Network security emulation system and its emulation method
An analog system and network security technology, applied in the transmission system, digital transmission system, data exchange network, etc., can solve the problem that network simulation software cannot simulate and simulate targeted network security issues, so as to improve scalability and use convenient effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
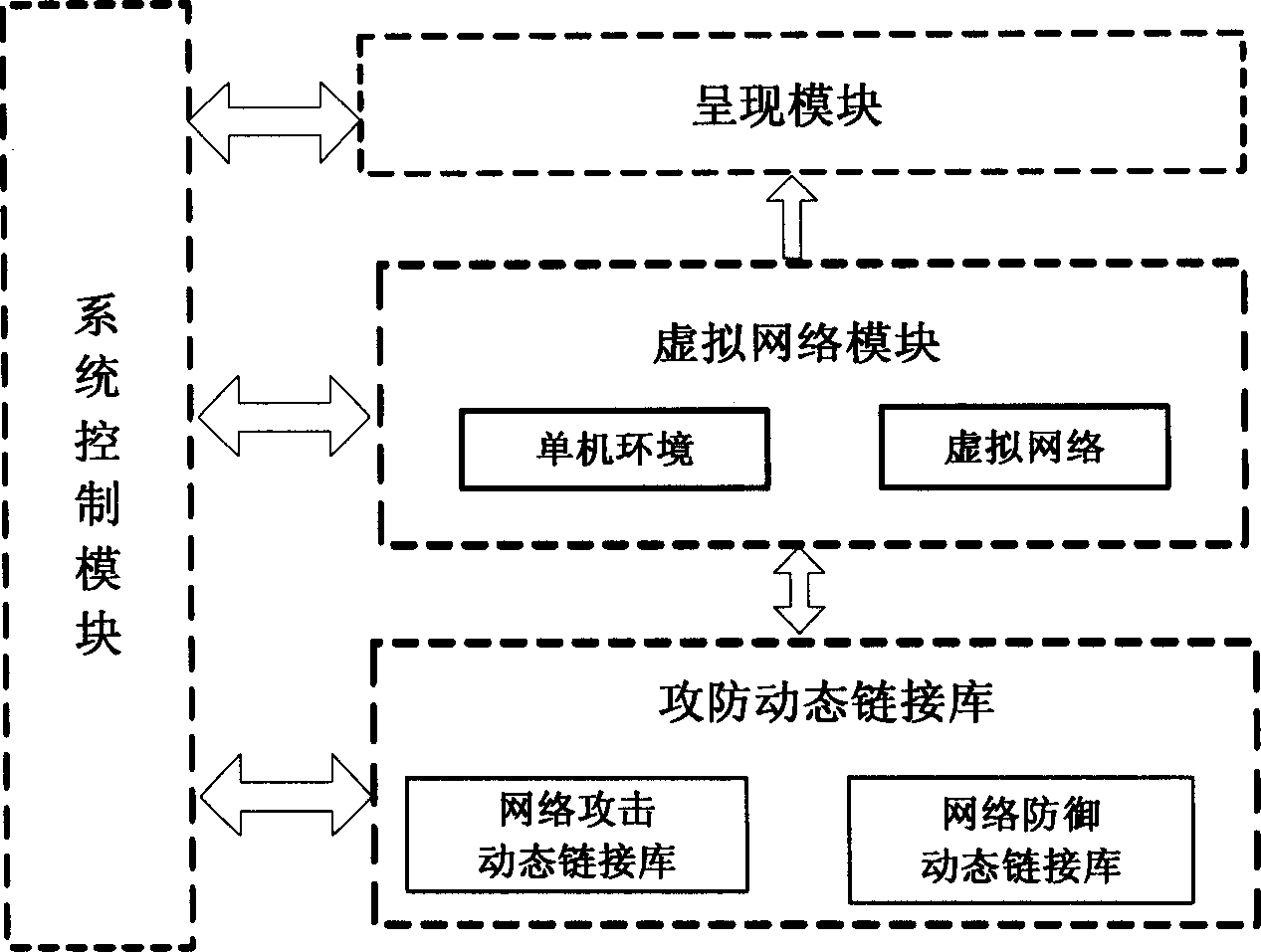
[0049] 1. System structure
[0050] refer to figure 1 , the logical structure of the network security simulation system of the present invention is composed of four parts, the virtual network module, the attack and defense dynamic link library, the system control module, and the presentation module, which cooperate with each other to form a logical structure of the network security simulation system. in:
[0051] The virtual network module is the platform and basic environment for network security simulation, and the network security simulation is carried out in the virtual network. A virtual network includes a real stand-alone environment and a virtual network environment. A real stand-alone environment refers to a stand-alone environment located in an actual physical network, where the actual network may be a local area network, a wide area network, or the Internet. A virtual network environment refers to a simulated network environment on a single host.
[0052]Offensiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com