Patents
Literature
61 results about "Data theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data theft is a growing phenomenon primarily caused by system administrators and office workers with access to technology such as database servers, desktop computers and a growing list of hand-held devices capable of storing digital information, such as USB flash drives, iPods and even digital cameras. Since employees often spend a considerable amount of time developing contacts and confidential and copyrighted information for the company they work for, they may feel they have some right to the information and are inclined to copy and/or delete part of it when they leave the company, or misuse it while they are still in employment. They can be sold and bought and then used by criminals and criminal organizations. Alternatively, an employee may choose to deliberately abuse trusted access to information for the purpose of exposing misconduct by the employer; From the perspective of the society such an act of whistleblowing can be seen as positive and is in certain situations protected by law in some jurisdictions, such as the USA.
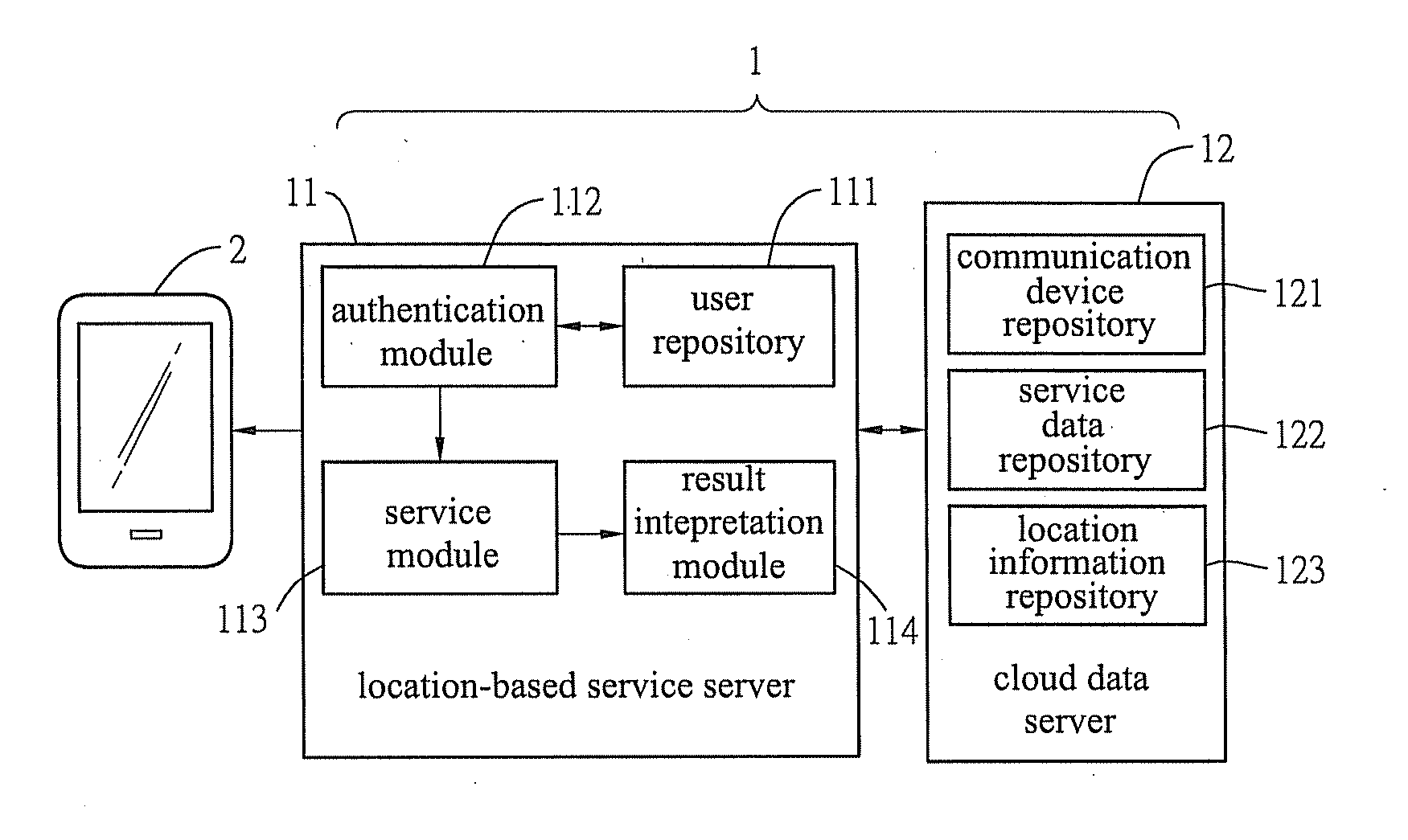
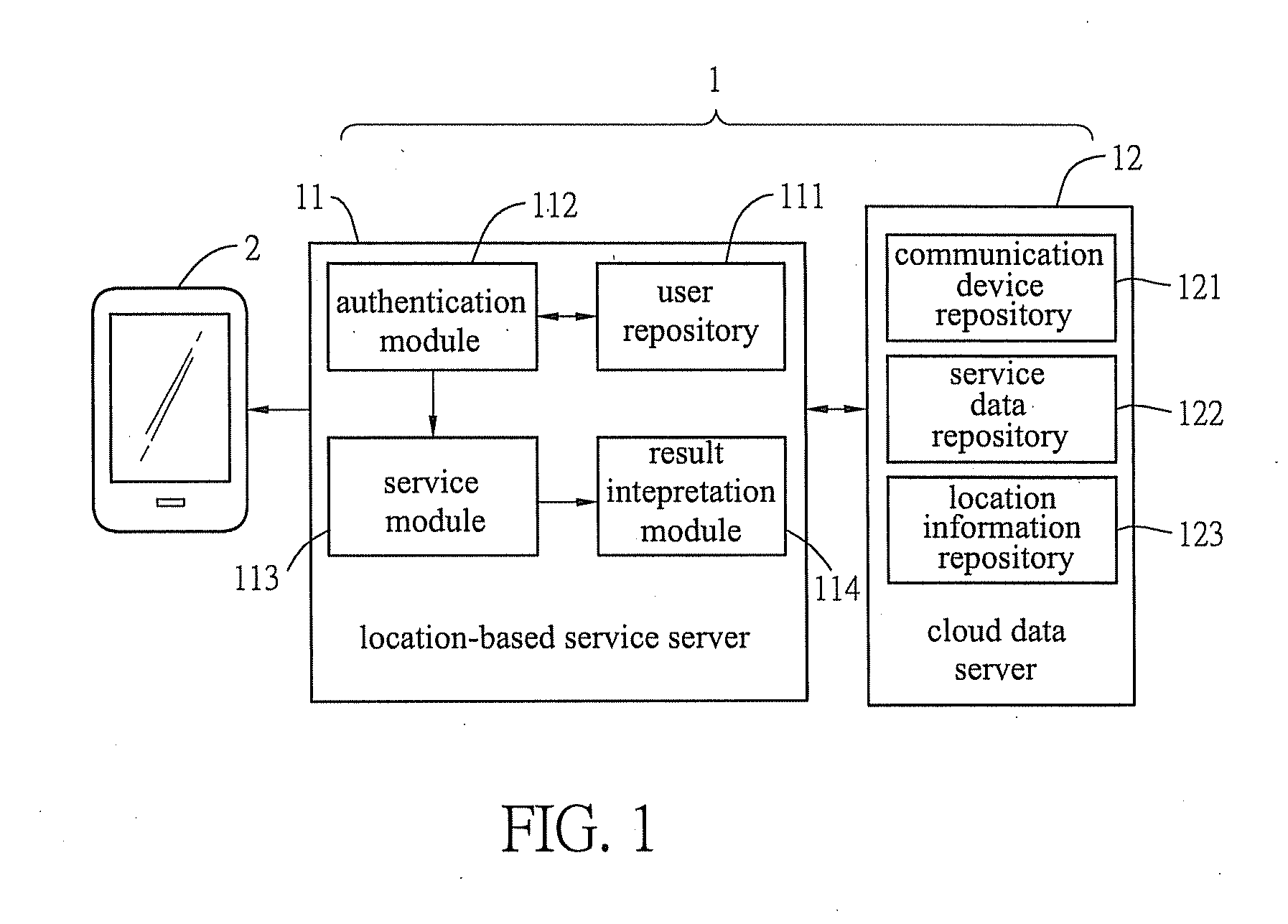
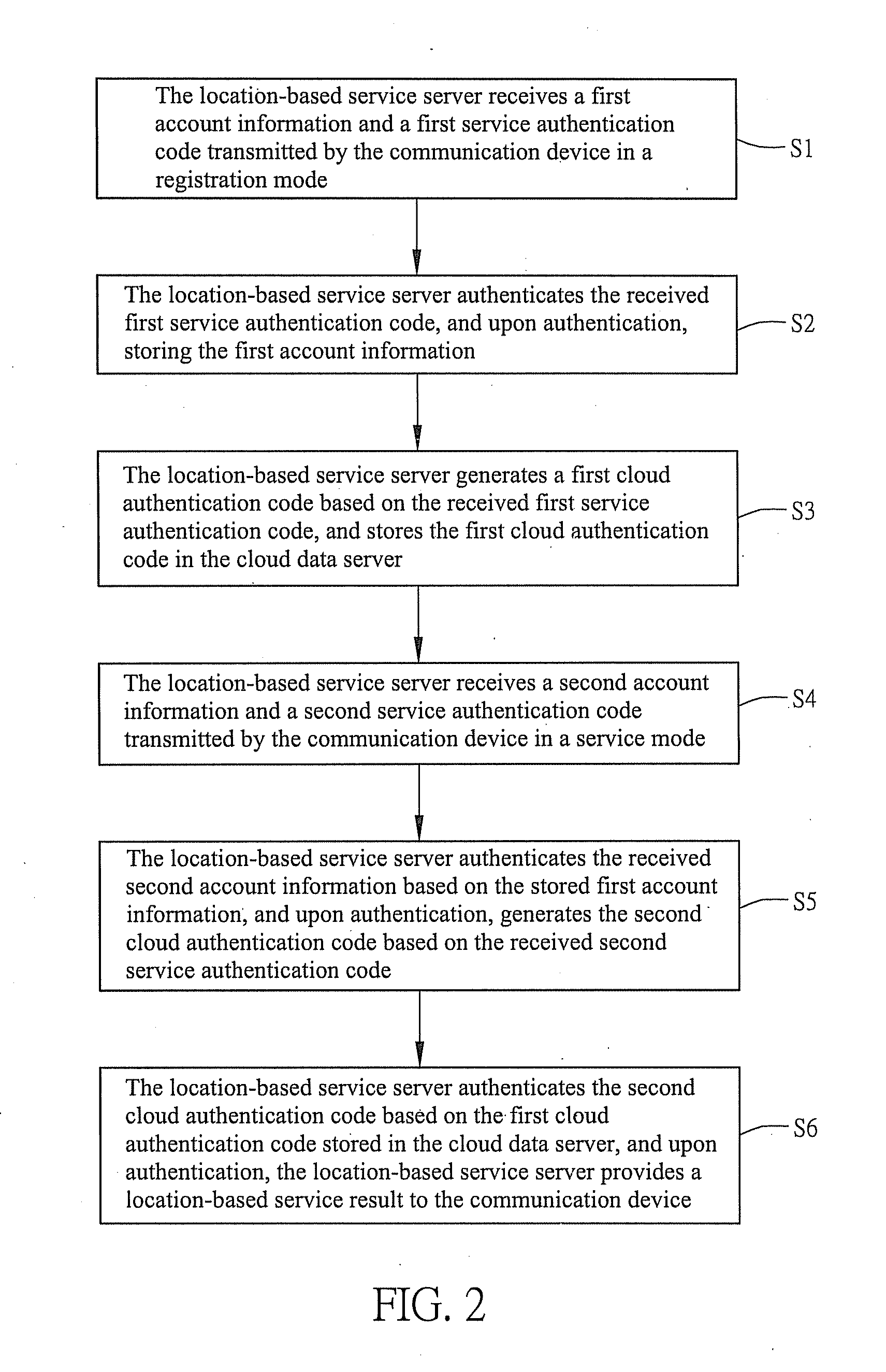
Location-based service system and serving method
ActiveUS20130122863A1Easy for forgingEasy to modifyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCloud dataService mode
A location-based service system and method, which allows a location-based service server connected with a communication device and a cloud data server to perform registration authorization procedures and service authorization procedures using an international mobile subscriber identity of the communication device that cannot be easily modified or forged in the registration and service modes, so that a user may obtain a specific location-based service result via the communication device, and this distributed authentication technique reduces the risk of data theft while increasing the flexibility and convenience in obtaining services.
Owner:NAT CHIAO TUNG UNIV
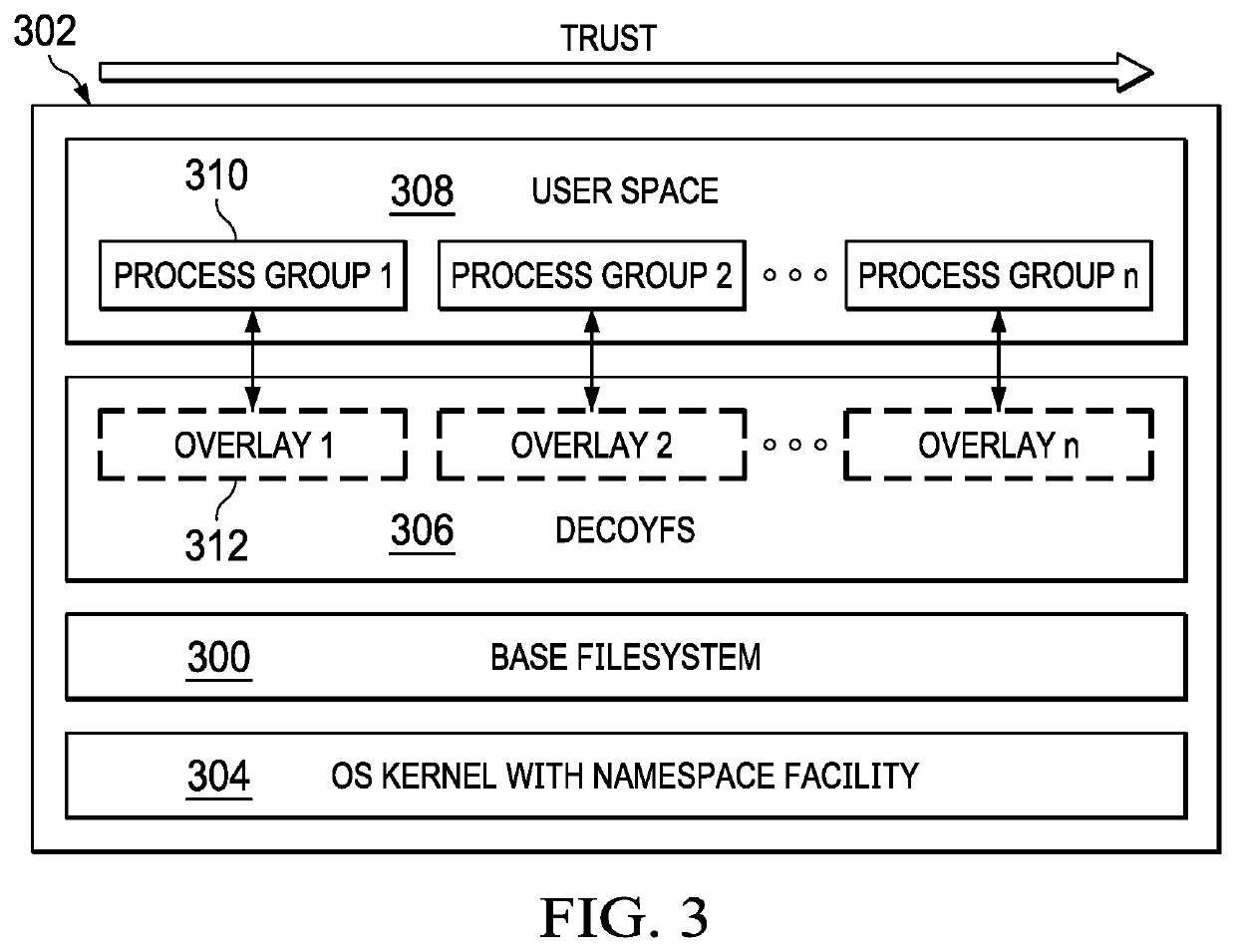
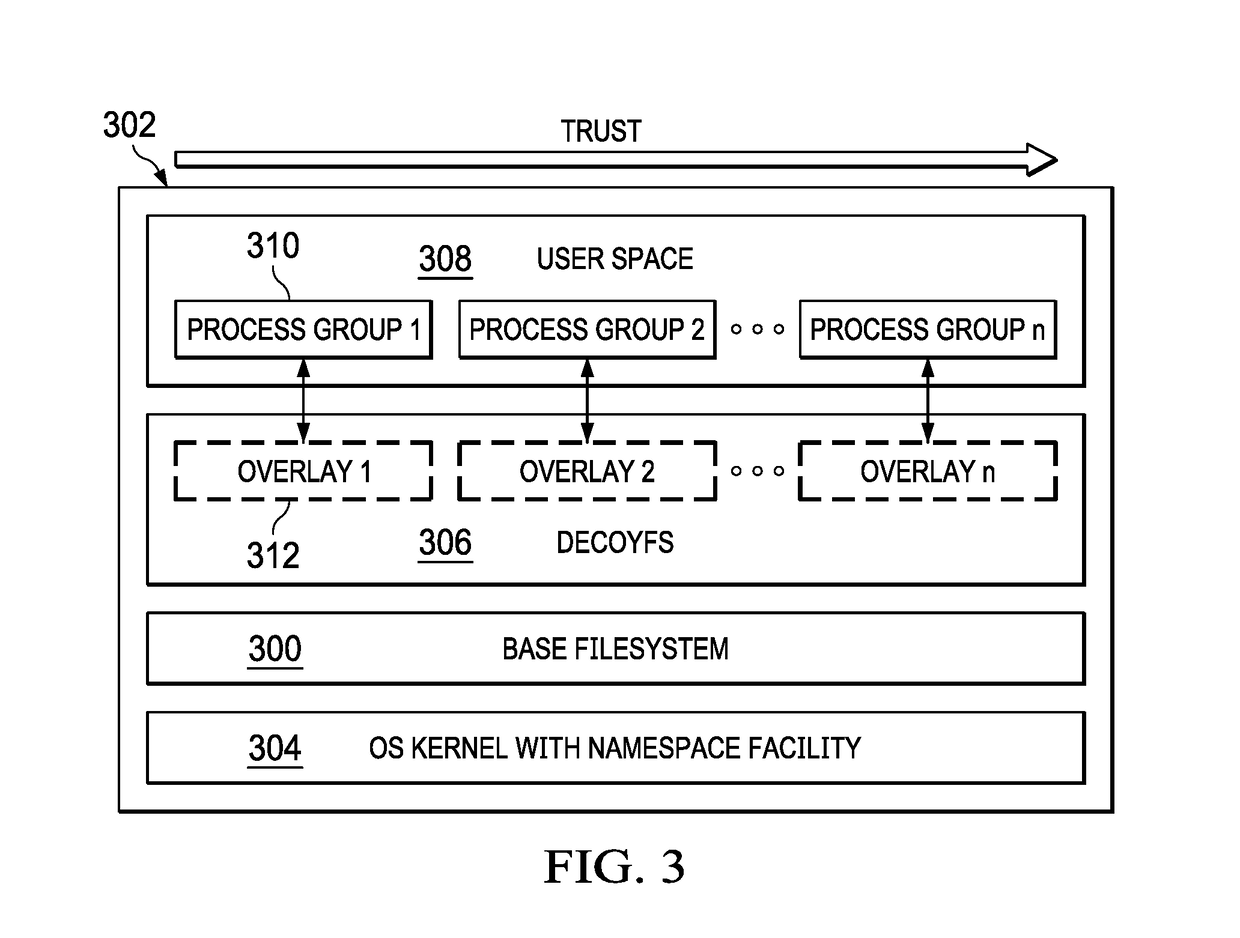
Filesystem view separation for data confidentiality and integrity using lattice-based security domains
ActiveUS20200004977A1Curtails data theftWithout incurring significant performance overheadDigital data protectionInternal/peripheral component protectionData integrityFile system
A stackable filesystem architecture that curtails data theft and ensures file integrity protection. In this architecture, processes are grouped into ranked filesystem views, or “security domains.” Preferably, an order theory algorithm is utilized to determine a proper domain in which an application is run. In particular, a root domain provides a single view of the filesystem enabling transparent filesystem operations. Each security domain transparently creates multiple levels of stacking to protect the base filesystem, and to monitor file accesses without incurring significant performance overhead. By combining its layered architecture with view separation via security domains, the filesystem maintains data integrity and confidentiality.
Owner:IBM CORP
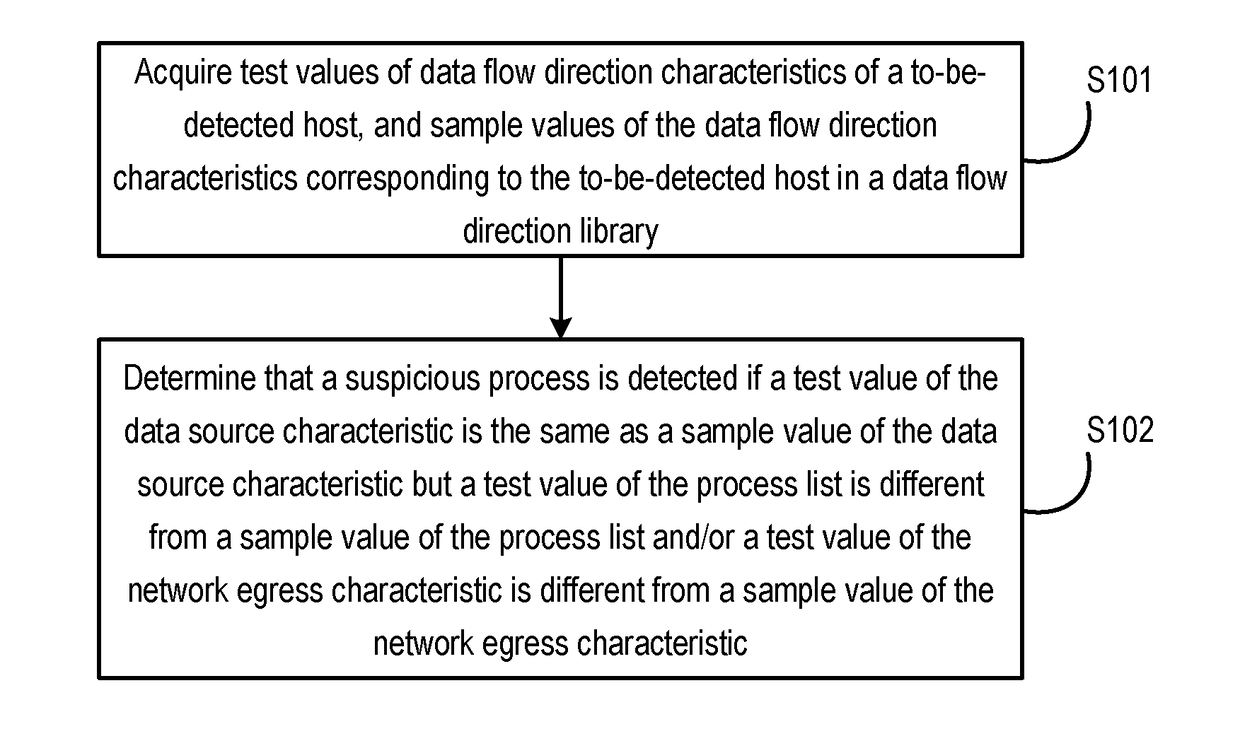
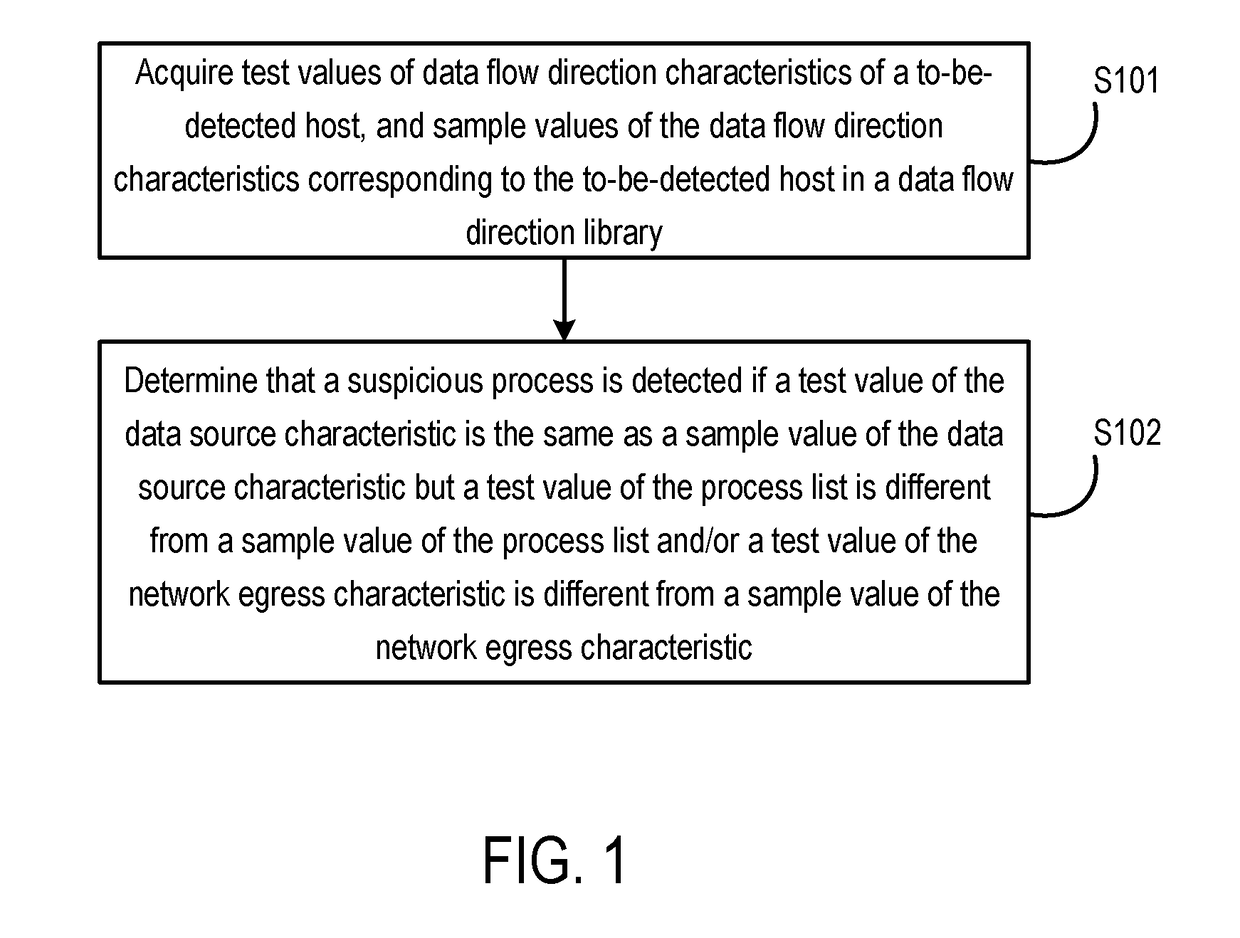
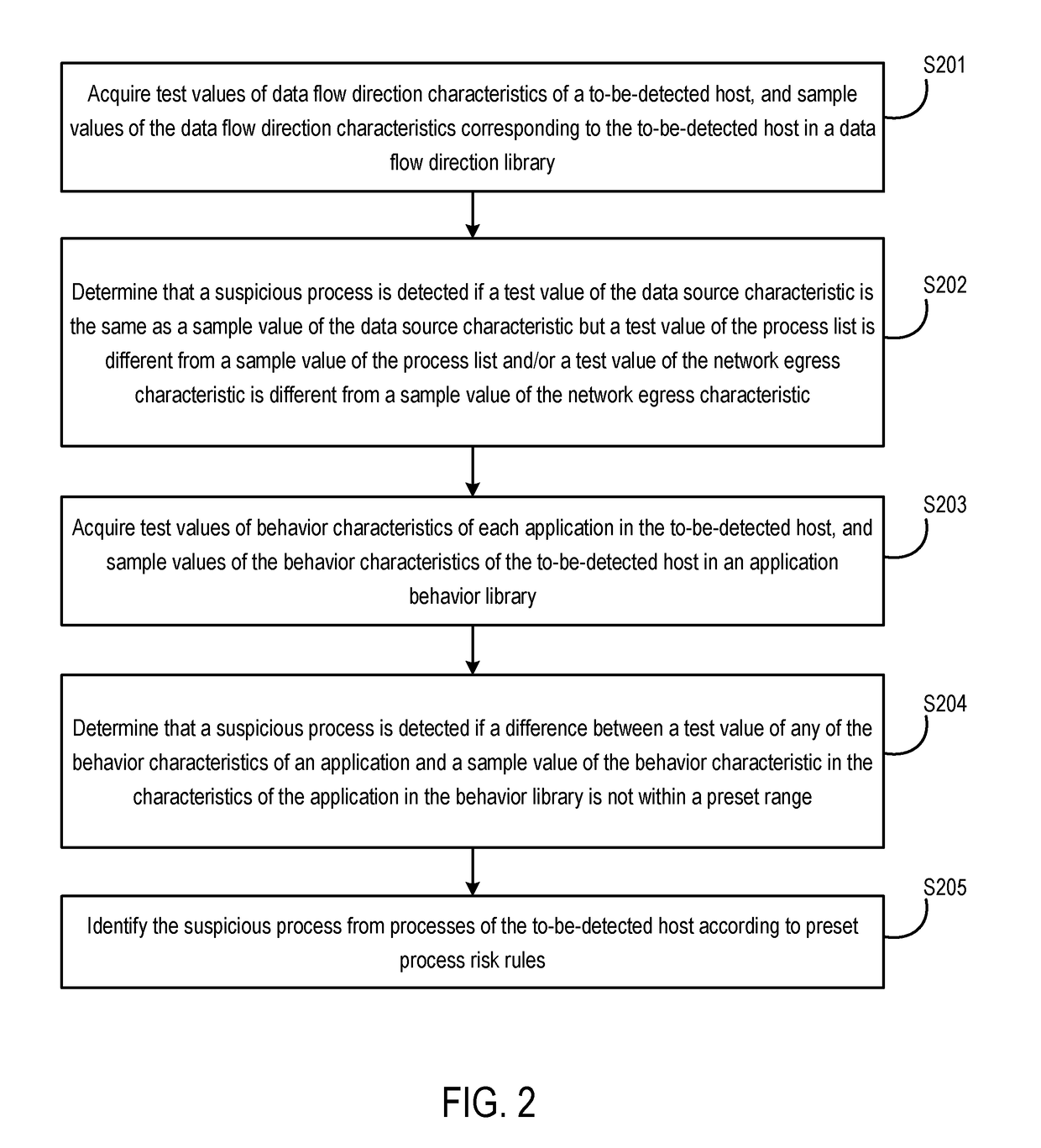
Method and device for detecting a suspicious process by analyzing data flow characteristics of a computing device
InactiveUS20180075240A1Accurate detectionDigital data protectionPlatform integrity maintainanceData streamData source
Disclosed are methods and devices for detecting a suspicious process. Test values of data flow direction characteristics of a to-be-detected host and sample values of the data flow direction characteristics corresponding to the to-be-detected host in a data flow direction library are acquired, wherein the data flow direction characteristics comprise at least one of a process list and a network egress characteristic, and a data source characteristic. It is then determined that a suspicious process is detected when a test value of the process list is different from a sample value of the process list and / or a test value of the network egress characteristic is different from a sample value of the network egress characteristic in the case that a test value of the data source characteristic is the same as a sample value of the data source characteristic. It can be seen that the disclosed methods and devices for detecting a suspicious process according detect a suspicious process based on the data flow direction characteristics rather than the attack behaviors of applications. Moreover, because data flow direction characteristics change whenever data theft occurs, the methods and devices can accurately detect a suspicious process in which data might be stolen.
Owner:ALIBABA GRP HLDG LTD
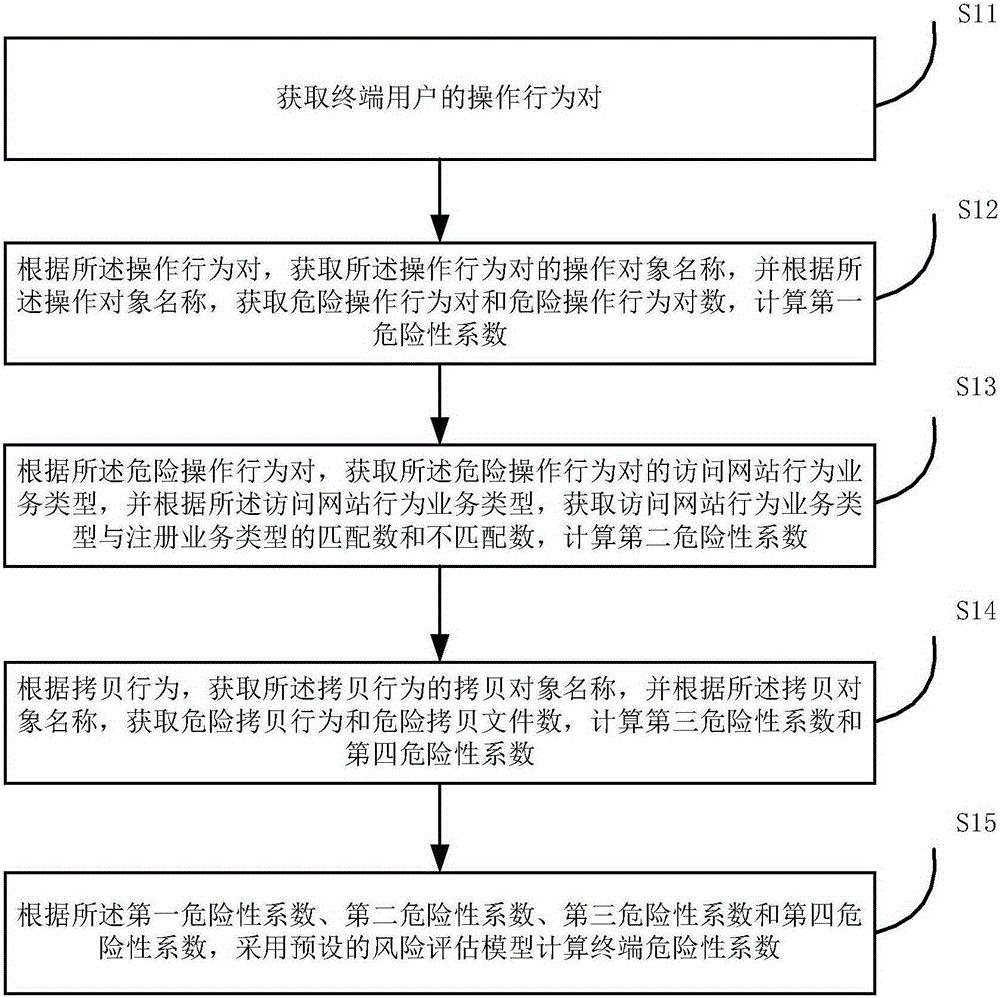
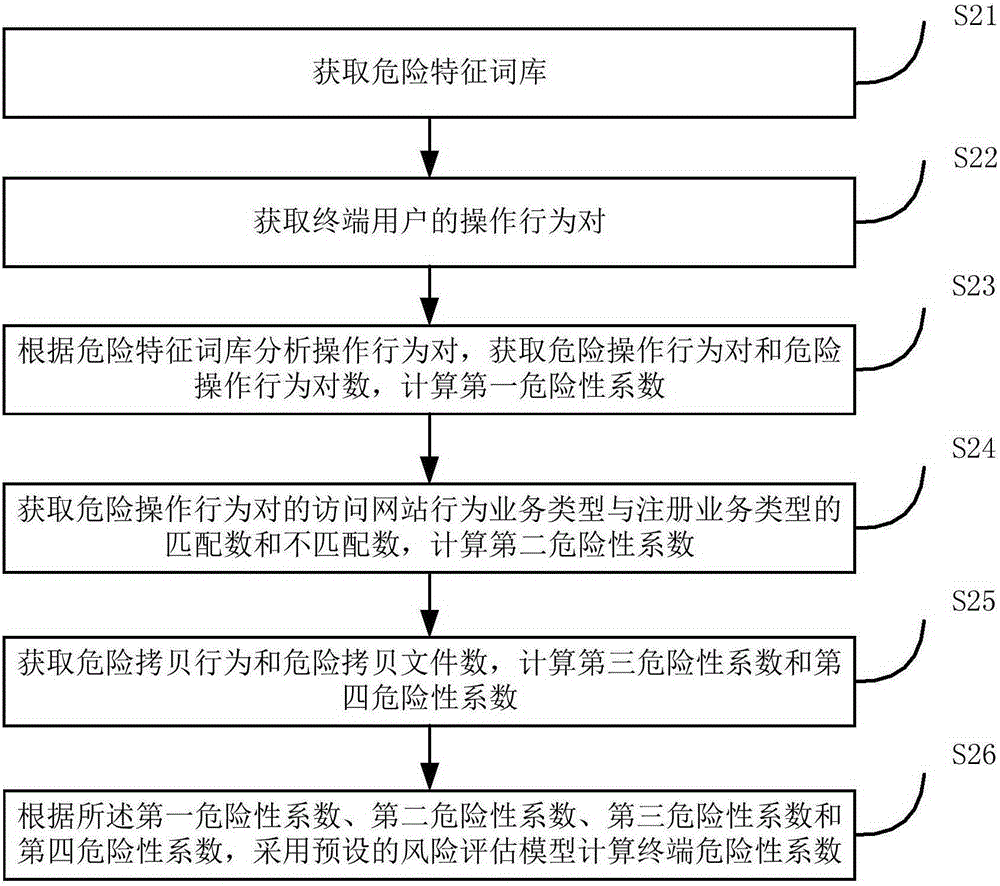
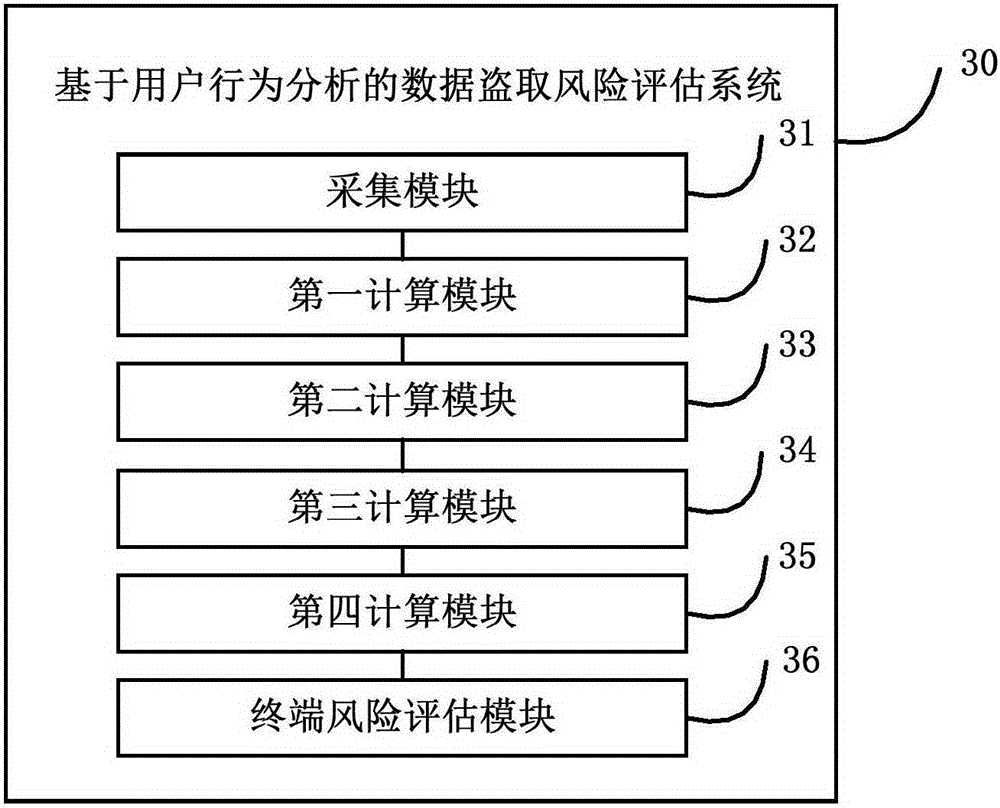
User behavior analysis-based data theft risk assessment method and system
ActiveCN105357217AImprove securityReduce lossesDigital data protectionData switching networksWeb siteInternet privacy
The invention provides a user behavior analysis-based data theft risk assessment method and system. The method includes the following steps that: operation behavior pairs of a terminal user are obtained; dangerous operation behavior pairs and the number of the dangerous operation behavior pairs are obtained according to the operation behavior pairs, and a first dangerousness coefficient is obtained; the matching number and mismatching number of web site visit behavior business types and registration business types are obtained according to the dangerous operation behavior pairs, and a second dangerousness coefficient is obtained; dangerous copy behaviors and the number of dangerous copy files are obtained according to copy behaviors, and a third dangerousness coefficient and a fourth dangerousness coefficient are calculated; and a preset risk assessment model is adopted to calculate the dangerousness coefficient of a terminal according to the first dangerousness coefficient, the second dangerousness coefficient, the third dangerousness coefficient and the fourth dangerousness coefficient. With the user behavior analysis-based data theft risk assessment method and system of the invention adopted, the network behaviors of the terminal user of an intranet are analyzed; potential terminals where risk operation may exist can be discovered; data security can be protected; the security of the intranet can be improved; and the losses of enterprises can be reduced.
Owner:BEIJING VRV SOFTWARE CO LTD
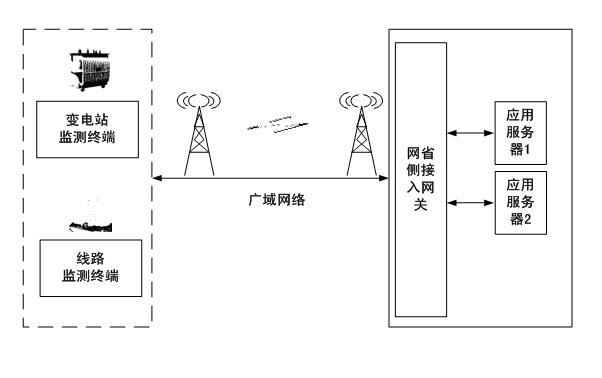
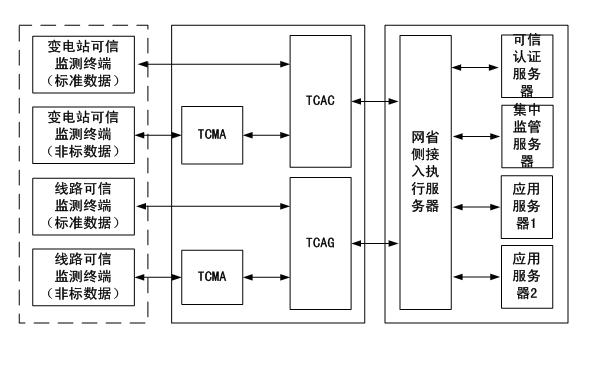
Power transmission and transformation equipment state monitoring system security protection method based on trust chain transmission
Owner:STATE GRID ELECTRIC POWER RES INST
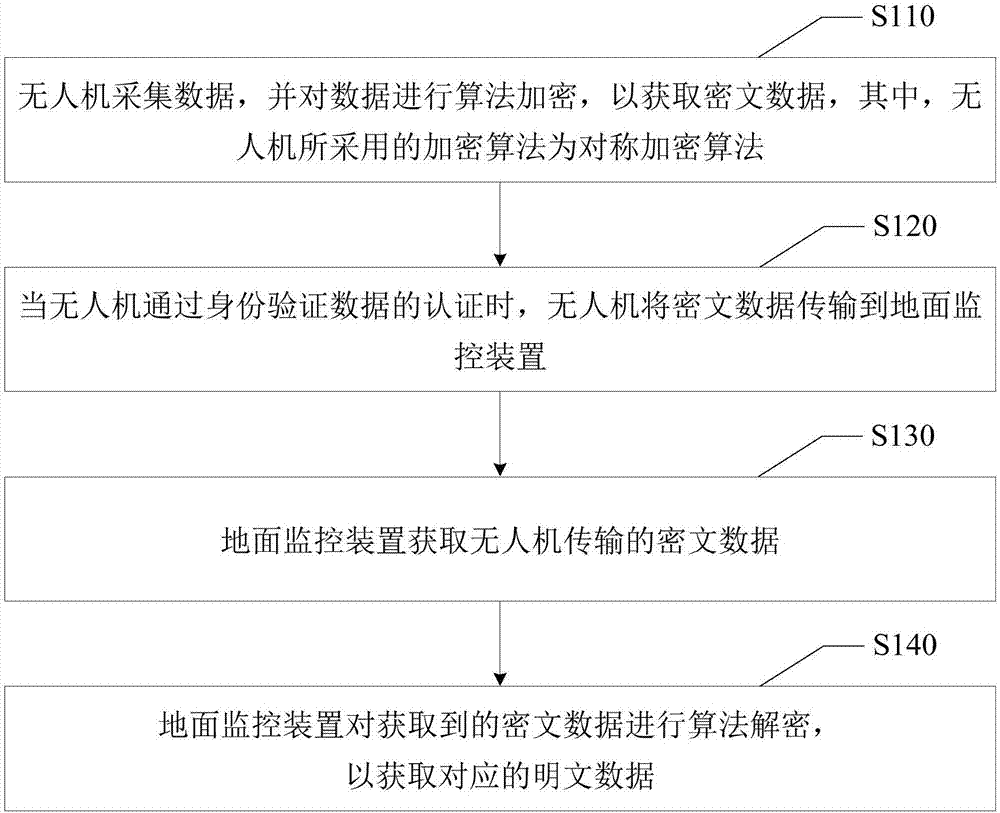
Flying drone data transmission method and flying drone data transmission system
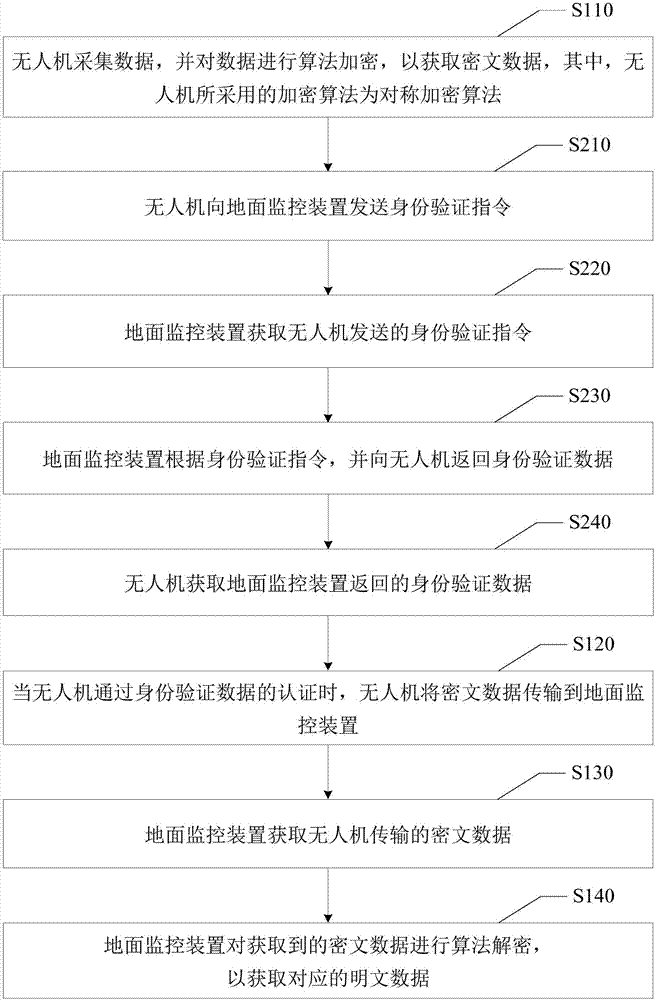
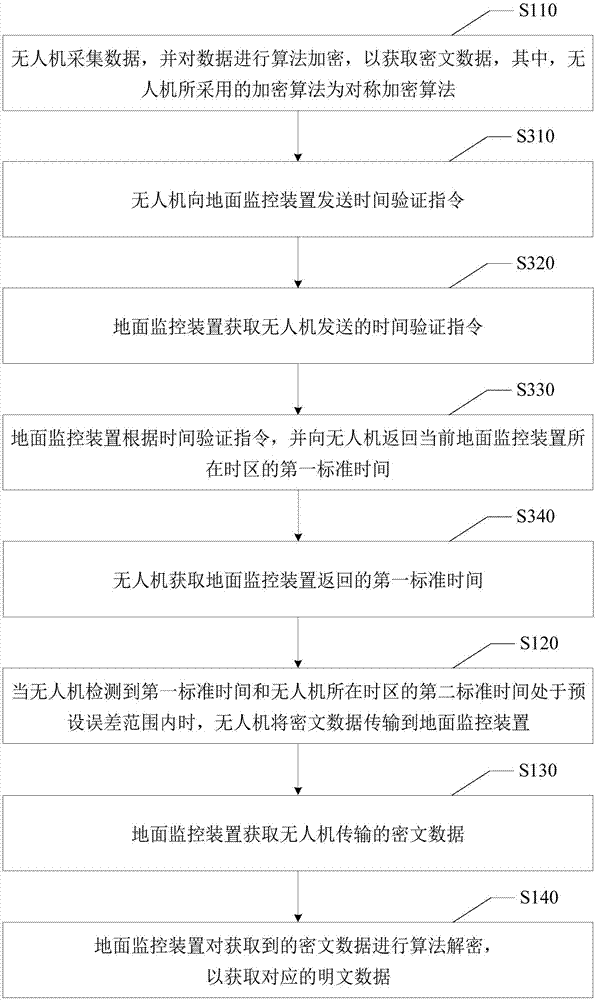
The invention discloses a flying drone data transmission method and a flying drone data transmission system, wherein the flying drone data transmission method comprises: the flying drone acquires data and performs algorithm ciphering to the data to obtain the ciphertext data wherein the ciphered algorithm the flying drone uses is a symmetrically ciphered algorithm; the flying drone transmits the ciphertext data to a ground monitoring device; the ground monitoring device obtains the ciphertext data transmitted from the flying drone; the ground monitoring device performs algorithm deciphering to the obtained ciphertext data to obtain corresponding clear data wherein the deciphering algorithm the ground monitoring device uses is the deciphering algorithm corresponding to the symmetrically ciphered algorithm used by the flying drone. According to the invention, through the manner of data ciphering, the data transmission security of the data transmission system of the flying drone is increased; the reliability of the data transmission is increased; therefore, the data theft or data tamp ering in the transmission process could be prevented, and the phenomenon of data leakage could also be avoided.
Owner:SHENZHEN ZHOUJI TONGHANG INVESTMENT HLDG CO LTD
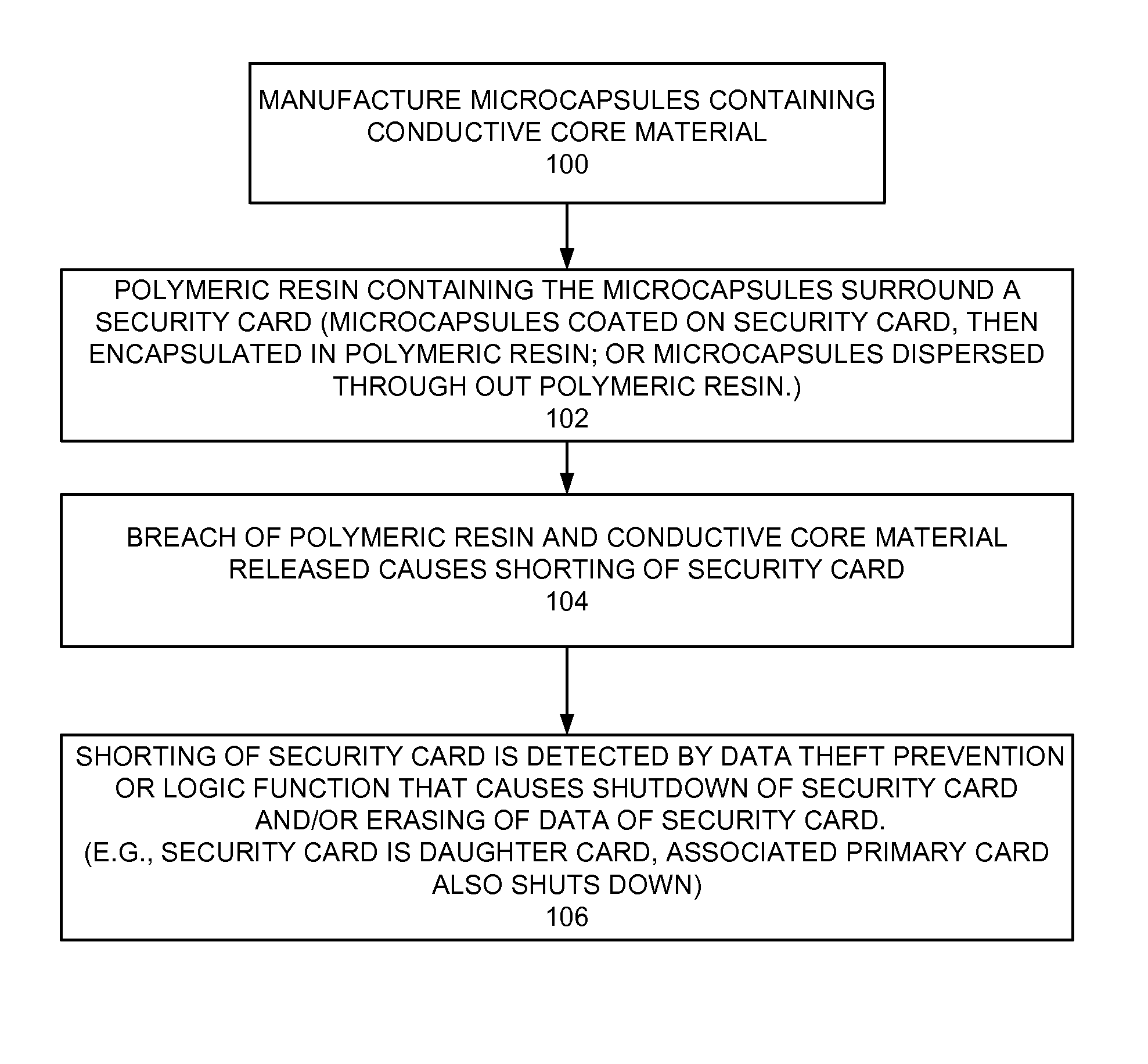
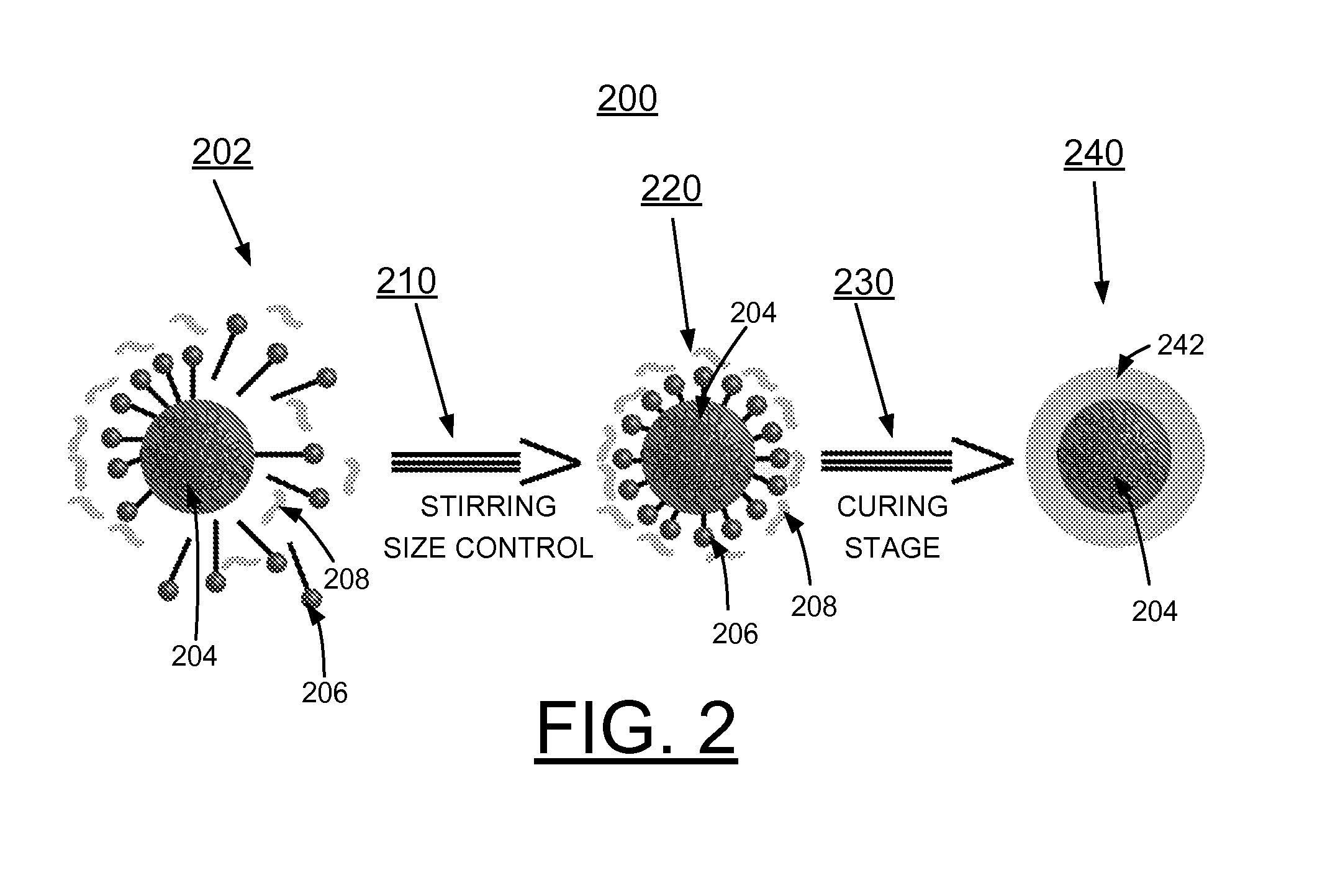
Iimplementing data theft prevention
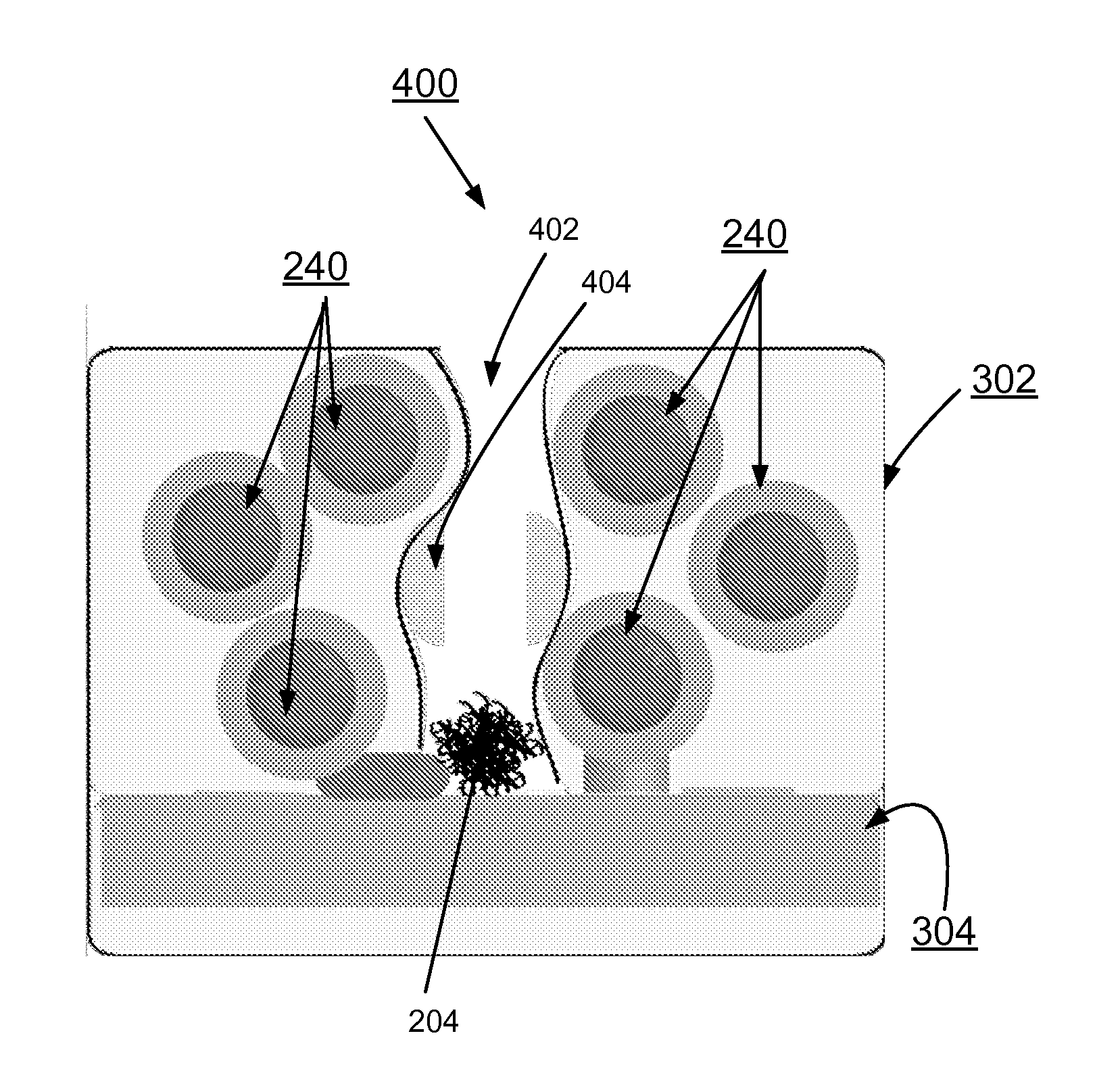
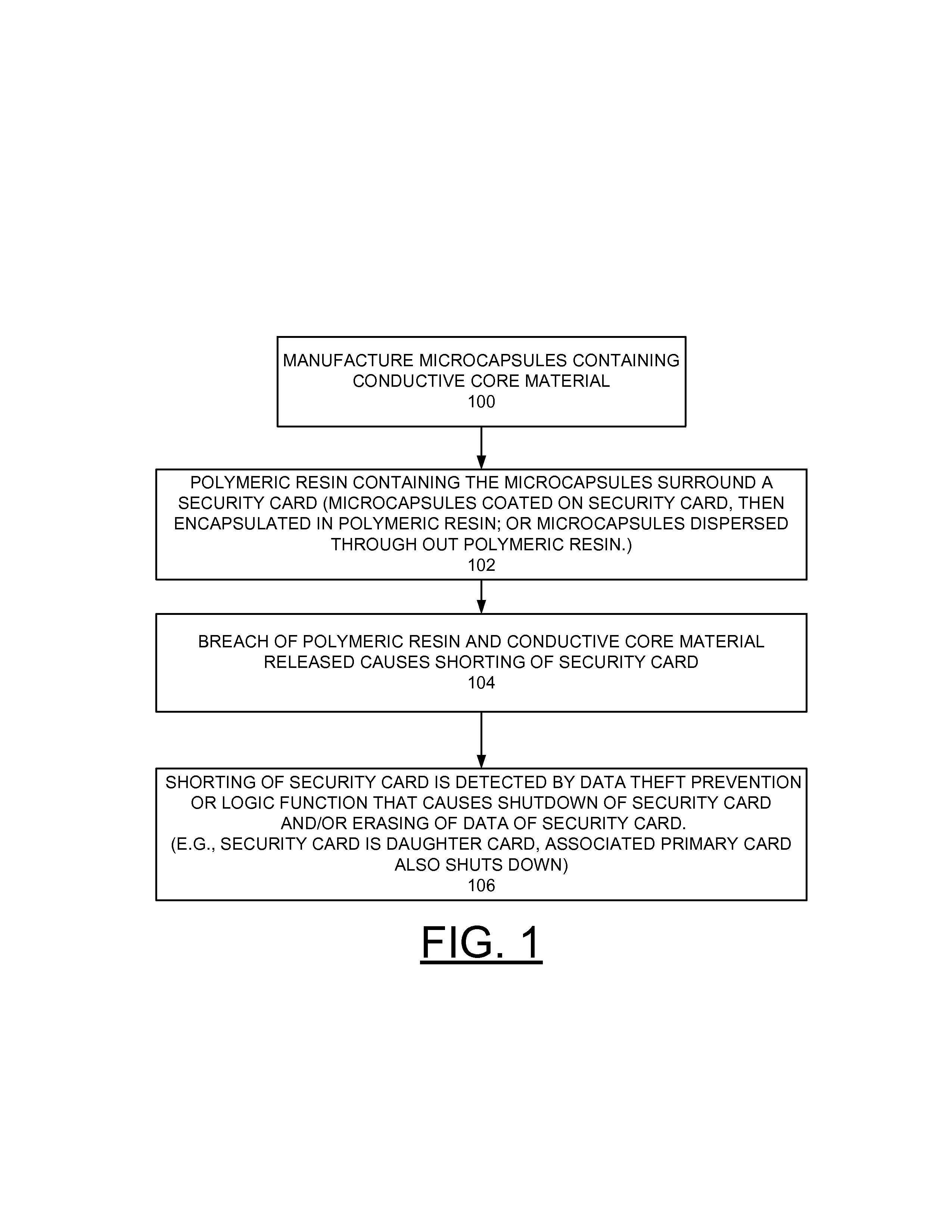
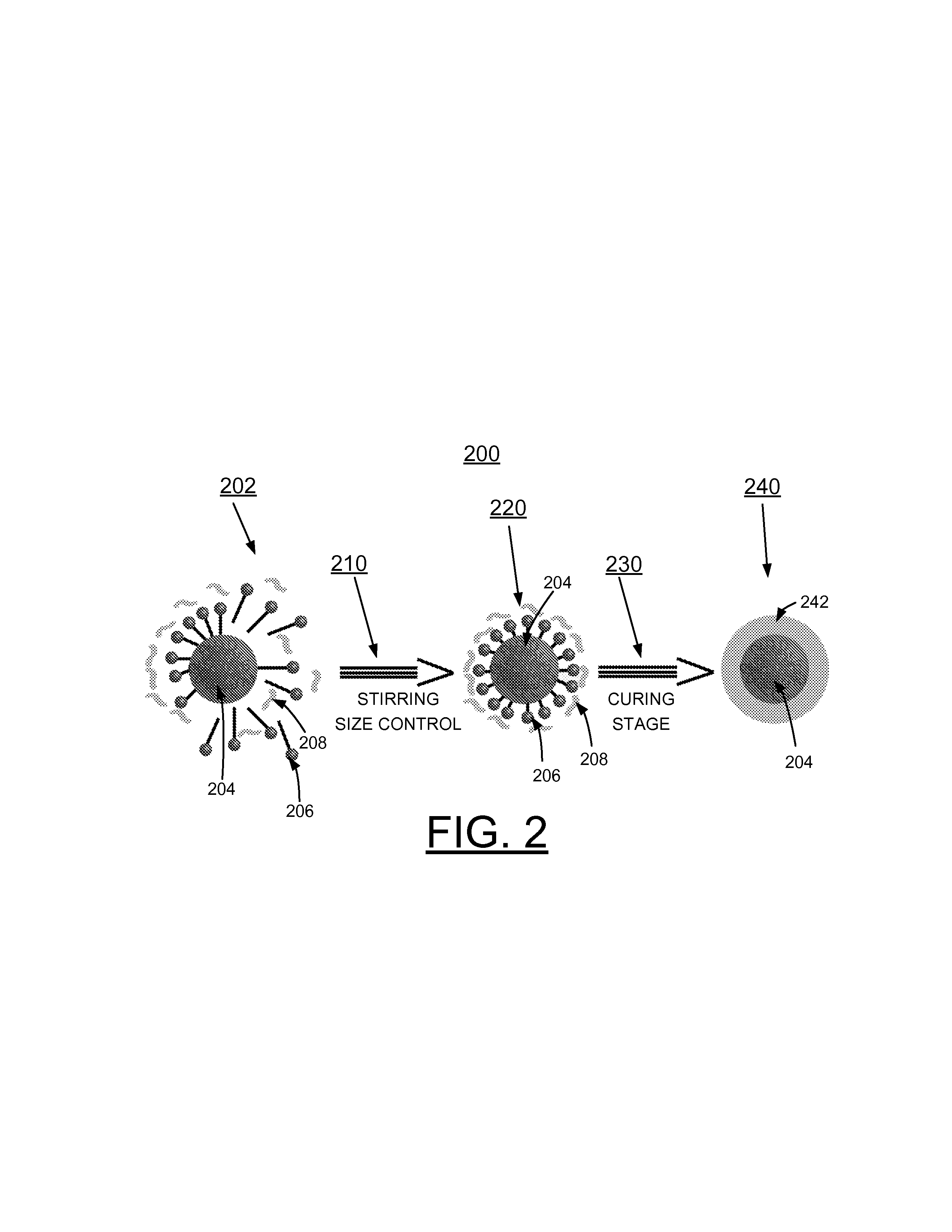
InactiveUS20130179996A1Error detection/correctionVolume/mass flow measurementPolymer resinConductive materials
A method and circuit for implementing data theft prevention, and a design structure on which the subject circuit resides are provided. A polymeric resin containing microcapsules surrounds a security card. Each microcapsule contains a conductive material. The conductive material of the microcapsule provides shorting on the security card responsive to the polymer resin and the microcapsule being breached, and a data theft prevention function using the shorting by the conductive material to prevent data theft.
Owner:IBM CORP
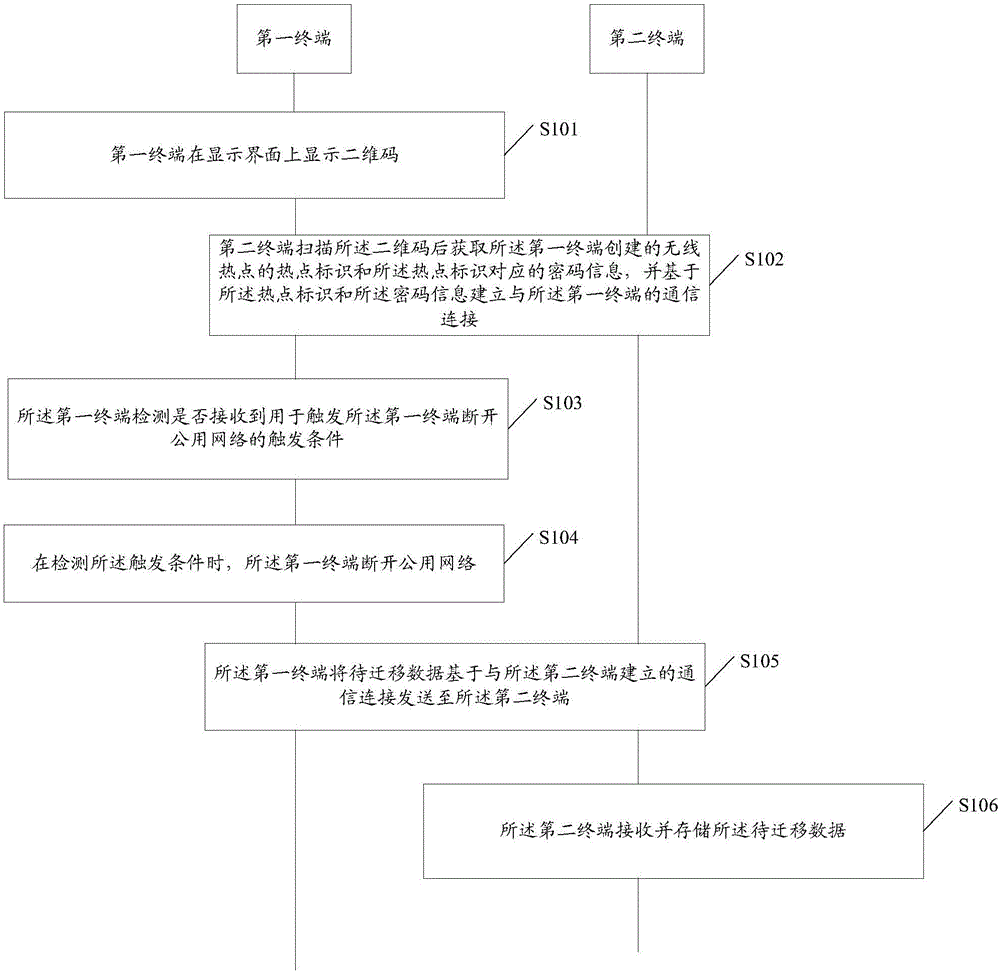
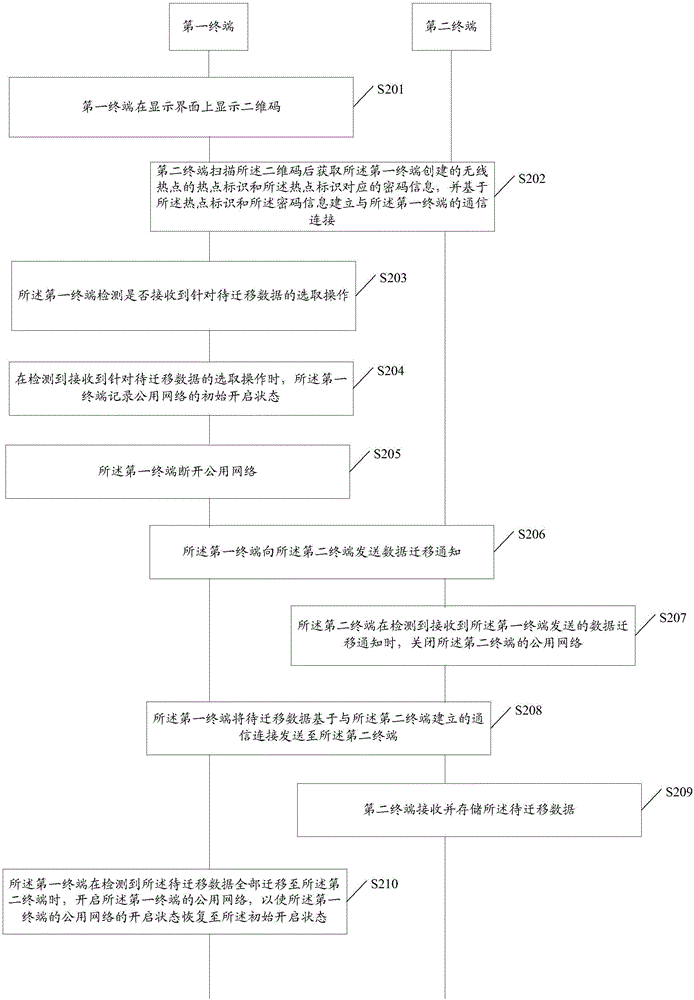
Data migration method and mobile terminal
InactiveCN106454805AImprove securityAvoid hidden dangersAssess restrictionConnection managementWi-FiPassword
The embodiment of the invention discloses a data migration method and a mobile terminal. The data migration method includes that a first terminal displays a two-dimensional code on a display interface, and the two-dimensional code is used for a second terminal to scan to acquire a hotspot identifier of a wireless hotspot created by the first terminal and password information corresponding to the hotspot identifier, and to establish a communication connection with the first terminal based on the hotspot identifier and the password information; the first terminal detects whether a trigger condition for triggering the first terminal to disconnect a public network is received; the first terminal disconnects the public network when the trigger condition is detected; and the first terminal transmits the data to be migrated to the second terminal based on the communication connection established with the second terminal so that the second terminal receives and stores the data to be migrated. The embodiment of the invention helps avoid the hidden danger of data theft caused by accessing the mobile data network or a wi-fi network, thereby further improving the security of data migration of the mobile terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
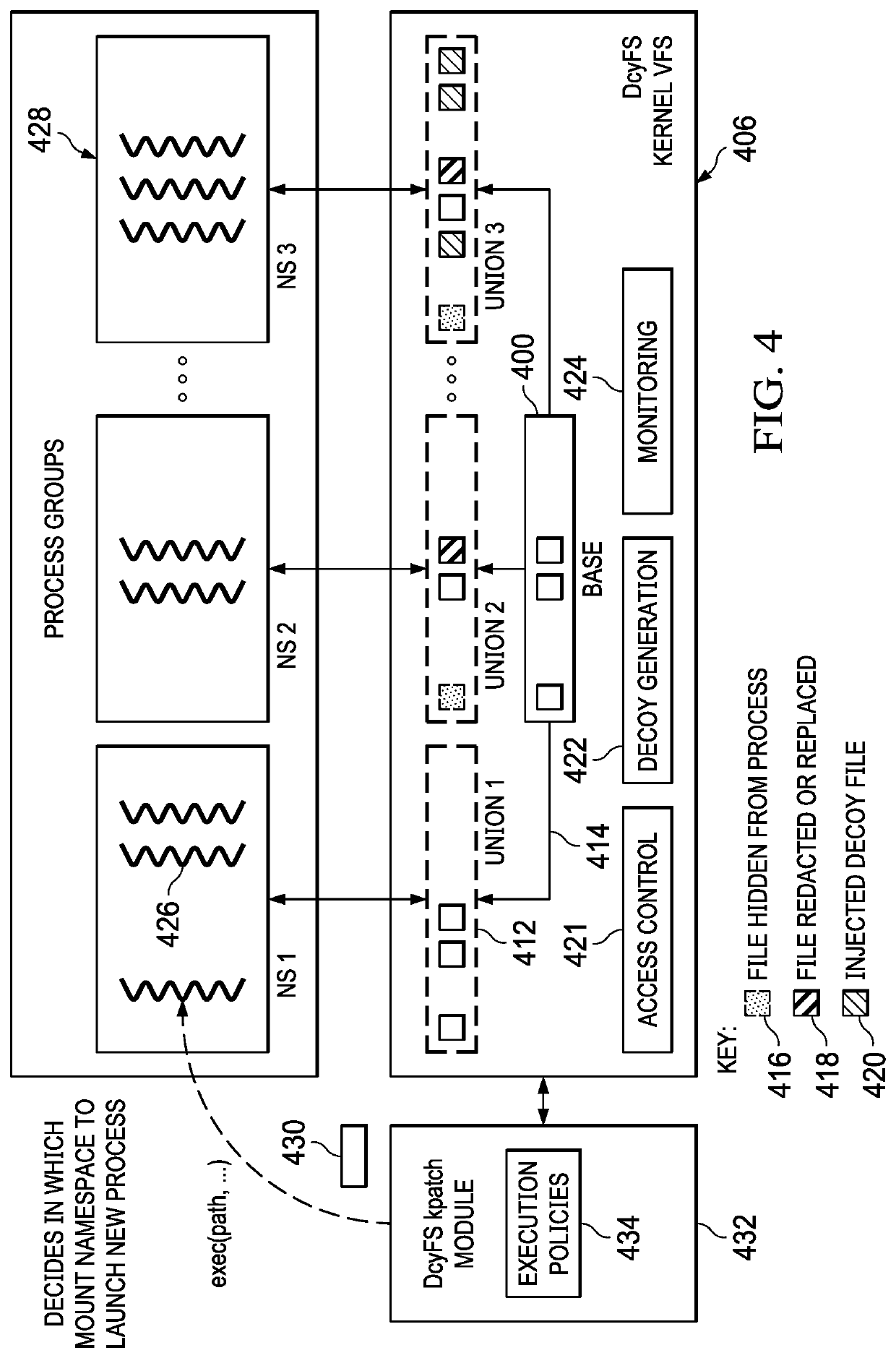
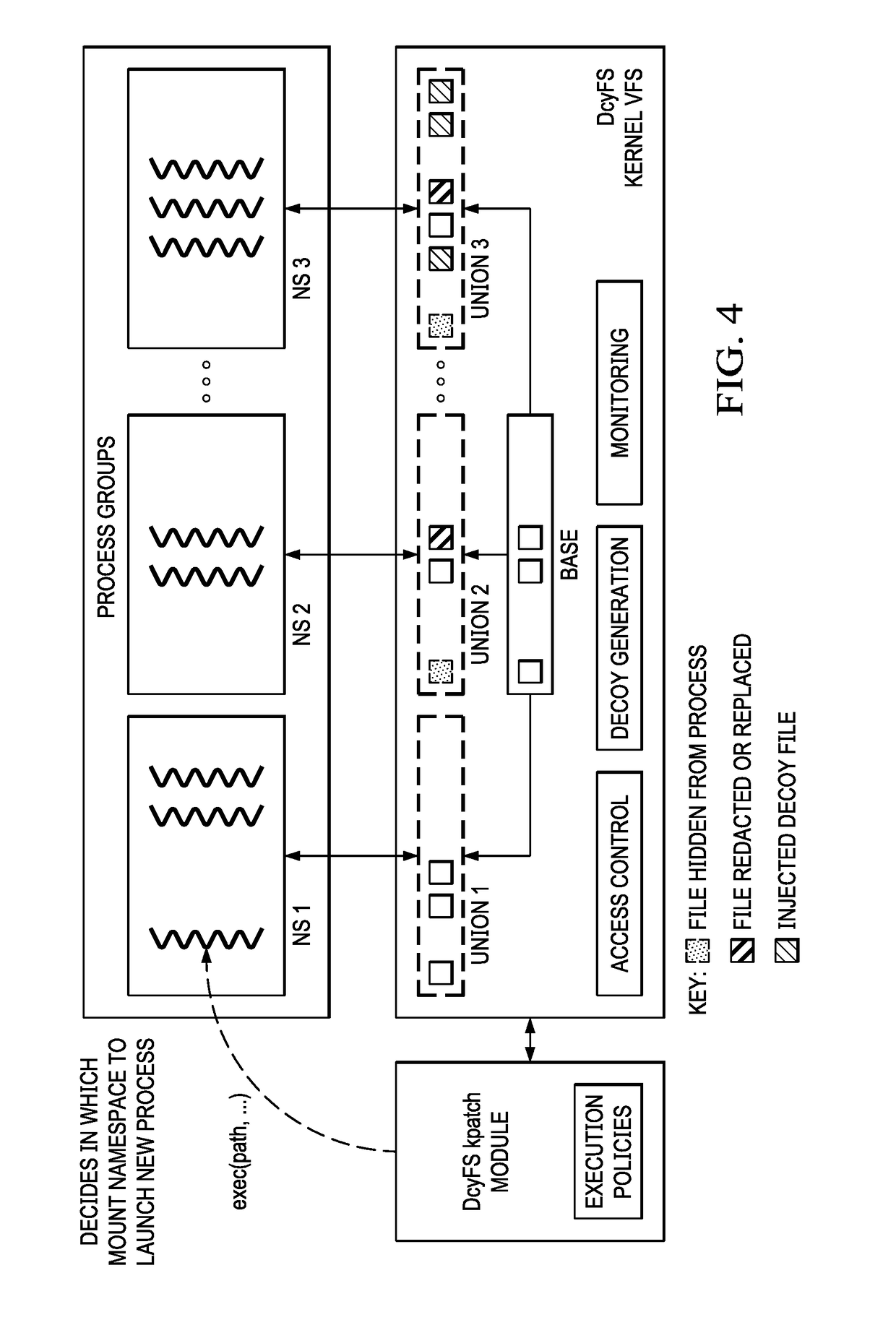
Integrity, theft protection and cyber deception using a deception-based filesystem
ActiveUS20190065745A1Digital data protectionInternal/peripheral component protectionFile systemDecoy
A decoy filesystem that curtails data theft and ensures file integrity protection through deception is described. To protect a base filesystem, the approach herein involves transparently creating multiple levels of stacking to enable various protection features, namely, monitoring file accesses, hiding and redacting sensitive files with baits, and injecting decoys onto fake system views that are purveyed to untrusted subjects, all while maintaining a pristine state to legitimate processes. In one implementation, a kernel hot-patch is used to seamlessly integrate the new filesystem module into live and existing environments.
Owner:IBM CORP
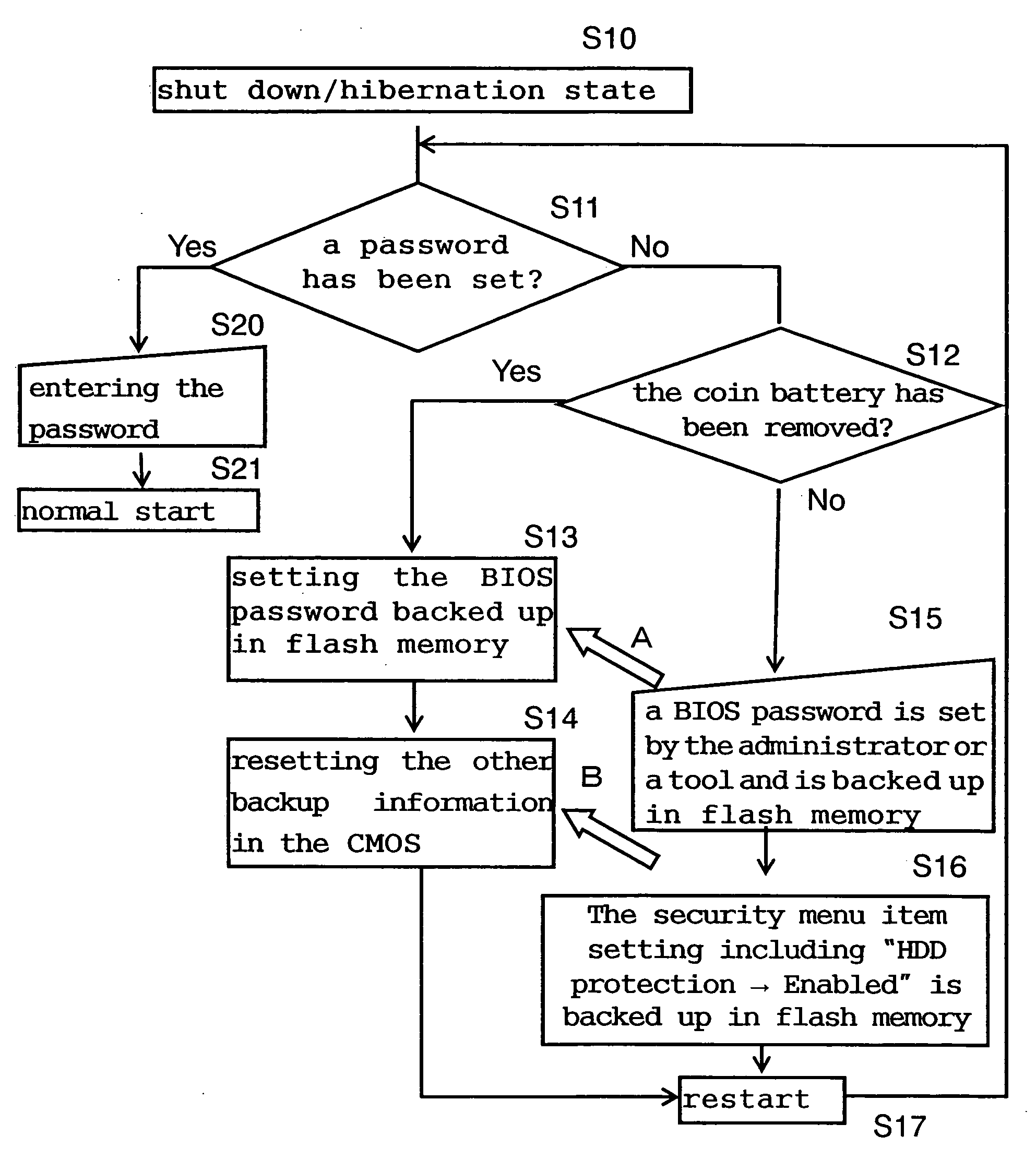
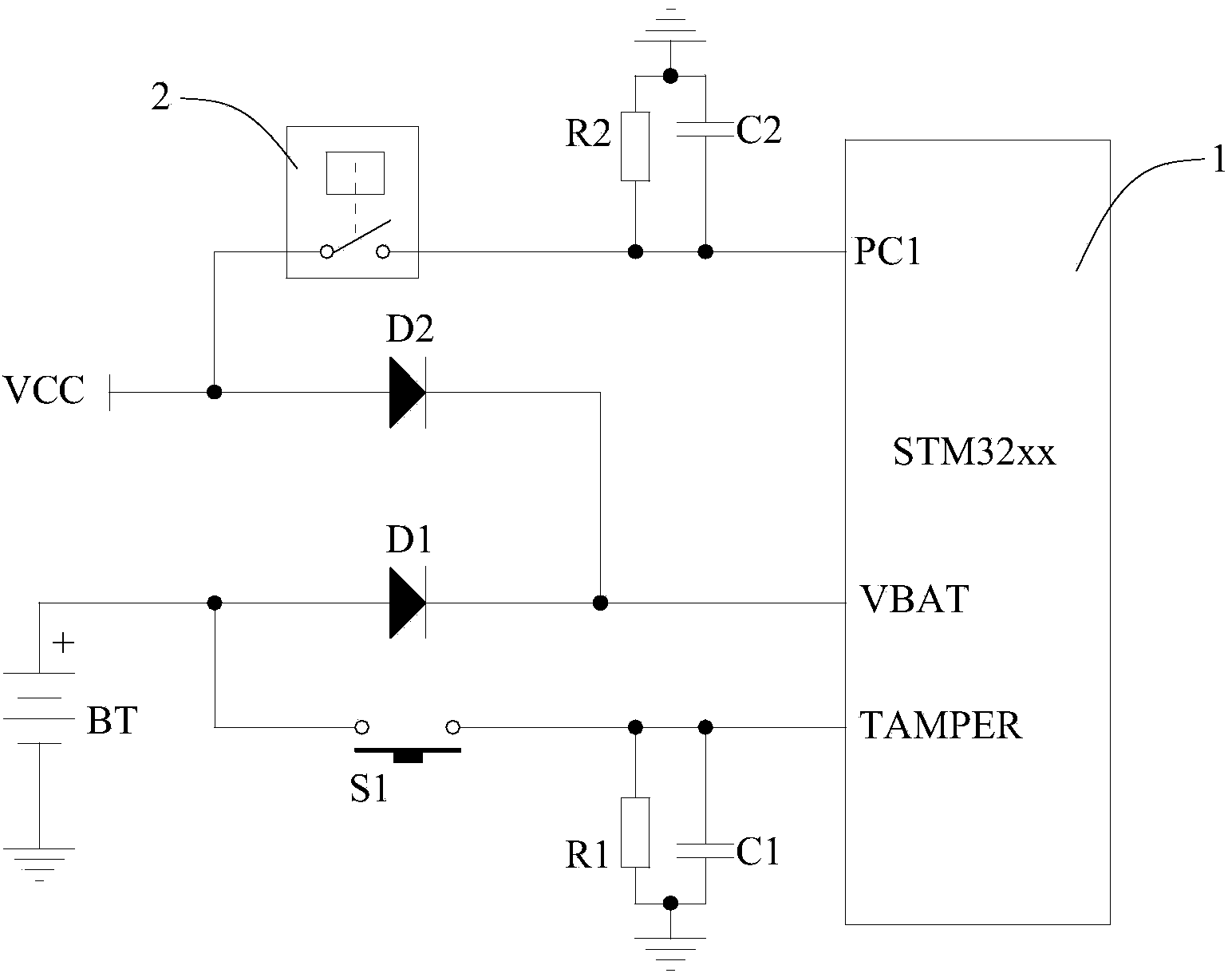
Security device and method for information processing apparatus
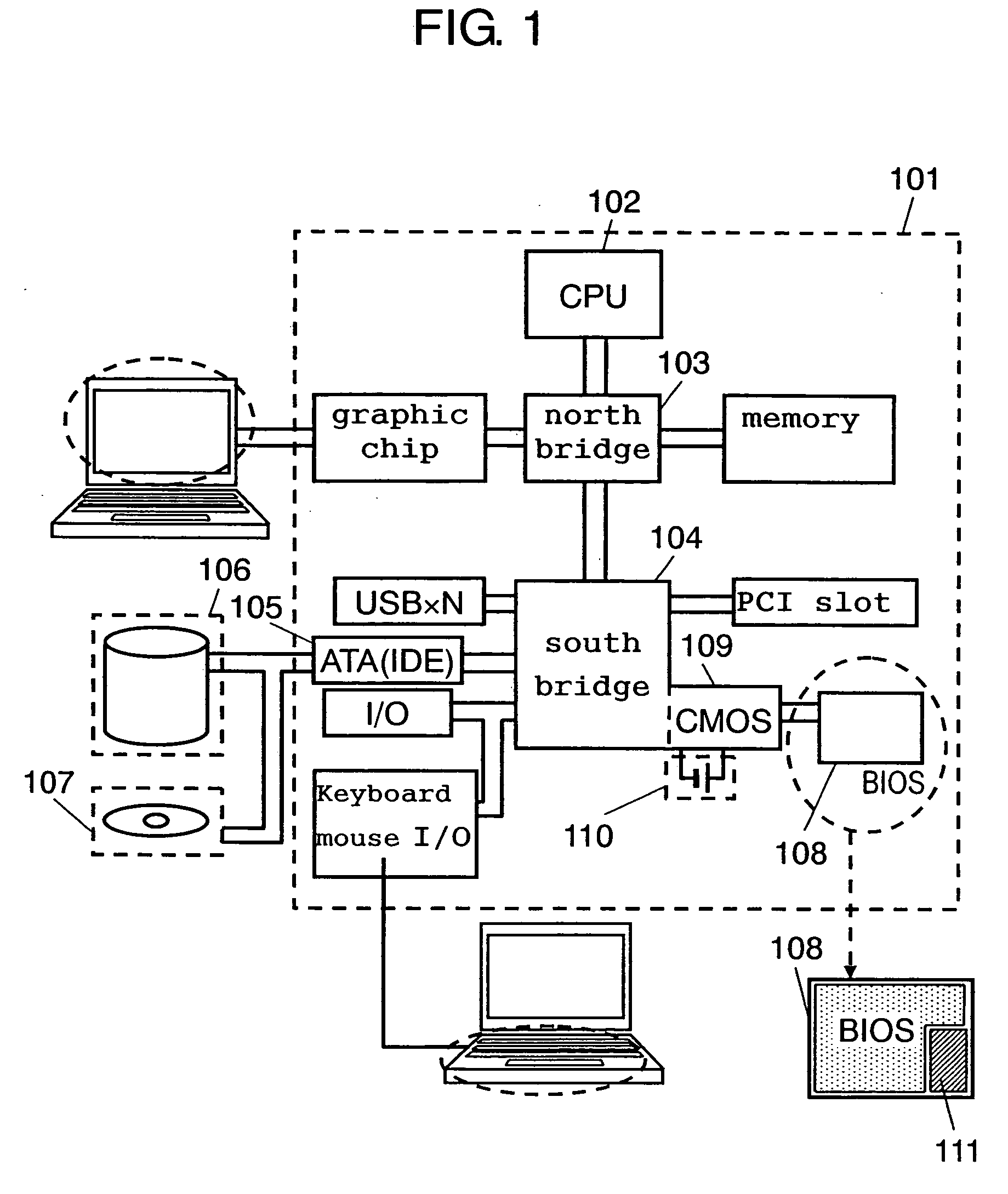
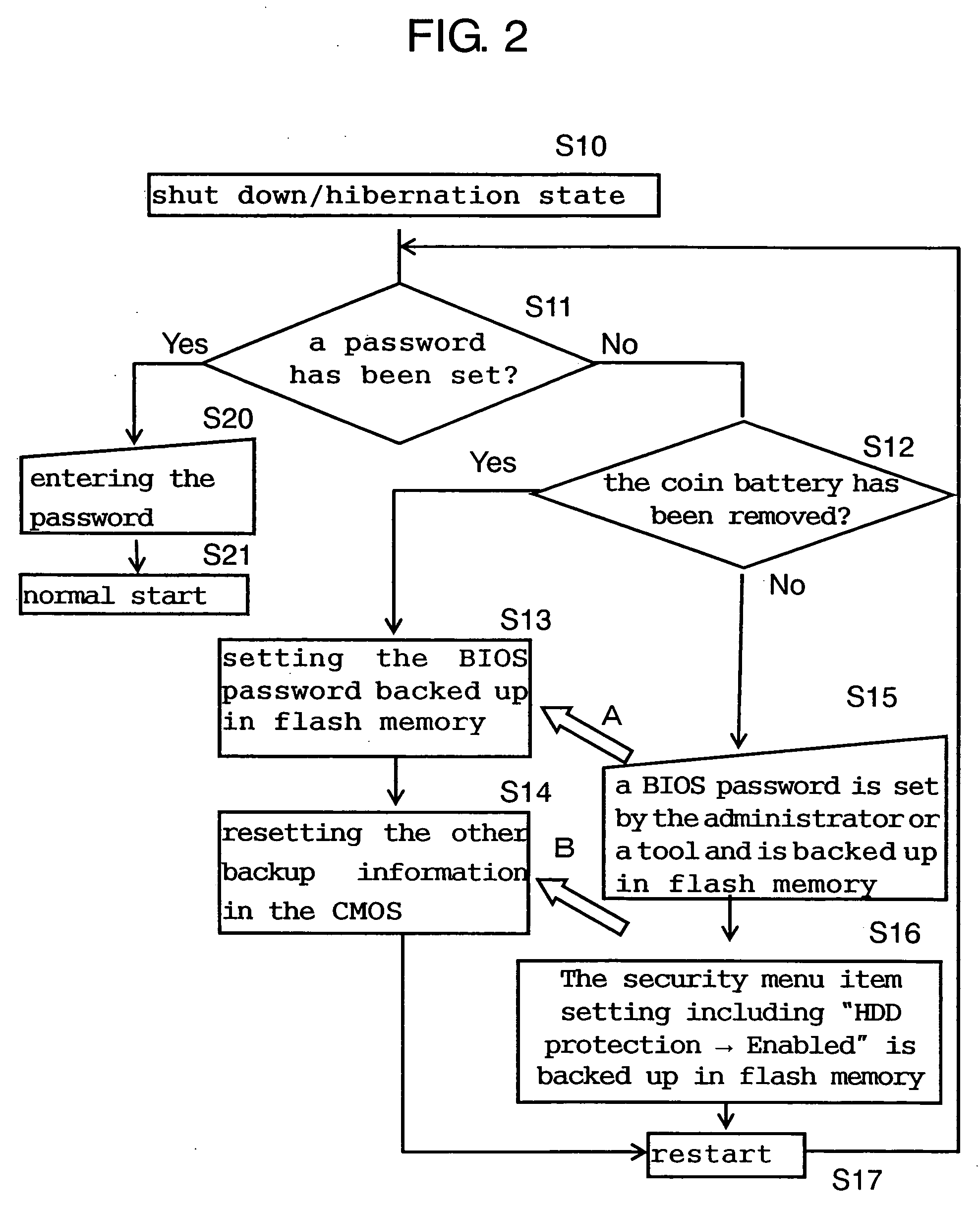
InactiveUS20060282902A1Avoid problemsDigital data processing detailsUnauthorized memory use protectionInformation processingCMOS
Security data such as a password is stored as backup in flash memory in a PC, and even if someone removes a coin battery for CMOS backup from the PC, the removal is detected and the data backed up in the flash memory is reset in the CMOS. This feature strengthens the prevention of data theft from recording media such as HDDs due to unauthorized use or access of PCs.
Owner:PANASONIC CORP
Method for protecting digital asset private key and handling private key loss or identity data theft
InactiveCN109560936AImprove protectionReduce the risk of theftFinanceUser identity/authority verificationComing outIdentity theft
The invention discloses a method for protecting a digital asset private key and handling private key loss or identity data theft. The method comprises the steps of: generating identity data of a private key for the user to save after the private key is generated; generating a new private key-address pair when the private key of the user is lost or stolen; initiating a loss reporting transaction bythe user or a thief, and depositing a guarantee deposit; verifying whether a signature is correct, and determining that the present loss report is invalid and the deposit is not refunded if the signature is not correct; locking the loss reporting behavior as a delay period by means of a blockchain node, wherein a private key corresponding to a loss reporting new address cannot transfer assets while an original private key can transfer assets; and allowing the private key corresponding to the loss reporting new address to transfer assets after the delay period ends. The method does not need tobackup a private key mnemonic word, truly realizes the effect that ''the private key cannot come out of hardware'', significantly reduces the stolen risk of the private key, is easy to retrieve the assets after the private key is lost, avoids the loss of the assets due to the loss of the private key, can protect the assets for a period of time after the private key is stolen, and enhances the anti-theft performance of digital assets.
Owner:四川链安信科技有限公司
Cloud computing terminal authentication method
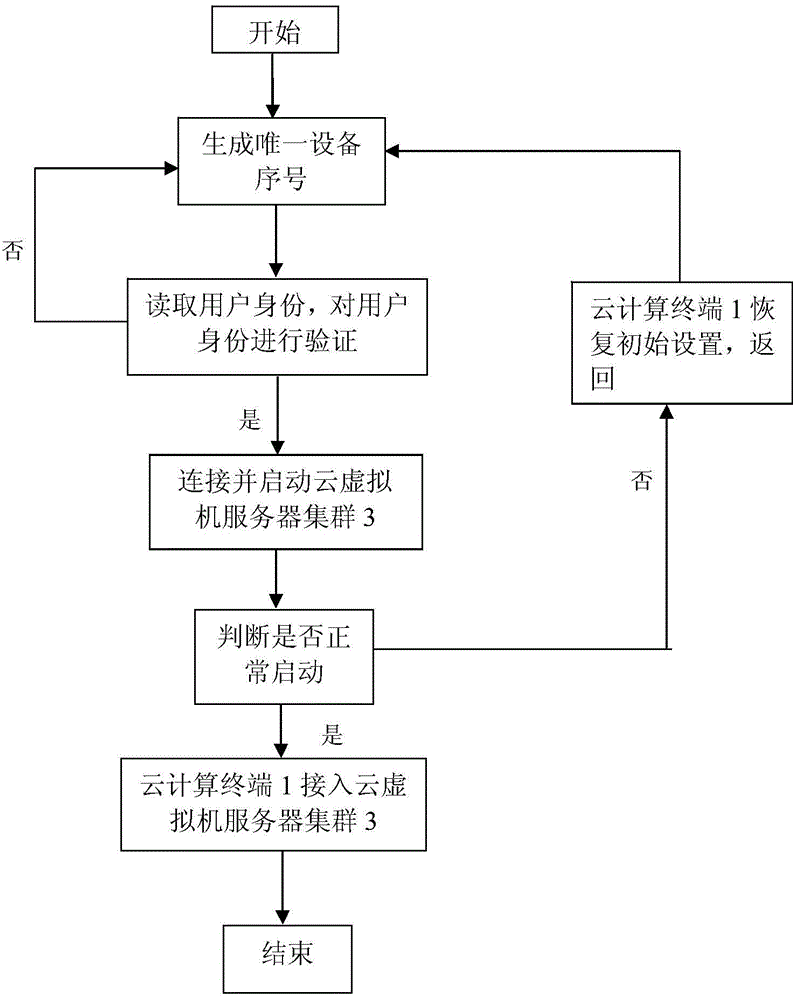
InactiveCN104468106AResolve the Leakage SituationAvoid lossUser identity/authority verificationClient-sideCloud computing
The invention provides a cloud computing terminal authentication method comprising the following steps: step 1, generating a unique device sequence number; step 2, reading a user ID and checking the user ID, if the user does not exist, the cloud computing terminal returns to initial setting, and return to step1; step 3, connecting and staring a cloud virtual machine server cluster through a client side connecting protocol; step 4, determining whether normal starting is carried out or not, if yes, start a step 6, if not, then start a step 5; the step 5, the cloud computing terminal returns to the initial setting and goes back to step 1; step 6, the cloud computing terminal is connected with the cloud virtual machine server cluster. The cloud computing terminal authentication method can effectively solve the problems that the cloud computing terminal is weak in protection, thus causing user information leakage; the cloud computing terminal authentication method can effectively prevent safety troubles like ID leakage, data theft, and information loss.
Owner:上海俊悦光纤网络科技有限公司
Numerical control machine communication interface security protection method and device
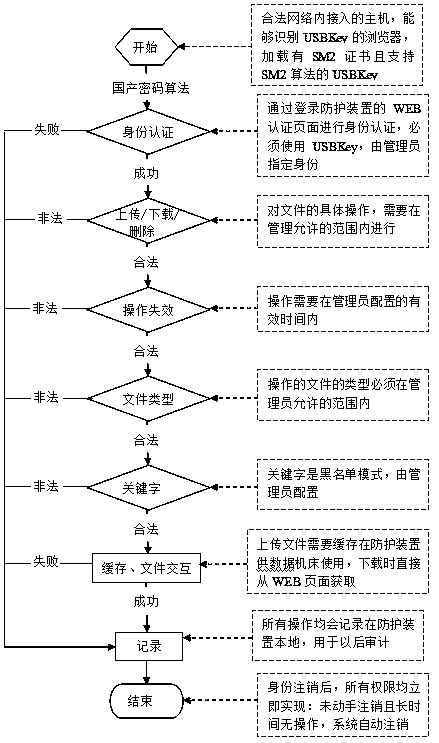
InactiveCN108429744AProtect communication data securityPrevent inflowTransmissionCommunication interfaceData stream
The invention provides a numerical control machine communication interface security protection method and device. The method comprises the steps that access monitoring is conducted on a peripheral interface needing access control in a numerical control machine; equipment to be accessing the numerical control machine all conduct access through access monitoring, wherein the specific control methodof access monitoring comprises the steps that identities of the access equipment are authenticated, and access is allowed only when the identities pass authentication; upload files are supplied to thenumerical control machine for use by means of caching of access monitoring; download files are acquired through a WEB page of access monitoring; and all operations of the access equipment are recorded. Accordingly, the communication data security of a numerical control system is effectively protected, abnormal data streams are prevented from flowing into the numerical control system, all networkattacks and illegal data theft behaviors which are conducted by means of the numerical control system are blocked, and normal and secure operation of the numerical control system and a numerical control machining network is guaranteed.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
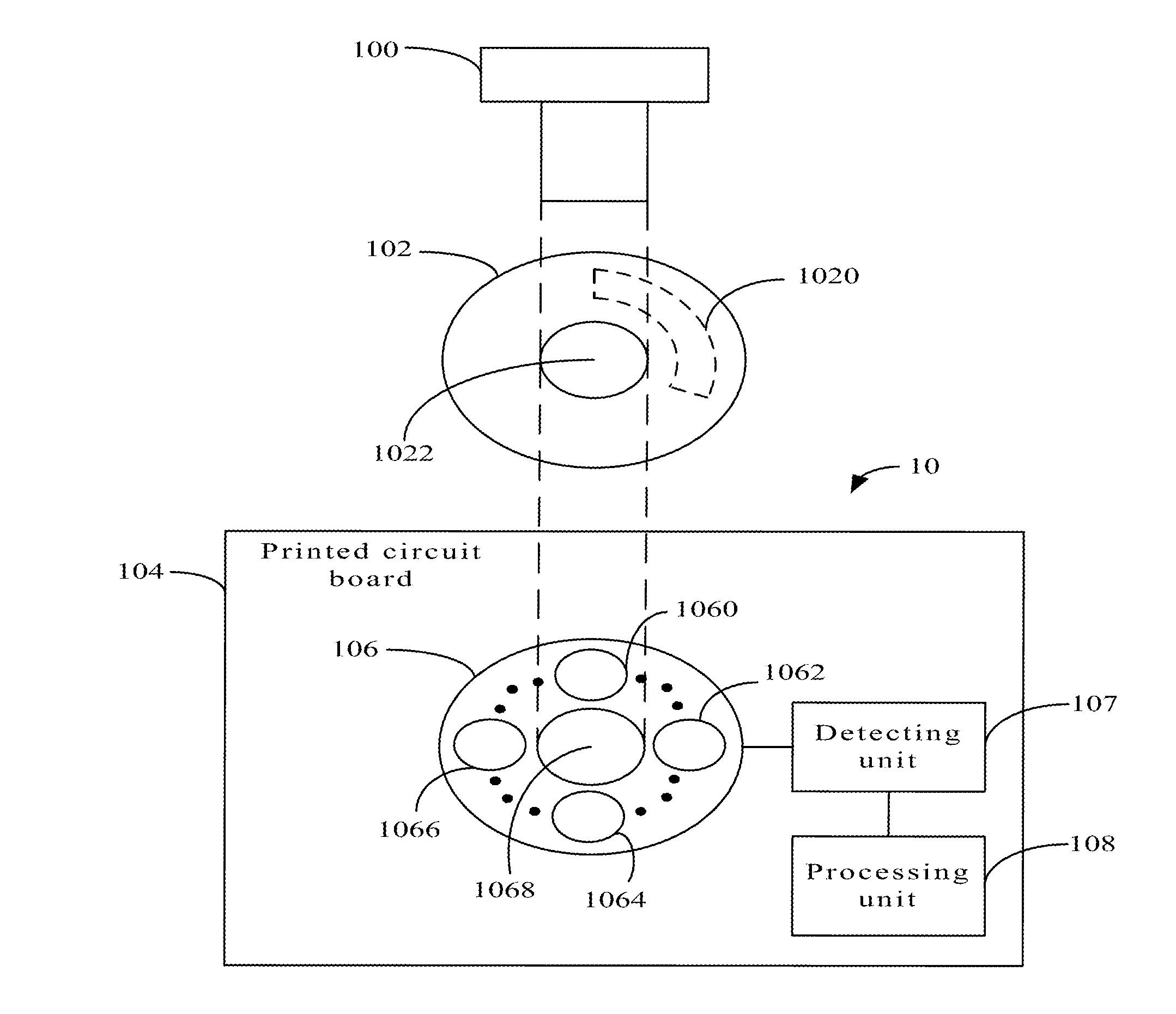
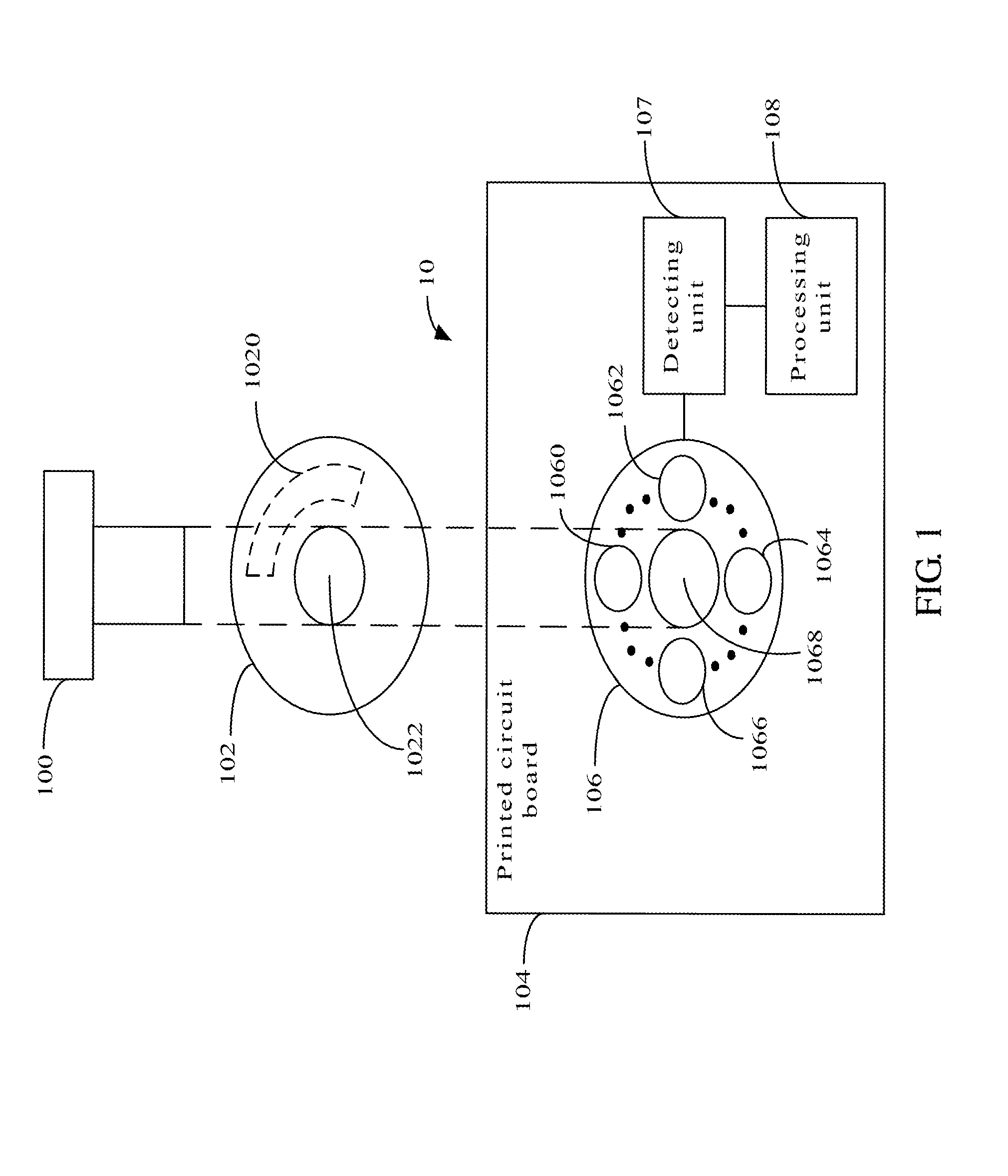
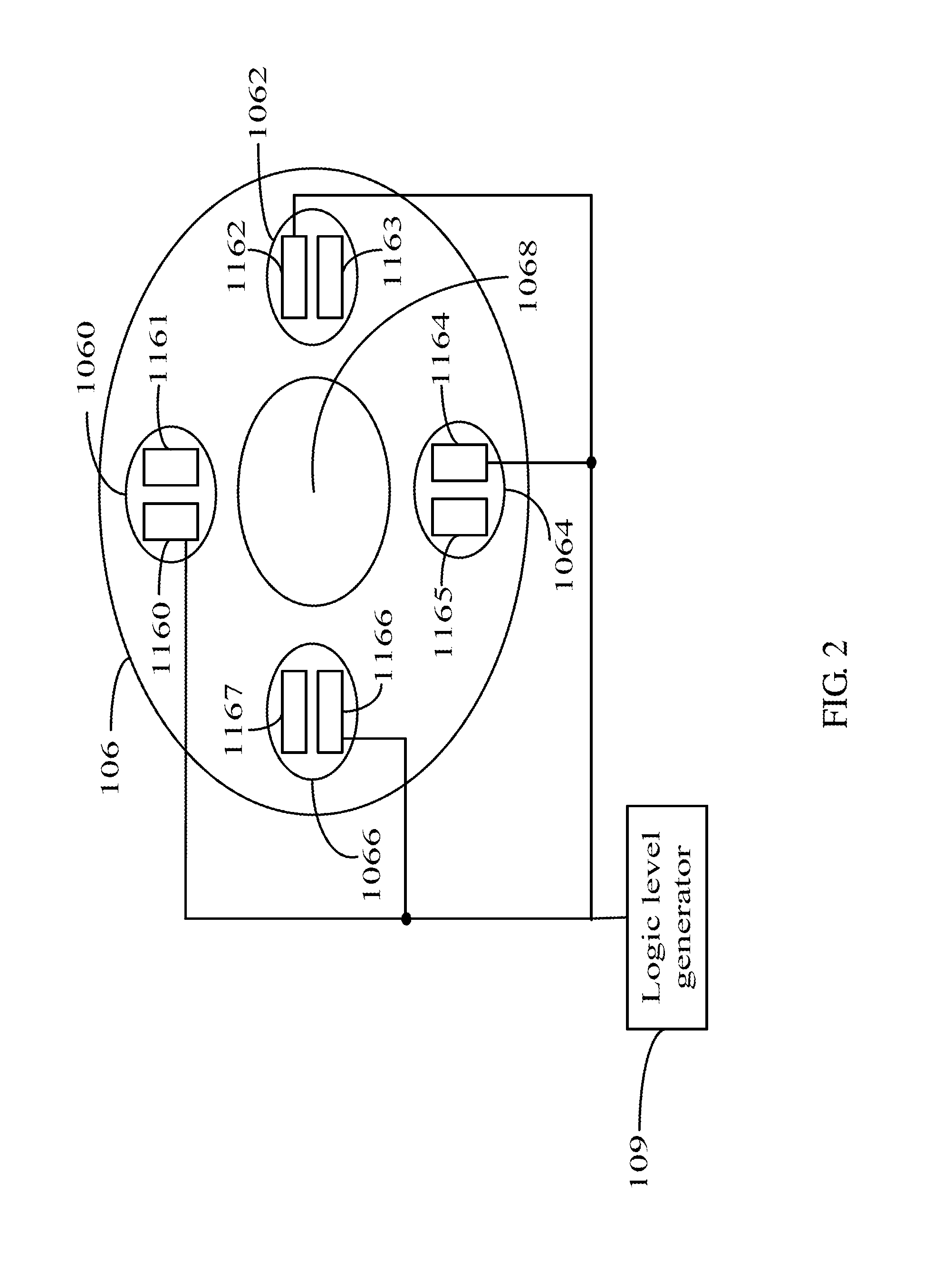
Electronic device using data theft protection
An electronic device includes a washer, a printed circuit board, and a screw. The printed circuit board includes a copper foil, a detecting unit and a processing unit. The copper foil comprises a plurality of electrical signal interfaces surrounding a first via defined in the copper foil. The washer defines a second via and includes a transmission metal. The screw combines the printed circuit board and the washer through the second via and the first via. The detecting unit stores an original logic level signal, and detects logic level signals of the electrical signal interfaces in real-time. The processing unit compares the original logic level signal and the detected logic level signal, to determine whether the electronic device is disassembled. If the electronic device is disassembled, the electronic device stops working.
Owner:CLOUD NETWORK TECH SINGAPORE PTE LTD
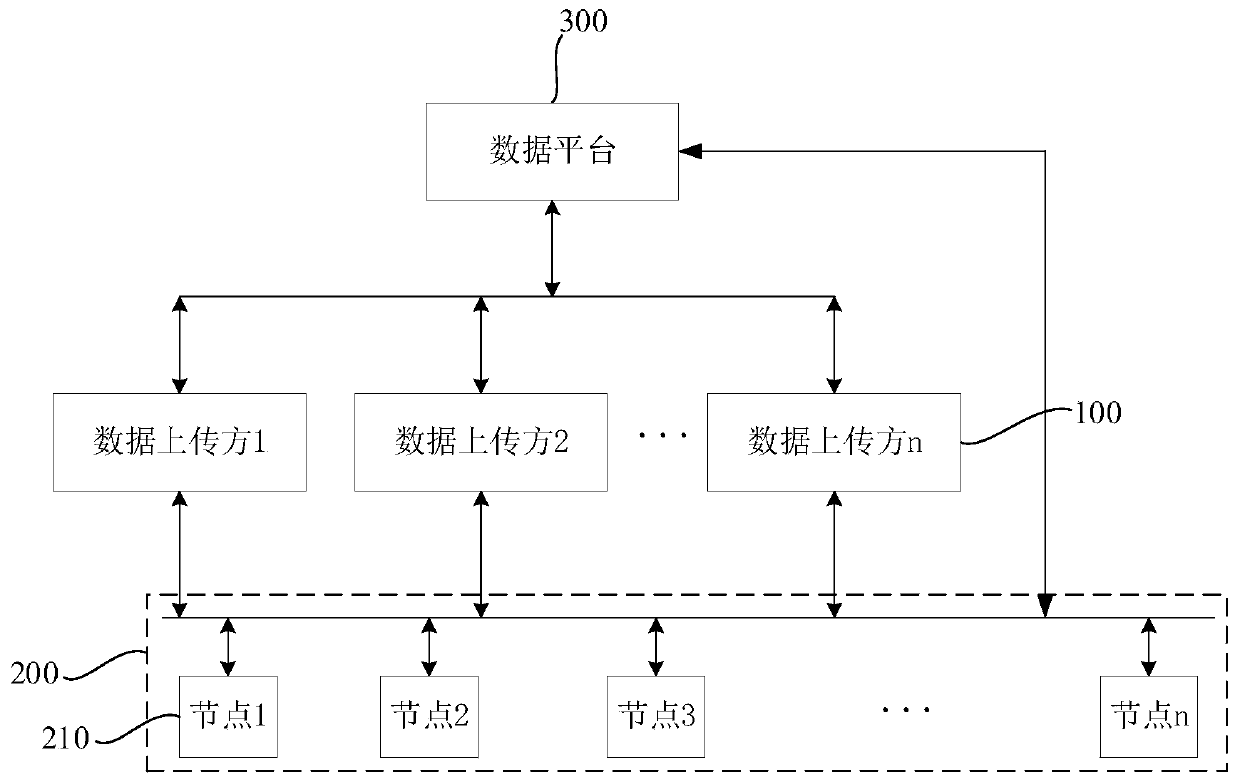
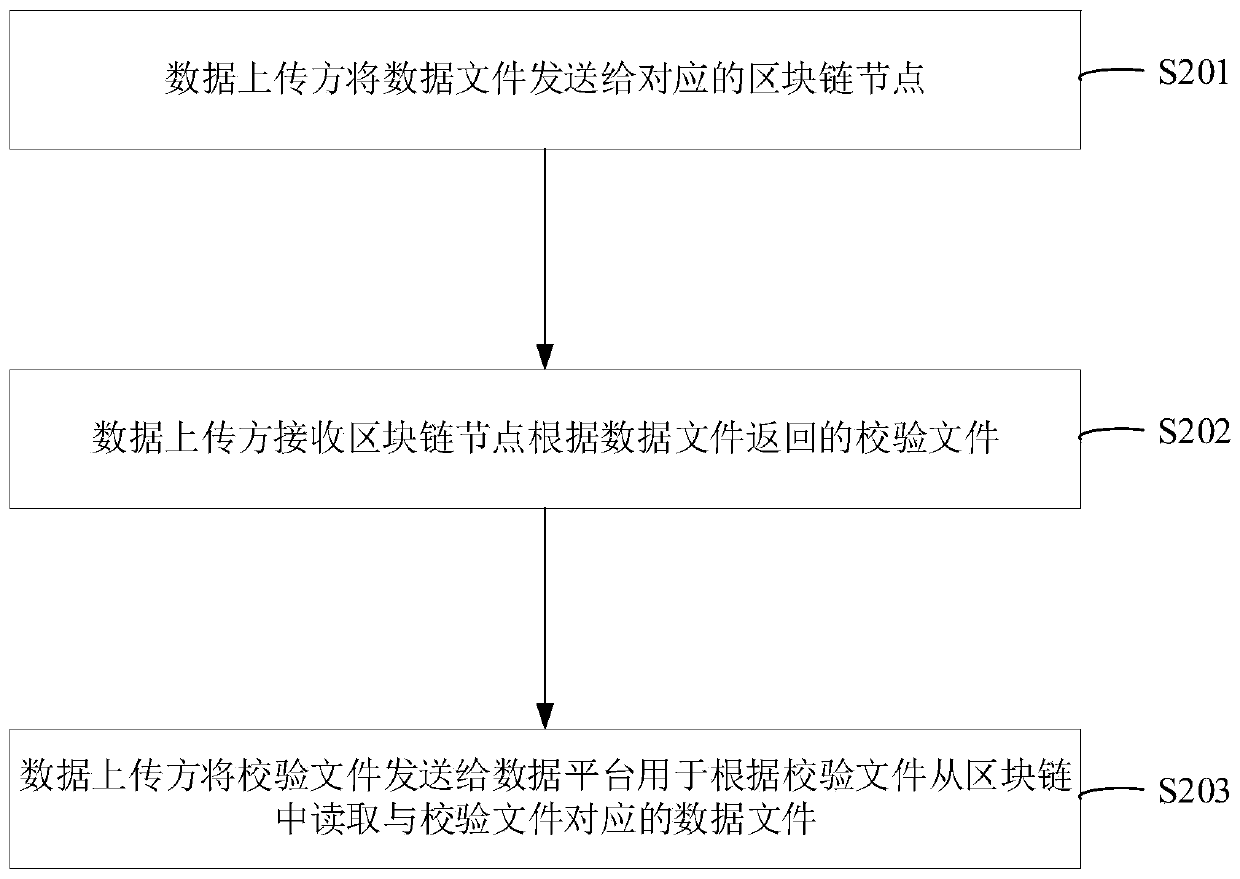
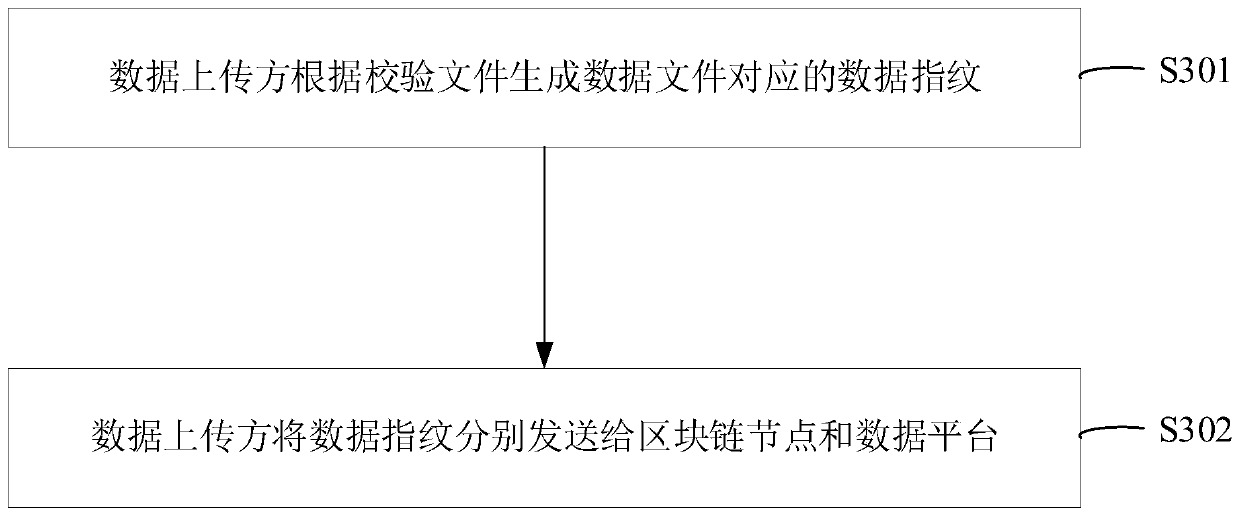
Data transmission method, device, system, electronic equipment and storage medium
ActiveCN110753105AAvoid lossReduce riskDigital data protectionTransmissionData platformSoftware engineering
The invention provides a data transmission method, a device, a system, electronic equipment and a storage medium, and relates to the technical field of data transmission. According to the embodiment of the invention, the method comprises the steps: carrying out the processing, the data uploader can send the data file to the blockchain node; receiving a verification file returned by the blockchainnode according to the data file; then, the data uploading party can send the verification file to the data platform. Therefore, the data platform can read the corresponding data file from the blockchain where the blockchain node is located according to the verification file. According to the invention, data transmission can be carried out between the data uploader and the data platform based on the blockchain formed by the blockchain nodes, so that when data transmission is carried out between the data uploader and the data platform, risks of data loss, data theft and the like can be avoided,and the safety of data is ensured.
Owner:CHINA CONSTRUCTION BANK
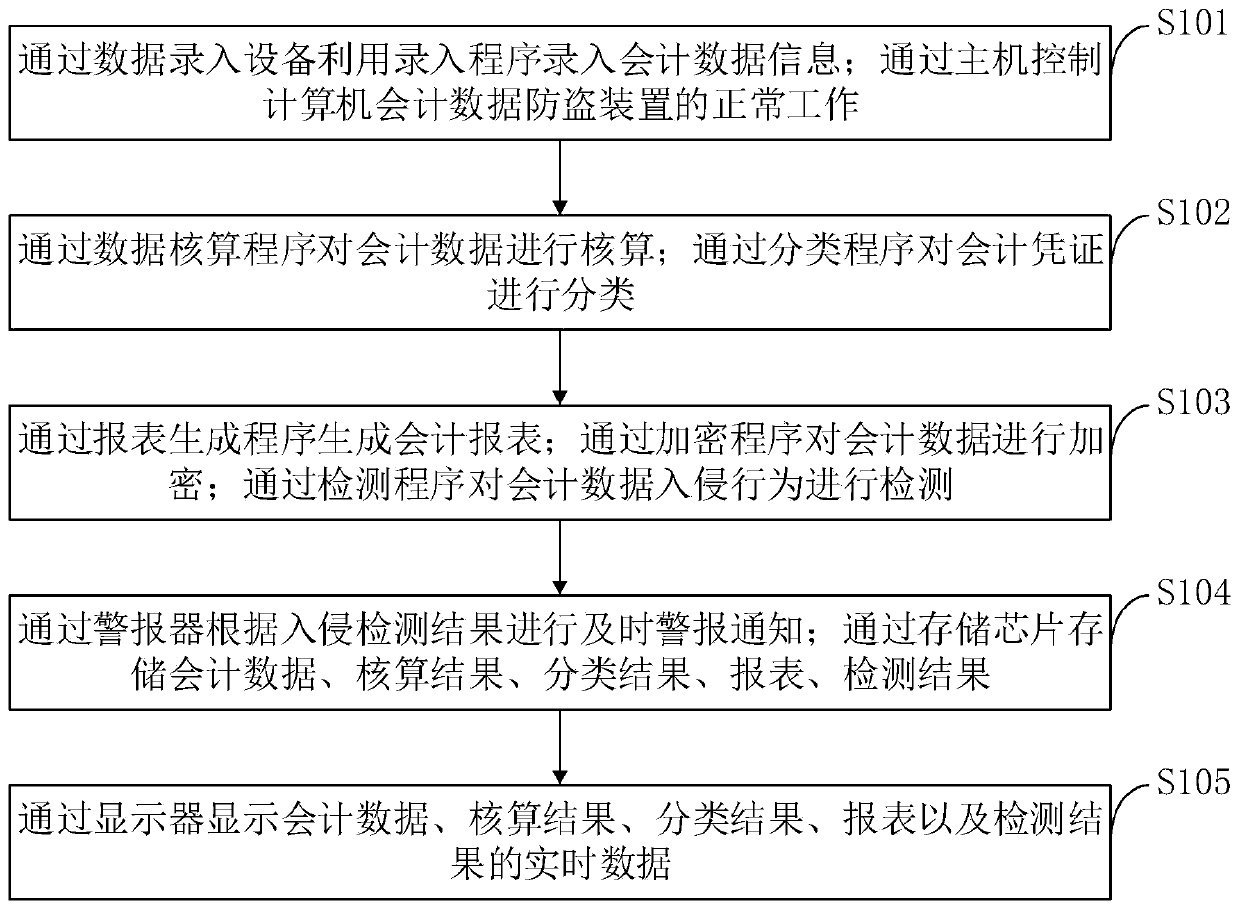
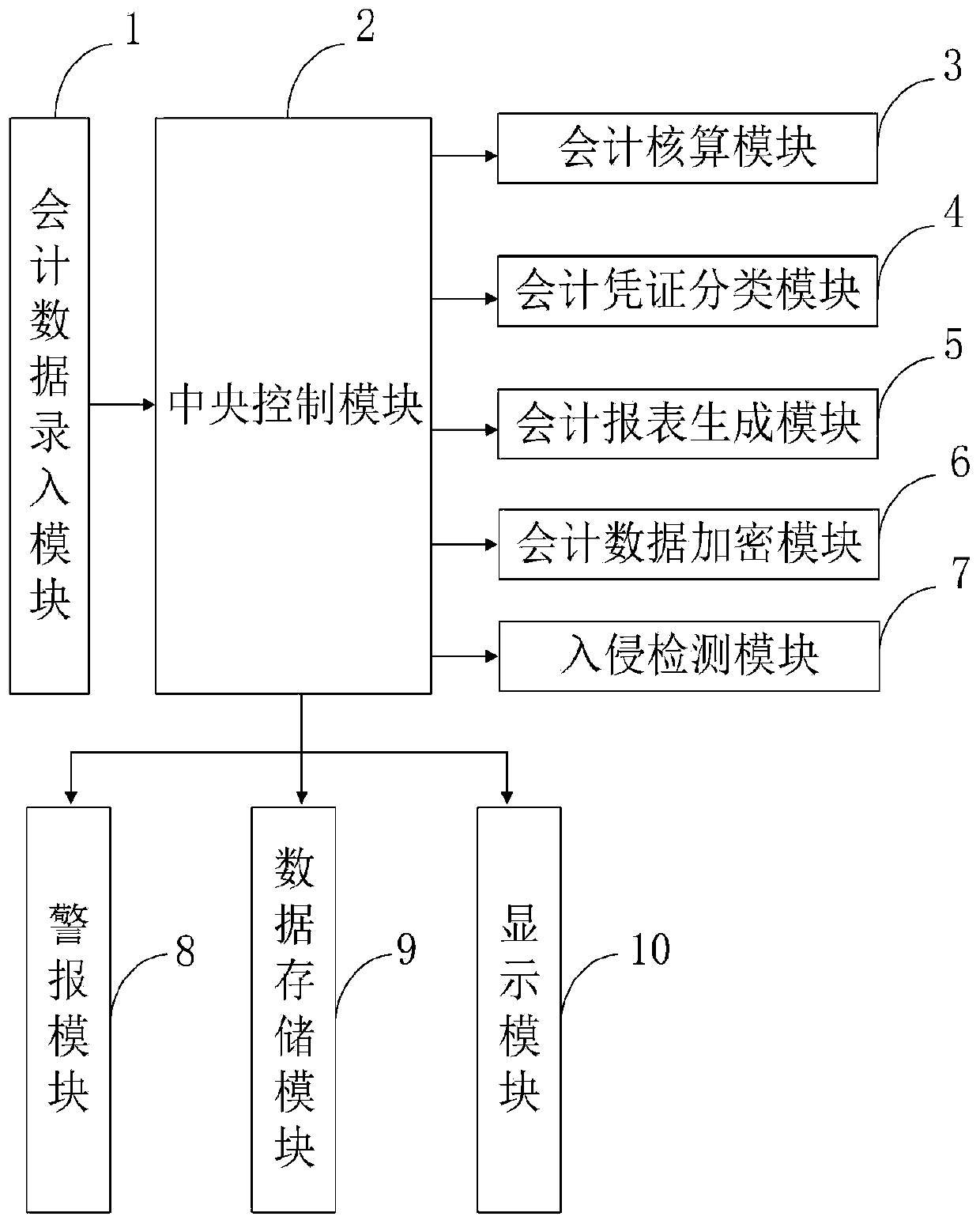
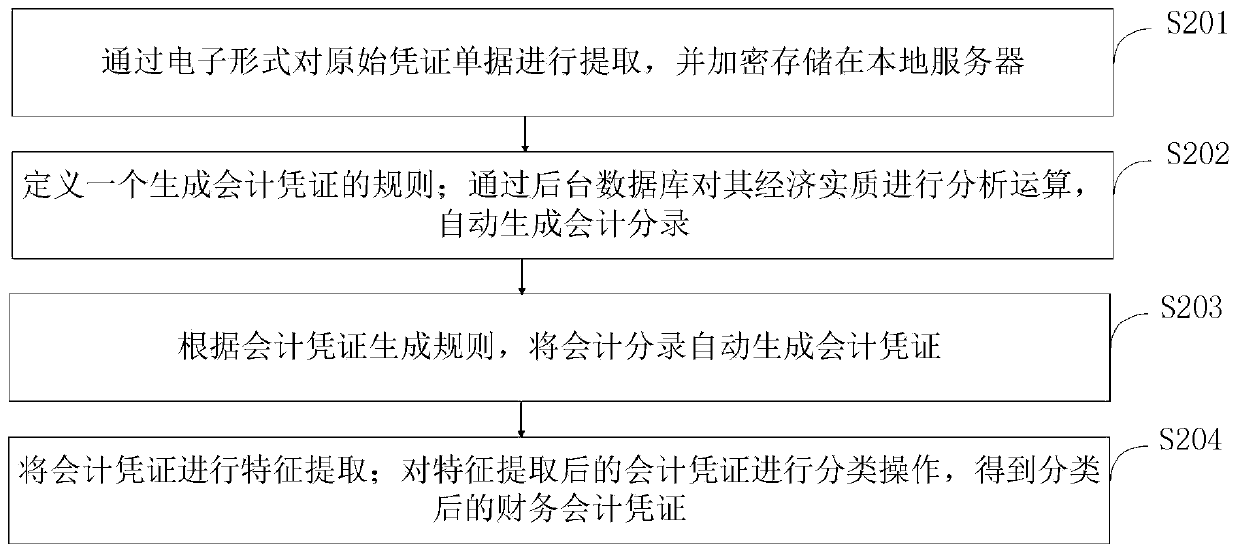
Computer accounting data anti-theft device and control method thereof
InactiveCN111339540AGenerate accuratelyHigh encryption strengthFinanceDigital data protectionClassification methodsData needs
The invention belongs to the technical field of computer accounting data theft prevention, and discloses a computer accounting data anti-theft device and a control method thereof. The computer accounting data anti-theft device comprises an accounting data input module, a central control module, an accounting module, an accounting voucher classification module, an accounting statement generation module, an accounting data encryption module, an intrusion detection module, an alarm module, a data storage module and a display module. A classification method adopted by the accounting document classification module is simple to operate and high in classification accuracy, the labor cost is reduced, and the working efficiency is improved; the adopted classification operation method can improve the accuracy of accounting document classification; meanwhile, the financial data is preprocessed through the accounting statement generation module, when the accounting statement is generated, only thecorresponding data needs to be read, operation is not needed, the accounting statement can be rapidly and accurately generated, and the processing speed and efficiency can be greatly improved.
Owner:SHANDONG LABOR VOCATIONAL & TECHN COLLEGE
Implementing data theft prevention
A method and circuit for implementing data theft prevention, and a design structure on which the subject circuit resides are provided. A polymeric resin containing microcapsules surrounds a security card. Each microcapsule contains a conductive material. The conductive material of the microcapsule provides shorting on the security card responsive to the polymer resin and the microcapsule being breached, and a data theft prevention function using the shorting by the conductive material to prevent data theft.
Owner:IBM CORP
Data protection device of terminal equipment
InactiveCN103902936APrevent theftIncrease costDigital data protectionInternal/peripheral component protectionMicrocomputerMicrocontroller
The invention discloses a data protection device of terminal equipment. The data protection device of terminal equipment comprises a self-reset switch, a reflective photoelectric switch and a single-chip microcomputer. The self-reset switch is abutted against a shell of the terminal equipment to be kept in a triggered state under abutting pressure of the shell and outputs an electric signal. The reflective photoelectric switch is arranged in the shell of the terminal equipment, a light ray signal sent by a transmitter of the reflective photoelectric switch is reflected by the shell and the received by a receiver, and the reflective photoelectric switch is kept in a triggered state and outputs an electric signal. The single-chip microcomputer is respectively connected with the self-reset switch and the reflective photoelectric switch to detect the electric signals outputted by the self-reset switch and the reflective photoelectric switch and clear application data when one of the two electric signals leaps, and accordingly dual protection of data in the terminal equipment is realized, data theft is effectively avoided on the basis that a shell material is unchanged, and increasing of production cost and processing cost is avoided.
Owner:GUANGDONG HUADA INTERNET CO LTD
Method to eliminate data theft through a phishing website
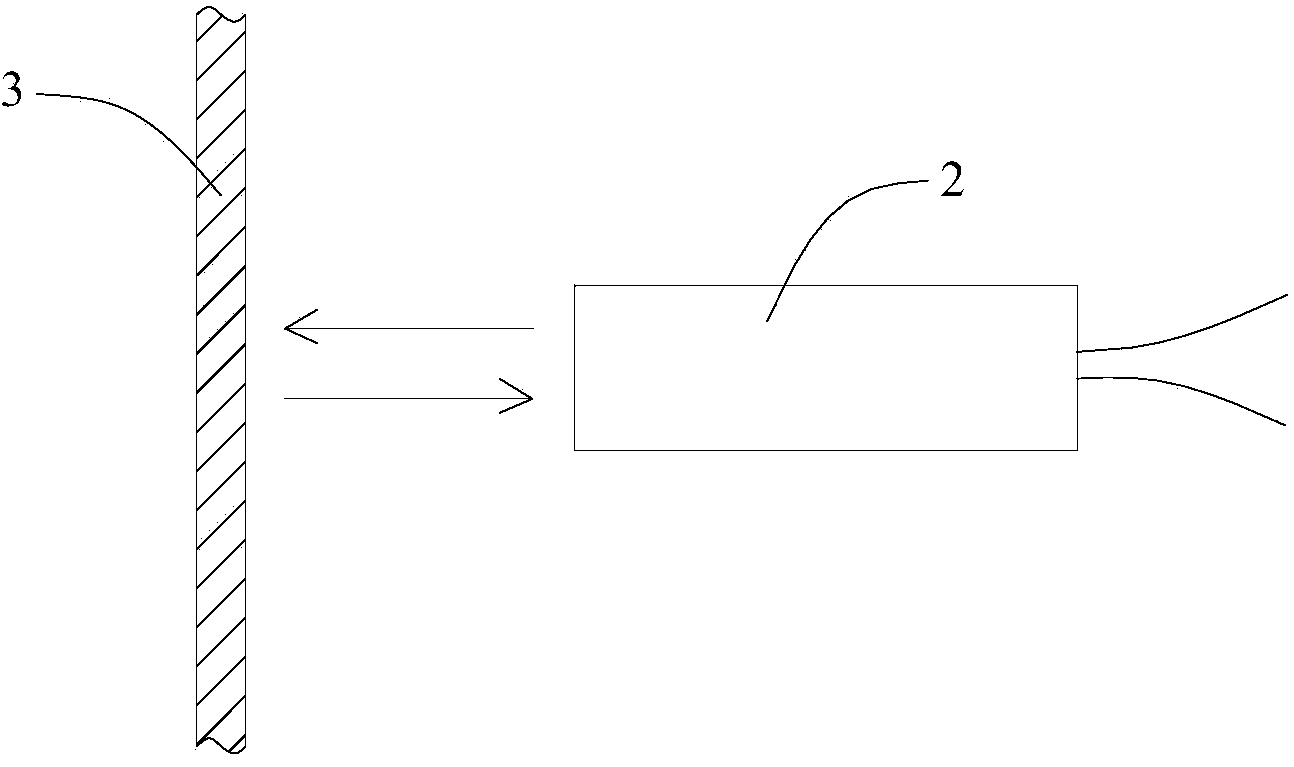
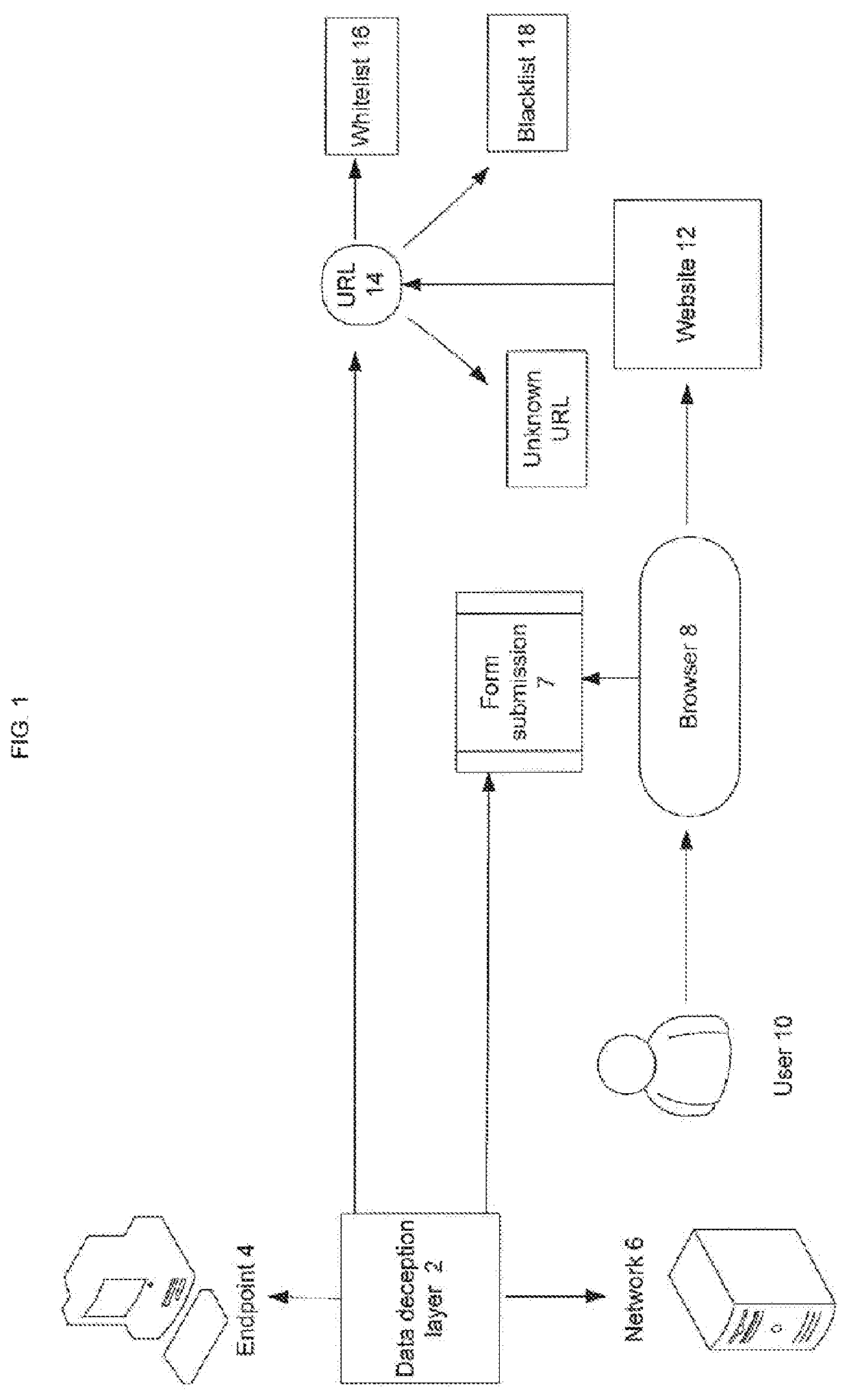
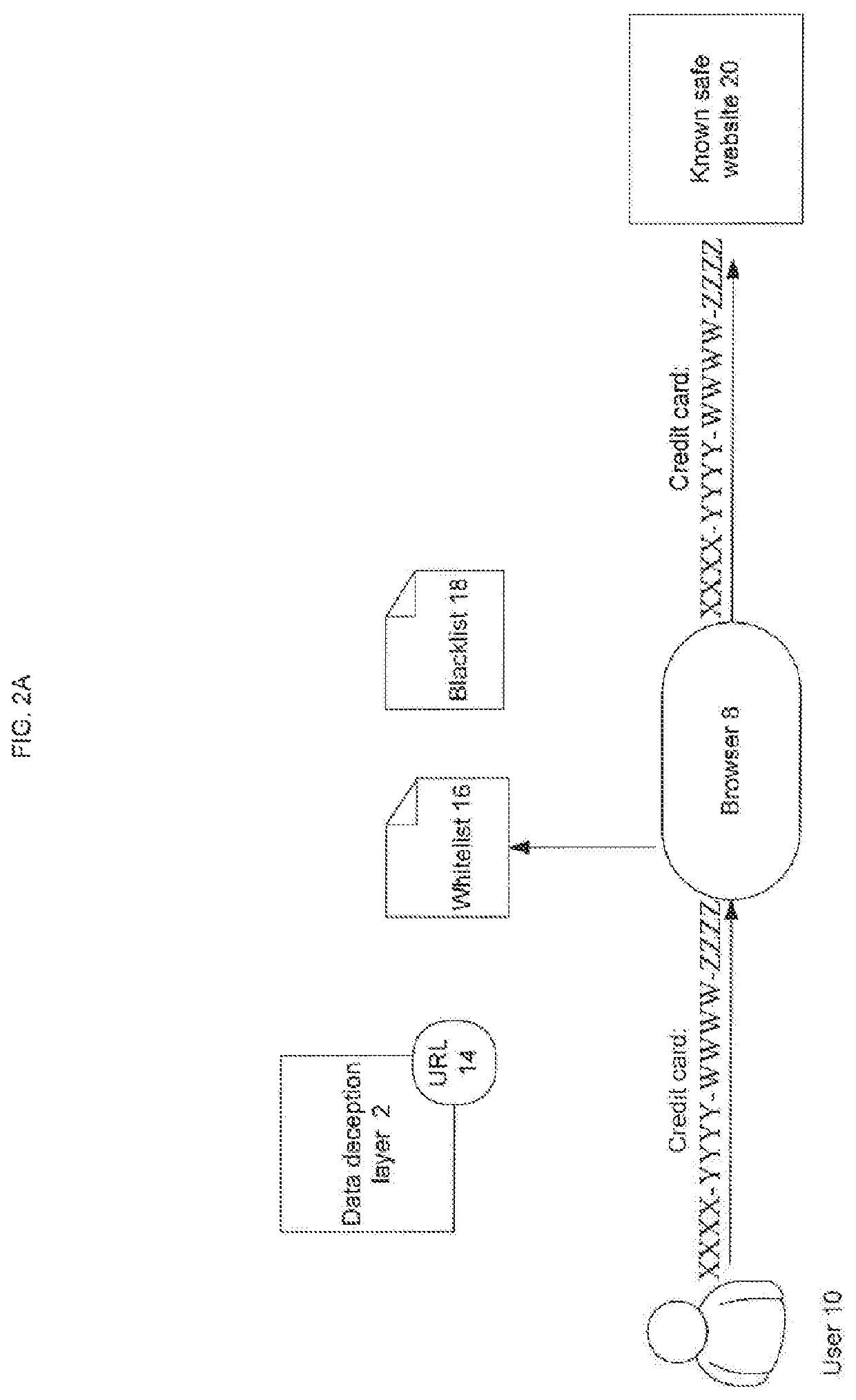
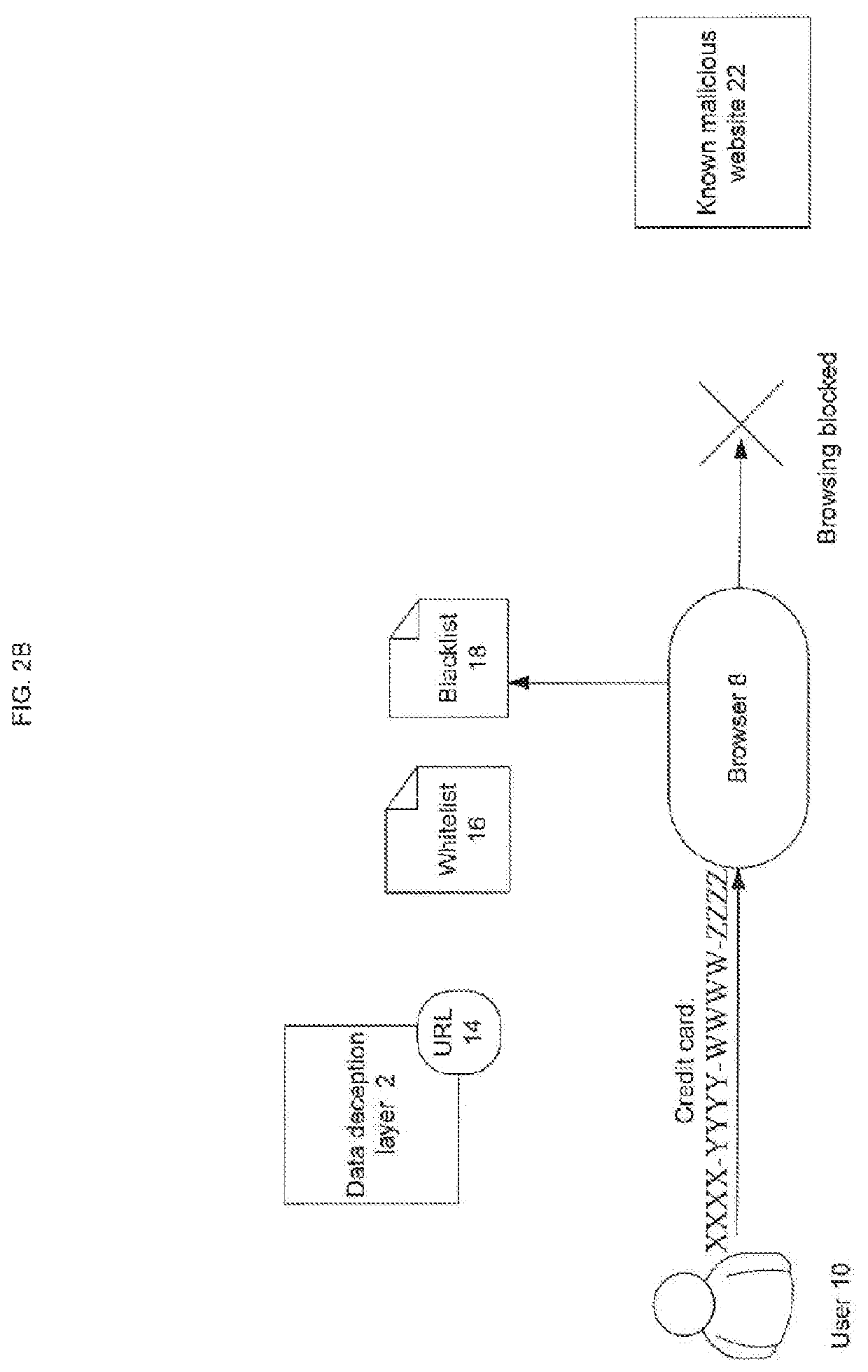
ActiveUS11470113B1Reduced usabilityAffects usabilityDigital data protectionSecuring communicationWeb siteControl layer
There is provided a method to eliminate data-theft through a phishing website by creating a layer of control between the user and the website to be visited that prevents submission of sensitive data to malicious servers. When there is a form submit event in a webpage, the data that is input (by the user or automatically) is modified by a data deception layer in a random manner that disguises the authentic content, while preserving the format of the data. Visual cues are provided to indicate that the data deception is enabled and that fake / generated data is being submitted instead of real data. The generated fake data is sent to unknown (potentially malicious) server while the users' actual private data is preserved (never submitted), with the results of the server response visible to the user.
Owner:COMODO SECURITY SOLUTIONS
Household NAS network memory
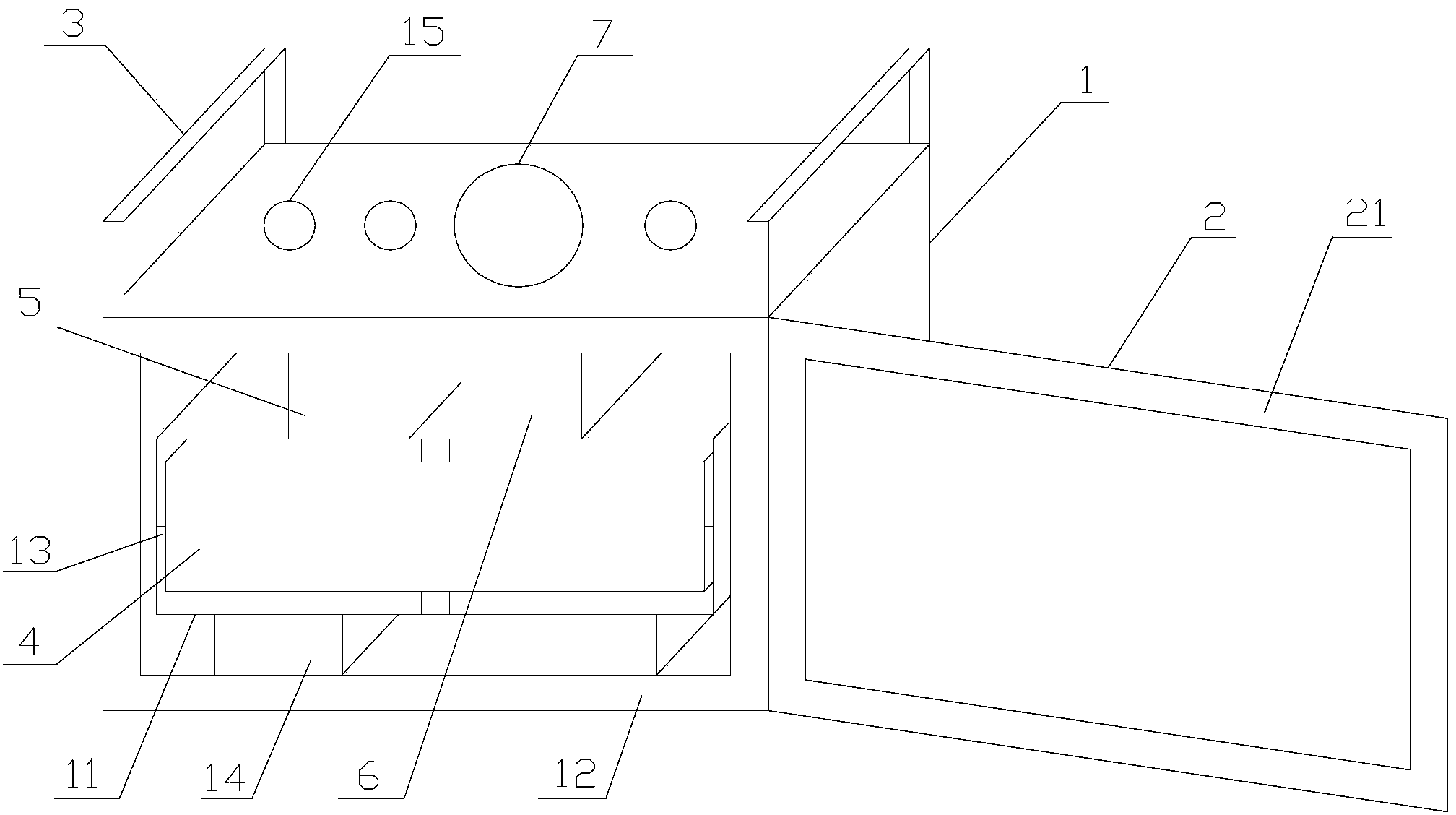
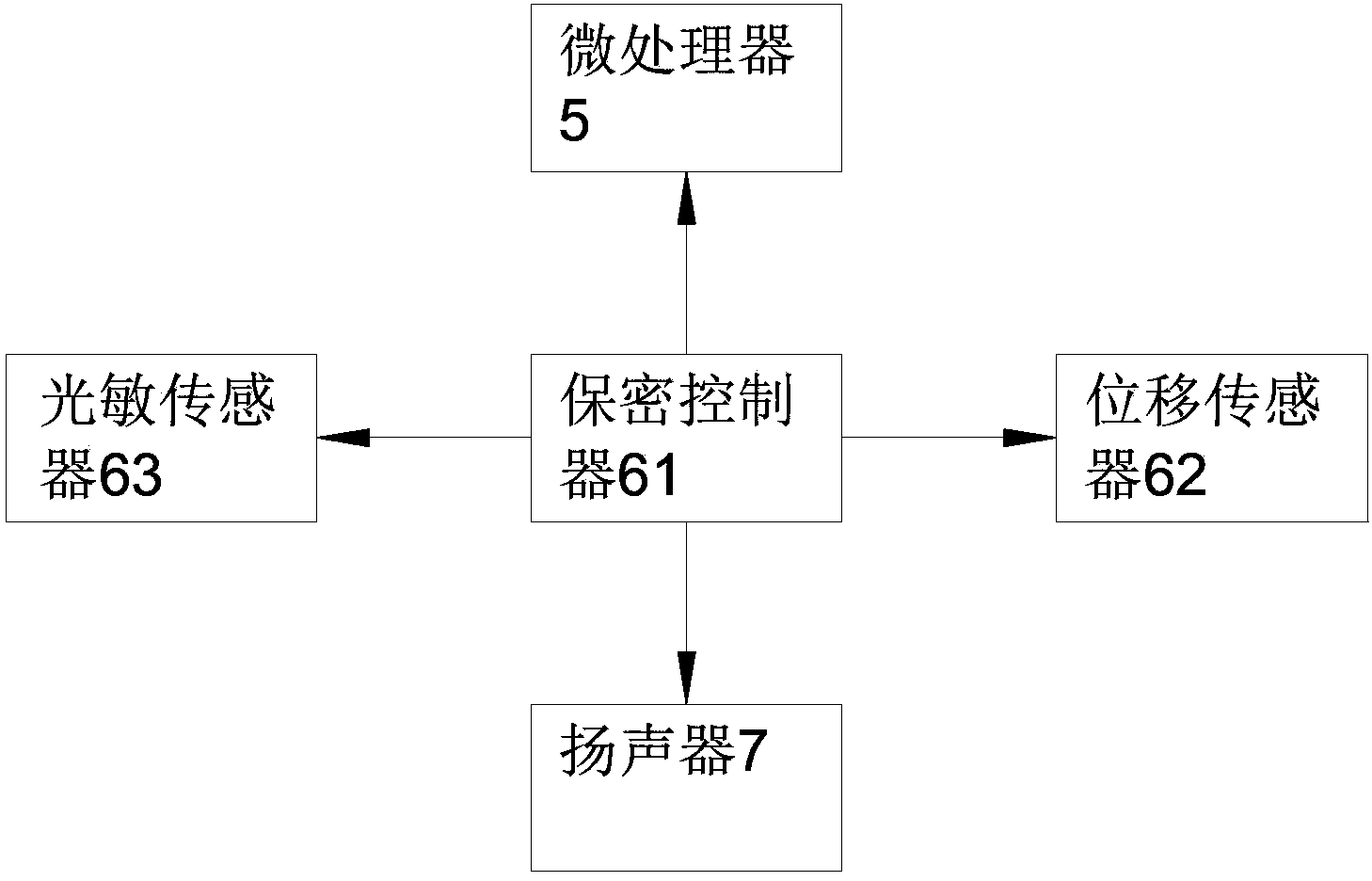
InactiveCN104301351APrevent theftLarge amount of data storageBurglar alarm mechanical actuationHermetically-sealed casingsLoudspeakerData theft
The invention discloses a household NAS network memory comprising a shell, a sealing door, a pair of lifting handles, one or multiple hard disks, a microprocessor, a secrecy mechanism and a loudspeaker. The sealing door is hinged with the shell. The pair of the lifting handles are respectively arranged at the two sides of the top part of the shell which is internally provided with a hard disk accommodating cavity. The internal wall of the shell is provided with a layer of damping pad. The hard disks are arranged in the hard disk accommodating cavity and are fixed via connecting members arranged at the periphery of the hard disks. The microprocessor and the secrecy mechanism are arranged above the hard disk accommodating cavity. The microprocessor is connected with the secrecy mechanism which is composed of a secrecy controller, a displacement sensor and a photosensitive sensor. The secrecy controller is respectively connected with the displacement sensor and the photosensitive sensor. The loudspeaker is arranged at the top part of the shell. The loudspeaker is connected with the secrecy mechanism. Data theft can be prevented via change of light rays and movement of the position of the hard disks. Besides, the shell is sealed so as to be dustproof and waterproof, the hard disks can be effectively protected and data security is ensured.
Owner:TIANJIN LIANGZHENG SCI & TECH
A container-based data exchange method
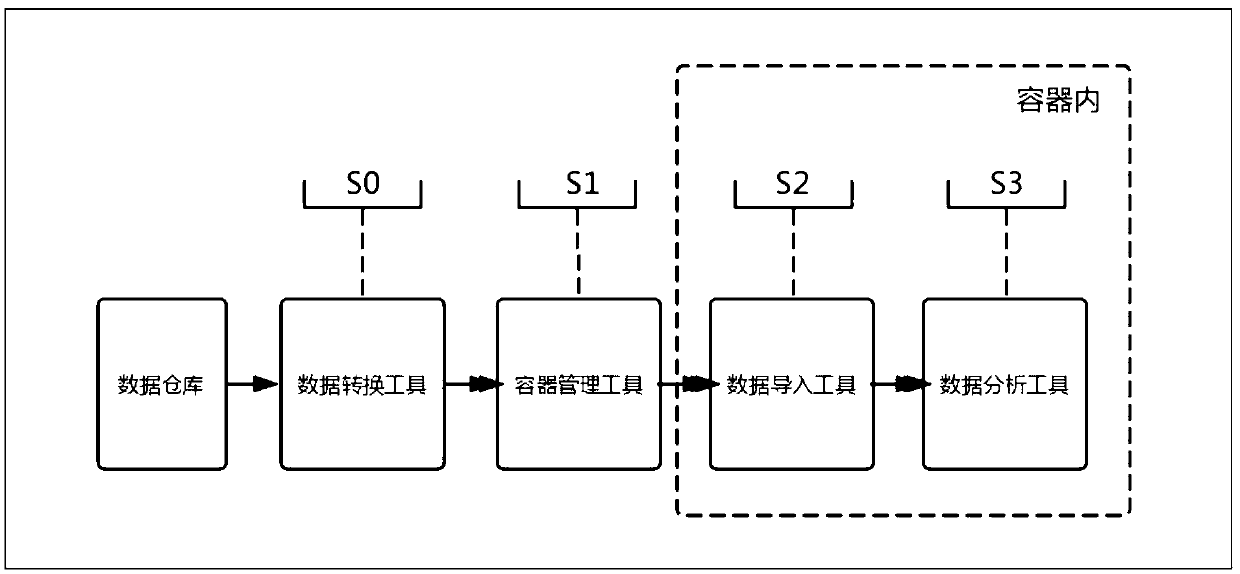
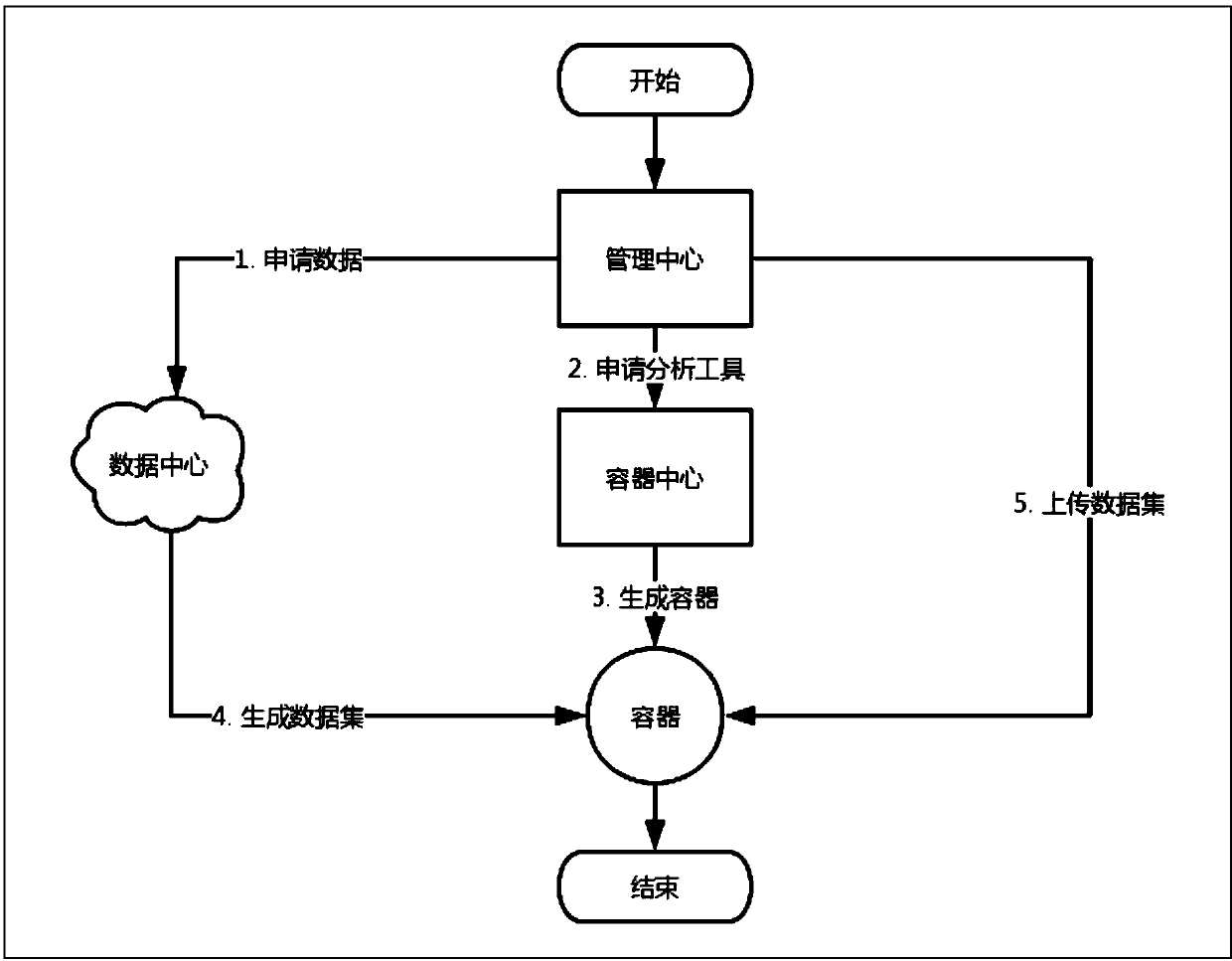
InactiveCN109635018AIncrease profitDatabase management systemsDigital data protectionData setManagement tool
The invention provides a container-based data exchange method, comprising the following steps: 1) providing a data conversion tool for converting data from different data sources into data sets; 2) Providing a container management tool including application, image and management; 3) providing a data exchange tool for importing and export data set, private data and result data; 4) Providing a container environment containing data analysis tools, which can be used for data fusion, analysis and mining. The invention provides a container-based data exchange method, which solves the problems of data exchange, data set fusion processing, model base formation and the like, aiming at the problems that the traditional data exchange mode cannot directly operate the data set for analysis and mining and the non-public data needs isolation environment, etc. At the same time, the container technology is used to isolate the calculation process, improve the data security, simplify the analysis processof the analysis and mining workers, and reduce the risk of data theft.
Owner:陕西艾特智慧信息技术有限公司
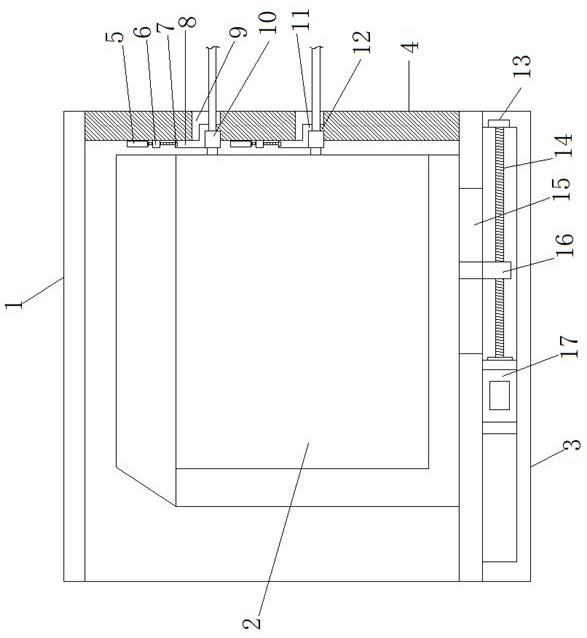
Anti-theft storage device below network data line
ActiveCN113135339APrevent removalNot easy to be stolenBuilding locksContainer/bottle contructionStructural engineeringNetwork data
The invention relates to the technical field of data theft prevention, in particular to an anti-theft storage device below a network data line. The anti-theft storage device comprises a containing box, a storage device is arranged on the inner side face of the containing box, and a baffle making contact with the storage device is rotationally connected to one side of the side face, located on the opening side, of the containing box through hinges. A connecting plate is arranged at the position, corresponding to a front panel of the storage device, on one side of the side face of the baffle, a locking block making contact with the inner top face of the containing box is fixedly connected to the side face of the baffle, a lock cylinder rotationally connected with the connecting plate is rotationally connected in the locking block, and an open groove rotationally connected with the lock cylinder is formed in the side face of the containing box. In the anti-theft storage device, a sliding plate is slidably connected through the open groove, after the storage device is placed in the containing box, the containing box and the baffle can be mutually fixed through the locking block, and therefore the containing box and the baffle can block the storage device, a hard disk in the storage device is prevented from being taken away, other people are not prone to stealing an NAS storage server, and the device is beneficial to data storage and is convenient to use.
Owner:CAPITAL UNIV OF ECONOMICS & BUSINESS
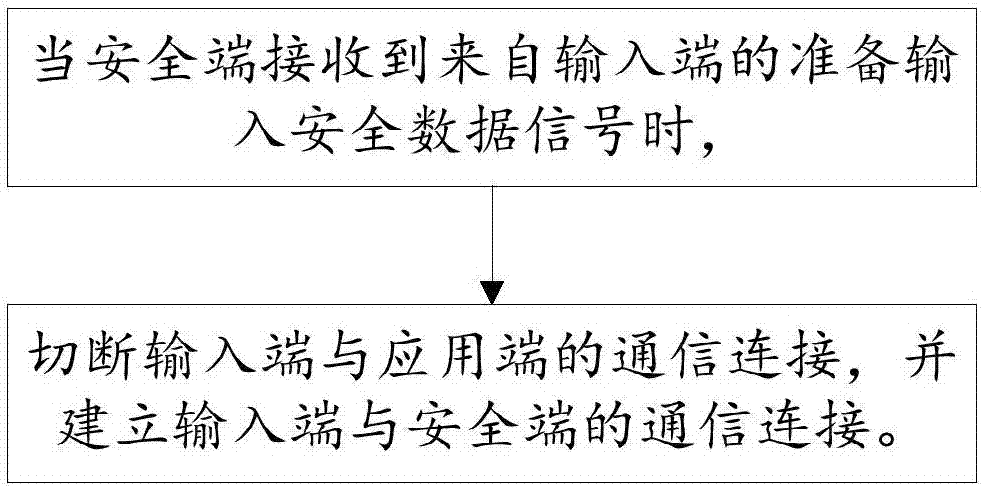
Data safety protection method and device
The invention relates to the field of information security, in particular to a data safety protection method and device. According to the data safety protection method and device, when a safety terminal receives a to-be-input safety data signal from an input terminal, the communication between the input terminal and an application terminal is built, and the communication between the input terminal and the safety terminal is built. Before a user inputs safety data, the communication between the input terminal and the application terminal is cut off, even if the application terminal is attacked by a cracker, the input signal generated by the input terminal can not be obtained, data theft is thus effectively prevented, and the data safety is improved.
Owner:上海汇尔通信息技术有限公司
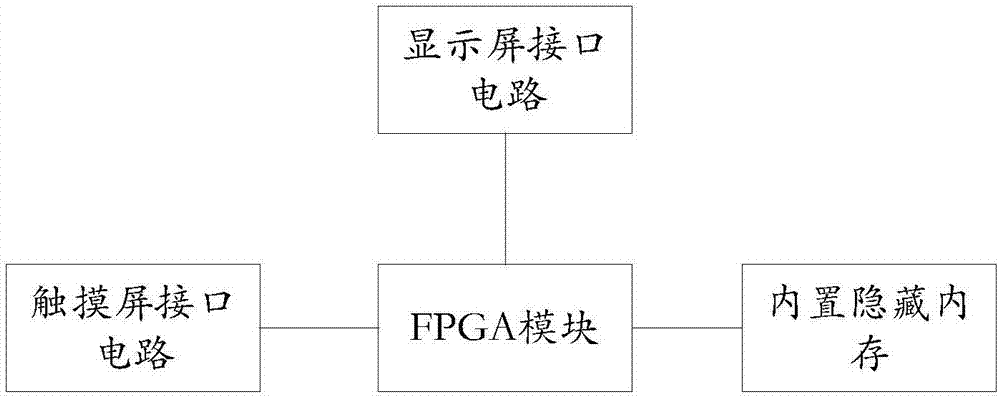
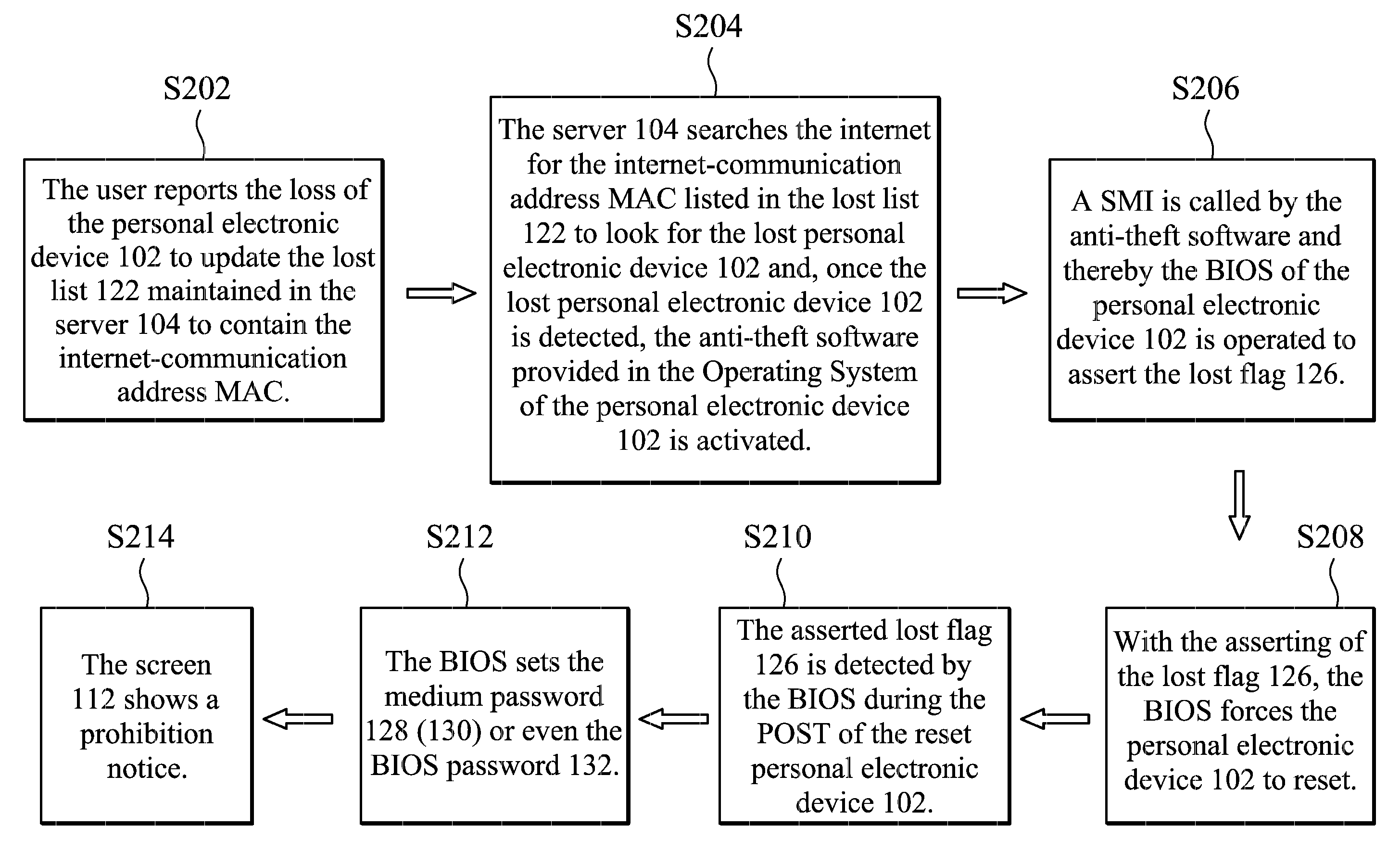
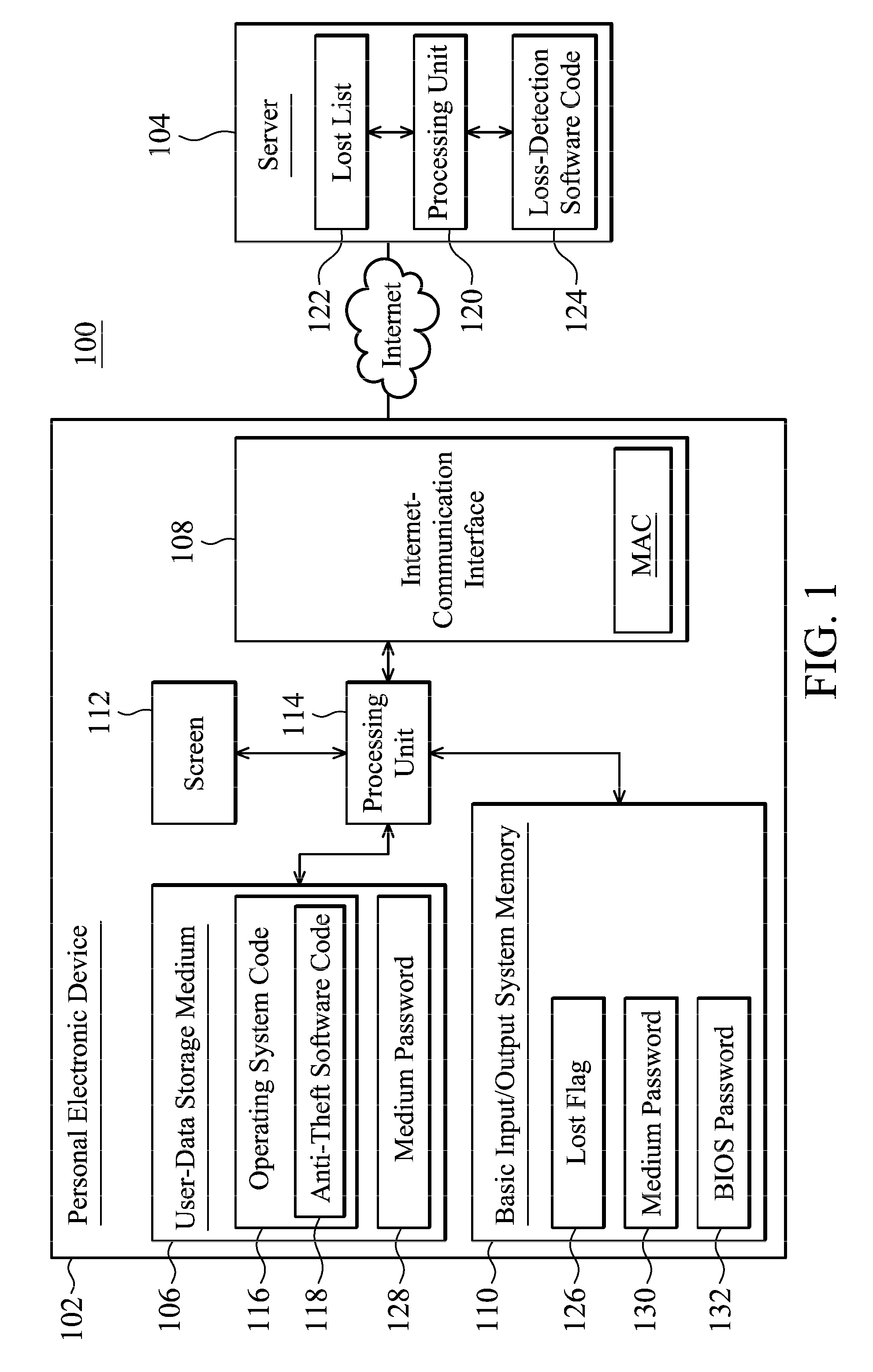
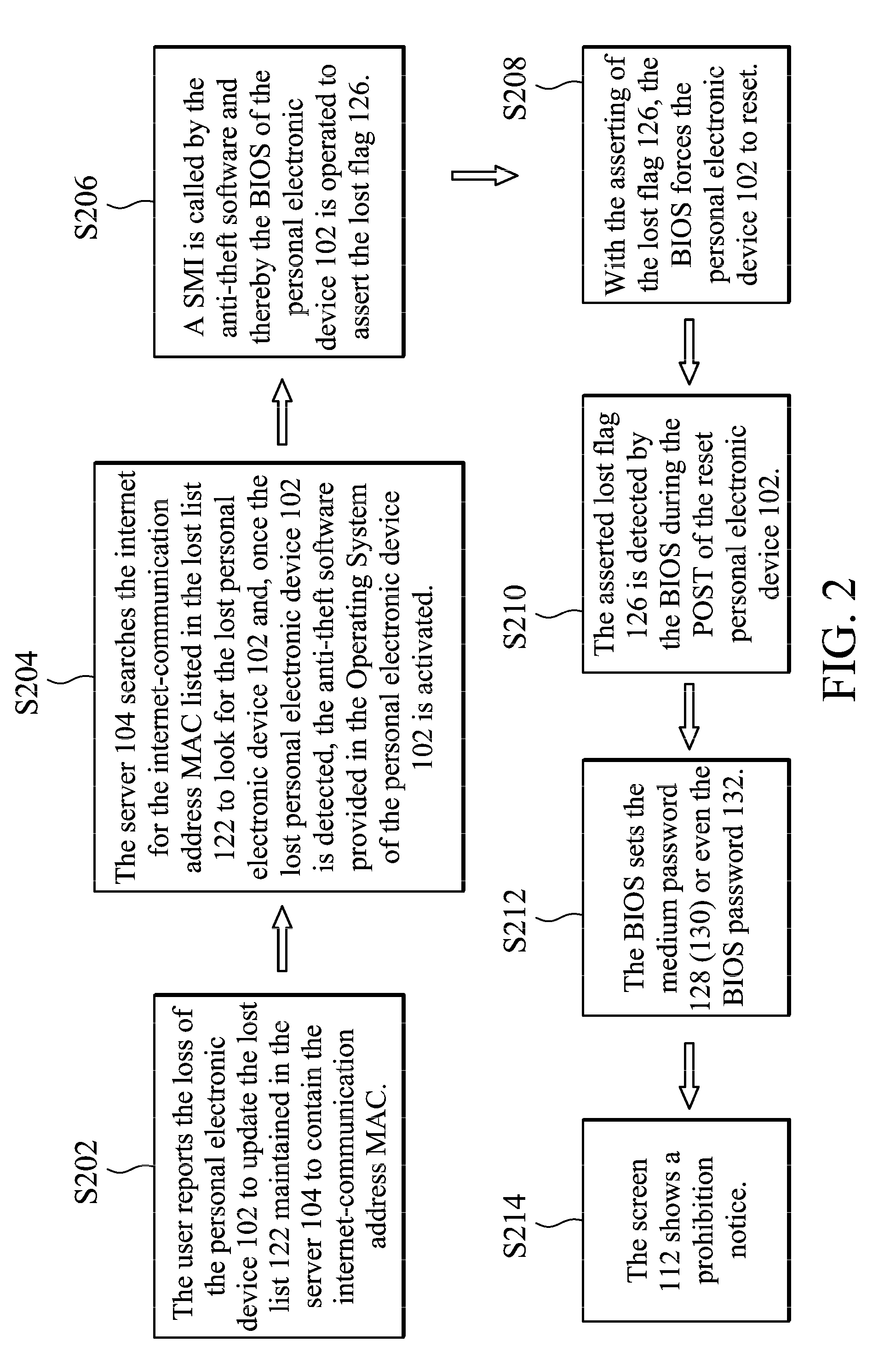
Personal electronic device and data theft prevention system and method thereof
ActiveUS9424434B2Digital data protectionInternal/peripheral component protectionInternet communicationPassword
Data theft prevention technology for a personal electronic device is provided. When an internet-communication address of the personal electronic device is detected by a server through the internet and the server determines that the detected internet-communication address has been listed in a lost list, a processing unit of the personal electronic device operates in accordance with anti-theft software to execute the codes contained in a BIOS memory of the personal electronic device to set a medium password for a user-data storage medium of the personal electronic device and to prohibit the use of the personal electronic device.
Owner:WISTRON CORP
Computer accounting data anti-theft device
PendingCN112347447APrevent theftSimple structureInternal/peripheral component protectionDigital data authenticationControl powerStructural engineering
The invention discloses a computer accounting data anti-theft device, which comprises a placing frame installed at the lower end of a workbench and a host arranged in the placing frame, wherein a fixing plate is installed behind the placing frame; rectangular openings are formed in the positions, right opposite to interfaces of the host, of the fixing plate; connectors are arranged in the rectangular openings; one end of each connector is inserted into the corresponding interface; pressing plates for pressing the connectors are arranged at the upper ends of the connectors; a shell is installedon the bottom face of the placing frame; and a driving mechanism for achieving power-on and power-off of the host is installed in the shell. The device is simple in structure, the host can be completely disconnected from a power connector, a data connector and the like, the host cannot be started, data theft is avoided, the device for controlling power-on and power-off of the host is a mobile phone of a host manager, other people cannot achieve power-on, and safety is improved.
Owner:JIUQUAN VOCATIONAL & TECHN COLLEGE
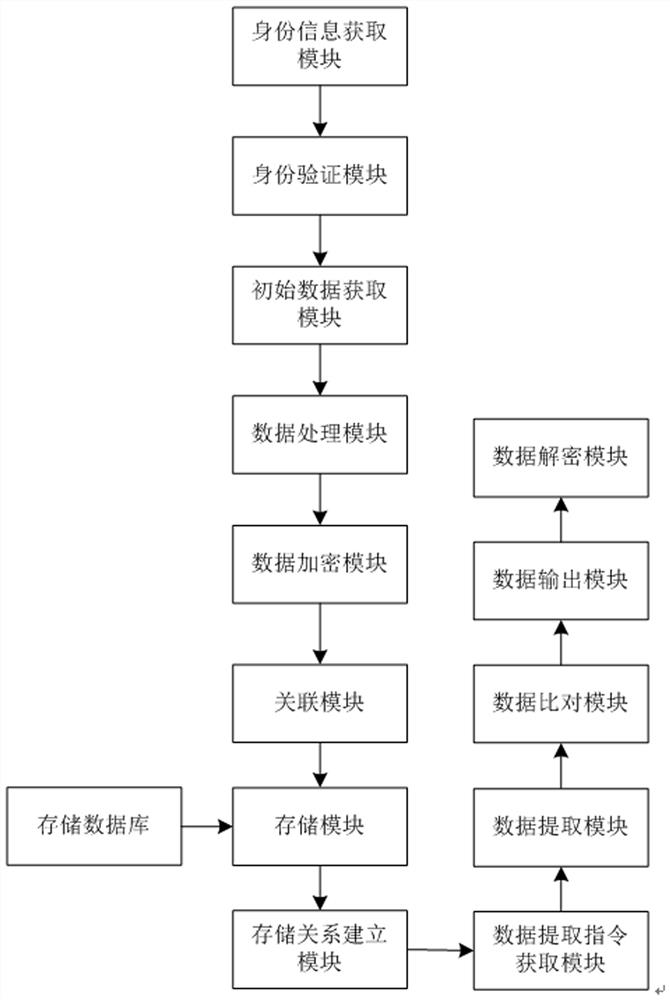
Computer data security storage system
InactiveCN111859345AReduce the possibility of theftWon't leakDigital data protectionDigital data authenticationData setData information
The invention relates to a computer data security storage system. The system comprises an identity information acquisition module, an identity verification module, an initial data acquisition module,a data processing module, a data encryption module, an association module, a storage database, a storage module and a storage relationship establishment module. Prior to data storage, the identity ofa data storage person is verified, so the security of data storage can be ensured, and the likelihood of data theft is reduced; after the authentication of an identity is passed, the initial data information is divided into at least two data sets with different data attributes, and different data sets are encrypted according to different encryption mechanisms; even if some data sets are illegallydecrypted, all the data sets cannot be decrypted, so the possibility that the data is stolen is further reduced, and the safety of data storage is improved; moreover, different encrypted data sets arestored in different storage areas, so the reliability of data storage is improved, and later data extraction is facilitated.
Owner:郑州奥腾网络科技有限公司
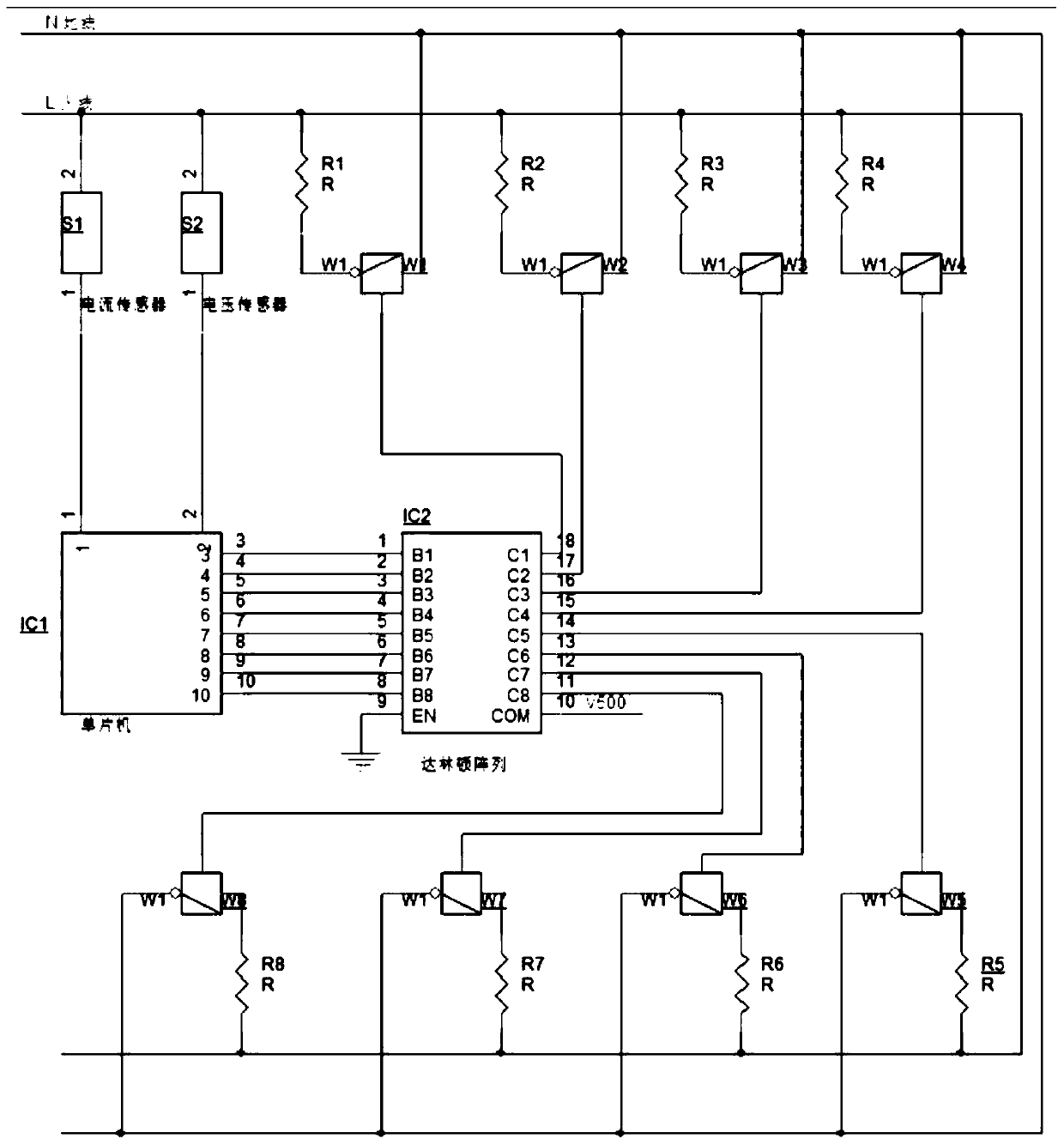
Method for tampering secret stealing information on power line and preventing interference
InactiveCN110808761ATamper to reachInterference reachesPower distribution line transmissionElectrical apparatus interference reductionCurrent sensorEngineering
The invention provides a method for tampering secret stealing information on a power line and preventing interference, and relates to the technical field of data theft prevention. The method for tampering secret stealing information on the power line and preventing interference comprises the following steps: 1) installing current and voltage sensors on a live wire and a zero wire, and then connecting the current and voltage sensors with an ADC of a single-chip microcomputer MCU; and 2) performing high-speed sampling on the power information by using a single-chip microcomputer, performing AD conversion on the information on the current sensor and the voltage sensor by the single-chip microcomputer, judging whether secret stealing information is transmitted on the power line or not throughcalculation, and if the secret stealing information is transmitted, calculating the Baud rate, the amplitude and the waveform starting time of the secret stealing information. After the amplitude of secret stealing information is analyzed through the single-chip microcomputer, proper loads are selected from the load array through calculation to form an interference load, the single-chip microcomputer drives the loads to be synchronously and randomly switched on and off at the frequency the same as that of the secret stealing information, and the purposes of interfering and tampering the secretstealing information are achieved under the condition that the network is not connected.
Owner:中科可来博(固安)航天电器制造有限公司
Method and system for reducing risk of data theft in data banks
ActiveCN106790056BImprove securityIncrease the difficultyDigital data protectionTransmissionPasswordEngineering
The invention discloses a method and a system for reducing a data stealing risk of a databank. The method comprises the following steps: S1, sending a first encrypted file obtained by packing a databank account and a login password and encrypting to a server by a client side, and after verifying that a login is successful, acquiring an identifier address information of user equipment by the client side; S2, sending a second encrypted file obtained by packing an identifier address and an access request and encrypting to the server by the client side; S3, decrypting and decompressing, by the server, the second encrypted file, detecting whether the identifier address information is bound with an identifier, executing a step S4 if no, and if yes, executing a step S5; S4, sending a security question to the user equipment, and if an answer input by the user equipment is correct, executing the step S5; and S5, giving a permission to the user equipment to access data. According to the method and the system disclosed by the invention, the security of the databank is improved, and the possibility that the data are stolen is reduced.
Owner:SUZHOU INST OF BIOMEDICAL ENG & TECH CHINESE ACADEMY OF SCI
Self-hiding data transmission port data theft prevention encryption device for computer
InactiveCN112671722AImprove data transfer efficiencyInternal/peripheral component protectionTransmissionHidden dataStructural engineering
The invention relates to the technical field of computer encryption, and discloses a self-hiding data transmission port data theft prevention encryption device for a computer, which comprises a mounting base, a reset spring is movably connected to the top of the mounting base, a connecting rod is movably connected to the top of the reset spring, and a push block is movably connected to the top of the connecting rod. The top of the push block is movably connected with an explosion-proof plate, the top of the explosion-proof plate is movably connected with a strong magnetic block, the left side of the strong magnetic block is movably connected with a transmission port, magnetism is generated by electrifying an electrified coil, and therefore an encryption spring is stretched to deform to drive an encryption magnet to move, and the encryption magnet moves to drive the transmission port to move. Meanwhile, the force compresses the reset spring to deform and then drive the explosion-proof plates to move, and the two explosion-proof plates move oppositely at the moment, so that the two strong magnetic blocks are separated, the connecting seat is completely exposed, and the effect of automatically hiding the data transmission port to prevent data from being stolen is achieved.
Owner:杭州墨磬智能技术有限公司
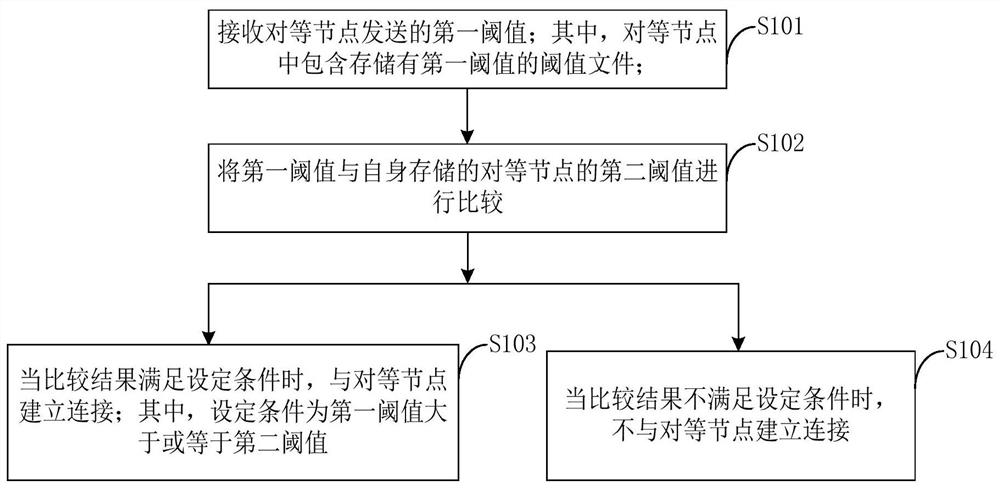
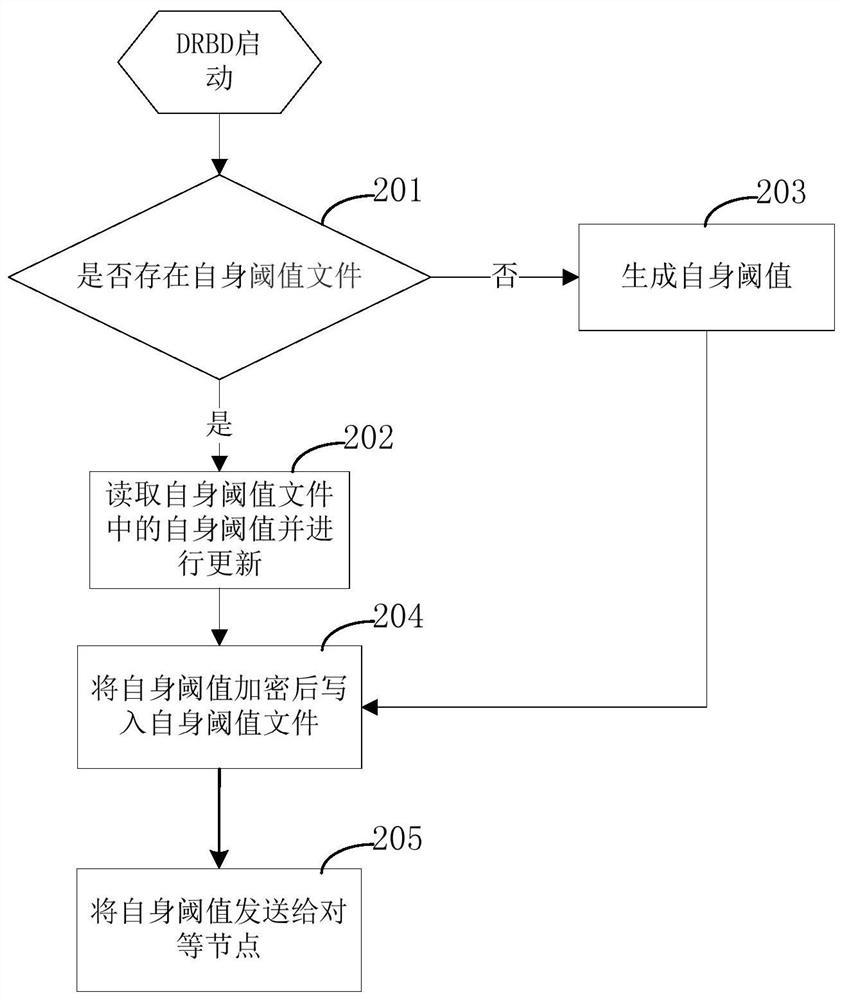
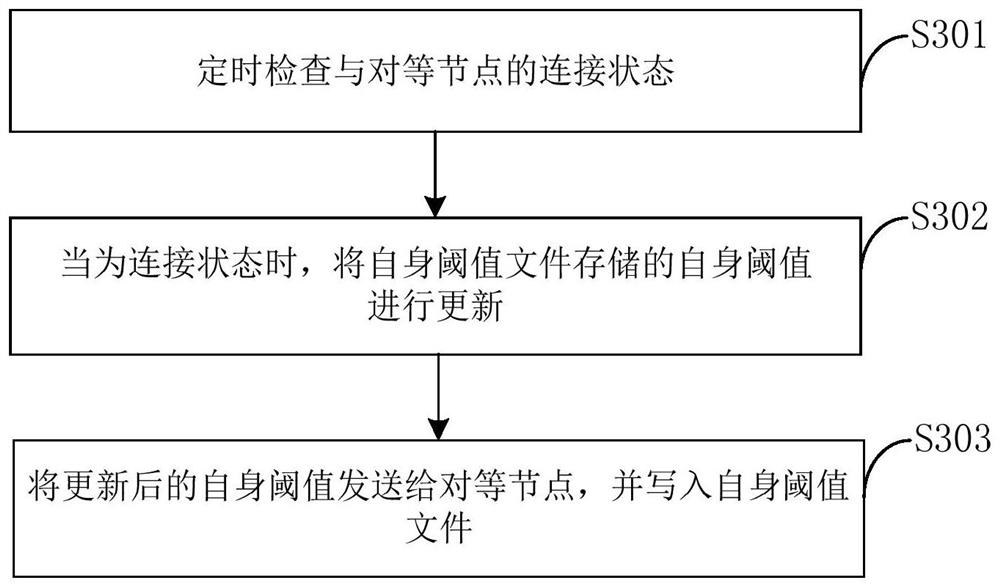
Method, system, server and computer-readable medium for preventing pseudo-node joining
The invention provides a method, system, server and computer-readable medium for preventing false nodes from joining, relates to the field of communication technology, and is applied to a distributed replication block device DRBD node, where the primary node and the secondary node of the DRBD node are peer nodes. , the method includes: receiving the first threshold sent by the peer node; wherein, the peer node contains a threshold file storing the first threshold; comparing the first threshold with the second threshold of the peer node stored by itself; when comparing When the result meets the set condition, a connection is established with the peer node; when the comparison result does not meet the set condition, the connection is not established with the peer node. The present invention can prevent false nodes from joining by setting a threshold, prevent the data of the master node from being stolen, and improve data security.
Owner:GUANGDONG ZHONGXING NEWSTART TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com