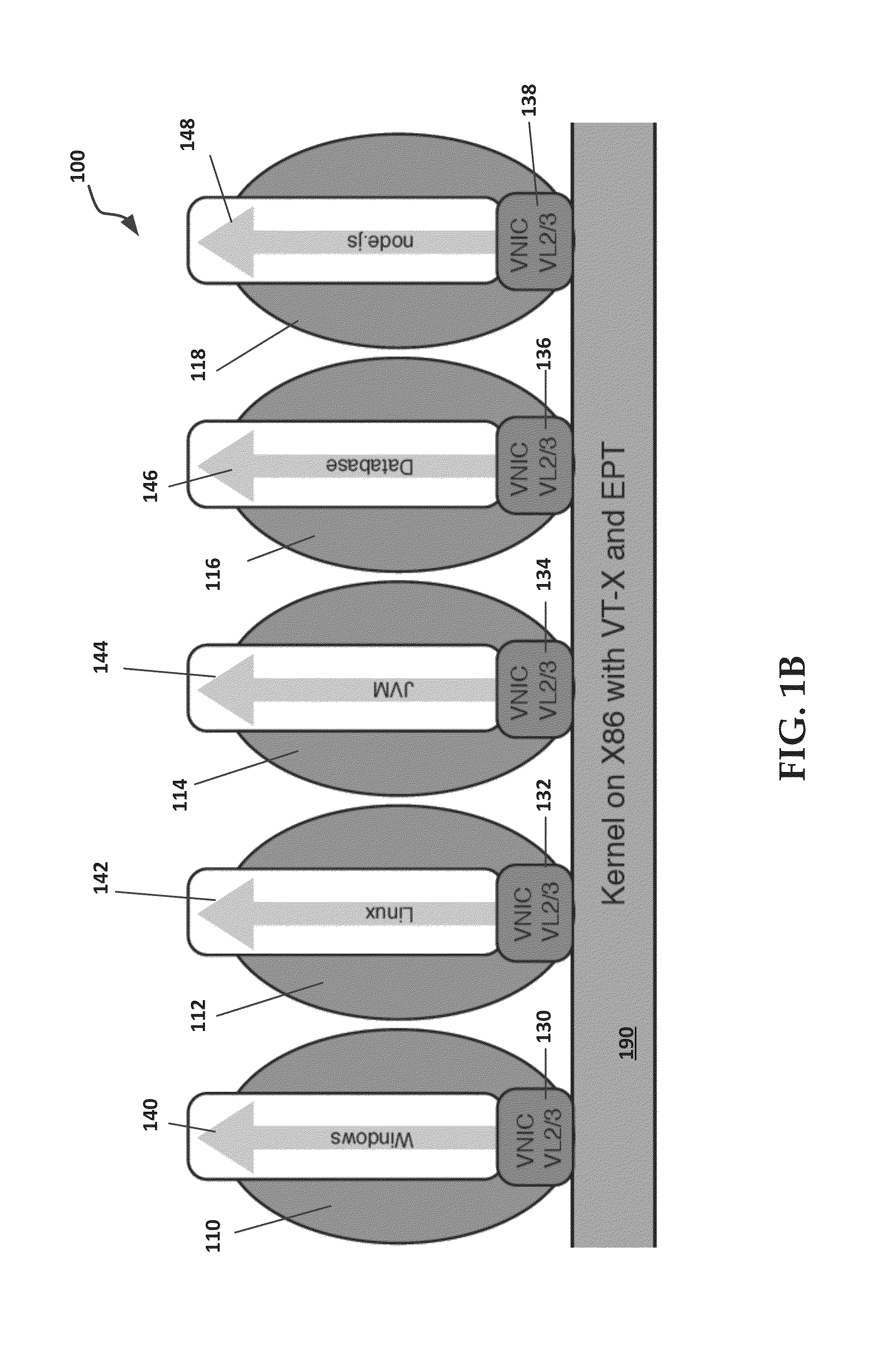
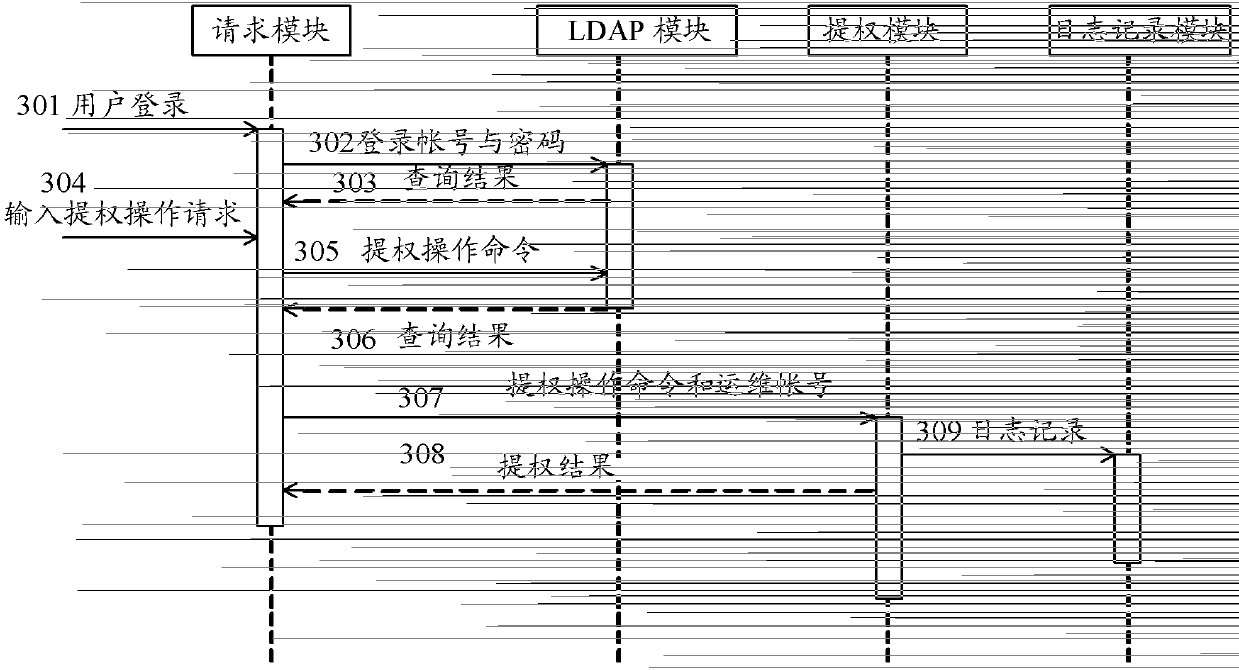
Patents
Literature
77 results about "Privilege escalation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Privilege escalation is the act of exploiting a bug, design flaw or configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user. The result is that an application with more privileges than intended by the application developer or system administrator can perform unauthorized actions.
Application of advanced cybersecurity threat mitigation to rogue devices, privilege escalation, and risk-based vulnerability and patch management
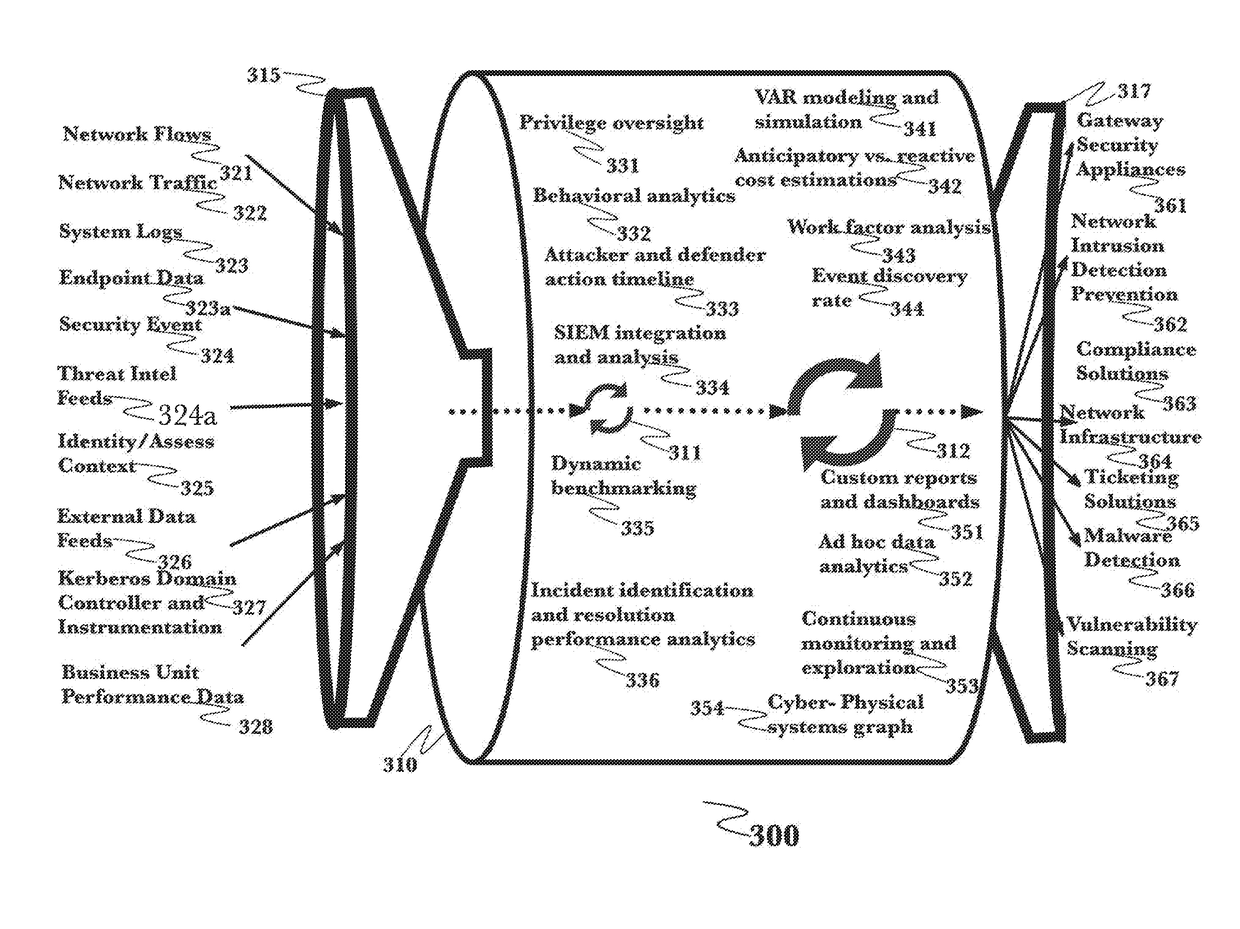
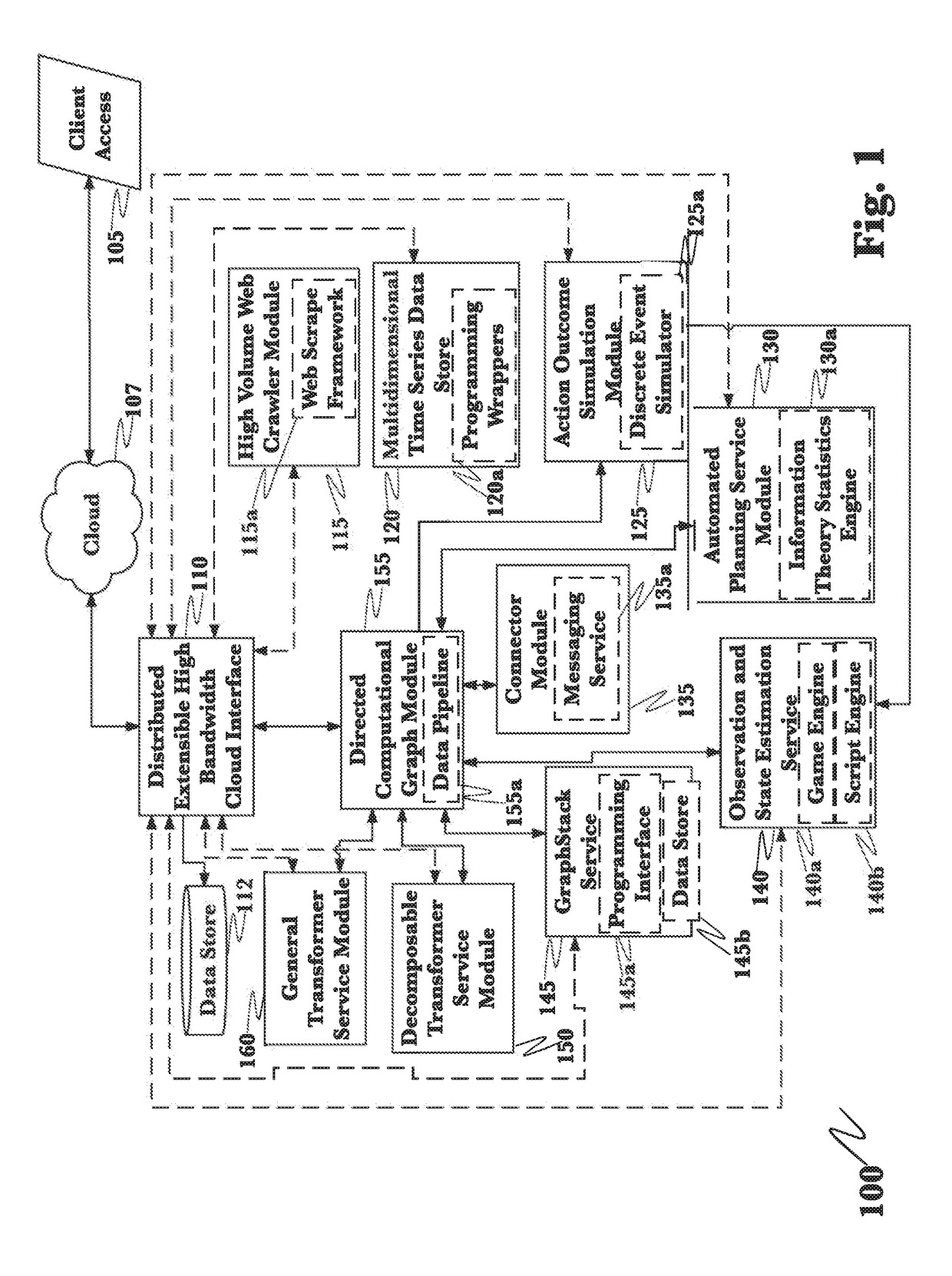
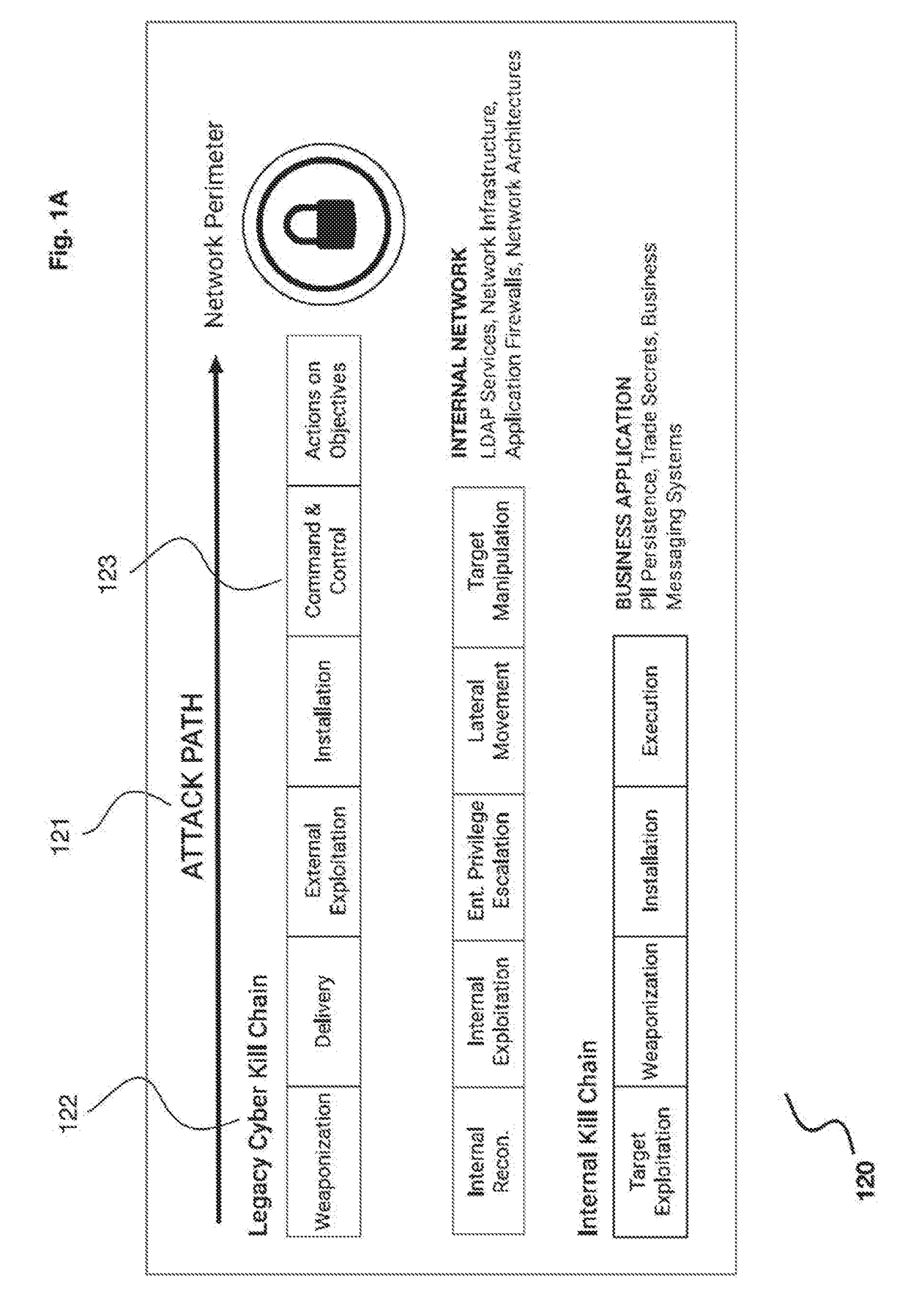
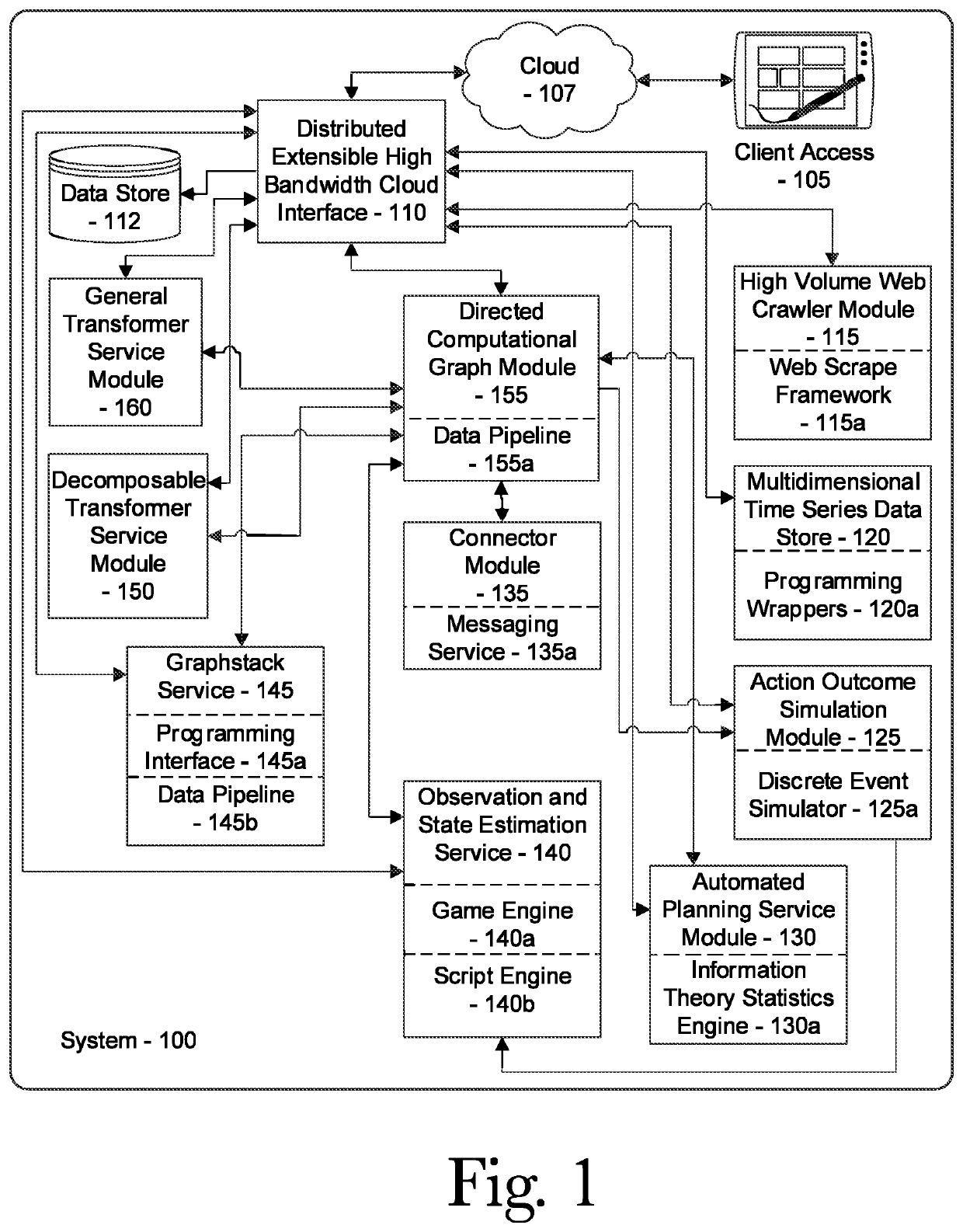
A system for mitigation of cyberattacks employing an advanced cyber decision platform comprising a time series data store, a directed computational graph module, an action outcome simulation module, and observation and state estimation module, wherein the state of a network is monitored and used to produce a cyber-physical graph representing network resources, simulated network events are produced and monitored, and the network events and their effects are analyzed to produce security recommendations.
Owner:QOMPLX INC
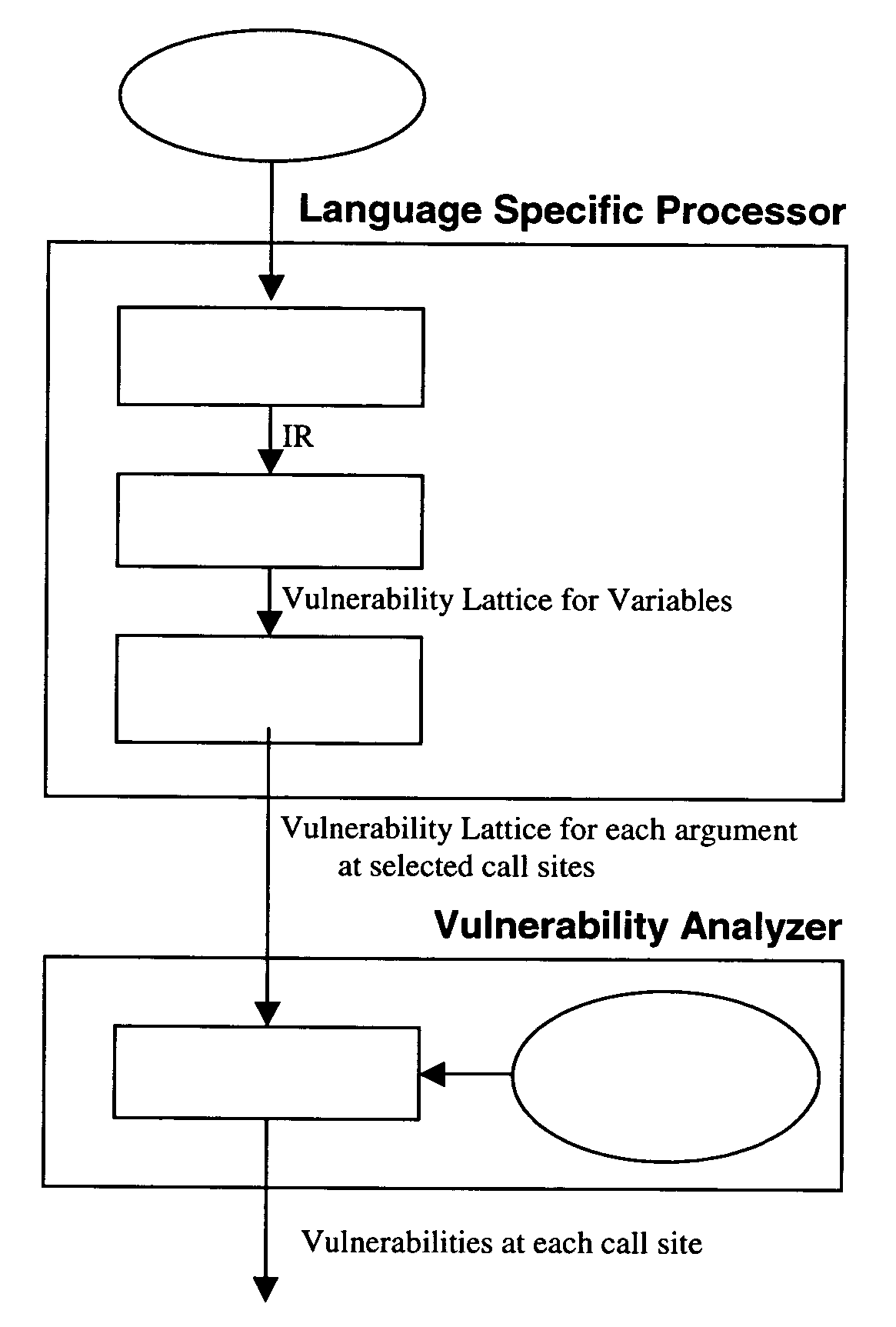
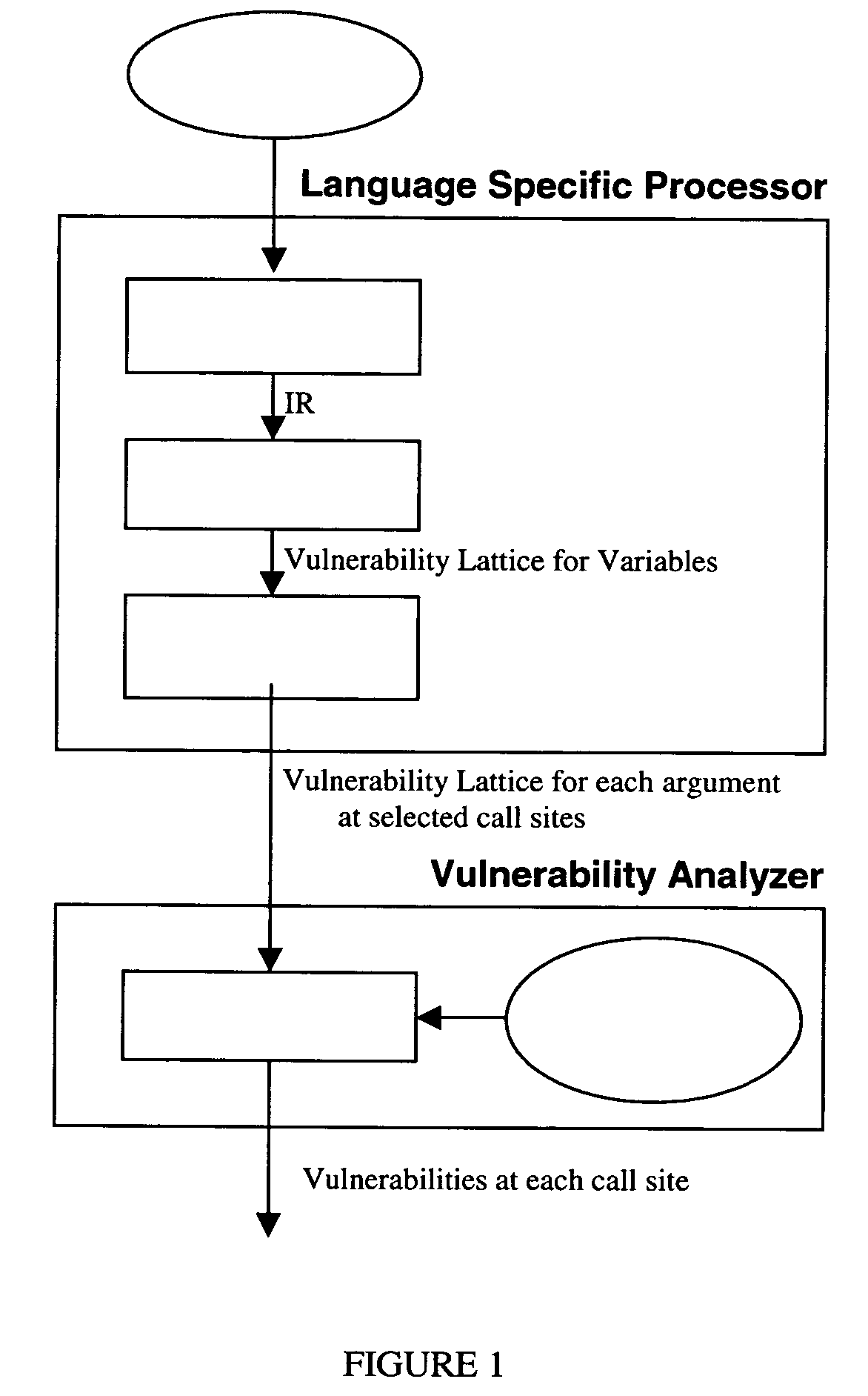
Method and system for detecting privilege escalation vulnerabilities in source code
InactiveUS20050010806A1Memory loss protectionDigital data processing detailsSource codePrivilege escalation
A method and system of detecting vulnerabilities in source code. Source code is parsed into an intermediate representation. Models are derived for the code and the models are then analyzed in conjunction with pre-specified rules about the routines to determine if the routine call posses one or more of pre-selected vulnerabilities.
Owner:IBM CORP
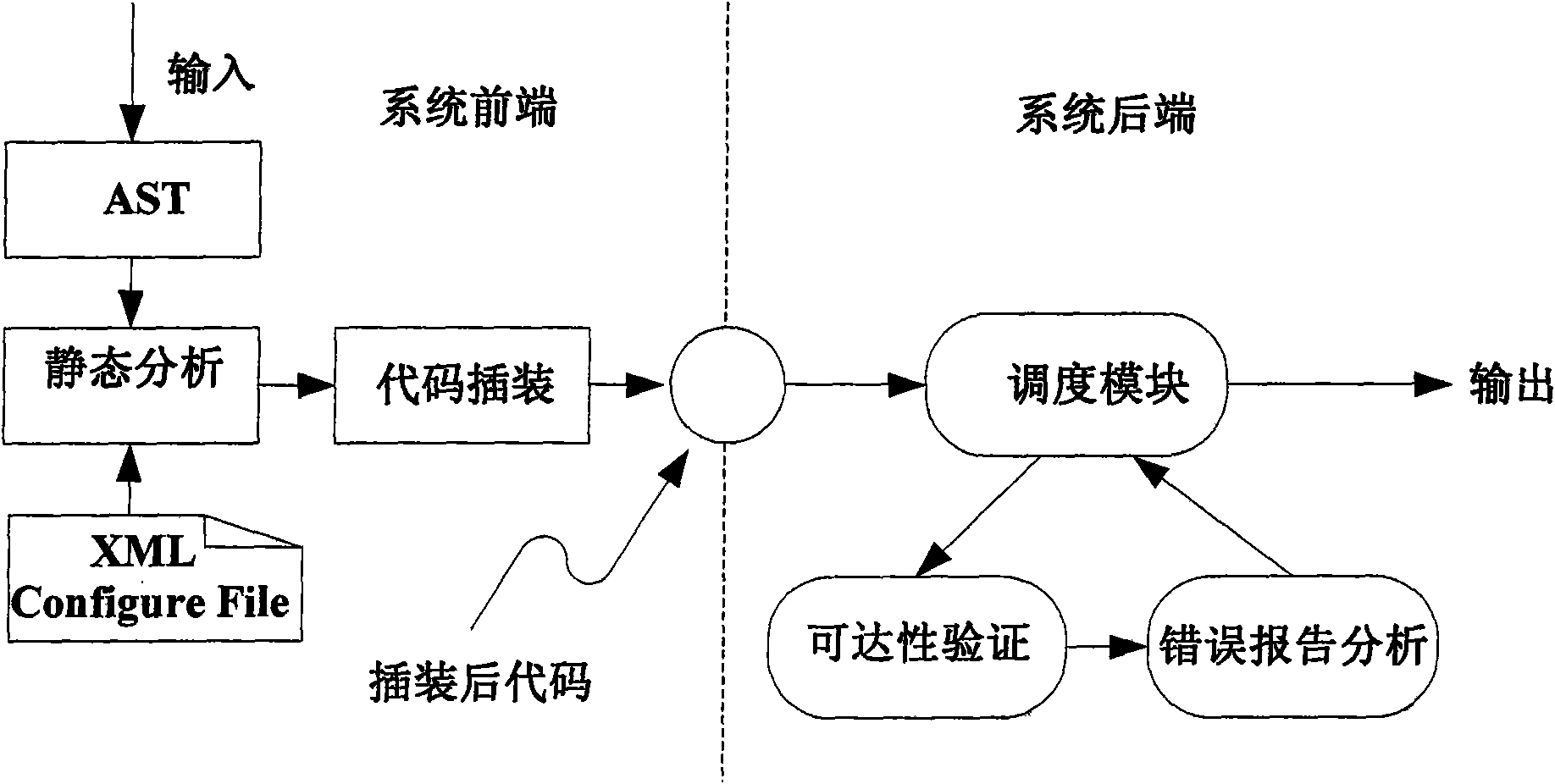
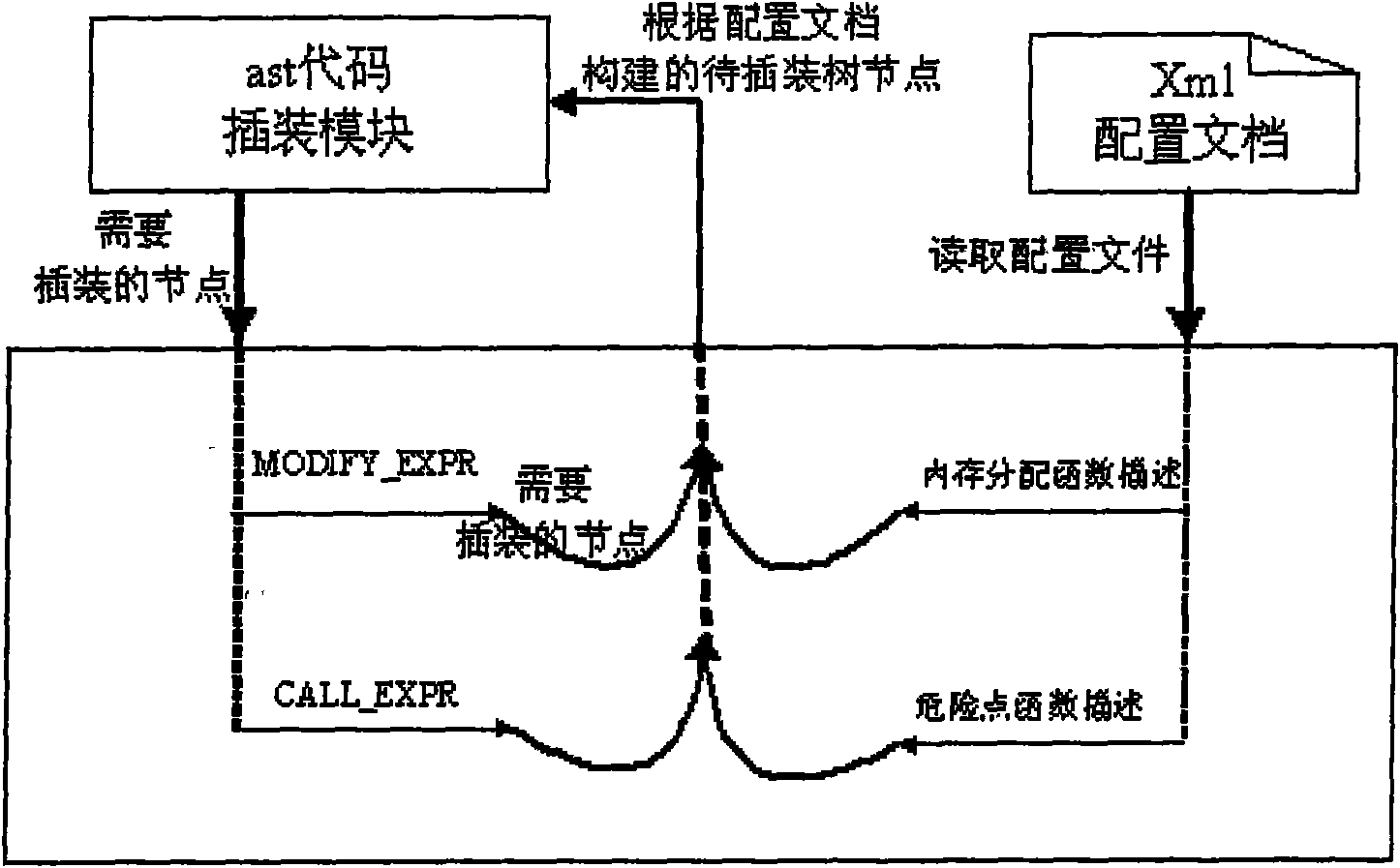
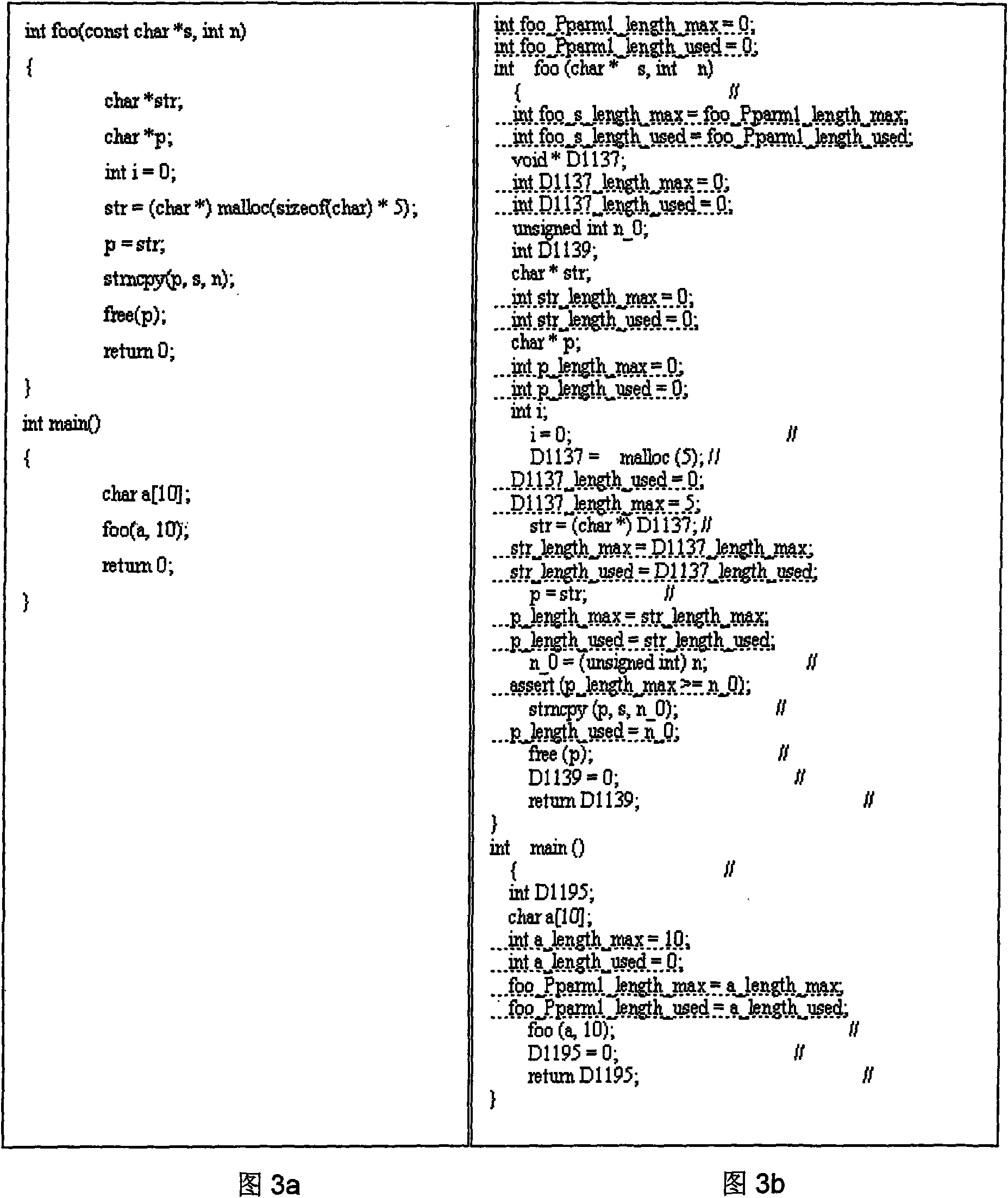
Method for detecting code security hole based on constraint analysis and model checking
The invention relates to a method for detecting a code security hole based on constraint analysis and model checking, which can extract the source code of a C program in a constraint way and detect the security hole of the program with the model checking. The main content comprises the following steps: buffer attribute information which is involved in the source code of the C program is extracted with a constraint analysis technology; the corresponding ASSERT sentence information of attribute generation, attribute transmission and attribute constraint is inserted into variable declaration, variable assignment and function call site with the buffer attribute information; the inserted code can be taken as the input of the model checking to judge whether the program is accessible, find whether the dangerous points in the program really has an accessible path and finally find the security hole in the source code. Currently, independent model checking can not detect the security hole of the buffer and the like, the method combines the static detecting technology of the constraint analysis with the model detecting technology to realize the detection of the security hole of the buffer overflow and the like, wherein, the detecting precision of the method is higher than that of the general static detecting technology. By extracting the other dangerous function information of the source code, corresponding inserting process is carried out. The invention also can detect the security holes such as formative character string, code injection, privilege escalation, etc.
Owner:BEIHANG UNIV
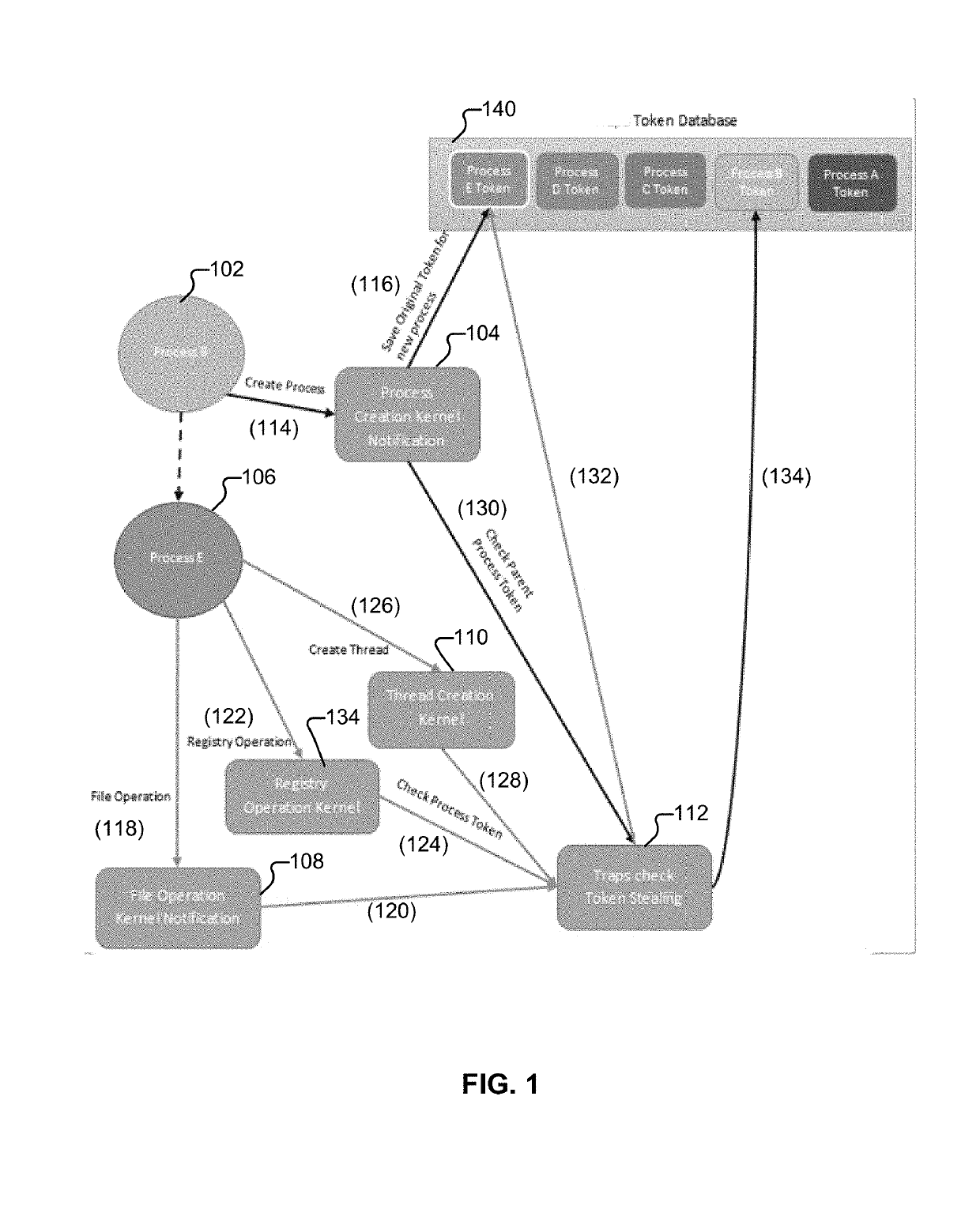
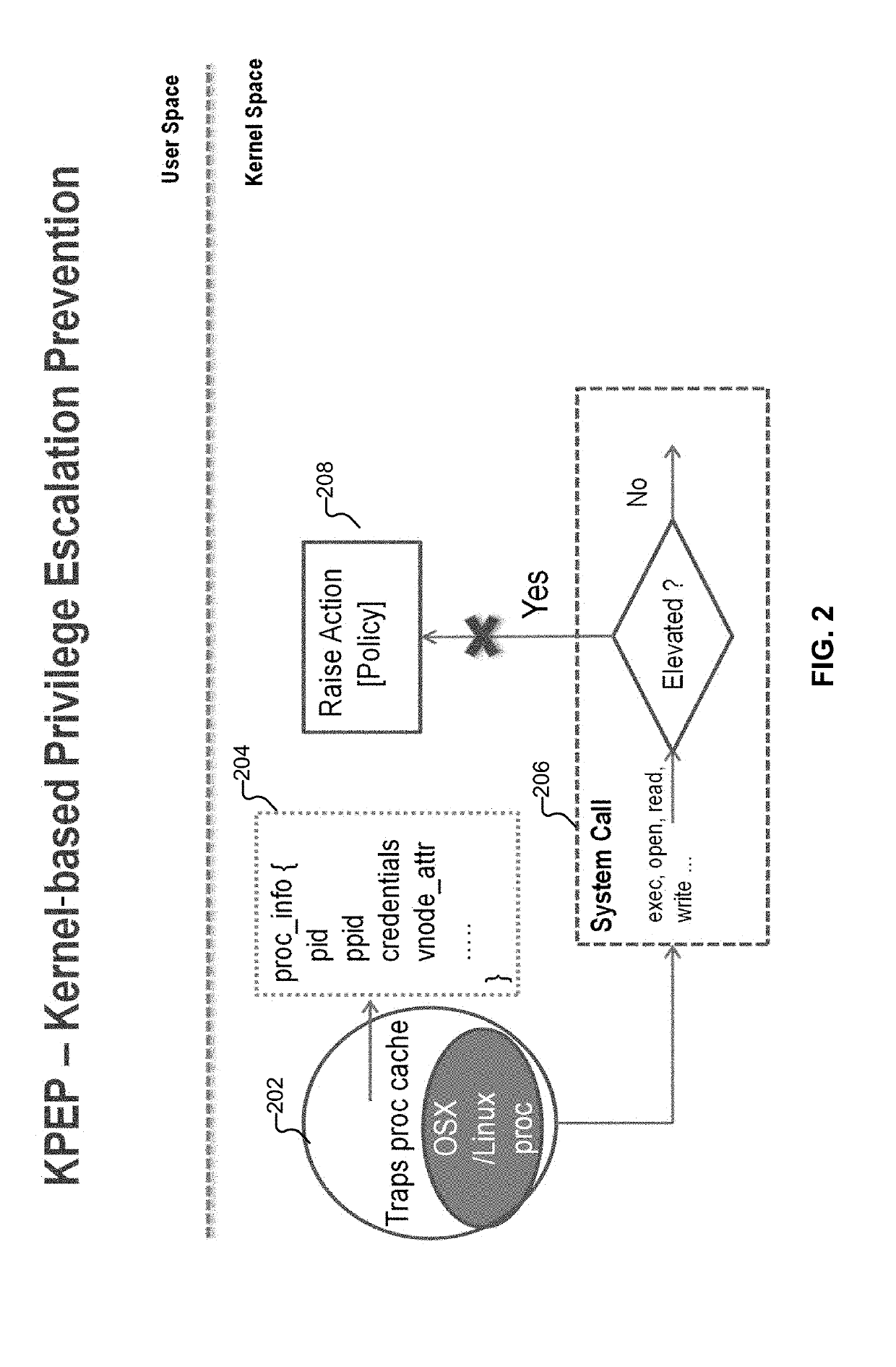
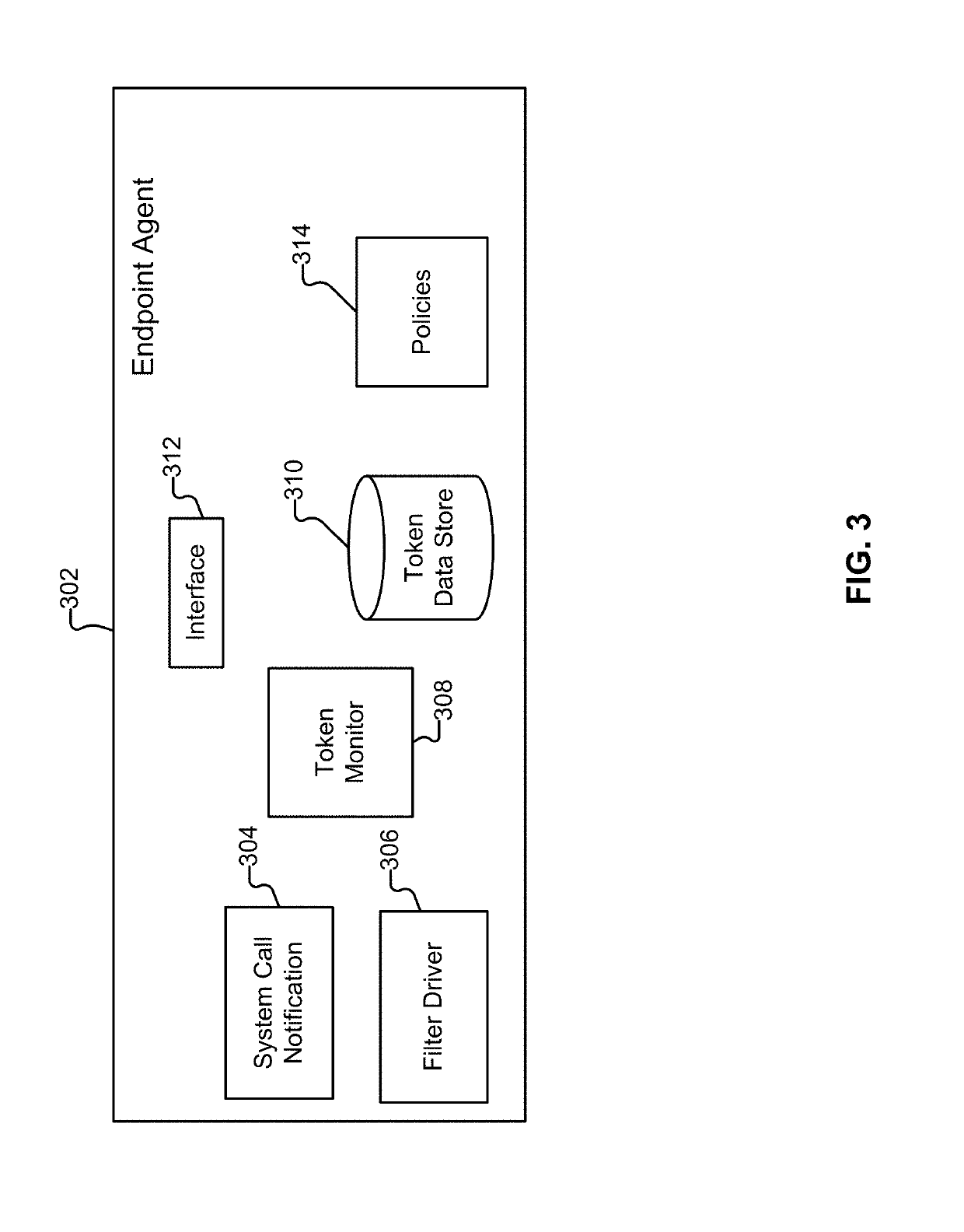
Privilege escalation protection
ActiveUS20190311115A1Digital data authenticationPlatform integrity maintainanceWhitelistSecurity policy
Techniques for privilege escalation protection are disclosed. In some embodiments, a system / process / computer program product for privilege escalation protection includes monitoring a process executed on a computing device, detecting an unauthorized change in a token value associated with the process, and performing an action based on a policy (e.g., a kernel protection security policy / rule(s), which can include a whitelisted set of processes and / or configured actions / responses to perform for other / non-whitelisted processes) in response to an unauthorized change in the token value associated with the process.
Owner:PALO ALTO NETWORKS INC
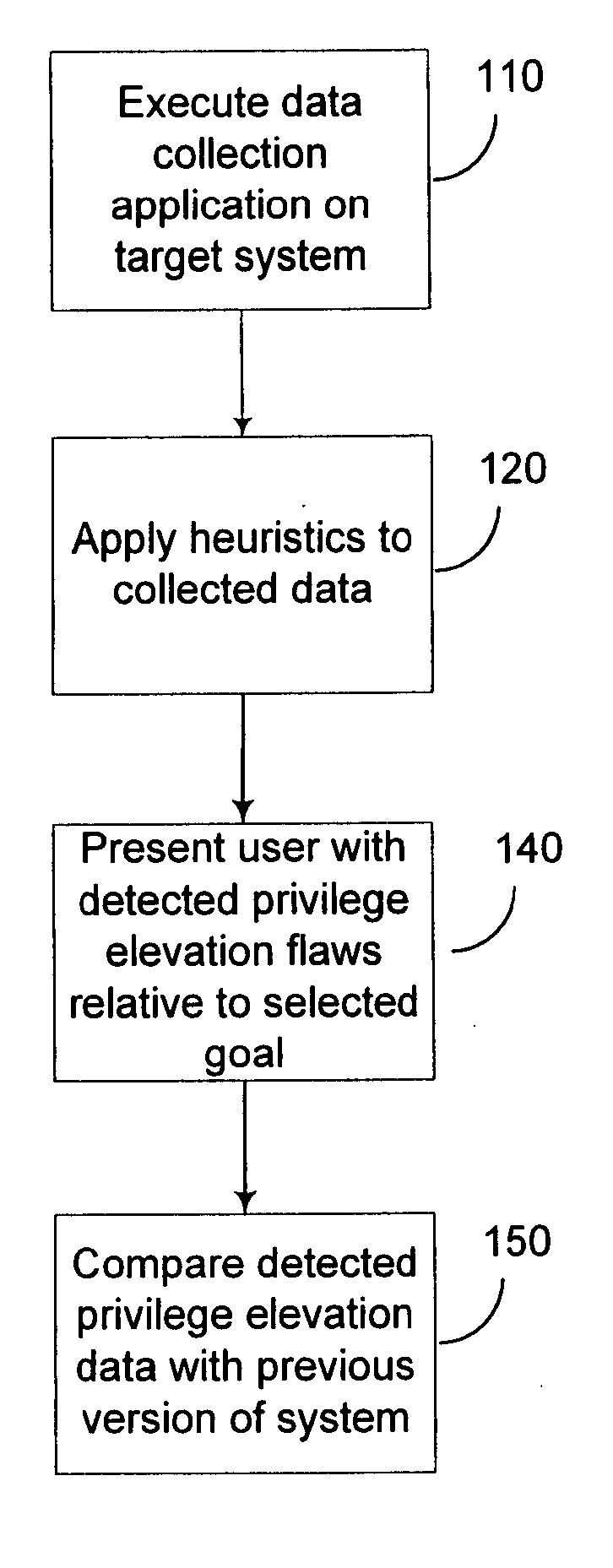
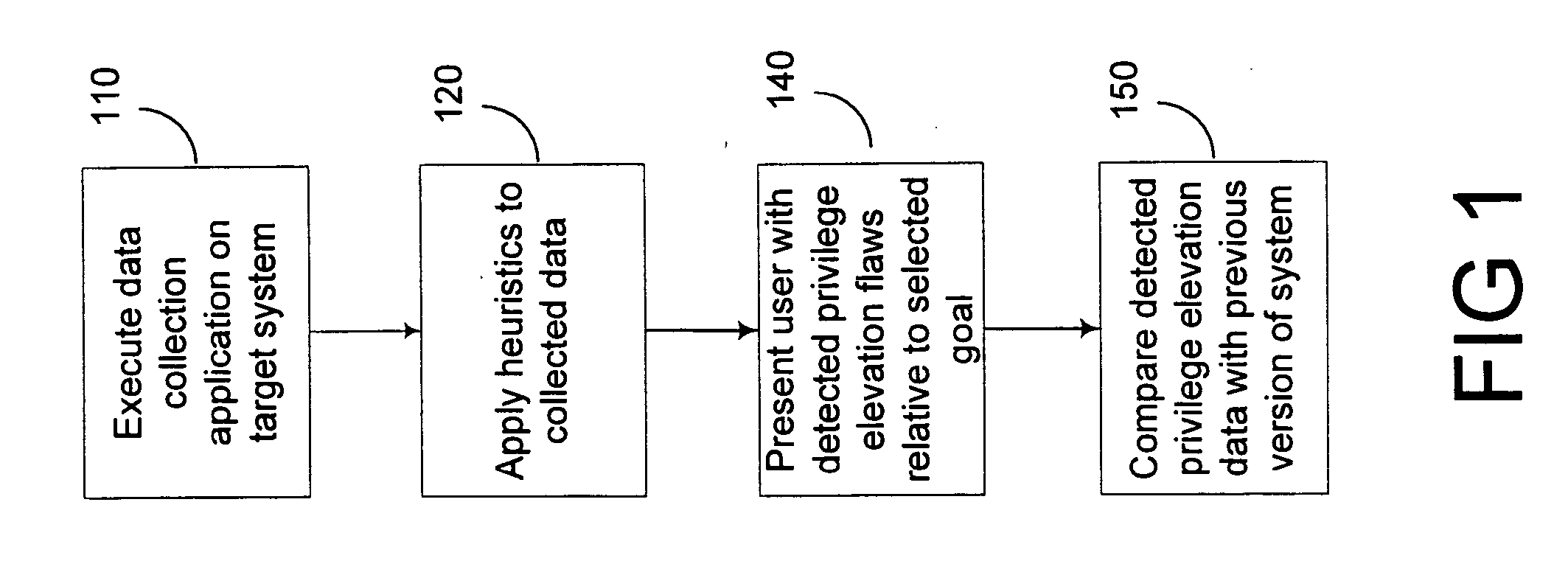
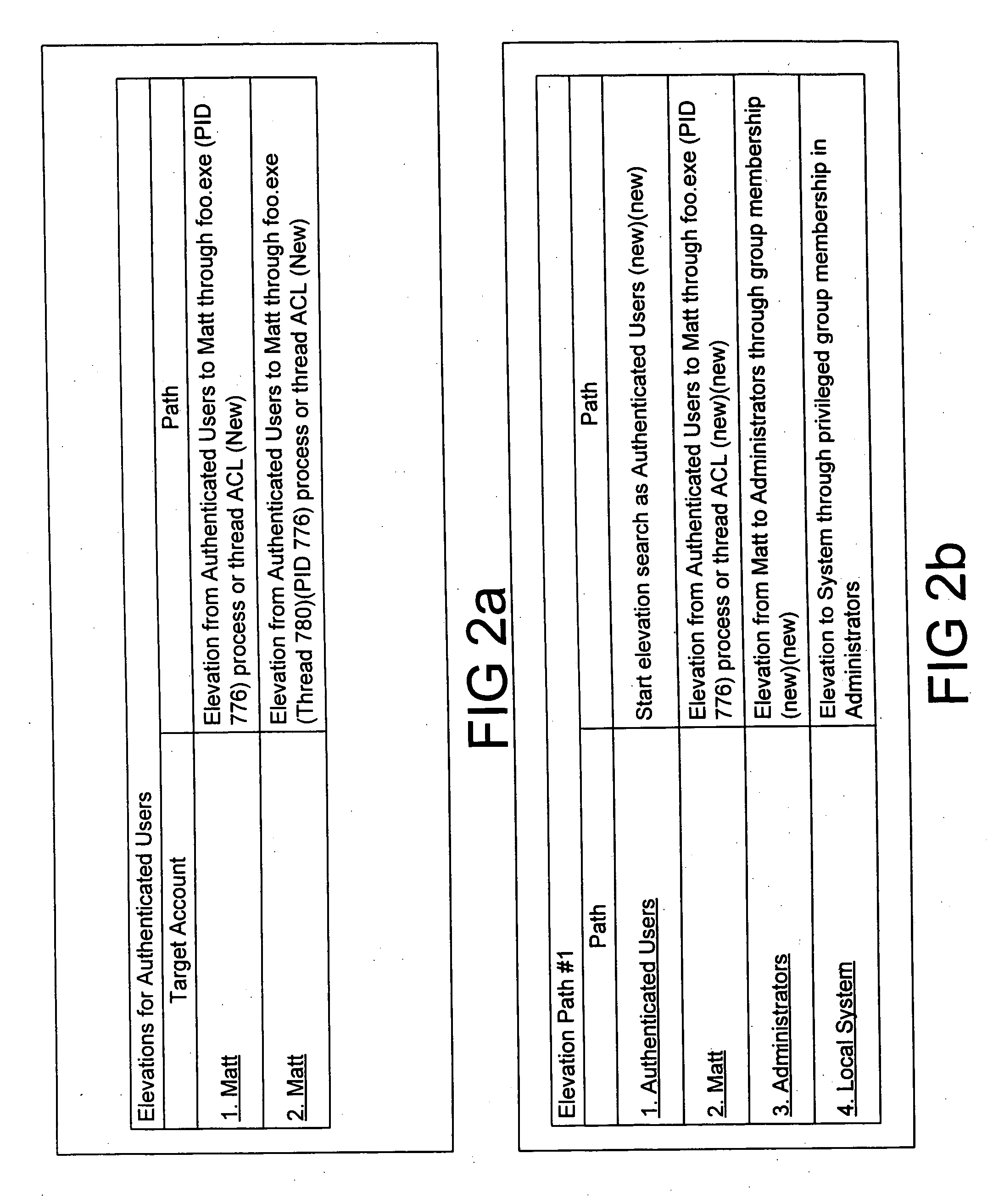
Expert system analysis and graphical display of privilege elevation pathways in a computing environment
A data collection application is executed on a target system. Various data indicative of privilege elevation pathways is collected, including user account data, file permission data, and system registry data. The collected data is analyzed according to heuristics. System accounts are displayed on a graph as nodes. Detected privilege elevations between the accounts are displayed as edges between their corresponding accounts. A user may customize the displayed graph to focus on particular goal accounts, and categories of privilege elevations.
Owner:MICROSOFT TECH LICENSING LLC
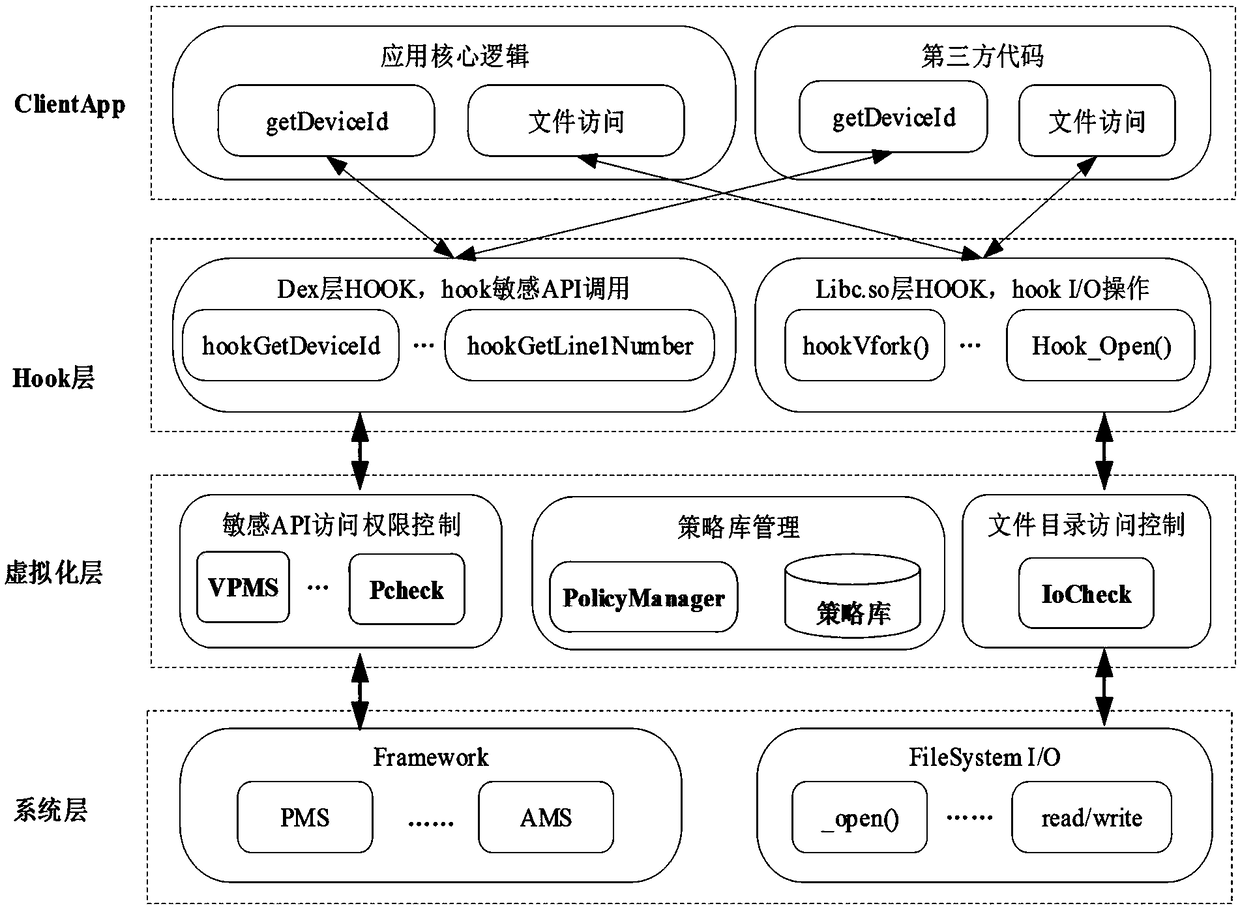
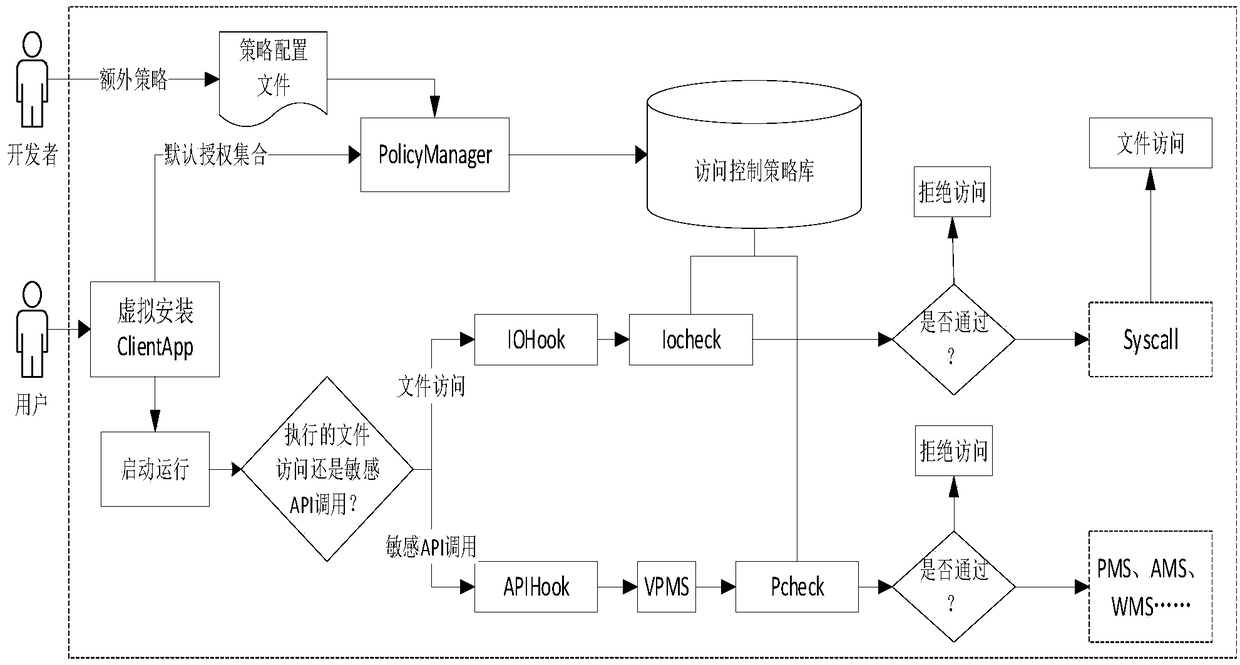
Control method and system of restricted access in Android application multi-running environment
InactiveCN108932427APermission restrictionLimited useComputer security arrangementsReal systemsThird party
The invention discloses a control method and system of restricted access in an Android application multi-running environment, an open source virtualization framework is extended, and a privilege escalation attack initiated by a ClientApp due to the sharing of a permission of a HostApp is limited. The method includes a step of judging whether a current sensitive API call operation is legal or not with the combination of loaded policy information if a current operation is the sensitive API call operation when the ClientApp is running, and allowing the ClientApp to call a real API if so, a step of triggering an IOHook module to obtain a currently accessed file directory if the current operation belongs to a file access operation, then allowing an IoCheck module to check whether current accessis legal or not with the combination of a policy library, and calling a real system for file operation if so, and a step of analyzing a permission list to be a default quasi-permission authorizationset while the HostApp loads the ClientApp, and forming an authorization set with the integration of a developer-configured policy. According to the method and the system, the sensitive API access control in a third-party application multi-running environment is achieved.
Owner:HUAZHONG UNIV OF SCI & TECH
Complex Application Attack Quantification, Testing, Detection and Prevention
ActiveUS20200351298A1Avoid attackEasy to learnMathematical modelsOffice automationRisk quantificationAttack
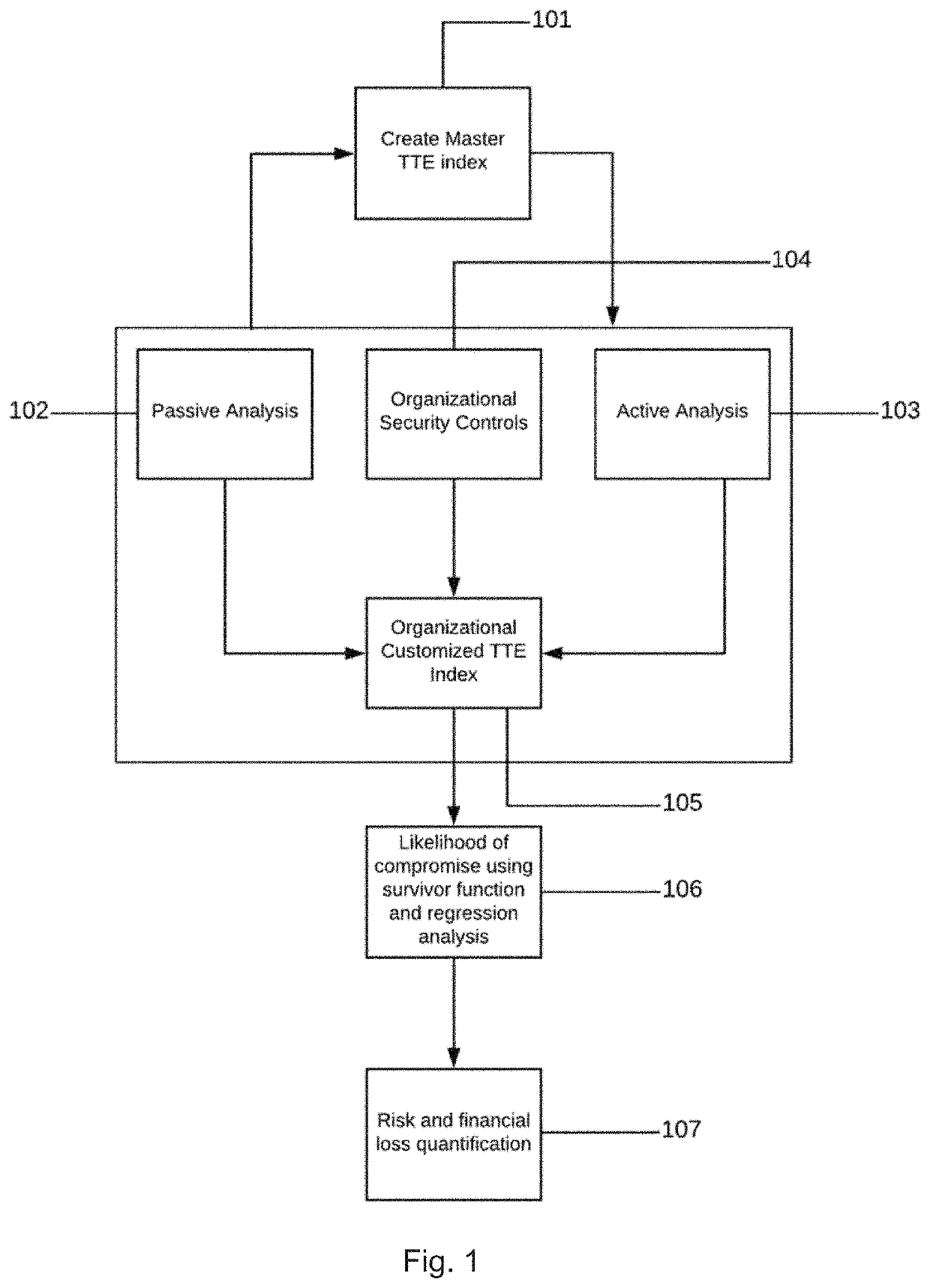
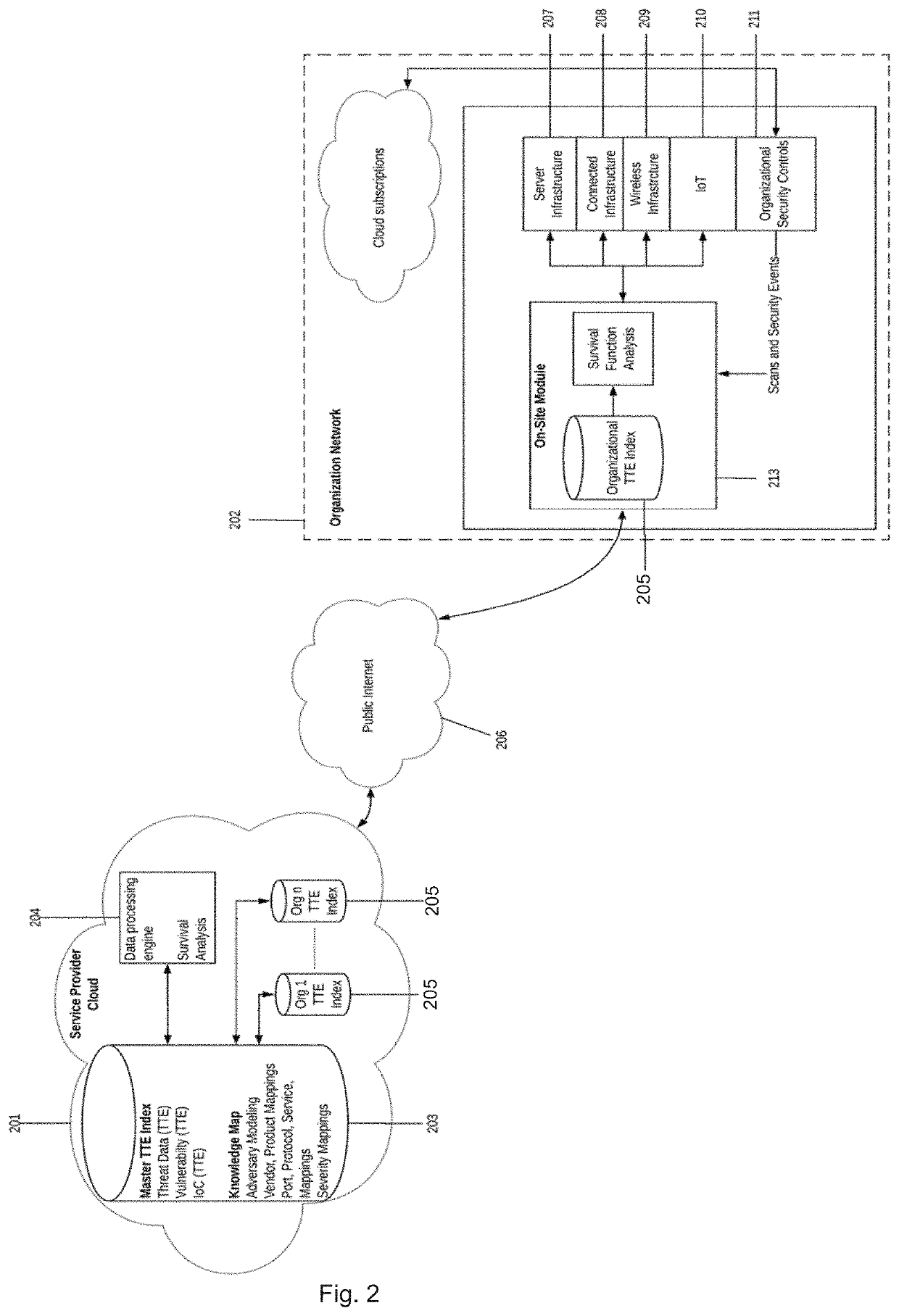
An apparatus and method for cyber risk quantification calculated from the likelihood of a cyber-attack on the target enterprise and / or cyber ecosystem based on its security posture. The cyber-attack likelihood can be derived as a probability-based time-to-event (TTE) measure using survivor function analysis. The likelihood probability measure can also be passed to cyber risk frameworks to determine financial impacts of the cyber-attacks. Embodiments of the present invention also relate to an apparatus and method (1) to identify and validate application attack surfaces and protect web applications against business logic-based attacks, sensitive data leakage and privilege escalation attacks; and / or (2) that protects web applications against business logic-based attacks, sensitive data leakage and privilege escalation attacks. This can include implementing an intelligent learning loop using artificial intelligence that creates an ontology-based knowledge base from application request and response sequences. Stochastic probabilistic measures are preferably applied to a knowledge base for predicting malicious user actions in real time.
Owner:IVANTI INC
Android privilege escalation attack detection system and method based on cloud platform
InactiveCN103023871AIncrease costAvoid complex judgment processesTransmissionSpecial data processing applicationsThird partyComputer terminal
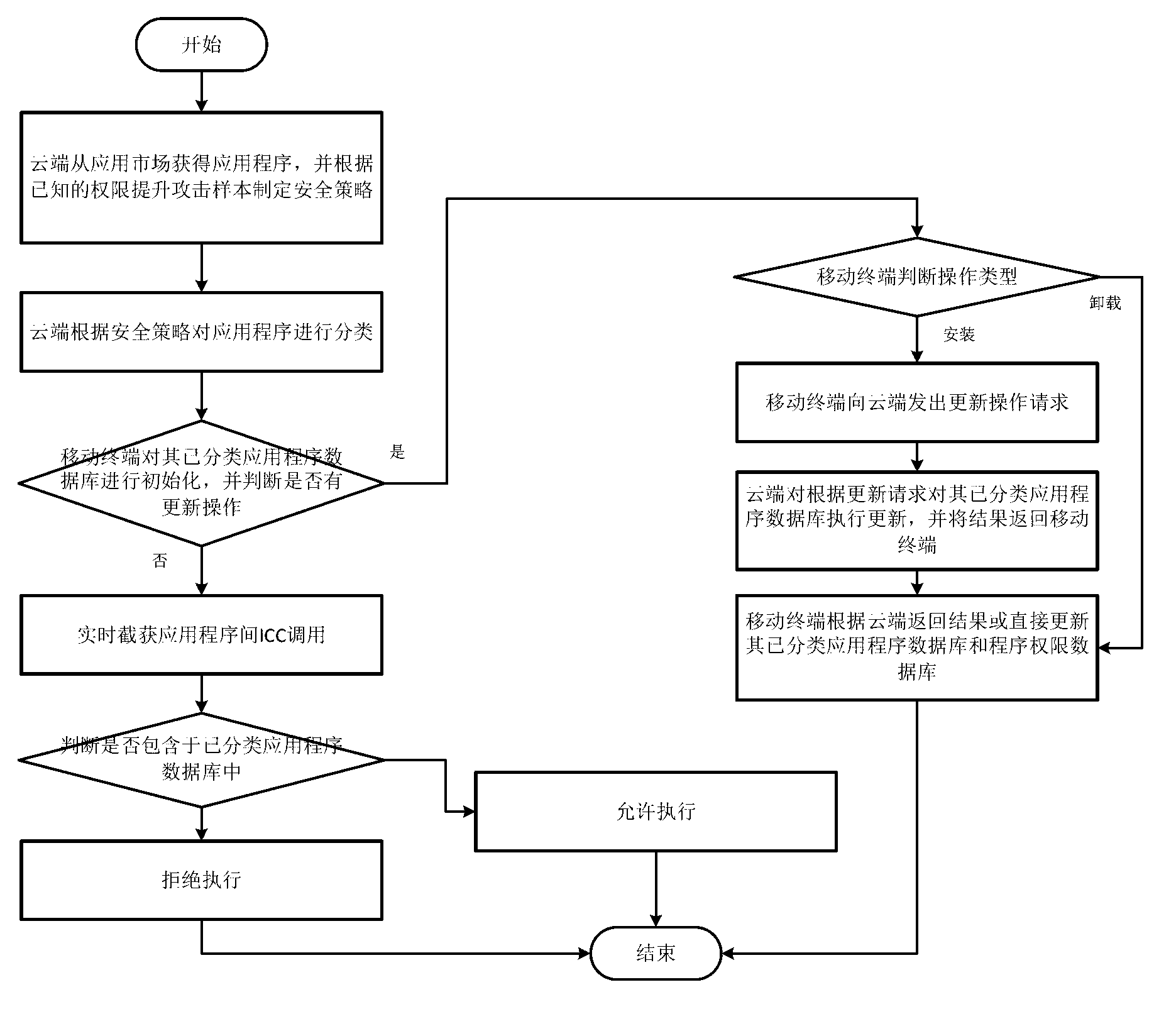
The invention discloses an android privilege escalation attack detection system and method based on cloud platform, which comprises the following steps: a cloud end downloads application programs from an application market and adds into an application program information database by using the crawler program, the application market comprises an official market and a third-party market, and formulates the security policy according to known privilege escalation attack sample, the cloud end classifies the application programs according to the security policy, the mobile terminal initializes the classified application program database and judges whether the application programs have update operation, if yes, the mobile terminal judges the type of the update operation is installation operation or un-installation operation, and the mobile terminal updates the classified application program database and the program privilege database directly or according to the result sent by the cloud end. By adoption of the method disclosed by the invention, the problem that the detection operation which wastes time and resource is performed every time when invoking the ICC (inter-component communication) is avoided.
Owner:HUAZHONG UNIV OF SCI & TECH
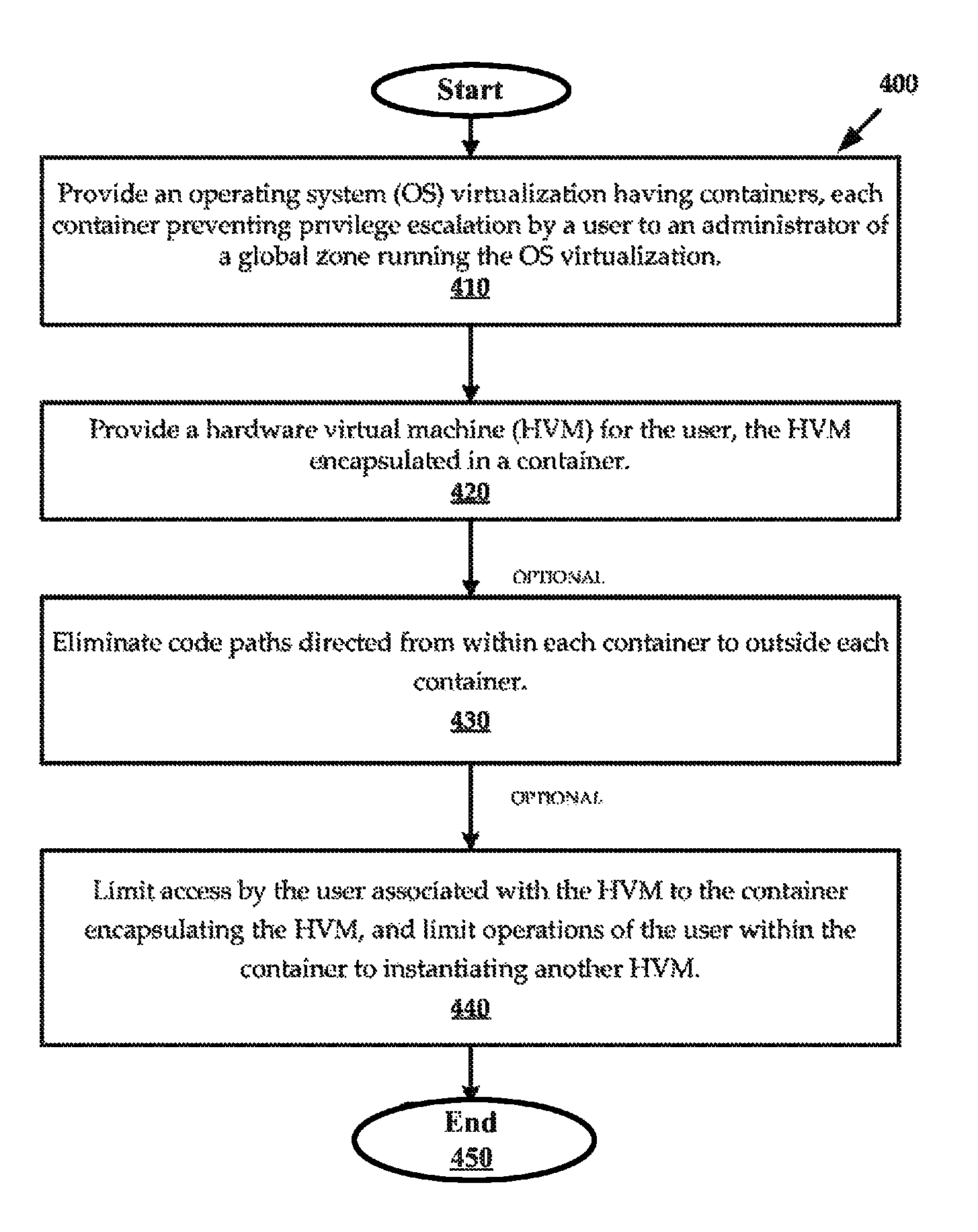
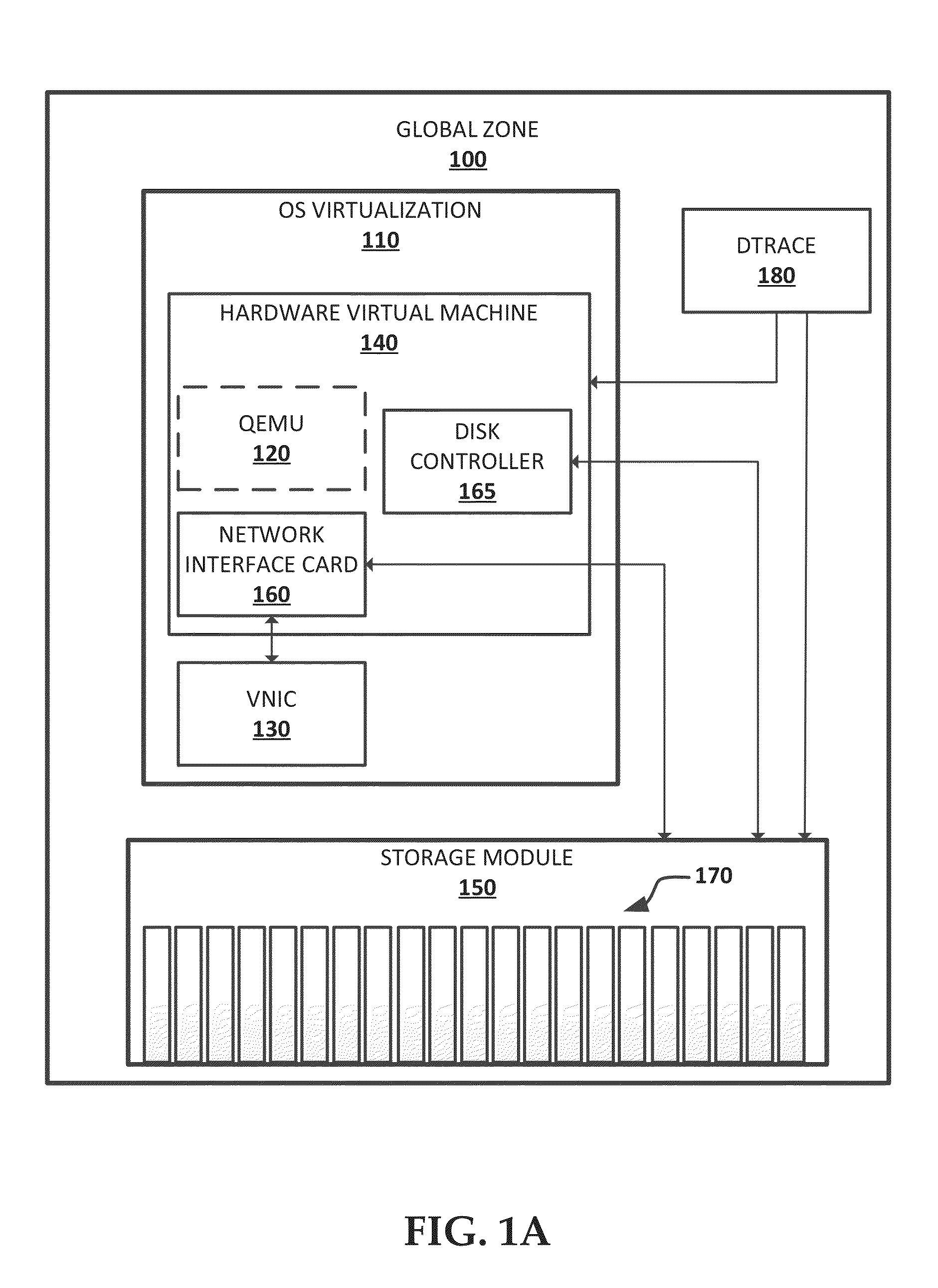
Systems and methods for double hulled virtualization operations
ActiveUS8793688B1Prevent privilege escalationLimiting user operationSoftware simulation/interpretation/emulationMemory systemsVirtualizationOperational system
A method for storing and processing data includes providing an operating system (OS) virtualization running on a processor and having a plurality of containers. Each container may prevent privilege escalation by a user to an administrator of a global zone running the OS virtualization. The method may also include providing a hardware virtual machine (HVM) for the user, the HVM encapsulated in one of the containers. A system for storing and processing data is provided that includes an operating system (OS) virtualization stored in a memory and running on a processor. The OS virtualization has a plurality of containers, and each container prevents privilege escalation by a user to an administrator of a global zone running the OS virtualization. The HVM may be encapsulated in one of the containers. A non-transitory computer readable storage medium having a program recorded thereon is provided.
Owner:JOYENT
Method for vulnerability detection in Windows operating environment based on instrumentation tool
InactiveCN105184169AAutomatic identificationAutomatic detectionPlatform integrity maintainanceBuffer overflowPrivilege escalation
The invention discloses a method for vulnerability detection in a Windows operating environment based on an instrumentation tool. The method comprises the steps that when it is detected that a target process executes a function call instruction, a next instruction address and a function return address are saved; if the instruction corresponding to the skip destination address of the target progress is not a start instruction of a function, ROP vulnerability existing is determined; when it is detected that the target process executes the function return address, whether the return address in a current thread stack is stored or not is detected, and if the return address is stored, a buffer overflow vulnerability is determined; whether the address of a function return instruction is same as the stored return address or not is judged, the address of the function return instruction is saved if the address of the function return instruction is not same as the stored return address, and it is judged that a ROP vulnerability exists in the target progress when it is detected that the address is executed for multiple times; a preset debugged progress is opened based on a function call interface, then whether the preset debugged progress can open the target process or not is judged, and if the preset debugged progress cannot open the target process, a local privilege escalation vulnerability exists. By means of the method, multiple samples can be automatically identified and detected concurrently.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Access control method and system for Android operation system
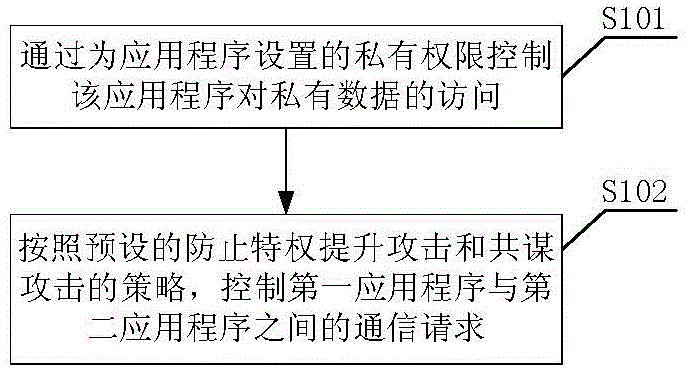
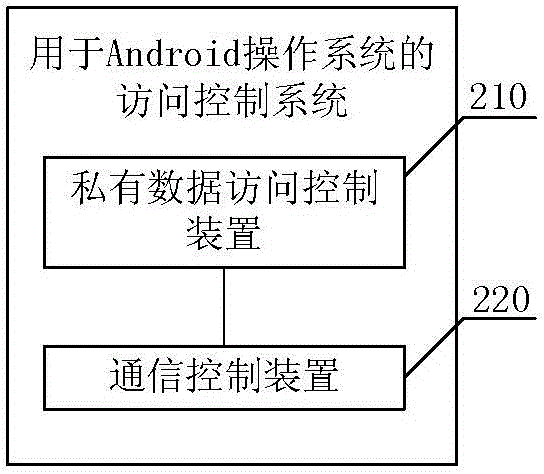
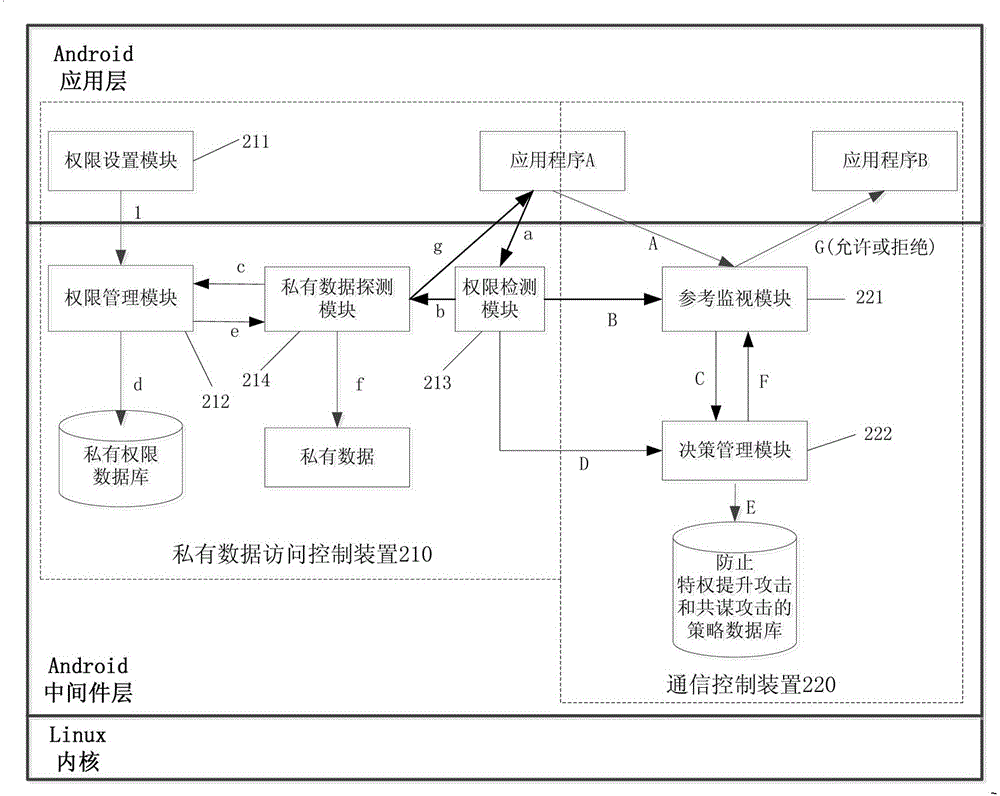
ActiveCN103559437AImprove securityIncrease flexibilityDigital data authenticationPlatform integrity maintainanceOperational systemApplication software
The invention relates to an access control method and system for an Android operation system, wherein the access control method for the Android operation system comprises the steps of step A, controlling the access of application programs to private data by the private permission set for the application programs; step B, according to a preset strategy for preventing privilege promoting attack and collusion attack, controlling the communication request between the first application program and the second application program. According to the access control method and system for the Android operation system, the safety when a single application program accesses the system resource or user private data is improved, and the safety during communication of multiple application programs is enhanced, so the flexibility of an Android permission mechanism is improved, the collusion attack and privilege enhancing attack can be effectively prevented, and the safety of a middleware layer in the Android operation is greatly improved.
Owner:INST OF INFORMATION ENG CAS
User privilege escalation method supporting mandatory access control
ActiveCN104036166AImprove securityImprove usabilityDigital data authenticationUser PrivilegeOperating system security
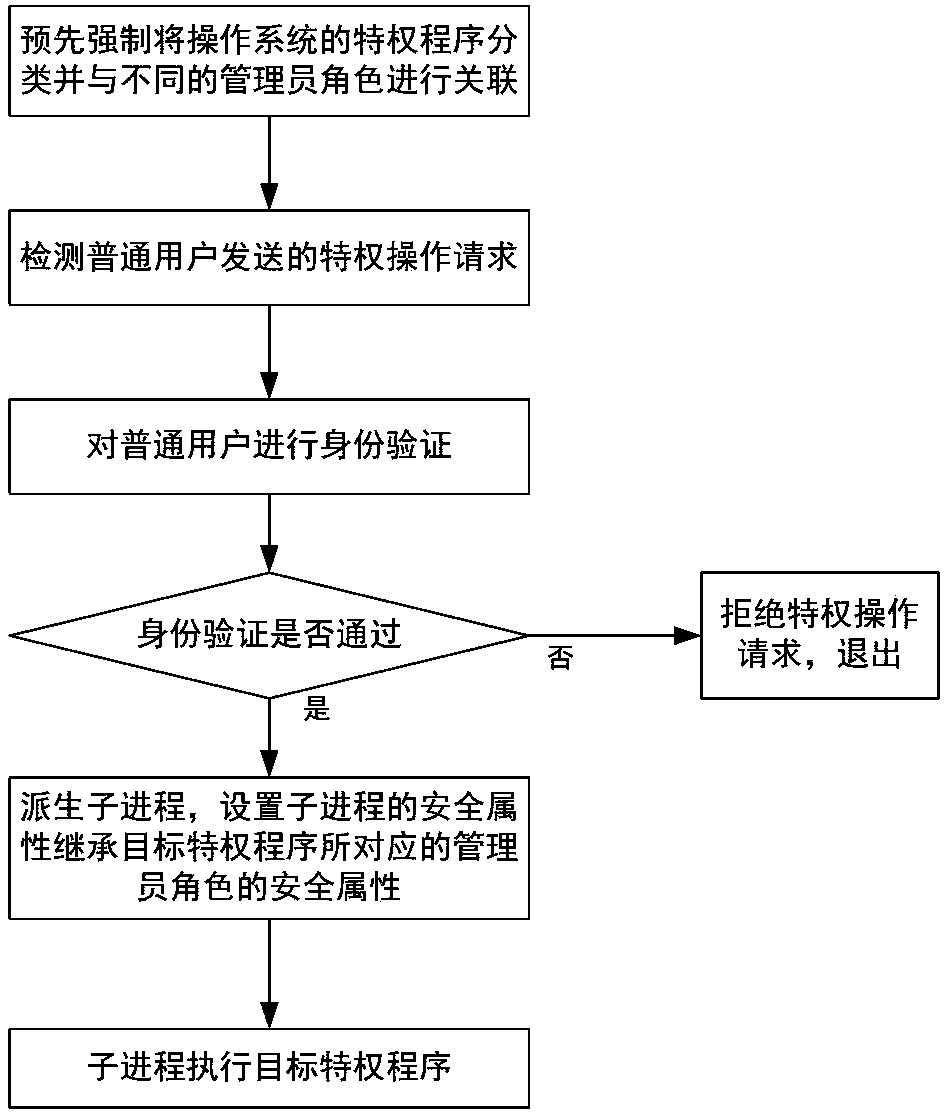
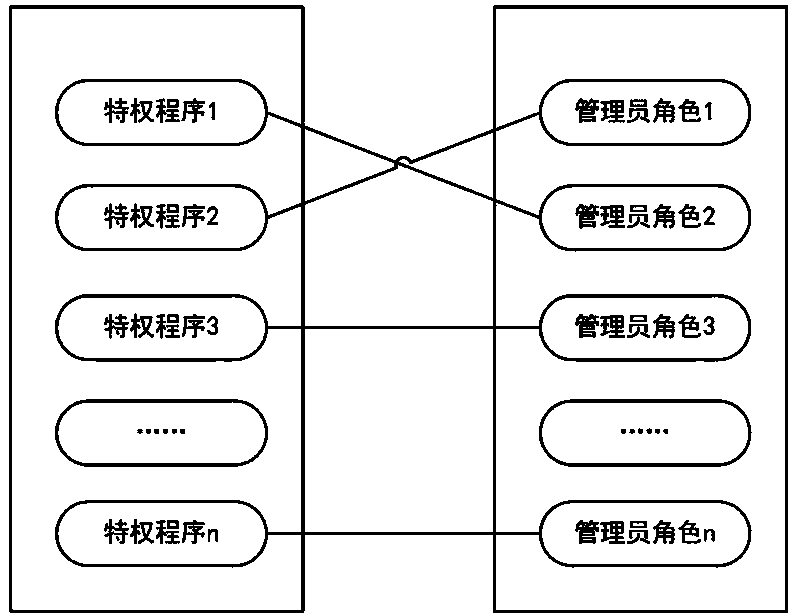
The invention discloses a user privilege escalation method supporting mandatory access control. The method comprises the following steps that: (1) privilege programs of an operating system are subjected to mandatory classification in advance and are correlated with different administrator roles; (2) access requests of users are detected, and when a privilege operation request is detected, jumping is carried out to execute the step (3); and (3) a user sending out the privilege operation request is authenticated, if the authentication is passed, a child process is derived, security attributes of the child process are set and are enabled to inherit security attributes of the administrator roles corresponding to the target privilege programs, and the target privilege programs are executed through the child process; and if the authentication is not passed, the privilege operation request of the user is refused, and exiting is carried out. The user privilege escalation method has the advantages that a realization method is simple; the privilege escalation operation of the user can be realized; in addition, the mandatory access control is supported; the safety of the operating system is high; and in addition, the usability is high.
Owner:NAT UNIV OF DEFENSE TECH
System and method for privilege delegation and control
InactiveUS20110093934A1FinanceDigital data processing detailsComputerized systemPrivilege escalation
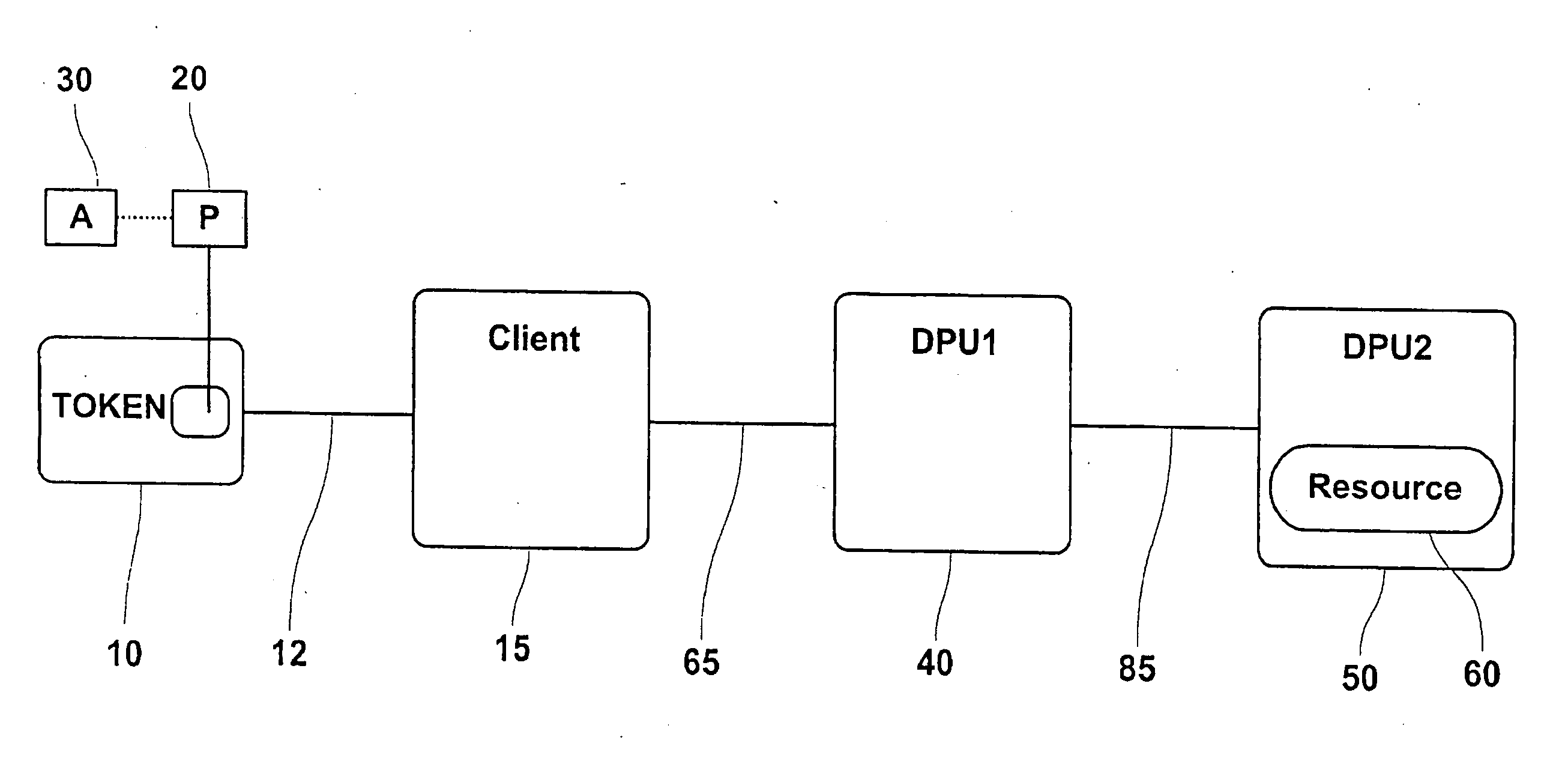
This invention provides a privilege delegation mechanism, which allows a privilege and associated control attributes to be delegated from a security token to another security token or an intelligent device such as a computer system. The privilege may be in the form of an attribute certificate, a key component of a cryptographic key, a complete cryptographic key, digital certificate, digital right, license or loyalty credits. The purpose of the delegation is to allow another security token or computer system to act as a surrogate for the security token or to access a resource which requires components from both units before access is permitted. Attributes associated with the delegated privilege control the scope and use of the privilege. The delegation may allow the surrogate to perform authentications, access data or resources included on another security token or computer system. Authentications are performed prior to transferring of the delegable privileges.
Owner:ASSA ABLOY AB
Integrated privilege separation and network interception
InactiveUS8635686B2Multiple digital computer combinationsProgram controlOperational systemFile system
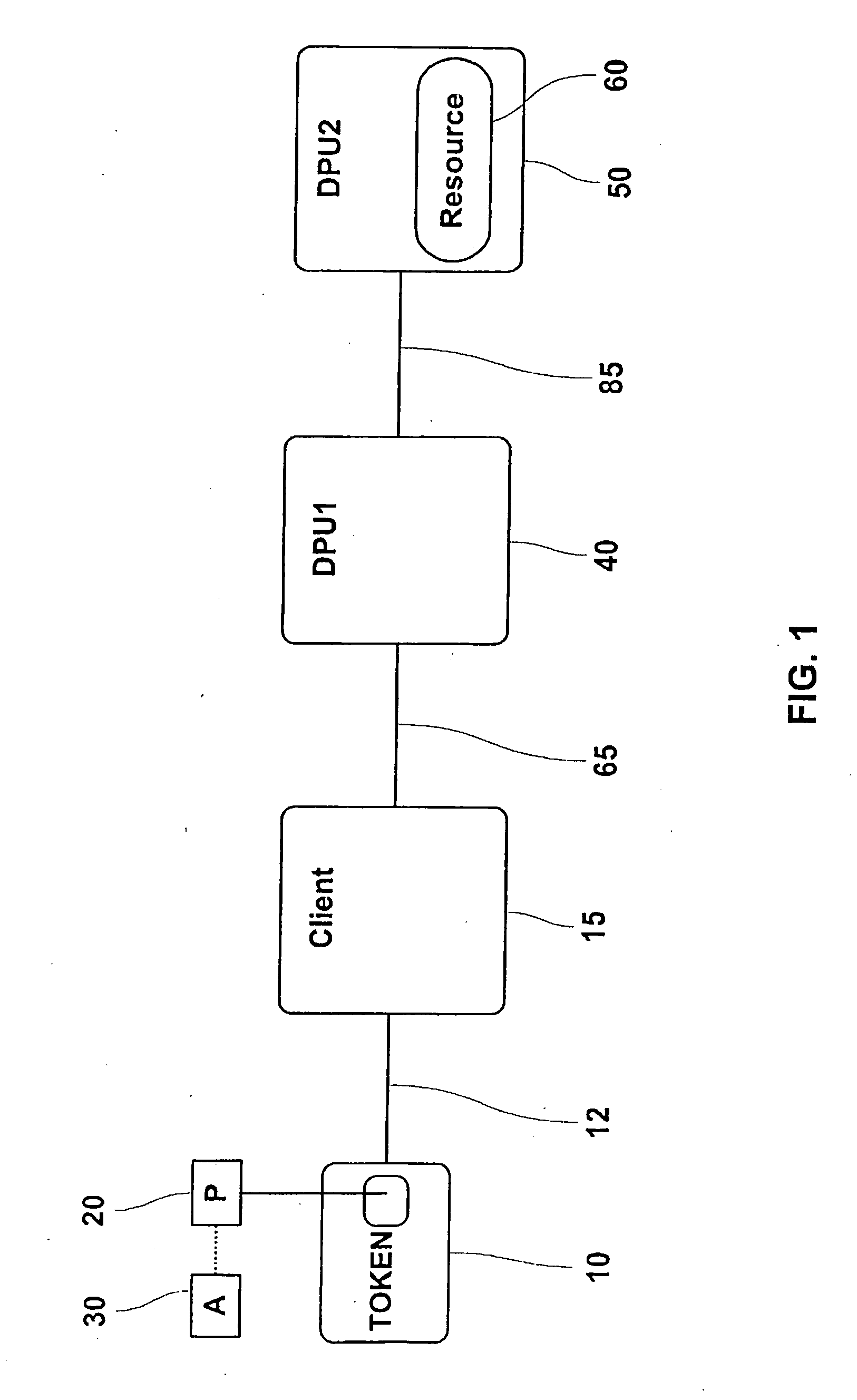
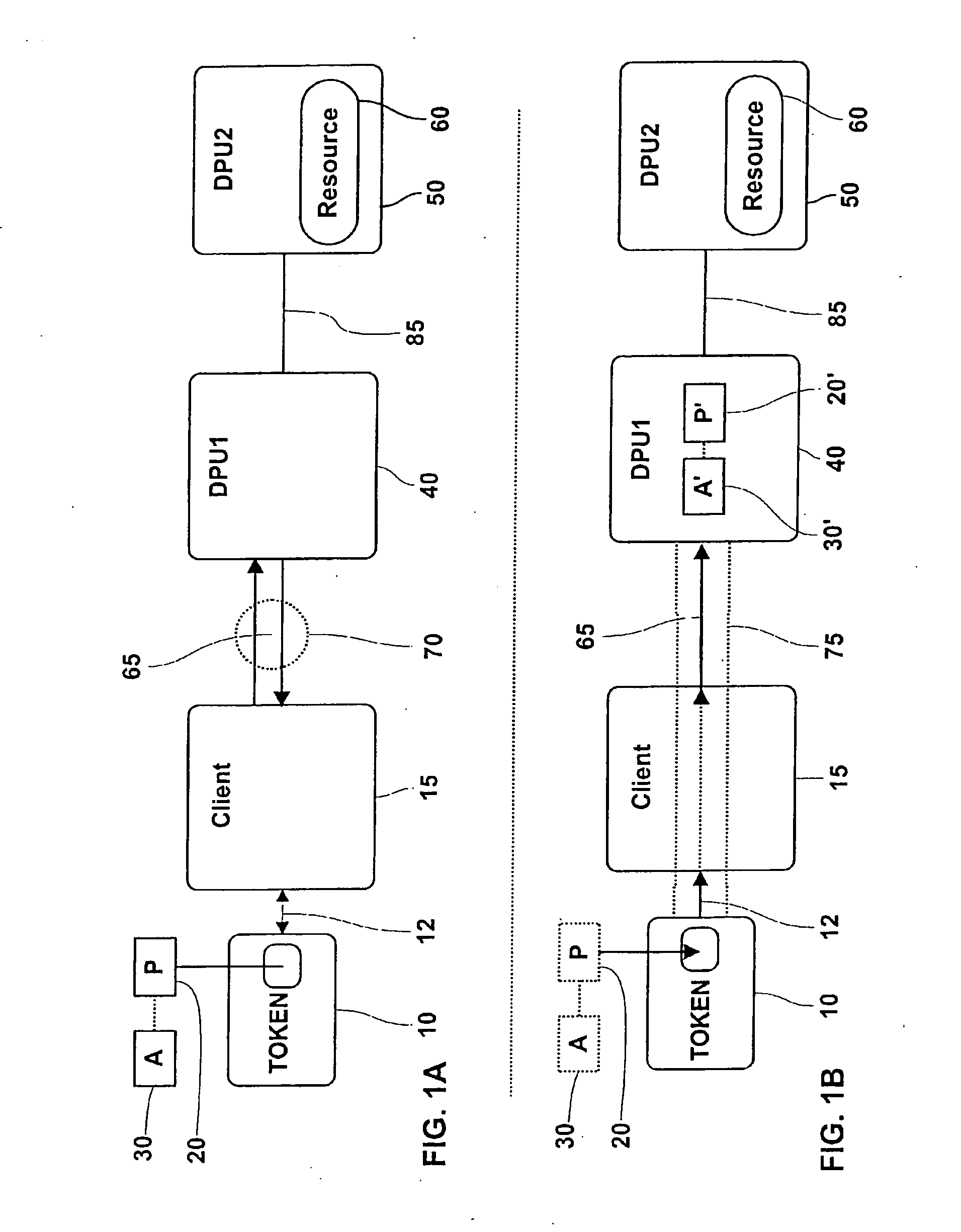
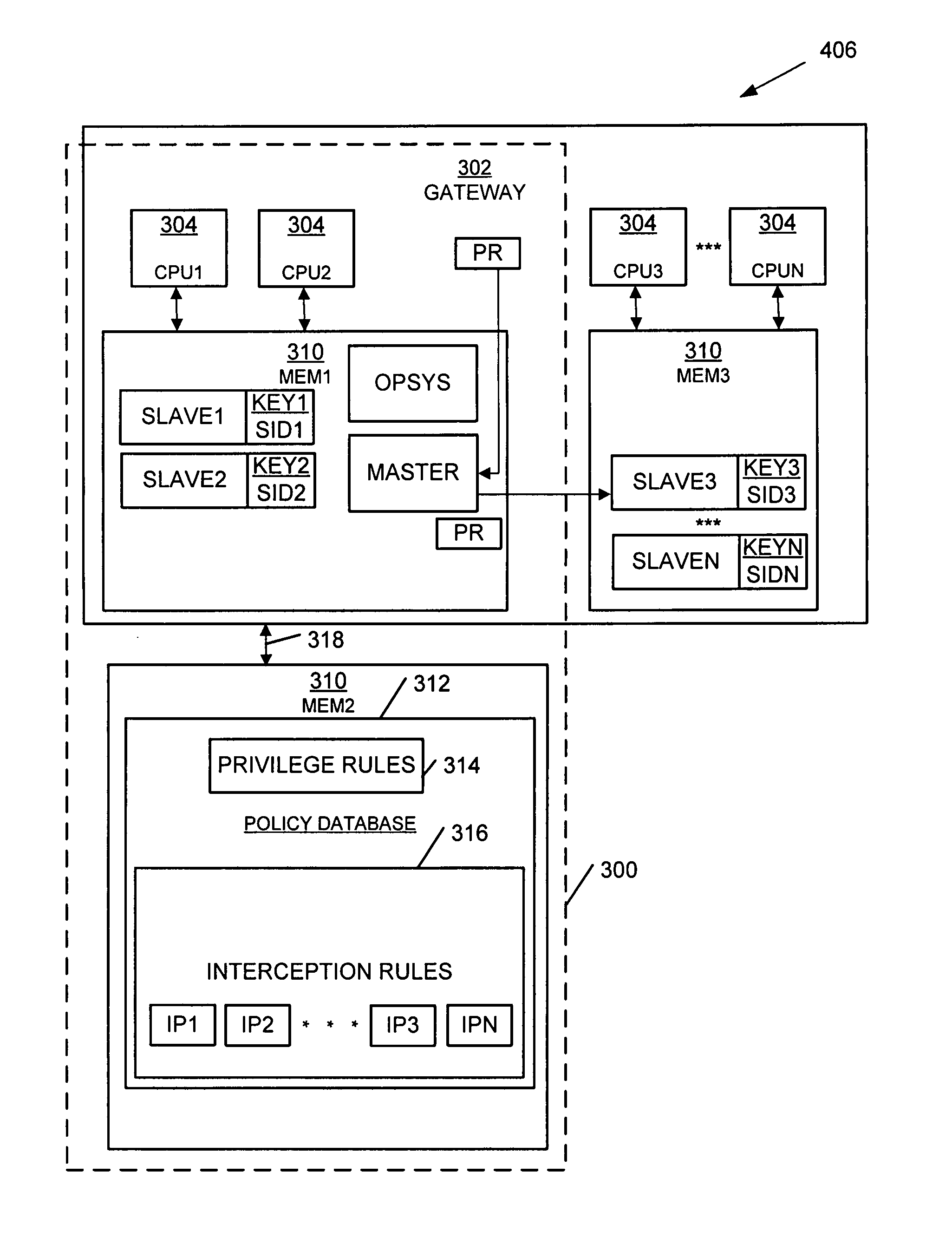
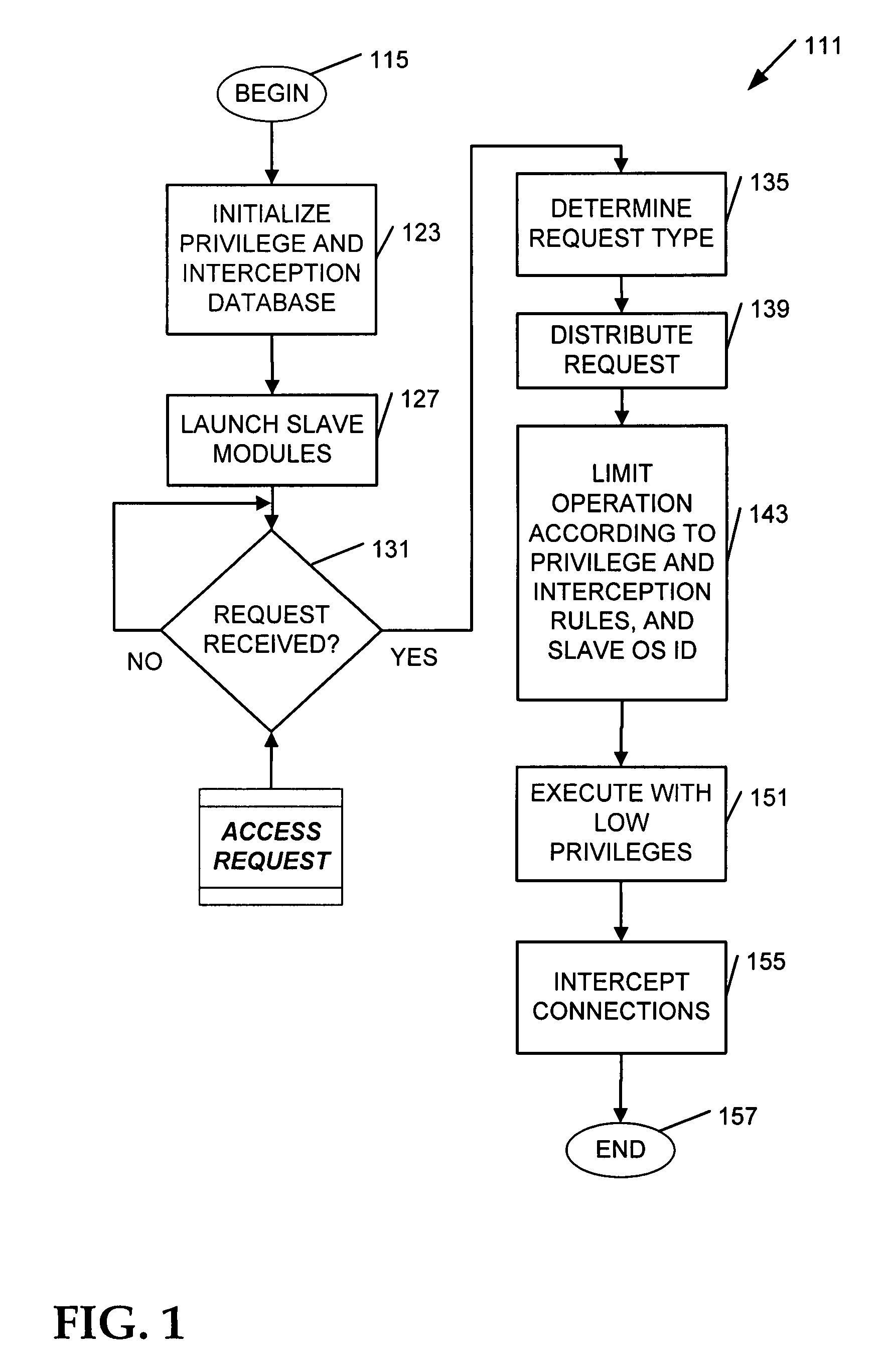
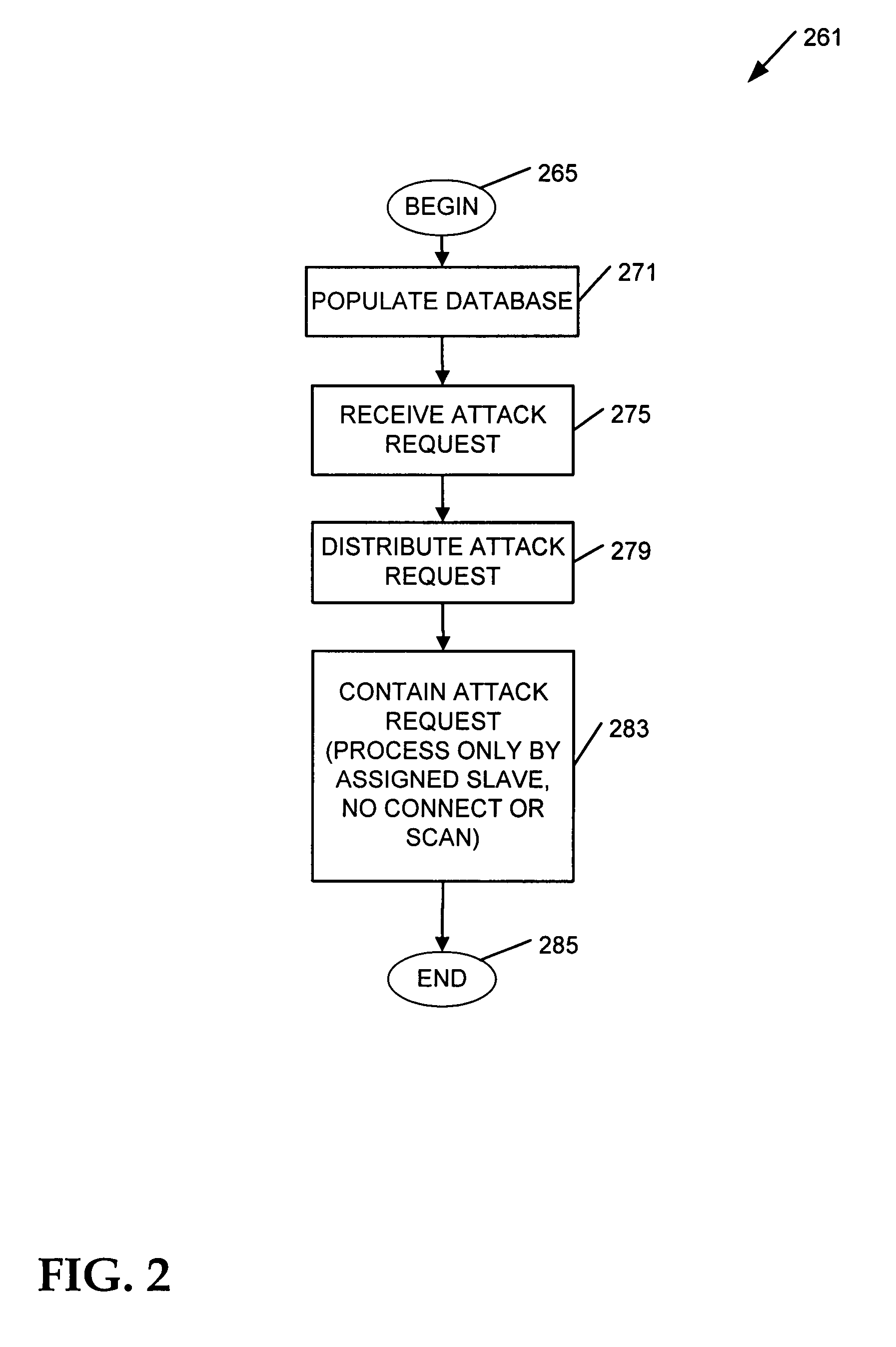
Apparatus, systems, and methods may operate to receive an attack request comprising operating system privilege use instructions associated with a gateway and slave process exploit code instructions. The attack request may be contained by processing the request as a user associated with an assigned slave module processing on the gateway. The slave module is prevented from connecting to or scanning any internet protocol address and port that is not specified in a policy database having network interception policy rules and file system privilege rules associated by a key comprising a slave module operating system identifier associated with the slave module. Additional apparatus, systems, and methods are disclosed.
Owner:APPLE INC
Fine-grained privilege escalation
InactiveUS20120151185A1Digital computer detailsSpecific program execution arrangementsProcessor registerPrivilege escalation
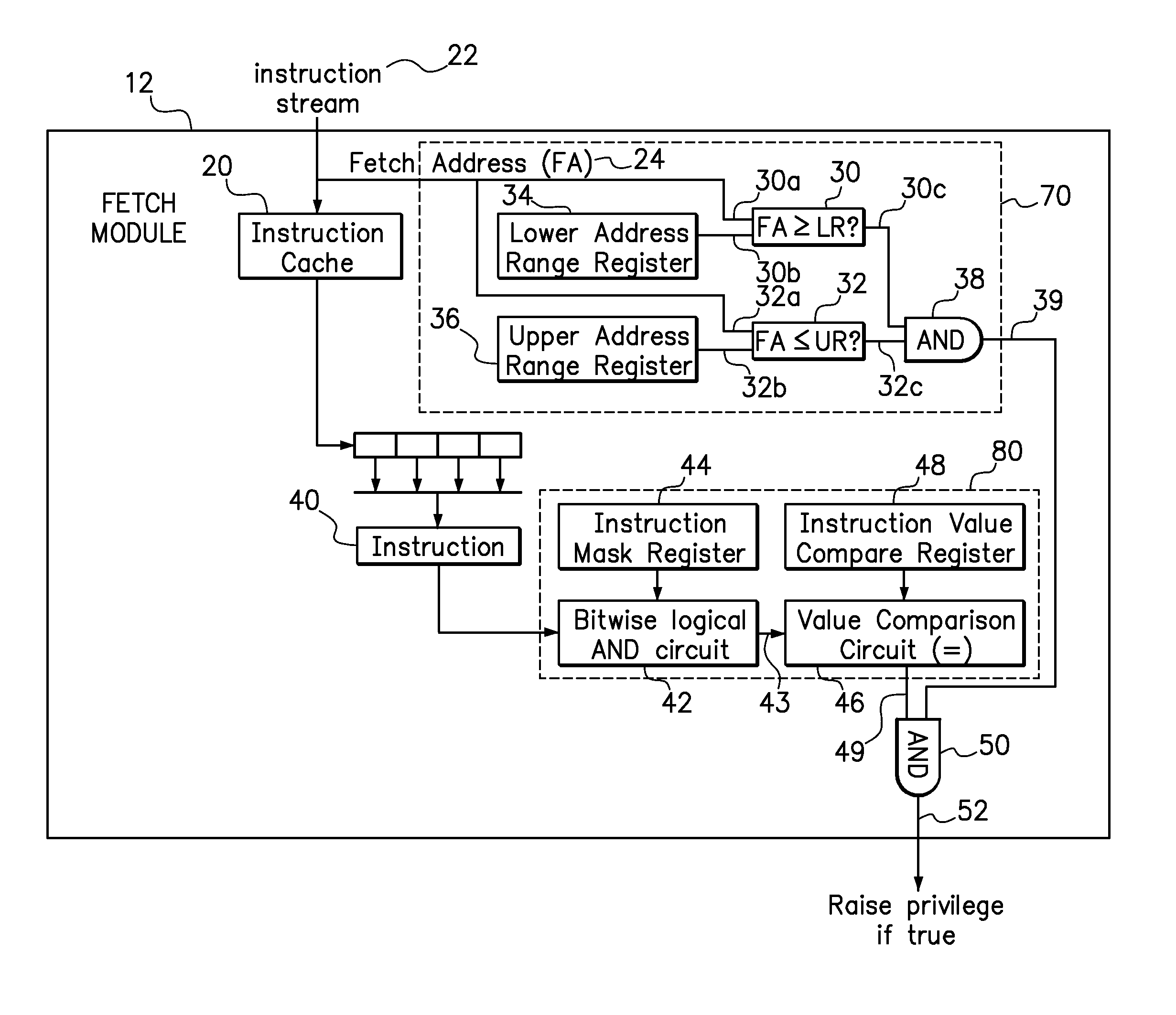
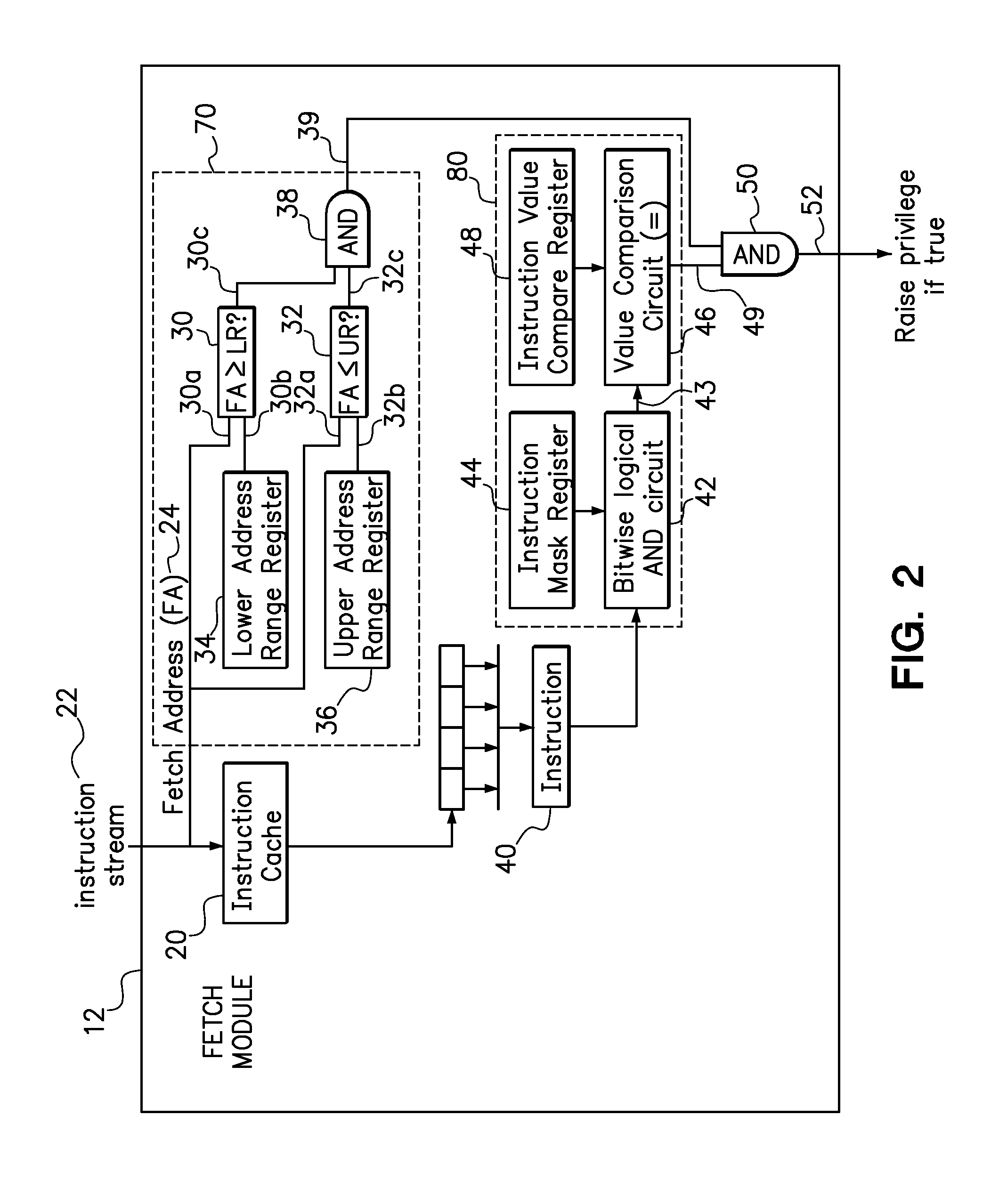
A processor and a method for privilege escalation in a processor are provided. The method may comprise fetching an instruction from a fetch address, where the instruction requires the processor to be in supervisor mode for execution, and determining whether the fetch address is within a predetermined address range. The instruction is filtered through an instruction mask and then it is determined whether the instruction, after being filtered through the mask, equals the value in an instruction value compare register. The processor privilege is raised to supervisor mode for execution of the instruction in response to the fetch address being within the predetermined address range and the filtered instruction equaling the value in the instruction value compare register, wherein the processor privilege is raised to supervisor mode without use of an interrupt. The processor privilege returns to its previous level after execution of the instruction.
Owner:IBM CORP
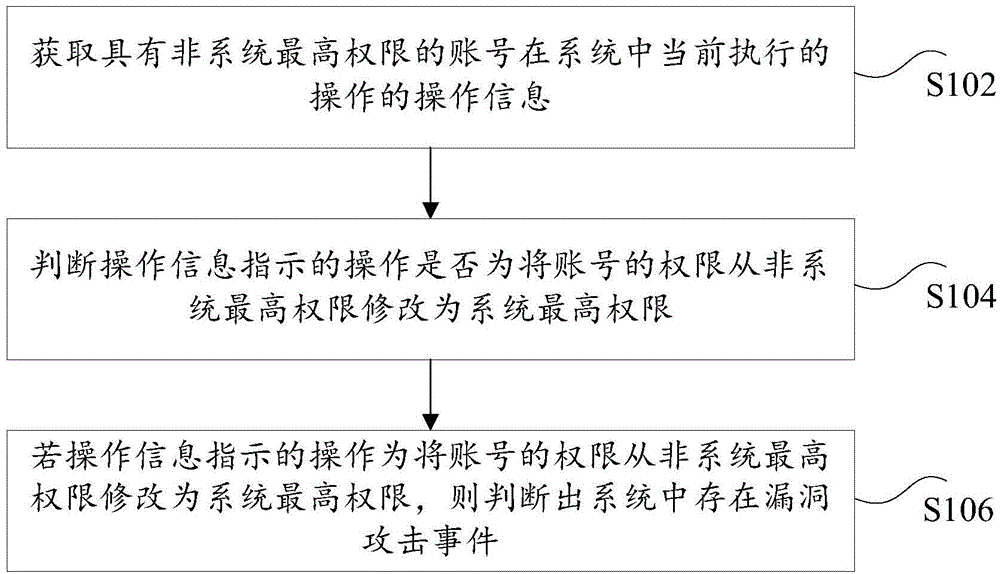
System bug attack detection method and apparatus
ActiveCN105224868AAccurate detectionSolve the low detection accuracyPlatform integrity maintainanceData miningPrivilege escalation
The invention discloses a system bug attack detection method and apparatus. The system bug attack detection method is provided according to one aspect of embodiments of the invention. The system bug attack detection method comprises: obtaining operation information of an operation currently performed by an account with a non highest system privilege in a system; and determining whether the operation indicated by the operation information is used for modifying a privilege of the account to a highest system privilege from the non highest system privilege or not, and if the operation indicated by the operation information is used for modifying the privilege of the account to the highest system privilege from the non highest system privilege, determining that a bug attack event exists in the system. With the adoption of the method and the apparatus, the problem of low detection accuracy of detecting a privilege escalation bug attack in the prior art is solved and the effect of detecting the system bug attack event timely and accurately is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
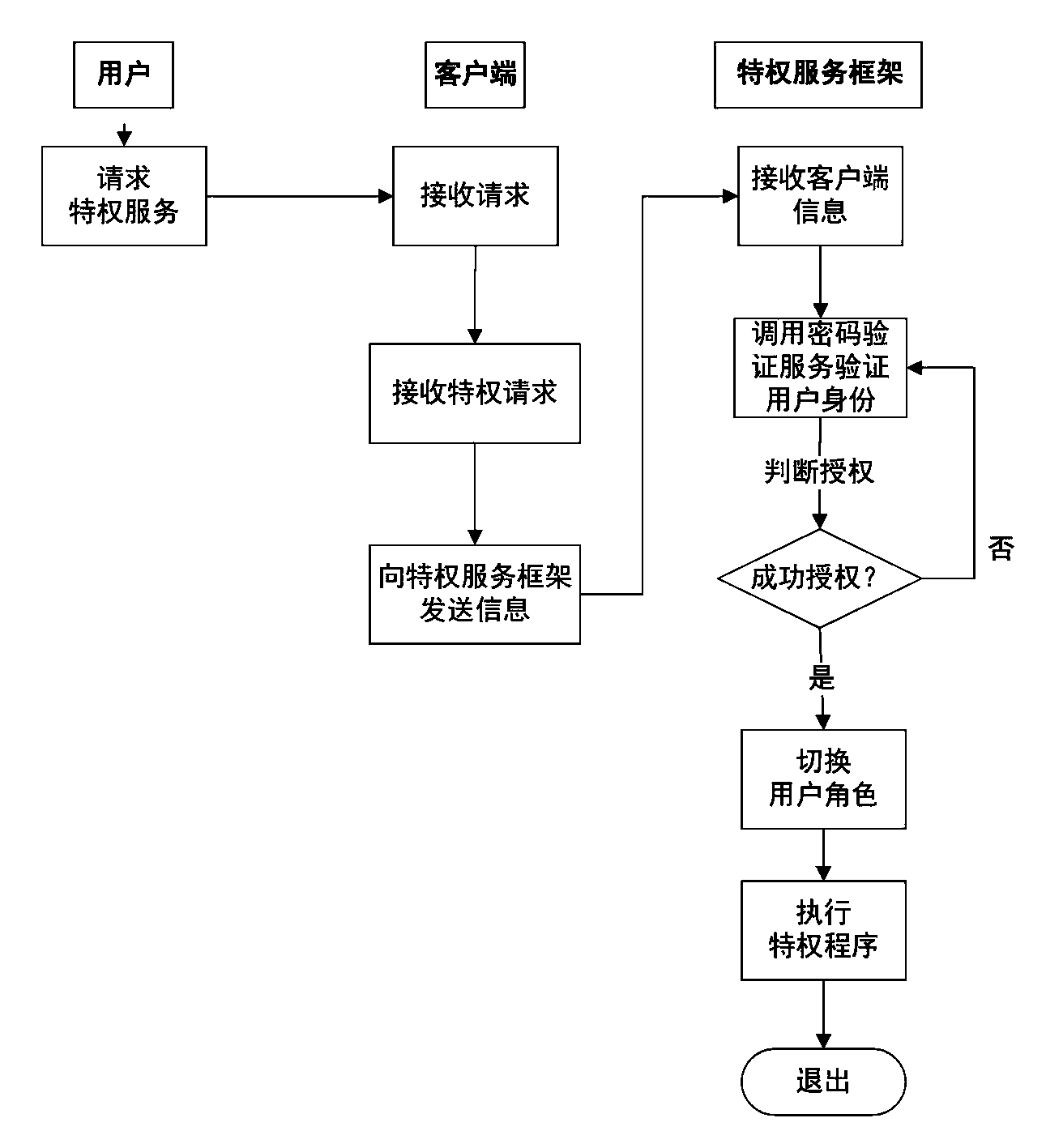
Method and apparatus for securely executing multiple actions using less than a corresponding multiple of privilege elevation prompts
Owner:ADOBE SYST INC
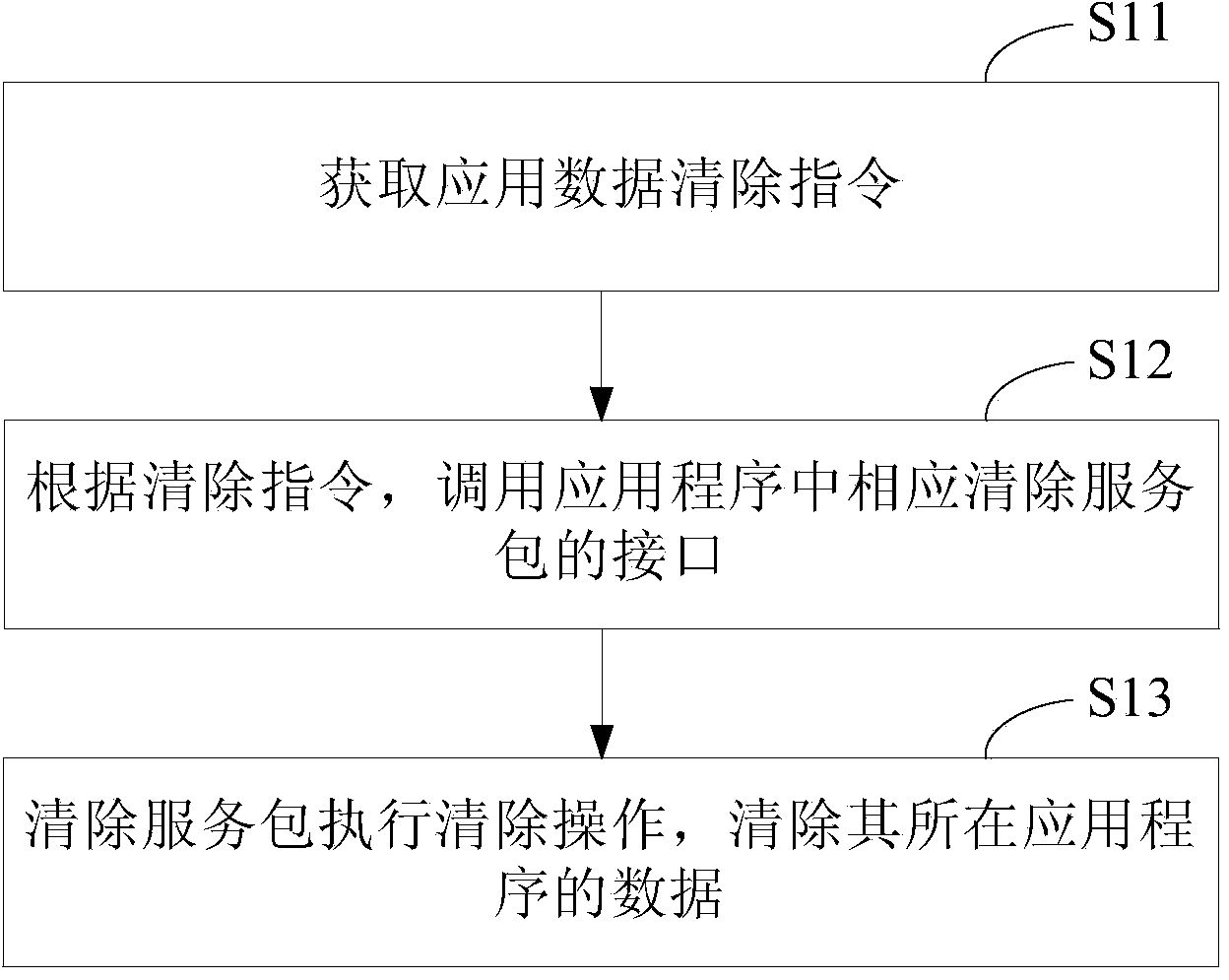
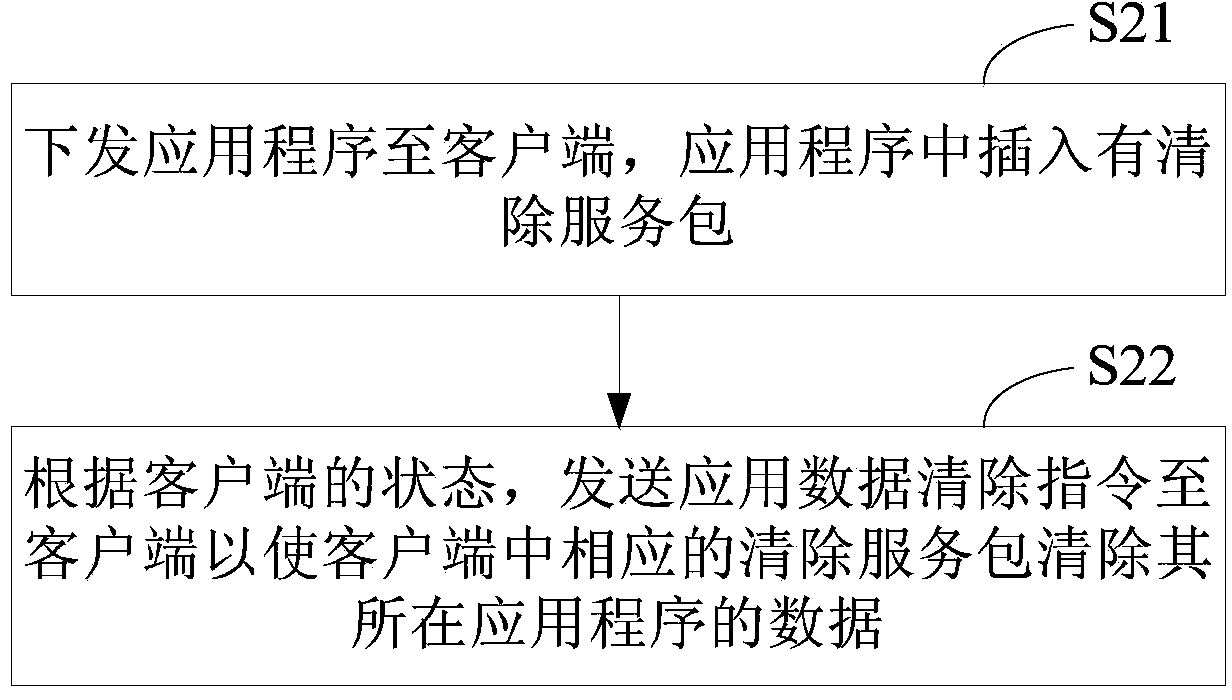
Method and device for clearing application data
ActiveCN104252373AReal-time monitoring statusEnsure safetyProgram loading/initiatingClient-sideApplication software
The invention provides a method for clearing application data. The method comprises the following steps: a server-side sends an application program to a client-side, and a cleanup service package is inserted into the application program; the server-side sends an application data clearing instruction to the client-side or the client-side locally sends an application data clearing instruction according to the state of the client-side; the client-side obtains the application data clearing instruction; an interface of a corresponding cleanup service package in the application program is called according to the clearing instruction; the cleanup service package executes the clearing operation and clears data of the application grogram which the cleanup service package belongs to. The invention also provides a device for clearing application data. According to the method, the device can be independent from privilege escalation, and can clear application data produced by corresponding programs.
Owner:BEIJING QIHOO TECH CO LTD
Filtering intrusion detection system events on a single host
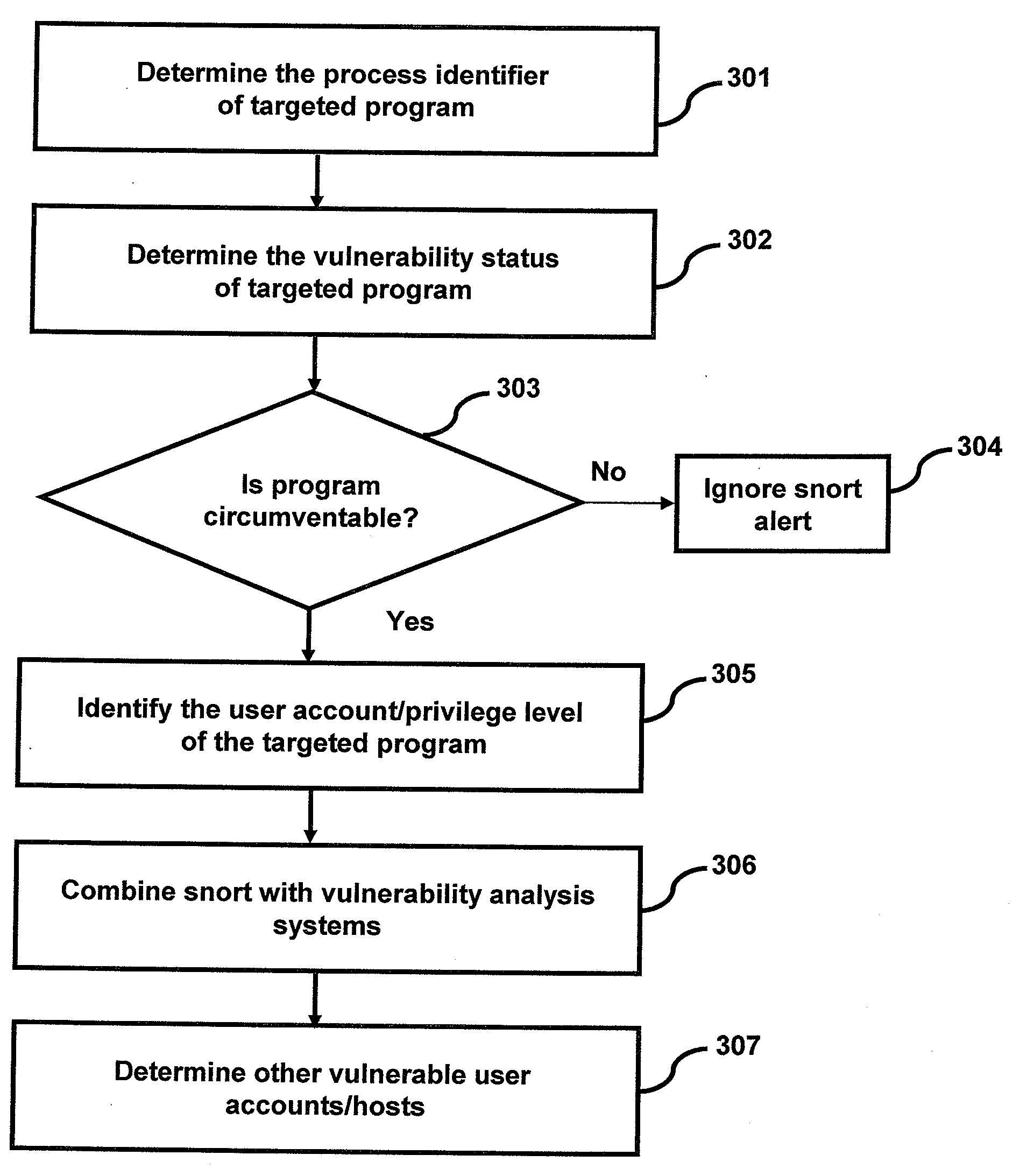
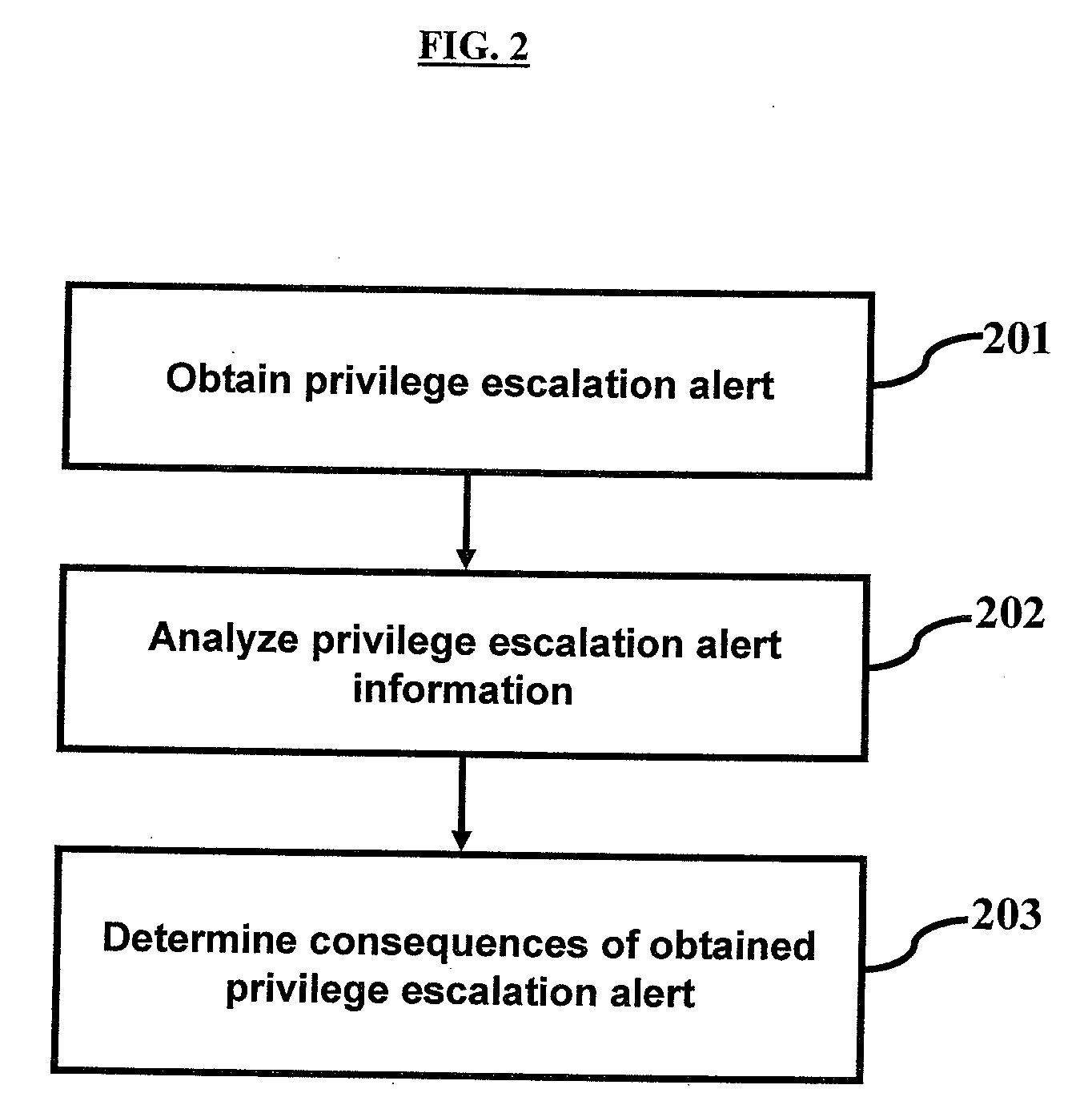
InactiveUS20090276853A1Memory loss protectionError detection/correctionPrivilege escalationIntrusion detection system
Embodiments disclosed herein describe a method to determine consequences of a privilege escalation alert from an intrusion detection system, the method comprising the steps of obtaining privilege escalation alert from the intrusion detection system and analyzing said privilege escalation alert information. The analysis further comprises of identifying the program affected by said privilege escalation alert and determining if it can be circumvented. The users affected by said privilege escalation alert and the transitive effects of said privilege escalation alert are identified.
Owner:MULVAL TECH
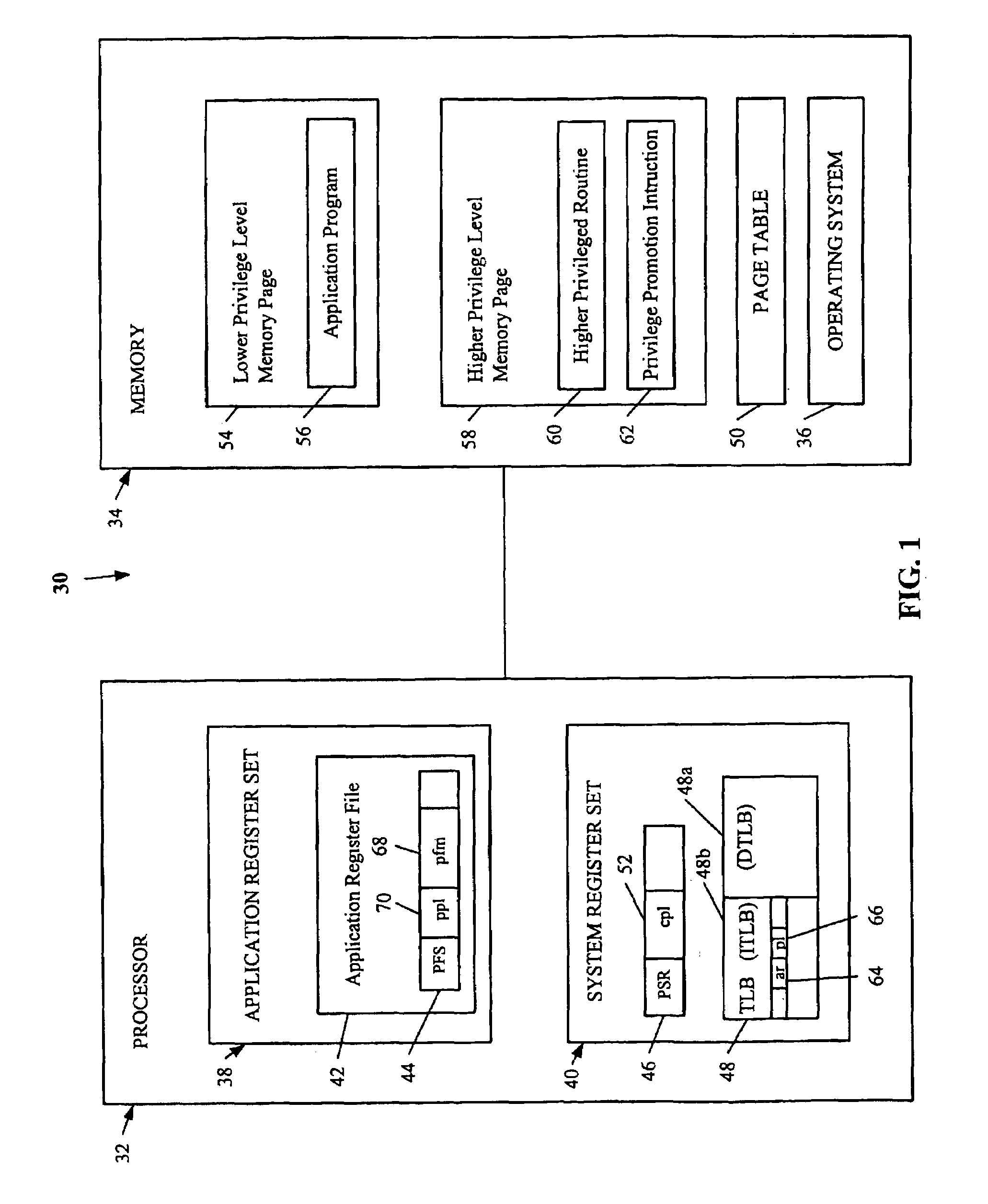
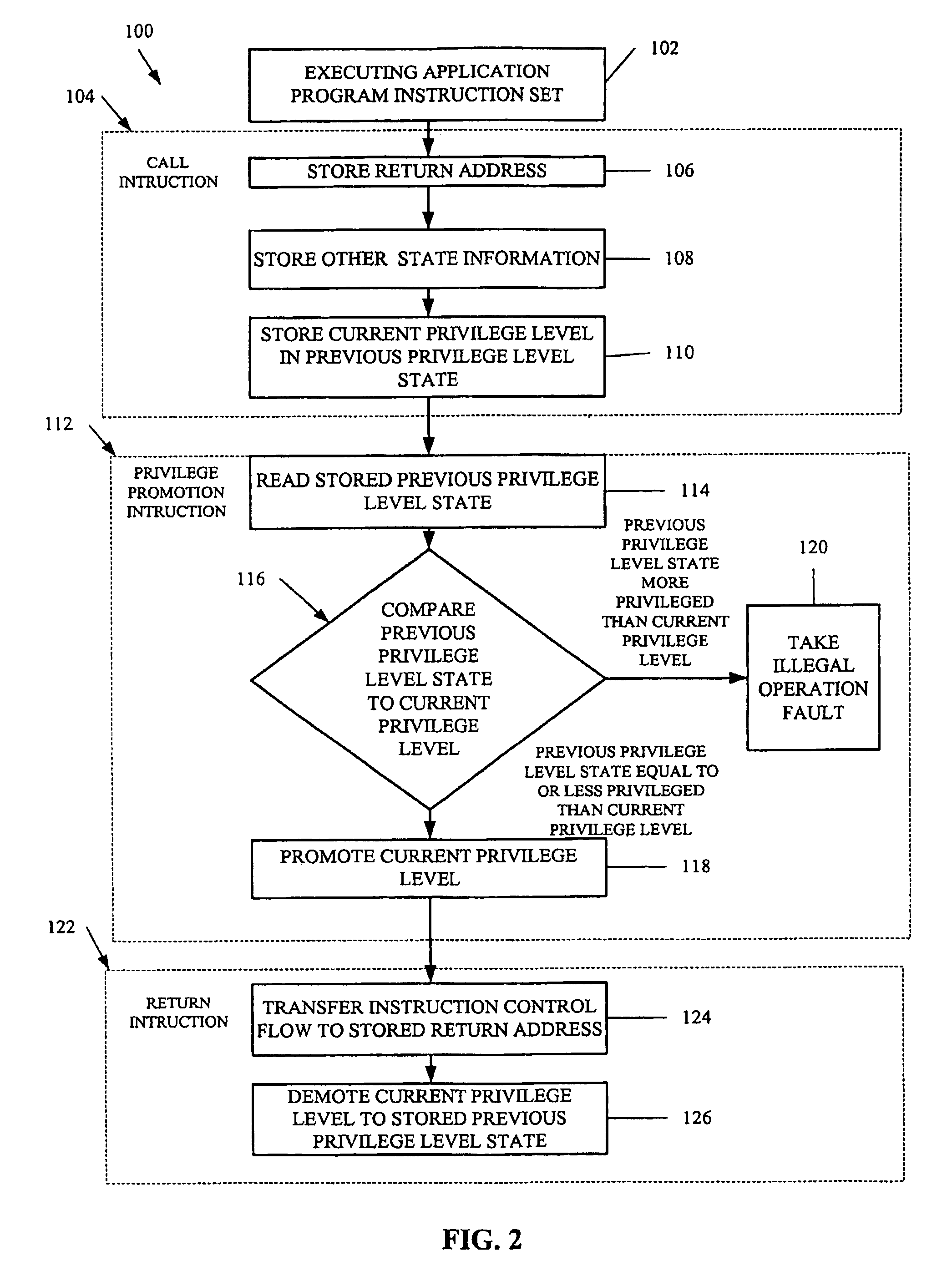
Privilege promotion based on check of previous privilege level
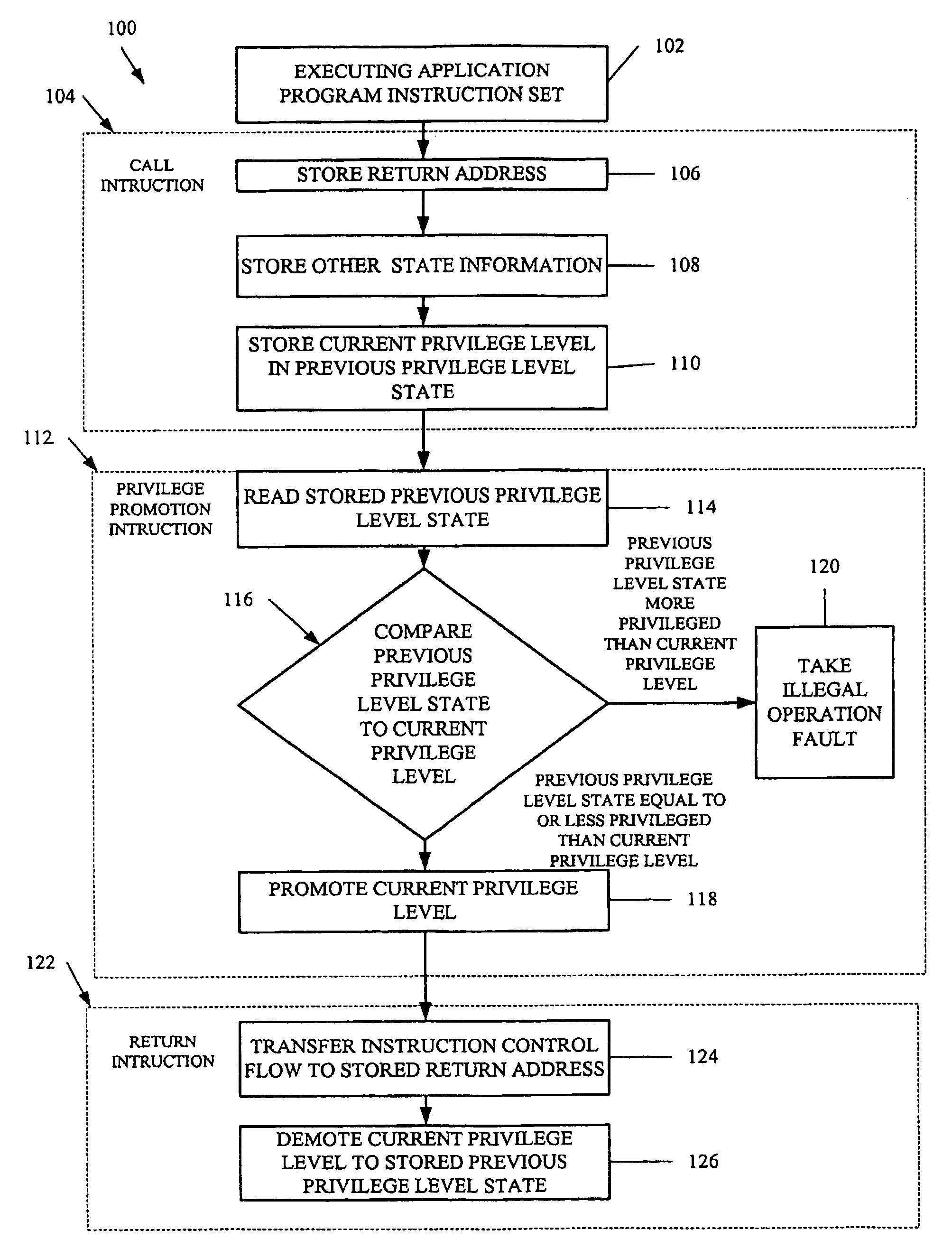
InactiveUS7680999B1Improve performanceSpecific access rightsDigital computer detailsComputerized systemApplication software
A secure promotion mechanism promotes a current privilege level of a processor in a computer system. The current privilege level controls application instruction execution in the computer system by controlling accessibility to system resources. An operating system performs a privilege promotion instruction, which is stored in a first page of memory not writeable by an application instructions at a first privilege level. The privilege promotion instruction reads a stored previous privilege level state, compares the read previous privilege level state to the current privilege level, and if the previous privilege level state is equal to or less privileged than the current privilege level, promotes the current privilege level to a second privilege level which is higher than the first privilege level.
Owner:INST FOR THE DEVMENT OF EMERGING ARCHITECTURES L L C
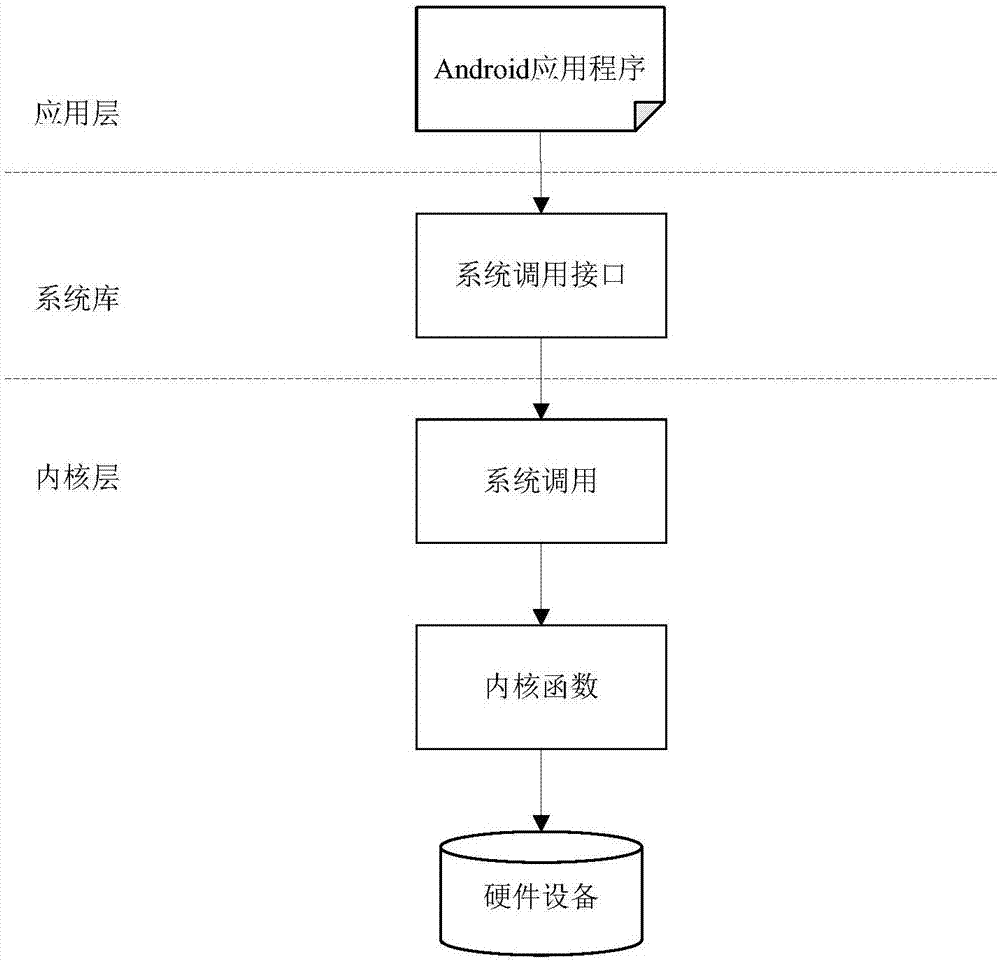
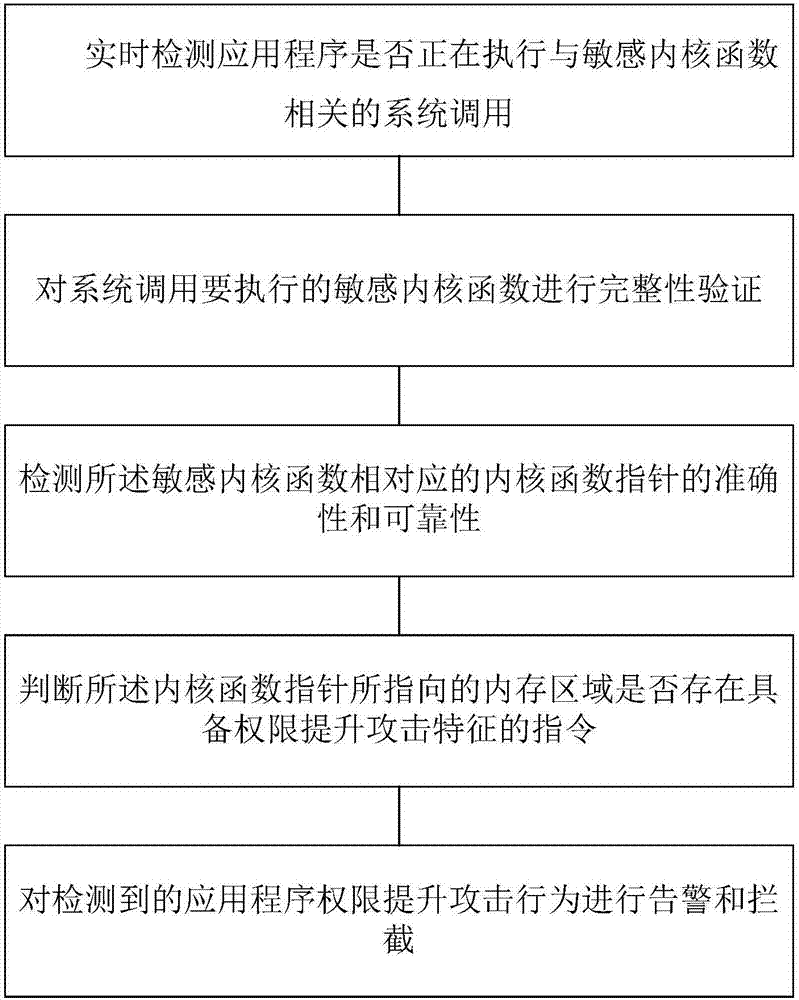
Security defense method and device of Android privilege escalation attack based on integrity verification
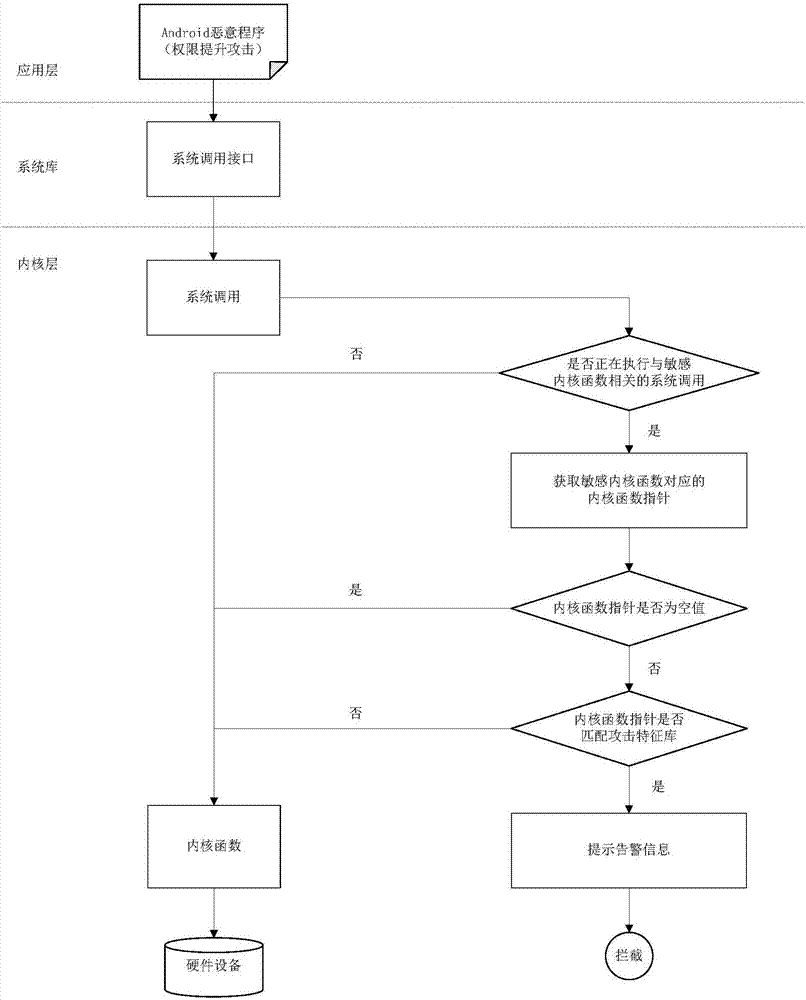
ActiveCN107016283AAvoid destructionReduce security threatsPlatform integrity maintainanceFunction pointerSystem call
The invention relates to a security defense method and device of the Android privilege escalation attacks based on integrity verifications. The method comprises the steps that the case that whether or not an application program is executing the system calls associated with sensitive kernel functions is detected in real time; integrity verifications are conducted on the sensitive kernel functions to be executed by the system calls; the accuracy and reliability of the kernel function pointer corresponding to the sensitive kernel functions are examined; the case that whether or not the internal storage pointed by the kernel function pointers has the commands for the privilege escalation attack features is evaluated; the detected application privilege escalation attacks are given warnings and blocked. According to the security defense method and device of the Android privilege escalation attacks based on integrity verifications, the privilege escalation attack behaviors of malicious programs are detected in real time and are given warnings and blocked, and the damages caused by attacks on the Android system are prevented, and the securities of the application and data are effectively protected. The security defense method and device of the Android privilege escalation attacks based on integrity verifications reduce security threats brought to the Android system by the privilege escalation vulnerabilities, and enhance the security of the Android system.
Owner:INST OF INFORMATION ENG CAS
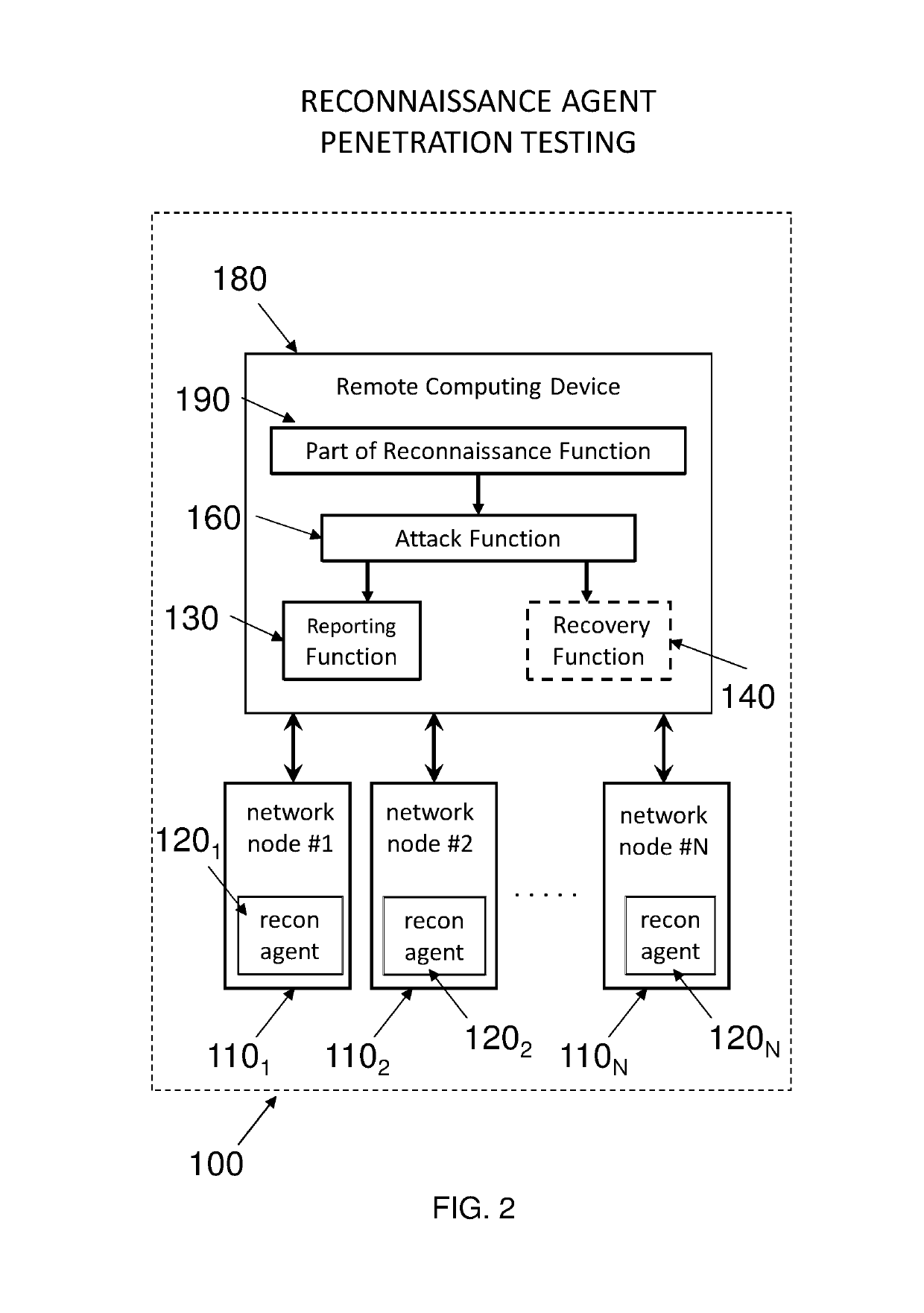
Taking privilege escalation into account in penetration testing campaigns
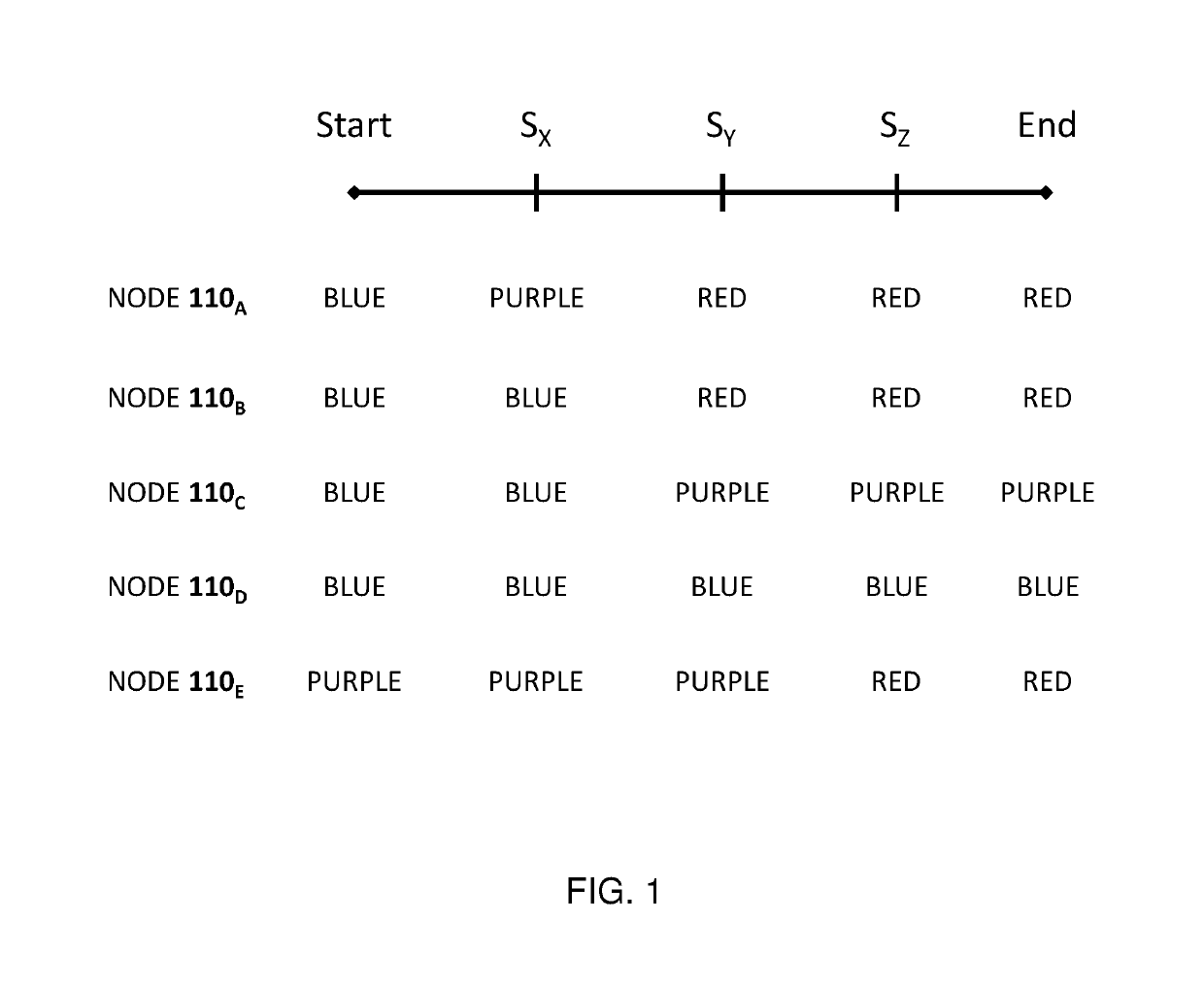
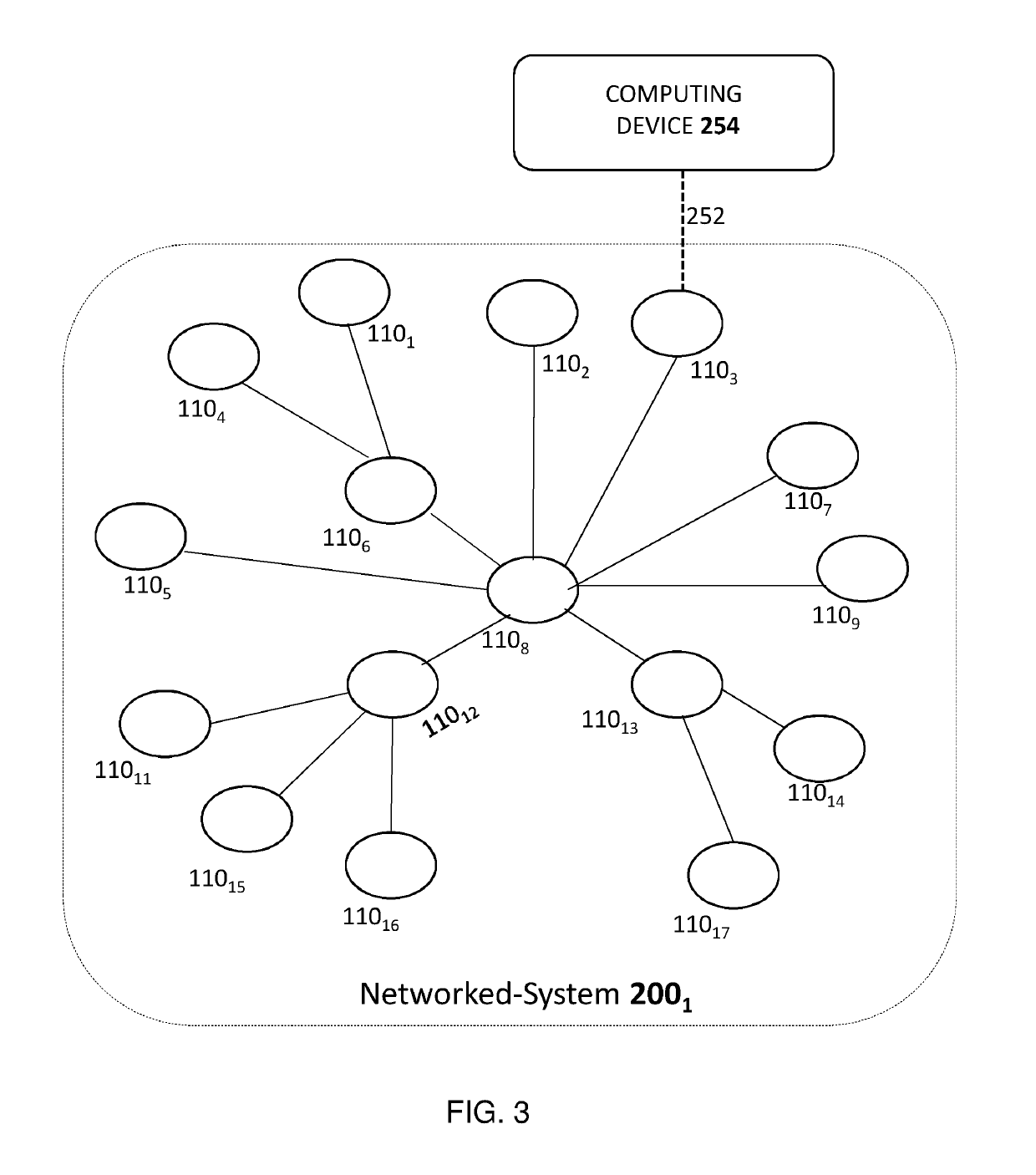
A simulated penetration testing system that assigns network nodes of the tested networked system to classes based on current information about the compromisability of the nodes at a current state of a penetration testing campaign, the classes consisting of (i) a red class for nodes known to be compromisable by the attacker in a way that gives the attacker full control of the nodes, (ii) a blue class for nodes that are not known to be compromisable by the attacker, and (iii) a purple class for nodes known to be compromisable by the attacker in a way that does not give the attacker full control of the purple-class-member network node. The campaign tests whether an attacker would be able to achieve full control of a target node by using privilege escalation techniques and one or more access rights achieved by compromising the target node.
Owner:XM CYBER LTD
Ai-driven defensive penetration test analysis and recommendation system
PendingUS20220201042A1Reduce sensitivityWeb data indexingComputer security arrangementsAttackNetworked system
A system and method for automated defensive penetration test analysis that predicts the evolution of new cybersecurity attack strategies and makes recommendations for cybersecurity improvements to networked systems based on a cost / benefit analysis. The system and method use captured system data to classify networked system based upon their susceptibility to privilege escalation attacks measured against the networked system's response to a penetration test. The system and method use machine learning algorithms to run simulated attack and defense strategies against a model of the networked system created using a directed graph. Recommendations are generated based on an analysis of the simulation results and system classifications against a variety of cost / benefit indicators.
Owner:QOMPLX INC
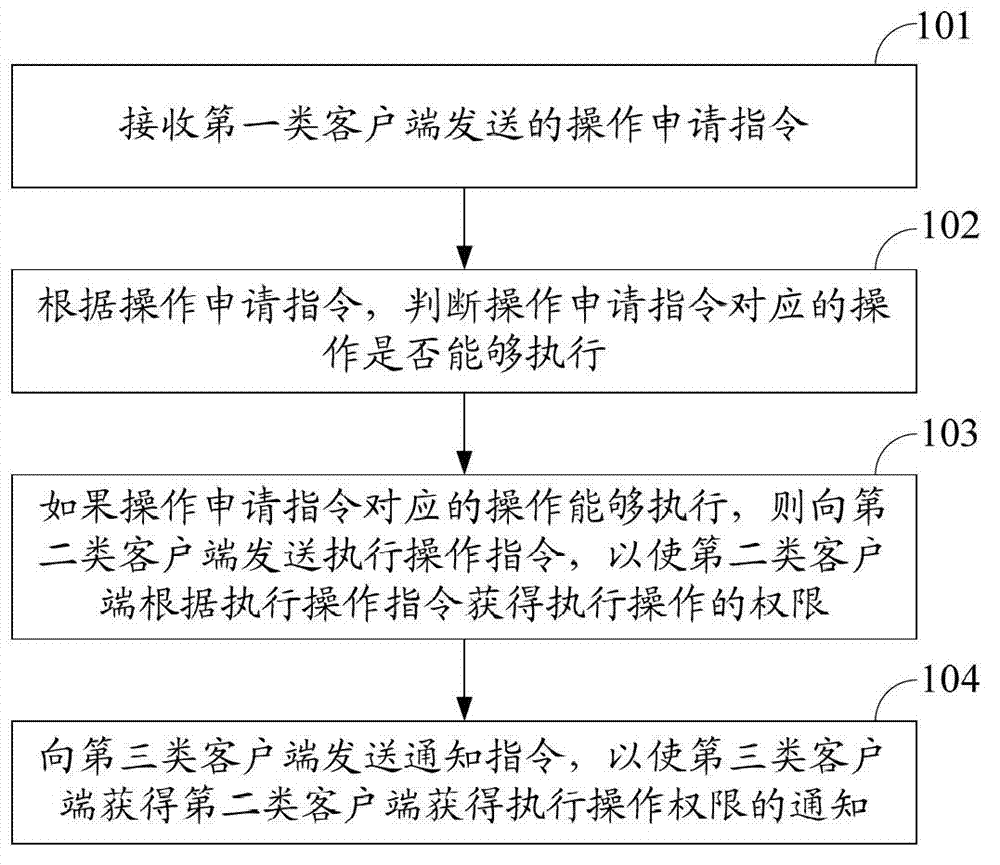
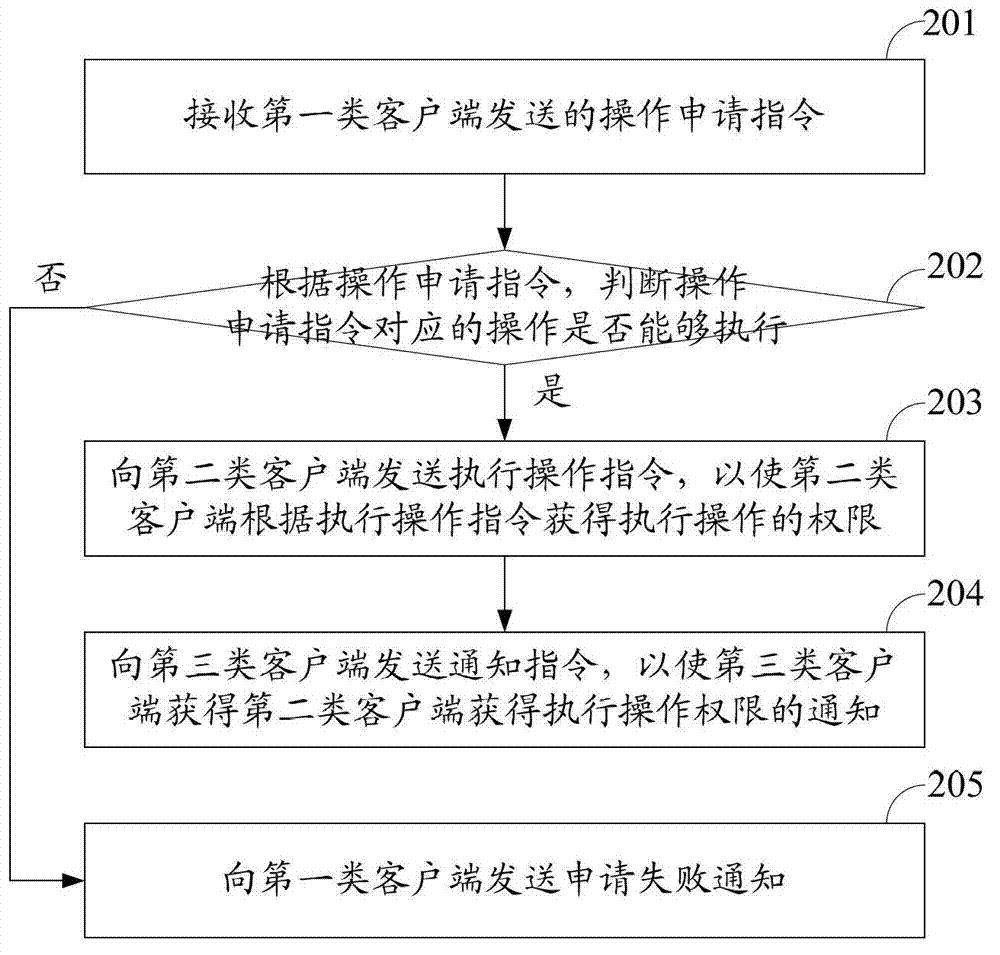
Method, relevant equipment and system for realizing privilege separation
The invention discloses a method for realizing privilege separation. The method is used for separating administrator rights from the rights of some special operations. The method comprises the steps of receiving the operation application instructions transmitted by a first-class client-side; judging whether the relevant operations of the operation application instructions can be executed according to the operation application instructions; if the relevant operations of the operation application instructions can be executed, transmitting the execution operation instructions to a second-class client-side to enable the second-class client- side to obtain the rights of executing the operation according to the execution operation instructions; and transmitting an informing instruction to a third-class client-side to enable the third-class client-side to obtain the information of executing the operation rights by the second-class client-side. The invention also discloses a device and a system for realizing the privilege separation.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Methods for feedback and matching of privilege escalation configuration information as well as corresponding devices
InactiveCN104346576AIncrease success ratePrecise optimization effectDigital data authenticationPlatform integrity maintainanceTerminal equipmentComputer terminal
The invention discloses a method for feedback of privilege escalation configuration information and a related device. The method comprises the following steps of obtaining a request containing characteristic information of terminal equipment; searching configuration information used for obtaining Root permission according to the characteristic information; sorting the searched configuration information according to history service data stored for the configuration information and forming a recommendation list containing the searched configuration information; responding to the request and pushing the recommendation list containing the sorted configuration information. The invention further discloses a method and a device for matching of the privilege escalation configuration information. The method comprises the following steps of transmitting a request containing the characteristic information collected by the terminal equipment; obtaining a configuration information recommendation list, which responds to the request and is used for obtaining the Root permission of the terminal equipment; applying privilege escalation to the terminal equipment by utilizing at least one piece of configuration information. According to the methods and the devices, a more effective scheme for obtaining highest permission of terminal equipment system is provided for a user.
Owner:BEIJING QIHOO TECH CO LTD +1
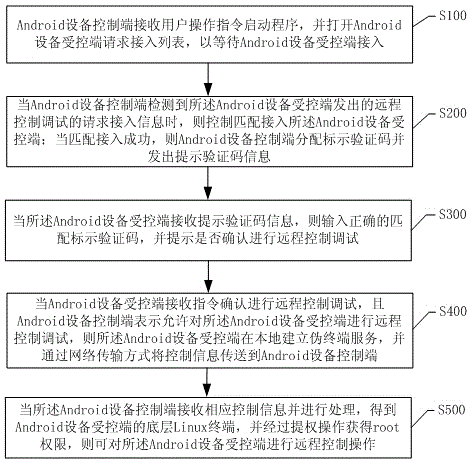
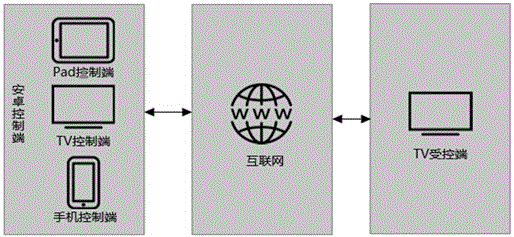
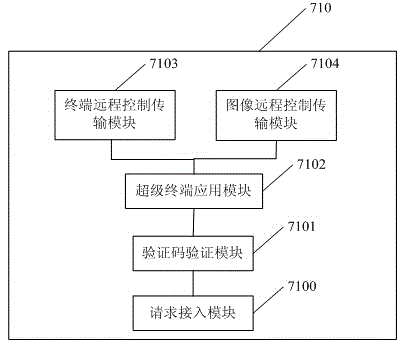
Remote control debugging method and system based on Android equipment
InactiveCN105141776ARealize remote controlImprove remote control debugging efficiencySubstation equipmentTransmissionRemote controlComputer science
The present invention discloses a remote control debugging method and system based on Android equipment. The method includes the steps as follows: a controlling terminal of the Android equipment receives remote control debugging information transmitted by a controlled terminal of the Android equipment, distributes and marks verification codes, and transmits verification code prompting information; when the controlling terminal receives correct verification code prompting information inputted by the controlled terminal, and acquires reception instruction confirmation of the controlled terminal for processing the remote control debugging, the controlled terminal establishes a pseudo-terminal service in local, the controlling terminal acquires a bottom layer linux terminal of the controlled terminal, and the controlling terminal acquires root privileges through a privilege escalation operation so that the controlled terminal is remotely controlled. The remote control debugging method and system based on Android equipment control remote terminals among Android equipment, and remotely control remote menus. The remote control debugging method and system based on Android equipment can greatly increase the remote control efficiency and reduce the realizing cost for remote control, and provide subscribers with convenience.
Owner:KONKA GROUP
Automatic detection of software that performs unauthorized privilege escalation
ActiveUS20180276383A1Specific access rightsInterprogram communicationAutomatic testingPrivilege escalation
Automatic detection of software that performs unauthorized privilege escalation is disclosed. The techniques cause a programmable device to obtain a trace event of a program from an event logger, parse the trace event to determine a privilege level for an event, compare the privilege level for the event to an expected privilege level, and block execution of the program based on the comparison.
Owner:MCAFEE LLC
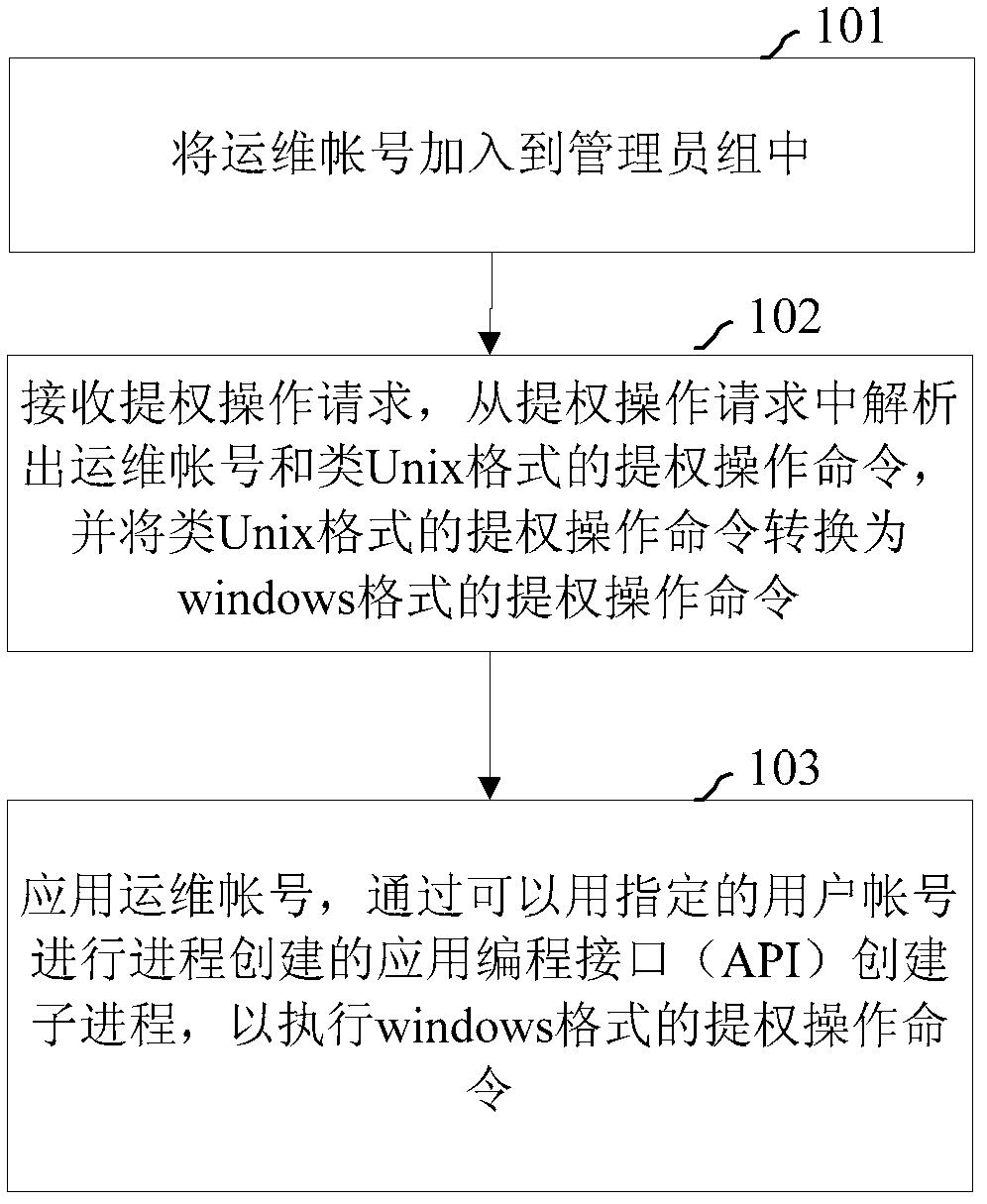
Privilege escalation method and system in Unix-like environment of windows system
The embodiment of the invention provides a privilege escalation method and system in a Unix-like environment of a windows system. The privilege escalation method comprises adding an operation and maintenance account into an administrator group; receiving an operation request of privilege escalation, analyzing out the operation and maintenance account and an operation command of privilege escalation of a Unix-like format from the operation request of privilege escalation, and converting the operation command of privilege escalation of the Unix-like format into an operation command of privilege escalation of a windows format; applying the operation and maintenance account and creating sub-processes through an API (application program interface) which allows a user to use an assigned user account for creating processes to execute the operation command of privilege escalation of the windows format. According to the privilege escalation method and system in the Unix-like environment of the windows system, the function of command privilege escalation in the Unix-like environment can be achieved in the windows system, environments of Cygwin and cmd in the windows system are compatible and supported, and path analyses of Cygwin and redirecting of output results are supported.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Generic privilege escalation prevention
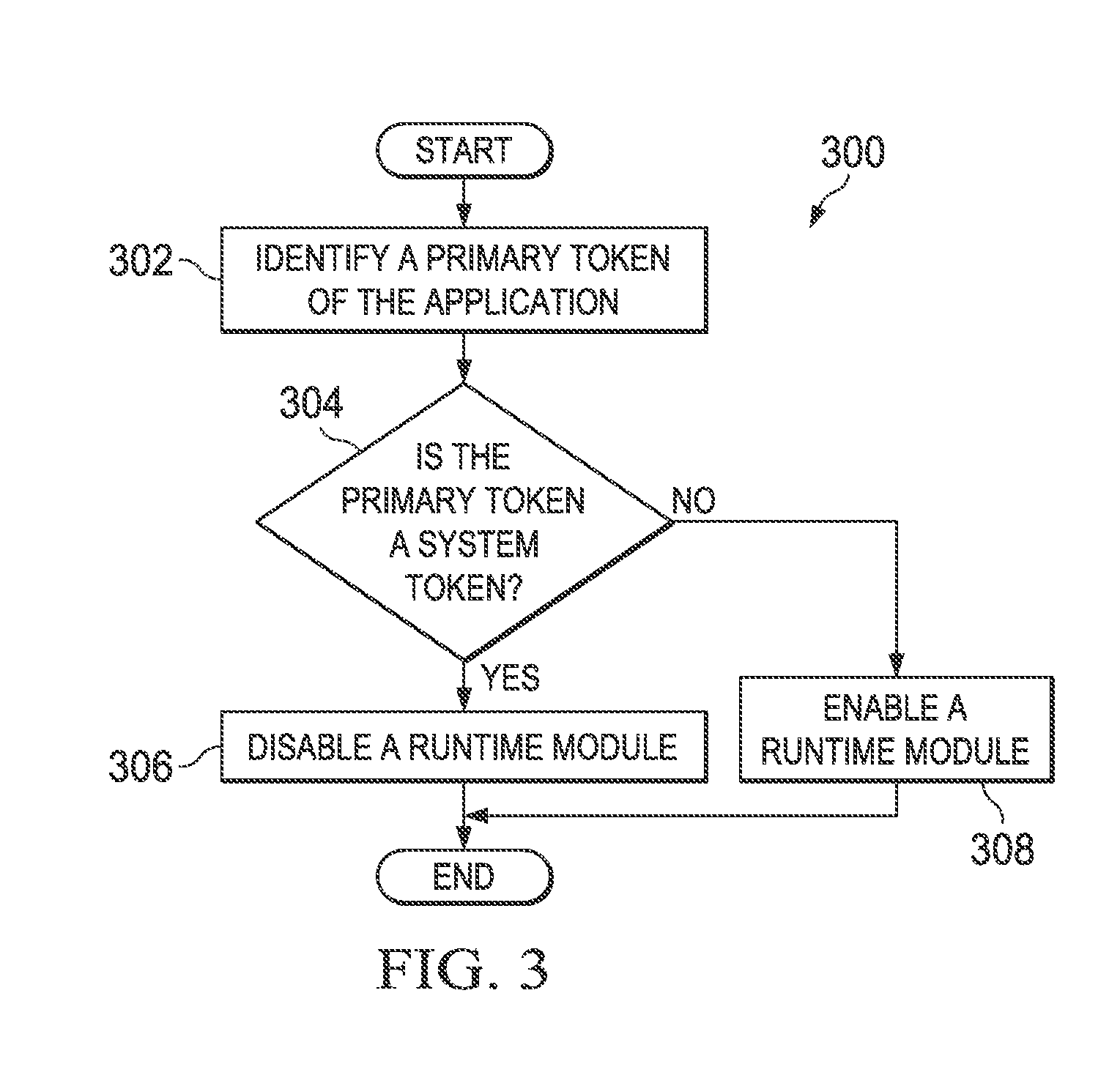
An apparatus, method, computer readable storage medium are provided in one or more examples and comprise accessing an application, identifying an access token of the application, determining if the access token is a system token, and responsive to the access token failing to be a system token, enabling a runtime module.
Owner:MCAFEE LLC
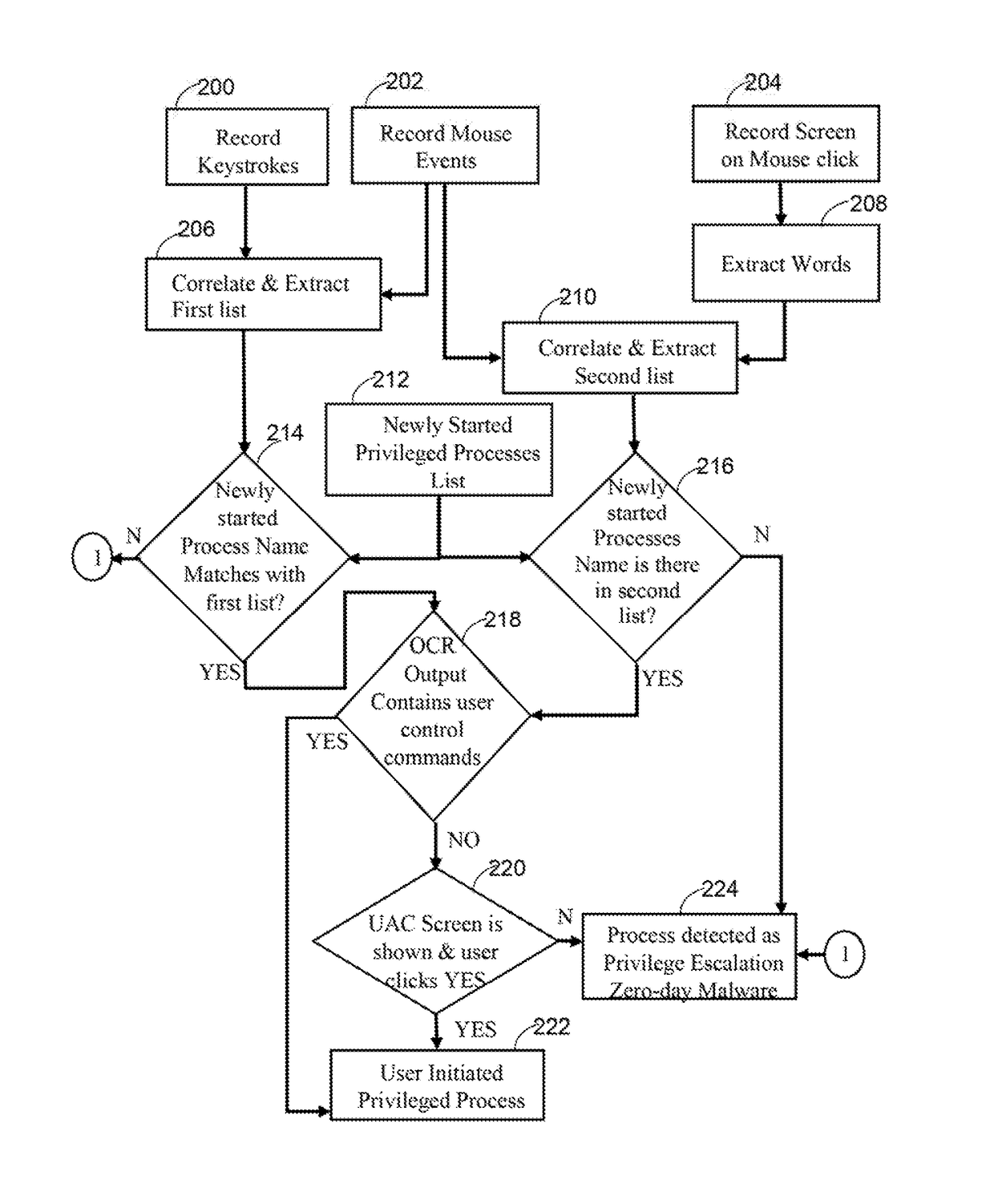
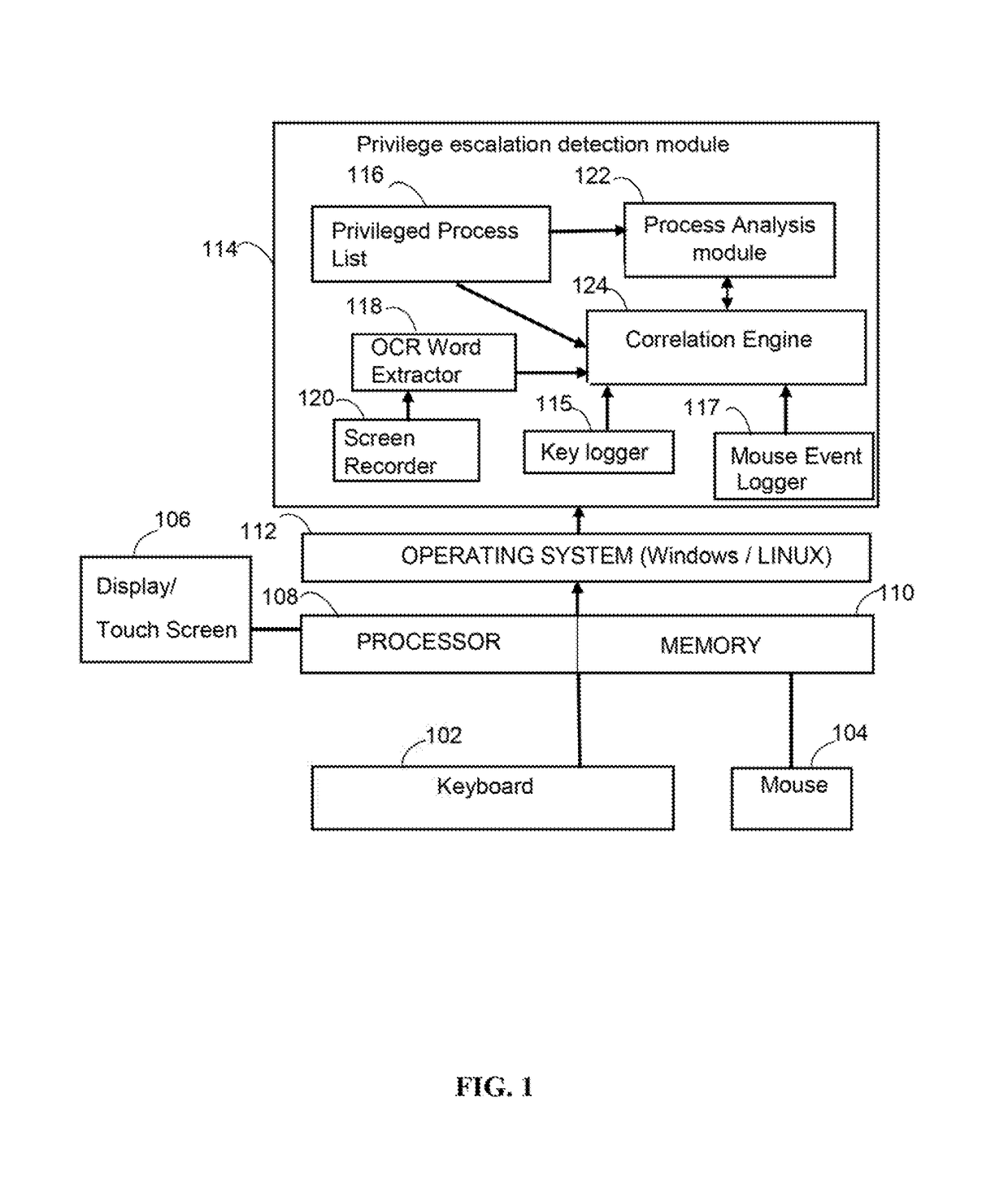
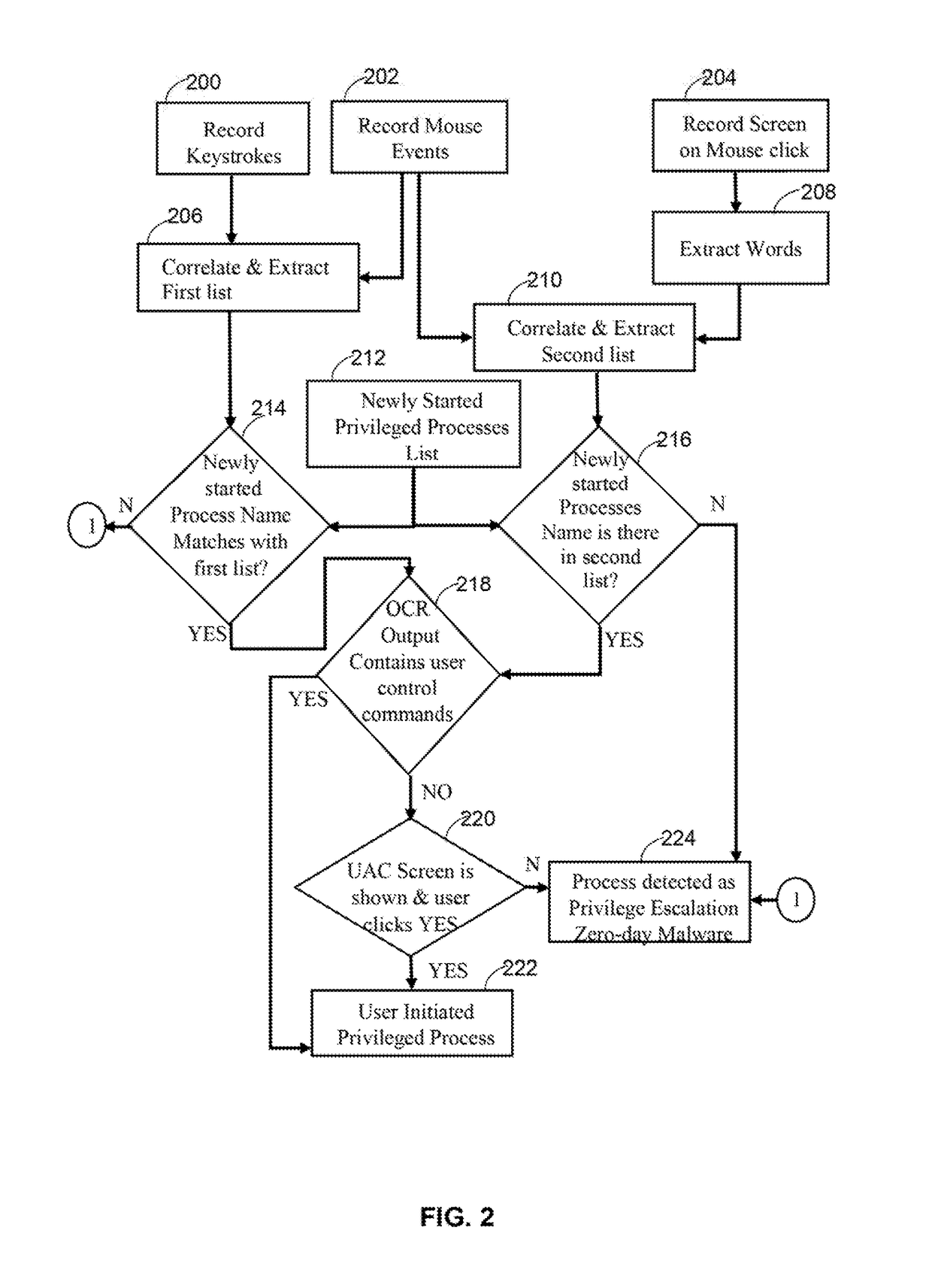
System and method for zero-day privilege escalation malware detection
The various embodiments herein disclose a system and method for detecting zero-day privilege escalation malware at host level. The method identifies whether a privileged escalation state is initiated and executed by a user or by a malware program. The method uses keystrokes, Mouse events along with OCR output extracted from recorded background screen image for checking if user has initiated the privilege escalation. If a new process starts automatically without any pattern in Key Strokes, Mouse Strokes and background screen, then the process is identified as zero-day privilege escalation malware.
Owner:INST FOR DEV & RES IN BANKING TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com