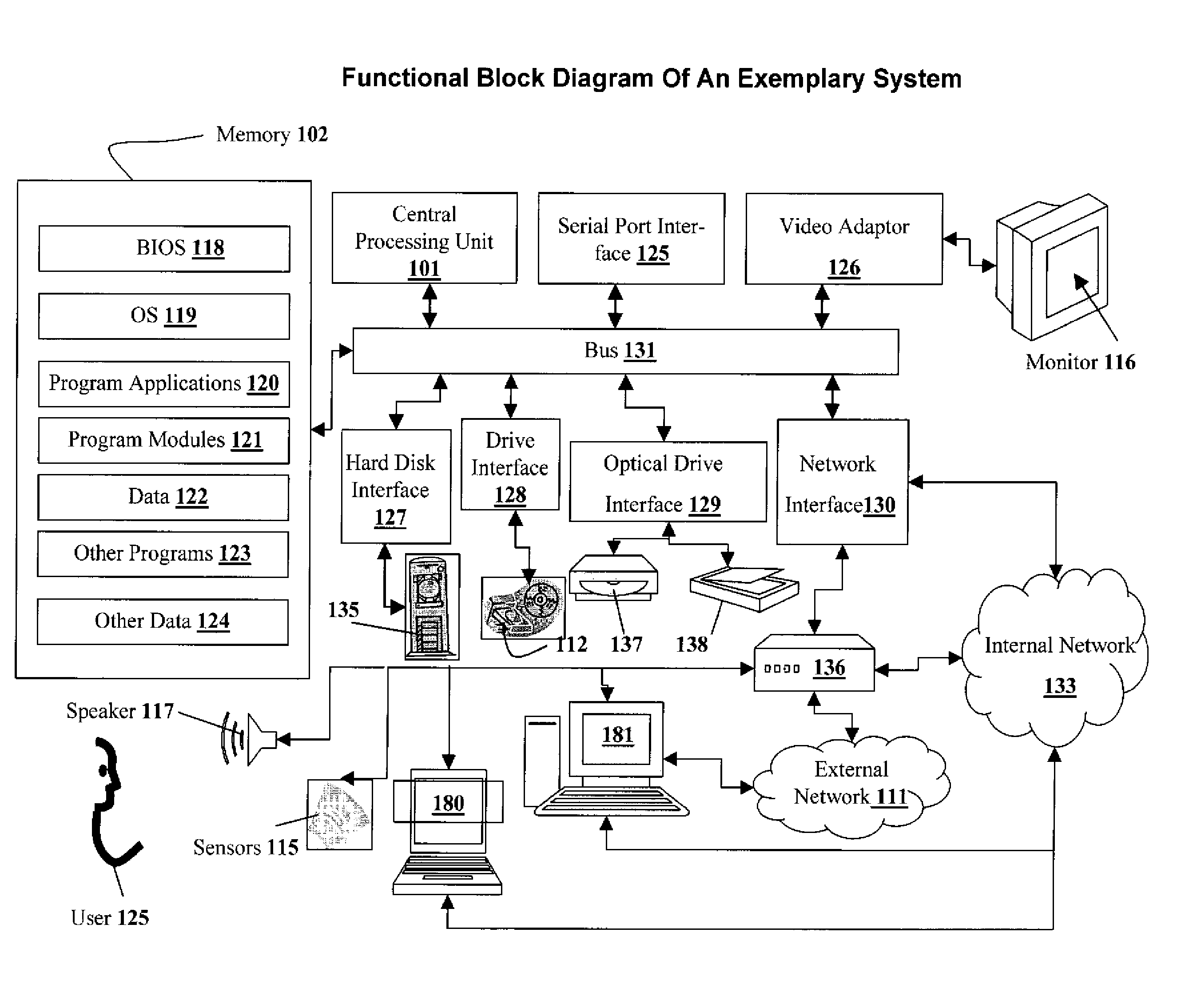
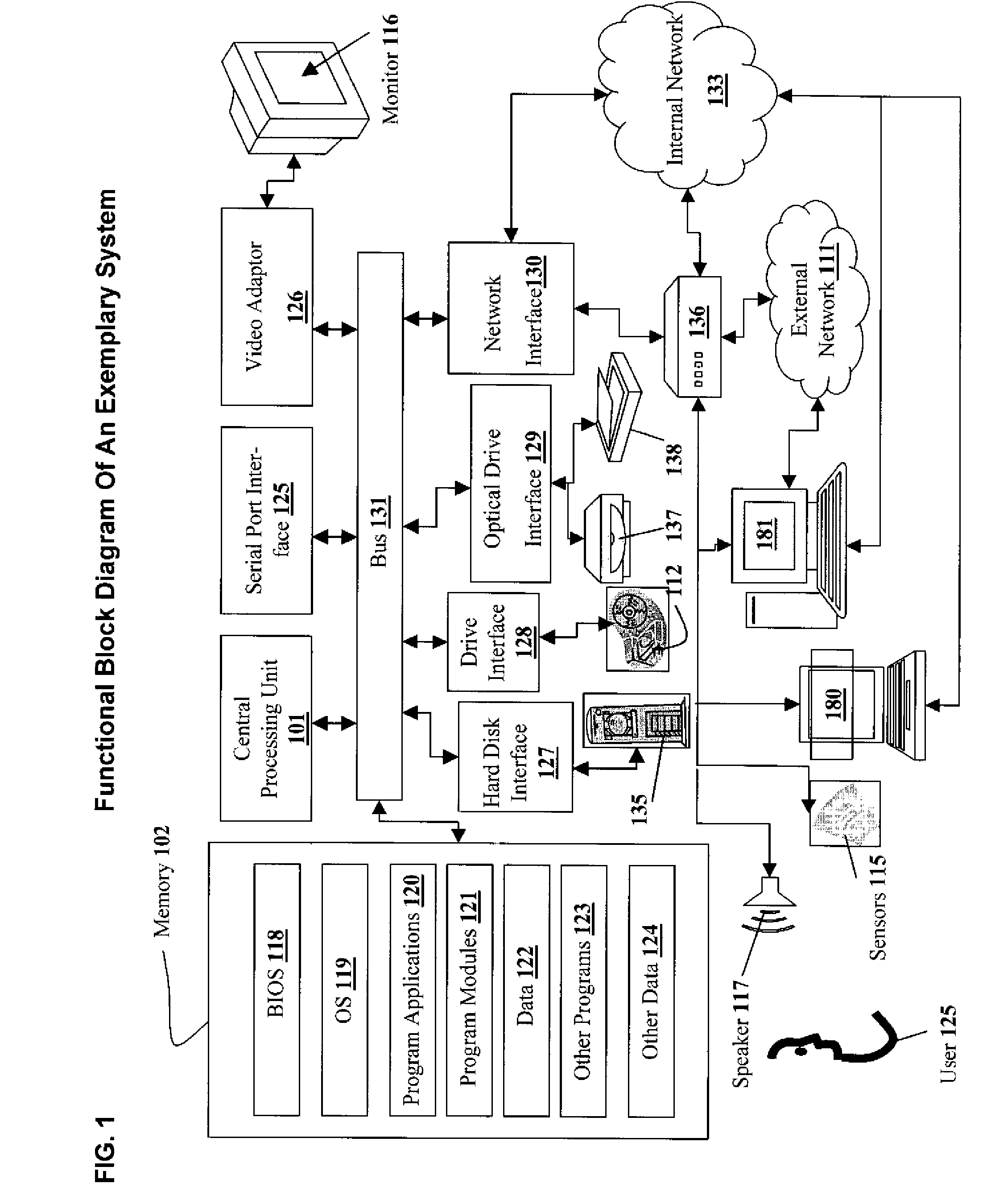
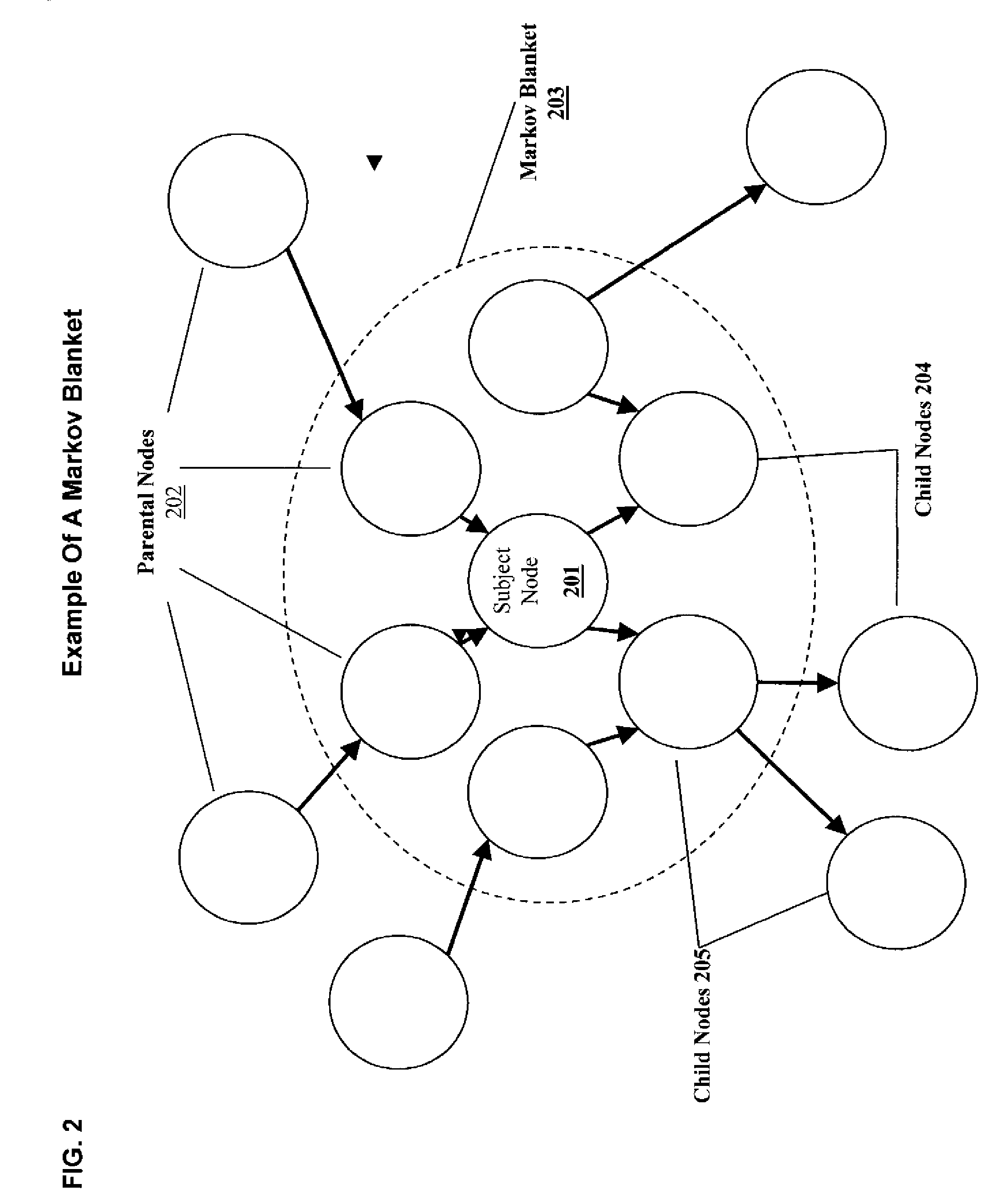
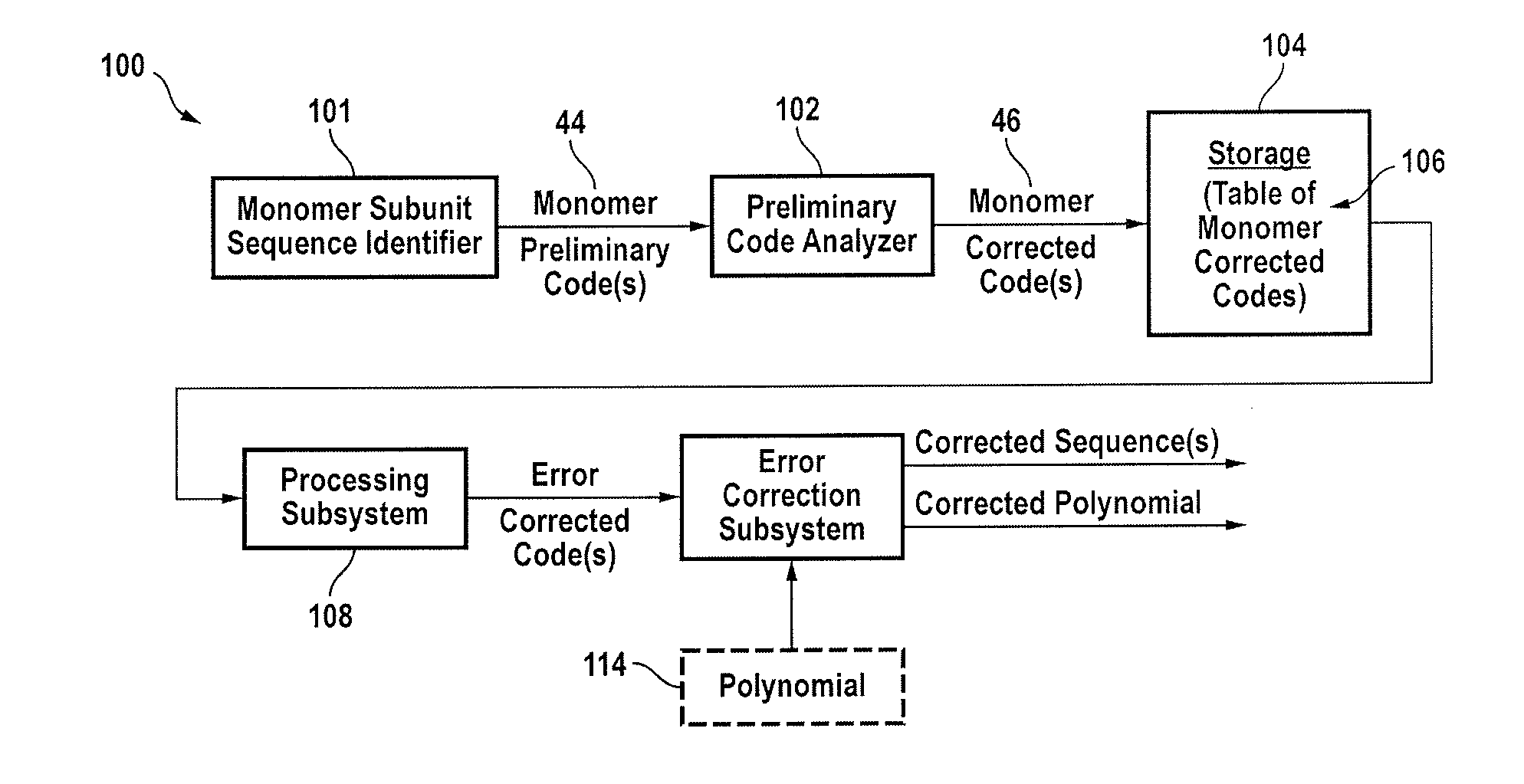
Patents
Literature
290 results about "Real systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Extensible bayesian network editor with inferencing capabilities
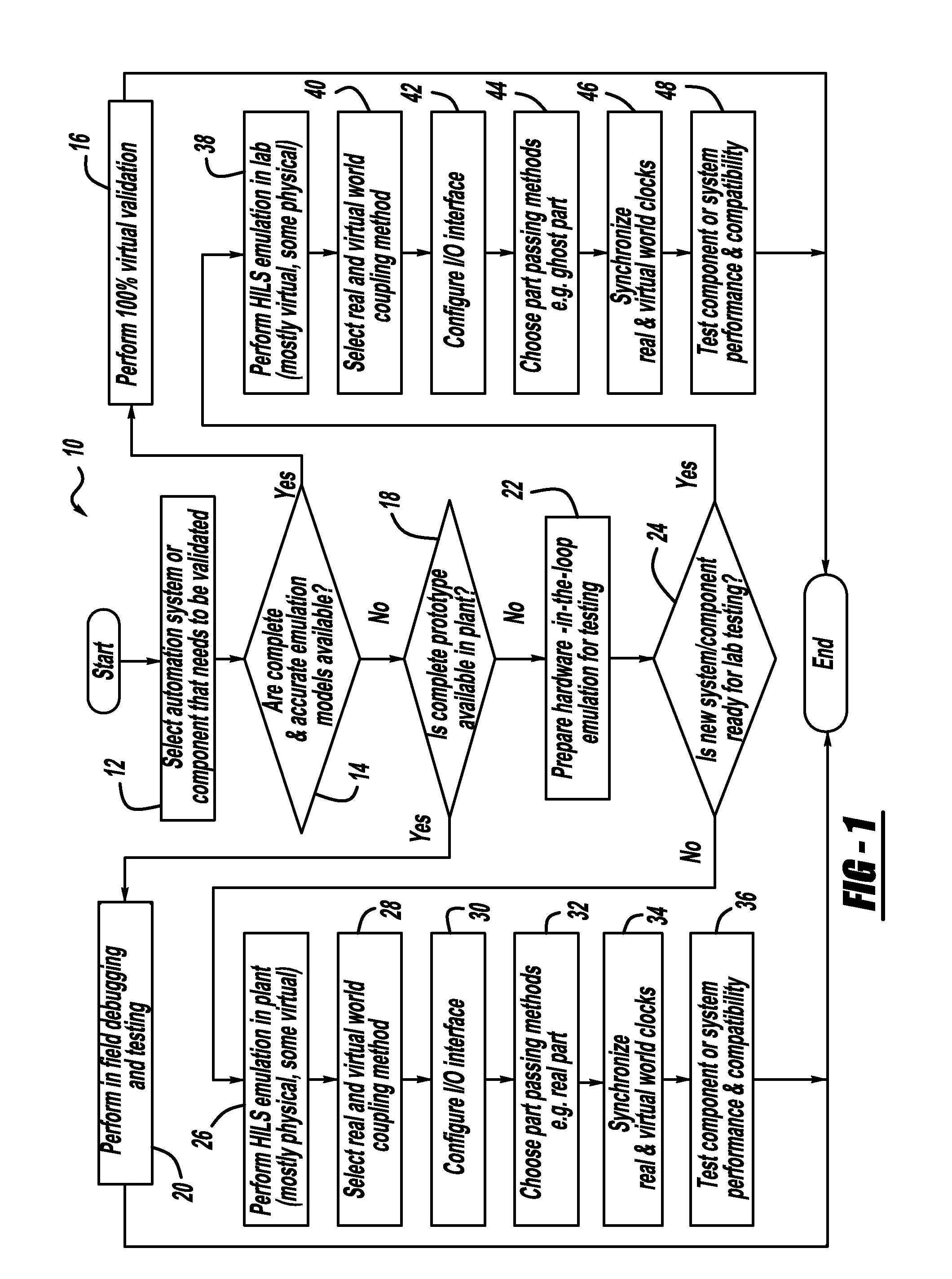
A system for the representation, editing, evaluation, and inference of graphical models is disclosed which can be used to construct and evaluate a graphical model or graphical network and to calculate inference values. An efficient method of updating graphical models is demonstrated, and provides the basis for an improved system for manipulation and evaluation of probabilistic models. The graphical network editor is useful in the construction of graphical modes such as Bayesian Networks. The graphical network and network graphical user interface (GUI) are used in conjunction with each other to model a system wherein failure probabilities and the current state of components are taken into account to monitor the health and progress of a system for an engineer or engineering software to evaluate and monitor. The evaluation is useful in the monitoring of assets and other real systems having multiple, dependent, and independently operating components such as a pump, a manufacturing plant, a production line, an assembly line, where asset health and quality control is a concern. The asset components each influencing some overall outcome of a system or situation. Success or failure or probability of success, probability of failure and health of the system can be monitored and manipulated by altering the values of prior probability and posterior probability values. Failure correlation between components can be evaluated wherein failure rates of asset is unknown. Production and quality can be monitored and altered.
Owner:QUANTUM LEAP RES
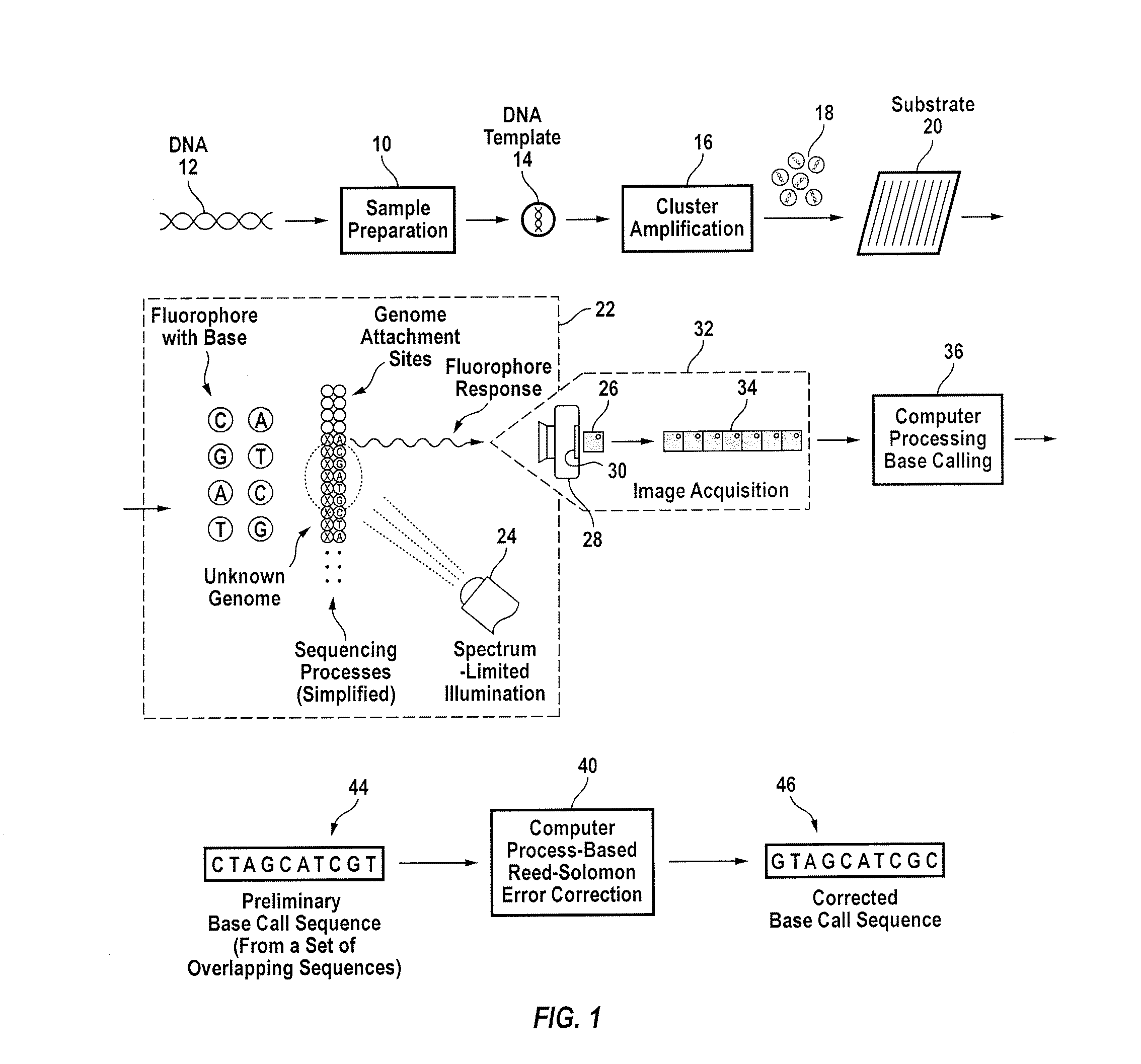
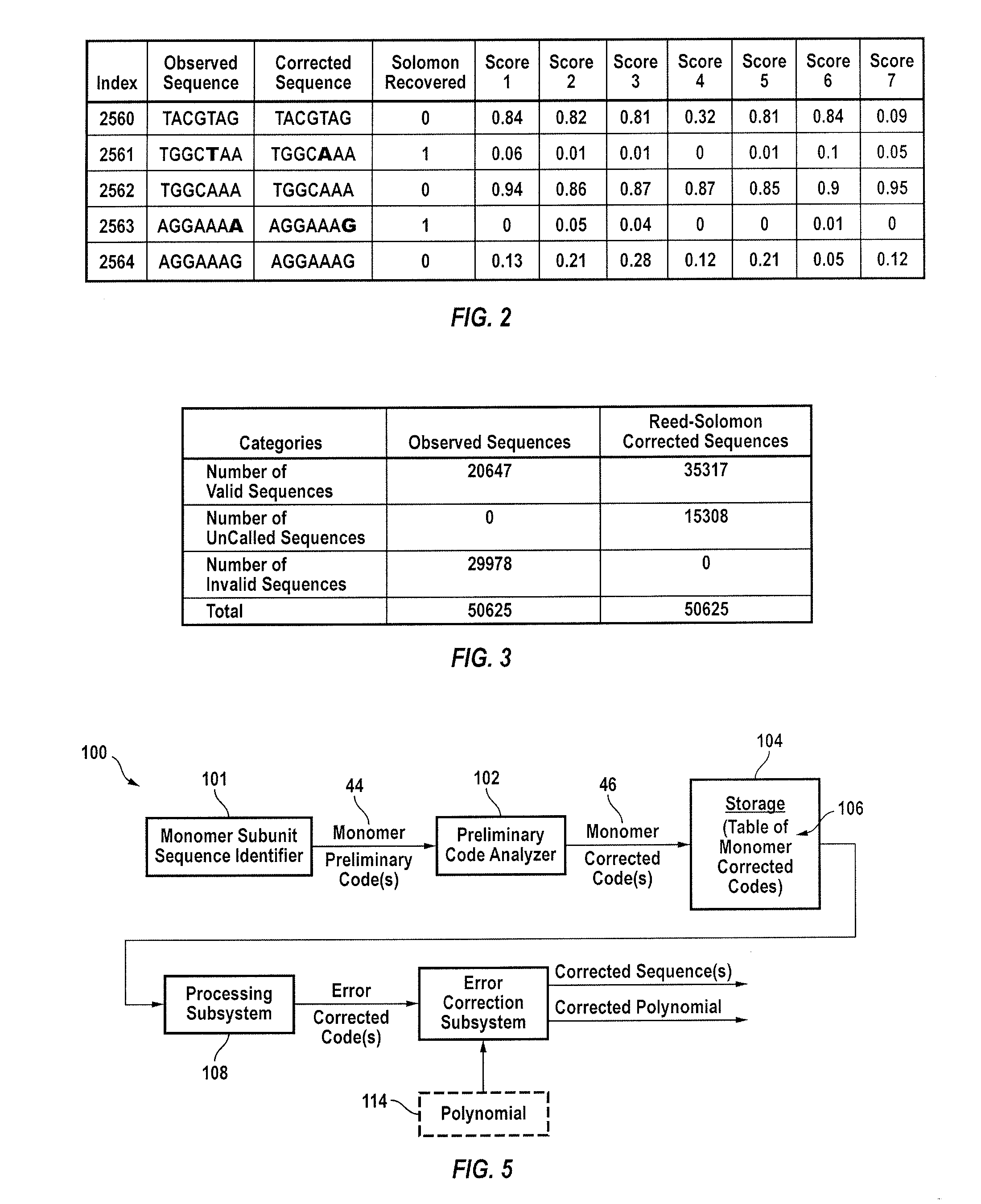
Method and apparatus for quantification of DNA sequencing quality and construction of a characterizable model system using reed-solomon codes
Data extracted from fluorosphore responses of fluorophore labeled bases in genetic material used in sequencing of unknown fragments from a defined set of for example a model system are converted into a class of block codes that are then employed in a computer-based process to compare and correct preliminary calls of calls of the categorically known genetic material. In a specific embodiment, the Reed-Solomon codes are employed to identify one or more errors as may occur in a finite block of codes. The methodology is also useful to identify elements of a real system containing known elements in the form of a tag. Reed-Solomon sensors may be employed with and in addition to other types of genome sensors.
Owner:COMPLETE GENOMICS INC
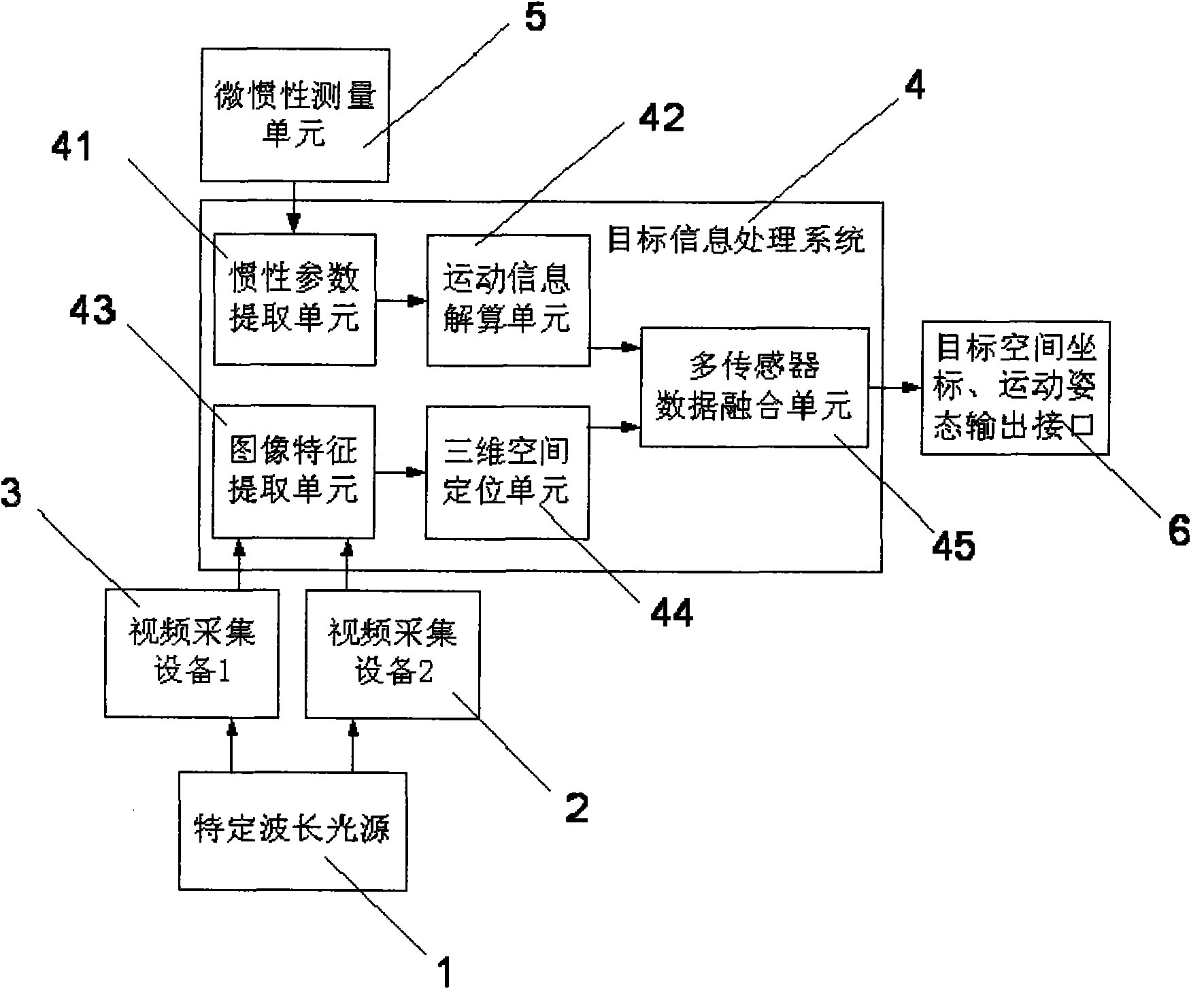
Movement tracking device for man-machine interaction and tracking method thereof
InactiveCN101859439AEasy to implementImprove tracking accuracyImage analysisInformation processingReal systems
The invention relates to a movement tracking device for man-machine interaction and a tracking method thereof. The invention comprises a movement tracking device and a target information processing device. The tracking method comprises the following steps of: (1) binding a micro inertial measurement unit and a specified-wavelength light source with a tested target; (2) transmitting target movement parameters to a target information processing system by the movement tracking device; (3) processing the acquired target movement information by the target information processing system; and (4) outputting accurate target movement information to a man-machine interaction interface through a target space coordinate and a movement posture information output interface. The invention provides the device and the tracking method thereof which can be applied to man-machine interaction, virtual reality, and enhancement of a real system and can effectively expand the movement tracking range.
Owner:HEFEI VRVIEW INFORMATION TECH
Nonlinear adaptive control of resource-distribution dynamics
InactiveUS20060013132A1Improves controller performanceImprove performanceError preventionTransmission systemsReal systemsResource Management System
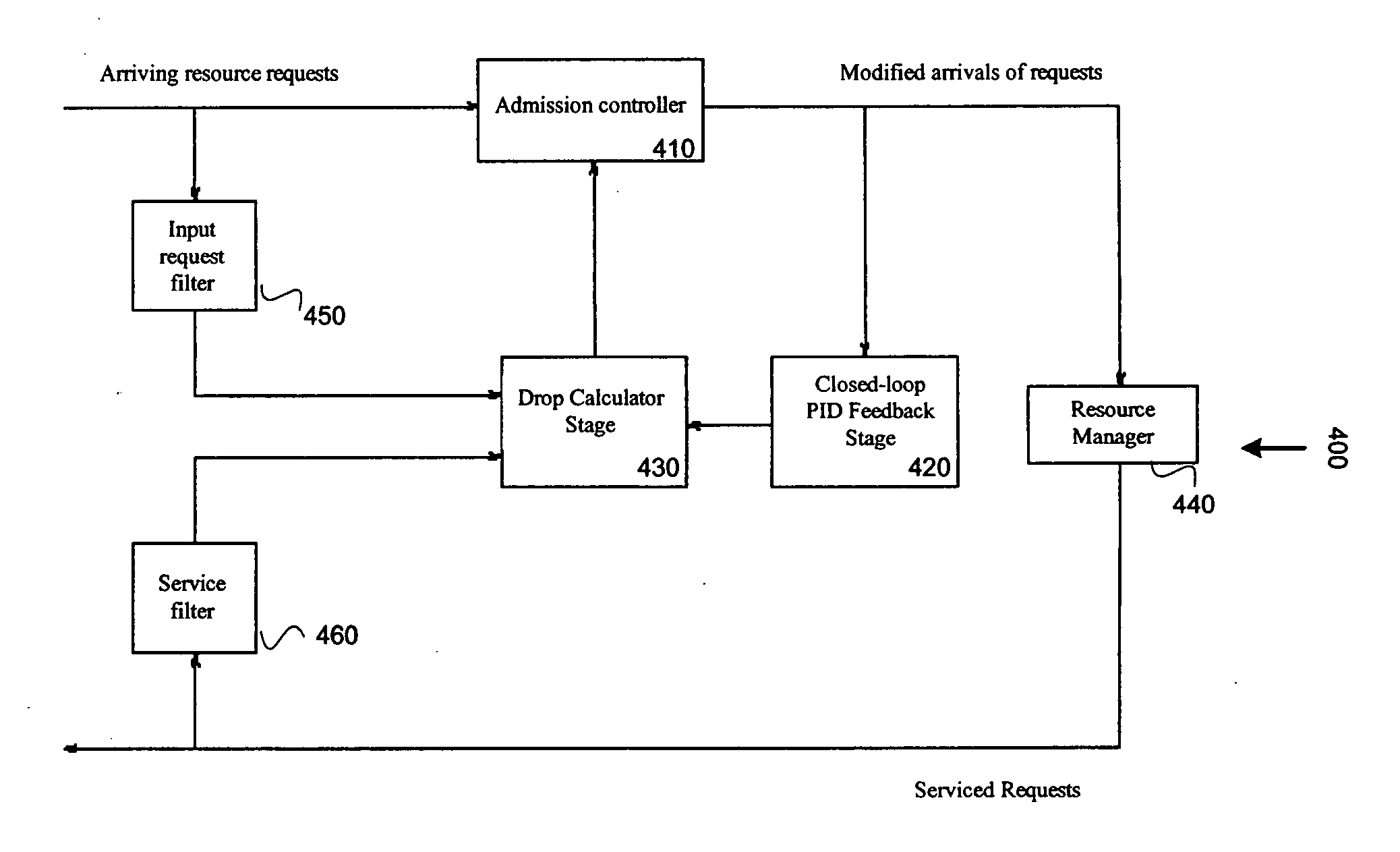
Nonlinear adaptive resource management systems and methods are provided. According to one embodiment, a controller identifies and prevents resource starvation in resource-limited systems. To function correctly, system processes require resources that can be exhausted when under high load conditions. If the load conditions continue a complete system failure may occur. Controllers functioning in accordance with embodiments of the present invention avoid these failures by distribution shaping that completely avoids undesirable states. According to one embodiment, a Markov Birth / Death Chain model of the resource usage is built based on the structure of the system, with the number of states determined by the amount of resources, and the transition probabilities by the instantaneous rates of observed consumption and release. A control stage is used to guide a controller that denies some resource requests in real systems in a principled manner, thereby reducing the demand rate and the resulting distribution of resource states.
Owner:CREATIVE TECH CORP
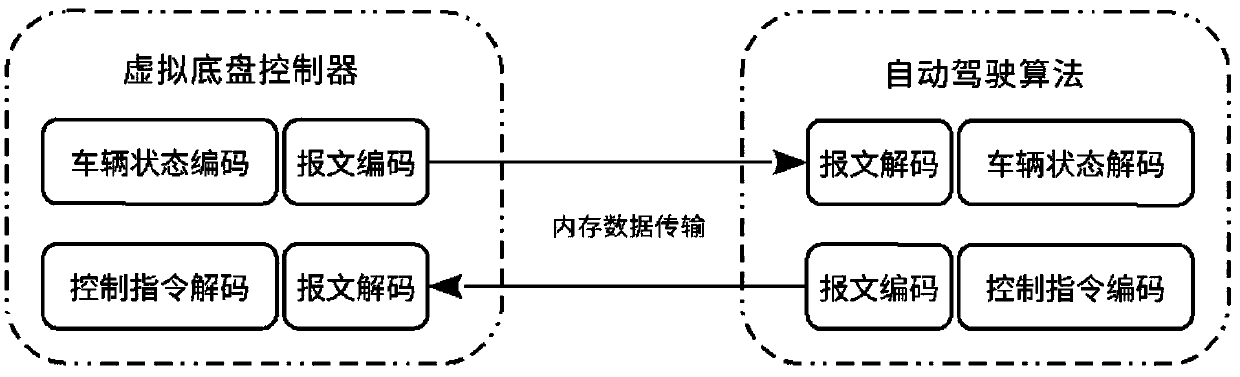
Multifunctional simulation system for automatic driving
ActiveCN108803607AImprove portabilityEfficient verificationPosition/course control in two dimensionsVehiclesVirtual vehicleData interface
The invention provides a multifunctional simulation system for automatic driving. The multifunctional simulation system comprises a virtual vehicle module, a virtual chassis control module, a virtualroad module, a virtual traffic module, a time control unit module and a visualized interactive interface module, the virtual road module provides cartographic information for an automatic driving algorithm and the virtual traffic module, the virtual traffic module provides road conditions including vehicles, pedestrian, traffic lights and the like for the automatic driving algorithm, the automaticdriving algorithm communicates with the virtual vehicle module through a virtual chassis so as to obtain vehicle information and send vehicle control instructions, a visualized interactive interfacesends human-computer interaction information to the simulation system and displays system information in a visualized three-dimensional effect, and finally, the time control unit module controls intervals of simulation time of the simulation system comprising the automatic driving algorithm. Data interfaces of the virtual modules are kept consistent with those of a real system, so that multifunctional modes, including hardware-in-loop simulation, of the simulation system can be realized.
Owner:北京领骏科技有限公司
Automatic embedded software block box testing system and method
InactiveCN103995777AImprove test efficiencyThe test result is accurateSoftware testing/debuggingTest efficiencyReal systems
The invention relates to the field of computers, and discloses an automatic embedded software block box testing system and method. The testing system comprises an upper computer and a lower computer. The upper computer is used for automatically generating a testing script and establishing a simulation model of a system cross-linked with a tested system, the simulation model and the tested system are connected through the lower computer, and after a testing order is received, the testing script corresponding to the testing order is called to the lower computer. The lower computer is used for testing the tested system according to the testing script and sending testing data of the tested system to the upper computer. The testing system can automatically generate the testing script, testing efficiency is improved, the tested system is brought into a real system environment, the tested system is connected with the system cross-linked with the tested system, the integral function testing is carried out on the tested system based on a closed loop testing method, and the testing result is real and accurate.
Owner:SHANGHAI KELIANG INFORMATION ENG
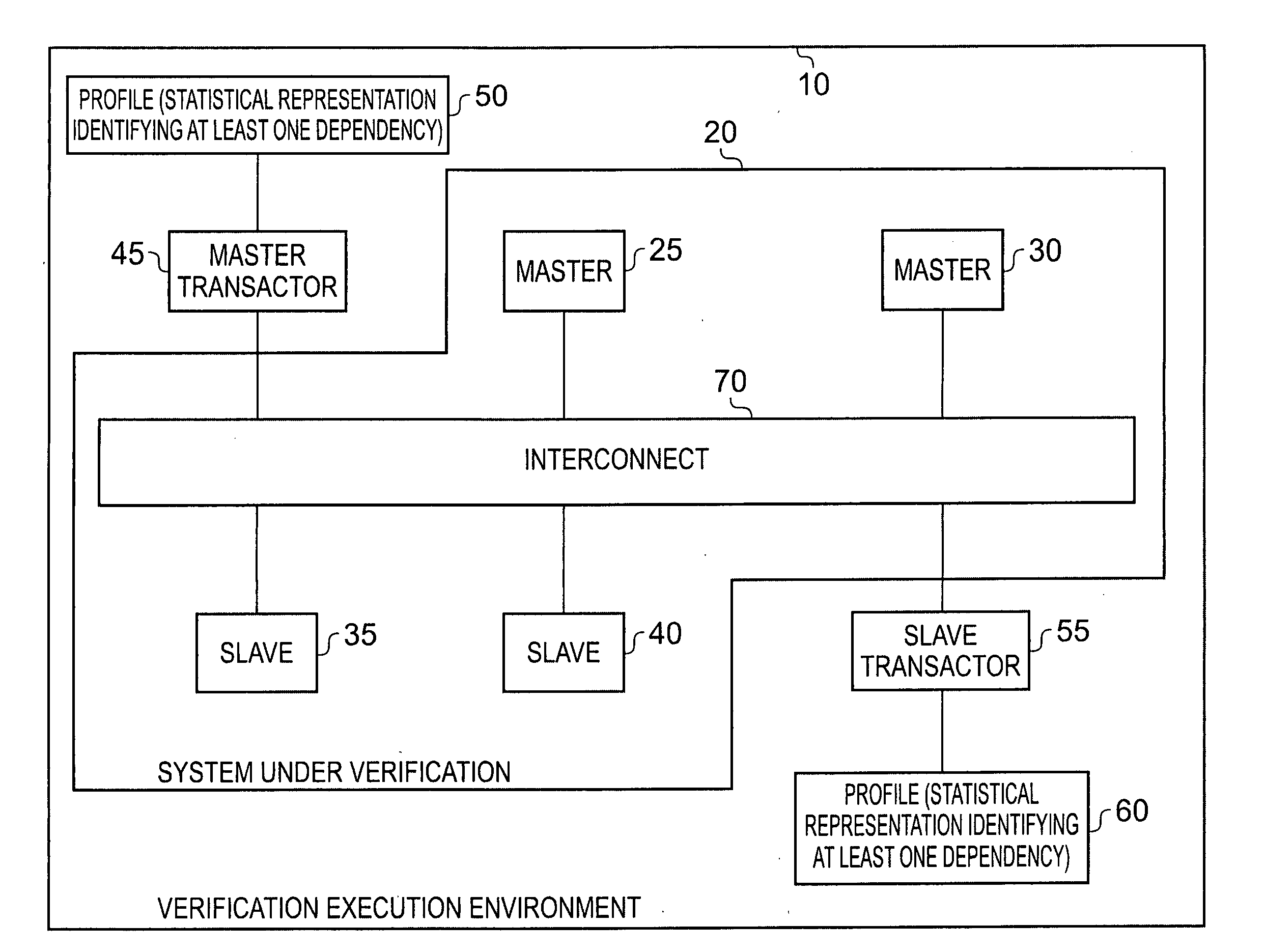
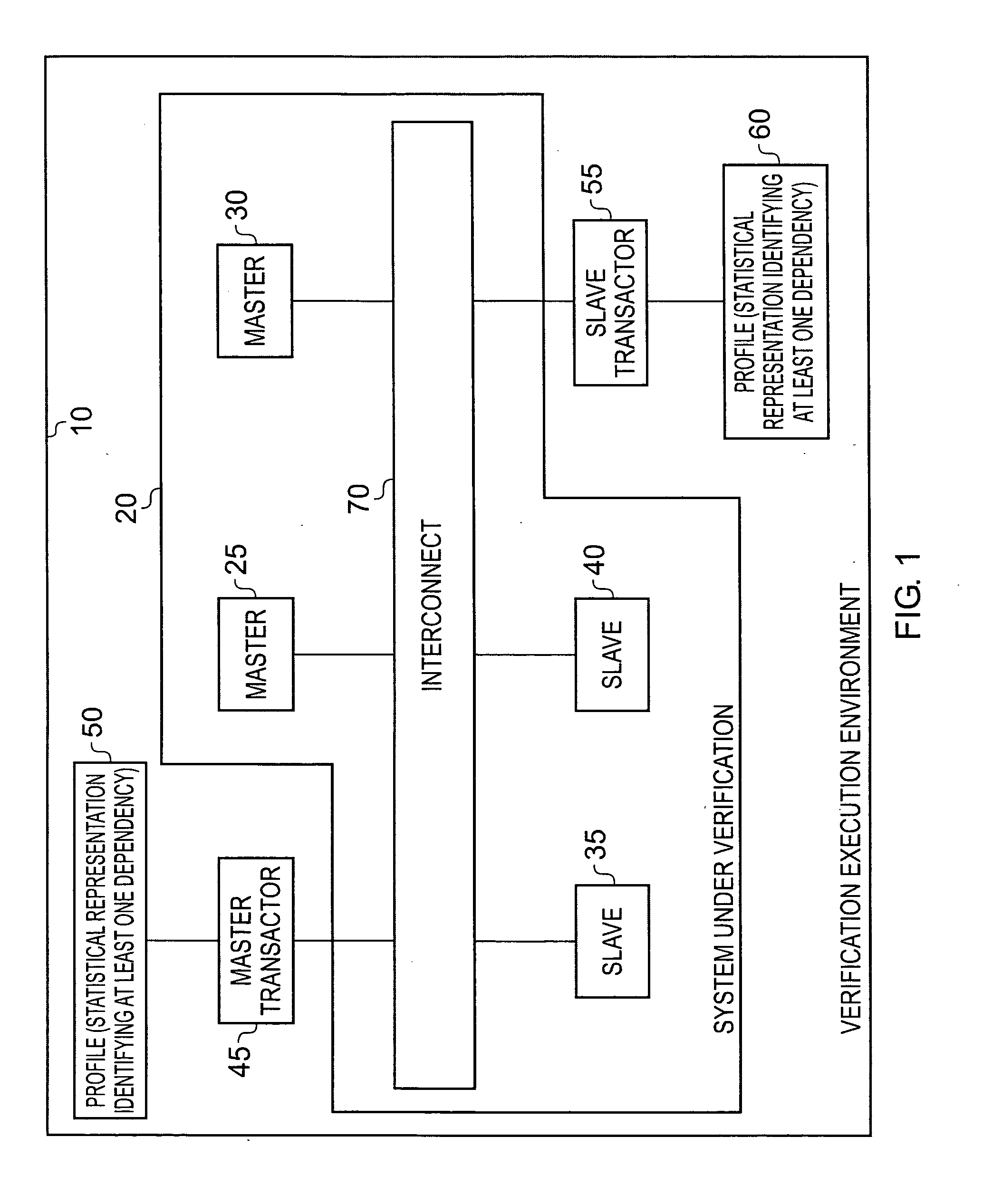
Use of statistical representations of traffic flow in a data processing system
InactiveUS20110145646A1Less likelihoodWork lessError detection/correctionElectrical testingData processing systemReal systems
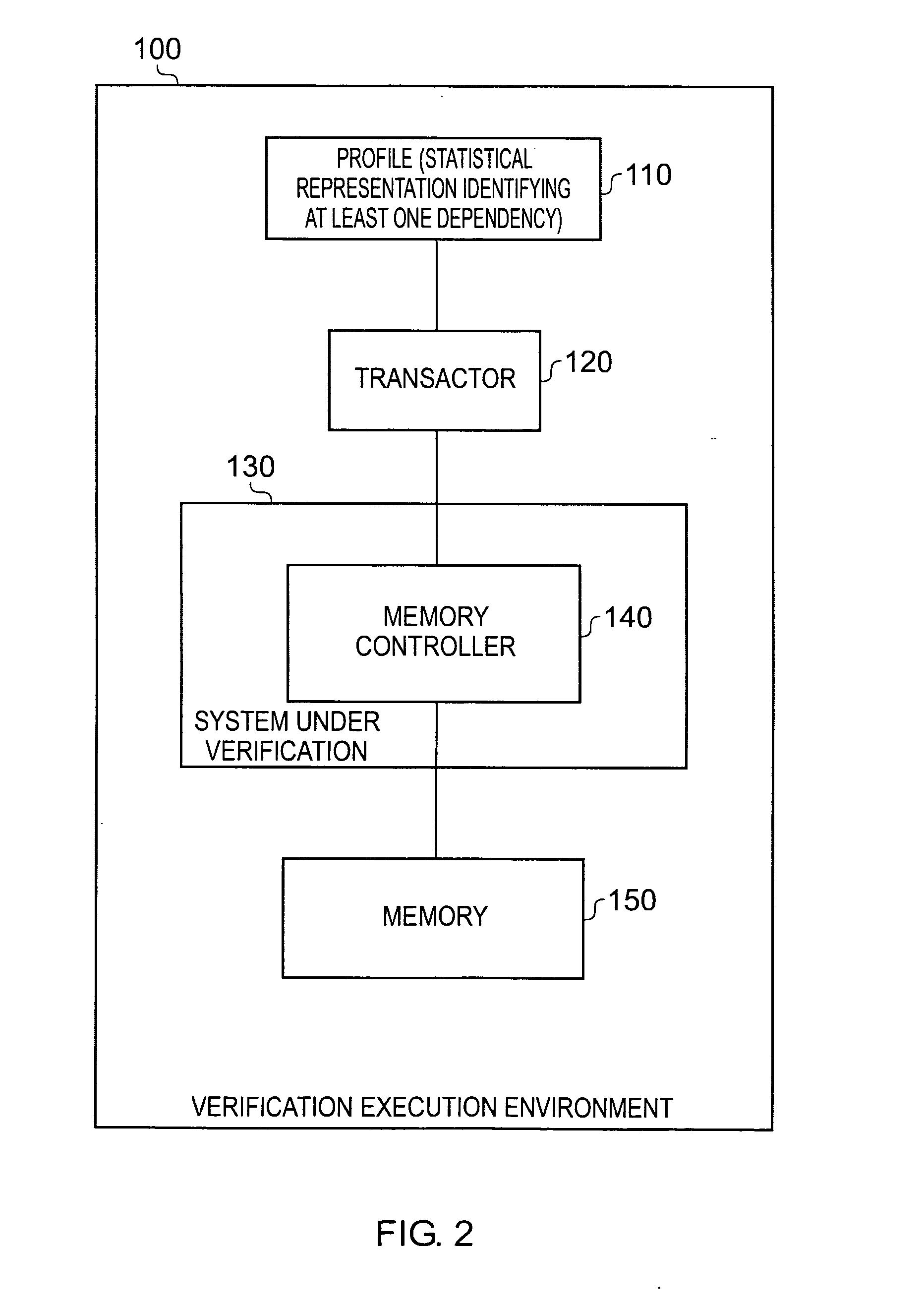
An apparatus and method are provided for performing verification tests for a design of a data processing system. The apparatus comprises a system under verification representing at least part of the design of the data processing system, and a transactor for connecting to an interface of the system under verification, and for generating signals for input to the system under verification via the interface during performance of the verification tests. Profile storage stores a profile providing a statistical representation of desired traffic flow at the interface, the statistical representation providing statistical information for a plurality of traffic attributes and also identifying at least one dependency between such traffic attributes. The transactor then references the profile in order to determine the signals to be generated, such that the signals generated take account of the specified dependencies identified in the profile. Such a mechanism enables the transactor to more realistically replicate the traffic flow that will be observed in the real system. Another aspect to the present invention provides a mechanism for generating such profiles.
Owner:ARM LTD
Robot positioning method based on wireless sensor network and geomagnetic map
InactiveCN106123892AEasy to associateImprove robustnessNavigational calculation instrumentsNavigation by terrestrial meansReal systemsWireless mesh network
The invention relates to a robot positioning method based on a wireless sensor network and a geomagnetic map. wireless sensor network nodes, during the movement of the robot, by activating A wireless sensor network node, use RSSI to obtain the observation model of wireless sensor network nodes and robots; then use PSO and multi-sensor information fusion to obtain the particle likelihood; at the same time obtain the weight of particles in the particle swarm optimization method; Resampling and fitness function judgment are used to obtain the position of the optimal particle, obtain a local geomagnetic map, and use the geomagnetic matching method to achieve precise positioning, and finally obtain the absolute position. The present invention is easy to associate data, no wrong association occurs during observation, and the robustness and accuracy of the network are improved; at the same time, a more realistic system state distribution prediction is obtained, which makes the positioning of the robot more accurate and reduces the calculation amount of geomagnetic matching. The real-time performance of the method is increased.
Owner:WUHAN UNIV OF SCI & TECH
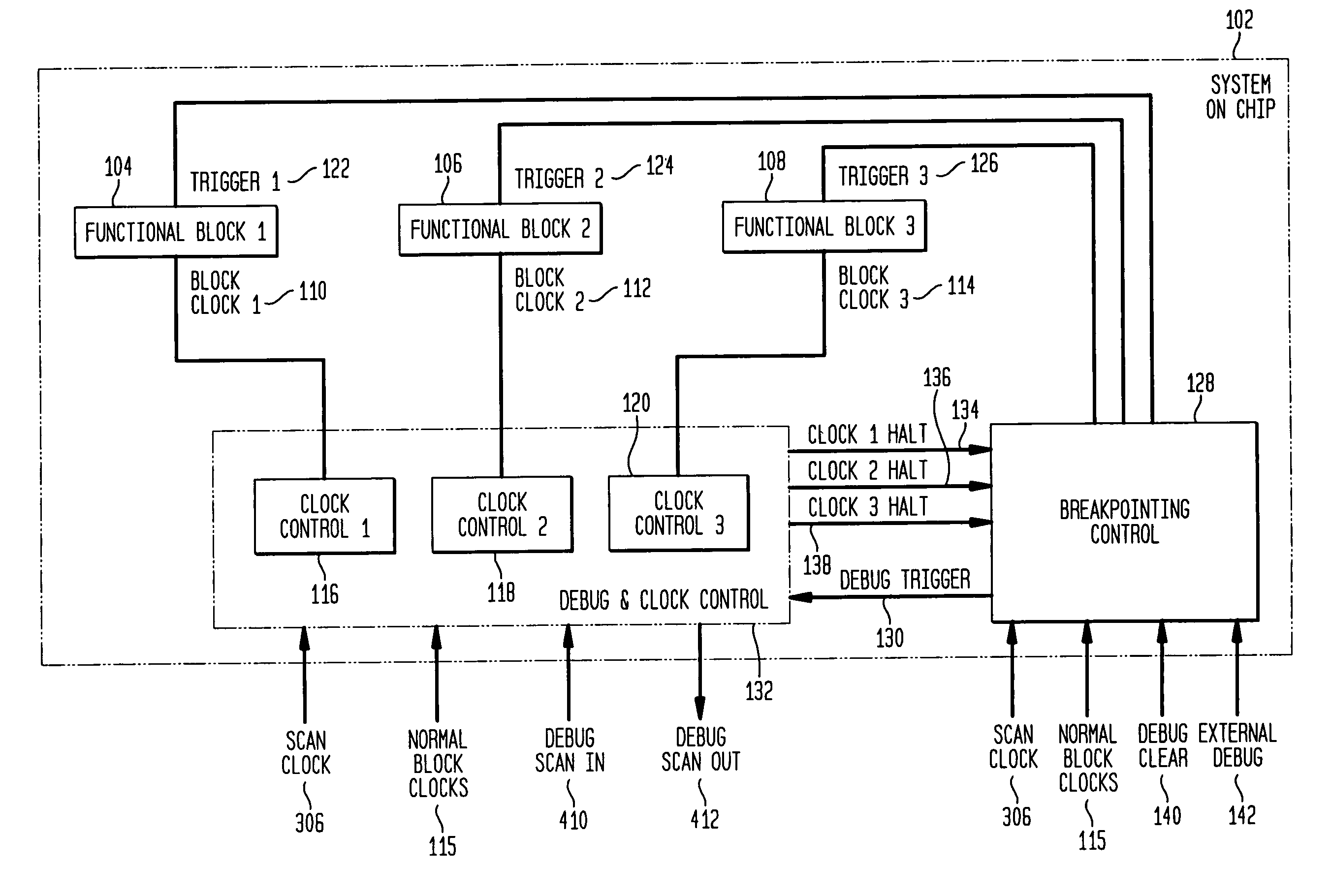
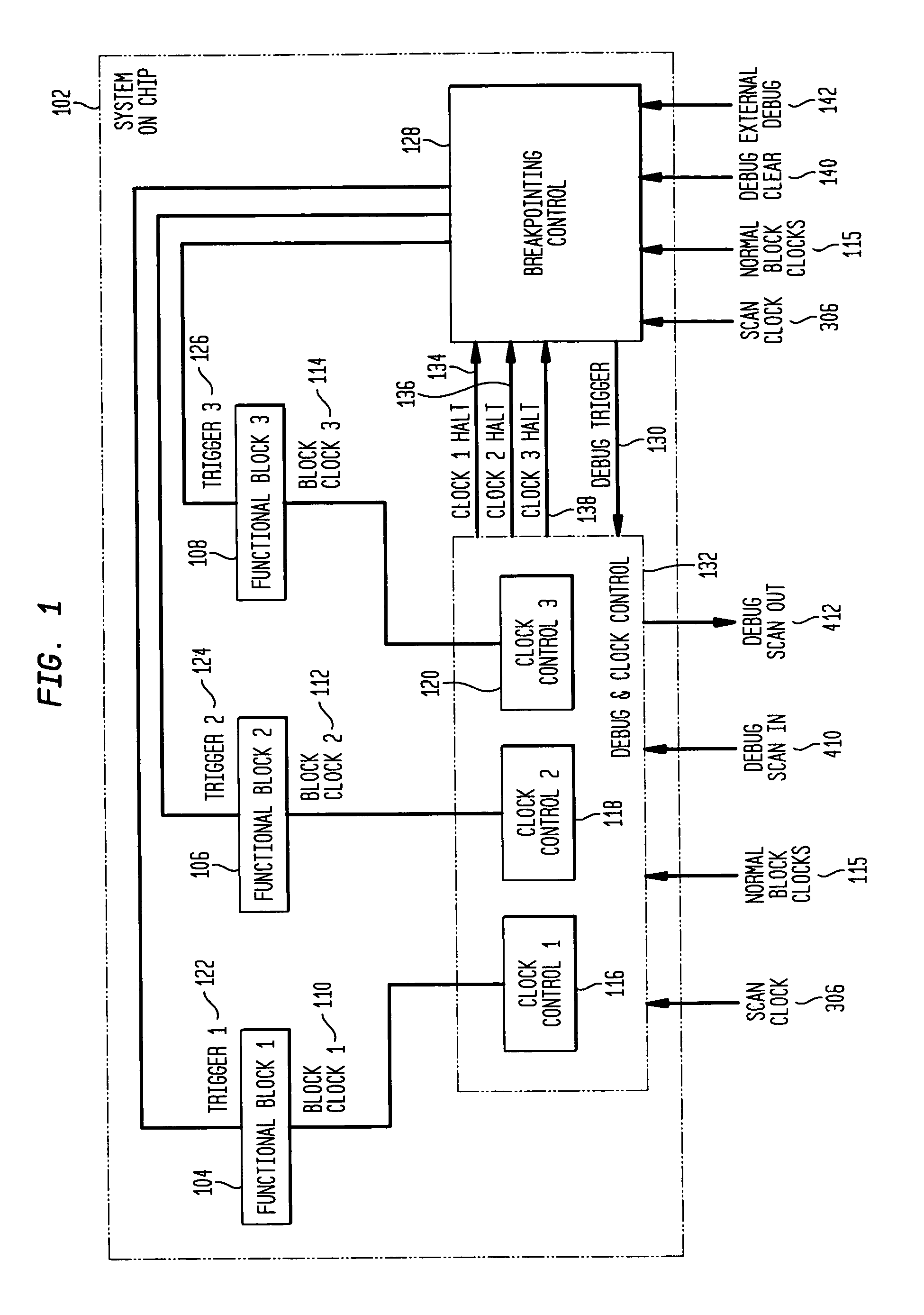
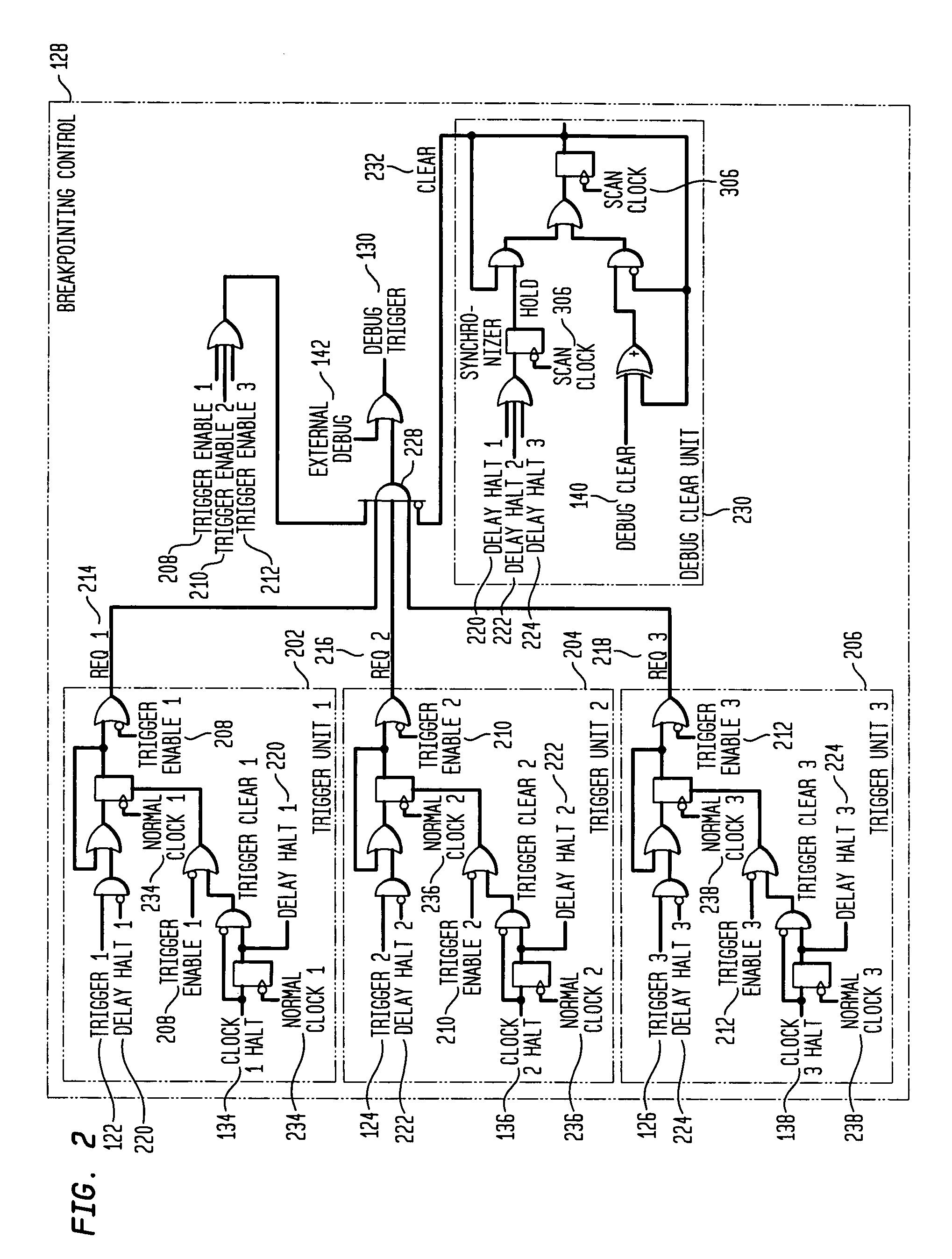
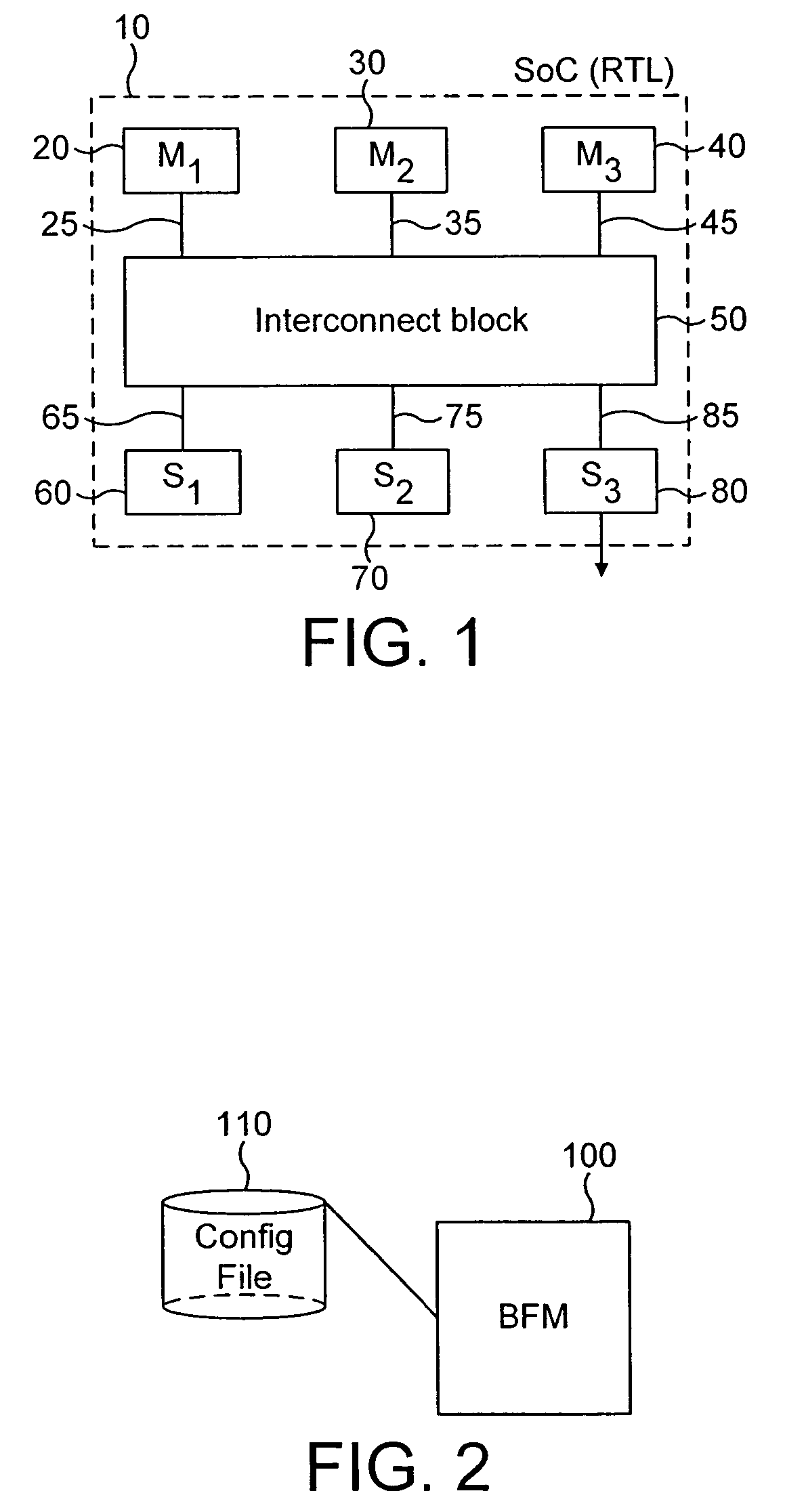
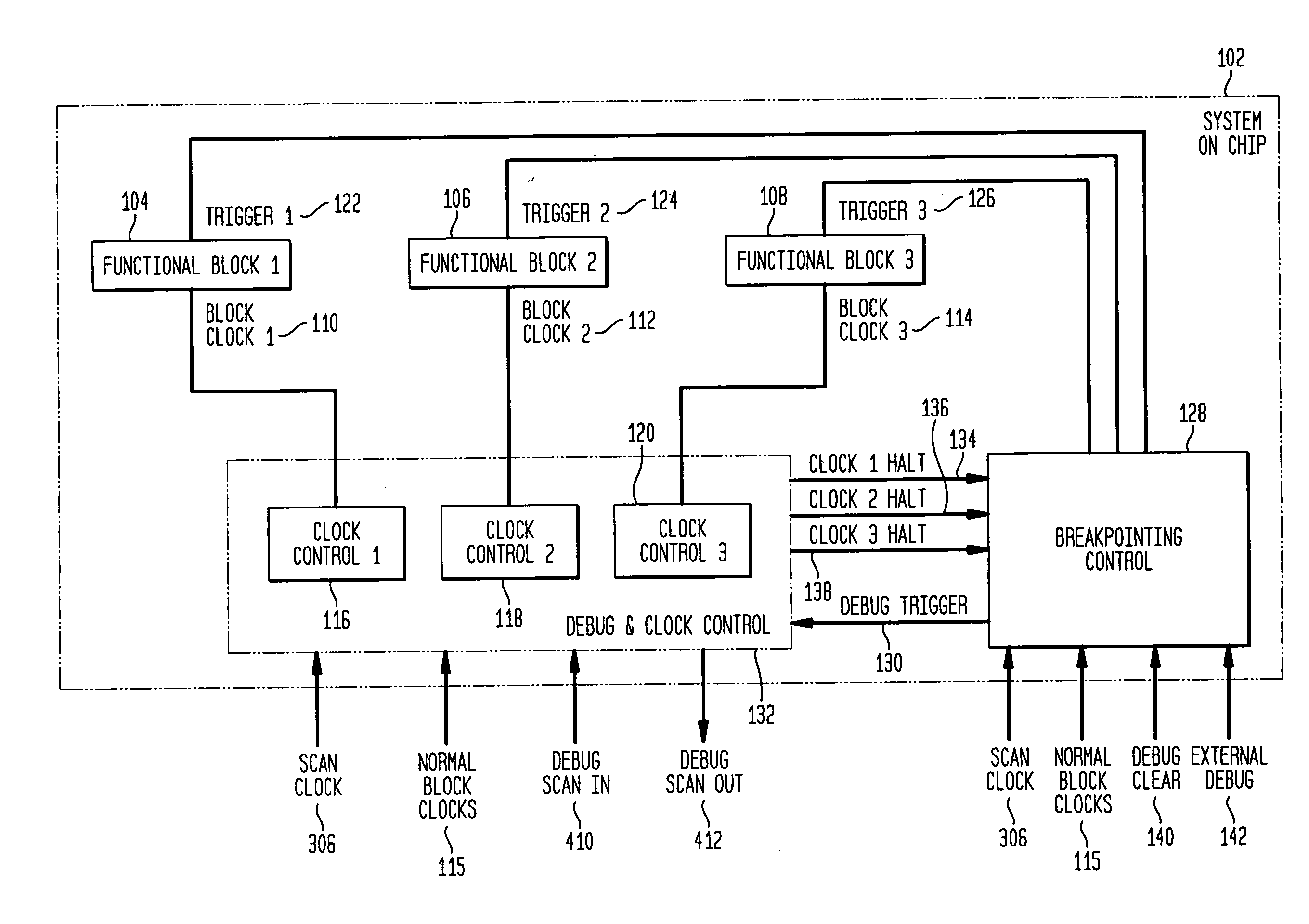
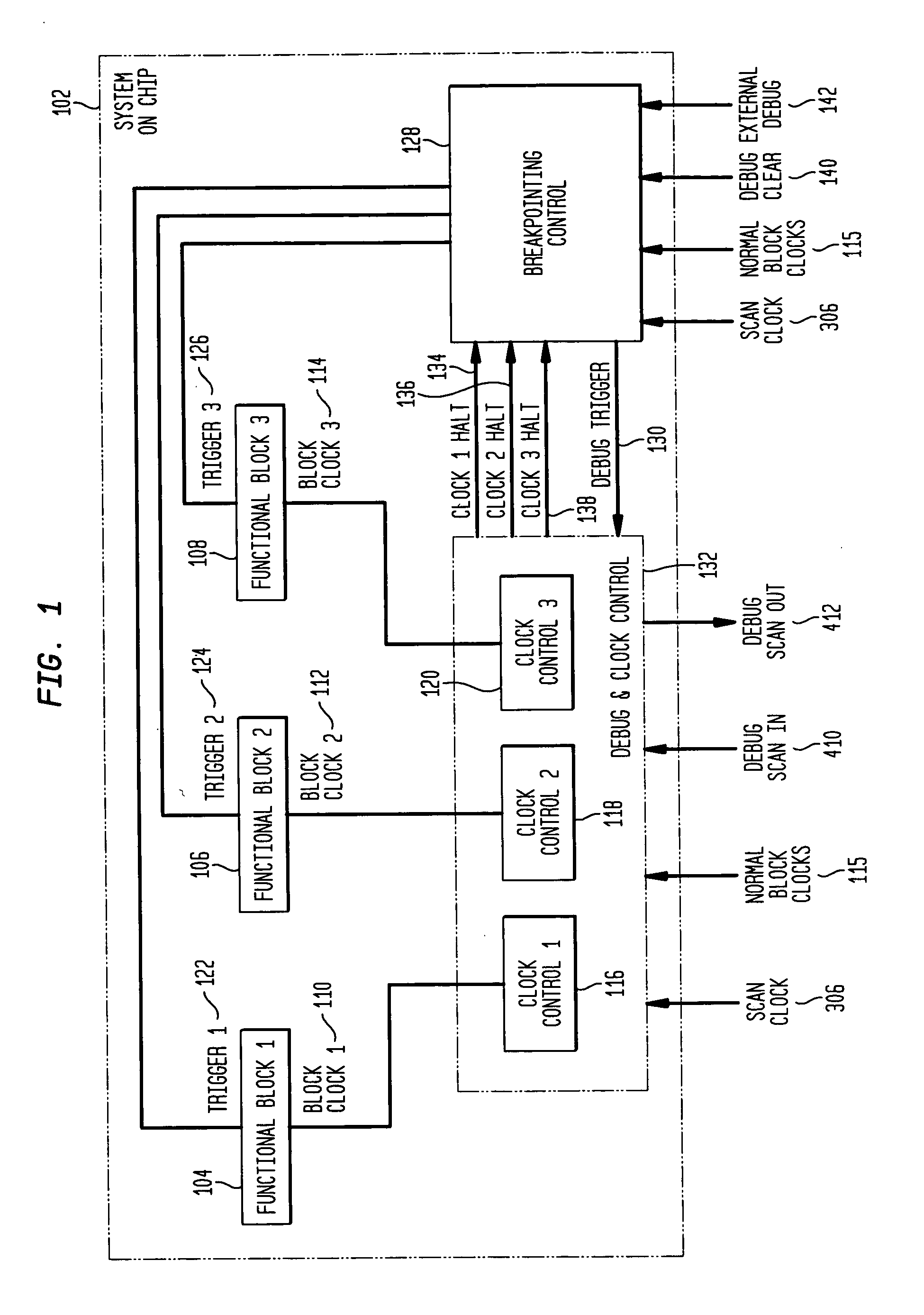
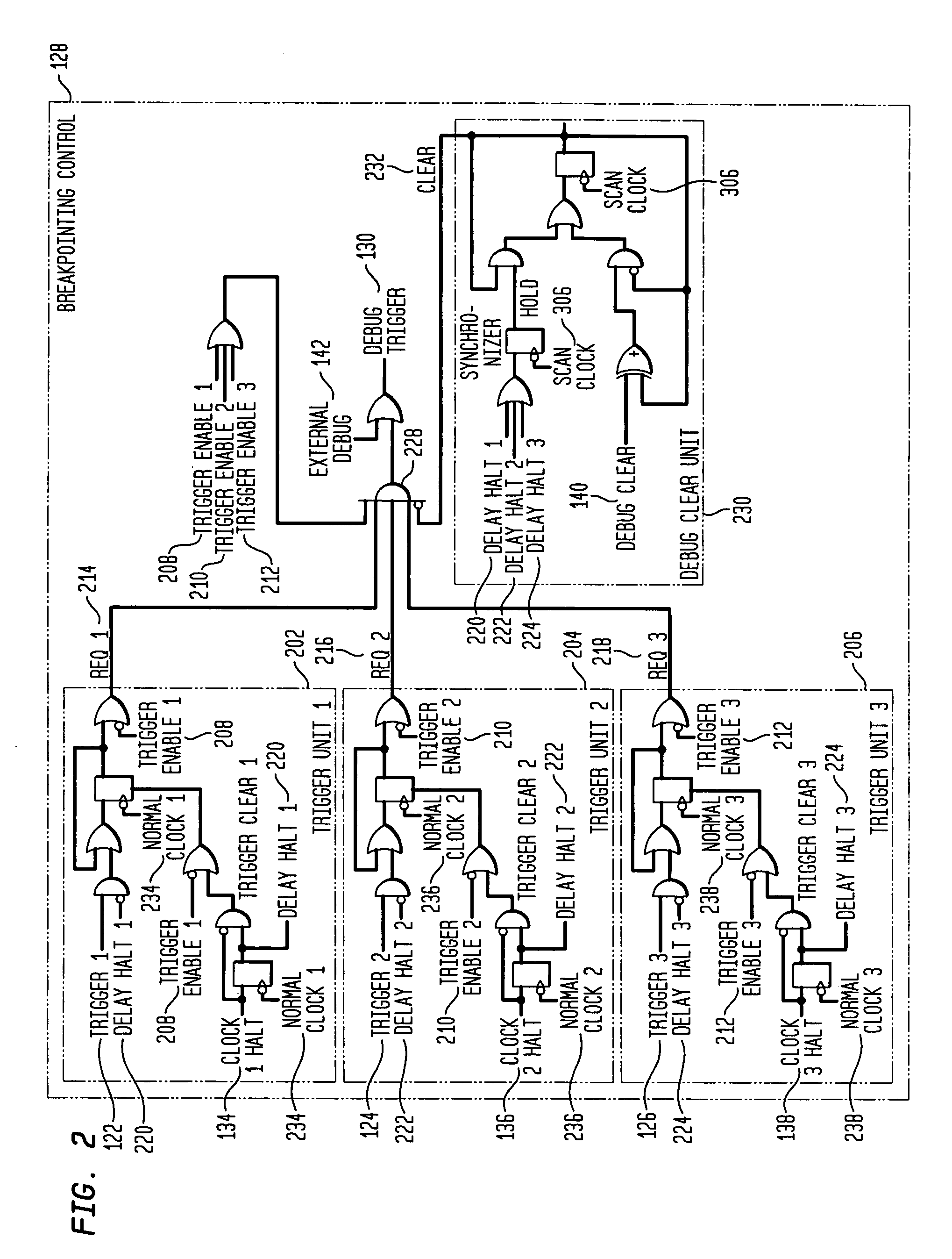
System and method for debugging system-on-chips using single or n-cycle stepping
InactiveUS7055117B2Digital circuit testingDetecting faulty computer hardwareReal systemsSoftware design
Large, complex SoCs comprise interconnections of various functional blocks, which blocks frequently running on different clock domains. By effectively controlling the clocks within the SoC, this invention provides a means to halt execution of a SoC and to then single or n-cycle step its execution in a real system environment. Accordingly, the invention provides an effective debugging tool to both the SoC designer and software designers whose code is executed by the SoC as it provides them the capability of studying the cause and effect of interactions between functional blocks. The invention is also applicable to SoCs containing only one functional block while containing complex circuitry operating on a clock different than the block's clock. In particular, the invention permits halting of the block clock and then single or n-cycle stepping its execution to permit analysis of the interactions between the block and the SoC circuitry.
Owner:BELL SEMICON LLC
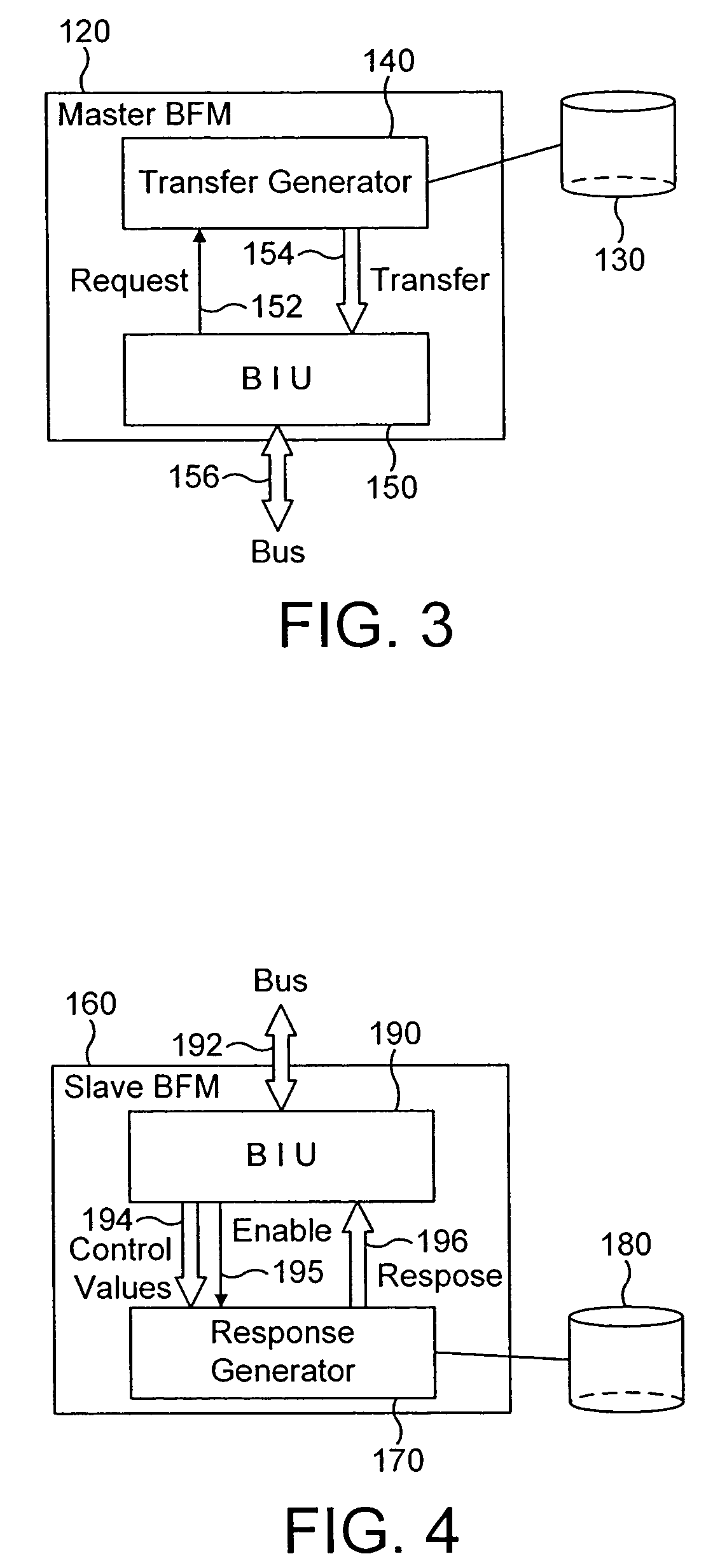
Test component and method of operation thereof
ActiveUS20040243334A1Many timesShorten the timeElectronic circuit testingError detection/correctionReal systemsEquipment under test
A test component and method of operation thereof are provided, the test component being arranged in a test environment to issue a test sequence over a bus to a device under test. A configuration file is provided to specify the behaviour of the test component, the configuration file comprising a plurality of regions with each region specifying attributes for use in determining the test sequence. A number of the regions specify constraint attributes defining allowable test sequences. The method of the present invention comprises the steps of: (a) when a test sequence is required to be issued, causing the test component to select, based on predetermined criteria, one of a number of regions provided by the configuration file; and (b) using the constraint attributes for that selected region to generate the test sequence to be issued on to the bus. It has been found that such an approach provides an efficient technique for enabling the test component to be configured to emulate the actual component which in the real system will interact with the device being tested. It has also been found that the time taken to write the tests required for the device under test is significantly reduced compared to prior art techniques.
Owner:ARM LTD
Active user detection and channel estimation method with adaptive overhead
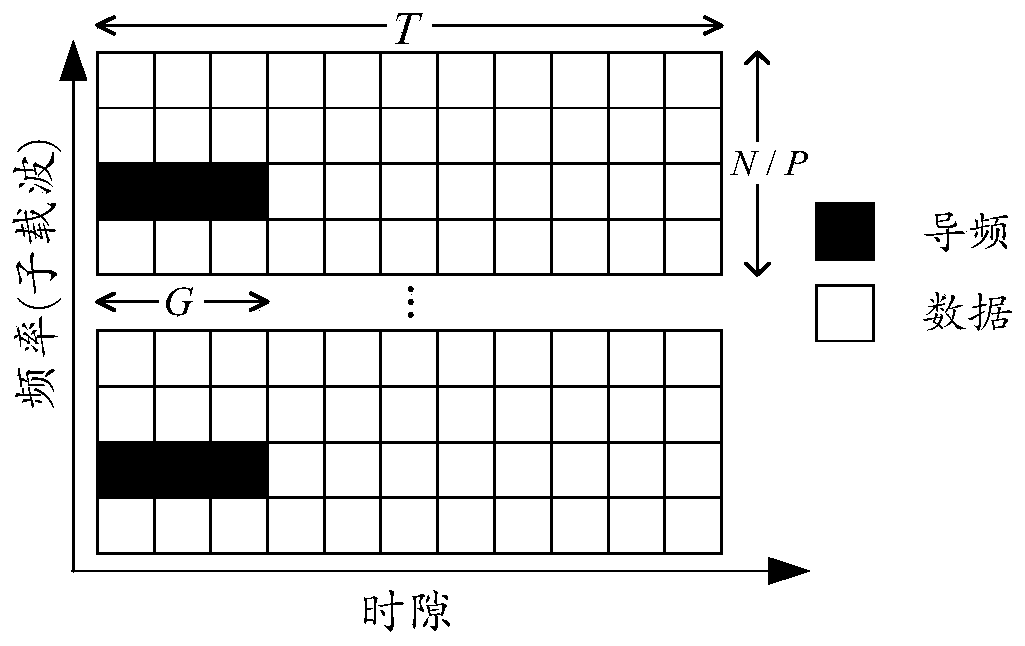
ActiveCN110071881AReduce access delayReliable estimateBaseband system detailsRadio transmissionQuality of serviceUplink transmission
The invention discloses an active user detection and channel estimation method with adaptive overhead. Using the estimated active user set and the channel thereof, the estimation quality is evaluatedby calculating the received signal error, and the time slot overhead of the pilot frequency in the frame structure can be adaptively adjusted according to the number of active users and the channel environment in the real system, so that the service quality is ensured with the access time delay as low as possible, and super-reliable active user detection and channel estimation are realized. The method also aims at an enhanced mobile broadband scene, large-scale machine type communication and other huge-address communication scenes in a cellular network in the future. According to the method, the pilot signal for broadband uplink unlicensed multiple access is reasonably designed by utilizing the sporadic characteristic of the uplink transmission flow of the user and the sparsity of a large-scale MIMO virtual angle domain channel, and an advanced compressed sensing technology is introduced, so that the access delay of the user can be greatly reduced.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Residual life prediction method for non-stationary degradation process with uncertain impact
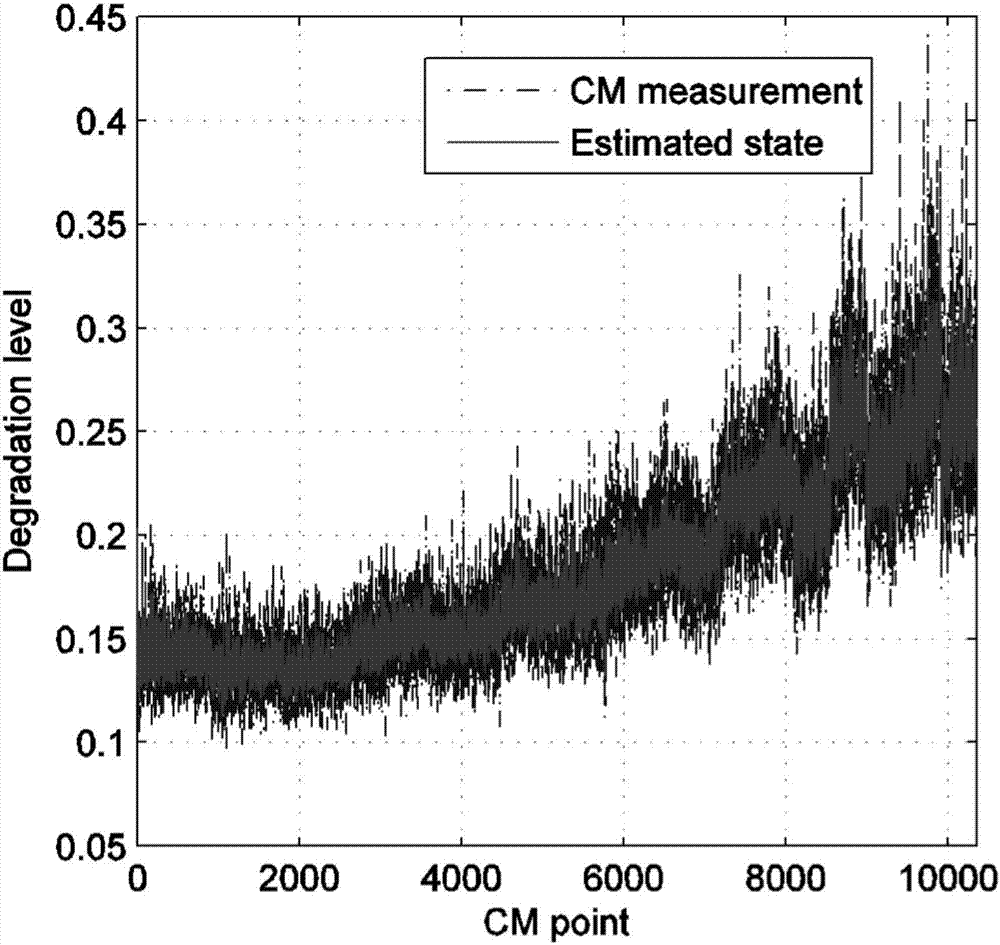
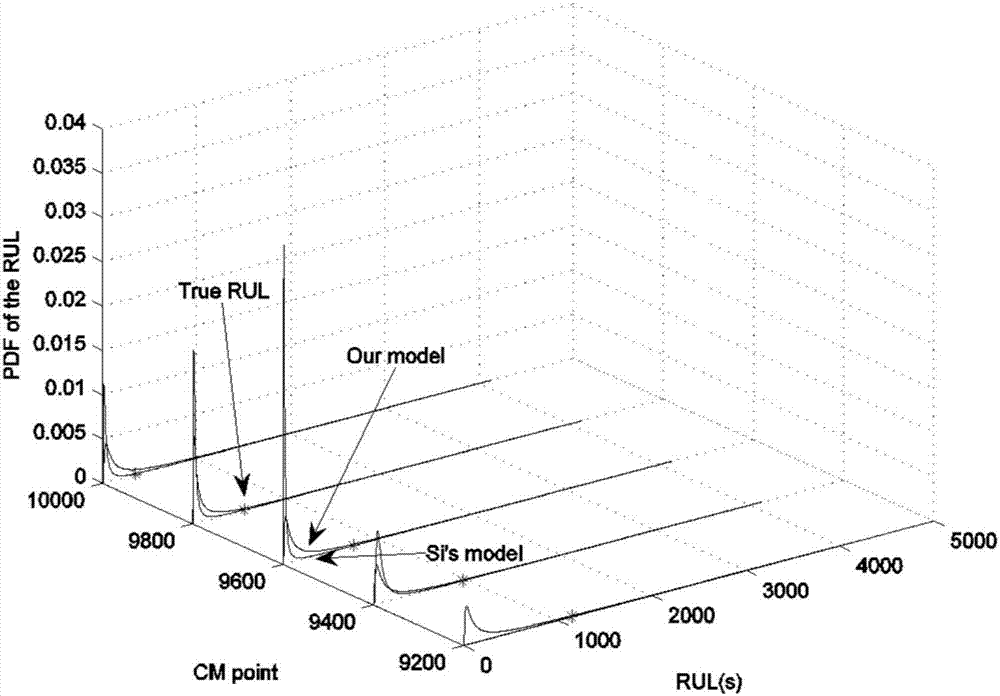
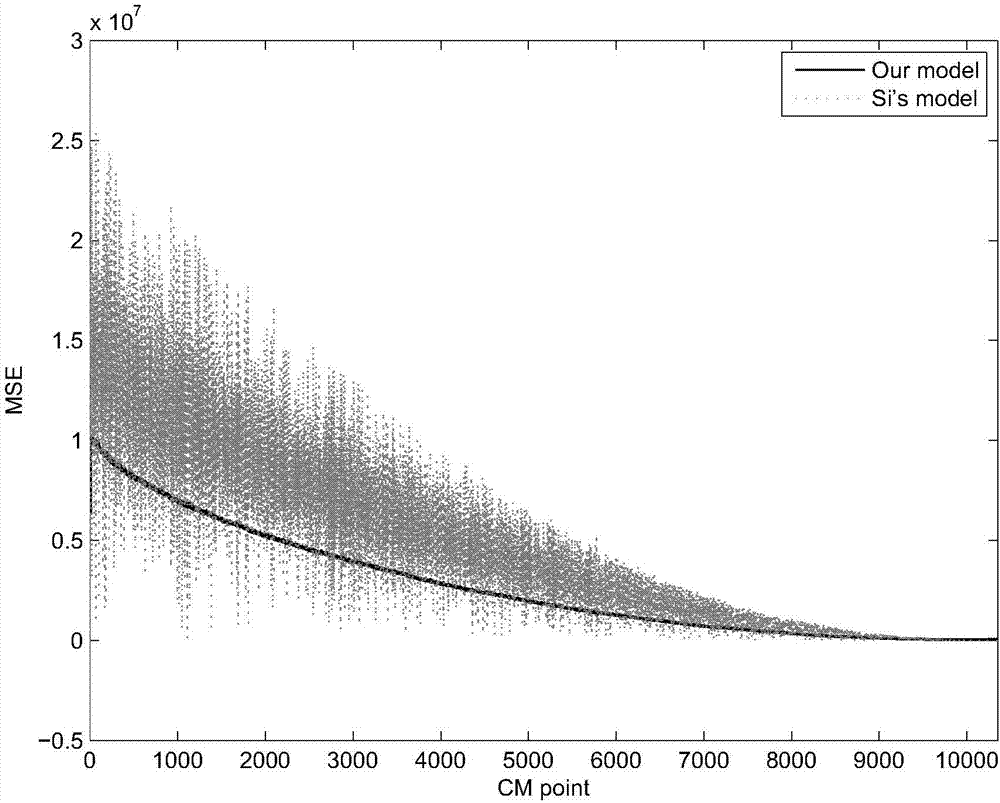
ActiveCN107145645ADetermining Online Remaining Life Prediction ResultsIn line with the actual degradationDesign optimisation/simulationSpecial data processing applicationsExpectation–maximization algorithmReal systems
The invention provides a residual life prediction method for a non-stationary degradation process with uncertain impact and belongs to the technical field of reliability engineering. The impact effect is combined with a continuous degradation process, thereby more reasonably describing the actual degradation process. In a state estimation phase, a new online state estimation algorithm is provided to identify the real system state and to provide a necessary support for subsequent residual life prediction. In a parameter estimation stage, unknown parameters in a model are obtained by adopting an expectation maximization algorithm. For residual life production, the uncertainty of state estimation and the influence of the impact effect are considered at the same time, and an expression is analyzed to give a probability density function and a cumulative probability density function of residual life prediction distribution. The provided model meets the actual degradation condition, a more accurate residual life prediction result can be obtained, and the residual life prediction method is of great significance in fault prediction and health management in engineering.
Owner:ZHEJIANG UNIV +1
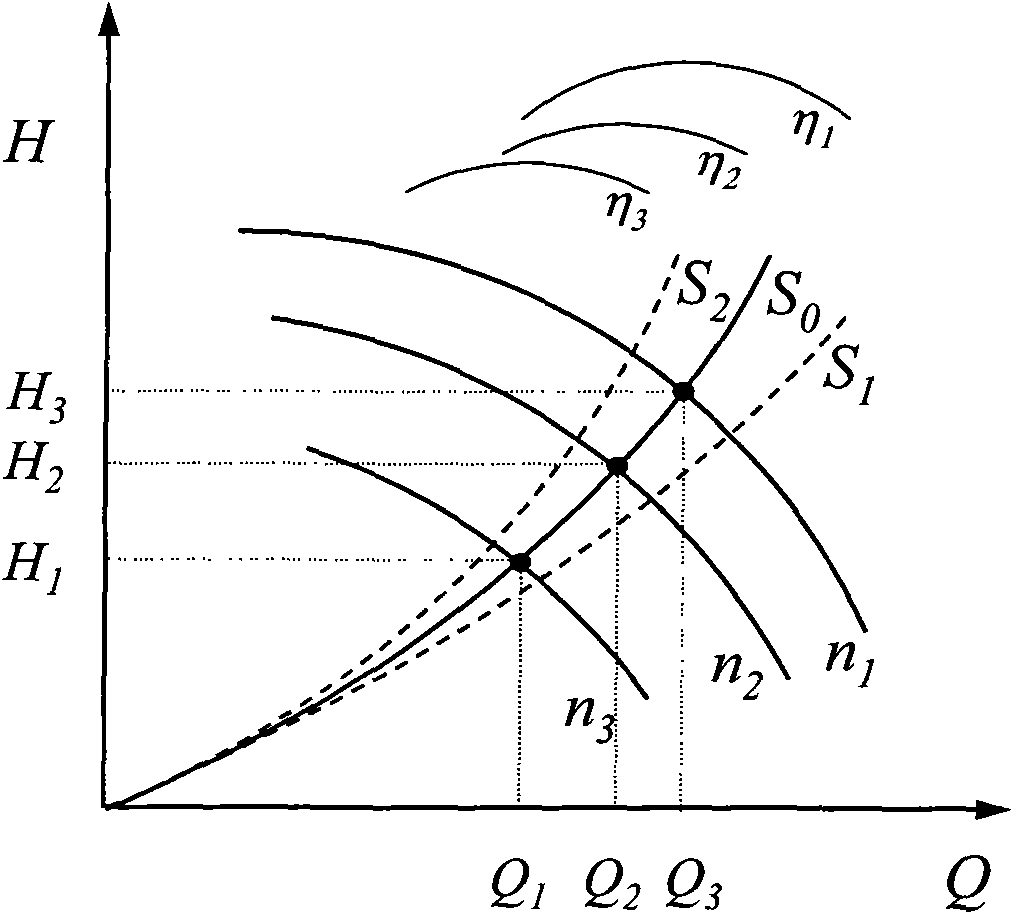
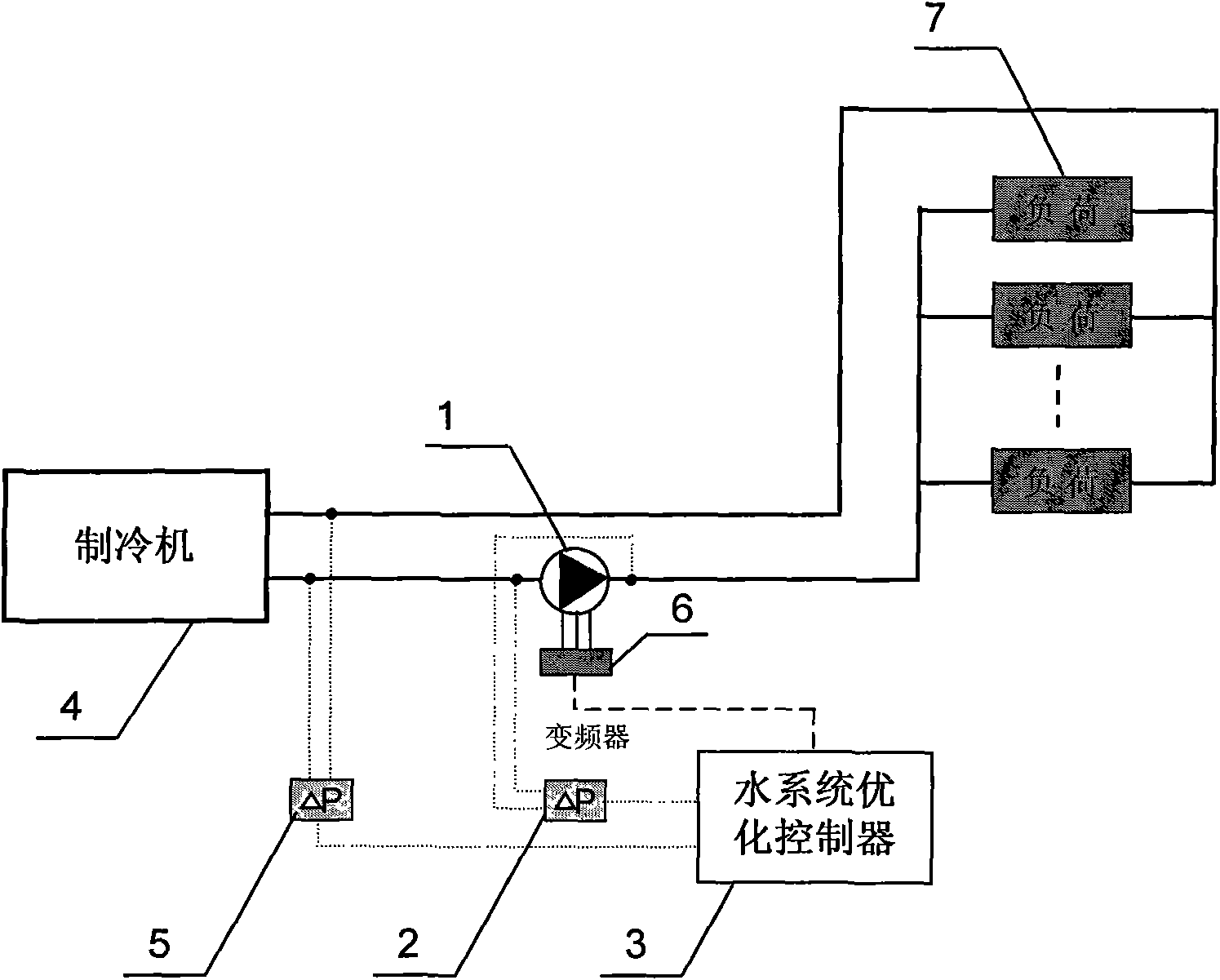
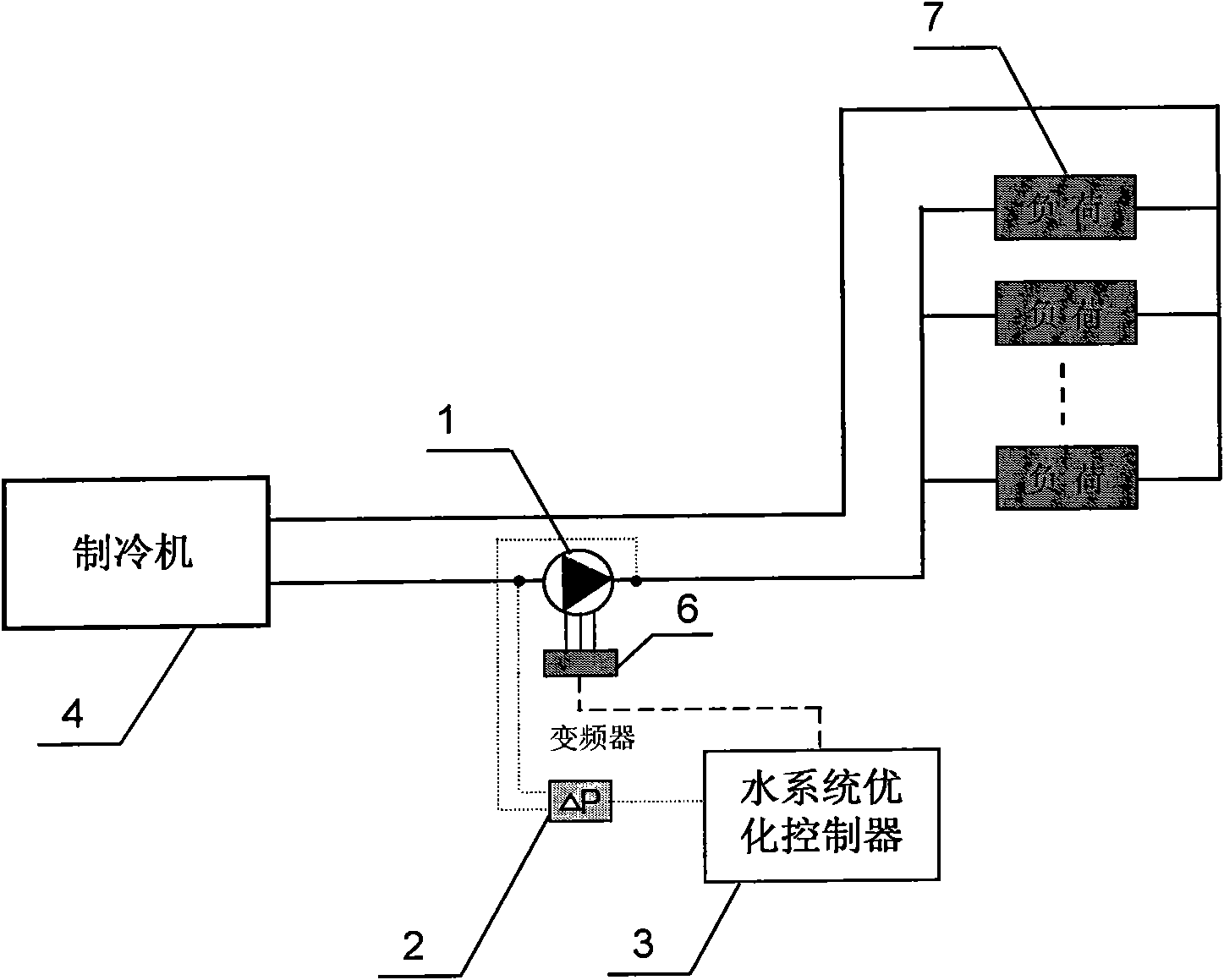
Optimal control method and device for water system of air conditioning
InactiveCN101782260AAvoid consumptionAvoid the disadvantage of very limited energy saving benefitsSpace heating and ventilation safety systemsLighting and heating apparatusReal systemsHigh energy
The invention relates to an optimal control method and a device for a water system of an air conditioning, which belongs to the field of building energy conservation and green air conditionings. In the invention, according to the measured pressure difference between the inlet and the outlet of a water pump, a certain algorithm is utilized to work out the flow rate of the water pump and the resistance characteristic value of the water system, and the frequency of the water pump is regulated so that the resistance characteristic value of the water system is kept within a certain range. The range of the resistance characteristic value is the system resistance characteristic value when the end valve of the water system is opened. The invention can overcome the defects of high cost for a flow sensor, which is installed in a real water system and is used for controlling the real system, and inaccurate measurement due to insufficient space and position for field installation; And the invention can overcome the defect of high energy consumption of a constant-speed pumping system under the loading condition at the end of the air conditioning, and the defects of high energy consumption and insufficient end cold energy of the constant-speed pumping system due to the unreasonable arrangement position and the unreasonable set value of a pressure difference control point. The invention is suitable for primary pump chilled water systems, secondary pump chilled water systems and air conditioning hot-water systems.
Owner:HUAZHONG UNIV OF SCI & TECH
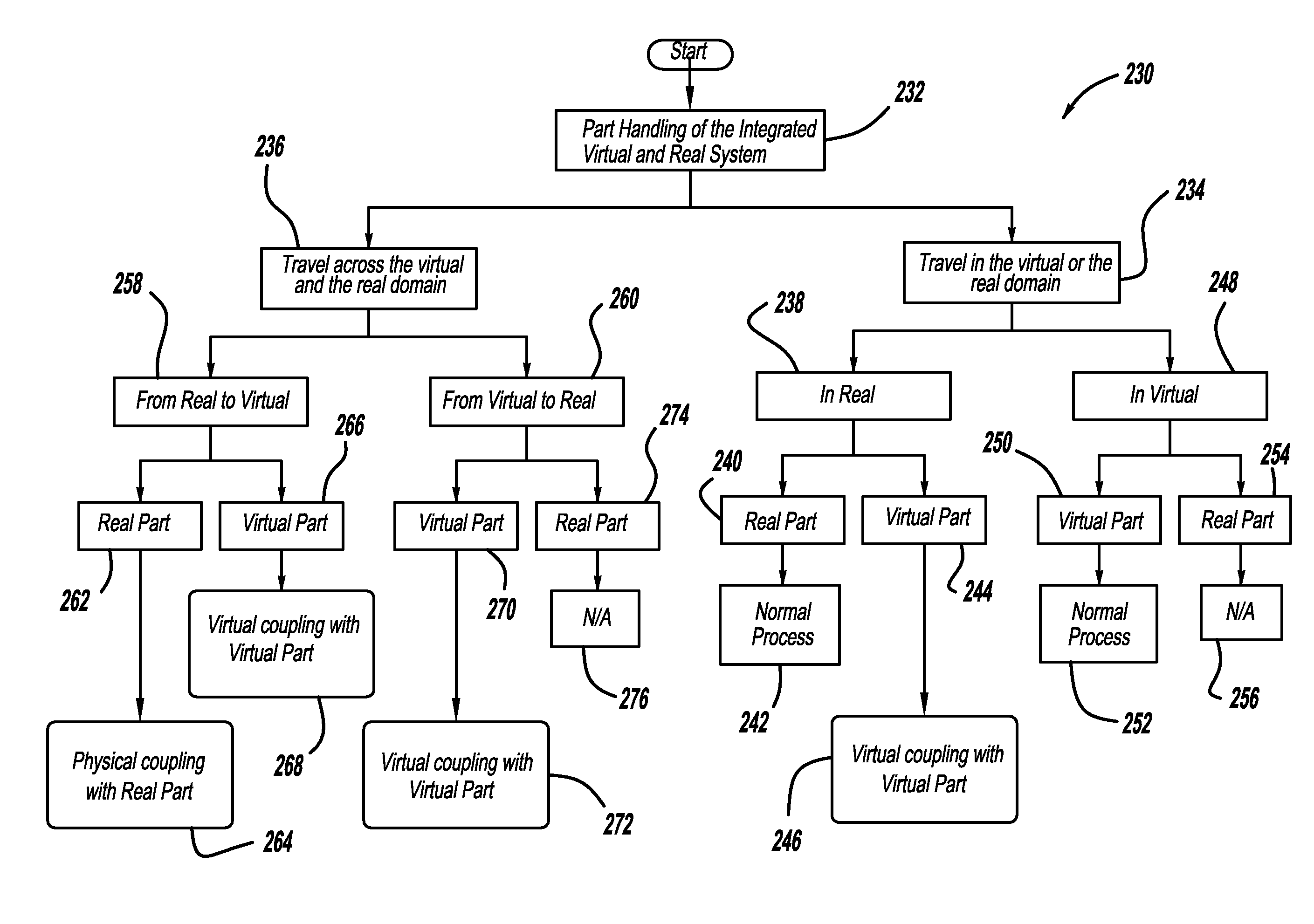
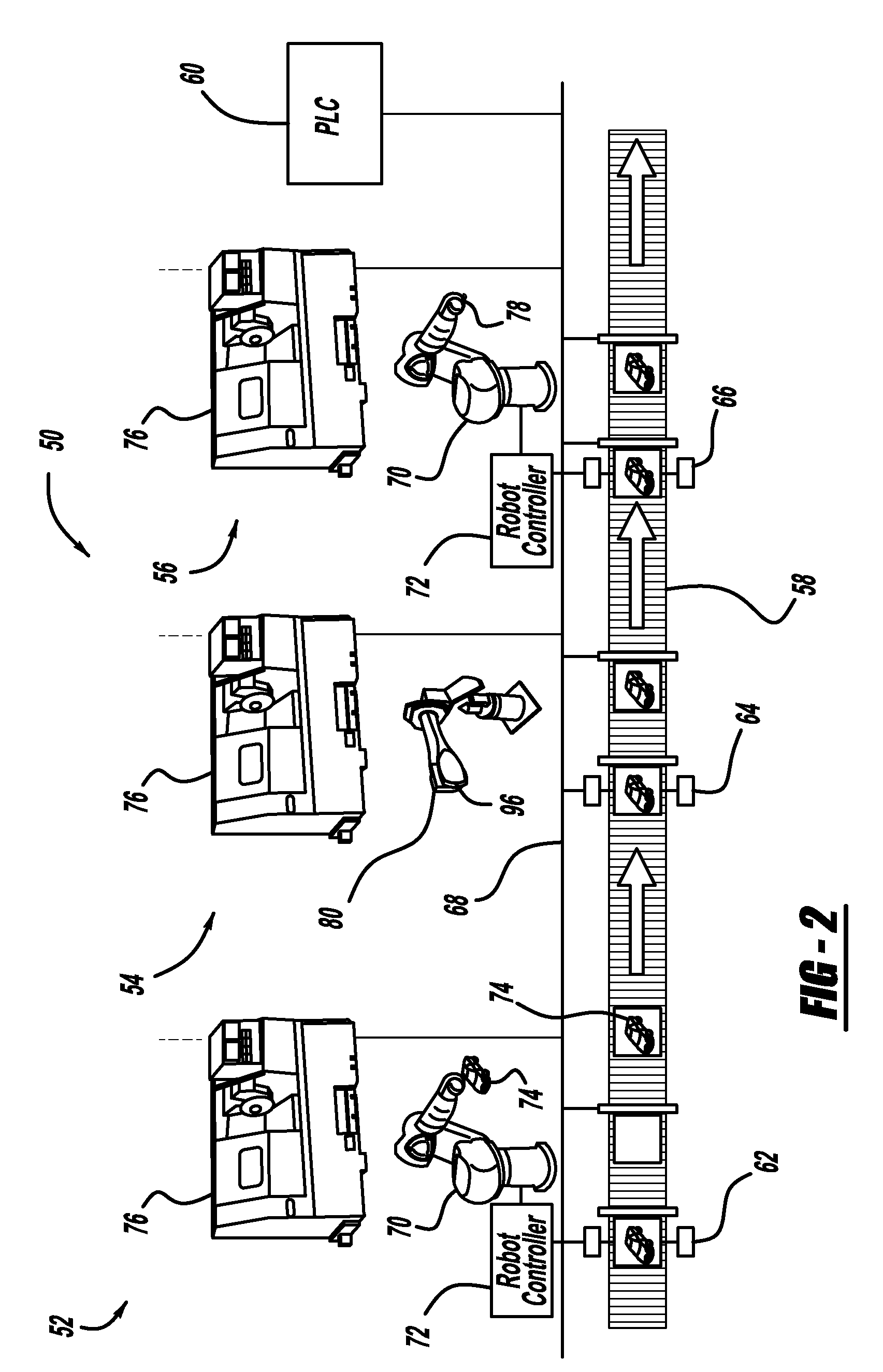
Manufacturing automation system components compatibility and performance testing with integrated virtual and real environment
InactiveUS20090088884A1Programme controlTotal factory controlReal systemsProgrammable logic controller
A system and method for providing an integrated virtual and real emulation environment for a manufacturing process to provide component compatibility testing and system performance prediction. In one embodiment, a real manufacturing system includes one or more real components that are controlled by a programmable logic controller. The real component can be replaced with a virtual component to determine whether it is compatible in the process, where the programmable controller sends signals to and receive signals from the virtual component as if it were the real component. For system performance prediction, a virtual manufacturing process is provided that includes virtual components where the virtual process is controlled by a programmable logic control as if it were a real process to determine the performance of a real system using the virtual process.
Owner:GM GLOBAL TECH OPERATIONS LLC
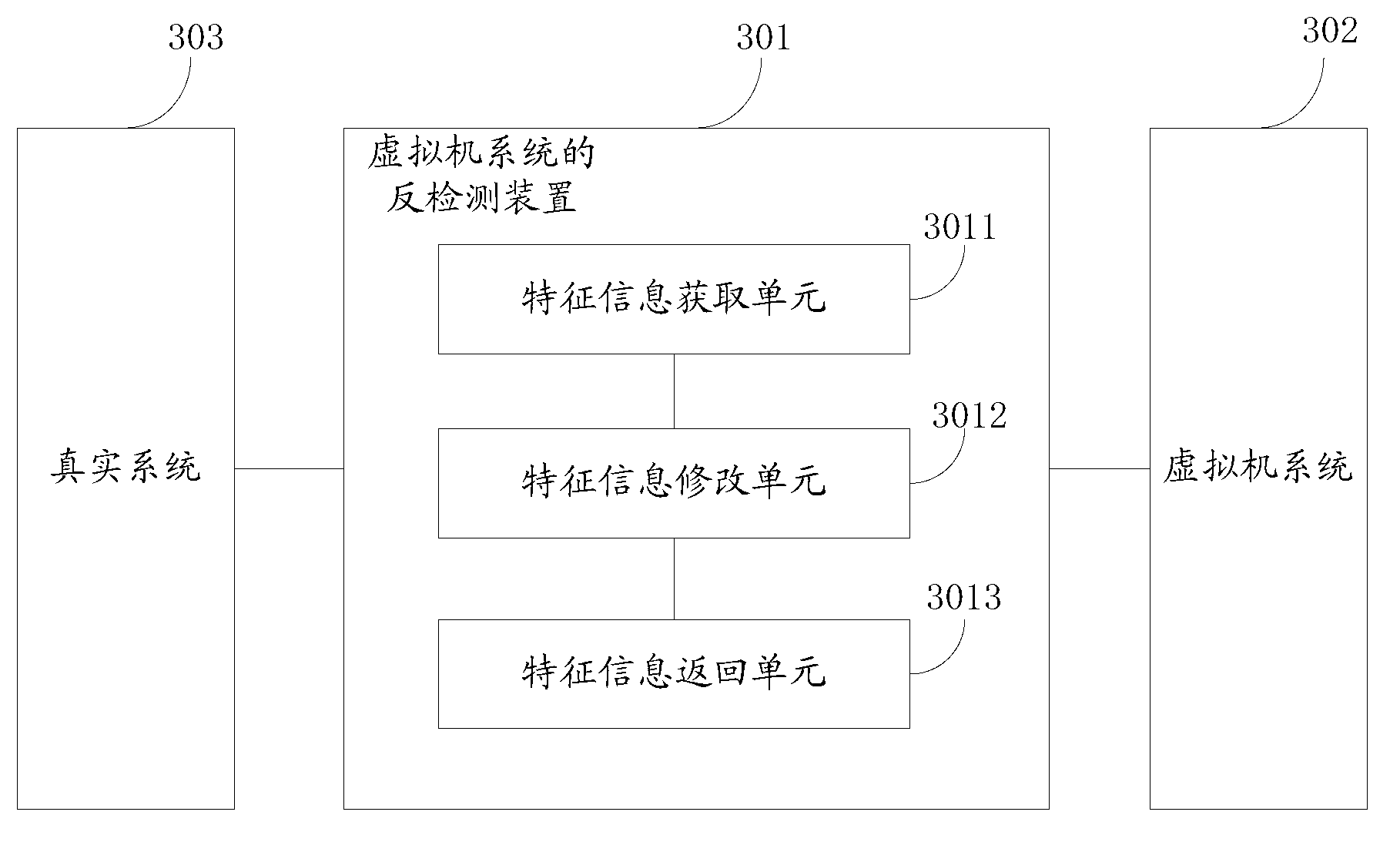
Anti-detecting method and device of virtual machine system
InactiveCN103020525ATo achieve the purpose of anti-detectionRealize discoveryPlatform integrity maintainanceReal systemsProgram analysis
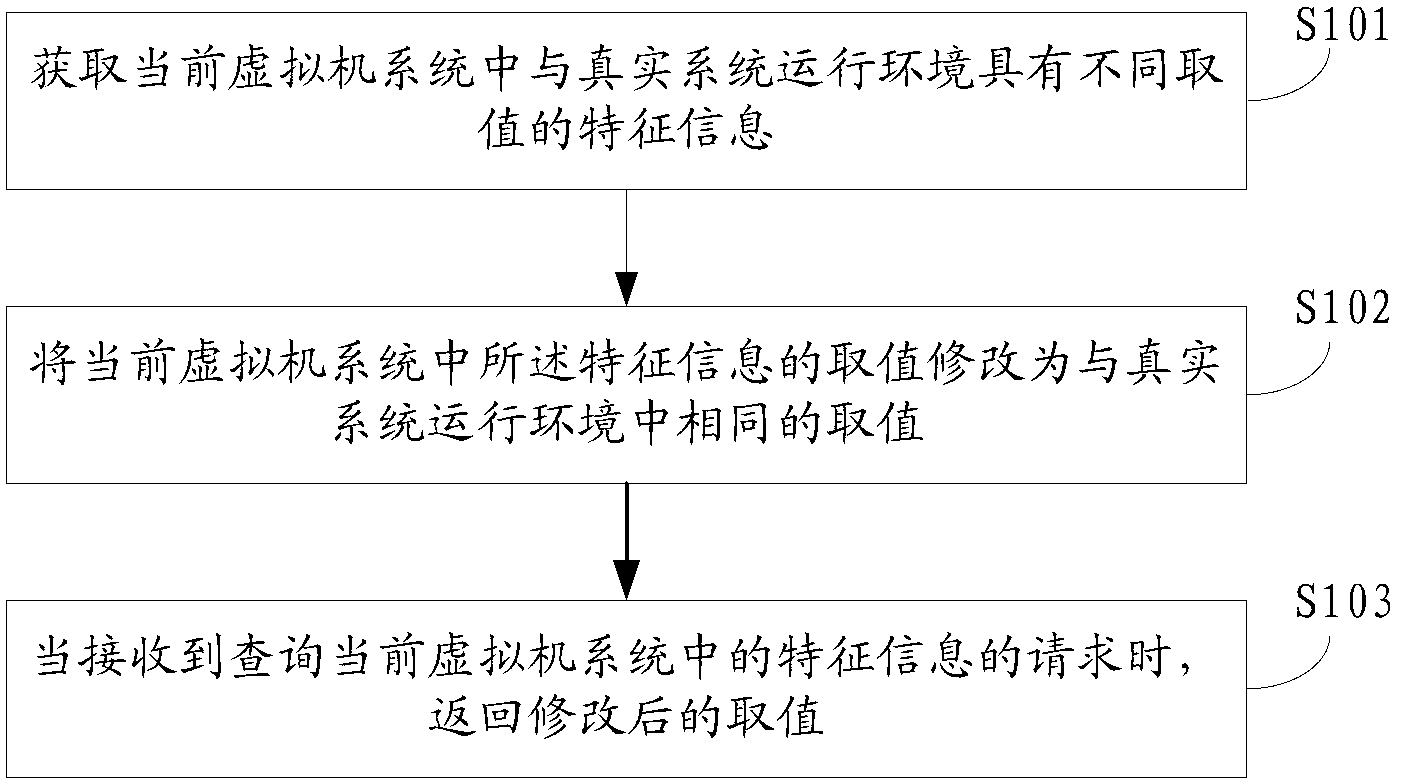
The invention discloses an anti-detecting method and an anti-detecting device of a virtual machine system. The method comprises the following steps that feature information with a different value in a current virtual machine system from the operating environment of a real system is obtained; the value of the feature information in the current virtual machine system is modified into the same value in the operating environment of the real system; and when a request that the feature information in the current virtual machine system is inquired is received, the modified value is returned, so that the inquired result in the virtual machine system is the same as that in the operating environment of the real system. Through the anti-detecting method, the anti-detecting purpose of a virtual machine can be achieved, so that the virtual machine can effectively support malicious program analysis.
Owner:BEIJING QIHOO TECH CO LTD +1
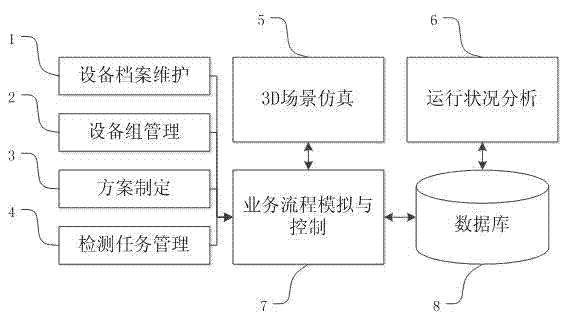
Automatic detection simulation analog system of ultra-large intelligent electric energy meter
The invention discloses an automatic detection simulation analog system of an ultra-large intelligent electric energy meter, and the automatic detection simulation analog system comprises a three-dimensional (3D) scene simulation module, an equipment archive maintenance module, an equipment unit management module, a scheme formulation module, a plan task compilation module, a service flow analog and control module, a database module and a running status analysis module. Aiming at the characteristics of the automatic detection system of the ultra-large intelligent electric energy meter that the process flow is complicated, multiple devices are needed, the production requirement is strict, and large difficulty is brought to the production management, task scheduling and new product research and development of the enterprise, instructions can be provided for multiple links of a real system such as the plan, design, equipment model selection, equipment manufacturing, installation, debugging and running by establishing the simulation analog system, scientific evidence can be provided for establishing relevant technical standards and operation strategies, the construction risk and the construction cost can be effectively reduced, and the construction period can be shortened.
Owner:ELECTRIC POWER SCI RES INST OF JIANGSU ELECTRIC POWER +3
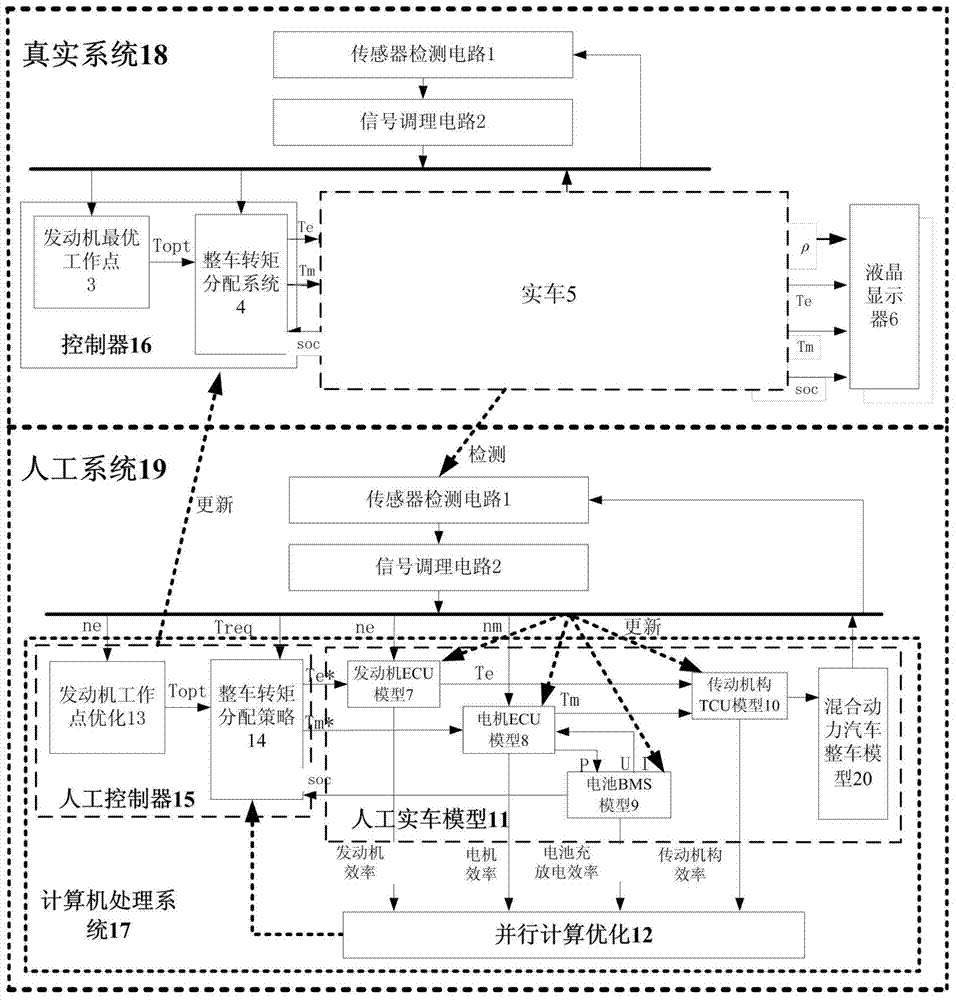
Finished hybrid power automobile torque distribution system and method based on parallel control
ActiveCN103935360AImprove robustnessImprove reliabilityHybrid vehiclesDriver input parametersReal systemsSignal conditioning circuits
The invention provides a finished hybrid power automobile torque distribution system and method based on parallel control and relates to the field of hybrid power automobile control. The finished hybrid power automobile torque distribution system based on the parallel control consists of a real system and an artificial system, wherein the real system is responsible for driving of actual running of a real automobile, the artificial system is responsible for real automobile modeling and controller parameter optimization in a real automobile real-time running state and parallel execution. The real system consists of a sensor detection circuit, a signal conditioning circuit, a controller and a liquid crystal display. The artificial system consists of a sensor detecting circuit, a signal conditioning circuit and a computer processing system. The finished hybrid power automobile torque distribution system based on the parallel control is simple in structure, easy to achieve and high in reliability, improves the engine fuel utilization rate, reduces emission and effectively improves the actual running performance and working efficiency of the real automobile within a whole service life.
Owner:CHANGCHUN UNIV OF TECH
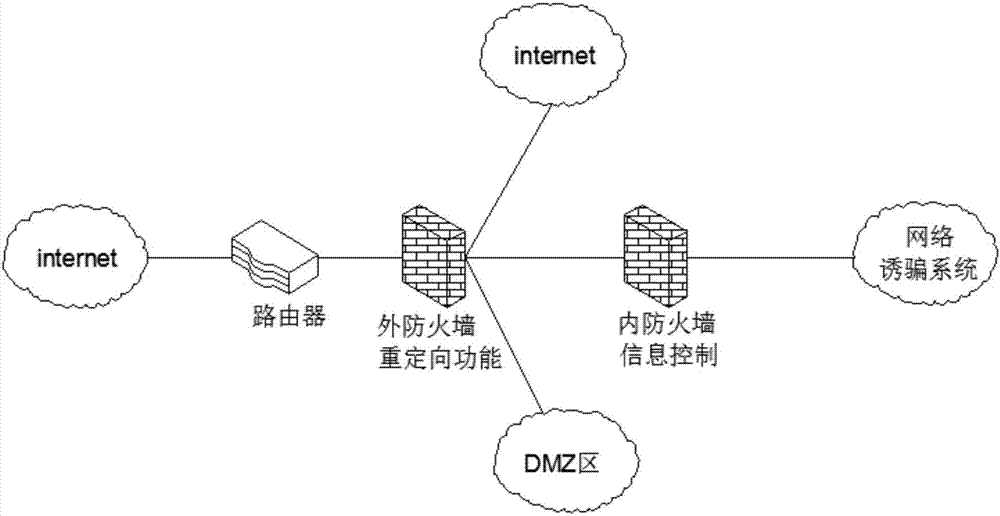
Network trapping method based on honey pot
The invention discloses a honeypot-based network trapping method, which comprises an outer firewall, an inner firewall and a network deception system. The beneficial effects of the invention are: the "wide entry" of the internal firewall is to confuse the intruder and let him "make the best use of it", while the "strict exit" ensures that the intruder's activities are limited to the "cage", and more data can be collected , evidence, and also prevent intruders from using the system as a springboard to conduct further attacks on other systems. Organizing information to deceive forged persons and locations also requires forged information such as salary, budget, and personal records. The more real the forged information is , the more you can avoid deception, and it is easy to be discovered. Network traffic simulation replicates all access connections, making the deception system very similar to the real system. Service camouflage writes a series of scripts in the system to simulate the characteristics of some application services, providing seemingly Normal service, leading the attacker to believe that the trapping system is a functioning system.
Owner:CHINA ELECTRONICS STANDARDIZATION INST +1
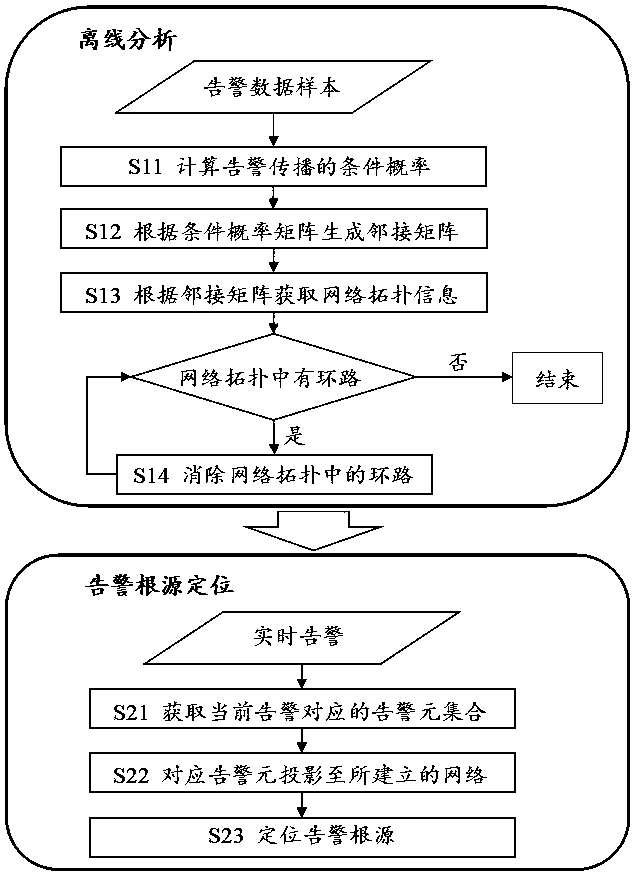
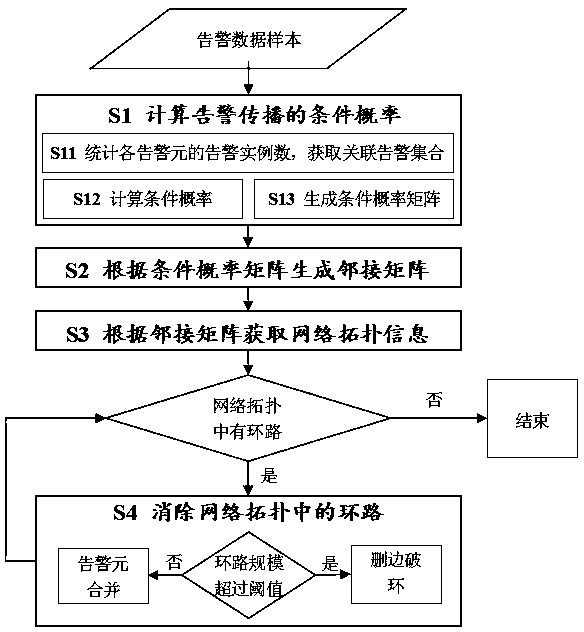
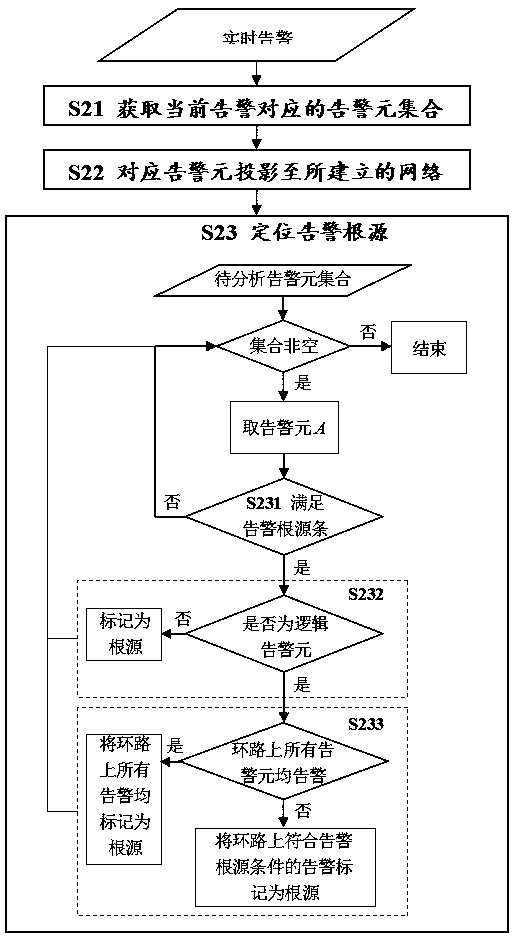
Network alarm source positioning method based on alarm data analysis
ActiveCN108600009AReduce development costsReduce maintenance costsData switching networksReal systemsNetworking hardware
The invention discloses a network alarm source positioning method based on alarm data analysis. The method includes a modeling analysis step based on alarm historical data and an online alarm source positioning step, and specifically includes the following operations: firstly, analyzing an alarm historical data sample, mining a time sequence correlation relationship between network alarms, and further establishing the network topology between alarm elements; and on this basis, mapping real-time alarms into the established network topology, and deducing alarm sources based on the relative positions of the alarm elements corresponding to the current alarms in the network topology. The method does not need to use network hardware connection relationships, service logic dependence relationships and other expert experience knowledge, and has low development and maintenance costs; and meanwhile, the method can make full use of the occurrence probability and distribution characteristics of the alarms in a real system, and has higher analysis accuracy.
Owner:北京思特奇信息技术股份有限公司
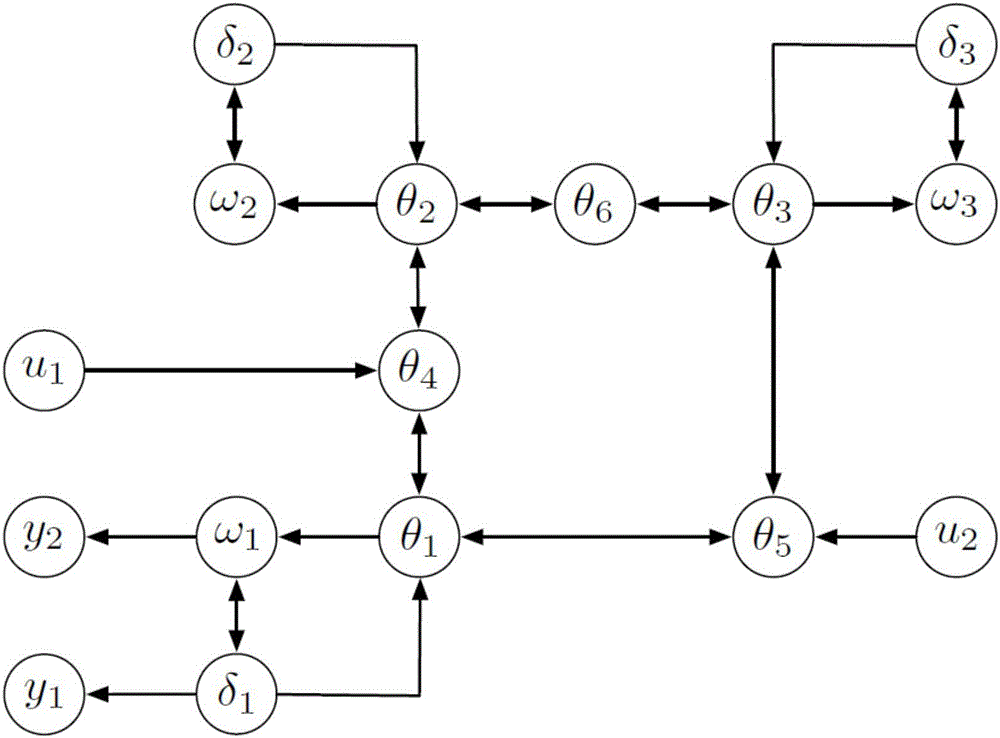
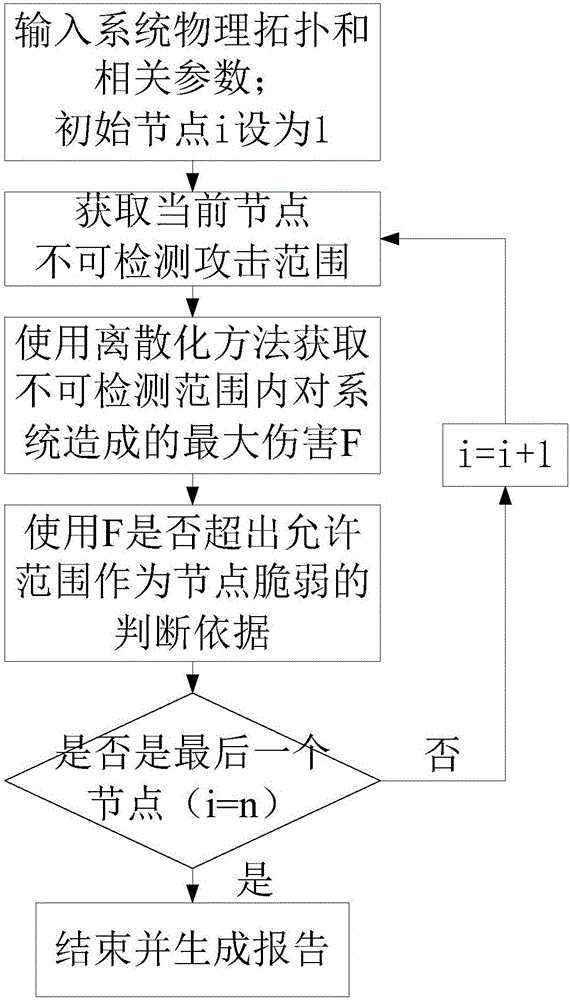
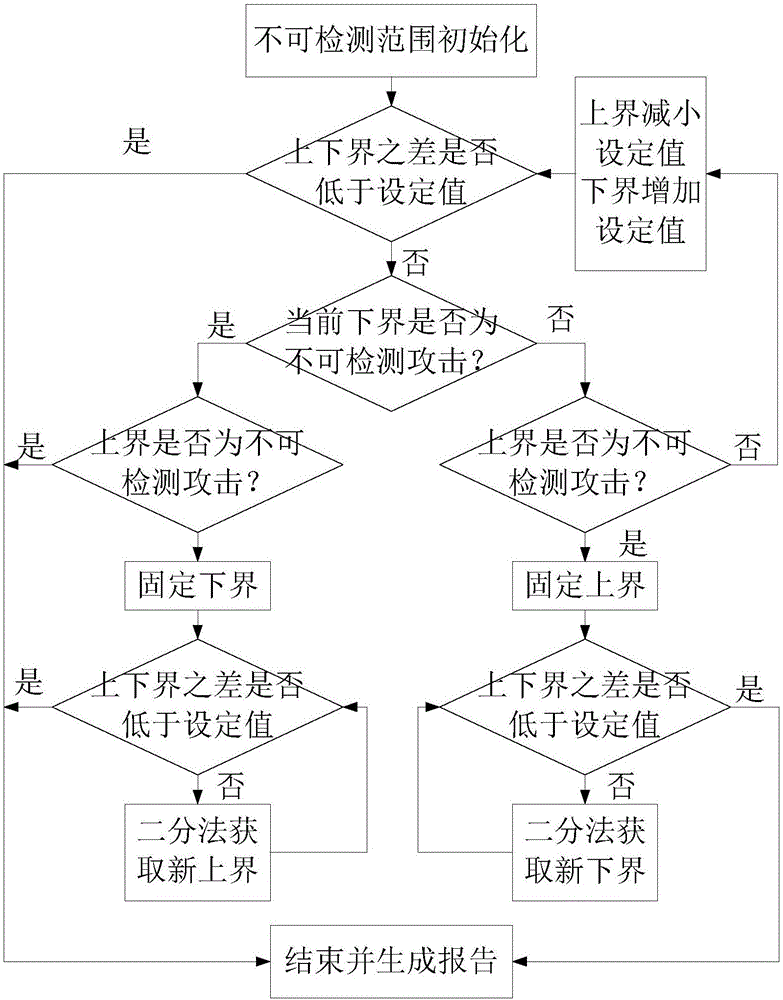
Method for evaluating vulnerability node of electric cyber-physical system based on undetectable information attack pre-warning technology
InactiveCN106713354ASafe and stable operationThe analysis result is accurateData switching networksReal systemsTopological graph
The invention discloses a method for evaluating a vulnerability node of an electric cyber-physical system based on an undetectable information attack pre-warning technology. A partial model of the electric cyber-physical system is generated according to a physical topological graph of an electric power system in the electric cyber-physical system, pre-warning of an undetectable information attack under a general information attack and topology condition is analyzed and the damage of the attack is evaluated, and the potential risk of the ECPS is perceived in advance to obtain a more accurate analysis result, so that a grid company can evaluate the running state of the ECPS from a global perspective and the protection for a vulnerability link is enhanced timely to protect the ECPS to run safely and stably. Pre-warning of a multi-node information attack is realized based on analysis of a single-node information attack. In addition, the information attack in the real system often has continuity, the method adds prediction of a continuity information attack on the basis of analysis of an instantaneous information attack, and the overall vulnerability of nodes and the ECPS is evaluated. A technical framework of the invention is more comprehensive.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Dynamic simulation apparatus and method for network layer performance of the third generation mobile communication system
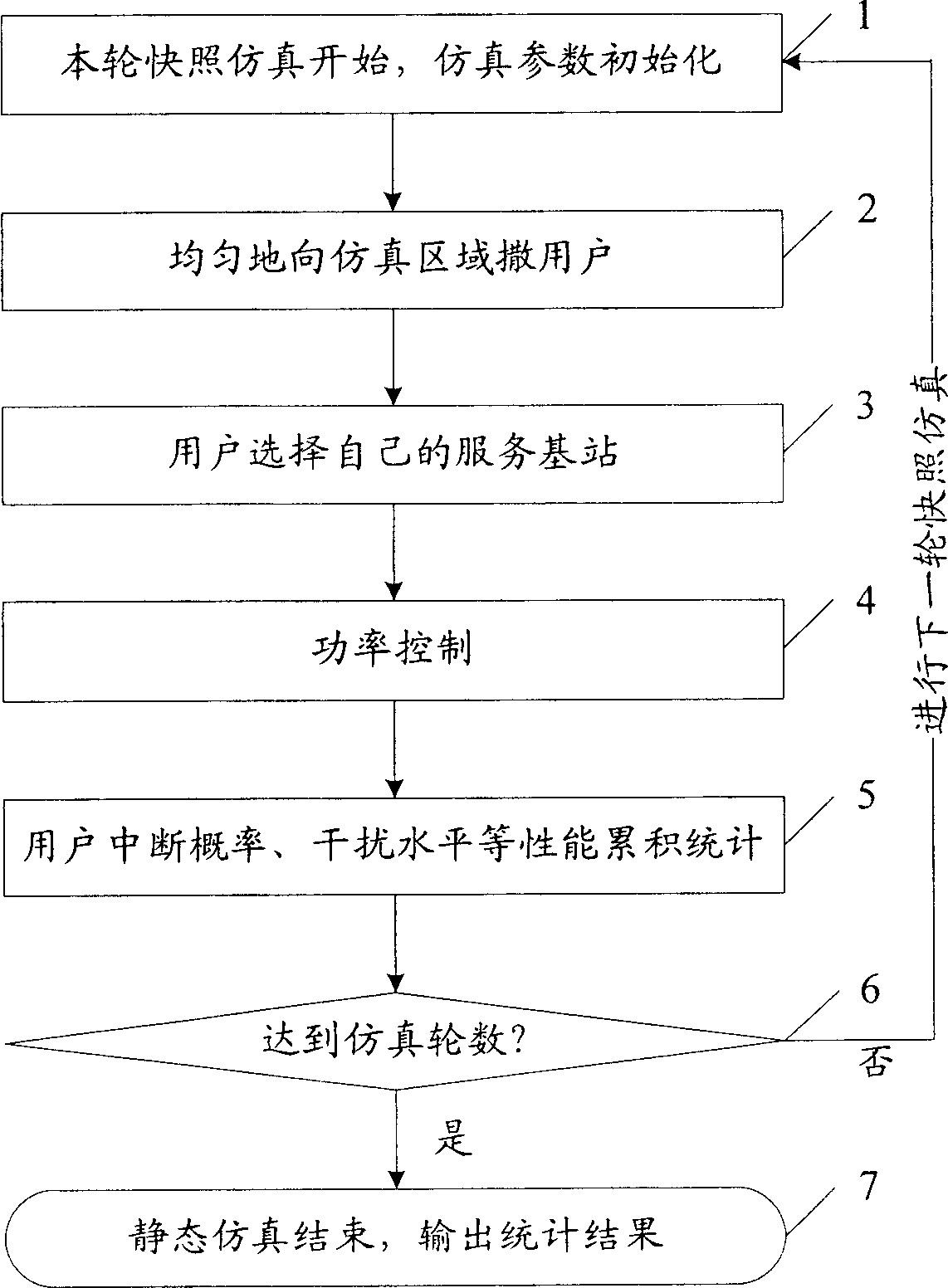
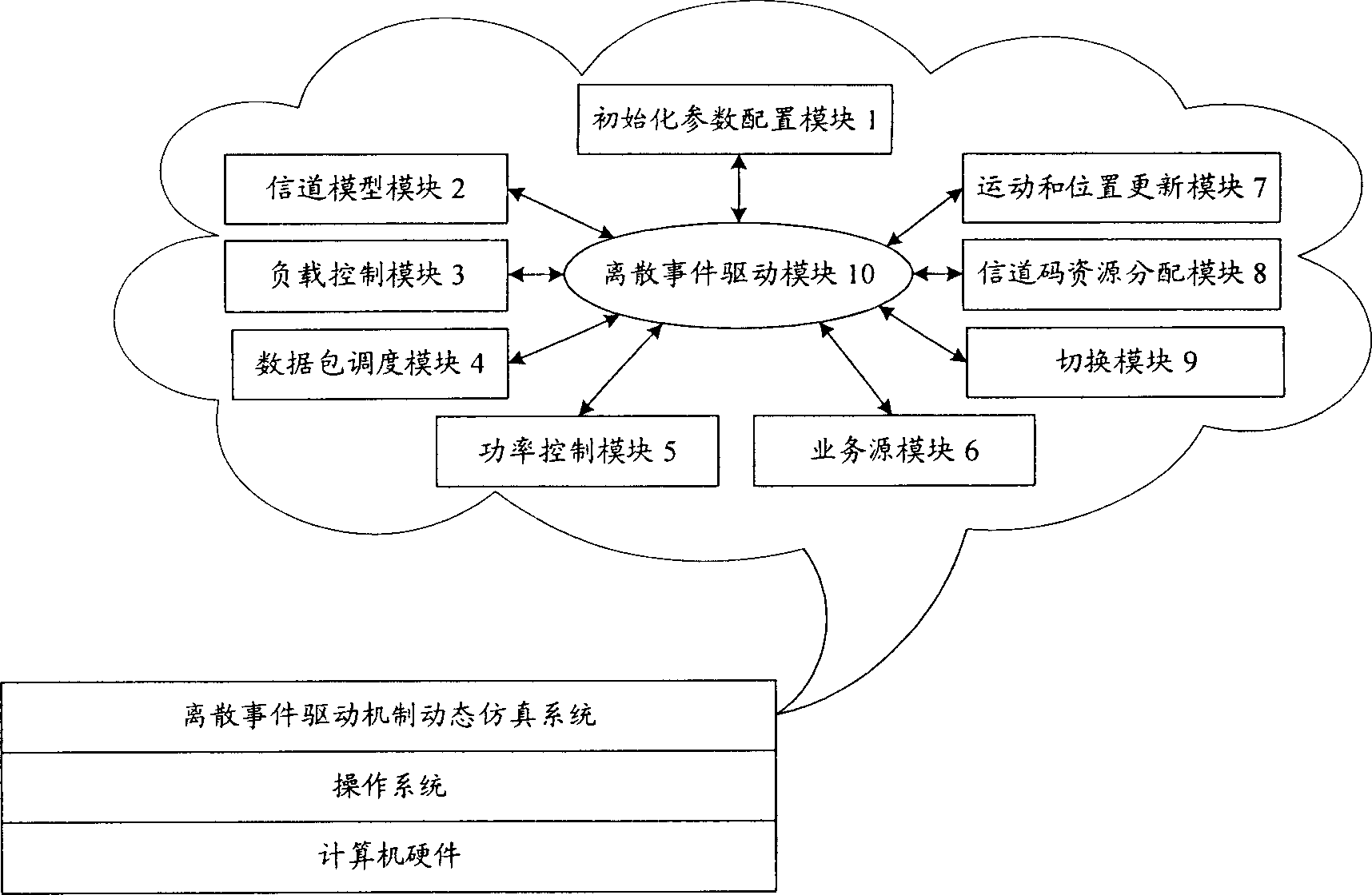
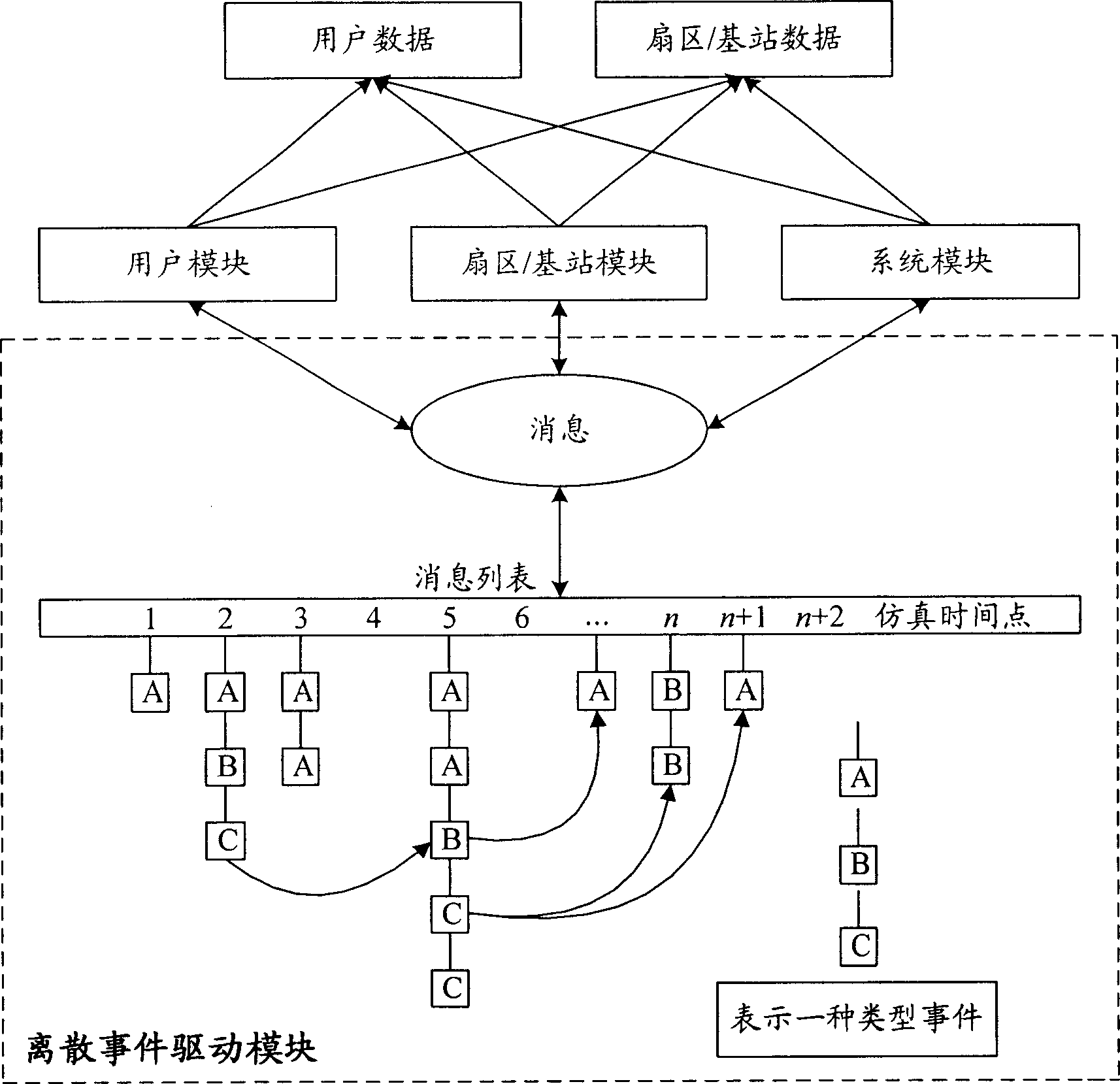
InactiveCN1885988AIncreased simulation timeIncrease performance curveTransmission control/equalisingRadio/inductive link selection arrangements3g mobile communicationsOperational system
The related dynamic simulator for performance of 3G mobile communication system network layer comprises: a common PC, and a corresponding software stored in HD with nine function modules. This invention uses discrete-affair drive mechanism for sending and process, has precise result to reflect real system dynamic performance well, and has bright application future.
Owner:BEIJING UNIV OF POSTS & TELECOMM
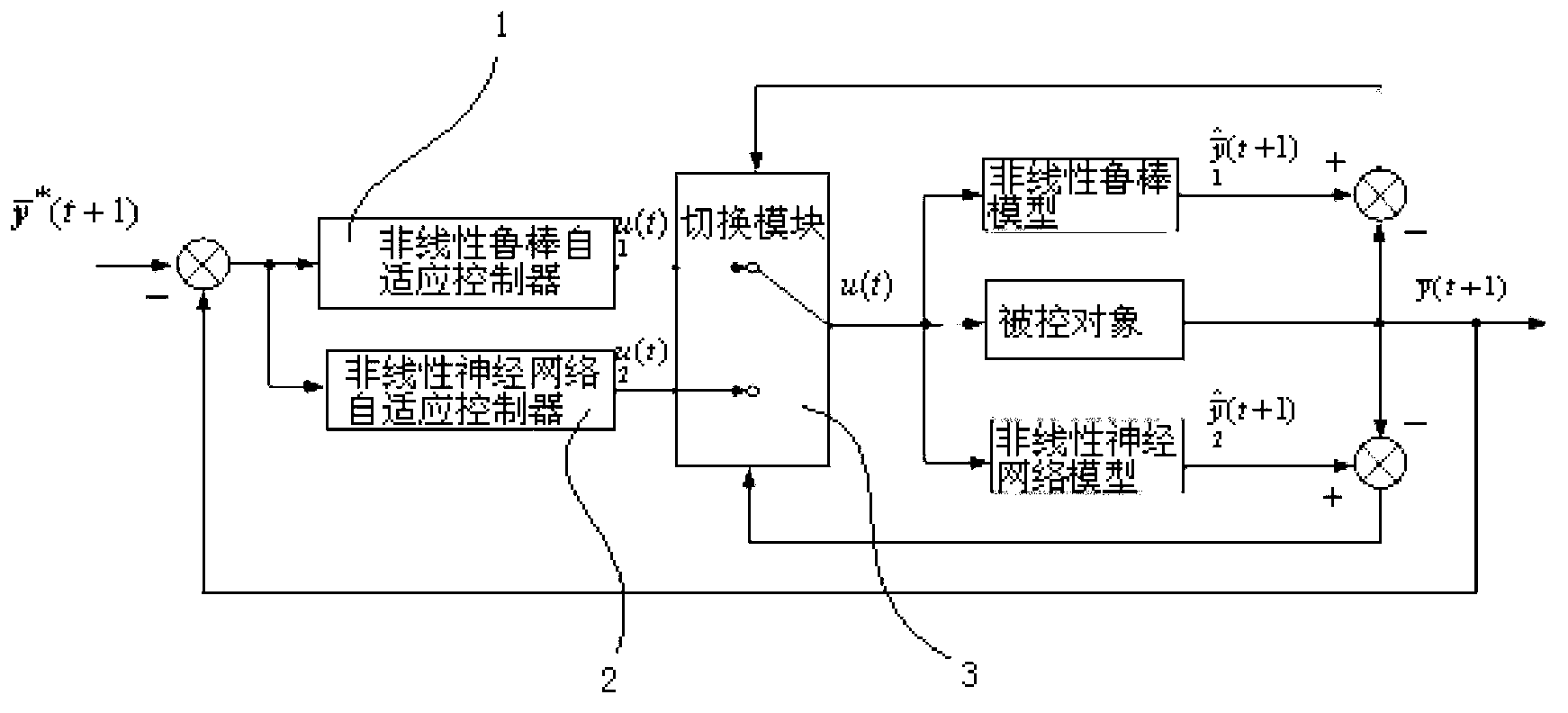
Multi-model self-adaptive controller and control method of zero-order closely-bounded nonlinear multivariable system
The invention discloses a multi-model self-adaptive controller and control method designed for a zero-order closely-bounded nonlinear multivariable system. The multi-model controller is provided with a nonlinear robust self-adaptive controller and a nonlinear neural network self-adaptive controller. Due to the fact that a nonlinear complementation item is introduced, the identification model of the nonlinear robust self-adaptive controller and the output errors of a real system are guaranteed to be bounded. The BIBO stability of the system can be guaranteed through a one-step advanced control law designed by utilizing model errors. System control signals are generated through the switching of the two controllers, and the performance of the system is improved through the neural network self-adaptive controller.
Owner:SHANGHAI JIAO TONG UNIV
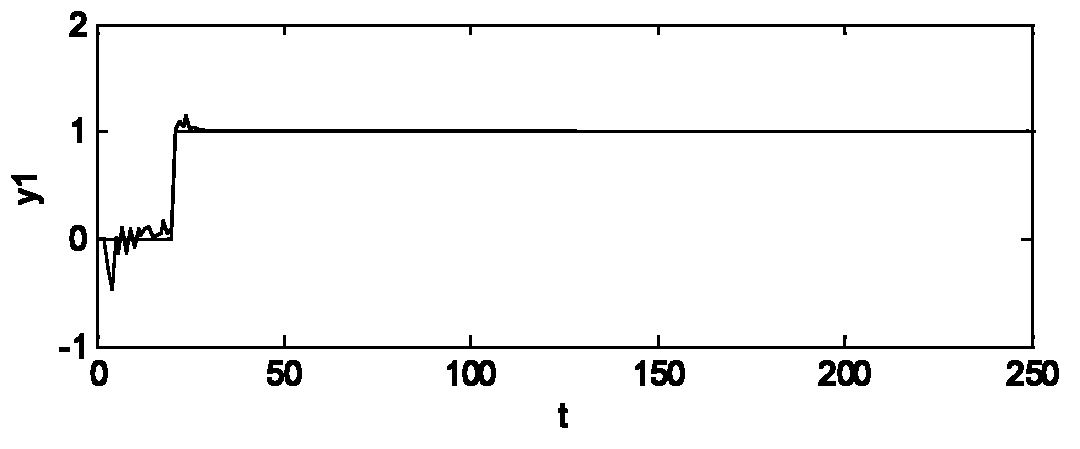
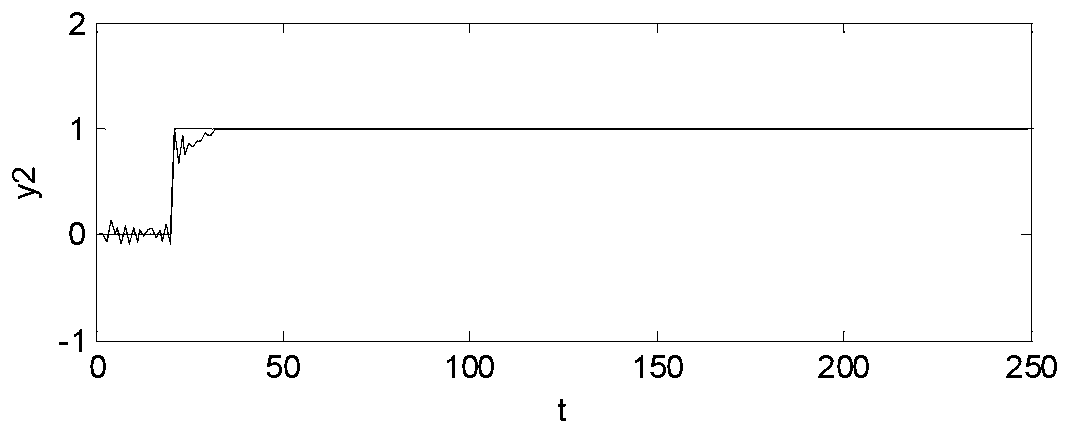
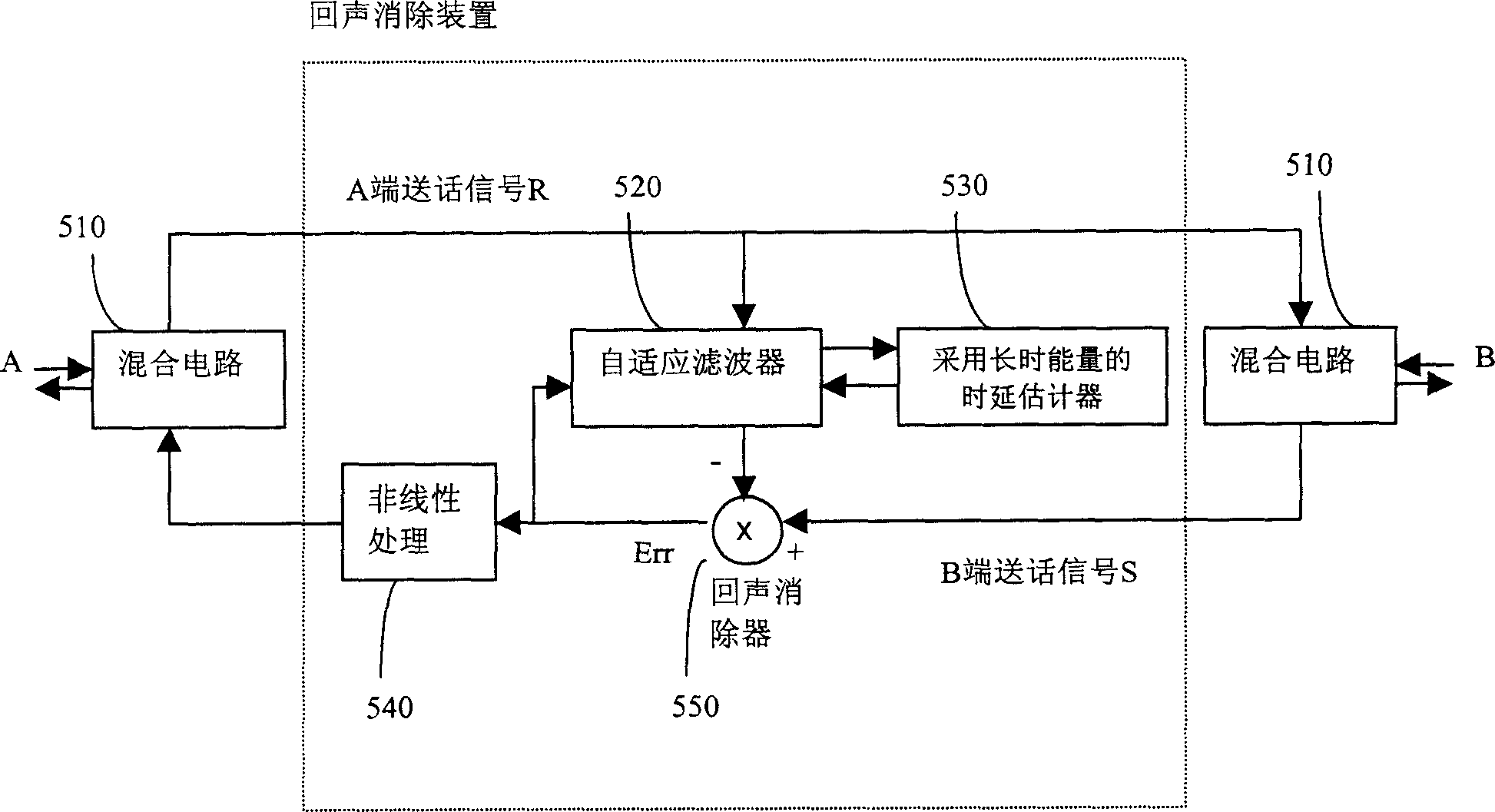
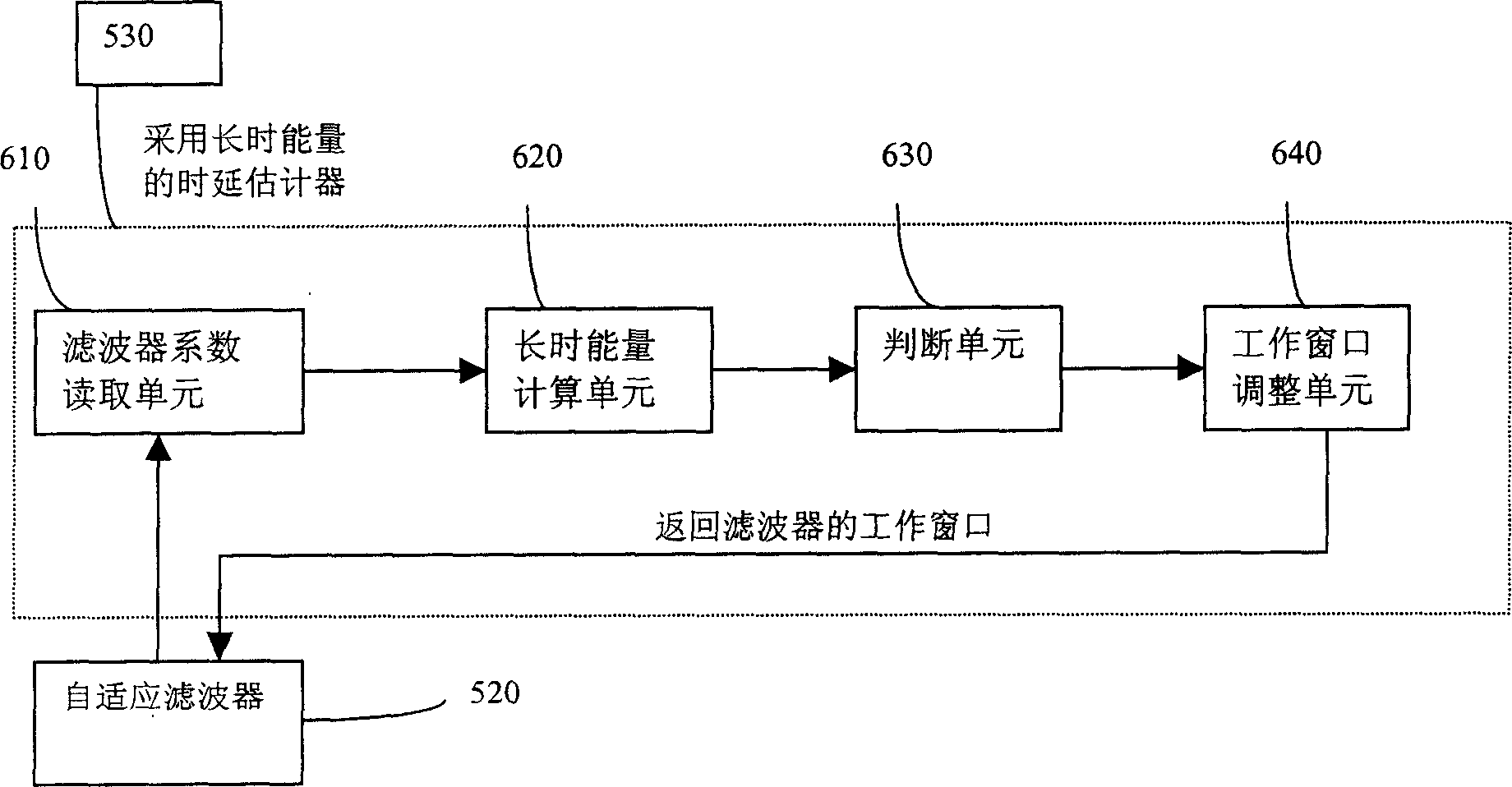
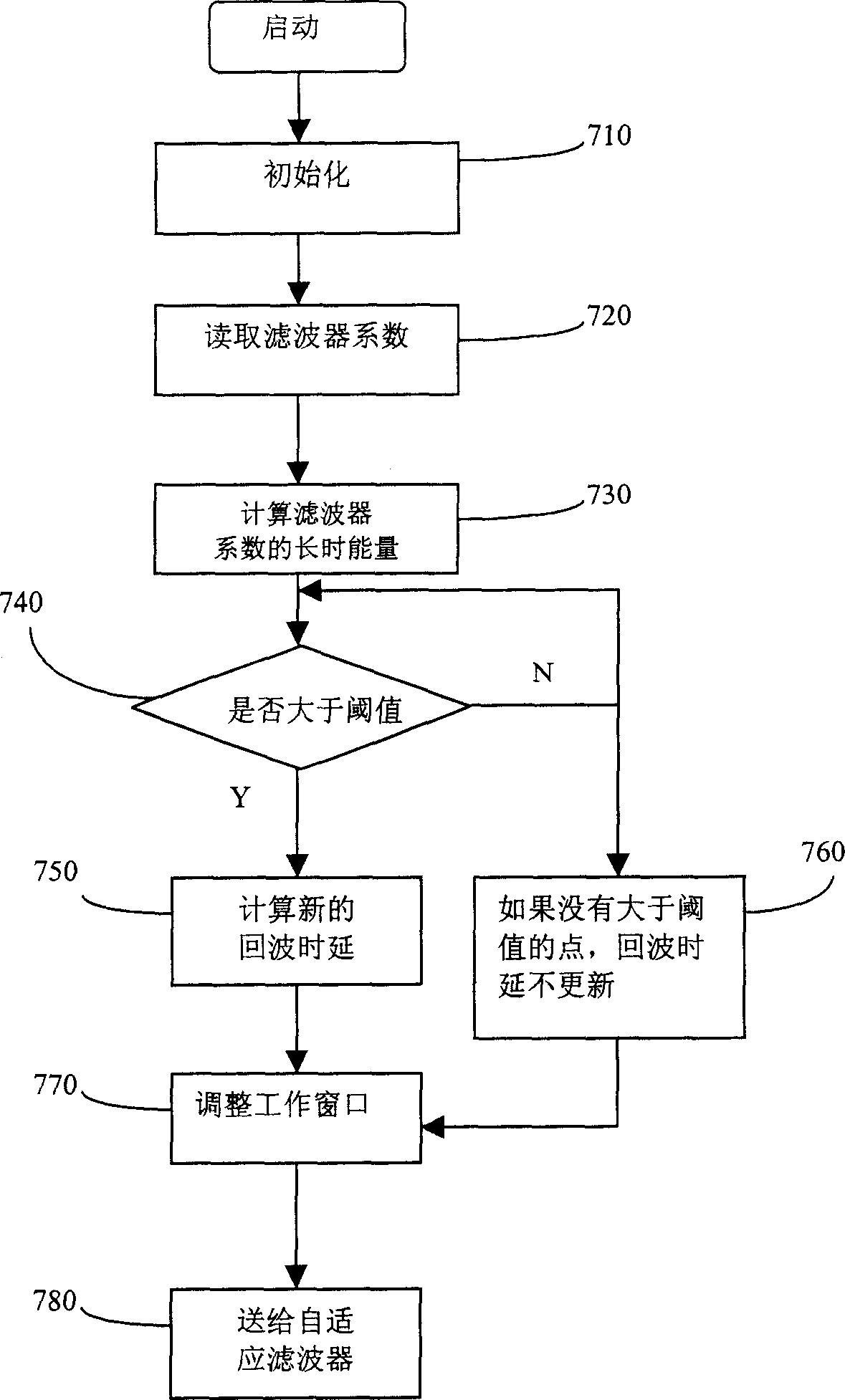
Echo eliminator
InactiveCN1691716ASmall amount of calculationAvoid using incompleteTwo-way loud-speaking telephone systemsLine-transmissionReal systemsAdaptive filter
A echo elimination device comprises adaptive filter, used to simulate echo signal in work window; delay estimator with long-term energy, used to estimate time delay of echo path and transmit work signal of adaptive filter in effective coverage to adaptive filter according to time delay simultaneous; echo elimination device is used to echo signal; nonlinear processor decides whether to set zero or pass entirely for output signal of echo elimination device. It can decrease amount of calculation of adaptive filter by the method. Compared with delay T1 by traditional delay estimation method, the invention can decide more accurately the delay T2 of echo path, more approach to real delay T3, and then avoid utility imperfection of effective zone of filter parameter, solve echo elimination imperfection by traditional method and the divergence problem in real system.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
System and method for debugging system-on-chips using single or n-cycle stepping
InactiveUS20050149892A1Efficient debuggingEffective controlDigital circuit testingDetecting faulty computer hardwareReal systemsSoftware design
Large, complex SoCs comprise interconnections of various functional blocks, which blocks frequently running on different clock domains. By effectively controlling the clocks within the SoC, this invention provides a means to halt execution of a SoC and to then single or n-cycle step its execution in a real system environment. Accordingly, the invention provides an effective debugging tool to both the SoC designer and software designers whose code is executed by the SoC as it provides them the capability of studying the cause and effect of interactions between functional blocks. The invention is also applicable to SoCs containing only one functional block while containing complex circuitry operating on a clock different than the block's clock. In particular, the invention permits halting of the block clock and then single or n-cycle stepping its execution to permit analysis of the interactions between the block and the SoC circuitry.
Owner:BELL SEMICON LLC
Self-adaption bit and power distribution method with low complex degree
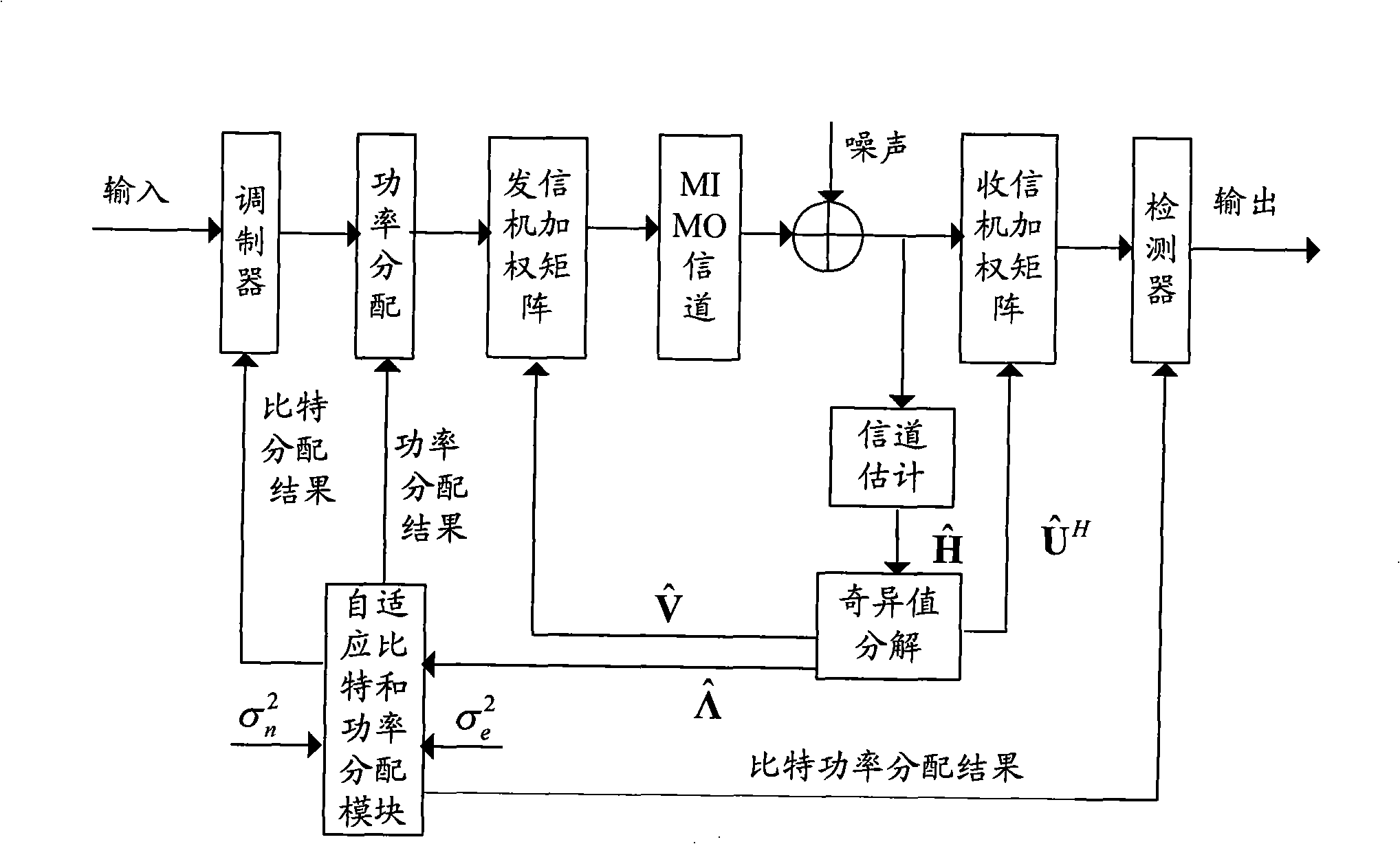
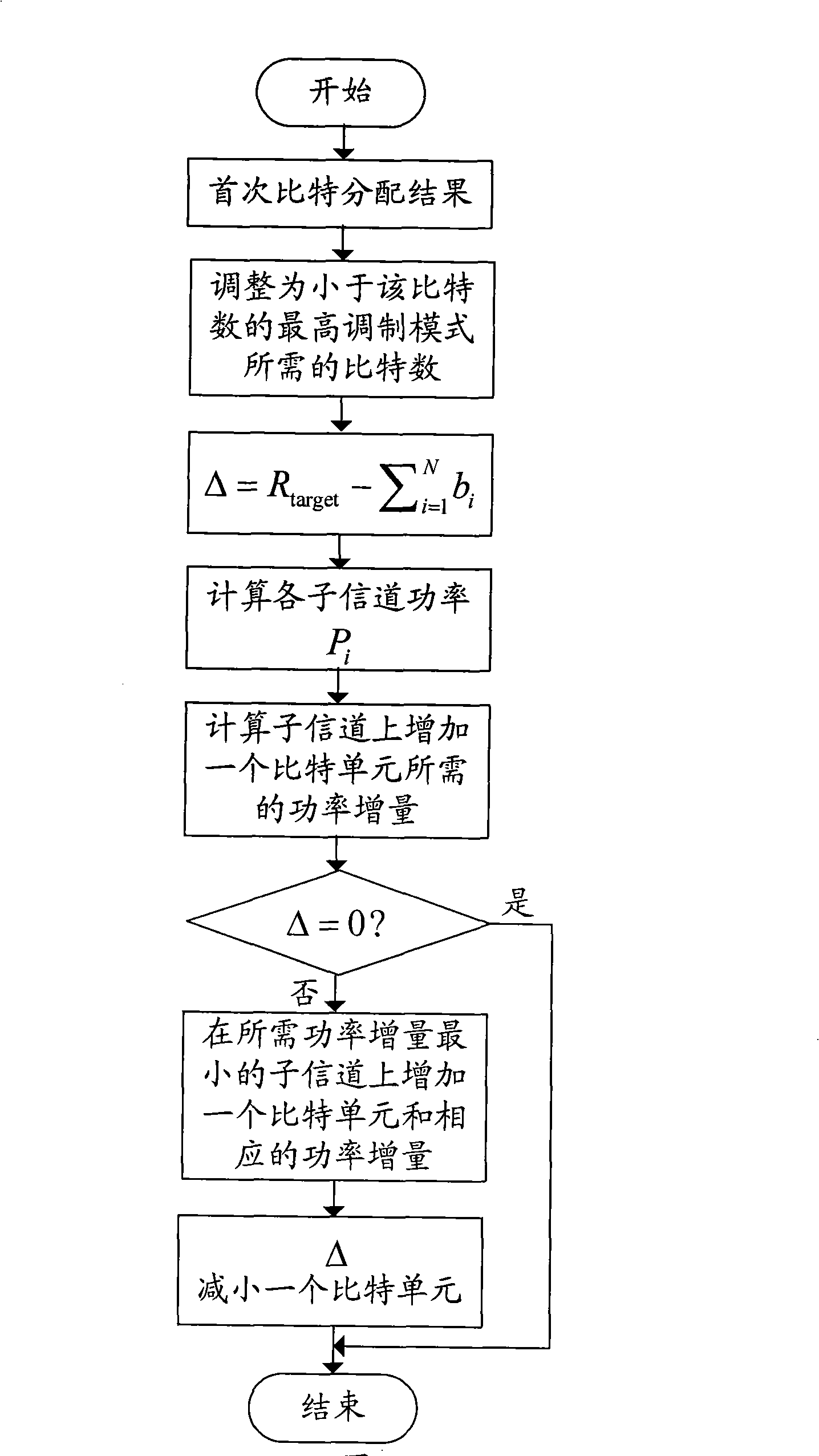
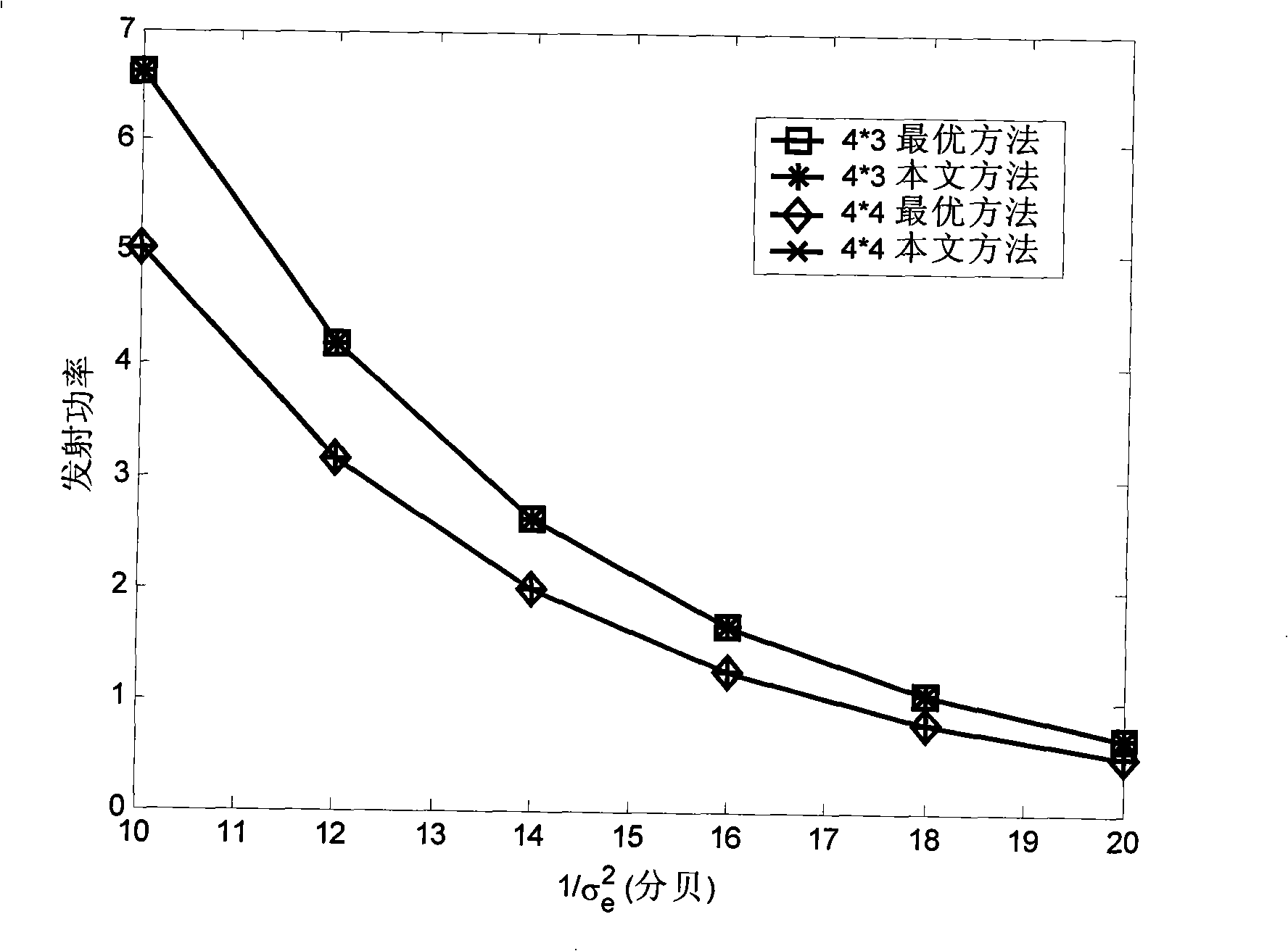
InactiveCN101304298AExcellent power efficiencyReduce operational complexityMulti-frequency code systemsError prevention/detection by diversity receptionBit allocationNon convex optimization
The invention discloses a self-adaptive bit and power allocation method with low complexity which is suitable for an MIMO system, and the method minimizes the total transmission power of the system under the condition that a sender cannot obtain an accurate channel state message and the bit error ratio of the system and the message transmission rate are restricted. The method is characterized in that signals to interference and noise ratios of equivalent sub-channels of the MIMO system under the condition of inaccurate channel state message are analyzed, thus obtaining an explicit relation between the transmission power of the sub-channels and the bit number; a non-convex optimization problem is converted into a convex optimization problem by adopting part monotonicity of functions, and then the closed optimal result in non-negative real number region of the optimization problem is calculated by adopting the Lagrangian approach; finally a real bit number is adjusted to a bit allocation result which requires the need of the real system and a corresponding power allocation is given. The invention is suitable for not only the MIMO system, but also an MIMO-OFDM system. The self-adaptive bit and power allocation method provided by the invention has the advantages of providing approximately optimal power efficiency under the condition of inaccurate channel state message and low operation complexity.
Owner:BEIJING UNIV OF POSTS & TELECOMM
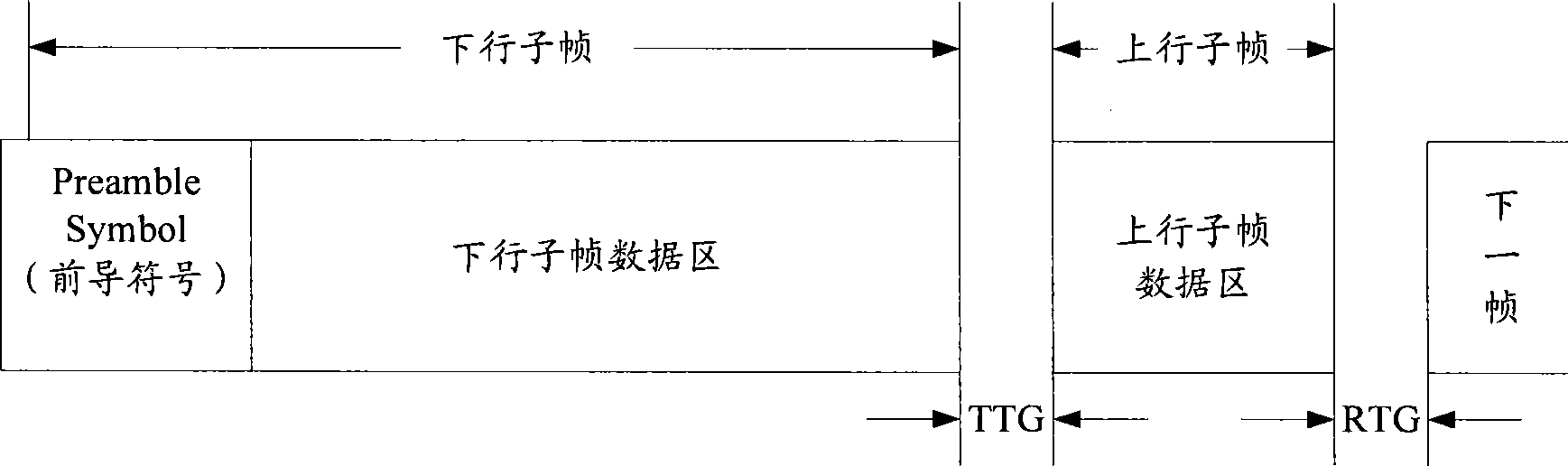
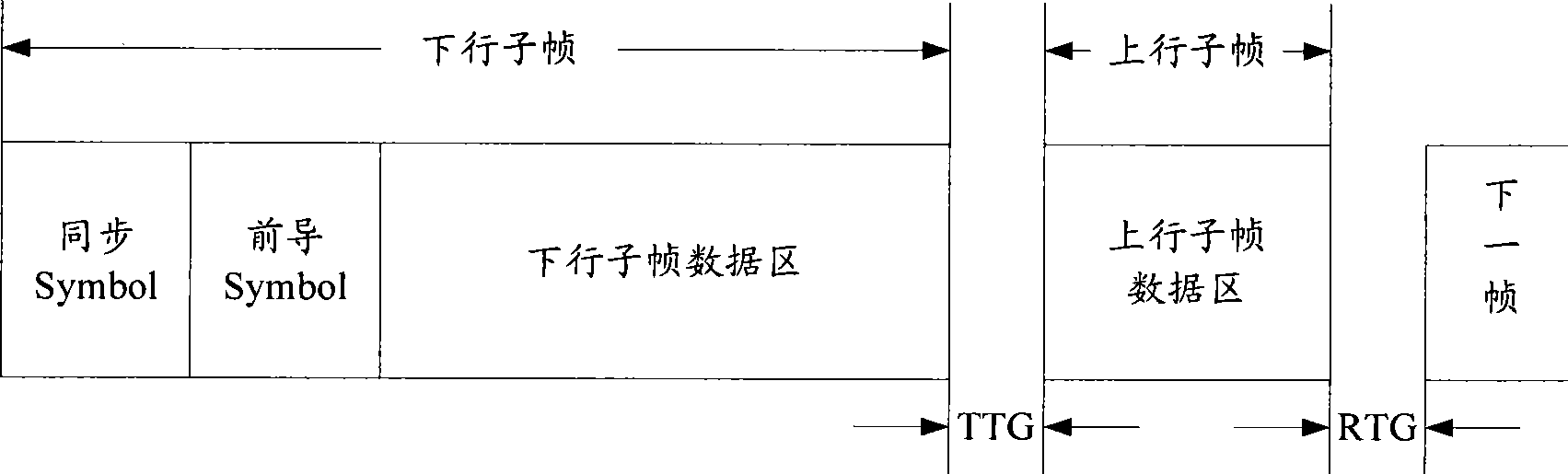
Sending, receiving, and transmitting method for preamble sequence
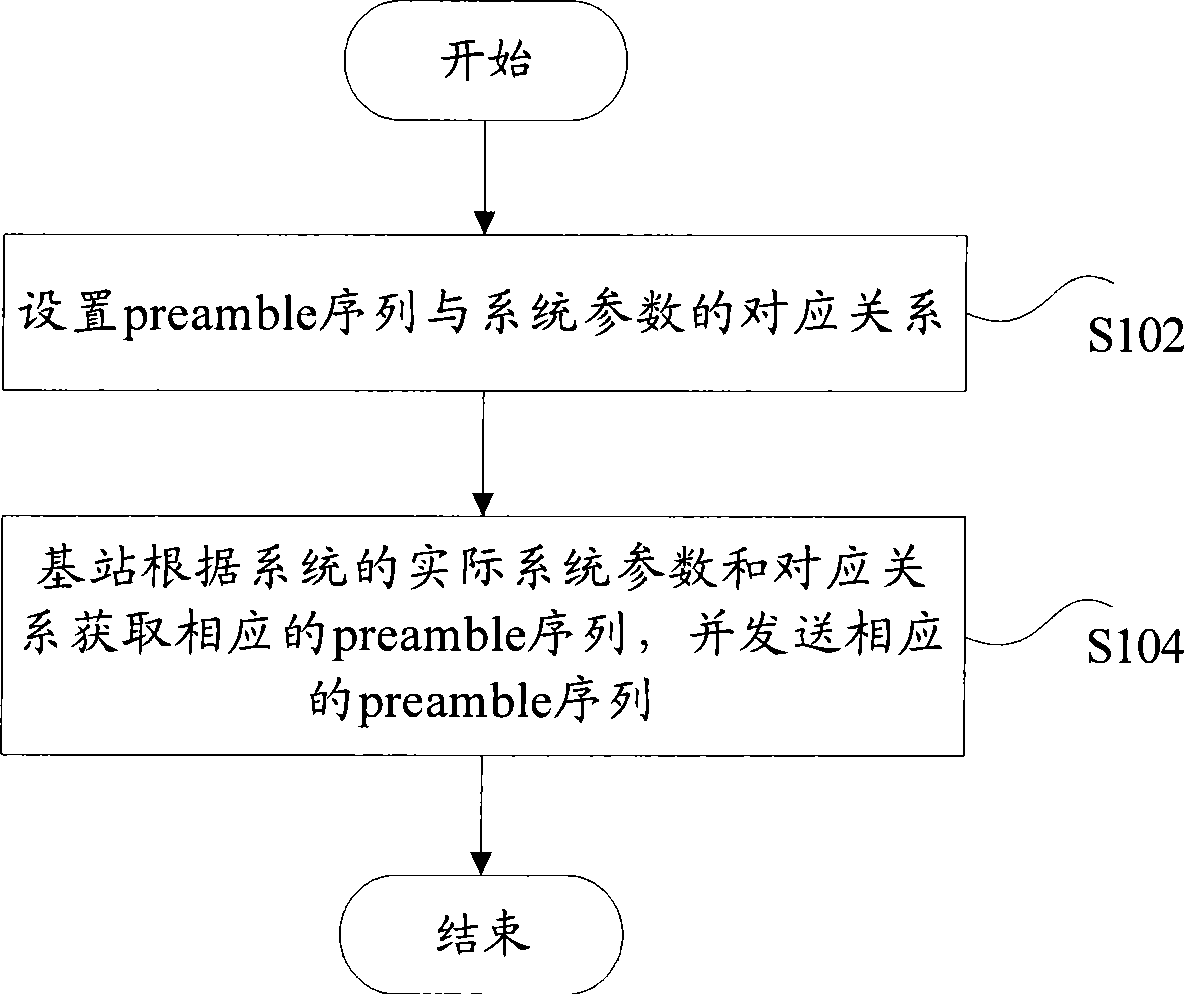
InactiveCN101483626AImprove transmission efficiencyMulti-frequency code systemsReal systemsSystem parameters
The invention discloses a preamble sequence sending method. The preamble sequence sending method comprises steps of S102, setting corresponding relationship between the preamble sequence and system parameters; S104, according to real system parameters and the corresponding relationship, obtaining the corresponding preamble sequence by a base station, and sending the corresponding preamble sequence. Otherwise, the invention also discloses a preamble sequence receiving method and a preamble sequence transmitting method. By using the invention, transmitting efficiency can be improved effectively under the premise of not affecting the system performances.
Owner:ZTE CORP
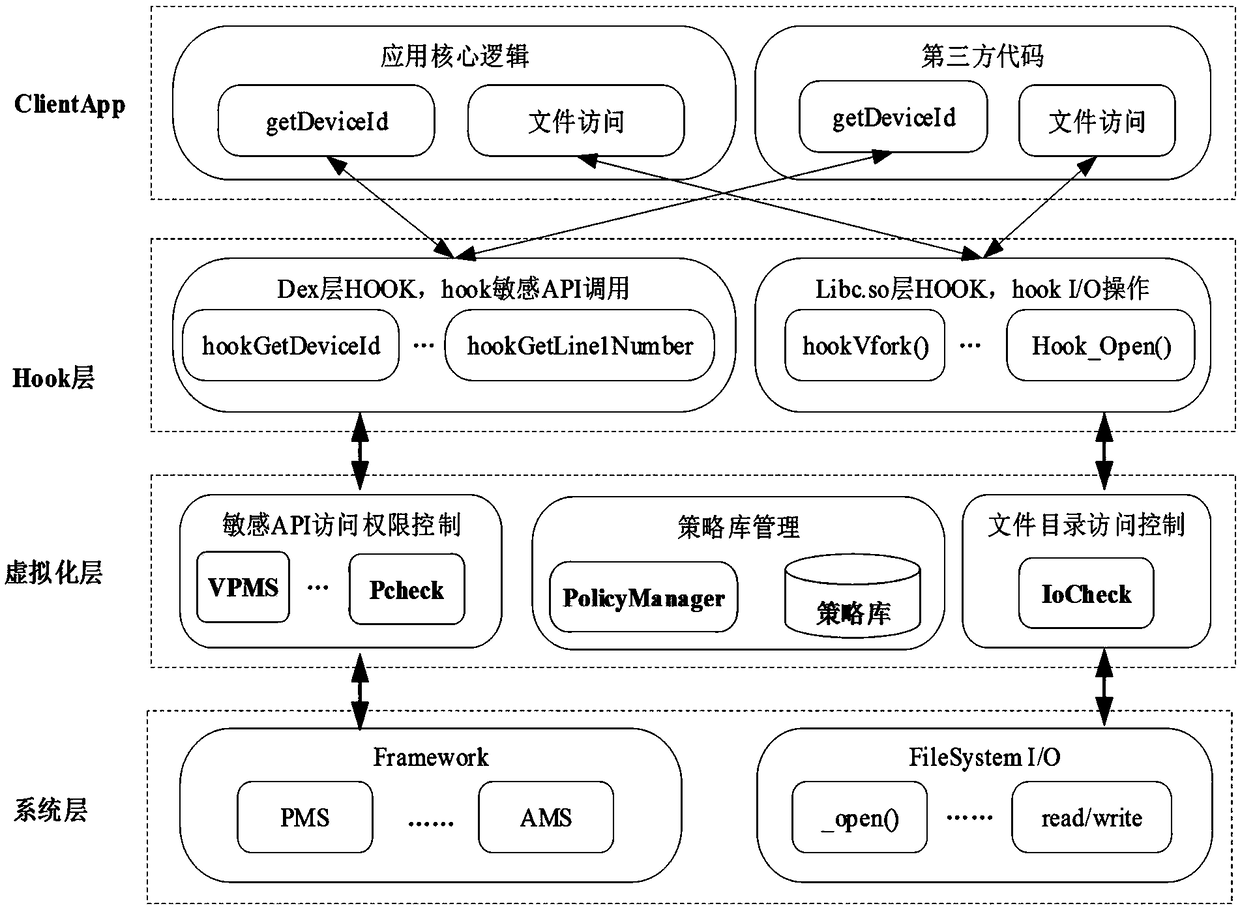
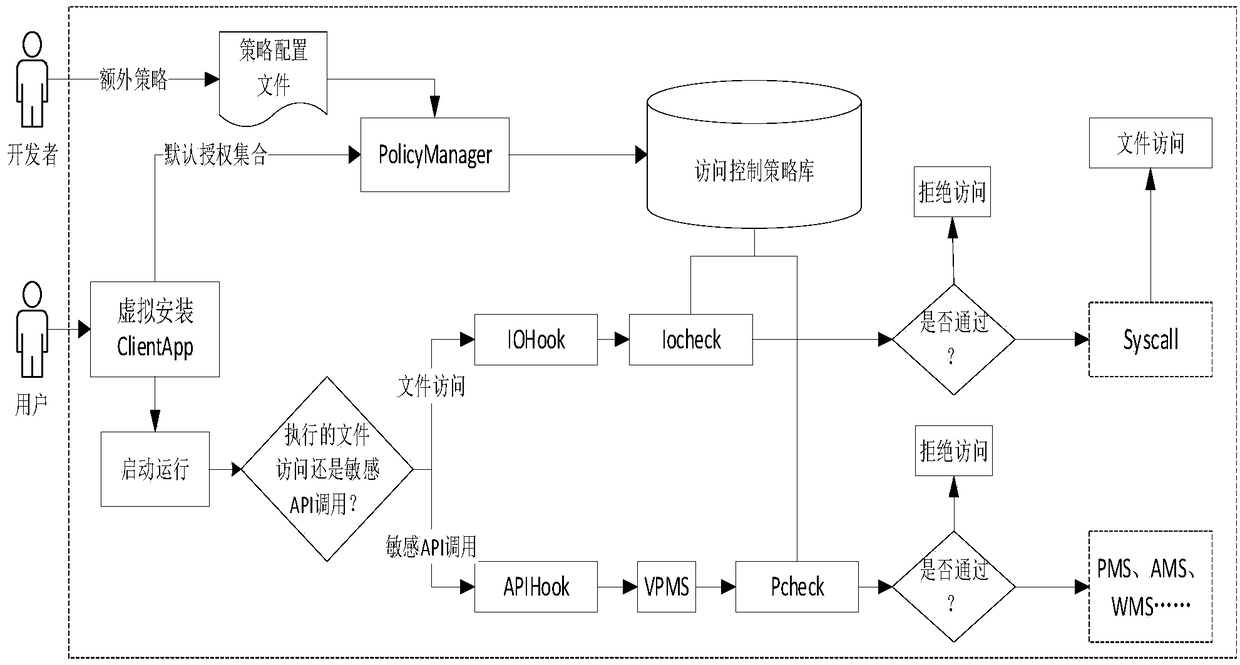
Control method and system of restricted access in Android application multi-running environment
InactiveCN108932427APermission restrictionLimited useComputer security arrangementsReal systemsThird party
The invention discloses a control method and system of restricted access in an Android application multi-running environment, an open source virtualization framework is extended, and a privilege escalation attack initiated by a ClientApp due to the sharing of a permission of a HostApp is limited. The method includes a step of judging whether a current sensitive API call operation is legal or not with the combination of loaded policy information if a current operation is the sensitive API call operation when the ClientApp is running, and allowing the ClientApp to call a real API if so, a step of triggering an IOHook module to obtain a currently accessed file directory if the current operation belongs to a file access operation, then allowing an IoCheck module to check whether current accessis legal or not with the combination of a policy library, and calling a real system for file operation if so, and a step of analyzing a permission list to be a default quasi-permission authorizationset while the HostApp loads the ClientApp, and forming an authorization set with the integration of a developer-configured policy. According to the method and the system, the sensitive API access control in a third-party application multi-running environment is achieved.
Owner:HUAZHONG UNIV OF SCI & TECH
Resource configuration method and device for backhaul link control channel information
ActiveCN102300270ASpecification design is simpleSimple designModulated-carrier systemsNetwork traffic/resource managementReal systemsInformation resource
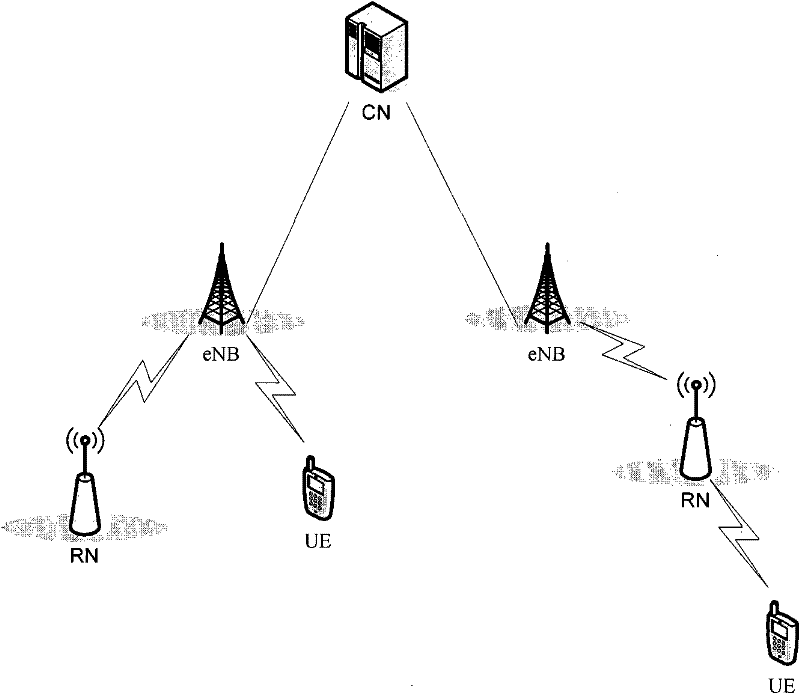
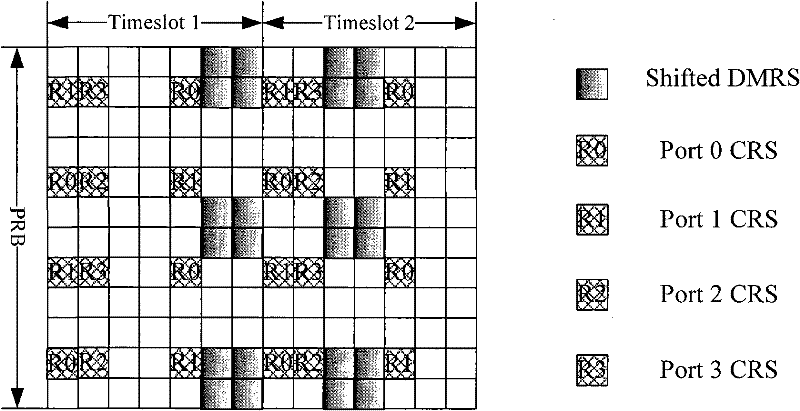
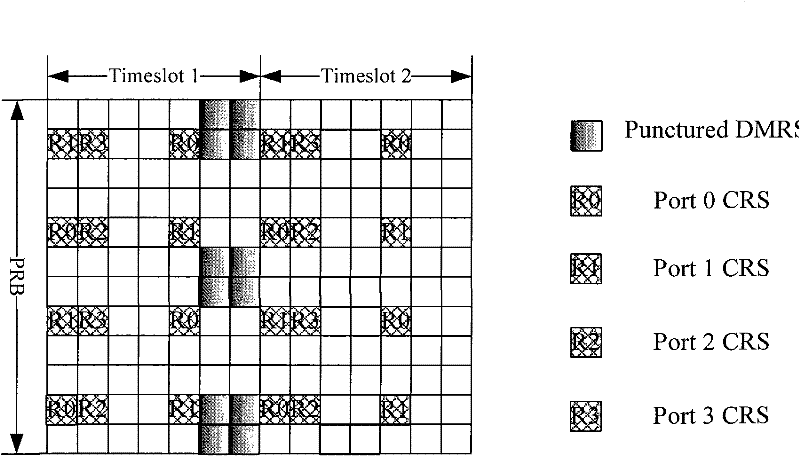
The present invention discloses a method and device for resource allocation of backhaul link control channel information. Upon application of technical solution proposed by embodiment of this invention and based on the condition of introducing DMRS and CSI-RS, make remaining REs in OFDM symbol that contains REs for transmitting CSI-RS and / or DM-RS constitute REG to transmit backhaul link control channel information or abandon them, thus, on the basis of maximizing the reservation of existing LTE system specification, specifying resource allocation scheme of backhaul link control channel information in corresponding physical resource block, giving consideration to both simple specification design and full utilization of resources, and realizing flexible design and allocation in light of the demand of real system.
Owner:DATANG MOBILE COMM EQUIP CO LTD
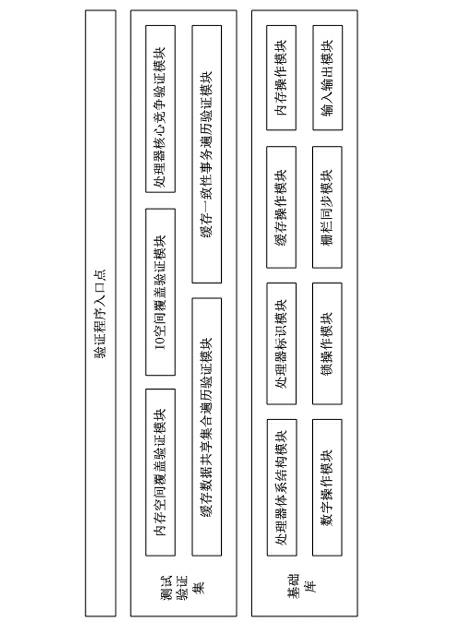
Correctness verifying method of cache consistency protocol
ActiveCN102681937AMake up for efficiencyMake up for poor verification coverageDigital computer detailsMultiprogramming arrangementsOperational systemTerm memory
The invention provides a correctness verifying method of a cache consistency protocol. After a computer enters an operating system, the complexity of a core and the application of the operating system is higher; the action of a processor is not easy to control accurately; therefore, in order to keep verification correctness, a verifying program for the cache consistency protocol is necessary to embed in a systematic procedure; the program is embedded in a BIOS (basic input / output system) code; after the initialization of a memory subsystem is completed at the initialization initial stage of the system, the verifying program is started to be executed; the verifying program needs to be capable of accurately controlling actions of each processor of the system, supports a user to select a verification item to be particularly executed, and feeds back a verification result to the user; by using the method, the verification of the correctness of the cache consistency protocol is realized at a system level; all application scenes of a real system can be completely covered; the disadvantages that a conventional verifying method based on an analog way is low in efficiency and poor in verification coverage rate are made up; the design period and the verifying period of an inter-domain cache consistency chip of the processor can be shortened; the one-time taping-out mission success rate of the chip can be guaranteed effectively; and therefore, the correctness verifying method has an extremely wide development prospect and an extremely high technical value.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Fundamental method and its hardware implementation for the generic prediction and analysis of multiple scattering of waves in particulate composites
InactiveUS20030167156A1Computation using non-contact making devicesScattering properties measurementsReal systemsFluid phase
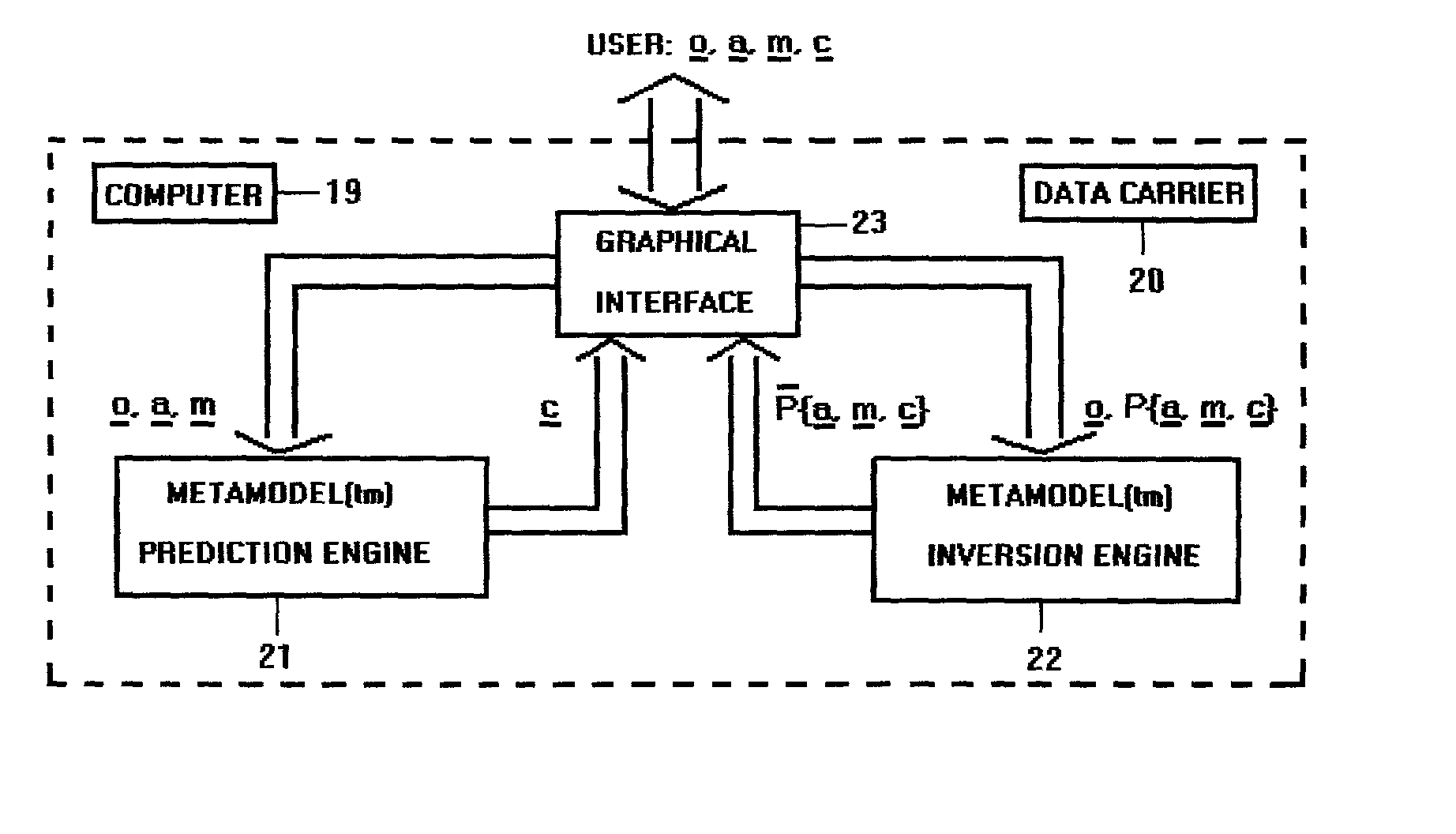
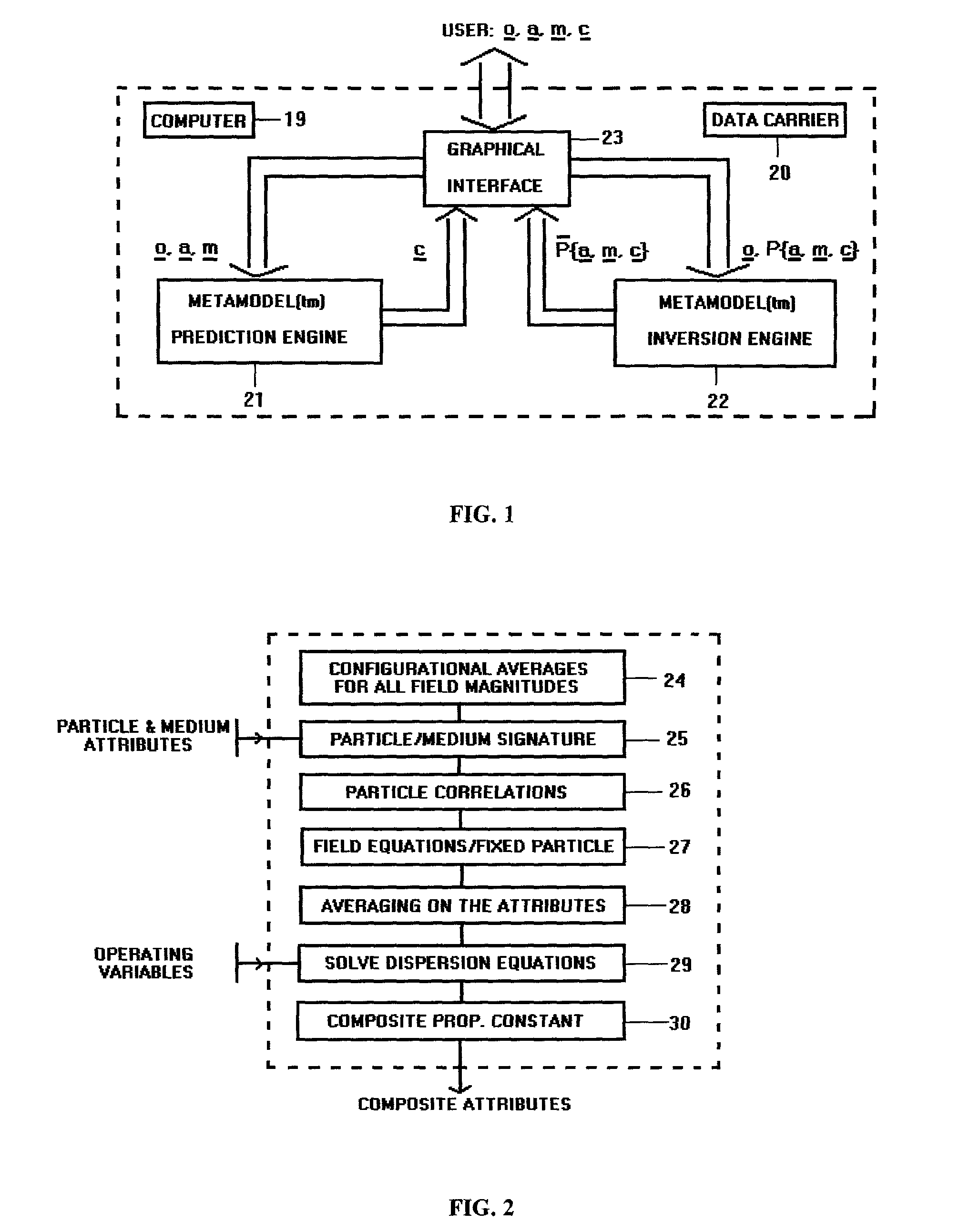
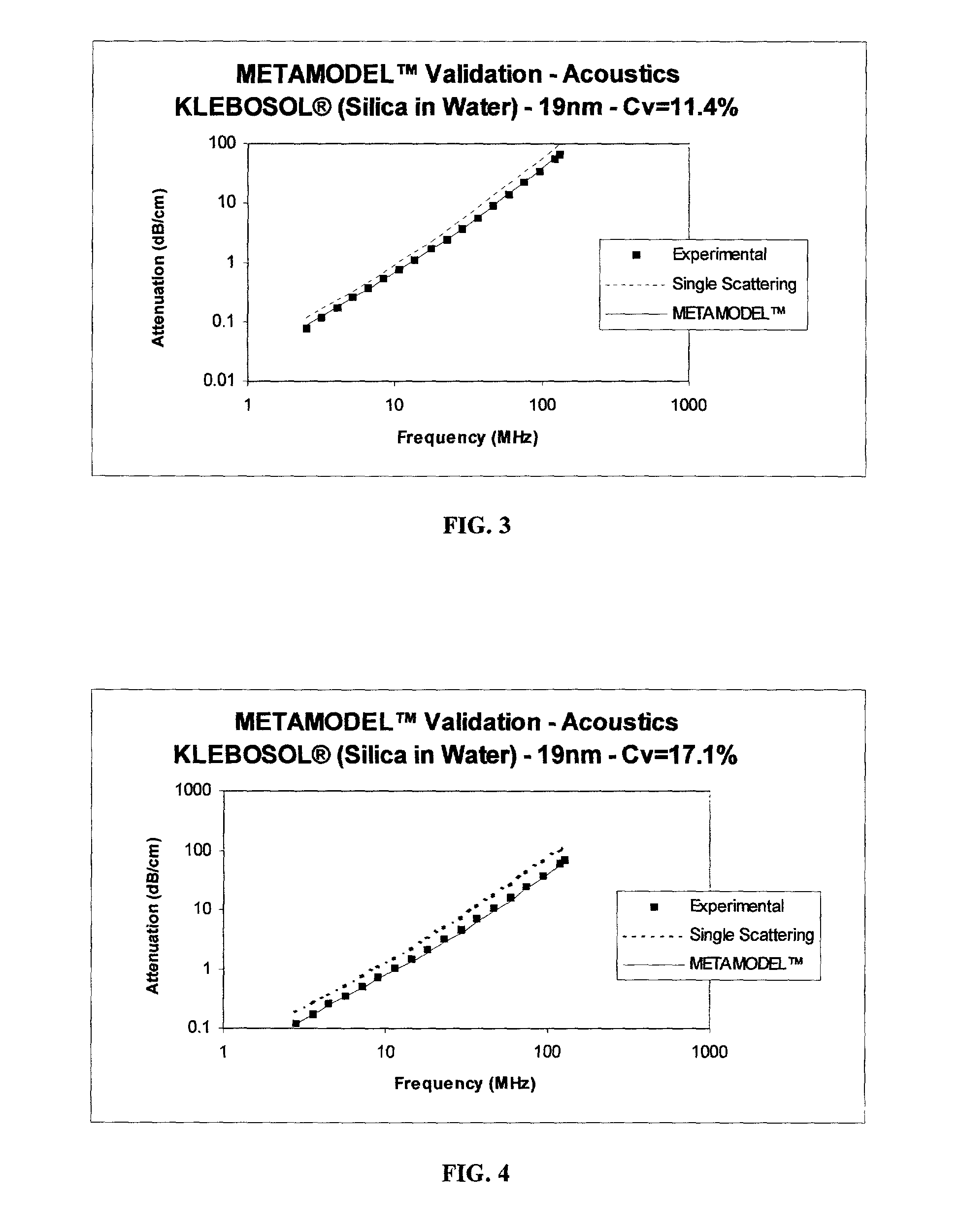
This invention relates to a method and apparatus for the fundamental prediction, analysis, and parametric studies of the interaction of multiply scattered waves of any nature (acoustic, electromagnetic, elastic) with particulate composites (solid or fluid particulate phases included in a solid or fluid phase). It comprises of: a) a Prediction Engine 21 to predict the composite physical attributes from those of the constituent phases, b) an Inversion Engine 22 to estimate a subset of the attributes of the constituent phases and composite from the rest of those attributes, and c) an ergonomic Graphical Interface 23 to allow the user to easily set up complex simulation experiments to assist in parametric studies, analysis, and synthesis of real systems in which waves of any nature interact with composites. The Prediction Engine 22 is suitable for integration into existing acoustic or optical particle size analyzers to thereby extending substantially their concentration ranges.
Owner:FELIX ALBA CONSULTANTS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com