Power transmission and transformation equipment state monitoring system security protection method based on trust chain transmission
A state monitoring system and power transmission and transformation equipment technology, applied in the field of network information security, can solve problems such as complex network structure and high security risks, and achieve the effect of protecting data security, preventing malicious program attacks, and realizing data leakage prevention functions
Active Publication Date: 2012-02-15
STATE GRID ELECTRIC POWER RES INST
View PDF12 Cites 16 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
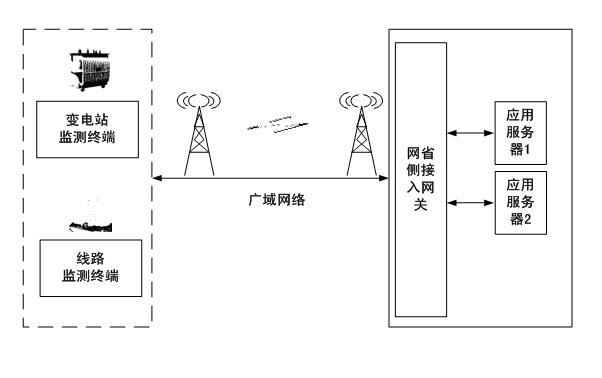
[0005] Since the monitoring terminal is connected to the power system intranet and spans wide-area networks such as wired
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
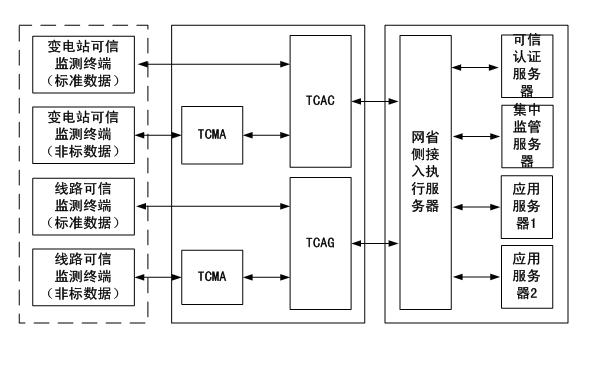
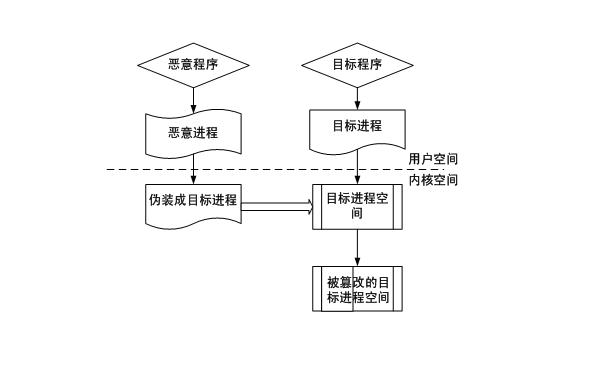
The invention relates to a power transmission and transformation equipment state monitoring system security protection method based on trust chain transmission, which carries out credible transformation to a power transmission and transformation equipment state monitoring system through identity authentication, platform authentication, integrity measurement, trust chain transmission and other methods. A credible authentication service, an access actuation server and a centralized regulation server are deployed in a main station, and a monitoring terminal, a state information access controller, a state information access gateway machine and a state monitoring proxy are transformed into a credible monitoring terminal, a credible state information access controller, a credible state information access gateway machine and a credible state monitoring proxy, so that the whole monitoring system is constructed into a credible system. The system can effectively prevent malicious program attack, malicious code injection attack, physical data theft, network tapping, sniffing attack and the like, and protect the security of the monitoring system and an internal power grid system; and the invention also provides a trust chain transmission model which is used for proving that under trust chain transmission, as long as each level of a trust chain is credible, the whole system is credible.
Description
technical field [0001] The invention is a security protection technology for the state monitoring system of power transmission and transformation equipment, which applies the trust chain transfer method to the state monitoring system of power transmission and transformation equipment, mainly solves the problem of network information security protection of the state monitoring system of power transmission and transformation equipment, and prevents various illegal attacks , belonging to the field of network information security. Background technique [0002] Power transmission and transformation equipment status monitoring system (referred to as "monitoring system") is a real-time perception, monitoring and early warning, analysis and diagnosis of various power transmission and transformation equipment operating status using various sensor technologies, wide-area communication technology and information processing technology Assess predictive monitoring systems. [0003] At p...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06
Inventor 曾荣张涛林为民陈亚东邵志鹏马卓
Owner STATE GRID ELECTRIC POWER RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com