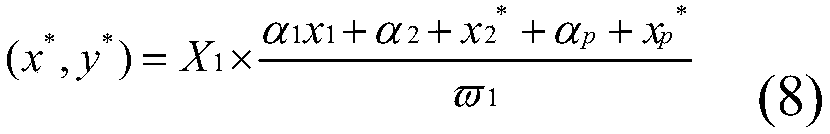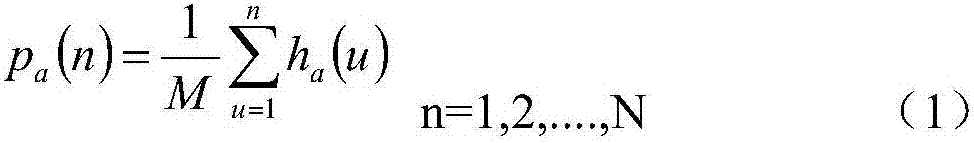Patents
Literature
129 results about "Response strategy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
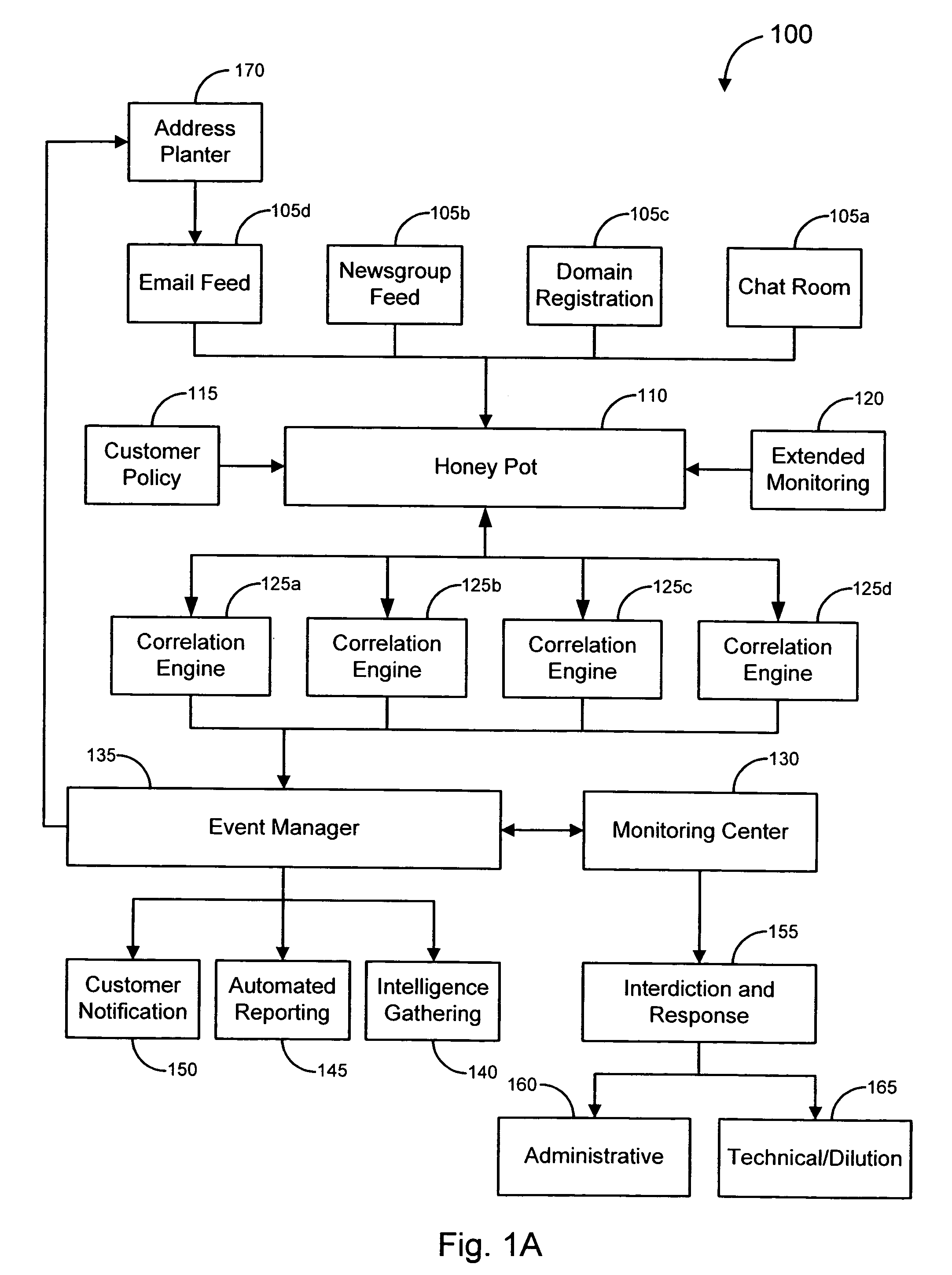
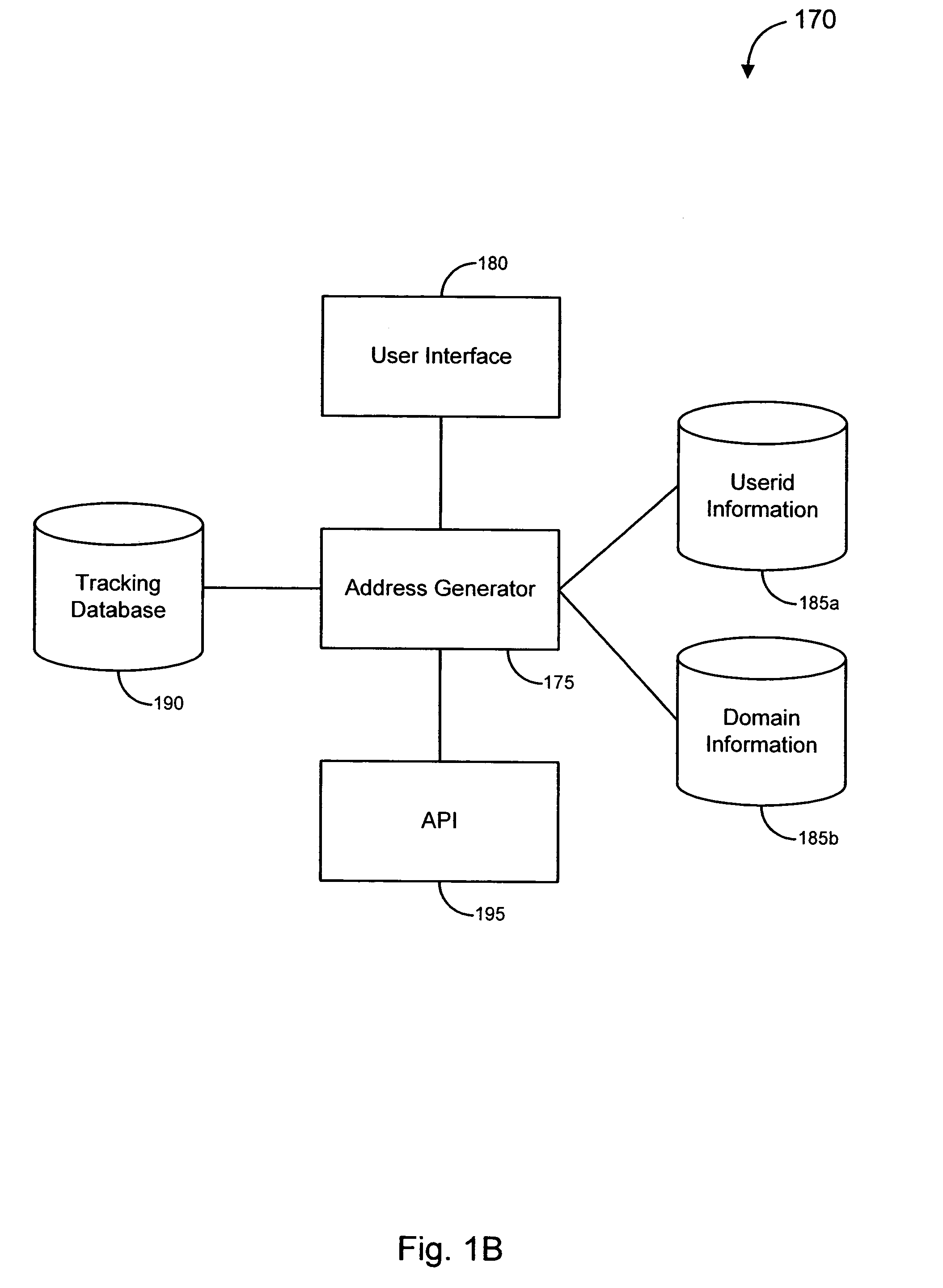
Geographic Response Strategies. Geographic Response Strategies ( GRS) are oil spill response plans tailored to protect a specific sensitive area from impacts following a spill. Environmental conditions at GRS sites frequently change according to season, storm impact, erosion, substrate redistribution, and other factors,...
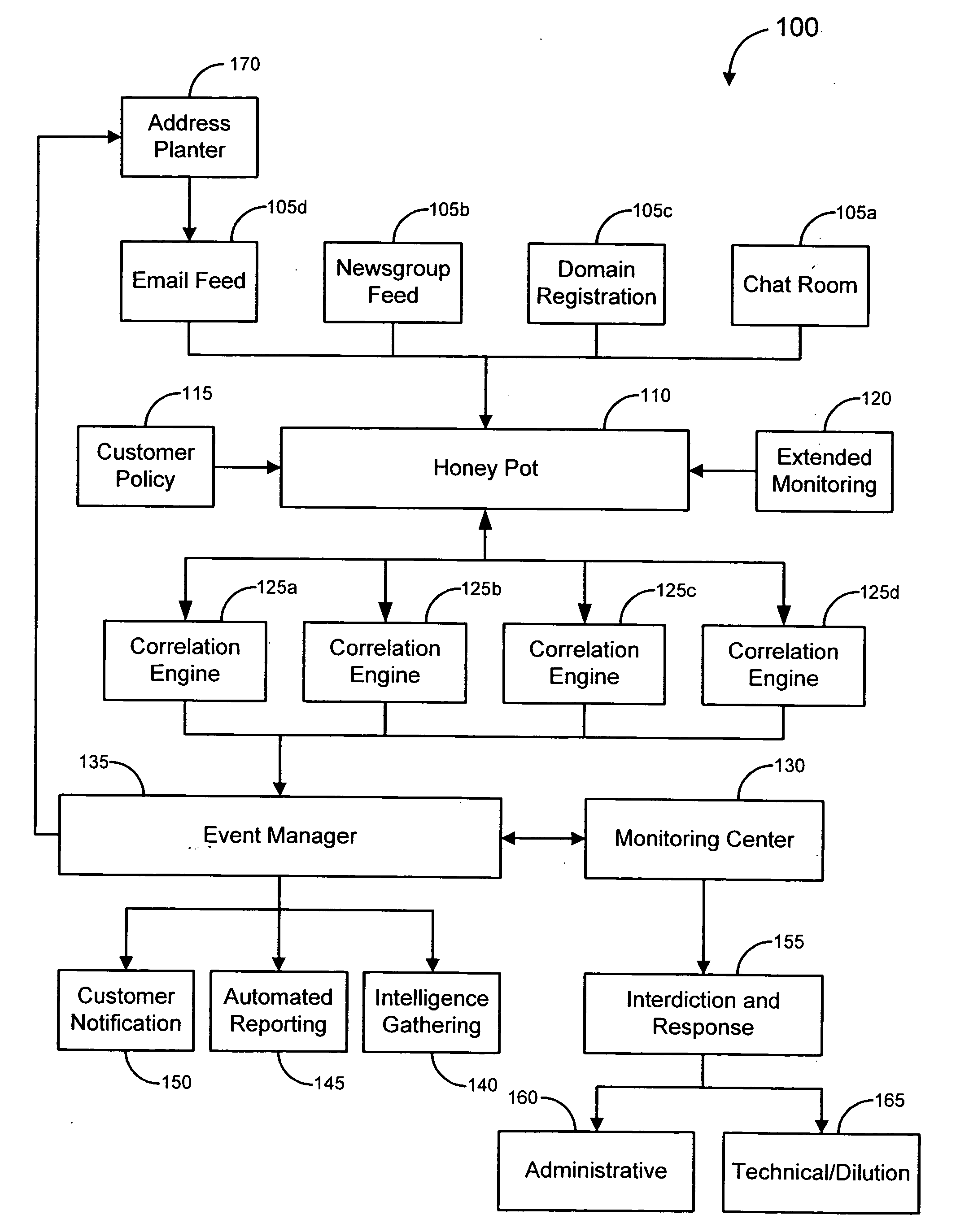
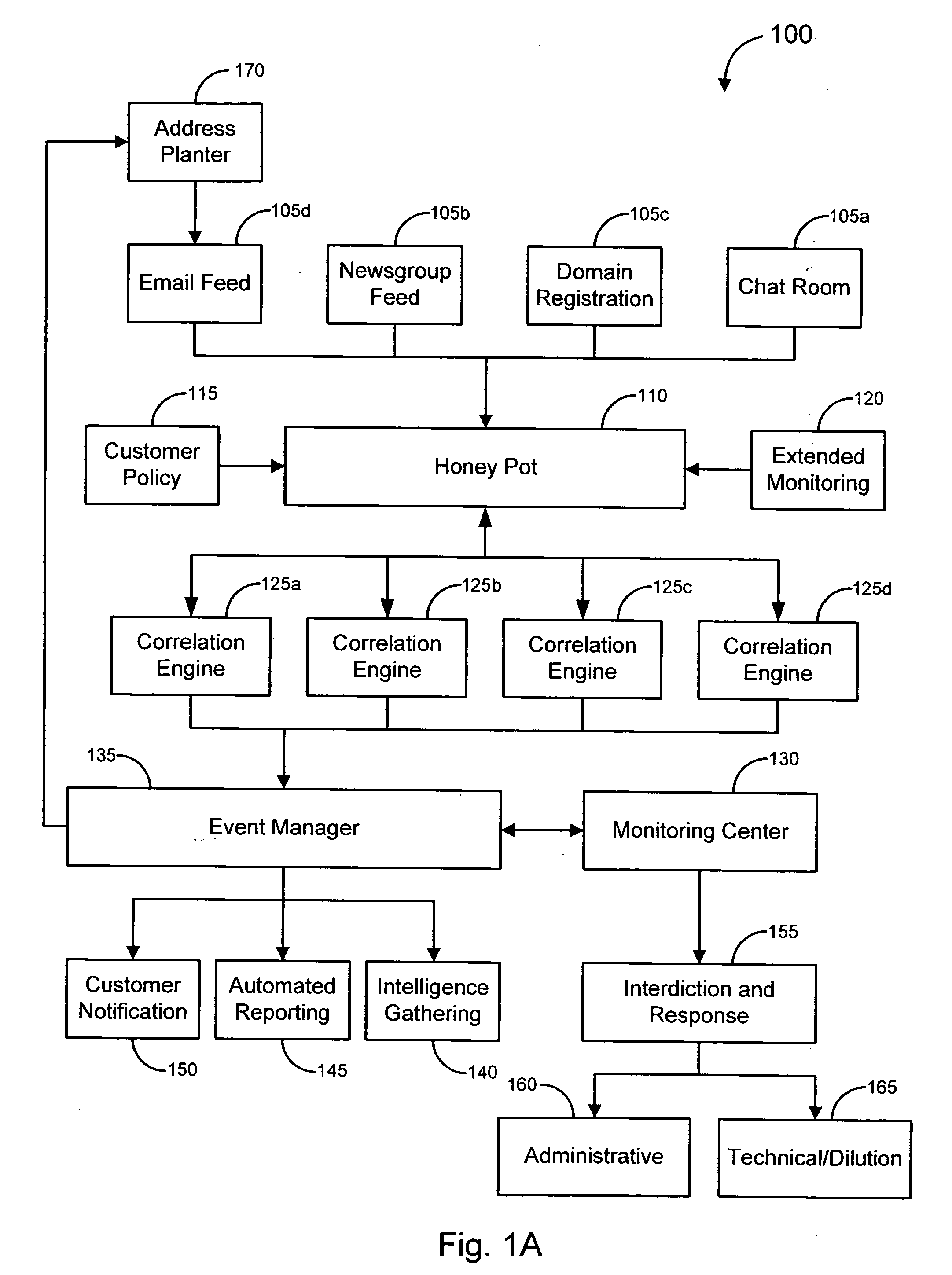
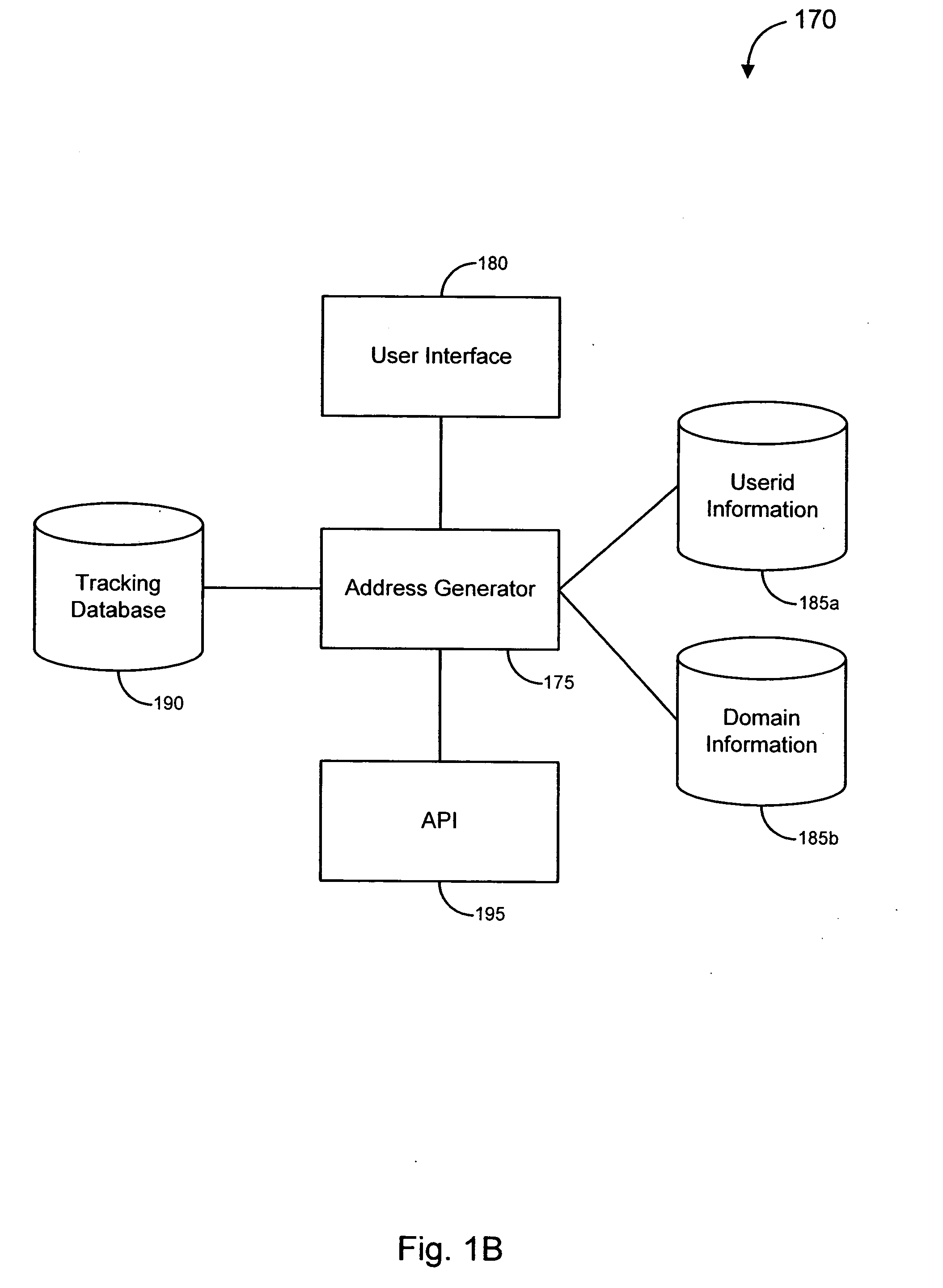
Enhanced responses to online fraud
ActiveUS20070294762A1Reduced effectivenessImprove responseMemory loss protectionDigital data processing detailsResponse strategyData science
Various embodiments of the invention provide solutions (including inter alia, systems, methods and software) for dealing with online fraud. In particular, various embodiments of the invention provide enhanced responses to an identified instance of online fraud. Such enhanced responses can incorporate one or more of a variety of strategies for defeating an attempt by a server to filter and / or otherwise avoid responses to its fraudulent activity. Merely by way of example, responses may be disguised (e.g., by transmitting the responses from a variety of computers, by transmitting responses that appear to originate from a computer different than the actual source of the responses, etc.). In some cases, a response strategy may be implemented that forces the server (and / or an operator thereof) to choose between accepting the responses and blocking potential responses from the targets of the fraudulent scheme. In these and other ways, embodiments of the invention can provide robust solutions to fraudulent activity, thereby diminishing the effectiveness of the fraudulent activity.
Owner:OPSEC ONLINE LTD
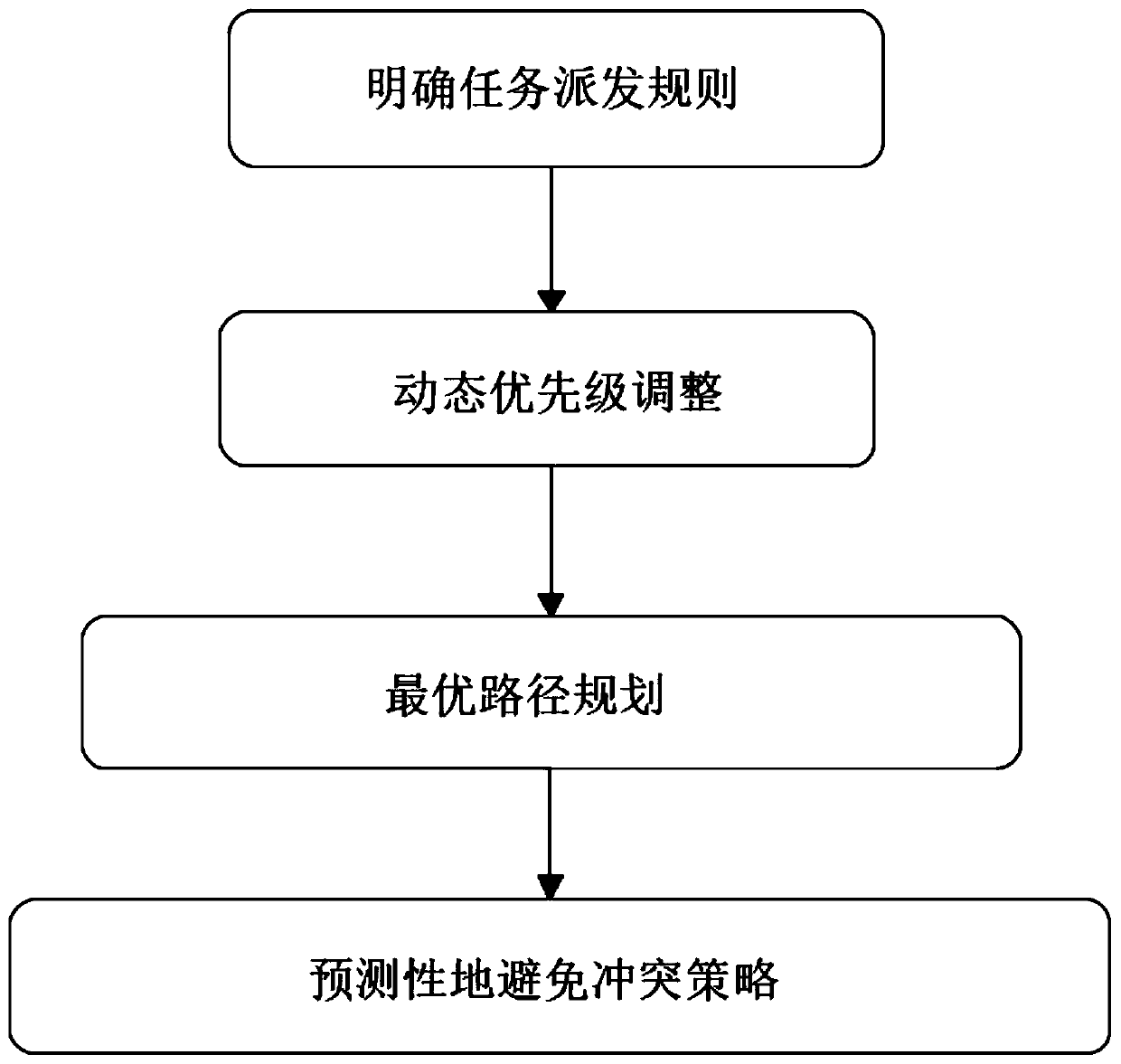
Intelligent warehousing route planning system and method based on multiple AGVs
The invention discloses an intelligent warehousing route planning method and system based on multiple AGVs. The method comprises the following steps: S100, defining a task distribution rule; dividing the priorities when the storage tasks are generated; S200, adjusting the dynamic priority; carrying out dynamic priority adjustment on the task of the AGV load in transportation; S300, planning an optimal path: dynamically and accurately calculating and locking a time window to reset a path so as to avoid conflicts, respectively carrying out coping strategy research on predictable vertical meeting conflicts and opposite meeting conflicts, and finally finding out a conflict-free shortest path; s400, predictively avoiding a conflict strategy; carrying out traffic rule making and unpredictable conflict detection and processing on traffic problems which may be encountered by a plurality of AGVs in the transportation process of a storage workshop. According to the system, the time cost of warehousing workshop tasks is reduced to the minimum, it is guaranteed that the path cost of the AGV is the minimum under the condition that vehicles are free of collision, and meanwhile the task scheduling efficiency and the vehicle scheduling efficiency are improved.
Owner:盐城品迅智能科技服务有限公司
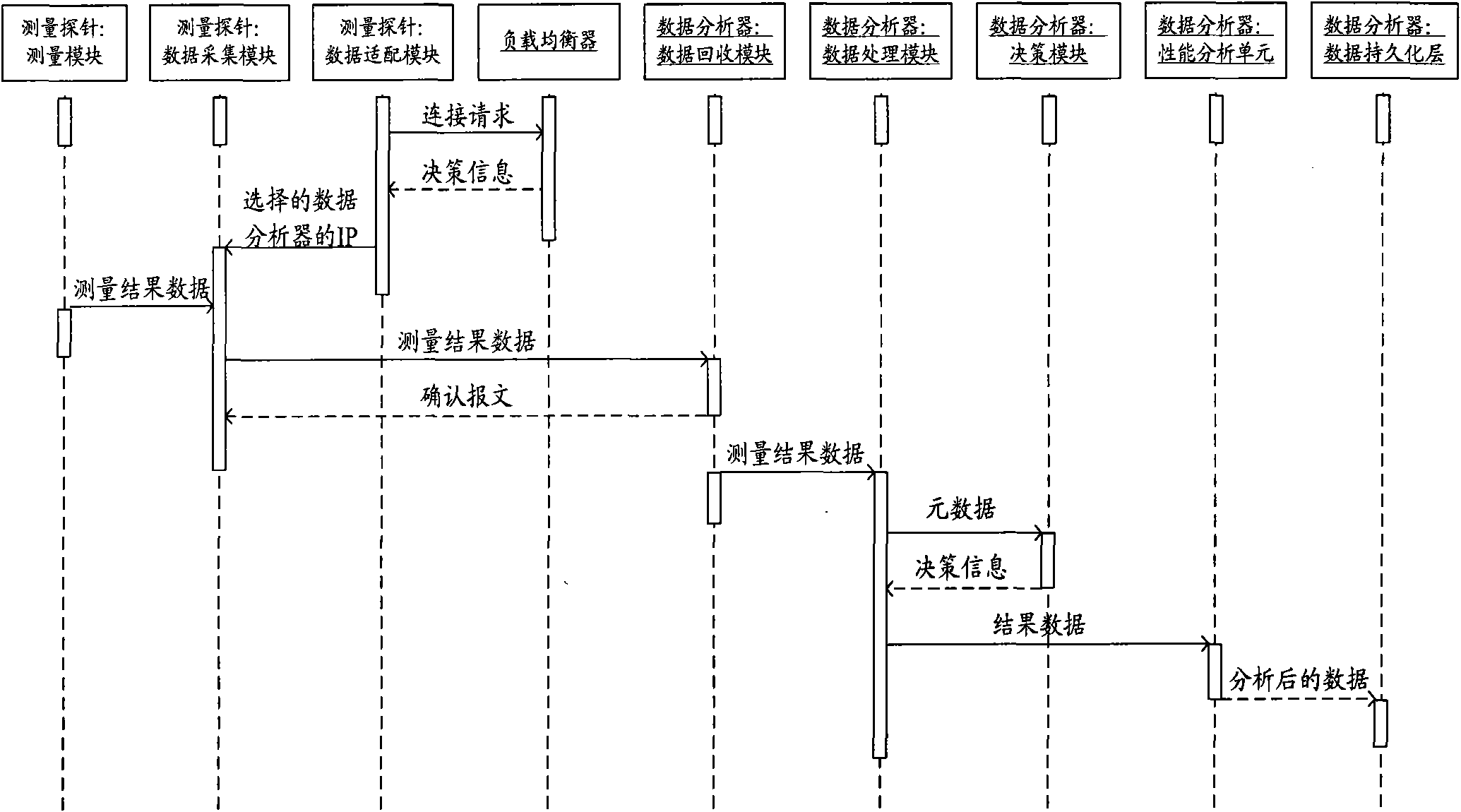
Cloud measurement device and method for IP network
InactiveCN102143022AEasy to handleFast data miningData switching networksMeasurement deviceData acquisition
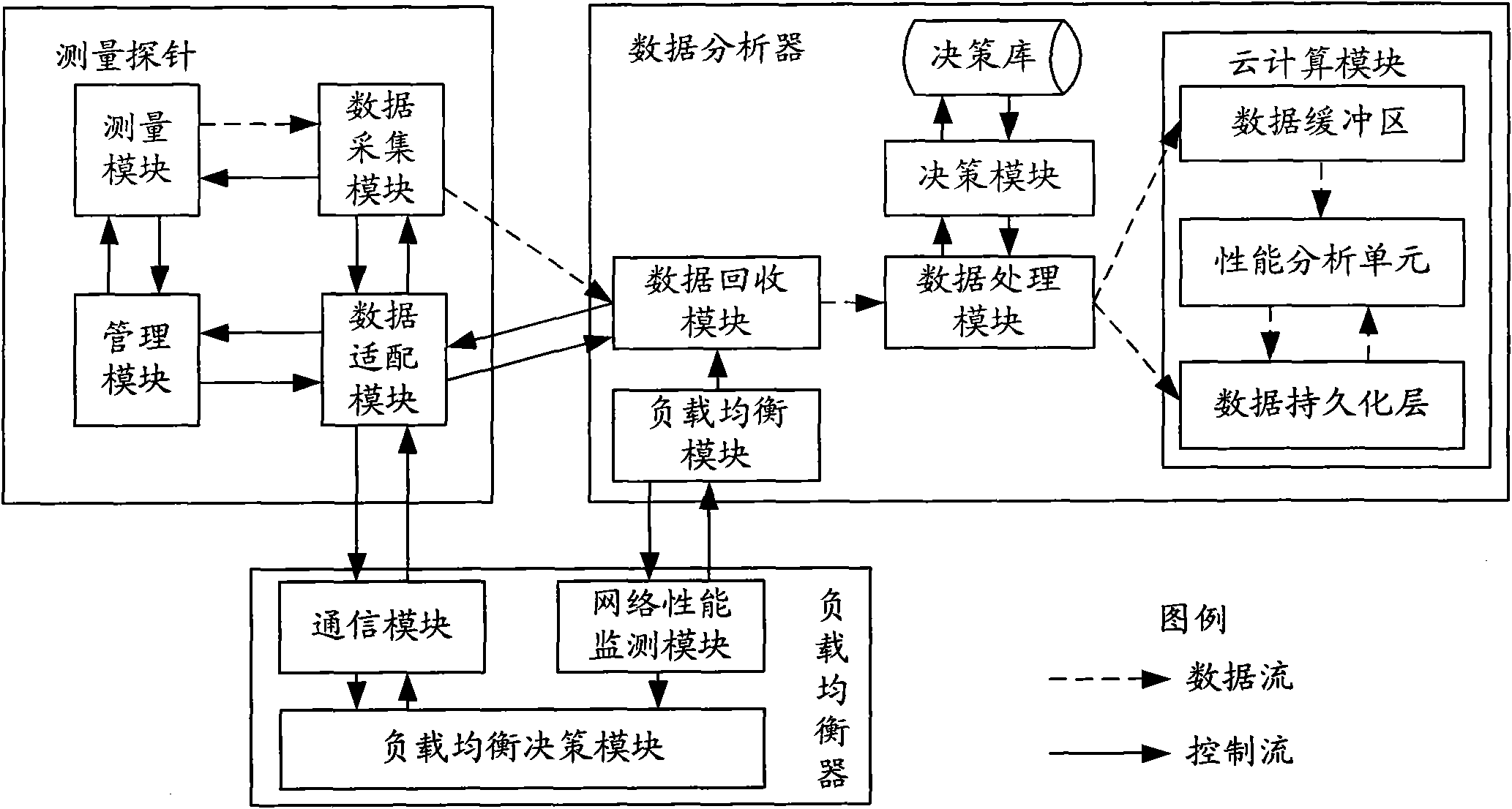
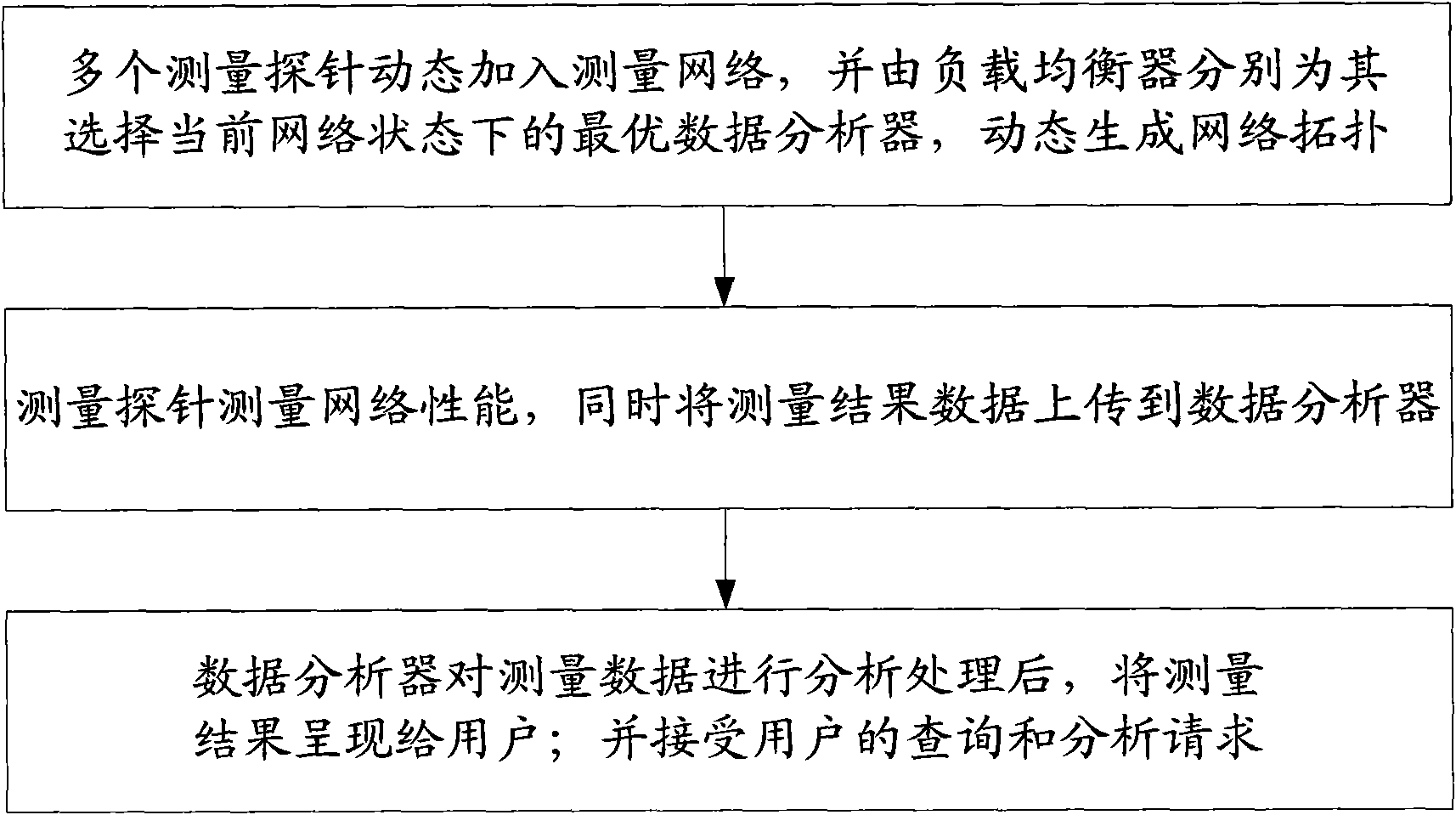
The invention provides a cloud measurement device and method for an IP network. The device is provided with three parts of a data analyzer, a measurement probe and a load balancer, wherein the data analyzer is provided with a data recovery module, a load balance module, a data processing module, a decision module and a cloud computing module; the measurement probe is provided with a measurement module, a data acquisition module, a data adaption module and a management module; and the load balancer is provided with a communication module, a network performance monitor module and a load balancedecision module. Huge measurement data is stored by using a cloud computing platform, reliability and expansibility of data storage are ensured, and rapid analysis and data mining are carried out on the huge measurement data by using a parallel processing mechanism of the cloud computing platform. The measurement probe supports multiple measurement algorithms and multiple formats of data acquisition. The measurement method provides a congestion response strategy and a load balance strategy. Therefore, the problems of data reliability and load balance between the multiple measurement probes and the data analyzer during storage and processing of the huge measurement data are solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
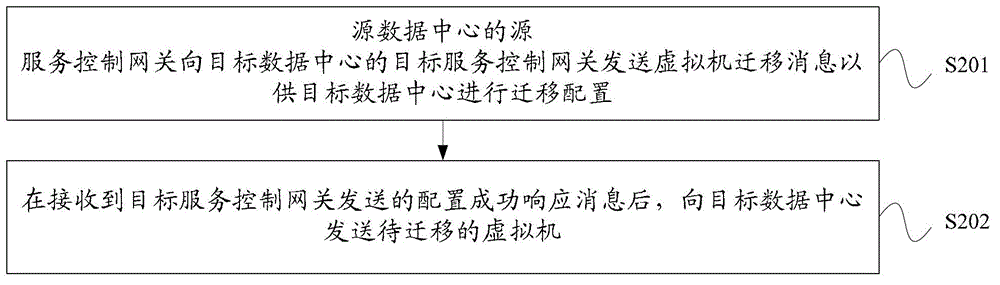
Cross-data-center virtual machine migration method, service control gateway and cross-data-center virtual machine migration
ActiveCN102884763AImplement automatic installationNo human intervention requiredNetworks interconnectionAuto-configurationService control
Embodiments of the invention provide a cross-data-center virtual machine migration method, a service control gateway and a cross-data-center virtual machine migration. The migration method comprises: a target service control gateway of a target data center receives virtual machine migration information sent by a source service control gateway of a source data center; the target service control gateway configures a response strategy, an internal data channel between an ingress router of the target data center and a target switch, and an external data channel between the target data center and a user on the target switch; the target service control gateway sends configuration success information to the source service control gateway; and the target service control gateway installs an virtual machine to be migrated on the target server and provides service for the user. According to the embodiments of the invention, the strategy of the target switch can be automatically installed, the external data channel from the user to the target data center can be automatically installed, and the internal data channel between the ingress router of the target data center and the target switch can be automatically installed, thereby achieving the automatic virtual machine migration across data centers.
Owner:HUAWEI TECH CO LTD
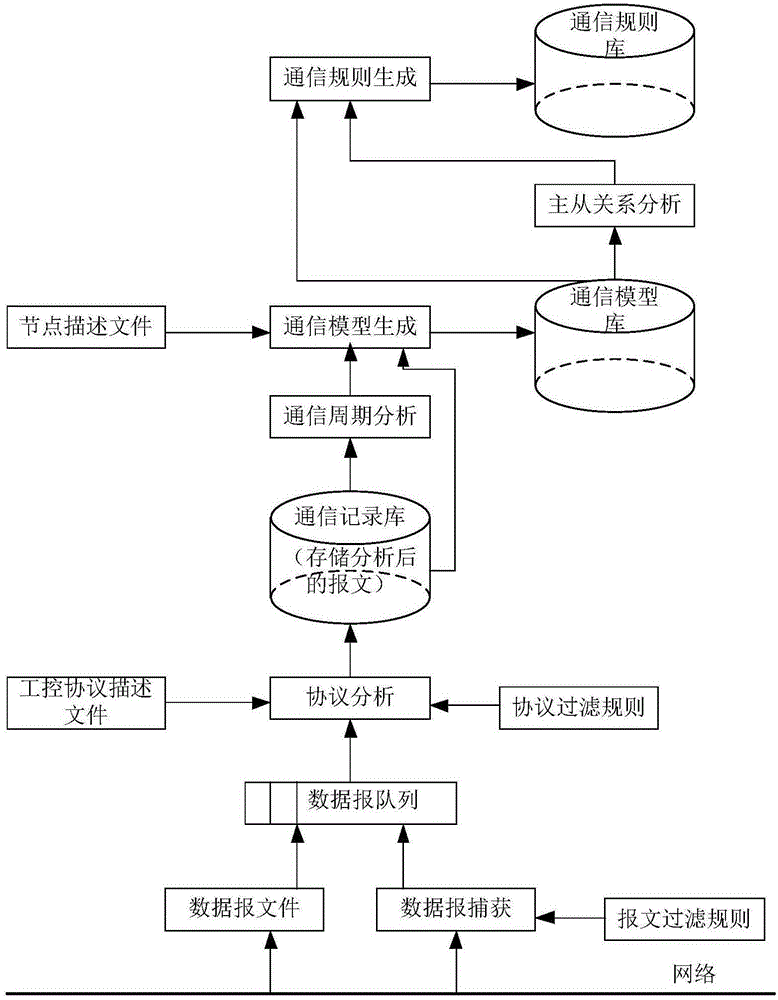
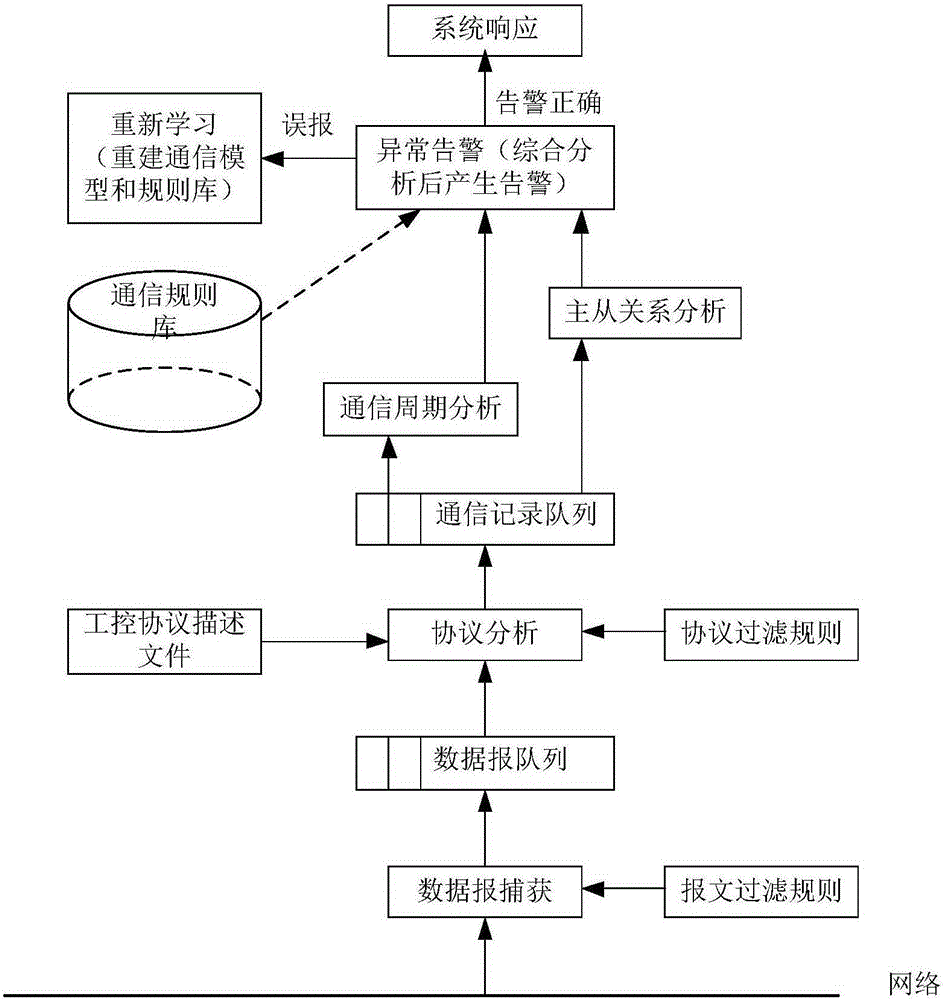
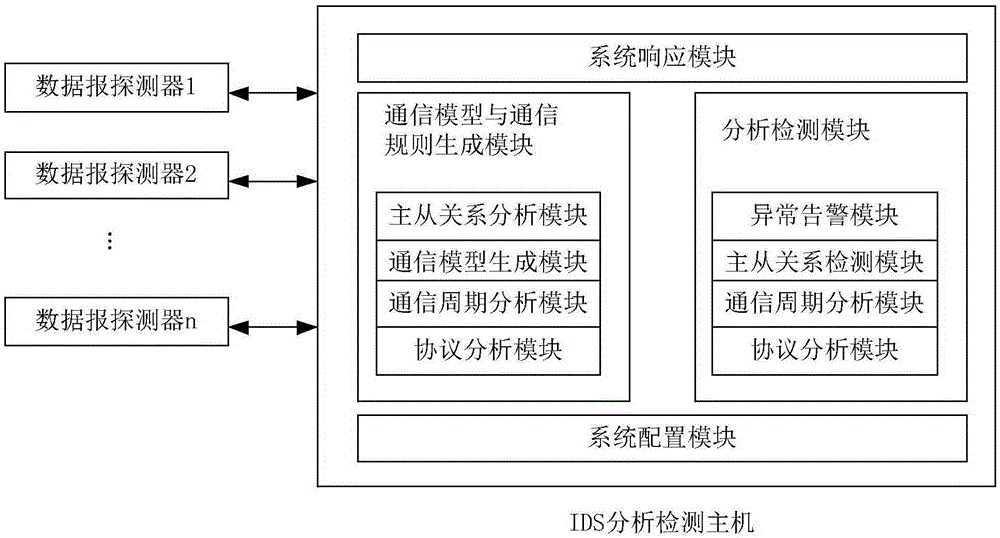
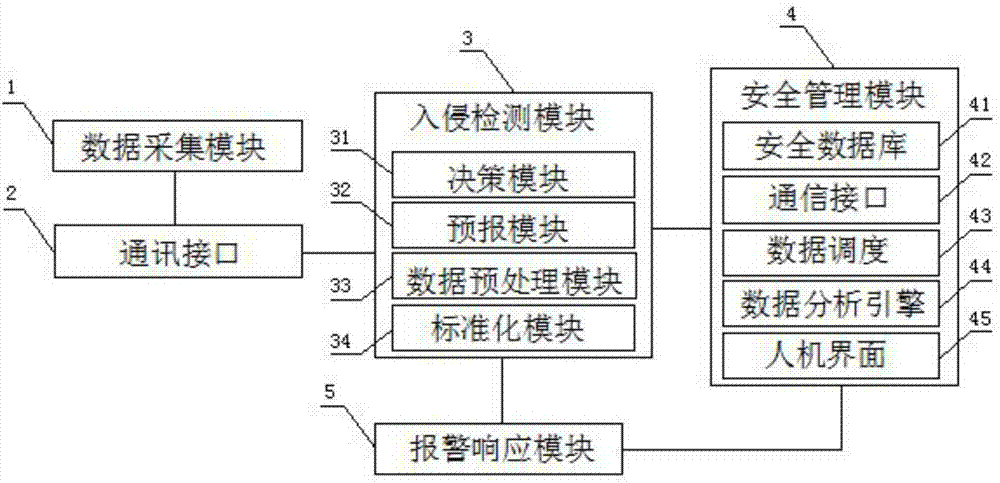
Intrusion detection method and intrusion detection system for industrial control system based on communication model
InactiveCN105204487AImprove accuracyGuaranteed practicalityElectric testing/monitoringComputer moduleResponse strategy
The invention provides an intrusion detection method and an intrusion detection system for an industrial control system based on a communication model. The accuracy of intrusion detection is improved to the maximum degree while the practicability is guaranteed. The intrusion detection method comprises the steps of firstly establishing a communication model and communication rules of the industrial control system, wherein the communication model comprises node information and communication connection information; generating a legal communication rule set on the basis of the communication model after the communication model of the industrial control system is established, learning in an installation and debugging stage and a stage before an attack happens of the industrial control system, and establishing a communication model and a communication rule set; then deploying detectors in an industrial control network, capturing a datagram, analyzing and extracting the communication connection information through the datagram, comparing the communication connection information with the generated legal communication rule set, and giving out an alarm when communication connection which violates the legal communication rule set exists; and calling a system response module to adopt corresponding response strategies if intrusion is discovered, and carrying out analysis and learning again if actual detection is wrong.
Owner:BEIJING UNIV OF POSTS & TELECOMM
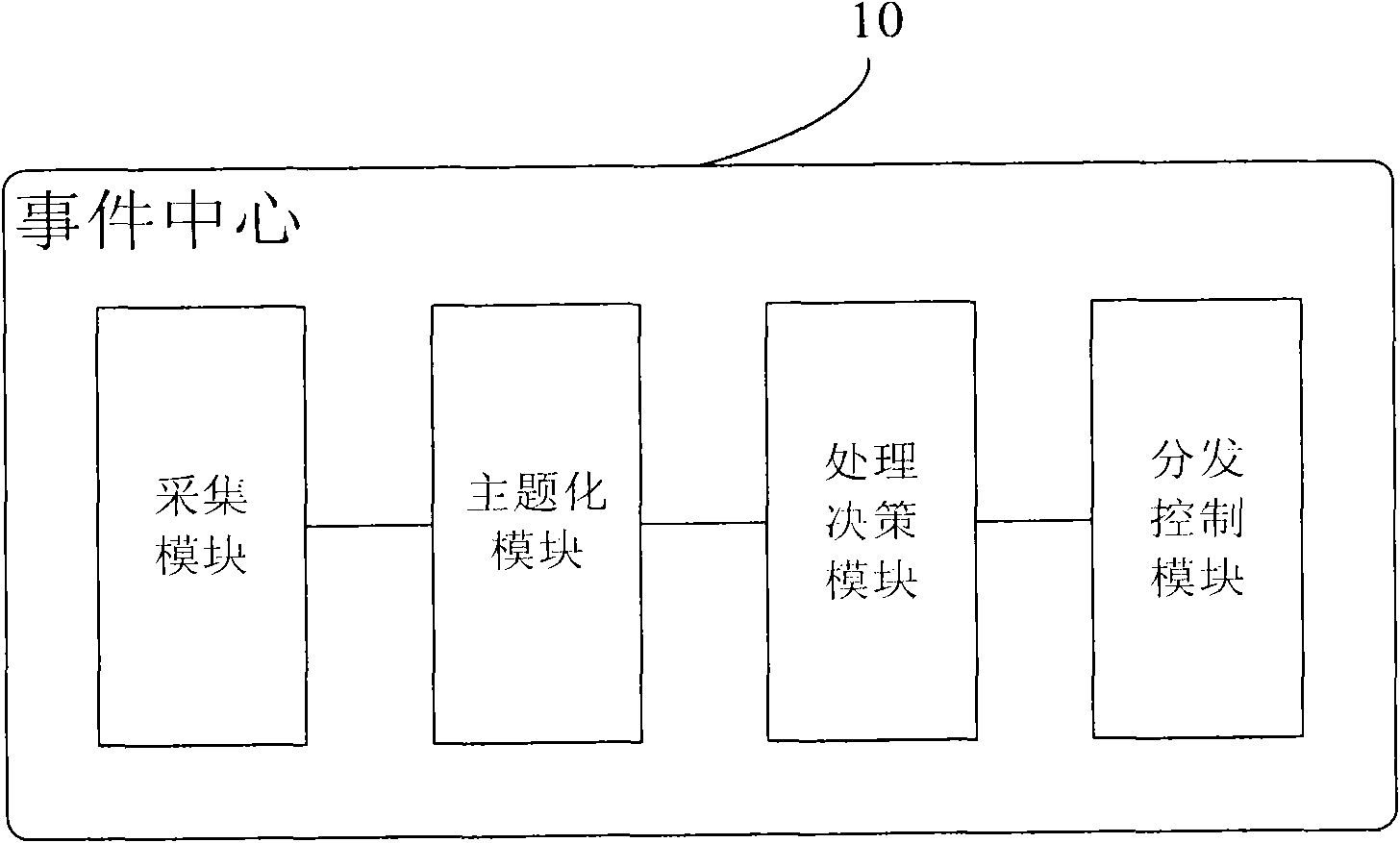
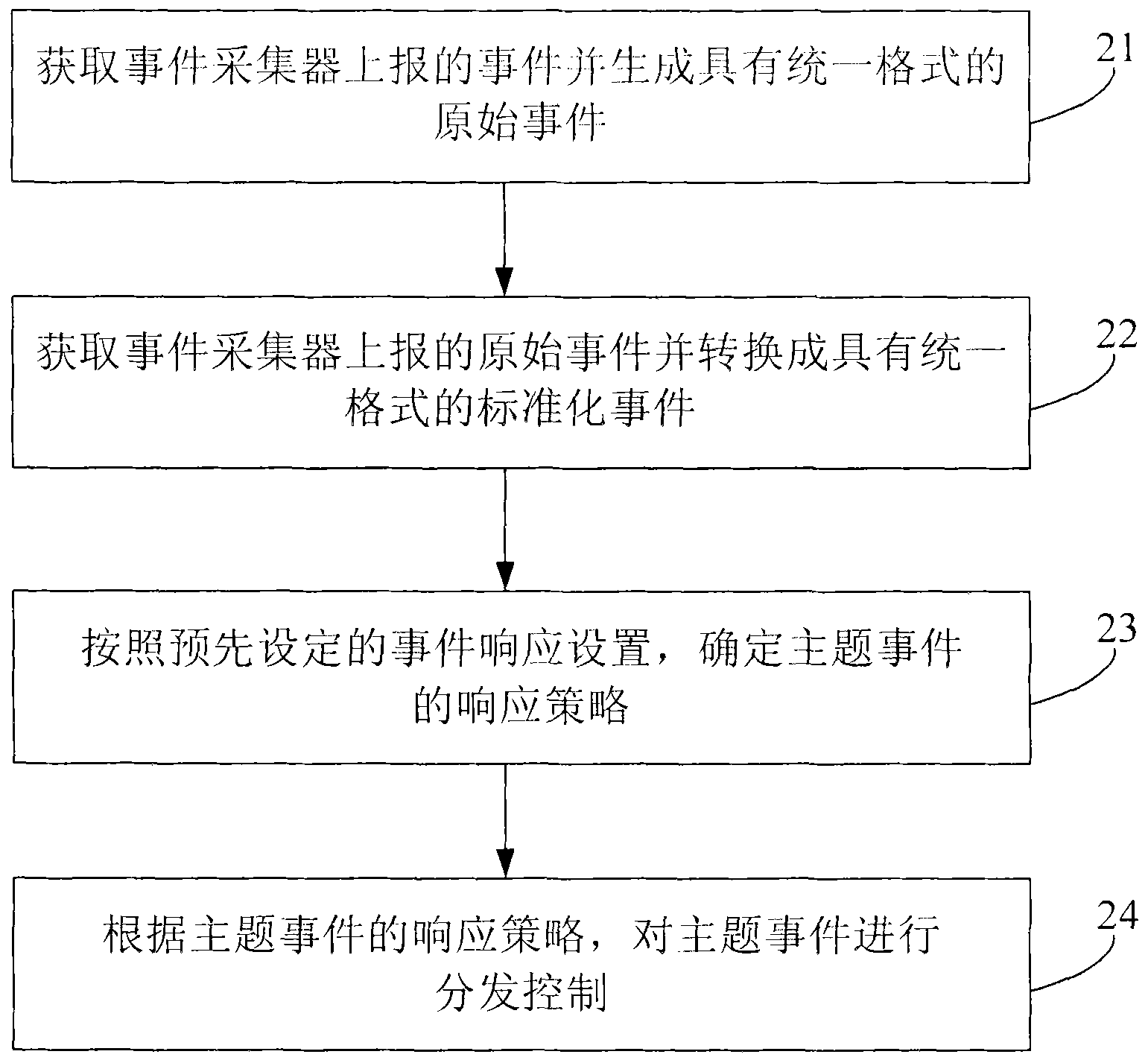
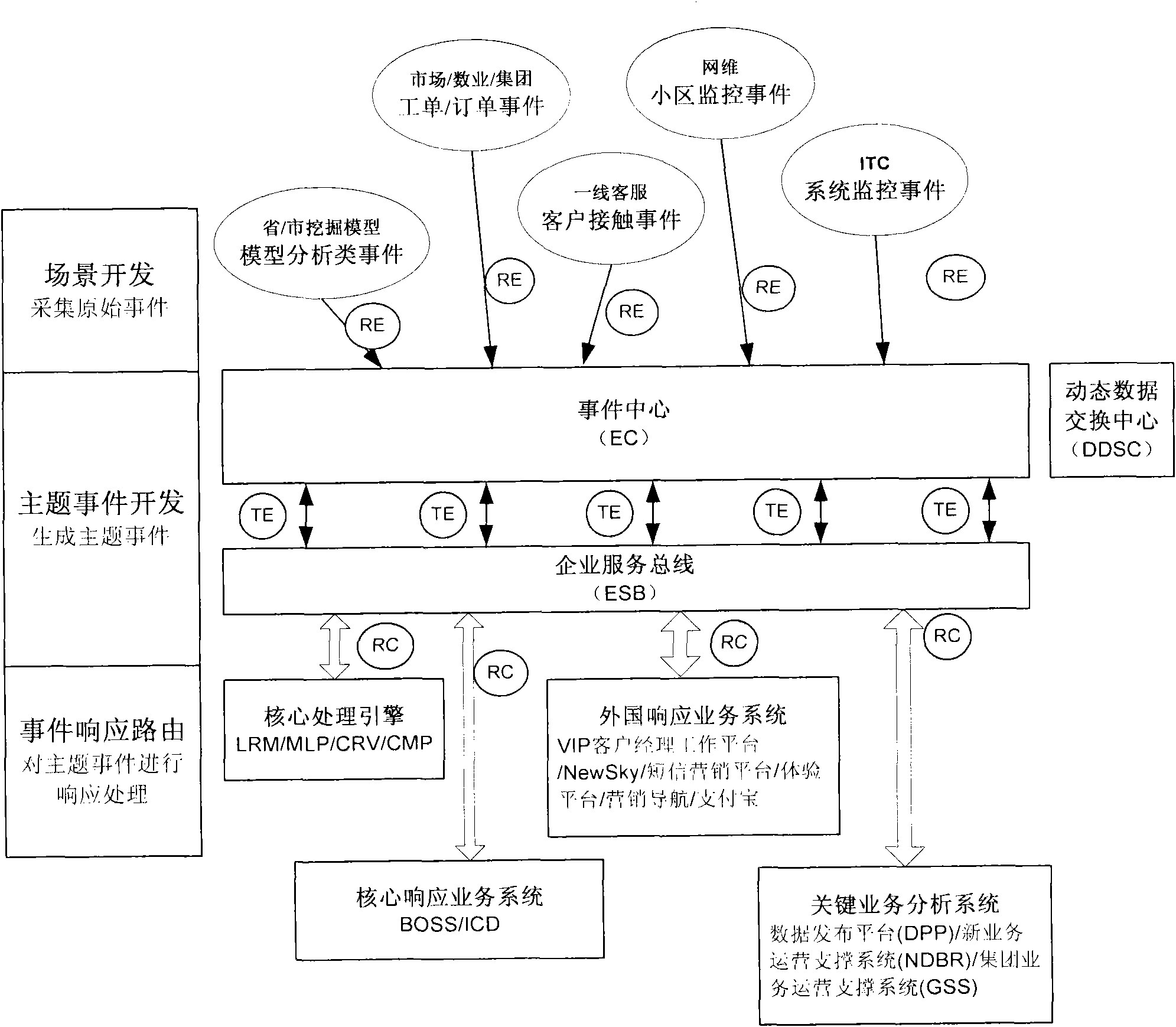
Event center supporting cross-system service linkage and event processing method of event center
InactiveCN102340495AImprove good performanceEasy maintenanceBus networksDistribution controlStructure of Management Information
The invention provides an event center supporting a cross-system service linkage and an event processing method of the event center. The event center comprises: an acquisition module, which is used for obtaining original events reported by event collectors of all systems in a network and converting the original events into standardized events having a unified format; a thematic module, which is used for carrying out thematic processing on the standardized events obtained by the acquisition module on the basis of a preset thematic mode so as to obtain theme events; a processing decision module, which is used for determining response strategies of the theme events according to preset event response arrangement; and a distribution control module, which is used for carrying out distribution and control on the theme event according to the response strategies of the theme events. According to the invention, events are collected and processed by employing a bus structure mode through an event center, so that service logics are concentrated; moreover, services are easy to expand and maintain.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
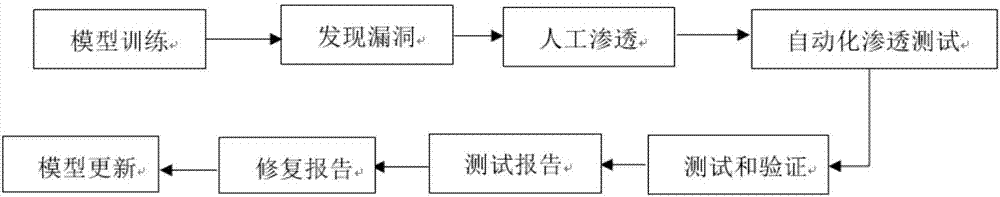
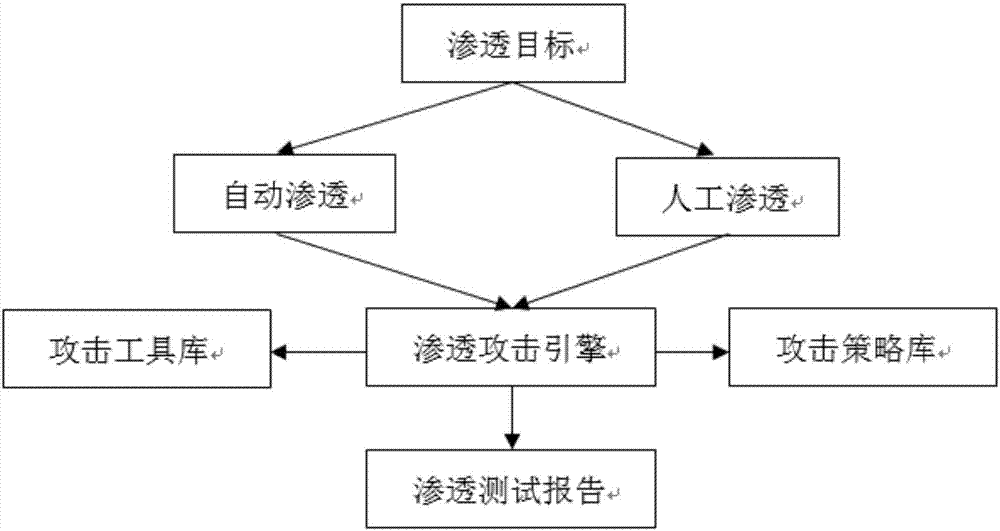
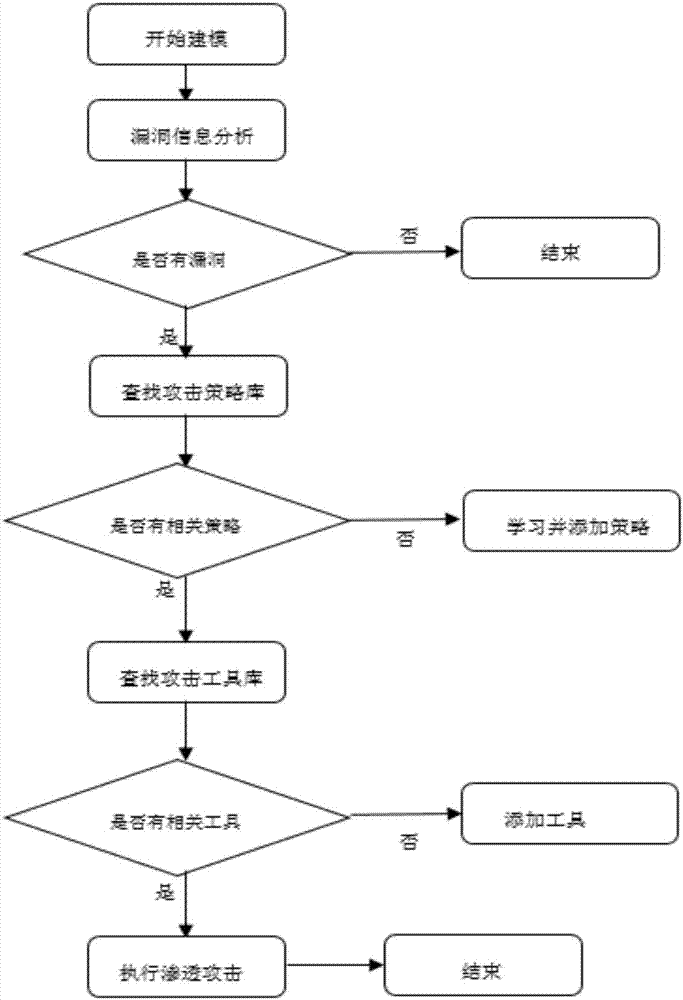
Automated safety penetration test method
ActiveCN107426227ARealize automatic callAchieve executionPlatform integrity maintainanceData switching networksAttack modelAttack strategy
The invention discloses an automated safety penetration test method, comprising: step 1, training an automated response model, establishing a corresponding model; step 2, scanning a target information system, obtaining host information; step 3, scanning vulnerability of the target information system, obtaining vulnerability information; step 4, according to the host information and the vulnerability information obtained in the step 2 and step 3, combined with an attack strategy library, establishing an attack model, according to the attack model, trying to attack the target information system, obtaining an attack feedback result; step 5, performing comprehensive analysis on a penetration test overall process, generating a penetration test report and teasing test steps and intermediate results, analyzing system security, providing a related solution; step 6, the response model updating in an adaptive manner, and regulating a response strategy.
Owner:CHINA INFOMRAITON CONSULTING & DESIGNING INST CO LTD
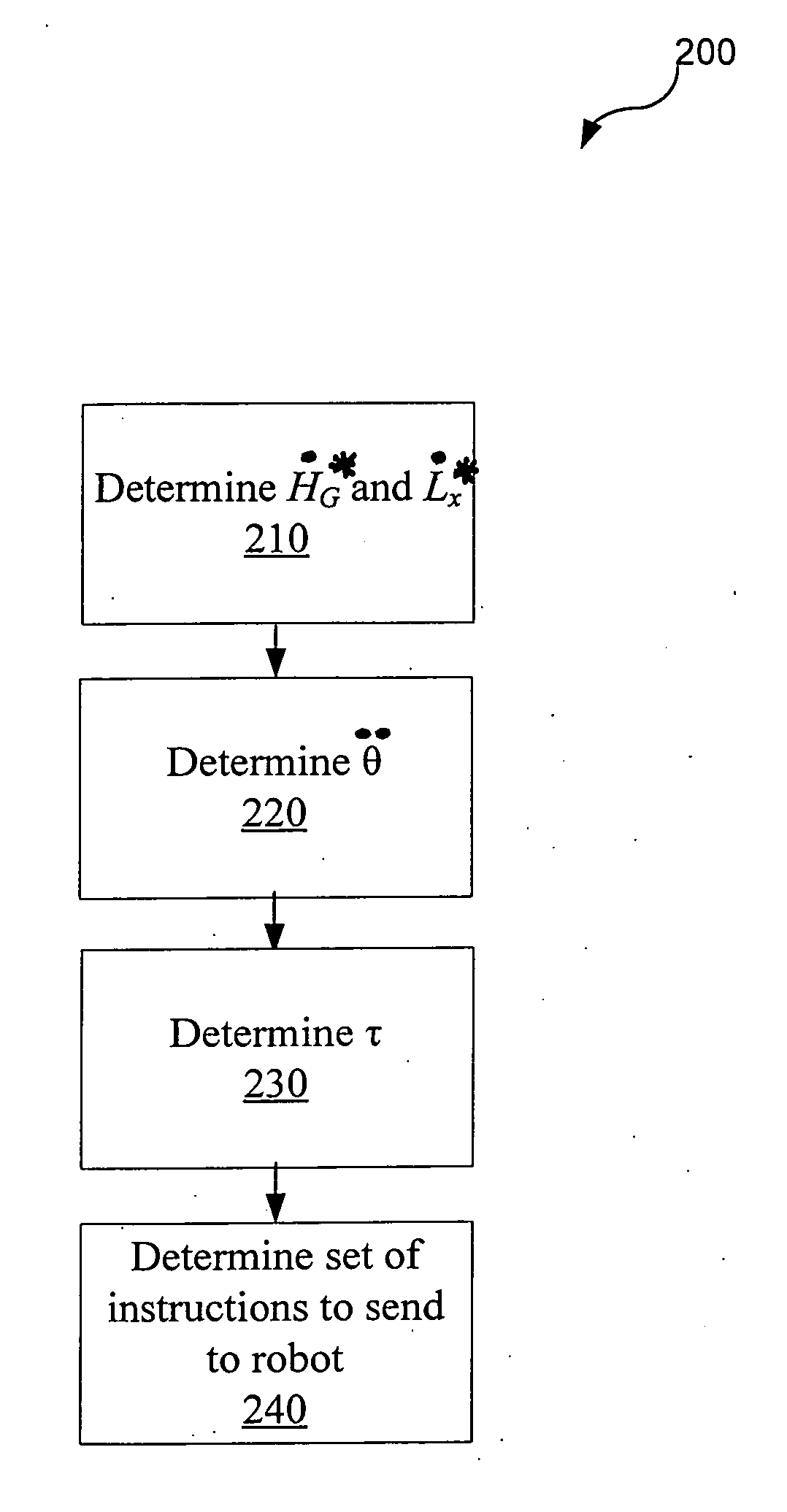
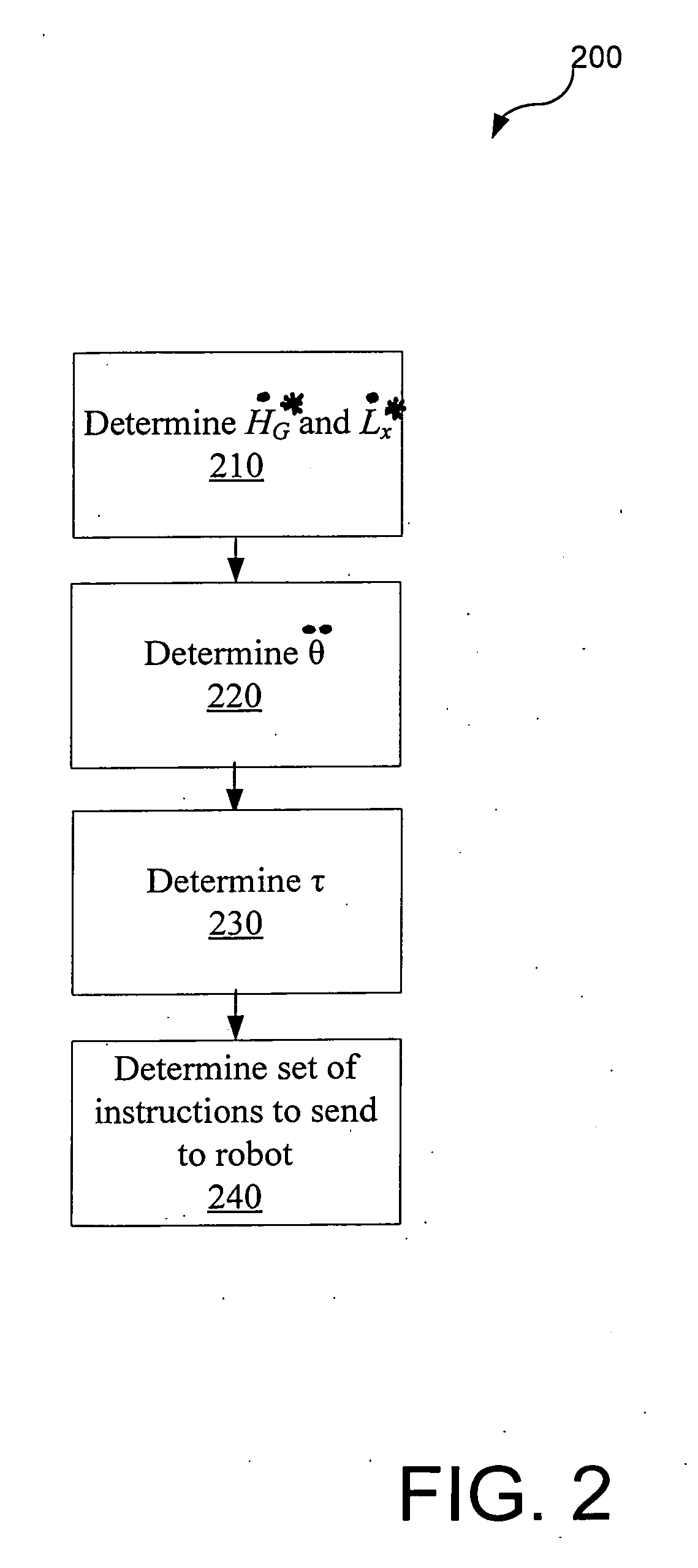
Systems and methods for controlling a legged robot using a two-phase disturbance response strategy
ActiveUS20060241809A1Maximize energyHigh energyProgramme-controlled manipulatorComputer controlMomentumControl system
Systems and methods are presented that enable a legged robot to maintain its balance when subjected to an unexpected force. In the reflex phase, the robot withstands the immediate effect of the force by yielding to it. In one embodiment, during the reflex phase, the control system determines an instruction that will cause the robot to perform a movement that generates a negative rate of change of the robot's angular momentum at its centroid in a magnitude large enough to compensate for the destabilizing effect of the force. In the recovery phase, the robot recovers its posture after having moved during the reflex phase. In one embodiment, the robot returns to a statically stable upright posture that maximizes the robot's potential energy. In one embodiment, during the recovery phase, the control system determines an instruction that will cause the robot to perform a movement that increases its potential energy.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
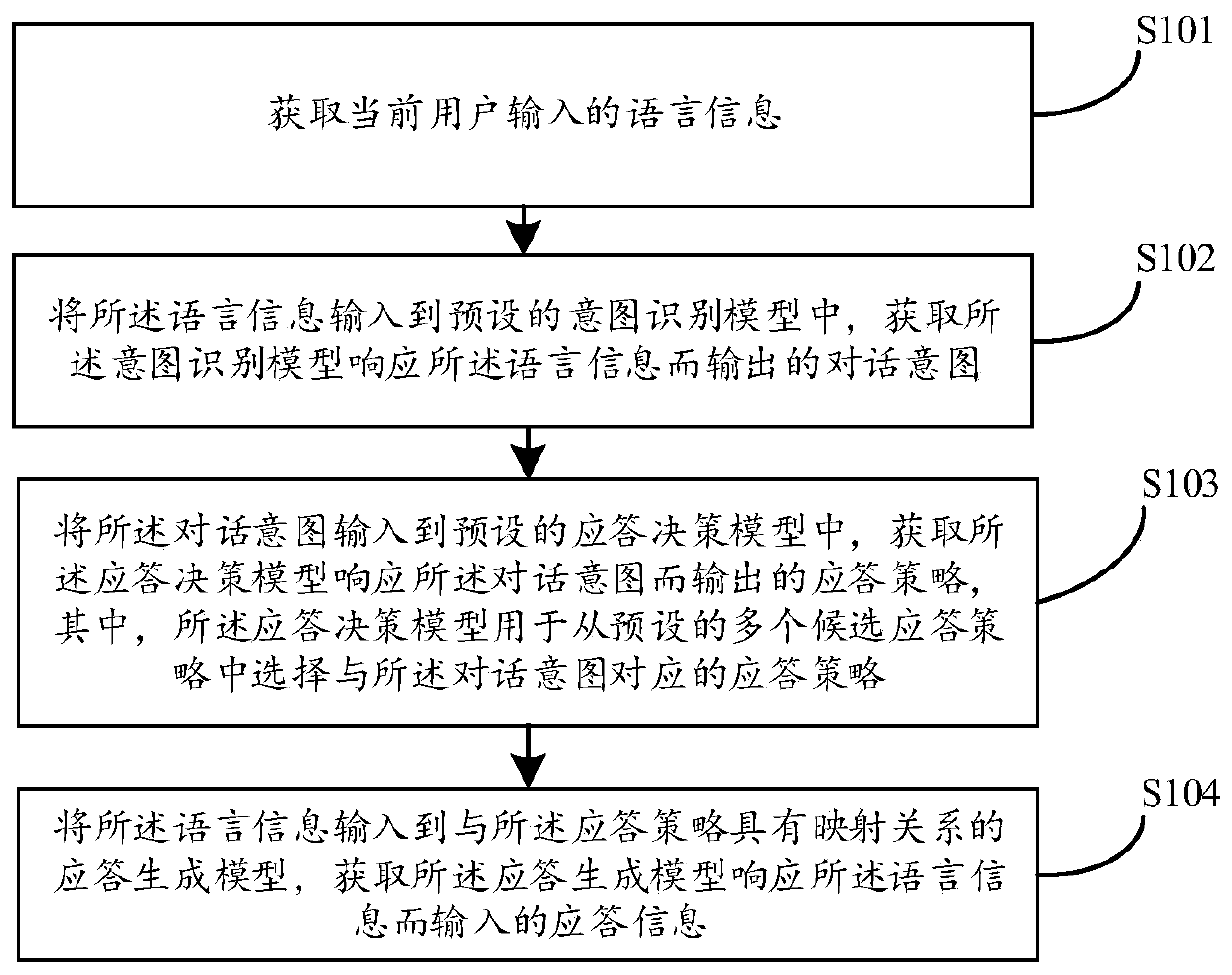
Machine dialogue method and device, computer equipment and storage medium
PendingCN110046221ADialogue diversificationCharacter and pattern recognitionNeural architecturesDecision modelResponse generation
The embodiment of the invention relates to the technical field of artificial intelligence, and discloses a machine conversation method and device, computer equipment and a storage medium, and the method comprises the following steps: obtaining language information input by a current user; inputting the language information into a preset intention recognition model, and obtaining a dialogue intention output by the intention recognition model in response to the language information; inputting the dialogue intention into a preset response decision model, and obtaining a response strategy output by the response decision model in response to the dialogue intention; and inputting the language information into a response generation model having a mapping relationship with the response strategy, and obtaining response information input by the response generation model in response to the language information. Through intention identification, a response generation model is determined, and responses of different types are generated, so that the dialogue is diversified and more interesting.
Owner:PING AN TECH (SHENZHEN) CO LTD
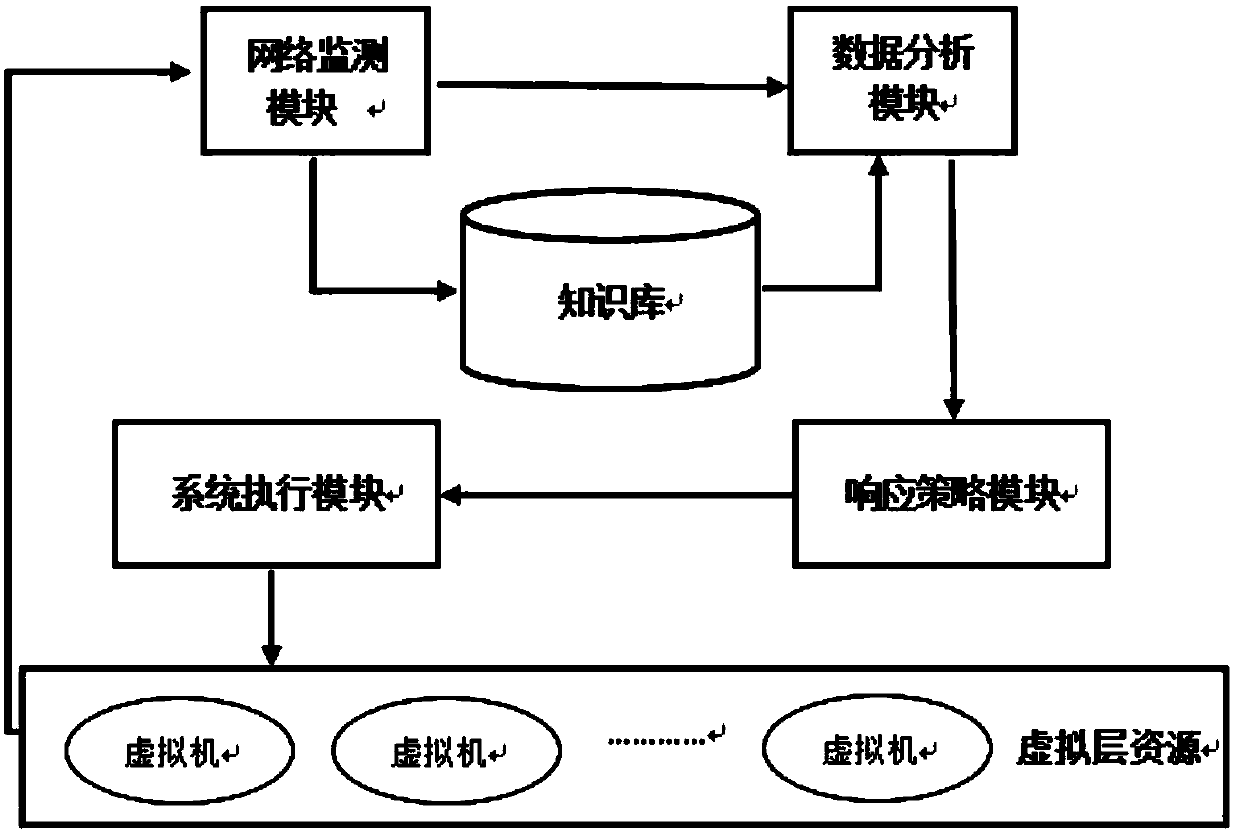
Data safety monitoring method and system for cloud platform
InactiveCN107707431AImprove accuracyLong monitoring cycleData switching networksFeature vectorResponse strategy
The invention provides a data safety monitoring method and system for a cloud platform. The system includes: a network monitoring module which is intended for searching the monitoring data of respective levels of a cloud platform and permanently saving the monitoring data to a knowledge base; a data analysis module which is intended for analyzing and saving the data that are input by the network monitoring module and invoked from the knowledge base; a response strategy module which is intended for, based on quantification information of the importance of a to-be-monitored target that is inputby the data analysis module, selecting a to-be-monitored target which is required for the next stage, and analyzing the possibility of faults of an abnormal degree prediction system; a system execution module which is intended for, based on the input that is input by the response strategy module, using a monitoring agent to execute dynamic adjustment of a to-be-monitored target and a monitoring period; and a knowledge base module which is intended for recording a load mode that is learnt in the operation and a corresponding feature vector so as to describe the normal operation state of the system.
Owner:HENAN UNIV OF SCI & TECH
Regional power utilization intelligent management system
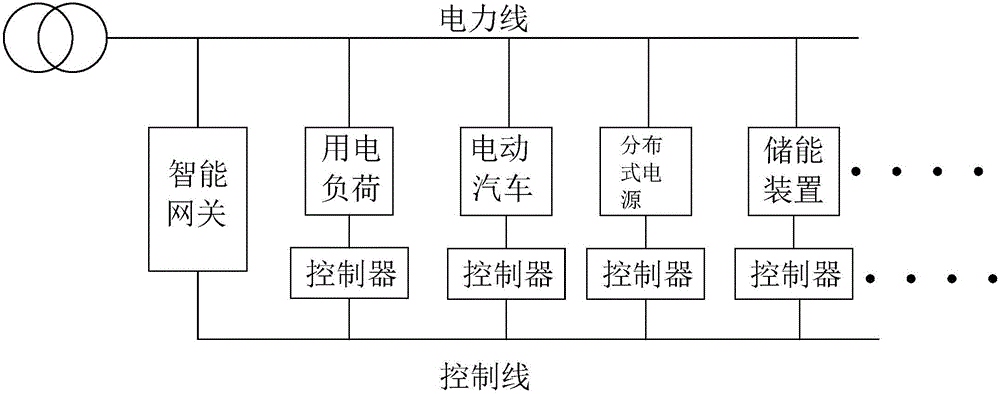
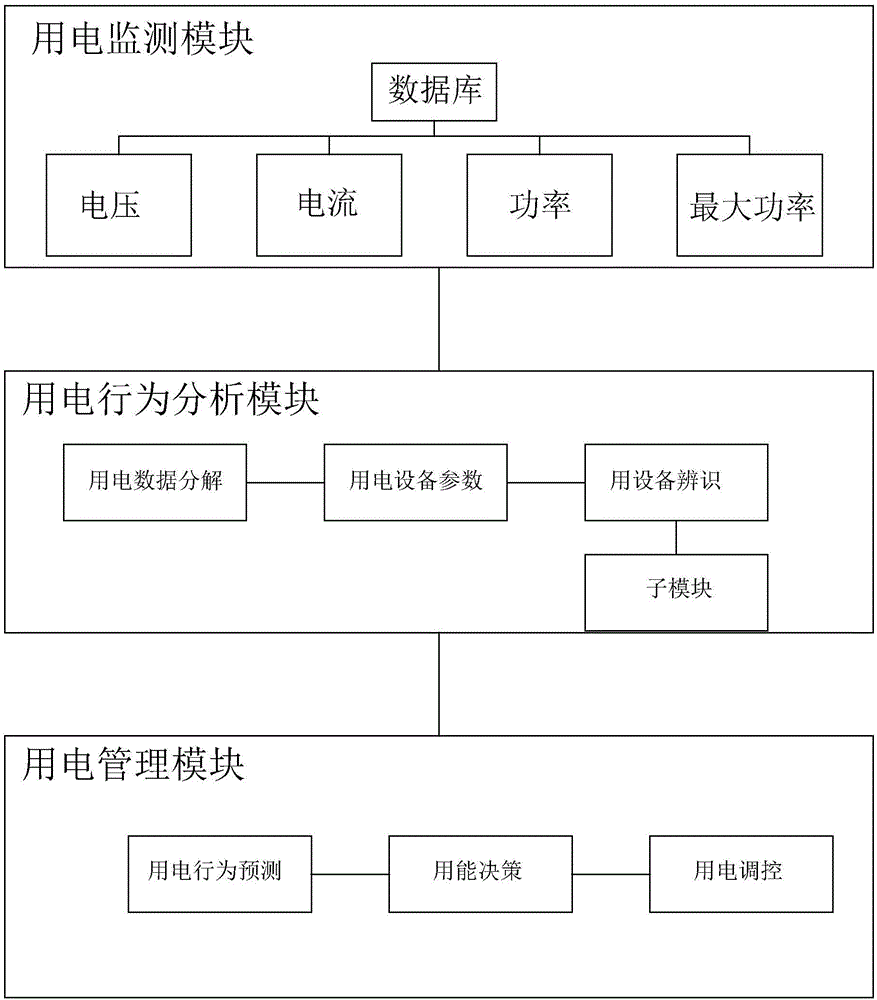
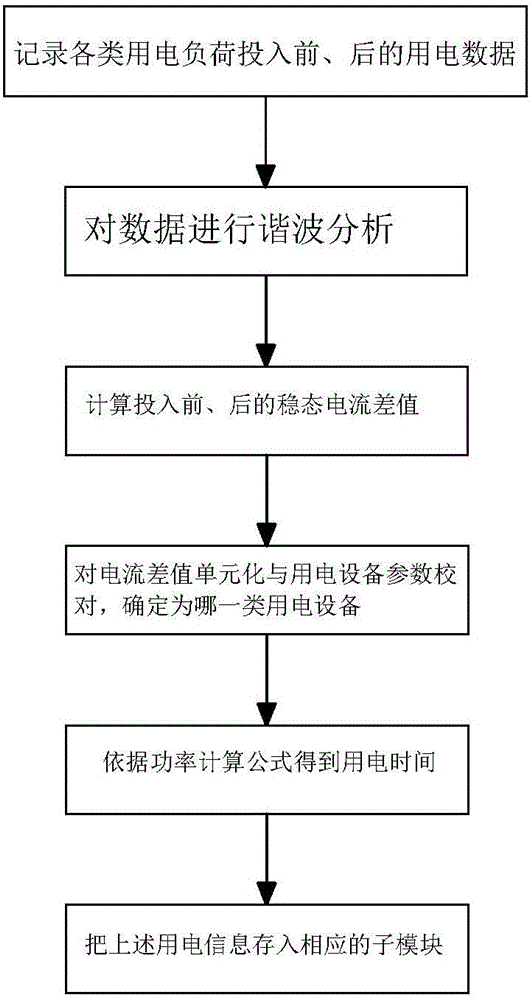
PendingCN106300349AFunction increaseImprove efficiencyLoad forecast in ac networkSystems intergating technologiesUtilization behaviorEngineering
The invention relates to a regional power utilization intelligent management system. By building a regional energy utilization monitoring system which is automatic, intelligent and networked, has complete functions and is wide in measurement range and high in adaptability, real-time power utilization energy consumption information of various power utilization equipment (electrical appliances) in a region is measured, power utilization behavior is recorded, stored and analyzed, a user power utilization mode optimization scheme is formed by machine learning, an optimization algorithm is developed, an automatic response strategy of a demand side is combined, load management (dispatching control) is performed on a power utilization terminal through access of a controller of the power utilization equipment by an intelligent gateway, reasonable and orderly power utilization, terminal energy use efficiency improvement and power utilization behavior optimization are finally realized, and the purposes of energy saving and efficiency increase are achieved.
Owner:BEIJING PURUI ELECTRONICS
Interaction method and device based on child emotions
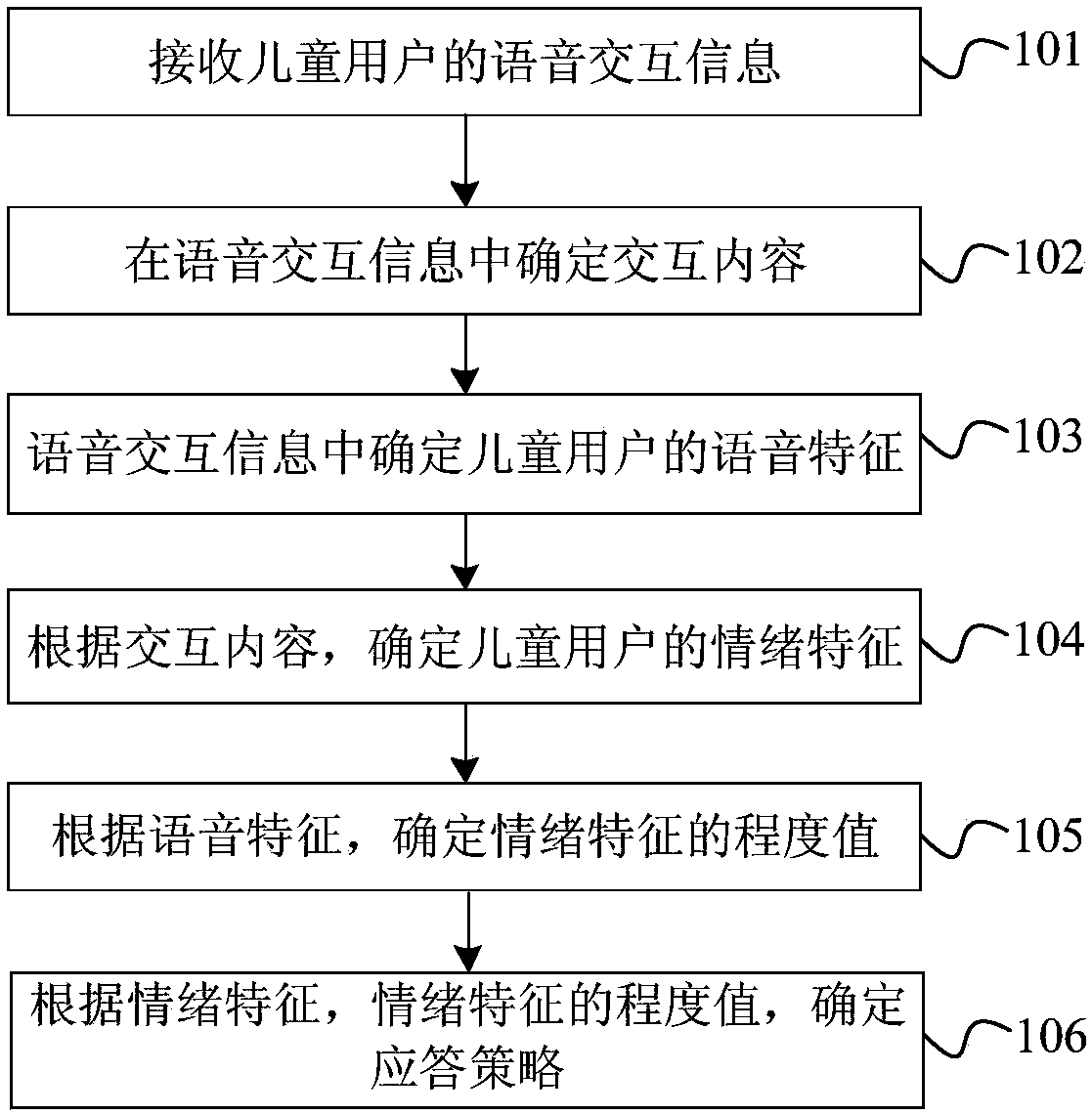
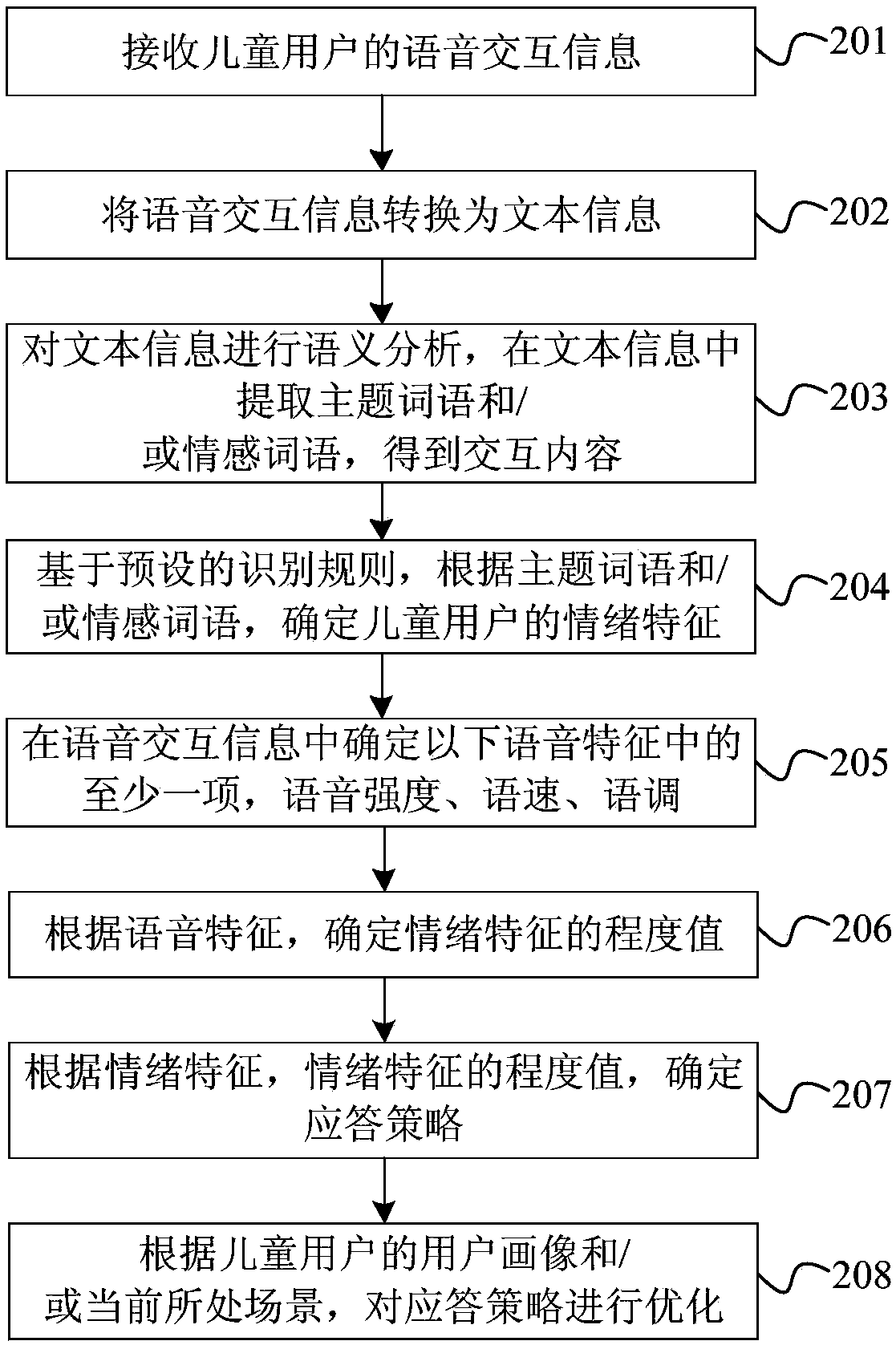
ActiveCN108536802AGuaranteed positive guidanceImprove fluencySemantic analysisSpecial data processing applicationsResponse strategyHuman–computer interaction
The invention provides an interaction method and device based on child emotions, electronic equipment and a readable storage medium. The interaction method includes the steps that voice interaction information of child users is received; the interaction content is determined in the voice interaction information; voice characteristics of the child users are determined in the voice interaction information; then according to the interaction content, emotion characteristics of the child users are determined; according to the voice characteristics, degree values of the emotion characteristics are determined; according to the emotion characteristics and the degree values of the emotion characteristics, a response strategy is determined. It is achieved that child emotions are accurately grasped,the concordance and the smoothness of child communication are improved, and good guidance for the child emotions is guaranteed.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD +1
Enhanced responses to online fraud
ActiveUS7992204B2Reduced effectivenessImprove responseMemory loss protectionDigital data processing detailsResponse strategyData science
Solutions (including inter alia, systems, methods and software) for dealing with online fraud. Certain of these solutions provide enhanced responses to an identified instance of online fraud. Such enhanced responses can incorporate one or more of a variety of strategies for defeating an attempt by a server to filter and / or otherwise avoid responses to its fraudulent activity. Merely by way of example, responses may be disguised (e.g., by transmitting the responses from a variety of computers, by transmitting responses that appear to originate from a computer different than the actual source of the responses, etc.). In some cases, a response strategy may be implemented that forces the server (and / or an operator thereof) to choose between accepting the responses and blocking potential responses from the targets of the fraudulent scheme.
Owner:OPSEC ONLINE LTD
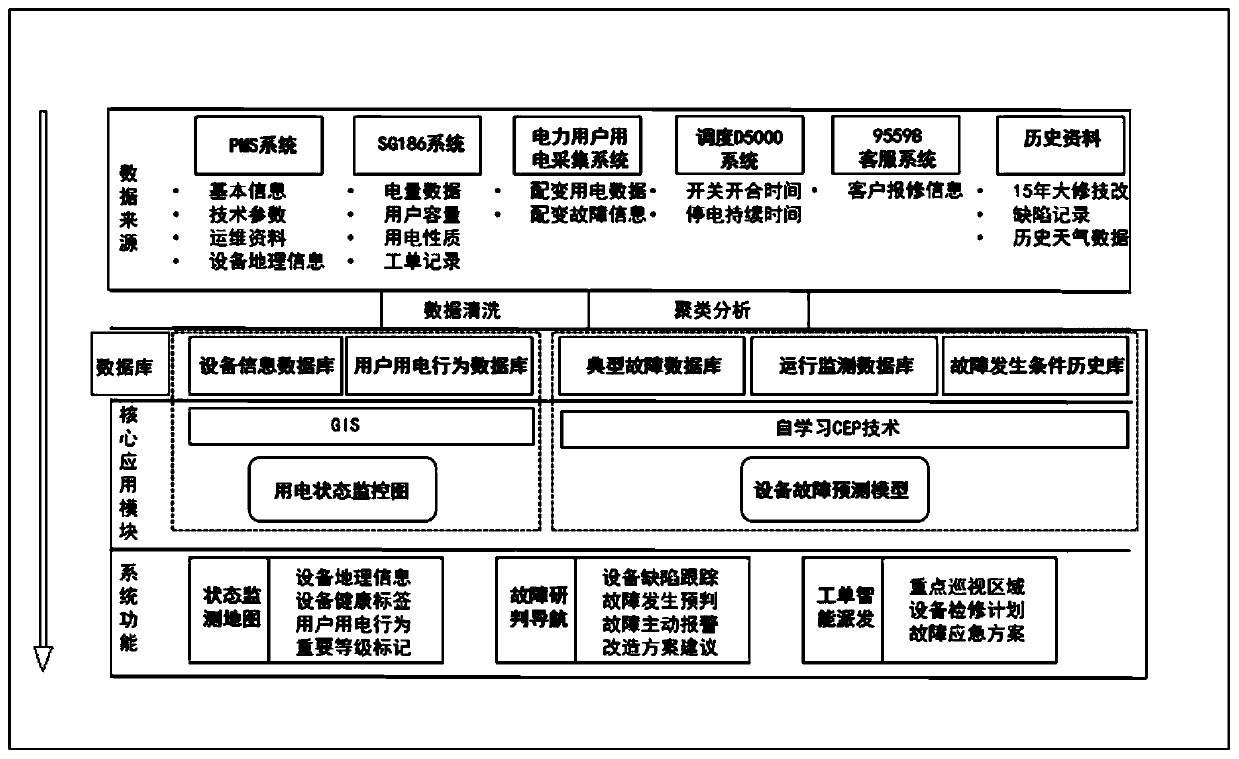
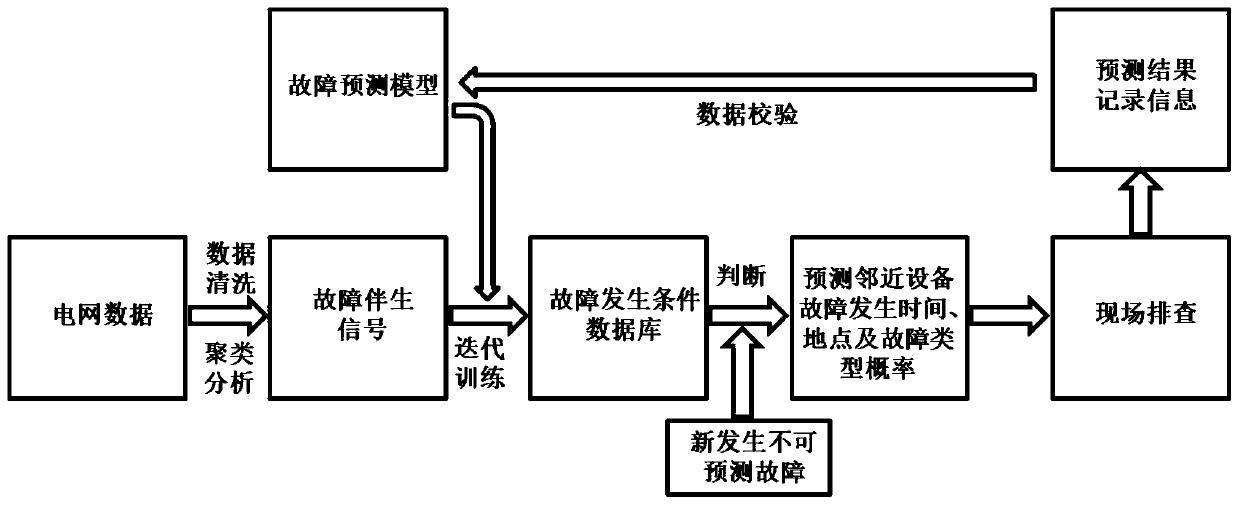
Method for enhancing operation and maintenance management and control of distribution network equipment
PendingCN110378492AEasy to handleLarge coverageForecastingInformation technology support systemElectricityMaintenance management
The invention aims at the characteristics of randomness and suddenness of power grid equipment faults. Therefore, the problem is difficult to accurately predict; the invention provides a method for enhancing operation and maintenance management and control of distribution network equipment. The invention belongs to the technical field of power grid equipment operation. Big data technologies such as clustering analysis, machine learning and the like are applied to effectively integrate and mine system data such as an electricity consumption information acquisition system, PMS2.0, D5000 and thelike; data islands among the systems are broken through, an equipment fault prediction model is established according to an adjacent propagation effect analysis theory, the equipment fault occurrenceprobability can be pre-judged in advance, equipment maintenance can be arranged in advance, the power failure frequency and time are reduced, the power supply quality is improved, and the operation and maintenance level of a distribution network is greatly improved. According to the method, an alarm signal is sent out before an equipment fault occurs, the equipment fault is pre-judged in advance,a coping strategy is provided, the big data technology is innovatively applied to predict the possibility that the equipment has faults in future according to historical fault records, and a passive repair working mode is changed into an active repair working mode.
Owner:长春电力设计有限公司 +2
Methods and systems for assessing security risks
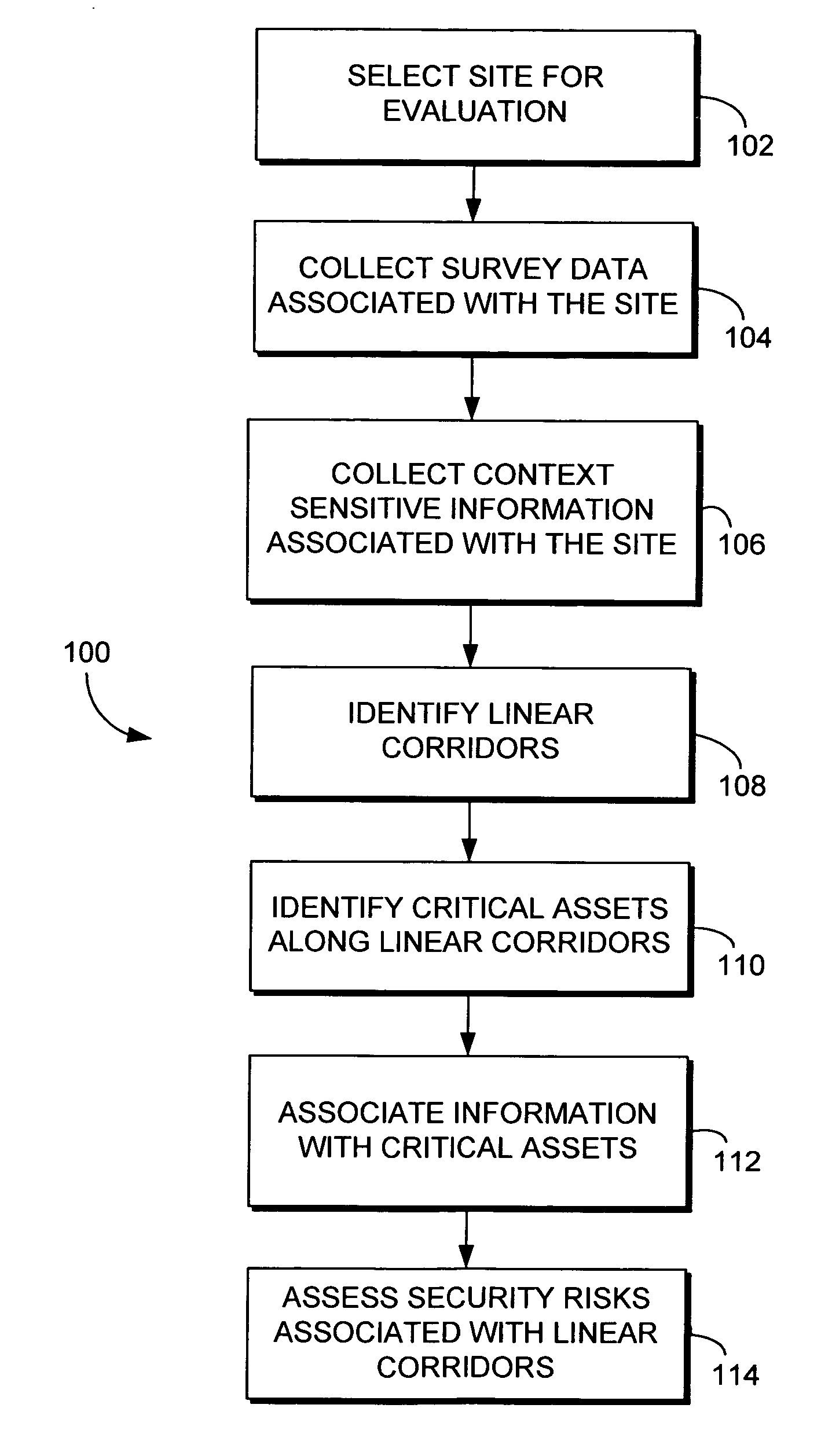
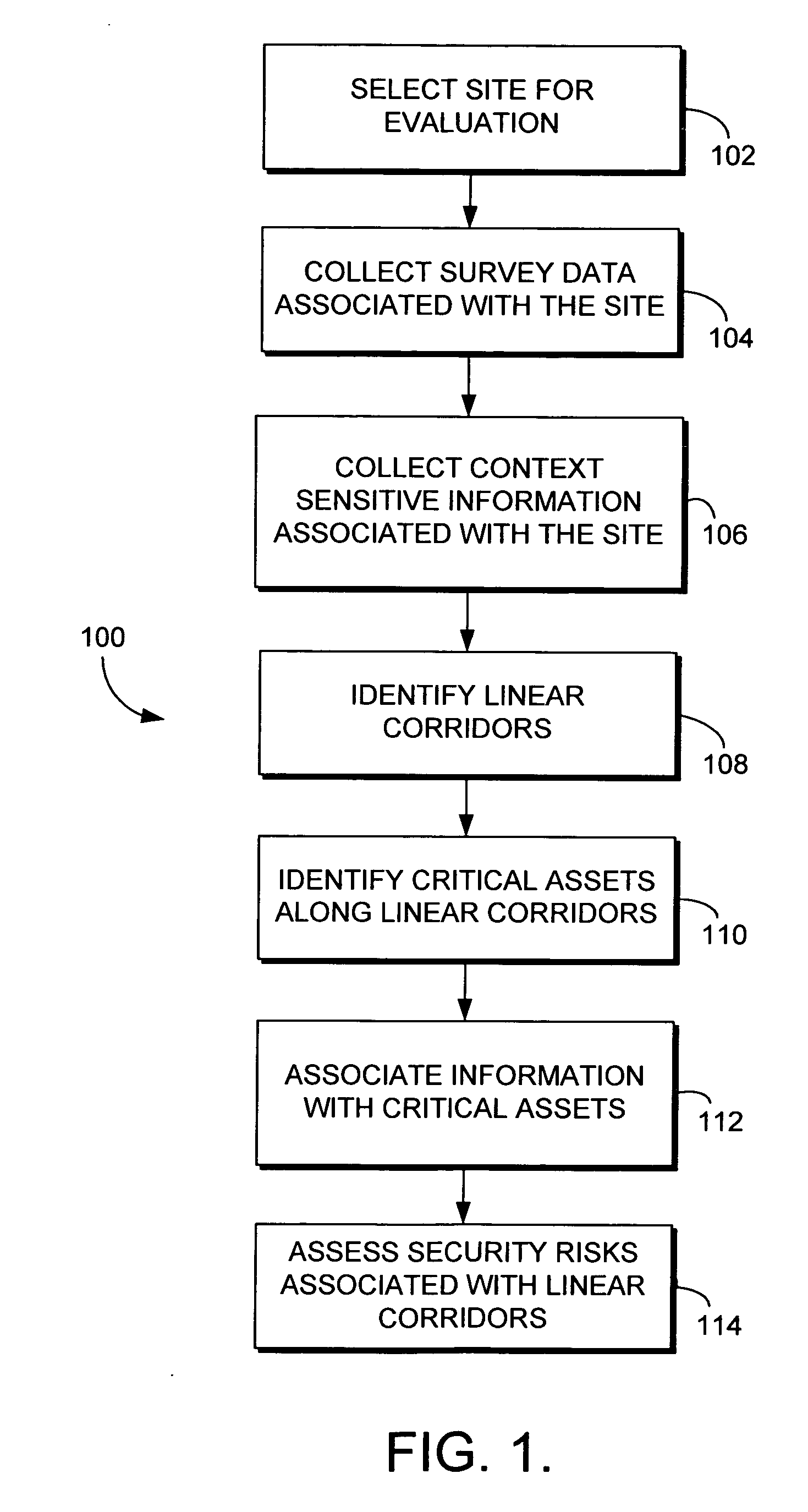
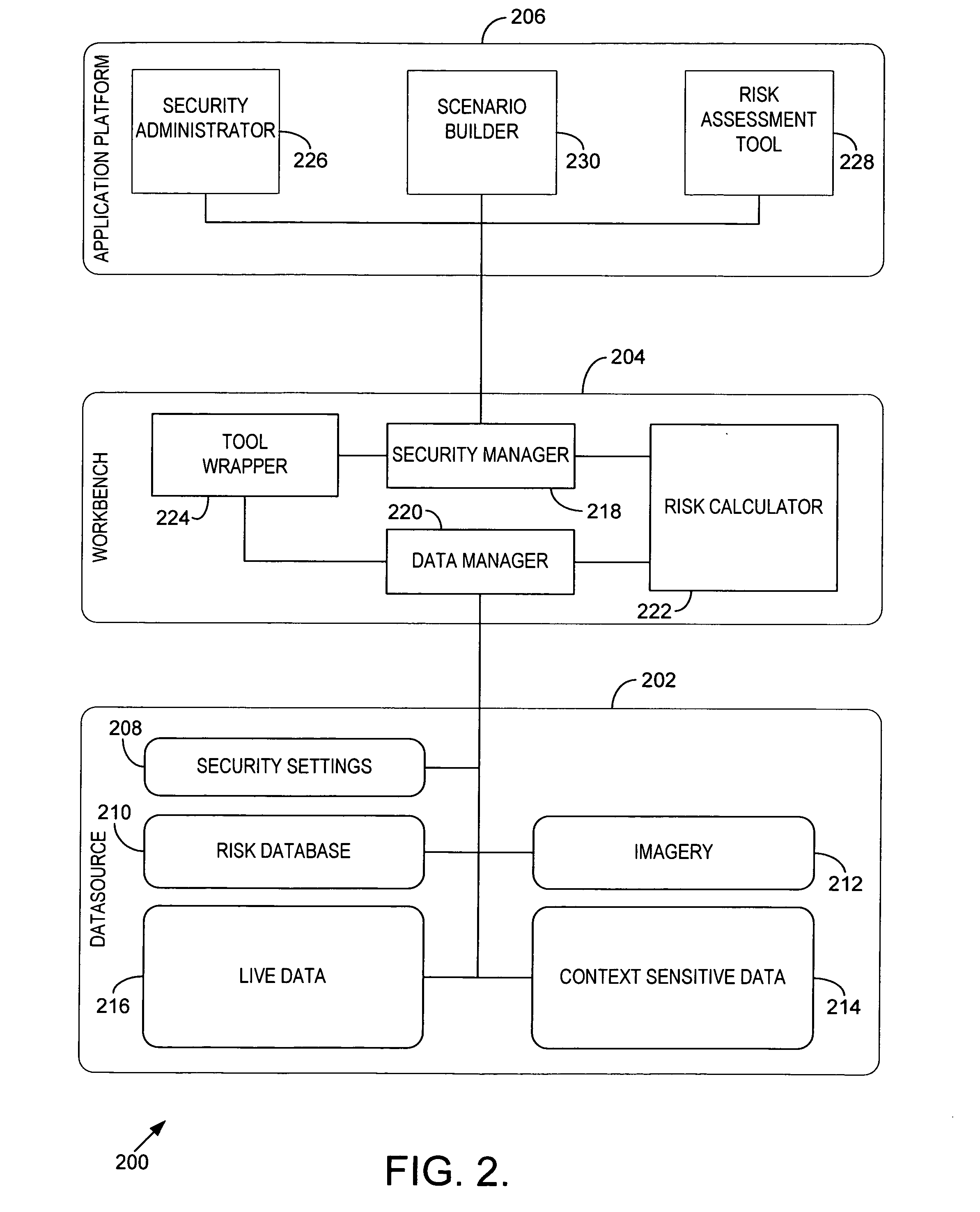
InactiveUS20060167728A1Improve developmentEase of evaluationMarket predictionsFinanceTransport corridorResponse strategy
The assessment of security risks associated with linear corridors, such as transportation corridors and utilities corridors, is provided. Initially, a site is selected for evaluation. Survey data and context sensitive information, such as demographic information, environmental information, corridor asset information, and the like, is collected for the site. Linear corridors are identified within the data, and critical assets within each linear corridor are also identified. Security risks associated with linear corridors may then be assessed using the survey data and context sensitive information. In addition, mitigation strategies, response strategies, and recovery strategies may be developed for the security risks assessed for the linear corridors.
Owner:HNTB HLDG
Service management method and device
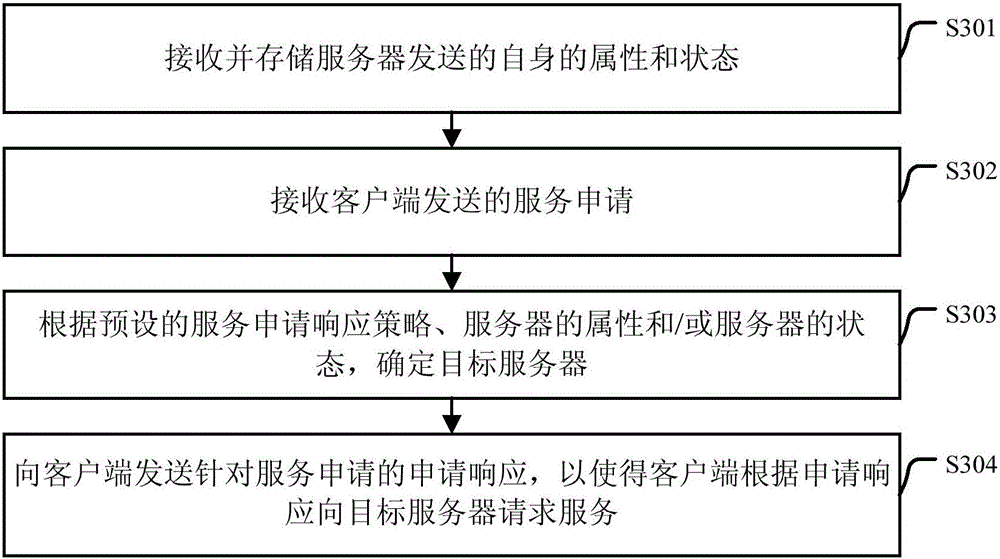
ActiveCN106060088AKeep abreast of the real situationTimely service requestTransmissionResponse strategyClient-side
The embodiment of the invention discloses a service management method and device, and relates to the technical field of computers. The service management method is applied to a manager in a service management system. The service management system comprises one manager, at least two servers and at least a client; the manager is in communication connection with the servers through a preset first port; and the manager is in communication connection with the client through a preset second port. The service management method comprises the steps of receiving and storing attribute and state of the server sent by the server per se; receiving a service application sent by the client; determining a target server based on a preset service application response strategy, the attributes of the servers and / or the states of the servers; and sending an application response aiming at the service application to the client to enable the client to apply for a service to the target server based on the application response, wherein the application response carries the attribute of the target server. By applying the scheme provided by the invention, the service request of the client can be responded in time.
Owner:NEW H3C TECH CO LTD
Page access control method and device
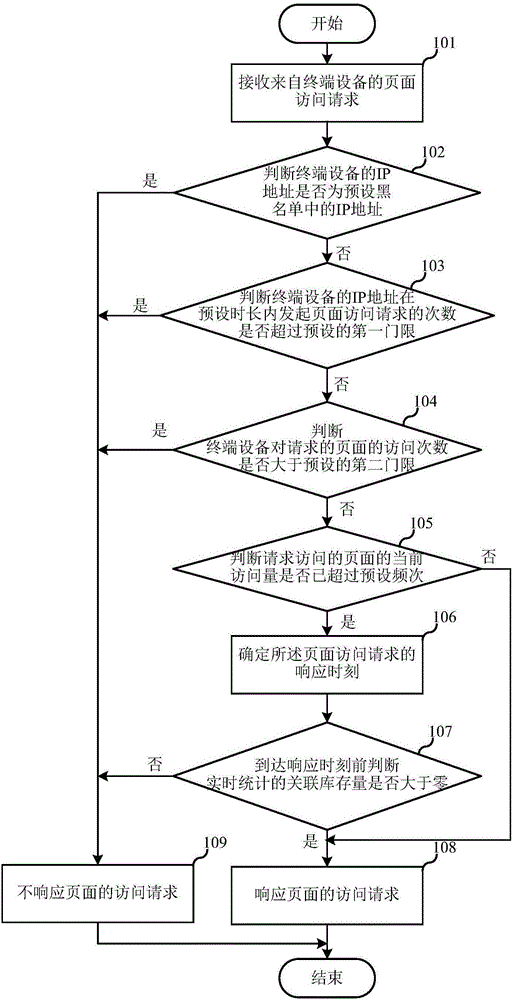
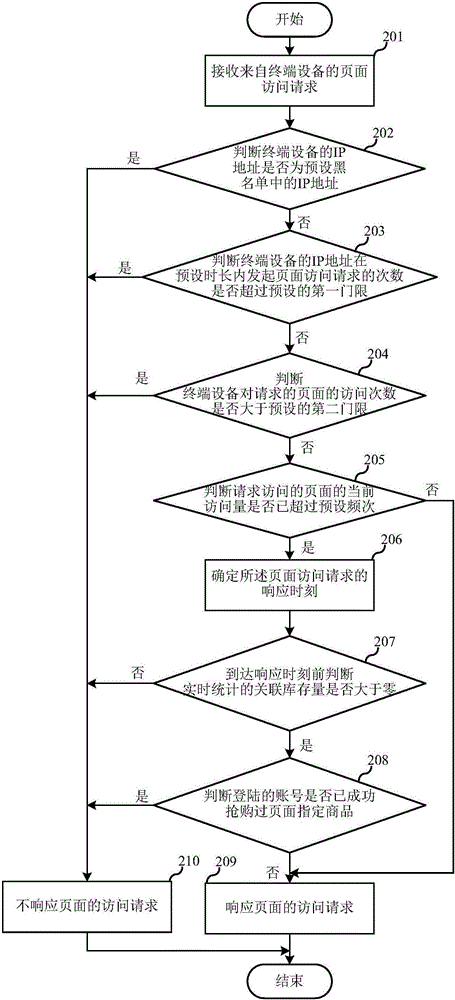
InactiveCN106101080AReduce in quantityIncrease your chances of qualifying for snap-upsBuying/selling/leasing transactionsTransmissionIp addressComputer network technology
The invention relates to the technical field of computer network, and discloses a page access control method and device. The method comprises the steps of: when a page access request is received from terminal equipment, according to the IP address of the terminal equipment and a page requested to access, judging whether the terminal equipment is allowed to access the requested page, and if the terminal equipment is allowed to access the requested page, generating a response strategy of the page access request according to the current access quantity of the page requested to access and the real-time statistics of an associated storage amount of the page requested to access. The invention further provides a page access control device, so that a system can filter most brush behaviors and guarantee that common customers get equal purchase opportunity.
Owner:LETV HLDG BEIJING CO LTD +1
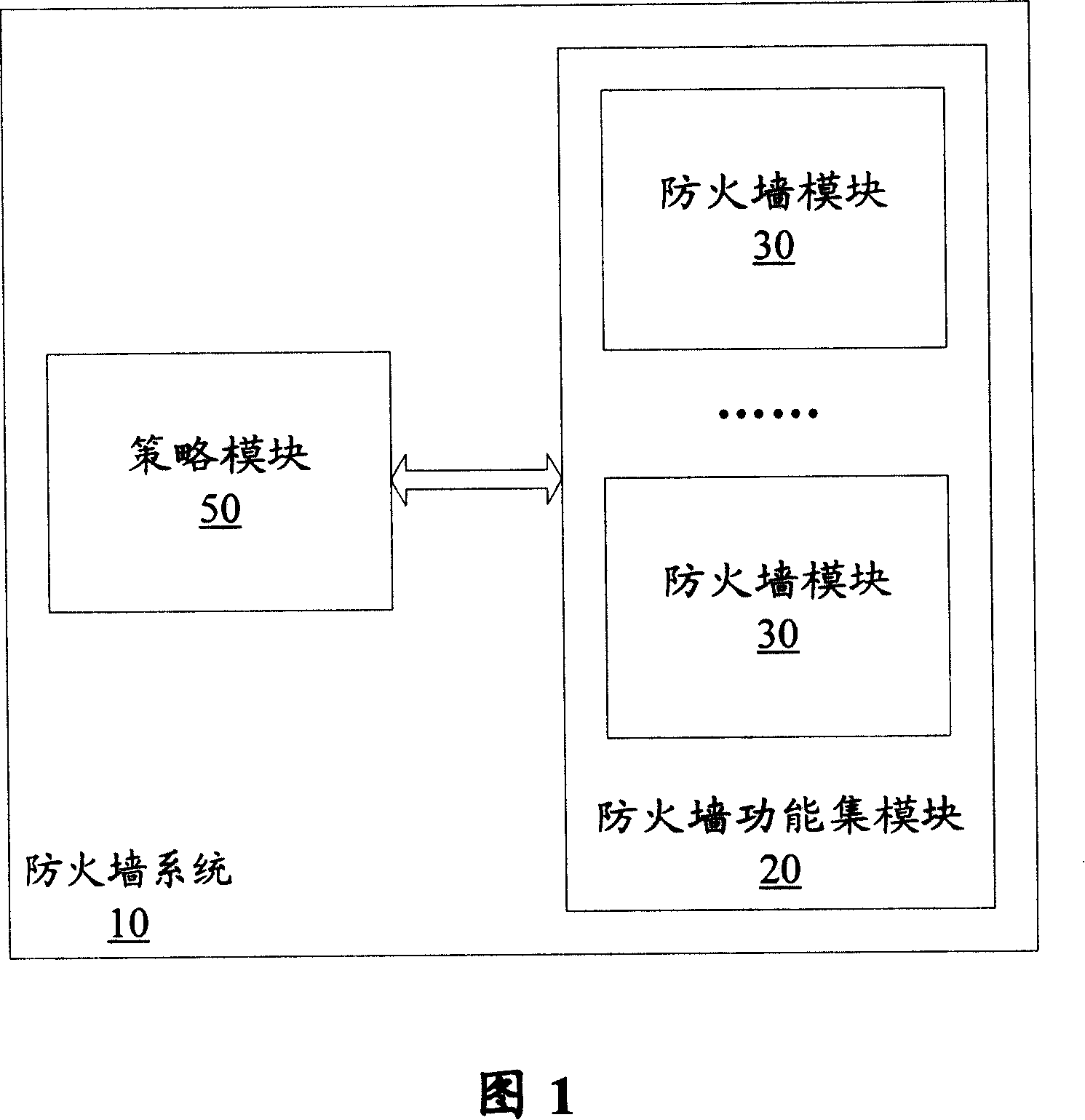
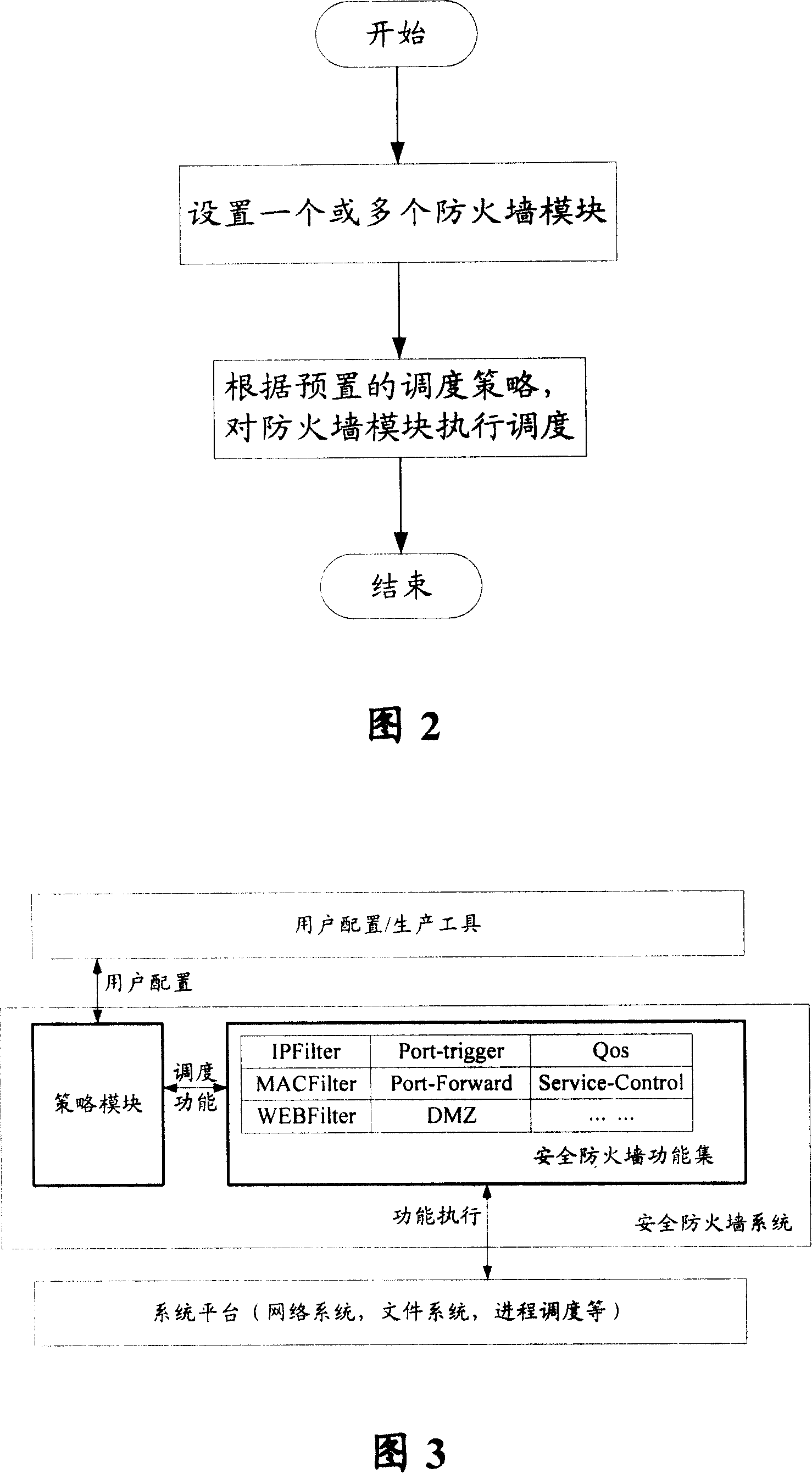
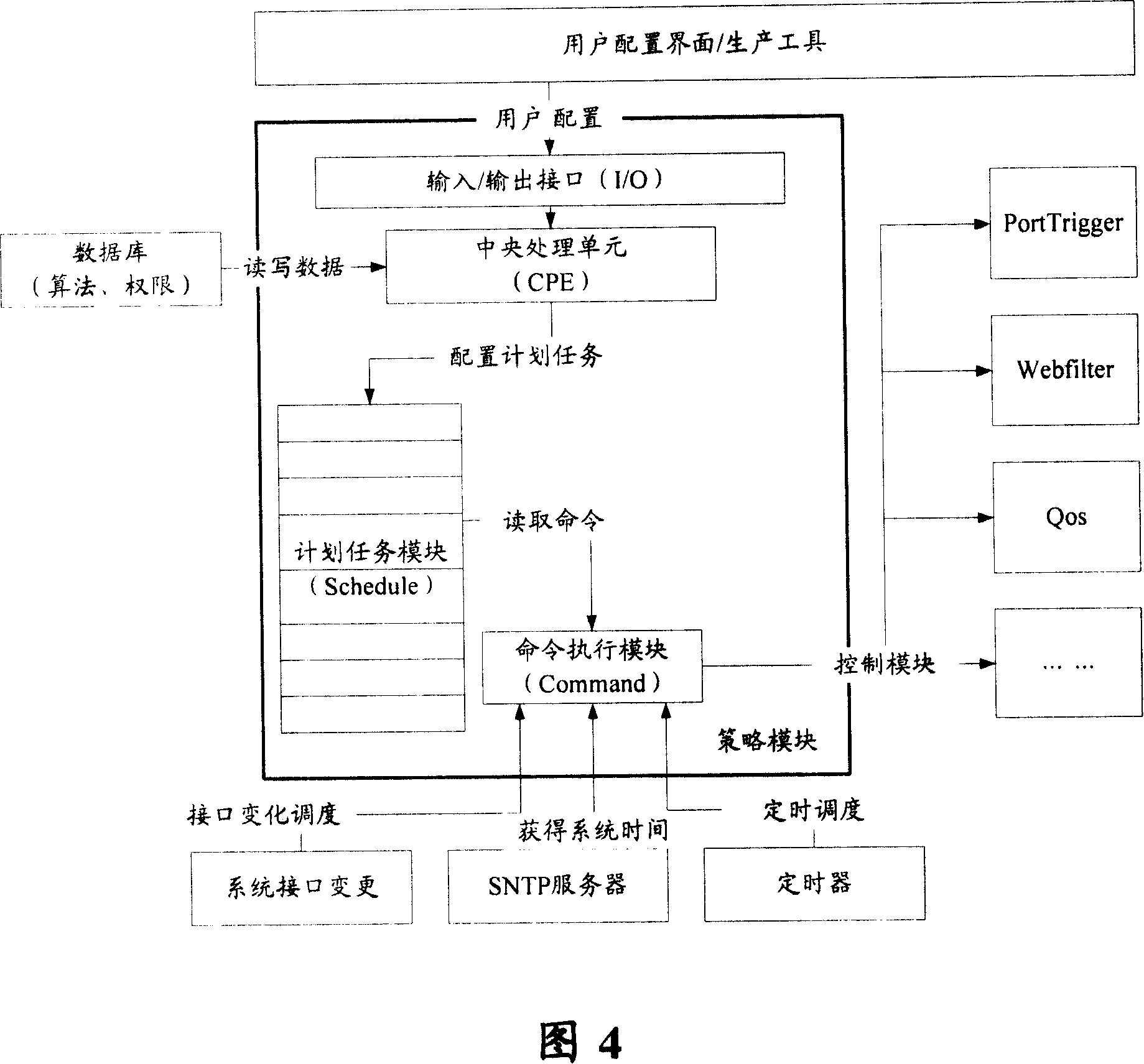
Tactic management based firewall system and dispatching method
The invention discloses a firewall system and scheduling method based on strategy management. The system comprises a firewall function set module that is provided with one or a plurality of firewall modules used for running or stopping a security firewall according to schedule; and a strategy module that contains a central processing unit used for performing schedule on the firewall module according to preset system strategies. The system strategy consists of a user configuration strategy, a strategy based on resources, a strategy based on the firewall, a strategy based on priority, and one of the intelligent response strategies which consist of a time strategy, an interface strategy, a port strategy, and at least one of intelligent strategies. The strategy security firewall system provided by the invention can effectively manage system resources and dynamically allocate the system resources to different function modules according to priority, so that maximum utilization of the system resources is realized. By making use of the system structure of the strategy firewall, complex security firewall functions can be accomplished and intelligent firewall can be realized.
Owner:ZTE CORP
Operation response method and related equipment
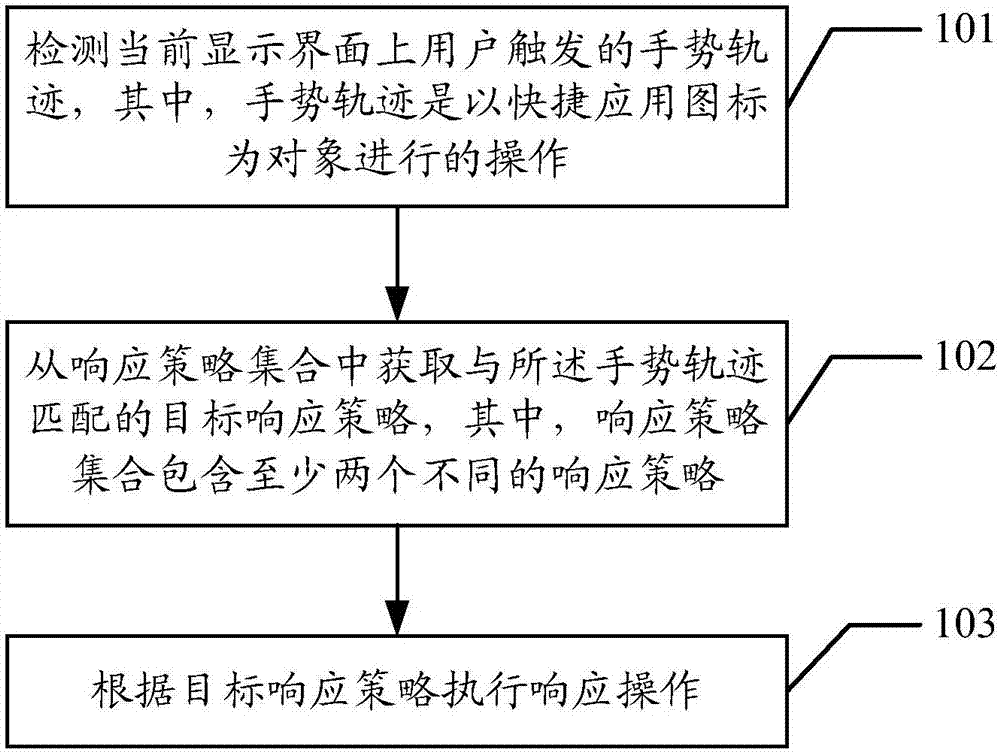
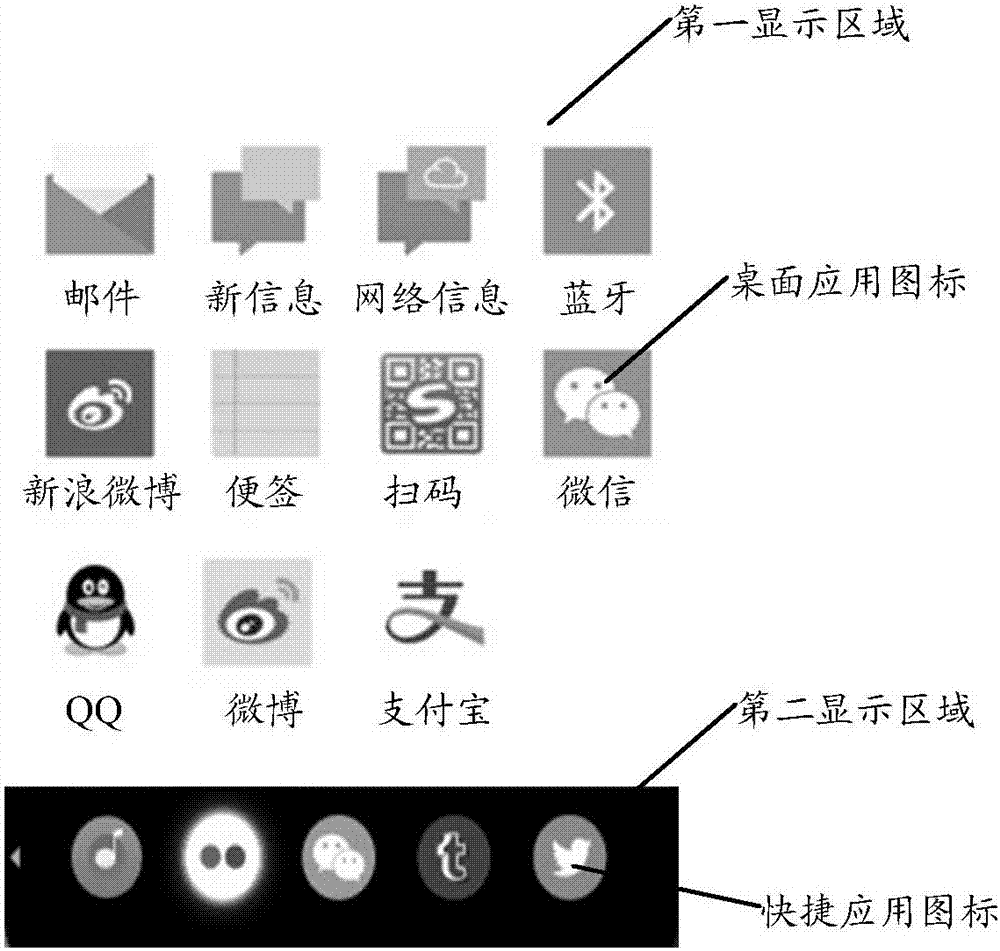
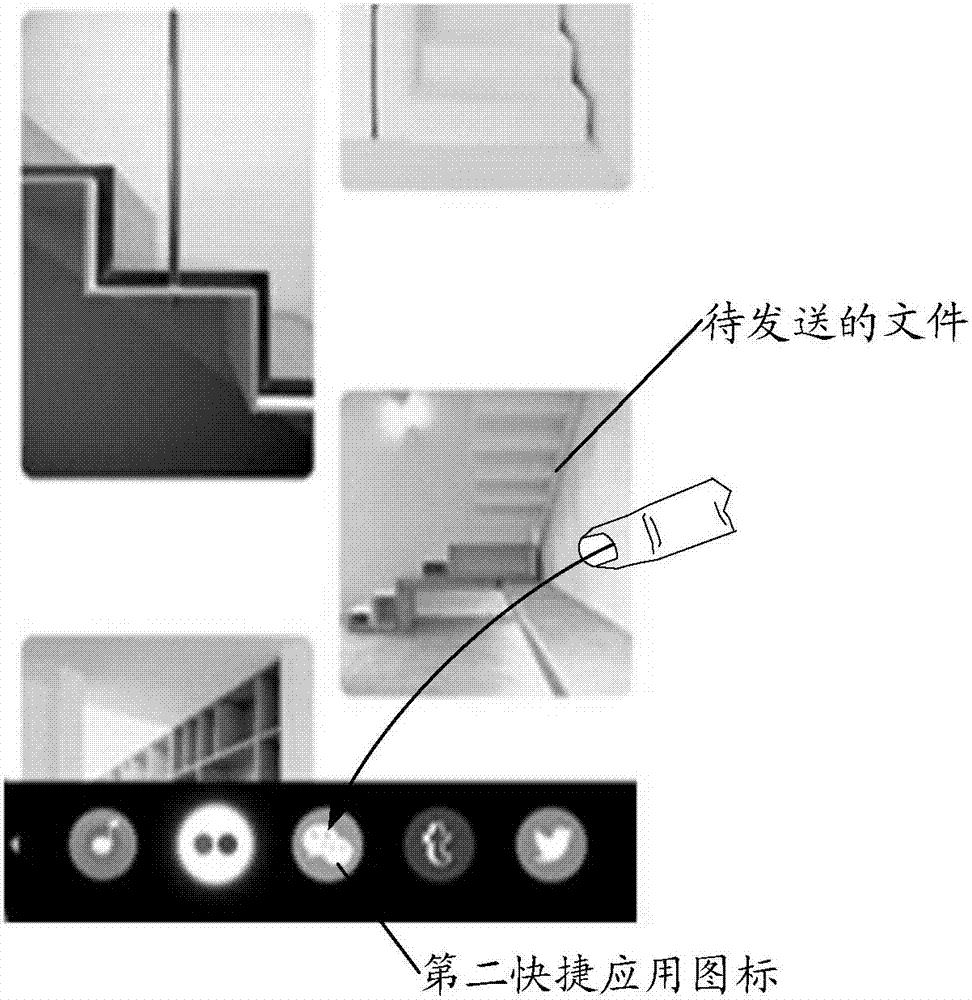
InactiveCN107239199AImprove operational efficiencyEasy to operateSpecific program execution arrangementsInput/output processes for data processingTarget ResponseResponse method
The embodiment of the invention discloses an operation response method for improving the operational efficiency of terminal equipment. The method comprises the steps that the method is applied to the terminal equipment, and a display interface of the terminal equipment comprises at least two display areas, wherein the first display area is used for displaying a desktop application icon, and the second display area is used for displaying a shortcut application icon; a gesture trajectory triggered by a user on a current display interface is detected, wherein the gesture trajectory is operation taking the shortcut application icon as an object; a target response strategy matched with the gesture trajectory is obtained from a response strategy set, wherein the response strategy set comprises at least two different response strategies; response operation is executed according to the target response strategy. The embodiment of the invention further discloses the terminal equipment.
Owner:MEIZU TECH CO LTD
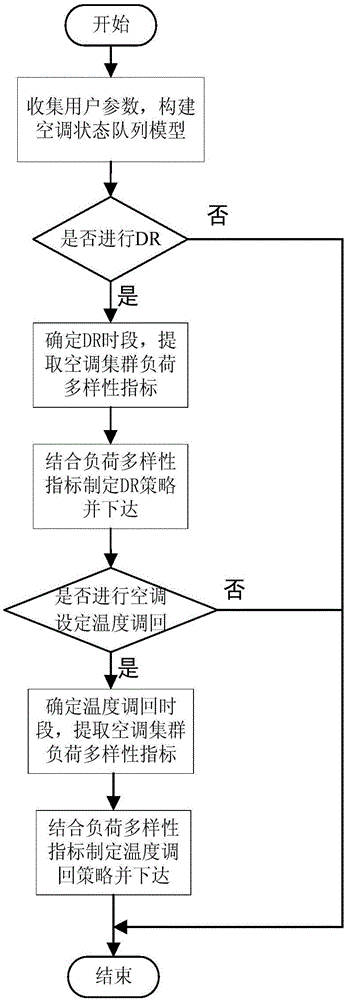
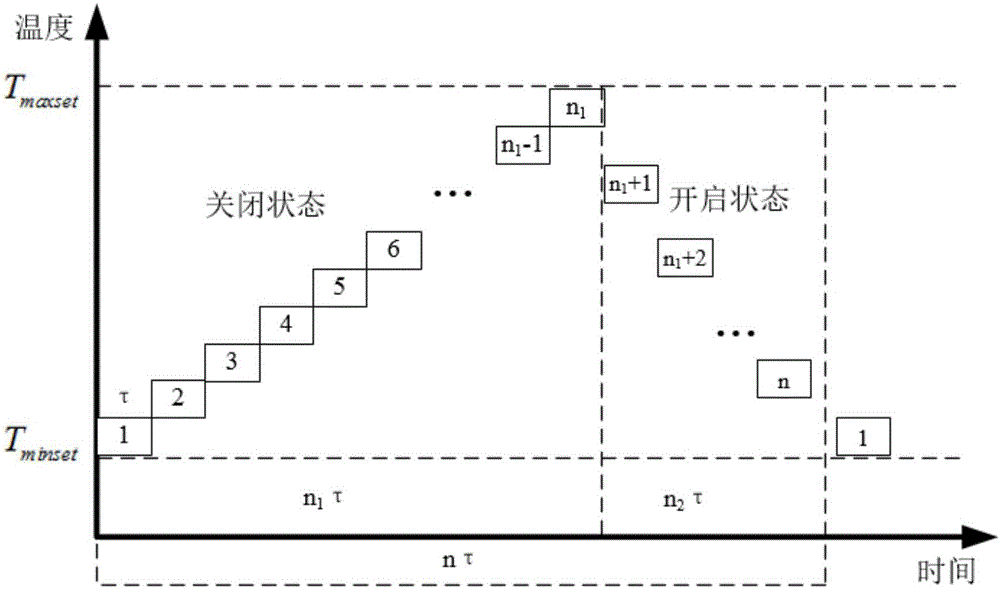
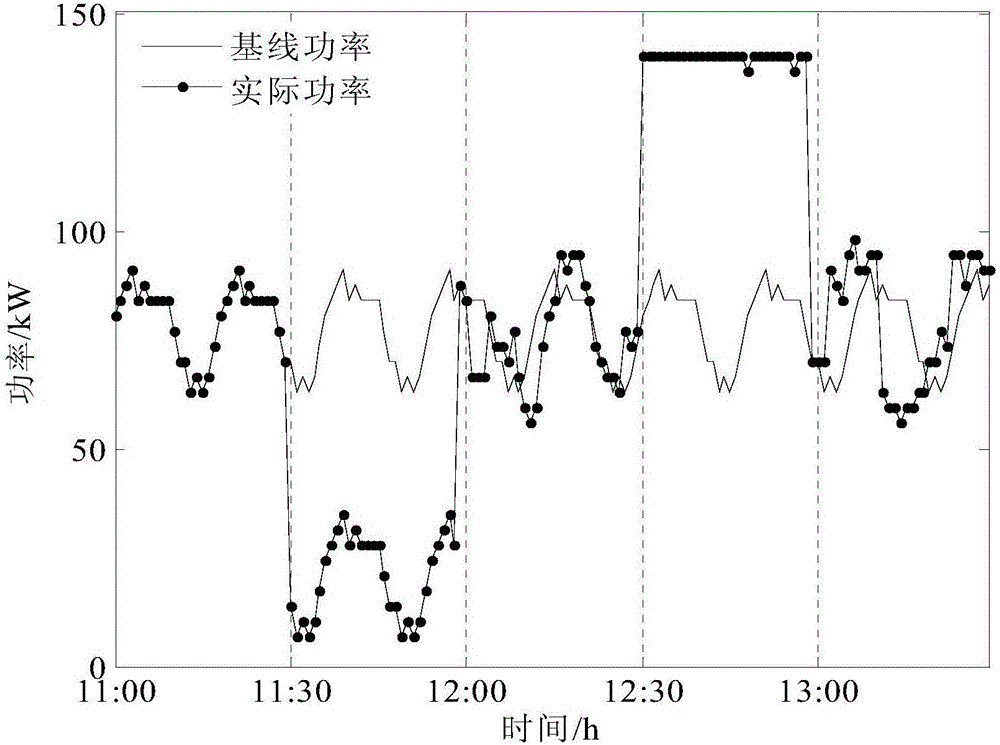
State diversity keeping type air conditioner load cluster control strategy
ActiveCN106765994AReduce shockFully consider the comfortMechanical apparatusSpace heating and ventilation safety systemsDiversity indexResponse strategy
The invention discloses a state diversity keeping type air conditioner load cluster control strategy. The strategy includes: collecting user's air conditioner parameters to construct a state queue model; judging whether to perform demand response or not; determining a demand response time period and extracting load diversity indexes of air conditioner clusters under a baseline state at the end moment of demand response; making response strategies according to the load diversity indexes, and implementing to adjust an air conditioner set temperature to a new range; judging whether to reset the air conditioner set temperature or not; determining a set temperature reset time period and extracting diversity indexes under the baseline state at the end moment of the reset time period, making reset strategies according to the indexes, and transmitting to reset the air conditioner set temperature to an initial range. The state diversity keeping type air conditioner load cluster control strategy has advantages that load diversity of the air conditioner clusters are taken into full consideration while regulation potential is exploited, user comfort is guaranteed, and defects of current air conditioner control strategies are overcome.
Owner:SOUTHEAST UNIV
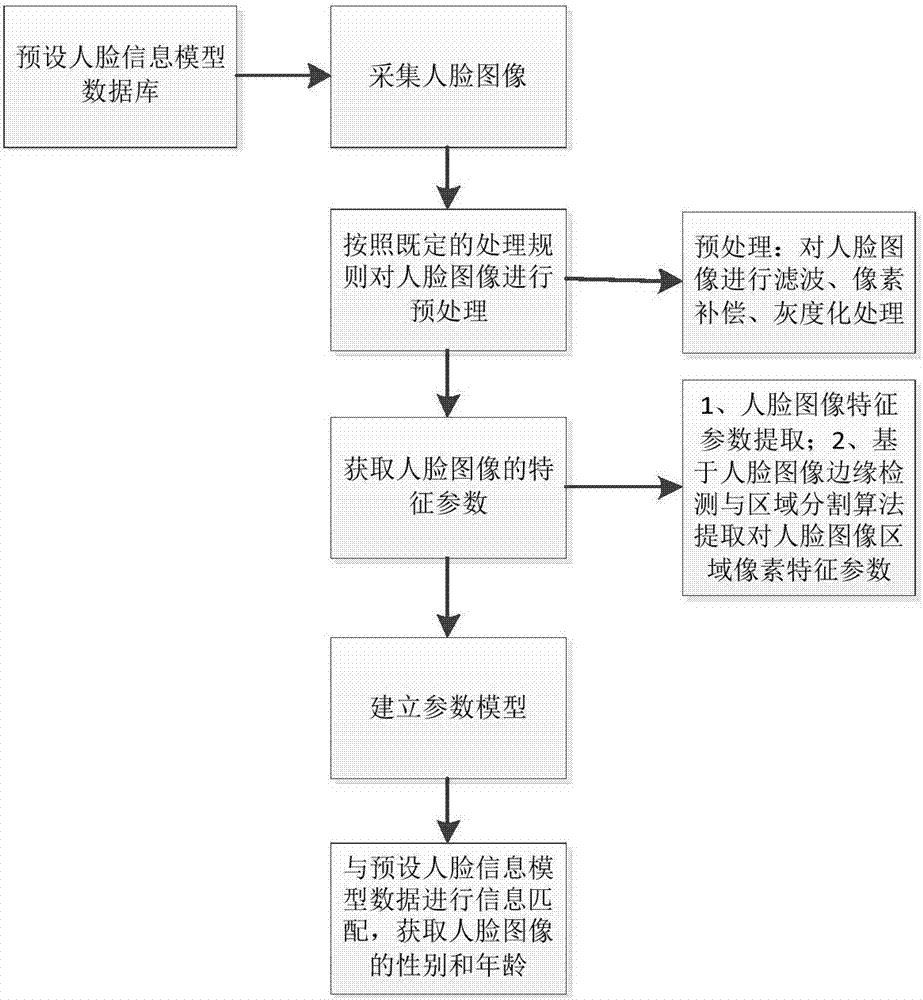
Face recognition method and system
InactiveCN107423696AImprove accuracyGood coping strategyCharacter and pattern recognitionMarket data gatheringData informationResponse strategy
The invention provides a face recognition method and system. The method comprises a step of collecting a face image and carrying out preprocessing on the face image, a step of obtaining feature parameters of the face image and establishing parameter models which comprise an age model and a gender model, and a step of comparing the parameter model data with preset face information model data and obtaining the gender and age of the face image. According to the method and the system, through the combination of the age model and the gender model, the gender and age of the face image are identified, the accuracy of the face image identification are improved, a user can carry out more comprehensive planning according to an obtained accurate result, analysis can be gradually refined according to business requirements, the data collection of consumption of customers of different ages and different genders of active population in different regions is carried out, detailed and accurate data information is effectively provided for the customers to make better strategies.
Owner:CHONGQING KAIZE TECH
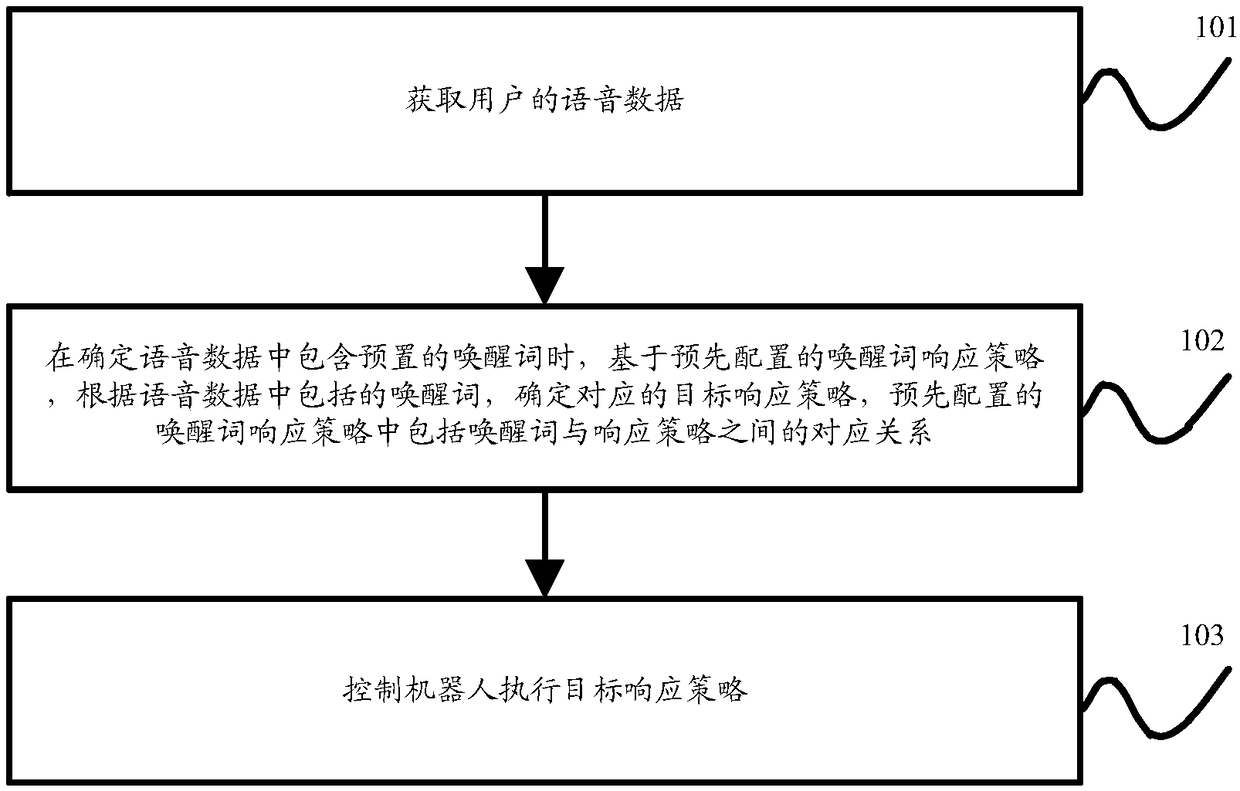
Robot wake-up control method, device and apparatus
InactiveCN109358751ARich response strategiesMeet the needs of multiple application scenariosInput/output for user-computer interactionSpeech recognitionTarget ResponseSimulation
The embodiment of the invention discloses a robot wake-up control method, device and apparatus, which are used for executing different response strategies according to the wake-up words and the current state of the robot, and enriching the response strategies of the robot to meet the requirements of multi-application scenes. The wake-up control method of the robot comprises the following steps: acquiring voice data of a user; determining a corresponding target response strategy according to the wake-up words included in the voice data based on a pre-configured wake-up word response strategy when it is determined that the pre-configured wake-up word is included in the voice data, wherein the pre-configured wake-up word response strategy includes a correspondence relationship between the wake-up words and the response strategy when determining that the voice data includes a preset wake-up word; controlling the robot to execute the target response strategy.
Owner:BEIJING ORION STAR TECH CO LTD
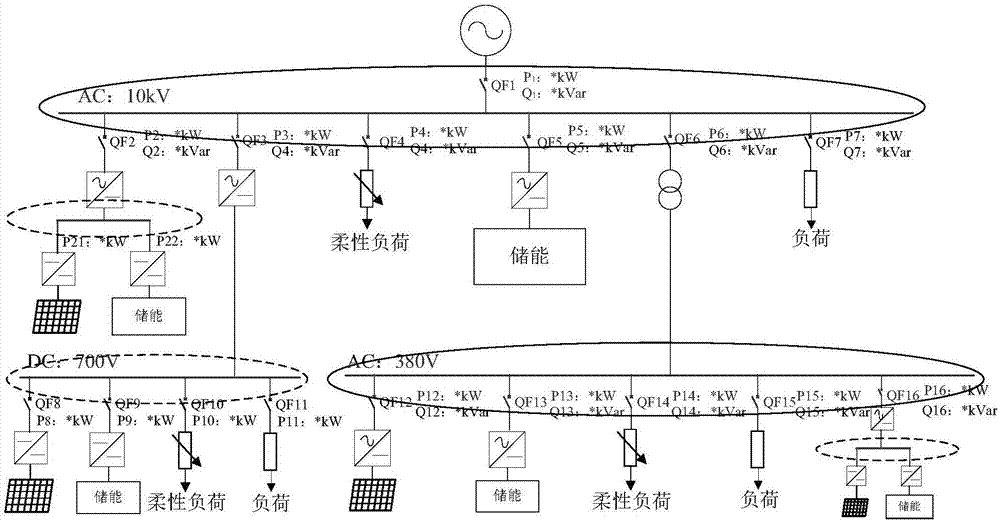
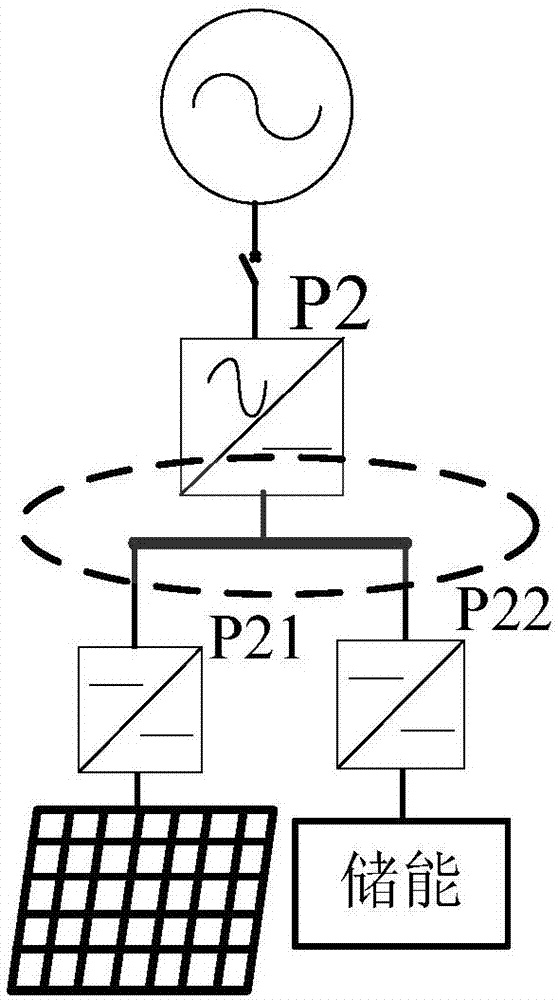
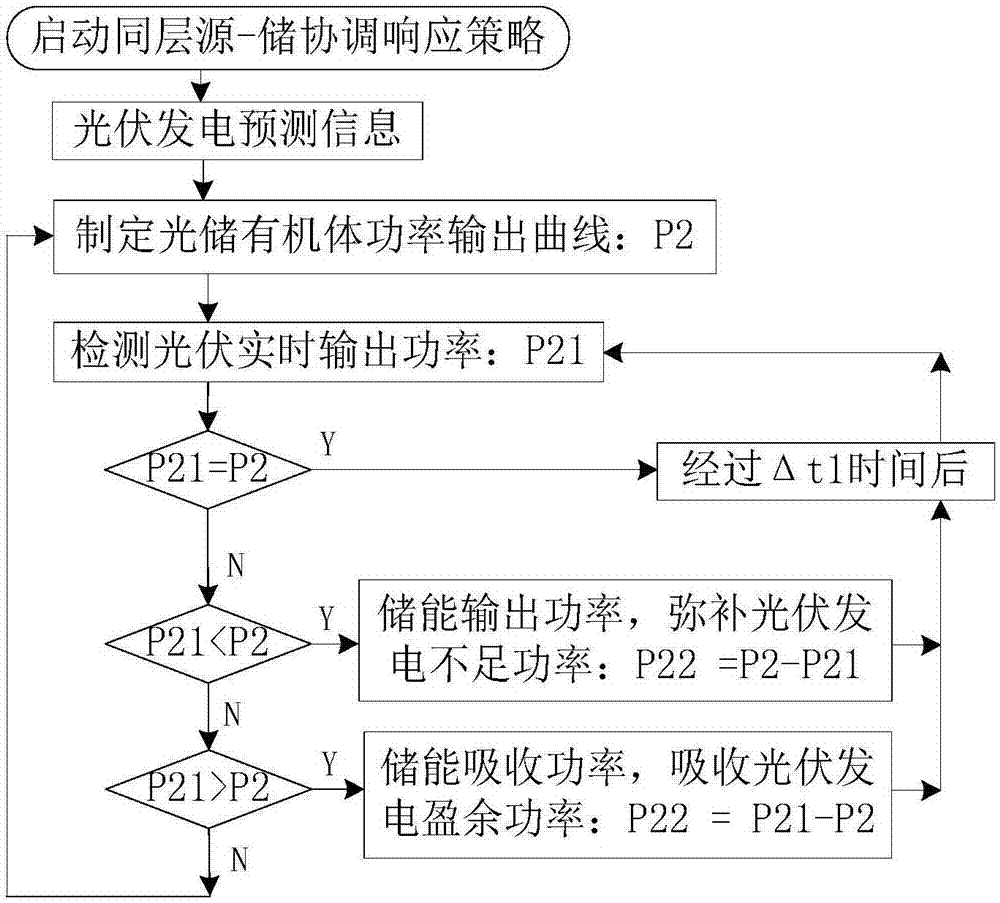
Active distribution network demand response control method based on hierarchical energy storage
ActiveCN106911149AImprove permeabilityValid responseSingle network parallel feeding arrangementsAc network load balancingThermal energy storageElectric power system
The invention relates to an active distribution network demand response control method based on hierarchical energy storage. The method comprises a same layer source-storage coordinated response strategy, a cross layer storage-storage coordinated response strategy, a same layer source-storage-charge coordinated response strategy and a cross layer source-storage-charge coordinated response strategy. The same layer source-storage coordinated response strategy is used for onsite smoothing distributed energy network access real-time power fluctuation. The cross layer storage-storage coordinated response strategy solves the problem fed back by the present layer by authorizing to the energy storage system in the previous layer of power grid and aims at enhancing the consumption capacity of the distributed power supplies. The same layer source-storage-charge coordinated response strategy and the cross layer source-storage-charge coordinated response strategy perform optimization control according to the priority of maximizing consumption distributed power generation, load power supply and energy storage economic operation. The energy storage system is hierarchically accessed to the distribution network so that the characteristics of energy storage can be fully exerted and the economic performance of its application can be enhanced, and scale application of energy storage in the electric power system can be facilitated.
Owner:XUJI GRP +2
Public opinion analysis method and corresponding device
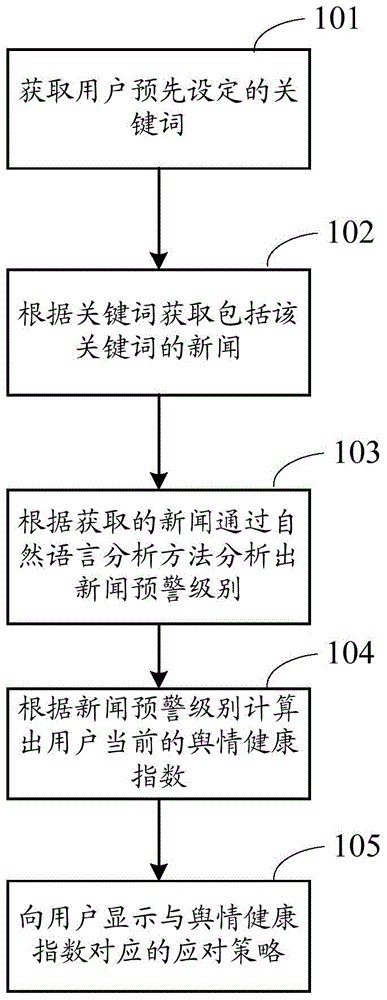
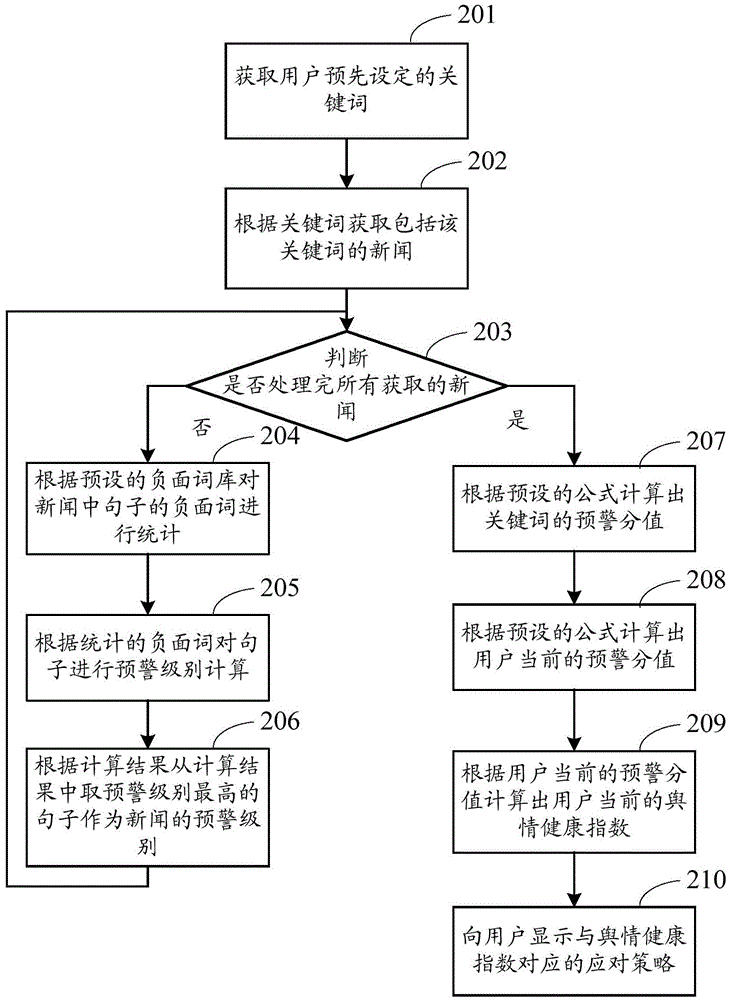
InactiveCN104657393AIntuitive decision referenceVisual guidanceWeb data indexingSpecial data processing applicationsHealth indexNatural language analysis
An embodiment of the invention discloses a public opinion analysis method, and further provides a corresponding device. The public opinion analysis method comprises the steps that the public opinion analysis device acquires a keyword which is set by a user in advance, news which includes the keyword is acquired according to the keyword, the early warning level of the news is analyzed through a natural language analysis method according to the acquired news, a current public opinion health index of the user is calculated, and a coping strategy corresponding to the public opinion health index is displayed to the user. By the adoption of the public opinion analysis method, current public opinion state analysis can be provided for the user, and the purpose that intuitive decision reference and guidance are provided for the user is achieved.
Owner:SHENZHEN SIECOM COMM TECH DEV CO LTD
Multiuser command speech recognition method and system and storage medium
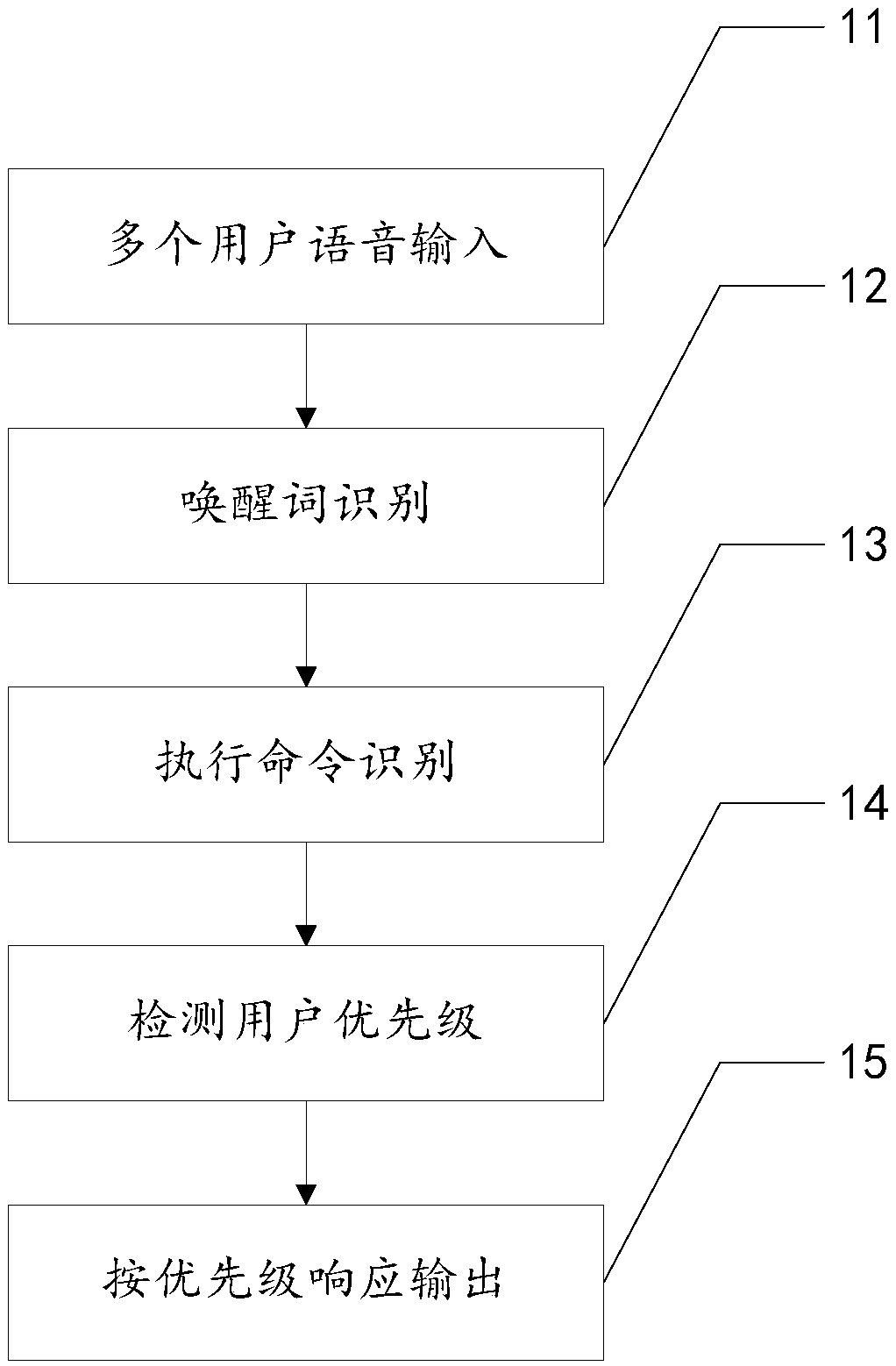
InactiveCN108962260AImprove speech recognition accuracyClear executionSpeech recognitionInput/output processes for data processingConfusionSpeech identification
The invention discloses a multiuser command speech recognition method comprising the steps that at least one user speech instruction is acquired; existence of at least one wake-up word in at least oneuser speech instruction is recognized and detected according to the user voiceprint characteristics; existence of at least one executive command in at least one user speech instruction is recognizedand detected according to the user voiceprint characteristics; at least one wake-up word and at least one executive command are matched according to the user voiceprint characteristics so as to obtainat least one response instruction corresponding to at least one user; and at least one response instruction is matched and responded according to the response strategy. The wake-up words and the executive commands of multiple users are recognized through the voiceprint characteristics of the users and responded according to the response strategy. The wake-up words and the executive commands are separately recognized so that the speech recognition accuracy can be enhanced, the speech commands of the users are executed according to the response strategy and the speech commands can be clearly executed without confusion.
Owner:FLYBALL ELECTRONIC SHENZHEN CO LTD
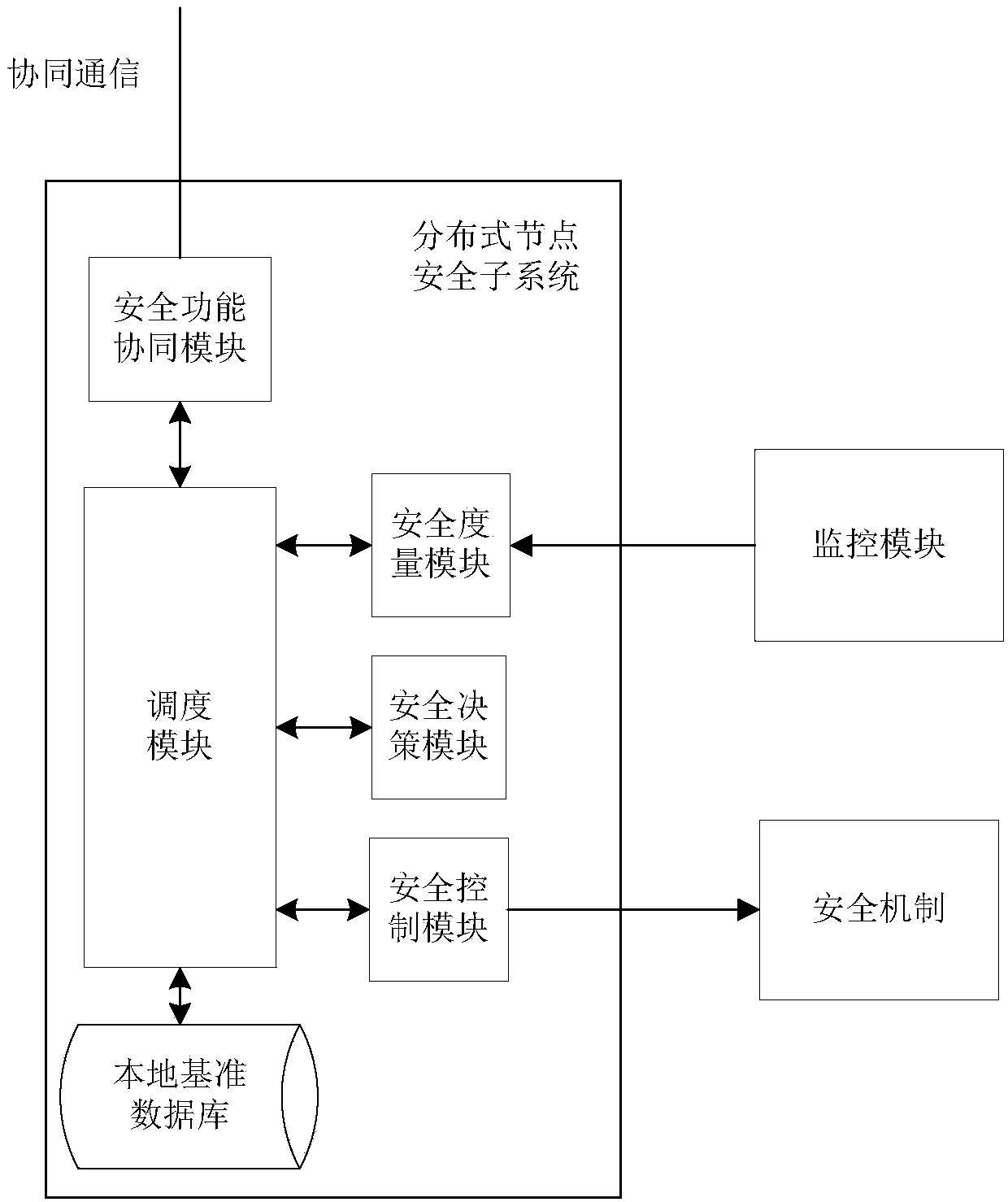
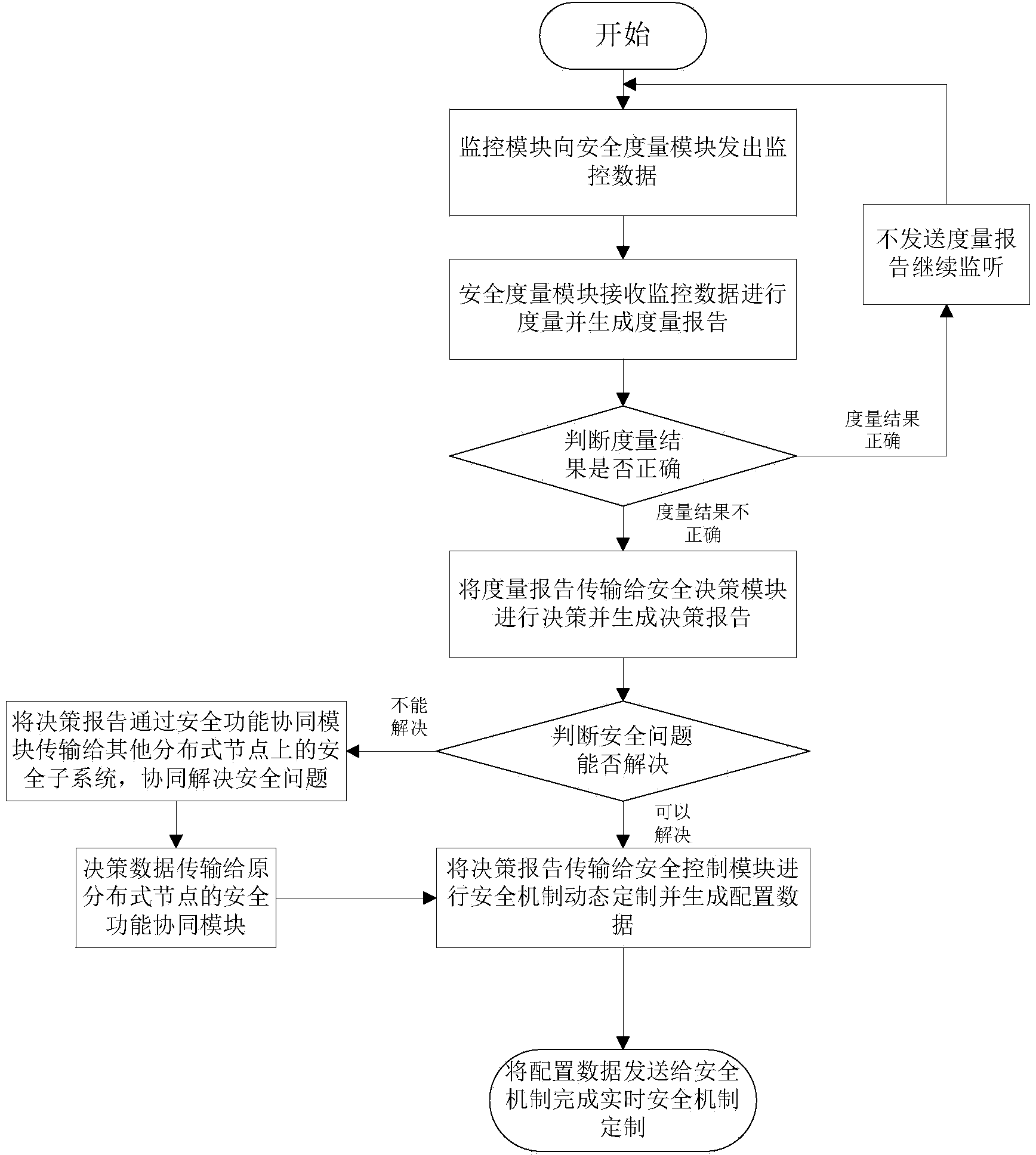
Safety monitoring method under distributed network environment
The invention discloses a safety monitoring method under a distributed network environment and relates to the safety monitoring problem in the field of information security. According to the method, the system is composed of a monitoring module, a safety module and a safety mechanism, wherein the safety module is composed of a safety function cooperation module, a safety control module, a safety measurement module, a safety decision module and a local benchmark database. Monitored dynamic data are transmitted out by the monitoring module, and the monitored dynamic data are transmitted to the safety measurement module for measurement and used for measuring safety of behaviors of monitoring nodes; the safety problem is determined by the safety decision module according to the measurement result; the safety mechanism in a monitored system is dispatched by the safety control module according to the decision result to perform a coping strategy; the safety function cooperation module is responsible for having communication with the safety measurement module, the safety decision module and the safety control module so that the safety function cooperation work can be achieved. A safety strategy can be dynamically made for the distributed network environment, and safety of the monitoring nodes under the distributed network environment is maintained.
Owner:BEIJING UNIV OF TECH
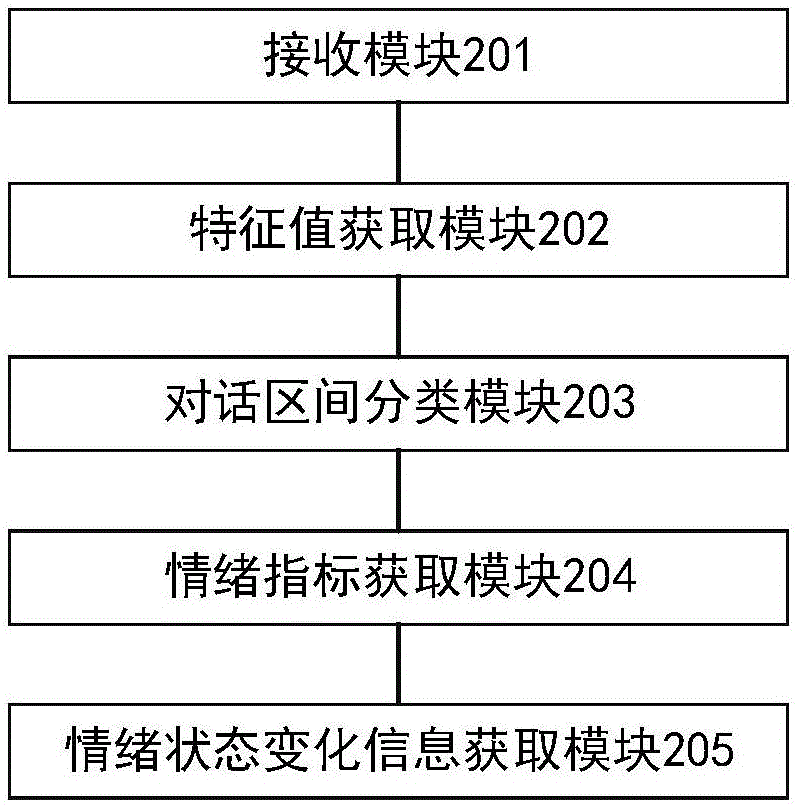
Acquisition method and device based on emotional state change information of emotion indexes
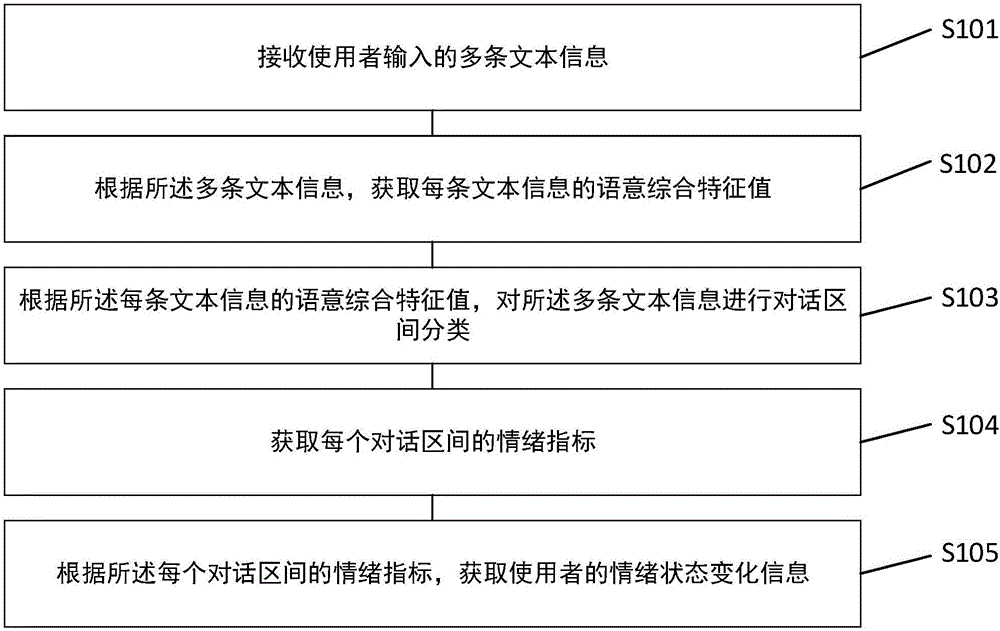
ActiveCN106775665AEarly detection of rising negative emotionsSoftware designSpecific program execution arrangementsDialog systemResponse strategy
The invention provides an acquisition method and device based on emotional state change information of emotion indexes. The method comprises the steps that a semanteme comprehensive characteristic value of multiple text messages input by a user is acquired, the multiple text messages are classified into multiple dialogue sections according to the semanteme comprehensive characteristic value, and the emotion index of every dialogue section is calculated. Through calculation of the emotion indexes, the emotional state changes during interaction between a user and a robot are grasped, and meanwhile the state of negative emotion increasing of the user for an artificial intelligence dialogue system can be found earlier to serve as reference of response mode conversion of the artificial intelligence dialogue system. Response strategy is adjusted by grasping the emotional state changes and coming to conclusions, and the method makes it possible to get closer to users and have an understanding of them.
Owner:EMOTIBOT TECH LTD
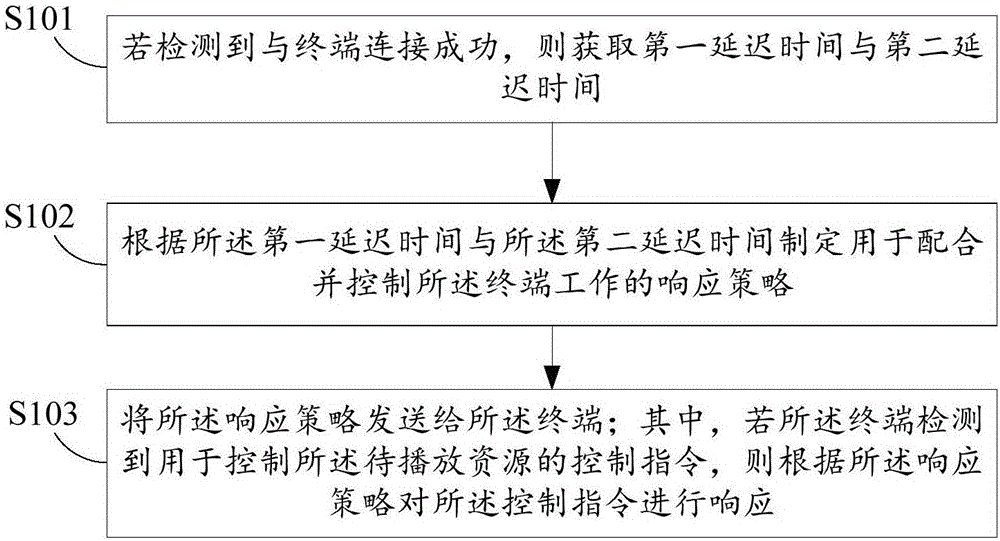
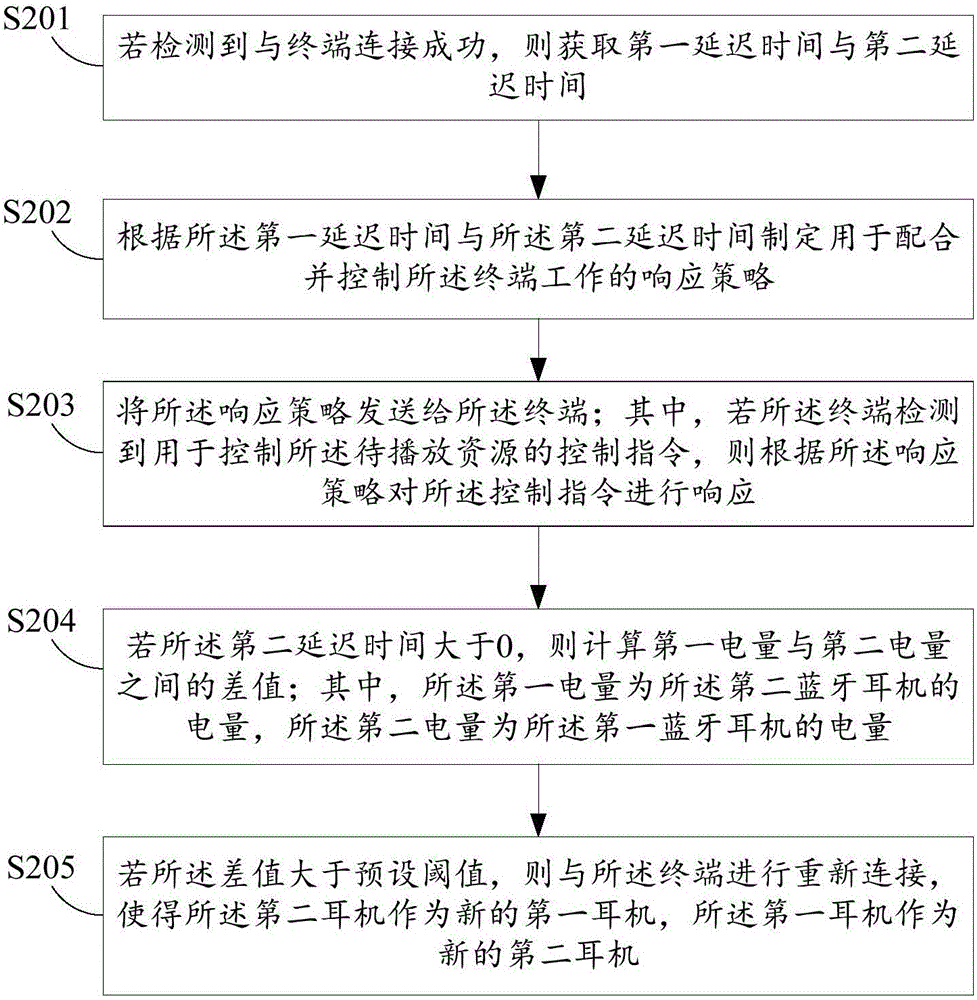
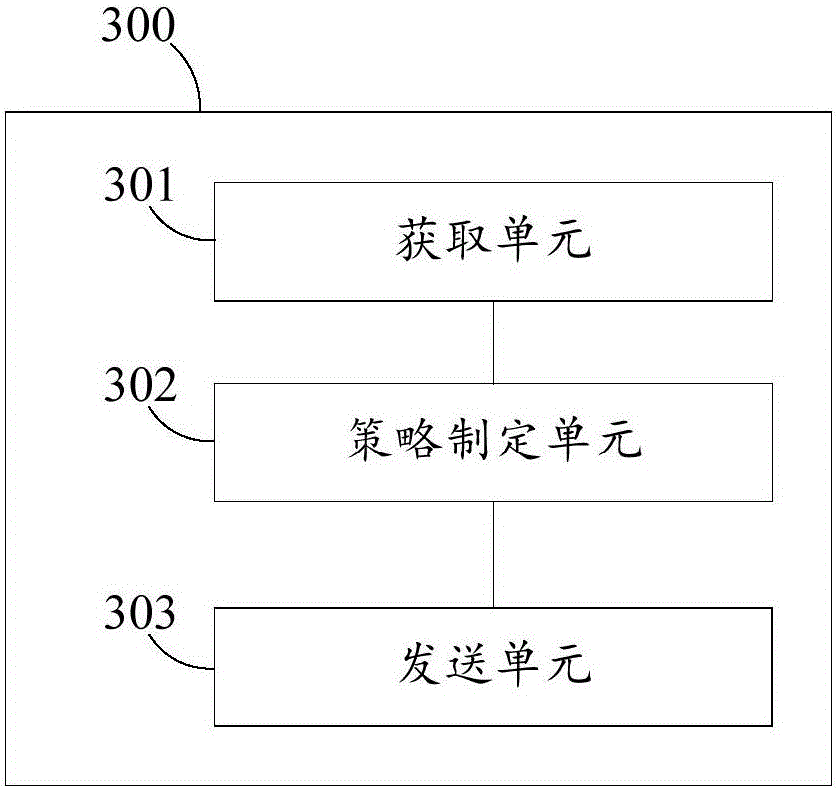
Method of controlling play resources of terminal, and bluetooth headset
The embodiment of the invention discloses a method of controlling play resources of a terminal, and a bluetooth headset. The method of controlling play resources of a terminal includes the steps: if detecting that connection with the terminal is successful, obtaining the first delay time and the second delay time, wherein the first delay time is used for identifying the data transmission delay time length between the terminal and a bluetooth headset and the second delay time is used for identifying the data transmission delay time length between a first bluetooth headset and a second bluetooth headset in the bluetooth headsets; according to the first delay time and the second delay time, making a response strategy for coordinating with and controlling working of the terminal; and sending the response strategy to the terminal, wherein if the terminal detects a control command for controlling the resources to be played, giving a response to the control command according to the response strategy. The method of controlling play resources of a terminal can eliminate the phenomenon that data transmission between the bluetooth headset and the terminal is delayed.
Owner:SHENZHEN GIONEE COMM EQUIP
Intrusion detection and analysis system on basis of service data flow of virtual machines
InactiveCN104753952AApplicable security defenseImprove robustnessData switching networksService flowData stream
The invention provides an intrusion detection and analysis system on the basis of service data flow of virtual machines. The intrusion detection and analysis system comprises a data acquisition module, an intrusion detection module, a communication interface, an alarm response module and a safety management module. The data acquisition module is used for acquiring audit data when access request operation is started; the intrusion detection module is used for analyzing the acquired audit data and detecting the audit data to determine whether the audit data are intrusion events or not; the intrusion detection module and the data acquisition module are bidirectionally communicated with each other via the communication interface; an intrusion detection system can generate alarm information by the aid of the alarm response module when the intrusion events occur, and the alarm information is transmitted to the safety management module by the aid of the alarm response module, so that the alarm information can be visually displayed; the safety management module is used for combining and scheduling forecasting methods, transmitting access control strategies, the forecasting methods and alarm correlation information to the intrusion detection module, transmitting response strategies to the alarm response module and receiving safety update information transmitted by the alarm response module.
Owner:CHENGDU SHUANGAOYANG TECH
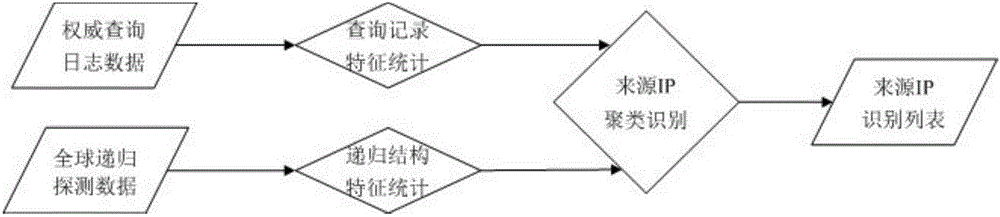
IP recognition method and system for domain name authority service source
ActiveCN105704259ADoes not affect normal operationRefined identificationTransmissionDomain nameFeature extraction
The invention discloses an IP recognition method and system for a domain name authority service source. The method comprises the steps: 1), a query record feature statistic module extracts the query record features of set source IPs from an authority query log of an authority server; 2), a recursion structure feature statistic module builds a recursion structure mapping relation table according to the read global recursion service detection data, and then carries out recursion structure feature extraction according to the recursion structure mapping relation table; 3), a source IP cluster recognition module carries out the clustering of the set source IPs according to the extracted query record features and the recursion structure features, dividing the source IPs into a plurality of different subsets, and sets a response strategy for each subset; 4), the authority judges which subset the IP corresponding to the query belongs to when the authority server receives the query, and then carries out the processing of the IP corresponding to the query according to the response strategy corresponding to the subset. The method can achieve the fine recognition of different types of source IPs, and carries out the corresponding processing of the IPs.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com