System and Method for High-Assurance Data Storage and Processing based on Homomorphic Encryption
a data storage and homomorphic encryption technology, applied in the field of data storage and processing, can solve the problems of data theft becoming a much bigger problem, data breaches and theft episodes being reported all over the world, etc., and achieve the effect of reducing service quality, assessing master node service quality, and reducing service quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025]The disclosed methods and systems below may be described generally, as well as in terms of specific examples and / or specific embodiments. For instances where references are made to detailed examples and / or embodiments, it should be appreciated that any of the underlying principles described are not to be limited to a single embodiment, but may be expanded for use with any of the other methods and systems described herein as will be understood by one of ordinary skill in the art unless otherwise stated specifically.
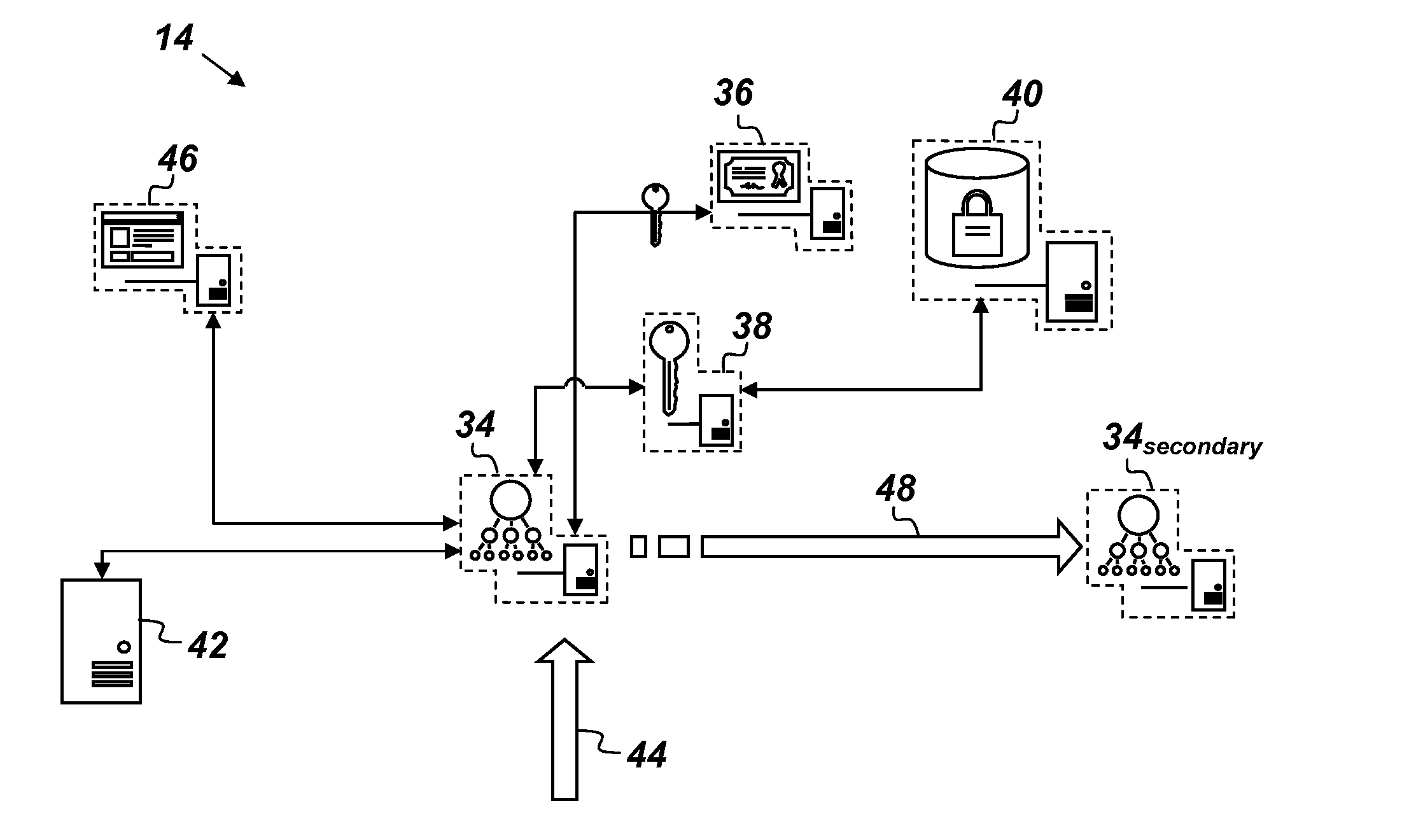
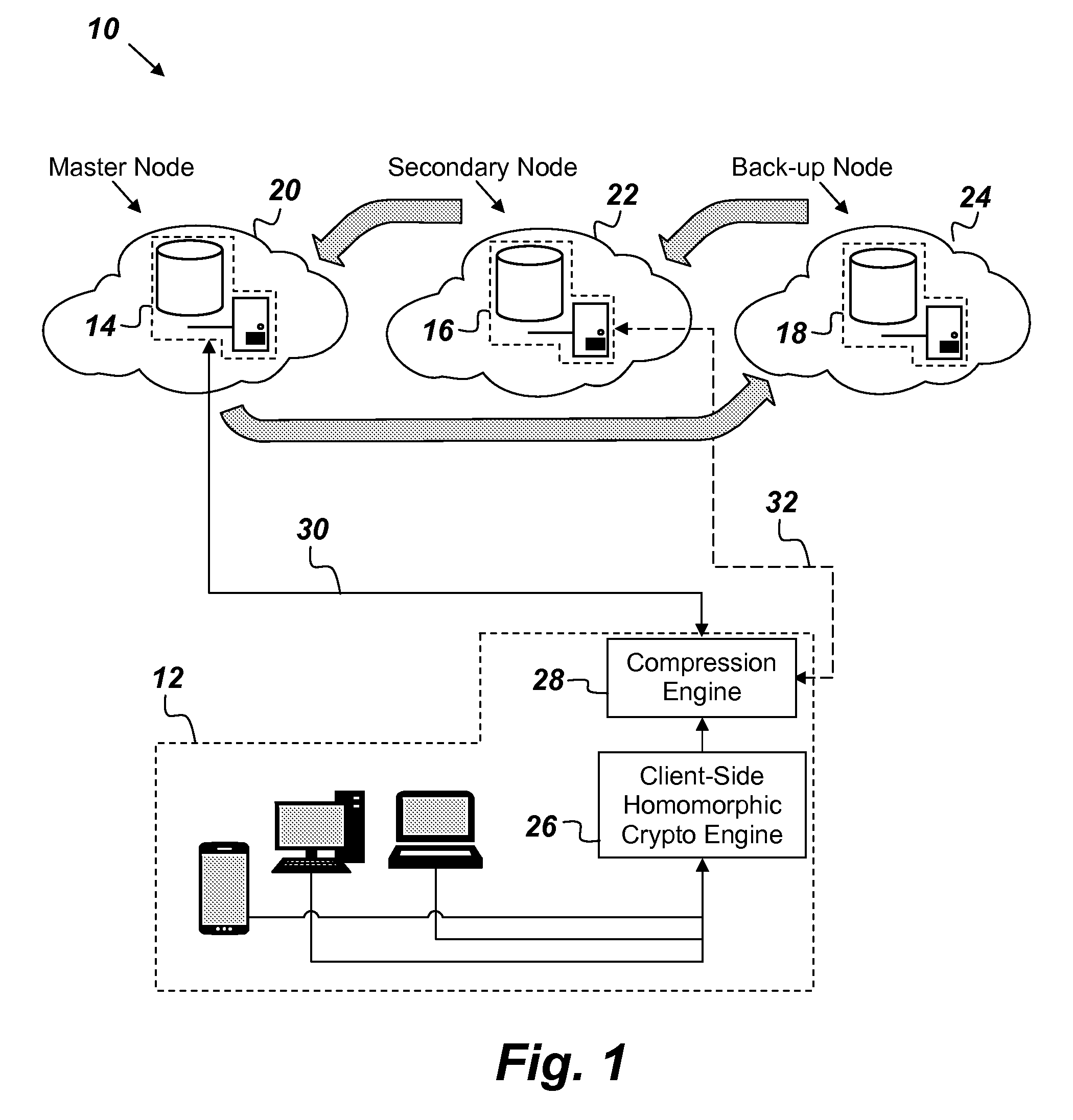
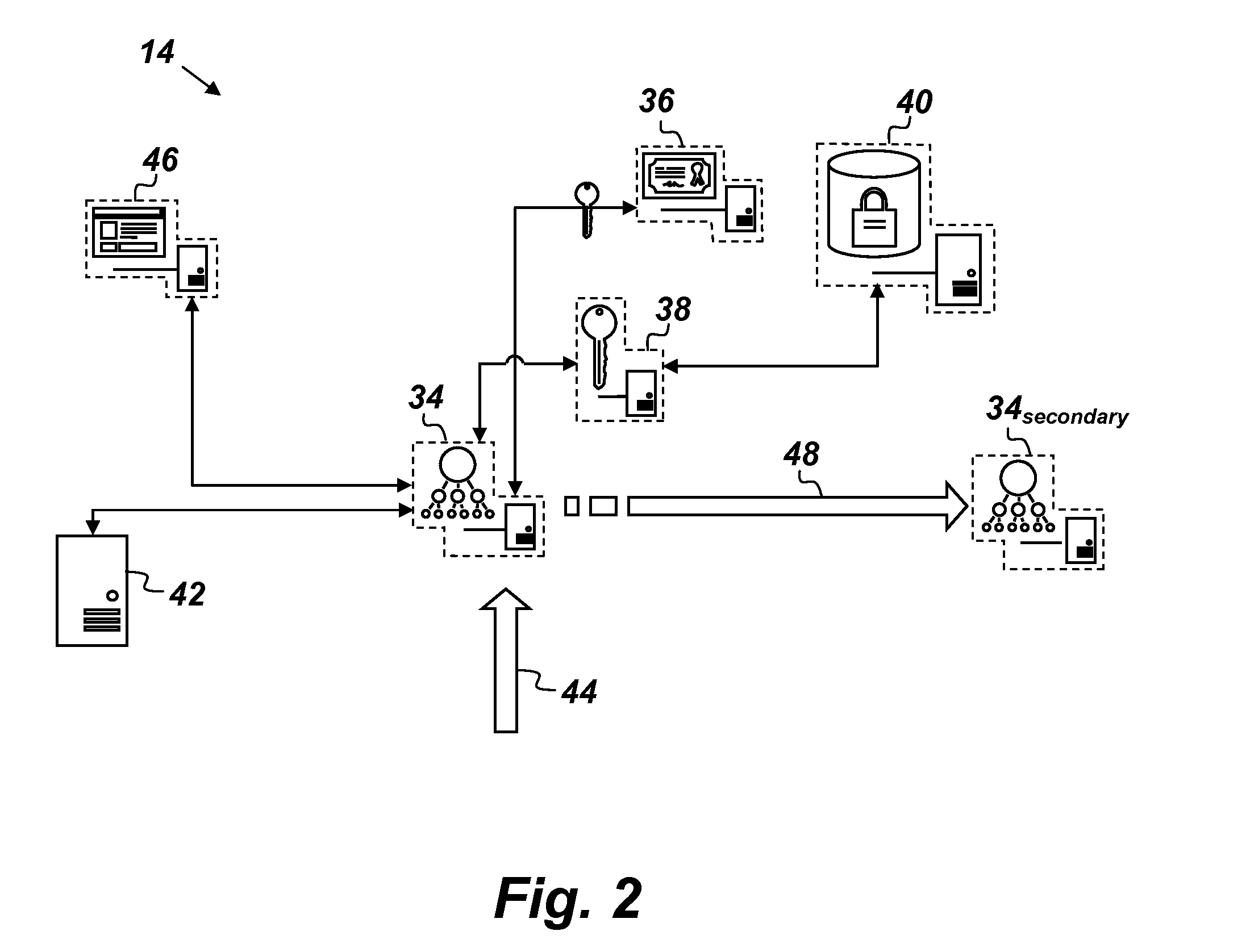
[0026]FIG. 1 is an illustration of a key value storage (KVS) system 10 comprising, consisting of, or consisting essentially of a client-side agent 12 and first, second, and third nodes 14, 16, and 18 respectively. The client-side agent 12 is configured to encrypt data, and only the client-side agent 12 can decrypt the data. The first, second, and third nodes 14, 16, and 18 are hosted respectively in first, second, and third clouds 20, 22, and 24 provided by different...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com