Parallelization security hole detecting method based on function call graph
A function call graph and vulnerability detection technology, which is applied in the field of parallel detection of source code vulnerabilities, can solve the problems of high false alarm rate, inability to directly detect program vulnerabilities, inability to detect more complex buffer operation security, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
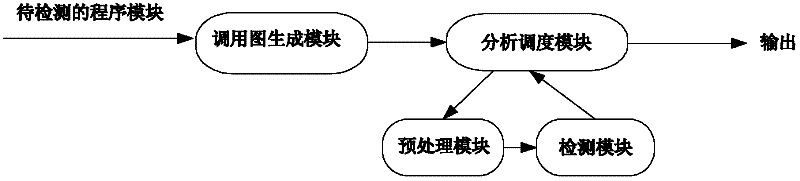
[0020] The present invention utilizes static analysis to track the calling relationship of functions in the program through the method of generating a function relationship calling graph, and provides corresponding scheduling information for the analysis and scheduling module, and then, on this basis, the files that need to be inserted are processed by the preprocessing module Finally, the parallel model detection is realized through the detection module, so as to realize the detection and analysis of security loopholes and ensure the accurate detection of source code loopholes. Structure diagram such as figure 1 .
[0021] 1. Call graph generation module
[0022] Firstly, this module generates the function call diagram of the software to be tested, which can conveniently start analysis and detection from the underlying functions, and can also conveniently schedule the entire detection process.
[0023] In the process of realization, we have utilized the features of GCC's Re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com