Filter location selection method for bandwidth consumption attacks
A technology for filtering location and bandwidth consumption, applied in transmission systems, electrical components, etc., can solve problems such as network performance impact and large economic losses, and achieve the effect of minimizing bandwidth resources, improving efficiency, and reducing state space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
experiment example
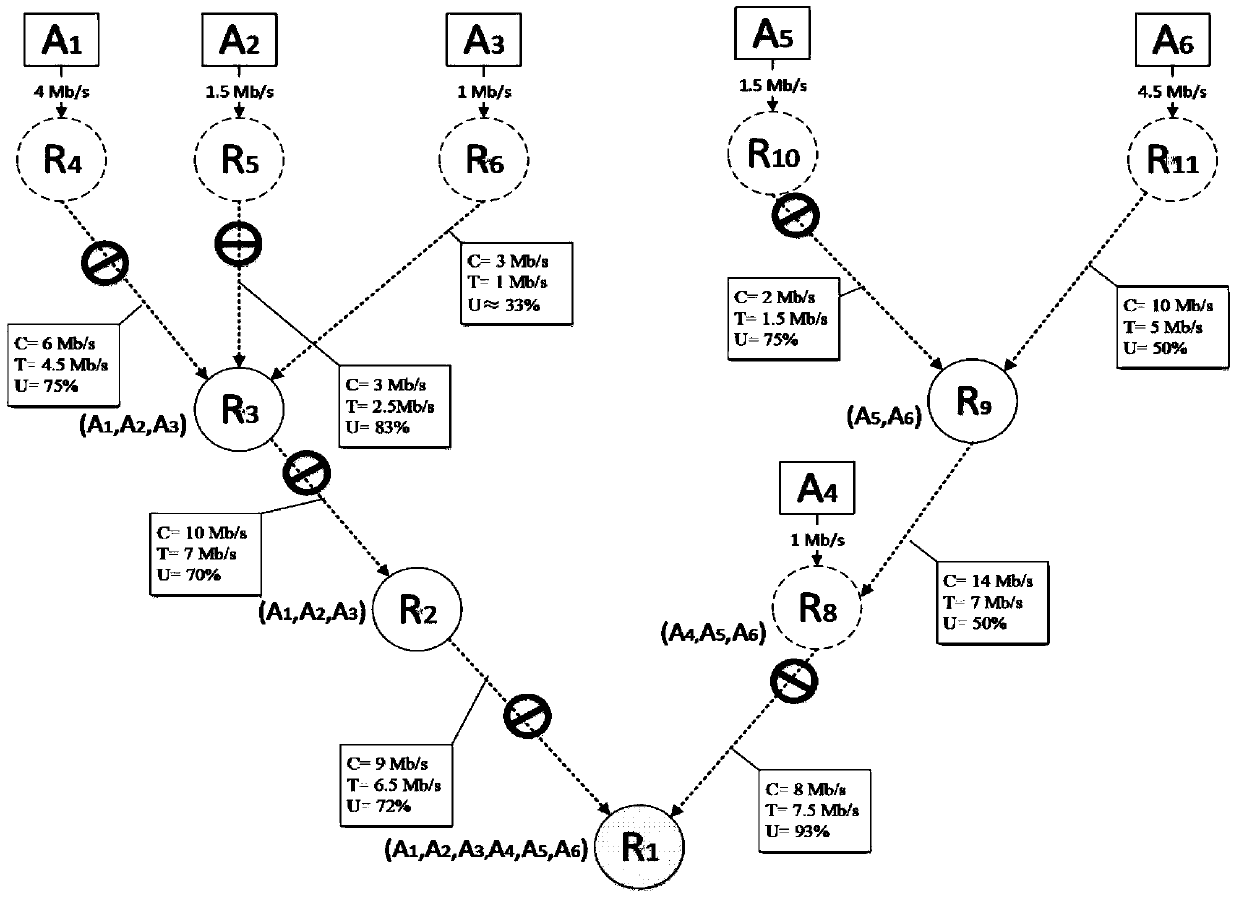
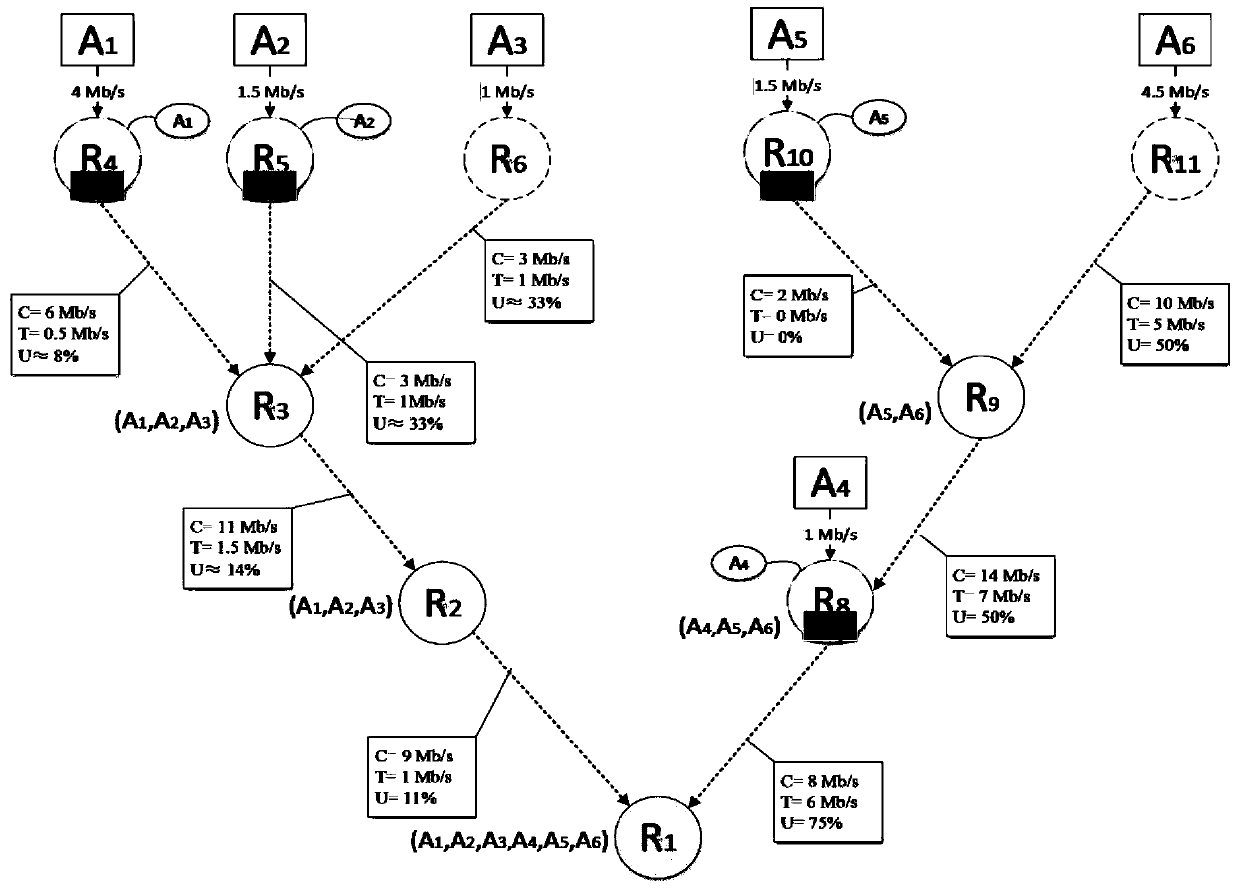
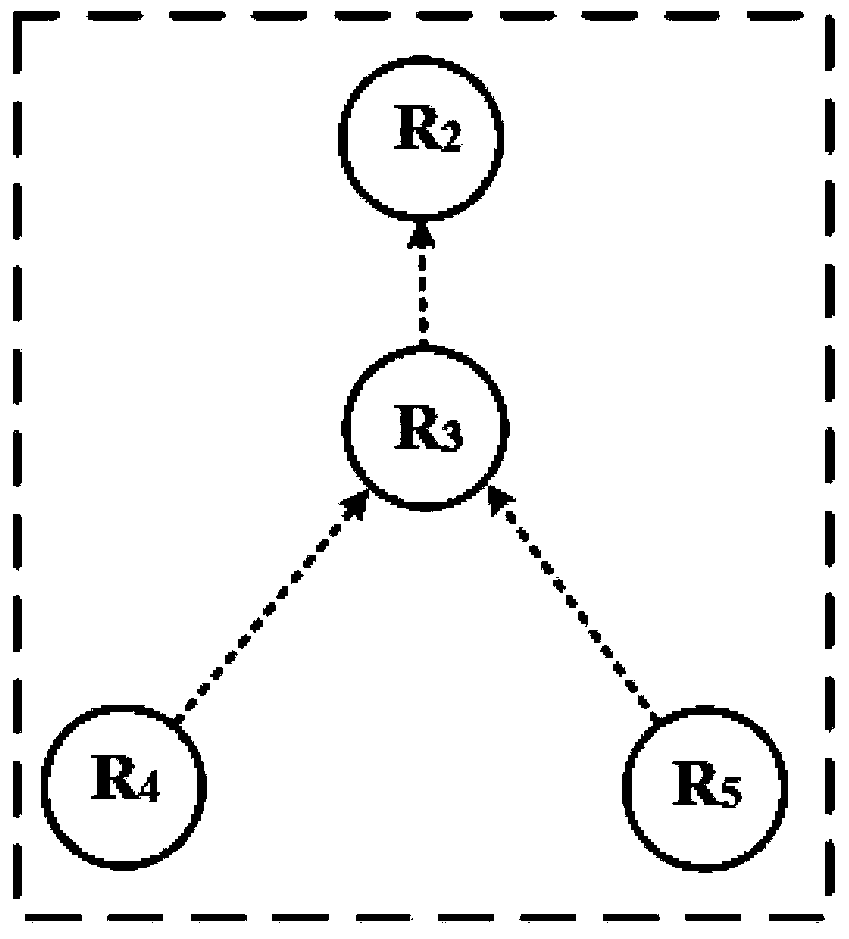
[0077] Experimental example: figure 1 is a given attack network (which can be constructed using the traceability method), figure 2 is the corresponding defense model. After an in-depth analysis of the attack behavior, the bandwidth-exhausting attack network can be defined as a multi-source and single-sink graph, denoted as G S ={V S , L S ,S S ,D S , R S ,F S ,C S , T S}, where, G S Indicates attack network, V S Indicates the attack network G S The set of nodes in L s Indicates the attack network G S The set of links in S s Indicates the attack network G S The set of attack sources in D s Indicates the attack network G S The root node in R S Indicates the attack network G S The set of attack flow rates in F S Represents the relationship set of nodes and attack paths in the attack network, C S Indicates the attack network G S The bandwidth utilization rate of the medium link, T s Indicates the actual flow set of each link.
[0078] Among them, the set ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com