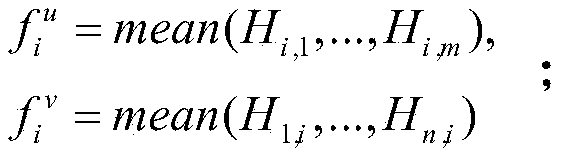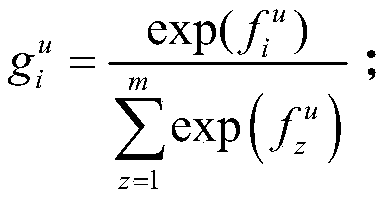Patents
Literature
729 results about "Computer network technology" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
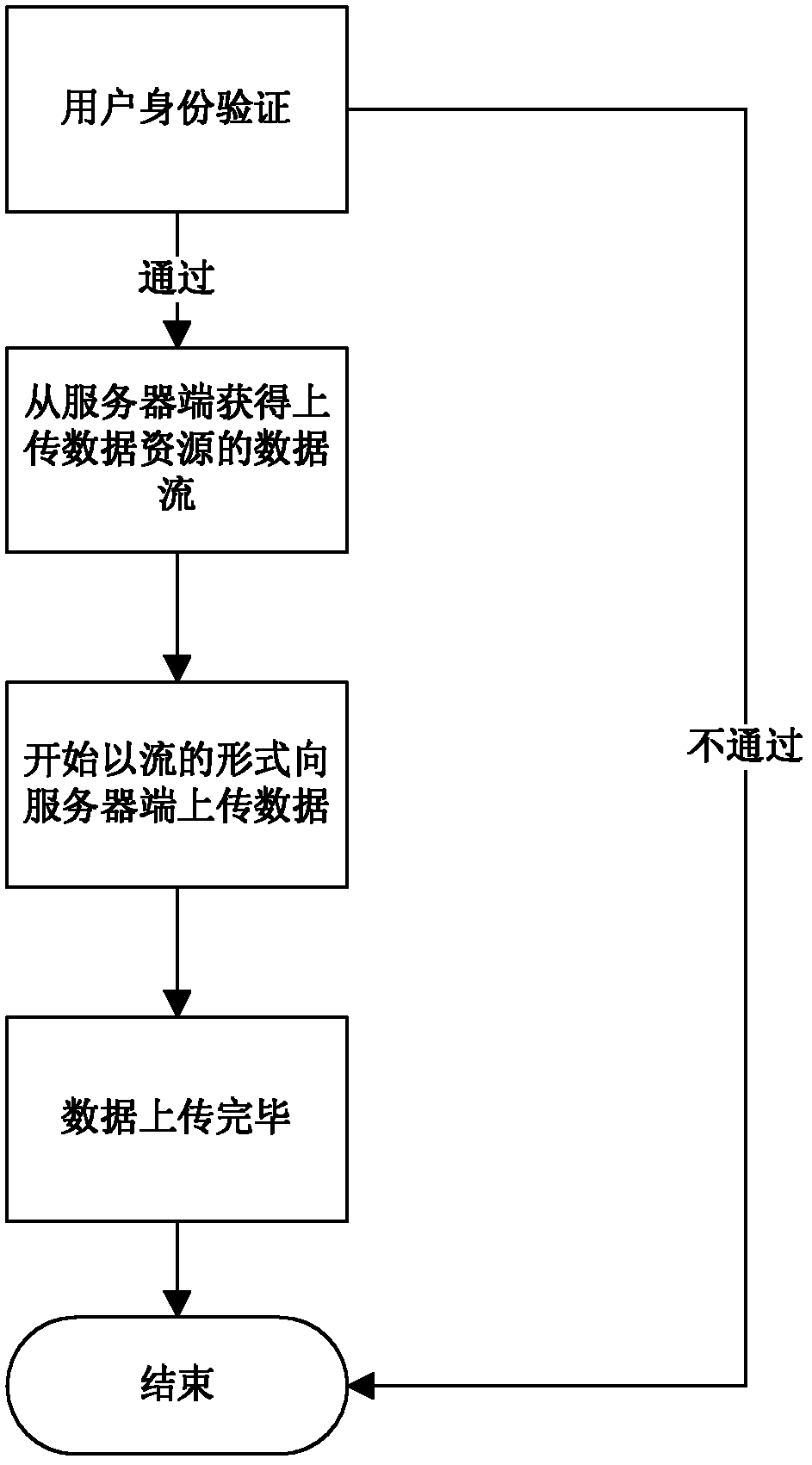
A Computer Network Technician is an information technology professional engaged in various businesses to build and troubleshoot computer networks. These individuals focus on setup, repair, and troubleshooting of both hardware and software products that are incorporated in a business’s operations.
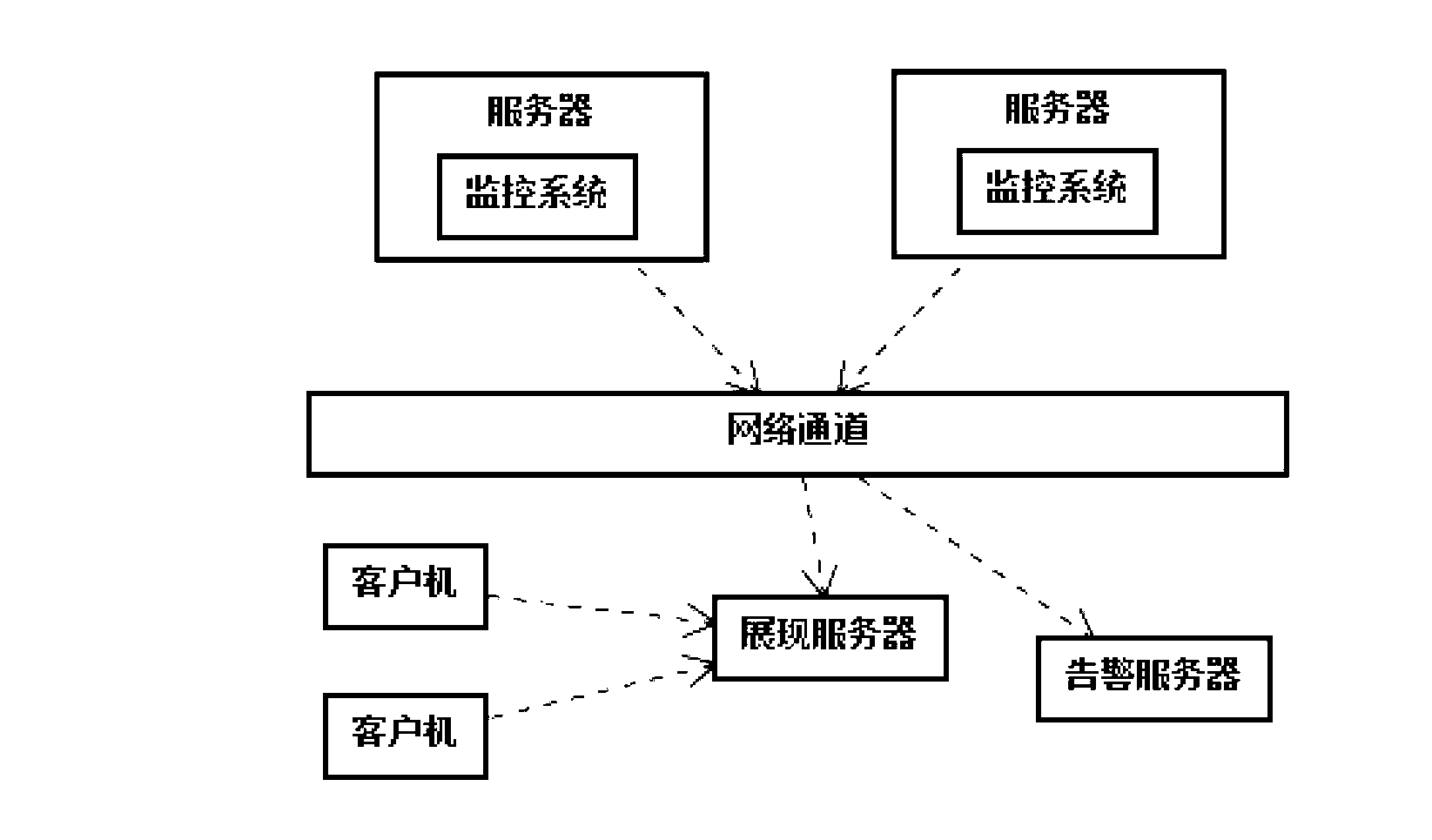
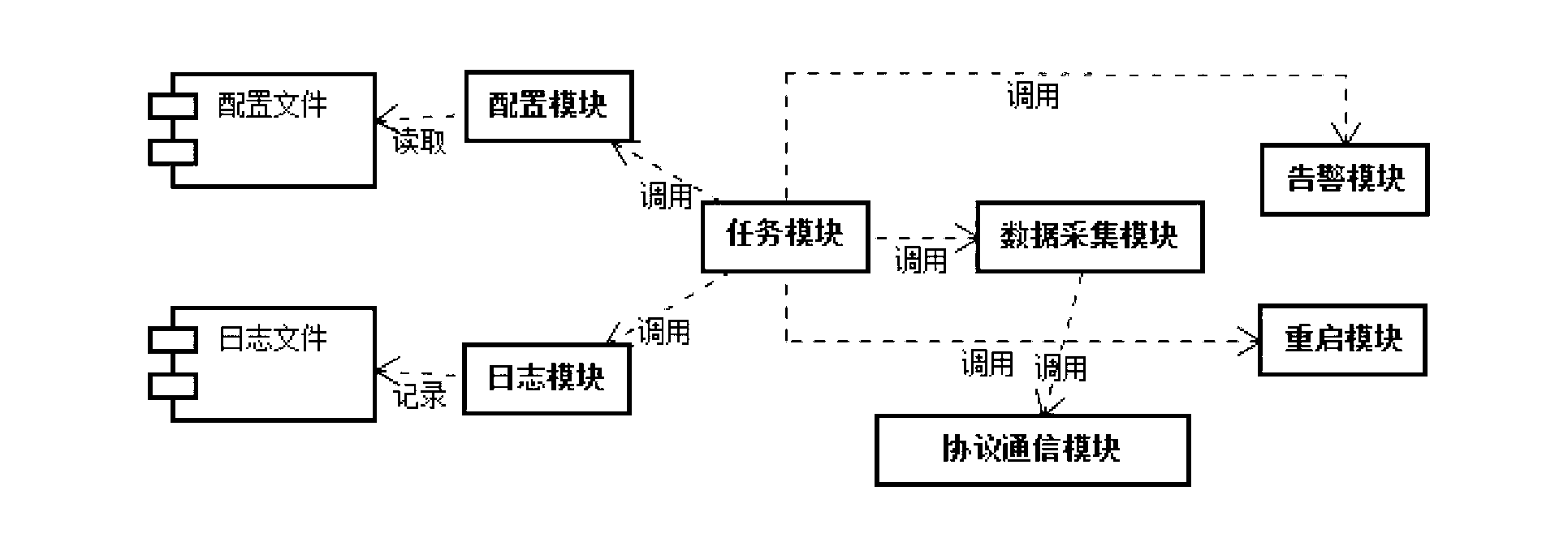
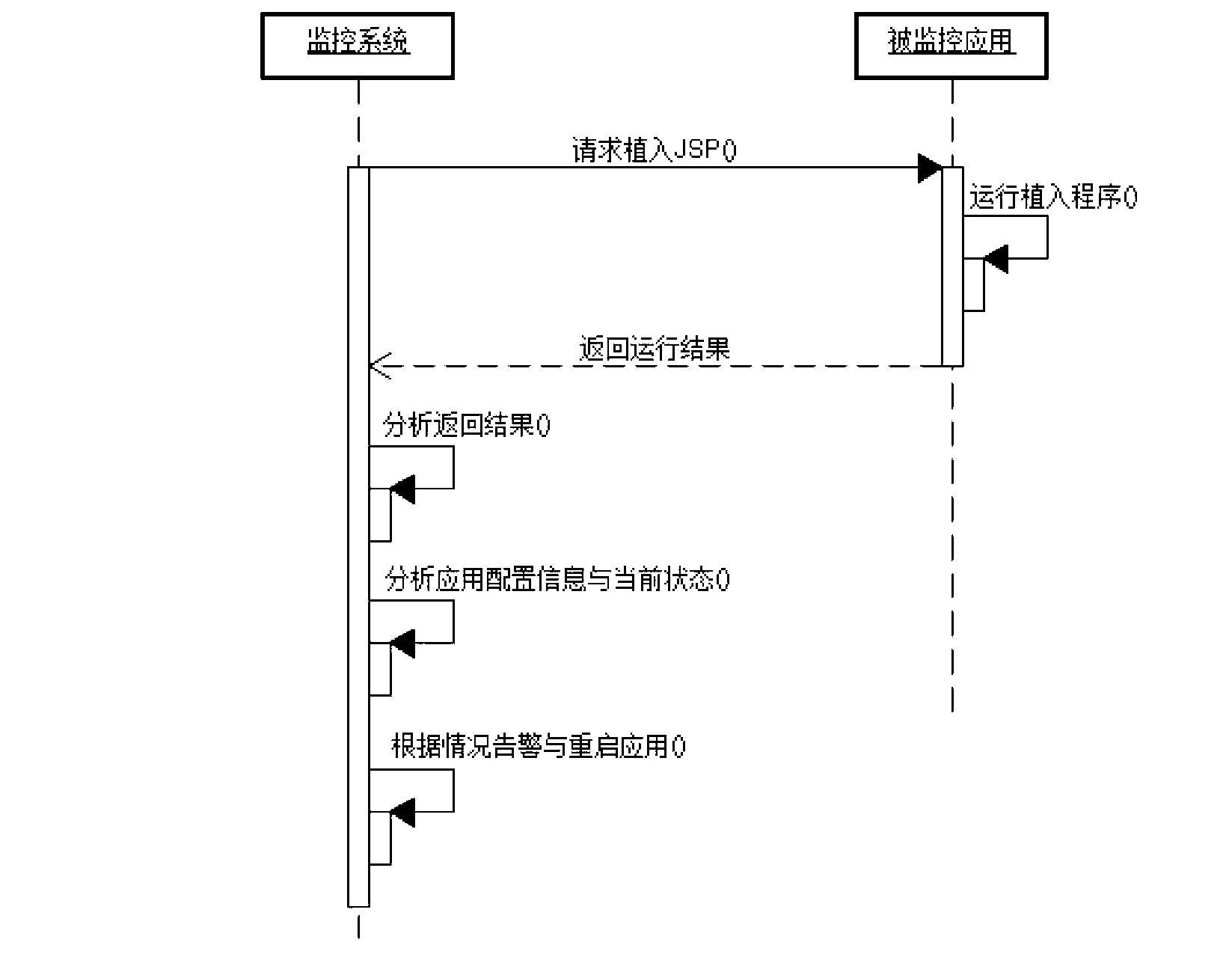
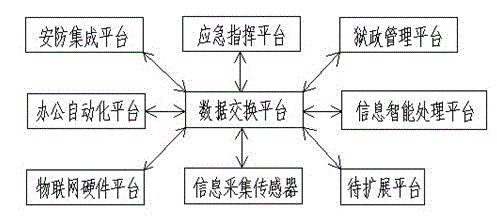
Wisdom skynet video behavior analyzing system
InactiveCN103297751AEffective trackingSave burdenClosed circuit television systemsBurglar alarmVisual technologyDistributed structure
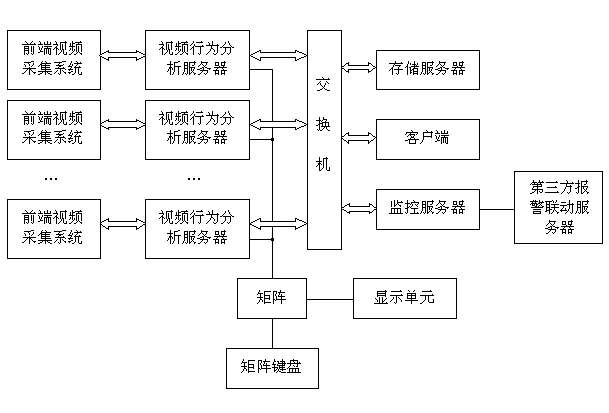
The invention discloses a wisdom skynet video behavior analyzing system which comprises a plurality of front end video collecting systems and a central monitoring system. The central monitoring system comprises a plurality of video behavior analyzing servers, a storage server, a monitoring server and a client side, wherein each video behavior analyzing server receives video information of one front end video collecting system respectively, automatically analyzes all kinds of exception behaviors by the adoption of an advanced image analyzing processing technology, a computer vision technology, a computer network technology and an artificial intelligent technology and generates alarming signals, the video behavior analyzing servers are respectively connected with the storage server, the monitoring sever and the client end through an interchanger, and the monitoring server is further connected with a third party alarm linkage server. The wisdom skynet video behavior analyzing system is provided with multiple detection modules, users can selectively install certain modules according to actual needs, installation is convenient, the operation is simple, and video behavior analysis can be carried out automatically. A distribution type structure is adopted by the wisdom skynet video behavior analyzing system, and data transmitting and processing speed can be improved.
Owner:四川天翼网络股份有限公司
Transaction commit method of distributed database system
InactiveCN101706811AReduce the number of log operationsImprove efficiencySpecial data processing applicationsComputer network technologyHigh availability
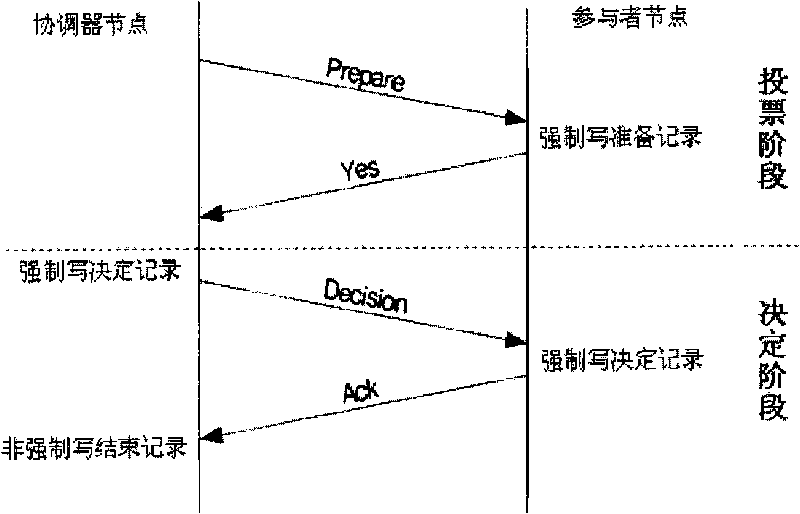
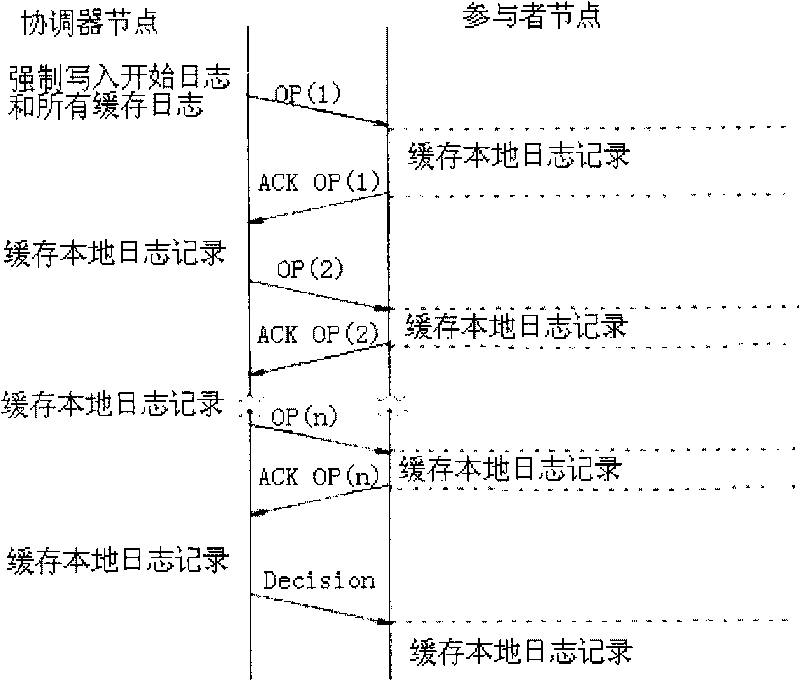
The invention discloses a transaction commit method of a distributed database system, belonging to the technical field of computer network. The transaction commit method comprises the following steps: 1) a cache area is respectively allocated in memories of participant nodes and coordinator nodes and used for caching transaction logs; 2) the coordinator nodes determine the participant nodes and establishes connection with the participant nodes according to the transaction content, and simultaneously determines operation request information of the transaction; 3) the coordinator nodes send the one-step operation request messages of the transaction to the participant nodes and simultaneously records the transaction request logs of each operation request; 4) the participant nodes process local logs according to the completion condition of each operation request and send corresponding messages to the coordinator nodes; and 5) the coordinator nodes judge whether the transaction is completed according to the received messages sent by all the participant nodes, and if so, a final decision is given. Compared with the prior art, the transaction commit method greatly reduces the operation times of logs, improves system efficiency and transaction efficiency and has extremely high availability.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
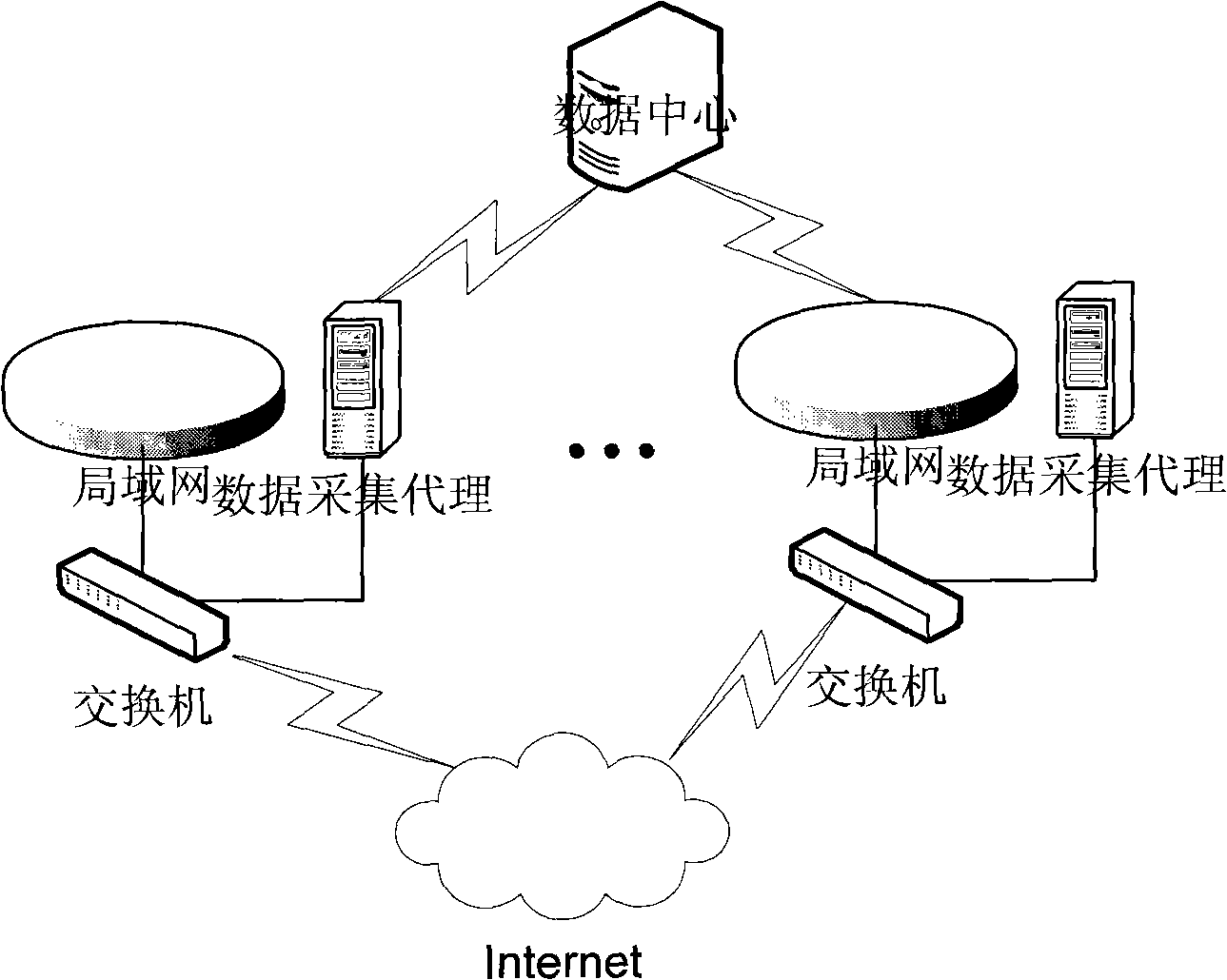
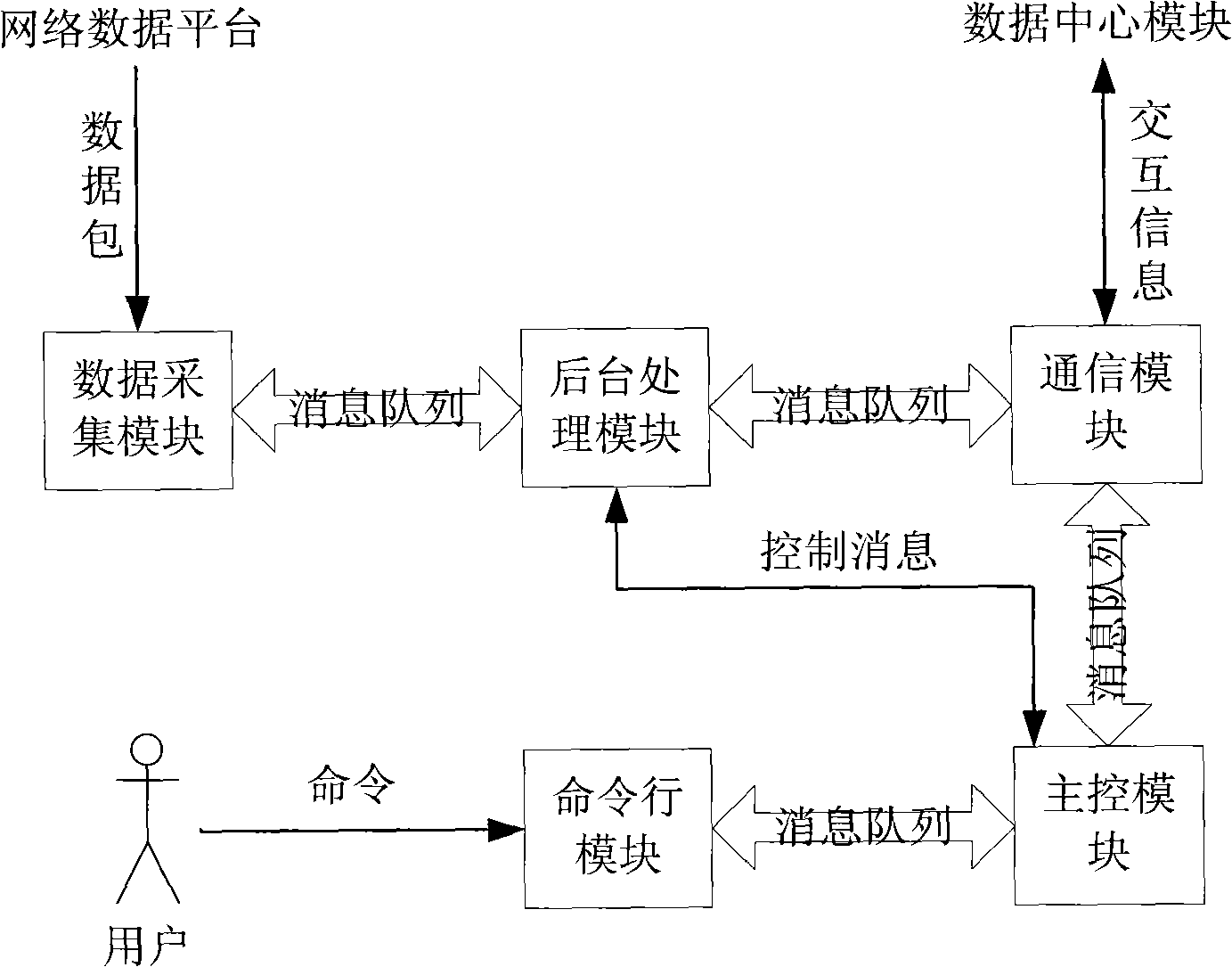
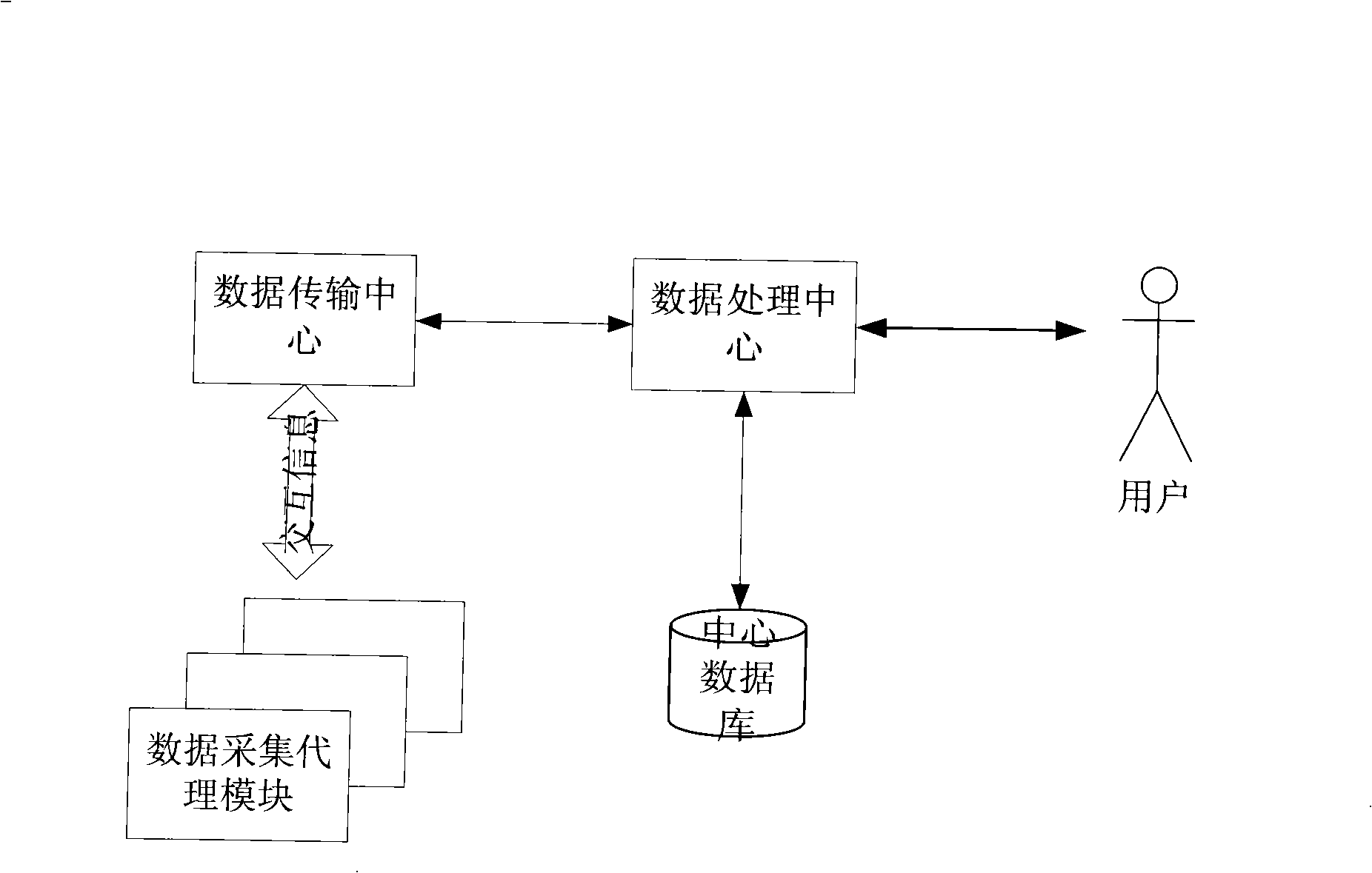
Dynamic configurable data monitoring system and method for distributed network
The invention relates to a system and a method for monitoring distributed network data with dynamic configuration in the technical field of computer network. In the invention, an agent module of data acquisition collects the data of an affiliated network data platform according to the configuration files set by users and carries out preprocessing of the collected data; the preprocessing comprises operations of data packet filtration and data packet disassembly, wherein, the data packet filtration refers to protocol filtration operation, namely, the invalid data pocket is discarded according to the filtration mechanism defined by the users; the data packet disassembly operation refers to that useful information in the data packets is extracted according to presented content by the users and the data required by the users is reported to a data center module in the form of XML document; the data center module is responsible for processing the data files reported by the agent module of data acquisition and in the form of XML, and carries out dynamic management on the agent module of data acquisition by inquiring, configuring and updating the XML documents. The system and the method of the invention simplify the design of the system, and improve the ability of the system to process data as well as usability and robustness of the system.
Owner:SHANGHAI JIAO TONG UNIV
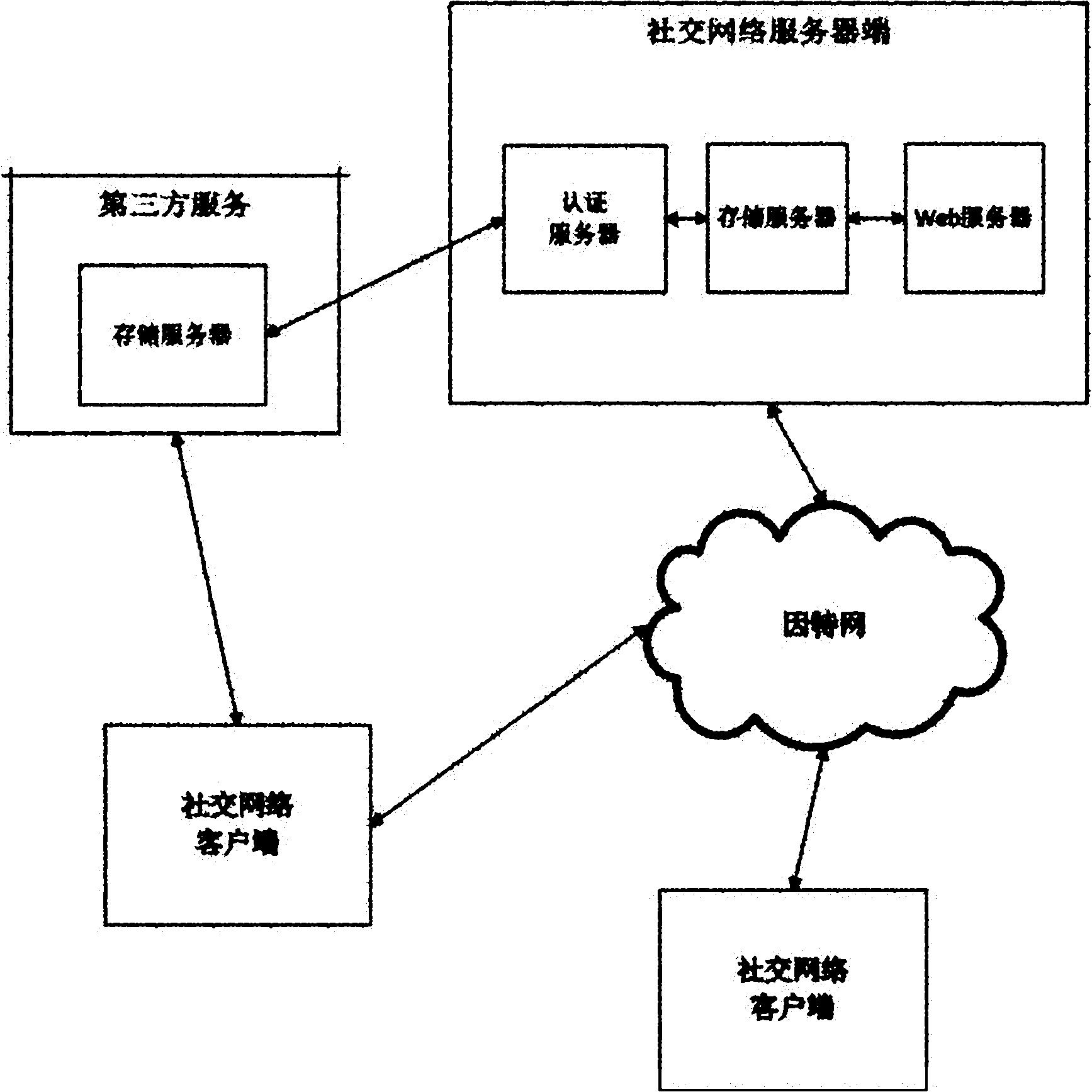
Method for sharing and acquiring data in social network service (SNS)
ActiveCN102158468ASafe storageReduce the possibility of malicious accessTransmissionOperational systemData store
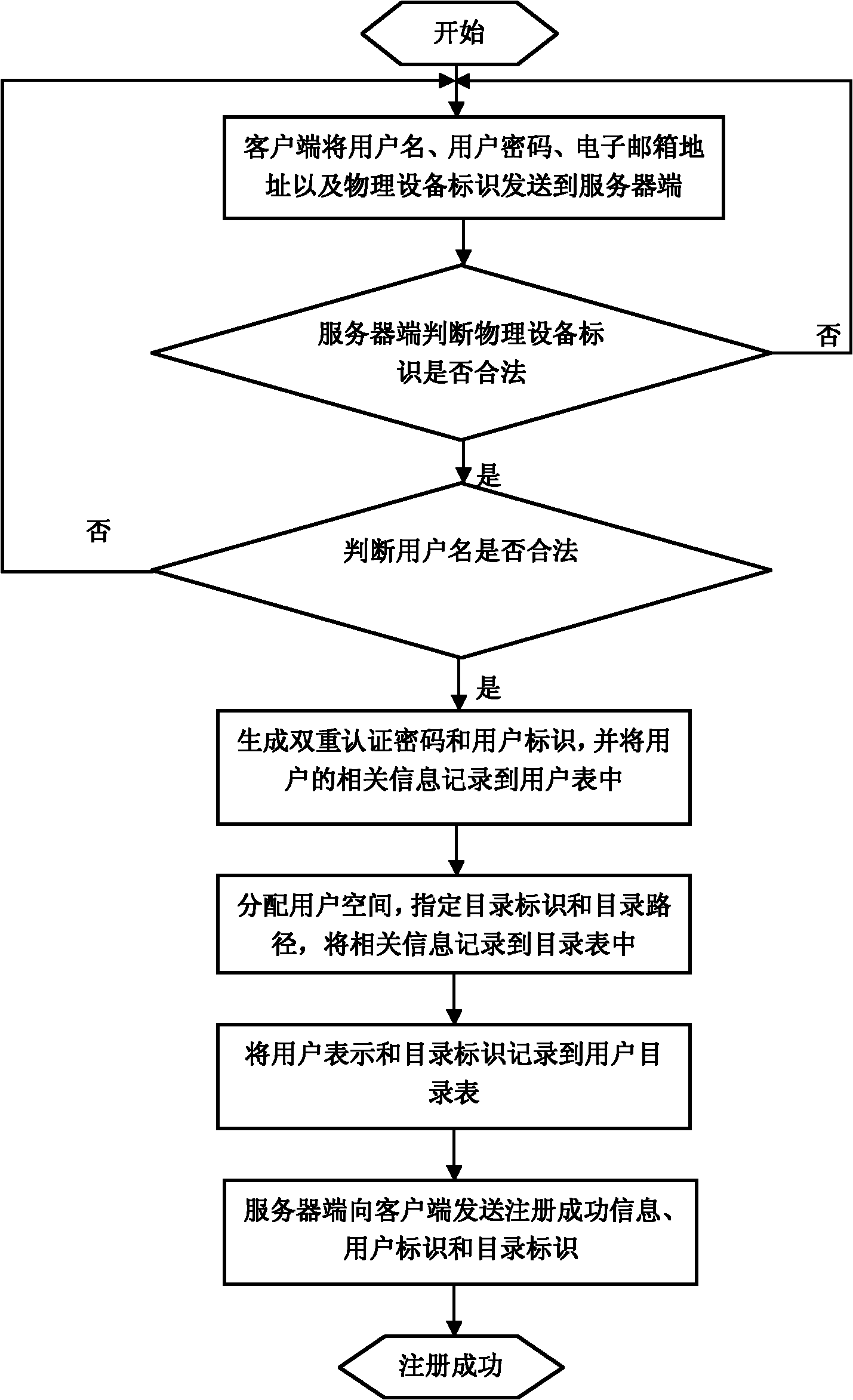
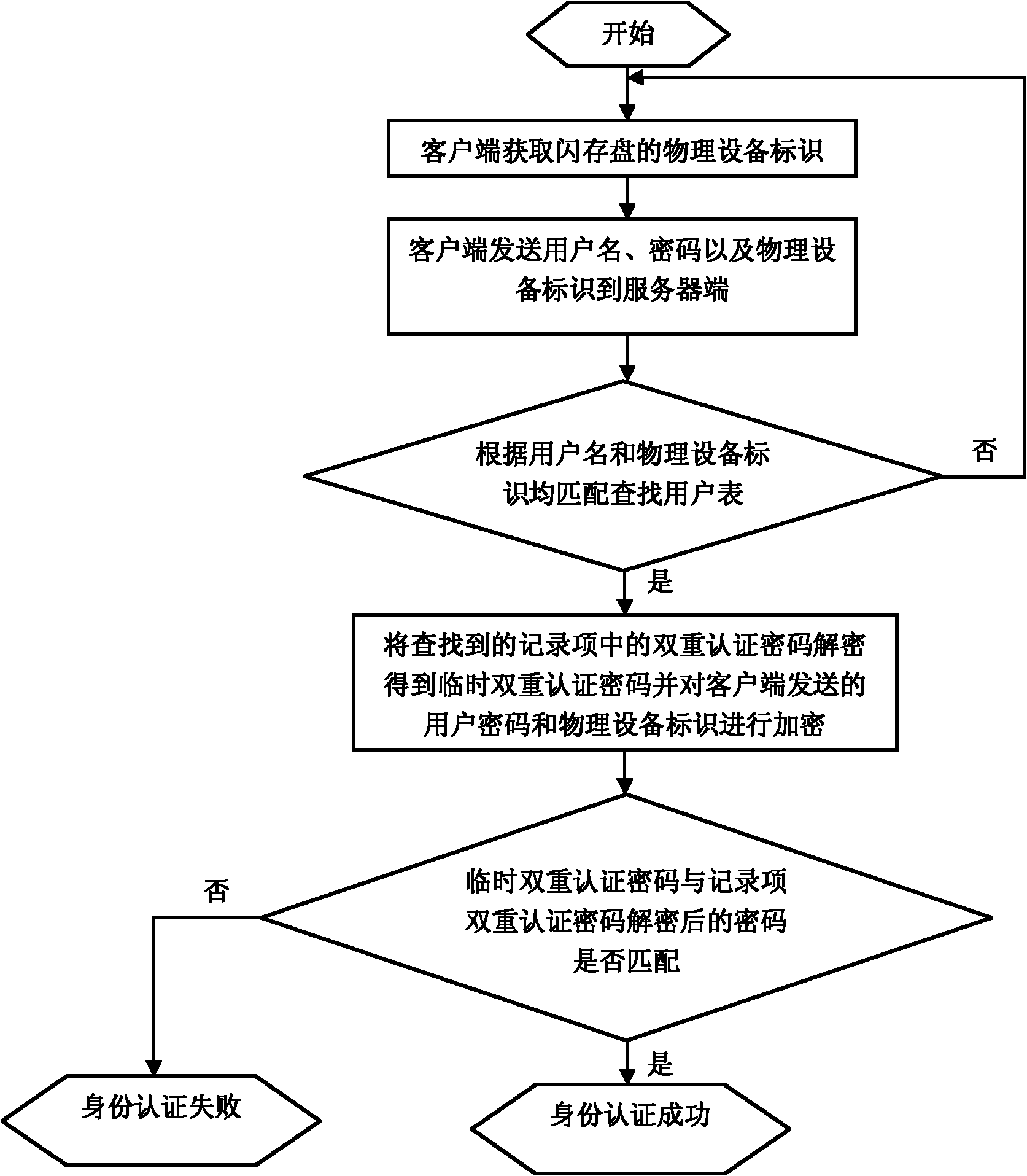
The invention relates to a method for sharing and acquiring data in a social network service (SNS), belonging to the technical fields of computer network and computer data storage. A flash disk is used as an identity authentication device. The method comprises the steps as follows: the SNS uses a server-side to carry out user registration, perform the identity authentication and access data on a user, and carry out social circle registration as well as read files under Web; the user carries out interaction with the server-side by a client-side; a remote server-side is logged in by double authentication, namely the physical identification of the identity authentication device and user password; a user personal space and a shared space which is not in the social circle are respectively mounted to a local operating system in the form of an catalog; and different catalogs are established in the shared space in accordance with different social circles, and the user reads files which are shared in the different social circles by accessing the corresponding catalogs. By using the method, the user can share data selectively in the different social circles without extra management.
Owner:TSINGHUA UNIV
Resource supply method oriented to Web application host platform
ActiveCN102130938AReduce usageReduce consumptionData switching networksWeb applicationOperational costs
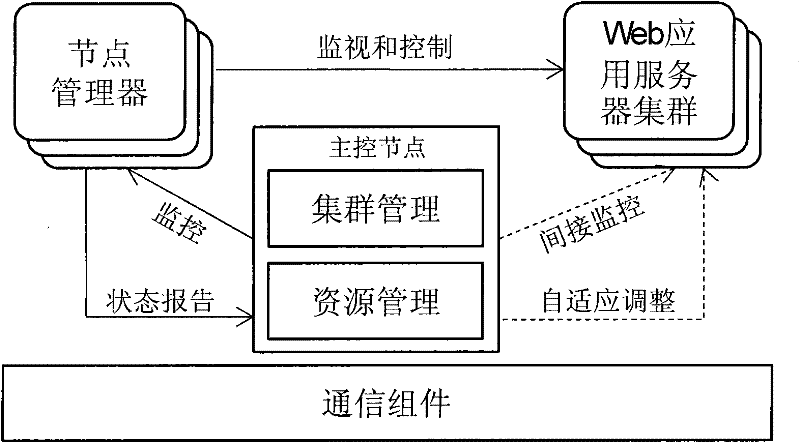
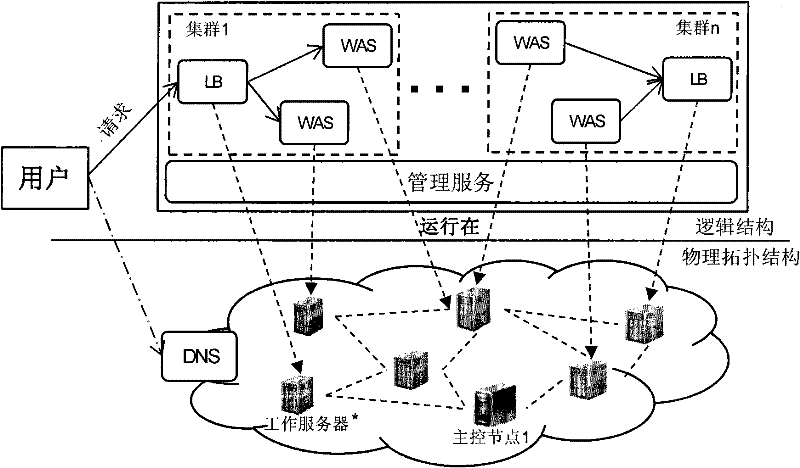
The invention discloses a resource supply method oriented to a Web application host platform, belonging to the technical field of computer networks. The method comprises the following steps: a main control node is arranged in the host platform and a node manager is arranged on each server in the platform; and the node manager monitors the performance of the server and a cluster node by adopting a performance abnormity detection method and feeds a monitoring result to the main control node, and the main control node generates a resource adjusting strategy according to the monitoring result, returns the adjusting strategy to the node manager and performs resource adjustment according to a received resource adjusting plan. Compared with the prior art, the invention has the advantages that the application amount of the server is lowered to the maximum extent, the resource consumption is lowered and the operating cost of a data center is reduced.
Owner:山东乾云信息科技集团有限公司
Intelligent confidential article identification management system on basis of internet of things
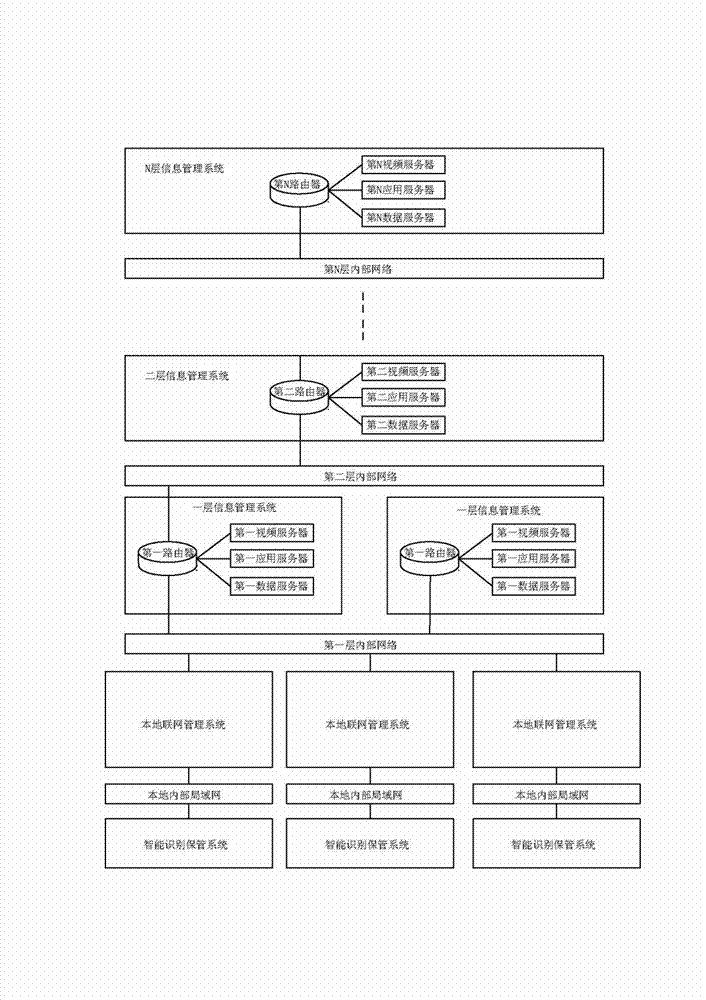
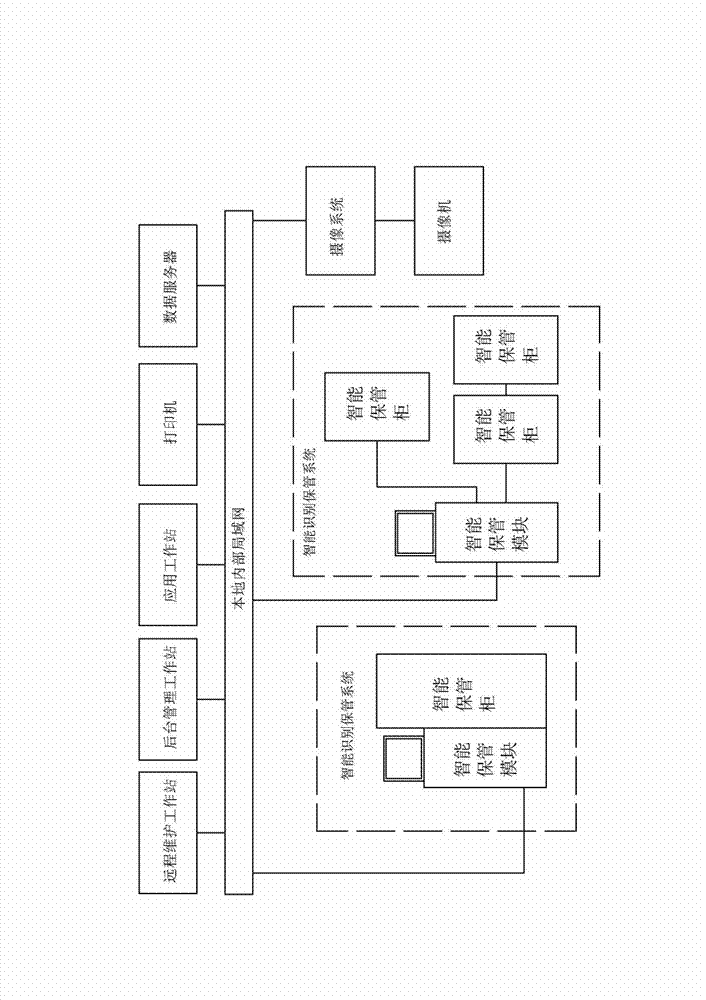
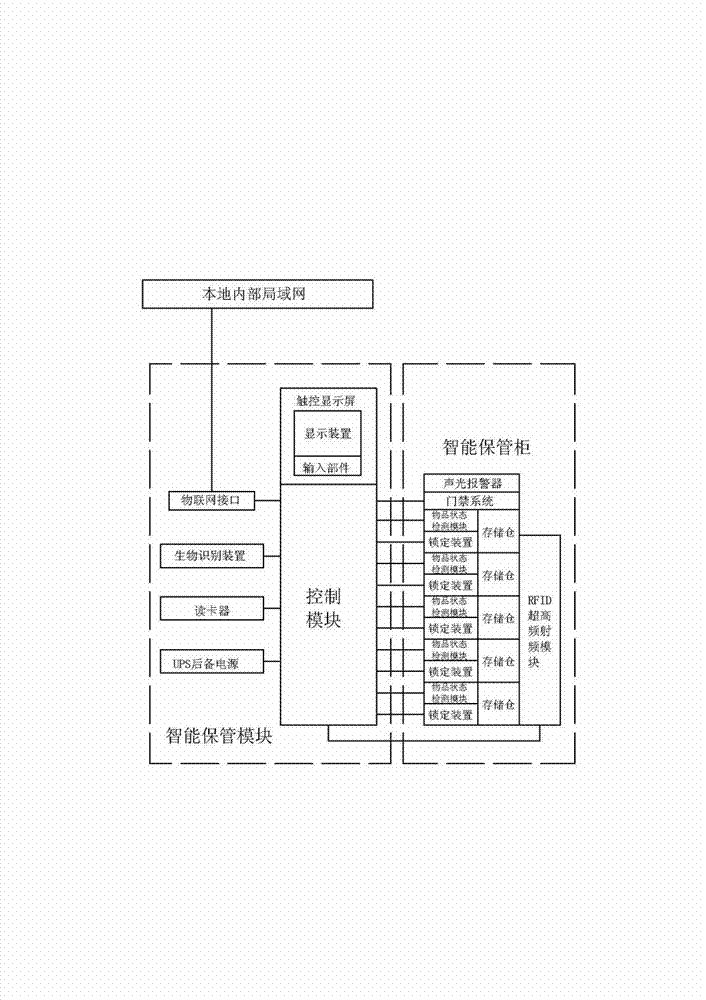
The invention discloses an intelligent confidential article identification management system on the basis of an internet of things. The intelligent confidential article identification management system comprises intelligent identification storage systems and information management systems. Ultrahigh RFID (radiofrequency identification) and biometric identification technologies, computer network technologies and the like are fused in the intelligent identification storage systems, so that storage states and access behavior of confidential articles in intelligent storage cabinets can be effectively identified and monitored, and intelligent and informationized management tools can be provided for management institutions for strictly managing materials in the aspects of intelligent confidential material identification, real-time managed and controlled article information aggregation, real-time confidential article inventory, whole-course liability traceability and the like. The intelligent confidential article identification management system has the advantages that the intelligent confidential article identification management system is based on existing advanced technologies of article perception, sensing and personnel identity authentication, and requirements of article and material information construction and the requirement on updating and upgrading management and control on important materials are considered in a certain aspect, so that the traditional manual management mode of material management and control is transited to a modern information management mode, and informationized, digital and real-time material management and control can be implemented.
Owner:广东中韬信息科技有限公司
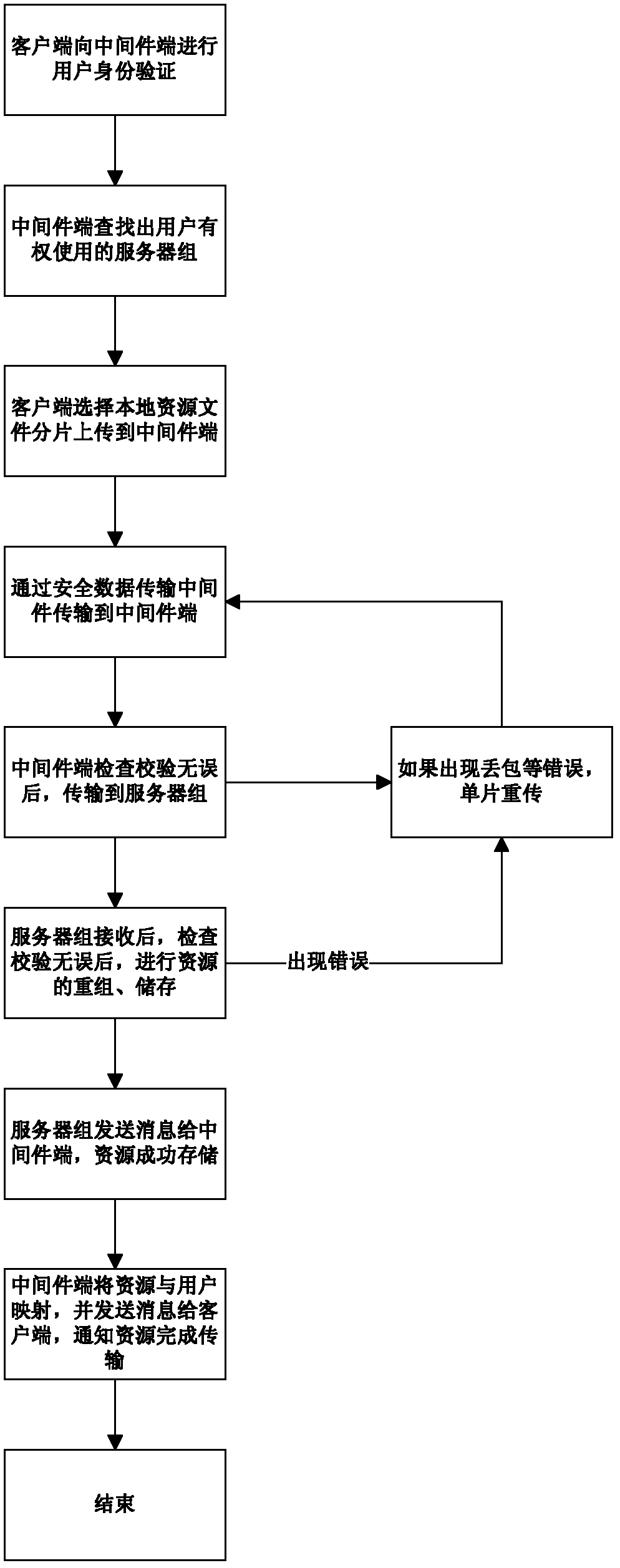
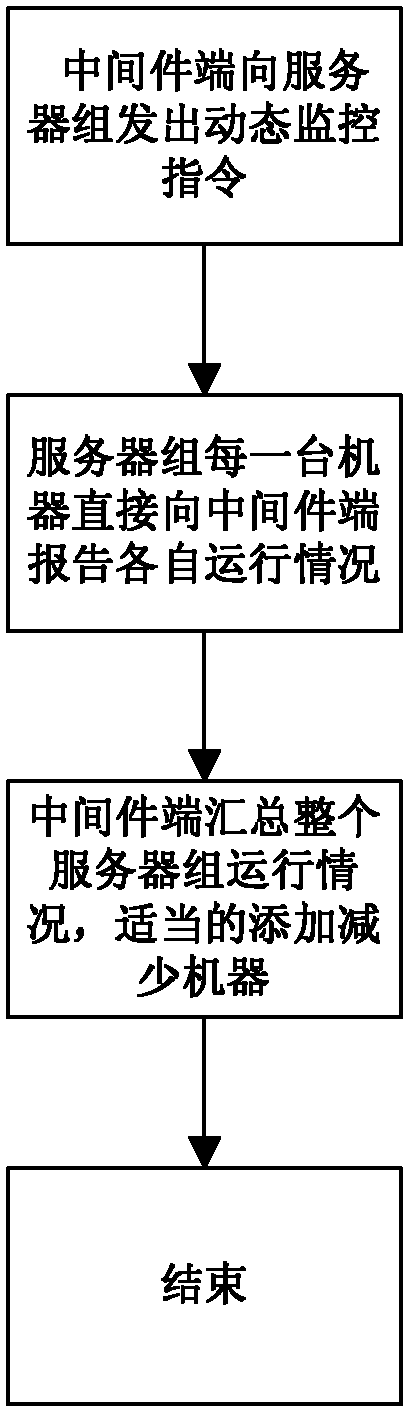
Cloud storage method for cloud computing server
InactiveCN102255974AFix security issuesGuaranteed correctnessTransmissionComputer network technologyClient-side
The invention discloses a cloud storage method for a cloud computing server, belonging to the technical field of computer networks. The method comprises the following steps: (1) a cloud computing server group server and a client registers on a middleware server respectively; (2) the middleware server searches a local database and looks up an operable file and a usable cloud computing server group for a current user; (3) the user selects an upload file, fragments the file and transmits the file fragments to the middleware server; (4) the middleware server verifies the upload file, requires the user to retransmit if the upload file is wrong, and transmits data to the cloud computing server group usable for the user if the upload file is correct; (5) the cloud computer server group rearranges and stores the received data and sends a success message to the middleware server; and (6) the middleware server establishes mapping between the name of the upload file and the user. According to the invention, the correctness and integrity of a data transmitting process and the privacy of data are ensured, and high reliability of normal work of the server group is ensured.
Owner:无锡中科方德软件有限公司
Blending MAC protocol design method suitable for wireless sensor network
InactiveCN101827378ALower latencyImprove throughputNetwork traffic/resource managementNetwork topologiesWireless mesh networkProtocol design
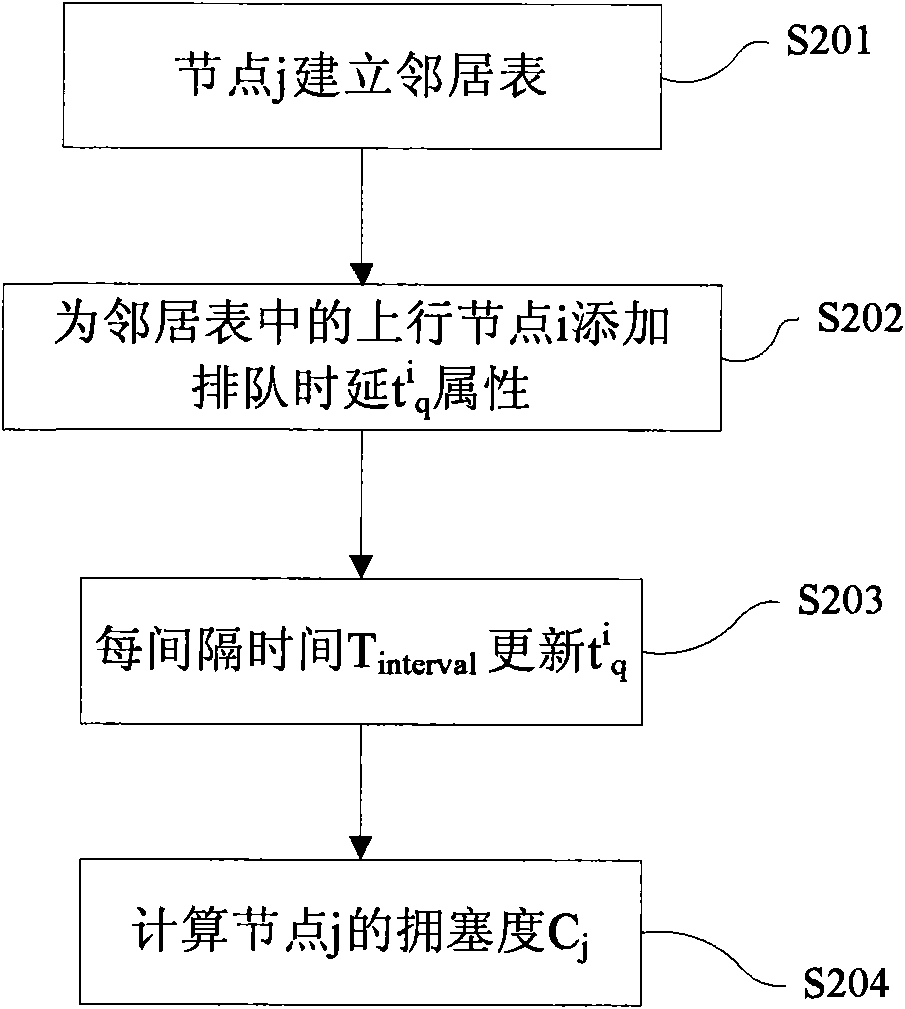
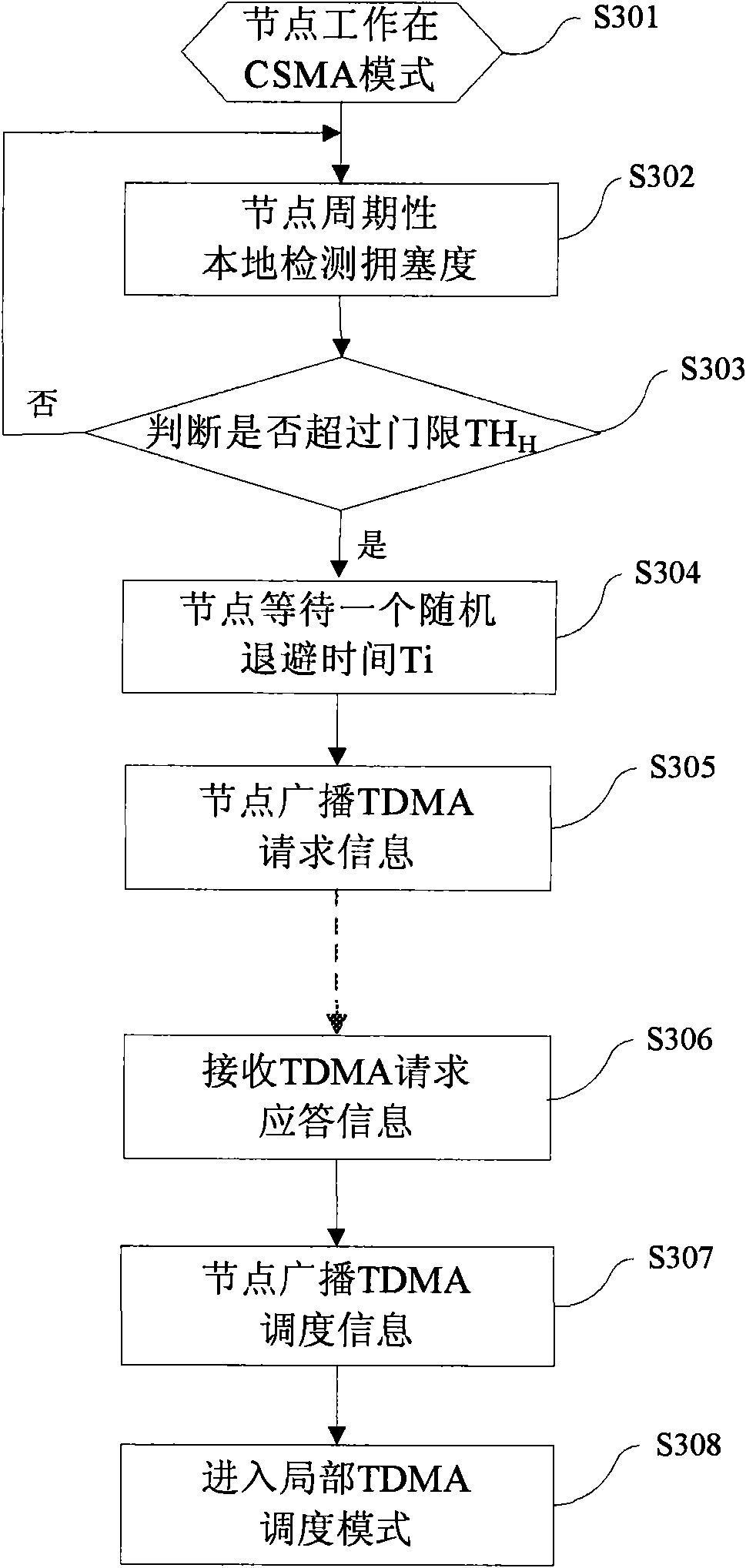
The invention discloses a jamming perception self-adaption blending MAC protocol which is suitable for a wireless sensor network and belongs to the field of computer networking technology. In the low loading network situation, a node runs the CSMAMAC protocol at the normal working condition; when the network has burst data or detects the jamming nearby the node of a bottleneck, a TDMA mechanism is embedded in the jamming area in a self-adaption way; the node of the jamming area runs the local TDMAMA protocol; and after the jamming releases, the node recovers the normal working condition and runs the CSMAMAC protocol. The invention detects the jamming according to the local information and does not need any synchronization algorithm; according to the jamming degree, the local TDMA is embedded in the CSMA network in a self-adaption way so that performance indexes such as the throughout capacity, packet loss rate and time delay and the like are improved and the performance of the network is increased.
Owner:BEIJING JIAOTONG UNIV
Remote intelligent meter reading system
InactiveCN102270383AReduce complaintsImprove information management levelTransmission systemsTransmissionMeasuring instrumentTransmission technology
The remote intelligent meter reading system of the present invention includes a database server, a data service center, an operation terminal, a concentrator, a collector and a client terminal, and one concentrator can be connected with multiple collectors; the concentrator receives various Effective command and responding to the command, send various operating information of the client to the concentrator, and the energy client includes a gas meter, a water meter or an electric meter. The remote intelligent meter reading system of the present invention integrates non-electric power detection technology, microelectronic control technology, radio technology, wireless digital transmission technology, computer network technology, information security technology and software technology and is independent of water, electricity and gas backbone networks. The extraction and data management of measurement data information of measuring instruments has improved the information management level of the industry.
Owner:李蓉
Cloud computing load balancing method and equipment
InactiveCN101873224AApply Dynamic JoinApplicable situationData switching networksService compositionComputer network technology
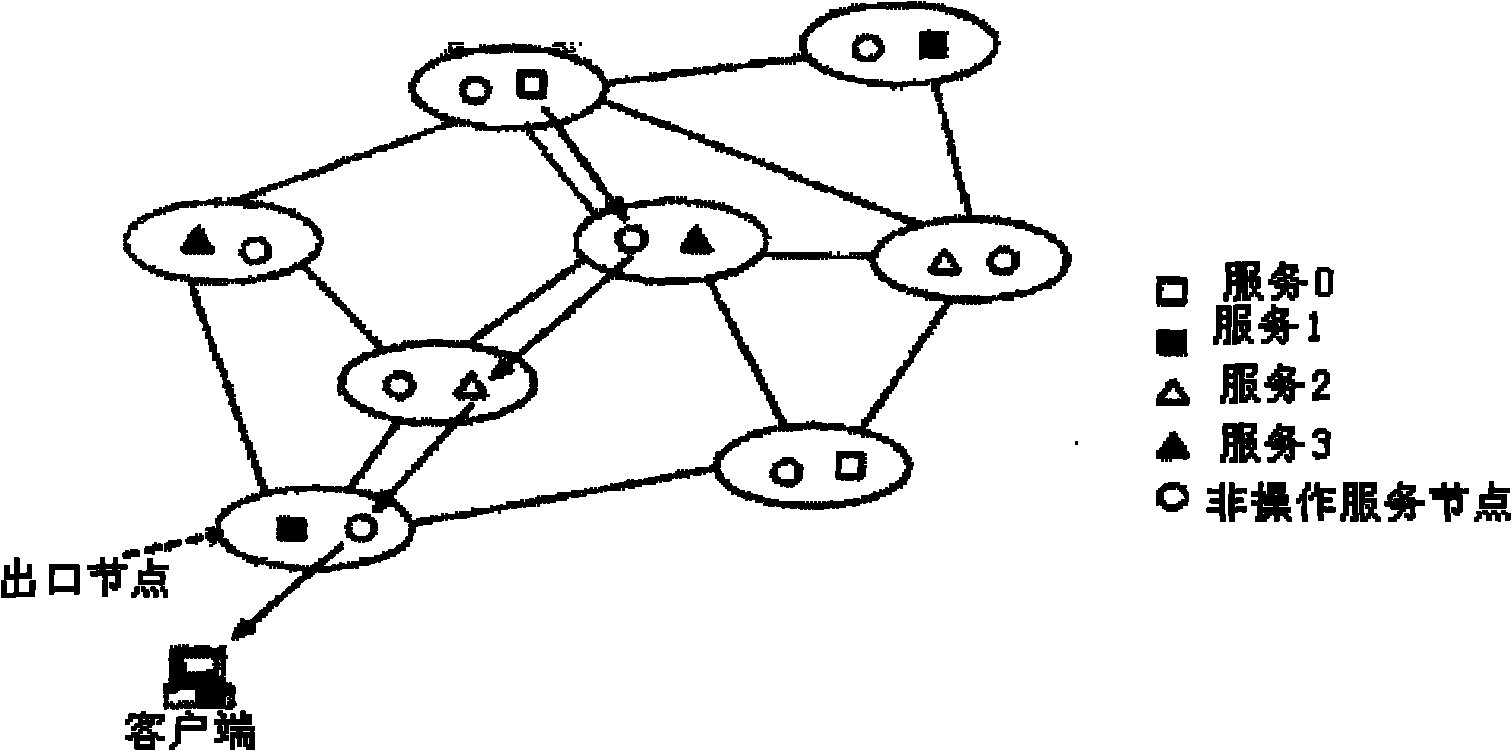
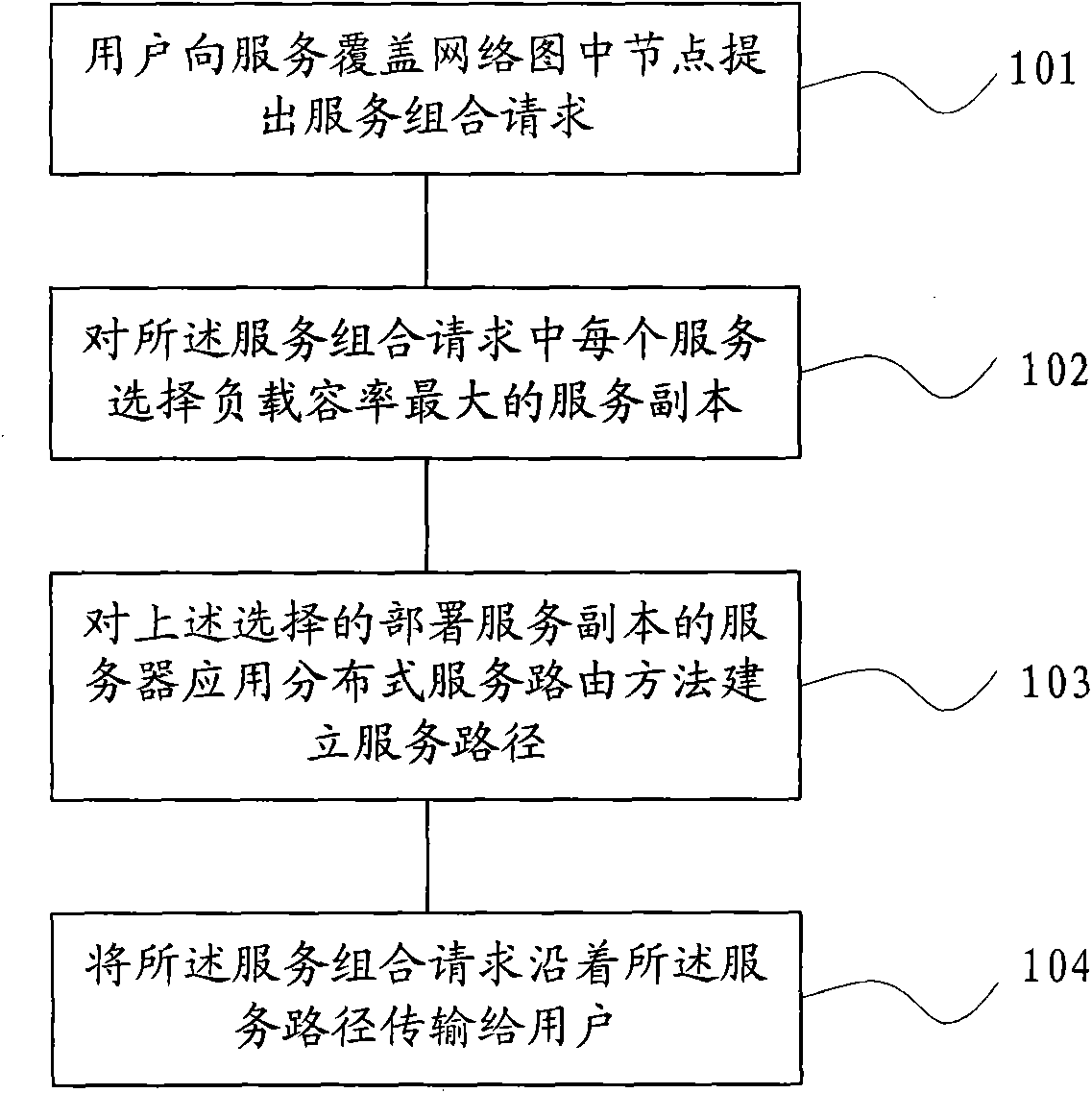
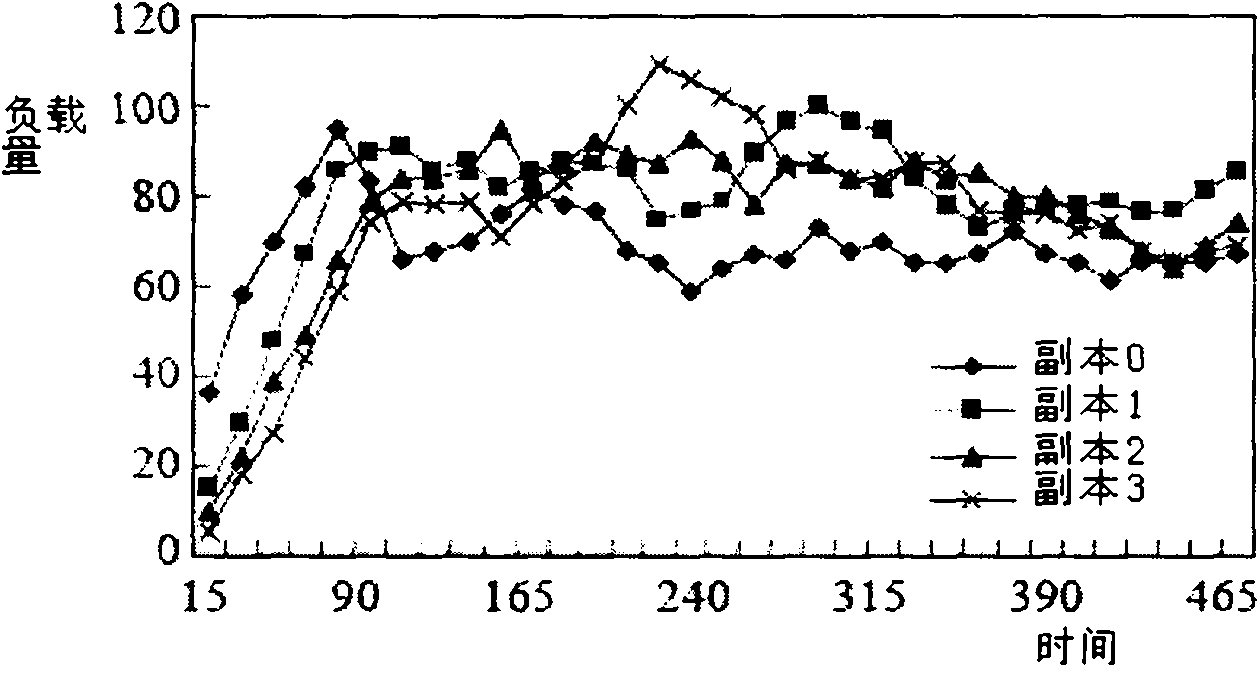
The invention discloses a cloud computing load balancing method and cloud computing load balancing equipment, and belongs to the technical field of computer networks. The cloud computing load balancing method comprises the following steps of: selecting a service copy according to the load capacity of each server in a service combination request raised by a user, establishing a service path for a server application distributed service routing method, and transmitting the service combination request raised by the user to the user along the service path. The cloud computing load balancing equipment comprises a service combination request module, a service copy selecting module and a service path establishing module. The load capacity of the server is acquired according to the load fluctuation condition of the server; because the load fluctuation condition of the server is continuously and adaptively adjusted, the load capacity of the server is adaptively changed; and the proper service copy is selected according to the load capacity of the server so as to ensure comparatively uniform load distribution on each copy and realize adaptive load balance of the server.
Owner:北京高森明晨信息科技有限公司
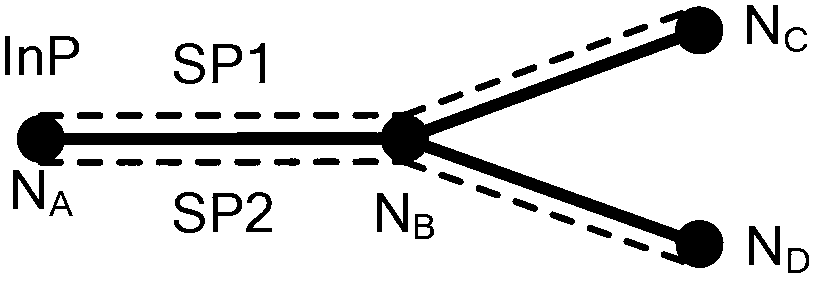
Virtual network resource allocation method
InactiveCN102710508AImprove performanceReduce complexityNetworks interconnectionService provisionNetwork processor
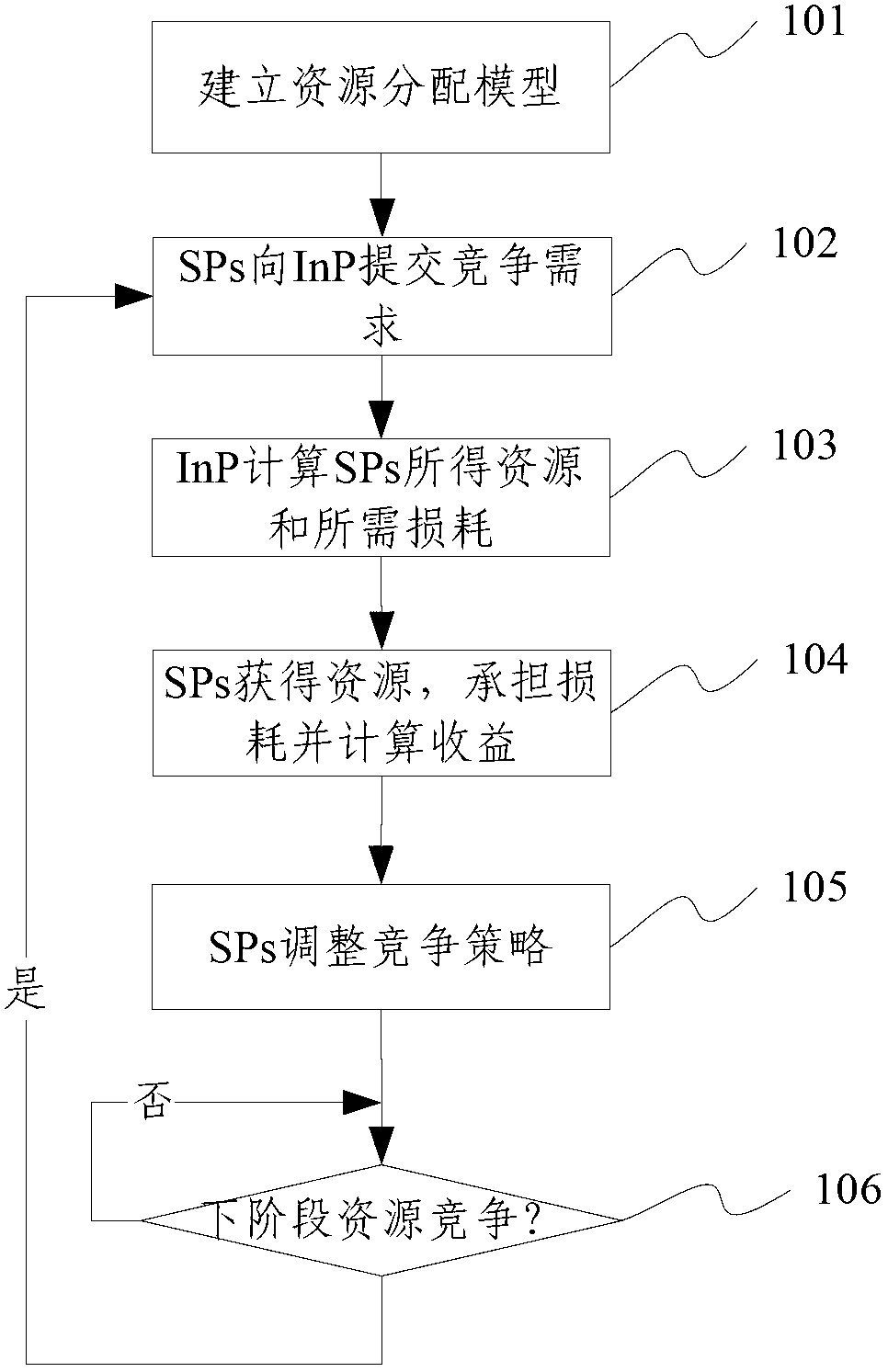
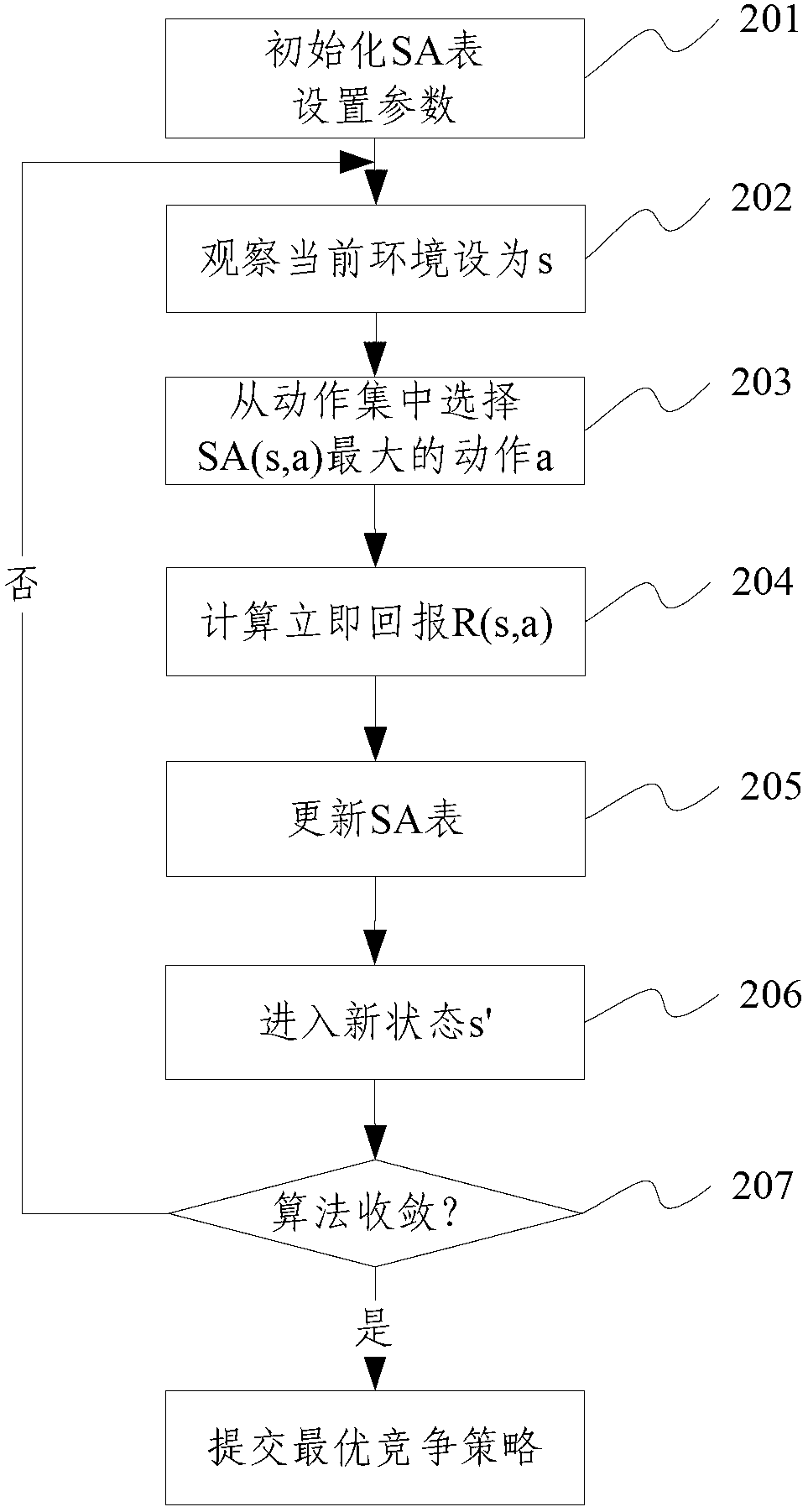
The invention relates to the technical field of computer networks, and provides a virtual network resource allocation method. The method comprises the steps of: building a resource allocation model; submitting competitive demands to an InP (Internal Network Processor) through SPs (Service Providers); calculating the quantity and consumption of the resource through the InP; acquiring the resource, assuming the consumption and calculating the income through each SP; adjusting the competitive strategies through each SP; and waiting for competing at the next time based on the adjusted competitive strategies. In the scheme of the invention, a novel virtual network resource allocation method is provided; the resource is periodically allocated to a plurality of service providers based on the trend of the demands on the virtual network resource, so that the resource allocation can be carried out as demands, and the performance of the whole network can be improved. Moreover, a scheme for effectively selecting the competitive strategies is provided at the same time; by using the scheme, the service providers can be guided to select the competitive strategies; the real network demands can be quickly obtained; the network performance can be improved; and the complexity of the algorithm can be effectively reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM
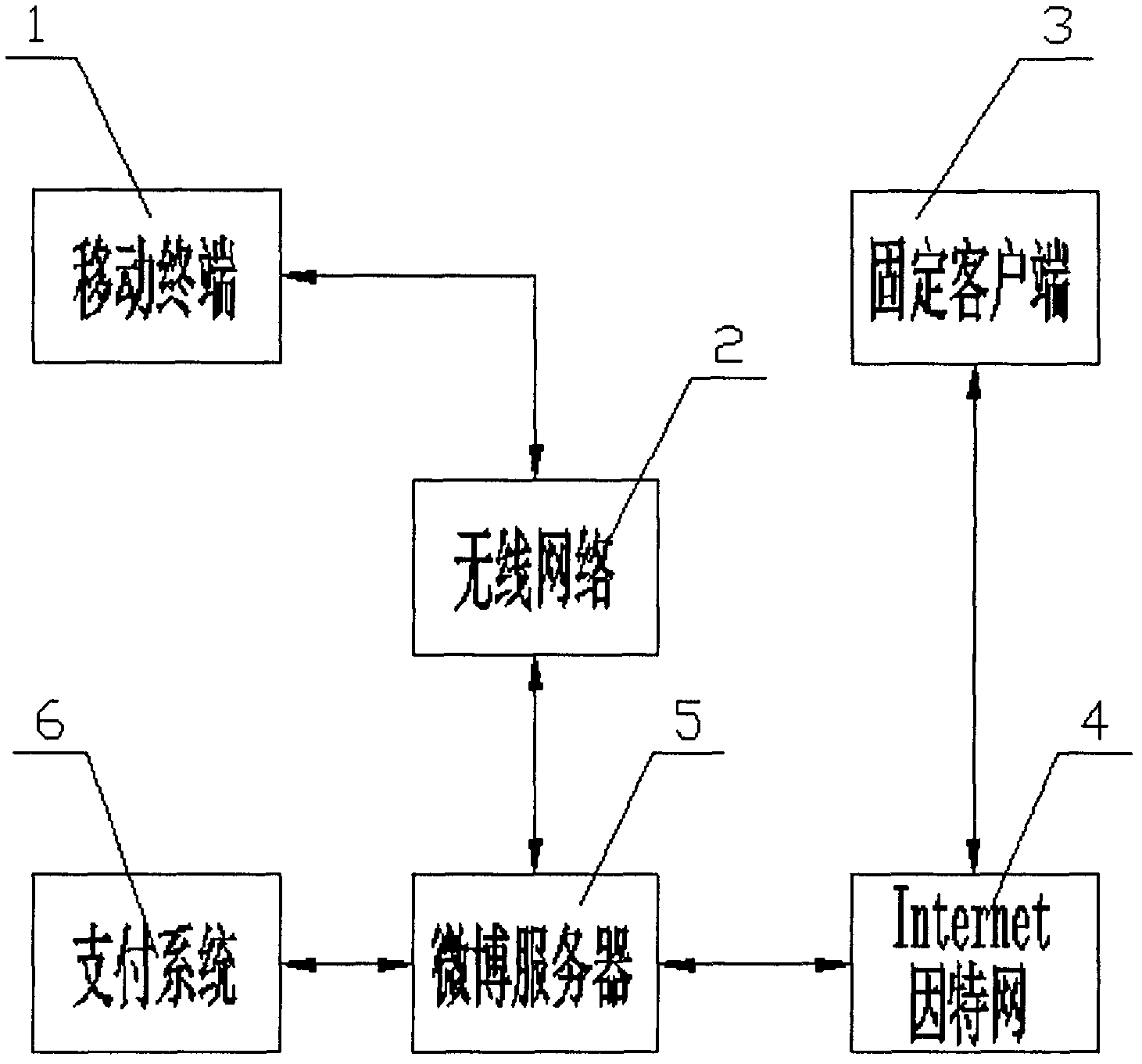
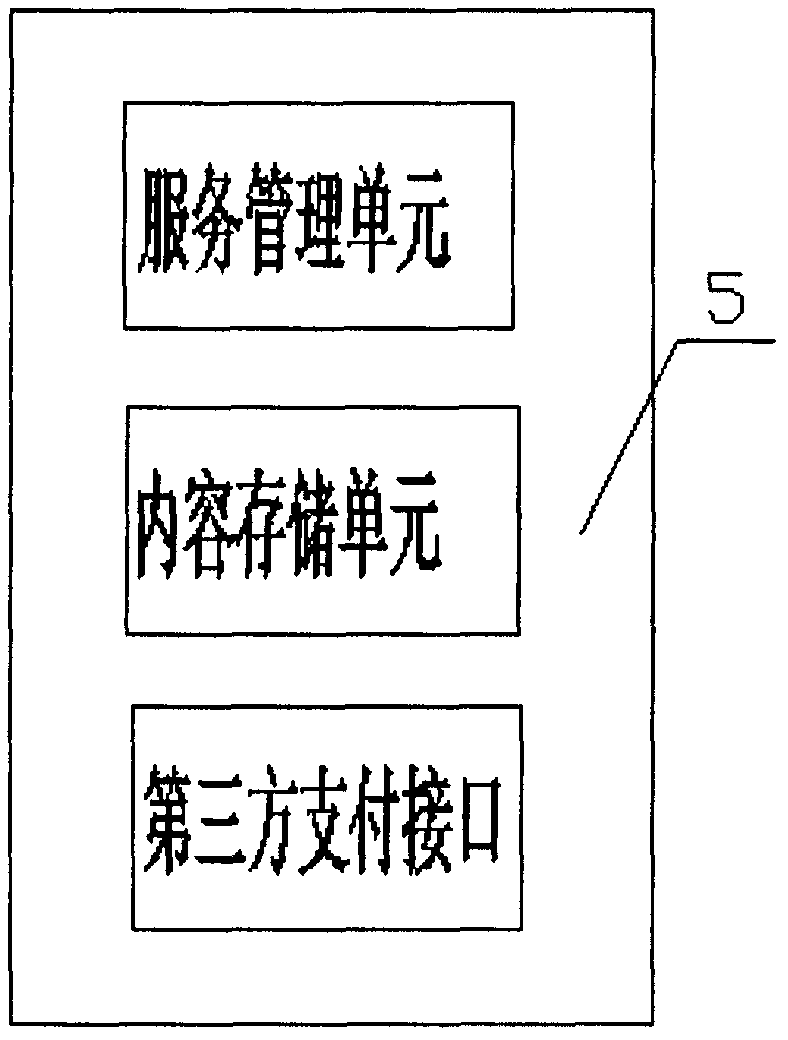
System and method for immediately combining MicroBlog social contact system with electronic commerce
InactiveCN102831520ACommercePayments involving neutral partyMicrobloggingComputer network technology
The invention relates to Internet systems, the field of computer networking technology and the field of electronic commerce, and discloses a system and a method for immediately combining a MicroBlog social contact system with electronic commerce. The system comprises a terminal and a MicroBlog server (5), wherein the MicroBlog server (5) is connected with a payment system (6). The construction method comprises the following steps sequentially: a user carries out registration and login; the user creates a shop; the user issues commodity information; the user listens shop information; the user inquires a commodity; the user replies the information; the user forwards the information; the user selects and purchases the commodity; the user pays an order online; and the user processes the information after the transaction is successful. According to the invention, the online shop and the electronic commerce functions of B2B or B2C are combined together, so that the function for shopping in an Internet social contact system is realized.
Owner:丁贵祥
Vehicle-carried intelligent terminal system and realization method thereof
InactiveCN102658804AVersatileEasy to operatePedestrian/occupant safety arrangementSignalling/lighting devicesVideo monitoringArea network
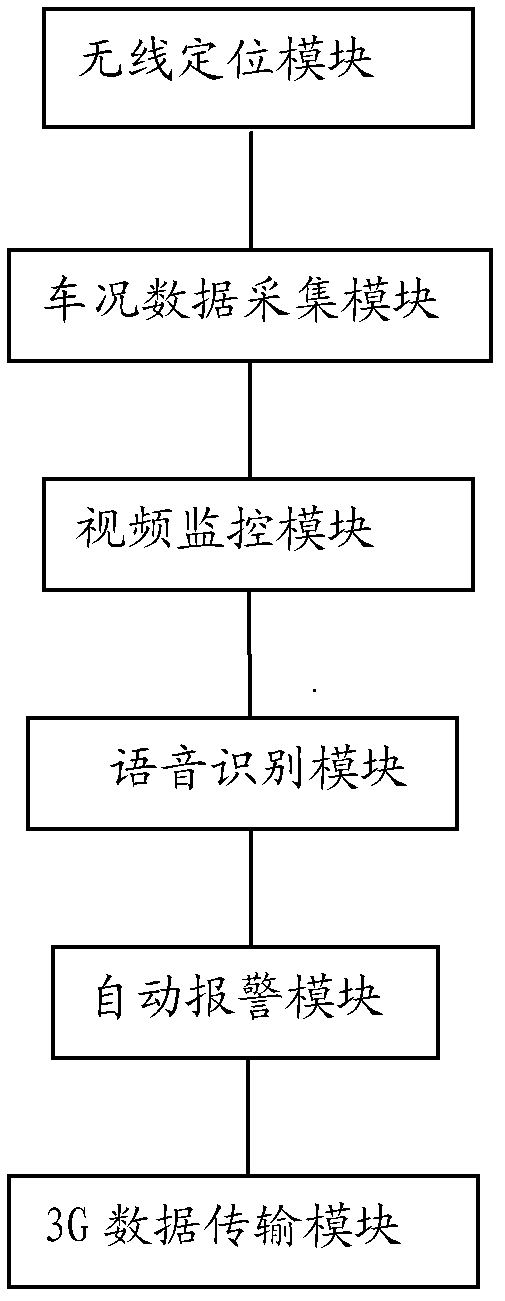
The invention discloses a vehicle-carried intelligent terminal system and realization method of the vehicle-carried intelligent terminal system, for the technical field of GPS (global positioning system) positioning. The system comprises a wireless positioning module for locating the current position of a vehicle to obtain current position data; a vehicle condition data acquisition module for acquiring the running state of the vehicle in a real-time manner via a CAN (controller area network) bus; a voice identification module for receiving and identifying a voice command of a host; a video monitoring module for performing human face identification on a driver and / or identification on a safety airbag; an automatic alarming module for giving a corresponding alarm according to the human face identification result, the safety airbag identification result and / or the vehicle internal running state; and a 3G data transmission module for transmitting the data acquired by the video monitoring module and / or the data for alarming sent out by the automatic alarming module. The invention adopts GPS technology combined with information technology such as CAN bus technology and computer network technology, so that the system function is complete, operation is convenient and practicability is high.
Owner:SHANGHAI QIHUI TELECOM TECH
Network contact list system achieving version management and authority management
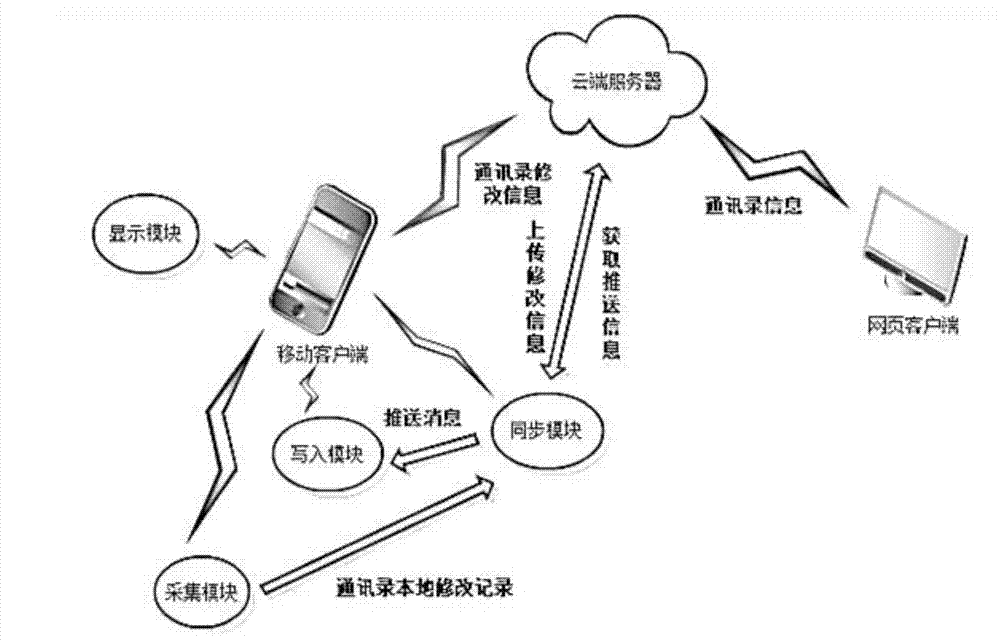
InactiveCN103095829AModify at willFreedom to control accessData switching networksTerminal serverComputer network technology
The invention discloses a network contact list system achieving version management and authority management,and belongs to the technical field of computer networks. The network contact list system achieving version management and authority management comprises a mobile client, a web client and a cloud terminal server. The mobile client is connected with the cloud terminal server. User contact list information is transmitted by the mobile client. The web client is connected with the cloud terminal server. The user contact list information is transmitted by the web client. User contact list revising information transmitted by a client terminal is received by the cloud terminal server and the user contact list revising information is written to a data base and is carried through a version controlling management. Change of user personal information is pushed to each relevant friend of the user according to friend-permission setting by the cloud terminal server and is output to a synchronization module of the mobile client. By means of the network contact list system achieving version management and authority management, defects that the prior network contact list lacks a version management mechanism and the authority management can not be carried out are overcome. Contact person information can be carried through the version controlling management and the authority management. Contact list update can be pushed to members of the specified group.
Owner:SHANGHAI JIAO TONG UNIV
Distributed paralled IP route searching method based on TCAM
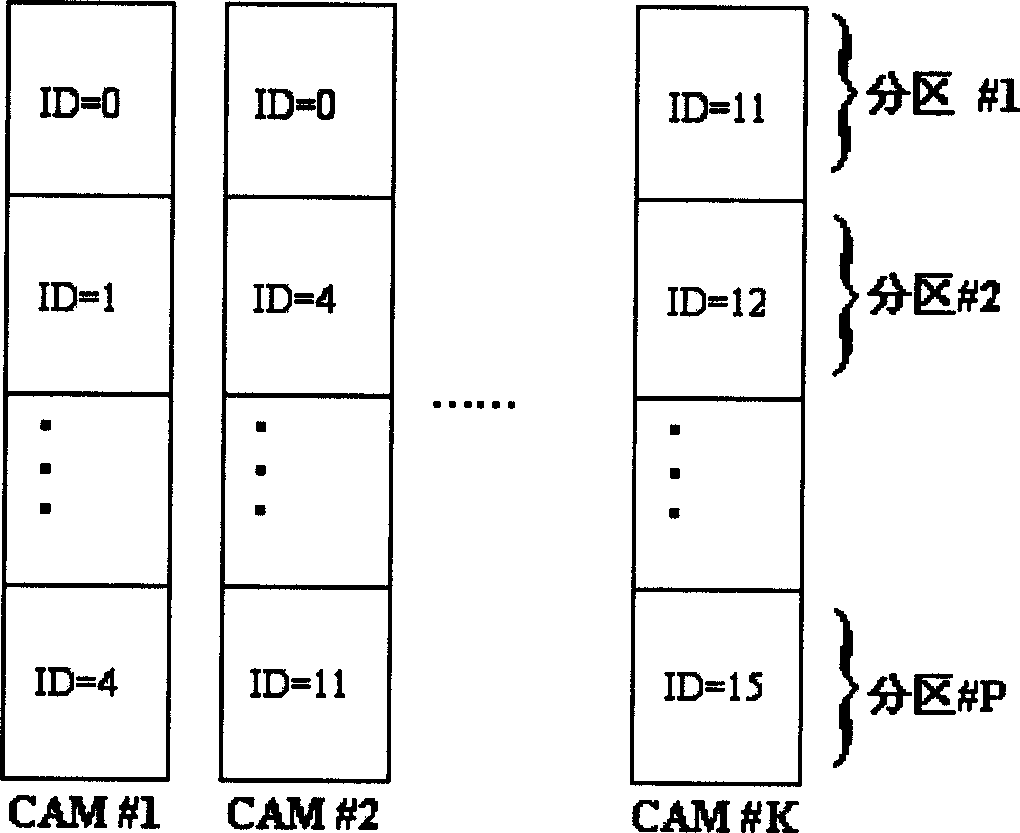
A distributed parallel IP route seek method based on TCAM characterizes in taking 10-13 bits of IP address or route prefix as its ID then to divide the prefix into 16 groups with the same ID to be separately stored in different regions in multiple TCAM chips so as to make it possible to seek in multiple chips at the same time. It allows the accessed prefix groups high frequency to exercise redundancy memory among TCAM chips to equalize the seek flow among TCAM.
Owner:TSINGHUA UNIV
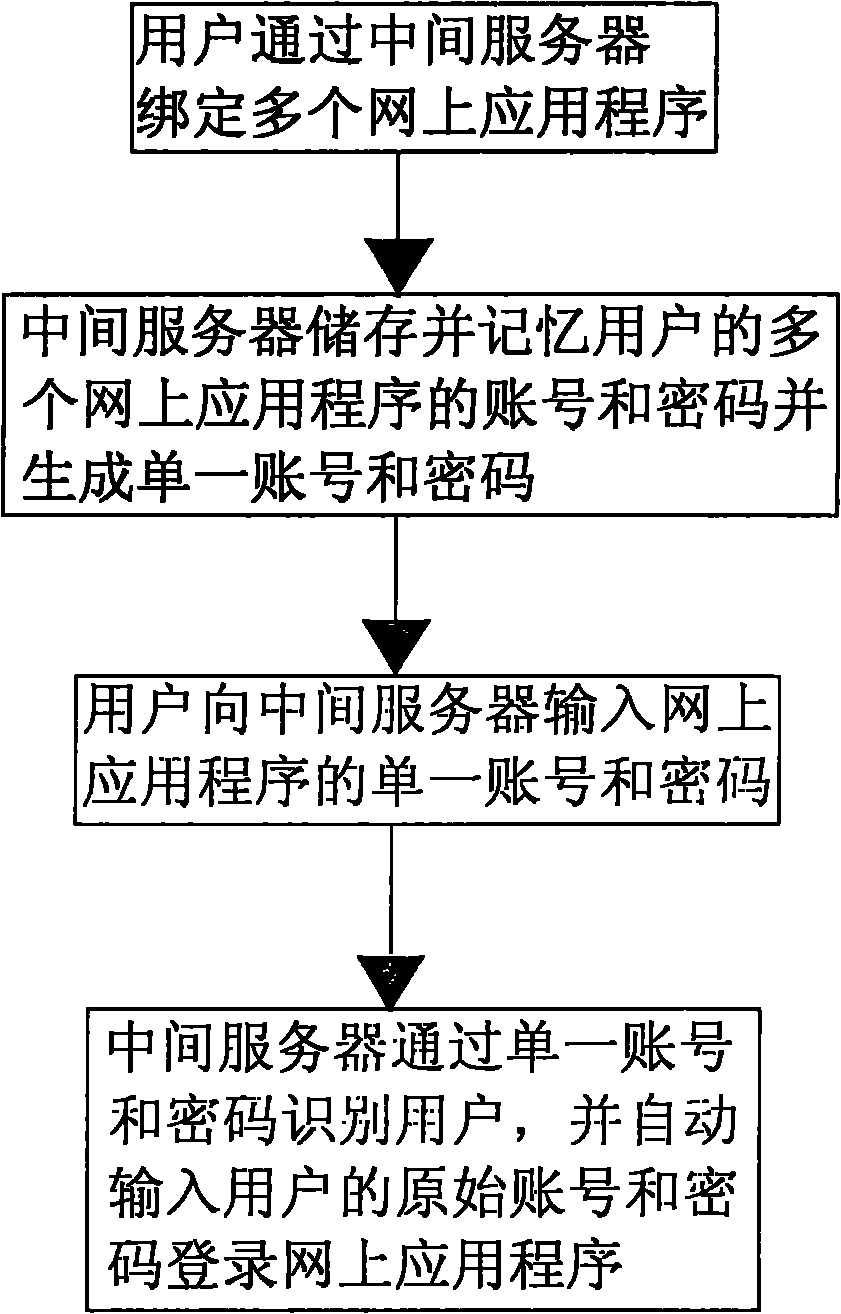
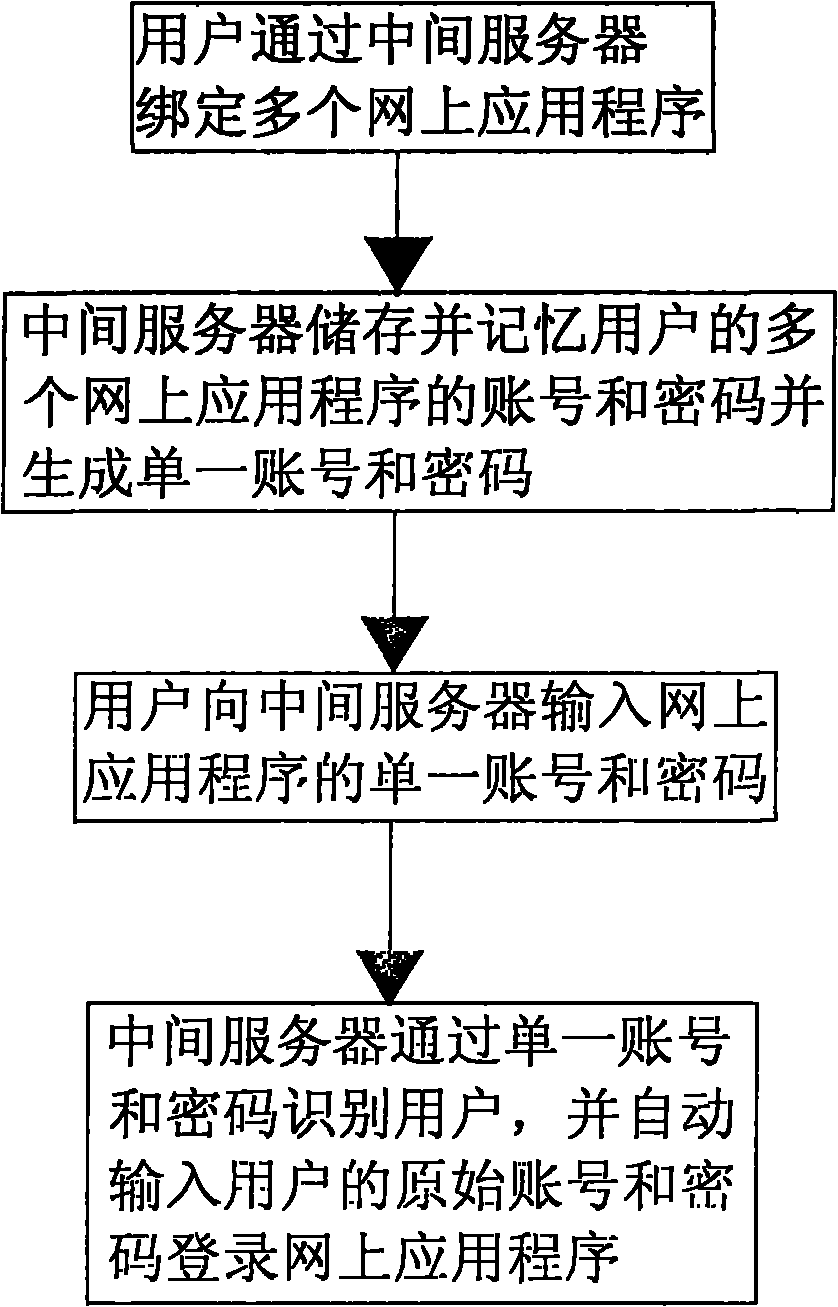
Method for logging in multiple web application programs with one account
The invention discloses a method for logging in multiple web application programs with one account, relating to the field of computer network technology. The method involves an intermediate server, accounts of an individual user for multiple web application programs, and corresponding login passwords of all the accounts of the web application programs. The login method comprises the following steps of: binding the multiple web application programs through the intermediate server, and memorizing and storing the accounts of the individual user for the multiple web application programs and the login password corresponding to the account of each web application program by the intermediate server; generating a single account and a corresponding password for the accounts of the individual user for the multiple web application programs and the login password corresponding to the account of each web application program by the intermediate server; and when the user logs in the web application programs once again, logging-in all the web application programs with the single account and the corresponding password, generated by the intermediate computer. The method has the advantages of avoiding the trouble in remembering too many login accounts and passwords.
Owner:深圳市闪电通讯技术有限公司
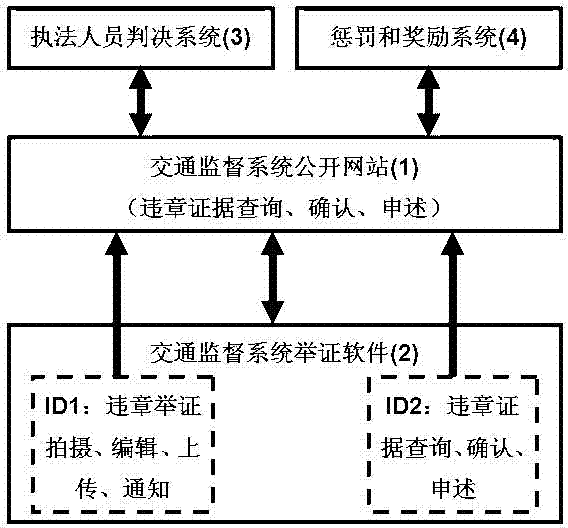
High-efficiency and low-cost traffic violation monitoring system and method
InactiveCN104778831AImprove complianceWide coverageRoad vehicles traffic controlComputer network technologyMonitoring system
The invention discloses a high-efficiency and low-cost traffic violation monitoring system and method and mainly solves the problems of high mounting and maintaining costs and small monitoring coverage range of monitoring systems such as an electronic eye in the prior art. By applying a modern computer network technology, each car owner can utilize intelligent equipment such as a mobile phone and an automobile data recorder to prove and report seen traffic offences of others, and the system automatically informs a party of confirming violation evidences, and automatically punishes the people violating traffic rules and gives awards to people putting to the proof after the party confirms the violation evidences. Because proofing is self-confirmed, participation of people does not exit basically in the whole process, and in combination with zero-cost replicability of software, the new cost cannot be increased with the increase of the people for monitoring and proofing, and the high-efficiency and low-cost traffic violation monitoring system can be largely replicated and popularized after being deployed at a time. Therefore, through giving awards to the people for putting to the proof, all people are promoted and encouraged to particulate in monitoring, the monitoring coverage rate of 100 percent can be realized at the low cost, and finally the purpose of promoting all people to consciously observe traffic regulations is achieved.
Owner:刘莎
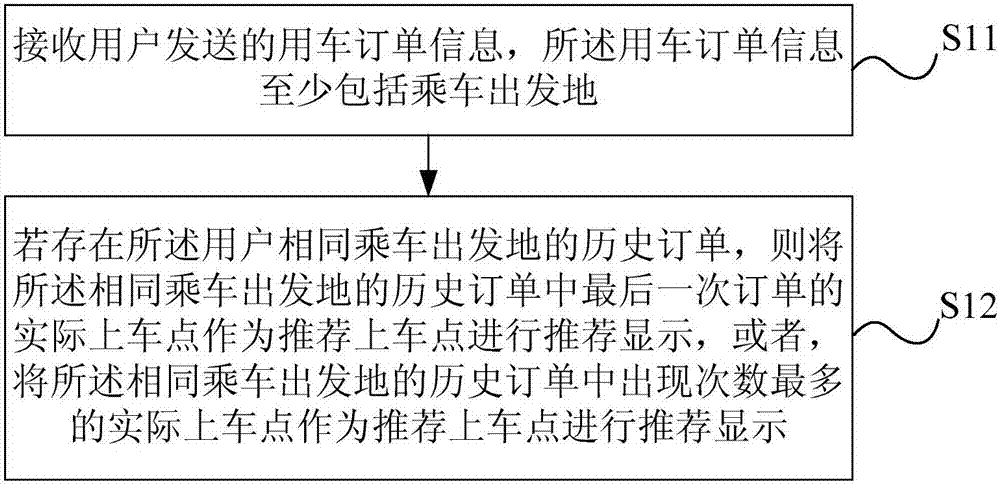
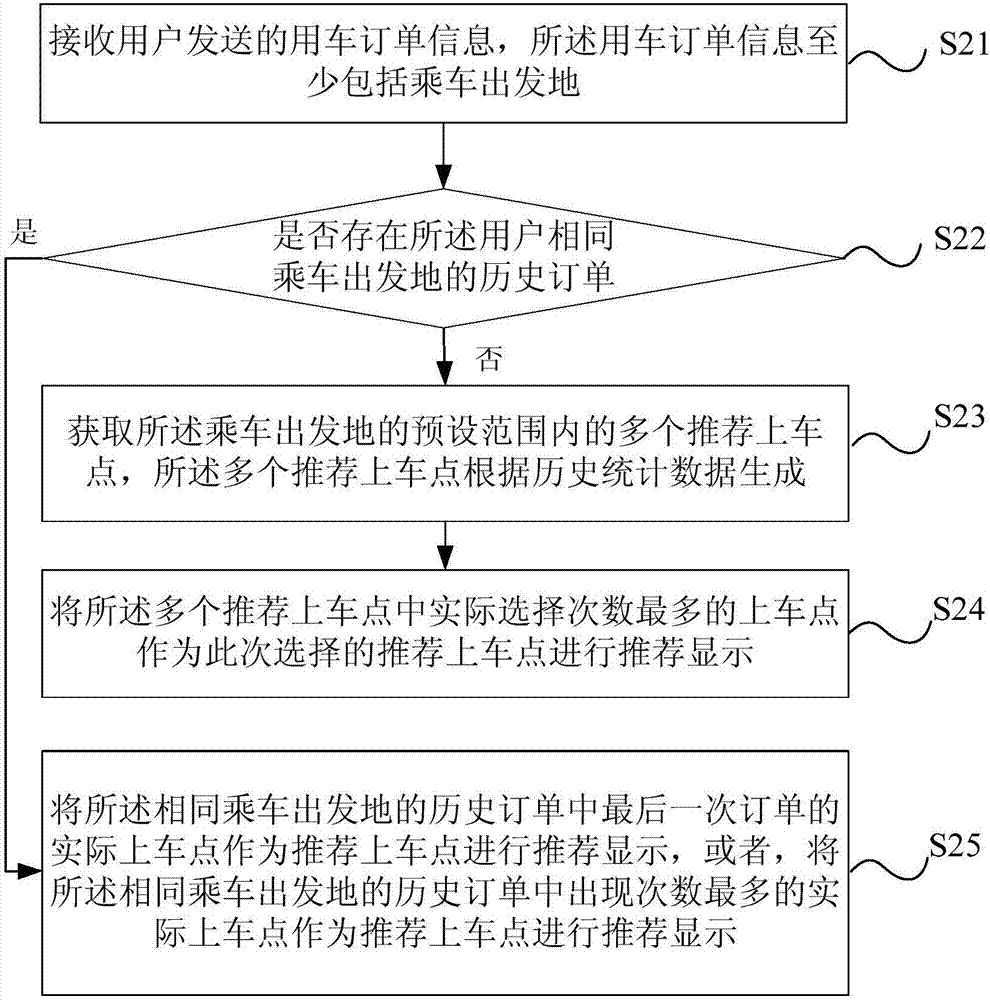
Boarding point recommendation processing method and system thereof
ActiveCN107492063AMeet individual needsImprove experienceTransportation facility accessLocation information based servicePersonalizationComputer network technology
The invention discloses a boarding point recommendation processing method and a system thereof and relates to the computer network technology field. The method comprises the following steps of receiving vehicle order information sent by a user, wherein the vehicle order information at least includes a place of departure; and if historical orders which include the same place of departure exist, taking an actual boarding point of last one of the historical orders of the same place of departure as a recommended boarding point and carrying out recommending and displaying, or taking the actual boarding point having a highest number of occurrence in the historical orders of the same place of departure as the recommended boarding point and carrying out recommending and displaying. In the technical scheme, according to the actual boarding point of last one of the historical orders of the same place of departure or the actual boarding point having the highest number of occurrence, recommendation of the boarding point is performed so that boarding point recommending and displaying based on an actual demand of the user are realized; and a personalized demand of the user is satisfied and a user experience is improved.
Owner:BEIJING DIDI INFINITY TECH & DEV
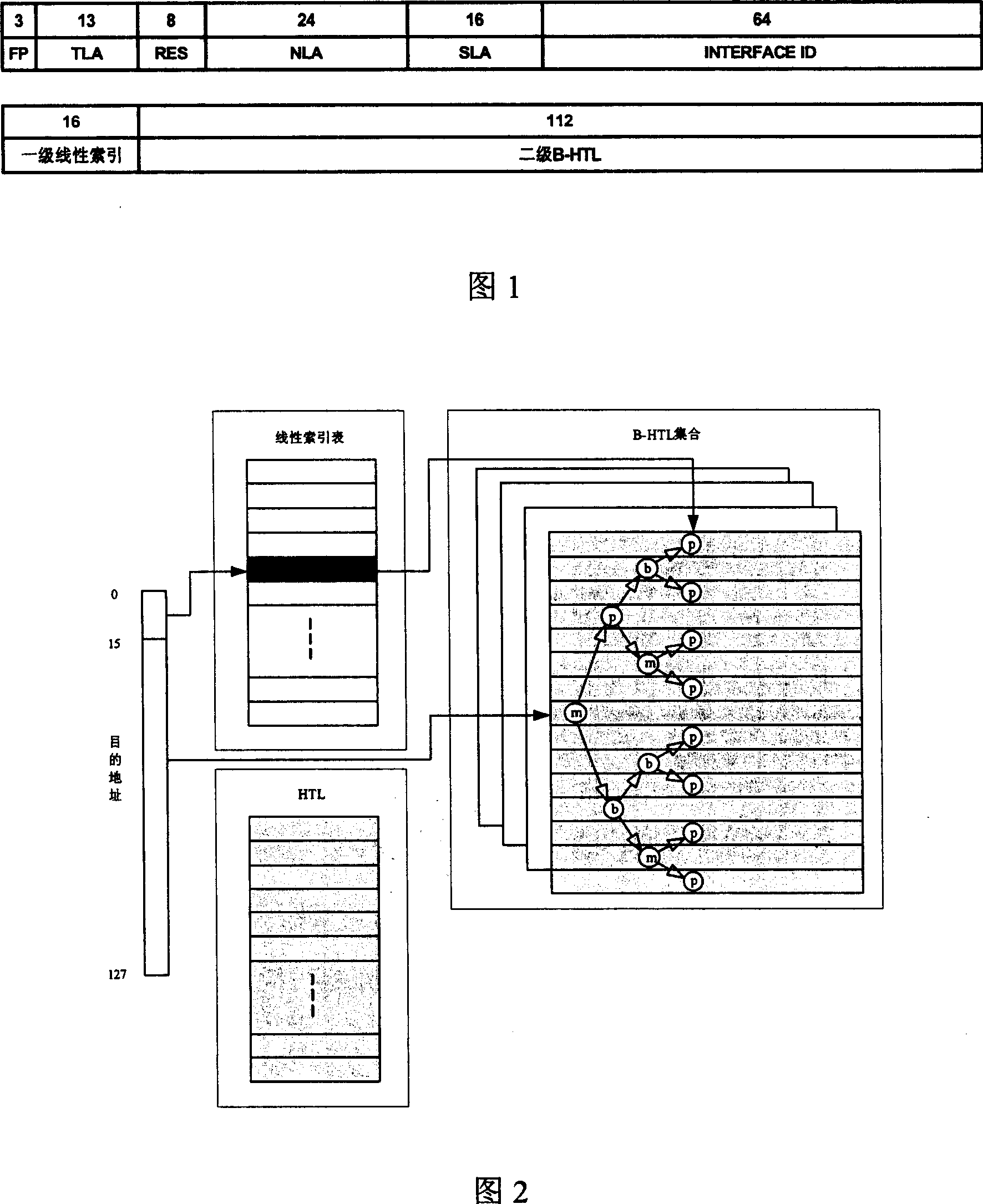
A method to quickly search and update IPv6 routing list
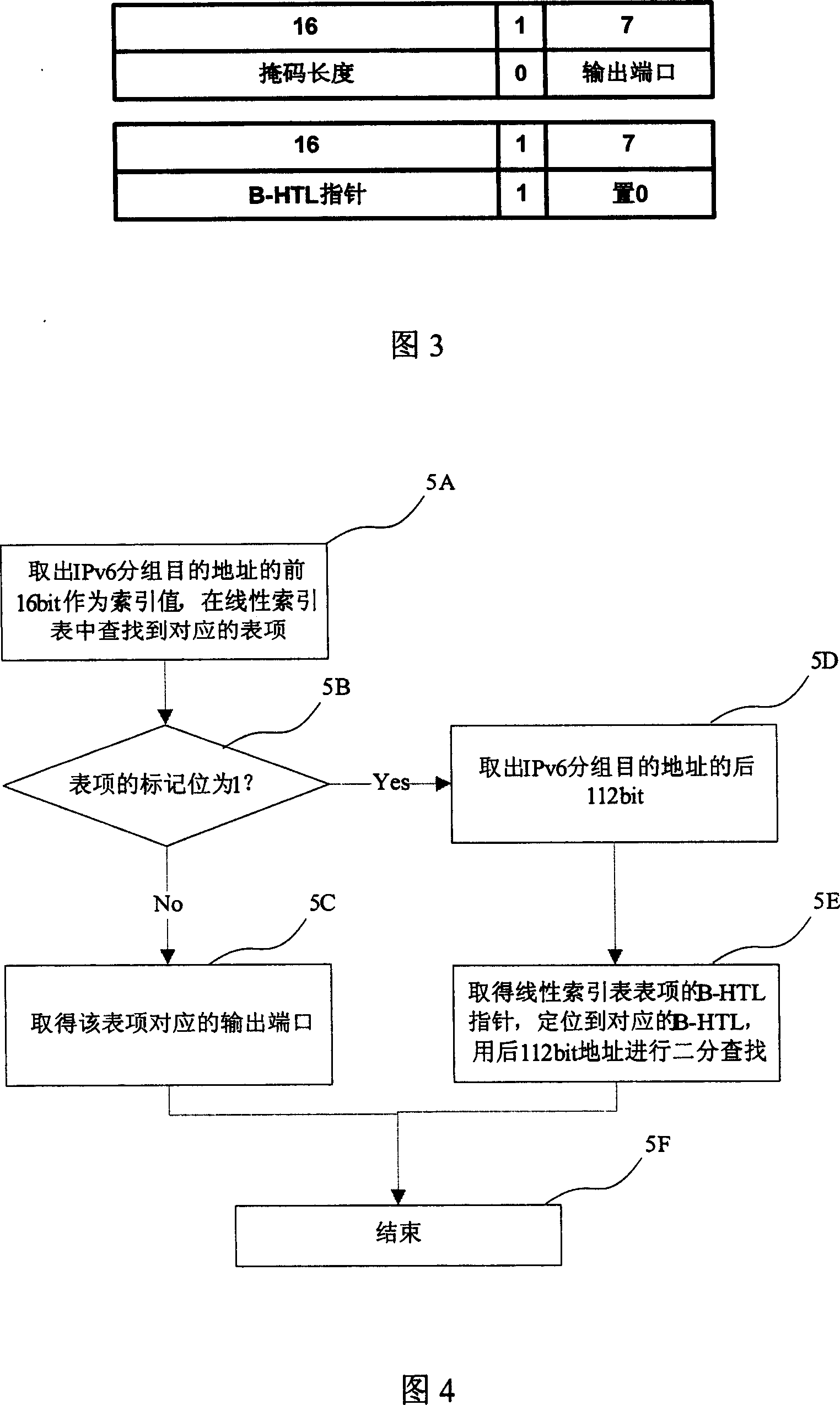
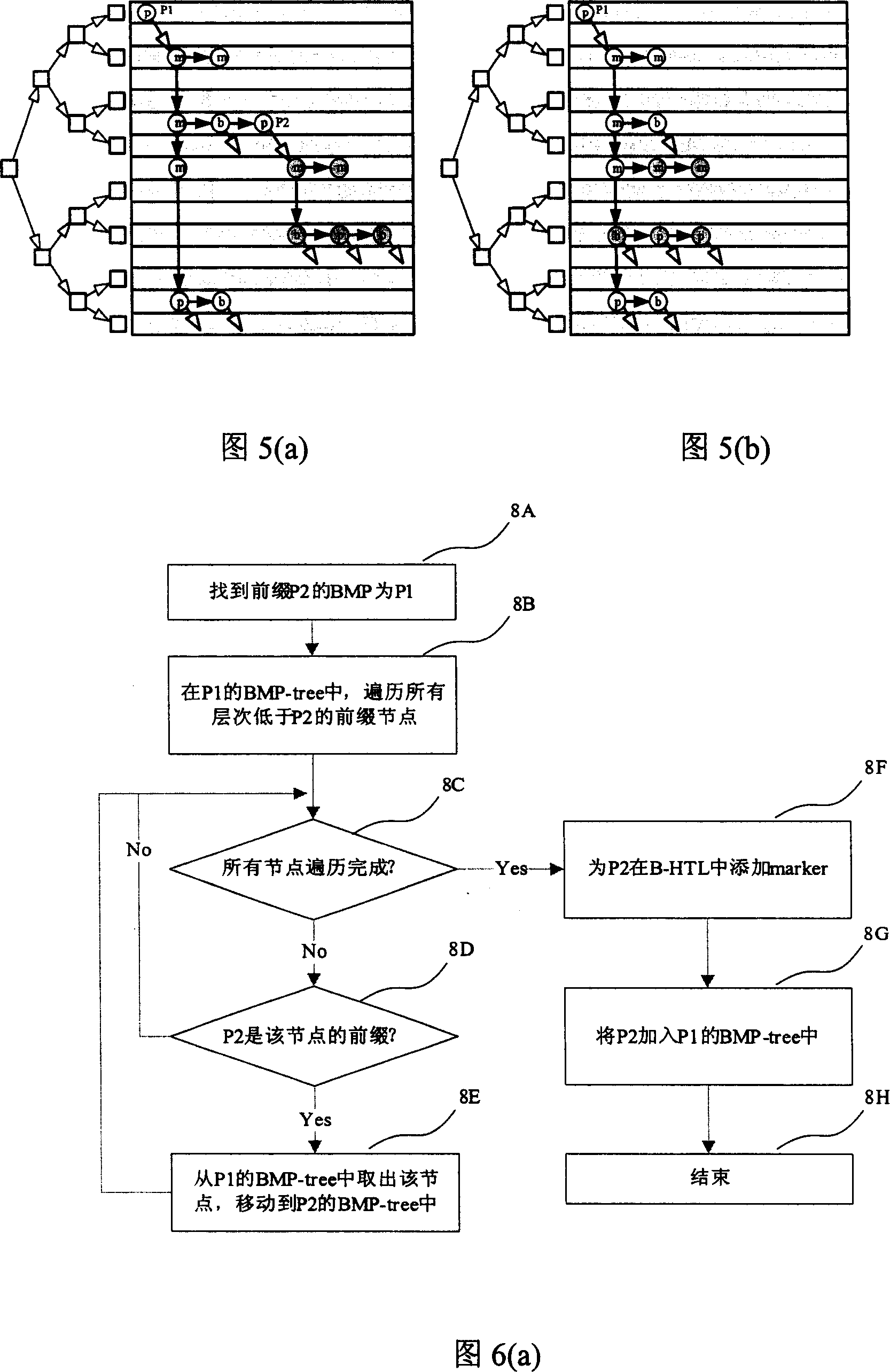
InactiveCN1964311AImprove update processImprove efficiencyData switching networksSpecial data processing applicationsRouting tableComputer network technology
The related fast lookup and update method for IPv6 route table comprises: using a first-linear index table and a second hash table issued by binary search tree for two-stage lookup; using BMP-tree to recombine prefix relation in data structure, and improving update efficiency. Compared with traditional method or other methods, this invention is more proper to the IPv6 network.
Owner:烟台惠通网络技术有限公司
Method for queue buffer management in linked list-based switched network
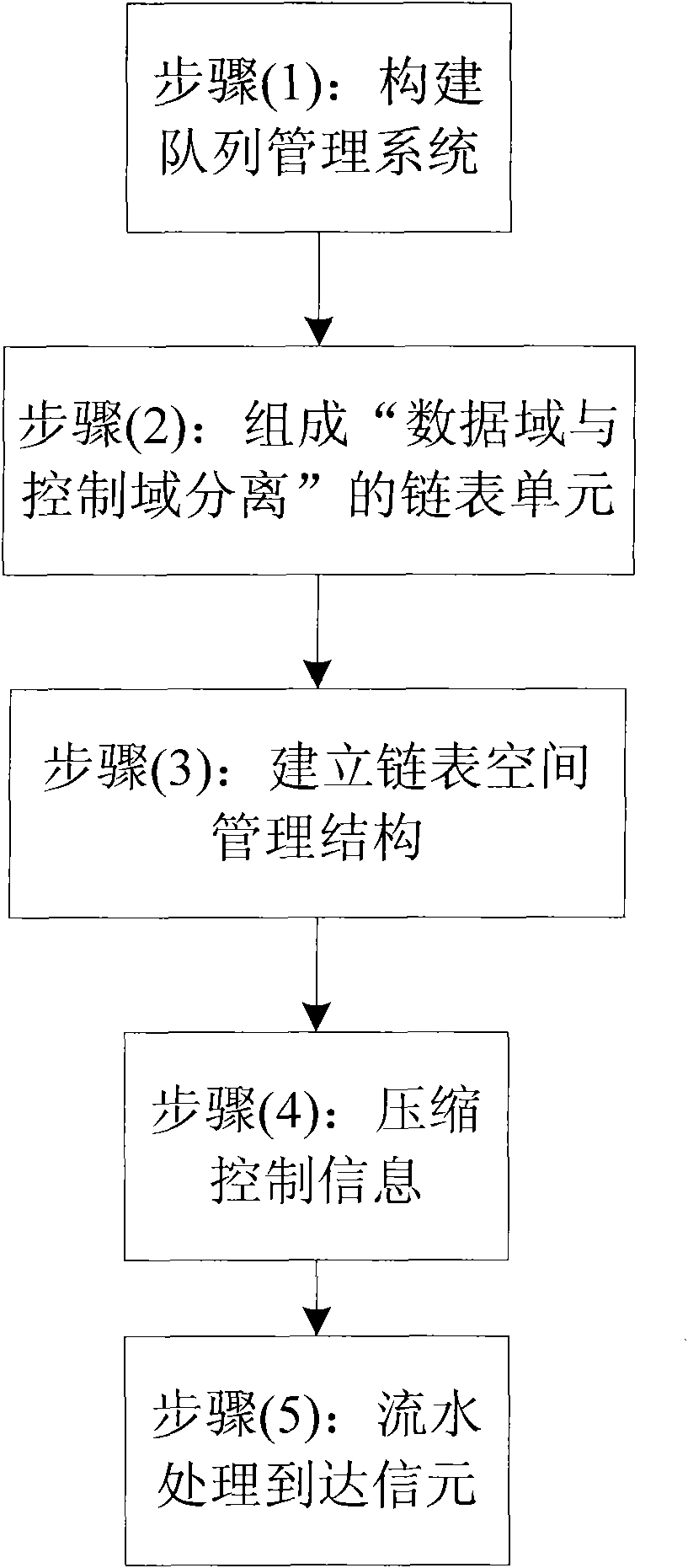
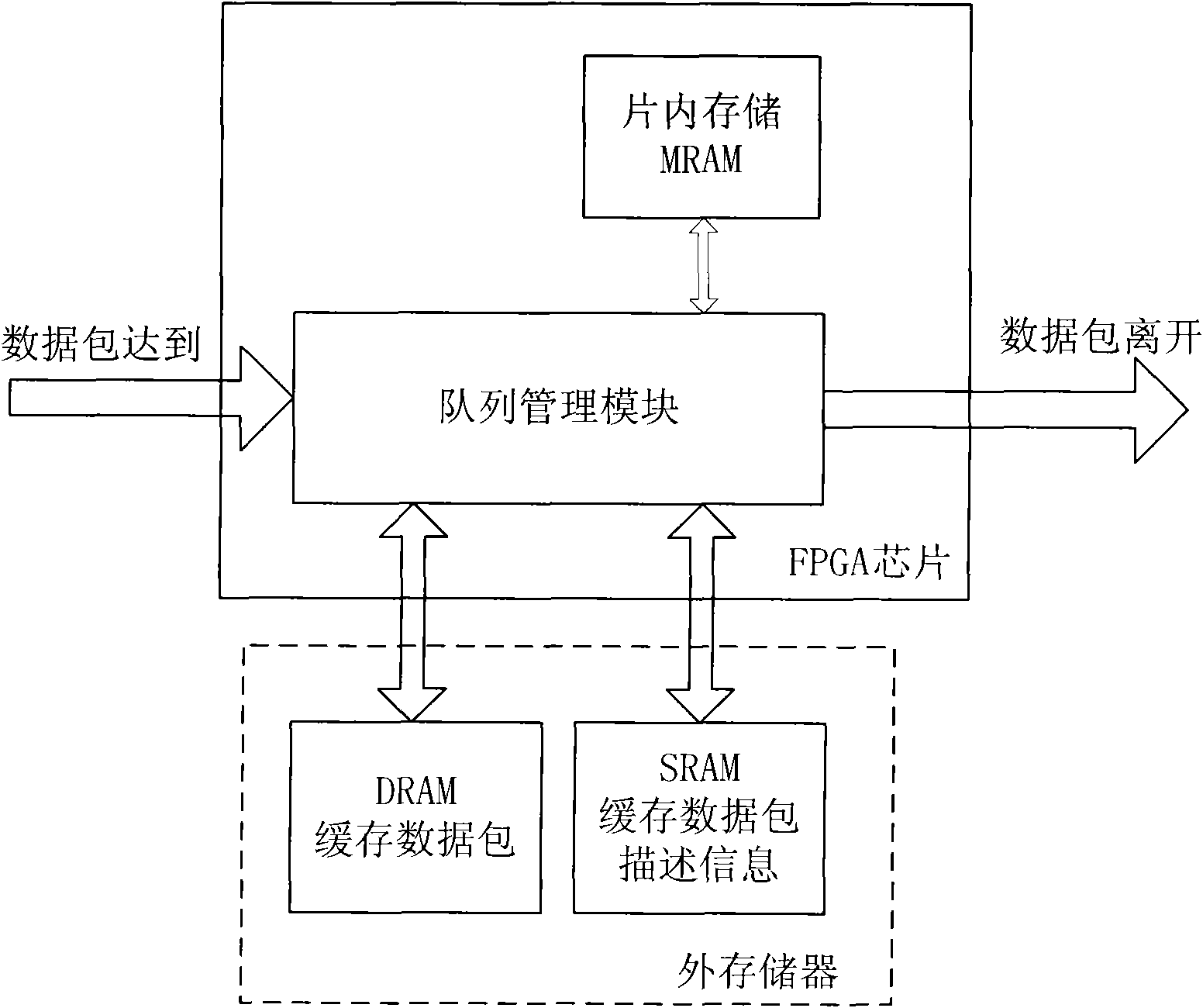
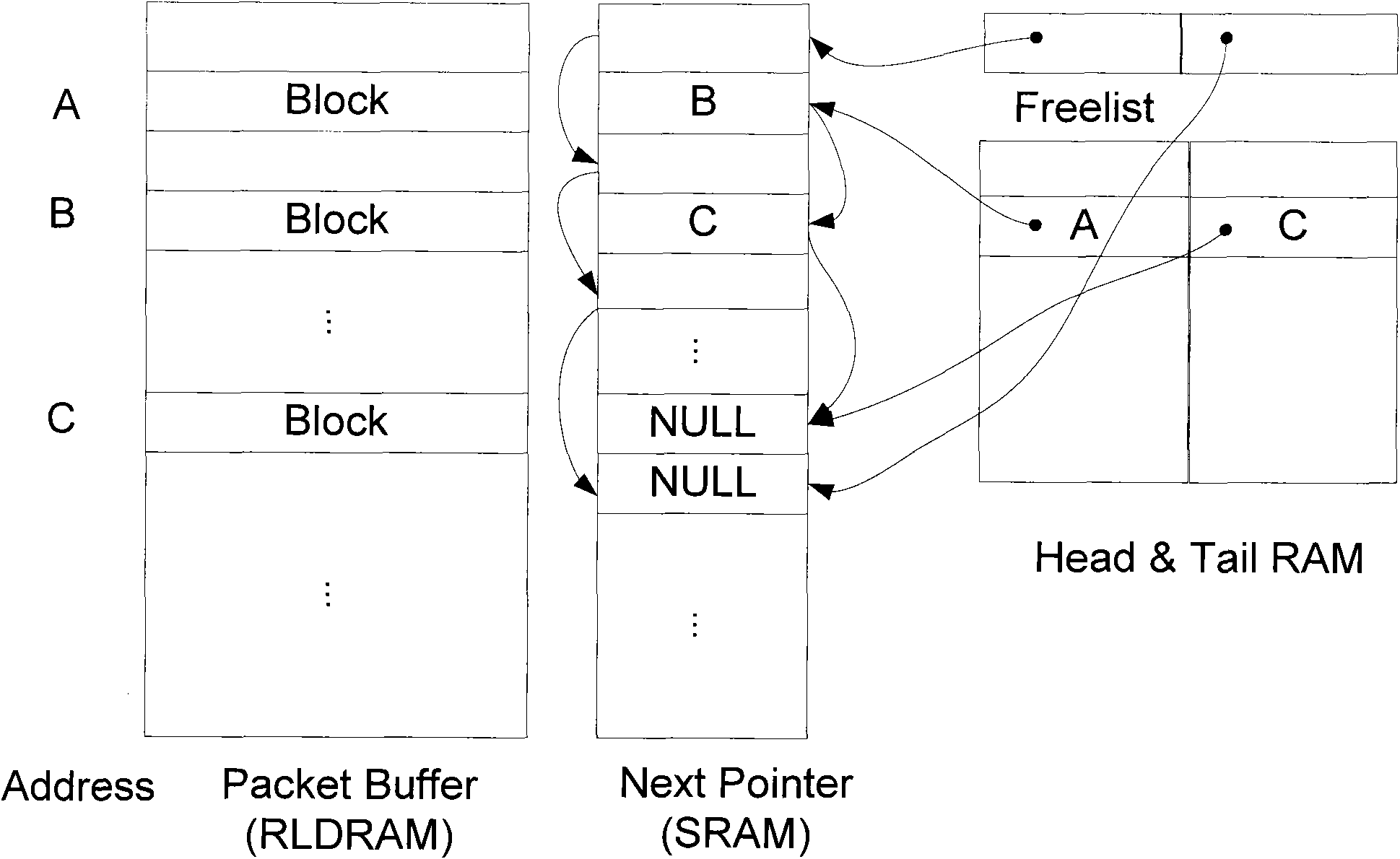
InactiveCN101594299AData switching networksSpecial data processing applicationsExchange networkComputer network technology
The invention relates to a method for queue buffer management in a linked list-based switched network, which belongs to the technical field of computer networks. The method is characterized in that: DRAM and SRAM are used together to build a linked list unit structure with separate data and control, and external memory space is managed in a lined list mode to realize a multi-queue structure; according to the characteristic that queue operation is carried out in data packet unit, control information in a storage linked list unit is compacted to improve the storage efficiency of the linked list unit; and the concurrent processing of a plurality of linked list units is realized, adverse effects of storage delay are prevented, and linked list operation efficiency is improved due to pipelining design. The method has the characteristics of high throughput rate and excellent expansibility.
Owner:TSINGHUA UNIV
Link prediction method based on network structure and text information
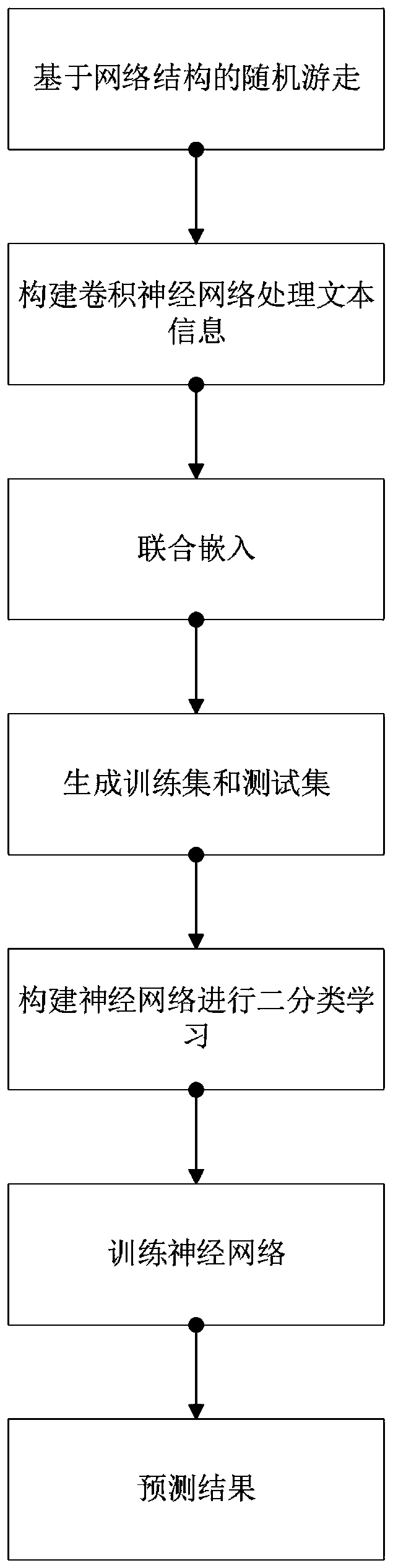
ActiveCN111368074AAvoid missingExcellent predictive experimentData processing applicationsNeural architecturesInformation embeddingComputer network technology
The invention relates to the technical field of computer networks, and discloses a link prediction method based on a network structure and text information, and the method comprises the steps: S1, obtaining a structure embedding vector of a node based on a random walk node in the network structure; s2, constructing a convolutional neural network to process the text information of the nodes to obtain text information embedding vectors of the nodes; s3, performing joint embedding on the structure embedding vector and the text information embedding vector of the node; s4, generating a training set and a test set; s5, constructing a neural network for binary classification learning; s6, training a neural network; and S7, result prediction: the link prediction method based on the network structure and the text information is simple in calculation process, small in error and high in prediction accuracy.
Owner:XIDIAN UNIV
Method for achieving hyper text transport protocol (http) service monitoring through embedding monitoring code
InactiveCN103067230AReduce investmentGuaranteed service qualityData switching networksProcessing InstructionFault tolerance
The invention relates to a method for achieving a hyper text transport protocol (http) service monitoring through embedding a monitoring code and belongs to the technical field of computer networks. By means of following steps, a monitoring to a monitored terminal http service by a monitoring terminal is achieved. The steps comprises a first step of embedding a dynamic page into a monitored terminal subscription address, the dynamic page is used for issuing a corresponding request of monitoring http service needing to be monitored and generating a visiting end value according to the http service response; a second step of starting a dynamic page visiting the subscription address at a fixed time; a third step of generating a corresponding visiting end value according to a returned value after receiving the corresponding request, of the monitoring http service needing to be monitored, issued by the visited dynamic page; a third step of issuing a processing instruction when the visiting end value is abnormal and abnormal times are more than fault tolerance threshold value, otherwise, going back to the second step. Therefor, even through the monitoring terminal is in a unattended-operation state, anomalies of the monitored terminal can be found timely and corresponding measures can be taken to enable the monitored terminal to return to normal, so that service quality is guaranteed, the personnel investment for maintaining and managing is greatly reduced and recovery time of the monitored terminal is shortened.
Owner:JIANGSU TIANZHI INTERCONNECTION TECH CO LTD
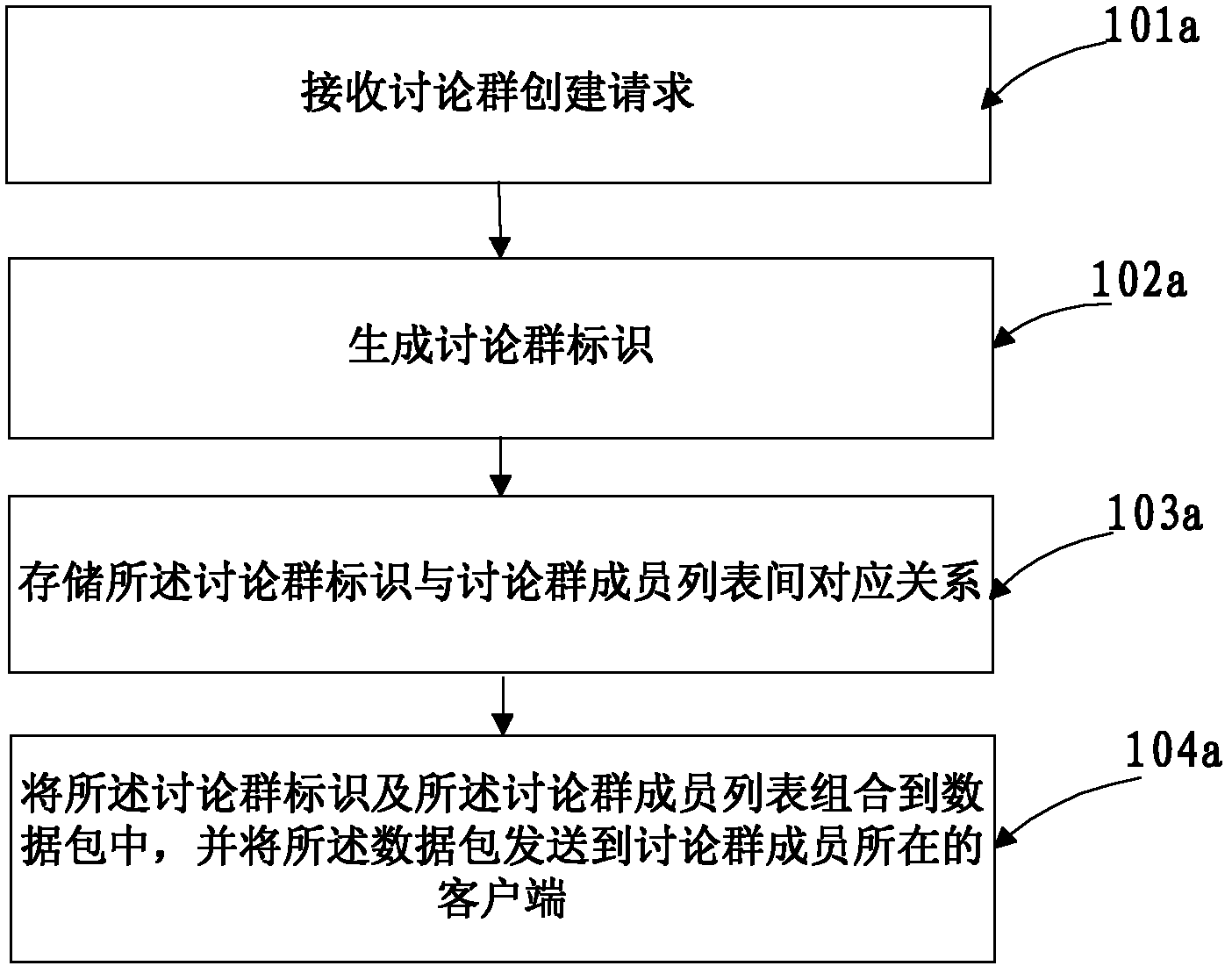
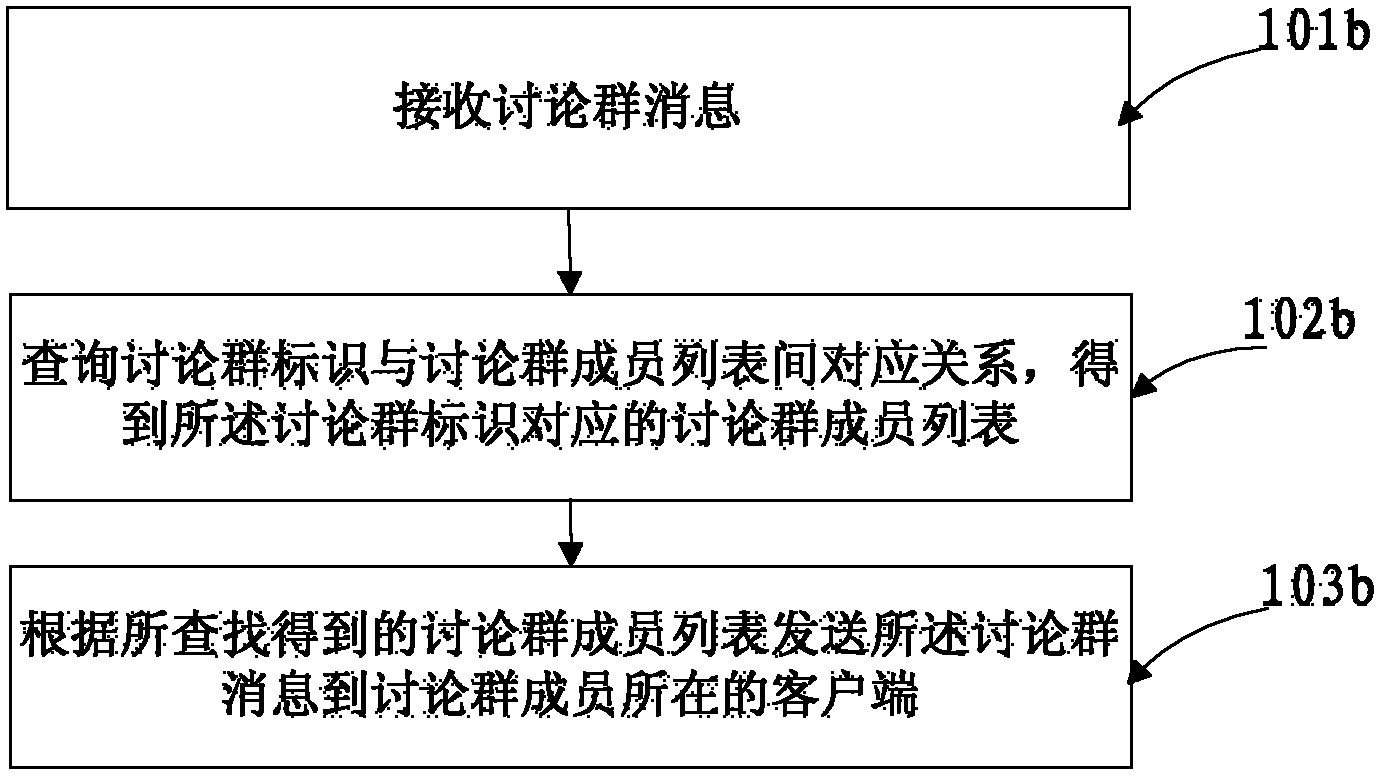
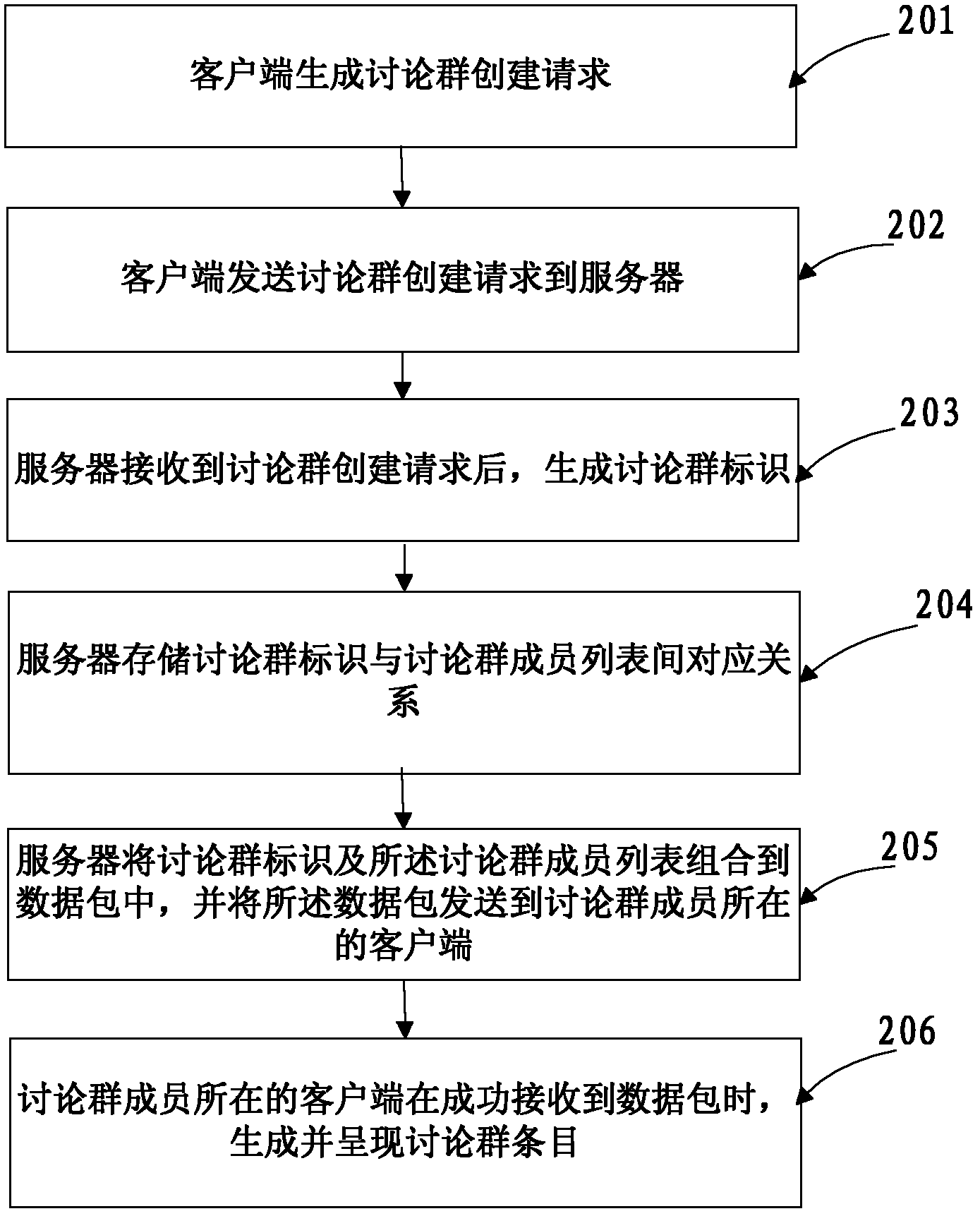
Discussion group creating method, and communication method, server and system based on discussion group
ActiveCN102624650AReduce the number of interactionsImprove efficiencyData switching networksComputer network technologyNetwork packet
The invention discloses a discussion group creating method, and a communication method, a server and a system based on a discussion group, and belongs to the technical field of computer networks. The discussion group creating method includes receiving a discussion group creating request which comprises a member list of the discussion group; generating a logo for the discussion group; storing a corresponding relation between the logo and the member list of the discussion group; and combining the logo and the member list of the discussion group to a data packet, sending the packet to a client of the discussion group members so that the client can generate and present discussion group items after receiving the data packet successfully. According to the discussion group creating method, and the communication method, the server and the system based on the discussion group, the discussion group members can start conversation according to the discussion group items presented by the client, the number of information interaction between the server and the client is reduced, and the discussion group creating efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
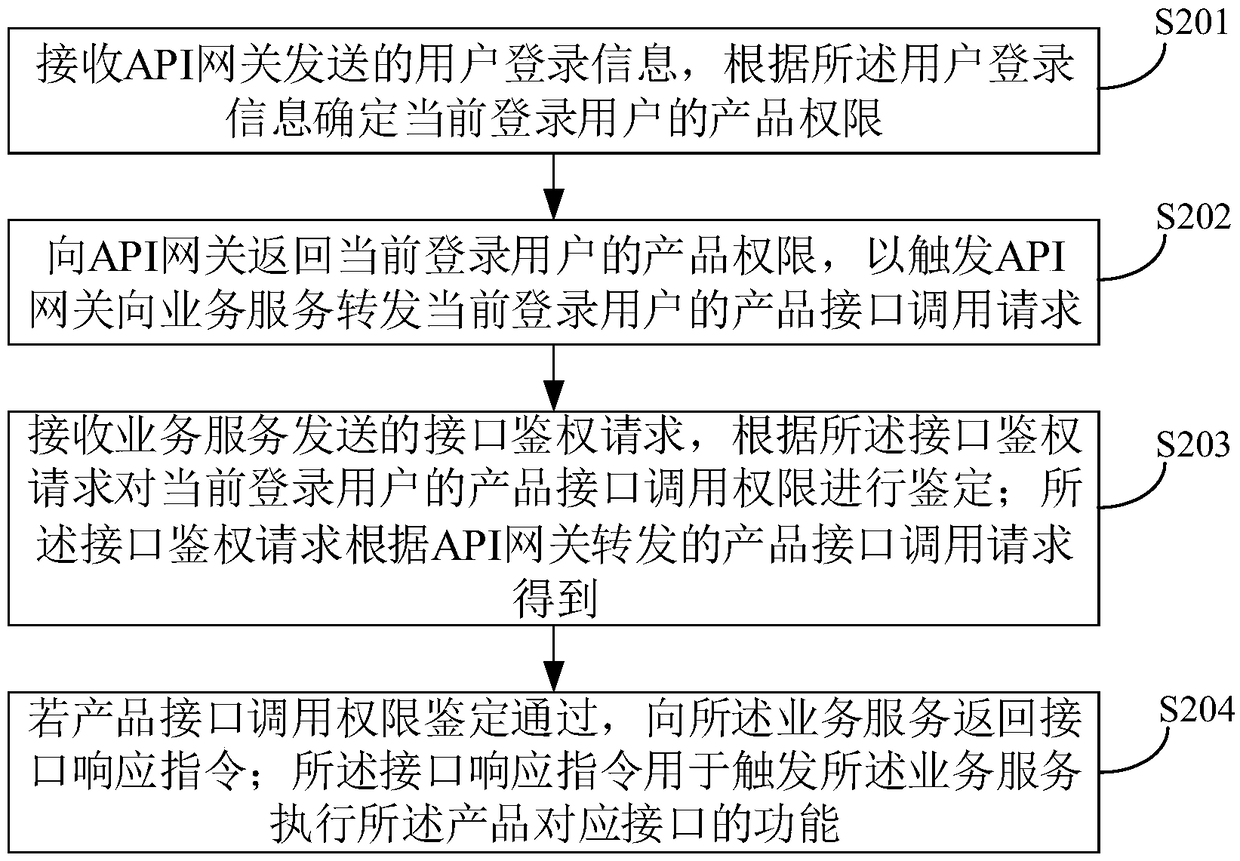
Control method and device for interface calling permission, computer equipment and storage medium
ActiveCN108924125AImprove the efficiency of authority controlTransmissionComputer network technologySoftware engineering
The invention relates to a control method and device for interface calling permission, computer equipment and a storage medium, and belongs to the technical field of a computer network. The method comprises the steps of: receiving user login information sent by an API gateway, and according to the user login information, determining product permission of a current login user; returning the productpermission to the API gateway to trigger the API gateway to forward a product interface calling request to a business service; receiving an interface authentication request sent by the business service, and according to the interface authentication request, carrying out authentication on product interface calling permission of the current login user; and if the product interface calling permission passes the authentication, returning an interface response instruction to the business service so as to trigger the business service to execute a function of an interface corresponding to the product. According to the technical scheme, problems of high complexity and low efficiency of permission control on interface calling of multiple users are solved, and effective permission control can be carried out on interface calling of a plurality of users in tenants.
Owner:招银云创信息技术有限公司
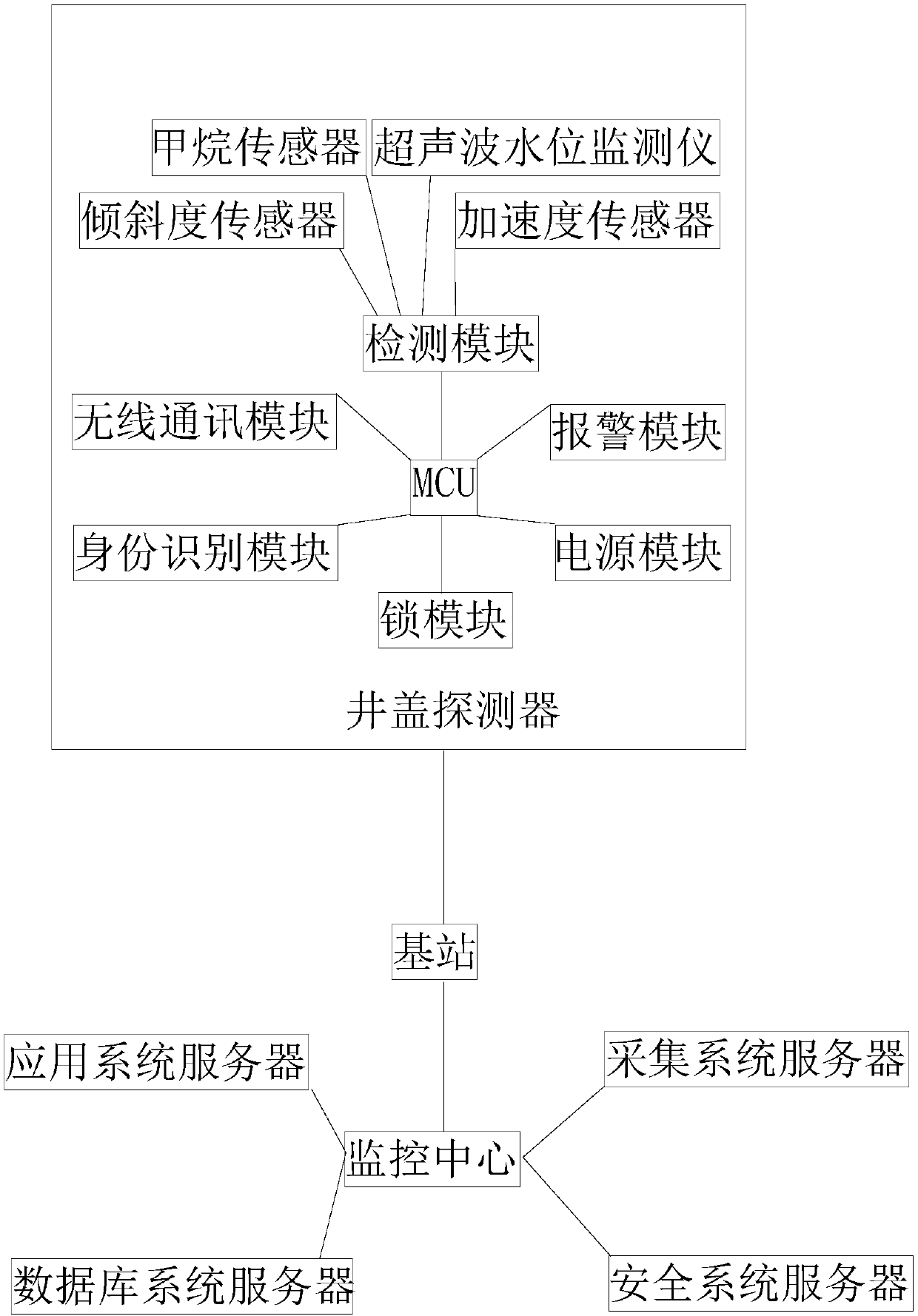
Urban intelligent manhole cover system and management method
InactiveCN107786640ARealize intelligenceNetworkingData processing applicationsMeasurement devicesComputer network technologyCovering system
The invention provides an urban intelligent manhole cover system. The urban intelligent manhole cover system comprises a manhole cover, a manhole cover detector installed on the manhole cover, a basestation and a monitoring center; and the manhole cover detector comprises an MCU and a detection module, a lock module, an alarm module, a power supply module, a wireless communication module and an identity identification module which are connected with the MCU, and the base station and the monitoring center achieve communication through the Ethernet or a CDMA network. The invention provides a management method of the urban intelligent manhole cover system on the basis of the urban intelligent manhole cover system. The urban intelligent manhole cover system and the management method have theadvantages that on the basis of Internet-of-Things technologies such as the sensor technology, the geographic information technology and the computer network technology, the intelligence, networking and spatial visualization of urban manhole cover management are achieved, the manhole cover management mode is innovated, resource sharing is achieved, the urban management efficiency is improved, andthe urban management level is increased.
Owner:上海邦芯物联网科技有限公司
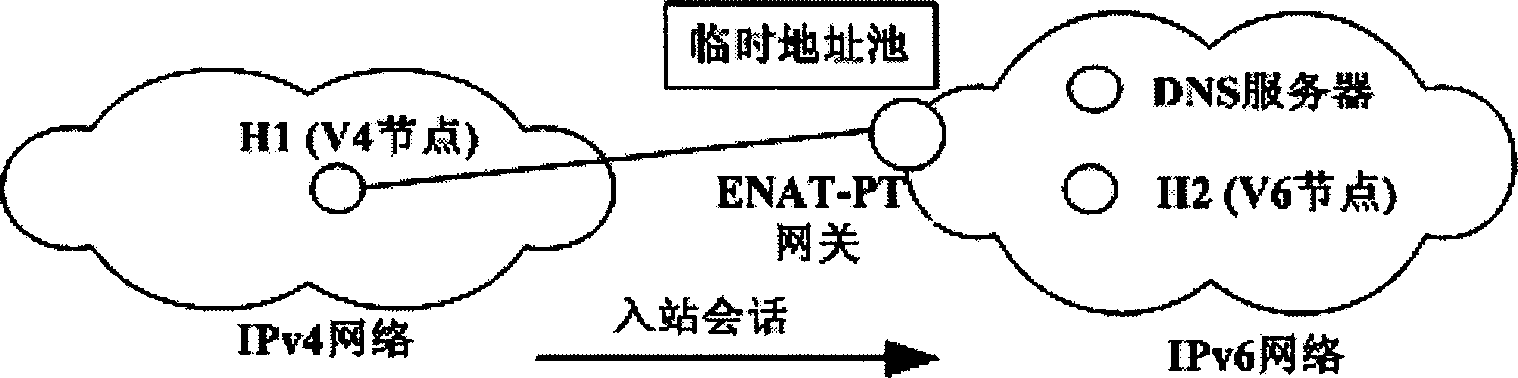
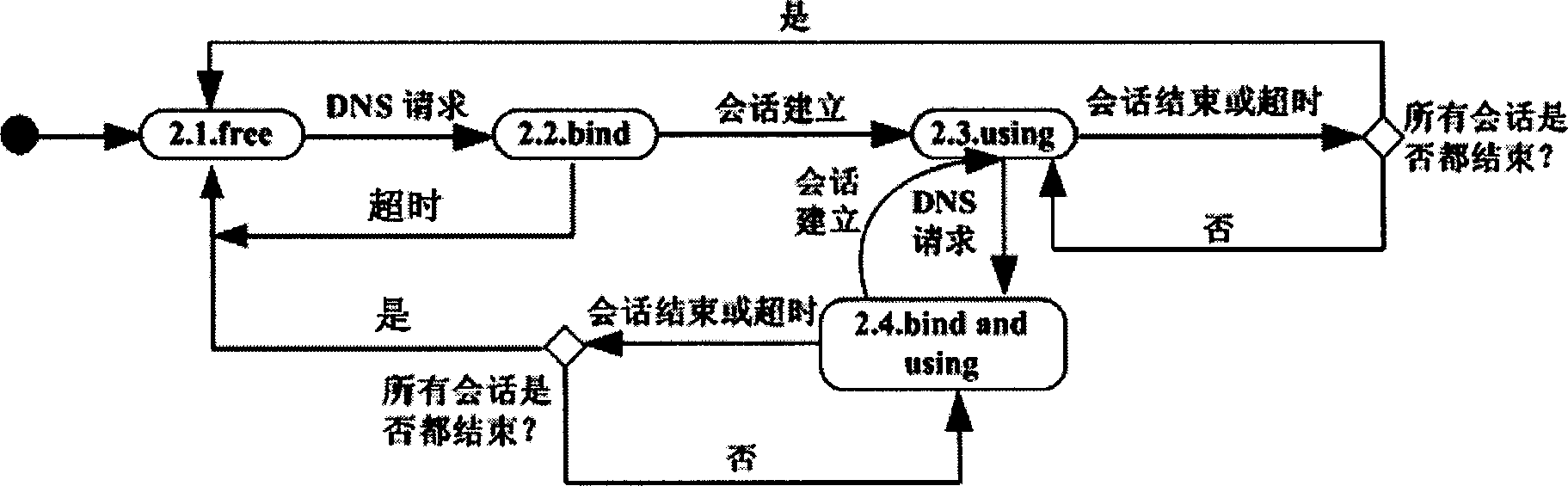
Enhanced NAT-PT protocol scheme
InactiveCN1380773AResolve mutual visitsRealize multiplexingStore-and-forward switching systemsNetwork connectionsComputer network technologyInterconnection
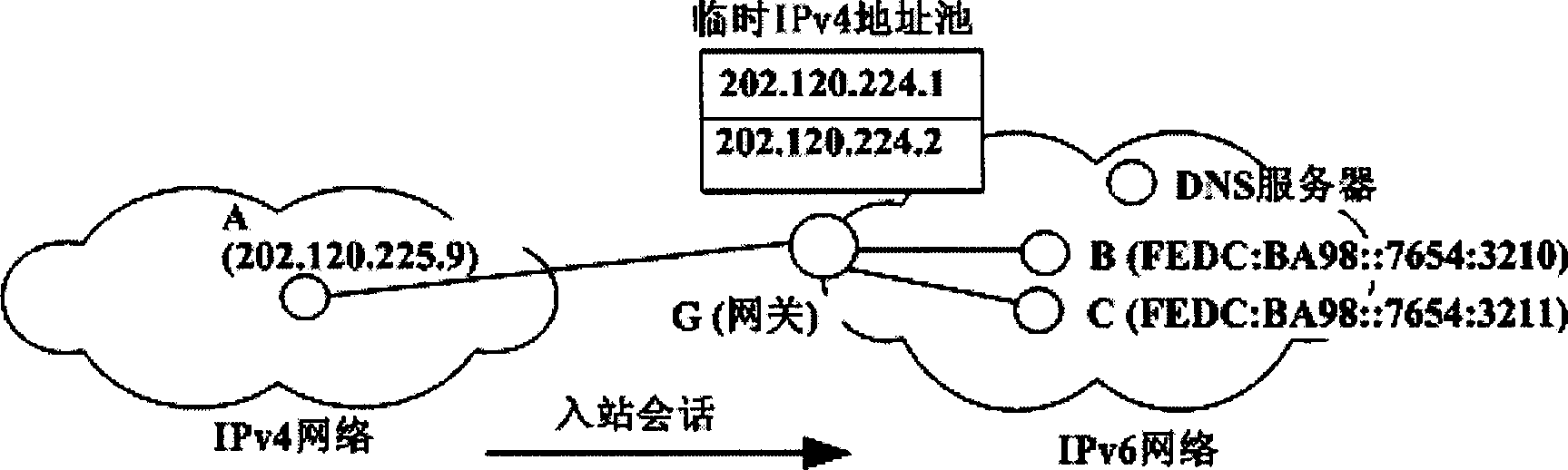
The invention relates to the ENAT-PT protocol, which can access both IPV4 and IPV6 networks, belonging to the area of computer network technique. The ENAT-PT protocol is composed of ENAT, NAPT and PTthree parts. The invented protocol solves the issue of accessing between IPV4 and IPV6 networks, and supports network interconnection by using only a small amount of IPV4 addresses.
Owner:FUDAN UNIV
System and method for redeeming and gifting credits
ActiveCN102800008AIncrease Loyalty StickinessReduce consumptionMarketingInformation processingComputer network technology
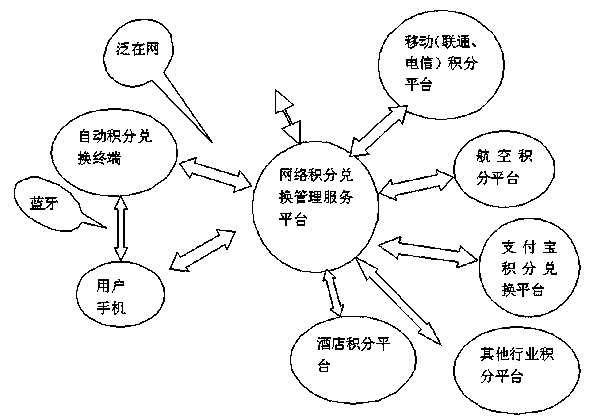
The invention relates to a system and a method for redeeming and gifting credits. The system comprises a cellphone, an automatic credit redeeming machine, a network credit redeeming management service platform and various industry credit platforms. According to the system and the method, an advanced computer network technology and an information processing technology are adopted, and the system and the method for redeeming and gifting credits are conveniently and fast provided for a consumer. By utilizing the system and the method, the consumer enjoys the benefits, the loyalty adhesion degree of the consumer to a service provider is improved, the consumption is promoted, and economic growth is stimulated. The system and the method are a novel technology applying the information technology and serving the general public.
Owner:HUNAN KIMMA INTELLIGENT EQUIP MFR
Integrated Internet of things application system for prison
InactiveCN102867236AImprove the ability to deal with emergenciesQuick treatmentNetwork topologiesResourcesInformation transmissionComputer network technology
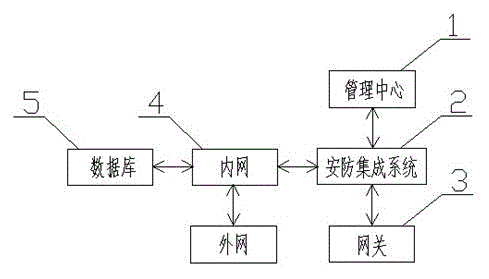
The invention belongs to the technical field of wireless communication, and relates to an Internet of things system, in particular to an integrated Internet of things application system for a prison. The system is also applied to supervision places such as a detention house, reeducation-through-labor office and a drug rehabilitation center. The system comprises a management center, an integrated security system, a gateway, an intranet and a database, wherein the database is connected with the intranet to store information collected by the integrated security system; and the integrated security system performs information transmission with the management center through the gateway. An Internet of things technology is used for real demands, and comprises integrated application technologies such as a communication technology, a sensing technology, a computer network technology and a radio frequency identification technology, and the actual service needs of the prison are combined to implement a platform-based integrated application solution, and the system has broad application prospect in the technical field of wireless communication.
Owner:都伊林
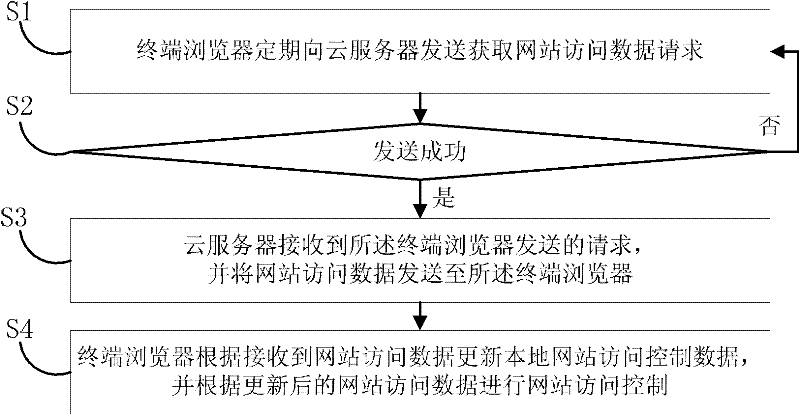
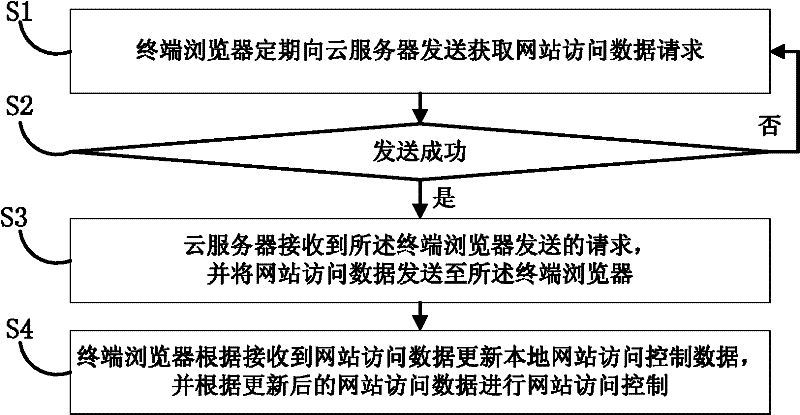
Website access control method
InactiveCN102195971AControl browsing page addressIntegrity guaranteedTransmissionComputer network technologyComputer terminal
The invention discloses a website access control method, relating to the field of computer network technology. The method comprises the steps that: S1, a terminal browser sends a request for acquiring website access data to a cloud server periodically; S2, if the request is successfully sent, the terminal browser waits for the data returned by the cloud server and the next step is continuously carried out, otherwise, the step S1 is carried out again; S3, the cloud server receives the request sent by the terminal browser and sends the website access data to the terminal browser; and S4, the terminal browser updates local website access control data according to the received website access data sent by the server, and performs website access control according to the updated website access data. The method of the invention can realize flexible control for the address of a browsed page of user, webpage access is monitored in real time and processed, top priority is given to the safety protection of webpage browsing of user, besides, system files are not required to be modified, thereby ensuring the integrity of the system files.
Owner:北京思创银联科技股份有限公司
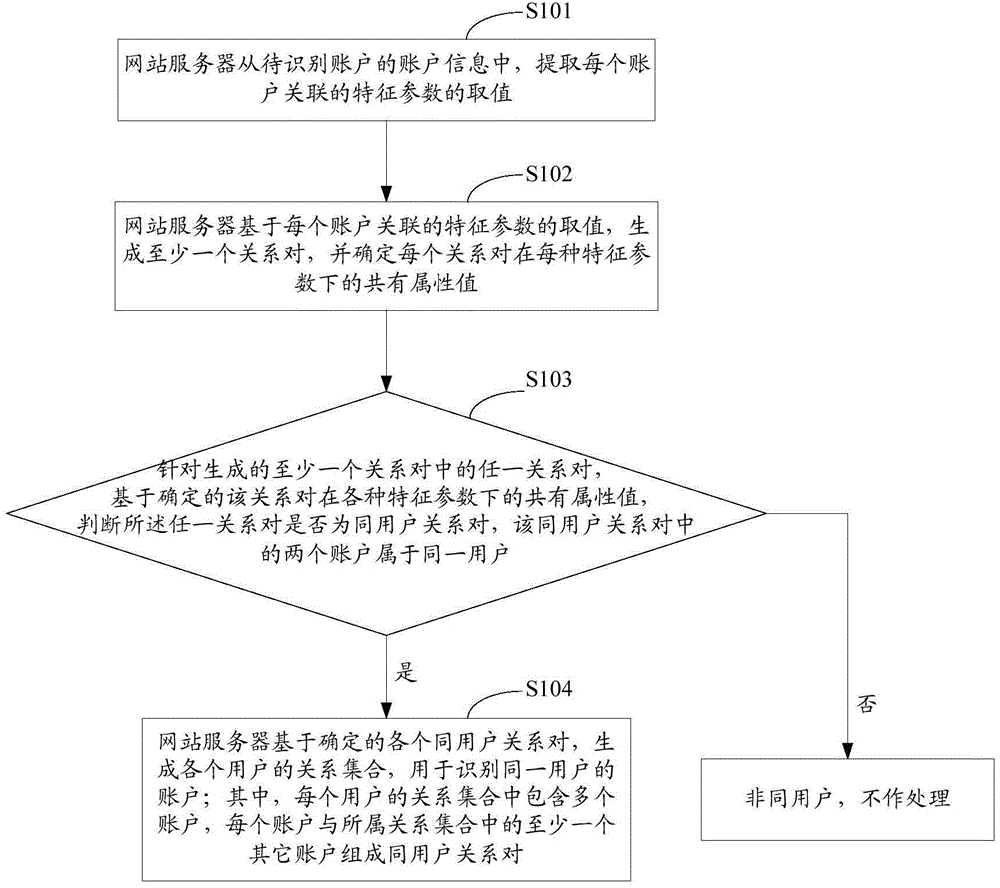
Account identification method and device
ActiveCN106034149AReduce processing duplicationImprove processing efficiencyTransmissionComputer network technologyData mining
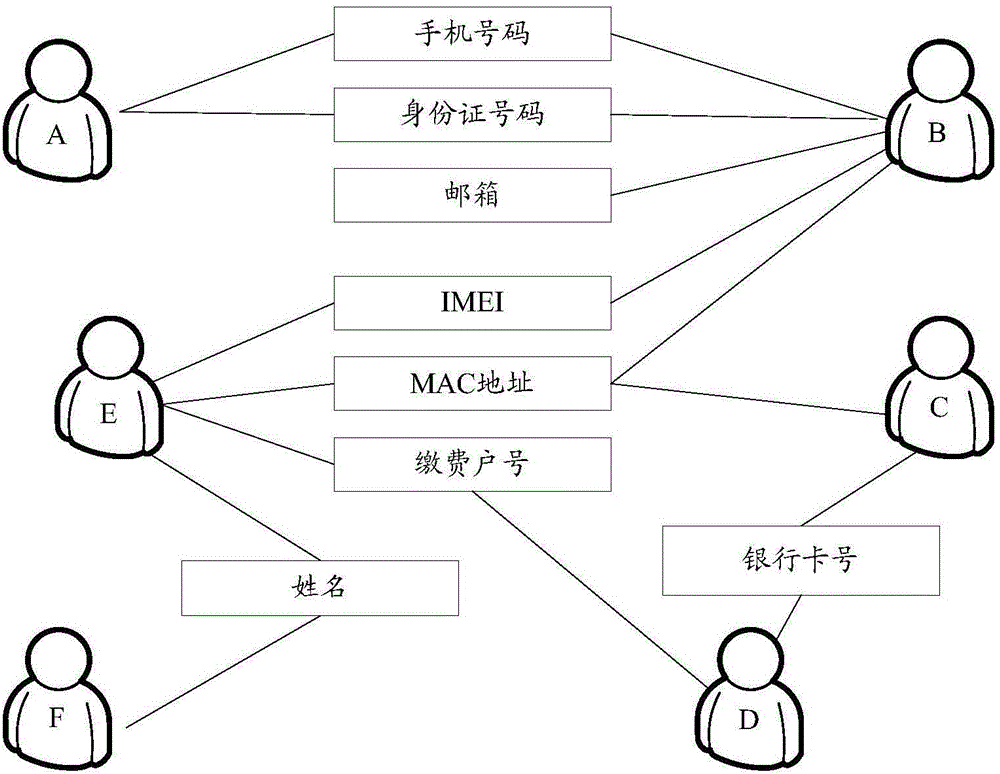
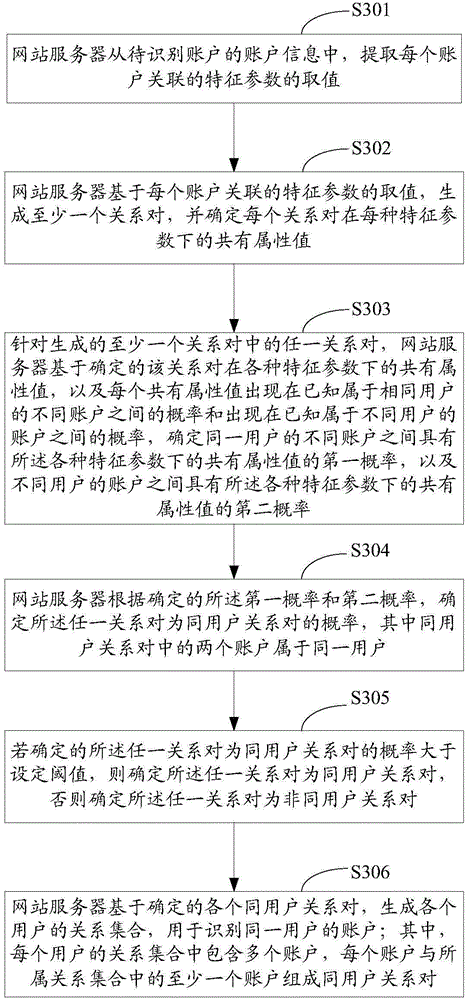
The invention relates to the computer network technology field, and particularly relates to an account identification method and device. The account identification method comprises steps: a website server extracts a value of a characteristic parameter correlated to each account on the basis of account information of an account to be identified, generates at least one relation pair, determines a common attribute value of each relation pair under each characteristic parameter, determines whether any relation pair is a common user relation pair on the basis of the determined common attribute value of the relation pair under various characteristic parameters, wherein two accounts in the common user relation pair belong to one user, and generates a relation set for all users for identifying the accounts of one user on the basis of the determined various common user relation pairs.
Owner:ADVANCED NEW TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com