Patents
Literature
237 results about "Network software" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
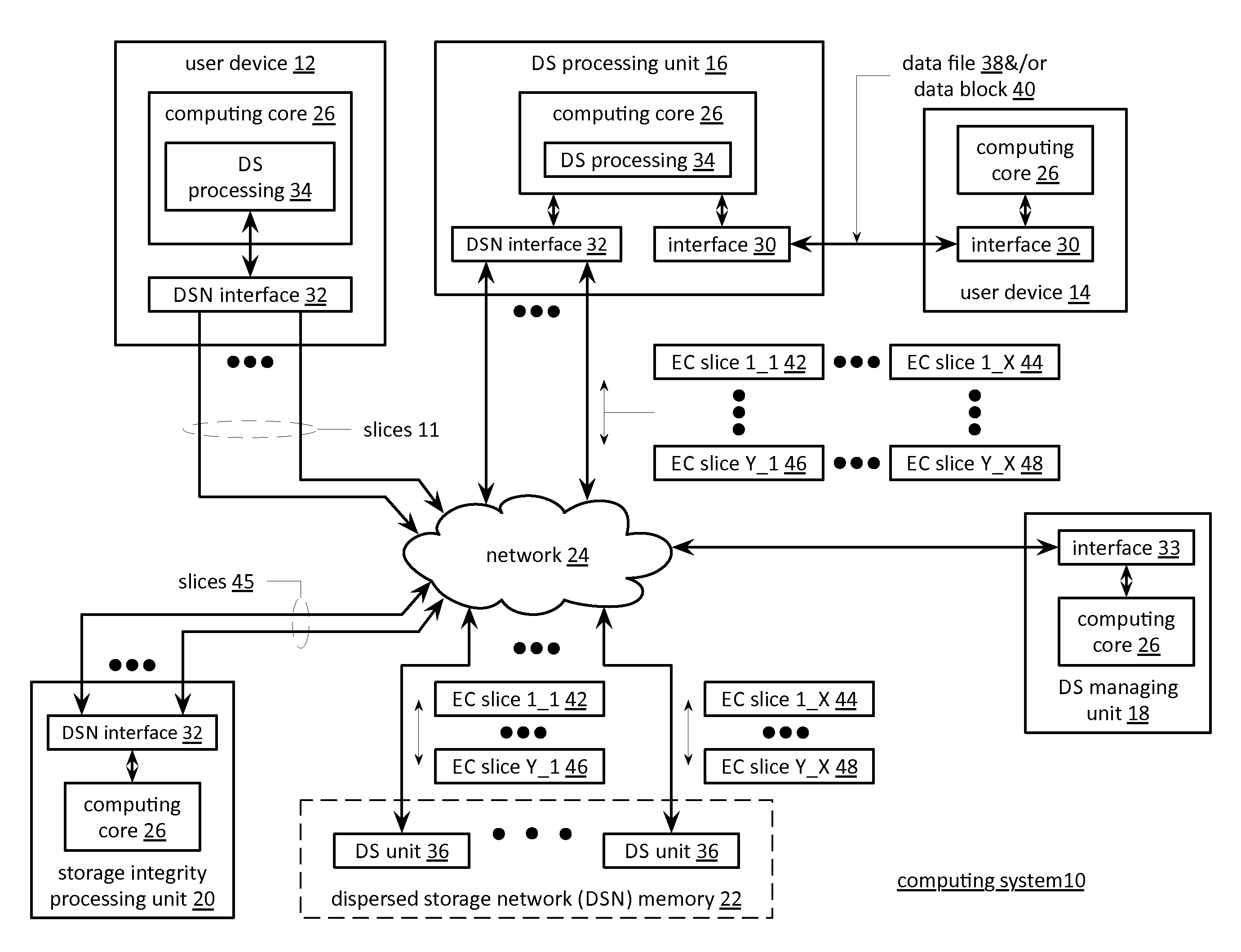
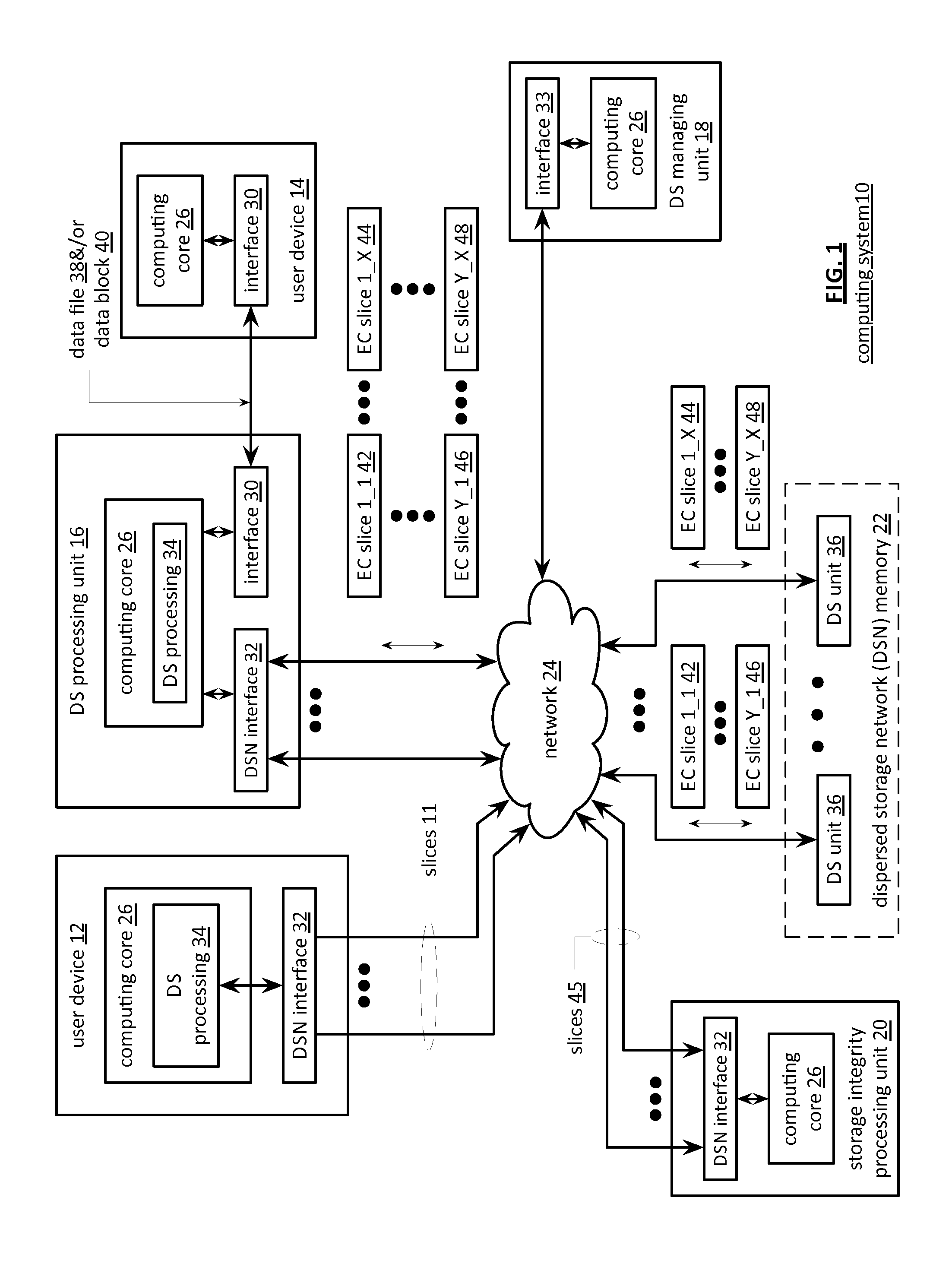
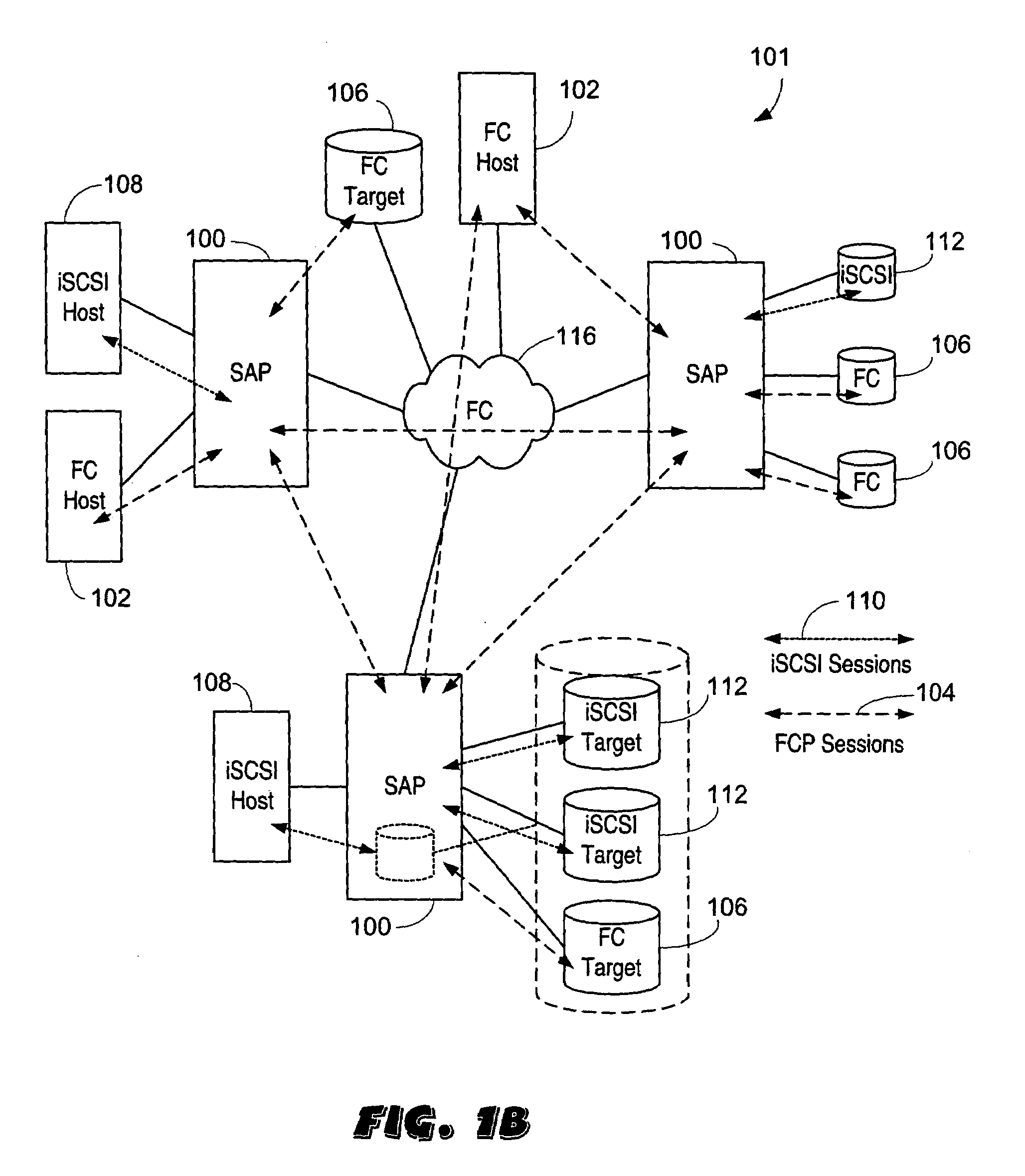
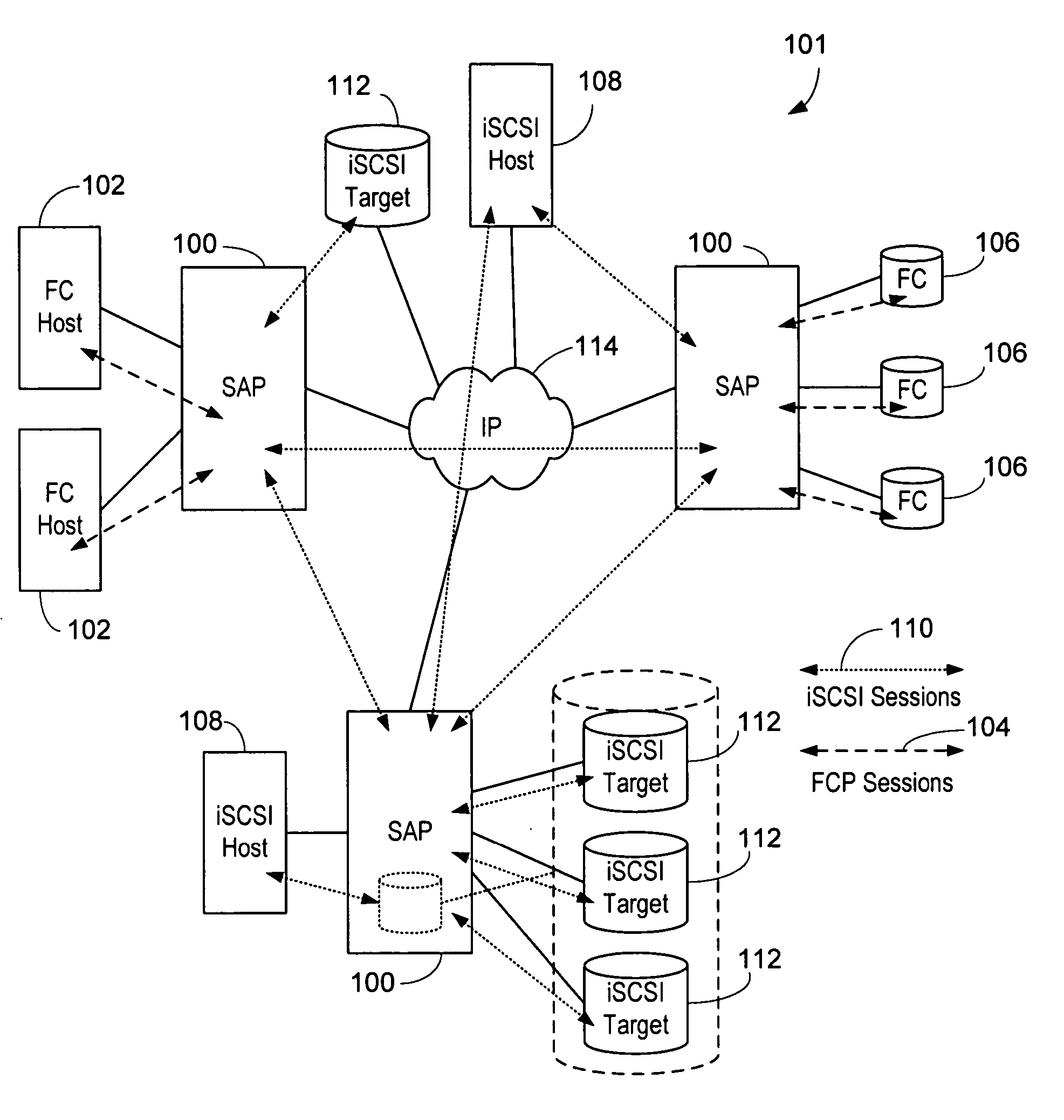
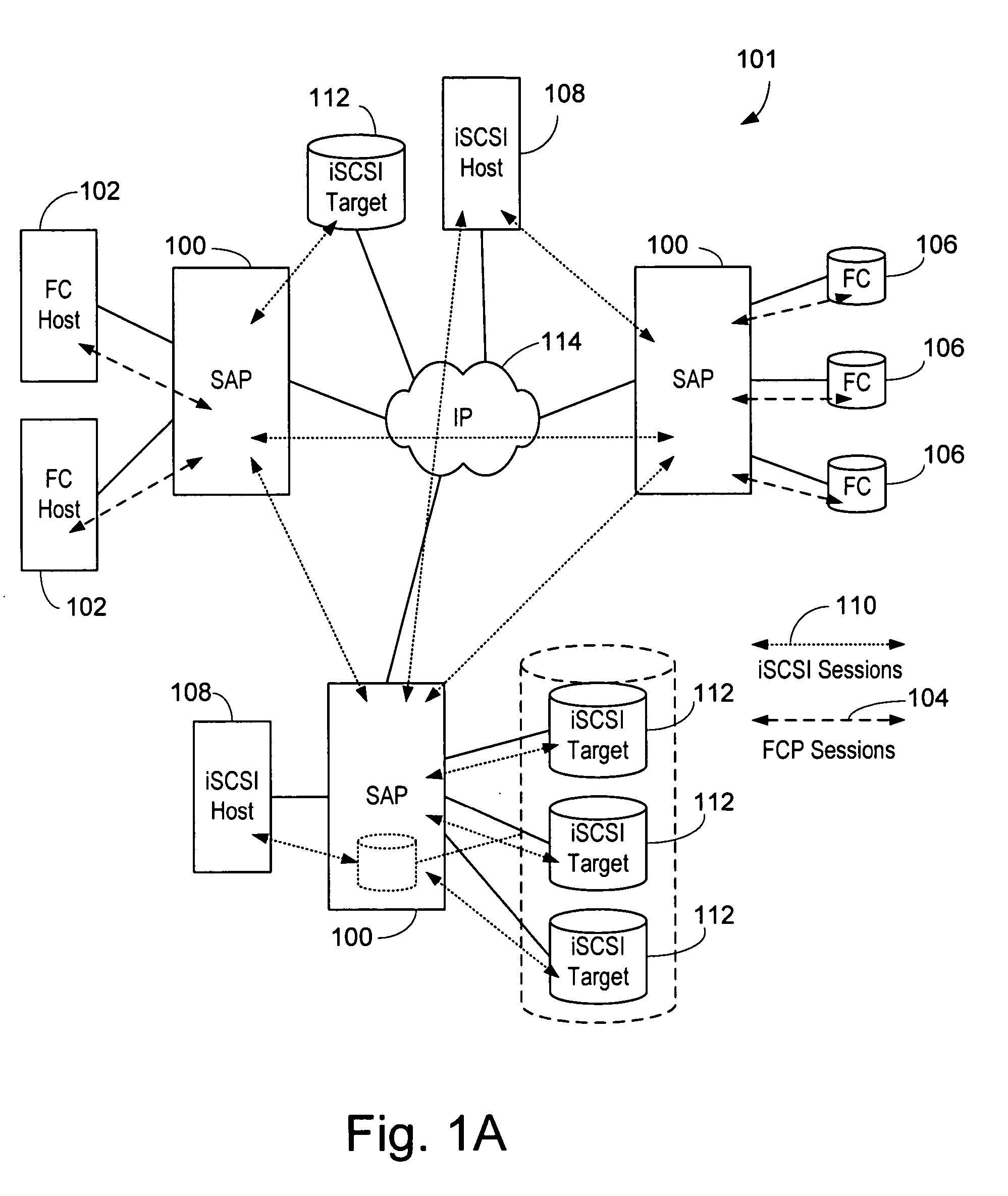
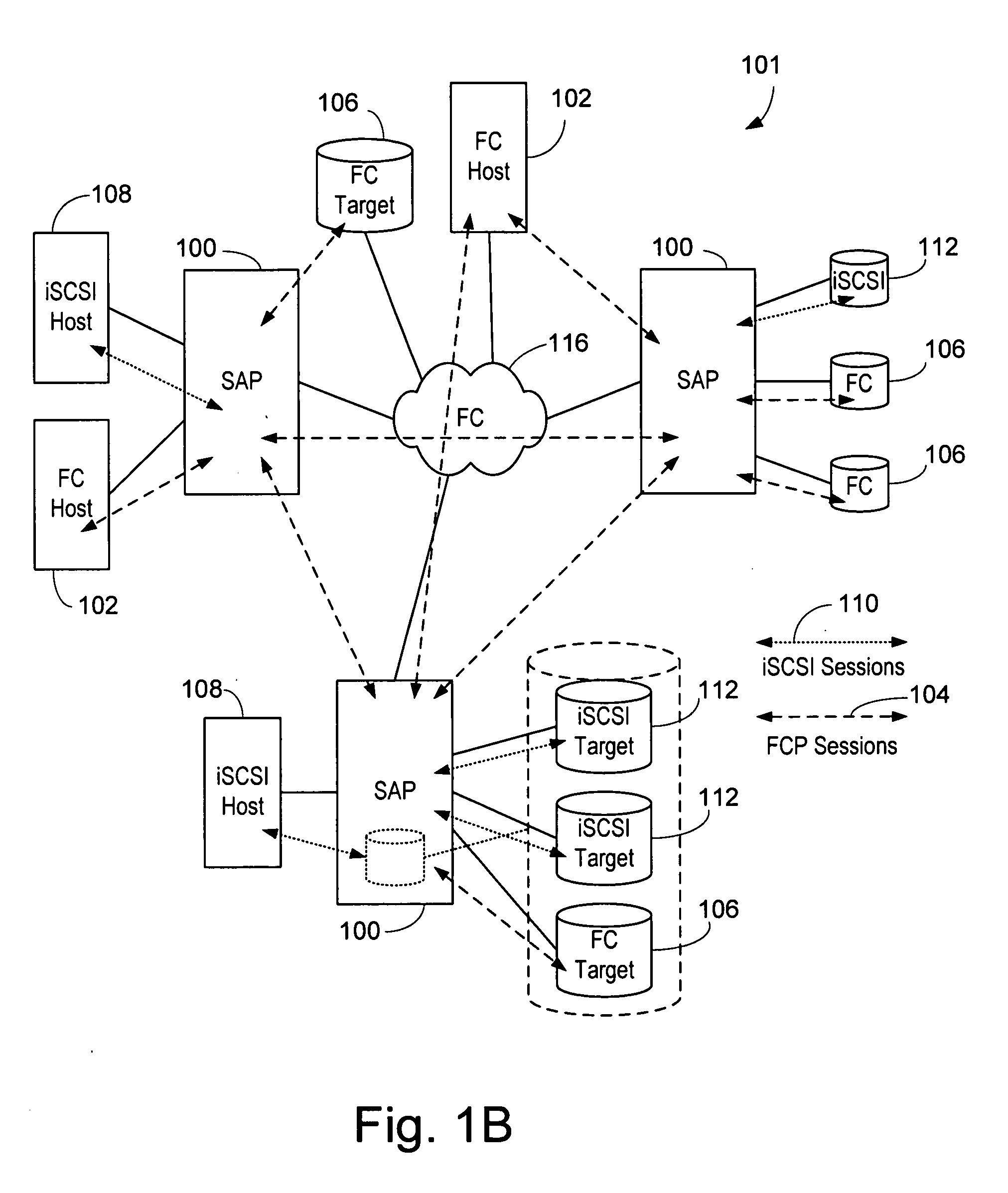
Updating distributed storage network software
ActiveUS20120311557A1Memory architecture accessing/allocationDigital computer detailsManagement unitSoftware update
A method begins by a management unit of a distributed storage network (DSN) sending a software update notice to a plurality of dispersed storage (DS) units, wherein the plurality of DS units supports a plurality of digital storage vaults, and wherein a set of DS units of the plurality of DS units supports a digital storage vault of the plurality of digital storage vaults. The method continues with a DS processing module determining an update strategy for updating software of the plurality of DS units such that at least a decode threshold number of DS units of the set of DS units is continually available to service access requests to the digital storage vault and updating the software of at least some of the plurality of DS units in accordance with the update strategy.
Owner:PURE STORAGE
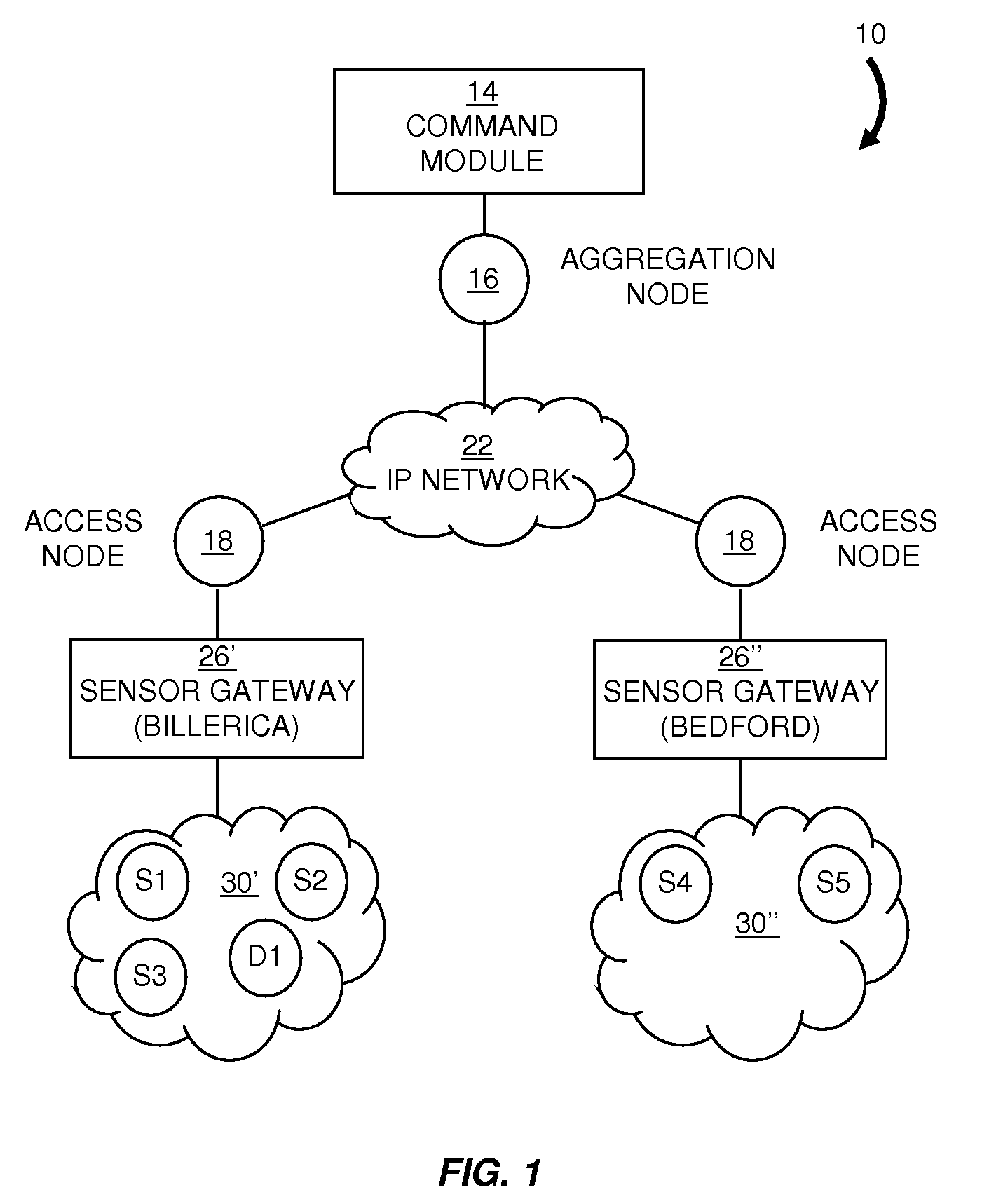
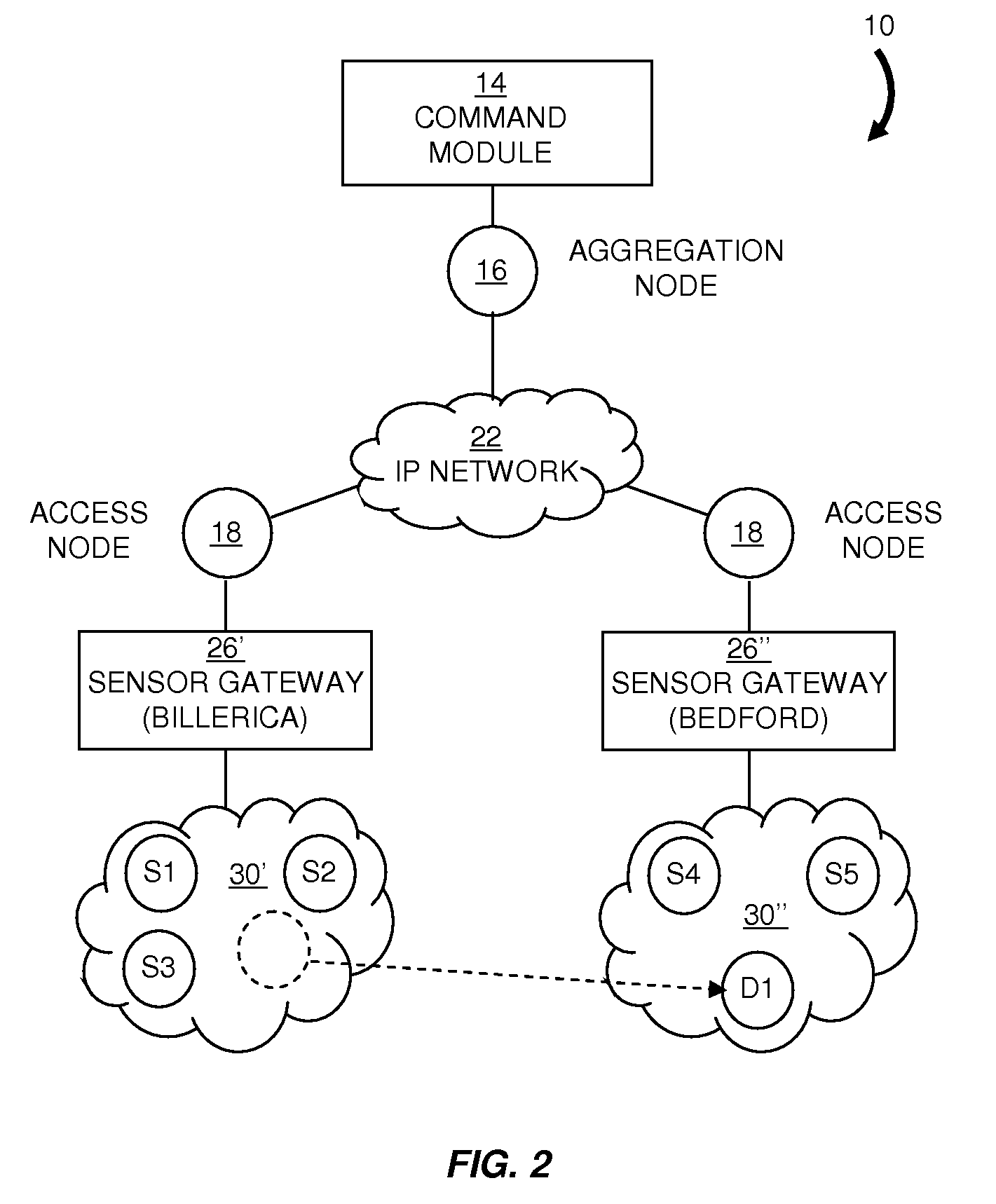
Dynamic sensor network registry
InactiveUS20090222541A1User identity/authority verificationNetwork topologiesNetwork connectionNetwork architecture
A scalable network architecture adapted to interface with various sensor types and sensor access mechanisms while providing real-time access to sensor data for distributed applications and organizations is described. A centralized sensor network service manages the registration, capabilities, near real-time status of the sensors and their current network connections. New sensors are discovered automatically through messaging between network access nodes and the sensor registry. The registry service can be made available to distributed sensor applications and sensor middleware, and facilitates the sharing of sensors across organizations. The sensor registry is automatically updated by network software and does not require manual configuration or reconfiguration each time a sensor is added to or relocated within the network. Authentication and authorization policies can be implemented to ensure that only authorized applications can query and view the registry. The registry can be implemented for multi-vendor sensor networks and can accommodate multiple addressing schemes.
Owner:RPX CLEARINGHOUSE
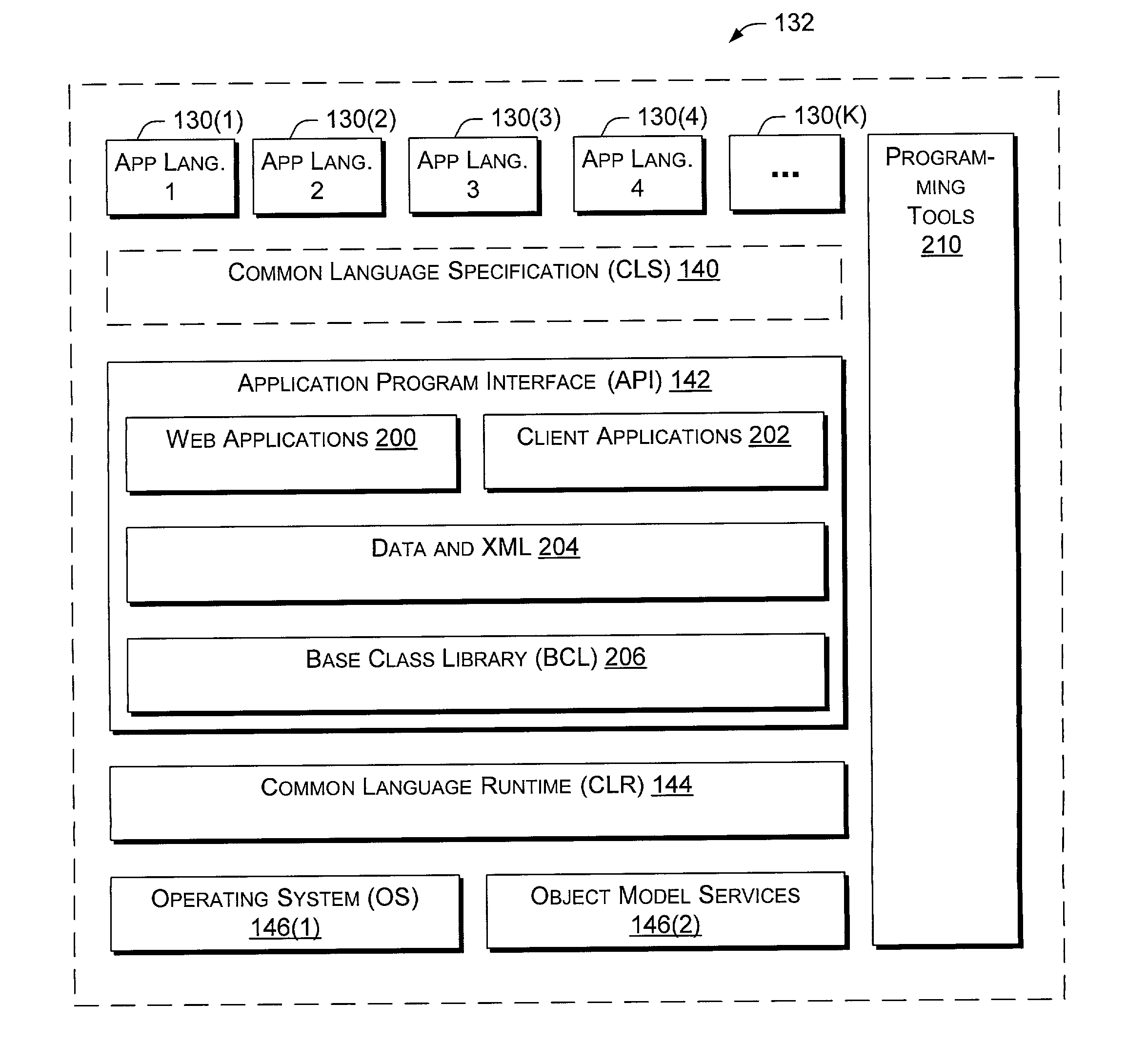
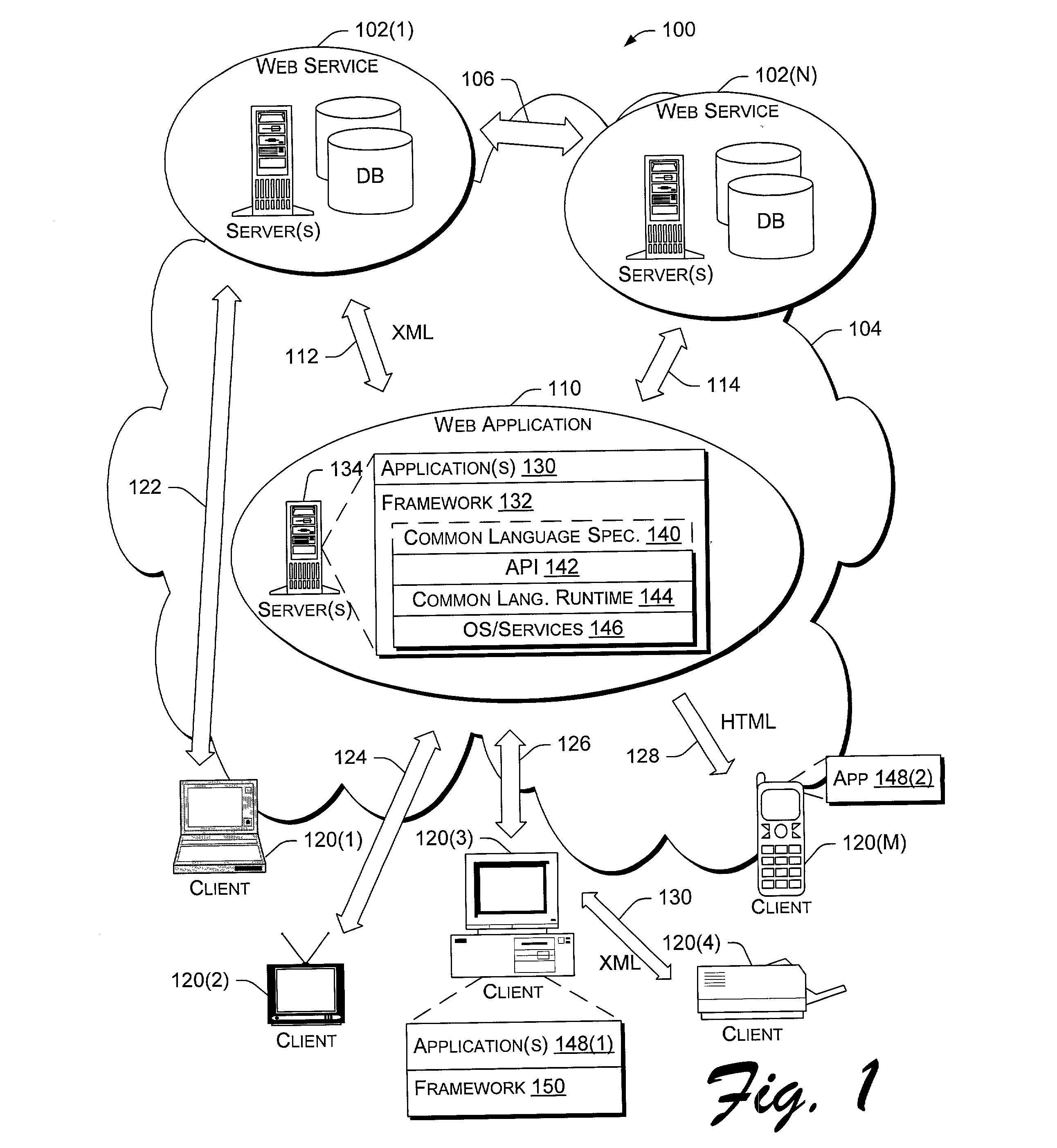
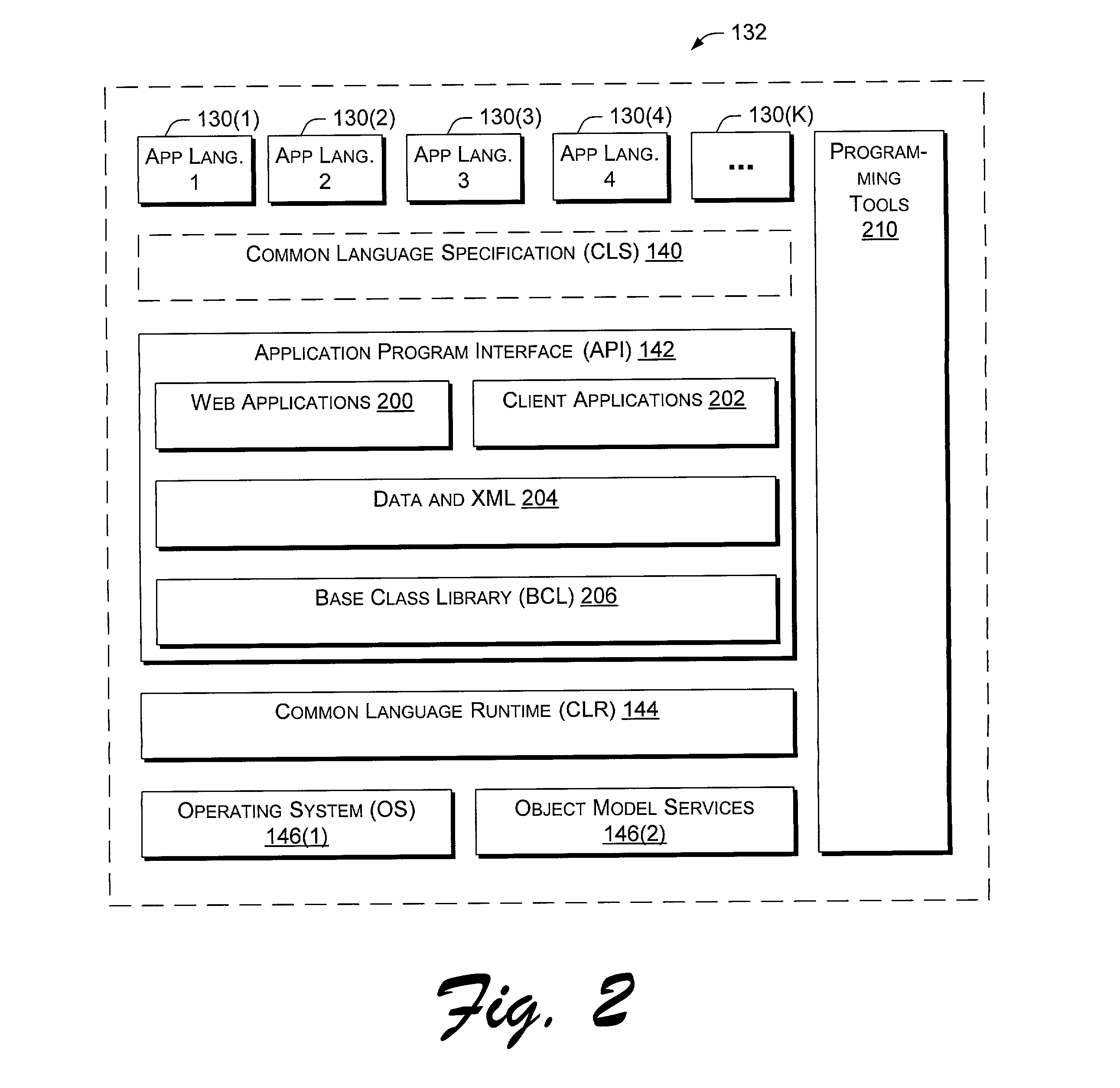
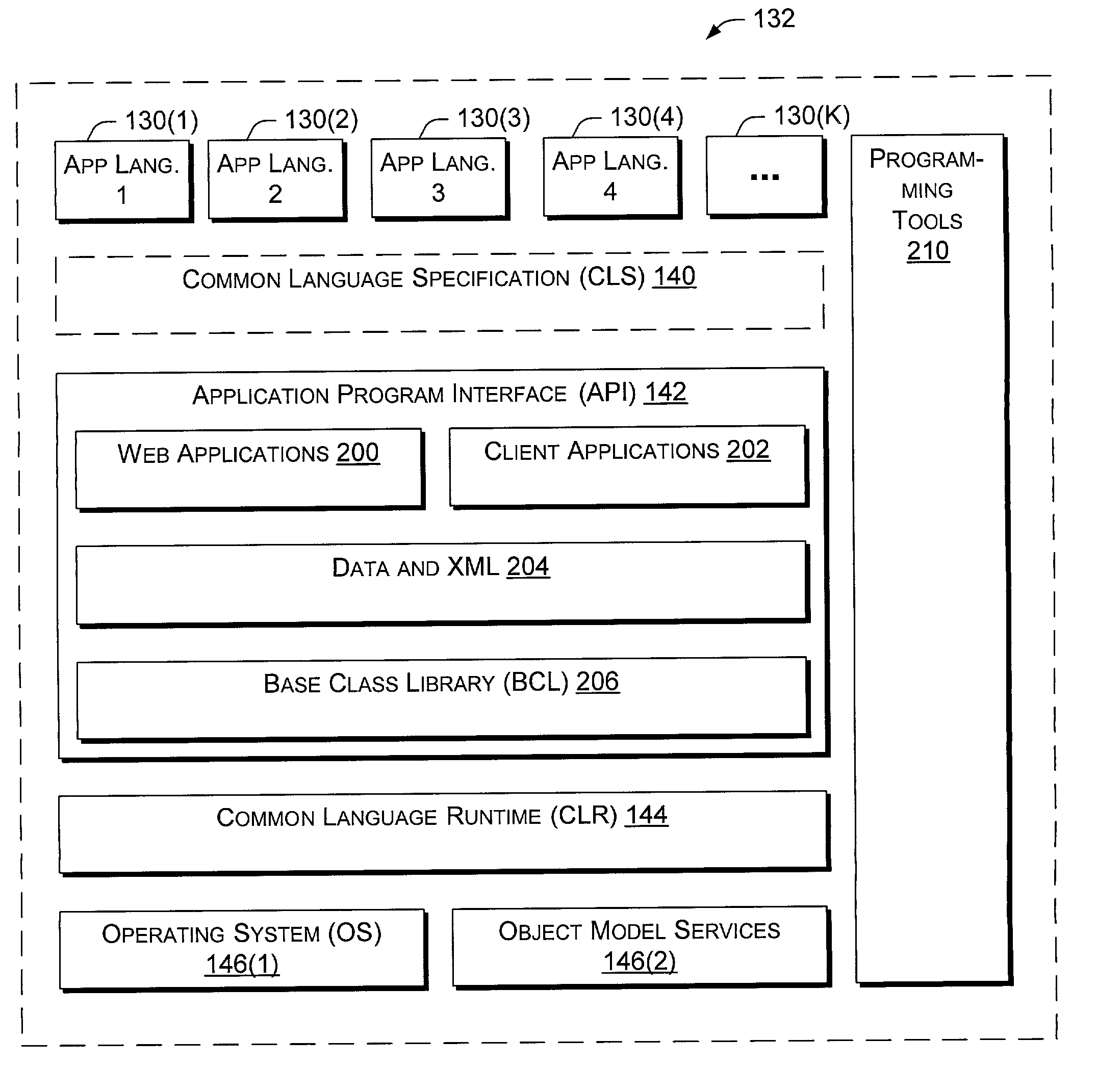
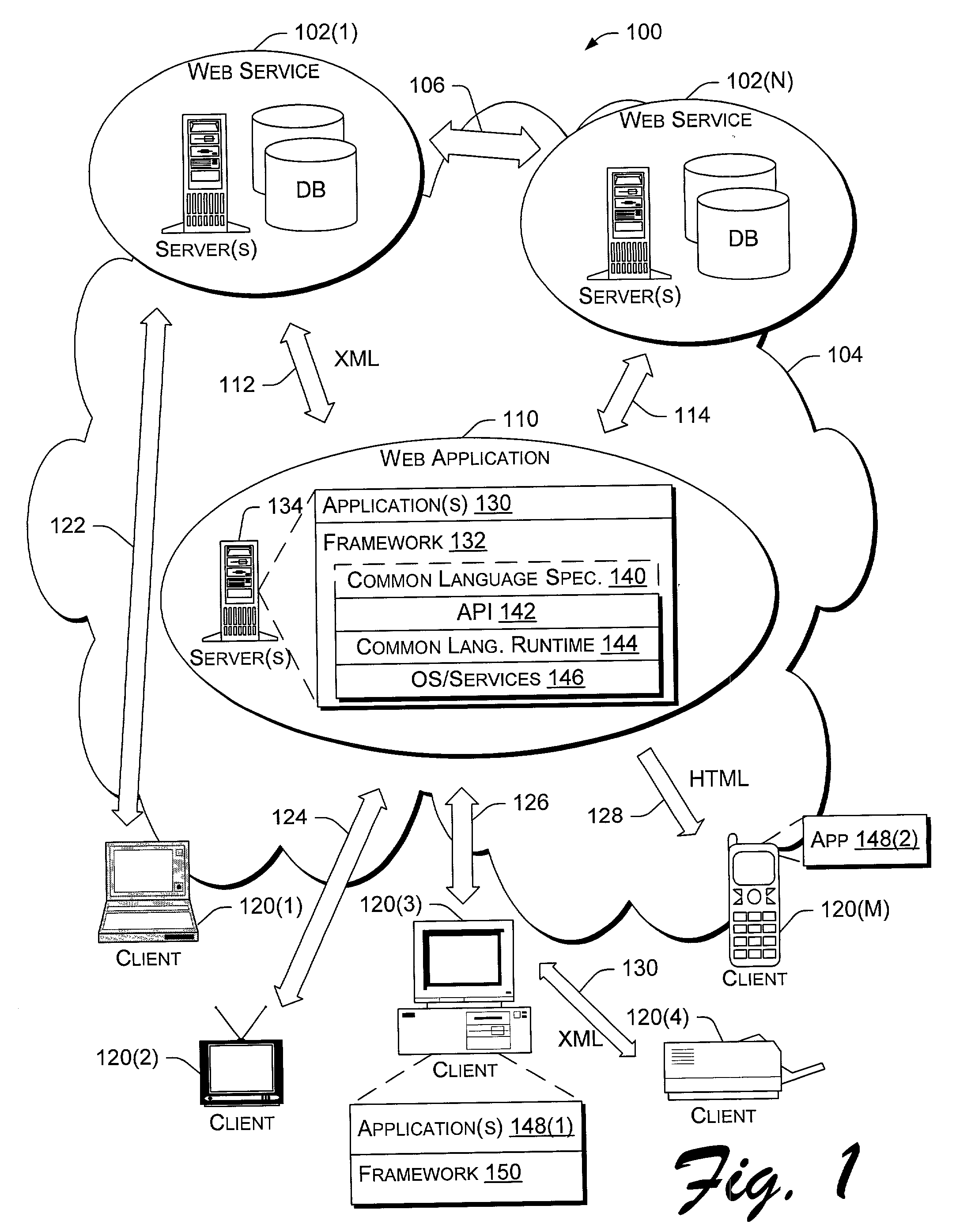
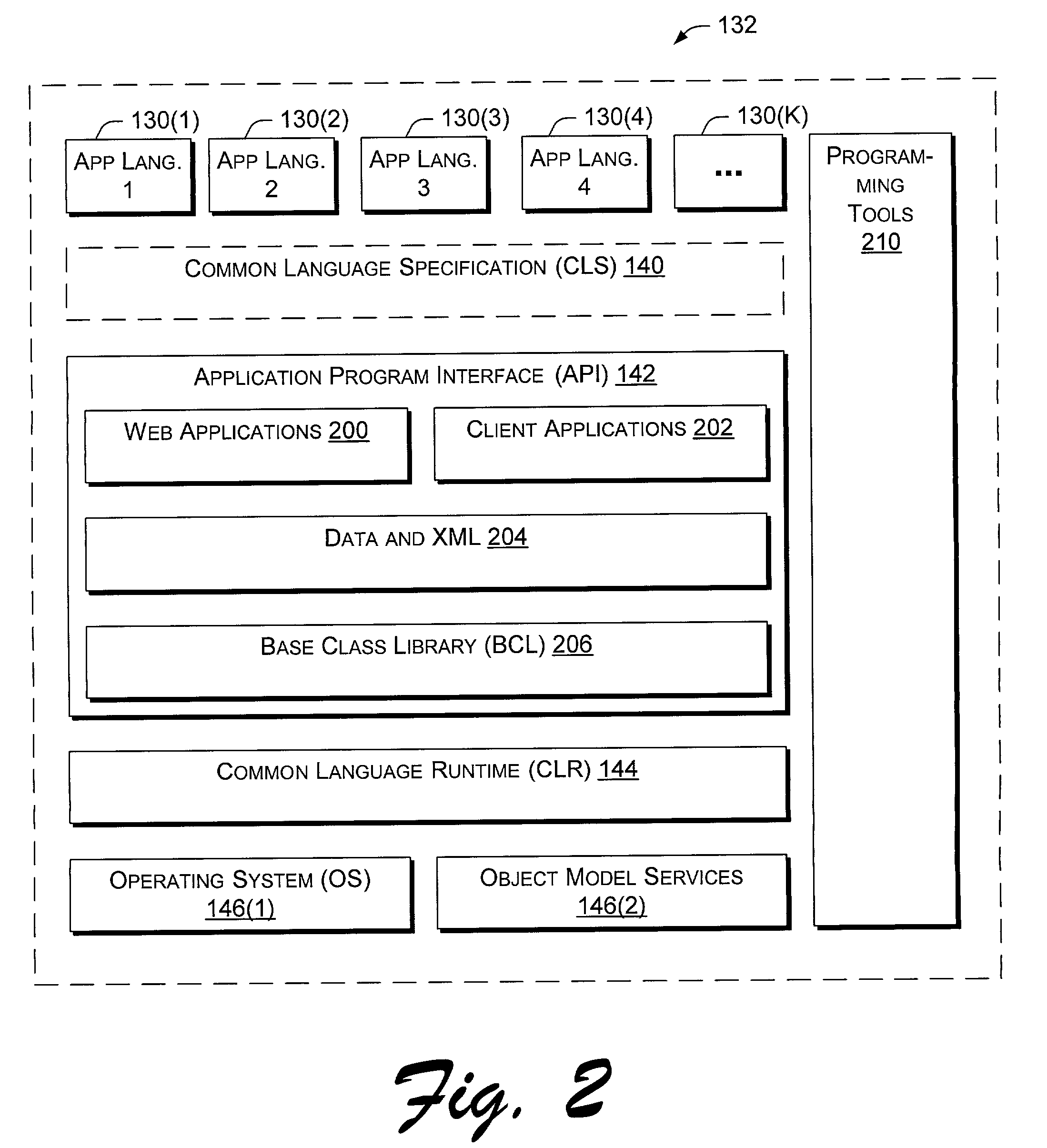
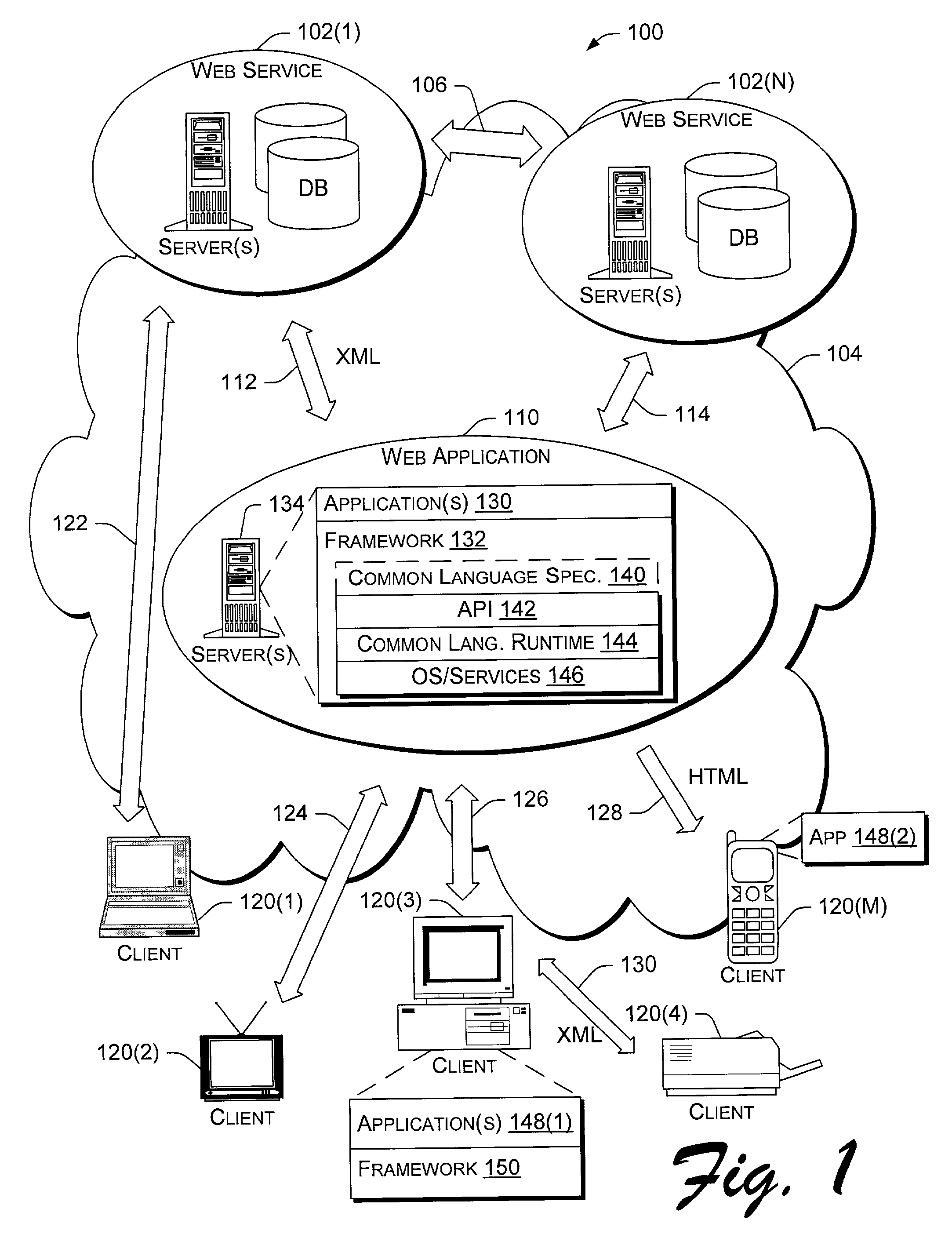
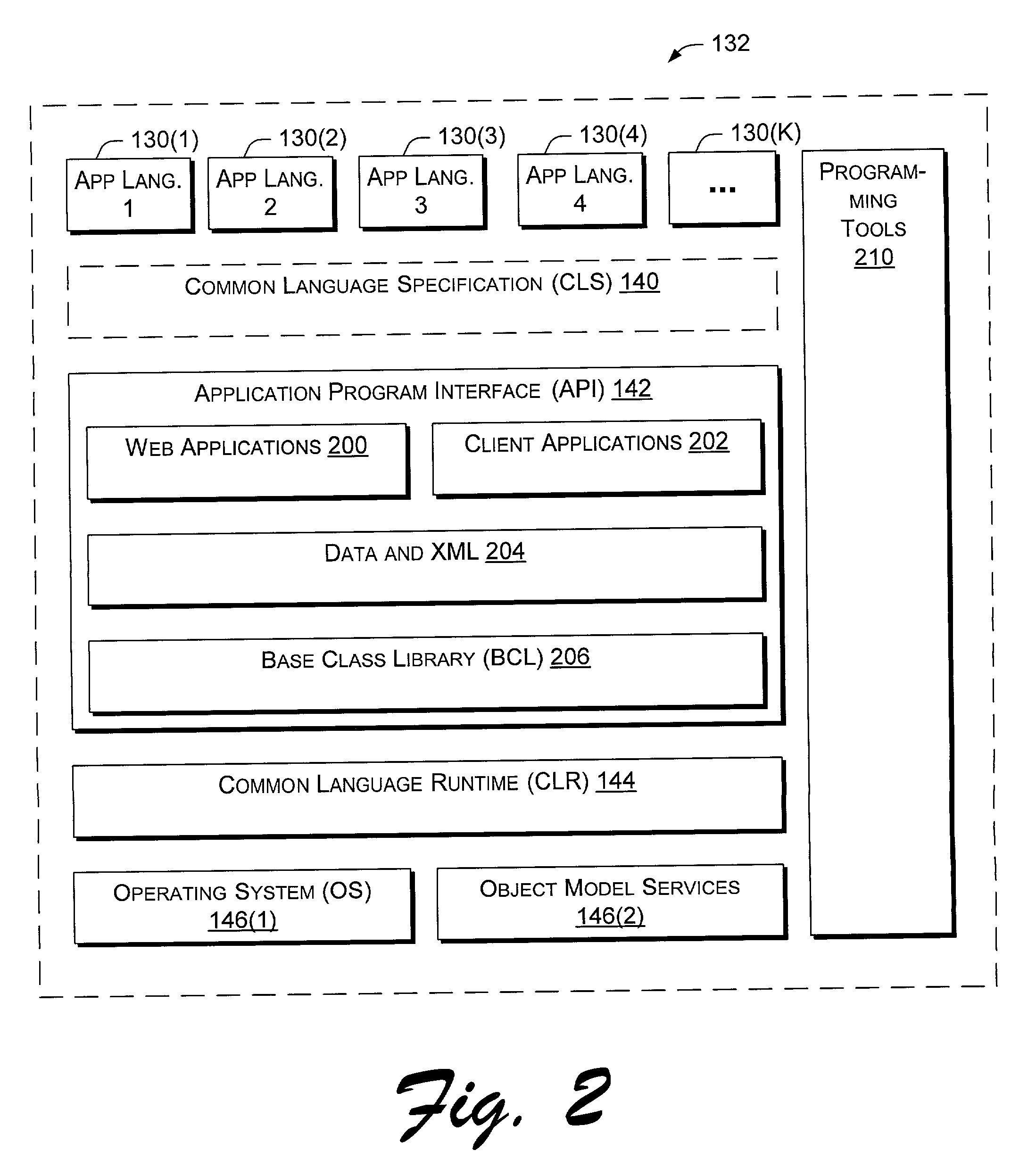
Application program interface for network software platform
InactiveUS20030172196A1Specific program execution arrangementsMemory systemsWeb applicationApplication programming interface
An application program interface (API) provides a set of functions that make available support for processing XML documents for application developers who build Web applications on Microsoft Corporation's .NET(TM) platform.
Owner:MICROSOFT TECH LICENSING LLC
Application program interface for network software platform
InactiveUS7165239B2Specific program execution arrangementsMemory systemsWeb applicationApplication programming interface
An application program interface (API) provides a set of functions that make available support for processing XML documents for application developers who build Web applications on Microsoft Corporation's .NET™ platform.
Owner:MICROSOFT TECH LICENSING LLC
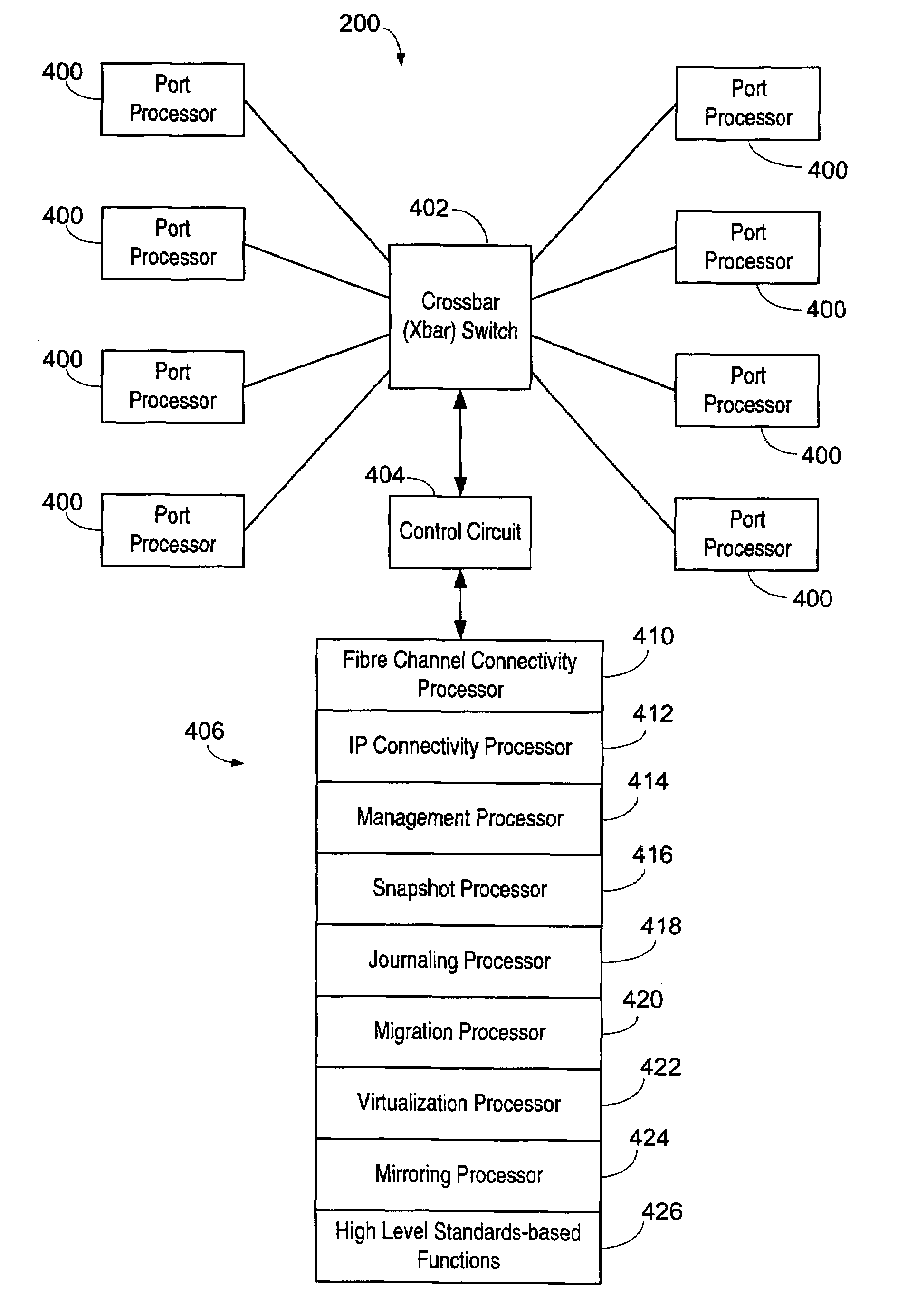
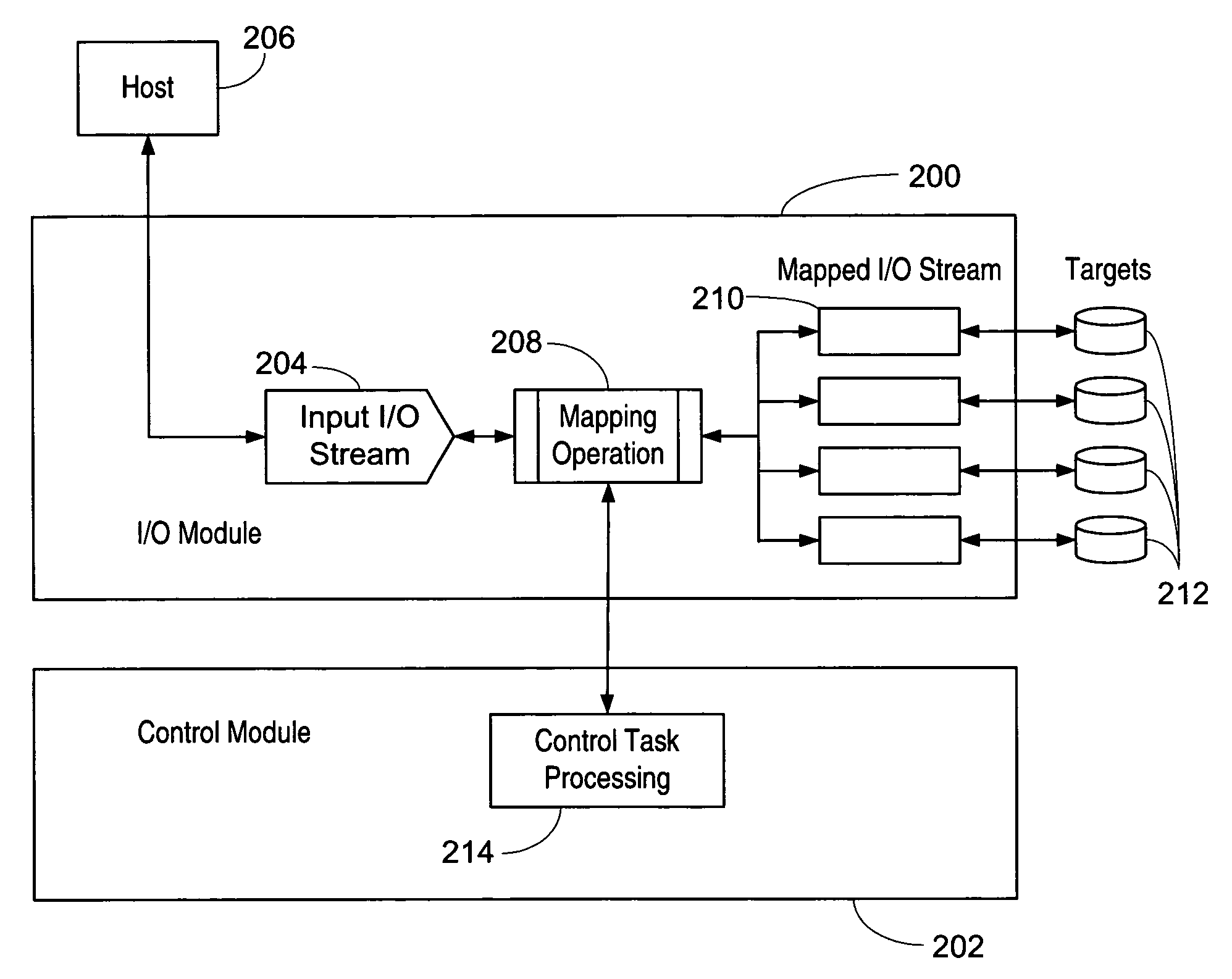
Apparatus and method for data virtualization in a storage processing device
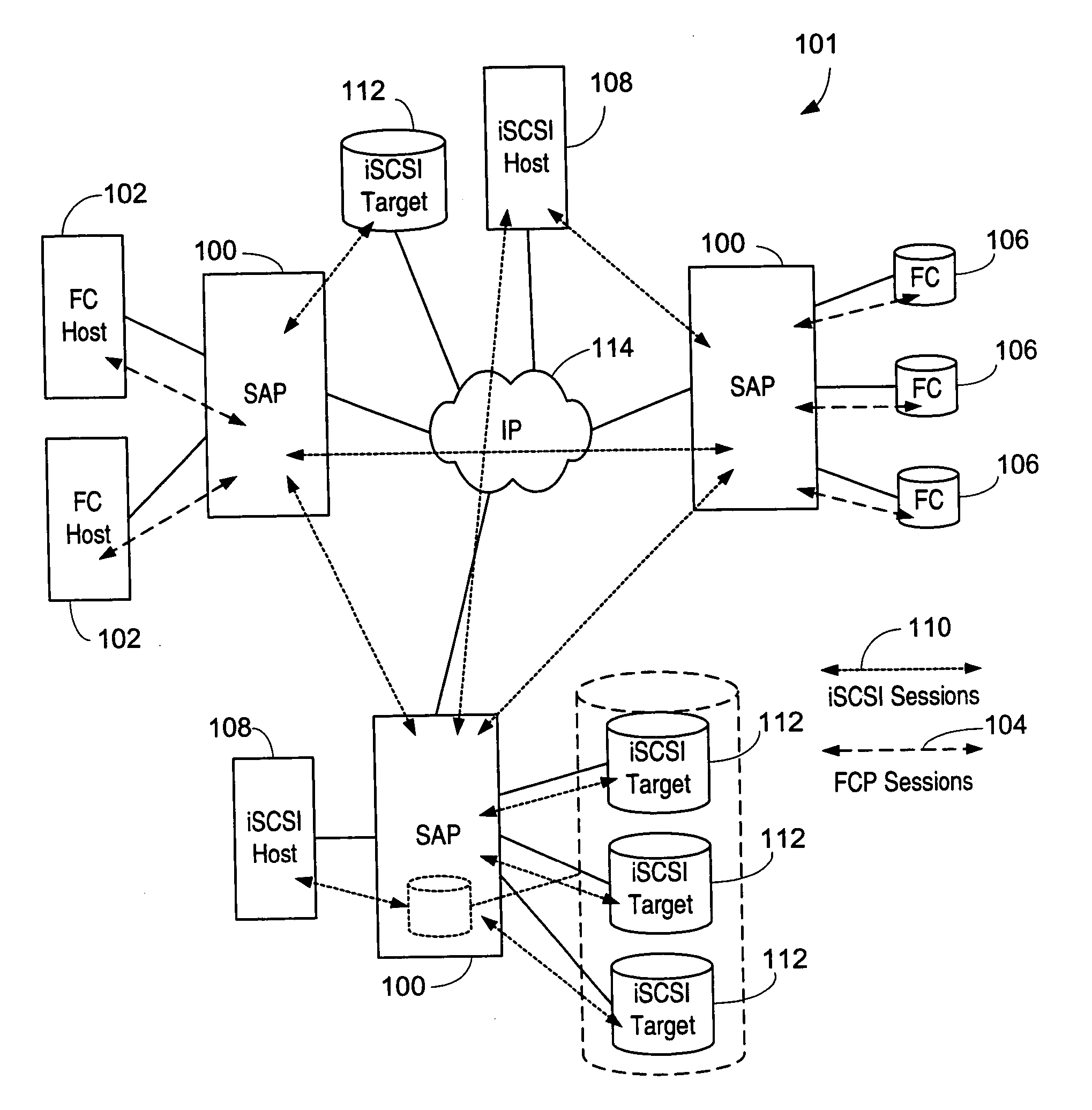
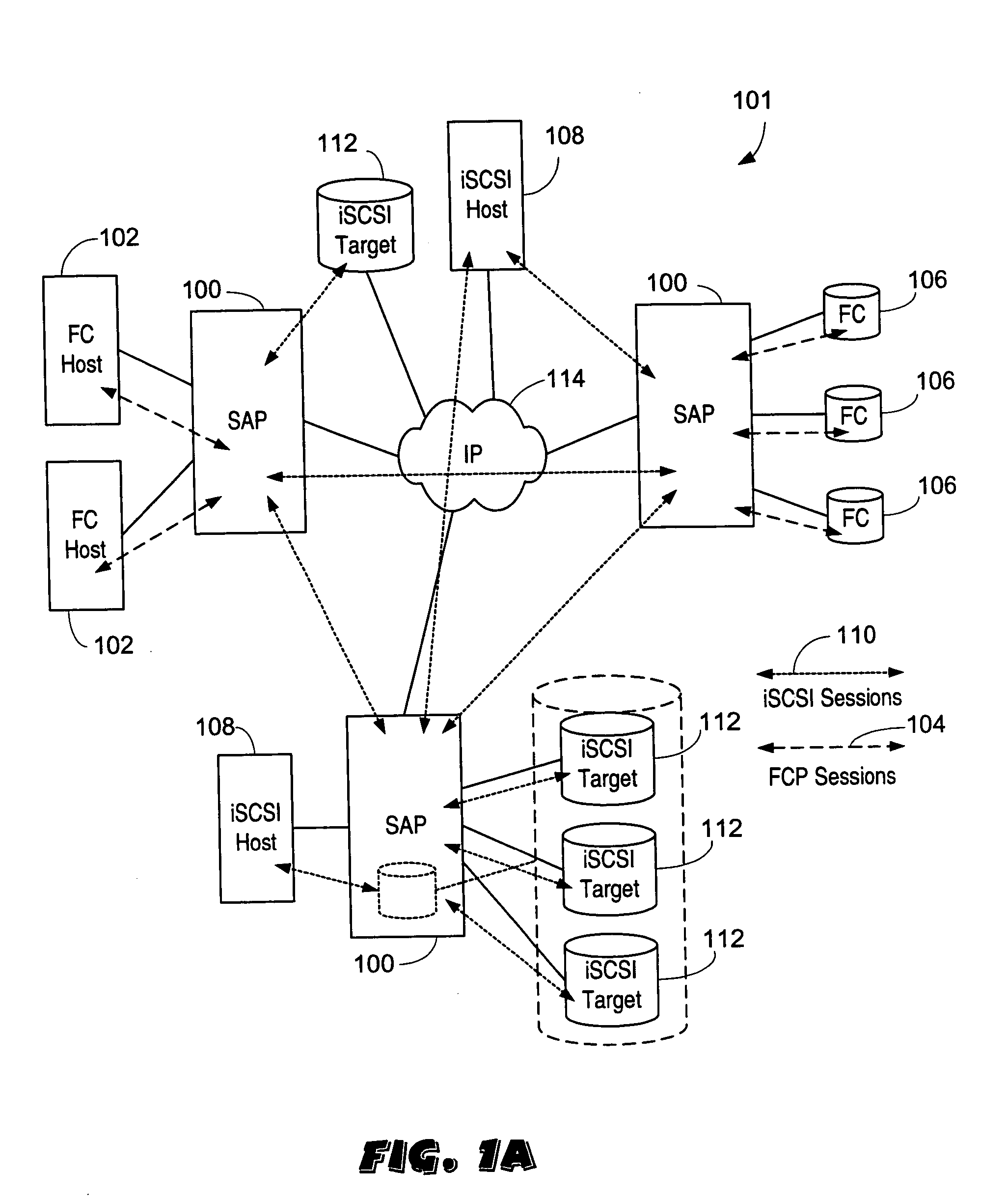
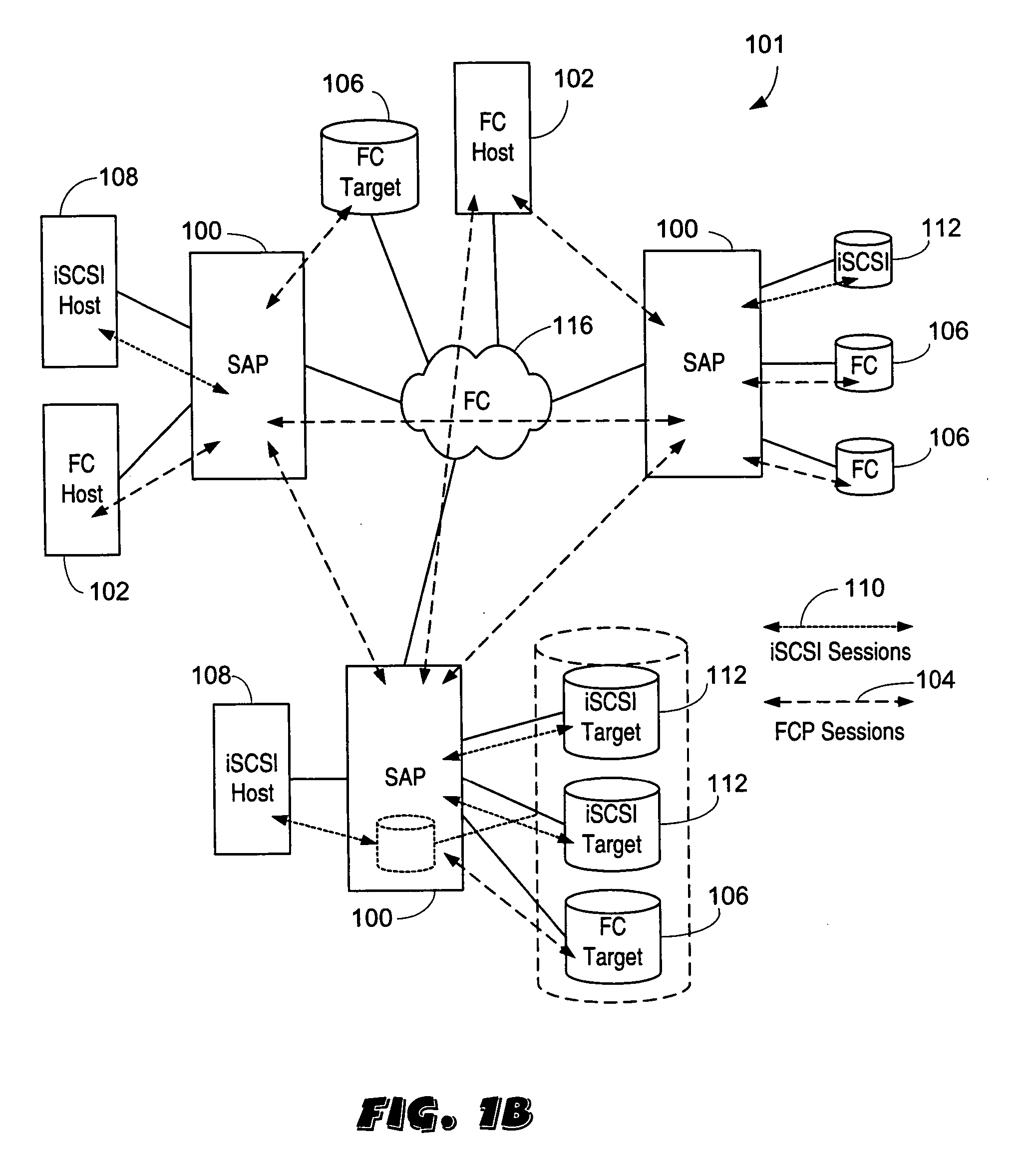
ActiveUS20050033878A1Achieve scaleProvide flexibilityMultiplex system selection arrangementsInput/output to record carriersInternet trafficMulti protocol
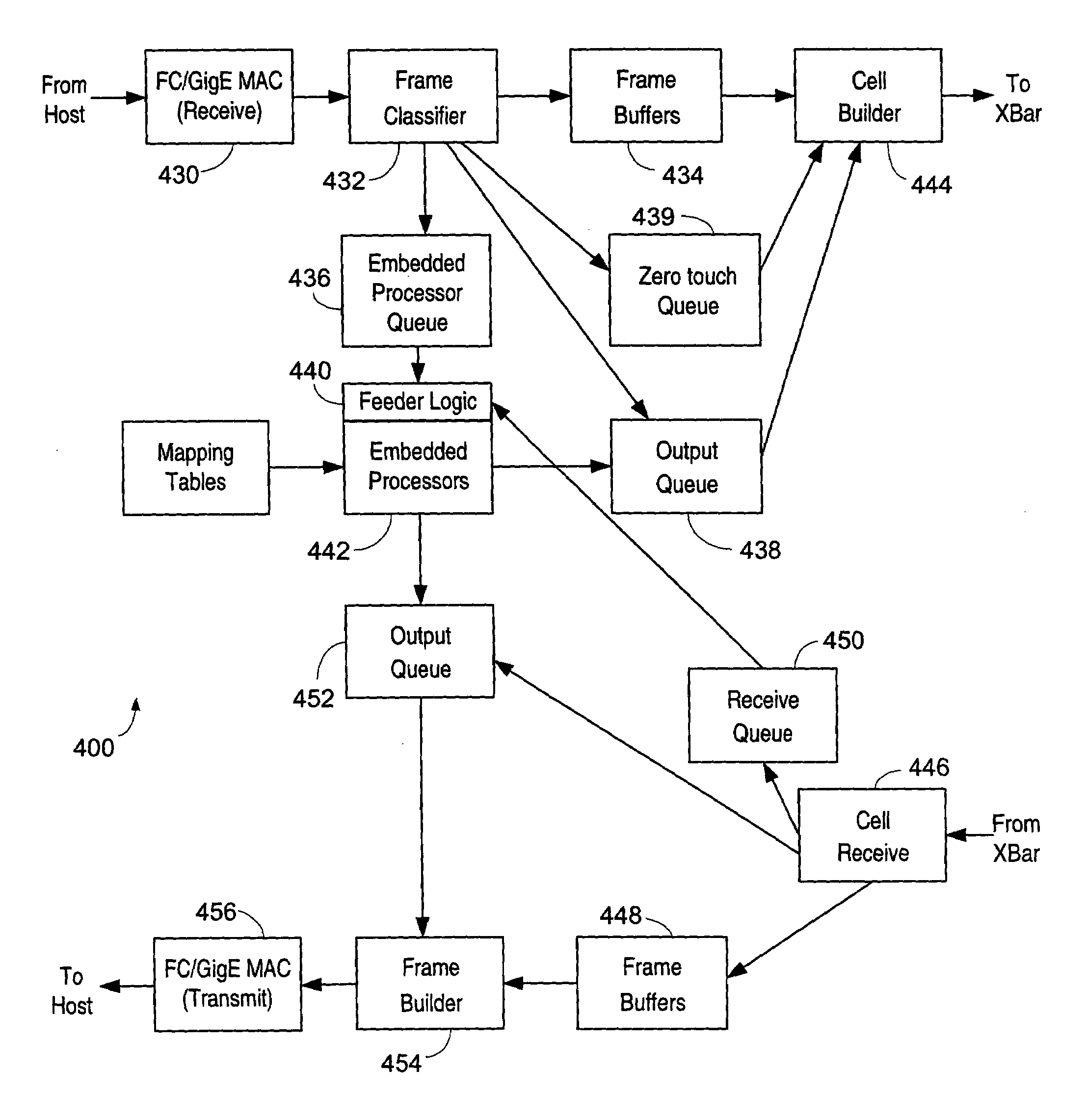
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:AVAGO TECH INT SALES PTE LTD
Software executables having virtual hardware, operating systems, and networks
InactiveUS20080028401A1Software simulation/interpretation/emulationMemory systemsOperational systemWeb browser
Owner:GEISINGER NILE JOSIAH
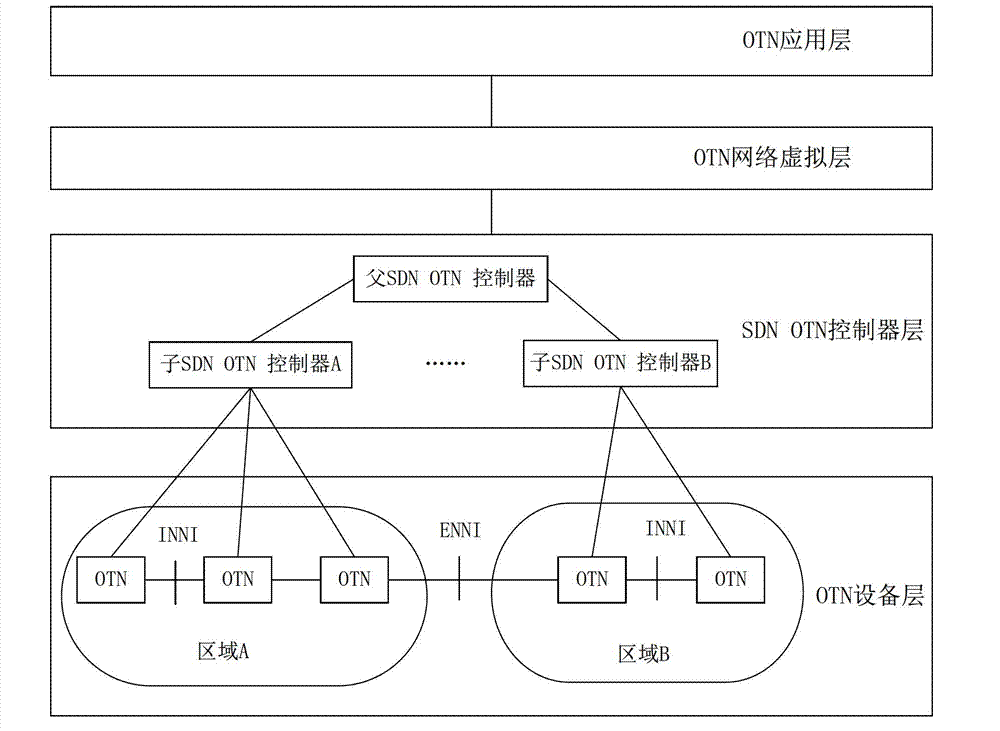
Framework system of grade software defined network software controller and implementation method thereof
ActiveCN103051565AResolve resource conflictsAvoid asyncData switching networksStructure of Management InformationNetwork control
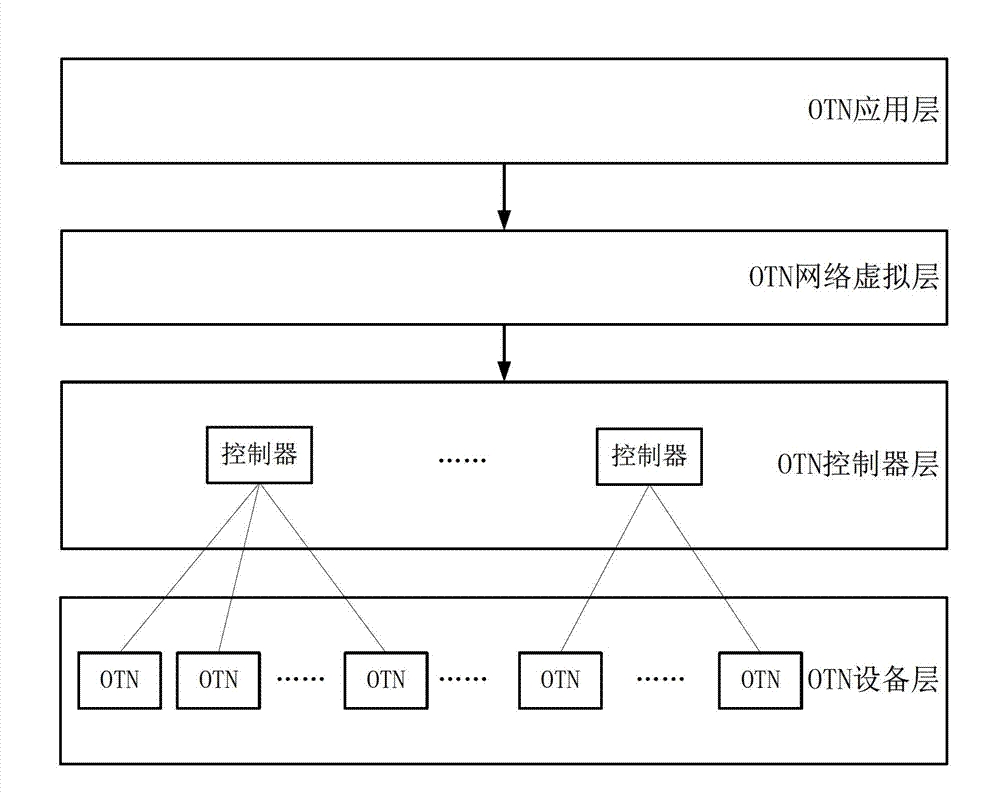
The invention discloses a framework system of a grade software defined network software controller and an implementation method thereof. The framework system and the implementation method are applied in a multi-domain optical transport network (OTN); an inter-domain mapping relation of a whole network view and a physical device network is established according to whole network topologic information by a primary (SDNOTN) controller; an inter-domain mapping processing request of the whole network view and the physical device network in each domain is sent to each auxiliary SDNOTN; and the domain mapping relation of the whole network view and the physical device network is established by the auxiliary SDNOTN controllers. Grade structures of the primary SDNOTN controller and the auxiliary SDNOTN controllers are arranged in the framework system, so that the mapping relation of the multi-domain whole network view and the overall physical device network in real sense is realized, and a whole network resource optimizing algorithm is realized in the real sense, so that the problem that the inter-domain link resource conflict occurs in a cross-domain service connection signaling process can be thoroughly solved.
Owner:ZTE CORP
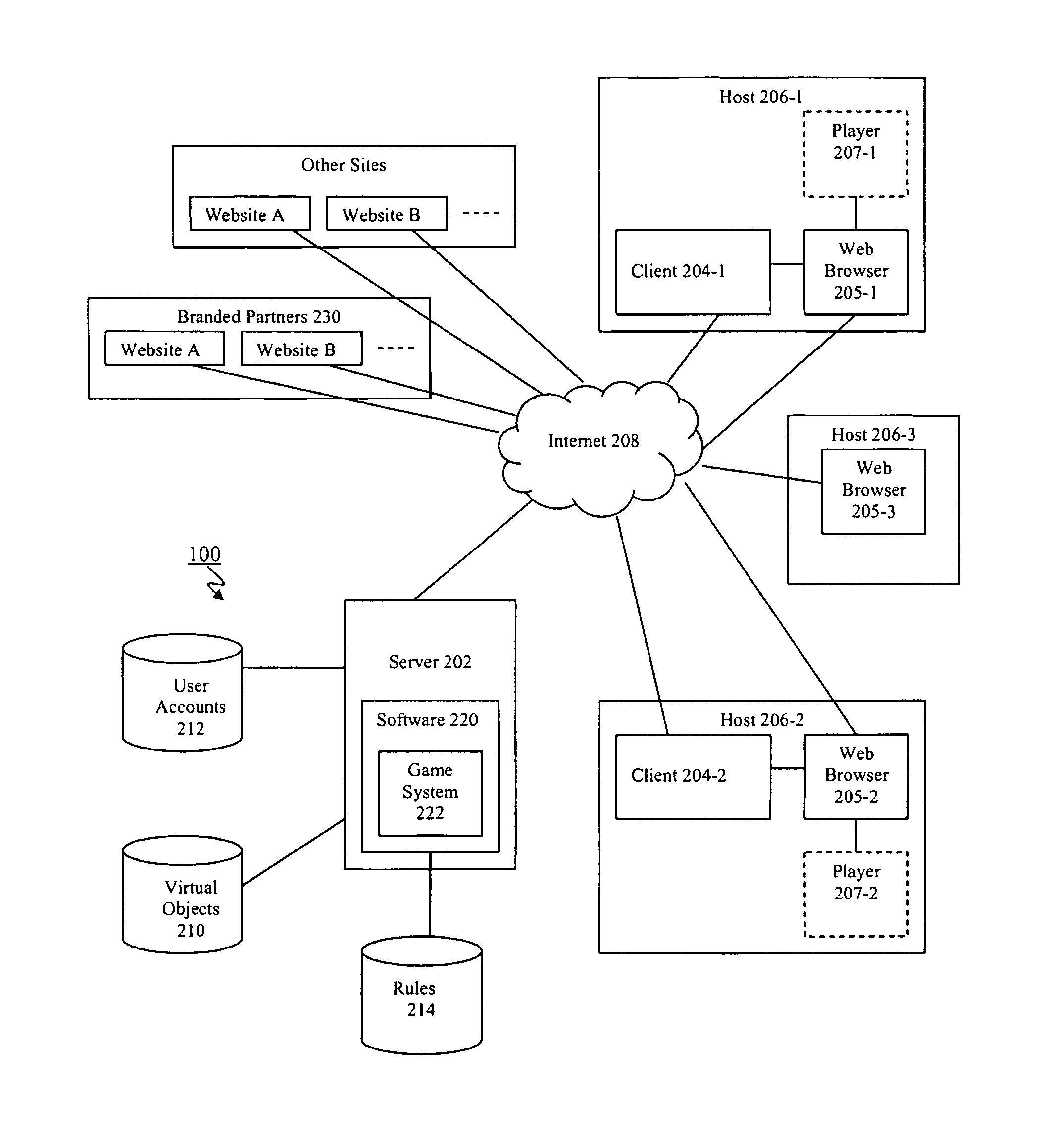
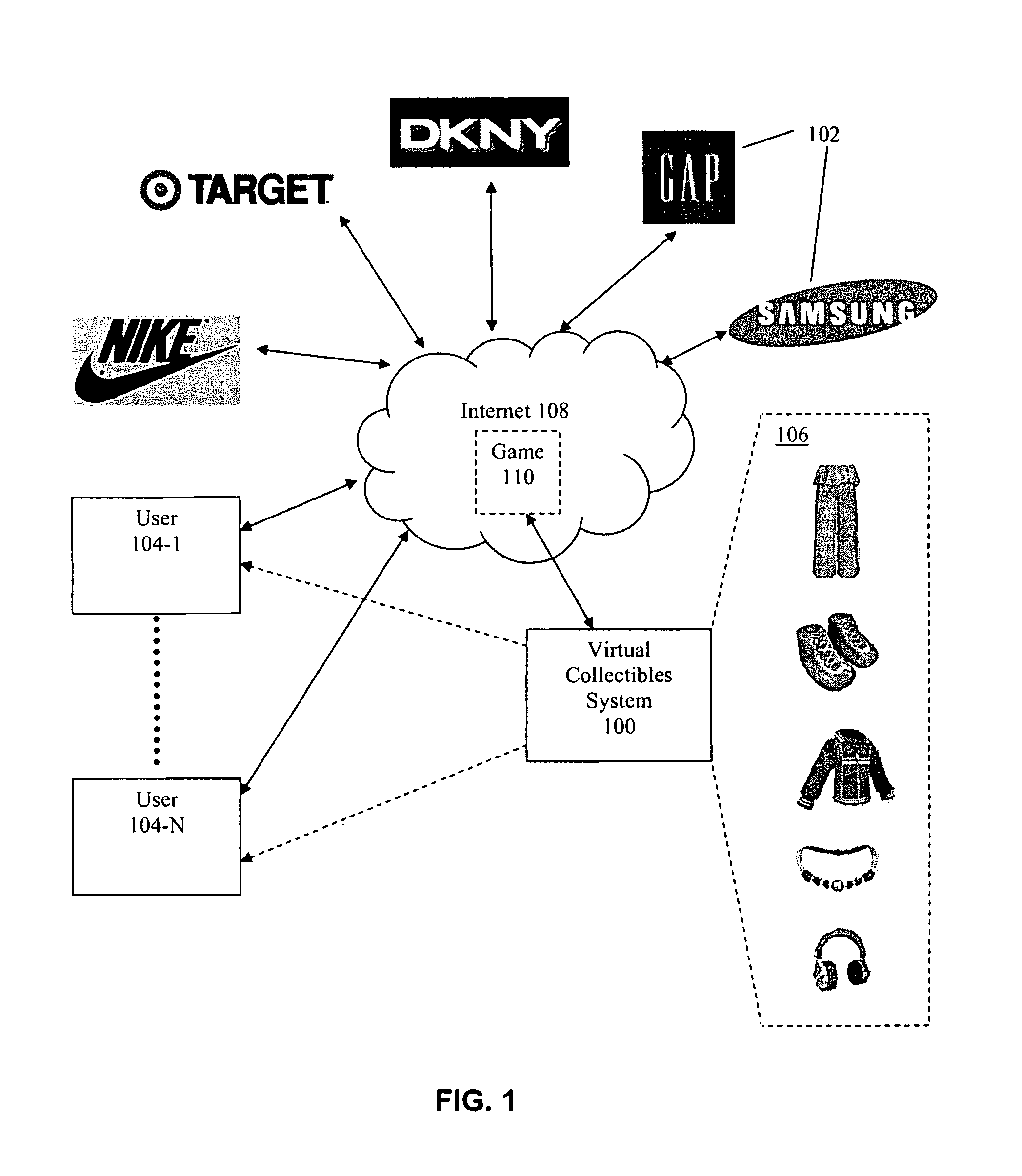
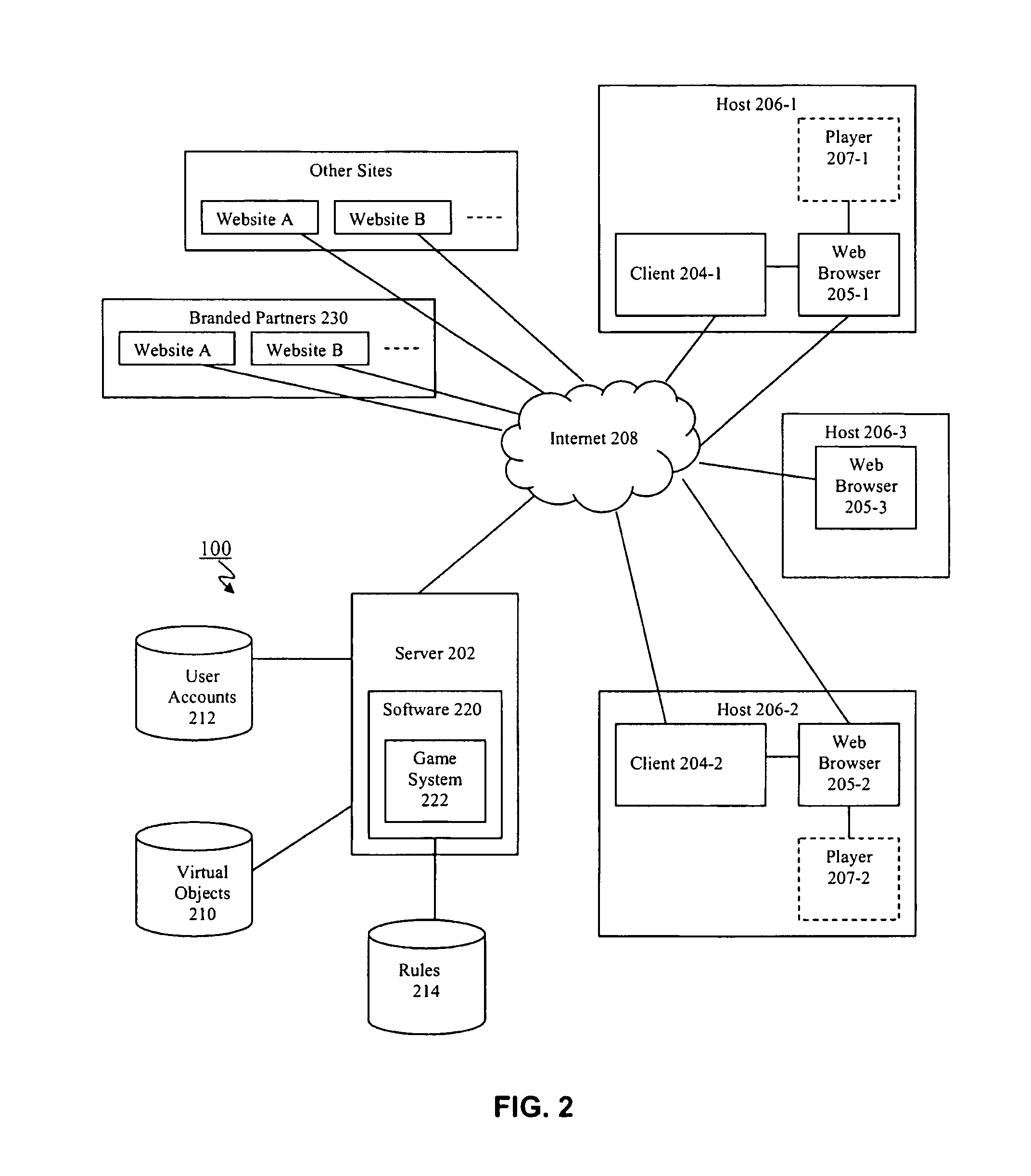
Method and apparatus for promoting desired on-line activities using on-line games
InactiveUS8239487B1Easy accessSuperior on-line advertising revenue opportunitiesMultiple digital computer combinationsArtificial lifeWeb siteVirtual space
The present invention relates generally to the field of computer and network software, and more particularly it relates to a computer system and method for promoting on-line activities on desired sites via a virtual entertainment system that provides games, interactions or activities that take place either partially or fully on the partner's website or within the virtual space associated with the partner's website. According to one aspect, the invention drives on-line traffic to partner sites using Virtual Collectibles and other prizes rewarded for participation in Internet-based games. The games are designed to promote users to visit and / or perform other activities on the partner sites, and can include give-aways, special offers, treasure hunts, combo puzzles, among many other types of games. According to other aspects, the games can be played by users in the course of or with very little effort in addition to casually surfing the web. According to other aspects, the invention provides on-line advertisers and / or partners having Internet sites with means to configure promotions that are tied to the games hosted by the system. According to some additional aspects of the invention, the system can provide superior on-line advertising revenue opportunities as compared to traditional banner ads and click-through advertising through the appeal of Virtual Collectibles. In addition, the present invention allows the system to be configured to allow advertiser and partner websites to configure the Virtual Collectibles and other prizes rewarded to users for desired effects.
Owner:LAVAMIND
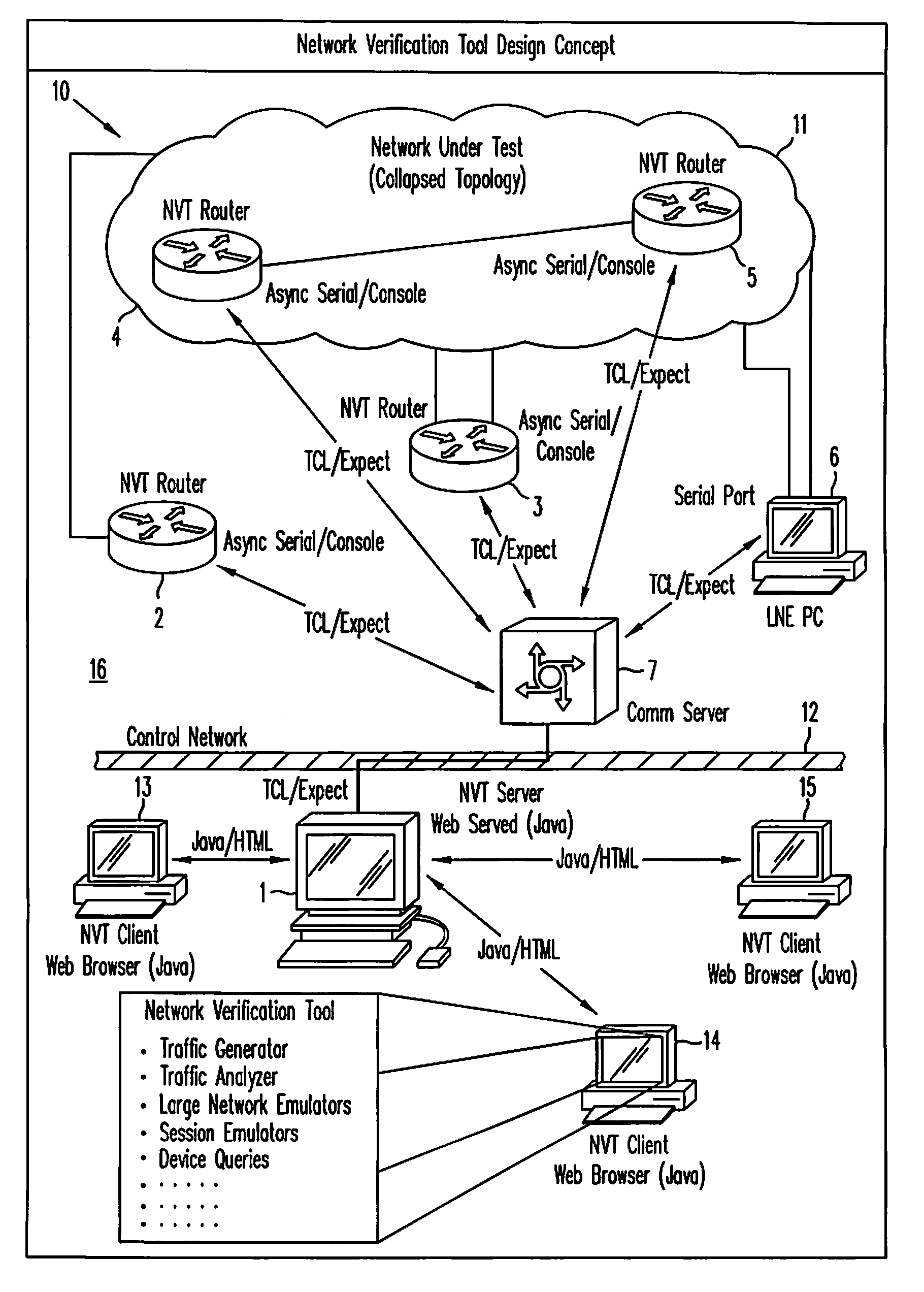
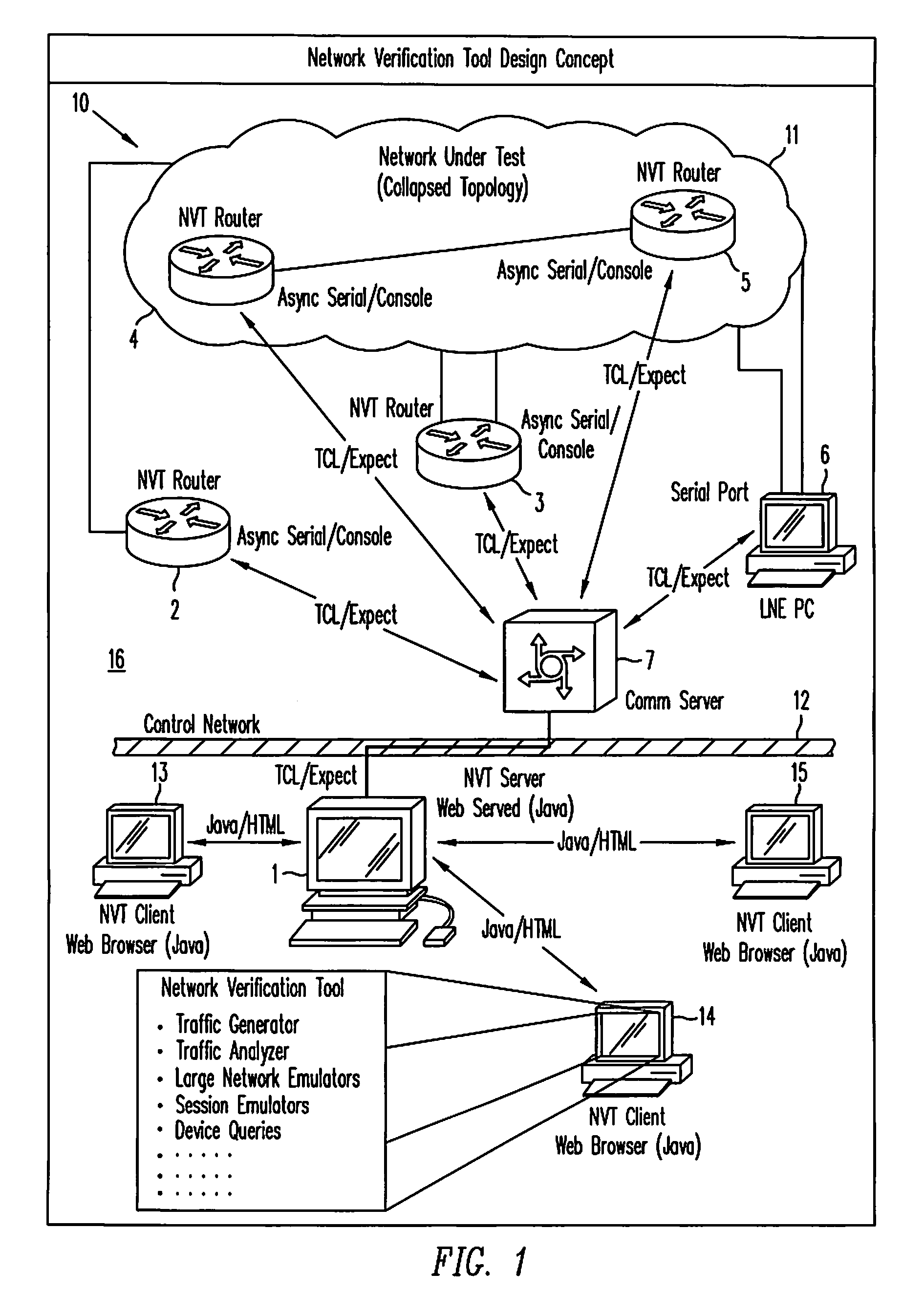
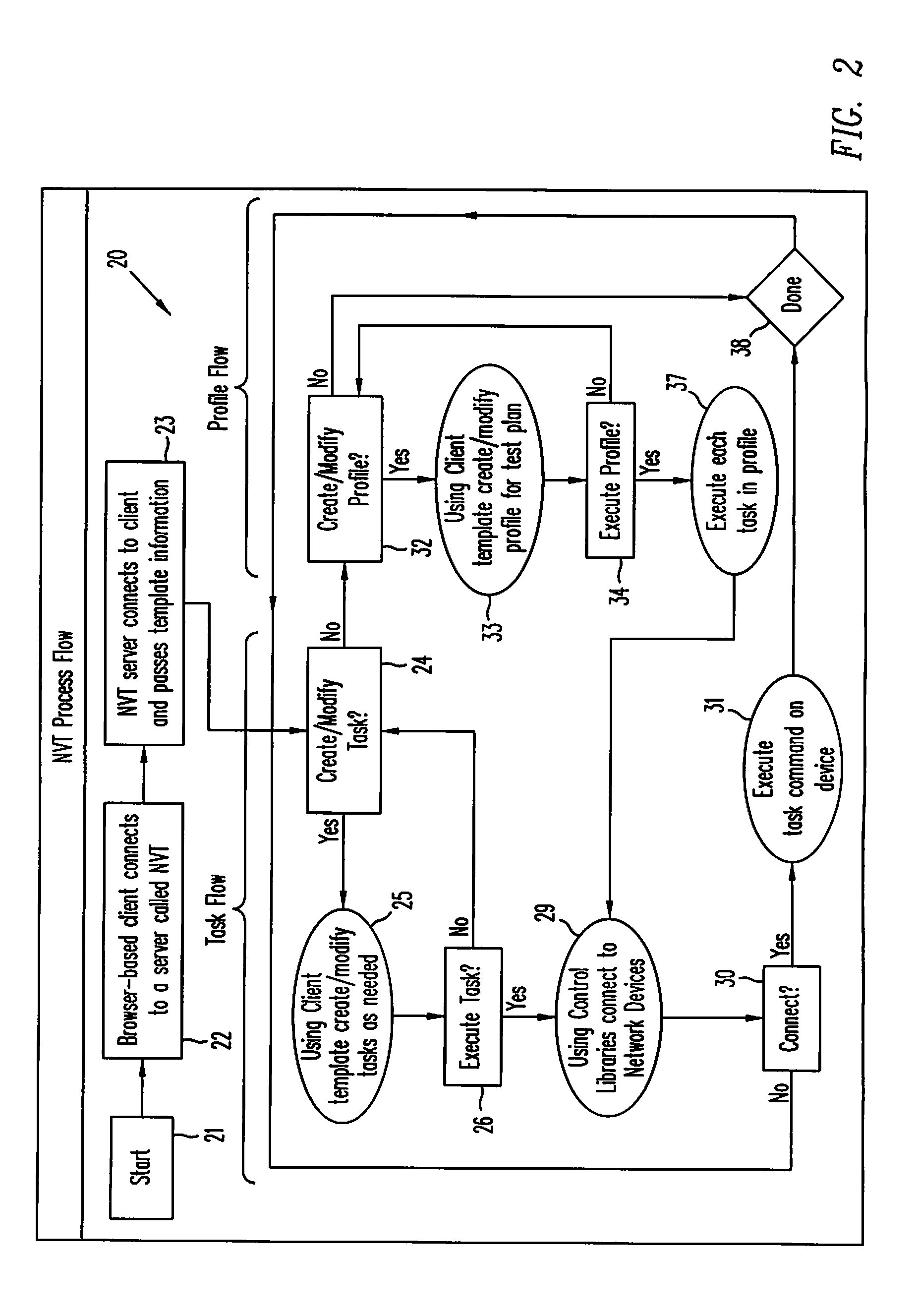
Network verification tool
InactiveUS7342897B1Easily set parameter requiredFacilitate joint resolutionError preventionFrequency-division multiplex detailsTraffic capacityClient-side
A network verification tool is presented that allows a user to easily create tasks for a collection of task types. The collection of task types are hosted by probe network devices that are coupled to a network under test. The network under test includes network devices executing generic network software and particular hardware or software that is being tested. The probe network devices are coupled to an NVT server, which transmits tasks to the task types and interfaces with one or more NVT clients. The NVT clients can create tasks by entering the appropriate parameters within templates supplied by the NVT server. Any collection of task types can be included in the network verification tool, including traffic generators, traffic analyzers, large network emulators, session emulators, device queries and script tasks.
Owner:CISCO SYSTEMS INC
Application program interface for network software platform
InactiveUS20030167356A1Specific program execution arrangementsMemory systemsWeb applicationApplication programming interface
Owner:MICROSOFT TECH LICENSING LLC
Malicious Attack Response System and Associated Method
InactiveUS20120023572A1Memory loss protectionError detection/correctionTraffic capacityNetwork software
A system and method for detecting and identifying intruders in a computer network environment by providing a network traffic evaluation and simulation module at the interface between a protected network and external traffic source. The evaluation and simulation module identifies suspected intruders by observing intrusion pattern behavior and then presents a simulated network to the intruder. The simulated network appears to offer the intruder valuable information and provides the intruder with the appearance of success in breaking down the layers of the simulated network to keep the intruder engaged in the intrusion effort while information is gathered to trace and identify the source of the intrusion. Intrusion attempts are identified and categorized in an intrusion analysis module. The network traffic evaluation and simulated network may be provided as a self contained physical module that does not require modification of existing network software.
Owner:Q TRACK CORP
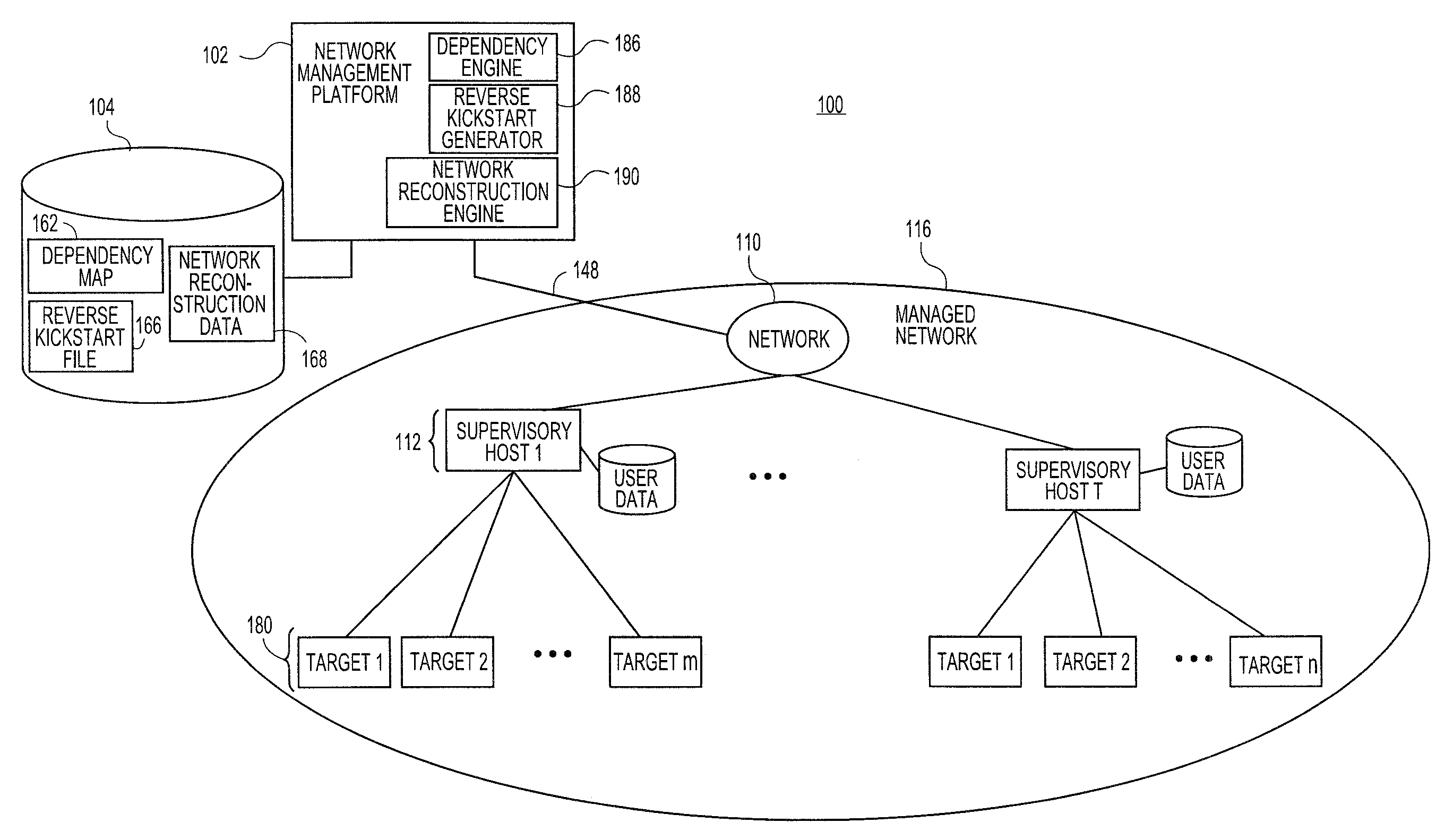
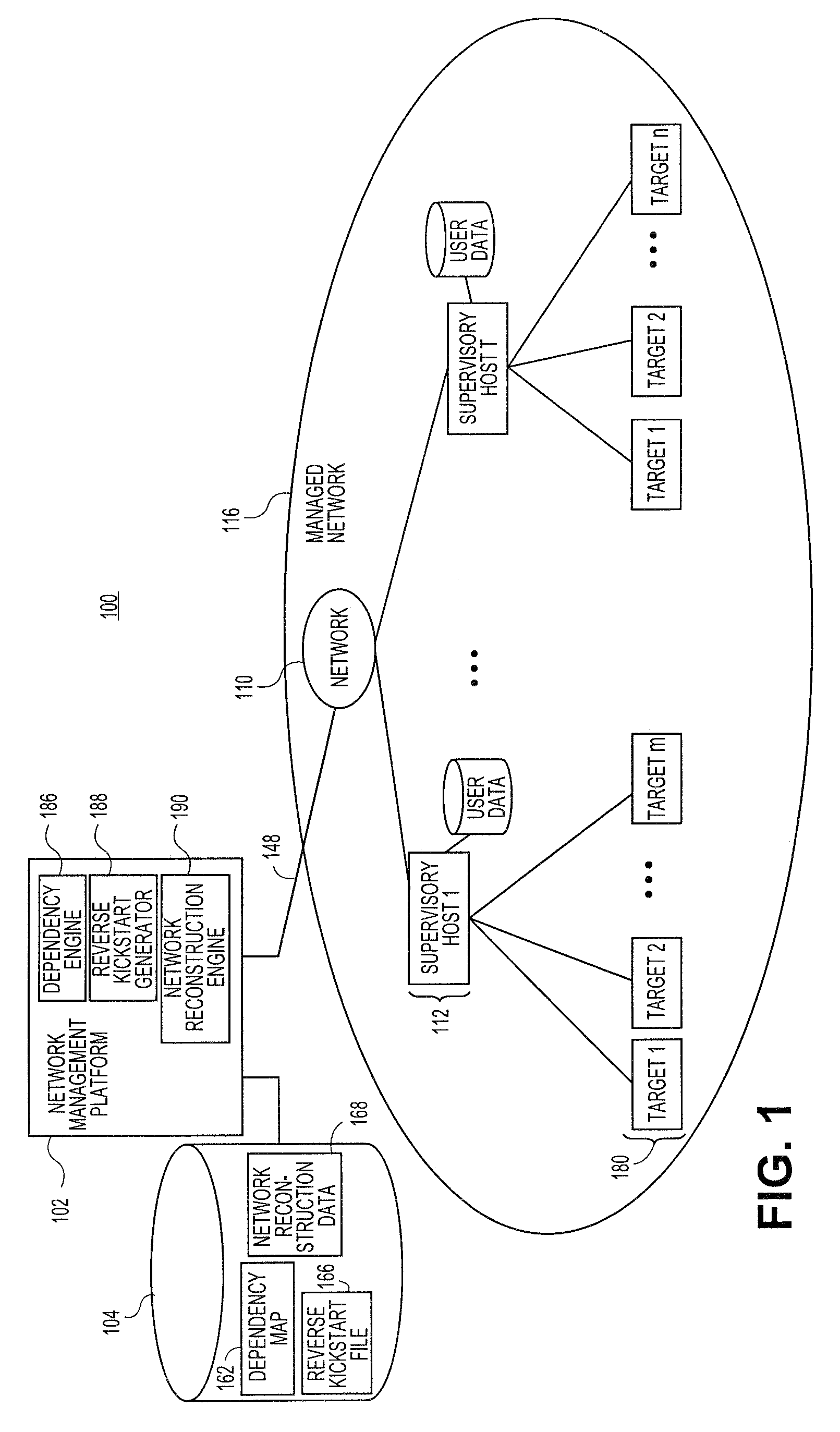
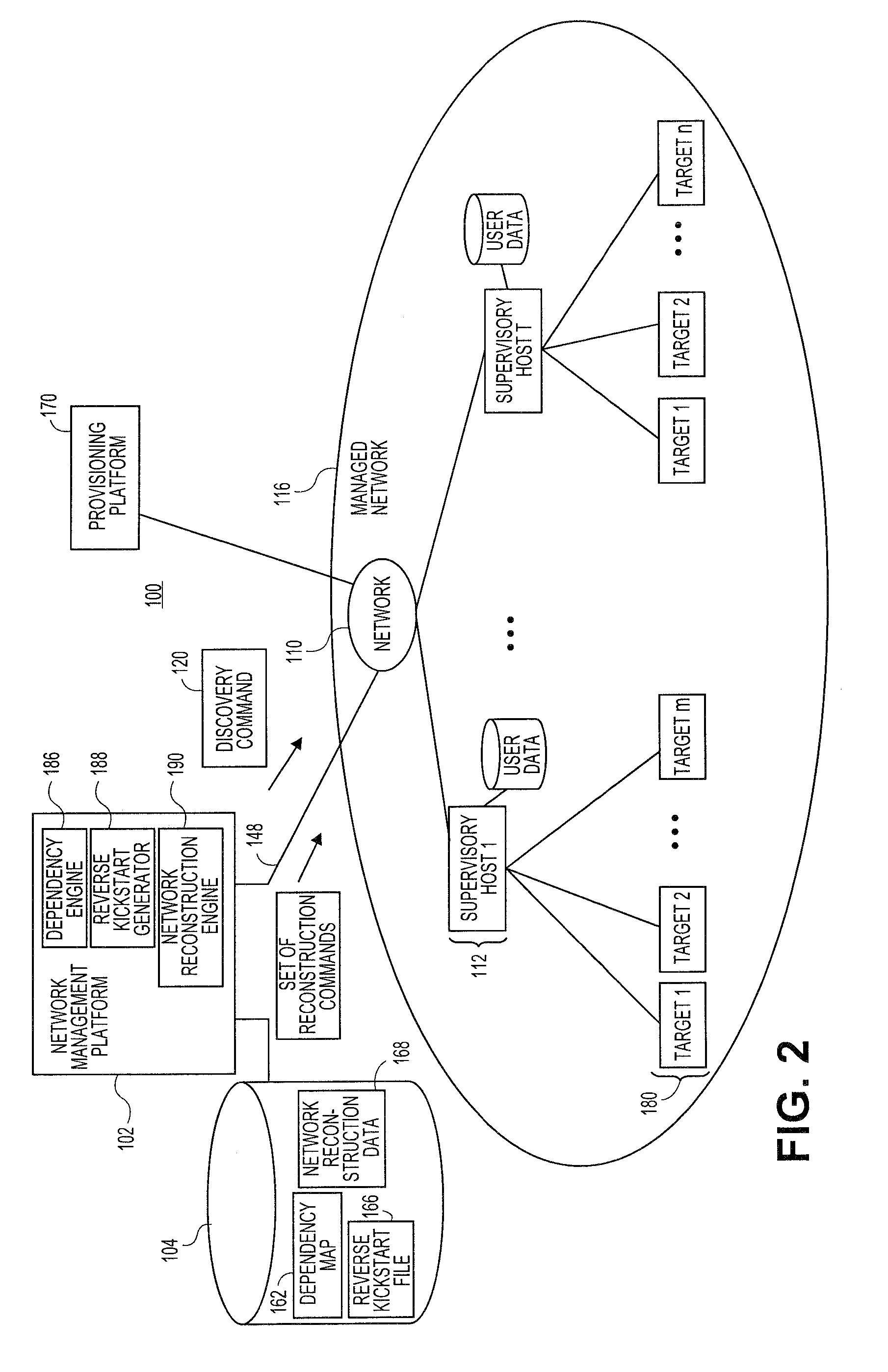
Systems and methods for automatic discovery of network software relationships
Embodiments relate to systems and methods for automatic discovery of network software relationships. A set of managed machines, such as personal computers or servers, can be managed by a network management platform communicating with the machines via a secure channel. The network management platform can issue a set of discovery commands interrogating nodes of the network to report software or services which they consume. The network management platform can build a dependency map encoding the dependency or other relationships between nodes in the managed network based on their use of software resources. Network restorations can therefore be conducted in a rational order, maintaining stability in the restored nodes and network.
Owner:RED HAT
Remote monitoring and controlling of network utilization
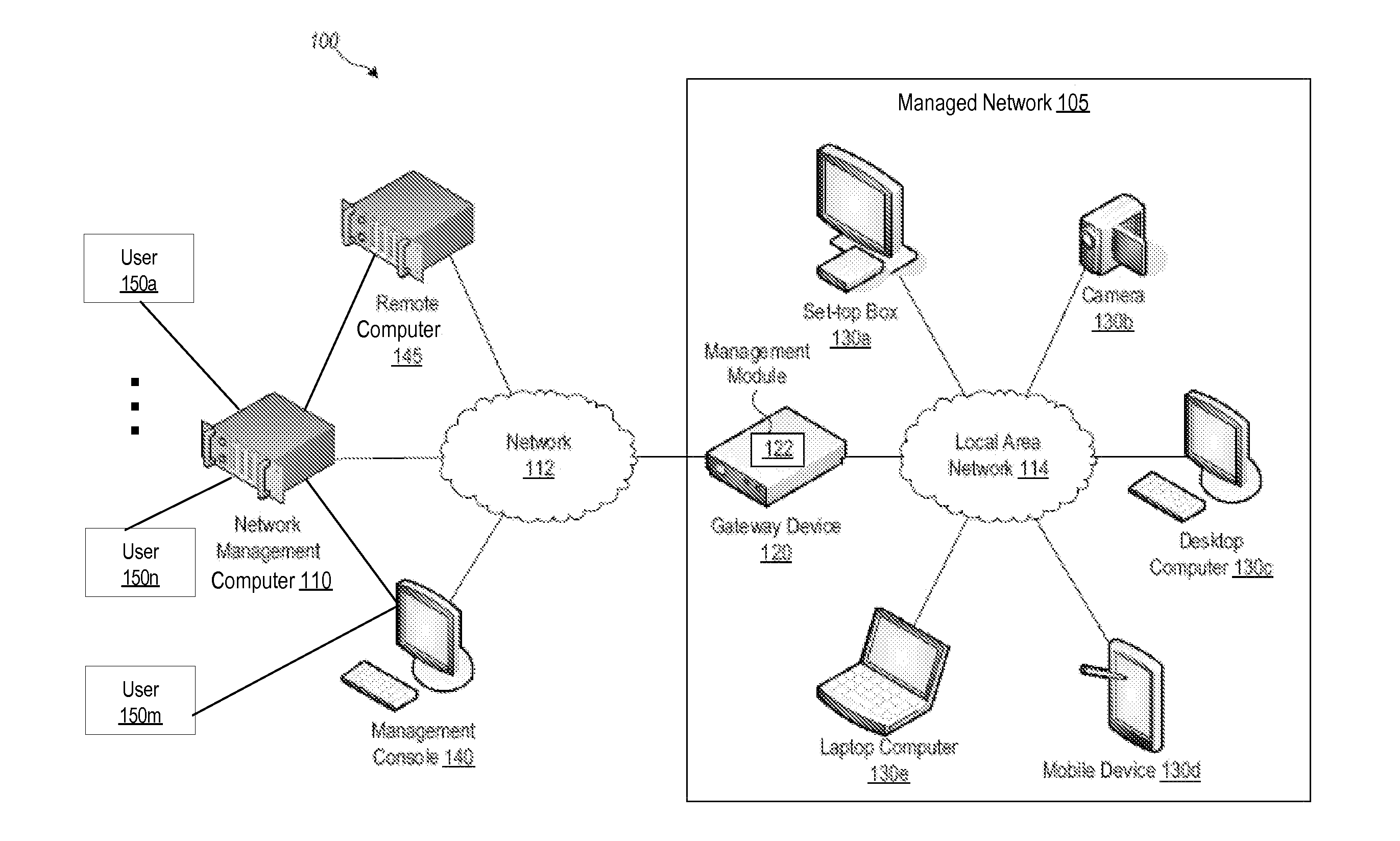
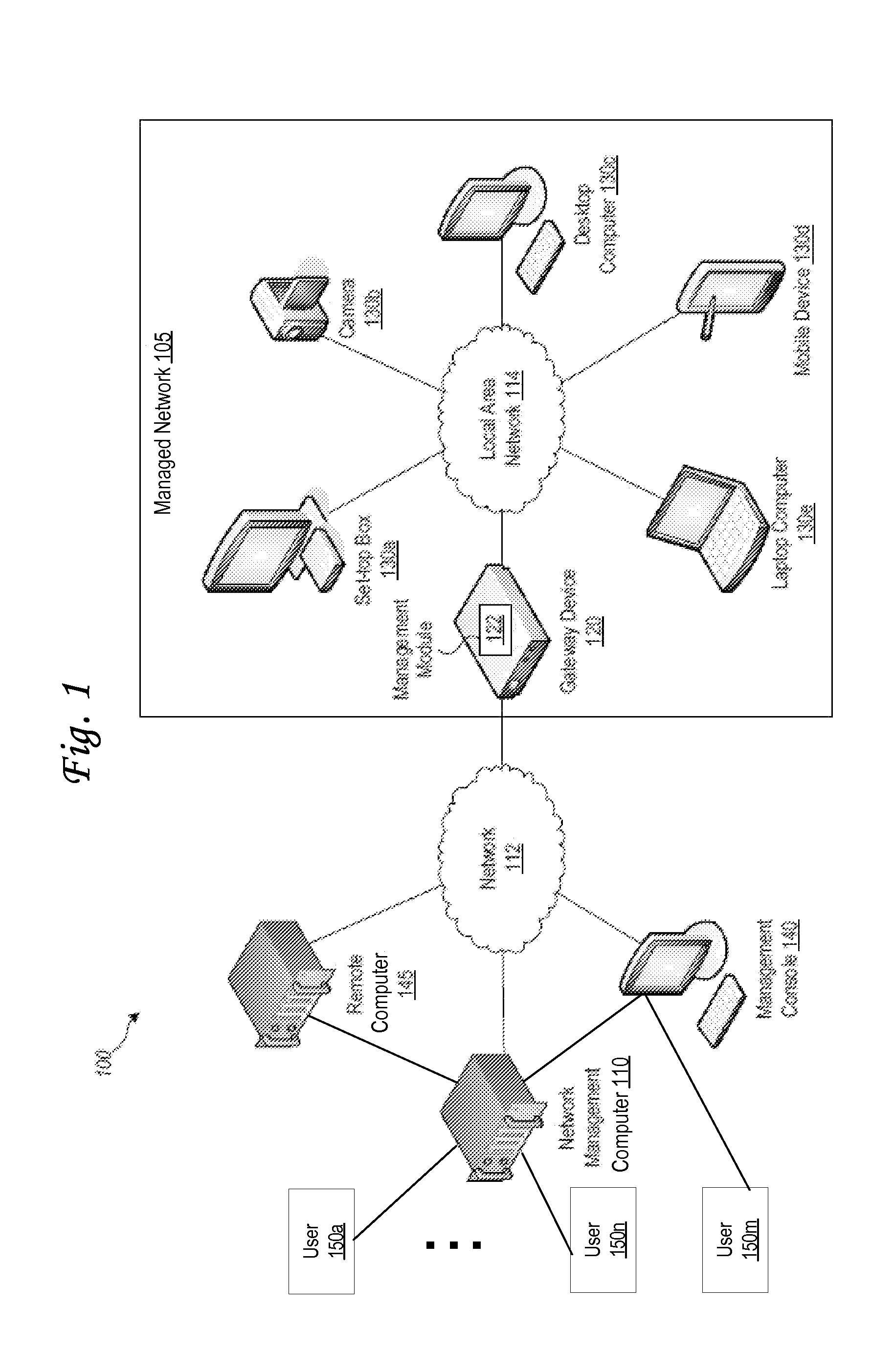
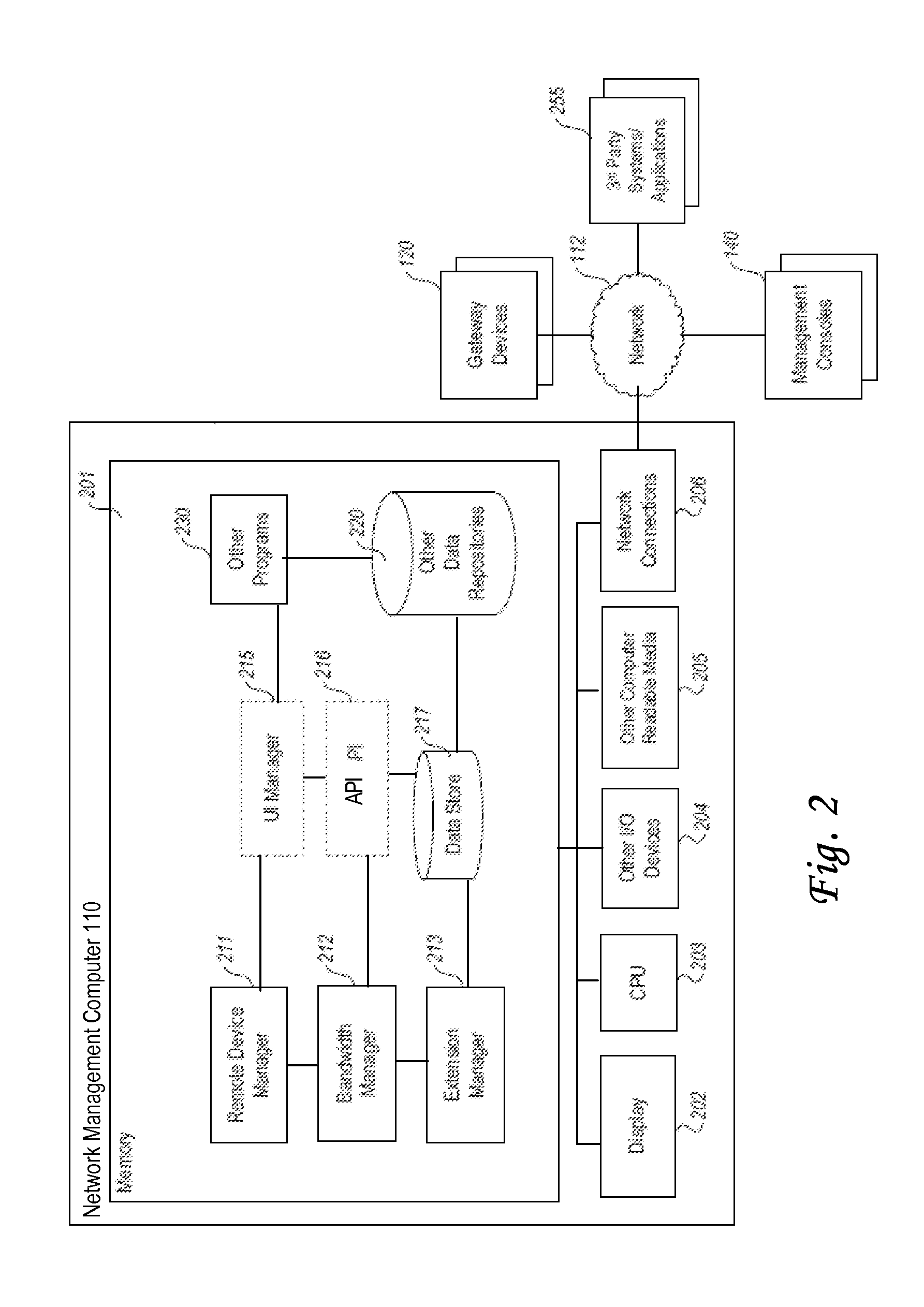
ActiveUS20130205016A1Digital computer detailsData switching networksComputer networkNetwork software
A non-transitory computer-readable storage medium storing instructions which, when executed by processors, cause the processors to perform: at a management computer, receiving, from a gateway located in a managed network, device information about devices in the managed network; for a particular device: determining a match between the device capabilities of the particular device and features of a particular network software application configured to control the particular device, and determining a particular protocol endpoint configured to communicate control instructions from the particular network software application to the particular device; receiving, from the gateway, aggregated data that reflects network utilization by the devices located in the managed network; for the particular device: based at least in part on the aggregated data, using the particular network software application, determining control instructions for the particular device; causing the particular protocol endpoint to transmit the control instructions for the particular device to the device.
Owner:CISCO TECH INC
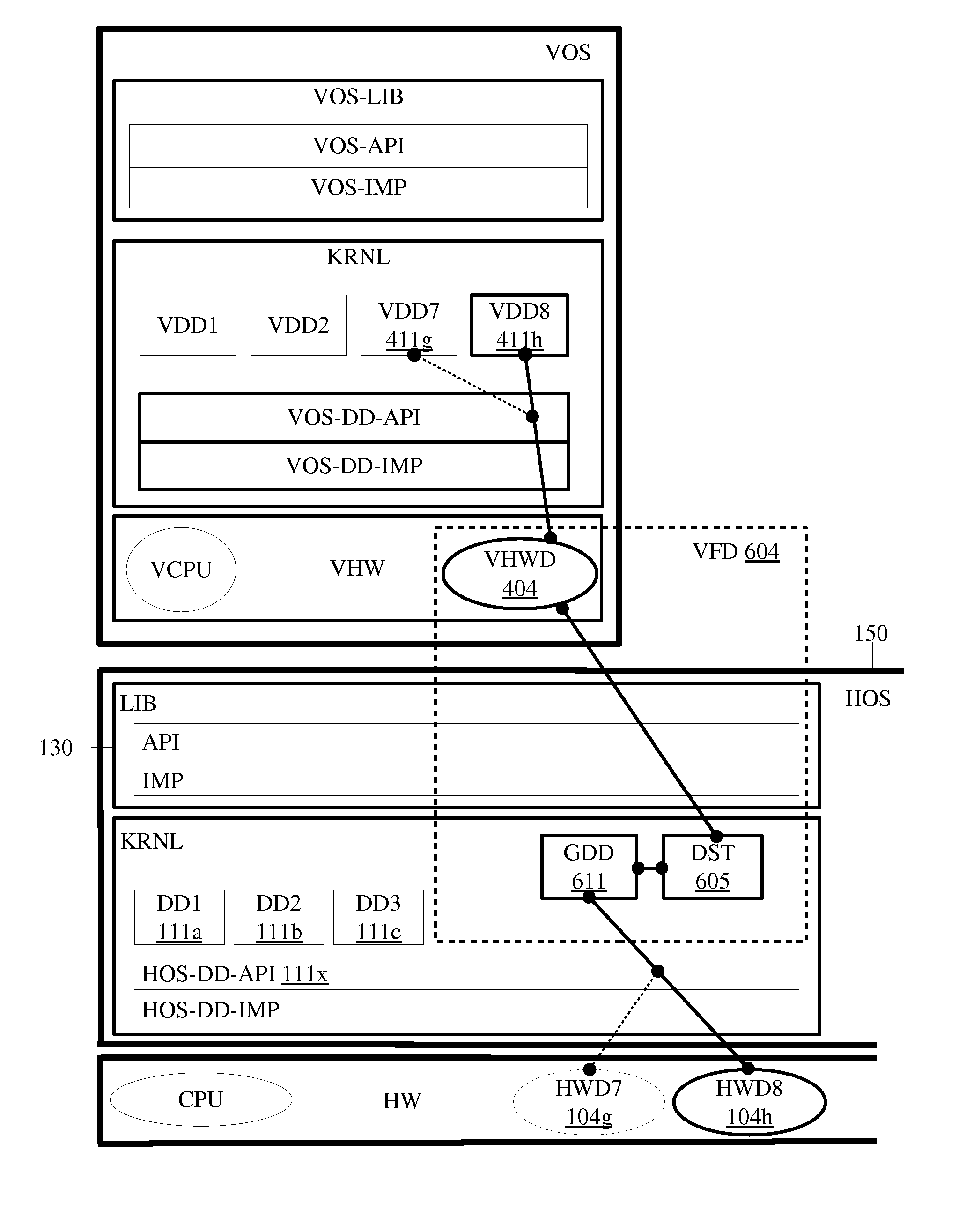
Software executables having virtual hardware, operating systems, and networks
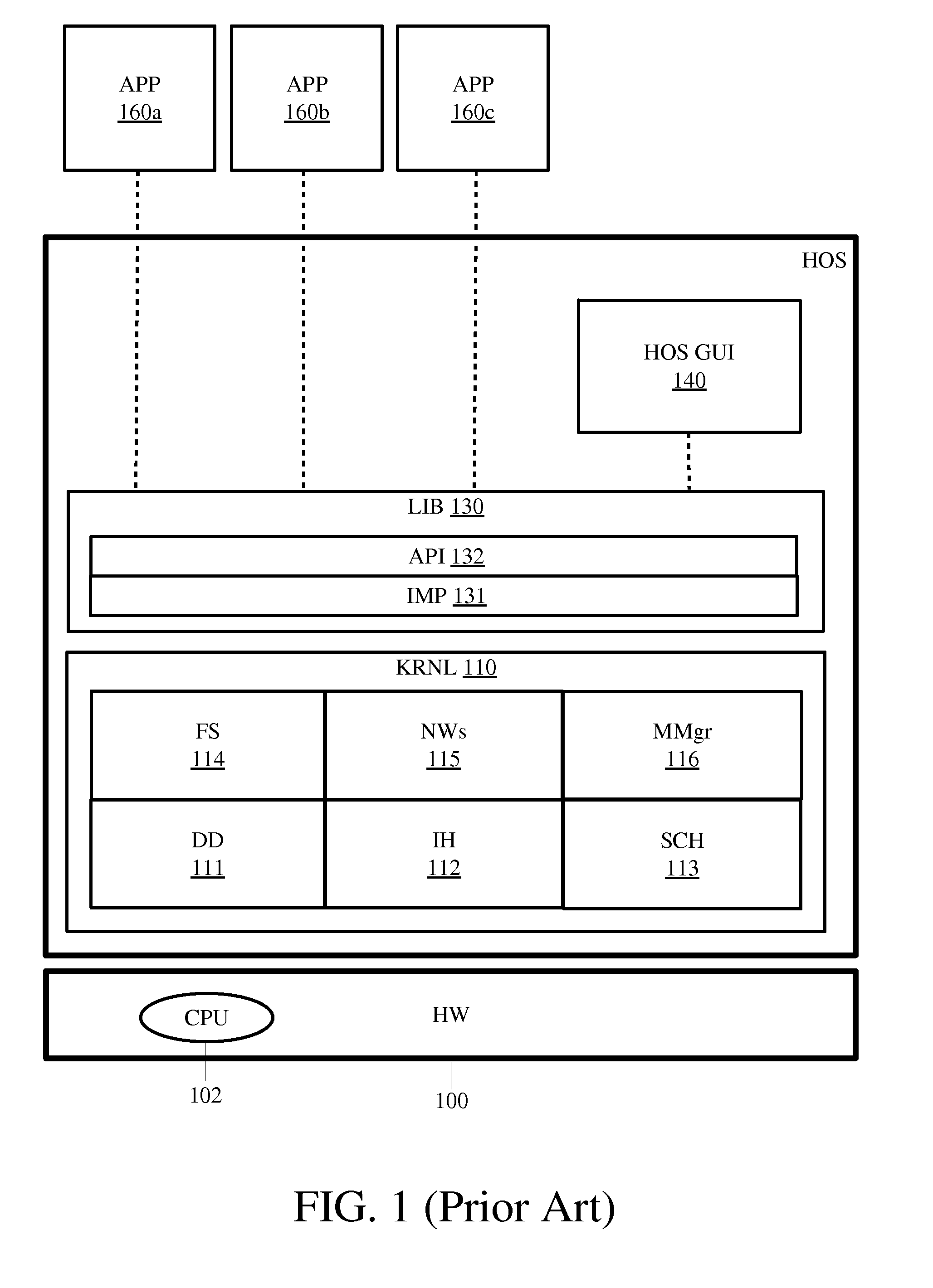
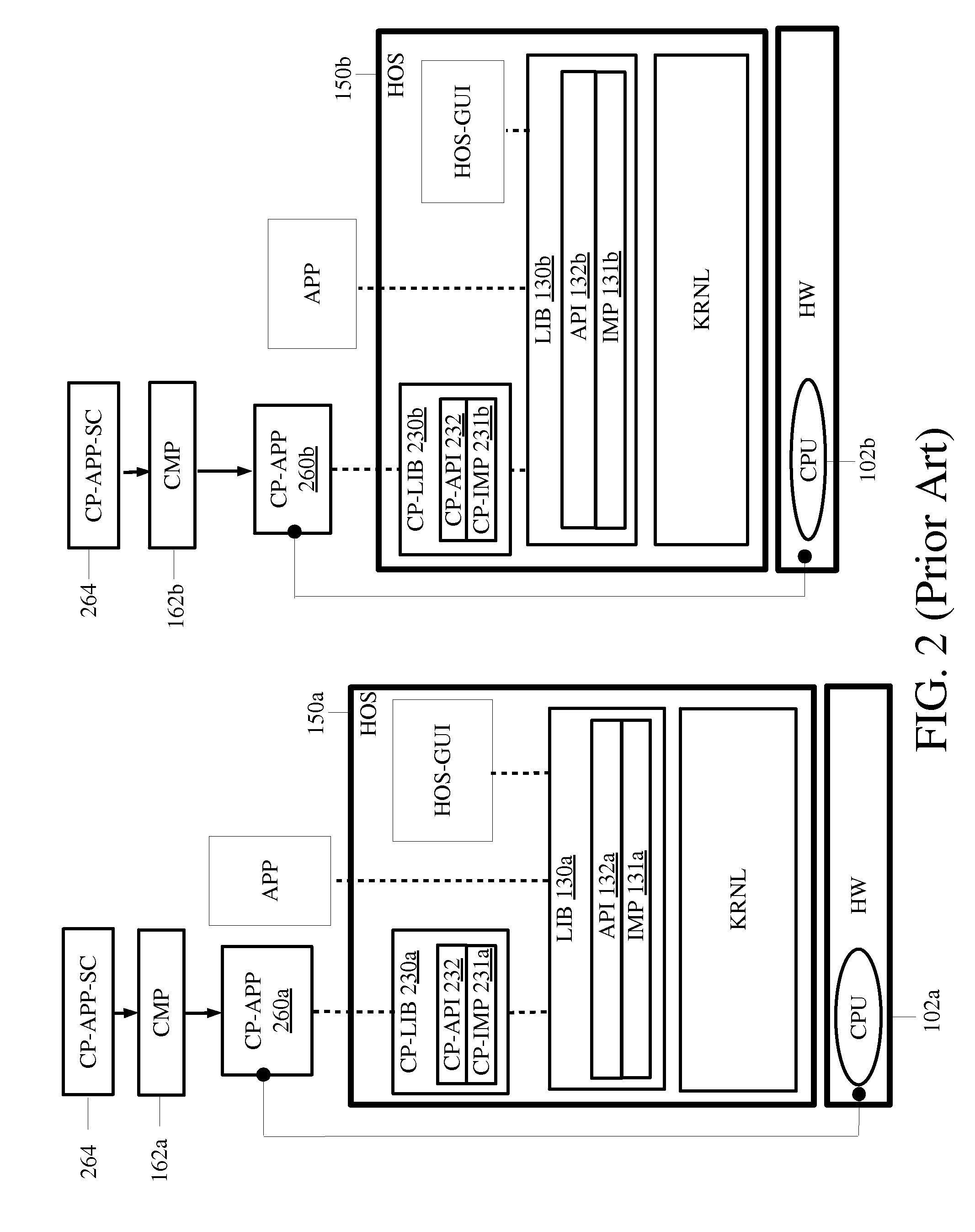
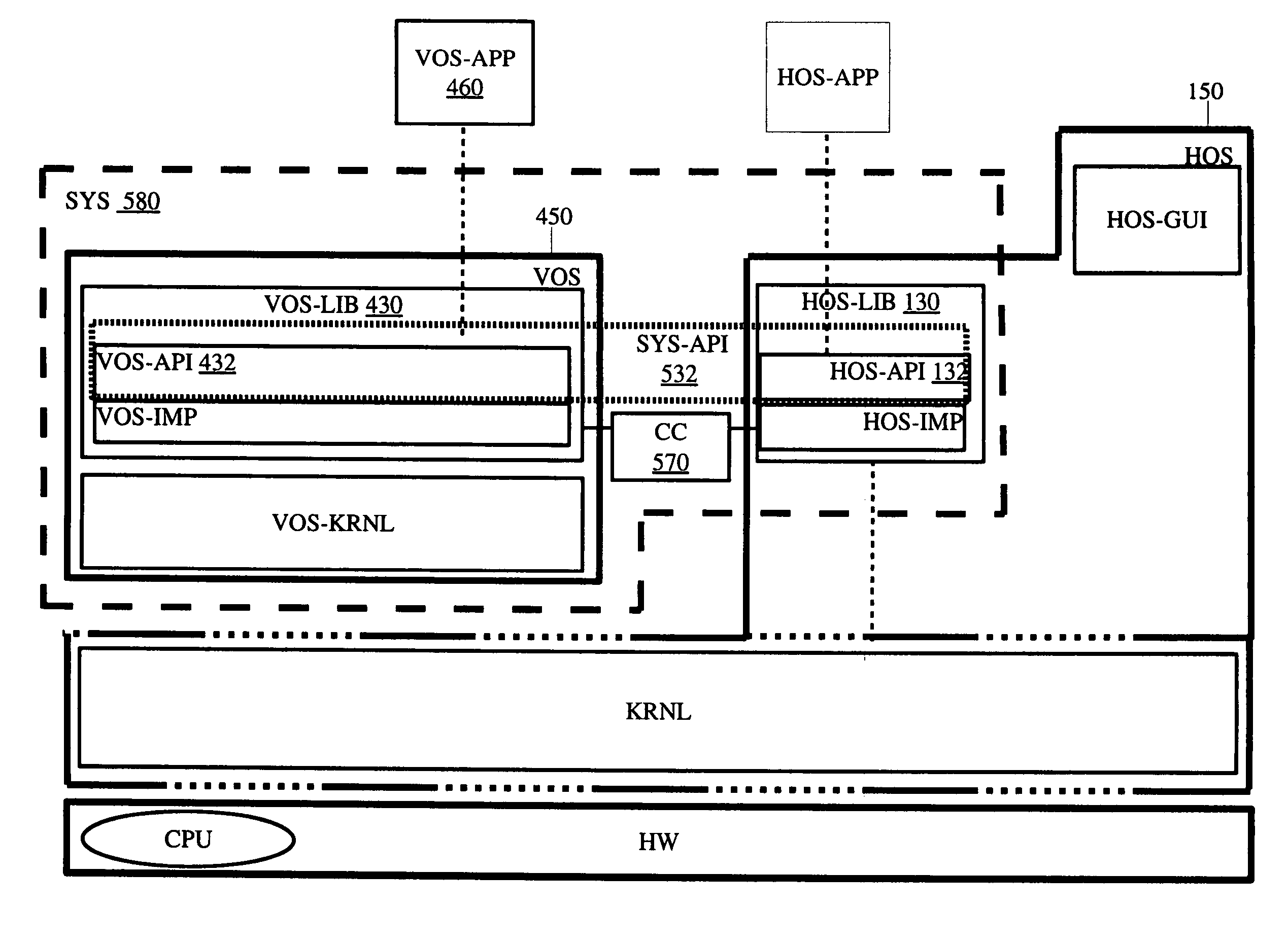
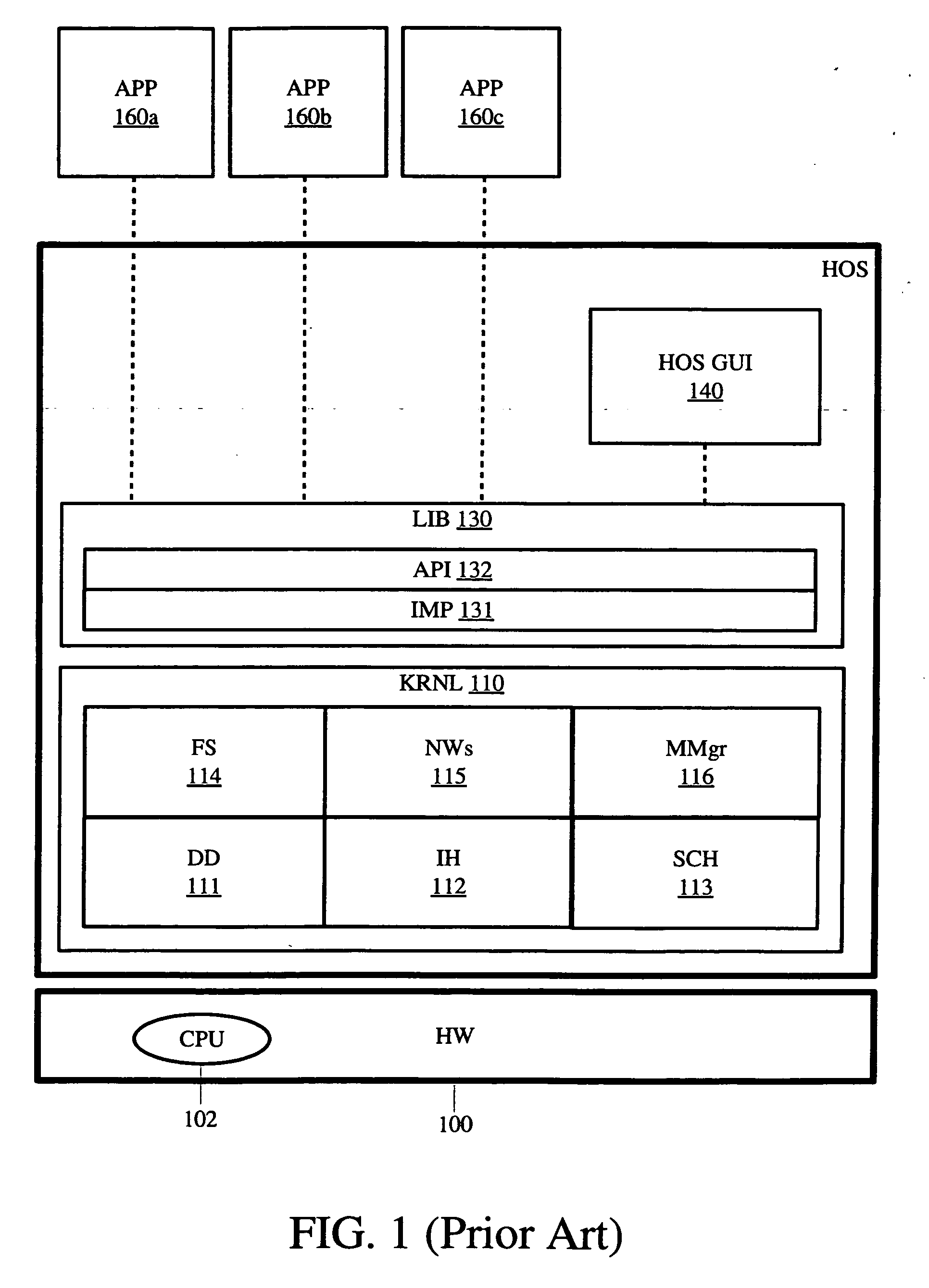
Software executables having virtual hardware, operating systems, and networks are described herein. In one embodiment, an example of a computing system includes, but is not limited to, a host operating system (HOS) including a HOS kernel, a virtual operating system (VOS) coupled to the HOS including a first virtual platform and a second virtual platform, an executable including a first application to be run on the first virtual platform and a second application to be run on the second virtual platform, and a dispatcher in response to the executable to dispatch the first application to the first virtual platform and the second application to the second virtual platform. Other methods and apparatuses are also described.
Owner:DLOO
Apparatus and method for storage processing through scalable port processors
InactiveUS7237045B2Achieve scaleProvide flexibilityMultiplex system selection arrangementsInput/output to record carriersWire speedMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:AVAGO TECH INT SALES PTE LTD
Apparatus and method for internet protocol data processing in a storage processing device
InactiveUS20060013222A1Achieve scaleProvide flexibilityError detection/correctionData switching by path configurationInternet trafficMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:BROCADE COMMUNICATIONS SYSTEMS
System and method for an online duel game
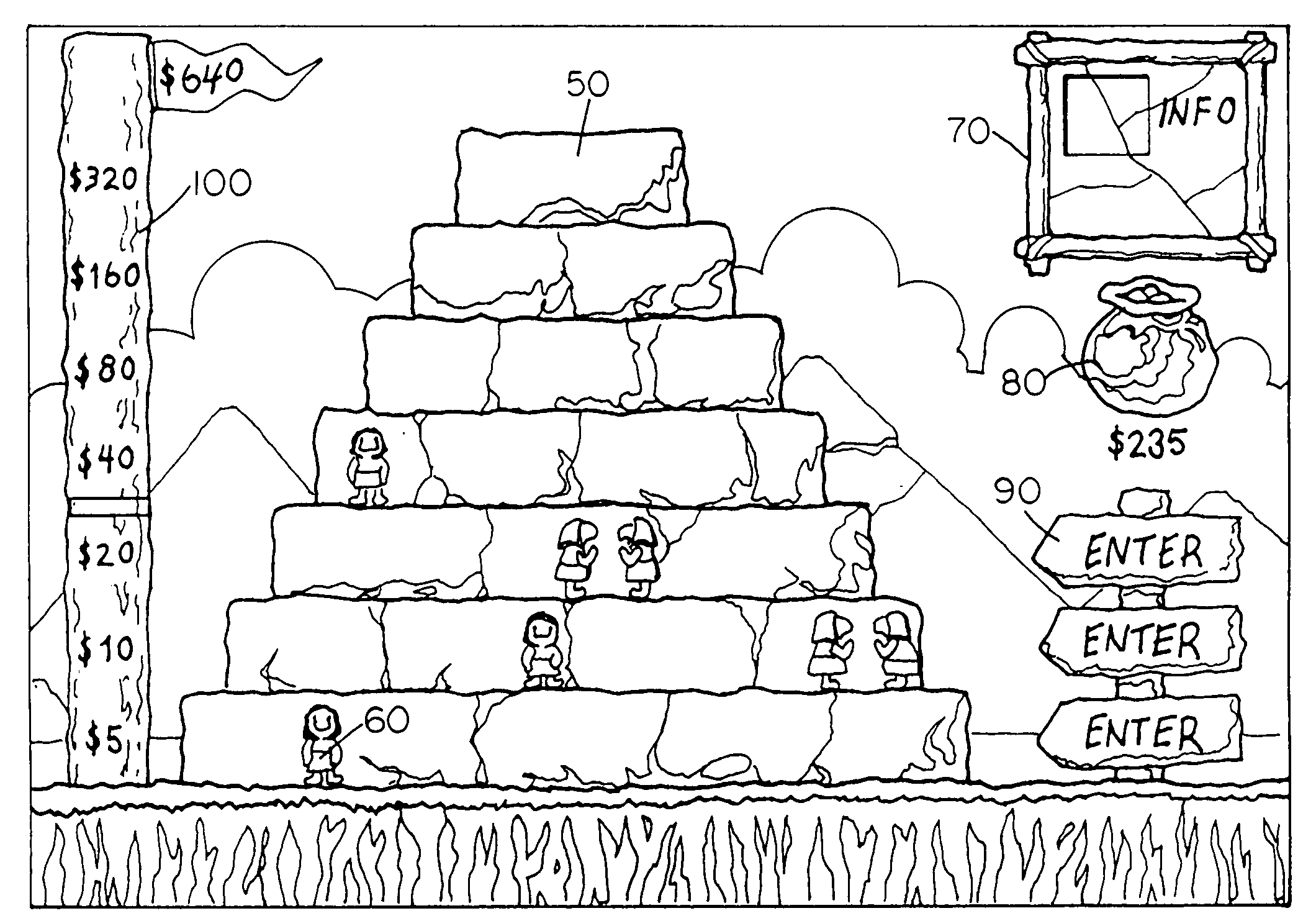
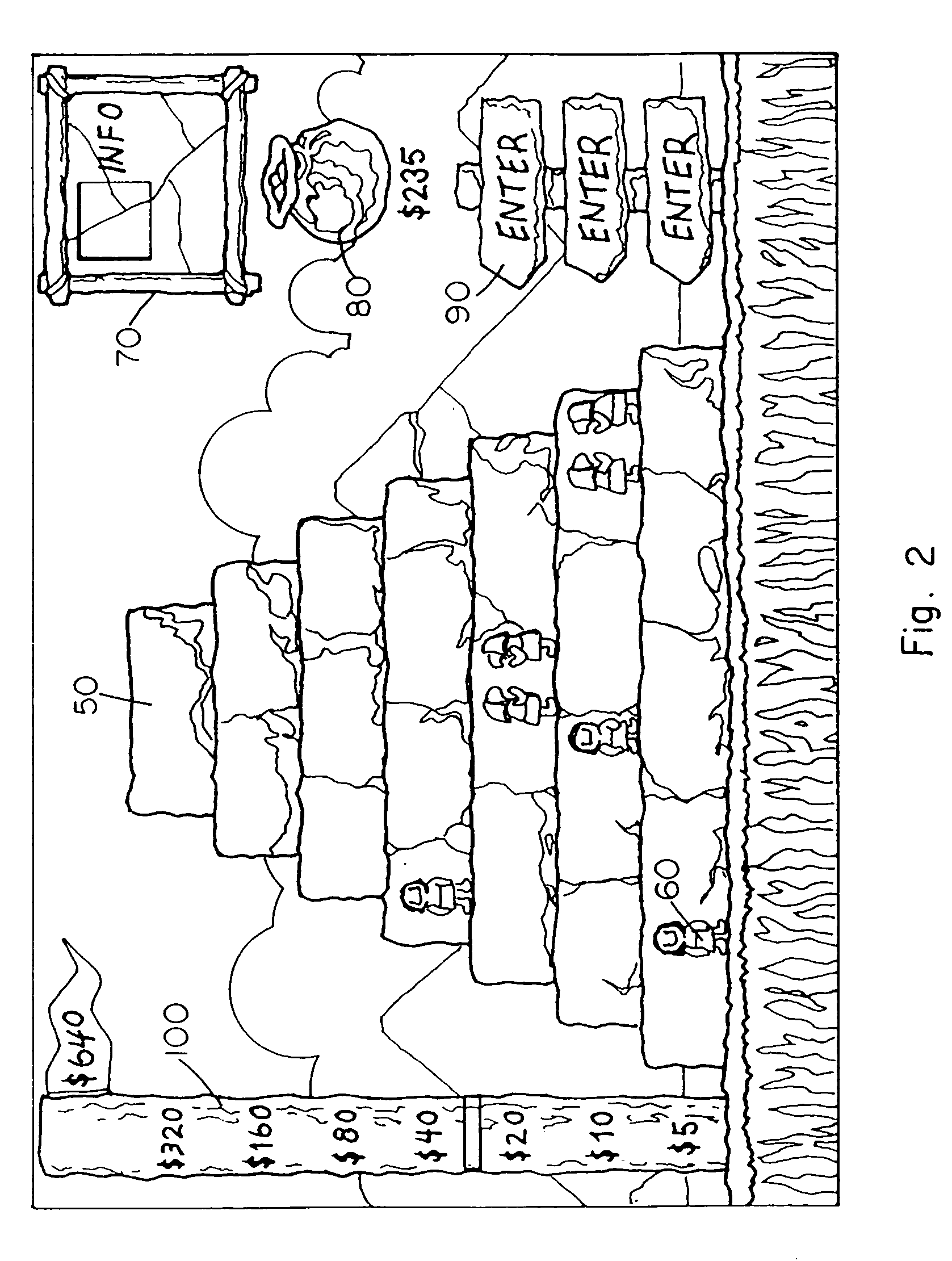
InactiveUS20050266925A1Exciting to playFun to playVideo gamesSpecial data processing applicationsThe InternetDistributed computing
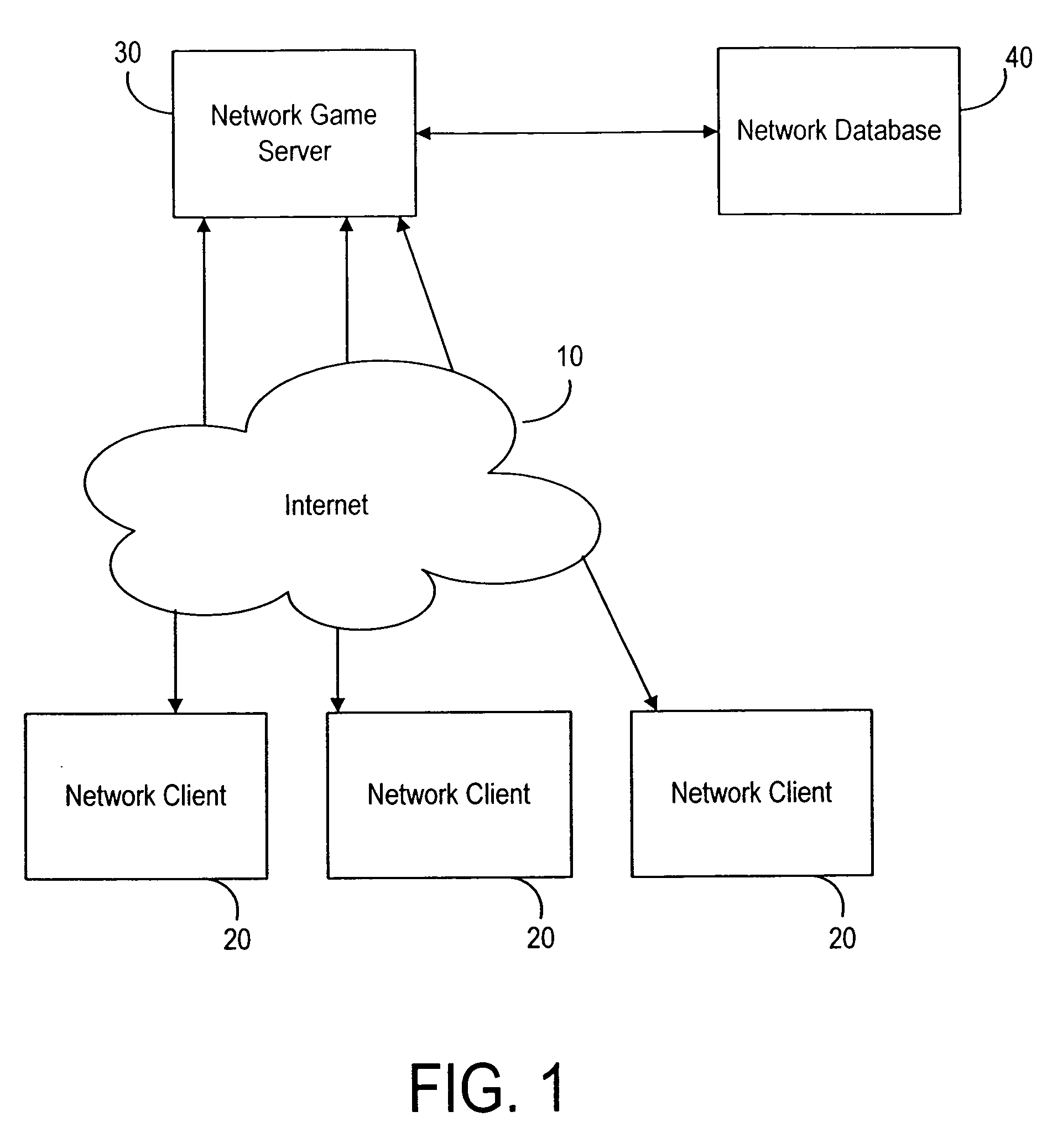
A network system and network method perform a pyramid tournament duel game, such as a Rock-Paper-Scissors duel game, between at least two participants online a network for data- and telecommunication such as the Internet. Network software is used for performing the online game and a readable storage medium stores the network software.
Owner:BWIN GAMES
System and method for detecting peer-to-peer network software
ActiveUS20060248525A1Platform integrity maintainanceProgram loading/initiatingRemote systemGoal system
The present invention provides a method for detecting whether or not a computer system is, has, or can participate in a Peer-to-Peer network. Scanning software is executed on a target system to be scanned or a remote system which will scan a target system. If Peer-to-Peer client software is detected the scanning software can notify the enforcing user, disable the Peer-to-Peer client software, or both.
Owner:KROLL INFORMATION ASSURANCE LLC
Method and system for connecting mobile terminal into network
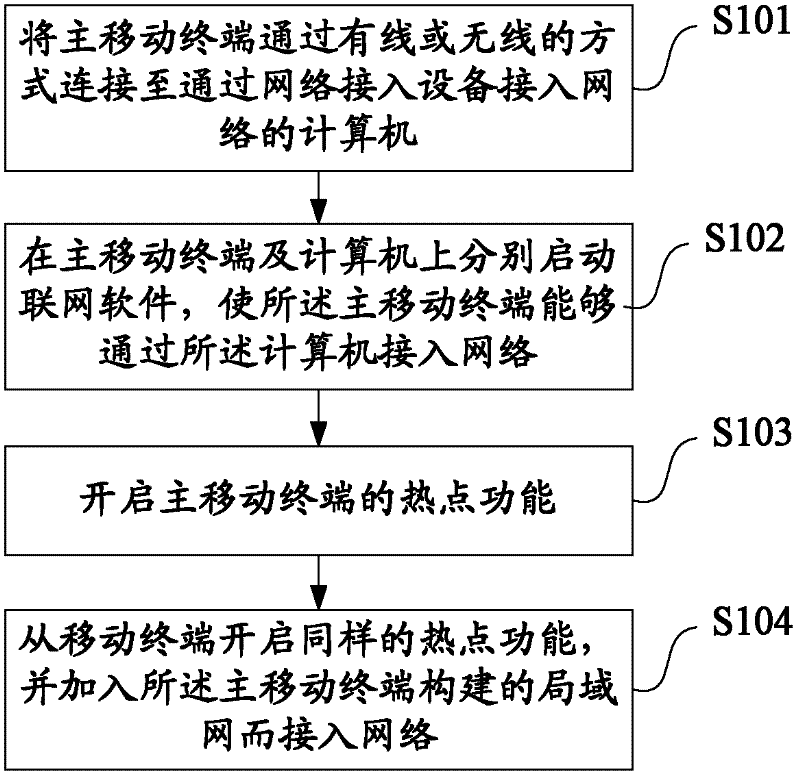
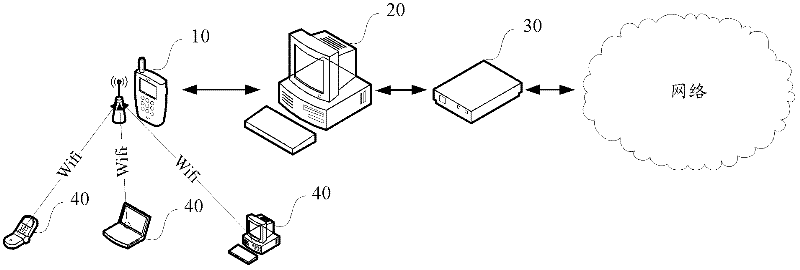
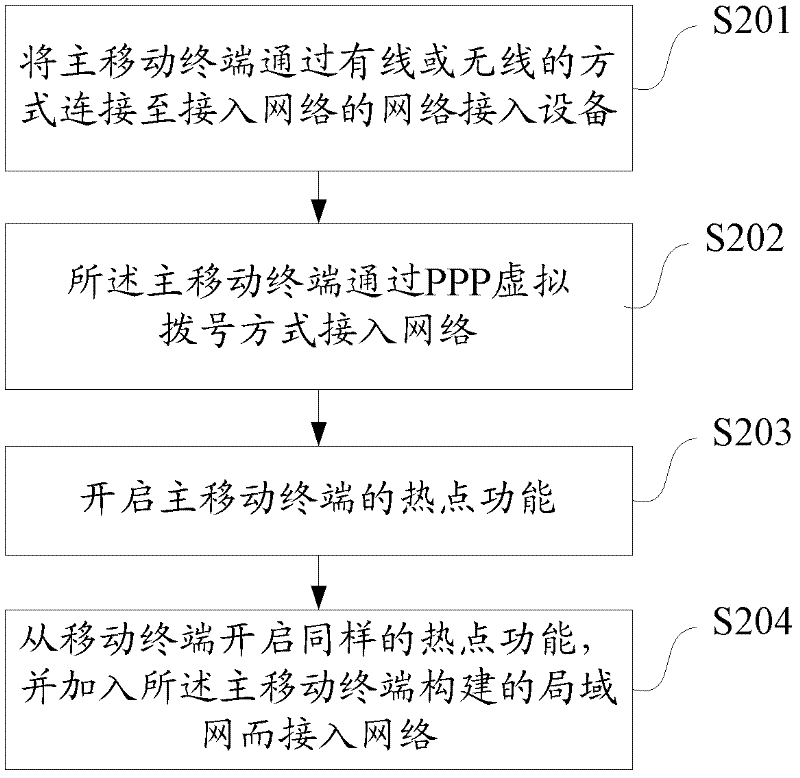
ActiveCN102364979ALow costSimple technical implementationAssess restrictionNetwork topologiesComputer terminalMobile phone
The invention discloses a method and a system for connecting a mobile terminal into a network. The method comprises the following steps of: connecting a master mobile terminal to a computer which accesses the network through network access equipment in a wire or wireless way; and starting networking software on the master mobile terminal and the computer respectively, so that the master mobile terminal accesses the network through the computer. By the method and the system, the mobile terminal (such as a mobile phone) which supports a wireless fidelity (WiFi) hotspot function is used as the conventional wireless WiFi access point equipment, so that the cost of a wireless local area network (WLAN) is saved.
Owner:ZTE CORP
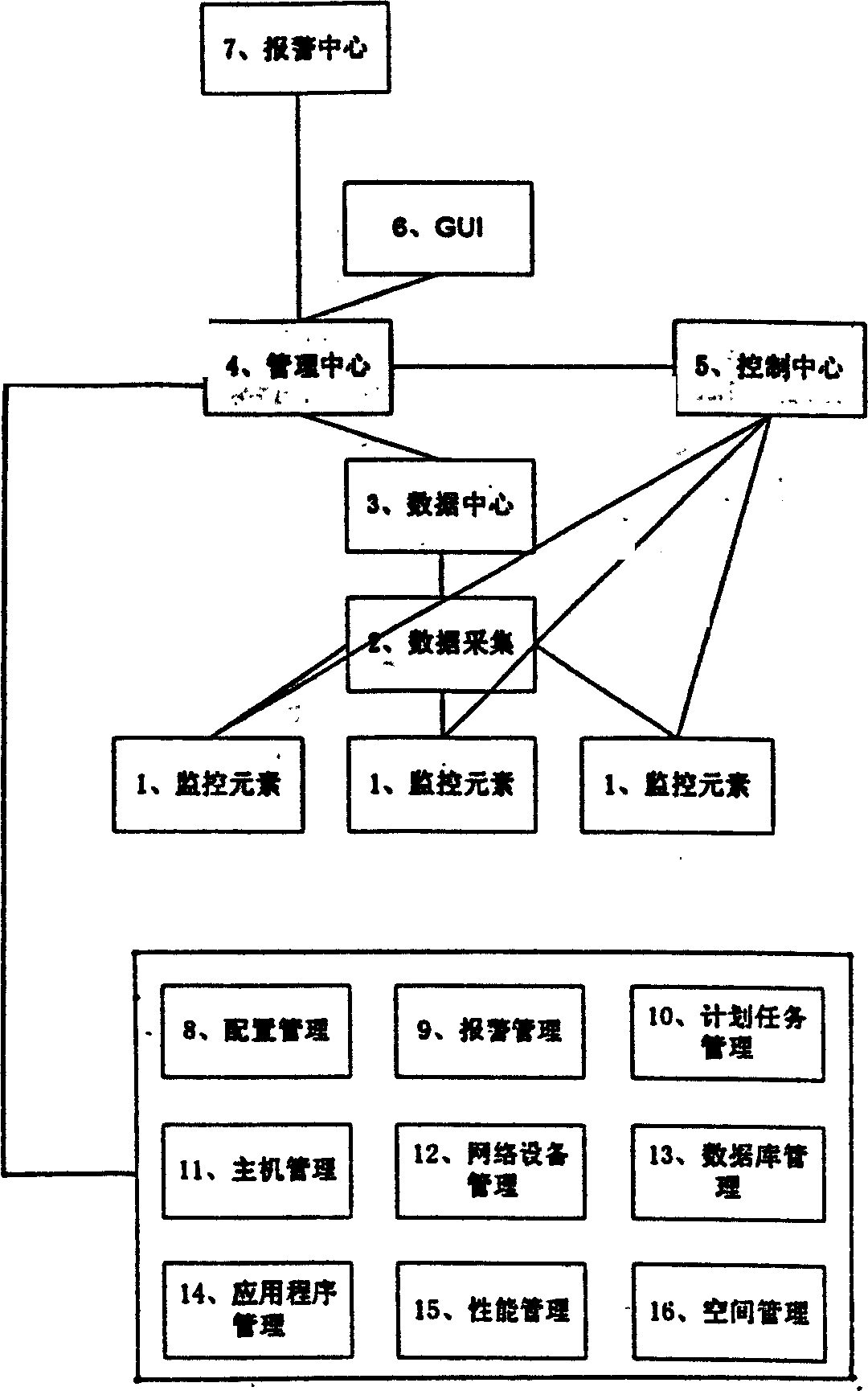
Network monitoring management system
InactiveCN1547120AOptimizationSimplify workHardware monitoringSpecific program execution arrangementsApplication procedureAcousto-optics
The invention is a kind of computer network software, which is a new multi-function network supervising management method. The host computer, network device, databank, and application procedure are defined as supervising element according to different particle size, the different domain supervising elements are allocated to different network supervising management joint, and the centre realizes grade management through center supervising. The states of the network device, databank and application system can be informed to the field network maintaining person and remote network maintaining person, at the same time, it can manages many kinds of databank, and application system. The states of the network devices can be sent to relative maintaining person with acousto-optic alarming, voice music alarming, message alarming, telephone alarming, Email alarming, messenger alarming. It can realize the supervising and management to many kinds of databank and application systems.
Owner:NEUSOFT CORP
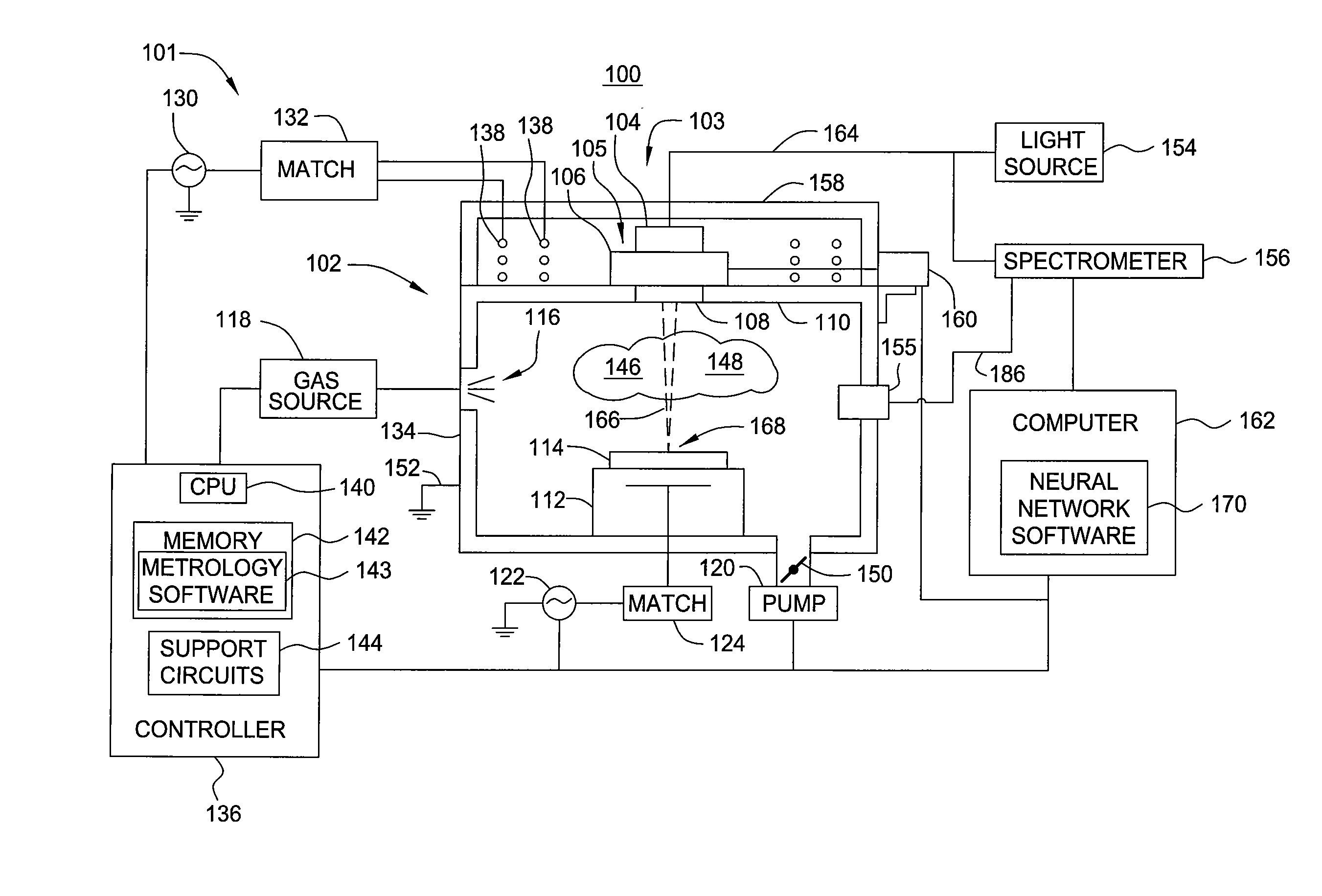
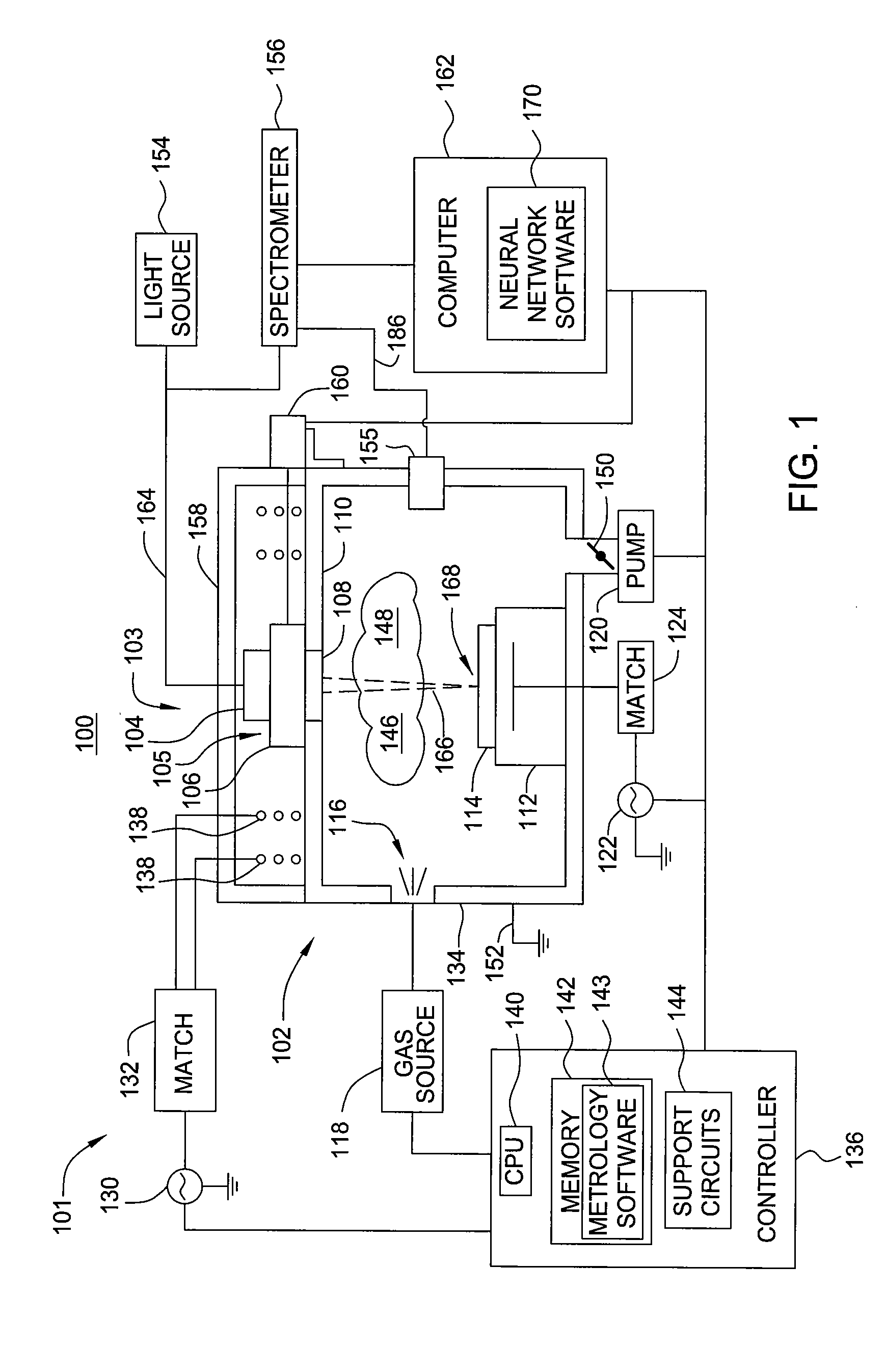
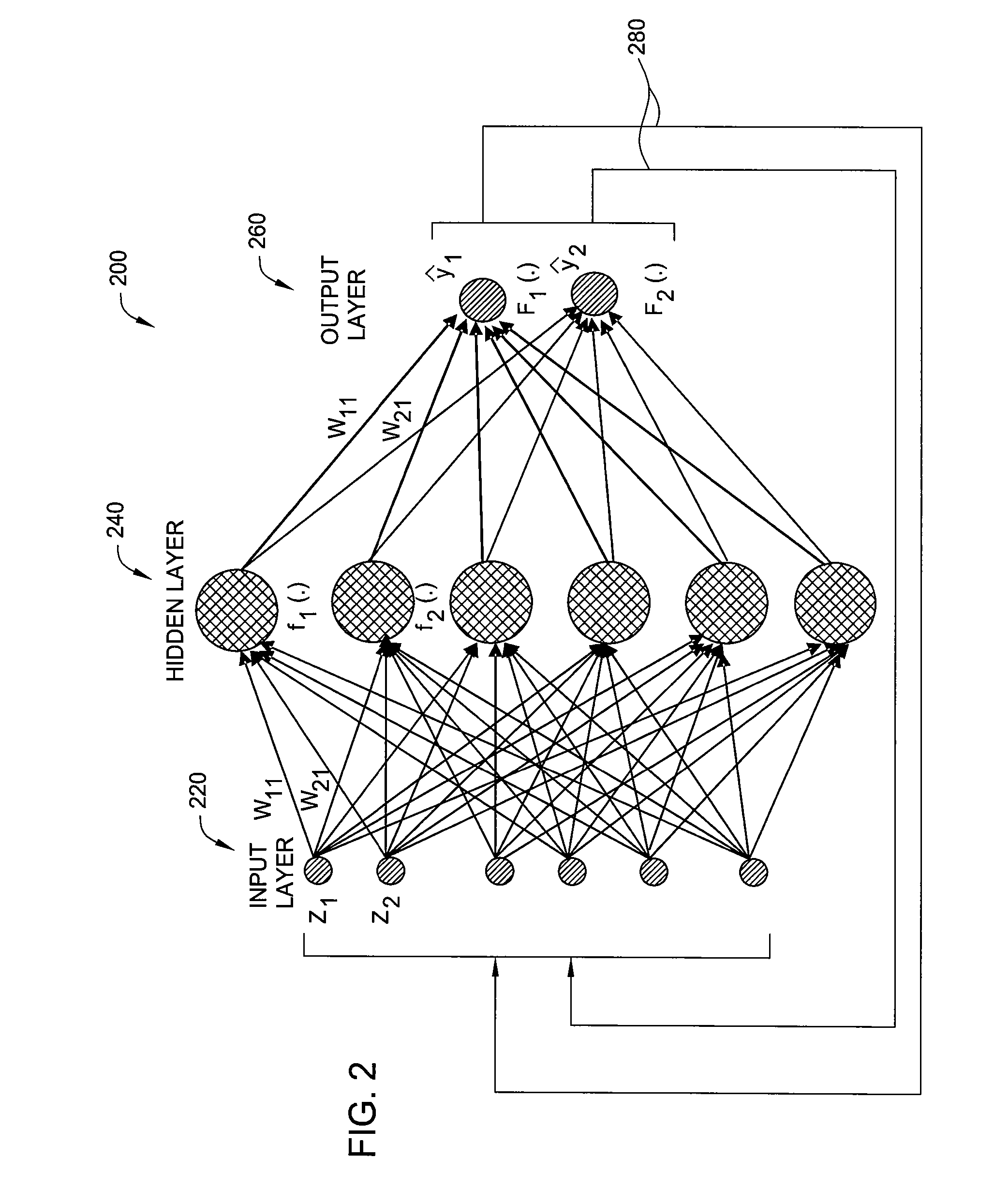
Neural Network Methods and Apparatuses for Monitoring Substrate Processing
InactiveUS20070249071A1Semiconductor/solid-state device testing/measurementSemiconductor/solid-state device manufacturingMetrologyElectromagnetic radiation
Aspects of the present invention include methods and apparatuses that may be used for monitoring substrate processing systems. One embodiment may provide an apparatus for obtaining in-situ data regarding processing of a substrate in a substrate processing chamber, comprising a data collecting assembly for acquiring training data related to a substrate disposed in a processing chamber, an electromagnetic radiation source, at least one in-situ metrology module to provide measurement data, and a computer, wherein the computer includes a neural network software, wherein the neural network software is adapted to model a relationship between the plurality of the training and other data related to substrate processing.
Owner:APPLIED MATERIALS INC
Apparatus and method for data virtualization in a storage processing device
ActiveUS7353305B2Provide flexibilityProvides managementMultiplex system selection arrangementsInput/output to record carriersWire speedMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:AVAGO TECH INT SALES PTE LTD
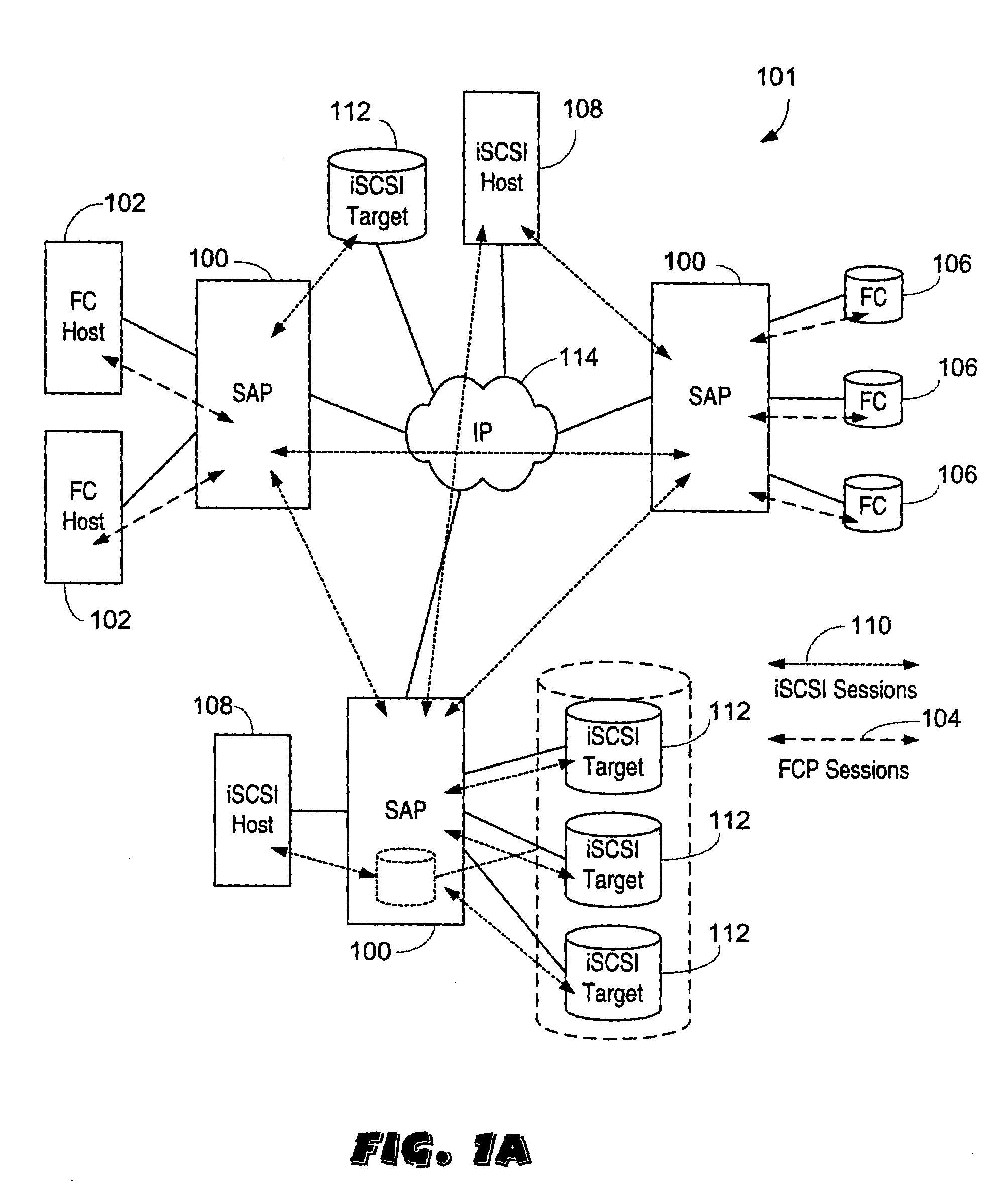
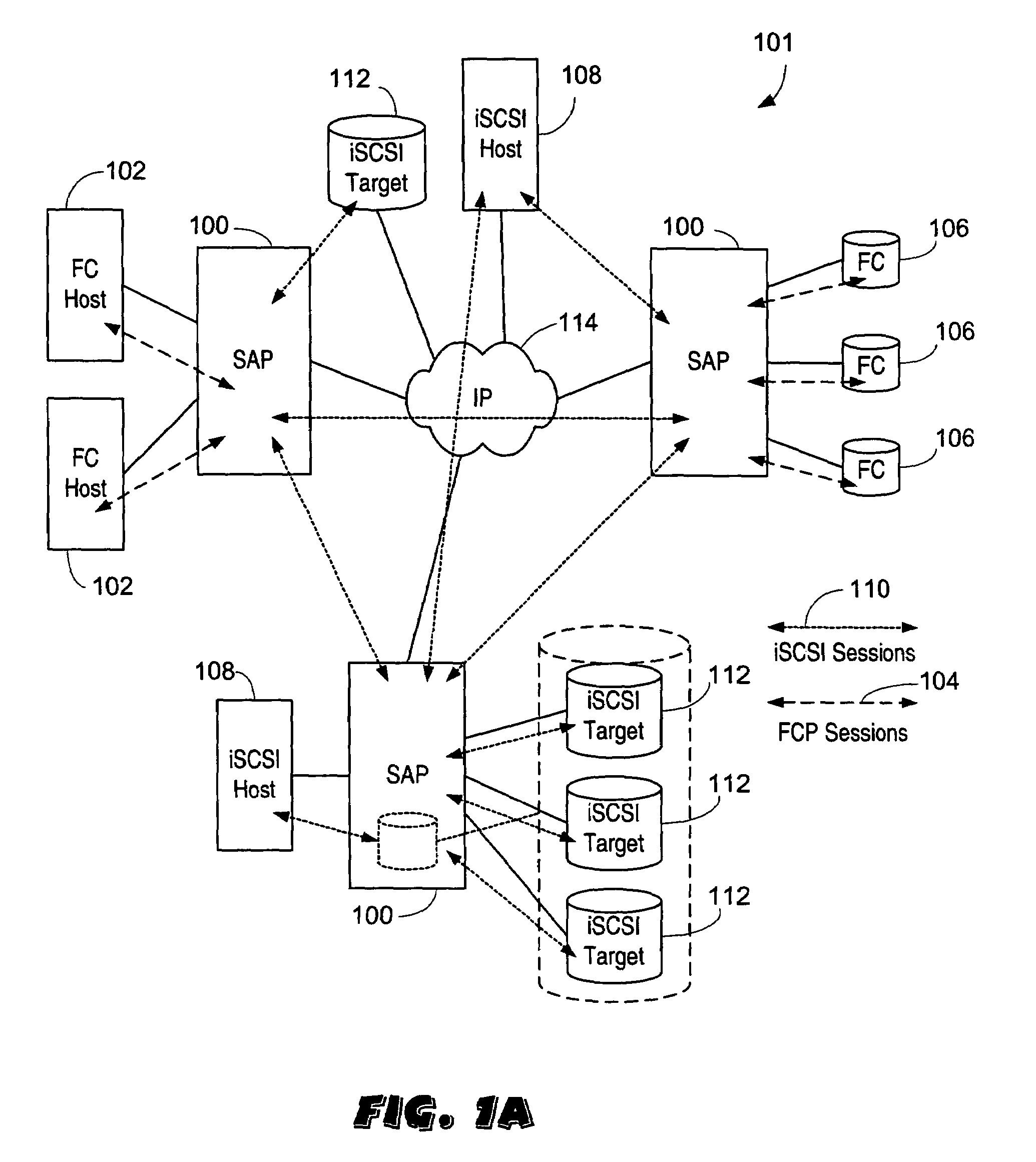
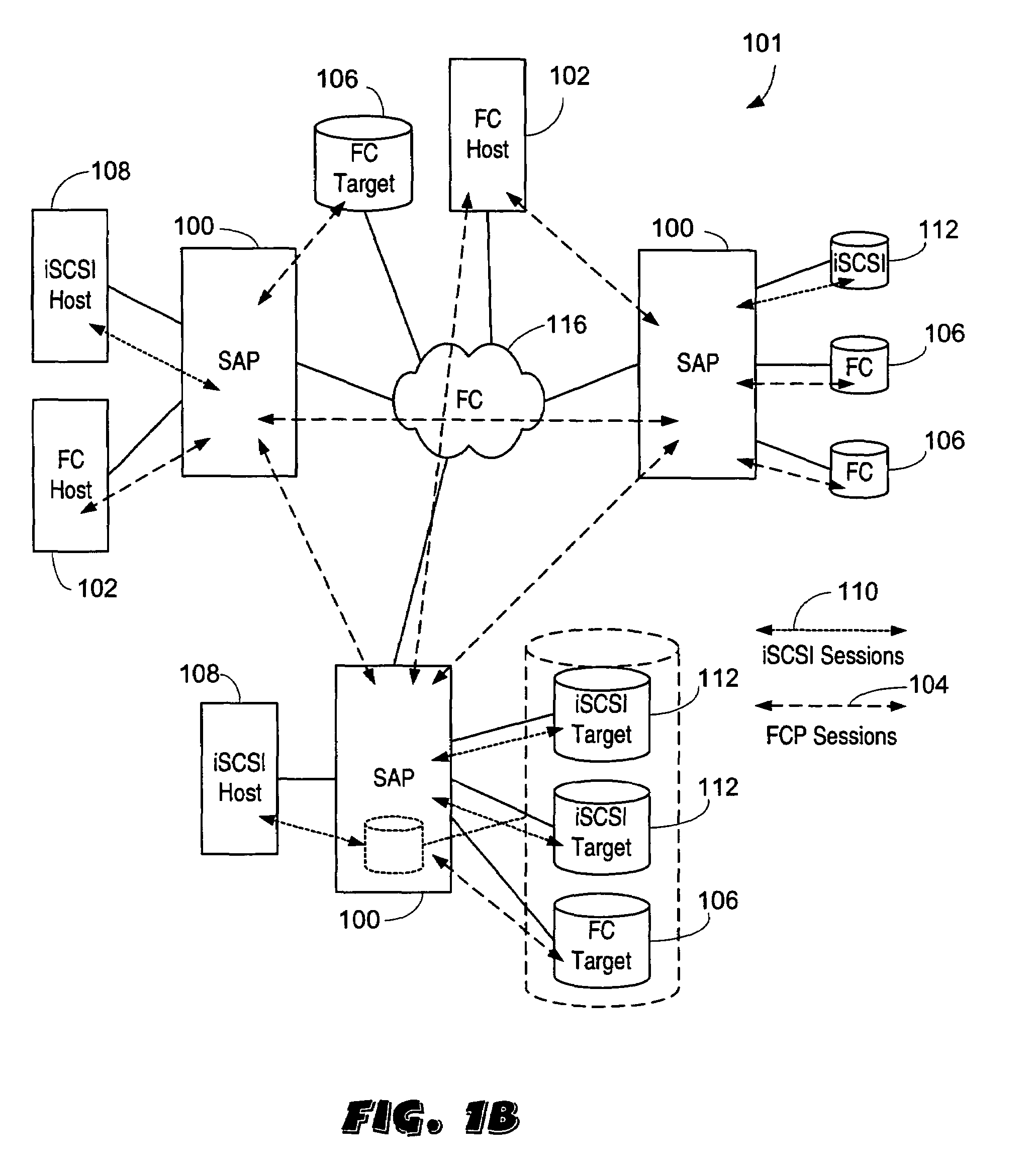
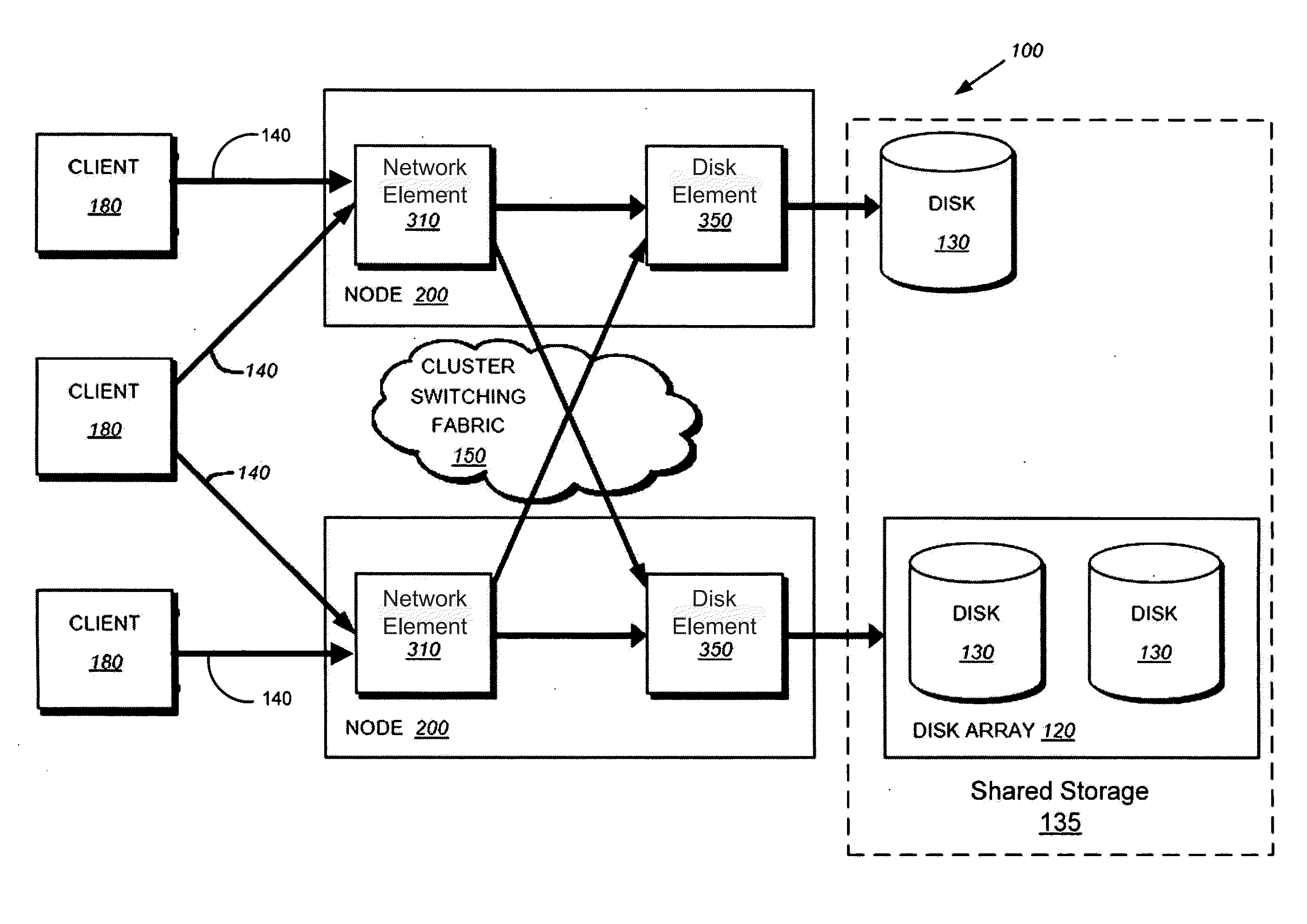
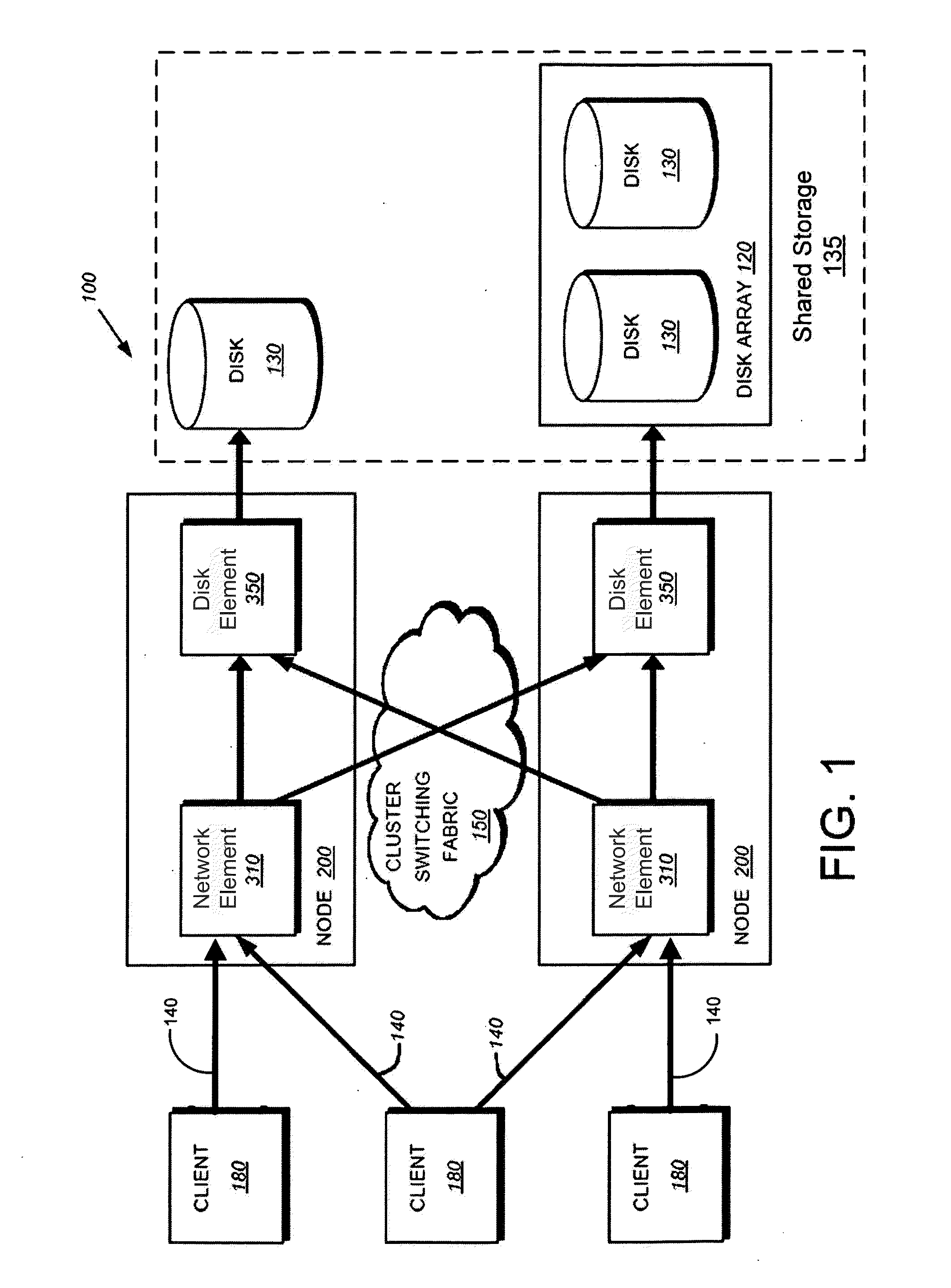
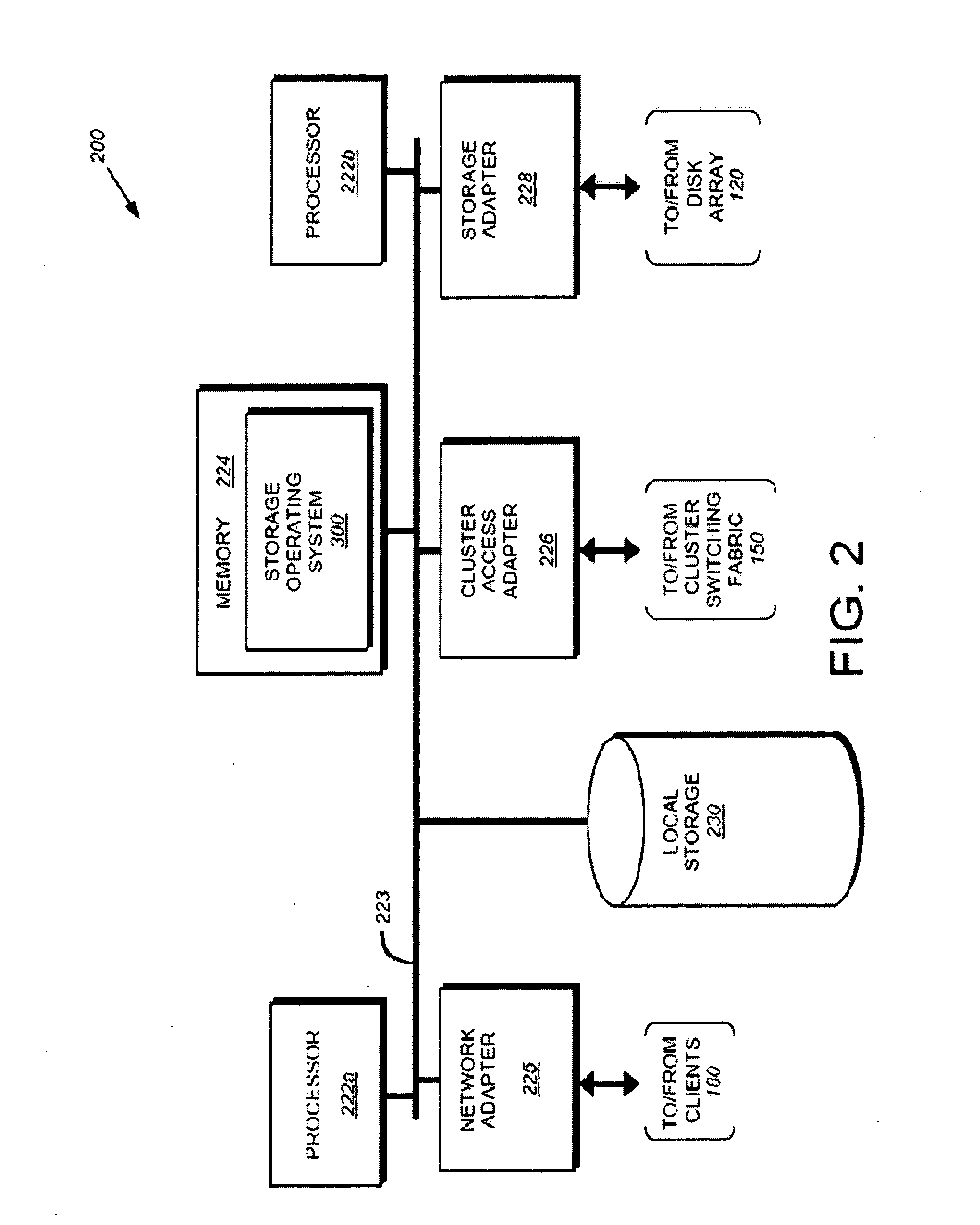
Servicing of Network Software Components of Nodes of a Cluster Storage System
InactiveUS20160239437A1Less disruptiveReduce disruptionMemory architecture accessing/allocationInput/output to record carriersNetwork connectionData access
Described herein are method and apparatus for servicing software components of nodes of a cluster storage system. During data-access sessions with clients, client IDs and file handles for accessing files are produced and stored to clients and stored (as session data) to each node. A serviced node is taken offline, whereby network connections to clients are disconnected. Each disconnected client is configured to retain its client ID and file handles and attempt reconnections. Session data of the serviced node is made available to a partner node (by transferring session data to the partner node). After clients have reconnected to the partner node, the clients may use the retained client IDs and file handles to continue a data-access session with the partner node since the partner node has access to the session data of the serviced node and thus will recognize and accept the retained client ID and file handles.
Owner:NETWORK APPLIANCE INC
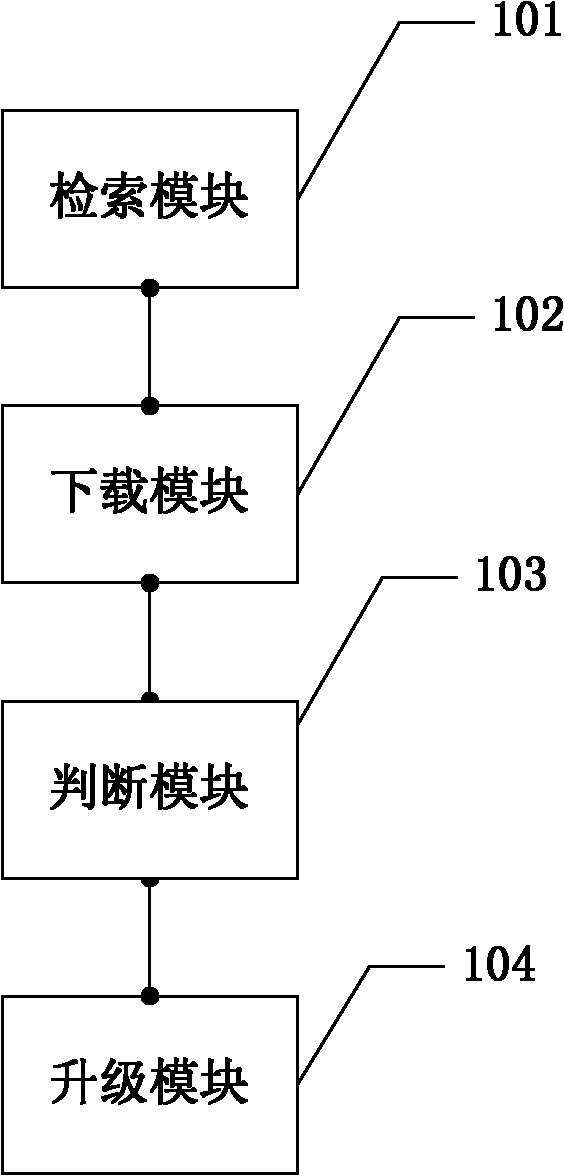
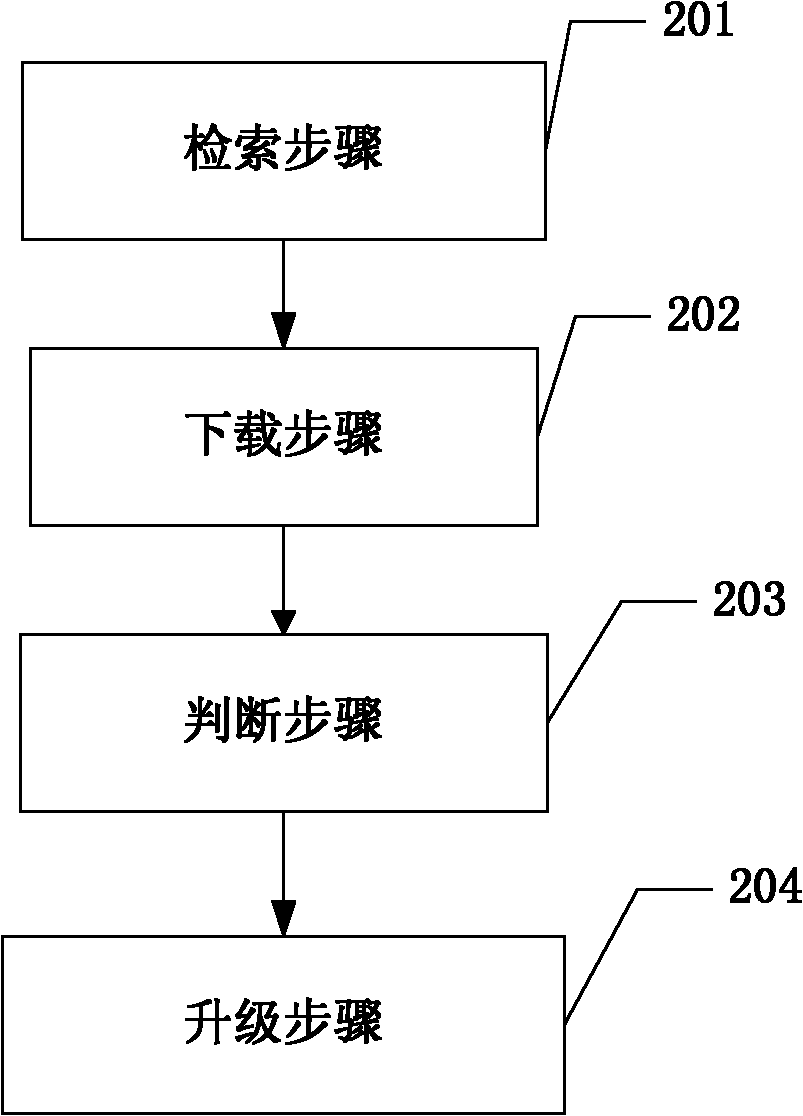
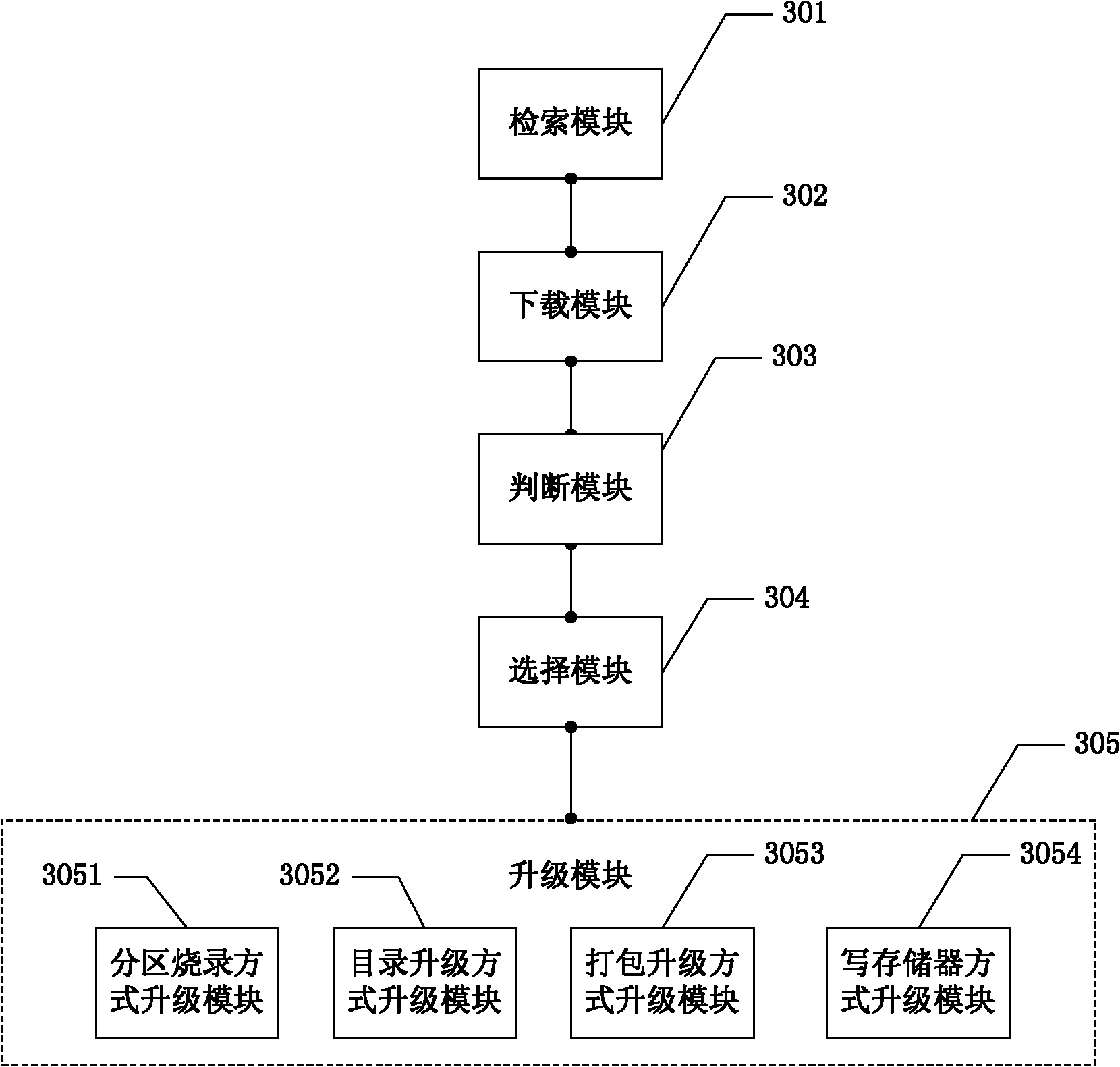
Method for updating network equipment and device for implementing method
The invention discloses a method and device for updating network equipment. The method comprises the followings steps: searching an update file which is contained in an update file list at a server side, wherein the update file comprises an update file header and an update data; downloading the file header; according to a software release and a hardware release, judging whether update is required; when the update is required, according to update types, downloading data and executing update operations on the network equipment by adopting a corresponding update mode based on description in the update types. The invention also provides a device for implementing the method. The technical scheme is applied, based on information carried by the downloaded file header, the corresponding update mode is selected to update network software, thus simplifying update procedures, saving network resources, saving storage space and improving update efficiency, diversifying update modes, having flexible expansibility, and meeting update requirements for different types of files and different types of network equipment.
Owner:SHENZHEN JIUZHOU ELECTRIC
Systems and methods for in-application and in-browser purchases
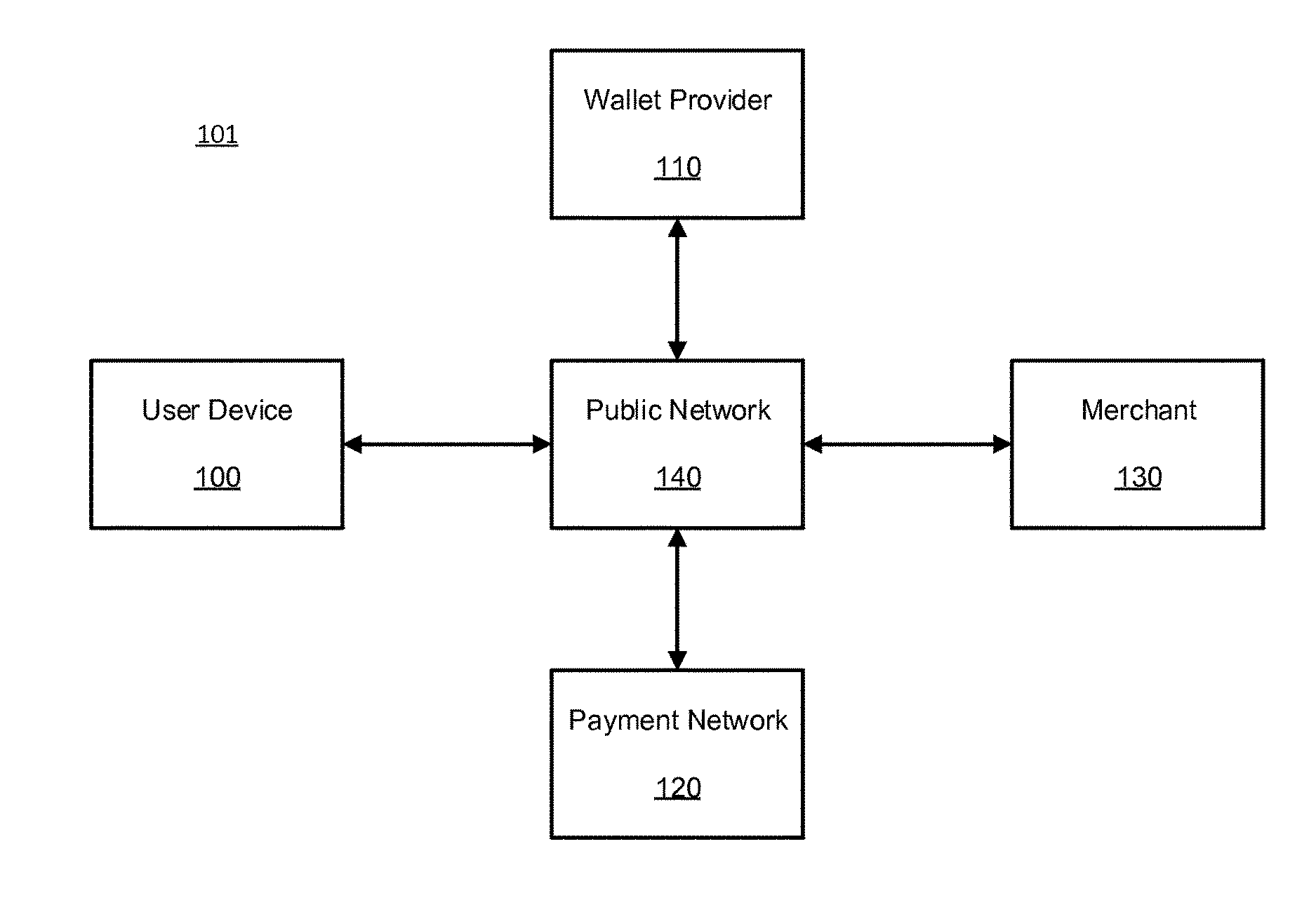
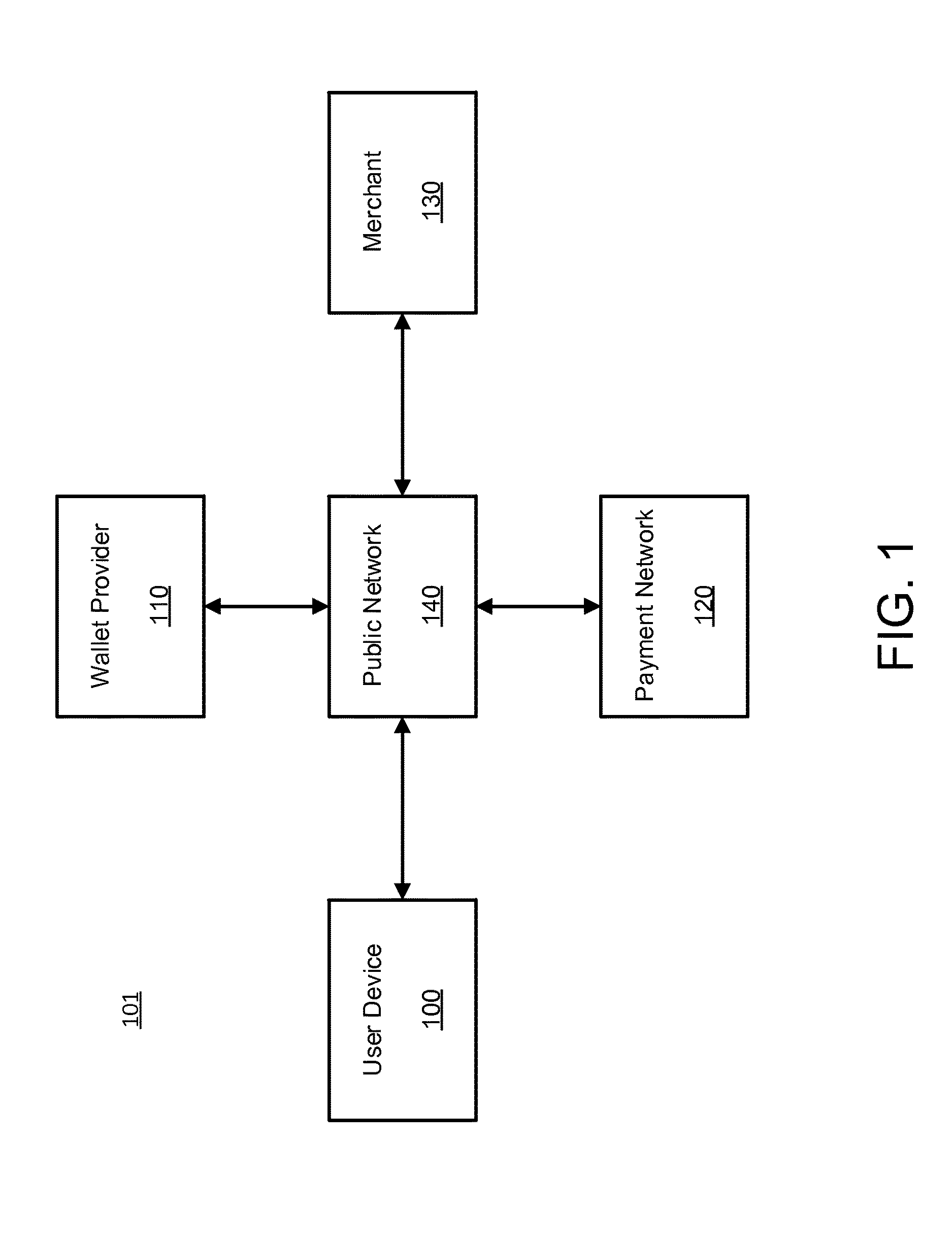
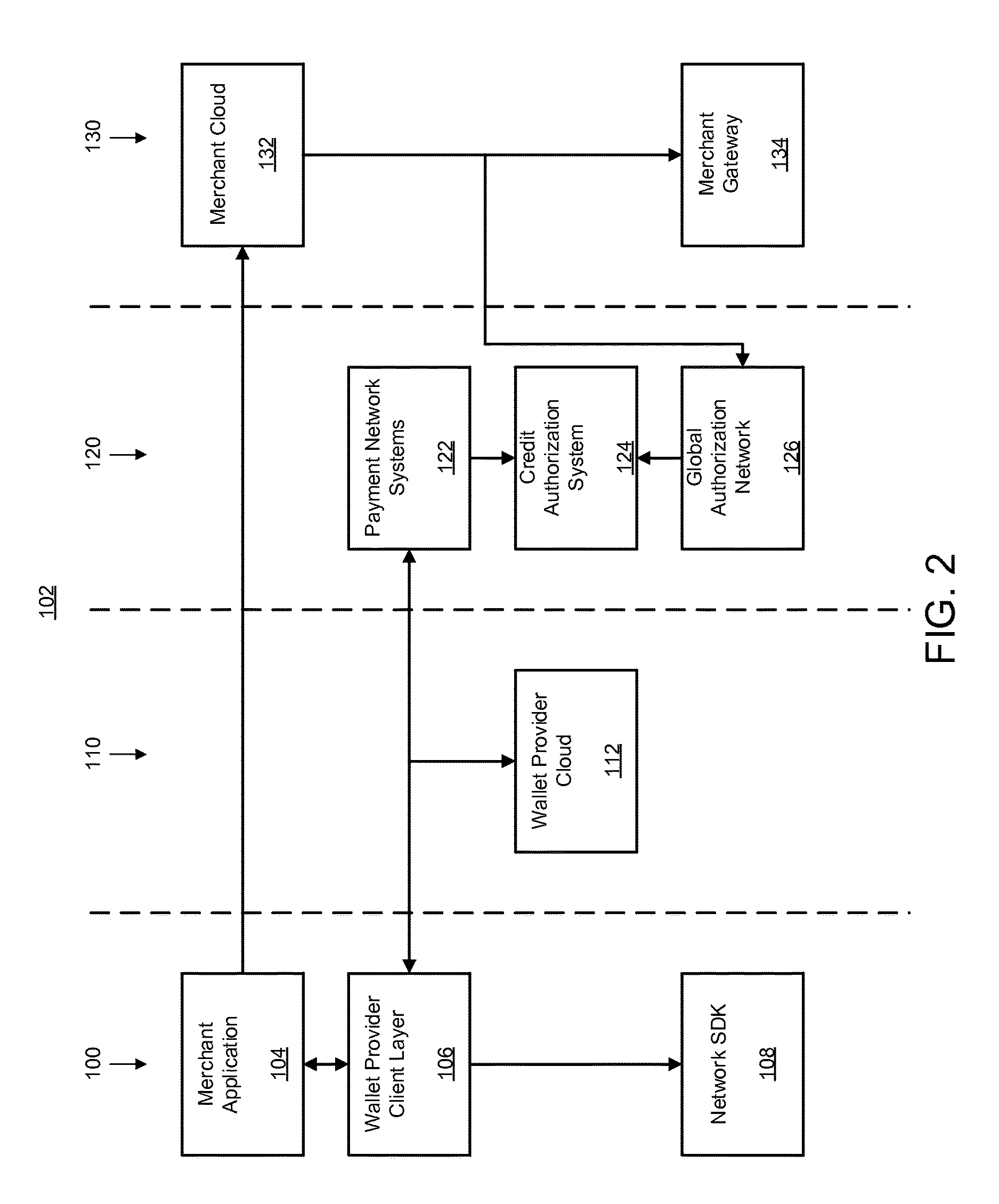
A system may receive a transaction request from a user device, and request an in-app cryptogram from a network software development kit (SDK) on the user device. The in-app cryptogram may include an unpredictable number, an application transaction counter (ATC), and a card verification result (CVR), and the ATC may be extracted from a limited use payment credential (LUPC). The system may transmit a token, a token expiry, and a token data block for an assessment by a payment network, with the token data block including the token, the token expiry, the ATC, and / or the in-app cryptogram. The system may further receive a request from the payment network to update the LUPC on the user device, and attest that the user device is secure in response to the request from the payment network to refresh the LUPC on the user device.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
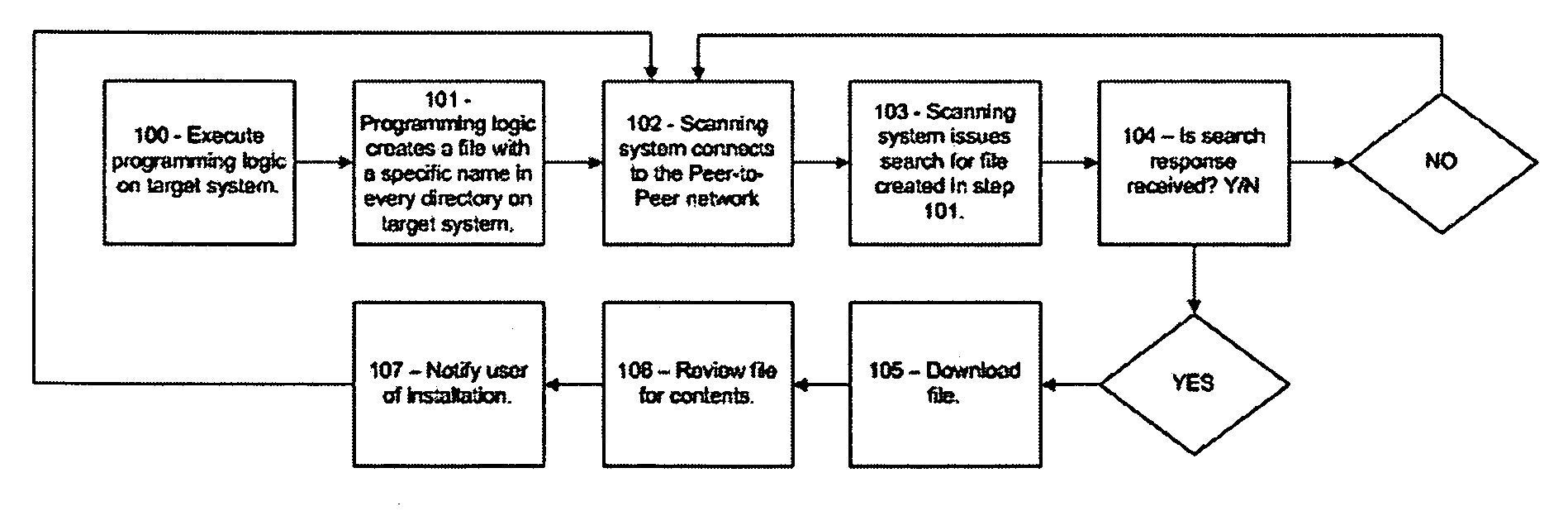
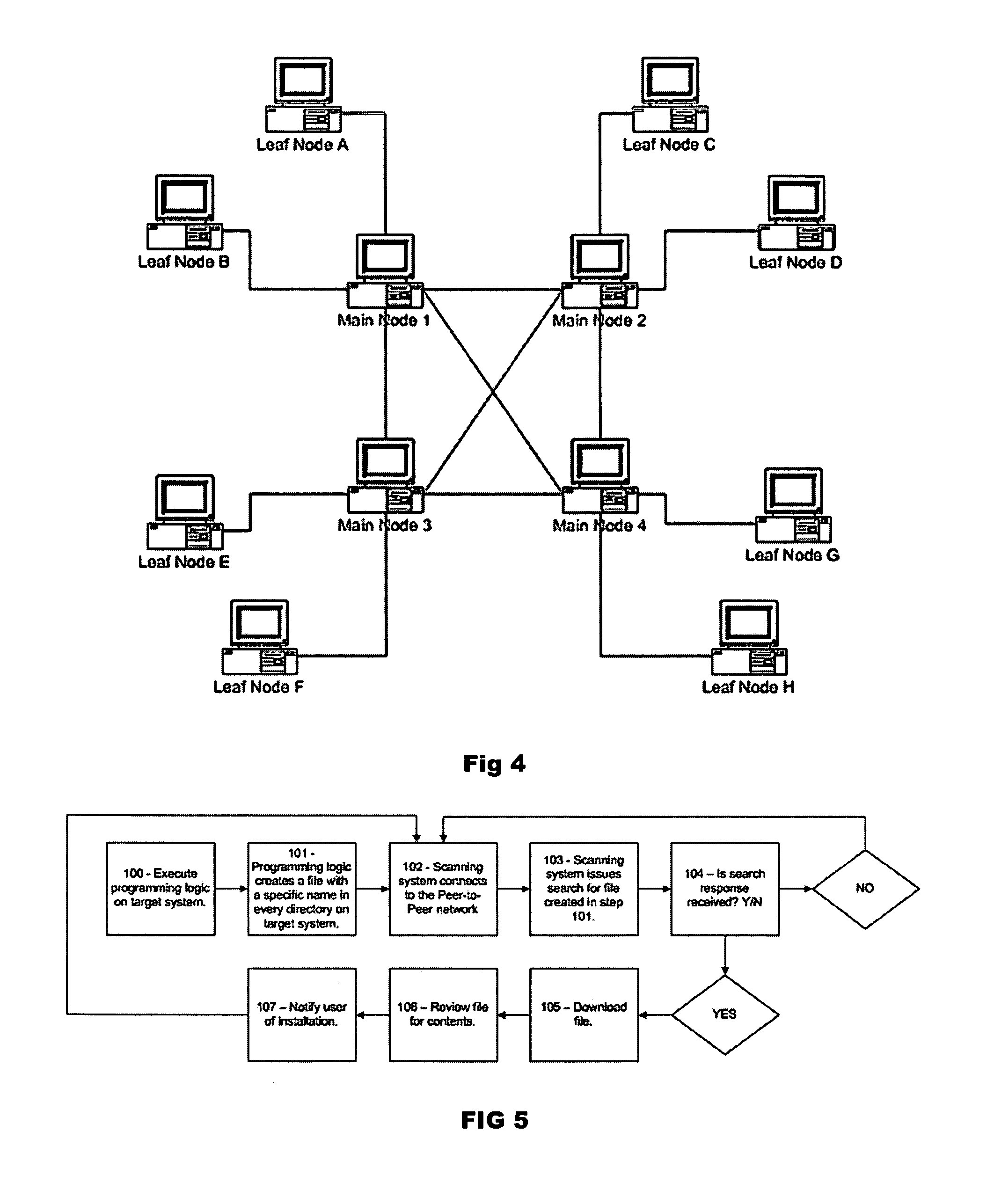
System for identifying the presence of Peer-to-Peer network software applications
ActiveUS20070078990A1Digital data processing detailsTime-division multiplexDistributed computingPeer-to-peer
A system and method for detecting peer-to-peer network software operating on a target computer. A target file is created, and placed in one or more folders on the target computer. A search is issued on a Peer-to-Peer network for the target file. Peer-to-peer software is detected to be operating on the target computer in accordance with results of the search.
Owner:KROLL INFORMATION ASSURANCE LLC
Apparatus and method for storage processing with split data and control paths
InactiveUS7376765B2Achieve scaleProvide flexibilityMultiplex system selection arrangementsInput/output to record carriersWire speedMulti protocol
A system including a storage processing device with an input / output module. The input / output module has port processors to receive and transmit network traffic. The input / output module also has a switch connecting the port processors. Each port processor categorizes the network traffic as fast path network traffic or control path network traffic. The switch routes fast path network traffic from an ingress port processor to a specified egress port processor. The storage processing device also includes a control module to process the control path network traffic received from the ingress port processor. The control module routes processed control path network traffic to the switch for routing to a defined egress port processor. The control module is connected to the input / output module. The input / output module and the control module are configured to interactively support data virtualization, data migration, data journaling, and snapshotting. The distributed control and fast path processors achieve scaling of storage network software. The storage processors provide line-speed processing of storage data using a rich set of storage-optimized hardware acceleration engines. The multi-protocol switching fabric provides a low-latency, protocol-neutral interconnect that integrally links all components with any-to-any non-blocking throughput.
Owner:AVAGO TECH INT SALES PTE LTD
Intelligent television system and intelligent television method capable of expanding cellphone
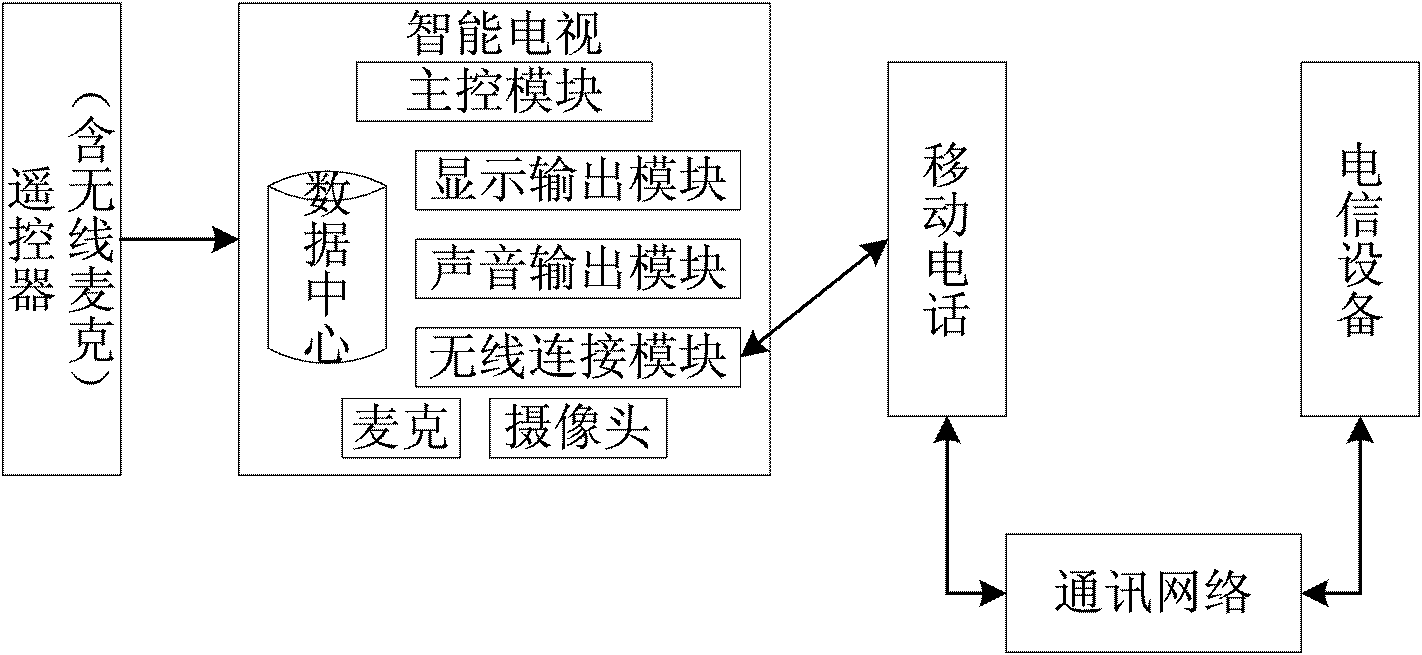
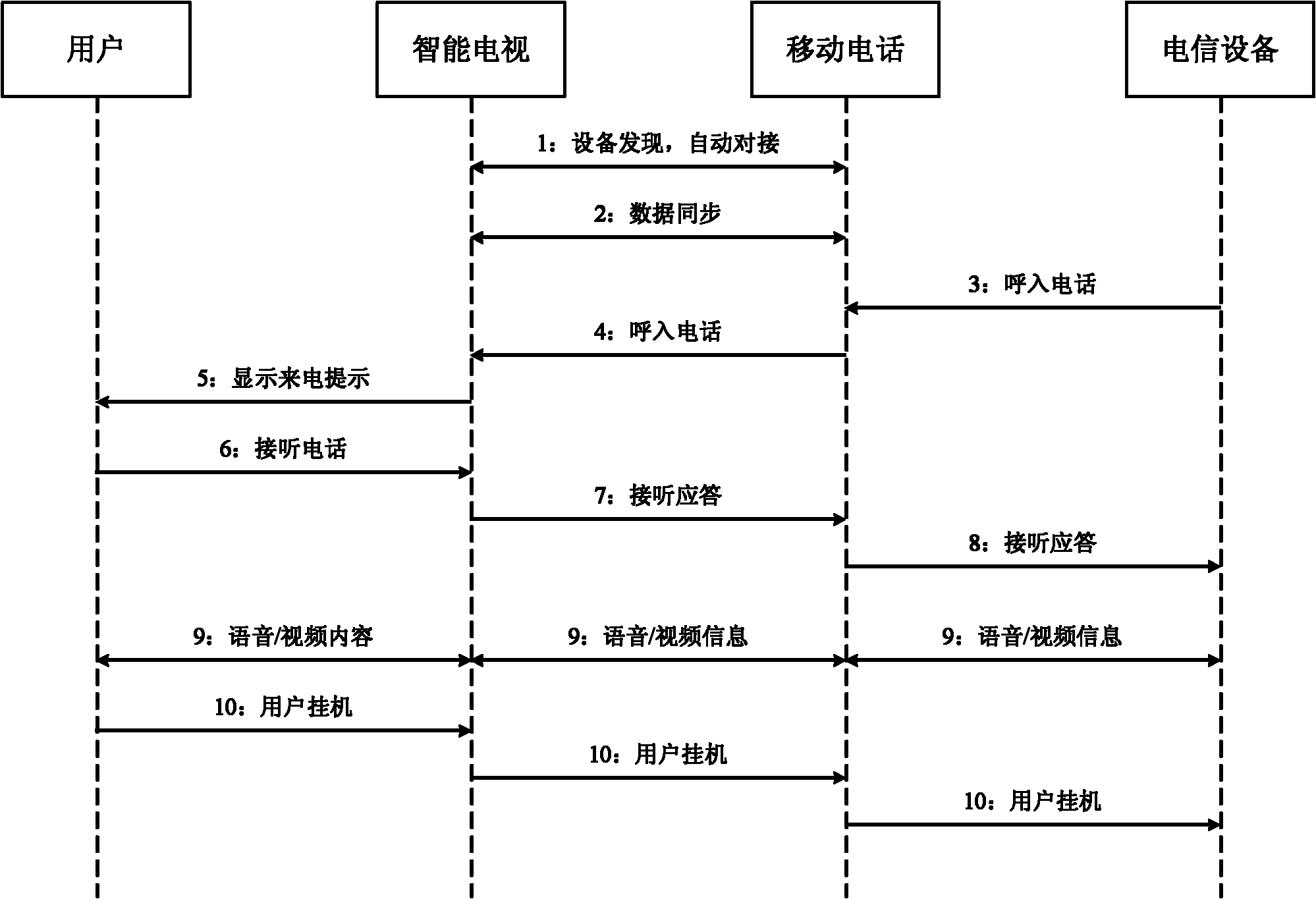
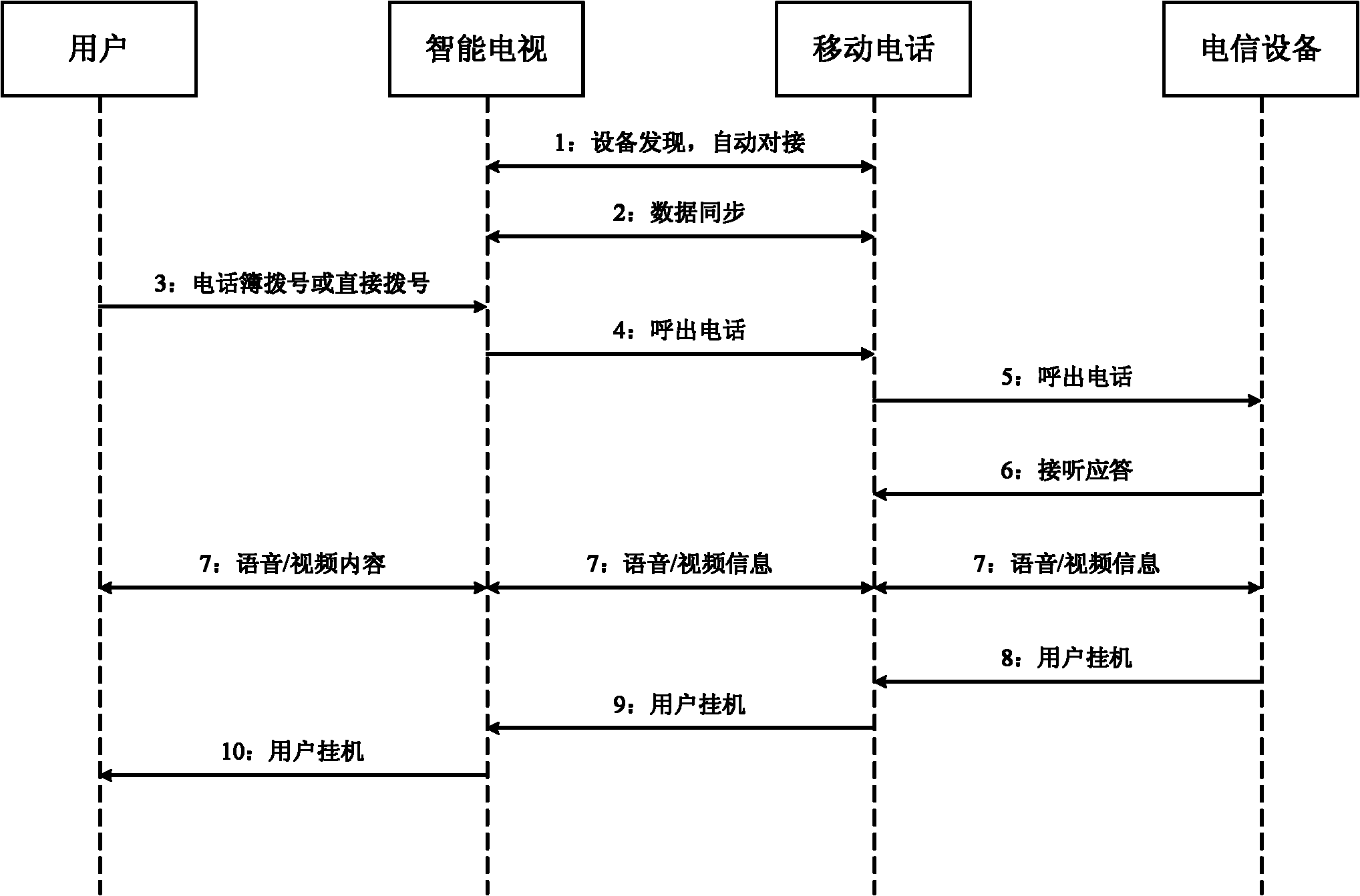
InactiveCN102572584AEasy to operateImprove experienceSubstation equipmentTwo-way working systemsTelevision systemCommunication effects
The invention relates to the technical field of intelligent televisions and provides an intelligent television system and an intelligent television method capable of expanding a cellphone. The system comprises an intelligent television, a cellphone, a communication network and telecommunication equipment, wherein the intelligent television is in butt joint with the cellphone in wireless connection mode, the cellphone can build speech / video phone communication connection with the telecommunication equipment through the communication network, the intelligent television can input speech / video phone message received from the telecommunication equipment by the cellphone; and / or the intelligent television can collect a speech / video phone message and send the phone message to the telecommunication equipment through the cellphone. The intelligent television can expand speech / video communication capacity to fully utilize the advantage that the television is strong in audio and video playing capacity, thereby enabling users to achieve good speech / video communication effects. Due to the fact that communication is not based on specific network software, user experience is enhanced and safety is improved.
Owner:HISENSE VISUAL TECH CO LTD
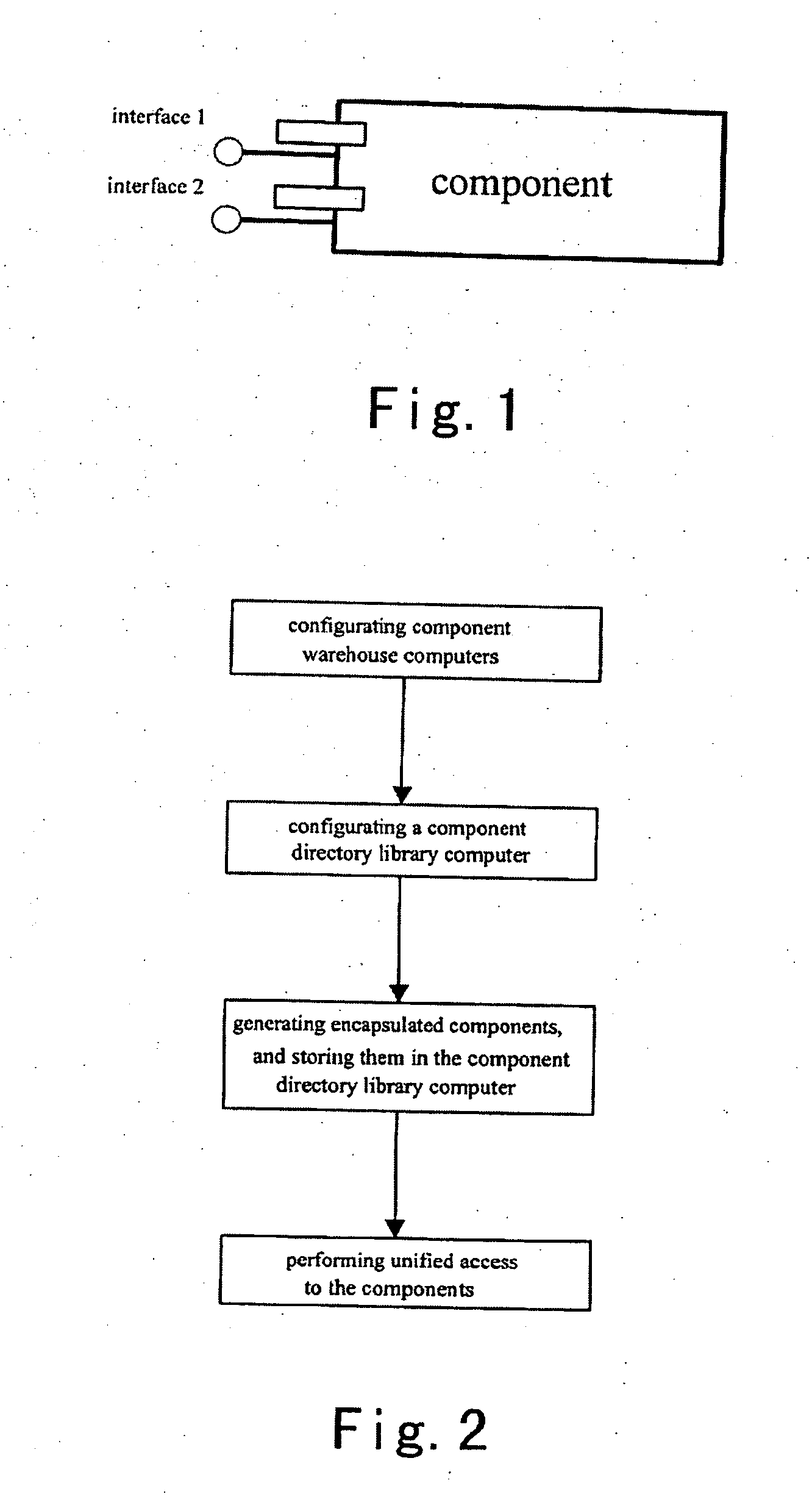
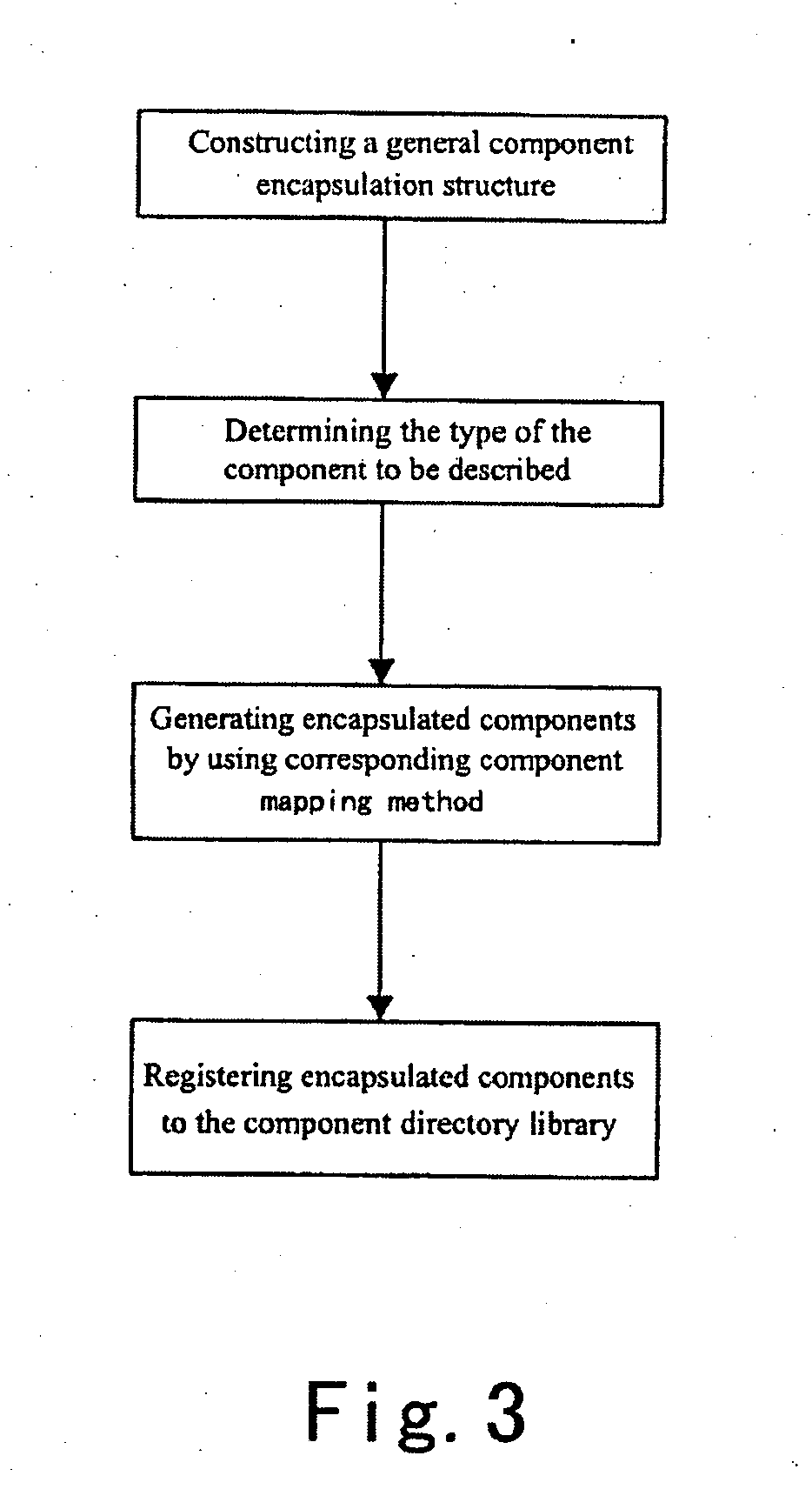
Encapsulation and unified access scheme for components
InactiveUS20060080336A1Improve reuse efficiencyImprove software development efficiencyDigital data processing detailsSoftware reuseThe InternetSoftware engineering
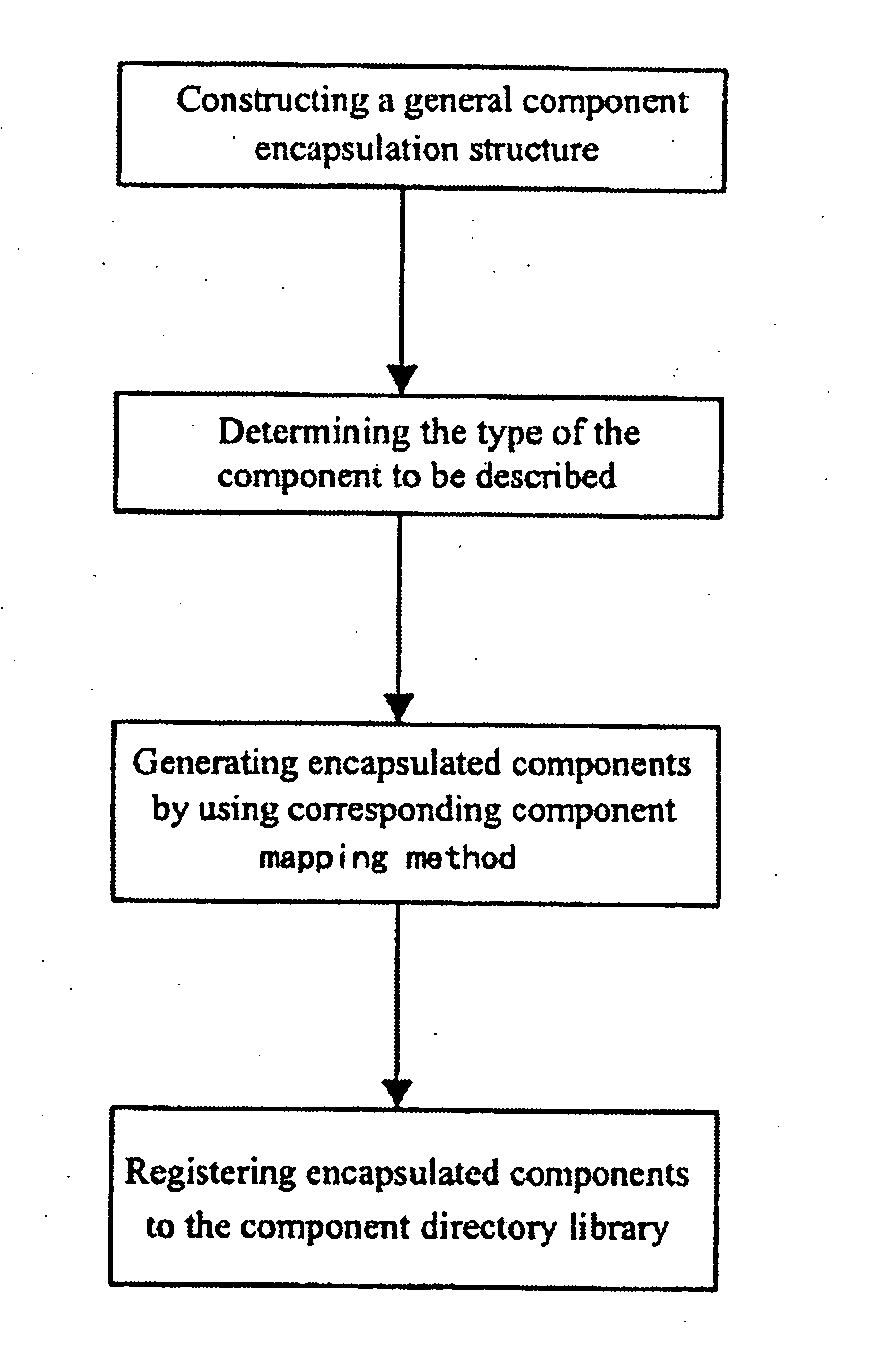
A method is provided for encapsulating and accessing components, comprising: configurating component warehouse and storing components acquired from the Internet into the component warehouse to form a component warehouse computer; configurating a component directory library on another computer to form a component directory library computer; fetching component from the component computer by a user computer, encapsulating the component to form a encapsulated component, and organizing and storing the encapsulated component in the component directory library computer; and performing unified access to component resources by a user computer based on the component encapsulation information in the component directory library computer. The method can implement unified description and efficient organization of the existing component resources, to thereby support efficient retrieval and unified access to the component resources by high level applications. The method can also improve the reuse of network software and the efficiency of software development in many application fields.
Owner:TSINGHUA UNIV
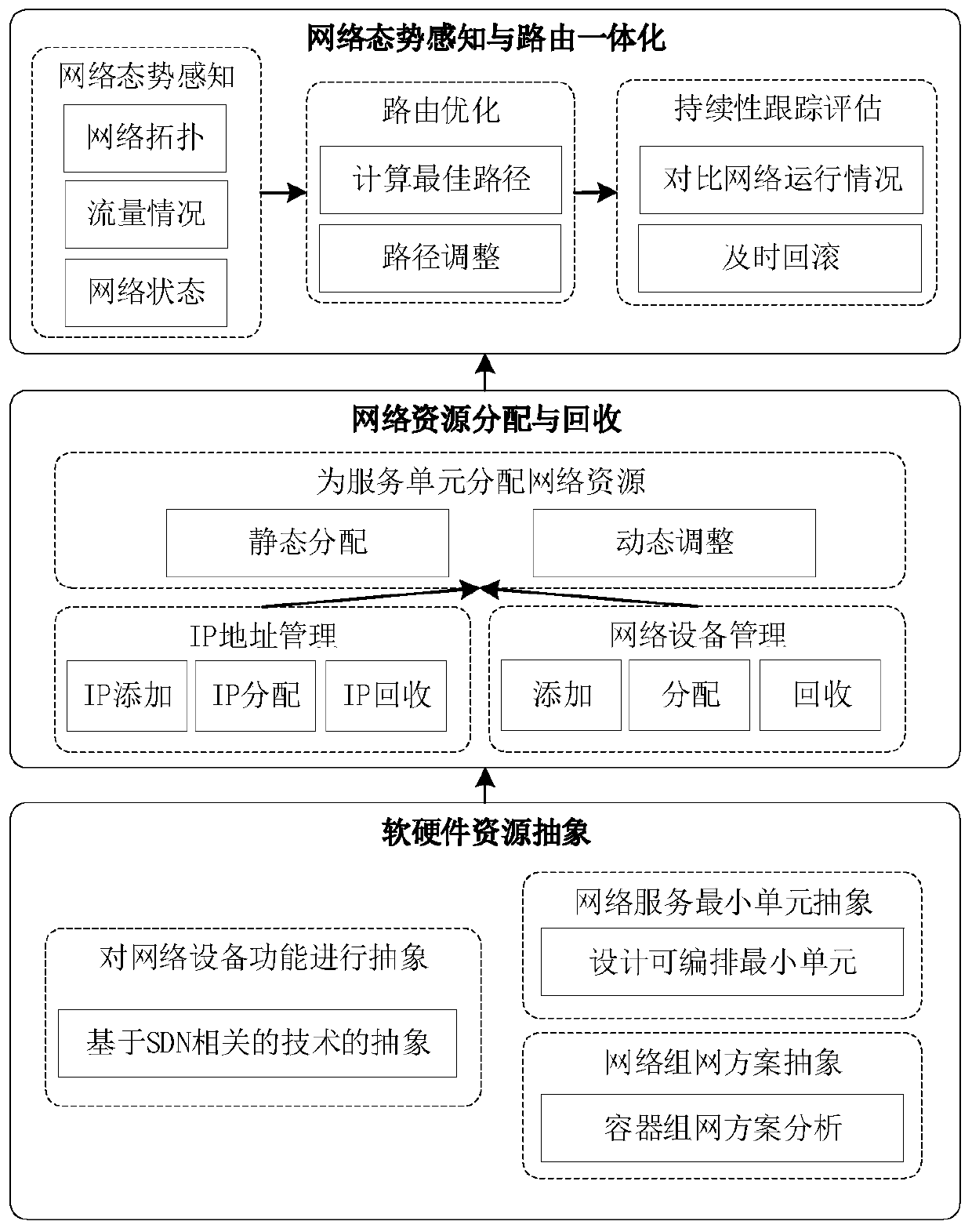
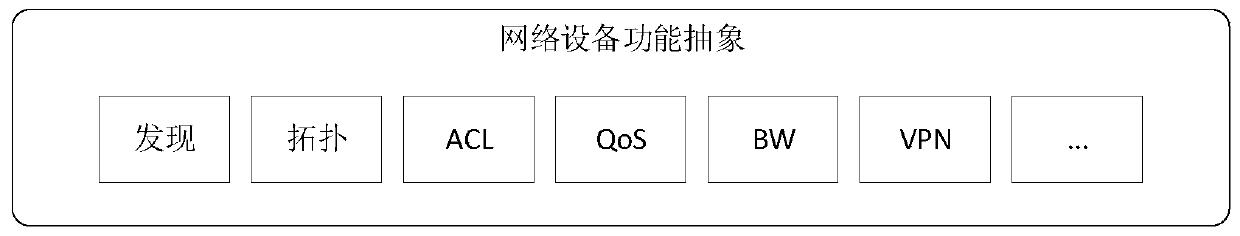
An SDN-based container network resource scheduling method
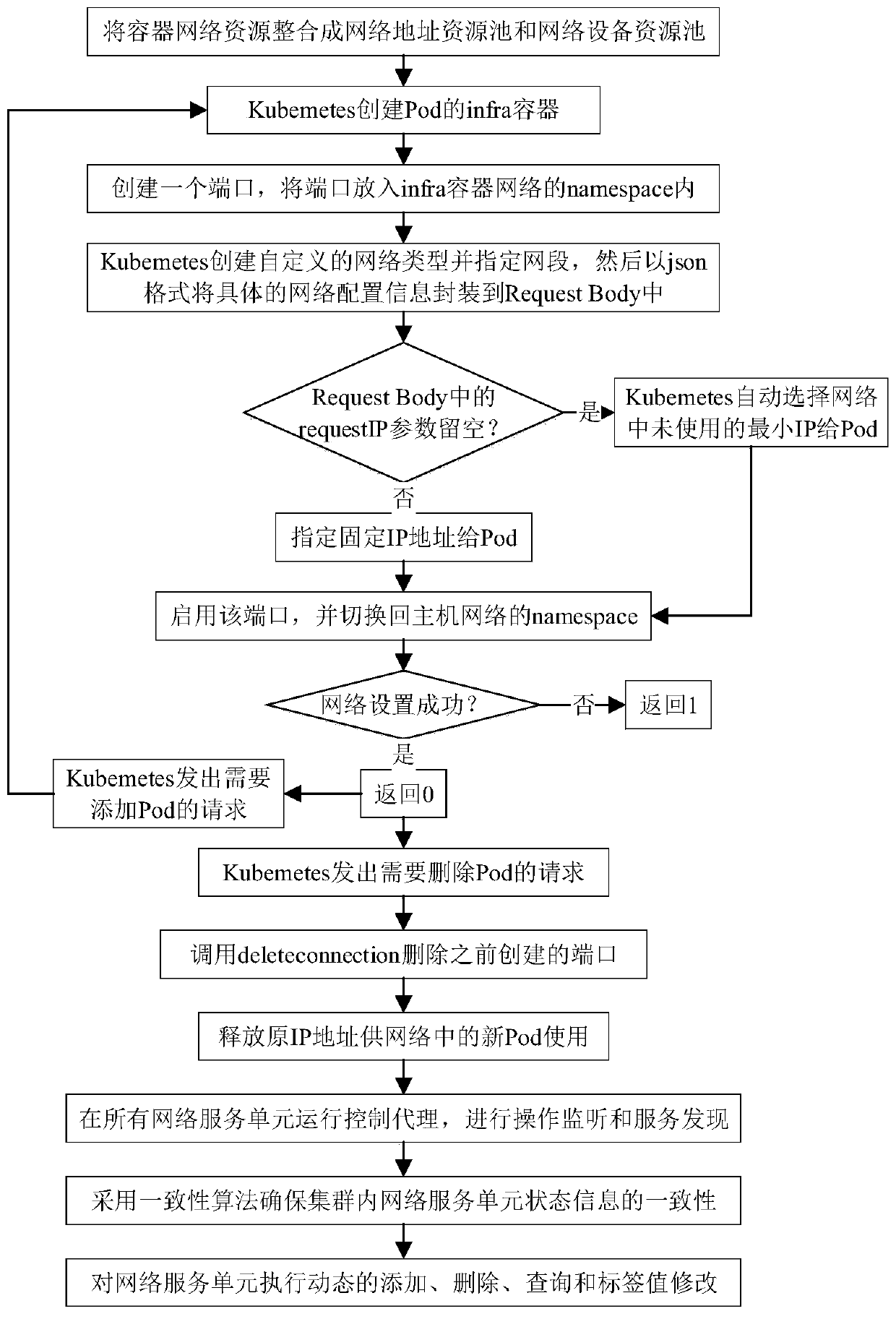
ActiveCN109743261AFully flexible sharingFlexible sharingData switching networksResource poolNetwork address
Aiming at the problem that resource segmentation and guarantee cannot be carried out according to requirements of a container network in the prior art, the invention provides an SDN-based container network resource scheduling method, which comprises the following steps of: 1, carrying out unified abstraction and description on network software and hardware resources based on an SDN / NFV technology;2, implementing resource allocation and recovery on the container network, integrating resources into a resource pool, establishing and managing a network address resource pool and a network equipment resource pool, providing network equipment resources as required, and recovering the network equipment resources in time when the network is destroyed; And step 3, based on the idea of SDN centralized control, deploying a centralized control server in the container network, and implementing network situation awareness and routing integration. The container network resource scheduling method integrates networking, routing and monitoring by intensively sensing the network situation and reasonably segmenting and recovering the container network resources in combination with the requirements oftasks, thereby realizing the optimal scheduling of the container network resources.
Owner:NAT UNIV OF DEFENSE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com