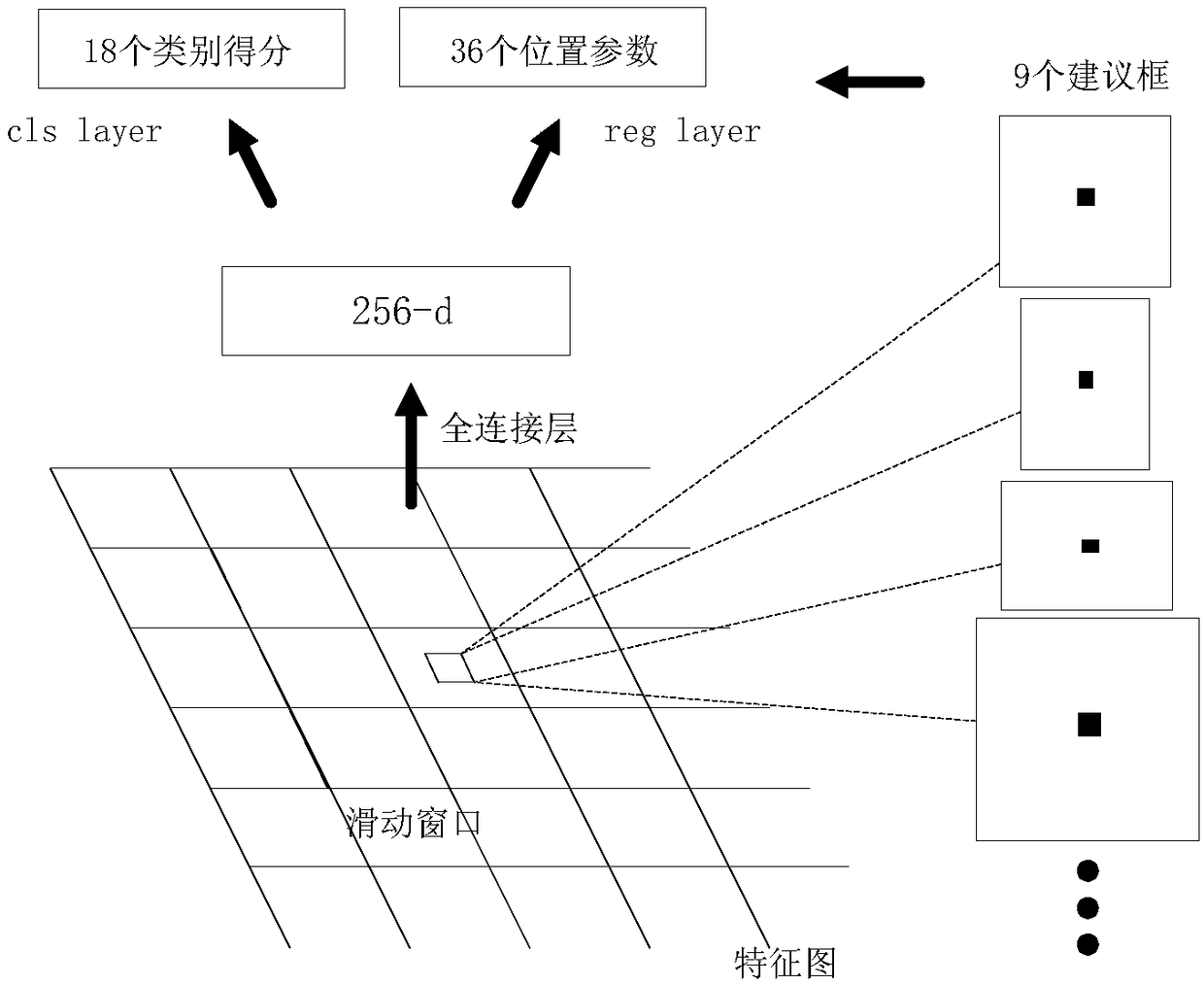
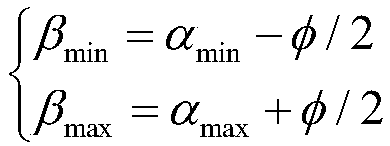Patents
Literature
38 results about "Constraint analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Constraint analysis. Constraint analysis focuses on the bottlenecks within an organization. Under this viewpoint, a manager should only focus on maximizing the utilization of a bottleneck, since the bottleneck controls the overall profitability of the business. Focusing on any other aspect of the business has no impact on profits.
Regional integrated energy system optimization control method
InactiveCN109784569ALow operating costImprove reliabilityForecastingSystems intergating technologiesReduction rateEnergy system optimization
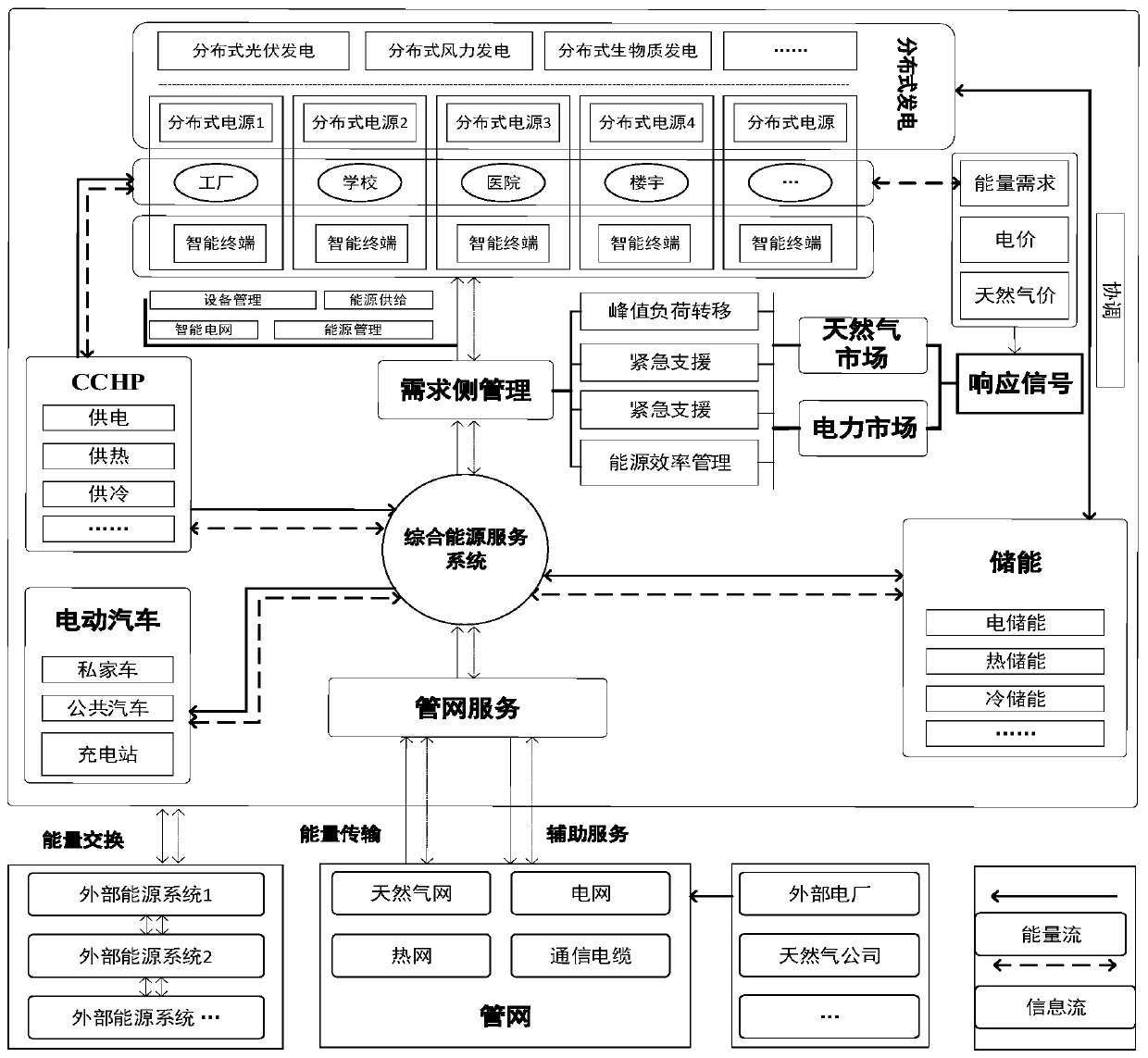
The invention discloses a regional integrated energy system optimization control method. The method comprises the following steps: S1, optimizing a control objective function of the regional integrated energy system; The purposes of the lowest total operation cost and the highest reliability and system emission reduction rate of the regional comprehensive energy system are achieved, and the objective function is divided into an operation cost model, an environment cost model and a system reliability model; including S11, constructing an objective function based on an operation cost model; S12,constructing an objective function based on an environment cost model; S13, constructing an objective function based on the system reliability model; S2, analyzing optimization control constraint conditions of the regional comprehensive energy system; S21, energy balance constraint analysis; S22, performing energy balance constraint analysis; And S23, system operation constraint. The control method aims at achieving the purposes that the total operation cost of the system is lowest, and reliability and system emission reduction rate are highest.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
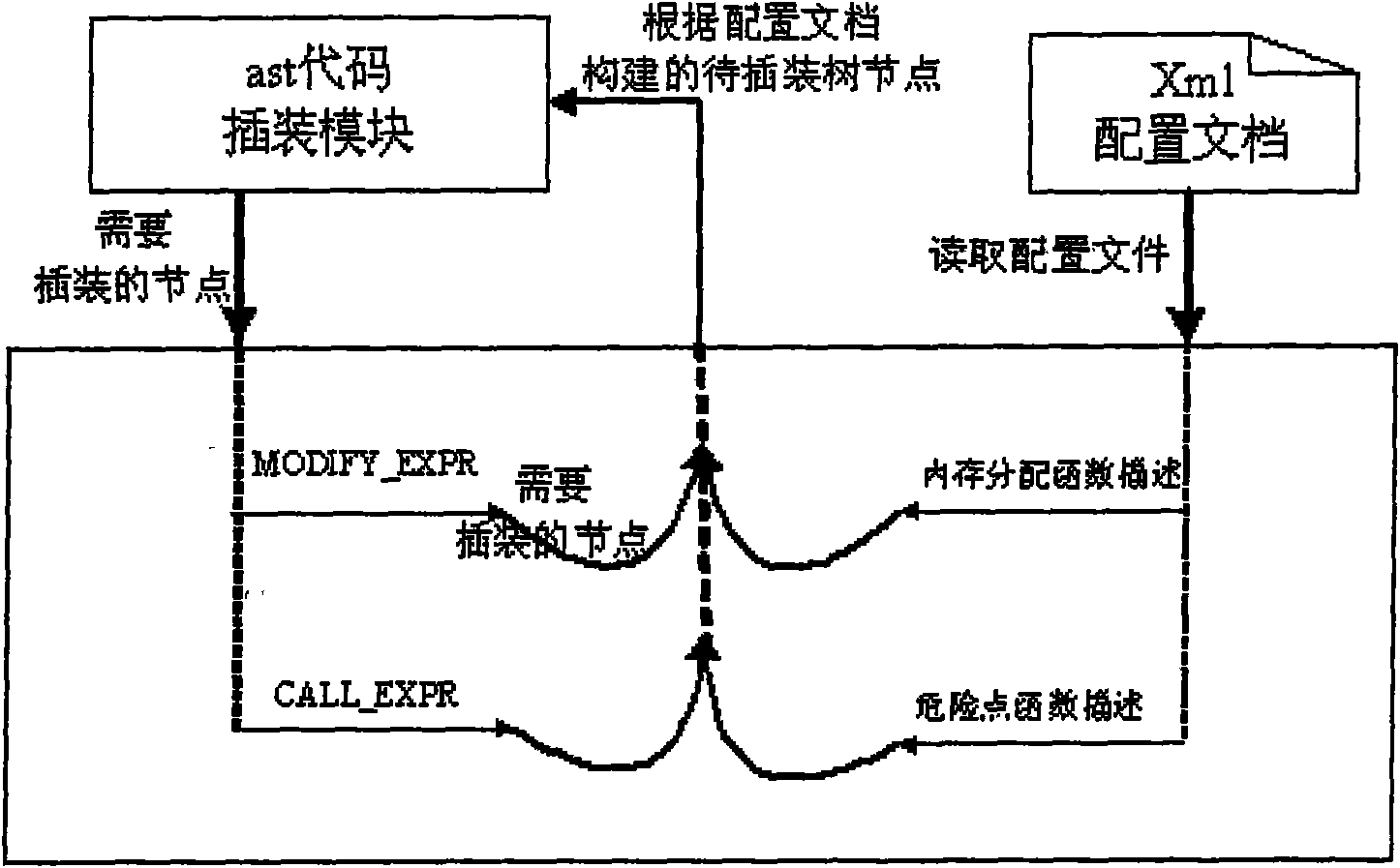
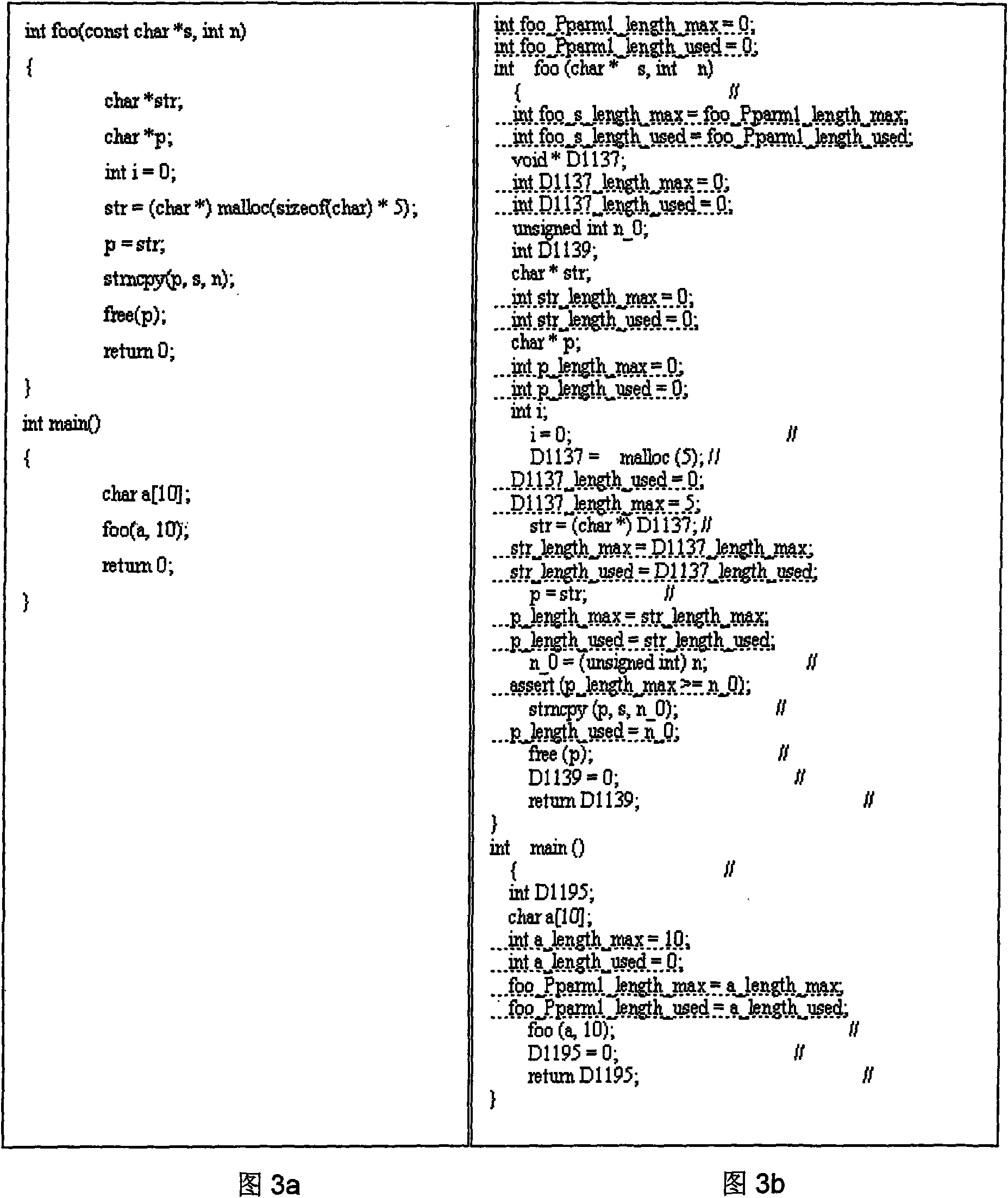
Method for detecting code security hole based on constraint analysis and model checking
The invention relates to a method for detecting a code security hole based on constraint analysis and model checking, which can extract the source code of a C program in a constraint way and detect the security hole of the program with the model checking. The main content comprises the following steps: buffer attribute information which is involved in the source code of the C program is extracted with a constraint analysis technology; the corresponding ASSERT sentence information of attribute generation, attribute transmission and attribute constraint is inserted into variable declaration, variable assignment and function call site with the buffer attribute information; the inserted code can be taken as the input of the model checking to judge whether the program is accessible, find whether the dangerous points in the program really has an accessible path and finally find the security hole in the source code. Currently, independent model checking can not detect the security hole of the buffer and the like, the method combines the static detecting technology of the constraint analysis with the model detecting technology to realize the detection of the security hole of the buffer overflow and the like, wherein, the detecting precision of the method is higher than that of the general static detecting technology. By extracting the other dangerous function information of the source code, corresponding inserting process is carried out. The invention also can detect the security holes such as formative character string, code injection, privilege escalation, etc.
Owner:BEIHANG UNIV
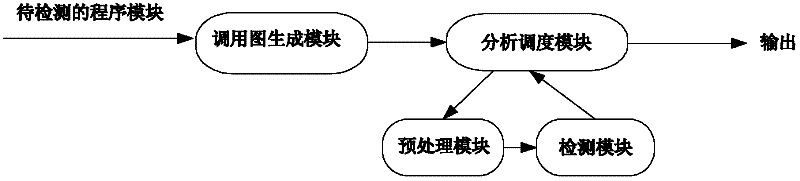
Parallelization security hole detecting method based on function call graph
InactiveCN102567200AEasy to analyzeEasy to detectSoftware testing/debuggingPlatform integrity maintainanceCall graphAccessibility
The invention relates to a parallelization security hole detecting method based on a function call graph, which is characterized in that a function set to be detected is determined by analyzing the function call relation in a C language module, instrumentation and assert analysis are performed for the function set by means of the preprocessing technology, and then security holes of a program are detected by the aid of model checking and the parallelization technology. The method mainly includes the steps: generating the function relation call graph, and determining C function information to be detected by analyzing the function relation call graph; extracting attribute information of a buffer area related to C program source codes by the aid of the constraint analysis technology, and inserting corresponding ASSERT statement information in a variable declaration, an assignment and a function call point by means of the attribute information of the buffer area; and performing accessibility judgment for the instrumented codes, and analyzing whether a dangerous point in the program includes an accessible path to discover the security holes in the source codes or not. The method detects the security holes such as buffer area overflow and the like by combining the constraint analysis static detecting technology, model checking and the parallelization technology, and the detecting precision of the method is higher than that of the general static detecting technology.
Owner:BEIHANG UNIV
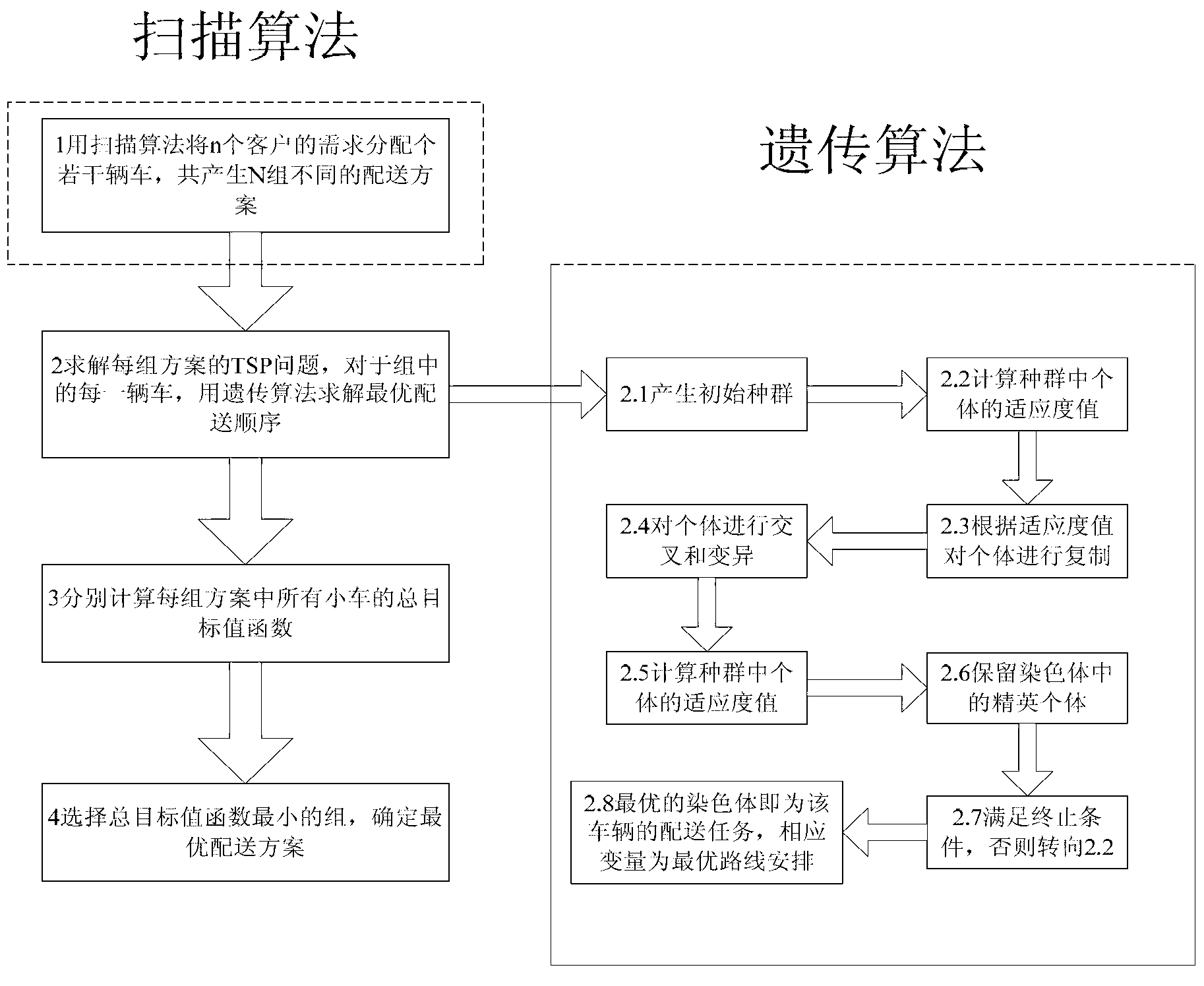
Numerically controlled workshop automatic delivery vehicle scheduling method
ActiveCN103279857ADelivery route optimizationIncrease productivityLogisticsDelivery vehicleGenetic algorithm
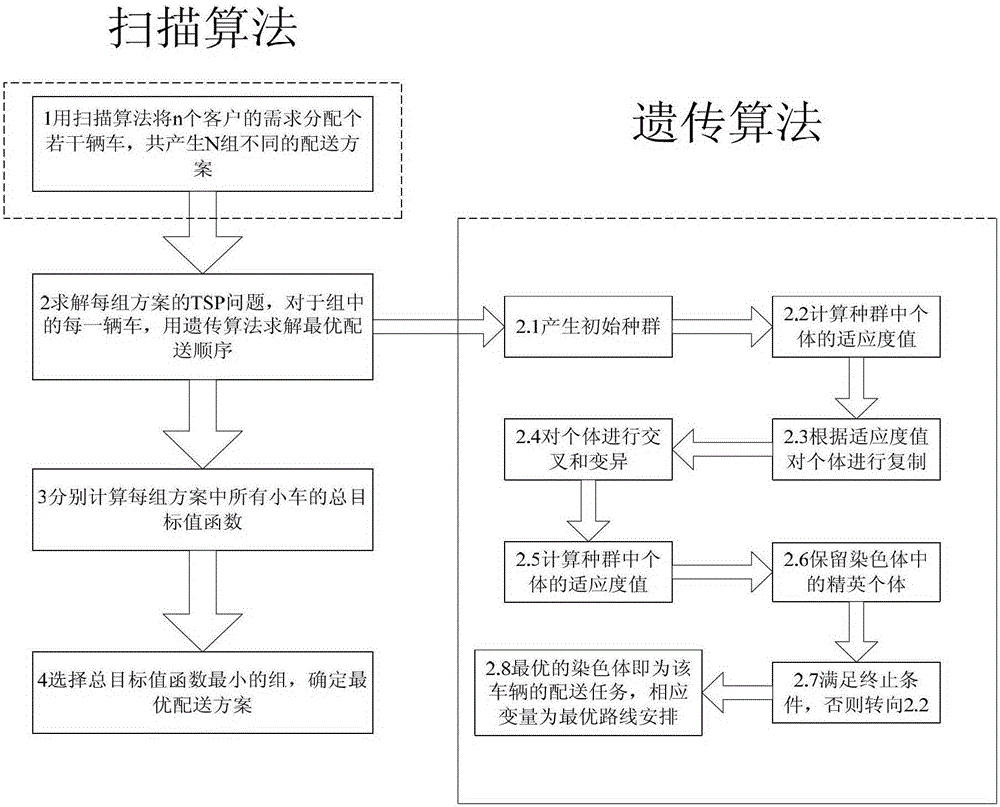
A numerically controlled workshop automatic delivery vehicle scheduling method is characterized in that firstly, on the basis that constraint analysis and mathematical modeling are conducted on the vehicle scheduling problem in a numerically controlled workshop, an original matrix scanning method is adopted to distribute distribution tasks to vehicles, initial population of a subsequent genetic algorithm is obviously optimized, then, an optimal distribution sequence of a single vehicle is solved through the genetic algorithm, aiming at driving characteristics of distribution vehicles in the numerically controlled workshop, practical driving distances of the vehicles are calculated through an original coordinate addition-subtraction method with directions, optimal distribution time of the vehicles are obtained through a golden section method based on the prior fact, local convergence of the algorithm are avoided through an elitism retention strategy, and therefore an ideal vehicle scheduling optimizing scheme is obtained. According to the numerically controlled workshop automatic delivery vehicle scheduling method, the problem that an existing vehicle scheduling algorithm is low in efficiency due to specific distribution of user points and the special distribution process in the numerically controlled workshop is solved, and the algorithm is efficient and feasible.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Multi-task-convolutional-neural-network-based detection method of fake-licensed car
InactiveCN108460328AHigh speedReduce processing stepsCharacter and pattern recognitionNeural architecturesEngineeringTime space
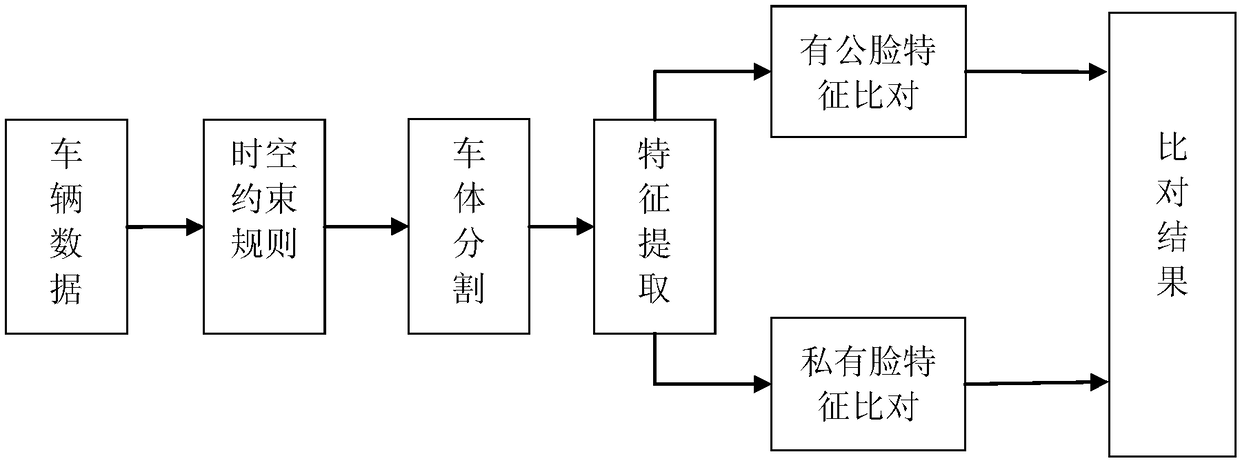
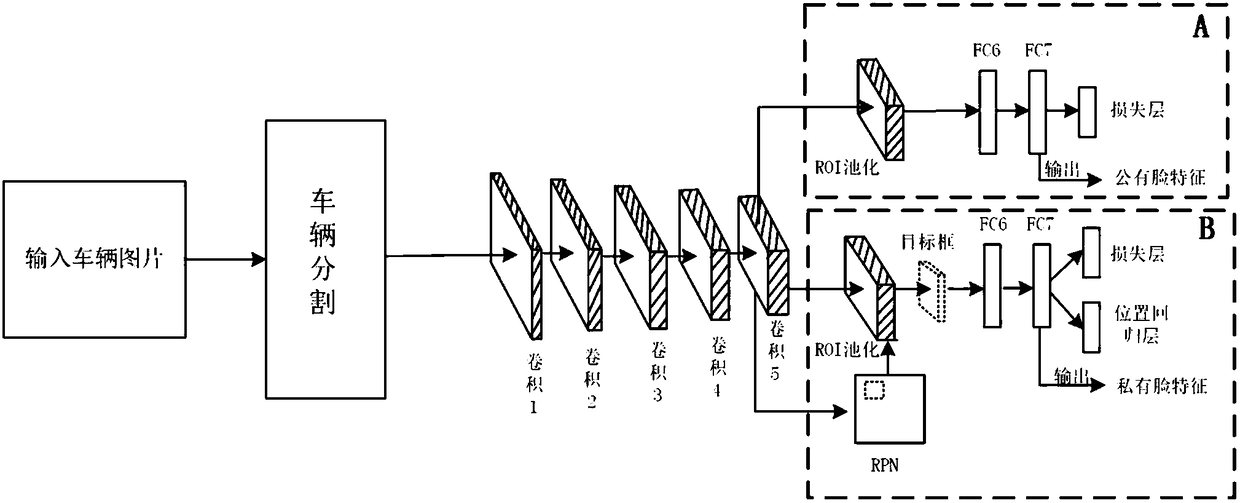
Provided in the invention is a multi-task-convolutional-neural-network-based detection method of a fake-licensed car. A suspected fake-licensed car is obtained by using time-space constraints; a car front-face part image is located and segmented by using Faster R-CNN; features of car public face parts being basic features of the car of the suspected fake-licensed car are compared; and then subtlefeatures of a car private face part being a car inspection identifier of the high-imitation fake-licensed car are detected and compared. Therefore, problems that low accuracy and difficult problem carlocking are caused by only utilization of the time-space constraint analysis as well as the high-imitation fake-licensed car can not be identified purely based on the car public face are solved; andthe accuracy and efficiency are high. The multi-task-convolutional-neural-network-based detection method is suitable for high-imitation fake-licensed cars.
Owner:ZHEJIANG UNIV OF TECH
Method for simplifying numerical map settlement place polygon by utilizing parametric design model
InactiveCN101930483AIncrease productivityGood effectMaps/plans/chartsSpecial data processing applicationsGraphicsAlgorithm
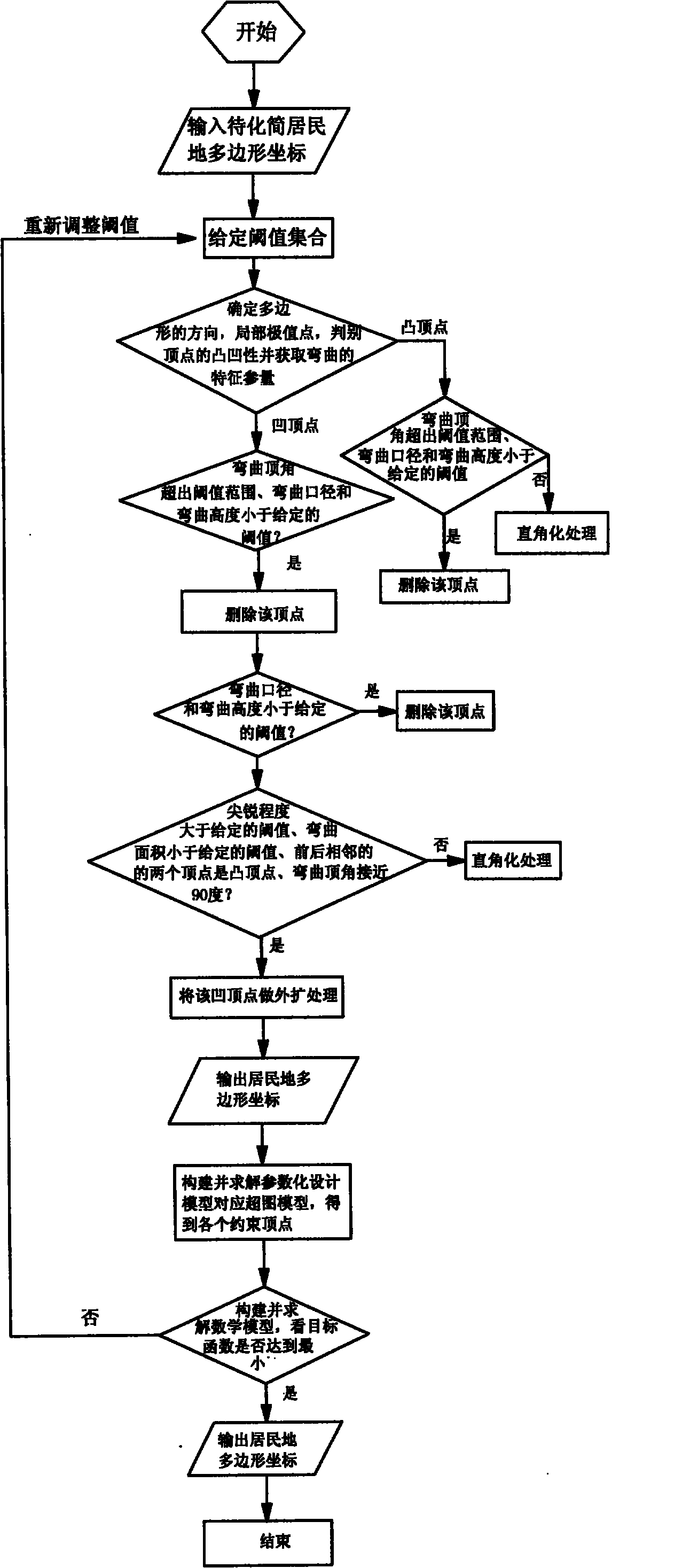
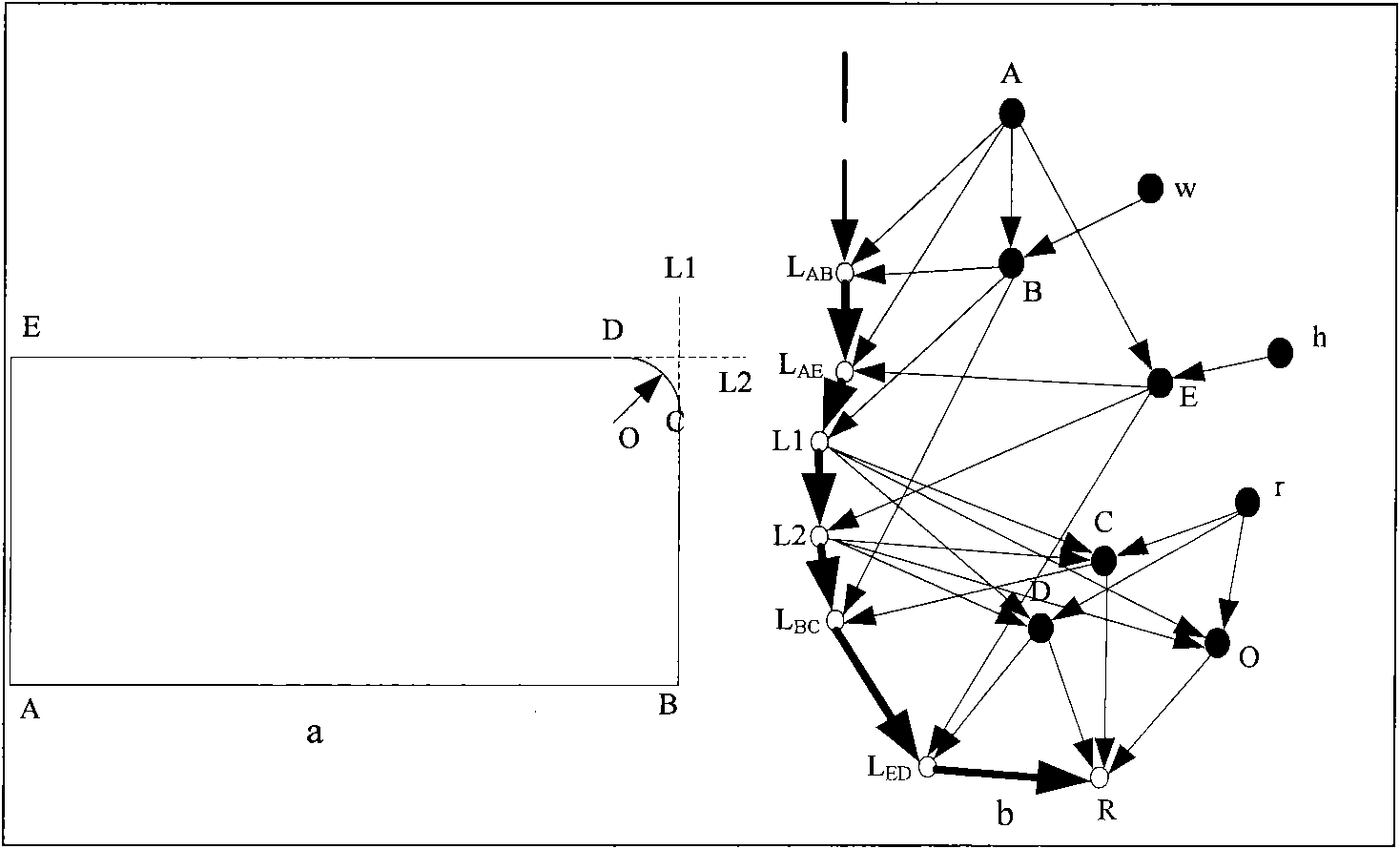
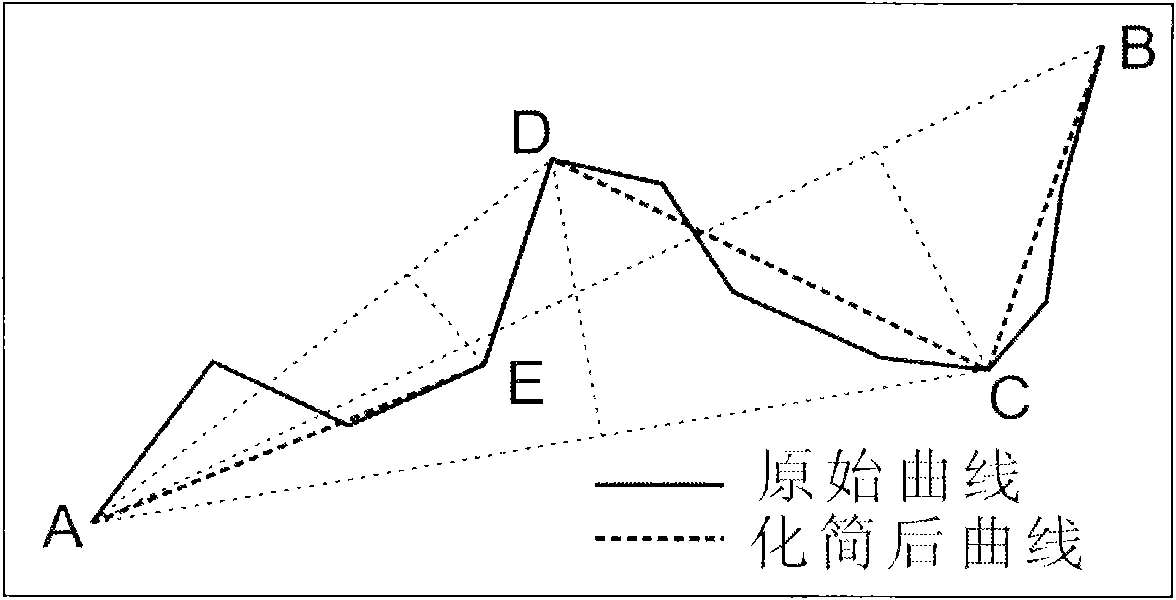
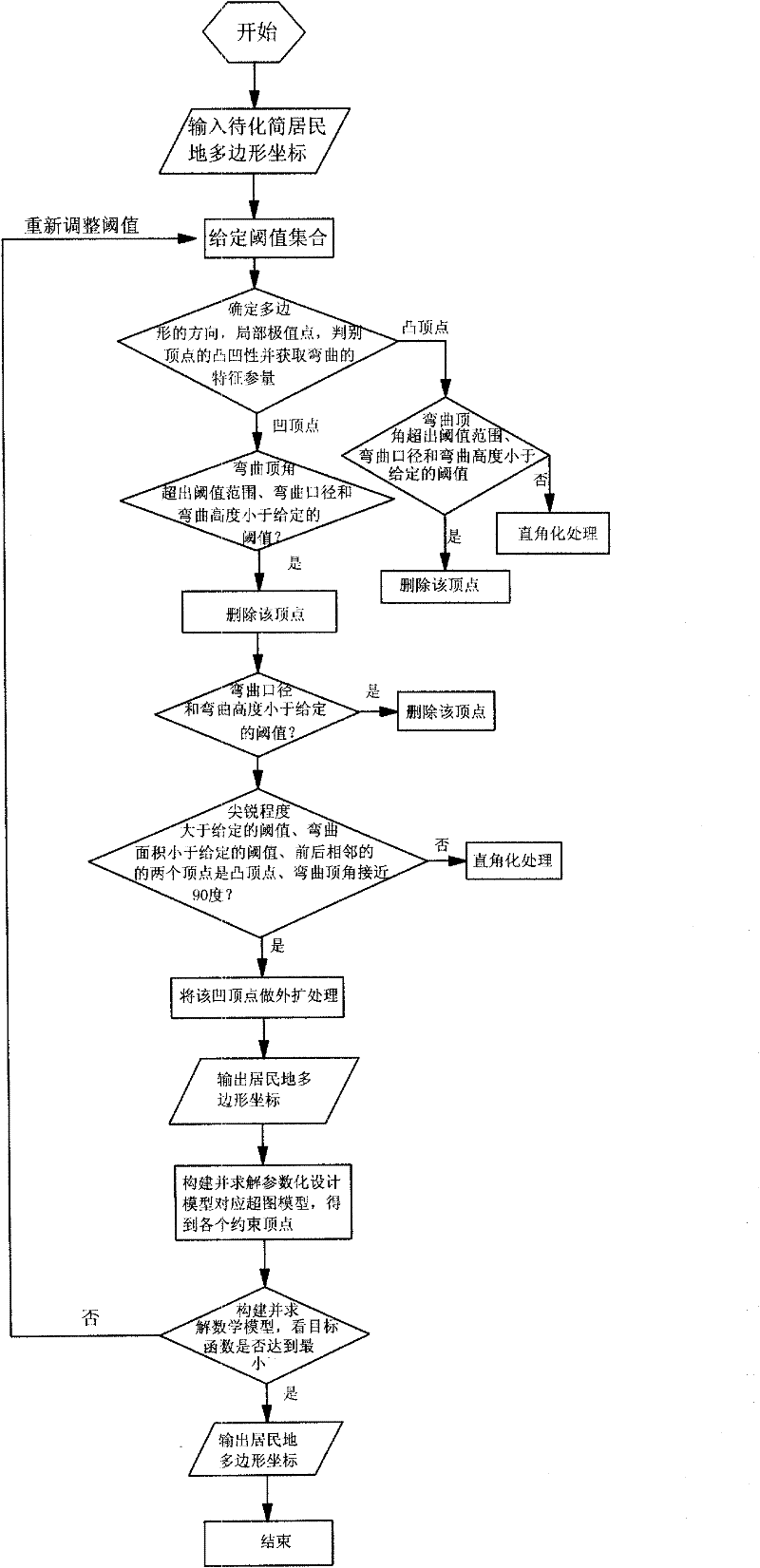
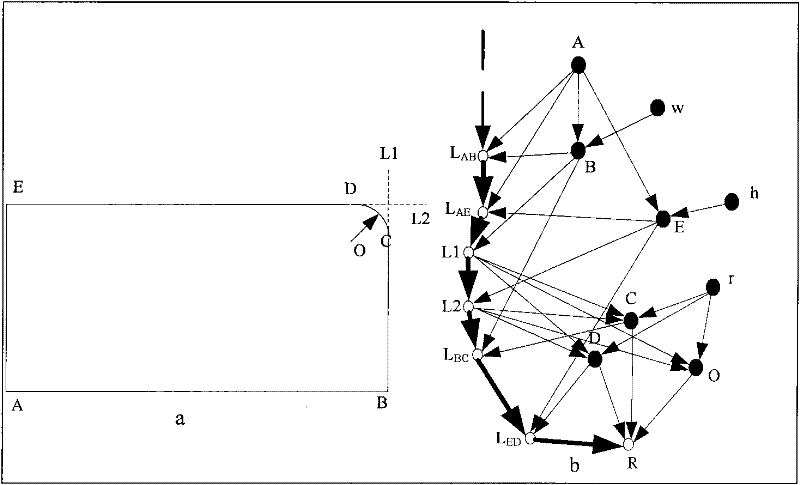
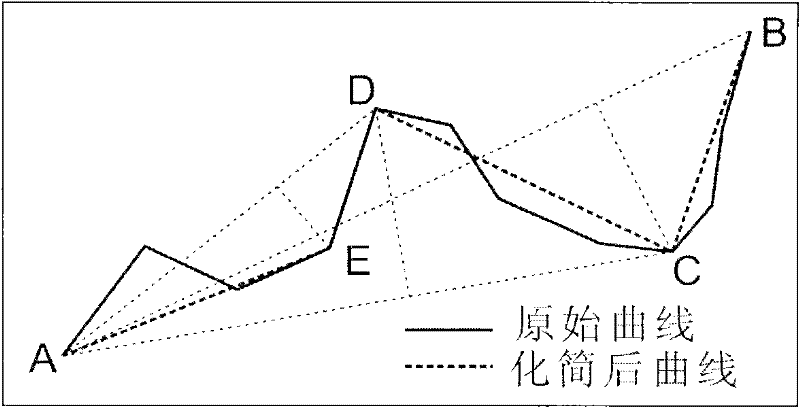
The invention relates to a method for simplifying a numerical map settlement place polygon by utilizing a parametric design model and effectively solves the problem of enabling the whole simplification process to accurate and quantitative, and ensuring good simplification effect. The method comprises the following steps: presetting the numeric area of the target function corresponding to the initial threshold value integrated digital model and simplification result quality and contribution weight; identifying the graph feature of the settlement place polygon, using coordinate monotonicity to identify local extremum point and basic bending, using adjacent edge vector multiplication cross to identify concavity of direction and culmination of the settlement place polygon; using gradual imaging simplification method to carry out primary simplification on the polygon and building the corresponding supergraph model to obtain the value of corresponding target culmination of each constrained edge in the model; using a mathematical model corresponding to the parametric design model to carry out constrained analysis on the constrained culmination, and constantly repeating iteration to obtain the final result. With coordinate data output by the computer, various settlement places can be simplified, and production efficiency and product quality of the numerical map can be improved.
Owner:THE PLA INFORMATION ENG UNIV
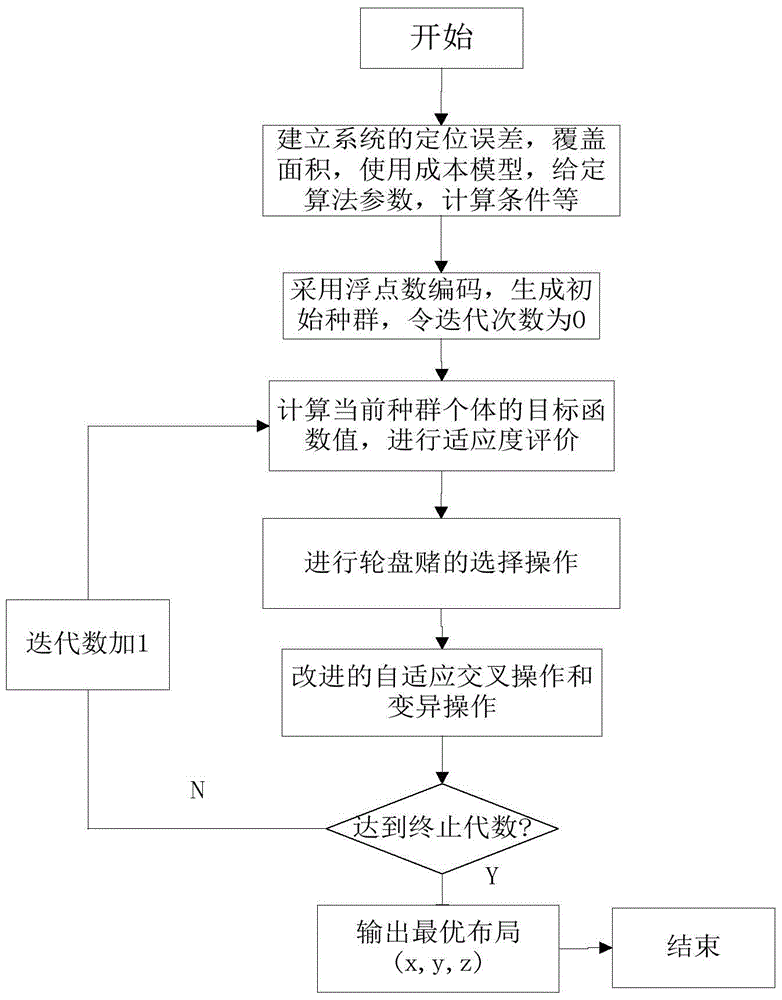
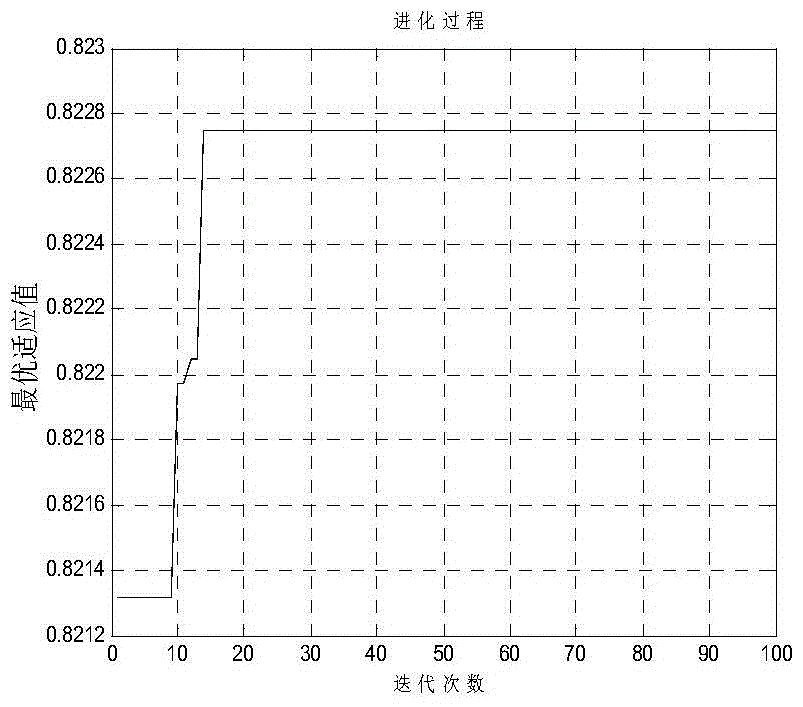
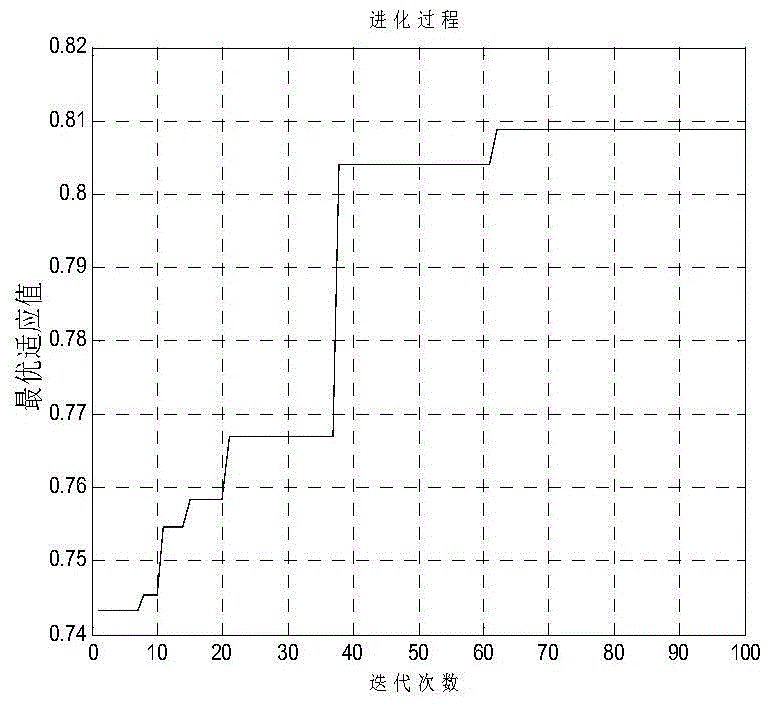
Survey station layout intelligent optimization method of spatial measurement positioning system
ActiveCN105069240AImprove global convergenceFast convergenceSpecial data processing applicationsNetwork measurementEngineering
A survey station optimization deployment problem is one of important problems in use of a spatial measurement positioning system. The present invention provides a survey station layout intelligent optimization method of a spatial measurement positioning system, so that an optimized survey station layout can fully cover a tested area under certain costs and a requirement of measurement accuracy can be met. According to the present invention, a proper positioning error model is established from three aspects of constraint analysis, optimization objective, and optimization means, a multi-goal optimizing function is defined, and survey station layout optimization of the spatial measurement positioning system is implemented by using a practical intelligent optimization algorithm. According to the survey station layout intelligent optimization method of a spatial measurement positioning system, a survey station network optimization deployment problem of the spatial measurement positioning system in an engineering application is effectively resolved. As a quantity of survey stations increases, the method has good expansibility, provides a new method for a multi-station networking measurement layout optimization problem based on an angle intersection principle, and has important theoretical value and practical significance.
Owner:LINGYUN GROUP WUHAN
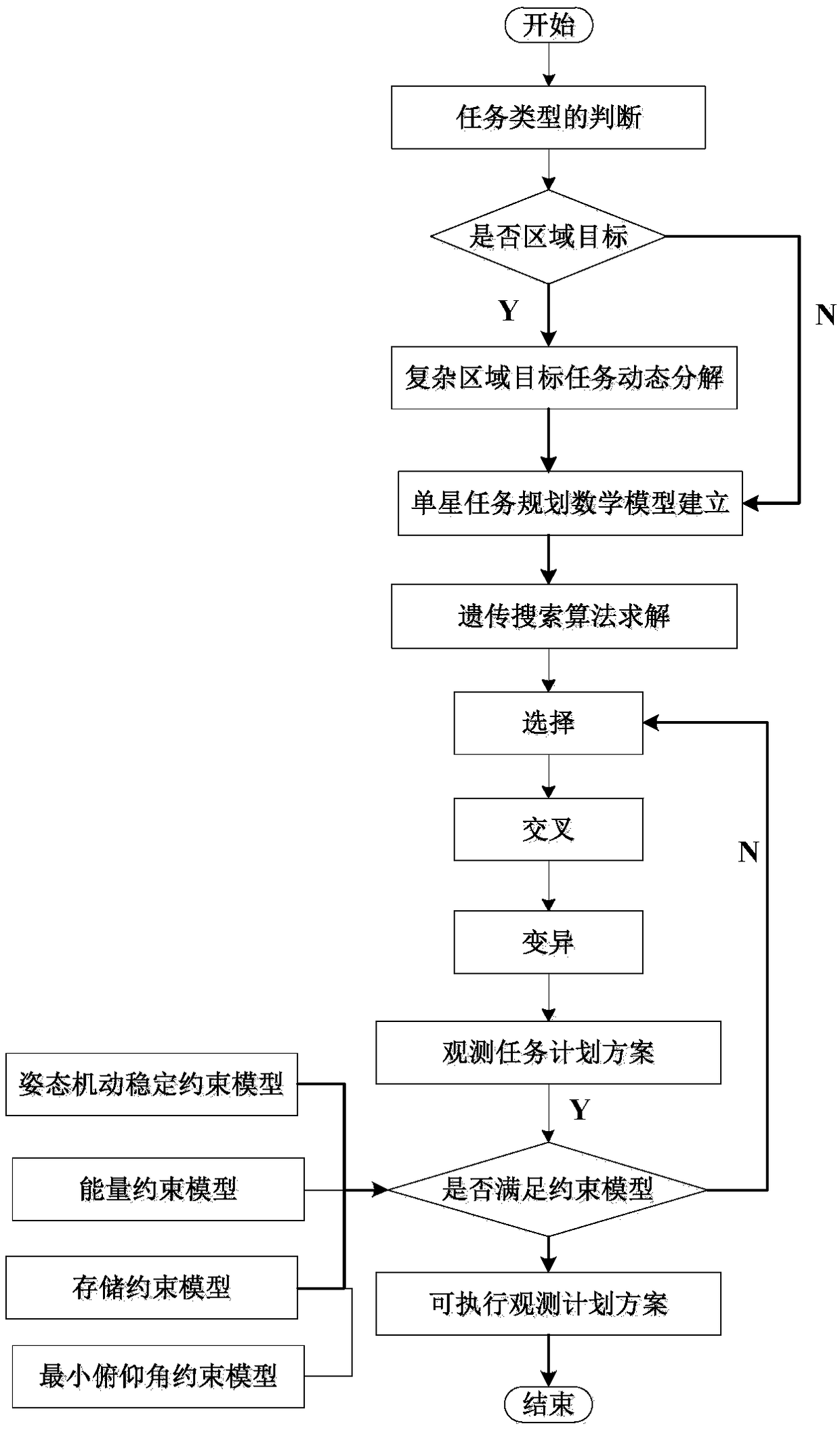
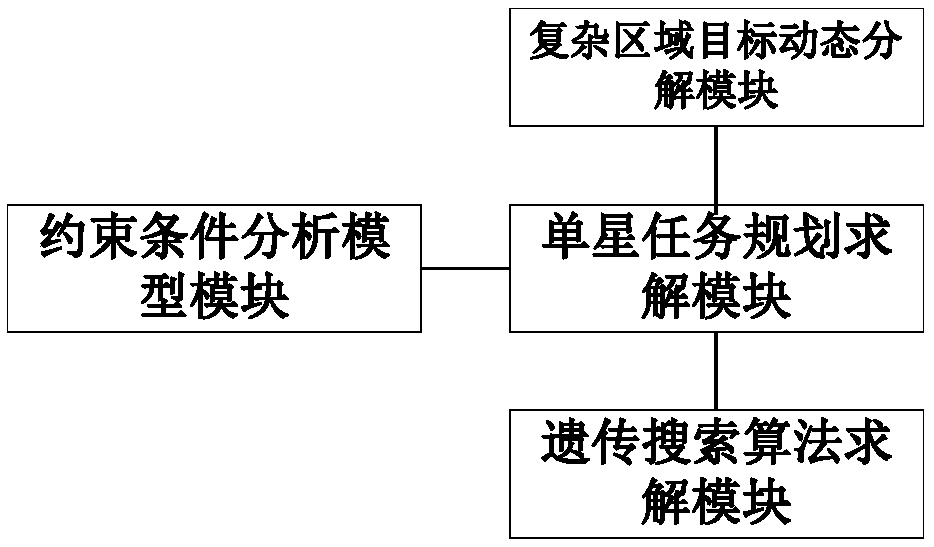
Agile satellite task planning and scheduling modeling method based on genetic optimization
InactiveCN109492834AIncrease profitSolve the problem of execution timelinessForecastingProgram planningMathematical model
The invention provides an agile satellite task planning and scheduling modeling method based on genetic optimization, which comprises the following steps of: dynamically decomposing a to-be-observed complex observation target task area according to an observation demand of a user and a resource condition of a satellite, and generating a meta-task set with a plurality of time windows; constructinga constraint analysis model according to the task constraint, the resource constraint and the relationship between the task constraint and the resource constraint, wherein the constraint analysis model comprises a satellite energy constraint model, a storage constraint model, a minimum pitch angle constraint model and an attitude maneuver stability constraint model; establishing a single-satellitetask planning mathematical model according to the multi-time window element task set; and utilizing a genetic search algorithm to optimize and solve the single-satellite task planning mathematical model, judging whether the established constraint analysis model is met or not, and generating a final executable observation plan scheme. According to the method, the task observation plan scheme meeting the maximum objective function and different constraint analysis can be generated, satellite resources are effectively utilized, and the task planning efficiency is improved.
Owner:SPACE STAR TECH CO LTD
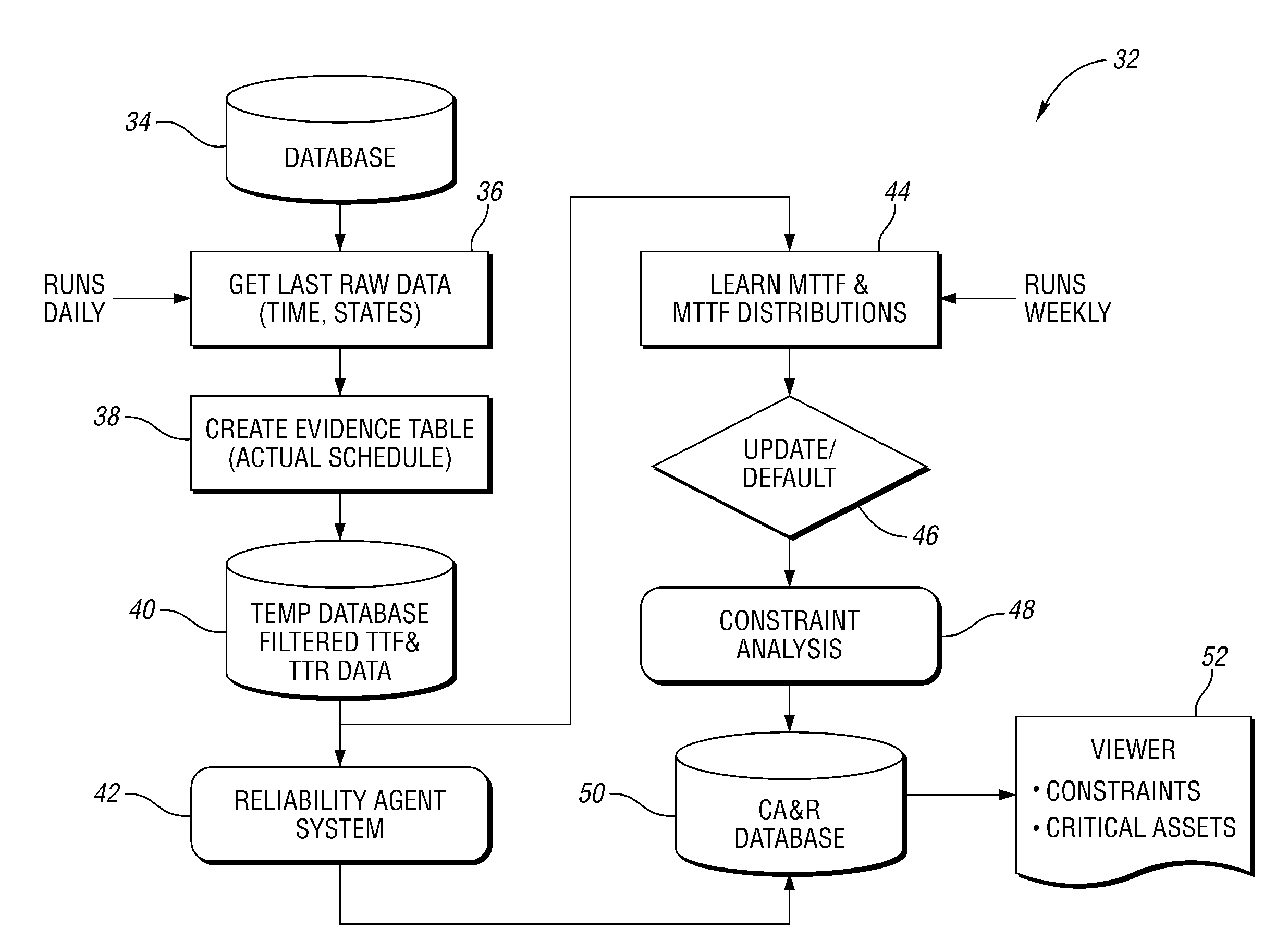
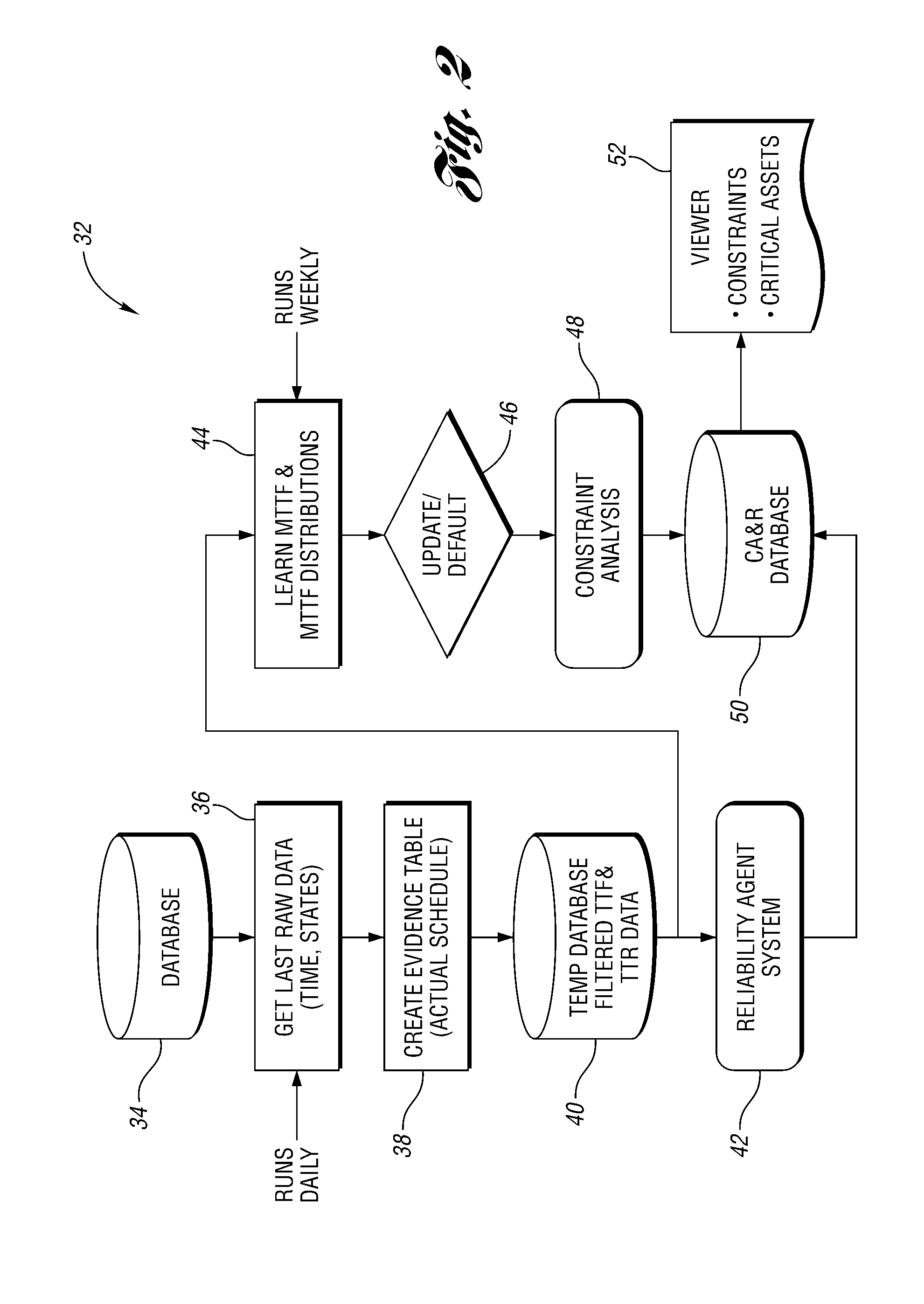
Method for analyzing operation of a machine
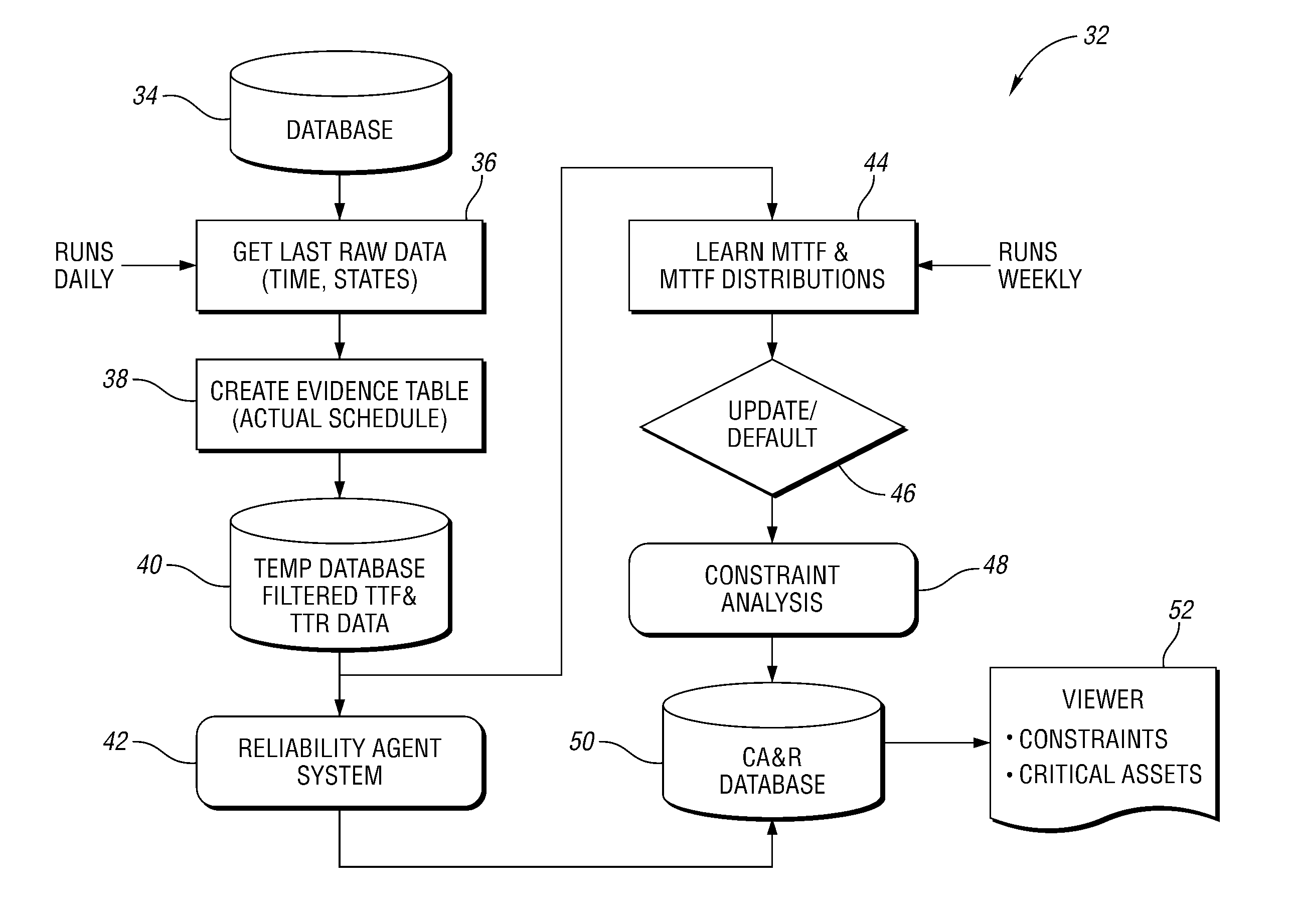
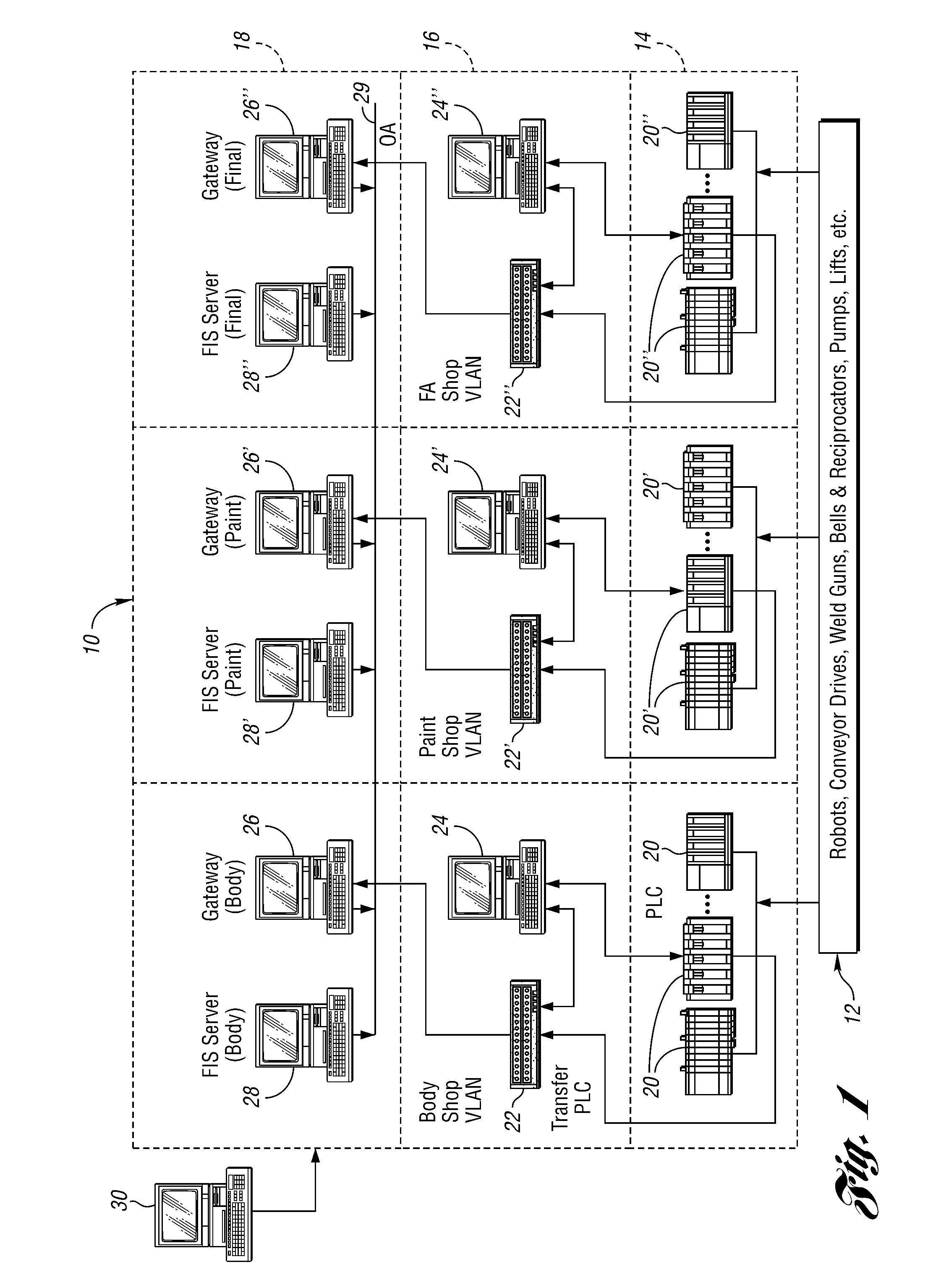
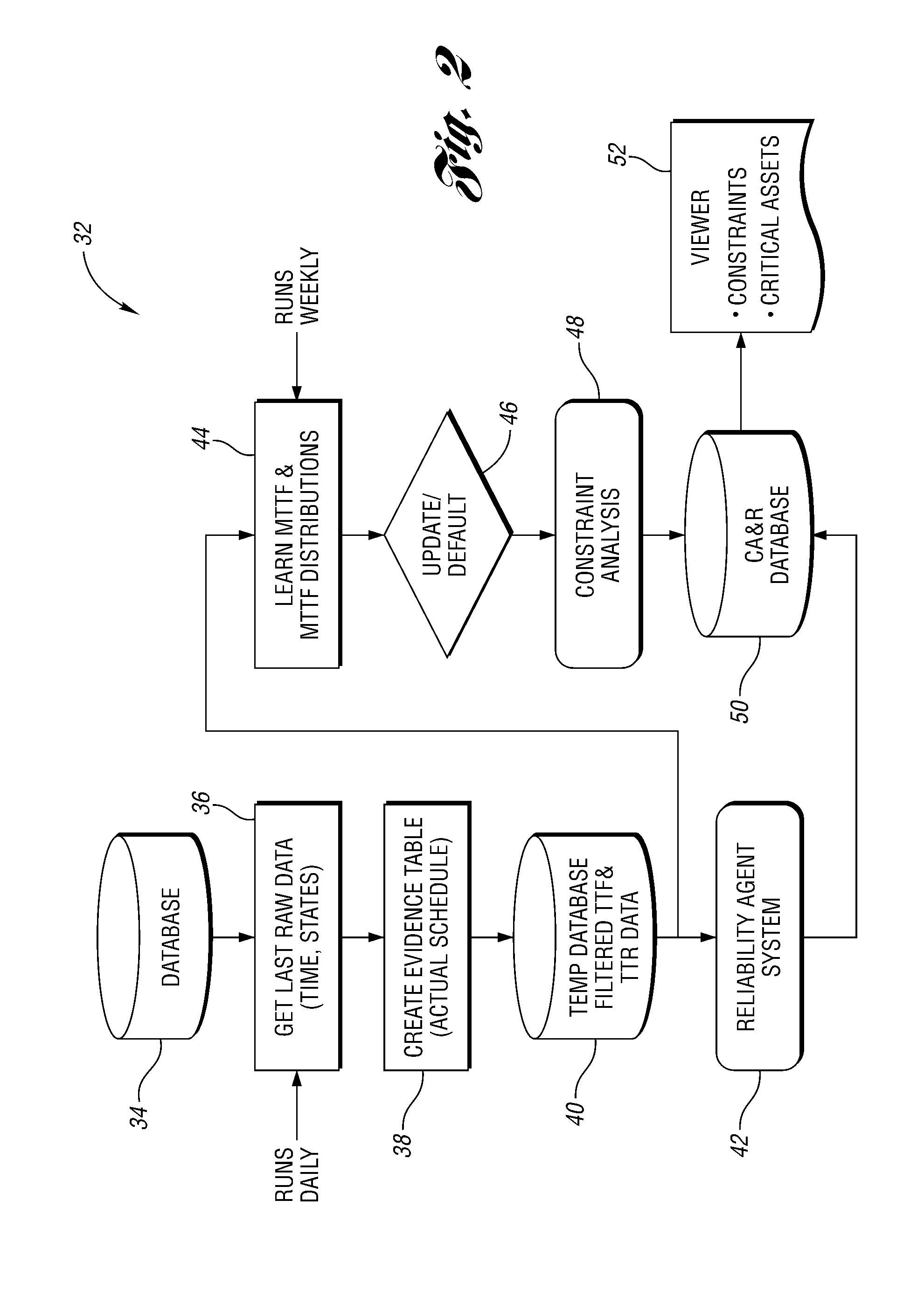
InactiveUS20080188973A1Improve accuracyAvoid inaccuraciesTesting/monitoring control systemsDigital computer detailsData setMutually exclusive events
A constraint analysis and reliability agent executes a method for analyzing operation of a manufacturing asset, and includes the steps of collecting operation data for a machine over a plurality of predetermined time periods. The operation data includes a plurality of mutually exclusive events that describe operation of the machine. For each of the predetermined time periods, it is determined whether the machine is in an “ON” or an “OFF” state. Data for the “OFF” states is removed from the collected data to generate a filtered data set. Reliability information is then generated based, at least in part, on the filtered data set. This facilitates predictions of future machine operation.
Owner:FORD MOTOR CO
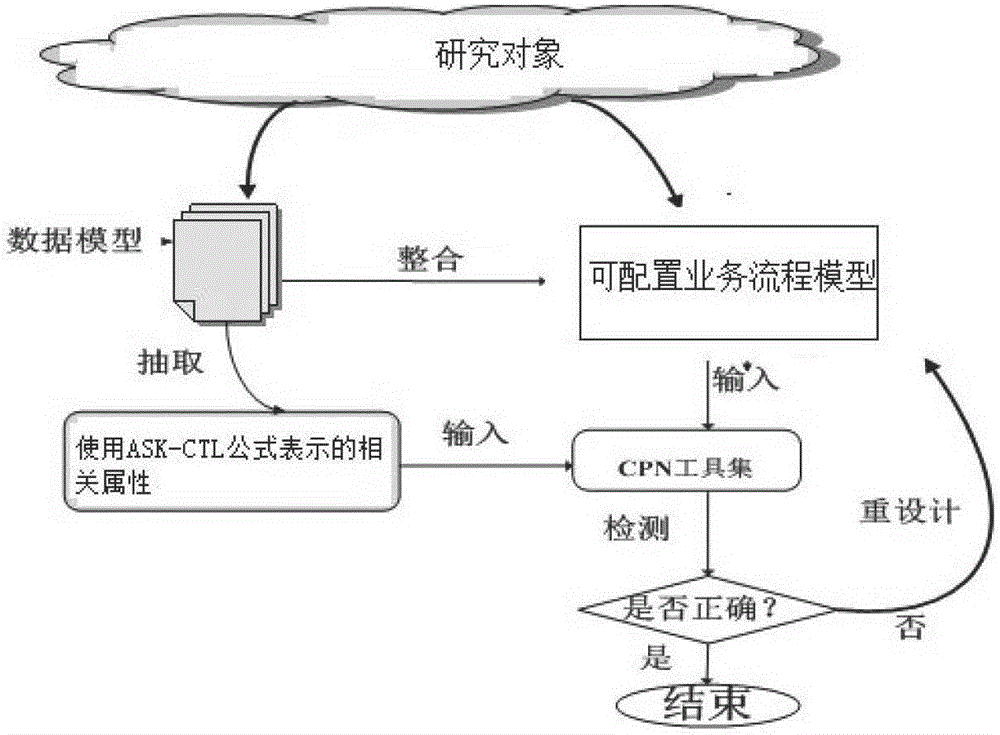
Configurable business process analyzing method based on data flow constraint
InactiveCN106169111ASolve the problem of data flow constraint relationshipAvoiding Unusual Behavior of Data SemanticsResourcesPersonalizationValidation methods
The invention discloses a configurable business process analysis method based on data flow constraints. First, according to a data flow model between related activities in a specific field, the execution relationship between the activities is determined, and a CPN-based business process model is designed; Then, the data flow model and the business process model are combined to form a business process model reflecting the data flow relationship, which is converted into a configurable business process model according to the needs and guidance of the field; and then the configurable business is analyzed and verified according to the personalized needs in the field. The correctness of the data flow constraint of the process; finally, the configurable business process model can be adjusted according to the verification result, so that the business process can maintain the correctness of the design during the configuration process. The method of the present invention proposes the data flow constraint of the configurable business process model The analysis and verification method effectively solves the data flow constraint relationship in business process variability management and avoids abnormal behavior of data semantics in the process of business process configuration.
Owner:TONGREN UNIV
Novel photovoltaic group string online fault diagnosis system and method in integrated inverter scheme
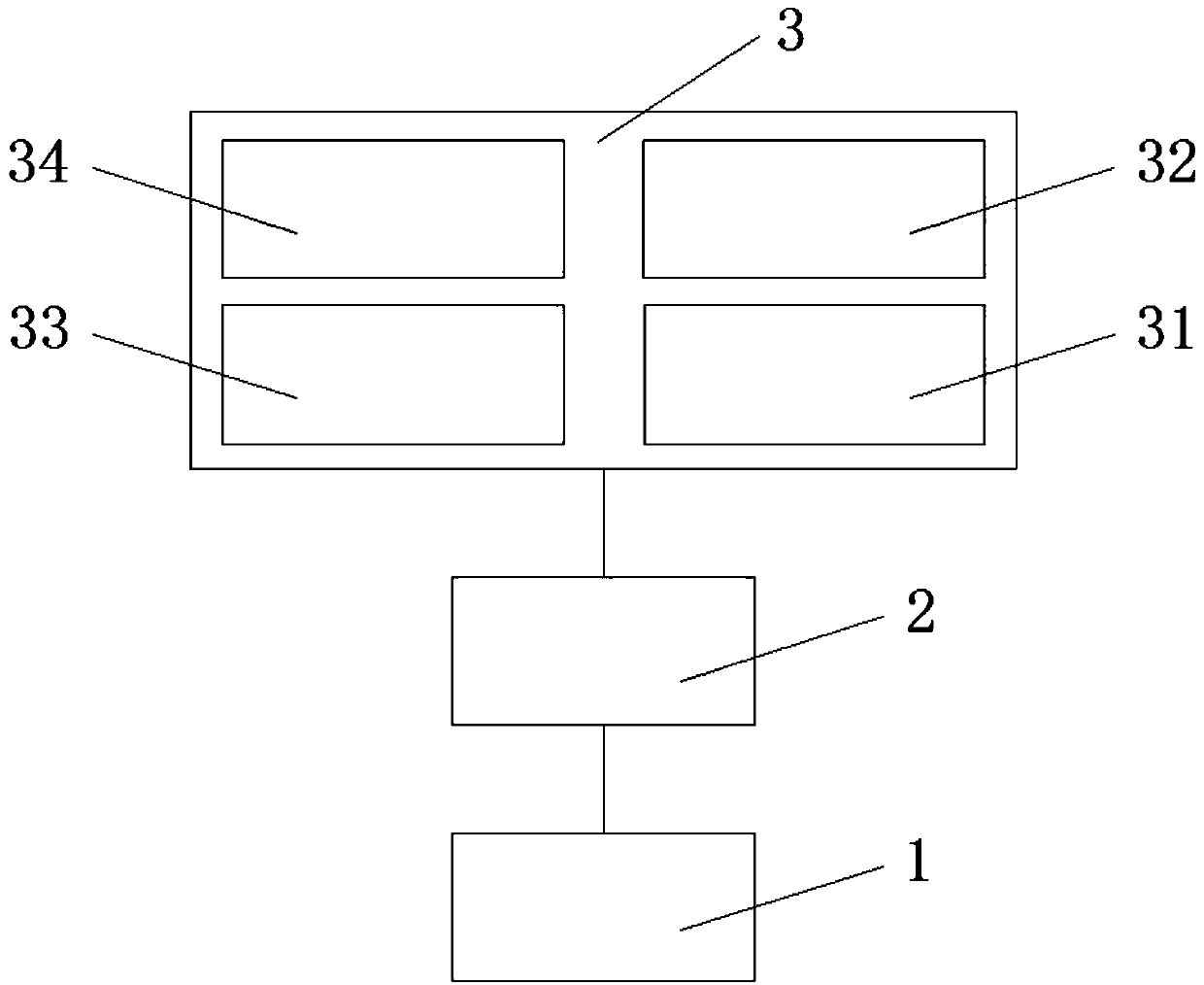
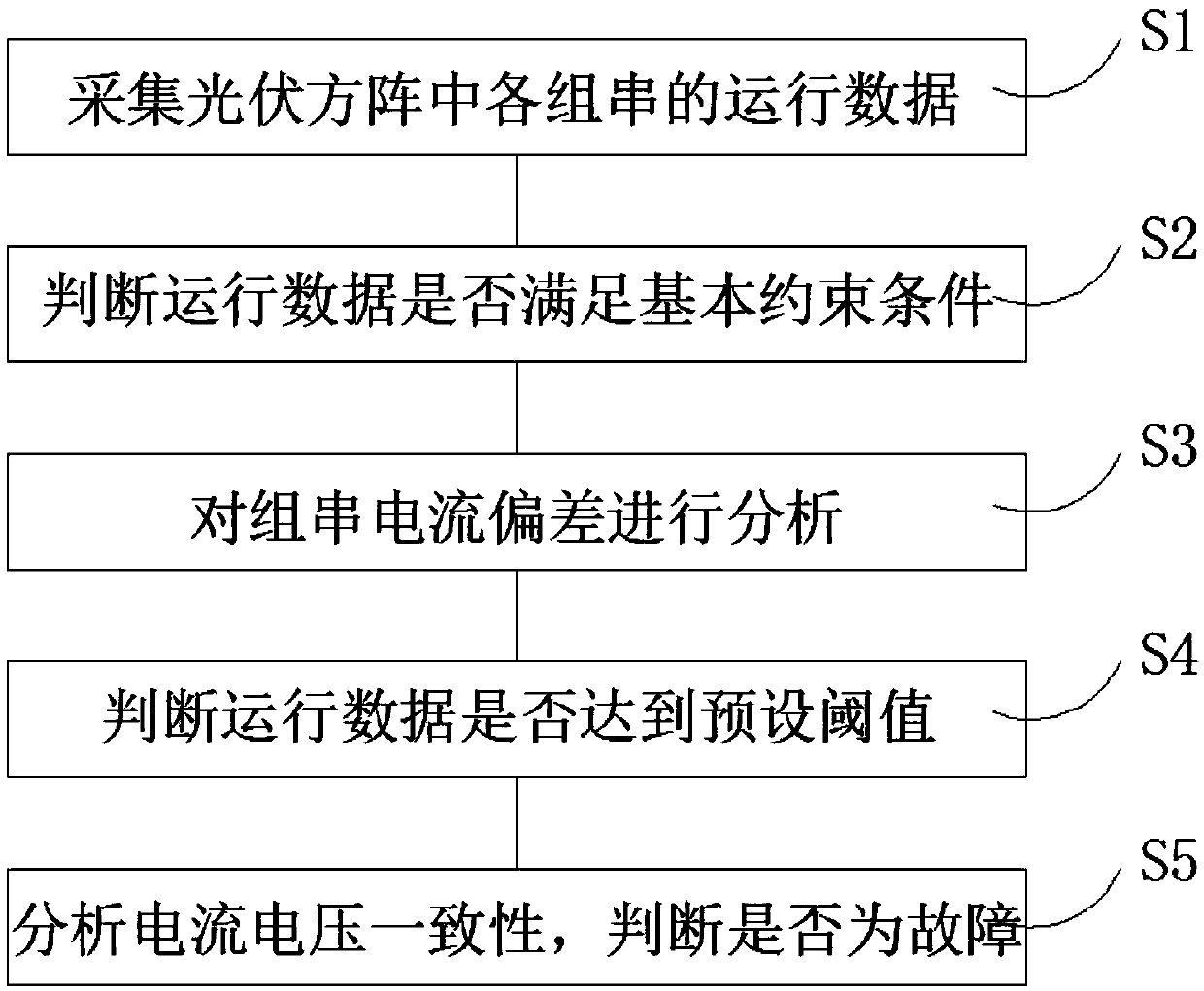
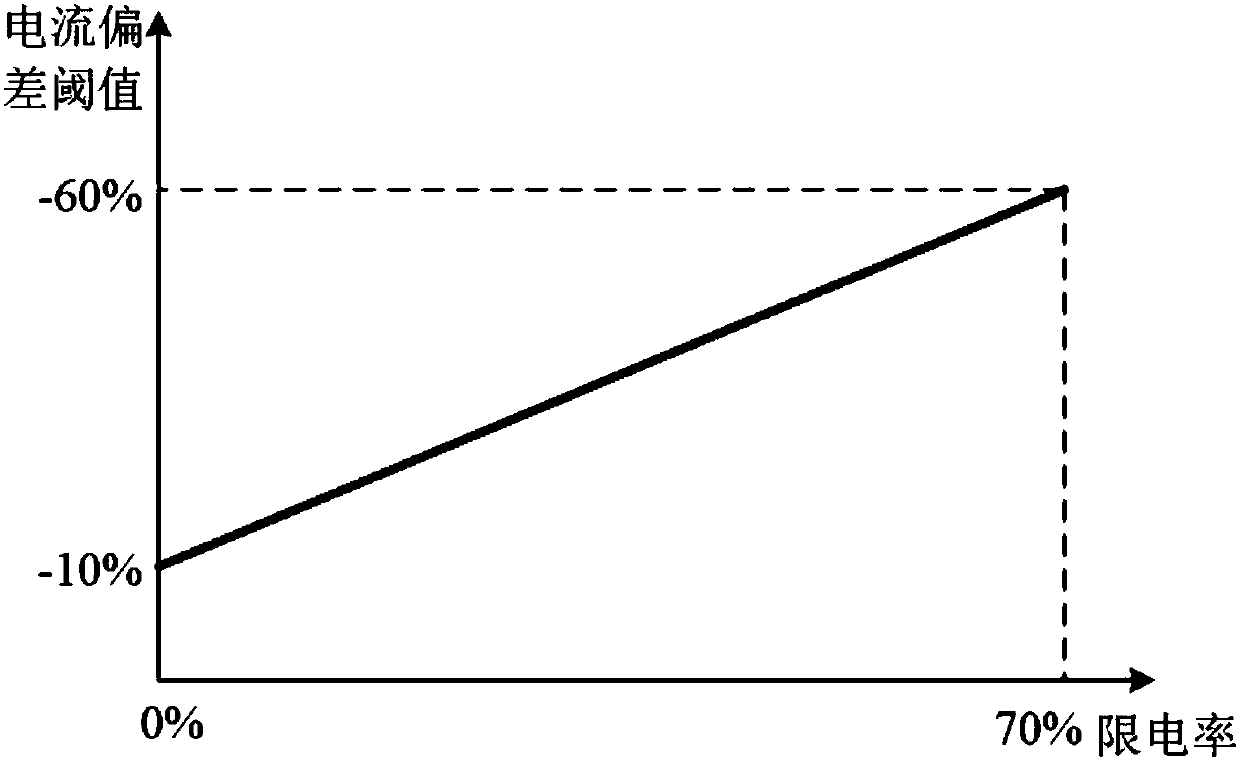
PendingCN107634719AHigh sensitivityReduce false alarm ratePhotovoltaic monitoringPhotovoltaic energy generationComputer moduleEngineering
The invention discloses a novel photovoltaic group string online fault diagnosis system in an integrated inverter scheme. The system comprises a collection module, a storage module and an analysis module, wherein the analysis module comprises a basic constraint analysis module, a current deviation analysis module, a threshold value analysis module and a voltage-current deviation consistency analysis module. The invention also discloses a novel photovoltaic group string online fault diagnosis system in the integrated inverter scheme. The method comprises the following steps: collecting the operating data of each group string; judging whether the operating data meet basic constraint conditions or not; carrying out analysis on the current deviation of each group string; judging whether the operating data of each group string reach preset threshold values or not; analyzing voltage-current deviation consistency and judging group string faults. The method has higher sensitivity and lower false alarm rate for voltage type faults occupying more than 90% of photovoltaic module faults, and the diagnosis result is stable and reliable; the method is simple to implement, small in one-time analysis range, short in inspection cycle, few in occupied resources, low in hardware requirement and convenient for large-scale popularization.
Owner:HUADIAN ELECTRIC POWER SCI INST CO LTD
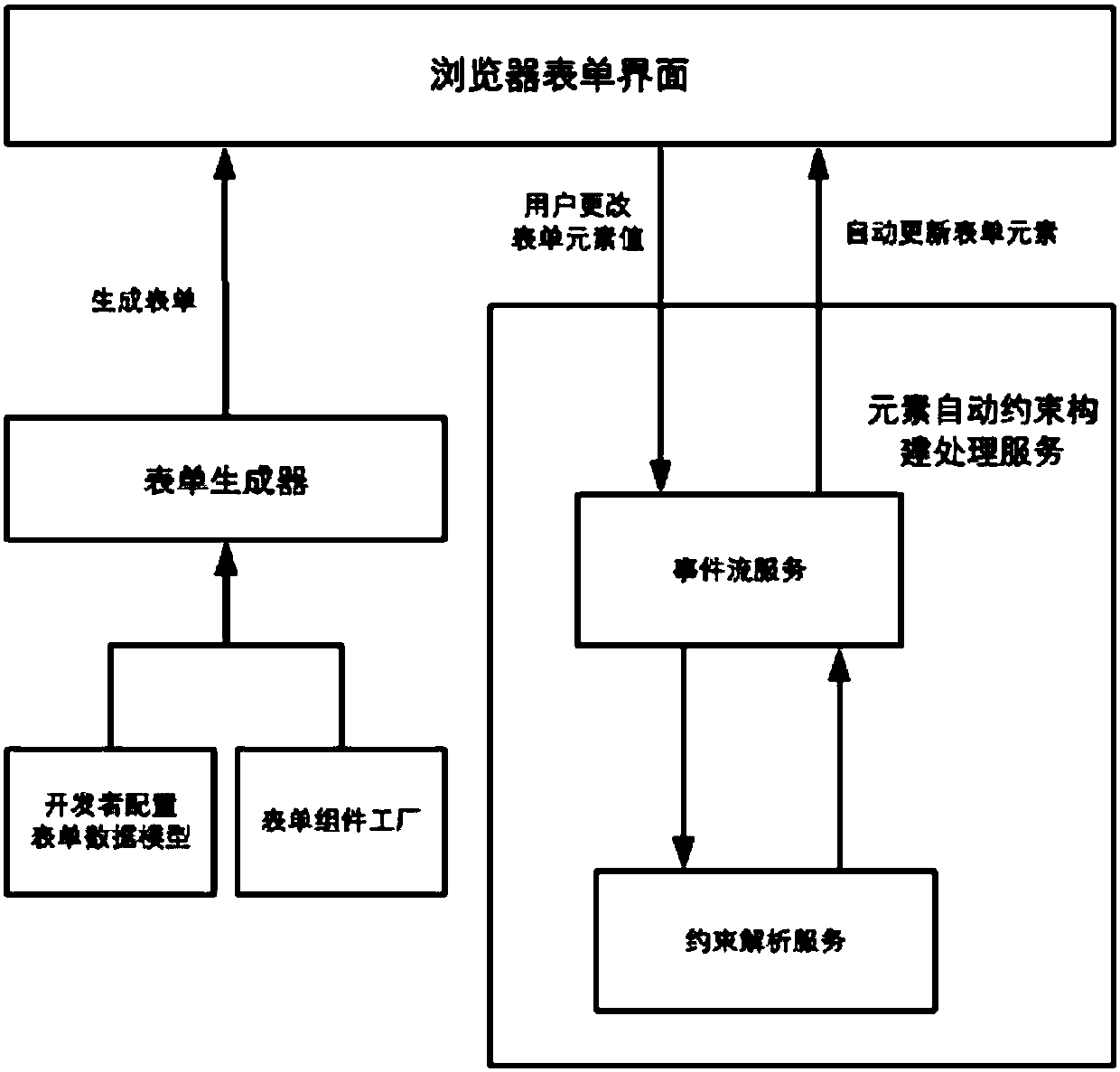
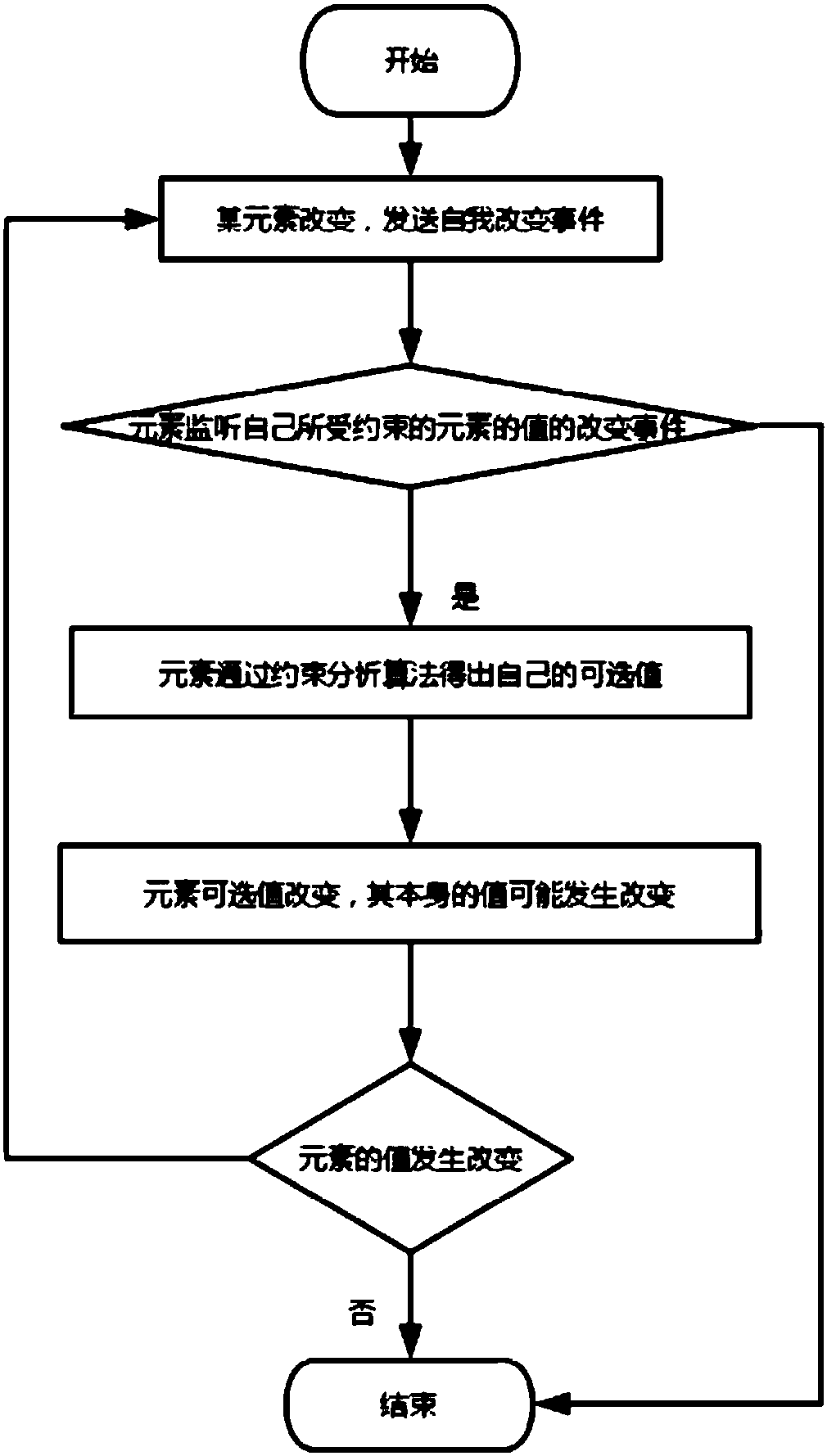
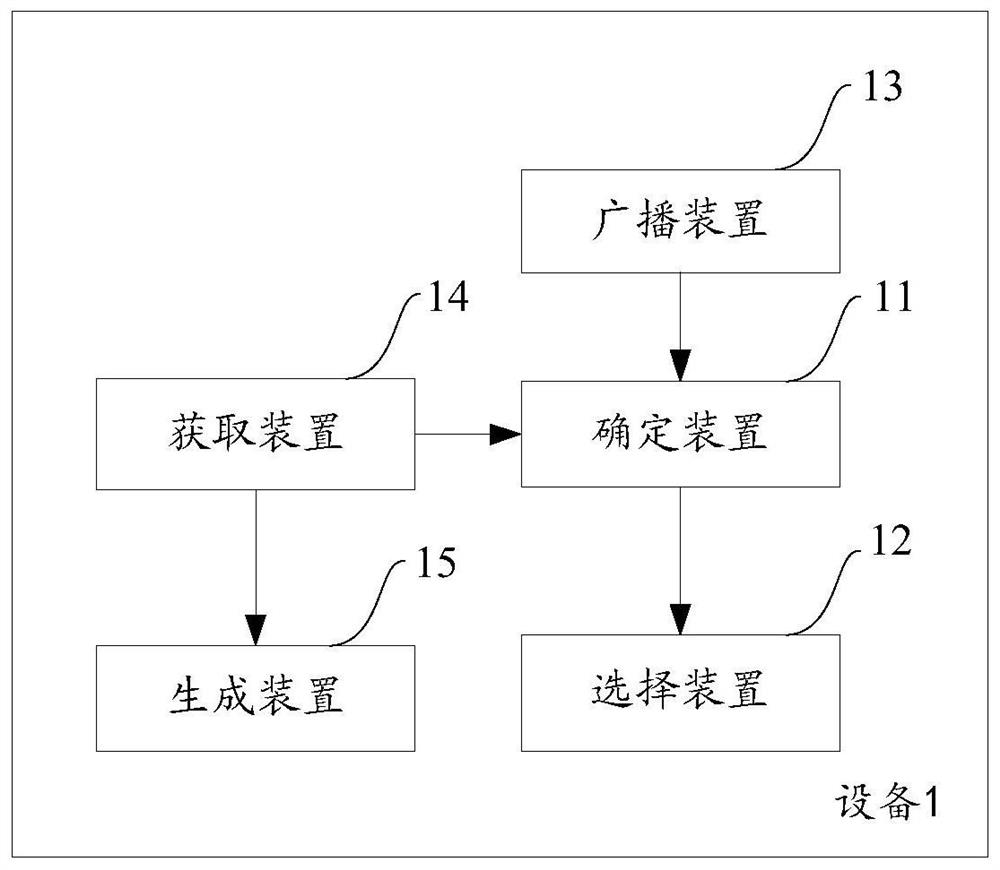
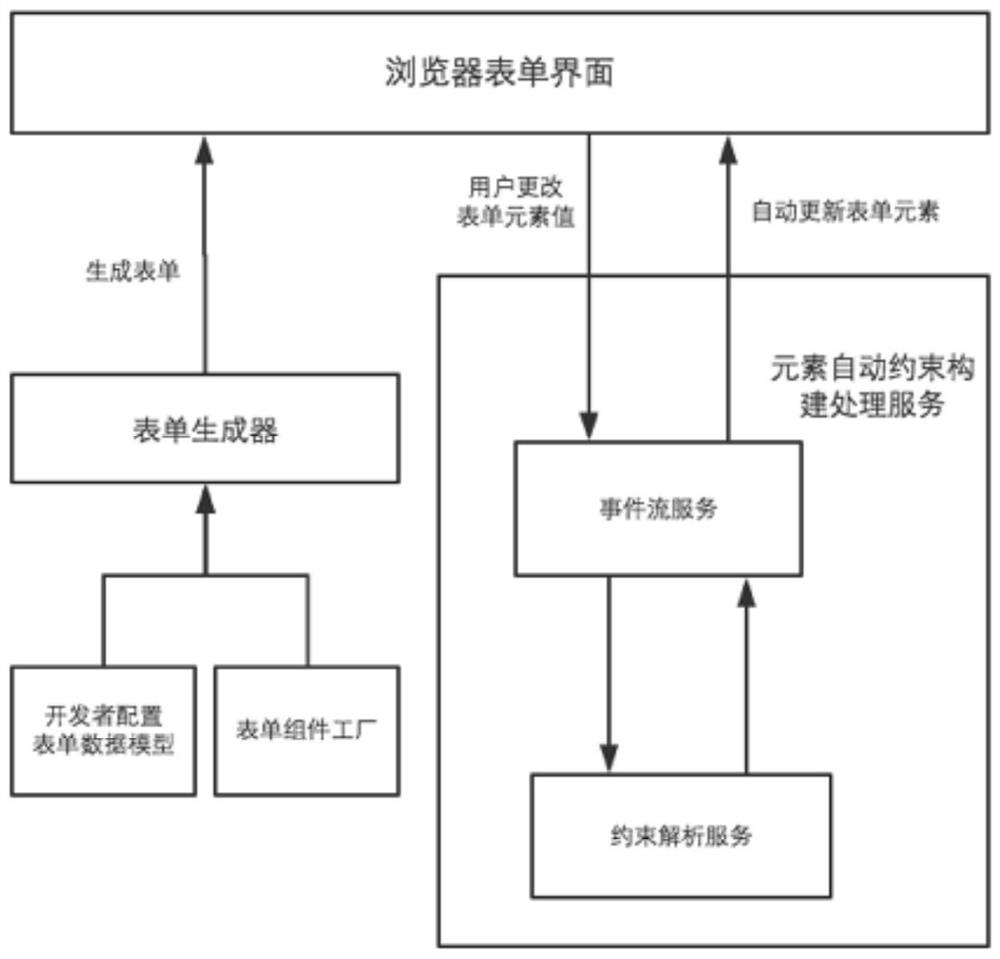
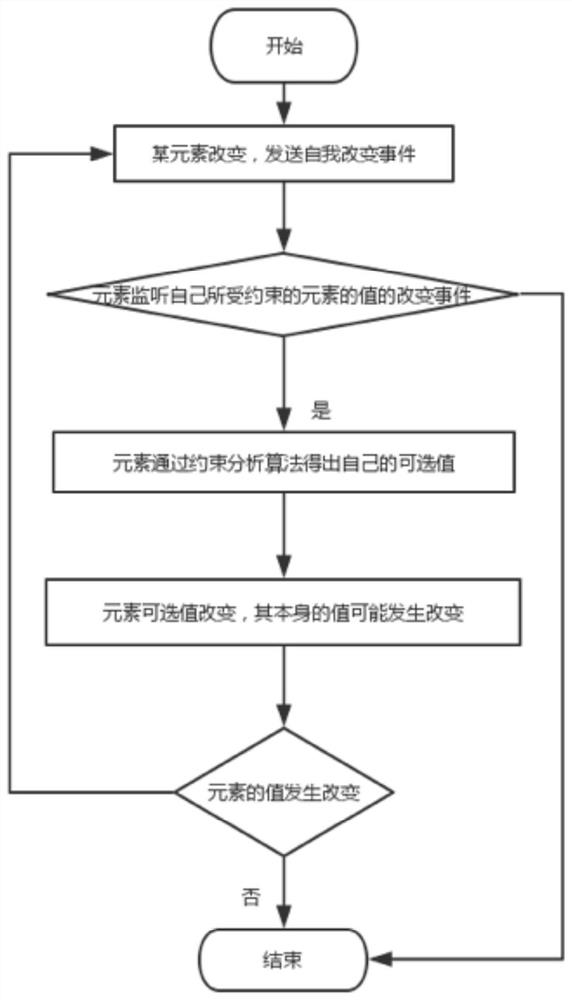
Form element linkage method and device
ActiveCN107766307AImprove scalabilityIncrease flexibilityText processingSpecial data processing applicationsReusabilityComputer science
The invention aims to provide a form element linkage method and device. When it is monitored that a constraint element value of a form is changed, corresponding optional values of a constrained element of the form are determined according to a constraint analysis algorithm and a corresponding constraint relationship, wherein the constraint relationship includes a corresponding relationship betweena constraint element and the constrained element; and then, the value corresponding to the constrained element is selected from the optional values. According to product function demands, the constraint relationship and the constraint analysis algorithm are configured; a form system is enabled to automatically process the optional values of the element; a form interface can finish automatic rendering according to the changes of the optional values of each element, so that the expansibility, flexibility and reusability of the form system are improved; and after the form product function demands are changed, codes of the form system are changed a little, so that the code correctness and robustness are improved.
Owner:ALIBABA GRP HLDG LTD
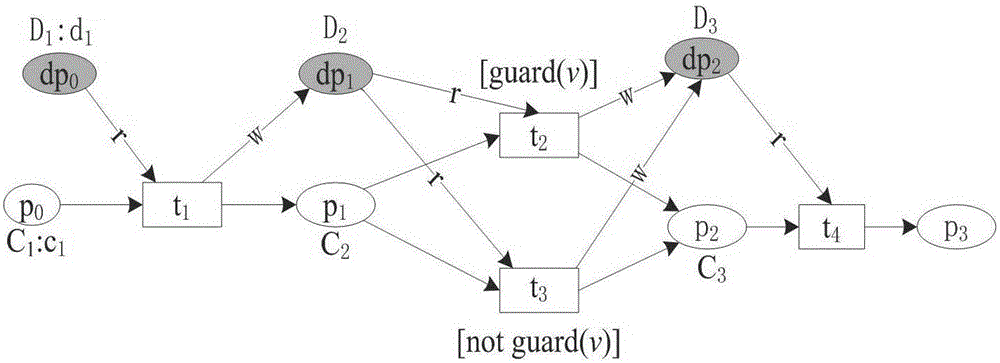
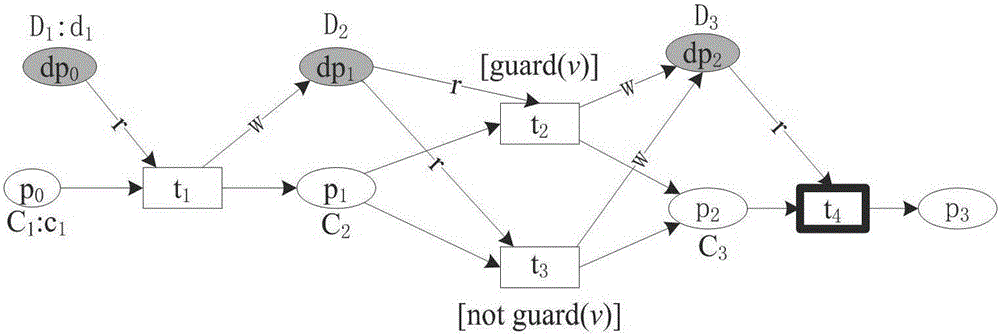
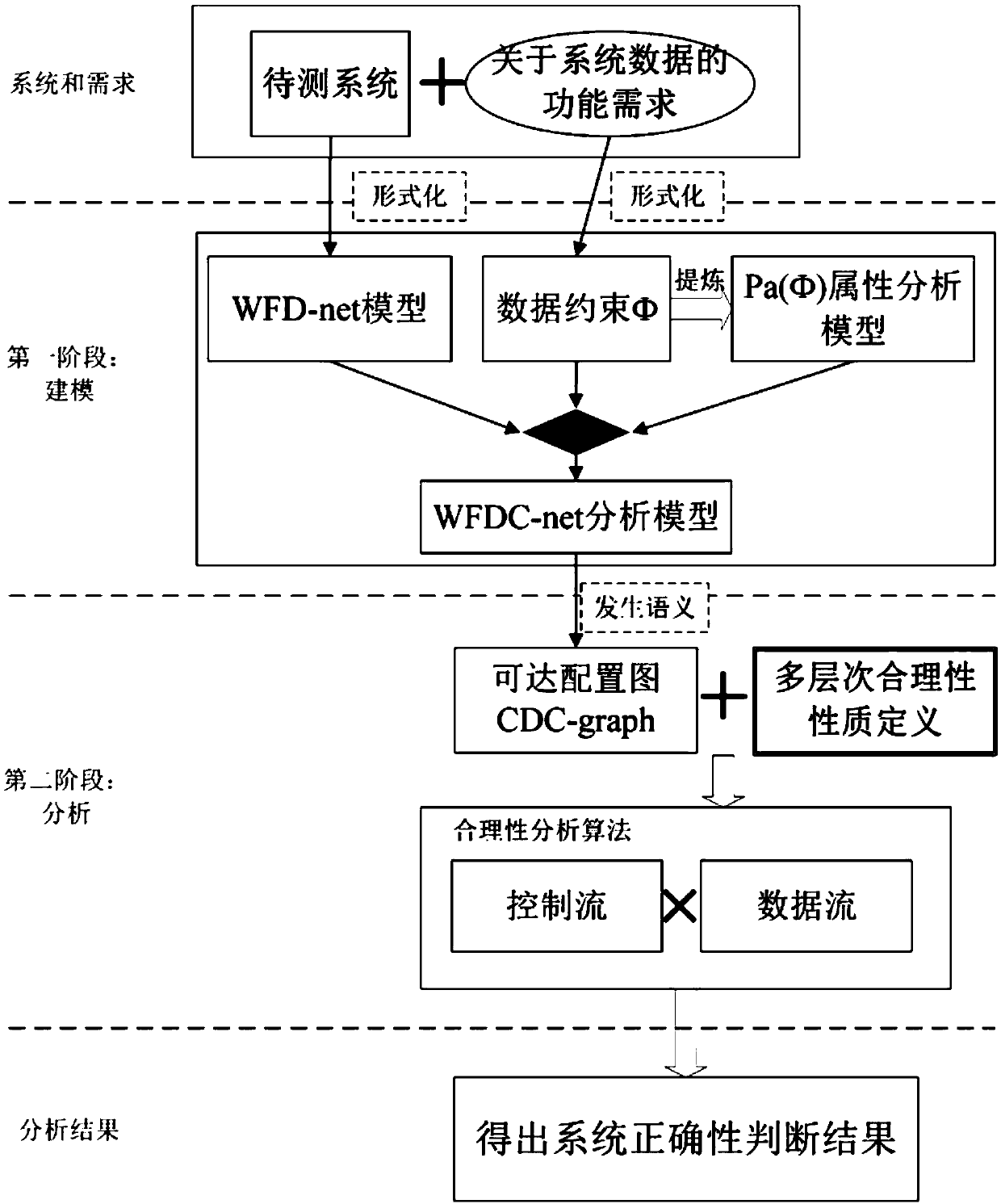
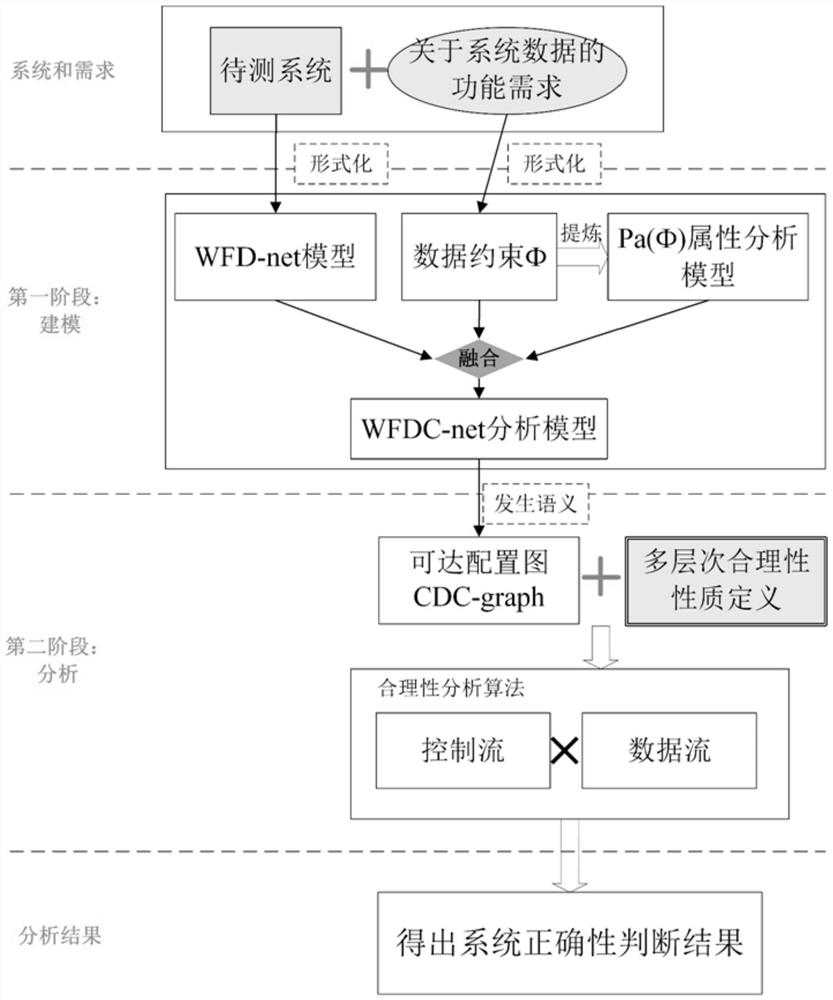
Abnormal fragment extraction method for workflow net inspection, readable storage medium and terminal
The invention provides an abnormal fragment extraction method for workflow net inspection, which comprises the following steps: a model initial WFD network is constructed and data constraints are generated; according to the data constraint, the corresponding constraint analysis mode, the corresponding relationship between the data and the positive and negative constraint, and the corresponding relationship between the constraint and the guard function value are constructed; a WFDC network model is generated; a reachable configuration CDC graph with data constraints is generated; according to the characteristics of WFDC network, the multi-layer rationality of WFDC network is defined; according to the WFDC network model and the multi-level rationality, the detection result is obtained by judging the rationality level of the network model; when the detection result is error, the reachable configuration CDC map is converted into a minimum complete CDC tree, and an abnormal path in which error state exists is extracted; according to the extracted abnormal paths and data constraint features, the abnormal segments of the abnormal paths are extracted. The invention solves the problem of automatically detecting abnormal fragments in the case of detection result failure of the system in the prior art.
Owner:TONGJI UNIV
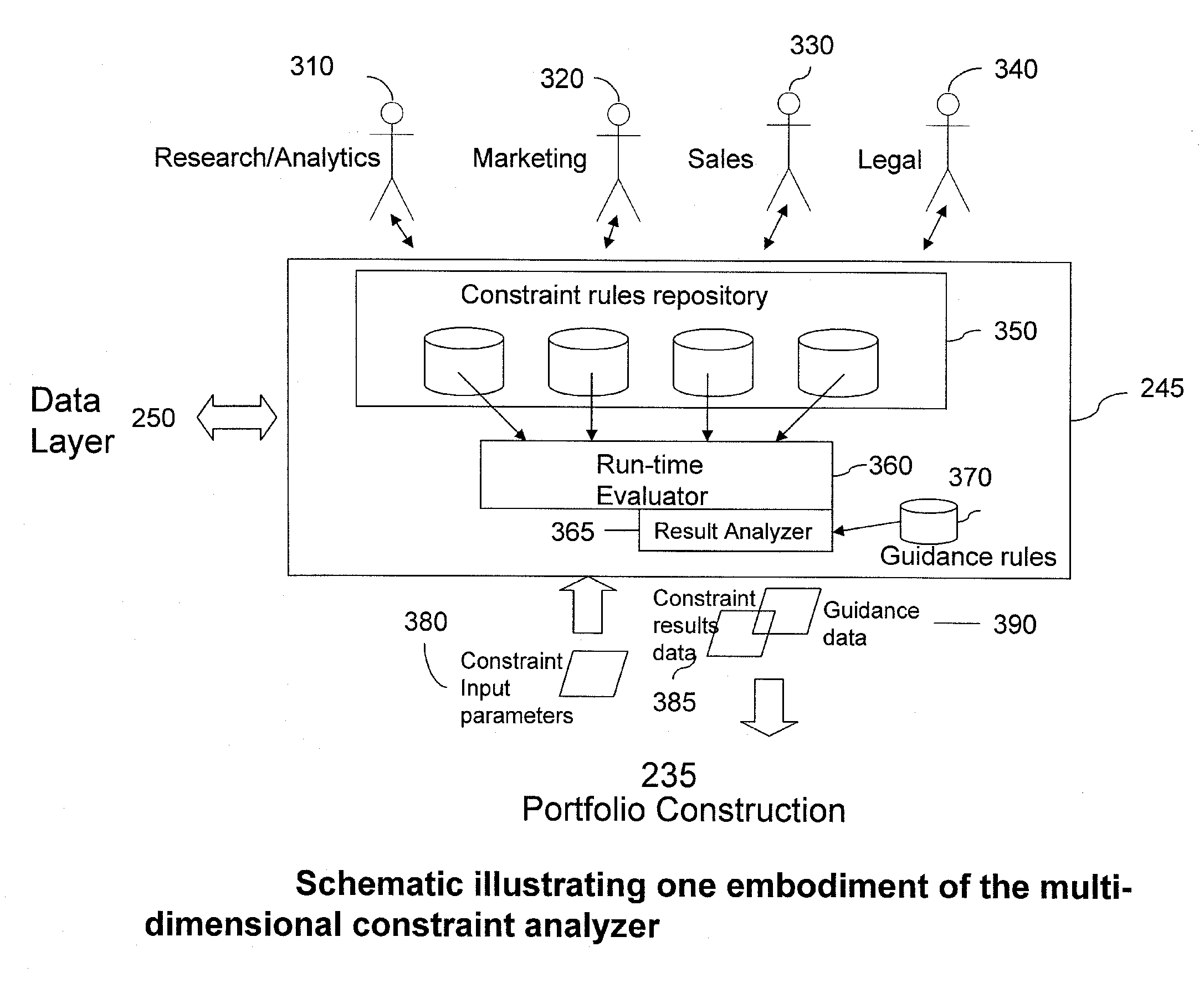
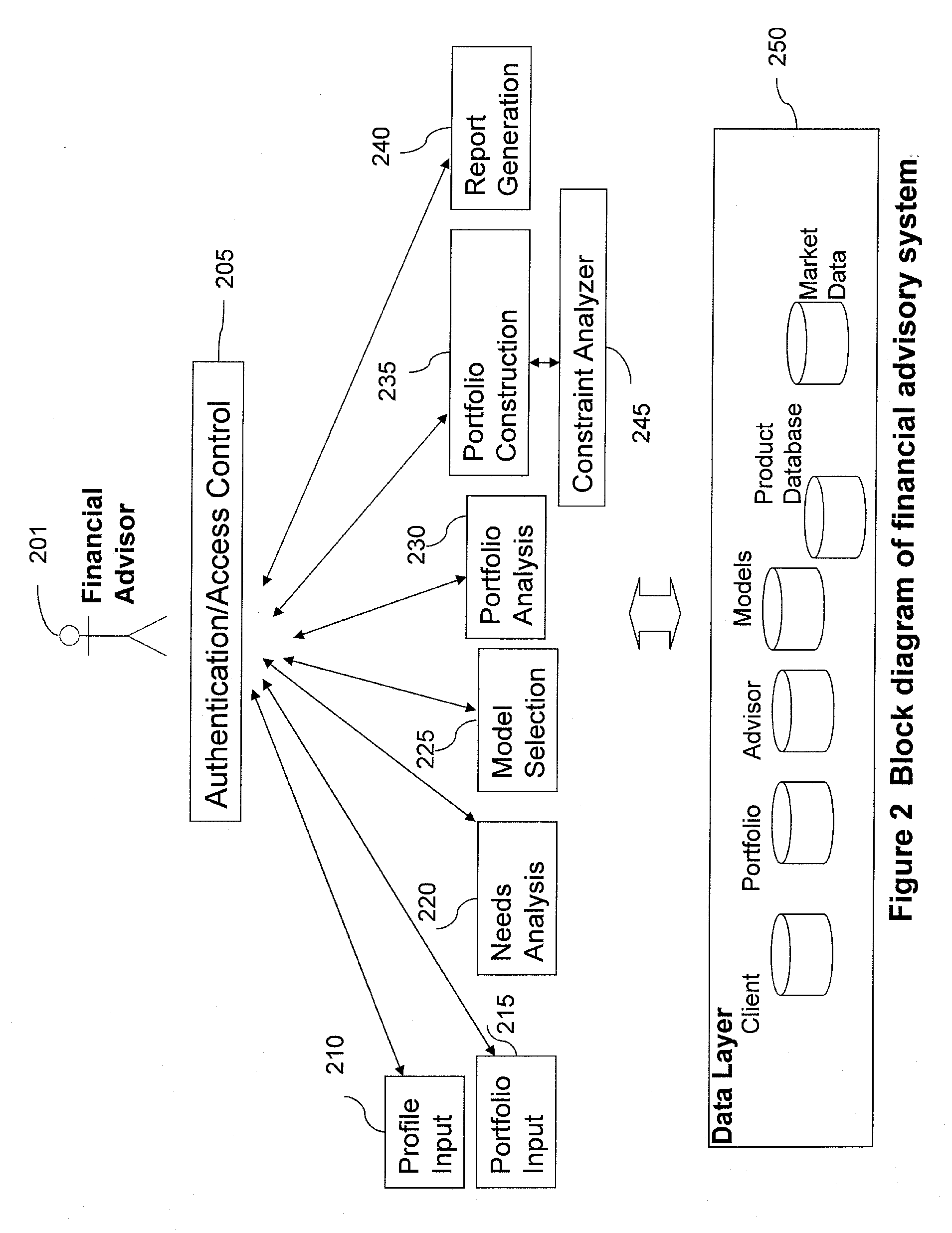
Systems and Methods for Real-time, Dynamic Multi-Dimensional Constraint Analysis of Portfolios of Financial Instruments
An automated method of managing or constructing a portfolio comprising at least one financial instrument defining portfolio attributes, the method using a system comprising a processor, a display and an input device. The method comprises defining at least one objective representing a desired state for the portfolio attributes and defining a set of constraints that are defined in relation to a computable, desired state of portfolio attributes in relation to the at least one objective. A constraints analysis module based upon the set of constraints is generated and provided to the processor. The portfolio is evaluated with the processor using the constraints analysis module and the state of the portfolio attributes based upon the evaluation is displayed. At least one option for altering portfolio attributes in order to more effectively meet the at least one objective is simultaneously displayed. The option is displayed with an interactive user input mechanism that allows for selection of an option and automatic evaluation and display of the state of the portfolio attributes due to selection of the option.
Owner:PERSPECTIVE PARTNERS
Method for analyzing operation of a machine
InactiveUS7966151B2Improve accuracyAvoid inaccuraciesTesting/monitoring control systemsNuclear monitoringData setMutually exclusive events
A constraint analysis and reliability agent executes a method for analyzing operation of a manufacturing asset, and includes the steps of collecting operation data for a machine over a plurality of predetermined time periods. The operation data includes a plurality of mutually exclusive events that describe operation of the machine. For each of the predetermined time periods, it is determined whether the machine is in an “ON” or an “OFF” state. Data for the “OFF” states is removed from the collected data to generate a filtered data set. Reliability information is then generated based, at least in part, on the filtered data set. This facilitates predictions of future machine operation.
Owner:FORD MOTOR CO
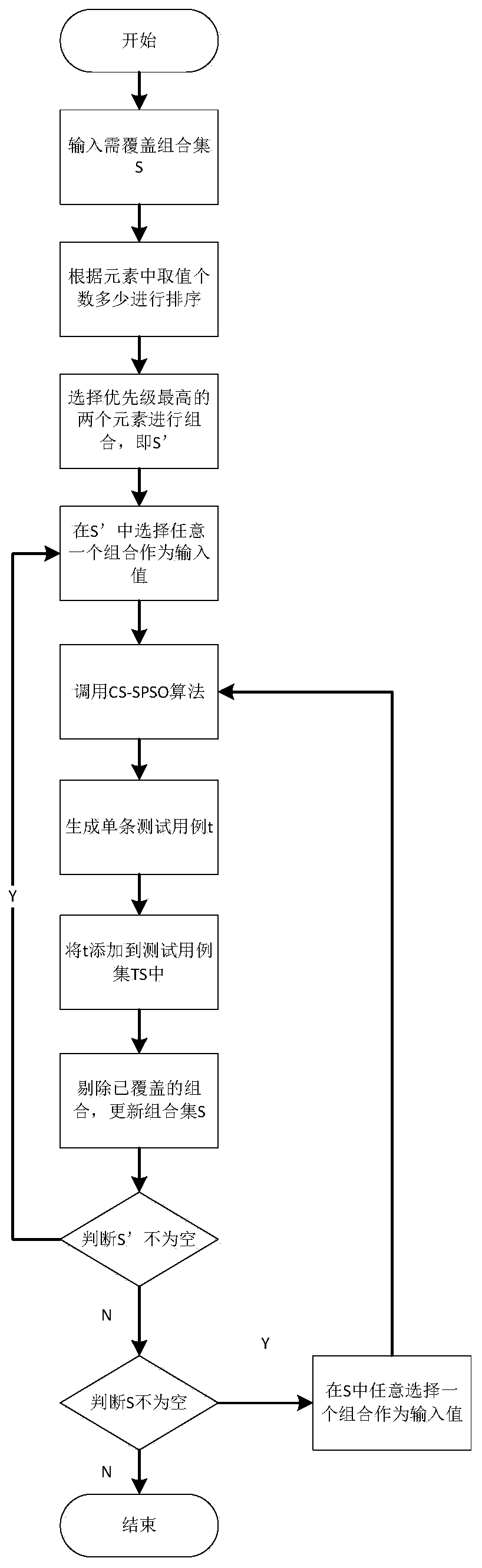
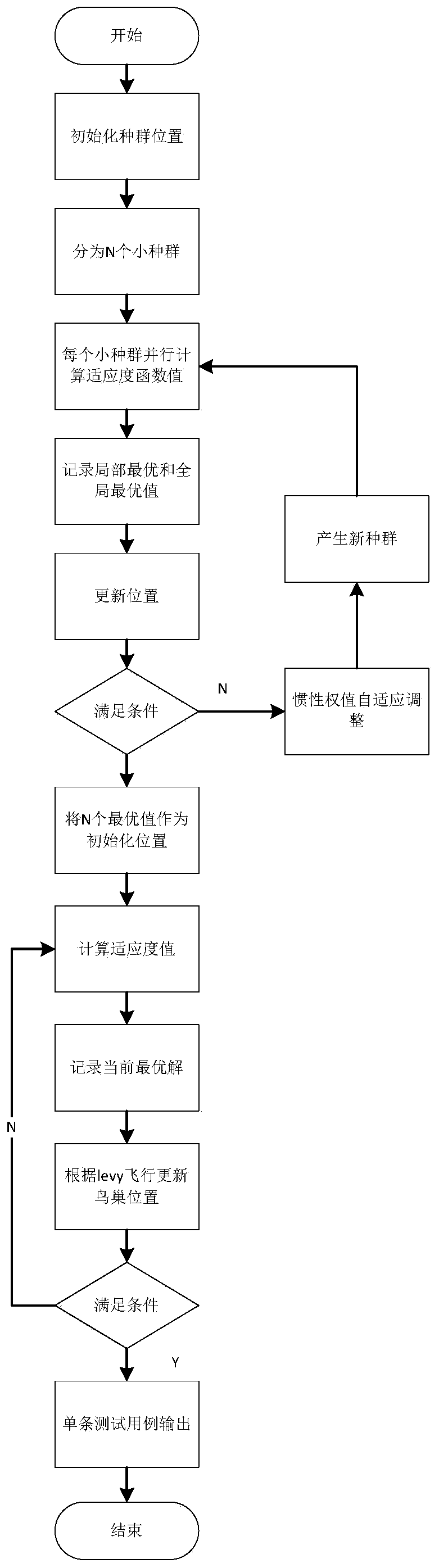
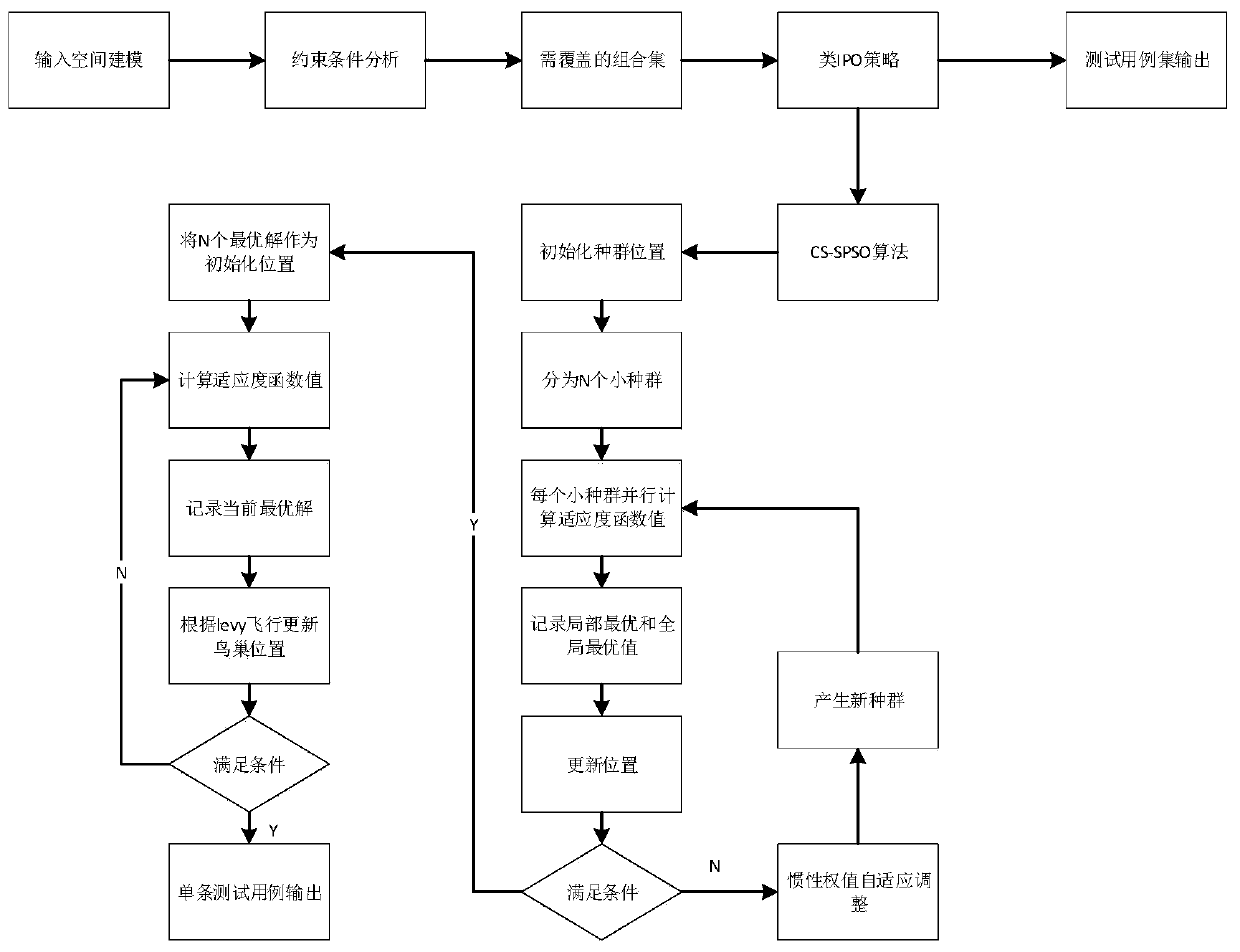
Combined test case generation method based on CS-SPSO algorithm
ActiveCN110334026AMaintain search capabilityImprove search capabilitiesArtificial lifeSoftware testing/debuggingCombined testAlgorithm
The invention discloses a combined test case generation method based on a CS-SPSO algorithm, and belongs to the field of software testing. The method comprises: obtaining a combination set needing tobe covered through constraint analysis; combining the two factors with the maximum values, and performing constraint analysis to obtain a final combination; determining all combinations of other elements according to a class IPO strategy; dividing the combination into N small populations, and carrying out local search on the N small populations by utilizing the simplified particle swarm, so that the advantages of local search of the simplified particle swarm are fully exerted; and taking the obtained N optimal particles as initial values of a cuckoo algorithm to carry out deep optimization, and generating a single test case. During position updating, a reflecting wall strategy is used for carrying out boundary processing on particle positions, and effective search space is prevented from flying out. The method can be suitable for the coverage tables with different coverage intensities, the scale of the combined test case set is effectively reduced, and the generation efficiency of thecombined test case is greatly improved.
Owner:ZHEJIANG SCI-TECH UNIV
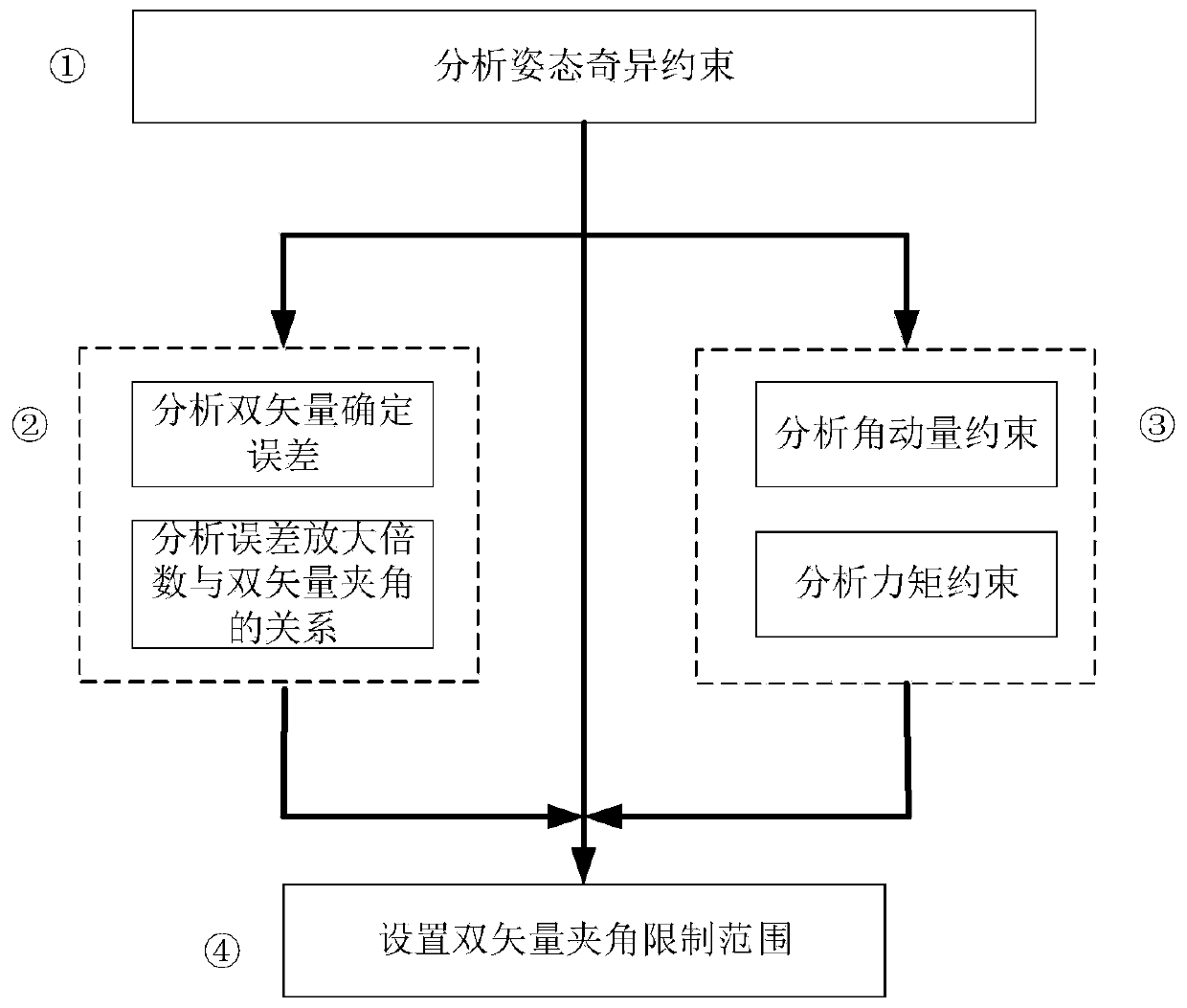
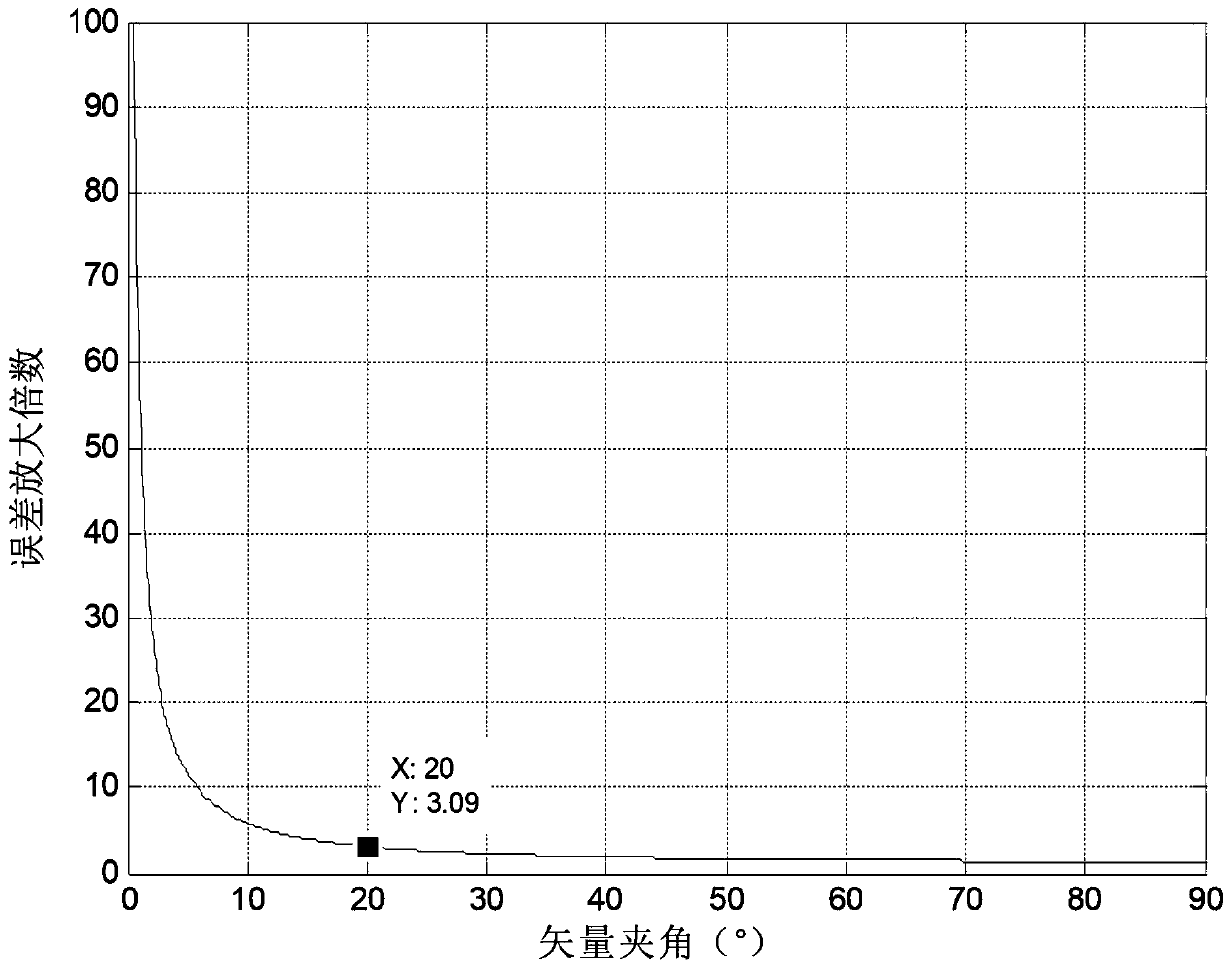
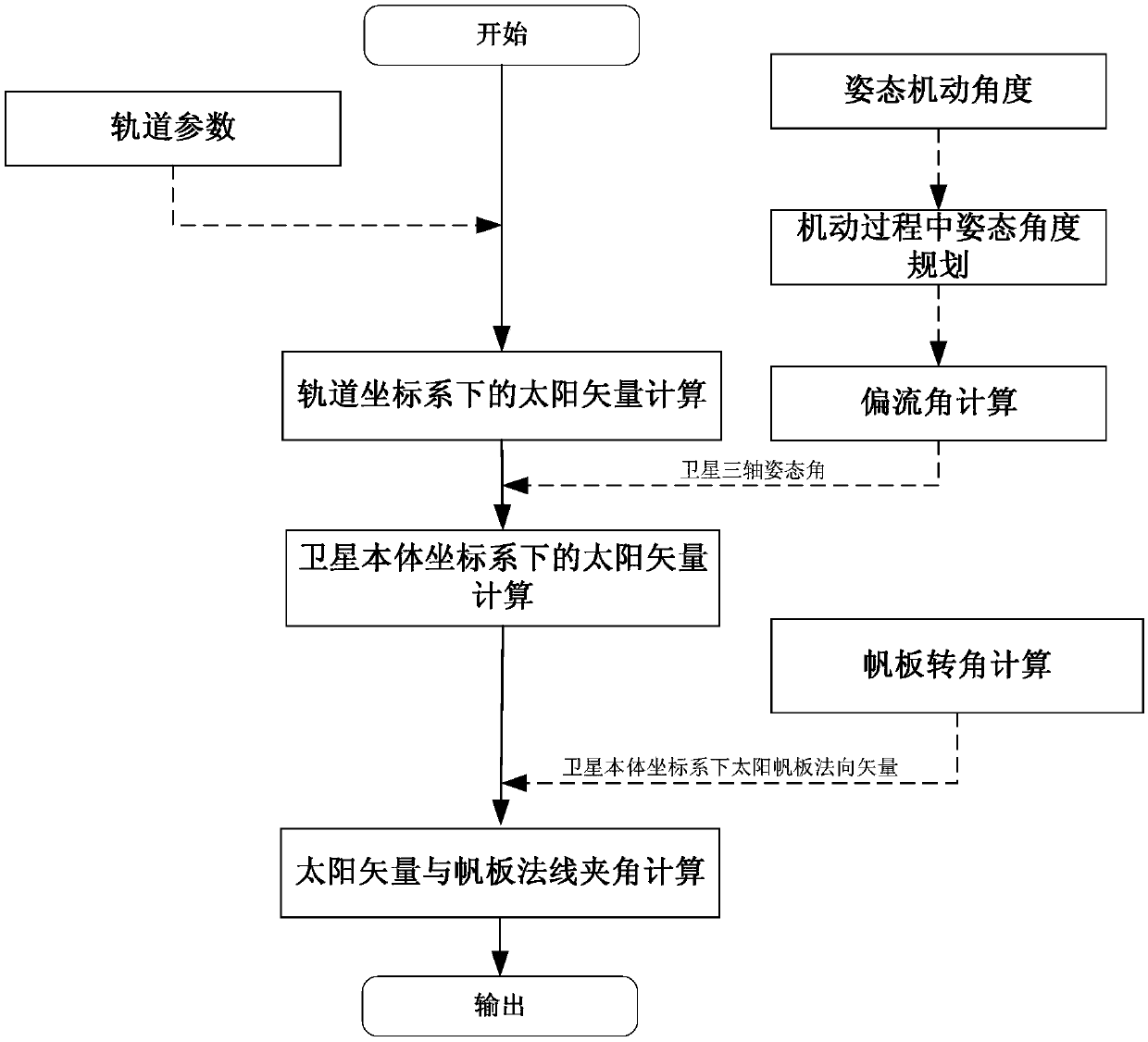
Double-vector included angle limiting range determining method and system based on constraint analysis
ActiveCN111123961ASolve the problem of determining the limited range of the angle between two vectorsSimple methodAttitude controlPosition/course control in three dimensionsAngular momentumControl theory
The invention provides a double-vector included angle limiting range determining method and a double-vector included angle limiting range determining system based on constraint analysis. The double-vector included angle limiting range determining method comprises analysis of attitude singular constraints, analysis of attitude benchmark determination error constraints, analysis of attitude maneuverability constraints and setting of a dual-vector included angle limiting range, and comprises the steps of: judging whether an attitude singularity phenomenon of attitude overturn occurs or not according to a three-axis attitude change rule determined by double vectors; according to the triaxial attitude determined by the double vectors, determining an error by analyzing an attitude reference, andjudging whether load pointing errors of an antenna, a camera and the like meet on-orbit requirements or not; judging whether angular momentum and moment meet the requirements or not by analyzing theattitude maneuver capability according to the triaxial attitude determined by the double vectors; and setting a double-vector included angle limiting range by integrating the attitude singularity constraint determined by the double vectors, the attitude reference determination error constraint and the attitude maneuver capability constraint. The double-vector included angle limiting range determining method solves the problem of determining the double-vector included angle limiting range based on constraint analysis, and is simple and easy to implement in engineering.
Owner:SHANGHAI SATELLITE ENG INST
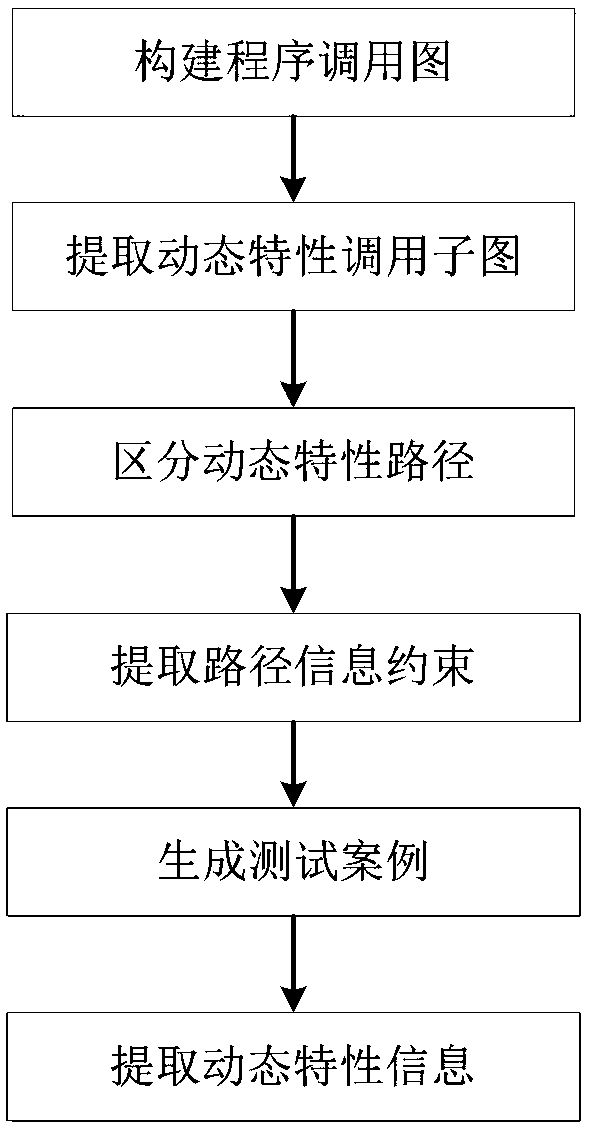
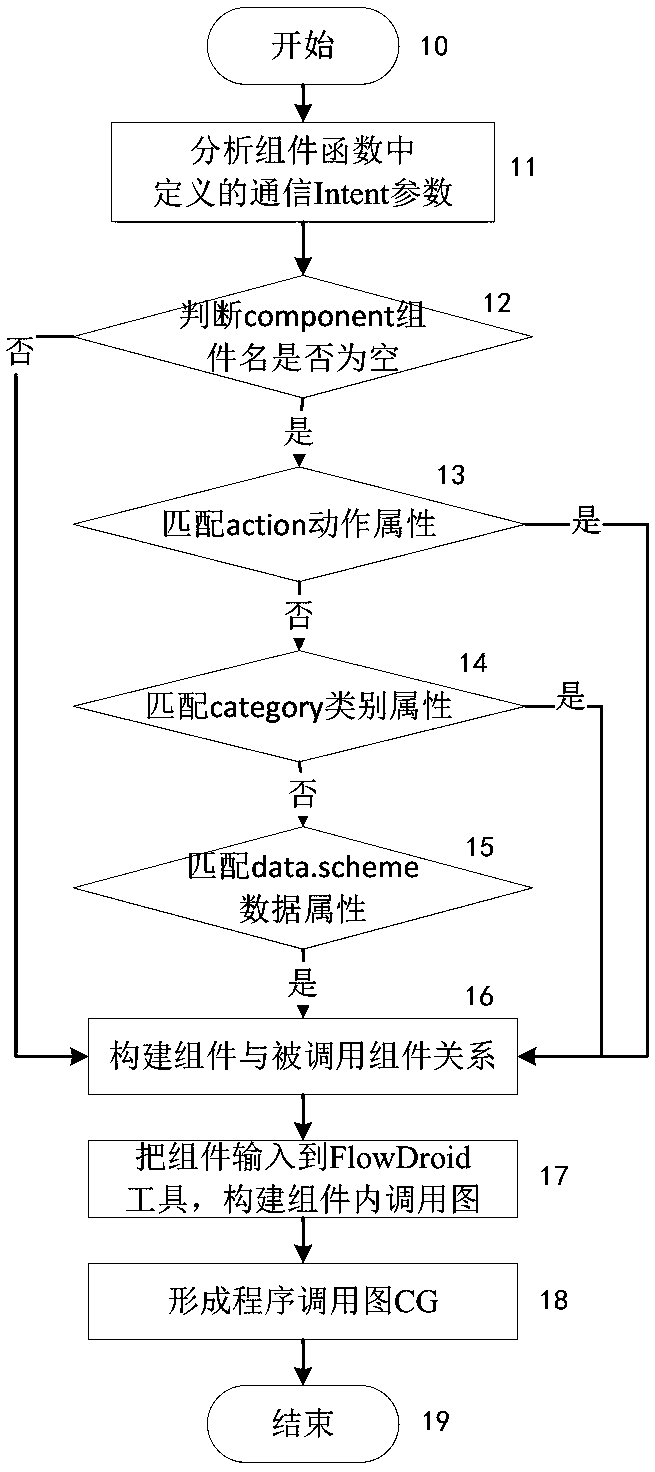
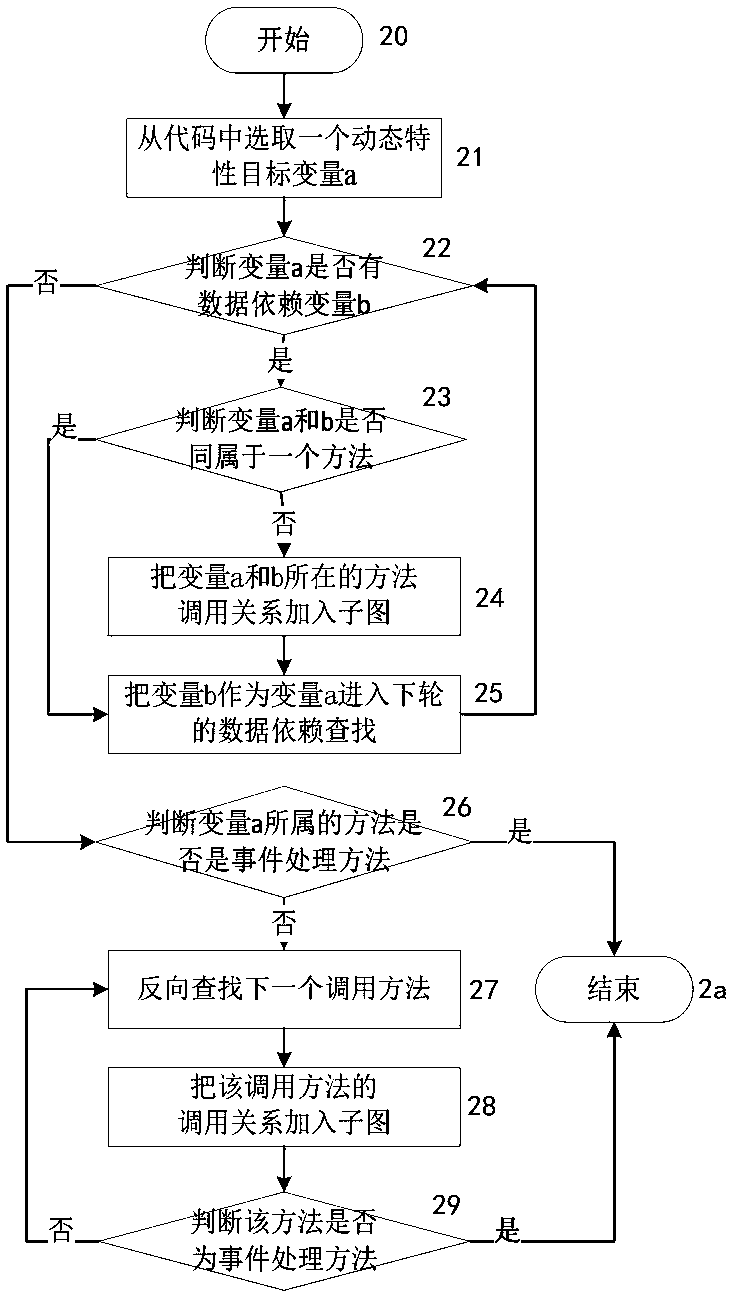
Android system privacy leakage detection-oriented dynamic characteristic information extraction method
The invention discloses an android system privacy leakage detection-oriented dynamic characteristic information extraction method. The method comprises the following steps of: extracting dynamic characteristics to call dynamic characteristic calling subgraphs on which reverse extraction depends on the basis of calling graphs between and in components, so as to decrease unnecessary code analysis and limit the analysis in relatively small program codes; dividing dynamic characteristic calling paths for the calling subgraphs according to different definition-using relationships of target parameters, so as to obtain more trigger calling paths; carrying out parameter constraint analysis on the basis of slice information of each calling path, and combining the parameters to generate test cases so as to construct more test cases; and inputting the test cases, and instructing dynamic test to obtain dynamic characteristic information so as to avoid random test. According to the method, the dynamic test takes static analysis as instruction, so that path sensitivity and context sensitivity are ensured, the coverage rate and accuracy of dynamic characteristic information obtaining are improved, the randomness of the dynamic characteristic information obtaining is avoided, and the coverage and obtaining efficiency of the dynamic characteristic information are improved.
Owner:NANJING UNIV
Product modeling method based on interactive feature pair
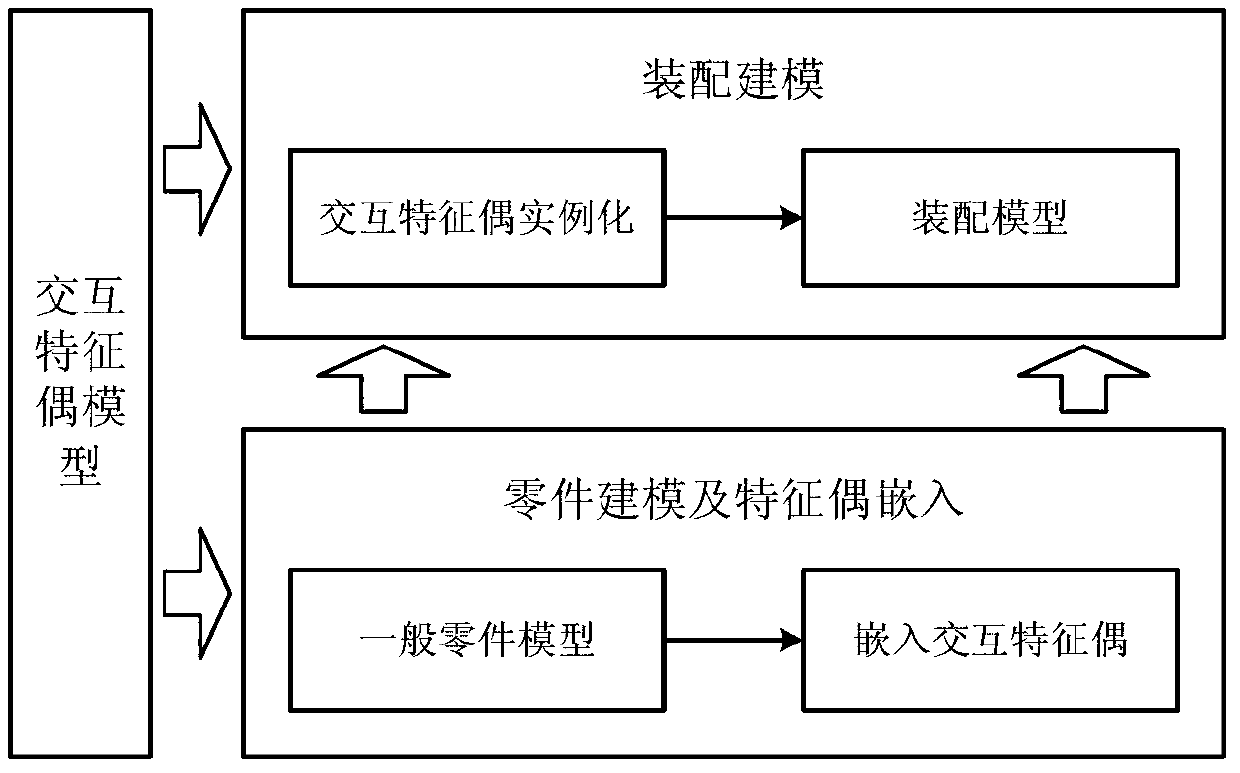
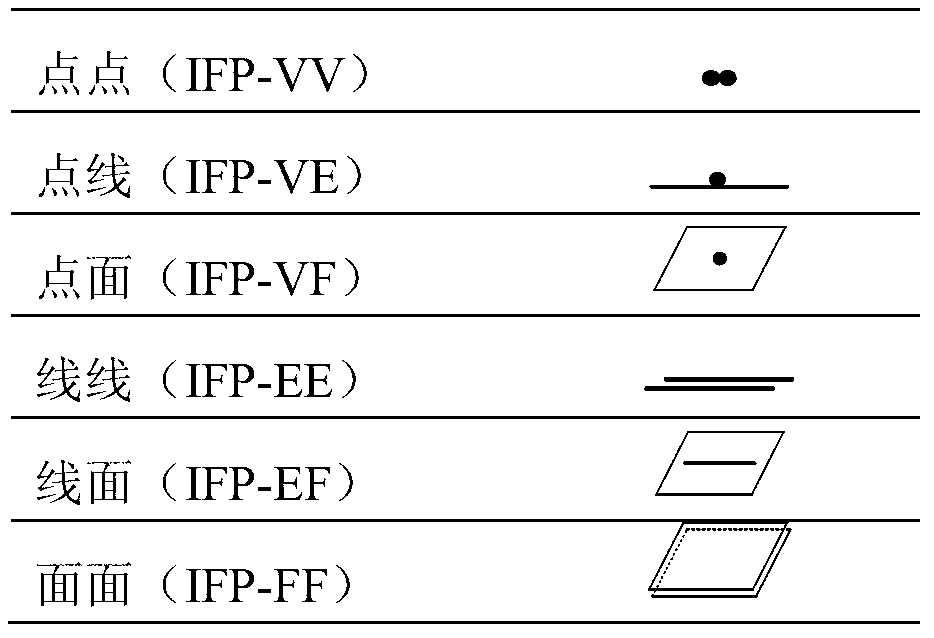
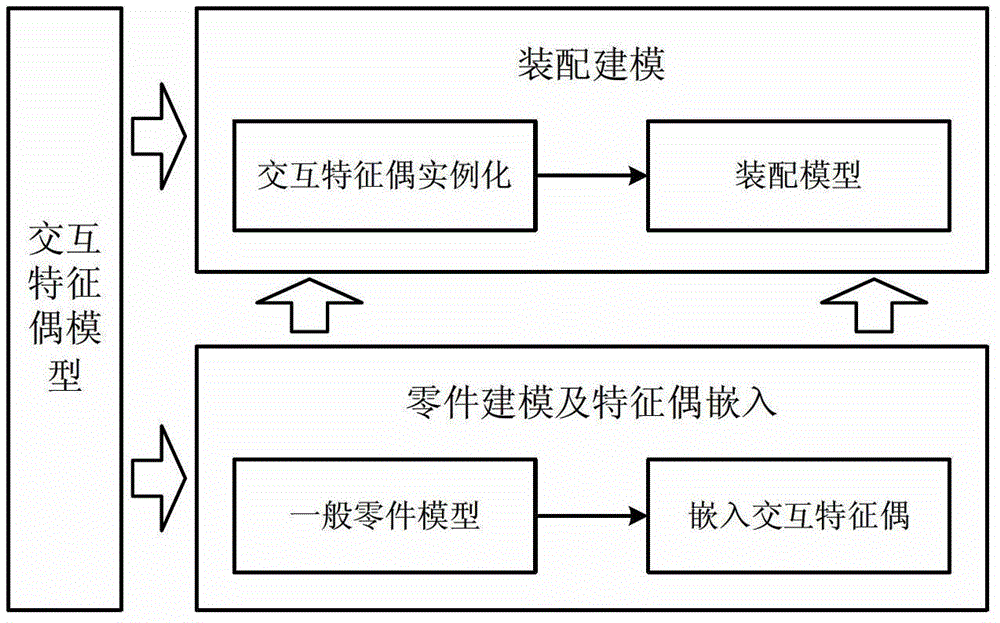
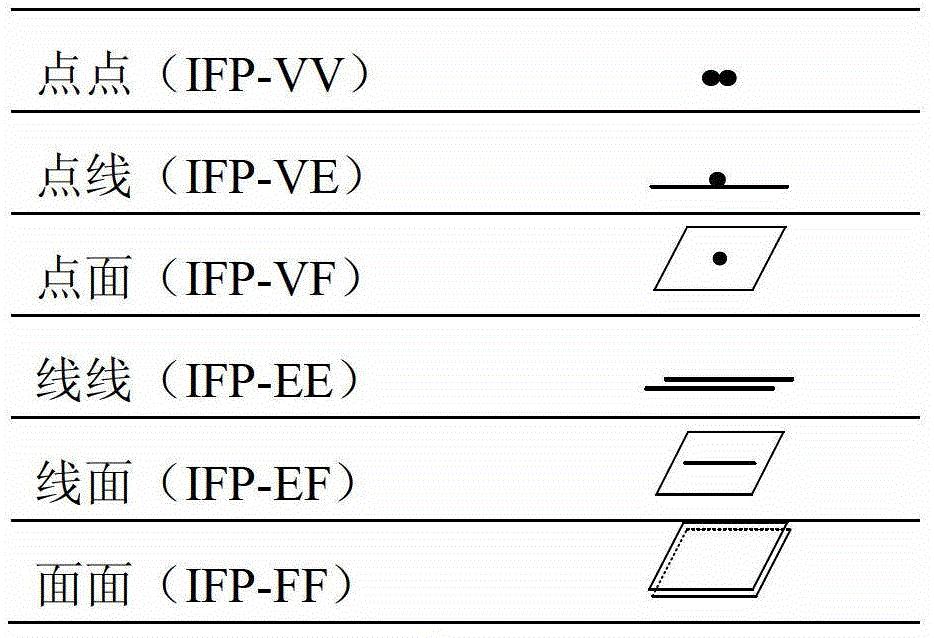
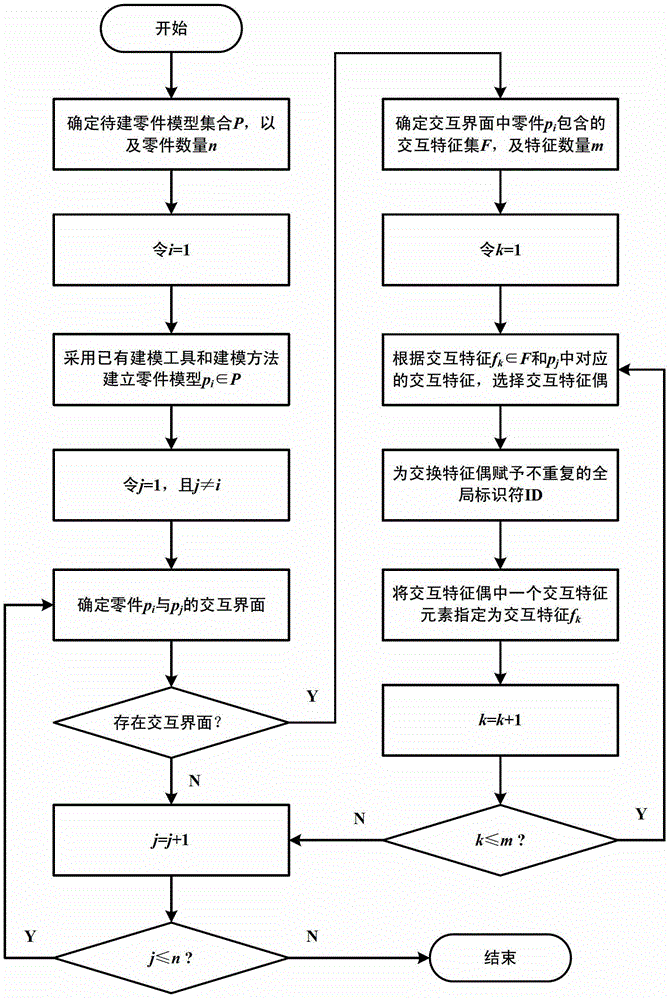
ActiveCN103279599AEnsure consistencySufficiently abstractSpecial data processing applicationsProduct modelingSimulation
The invention provides a product modeling method based on an interactive feature pair. The method includes the steps of firstly, conducting product part modeling, and enabling the interactive feature pair to be embedded in a part model on the basis of interactive interfaces among product parts, then, achieving assembly modeling through feature elements of the fully specified interactive feature pair on the basis of the part model where the interactive feature pair is embedded. The product modeling method based on the interactive feature pair has the advantages that the interactive feature pair is divided into six types of highly abstracted basic classifications, in the assembly modeling method from top to bottom, ports are set up through the interactive feature pair so that enough abstraction and generality can be ensured, consistency of constraints analysis for designers can be ensured when the interactive feature pair is embedded in the part model in comparison with a traditional assembly modeling method from bottom to top, and the interactive feature pair can be used for geometric reasoning in a downstream technology design process. Through the product modeling method based on the interactive feature pair, the advantages of the assembly modeling technology from top to bottom and the advantages of the assembly modeling technology from bottom to top can be combined, and therefore product assembly modeling can be better conducted.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Mechanical modeling method for nonholonomic constraint system
ActiveCN106383973AAvoid double countingReduce computing timeGeometric CADDesign optimisation/simulationArray data structureReverse order
The invention discloses a mechanical modeling method for a nonholonomic constraint system. The mechanical modeling method comprises the steps of introducing an intermediate variable to describe a nonholonomic constraint relation according to the complexity of nonholonomic constraints when constraint analysis is carried out; revealing independent generalized velocity information included in kinetic energy through the constraint analysis, extracting a coefficient of a product item of independent generalized velocity and defining the coefficient as the intermediate variable, and changing the kinetic energy into a new form of expression; in a modeling process, calculating partial derivatives of some function variables to generalized coordinates or total derivatives of the function variables to time massively, establishing a function-variable implication relation table and introducing composite derivation to solve by analyzing a variable subordinate structure; and defining several structural arrays to store calculation results since the calculation of the influence of the nonholonomic constraints on the system is more complex. In order to avoid a model expansion problem caused by back substitution of the intermediate variable, the calculation expression of the model needs to be outputted in a reverse order.
Owner:GUILIN UNIV OF ELECTRONIC TECH
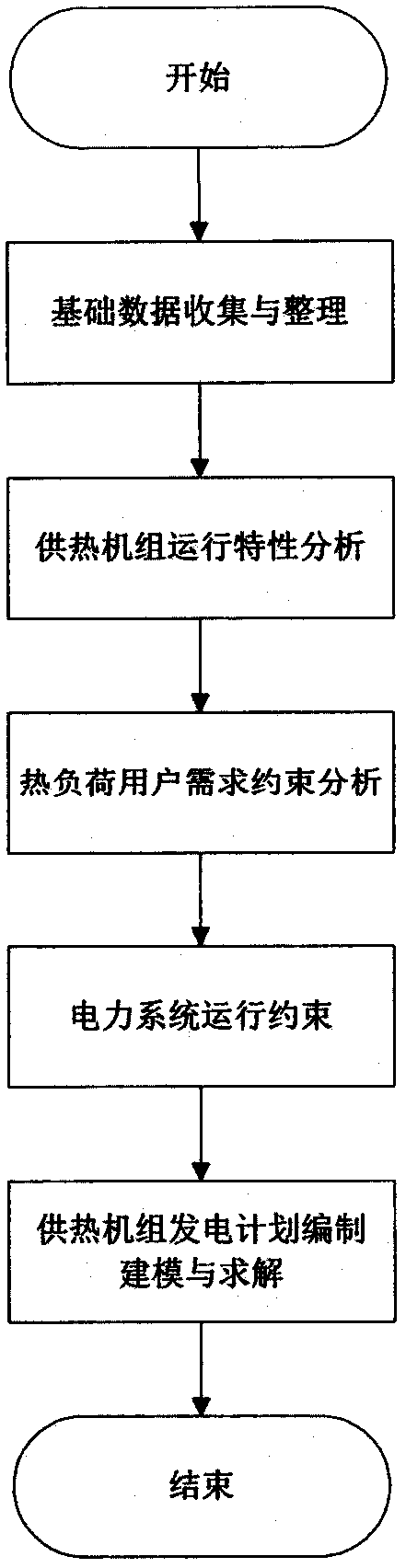
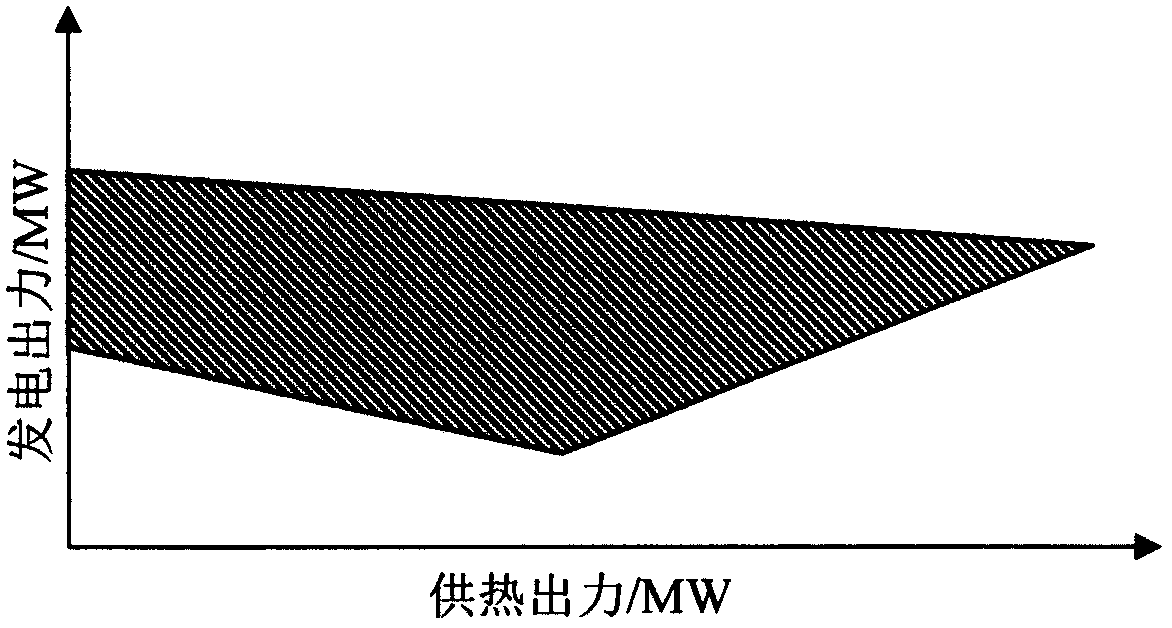
Heat supply unit power generation plan making method taking peak shaving capacity maximization as target
The invention relates to a heat supply unit power generation plan making method taking peak shaving capacity maximization as a target, and the method is characterized by comprising the steps: (1) collecting and arranging basic data; (2) analyzing the operation characteristics of the heat supply unit; (3) carrying out thermal load user demand constraint analysis; (4) carrying out power system operation constraint; and (5) compiling, modeling and solving a power generation plan of the heat supply unit. The method is mainly applied to mining the peak shaving potential of the heat supply unit, maximizes the peak shaving capacity of the system on the basis of meeting the heat supply requirement and the electric power balance requirement, and is beneficial to absorption of clean energy such as wind power and the like.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
A remote sensing satellite energy balance constraint analysis system and method
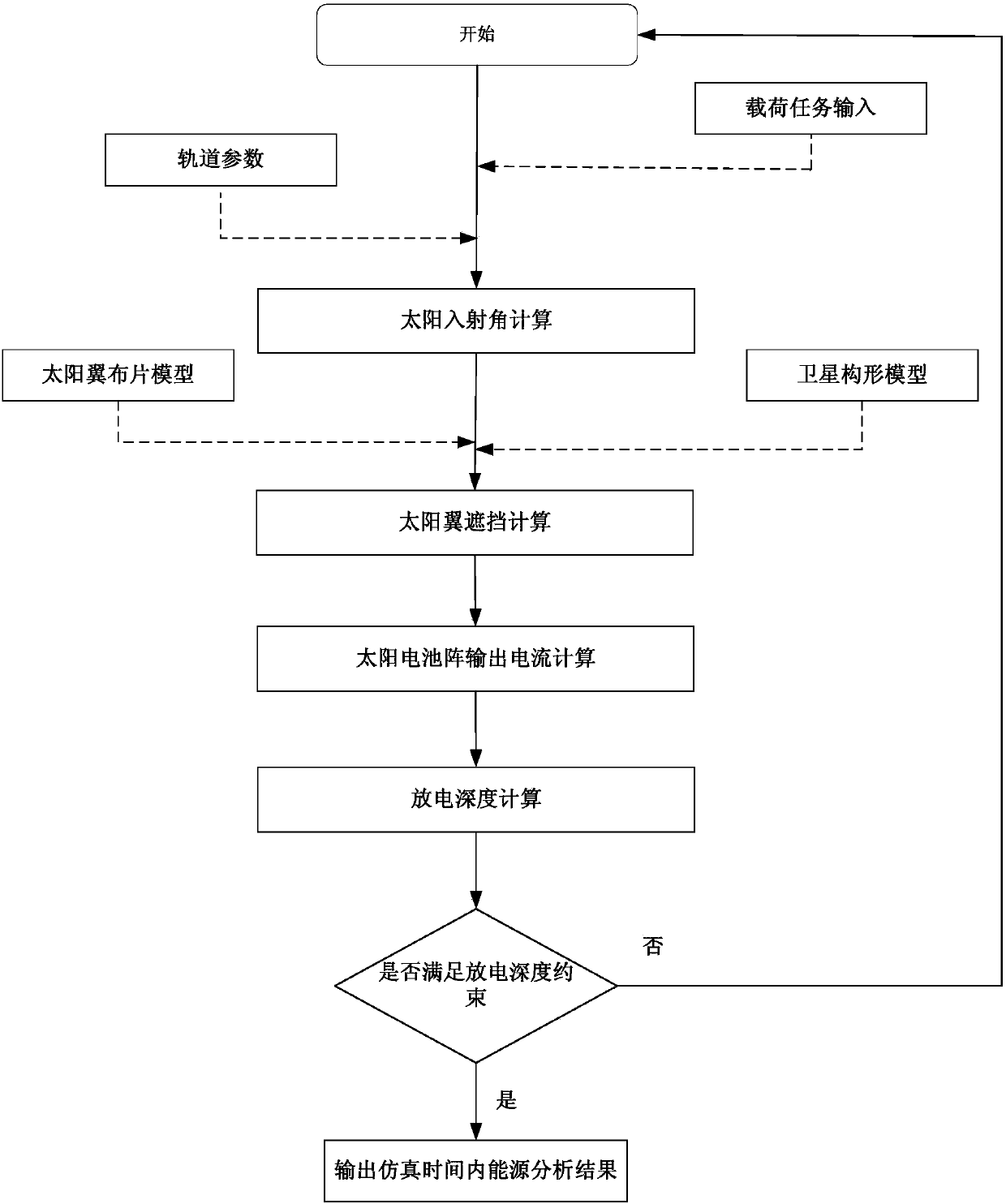
ActiveCN106324631BAccurate assessmentMeet constraintsSatellite radio beaconingEnergy balancingIrradiation
The present invention relates to a remote sensing satellite energy balance constraint analysis system and belongs to the technical field of satellite task simulation. The complex task planning and the complex configuration of a high-resolution remote sensing satellite and the dynamic analysis of the energy balance of the satellite are enabled, wherein the satellite has rapid attitude maneuvering requirements. According to the technical scheme of the invention, the satellite discharge depth of the satellite at each load task ending moment is calculated, and then the number of turns required for the energy balance of the satellite at the ending moment of each solar irradiation region is obtained. Meanwhile, according to a discharge depth safety threshold, whether the task of the satellite can meet the energy constraint condition or not is judged. For example, on the condition that the satellite can meet the energy constraint condition, an energy analysis result is outputted. Otherwise, the calculation result is returned to an upper-level task planning system. According to the energy balance condition of each turn and the discharge depth at each task ending moment, the re-adjustment is conducted and a new task planning is input for calculation.
Owner:BEIJING INST OF SPACECRAFT SYST ENG
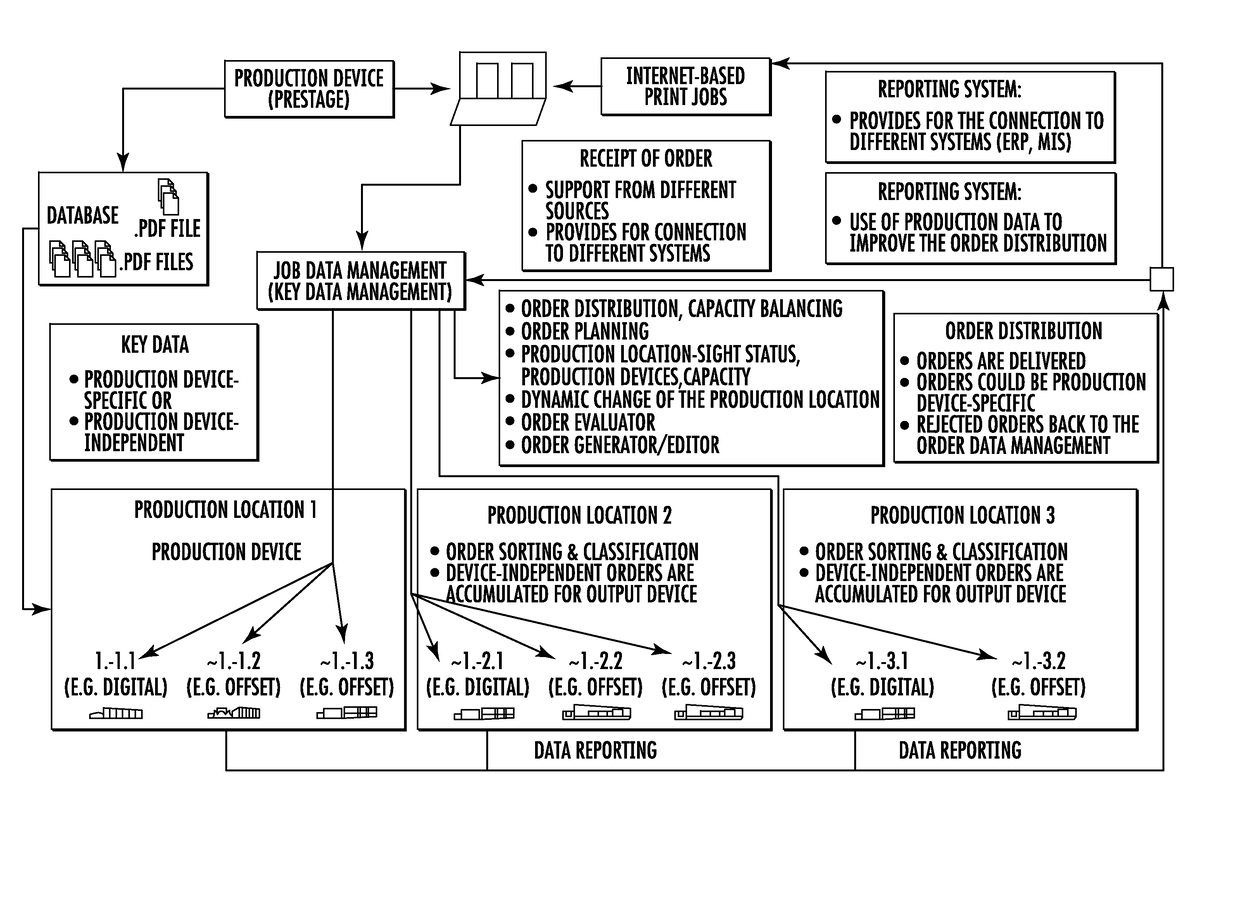
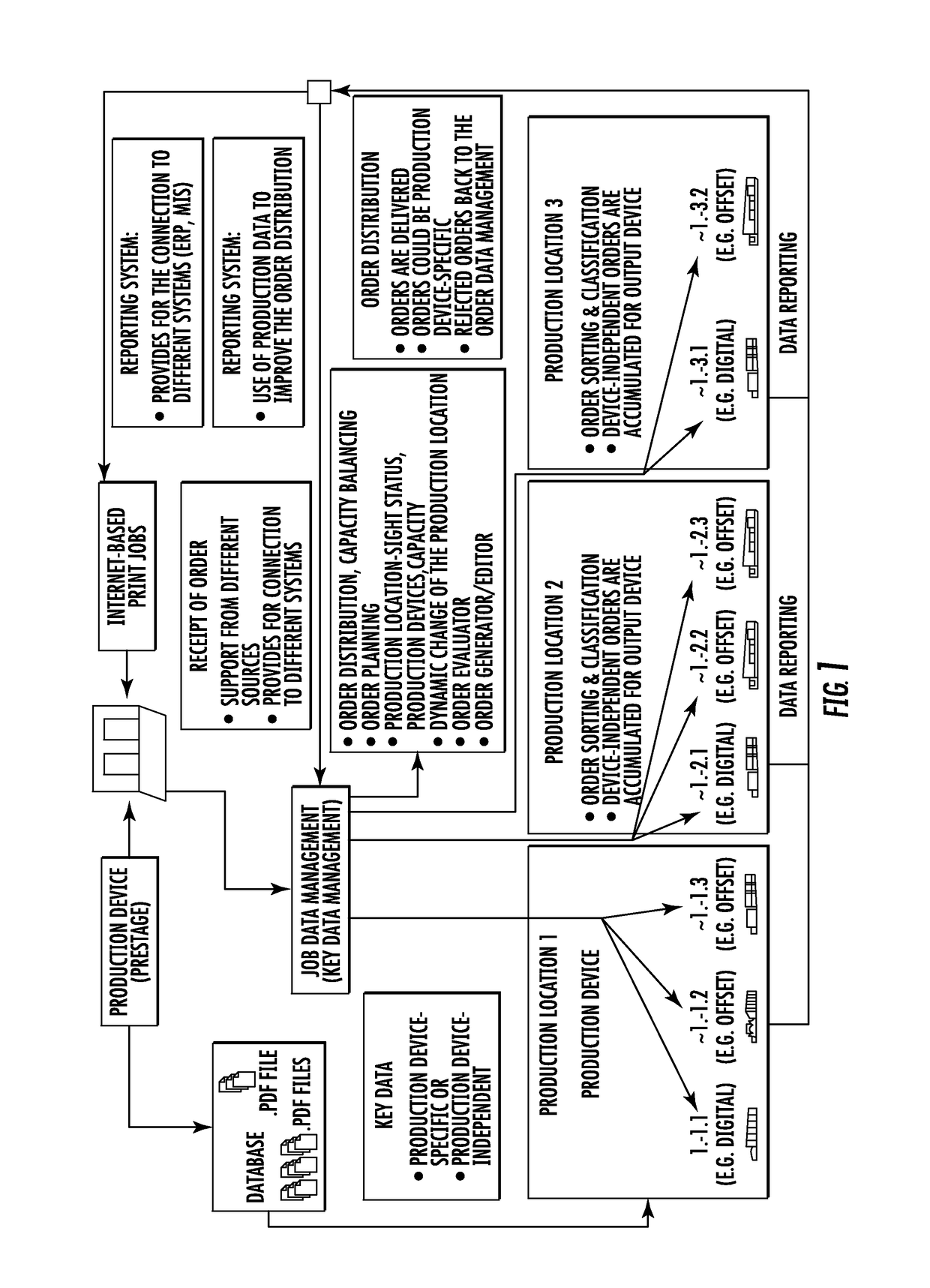
Method for Planning and Assigning Productions
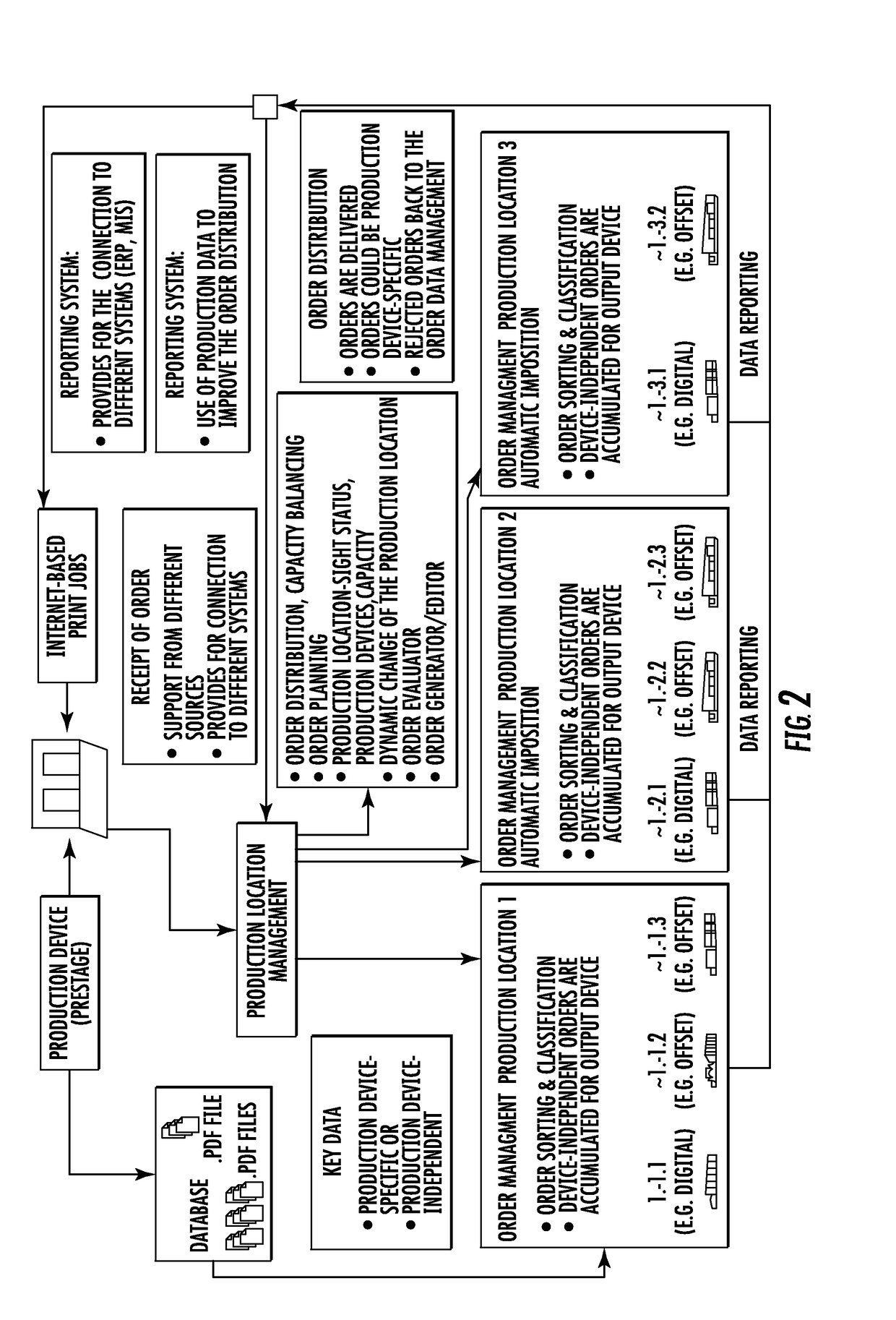
InactiveUS20170091684A1Low maintenance resultAvoid excessive errorResourcesComputer scienceConstraint analysis
A method for a assigning at least one production order comprising known job data from one or a plurality of production orders, which are in line for processing, to a particular production device of a plurality of production devices, wherein production device data with regard to the production options thereof can be written to each of the production devices, by means of which an efficiency-optimized assignment of at least one production order to a particular production device is made possible without manual interventions and person-bound analysis. The method permits the assignment of the at least one production order to a particular production device with regard to at least one sorting criterion to be carried out automatically.
Owner:MANROLAND WEB SYST
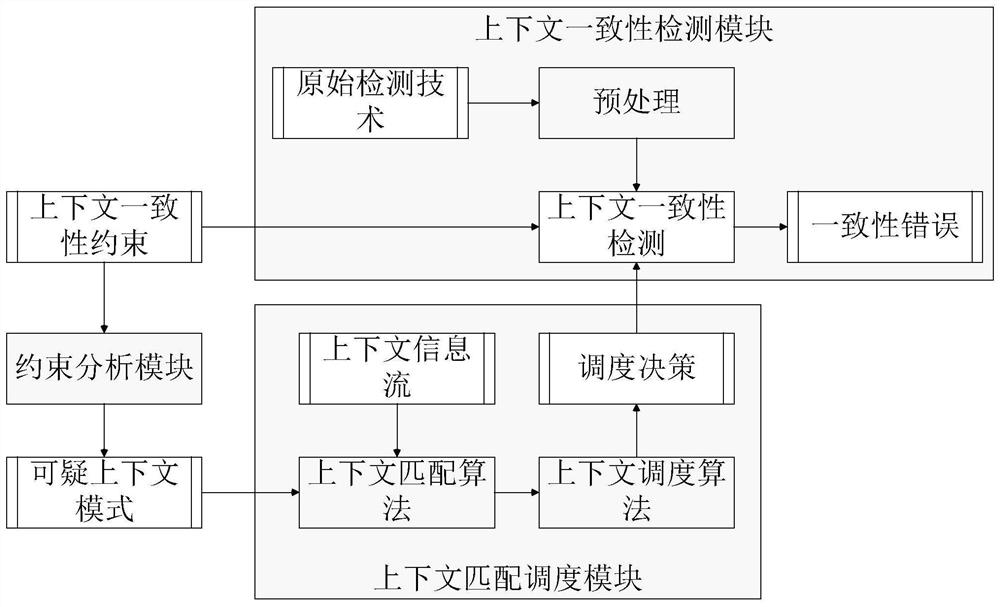
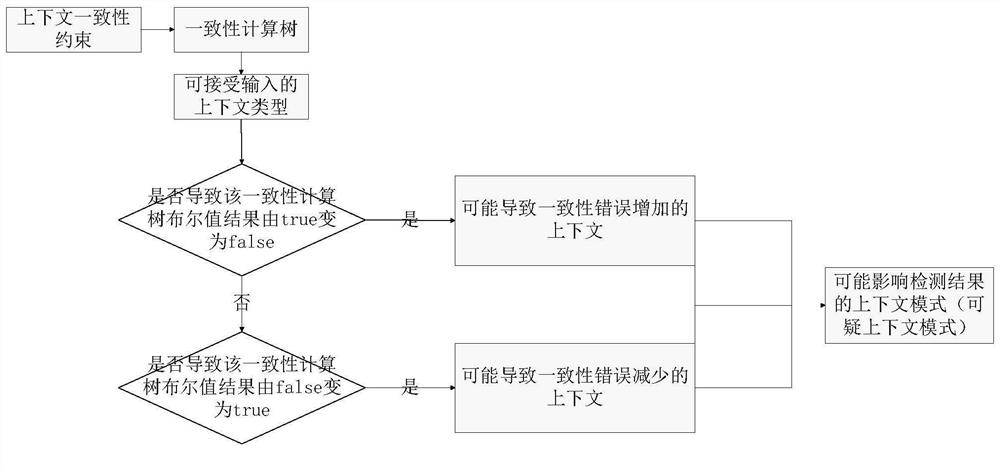
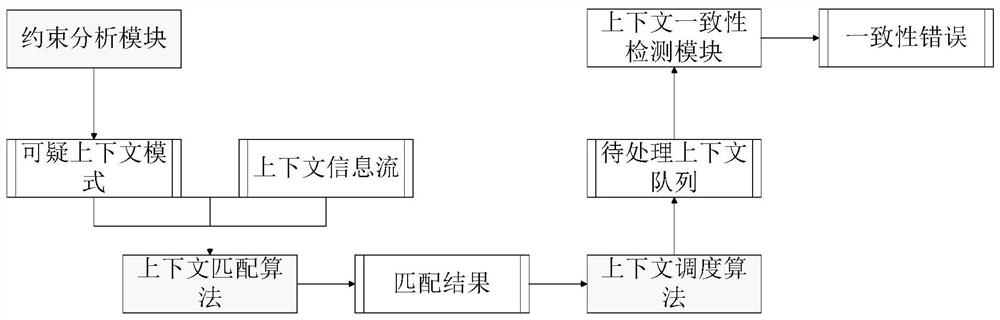
A detection system and detection method for realizing context consistency
ActiveCN107844327BReduce detection frequencyImprove detection efficiencySubstation equipmentExecution paradigmsStructure analysisPattern matching
The invention provides a detecting system for realizing context consistency. The system comprises a constraint analysis module, a context matching and scheduling module and a consistency detecting module. By means of the constraint analysis module, through the structural analysis of a series of consistency constraints needing to be met by a self-adaptive program, any suspicious context informationcombination mode probably causing new consistency error undetectable can be obtained through analysis in advance; a context information stream is matched with the suspicious combination mode throughthe context matching and scheduling module, and the detecting technology is scheduled and a proper scheduling decision is made in a self-adaptive mode according to the matching result guidance; the consistency error detecting module calls an existing consistency detecting technology according to the scheduling decision making result to detect a context queue for decision making. The invention further provides a detecting method for realizing context consistency.
Owner:NANJING UNIV
Abnormal segment extraction method, readable storage medium and terminal for workflow network inspection
The invention provides a method for extracting abnormal fragments of workflow network inspection, including: constructing an initial WFD network of the model, and generating data constraints; constituting a corresponding constraint analysis mode according to the data constraints, the corresponding relationship between data and positive and negative constraints, and constraints and Correspondence between guard function values; generate WFDC network model; generate reachable configuration CDC diagram with data constraints; define multi-level rationality of WFDC network according to network characteristics of WFDC network; To determine the rationality level of the network model, obtain the detection result, and convert the reachable configuration CDC graph into the minimum complete CDC tree when the detection result is an error, and extract the abnormal path in which there is an error state; according to the obtained The extracted abnormal path and data constraint features are used to extract the abnormal fragment of the abnormal path. The invention solves the problem of automatic detection of abnormal fragments in the prior art when a detection result failure occurs in the system.
Owner:TONGJI UNIV
A Product Modeling Method Based on Interaction Feature Pair
ActiveCN103279599BEnsure consistencyEasy to implementSpecial data processing applicationsProduct modelingSimulation
The invention provides a product modeling method based on an interactive feature pair. The method includes the steps of firstly, conducting product part modeling, and enabling the interactive feature pair to be embedded in a part model on the basis of interactive interfaces among product parts, then, achieving assembly modeling through feature elements of the fully specified interactive feature pair on the basis of the part model where the interactive feature pair is embedded. The product modeling method based on the interactive feature pair has the advantages that the interactive feature pair is divided into six types of highly abstracted basic classifications, in the assembly modeling method from top to bottom, ports are set up through the interactive feature pair so that enough abstraction and generality can be ensured, consistency of constraints analysis for designers can be ensured when the interactive feature pair is embedded in the part model in comparison with a traditional assembly modeling method from bottom to top, and the interactive feature pair can be used for geometric reasoning in a downstream technology design process. Through the product modeling method based on the interactive feature pair, the advantages of the assembly modeling technology from top to bottom and the advantages of the assembly modeling technology from bottom to top can be combined, and therefore product assembly modeling can be better conducted.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Information system testing method based on Internet of Things
The invention discloses an information system testing method based on the Internet of Things. The method comprises the following steps: firstly, carrying out multi-label dimension reduction on underlying communication abnormal data of the Internet of Things, carrying out constraint analysis on related data in combination with a particle swarm algorithm, and on the basis, completing recognition onthe underlying Internet of Things abnormal data by applying a support vector machine method through an iterative classification constraint technology; and finally, carrying out related distinguishingon the abnormal data by utilizing a support vector machine method so as to detect the characteristics of the abnormal data of the Internet of Things. Experimental data results show that the method isadopted to detect abnormal data characteristics, and the detection accuracy is high.
Owner:佛山市湘訾科技服务有限公司
Scheduling method for automatic distribution vehicles in CNC workshop
ActiveCN103279857BDelivery route optimizationIncrease productivityLogisticsSpecial data processing applicationsNumerical controlDelivery vehicle
An automatic distribution vehicle scheduling method in a CNC workshop, which is characterized by: on the basis of constraint analysis and mathematical modeling of the vehicle scheduling problem in the CNC workshop, an original matrix scanning method is first used to allocate distribution tasks to vehicles, which significantly optimizes The initial population of the subsequent genetic algorithm is then used to solve the optimal delivery sequence of a single vehicle. Based on the driving characteristics of the delivery vehicles in the CNC workshop, the original coordinate addition and subtraction method with direction is used to calculate the actual driving distance of the vehicle. On this basis The golden section method is used to obtain the optimal delivery time of the vehicle, and the elite retention strategy is used to avoid the local convergence of the algorithm, thereby obtaining an ideal vehicle scheduling optimization solution. The invention solves the problem of inefficiency of the existing vehicle scheduling algorithm in the CNC workshop due to the specific distribution of user points and the special process of distribution, and the algorithm is efficient and feasible.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method and device for linking form elements
ActiveCN107766307BImprove scalabilityIncrease flexibilityText processingInput/output processes for data processingTheoretical computer scienceReusability
The purpose of this application is to provide a method and device for linkage of form elements, by determining the constrained elements of the form according to the constraint analysis algorithm and its corresponding constraint relationship when the value of the constrained element of the form is monitored. The corresponding optional values of , wherein the constraint relationship includes the correspondence between the constrained element and the constrained element; then, select the value corresponding to the constrained element from the optional values. According to the functional requirements of the product, configure the constraint relationship and constraint analysis algorithm, let the form system automatically process the optional values of the elements, and the form interface can be automatically rendered according to the change of the optional values of each element, improving the scalability and flexibility of the form system and reusability, and after the functional requirements of the form product are changed, the code of the form system is changed less, and the correctness and robustness of the code are improved.
Owner:ALIBABA GRP HLDG LTD
Method for simplifying numerical map settlement place polygon by utilizing parametric design model
InactiveCN101930483BIncrease productivityImprove product qualityMaps/plans/chartsSpecial data processing applicationsGraphicsAlgorithm
The invention relates to a method for simplifying a numerical map settlement place polygon by utilizing a parametric design model and effectively solves the problem of enabling the whole simplification process to accurate and quantitative, and ensuring good simplification effect. The method comprises the following steps: presetting the numeric area of the target function corresponding to the initial threshold value integrated digital model and simplification result quality and contribution weight; identifying the graph feature of the settlement place polygon, using coordinate monotonicity to identify local extremum point and basic bending, using adjacent edge vector multiplication cross to identify concavity of direction and culmination of the settlement place polygon; using gradual imaging simplification method to carry out primary simplification on the polygon and building the corresponding supergraph model to obtain the value of corresponding target culmination of each constrained edge in the model; using a mathematical model corresponding to the parametric design model to carry out constrained analysis on the constrained culmination, and constantly repeating iteration to obtain the final result. With coordinate data output by the computer, various settlement places can be simplified, and production efficiency and product quality of the numerical map can be improved.
Owner:THE PLA INFORMATION ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com