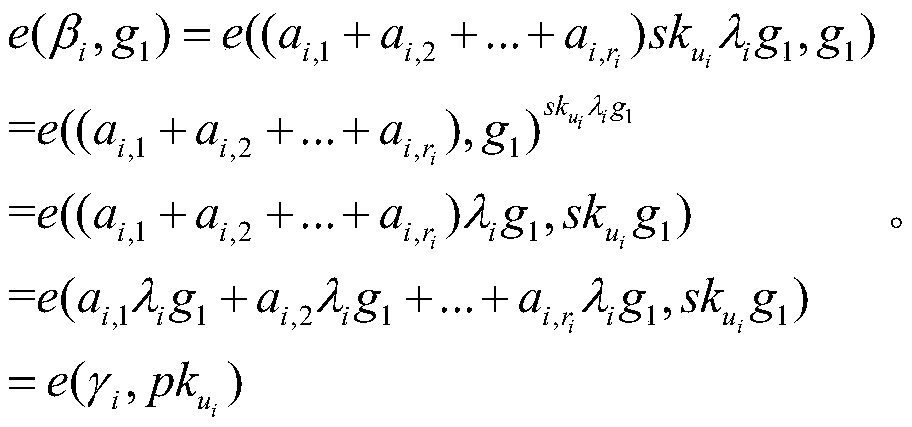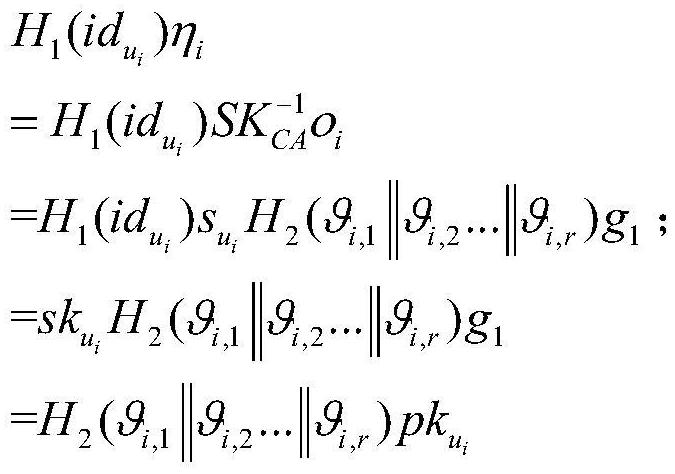Patents
Literature
104results about How to "Flexible sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Logistics management method, equipment and system based on cloud computing
InactiveCN102467703AReal-time trackingFlexible deploymentLogisticsLogistics managementTerminal equipment
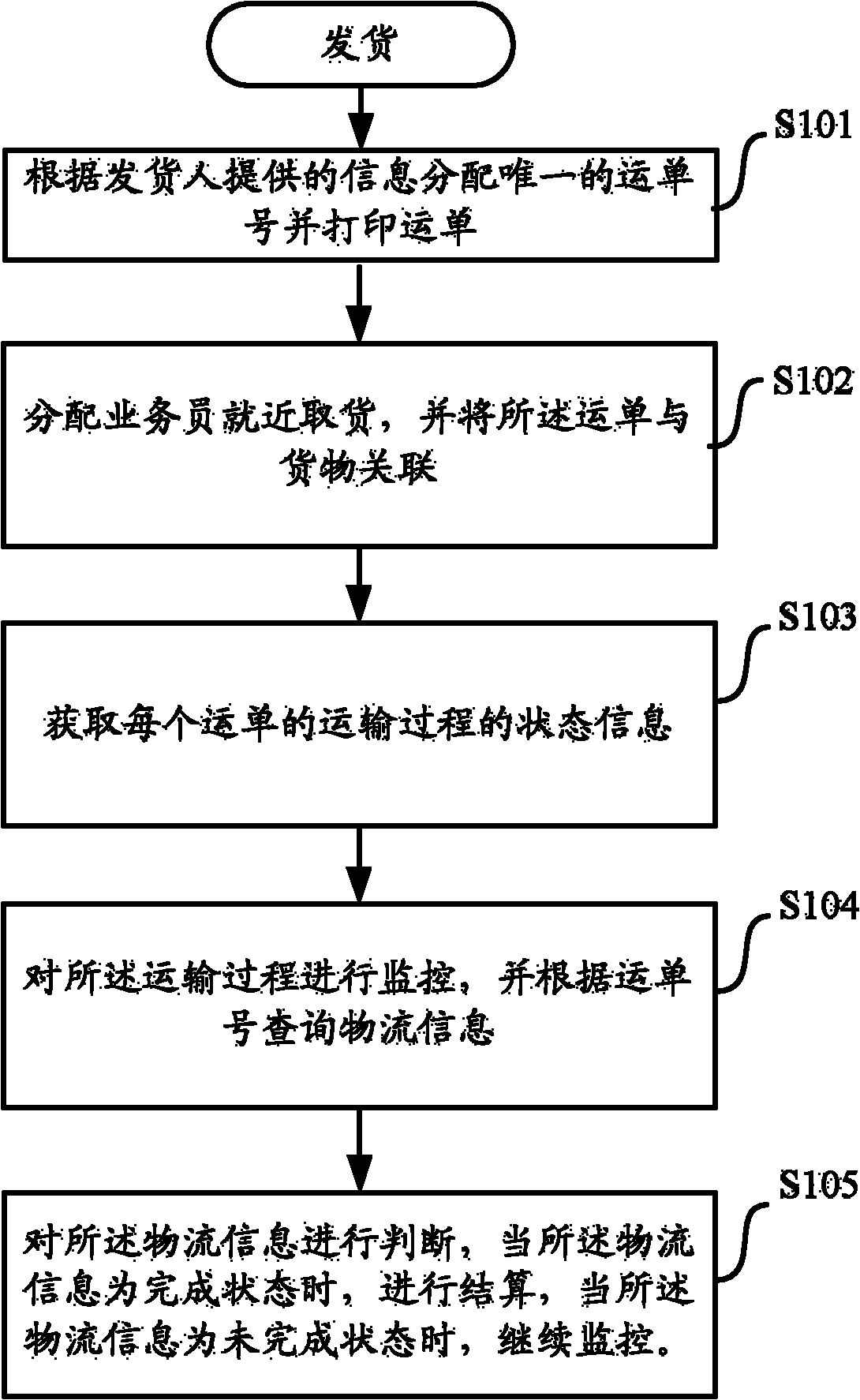
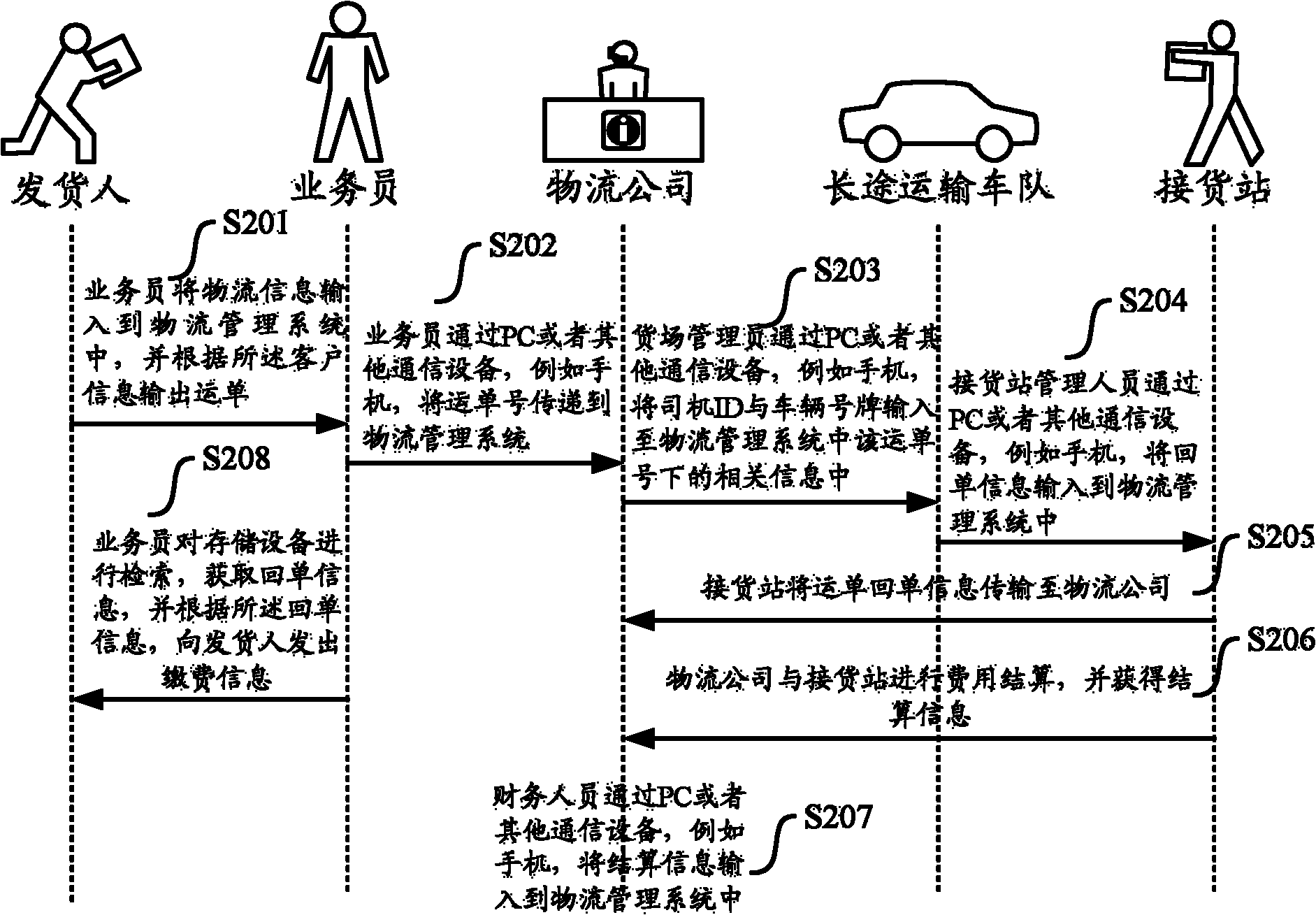
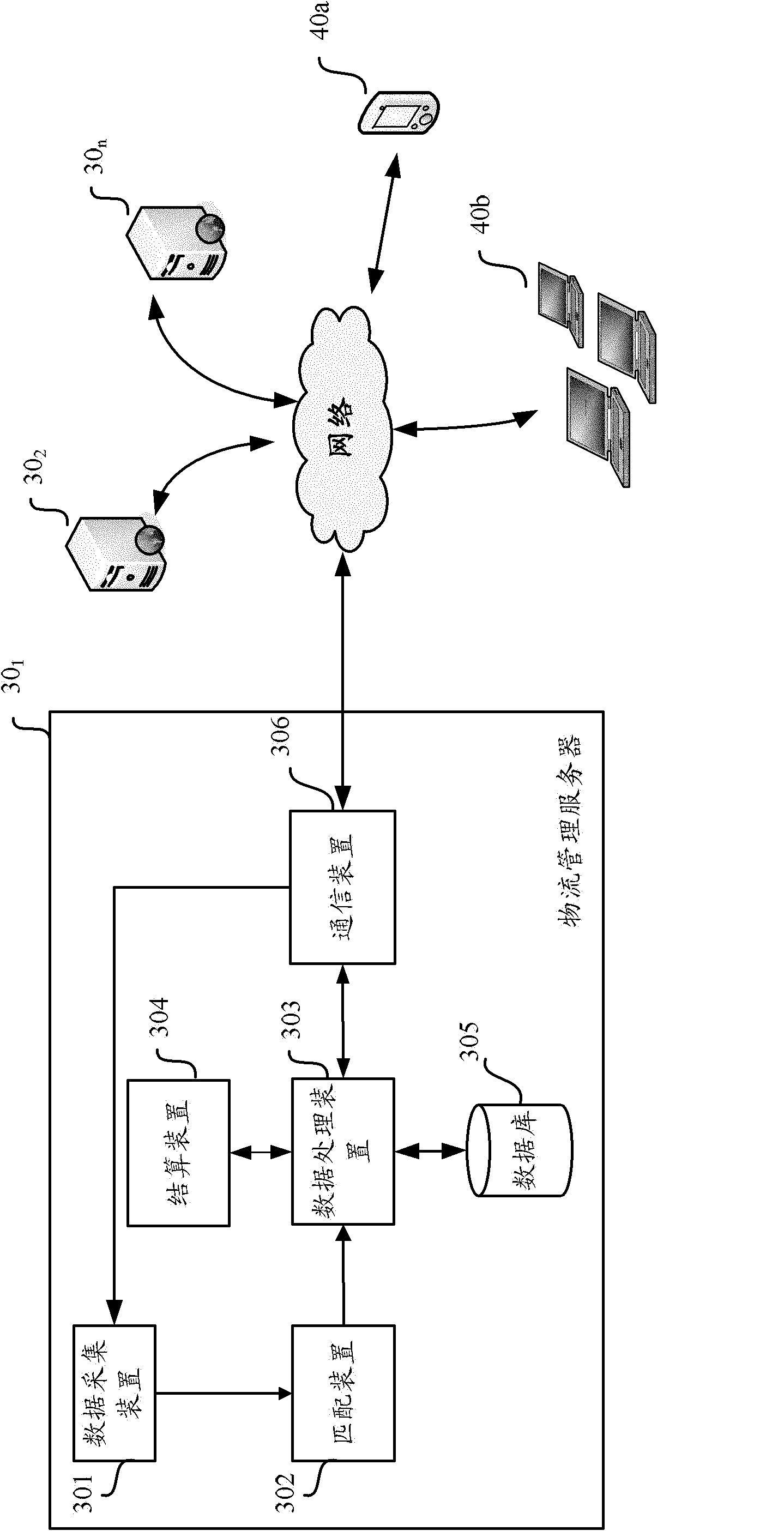
The invention provides a logistics management method based on a cloud computing technology. After one or more logistics agencies and staff thereof register / login a logistics management server, the logistics management method is characterized by comprising the following steps of: registering logistics information; allocating a unique waybill number; based on the logistics information and the state of each logistics agency and the staff of the logistics agency, allocating a logistics task to an appropriate logistics agency and parties of the logistics agency; sending the logistics information and the waybill number to the terminal equipment of the parties; attaching a waybill having the waybill number or a radio frequency identification (RFID) tag, on which the waybill number is recorded, to corresponding goods; monitoring and recording the parties and position of the goods in the logistics process; providing logistics state information; and after the logistics process is finished, settling accounts. The invention also provides the logistics management server and a logistics management system. By adoption of the logistics management method, functions of tracking logistics state, sharing logistics resources and settling the accounts among a plurality of logistics companies can be realized.
Owner:BEIJING TIANDE SHITONG TECH DEV
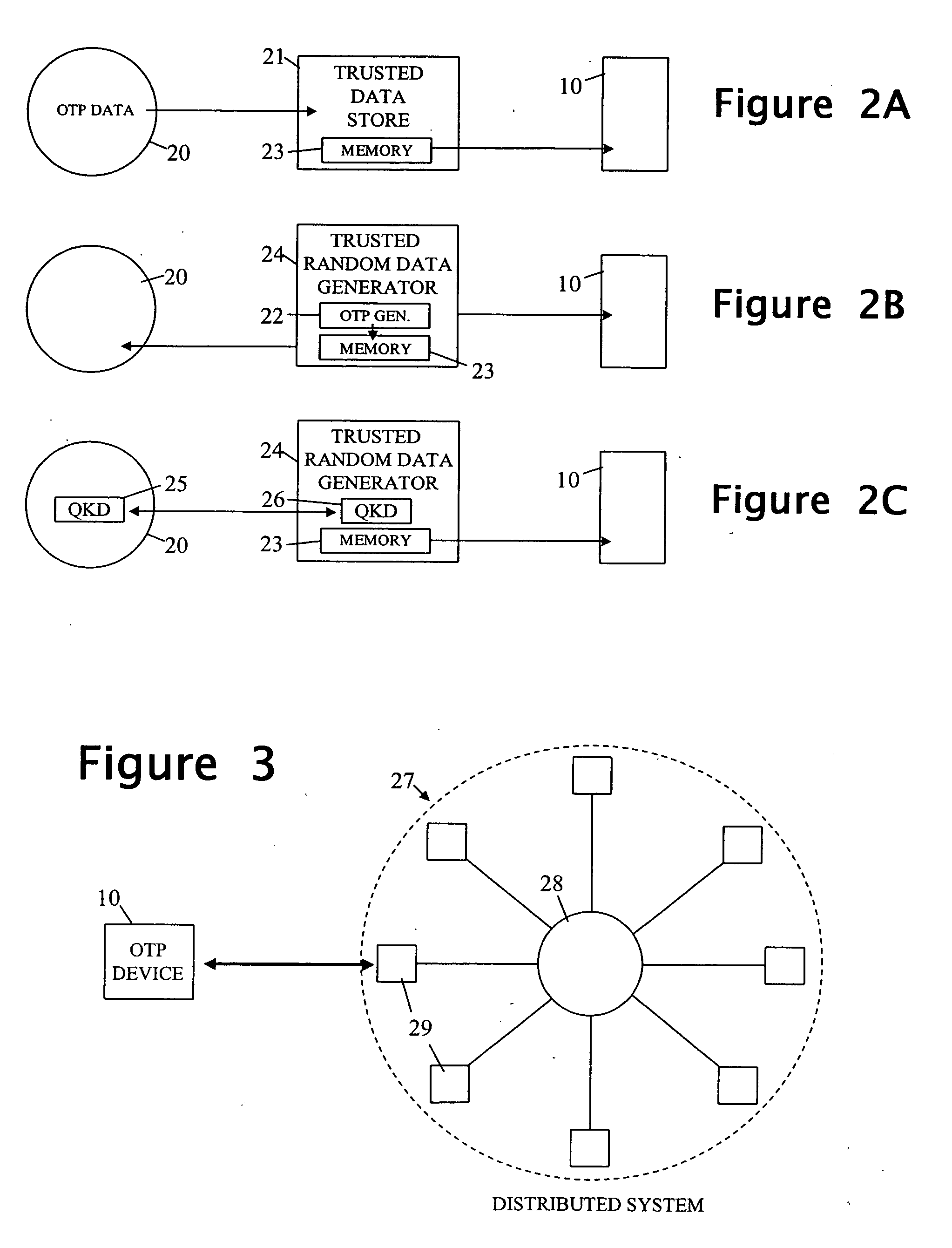
Device with multiple one-time pads and method of managing such a device
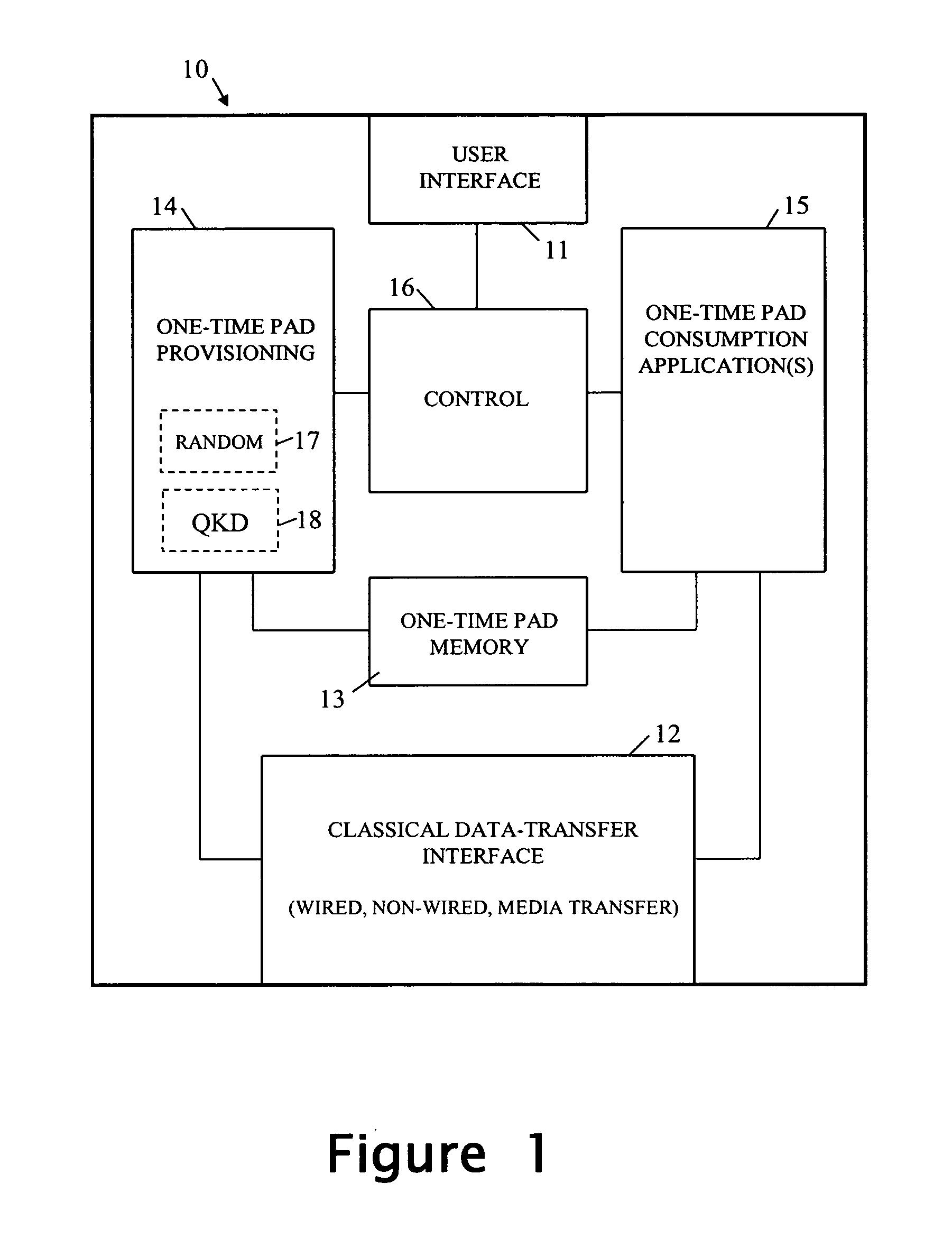
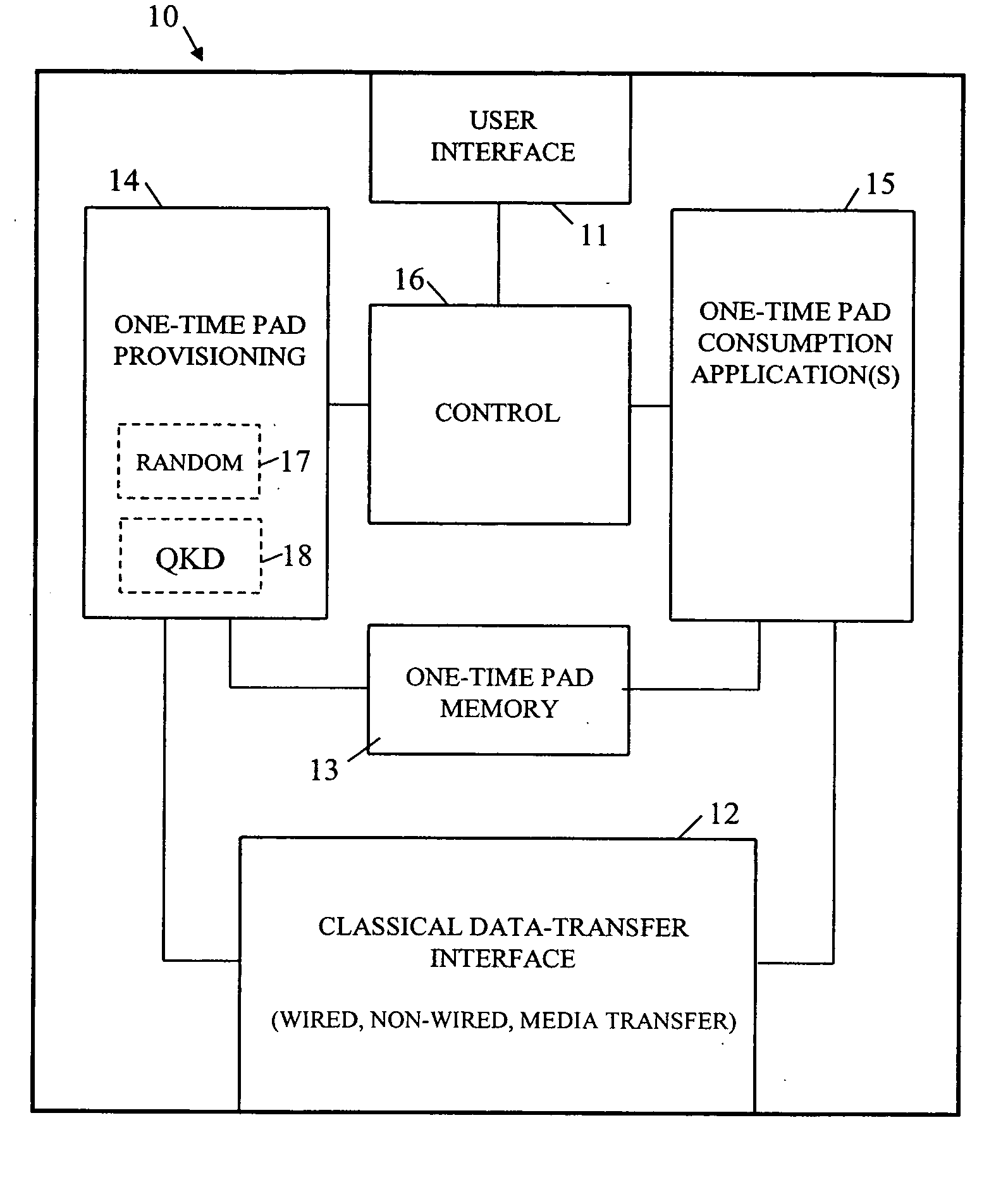
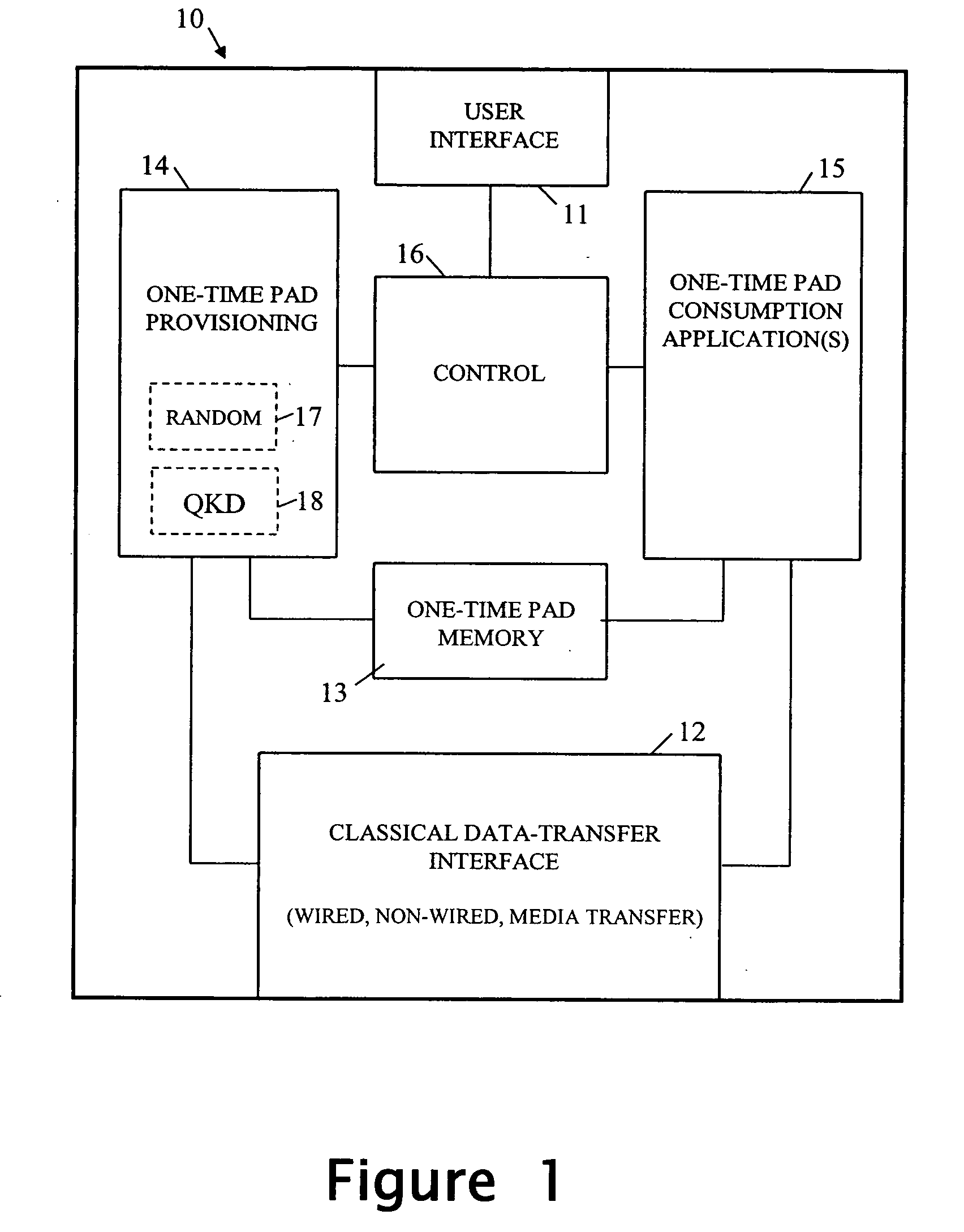
ActiveUS20080031456A1More dataFlexible sharingKey distribution for secure communicationComputer scienceTime data
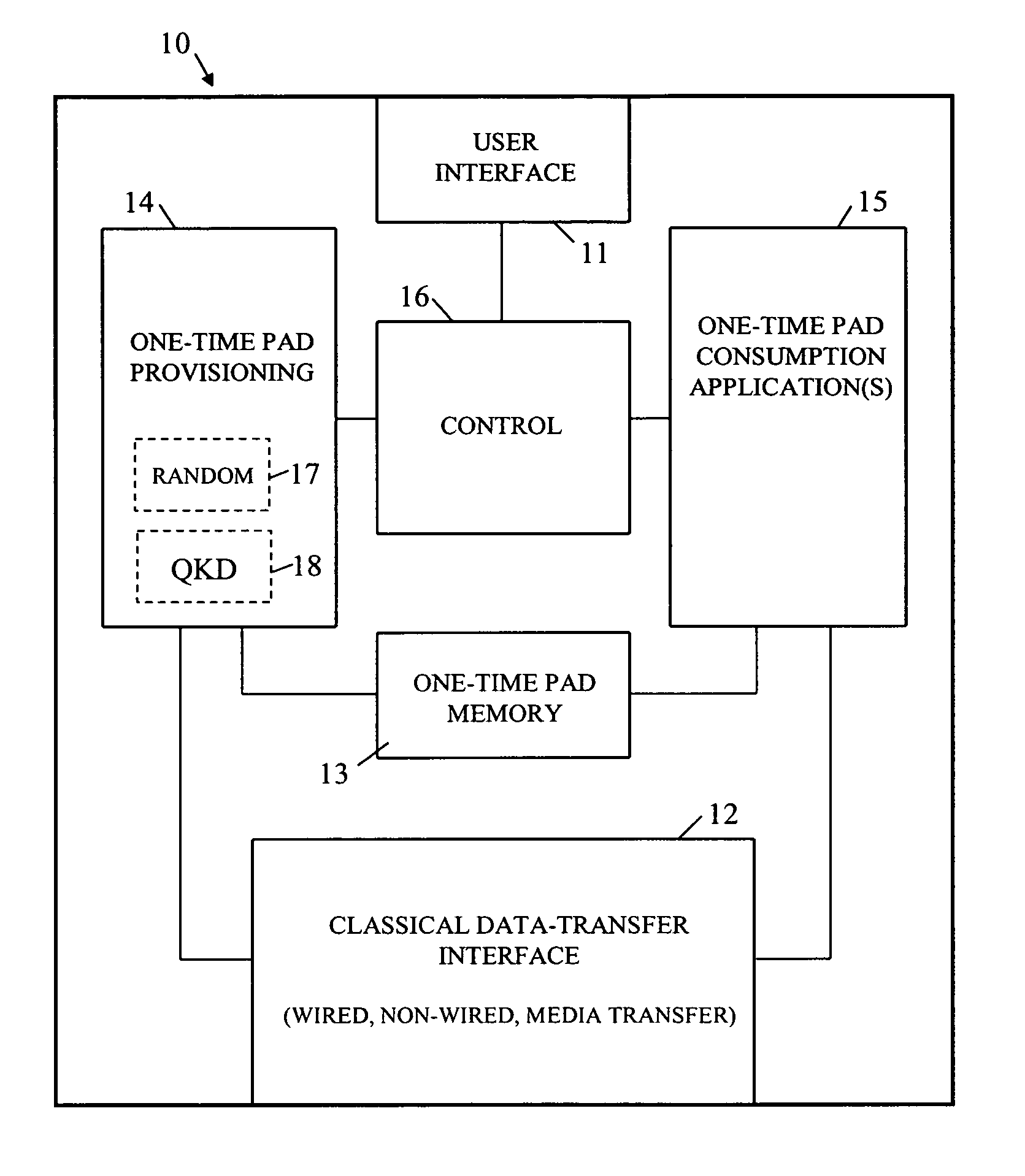
A device is arranged to carry out security-related tasks using one-time pad data. The device has a memory for holding multiple one-time pads, each pad having a different security rating and being intended for use by the device in executing a task to that security rating. Provisioning of the pads with one-time pad data involves carrying out a process for obtaining new secret random data. This process has a security rating with the value of this rating varying according to the nature and parameters of the process concerned. The security rating of the process used to obtain the new secret random data is matched to that of the pad to be provisioned with one-time data, or the other way around, such that the security rating of the process is as least as good as that of the pad to be provisioned.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method of operating a one-time pad system and a system for implementing this method
InactiveUS20070074276A1More dataFlexible sharingKey distribution for secure communicationDigital data processing detailsComputer hardwareEngineering
A system is disclosed in which a plurality of devices are arranged to use one-time pad data to interact with apparatus holding the same one-time pad data. Each of the devices and the apparatus has its own one-time pad and the pads are all provisioned with the same new one-time pad data. Upon any one of the devices wishing to effect an interaction with the apparatus using one-time pad data, an alignment operation is carried out between a set of entities comprising at least the apparatus and the device wishing to carry out the interaction. The alignment operation serves to reduce the level of the one-time pad of at least the device wishing to carry out the interaction, to the level of the lowest one-time pad of the set of entities involved in the alignment operation.
Owner:HEWLETT PACKARD DEV CO LP
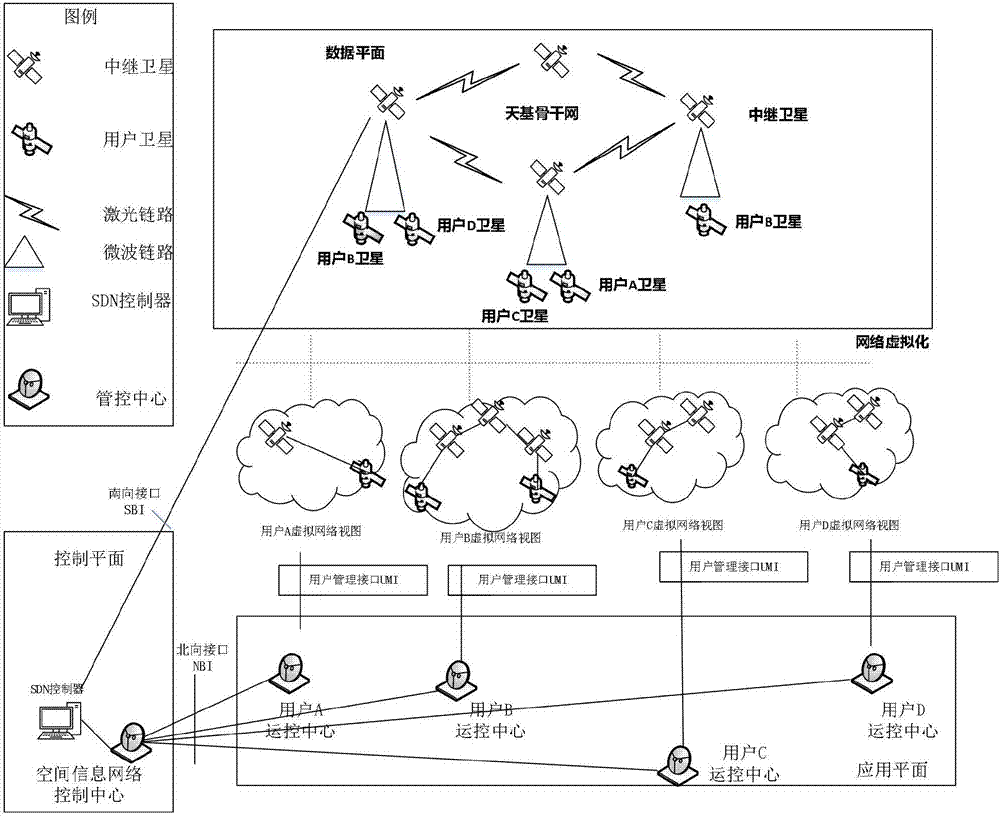
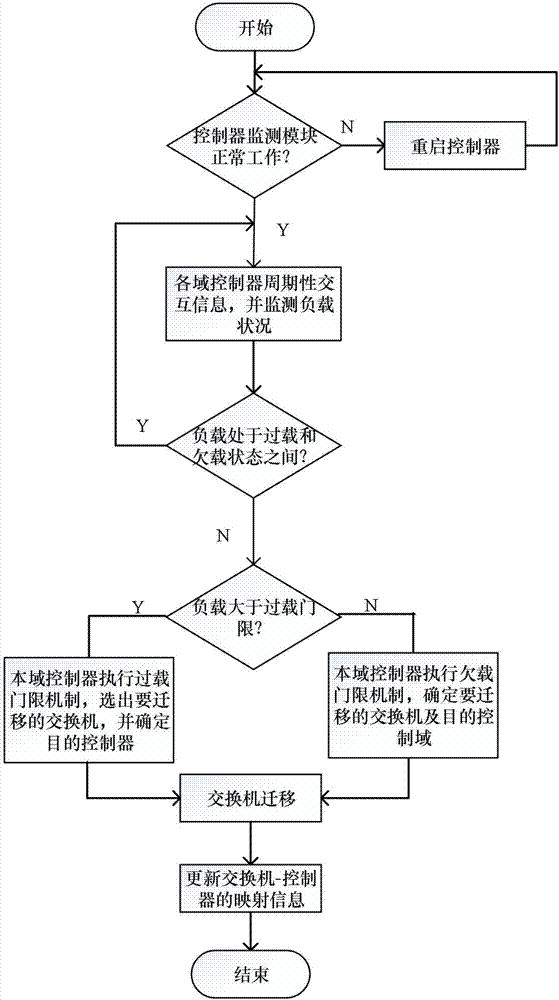
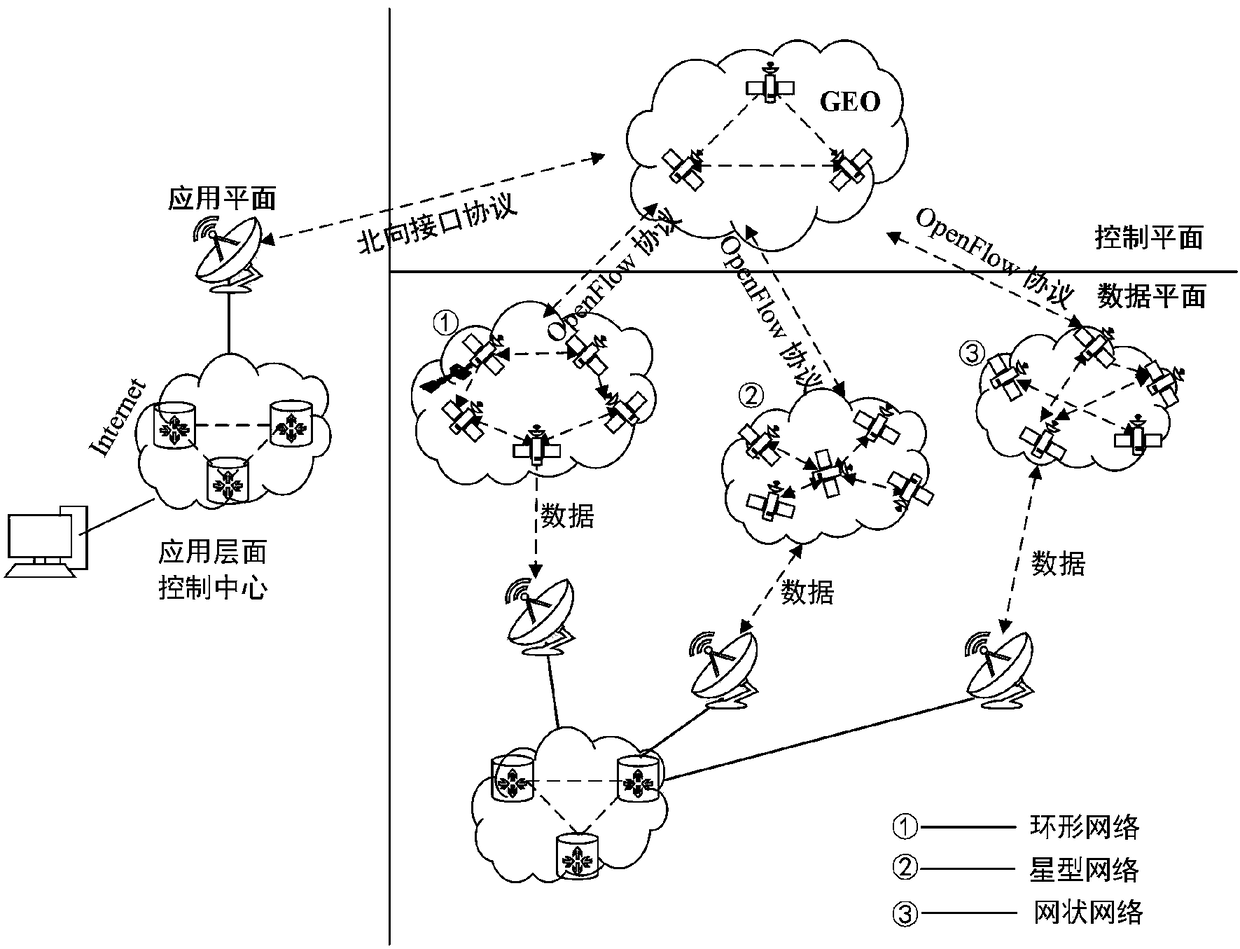
Multi-controller dynamic deployment method of software defined spatial information network
ActiveCN107276662AReduce overheadGood control effectRadio transmissionData switching networksTraffic capacityTarget control
The invention discloses a multi-controller dynamic deployment method of a software defined spatial information network. In the case of flow surge of switching nodes, the overload switch node can be migrated to an adjacent non-overload area by means of the collaboration of the controllers to realize the dynamic migration of the switch so as to reduce the processing pressure of the controllers and realize load balance of multiple controllers. A multi-target optimization method based on switch flow r, an interaction delay t and a controller volume f is provided in view of the migration problem of the overload switch by the controllers, a proper migration switch is selected according to the three parameters, and a target controller is selected according to the supportable residual load of the target controller; and with respect to the underload controller, the target is migrated by considering the requirement that the load of the other controllers can bear the migration of all switches in the underload controller, and then the underload controller is closed. By adoption of the multi-controller dynamic deployment method disclosed by the invention, the network response delay is shortened, the network throughput is improved, and the load balance among the controllers is guaranteed.
Owner:DALIAN UNIV
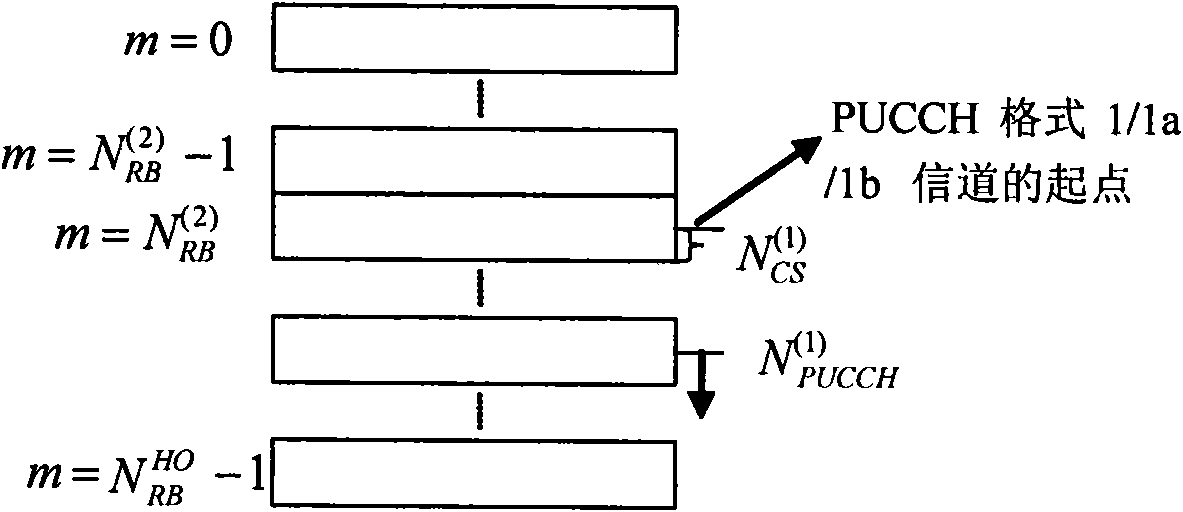
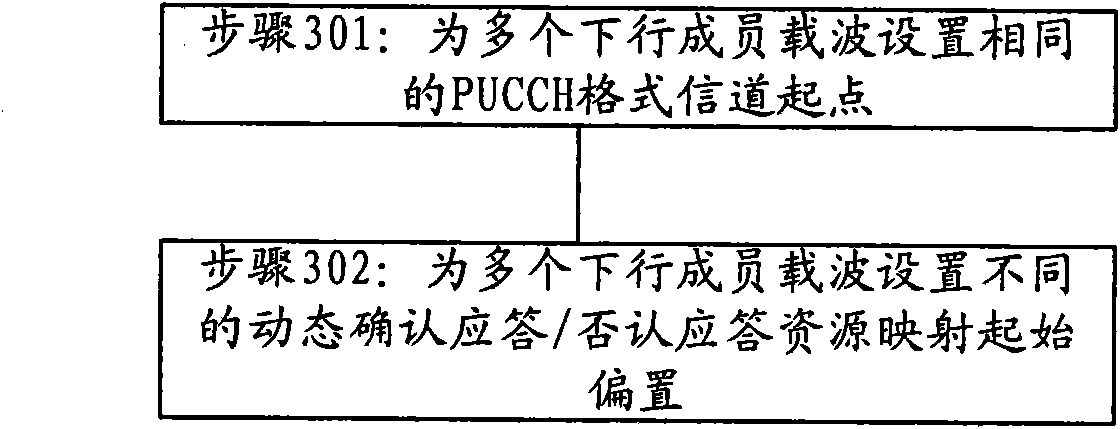
Configuration and sending method of PUCCH (Physical Uplink Control Channel) resources as well as device thereof
ActiveCN101778419AFlexible sharingAchieving Overhead CompressionNetwork traffic/resource managementTransmissionCarrier signalControl channel
The invention relates to a configuration method of PUCCH (Physical Uplink Control Channel) resources. The method comprises the following steps of: arranging the same PUCCH format channel starting point for a plurality of downlink component carriers, and arranging different dynamic Acknowledgement / Negative-Acknowledgement (ACK / NACK) resource mapping start offsets, wherein the PUCCH resources of the downlink component carriers correspond to the same uplink component carrier. In the invention, the flexible PUCCH resource sharing is realized by arranging the same PUCCH format channel starting point for the downlink component carriers, and the overhead compaction of dynamic ACK / NACK mapping resources is realized by arranging different dynamic ACK / NACK resource mapping start offsets.
Owner:HUAWEI TECH CO LTD
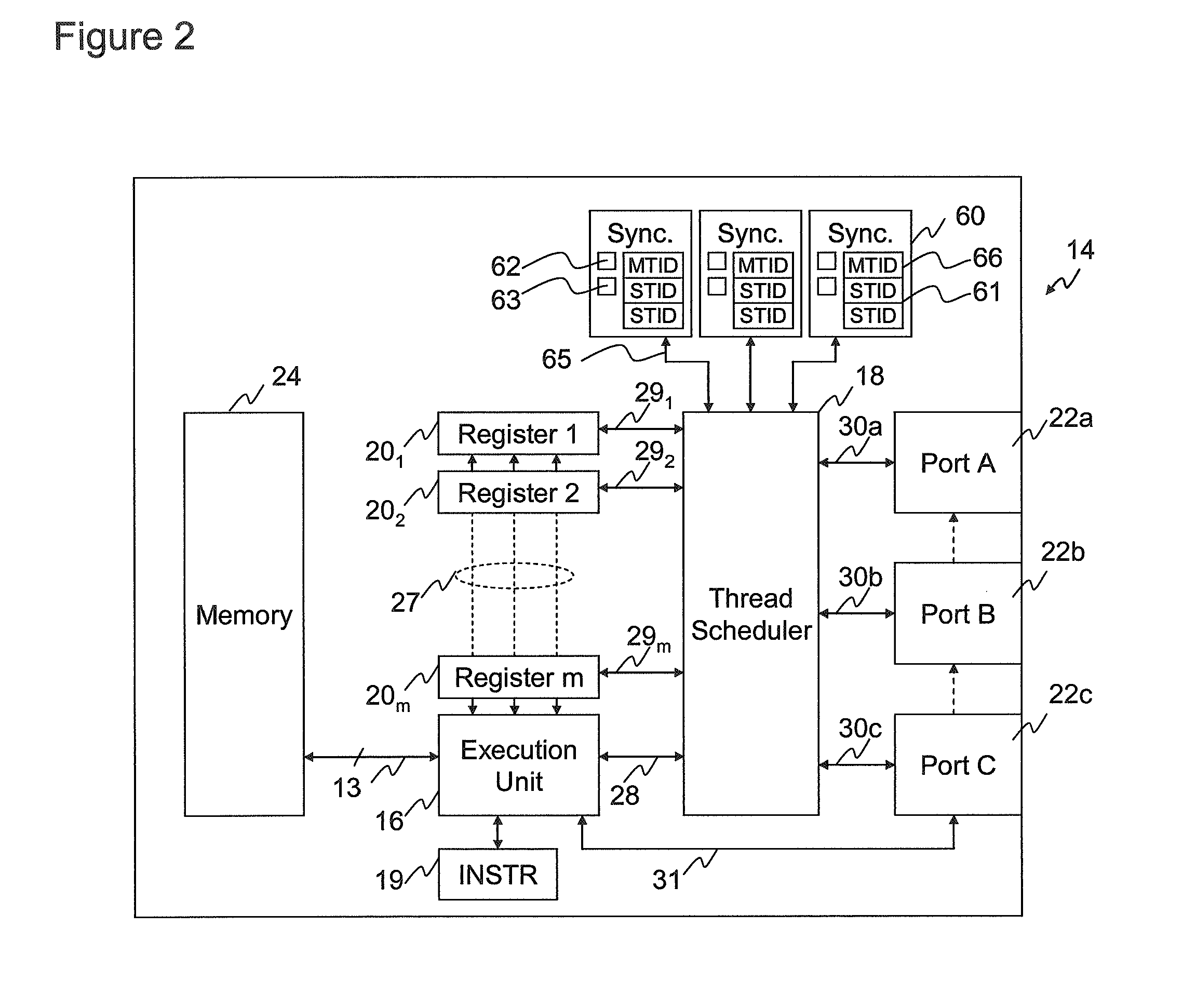
Synchronisation
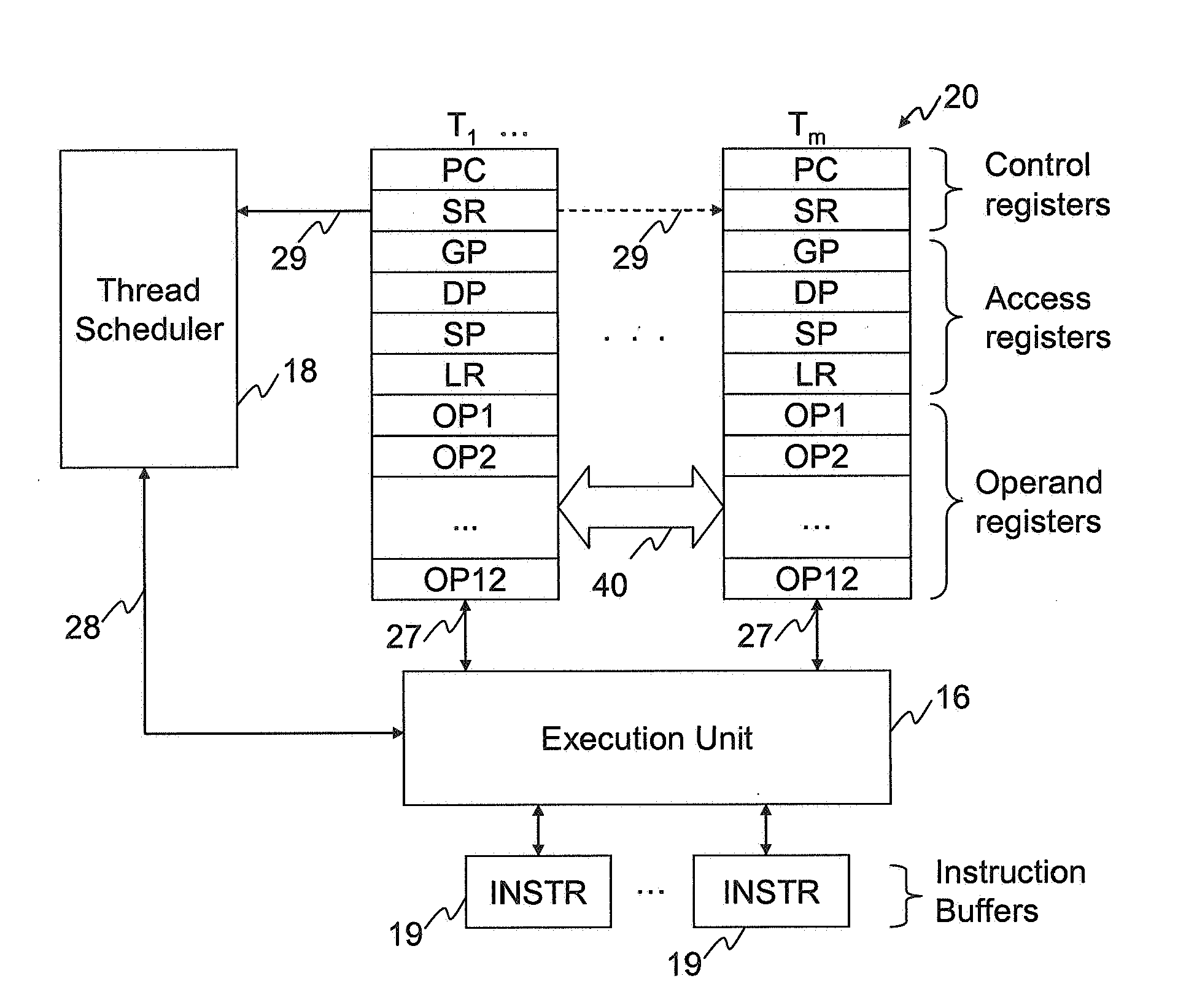
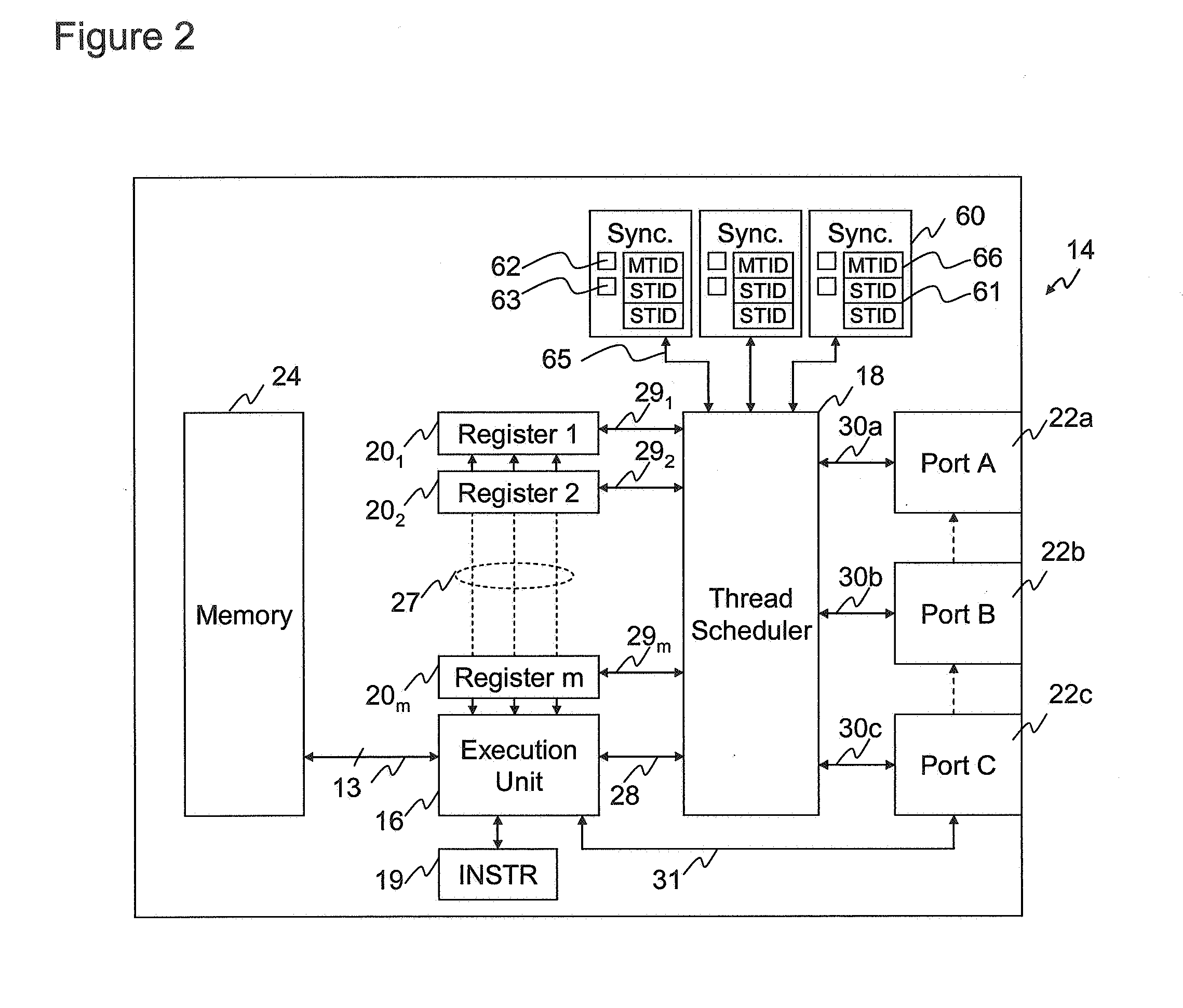
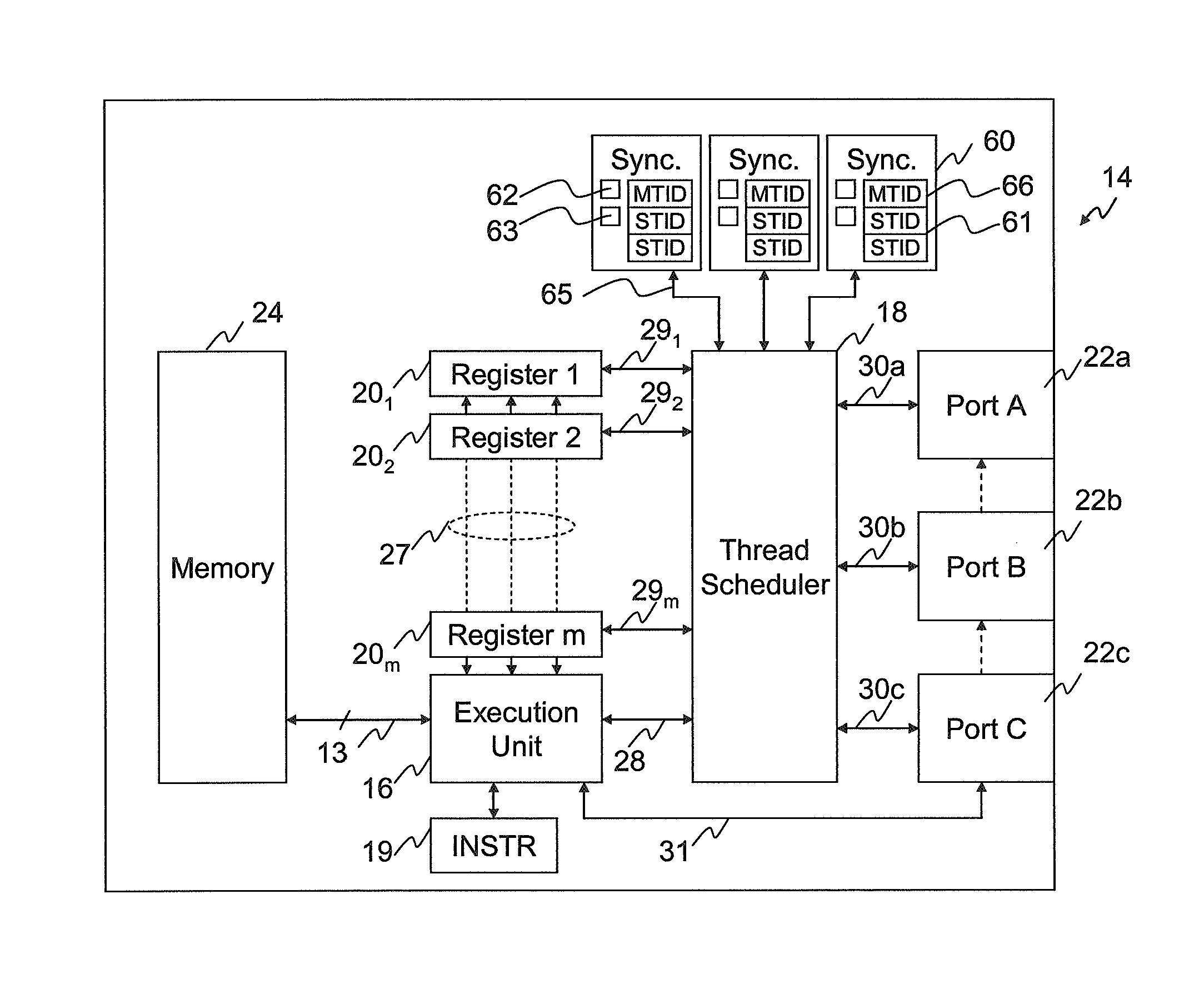
ActiveUS20090013323A1Reduce sync delayIncrease synchronisation code densityMultiprogramming arrangementsMemory systemsParallel computingExecution unit
The invention provides a processor comprising an execution unit arranged to execute multiple program threads, each thread comprising a sequence of instructions, and a plurality of synchronisers for synchronising threads. Each synchroniser is operable, in response to execution by the execution unit of one or more synchroniser association instructions, to associate with a group of at least two threads. Each synchroniser is also operable, when thus associated, to synchronise the threads of the group by pausing execution of a thread in the group pending a synchronisation point in another thread of that group.
Owner:XMOS
An SDN-based container network resource scheduling method
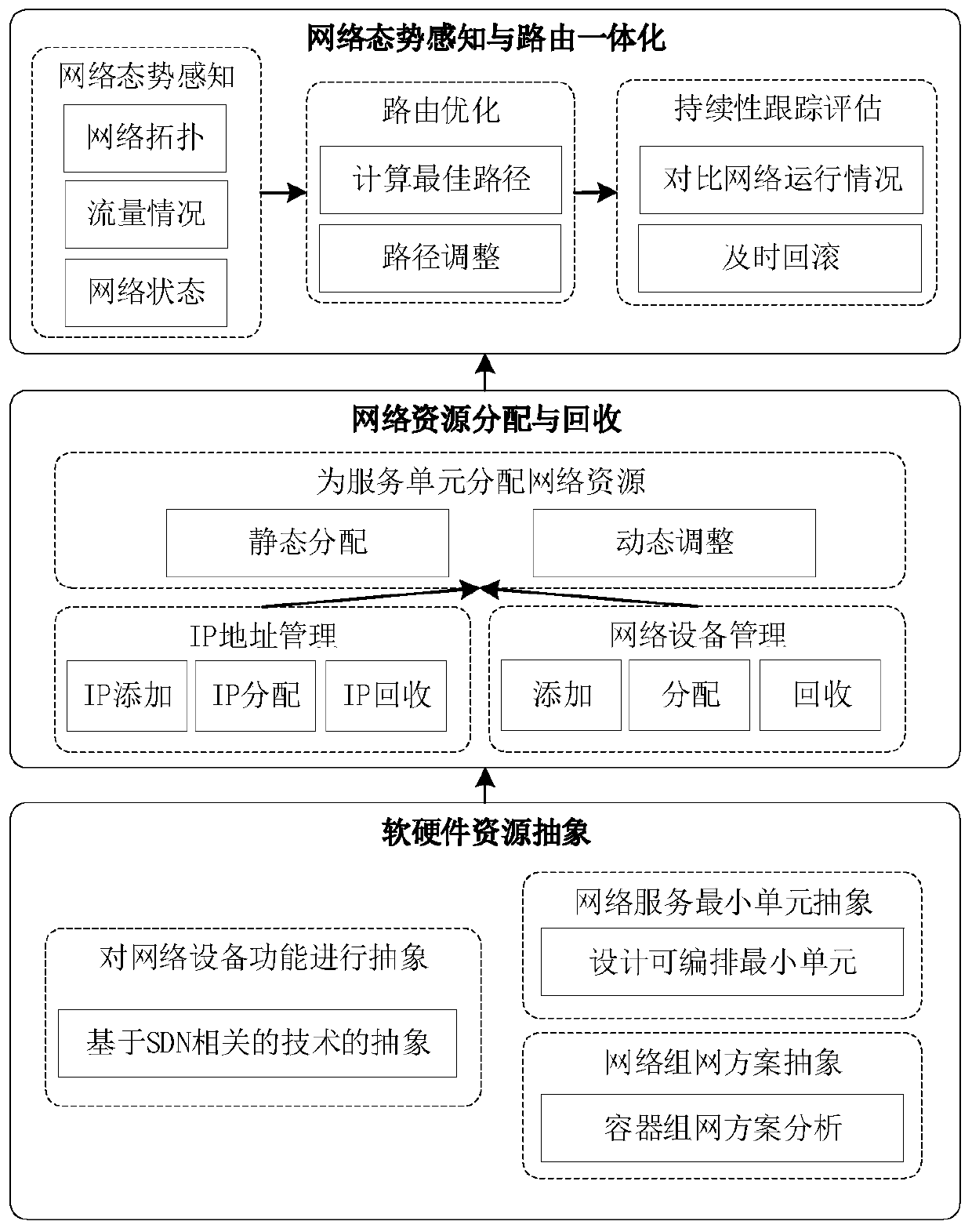
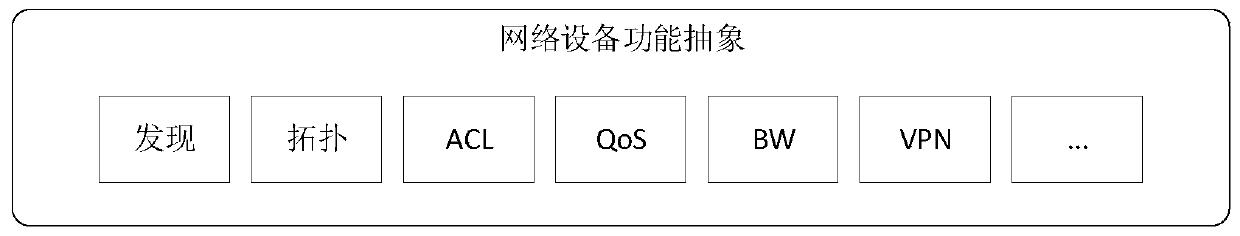
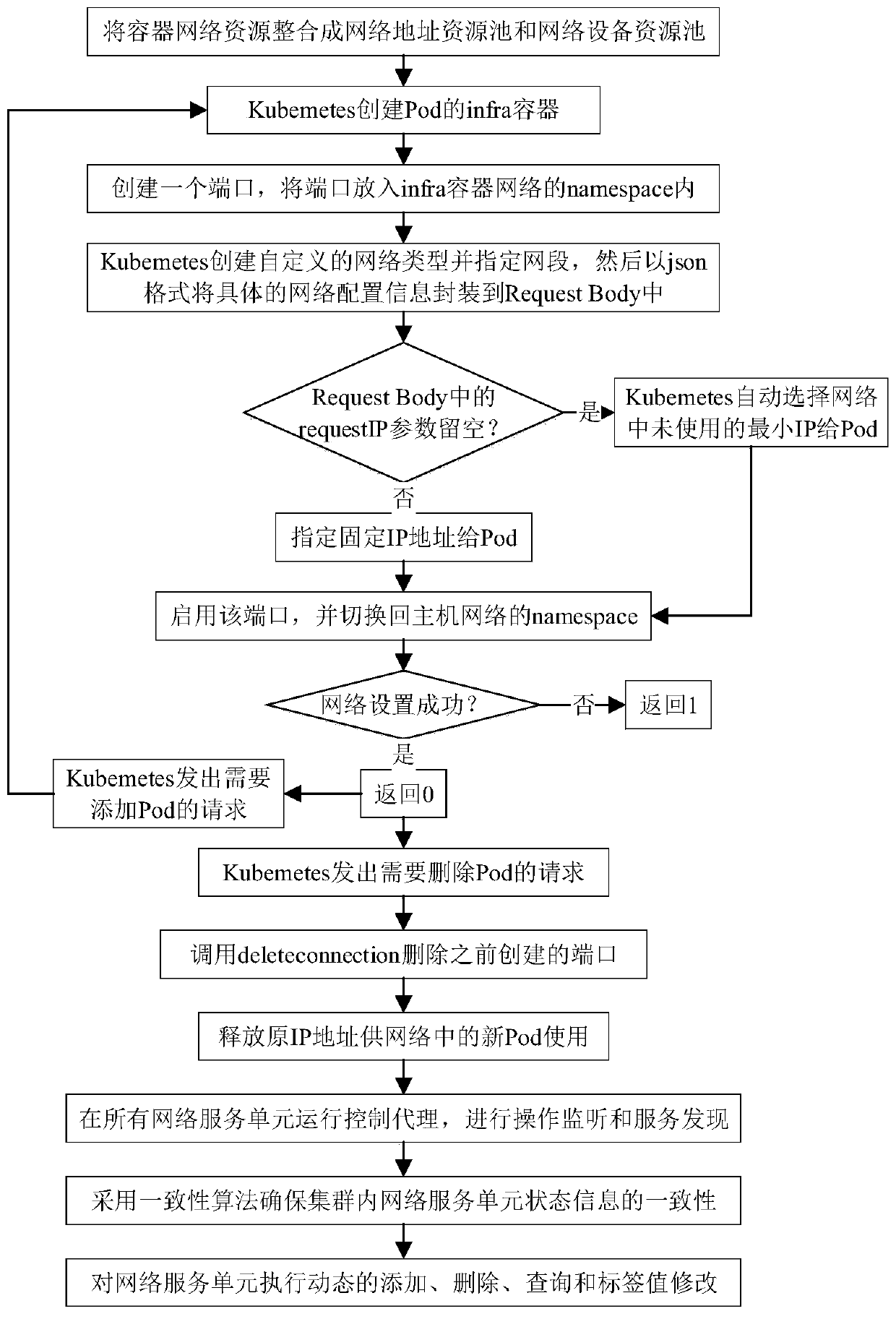
ActiveCN109743261AFully flexible sharingFlexible sharingData switching networksResource poolNetwork address
Aiming at the problem that resource segmentation and guarantee cannot be carried out according to requirements of a container network in the prior art, the invention provides an SDN-based container network resource scheduling method, which comprises the following steps of: 1, carrying out unified abstraction and description on network software and hardware resources based on an SDN / NFV technology;2, implementing resource allocation and recovery on the container network, integrating resources into a resource pool, establishing and managing a network address resource pool and a network equipment resource pool, providing network equipment resources as required, and recovering the network equipment resources in time when the network is destroyed; And step 3, based on the idea of SDN centralized control, deploying a centralized control server in the container network, and implementing network situation awareness and routing integration. The container network resource scheduling method integrates networking, routing and monitoring by intensively sensing the network situation and reasonably segmenting and recovering the container network resources in combination with the requirements oftasks, thereby realizing the optimal scheduling of the container network resources.
Owner:NAT UNIV OF DEFENSE TECH
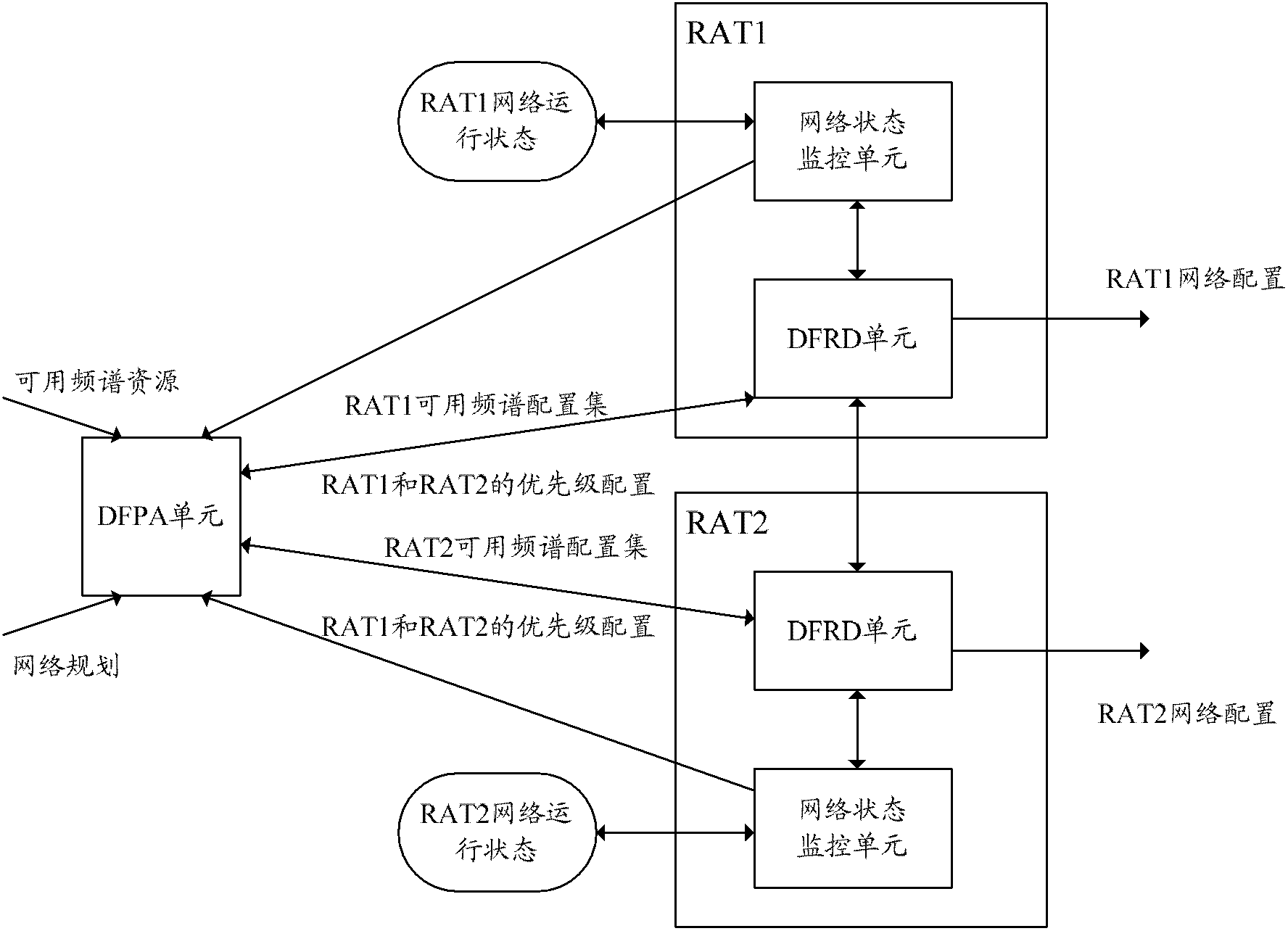
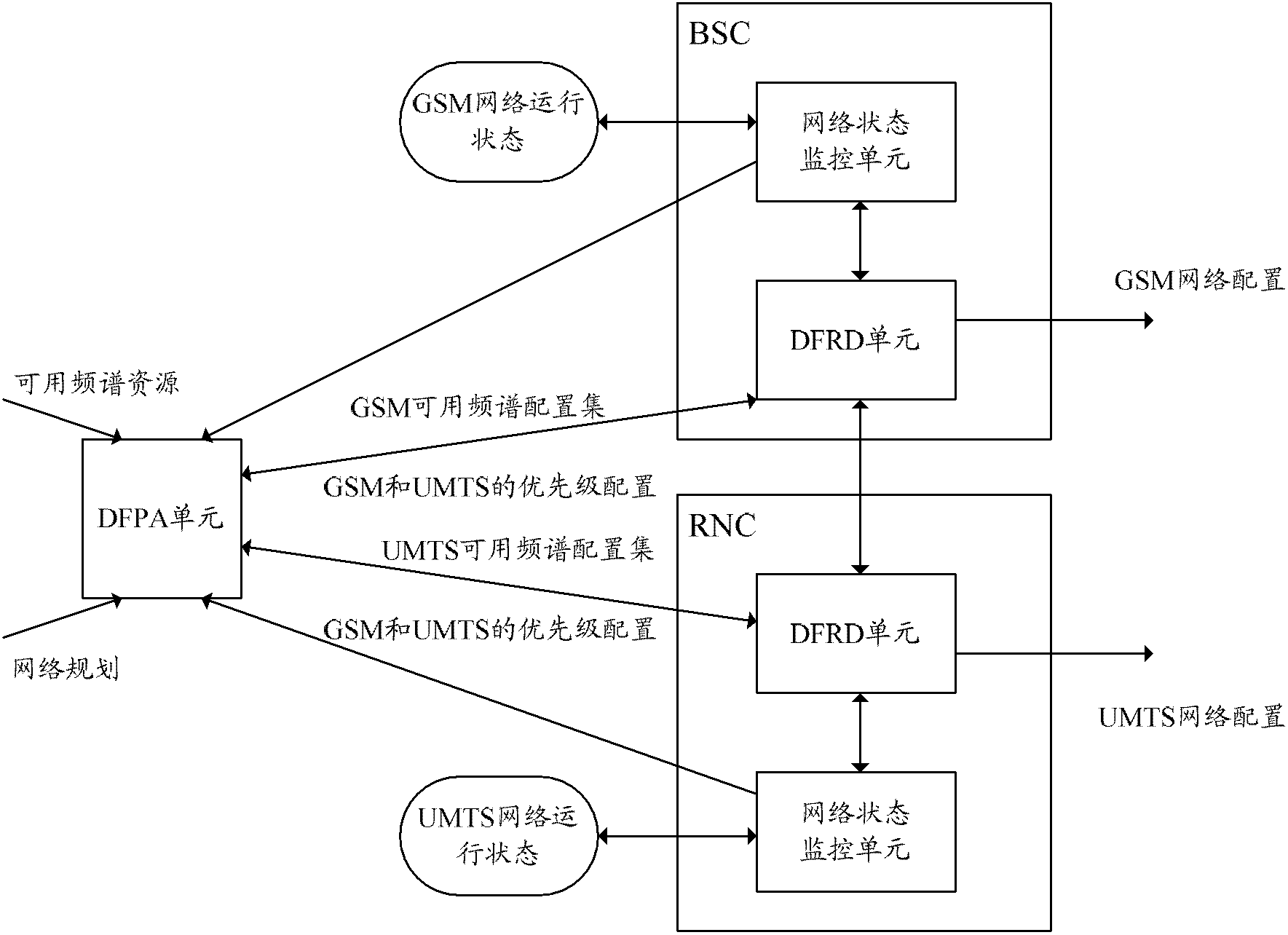
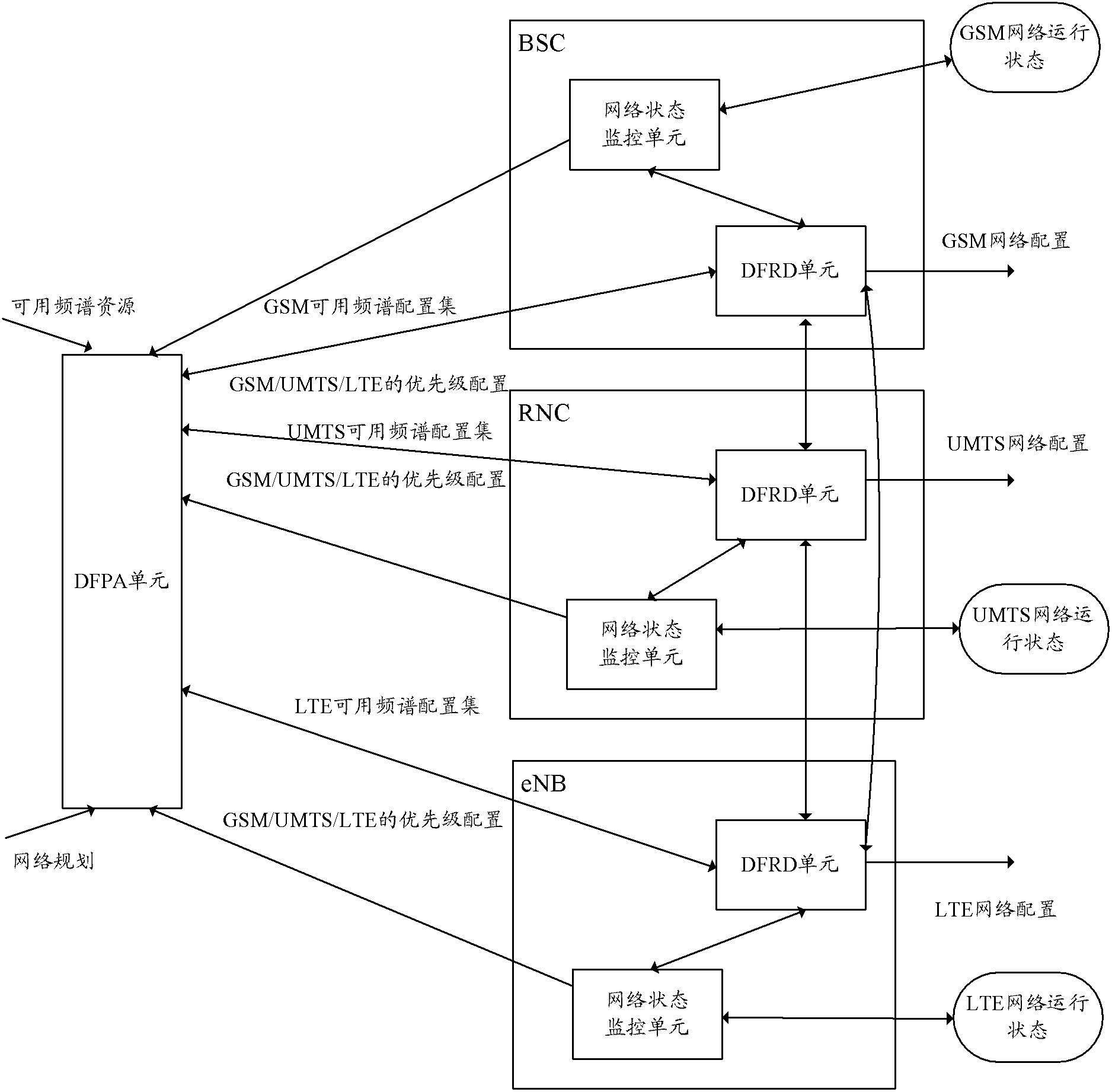
System and method for sharing dynamic frequency spectrum
The invention discloses a system for sharing a dynamic frequency spectrum. A DFPA (Dynamic Frequency Planning Adjustment) unit is used for planning and configuring available frequency spectrum resources to a plurality of wireless systems. The invention further discloses a method for sharing the dynamic frequency spectrum. When the sharing of the dynamic frequency spectrum is started and after the DFPA unit receives information of starting the sharing of the dynamic frequency spectrum, relevant frequency spectrum information is transmitted to DFRD (Dynamic Frequency Reframing Decision) units residing on different wireless systems; and after the DFRD units receive the relevant frequency spectrum information, the available frequency spectrum resources of the wireless network are determined. The system and the method which are disclosed by the invention are used for dynamically sharing wireless frequency spectrum resources under the condition that the wireless systems coexist, therefore, the wireless frequency spectrum can be shared more effectively and flexibly, the utilization rate of network resources is improved and the user experience is improved.
Owner:ZTE CORP
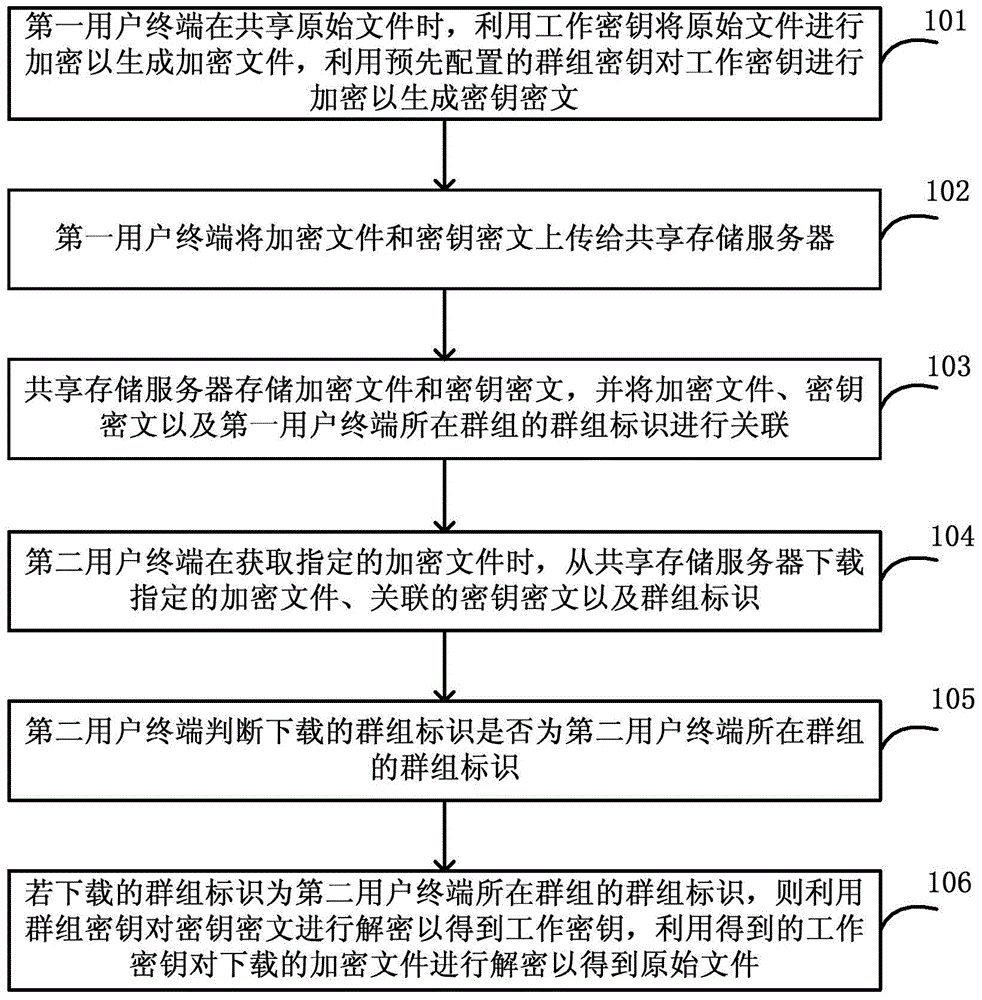
File secure sharing method and system based on group key
ActiveCN104917787AReduce the Risk of ConfidentialityFlexible sharingKey distribution for secure communicationCiphertextControllability
The invention discloses a file secure sharing method and system based on a group key. When a first user terminal shares an original file, the original file is encrypted by use of a work key so as to generate an encryption file, the work key is encrypted by use of the group key so as to generate key cryptograph, and the encryption file and the key cryptograph are uploaded to a shared storage server; a second user terminal downloads a specific encryption file, a key cryptograph associated with the specific encryption file, and a group identification from the shared storage server; and the second user terminal, when determining that the downloaded group identification is the group identification of a group where the second user terminal is located, decrypts the key cryptograph by use of the group key and decrypts the encryption file by use of the work key so as to obtain the original file. According to the invention, the work key is encrypted by use of the group key, the encryption file can be securely and flexibly shared with user controllability and easy key management, and the risk that a user file is leaked in a sharing process is reduced.
Owner:CHINA TELECOM CORP LTD
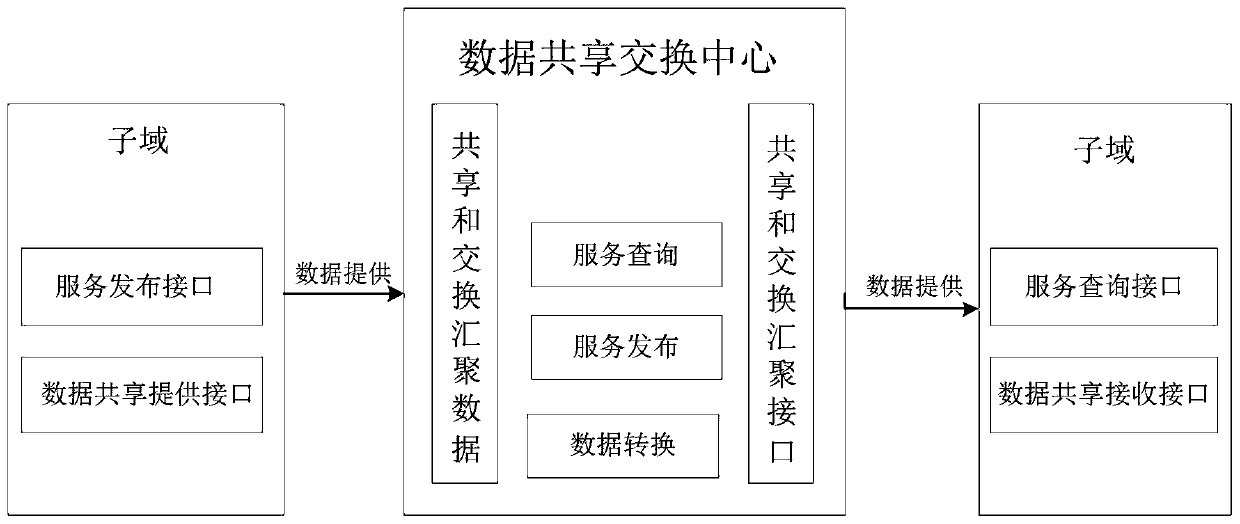
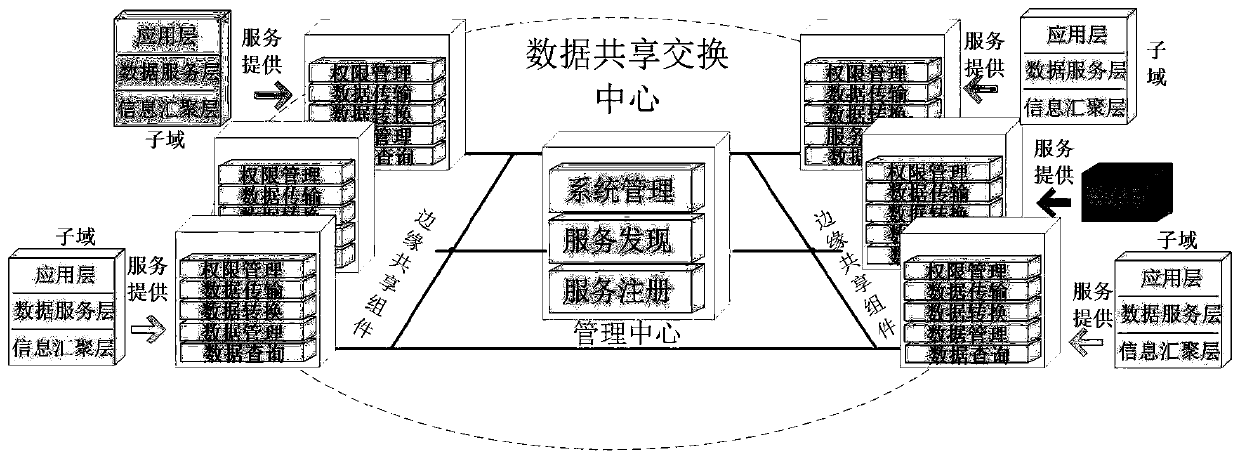
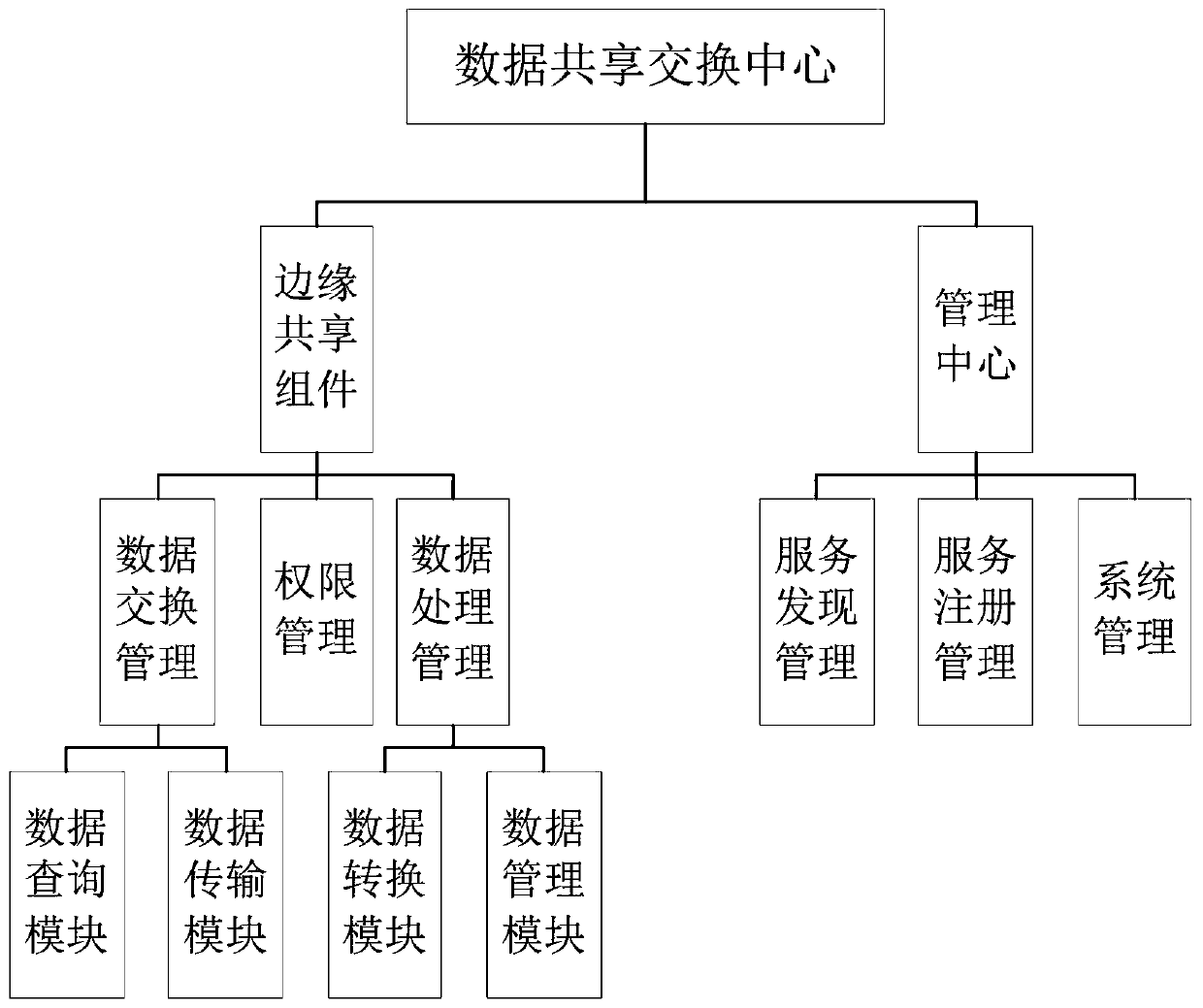
Multi-domain data sharing exchange platform architecture based on block chain
The invention belongs to the technical field of data exchange of the Internet of Things, and discloses a multi-domain data sharing exchange platform architecture based on a block chain, which comprises a data sharing exchange center module used for connecting other subdomain modules in series so as to achieve interconnection and intercommunication among subdomains and the sharing exchange of dataamong the subdomain, and managing sub-domain services and sub-domain data, and integrating all Internet of Things resources into a unified Internet of Things data and service providing platform; subdomains, each domain being customized by a local service provider to meet the protocol specification implementation of the data sharing exchange center. The data generated by the subdomains are stored locally, when data sharing is needed, the data needs to be opened or obtained from other domains, and the idea of taking the data as the center is achieved; when data sharing exchange needs to be carried out between domains, authority judgment is carried out through the data sharing exchange center, interconnection and intercommunication are carried out, the subdomain coupling degree is low, and data sharing with other subdomains can be flexibly carried out.
Owner:XIDIAN UNIV
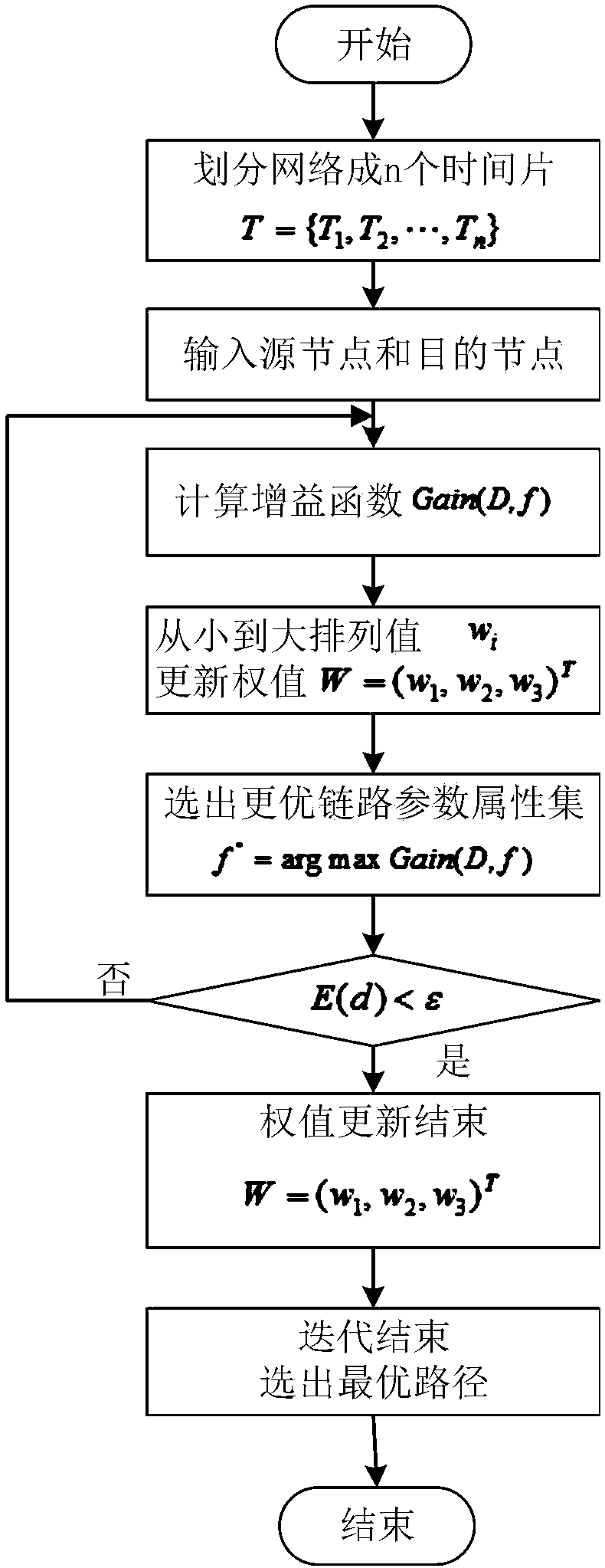
SDSIN-based multi-task routing method
ActiveCN108307435ARealize dynamic controlAchieve sharingNetwork traffic/resource managementNetwork topologiesState parameterMathematical model
The invention discloses a SDSIN-based multi-task routing method. The method comprises the following steps: establishing a reasonable network model; carrying out spatial task level division; establishing a mathematical model based on an SDSIN multi-task routing method; making a link parameter decision; and carrying out weight updating. On the basis of the machine learning algorithm, the method considers a plurality of factors such as link state parameters and spatial tasks fully to realize optimal path selection, so that the utilization rate of network resources is increased and a congestion phenomenon of local links is avoided. Meanwhile, QoS requirements of various spatial tasks are met. With full consideration of link characteristics like transmission delay, a packet loss rate and a remaining bandwidth, a training set is trained based on the parameters; the link parameter weights are updated; and thus the multi-tasking routes are selected and recorded. Therefore, the utilization rateof the underlying resources is increased and the load balancing across the entire network is realized.
Owner:DALIAN UNIV
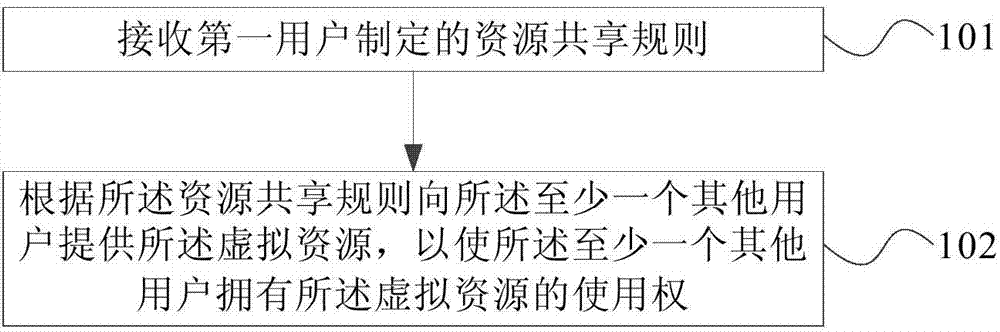
Virtual resource sharing method, device and system
InactiveCN104125297AFlexible sharingAccessibilityTransmissionSoftware simulation/interpretation/emulationTime rangeDistributed computing
The embodiment of the invention provides a virtual resource sharing method, device and system. The method comprises receiving resource sharing rules set by a first user, wherein the resource sharing rules comprise the variety and the quantity of virtual resources, which can be provided for at least one other user, and the time range during which the virtual resources can be provided; according to the resource sharing rules, providing the virtual resources to the at least one other user to enable the at least one other user to obtain the use right of the virtual resource. According to the virtual resource sharing method, the executing main body for setting sharing strategies is transferred from an operator to the user, so that multiple users can rapidly and flexibly share the virtual resources, the utilization rate of the virtual resources can be improved, and the cost of the operator can be saved.
Owner:HUAWEI TECH CO LTD
Data sharing method and device
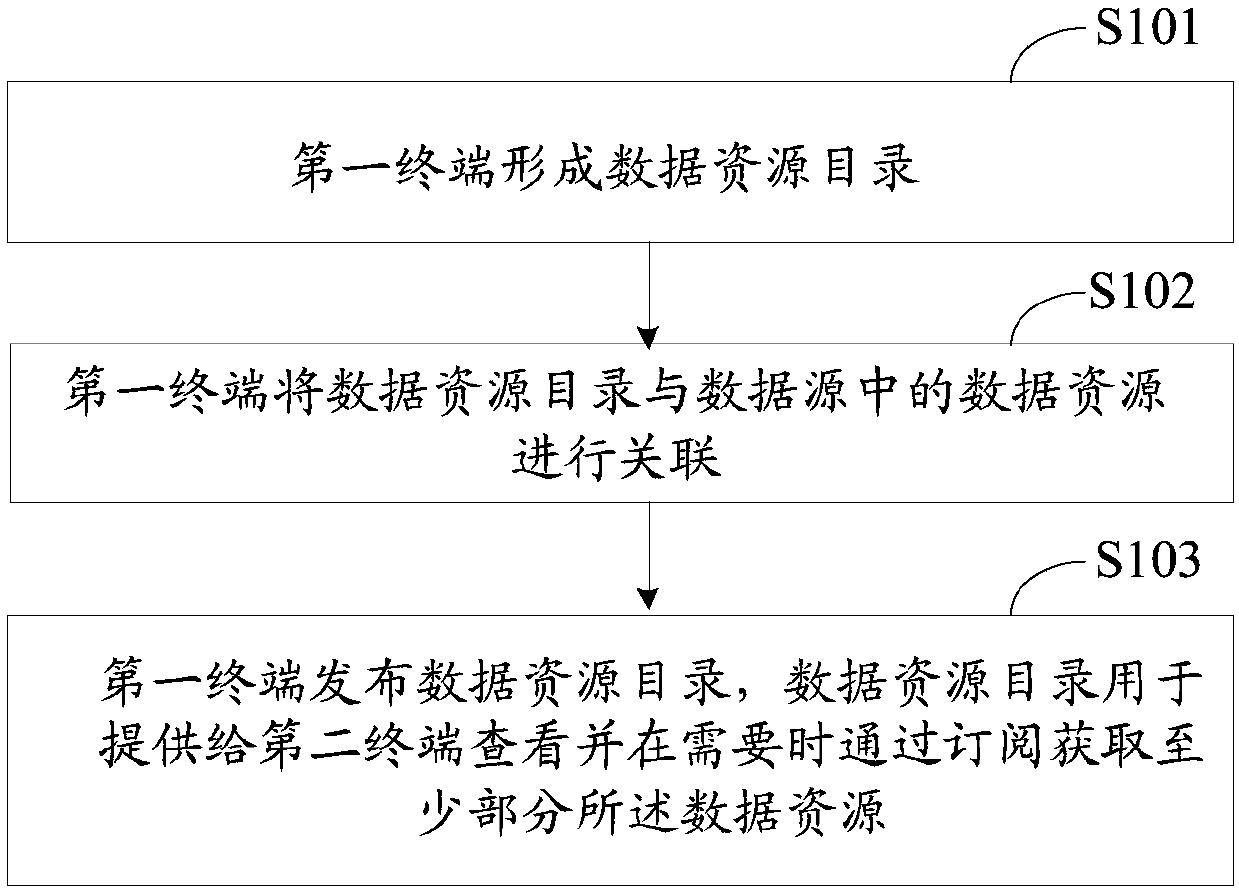
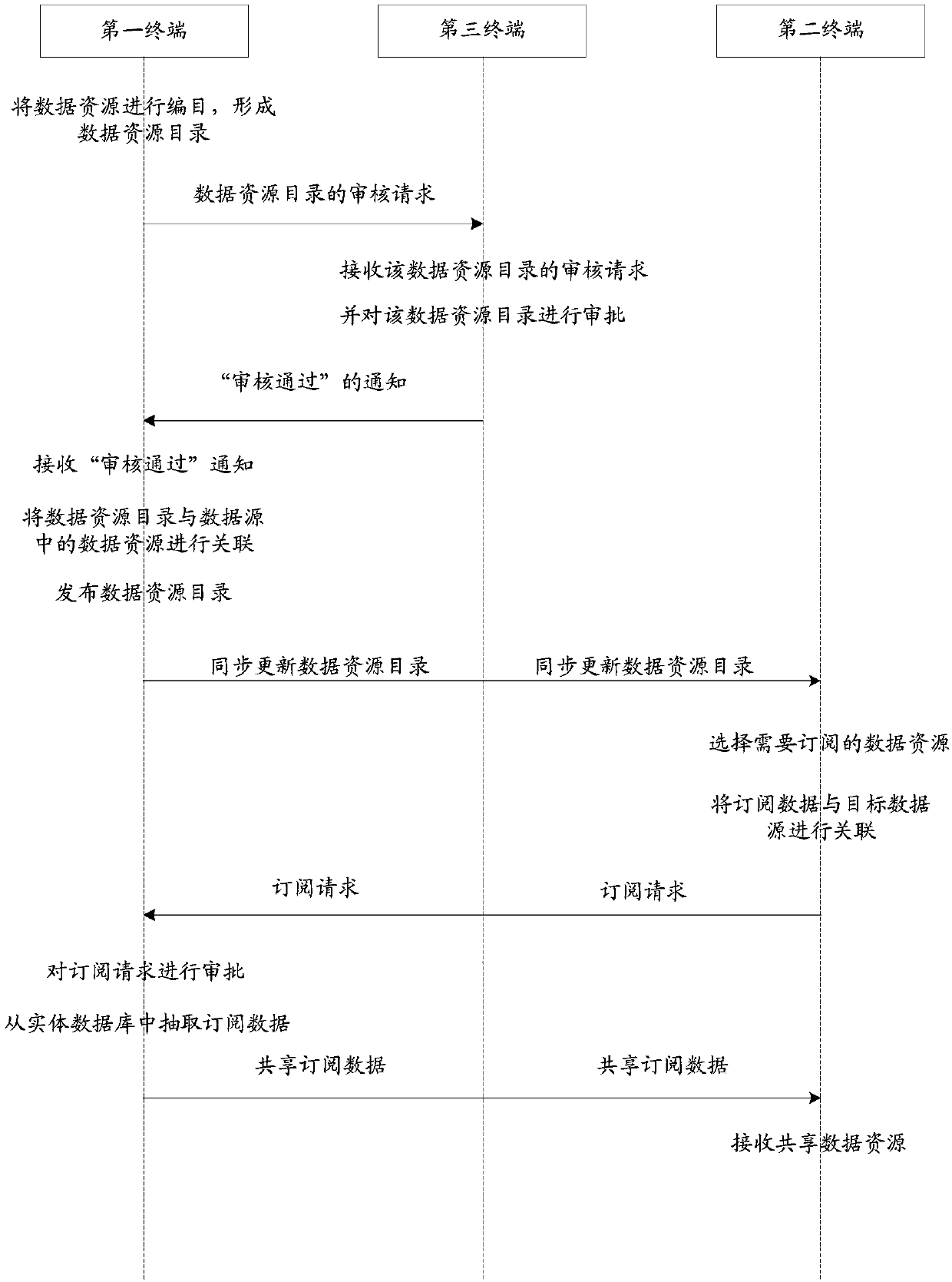
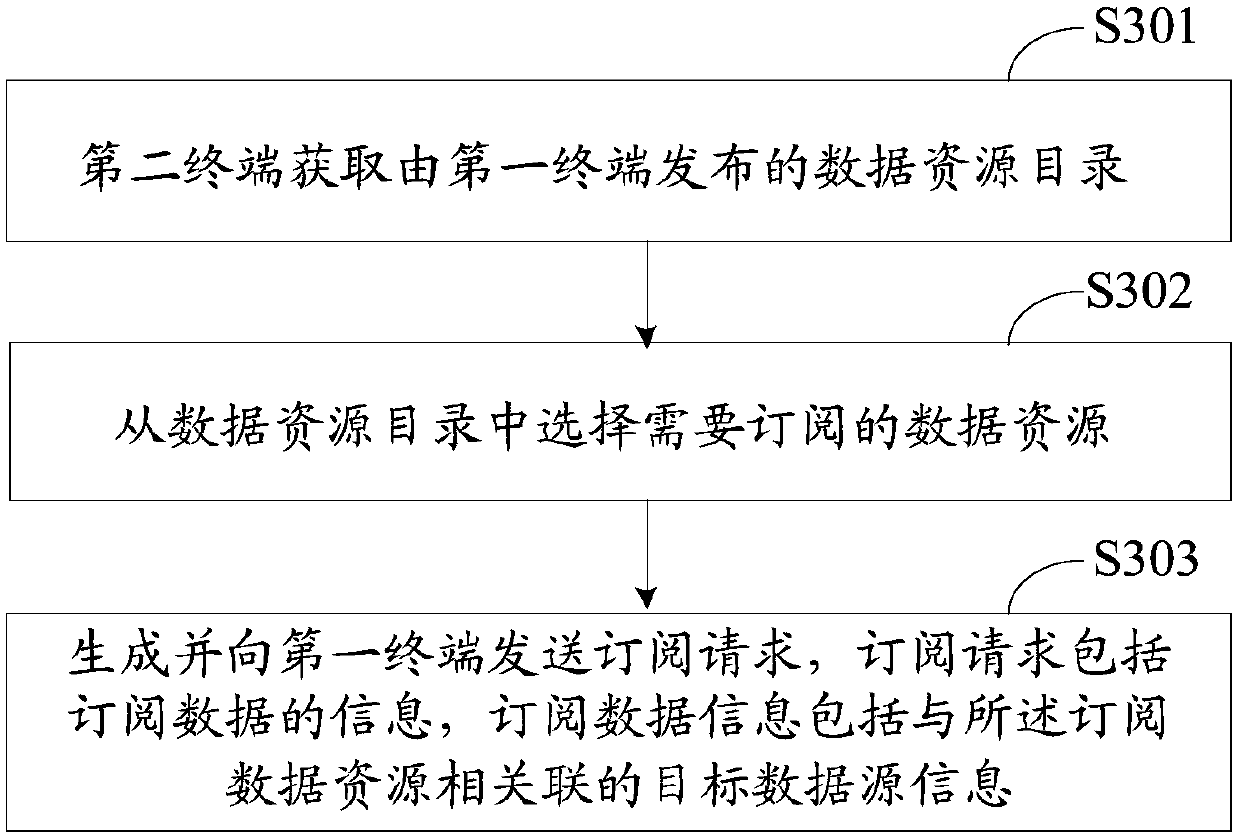
InactiveCN107920110AReduce the amount of data transferredEnsure safetyTransmissionData sharingData resources
The invention, which relates to the technical field of data sharing, discloses a data sharing method and device. The method comprises: a data resource catalog is formed by a first terminal; the firstterminal associates the data resource catalog with data resources in a data source; and the first terminal issues the data resource catalog that is provided for a second terminal for checking and is used for obtaining at least parts of data resources by subscription if needed. Therefore, data sharing flexibility and security are improved.
Owner:JIANGSU FEIBO SOFTWARE TECH
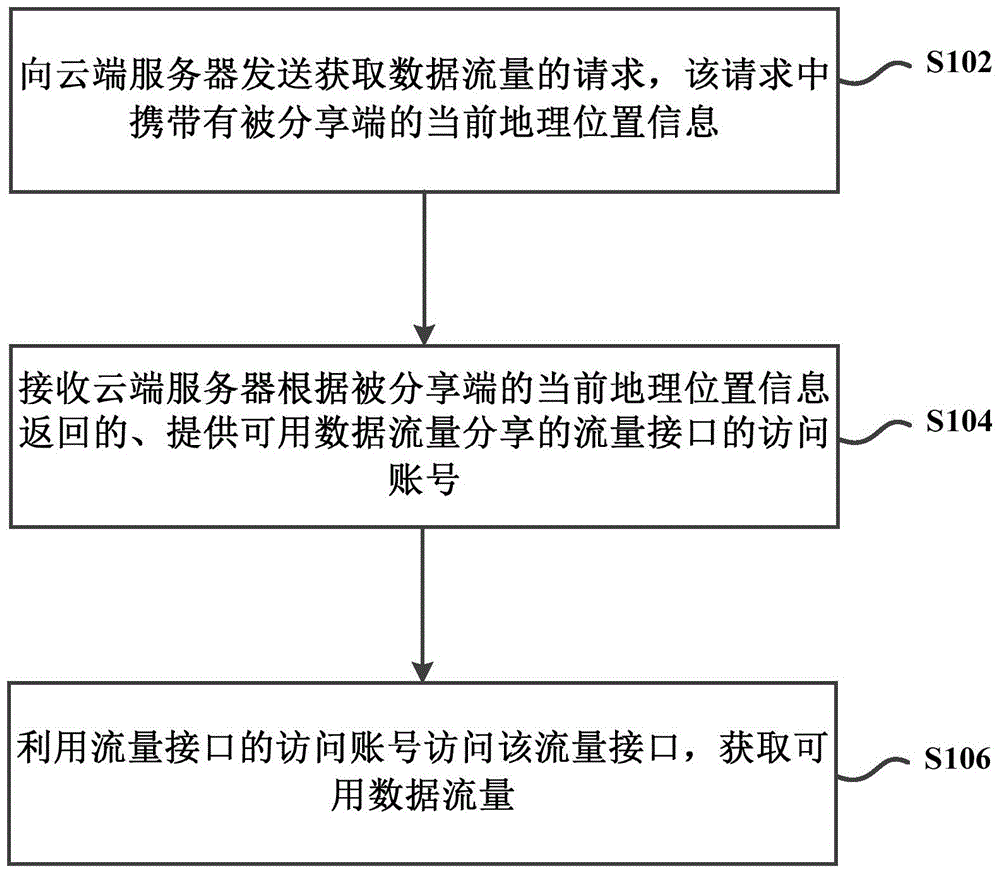
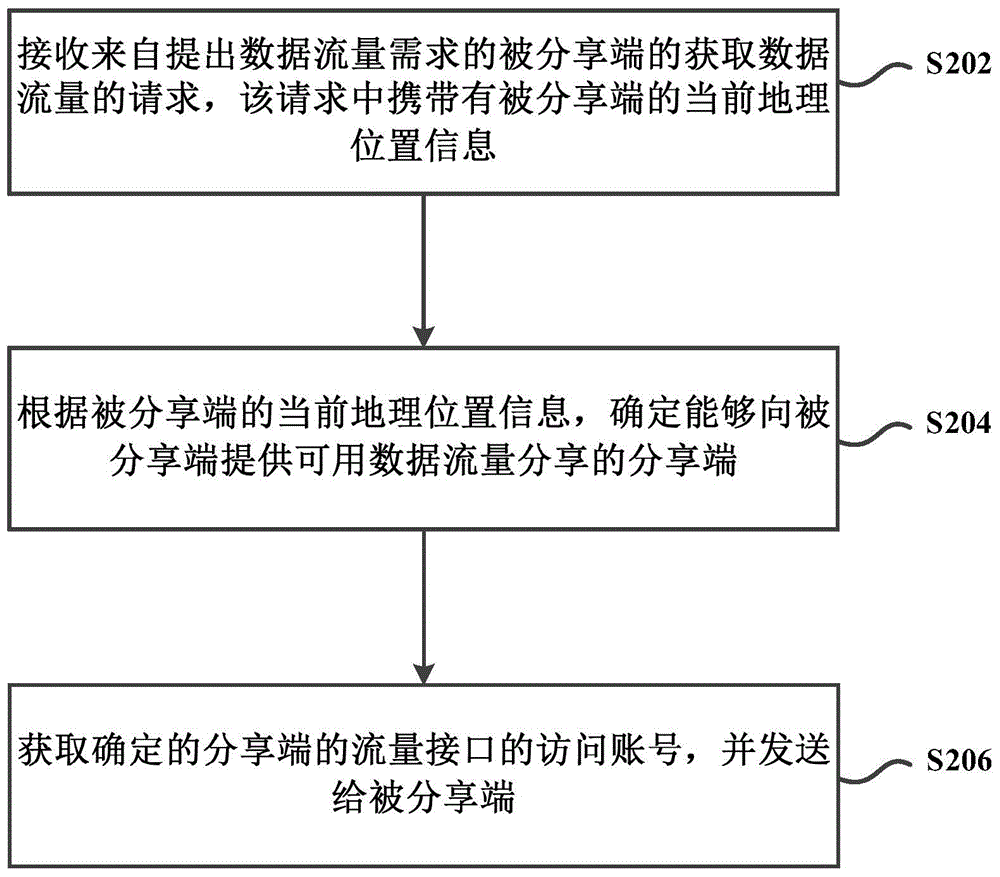
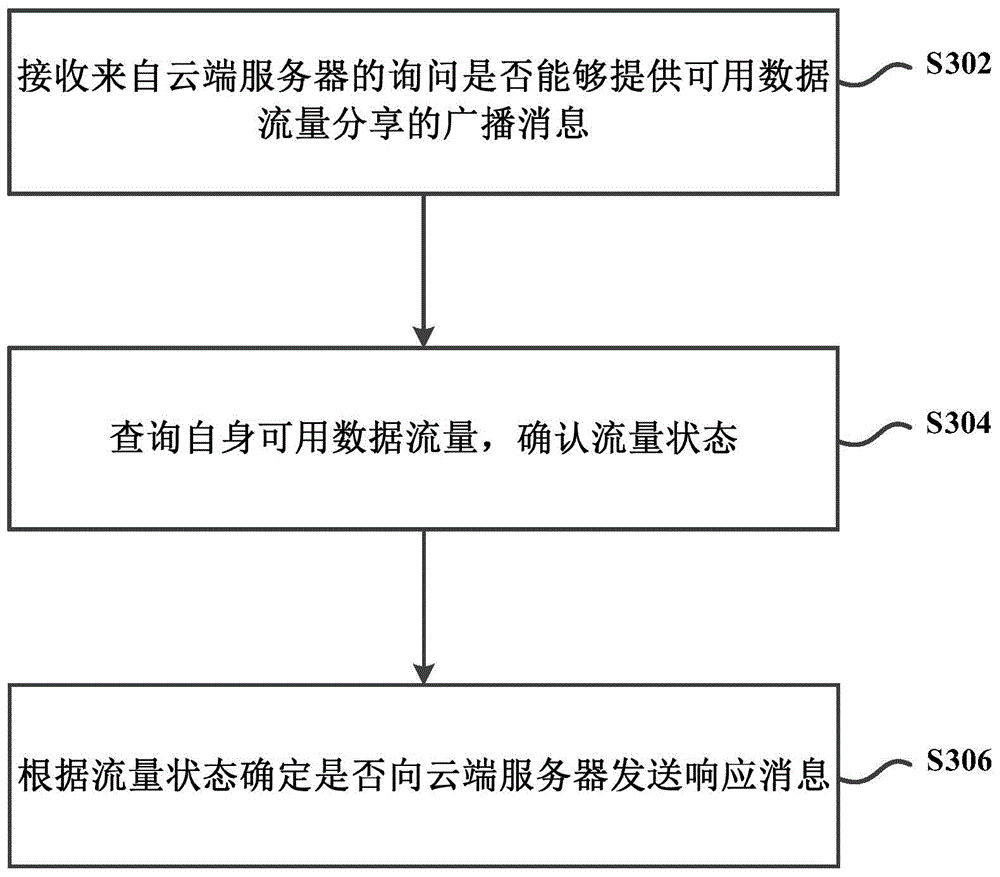
Dataflow share method, device and system between mobile terminals
InactiveCN104883673AEasy to useIncrease profitAccounting/billing servicesConnection managementTraffic capacityData traffic
The invention provides a dataflow share method, device and system between mobile terminals; the method comprises the following steps: sending a dataflow obtain request to a cloud server, wherein the request carries present geography position information of a shared end; receiving a visit account having a usable dataflow share flow interface and returned by the cloud server according to the present geography position information of the shared end; using the flow interface visit account to visit the flow interface, thus obtaining the usable dataflow. The shared end sending the dataflow demand can share the usable dataflow of a sharing end, providing dataflow sharing, through the cloud server, so the usable dataflow of the sharing end can be fully used, thus improving usable dataflow utilization rate.
Owner:BEIJING QIHOO TECH CO LTD
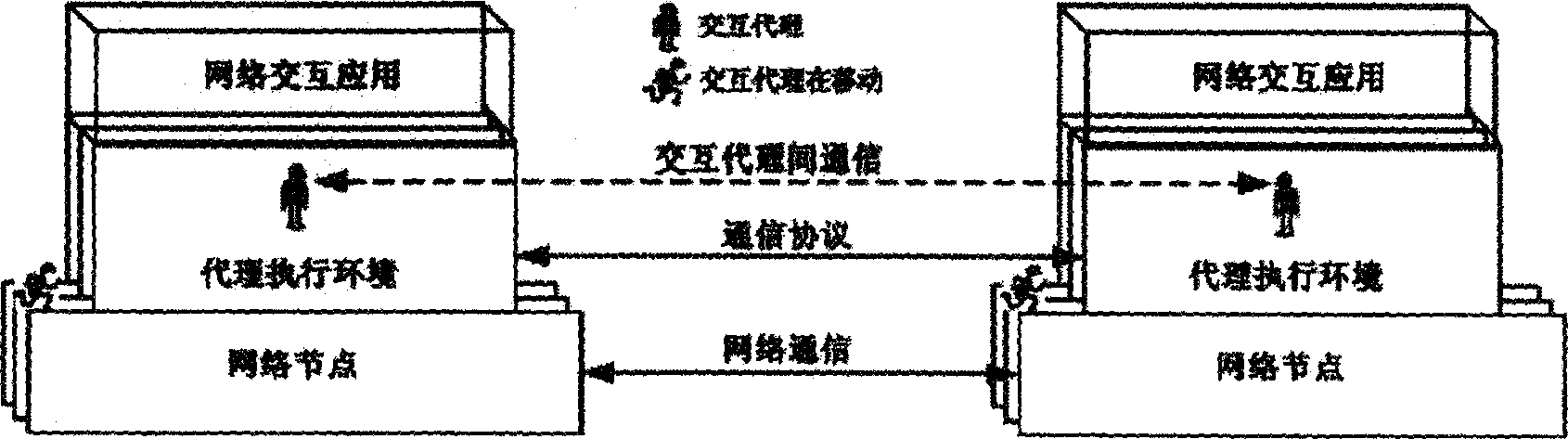
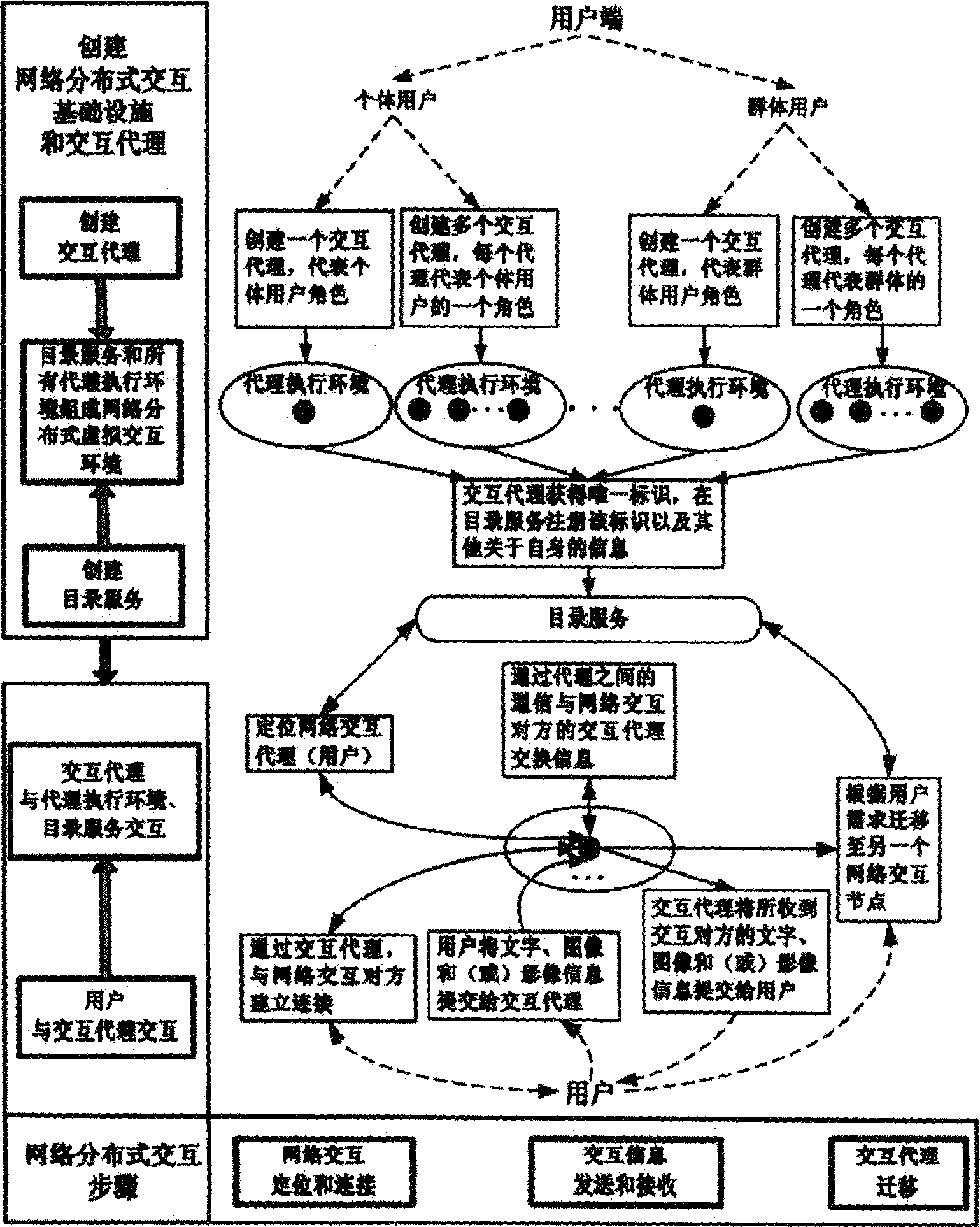
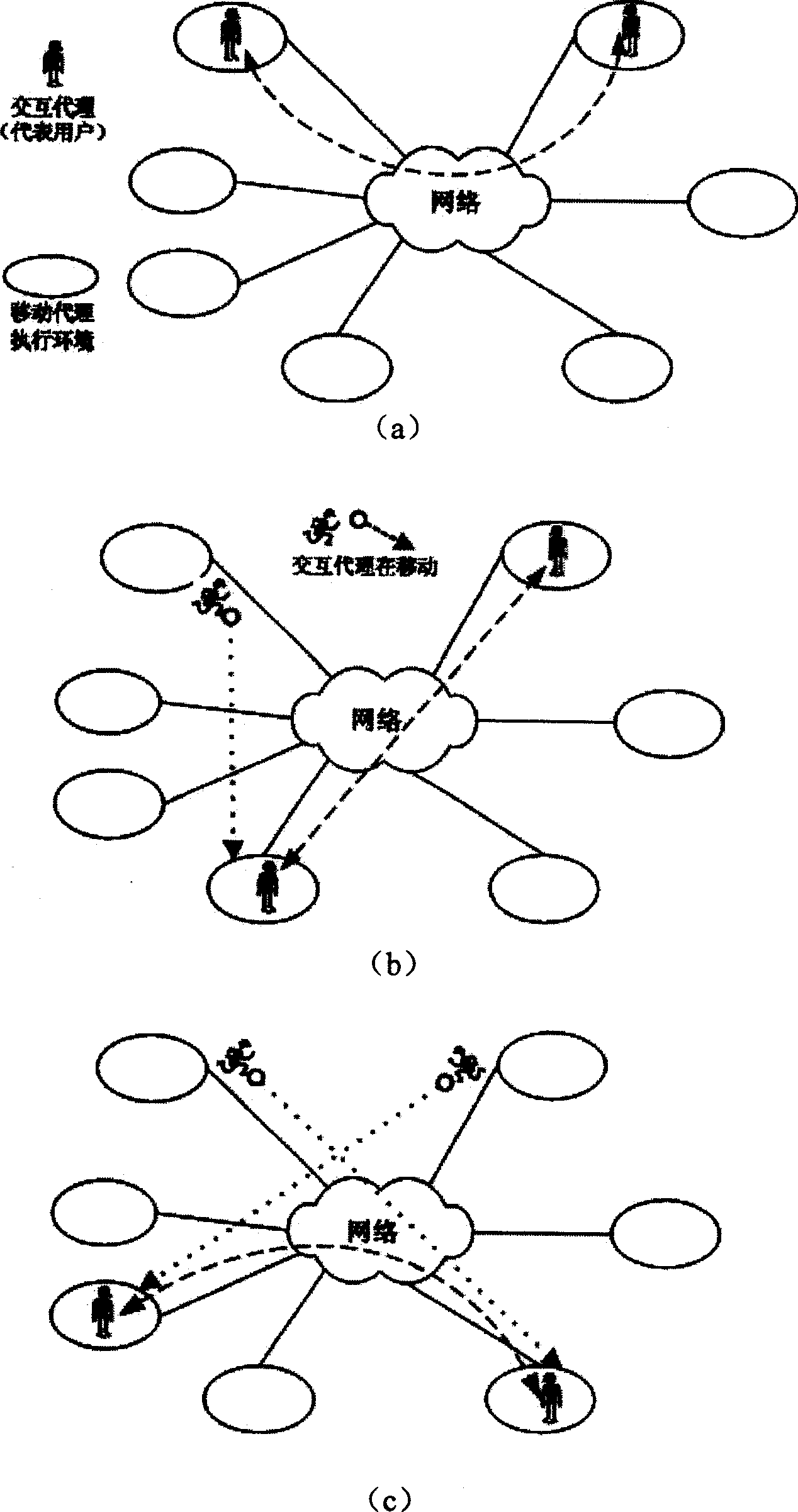
Mobile agent based network distributed interacting method
InactiveCN1744503AAchieve transparencyAchieve interactionData switching by path configurationStore-and-forward switching systemsInteraction agentInformation sharing
Through mobile agent implemented interaction agent, user interacts with network. Representing user, interaction agent as peer entity in interaction is migrated in network and keeps interaction state based on need. Network agent executive environment provides each functional support such as creating, operating and transferring for the interaction agent. Servers provide directory services in one or multiple levels for the interaction agent. The agent executive environment and directory services constitute distributed virtual interaction environment for interaction agent. Modes of each action and cooperated operation customized by interaction agent are corresponding to multiple interaction modes among units and groups in different interaction applications. The invention realizes transparent, intelligent and mobile interaction process among network interaction entities, interactive service in time and flexible information sharing mode.
Owner:NANJING UNIV OF POSTS & TELECOMM
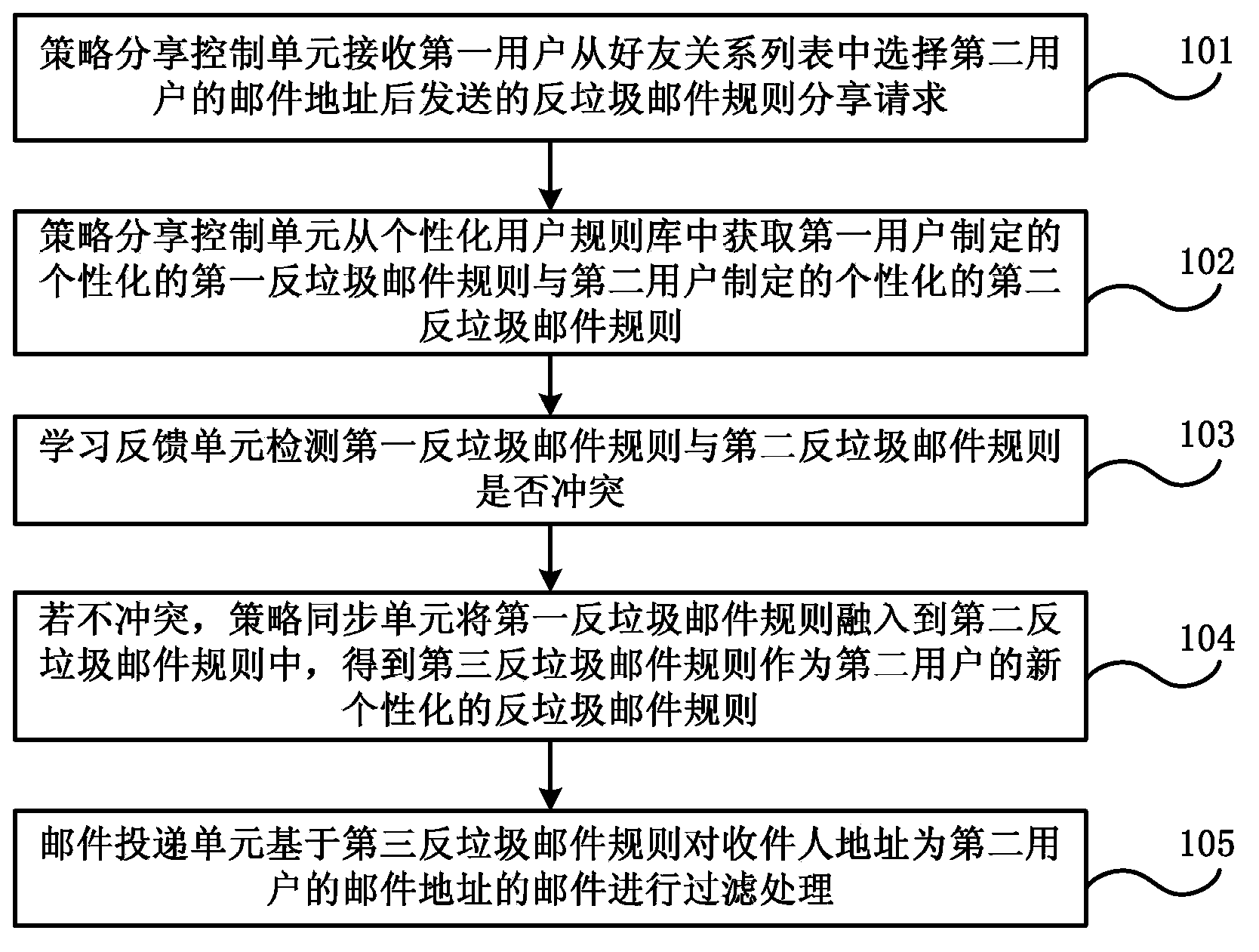
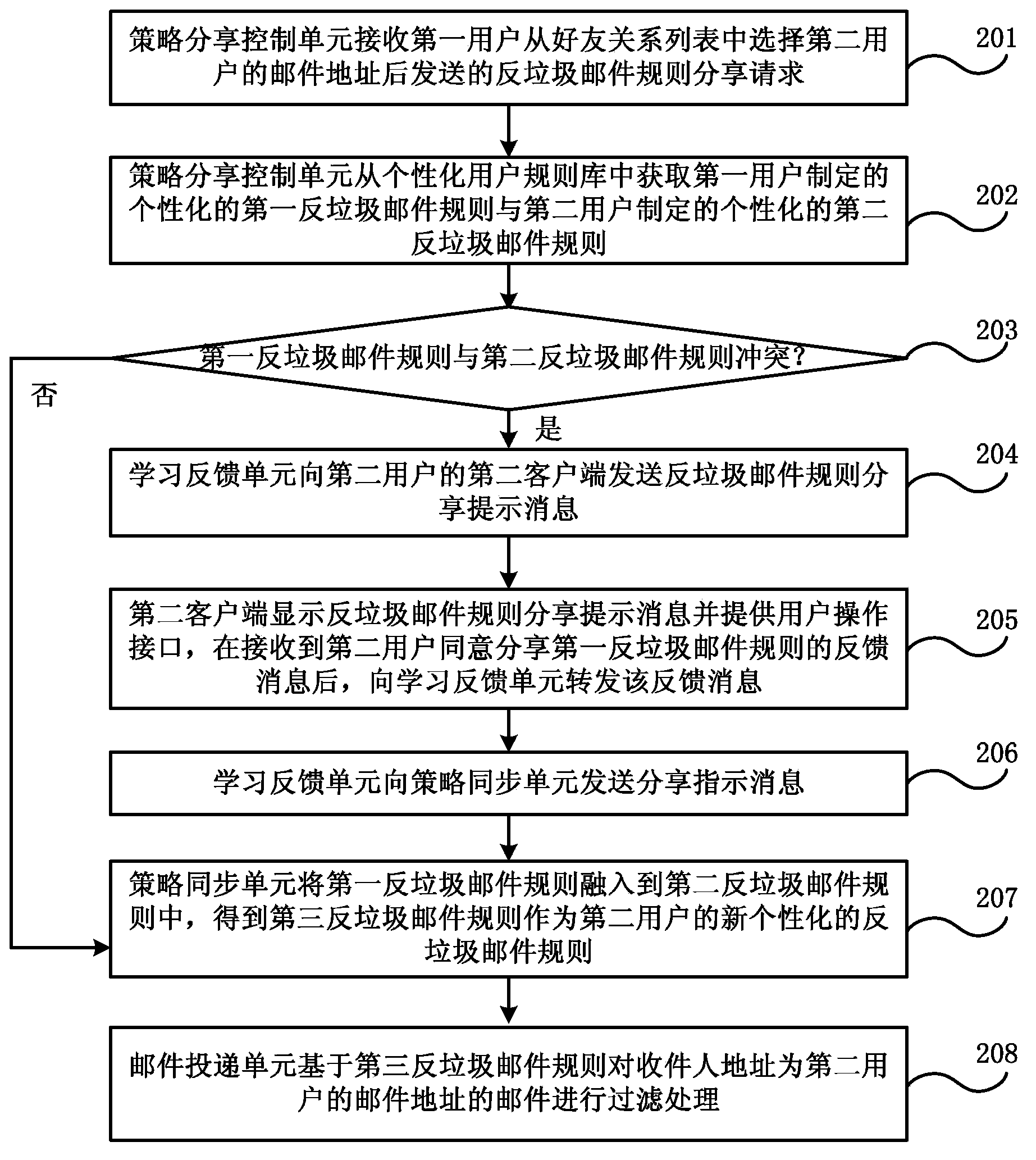
Spam mail filtering processing method and system
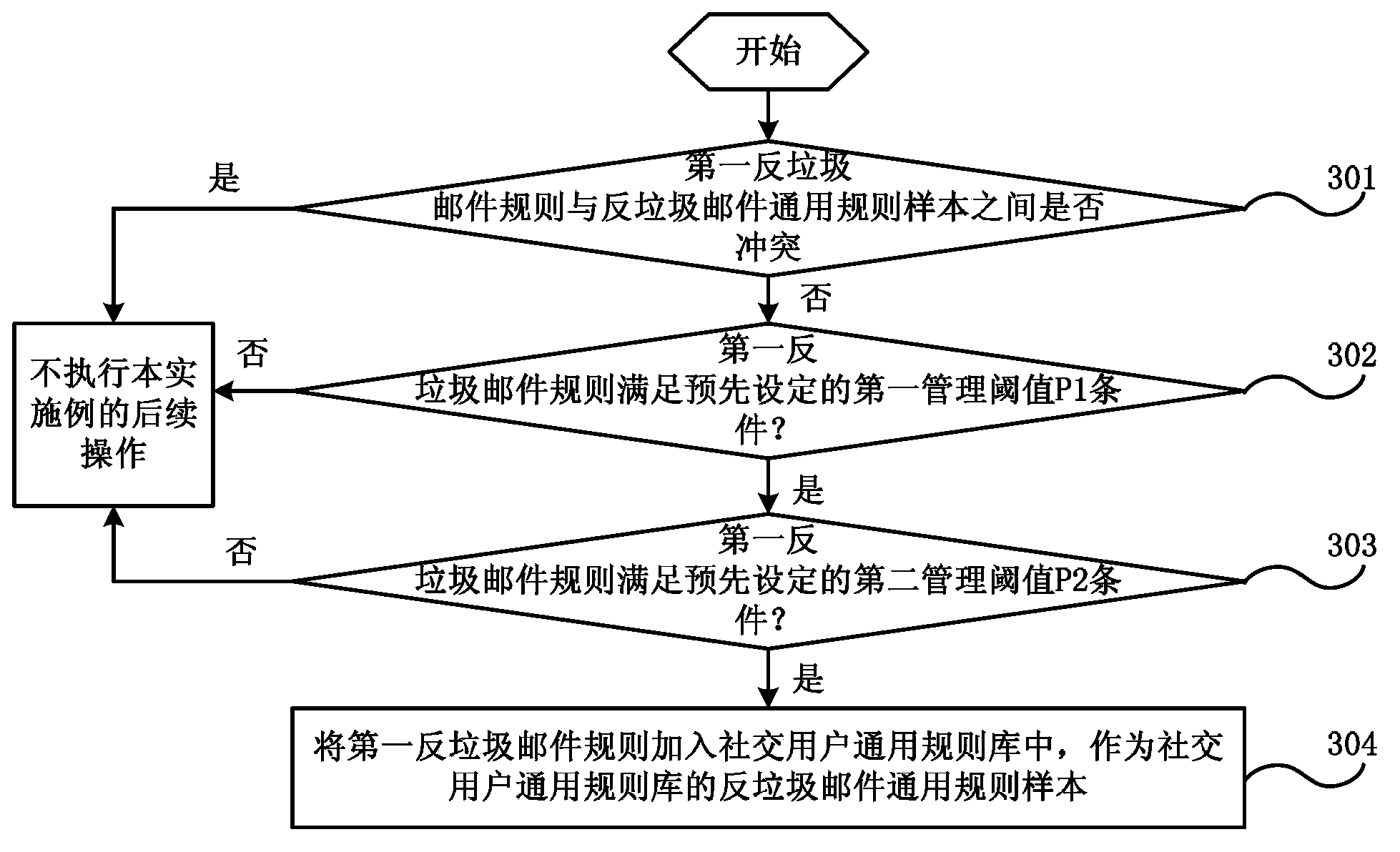
ActiveCN103684982AImprove filtering effectFlexible sharingData switching networksPersonalizationFiltering rules
The embodiment of the invention discloses a spam mail filtering processing method and a system. The method comprises that: an anti-spam mail rule sharing request sent by a first user after selection of a mail address of a second user from a friend relation list is received; an individualized first anti-spam mail rule formulated by the first user and an individualized second anti-spam mail rule formulated by the second user are acquired from an individualized user rule base; whether a first anti-spam mail rule is conflicted to a second anti-spam mail rule is detected; and if the first anti-spam mail rule is not conflicted to the second anti-spam mail rule, the first anti-spam mail rule is integrated into the second anti-spam mail rule so that a third anti-spam mail rule is obtained and acts as a newly individualized anti-spam mail rule for the second user, and a mail whose recipient address is the mail address of the second user is filtered on the basis of the third anti-spam mail rule. The filtering rules can be shared between the users so that effect of filtering spam mails is enhanced.
Owner:CHINA TELECOM CORP LTD
Book resource access control method based on ciphertext attribute authentication and threshold function
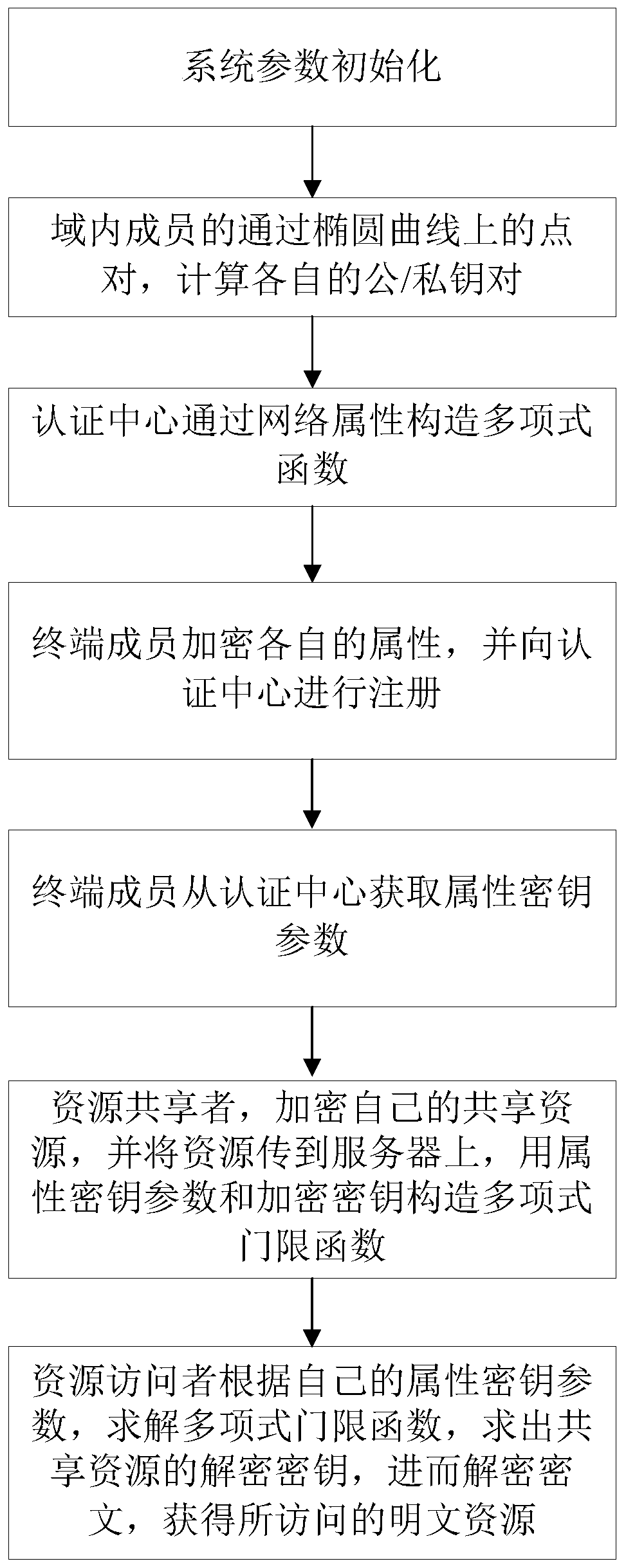
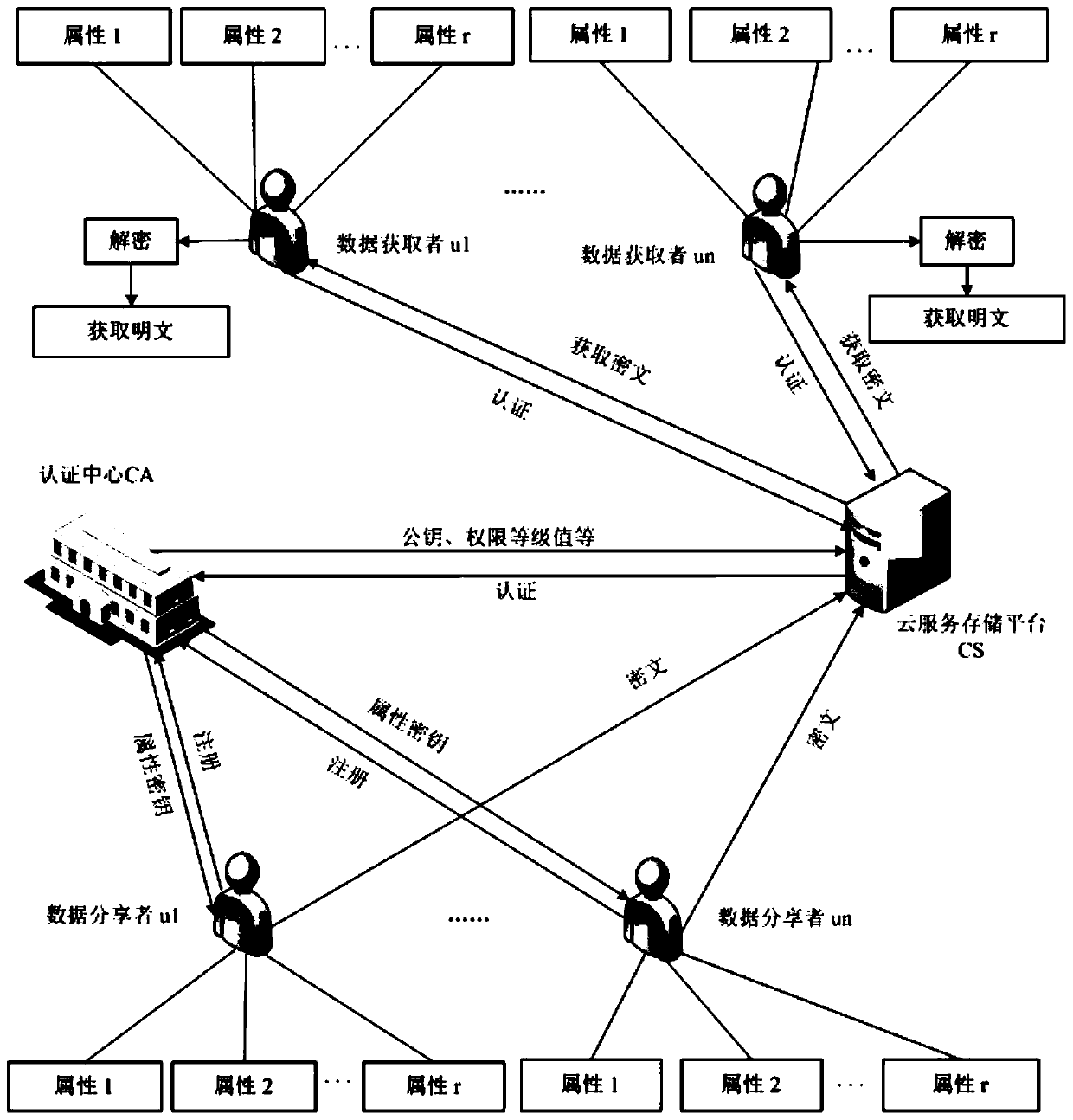
ActiveCN110912897AReduce computational and communication overheadAvoid Collusion AttacksPublic key for secure communicationInformation resourceThreshold function
The invention provides a book resource access control method based on ciphertext attribute authentication and a threshold function. The book resource access control method comprises the following steps that an authentication center and terminal members generate respective public / private key pairs; the terminal members interact with the authentication center to perform attribute authentication to obtain permission level values, and each terminal member sends the public key and the permission level value to the authentication center, and sends the public key and the permission level value to thecloud service platform after verification; the terminal member calculates an encryption key and a decryption key, encrypts the shared resource information into a ciphertext and uploads the ciphertextto the cloud service platform; and the terminal member determines a ciphertext resource to be checked according to the ciphertext, the cloud service platform verifies the identity of the ciphertext resource and opens an access link of the ciphertext resource, and the terminal member downloads the ciphertext for decryption. Personal privacy is protected by adopting a ciphertext attribute authentication technology, access permission is controlled by setting a threshold function to guarantee the safety of resource sharing, and collusion attack is prevented by adopting identity and permission dual authentication, so that information resource sharing in the Internet of Things is more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
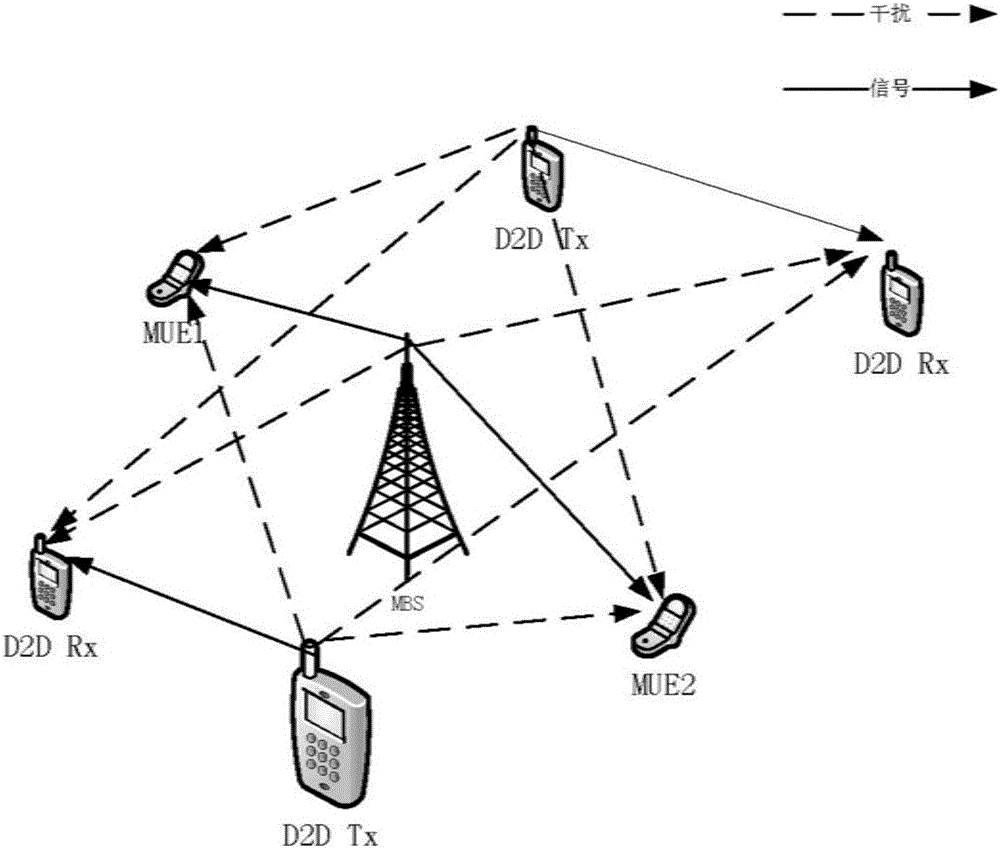
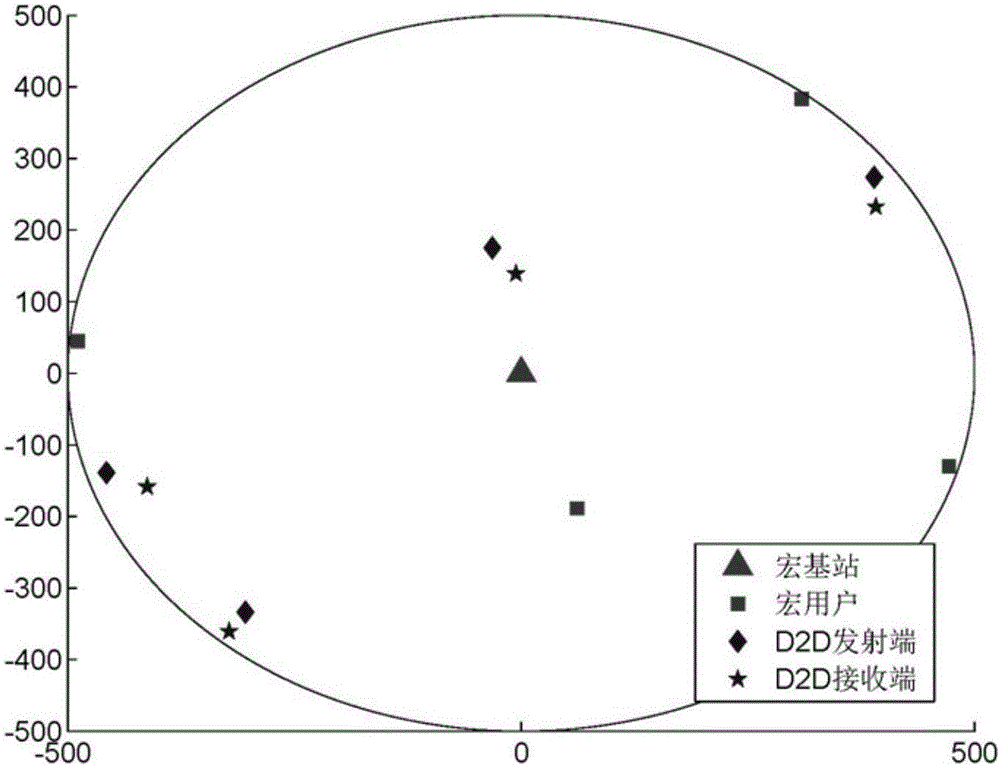
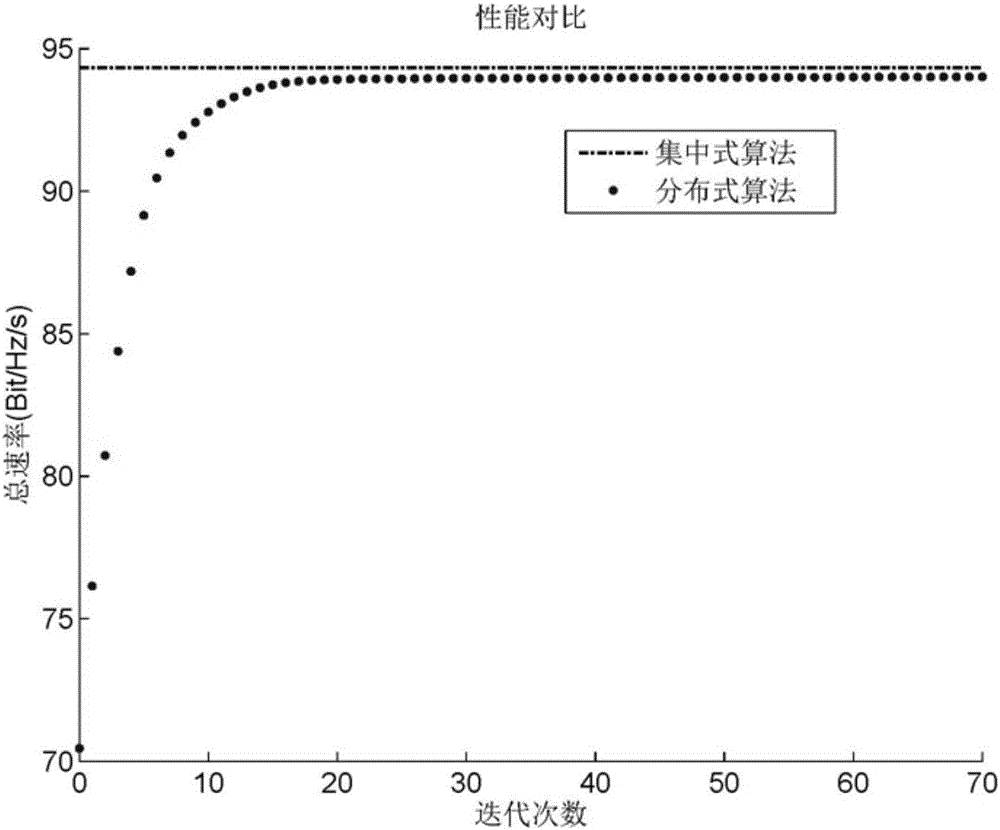
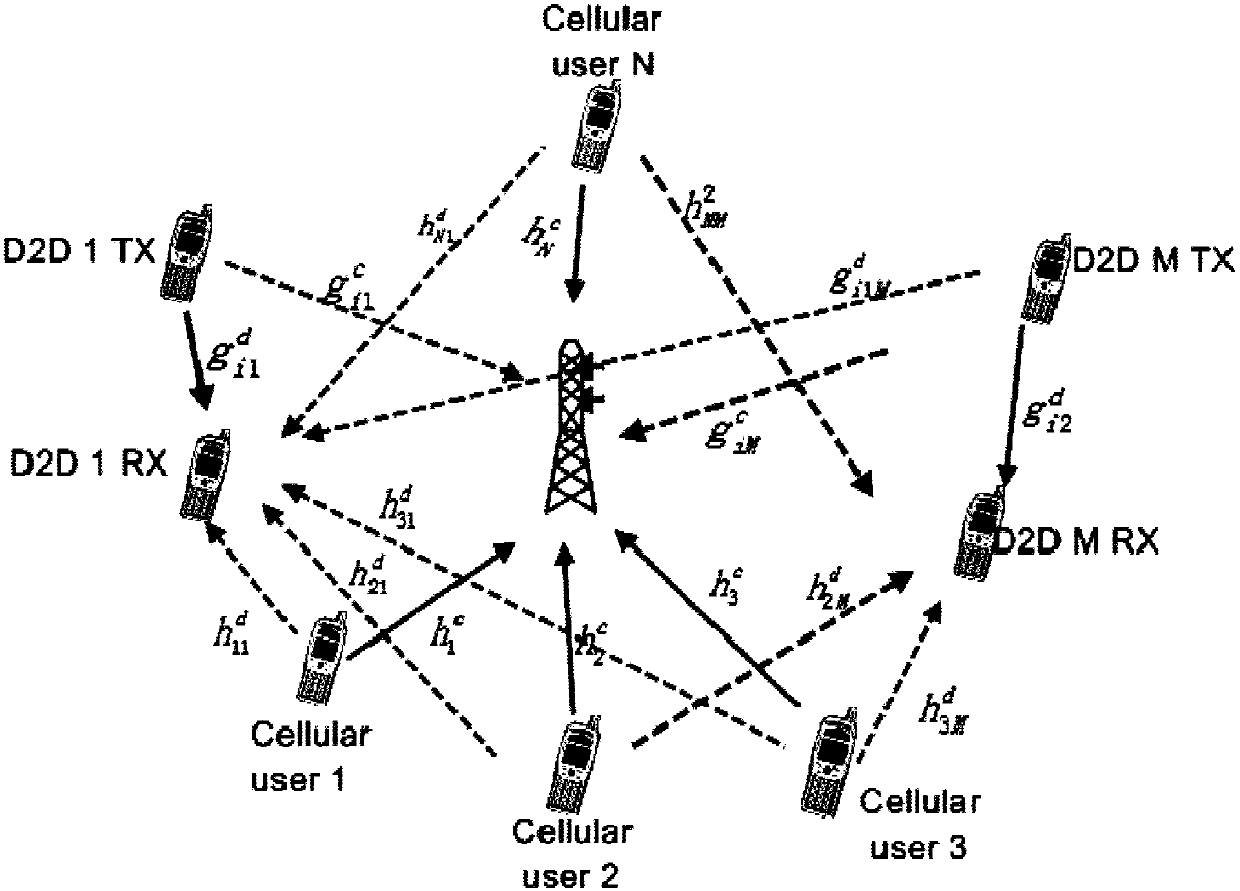
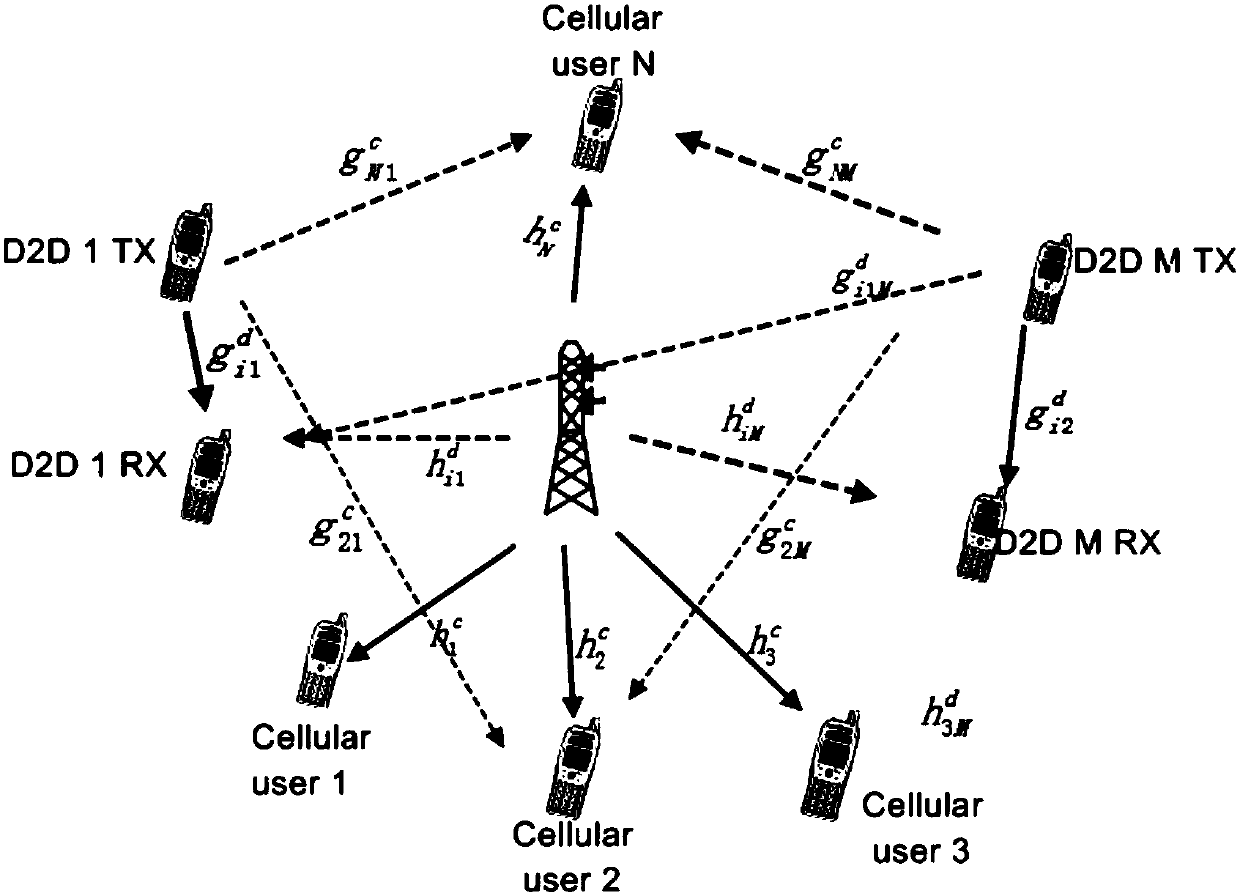
D2D distributed power optimization method in cellular network
ActiveCN105813189AIncrease flexibilityFast convergencePower managementFrequency spectrumDistributed power
The invention discloses a D2D distributed power optimization method in a cellular network. The transmission power of a base station and a D2D user is solved in a distributed manner through fixed point iteration, so that the power distribution and communication rate of a D2D device and the base station on different channels are obtained. According to the invention, a non-convex problem is approximated as a divisible convex optimization problem by using a convex approximation method and an optimal solution of the convex problem is obtained through multi-layer iteration rapid convergence. The method provided by the invention is wide in application range, realizes frequency spectrum resource sharing, improves system performance flexibly, reduces computation amount and improves computation speed.
Owner:SOUTHEAST UNIV
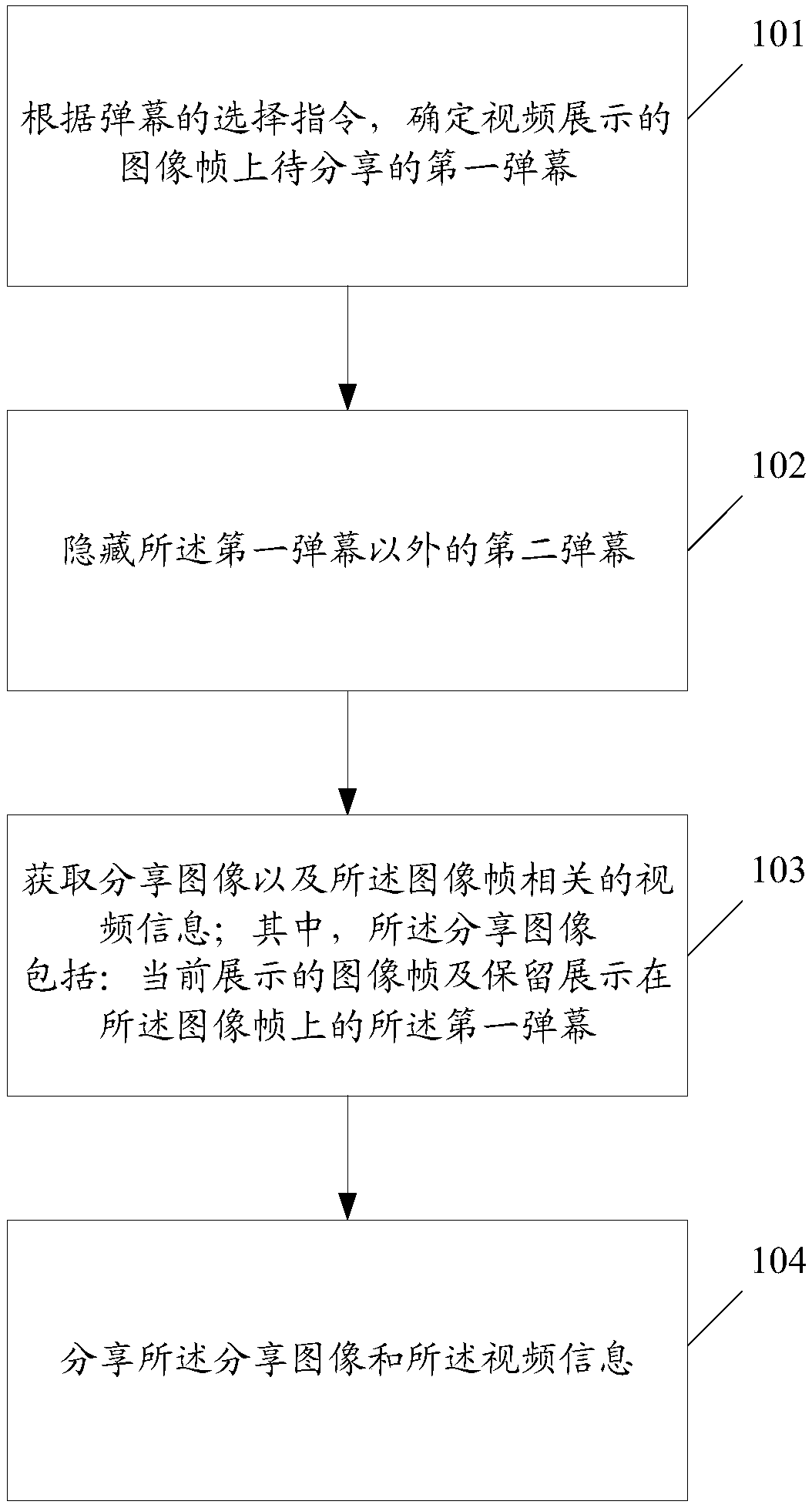
Method and device for sharing video
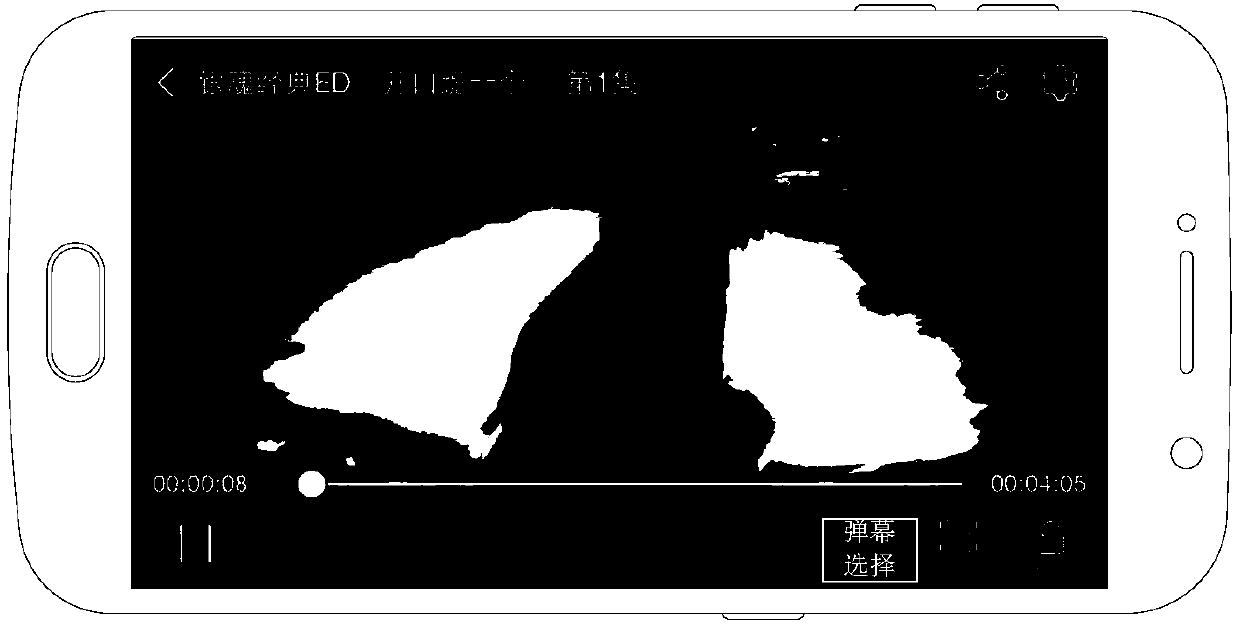
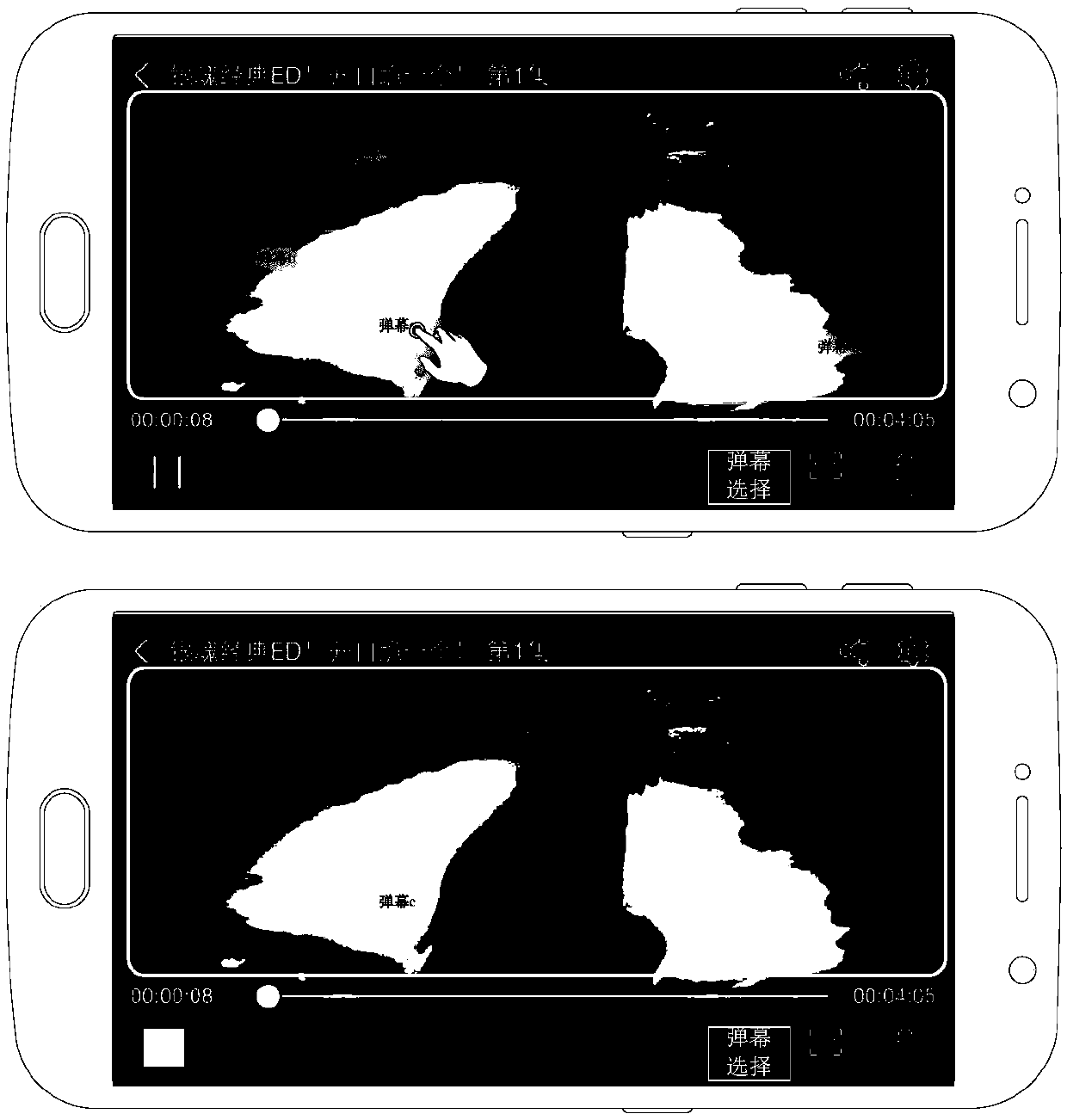
ActiveCN107786905AFlexible sharingSelective content distributionComputer graphics (images)Image frame
The invention discloses a method for sharing a video. The method comprises the steps that a first bullet screen to be shared on an image frame is determined according to a bullet screen selecting instruction; a second bullet screen expect for the first bullet screen is hidden; a shared image and video information of the image frame are acquired, wherein the shared image comprises the currently shown image frame and the first bullet screen reserved and shown on the image frame; the shared image and the video information are shared.
Owner:MIGU COMIC CO LTD
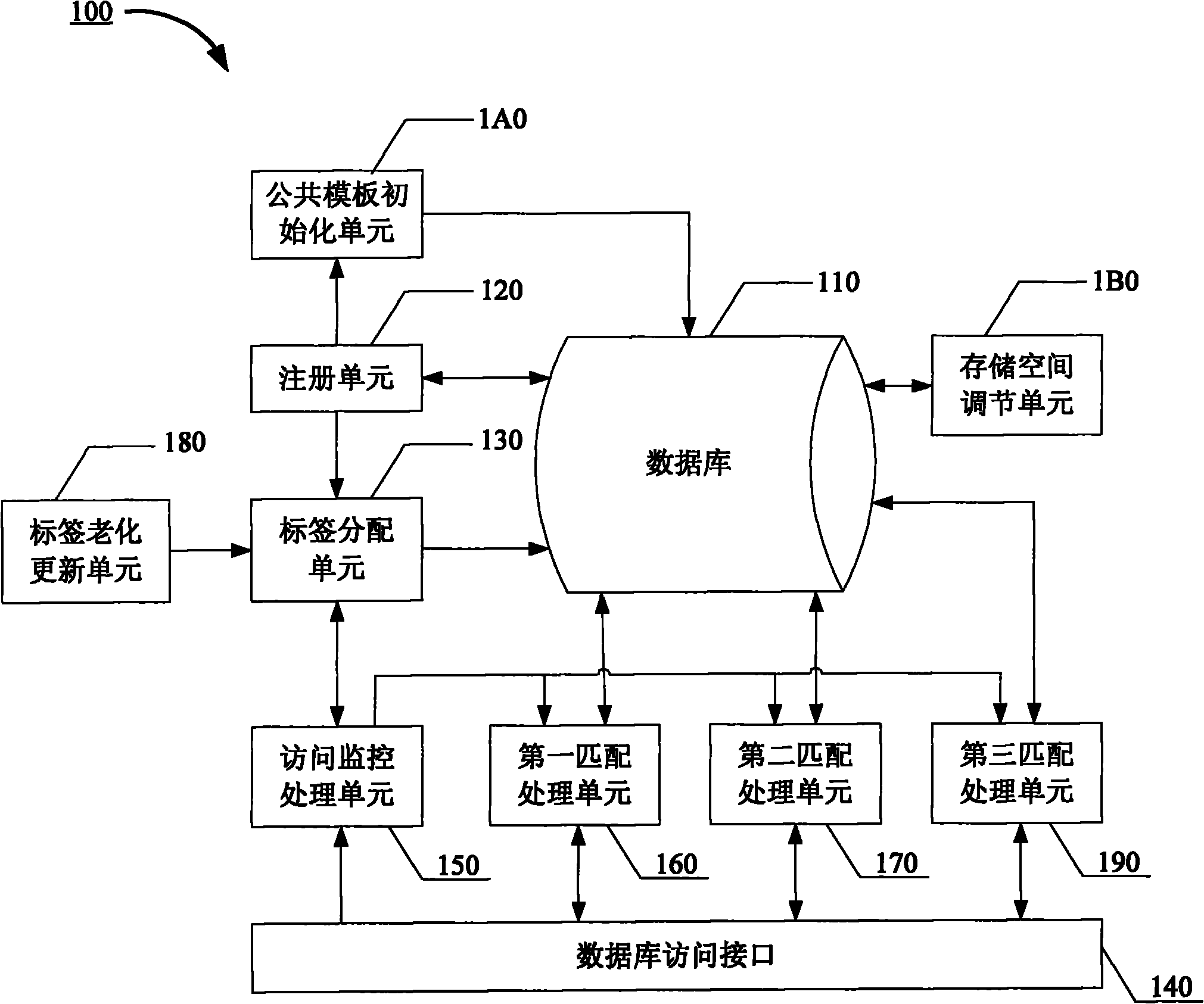
Information database system and access control method thereof
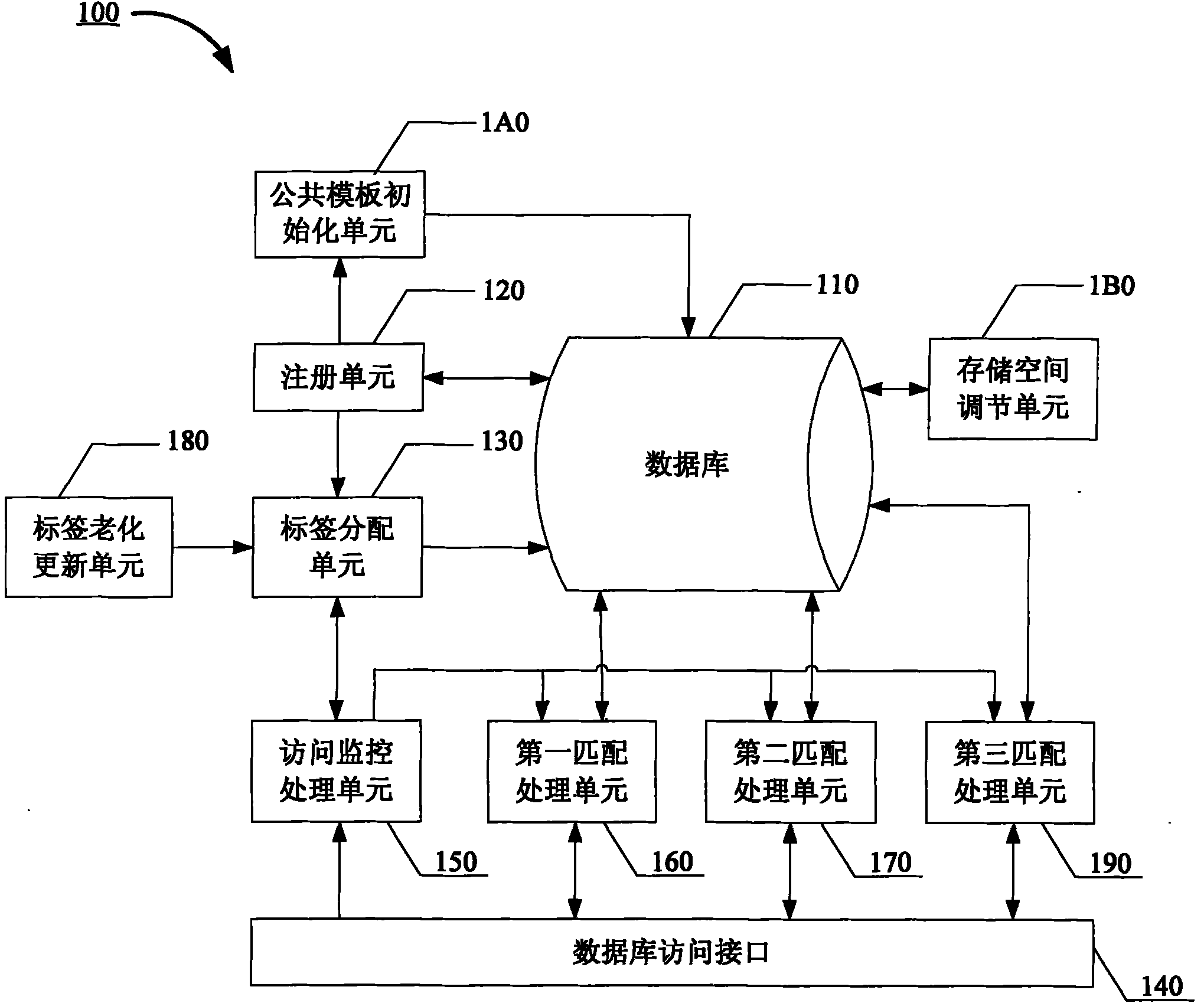
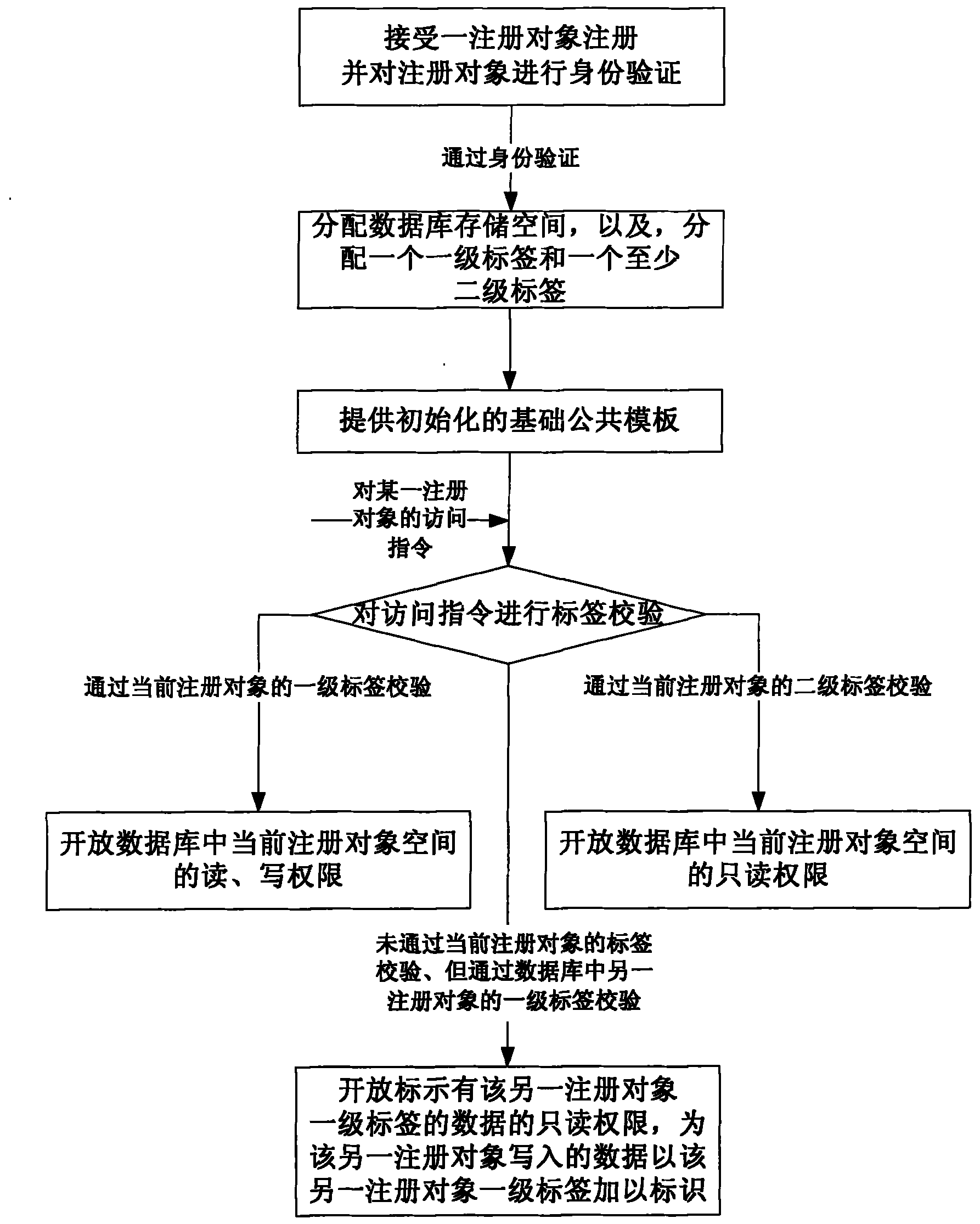
InactiveCN102063431AFlexible sharingSecurity enables sharingDigital data protectionSpecial data processing applicationsInformation confidentialityDatabase
The invention discloses an information database system and an access control method thereof. The access control method of the information database system comprises the following steps: allotting one first-order label and at least one second-order label to each registered object, and checking the labels of for an access command; opening the spacial read and write authority of the currently registered object space in a database to public use under the condition that the access command passes the check of the first-order label of the currently registered object; and opening the spacial read-onlyauthority of the currently registered object space in the database to public use under the condition that the access command passes the check of the second-order label of the currently registered object. Due to the adoption of the invention, the information database information can be kept secret, exchanged and shared flexibly and safely.
Owner:郭承运
System for processing graphic objects including a secured graphic manager
InactiveUS20100058116A1ReduceFlexible sharingFault responseCathode-ray tube indicatorsGraphicsSpecific storage
The general field of the invention is that of viewing systems that have to display information or images having different criticality levels. The viewing system according to the invention comprises at least one secure graphic manager with a criticality level at least equal to the highest criticality level of the graphic applications. The manager has the following detection means: violation of the segregation of the applications in their respective display window; overrunning of the processing times of each application; and violation of the specific storage spaces of the graphic applications.
Owner:THALES SA
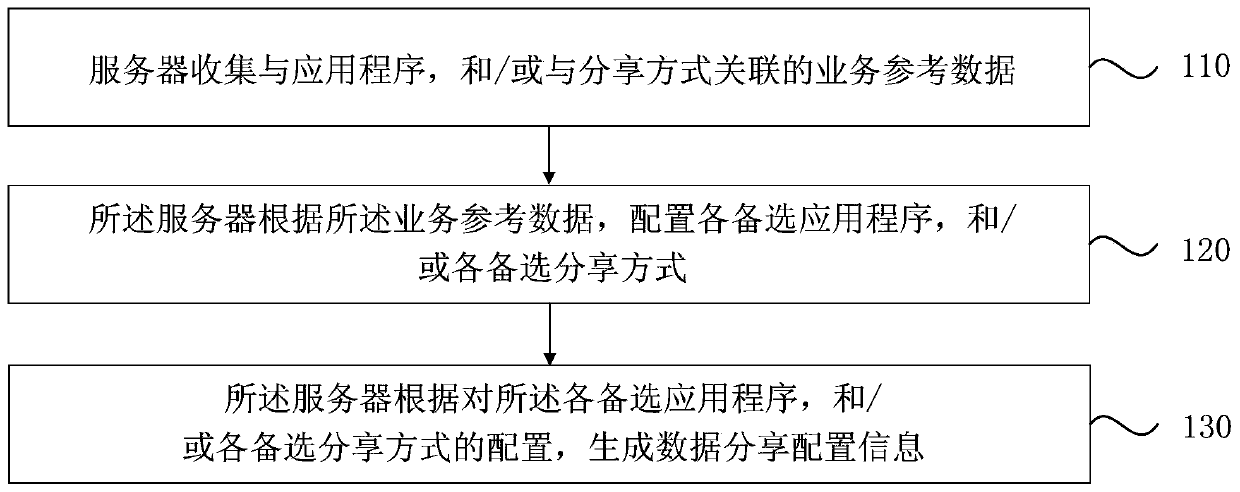
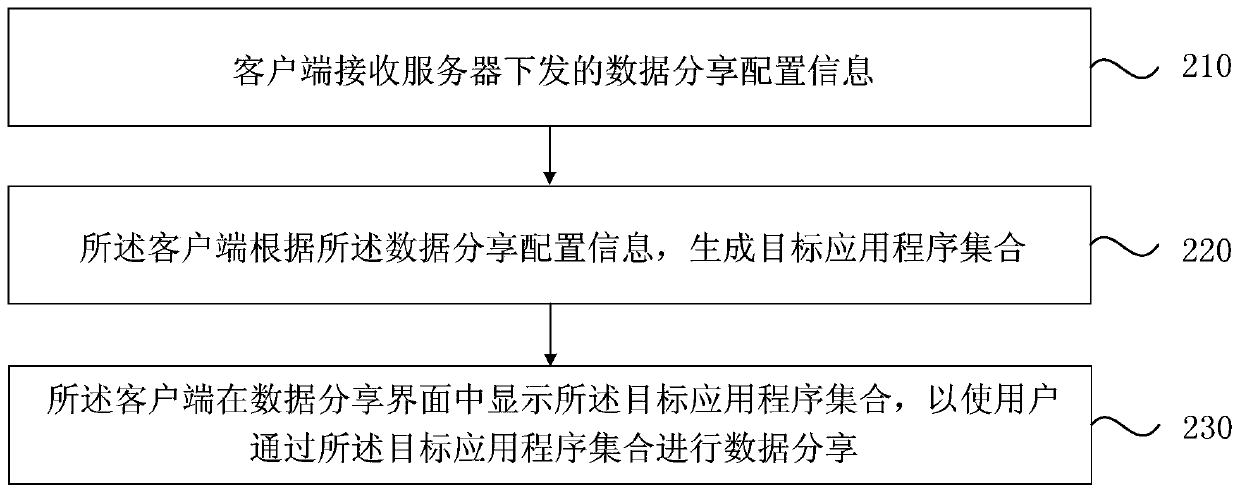
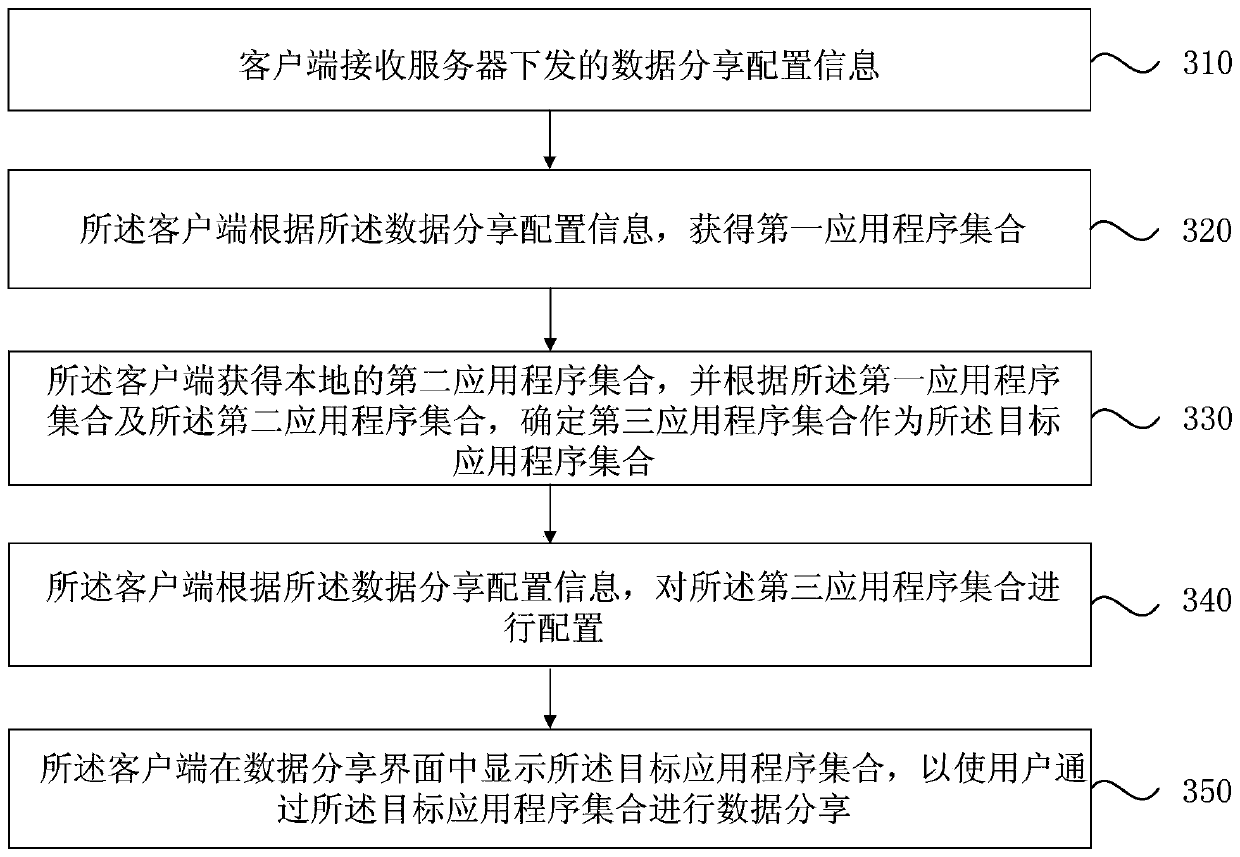
Data sharing method, device and equipment and medium
The embodiment of the invention discloses a data sharing method and device, equipment and a medium. The method comprises the steps that a server collects service reference data associated with an application program and / or a sharing mode; the server configures each alternative application program and / or each alternative sharing mode according to the service reference data; the server generates data sharing configuration information according to the configuration of each alternative application program and / or each alternative sharing mode; wherein the data sharing configuration information is used for being issued to at least one client, and indicating the client to generate a target application program according to the data sharing configuration information and display the target application program in a data sharing interface. According to the technical scheme provided by the embodiment of the invention, the effect of flexibly configuring the sharing application program in the data sharing interface or the sharing mode used by the sharing application program is achieved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
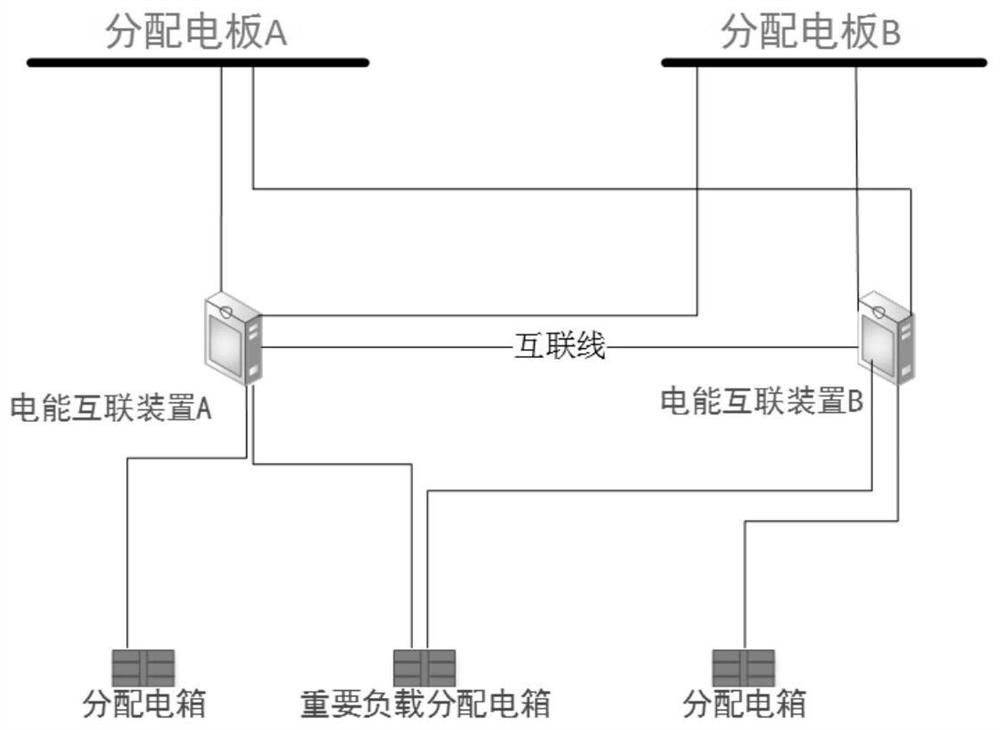
Ship tail end power distribution system
PendingCN111769551AReduce complexityRealize the flattening of power distributionSelective ac load connection arrangementsSingle network parallel feeding arrangementsElectric power transmissionInformation networks
The invention provides a ship tail end power distribution system. The system comprises a power network used for power transmission and an information network used for managing a regional power distribution system, a digital control mode is adopted, the power flow of all branches or ports is accurately controlled, the power scheduling function is optimized, the simultaneous parallel power supply ofmultiple paths of power sources is achieved, and a power supply mode is converted from passive power distribution to active power distribution; by connecting an electric energy interconnection deviceand port equipment thereof and communicating with a ship energy management system and a comprehensive platform management network, the accurate guarantee and reasonable distribution of the electric energy in the area are effectively performed as required, and the fusion of the energy flow and the information flow is realized.
Owner:CHINA SHIP DEV & DESIGN CENT
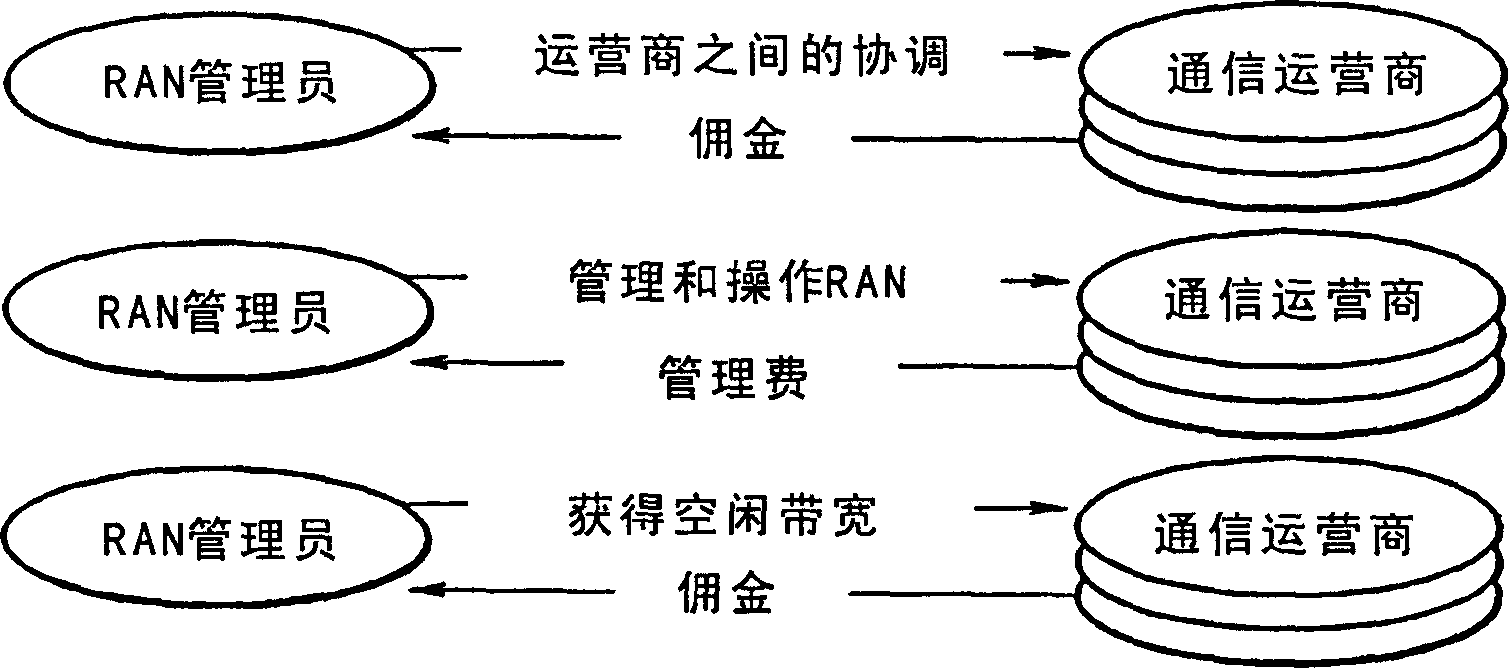
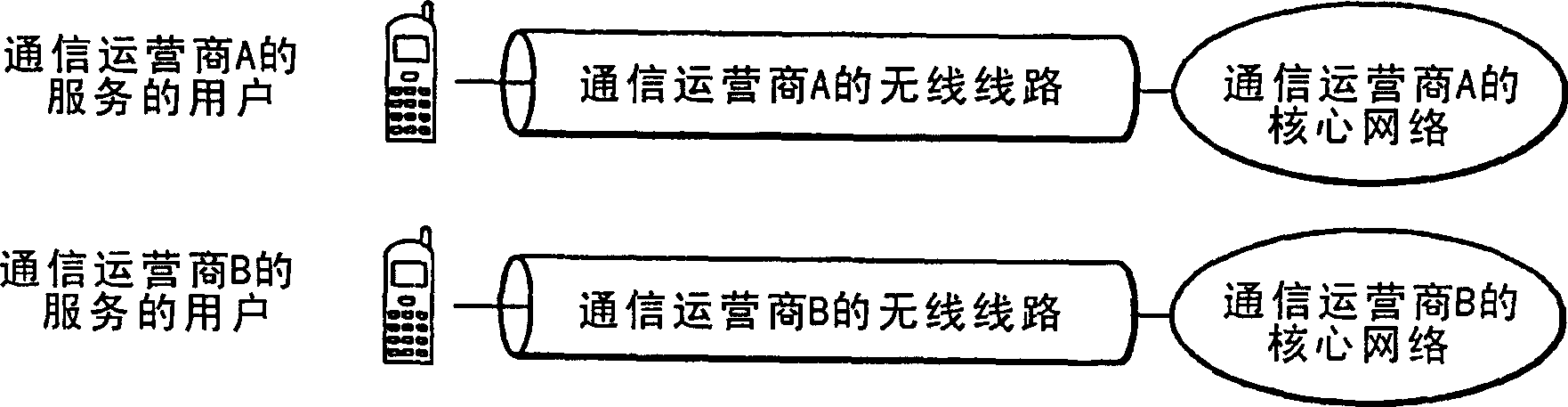
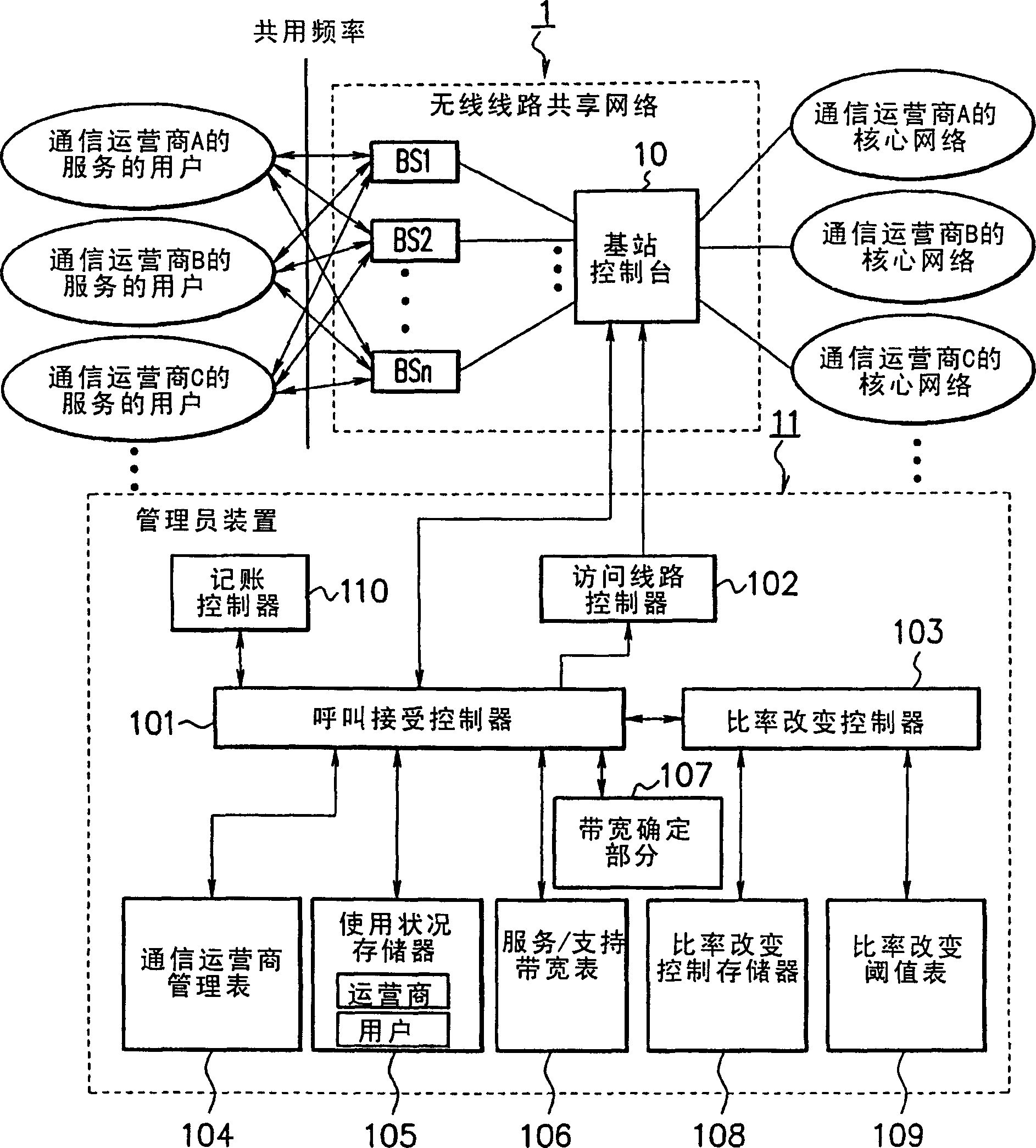
Wireless-line-shared network system, and management apparatus and method therefor
InactiveCN1860809AReduce trafficFair shareAccounting/billing servicesNetwork traffic/resource managementCharge controlNetworked system
A wireless-line-shared network system capable of charging in accordance with use of a wireless communication network so as to reduce the investment costs of communication providers. The user terminals of the communication providers use radio frequencies, which are permitted by authorities, to connect with the corresponding communication provider networks via radio base stations (BS) and a controlstation (10). In response to call connection requests, a call acceptance control part (101) performs call acceptances and band managements based on wireless band allocation patterns, which established by subscriptions, and based on current use statuses. A bandwidth decision part (107) decides bandwidths for the call connection requests by use of the call connection requests, call connection responses and a bandwidth table (106). A rate change control part (103) adjusts the bandwidths of the user terminals such that the currently used bandwidths of the communication providers are kept within predetermined ranges. A charge control part (110) charges the communication providers in accordance with their wireless band rental subscriptions.
Owner:NEC CORP
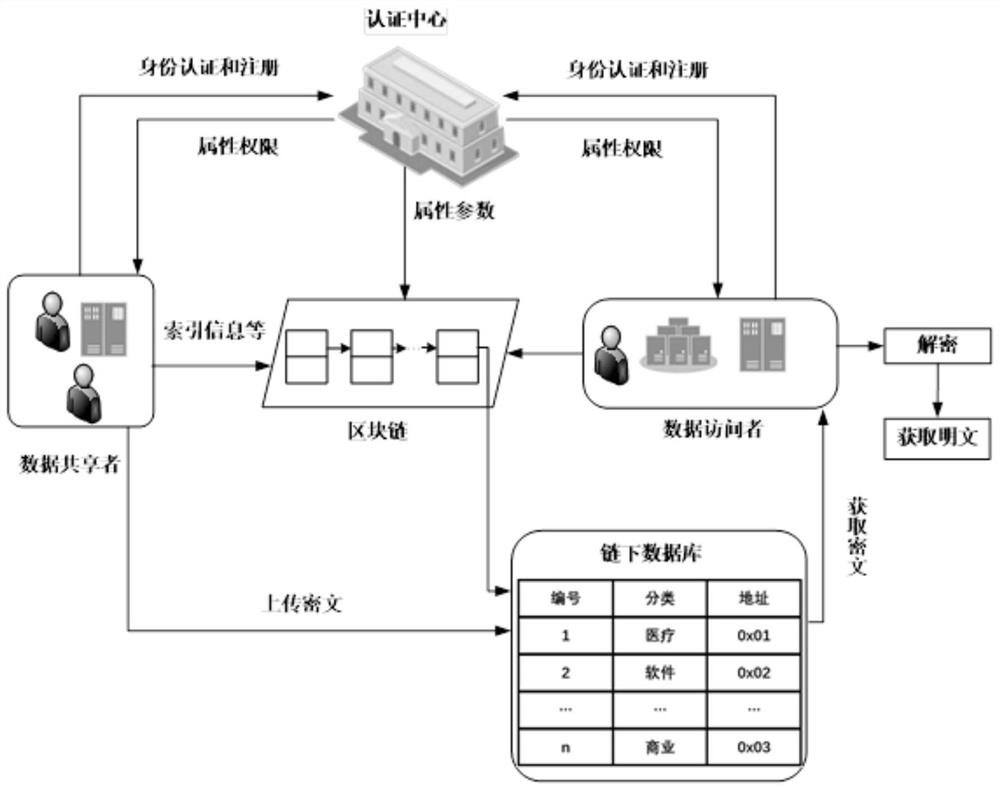
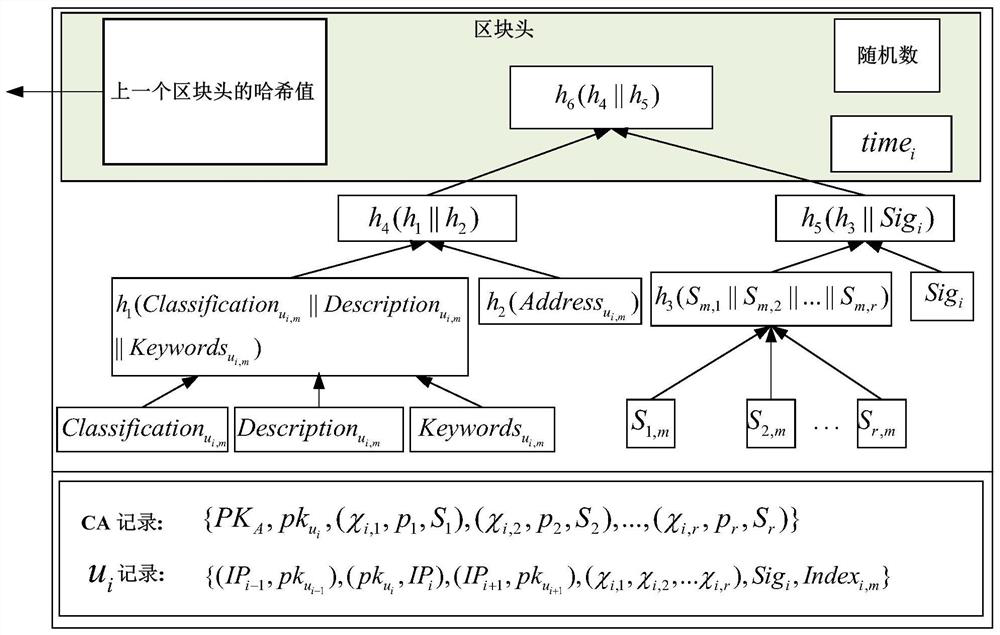
Internet of Things data security sharing method based on privacy protection
ActiveCN112165472AReduce calculationReduce communication overheadKey distribution for secure communicationUser identity/authority verificationInformation resourceAttack
The invention provides an Internet of Things data security sharing method based on privacy protection. The method comprises the following steps: initializing protocol parameters in an information sharing network domain; registering a terminal member; enabling the terminal member to acquire own attribute authority parameters, calculating encryption keys according to the Chinese remainder theorem, encrypting shared information resources and storing the encrypted information resources in an off-chain database; calculating intermediate parameters required for storing the information resources, generating index information of the shared ciphertext and packaging the index information in a block, and so on, enabling each terminal member to store related information of the ciphertext in the blockto generate a block chain; and accessing and sharing the ciphertext. Identity and attribute parameter matching dual authentication is adopted to prevent collusion attacks and protect personal privacy,an attribute matching access control strategy is combined with a block chain technology to guarantee the safety of shared resource information, the storage burden is reduced, information resource sharing in the industrial Internet of Things is more flexible, efficient and practical, and the method has important field research significance and commercial application value.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
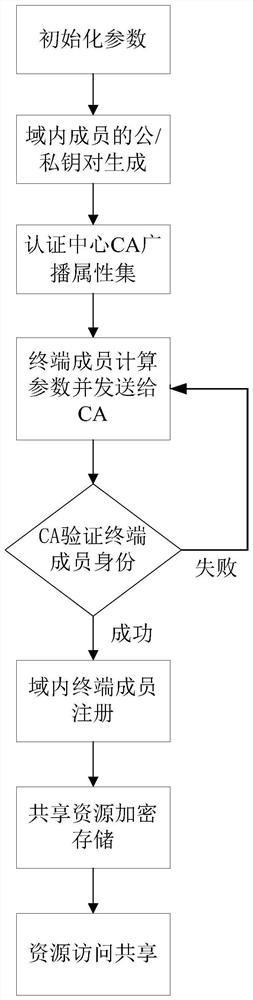
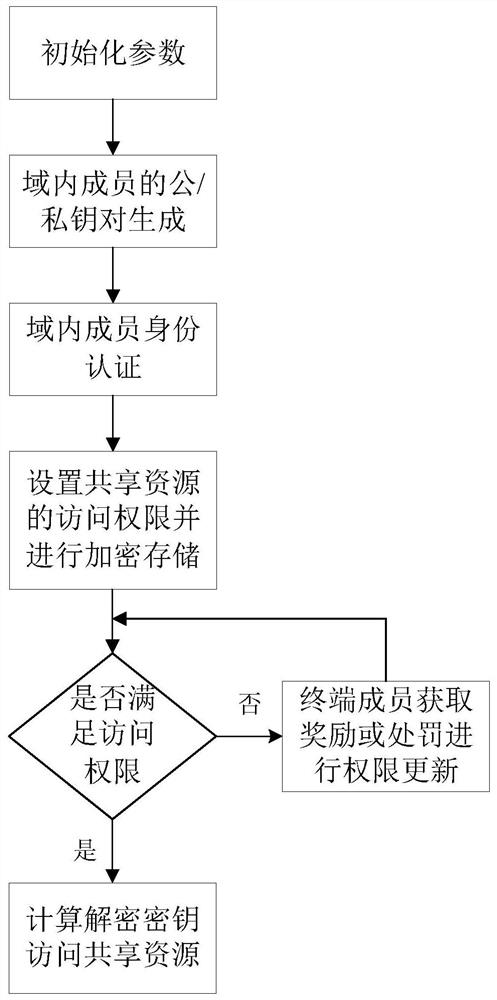
Dynamic authority access control method based on privacy protection
ActiveCN112383550AReduce calculationReduce communication overheadTransmissionInformation sharingCiphertext
The invention provides a dynamic authority access control method based on privacy protection, which comprises the following steps: initializing protocol parameters in an information sharing network domain, carrying out identity authentication of hidden attributes on terminal members, and after the authentication succeeds, setting, by a data sharer, the access authority of the shared resources according to the attribute parameters of the data sharer, encrypting the shared resources and storing the encrypted shared resources into an encrypted database; searching for, by a data acquirer, the shared resource to be accessed according to a keyword, acquiring a ciphertext storage link after verifying the access authority, downloading the ciphertext resource through the link, and calculating a decryption key to decrypt and acquire the ciphertext resource; and meanwhile, updating, by a terminal member, the access authority of the terminal member by acquiring rewards or punishment and the like.Double authentication is used to prevent collusion attacks, the safety of shared resources is guaranteed, personal privacy is protected, flexible and fine-grained data resource access is achieved based on attribute matching dynamic access control, access management is greatly simplified, and resource sharing is more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Synchronising groups of threads with dedicated hardware logic
ActiveUS8966488B2Synchronisation can be simplifiedReduce delaysMultiprogramming arrangementsConcurrent instruction executionParallel computingExecution unit
Owner:XMOS
Fast optimization algorithm of D2D power distribution in case of single-channel cellular users
ActiveCN105142224AFast convergenceFlexible sharingWireless commuication servicesFast optimizationTransmitted power
The invention discloses a fast optimization algorithm of D2D power distribution in case of single-channel cellular users. A communication rate optimization problem of D2D users based on a cellular system is a complex nonconvex nonlinear optimization problem. The cellular users that the fast optimization algorithm aims at utilize a single channel, while the D2D users utilize multiple channels; the algorithm can be used for quickly optimizing and solving the transmitting power pi of the cellular users and the transmitting power qi of the D2D users in a plurality of cases such as cellular users, power limitation and independent power limitation, and D2D users, power limitation and independent power limitation, and the like. The transmitting power obtained by use of the optimization algorithm is capable of ensuring the communication rate requirements of the cellular users and maximizes the sum of the communication rate of all the D2D users on all the cellular frequency bands. The algorithm has the advantages of high convergence rate, small calculation amount, easy implementation, high result accuracy and the like.
Owner:SOUTHEAST UNIV
Optical network unit device for mutual-excitation multi-wavelength dynamic scheduling in passive optical network (PON)
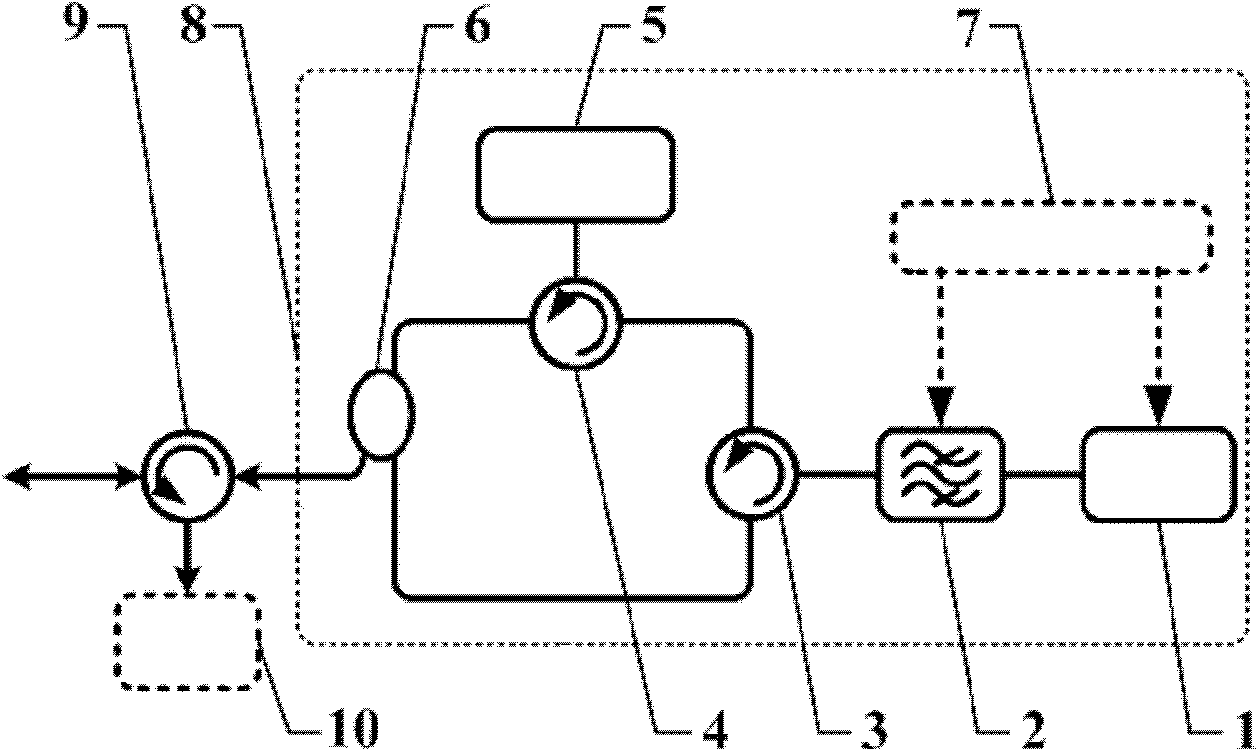
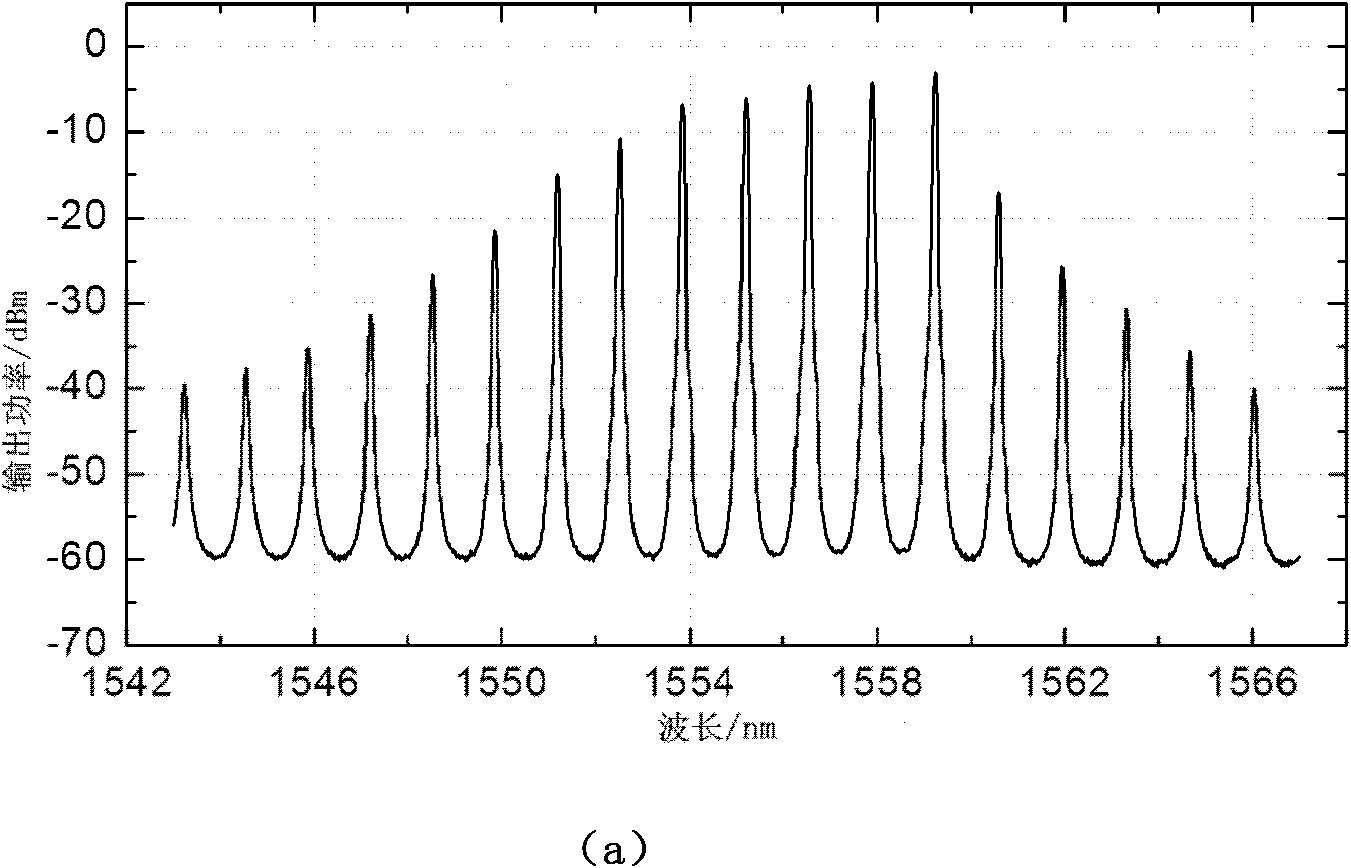
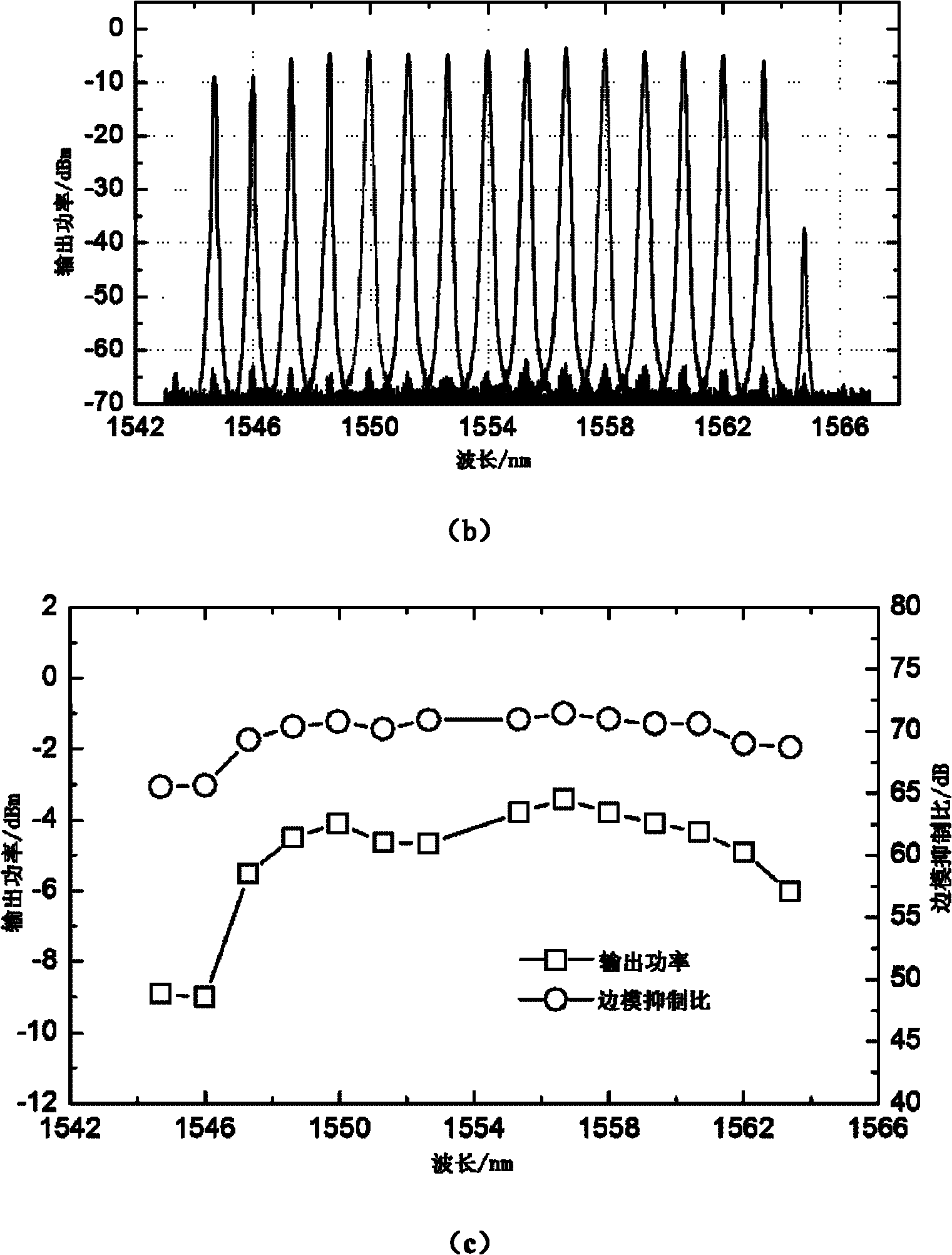
InactiveCN101895795AIncrease upstream transmission bandwidthIncrease profitMultiplex system selection arrangementsElectromagnetic network arrangementsLongitudinal modelMulti wavelength
The invention discloses an optical network unit device for mutual-excitation multi-wavelength dynamic scheduling in a passive optical network (PON), belonging to the technical field of optical communication. The optical network unit device comprises an uplink data transmitter, a downlink data receiver and an optical circulator, wherein the output end of the optical circulator is connected with the uplink data transmitter so as to transmit downlink data optical signals, and the input end of the optical circulator is connected with the uplink data transmitter so as to transmit uplink data optical signals; and the uplink data transmitter comprises two FP multi-longitudinal model lasers with the same model intervals, an adjustable band-pass filter, two optical circulator, an optical splitting and coupling device and a control module. Based on the mutual-excitation working mode of two FP multi-longitudinal model lasers, the invention can dynamically generate uplink optical carrier with adjustable multi-wavelength, flexibly and effectively share all uplink wavelength resources, improve the utilization rate of the uplink wavelength resources, has simple structure and low cost, and meet the development requirement on rapid increase of user uplink access capability.
Owner:SHANGHAI JIAO TONG UNIV +1
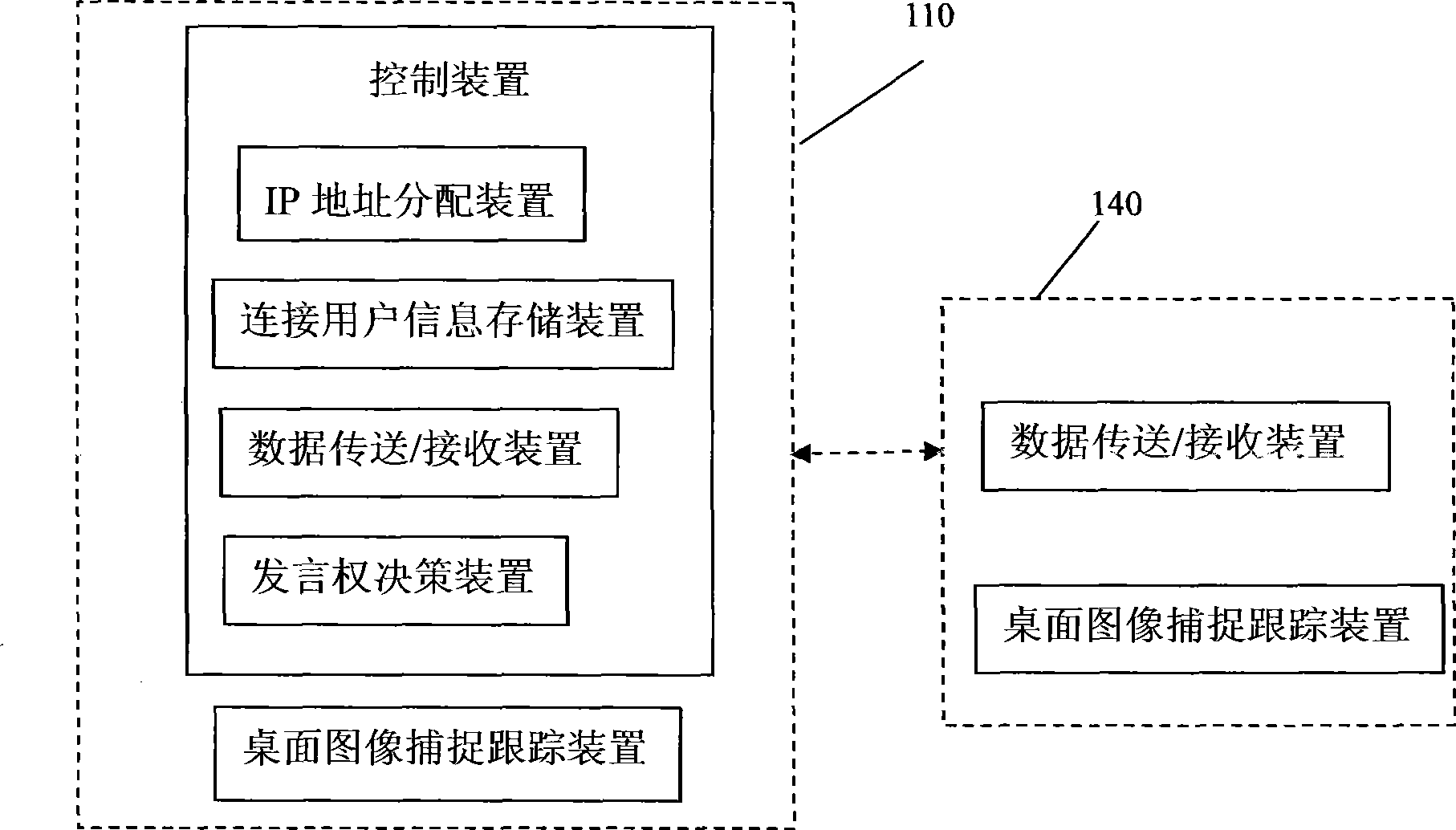
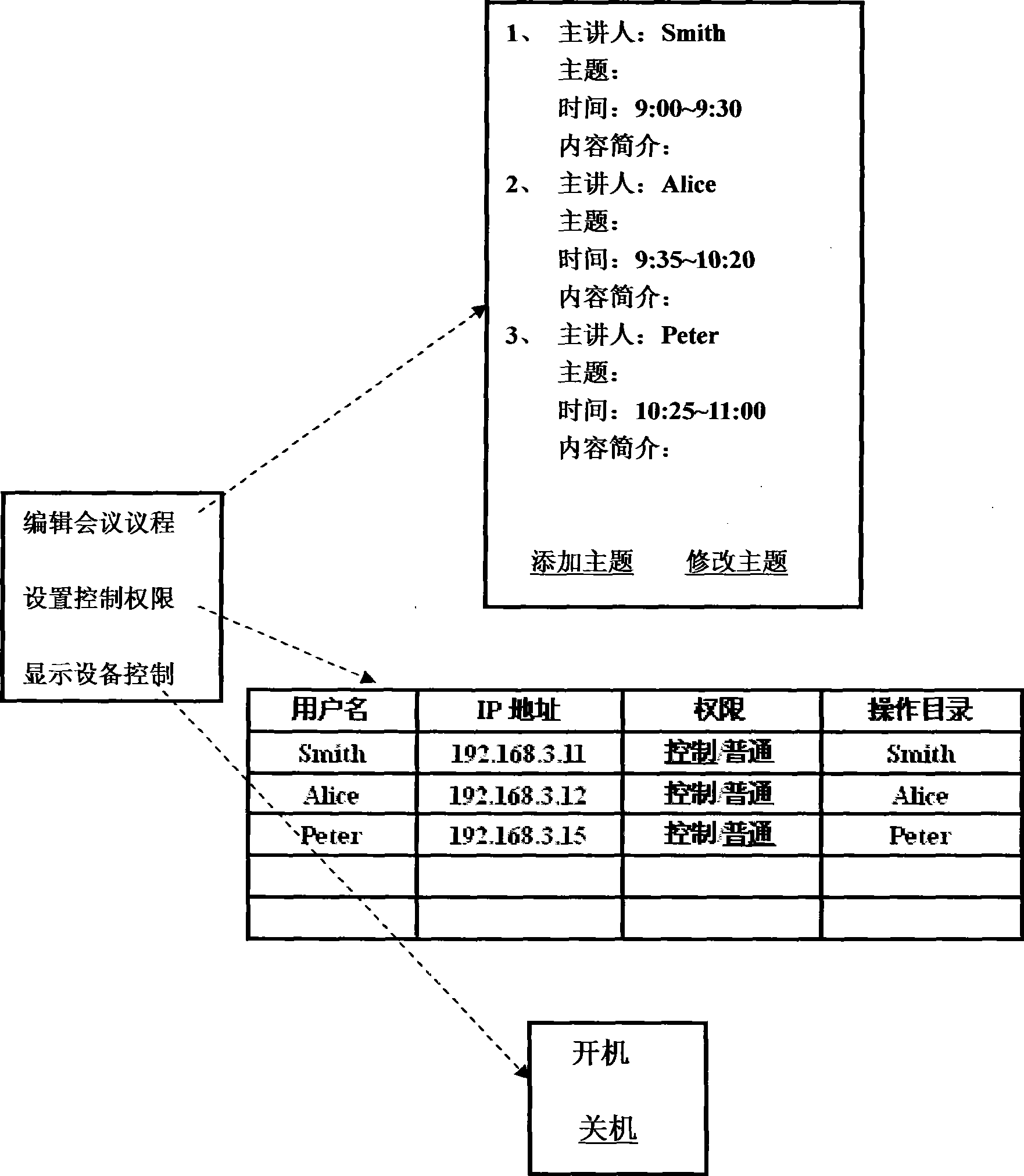
Wireless meeting system
InactiveCN101364886BFirmly connectedFacilitate communicationSpecial service provision for substationData switching by path configurationNon localClient-side
Owner:广州飞瑞敖电子科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com