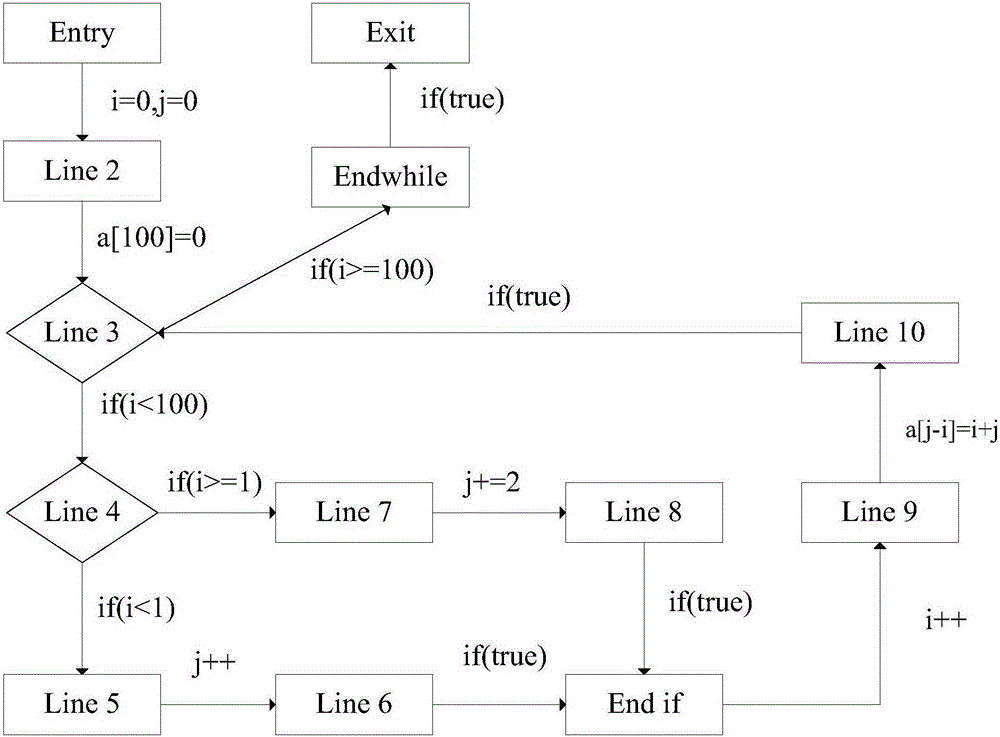
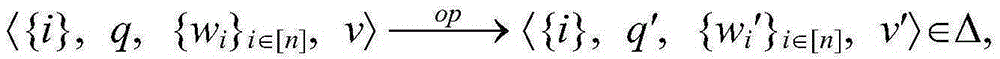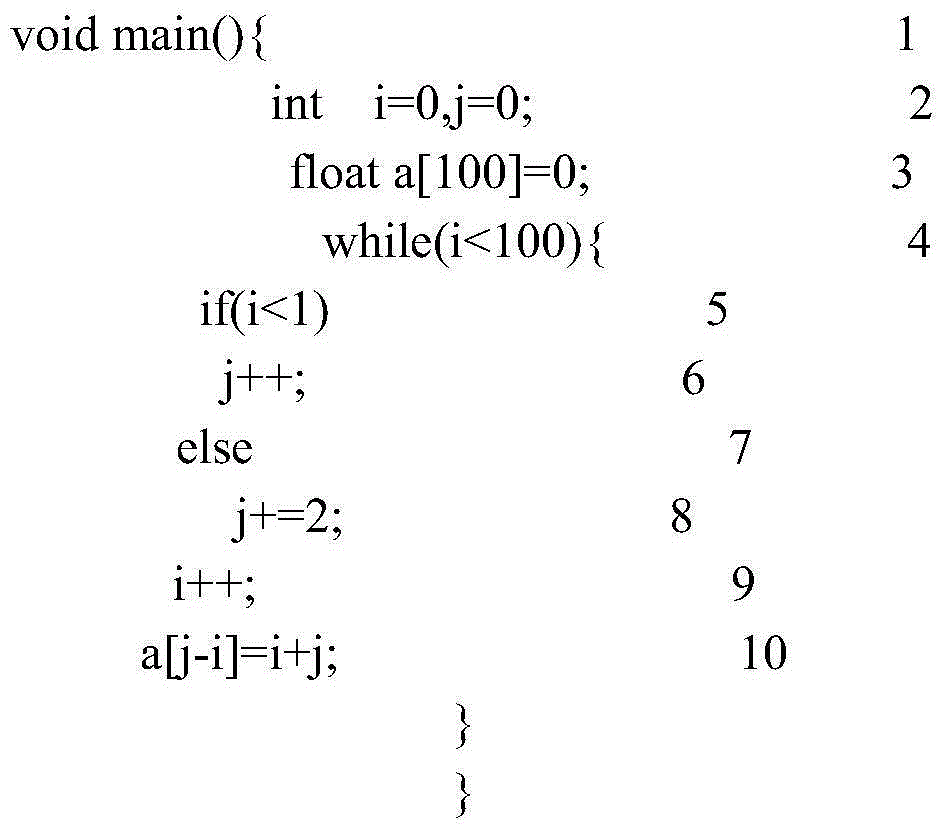Patents
Literature
39results about How to "Shrink state space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Parallelization security hole detecting method based on function call graph
InactiveCN102567200AEasy to analyzeEasy to detectSoftware testing/debuggingPlatform integrity maintainanceCall graphAccessibility
The invention relates to a parallelization security hole detecting method based on a function call graph, which is characterized in that a function set to be detected is determined by analyzing the function call relation in a C language module, instrumentation and assert analysis are performed for the function set by means of the preprocessing technology, and then security holes of a program are detected by the aid of model checking and the parallelization technology. The method mainly includes the steps: generating the function relation call graph, and determining C function information to be detected by analyzing the function relation call graph; extracting attribute information of a buffer area related to C program source codes by the aid of the constraint analysis technology, and inserting corresponding ASSERT statement information in a variable declaration, an assignment and a function call point by means of the attribute information of the buffer area; and performing accessibility judgment for the instrumented codes, and analyzing whether a dangerous point in the program includes an accessible path to discover the security holes in the source codes or not. The method detects the security holes such as buffer area overflow and the like by combining the constraint analysis static detecting technology, model checking and the parallelization technology, and the detecting precision of the method is higher than that of the general static detecting technology.
Owner:BEIHANG UNIV
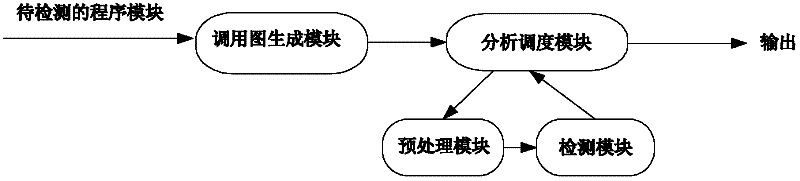
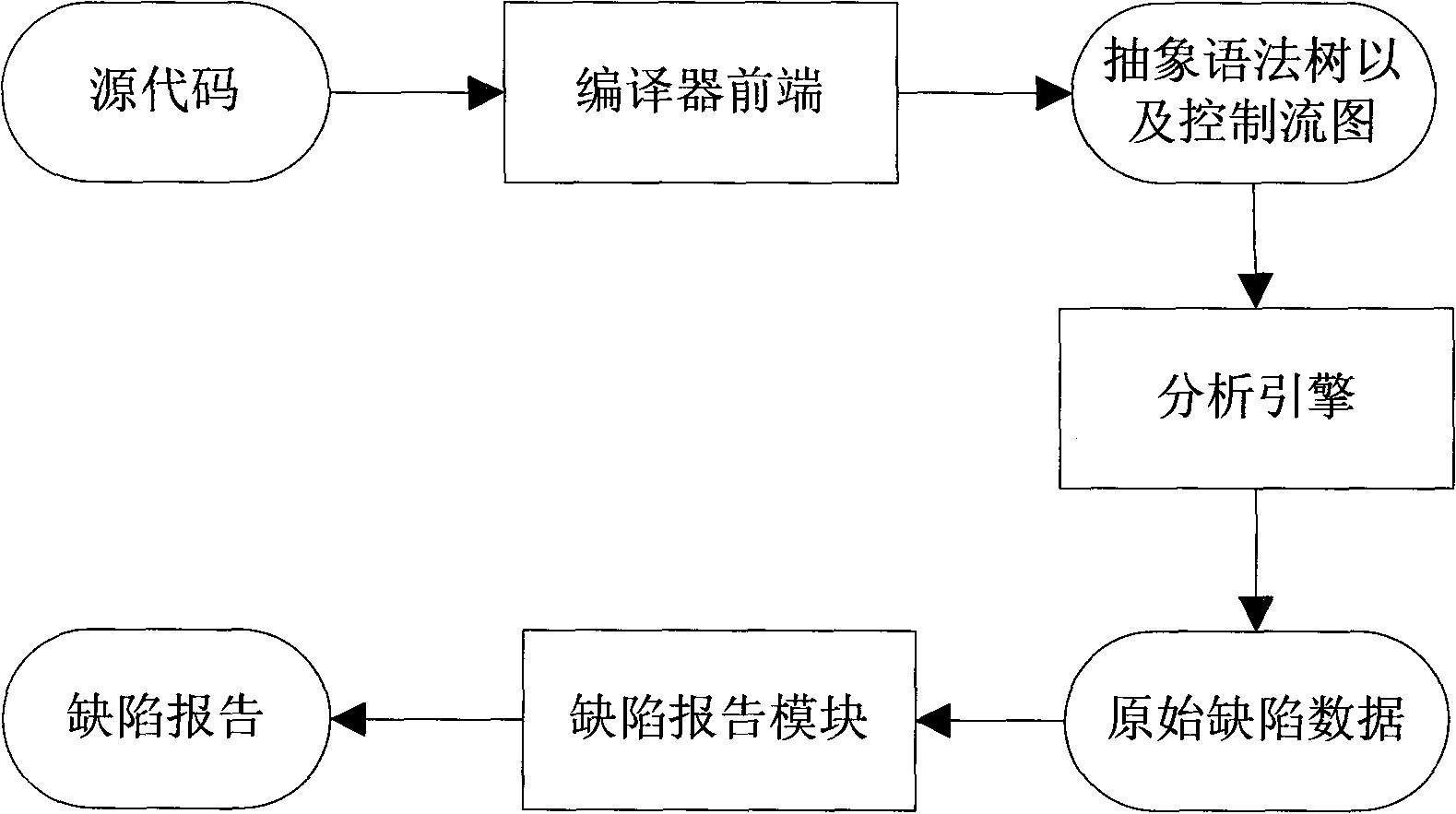
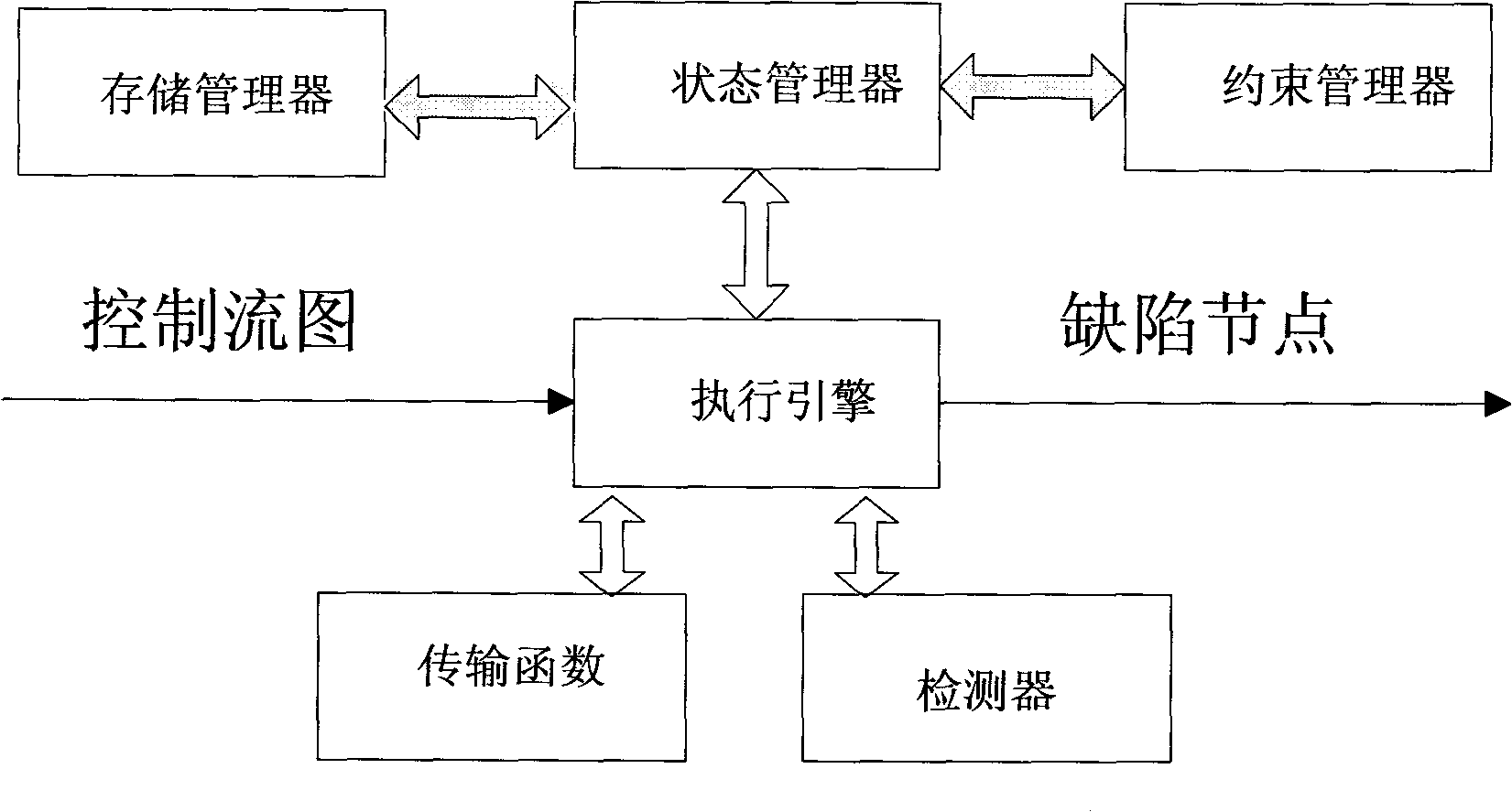
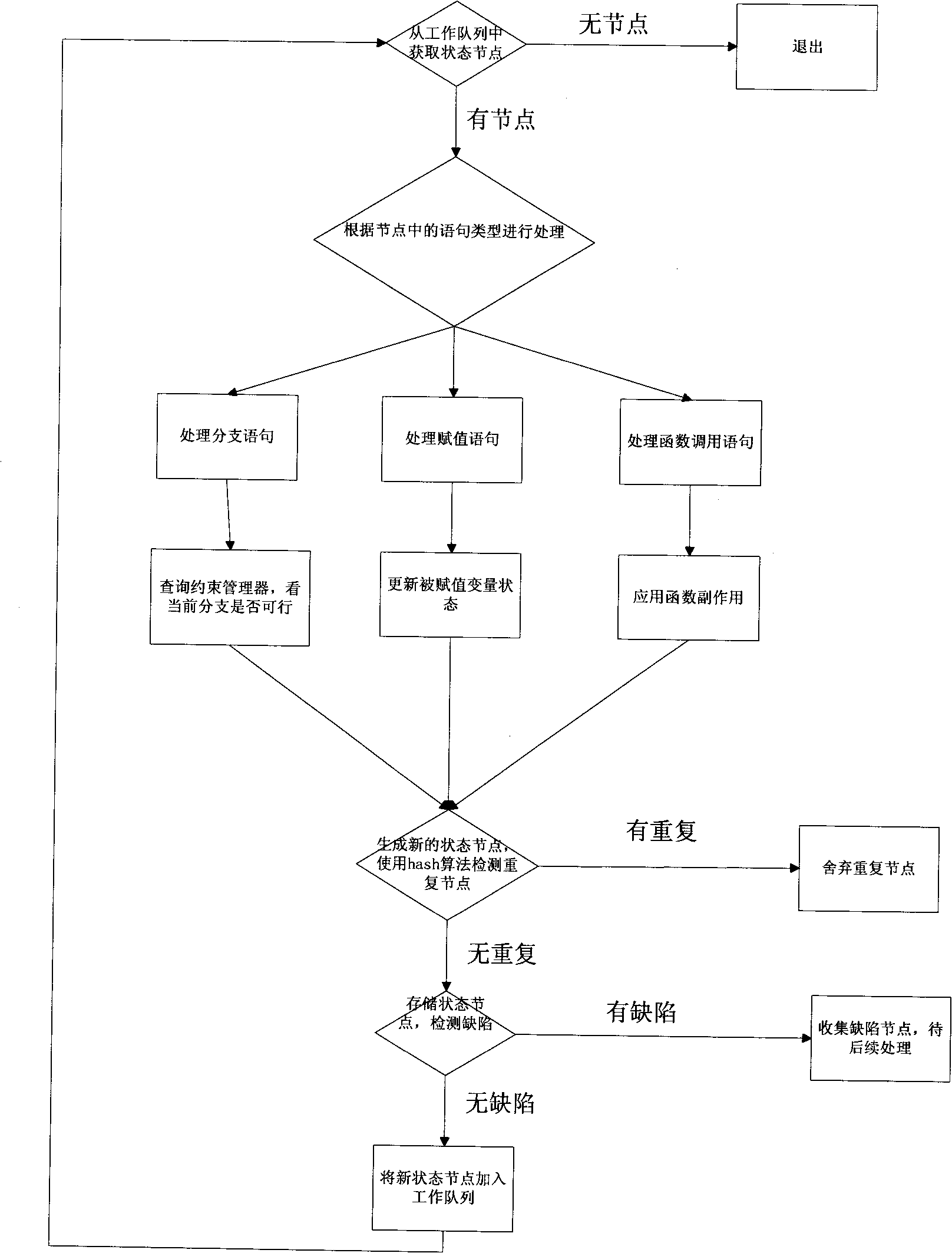
High-extensibility and high-maintainability source code defect detection method and device
InactiveCN101937388AHighly scalableStrong maintainabilitySoftware testing/debuggingModularityCompiler
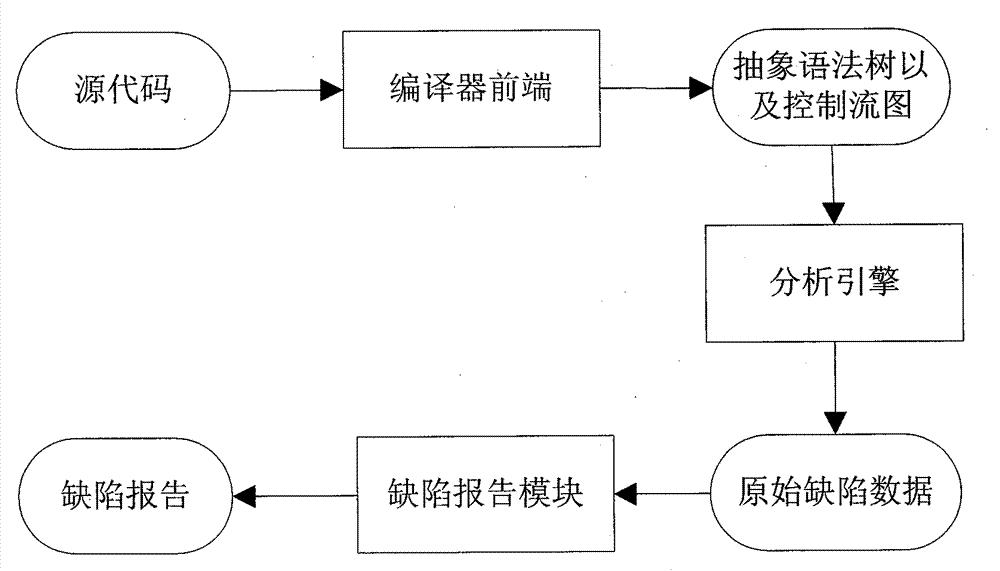
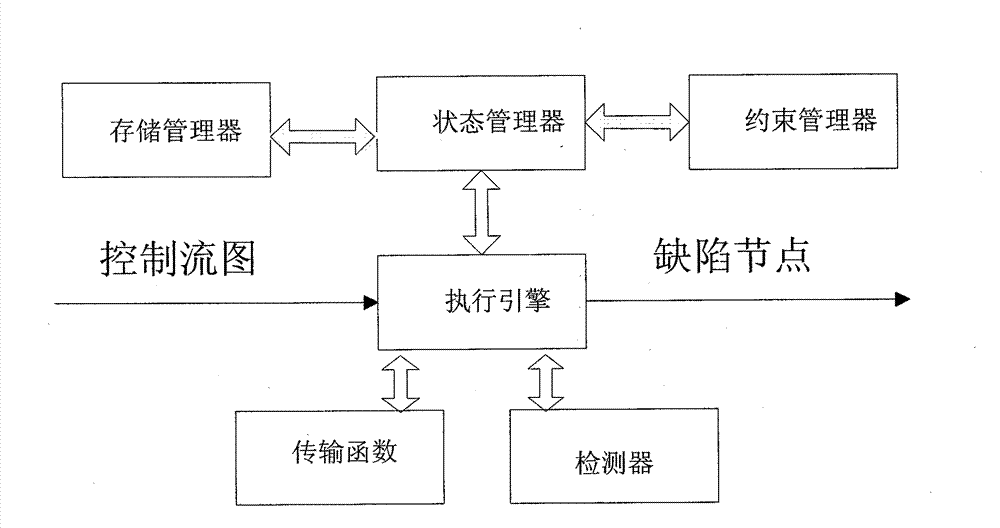
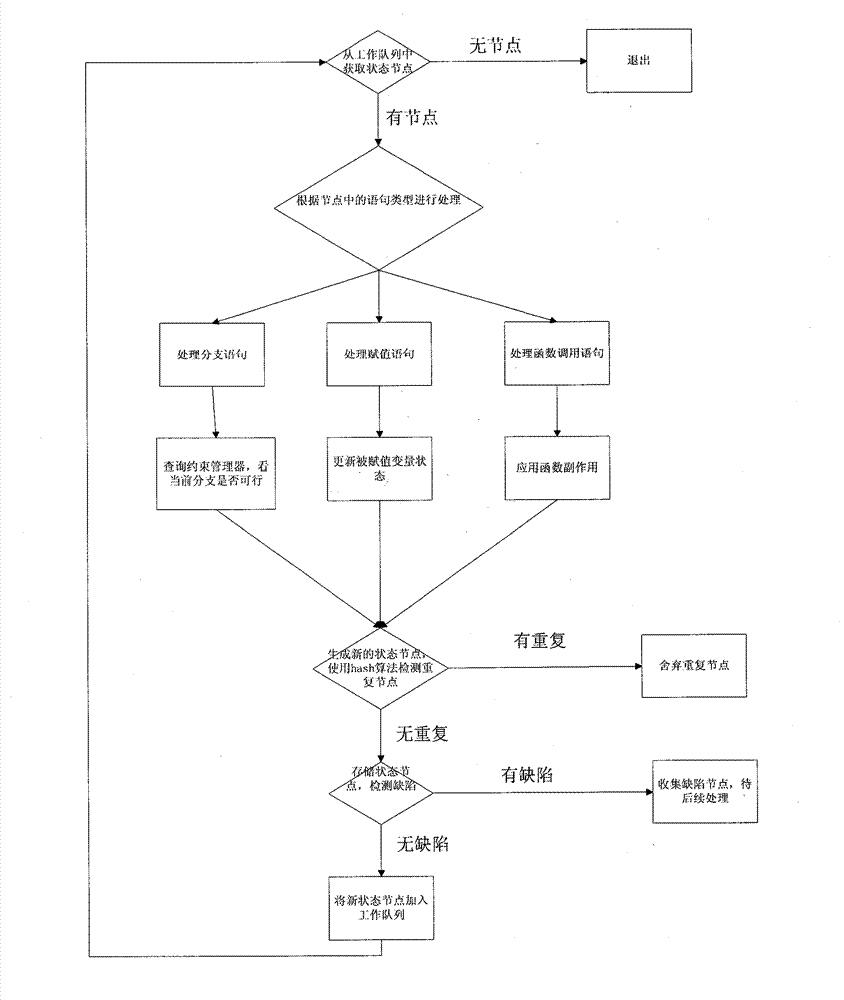
The invention provides a high-extensibility and high-maintainability source code defect detection method and a high-extensibility and high-maintainability source code defect detection device. The method comprises the following steps of: (1) converting a source code which is configured by a user and needs to be detected into an abstract syntax tree and a control flow chart and transmitting the abstract syntax tree and the control flow chart into an analytical engine; (2) performing flow-insensitive analysis on the source code according to the abstract syntax tree and the control flow chart, submitting an analysis result to a defect reporting module, and entering a step 3 to perform path-sensitive analysis; (3) performing various types of path-sensitive modeling and analysis on the source code to generate original defect information according to the abstract syntax tree and the control flow chart; and (4) reducing and simplifying a defect path and reporting the defect path to the user according to the original defect information. The device comprises three functional modules, namely a compiler front end, the analytical engine and the defect reporting module. The invention aims to provide the source code defect detection method and the source code defect detection device which have the characteristics of high extensibility, high maintainability, modularization and the like.
Owner:UNKNOWN
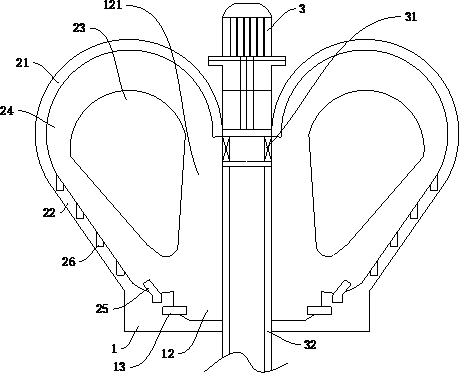
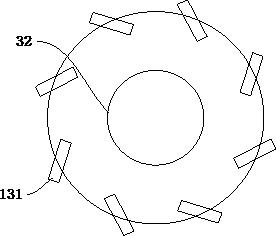
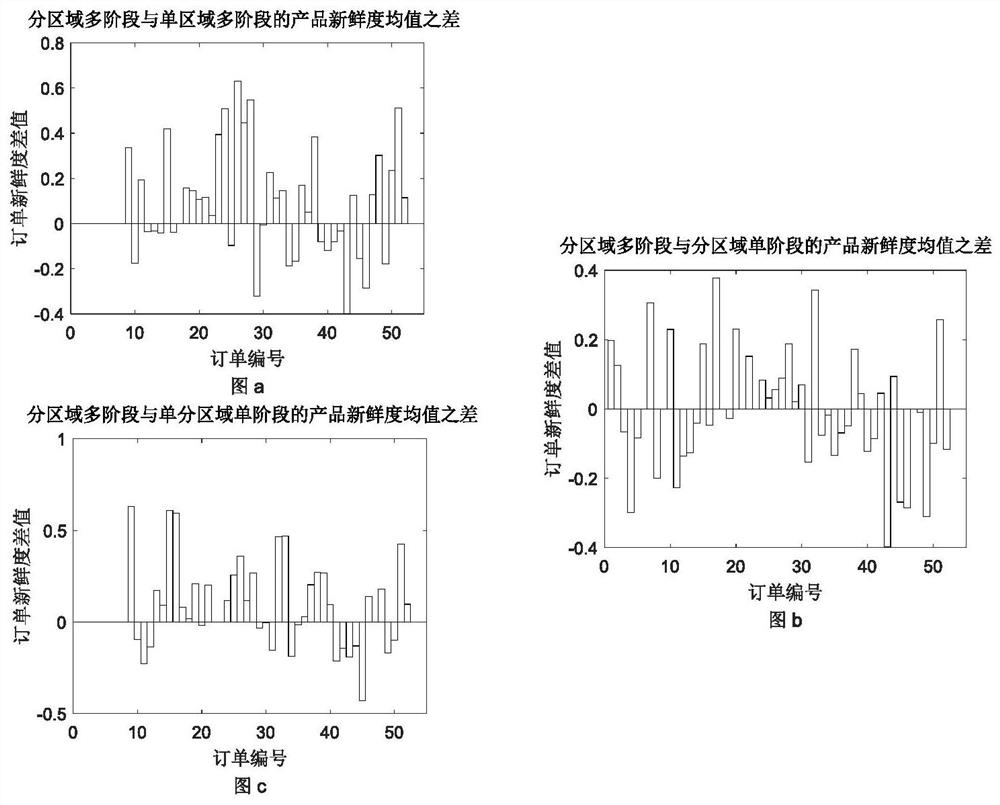
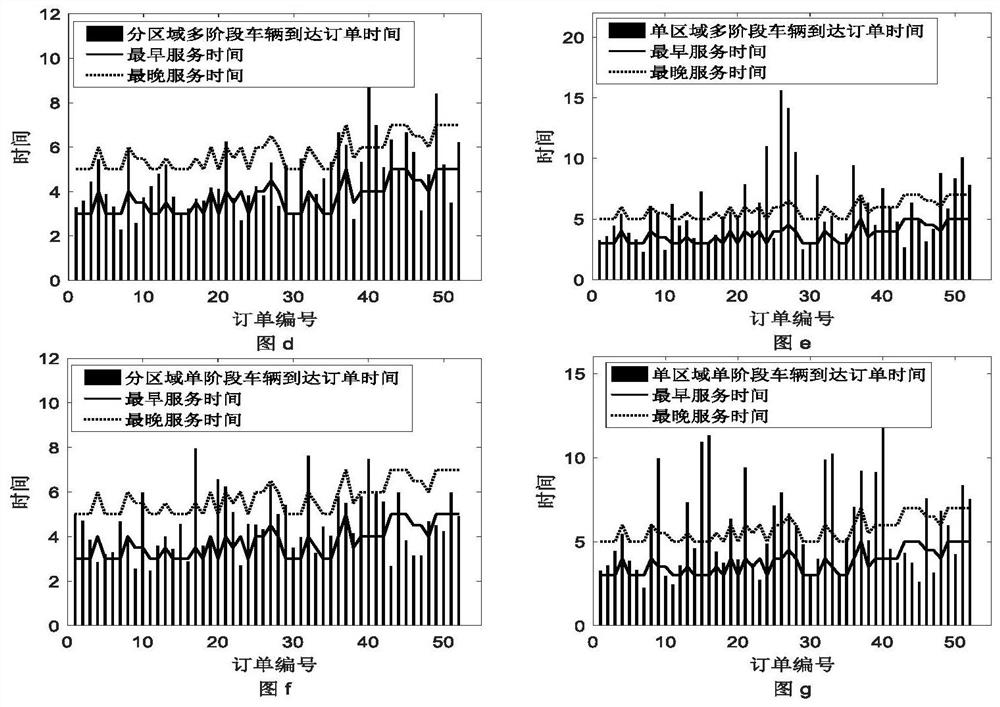
Multi-stage dynamic vehicle routing optimization method for fresh agricultural products in different regions
InactiveCN109002902AImprove solution efficiencySolve the path problemForecastingLogisticsMathematical modelPhases of clinical research
The invention discloses a multi-stage dynamic vehicle routing optimization method for fresh agricultural products in different regions, which comprises the following steps of: data obtaining; regionaldivision; time division; design of a freshness attenuation function and establishment of a mathematical model of minimum total distribution cost; algorithm design of a mathematical model for minimumtotal distribution cost; solution of a mathematical model of minimum total distribution cost. The invention effectively improves the distribution efficiency and reduces the total distribution cost, and has high practical significance.
Owner:EAST CHINA UNIV OF SCI & TECH
All-terminal reliability calculating method through communication community division based on modularity
ActiveCN107944705AReduce collection spaceFull-stack reliability and accuracyResourcesDecompositionModularity
The invention discloses an all-terminal reliability calculating method through communication community division based on modularity. The method includes electric power communication network communitydivision based on the modularity and all-terminal reliability calculation based on a minimum path set, the complexity of a network topology is substantially reduced through the mode of community division, the state space of the network is greatly reduced through spatial decomposition, the problem of state space explosion is alleviated to a certain degree, and the time for searching the minimum path set by an algorithm is reduced. The complexity of the internal topology structures of the communication communities divided through the modularity are far lower than the overall electric power communication, the topology structures are independent from each other, parallel calculation is introduced to the internal all-terminal reliability analysis thereof, the finally obtained connection topology structures of the communication communities are simple, and the consumption of the analysis time of the all-terminal reliability thereof is low.
Owner:STATE GRID HENAN INFORMATION & TELECOMM CO +1
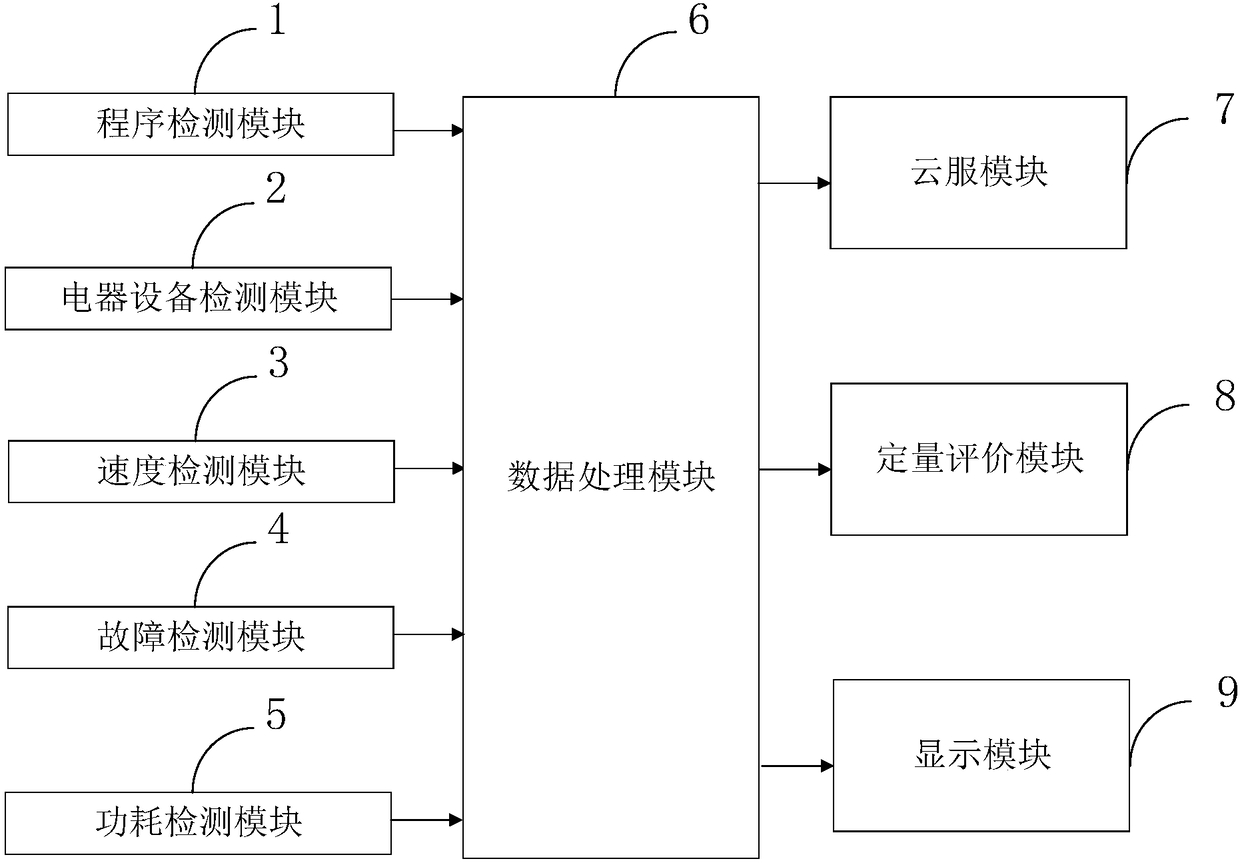
Intelligent unmanned vehicle quantitative evaluation system
InactiveCN108536977AImprove analysis processing speedDriving safetyDesign optimisation/simulationSpecial data processing applicationsService moduleElectric equipment
The invention belongs to the technical field of unmanned driving, and discloses an intelligent unmanned vehicle quantitative evaluation system. The intelligent unmanned vehicle quantitative evaluationsystem comprises a program detecting module, an electric equipment detecting module, a speed detecting module, a fault detecting module, a power consumption detecting module, a data processing module, a cloud service module, a quantitative evaluation module, a display module and a recorder module. Due to the cloud service module, the data analysis processing speed can be greatly increased, and the quantitative evaluation efficiency can be improved; meanwhile, due to the quantitative evaluation module, unmanned vehicles can be quantitatively evaluated more scientifically and accurately, the improvement direction can be found, rapid development for the unmanned vehicle technology is promoted, and therefore it is ensured that the unmanned vehicle can be safely driven under the real traffic environment.
Owner:北京京大律业知识产权代理有限公司
Method and system for constructing interpolation curve or curved surface based on B-spline
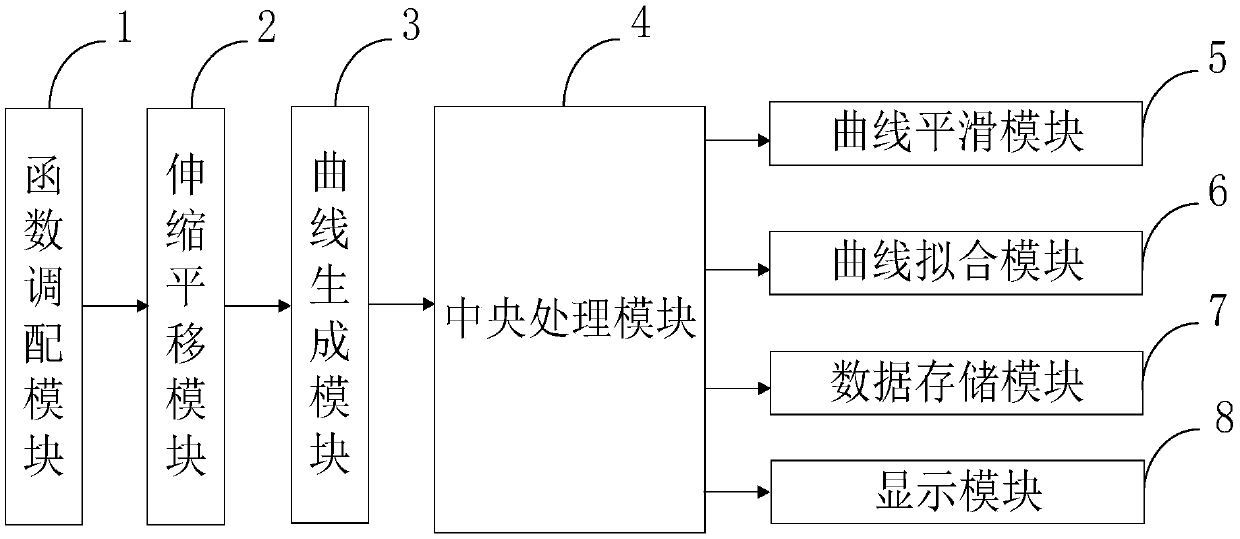
InactiveCN108804391AImplement map reconstructionEasy to handleComplex mathematical operationsComputer resourcesCurve fitting
The present invention belongs to the technical field of geometric modeling, and discloses a method and a system for constructing an interpolation curve or a curved surface based on a B-spline. The system comprises: a function deployment module, a telescopic translation module, a curve generation module, a central processing module, a curve smoothing module, a curve fitting module, a data storage module, and a display module. According to the technical scheme of the present invention, by using the curve smoothing module, a smoothing operation is performed on the curve in the image, the unsmoothcurve segment in the image can be effectively smoothed, and the curve after being subjected to the smoothing operation has substantially no defect with respect to the original curve, does not deviatemuch from the actual curve, and can adjust the degree of smoothness of the curve by adjusting the interval size by itself; and at the same time, by using the curve fitting module, the mapping reconstruction of the rotary part along the direction of the rotation axis can be realized, the data processing process can be simplified in a facilitated manner, and the consumption of computer resources can be reduced.
Owner:HUNAN AGRICULTURAL UNIV
Big data based position privacy protection system with homomorphic encryption mechanism
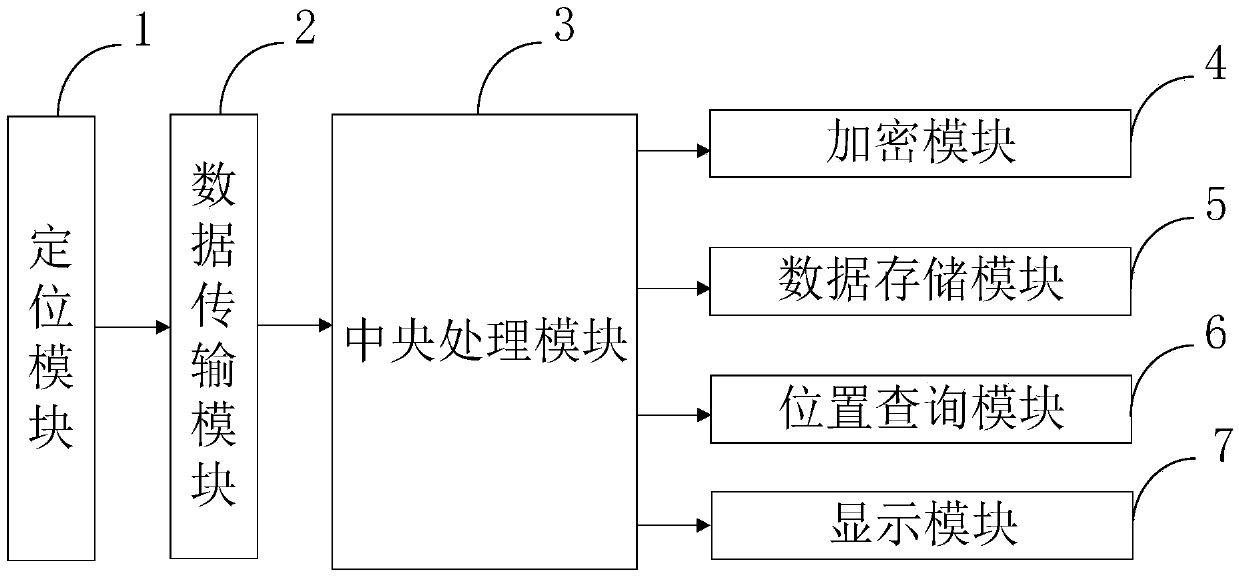
InactiveCN108650675AReduce computational overheadProtect location privacyLocation information based serviceSpecial data processing applicationsPrivacy protectionComputer module
The invention belongs to the technical field of privacy protection, and discloses a big data based position privacy protection system with a homomorphic encryption mechanism. The big data based position privacy protection system with the homomorphic encryption mechanism comprises a positioning module, a data transmission module, a central processing module, an encryption module, a data storage module, a position inquiry module and a display module. According to the invention, by the encryption module, in the same environment configuration, compared to the bootstrap process in an original scheme, the bootstrap process is reduced by 47%; safety of the scheme can be specified to the LWE problem, and can reach safety of 128 bits; and meanwhile, according to the invention, a cloud server and ahomomorphic encryption algorithm are introduced by the position inquiry module, a user can obtain a corresponding inquiry result only by implementing homomorphic encryption for once, homomorphic multiplication for once and subtraction operation for once, so that calculation cost of the user is reduced.
Owner:XUCHANG UNIV
Interpolation Based Path Reduction Method in Software Model Checking
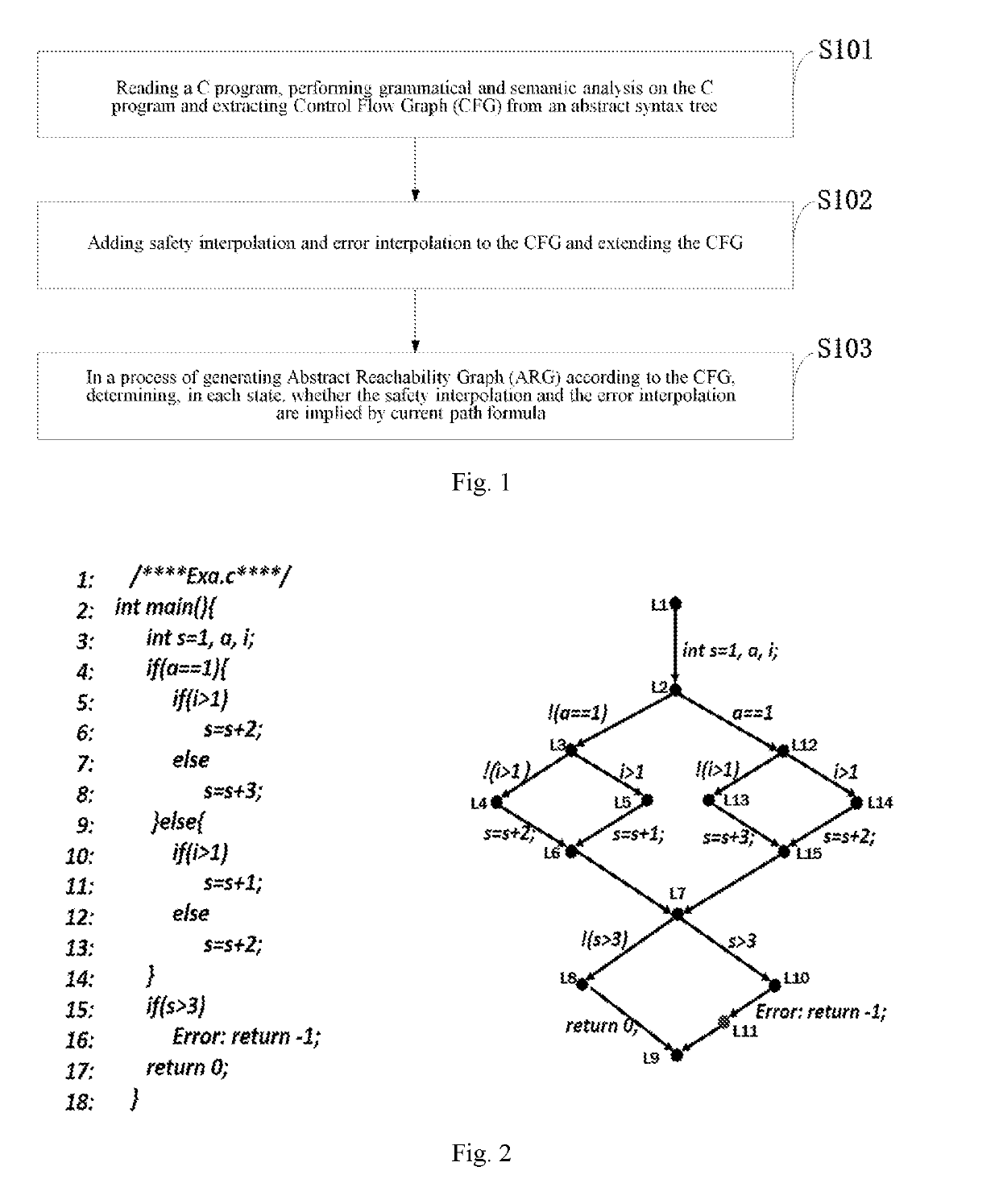
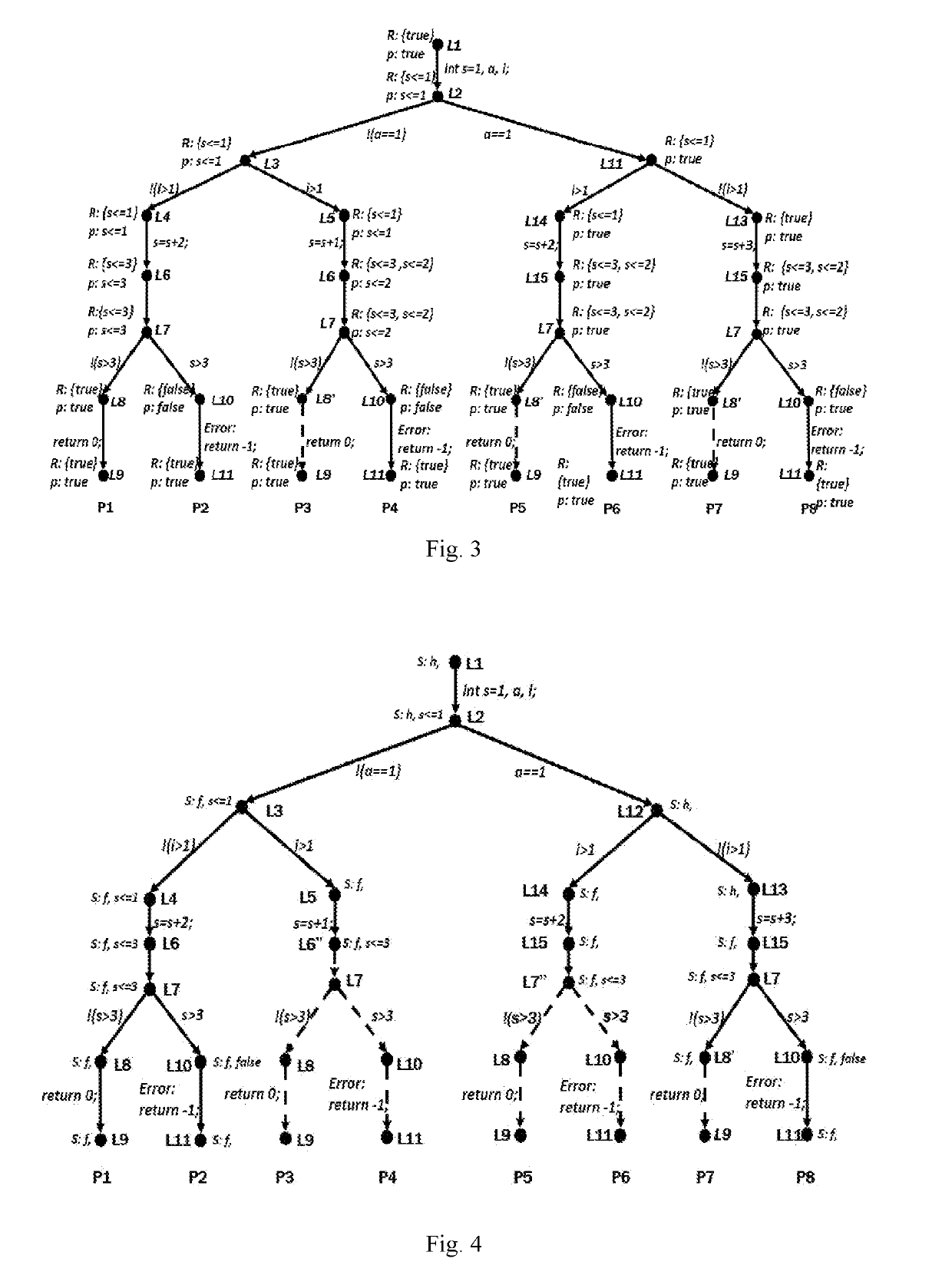
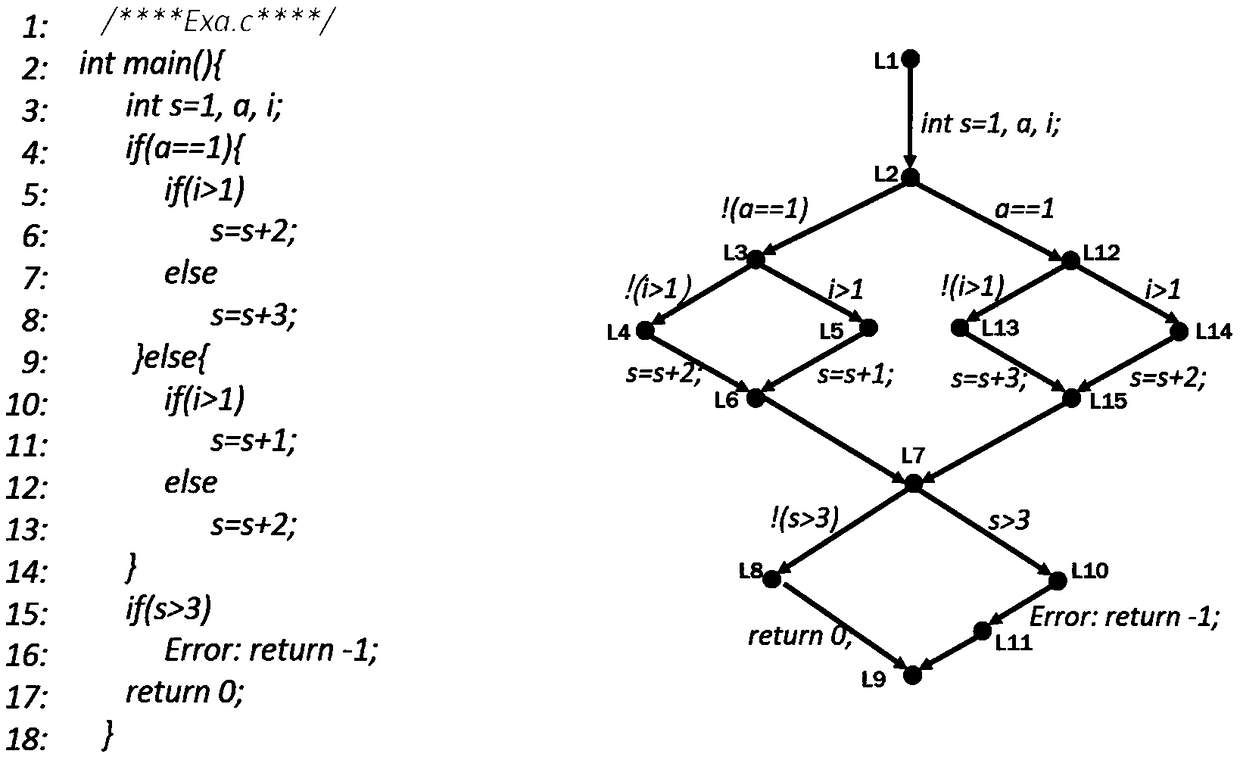
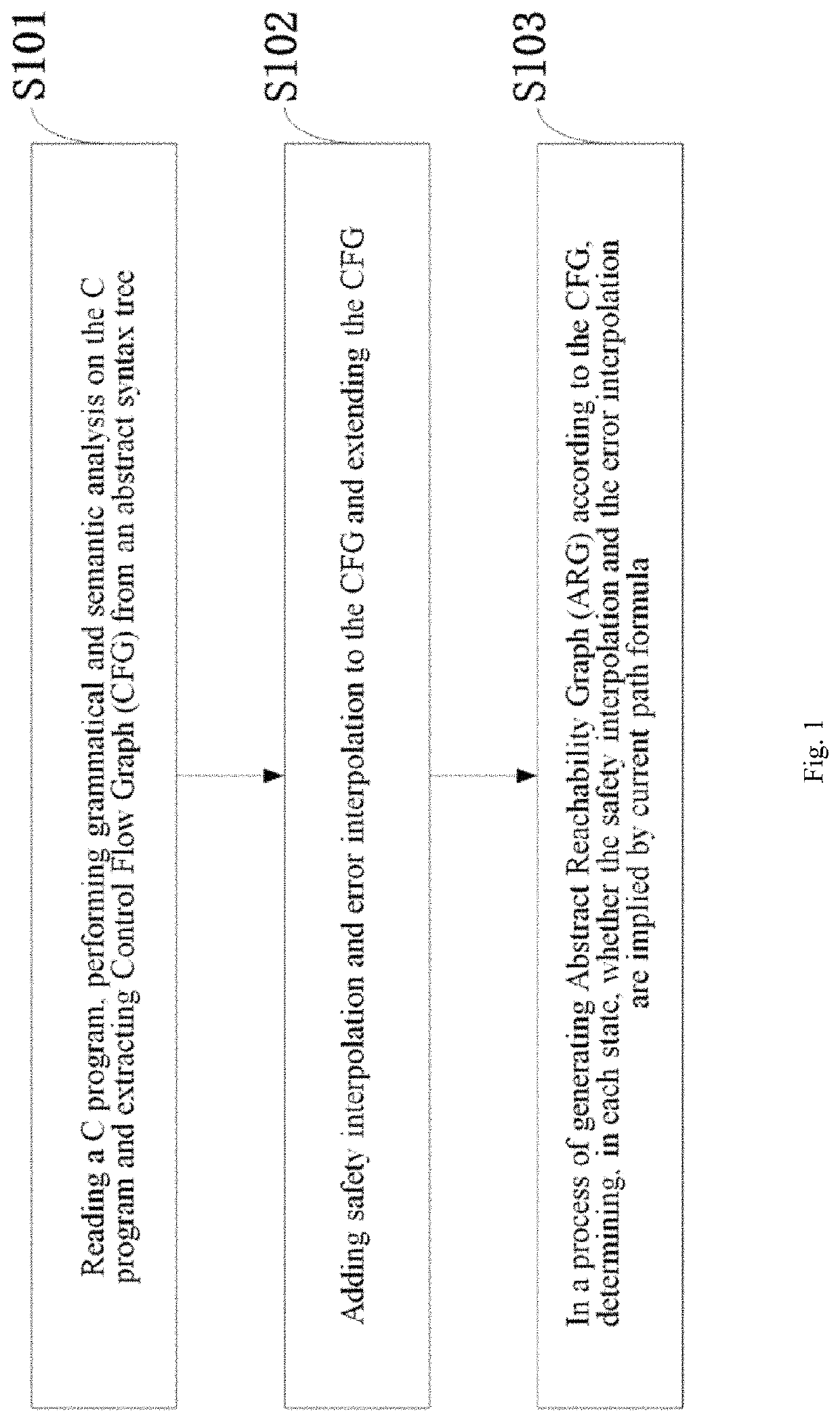
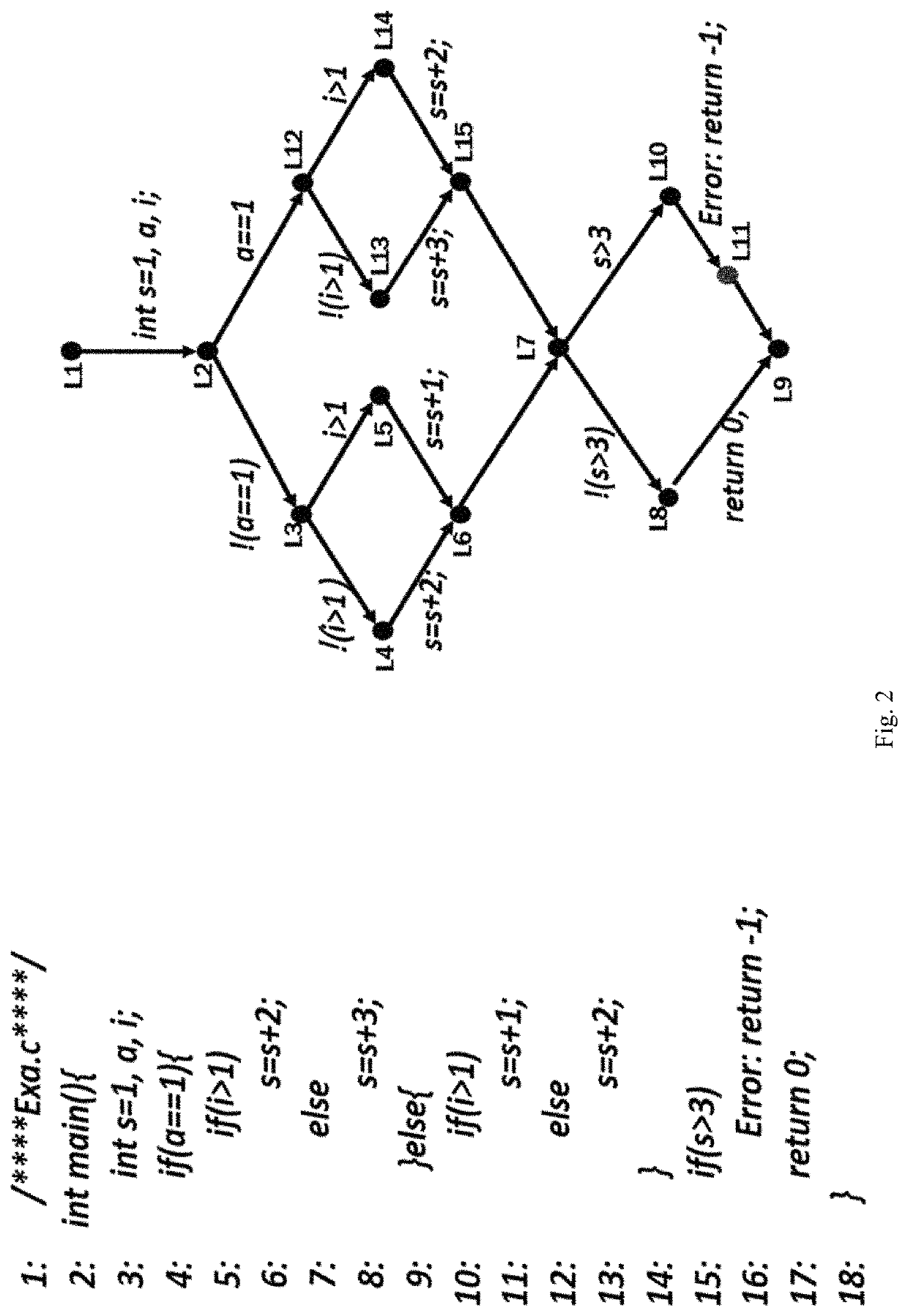
ActiveUS20190095314A1Reduces path search spaceImprove verification efficiencySoftware testing/debuggingErrors and residualsAbstract syntax tree
A method for model checking path reduction based on interpolation comprises: reading a C program, performing grammatical and semantic analysis on the C program, and extracting CFG from an abstract syntax tree; adding safety (S) interpolation and error (E) interpolation to the CFG and extending the CFG; in a process of generating ARG according to the CFG, determining, in each state, whether the safety interpolation and the error interpolation are implied by current path formula. The method improves the verification efficiency by computing the S interpolation and the E interpolation, which makes the algorithm of the model checking a better use in large-scale programs. The S interpolation can be used to avoid the unnecessary traversal, greatly reducing the number of ARG state. The E interpolation can be used to quickly determine whether there is a true counterexample in the program, accelerating the program's verification and improving the efficiency.
Owner:XIDIAN UNIV
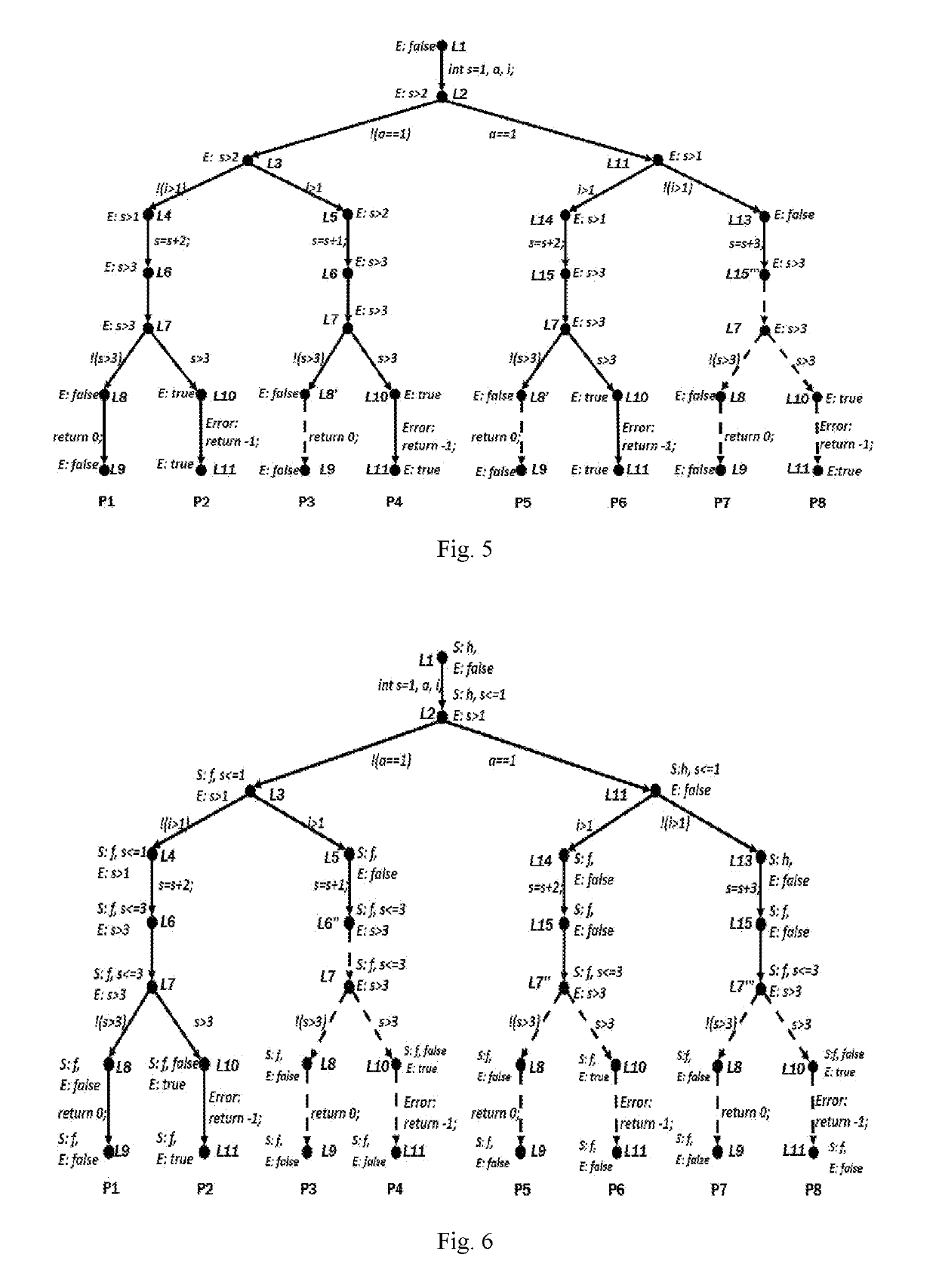
Method for unsupervised learning of grammatical parsers
ActiveUS9460076B1Shrink state spaceNatural language data processingNeural learning methodsLinguistic ruleUnsupervised learning
The invention comprises a core algorithm to use language regularity in large collections of human created textual documents, as well as optimization techniques to make the algorithm tractable. The core algorithm includes receiving tuples of text units that may be grammatically linked and processing a stream of such tuples to discover language regularities. After this learning is completed, the algorithm's output is used to evaluate the perceived likelihood that different interpretations of novel sentences would have been intended by a speaker of the language.
Owner:LEXALYTICS
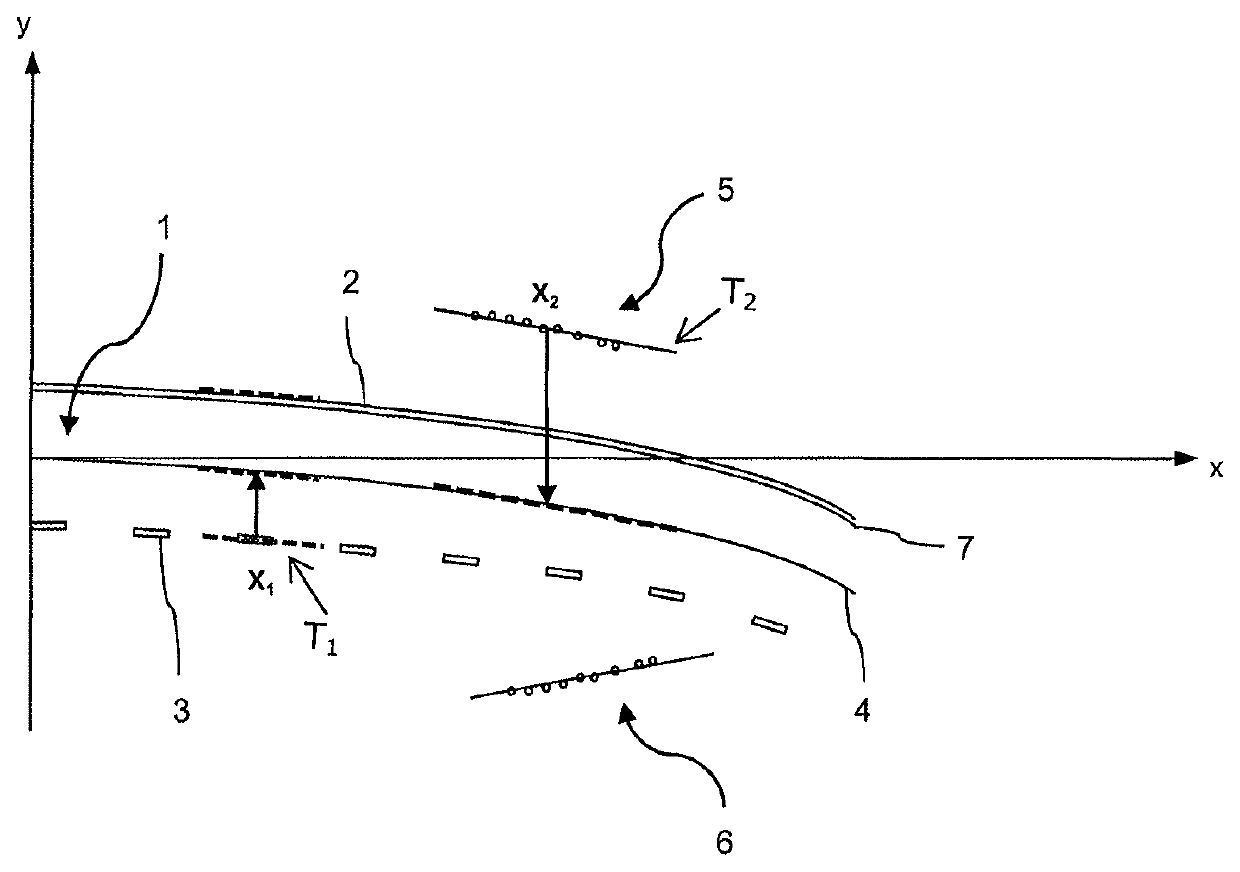
Method for determining the course of the road for a motor vehicle
ActiveUS10776634B2Accurate modelingMore robustAnti-collision systemsCharacter and pattern recognitionSimulationArtificial intelligence
A method for determining the course of the road for a moving motor vehicle having a surroundings sensor system. Sensor data generated by the surroundings sensor system are evaluated to detect lane-relevant features. A lane model having at least one lane model parameter that determines the course of the lane is generated for the road, structures of at least one distance range that are parallel to the road are detected in the sensor data, the tangential direction of at least the one structure that is parallel to the road is determined, and the value of the tangential direction of the structure that is parallel to the road is adopted as the value of the direction of the tangent line at the point of contact with the structure that is parallel to the road to determine at least the one lane model parameter by predictive estimation in the lane model.
Owner:CONTI TEMIC MICROELECTRONIC GMBH
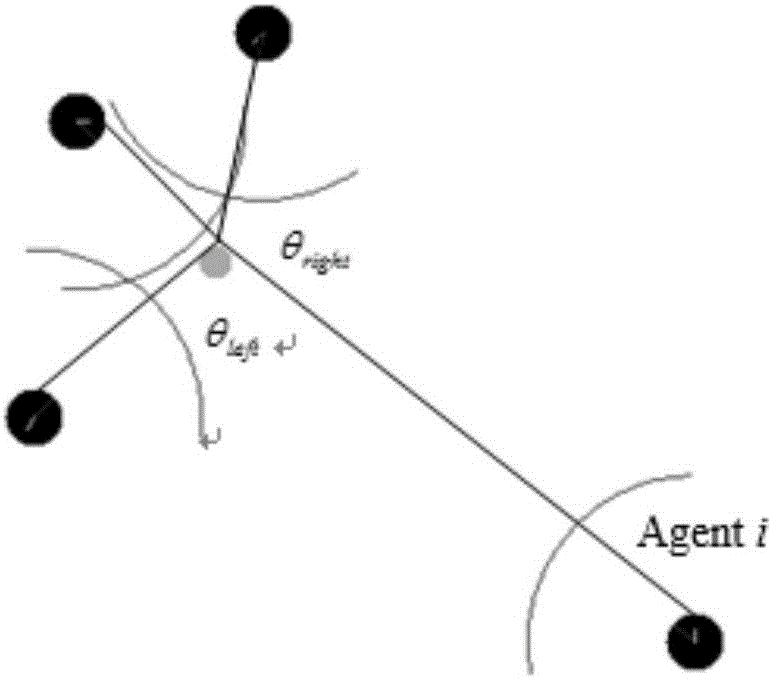
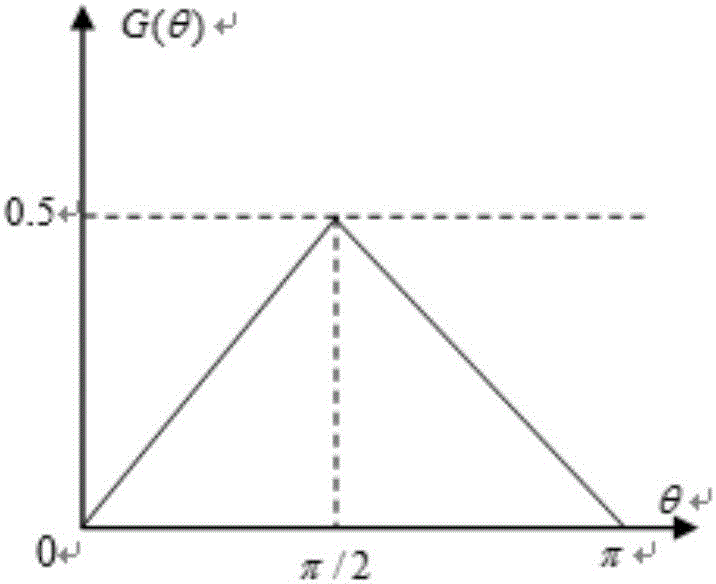
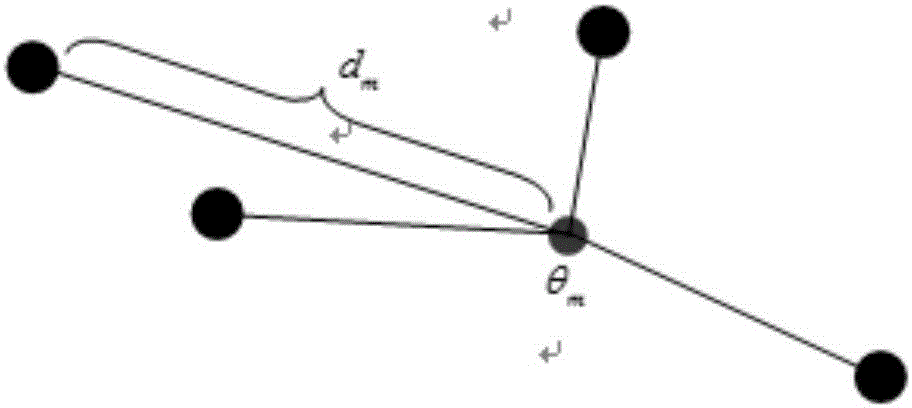
Multi-Agent stalking-foraging behavior control method
ActiveCN106843220AImprove roundup efficiencyHigh precisionPosition/course control in two dimensionsSimulationAtomic actions
The invention relates to a multi-Agent stalking-foraging behavior control method comprising the following steps: 1) dividing a state space formed by multiple agents and the current position of prey; 2) designing a reward function; 3) performing reinforced learning according to the state space divided in the step 1) and the reward function in the step 2), controlling the Agents to perform corresponding atomic actions to stalk the prey, and stopping when a stalking success condition is satisfied so as to achieve a foraging effect. Compared with the prior art, the method has high stalking efficiency.
Owner:TONGJI UNIV
Temporal dynamic push-down network converting method
ActiveCN105183652ASolving Accessibility IssuesReduced clock intervalSoftware testing/debuggingAsynchronous communicationTheoretical computer science
The invention discloses a temporal dynamic push-down network converting method used for describing real-time concurrent recursive modeling including recursive and dynamic thread creation. The converting method includes the steps that a global clock for describing continuous time and real number clocks capable of describing global variables and stack character ages related to time are introduced in DPN, so that asynchronous communication is achieved based on shared memories, and a real-time concurrent system with dynamic thread creation is modeled; for a clock equivalence technology based on integer division, an optimization technology based on a clock key point is given, a clock interval is reduced, and therefore state space obtained after conversion is reduced. As temporal dynamic push-down networks are abstract models of one kind of real-time concurrent recursive programs, the models are converted into the dynamic push-down networks by the clock equivalence optimization technology based on the key point, in this way, it is detected that the models are errors or bugs in the corresponding concurrent recursive program by verifying whether execution of the dynamic push-down networks operates into an error state or not.
Owner:GUILIN UNIV OF ELECTRONIC TECH
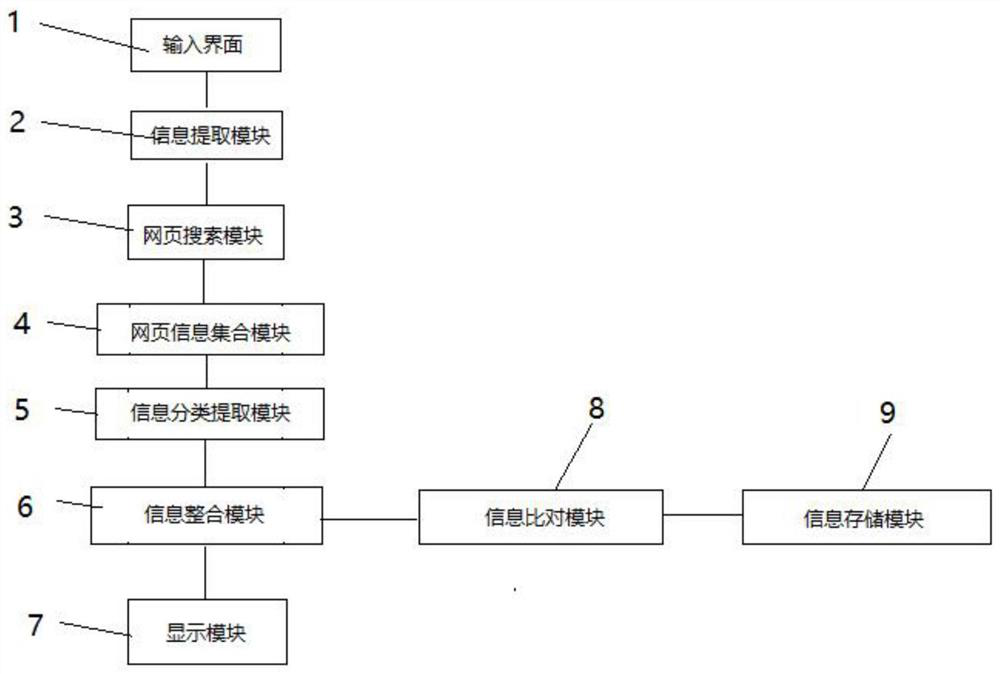
Internet people searching information integration analysis control method
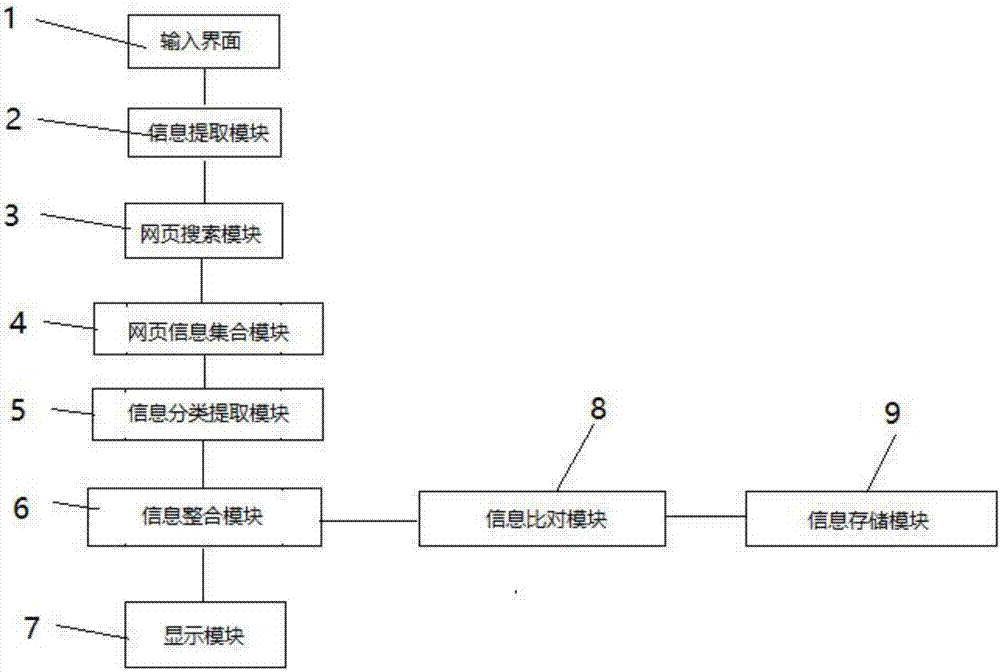
ActiveCN108009298AEfficient searchAvoid omissionsWeb data indexingSpecial data processing applicationsInternet searchingInformation searching
The invention belongs to the field of internet searching and discloses an internet people searching information integration analysis control method. According to the method, a webpage information collection module is utilized to integrate fragmentary information searched by a webpage searching module, classification is conducted by an information classification and extraction module, the searchinginformation is classified into identity information, account information and the like, and after the information is compared by an information comparison module, unknown information is stored into aninformation storage module or known information in the information storage module is read. By means of the method, internet searching information can be integrated, information can be stored into theinformation storage module for use later, and integration of scattered information on the internet is facilitated; moreover, searching is more efficient, and careless omission in manual searching canbe avoided.
Owner:海口经济学院
High-extensibility and high-maintainability source code defect detection method and device
InactiveCN101937388BImprove scalabilityImprove maintainabilitySoftware testing/debuggingControl flowExtensibility
Owner:UNKNOWN
Adaptive signal control method and system based on reinforcement learning and phase competition
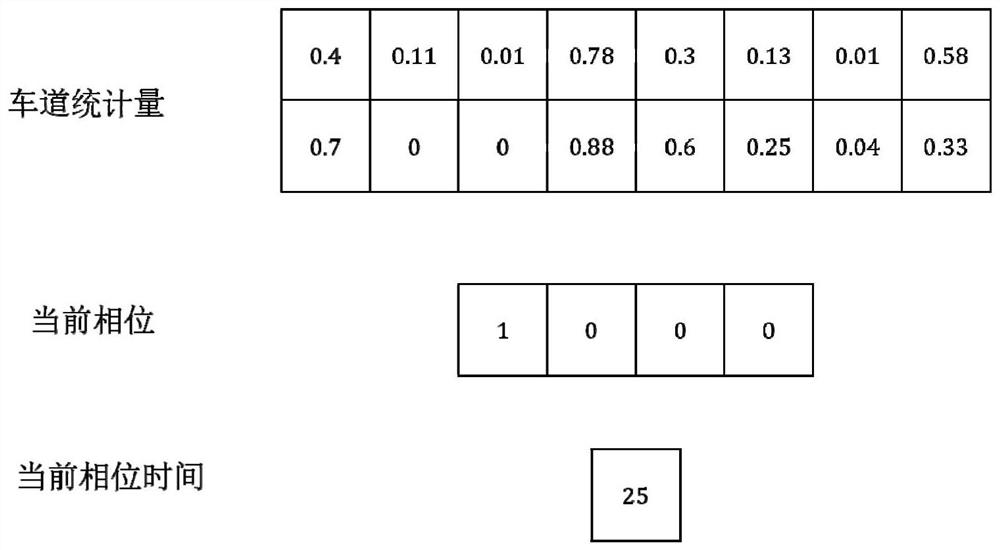
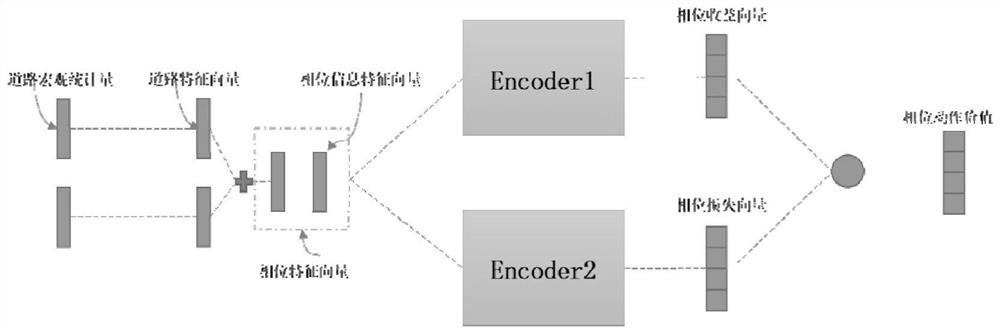
PendingCN114419884AGood convergenceGood control effectControlling traffic signalsDetection of traffic movementSelf adaptiveEngineering
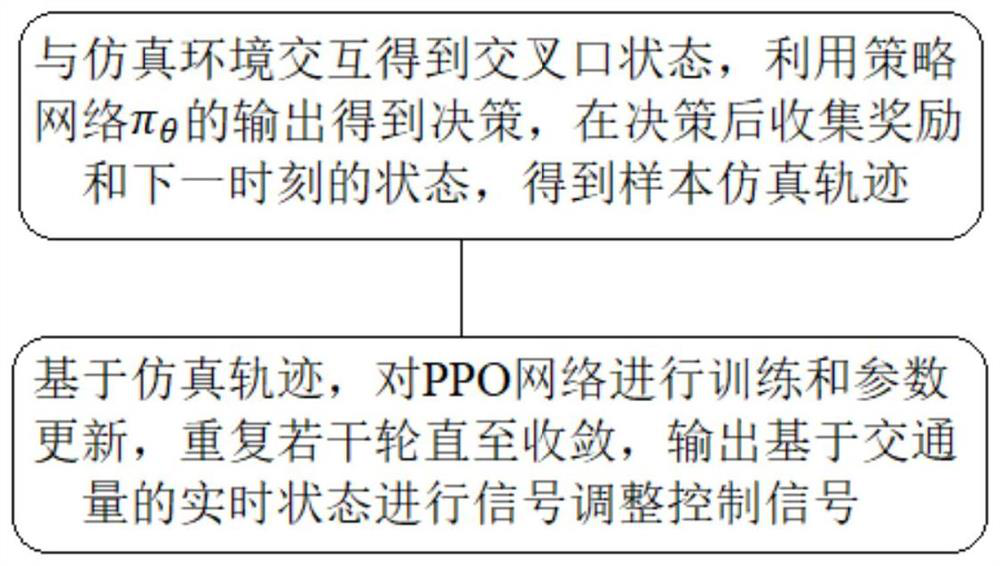
The invention relates to a self-adaptive signal control method and system based on reinforcement learning and phase competition, and the method comprises the steps: obtaining an intersection state through interaction with a simulation environment, obtaining a decision through the output of a strategy network pi theta, collecting rewards and a state at a next moment after the decision, and obtaining a sample simulation track; and training and parameter updating are performed on the PPO network based on the simulation trajectory, and the operation is repeated for a plurality of rounds until convergence. And after convergence, the model can perform signal adjustment and signal control based on the real-time state of the traffic flow. The method can be suitable for different intersections while ensuring the signal control effect. The method can be widely applied to the field of urban traffic signal control.
Owner:TSINGHUA UNIV
Path planning method of improved A* algorithm based on graph preprocessing
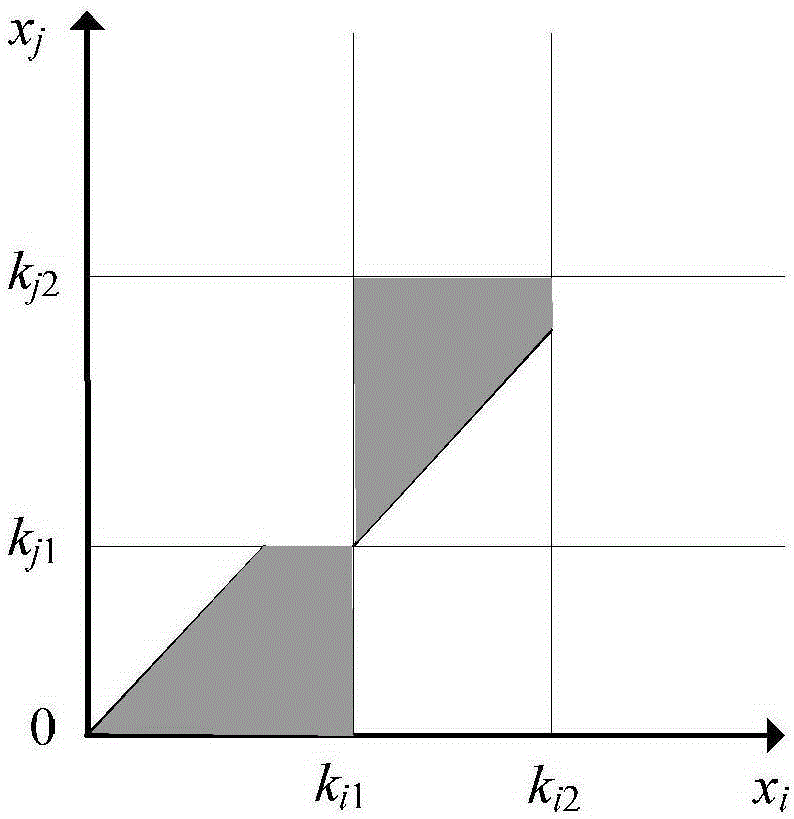
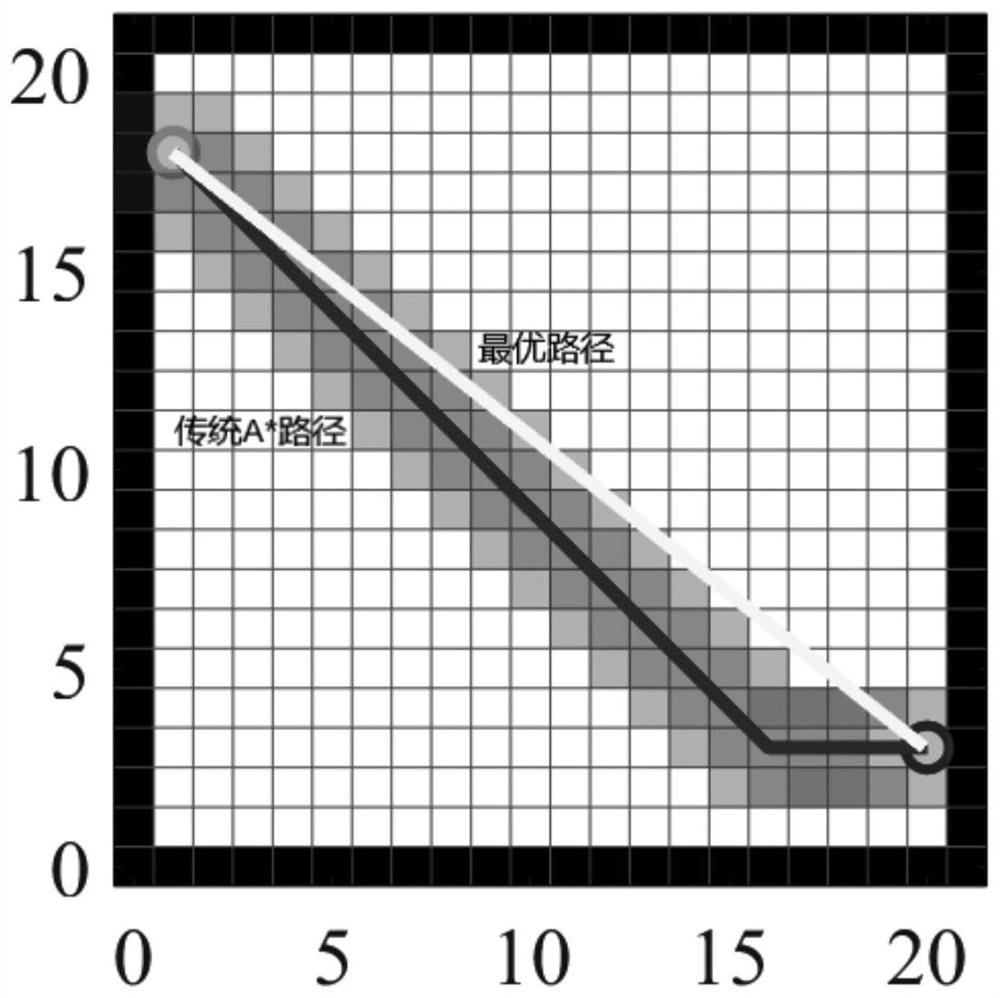
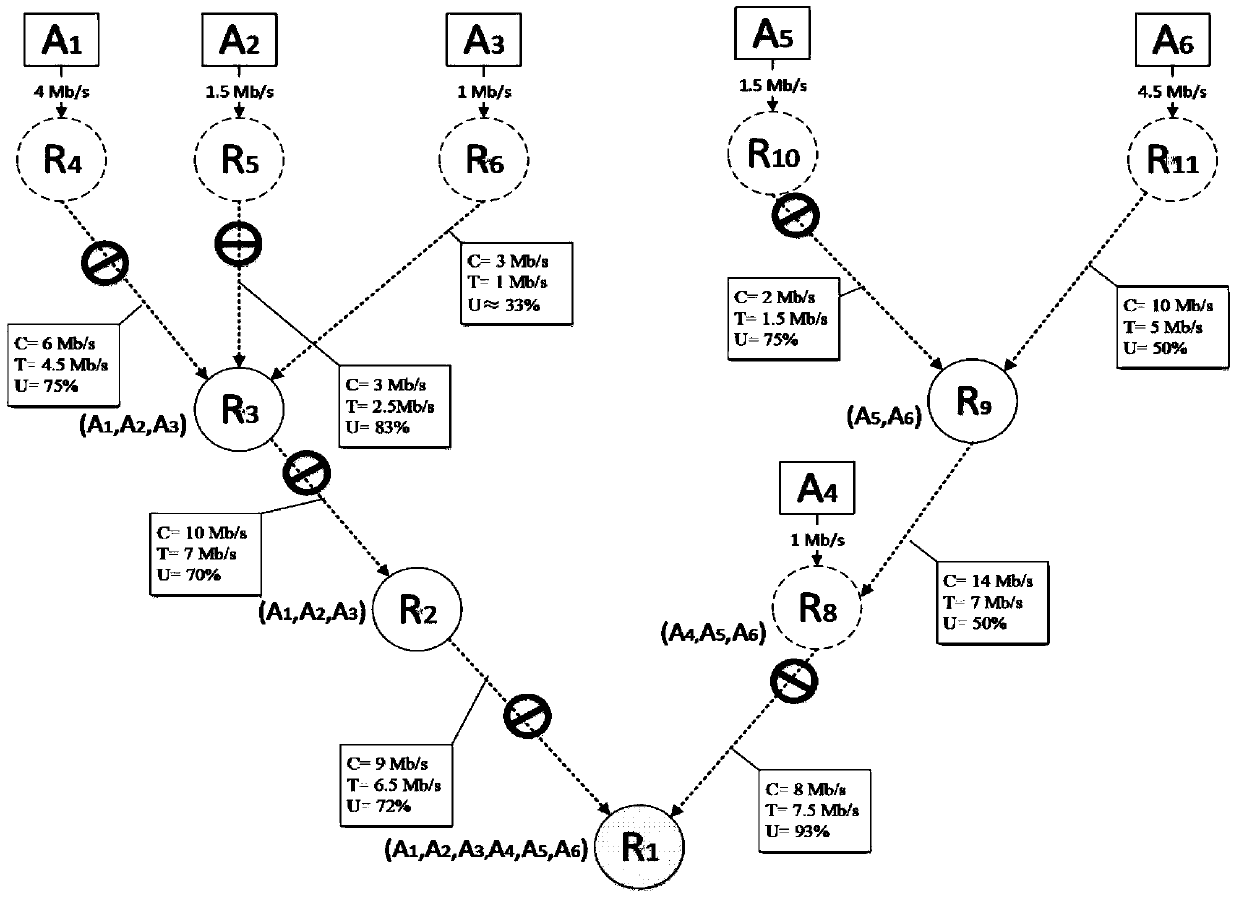
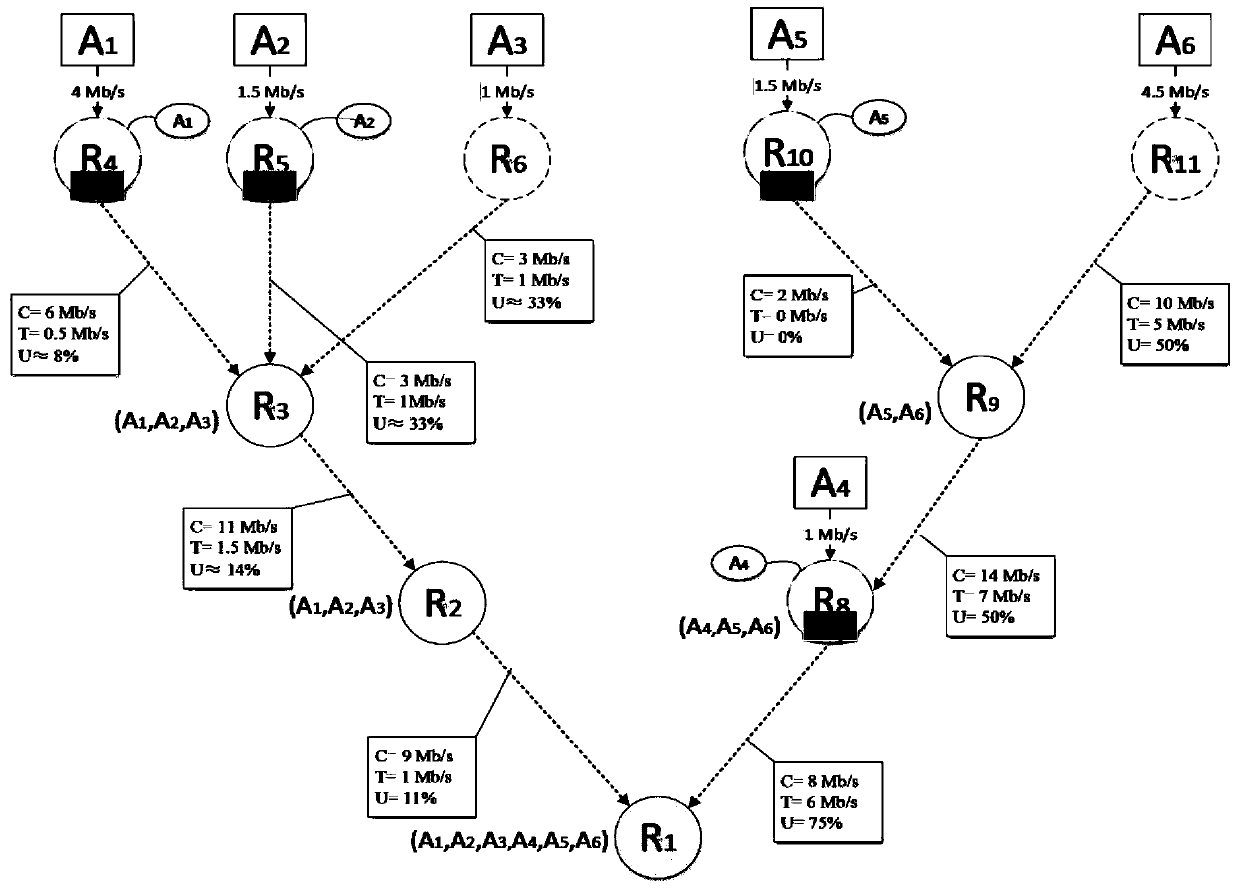
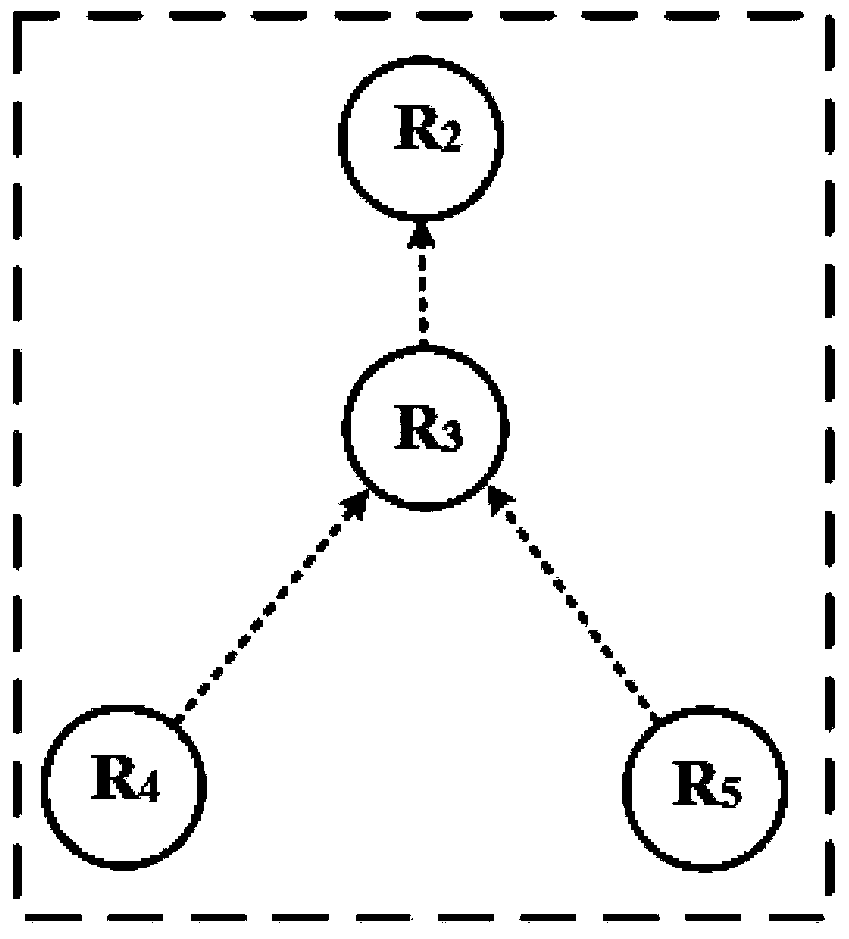
PendingCN113325834AImprove search efficiencyShrink state spacePosition/course control in two dimensionsVehiclesPathPingNeighborhood search
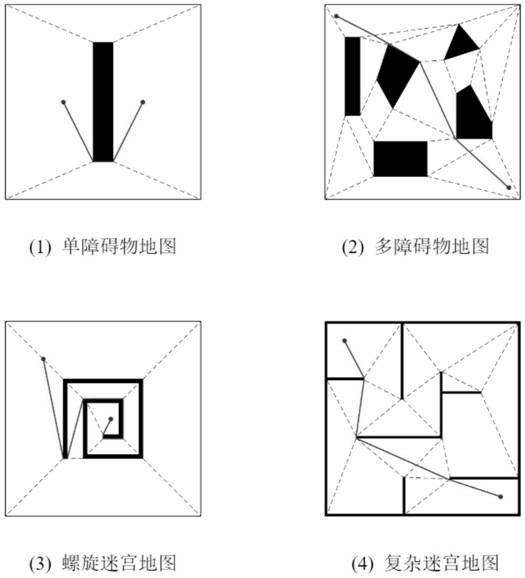
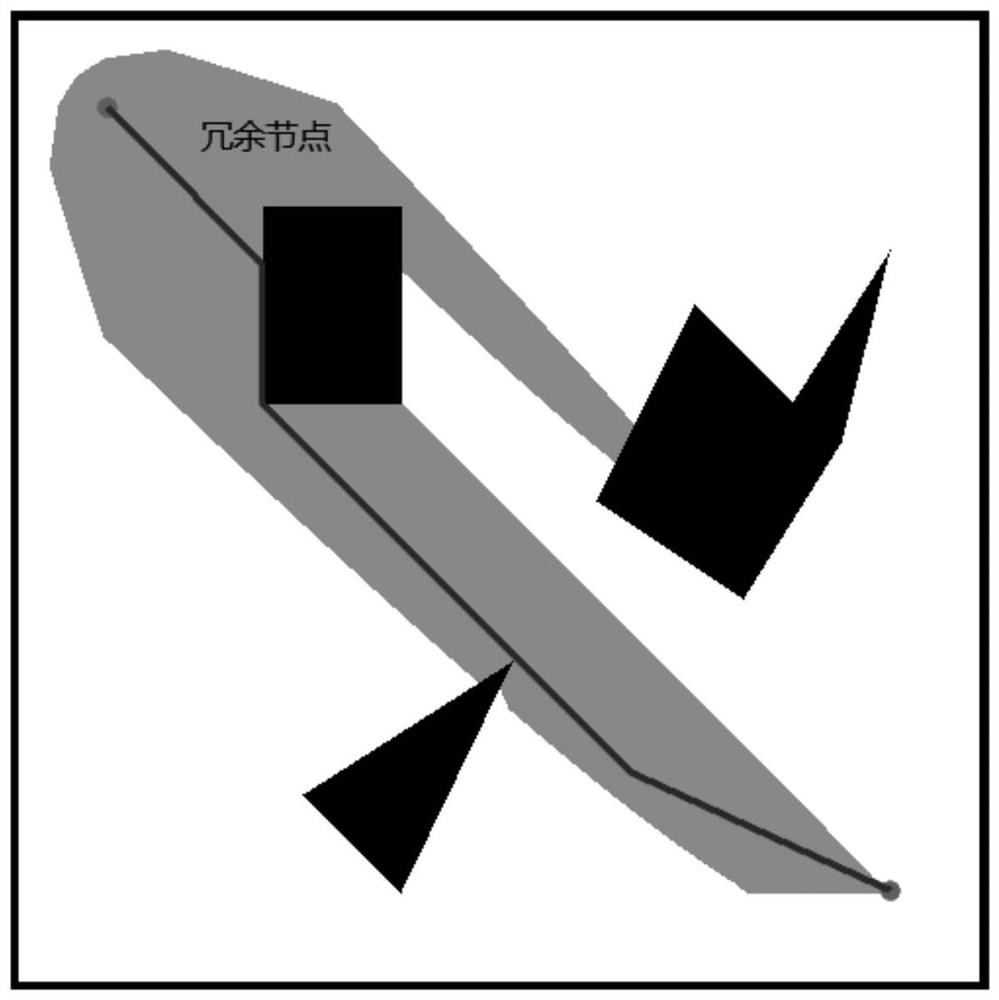
The invention discloses a path planning method of an improved A* algorithm based on graph preprocessing. Due to problems of complexity of map modeling and the like, path-finding efficiency is greatly reduced (as shown in Figure 1) due to large calculation amount and high redundancy of a traditional A* algorithm, and a large amount of performance consumption is caused. Due to the limitation of neighborhood search in a grid map, the traditional A * algorithm cannot actually realize the optimal path in the global sense. In order to solve the problems, firstly, an improved Maklink graph method is used for decomposing a free space on a map into a plurality of convex polygon areas, then all the areas are coded into feature nodes, finally, an optimal area channel is solved based on the principle of an A * algorithm, and a globally optimal path solution is obtained in the channel. The problems that a traditional A * algorithm is low in neighborhood search efficiency, the planned path is not optimal and the like are solved, and compared with other common algorithms, the proposed algorithm has remarkable advantages in the aspects of planning speed, path length, stability, completeness and the like.
Owner:BEIHANG UNIV
Self-adaptive heuristic global path planning method and system for robot
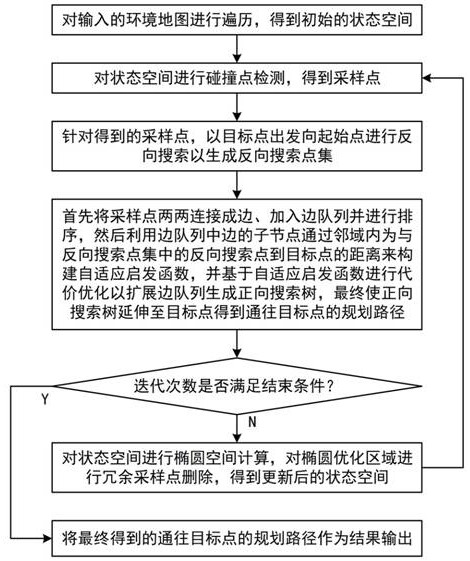
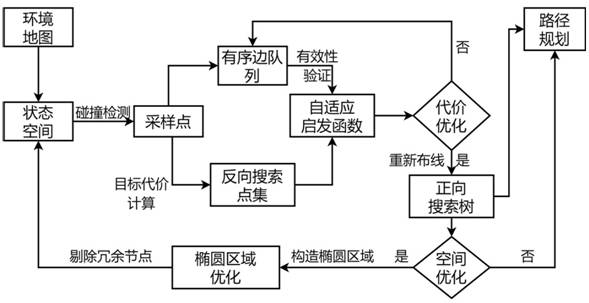
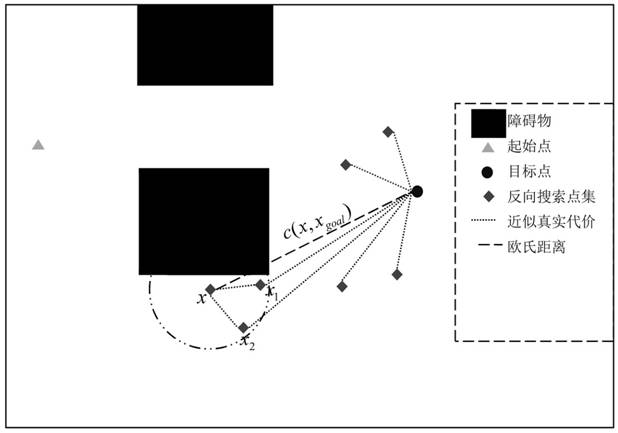
ActiveCN114705196AShrink state spaceFast path planningNavigational calculation instrumentsOther databases indexingAlgorithmEngineering
The invention discloses a self-adaptive heuristic global path planning method and system for a robot. The method comprises the following steps: traversing an input environment map to obtain an initial state space, and carrying out collision point detection to obtain sampling points; aiming at the obtained sampling points, carrying out reverse search by starting from a target point to generate a reverse search point set, connecting the sampling points into edges and sorting the edges, and then constructing an adaptive heuristic function by utilizing child nodes of the ordered edges and the reverse search point set; and performing cost optimization based on an adaptive heuristic function, extending an ordered edge queue from a starting point to generate a forward search tree, extending the forward search tree to a target point to obtain a planned path, and repeating the steps for multiple times to obtain a final planned path. According to the method, rapid and accurate path planning can be realized, a relatively shortest path can be planned, and the planning success rate and the effectiveness on a complex obstacle map are improved.
Owner:湖南欣欣向荣智能科技有限公司
Soft bit value generation in a sequence estimator
ActiveUS8223896B2Reduce computational complexityReduce complexityData representation error detection/correctionCode conversionComputation complexityState space
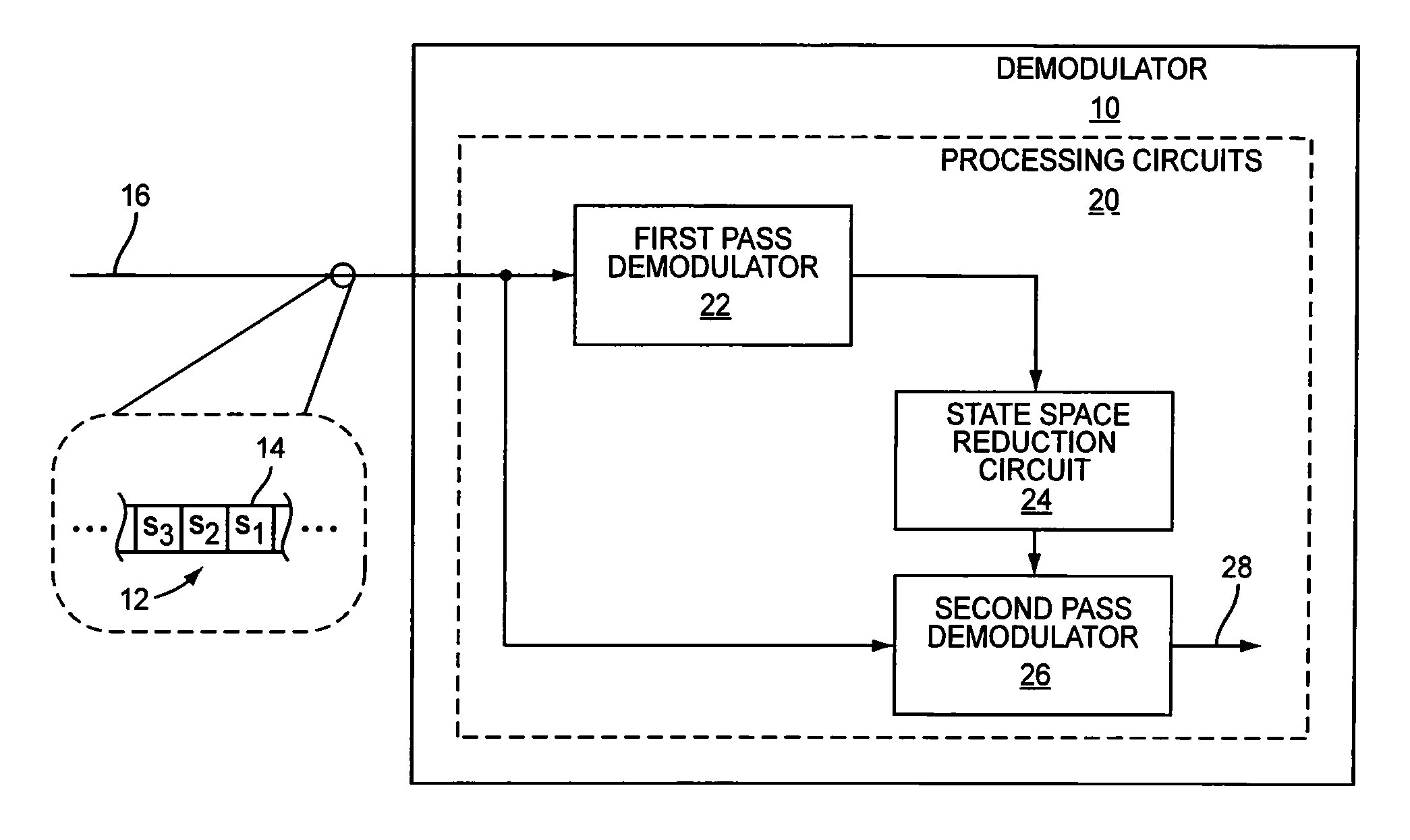
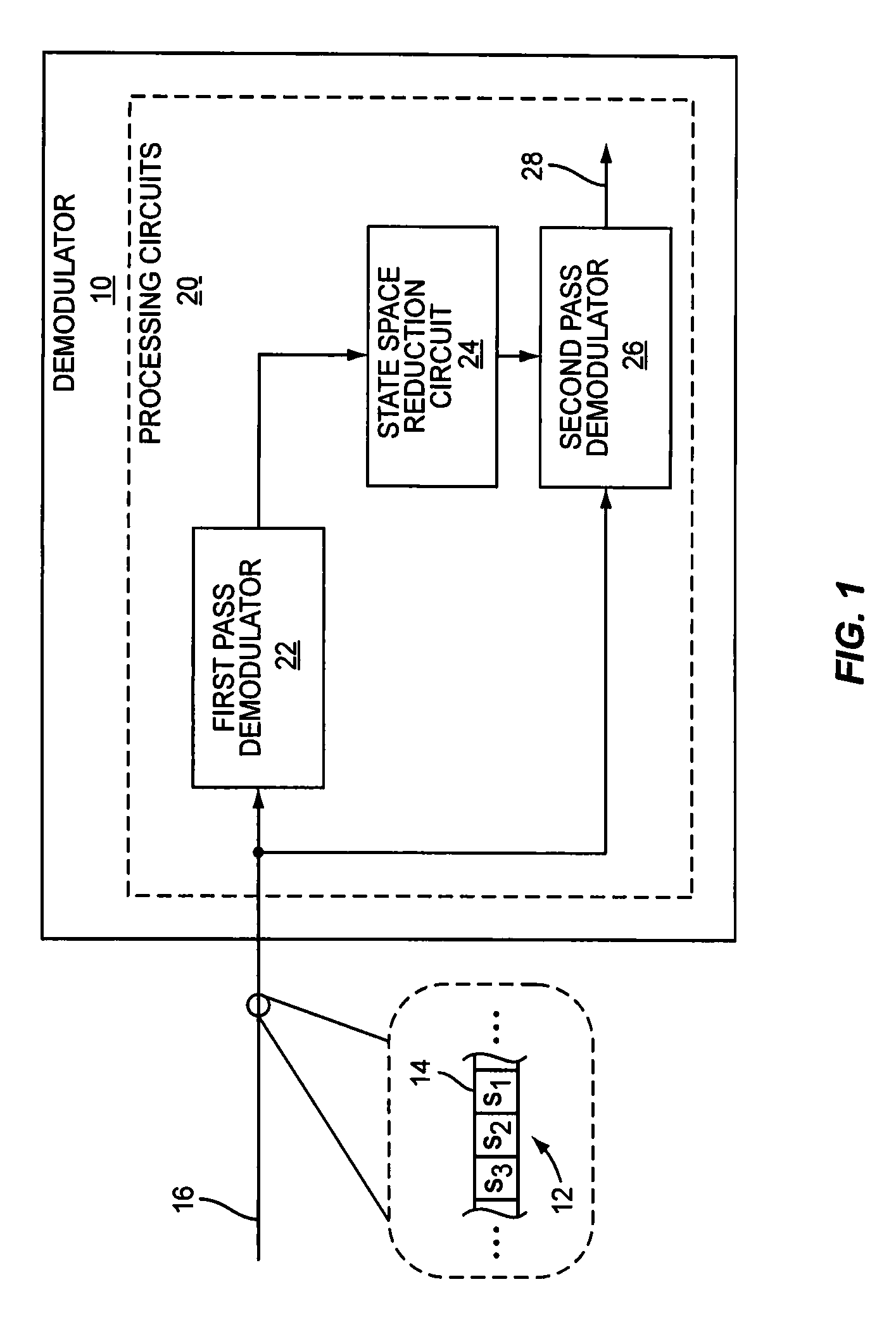
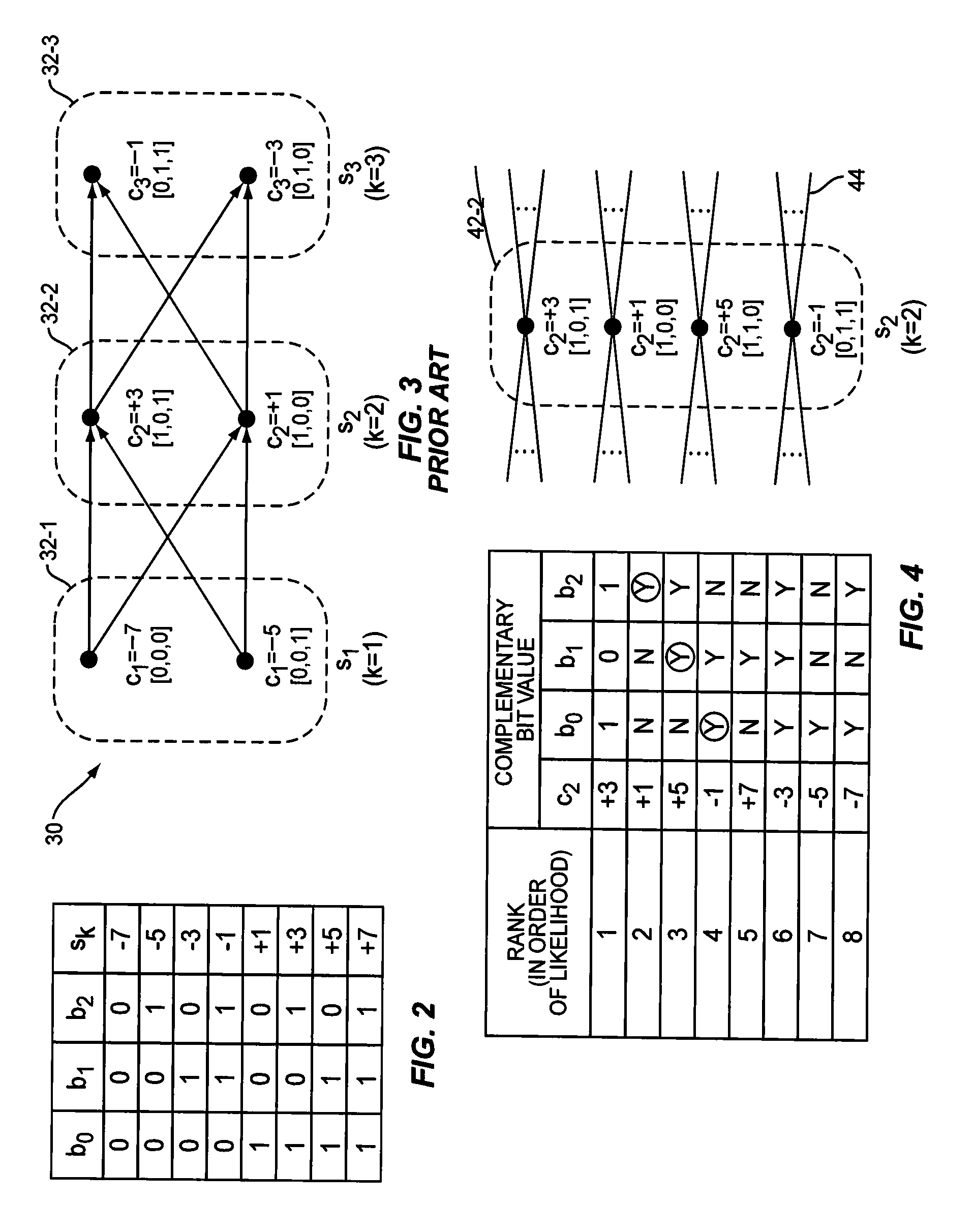
Teachings presented herein offer reduced computational complexity for symbol sequence estimation, and also provide for the generation of soft bit values representing the reliability of that estimation. A demodulator is configured to generate these soft bit values by identifying a candidate value for each symbol in the sequence which is more likely than at least one other in a defined set of candidate values. Based on the candidate value identified for each symbol, the demodulator forms a reduced set of candidate values for the symbol by selecting as many additional candidate values from the defined set as are needed to have complementary bit values for each bit value in that identified candidate value. The demodulator calculates soft bit values for the symbol sequence based on a sequence estimation process whose state space for each symbol is constrained to the corresponding reduced set.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
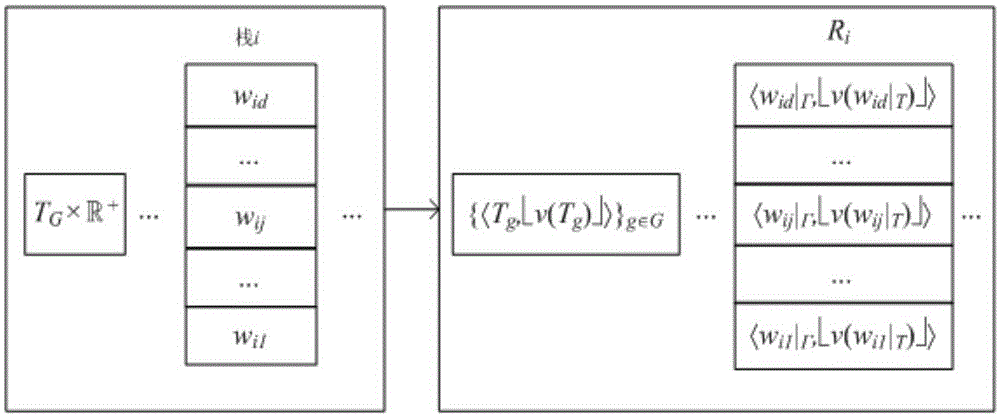
Static conversion method for time multi-stack push-down network
ActiveCN105260295AEfficient analysisShrink state spaceSoftware testing/debuggingPlatform integrity maintainanceTime systemFormal verification
The invention discloses a static conversion method for a time multi-stack push-down network. Firstly, to describe a concurrent recursive mechanism in a real-time system and interaction between threads, a clock is introduced on the basis of MPDN; a TMPDN model is provided; grammars and operational semantics of the TMPDN model are given; and secondly, the continuous-time TMPDN model is converted into a discrete MPDN model through the static conversion method by utilizing a clock domain equivalent optimization technology. According to the invention, description of the real-time performance and the concurrency of a real-time concurrent system can be realized simultaneously; and guarantee can be provided for formal verification of a real-time concurrent program.
Owner:GUILIN UNIV OF ELECTRONIC TECH
A method for integrated analysis and control of Internet person search information
ActiveCN108009298BEfficient searchAvoid omissionsWeb data indexingSpecial data processing applicationsInternet searchingEngineering
The invention belongs to the field of Internet search, and discloses an integrated analysis control method for Internet character search information. The fragmentary information searched by the webpage search module is integrated by using the webpage information collection module, and the search information is divided into categories through the information classification and extraction module. Identity information, account information and other types are compared by the information comparison module, and the unknown information is stored in the information storage module or the known information in the information storage module is read. The invention can integrate Internet search information and store the information in the information storage module for future use, which is beneficial to integrate scattered information on the Internet; more efficient search and can prevent manual search omissions.
Owner:海口经济学院
Energy-saving fluidized bed type jet mill
ActiveCN113967521AImprove crushing effectGuaranteed crushing effectGrain treatmentsRotational axisFluidized bed
The invention relates to the technical field of fluidized bed type jet mill equipment, and provides an energy-saving fluidized bed type jet mill. The mill comprises a base, a plurality of circulating petals and a classifier. A first crushing cavity is formed in the base; the plurality of circulating petals are distributed on the base circumferentially in an array manner with the axis of the base as the rotating axis, and second crushing cavities are formed in the circulating petals; the first crushing cavity is communicated with the second crushing cavities; the classifier is arranged at the axis of the base; a first crushing nozzle assembly which is horizontally arranged is arranged in the first crushing cavity; flow guide islands are arranged in the second crushing cavities, the flow guide islands and the circulating petals form a flow guide channel, and a second crushing nozzle assembly is arranged in an air inlet channel of the flow guide channel; and an air outlet of the flow guide channel faces the working face of the first crushing nozzle assembly. Under the action of the second crushing nozzle assembly, the flow guide channel forms circulating air flow along the air inlet channel, the air outlet and the first crushing cavity; and according to the jet mill, materials can be efficiently crushed, and compared with traditional fluidized bed type airflow crushing equipment, the jet mill has better energy-saving and environment-friendly effects.
Owner:四川瑞驰拓维机械制造有限公司
Multi-stage dynamic vehicle routing optimization method for fresh agricultural products in different regions
InactiveCN109002902BImprove solution efficiencySolve the path problemForecastingLogisticsAgricultural scienceMathematical model
The invention discloses a dynamic vehicle route optimization method for fresh agricultural products divided into regions and multi-stages, which comprises the following steps: acquiring data; dividing regions; dividing time periods; designing freshness attenuation functions; minimizing the total distribution cost mathematical model; and minimizing the total distribution cost Mathematical model algorithm design; minimum distribution total cost mathematical model solution; the present invention effectively improves distribution efficiency and reduces distribution total cost, and has high practical significance.
Owner:EAST CHINA UNIV OF SCI & TECH
Preparation method of inorganic and organic coated rutile titanium dioxide
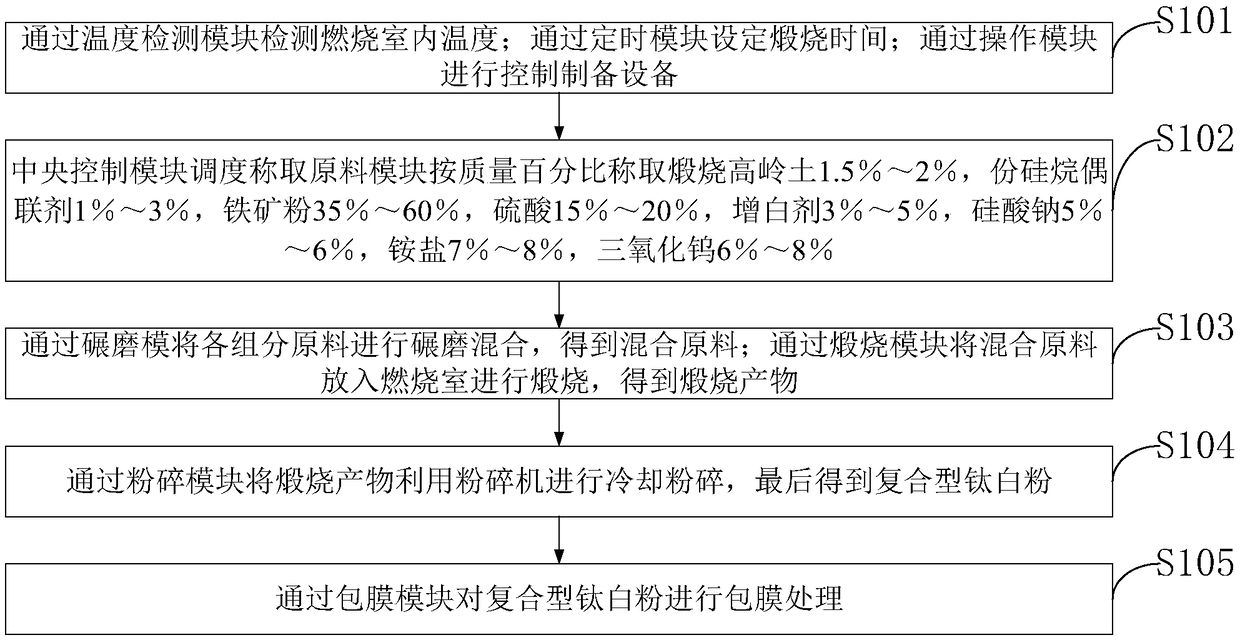
InactiveCN108822583AUniform particle size distributionImprove performanceInorganic pigment treatmentProgram loading/initiatingSilicic acidRutile
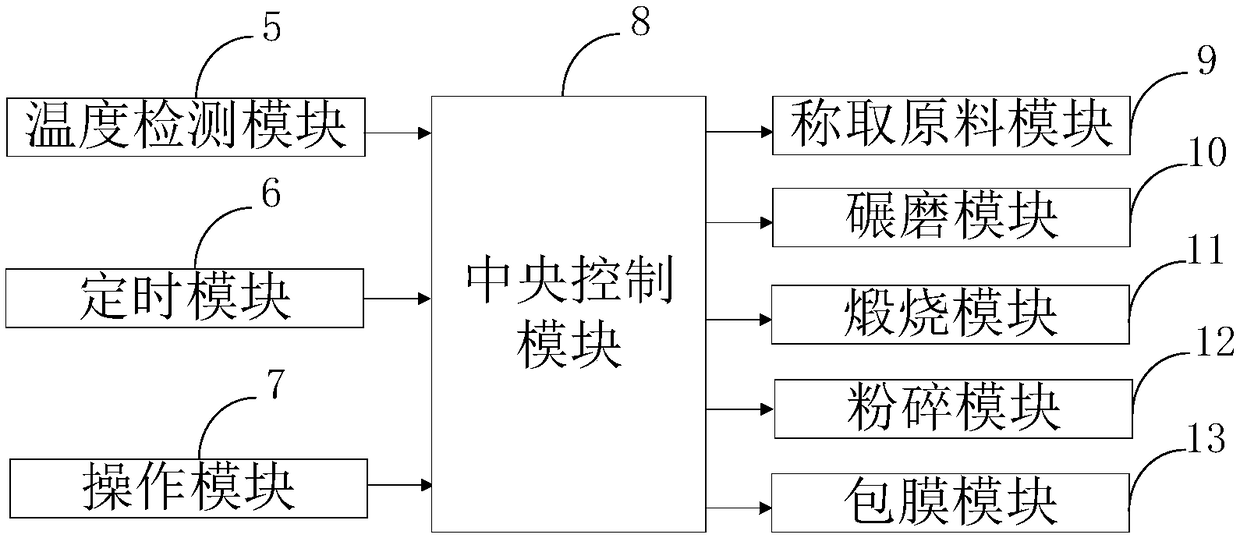
Belonging to the technical field of materials, the invention discloses a preparation method of inorganic and organic coated rutile titanium dioxide. The preparation system includes: a temperature detection module, a timing module, an operation module, a central control module, a raw material weighing module, a grinding module, a calcination module, a crushing module and a coating module. The composite titanium dioxide prepared by the method provided by the invention simplifies the production process and saves production cost, and moreover, the composite titanium dioxide has uniform particle size distribution and superior performance. According to the invention, the coating module adopts orthosiliconic acid as the silicon source, employs low alkalinity sodium metaaluminate, or employs low alkalinity sodium metaaluminate and aluminum sulfate as the aluminum coating raw materials for compact silicon-aluminum coating of titanium dioxide, thus providing a new way for coating of titanium dioxide. The method provided by the invention has the characteristics of simple operation, low production process labor intensity and low cost, and is worth popularizing and applying.
Owner:HUNAN UNIV OF TECH
A full-terminal reliability calculation method for dividing communication communities based on modularity
ActiveCN107944705BReduce collection spaceFull-stack reliability and accuracyResourcesConcurrent computationModularity
The invention discloses a method for computing full-terminal reliability based on modularity-based division of communication communities, including power communication network community division based on modularity and full-terminal reliability calculation based on minimum road sets. By reducing the complexity of the network topology, the state space of the network is greatly reduced through space decomposition, and the problem of "state space explosion" is alleviated to a certain extent, thereby reducing the time spent by the algorithm on finding the minimum path set. The complexity of the internal topological structure of the communication community divided by modularity is much lower than that of the entire electric power communication and is independent of each other. Parallel computing is introduced into the internal full-terminal reliability analysis, and the final connection topology of the communication community is relatively simple. Analysis of its full-stack reliability is less time consuming.
Owner:STATE GRID HENAN INFORMATION & TELECOMM CO +1
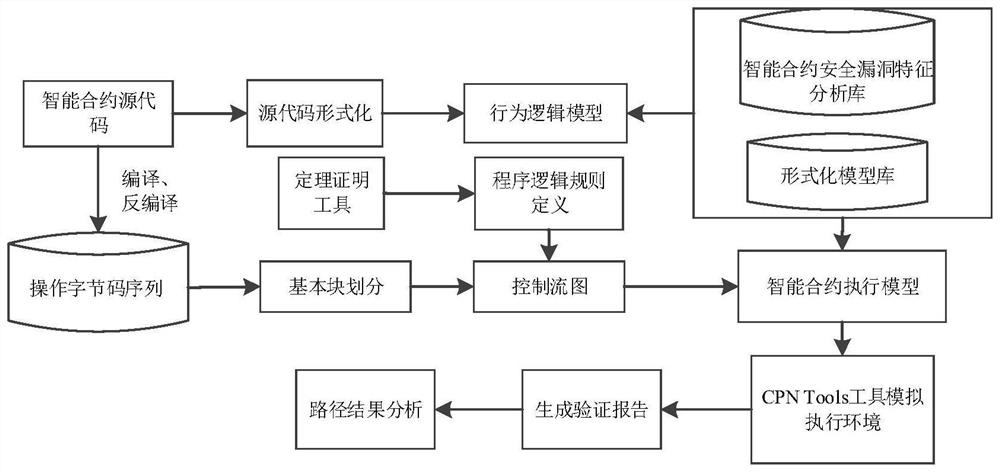
A system and method for formal verification of smart contracts based on state space
ActiveCN111062038BEasy to implementImprove efficiencyPlatform integrity maintainanceSoftware simulation/interpretation/emulationLogisimByte
The present invention relates to a system and method for formal verification of smart contracts based on state space. The system includes: a code compilation module for compiling smart contract source codes into source codes and virtual machine operation instruction byte code sequences; basic block division The module is used to divide the byte code sequence of the virtual machine operation instruction into a set of basic blocks; the control flow graph generation module is used to generate the control flow graph containing the condition identifier; the logic rule module is used to convert the condition identifier into a logic rule condition ; The source code formalization module is used to analyze the behavior elements from the source code and save it as a formal behavior file; the model generation module is used to generate a behavior model file according to the formal behavior file; generate execution according to the logic rule condition and control flow graph Model files; Execution and Validation Modules for obtaining state space reports and state space directed graphs. Compared with the prior art, the invention has the advantages of comprehensive detection, high efficiency, and ability to intuitively reflect abnormal states.
Owner:TONGJI UNIV
Filter location selection method for bandwidth consumption attacks
The invention discloses a filtering location selection method for bandwidth consumption attacks, which includes the following steps: establishing a link congestion complete dependency set CDS of routing nodes in an attack tree. set ;According to the link congestion fully dependent set CDS set Based on the upstream and downstream dependencies of the link, a corresponding link congestion dependency tree is established; all link congestion dependency trees form a link congestion dependency forest; the leaf routes of each link congestion dependency tree in the link congestion dependency forest are The node is the optimal filtering position of the routing node in the attack tree for bandwidth-consuming attacks. By adopting the filtering location selection method of the present invention, only 25% of the filtering routing nodes of the existing filtering strategy are needed to clear all congested links, so that the two can reach a balance and greatly reduce the network delay caused by router filtering. .
Owner:NORTHEASTERN UNIV LIAONING
An energy-saving fluidized bed jet mill
ActiveCN113967521BImprove crushing effectGuaranteed crushing effectGrain treatmentsFluidized bedEngineering
The invention relates to the technical field of fluidized bed airflow pulverizer, and provides an energy-saving fluidized bed airflow pulverizer, which includes a base; a first pulverization chamber is arranged inside it; Circulation flap; there is a second crushing chamber in the circulation flap; the first crushing chamber and the second crushing chamber are connected; the classifier is arranged at the axis of the base; the first crushing chamber is equipped with a horizontal first crushing nozzle assembly ;The second crushing chamber is provided with a diversion island, the diversion island and the circulation valve form a diversion channel, and the air inlet channel of the diversion channel is provided with a second crushing nozzle assembly; the air outlet of the diversion channel faces the first crushing nozzle The working surface of the assembly is set; under the action of the second crushing nozzle assembly, the guide channel forms a circulating air flow along the air inlet channel, the air outlet and the first crushing chamber; the present invention can efficiently crush materials, compared with the traditional flow The chemical bed airflow pulverization equipment has good energy saving and environmental protection effects.
Owner:四川瑞驰拓维机械制造有限公司
Interpolation based path reduction method in software model checking
ActiveUS10503628B2Reduce in quantityImprove verification efficiencySoftware testing/debuggingAbstract syntax treeString interpolation
Owner:XIDIAN UNIV
A dynamic conversion method for temporal multi-stack pushdown network
ActiveCN105260296BEfficient analysisResolve uncertaintySoftware testing/debuggingNetwork modelOperational semantics
The invention discloses a dynamic conversion method for a time multi-stack push-down network. Firstly, a clock is introduced on the basis of MPDN; a TMPDN model is provided; grammars and operational semantics of the TMPDN model are given; and secondly, the continuous-time TMPDN model is converted into a discrete multi-stack push-down network model through the dynamic conversion method by utilizing a clock domain equivalent optimization technology. According to the invention, description of the real-time performance and the concurrency of a real-time concurrent system can be realized simultaneously; and guarantee can be provided for formal verification of a real-time concurrent program.
Owner:GUILIN UNIV OF ELECTRONIC TECH
A Runtime Error Analysis Method Based on Abstract Interpretation and Model Validation
ActiveCN103617115BShrink state spaceImprove inspection efficiencySoftware testing/debuggingHypothesisRunning time
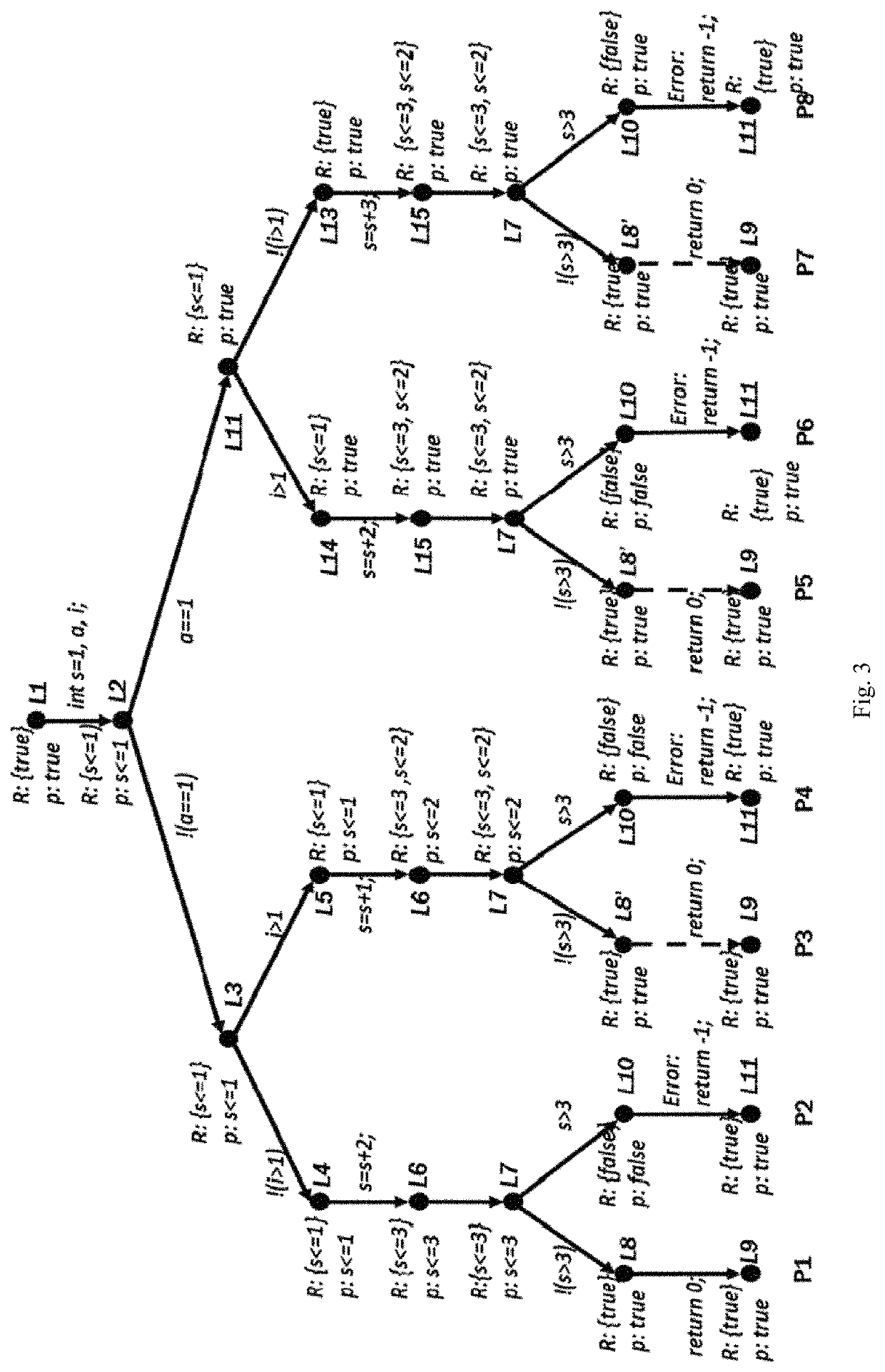
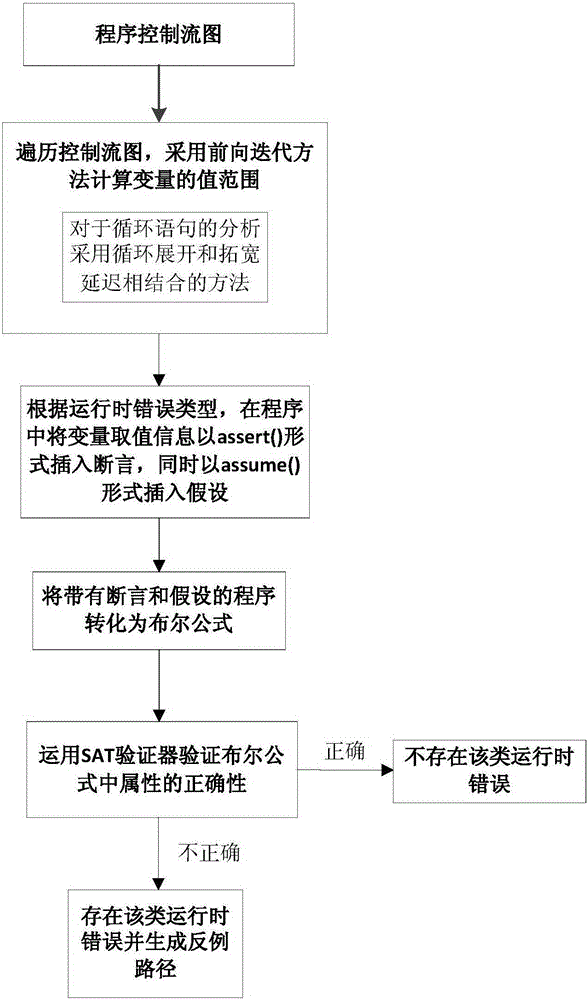
The invention discloses a runtime error analytical method based on abstract interpretation and model verification. The method includes the following steps that on the basis of the abstract interpretation theory, the program numerical variable value range is analyzed by the adoption of a forward iteration method, the variable value range information is obtained when program points are stable, and the iterative computations of loop nodes are achieved by the way that loop unrolling and delay widening are combined; the variable value range information at the relevant program points needing to be detected is converted to be in an assertion or hypothesis mode to be plugged into a program according to a runtime error type to be analyzed; the assertion or hypothesis programs are converted into a Boolean formula, wherein the Boolean formula comprises limiting conditions and attributes; the correctness of the attributes in the Boolean formula is judged through an SAT verifier, if correct, it shows that relevant runtime errors do not exist, if not correct, it shows that the relevant runtime errors exist, and relevant counter example paths are output. By means of the method, an equilibrium point is acquired between runtime error analysis precision and efficiency.
Owner:中国航天系统科学与工程研究院
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com