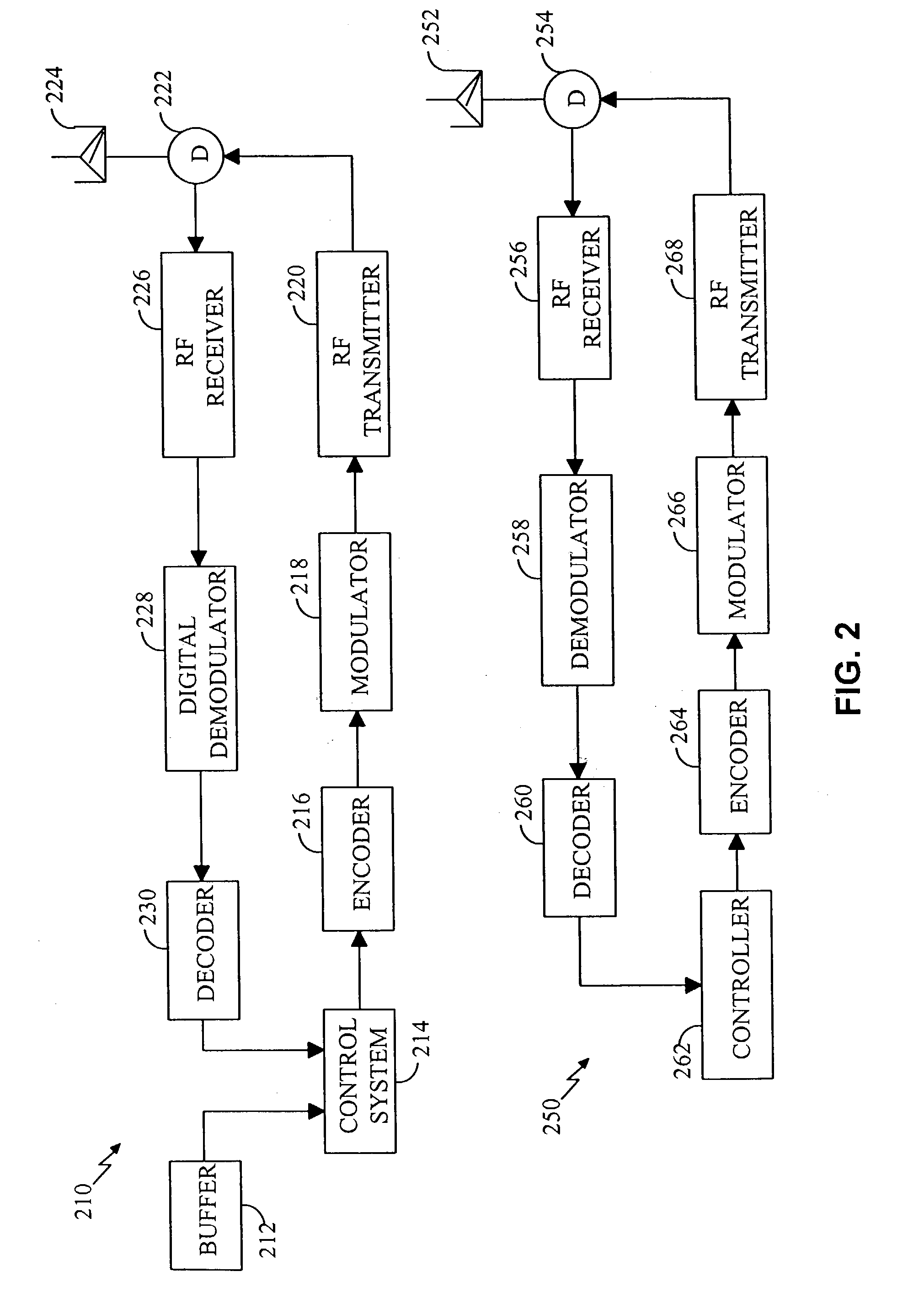
Patents
Literature
203 results about "Protocol design" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
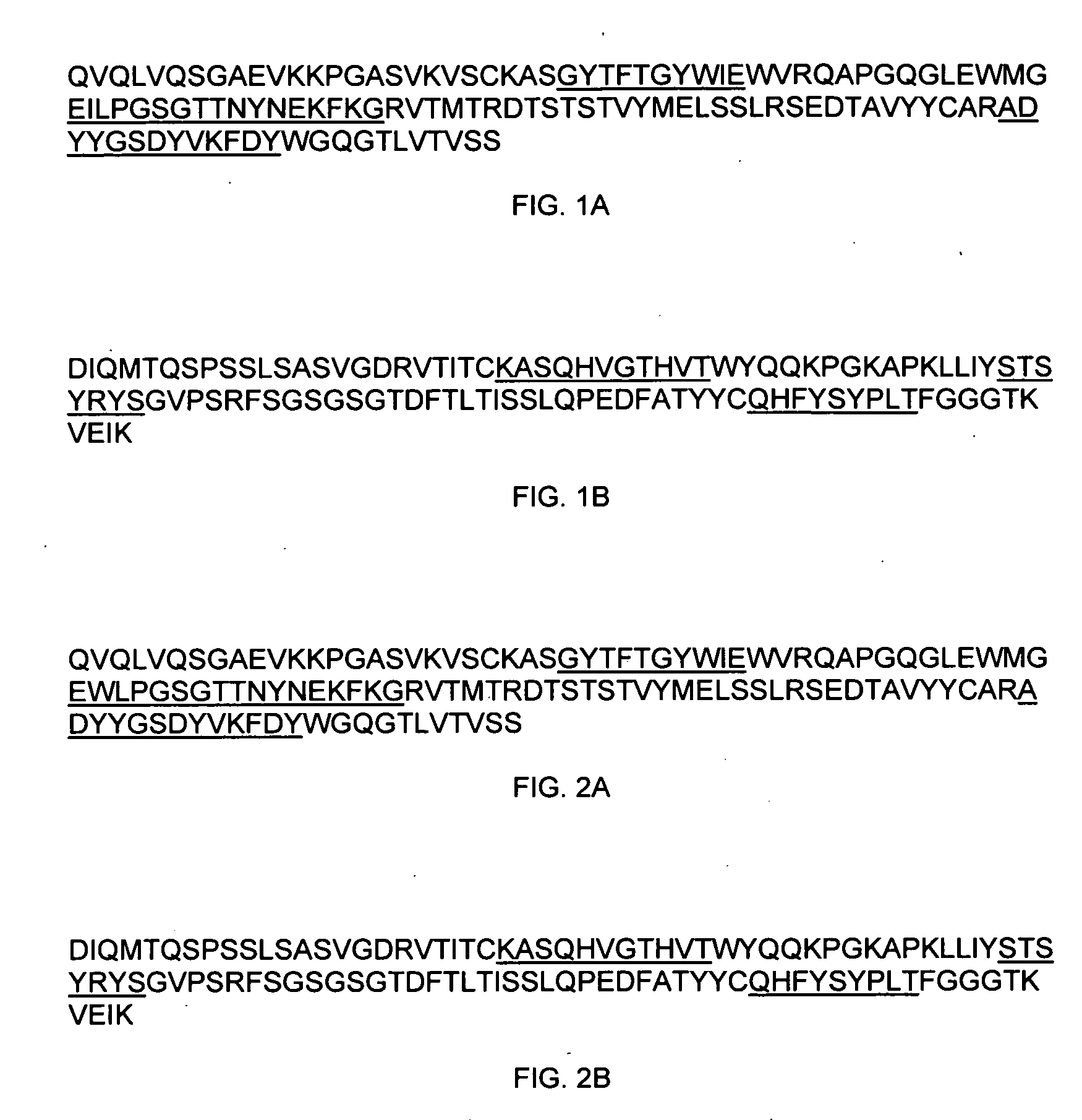
Therapeutic application of chimeric and radiolabelled antibodies to human B lymphocyte restricted differentiation antigen for treatment of B cell lymphoma
Disclosed herein are therapeutic treatment protocols designed for the treatment of B cell lymphoma. These protocols are based upon therapeutic strategies which include the use of administration of immunologically active mouse / human chimeric anti-CD20 antibodies, radiolabeled anti-CD20 antibodies, and cooperative strategies comprising the use of chimeric anti-CD20 antibodies and radiolabeled anti-CD20 antibodies.
Owner:IDEC PHARM CORP
Therapeutic application of chimeric and radiolabelled antibodies to human B lymphocyte restricted differentiation antigen for treatment of B cell lymphoma
Disclosed herein are therapeutic treatment protocols designed for the treatment of B cell lymphoma. These protocols are based upon therapeutic strategies which include the use of administration of immunologically active mouse / human chimeric anti-CD20 antibodies, radiolabeled anti-CD20 antibodies, and cooperative strategies comprising the use of chimeric anti-CD20 antibodies and radiolabeled anti-CD20 antibodies.
Owner:BIOGEN INC
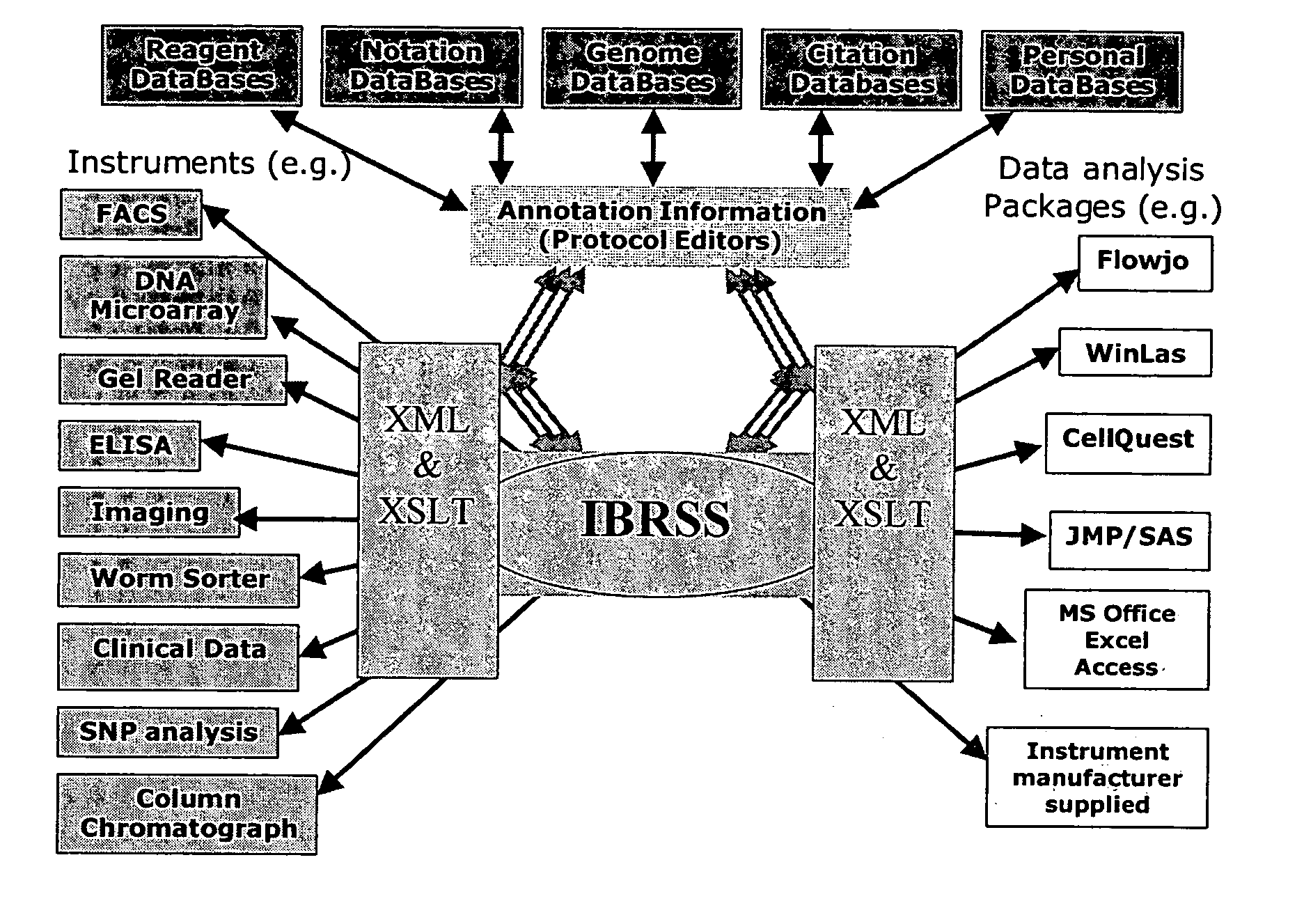
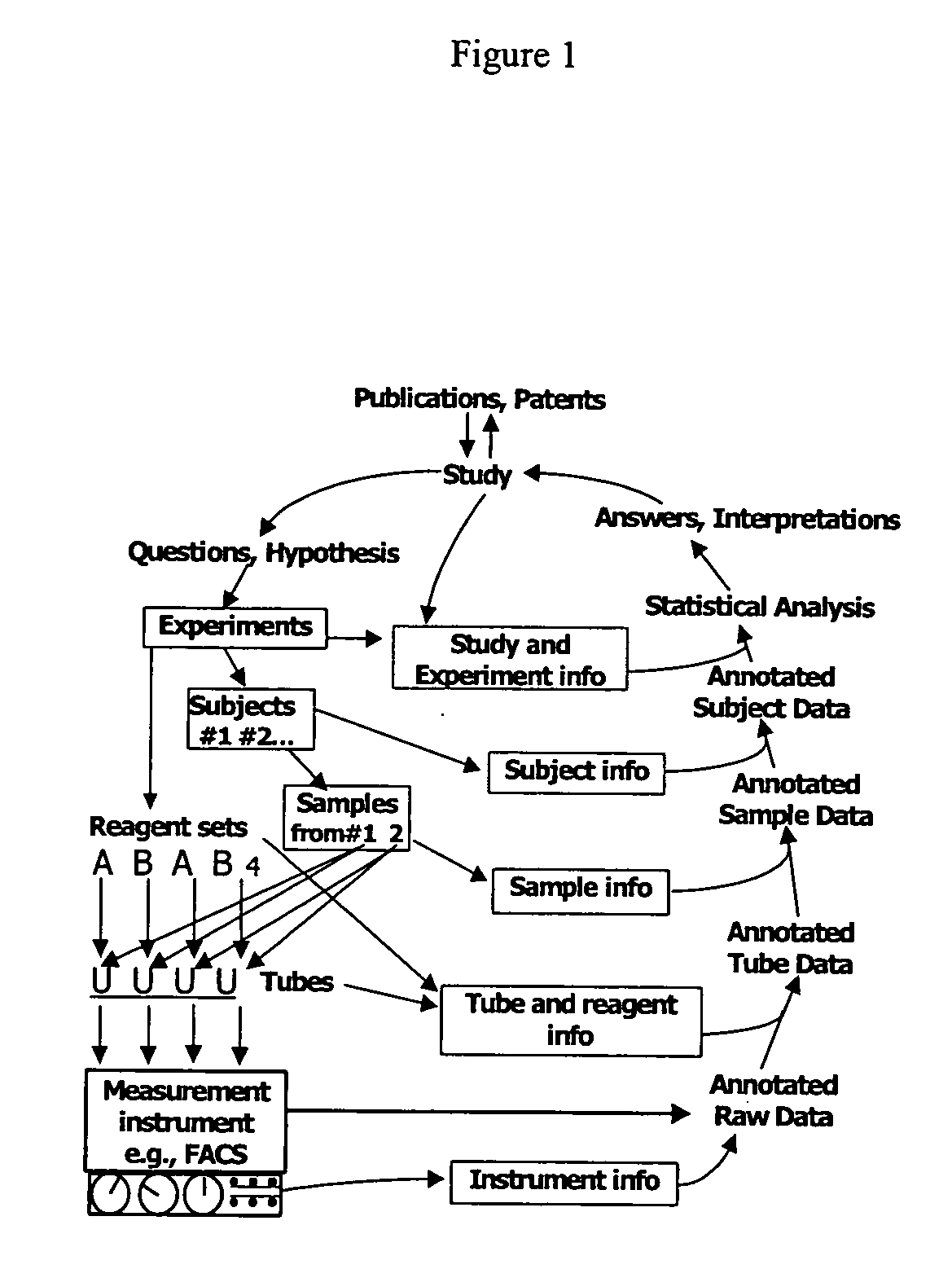
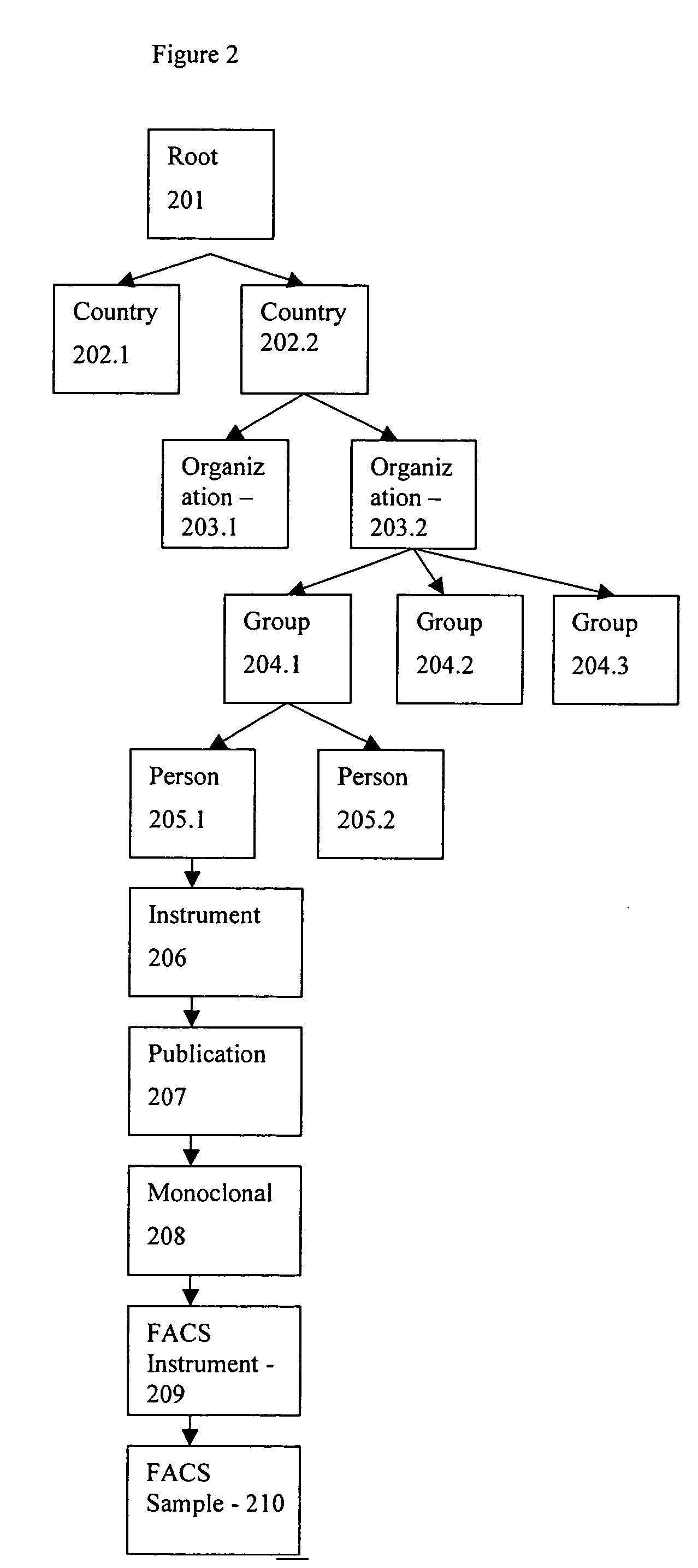
System and method for internet-accessible tools and knowledge base for protocol design, metadata capture and laboratory experiment management
InactiveUS20050044110A1Easy to share dataData is delayedData processing applicationsDigital data processing detailsProtocol designThe Internet
The present invention is related to databases and the exchange of scientific information. Specifically the invention discloses a laboratory data management system including a knowledge base that stores characteristics of laboratory reagents, experiment subjects, tissues and cells. The invention also includes an experiment input module that accepts input of parameters of an experiment and data from a knowledge base module. Further, the invention includes a protocol creator connected to the knowledge base module and the experiment input module that creates a laboratory protocol for an experiment based on data supplied from the knowledge base module and the experiment input module. The invention also includes methods to use the described system.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
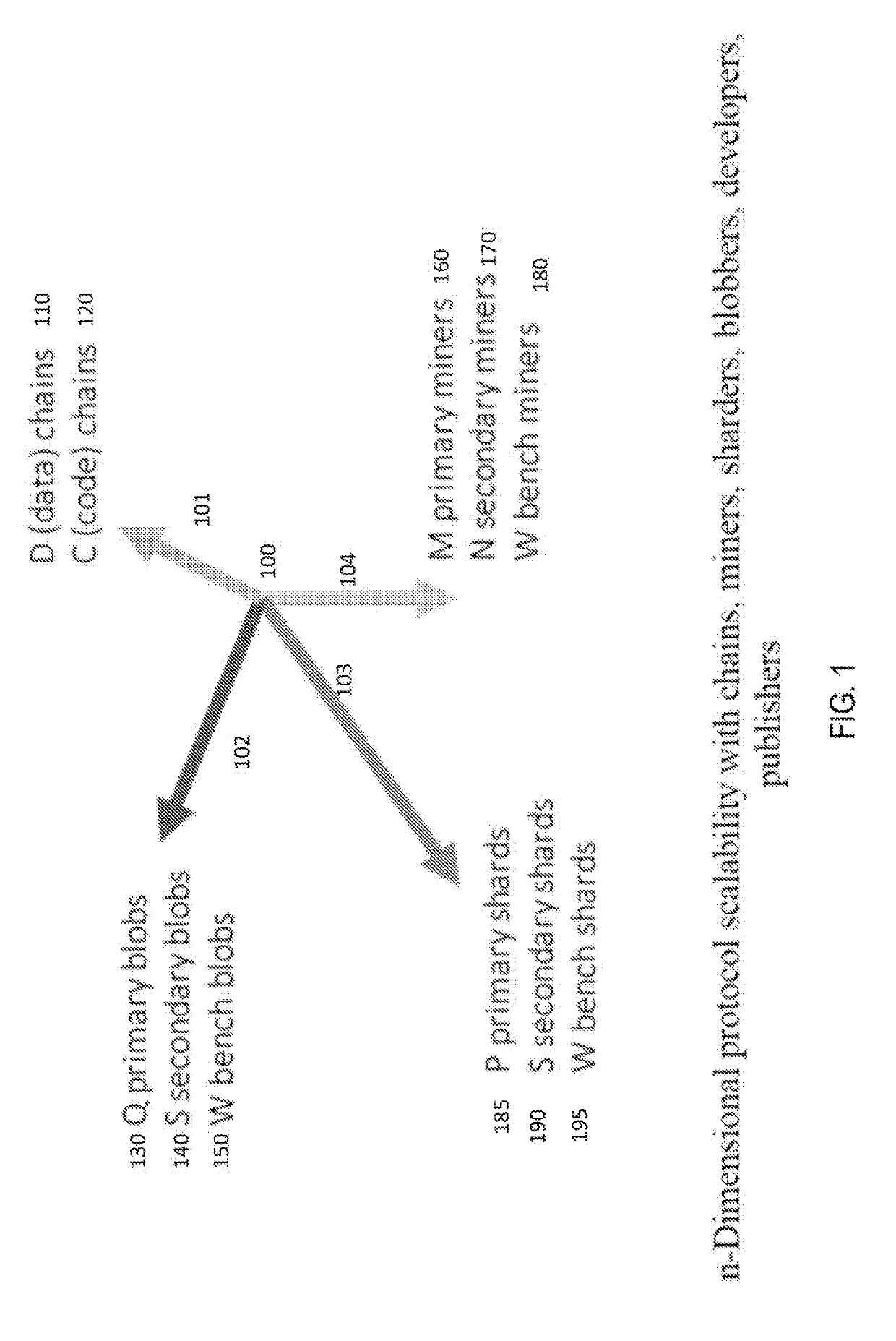
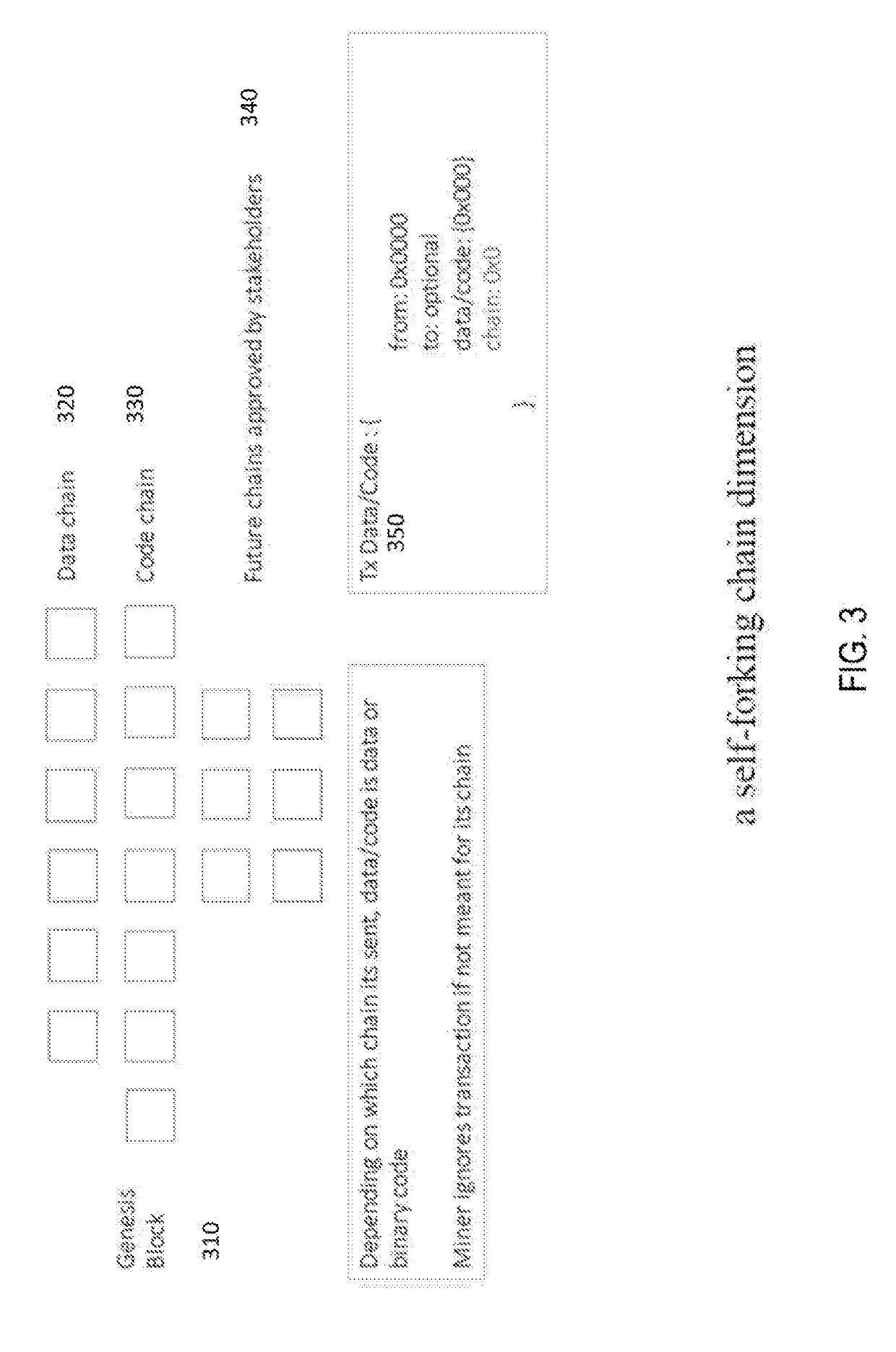
Systems and methods of self-forking blockchain protocol
ActiveUS20190123892A1Avoid OverloadingAccessKey distribution for secure communicationEncryption apparatus with shift registers/memoriesProtocol designMulti dimensional
A multi-dimensional blockchain protocol designed to self-fork into multiple chains, scale infinitely, achieve zero cost transactions, sub-second finality and open new markets for sharders, blobbers, developers, and content publishers, while managing a low inflation rate.
Owner:0CHAIN LLC
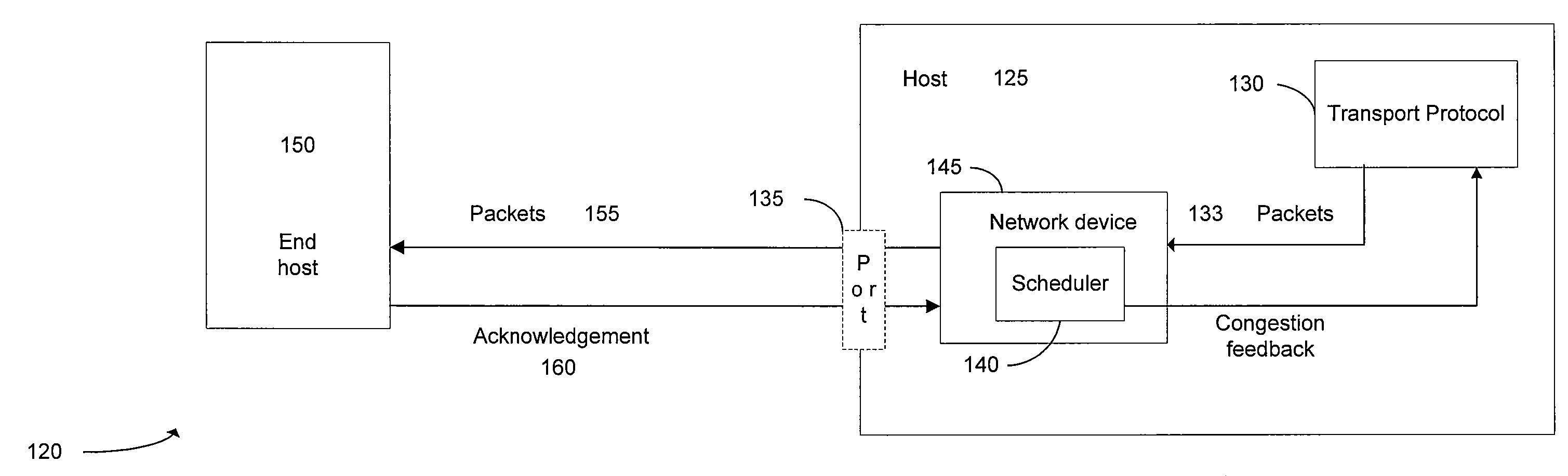
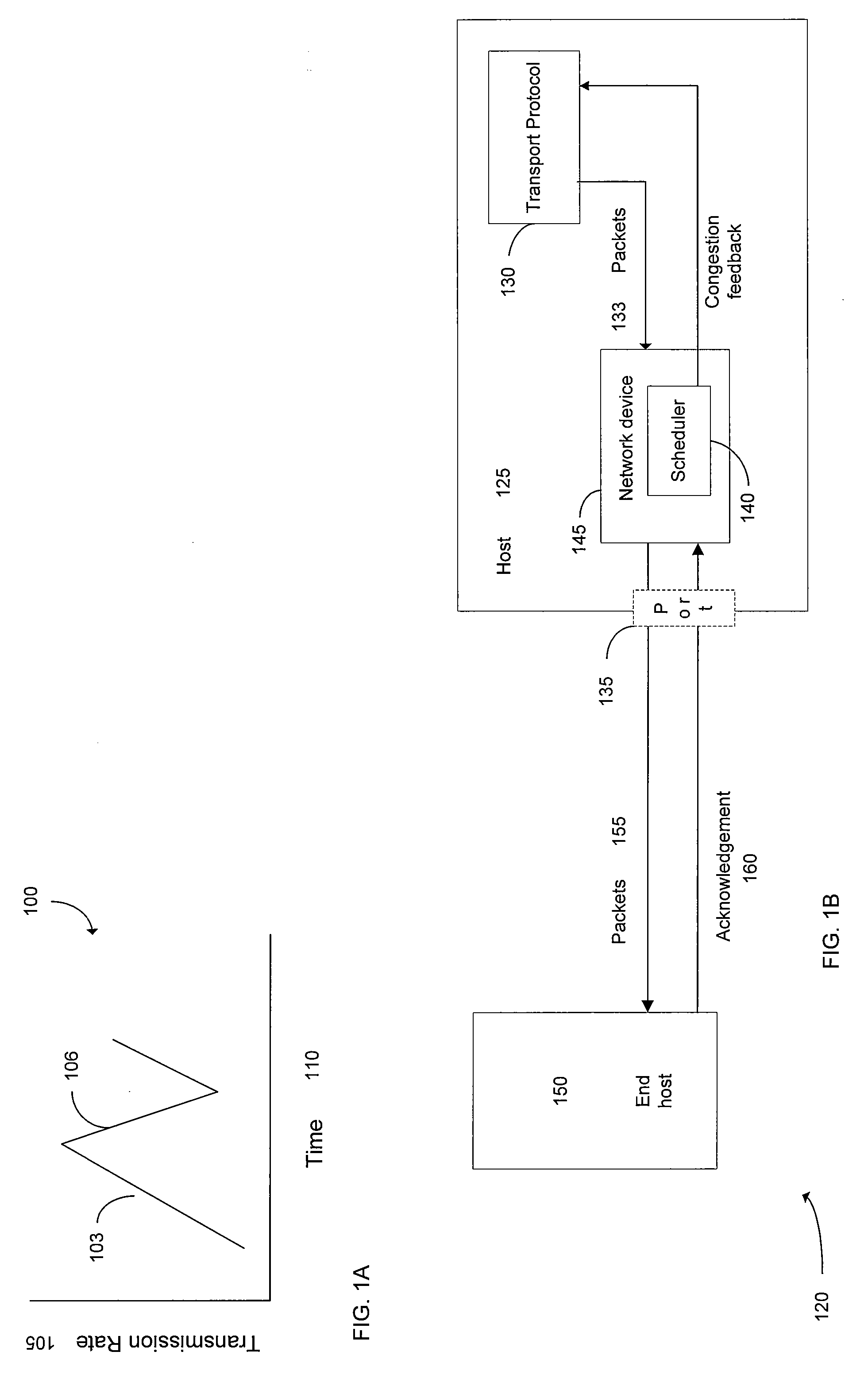
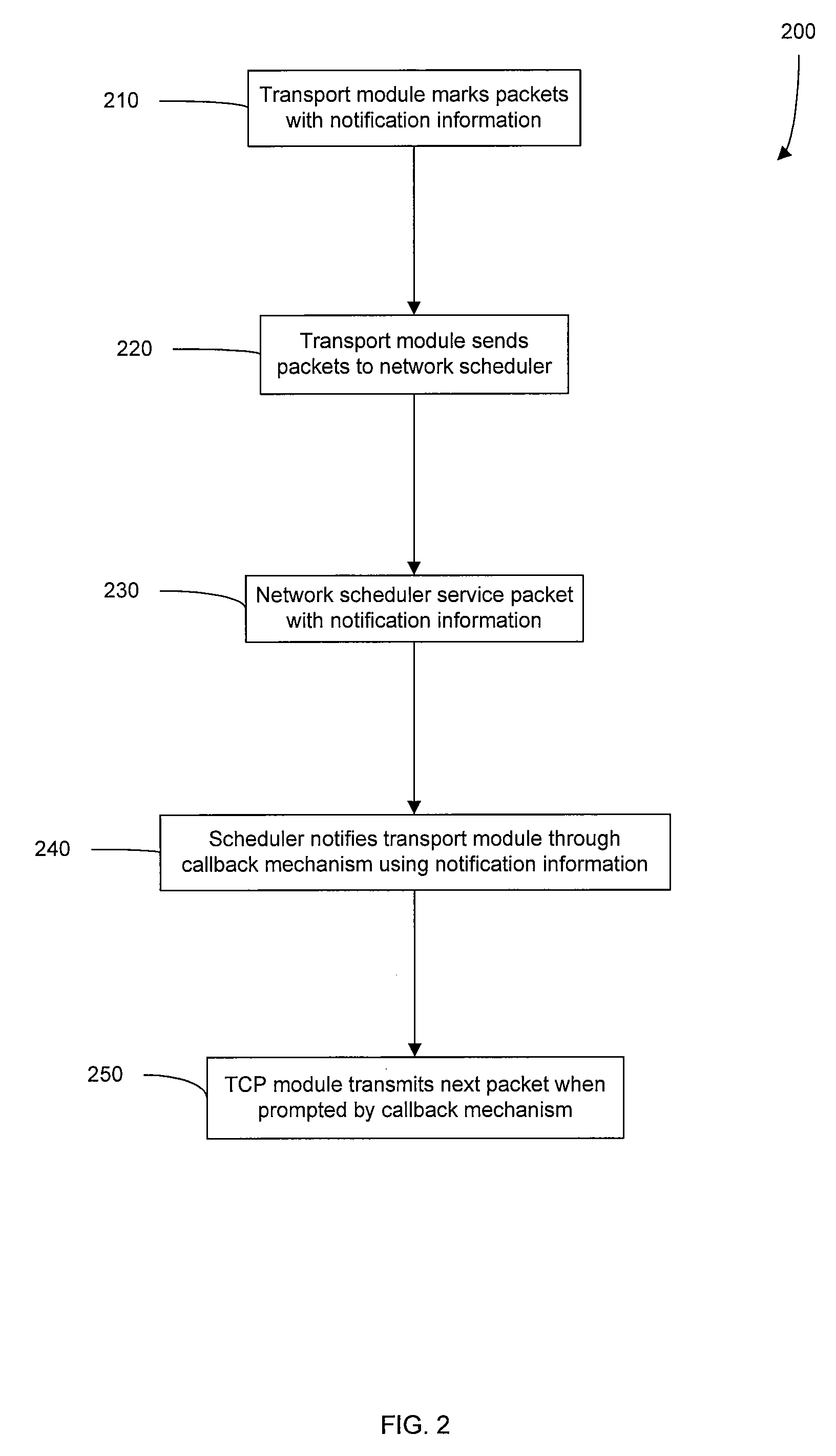
Cooperative Operation of Network Transport and Network Quality of Service Modules
ActiveUS20070297414A1Efficient and flexible networking quality of serviceImprove performanceData switching by path configurationStore-and-forward switching systemsQuality of serviceProtocol design
Methods, systems, and apparatus provide efficient and flexible networking quality of service as well as transport protocol design. A hybrid transport / network quality of service (HNTQ) scheme improves the performance of TCP over specific links or network paths that are subject to high latency, a high bandwidth-delay product, high packet loss, and / or bit errors. A callback mechanism can be used between a packet scheduler and a transport module to control the transmission rate of packets across one or more connections or links.
Owner:RIVERBED TECH LLC
Protocol for maintaining cache coherency in a CMP
ActiveUS20050144390A1Memory adressing/allocation/relocationMicro-instruction address formationProtocol designParallel computing
Owner:INTEL CORP
Method, device and system for data distribution in LET-A system
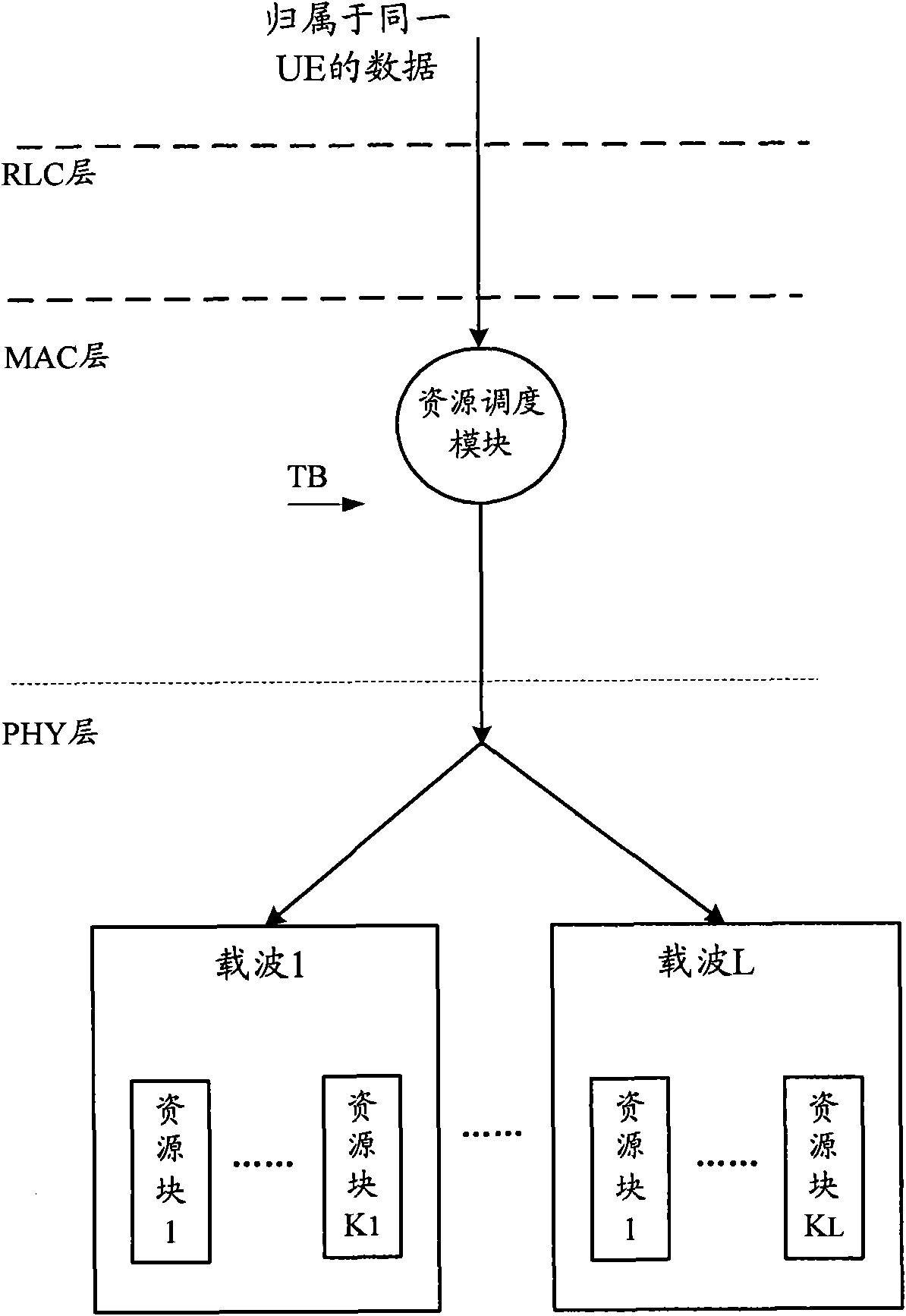
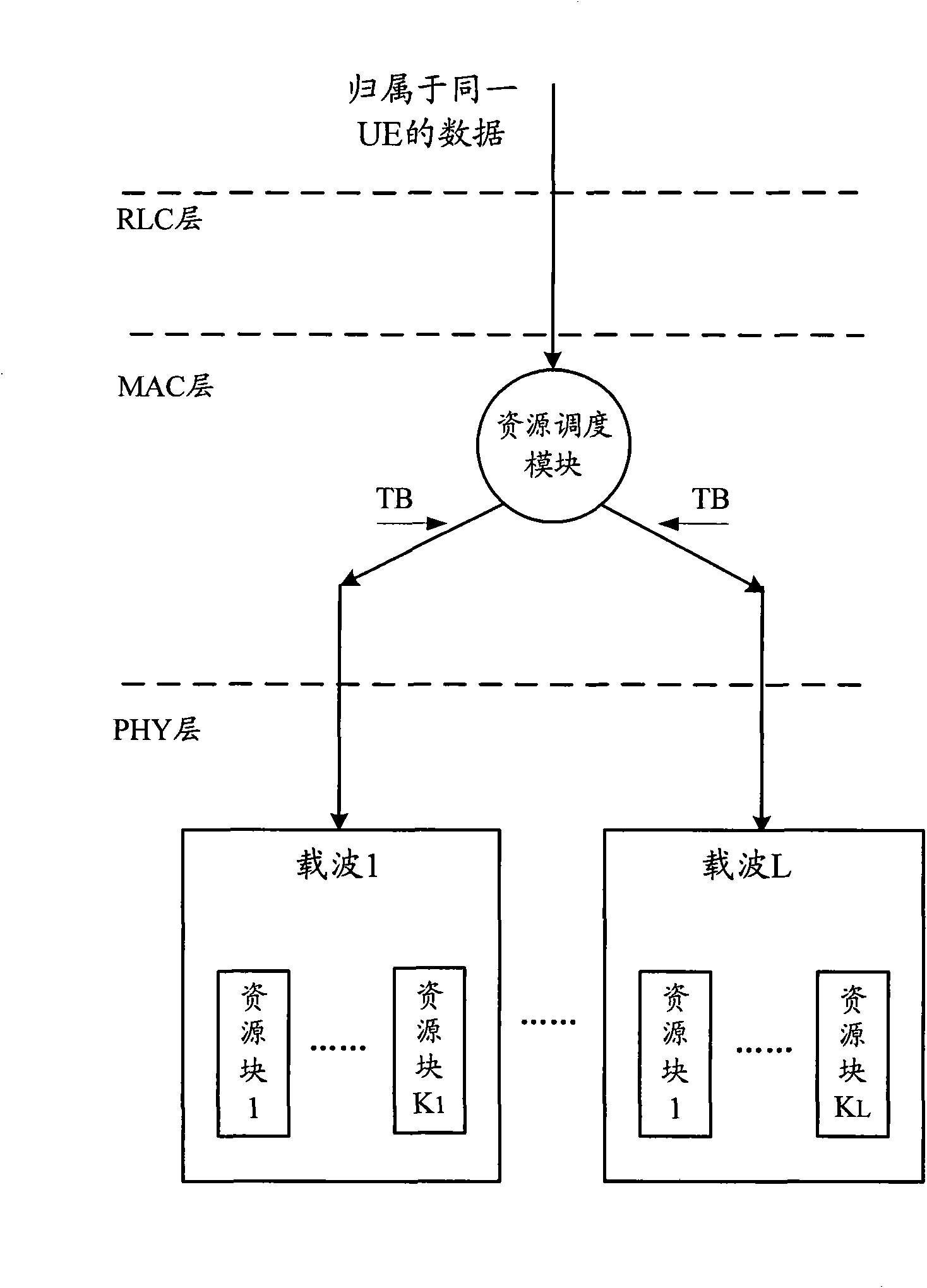
The invention discloses a method for data distribution in a LTE-A system, which comprises that: an RLC layers of network nodes receive a plurality of RLC SDUs transmitted by PDCP layers, wherein the RLC SDUs comprise communication data of at least one communication opposite terminal; and the RLC layers distribute the plurality of received RLC SDUs to carriers according to preset scheduling policies and transmit plurality of distributed RLC SDUs to the communication opposite terminals through protocol layers below the layer. Thus, compared with the LTE system, the LTE-A system has the advantages of avoiding the change of the protocol design and equipment of the protocol layers below the RLC layers of the network nodes and consequently saving research and development cost to a great extent. In addition, the invention also discloses a communication device and the LTE-A system.
Owner:CHINA MOBILE COMM GRP CO LTD
Blending MAC protocol design method suitable for wireless sensor network
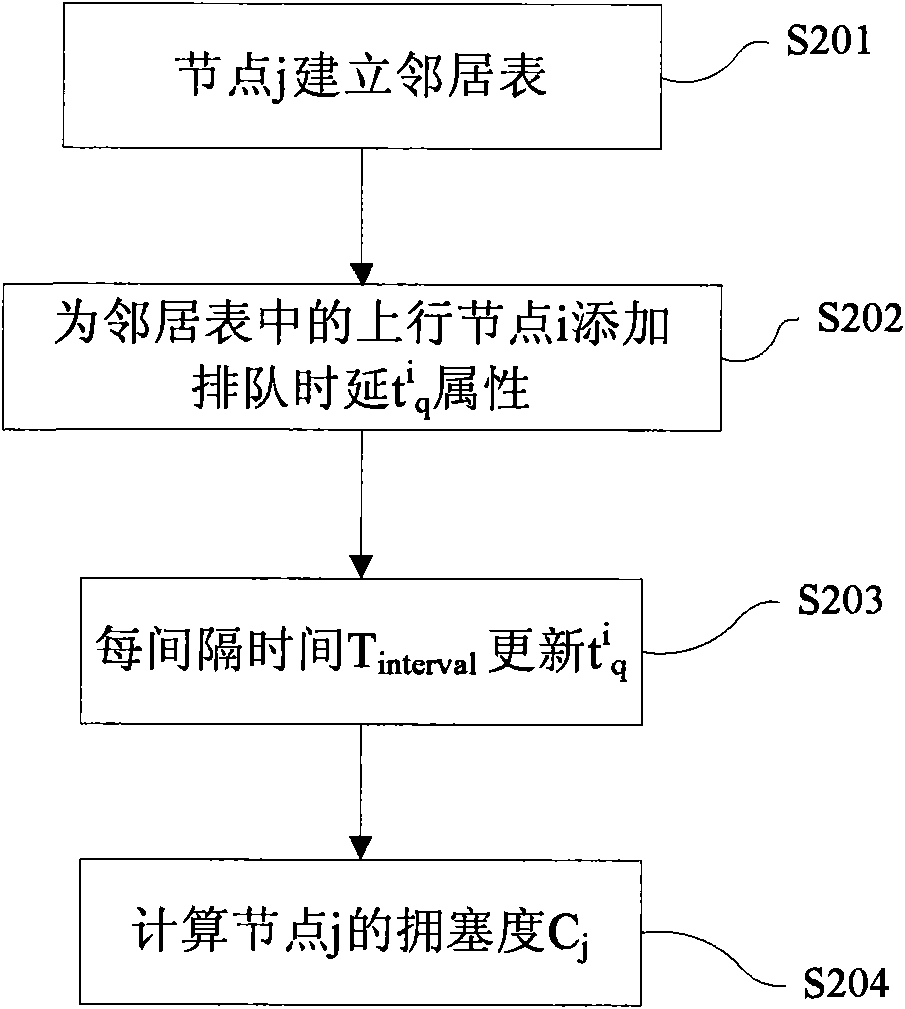
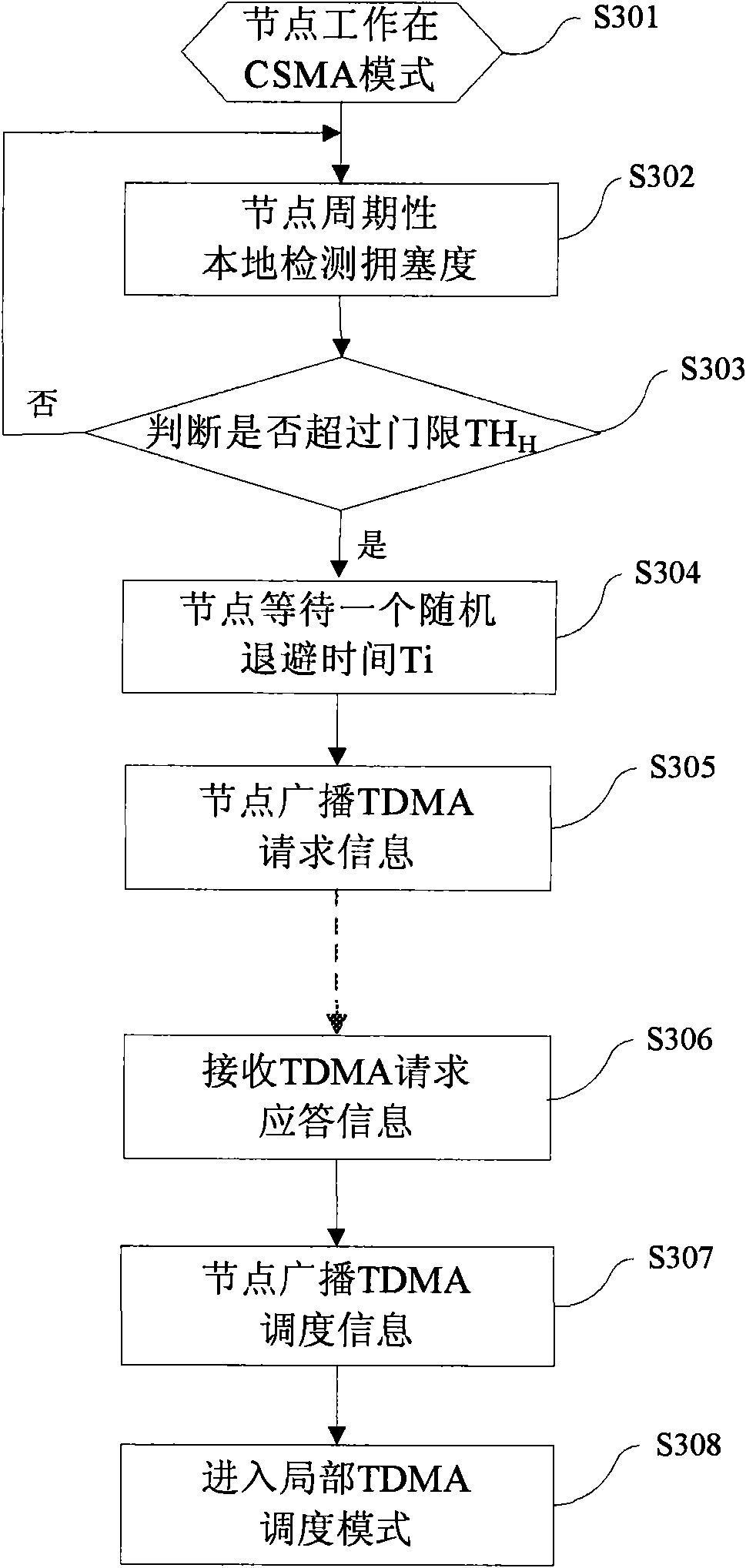
InactiveCN101827378ALower latencyImprove throughputNetwork traffic/resource managementNetwork topologiesWireless mesh networkProtocol design
The invention discloses a jamming perception self-adaption blending MAC protocol which is suitable for a wireless sensor network and belongs to the field of computer networking technology. In the low loading network situation, a node runs the CSMAMAC protocol at the normal working condition; when the network has burst data or detects the jamming nearby the node of a bottleneck, a TDMA mechanism is embedded in the jamming area in a self-adaption way; the node of the jamming area runs the local TDMAMA protocol; and after the jamming releases, the node recovers the normal working condition and runs the CSMAMAC protocol. The invention detects the jamming according to the local information and does not need any synchronization algorithm; according to the jamming degree, the local TDMA is embedded in the CSMA network in a self-adaption way so that performance indexes such as the throughout capacity, packet loss rate and time delay and the like are improved and the performance of the network is increased.
Owner:BEIJING JIAOTONG UNIV
Method and apparatus for providing configurable layers and protocols in a communications system
InactiveUS20030118049A1Easy to implementMinimal levelNetwork traffic/resource managementTime-division multiplexProtocol designCommunications system
The layers and protocols of an air interface layering architecture are designed to be modular and can be modified and upgraded to support new features, perform complex tasks, and implement additional functionality. Prior to commencement of data communication between a first entity (e.g., an access terminal) and a second entity (e.g., a radio network), a set of layers and / or protocols is selected for negotiation. For each selected layer and protocol (i.e., each attribute), a list of attribute values considered acceptable to the first entity is determined. The selected attributes and their associated attribute values are sent from the first entity and, in response, a list of processed attributes and their associated lists of processed attribute values are received. Each list of processed attribute values includes attribute values considered acceptable to the second entity. The layers and protocols in the first entity are then configured in accordance with the received list of processed attributes and their associated processed attribute values. Other features related to configurable layers and protocols are also provided.
Owner:QUALCOMM INC
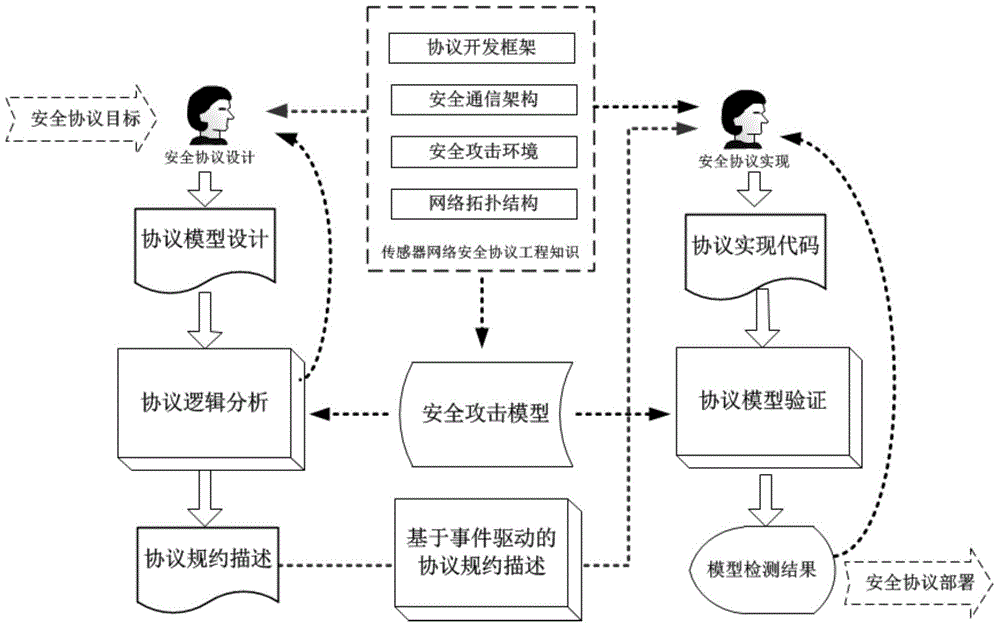
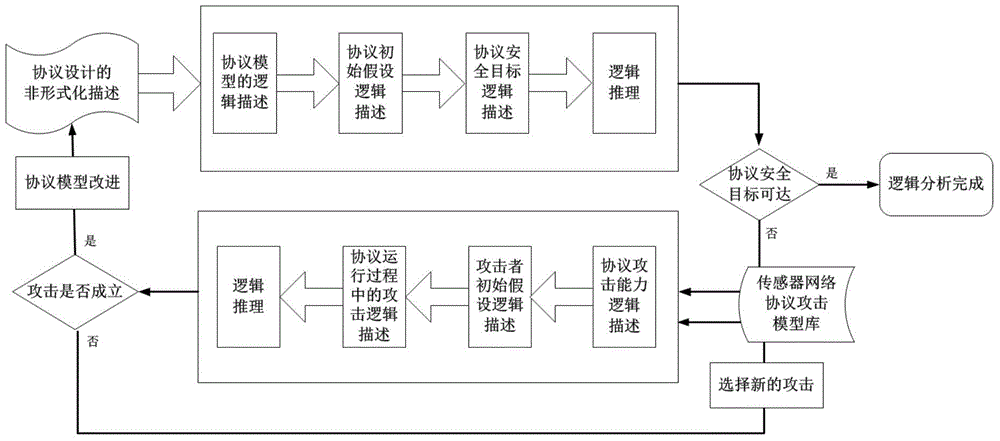
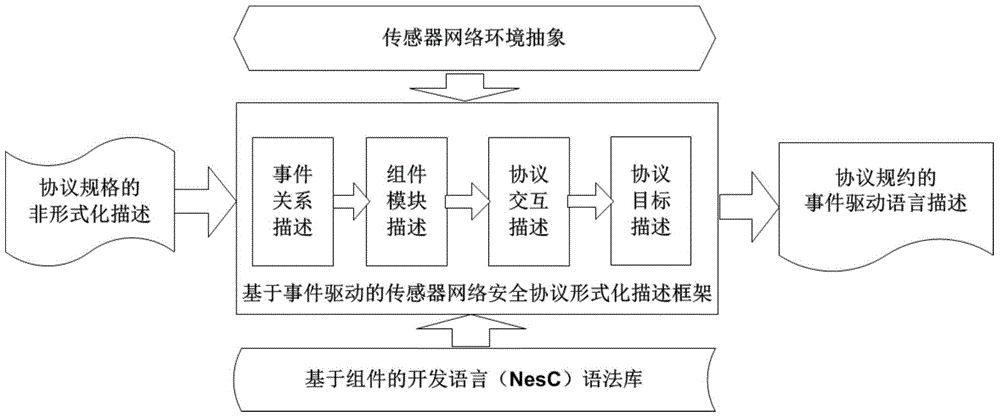
Formal verification method for facing design and accomplishment of wireless sensing network safety protocol
ActiveCN104135397ASimple designImprove development efficiencyData switching networksProtocol designValidation methods
A formal verification method for facing design and accomplishment of a wireless sensing network safety protocol, comprises the following steps: (1) a sensing network safety protocol design method based on logical analysis: a designer of the sensor network safety protocol accepting a protocol design goal, and designing a protocol rudiment based on analysis of sensor network environmental factors; establishing a logical reasoning system to accomplish protocol modeling and logical analysis, amending the protocol design plan according to the analysis result, and repeating logical analysis until the logic of the protocol is correct; and giving description of the protocol specification which is not formalized finally; (2) a safety protocol specification description language facing the sensing network developing environment; and (3) a safety protocol code automatic verification method based on model checking. The present invention effectively ensures safety and efficiency of the design and development and has good expansibility.
Owner:ZHEJIANG UNIV OF TECH
Multi-factor decision making route protocol based on connectivity in VANET
ActiveCN106961707APriority ConnectivityPrioritize short pathsTransmissionWireless communicationTime informationProtocol design
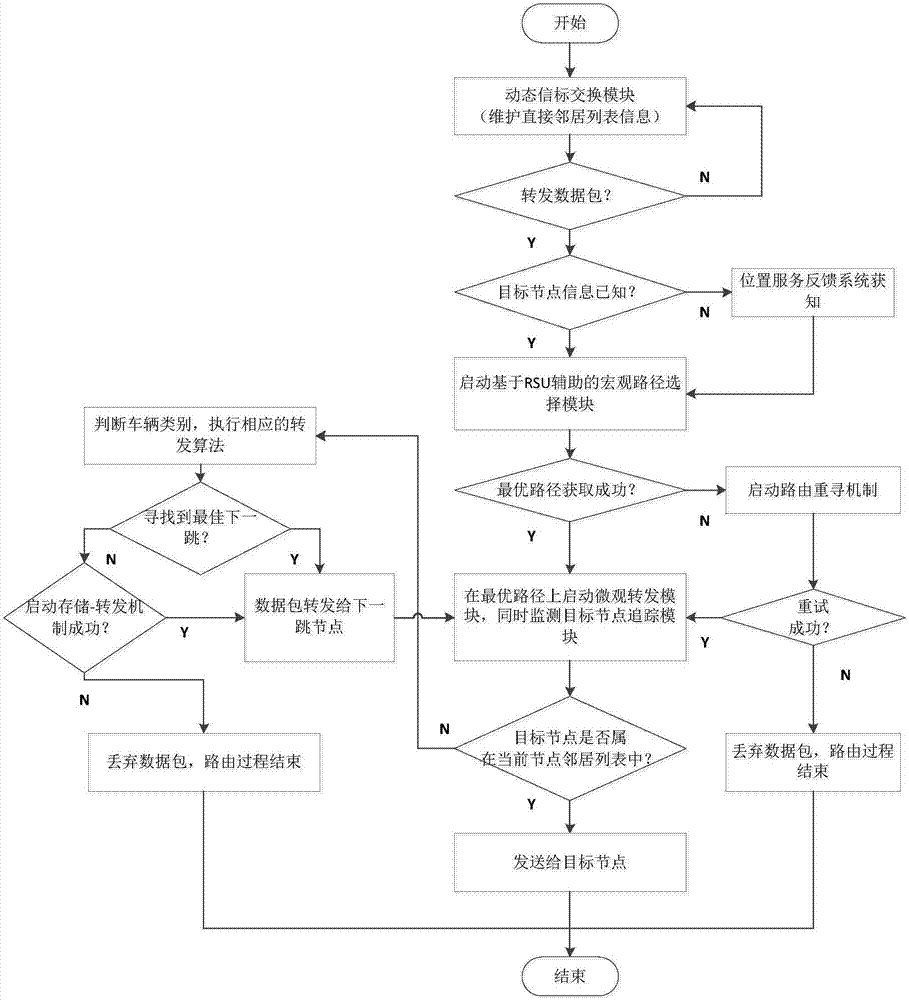
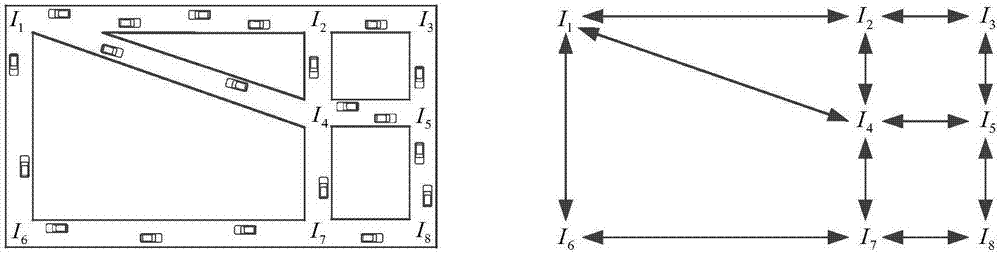
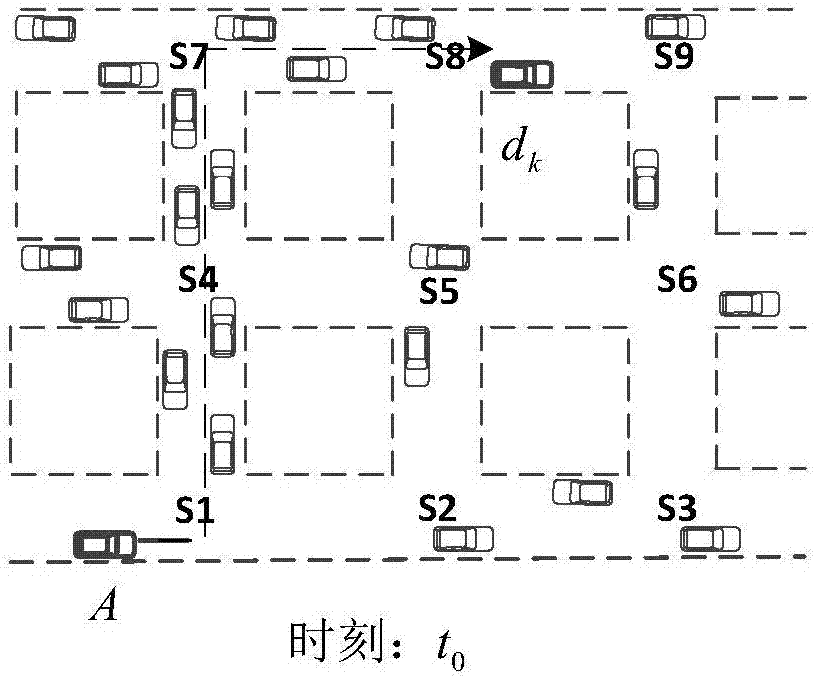
The invention relates to a multi-factor decision making route protocol based on connectivity in VANET, wherein the route protocol combines city VANET features with route protocol designing problems, and is suitable for the city scenes; each vehicle node in the multi-factor decision making route protocol is provided with a navigation positioning system and electronic map equipment, thus periodically obtaining self information, and obtaining RSU positions and a road topology structure in the same time; when the vehicle node in the network needs to send a data package to a target node, the target node real time information can be obtained through a position service feedback system, and added into a data package header. The multi-factor decision making route protocol can use the vehicle node and deployed roadside RSU information interaction and various types of V2R message statistics to obtain the vehicle distribution conditions on the road, thus calculating the road density, and using a principle ensuring the connectivity and short path priority to select the optimal path connecting the source node with the target node.
Owner:HARBIN ENG UNIV
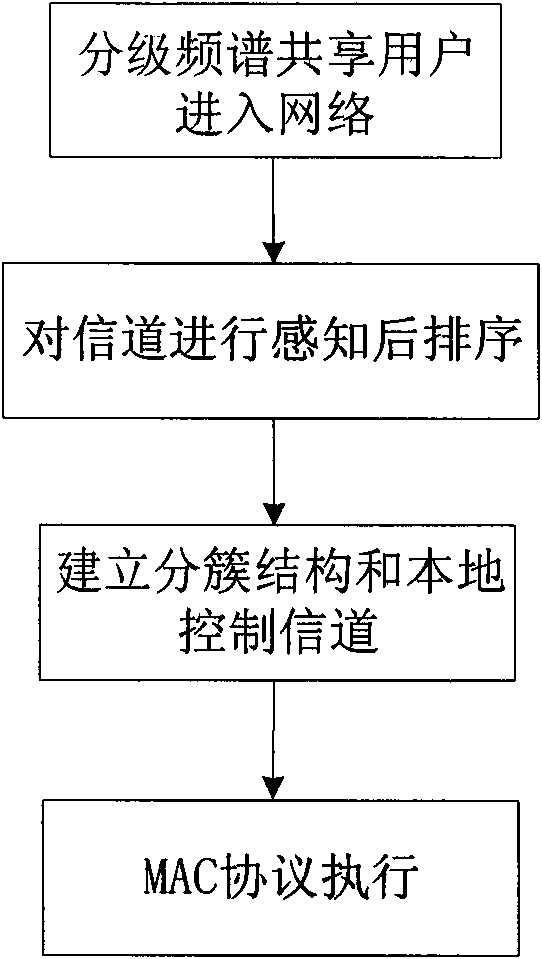
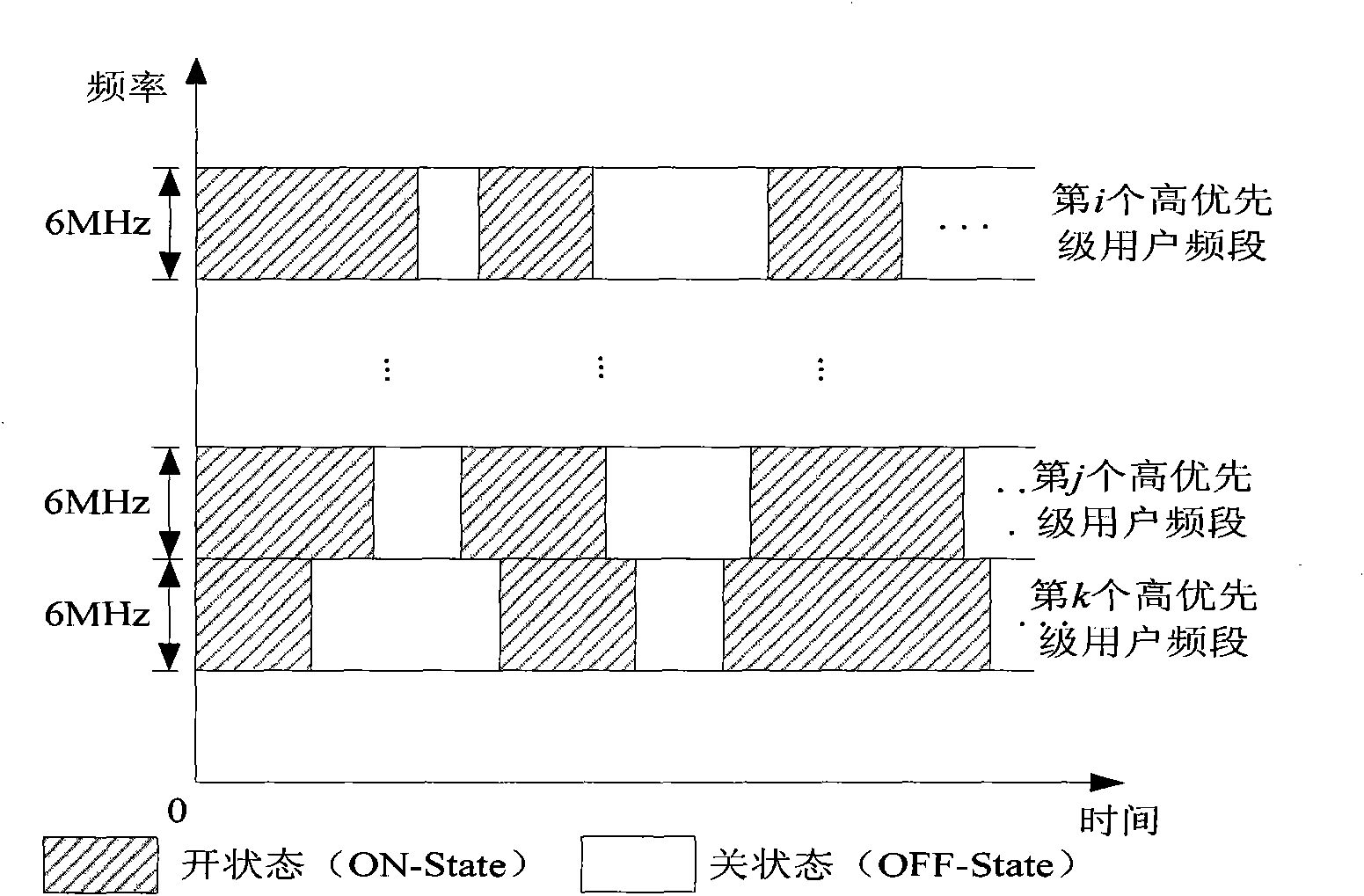
Method for establishing control channel of hierarchical spectrum sharing network
InactiveCN101594617ASolve the problem of not having a common control channelTransmission monitoringNetwork planningFrequency spectrumProtocol design
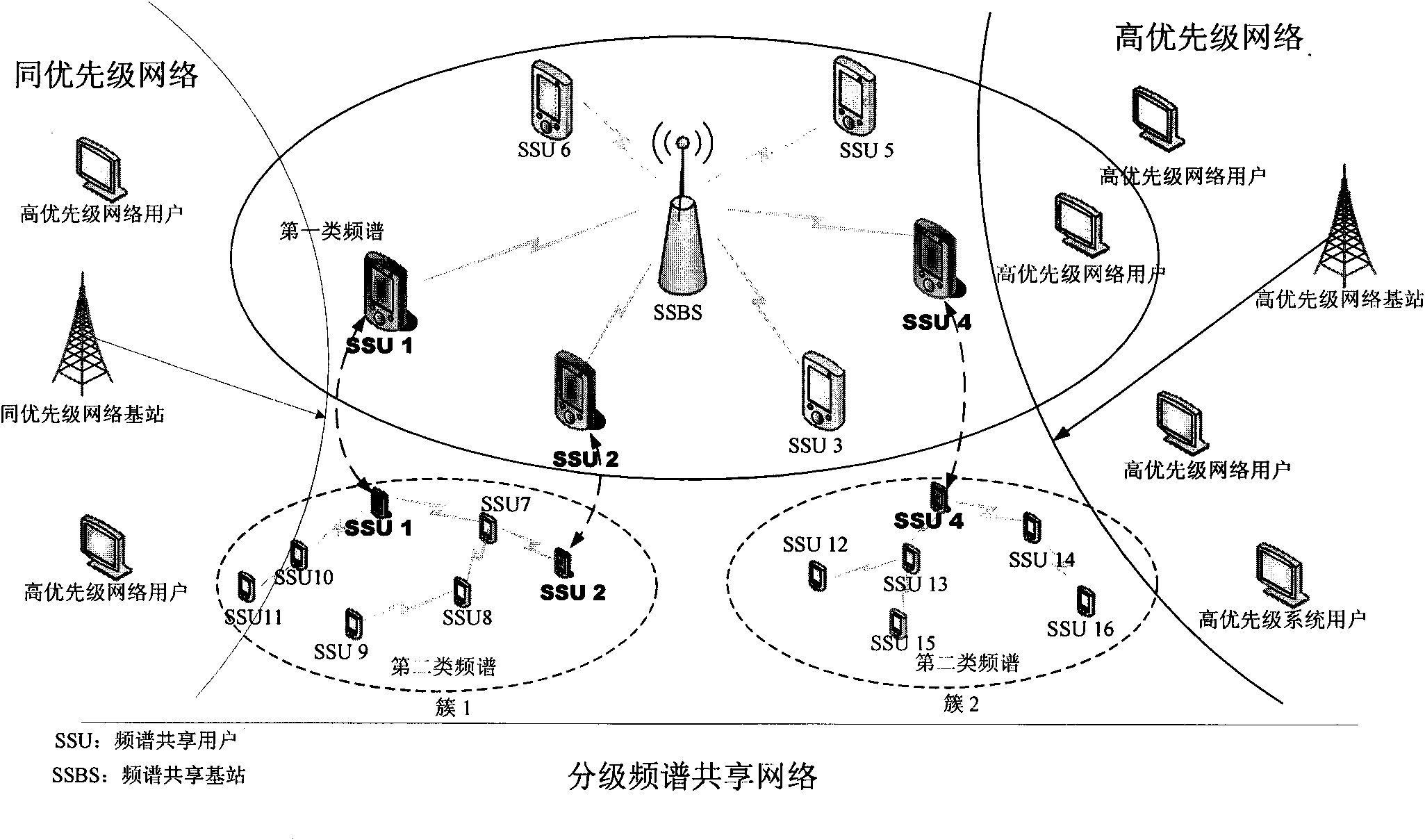
The invention relates to a method for establishing a control channel of a hierarchical spectrum sharing network. In the hierarchical spectrum sharing network, the number of high priority users is N, the number of hierarchical spectrum sharing users is H, and a frequency band F capable of being supported by a radio-frequency head can be averagely divided into M sub-channels. The method is characterized by comprising the following steps: S1, sorting the M sub-channels by calculating a perceptible high priority user channel weight by the hierarchical spectrum sharing users; S2, establishing the hierarchical spectrum sharing users accessing the same channel into the same cluster, and taking the channel as a local control channel of the cluster; and S3, managing multiple functions of different time slots of the clustered hierarchical spectrum sharing users through MAC protocol design. The method has the advantages that: the local control channel is established in the hierarchical spectrum sharing network through the steps for signal interaction of the hierarchical spectrum sharing users so as to effectively solve the problem that a public control channel does not exist in cognitive radio.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
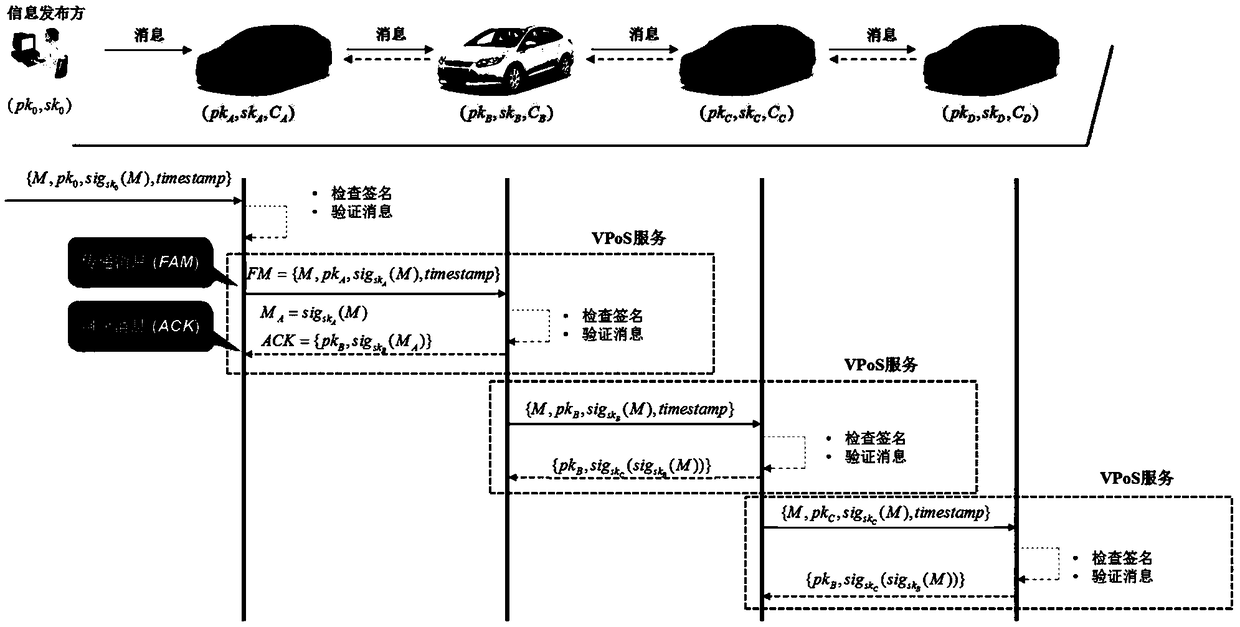
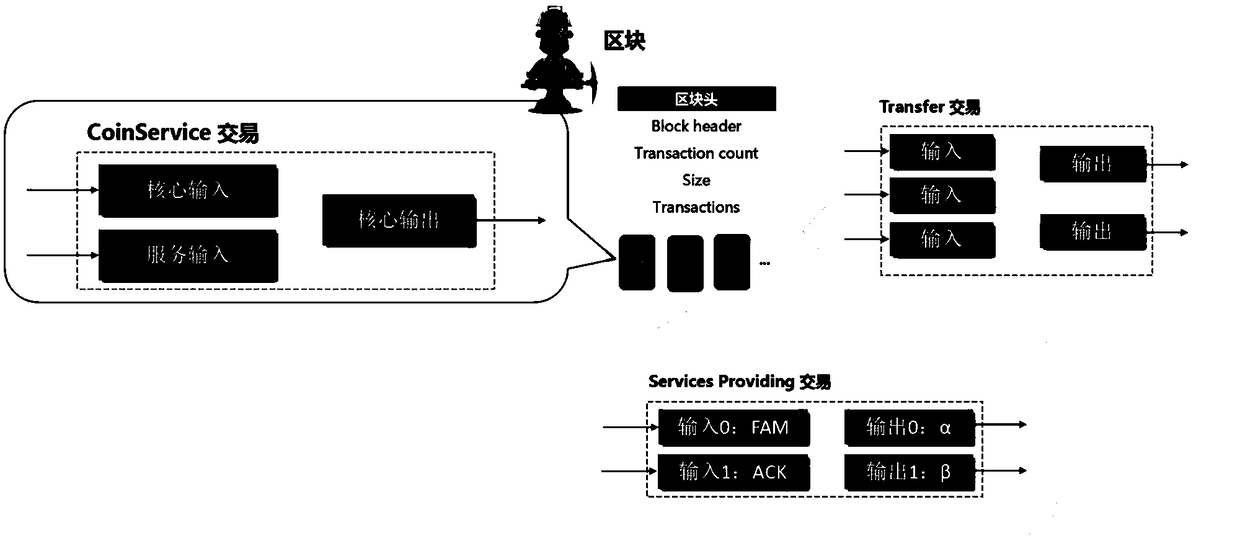
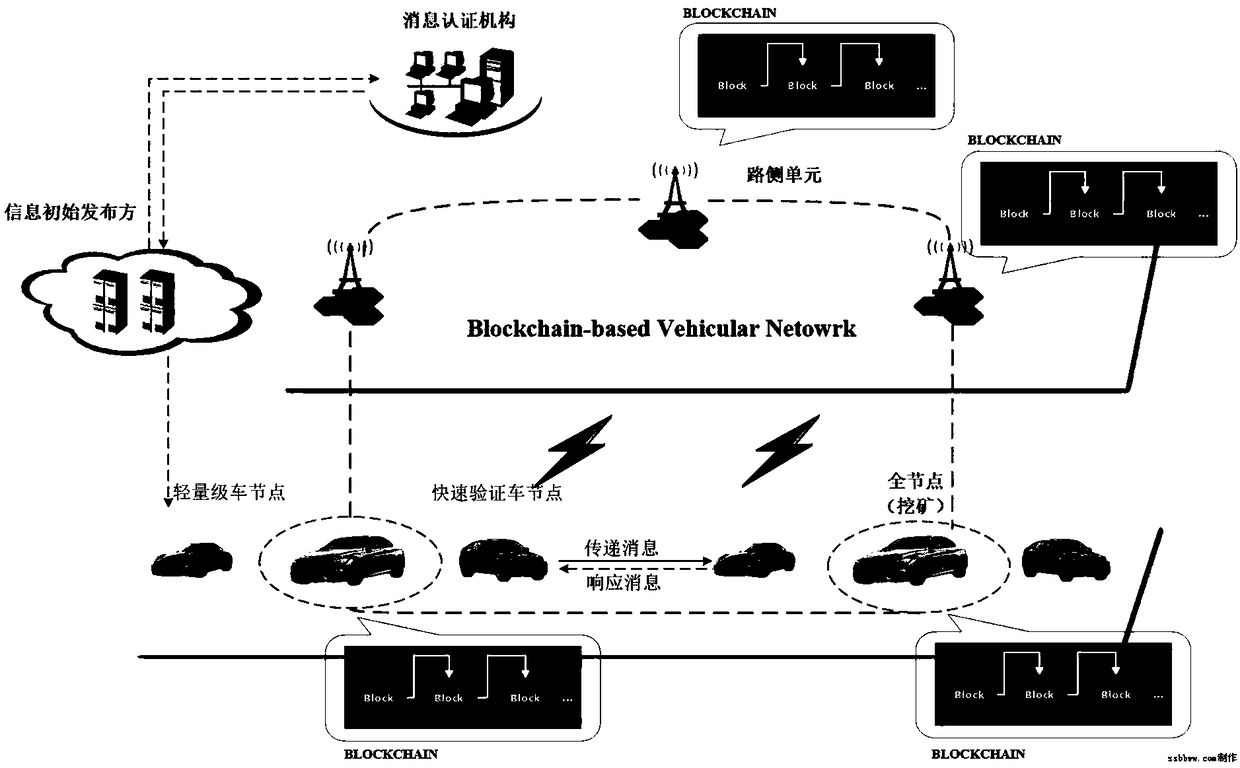
A consensus protocol design based on service proof and a vehicle networking application method thereof
ActiveCN109275122AEnsure safe and effective transmissionReduce consumptionKey distribution for secure communicationFinanceThird partyProtocol design
The invention discloses a consensus protocol design based on service proof and a vehicle networking application method thereof. In the consensus protocol, a vehicle can obtain an incentive (VPoSCoin)by providing service proof without relying on a third party messageable certification authority. VPoSCoin enables more nodes to actively cooperate with other vehicles by motivating vehicles to participate in V2V communication. In the scheme, a consensus protocol based on Proof of Services (Proof of Services) is designed. The whole block chain system is maintained by the roadside unit in the vehicle network, and the information is highly transparent.
Owner:JINAN UNIVERSITY
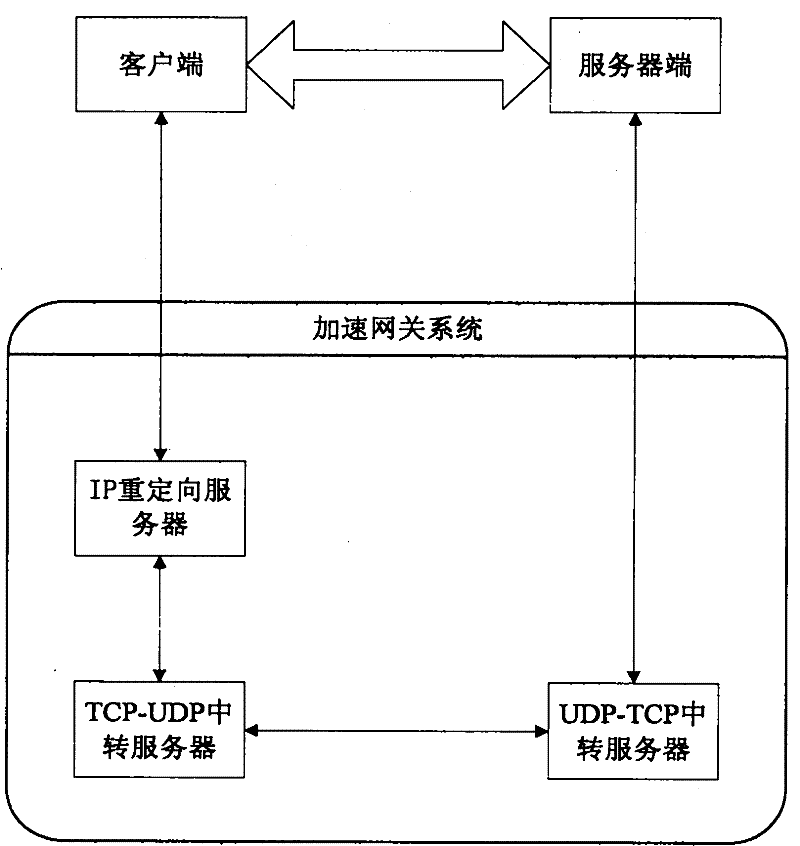
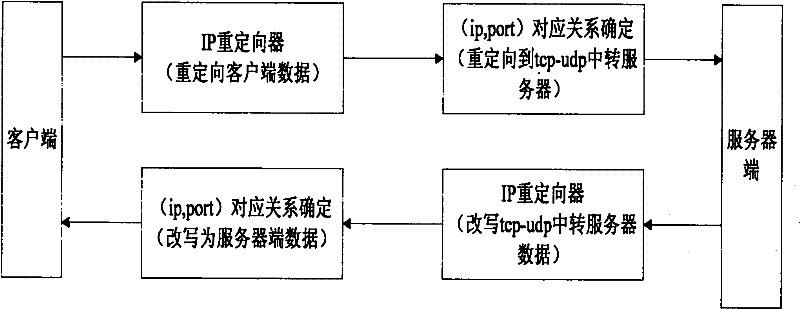
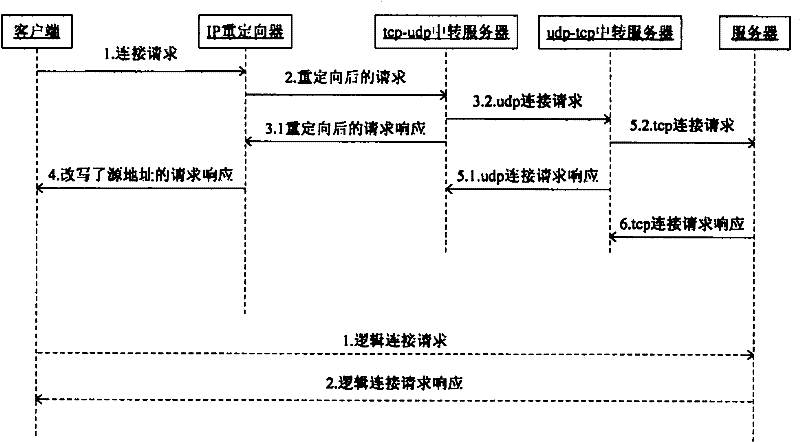
Reliable, transparent and general acceleration gateway system based on UDP protocol
InactiveCN102244645AImprove reliable transmission speedLower deployment costsNetwork connectionsData packReliable transmission
The invention discloses a reliable, transparent and general acceleration gateway system based on an UDP protocol. The invention belongs to the communication network protocol design field. In the invention, a TCP-UDP transferring device and a UDP-TCP transferring device are respectively arranged between original communication nodes and a TCP connection is converted into three connections of TCP-UDP, UDP-UDP, UDP-TCP through adding the reliable UDP protocol transmission between the transferring devices. In the invention, a high efficient and rapid characteristic of the UDP protocol is fully used; the reliable transmission based on the UDP protocol is realized; the reliable transmission between the original communication nodes is guaranteed. By using the system of the invention, automatic redirection of an IP data packet can be realized and transparent acceleration transmission can be performed by an original communication protocol without modification. The system of the invention does not assume to realize acceleration for one kind of software based on the TCP protocol, and the system is the general acceleration gateway system. The invention is suitable for an Internet field which needs high-speed data transmission and is inconvenient to change a current network architecture and a software architecture, and especially suitable for a CDN field which has a huge transmission quantity.
Owner:BEIJING FASTWEB TECH
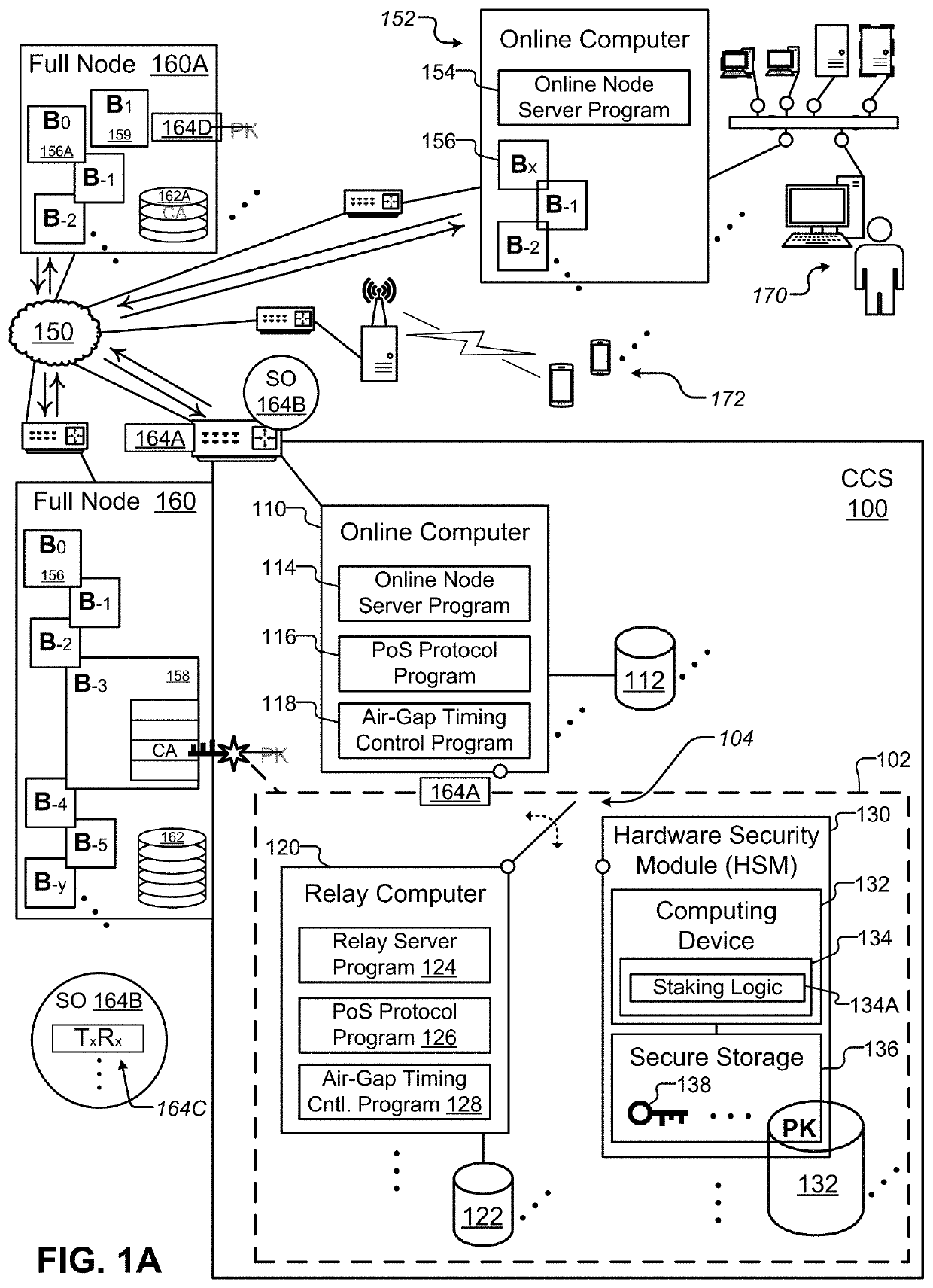
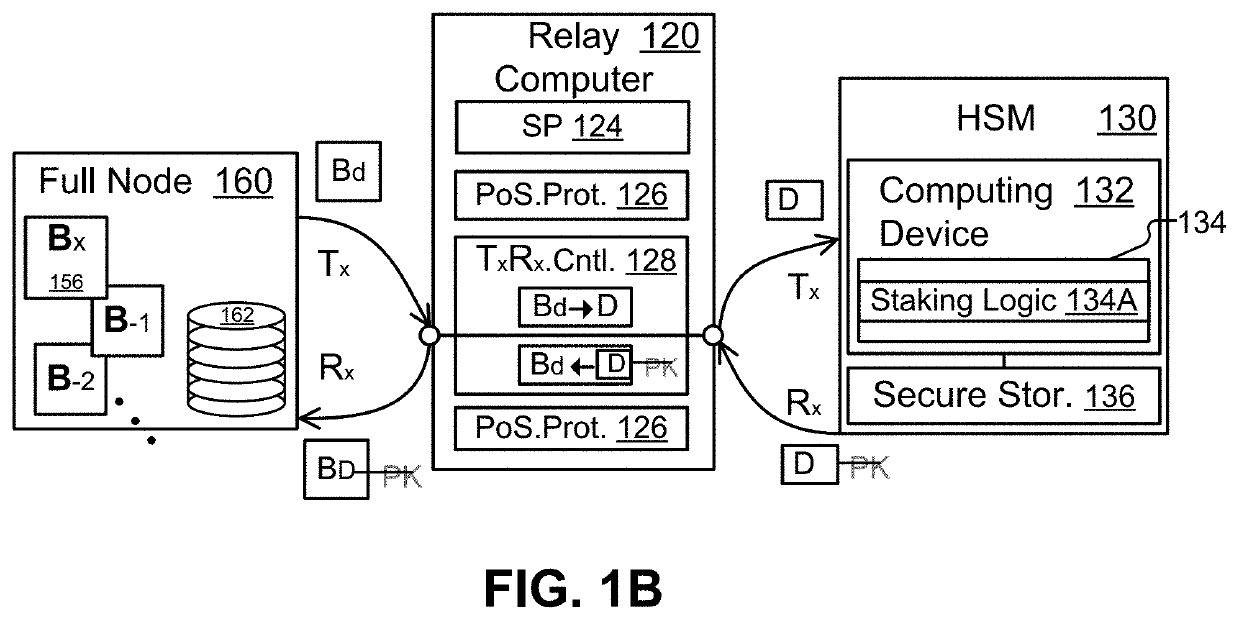
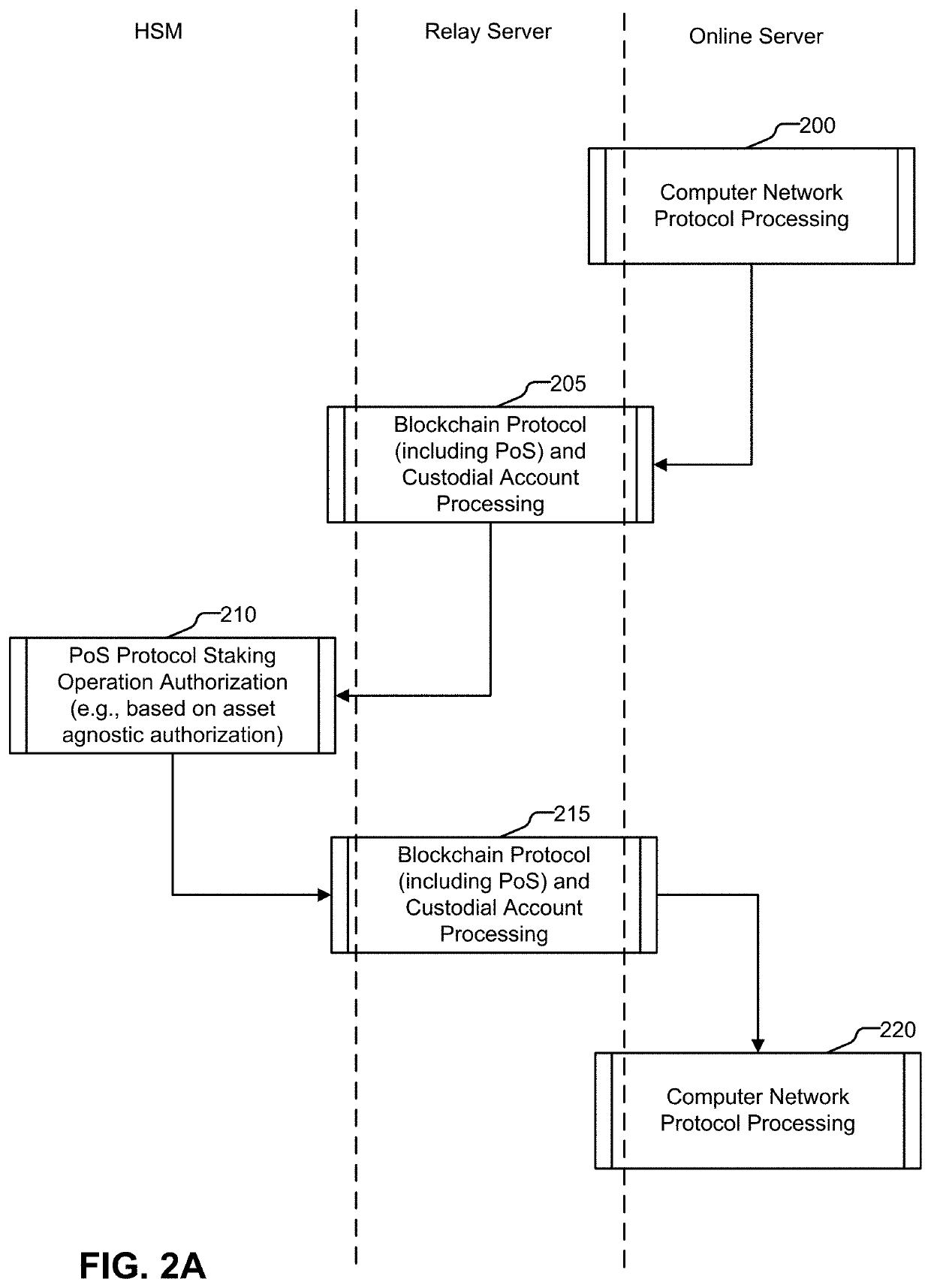
Cryptoasset custodial system with proof-of-stake blockchain support
ActiveUS20210056547A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesProtocol designHardware security module
Methods and systems for secure storage and retrieval of information, such as private keys, useable to control access to a blockchain, include: receiving, in a cryptoasset custodial system, a request to authorize a staking operation associated with a blockchain, wherein the staking operation is associated with a private key of an asymmetric cryptographic key pair, the private key is usable to control ownership of a cryptoasset recorded in the blockchain, and the private key is securely held in the custodial system; performing, in response to the request, a portion of the proof-of-stake protocol in a hardware security module using logic designed for the protocol, wherein the logic in the hardware security module is configured to authorize the staking operation by digitally signing an associated staking transaction; and sending the digitally signed staking transaction to another computer to effect the staking operation on behalf of the user.
Owner:ANCHOR LABS INC
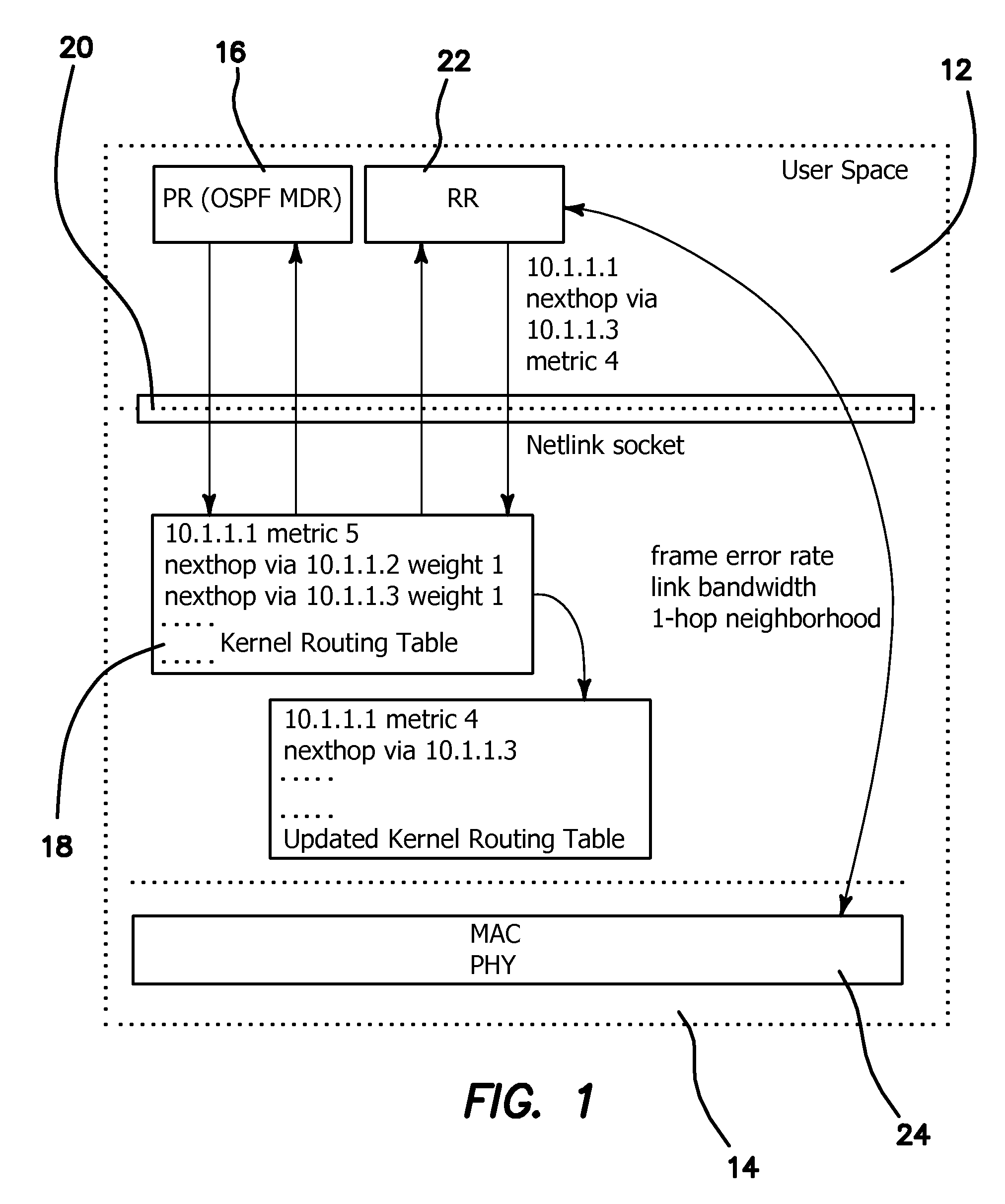
Hybrid Cross-Layer Routing Protocol for MANETs
ActiveUS20120294152A1Short delayEasy to deployError preventionTransmission systemsRouting decisionProtocol design
A Hybrid Cross-Layer Routing (HCLR) protocol designed and implemented based on the premise of being able to leverage a pair of proactive and reactive routing schemes in Mobile Ad Hoc Networks (MANETs) which is used to compensate against wireless link effects thereby allowing for making more intelligent routing decisions. Compared to standalone proactive or reactive routing protocols, HCLR provides a two-tier improvement logic by performing local on-demand search in an n-hop neighborhood utilizing a 2-tuple cross-layer routing metric. HCLR is implemented in a Linux Quagga suite and its performance improvements compared to OSPF MANET Designated Routing (MDR) through emulation studies is demonstrated.
Owner:RGT UNIV OF CALIFORNIA
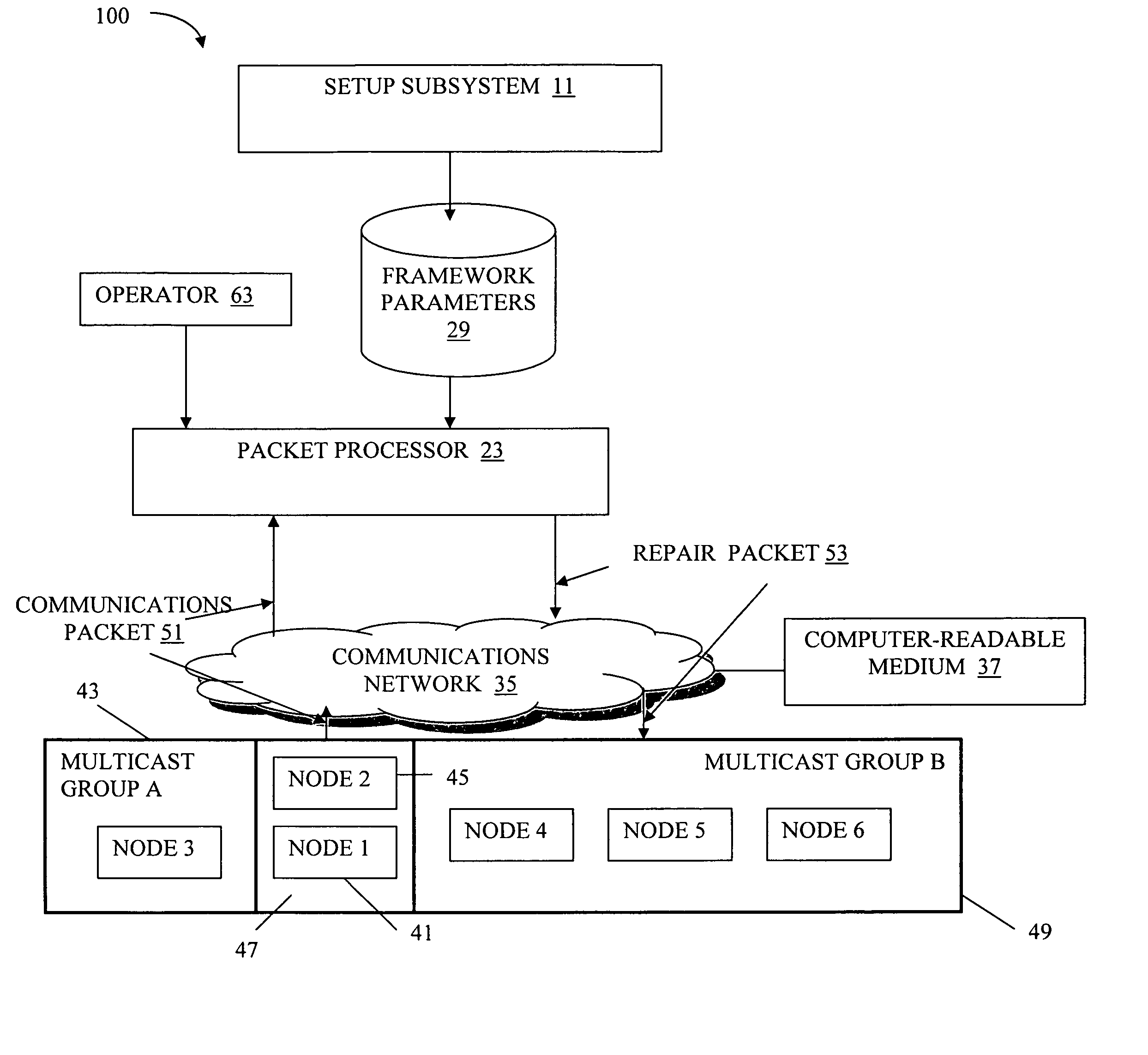
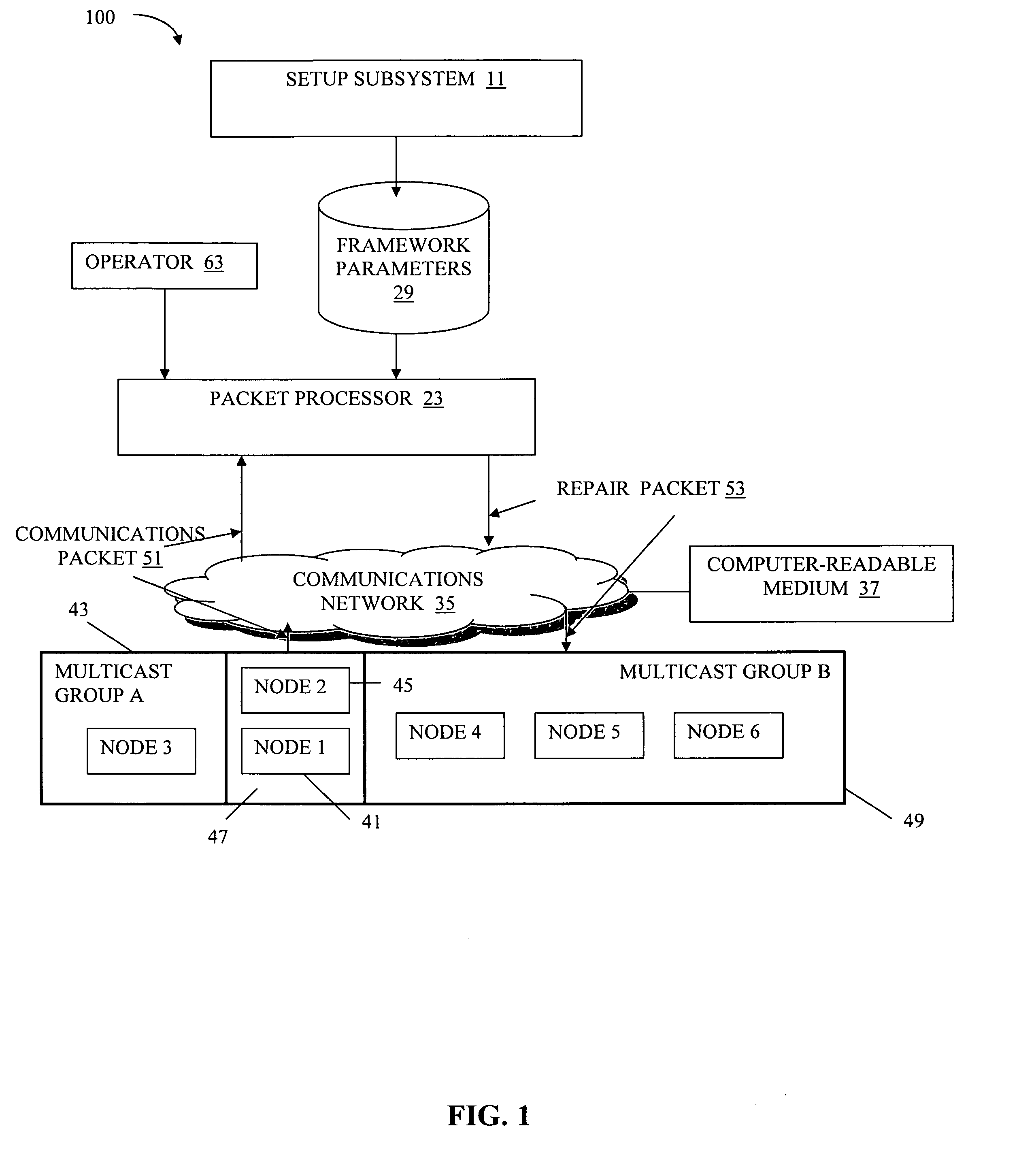
Lateral error correction for time-critical multicast
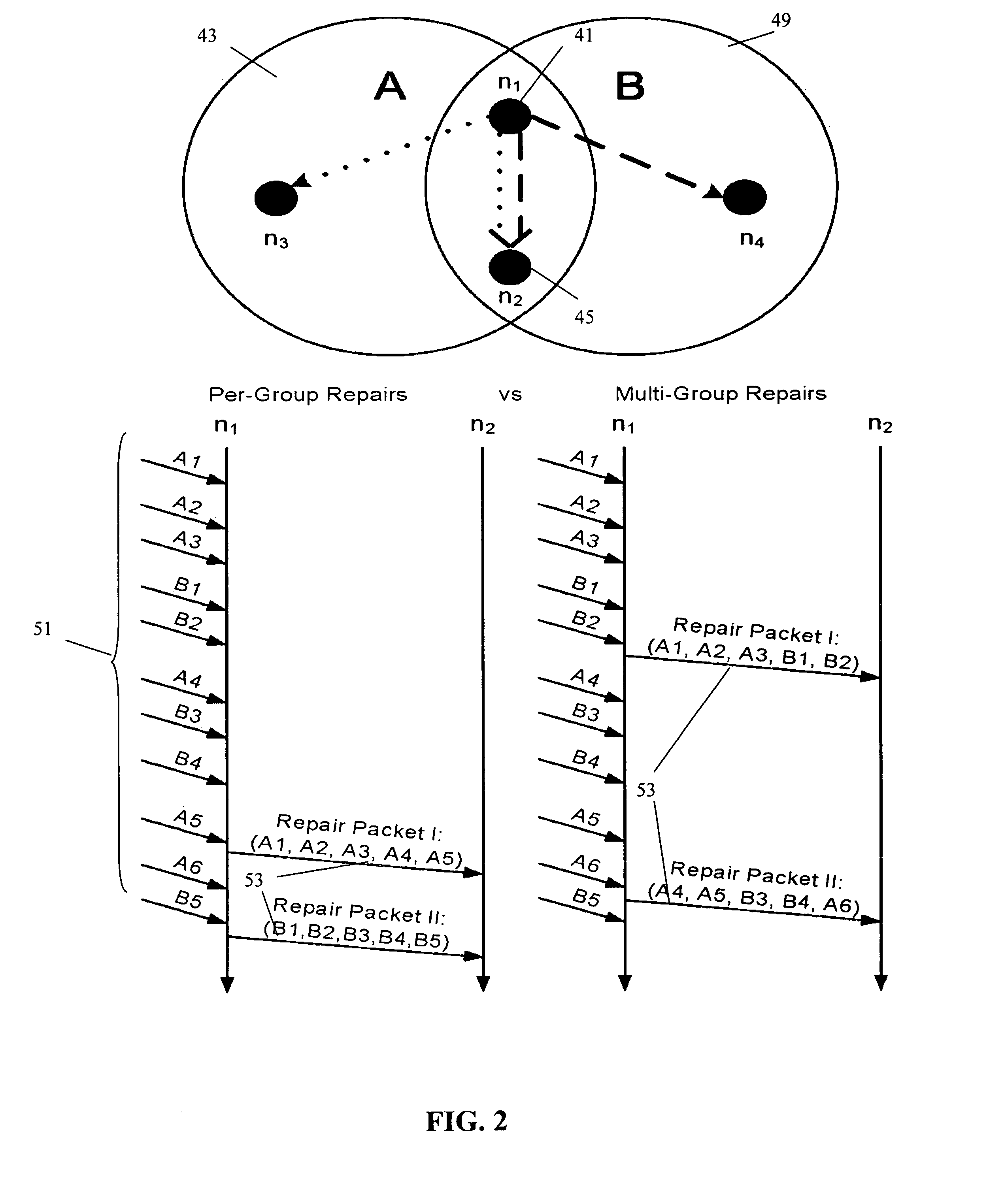
A system and method for providing a low-latency reliable multicast protocol designed for time-critical clustered applications. Internet Protocol (IP) multicast is used to transmit data and recovers from packet loss in end-hosts using a repair mechanism involving the exchange of XOR repairs between receivers and across groups. The system and method of the present invention can be embodied in a scalable, reliable and fast multicast primitive that can be layered under high-level abstractions such as publish-subscribe, group communication and replicated service / object infrastructures.
Owner:CORNELL RES FOUNDATION INC
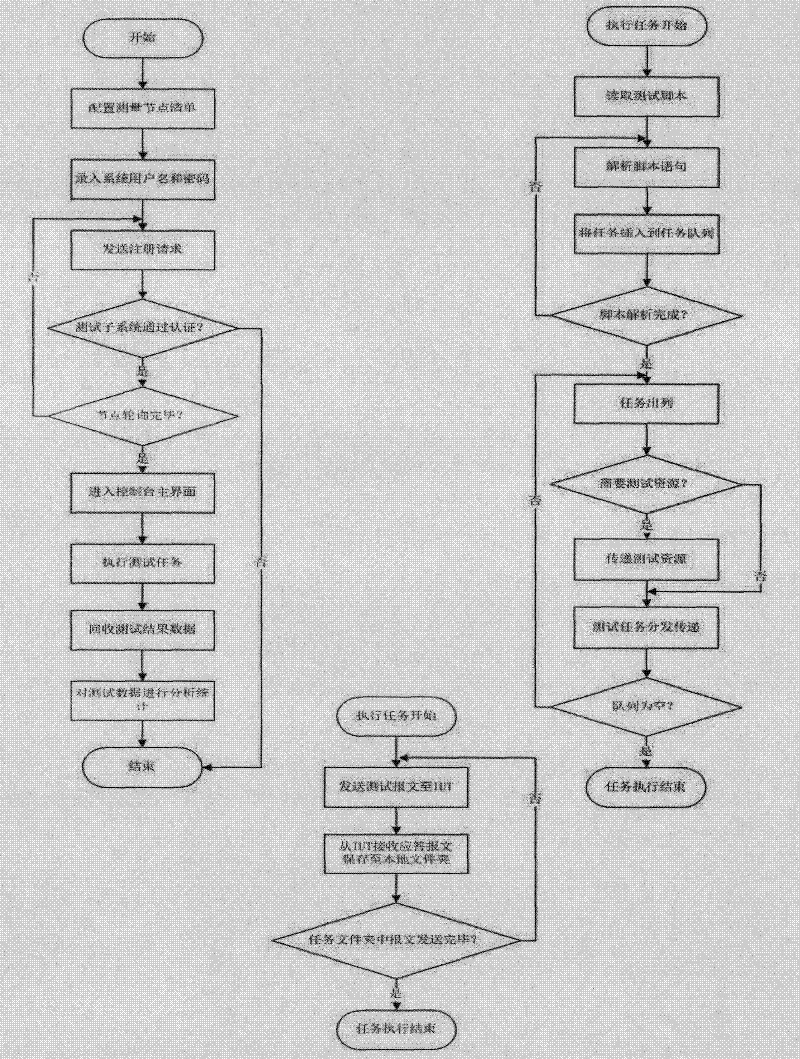
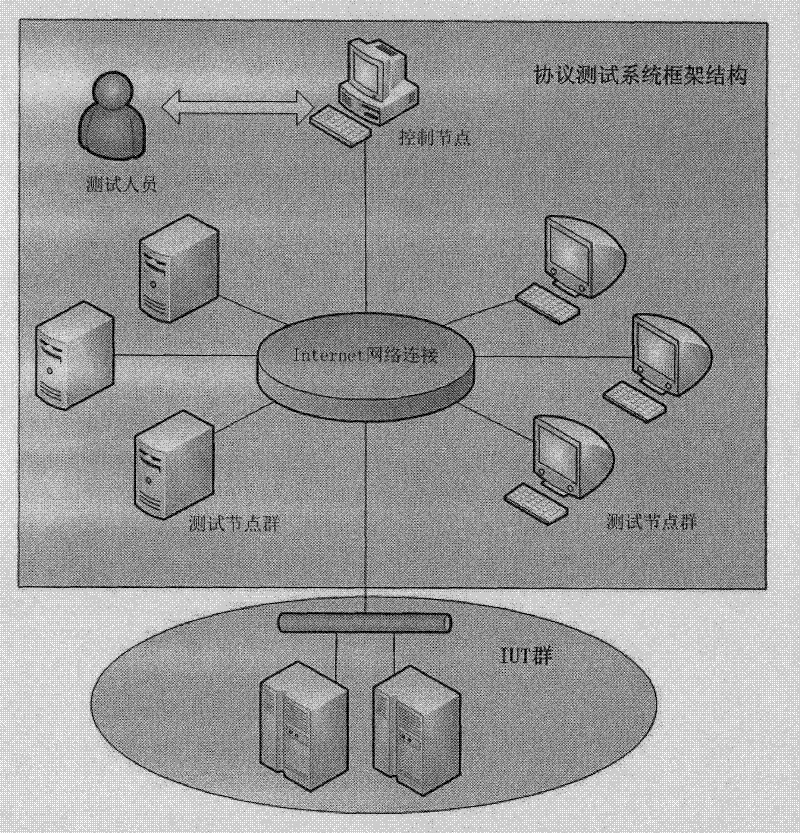
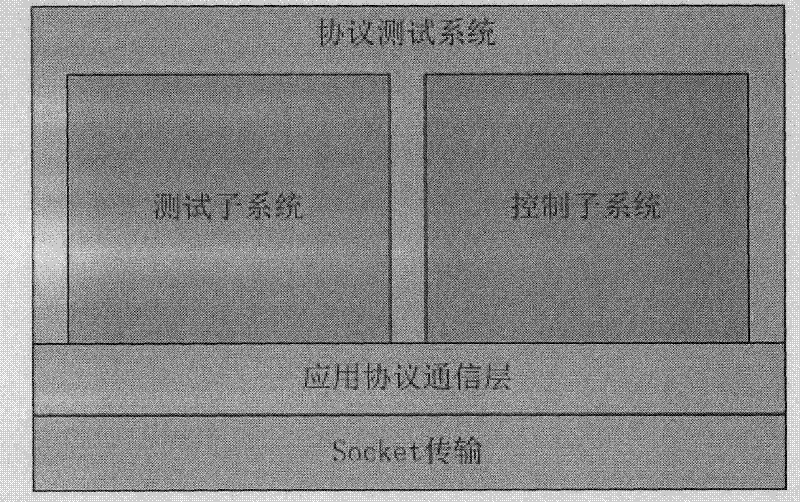
Distributed protocol test system and method
InactiveCN102420727ASolve deployment difficultiesOrderly managementData switching networksTest efficiencyProtocol design
Owner:BEIJING UNIV OF POSTS & TELECOMM
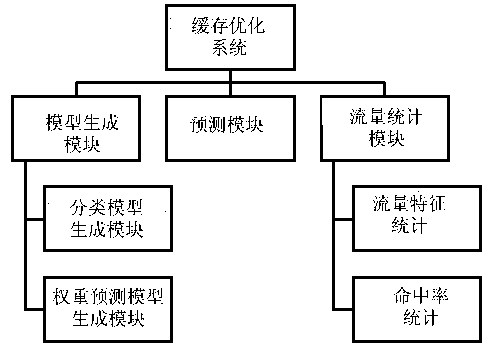
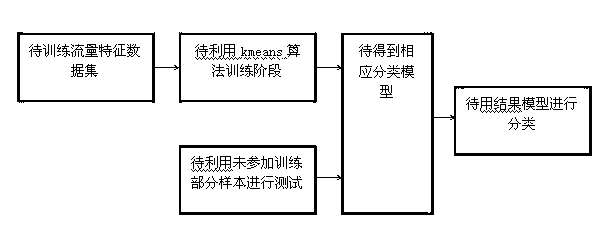
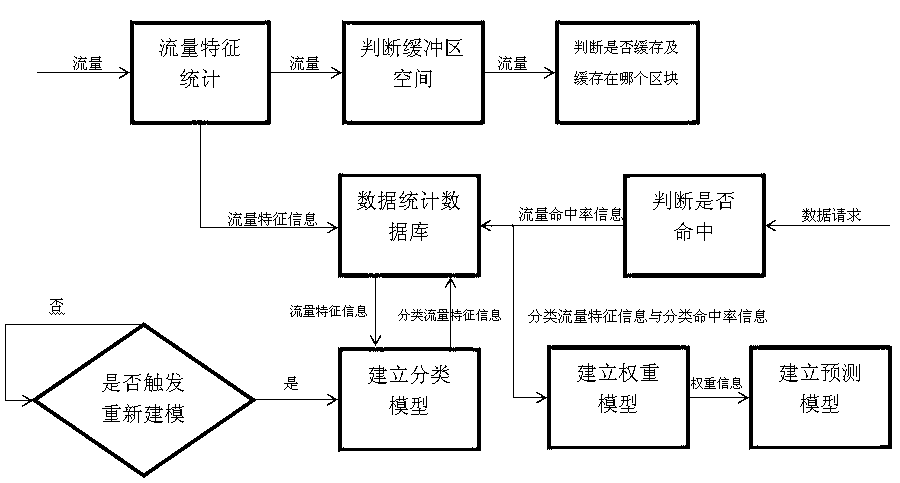
Network intermediate node cache optimization method based on flow characteristic analysis
InactiveCN103023801AMaximize utilizationTraffic conditions are closely relatedData switching networksProtocol designCache optimization
The invention belongs to the field of computer network communication and particularly relates to a network intermediate node cache optimization method based on flow characteristic analysis. The method includes when the flow passes the intermediate node, firstly classifying the flow, and then according to the type of the flow, determining how to process the flow in divided buffer area space of the type according to the cache condition of the area and combining a least recently used (LRU) algorithm. The system can update flow classification models and redistribute buffer space to different new classifications regularly. The method mainly focuses on solving the transparency problem of a network intermediate node cache strategy, namely, algorithm design of the network intermediate node cache is guaranteed to be unrelated to a specific user layer protocol design, and the efficiency of the strategy which satisfies the programming transparency is managed to be optimal.
Owner:FUDAN UNIV
Methods of Preventing or Treating Respiratory Conditions
InactiveUS20090186038A1Reduce developmentAvoid and reduce side effectAntibacterial agentsAntimycoticsProtocol designRespiratory infection
Owner:MEDIMMUNE LLC
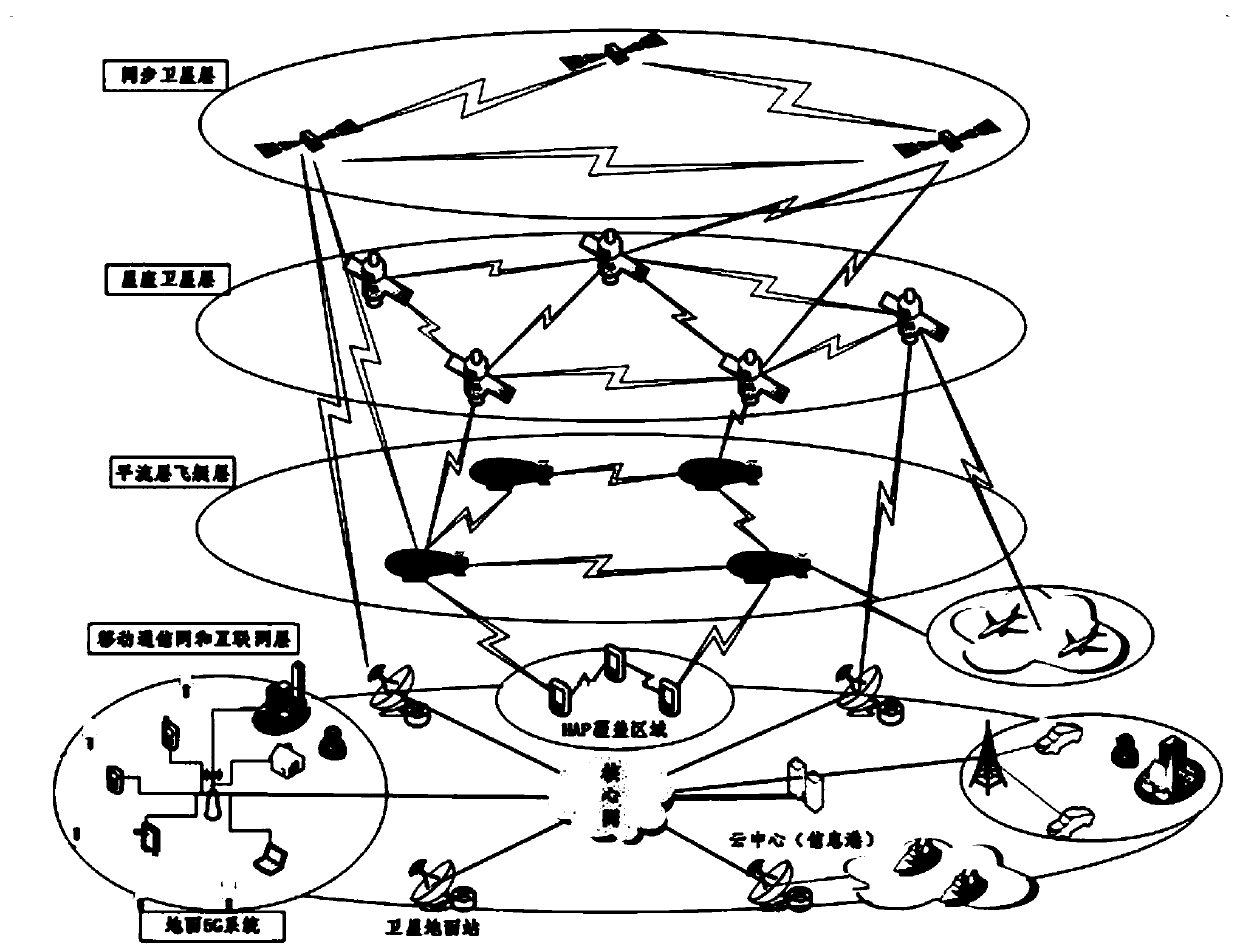
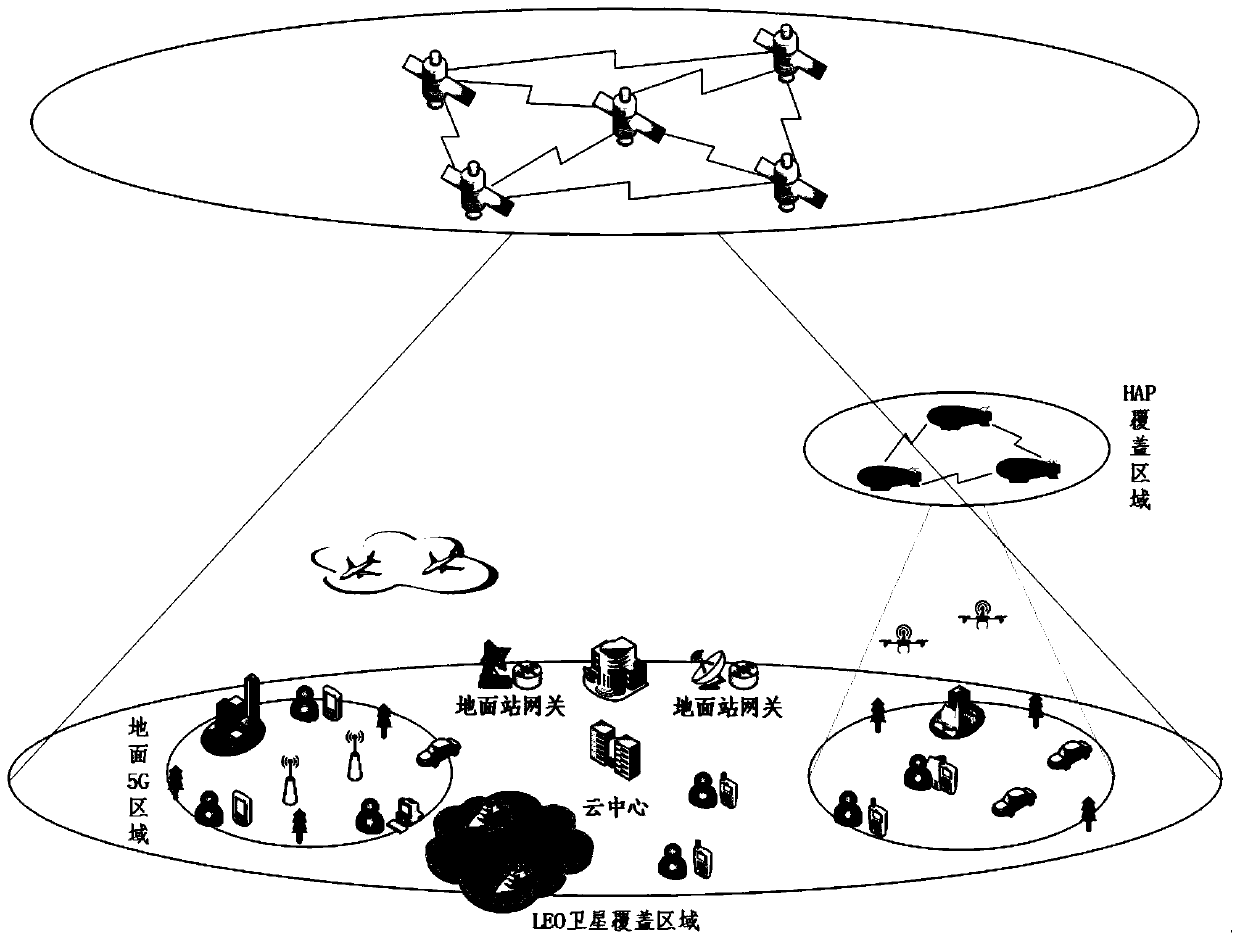
Air-space-ground integrated network system architecture based on near space platform and design method
ActiveCN110493791AIncrease available bandwidthIncrease link capacityRadio transmissionNetwork planningProtocol designTelecommunications link
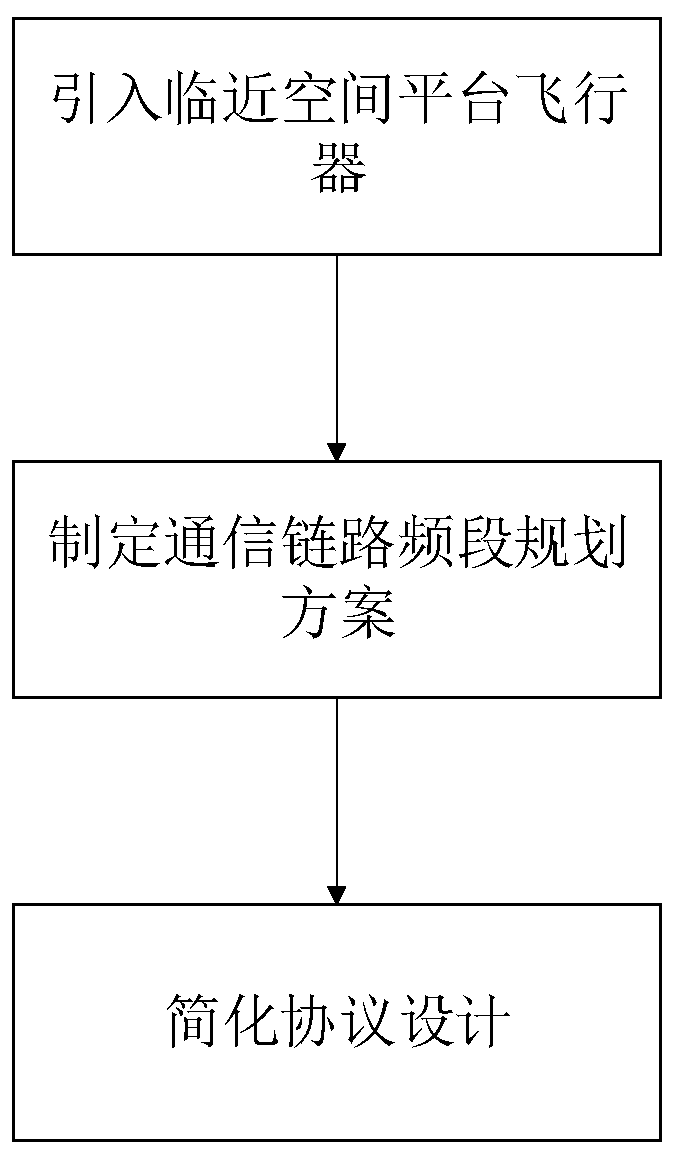
The invention discloses an air-space-ground integrated network system architecture based on a near space platform and a design method, and belongs to the technical field of wireless communication, andthe design method comprises the following steps: S1, introducing a near space platform aircraft; S2, formulating a communication link frequency band planning scheme; S3, simplifying protocol design.When communication link selection is carried out, the communication link selection is carried out based on the principle of minimizing propagation time delay and routing hops according to the geographical location relationship and the service type of two users carrying out communication. According to the invention, the near space platform aircraft is introduced into the network system architecture; a satellite network and a ground network are fused; global coverage is realized; the communication service quality of a non-ground network coverage area is effectively improved, extremely high robustness is achieved, the rerouting rate, the switching rate, the system delay overhead, the system access capacity and the like can be remarkably improved by designing a simplified protocol process, a frequency band planning scheme and a link selection scheme, and the method is worthy of application and popularization.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 38 RES INST
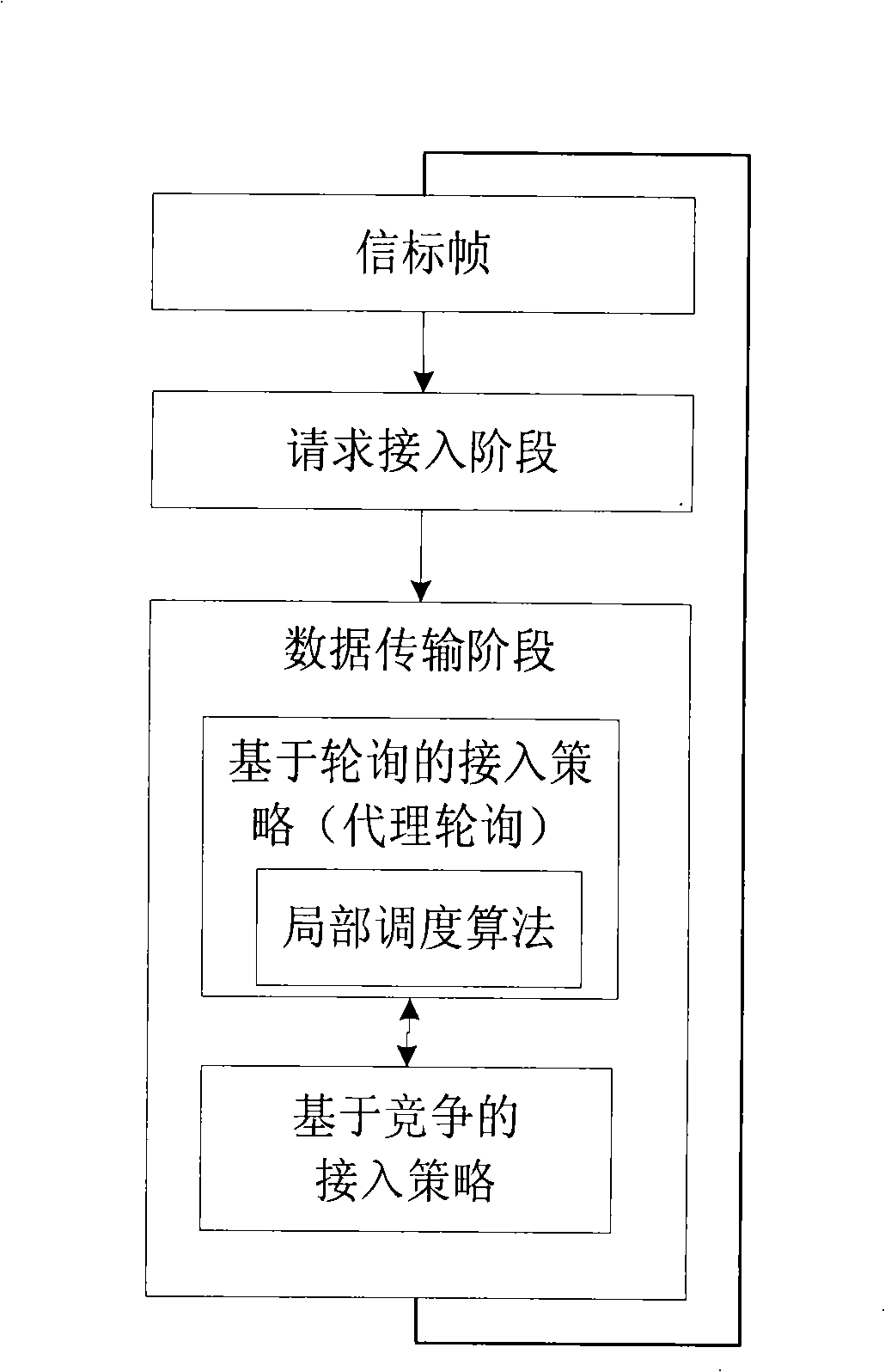
Distributed media access control protocol for increasing capacity of wireless local area network
InactiveCN101286980ALarge capacityImprove QoS performanceData switching networksWireless communicationProtocol designTraffic flow
The invention discloses a distributed media access control protocol, in particular to a proxy polling mixed access protocol for increasing the capacity of a wireless local area network. The invention designs an access strategy based on polling to avoid channel conflicts, namely, according to a partial schedule strategy designed by the protocol, the existing transmission traffic flow substitutes an AP to select next transmission traffic flow, which leads the traffic flow in a network to be transmitted in sequence in a relay way. Meanwhile, the protocol adopts an access strategy based on competition as supplement to solve problems arising when a polling decision is wrong. The partial schedule strategy of the invention provides a service differentiating system based on conditions, which promotes the fairness of services with low priority when network load is relatively low. On the basis of a strategy for forecasting queue information, the partial schedule strategy further adopts a periodic polling strategy as supplement to modify wrong polling decisions on time, so as to adapt to service arrival models. The protocol remarkably increases the capacity of networks and has good performance.
Owner:HUAZHONG UNIV OF SCI & TECH
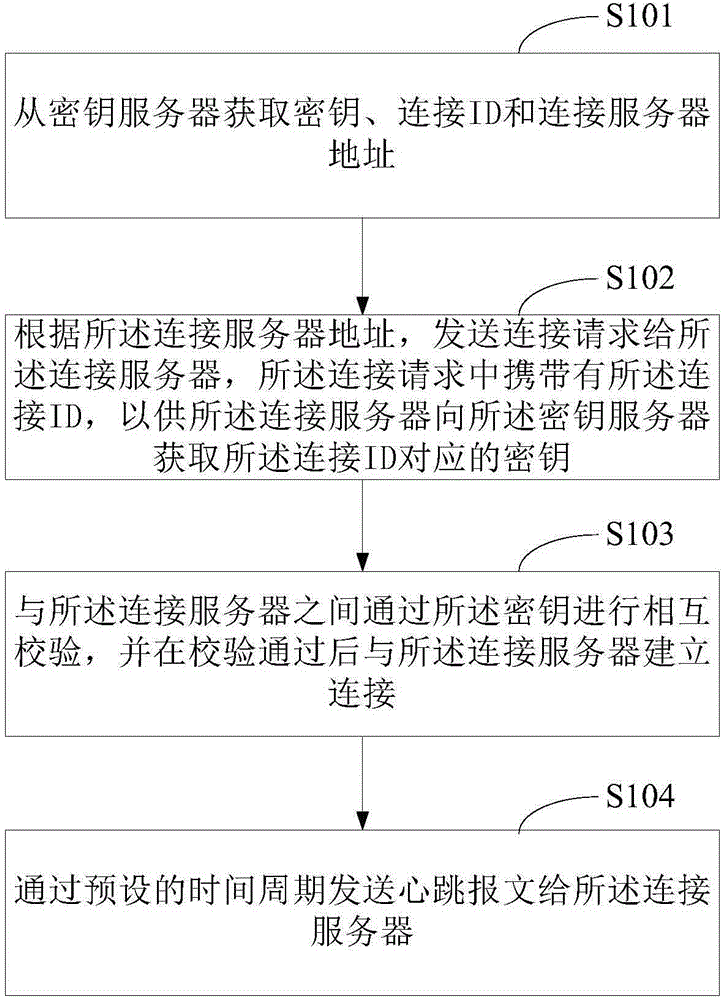
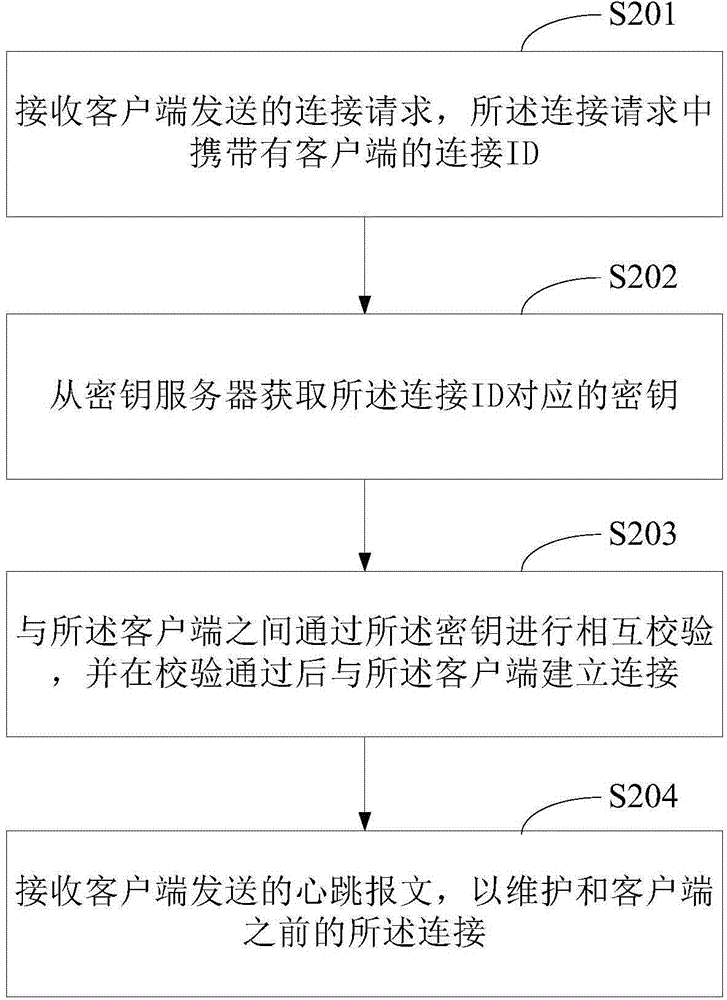
Method of establishing long connection of client and server and apparatus thereof
ActiveCN105337935AImplement encryptionImprove securityUser identity/authority verificationProtocol designClient-side
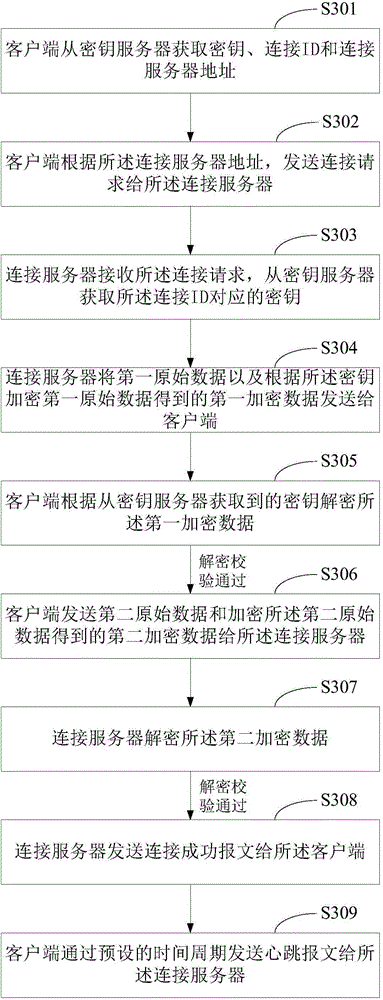
The invention provides a method of establishing long connection of a client and a server and an apparatus thereof. The method comprises the following steps of acquiring a secret key, a connection ID and a connection server address from a secret key server; according to the connection server address, sending a connection request to a connection server, wherein the connection request carries the connection ID so that the connection server acquires a secret key corresponding to the connection ID from a secret key server; carrying out mutual decryption verification with the connection server through the secret key, and after the decryption verification is passed, establishing connection with the connection server; through a preset time period, sending a heartbeat message to the connection server. In the invention, a communication protocol designed autonomously is used; long connection between the client and the server is established; simultaneously, encryption processing is performed on data transmitted by a user and safety is high.
Owner:ADVANCED NEW TECH CO LTD
Method and system for deploying and evaluating networks in indoor environments
InactiveUS20110032826A1Minimal effortAccurate knowledgeError preventionTransmission systemsNetworking protocolProtocol design
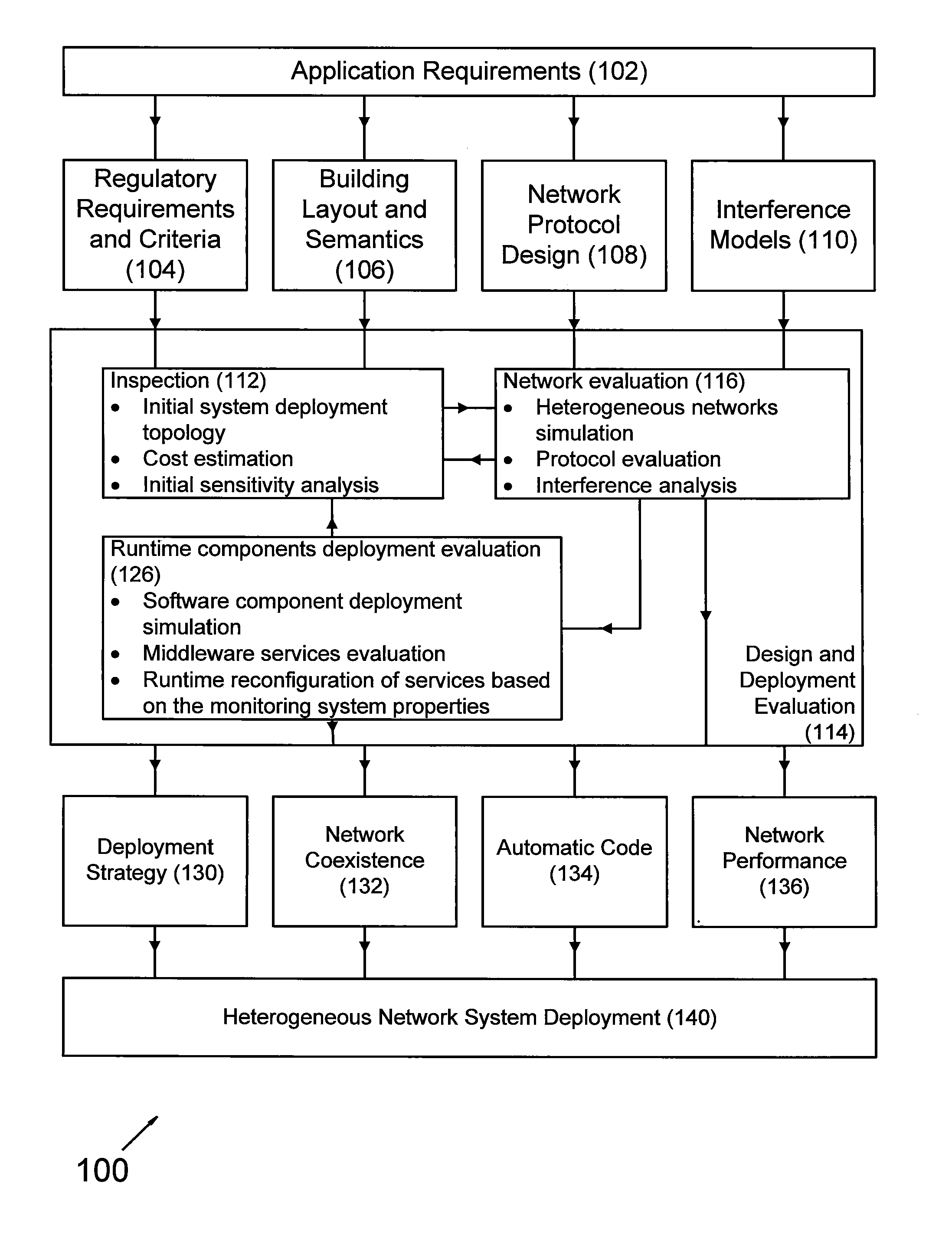
A method for deploying and evaluating a network system includes providing an electronic two- or three-dimensional representation of a layout of a building, placing a plurality of nodes of the network system in the building, and communicatively coupling the nodes together to form the network system. The nodes are inspected dependent upon a regulatory requirement and / or the representation of the layout of the building. The network is evaluated dependent upon data collected during the inspecting and dependent upon a network protocol design and / or an interference model. The inspecting of the nodes and the evaluating of the network are performed automatically by use of at least one electronic processor.
Owner:ROBERT BOSCH GMBH
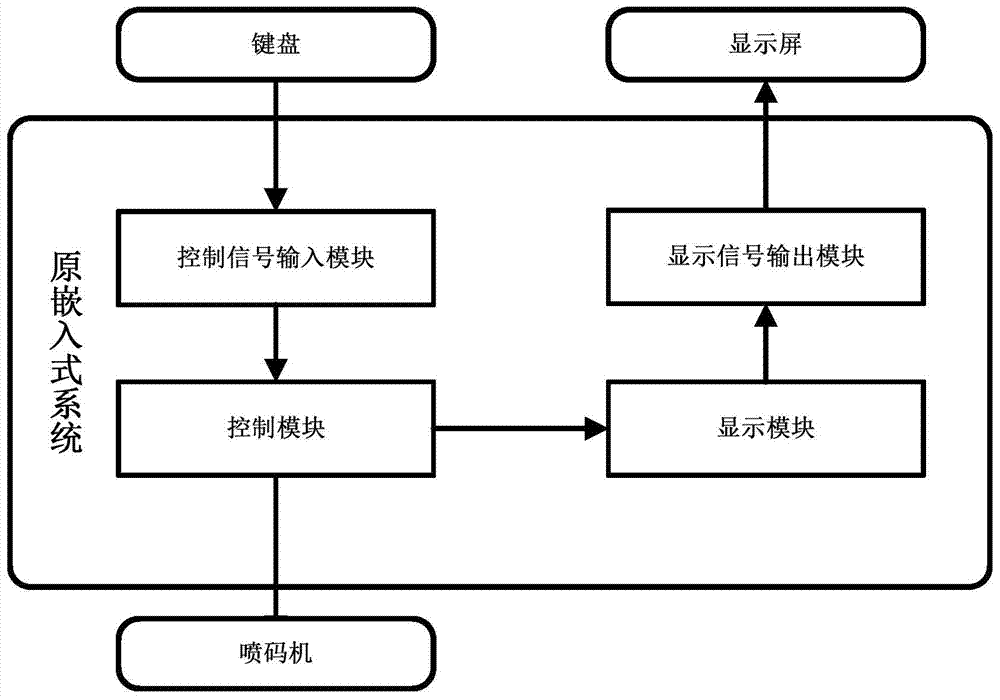
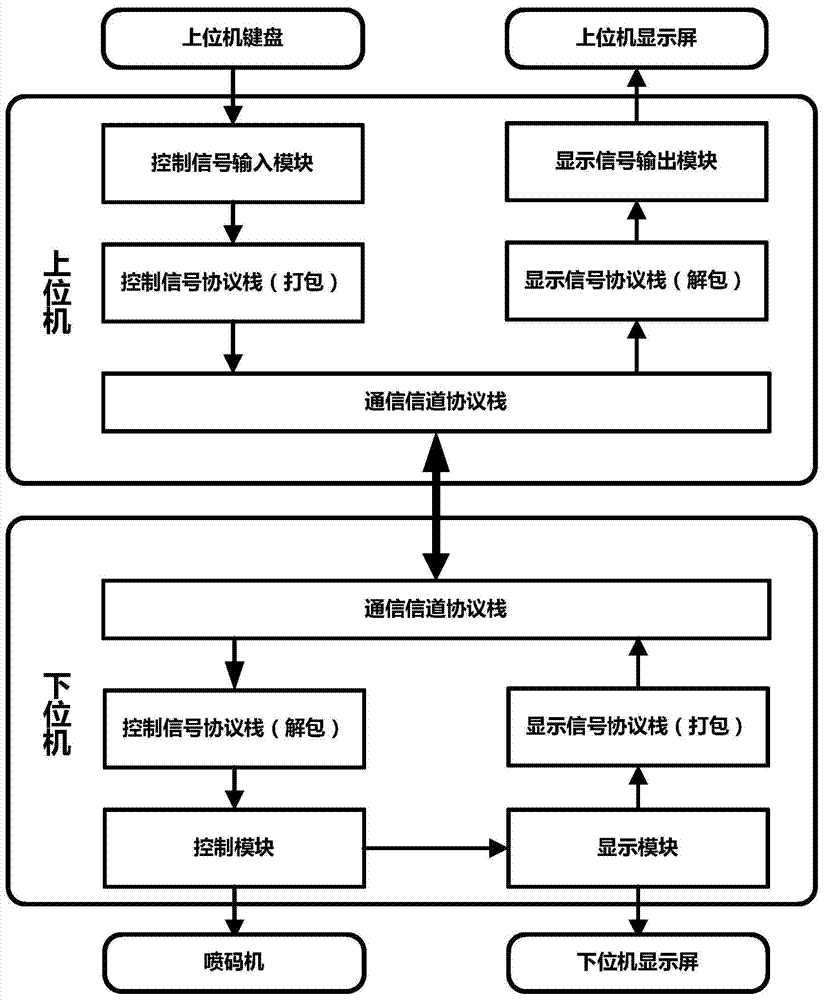
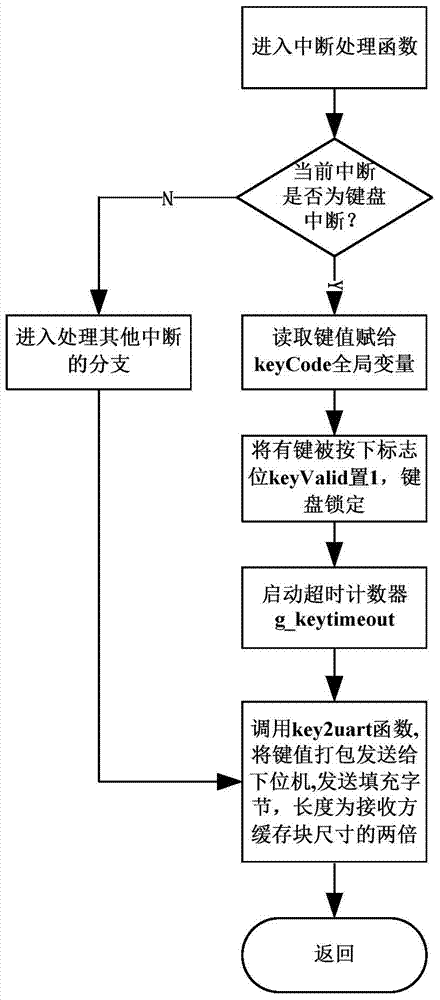
Remote implementation method based on industrial inkjet printer control system
InactiveCN103802509AAchieve echoRealize same-screen transmissionOther printing apparatusHardware structureProtocol design
A remote implementation method based on a traditional industrial inkjet printer local control system comprises the following steps of a local control equipment hardware remote step including reconstituting hardware structures of far-end control systems of an upper computer and a lower computer; a remote communication protocol design step including adding a communication channel protocol stack module; a packing protocol and unpacking protocol design step of transmission data, which includes adding a transmitting and receiving protocol stack module; a far-end packing information sending and receiving program design step which includes completing an I / O module of control data and display data. The remote implementation method based on the traditional industrial inkjet printer control system achieves remote operation of the industrial inkjet printer, effectively protects a site operator to stay away from an operation site harmful to a human body; meanwhile, the remote implementation method is based on the traditional industrial inkjet printer local control system, is low in costs and easy to implement; a completed remote control system accords with an original local control system mode and method, retraining on site operators is not needed, centralized control is facilitated, and human cost is further reduced.
Owner:BEIHANG UNIV
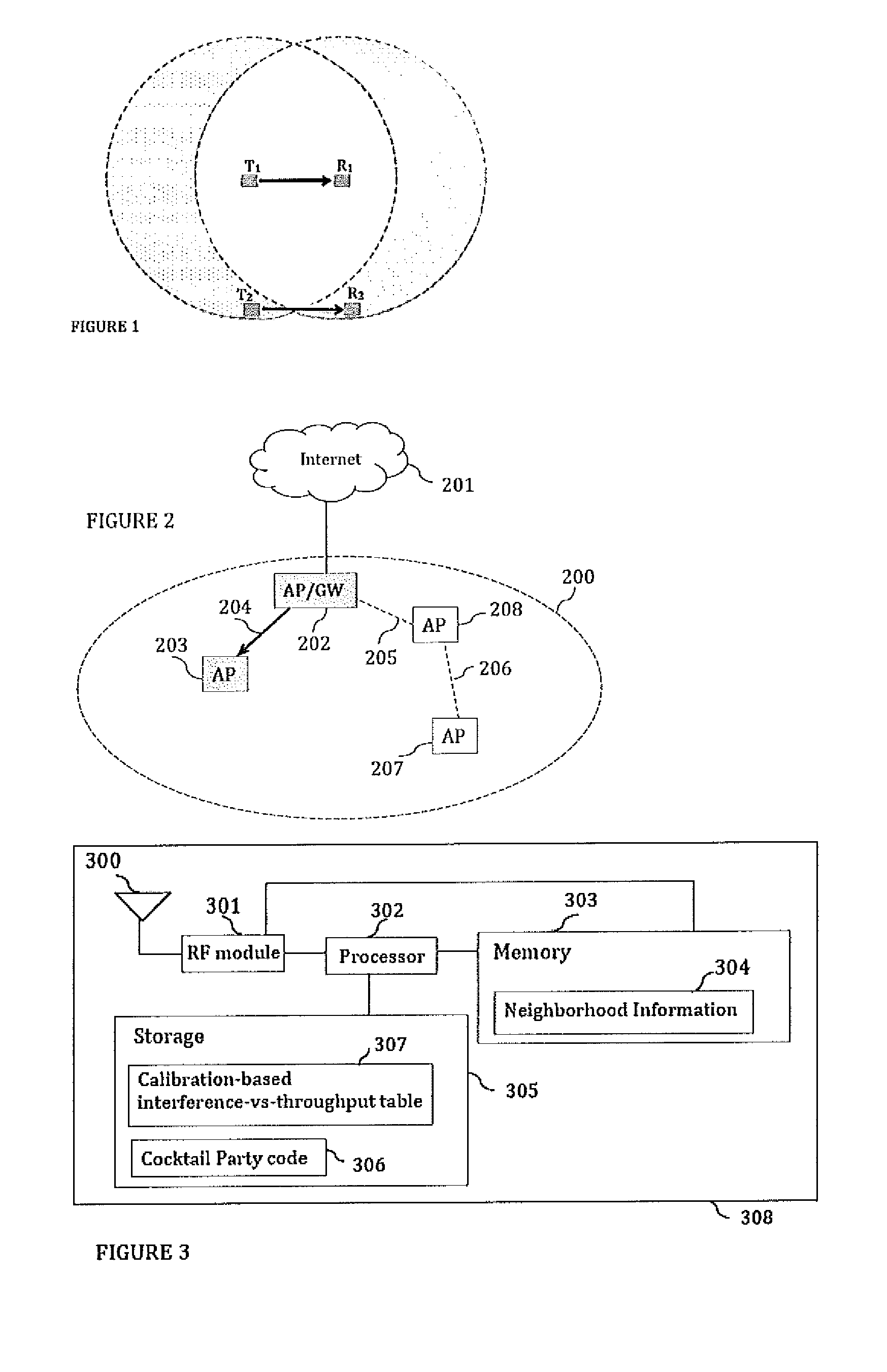
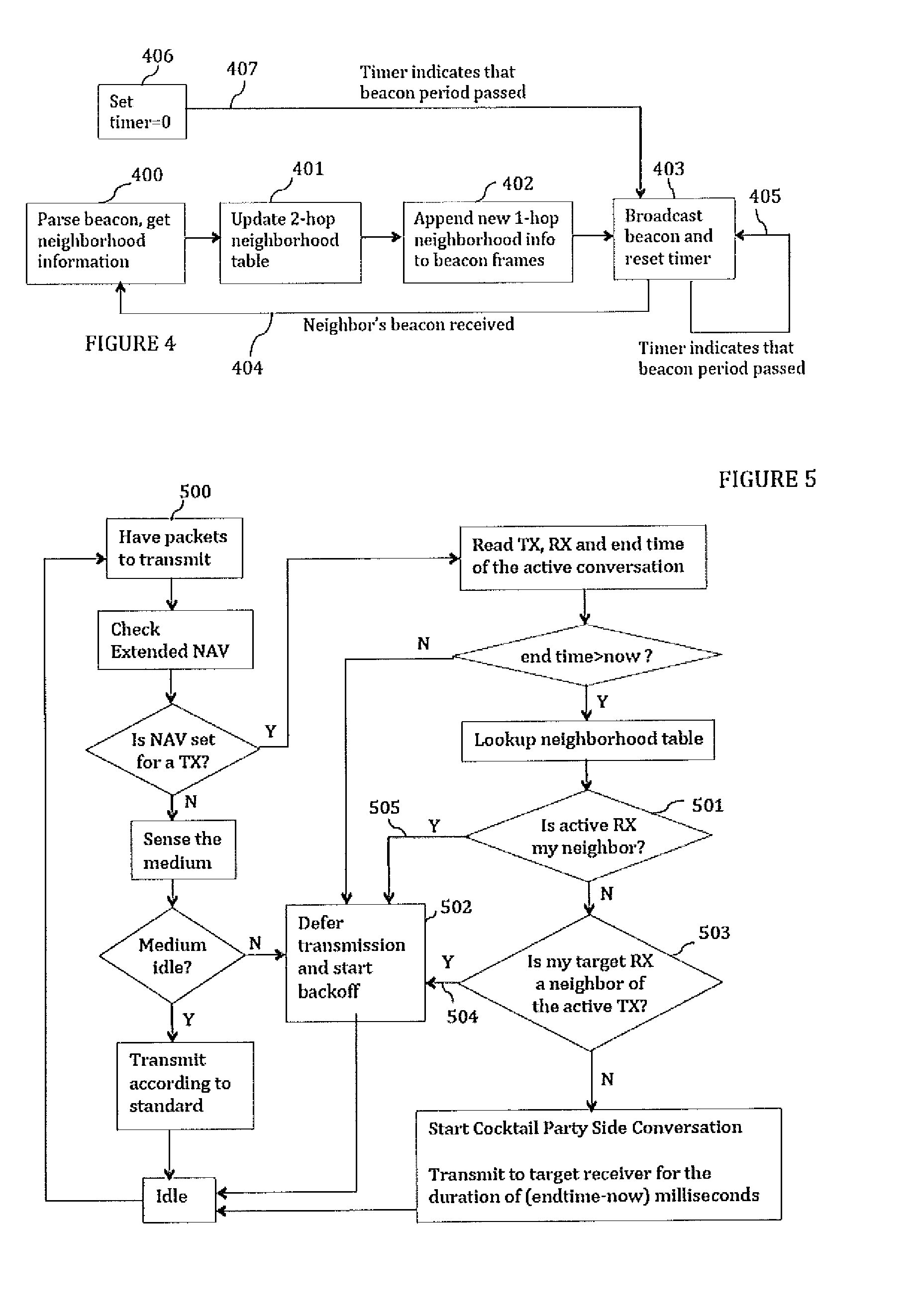
Cocktail party: side conversations and talking over in wireless mesh networks
ActiveUS20140254459A1Minimize jitterSpecial service provision for substationNetwork topologiesDistributed coordination functionProtocol design
The present disclosure proposes a method for minor modifications to the Distributed Coordination Function (DCF) channel access mechanism in order to enable a greater number of concurrent communications in a unit area in compliance with the current protocol design. The method comprises equipping nodes with wider neighborhood information than what is obtained with IEEE 802.11, and with a device calibration that equips the device with the knowledge of its performance in the presence of interference. The present disclosure medium access mechanism increases the aggregate throughput with every additional concurrent communication that is enabled in the shared medium. Cocktail Party-capable devices can fairly coexist with 802.11 legacy DCF devices, and co-operate with these devices in the same network without changes to those devices or to the standard. The same or similar mechanisms can be applied to other systems and standards in order to enable concurrent communications in the same contention area.
Owner:AIRTIES SAS
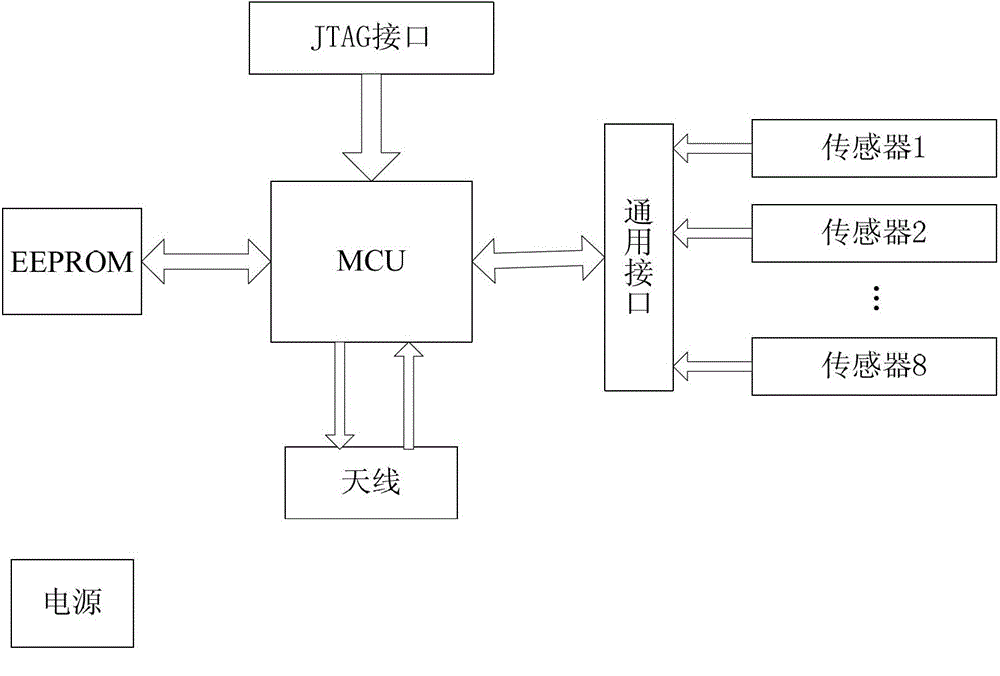
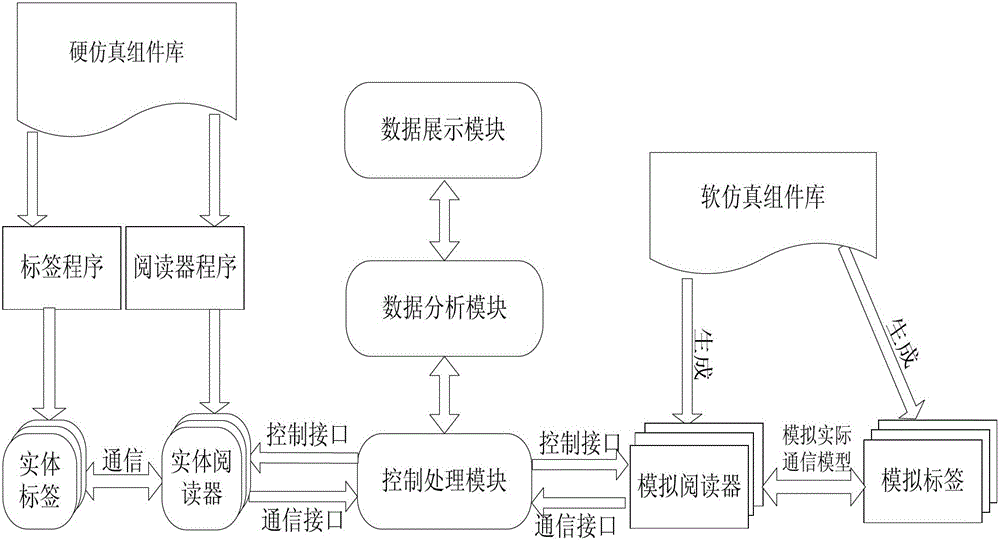
Open type frequency identification device (RFID) experiment platform and tag
InactiveCN103065166AHas the ability to developSimple designCo-operative working arrangementsRecord carriers used with machinesData displayProtocol design
The invention discloses an open type frequency identification device (RFID) experiment platform and a tag. The open type RFID experiment platform and the tag can be used as a RFID tag which integrates all sorts of sensors to perform development of perception ability and also can be used as a testing and verifying platform of RFID protocol design. The open type RFID experiment platform comprises a passive programmable RFID tag and a RFID integrated simulator (RFID-IS). The passive programmable RFID tag comprises a micro processing unit, a JTAG interface, a general interface, a storage device and an antenna and is used for providing a sensing tag hardware testing platform. The RFID-IS is used for providing soft and hard simulation conditions and comprises a soft simulation module library, a hard simulation module library , a control processing module, a data analyzing module and a data displaying module. Rapid development and software simulation of the RFID protocol and a perception function can be done based on the RFID-IS. Meanwhile, hardware development based on the passive programmable RFID tag is supported. The open type RFID experiment platform and the tag can be widely applied to all sorts of RFID application, verification of research and development, development speed is improved and further enrichment and development of the RFID and Internet of Things technology are supported.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Error code testing system based on FPGA (Field Programmable Gate Array)
ActiveCN102143023AIncrease flexibilityImprovement of design conceptData switching networksProduction lineProtocol design
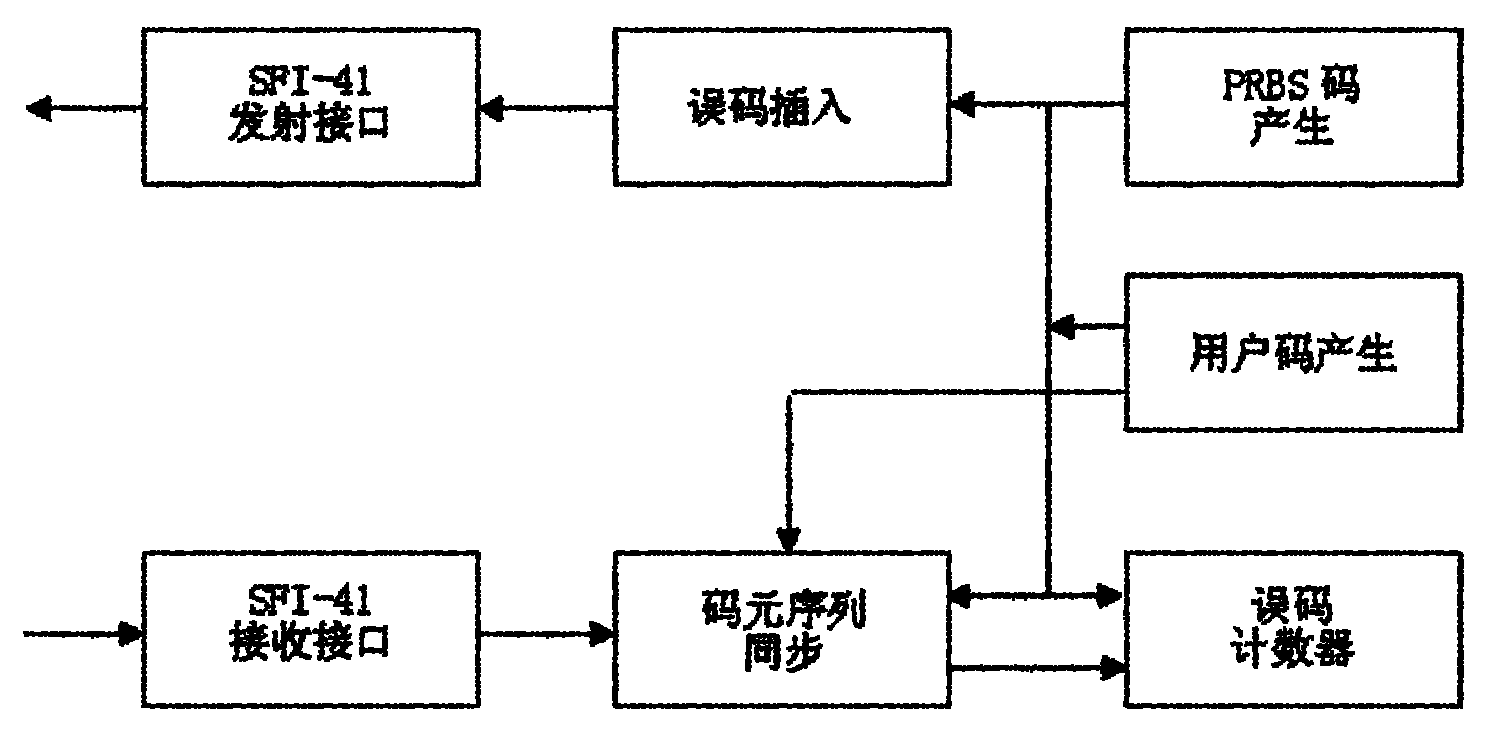
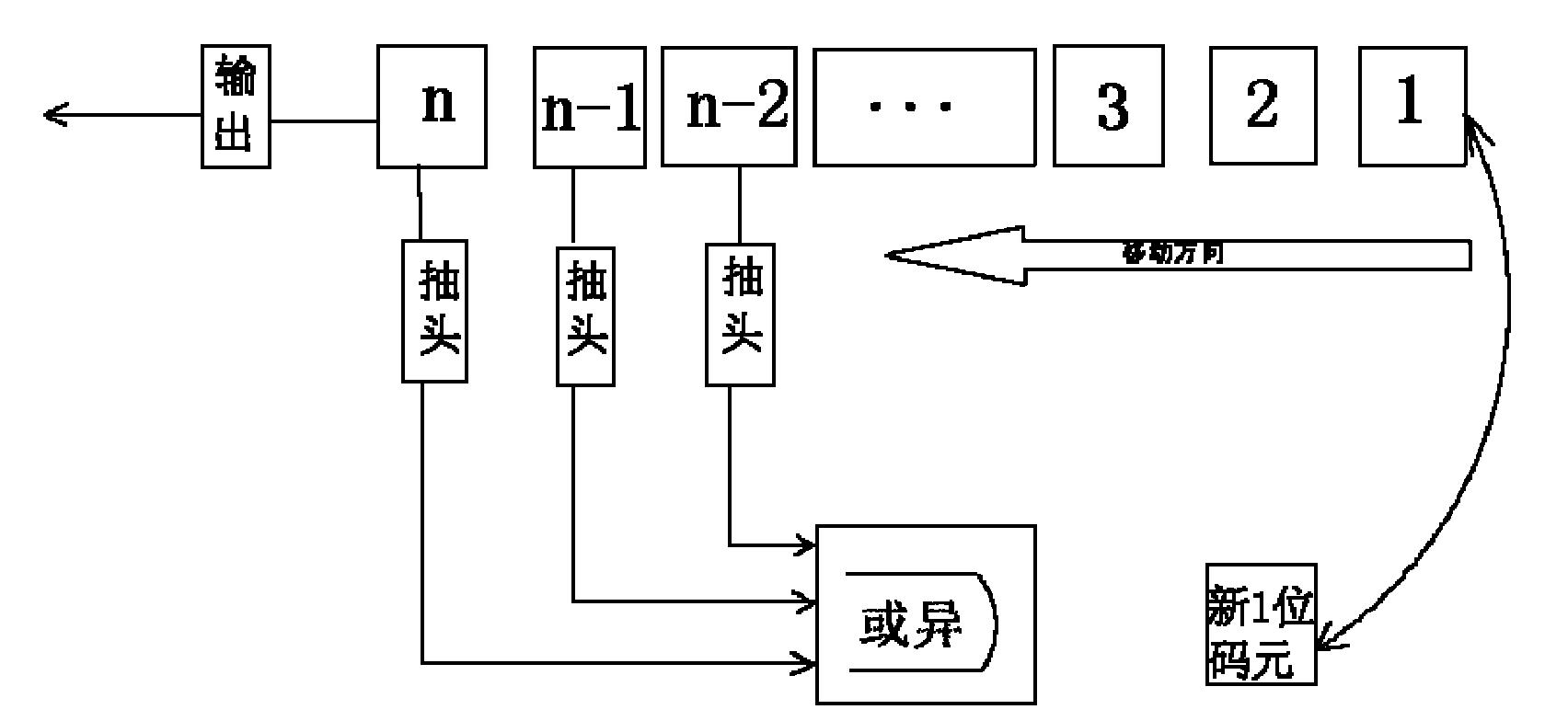
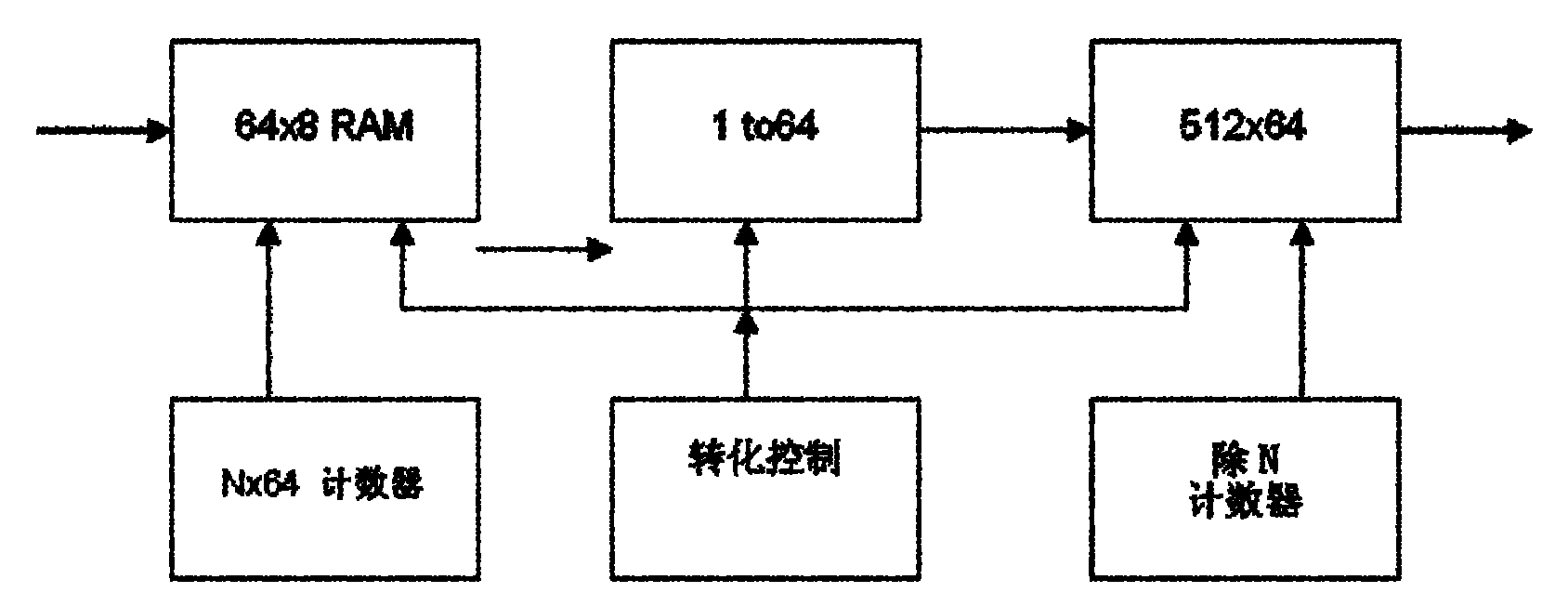
The invention discloses an error code testing system based on an FPGA (Field Programmable Gate Array), which comprises a code element sequence synchronization module, an error code counter, a user code generation module and a PRBS (Pseudo Random Binary Sequence) module, wherein the code element sequence synchronization module is used for realizing the synchronization of a receiving code element and a local code element; the error code counter is used for counting number of code element errors in same time period; the user code generation module is used for generating a custom code; and the PRBS module is used for generating a PRBS code element. The error code testing system disclosed by the invention improves the principles of the traditional circuit, apparatus and communication protocol design by applying integration and flexibility of the FPGA, and can be applied to a production line and research and development to be used as a main control chip of an error code testing apparatus.
Owner:SOURCE PHOTONICS CHENGDU
Multi-path coordinative communication method for underwater sound sensor network
ActiveCN104601280AImprove protocol efficiencyReliable data transmissionError prevention/detection by using return channelProtocol designComputer science
The invention discloses a multi-path coordinative communication method for an underwater sound sensor network, belongs to the technical field of underwater sound communication, and aims at solving the problem that unstable point-to-point underwater sound communication in the underwater sound sensor network leads to increase network delay and even paralysis. The method is that different signals are transferred to the same collecting node through different relay nodes to obtain space diversity gain provided by different channels for receiving and decoding, and therefore, the reliability of underwater sound communication under the network environment can be improved. According to the method, the underwater sound physical communication technology and the route technology are combined by the cross-layer type protocol design method according to the application feature of the underwater sound sensor network, and meanwhile, the optimal selection of the reliable underwater sound communication and the relay node can be achieved, and therefore, the network protocol efficiency can be obviously increased.
Owner:THE 715TH RES INST OF CHINA SHIPBUILDING IND CORP
Design scheme for wireless sensor network sector protocol based on CDMA and TDMA
InactiveCN101237453ARelaxation of restrictionsImprove spectral efficiencyTime-division multiplexData switching by path configurationFrequency spectrumProtocol design
The invention discloses a clustering sensor network protocol design proposal on the basis of the CDMA and the TDMA DTSA. The proposal clusters the sensor network nodes according to certain strategy and distributes one orthogonal OVSF for each cluster to realize the concurrence of a plurality of clusters. The node in the cluster divides a plurality of time slots according to the service conditions. The dynamic time slot subscription strategy is adopted to distribute the time slots, thereby realize that a plurality of nodes work at the same time. Therefore, the frequency spectrum efficiency and the energy efficiency of the system are raised and the limits on the frequency band resource and the energy resource are released.
Owner:JIAXING WIRELESS SENSOR NETWORKS CENT CAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com