Patents
Literature
676results about How to "Reduce communication overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
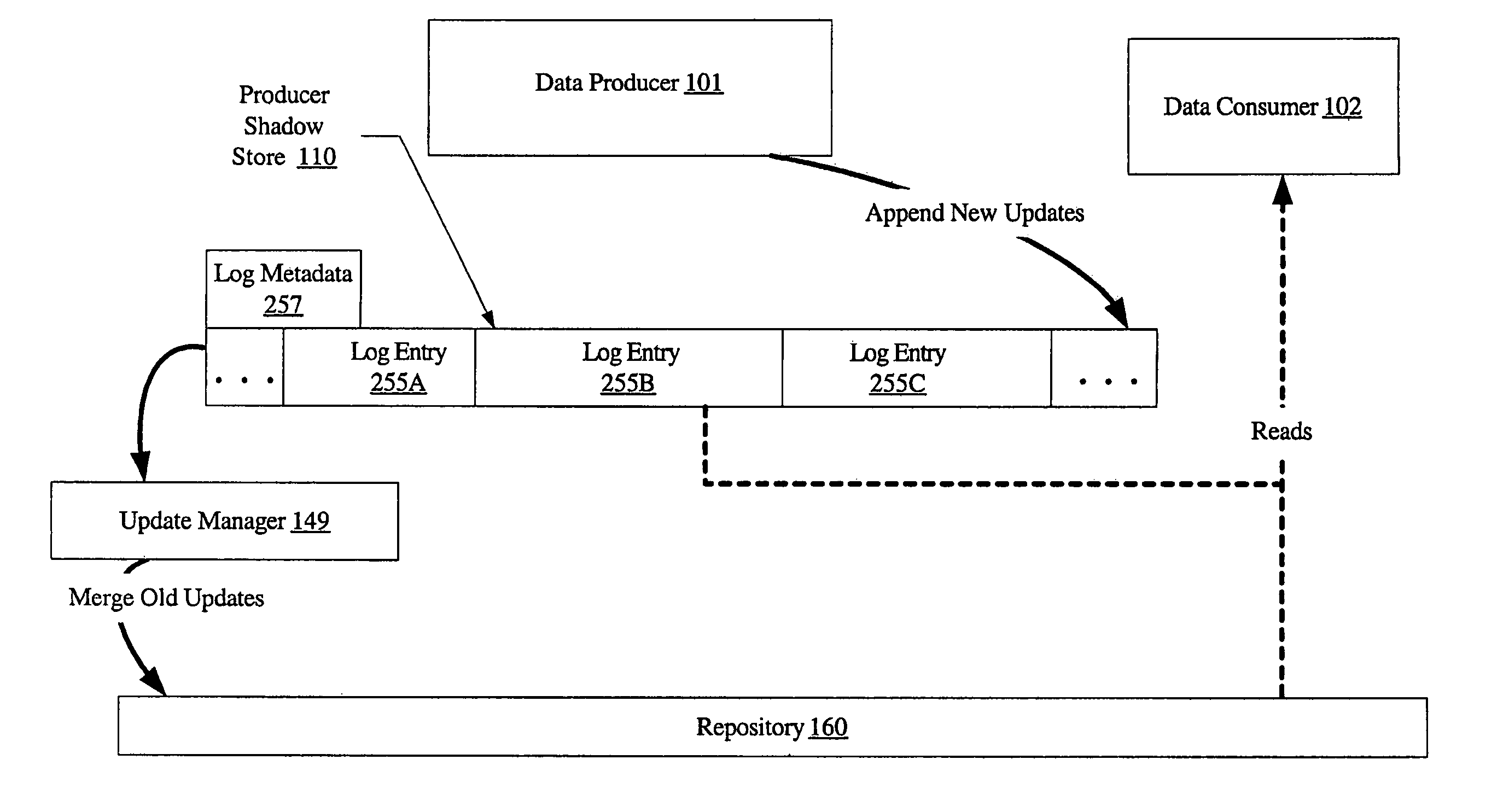
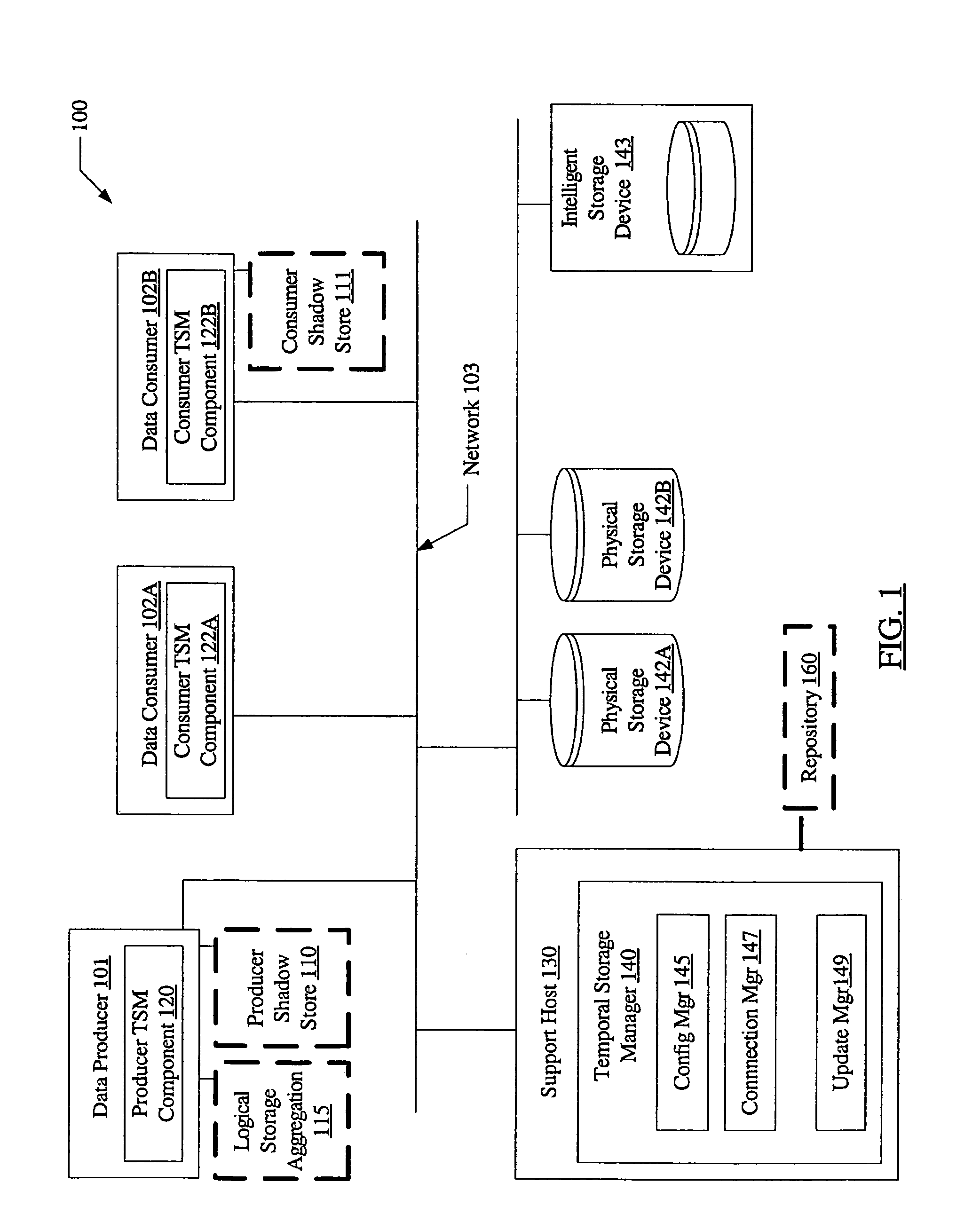
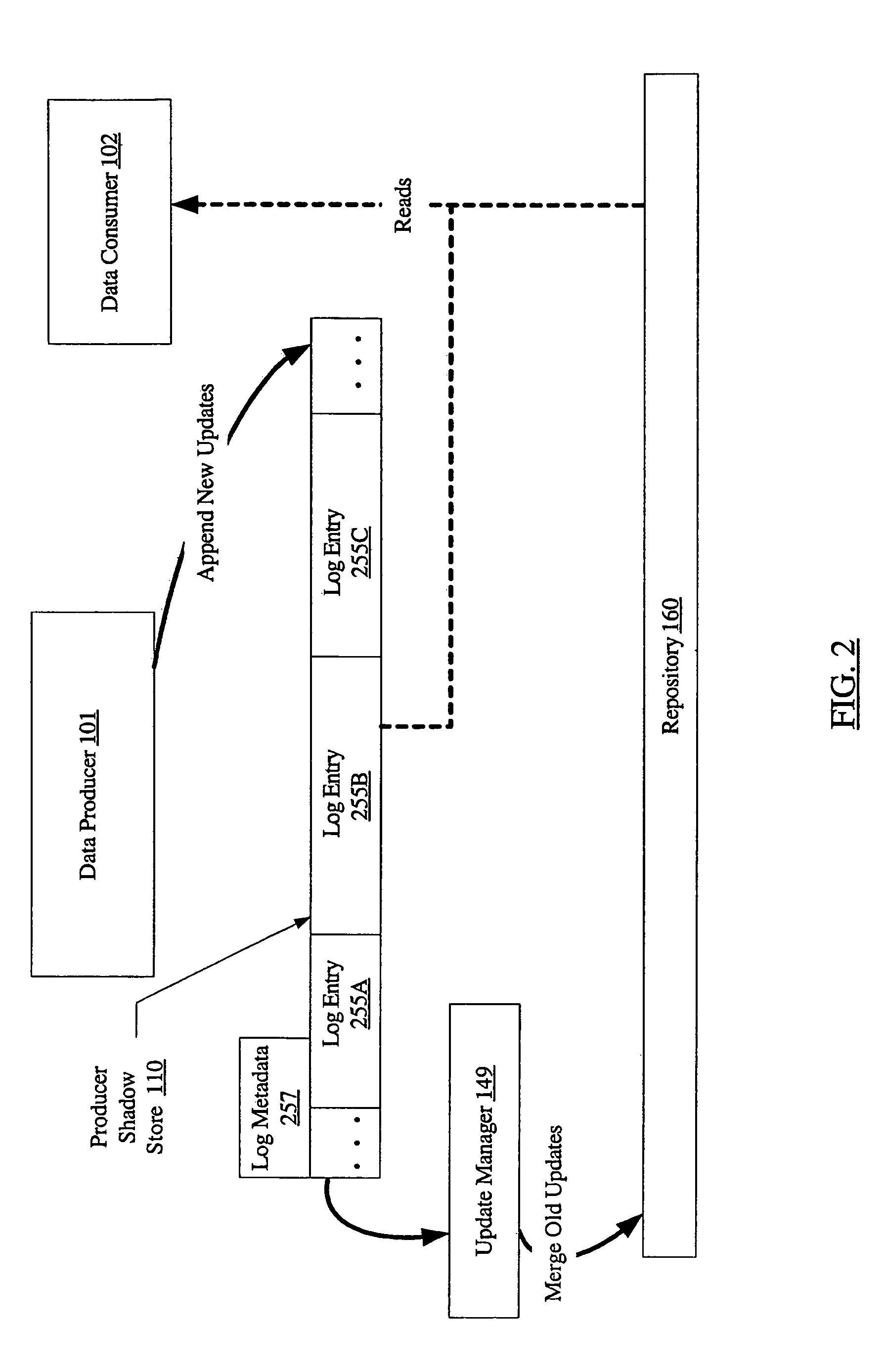
System and method for loosely coupled temporal storage management
ActiveUS7257689B1Prevent corruptionHigh degreeData processing applicationsDigital data information retrievalStorage managementDatabase
A system for loosely coupled temporal storage management includes a logical storage aggregation including a plurality of data blocks, a data producer, one or more data consumers, and a temporal storage manager. The temporal storage manager may be configured to maintain a producer shadow store including entries stored in a log-structured logical volume, where each entry is indicative of one or more data blocks of the logical storage aggregation that have been modified by the data producer. The temporal storage manager may also be configured to maintain a repository containing a baseline version of the logical storage aggregation, and to provide the data consumers with read-only access to the producer shadow store and the repository.
Owner:SYMANTEC OPERATING CORP
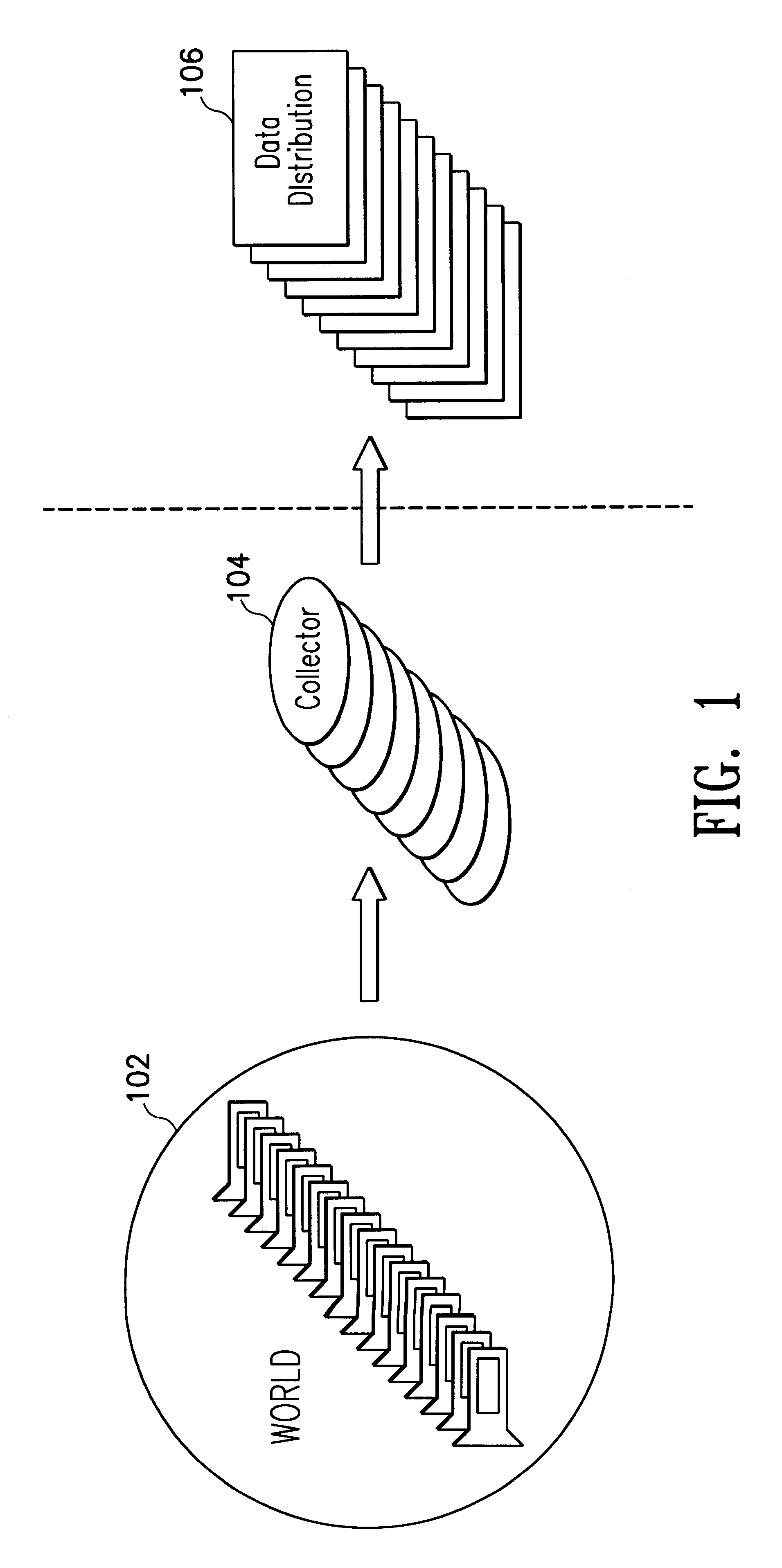
Collaborative team crawling:Large scale information gathering over the internet
InactiveUS6182085B1Reduce processing overheadEfficient accessDrawing from basic elementsData processing applicationsTree (data structure)Workload
A distributed collection of web-crawlers to gather information over a large portion of the cyberspace. These crawlers share the overall crawling through a cyberspace partition scheme. They also collaborate with each other through load balancing to maximally utilize the computing resources of each of the crawlers. The invention takes advantage of the hierarchical nature of the cyberspace namespace and uses the syntactic components of the URL structure as the main vehicle for dividing and assigning crawling workload to individual crawler. The partition scheme is completely distributed in which each crawler makes the partitioning decision based on its own crawling status and a globally replicated partition tree data structure.
Owner:IBM CORP
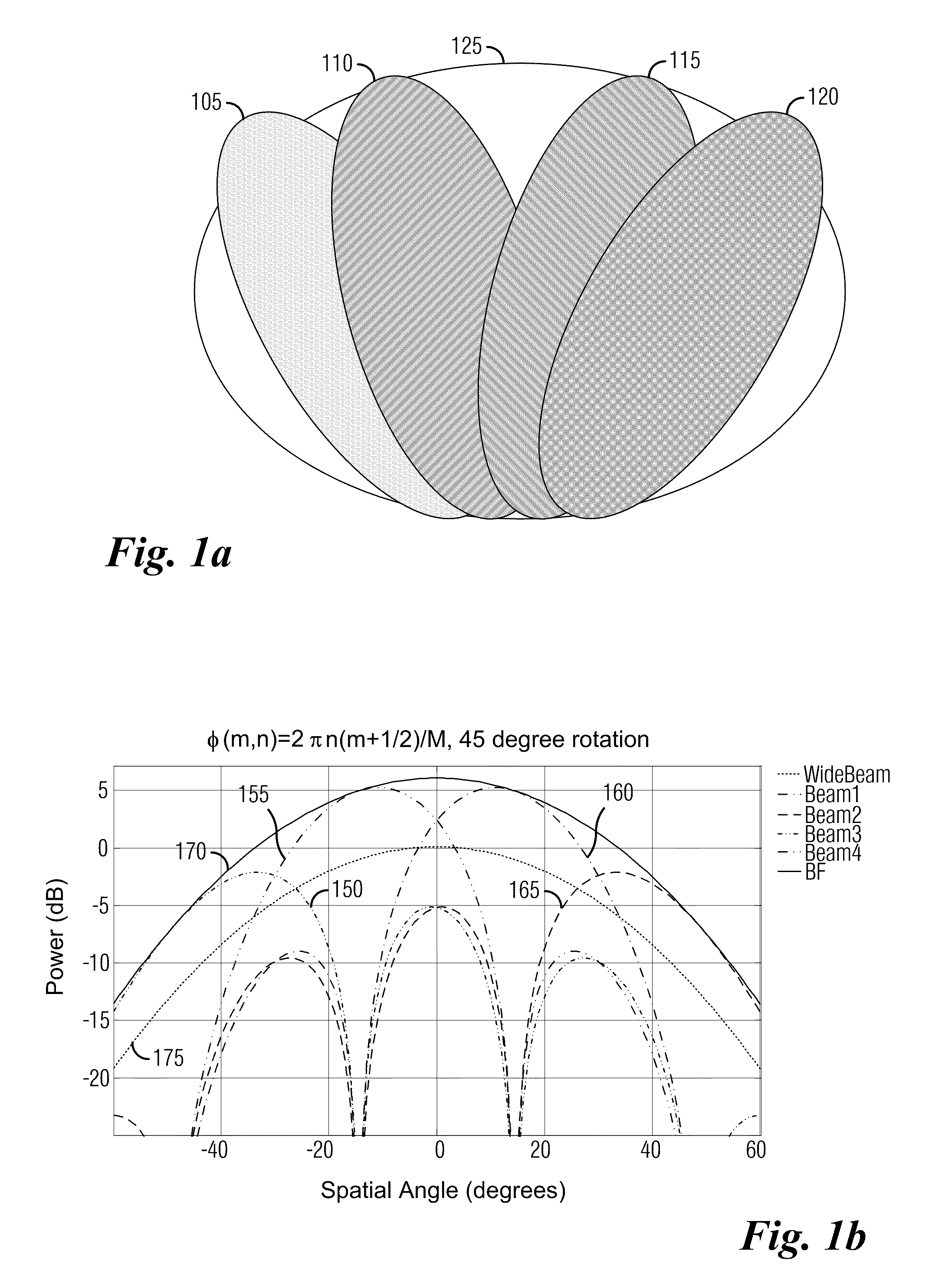
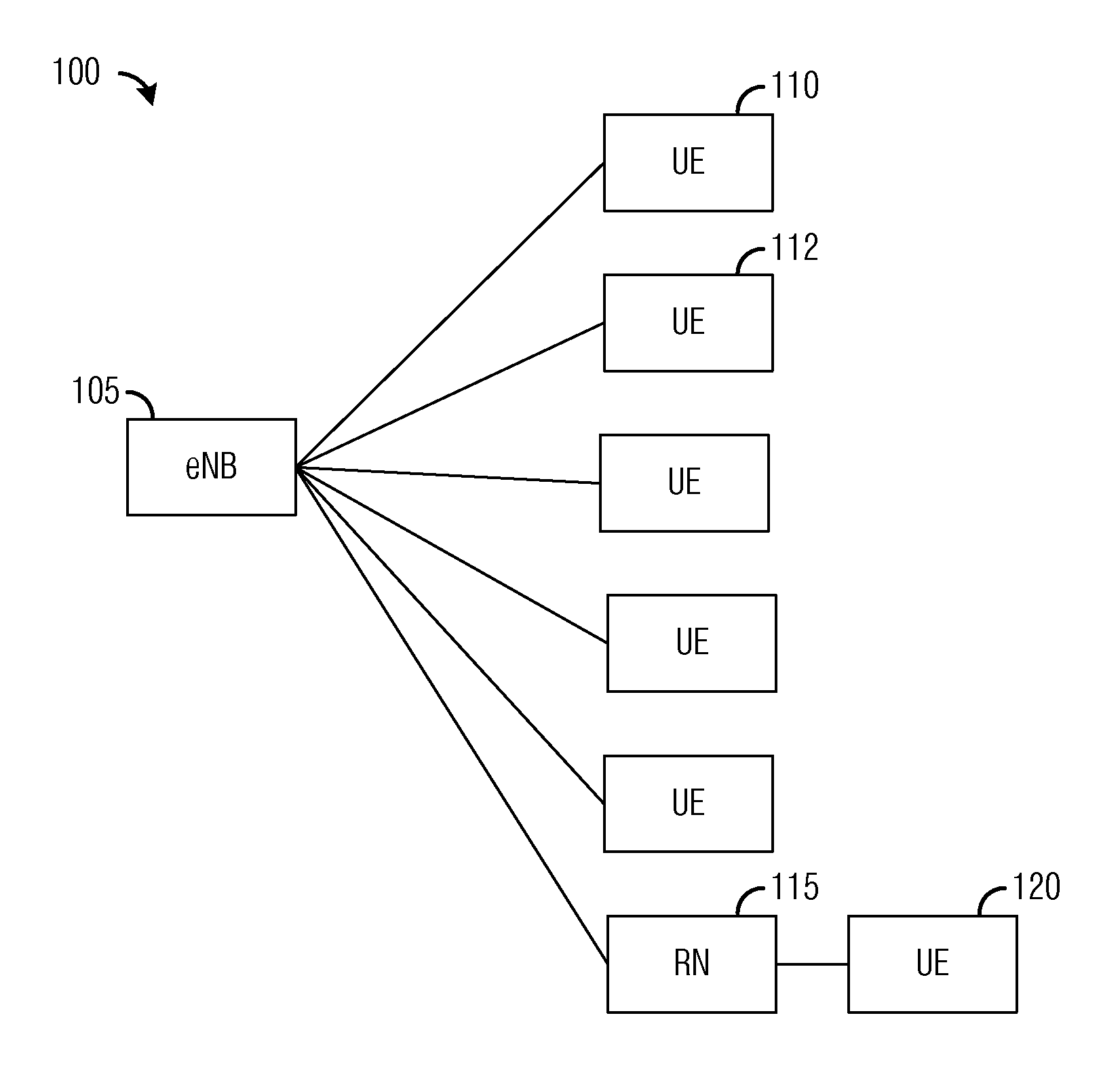
System and Method for Enabling Coordinated Beam Switching and Scheduling
ActiveUS20100075705A1Reduce computational overheadReduce communication overheadSite diversitySubstation equipmentCommunications systemBeam pattern
A system and method for enabling coordinated beam switching and scheduling in a wireless communications system. A method for controller operation includes indicating that the controller is operating in a cooperative beam switching mode, transmitting a beam formed reference signal (BFRS), from each communications device being served by the controller, receiving a measurement of a communications channel between the controller and the communications device and an indicator indicating a transmission unit corresponding to the measurement of the communications channel, receiving a transmission intended for a communications device, and causing the transmission to be transmitted to the communications device. The BFRS is beam formed using a plurality of beam patterns, the beam pattern used in beam forming the BFRS changes once per transmission unit, and the transmission is transmitted using measurement of the communications channel and the indicator from the communications device.
Owner:FUTUREWEI TECH INC
Sensor network system for acquiring high quality speech signals and communication method therefor
InactiveUS8600443B2Reduce network trafficData efficientMicrophonesInterconnection arrangementsComputer scienceSignal source
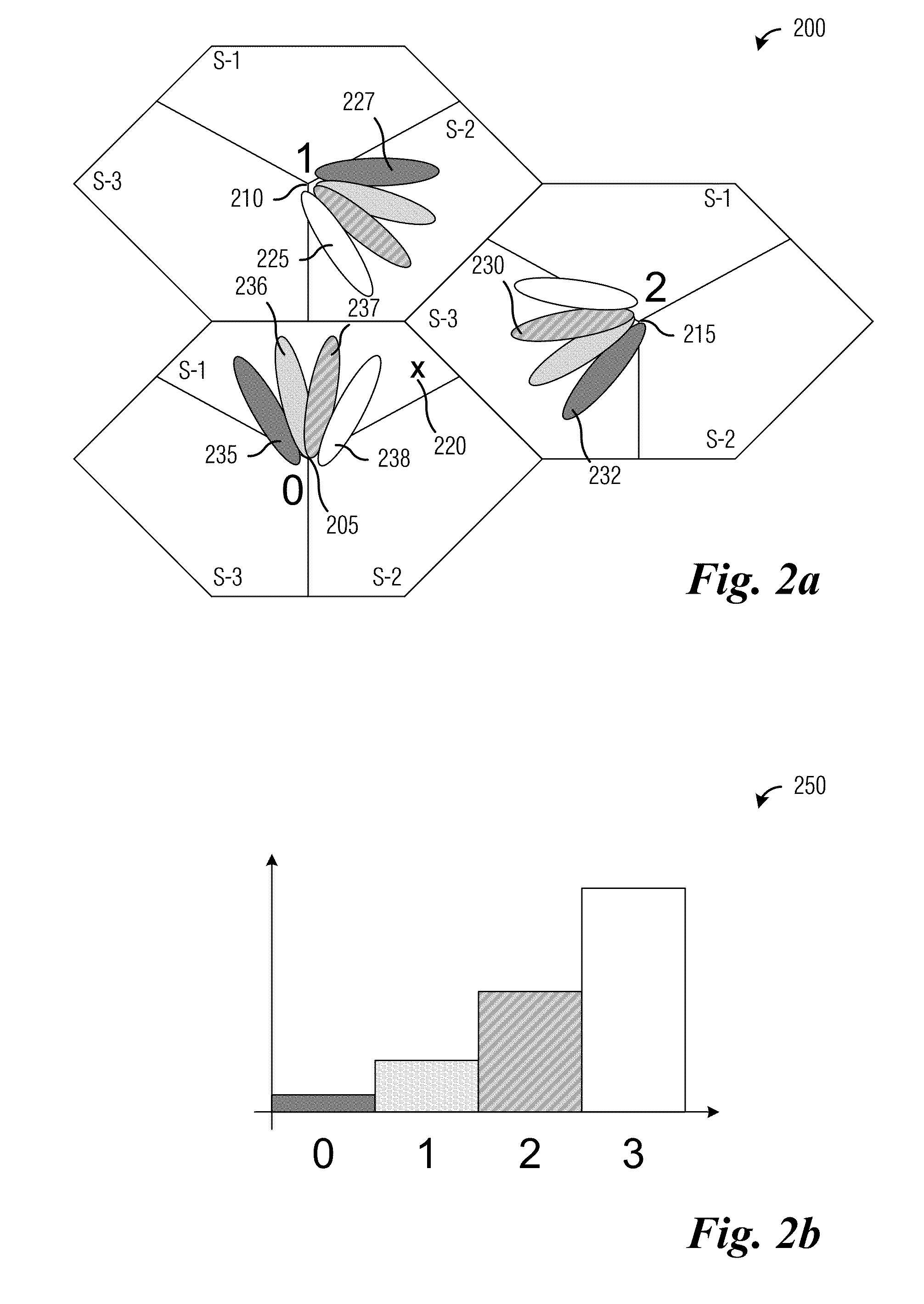
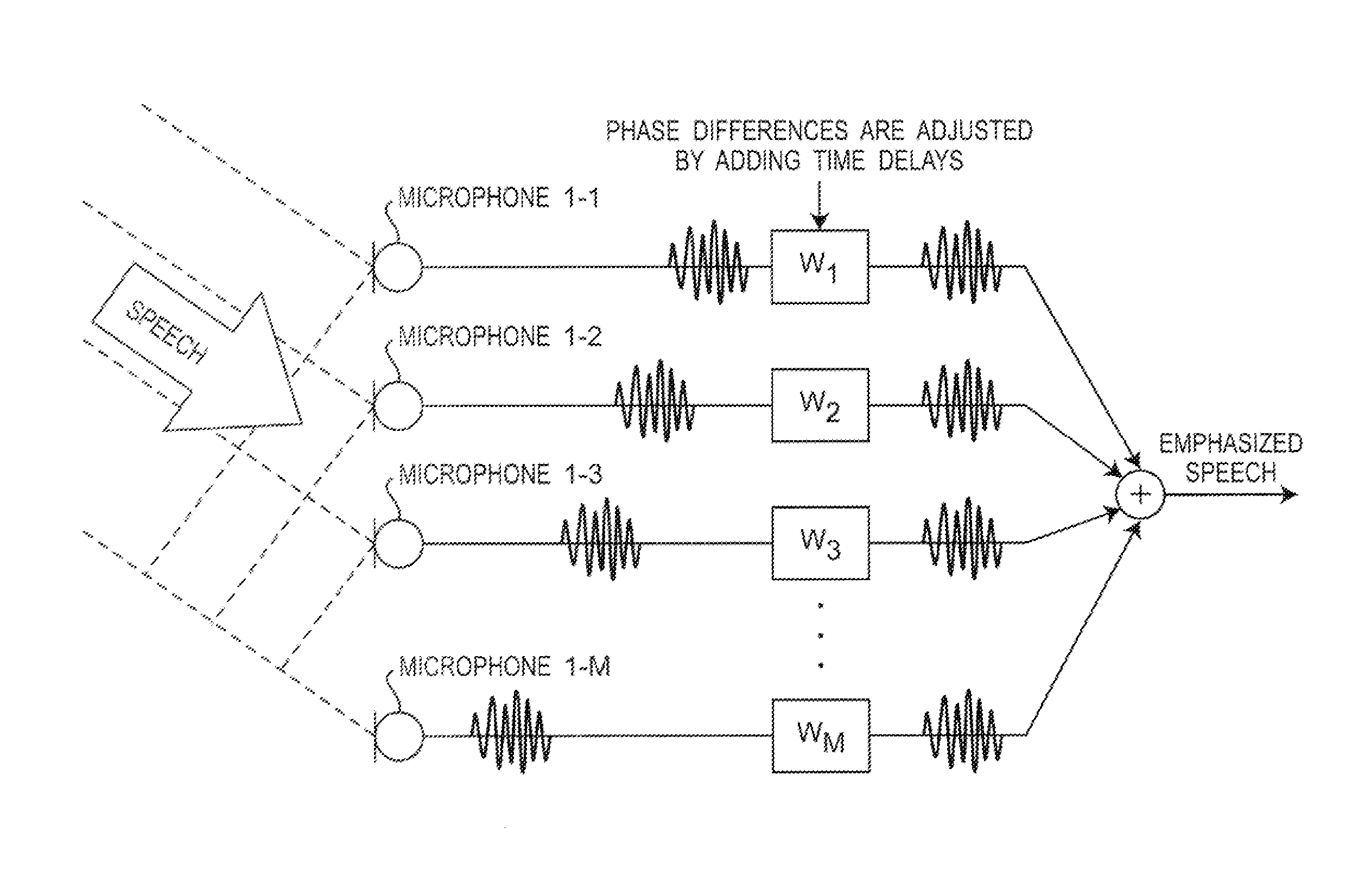
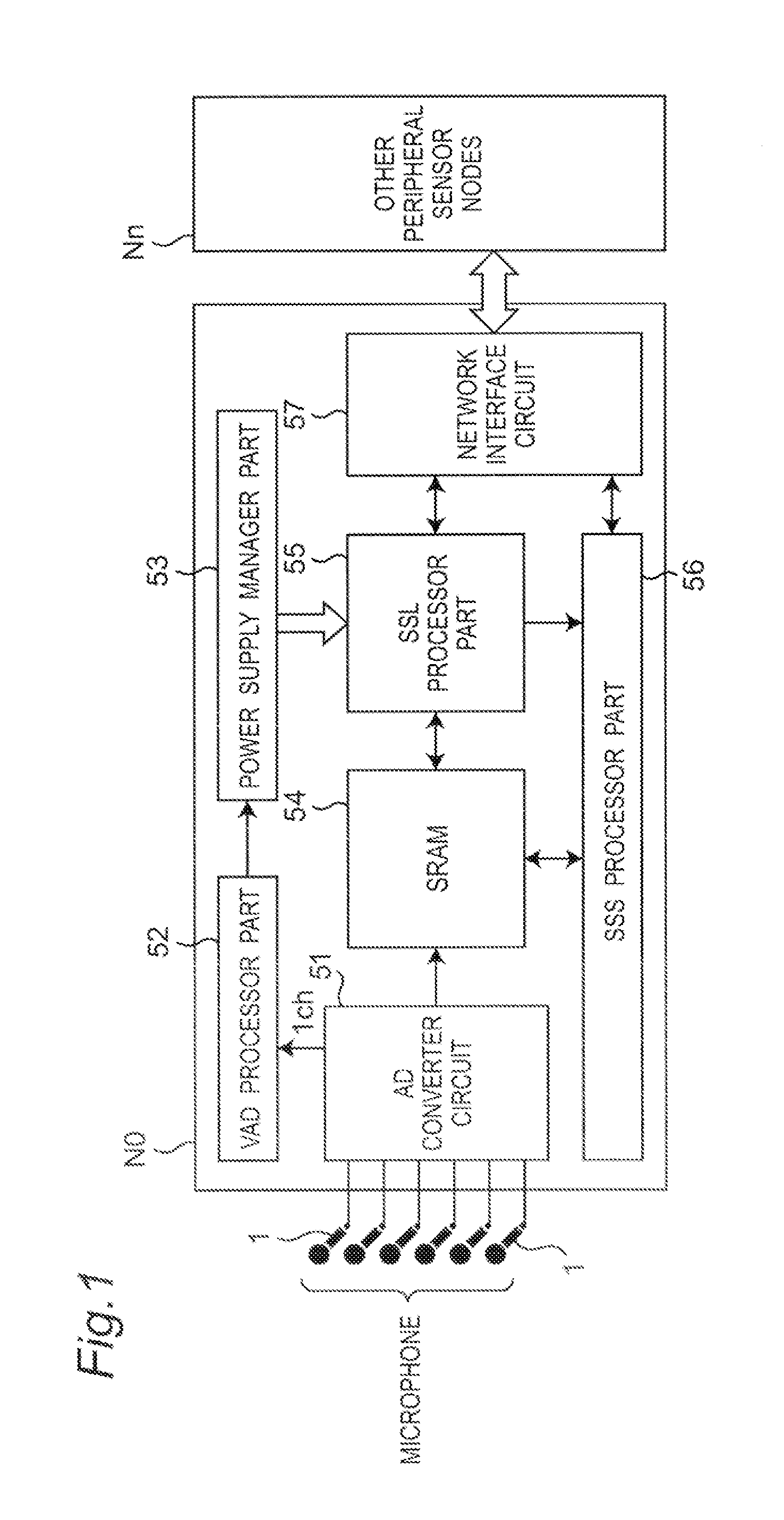
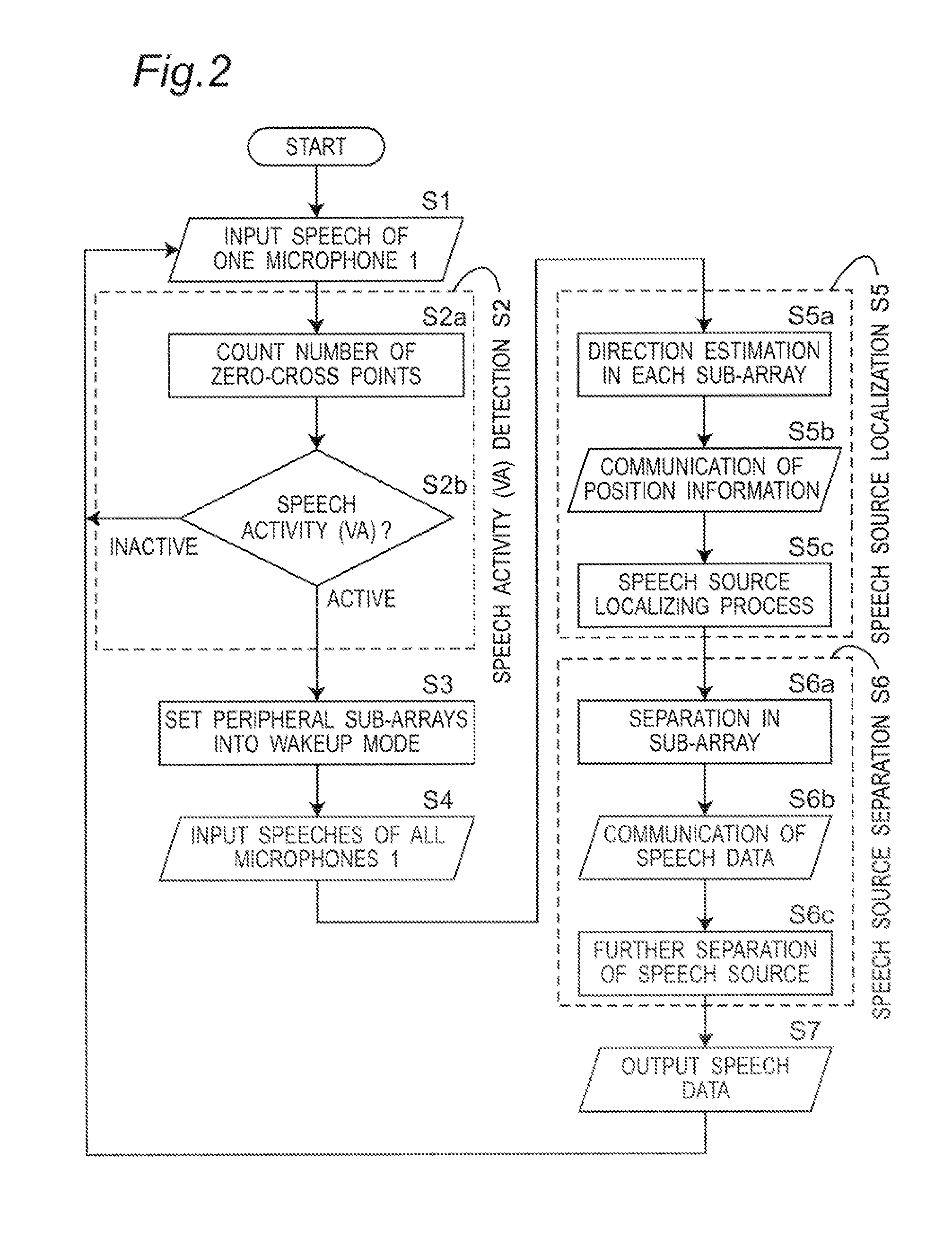
A sensor network system including node devices connected in a network via predetermined propagation paths collects data measured at each node device to be aggregated into one base station via a time-synchronized sensor network system. The base station calculates a position of the signal source based on the angle estimation value of the signal from each node device and position information thereof, designates a node device located nearest to the signal source as a cluster head node device, and transmits information of the position of the signal source and the designated cluster head node device to each node device, to cluster each node device located within the number of hops from the cluster head node device as a node device belonging to each cluster. Each node device performs an emphasizing process on the received signal from the signal source, and transmits an emphasized signal to the base station.
Owner:SEMICON TECH ACADEMIC RES CENT
System and Method for Transmission and Reception of Control Channels
ActiveUS20120250642A1Increase the number ofReduce communication overheadAssess restrictionWireless commuication servicesControl channelCommunication control
A method for transmitting control information to a wireless node includes determining, by a communications controller, a first resource assignment parameter according to a pseudo-random sequence derived from an identifier, and mapping, by the communications controller, using the first resource assignment parameter, a demodulation reference signal associated with the wireless node onto a first resource located in a data region of a subframe. The method also includes mapping, by the communications controller, modulated control information associated with the wireless node onto a second resource located in the data region of the subframe, and transmitting, by the communications controller, the subframe to the wireless node.
Owner:FUTUREWEI TECH INC
Method and system for parallelizing database requests
ActiveUS20110202929A1Reduce communication overheadReduced response timeDigital data information retrievalMultiprogramming arrangementsClient-sideSingle process
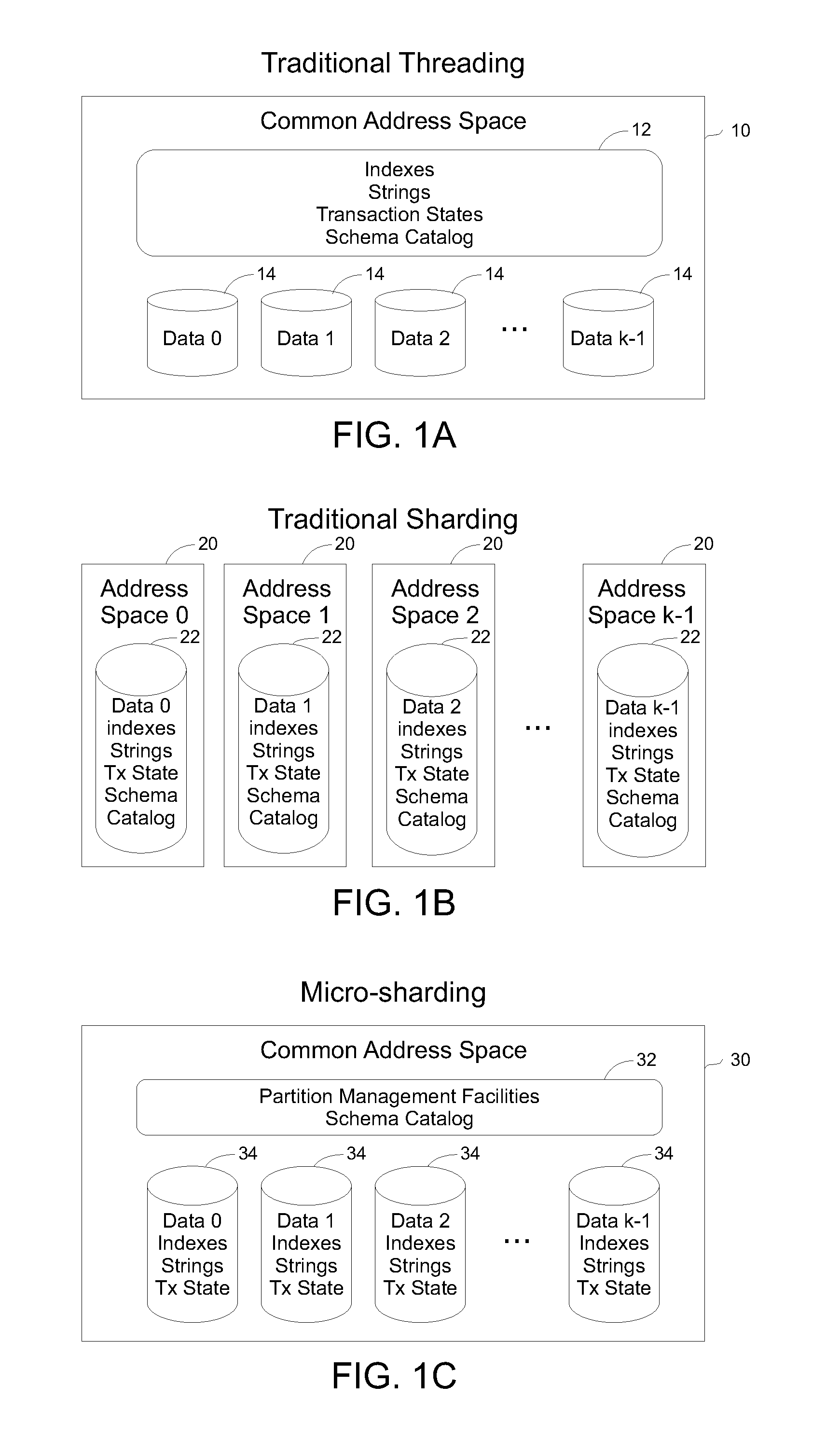
Methods and systems are described for applying the use of shards within a single memory address space. A database request is processed by providing the request from a client to a processor, the processor then distributing the request to multiple threads within a single process but executing in a shared memory address environment, wherein each thread performs the request on a distinct shard, and aggregating the results of the multiple threads being aggregated and returning a final result to the client. By parallelizing operations in this way, the request response time can be reduced and the total amount of communication overhead can be reduced.
Owner:ORACLE INT CORP
Method and system for distributed calculating and enquiring magnanimity data in on-line analysis processing
InactiveCN101183368ASave storage spaceSmall returned resultSpecial data processing applicationsData setCluster systems
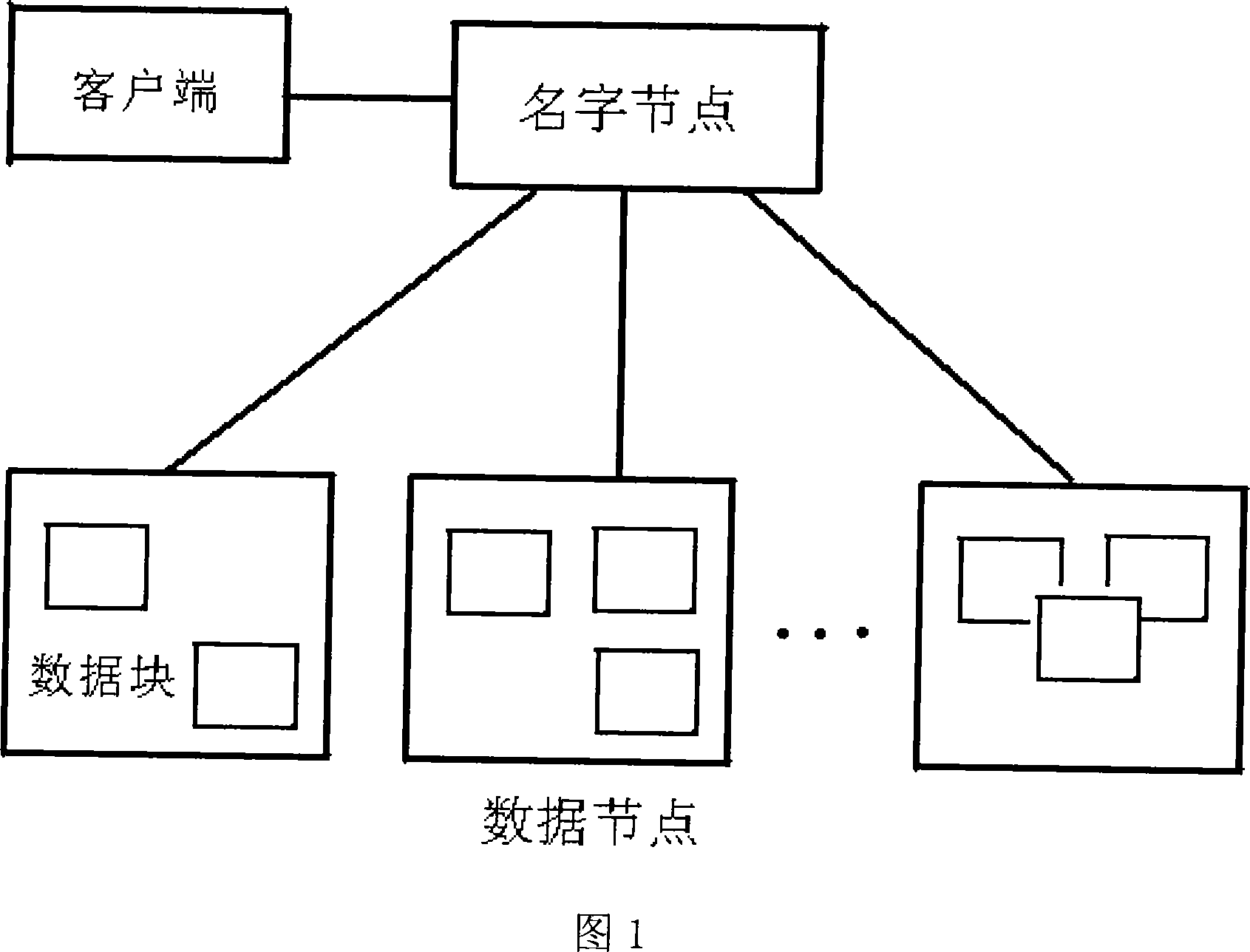
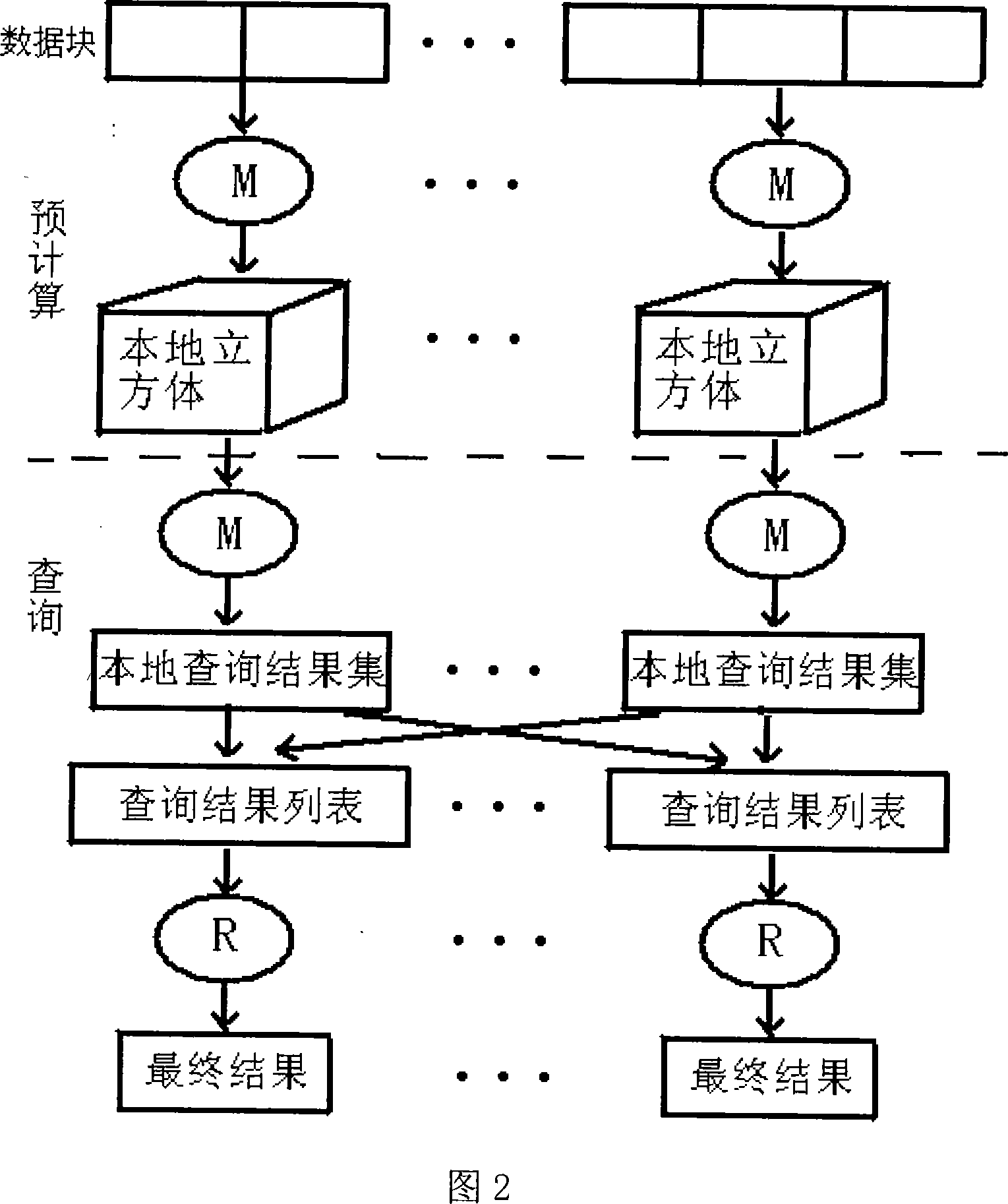
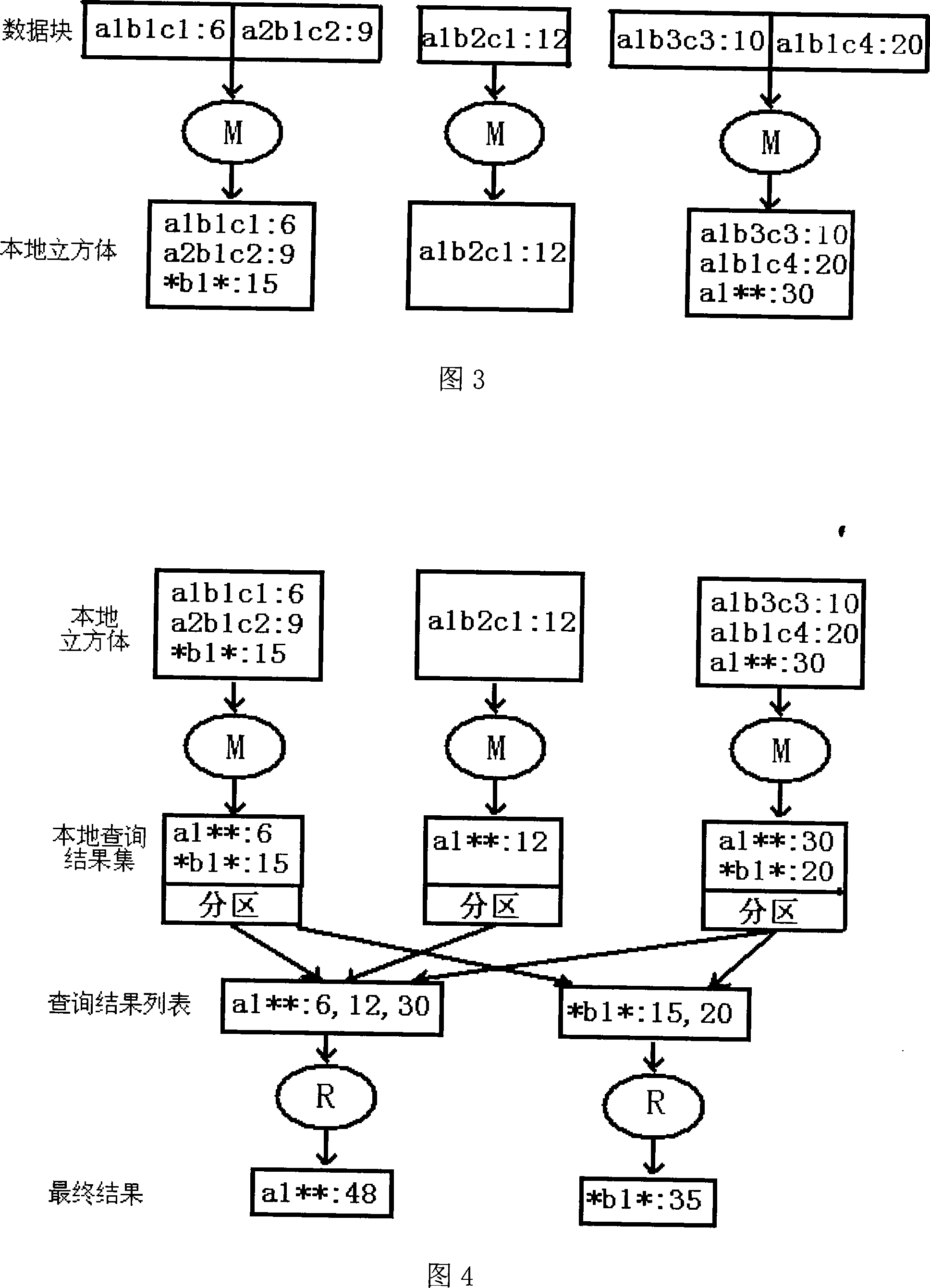
The invention discloses a method and system for distributed computing and querying massive data in online analysis and processing. The method uses a cluster system to perform distributed pre-calculation and querying on data cubes. Based on the MapReduce framework, the present invention divides large-capacity data sets into blocks and distributes them to each node through MapReduce, then the Map task on the node calculates a corresponding local closed cube for each data block, and finally starts the Map task on different nodes Parallel query is performed on each local closed cube, and the Reduce task merges the metric values obtained from the query. The present invention can simply and effectively perform pre-calculation and query on-line analysis and processing of large-capacity data, greatly compress the storage space of the data cube, and can quickly respond to user queries.
Owner:SOUTH CHINA UNIV OF TECH
Telecommunication and computing platforms with serial packet switched integrated memory access technology
ActiveUS20080052436A1Efficiently provide packet-based serial self-clocked communicationReduce communication overheadMultiplex system selection arrangementsTime-division multiplexTraffic congestionAccess technology
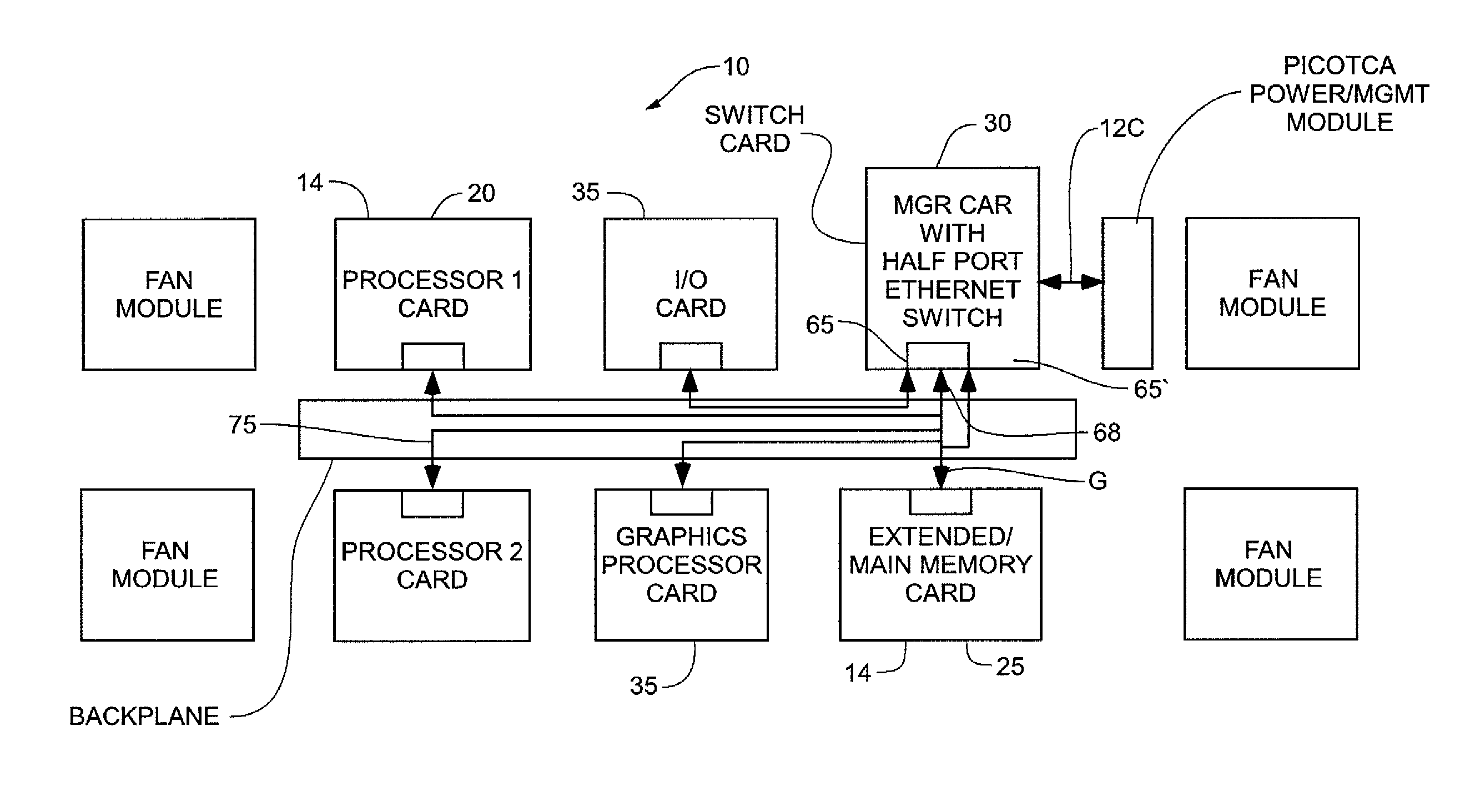
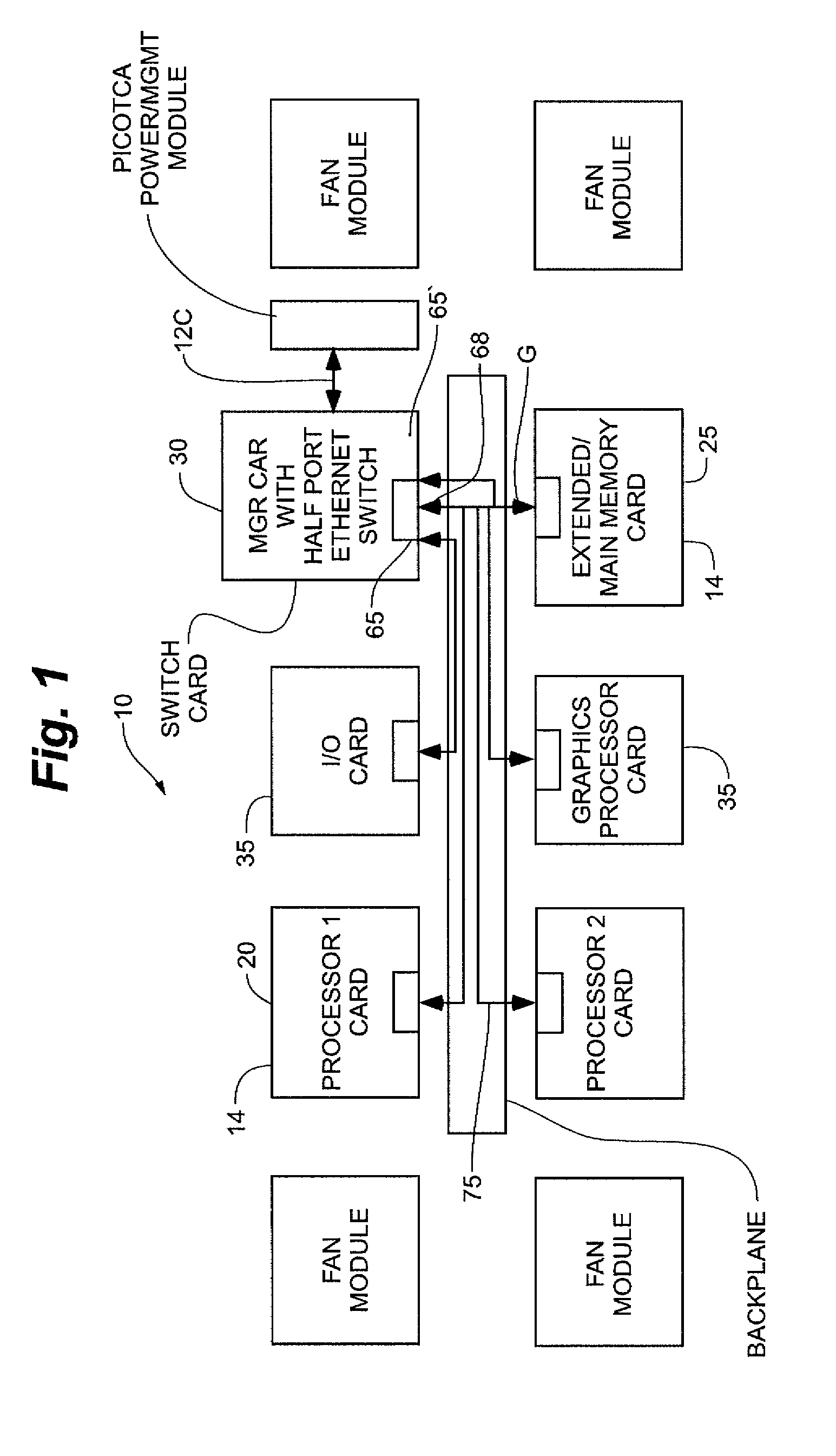
A computing and communication architecture utilizes a serial protocol based switched fabric among circuit cards housed in packaging arrangement. In one embodiment, each circuit card connected to the serial protocol based switched fabric in the packaging arrangement is provided with a protocol processor that enables all of the circuit cards to efficiently provide packet-based serial self-clocked communications at line speed. As a result, it is not necessary to arrange the circuit cards in a hierarchical manner in order to address the problems of switch blocking and related traffic congestion issues that would otherwise limit the implementation of the serial protocol based backplane arrangement for housing circuit cards.
Owner:KIRITIN INC
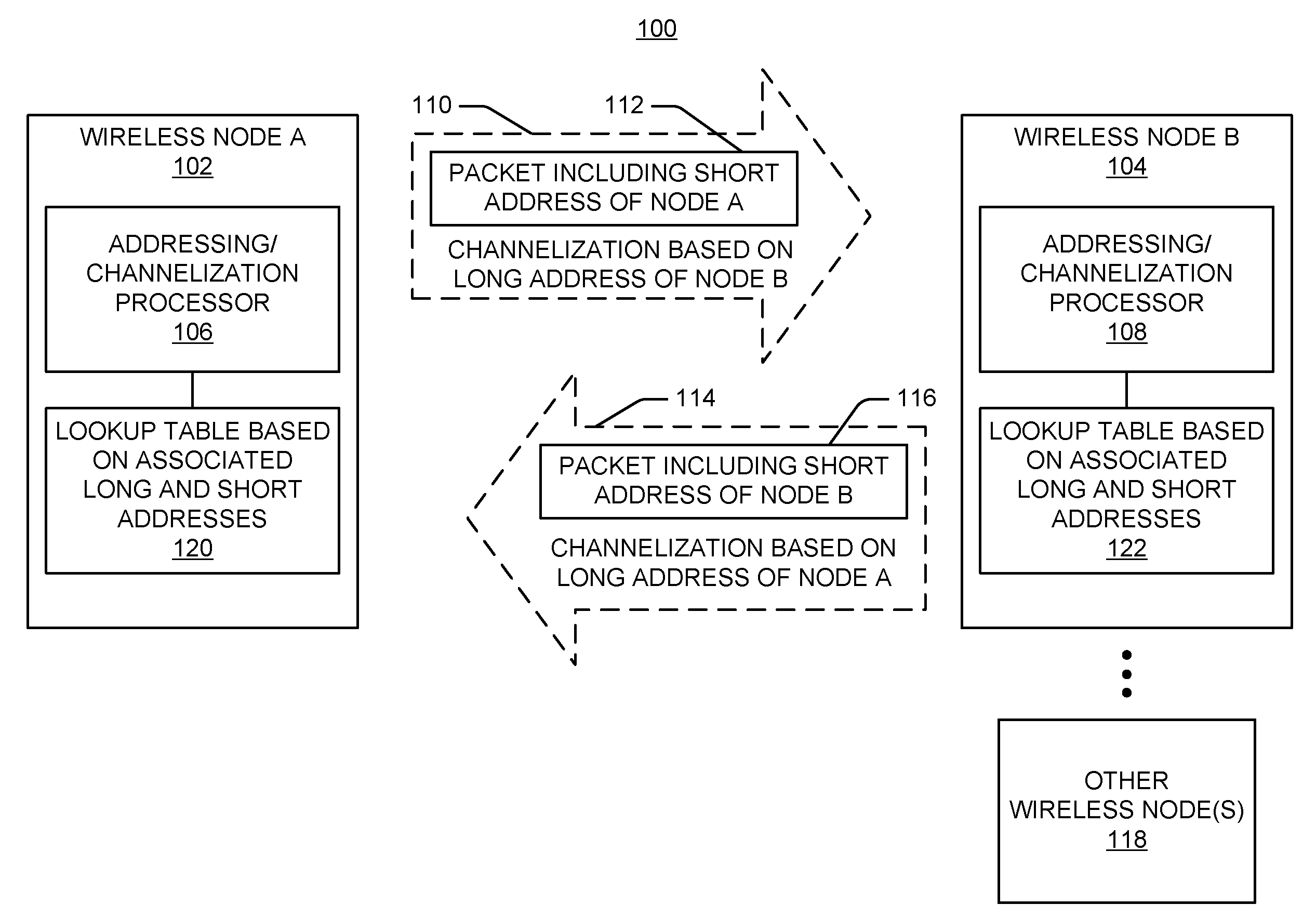
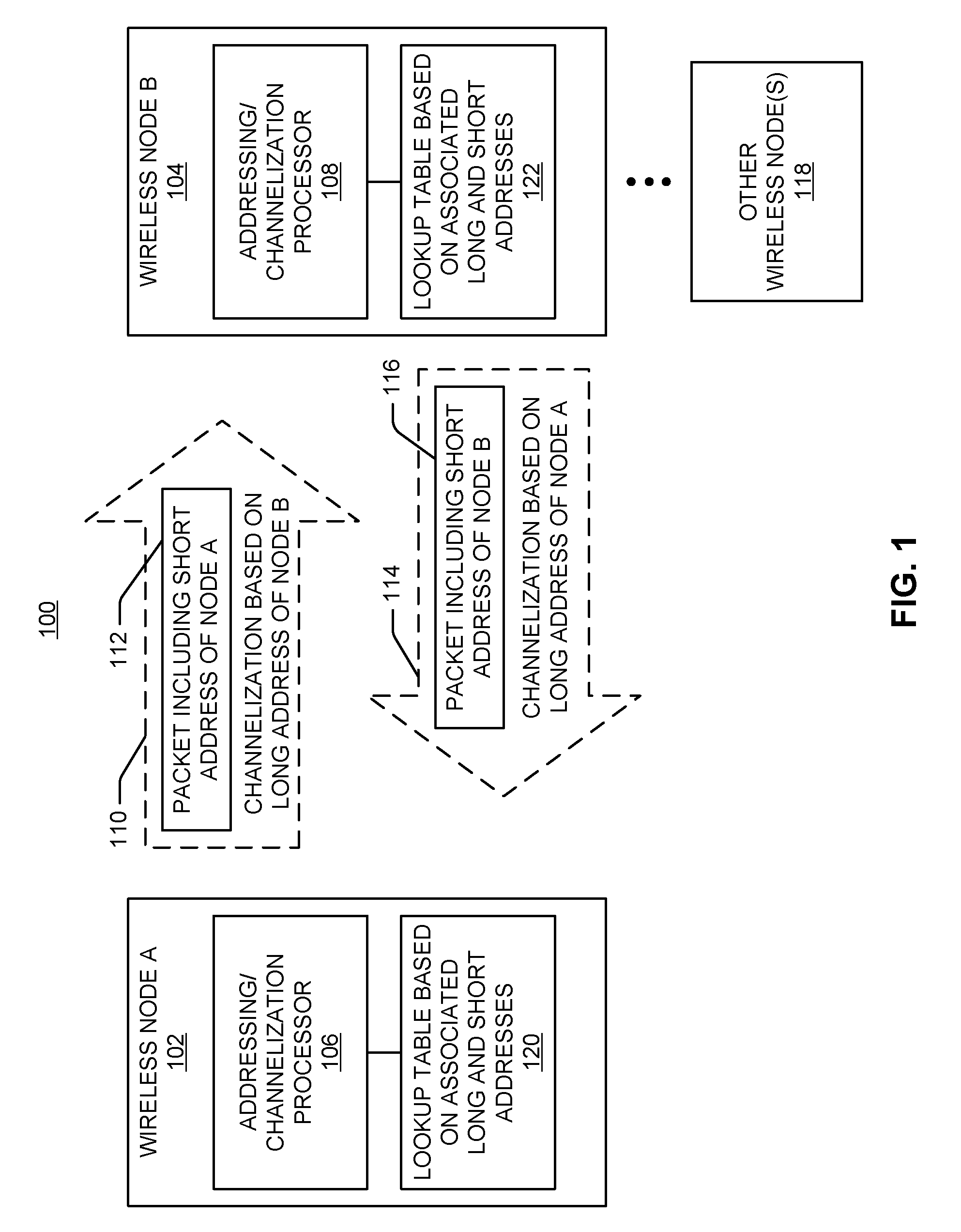
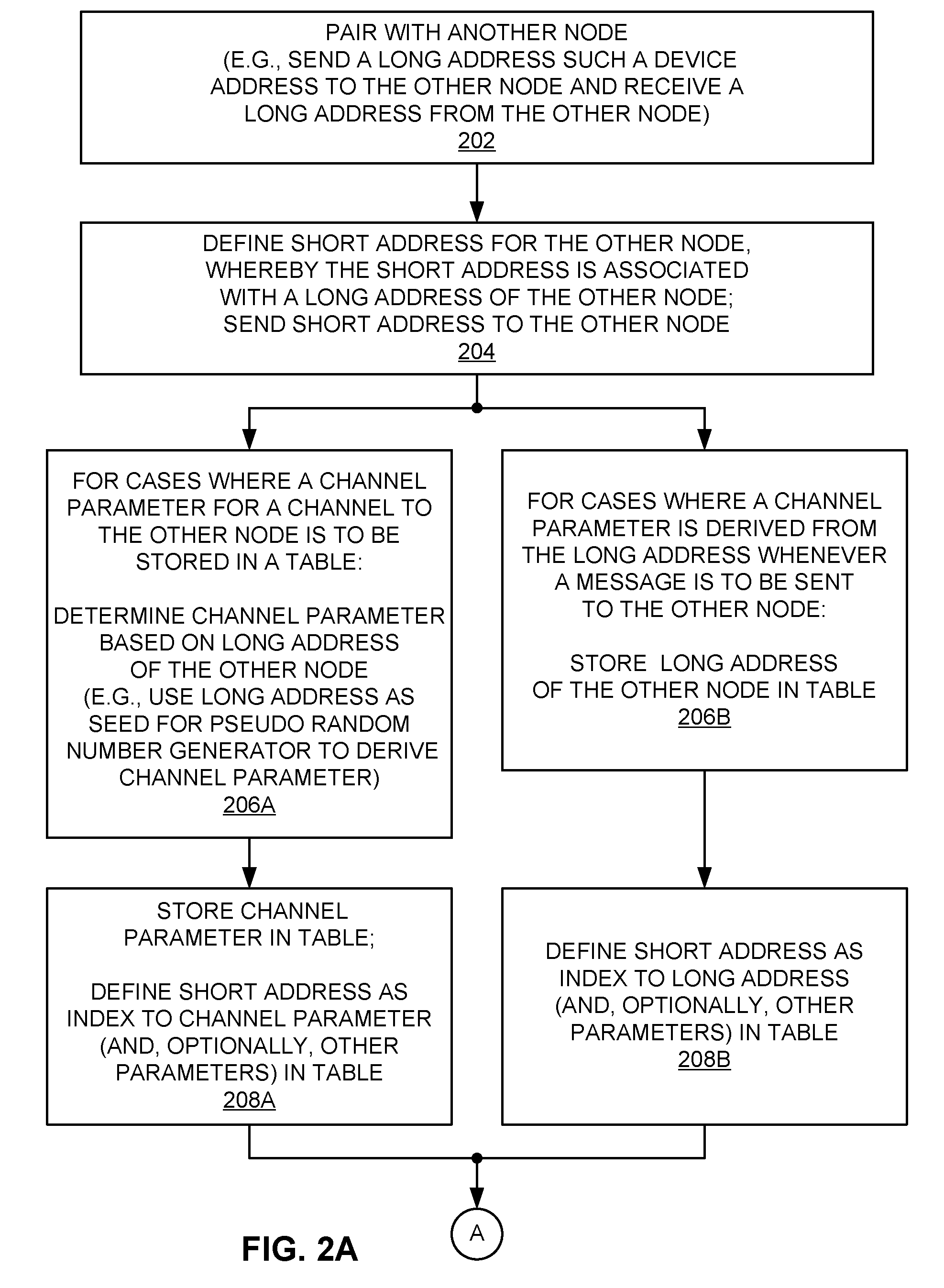
Addressing schemes for wireless communication
ActiveUS20100046443A1Reduce communication overheadMechanical clocksNetwork topologiesWireless communication systemsUnique identifier
In an addressing scheme for wireless communication a communication channel may be defined based on a unique identifier associated with a destination node or a source node. In addition, a short identifier may be included in messages sent over the communication channel such that a node may uniquely identify the source node or destination node for the message. A node may use a short identifier as an index into a lookup table to determine one or more parameters to be used for communicating with another node.
Owner:QUALCOMM INC
Wireless sensing network node positioning method based on optimal beacon set
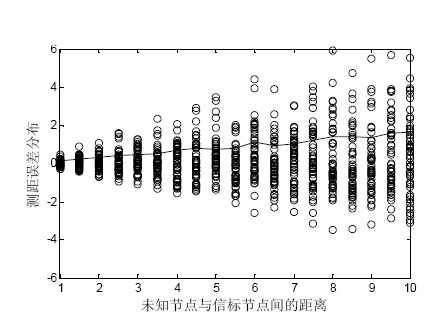
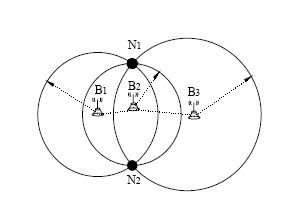
ActiveCN101965052AReduce complexityReduce communication overheadNetwork topologiesTransmission monitoringLow complexityWireless sensor networking
The invention relates to a wireless sensing network node positioning method based on an optimal beacon set, which comprises the following steps of: 1, establishing a wireless sensor network comprising beacon nodes assisting for positioning and a target node to be positioned; 2, when an unknown node moves, updating the position of the unknown node and sending a positioning request packet, and whenthe beacon nodes receive the positioning request packet, sending an information packet comprising the node and the position coordinates; 3, after the unknown node receives the information packet of the beacon nodes, sequencing the beacon nodes from big to small according to an RSSI value, and establishing the mapping of a distance from the RSSI and the unknown node to the beacon node; 4, selecting four nodes nearest the unknown node from the beacon node set, wherein each three beacon nodes form a set of beacon set, and one set with minimum collinearity is the optimal beacon set; and 5, obtaining the initial position of the unknown node by adopting a maximum likelihood method. The invention has the advantages of low complexity of algorithm, little communication overhead among the nodes andhigh positioning precision.
Owner:ZHEJIANG UNIV OF TECH
High-efficiency difference disturbance location privacy protection system and method
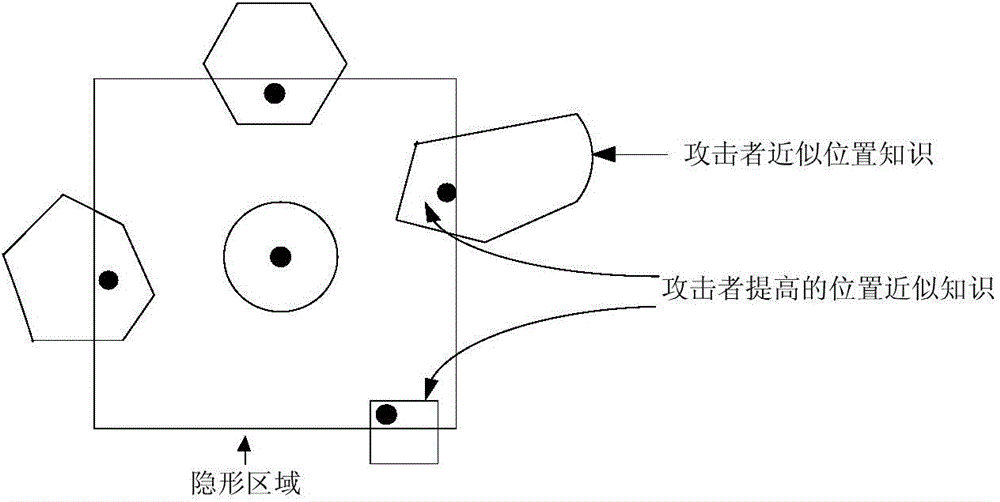
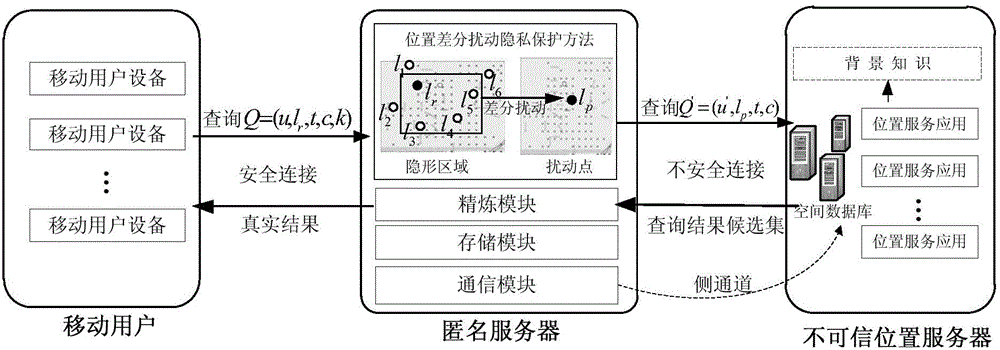
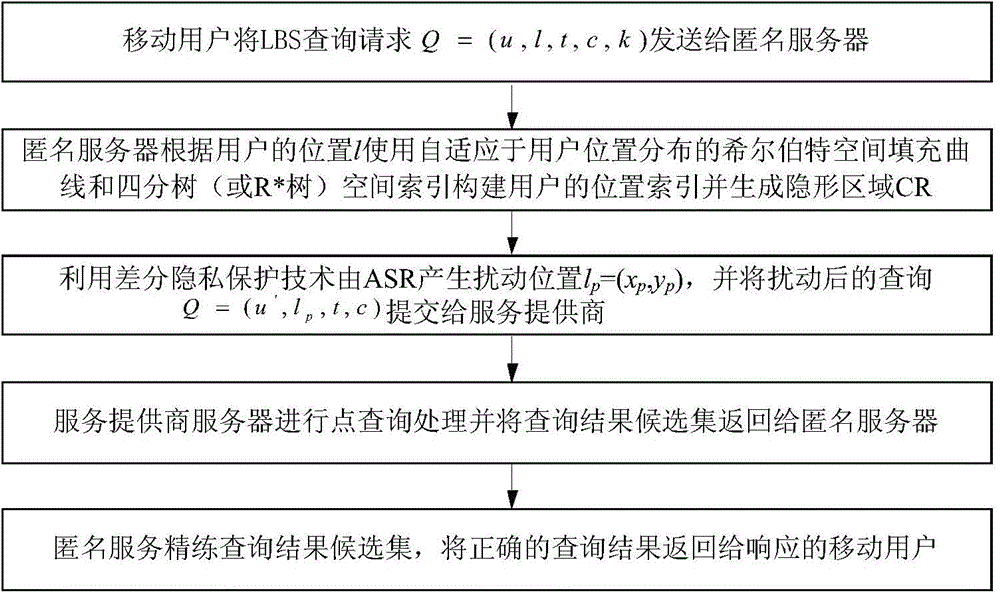
ActiveCN104394509AGenerate efficientlyGuaranteed correctnessTransmissionLocation information based serviceK-anonymitySide information
The invention discloses a high-efficiency difference disturbance location privacy protection system and a method, considering that the attacker has the challenge to the location privacy protection method based on the location disturbance and fuzzy technology about the background knowledge of the user side information, the difference privacy protection technology is guided to the location fuzzy privacy protection method, the Hilbert space filling curve capable of self-adaption transition on the user location according to the distributed change features in the geographic space of the mobile user and the current fashionable quadtree or R tree spatial index are used for forming the location index for all mobile users in the geographic space, and the K anonymity contact area satisfying the principle of reciprocity is effectively generated. Then, the difference privacy protection technology is used for generating the location disturbance point reasonable near user real location of k location points of the contact area as the query location of LBS user for requesting service from the LBS service provider, the problems and deficiencies of the existing method can be overcome.
Owner:XI AN JIAOTONG UNIV
Method for distributing and routing optimal services of multi-layer satellite network based on minimum time delay
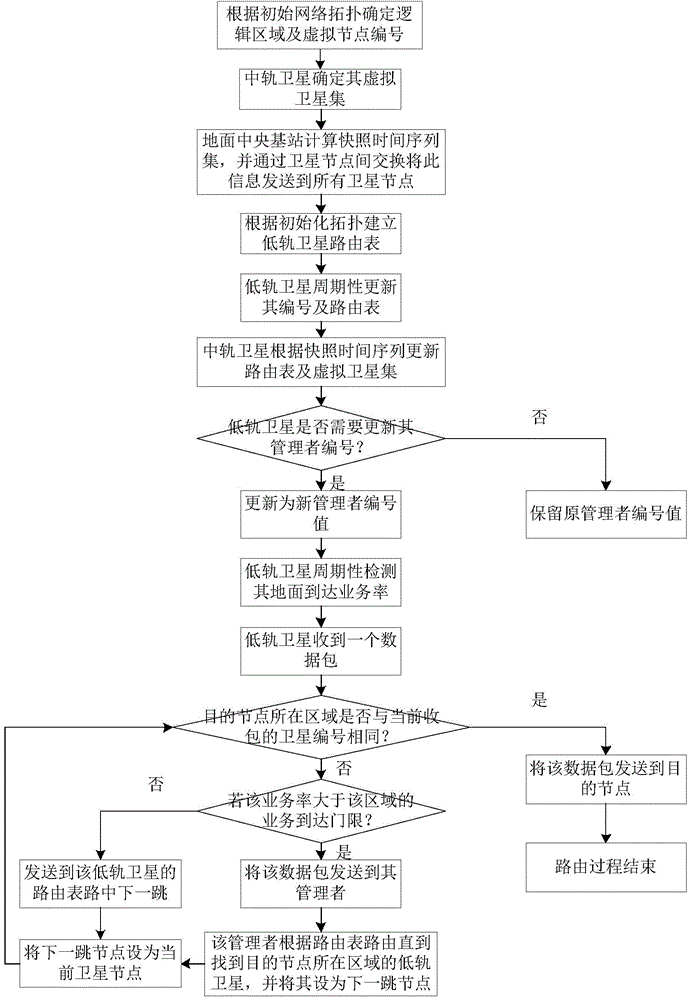
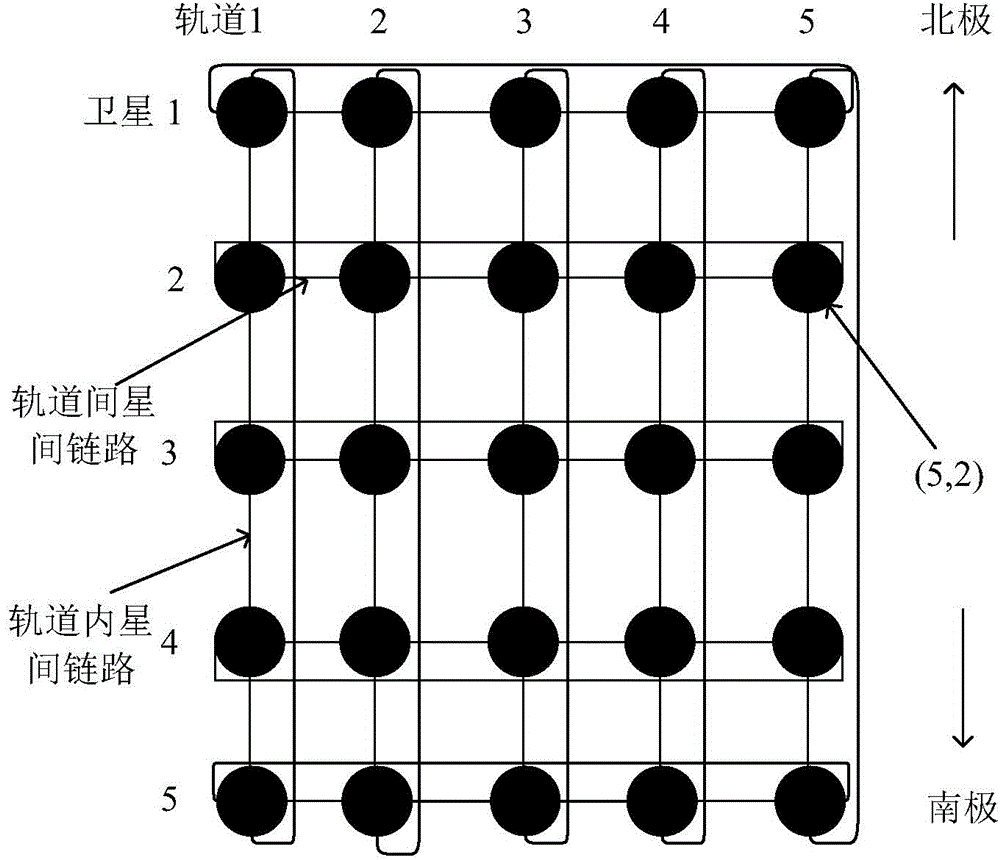
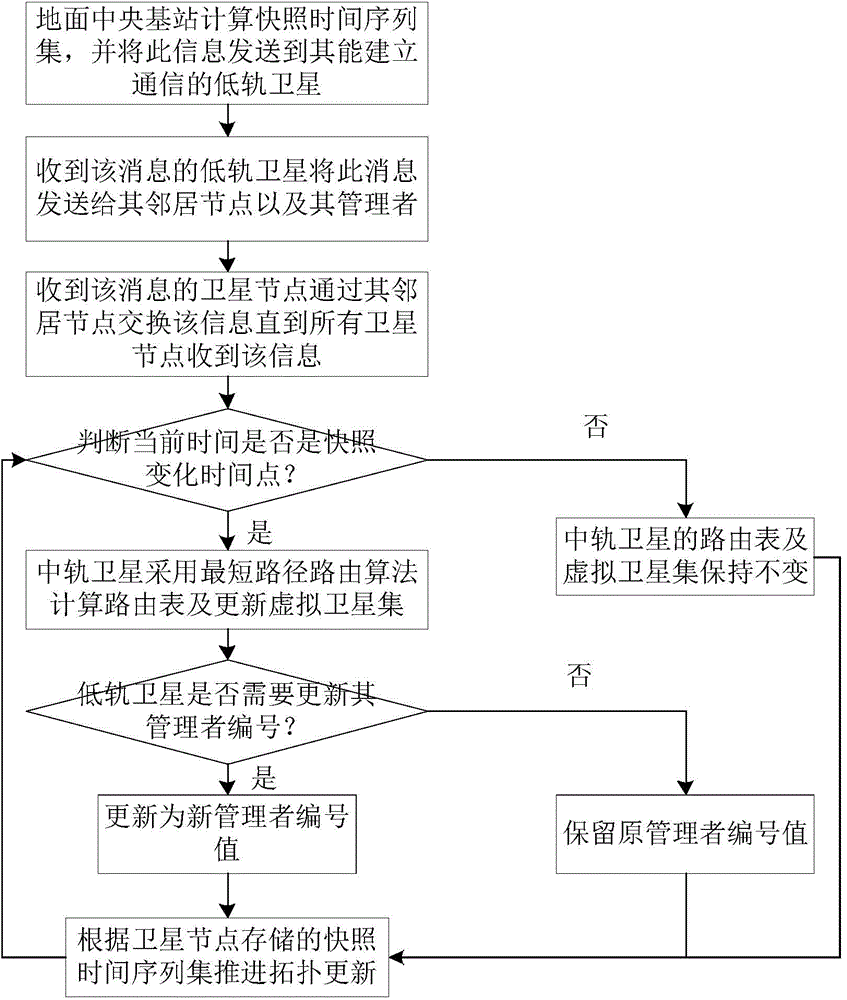
ActiveCN104683016ASolve congestionImprove throughputRadio transmissionData switching networksMinimum timeLow earth orbit
The invention discloses a method for distributing and routing optimal services of multi-layer satellite network based on minimum time delay, and aims to solve the problems of large end-to-end time delay, low handling capacity and insufficient utilization of network resource of a multi-layer satellite communication network routing method. The method comprises the following steps: determining a logic area, a virtual node number and a low-earth-orbit satellite routing list according to the initial network topology; periodically updating the node number and the routing list by a low earth orbit; updating a virtual satellite set and a member routing list according to the snapshot time sequence set by a medium earth orbit, and synchronously updating the number of an administrator by the low earth orbit; if the services arrive and the arrival rate of the current satellite area is less than the arrival rate threshold of the ground service supported by the area based on the minimum end-to-end time, transmitting the service in the low earth orbit, and otherwise, transferring the service to a high-level satellite to route, and finally sending a target node. With the adoption of the method, the performance of the multi-layer satellite communication network is improved; the method can be applied to the routing of the multi-layer satellite communication network.
Owner:XIDIAN UNIV
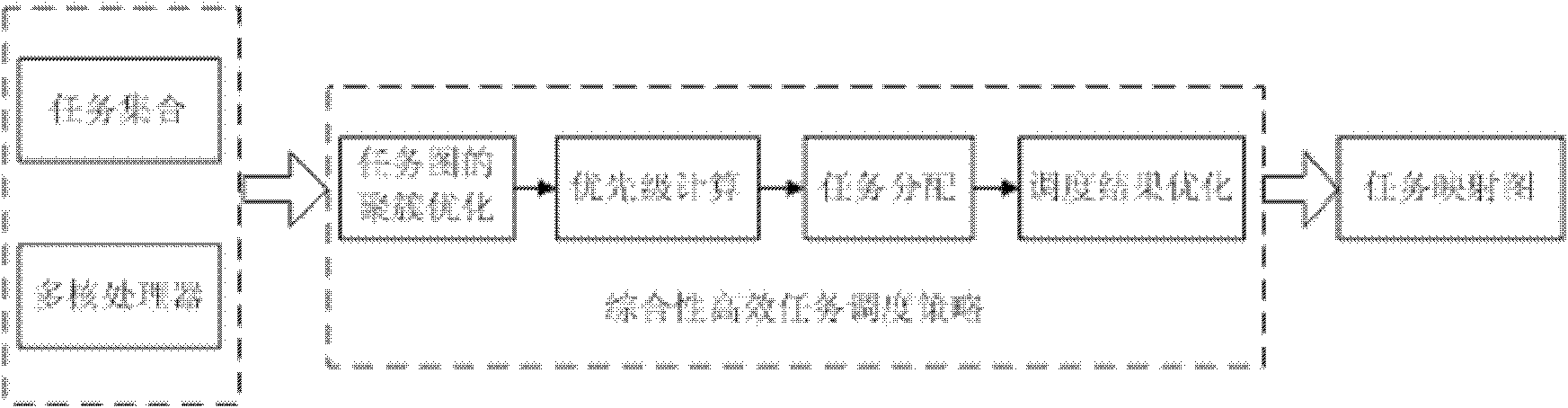
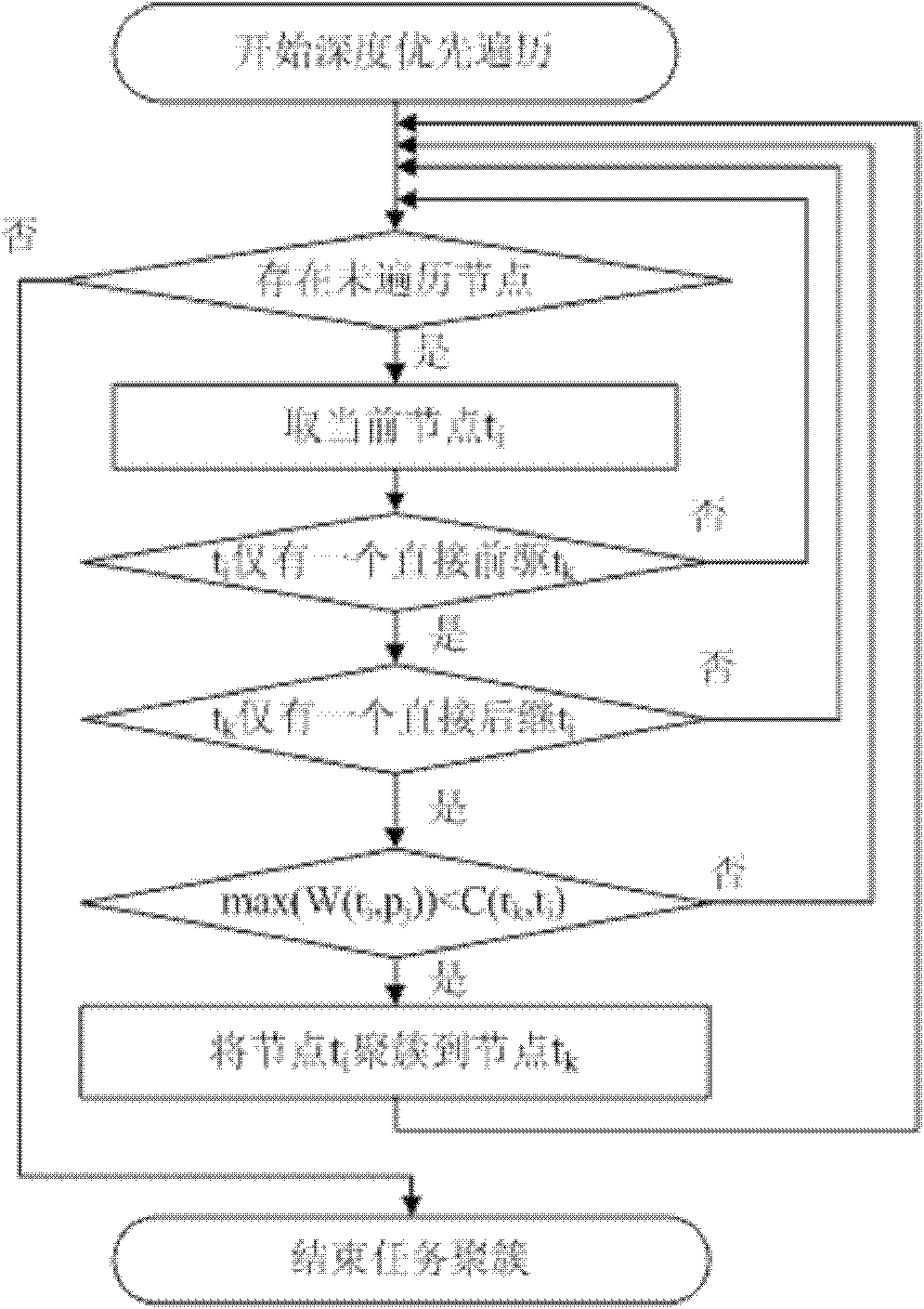
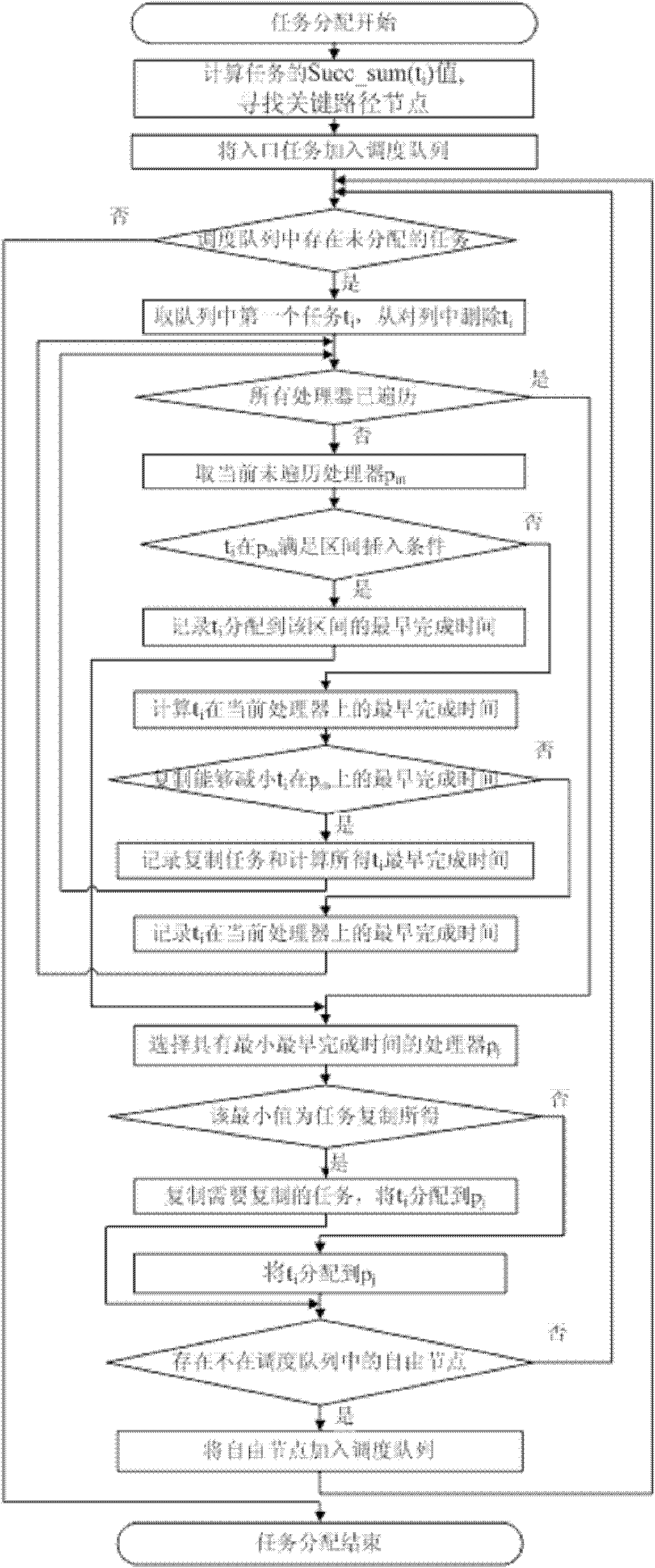
Method for high-efficiency task scheduling of heterogeneous multi-core processor
InactiveCN102193826ARaise priorityOptimize calculation resultsEnergy efficient ICTResource allocationEarliest finish timeCritical path method
The invention provides a method for high-efficiency task scheduling of a heterogeneous multi-core processor. The method comprises the following steps of: clustering certain special tasks which are large in communication overhead and easy to cluster in a task image to a precursor node of the tasks by adopting a linear task clustering method; starting from a topological structure of the whole task image, selecting parameters capable of comprehensively reflecting the importance of the task in the whole task image as priority weights; selecting a free critical path node to perform allocation first, and if multiple free critical path nodes exist, allocating the free critical path nodes in a sequence from high to low according to the node priority weights, and allocating all non-critical path free nodes in a sequence from high to low according to the priority weights; performing redundancy judgment, and deleting redundant tasks in a scheduling result; and performing adjustment according to the scheduling result after deleting the redundant tasks, and recalculating the earliest finish time of each task. According to the method, the efficiency of the task scheduling of the heterogeneous multi-core processor is improved, the power consumption of the processor is reduced, and the performance of the multi-core processor is promoted.
Owner:HARBIN ENG UNIV
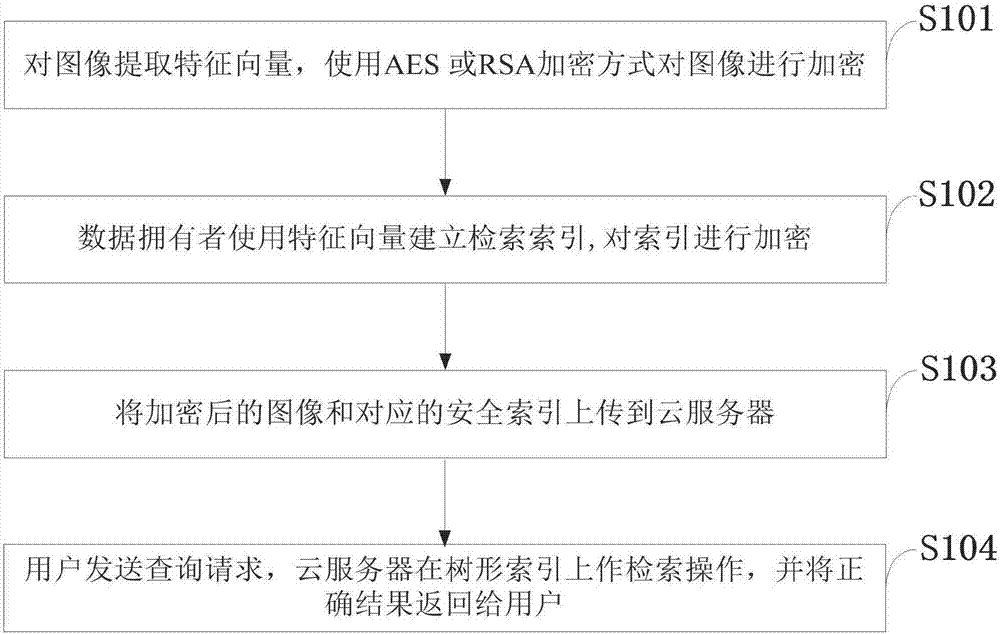
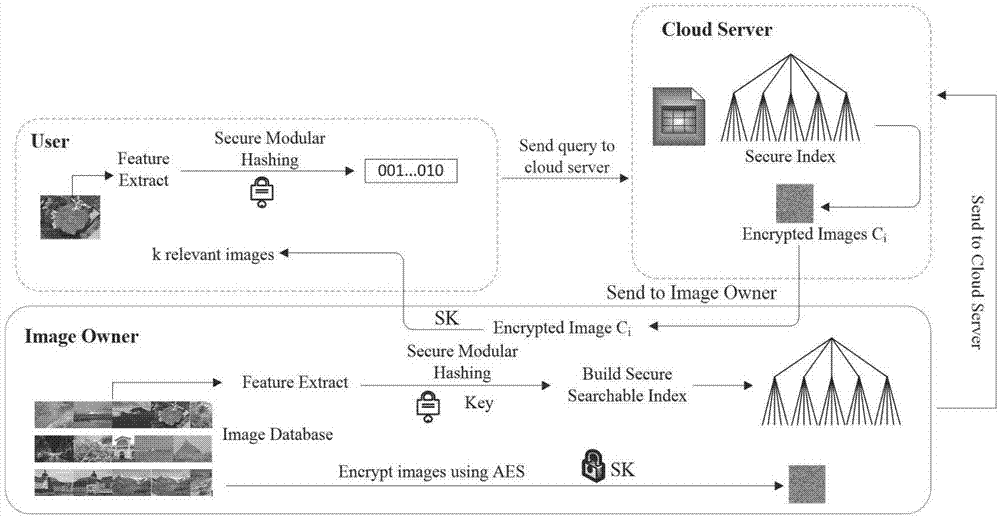
Efficient cryptograph image retrieval method capable of supporting privacy protection under cloud environment
ActiveCN107480163AGuaranteed privacyReduce computational overheadImage data processing detailsTransmissionImage extractionPlaintext
The invention belongs to the technical field of image retrieval and discloses an efficient cryptograph image retrieval method capable of supporting privacy protection under a cloud environment. The efficient cryptograph image retrieval method capable of supporting the privacy protection under the cloud environment comprises the steps that an image owner firstly extracts characteristic vectors of an image in a database and encrypts the image by an AES or RSA encryption manner; the owner establishes indexes using a hierarchical K-means algorithm based on the characteristic vectors and uses a safe mode Hash technology to encrypt the indexes; and the encrypted image and indexes are uploaded to a cloud server, and a retrieval operation is executed. According to the invention, the privacy protection of the cryptograph image retrieval can be achieved, and retrieval accuracy equivalent with public image retrieval can be reached. In addition, detailed safety analysis of the disclosed method is conducted, and experimental assessment of efficiency and accuracy is conducted in different datasets. Results indicate that the method disclosed by the invention can reach expected safety targets, and can increase retrieval efficiency on the premise of ensuring retrieval accuracy.
Owner:XIDIAN UNIV
Dependence-based parallel task packet scheduling method used on multi-core cluster server
ActiveCN103235742AReduce usageReduce idle timeEnergy efficient ICTResource allocationIdle timeResource utilization
The invention particularly discloses a dependence-based parallel task packet scheduling method used on an isomorphic multi-core cluster server. Through calculating the dependence between execution paths and under the premise of not increasing the maximum loads of the execution paths, execution paths with large dependence are combined, compared with the original algorithm, the method can reduce unnecessary task duplication expenditure, communication expenditure between processors and the idle time energy consumption of the processors are reduced, the load of the processors is more balanced, and the overall energy consumption is lowered. The dependence-based parallel task packet scheduling method has the greatest features that the number of the processors is effectively reduced, the resource utilization efficiency is improved, the load of the processors is more balanced, and accordingly, the overall energy consumption is reduced.
Owner:济南云腾智能科技有限公司
Federal learning computing unloading computing system and method based on cloud side end
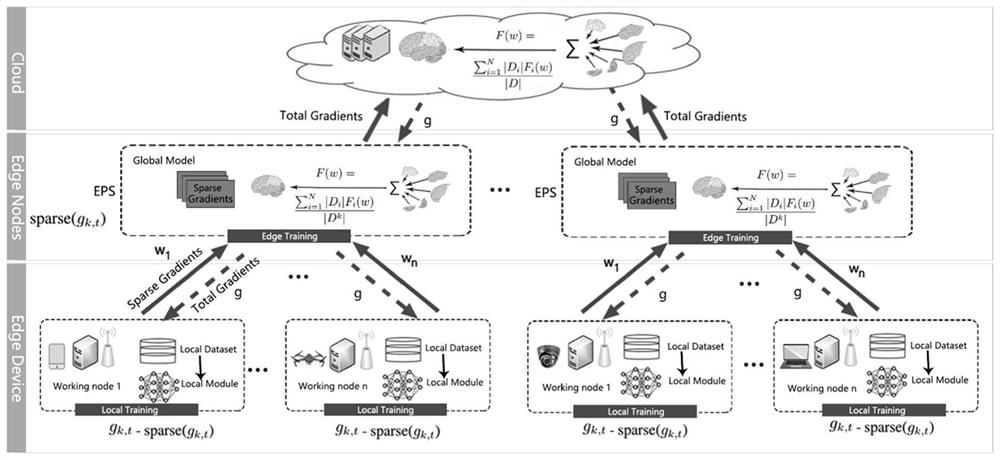
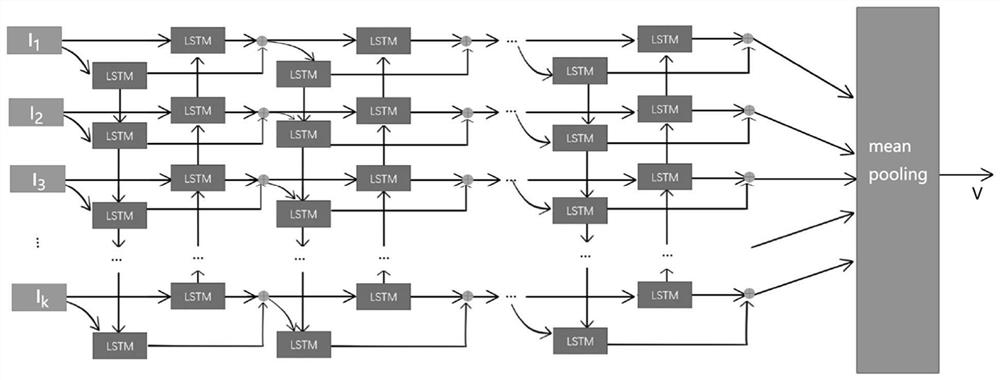
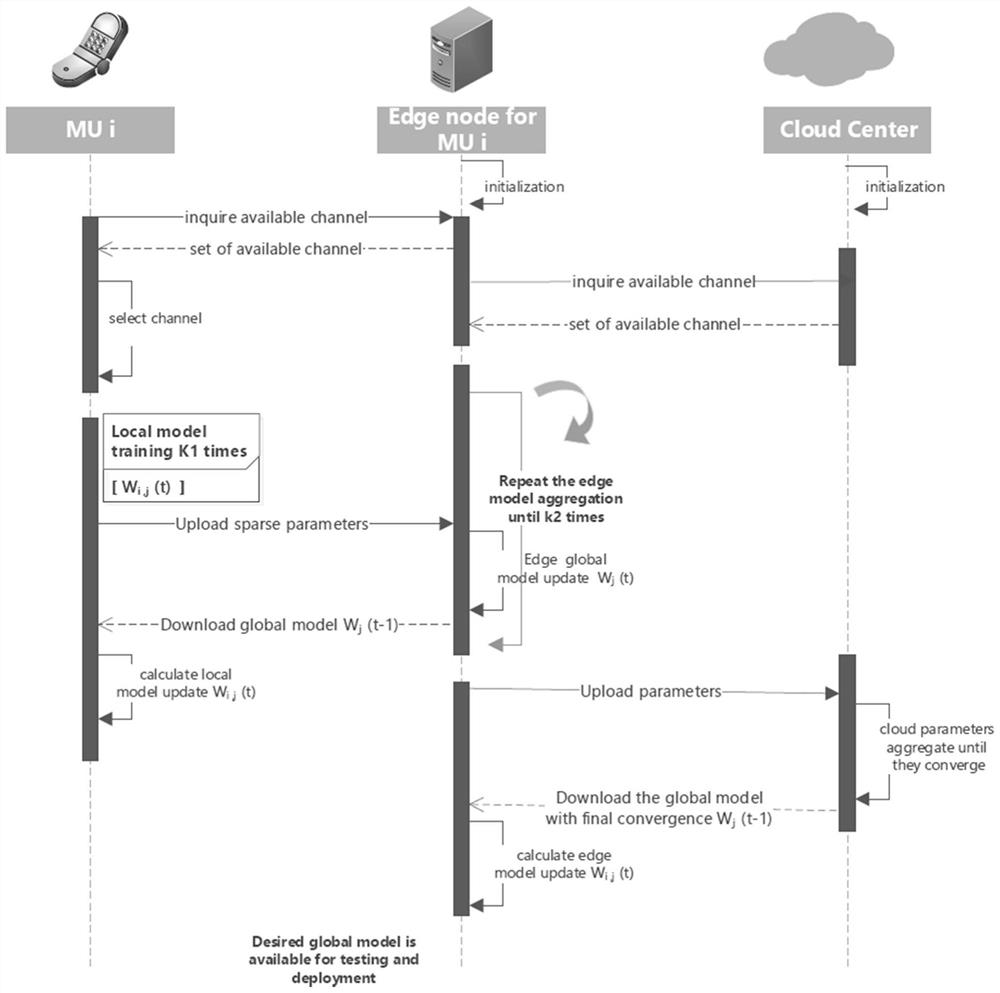
InactiveCN112817653AMake up for deficienciesAccurate decisionProgram initiation/switchingResource allocationComputation complexityEdge node
The invention discloses a federated learning computing unloading resource allocation system and a method based on a cloud side end, and aims to make an accurate decision for computing task unloading and resource allocation, eliminate the need for solving a combinatorial optimization problem and greatly reduce the computing complexity. Based on cloud side three-layer federated learning, the adjacent advantage of edge nodes to a terminal is comprehensively utilized, core powerful computing resources in cloud computing are also utilized, the problem that the computing resources of the edge nodes are insufficient is solved, a local model is trained at each of multiple clients to predict an unloading task. A global model is formed by periodically executing one-time parameter aggregation at an edge end, the cloud end executes one-time aggregation after the edge executes the periodic aggregation until a global BiLSTM model is formed through convergence, and the global model can intelligently predict the information amount of each unloading task. Therefore, guidance is better provided for calculation unloading and resource allocation.
Owner:XI AN JIAOTONG UNIV
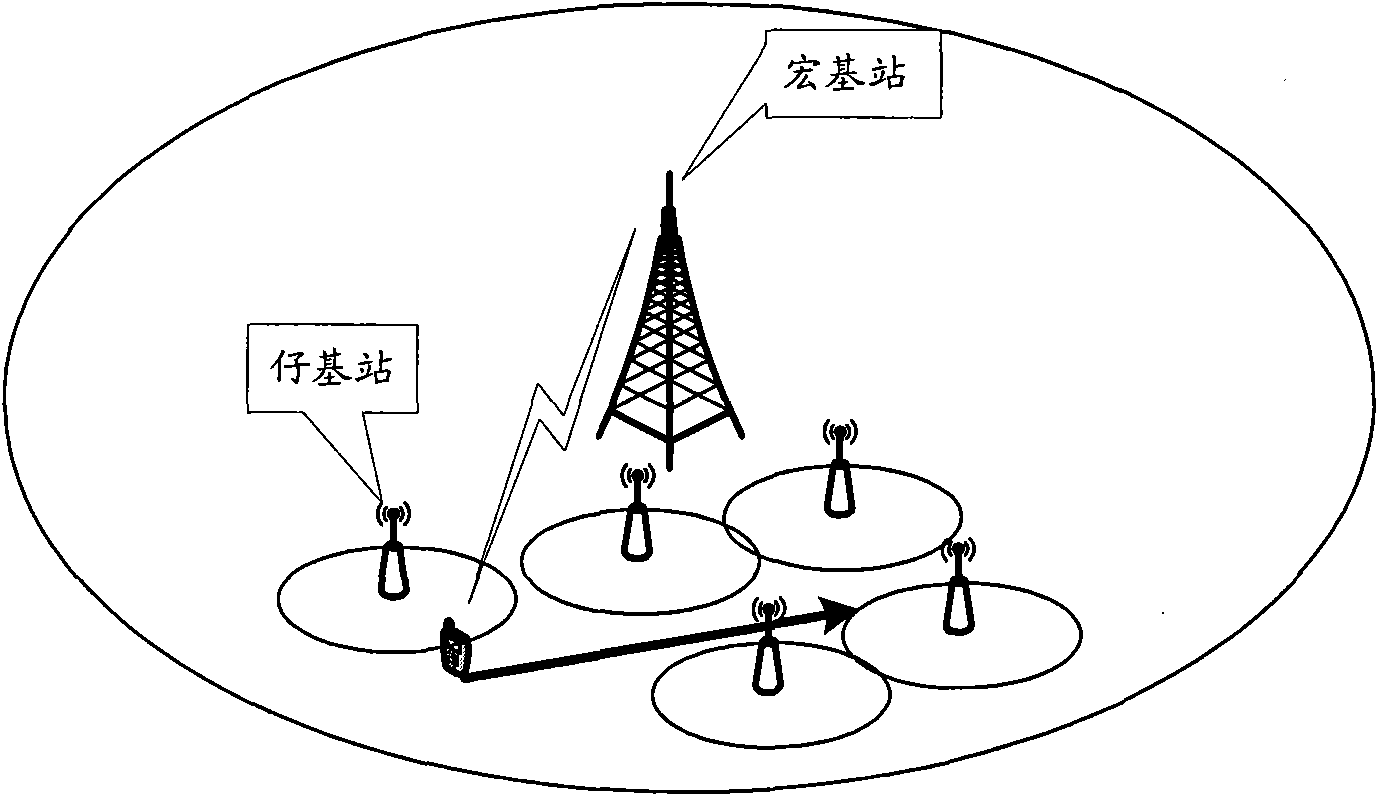
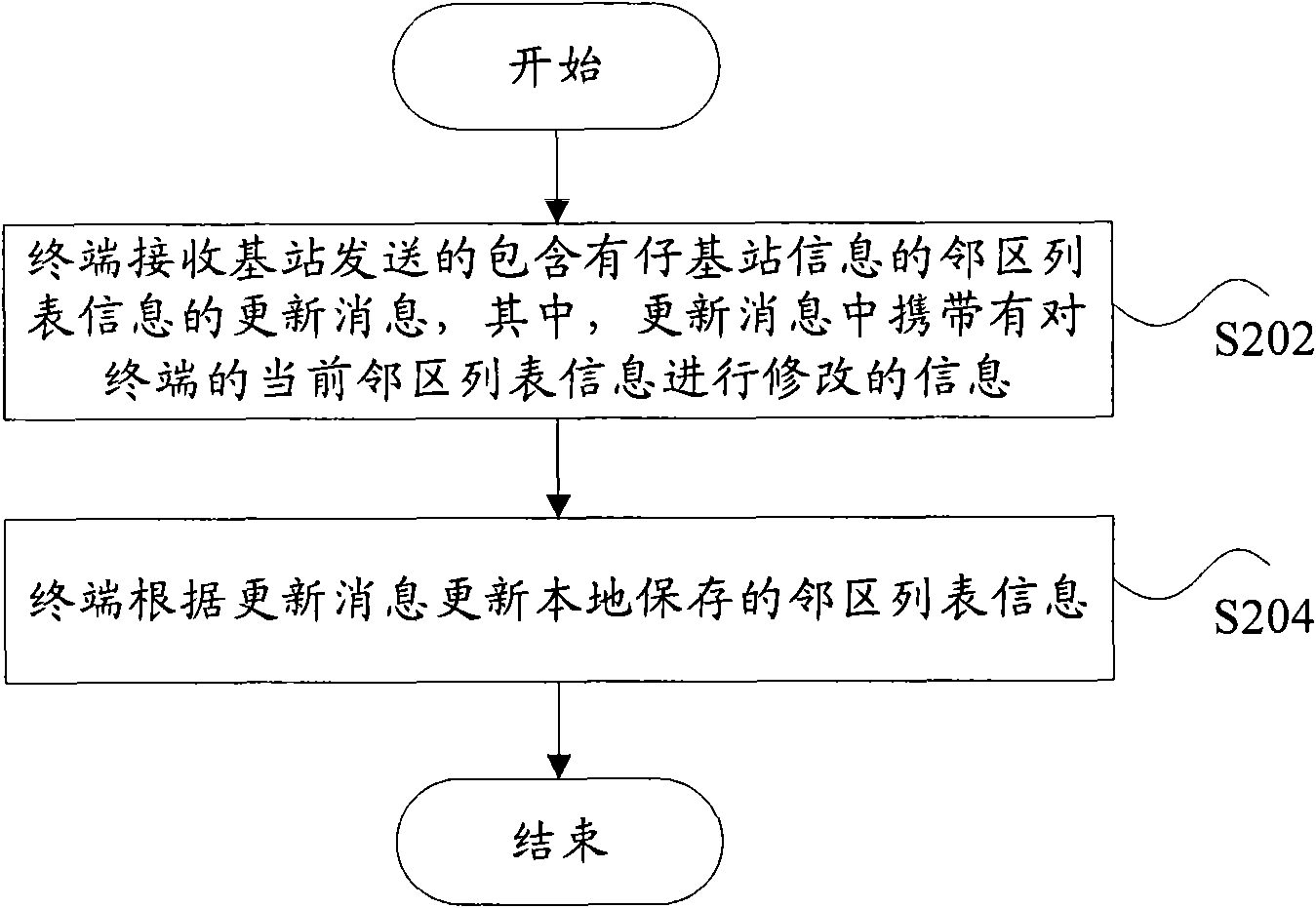
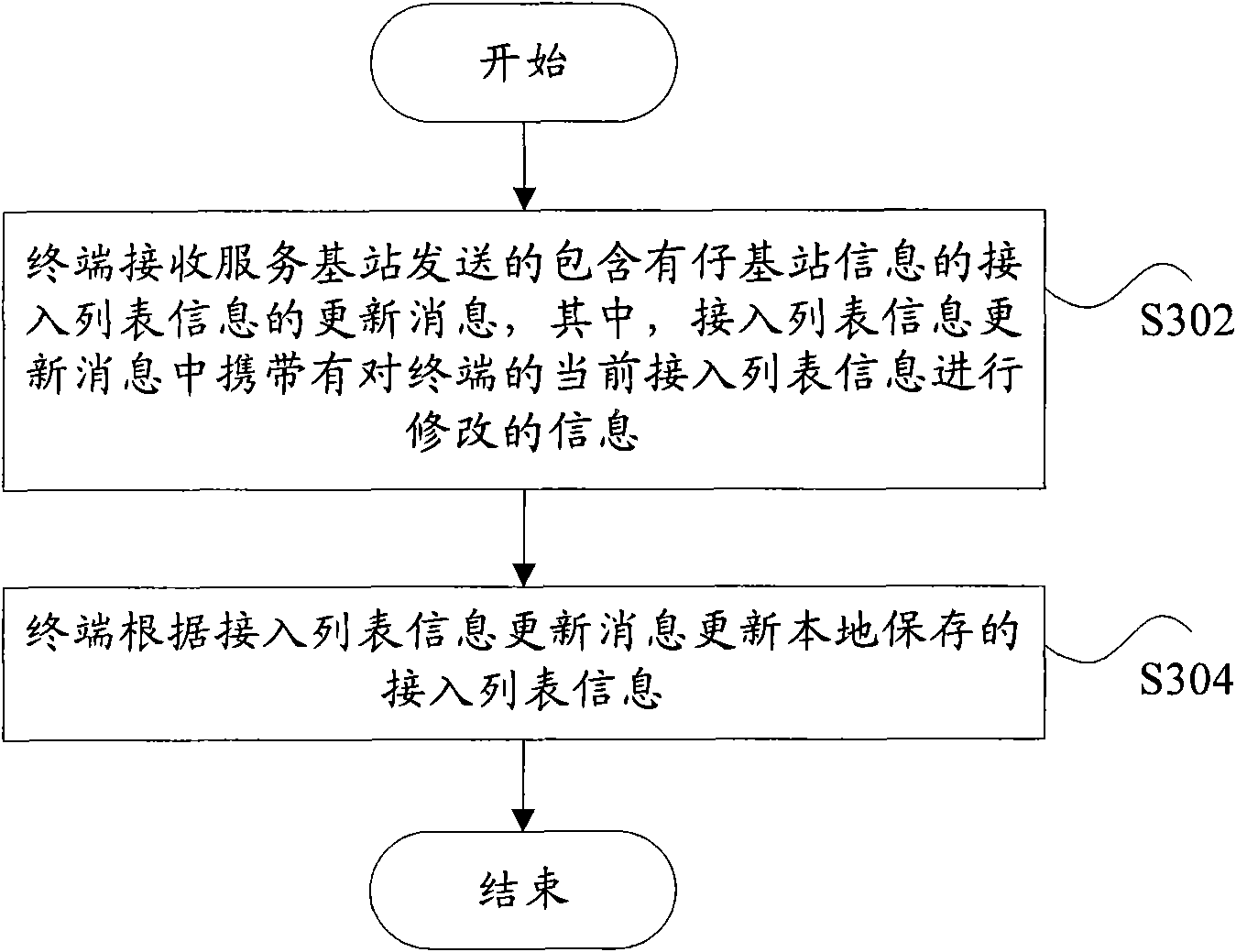
Adjacent area list information and access list information updating method and terminal and base station thereof
InactiveCN101772098AReduce communication overheadEasy to switchAssess restrictionCommunications systemBase station
The invention discloses an adjacent area list information and access list information updating method and a terminal and a base station thereof, wherein the adjacent area list information updating method comprises the following steps that: the terminal receiving base station sends the updating information of the adjacent area list information comprising sub-base station information, wherein the updating information carries information of revising the current adjacent area list information to the terminal; and the terminal updates the adjacent area list information stored locally according to the updating information. Through the technical scheme, the invention can effectively reduce the communication overhead between the base station and the terminal, and simultaneously, improve the switching and the accessing performance of the wireless communication system.
Owner:ZTE CORP
System And Method For Reduced Signaling Transmissions In A Communications System
ActiveUS20140254455A1Reduce communication overheadSignaling required for reducedReceiver specific arrangementsBroadcast transmission systemsCommunications systemEngineering
A method for operating a communications controller includes assigning one or more code domain elements (CDE) of a transmission zone to each user equipment (UE) of a plurality of UEs being served by the communications controller and operating in the transmission zone and having a transmission available. The method also includes transmitting downlink information located in the one or more CDEs to the UEs without utilizing dynamic control signaling.
Owner:HUAWEI TECH CO LTD
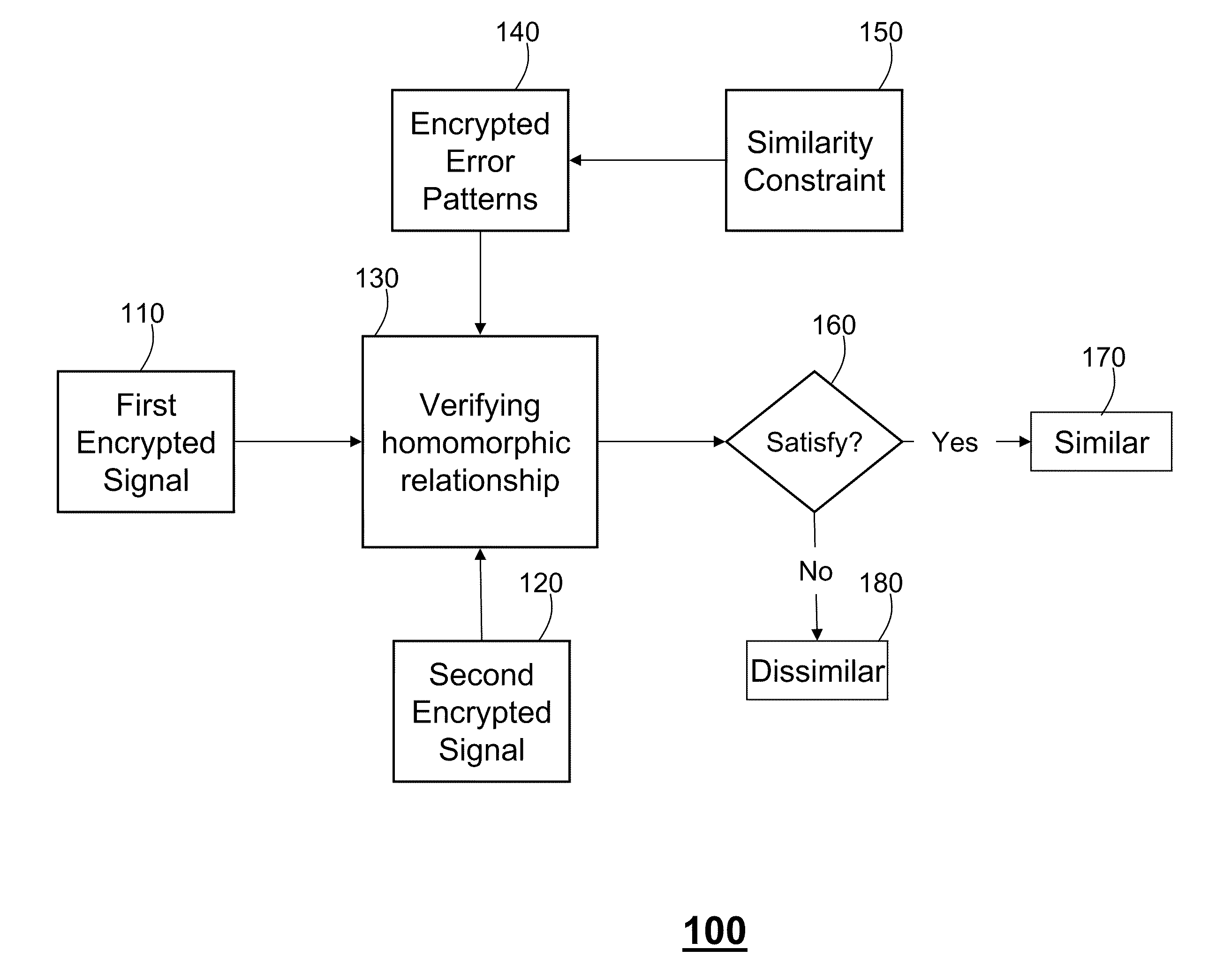
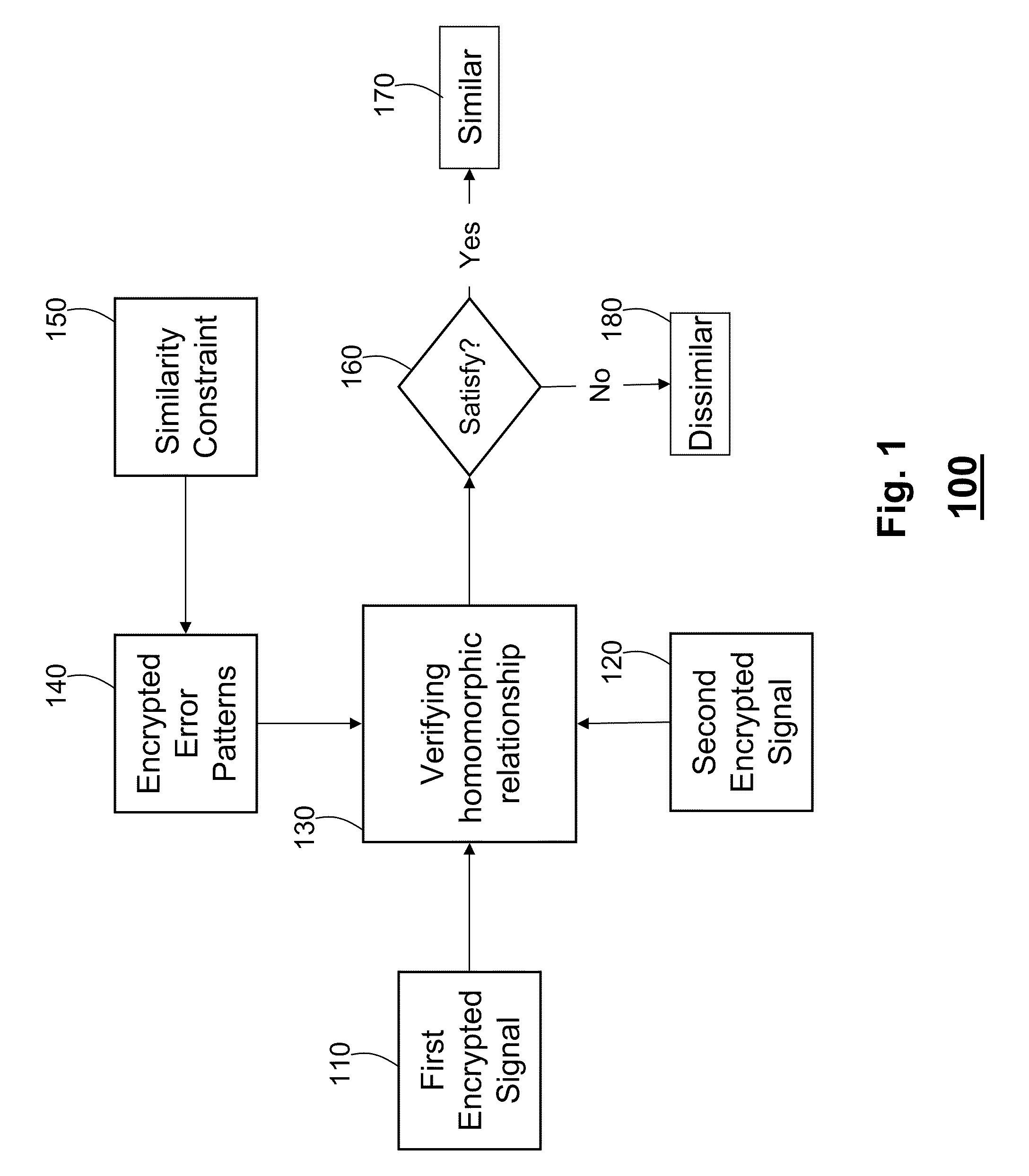
Secure Similarity Verification Between Encrypted Signals
ActiveUS20100246812A1Reduce communication overheadDigital data processing detailsComputer security arrangementsComputer hardwareHomomorphic encryption
A method for verifying a similarity between a first signal and a second signal is described. The first and the second signals are encrypted homomorphically using a key. First, we acquire a set of error patterns determined by a similarity constraint. Then, each error pattern is homomorphically encrypted using the key and presented to a verifier in the setup phase. The verifier declares the first signal similar to the second signal, if any error pattern in the set of error patterns satisfies a homomorphic relationship between the first encrypted signal and the second encrypted signal.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Processor chip arcitecture having integrated high-speed packet switched serial interface
InactiveUS20080244150A1Reduce communication overheadGeneral purpose stored program computerMultiple digital computer combinationsChip architectureProtocol processing
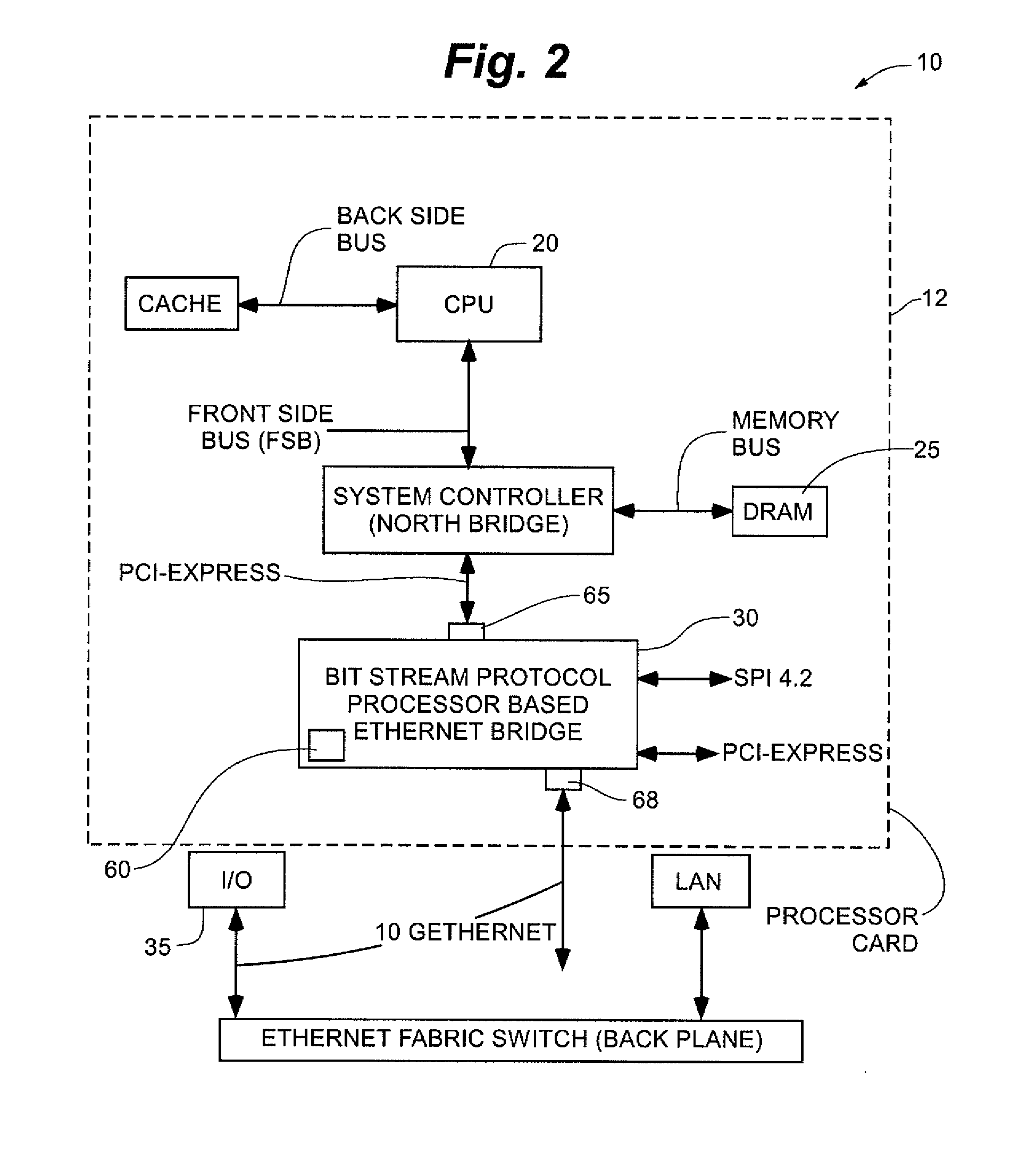
A computing and communication chip architecture is provided wherein the interfaces of processor access to the memory chips are implemented as a high-speed packet switched serial interface as part of each chip. In one embodiment, the interface is accomplished through a gigabit Ethernet interface provided by protocol processor integrated as part of the chip. The protocol processor encapsulates the memory address and control information like Read, Write, number of successive bytes etc, as an Ethernet packet for communication among the processor and memory chips that are located on the same motherboard, or even on different circuit cards. In one embodiment, the communication over head of the Ethernet protocol is further reduced by using an enhanced Ethernet protocol with shortened data frames within a constrained neighborhood, and / or by utilizing a bit stream switch where direct connection paths can be established between elements that comprise the computing or communication architecture.
Owner:KIRITIN INC
Method for determining location of wireless devices
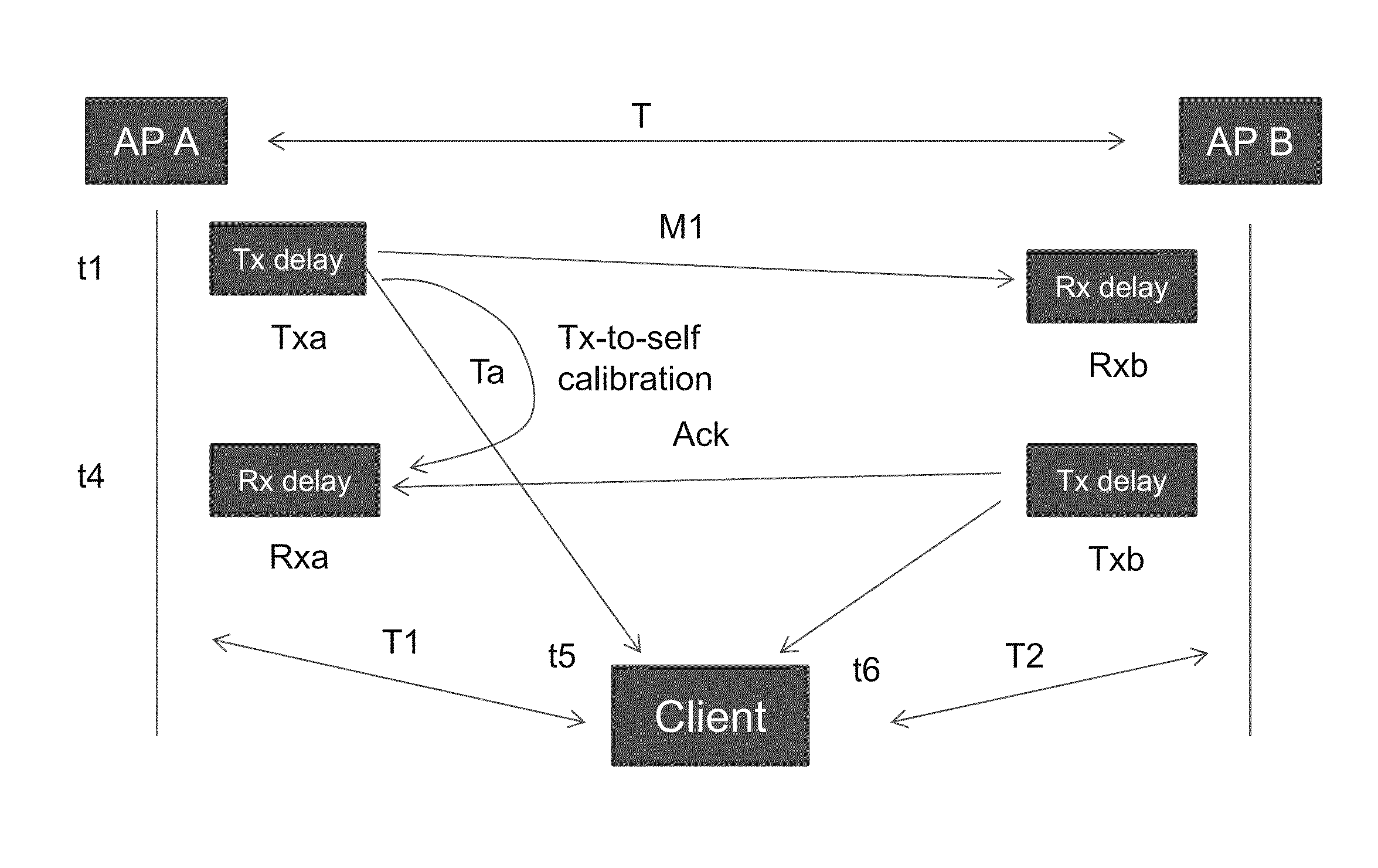
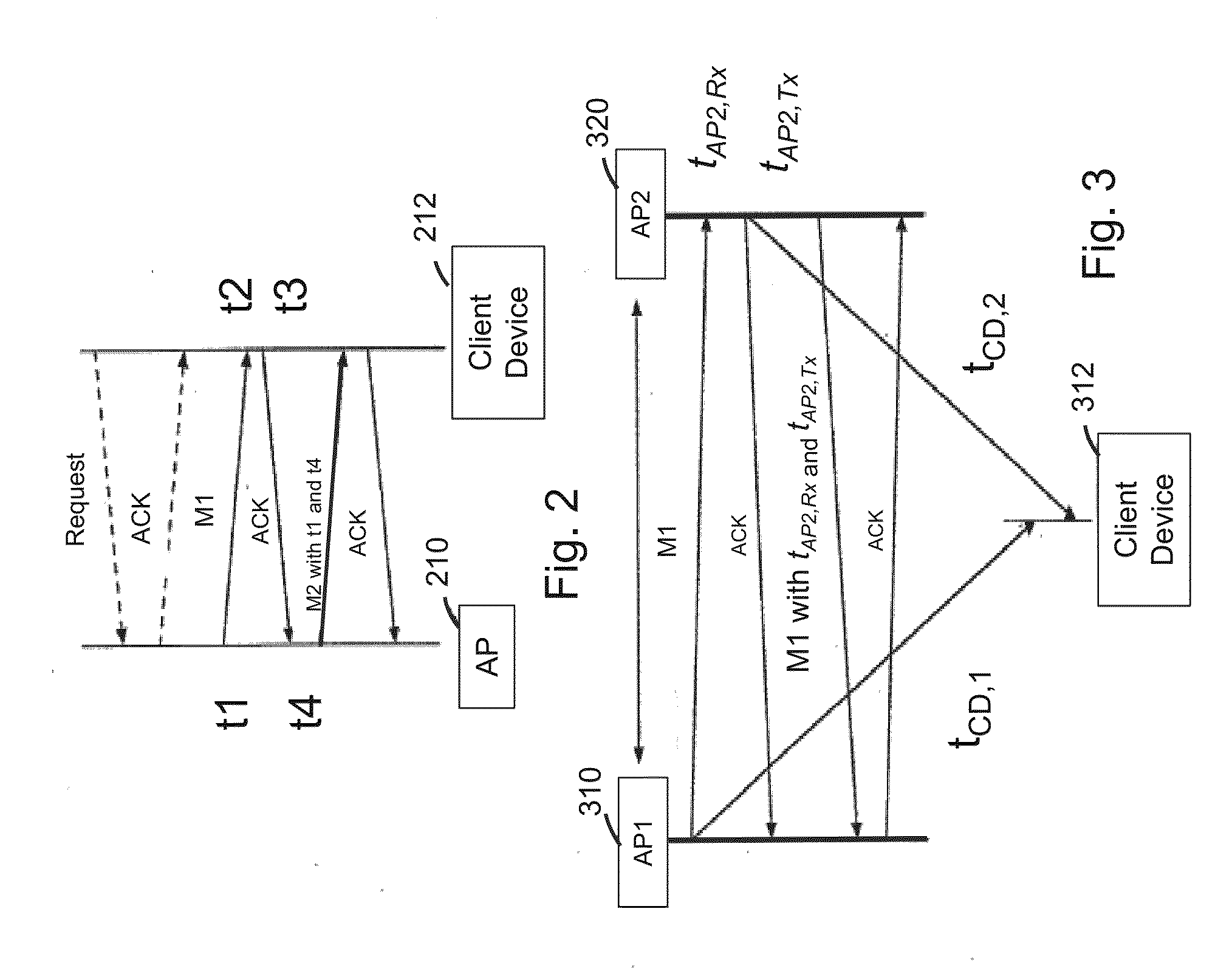
InactiveUS20150382152A1Improve accuracyReduce the burden onNetwork topologiesPosition fixationClient-sideWireless network
Methods for determining a location of a client device in a wireless network having at least a first other network device with a known location are disclosed. Transmission-to-self calibrations are performed at the first other network device and / or the client device to determine RF group delay of the first other network device and / or the client device. The client device receives messages and acknowledgements from the other network devices and determines its location based on information received including the time at which it received the messages, the acknowledgements and the RF group delay of the first other network device. As such, the location calculation can be refined by accounting for the RF group delays of the first other network device and / or the client device.
Owner:QUALCOMM TECH INT
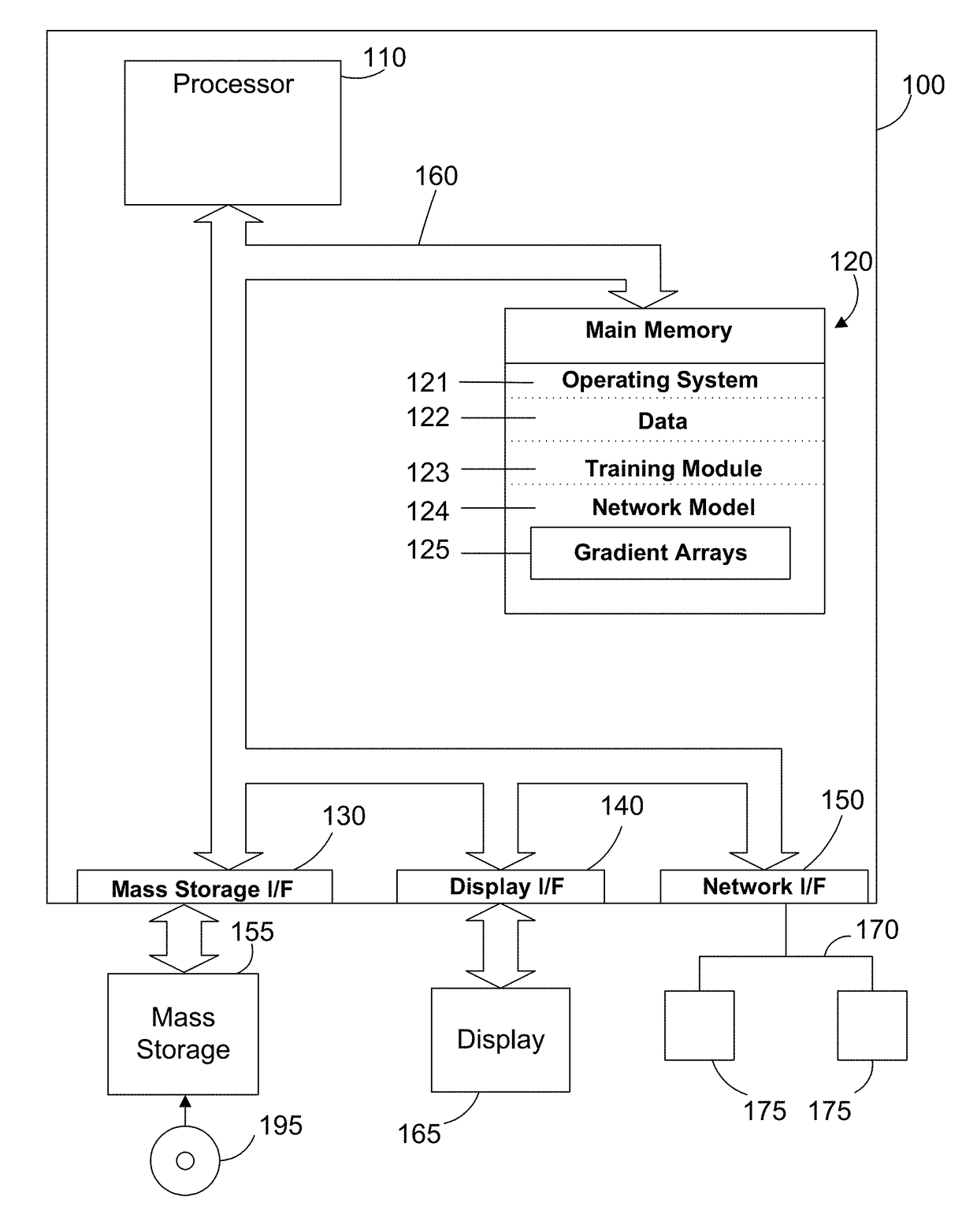
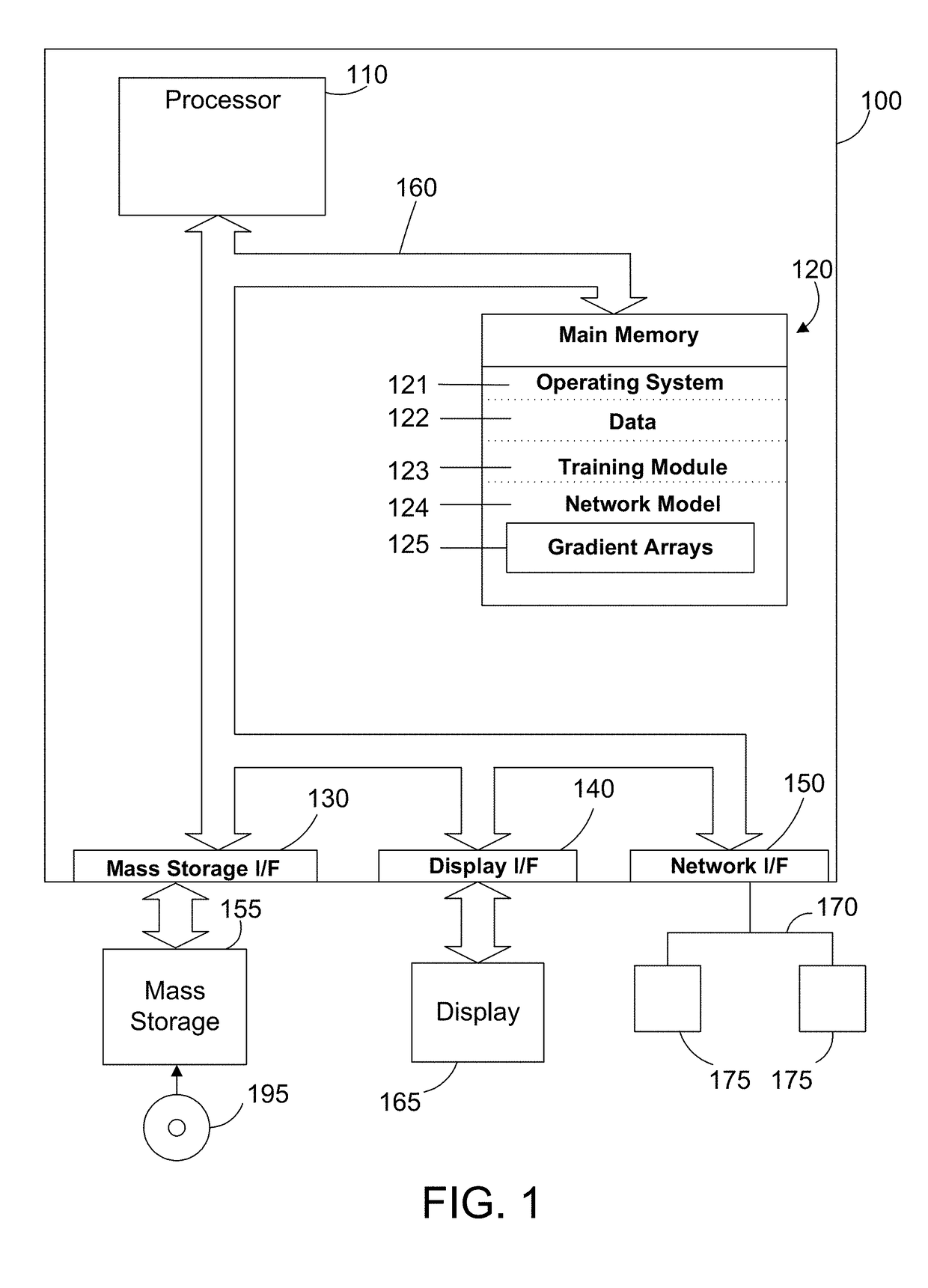
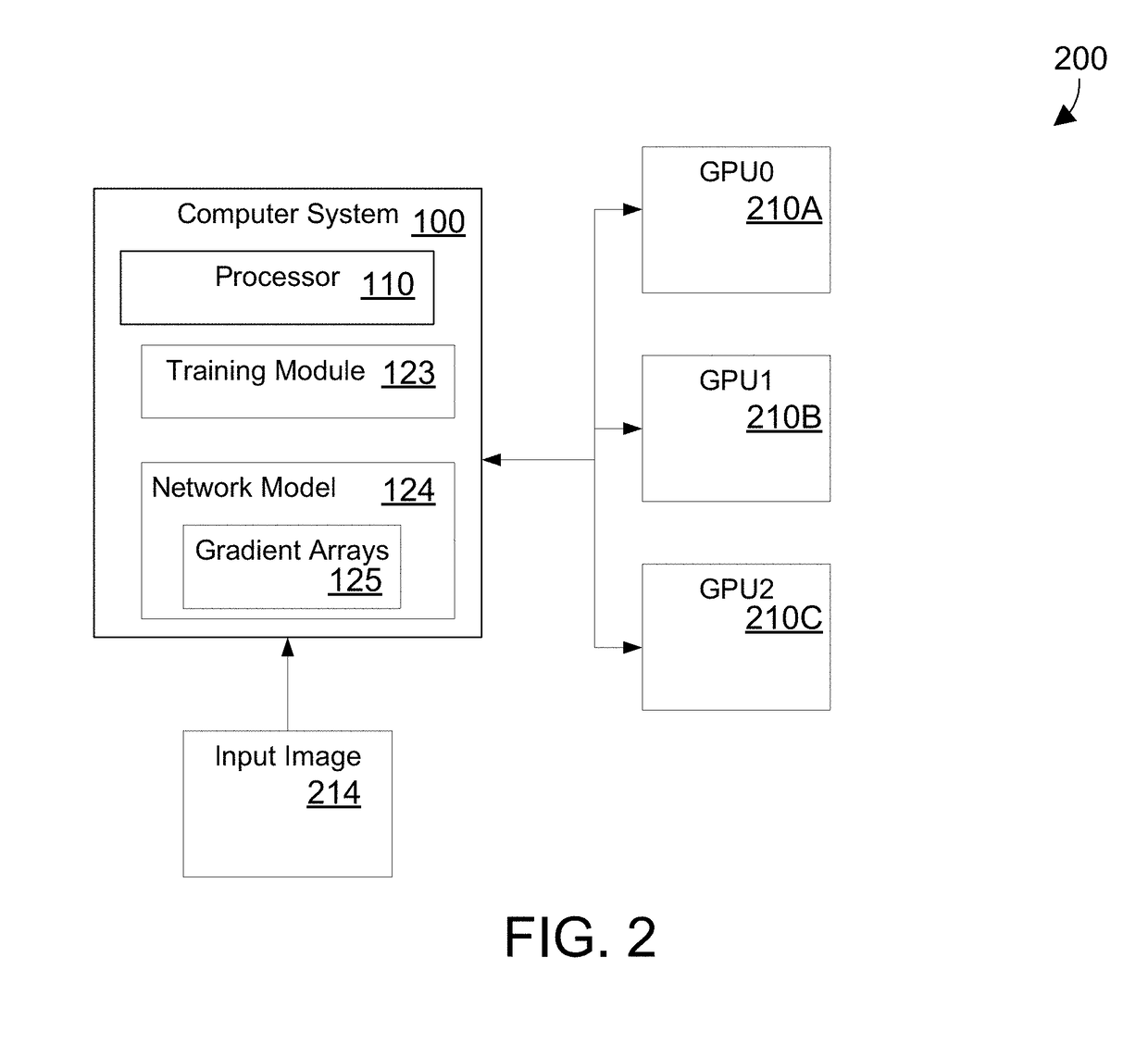
Efficient parallel training of a network model on multiple graphics processing units
ActiveUS20180121806A1Reduce communication overheadShorten the timeNeural architecturesNeural learning methodsGraphicsNerve network
A system and method provides efficient parallel training of a neural network model on multiple graphics processing units. A training module reduces the time and communication overhead of gradient accumulation and parameter updating of the network model in a neural network by overlapping processes in an advantageous way. In a described embodiment, a training module overlaps backpropagation, gradient transfer and accumulation in a Synchronous Stochastic Gradient Decent algorithm on a convolution neural network. The training module collects gradients of multiple layers during backpropagation of training from a plurality of graphics processing units (GPUs), accumulates the gradients on at least one processor and then delivers the gradients of the layers to the plurality of GPUs during the backpropagation of the training. The whole model parameters can then be updated on the GPUs after receipt of the gradient of the last layer.
Owner:IBM CORP
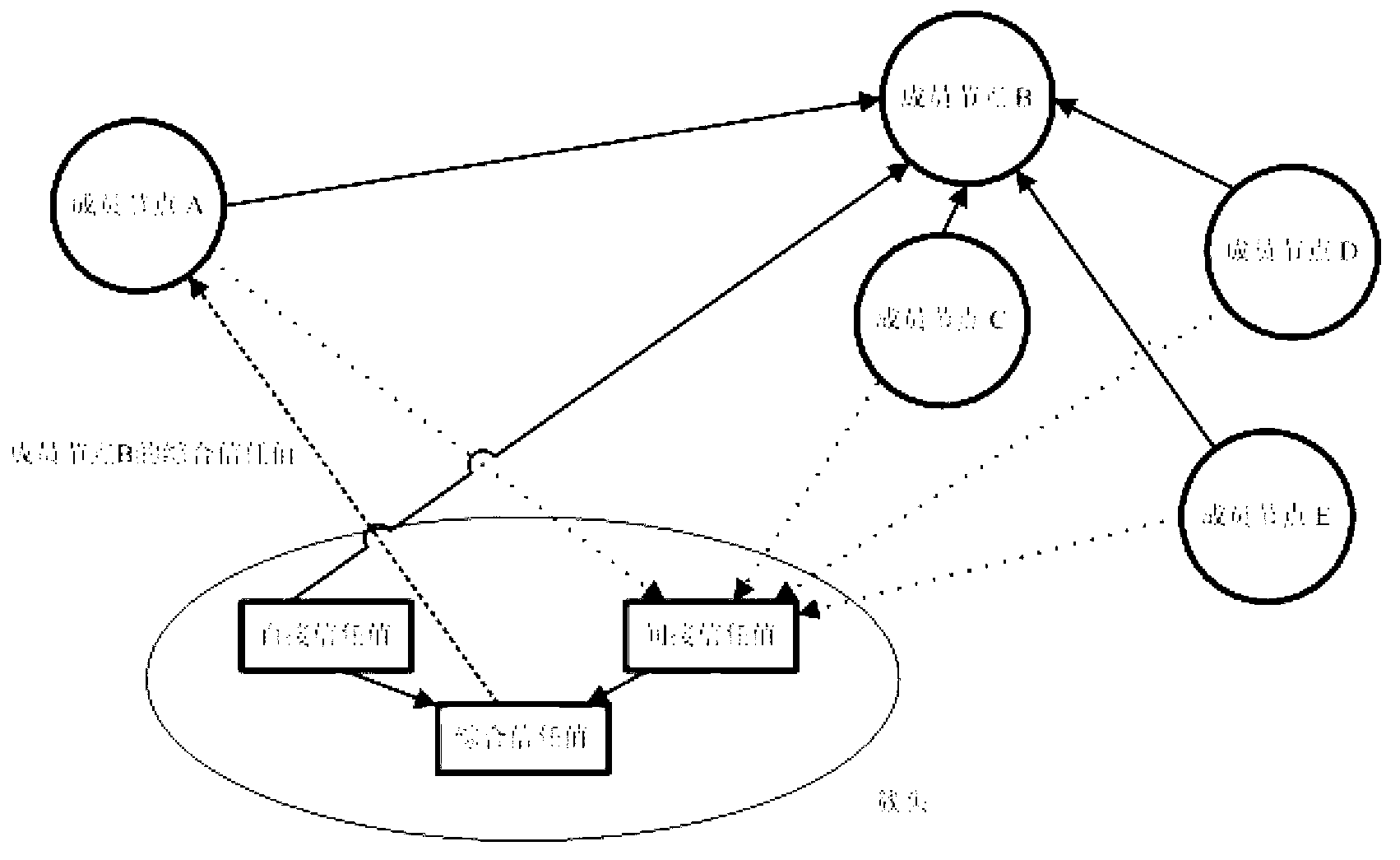
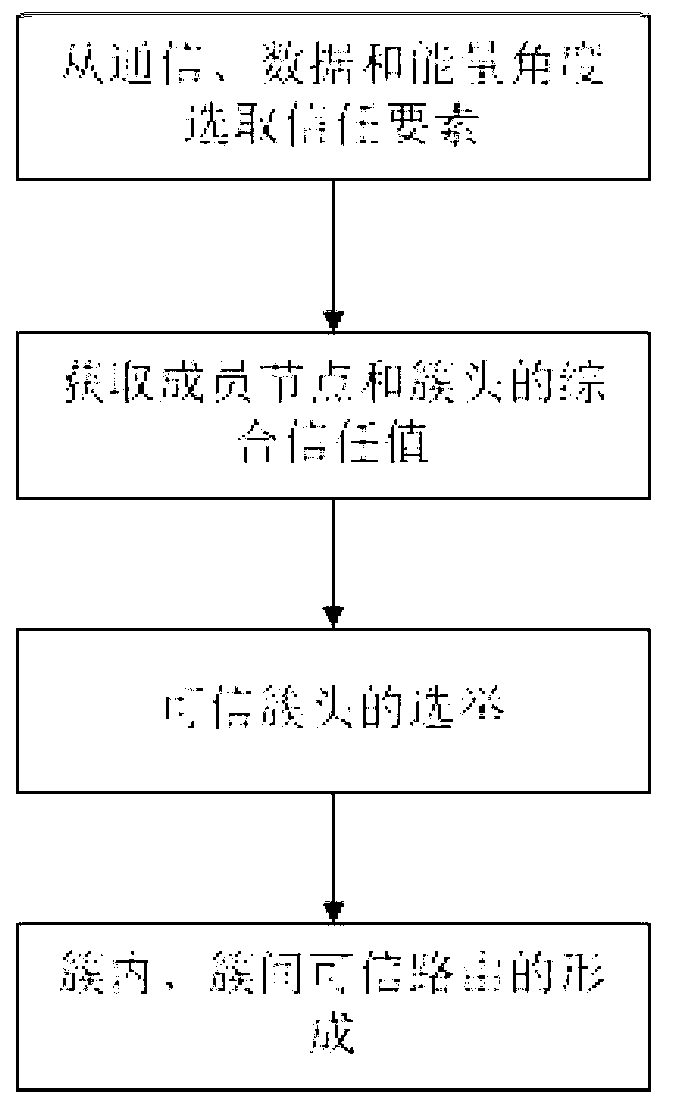
Cluster routing method based on multi-factor trust mechanism
InactiveCN103237333AAvoid communicating with each otherReduce communication overheadNetwork topologiesHigh level techniquesWireless sensor networkingData transmission
The invention discloses a cluster routing method based on a multi-factor trust mechanism developed for a wireless sensor network. The multi-factor trust mechanism is adopted for guaranteeing safety and reliability of nodes. Trust factors are selected by angles of communication, data and energy by the trust mechanism. A 'low-return and high-punishment' mechanism is adopted for preventing malicious nodes from increasing trust values rapidly through short-period lawful actions or surviving in the network in long terms by utilizing low trust values. Meanwhile, when a network topology is established, comprehensive trust values of the nodes are combined with cluster head election values and route communication cost to guarantee trusted cluster head election and trusted route selection. In the process of data transmission, the malicious nodes, selfish nodes and low-competitive nodes are removed according to the comprehensive trust values of the nodes, and thus, a safe and trusted network environment is established.
Owner:SOUTHEAST UNIV
Matrix multiplication parallel computing system based on multi-FPGA
InactiveCN101089840AReduce resource requirementsImprove computing powerDigital computer detailsData switching networksBinary multiplierParallel algorithm
A matrix multiplication parallel calculation system based on multi-FPGA is prepared as utilizing FPGA as processing unit to finalize dense matrix multiplication calculation and to raise sparse matrix multiplication calculation function, utilizing Ethernet and star shaped topology structure to form master-slave distributed FPGA calculation system, utilizing Ethernet multicast-sending mode to carry out data multicast-sending to processing unit requiring the same data and utilizing parallel algorithm based on line one-dimensional division output matrix to carry out matrix multiplication parallel calculation for decreasing communication overhead of system.
Owner:ZHEJIANG UNIV
Light-weight authentication key negotiation method based on implicit certificate
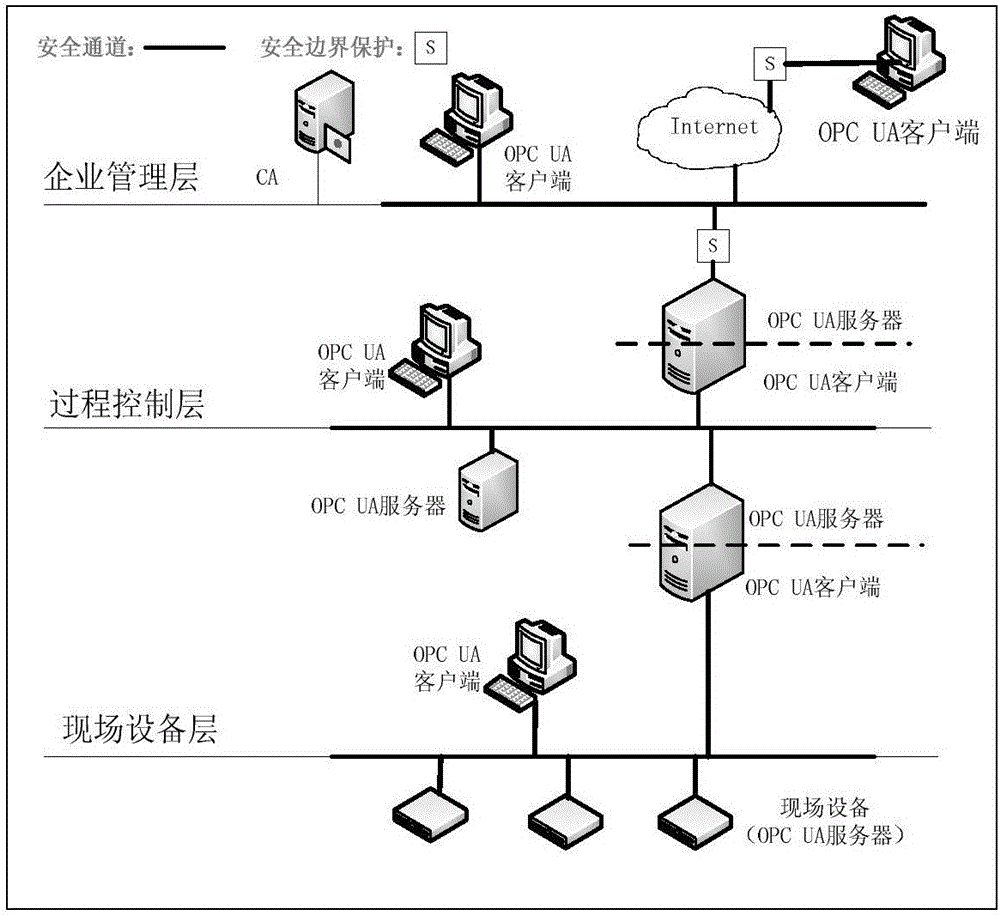
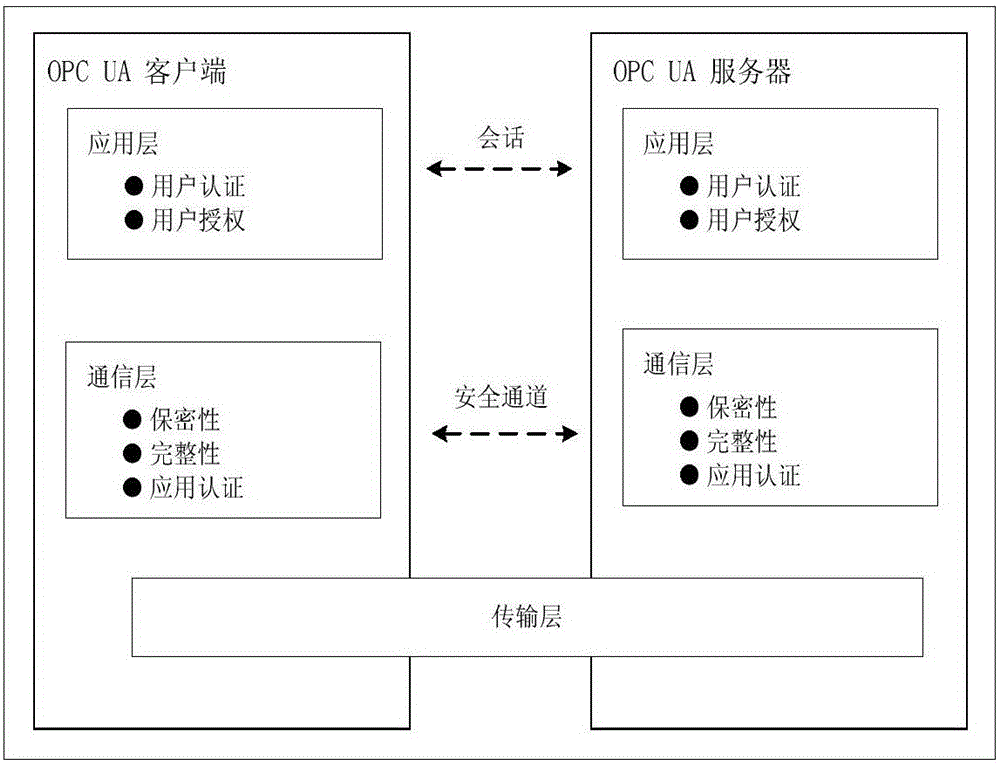
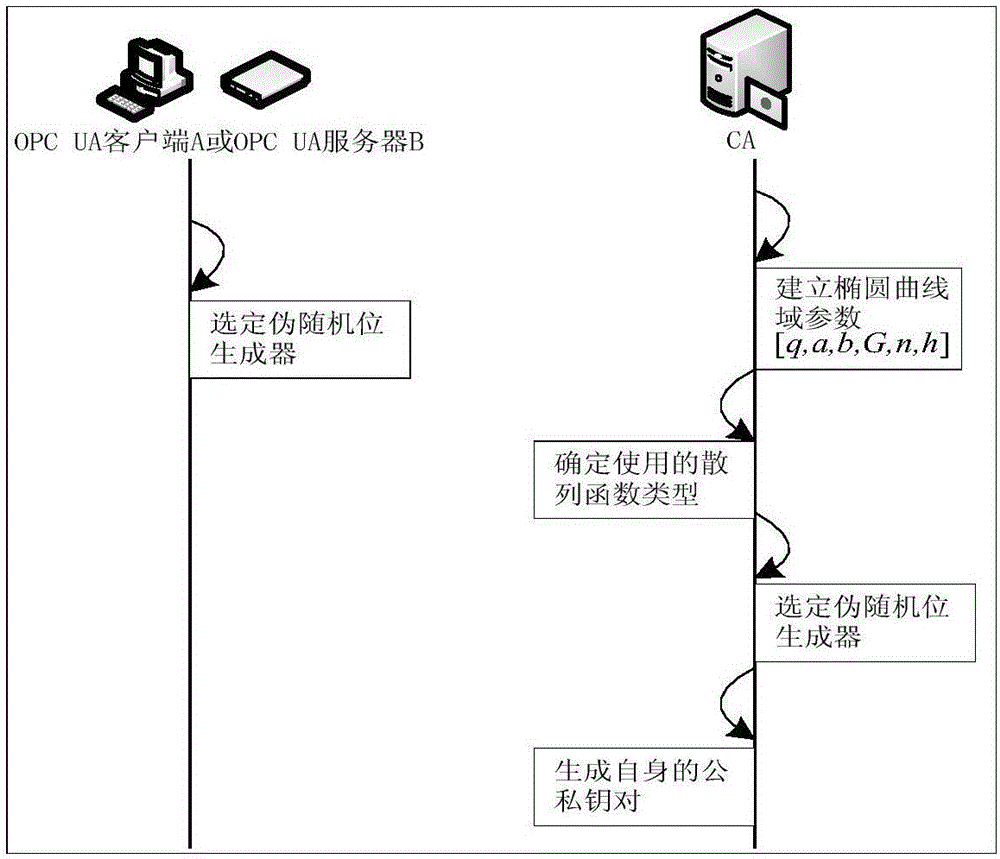
ActiveCN106411528ACalculation speedReduce the probability of collisionKey distribution for secure communicationPublic key for secure communicationClient-sideSecure channel
The invention relates to a light-weight authentication key negotiation method based on an implicit certificate, and belongs to the technical field of identity authentication. The method is used for establishing a secure channel between an OPC UA server and an OPC UA client and generating of a session key. Three entities, a credible certification authority (CA), the OPC UA client A and the OPC UA server B, are involved in an authentication key negotiation process. The OPC UA server B and the OPC UA client A acquire the own implicit certificates after the CA completes identity registration. Then the OPC UA server B and the OPC UA client A complete bidirectional authentication and key negotiation between the entities by using a light-weight algorithm. According to the method provided by the invention, the light-weight authentication key negotiation method based on the implicit certificate is provided aiming at the problem that an existing OPC UA security mechanism is not applicable to a resource-constrained communication environment. The method provided by the invention can be efficiently and safely applicable to an industrial network with a large amount of resource-constrained embedded OPC UA equipment.
Owner:KYLAND TECH CO LTD
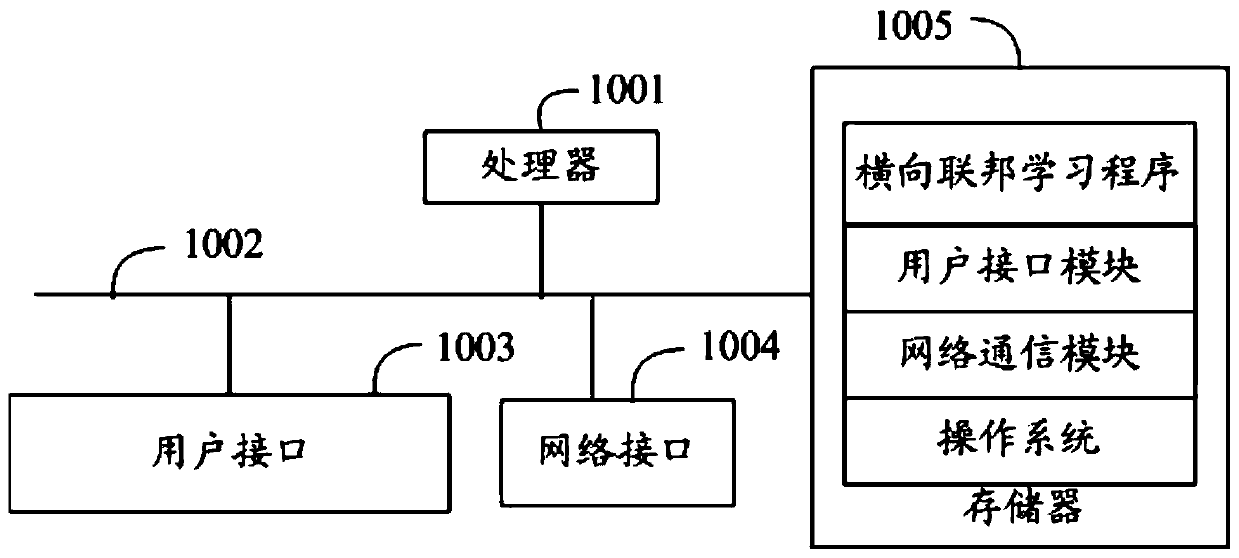
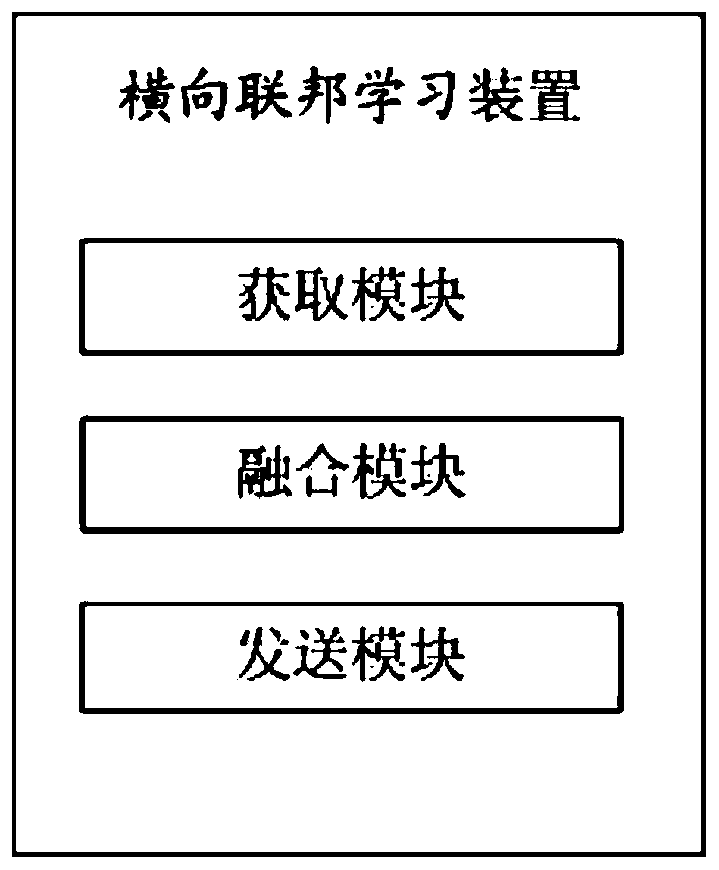
Transverse federated learning method, device and equipment and computer storage medium
PendingCN110263936AReduce the number of updatesReduce overheadFinanceMachine learningFederated learningGlobal model
The invention relates to the technical field of Fintech, and discloses a transverse federated learning method. The method comprises the following steps: a community coordinator acquiring global model parameters sent by a central coordinator and sending the global model parameters to each participant; obtaining model parameter update which is sent by each participant and is obtained by performing model training based on the global model parameters, fusing the model parameter update to obtain community model parameter update, and determining whether the community model parameter update needs to be sent to the central coordinator or not; and if yes, sending the community model parameter update to the central coordinator, obtaining global model parameter update returned by the central coordinator, and sending the global model parameter update to each participant, thereby enabling each participant to carry out model training based on the global model parameter update. The invention further discloses a transverse federated learning device and equipment and a computer storage medium. According to the invention, the learning efficiency of transverse federal learning is improved.
Owner:WEBANK (CHINA)
Secure protocol execution in a network
ActiveUS20140115666A1Minimizing connectivity requirementMinimize workloadDigital data processing detailsUser identity/authority verificationCryptographic protocolWorkload
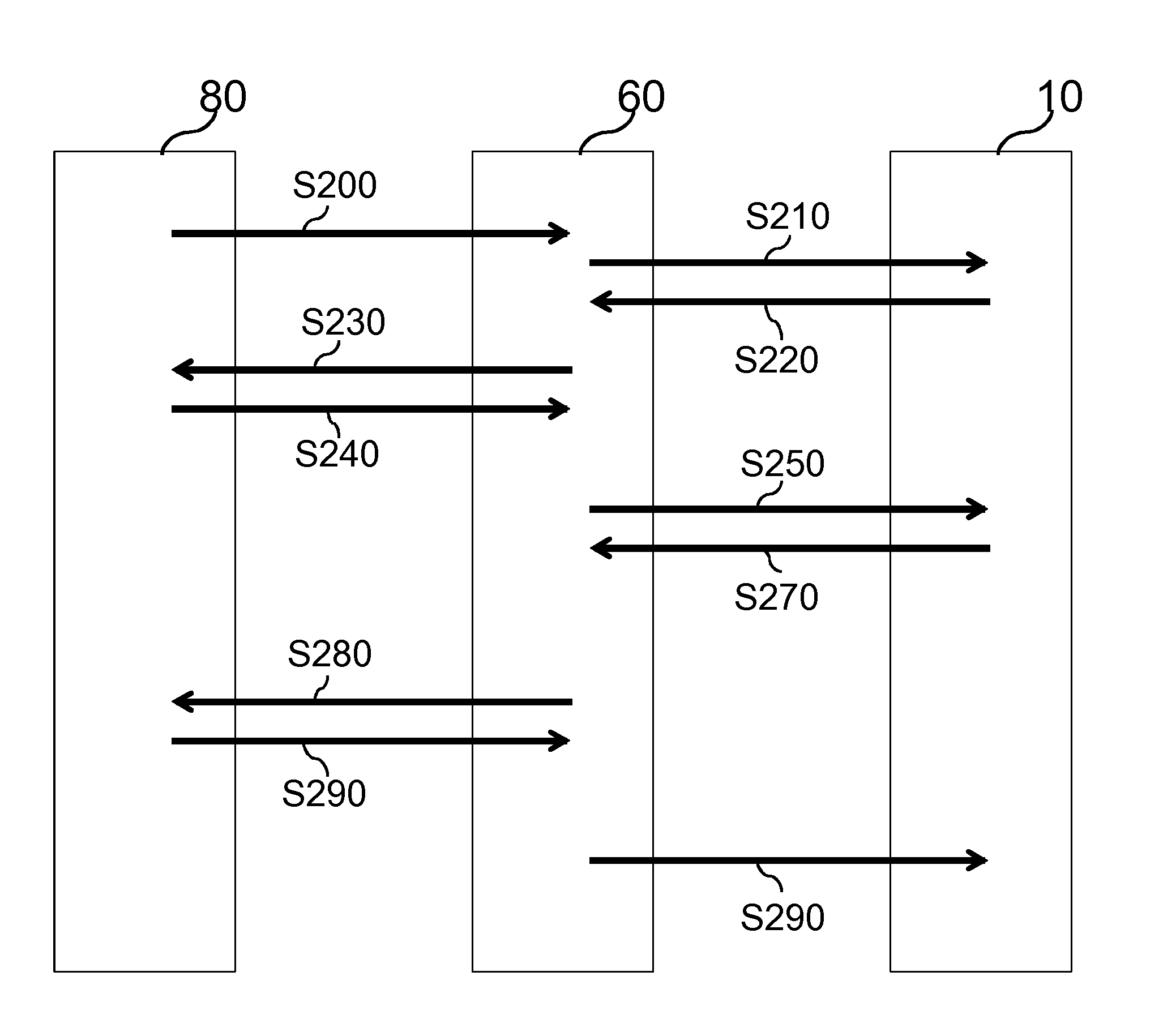
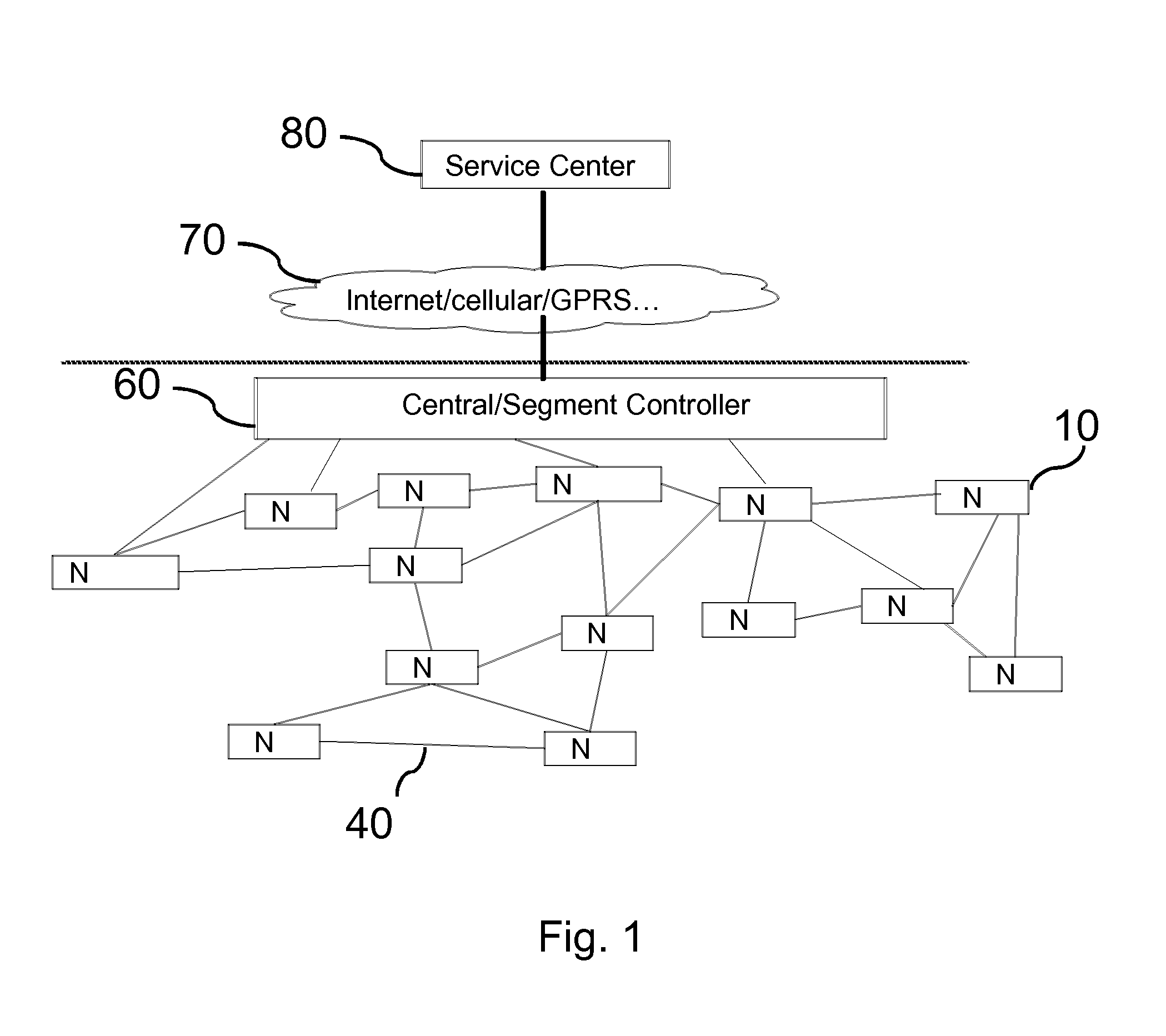
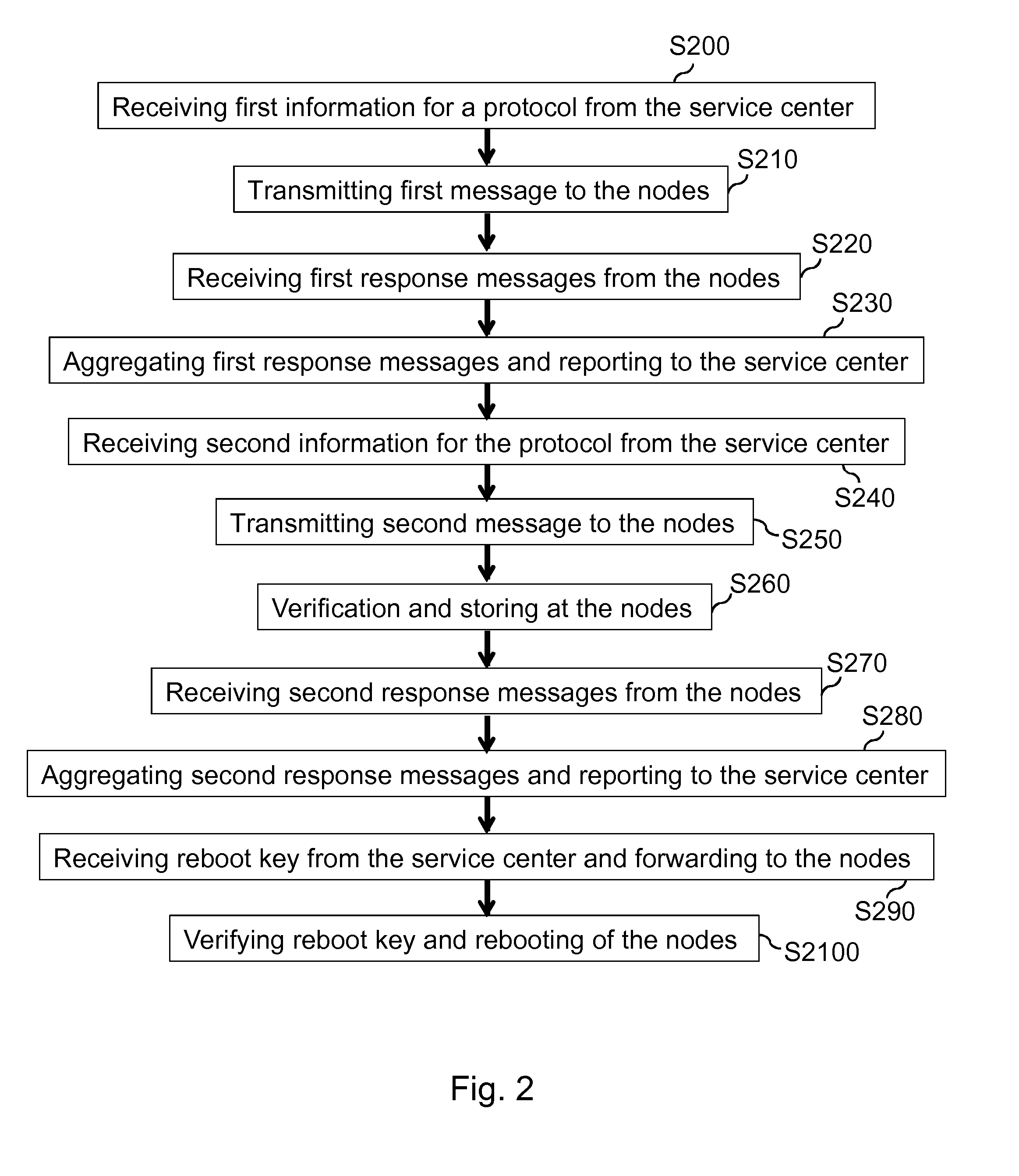
For secure configuration of network nodes from a backend with low connectivity requirements and workload at the backend and reduced communication overhead, a system, a control unit for a segment controller and a method for secure protocol execution in a network are provided, wherein protocol information is provided to a segment controller (60) for controlling a node (10) and a protocol is performed based on the protocol information to control the node (10), at least one response message of the node (10) being required at the segment controller (60) for performing one or more steps of the protocol.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
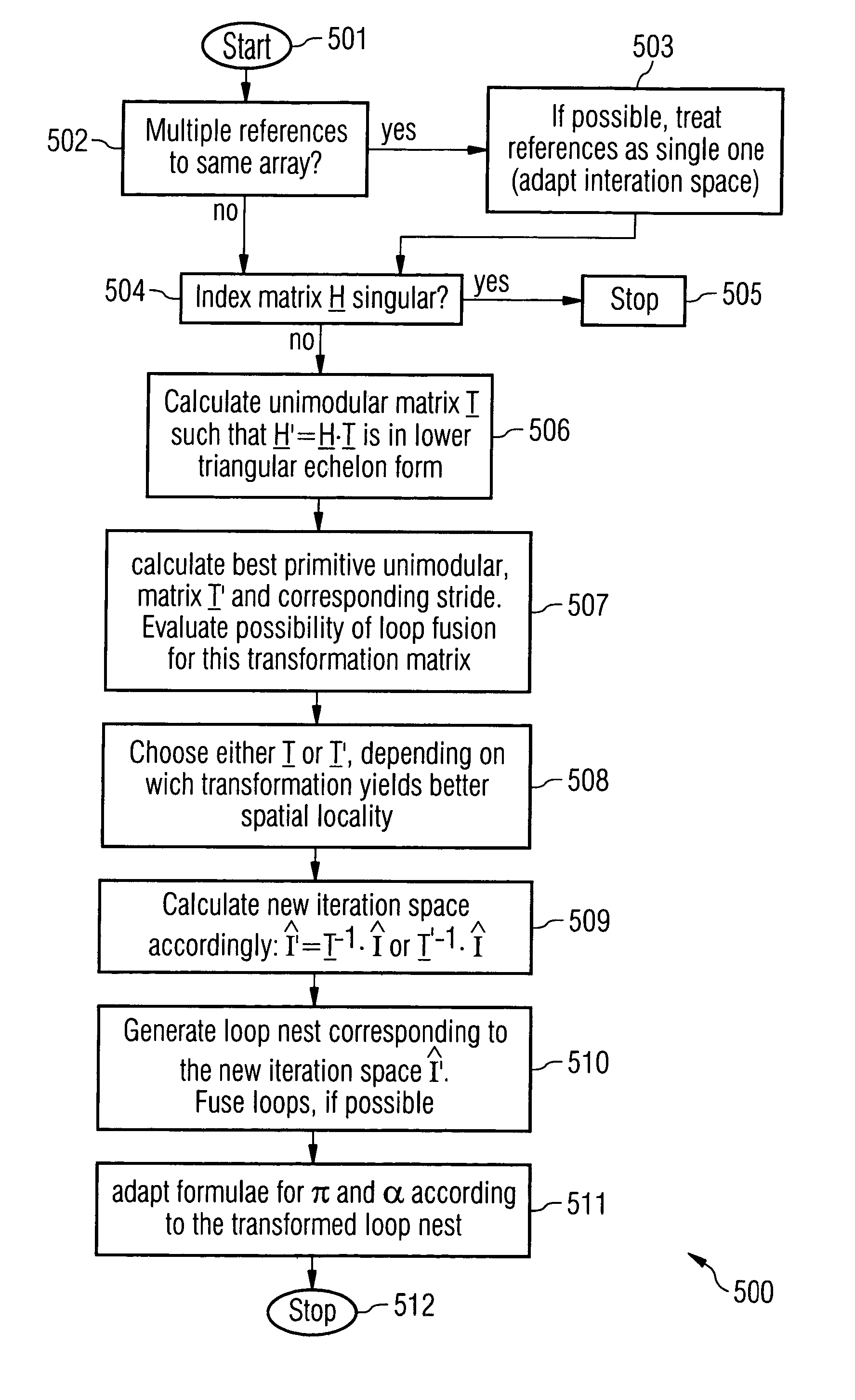
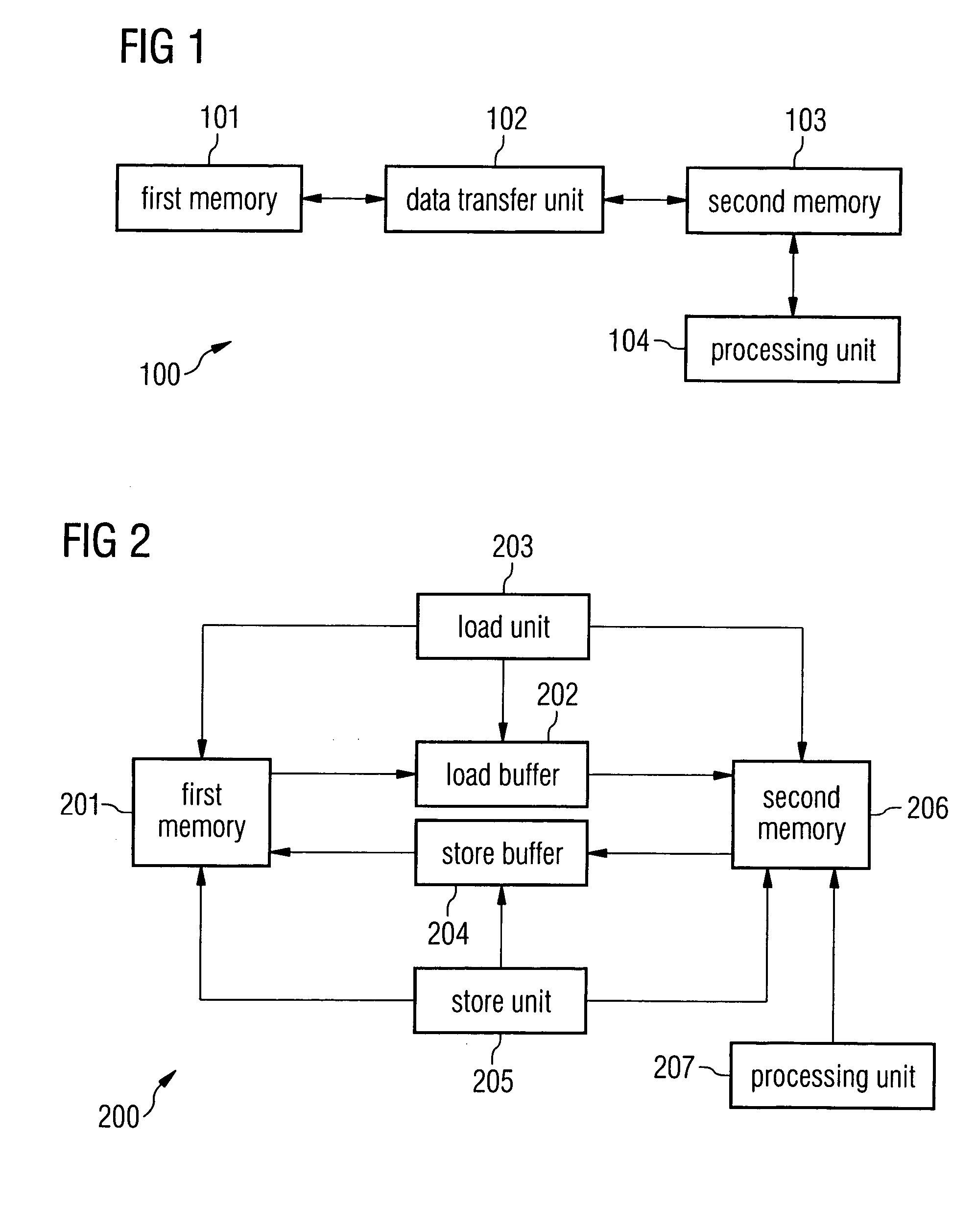
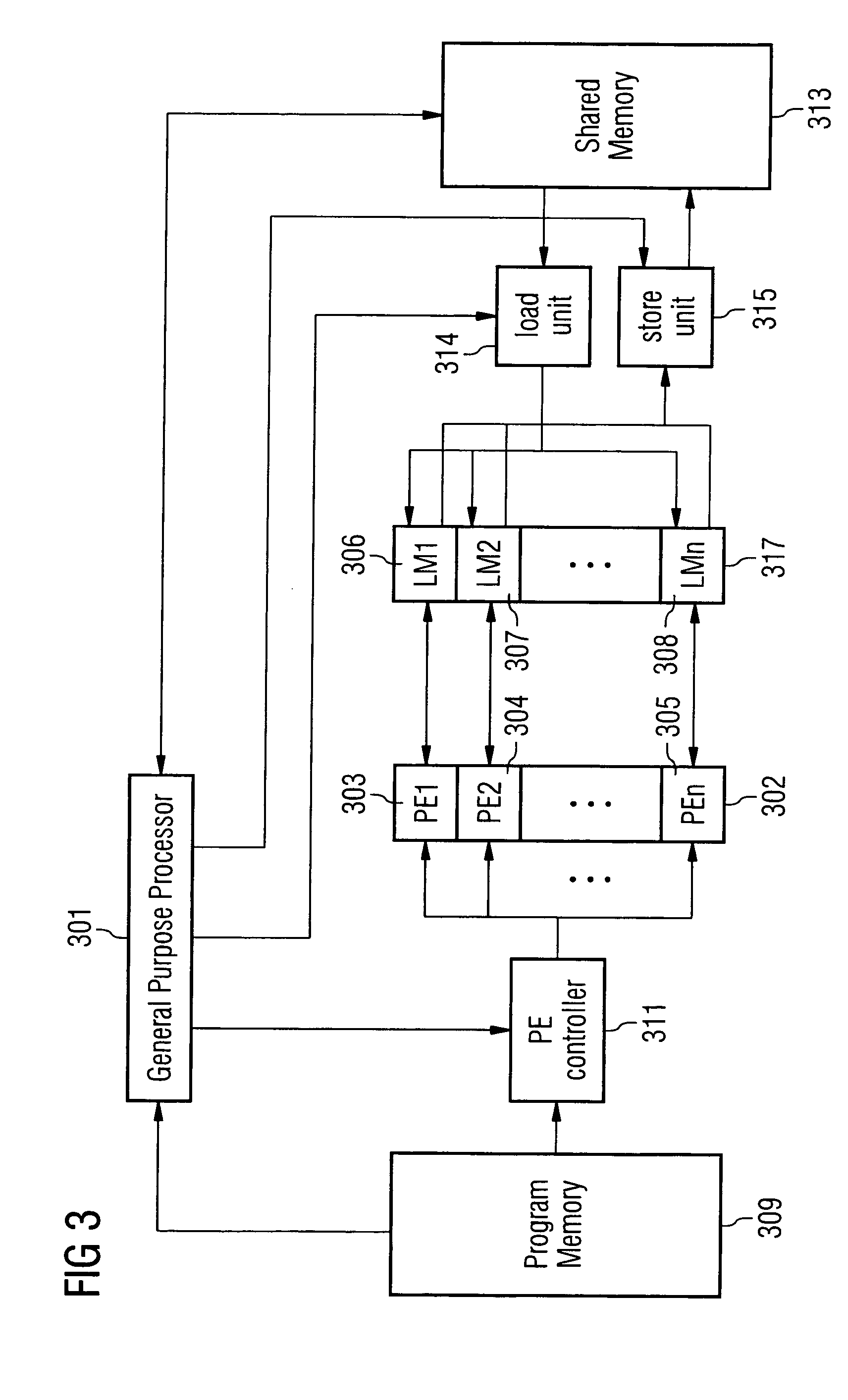
Computer system for data processing and method for the transfer of an array segment of an affine-indexed multi-dimensional array referenced in a loop nest from a first memory to a second memory
InactiveUS20060031652A1Increase freedomProcessing speedSoftware engineeringMemory systemsParallel computingMulti dimensional
Computer system for electronic data processing having programmable data transfer units used for transferring data from a first memory in which data is stored in a form of a multi-dimensional array to a second memory in such a way, that spatial or temporal locality for the transfer is established.
Owner:INFINEON TECH AG
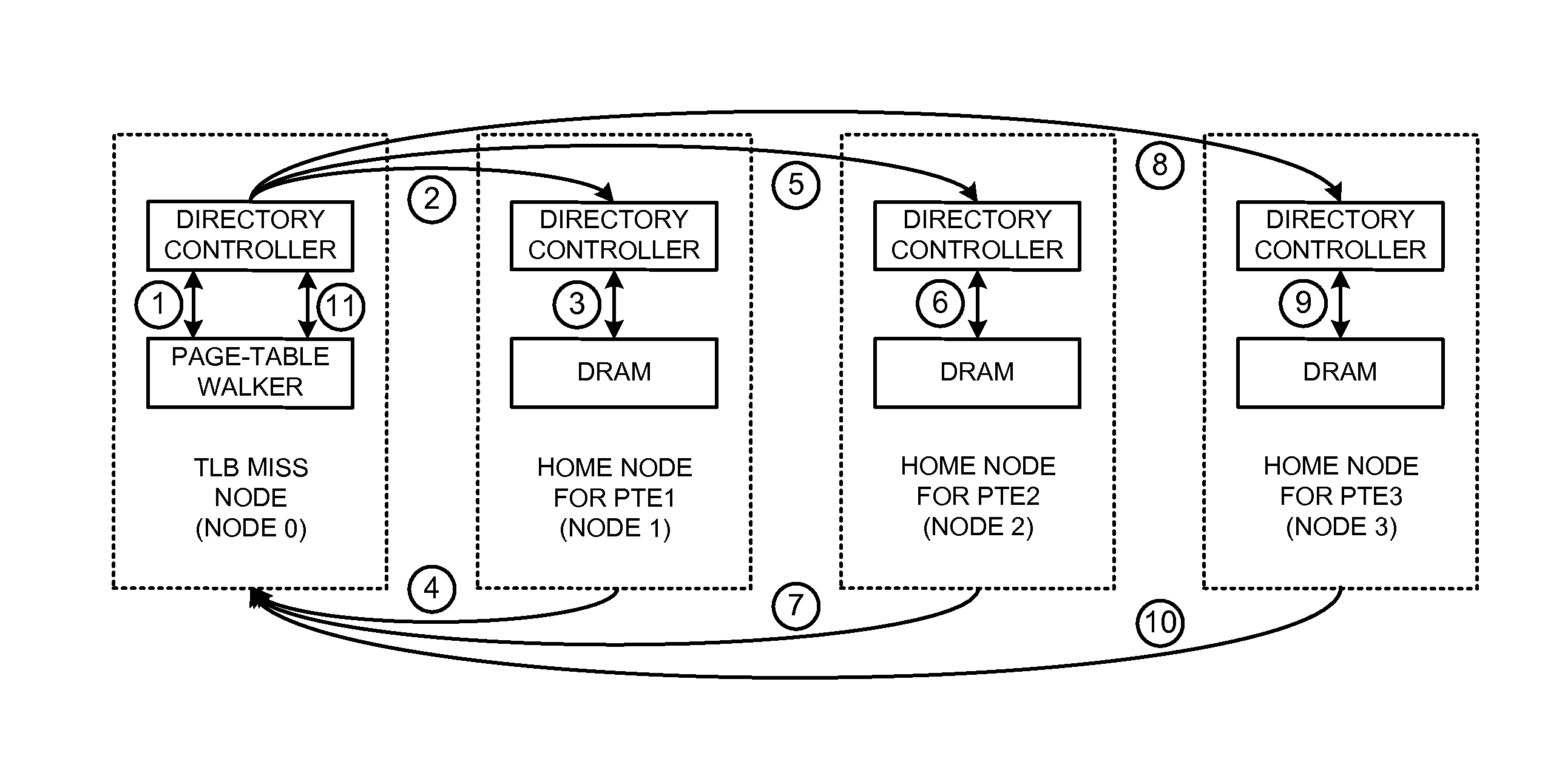
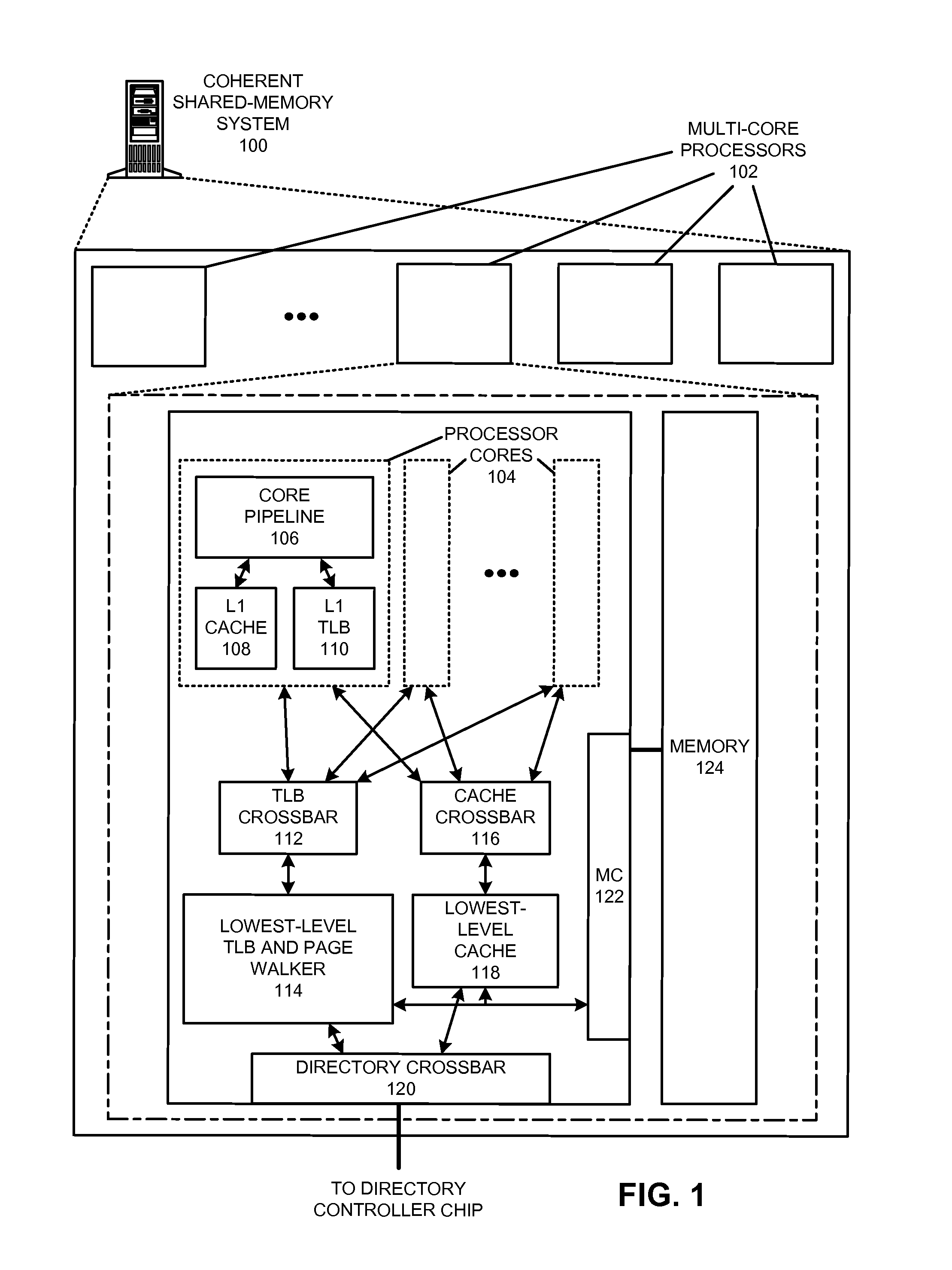
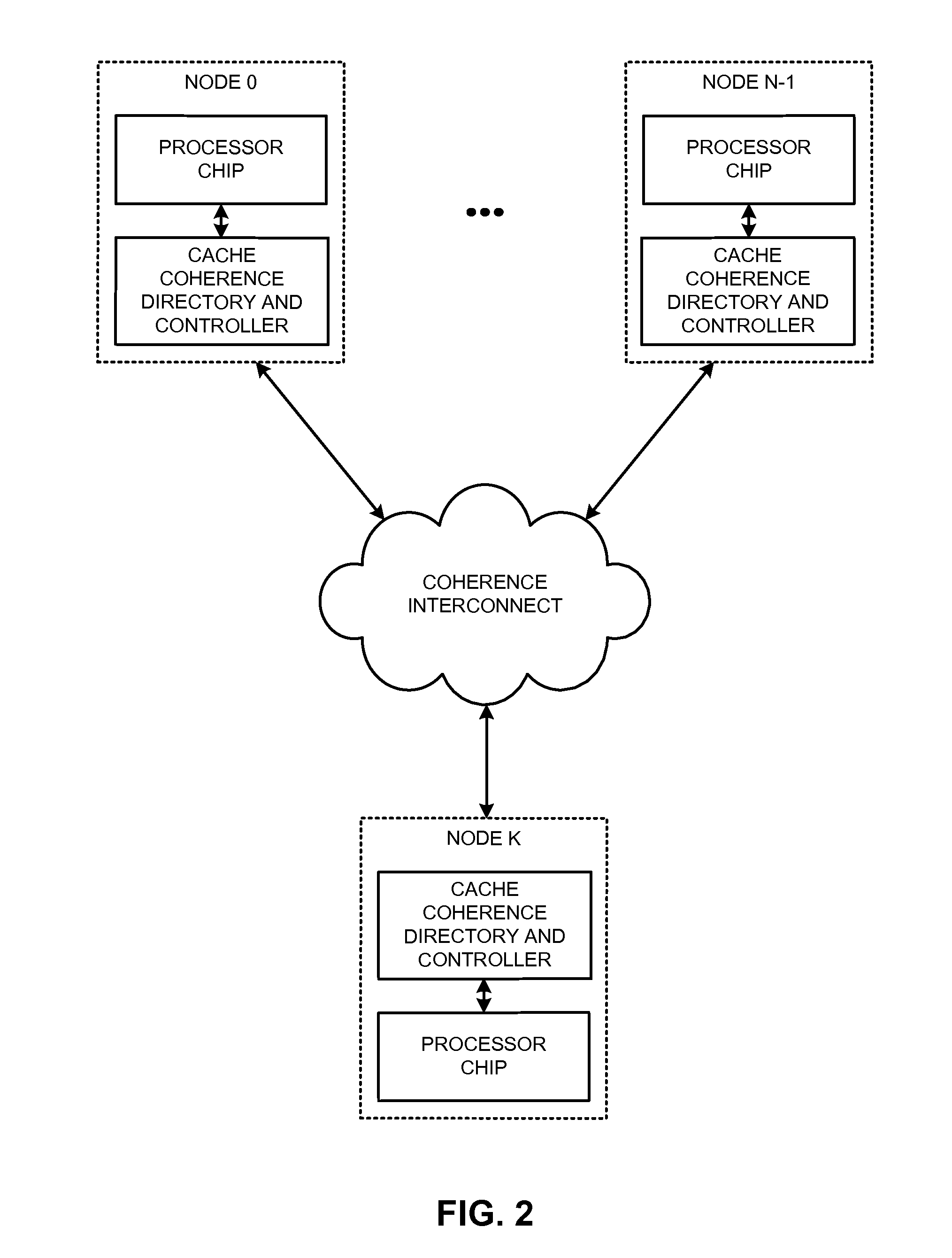
Distributed page-table lookups in a shared-memory system
ActiveUS20140089572A1Reduce address-translation latencyReduce communication overheadMemory architecture accessing/allocationMemory adressing/allocation/relocationPhysical addressPage table
The disclosed embodiments provide a system that performs distributed page-table lookups in a shared-memory multiprocessor system with two or more nodes, where each of these nodes includes a directory controller that manages a distinct portion of the system's address space. During operation, a first node receives a request for a page-table entry that is located at a physical address that is managed by the first node. The first node accesses its directory controller to retrieve the page-table entry, and then uses the page-table entry to calculate the physical address for a subsequent page-table entry. The first node determines the home node (e.g., the managing node) for this calculated physical address, and sends a request for the subsequent page-table entry to that home node.
Owner:ORACLE INT CORP
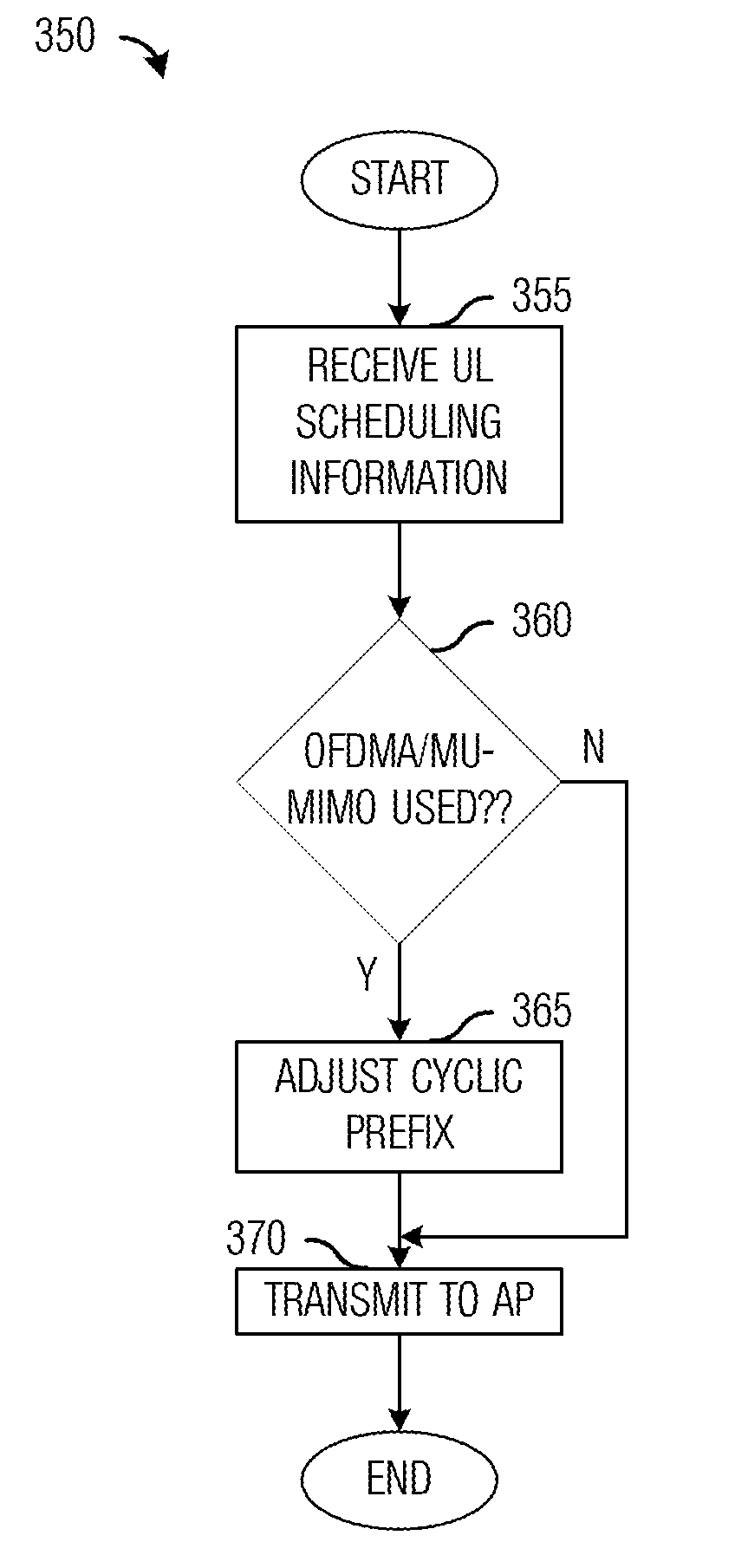
System and Method for Setting Cyclic Prefix Length
ActiveUS20150117363A1Reduce communication overheadSpatial transmit diversityNetwork traffic/resource managementCommunications systemUplink transmission
A method for communicating in a wireless communications system includes receiving scheduling information including information for an uplink transmission scheduled for the station, and determining a first length of a first cyclic prefix for a transmission in accordance with the scheduling information. The method also includes transmitting the transmission with the first cyclic prefix.
Owner:FUTUREWEI TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com