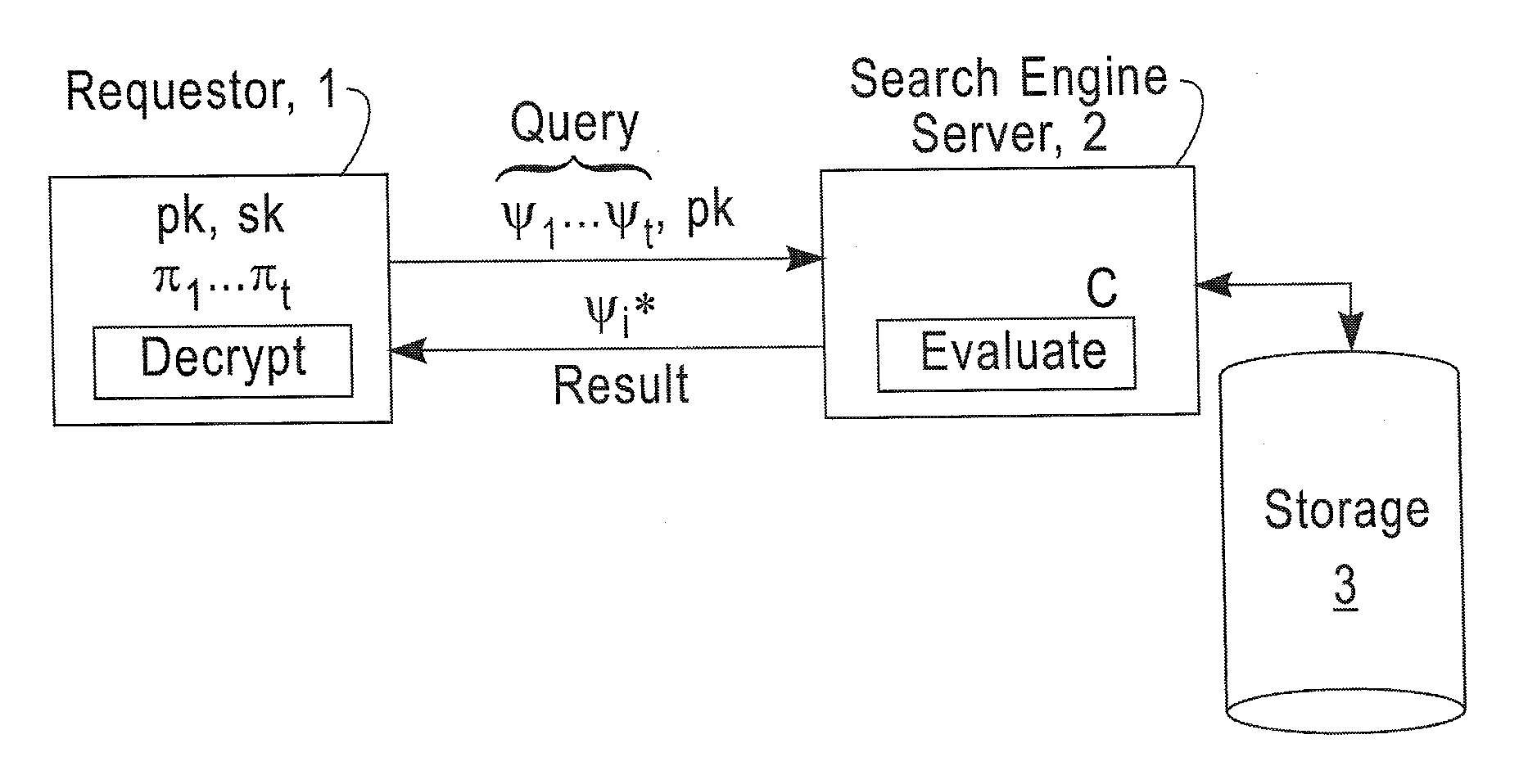
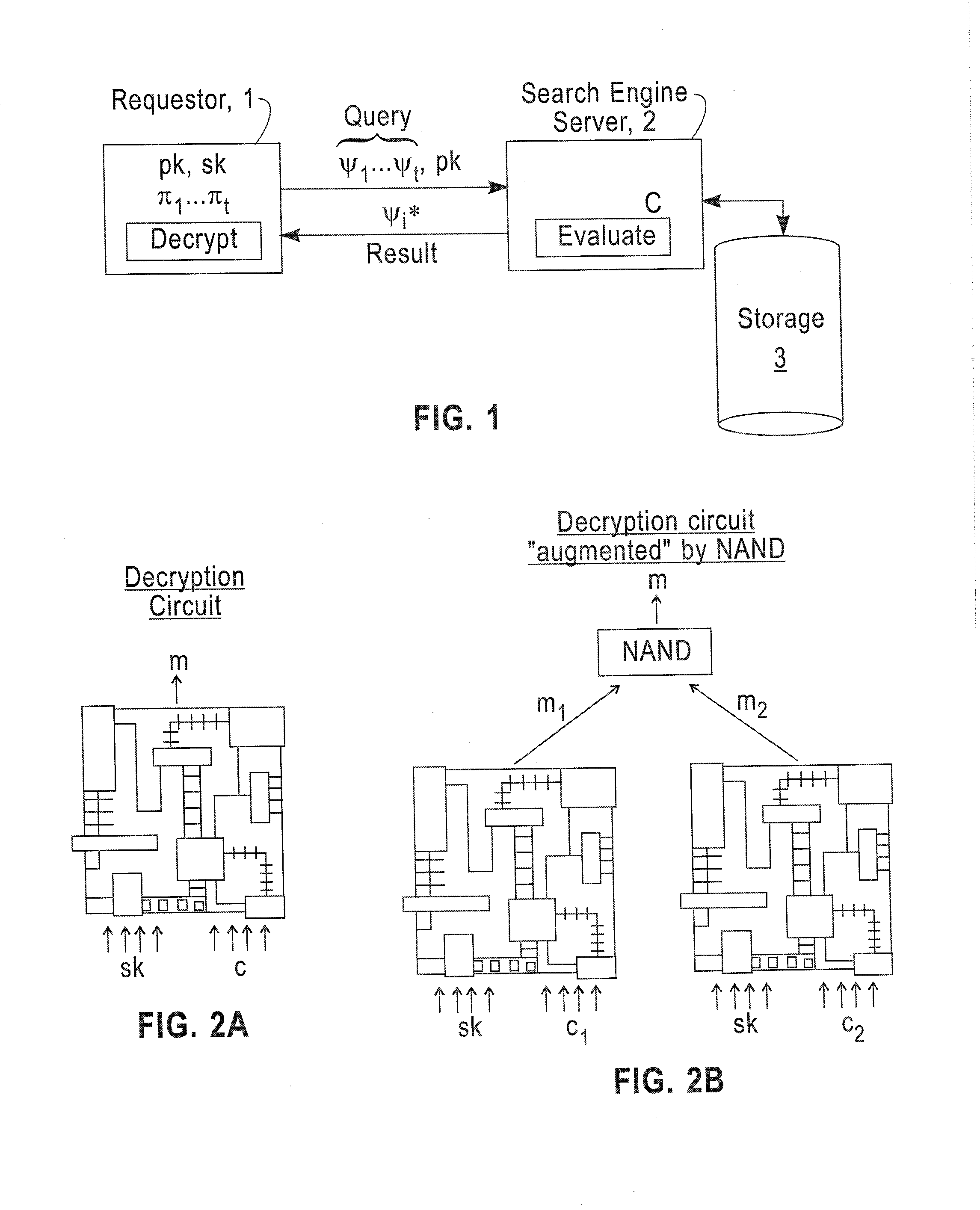
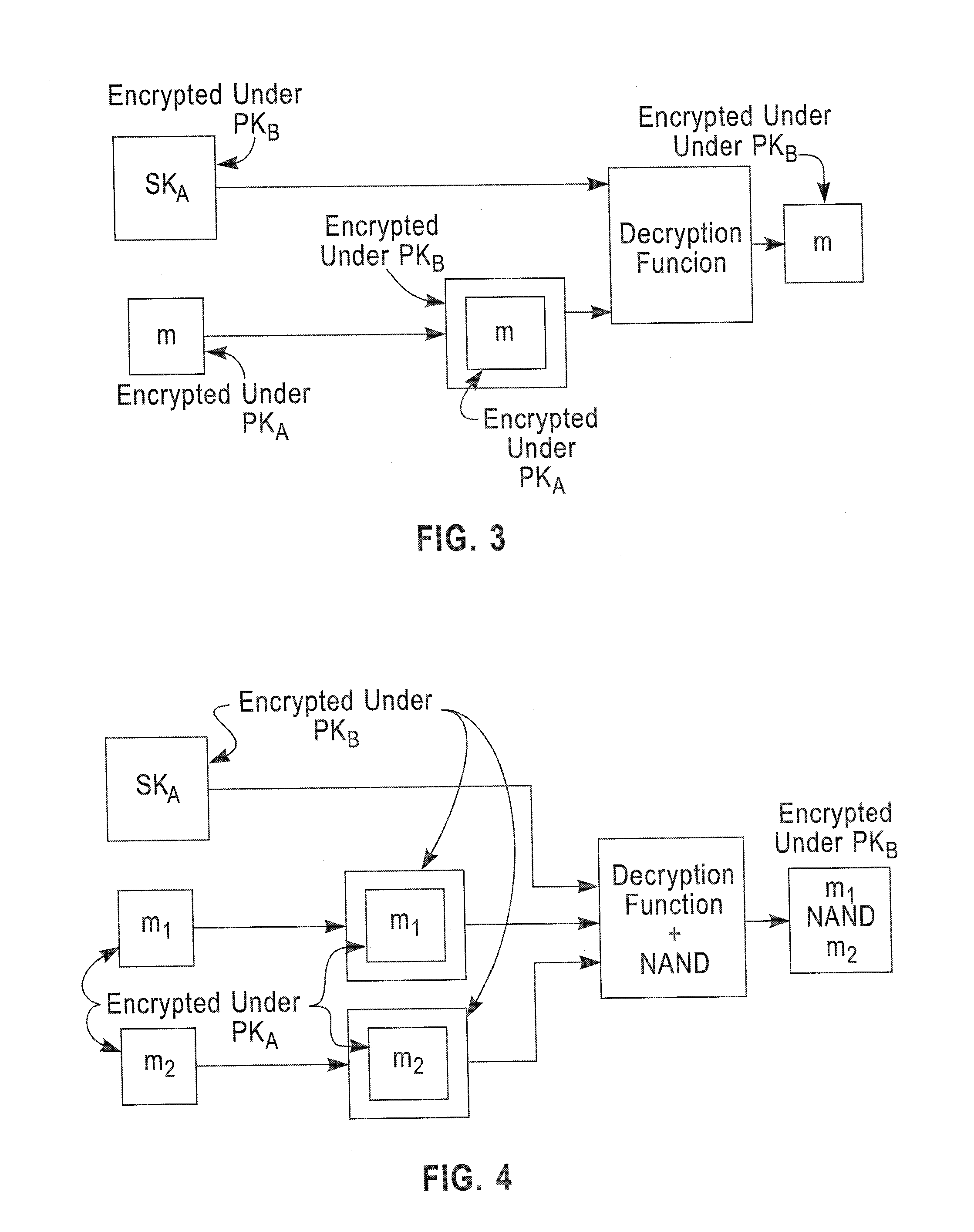
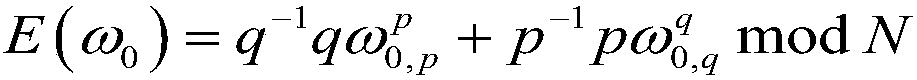Patents
Literature
1201 results about "Homomorphic encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Homomorphic encryption is a form of encryption that allows computation on ciphertexts, generating an encrypted result which, when decrypted, matches the result of the operations as if they had been performed on the plaintext.
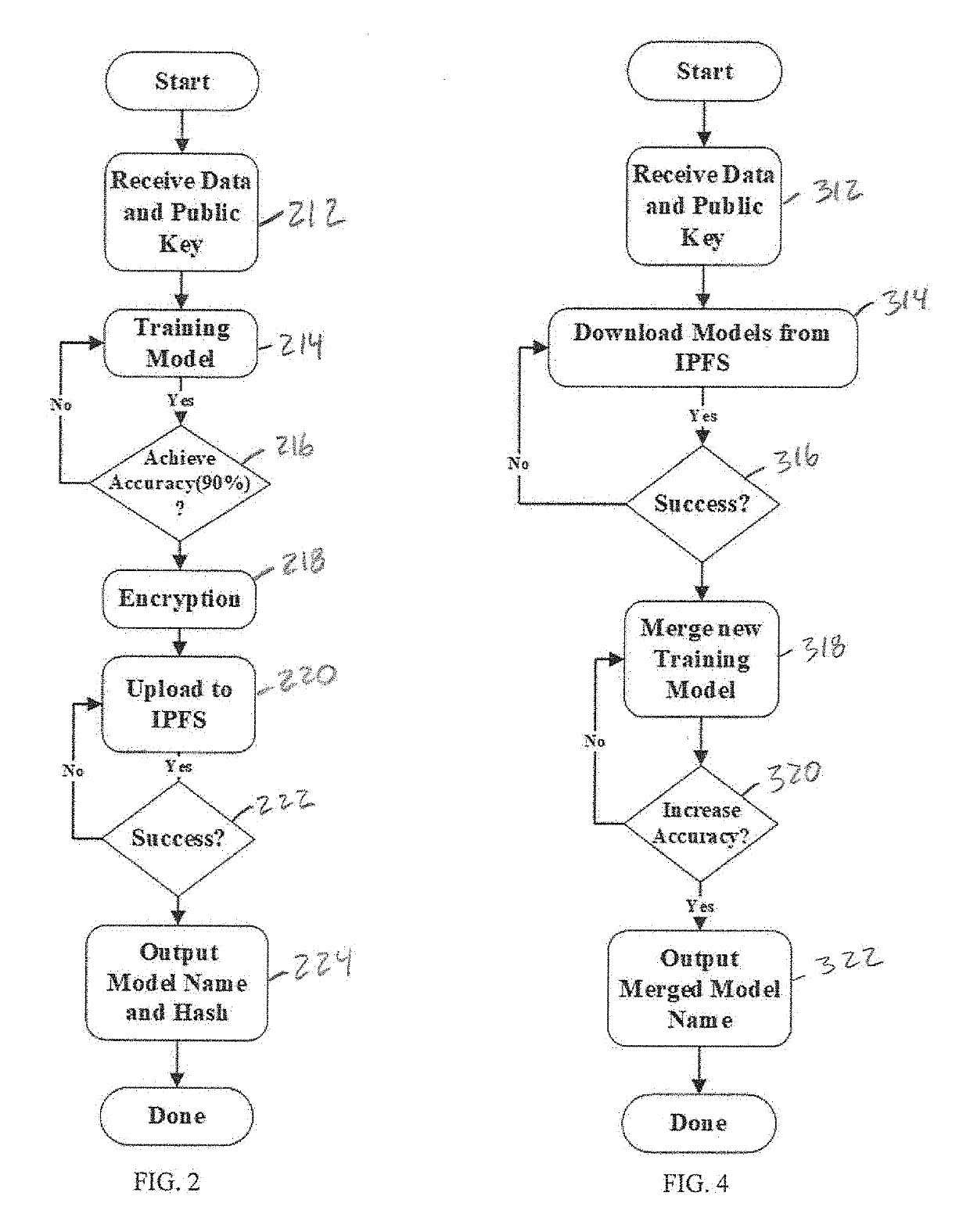
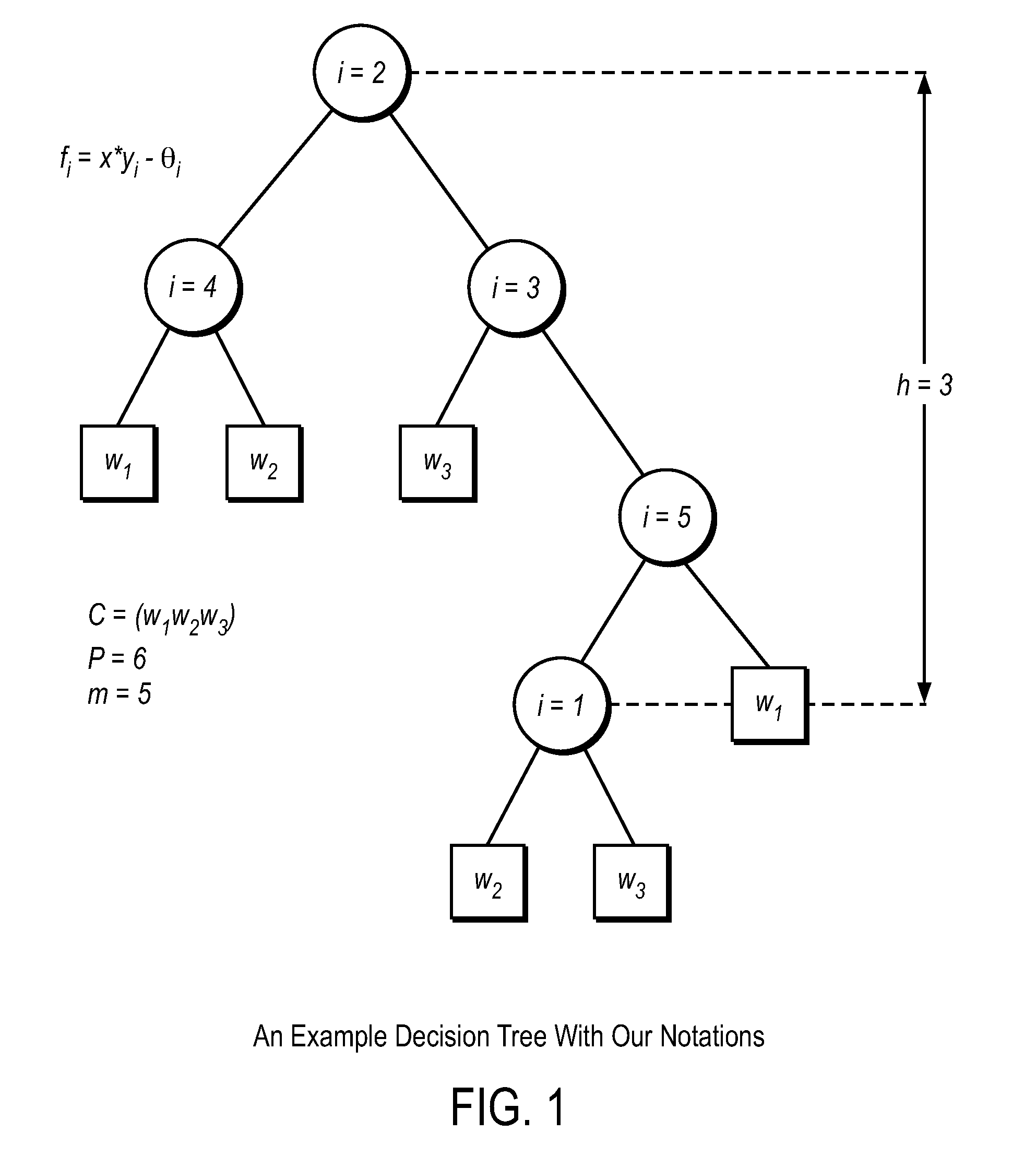
Fully homomorphic encryption method based on a bootstrappable encryption scheme, computer program and apparatus
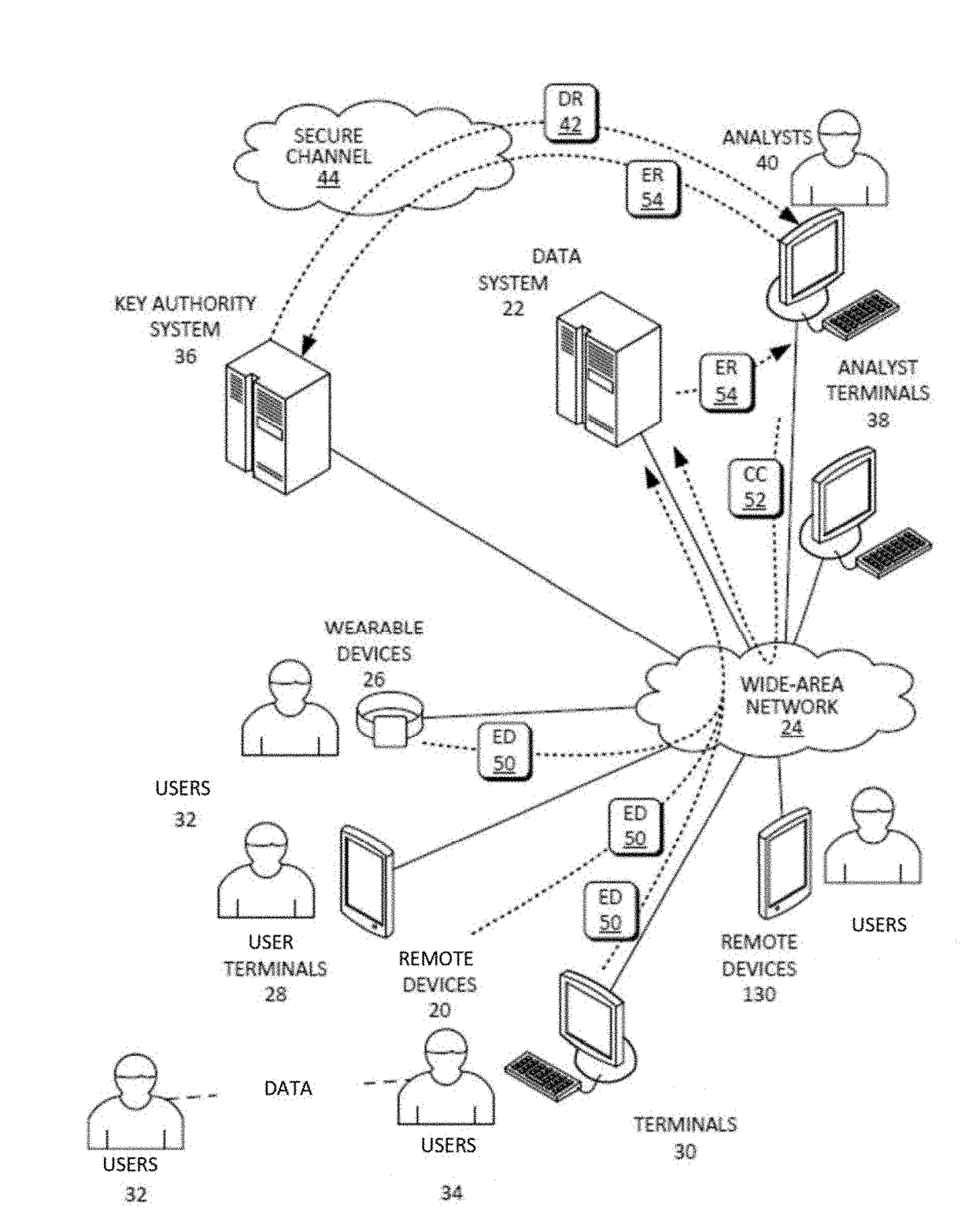
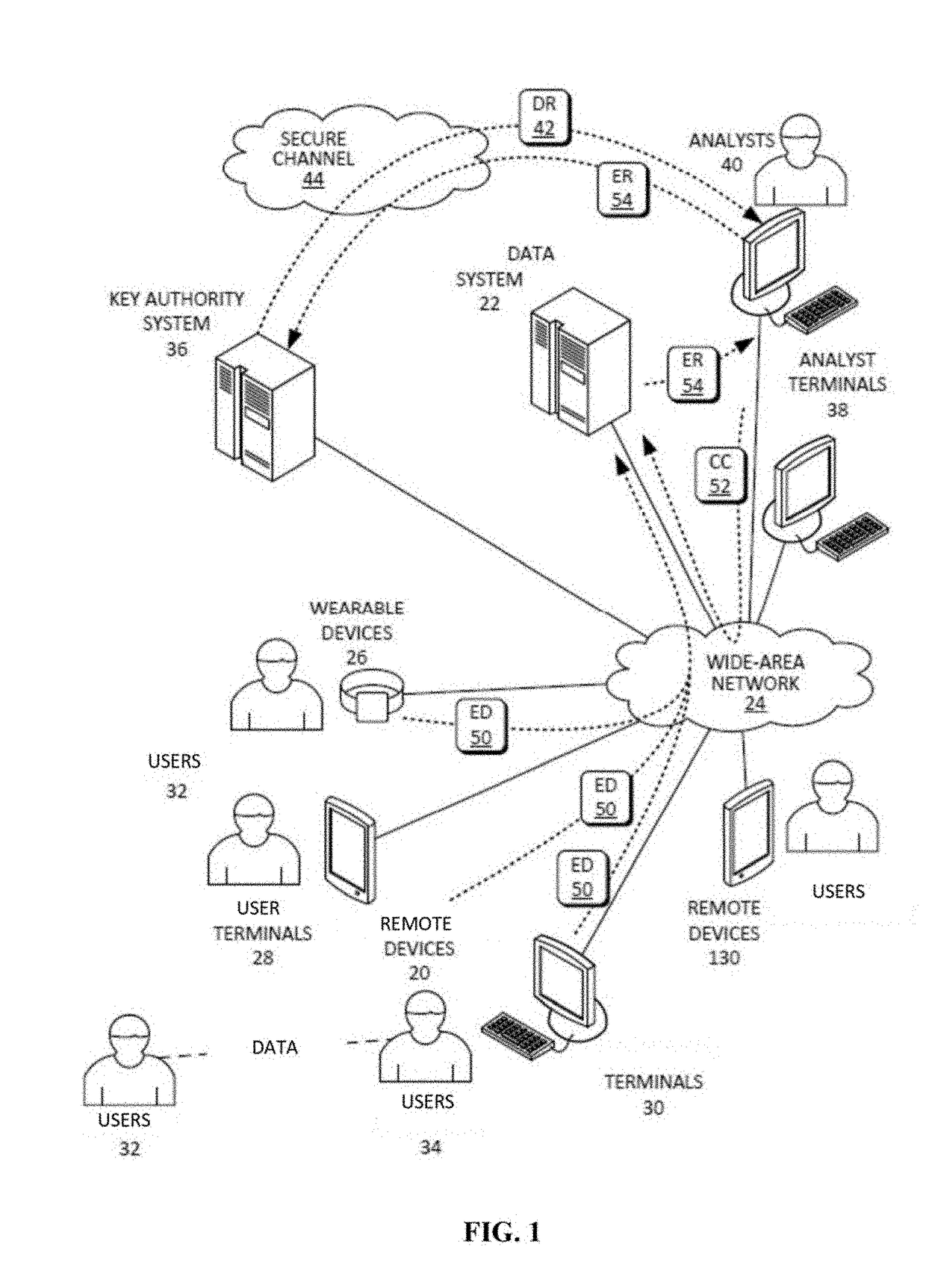
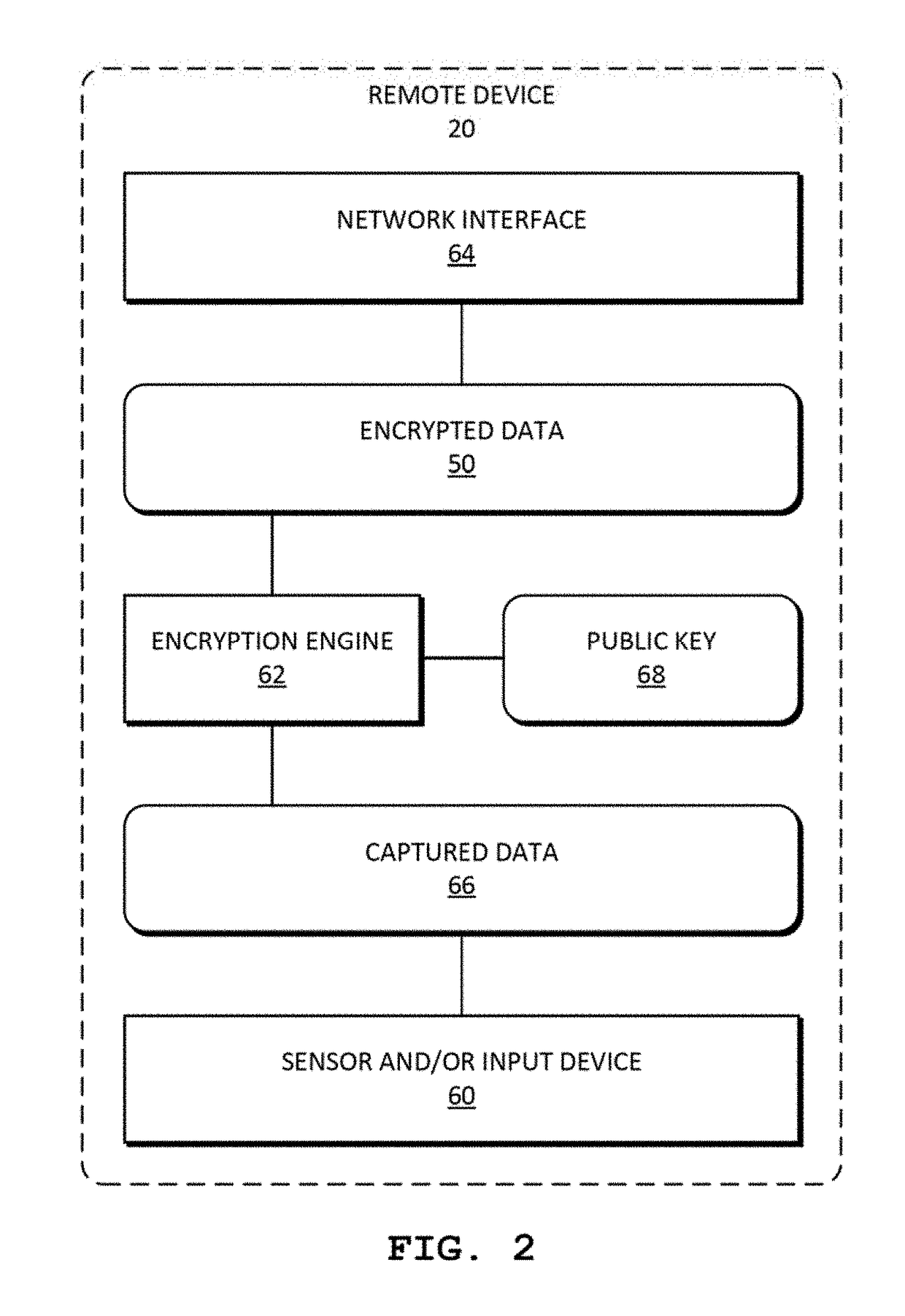
ActiveUS20110110525A1Key distribution for secure communicationMultiple keys/algorithms usageAssessment dataData application
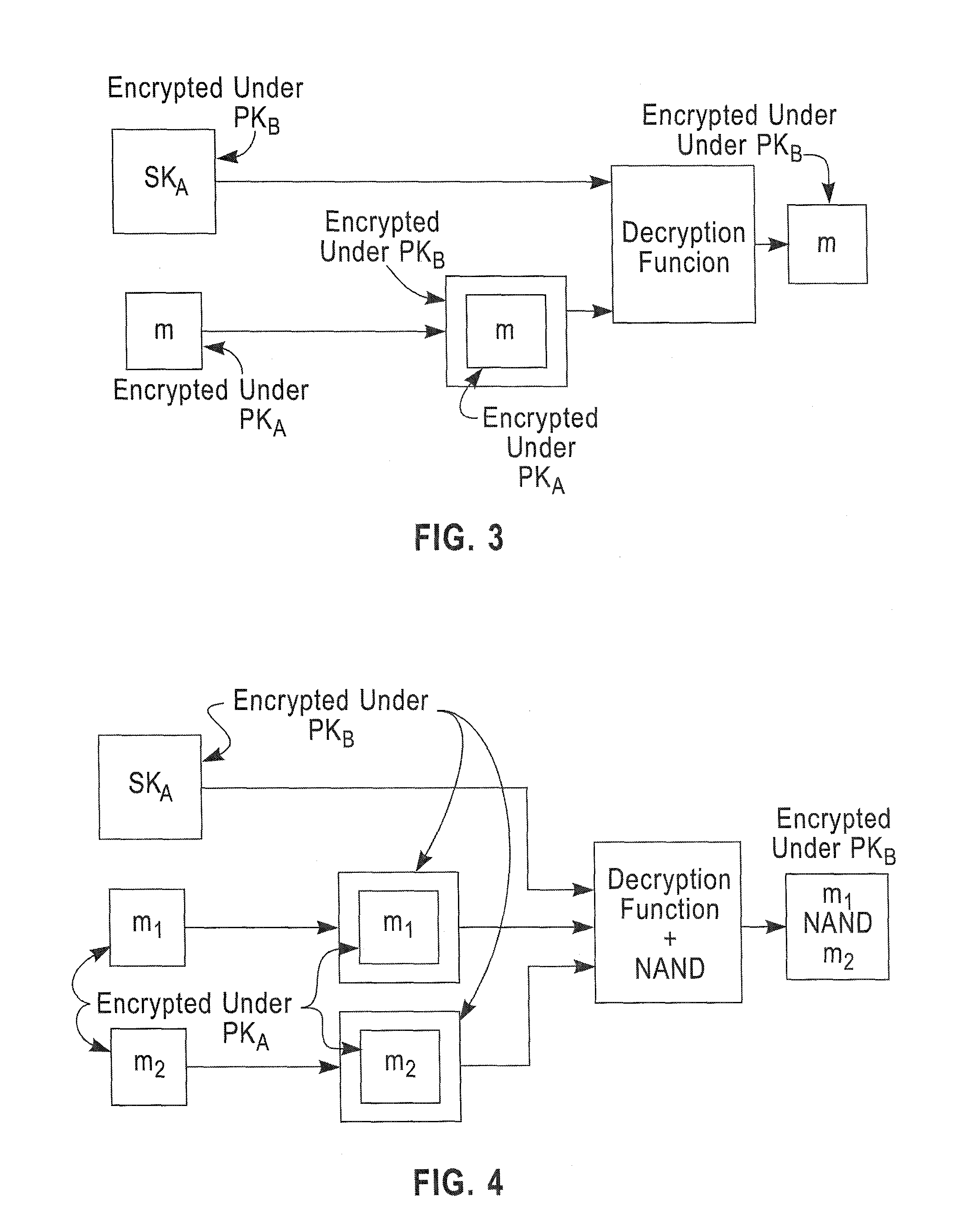
A method includes encrypting information in accordance with an encryption scheme that uses a public key; encrypting a plurality of instances of a secret key, each being encrypted using at least one additional instance of the public key; sending the encrypted information and the plurality of encrypted instances of the secret key to a destination; receiving an encrypted result from the destination; and decrypting the encrypted result. A further method includes receiving a plurality of encrypted secret keys and information descriptive of a function to be performed on data; converting the information to a circuit configured to perform the function on the data; and applying the data to inputs of the circuit and evaluating the data using, in turn, the plurality of encrypted secret keys.
Owner:IBM CORP
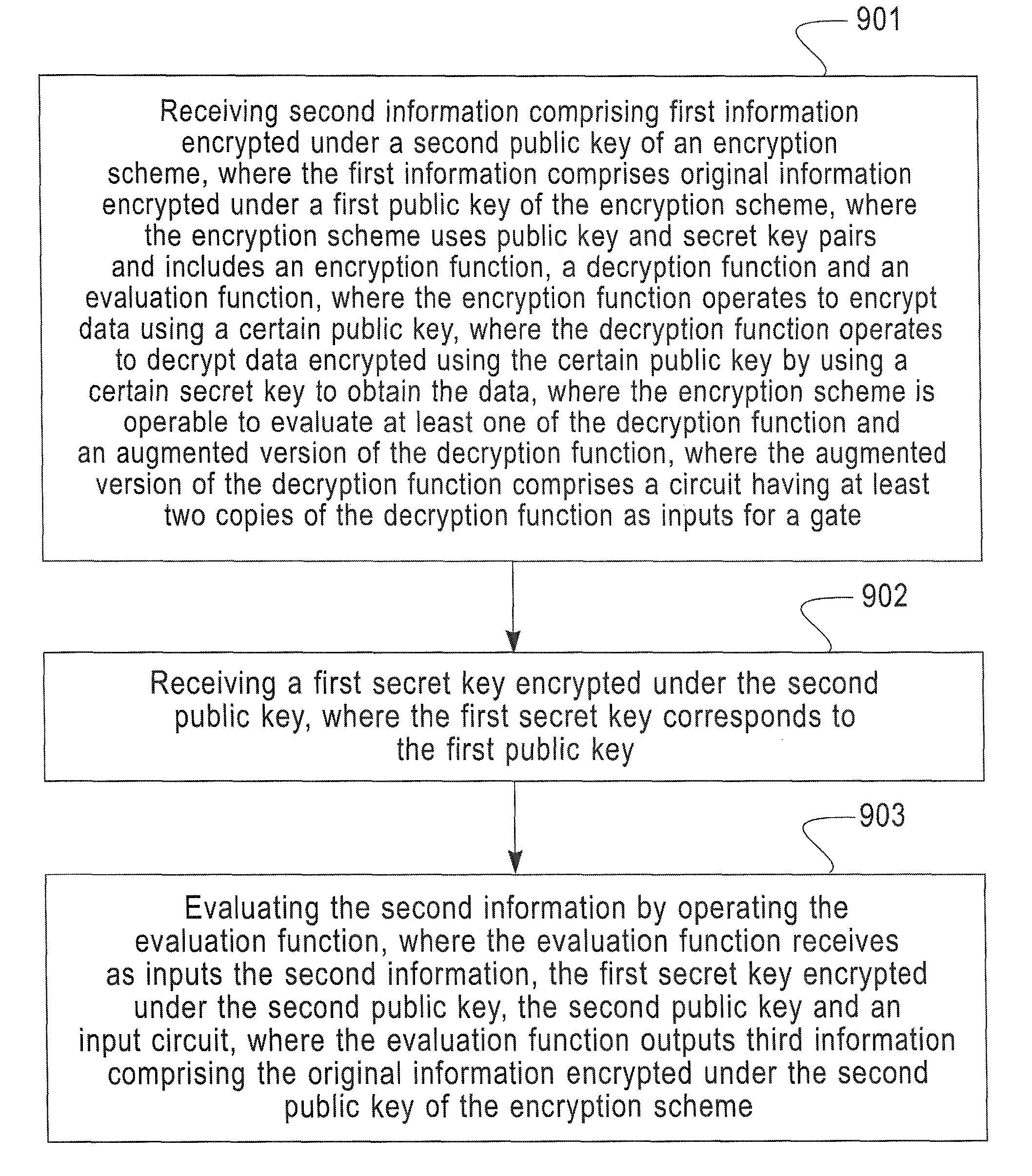
Bootstrappable homomorphic encryption method, computer program and apparatus
ActiveUS8515058B1Secret communicationCommunication with homomorphic encryptionComputer hardwareComputer program
Embodiments of the present invention describe a fully homomorphic encryption scheme using a “bootstrapable” homomorphic encryption scheme that evaluate a function ƒ when ƒ is the encryption schemes own decryption function. Specifically, the fully homomorphic encryption scheme uses the “bootstrapable” homomorphic encryption scheme to determine the decryption function to decrypt data encrypted under the fully homomorphic encryption scheme.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Fully Homomorphic Encryption
InactiveUS20130170640A1Reduce noise levelGrowth inhibitionPublic key for secure communicationSecret communicationRoundingNoise level
In one exemplary embodiment of the invention, a method and computer program include: receiving first and second ciphertexts having first and second data encrypted per an encryption scheme, the encryption scheme has public / secret keys and encryption, decryption, operation and refresh functions, the encryption function encrypts data, the decryption decrypts ciphertext, the operation receives ciphertexts and performs operation(s) on them, the refresh operates to prevent growth of the magnitude of noise for a ciphertext while reducing the modulus of the ciphertext without using the secret key, utilizing a modulus switching technique that involves transforming a first ciphertext c modulo q into a second ciphertext c′ modulo p while preserving correctness, the technique includes scaling by p / q and rounding, p<q; using the operation function(s), performing operation(s) on them to obtain a third ciphertext; and reducing a noise level of the third ciphertext using the refresh function.
Owner:IBM CORP
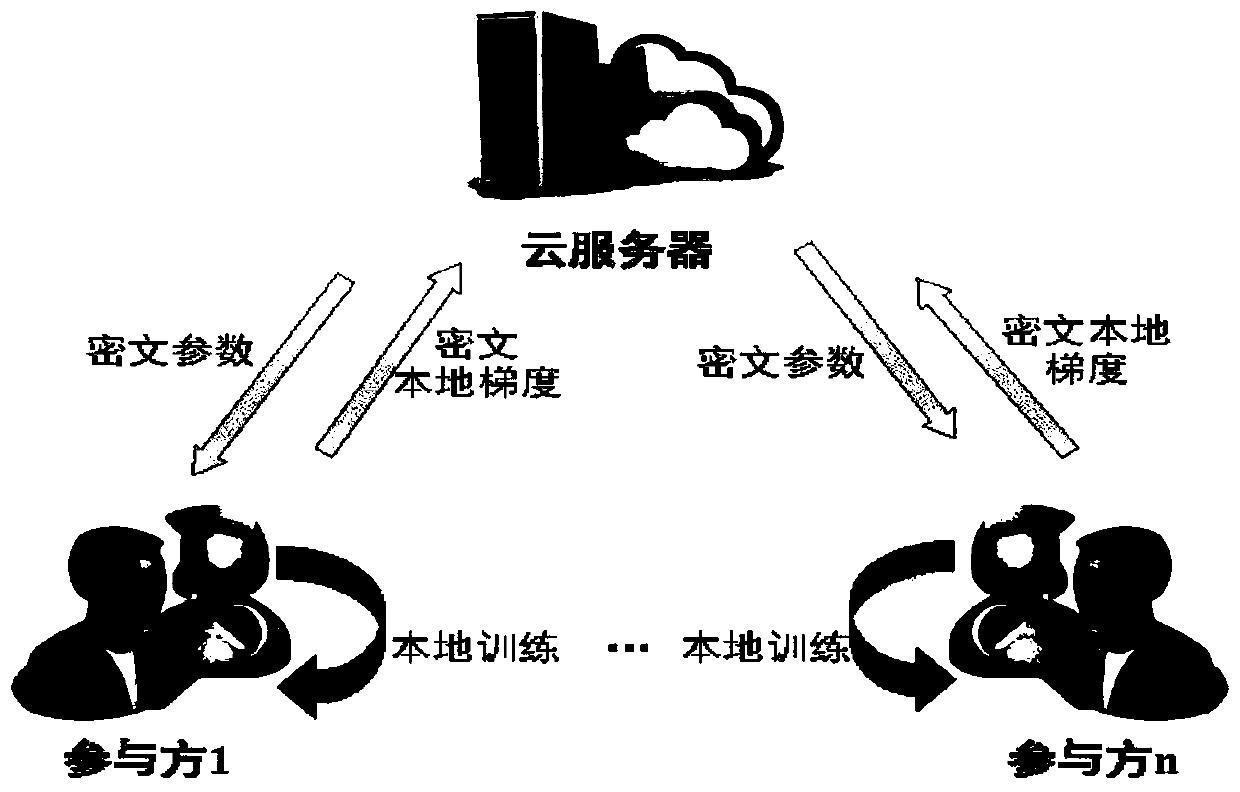
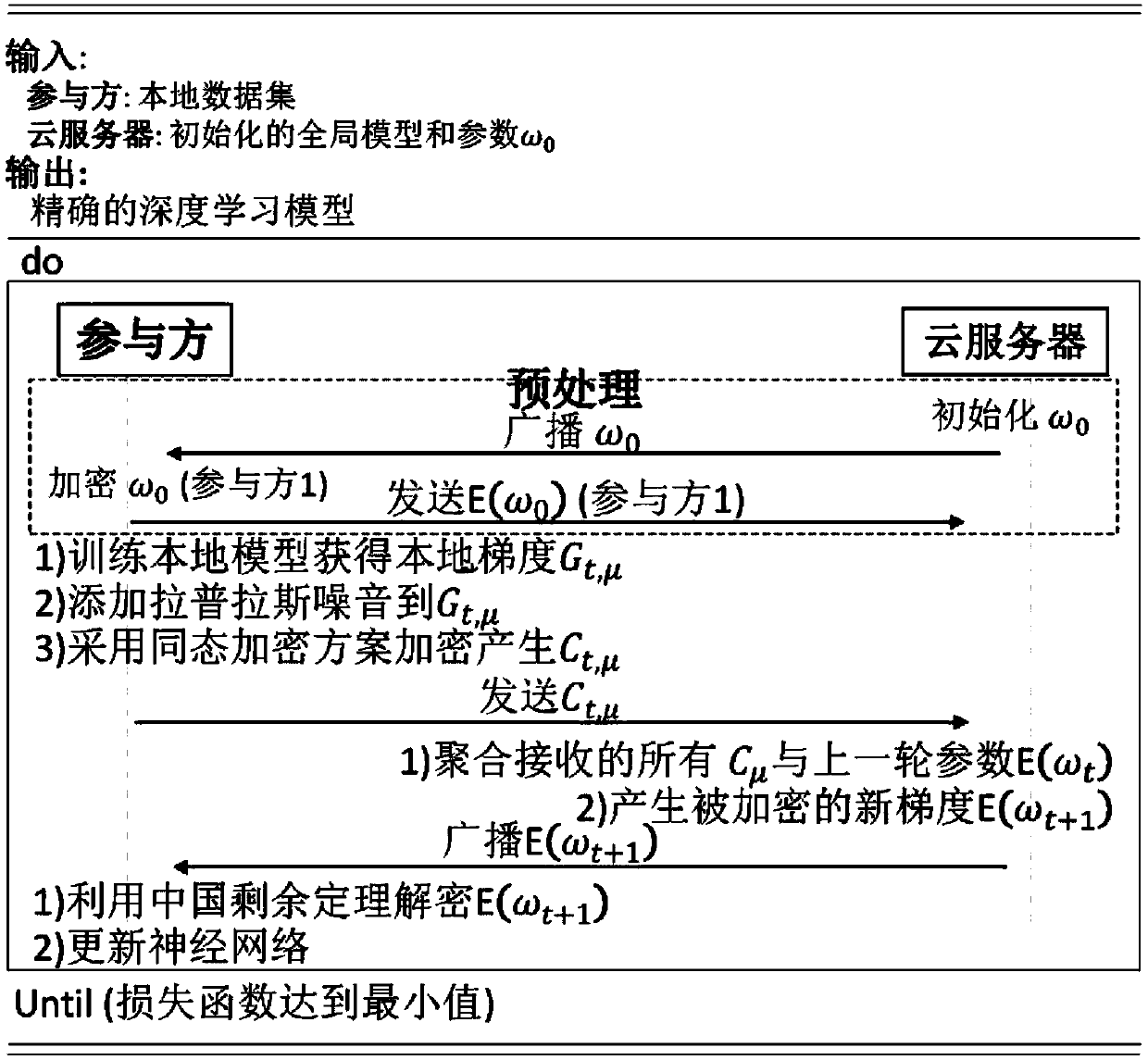
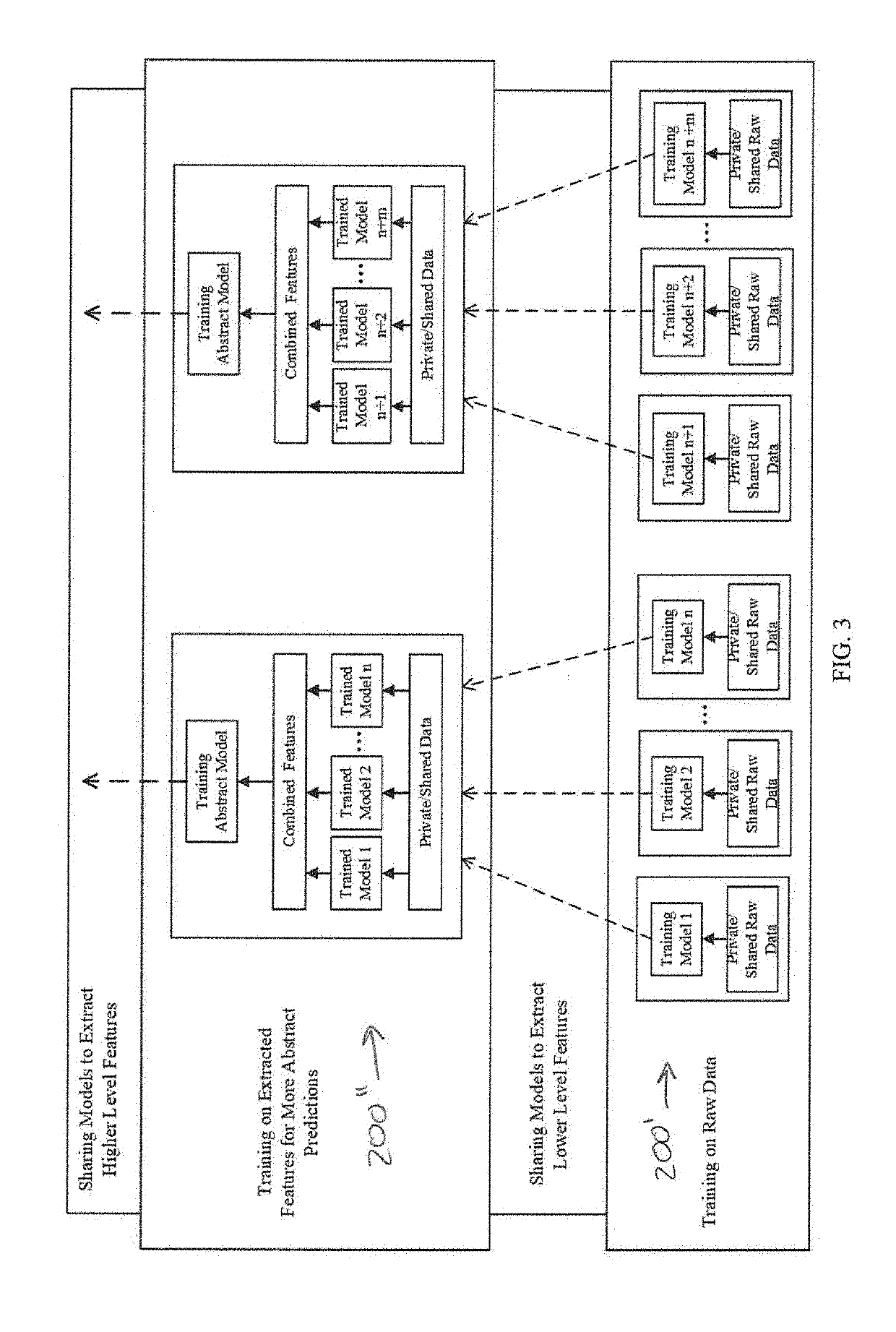
A combined deep learning training method based on a privacy protection technology
ActiveCN109684855AAvoid gettingSafe and efficient deep learning training methodDigital data protectionCommunication with homomorphic encryptionPattern recognitionData set
The invention belongs to the technical field of artificial intelligence, and relates to a combined deep learning training method based on a privacy protection technology. The efficient combined deep learning training method based on the privacy protection technology is achieved. In the invention, each participant first trains a local model on a private data set to obtain a local gradient, then performs Laplace noise disturbance on the local gradient, encrypts the local gradient and sends the encrypted local gradient to a cloud server; The cloud server performs aggregation operation on all thereceived local gradients and the ciphertext parameters of the last round, and broadcasts the generated ciphertext parameters; And finally, the participant decrypts the received ciphertext parameters and updates the local model so as to carry out subsequent training. According to the method, a homomorphic encryption scheme and a differential privacy technology are combined, a safe and efficient deep learning training method is provided, the accuracy of a training model is guaranteed, and meanwhile a server is prevented from inferring model parameters, training data privacy and internal attacksto obtain private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
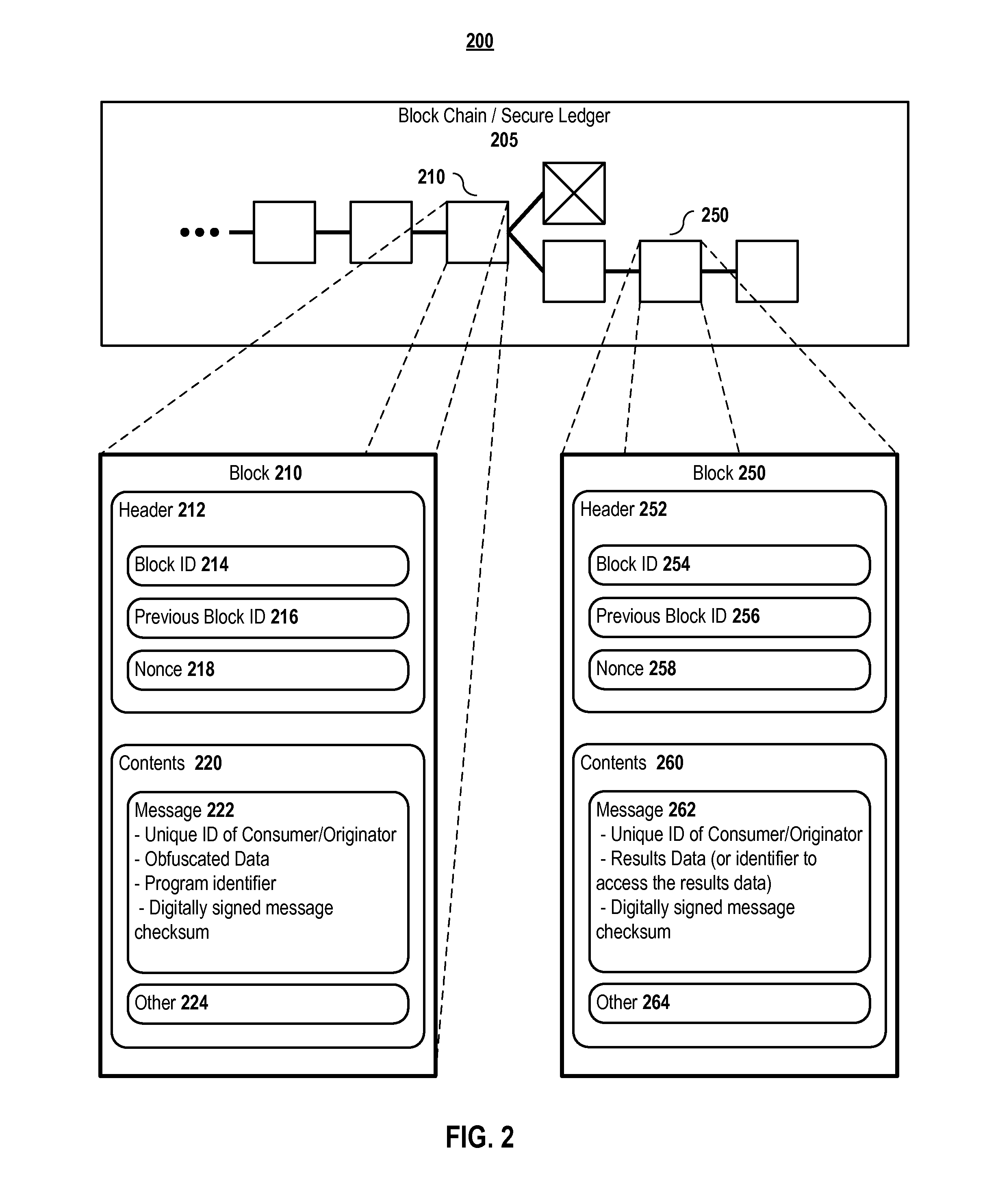
Methods and systems for obfuscating data and computations defined in a secure distributed transaction ledger
ActiveUS20160261404A1Digital data protectionCommunication with homomorphic encryptionConfidentialityDistributed transaction
Aspects of the present invention provide systems and methods that facilitate computations that are publically defined while assuring the confidentiality of the input data provided, the generated output data, or both using homomorphic encryption on the contents of the secure distributed transaction ledger. Full homomorphic encryption schemes protect data while still enabling programs to accept it as input. In embodiments, using a homomorphic encryption data input into a secure distributed transaction ledger allows a consumer to employ highly motivated entities with excess compute capability to perform calculations on the consumer's behalf while assuring data confidentiality, correctness, and integrity as it propagates through the network.
Owner:DELL PROD LP
Efficient Homomorphic Encryption Scheme For Bilinear Forms
InactiveUS20110243320A1Public key for secure communicationSecret communicationComputer hardwareCiphertext
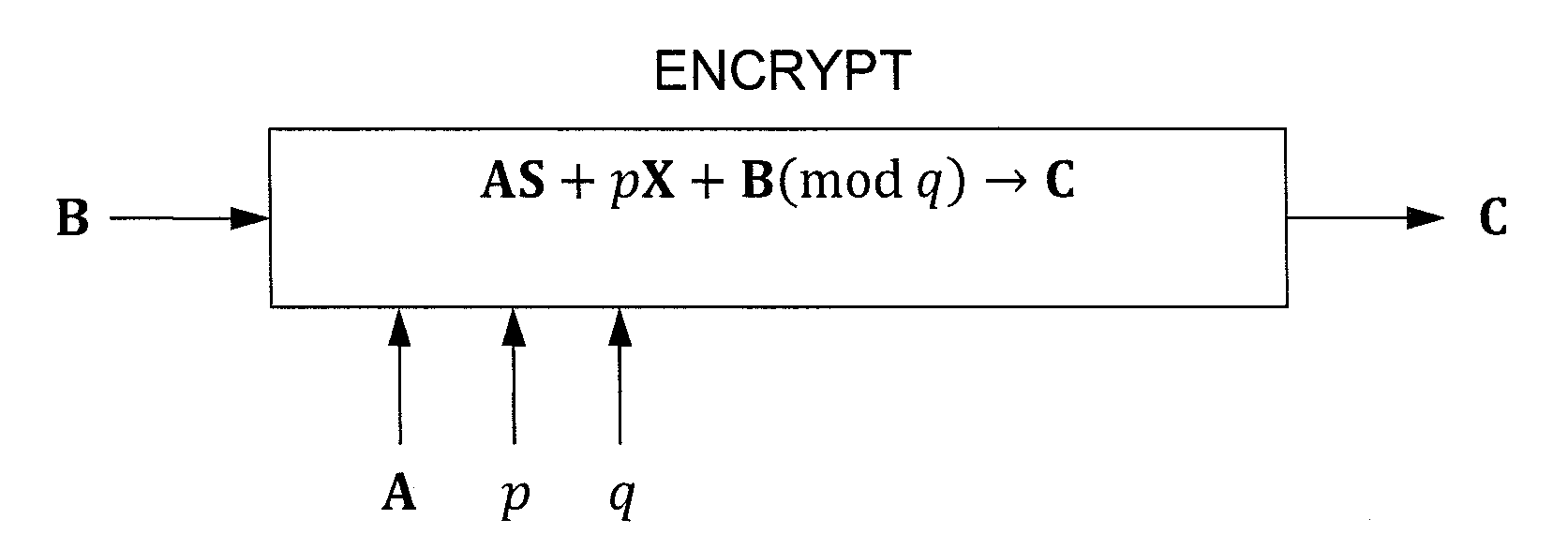
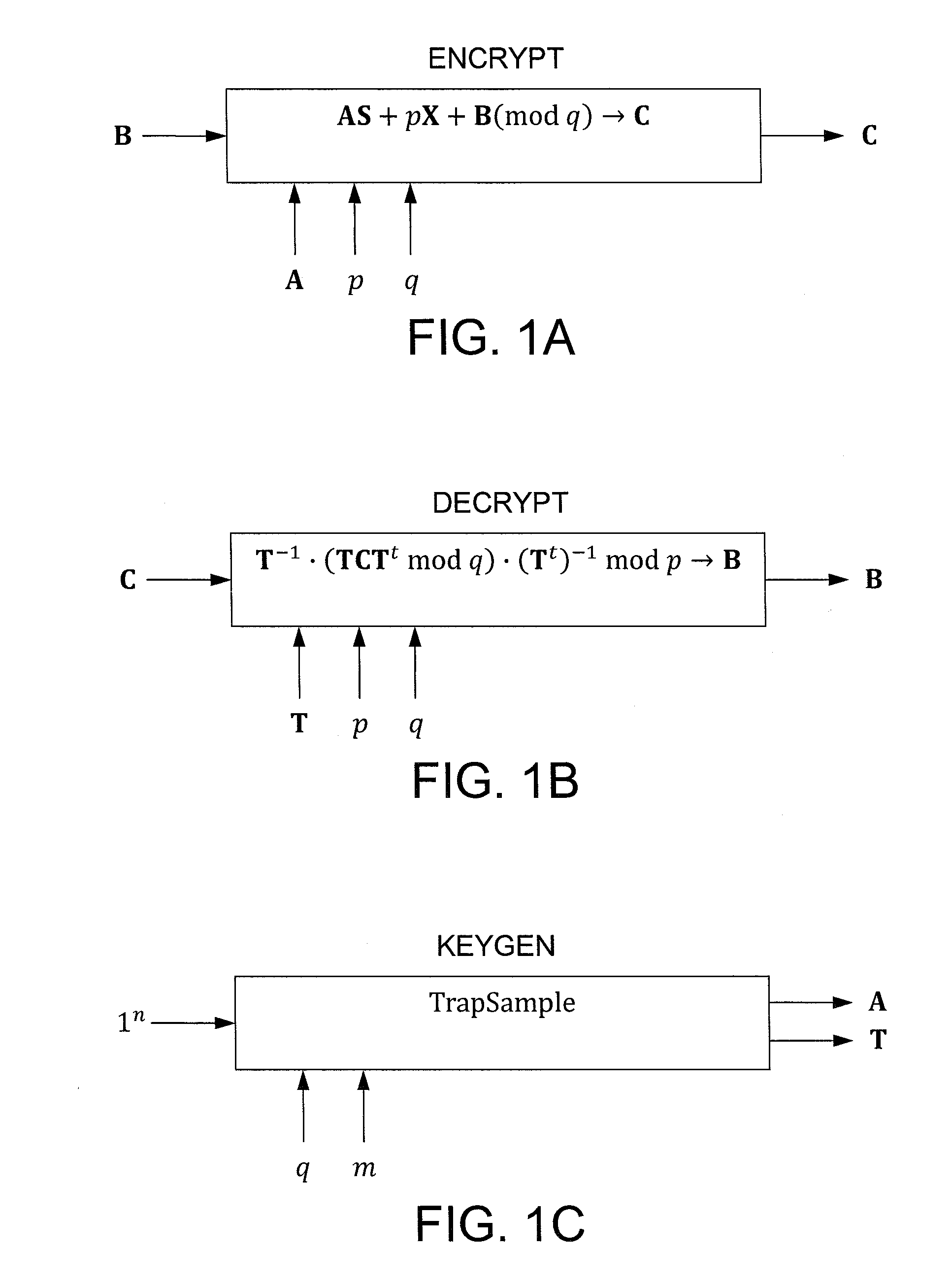
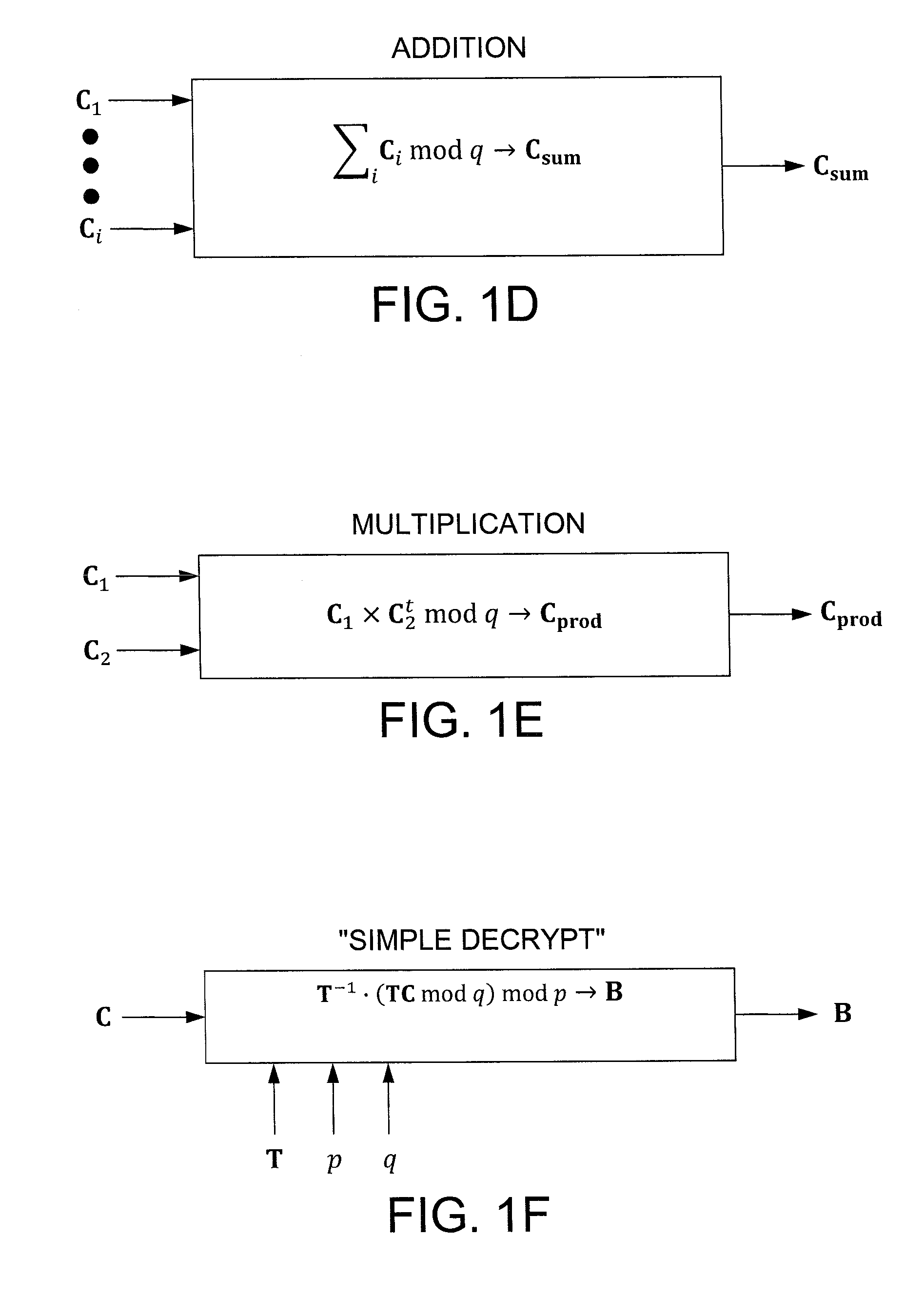
In one exemplary embodiment, a computer readable storage medium tangibly embodying a program of instructions executable by a machine for performing operations including: receiving information B to be encrypted as a ciphertext C in accordance with an encryption scheme having an encrypt function; and encrypting B in accordance with the encrypt function to obtain C, the scheme utilizes at least one public key A, where B, C, and A are matrices, the encrypt function receives as inputs A and B and outputs C as C→AS+pX+B (mod q), S is a random matrix, X is an error matrix, p is in integer, q is an odd prime number. In other exemplary embodiments, the encryption scheme includes a decrypt function that receives as inputs at least one private key T (a matrix) and C and outputs B as B=T−1·(TCTt mod q)·(Tt)−1 mod p.
Owner:IBM CORP
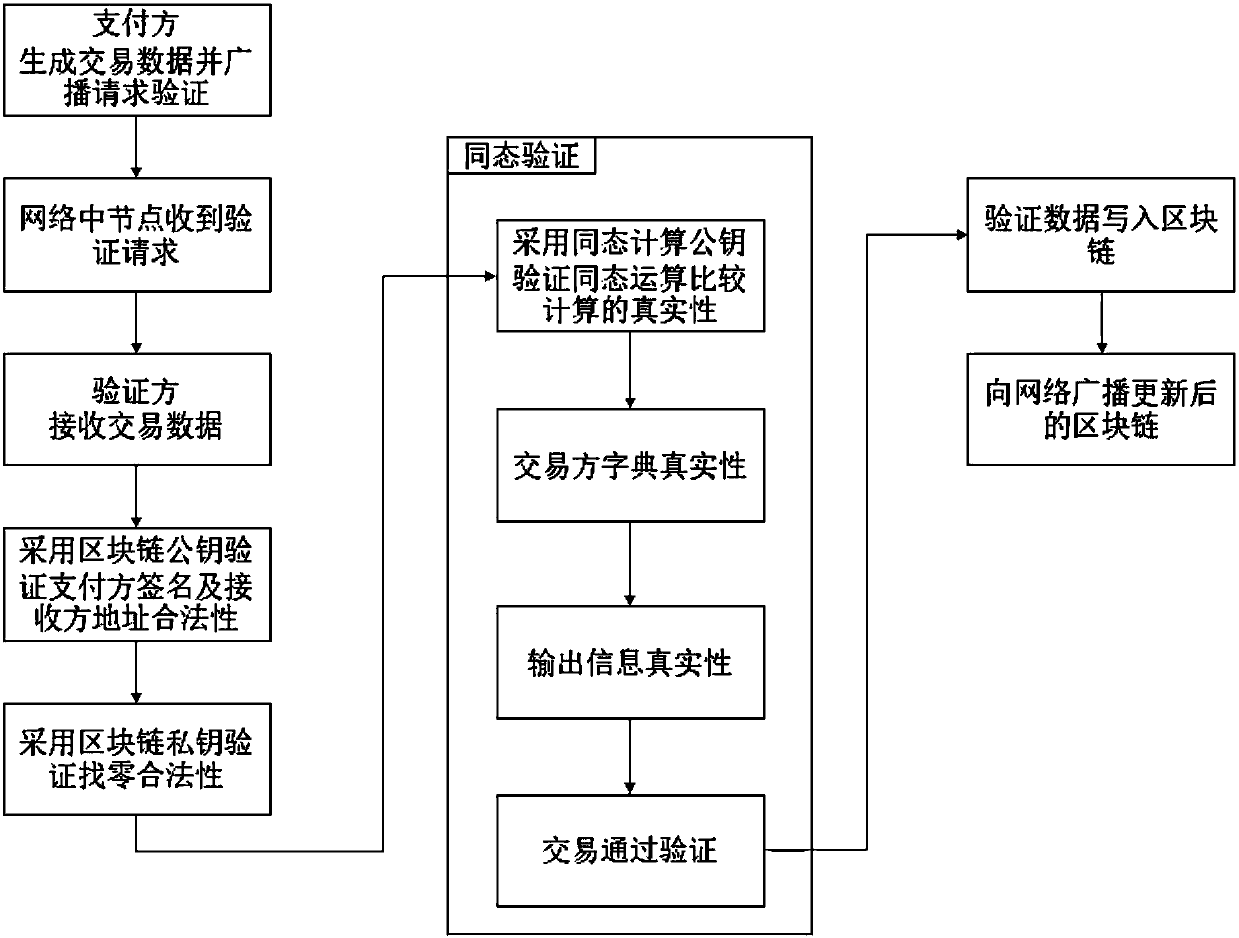
Method of blockchain information encryption based on complete homomorphic encryption method
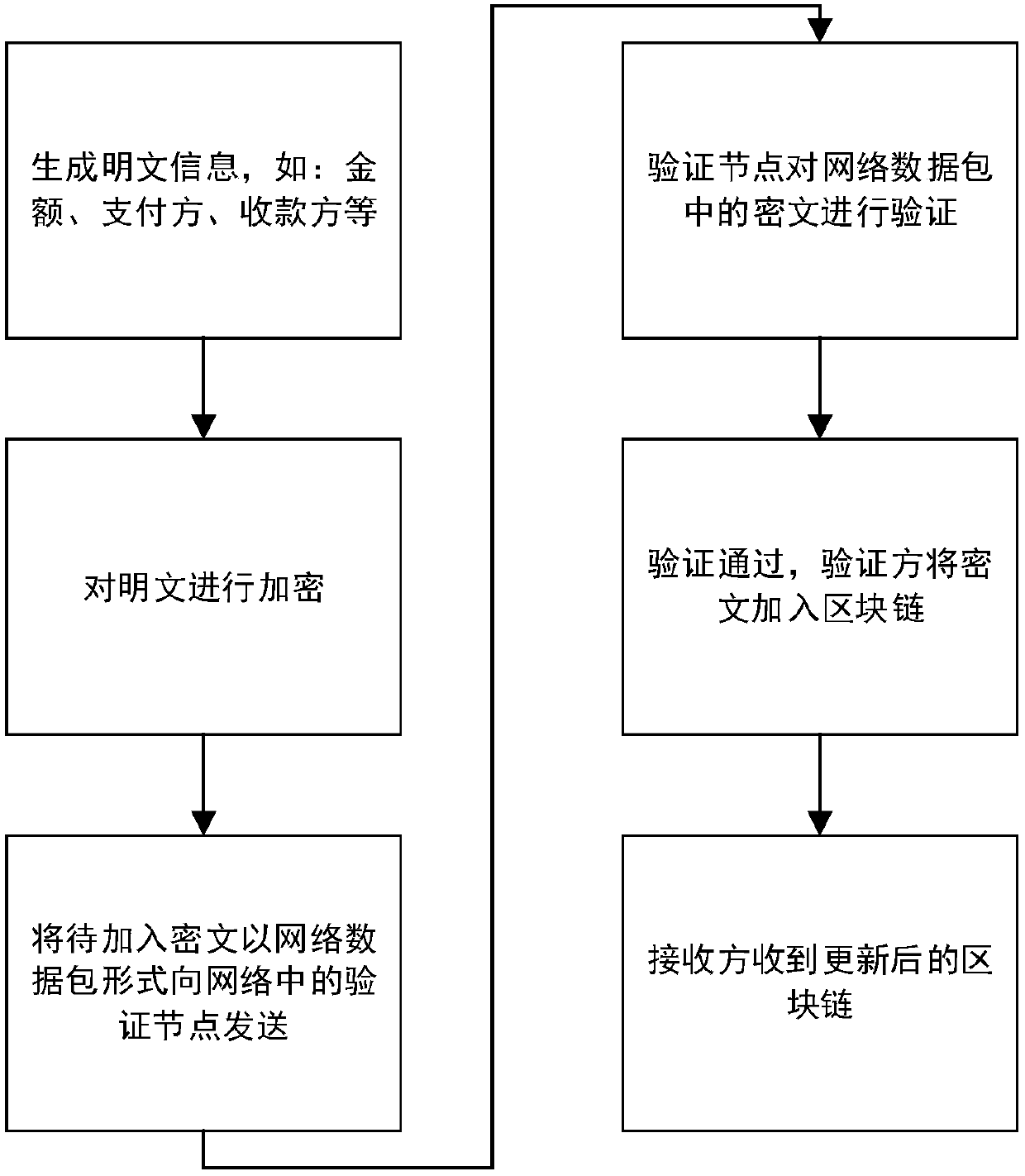
ActiveCN107666388AImprove data securityImprove confidentialityUser identity/authority verificationDigital data protectionPlaintextThird party
A method of blockchain information encryption based on a complete homomorphic encryption method comprises: performing complete homomorphic encryption of a plaintext to be encrypted through an information encryption side and then performing signature; publishing a verification request to all the nodes in a network in public through adoption of an encrypted plaintext; respectively employing blockchain public keys by all the nodes to perform blockchain verification of the signature and an information receiving side, and employing complete homomorphic public keys to perform homomorphic encryptionoperation verification of the ciphertext; and after the verification passes, packing the information encryption side information, the information receiving side information and the ciphertext to generate an updated blockchain, performing broadcast of the network, and completing updating operation of the blockchain. The method provided by the invention greatly improve data safety and privacy of theblockchain technology, is more concise in the whole structure and effective, does not need to introduce a trusted third party and greatly extend and improve an original blockchain technology model, and only needs the smallest improvement to reach a secrecy effect.
Owner:郑珂威
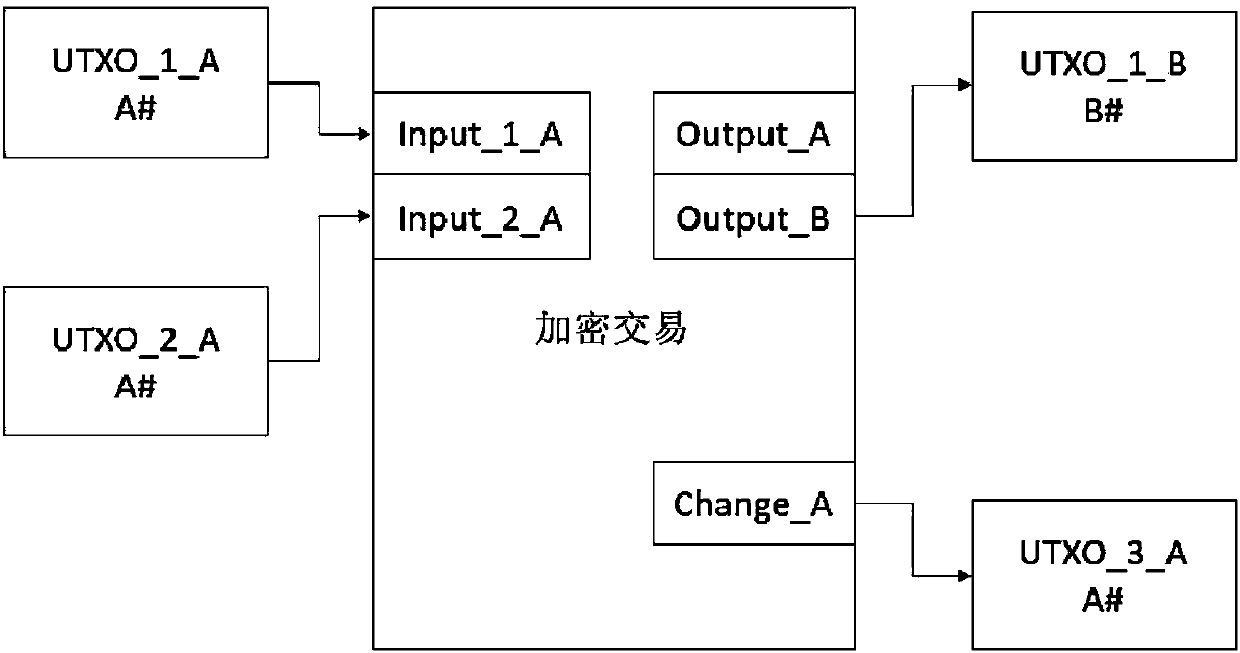
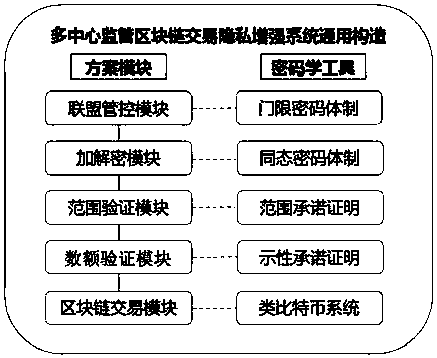
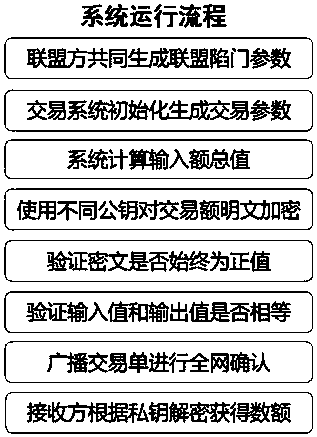
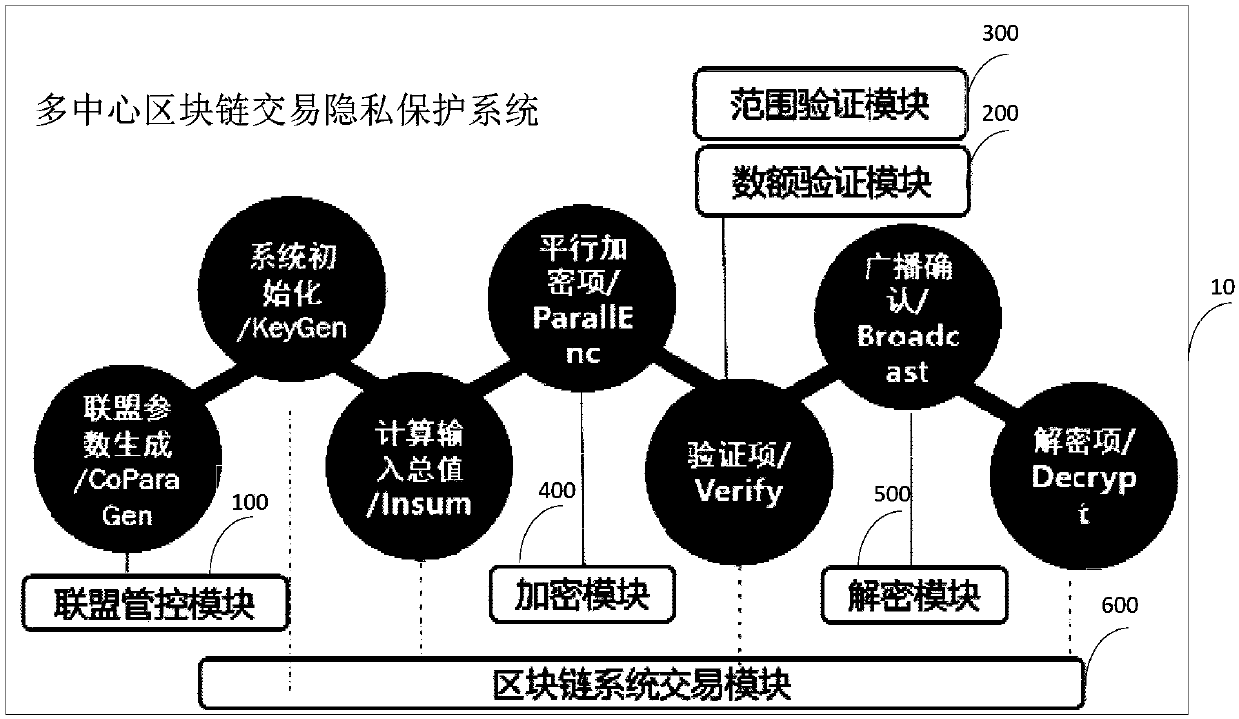
Multi-center block chain transaction privacy protection system and method
InactiveCN108021821ARealize privacy protectionEnhance the security of plaintext amountDigital data protectionCommunication with homomorphic encryptionDigital currencyCiphertext
The invention discloses a multi-center block chain transaction privacy protection system and method. The system comprises an alliance control module, an amount verification module, a range verification module, an encryption module, a decryption module and a block chain system transaction module, wherein the alliance control module is used for generating alliance parameters by multiple participants; the amount verification module is used for verifying that input and output of an encrypted ciphertext amount in a transaction are equal; the range verification module is used for verifying that theencrypted ciphertext amount in the transaction is in a specific interval and is constantly positive; the encryption module and the decryption module are used for carrying out homomorphic encryption and decryption on the amount in transmission and reception processes; and the block chain system transaction module is used for complete bitcoin-like digital currency transaction systems, and has a complete transaction process which comprises transmission, reception, broadcasting and block confirmation. The system is capable of enhancing general structures through block chain transaction privacies under a multi-center supervision mode, so as to realize privacy protection for trapdoor parameters under joint control of multiple parties and transaction metadata in transaction process, and effectively strengthen the safety of plaintext amounts in multi-center block chain system transaction process.
Owner:BEIHANG UNIV
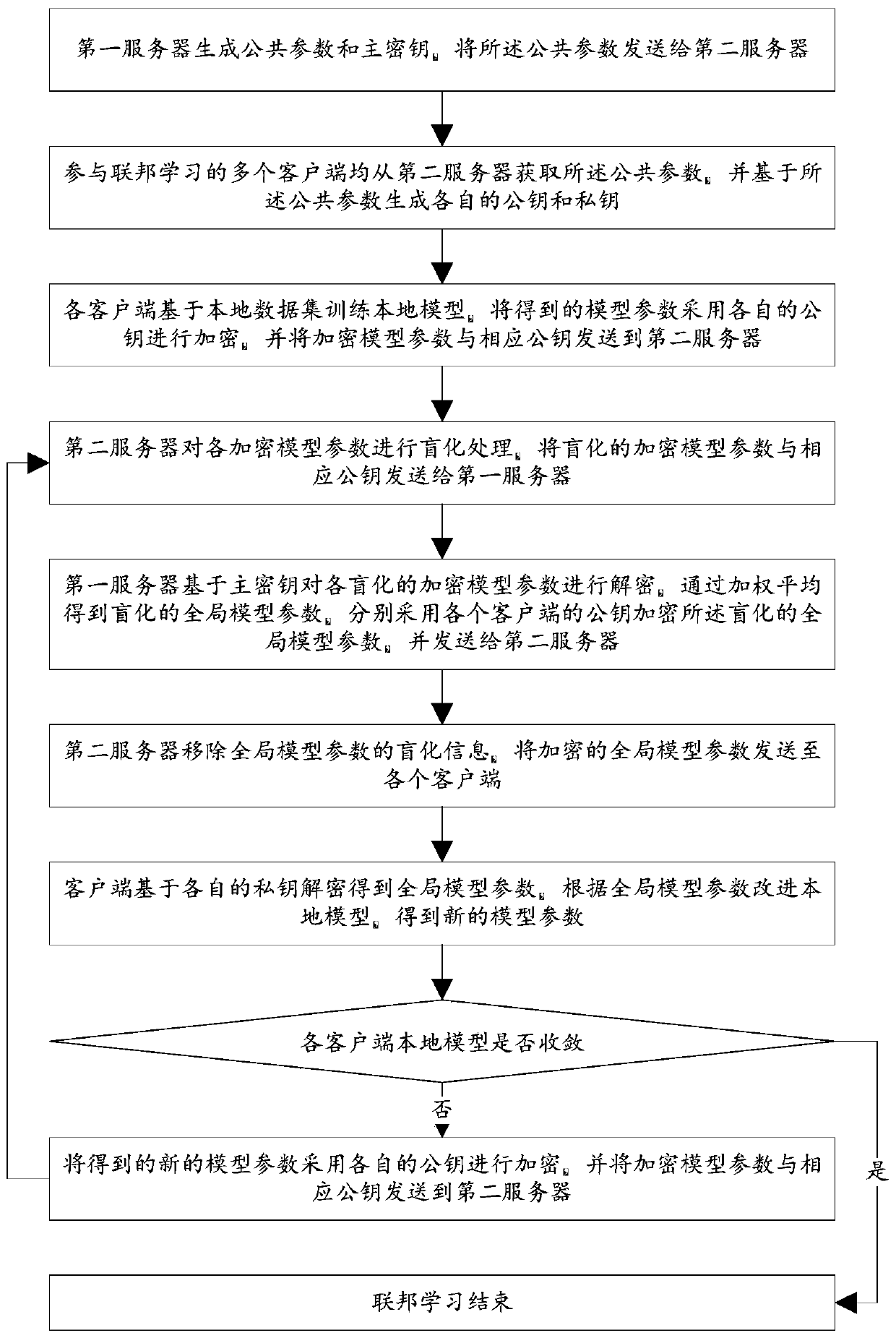
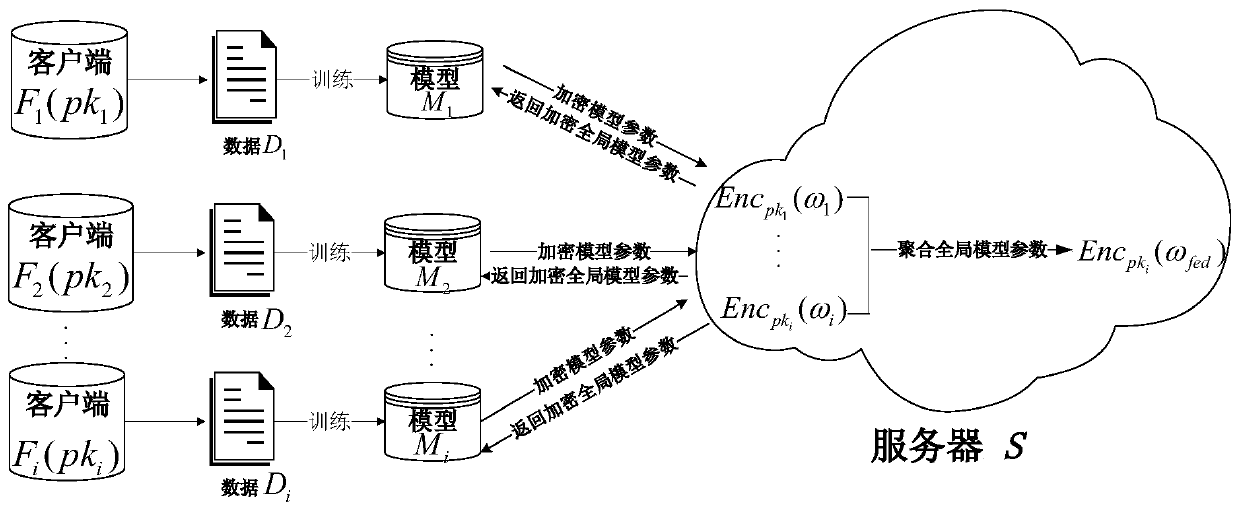
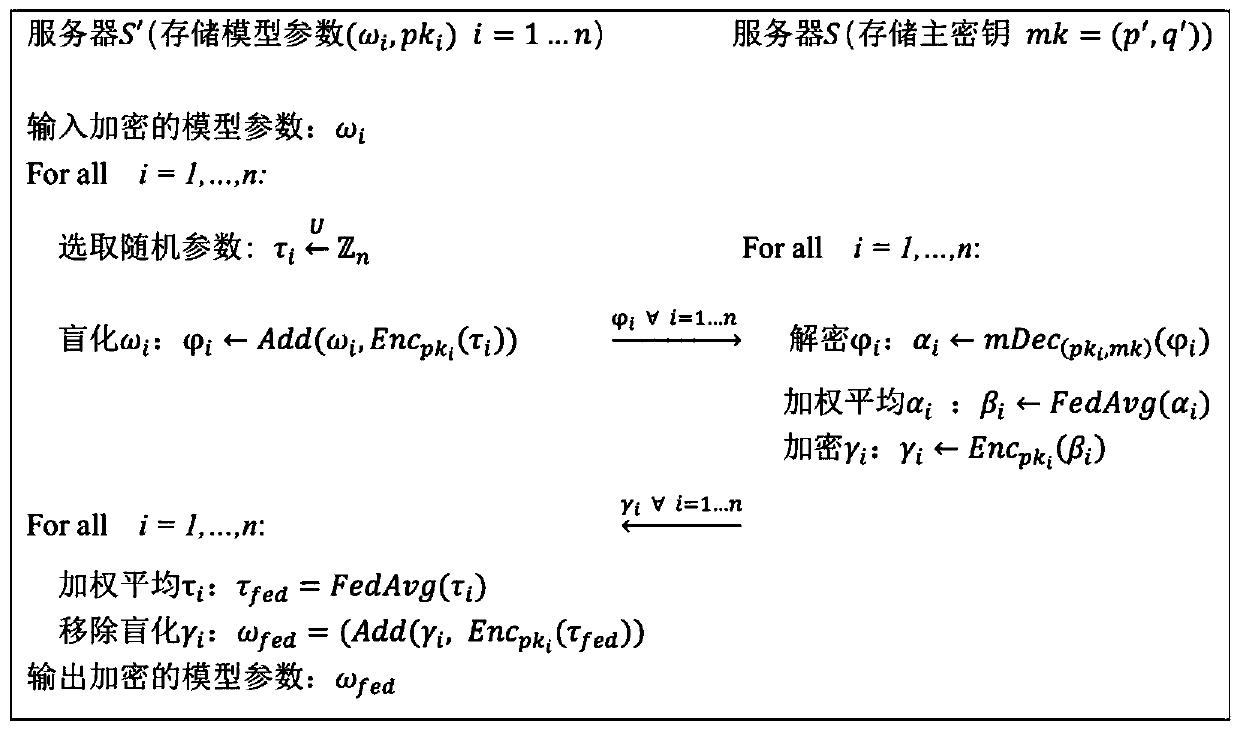
Federated learning training data privacy enhancement method and system
ActiveCN110572253AEnsure safetyEasy to joinCommunication with homomorphic encryptionModel parametersMaster key
The invention discloses a federated learning training data privacy enhancement method and system, and the method comprises the steps that a first server generates a public parameter and a main secretkey, and transmits the public parameter to a second server; a plurality of clients participating in federated learning generate respective public key and private key pairs based on the public parameters; the federated learning process is as follows: each client encrypts a model parameter obtained by local training by using a respective public key, and sends the encrypted model parameter and the corresponding public key to a first server through a second server; the first server carries out decryption based on the master key, obtains global model parameters through weighted average, carries outencryption by using a public key of each client, and sends the global model parameters to each client through the second server; and the clients carry out decrypting based on the respective private keys to obtain global model parameters, and the local models are improved, and the process is repeated until the local models of the clients converge. According to the method, a dual-server mode is combined with multi-key homomorphic encryption, so that the security of data and model parameters is ensured.
Owner:UNIV OF JINAN
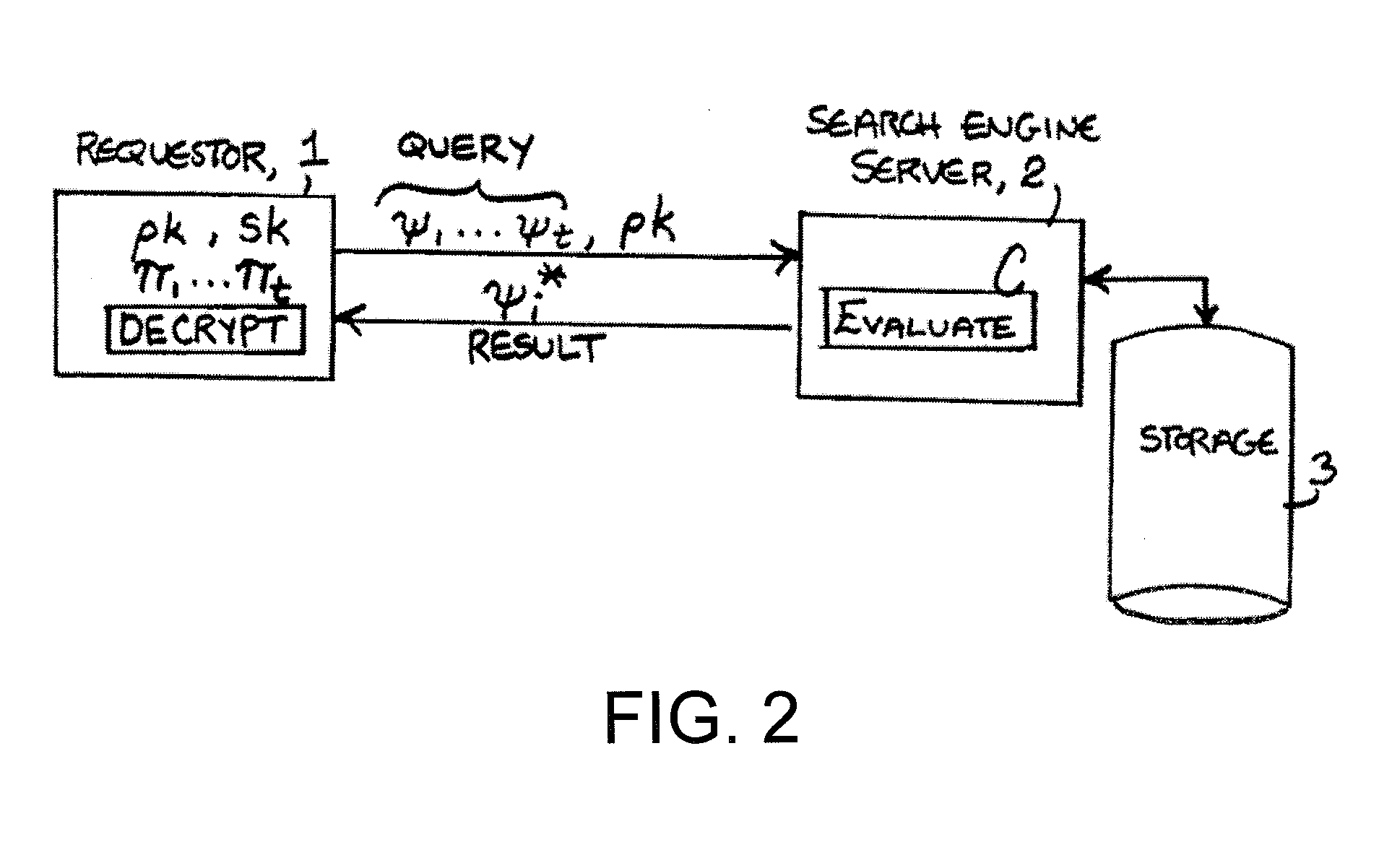
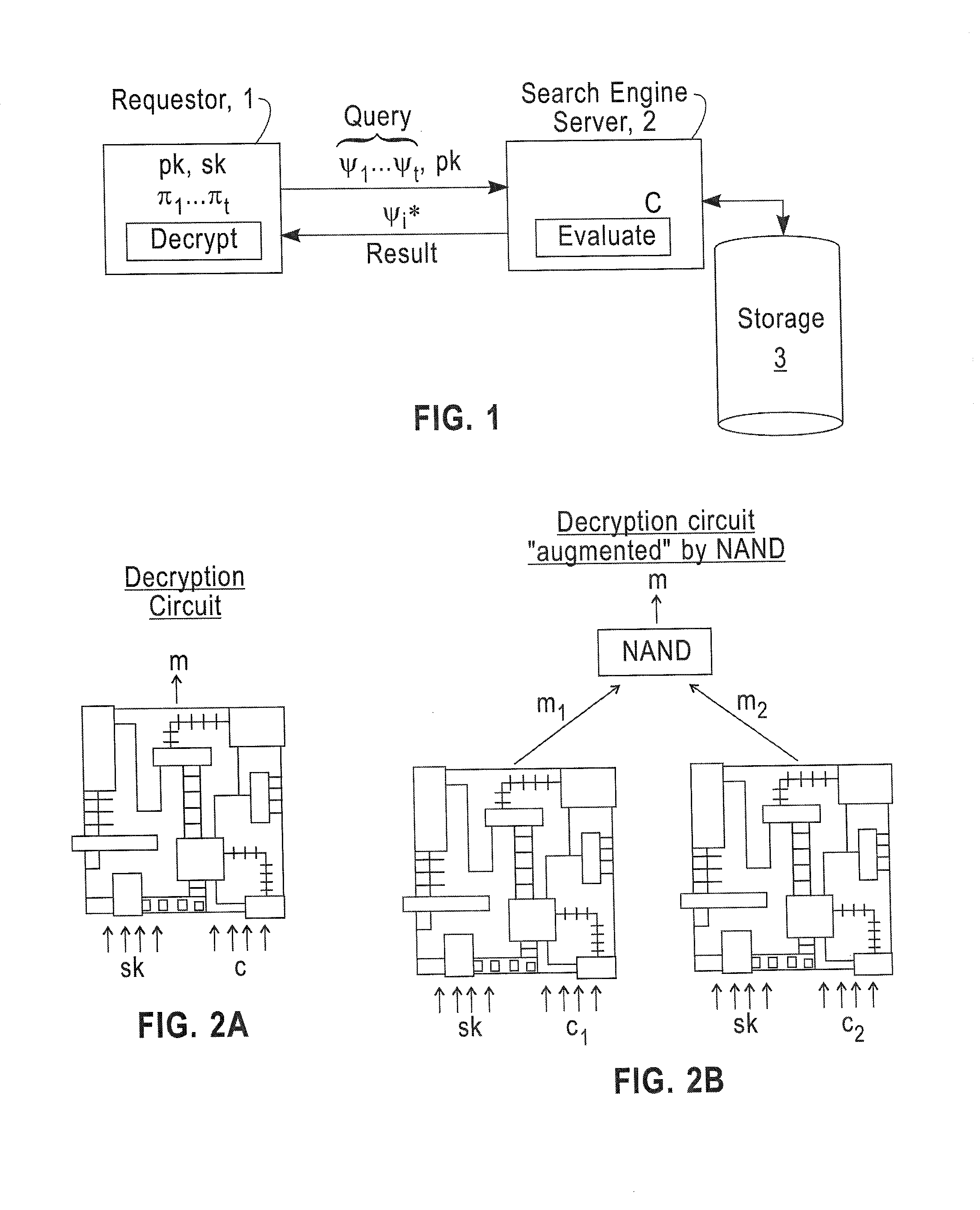
Systems and methods for communication, storage, retrieval, and computation of simple statistics and logical operations on encrypted data
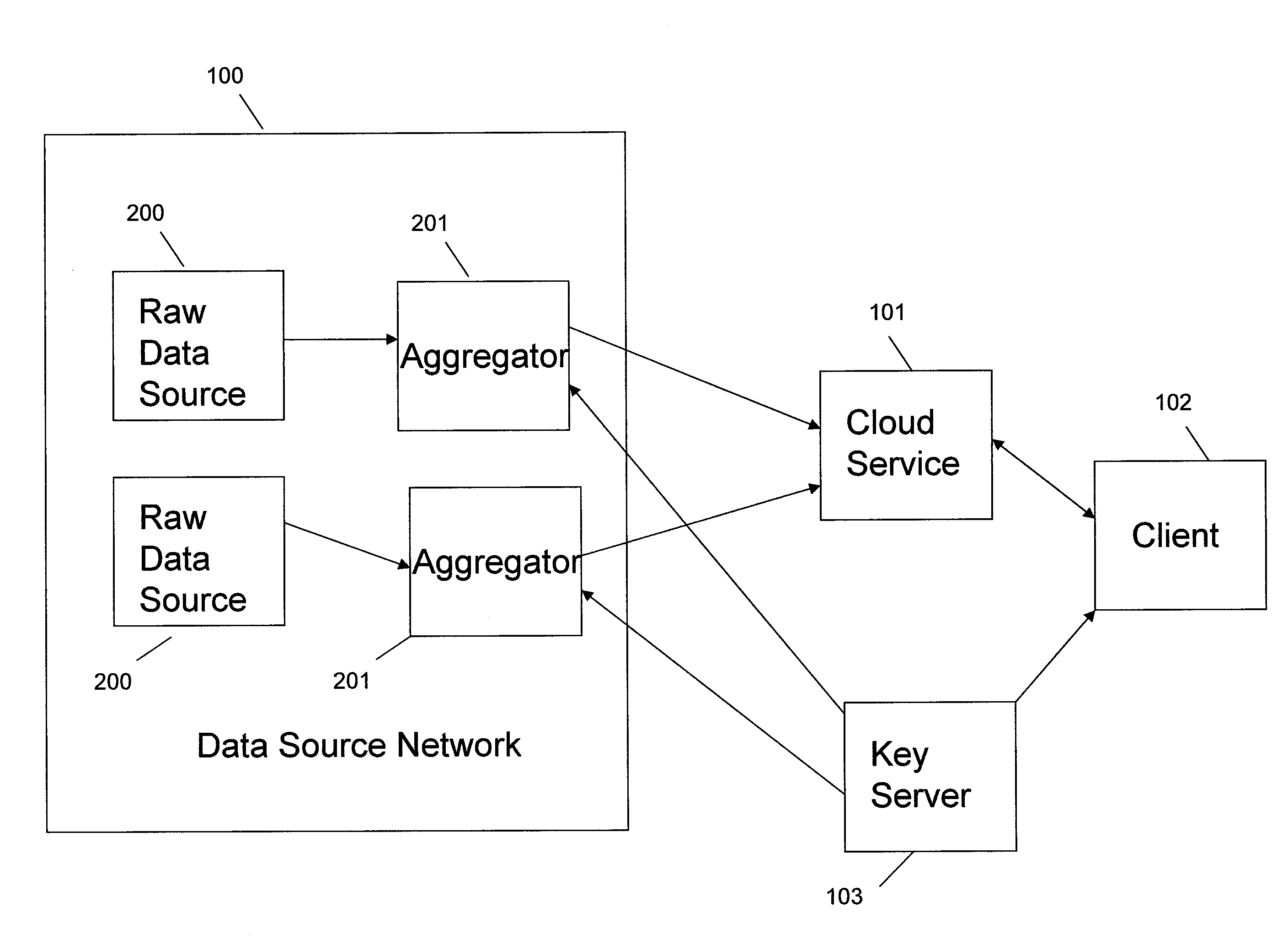
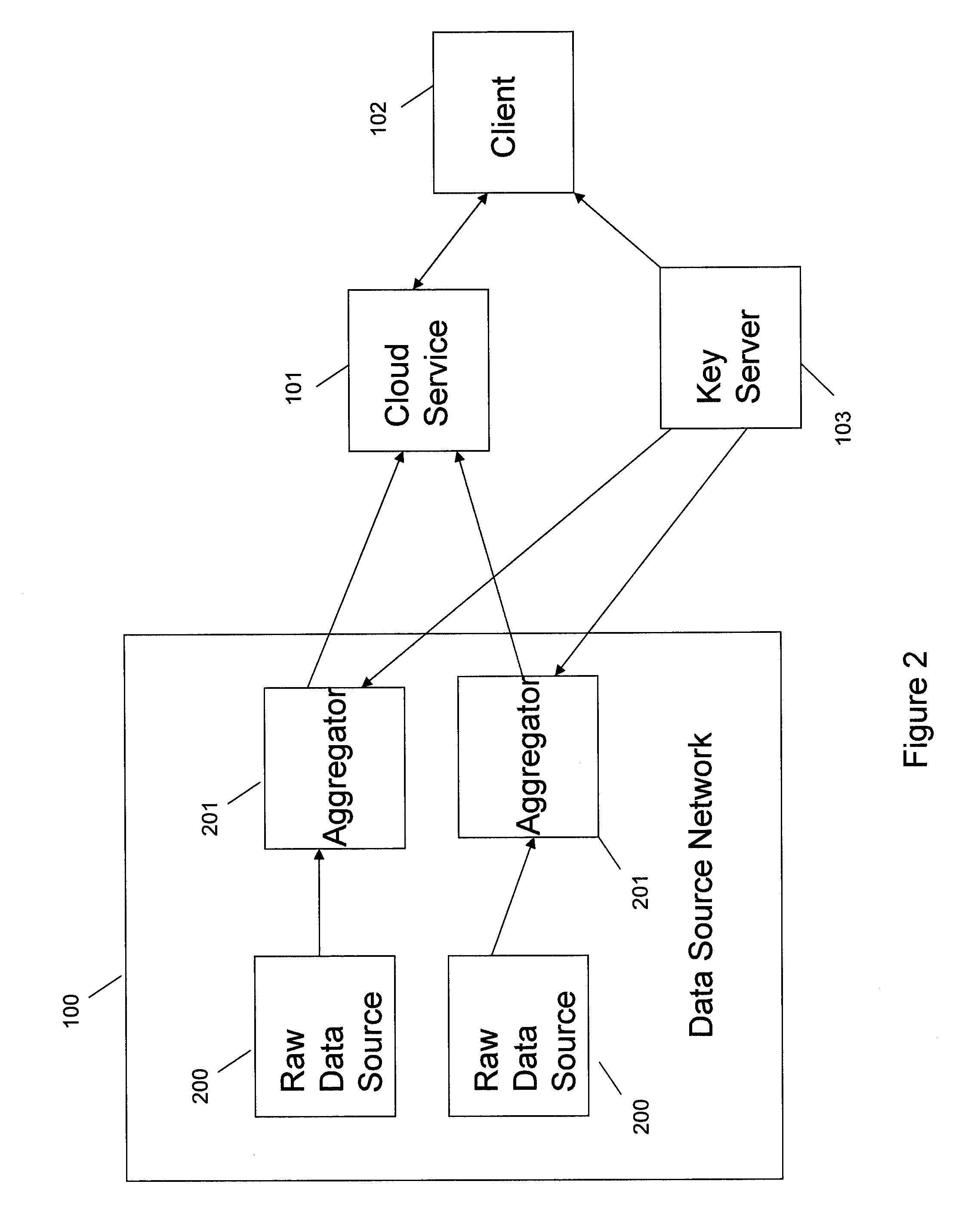
InactiveUS20110264920A1Unauthorized memory use protectionHardware monitoringLogical queryData system
Systems and methods provide for a symmetric homomorphic encryption based protocol supporting communication, storage, retrieval, and computation on encrypted data stored off-site. The system may include a private, trusted network which uses aggregators to encrypt raw data that is sent to a third party for storage and processing, including computations that can be performed on the encrypted data. A client on a private or public network may request computations on the encrypted data, and the results may then be sent to the client for decryption or further computations. The third party aids in computation of statistical information and logical queries on the encrypted data, but is not able to decrypt the data on its own. The protocol provides a means for a third party to aid in computations on sensitive data without learning anything about those data values.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Blockchain-empowered crowdsourced computing system
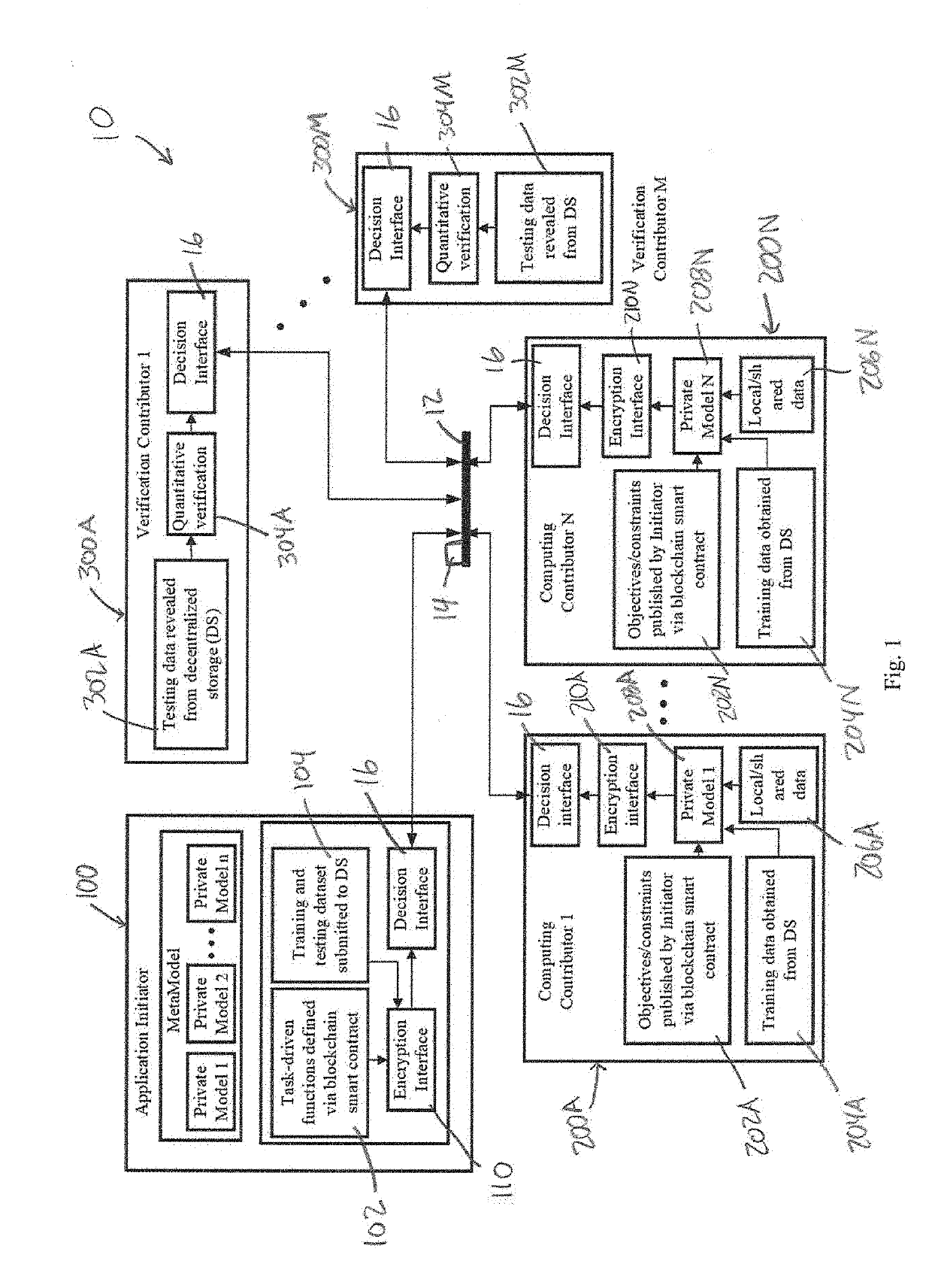
ActiveUS20190334716A1User identity/authority verificationMachine learningInterface designPrivacy preserving
In various embodiments, the present invention is directed to a decentralized and secure method for developing machine learning models using homomorphic encryption and blockchain smart contracts technology to realize a secure, decentralized system and privacy-preserving computing system incentivizes the sharing of private data or at least the sharing of resultant machine learning models from the analysis of private data. In various embodiments, the method uses a homomorphic encryption (HE)-based encryption interface designed to ensure the security and the privacy-preservation of the shared learning models, while minimizing the computation overhead for performing calculation on the encrypted domain and, at the same time, ensuring the accuracy of the quantitative verifications obtained by the verification contributors in the cipherspace.
Owner:THE UNIVERSITY OF AKRON
Decrypting data
ActiveUS9584311B2Prevent tamperingGuaranteed normal executionSecret communicationCommunication with homomorphic encryptionHomomorphic encryptionComputer program
A device for decrypting data includes a number of devices secured by at least one security device. The secured devices include a receiver for receiving calculation data encrypted using a homomorphic encryption function and a decryptor for decrypting the encrypted calculation data by carrying out the inverse of the homomorphic encryption function on the encrypted calculation data using a private key assigned to the homomorphic encryption function. A method and a computer program product for decrypting data are also provided.
Owner:SIEMENS AG
Compact fuzzy private matching using a fully-homomorphic encryption scheme
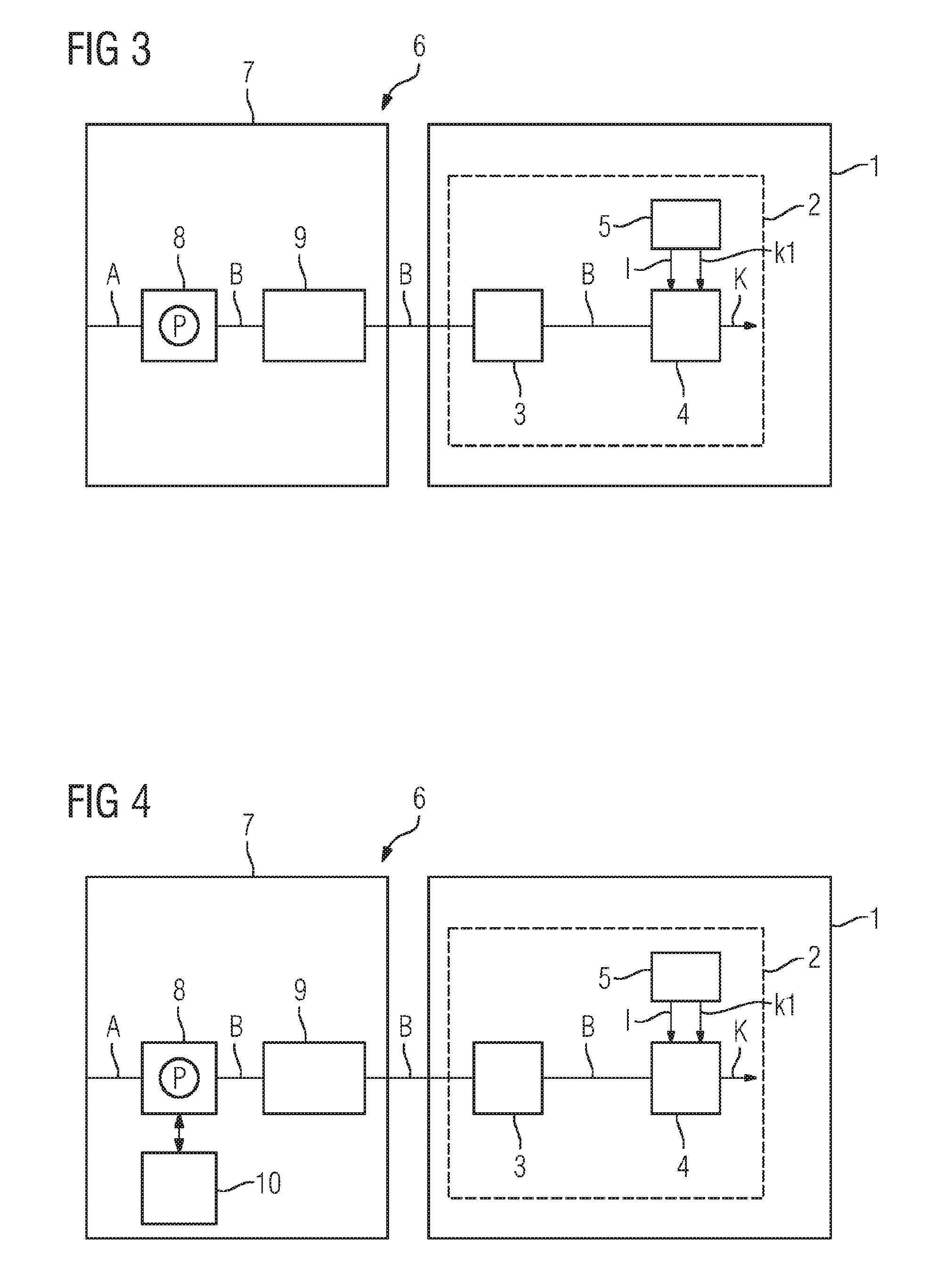
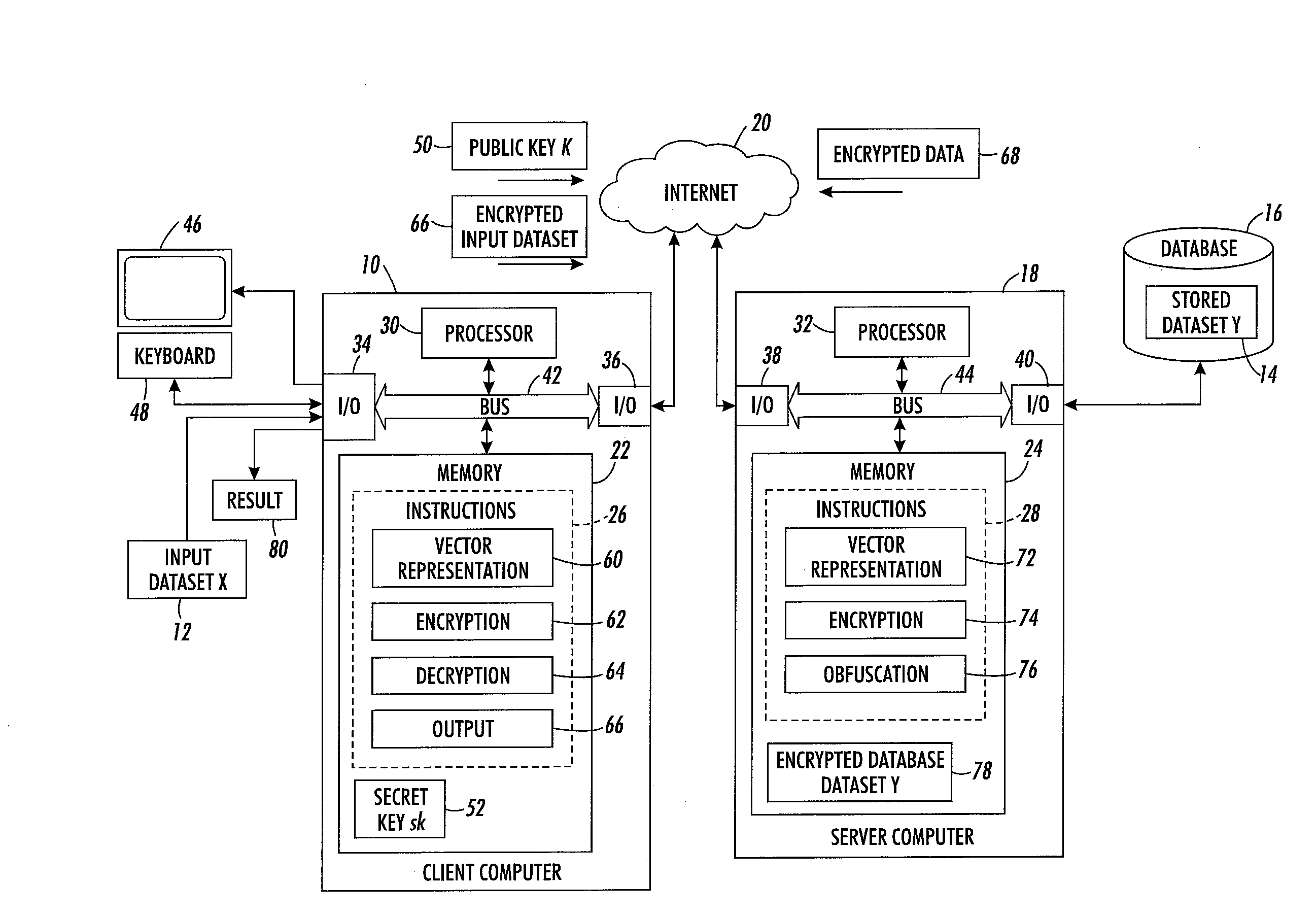
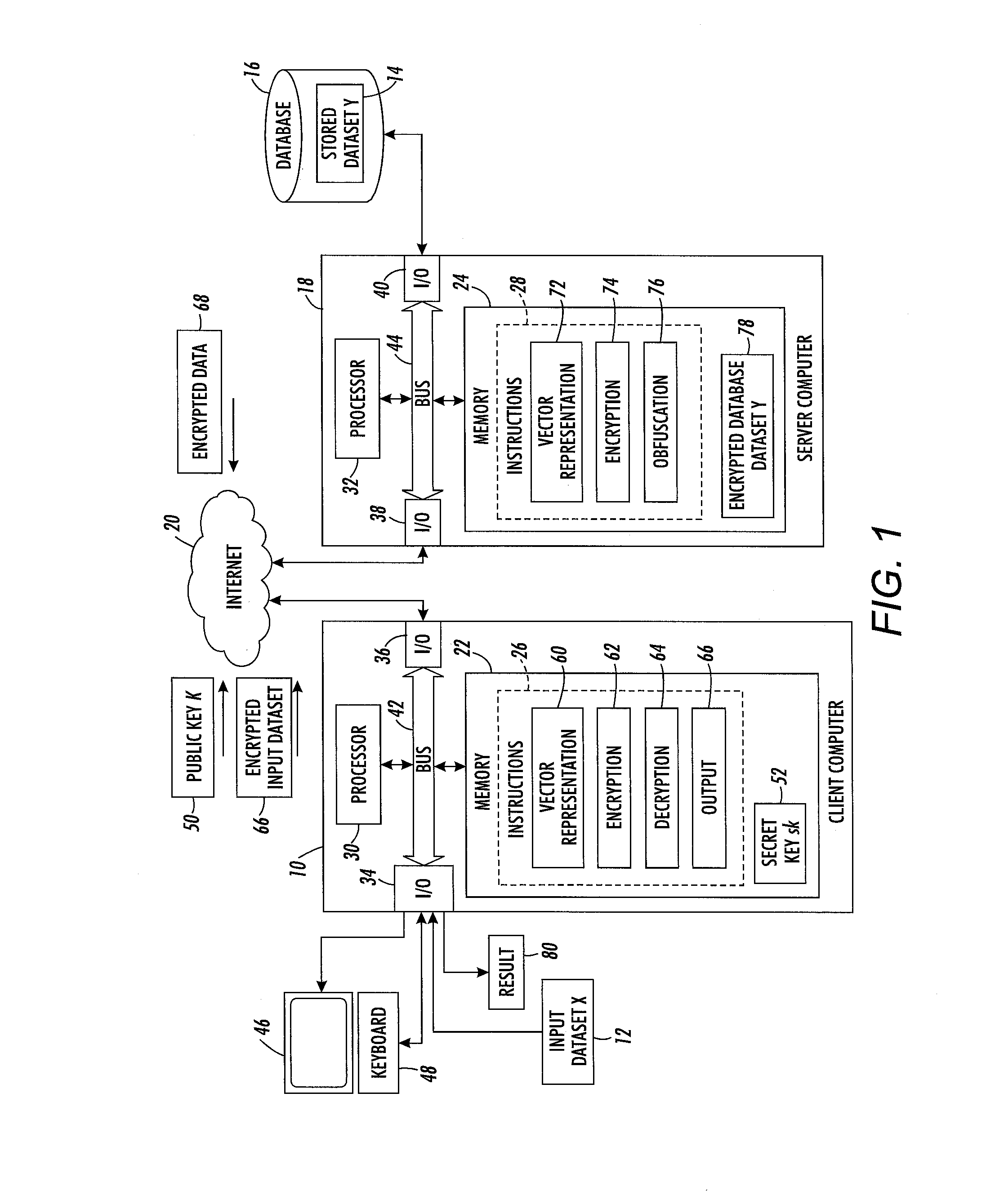
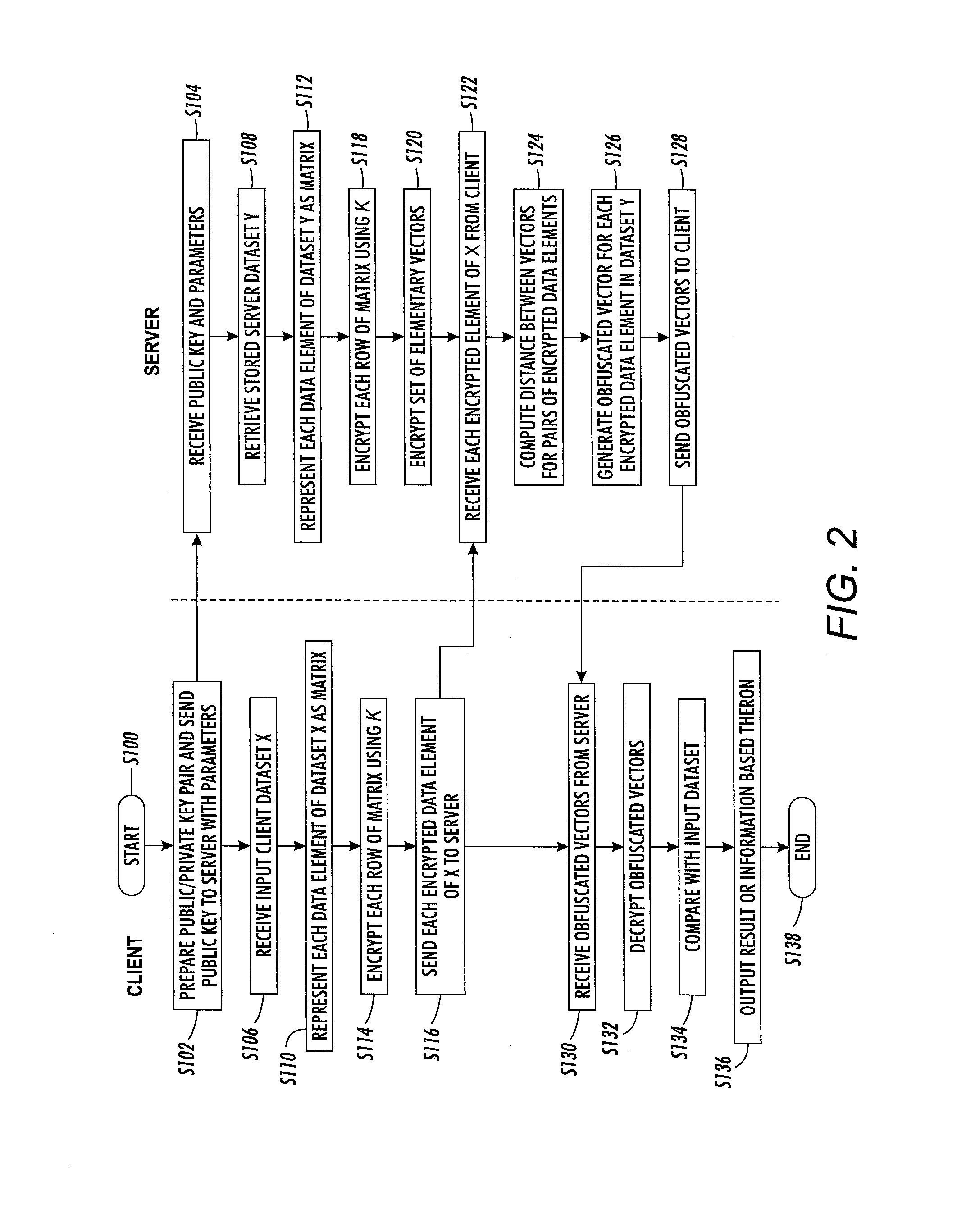
ActiveUS20160119119A1Public key for secure communicationComputer security arrangementsData matchingData element
A method for data matching includes providing two sets of encrypted data elements by converting data elements to respective sets of vectors and encrypting each vector with a public key of a homomorphic encryption scheme. Each data element includes a sequence of characters drawn from an alphabet. For pairs of encrypted data elements, a comparison measure is computed between the sets of encrypted vectors. An obfuscated vector is generated for each encrypted data element in the first set, which renders the first encrypted data element indecipherable when the comparison measure does not meet a threshold for at least one of the pairs of data encrypted elements comprising that encrypted data element. The obfuscated vectors can be decrypted with a private key, allowing data elements in the first set to be deciphered if the comparison measure meets the threshold for at least one of the data elements in the second set.
Owner:XEROX CORP
Efficient Implementation Of Fully Homomorphic Encryption
ActiveUS20120039473A1Public key for secure communicationUser identity/authority verificationCiphertextComputer science
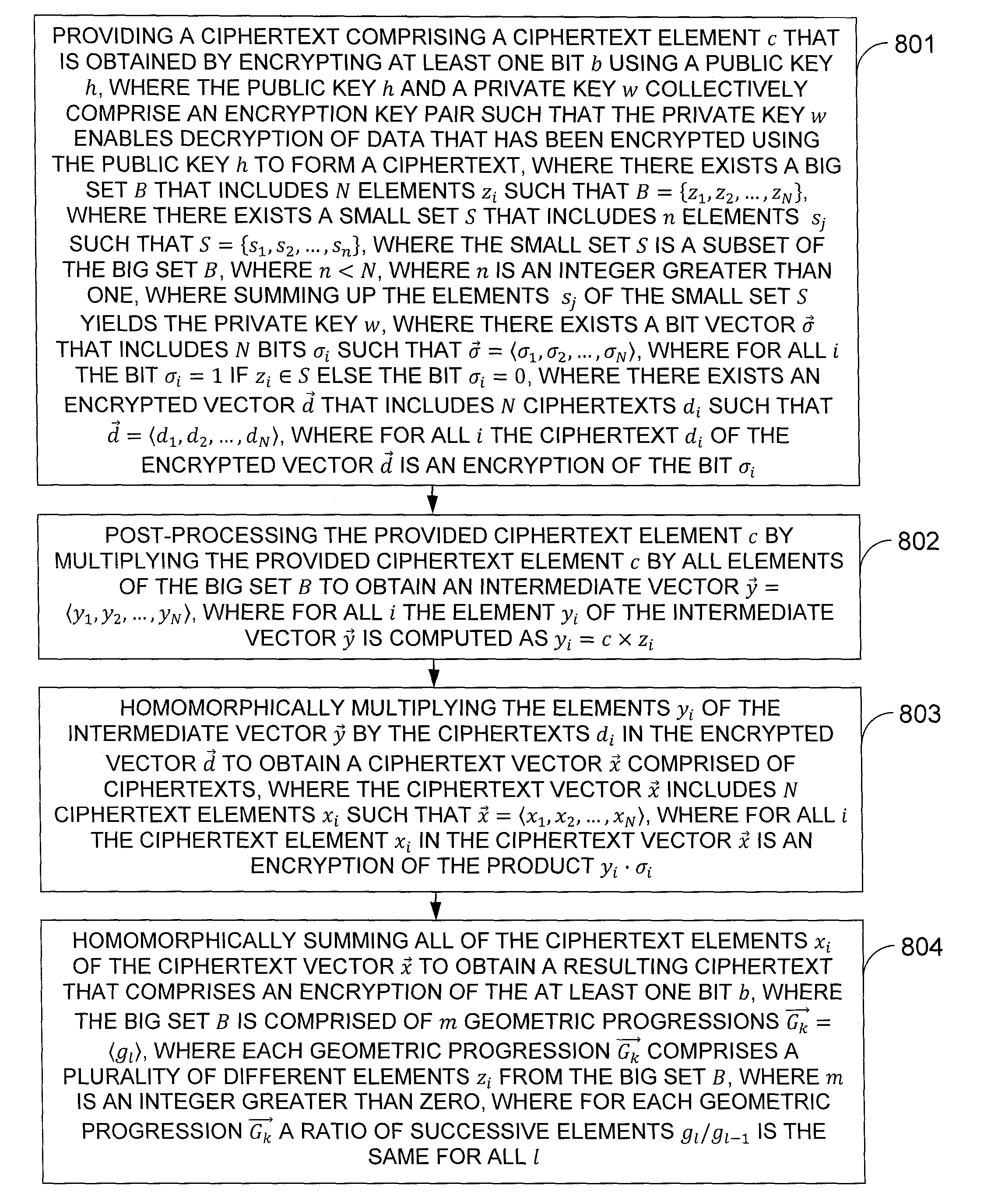
In one exemplary embodiment of the invention, a method for homomorphic decryption, including: providing a ciphertext with element c, there exists a big set B having N elements zi so B={z1,z2, . . . , zN}, there exists a small set S having n elements sj so S={s1, s2, . . . , sn}, the small set is a subset of the big set, summing up the elements of the small set yields the private key, there exists a bit vector {right arrow over (σ)} having N bits σi so {right arrow over (σ)}=σ1, σ2, . . . , σN, σi=1 if zi ∈ S else σi=0, there exists an encrypted vector {right arrow over (d)} having N ciphertexts di so d=d1, d2, . . . , dN, di is an encryption of σi; post-processing c by multiplying it by all zi to obtain an intermediate vector {right arrow over (y)}=y1, y2, . . . , yN with yi computed yi=c×zi; homomorphically multiplying yi by di obtaining a ciphertext vector {right arrow over (x)} having N ciphertexts xi so z=x1, x2, . . . , xN, where xi is an encryption of the product yi·σi; and homomorphically summing all xi to obtain a resulting ciphertext that is an encryption of the at least one bit, where the big set is partitioned into n parts with each part having a plurality of different elements from the big set, where the elements of the small set are one element from each part.
Owner:IBM CORP
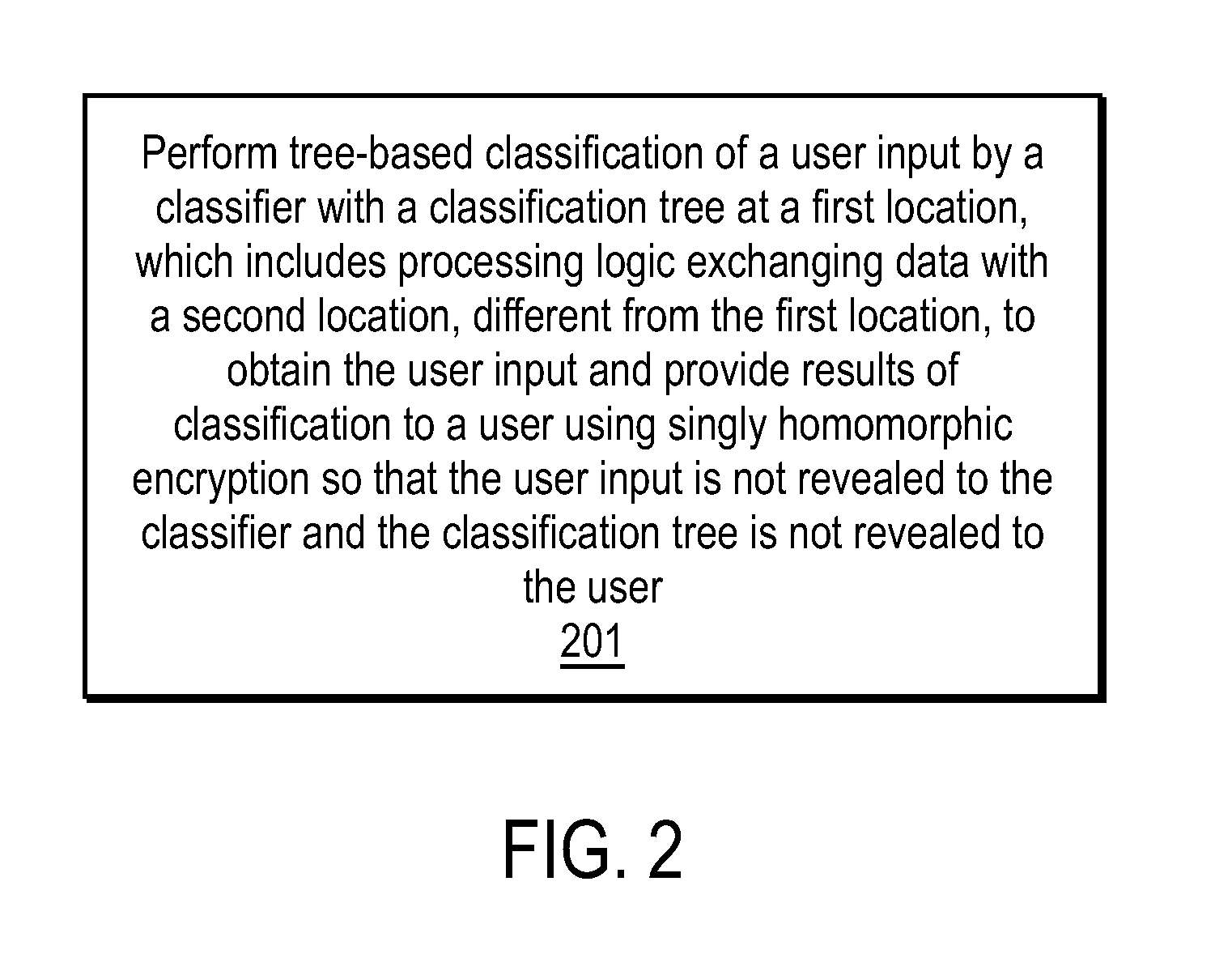
Efficient, remote, private tree-based classification using cryptographic techniques
InactiveUS20120201378A1Digital data protectionInternal/peripheral component protectionUser inputData mining
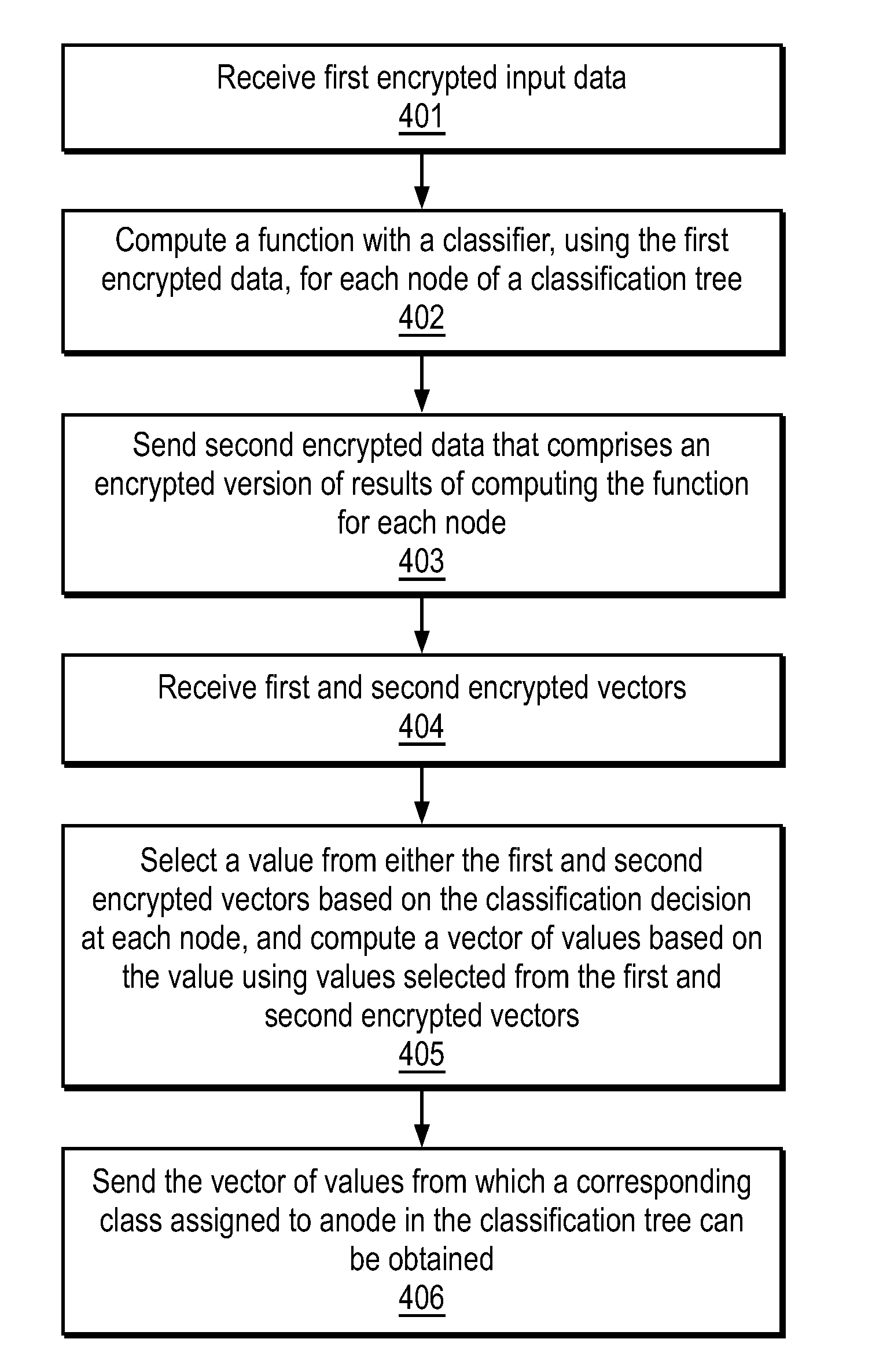
A method and apparatus are disclosed herein for classification. In one embodiment, the method comprises performing tree-based classification of a user input by a classifier with a classification tree at a first location, including exchanging data with a second location, different from the first location, to obtain the user input and provide results of classification to a user using singly homomorphic encryption so that the user input is not revealed to the classifier, the classification tree is not revealed to the user and the classifier's output is not revealed to the classifier.
Owner:RICOH KK
Fully homomorphic encryption method based on a bootstrappable encryption scheme, computer program and apparatus
ActiveUS8630422B2Key distribution for secure communicationMultiple keys/algorithms usageAssessment dataData application
A method includes encrypting information in accordance with an encryption scheme that uses a public key; encrypting a plurality of instances of a secret key, each being encrypted using at least one additional instance of the public key; sending the encrypted information and the plurality of encrypted instances of the secret key to a destination; receiving an encrypted result from the destination; and decrypting the encrypted result. A further method includes receiving a plurality of encrypted secret keys and information descriptive of a function to be performed on data; converting the information to a circuit configured to perform the function on the data; and applying the data to inputs of the circuit and evaluating the data using, in turn, the plurality of encrypted secret keys.
Owner:INT BUSINESS MASCH CORP
Matrix fully homomorphic encryption method
InactiveCN103259643AInput protectionSatisfy the requirement of full homomorphismSecuring communicationComputer hardwareCiphertext
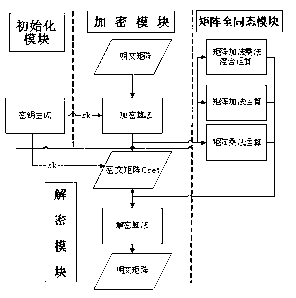
The invention discloses a matrix fully homomorphic encryption method. The matrix fully homomorphic encryption method comprises an initialization module, an encryption module, a decryption module and a matrix fully homomorphic module. The initialization module is used for generating secret keys needed by encryption and decryption according to dimensions of matrices to be encrypted, encryption types and ranges of matrix element values. The encryption module is used for utilizing encryption algorithms and the secret keys to conduct encryption on plaintext matrices and outputting ciphertext matrices according to the given plaintext matrices. The decryption module is used for utilizing the secret keys and decryption algorithms to conduct decryption on ciphertext matrices and outputting the plaintext matrices according to the given ciphertext matrices. According to the matrix fully homomorphic module, additive operation and multiplying operation of the matrices meet homomorphic properties of the matrices, output generated by the additive operation and the multiplying operation of the matrices still meets the homomorphic properties, namely, fully homomorphic properties of the matrices are met. The matrix fully homomorphic encryption method has the advantages of meeting safety requirements, meeting fully homomorphic requirements of the matrices and remarkably increasing the operating rate of the ciphertext matrices.
Owner:SUZHOU UNIV
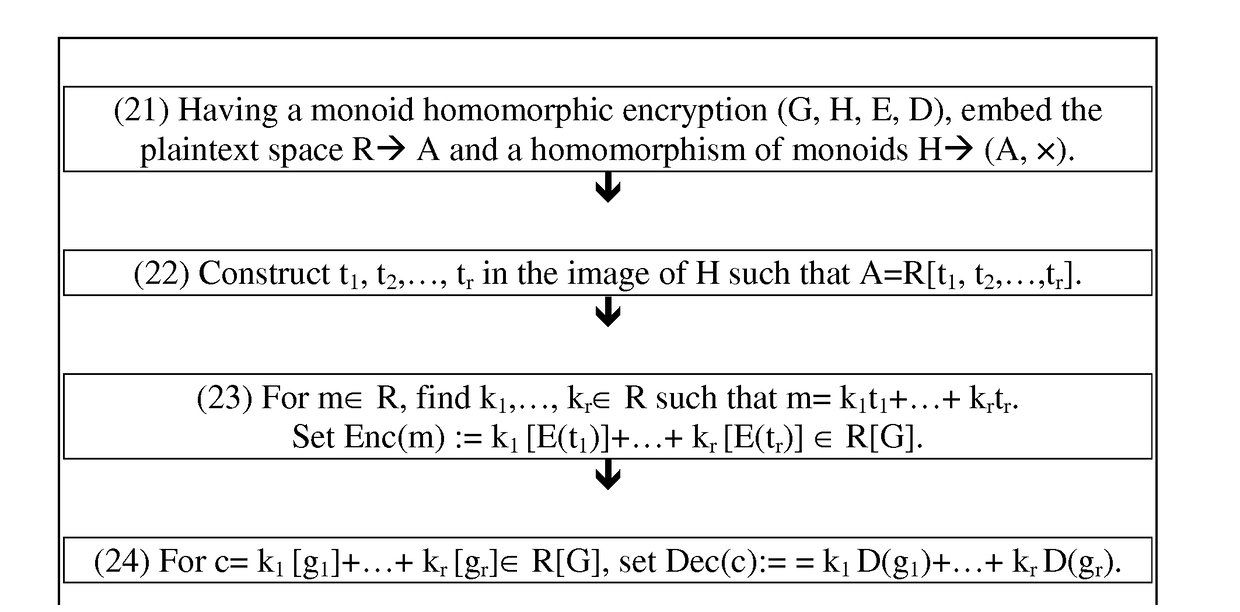
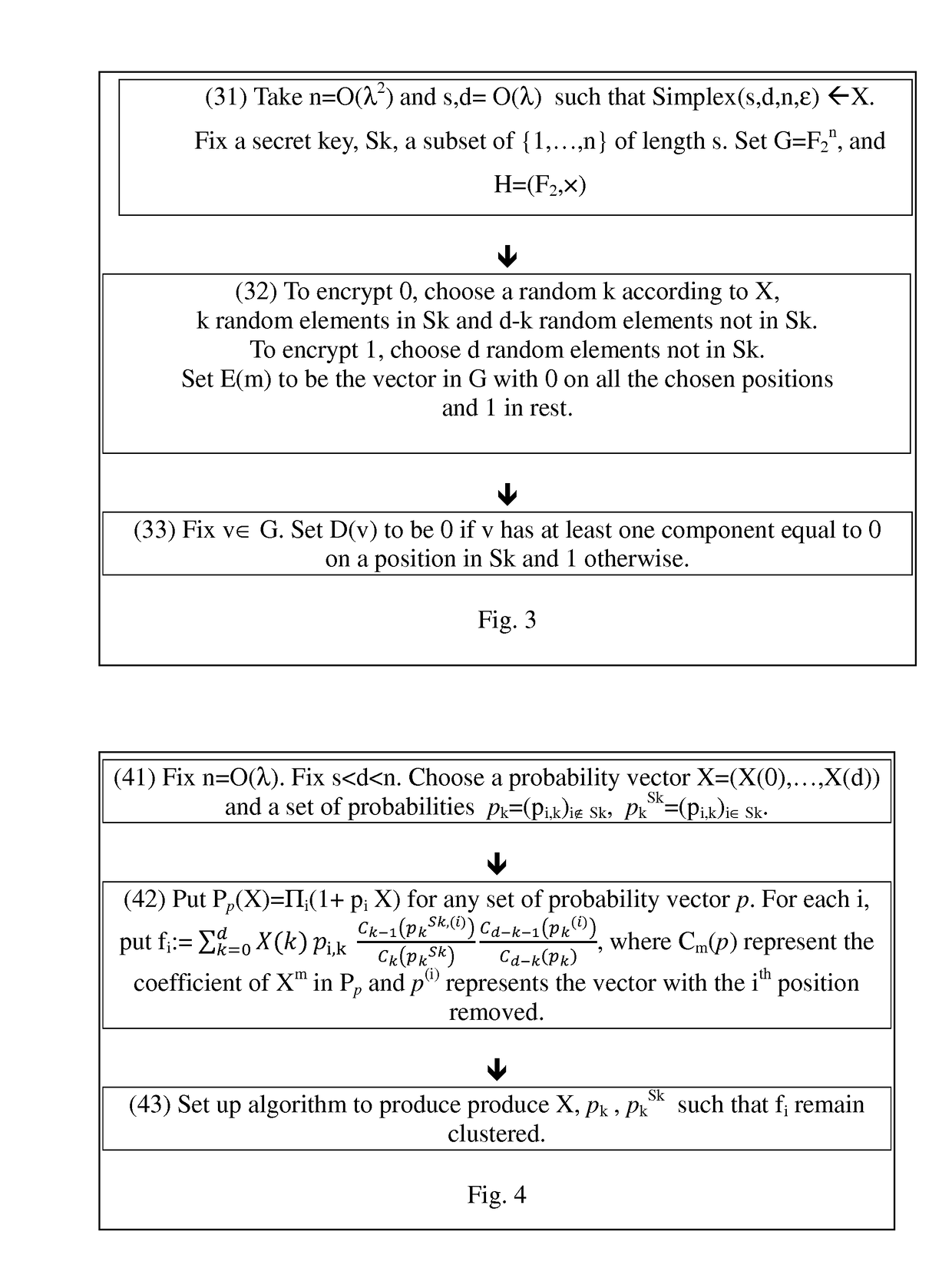
Fully Homomorphic Encryption from Monoid Algebras
ActiveUS20170134158A1Improve securityReduce chancePublic key for secure communicationCommunication with homomorphic encryptionCiphertextSecurity parameter
A blueprint that produces a family of FHE schemes given any homomorphic monoidal encryption scheme. The ciphertext space is a subspace of the monoid algebra over F2 generated by the initial encryption monoid. The method can be generally applied to any monoid encryption schemes. Advantageously, monoid encryption schemes produce efficient FHE schemes with the inventive blueprint. Furthermore, the corresponding FHE scheme can correctly decrypt and efficiently compute circuits with low (polynomial in the security parameter) additive depth, a feature not realized by prior encryption methods.
Owner:CERTSIGN SA
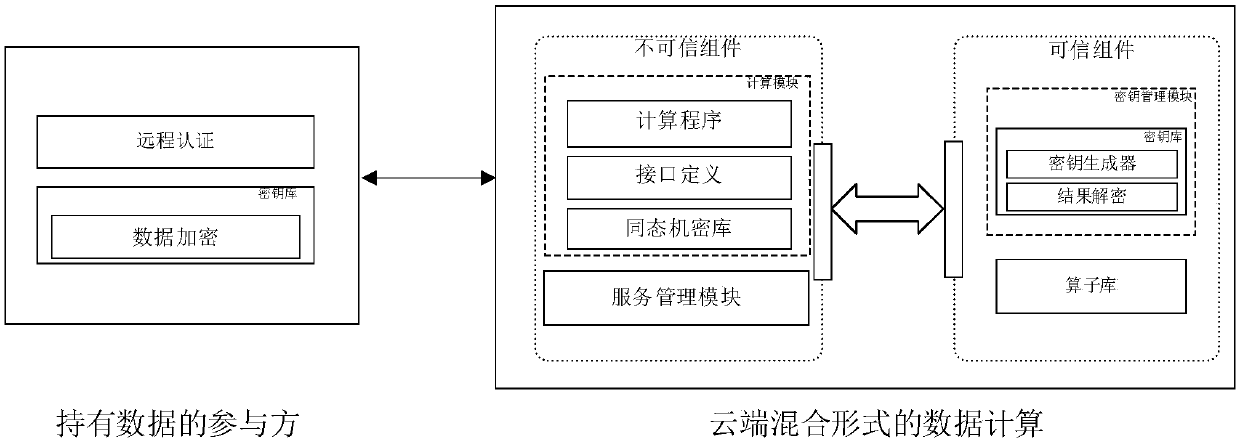
A method to solve the problem of data privacy disclosure in multi-party computing
ActiveCN109101822AGuaranteed scalabilityAddress privacy breachesDigital data protectionPlatform integrity maintainanceThird partyData profiling
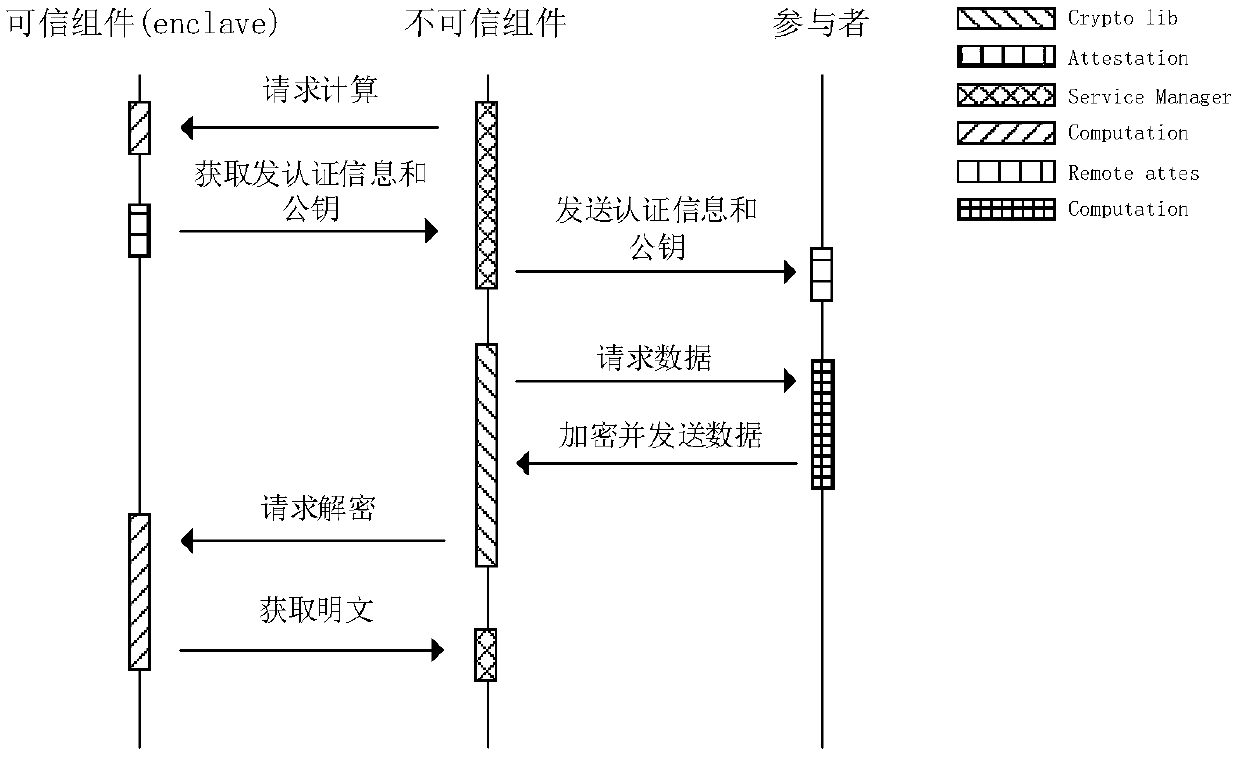
The invention discloses a method for solving the problem of data privacy disclosure in multi-party computation Using a trusted execution environment at the cloud hardware level. In the absence of a trusted third party, Participants who hold the data are able to authenticate remotely the key management program that executes in a trusted execution environment in the cloud, after confirming that theprogram has not been tampered with, the program encrypts its own data with the public key obtained from the program, transmits the data to the cloud, and performs the analysis and calculation of multi-party data in the form of mixed operation based on partial homomorphic encryption technology and hardware-level trusted execution environment at the cloud. The method does not require a centralized authority to complete the computation, so that the data analyst can analyze the data without requiring a third-party trustworthy mechanism, Completing the analysis and calculation of multi-party data can effectively reduce the risk of data privacy leakage in multi-party computation. Compared with the method based on garbled circuit, the method does not need complex key agreement mechanism and has high efficiency.
Owner:XI AN JIAOTONG UNIV
Efficient and privacy-preserving single-layer perceptron learning scheme in cloud computing environment
ActiveCN108259158APrivacy protectionComputationally efficientKey distribution for secure communicationCharacter and pattern recognitionCiphertextPrivacy preserving
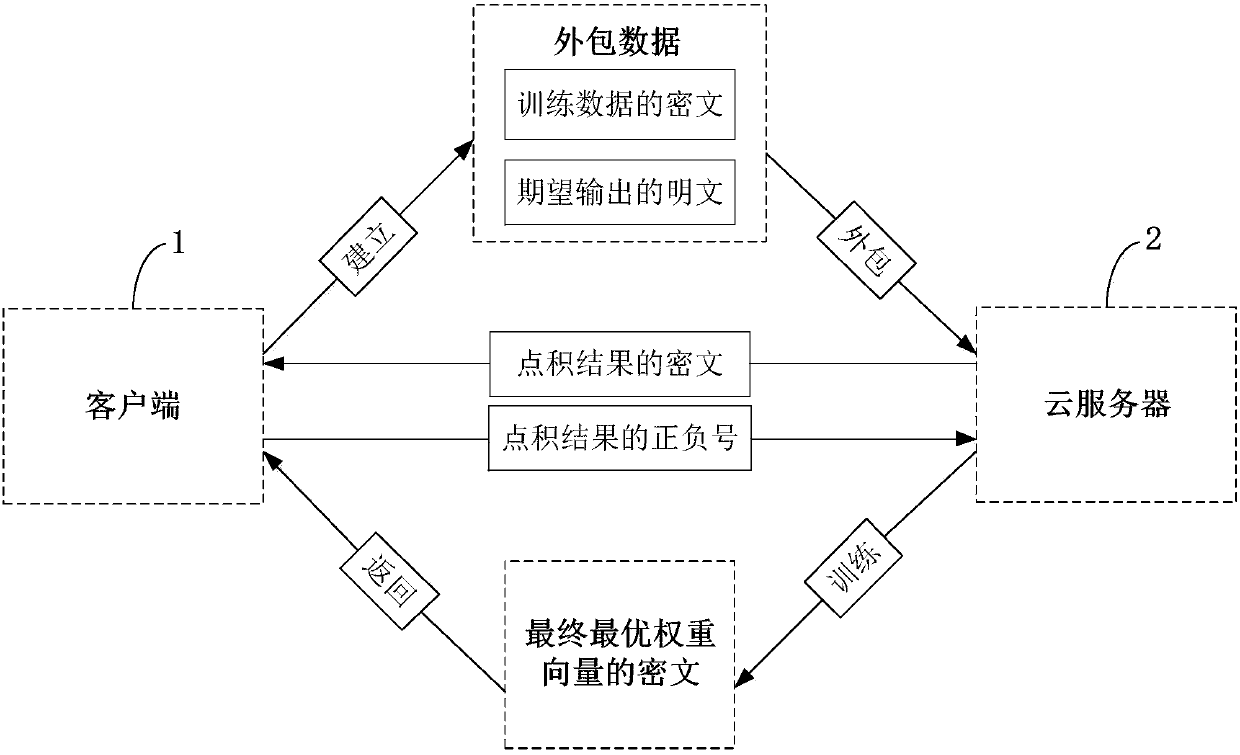
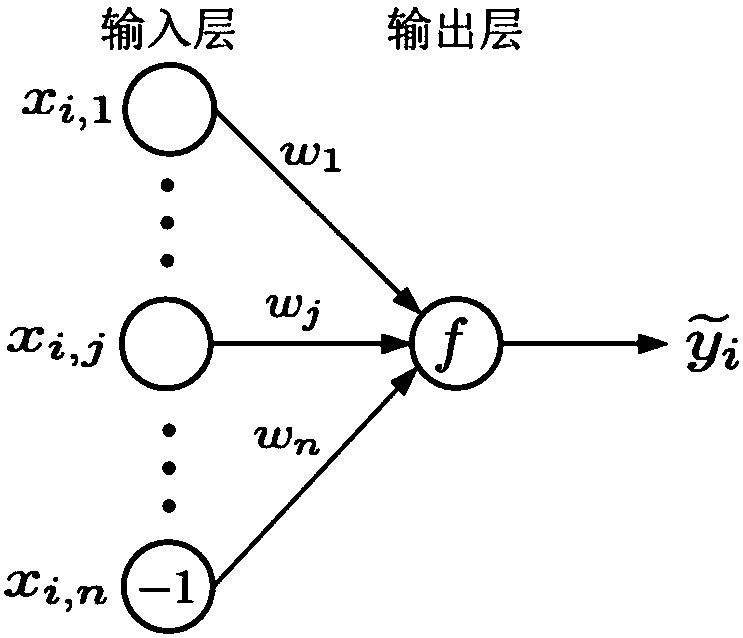
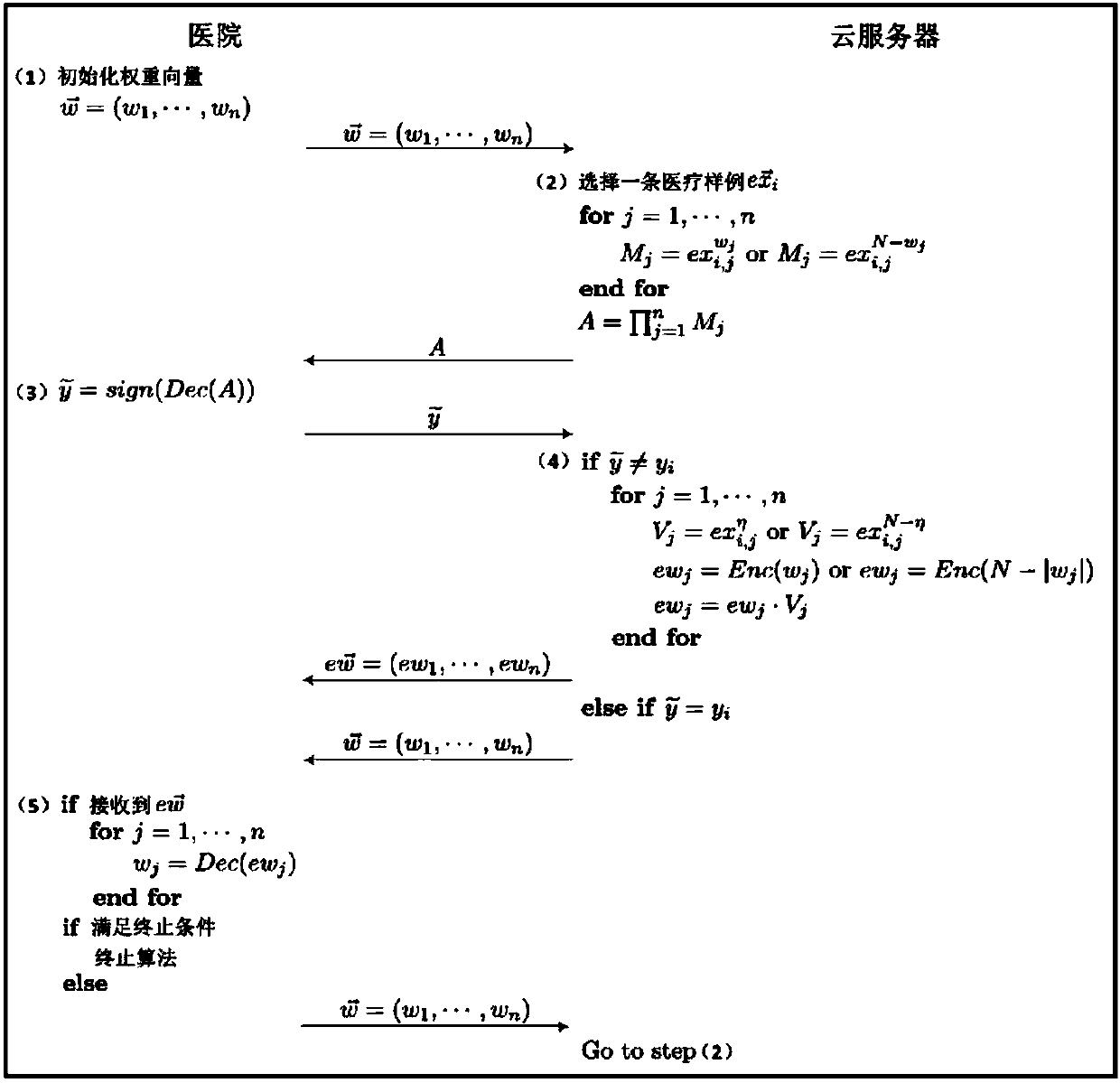
The invention belongs to the technical field of cloud computing and discloses an efficient and privacy-preserving single-layer perceptron learning scheme in a cloud computing environment. The scheme comprises the steps that a client provides a security parameter, operates a key generation algorithm of a symmetric homomorphic encryption algorithm to calculate a public parameter and a key, then operates an encryption algorithm, encrypts training data through utilization of the key to obtain a corresponding ciphertext, and sends the ciphertext and related expectation to a cloud server, assists acloud server to judge a positive or negative characteristic of a dot product result in a training process, and decrypts the ciphertext of the received final optimum weight vector after a training taskis finished, thereby obtaining a single-layer perceptron prediction model; and the cloud server stores the training mode, trains a single-layer perceptron model and sends the ciphertext of the finaloptimum weight vector to the client after the training task is finished. The safety analysis shows that according to the scheme, in the training process, the privacy of the training data, an intermediate result and the optimum prediction model can be preserved, and the scheme is efficient in computing overhead and communication overhead aspects.
Owner:XIDIAN UNIV
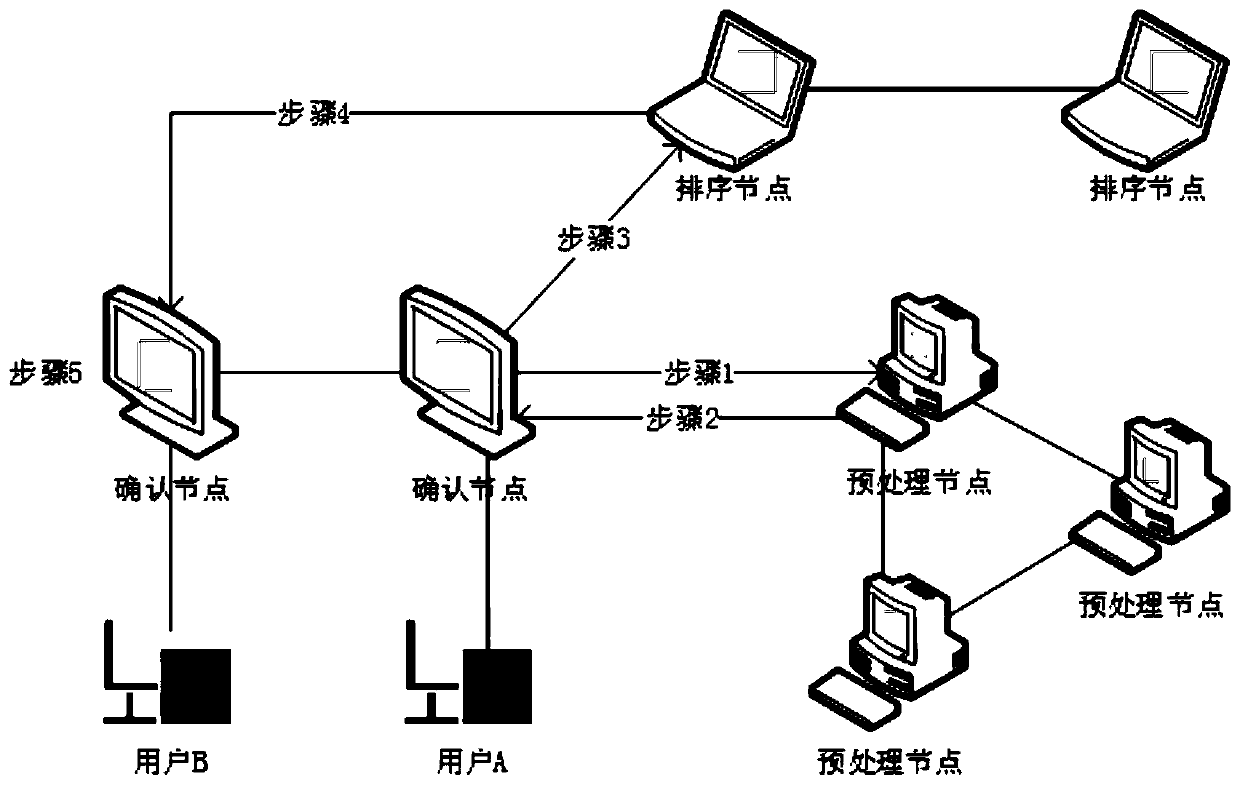
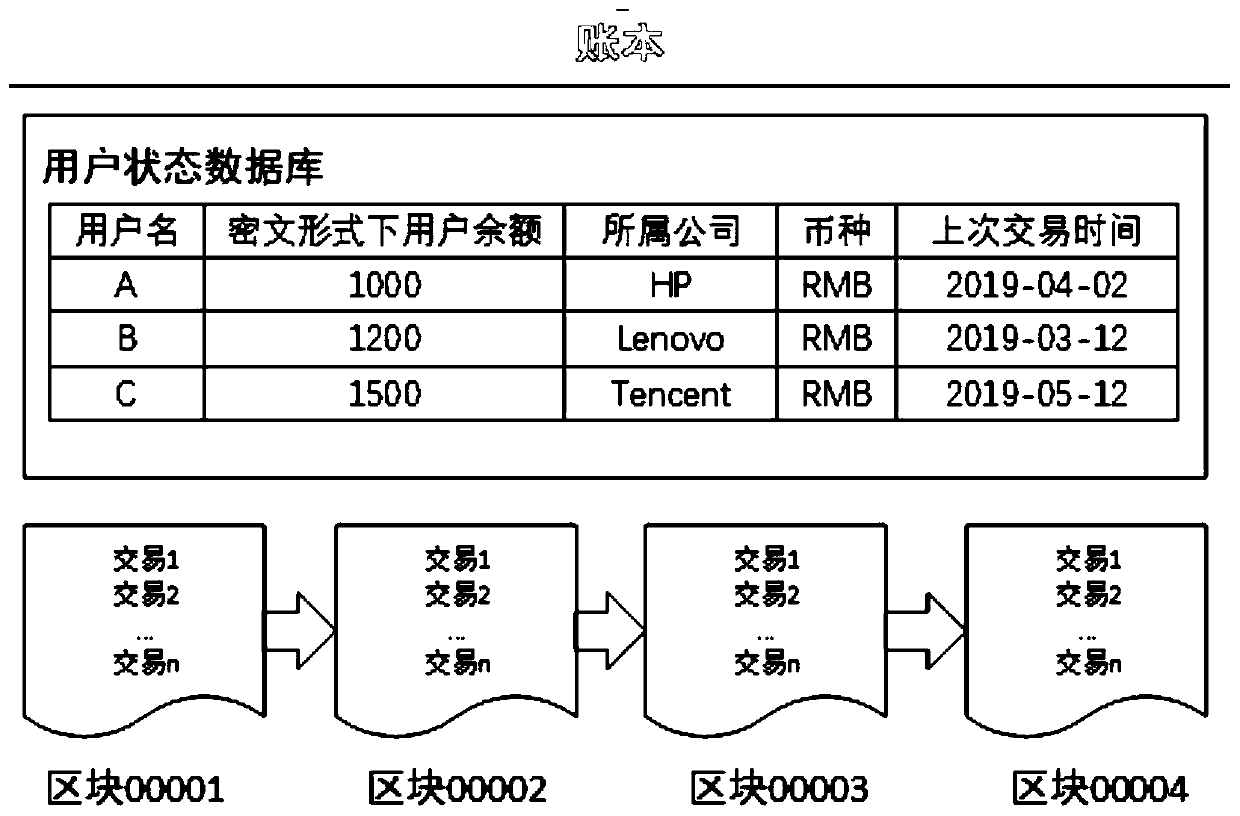
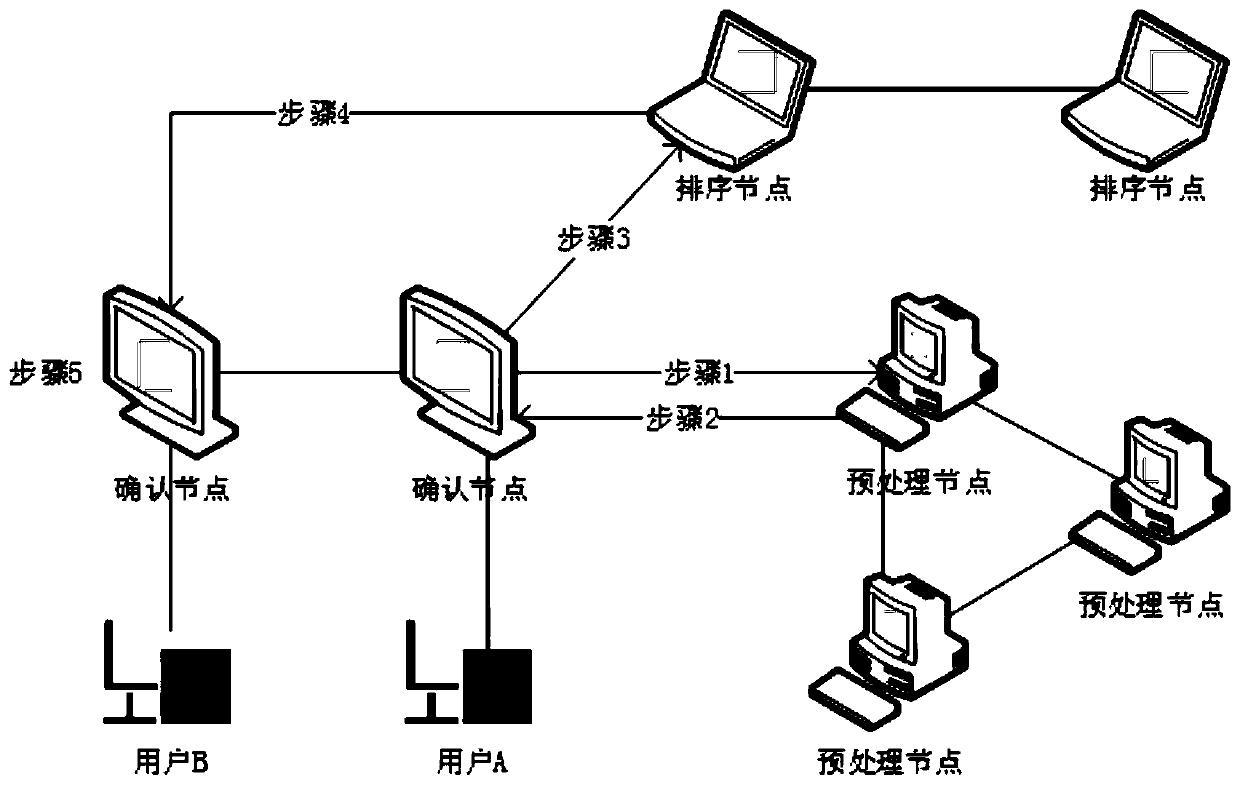
Block chain privacy protection system and method based on homomorphic encryption
InactiveCN109840771AImprove confidentialityCannot be tampered withFinanceDigital data protectionEncrypted functionPrivacy protection
The invention provides a block chain privacy protection system and method based on homomorphic encryption. The privacy protection system comprises an authentication center which is used for carrying out identity verification, issuing a certificate and periodically checking an account book; The block chain nodes are used for collecting transactions, verifying the transactions, sorting the transactions and generating blocks; Wherein the block chain nodes comprise a preprocessing node, a confirmation node and a sorting node; And a user: one user corresponds to one confirmation node. According tothe block chain privacy protection system and method based on homomorphic encryption provided by the invention, the block chain privacy protection scheme can realize transaction information confidentiality; The blockchain privacy protection scheme can ensure that the transaction information cannot be tampered; The blockchain privacy protection scheme can ensure transaction legality; The re-encryption function in the blockchain privacy protection scheme is secure.
Owner:XIDIAN UNIV
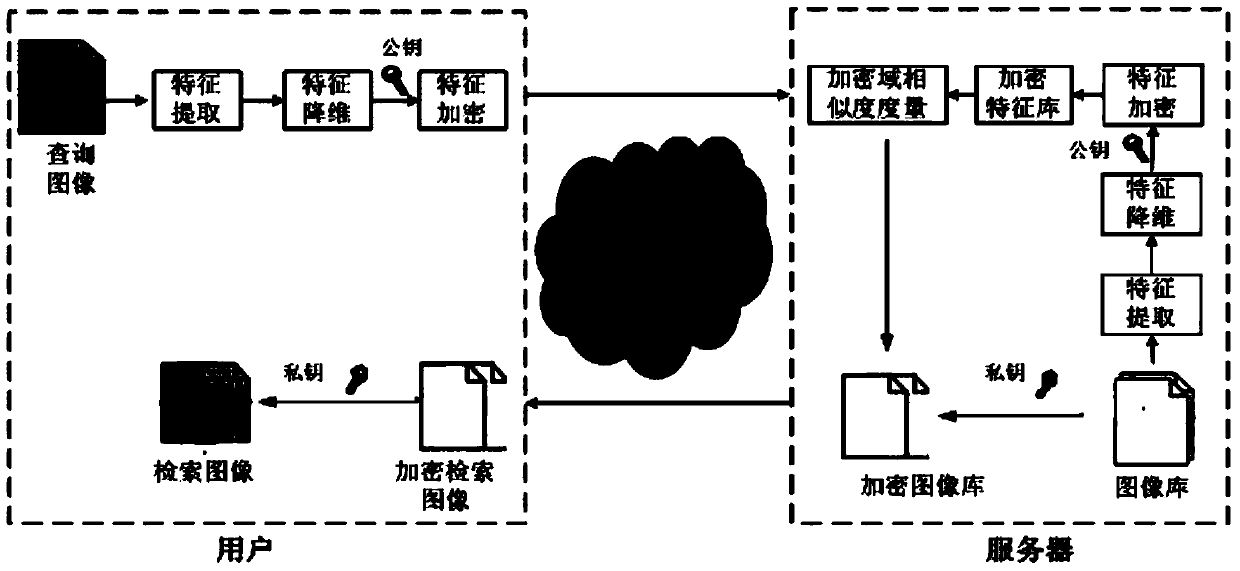
Secure image retrieval method based on homomorphic encryption
ActiveCN103744976ADoes not affect retrieval performanceCharacter and pattern recognitionComputer security arrangementsImage retrievalImaging Feature
The invention relates to a secure image retrieval method based on homomorphic encryption. The secure image retrieval method includes: firstly, extracting features, such as colors, textures, shapes and the like and reducing dimensions of the image features by a LPP method; secondly, protecting the image features by a Paillier homomorphic encryption algorithm; thirdly, conducting similarity matching of the image features which are encrypted and sending back retrieval results of K images with highest similarity to users. The secure image retrieval method is based on a CBIR structure and adopts a homomorphic encryption technology, so decryption is not needed and direct similarity measurement of the image features which are encrypted can be realized by using by using the homomorphic features of the Paillier encryption algorithm. Accordingly, the problem that the direct retrieval of the image features which are encrypted cannot be realized by the prior retrieval method can be solved. Experiment results prove that the retrieval results of the secure image retrieval method is consistent with the retrieval results of a plaintext CBIR method in the prior art under the condition of ensuring the security of image information, so that the encryption cannot influence the image retrieval performance.
Owner:数安信(北京)科技有限公司
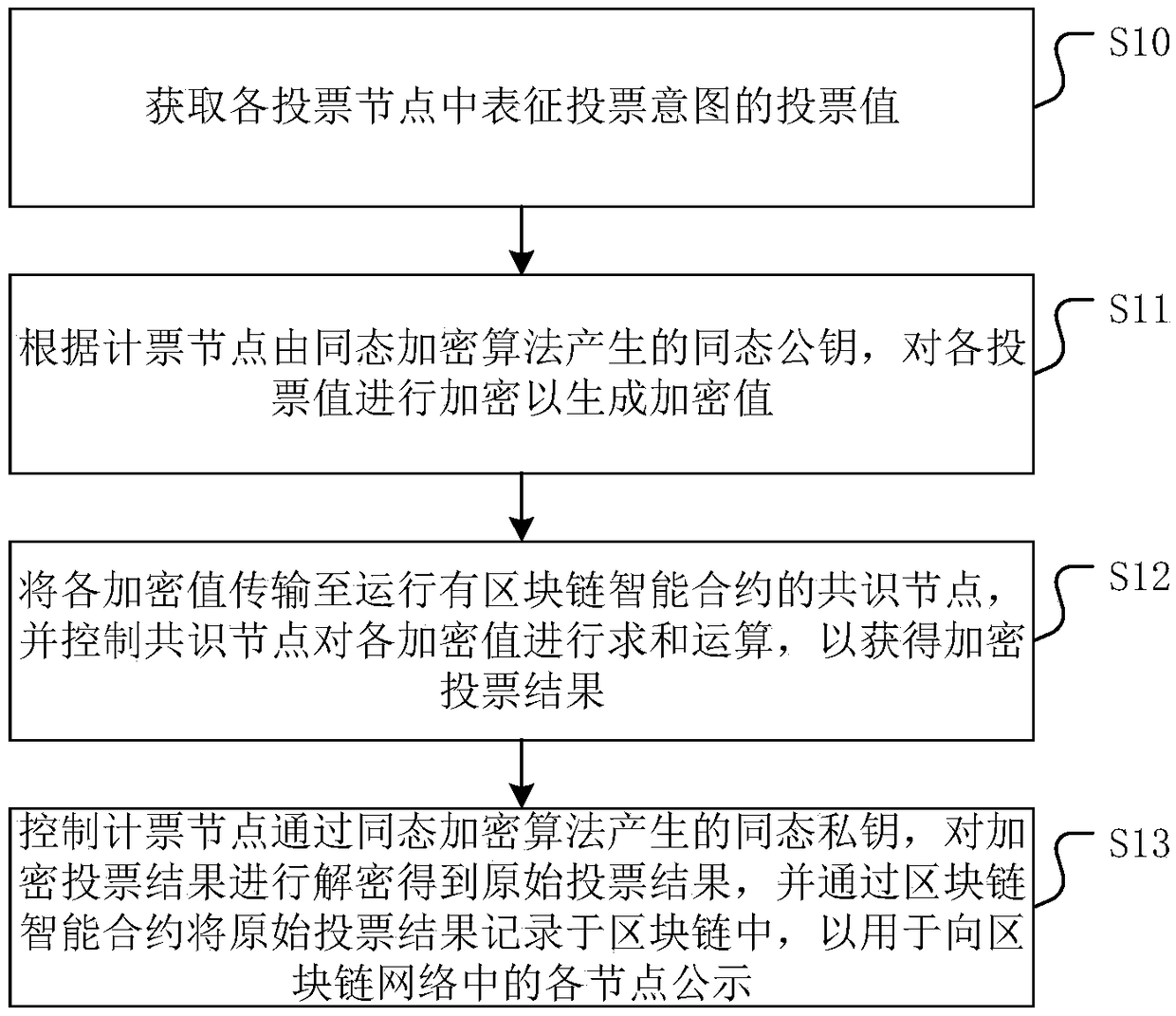
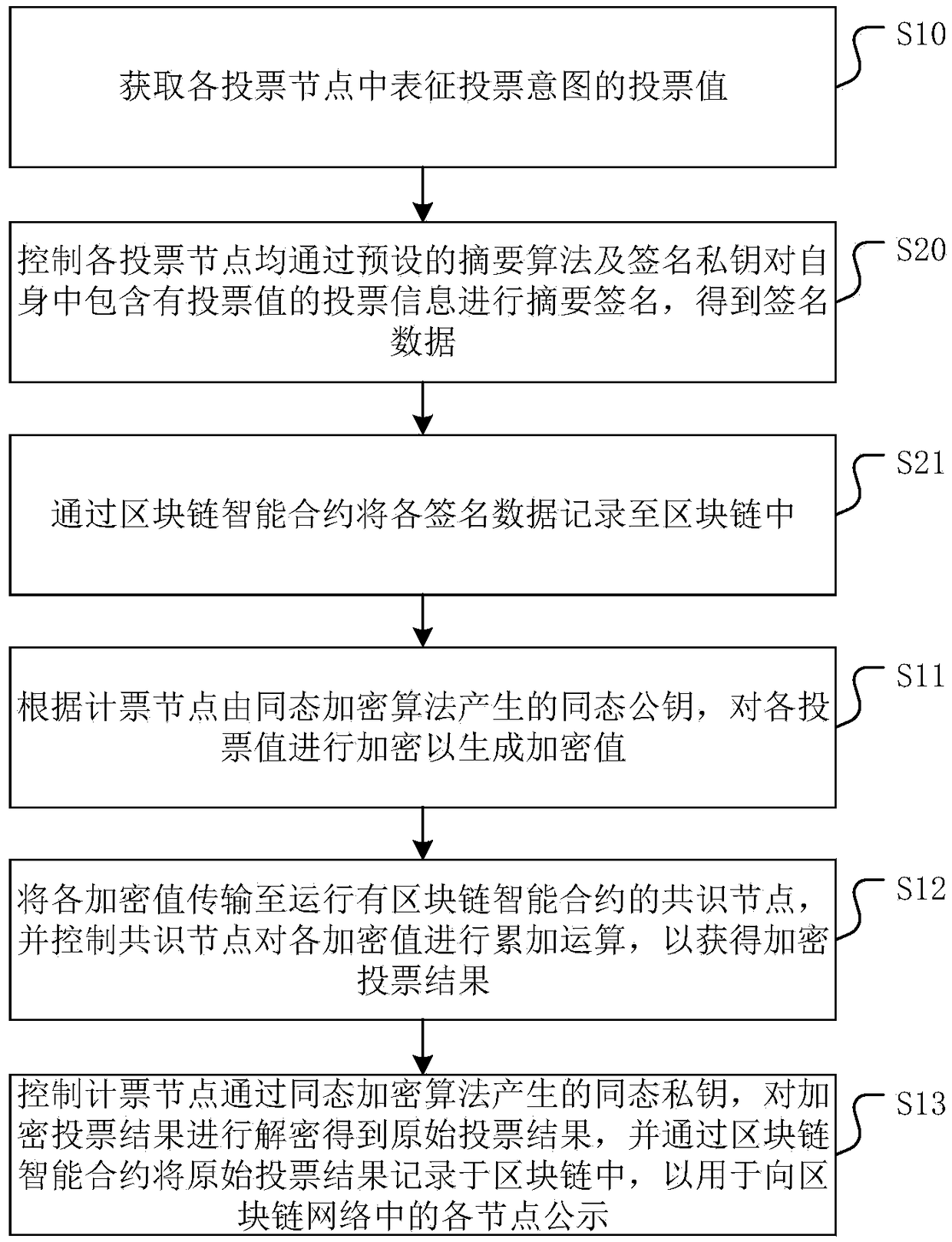
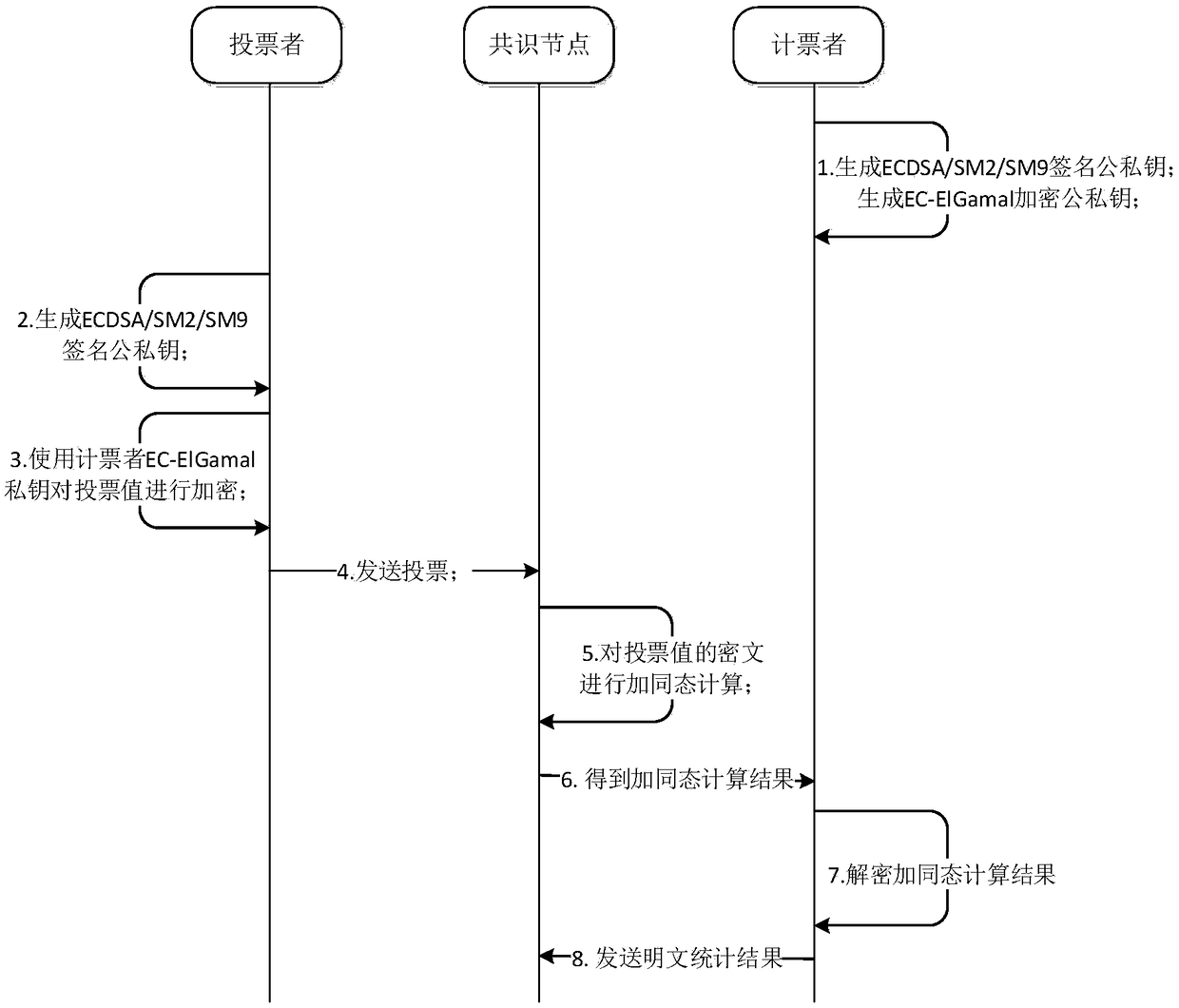
Voting method, device and equipment based on Blockchain, and medium
ActiveCN108768607AEnsure safetyGuarantee fairnessEncryption apparatus with shift registers/memoriesPublic key for secure communicationSmart contractHomomorphic encryption
The invention discloses a voting method, a voting device and voting equipment based on Blockchain, and a medium. The method comprises the steps of: obtaining voting values representing a voting intention in each voting node; encrypting each voting value according to the homomorphic public key of the counting nodes generated by a homomorphic encryption algorithm to generate encrypted values; transmitting each encrypted value to a consensus node running a blockchain smart contract, and controlling the consensus node to perform a summation operation on each encrypted value to obtain an encryptedvoting result; decrypting the encrypted voting result by controlling the homomorphic private key of the counting nodes generated by the homomorphic encryption algorithm to obtain an original voting result, and recording the original voting result in the blockchain through the blockchain smart contract for publicity for each node in the blockchain network. This method ensures the fairness of the counting process and the overall voting efficiency. In addition, the invention also provides a voting device and voting equipment based on Blockchain, and a medium, having the beneficial effects the same as described above.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院
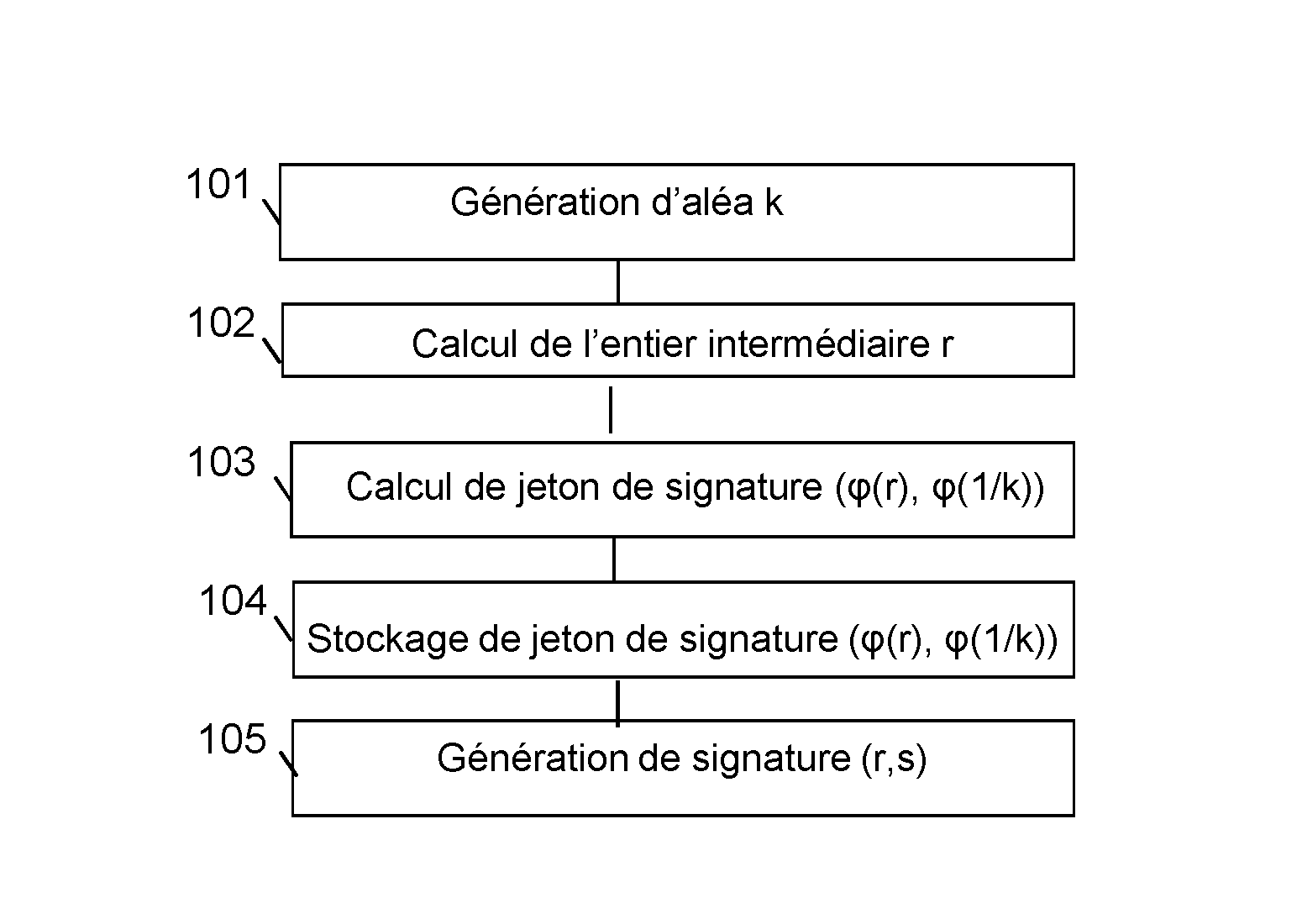
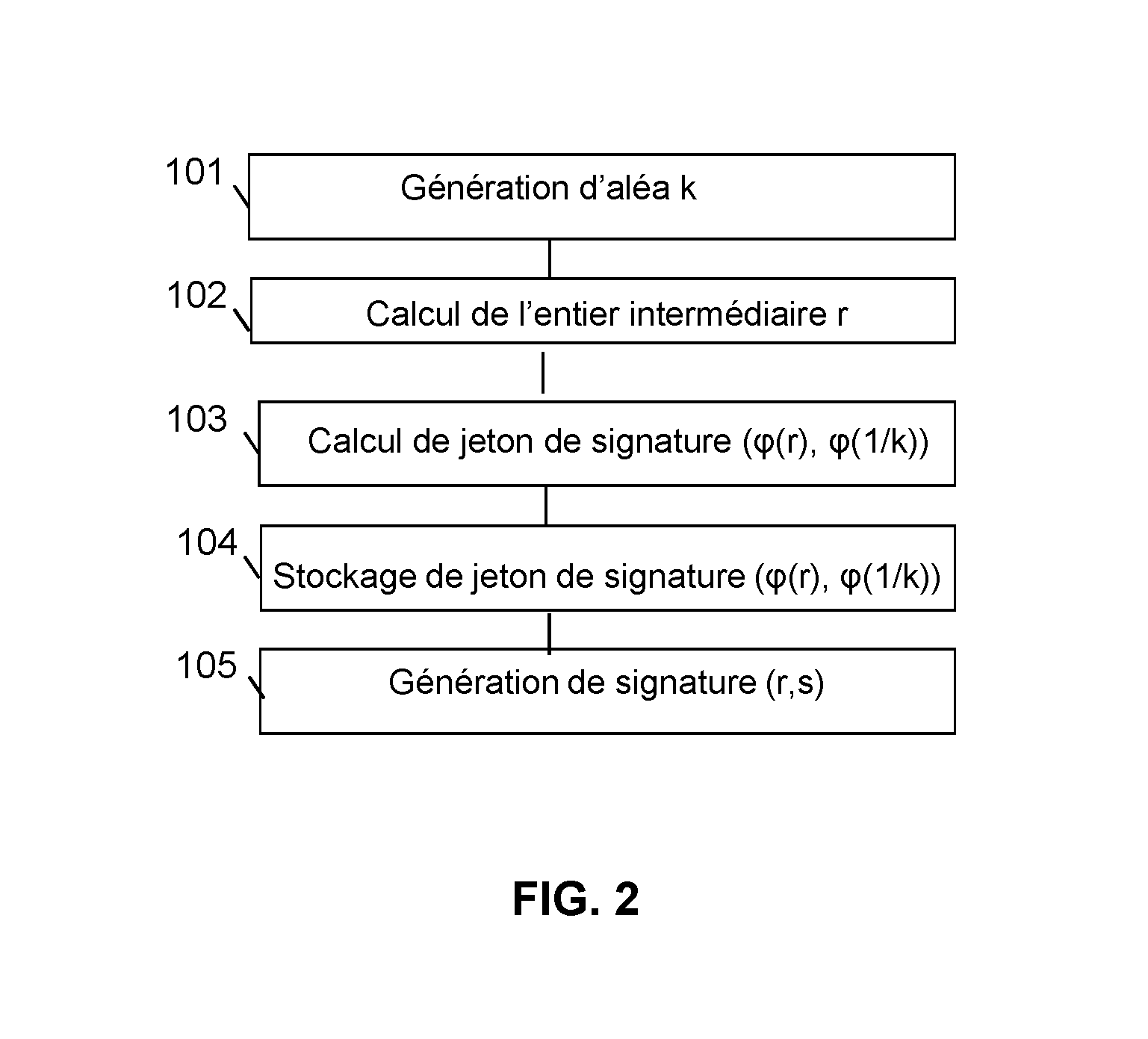
Method for generating a message signature from a signature token encrypted by means of a homomorphic encryption function
ActiveUS20160344557A1Not to endanger securityReduce power generation costsPublic key for secure communicationUser identity/authority verificationHardware security modulePrecomputation
The invention relates to a method for generating a message signature intended to be validated by a verifier server, a client device being configured to hold a private key and a corresponding public key and comprising steps of:offline precomputation (103) by a hardware security module of a signature token, a result of encryption by means of a homomorphic encryption function,storage (104) of said signature token;generation (105) of said signature of said encrypted message by means of said homomorphic encryption function from the result of the encryption by said homomorphic encryption function of the private key stored by the client device, of the signature token and of said message, said signature being intended to be validated by said verifier server by means of said public key.
Owner:IDEMIA IDENTITY & SECURITY FRANCE
System and methods for validating and performing operations on homomorphically encrypted data
InactiveUS20170293913A1Acceptable performancePrivacy protectionDiagnostic signal processingMultiple keys/algorithms usageInternet privacyTransaction data
A system and method of validating and performing operations on homomorphically encrypted data are described herein. The methods include processing a secure financial transaction by receiving a transaction request to complete a financial transaction, with at least a portion of the request encrypted according to a homomorphic encryption scheme, and the transaction request comprising confidential cardholder data including an account number, non-confidential cardholder data, and transaction data, and retrieving one or more sets of encrypted comparison cardholder data encrypted according to a homomorphic encryption scheme. The confidential cardholder data is then compared to each set of the comparison cardholder data using one or more homomorphic operations to determine which set of comparison cardholder data matches the confidential cardholder data and validating the confidential cardholder data. An encrypted indicator is generated indicating authorization or rejection of the request and forwarded to a party seeking authorization to complete the financial transaction.
Owner:LORICA CYBERSECURITY INC
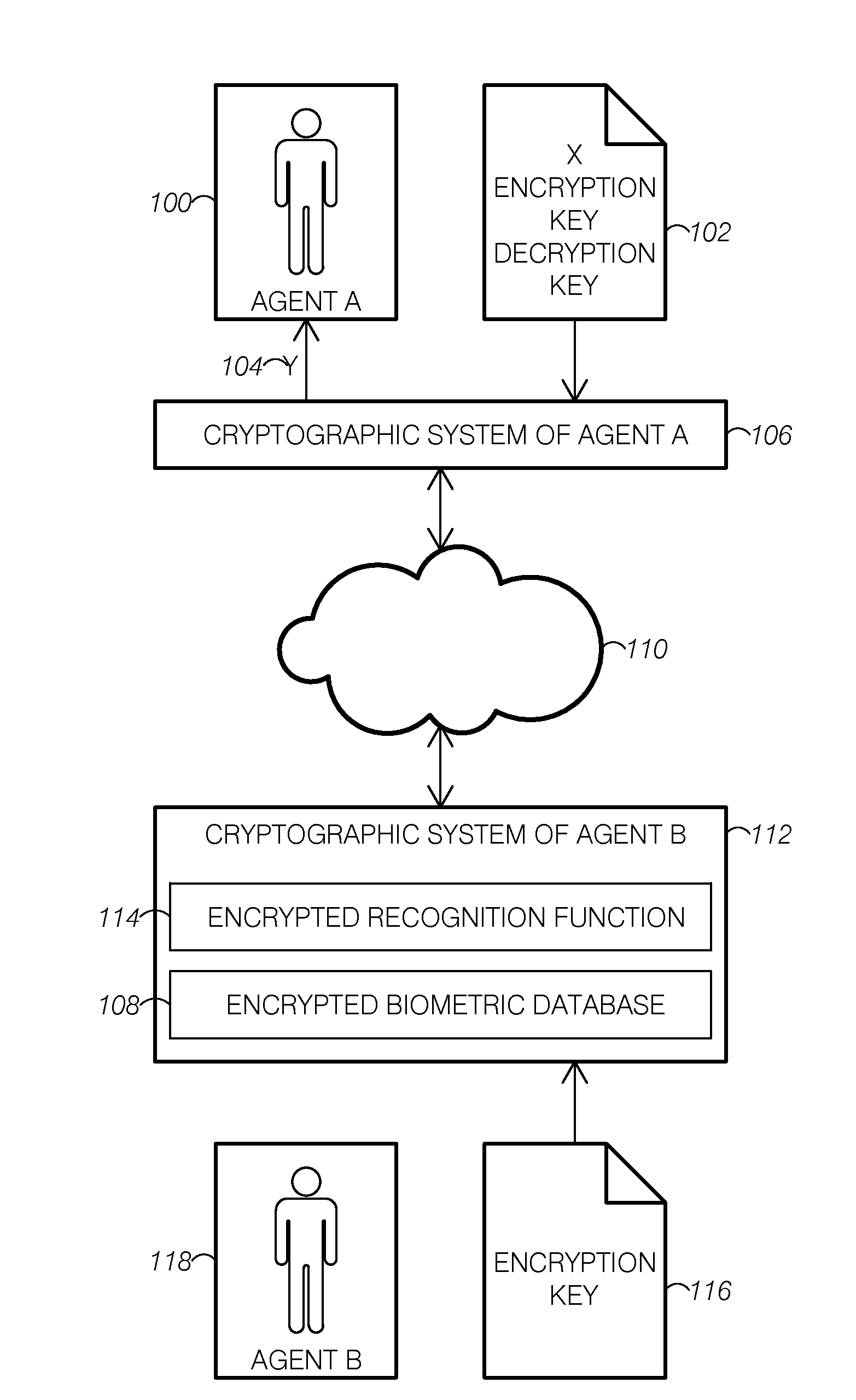
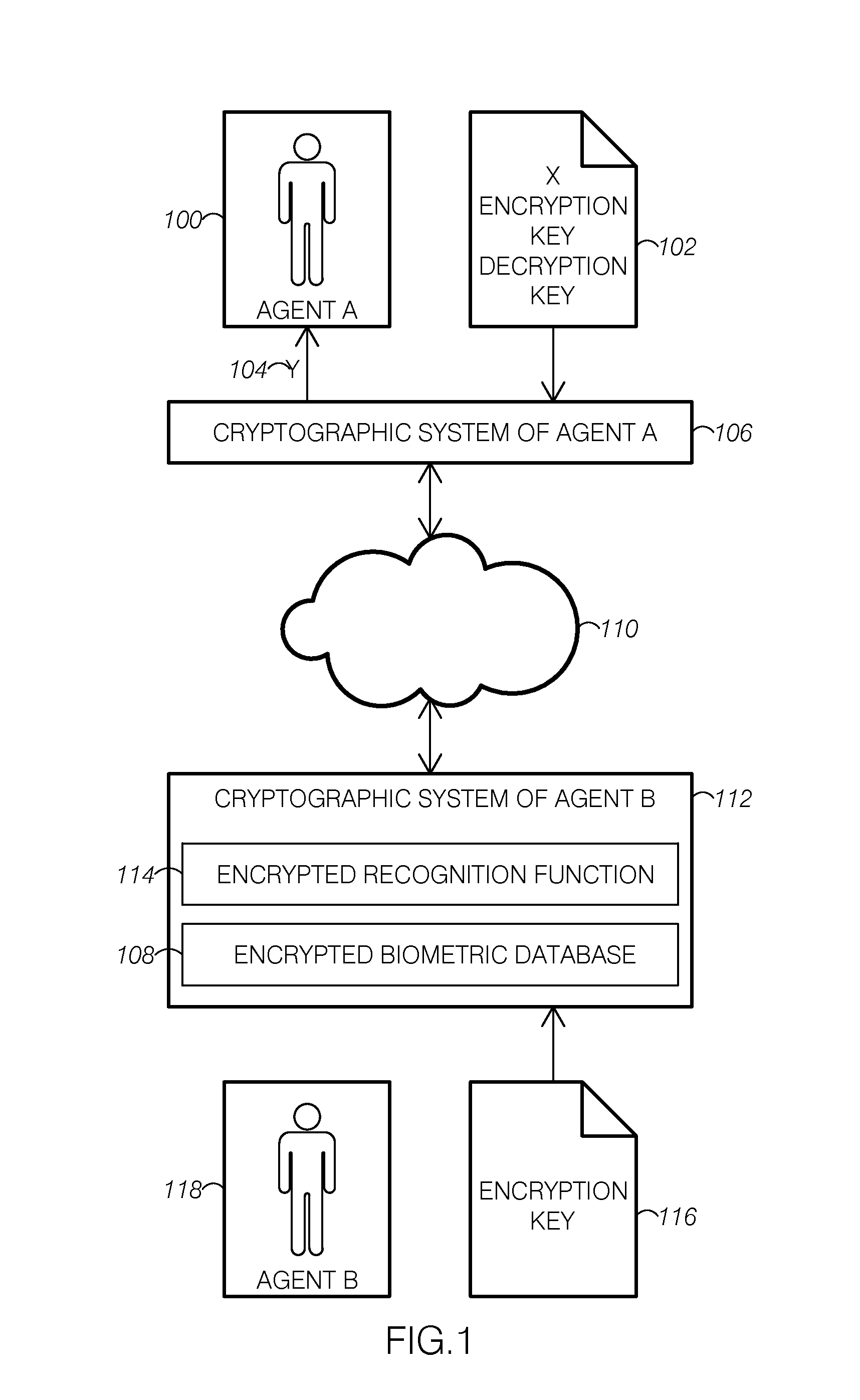
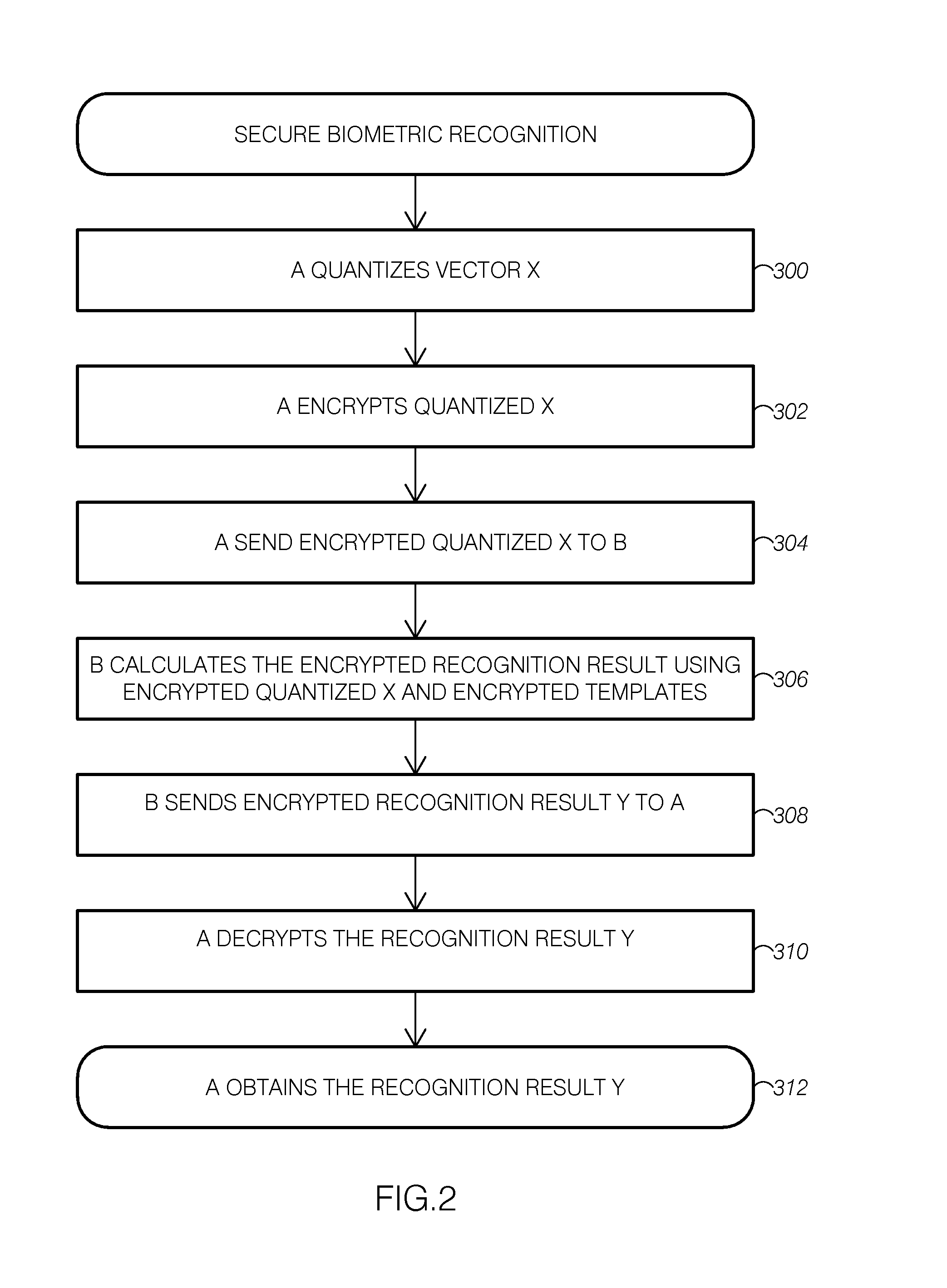
System for secure image recognition
ActiveUS20130148868A1Digital data authenticationBiometric pattern recognitionImaging processingBiometric system
Disclosed embodiments include methods, apparatuses, and systems for secured image processing, image recognition, biometric recognition, and face recognition in untrusted environments. The disclosure includes a system for secure image recognition that comprises a secure biometric recognition system configured to work directly with encrypted signals, and the secure biometric recognition system comprises an input quantization system and a homomorphic encryption system configured for noninteractive biometric recognition.
Owner:GRADIANT
Information sharing and secure multi-party computing model based on block chain
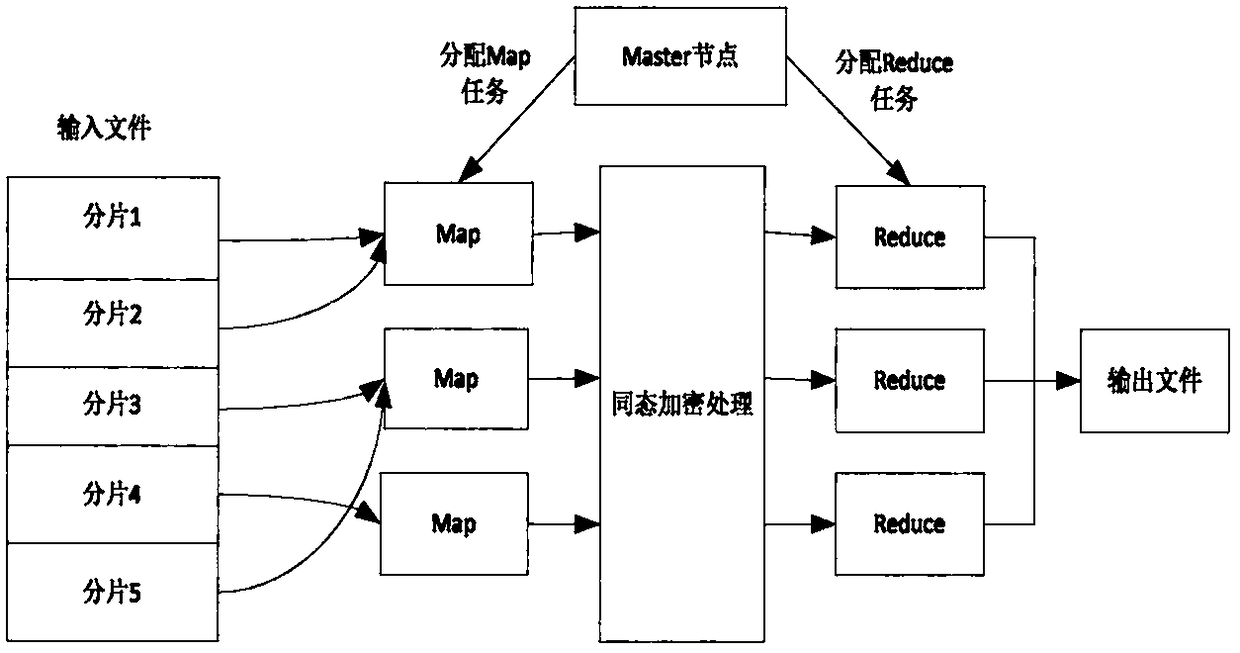
The invention discloses an information sharing and safe multi-party computing protocol based on a block chain, mainly solves the problem that the existing secure multi-party computation is easy to cause the user to be unable to control the data independently that is easy to get the data by the third party. The technical solutions are as follows: 1) constructing the storage model, and storing the index table information on the chain and the database under the chain in the way. 2) constructing a data sharing model,wherein users can access their data by authorizing a third party or revoke their privileges at any time. 3) using the consensus mechanism of the block chain to ensure the consistency among nodes; 4) Based on the correctness of nodes, using MapReduce programming model, the model isdivided into two phases: Map and Reduce, and the master node assigns the tasks of Map and Reduce to the nodes; 5) Map node uses the improved homomorphic encryption algorithm for encryption calculation; 6) Reduce node integrates the encrypted data to output data files.
Owner:全链通有限公司
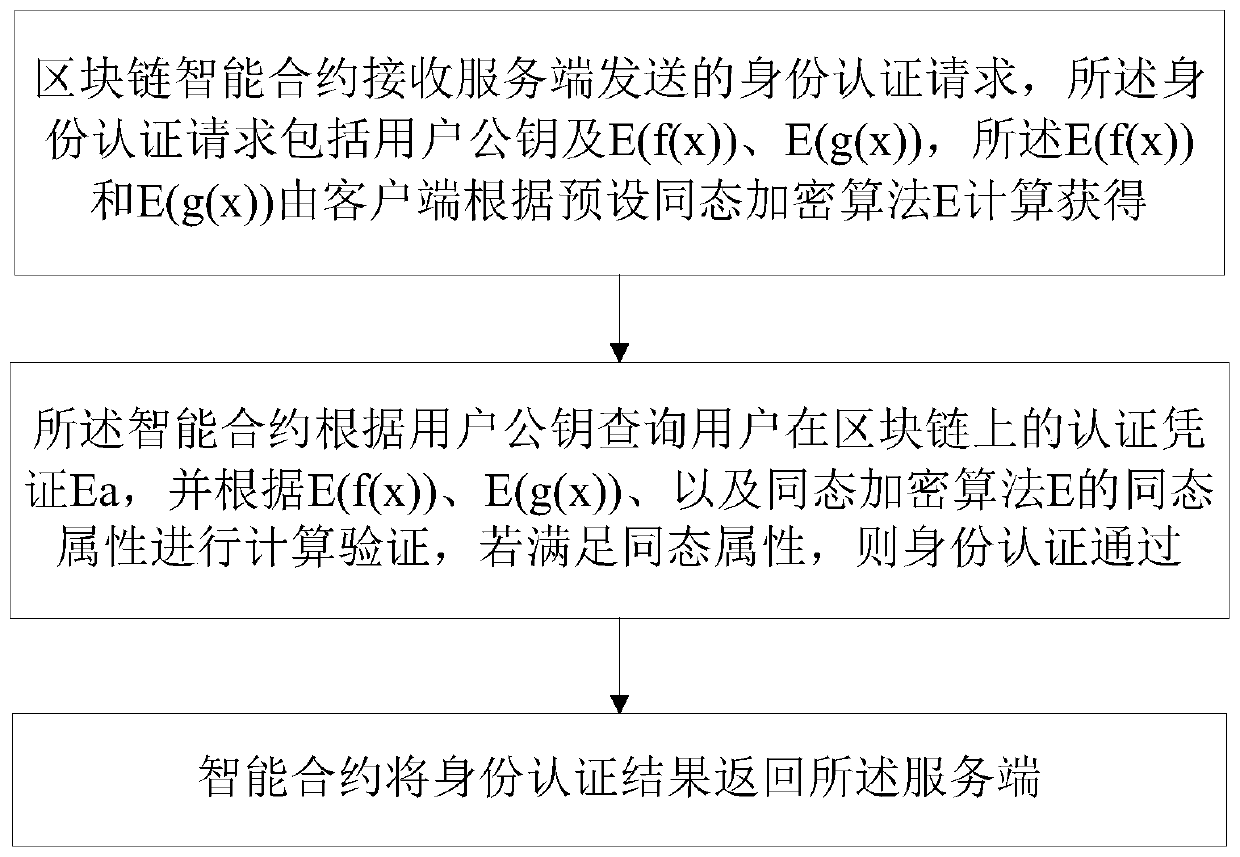
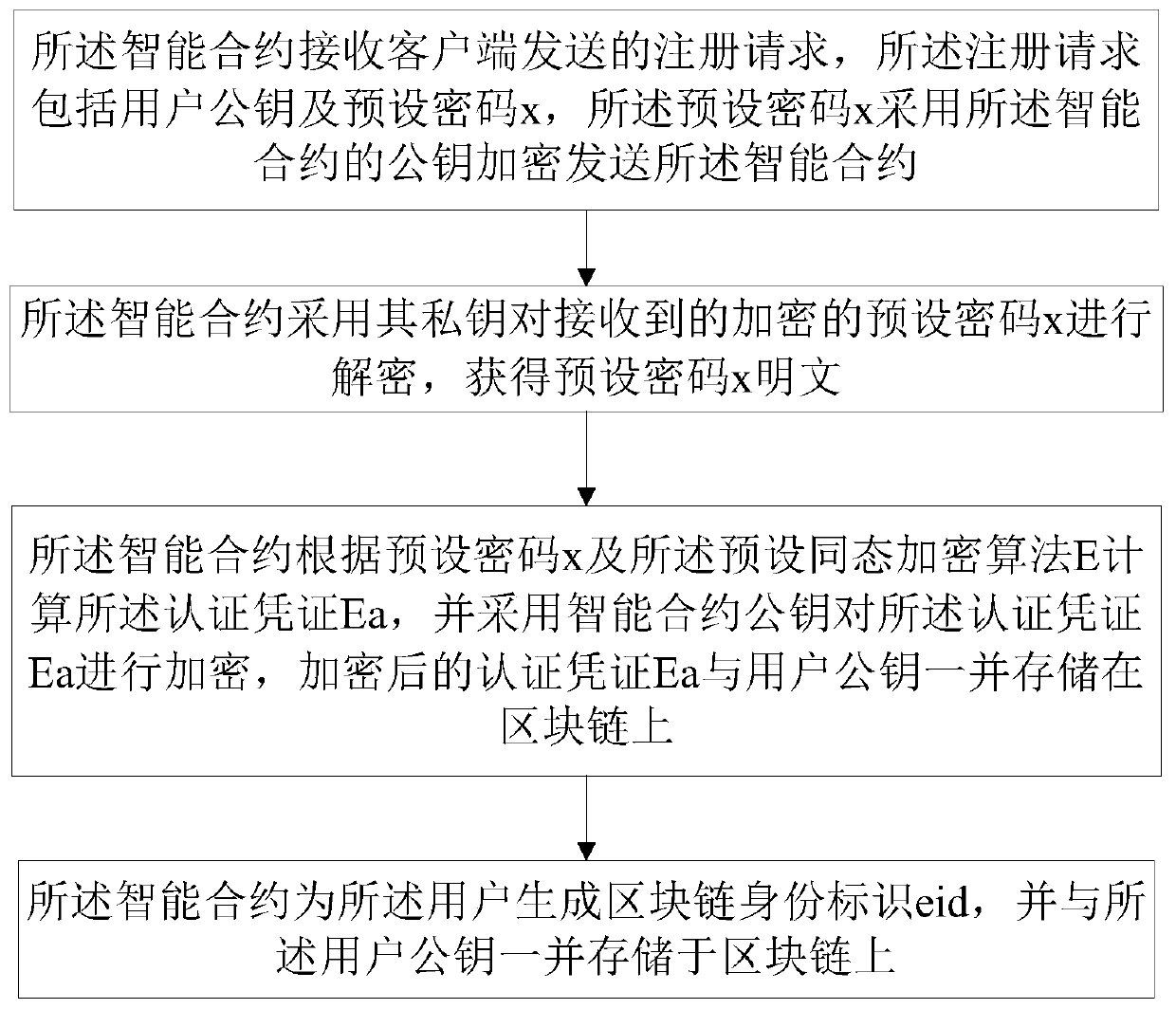
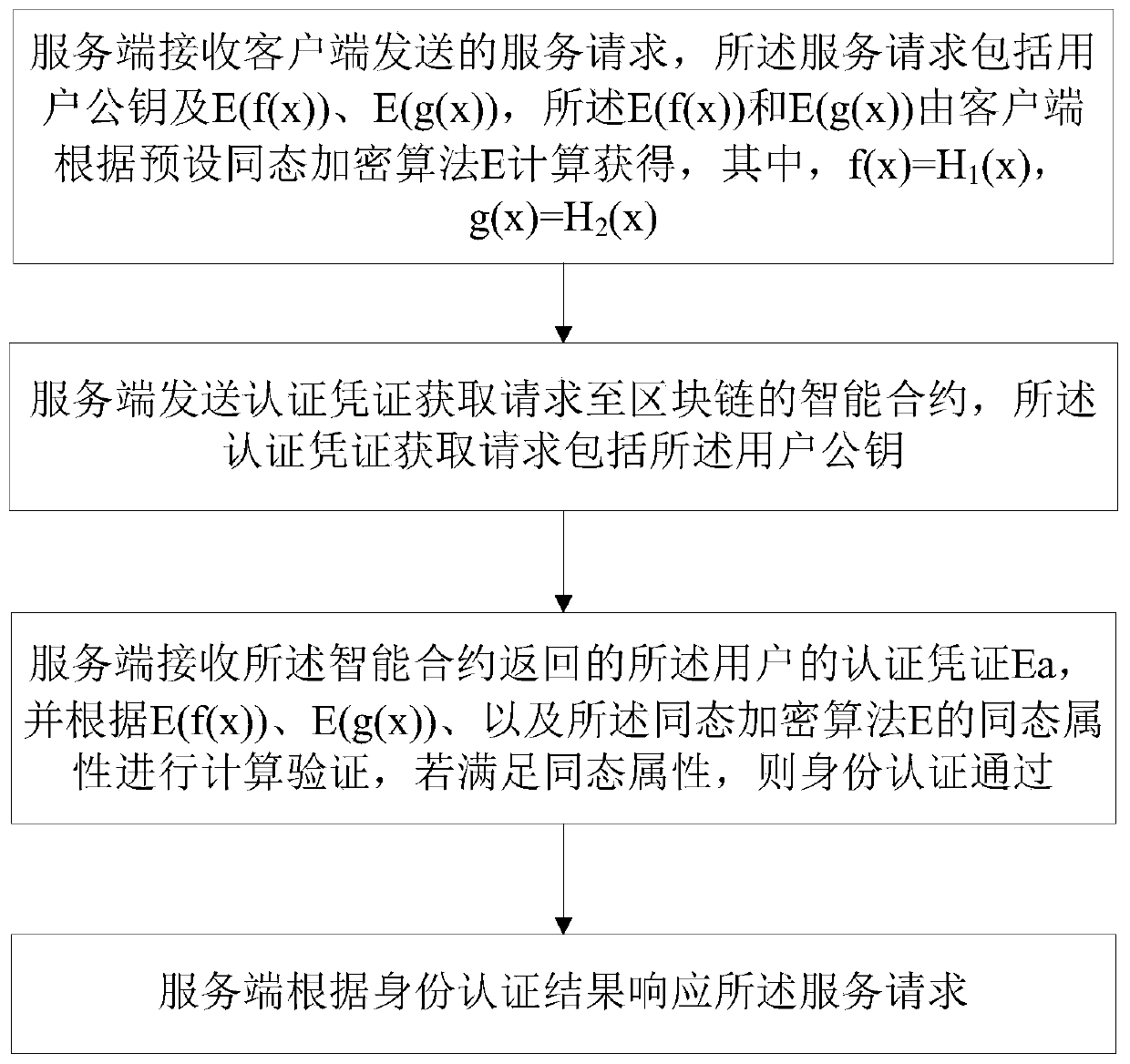
A blockchain-based identity authentication method and a blockchain-based identity authentication system
ActiveCN109922077AGuaranteed not to movePrevent leakageSecuring communicationSmart contractClient-side
The invention relates to a blockchain-based identity authentication method and a blockchain-based identity authentication system. The identity authentication method based on the block chain comprisesthe following steps that an intelligent contract of the block chain receives an identity authentication request sent by a server side, the identity authentication request comprises a user public key and E(f (x)), and the E(g (x)), the E(f (x)) and the E(g (x)) are obtained through calculation by a client side according to a preset homomorphic encryption algorithm E; the intelligent contract inquires an authentication certificate Ea of the user on the block chain according to the public key of the user, carries out calculation and verification according to E (f (x)) , E (g (x)) and the homomorphic attribute of a homomorphic encryption algorithm E, and passes identity authentication if the homomorphic attribute is met; and the smart contract returns the identity authentication result to theserver. The method has the beneficial effects that based on the characteristics of the block chain, the threats of replay attacks and violent cracking can be resisted, so that the attack cost is increased. By utilizing a homomorphic encryption attribute equation, the nizk can be constructed, and under the condition that an original credential for user identity authentication is not leaked, the user is proved to have the credential, so that the identity of the user is proved.
Owner:朗新数据科技有限公司
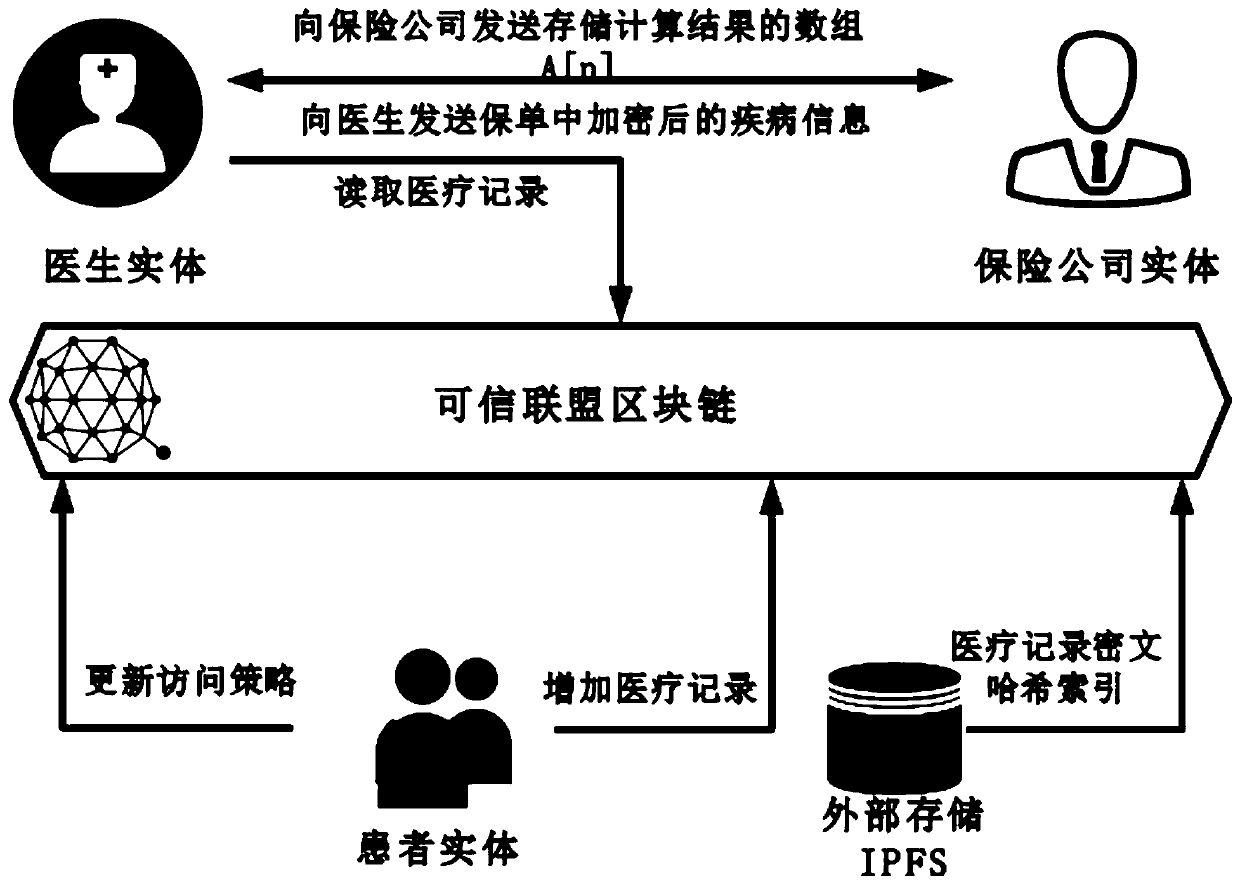
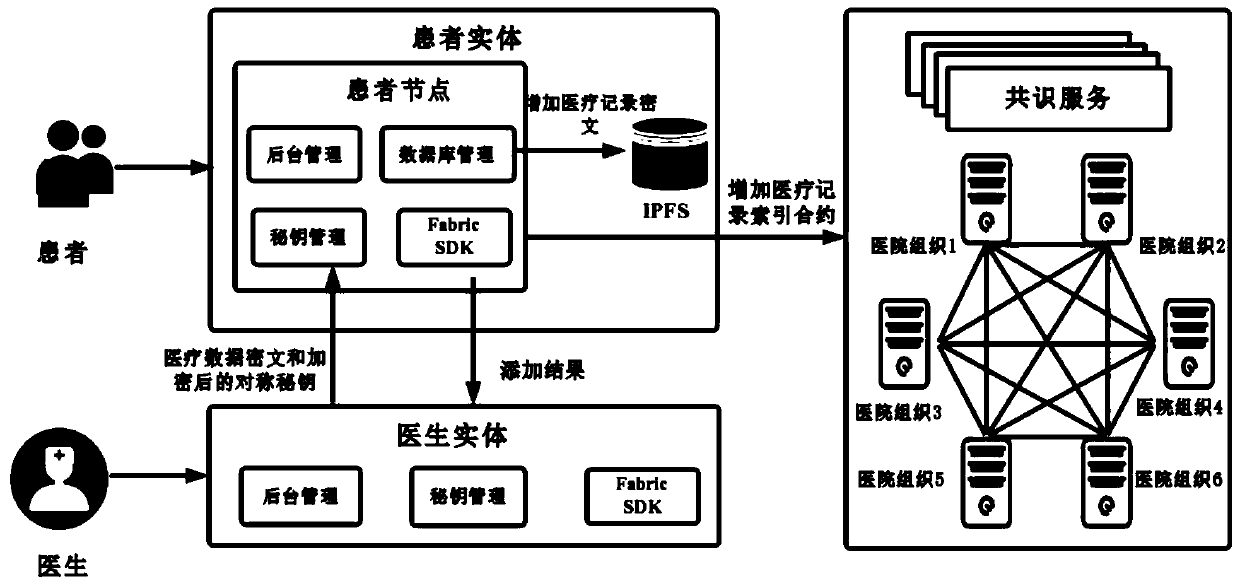
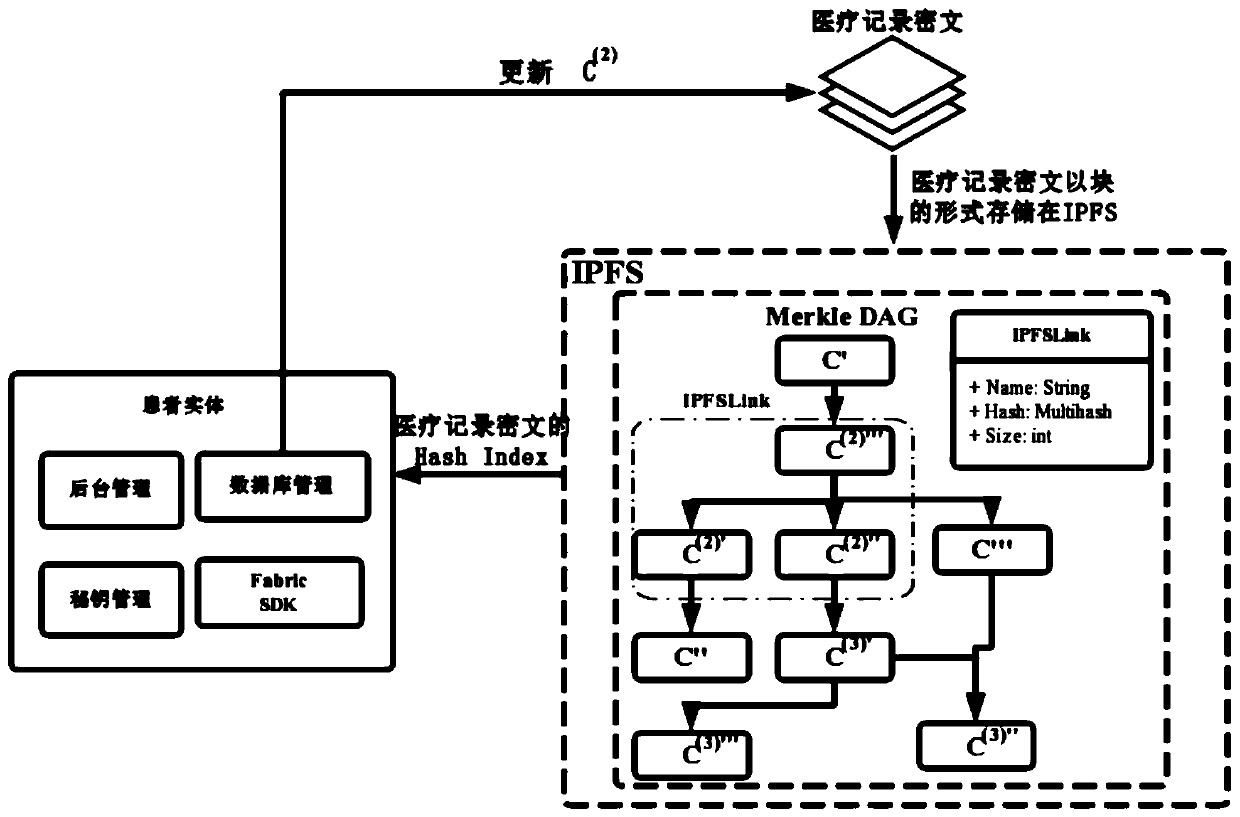
Medical record storage, sharing and security claim settlement model and method based on a block chain
ActiveCN110008746AGuaranteed privacyIncrease resistanceDigital data protectionPatient healthcareMedical recordThird party
The invention belongs to the technical field of medical data management, and relates to a medical record storage, sharing and security claim settlement model and method based on a block chain. Firstly, credible sharing of medical data of patients among medical institutions is achieved through the blockchain technology, and a lifelong medical record is established for the patients; based on a Hashchain type storage structure, the medical data cannot be tampered; secondly, an improved CP-ABE-based cryptographic primitive SHDPCPC-CP-ABE is proposed, security encryption and fine-grained access control on the medical data are realized, and a patient can conveniently and efficiently access and authorize a medical institution to read the medical data; and finally, a Paillier homomorphic encryption technology is utilized to realize safe medical insurance claim settlement, and the privacy of the patient is protected when the patient interacts with a third-party non-medical institution. According to the invention, security, confidentiality, reliability and integrity of medical data can be realized, and confidential sharing of private data is supported.
Owner:DALIAN UNIV OF TECH
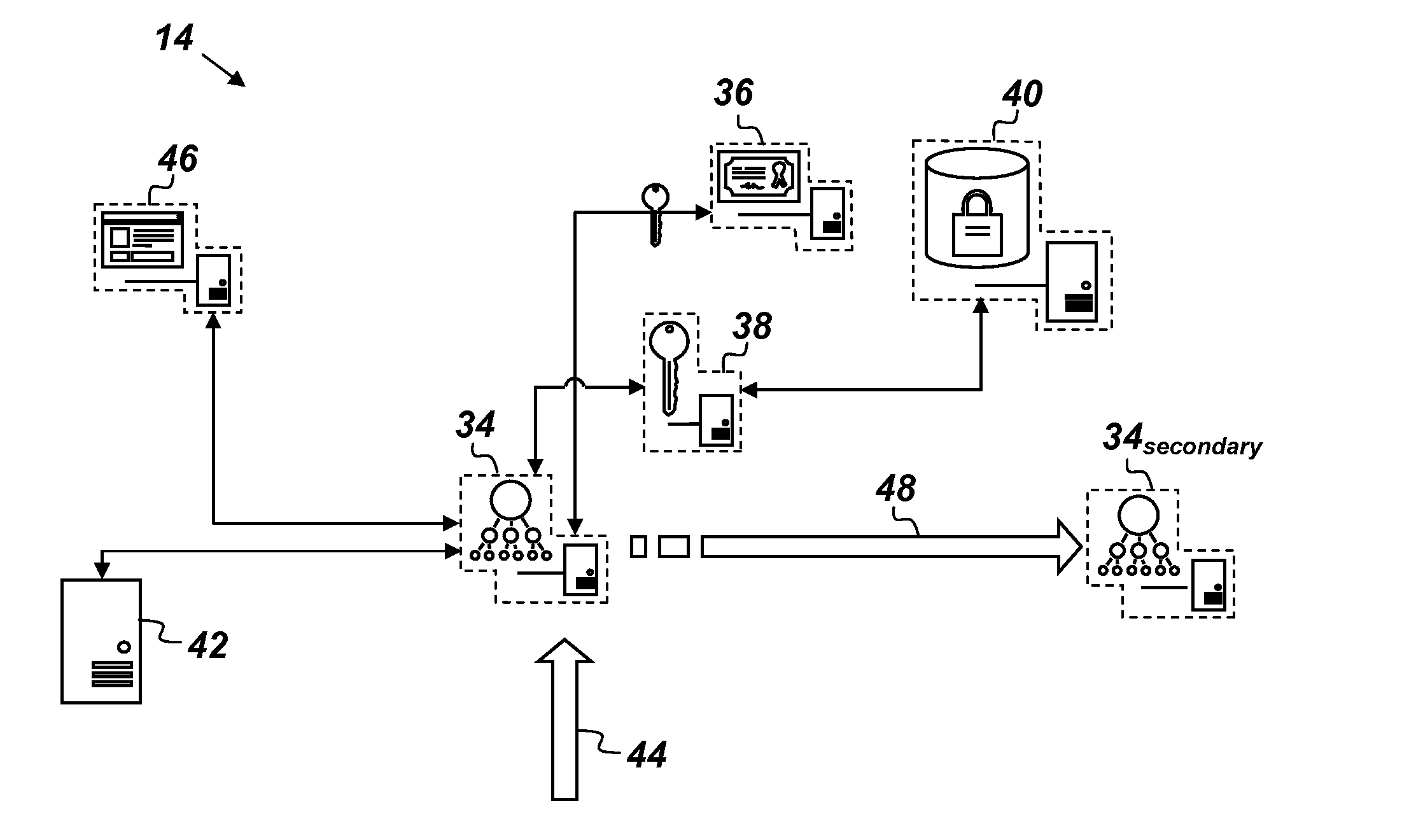
System and Method for High-Assurance Data Storage and Processing based on Homomorphic Encryption
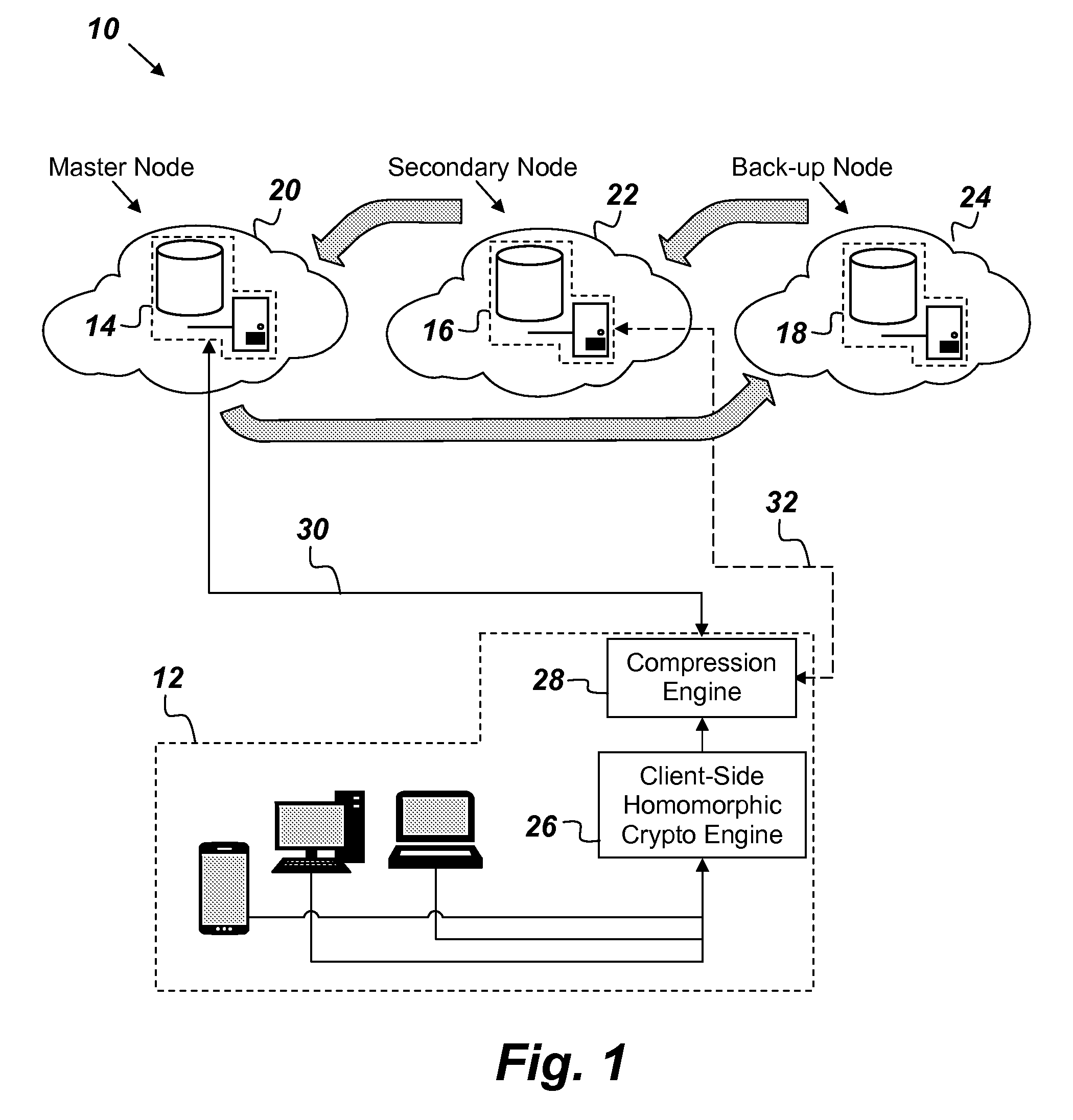
ActiveUS20160323098A1Quality of serviceLower quality of serviceKey distribution for secure communicationSoftware simulation/interpretation/emulationQuality of serviceClient-side
A key value storage (KVS) system comprising: a client-side agent configured to encrypt data; three nodes hosted respectively in three cloud service providers, wherein each node comprises: a management node configured to receive encrypted data from the client-side agent, a homomorphic encryption (HE) key manager configured to fetch a public key of a given object in the KVS system, a homomorphic encryption and processing engine configured to execute commands over the encrypted data without decrypting it, a homomorphic memory store, a hypervisor configured to monitor performance of the management node in order to assess the quality of service of the management node; and wherein each node serves on a rotating basis in a master node role, a secondary node role, or a back-up node role, wherein the nodes rotate their roles when the master node's hypervisor detects a reduced quality of service of the master node's management node.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com