Intrusion detection method and intrusion detection system for industrial control system based on communication model
An industrial control system and communication model technology, applied in the field of information security, can solve problems such as false positive rate, high false positive rate, lack of practicability, and reduced availability of control systems, so as to improve accuracy, ensure practicability, and reduce leakage. The effect of positive rate and false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
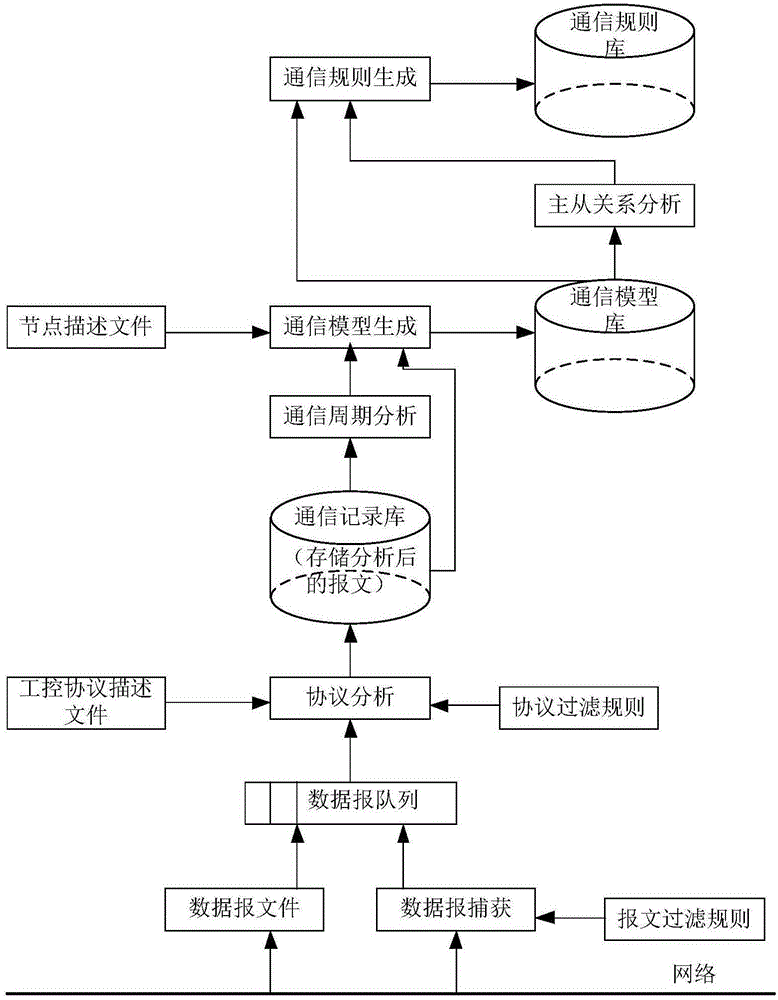
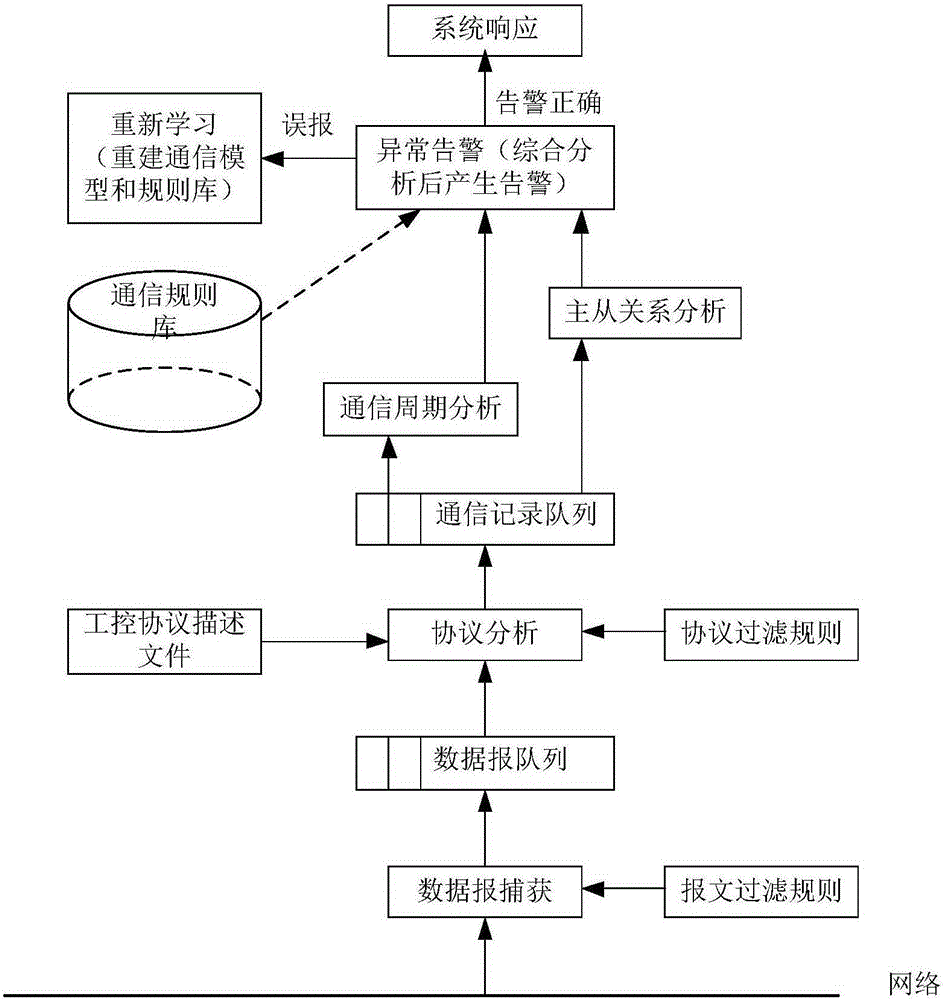
[0095] Example 1: Worms. If a node in the industrial control system is infected with a worm, the node will send a scanning detection message to the network. The communication connection mode of the scanning detection message does not match the communication rules of the industrial control system established by the present invention, and at this time, the IDS analysis and detection host will generate an alarm.
example 2
[0096] Example 2: Control command injection. If a control command is injected into the industrial control network, the period of the control command message does not match the original period of the control command. At this time, the IDS analysis and detection system will detect that the command period is abnormal and generate an alarm.
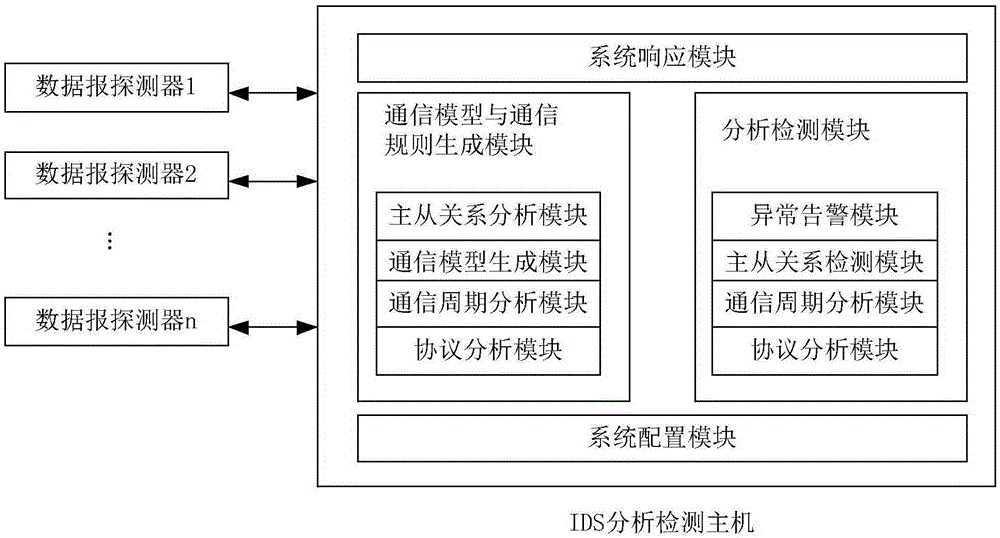
[0097] Example 3: The master-slave communication timing and polling sequence between the master station and the slave station are disordered due to control command hijacking. A typical example is that the Stunex virus can hijack the control commands of the Siemens industrial control system, making the Siemens S7-300PLC switch between start and stop. If there are S7-300PLCs in the master station and the slave station, the relationship between the master-slave communication timing and polling sequence will be confused. If there is similar hijacking of fame and fortune, the master-slave analysis and detection module in the present invention wil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com