Data safety protection method and device
A security protection device and security protection technology, applied in the field of data security protection methods and devices, can solve the problems of poor security of POS machines, easy to be attacked by hackers, stealing passwords, etc., to prevent data from being stolen and improve data security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
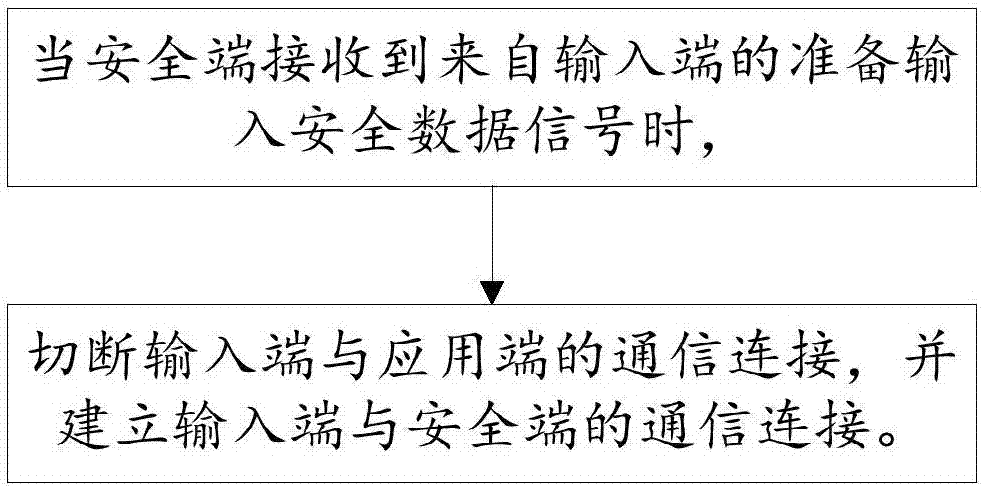
[0061] This embodiment provides a data security protection method, including:
[0062] S1. When the safety terminal 6 receives the ready-to-input safety data signal from the input terminal 4, cut off the communication connection between the input terminal 4 and the application terminal 5, and establish the communication connection between the input terminal 4 and the safety terminal 6; The data signal is a card swiping signal;
[0063] Among them, the method of cutting off the communication connection between the input terminal 4 and the application terminal 5, and establishing the communication connection between the input terminal 4 and the safety terminal 6 includes the following implementation methods:
[0064] The first implementation mode: obtain the level control signal from the safety terminal 6; control the analog switch to cut off the communication connection between the input terminal 4 and the application terminal 5 according to the level control signal, and establ...
Embodiment 2
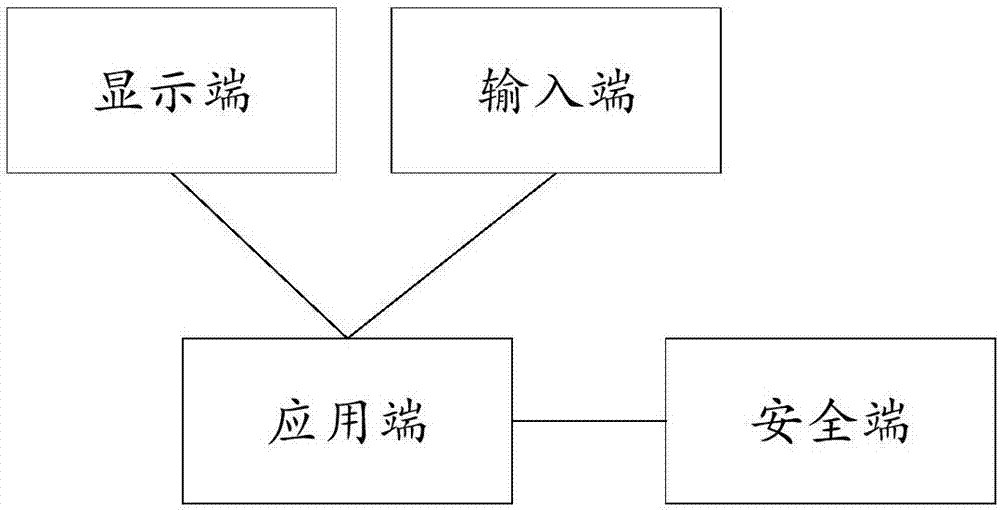
[0069] like Figure 4 As shown, this embodiment provides a data security protection device, including a switching module 1 and a building module 2, a display terminal 3, an input terminal 4, an application terminal 5 and a security terminal 6;
[0070] The switching module 1 is configured to cut off the communication connection between the input terminal 4 and the application terminal 5 and establish the communication connection between the input terminal 4 and the security terminal 6 when the safety terminal 6 receives a signal ready to input safety data from the input terminal 4 ;
[0071] The establishment module 2 is used to establish a communication connection between the input terminal 4 and the application terminal 5 when the security terminal 6 receives the data input completion signal from the input terminal 4;
[0072] The display terminal 3 is used for displaying the processing result of the application terminal or displaying a user interface.
Embodiment 3
[0074] This embodiment provides a data security protection device, including a switching module 1, a display terminal 3, an input terminal 4, an application terminal 5, and a security terminal 6; the display terminal 3 is used to display processing results of the application terminal or display a user interface.
[0075] Among them, the input terminal 4 includes input devices such as touch screen and keyboard; the security terminal 6 includes a security CPU that conforms to UPTS or PCI specifications, such as Freescale’s K21 / K81, MAXIM’s MAX32555, Broadcom’s BCM58101, and Zhaoxun’s MH1902; the application terminal 5 includes General-purpose CPUs that can run Android or Linux, such as Qualcomm processor MSM8909, MTK processor X30, Huawei's Kirin processor;
[0076] Wherein, the switching module 1 has the following implementation methods:
[0077] like Figure 5 As shown, the first implementation is that the switching module 1 includes a first acquisition unit 11 and a first co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com