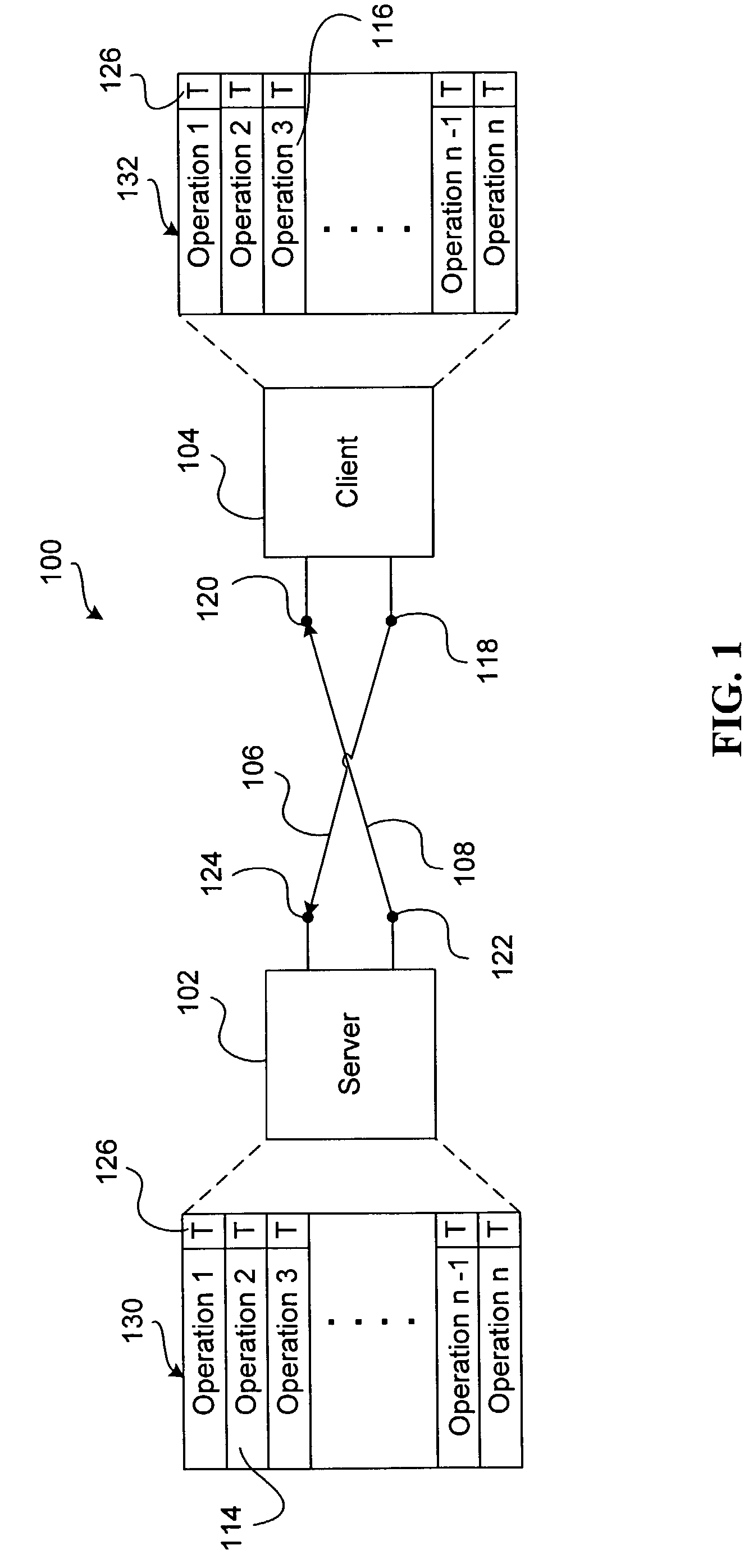
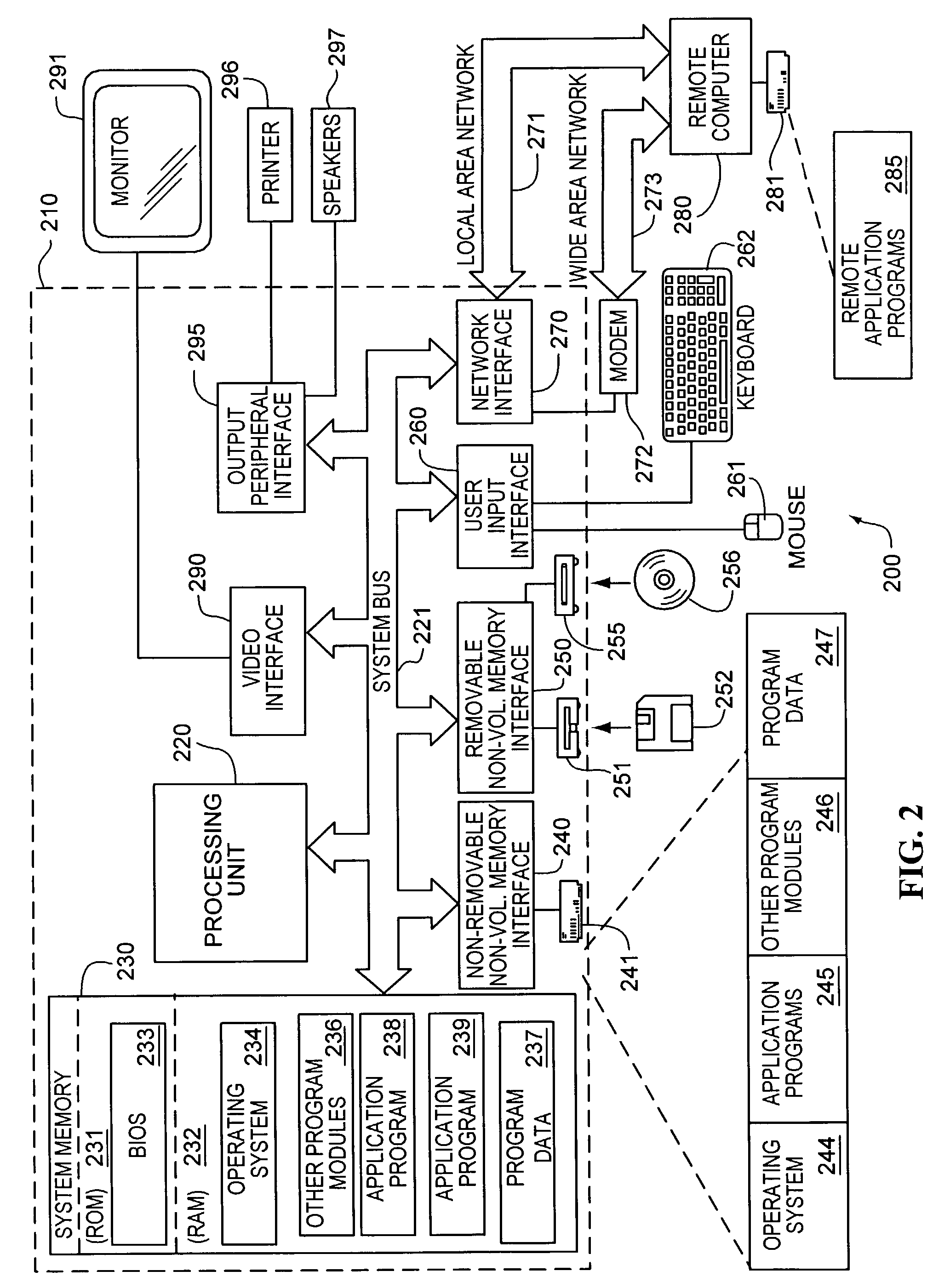
Patents
Literature
382 results about "Model checking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
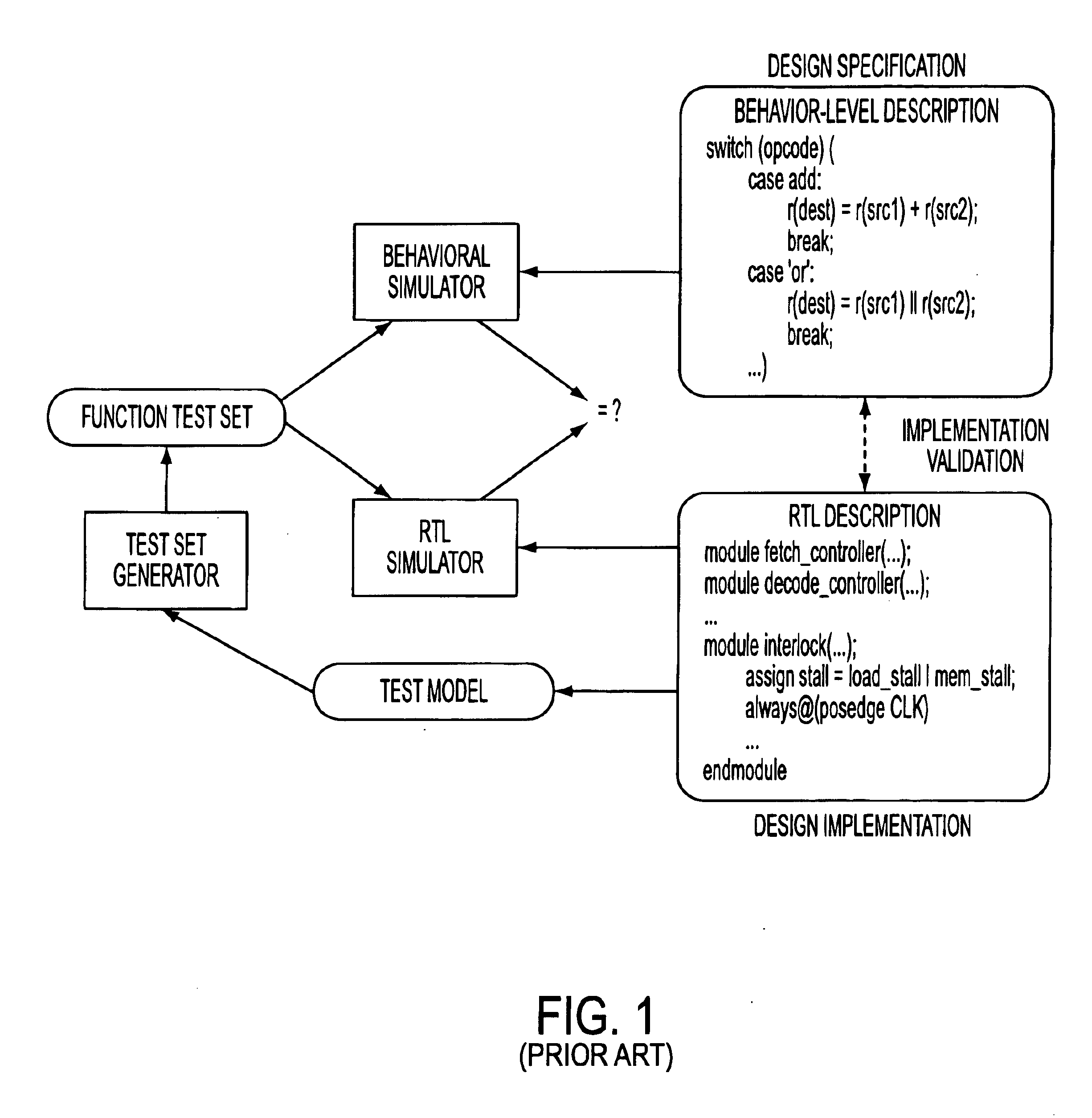
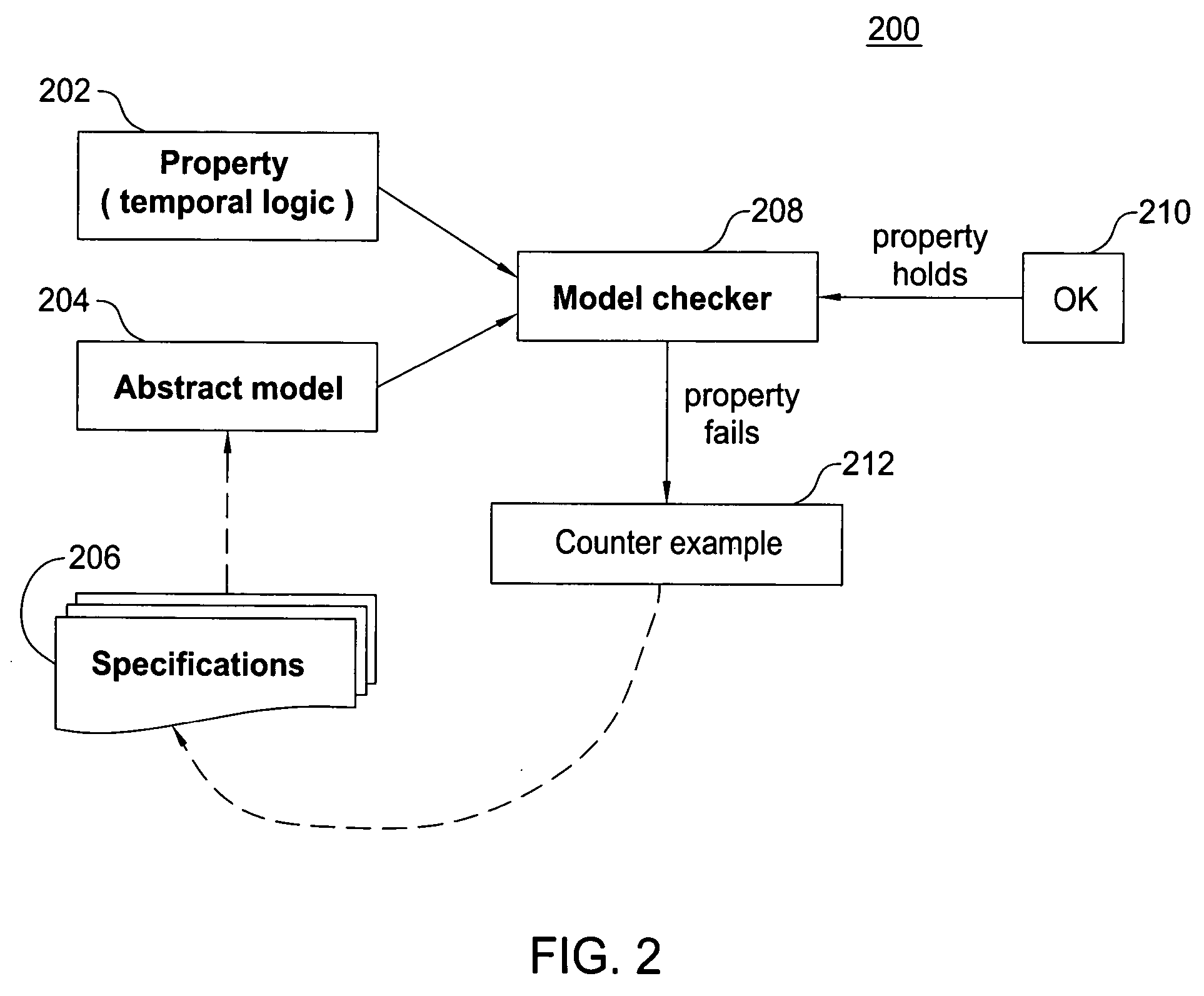
In computer science, model checking, or property checking, is, for a given finite-state model of a system, exhaustively and automatically checking whether this model meets a given specification (a.k.a. correctness properties). Typically, one has hardware or software systems in mind, whereas the specification contains safety requirements such as the absence of deadlocks and similar critical states that can cause the system to crash, as well as liveness requirements.
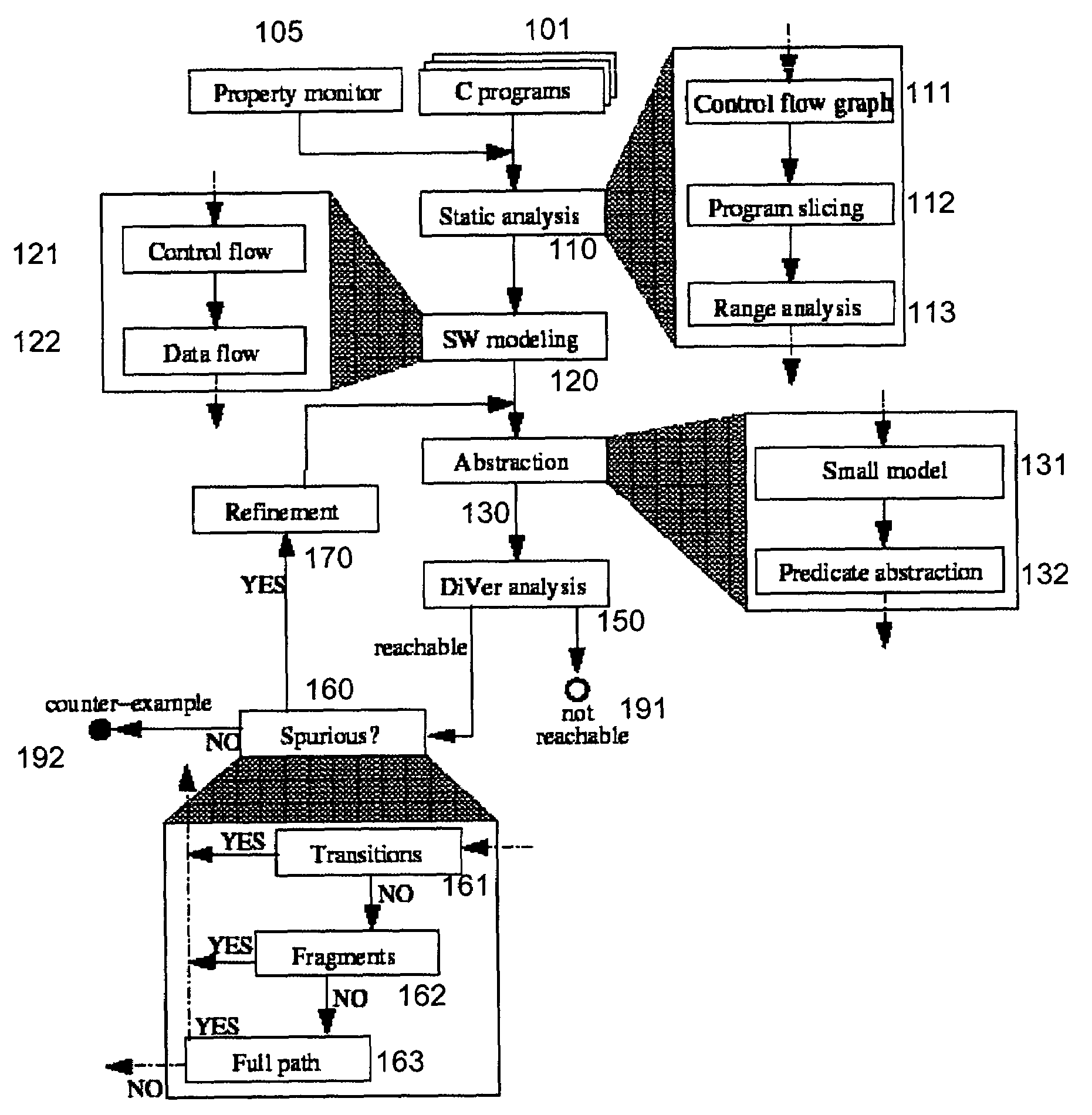
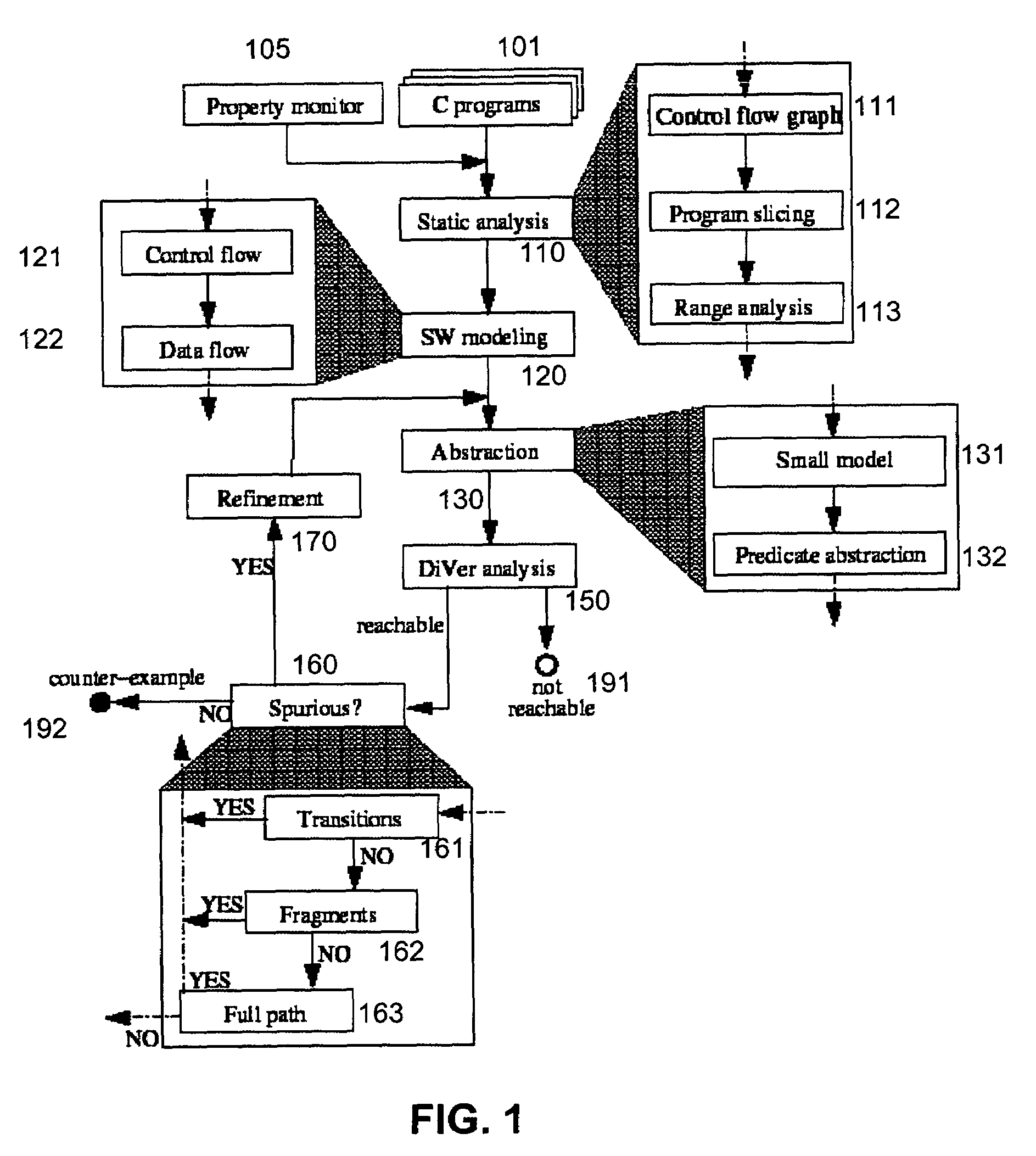
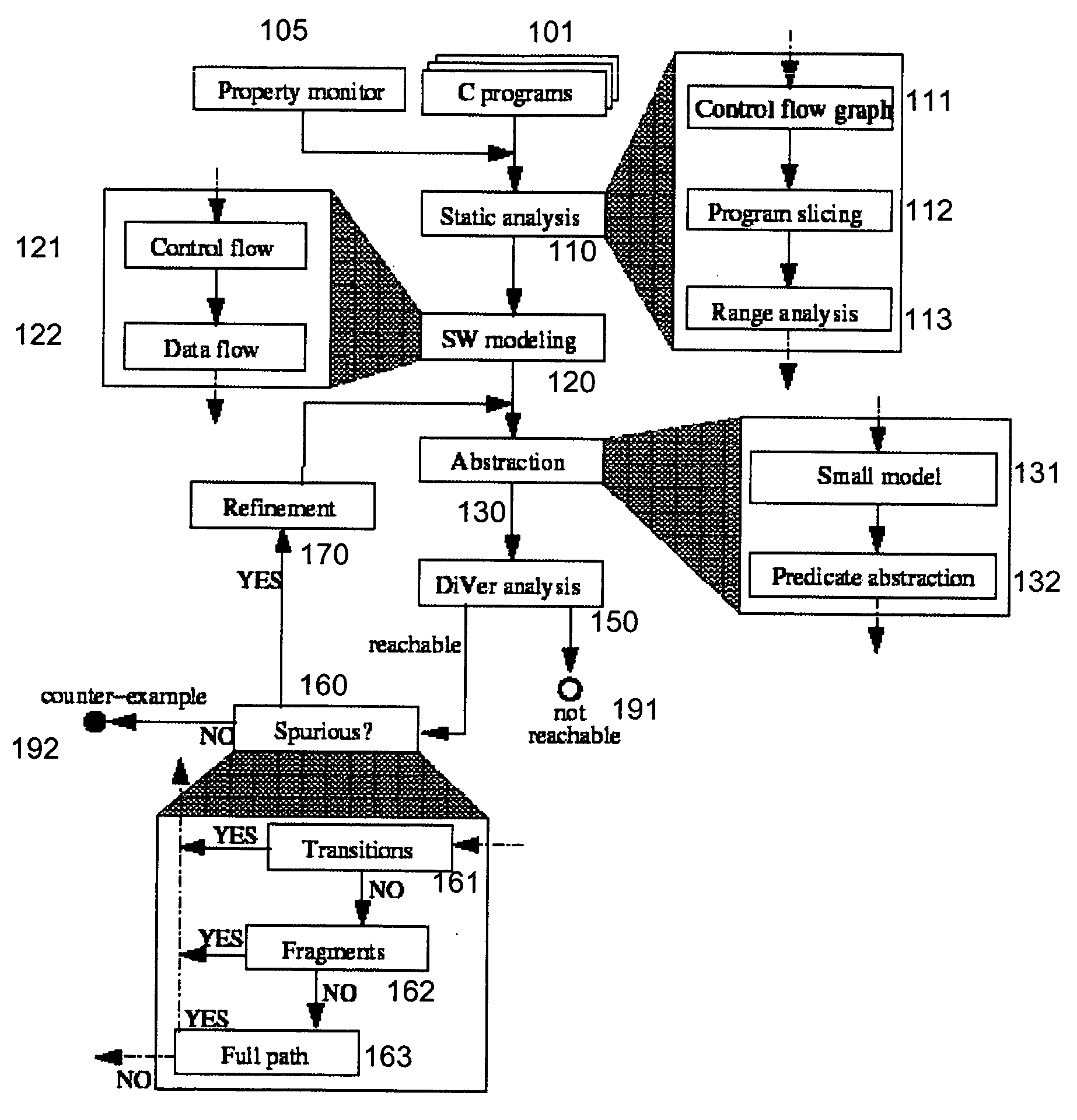
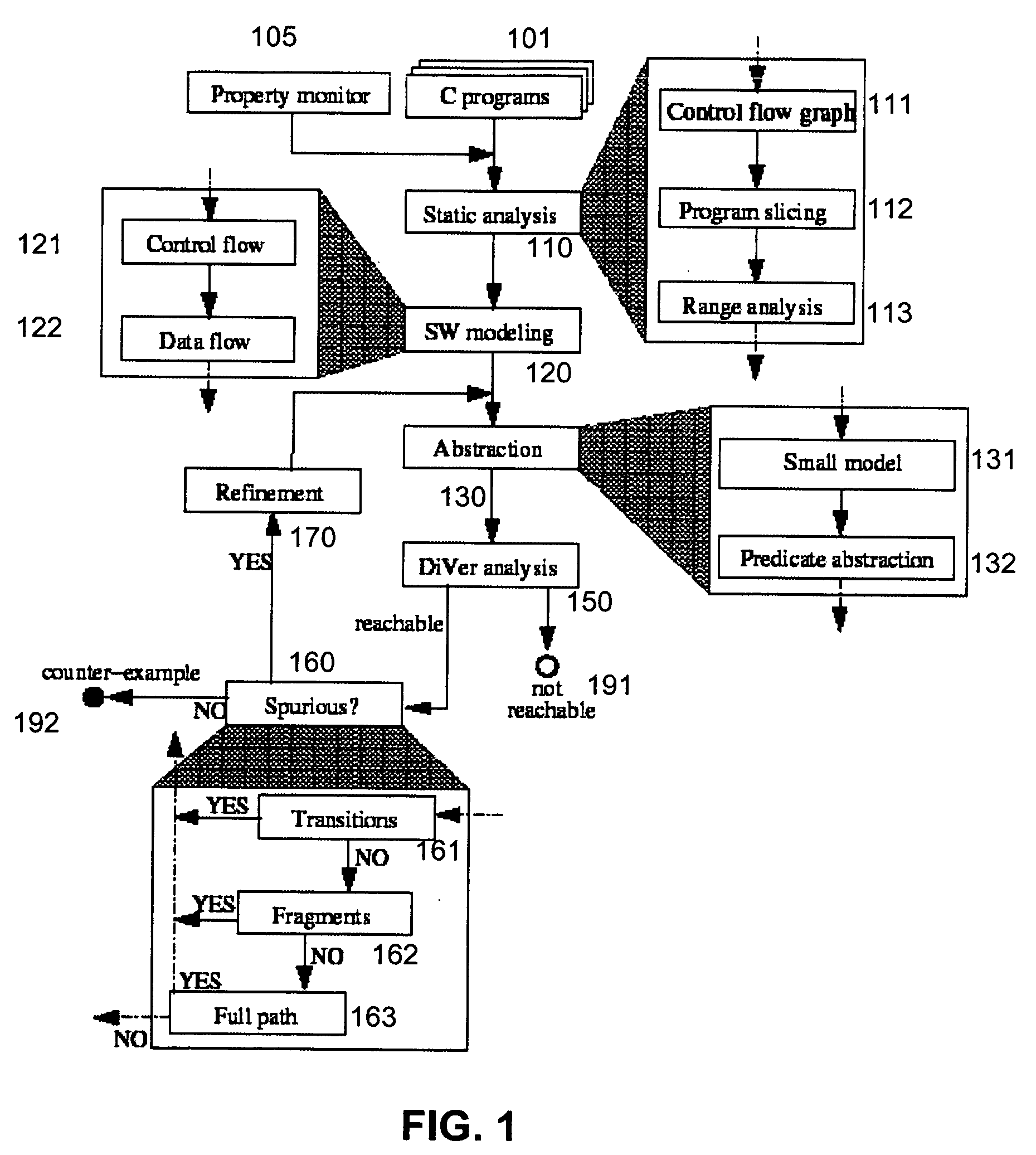
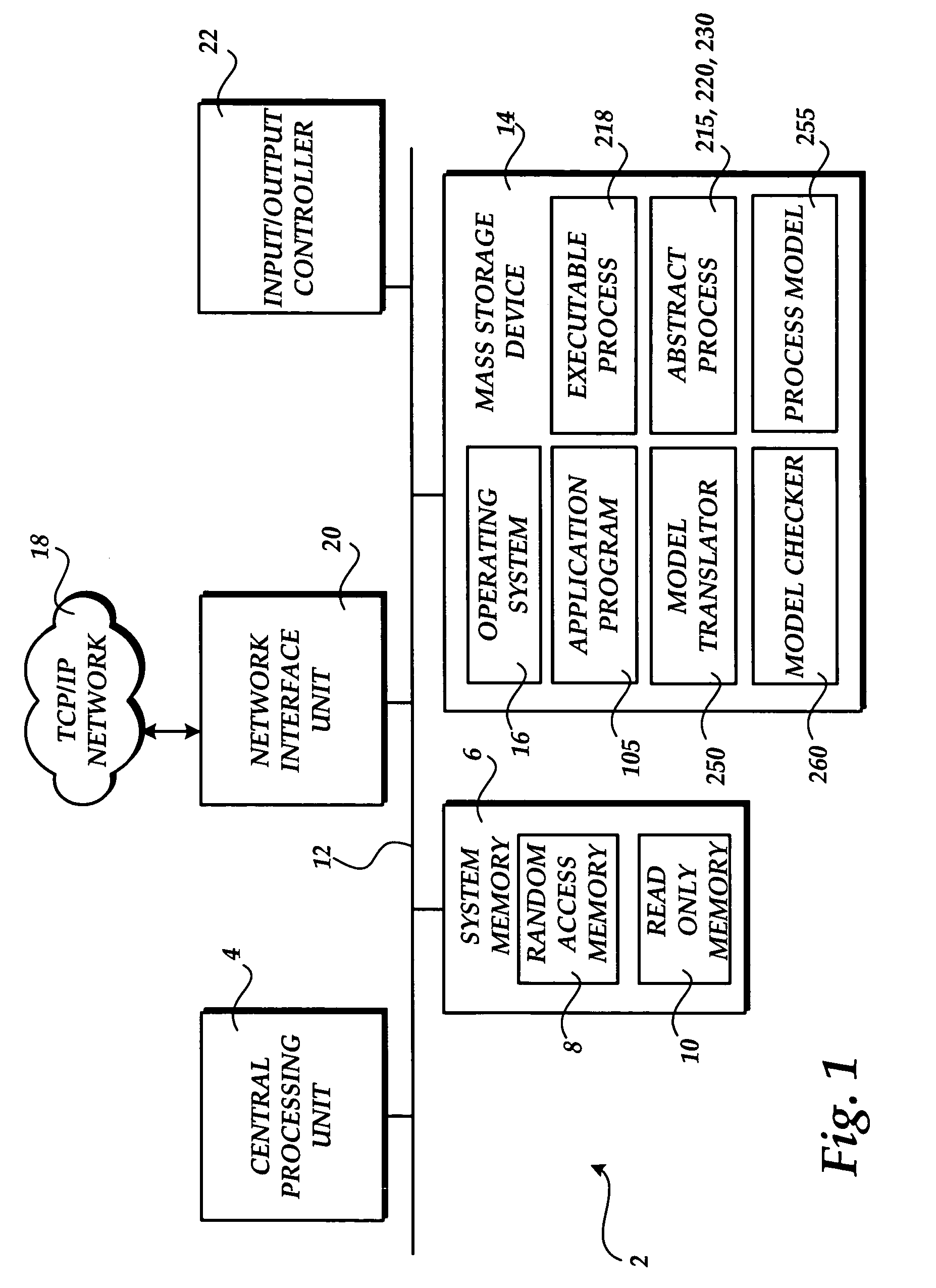
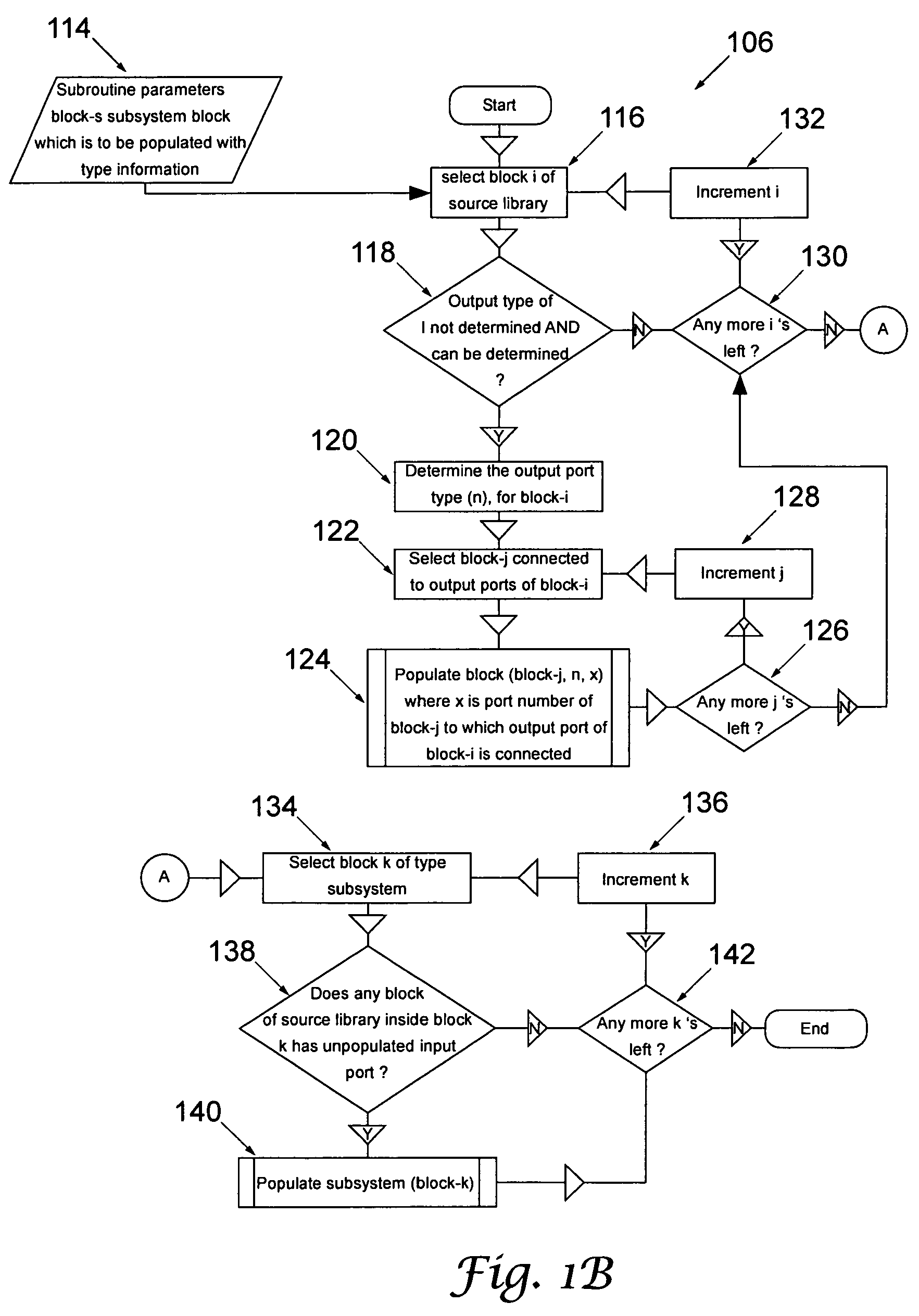
System and method for modeling, abstraction, and analysis of software
ActiveUS7346486B2Improve verification efficiencyImprove translationError detection/correctionComputation using non-denominational number representationBasic blockSoftware
A system and method is disclosed for formal verification of software programs that advantageously translates the software, which can have bounded recursion, into a Boolean representation comprised of basic blocks and which applies SAT-based model checking to the Boolean representation.
Owner:NEC CORP
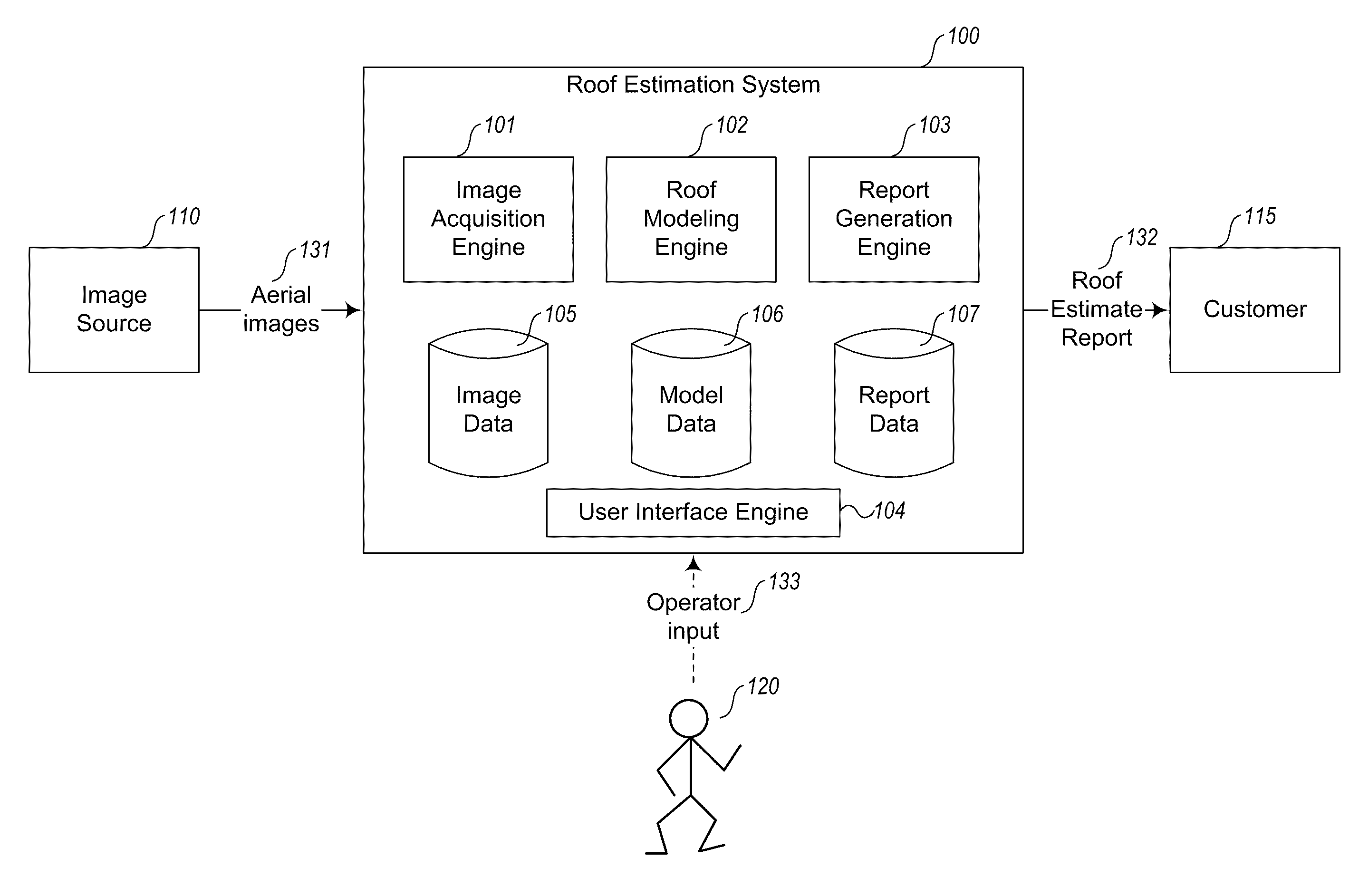
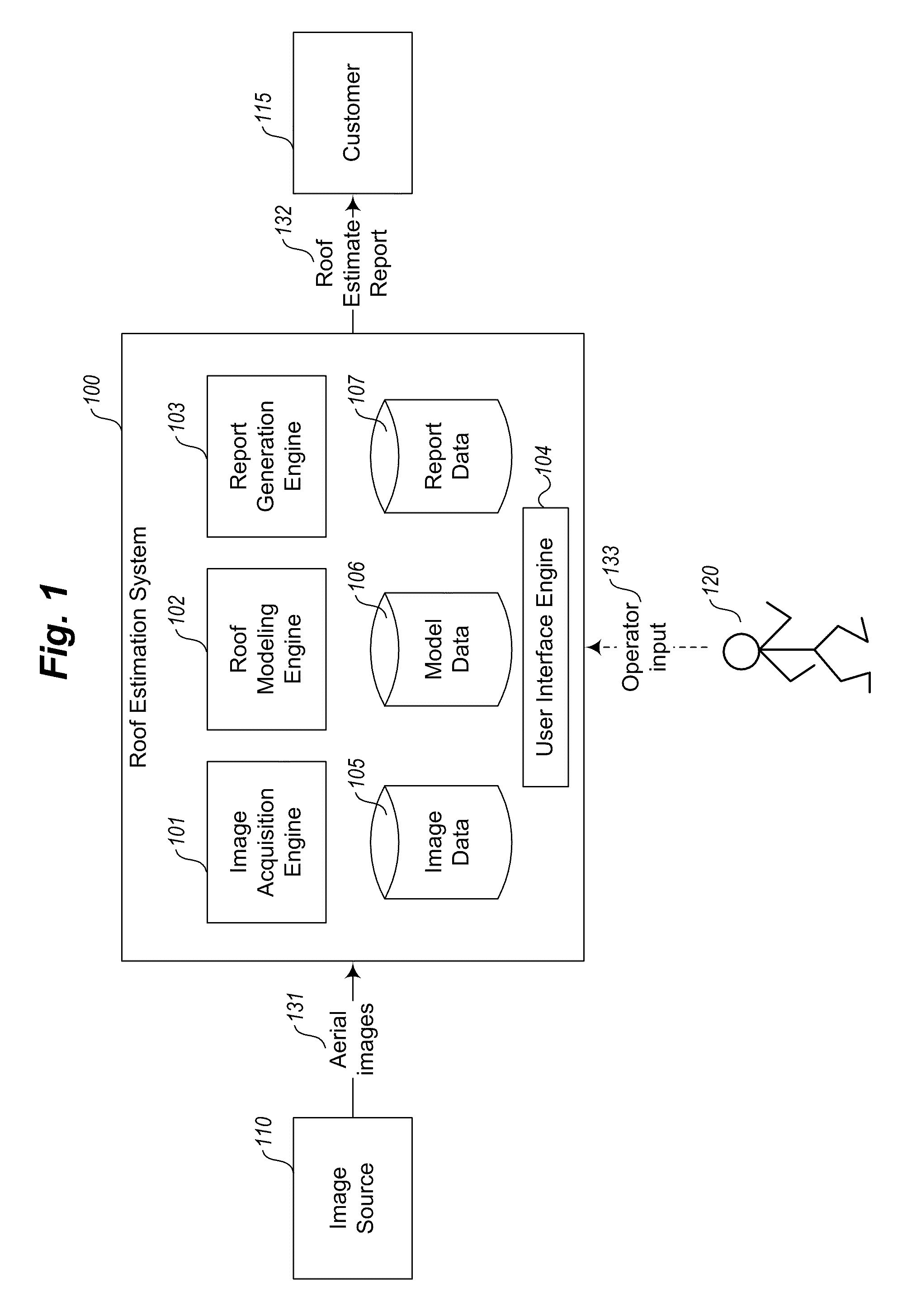
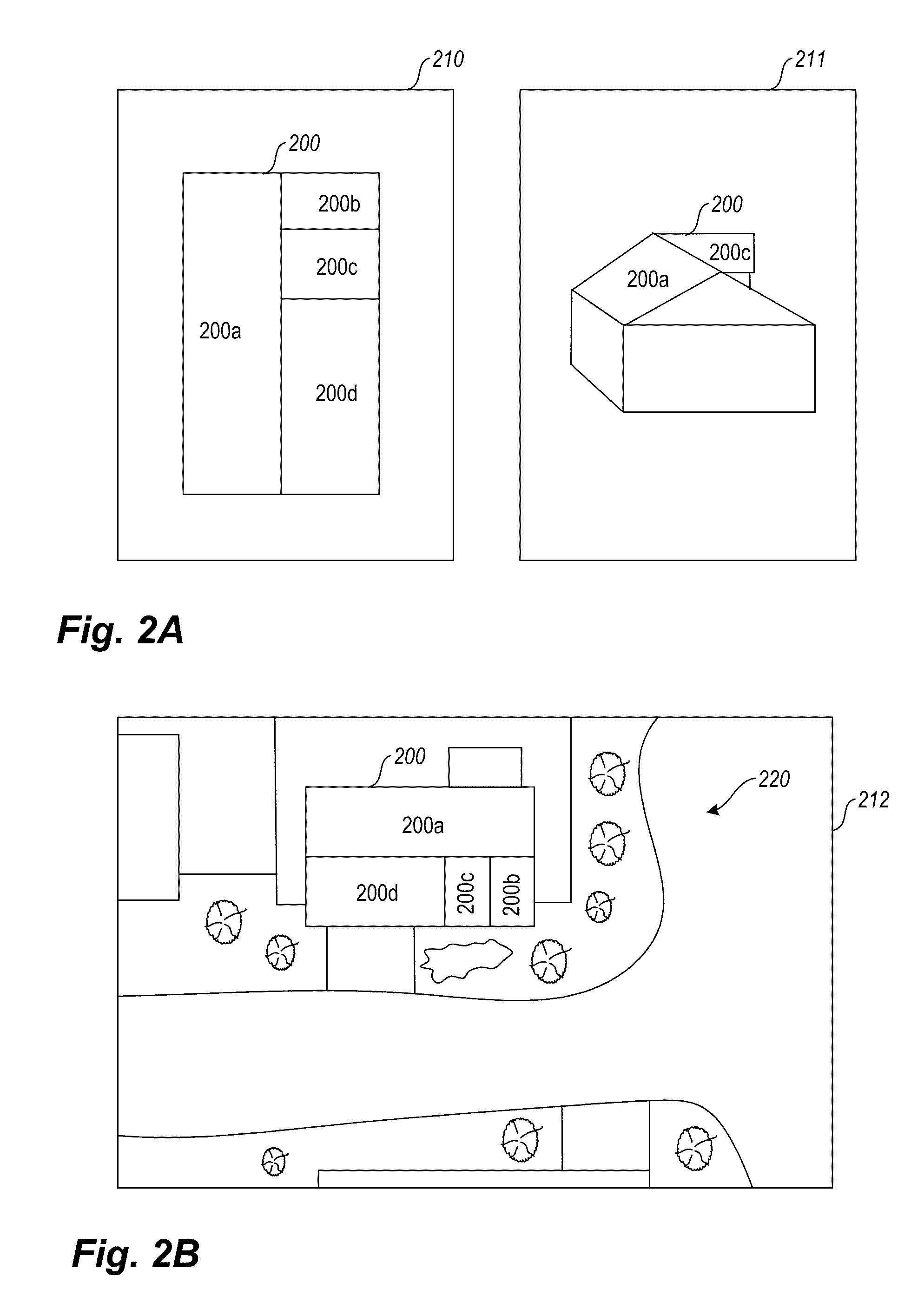
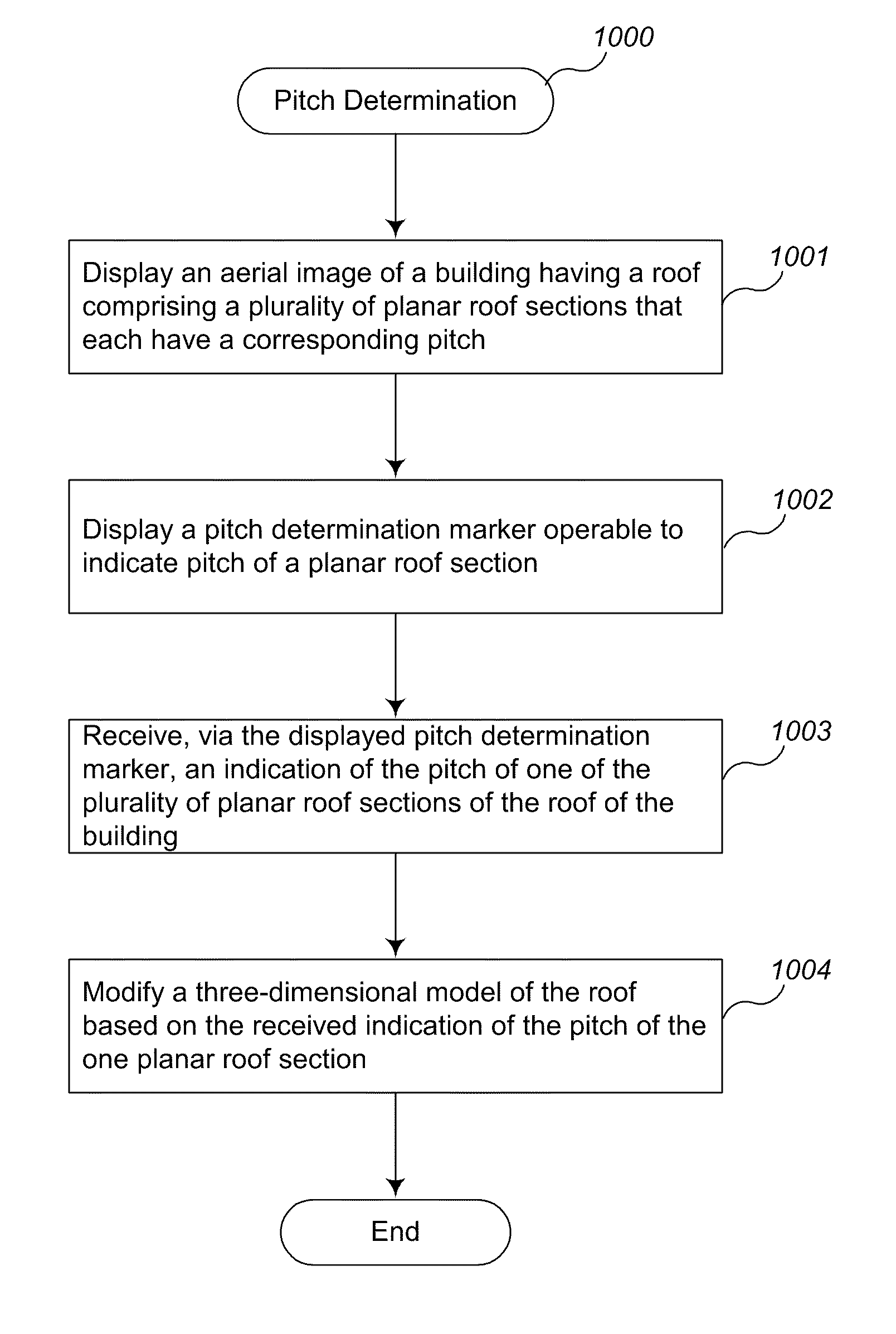
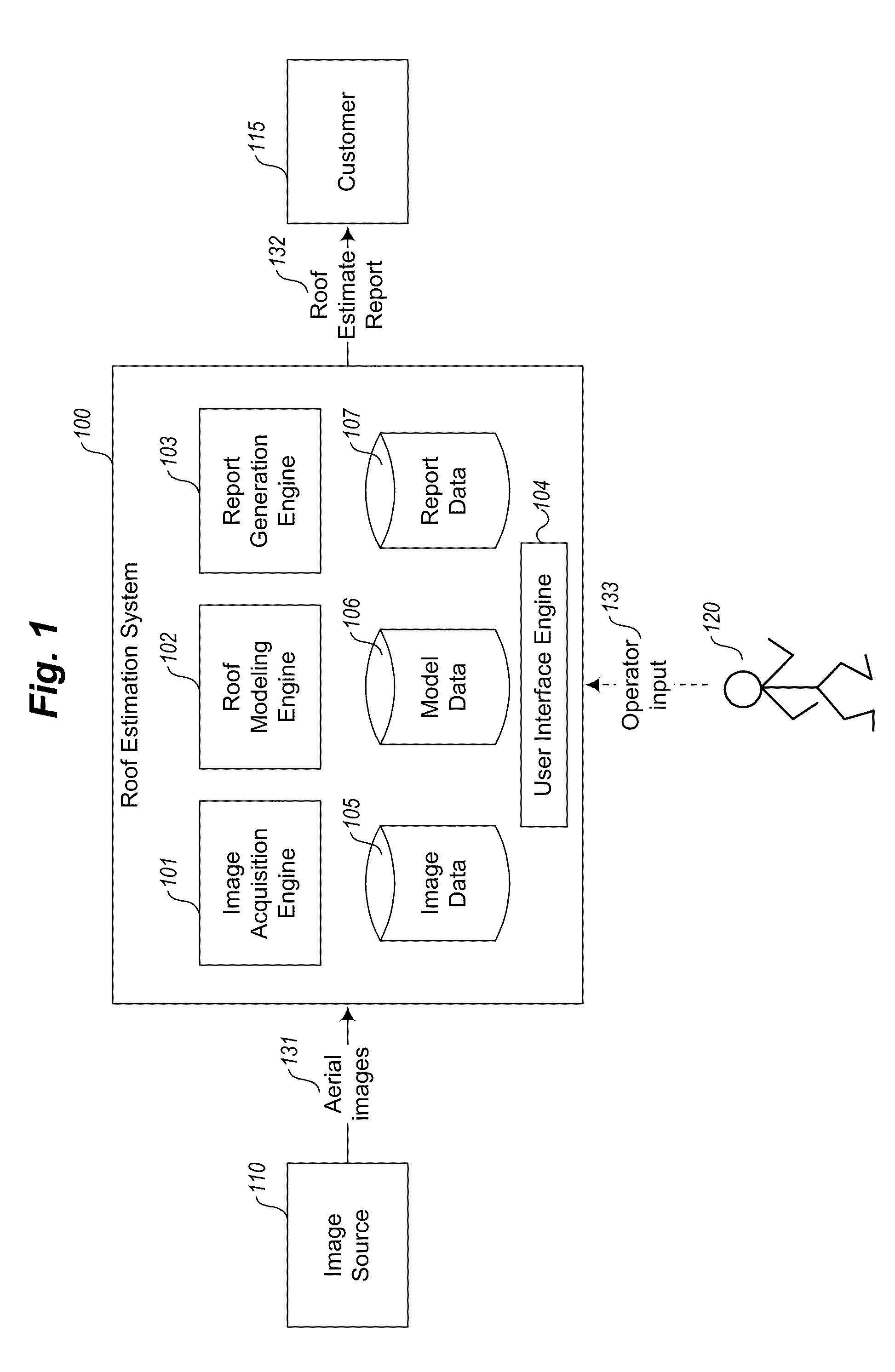
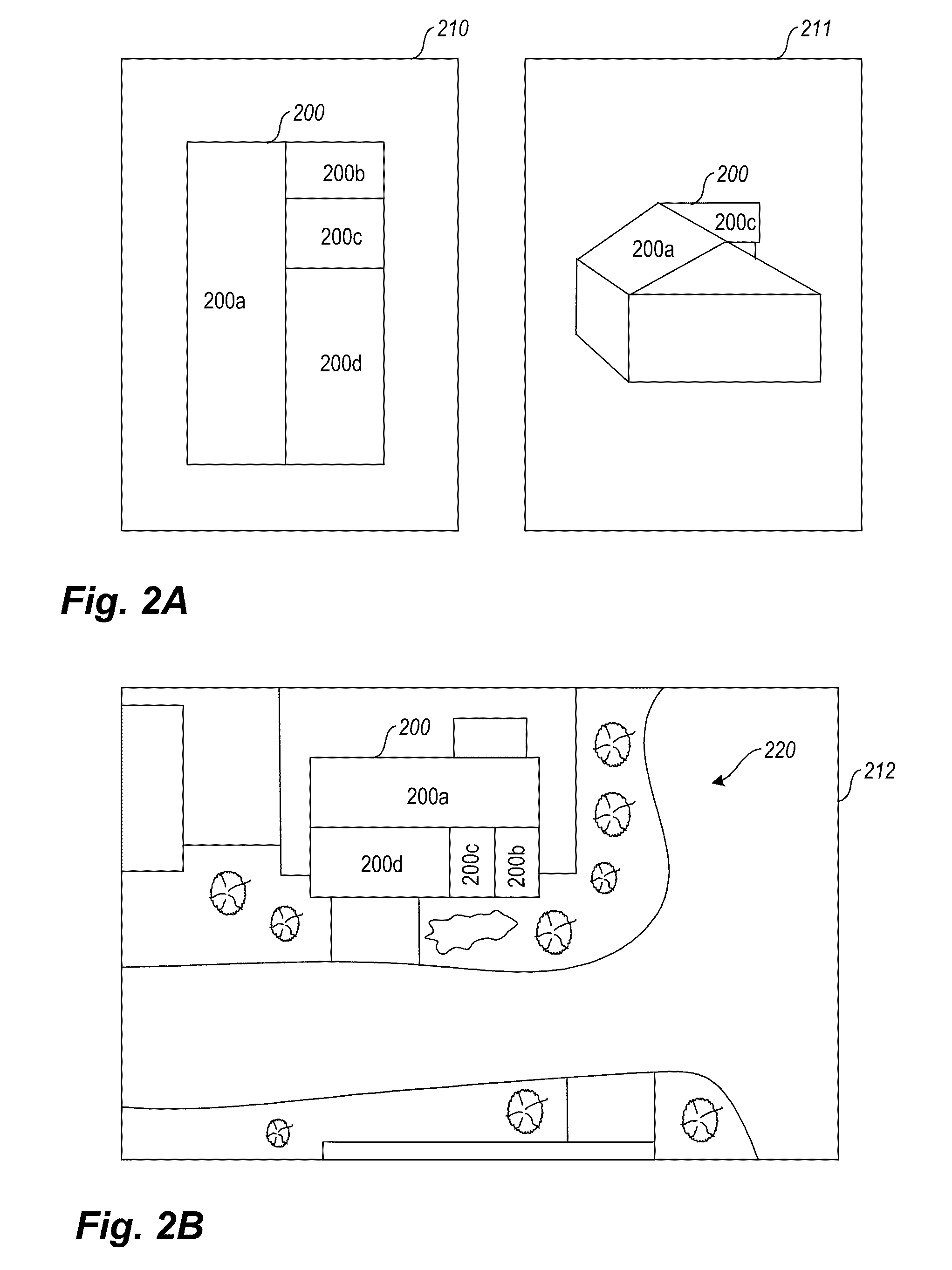
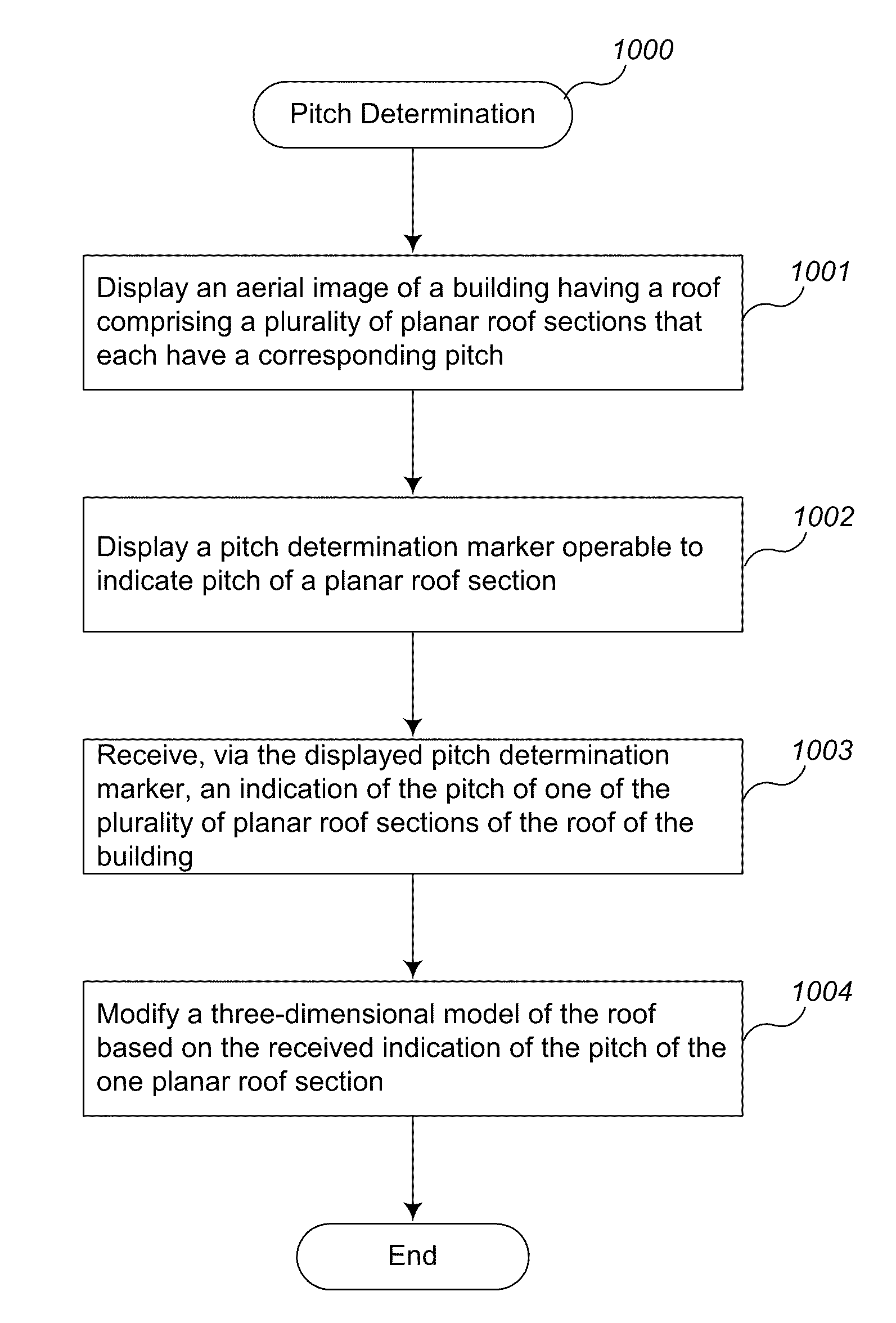
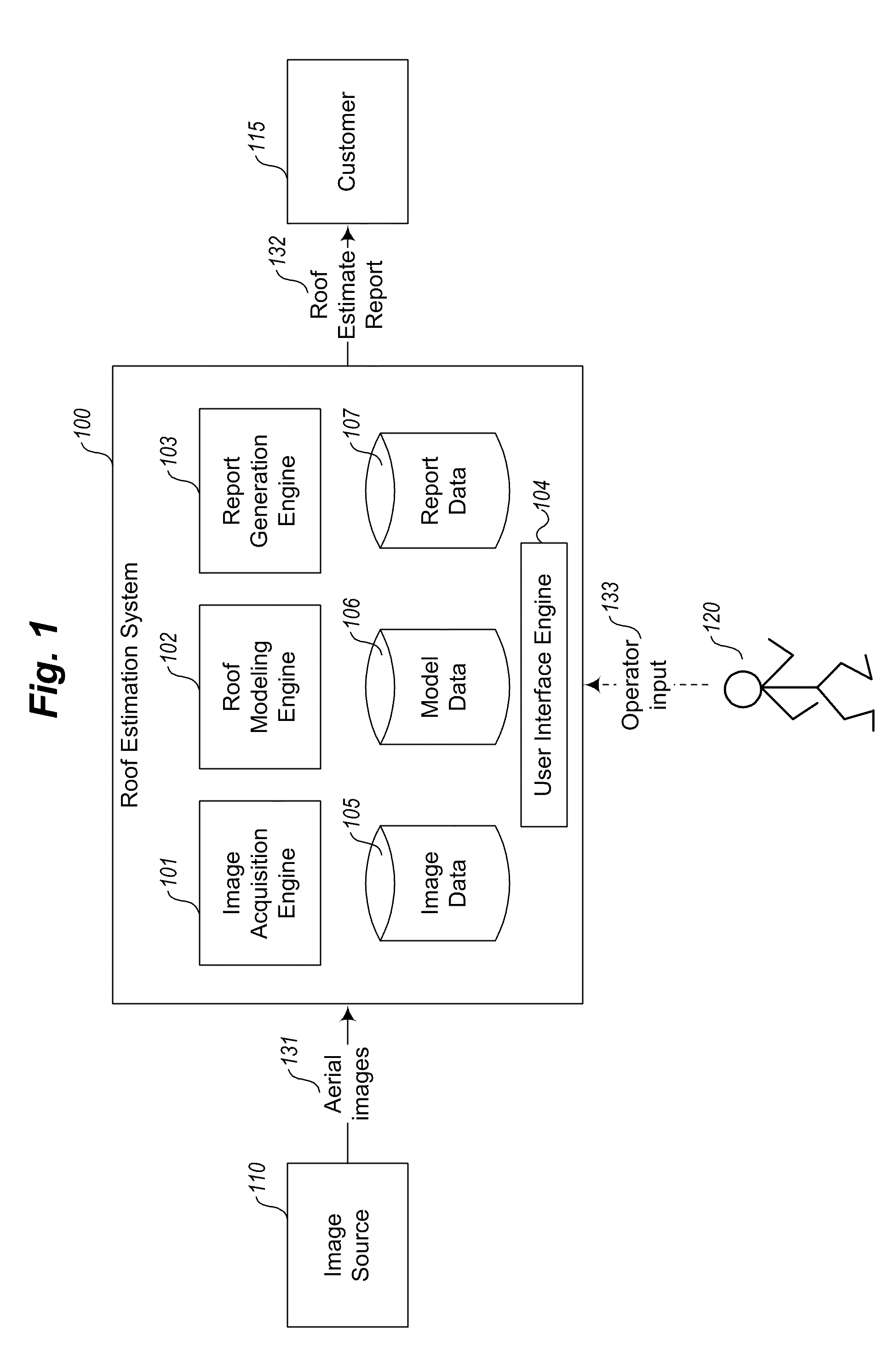
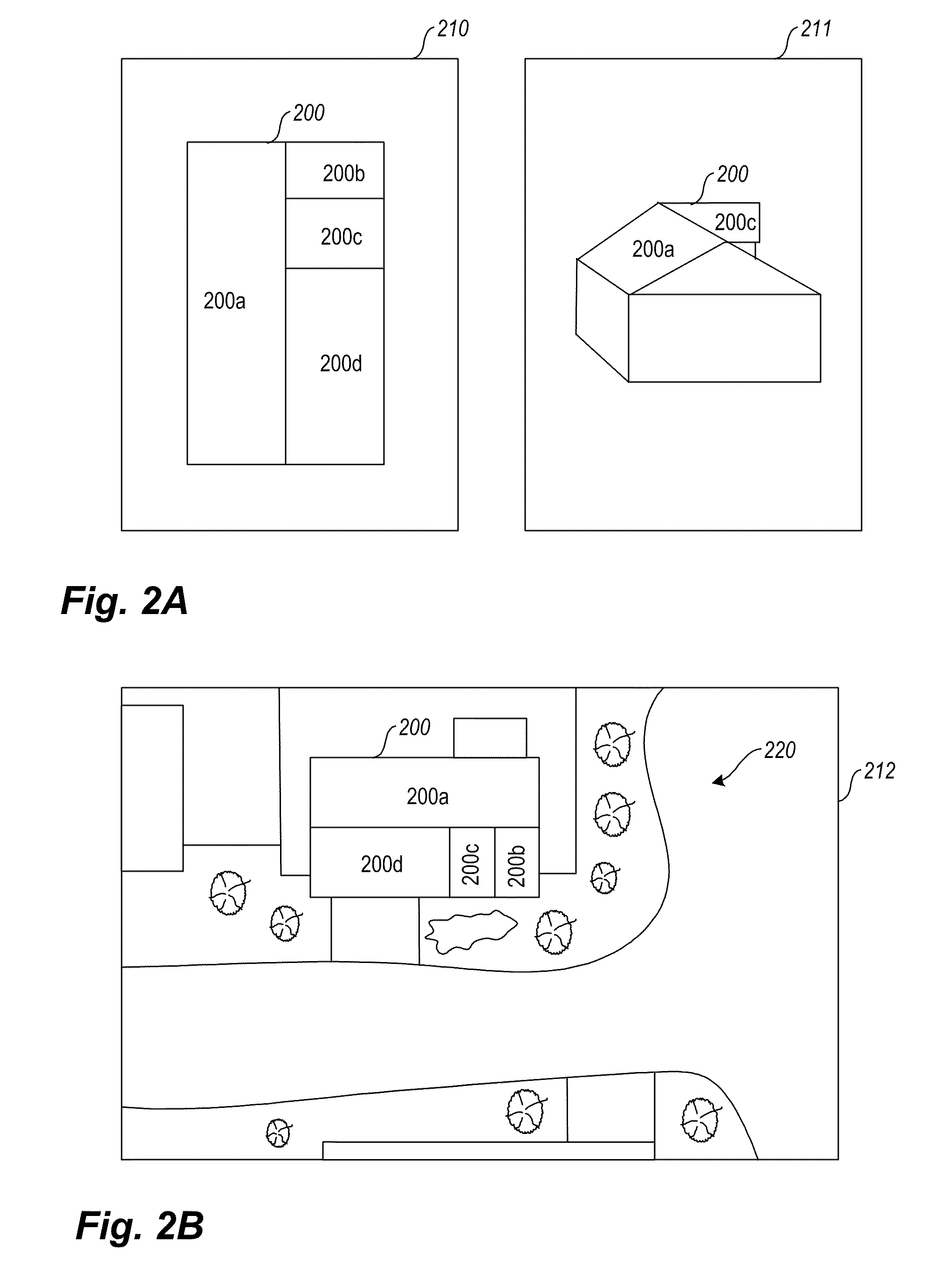
Pitch determination systems and methods for aerial roof estimation
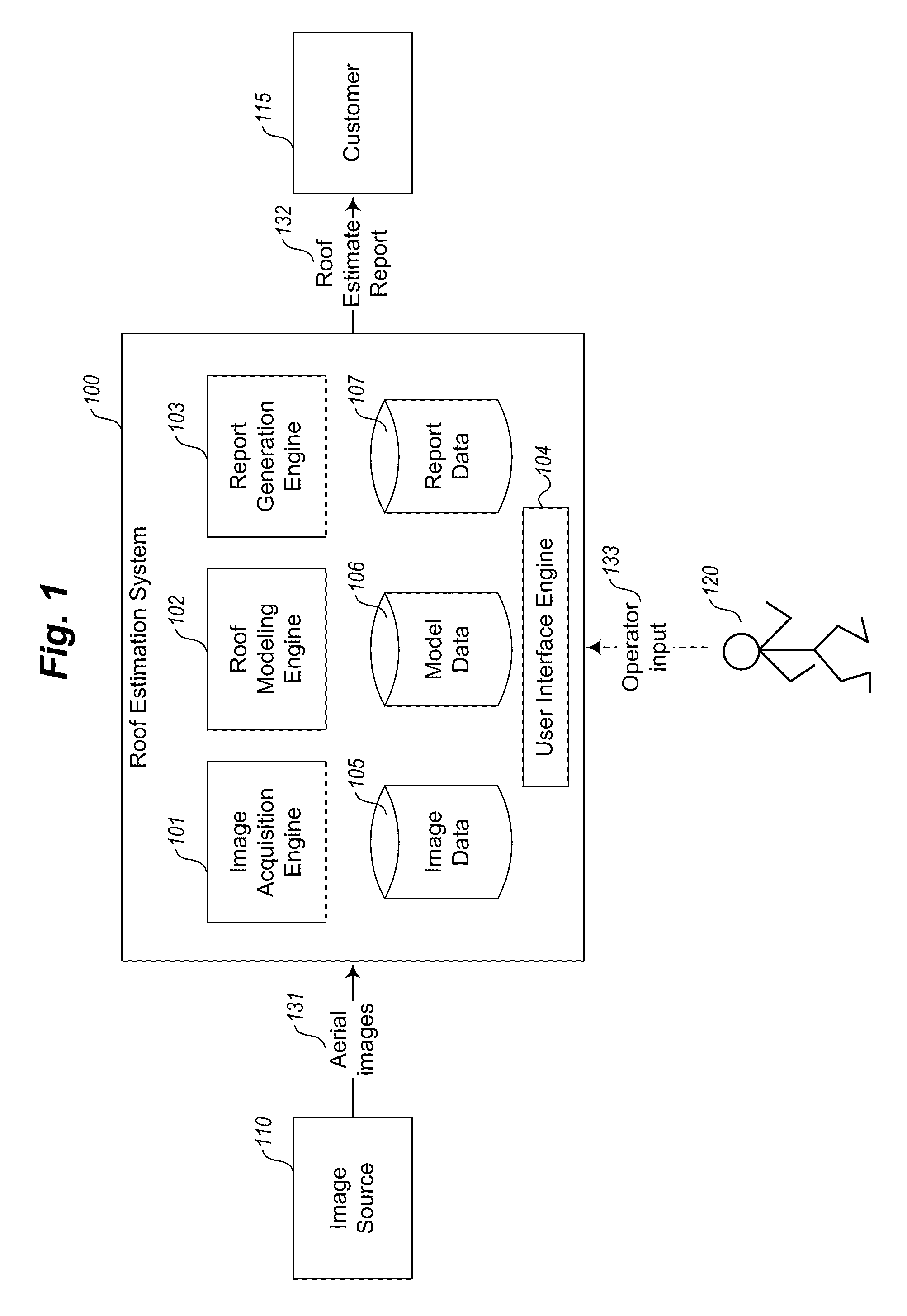
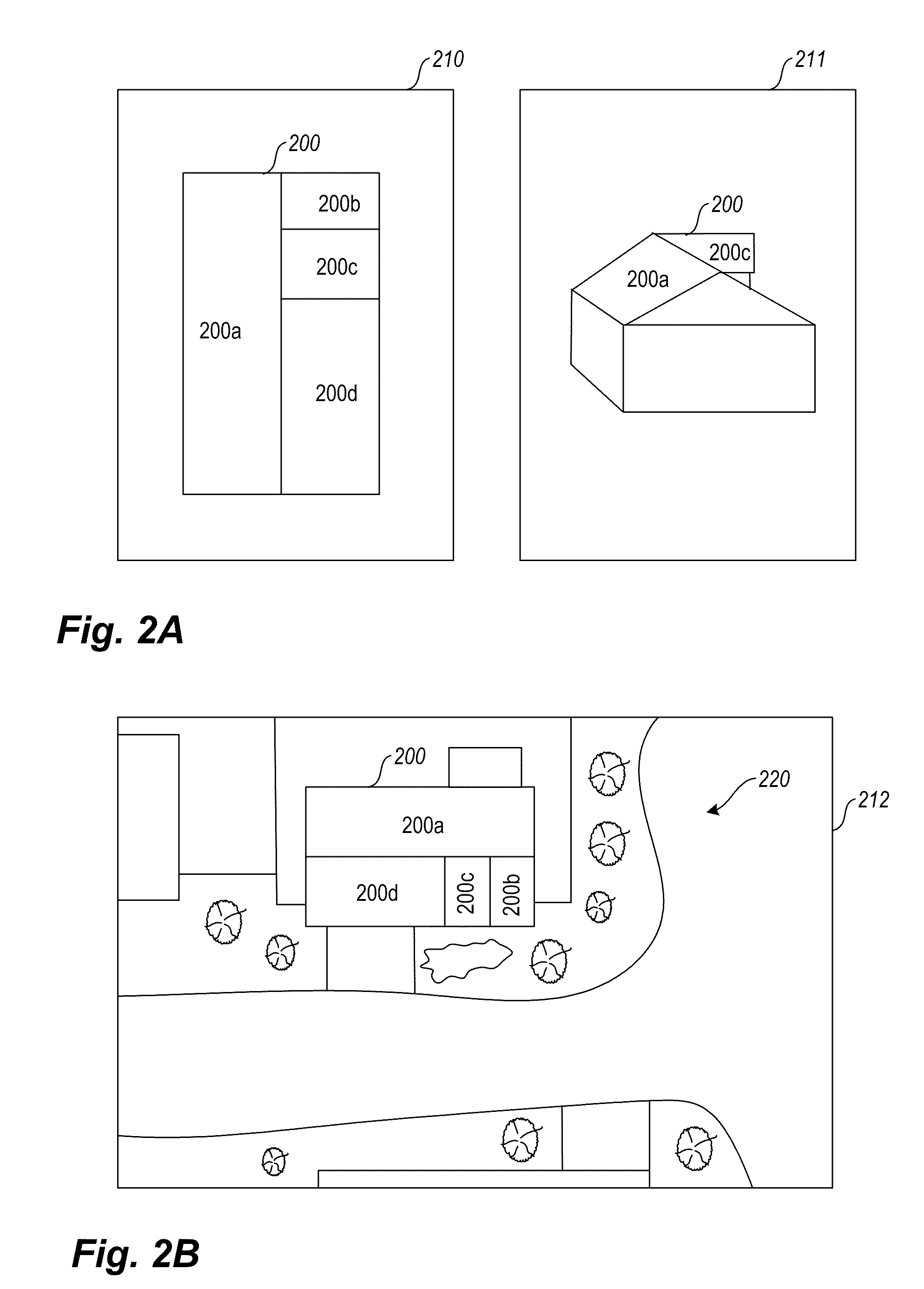
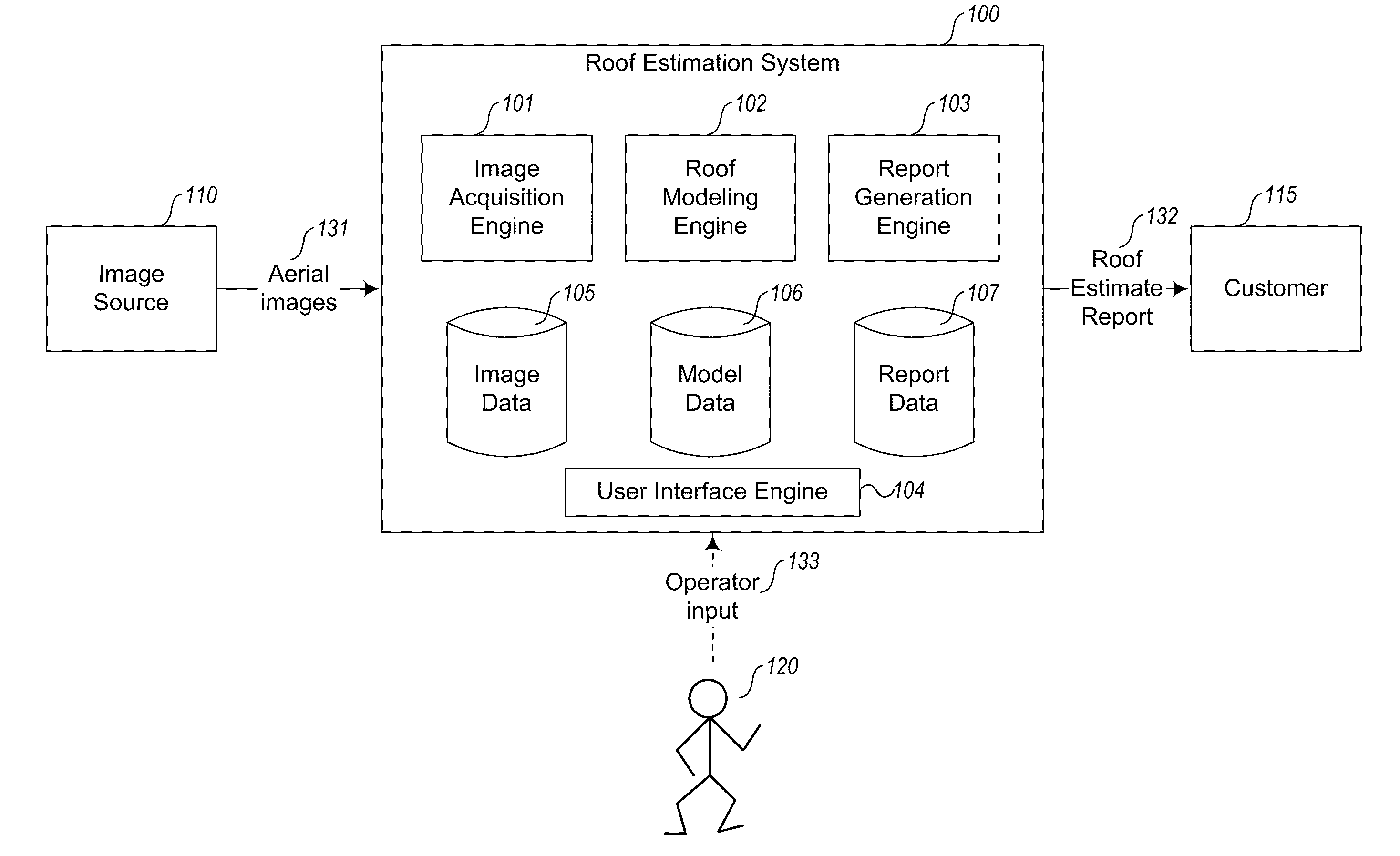
User interface systems and methods for roof estimation are described. Example embodiments include a roof estimation system that provides a user interface configured to facilitate roof model generation based on one or more aerial images of a building roof. In one embodiment, roof model generation includes image registration, image lean correction, roof section pitch determination, wire frame model construction, and / or roof model review. The described user interface provides user interface controls that may be manipulated by an operator to perform at least some of the functions of roof model generation. In one embodiment, the user interface provides user interface controls that facilitate the determination of pitch of one or more sections of a building roof. This abstract is provided to comply with rules requiring an abstract, and it is submitted with the intention that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:EAGLEVIEW TECH
Concurrent display systems and methods for aerial roof estimation
User interface systems and methods for roof estimation are described. Example embodiments include a roof estimation system that provides a user interface configured to facilitate roof model generation based on one or more aerial images of a building roof. In one embodiment, roof model generation includes image registration, image lean correction, roof section pitch determination, wire frame model construction, and / or roof model review. The described user interface provides user interface controls that may be manipulated by an operator to perform at least some of the functions of roof model generation. The user interface is further configured to concurrently display roof features onto multiple images of a roof. This abstract is provided to comply with rules requiring an abstract, and it is submitted with the intention that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:EAGLEVIEW TECH
Pitch determination systems and methods for aerial roof estimation
Owner:EAGLEVIEW TECH
Concurrent display systems and methods for aerial roof estimation
User interface systems and methods for roof estimation are described. Example embodiments include a roof estimation system that provides a user interface configured to facilitate roof model generation based on one or more aerial images of a building roof. In one embodiment, roof model generation includes image registration, image lean correction, roof section pitch determination, wire frame model construction, and / or roof model review. The described user interface provides user interface controls that may be manipulated by an operator to perform at least some of the functions of roof model generation. The user interface is further configured to concurrently display roof features onto multiple images of a roof. This abstract is provided to comply with rules requiring an abstract, and it is submitted with the intention that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:EAGLEVIEW TECH
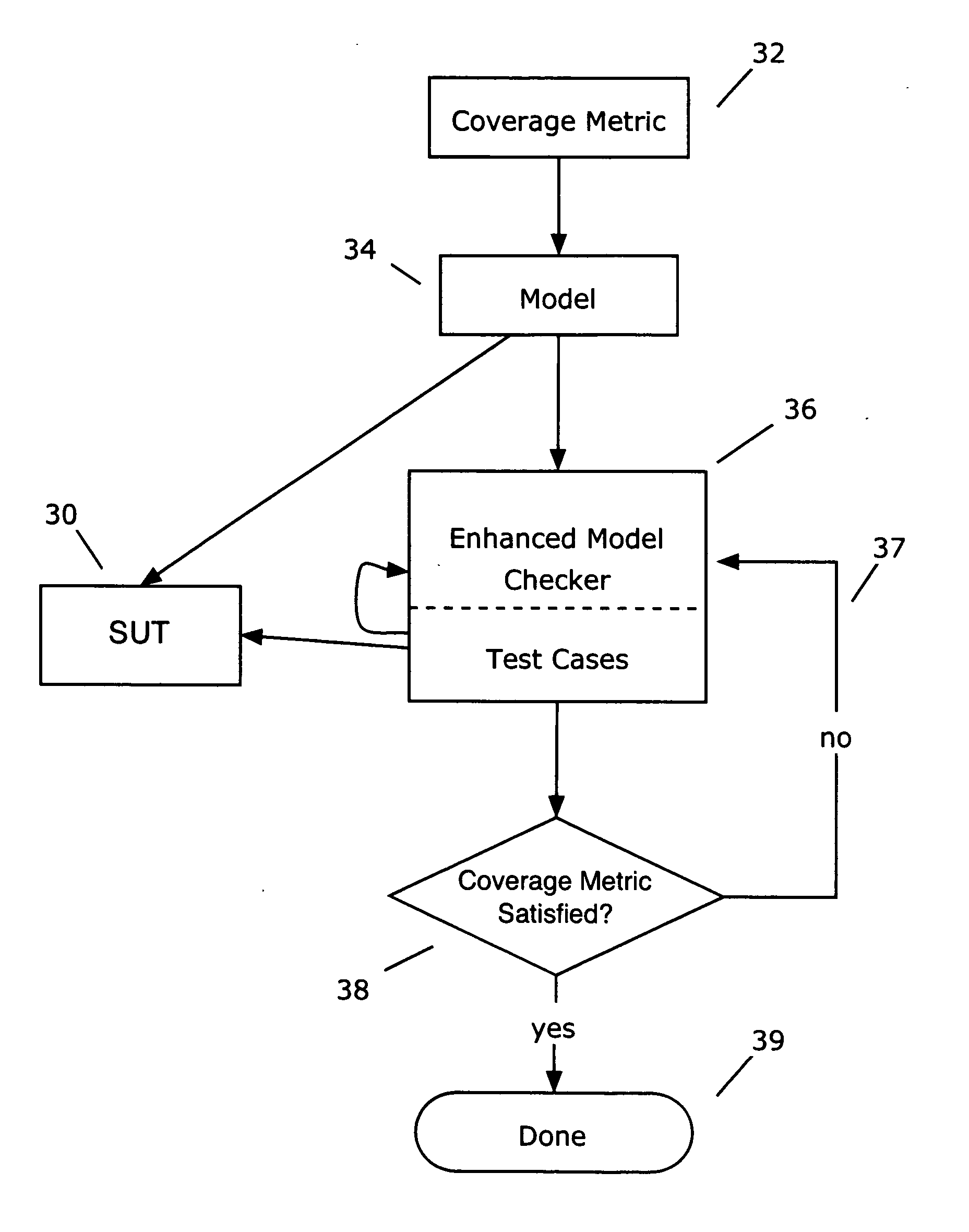
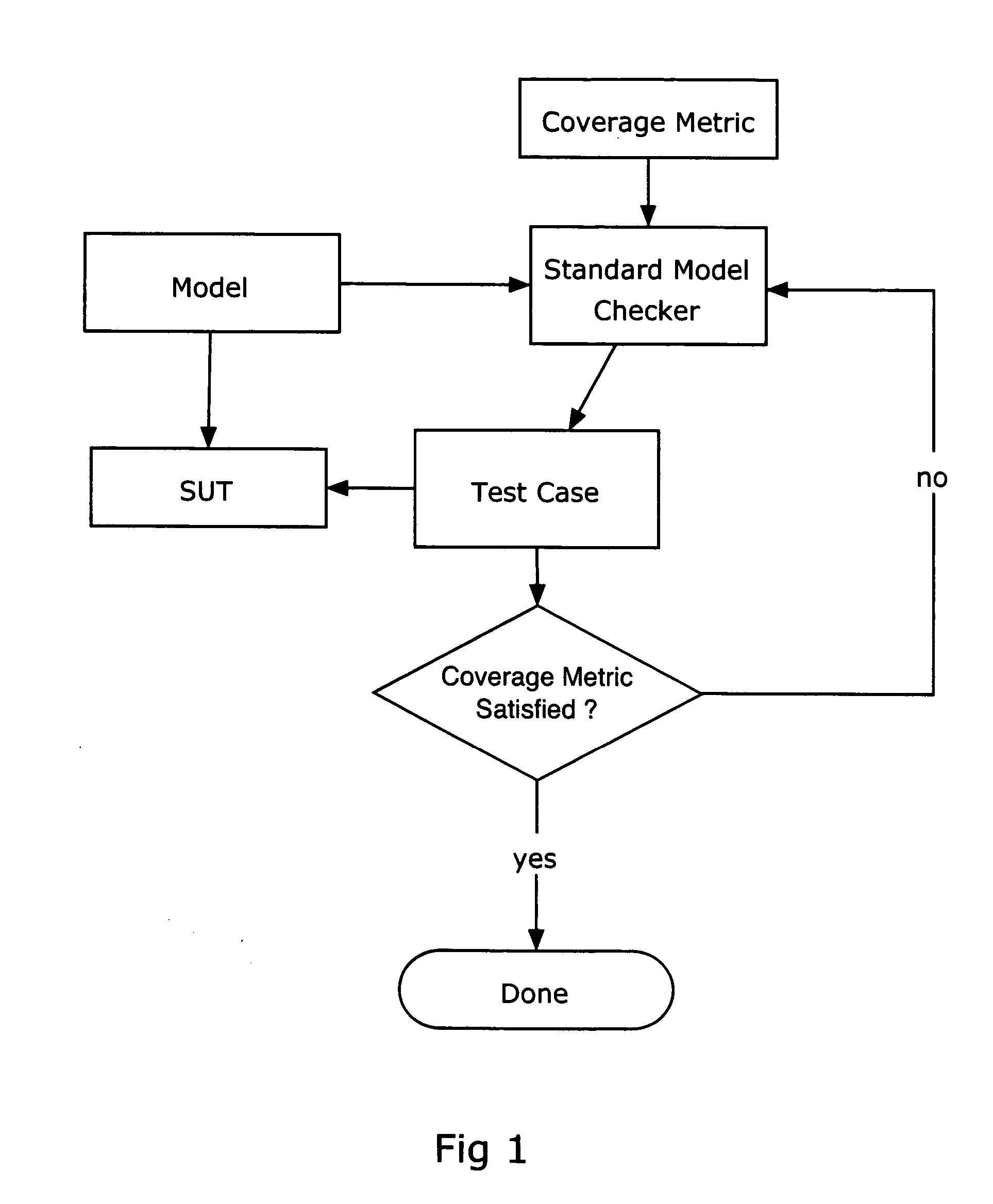
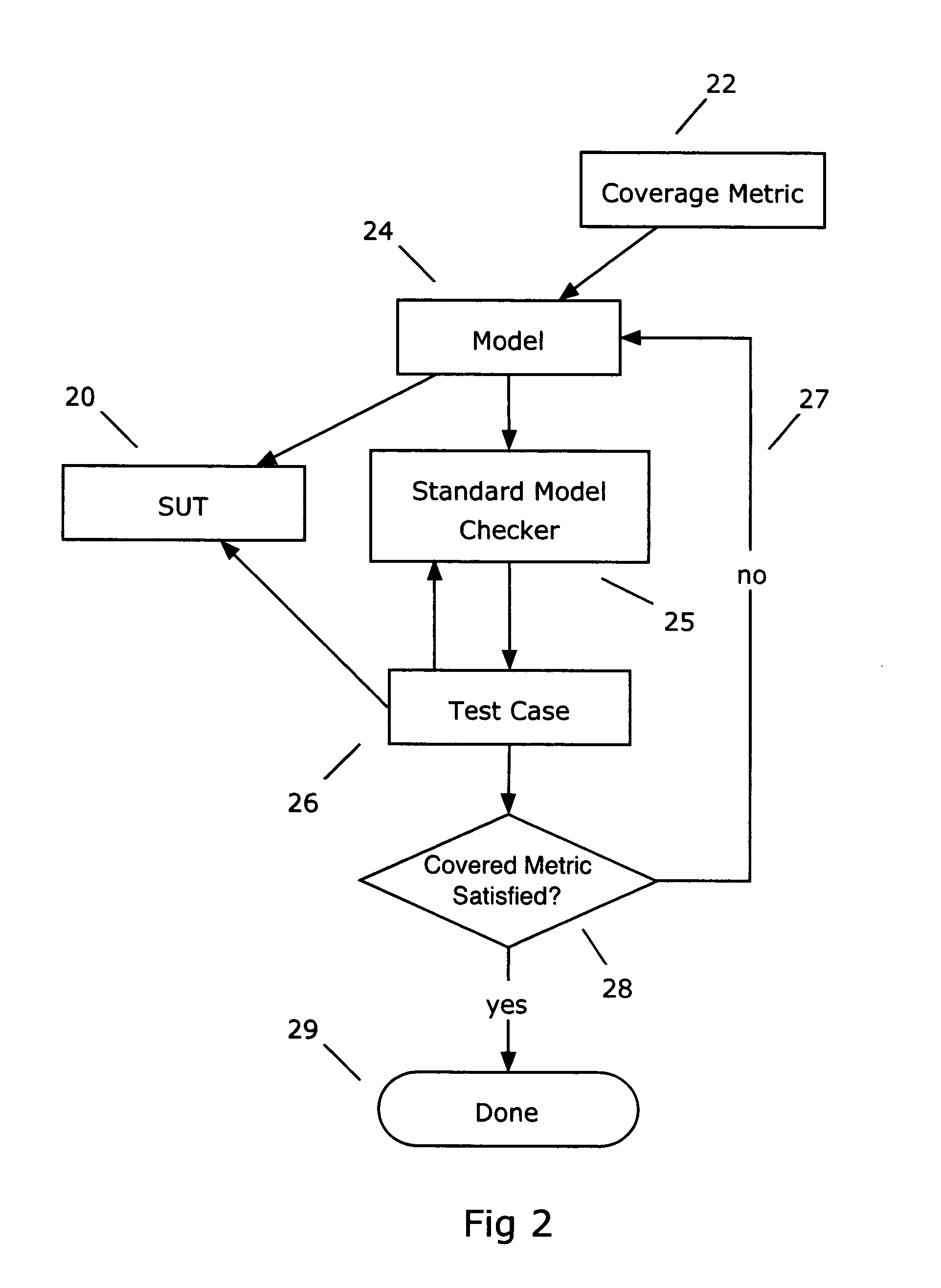
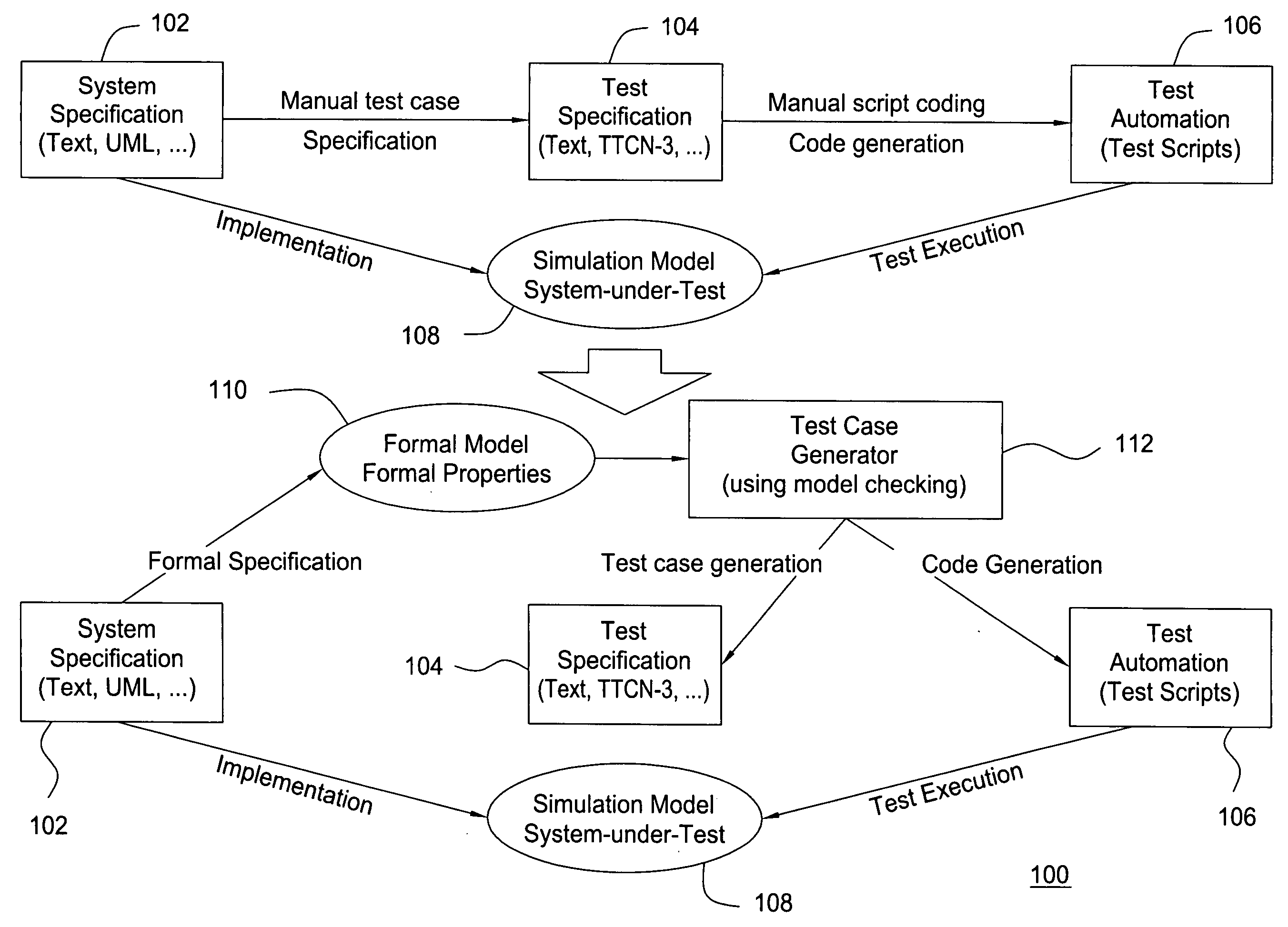
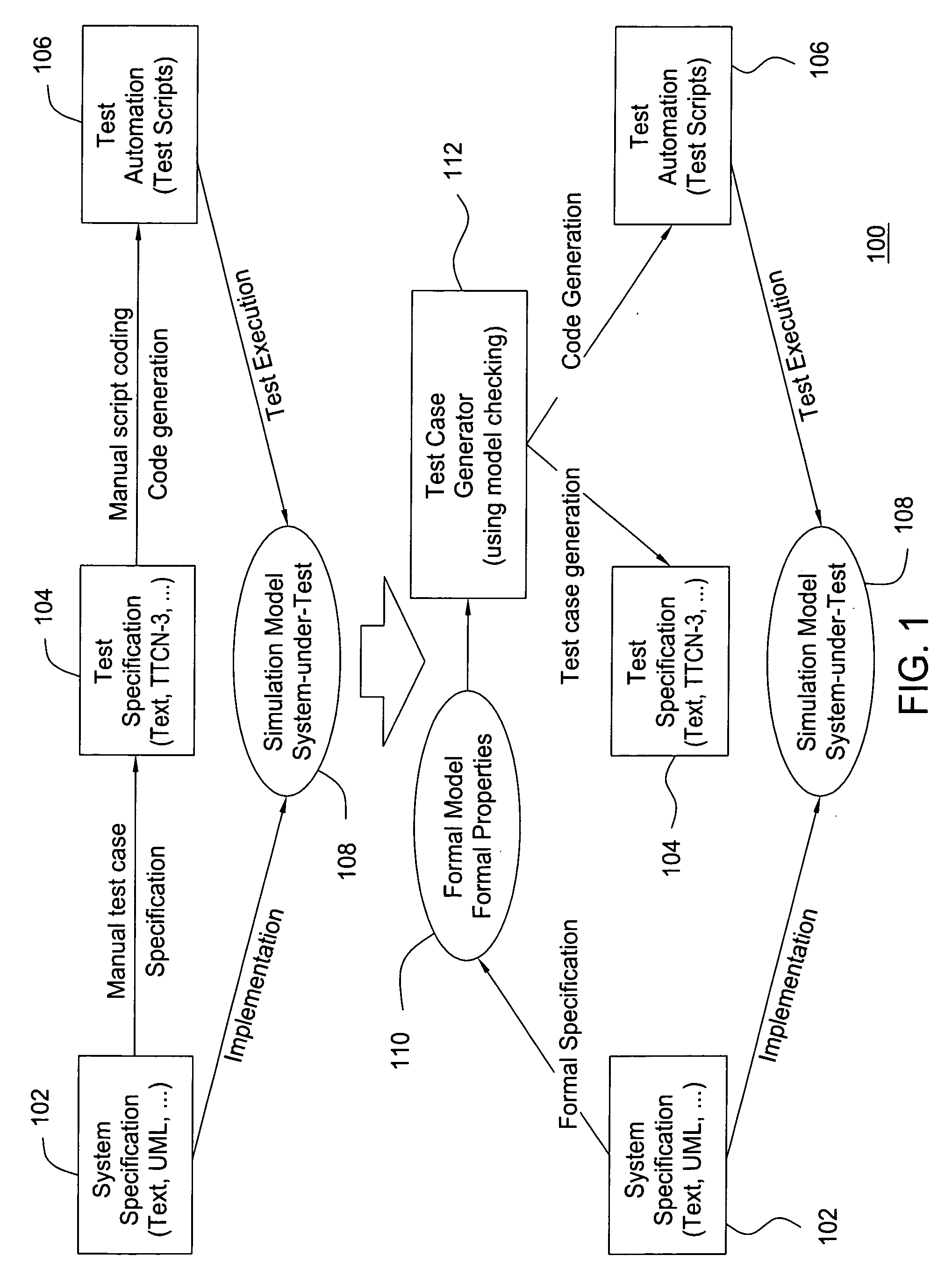
Formal methods for test case generation
ActiveUS20060010428A1Reduce development costsQuick testError detection/correctionComputation using non-denominational number representationSoftware systemFormal methods
The invention relates to the use of model checkers to generate efficient test sets for hardware and software systems. The method provides for extending existing tests to reach new coverage targets; searching *to* some or all of the uncovered targets in parallel; searching in parallel *from* some or all of the states reached in previous tests; and slicing the model relative to the current set of coverage targets. The invention provides efficient test case generation and test set formation. Deep regions of the state space can be reached within allotted time and memory. The approach has been applied to use of the model checkers of SRI's SAL system and to model-based designs developed in Stateflow. Stateflow models achieving complete state and transition coverage in a single test case are reported.
Owner:SRI INTERNATIONAL
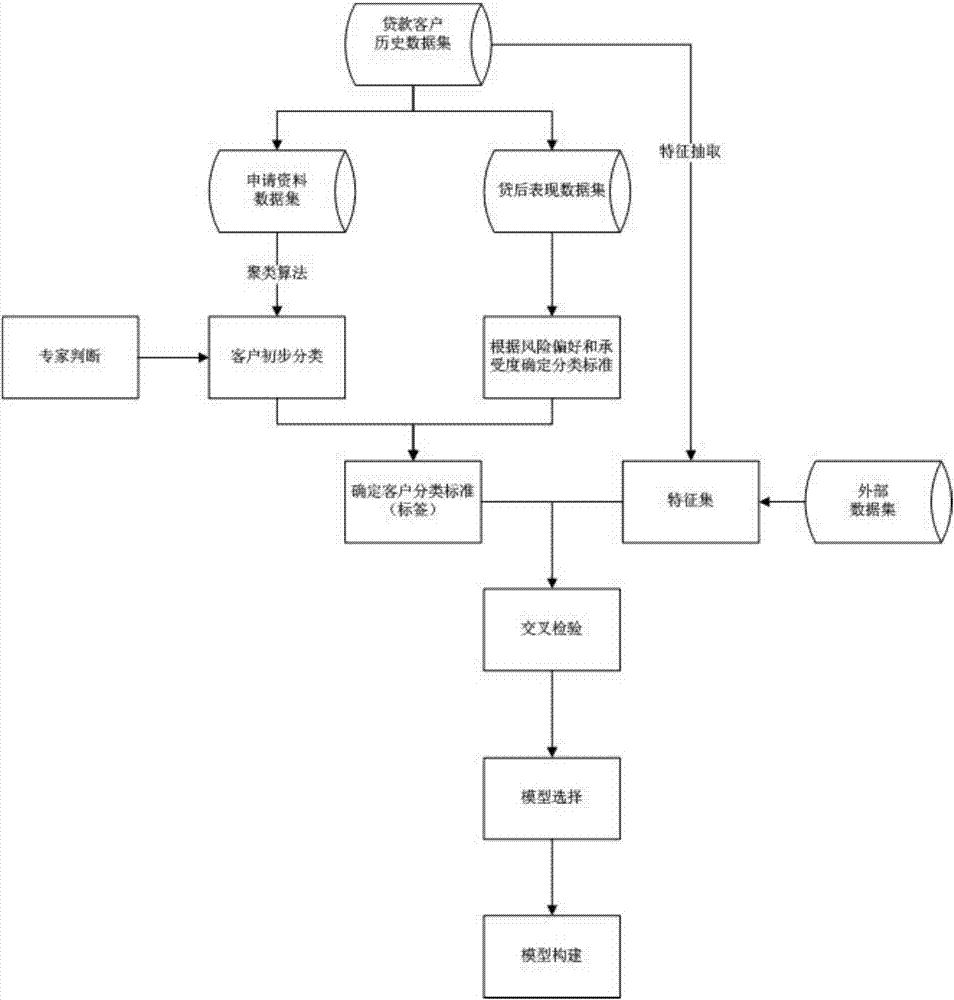
Hybrid machine learning credit scoring model building method
InactiveCN106897918AResolve accuracySolve efficiency problemsFinanceBuying/selling/leasing transactionsData setFeature set
The invention discloses a hybrid machine learning credit scoring model building method. The method comprises the steps of 1, determining client risk classification standards based on a loan client historical data set; 2, based on the loan client historical data set, obtaining a loan client data feature set through feature extraction; 3, selecting at least two model algorithms from an alternative model library, building corresponding models based on the selected algorithms, performing model performance check on the built models by adopting a K-fold cross check method, performing standard check on the models about to pass the model performance check based on model check standards, obtaining evaluation index statistical quantity values, and selecting a model type used by final modeling according to the evaluation index statistical quantity values returned by the standard check of the models; and 4, based on the algorithm corresponding to the selected model type, building a credit scoring model. The technical effect of efficiently and accurately finishing user credit evaluation through the built hybrid machine learning credit scoring model is achieved.
Owner:上海易贷网金融信息服务有限公司
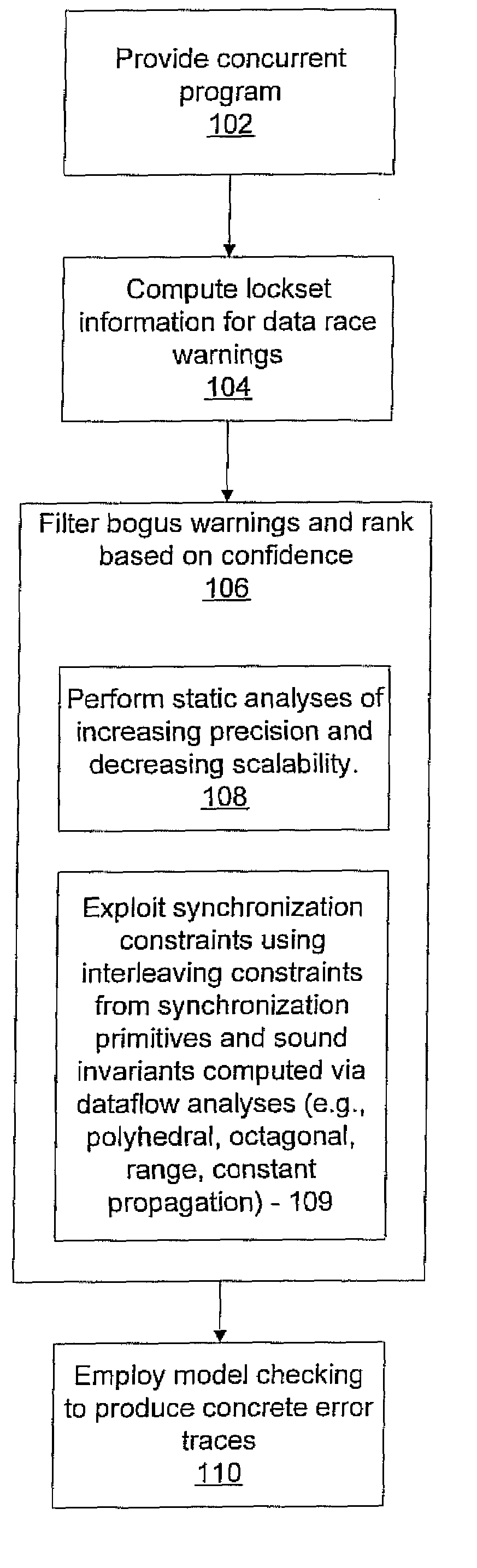
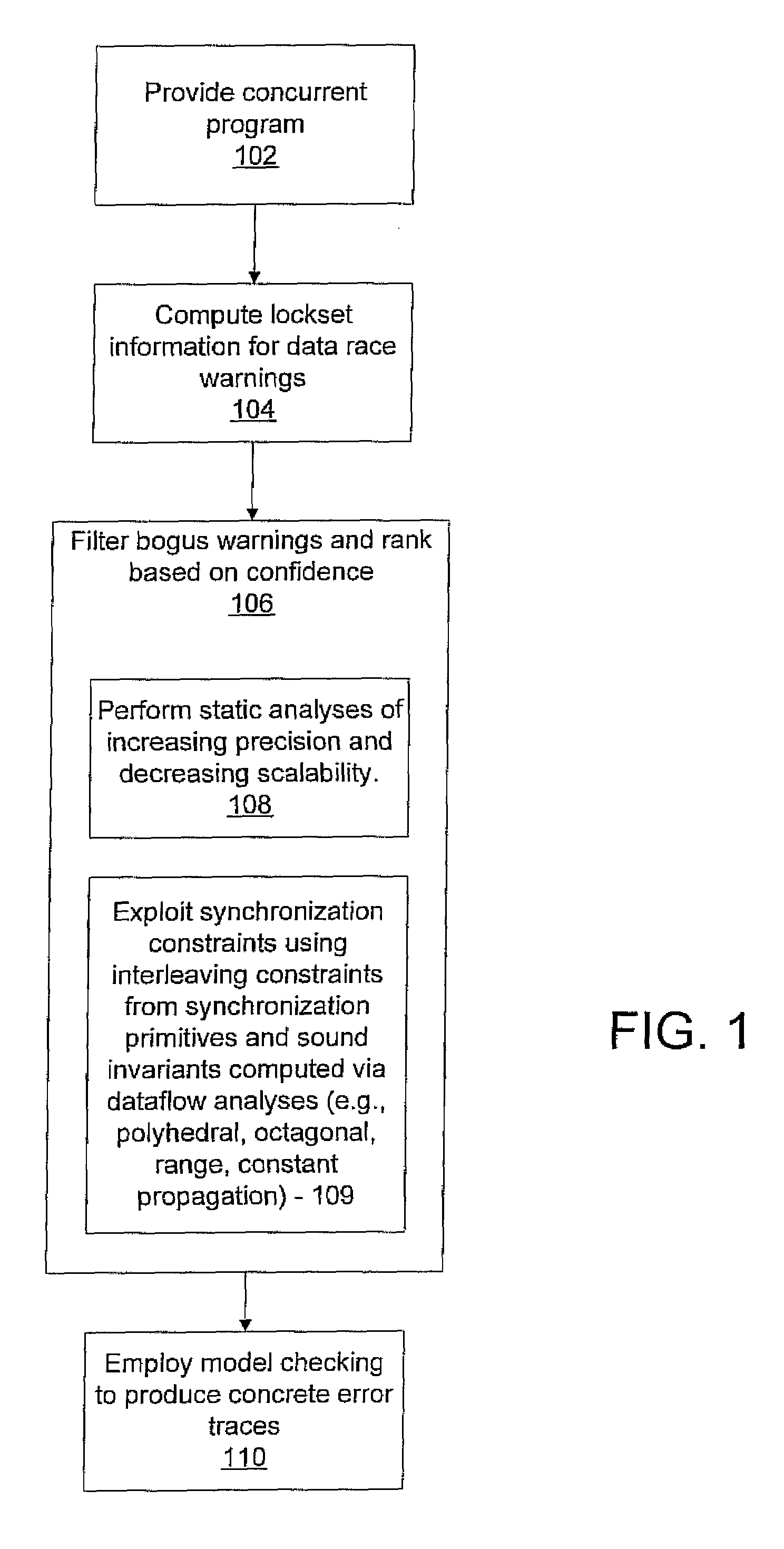
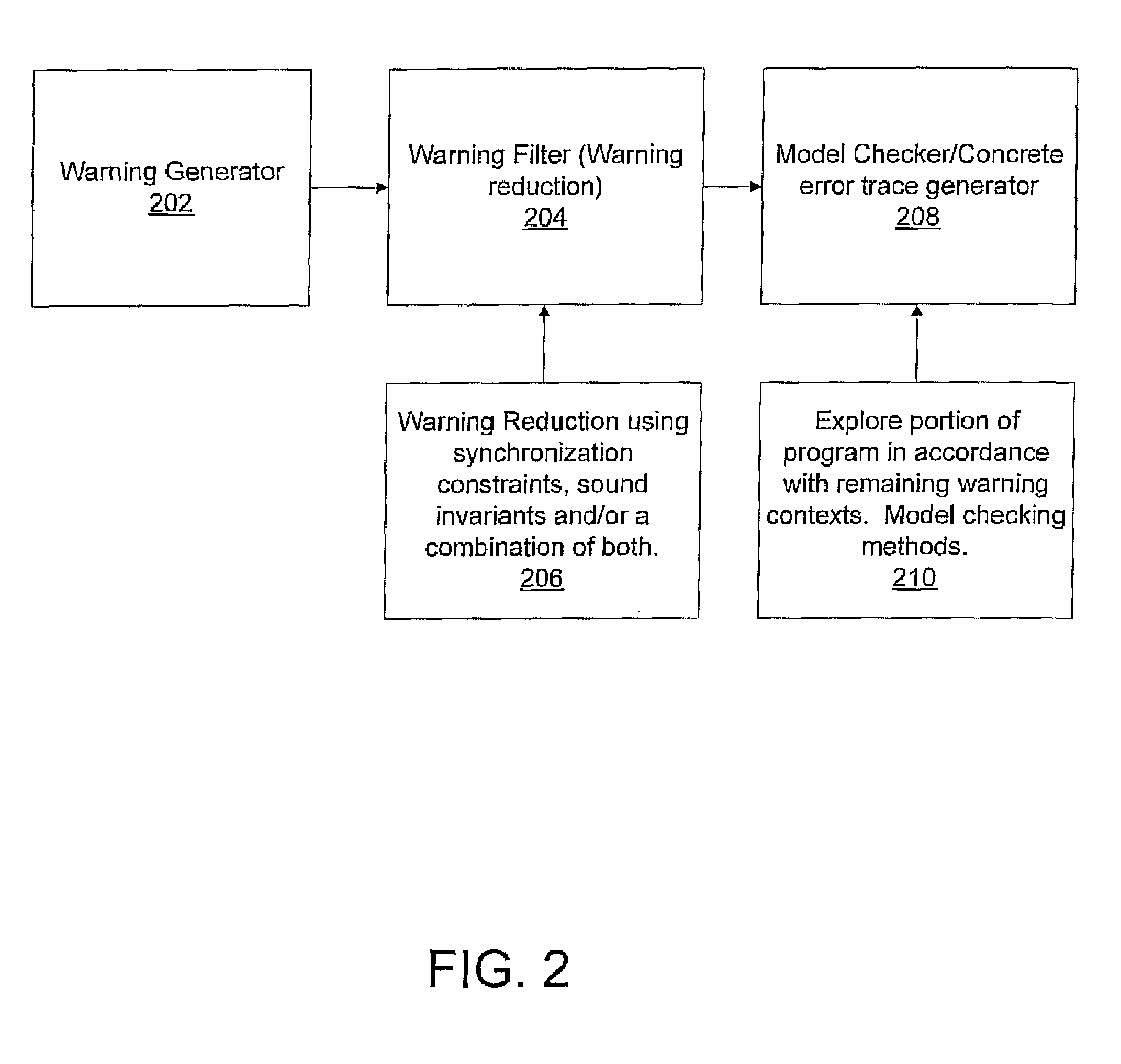
System and method for generating error traces for concurrency bugs
ActiveUS20090125887A1Error detection/correctionSpecific program execution arrangementsData streamProgram validation
A system and method for program verification includes generating a product transaction graph for a concurrent program, which captures warnings for potential errors. The warnings are filtered to remove bogus warnings, by using constraints from synchronization primitives and invariants that are derived by performing one or more dataflow analysis methods for concurrent programs. The dataflow analysis methods are applied in order of overhead expense. Concrete execution traces are generated for remaining warnings using model checking.
Owner:NEC CORP
System and method for modeling, abstraction, and analysis of software
ActiveUS20050166167A1Improve verification efficiencyImprove translationError detection/correctionComputation using non-denominational number representationBasic blockSoftware
A system and method is disclosed for formal verification of software programs that advantageously translates the software, which can have bounded recursion, into a Boolean representation comprised of basic blocks and which applies SAT-based model checking to the Boolean representation.
Owner:NEC CORP
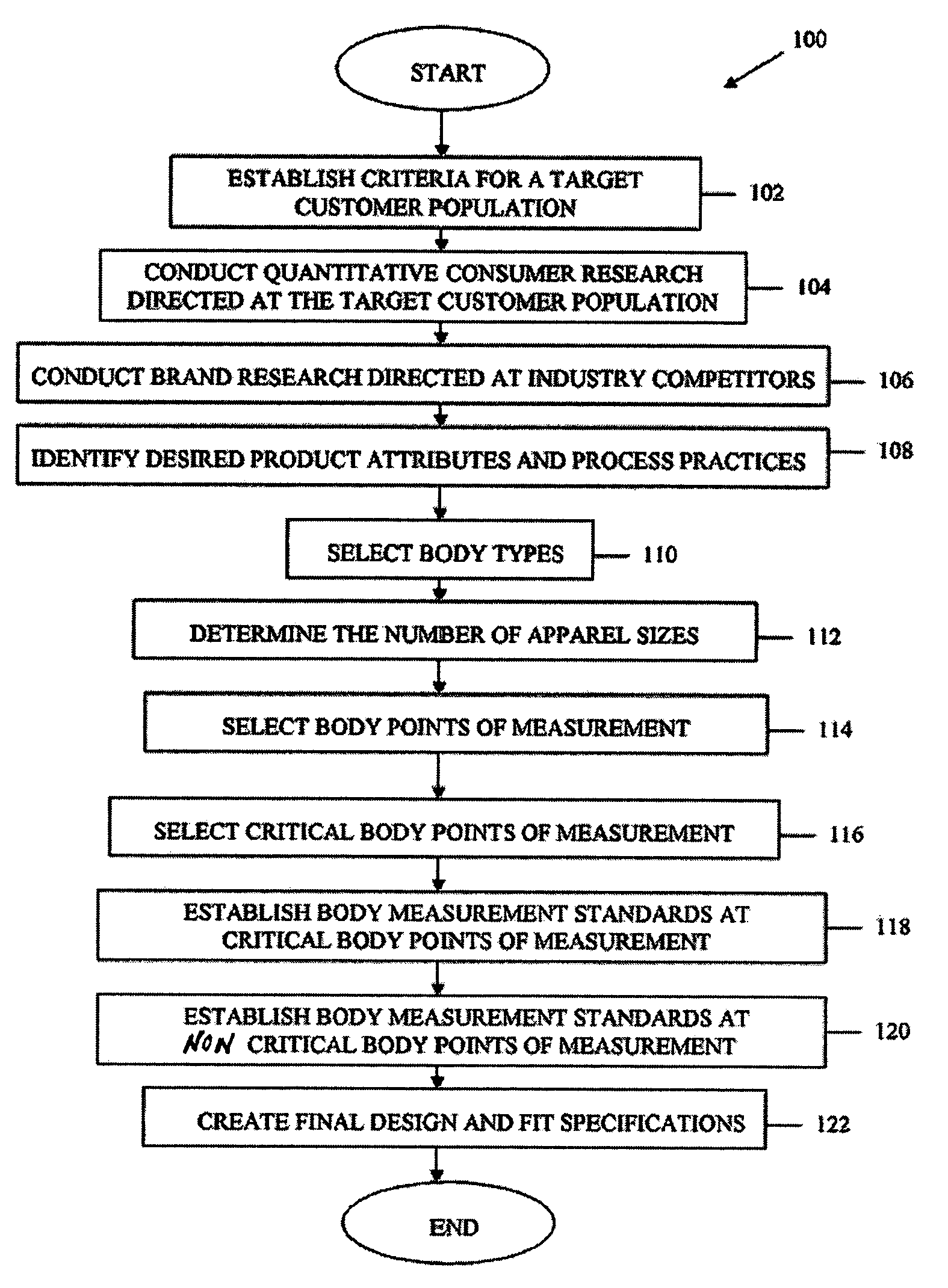
Systems and methods for improved apparel fit
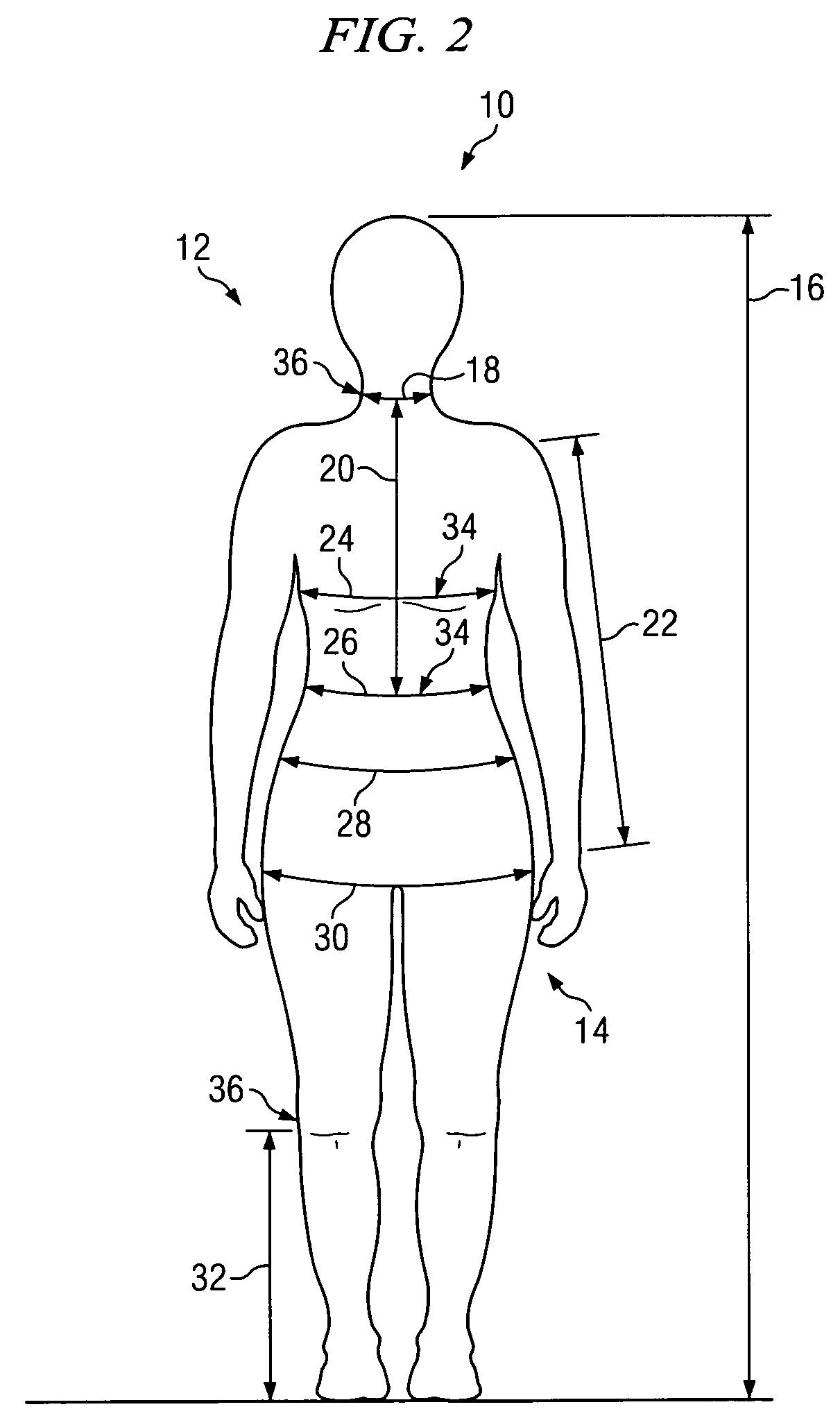
ActiveUS7092782B2Accurate methodIncreasing retail inventoryBuying/selling/leasing transactionsSpecial data processing applicationsEngineeringType selection
Systems and methods for providing garments with improved and customized fits to one or more target consumer groups fit are described in the present invention. One method provides for a garment fit to a target consumer group comprising the steps of determining common body types for the target consumer group, establishing customized body measurement standards for each body type, selecting at least one real fit model for each body type, creating a sample garment in a range of sizes using grading rules, checking each sample garment on a fit model selected for each size and body type, preparing a block for each sample garment size and body type, and using the block to provide a garment fit for a target consumer group. Additional aspects are also disclosed.
Owner:ADVANTAGE PLATFORM SERVICES INC
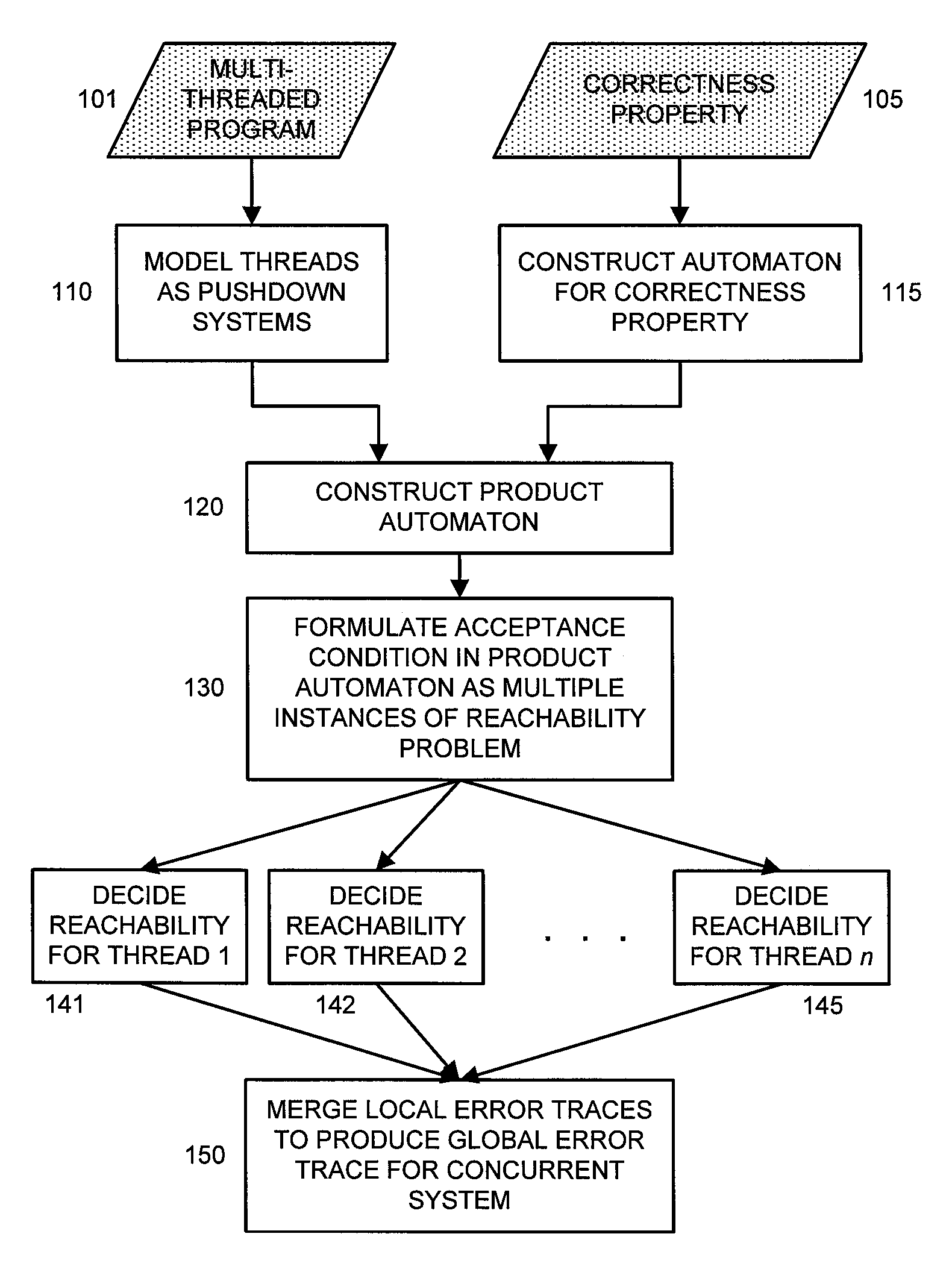
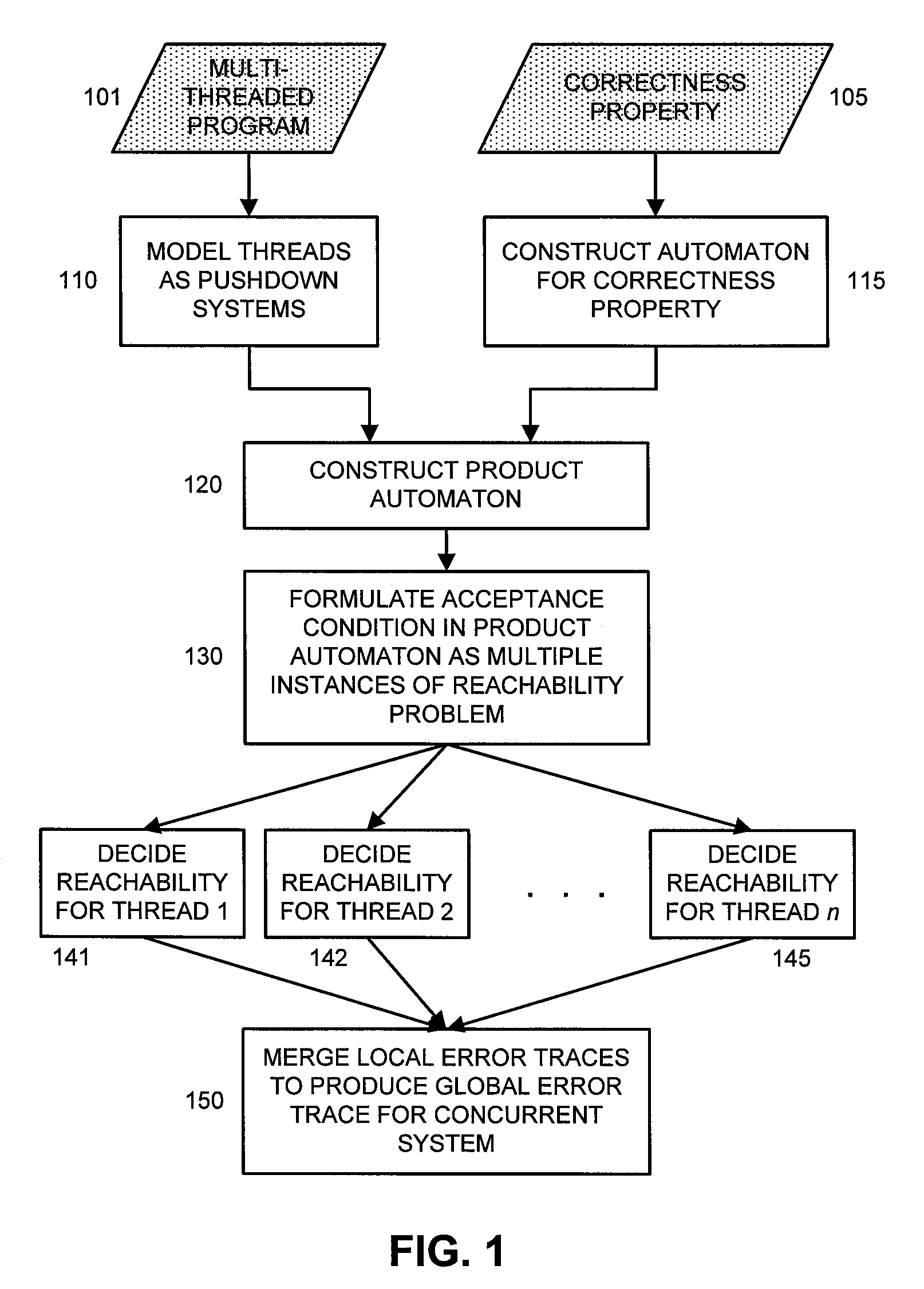
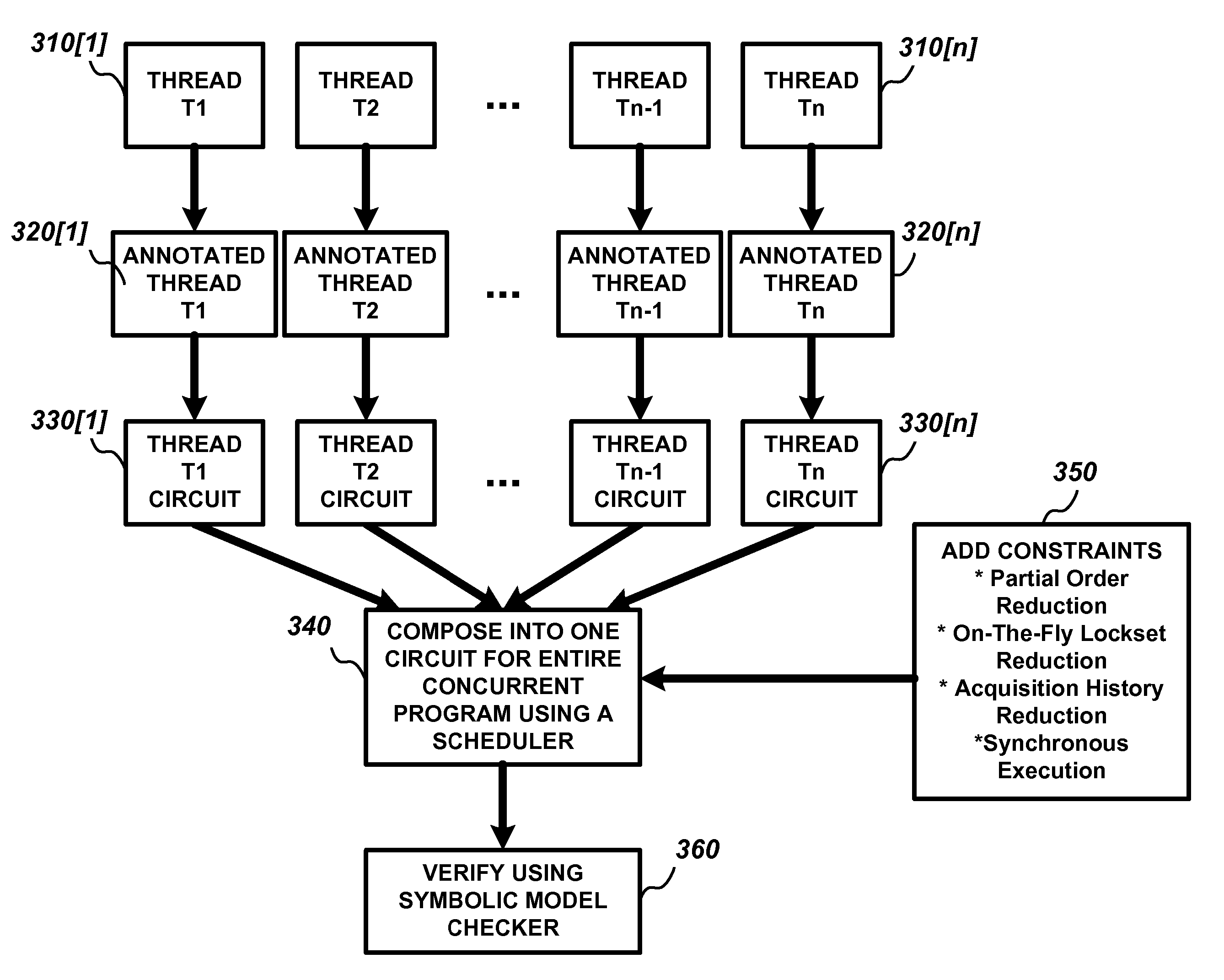
Model Checking of Multi Threaded Software
ActiveUS20060218534A1Avoid problemsError detection/correctionSpecific program execution arrangementsTemporal logicLinearity
A technique for model checking of multi-threaded software is herein disclosed which advantageously can be used to verify correctness properties expressed using temporal logic, e.g., linear time temporal logic and branching time temporal logic. The model checking problem of a concurrent system is decomposed into a plurality of model checking problems on individual threads of the multi-threaded software.
Owner:NEC CORP
IEC61970CIM model checking method
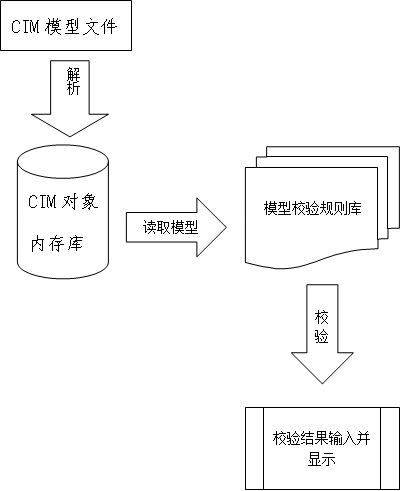
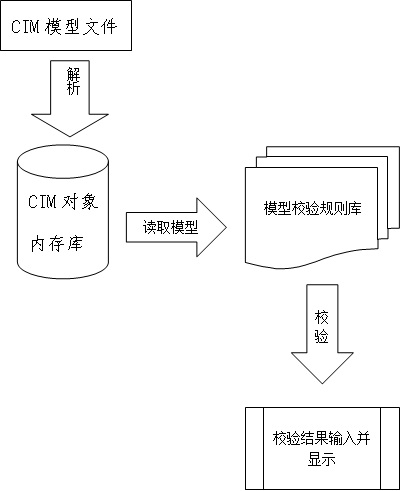
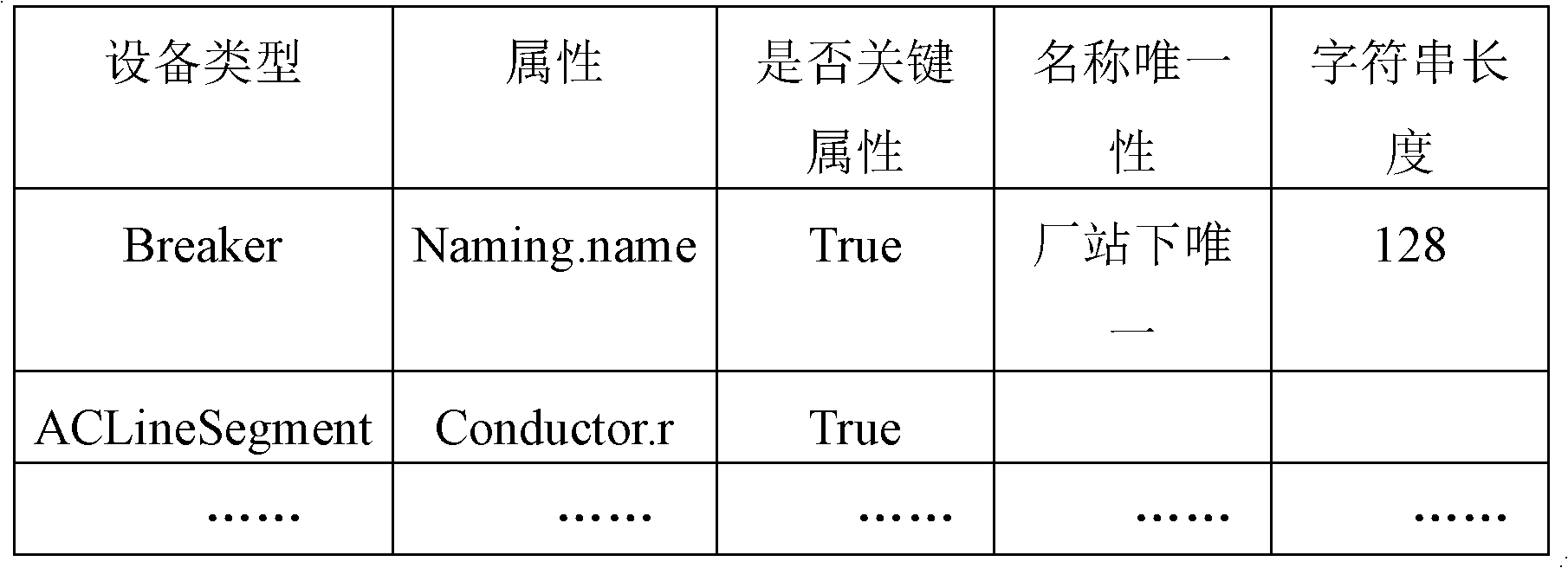
InactiveCN102663094ASolve problems that consume a lot of timeAvoid wrong creationSpecial data processing applicationsInternal memorySemantics
The invention discloses an IEC61970CIM model checking method, which comprises the following steps: at first, a device object in a CIM (Common information Model) is read into a CIM object internal memory bank, an incidence relation in a form of character string in the original CIM model file is replaced by a pointer, so that the problem of consumption of plenty of time caused by repeatedly reading the CIM model file is solved, and grammar checkout, semantics checkout, parameter completeness checkout, relation consistency checkout, topology integrity checkout and the like can be carried out on the model in the CIM object internal memory bank according to a defined checkout rule, a result which does not conform to the checkout rule can be output and shown to a user, so that the CIM model is convenient to modify quickly by the user, and the mistaken establishment of an electric network model in the other system is avoided, and therefore, a large amount of manpower and material resources can be saved.
Owner:NARI TECH CO LTD
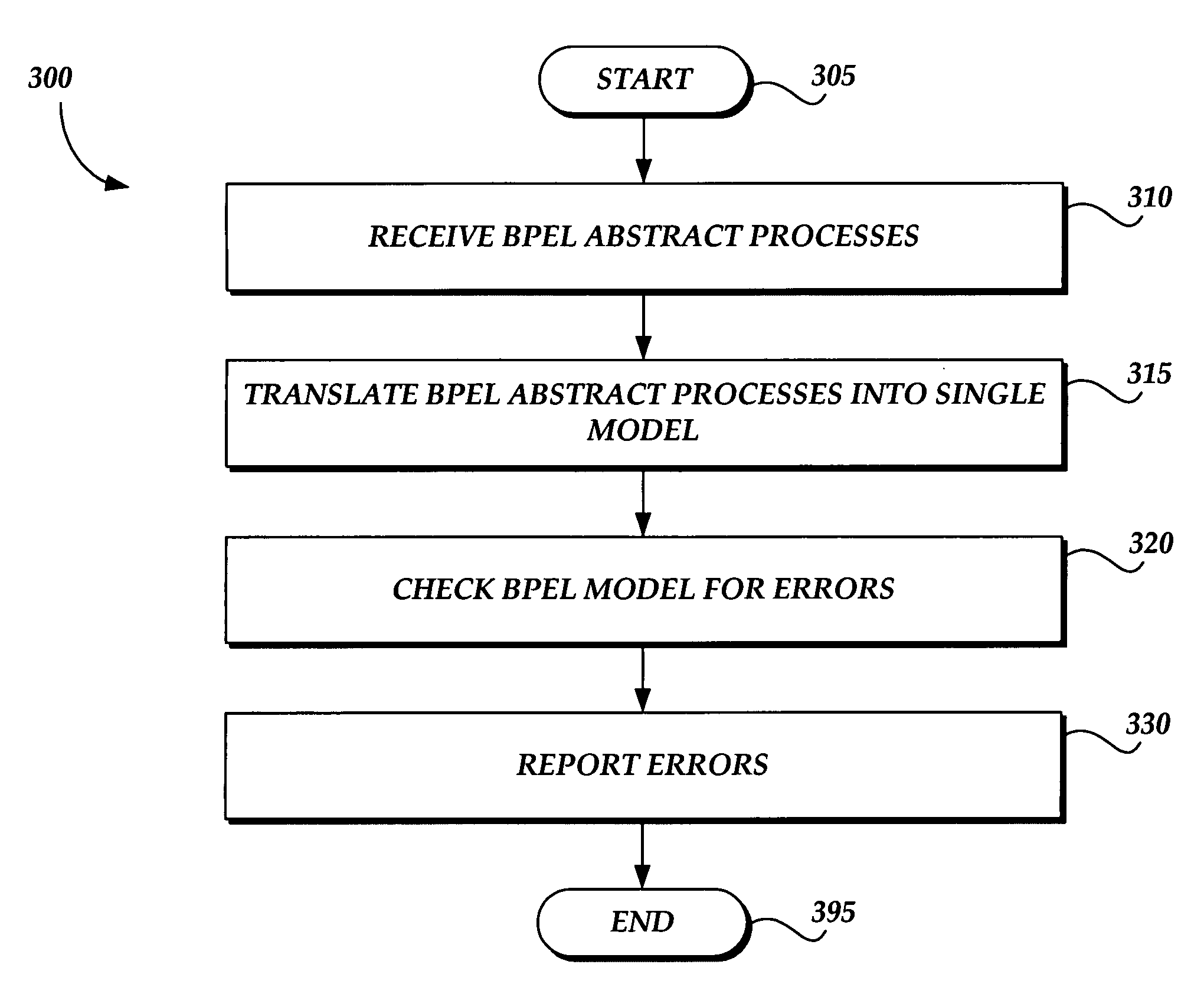
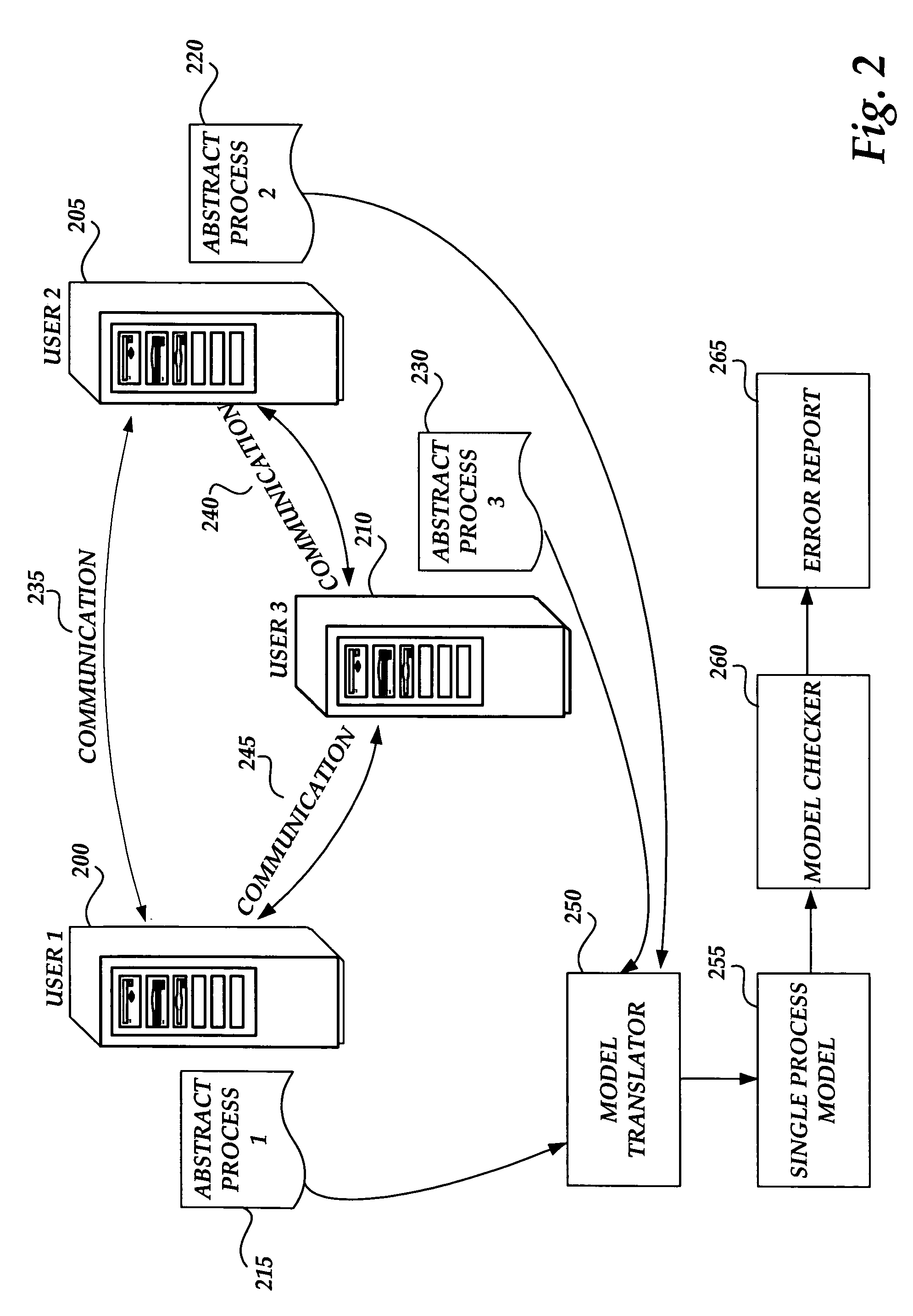
Error detection in web services systems
Methods and systems are provided for automatically generating an accurate model of communications processes between disparate computing systems that may be analyzed in an efficient manner for error detection in web services systems. Business Process Execution Language for Web Services (BPEL) descriptions are automatically generated for the BPEL-based executable processes utilized by each communicating computing system in a given web services system. The BPEL abstract process descriptions for each communicating computing system are translated into a combined process model according to a suitable modeling language. The process model is tested by a model checking software application. Communications errors between the disparate computing systems are detected by automatically testing the combined process model according to a variety of potential communications scenarios.
Owner:MICROSOFT TECH LICENSING LLC
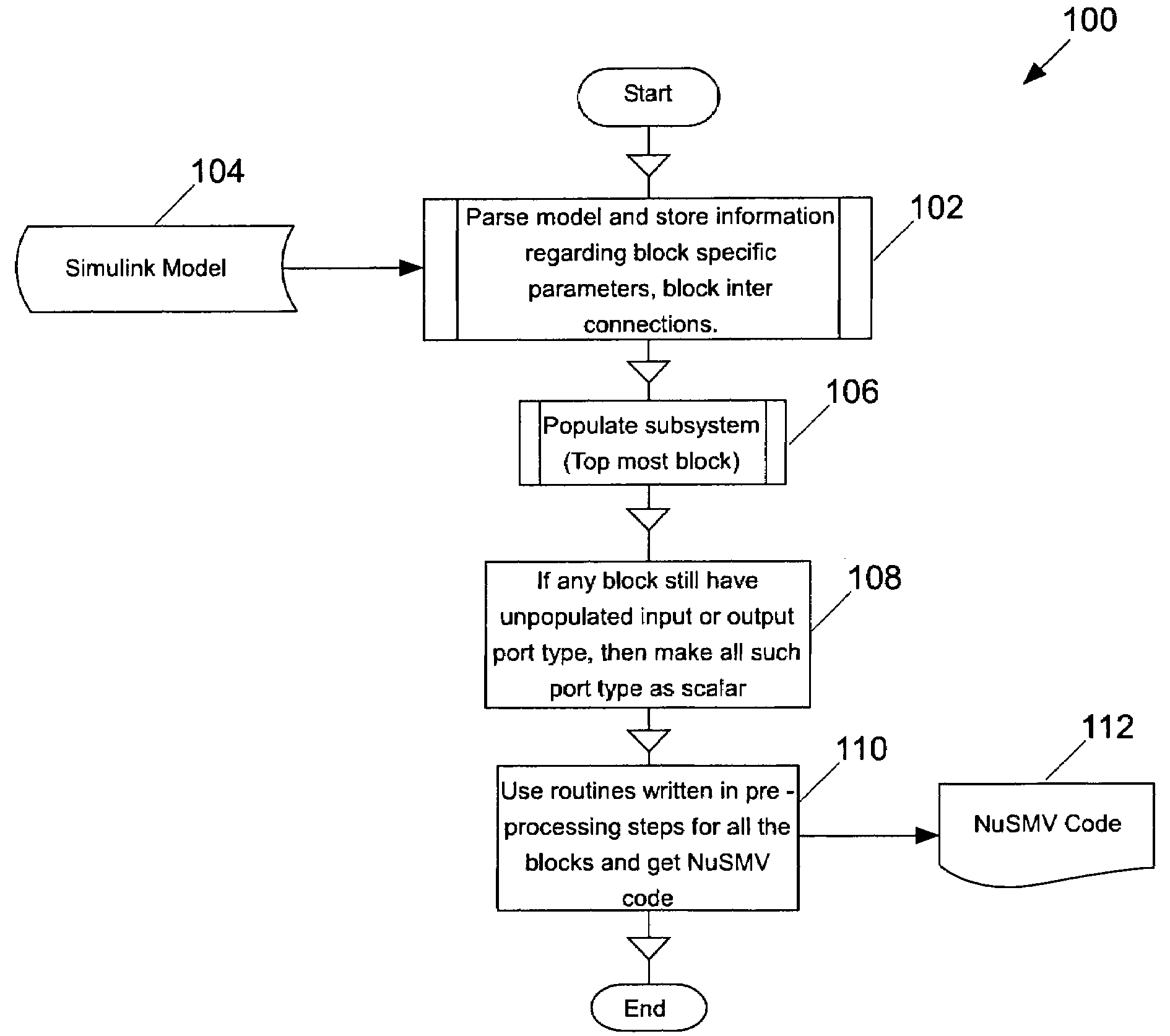
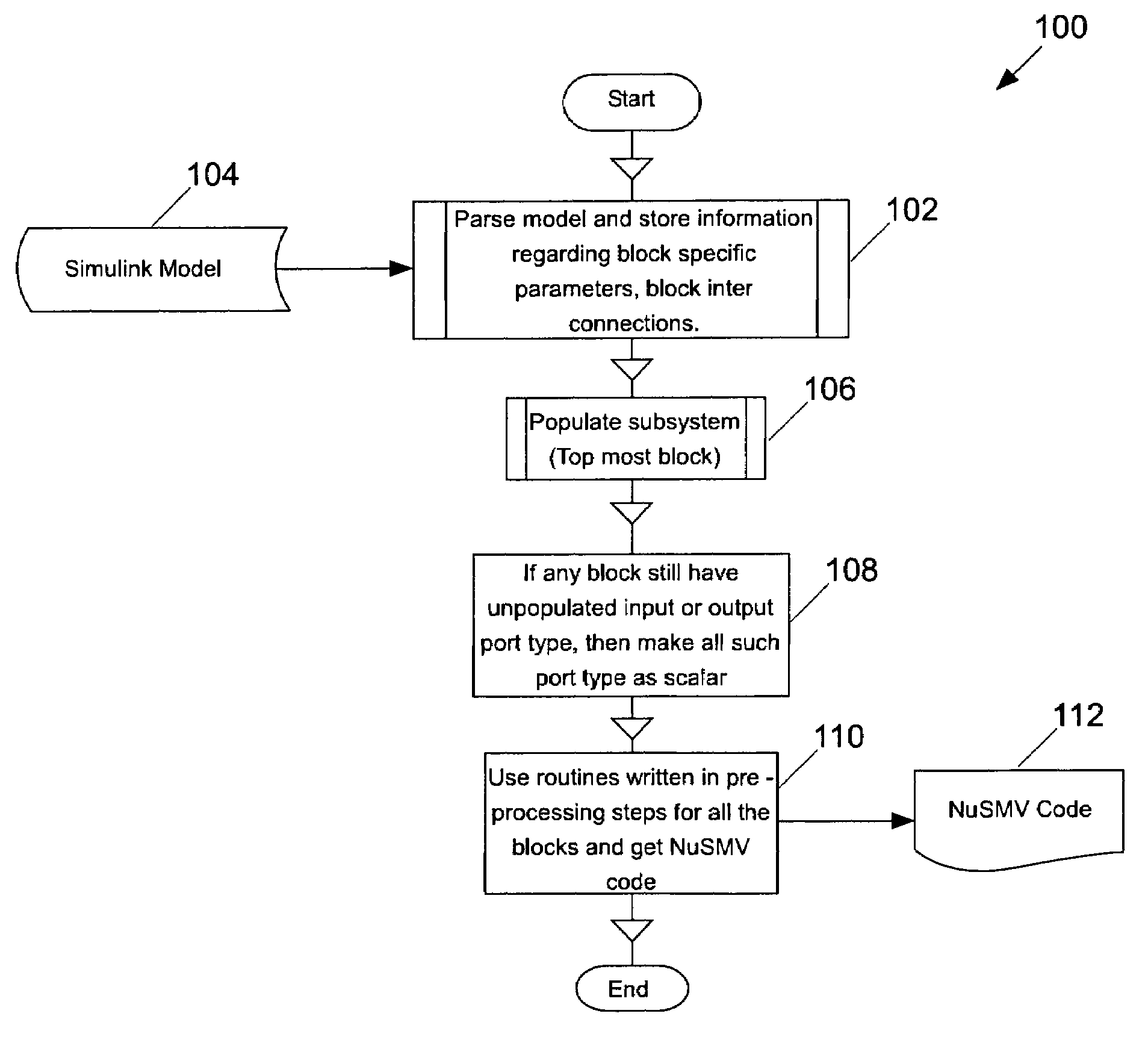
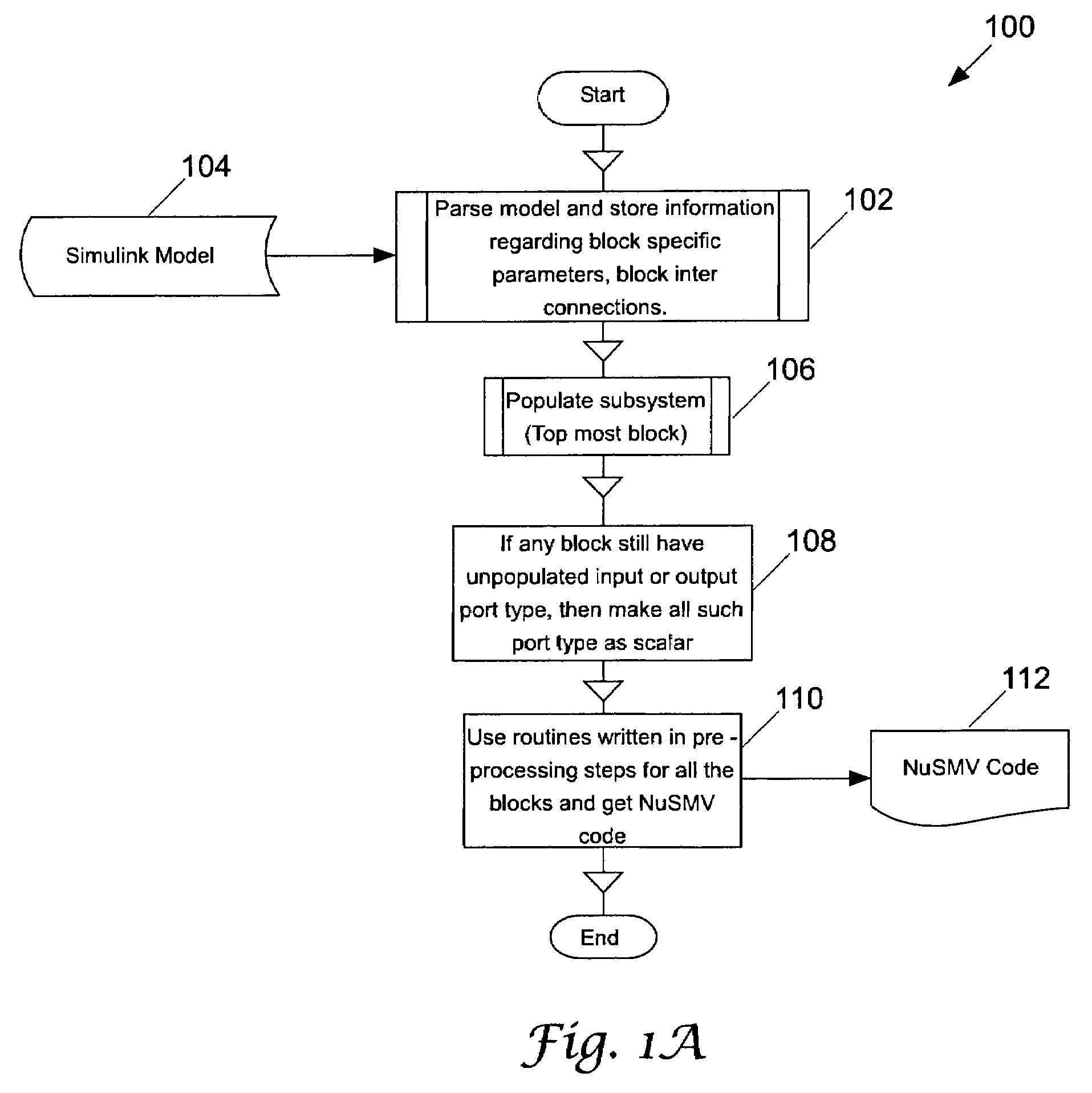
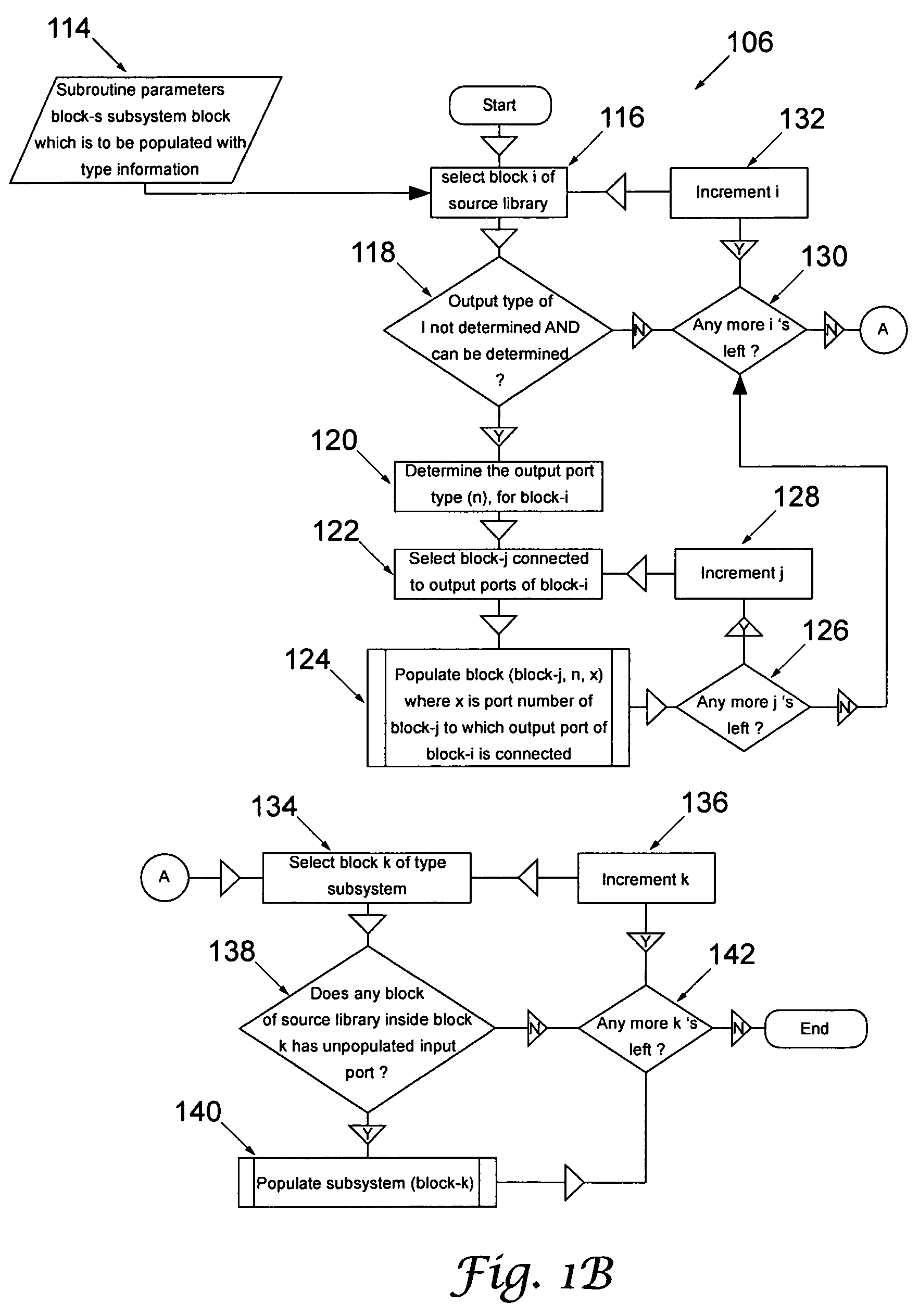
Automatic translation of simulink models into the input language of a model checker
InactiveUS20080086705A1Software simulation/interpretation/emulationSpecial data processing applicationsAutomatic translationInput language
A translator converts an input model, such as resulting from a simulation of a design to be verified, into an output model suitable for verification by a model checker. The input model, for example, may be produced using Simulink, and the output model, for example, may be a NuSMV model.
Owner:HONEYWELL INT INC
Efficient SAT-based unbounded symbolic model checking
ActiveUS20050240885A1Improve performanceReduce stepsComputation using non-denominational number representationComputer aided designFixed point computationQuantifier elimination
An efficient approach for SAT-based quantifier elimination and pre-image computation using unrolled designs that significantly improves the performance of pre-image and fix-point computation in SAT-based unbounded symbolic model checking.
Owner:NEC CORP
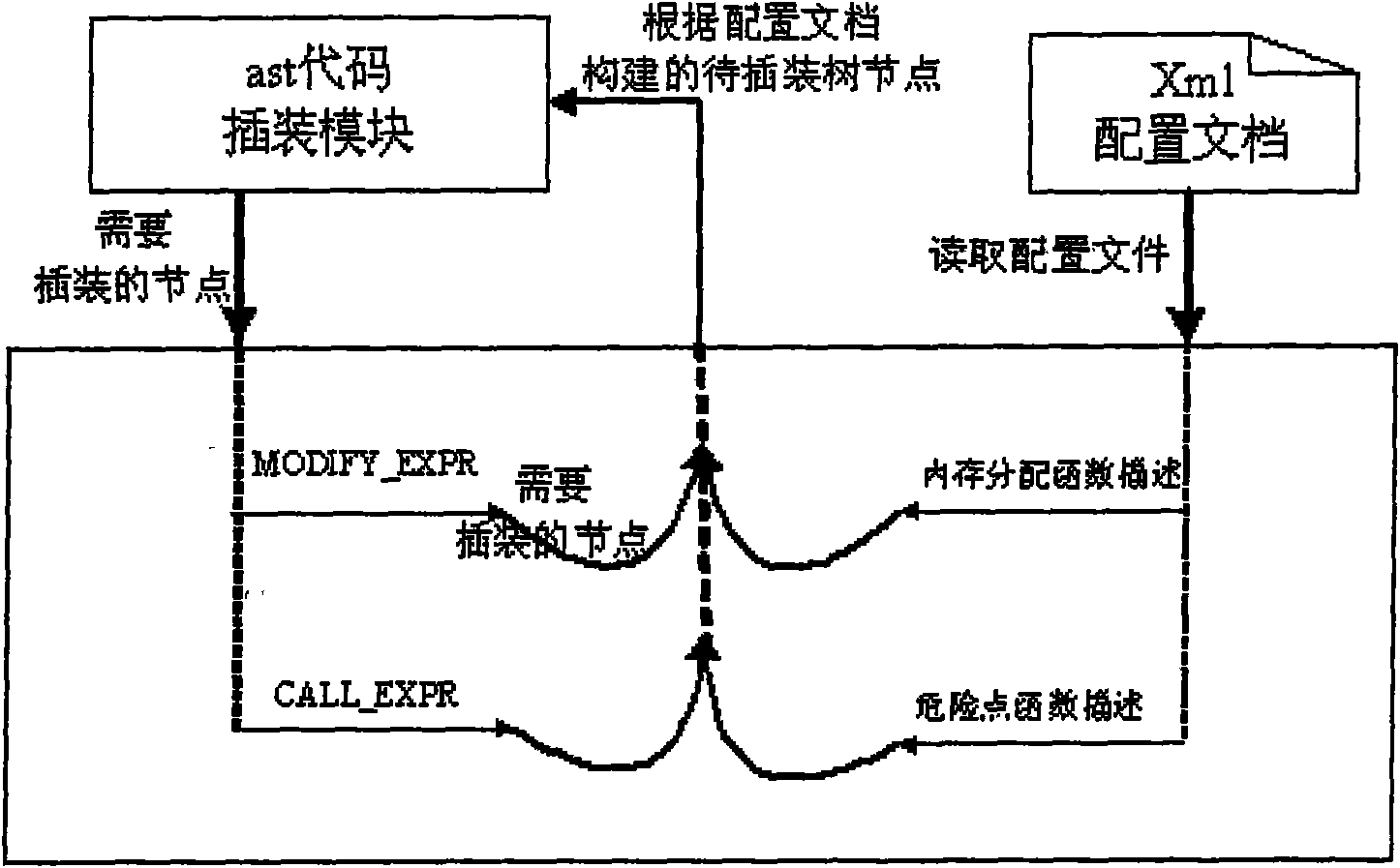
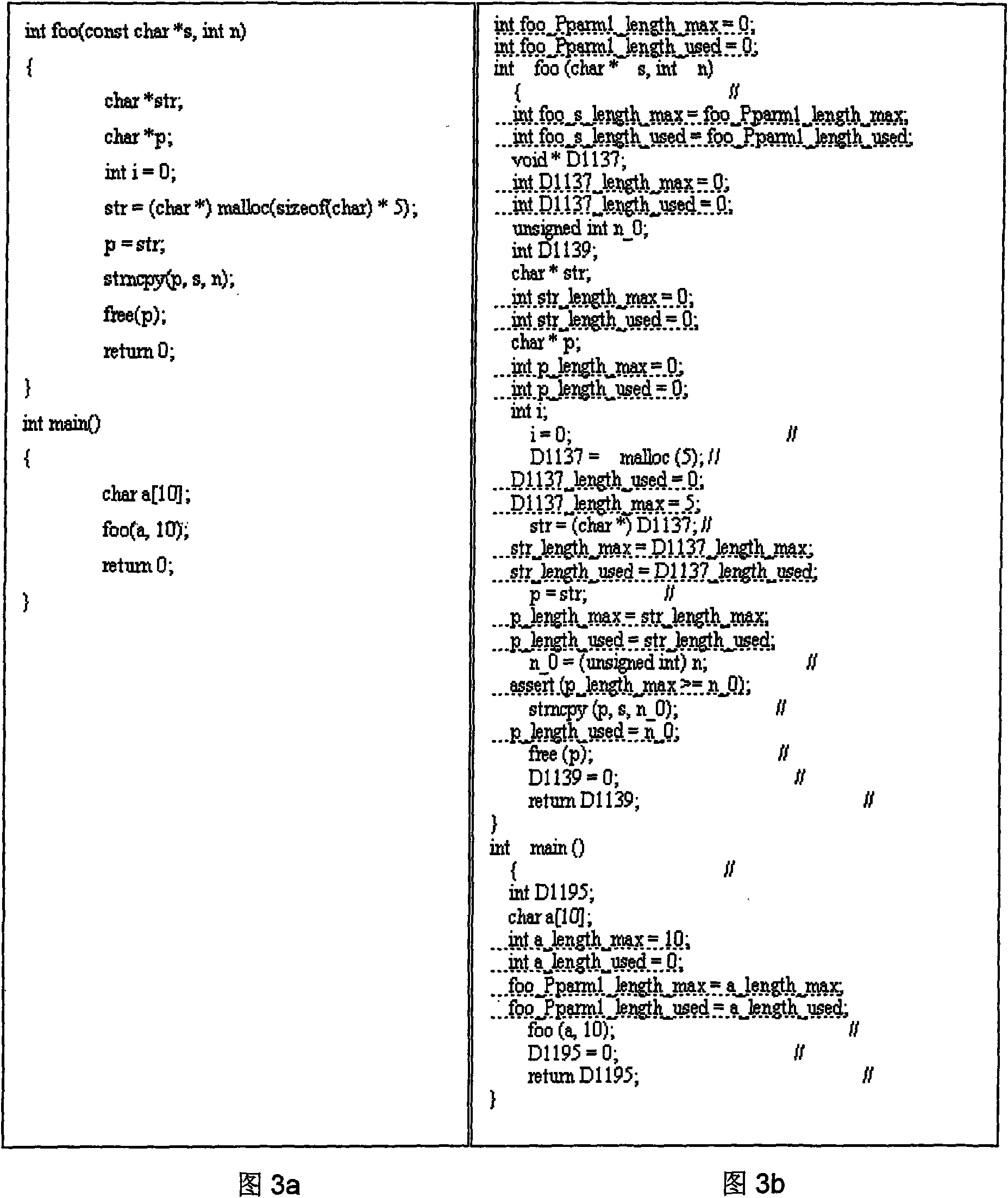
Method for detecting code security hole based on constraint analysis and model checking
The invention relates to a method for detecting a code security hole based on constraint analysis and model checking, which can extract the source code of a C program in a constraint way and detect the security hole of the program with the model checking. The main content comprises the following steps: buffer attribute information which is involved in the source code of the C program is extracted with a constraint analysis technology; the corresponding ASSERT sentence information of attribute generation, attribute transmission and attribute constraint is inserted into variable declaration, variable assignment and function call site with the buffer attribute information; the inserted code can be taken as the input of the model checking to judge whether the program is accessible, find whether the dangerous points in the program really has an accessible path and finally find the security hole in the source code. Currently, independent model checking can not detect the security hole of the buffer and the like, the method combines the static detecting technology of the constraint analysis with the model detecting technology to realize the detection of the security hole of the buffer overflow and the like, wherein, the detecting precision of the method is higher than that of the general static detecting technology. By extracting the other dangerous function information of the source code, corresponding inserting process is carried out. The invention also can detect the security holes such as formative character string, code injection, privilege escalation, etc.
Owner:BEIHANG UNIV
Method for design validation using retiming
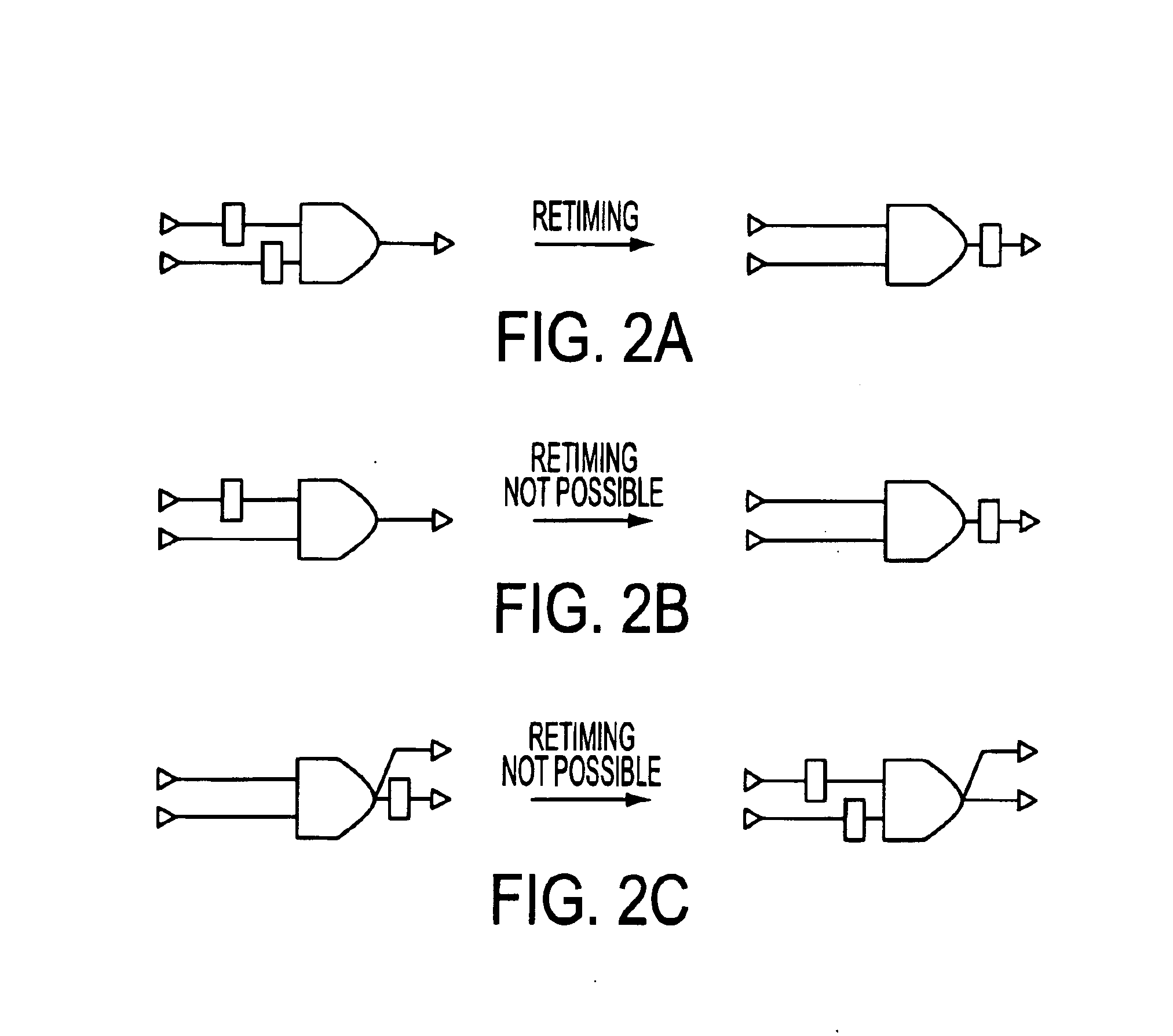
InactiveUS6874135B2Minimize the numberReduce complexityDetecting faulty computer hardwareCAD circuit designDesign testingTest sequence
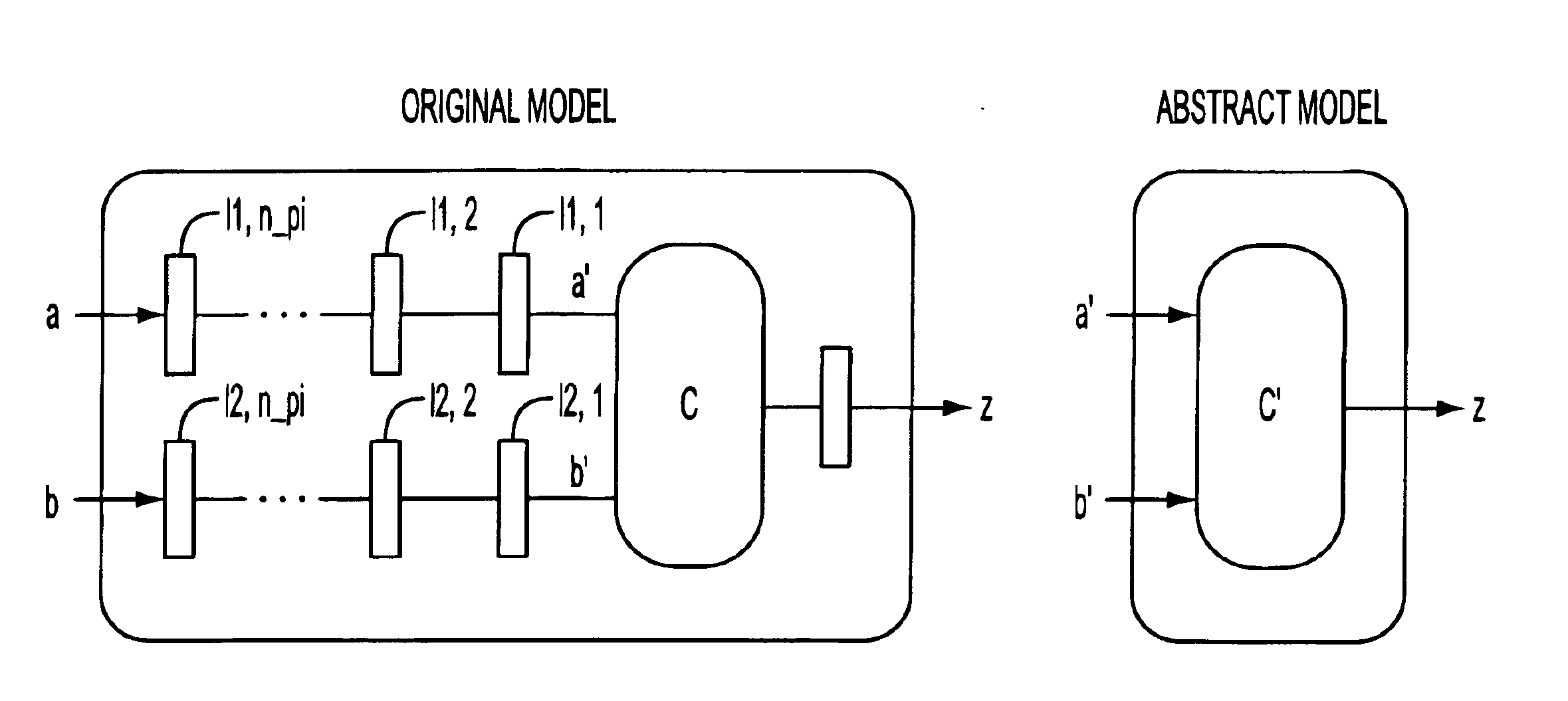
A method for derivation and abstraction of test models for validation of industrial designs using guided simulation is described. The method employs automatic abstractions for the test model which reduce its complexity while preserving the class of errors that can be detected by a transition tour. A method for design validation comprising generating a state-based test model of the design. The test model is abstracted by retiming and latch removal. Finally, a validation technique is applied on the abstracted test model. First, the number of internal (non-peripheral) latches in a design is minimized via retiming using a method of Maximal Peripheral Retiming (MPR). According to the MPR method, internal latches are retimed to the periphery of the circuit. Subsequently, all latches that can be retimed to the periphery are automatically abstracted in the test model. The validation technique may comprise of model checking, invariant checking or simulation using test sequences generated from the abstracted test model.
Owner:NEC CORP
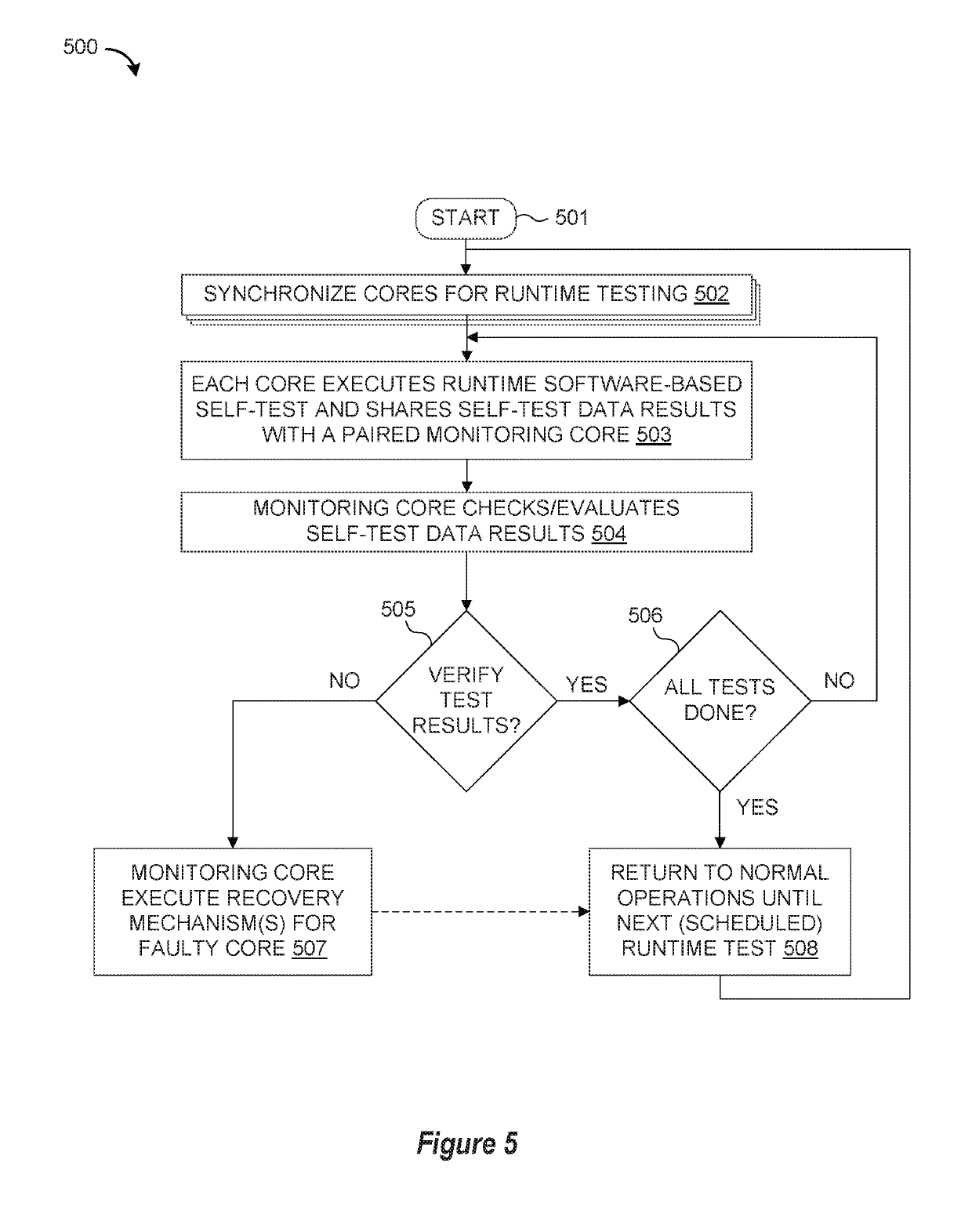
Runtime Software-Based Self-Test with Mutual Inter-Core Checking
A method, apparatus, article of manufacture, and system are provided for detecting hardware faults on a multi-core integrated circuit device by executing runtime software-based self-test code concurrently on multiple processor cores to generate a first set of self-test results from a first processor core and a second set of self-test results from a second processor core; performing mutual inter-core checking of the self-test results by using the first processor core to check the second set of self-test results from the second processor core while simultaneously using the second processor core to check the first set of self-test results from the first processor core; and then using the second processor core to immediately execute a recovery mechanism for the first processor core if comparison of the first set of self-test results against reference test results indicates there is a hardware failure at the first processor core.
Owner:NXP BV
Test case generation algorithm for a model checker
InactiveUS20070250799A1Aerodynamics improvementComputer aided designHardware software systemTest case
A method is provided for generating test cases automatically using an abstract system description in combination with a model-checking tool. The abstract system description can be used to design hardware / software systems and the generated test cases can be reused to verify the correctness of the implementation.
Owner:ALCATEL-LUCENT USA INC
Parallelization security hole detecting method based on function call graph
InactiveCN102567200AEasy to analyzeEasy to detectSoftware testing/debuggingPlatform integrity maintainanceCall graphAccessibility
The invention relates to a parallelization security hole detecting method based on a function call graph, which is characterized in that a function set to be detected is determined by analyzing the function call relation in a C language module, instrumentation and assert analysis are performed for the function set by means of the preprocessing technology, and then security holes of a program are detected by the aid of model checking and the parallelization technology. The method mainly includes the steps: generating the function relation call graph, and determining C function information to be detected by analyzing the function relation call graph; extracting attribute information of a buffer area related to C program source codes by the aid of the constraint analysis technology, and inserting corresponding ASSERT statement information in a variable declaration, an assignment and a function call point by means of the attribute information of the buffer area; and performing accessibility judgment for the instrumented codes, and analyzing whether a dangerous point in the program includes an accessible path to discover the security holes in the source codes or not. The method detects the security holes such as buffer area overflow and the like by combining the constraint analysis static detecting technology, model checking and the parallelization technology, and the detecting precision of the method is higher than that of the general static detecting technology.
Owner:BEIHANG UNIV
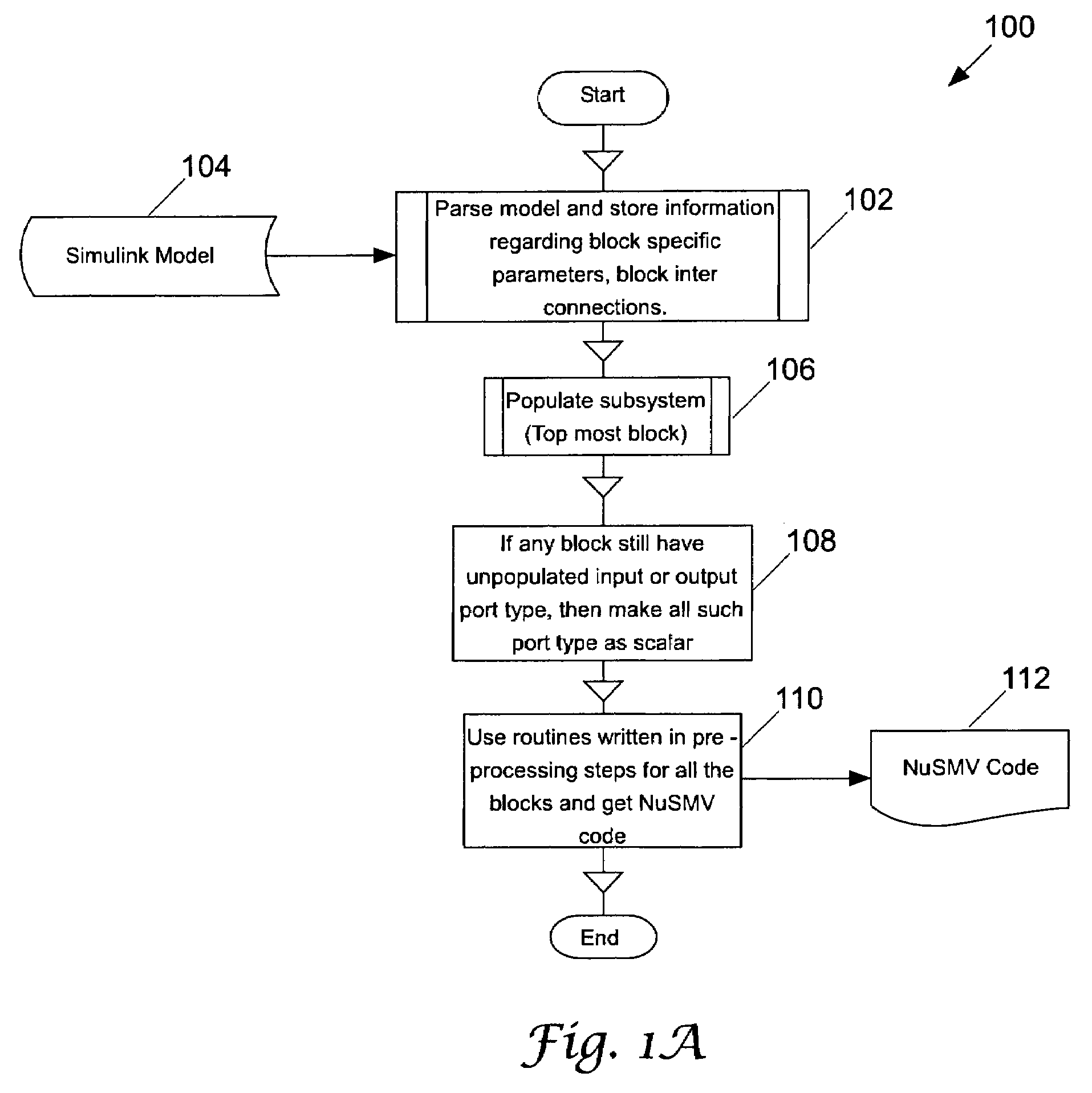
Automatic translation of simulink models into the input language of a model checker
InactiveUS7698668B2Software simulation/interpretation/emulationSpecial data processing applicationsAutomatic translationInput language
Owner:HONEYWELL INT INC
Systems and methods for discovery of data that needs improving or authored using user search results diagnostics
ActiveUS20060248057A1Digital data information retrievalSpecial data processing applicationsResult listInformation retrieval
A search mechanism is evaluated or a relevance model checked using session level and result level diagnostics based on user behavior during a search session with respect to queries entered and user responses to result lists. Tracking occurs of when content desired by a user exists, but is not returned in a search result list when a query is made by the user with intent to find the desired content, when content desired by the user does not exist, when content desired by a user exists, but is not recognized by the user in a result list or is too low in a result list. A user's intent and search context is also taken into consideration when performing search mechanism diagnostics.
Owner:MICROSOFT TECH LICENSING LLC
System, method and computer-accessible medium for security verification of third party intellectual property cores
ActiveUS20160098565A1Memory loss protectionError detection/correctionThird partyIntellectual property
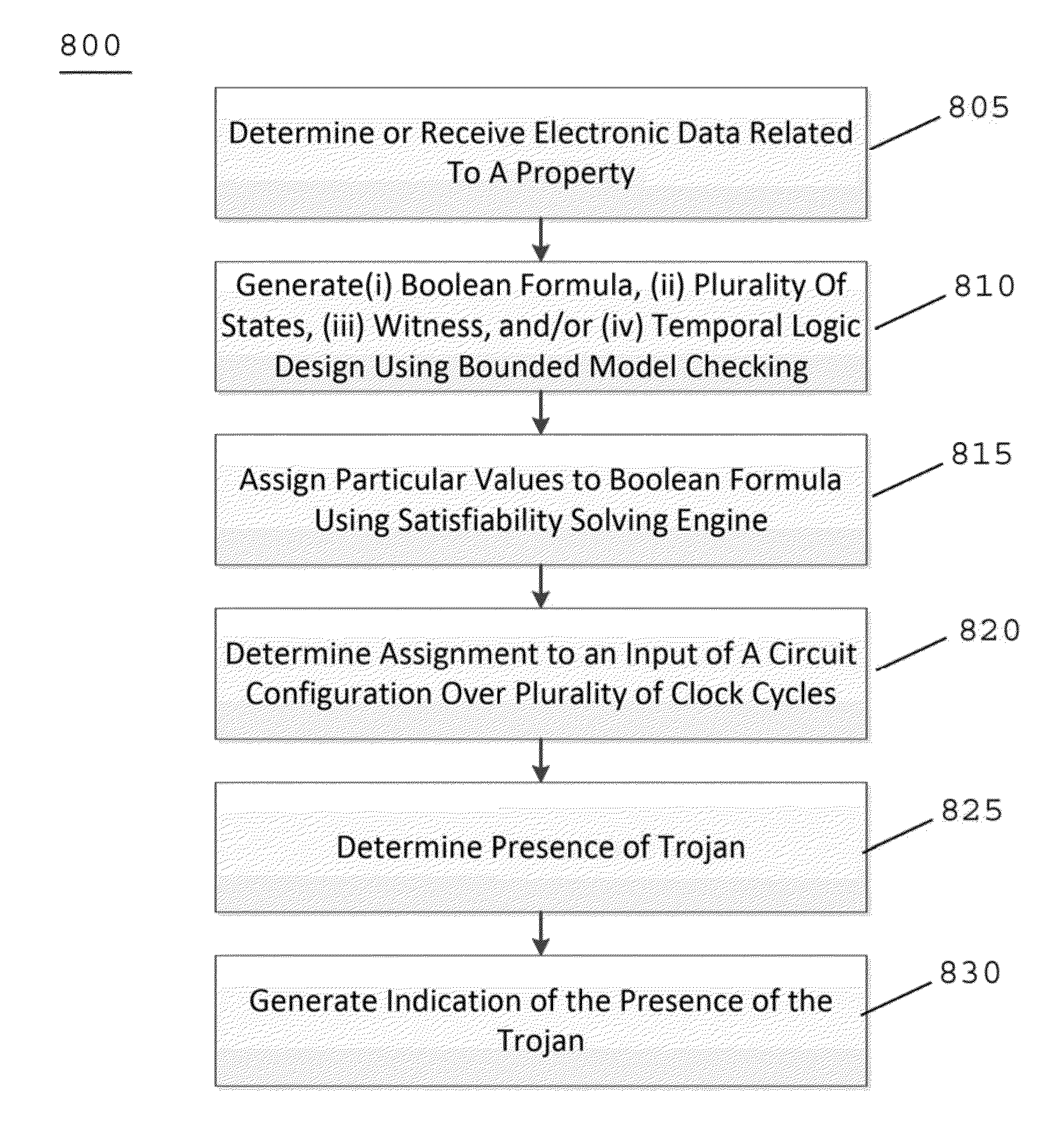
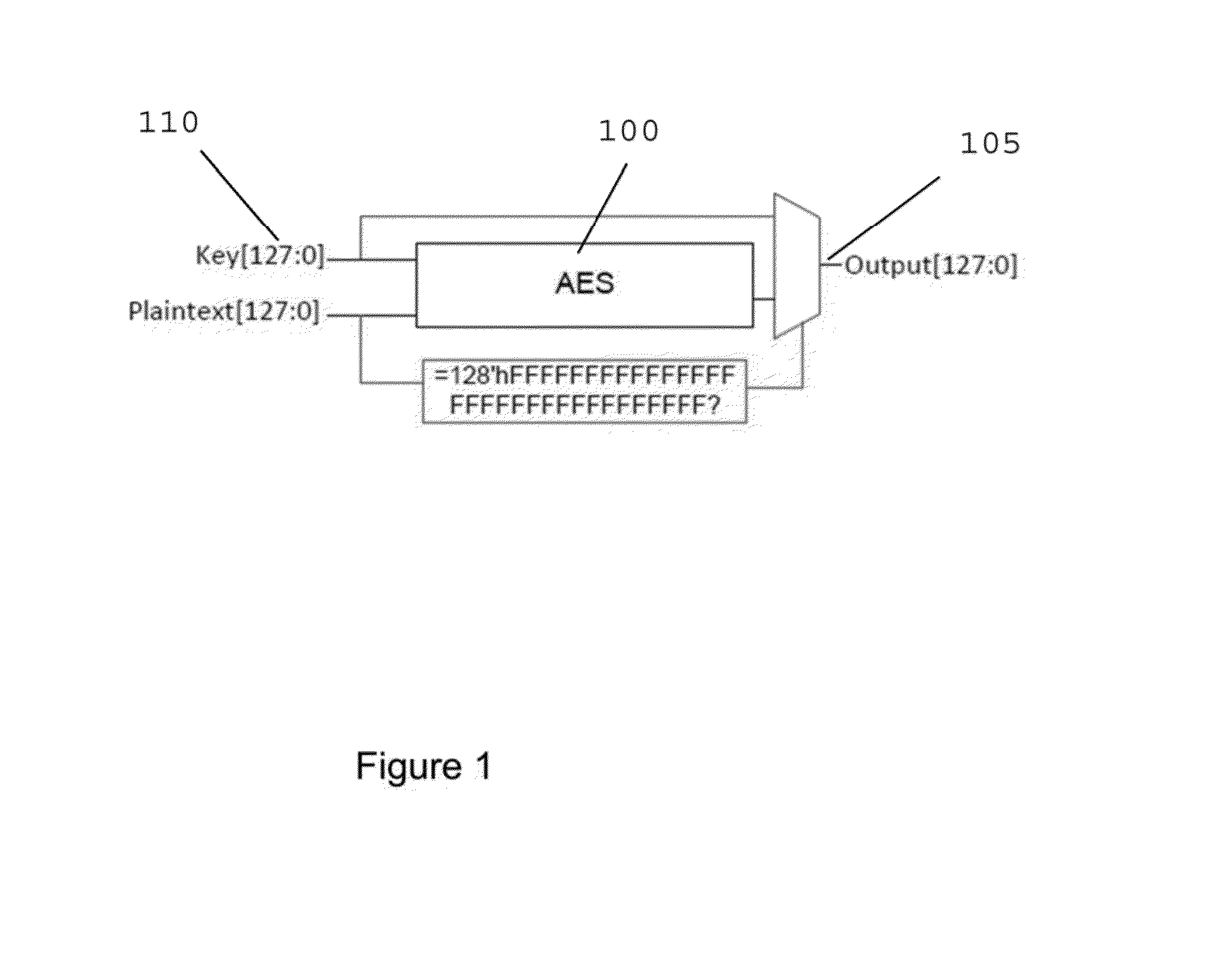
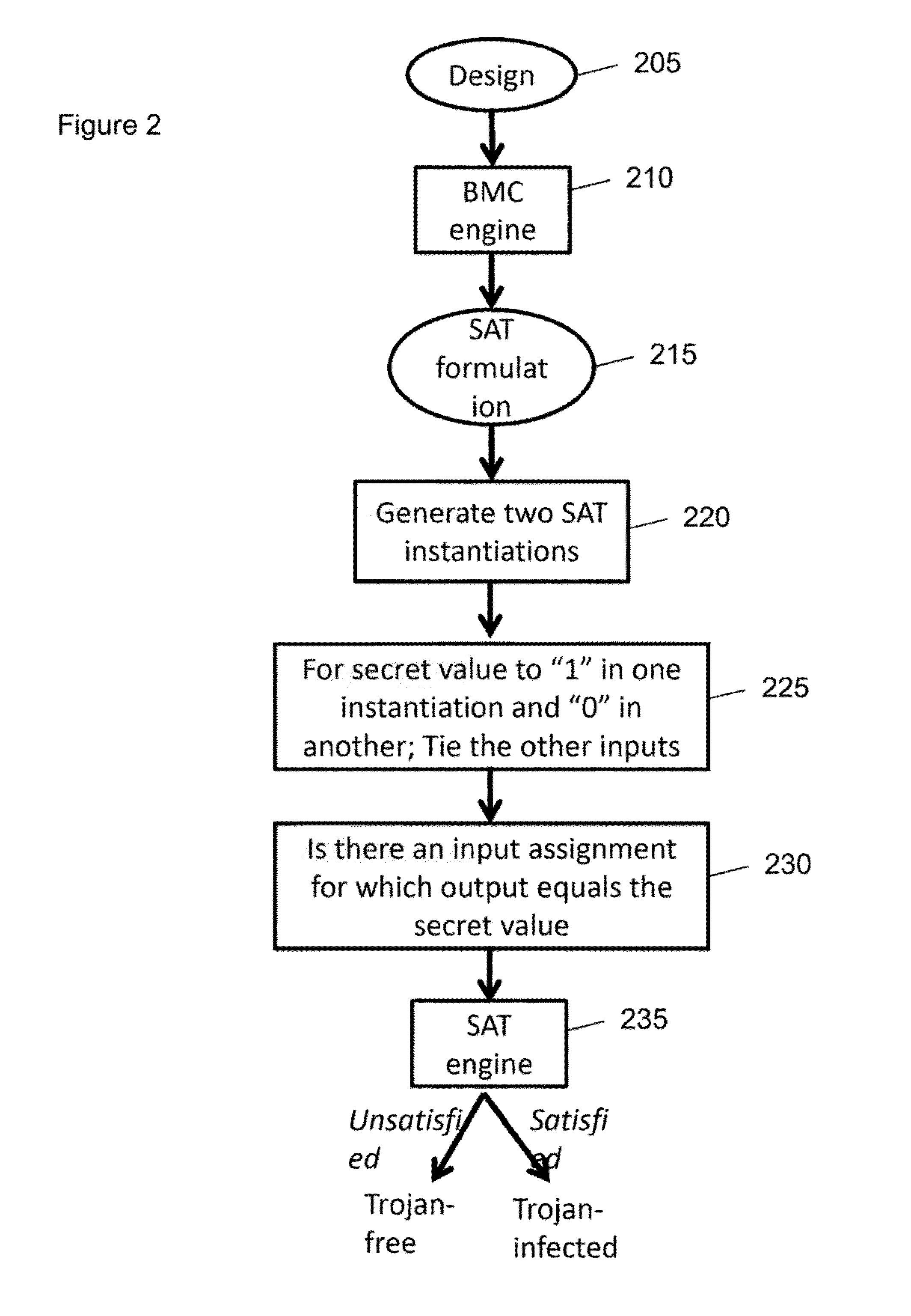
An exemplary system, method and computer-accessible medium for detecting the presence of a Trojan(s) in a circuit(s), can include, for example, receiving information related to a property(s) configured to determine the presence of the Trojan(s), and determining the presence of the Trojan(s) based on the property(s) and a design(s) of the circuit(s) using a bounded model checking tool.
Owner:NEW YORK UNIV
Transformer fault prediction method based on monitoring data of dissolved gas in oil of transformer
ActiveCN104820146AReflect individual characteristicsGuaranteed reliabilityElectrical testingForecastingTransformer oilData prediction
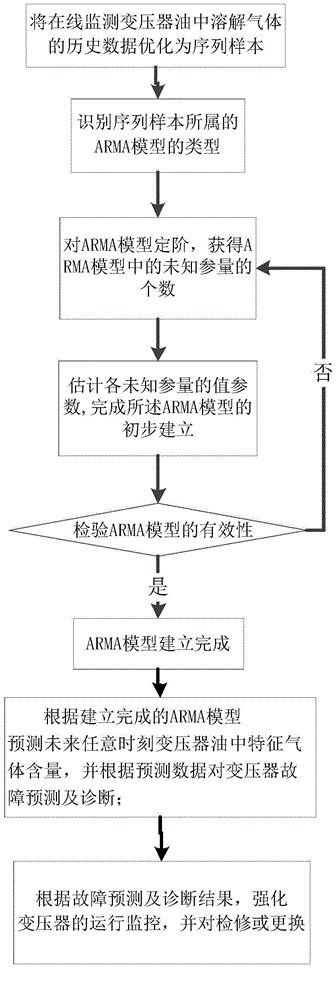
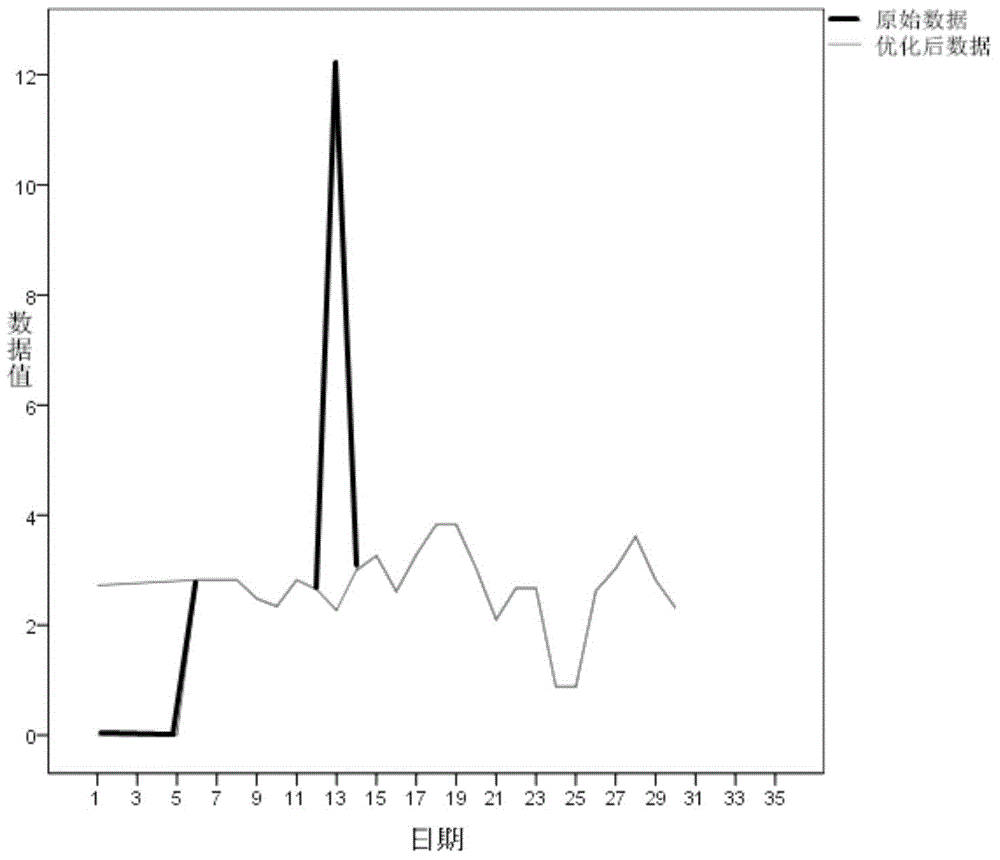
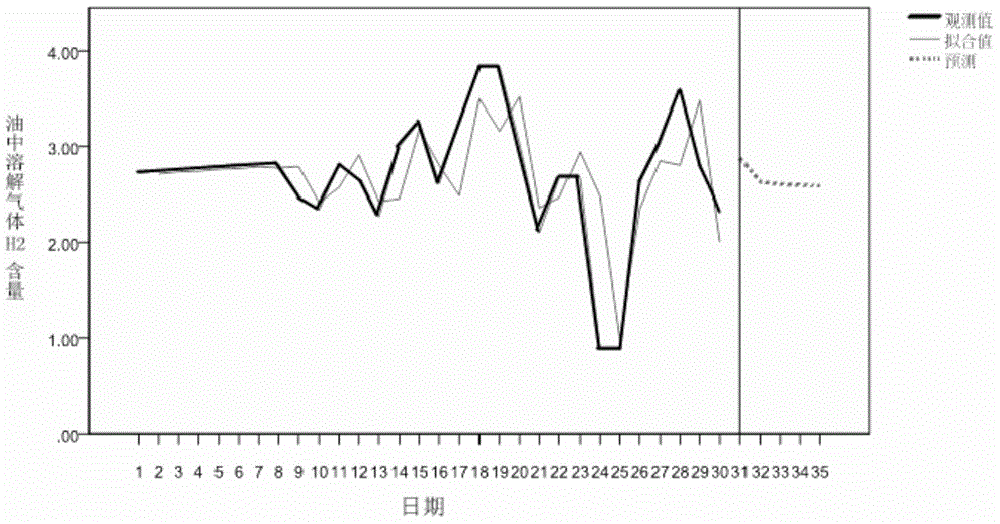
The invention provides a transformer fault prediction method based on monitoring data of a dissolved gas in the oil of a transformer. The method includes the following steps of: optimization of historical online data of the dissolved gas in the oil of the transformer, model identification of the optimized data, estimation of auto-regression moving average model parameters, model checking and establishment. With the transformer fault prediction method adopted, the content of the characteristic gas in the oil of the transformer at any time point in the future can be predicted, and therefore, the faults of the transformer can be judged, and maintenance measures can be put forward. Compared with the prior art, the method can improve sample quality, embody individual characteristics of the transformer and reflect a characteristic that the dissolved gas in the oil changes with time. Since data obtained through adopting the method do not change abruptly, the method can make more stable and concise physical interpretation compared with a prediction model which is established through adopting traditional machine learning. With the transformer fault prediction method adopted, the accuracy of online data prediction of the dissolved gas in the oil of the transformer can be improved, and fault prediction and maintenance measures can be more accurate and reliable; a reliable guarantee can be provided for the maintenance and use of the transformer; and the service life of the transformer can be prolonged.
Owner:CHINA ELECTRIC POWER RES INST +2
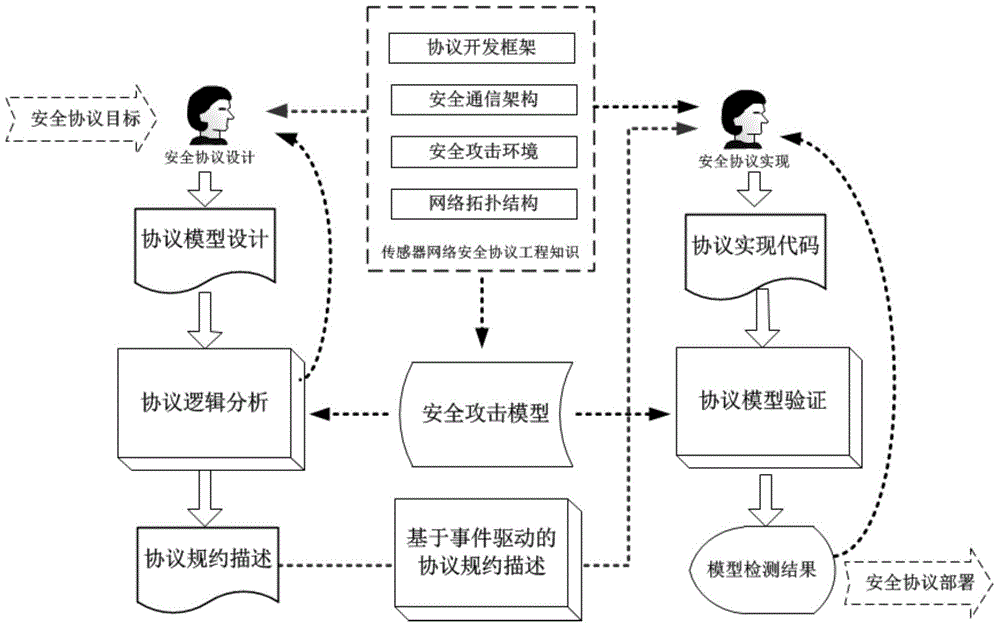
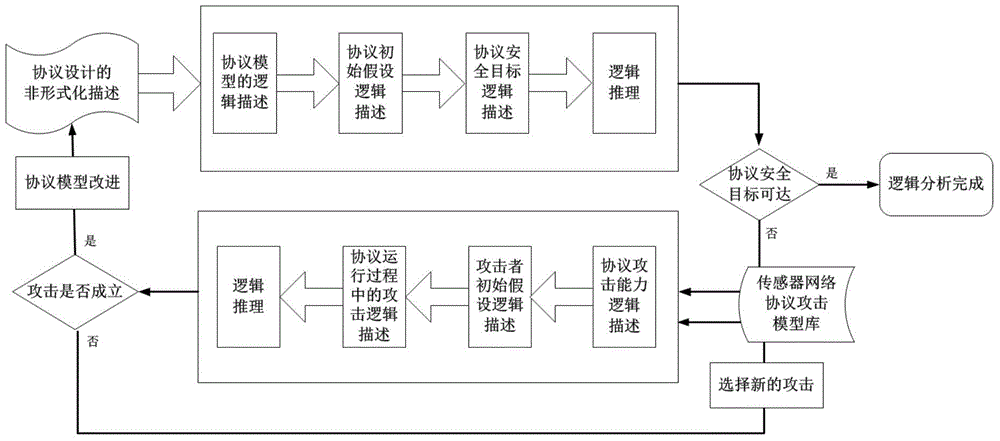
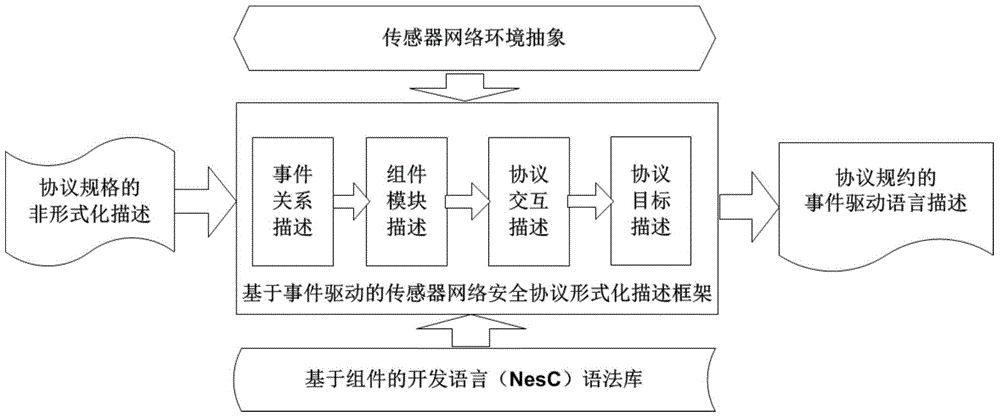
Formal verification method for facing design and accomplishment of wireless sensing network safety protocol
ActiveCN104135397ASimple designImprove development efficiencyData switching networksProtocol designValidation methods
A formal verification method for facing design and accomplishment of a wireless sensing network safety protocol, comprises the following steps: (1) a sensing network safety protocol design method based on logical analysis: a designer of the sensor network safety protocol accepting a protocol design goal, and designing a protocol rudiment based on analysis of sensor network environmental factors; establishing a logical reasoning system to accomplish protocol modeling and logical analysis, amending the protocol design plan according to the analysis result, and repeating logical analysis until the logic of the protocol is correct; and giving description of the protocol specification which is not formalized finally; (2) a safety protocol specification description language facing the sensing network developing environment; and (3) a safety protocol code automatic verification method based on model checking. The present invention effectively ensures safety and efficiency of the design and development and has good expansibility.
Owner:ZHEJIANG UNIV OF TECH
Symbolic model checking of concurrent programs using partial orders and on-the-fly transactions
InactiveUS20070143742A1Improved conditional dependency detectionFine granularityReverse engineeringSpecific program execution arrangementsState spaceOrder form
A set of techniques for analyzing concurrent programs that combines the power of symbolic model checking to explore large state spaces, and partial order and transaction-based reduction techniques to manage the size of explored state space.
Owner:NEC LAB AMERICA
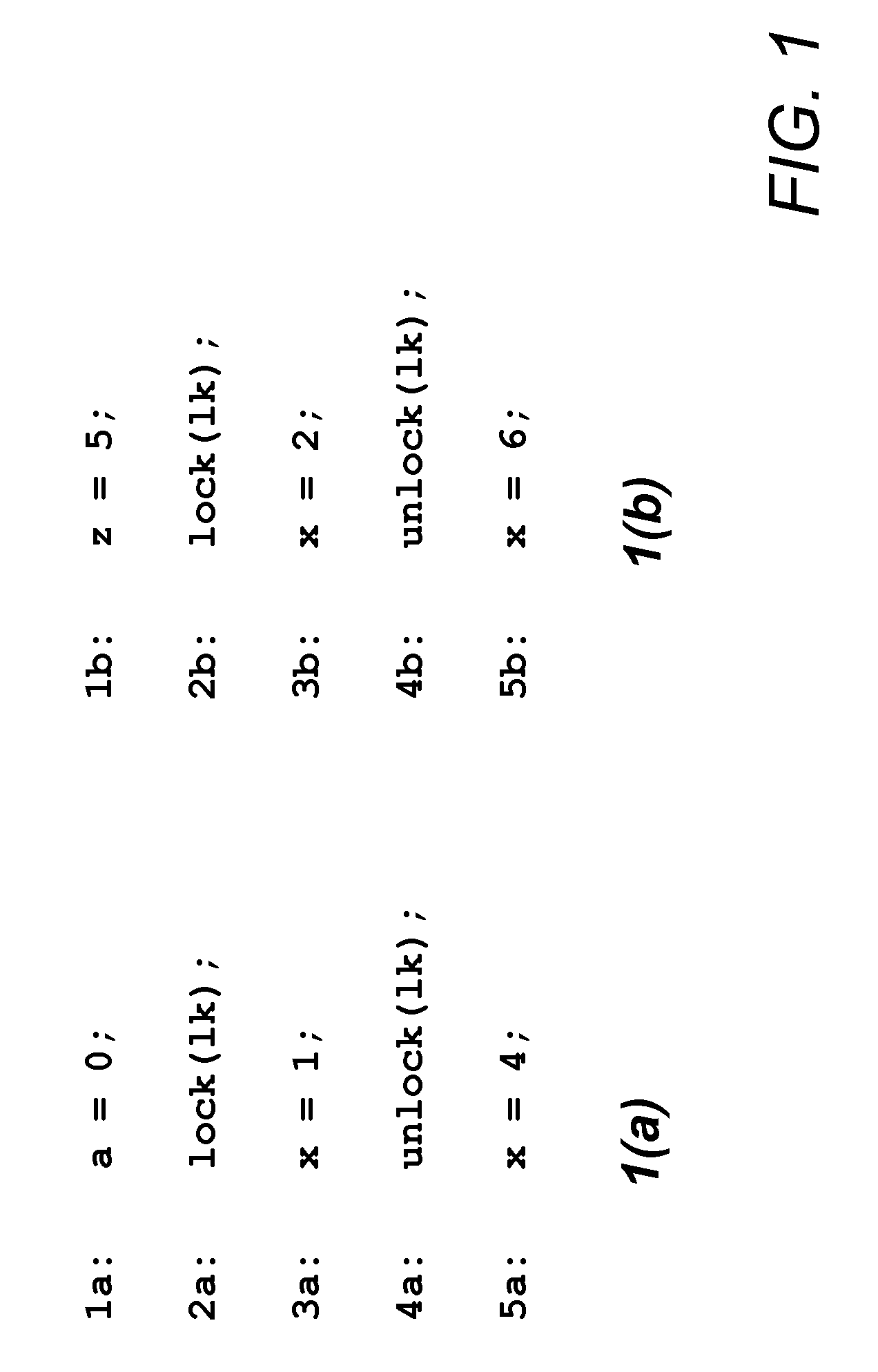
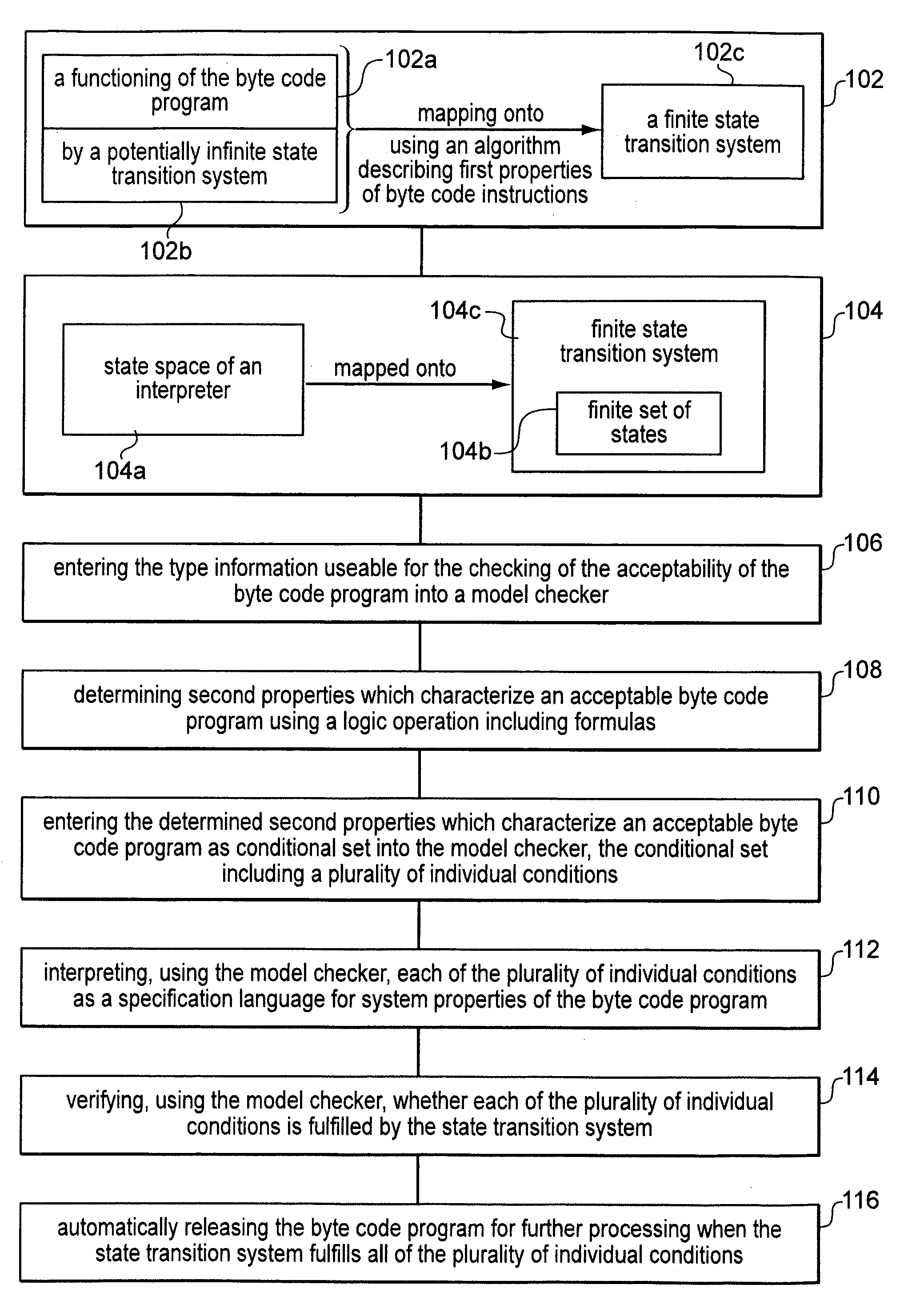
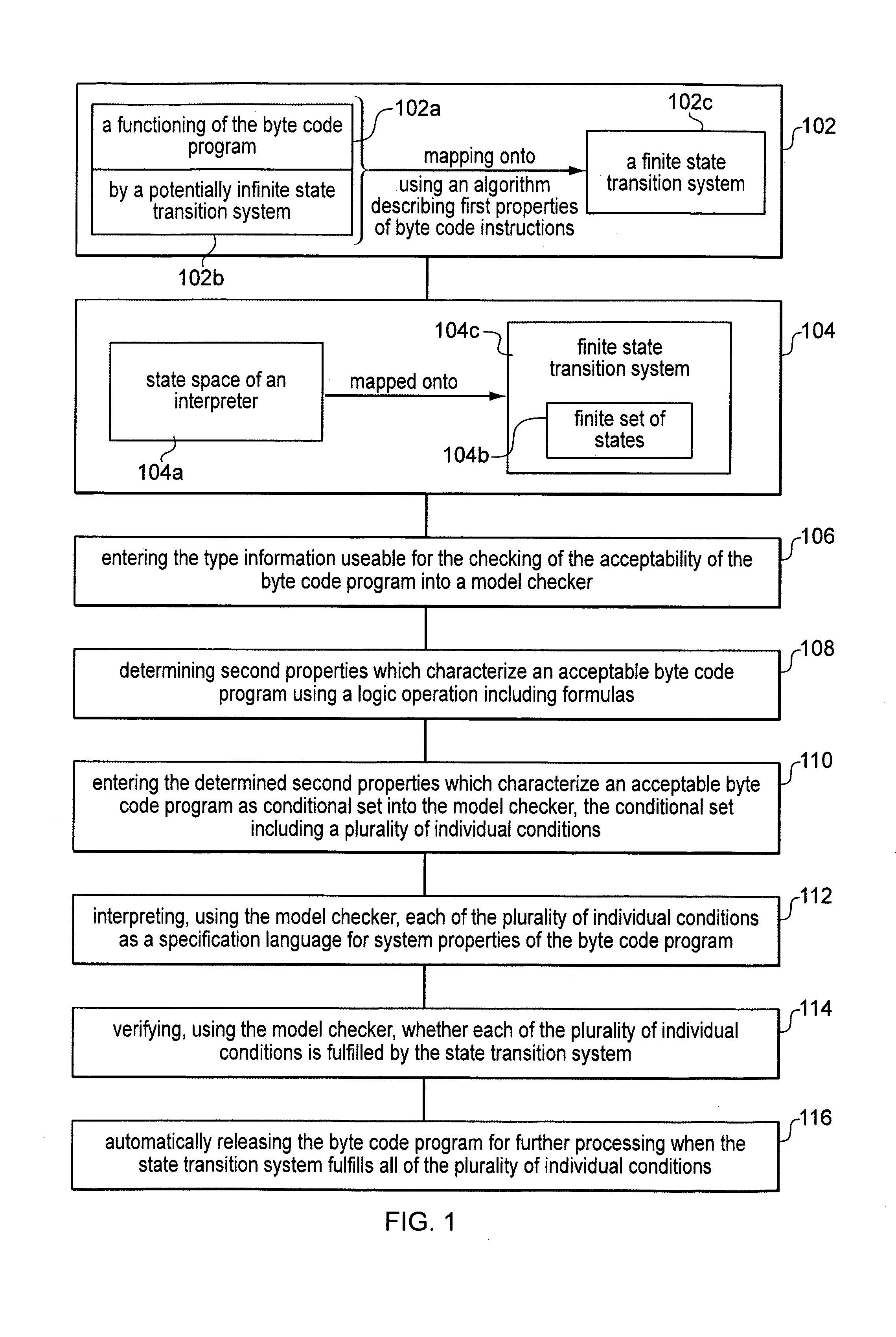
Method for verifying safety properties of java byte code programs
InactiveUS7181725B1Raise security concernsSoftware testing/debuggingProgram loading/initiatingState spaceSecurity properties
In a method for verifying the safety properties of Java byte code programs, the functioning of the byte code program to be verified is modeled on a finite state transition system M, and the state space of the Java Virtual Machine (JVM) on a finite set of states in M. Once entered into a model checker, the data of finite state transition system M are compared to the data entered in the model checker as conditional set S to determine properties characterizing an acceptable byte code program. The byte code program to be checked is released for further processing only when the state transition system M fulfills all conditions of conditional set S.
Owner:JOLLY SEVEN SERIES 70 OF ALLIED SECURITY TRUST I +1
Symbolized model detection method
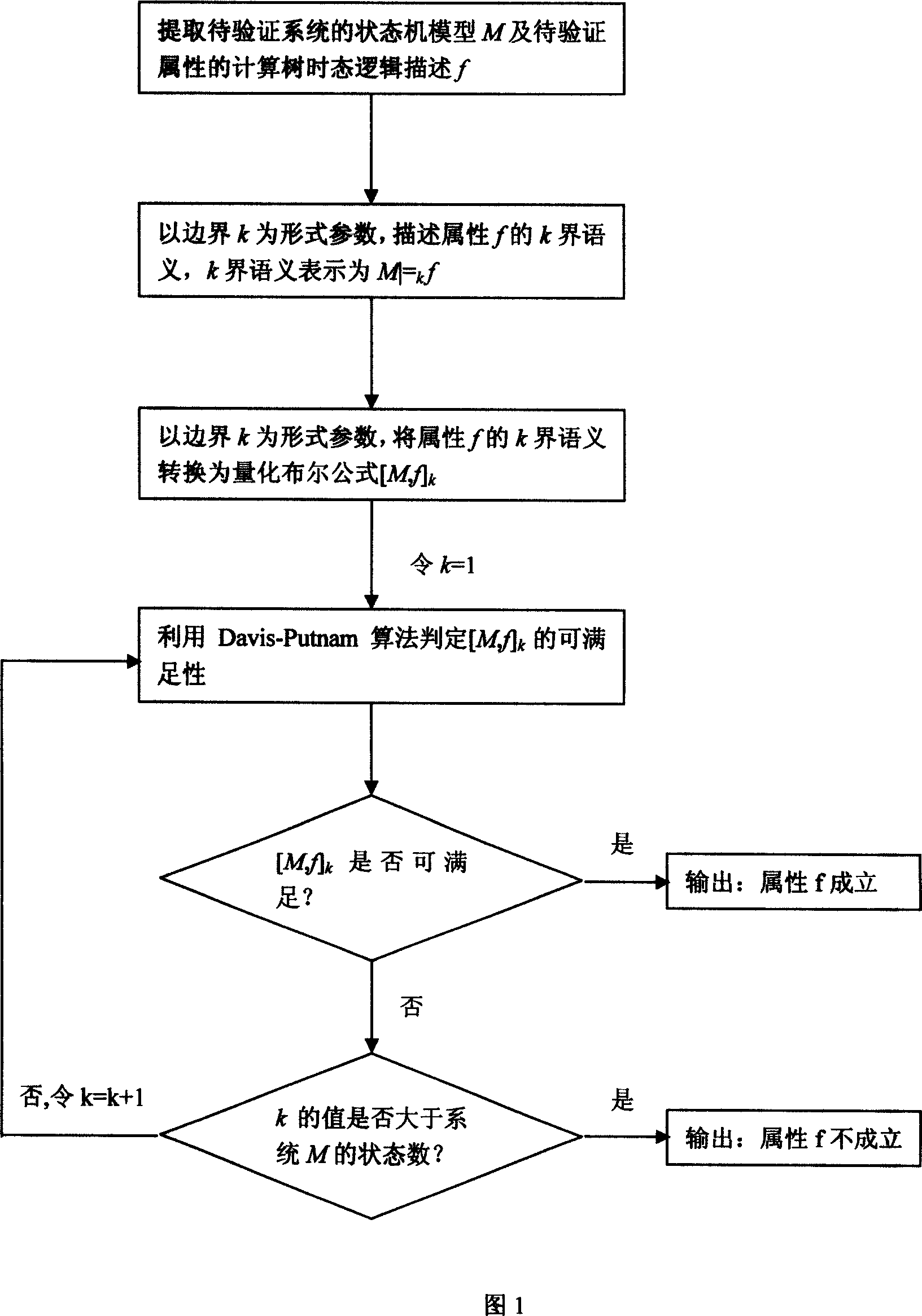
InactiveCN101013452AOvercoming the state space explosion problemImprove reliabilitySpecial data processing applicationsTemporal logicModel testing
This symbol model detection method is a method to make the model testing practical; the main principle is to use Boolean formula quantitative determination to instead of the CTL model testing. Their method: 1.) extract state machine M of the tested system and the attributes of the tested tree temporal logic description; 2.) taking border k as the form parameters, describe k sector semantics of the attributes f; 3.) taking border k as the form parameters, convert the k sector semantic of attribute f to quantify Boolean formula [M, f] k: 4.) progressive determine whether the system M meets the reliable attribute f: the approach integrates the advantages of symbol model testing based on binary decision diagram and bounded model checking based proposition equitation meeting judgment, also overcomes their shortcomings, which are not dependent on the sort of Boolean variables, or dependent on the property to verify the full name attribute.
Owner:JIANGSU UNIV
Method and system for partitioning an integrated circuit design
InactiveUS7047510B1Minimal numberComputationally efficientCAD circuit designSoftware simulation/interpretation/emulationComputer architectureGranularity
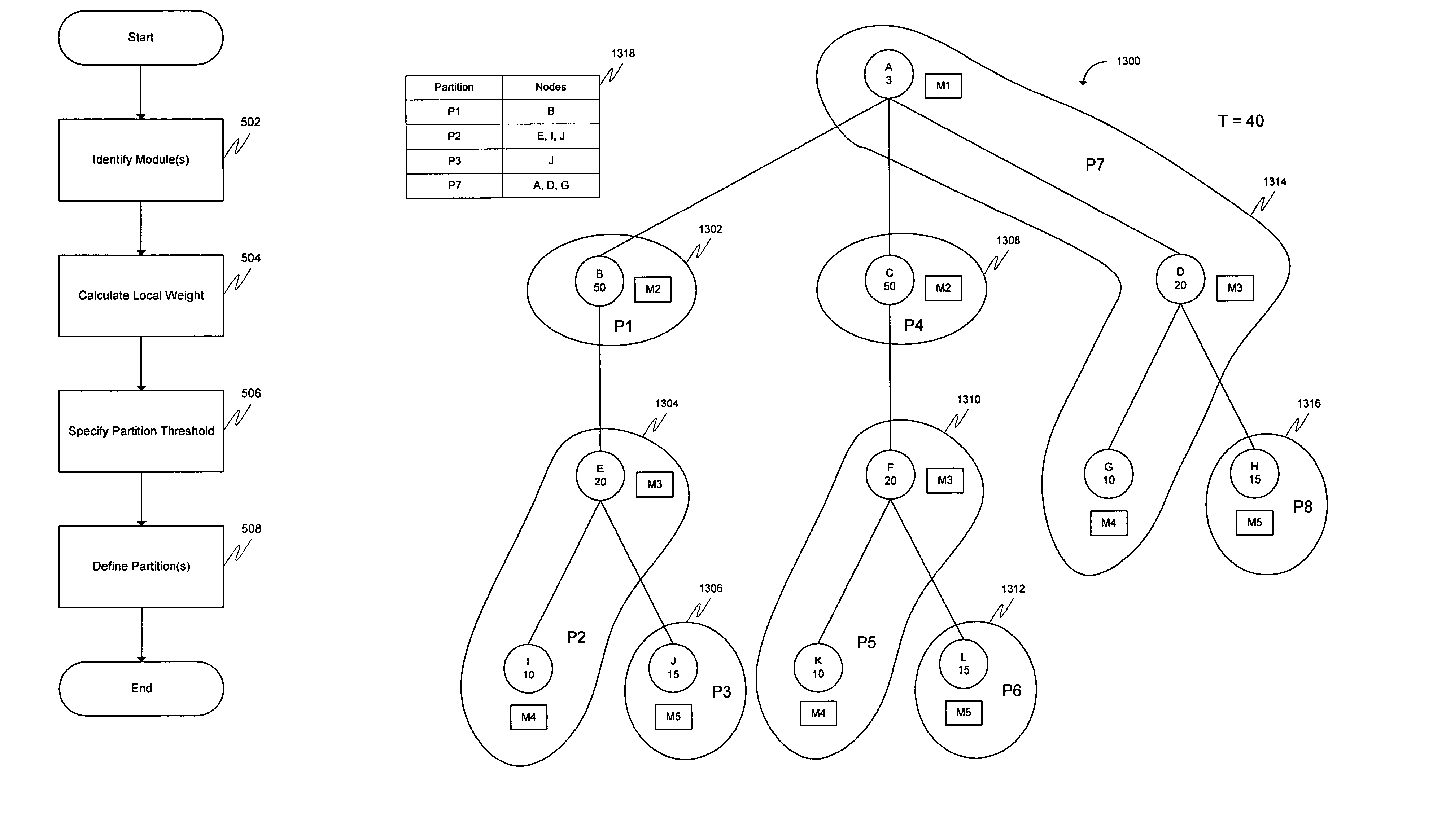
A method and system for verifying integrated circuit designs through partitioning. In an embodiment, a design is partitioned, then each partition is verified. In one embodiment, the design is partitioned at the granularity of modules. In another embodiment, the design is partitioned at the granularity of instances. In a third embodiment, instances are grouped together, subject to a weight threshold, so as to form possibly overlapping partitions of instances that are contiguous in the design hierarchy, with the purpose of avoiding, to the extent possible, false negatives. In a further embodiment, the design is partitioned to avoid redundant partitions. In an embodiment, model checking is applied to one or more local properties in each partition. In another embodiment, simulation is used to verify each partition.
Owner:CADENCE DESIGN SYST INC
Behavioral analysis for message-passing application programs
InactiveUS7203924B2Multiprogramming arrangementsSoftware testing/debuggingApplication softwareDependability
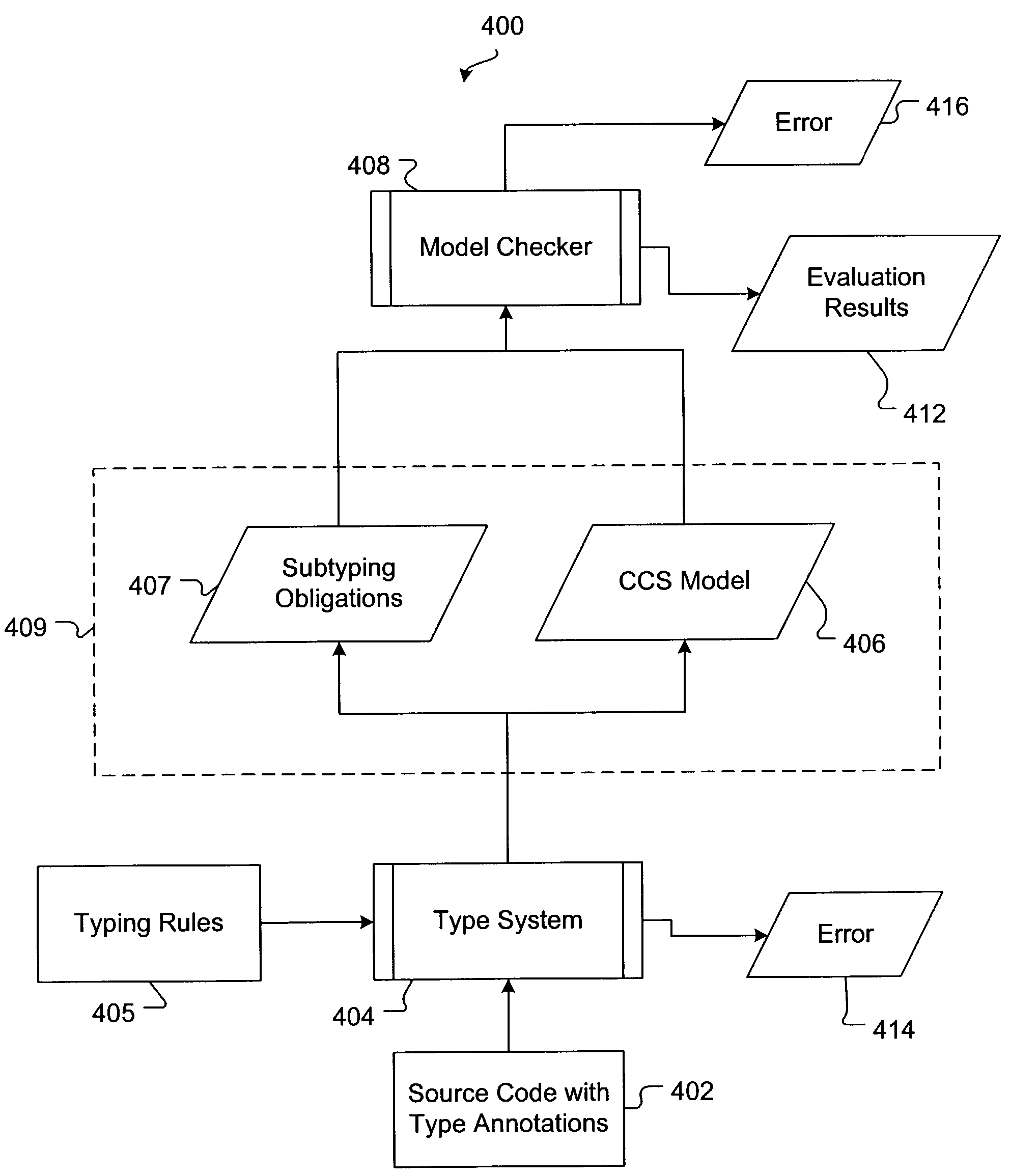
A system and method for modeling a message-passing program module using type annotations is disclosed. The message-passing program module is constructed with operations that communicate with operations of other message-passing program modules in an asynchronous computing environment. Type annotations are communication protocols that represent processes of input and / or output actions that the program module developer expects each operation to perform or take on a selected set of communication channels. During development of the program module, the type annotations are declared at each operation of the program module. Soundness of the type annotations and whether implementation of the program module conforms to the type annotations is checked using a type system. If the program module is well-typed and well-implemented, the type system abstracts a behavioral module of the message-passing program module that reflects the relevant processes expressed by the type annotations. A model checker determines whether the behavioral module is in fact a valid abstraction of the implementation, and if so, evaluates one or more properties of the behavioral module to render a conclusion about these properties for the program module.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com