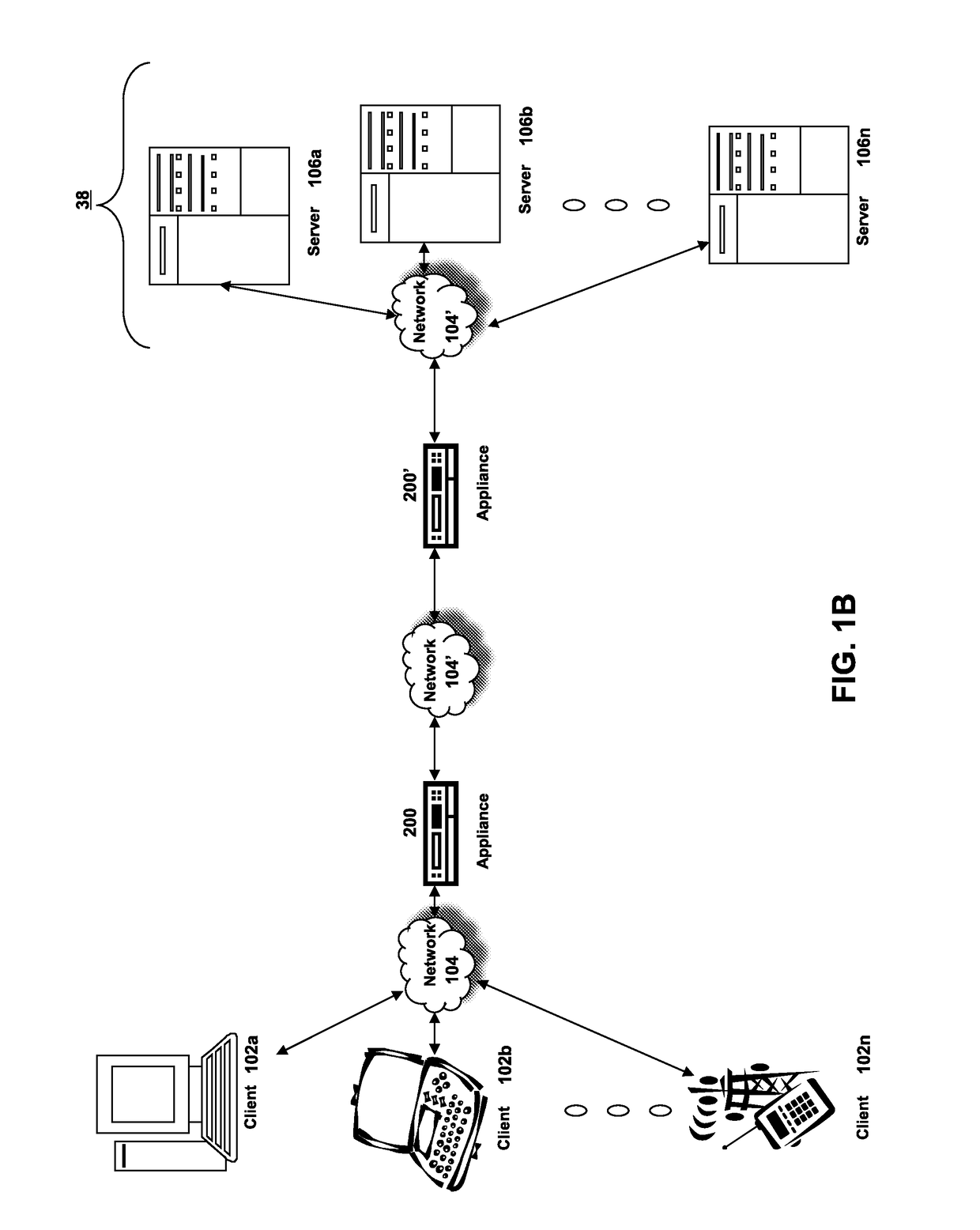
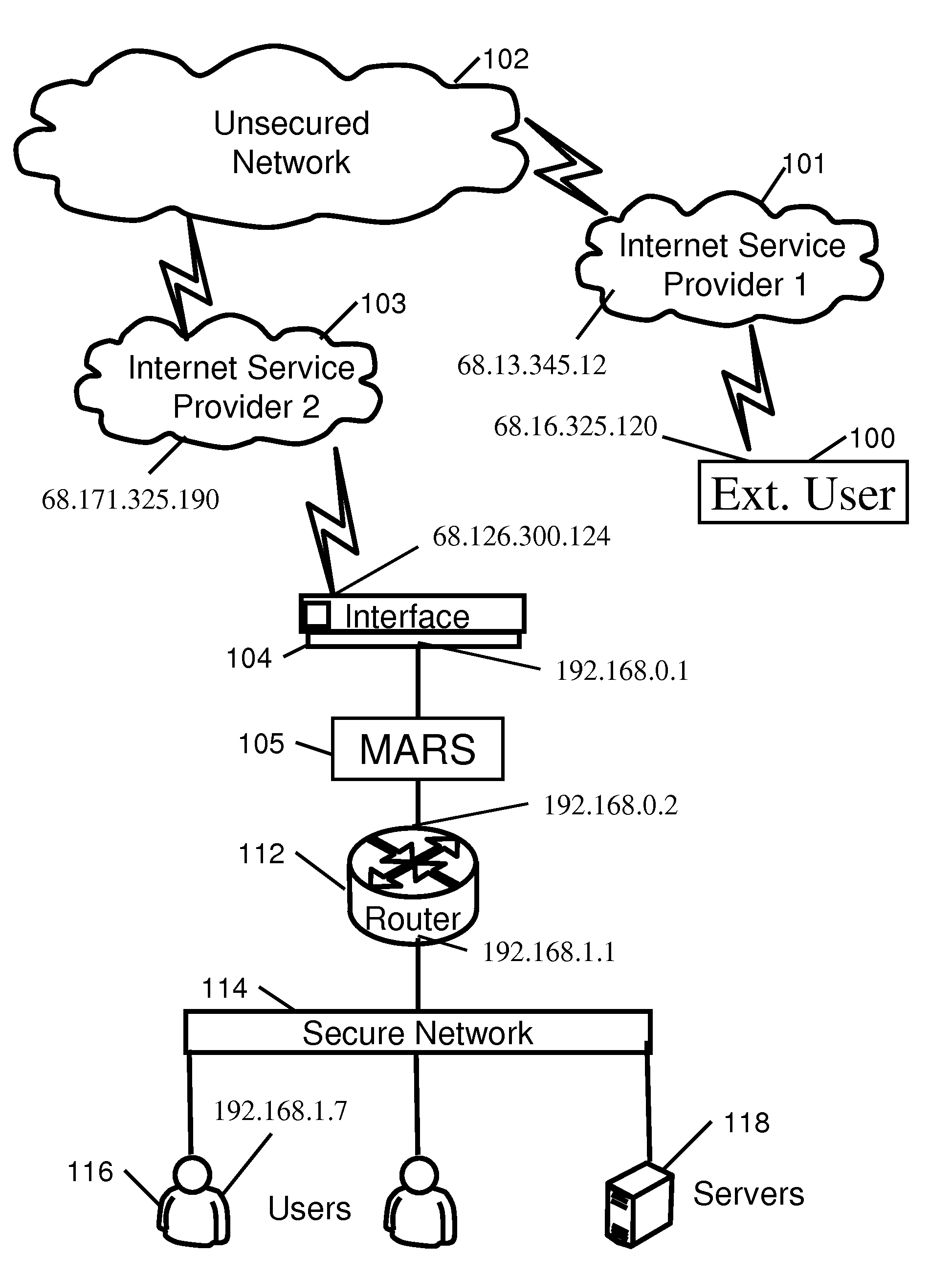
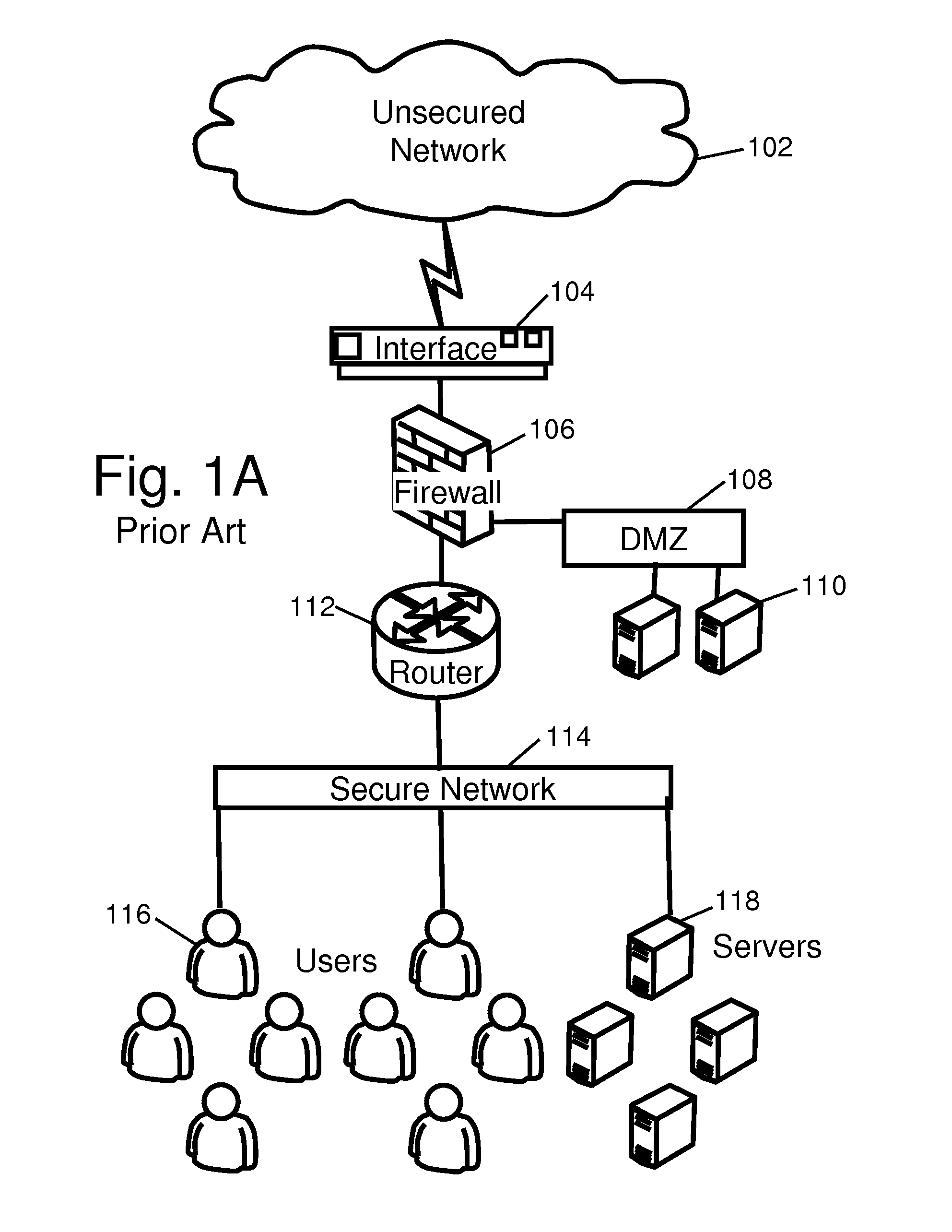
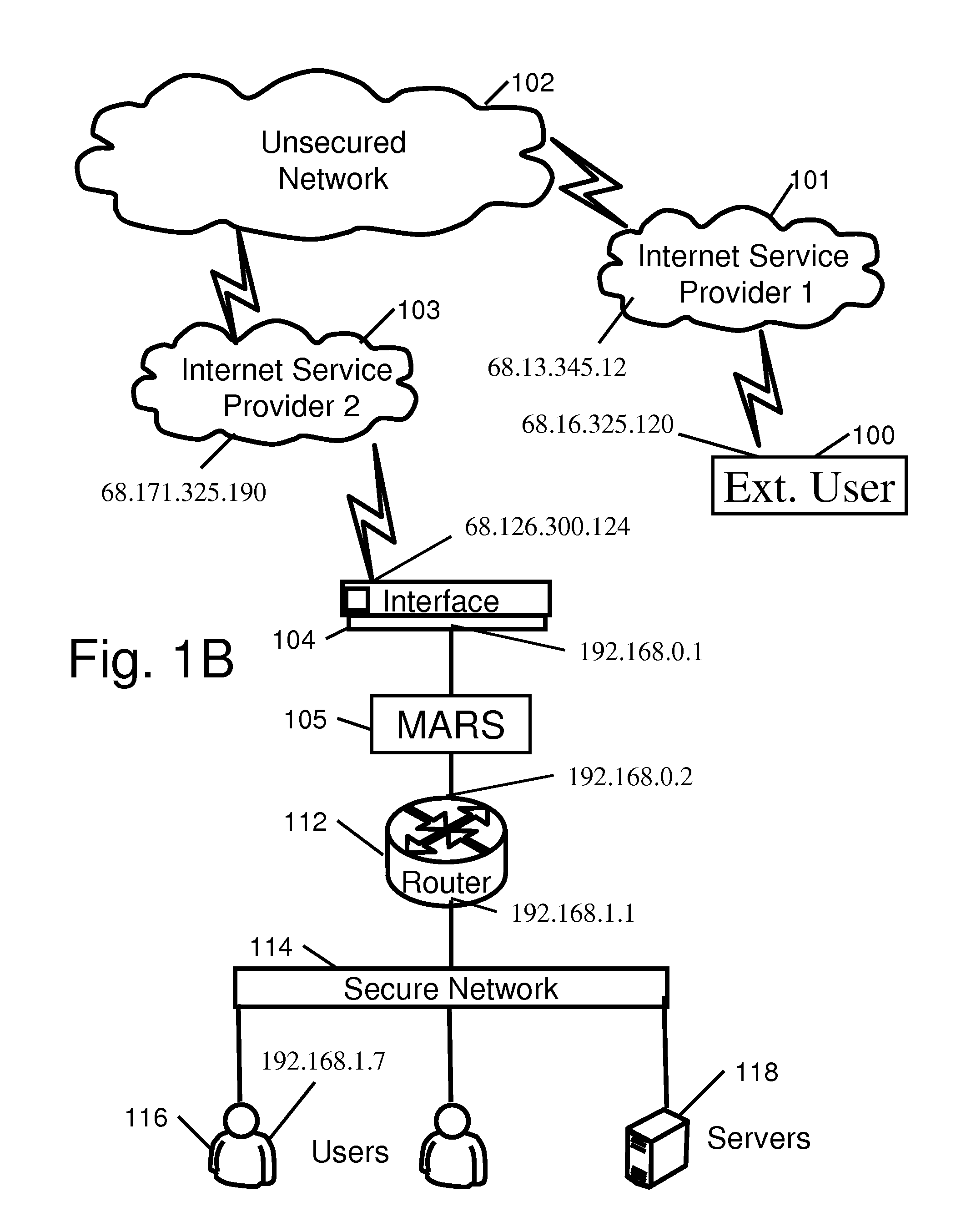
Patents
Literature
183 results about "Network traffic simulation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network traffic simulation is a process used in telecommunications engineering to measure the efficiency of a communications network.
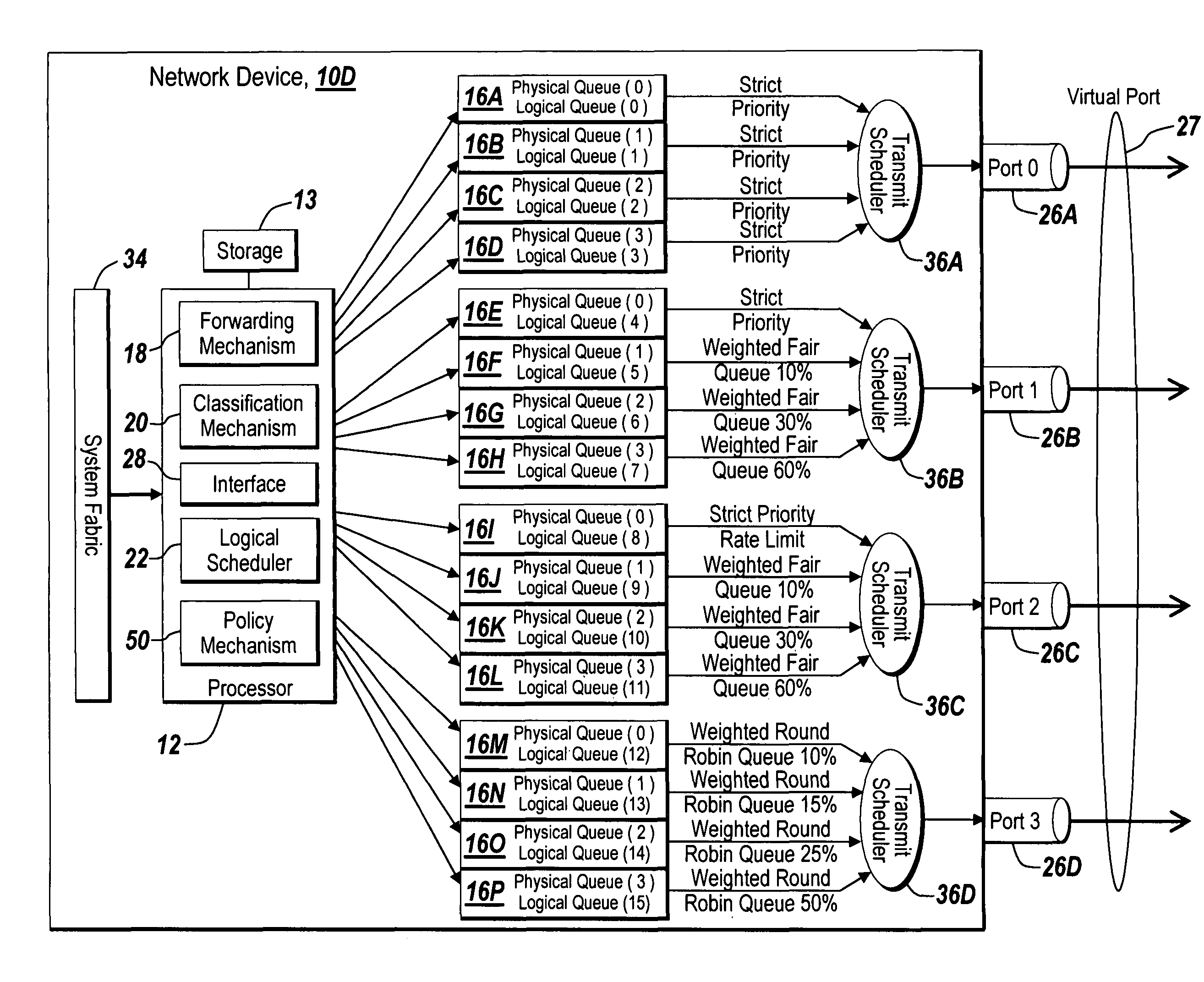
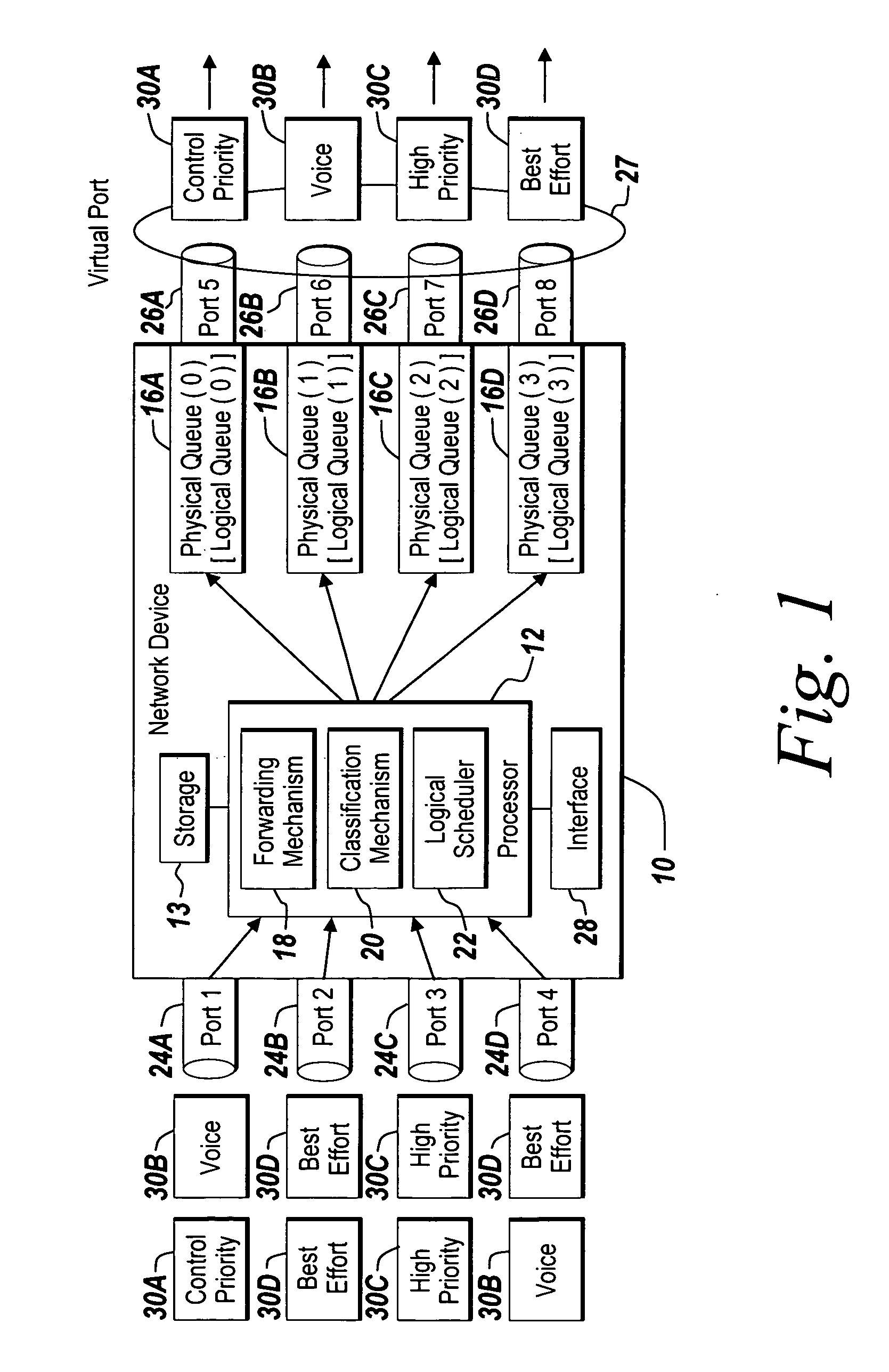
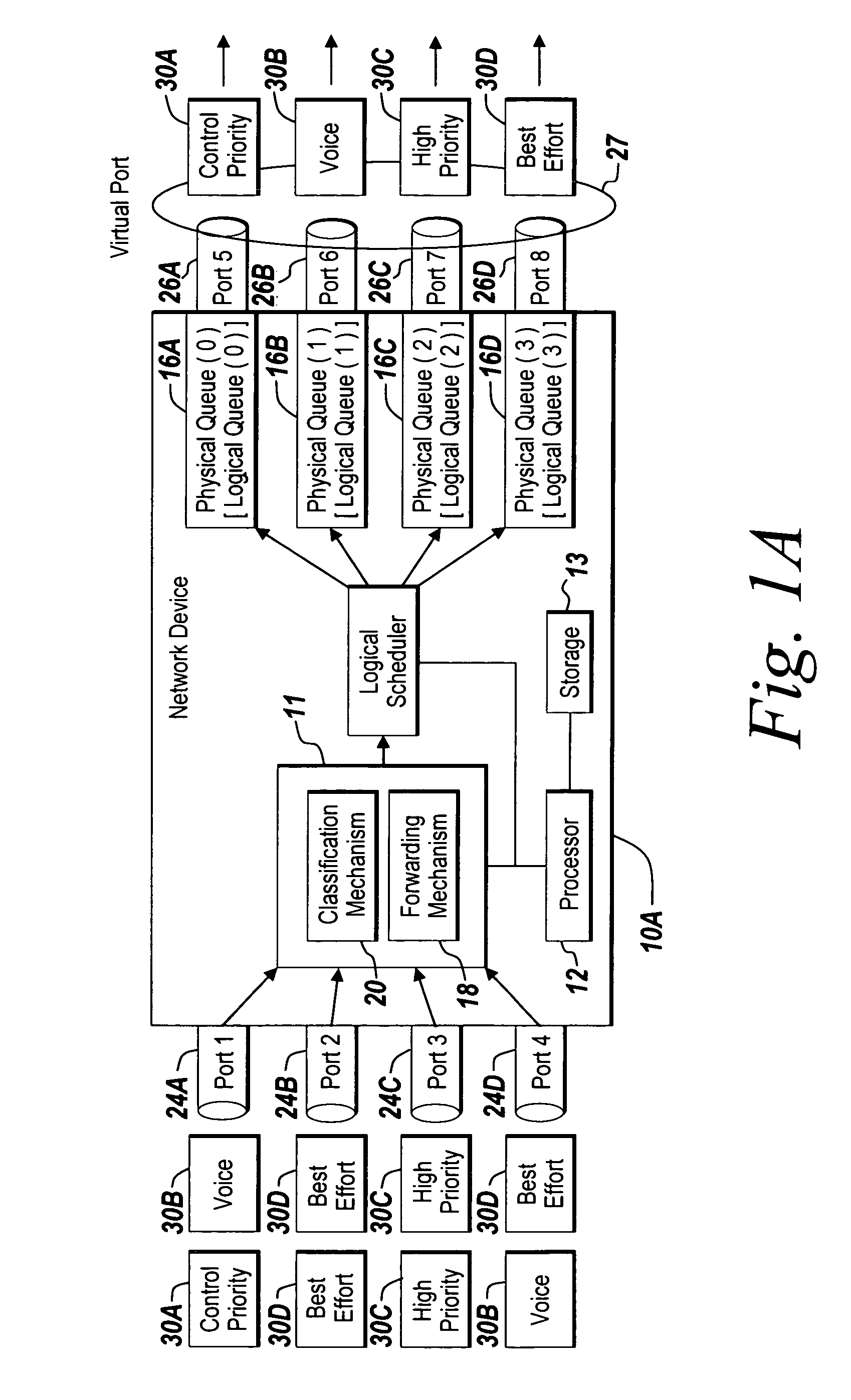
Method and apparatus of virtual class of service and logical queue representation through network traffic distribution over multiple port interfaces
ActiveUS7936770B1Improve abilitiesIncrease volumeMultiplex system selection arrangementsData switching by path configurationTraffic capacityVirtual class
A method and apparatus are provided that allows for the representation of a larger number of classes of network traffic and logical queues than is physically available on a per port basis within a network device. A number of logical queues, whose number can match the number of classes of network traffic a network device handles, may be supported across an aggregated set of ports even though the network device has fewer physical queues per port than there are classes of network traffic. The method and apparatus improve the management of network traffic sensitive to time delay and jitter, and further facilitates the operation of these applications in a simultaneous or near simultaneous manner.
Owner:EXTREME NETWORKS INC
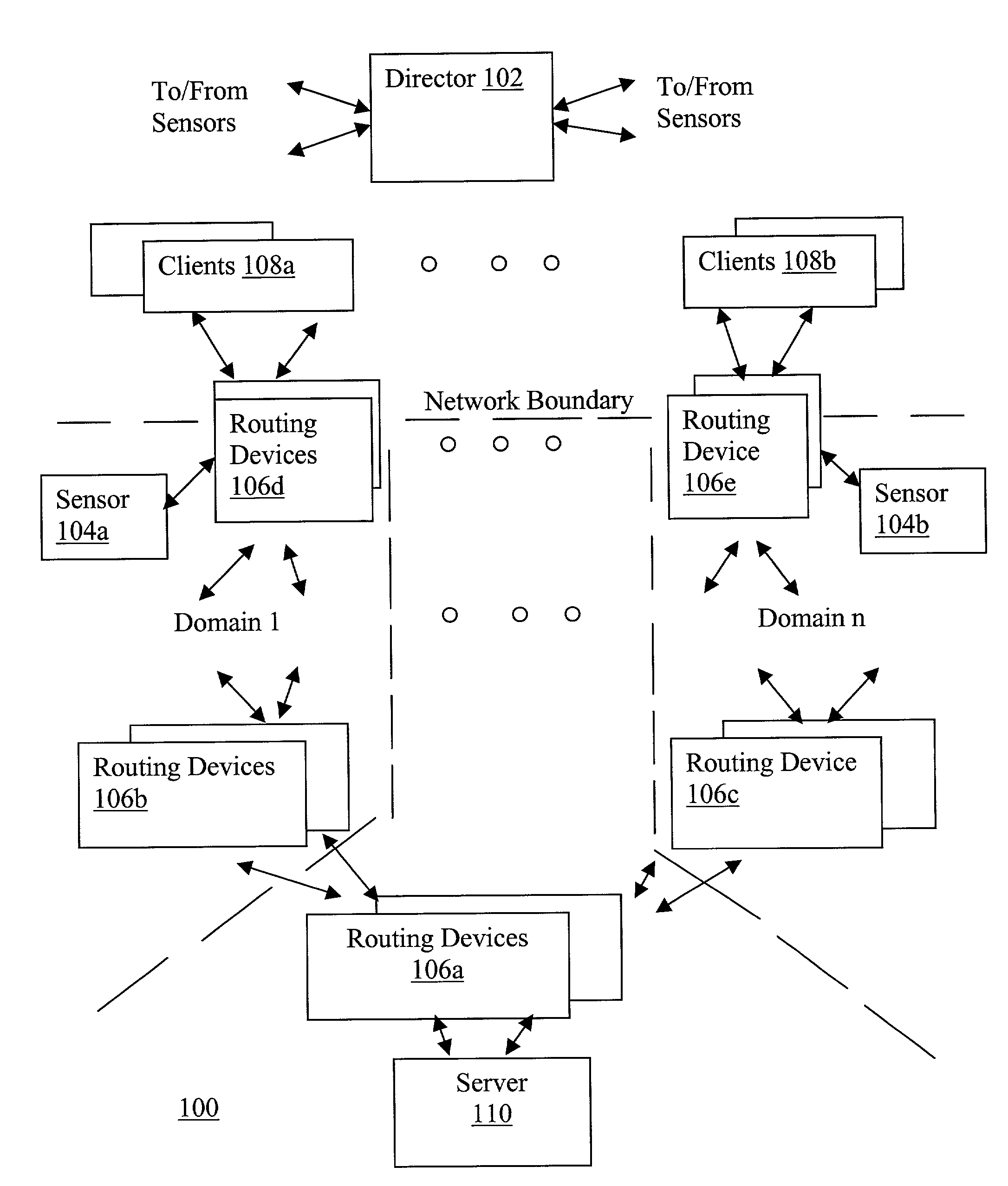
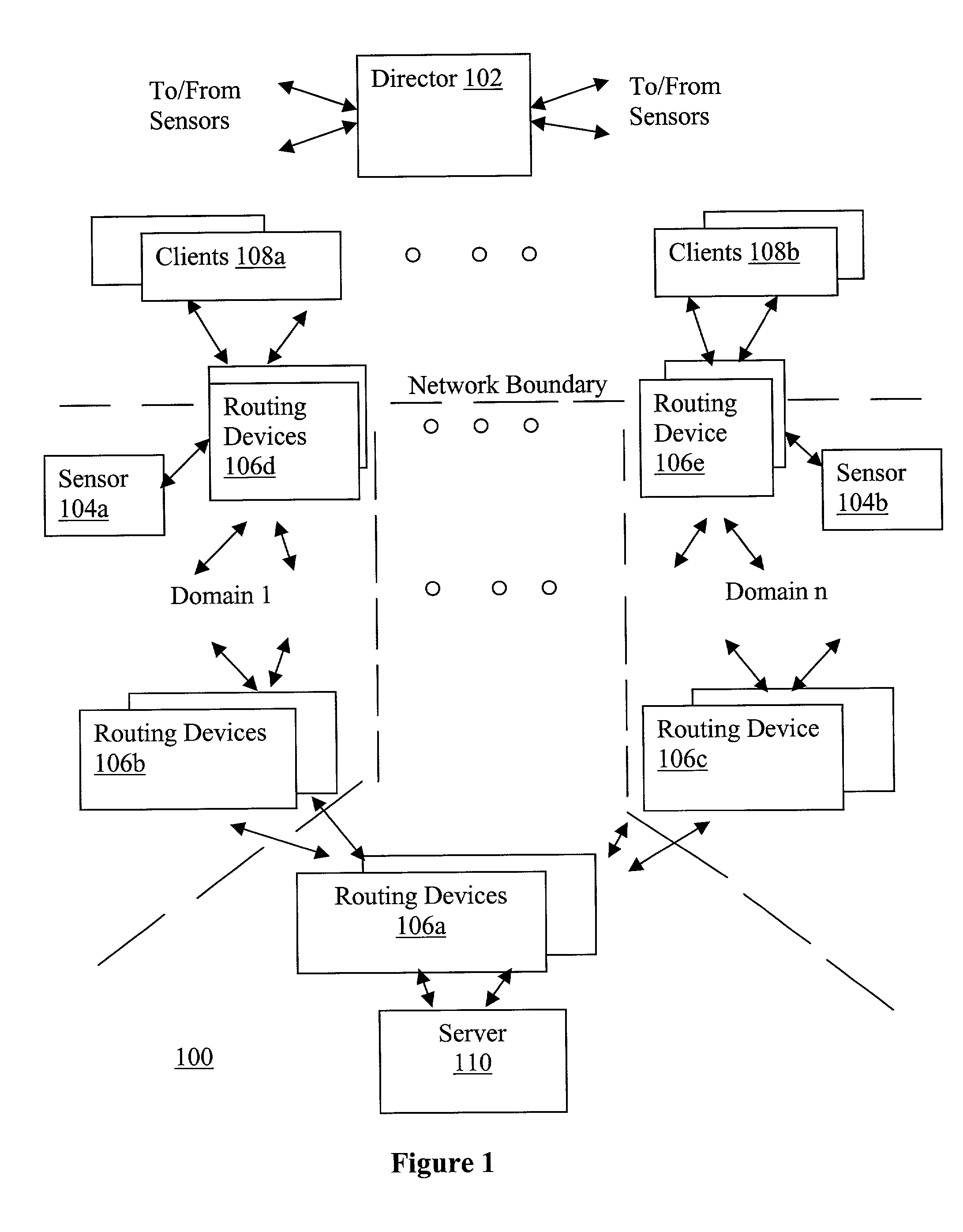
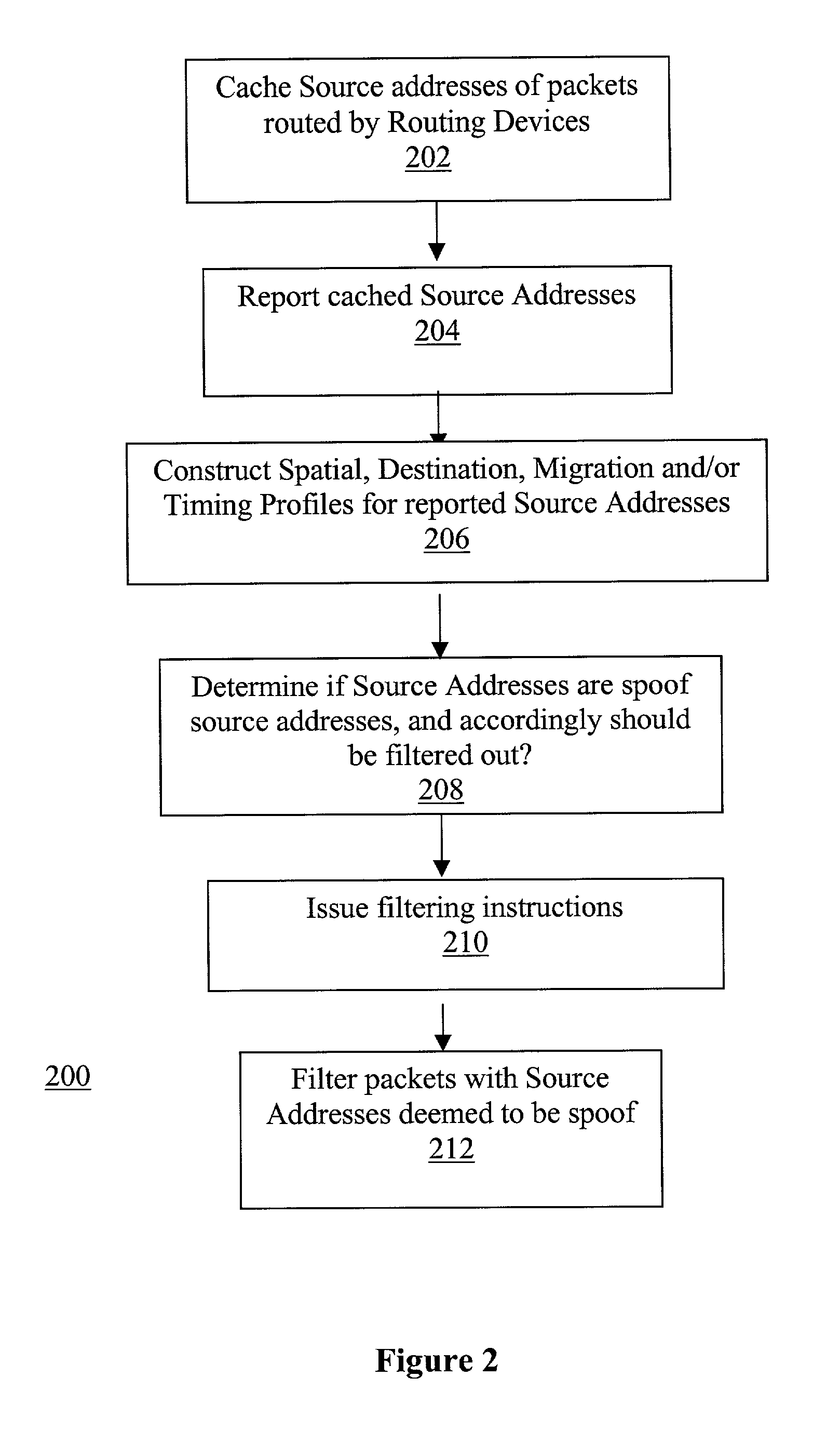
Network traffic regulation including consistency based detection and filtering of packets with spoof source addresses
InactiveUS7444404B2Ensuring quality of serviceEnsure qualityRandom number generatorsUser identity/authority verificationTraffic capacityReporting source
A director is provided to receive source address instances of packets routed through routing devices of a network. The director determines whether any of the reported source address instances are to be deemed as spoof source address instances. The director further determines where filtering actions are to be deployed to filter out packets having certain source addresses deemed to be spoof instances. The director makes its determinations based at least in part on a selected one of a number of consistency measures. The consistency measures may include but are not limited to spatial consistency, destination consistency, migration consistency, and temporary consistency. The consistency measures are evaluated using spatial, destination source address range, migration and timing S / D / M / T distribution profiles of the reported source addresses. In some embodiments, the determinations are based further in view of reference S / D / M / T distribution profiles, which may be an exemplary S / D / M / T distribution profile of a typical non-spoof source address or a historical S / D / M / T distribution profile of the source address.
Owner:ARBOR NETWORKS
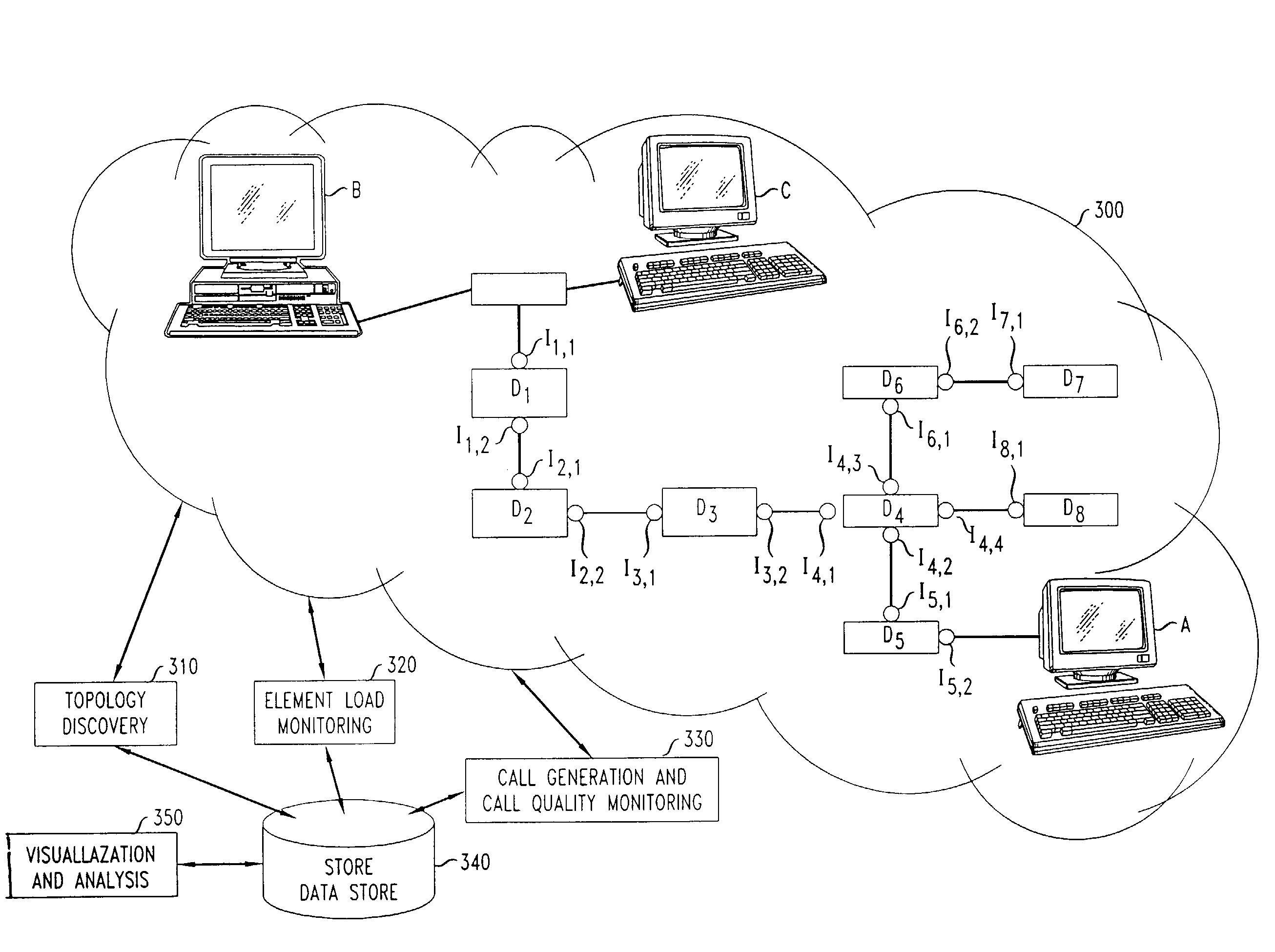
Network traffic generation and monitoring systems and methods for their use in testing frameworks for determining suitability of a network for target applications
ActiveUS7633942B2Overcome limitationsOvercomes shortcomingDigital computer detailsSupervisory/monitoring/testing arrangementsQuality of serviceMonitoring system
A system for monitoring traffic on a network first discovers the network so as to map the various devices and links in the network. Statistics are then gathered from various points in the network relating to quality of service, and especially loads on the network devices. Synthetic calls are generated at selected points of the network while monitoring the network. This data is then stored and displayed in a manner that is easy for the operator to analyze, with more detailed displays being available through the use of a mouse or keystrokes.
Owner:GULA CONSULTING LLC
Using network traffic logs for search enhancement
ActiveUS7398271B1Handy search resultsImprove the level ofData processing applicationsWeb data indexingTraffic capacityLink weight
A method and apparatus for using network traffic logs for search enhancement is disclosed. According to one embodiment, network usage is tracked by generating log files. These log files among other things indicate the frequency web pages are referenced and modified. These log files or information from these log files can then be used to improve document ranking, improve web crawling, determine tiers in a multi-tiered index, determine where to insert a document in a multi-tiered index, determine link weights, and update a search engine index.
Owner:R2 SOLUTIONS
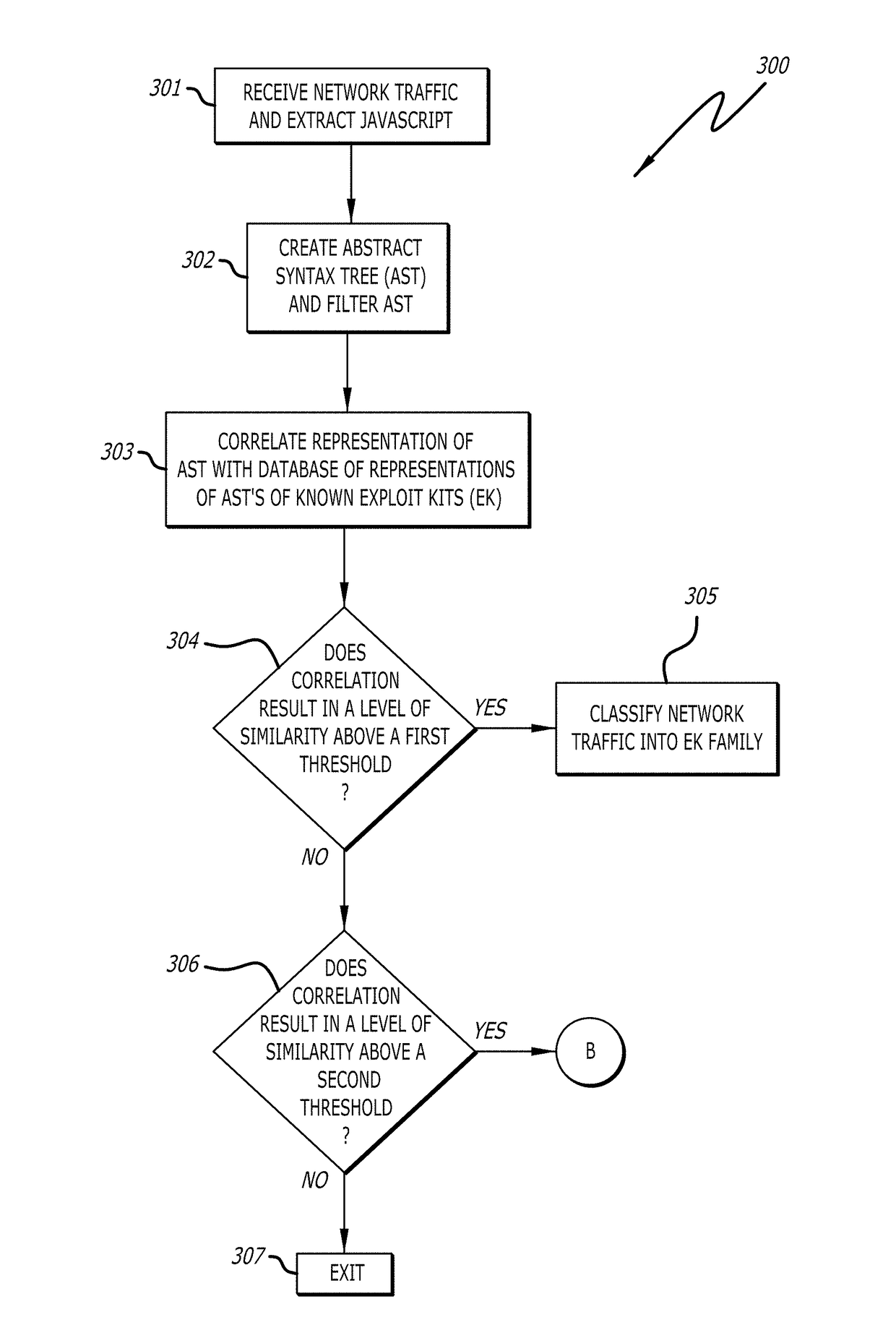
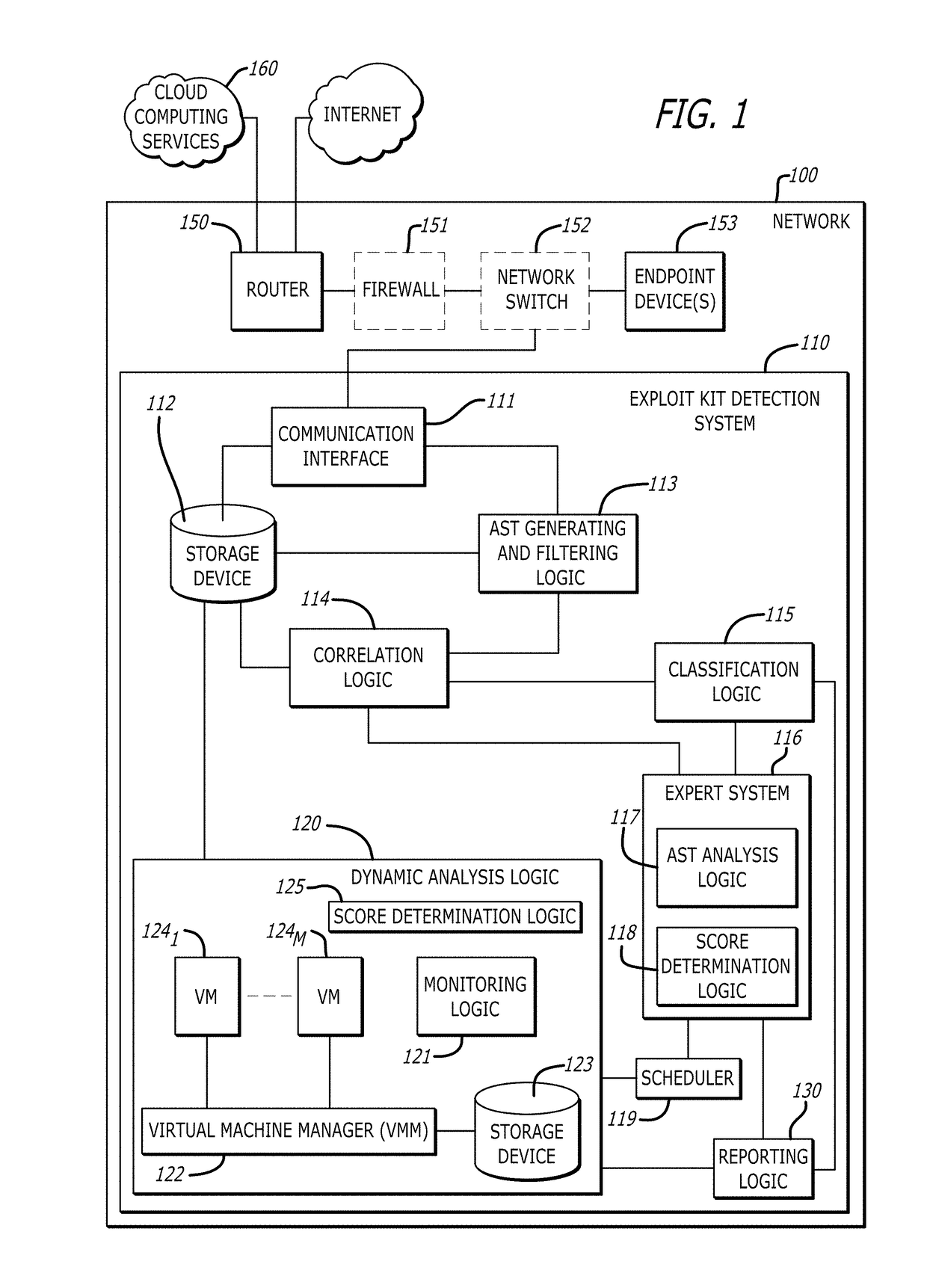
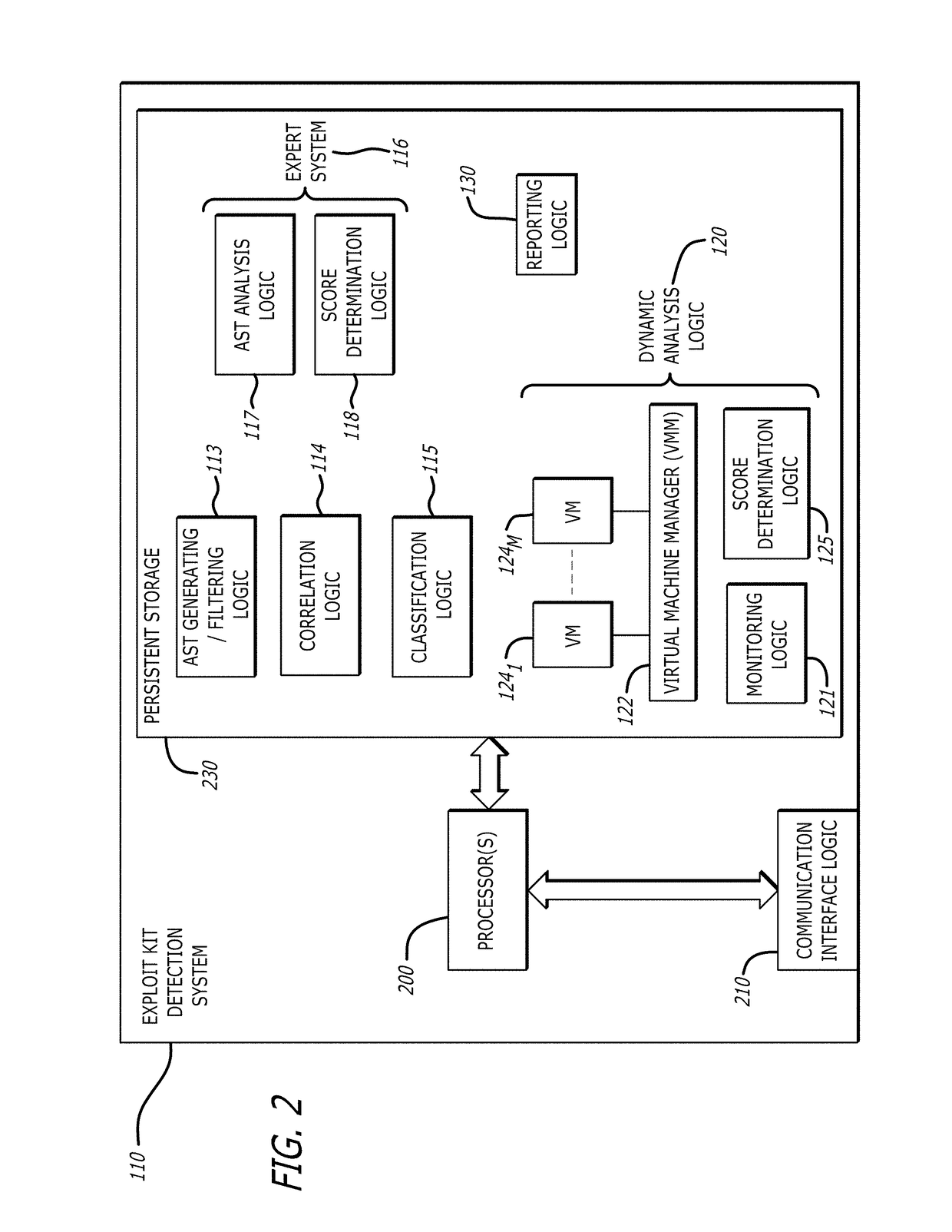
Detection and classification of exploit kits
ActiveUS9825976B1Computer security arrangementsProbabilistic networksExploit kitTheoretical computer science
A non-transitory computer readable storage medium having stored thereon instructions executable by a processor to perform operations including: responsive to determining that a correlation between a representation of the first portion of network traffic and a representation of a known exploit kit results in a score above a first prescribed score value, classifying the representation of the first portion of the received network traffic into an exploit kit family corresponding to the representation the known exploit kit; and responsive to determining that the score is below the first prescribed score value and above a second prescribed score value, (i) analyzing the representation of the first portion of the received network traffic, and (ii) processing, within a virtual machine, a second portion of the received network traffic to determine whether processing of the received network traffic results in behavior indicative of an exploit kit is shown.
Owner:FIREEYE SECURITY HLDG US LLC
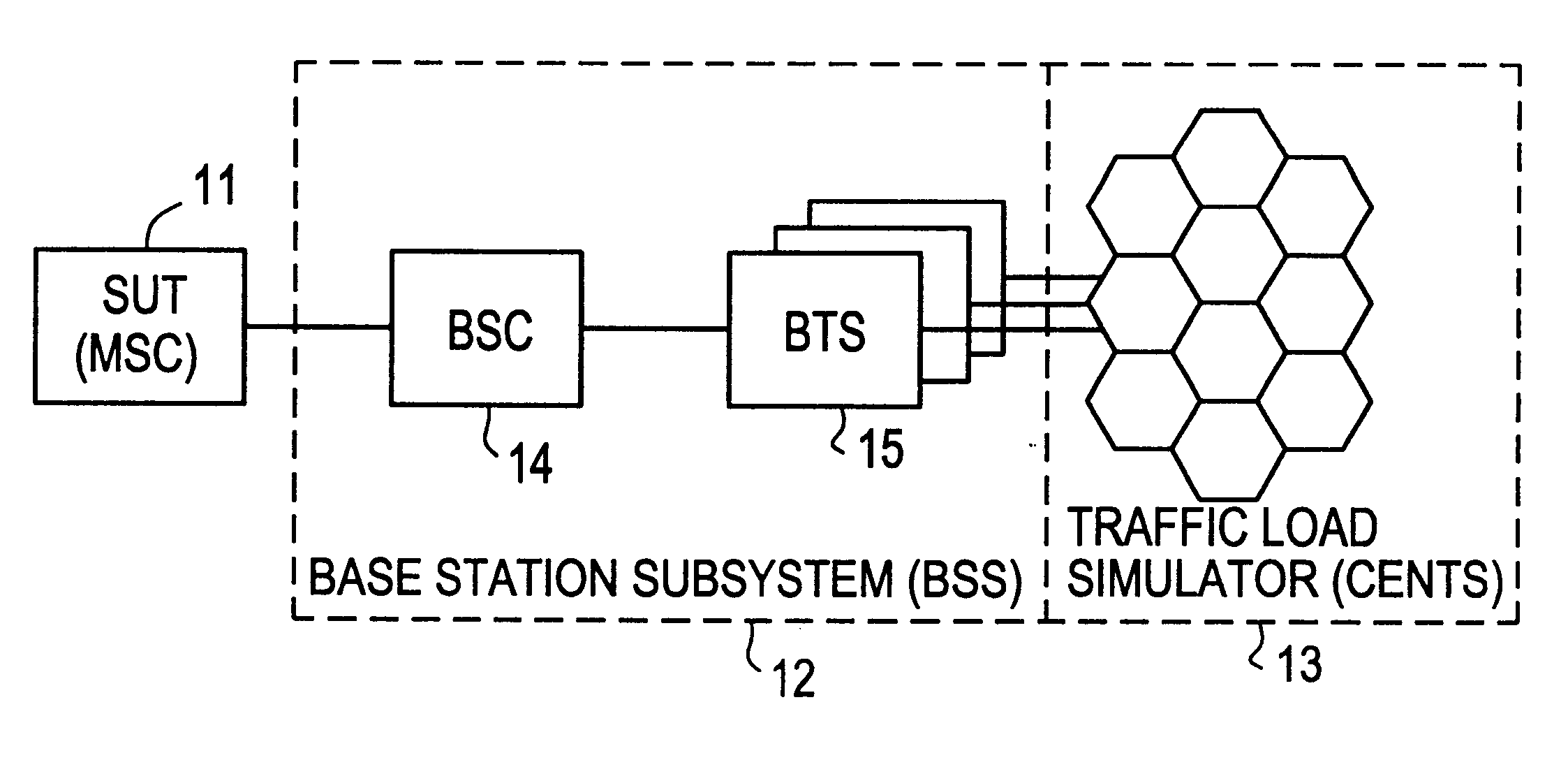
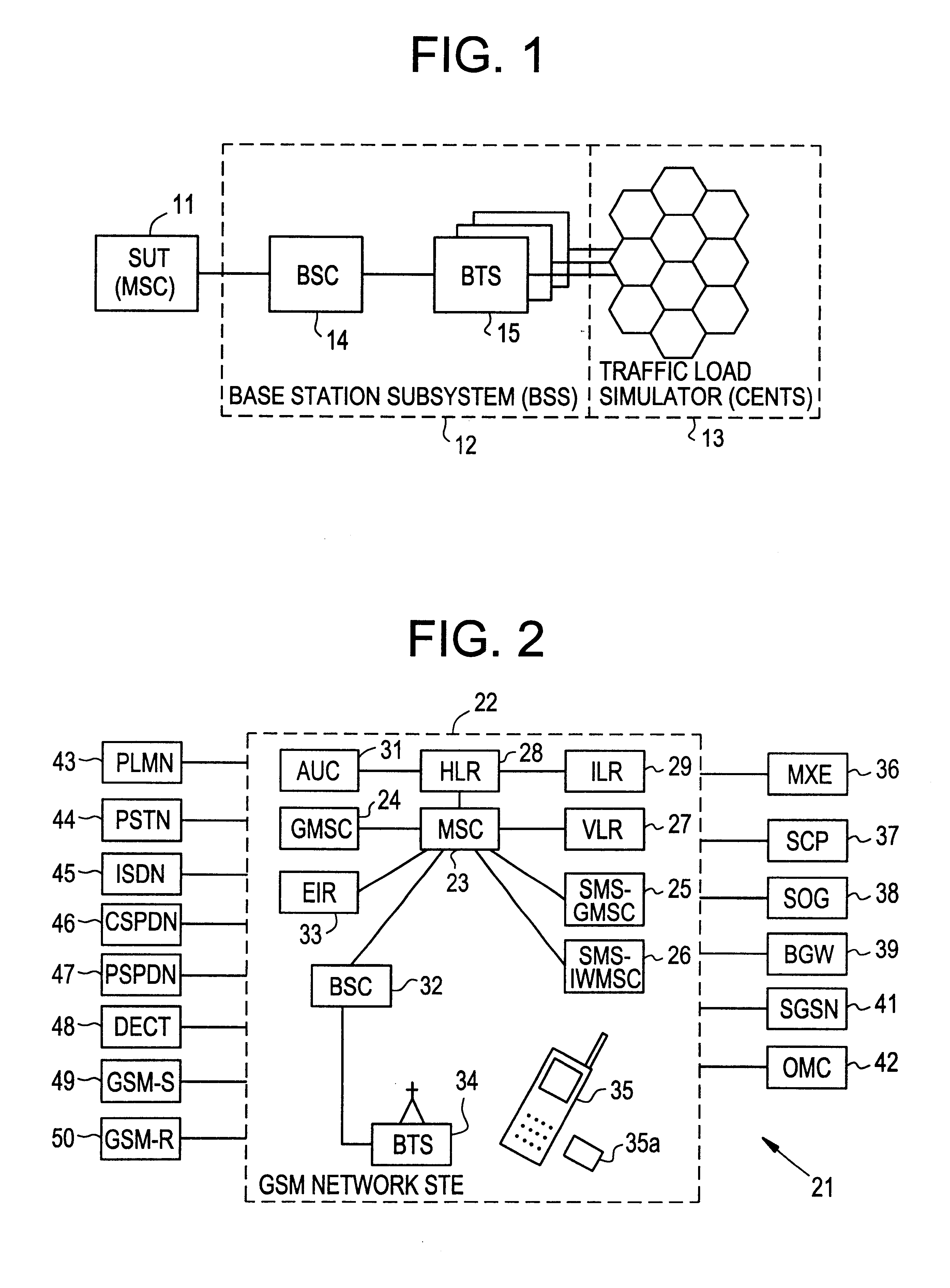
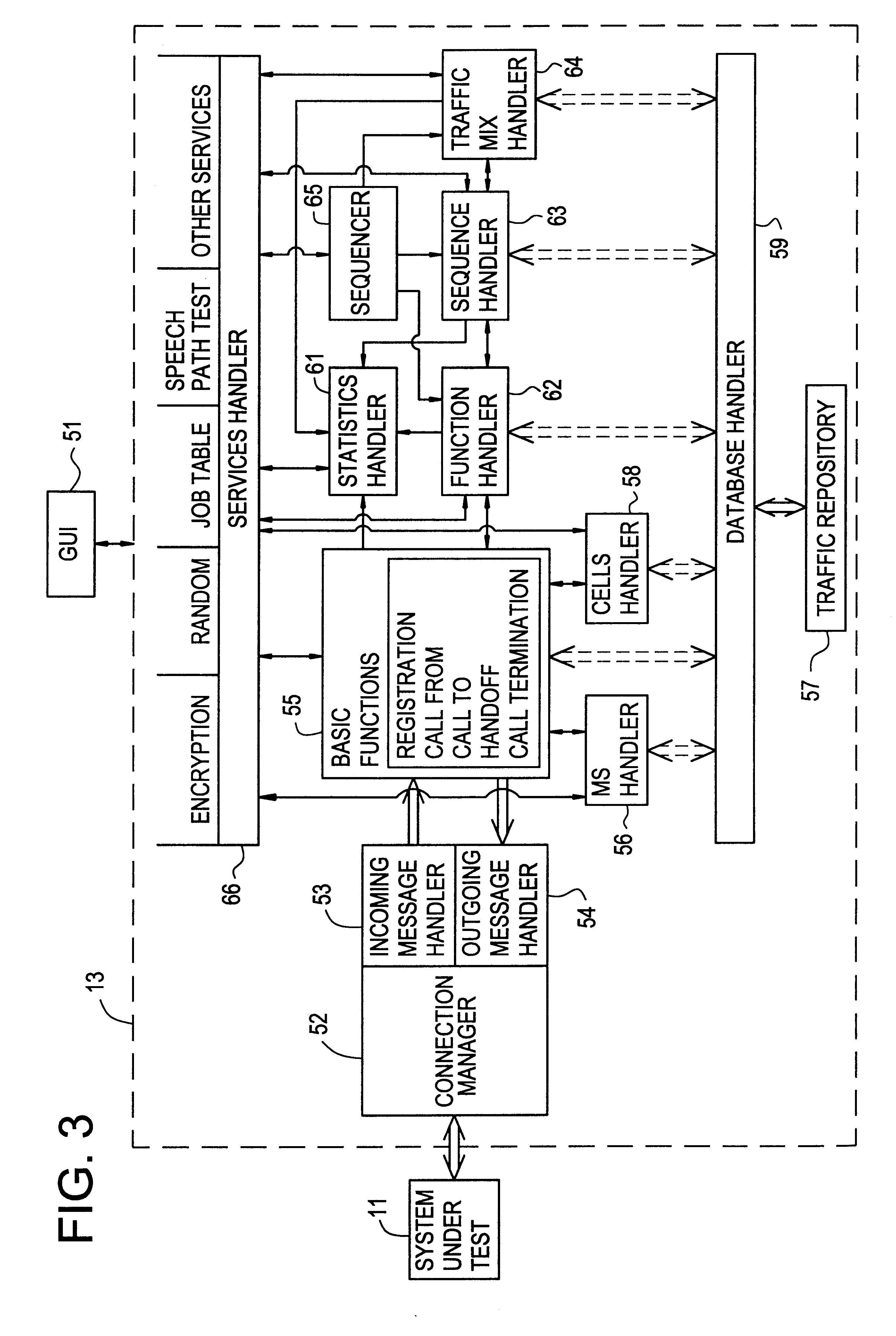
Cellular network traffic simulator (cents)
A traffic simulator for a cellular radio telecommunications network. The traffic simulator includes a function handler which generates a plurality of basic call functions performed by mobile stations (MSs) over an air interface link with the network. A sequence handler utilizes the basic functions to generate a plurality of call sequences, and a traffic mix handler utilizes the plurality of call sequences to generate an overall traffic mix. A MS handler includes a plurality of MS state machines for different types of MSs and a database of MS properties. The MS handler interfaces with the basic functions to generate realistic inputs to the sequence handler. A cells handler includes a database of cells in the network and parameters relating to radio conditions. The cells handler also interfaces with the basic functions to generate realistic inputs to the sequence handler. A traffic repository may inject recorded real mobile station traffic into the traffic mix. A connection manager sends the traffic mix to external network components, and a graphical user interface (GUI) enables an operator to interface with the traffic simulator and generate specified traffic scenarios.
Owner:INFOVISTA
Framework for explaining anomalies in accessing web applications
ActiveUS20170126718A1Improve computing efficiencyIncrease speedTransmissionWeb applicationClient-side
The present disclosure is directed towards systems and methods for characterizing anomalous network traffic. The system includes a device intermediary to clients and servers. The device includes a network traffic engine to receive network traffic including an anomaly. The device includes a univariate policy manager to determine whether the network traffic satisfies at least one of the rules of a univariate policy based on a respective single independent network traffic feature. The device includes a multivariate policy manager to determine, responsive to determining that the network traffic does not satisfy the rules of the univariate policy, that the network satisfies a multivariate policy including a plurality of anomaly explanation tests. The device includes an anomaly explanation selector to select, responsive to determining that the network traffic satisfies the multivariate policy, an anomaly explanation. The device includes a message generator to generate an anomaly explanation output including the selected anomaly explanation.
Owner:CITRIX SYST INC
Malicious Attack Response System and Associated Method
InactiveUS20120023572A1Memory loss protectionError detection/correctionTraffic capacityNetwork software
A system and method for detecting and identifying intruders in a computer network environment by providing a network traffic evaluation and simulation module at the interface between a protected network and external traffic source. The evaluation and simulation module identifies suspected intruders by observing intrusion pattern behavior and then presents a simulated network to the intruder. The simulated network appears to offer the intruder valuable information and provides the intruder with the appearance of success in breaking down the layers of the simulated network to keep the intruder engaged in the intrusion effort while information is gathered to trace and identify the source of the intrusion. Intrusion attempts are identified and categorized in an intrusion analysis module. The network traffic evaluation and simulated network may be provided as a self contained physical module that does not require modification of existing network software.
Owner:Q TRACK CORP
Network user usage profiling
ActiveUS20100162359A1Error preventionFrequency-division multiplex detailsTraffic capacityInformation type
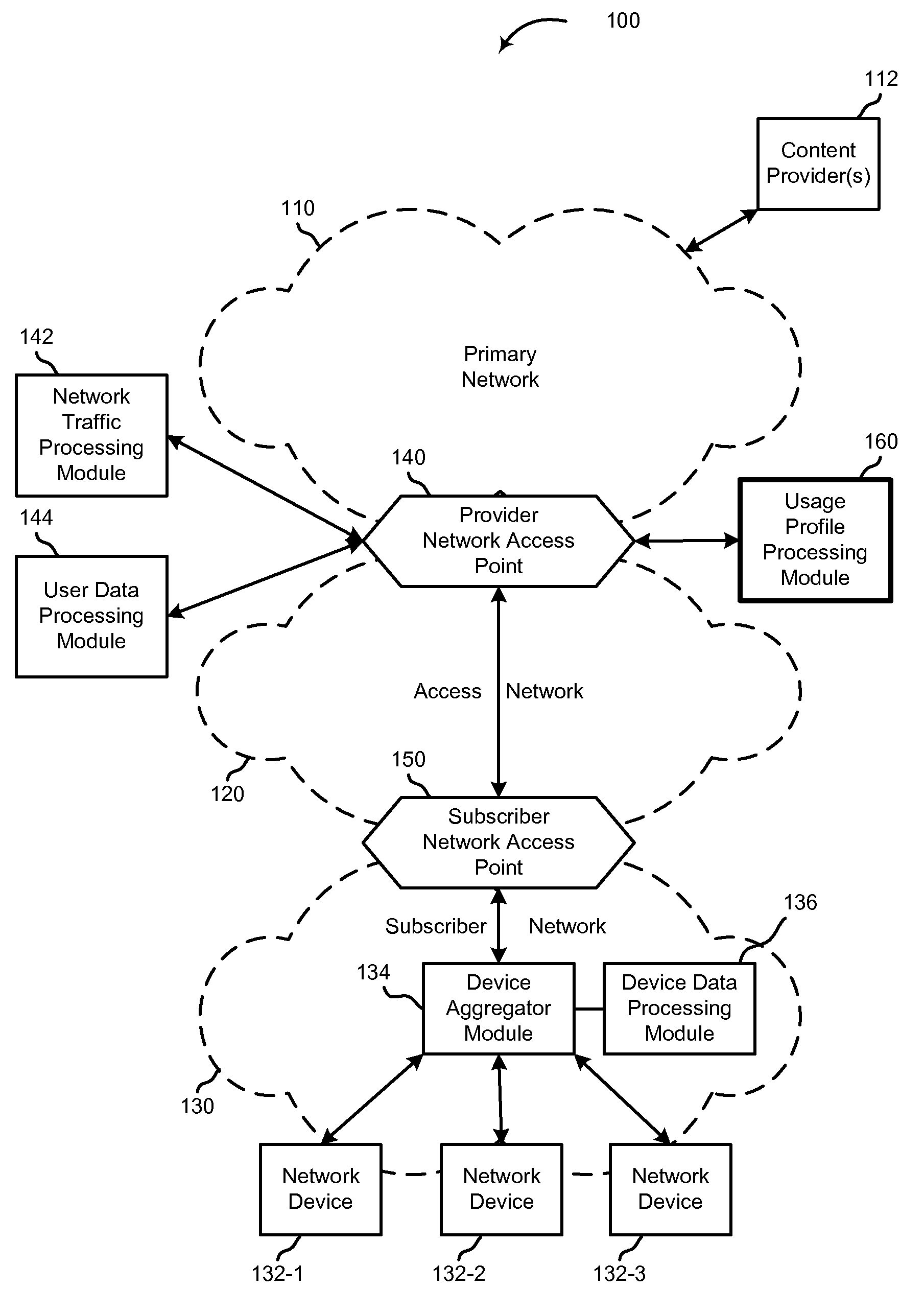
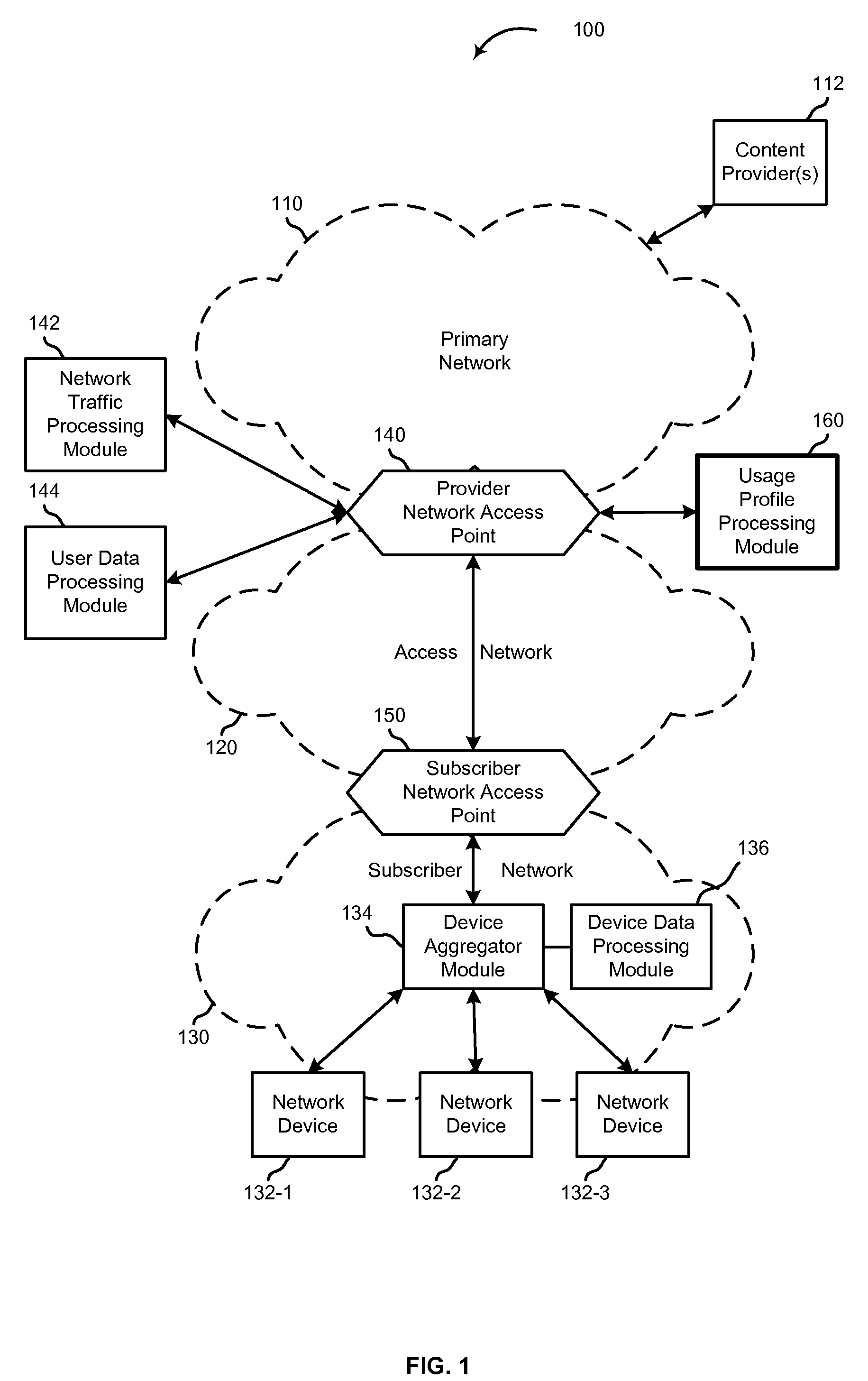
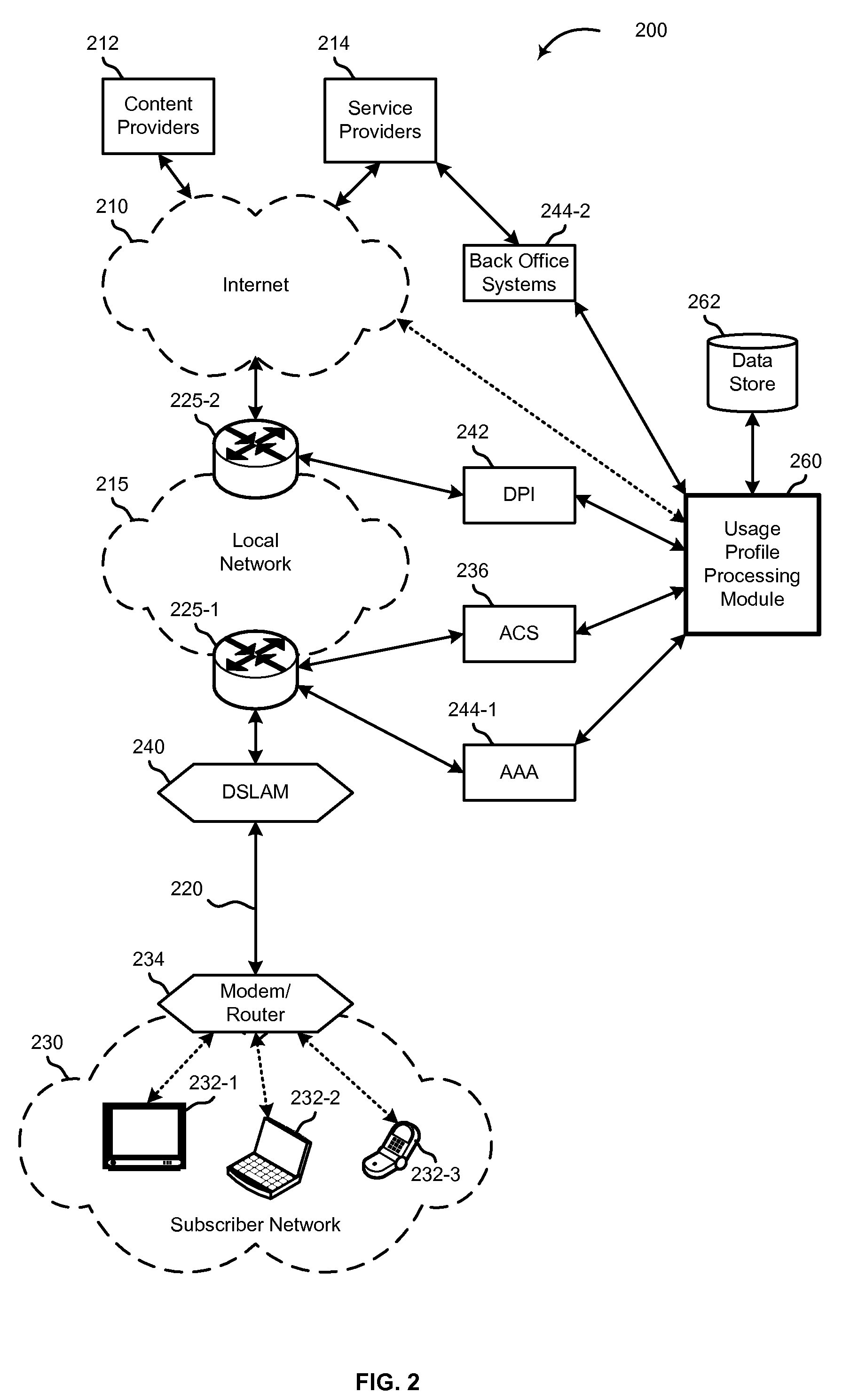
Methods, systems, devices, and software are disclosed for generating a network usage profile. Certain embodiments of the network usage profile include a devices-by-node profile, indicating the set of customer devices available for use in communicating with a customer-side network node located at a customer side of an access network over a period of time, where some of the customer devices are not in operative communication with the customer-side network node during a portion of that time. Other embodiments associate the network usage profile with customer information to generate device-by-customer profiles. Still other embodiments associate the network usage profile with network traffic information to generate traffic-by-device profiles. Even other embodiments associate the multiple sources and types of information to generate traffic-by-customer profiles and / or traffic-by-device-by-customer profiles. Any of the profiles may then be accessed by one or more parties for use in affecting various network services, including targeting content delivery.
Owner:CENTURYLINK INTPROP
Network traffic synchronization and data compression in redundant network topologies
ActiveUS7599283B1Good synchronizationImprove efficiencyError preventionTransmission systemsData compressionFailover
Synchronization of network traffic compression mechanisms deployed in redundant network topologies. In one implementation, the present invention features the synchronization of compression statistics on redundant network devices to facilitate failover and load sharing operations in the management of data flows traversing computer network environments. In one implementation, compression meta data is appended to synchronization packets and transmitted to one or more partner or redundant network devices. The receiving network devices use the compression meta data to synchronize one or more data flow control processes or data structures. Implementations of the present invention also feature process flows that increase the efficiency of synchronizing compression related operations.
Owner:CA TECH INC
Content distribution network load scheduling method and system
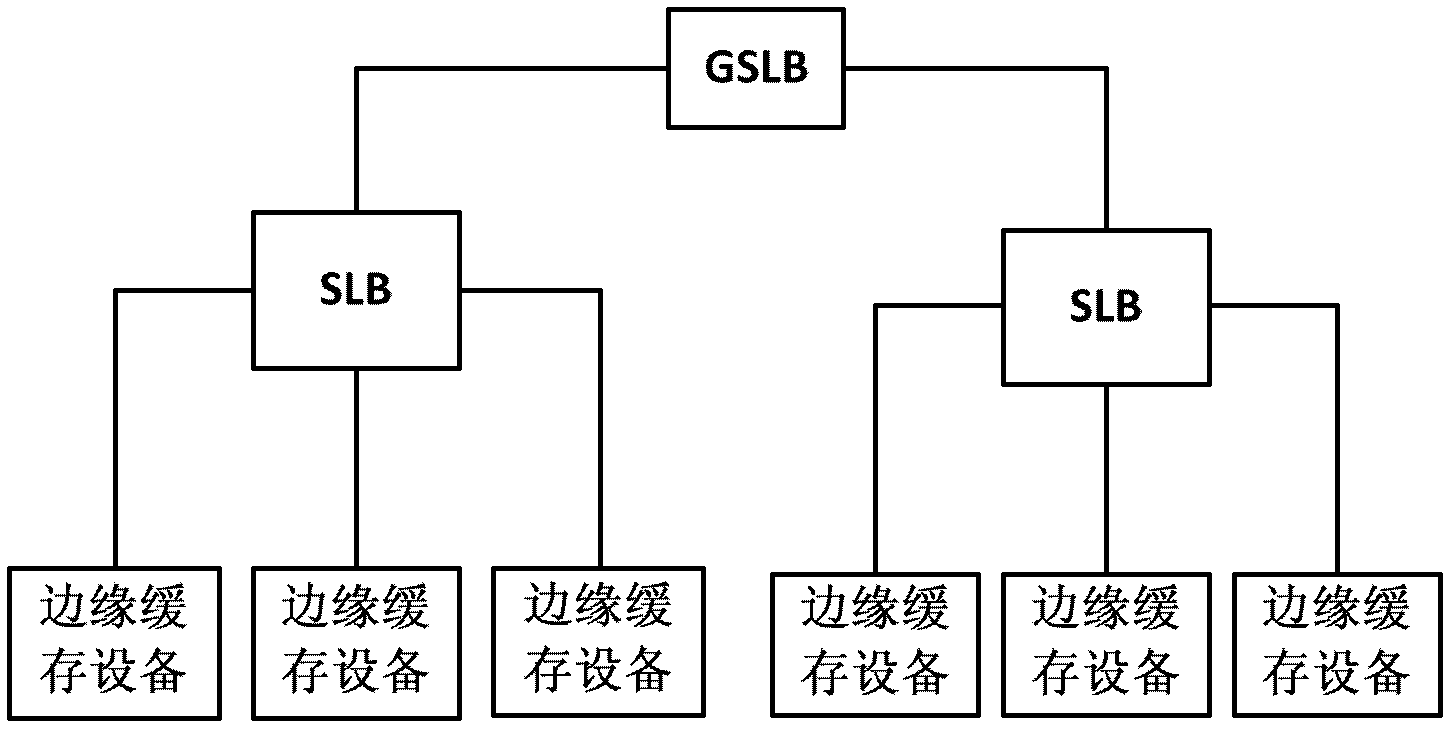
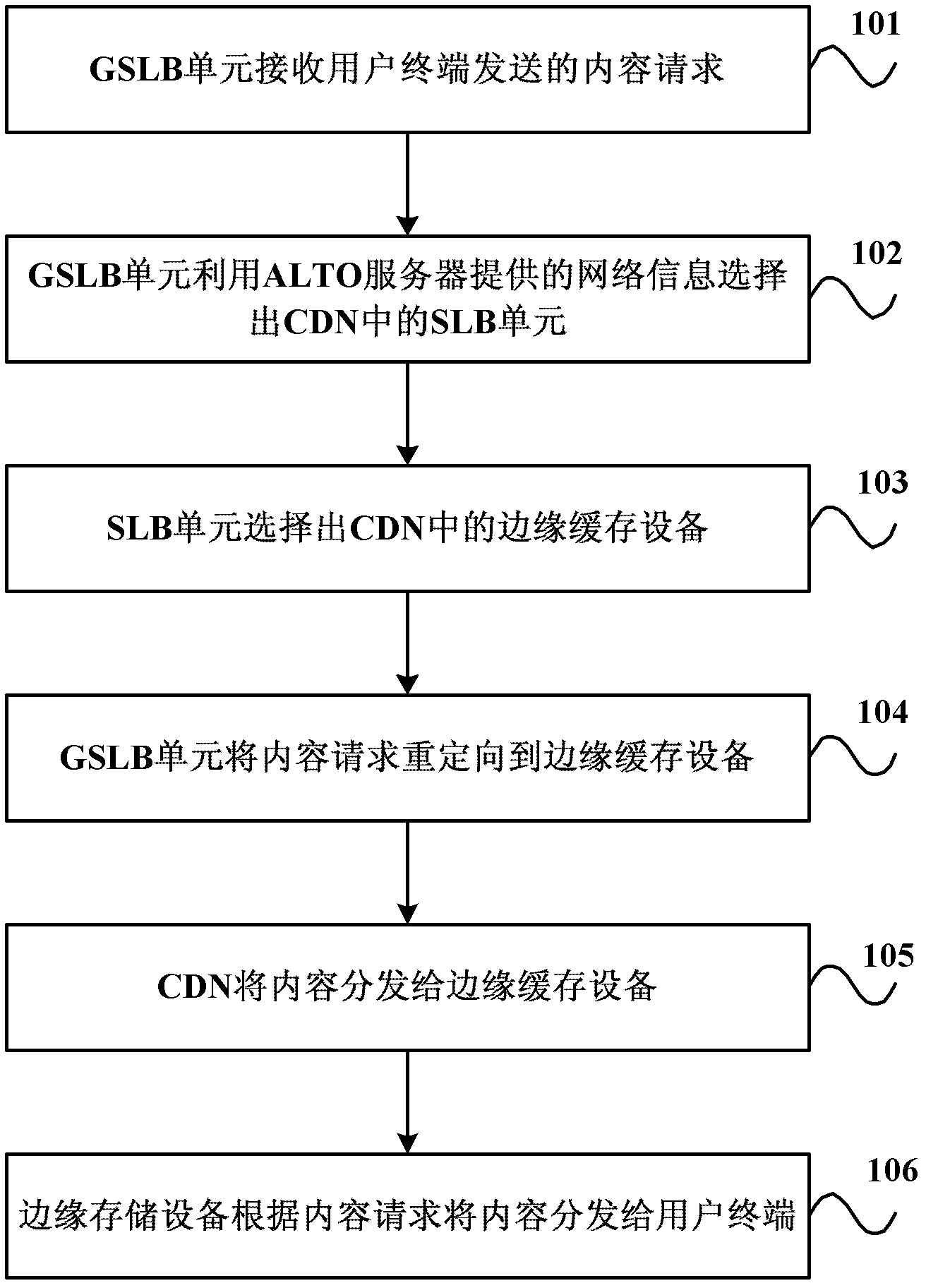
ActiveCN102291447AAccurately reflectGood service nearbyTransmissionContent distributionLoad distribution
The invention discloses a content distribution network load scheduling method and system. Among them, in the content distribution network load scheduling method, the content distribution network receives the content request sent by the user terminal; the global load balancing unit uses the network information provided by the application layer traffic optimization server to select the local load balancing unit according to the first selection strategy; the local load balancing unit The unit selects an edge cache device according to the second selection strategy; the content distribution network redirects the content request to the edge cache device, and distributes the content to the edge cache device; the edge cache device selects the edge cache device according to the content request The content is distributed to user terminals. Since the network information provided by the application-layer traffic optimization server more accurately reflects information such as network topology and network traffic, the global load balancing unit can direct user requests to the nearest node or area, which facilitates the content distribution network to better provide users with Nearby service.
Owner:CHINA TELECOM CORP LTD
Smart data dissemination
ActiveUS20070239862A1Easily configurableEasily modifiableNetwork topologiesMultiple digital computer combinationsQuality of serviceWireless mesh network
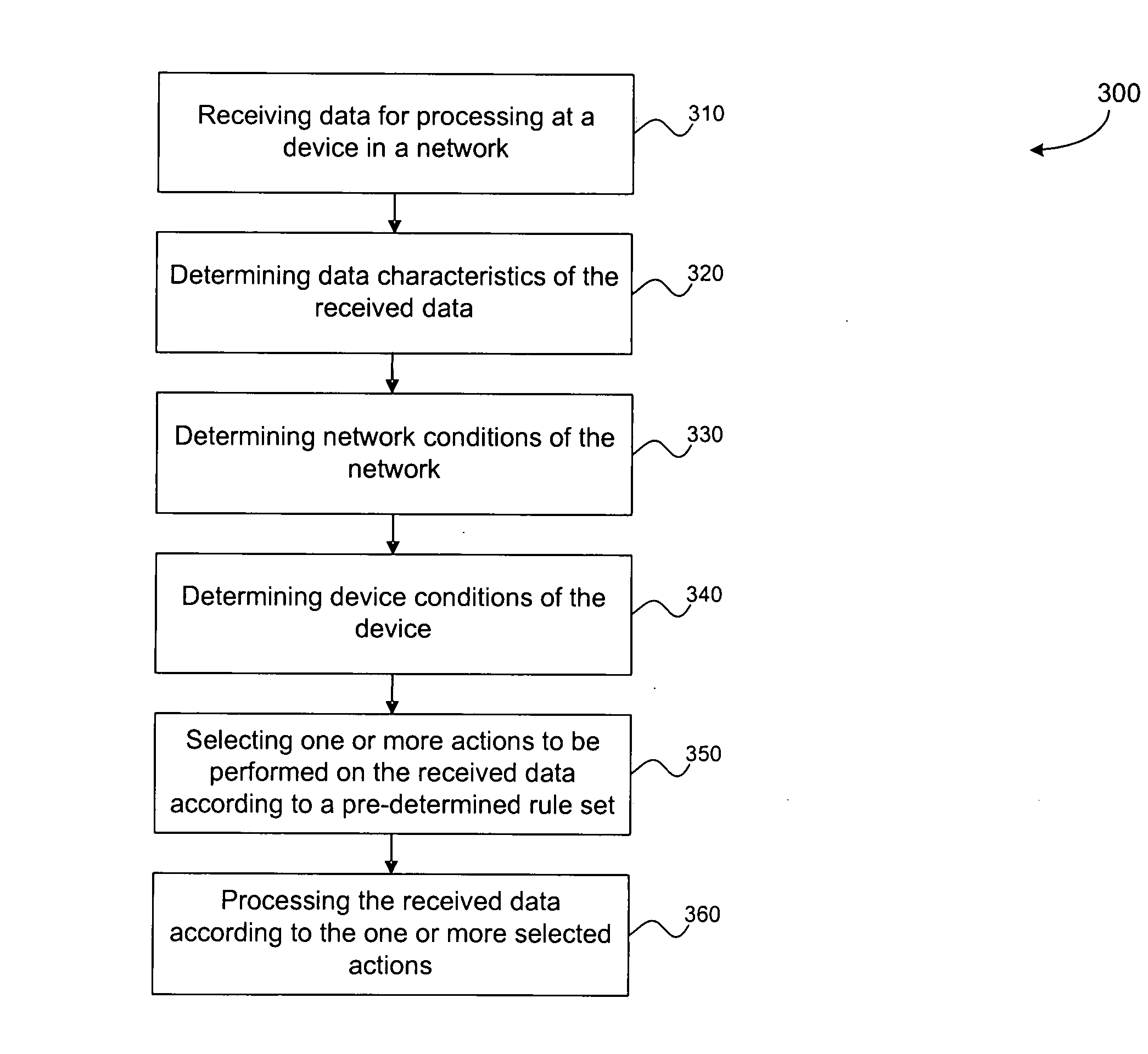
Methods and systems for smart data processing and dissemination in wireless sensor networks are provided herein. In one aspect, the present invention provides dynamic and independent data processing and dissemination at individual sensor nodes in a wireless sensor network. In another aspect, the present invention provides data processing and / or dissemination methods at a sensor node that are responsive to, among other parameters, network traffic conditions, network connectivity conditions, conditions at the sensor node, and the data characteristics and QOS (Quality of Service) requirements of the data being processed and / or disseminated. In yet another aspect, data processing and / or dissemination rules according to the present invention are easily configurable and modifiable depending on the specific sensor networking application.
Owner:MITRE SPORTS INT LTD
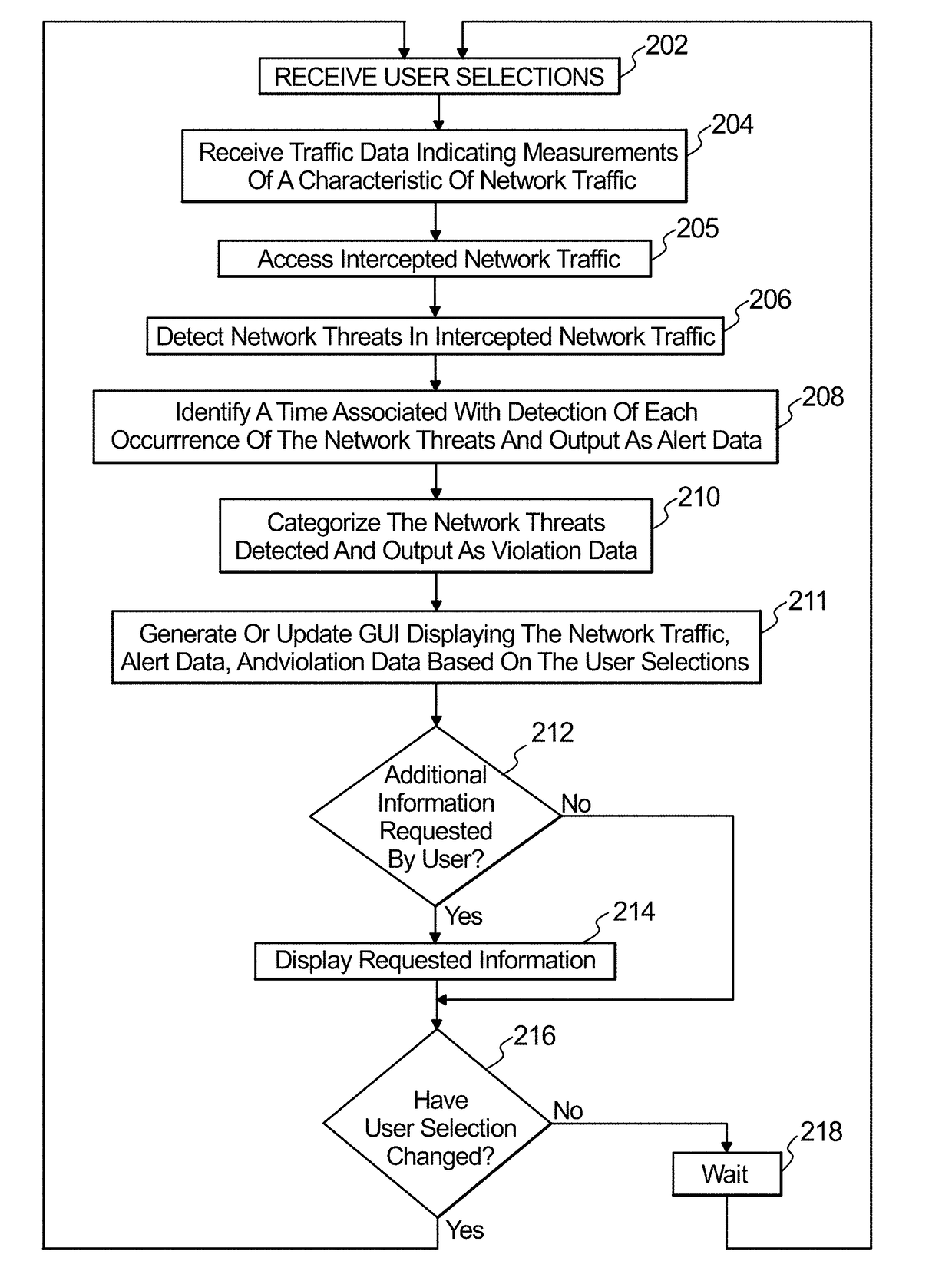
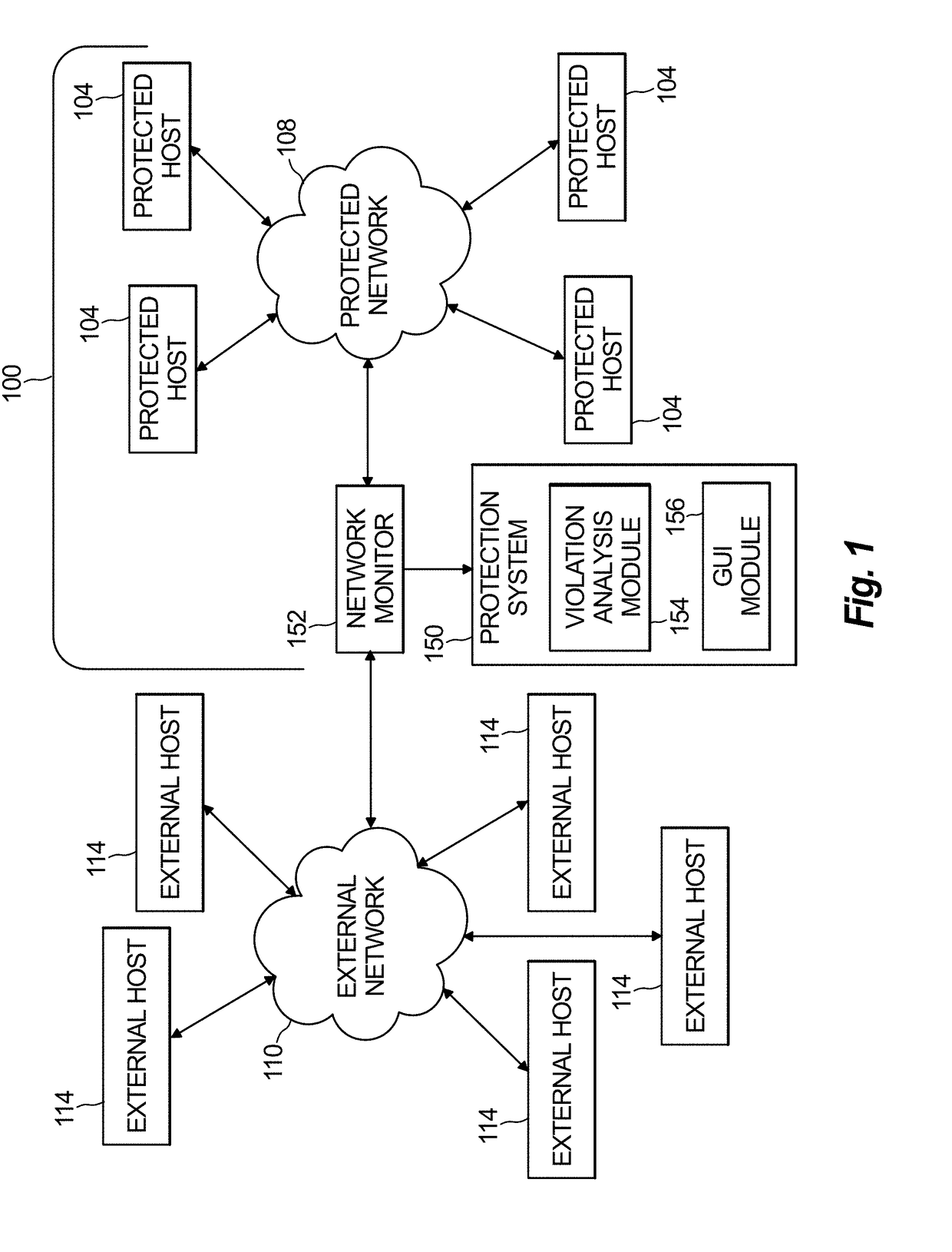
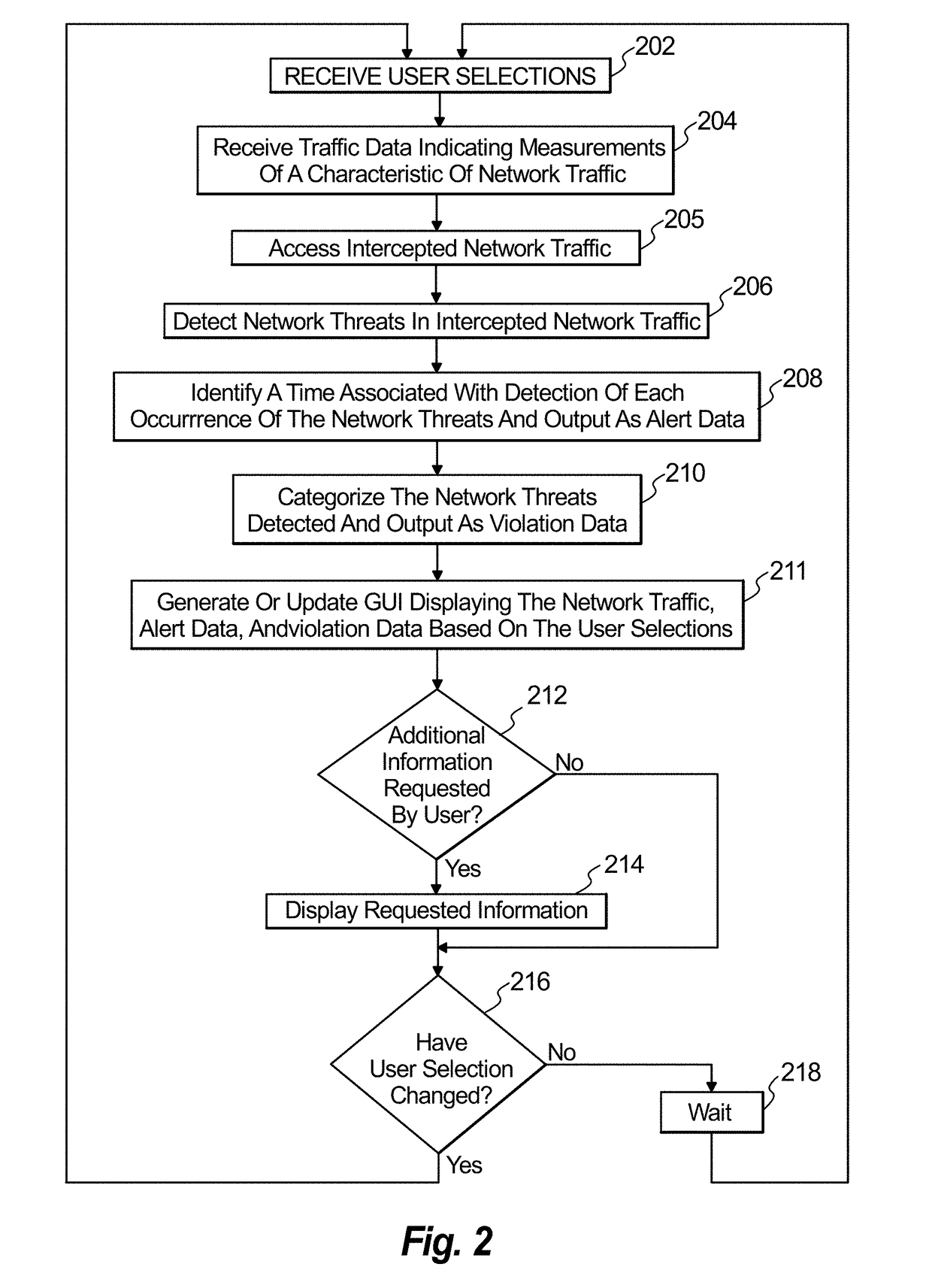
Visualization of network threat monitoring
A method to monitor a network is provided, including receiving traffic metric data indicating measurements related to a characteristic of network traffic flowing in the network and identifying network threats in intercepted traffic of the network traffic. The method further includes identifying a time associated with detection of each occurrence of the network threats and generating a graphical user interface having a GUI that includes a display of a time series graph that corresponds to a selected time period. The display includes a network traffic plot and an alert plot adjacent to the network traffic plot. The network traffic plot indicates a characteristic of network traffic relative to a timeline displayed along a first axis. The alert plot includes alert indicators, wherein each alert indicator is associated with detection of a network threat and aligned relative to the timeline based on the time identified for each occurrence of the detected network threats.
Owner:ARBOR NETWORKS
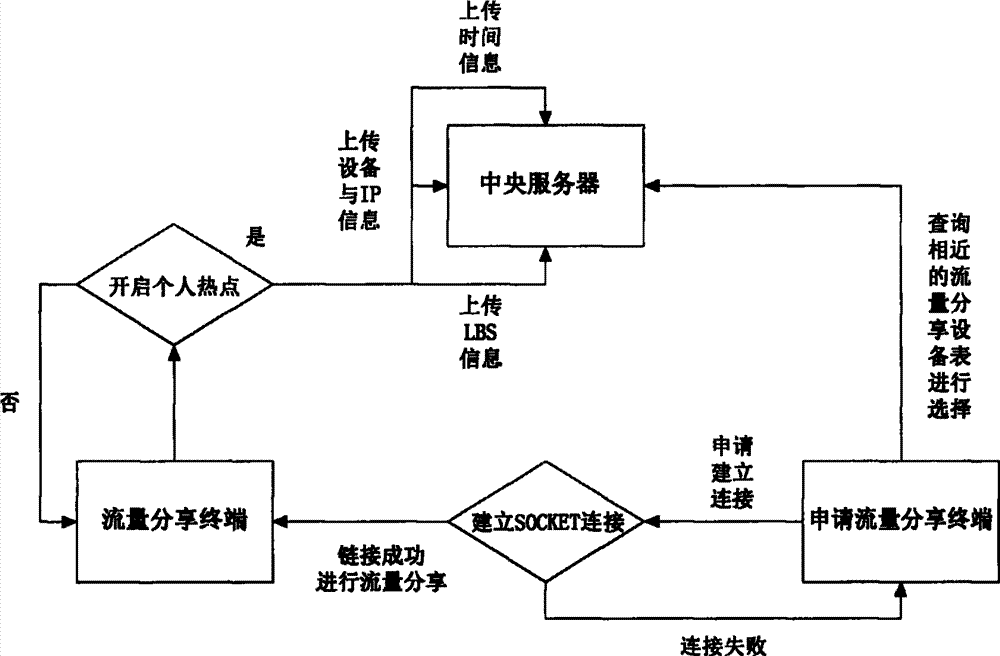
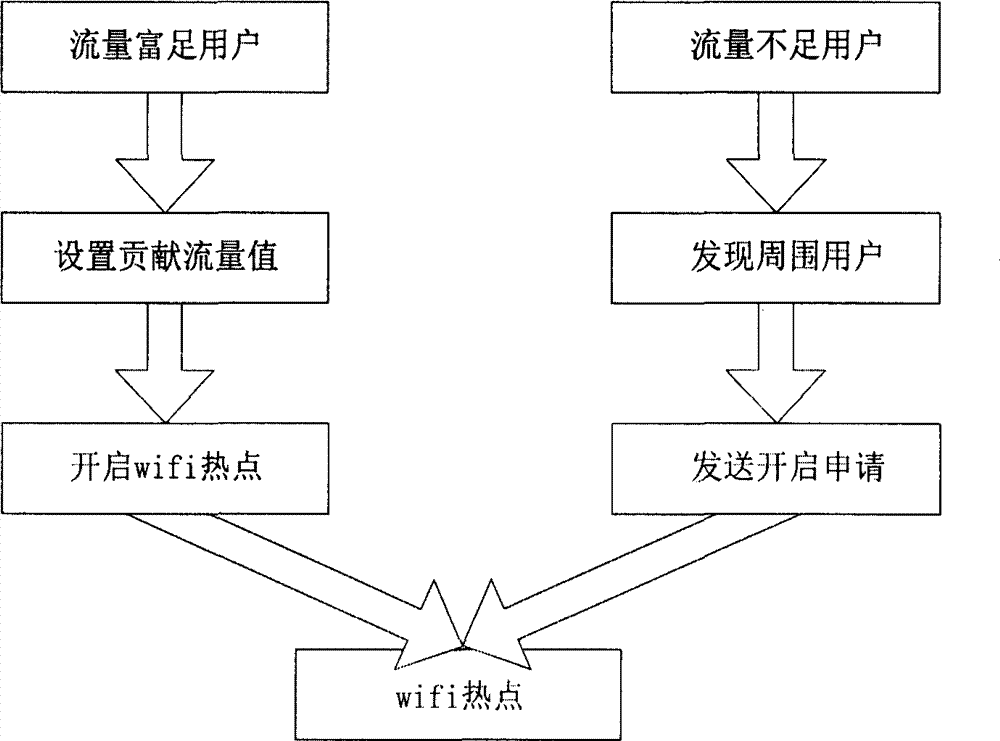
Mobile phone traffic sharing method
The invention relates to a mobile phone traffic sharing method. Users with residual 3G (the 3rd generation telecommunication) traffic are linked with users with insufficient 3G traffic through wireless hotspots to achieve mobile phone traffic sharing, and the linked users can chat and the like. The method includes the steps of S1, by a mobile terminal, accessing to a GPRS (general packet radio service) network; S2, starting a personal hotspot of the mobile terminal; S3, building a SOCKET connection; and S4, starting network traffic sharing, surfing on the Internet or chatting on the building SOCKET connection and the like.
Owner:南京安讯科技有限责任公司
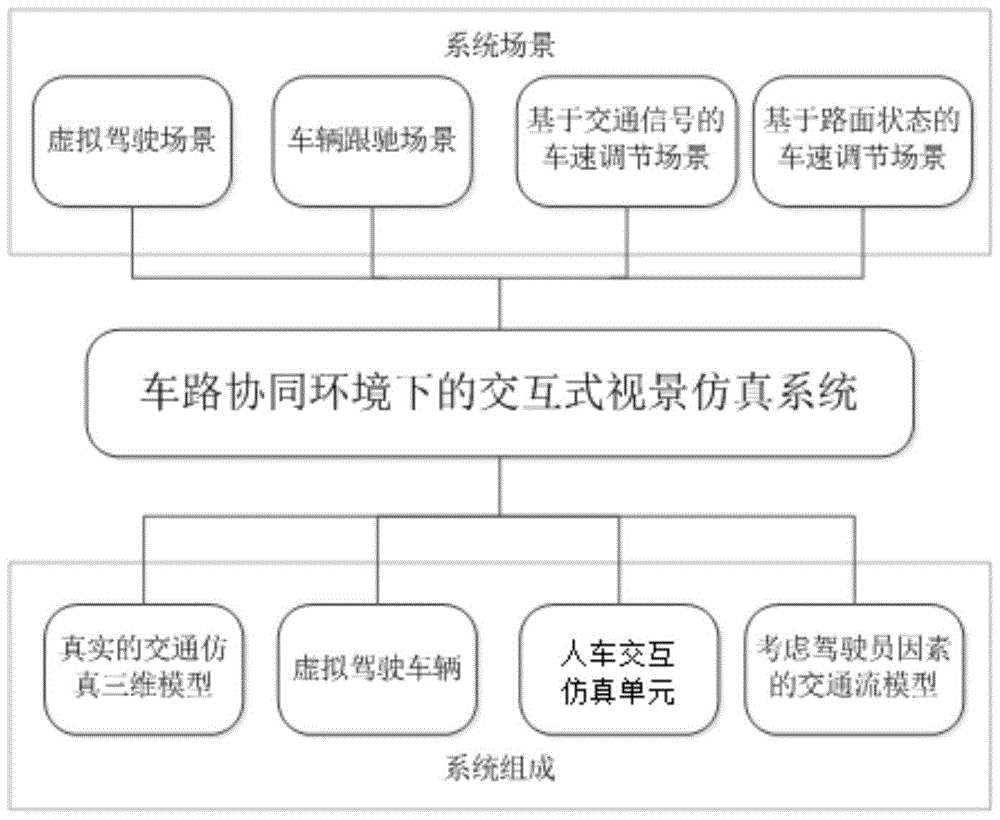
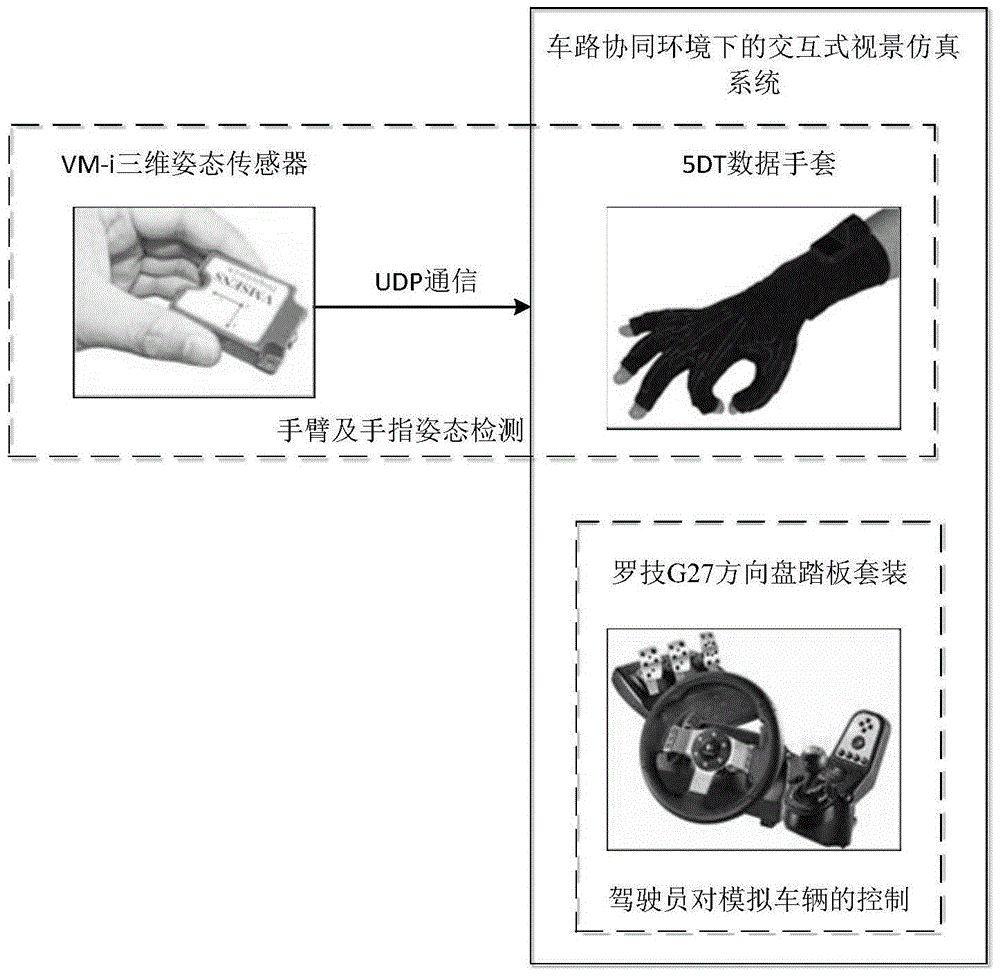
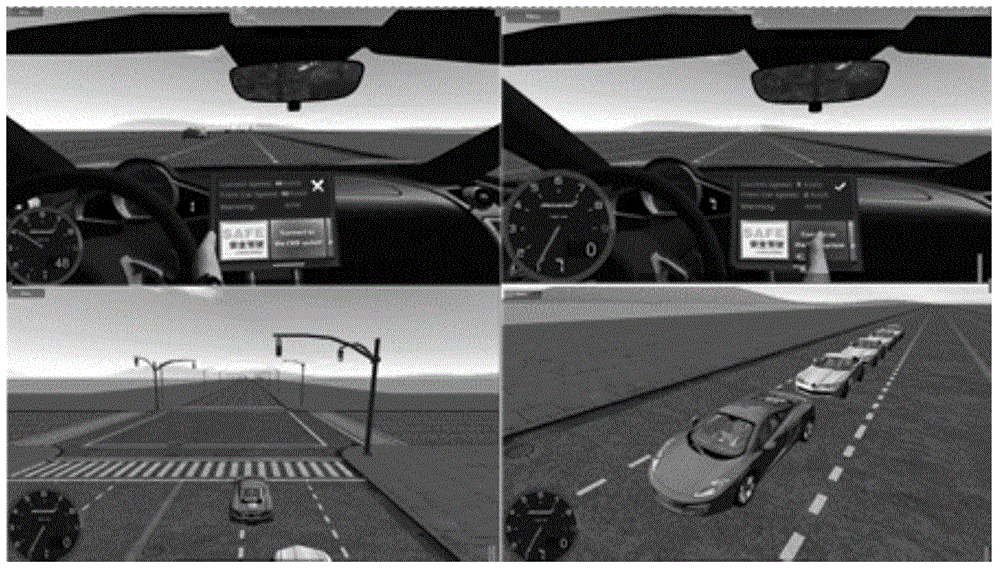
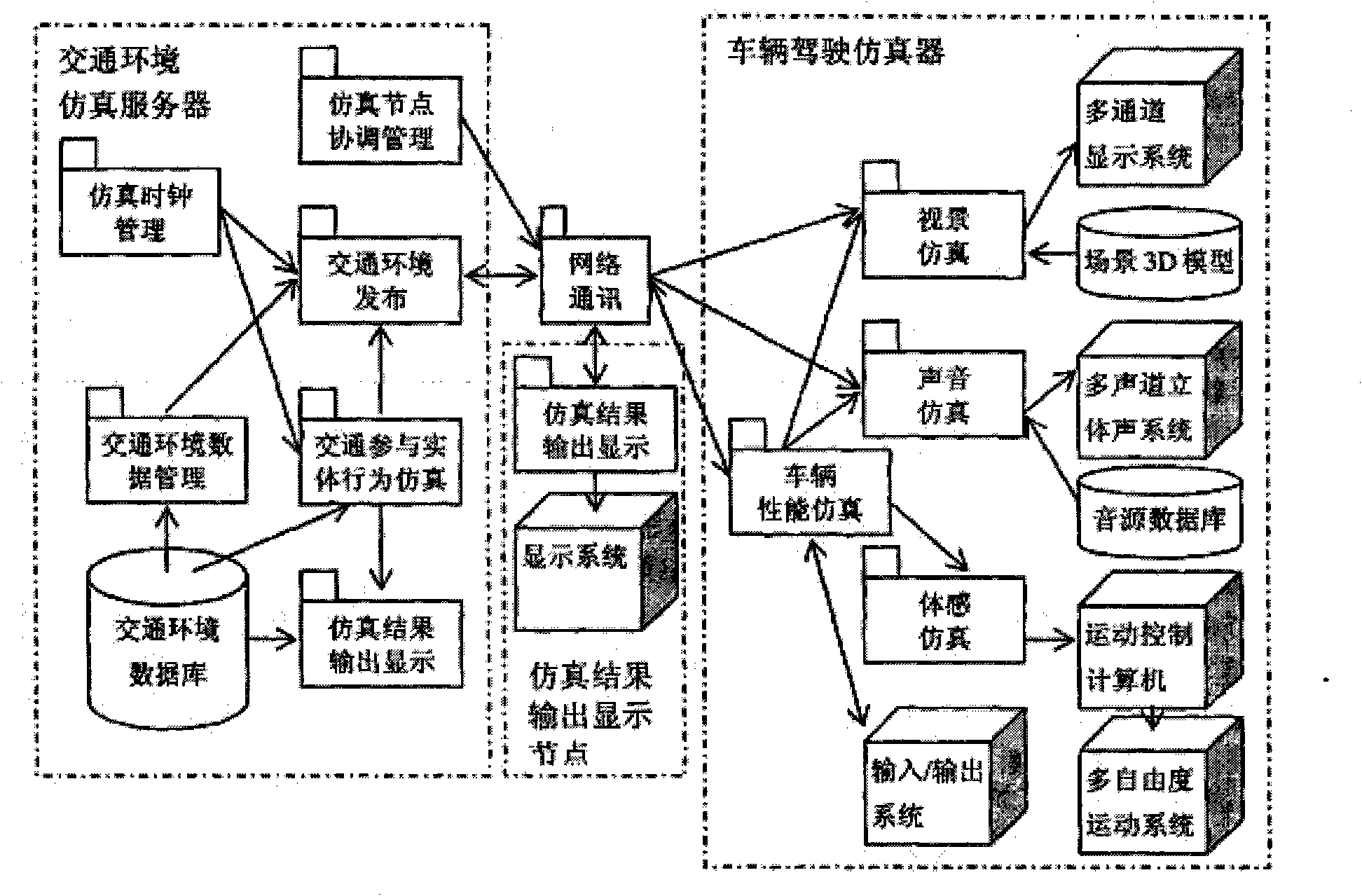
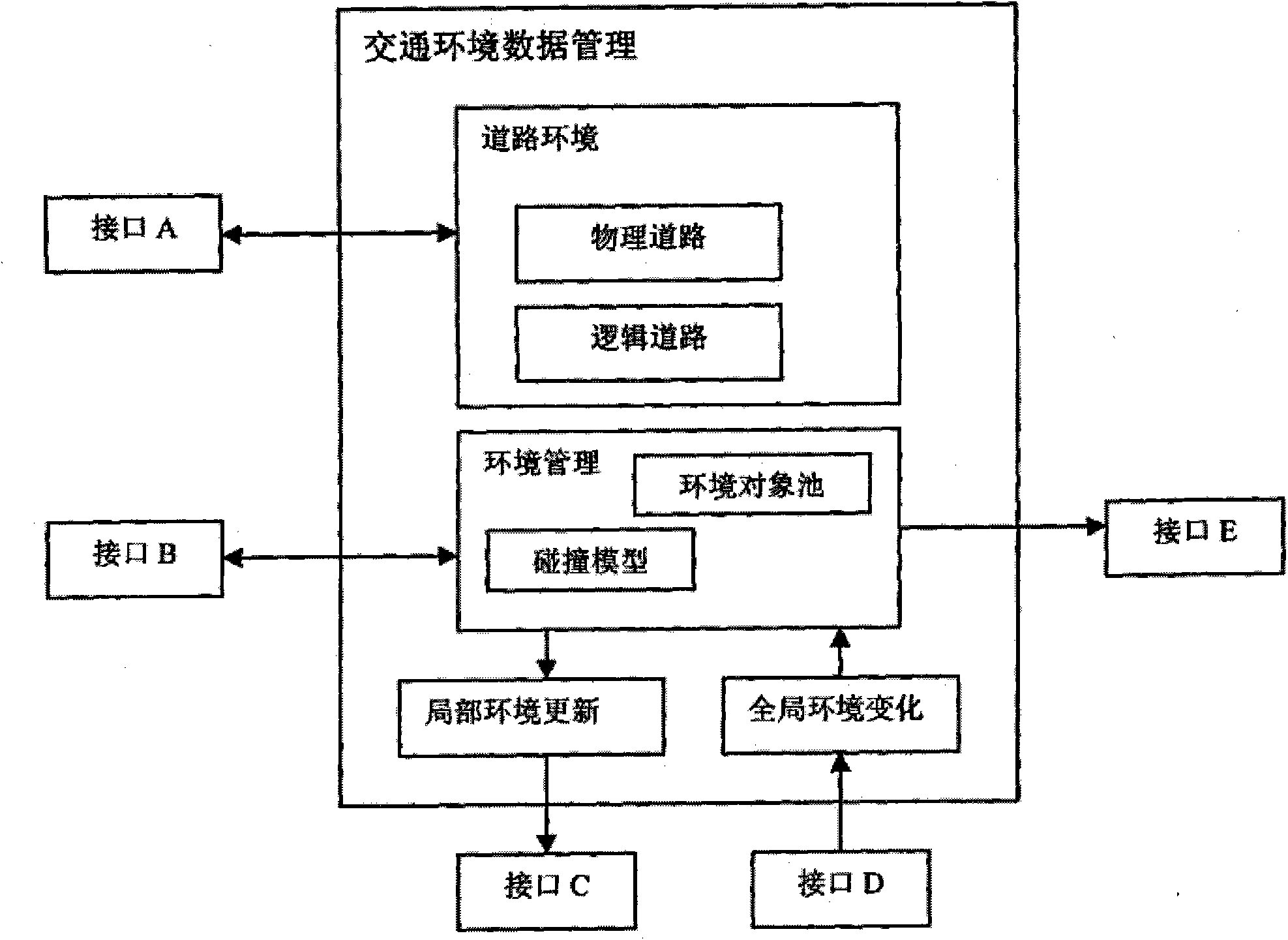
Interactive type visual simulation system under vehicle road collaborative environments
ActiveCN105718065AImprove realismImprove immersionInput/output for user-computer interactionGraph readingThree dimensional simulationDriver/operator
An embodiment of the invention provides an interactive type visual simulation system under the vehicle road collaborative environments.The system comprises a real traffic simulation three-dimensional model, a virtual driving vehicle, a driver-vehicle interactive simulation unit and a traffic flow model, and the traffic flow model considers driver factors and combines a vehicle starting and stop module.The system is based on the three-dimensional simulation environments, an interactive type dynamic mapping model corresponding to the virtual vehicle, different typical scene simulation and the like, the traffic flow model considering the driver behavior is designed, the behavior and the effect of a cooperative vehicle infrastructure system can be displayed to a user from multiple angles, at the same time, the acceptance degree of the driver on vehicle road collaboration certain functions and the design rationality of certain functions are analyzed, and a virtual driving environment with sense of reality and sense of immersion can be provided for the driver.
Owner:BEIJING JIAOTONG UNIV
Cellular automaton model based urban road network traffic flow simulation design method
ActiveCN104298829AIncrease authenticityPracticalSpecial data processing applicationsCellular automationSimulation
The invention provides a cellular automaton model based urban road network traffic flow simulation design method. The cellular automaton model based urban road network traffic flow simulation design method comprises the following steps of 1 establishing an urban road network consisting of a plurality of bidirectional two-lane roads; 2 establishing an on-lane vehicle update rule; 3 establishing a vehicle update rule at intersection positions and establishing a deadlock avoiding rube, wherein vehicles on the cells in the intersections and cells on the peripheries of the intersections follow different update rules; 4 distributing N vehicles in the urban road network to perform a simulation experiment, wherein the vehicles rung by following the rule in the step 2 and the rule in the step 3; 5 acquiring outgoing data of the vehicles in the step 4 and performing calculation and analysis so as to evaluate the characteristic of traffic flows of the urban road network. By means of the cellular automaton model based urban road network traffic flow simulation design method, the running states of complicated traffic flows of the bidirectional two-lane roads and the intersections can be really reflected, and the truthfulness of traffic simulation can be improved.
Owner:ZHEJIANG NORMAL UNIVERSITY
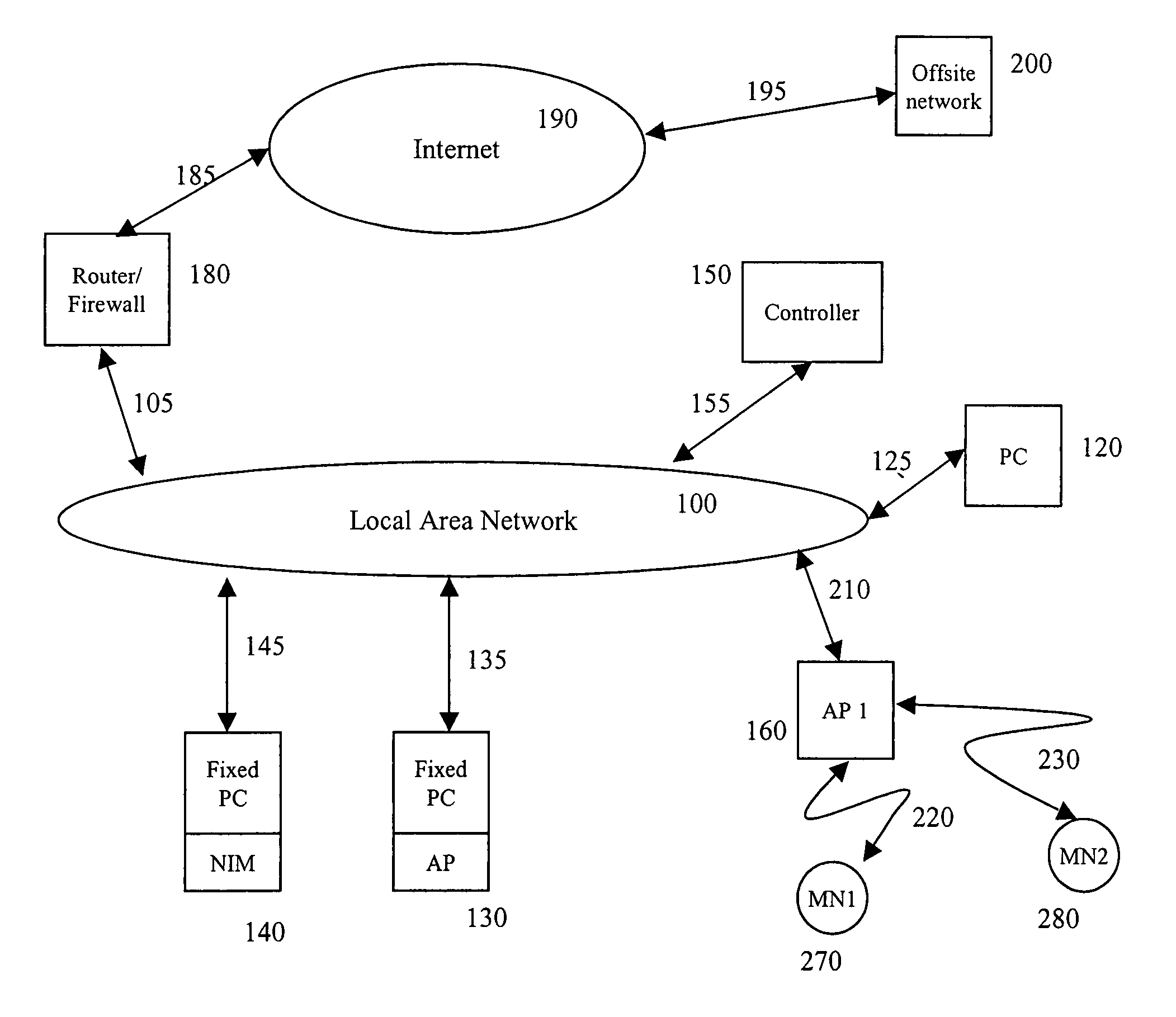
Wireless network having control plane segregation
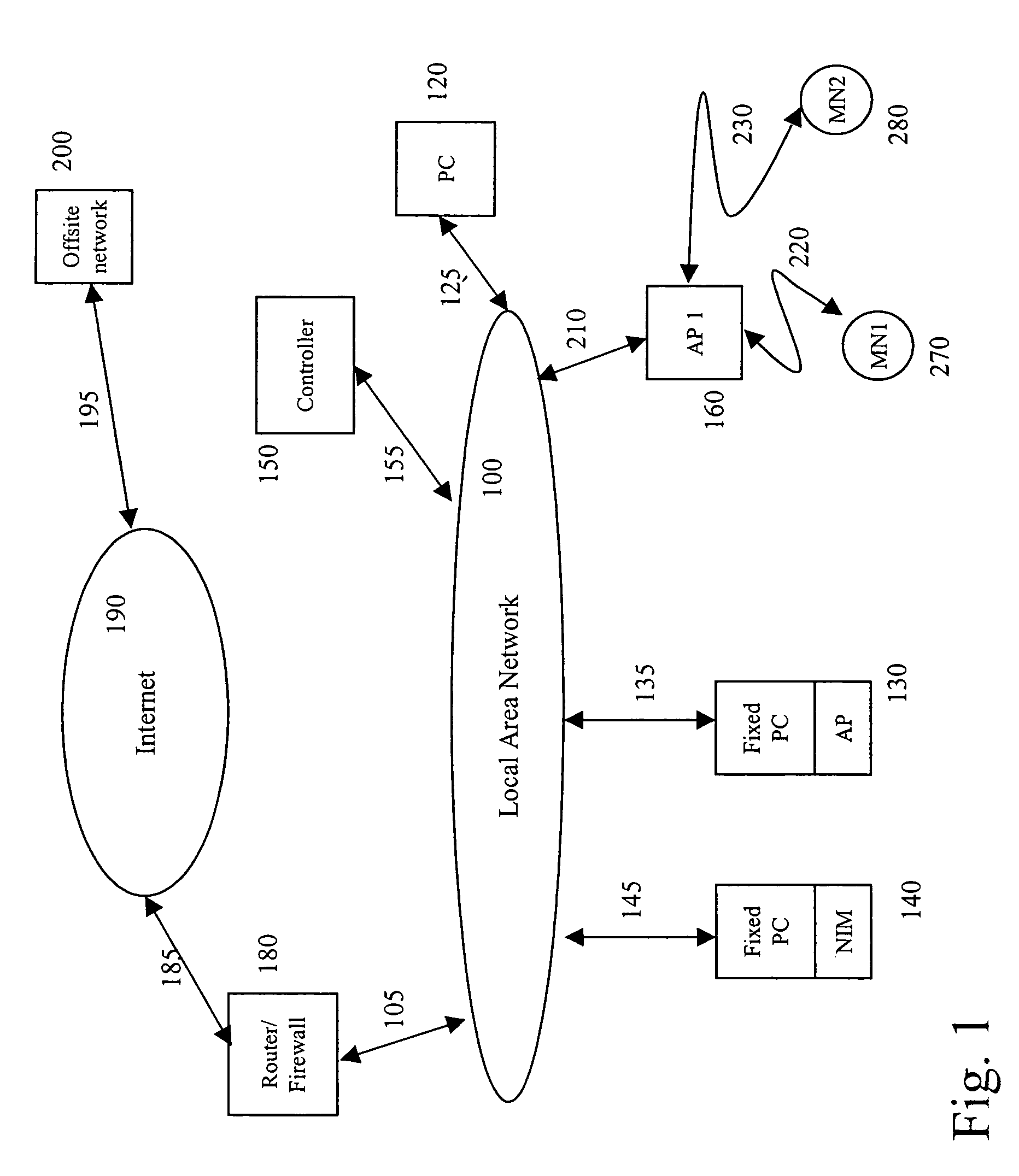
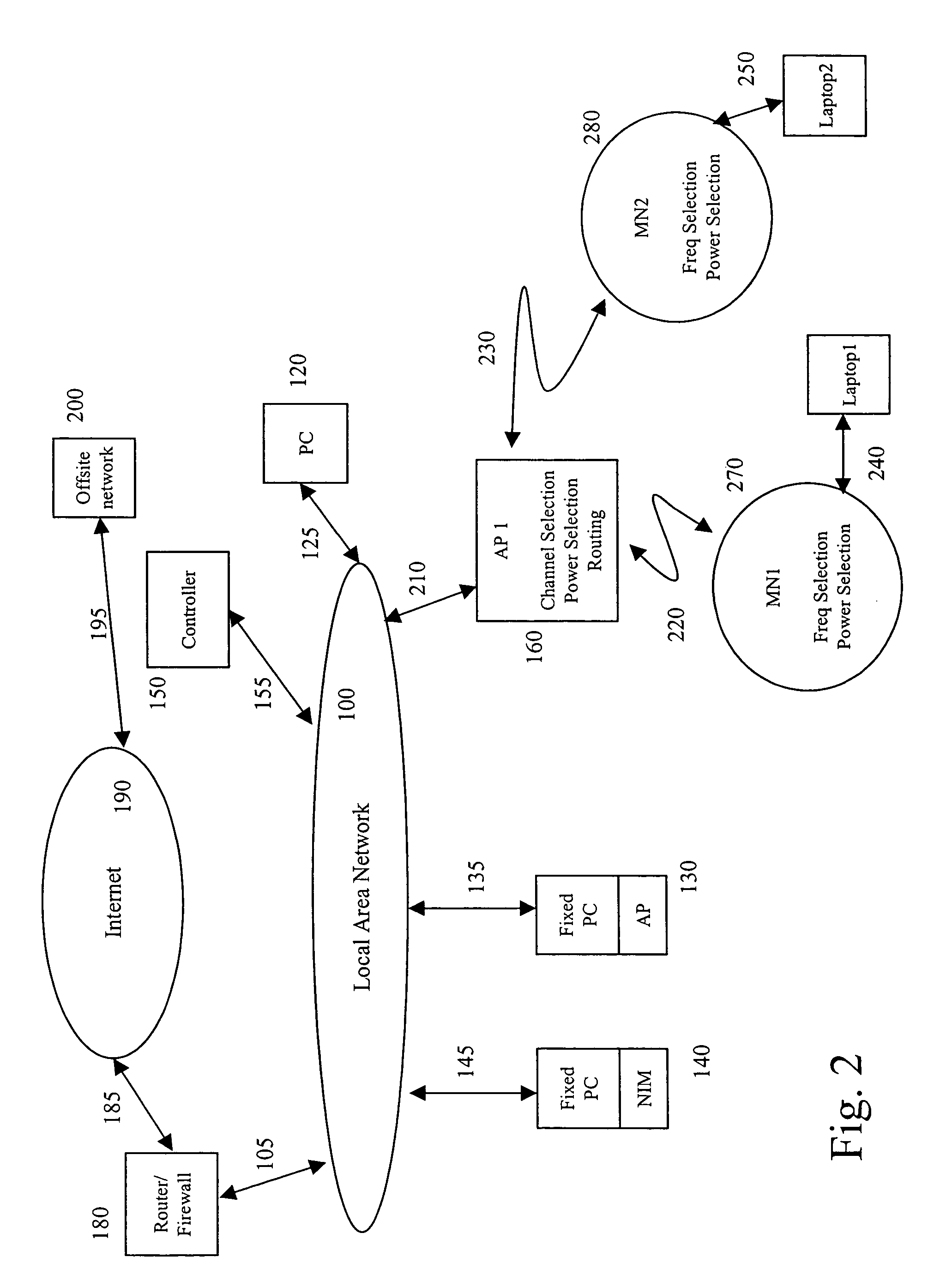
A wireless network having control plane segregation is described herein. In one embodiment, an exemplary network architecture includes, but is not limited to, multiple access points coupled to a wired network, where each of the access points is capable of communicating with one or more mobile nodes over a wireless network. The exemplary network architecture further includes a controller coupled to the access points over the wired network, where the controller maintains network traffic information of the wireless network and communicates the network traffic information with the access points to enable the access points to cooperate with each other to provide network services to the one or more mobile nodes over the wireless network. Other methods and apparatuses are also described.
Owner:GIDWANI SANJAY M
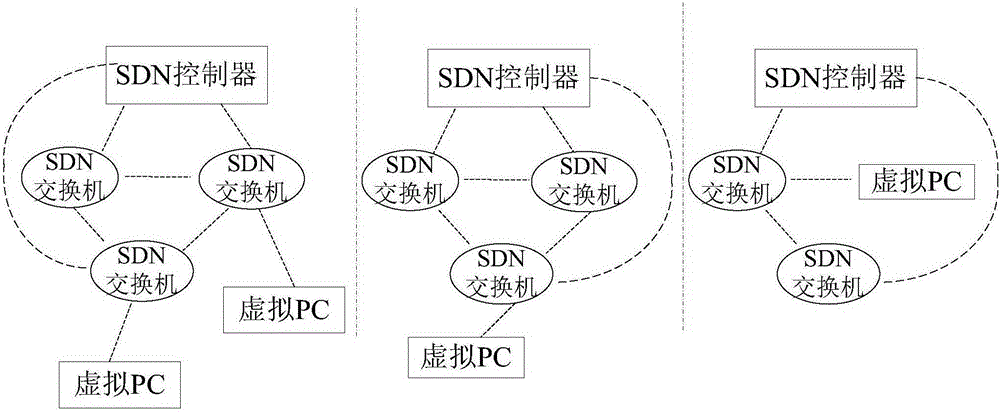
OpenStack based software defined network simulation system and method
ActiveCN105227344AIncreased setup flexibilityConvenience needsData switching networksSoftware simulation/interpretation/emulationStructure of Management InformationSoftware engineering
Owner:FENGHUO COMM SCI & TECH CO LTD
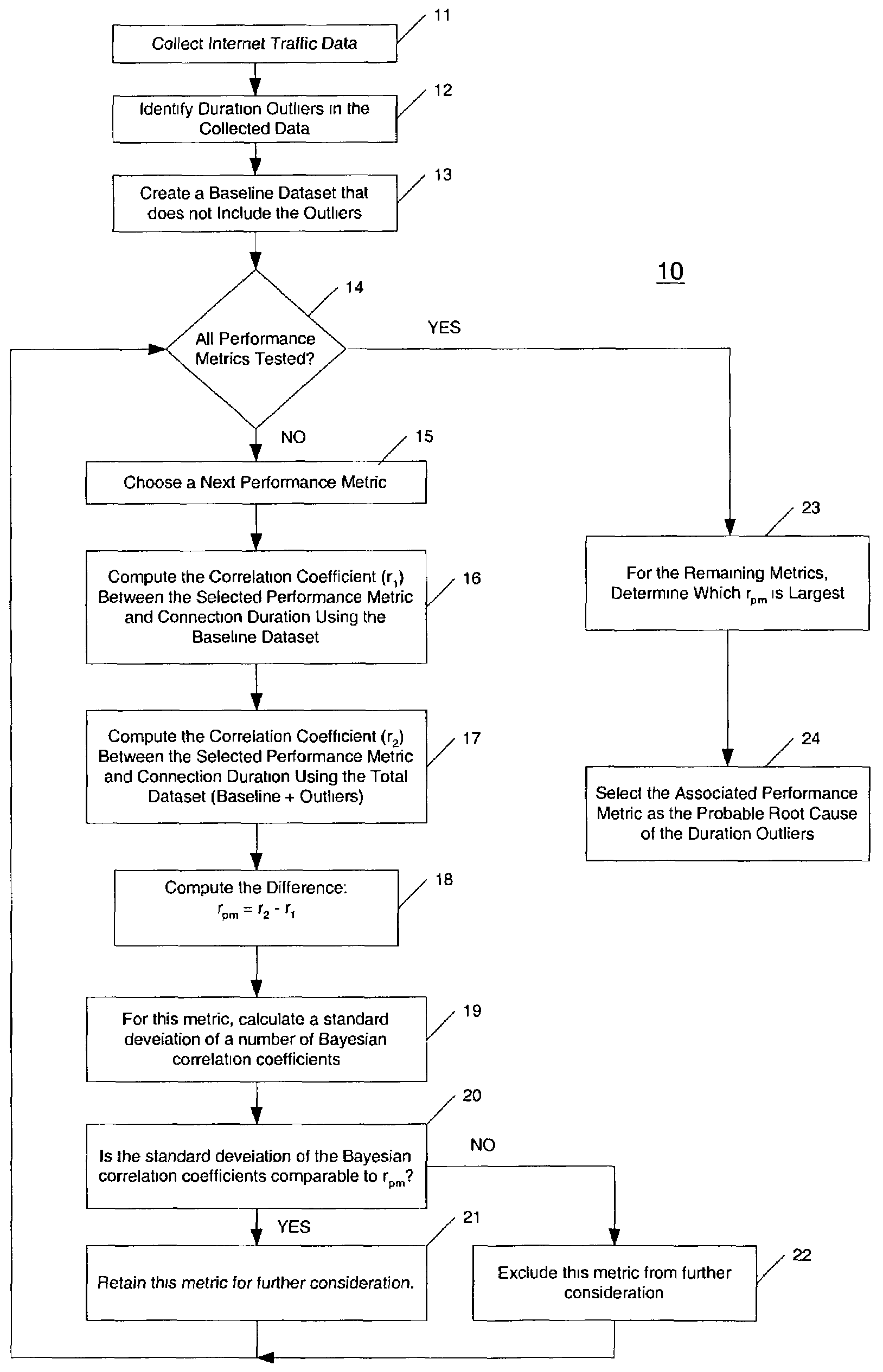
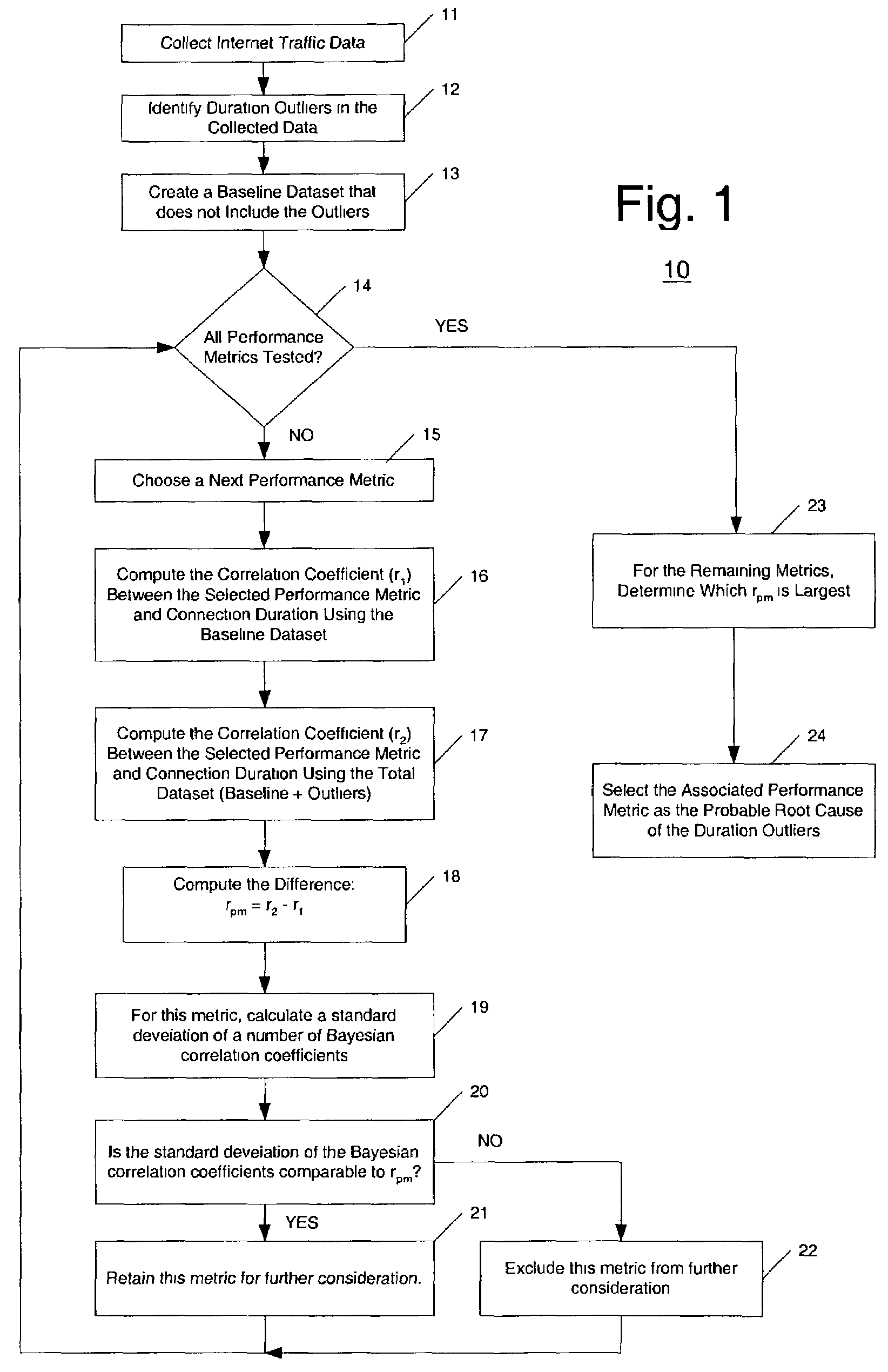
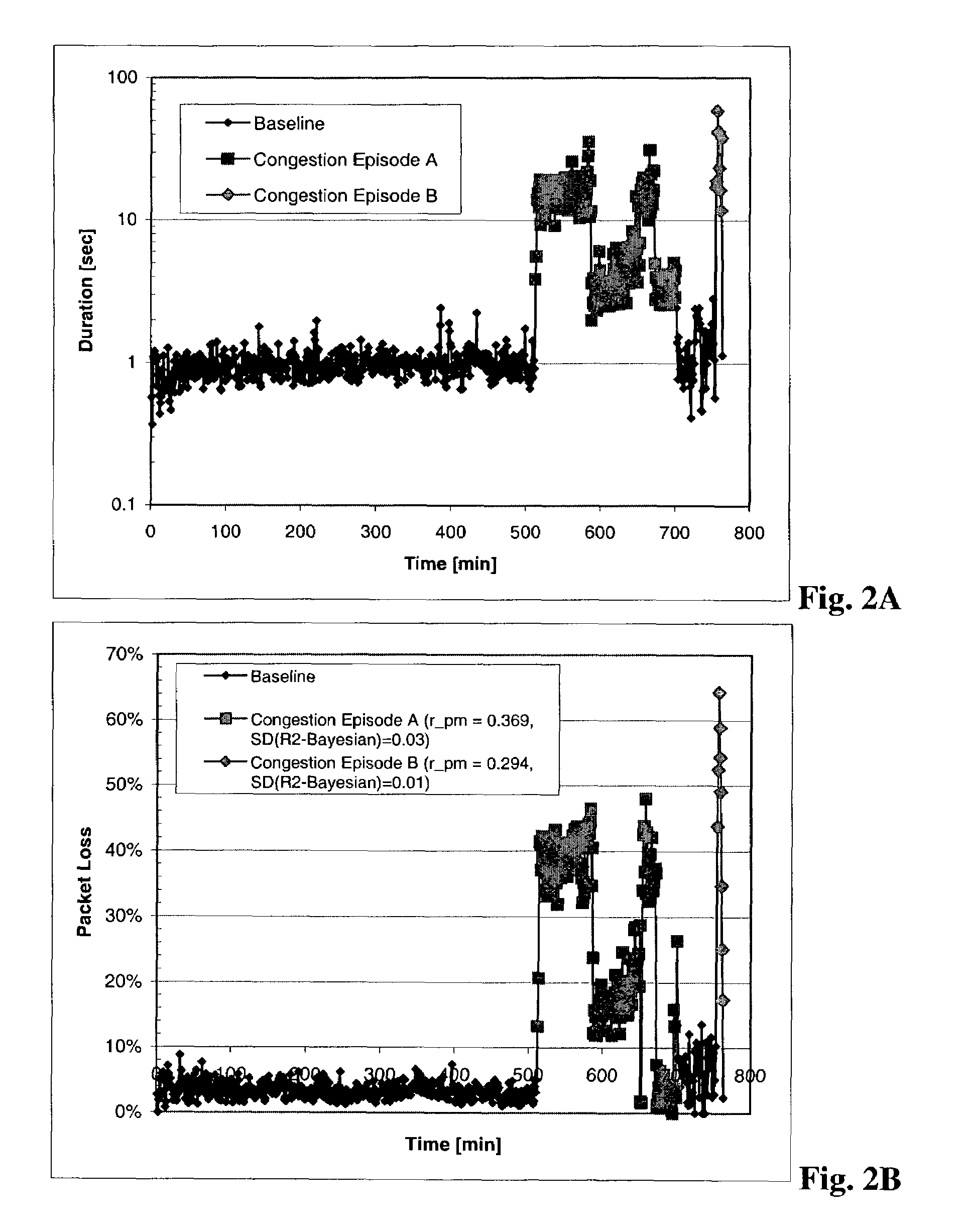
Bayesian approach to correlating network traffic congestion to performance metrics
For each of a number of network performance metrics, an associated value rpm that represents a difference between a first correlation coefficient r1 computed for a baseline data set and a second correlation coefficient r2 computed for a second data set that includes the baseline data set and other data points classified as duration outliers is computed. The first and second correlation coefficients for each network performance metric represent correlation between that network performance metric and durations of network connections. The network performance metric that has a largest associated rpm value of all statistically significant rpm values computed is selected as representing the probable root cause of the duration outliers. Statistical significance is measured through comparison of an rpm value with a statistical property of a set of Bayesian correlation coefficients computed for each performance metric.
Owner:RIVERBED TECH LLC
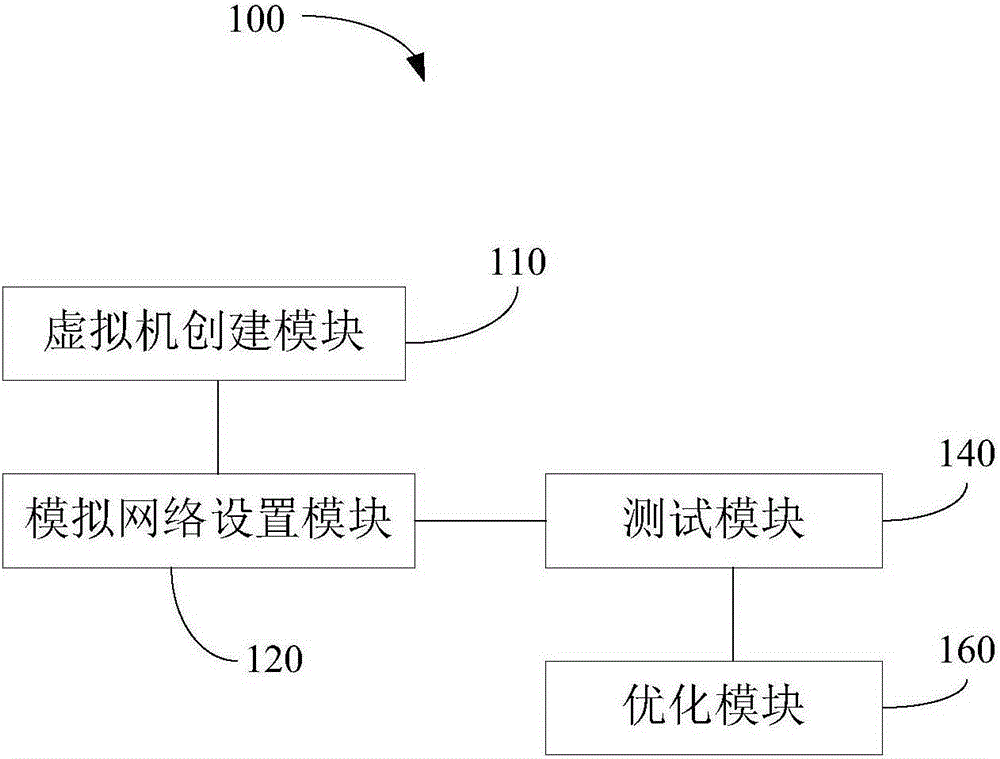
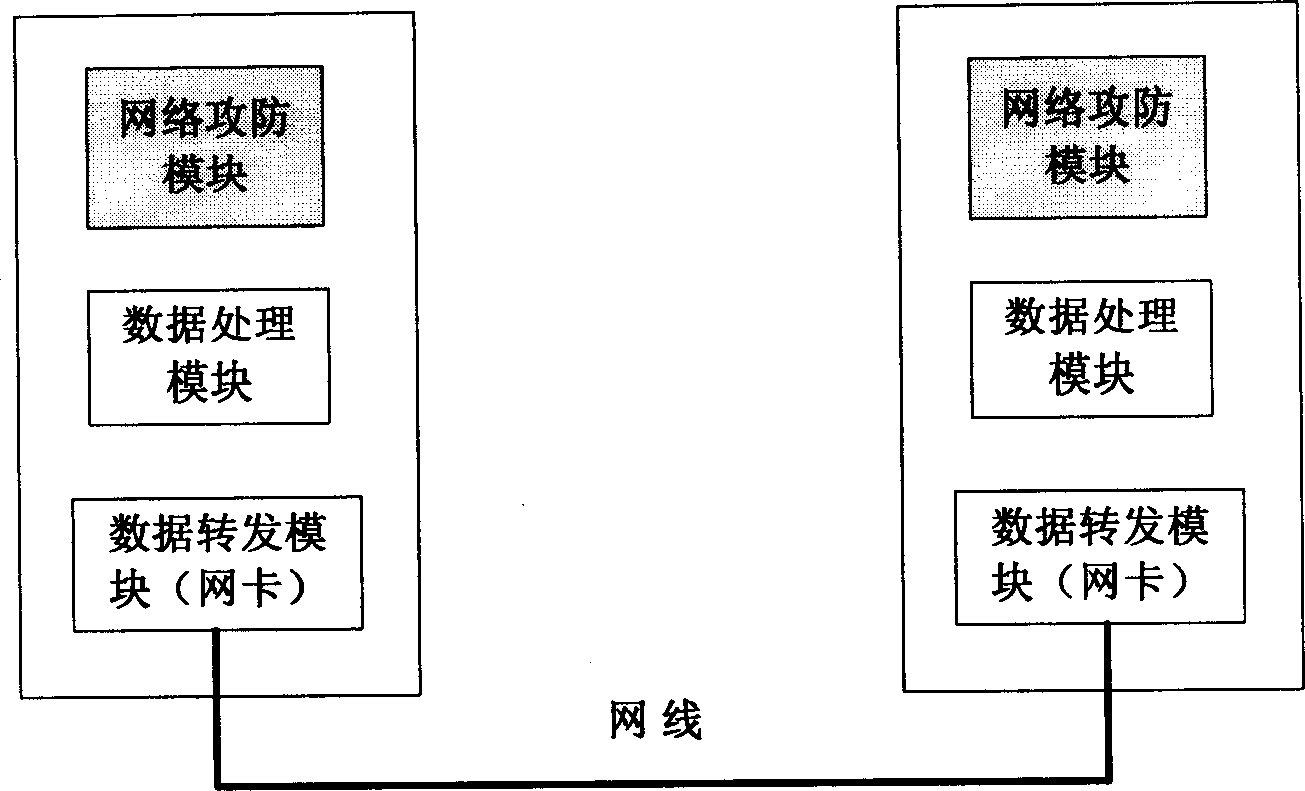
Hardware based network simulation system and method
The invention discloses a hardware based network simulation system. The system comprises a network simulation unit and multiple simulation nodes, wherein the network simulation unit adjusts the topological graph of the simulation nodes in a simulation network according to users, and configures characteristic parameters of a simulation link connected to the simulation nodes; and based on the adjusted network topological graph and the configured link characteristic parameters, the simulation nodes implements simulated experiments on the network protocols or server program via the simulation link. The invention further discloses a simulation method based on the network simulation system. Compared with a traditional network experiment platform, a network simulator computer (or embedded equipment) is connected with multiple simulation node computers, a simulation control system of the network simulator computer is operated to realize network topology change and configuration of the characteristic parameters of the simulation link, and the network protocol can be verified under different network topologies and link characteristic parameters via fewer common computers.
Owner:BEIJING JIAOTONG UNIV
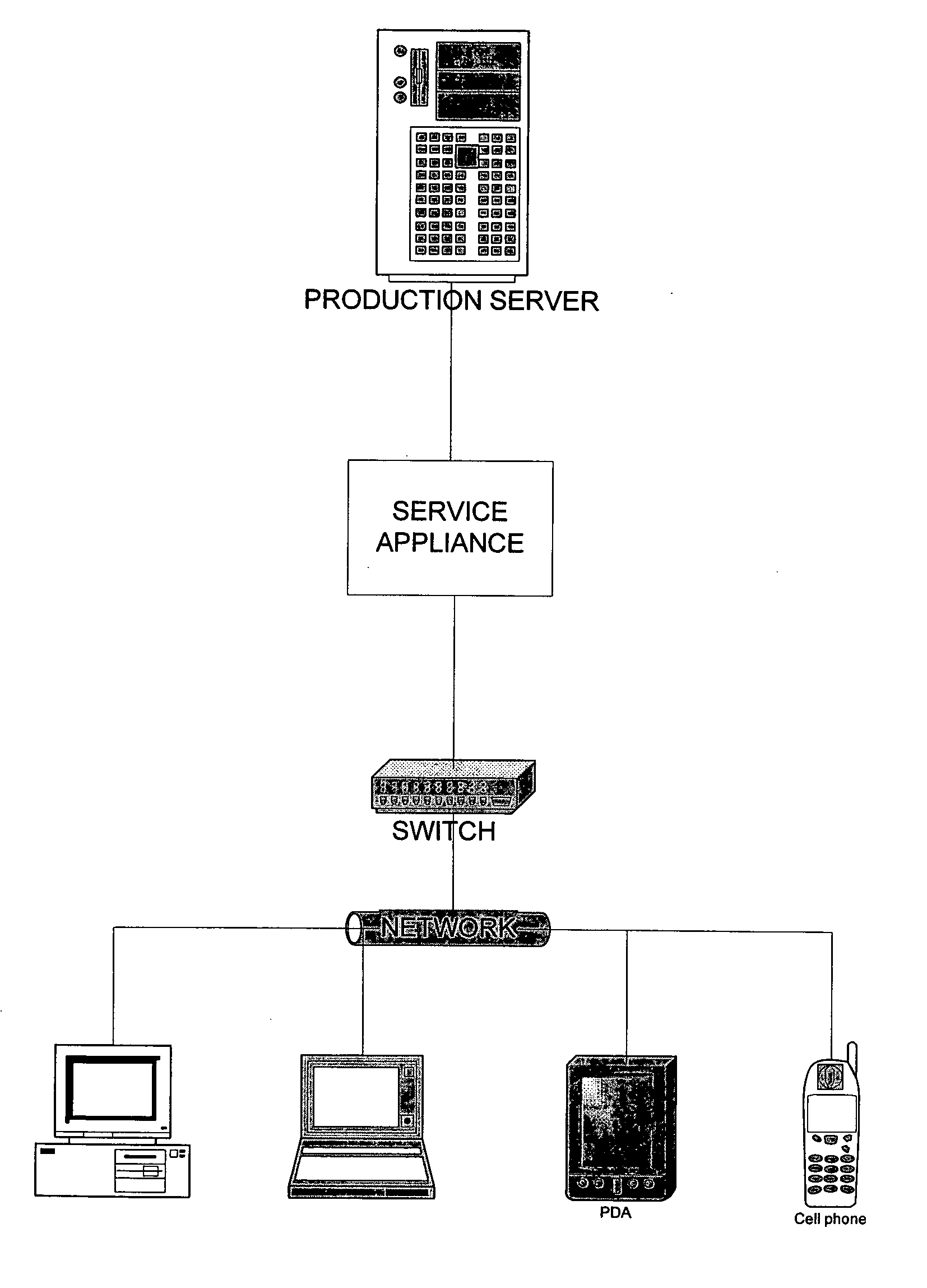
Network traffic routing
ActiveUS20060015645A1Error detection/correctionDigital computer detailsTraffic capacityApplication software
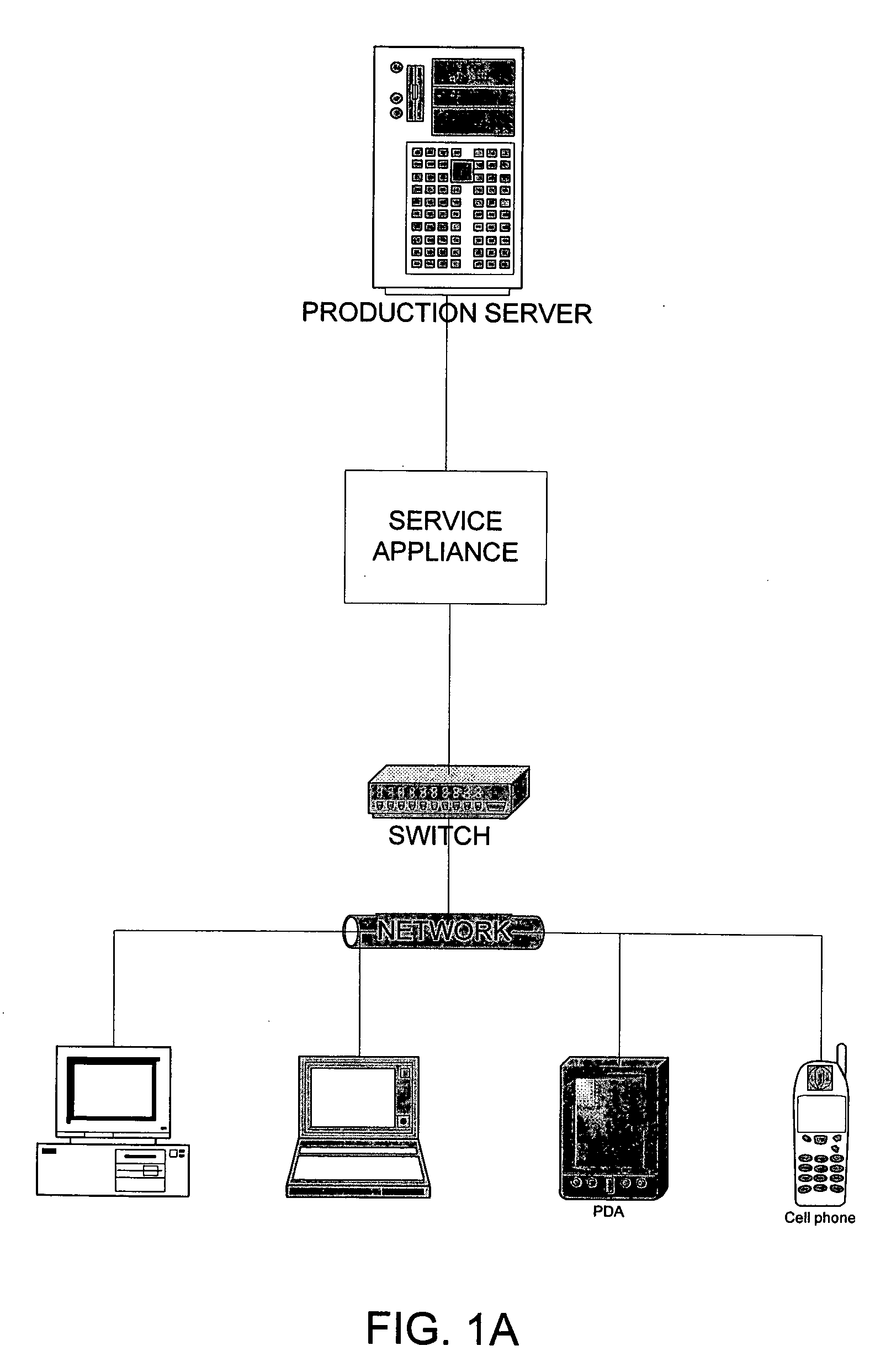
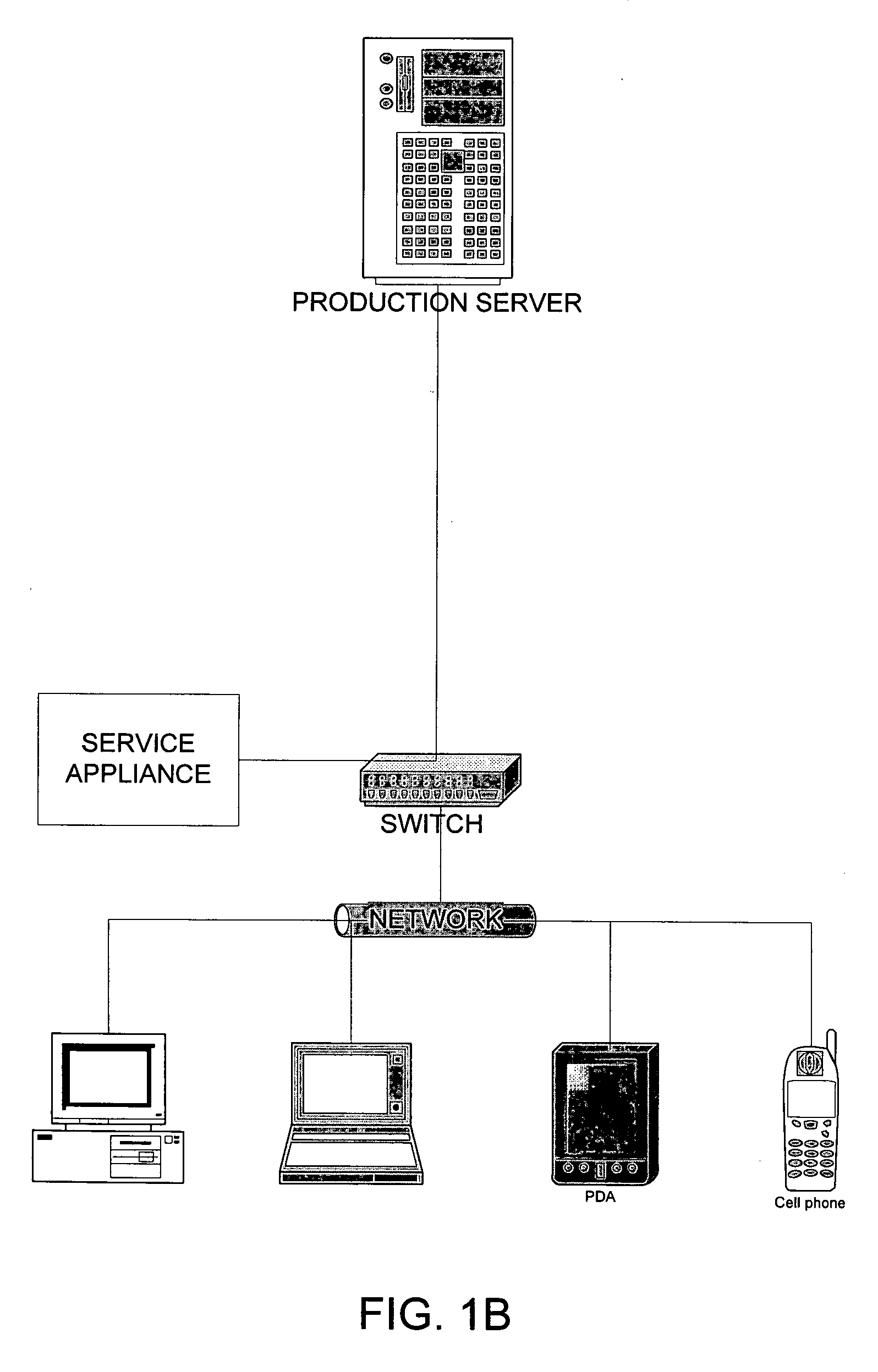
A service appliance is installed between production servers running service applications and service users. The production servers and their service applications provide services to the service users. In the event that a production server is unable to provide its service to users, the service appliance can transparently intervene to maintain service availability. To maintain transparency to service users and service applications, service users are located on a first network and production servers are located on a second network. The service appliance assumes the addresses of the service users on the second network and the addresses of the production servers on the first network. Thus, the service appliance obtains all network traffic sent between the production server and service users. While the service application is operating correctly, the service appliance forwards network traffic between the two networks using various network layers.
Owner:ONGOING OPERATIONS
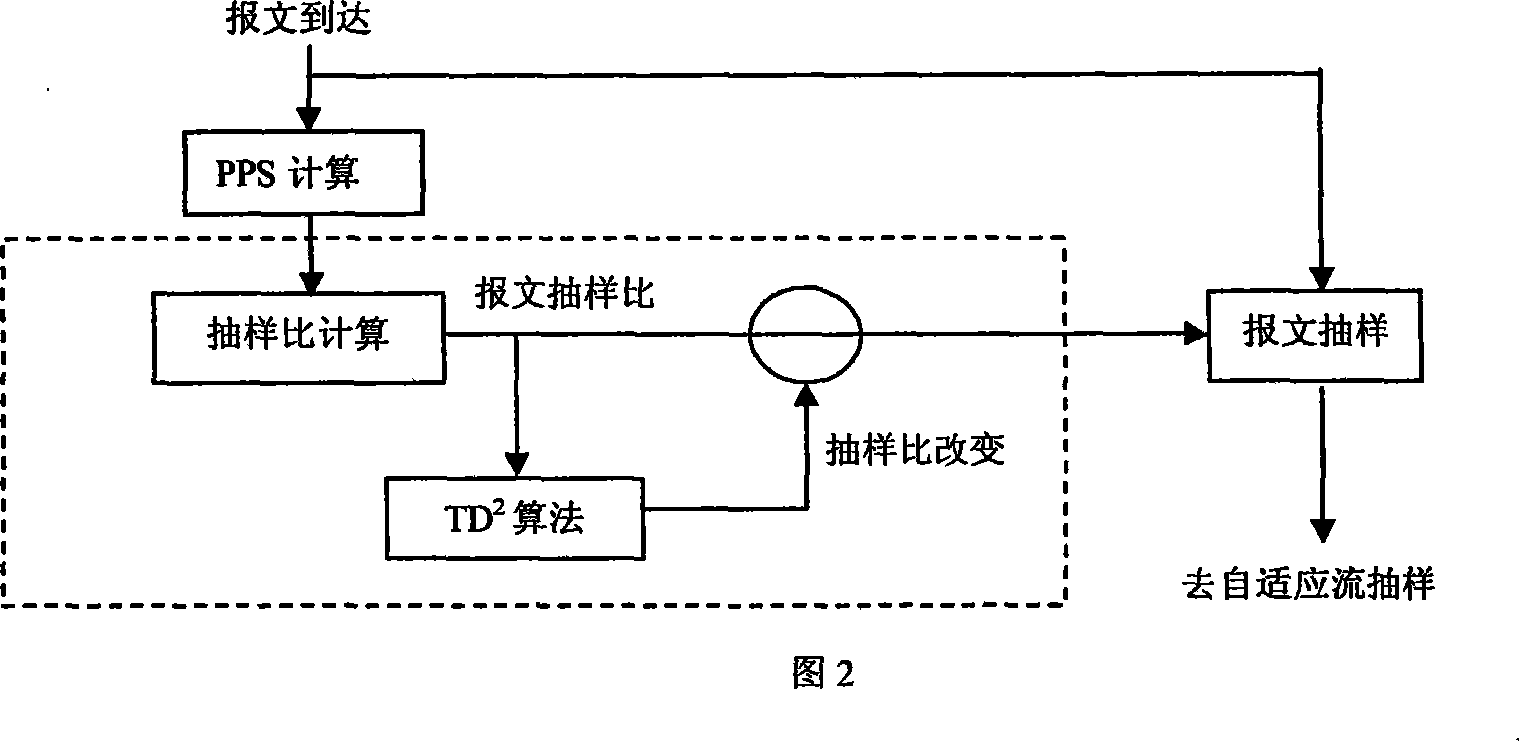
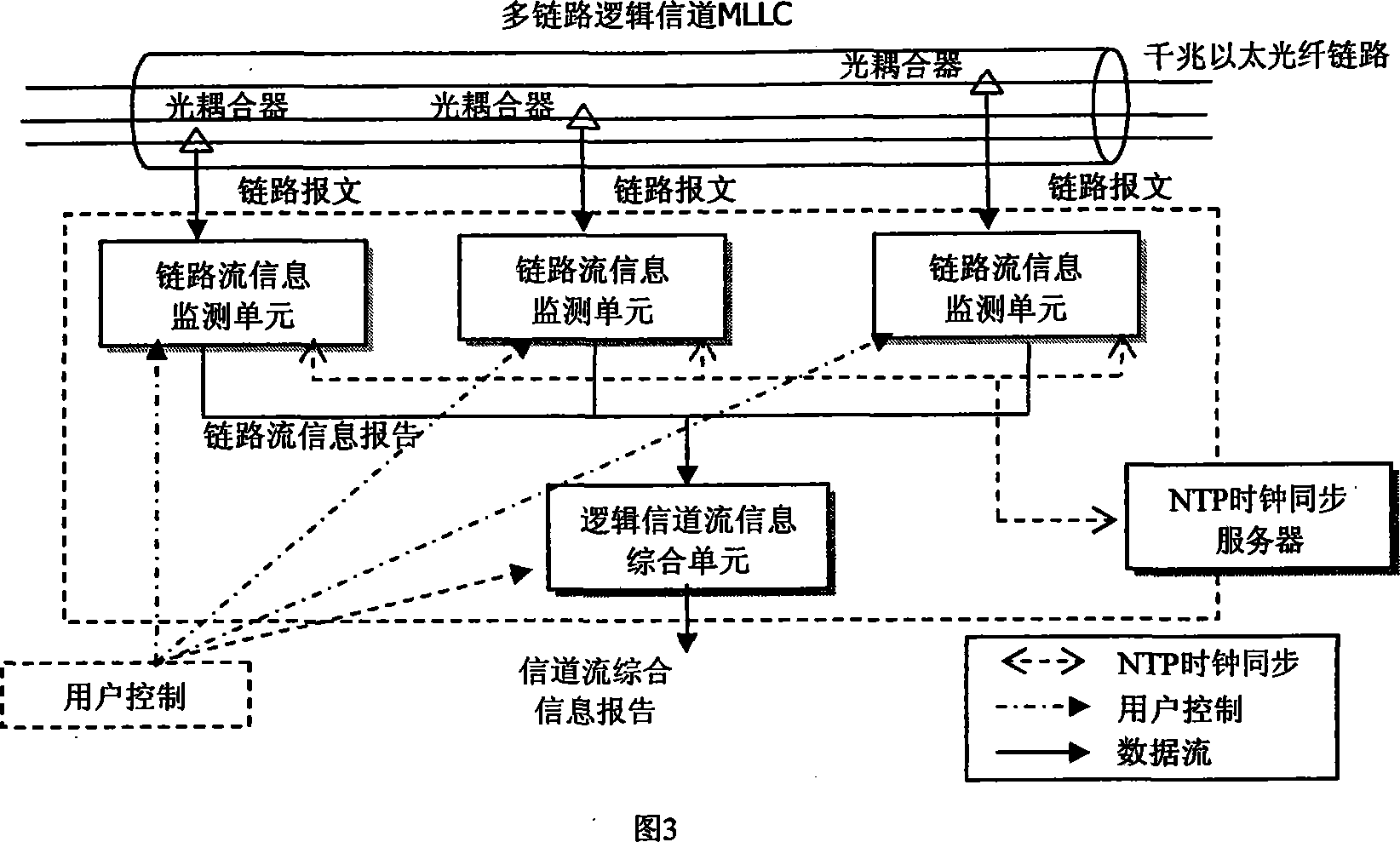
Self adaption sampling stream measuring method under high speed multilink logic channel environment
The method is designed based on NetraMet and NetFlow system. It uses a sampling ratio supporting a high-speed multi-link logical channel network traffic measurement, which can makes self-adaption to the message sampling ratio and the traffic sampling ratio according to the network traffic state and supports to use time slice approach to output the stream message. It uses a general approach to monitor the traffic in any channels.
Owner:SOUTHEAST UNIV
Network security emulation system and its emulation method
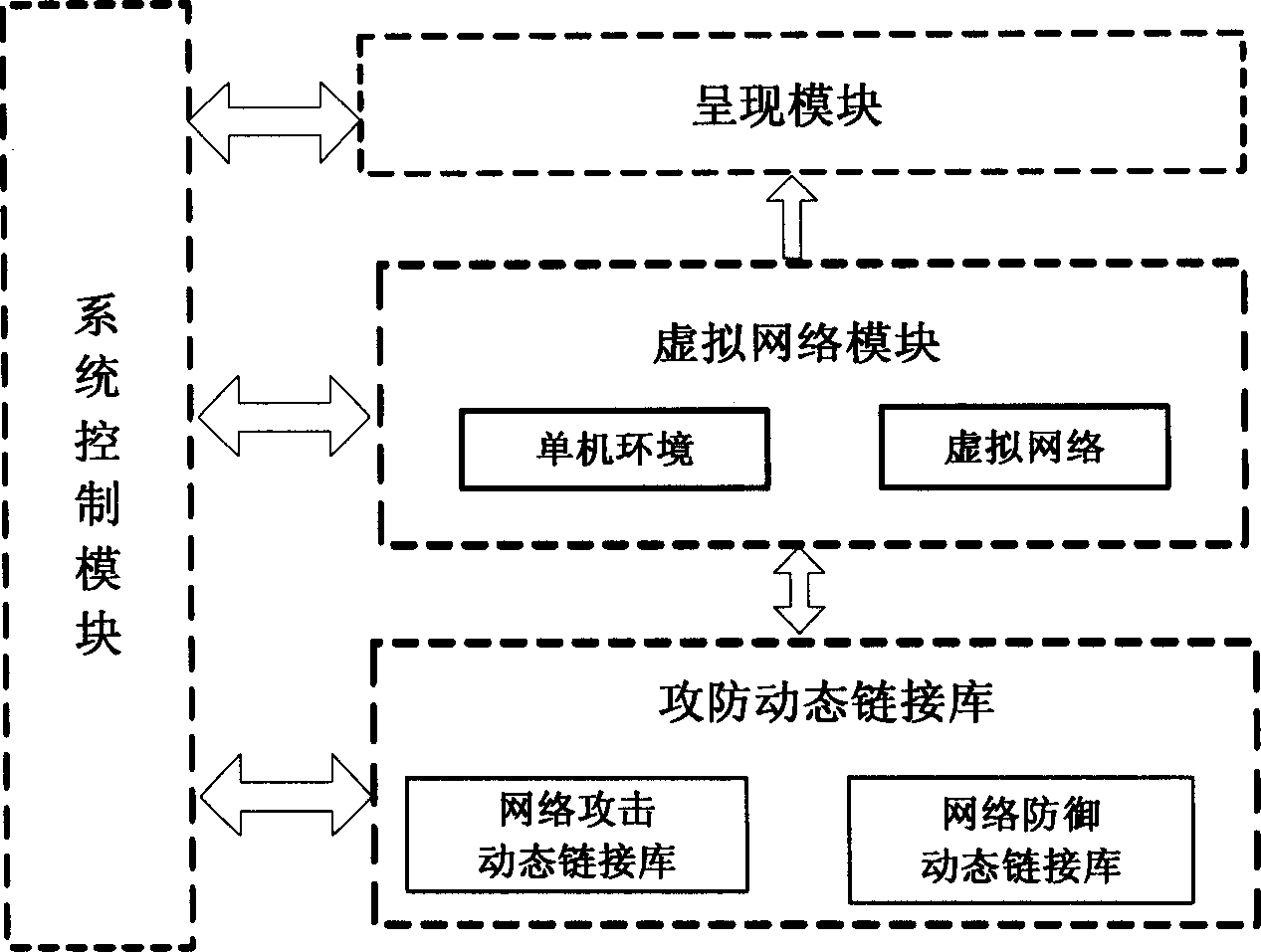
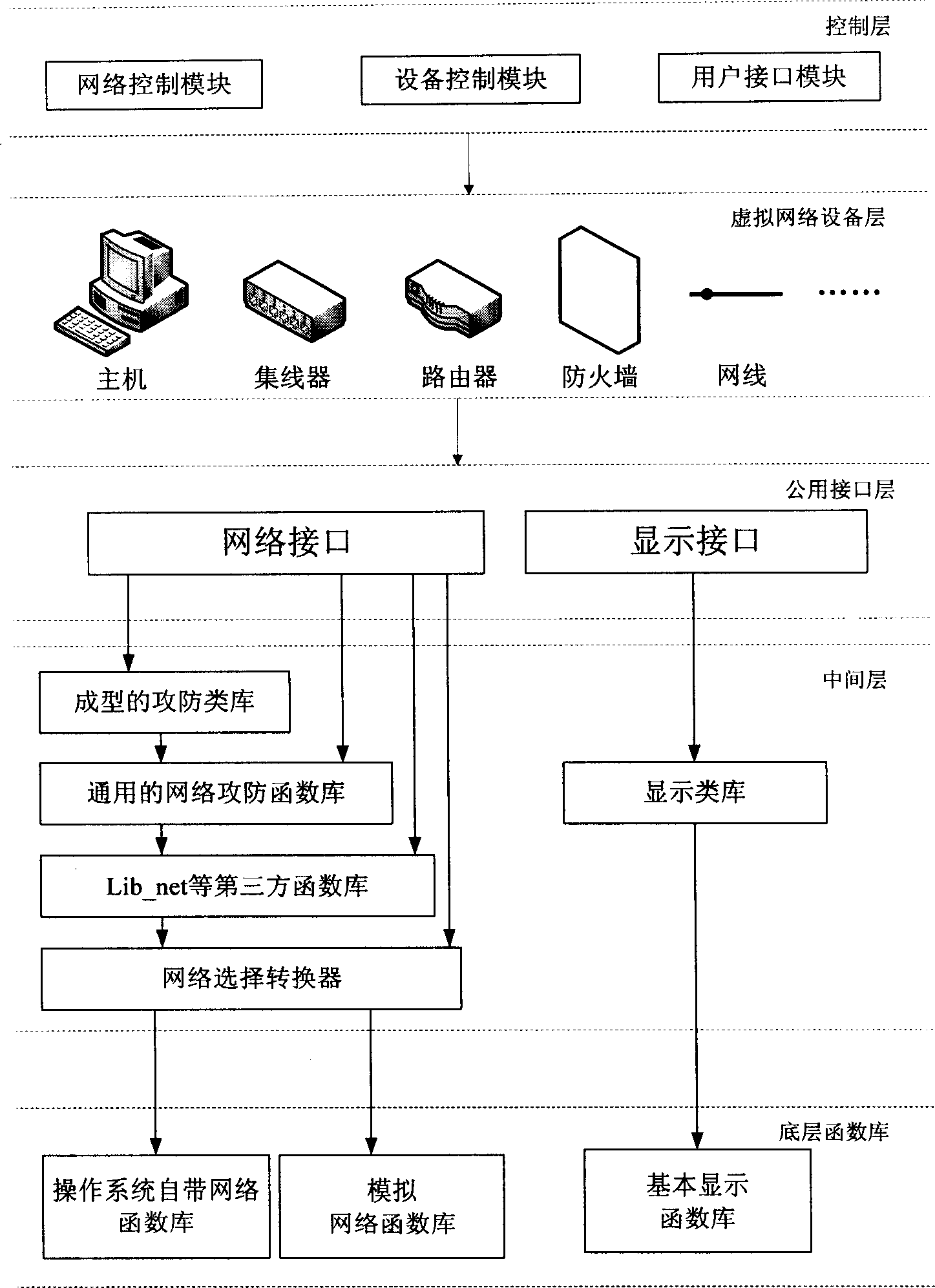
InactiveCN1805385ASolve environmental problemsTroubleshooting Emulation Platform IssuesData switching networksSpecial data processing applicationsPublic interfaceControl layer
The invention relates to a network safe simulation system and relative imitation method. The logical function of said network safe simulation system comprises: a virtual network module, a attack-defend dynamic chain connection base, a system control module, and a display module, while said logical functions are displayed by the control layer, virtual network device layer, public interface layer, middle layer and bottom function base. The virtual network device can simulate the host machine, router, firewall, network card, concentrator, and network wire on the single machine to connect each virtual network device to form the virtual network. The process that using said virtual network to process the safe simulation comprises: first, setting the user program; distributing system parameter document; coding the system; imitated operating the coded system in the operating system; at last collecting the simulated data according to which makes the network safety analyst. The invention has easy operation and extended availability, which can be used as network safety research simulation environment and imitation platform.
Owner:KUNSHAN RUIXIANG XUNTONG COMM TECHCO
Hybrid prediction method for network traffic
InactiveCN105376097AAccurate descriptionGood non-linear predictive abilityData switching networksLearning machineTraffic prediction
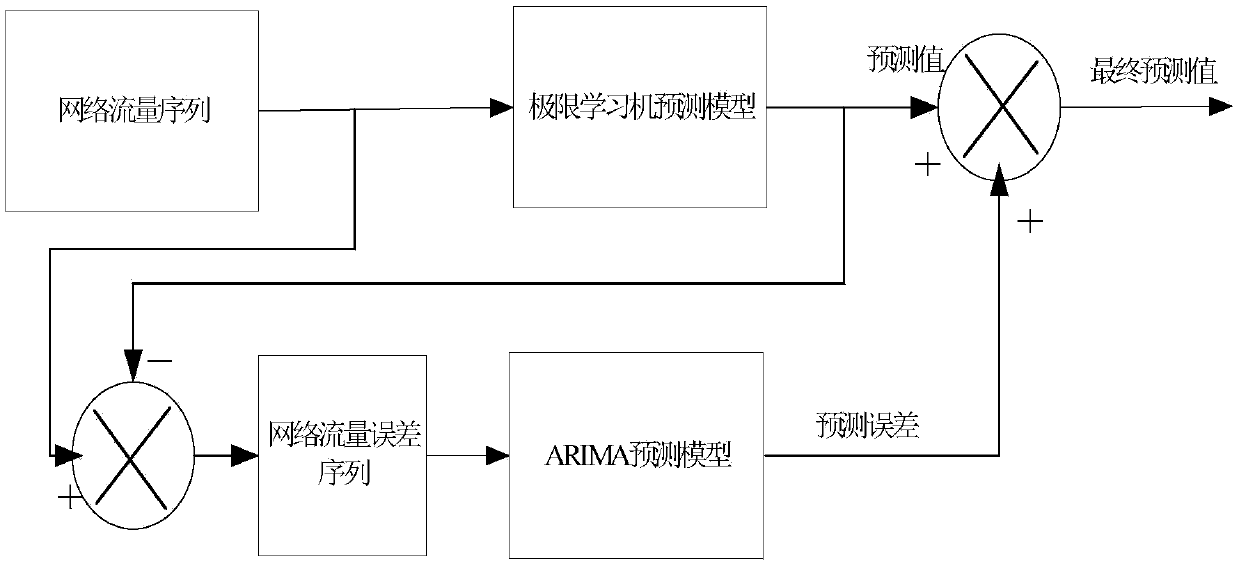
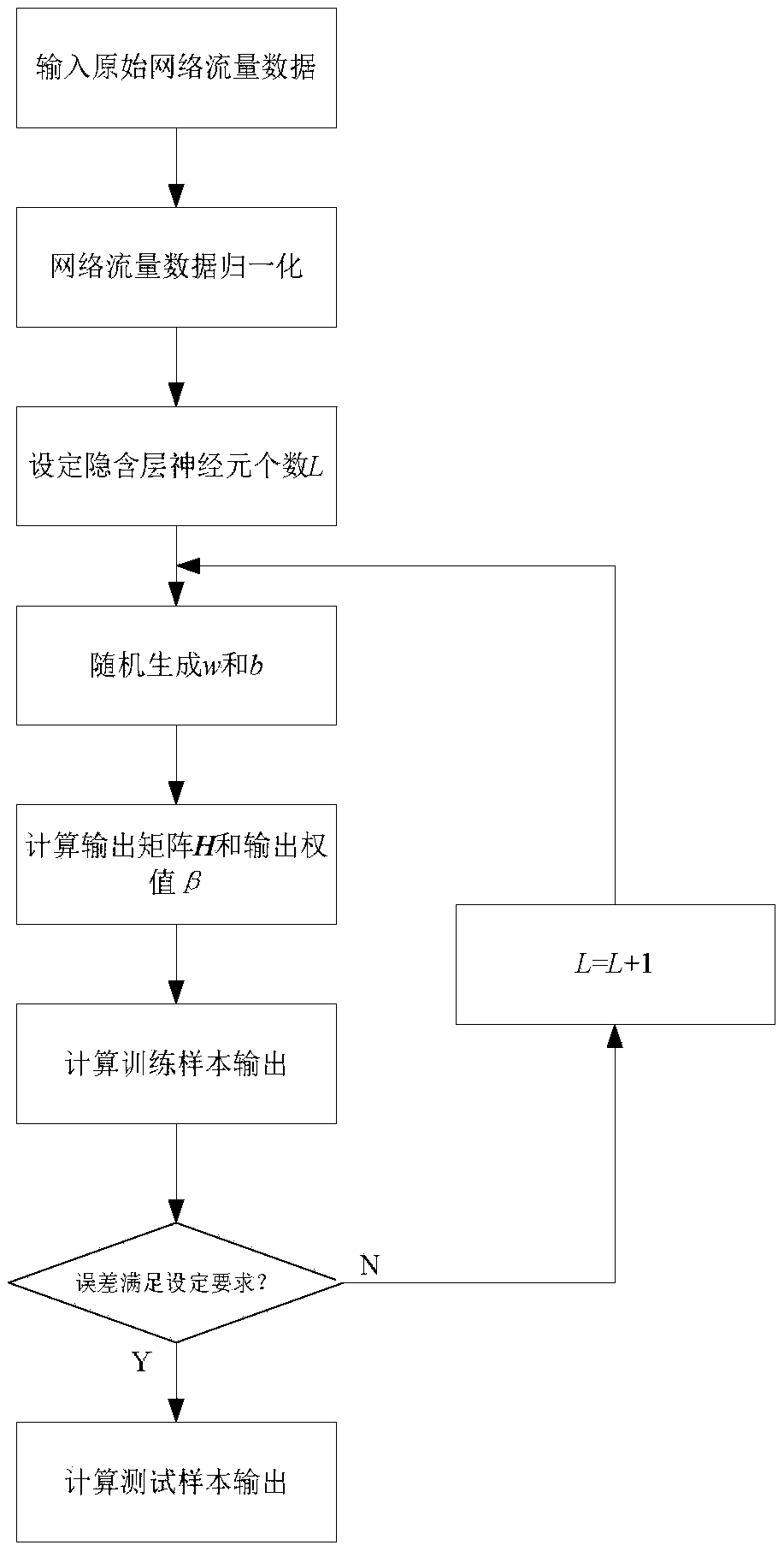
The invention discloses a hybrid prediction method for network traffic. The method is characterized in that a network traffic prediction method with an extreme learning machine (ELM) being compensated by autoregressive integrated moving average (ARIMA), namely, a network traffic prediction method with the ELM being compensated by a Farctal autoregressive integrated moving average model is provided through a self-similarity analysis of a network traffic sequence. The method comprises the following steps: firstly, predicting the network traffic sequence with the ELM; secondly, correcting an error sequence of network traffic prediction through an ARIMA model; and lastly, overlaying an ELM predicted value and an ARIMA model correction value to obtain a final predicted value. According to the method, prediction error data is fitted by the ARIMA model, and the predicted value of the ELM is overlaid with a residual error of ARIMA prediction to obtain the final predicted value. Residual error compensation is performed through the ARIMA model, thereby effectively increasing the prediction accuracy.
Owner:SHENYANG POLYTECHNIC UNIV
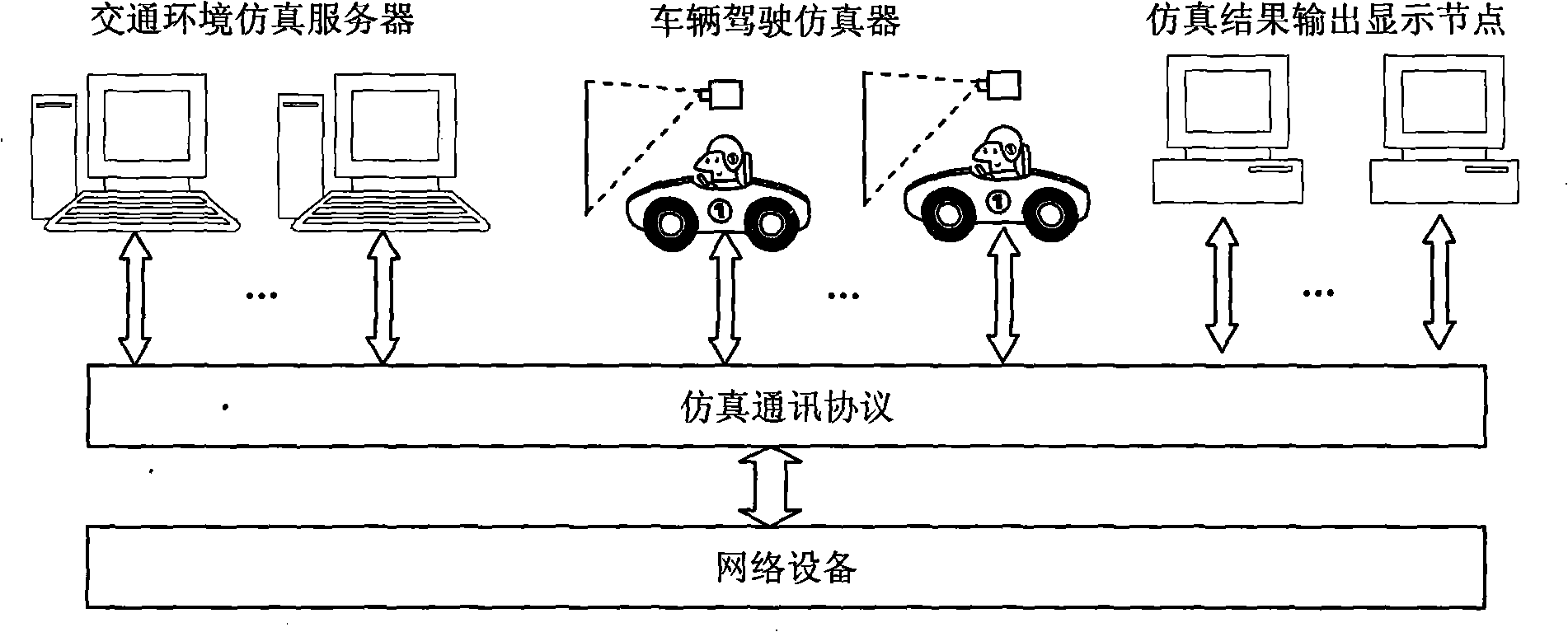
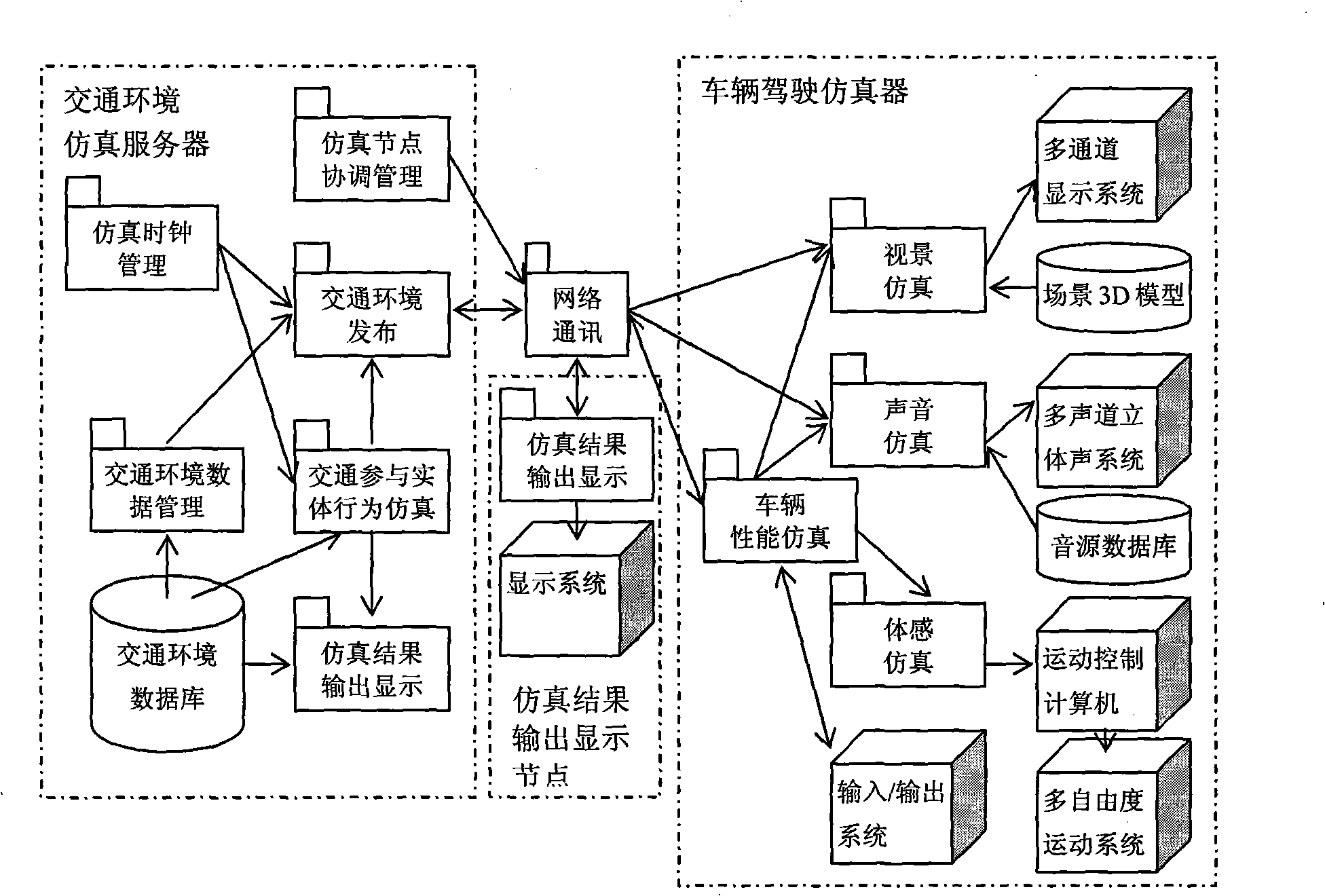
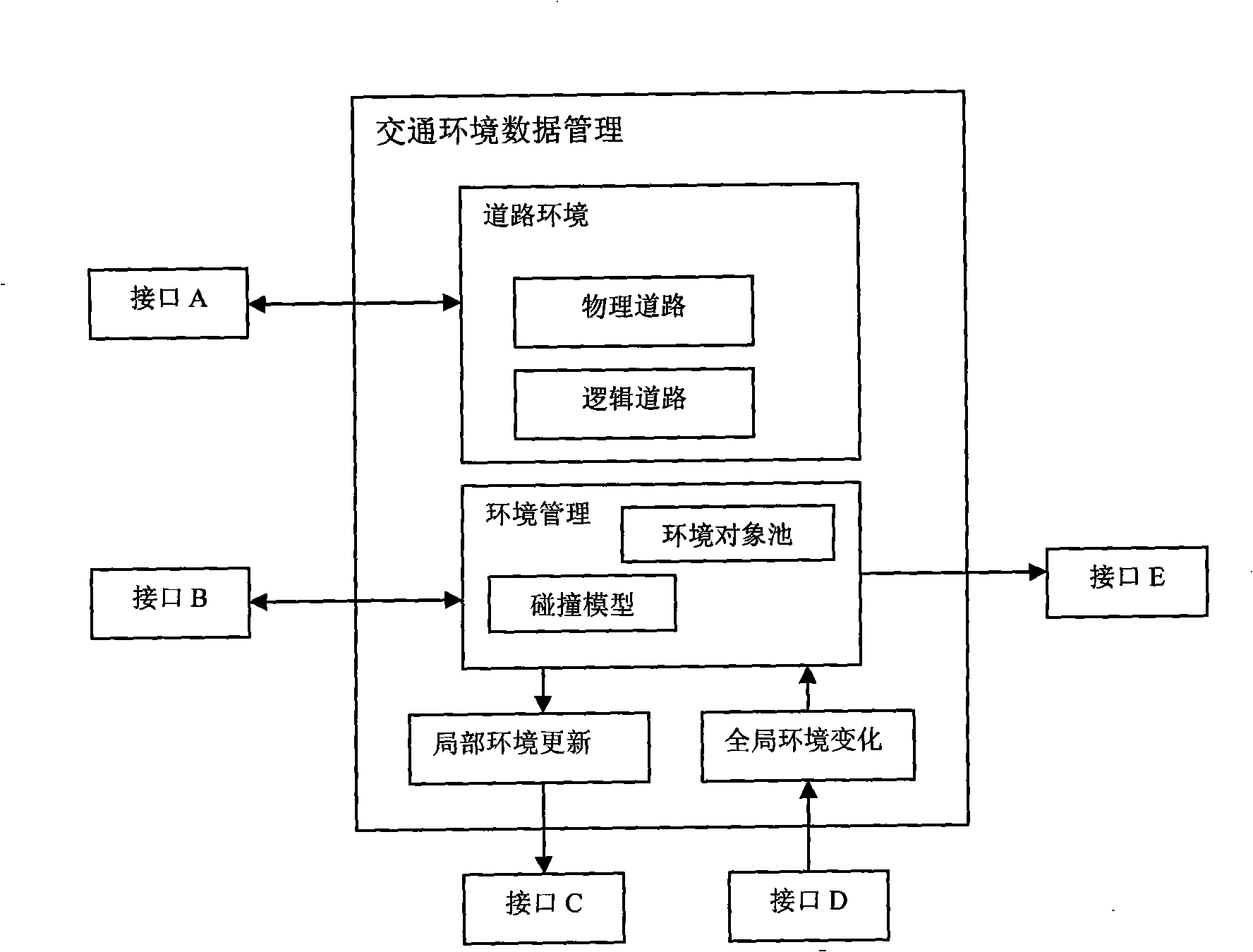
Interactive traffic simulation system
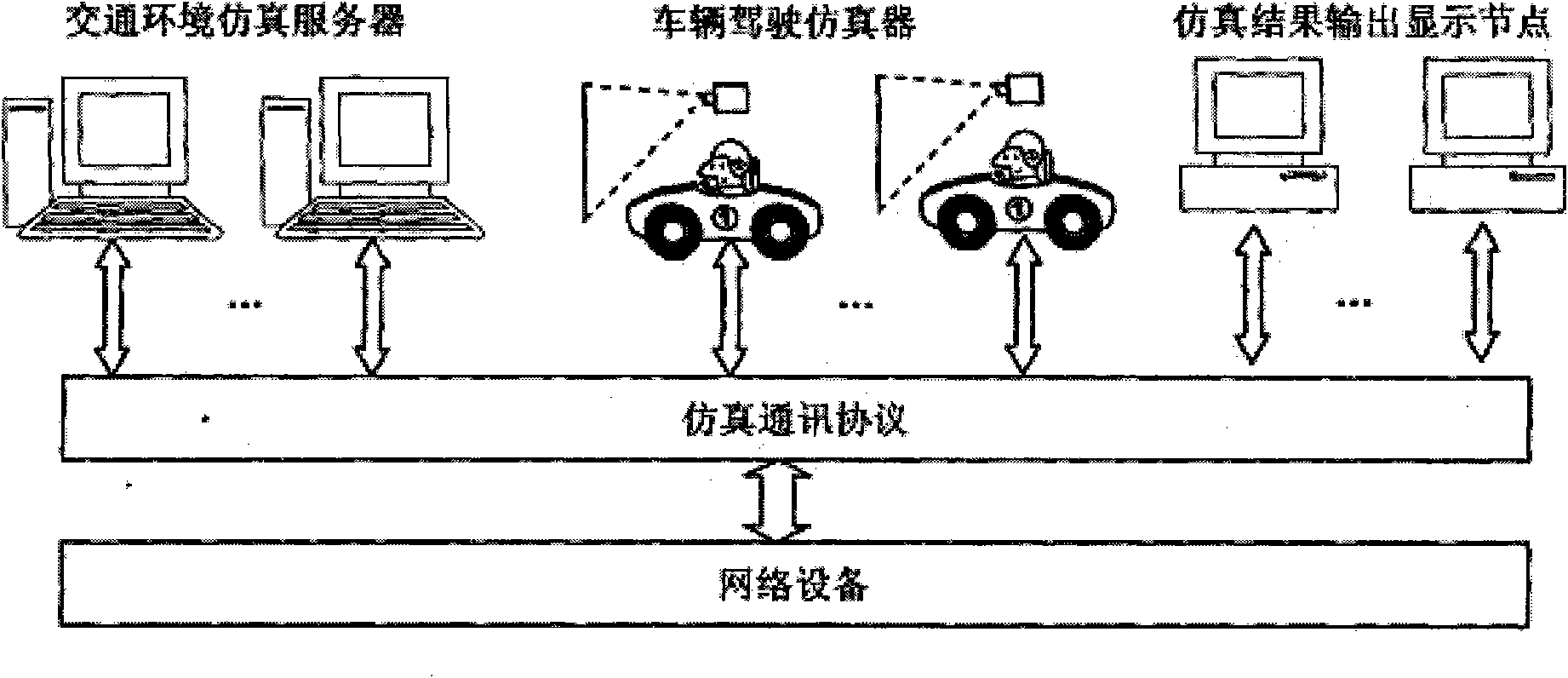
InactiveCN102467589AEnable co-simulationFlexible structureRoad vehicles traffic controlSpecial data processing applicationsCo-simulationTraffic simulation
The invention aims to provide an interactive traffic simulation system with a distributed system structure, which is a novel traffic-driving hybrid simulation system. The core is that: a returning vehicle driving simulator for a person serves as a traffic participation entity and is introduced into the traffic simulation system. The vehicle driving simulator serving as the traffic participation entity controlled by a user driving behavior and a virtual traffic participation entity generated in the traffic simulation system interact and participate traffic simulation calculation together so as to realize cooperative simulation of a plurality of vehicle driving simulators and a plurality of traffic environment simulation servers in the same virtual traffic environment. The invention has the characteristics that: the traffic simulation system has a flexible structure, is convenient to expand, supports man-machine interaction and is high in simulation confidence, and the like; and the system can be used in the fields of traffic simulation and driving simulation and can provide a novel platform for research and application in the fields of driving behaviors, driving psychology, traffic safety, intelligent transportation, road and bridge design and the like.
Owner:上海日浦信息技术有限公司
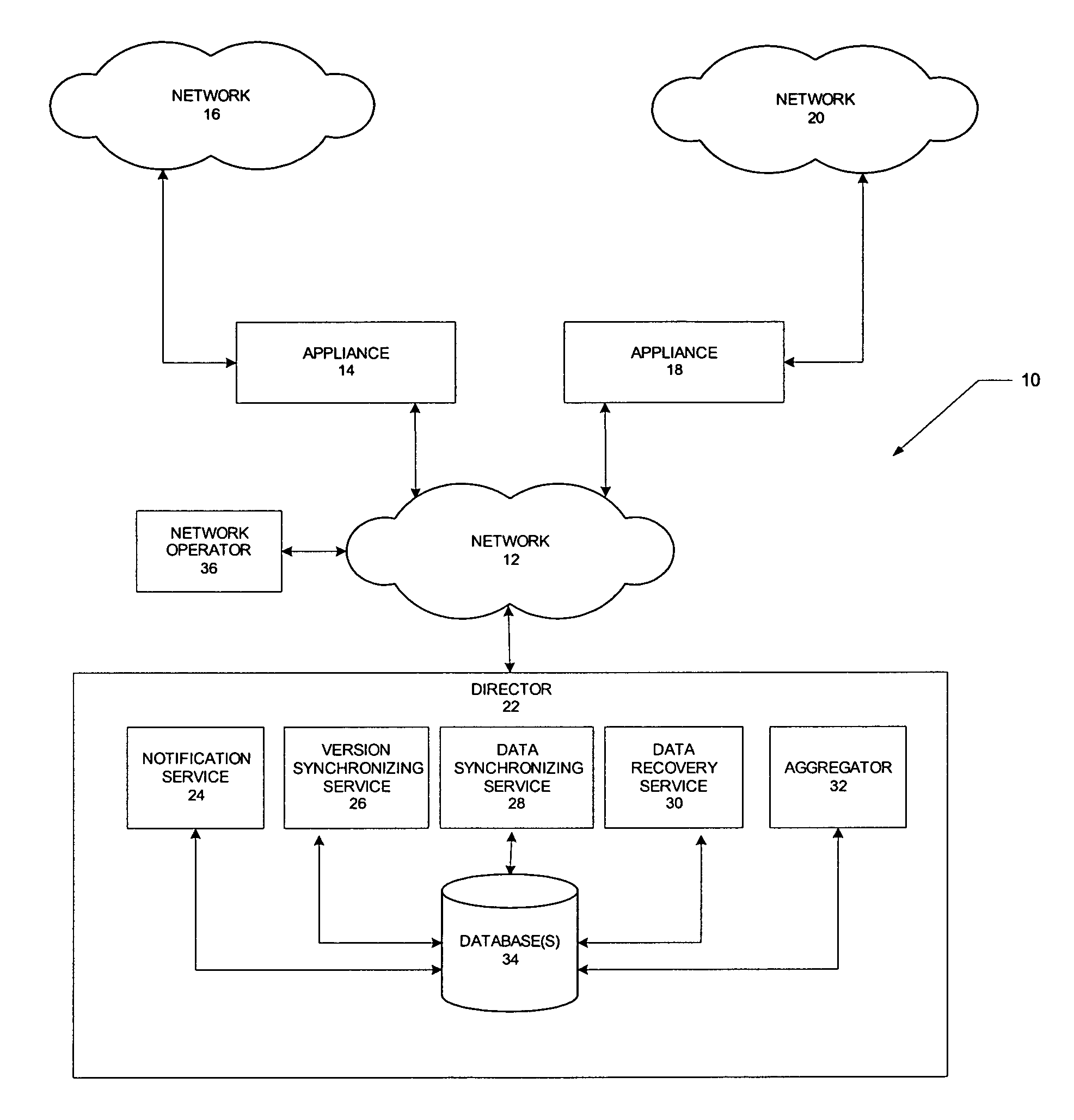
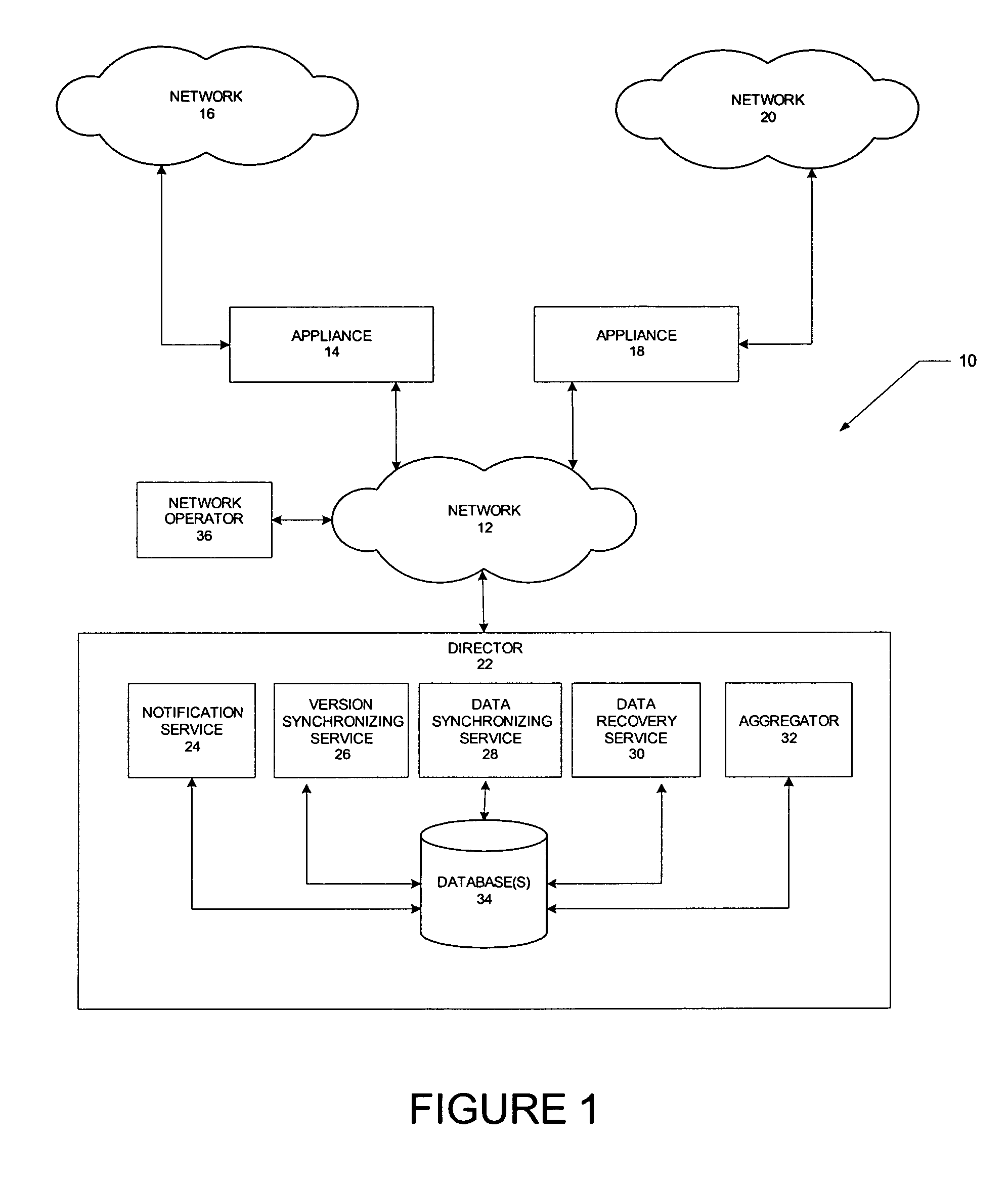
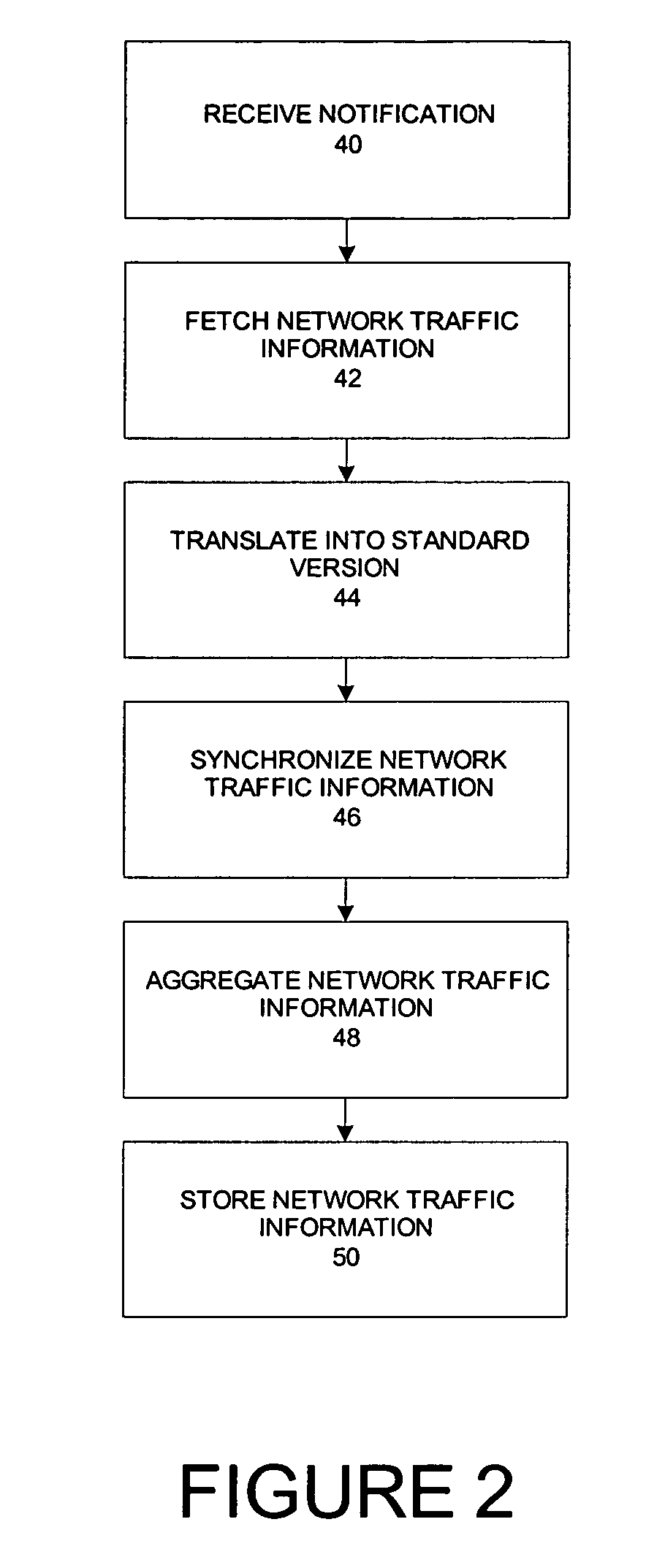
Method and system for collecting and consolidating network traffic information
A distributed network monitoring system includes a central monitoring device configured to fetch network traffic information from one or more remote monitoring devices in response to receiving a notification from the remote monitoring devices that the network traffic information is available, the remote monitoring devices being communicatively coupled to the central monitoring device. The network traffic information is associated with a timestamp which indicates a time period at which the network traffic information was collected by the remote monitoring devices. The central monitoring device further synchronizes the network traffic information from the remote monitoring devices by comparing the timestamp of the network traffic information with a system timestamp provided by a system clock or network time protocol (NTP) server. The network traffic information is identified as unavailable if the timestamp cannot be located when compared to the system timestamp. In addition, the central monitoring device starts a timeout wait period for the remote monitoring device with the unavailable network traffic information and further ceases collecting the network traffic information if the timeout wait period expires. The synchronized network traffic information is further consolidated to provide information regarding the overall performance of a network system.
Owner:RIVERBED TECH LLC
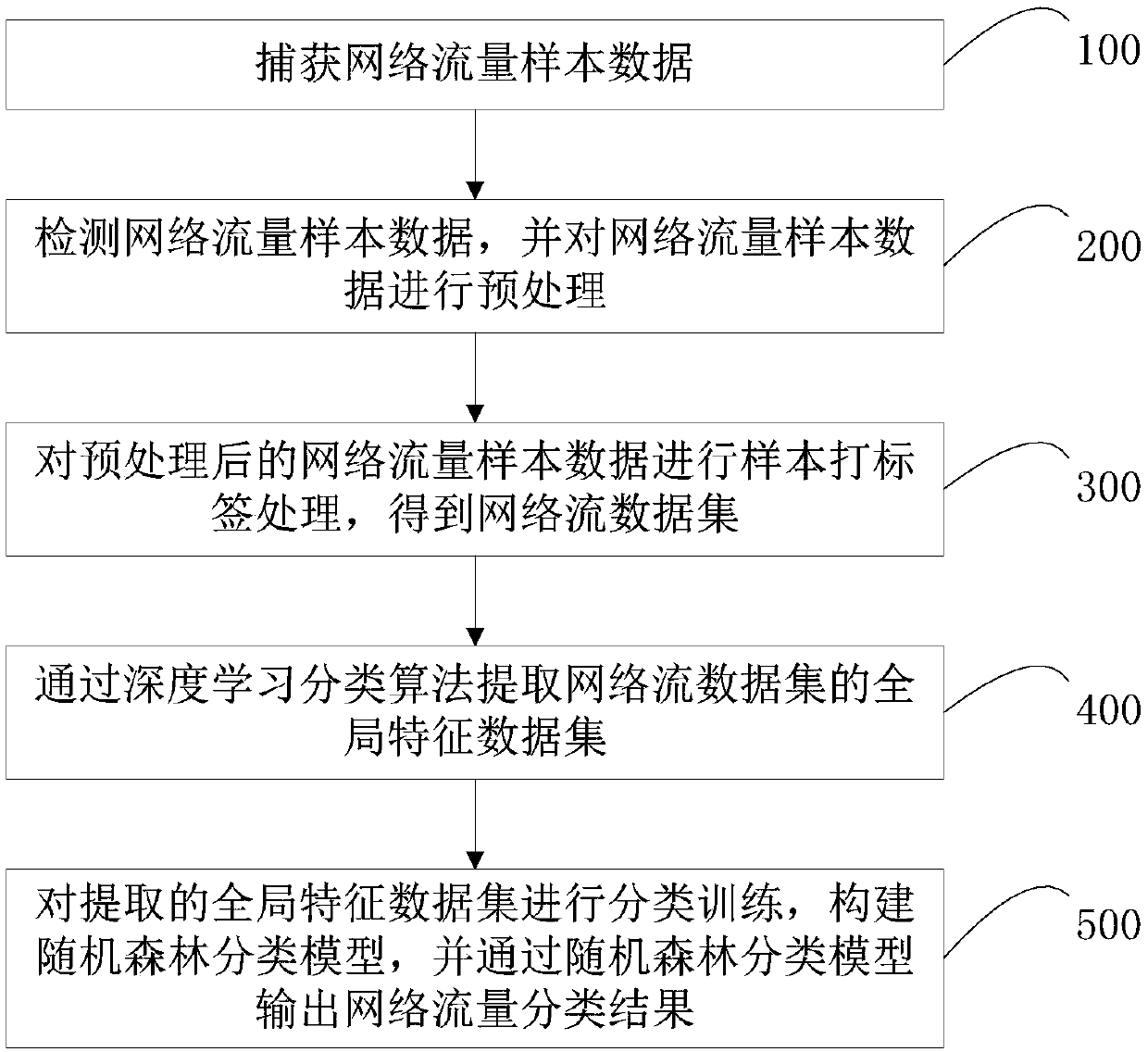
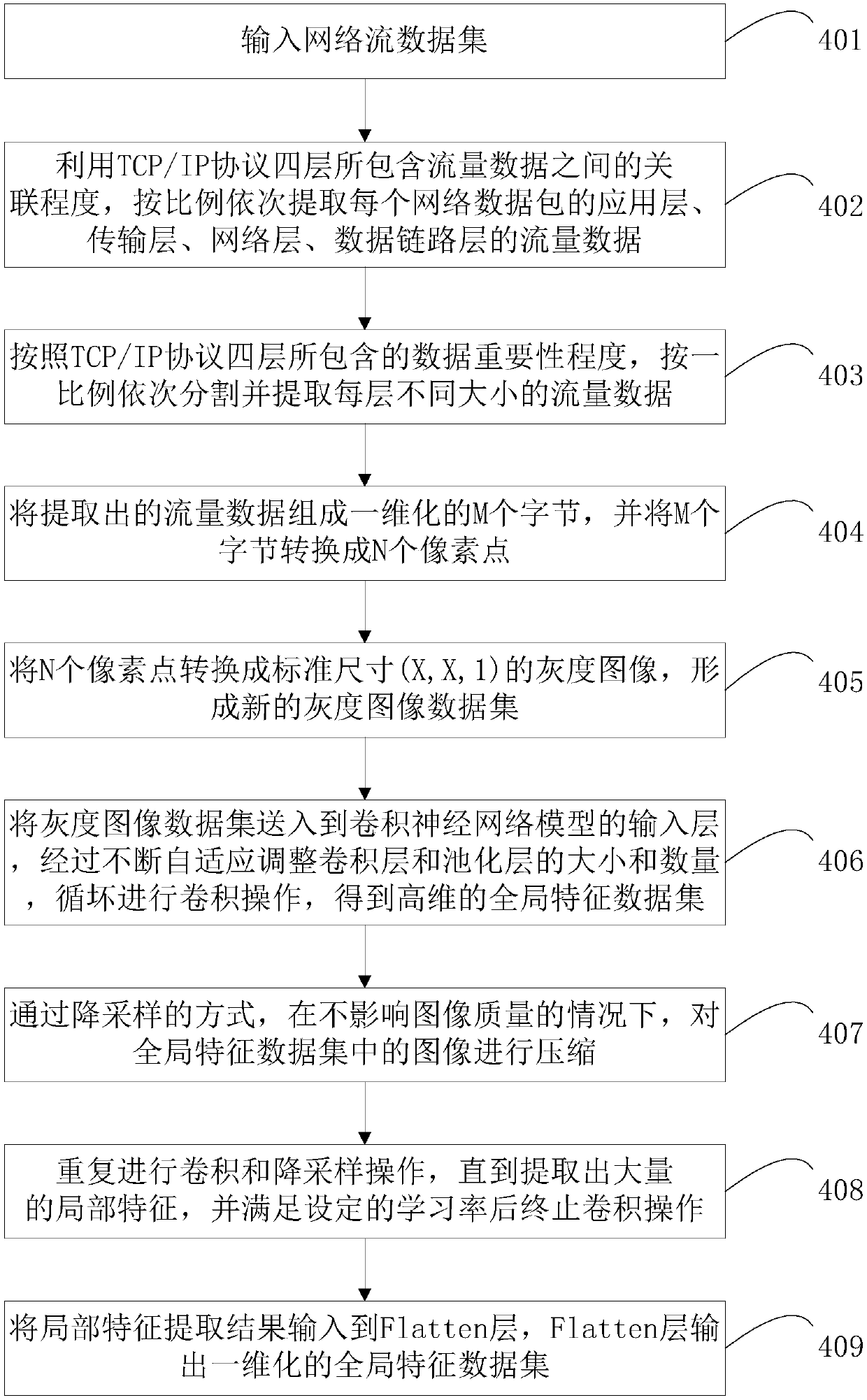
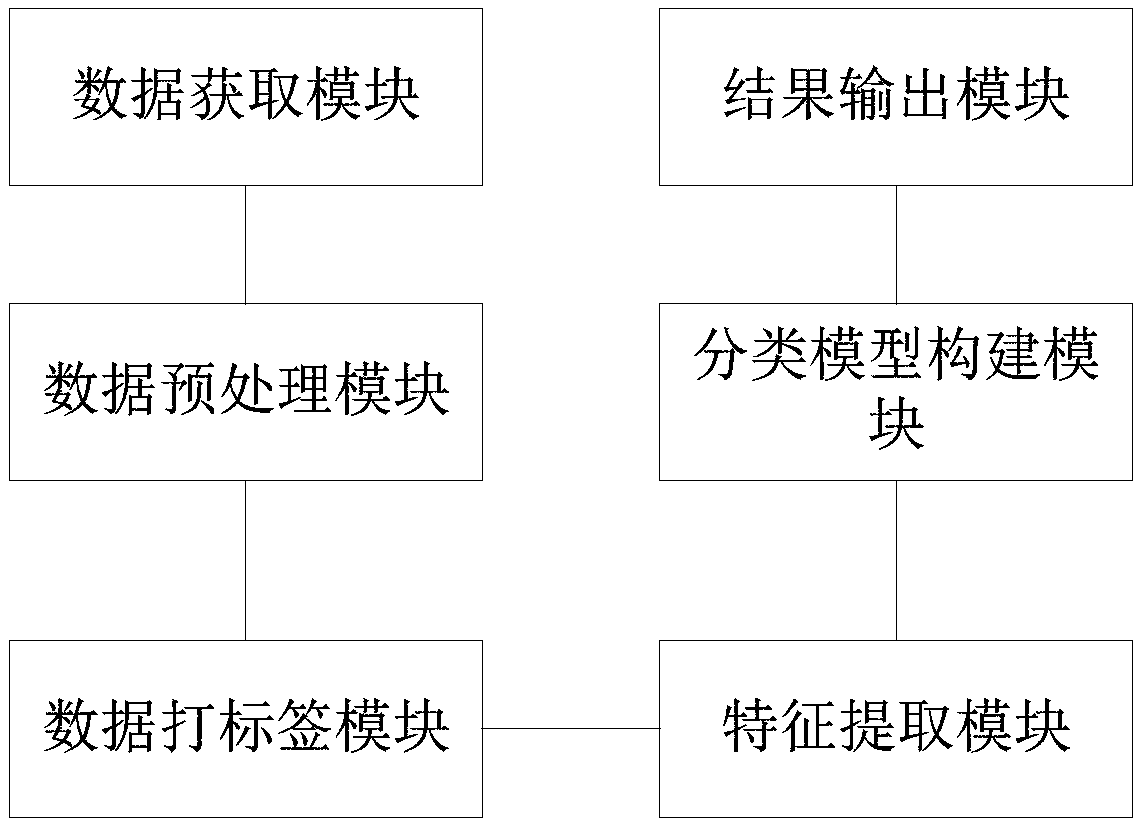
Network traffic classification method and system based on deep learning, and electronic equipment
ActiveCN109639481AImprove classification accuracyImprove classification efficiencyNeural architecturesData switching networksData setClassification methods
The application relates to a network traffic classification method and system based on deep learning, and electronic equipment. The method comprises the following steps: step a, capturing network traffic sample data; step b, extracting a global feature data set of the network traffic sample data through a deep learning classification algorithm; and step c, constructing a random forest classification model according to the global feature data set, and outputting a network traffic classification result through the random forest classification mode. The random forest classification model is trained by utilizing the extracted global feature, the result shows a stable classification performance, and the ultra-high-dimension traffic data can be processed, and the feature selection is avoided. Compared with the prior art, the high-precision and high-performance of the network traffic classification can be effectively guaranteed; and meanwhile, the classification efficiency can be improved, the training time is shortened, and the computation overhead is reduced.
Owner:SHENZHEN INST OF ADVANCED TECH
Interactive traffic simulating system
InactiveCN101308616AEnable co-simulationFlexible structureEducational modelsCo-simulationTraffic simulation
The invention aims at providing a distributed interactive traffic simulation system which is a new traffic-driving simulation system. The key point of the traffic simulation system lies in introducing a vehicle driving emulator on the route of the user into the traffic simulation system as a traffic entity. The vehicle driving emulator, as a traffic entity controlled by the driving of the user, interacts with the virtual traffic entity produced by the traffic simulation system, and the traffic entity and the virtual traffic entity together participate in traffic simulation calculation, thus realizing cooperated simulation of a plurality of vehicle driving emulators and a plurality of traffic condition simulation servers under the same virtual traffic condition. The distributed interactive traffic simulation system is flexible in structure, convenient to extend and is high in simulation credibility and supports man-machine interaction. The system not only can be applied to traffic simulation and driving simulation but also provides a new platform for the research and application in the field of driving behavior, driving mentality, traffic safety, intelligent traffic, as well as road and bridge design.
Owner:成都合纵连横数字科技有限公司
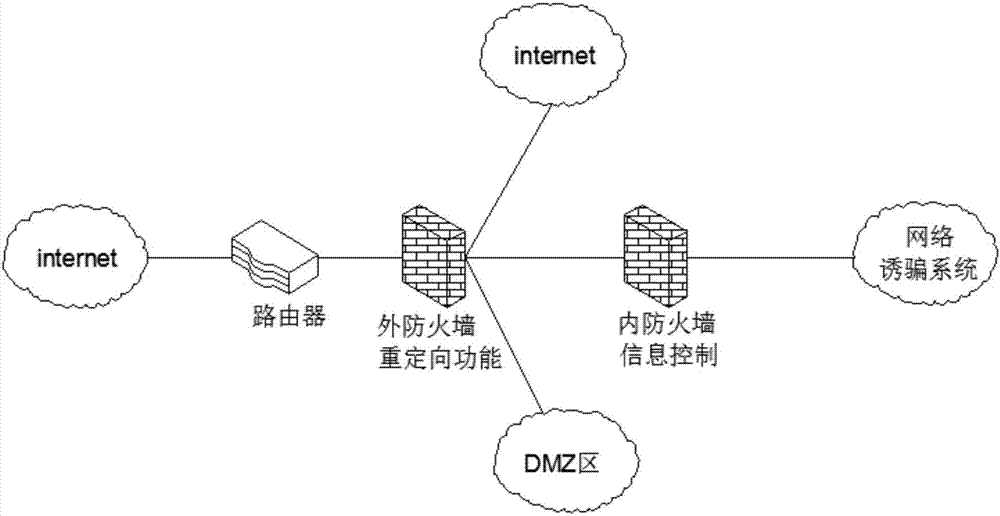
Network trapping method based on honey pot
The invention discloses a honeypot-based network trapping method, which comprises an outer firewall, an inner firewall and a network deception system. The beneficial effects of the invention are: the "wide entry" of the internal firewall is to confuse the intruder and let him "make the best use of it", while the "strict exit" ensures that the intruder's activities are limited to the "cage", and more data can be collected , evidence, and also prevent intruders from using the system as a springboard to conduct further attacks on other systems. Organizing information to deceive forged persons and locations also requires forged information such as salary, budget, and personal records. The more real the forged information is , the more you can avoid deception, and it is easy to be discovered. Network traffic simulation replicates all access connections, making the deception system very similar to the real system. Service camouflage writes a series of scripts in the system to simulate the characteristics of some application services, providing seemingly Normal service, leading the attacker to believe that the trapping system is a functioning system.
Owner:CHINA ELECTRONICS STANDARDIZATION INST +1
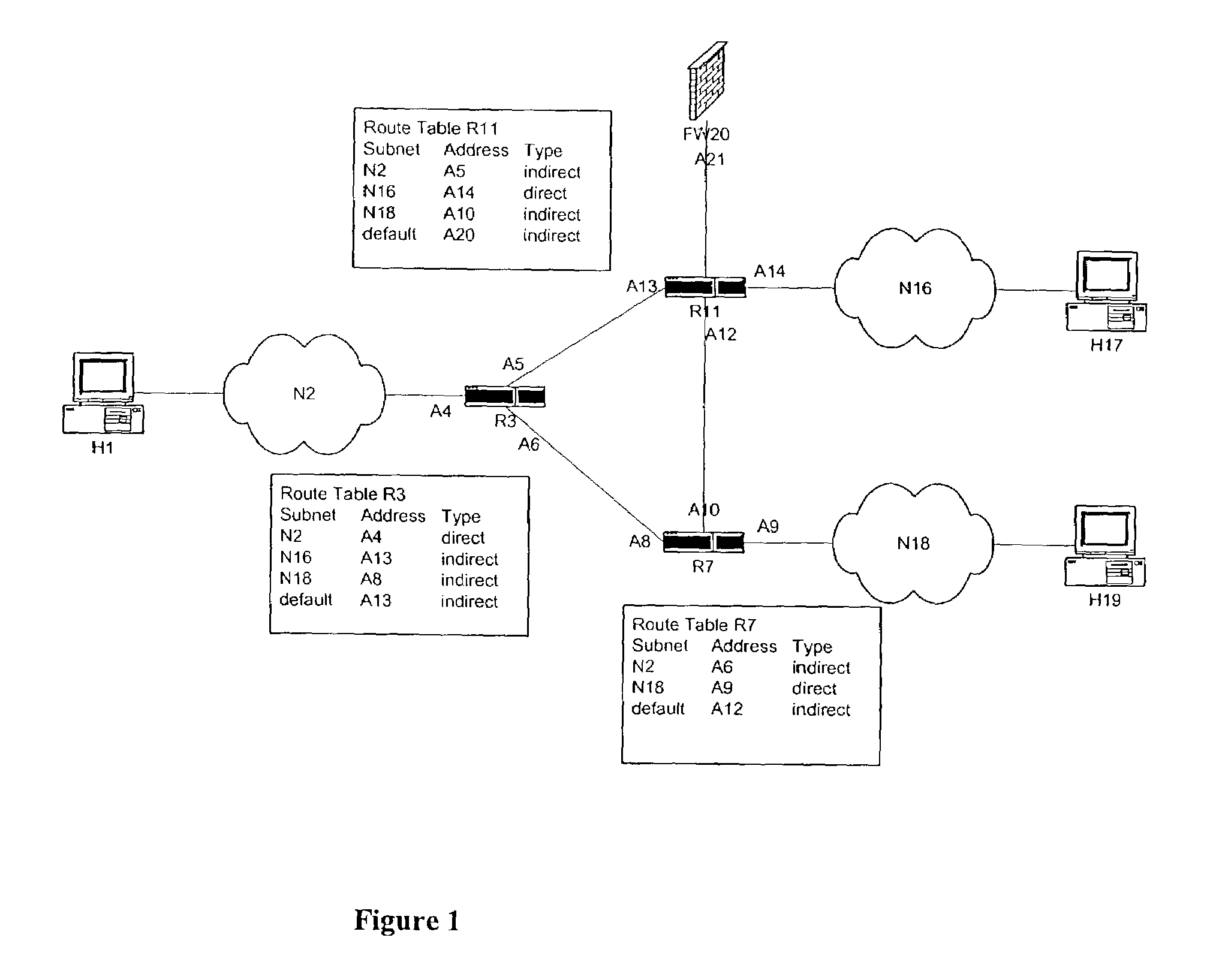
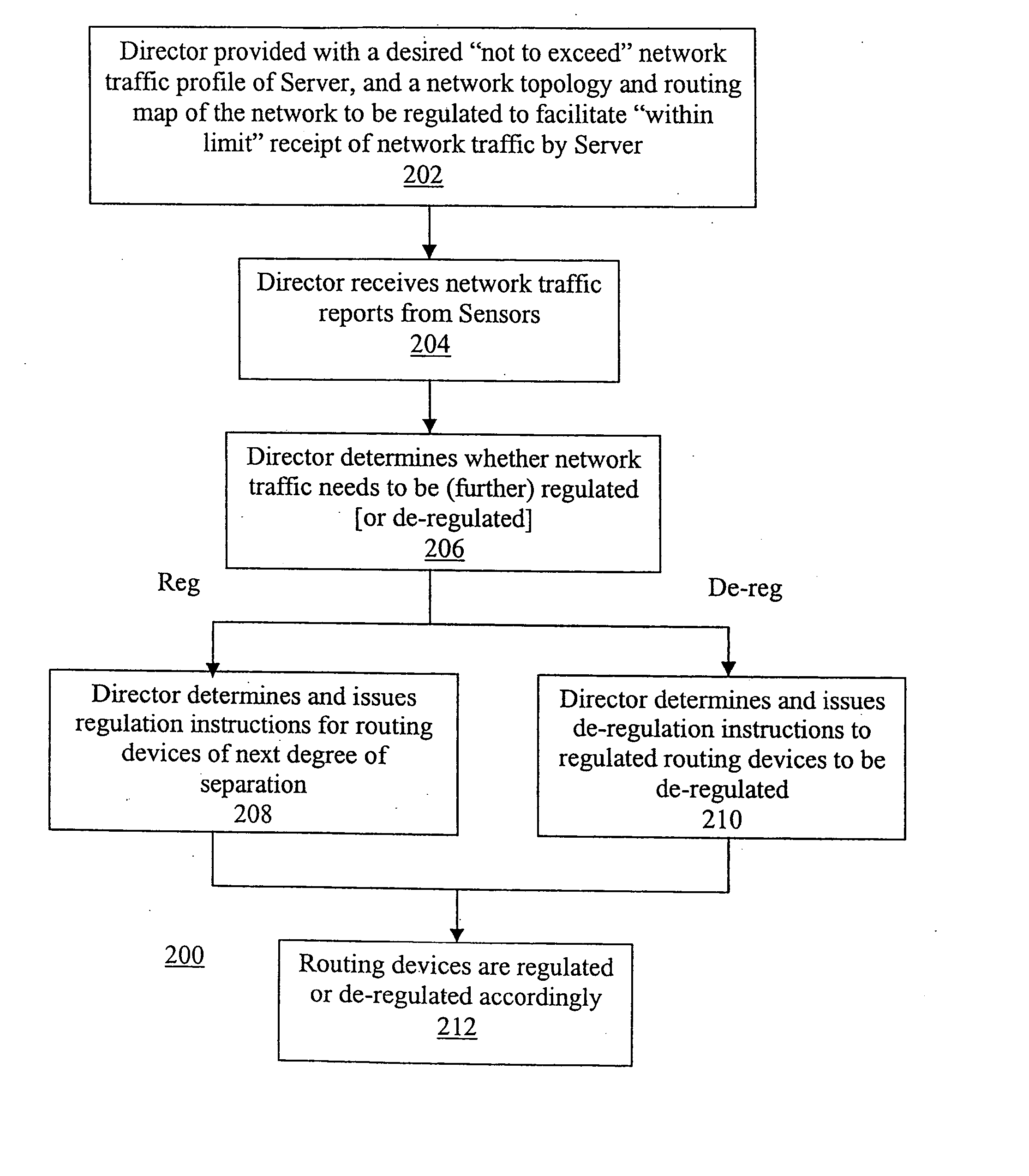
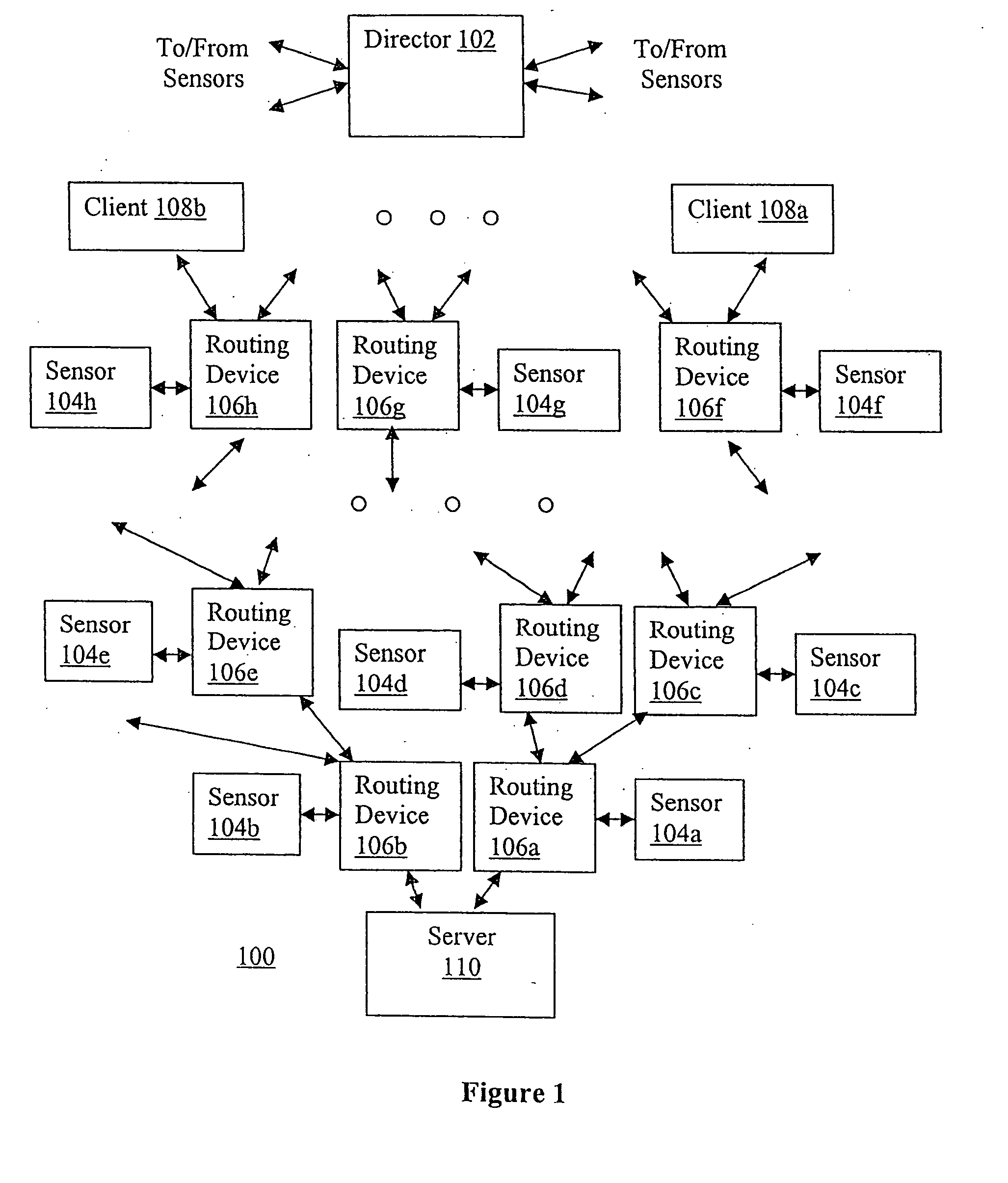
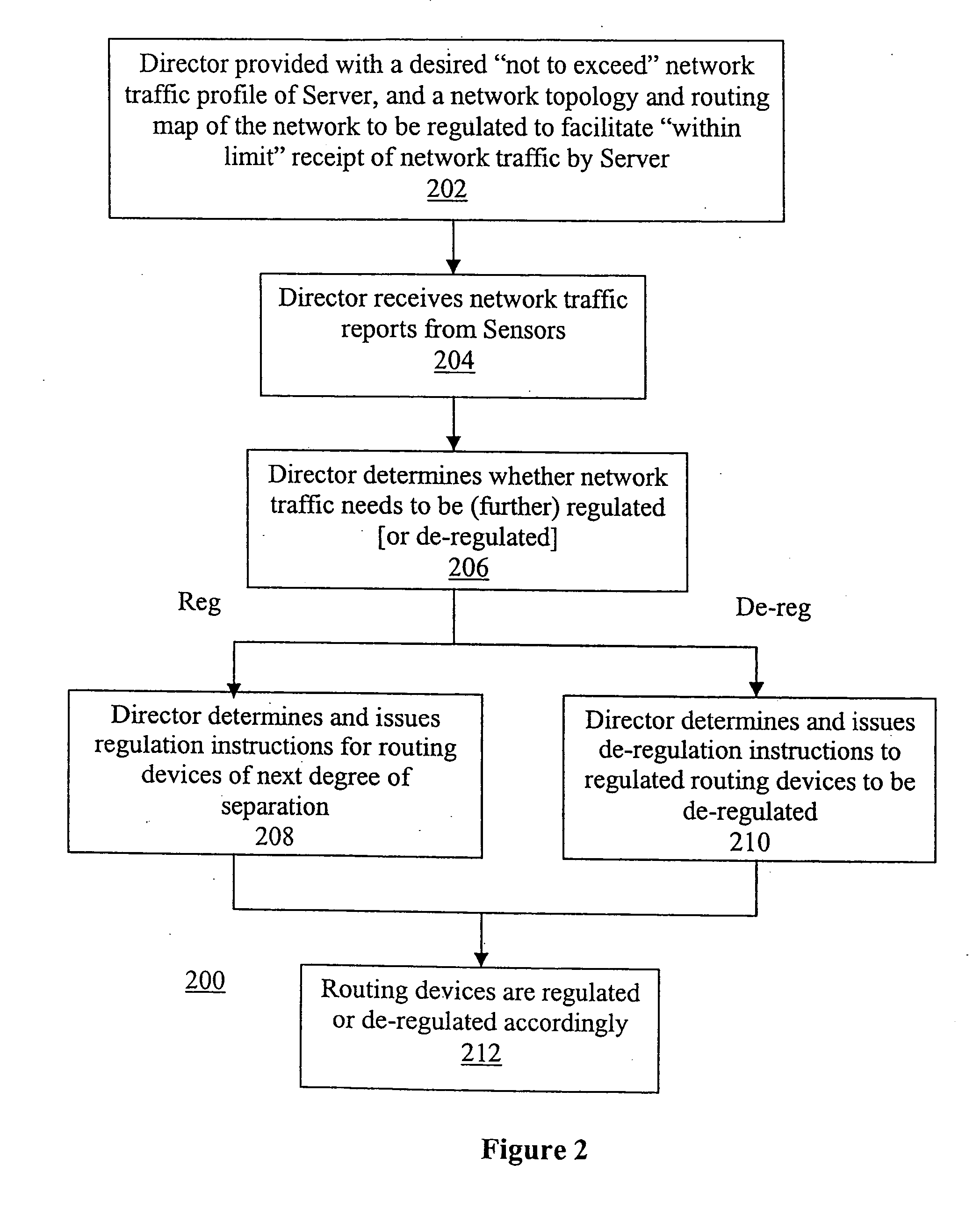
Progressive and distributed regulation of selected network traffic destined for a network node
InactiveUS20050018608A1Improve service qualityError preventionFrequency-division multiplex detailsTraffic capacitySelection criterion
An apparatus is equipped to receive network traffic data for network traffic routed through a number of routing devices with one or more degrees of separation from a network node. The network traffic data include at least network traffic data for network traffic destined for the network node which meet a traffic type selection criteria and are routed by the routing devices to the network node. The apparatus is further equipped to progressively regulate and de-regulate network traffic routing by the routing devices based at least in part on the received network traffic data and the degrees of separation of the routing devices from the network node. Regulation extends from routing devices with the lowest degree of separation from the network node to routing devices with the highest degree of separation, following in the reverse direction of the routing paths traversed by the packets to reach the network node. In one embodiment, the extension or push back is made one degree of separation at a time. In one embodiment, deregulation follows the reverse path, whereas in another embodiment, deregulation is determined and implemented locally, whenever regulation or the extent of regulation is no longer needed. In one embodiment, regulation is made in accordance with a not-to-exceed profile, and the not-to-exceed limit or limits are divided up as regulation extends away from the network node.
Owner:ARBOR NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com