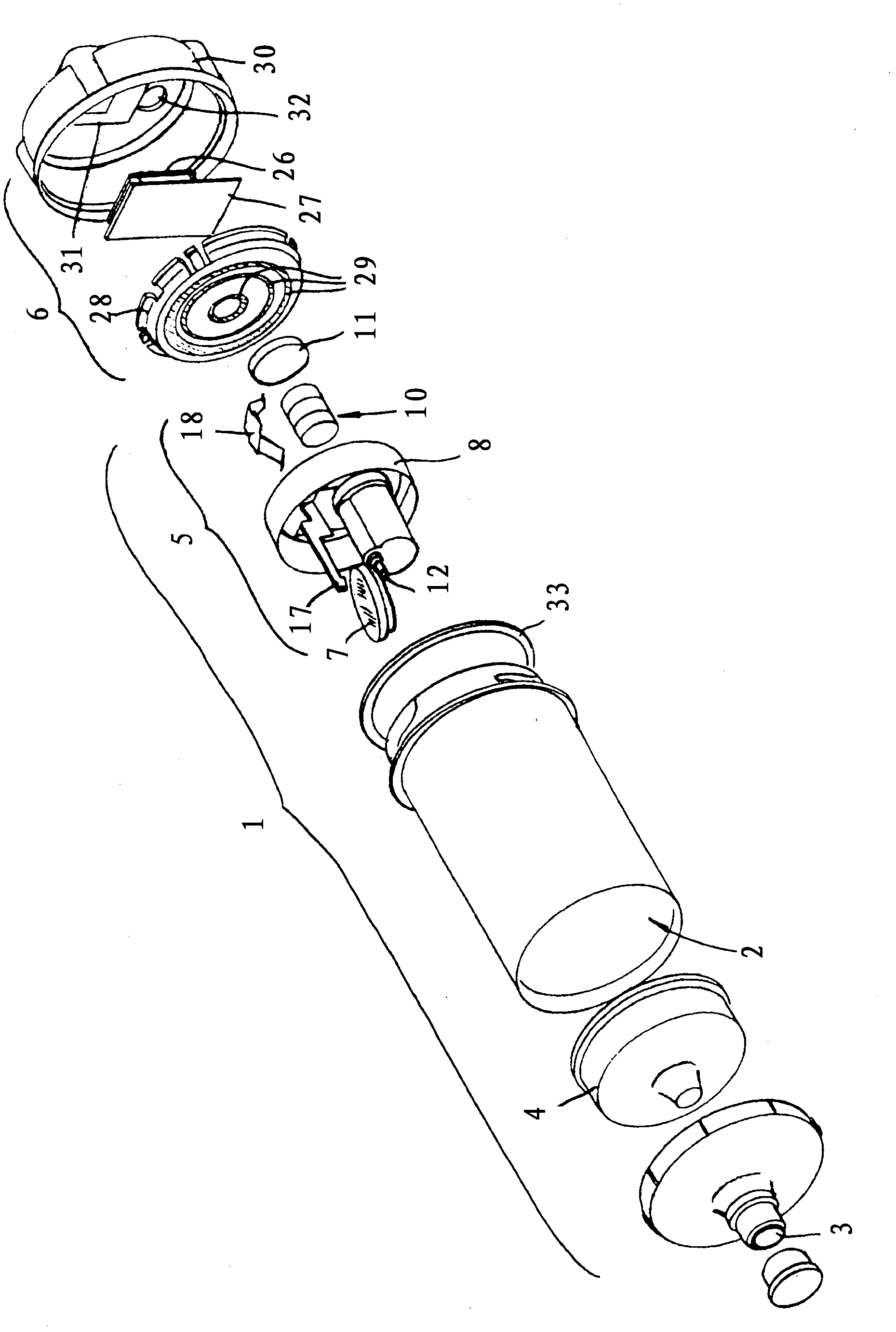
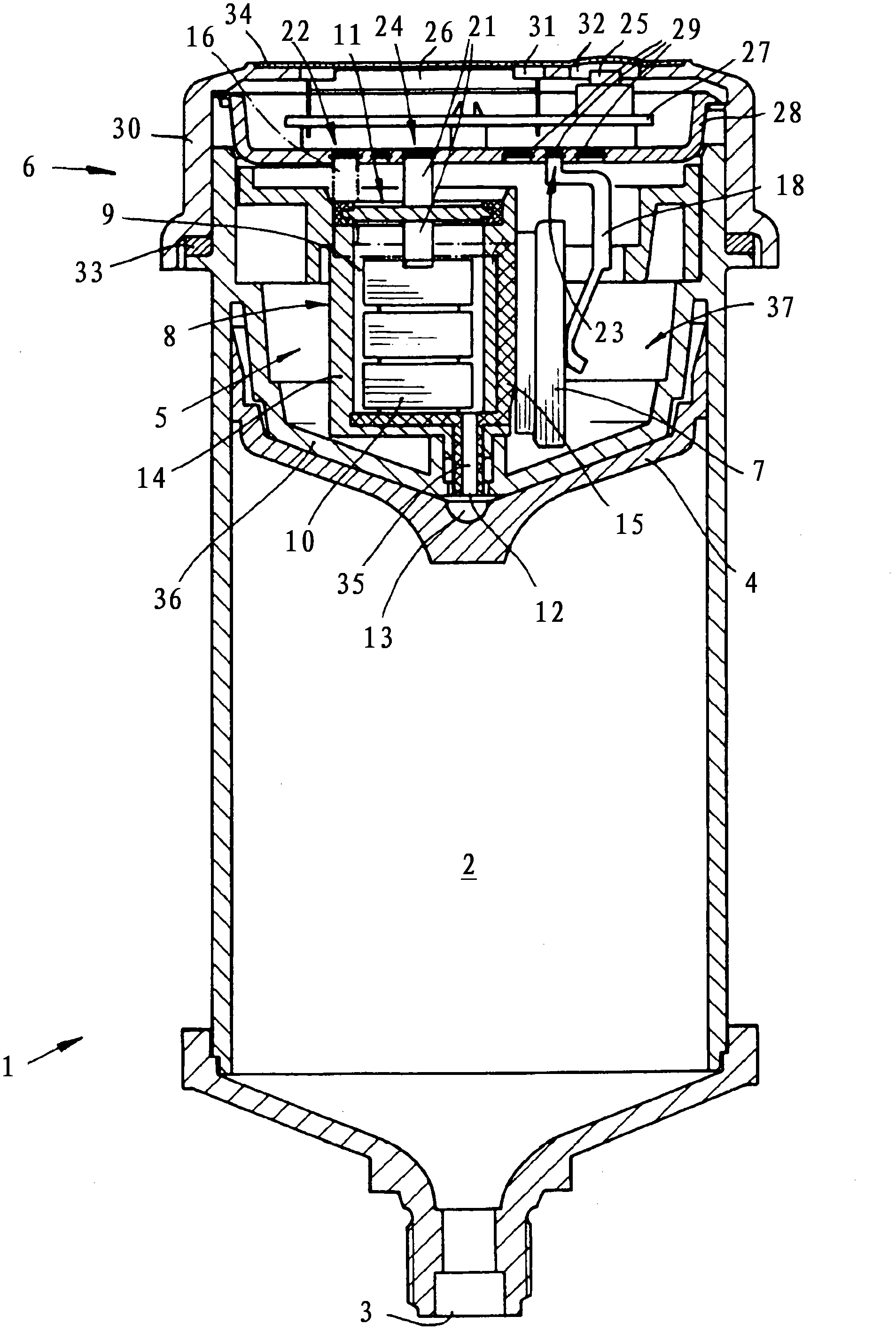
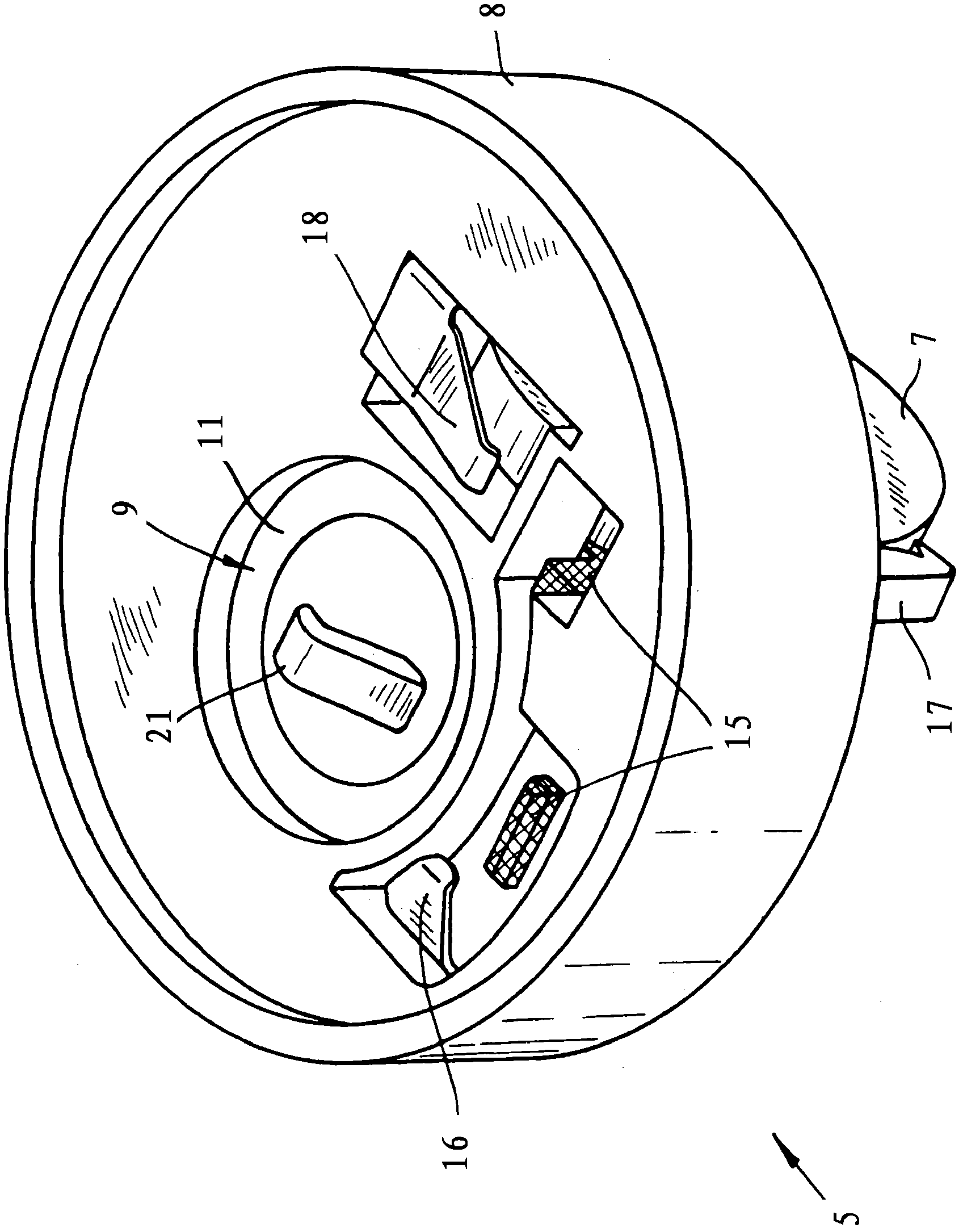
Patents
Literature
403results about How to "Reduce the risk of theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
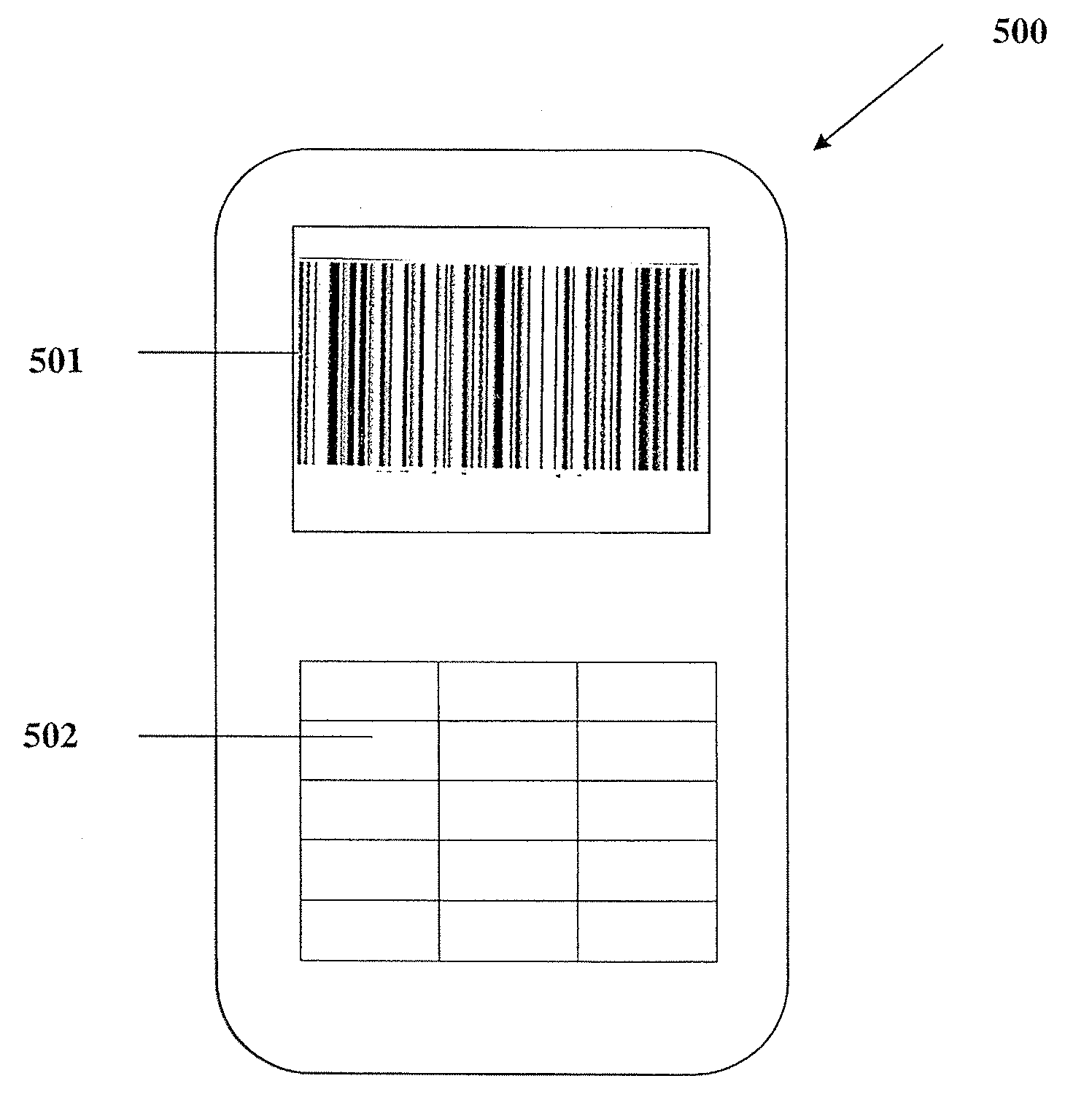
System and method for completing a secure financial transaction using a wireless communications device
InactiveUS7909243B2Low costReduce the risk of theftComplete banking machinesFinanceInternet privacyBarcode
A system and method for completing a financial transaction using a wireless communication device is provided. A transaction authorization request is sent from the device to an issuer using SMS. An authentication message is sent from the issuer to the device, and a response is sent by a user of the device to confirm the identity of the user. Once the identity of the user is verified, a surrogate account number, in a bar code format, is sent to the mobile communication device to be read by a POS device to complete the financial transaction. A computer program product enabling the systems and methods described is also provided.
Owner:LIBERTY PEAK VENTURES LLC
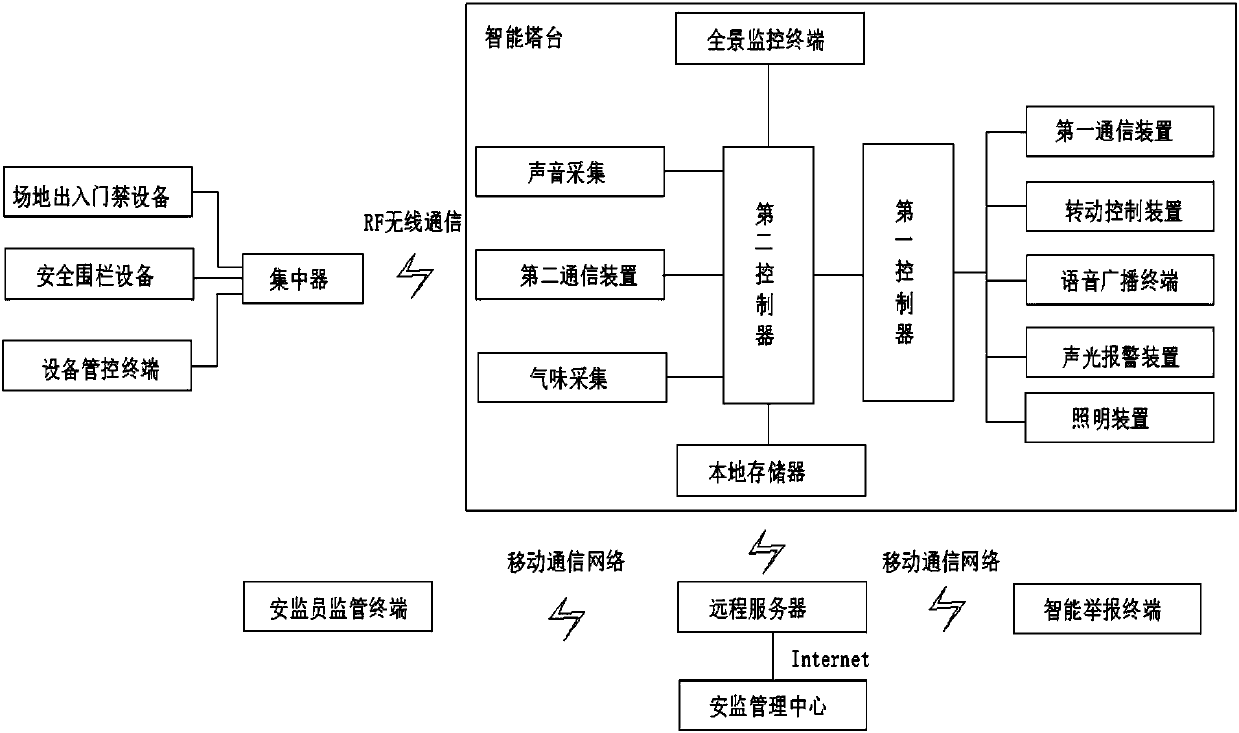
Construction site intelligent safety supervision system and control method thereof
ActiveCN107730428ARealize security monitoringAvoid undocumented jobsData processing applicationsAlarmsInternet networkComputer terminal
The invention provides a construction site intelligent safety supervision system and a control method thereof. The system comprises a site access control device, a safety fence device, a device control terminal, a smart tower and a remote server, wherein the intelligent tower is used for realizing construction site panoramic view monitoring, construction on-site sound collection, odor collection,on-site lighting and voice broadcast and realizing sound-light alarm under abnormal circumstances, and the remote server is in communication connection with the intelligent tower, the safety supervision terminal and an intelligent reporting terminal through a mobile communication network and transmits corresponding data to a safety supervision management center through an Internet network. With the construction site intelligent safety supervision system and the control method thereof of the invention, the image information and environmental information of a construction site can be acquired inreal time; the unified control of construction workers and construction equipment can be realized; auxiliary lighting can be realized; alarm prompts can be given out when an abnormal condition occurs, and the abnormal condition is reported to the a safety monitoring management department; and actual all-round and no-dead-corner safety supervision can be realized.
Owner:浙江龙腾畅想软件有限公司
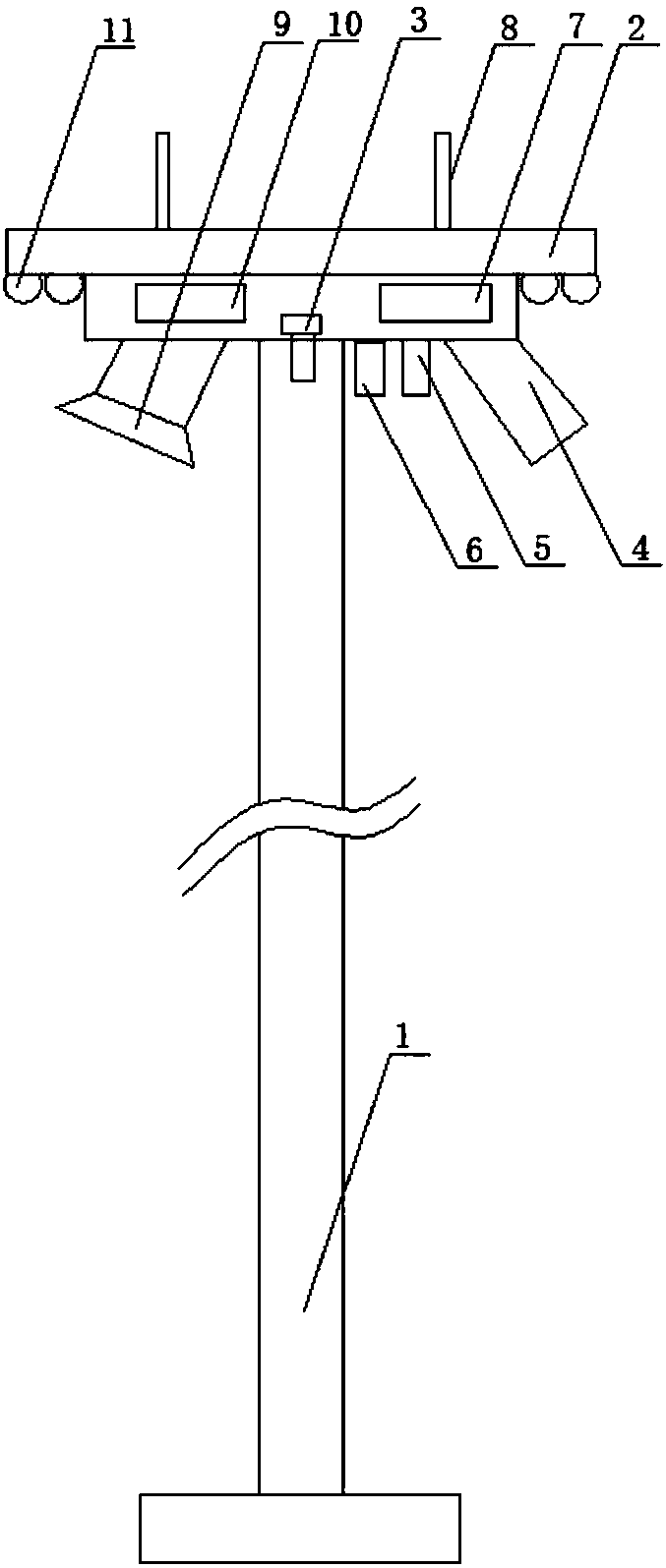
Access control system and control method thereof
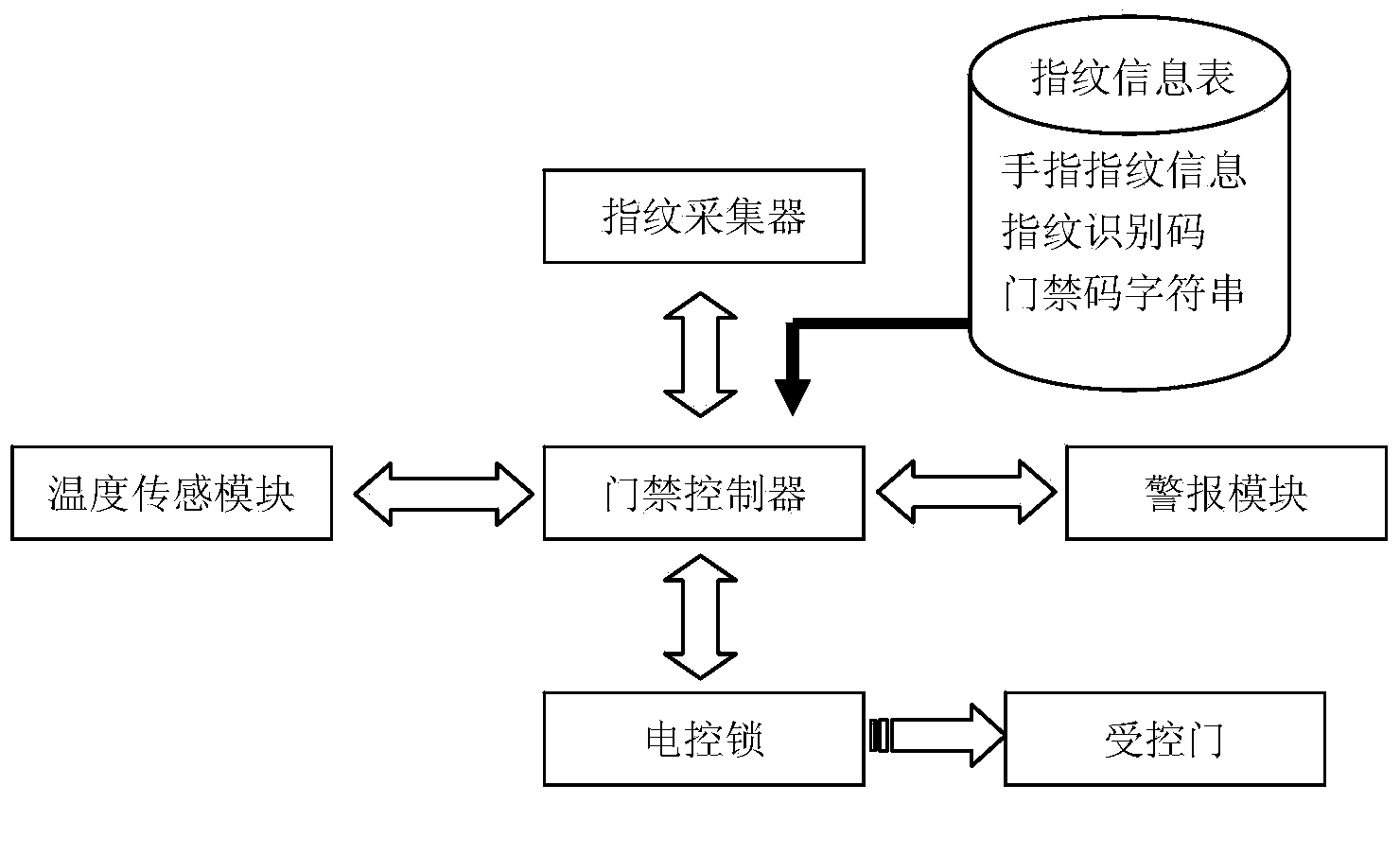
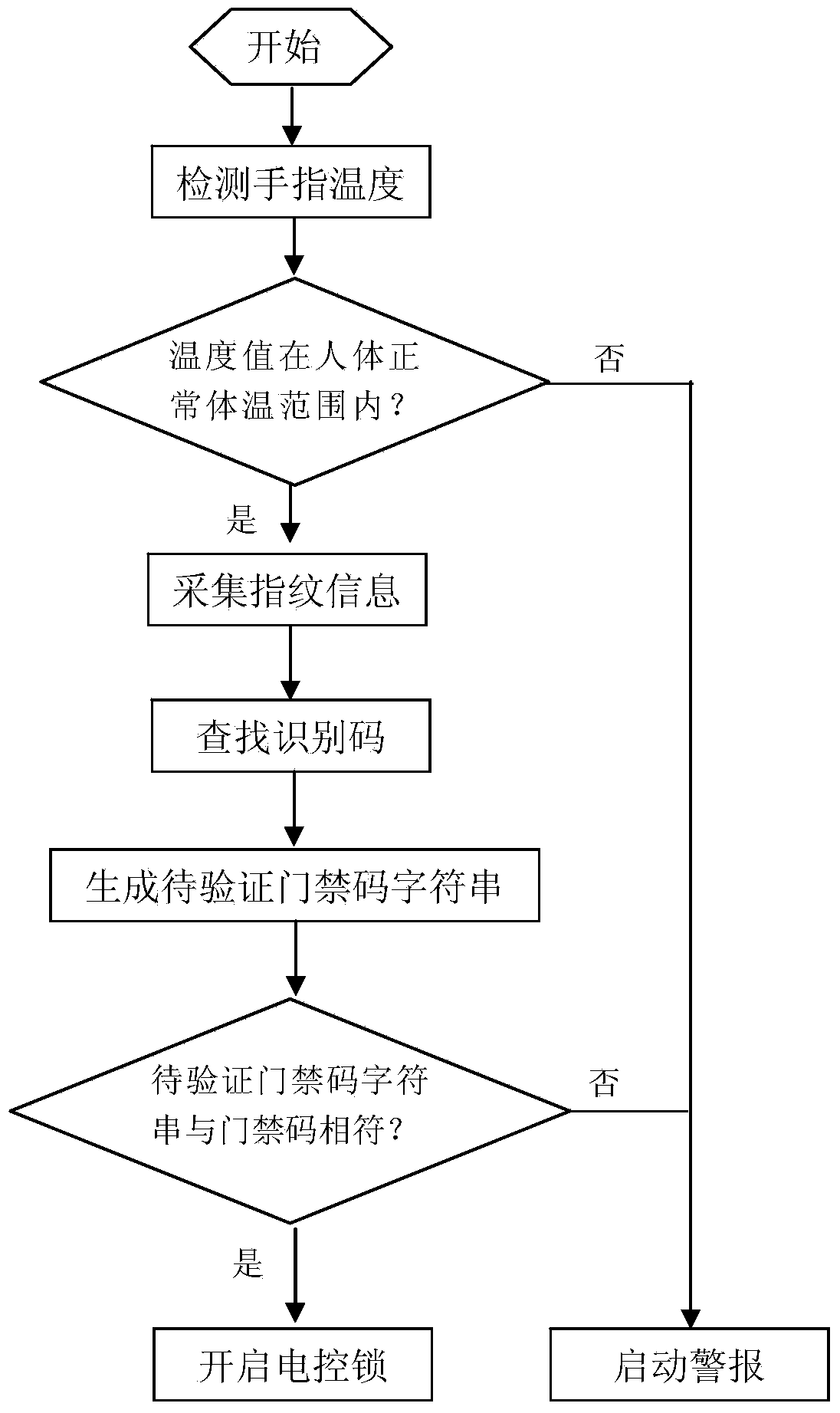
InactiveCN103400436AReduce the risk of theftPrevent the risk of masquerading authenticationIndividual entry/exit registersElectric controlEmbedded system
The invention discloses an access control system and a control method thereof. The access control system is characterized by comprising an access control controller, a fingerprint collector and an electric control lock. The access control controller is connected to the fingerprint collector and the electric control lock, and is used for controlling the electric control lock to open and close according to the fingerprint information collected by the fingerprint collector. The access control controller stores the fingerprint information table, which contains fingerprint information of different fingers of legal users, identification codes corresponding to the fingerprint information of each finger, and access control codes of each legal user. The fingerprint collector is used for collecting fingerprint information of users and transmitting the information to the access control controller. The electric lock is used for controlling the door to open and close according to the instructions sent by the access control controller. The access control system integrates the advantages of code input and fingerprint input together and largely improves the safety of the access control system.
Owner:慈溪市科创电子科技有限公司
Information transmission method, client, server and computer readable storage medium
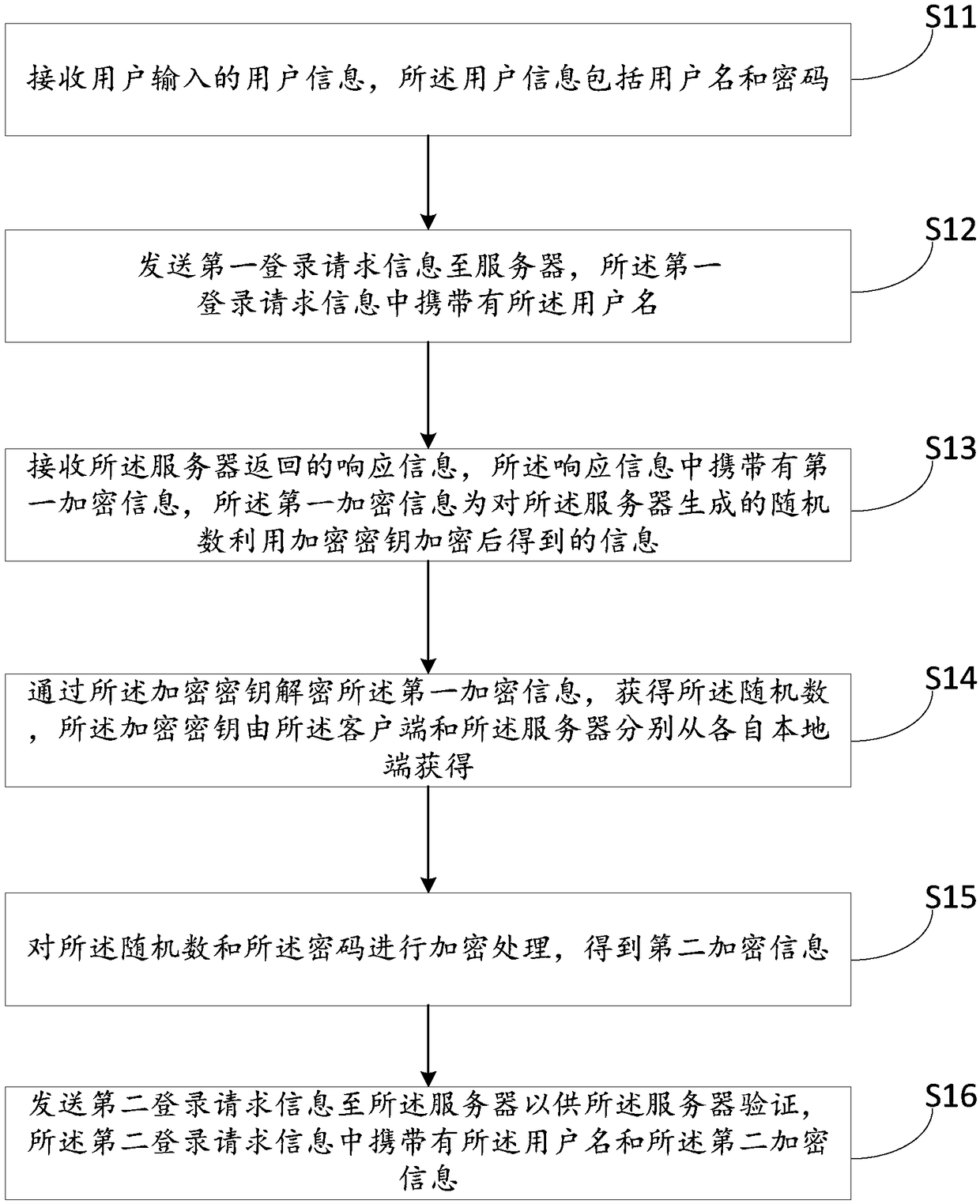
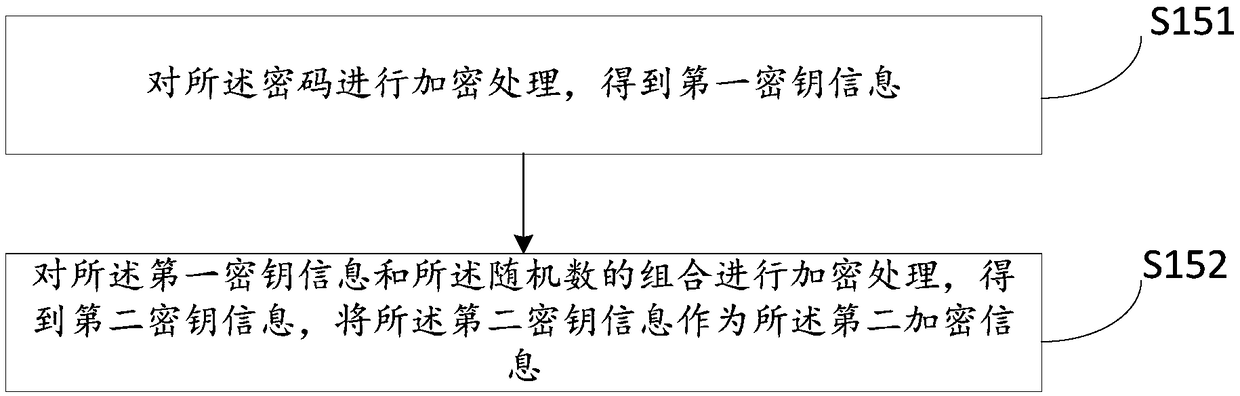
ActiveCN109347835AEnsure safetyPrevent theftKey distribution for secure communicationInformation transmissionPassword
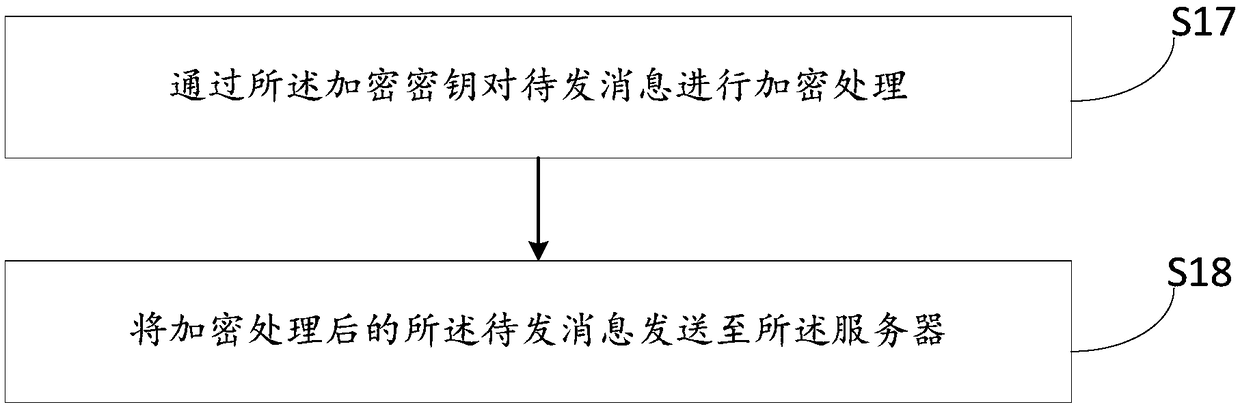
The invention relates to the technical field of communications, and discloses an information transmission method, a client, a server and a computer readable storage medium. The method comprises the following steps: receiving user information input by a user; sending first login request information to the server; receiving response information returned by the server, the response information carrying first encrypted information, and the first encrypted information being information acquired by encrypting a random number generated by the server by an encryption key; decrypting the first encrypted information through the encryption key to acquire the random number, the encryption key being acquired by the client and the server respectively from own local sides; encrypting the random number and a password to acquire second encrypted information; and sending second login request information to the server, the second login request information carrying a user name and the second encrypted information. Verification information for each login is different, so that a replay attack can be prevented; and furthermore, the encryption key is not required to be subjected to network switching between the client and the server, so that the security of the encryption key is guaranteed.
Owner:SUZHOU KEDA TECH
Login verification method and terminal device
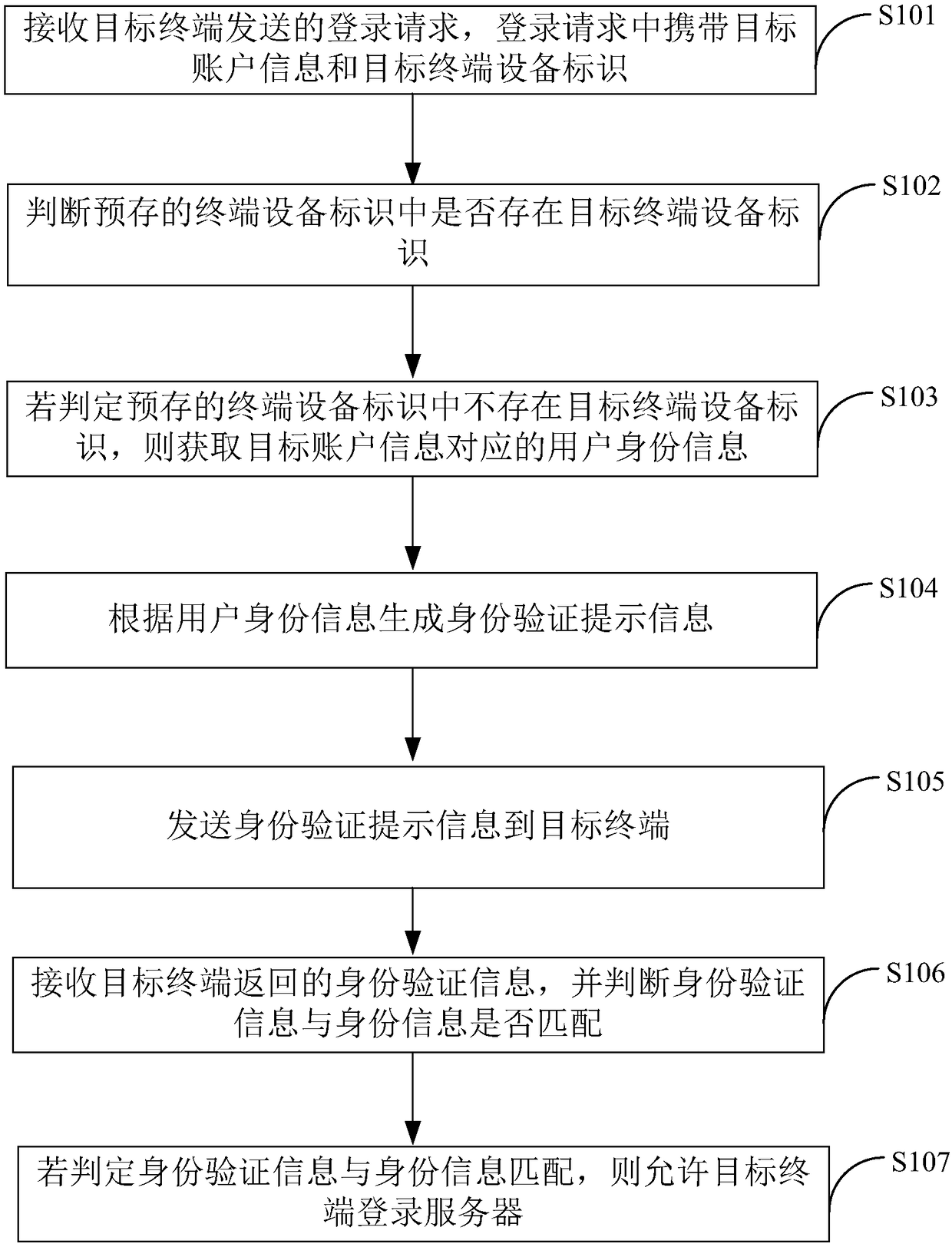
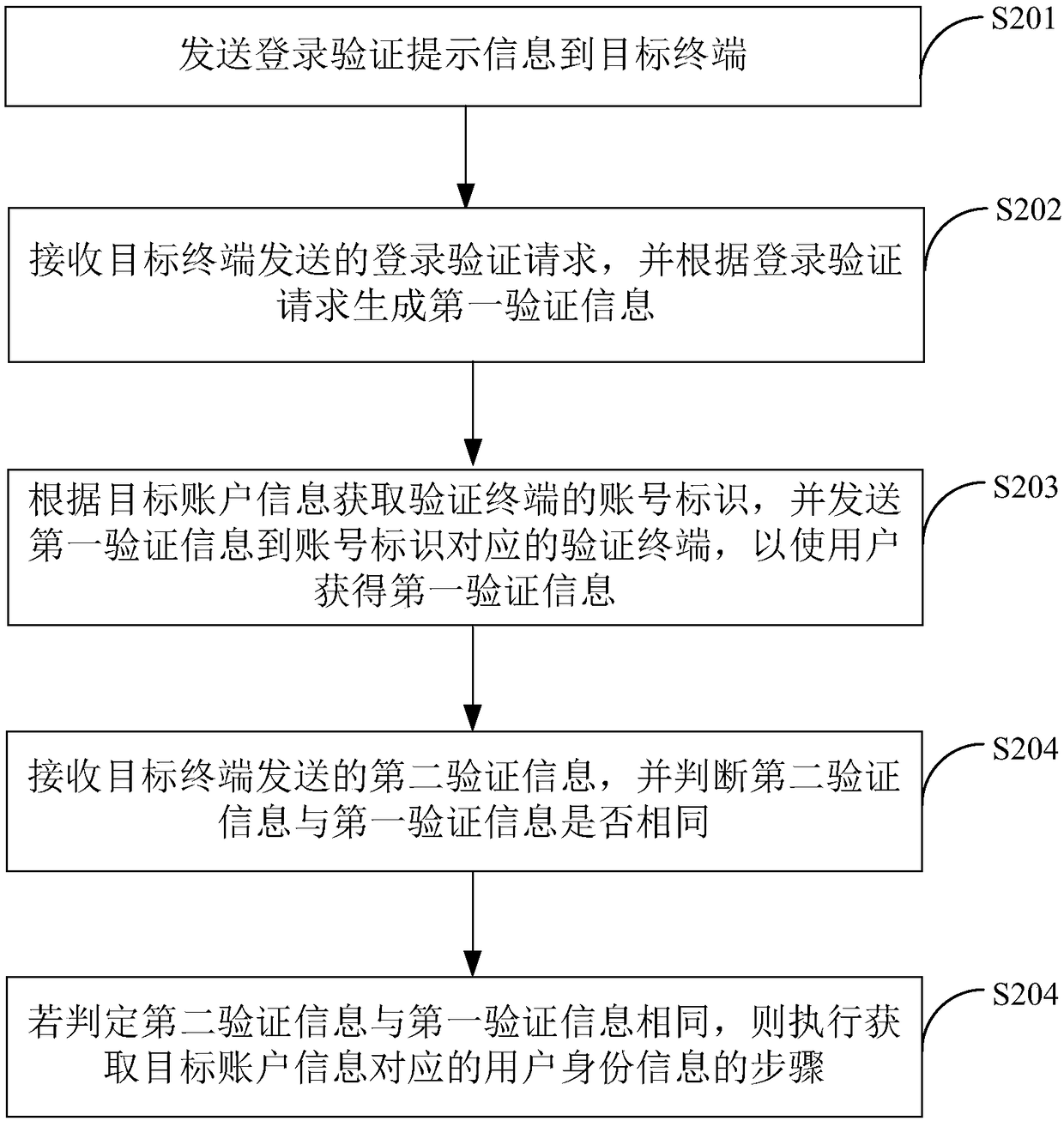
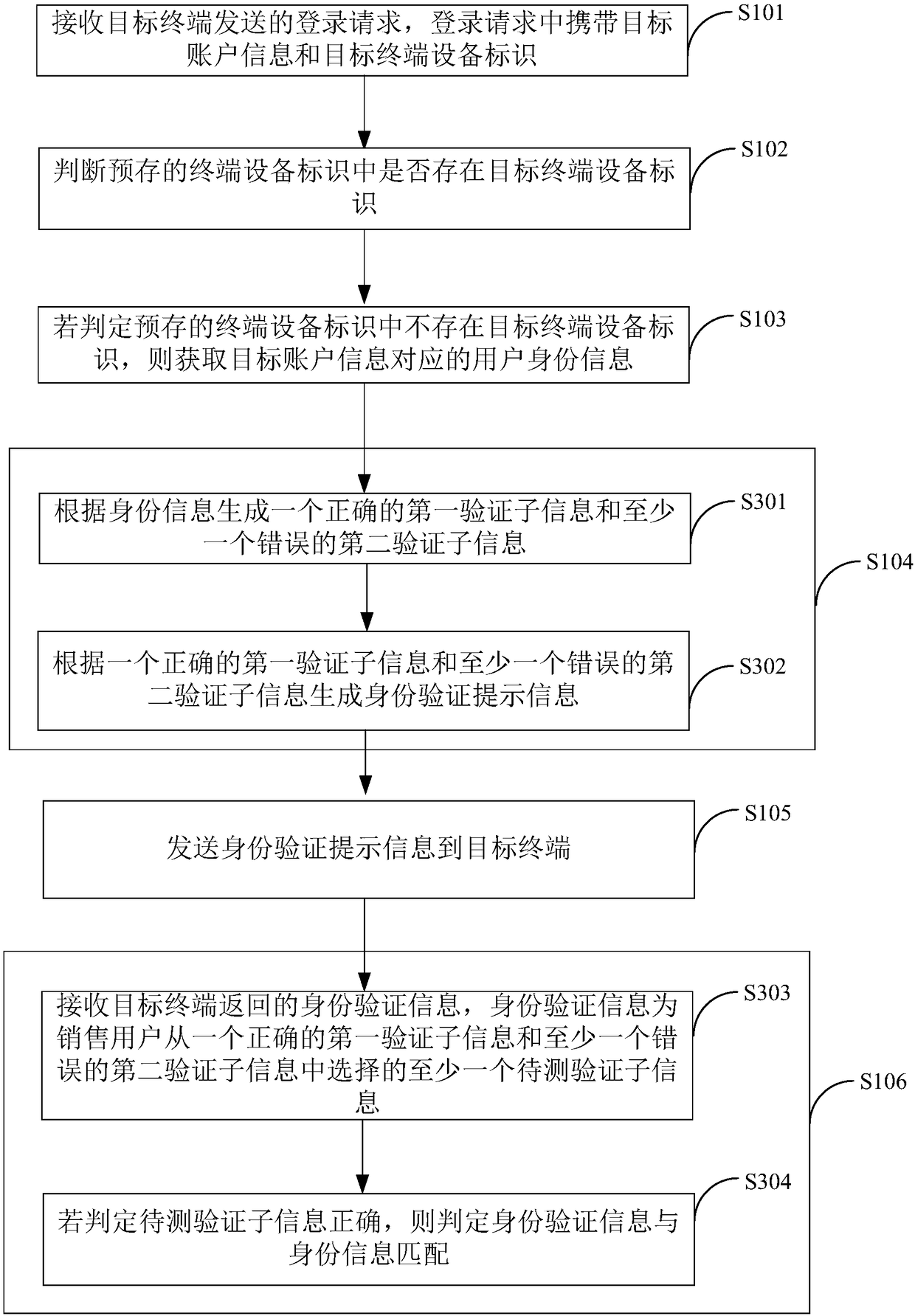
InactiveCN108183924AEnsure safetyReduce the risk of theftTransmissionValidation methodsTerminal equipment
The invention belongs to the technical field of communications, and provides a login verification method and a terminal device. The method comprises the following steps: receiving a login request sentby a target terminal, wherein the login request carries target account information and a target terminal device identifier; judging whether the target terminal device identifier exists in a pre-stored terminal device identifier; if it is judged that the target terminal device identifier does not exist in the pre-stored terminal device identifier, obtaining user identity information correspondingto the target account information; generating identity authentication prompt information according to the user identity information; sending the identity authentication prompt information to the target terminal; receiving identity authentication information returned by the target terminal, and judging whether the identity authentication information is matched with the identity information; and ifit is judged that the identity authentication information is matched with the identity information, allowing the target terminal to log in a server. As the login verification needs to be performed onthe login device for multiple times, the security of the login account is ensured, and the steal risk of the login account is reduced.
Owner:SHENZHEN MAIMAITI INFORMATION TECH CO LTD
Information storage system
ActiveUS20050188005A1Reduce the risk of theftReduce credit riskUser identity/authority verificationUnauthorized memory use protectionCredit cardClient-side
A system for storing information having a predetermined use which requires the information to be secured. The information may comprise credit card details used to complete a transaction. The system includes: (a) A client system for storing an encoded version of the information and an identifier. The encoded version is generated from first data of the information and an encoded version of the second data of the information. The information can be generated from the first data and the second data, and the predetermined use is infeasible with only one of the first data and the second data, (b) A remote server for storing the second data and an encoded identifier generated from the identifier. The client system sends at least the encoded version of the second data to the remote server. The client system or the remote server is able to generate the information from the first data and the second data. Accordingly, only part of the information to be secured is stored locally on the client system, whilst the other part is stored on the remote server, and neither the client system nor the remote server have a record of the entire information.
Owner:ENDRESZ ALLAN
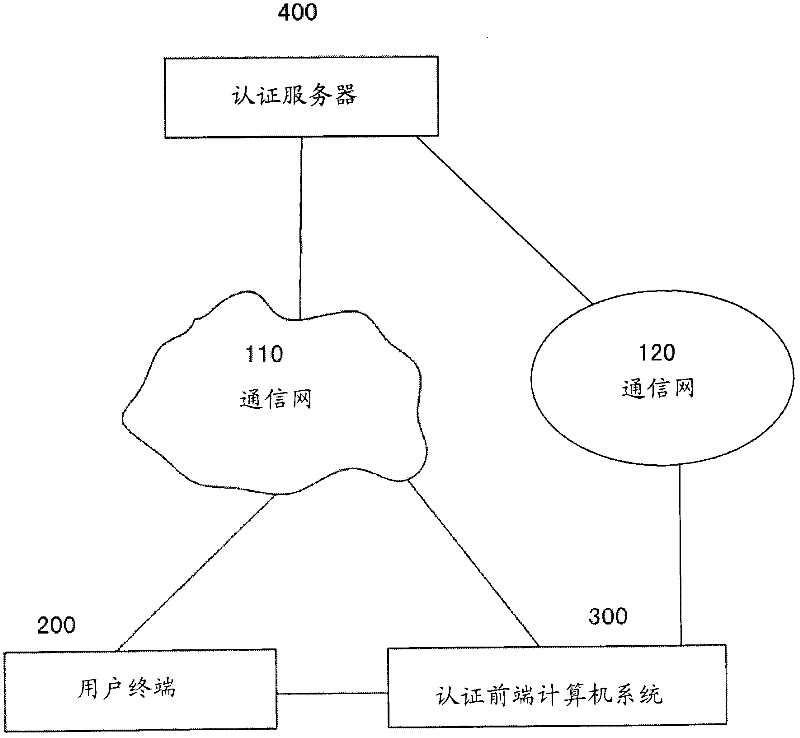
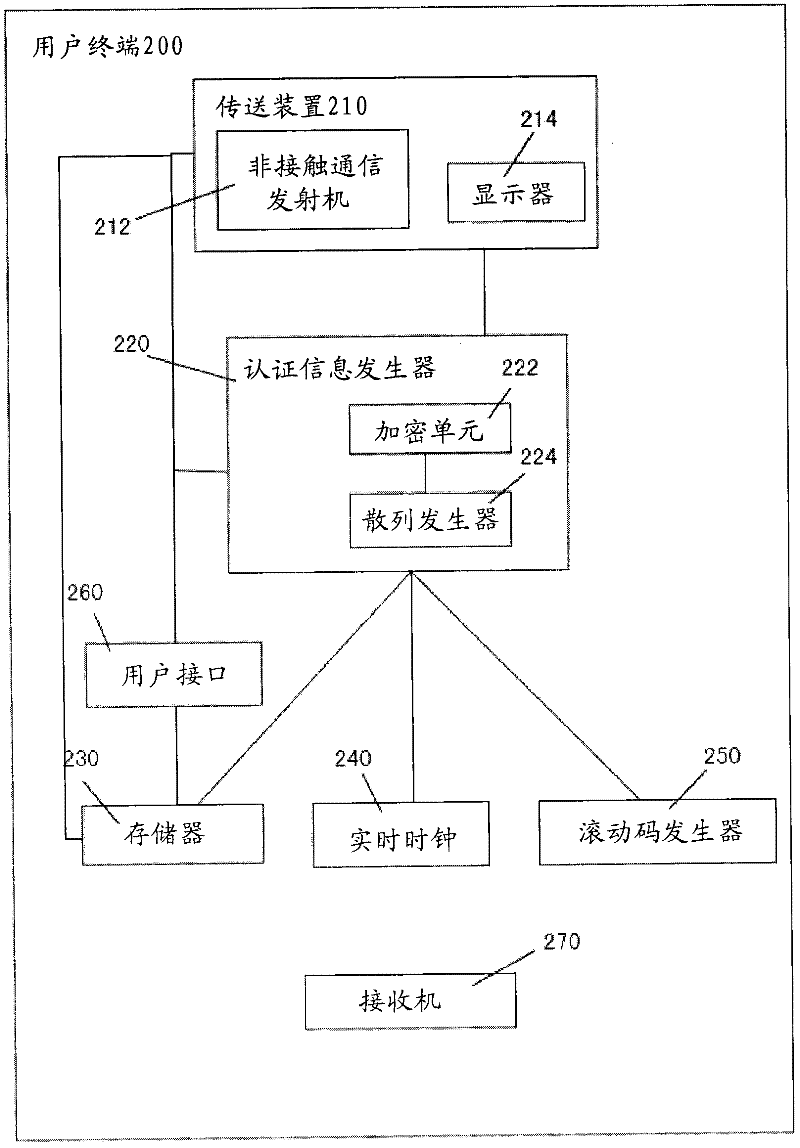
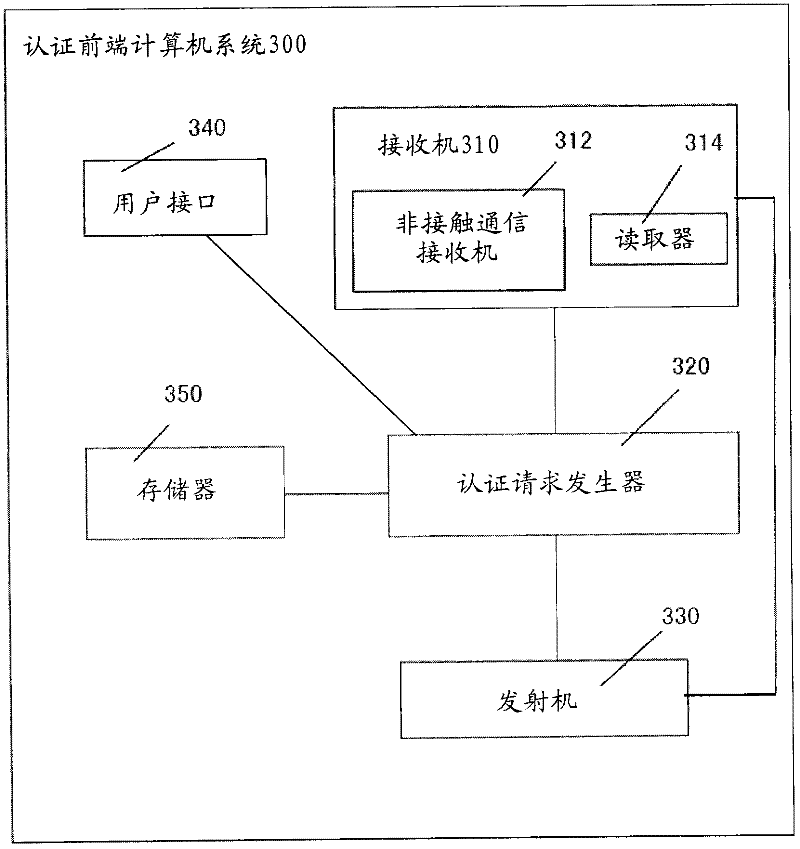
Method, system and device for identifying user's identity
InactiveCN102497354AEnsure safetyEasy to installUser identity/authority verificationEngineeringData mining
The invention relates to a method and a system for identifying a user's identity, as well as a user terminal, an identification front end computer system and an identification server. According to the invention, the user terminal transmits identification indication containing identification information to the identification front end computer system; the identification front end computer system sends an identification request containing the identification information to a specific identification server; after receiving the identification request, the identification server identifies a user's identity according to the identification information; and preferably, the identification server sends an identification result to the identification front end computer system. When the user pays a certain amount of money to an operator, and after successful identification, the identification server pays a certain amount of money to a specific operator's account from a specific user's payment account.
Owner:陈嘉贤
Multi-protocol communication method, smart home gateway and multi-protocol communication system
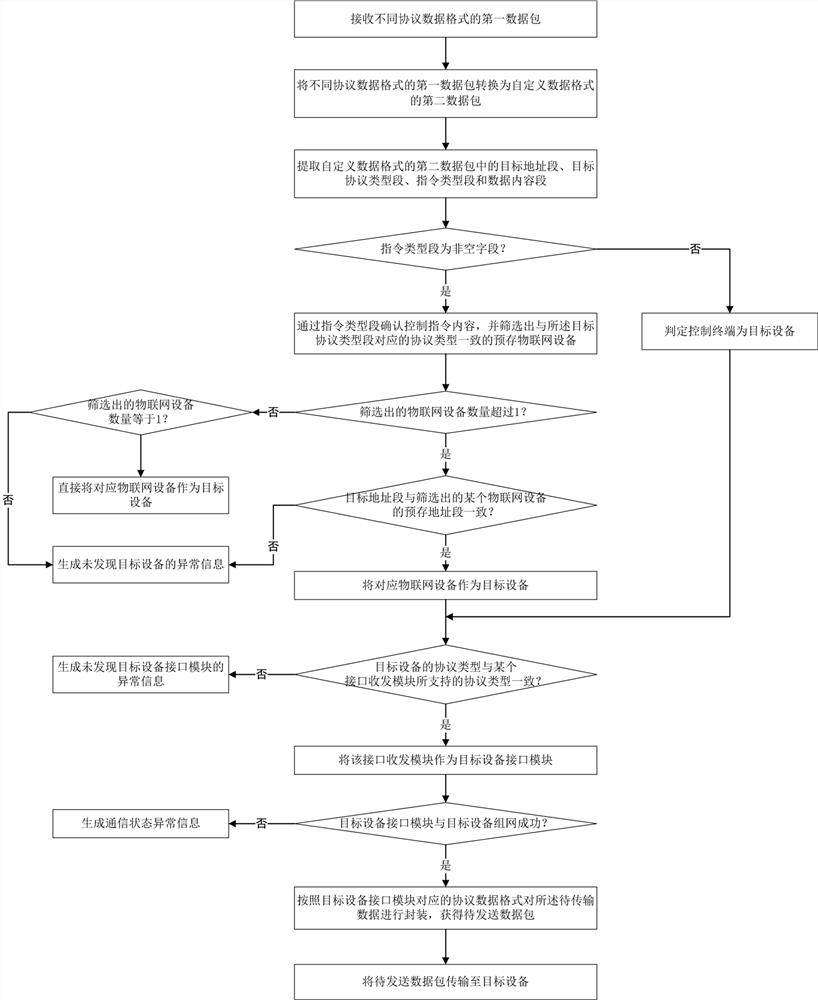
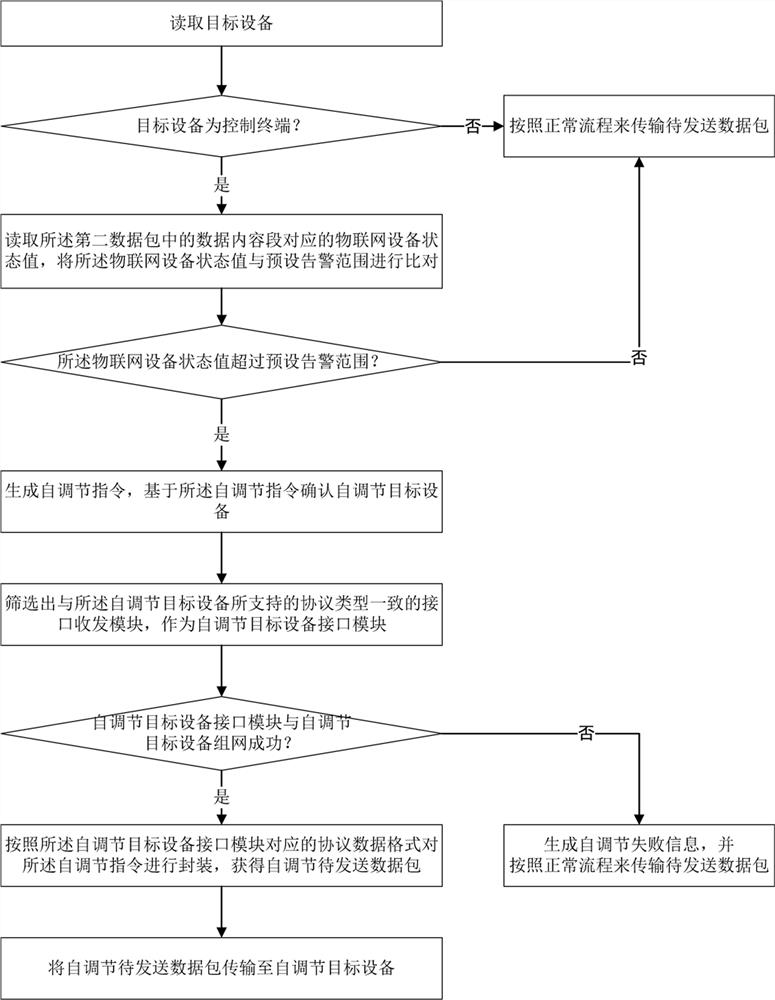
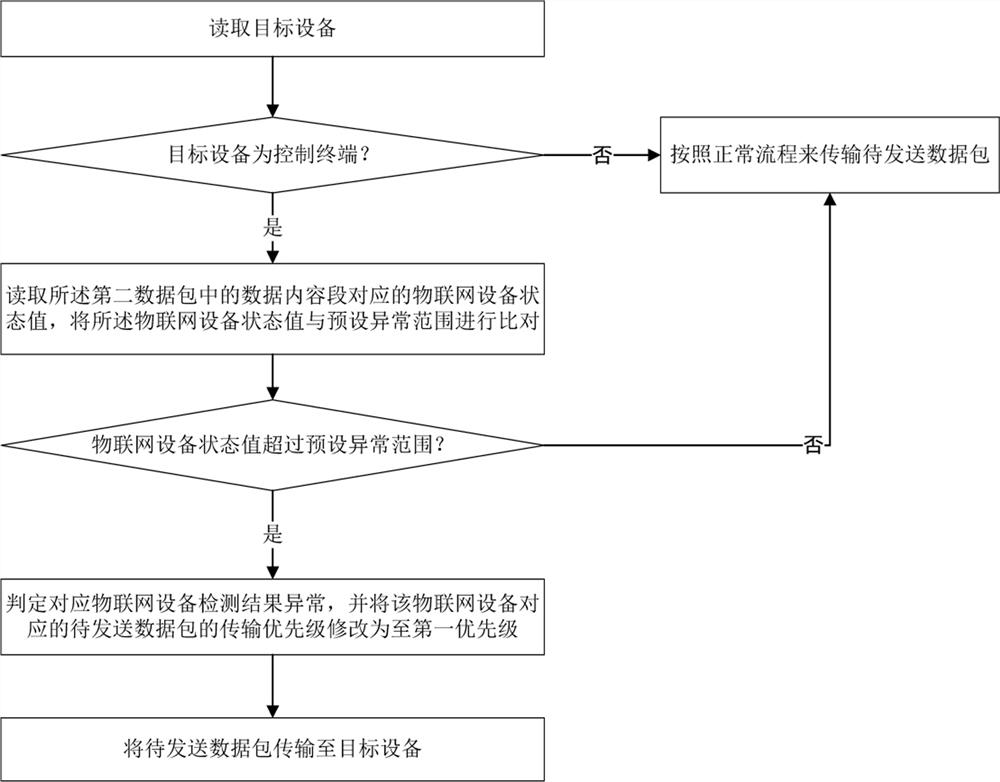
ActiveCN112087441AHighlight substantiveSignificant progressDigital data authenticationNetwork connectionsData packCommunications system
The invention provides a multi-protocol communication method, a smart home gateway and a multi-protocol communication system. The method comprises the the steps of receiving first data packets of different protocol data formats; converting the first data packets of different protocol data formats into second data packets of a self-defined data format; extracting a target address segment, a targetprotocol type segment, an instruction type segment and a data content segment in the second data packet with the self-defined data format; and if the extracted instruction type segment is a non-emptyfield, determining the content of the control instruction through the instruction type segment, screening out pre-stored Internet of Things devices and the like consistent with the protocol type corresponding to the target protocol type segment, and if the number of the screened Internet of Things devices is equal to 1, directly taking the corresponding Internet of Things device as a target deviceand the like. According to the invention, while the compatibility and universality of the gateway are improved, the design and development difficulty of a gateway application layer is reduced, the multi-protocol communication efficiency is improved, and the operation cost of the multi-protocol gateway is reduced.
Owner:郑州信大先进技术研究院
Identity authentication method, terminal device, authentication server, and electronic device
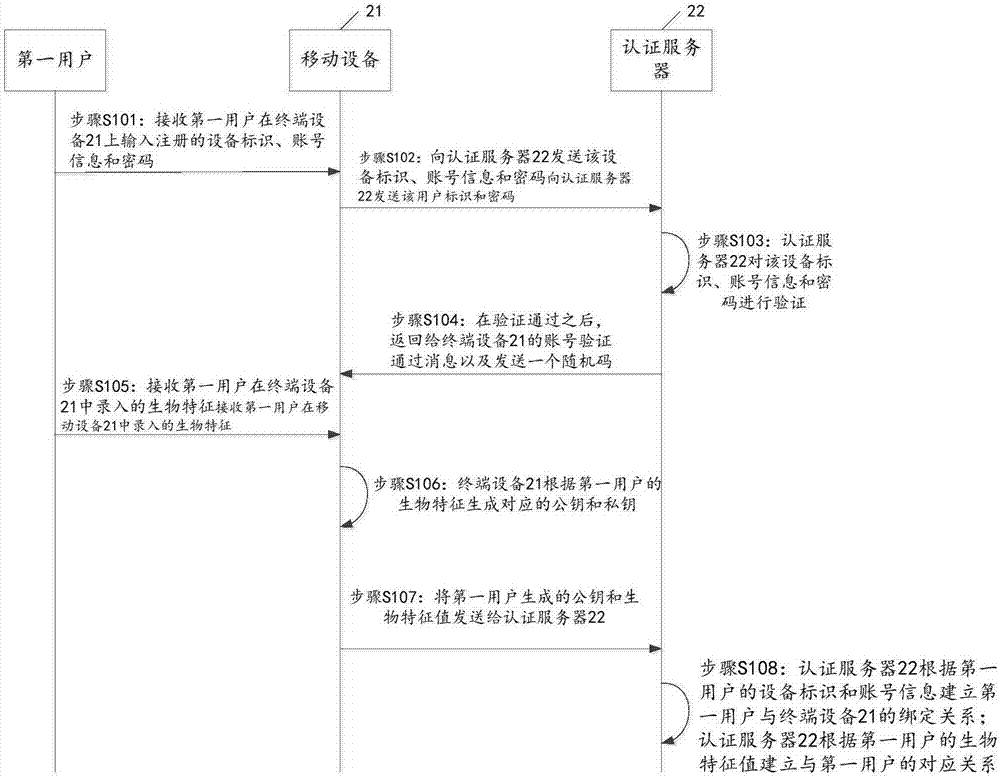
ActiveCN107079034AEasy to operateEnsure safetyKey distribution for secure communicationDigital data authenticationTerminal equipmentComputer terminal
The invention discloses an identity authentication method, a terminal device, an authentication server, and an electronic device. The method comprises the following steps: receiving biological features of a first user, and obtaining account number information of the first user and a device identity of the terminal device; sending an identity authentication request to the authentication server; receiving identity confirmation information returned by the authentication server; receiving input biological features of a second user; sending a verification request to the authentication server; and receiving a log-in code returned by the authentication server, and making the second user log in through the log-in code. In the above way, the terminal device, where the first user succeeds in authentication, serves as a device for the second user to carry out authentication and log-in, and identities of the first user and the second user are authenticated on the same device, so the second user can succeed in logging in only when the first user provides guarantee, thereby ensuring that the second user utilizes a secure device to log in and guaranteeing security and reliability.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
Data transmitting method and device, and data receiving method and device
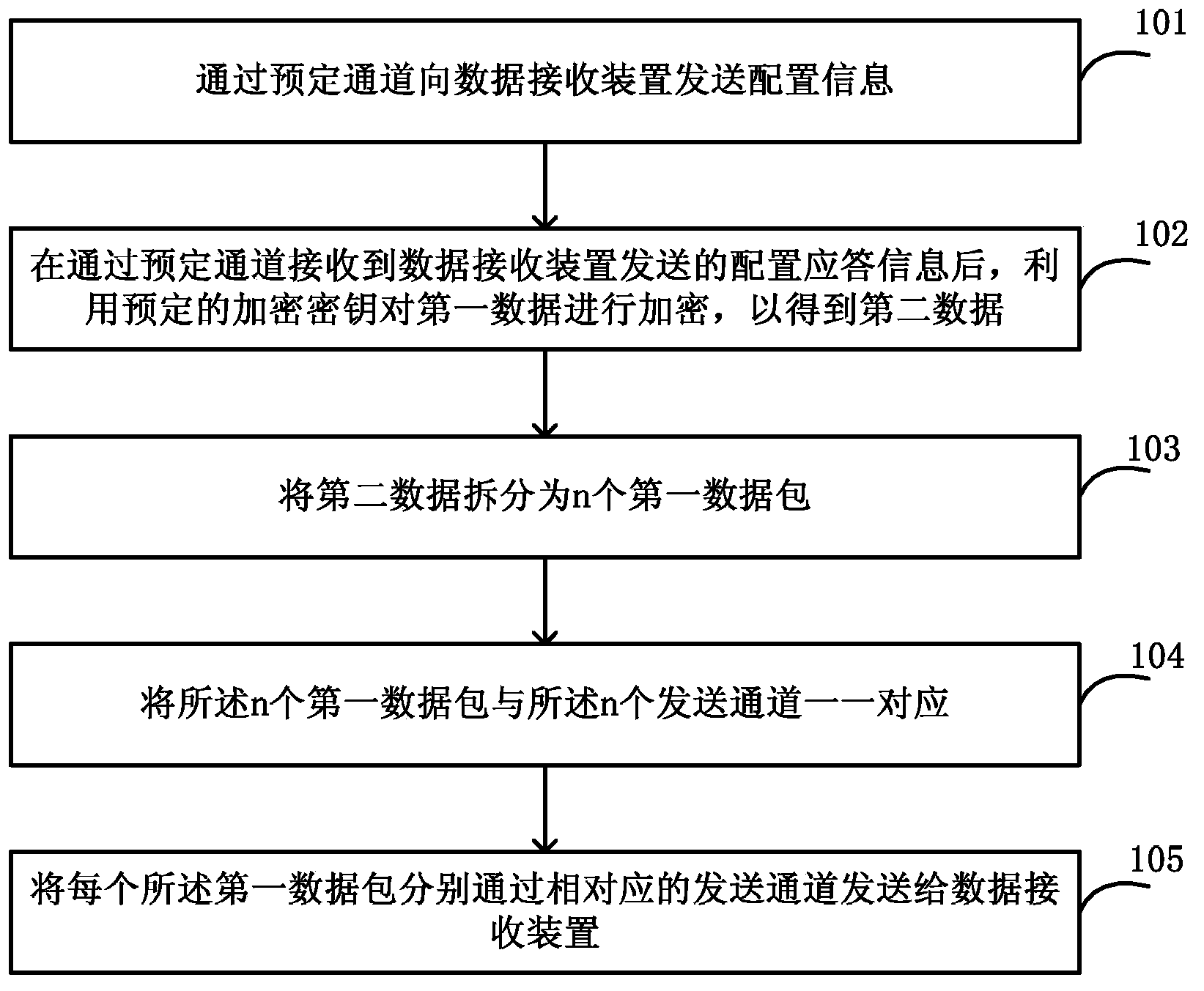
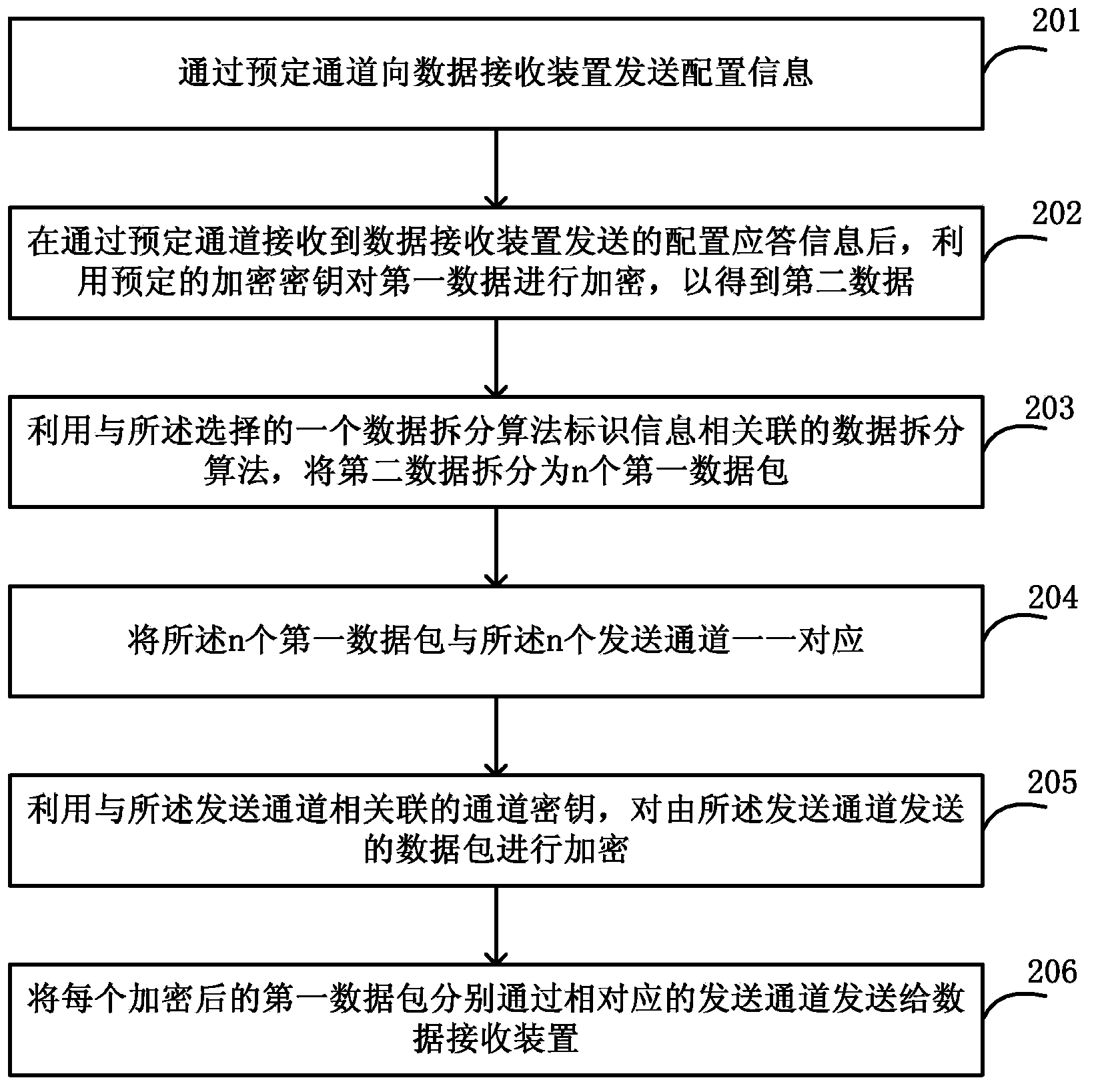
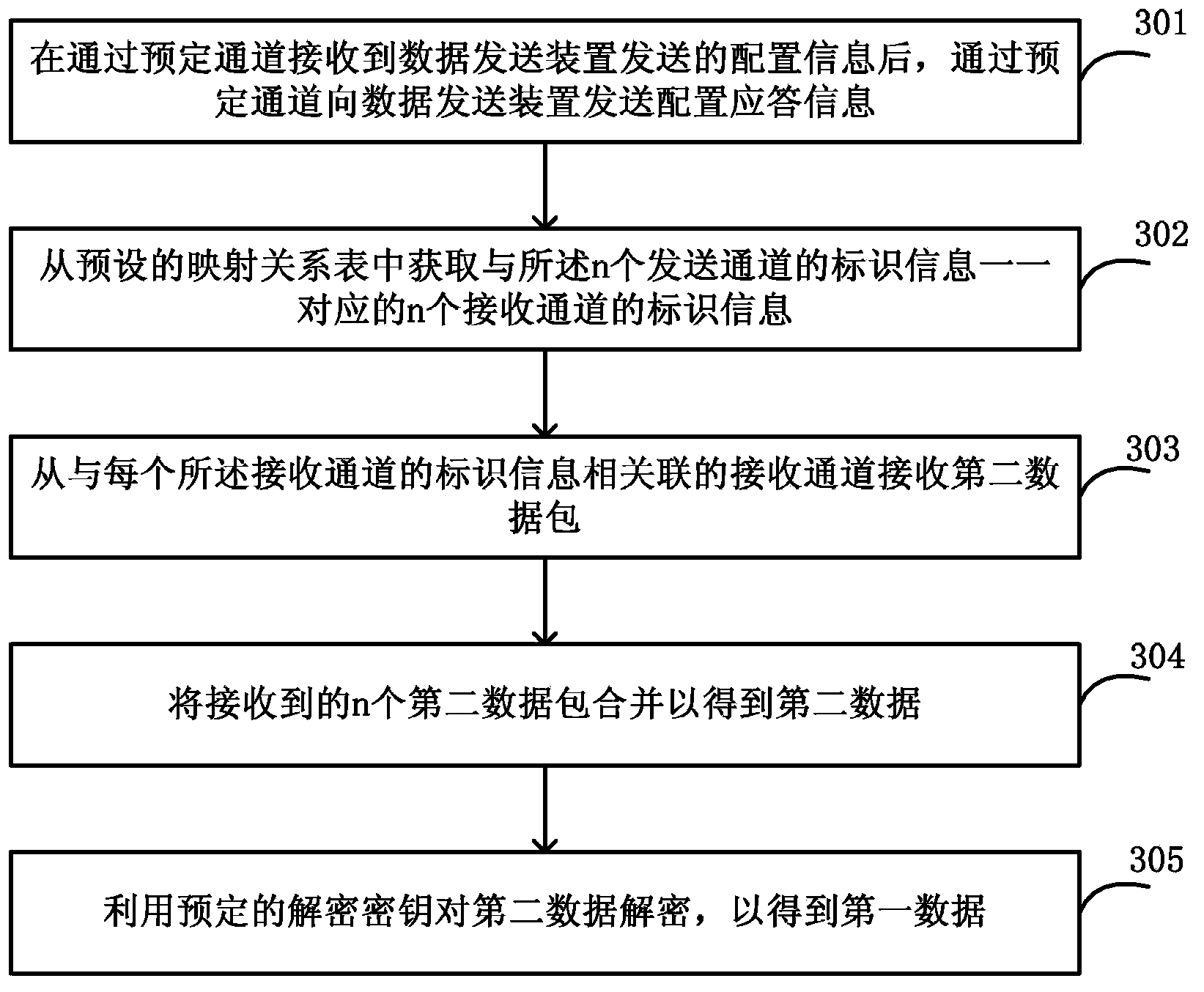
InactiveCN103780375AIncrease the difficultyReduce the risk of theftEncryption apparatus with shift registers/memoriesNetwork packetData transmission
The invention discloses a data transmitting method and system, and a data receiving method and system. In the data transmitting method, configuration information is transmitted to a data receiving device through a predetermined channel, wherein the configuration information comprises identification information of n transmitting channels adopted in the first data transmitting process. Encryption is performed on the first data through a predetermined encryption key to obtain second data, the second data is divided into n first data packets, the n first data packets correspond to the n transmitting channels in a one-to-one manner, and each first data packet is transmitted to the data receiving device through a corresponding transmitting channel separately. The transmitted data is divided into a plurality of data packets after encryption, and the data packets are transmitted to the receiver through different physical channels, so the data crack difficulty can be increased, the data transmission safety can be enhanced, and the risk that the data is stolen can be greatly reduced.
Owner:CHINA TELECOM CORP LTD
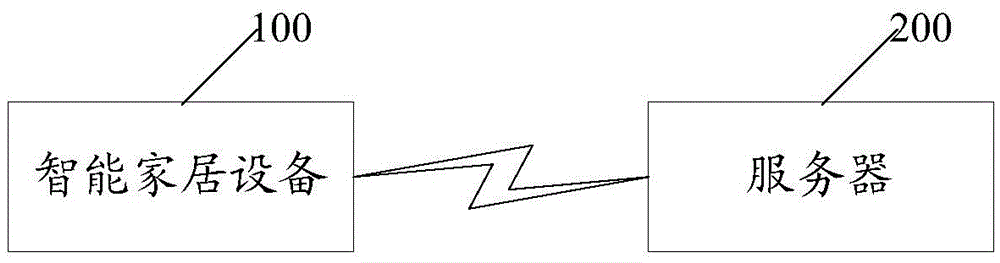
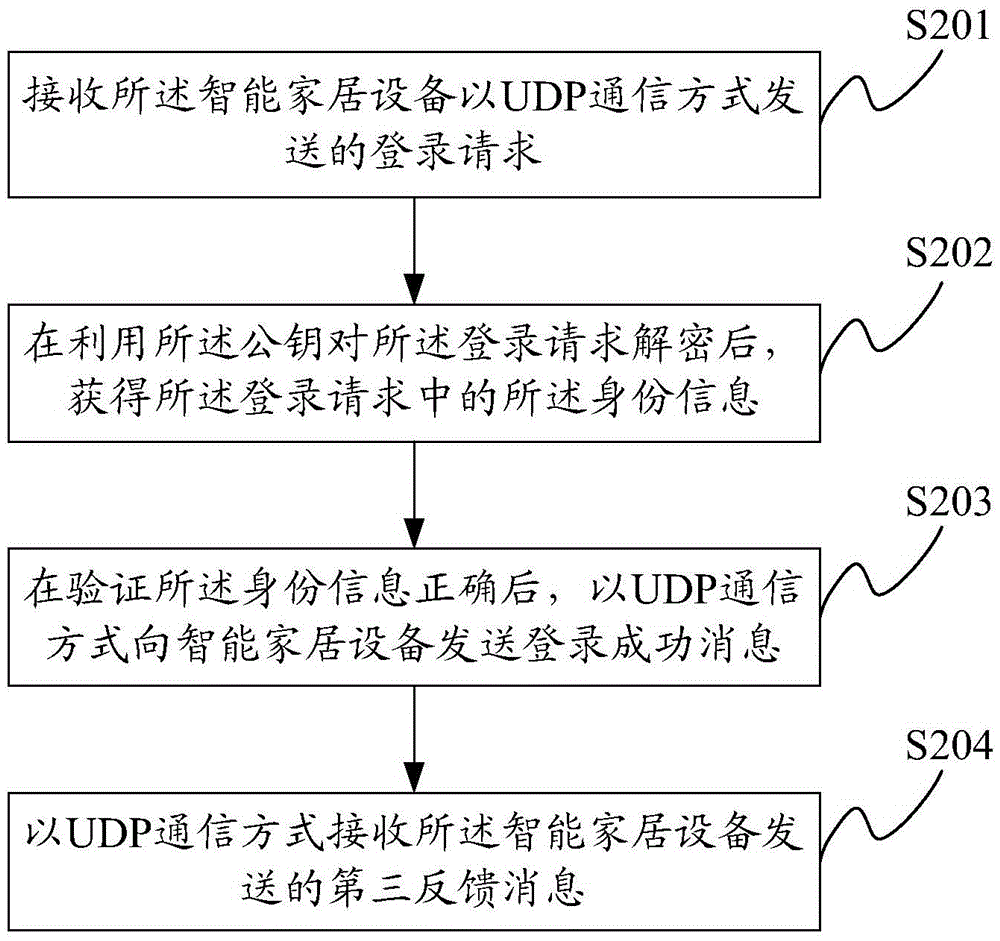
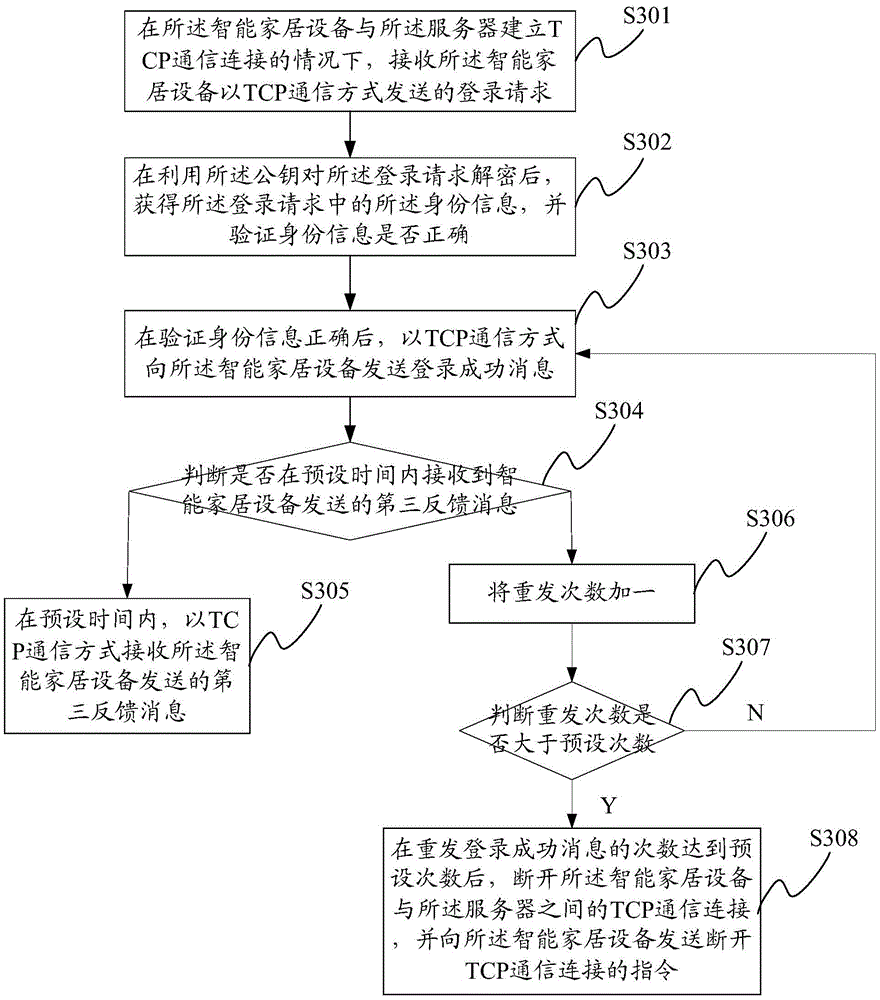
Data transmission method and IoT (Internet of Things) system
The invention provides a data transmission method and an IoT system. The method comprises that in the process that intelligent household equipment makes UDP communication with a server via a first secrete key, a secret key changing instruction is sent to the intelligent household equipment in a UDP communication manner; a first feedback message sent by the intelligent household equipment in the UDP communication manner is received; under the condition that the intelligent household equipment establishes TCP communication connection with the server, a secret key changing request sent by the intelligent household equipment in the TCP communication manner is received; a second secret key which is generated randomly is sent to the intelligent household equipment in the TCP communication manner; and after that the intelligent household equipment receives the second secret key successfully, a second feedback message sent by the intelligent household equipment is received in the TCP communication manner. The secret key in the invention is changeable but not fixed, the changed secret key is transmitted in the TCP communication manner, and thus, the safety of data to be transmitted between the intelligent household equipment and the server is ensured.
Owner:GREE ELECTRIC APPLIANCES INC
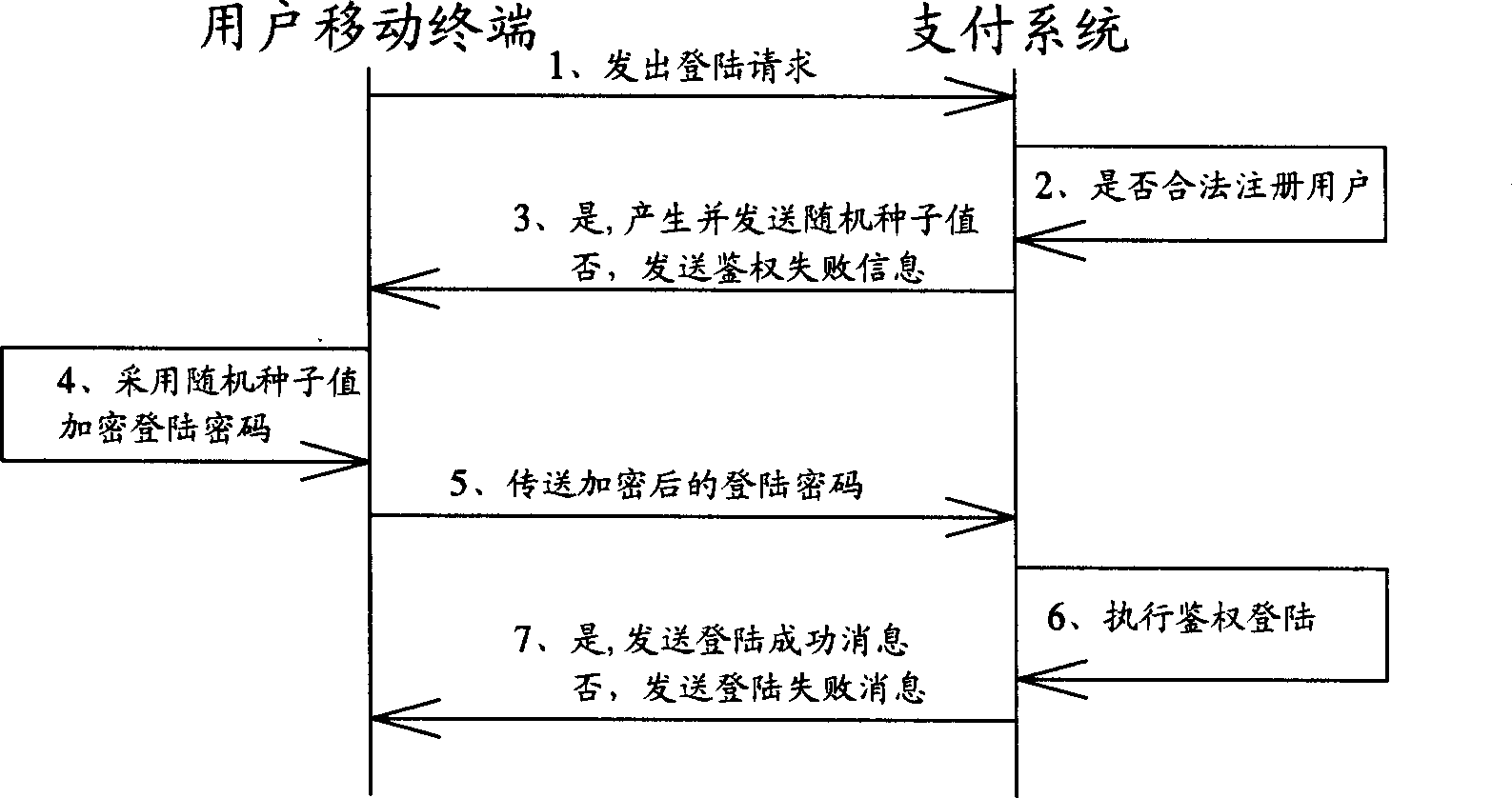
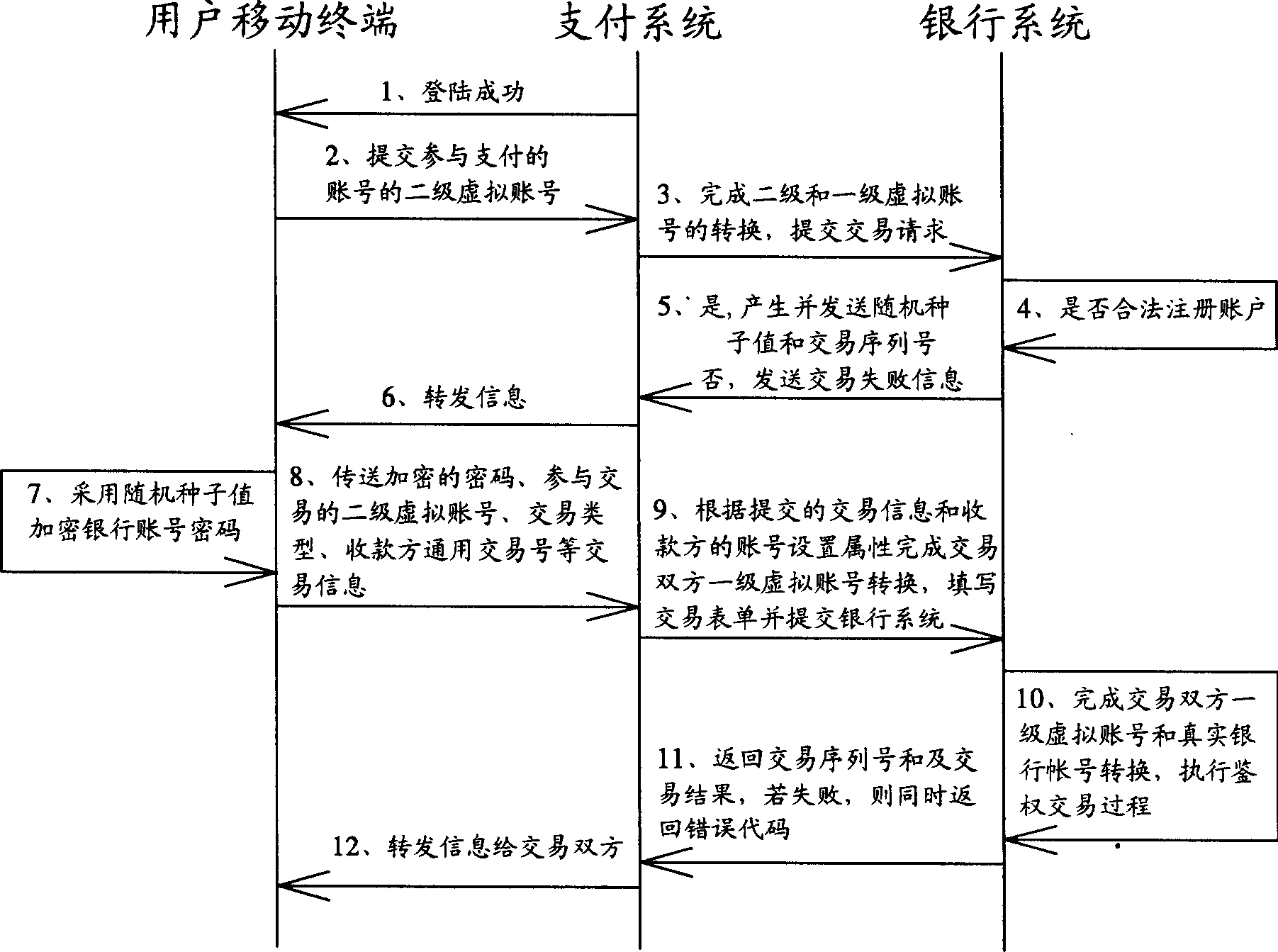
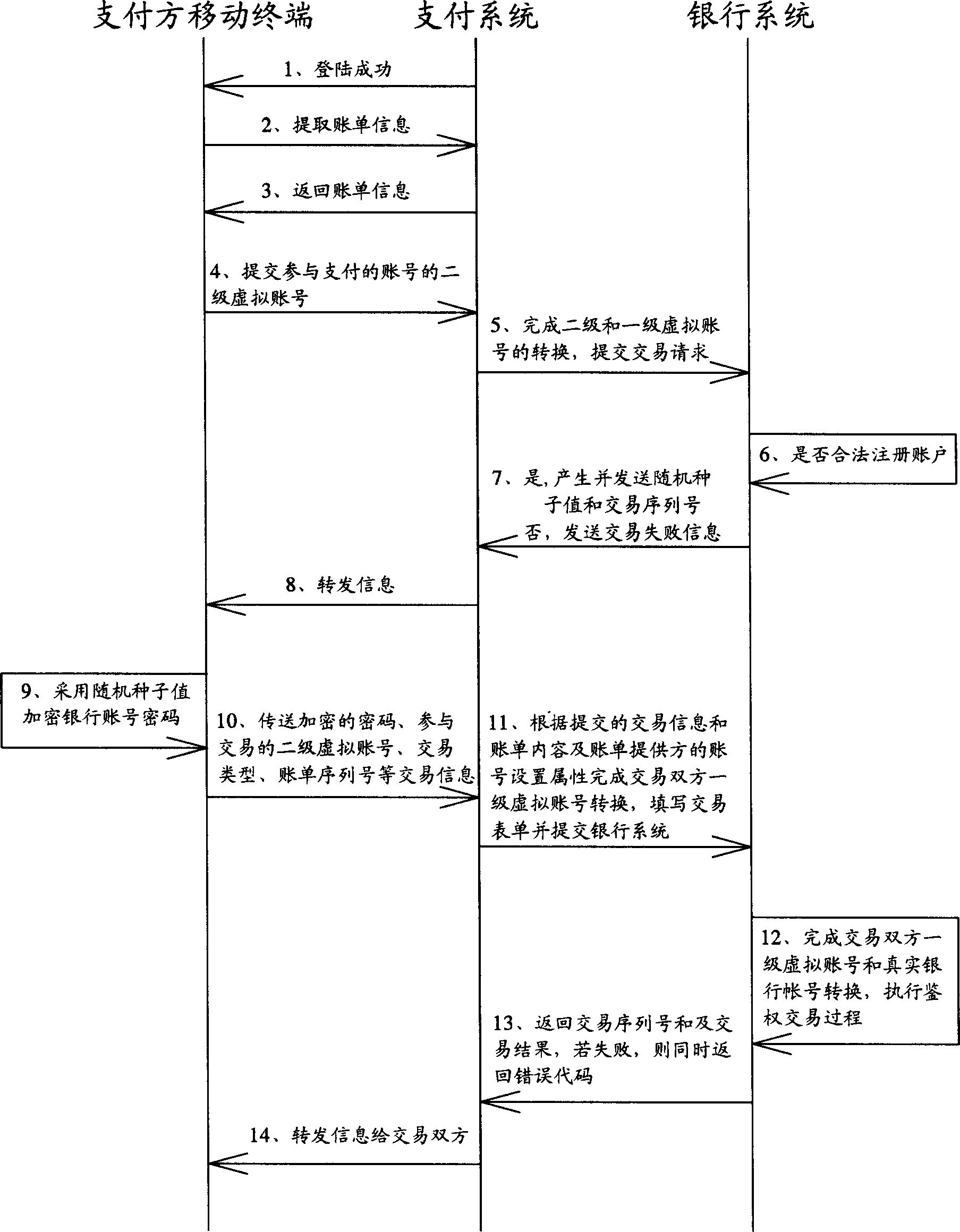
Mobile-terminal-based general transaction method and its system
InactiveCN1776732APrevent theftEnsure safetyFinancePayment architectureEmbedded systemPayment system
Purpose of the invention is to disclose secure general transaction system, which is capable of connecting to multiple bank system and diversified mobile terminals. Thus, mobile terminal possesses payment function and function of collection of payment. Main technique is to setup payment system between mobile terminal and bank system. Through payment system, mobile terminal can connect to multiple bank system to implement transaction. Through the payment system, security of transaction is guaranteed.
Owner:肖勇 +1
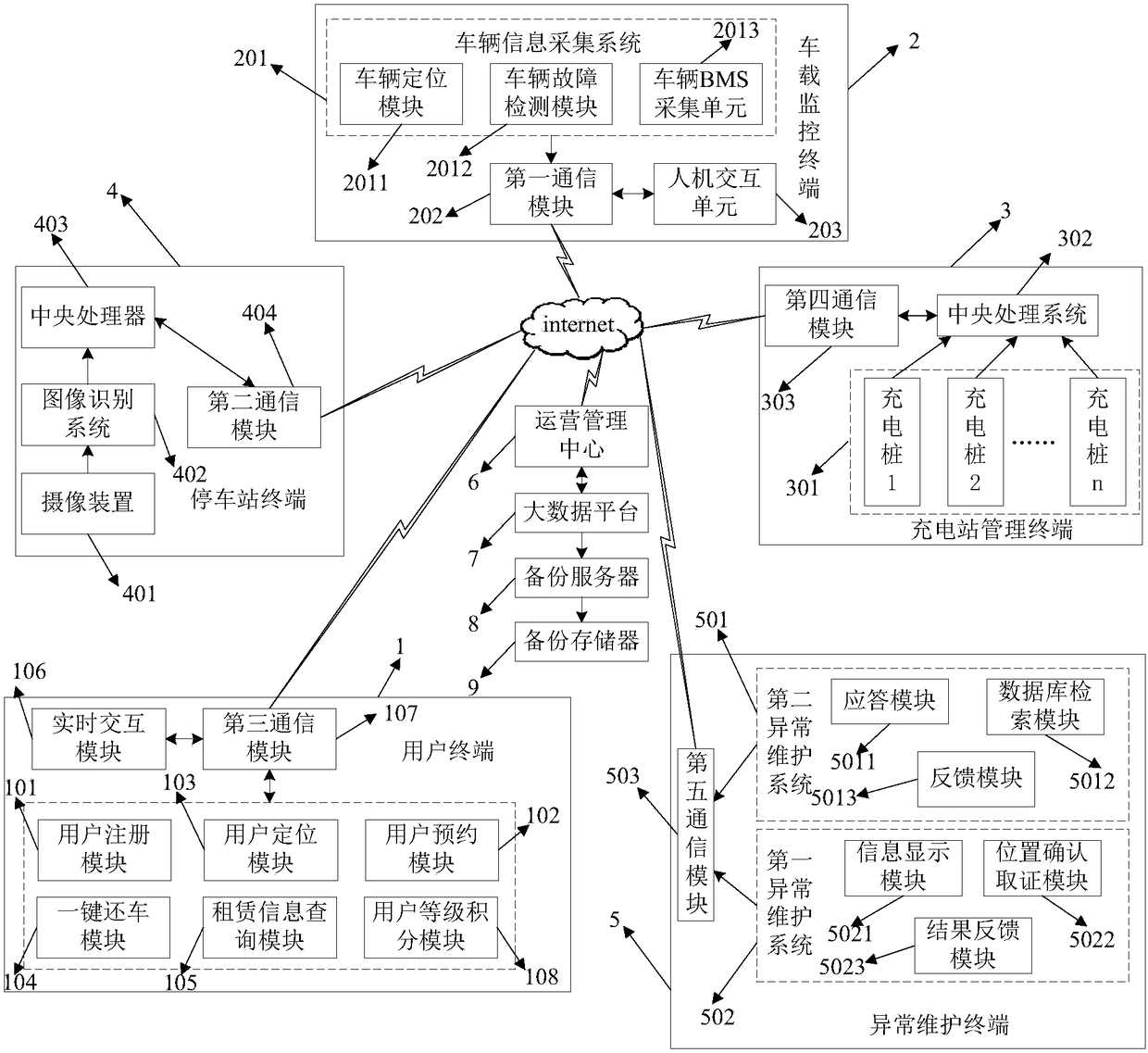
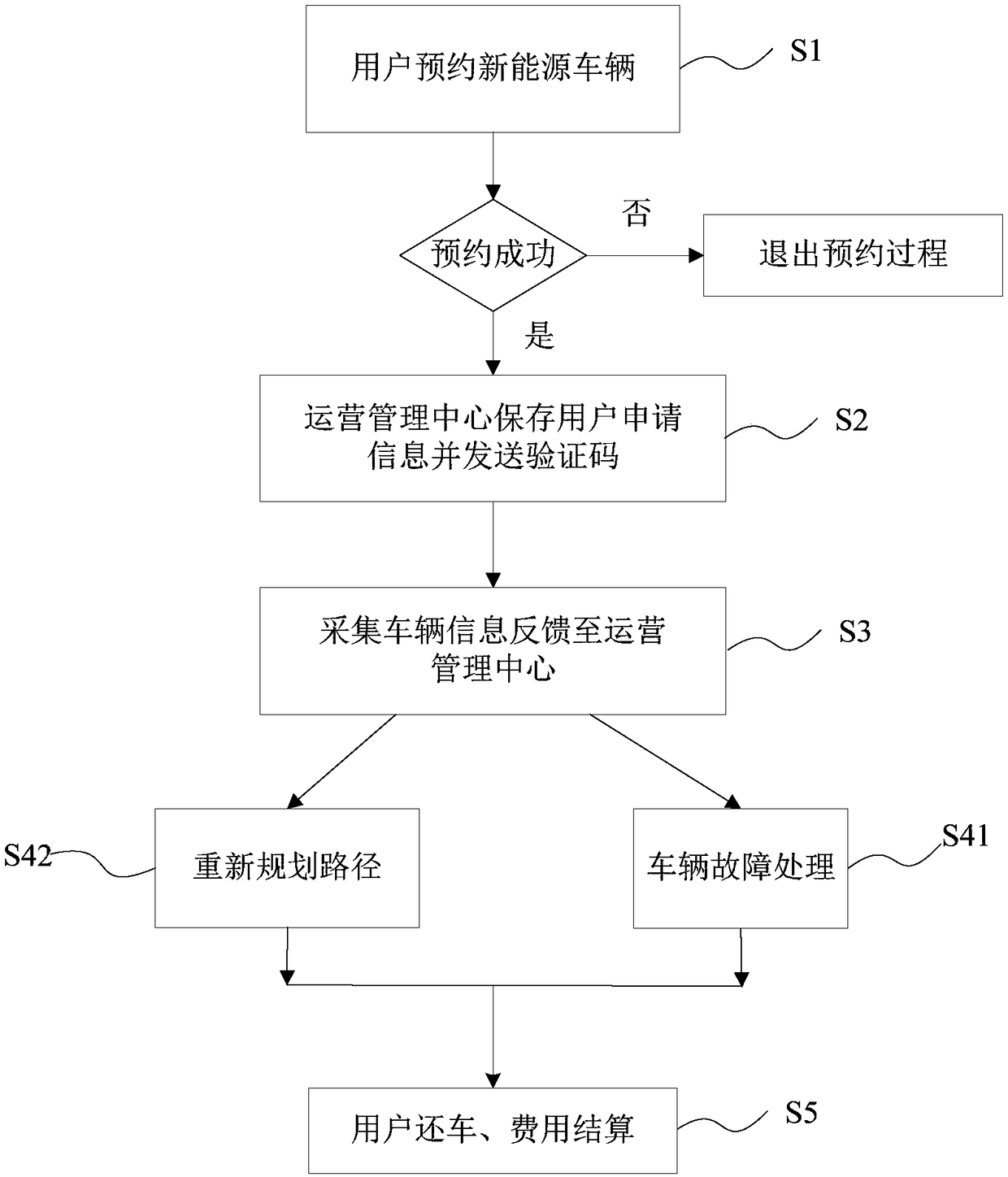
New energy vehicle operation and management method based on internet information system
InactiveCN108335178AConducive to unified deployment managementEnsure safetyDiscounts/incentivesReservationsNew energyThe Internet
The invention discloses a new energy vehicle operation and management method based on an internet information system. The method comprises the specific steps that users reserve new energy vehicles; anoperation and management center saves user application information and sends verification codes; vehicle-mounted monitoring terminals collect vehicle information and feed the vehicle information backto the operation and management center; the operation and management center re-plans paths and conducts vehicle fault handling; the users return the vehicles and pay money, and therefore the whole renting process is completed. The method aims at overcoming the endurance mileage defect of the new energy vehicles, the monitoring system integrates the new energy vehicles, charging stations and parking stations through the internet, the unified vehicle allocation and management of vehicle operation companies are facilitated, the method helps the users to easily obtain charging station information, the problem that the vehicles cannot be driven due to the power shortage of batteries of the vehicles is solved, the operation of renting and returning the vehicles by the users is simple and convenient, the vehicle stealing risk is reduced, and the operation income is increased.
Owner:河南智行新能源科技有限公司
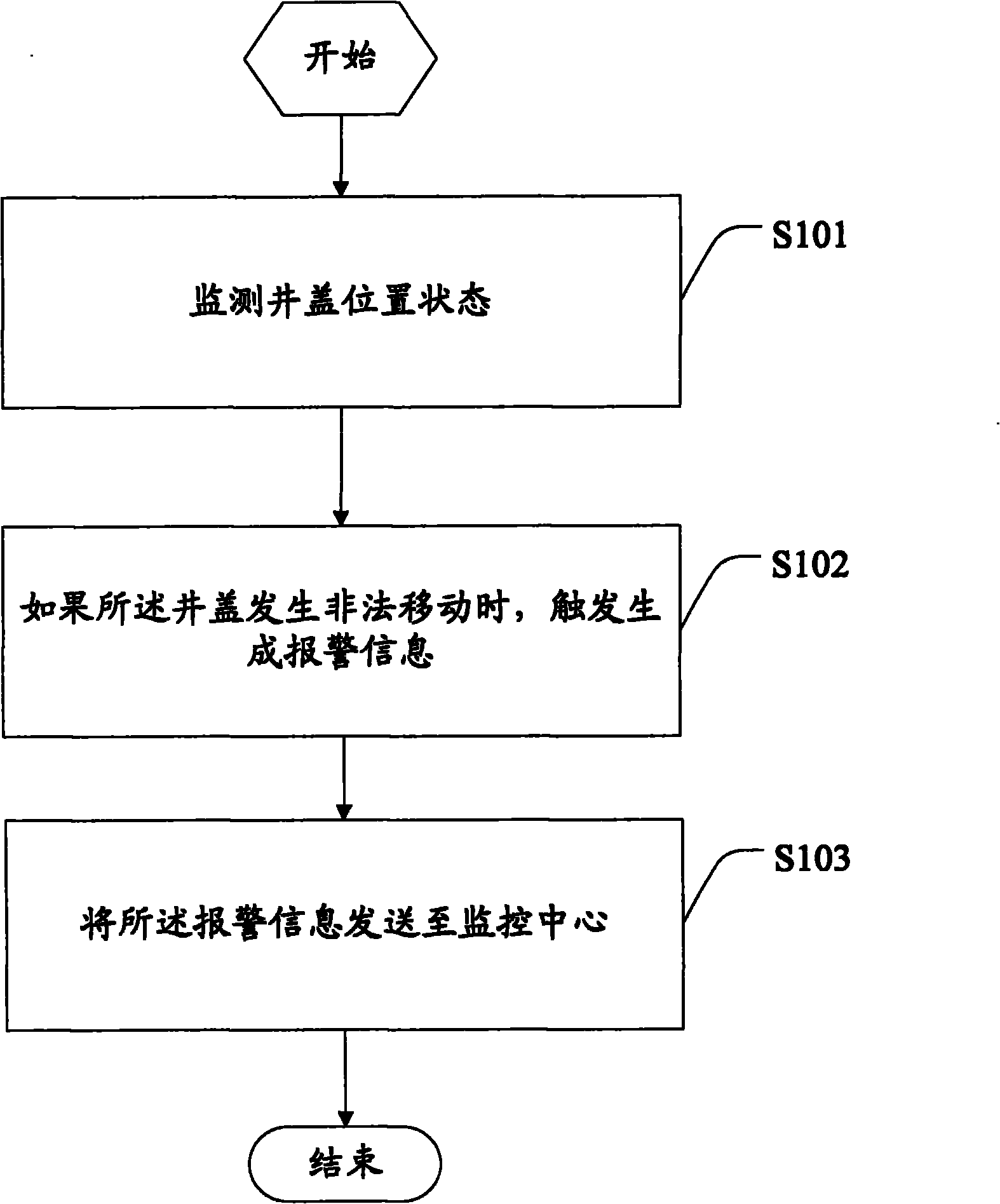
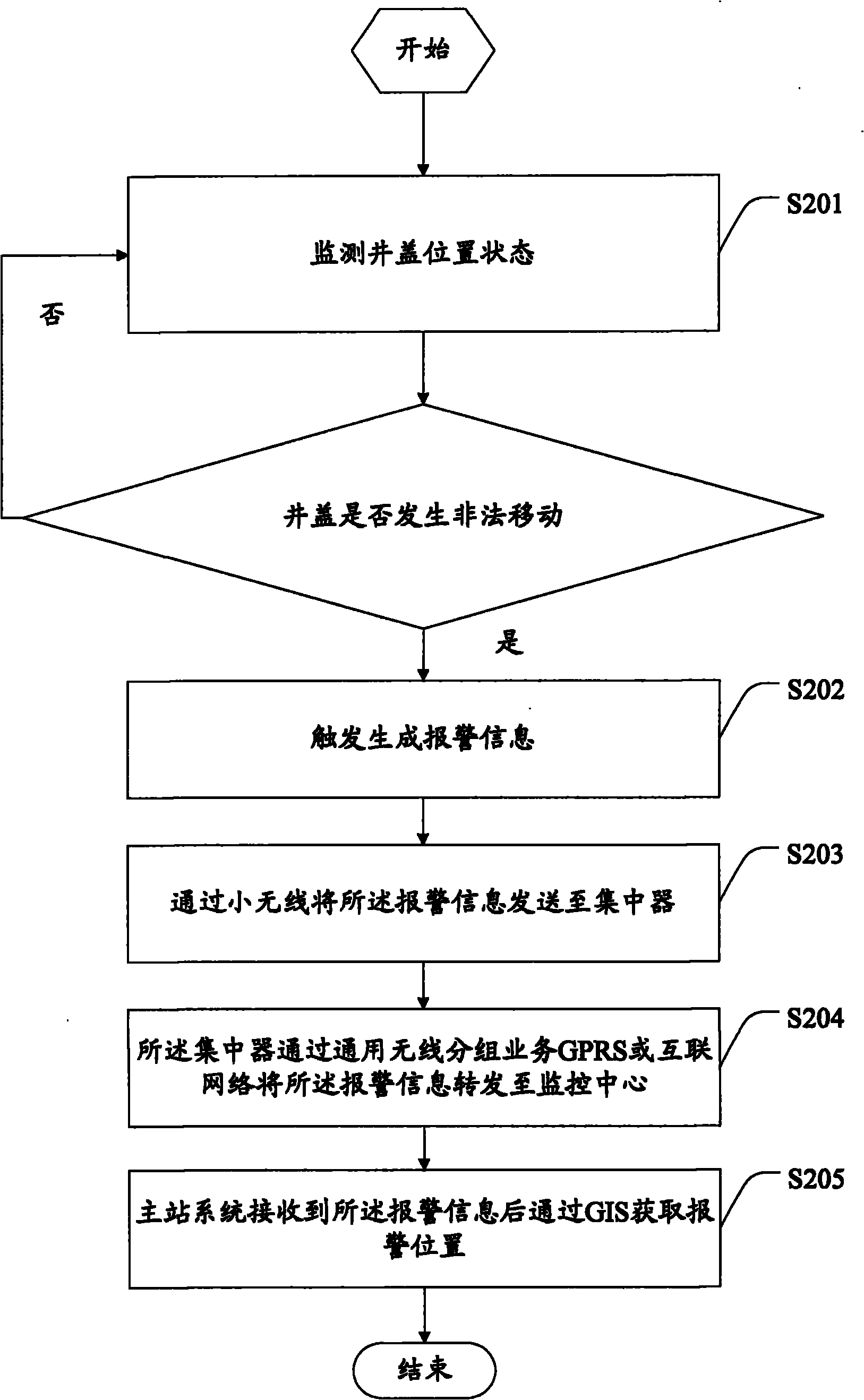
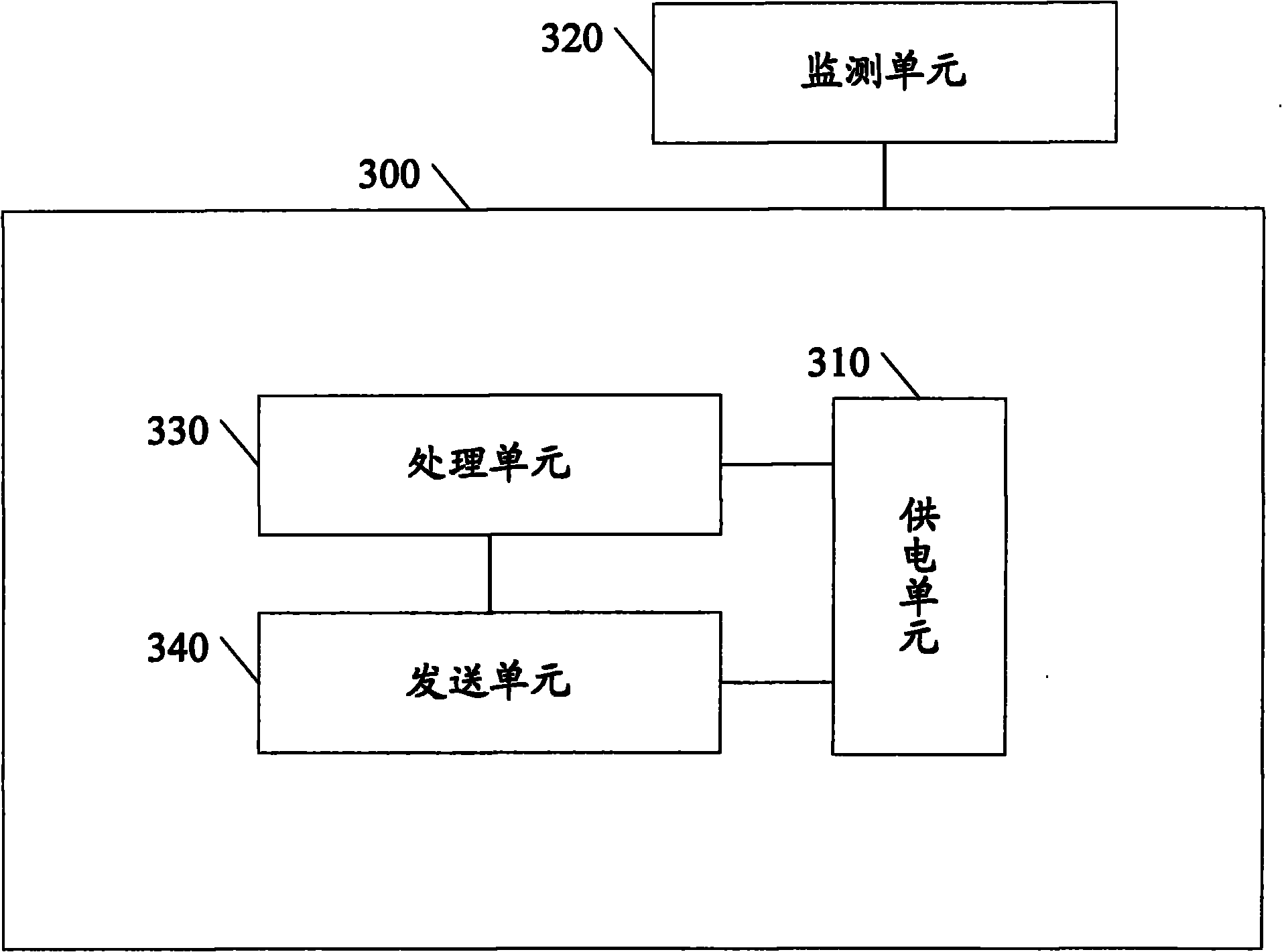
Well cover monitoring method and terminal equipment
InactiveCN102184608AReduce the risk of theftReduce the difficulty of supervisionBurglar alarm mechanical actuationTerminal equipmentEngineering
The invention discloses a well cover monitoring method, which comprises the following steps of: monitoring the position state of a well cover; triggering to generate alarm information if the well cover is illegally moved; and transmitting the alarm information to a monitoring center. Correspondingly, the invention discloses terminal equipment for implementing the method, which comprises a shell, a power supply unit, a monitoring unit, a processing unit and a transmitting unit, wherein the monitoring unit is used for providing a well cover position state signal; the processing unit is used for judging whether the well cover is illegally moved or not according to the well cover position state signal which is provided by the monitoring unit, and if so, triggering to generate the alarm information; and the transmitting unit is used for transmitting the alarm information generated by the processing unit to the monitoring center. By the embodiment of the method and the equipment, the alarm information can be timely transmitted when the well cover is moved, the risk that the well cover is stolen is reduced, and the supervision difficulty of maintenance personnel is reduced simultaneously.
Owner:AEROSPACE SCI & IND SHENZHEN GROUP
Lifting vertical-and-horizontal translation type stereo garage
InactiveCN101761256APrevent reverseAvoid scratched traffic accidentsParkingsMobile vehicleControl system
The invention relates to a parking device, in particular to a lifting vertical-and-horizontal translation type stereo garage. The garage comprises a multi-layer frame, wherein a vertical-and-horizontal translation guide rail is arranged on the frame and on the ground; a vehicle loading plate capable of moving along the guide rail is arranged on the vertical-and-horizontal translation guide rail at the bottom layer; a back-and-forth moving lift capable of moving along the guide rail is arranged on the vertical translation guide rail at the upper layer; and the back-and-forth moving lift is connected with a lifting frame of the vehicle loading plate and a horizontal moving vehicle loading plate by a sling. The space of a parking lot can be utilized to the maximum degree, a middle passage is used for vehicles coming in and going out, thereby avoiding backing off, turning around and other procedures of the vehicle in the garage; the coming-in and going-out speed of the vehicle can be improved, thereby avoiding the scratching accident when the vehicle is back off and turns around. Back-off time can avoid scratching; the parking position can be locked by a control system, and only when the control system is opened, the parking position can be placed at the position where the vehicles can freely come in and go out, and the vehicles can go out of the garage only from the passage; in addition, the parking positions are not located on the passage, thereby greatly reducing the risk of vehicle theft.
Owner:宋强
Private key storage method and device and related equipment
ActiveCN111431713AImplement storageEnable secure storageKey distribution for secure communicationInternet privacyCiphertext
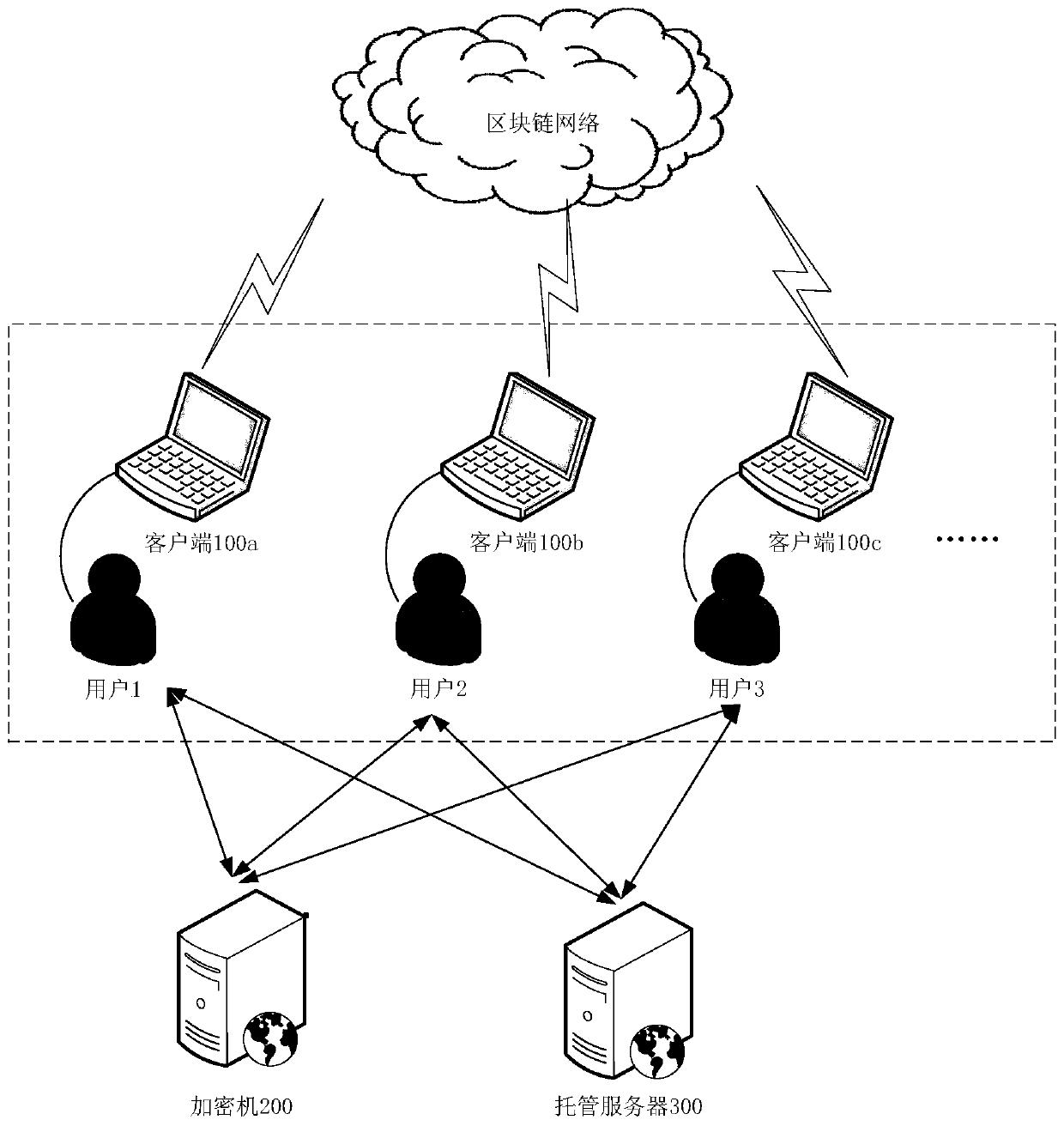
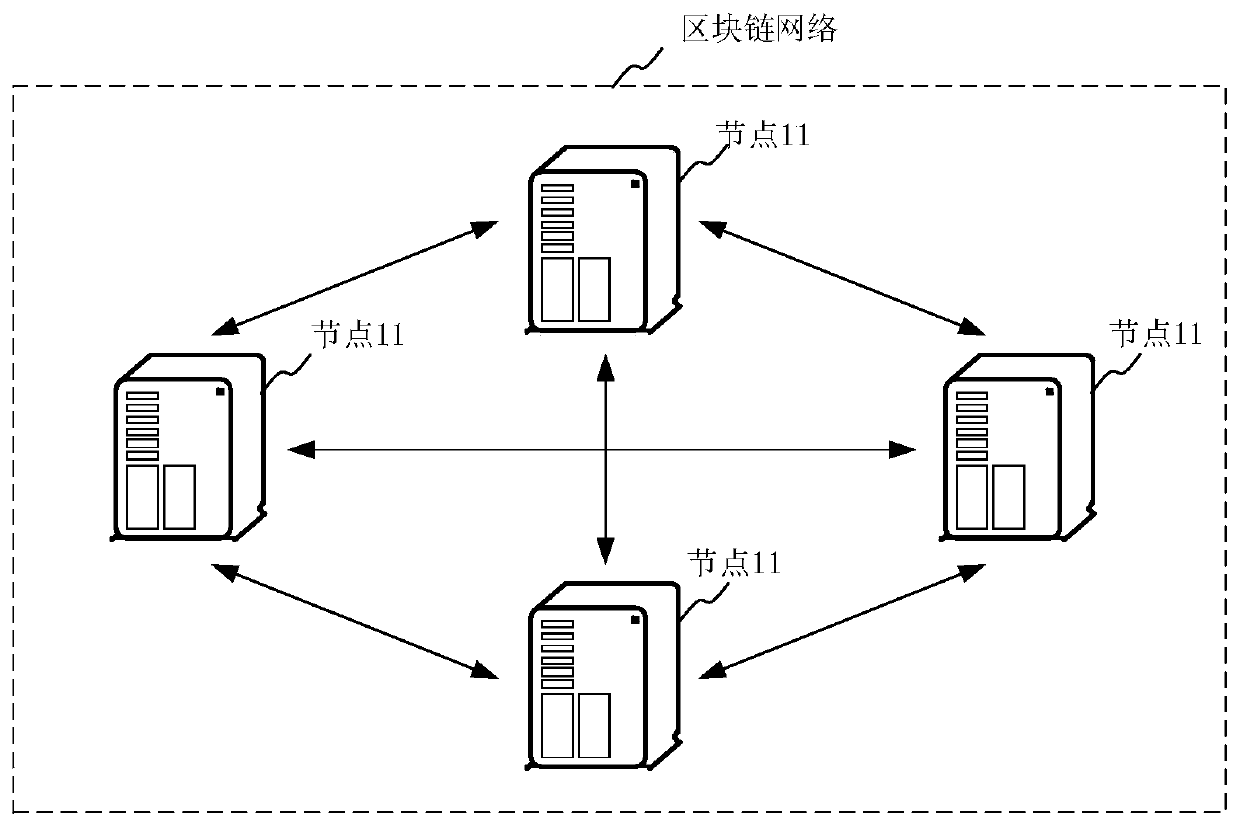
The invention discloses a private key storage method and device, and related equipment. The private key storage method comprises the steps that a key negotiation application sent by a client is received, a corresponding key position is formulated according to the key negotiation application, a corresponding encryption key is generated at the key position, and the key position is a key position inan encryption machine; a private key of a target user sent by the client is received, and the private key is encrypted according to the encryption key to obtain an encrypted ciphertext corresponding to the private key; wherein the private key is used for signing, encrypting and decrypting transaction data in a target account so as to use virtual assets in the target account; and the encrypted ciphertext corresponding to the private key is sent to a trusteeship server, so that the trusteeship server stores the encrypted ciphertext corresponding to the private key. By adopting the embodiment ofthe invention, the user private key can be encrypted through the encryption machine, and the leakage of the user private key is effectively prevented, so that the security of the virtual assets of theuser in the blockchain network is ensured.
Owner:TENPAY PAID TECH
User account login method and apparatus, electronic device and storage medium
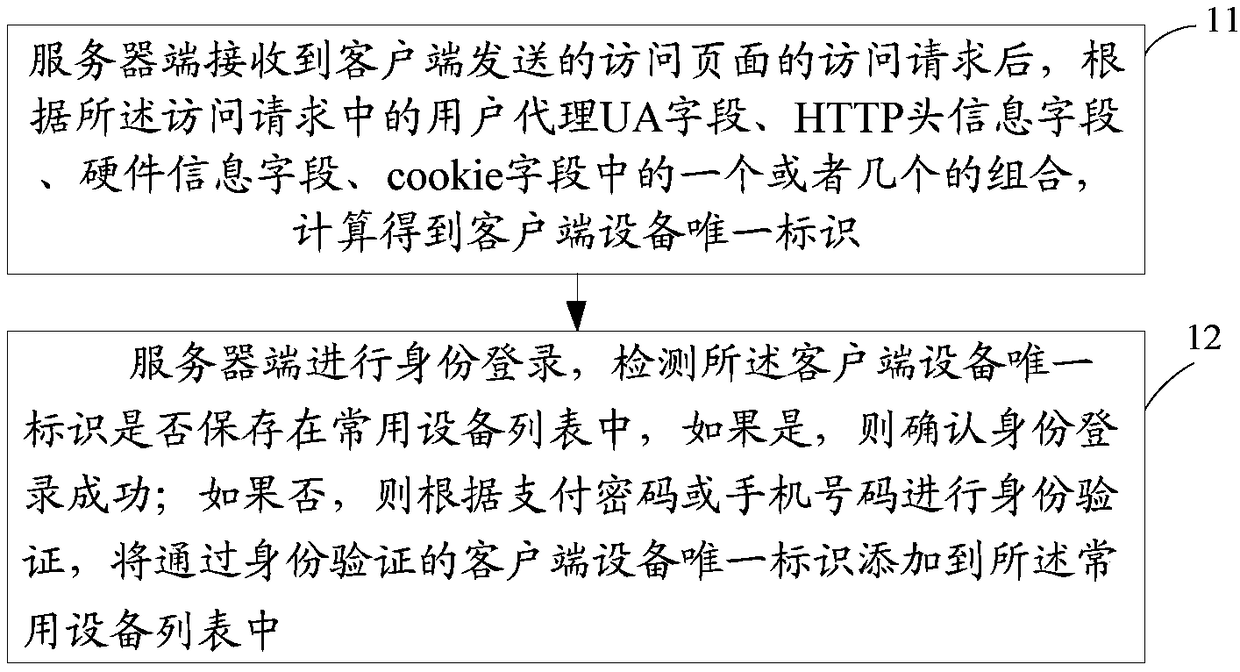
InactiveCN109039987AProtect fundamental interestsConvenient and flexible managementTransmissionPaymentPassword
The invention provides a user account login method. The method comprises the following steps: after receiving the access request of the access page sent by the client end, the server end calculates the unique identifier of the client end equipment according to one or a combination of one or several of the user agent UA field, HTTP header information field, hardware information field and cookie field in the access request; At that server end, the identity login is carried out, whether the unique identification of the client equipment is saved in the common equipment list or not is detected, andif yes, the identity login is confirmed to be successful; If not, authentication is performed according to a payment password or a mobile phone number, and an authenticated client device unique identity is added to the list of commonly used devices. The present application also provides a user account login apparatus. The invention can improve the safety of the user account.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Vehicle body control system for electric vehicle and method for calculating road gradient
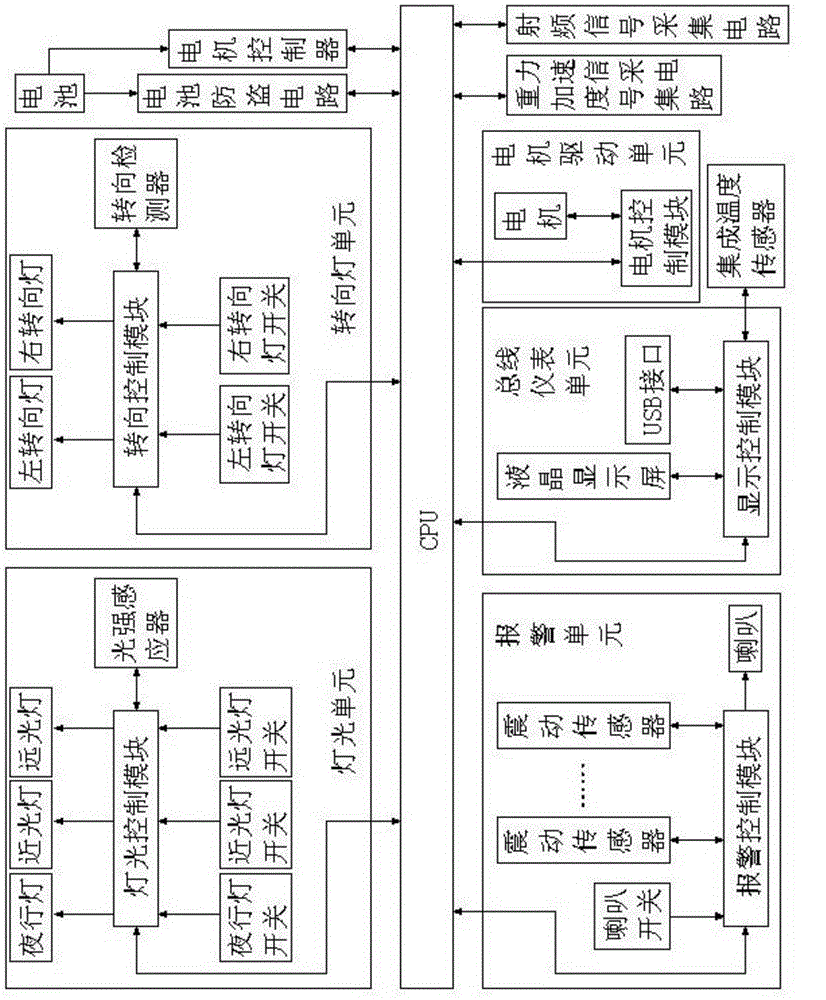
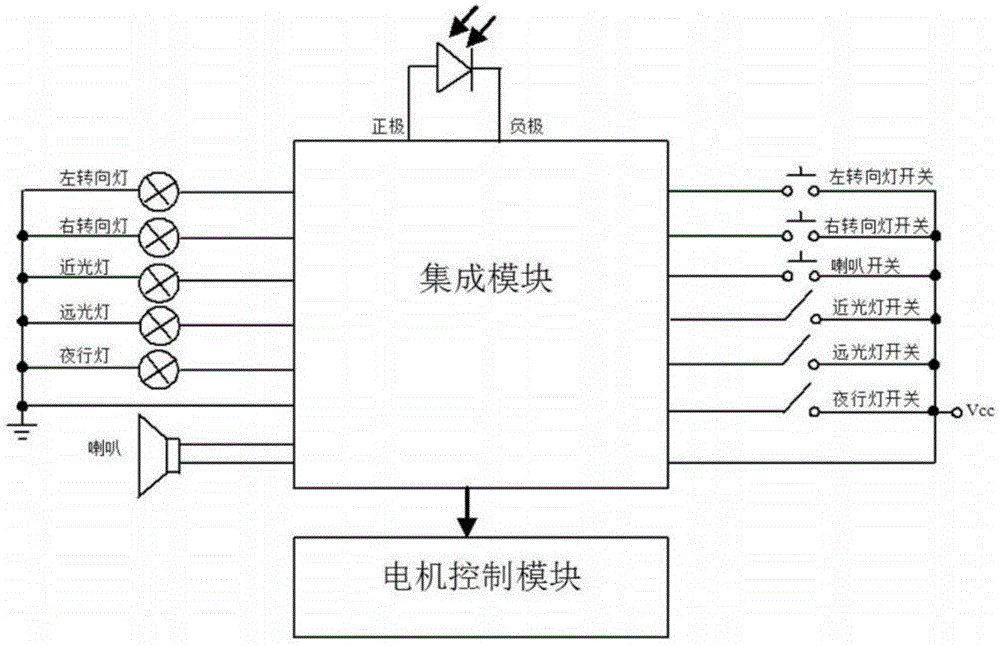
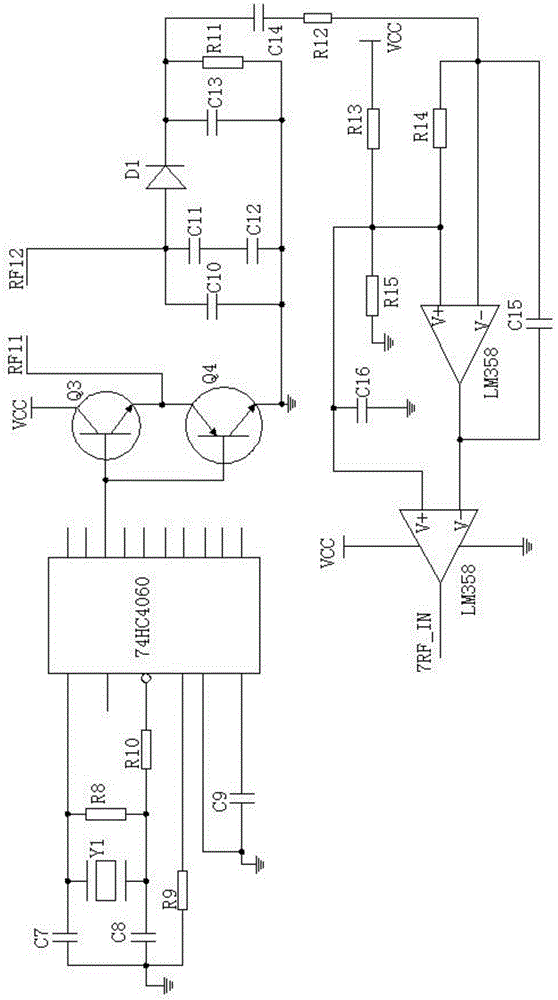
ActiveCN103979012AIncrease contentPowerfulSteering linkagesAutomatic steering controlTrip distanceElectrical battery
The invention relates to the field of electric vehicles, and discloses a vehicle body control system for an electric vehicle and a method for calculating the road gradient. The vehicle body control system comprises a lamplight control module, an alarm control module, a display control module and a steering control module, wherein at least one control module in the lamplight control module, the alarm control module, the display control module and the steering control module is integrated onto the same integrated chip together with a CPU (Central Processing Unit). The control modules for controlling the working state of each unit is integrated onto the same chip together with the CPU, and are centralized, so that wiring is simplified, wiring harnesses become simpler, and the cost is lowered; the CPU is used for acquiring signals of a three-axle gravity acceleration sensor and automatically calculating the gradient value of a road on which the electric vehicle runs in order to transmit gradient information to the motor controller; the motor controller is used for adjusting the output torque of the motor according to the current road gradient information, so that an intelligent energy output adjusting function is realized, unnecessary consumption of battery power is lowered, and the trip distance is prolonged.
Owner:ZHEJIANG JINKAI ELECTRONICS TECH CO LTD
Concurrent job backup method for mass data backup
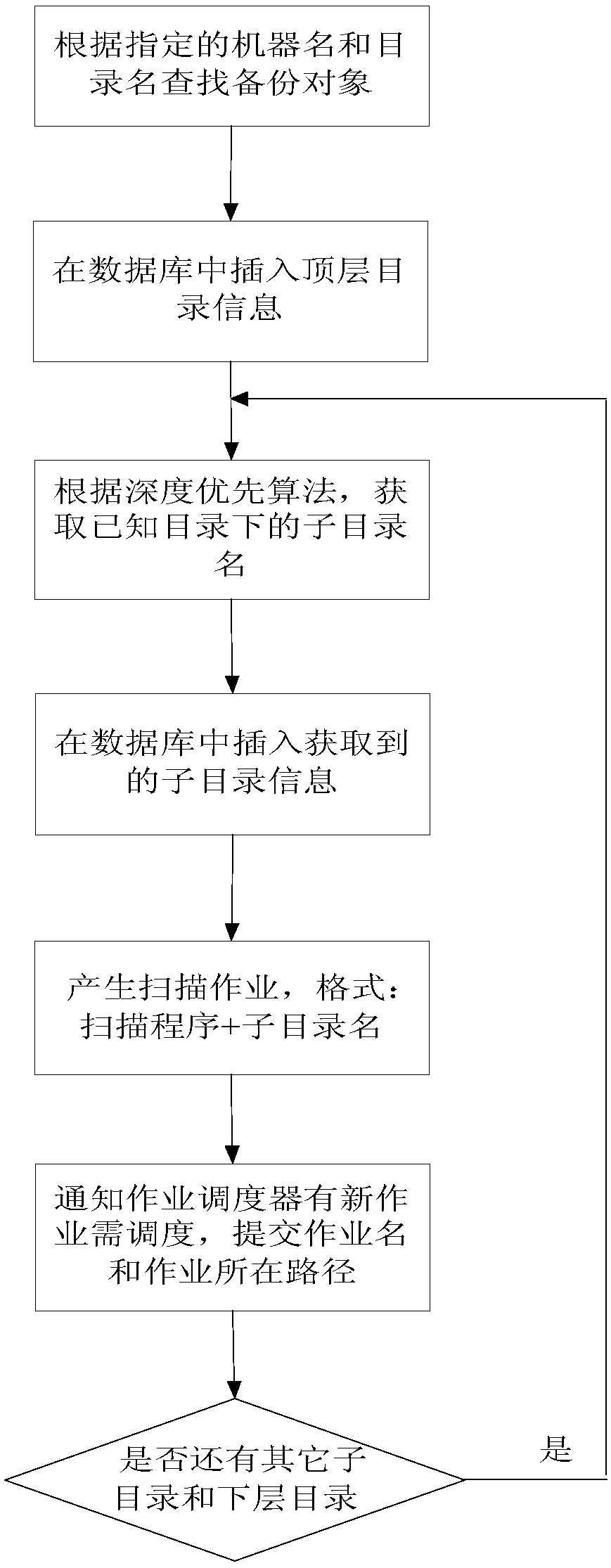
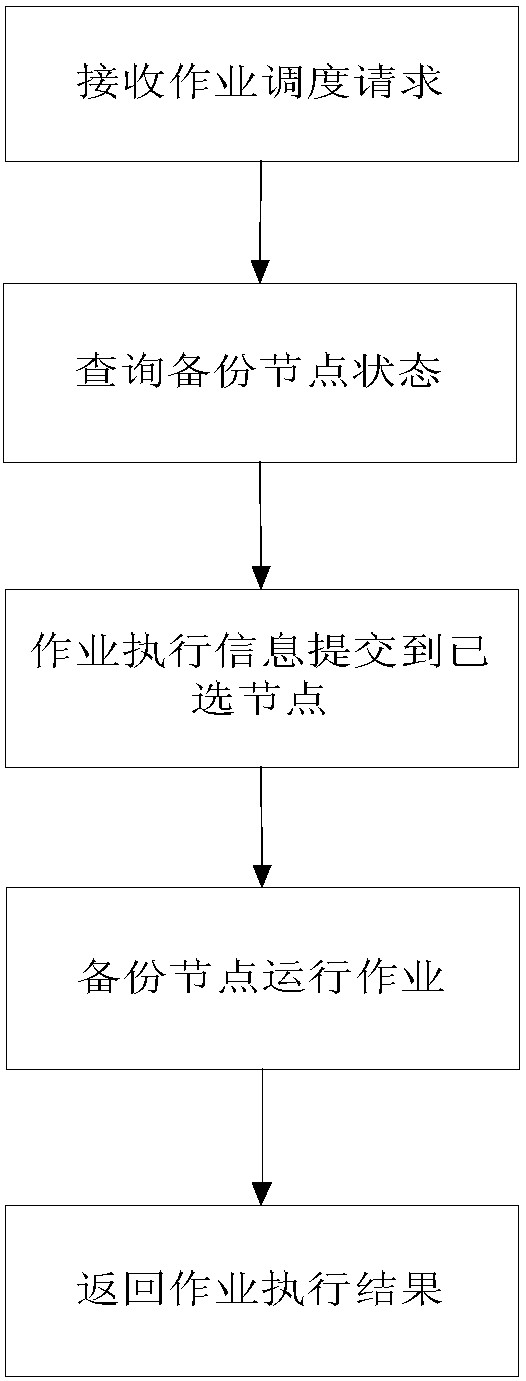
ActiveCN108804253ASpeed up recoveryImprove usabilityRedundant operation error correctionDirectory structureJob scheduler
The invention discloses a concurrent job backup method for mass data backup. The method comprises the following steps of: 1) selecting multiple backup nodes to for a backup cluster, wherein the backupnodes have uniform configuration; 2) selecting a backup node to serve as a backup management server by a terminal, and starting a backup strategy of an object needing backup; 3) selecting a backup node to serve as a job scheduler by the backup management server, obtaining a directory structure corresponding to the object needing backup layer by layer, and generating a scanning job when a directory is obtained; 4) submitting a job path corresponding to each scanning job to the job scheduler by the backup management server, and sending the job paths to the backup nodes by the job scheduler so as to scan target directories in the scanning jobs; 5) selecting a file needing backup by the backup management server and generating a plurality of file sub-tables, generating a copy job according toeach sub-table, and sending the copy jobs to the jog scheduler; and 6) sending different copy jobs to different backup nodes by the job scheduler so as to copy the file needing backup to a corresponding position.
Owner:INST OF HIGH ENERGY PHYSICS CHINESE ACAD OF SCI
Park vehicle anti-theft system, park vehicle management method and park vehicle control method
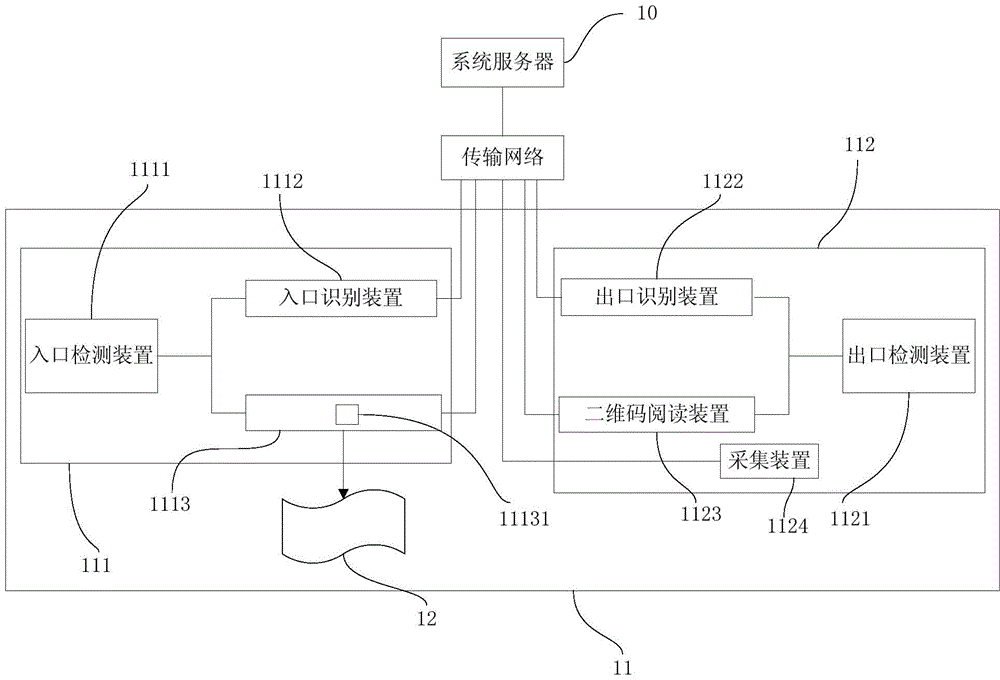
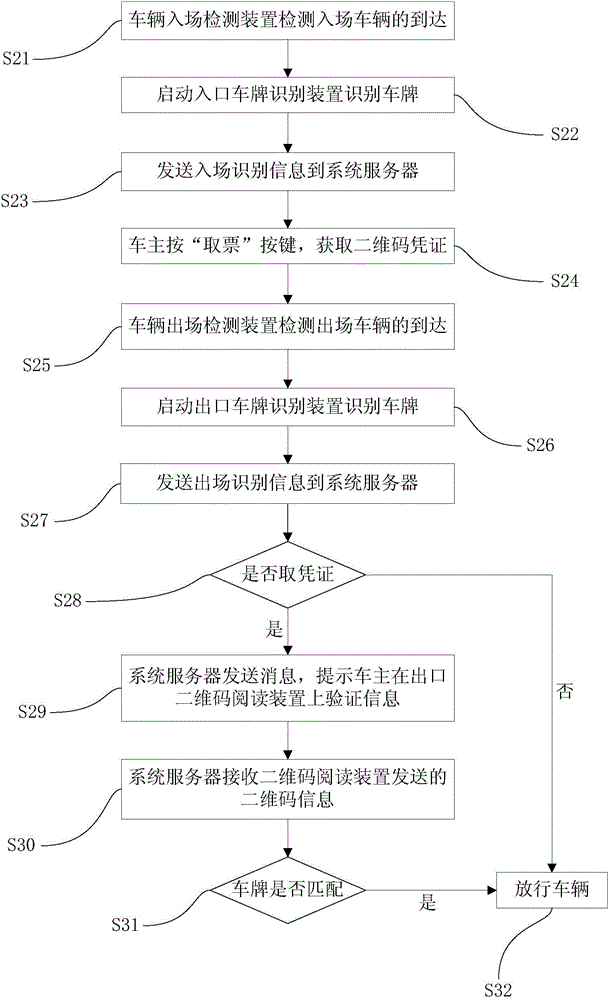
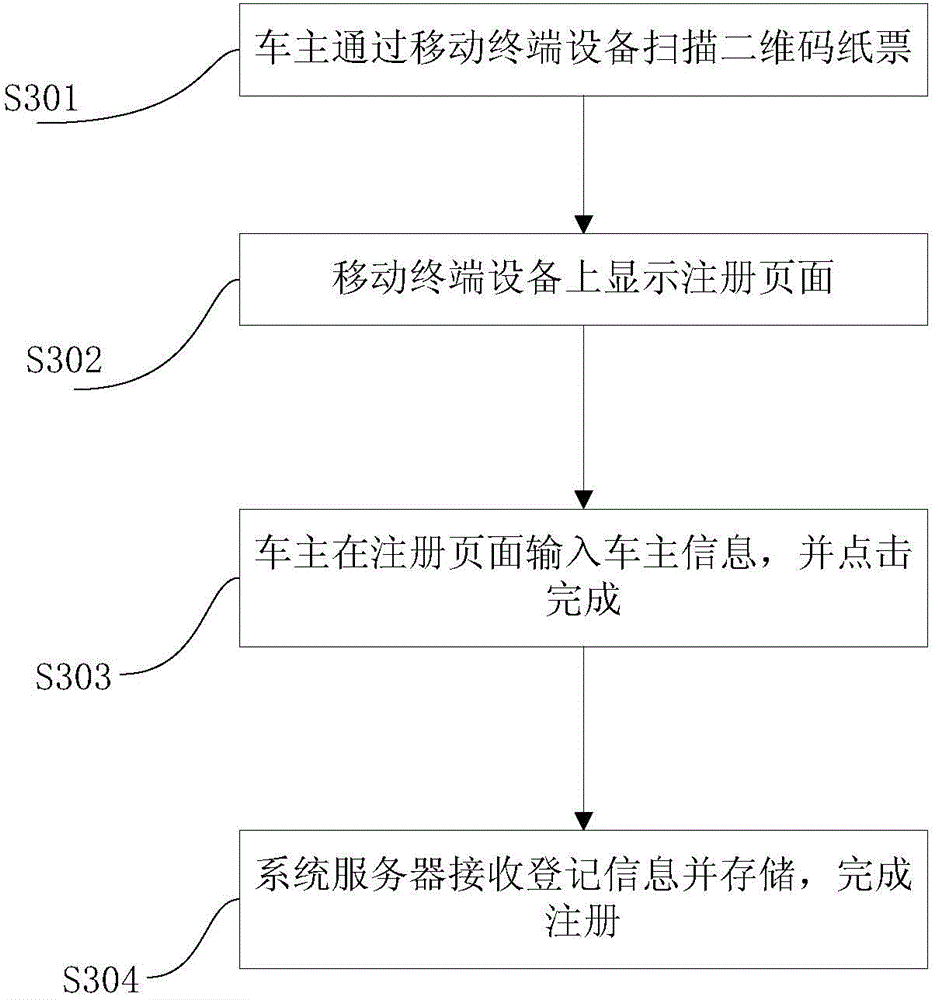
ActiveCN104794901AReduce the risk of theftSafe ParkingTicket-issuing apparatusRoad vehicles traffic controlSystem serviceAnti theft
The invention discloses a park vehicle anti-theft system comprising a system server, a park unit, a QR (quick response) code device, a reader and a barrier unit. The system server exchanges data with the park unit and stores vehicle information. The park unit comprises recognizing devices disposed at an entry of and an exit of a park; the recognizing devices are used for recognizing the vehicle information and outputting the same to the system server. The QR code device is disposed at the entry of the park, acquires information of a currently entering vehicle from the system server and outputs a QR code certificate; the reader disposed at the exit of the park is used for reading the QR code certificate and outputting the read information of the QR code certificate to the system server; the barrier unit disposed at the exit is configured to receive an opening signal of the system server to let go of the vehicle; the system server generates the opening signal to the barrier unit according to the stored vehicle entering information and the received QR code information. The park vehicle anti-theft system has the advantages that accessing the park is finished through the QR code certificate, parking safety is guaranteed and vehicle theft is effectively prevented.
Owner:SHENZHEN EPARKING TECH
Stereo modular tower-type bicycle parking mechanical device
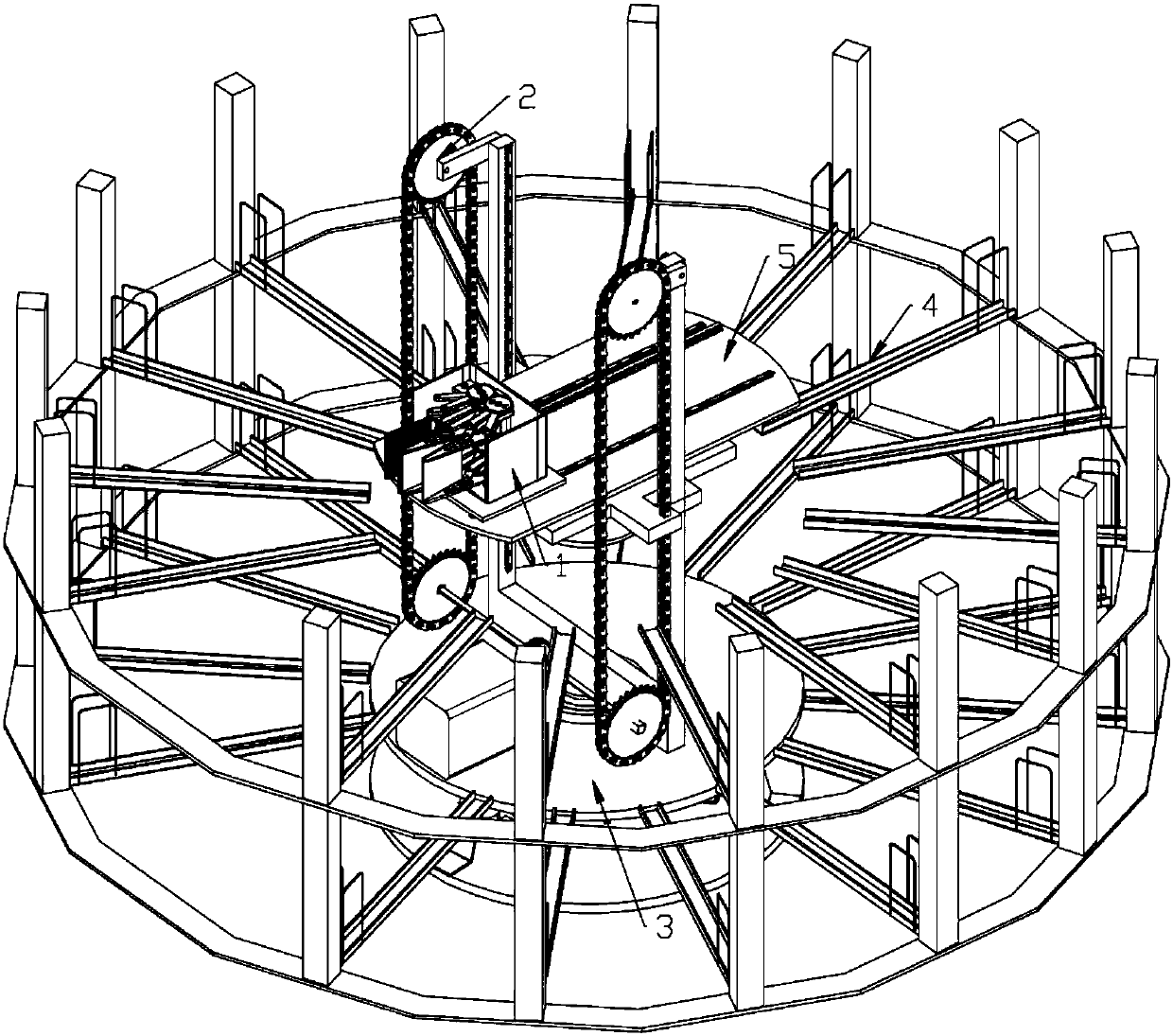
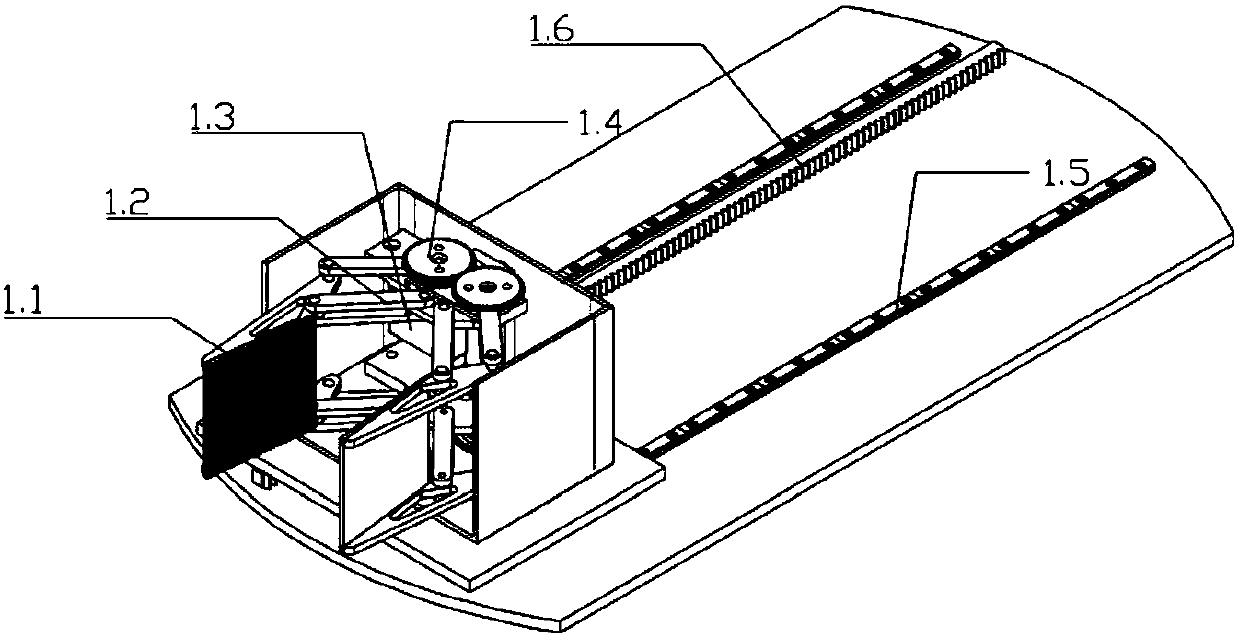
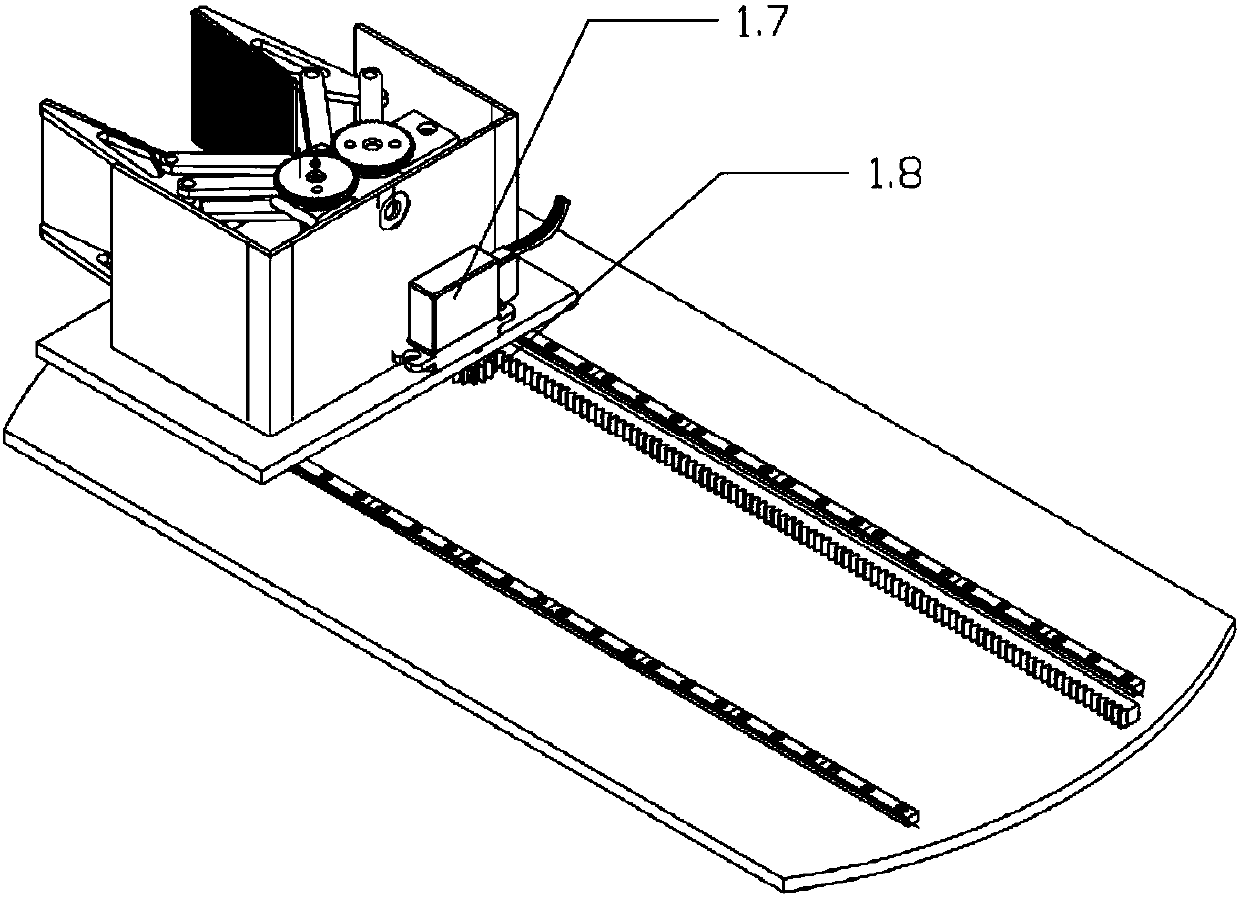
The invention discloses a stereo modular tower-type bicycle parking mechanical device. The stereo modular tower-type bicycle parking mechanical device comprises a rotating mechanism (3) used for rotating bicycles, a lifting mechanism (2) arranged on the rotating mechanism (3), a parking platform (5) arranged on the lifting mechanism (2), capable of rising and falling along the lifting mechanism (2) and used for bearing the bicycles, a clamping mechanism (1) arranged on the parking platform (5) for clamping front wheels of the bicycles, and positioning mechanisms (4) arranged on the periphery of the rotating mechanism (3) for fixing parking places. The stereo modular tower-type bicycle parking mechanical device is used for orderly parking the more bicycles in a limited area so as to solve the problem that parking of the bicycles is difficult in the area with the high crowd density.
Owner:XI AN JIAOTONG UNIV
Vehicle alarm method and device
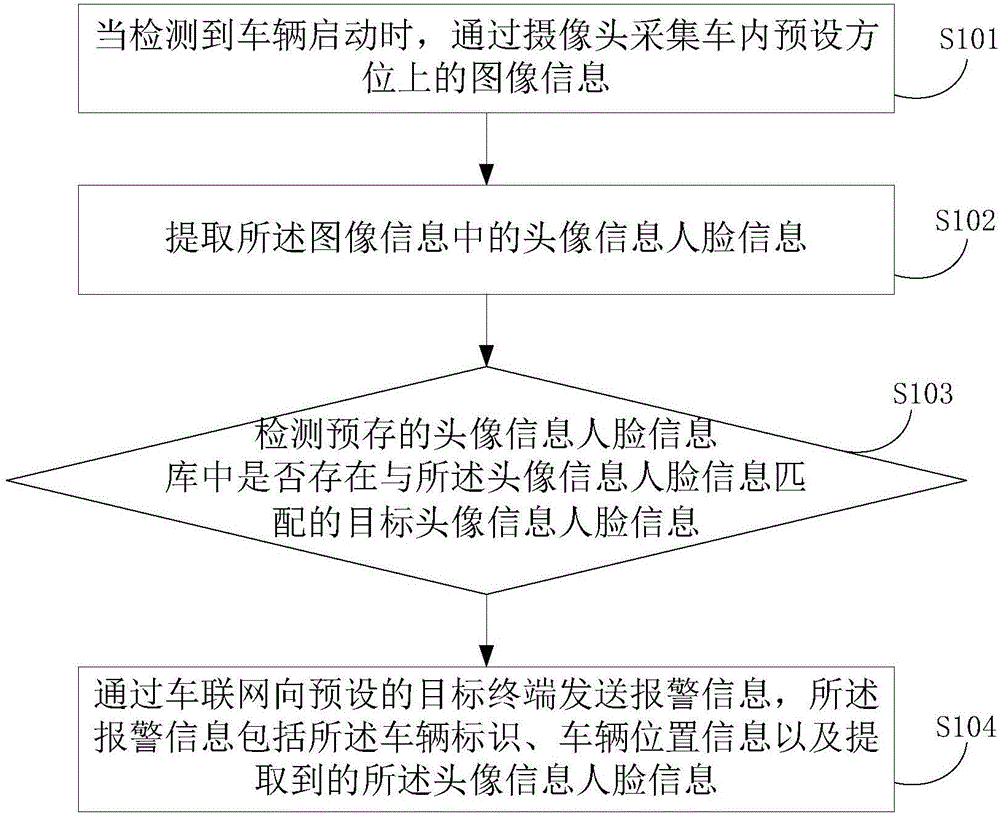
InactiveCN106599774ATrack in timeReduce the risk of theftCharacter and pattern recognitionTransmissionInformation repositoryThe Internet
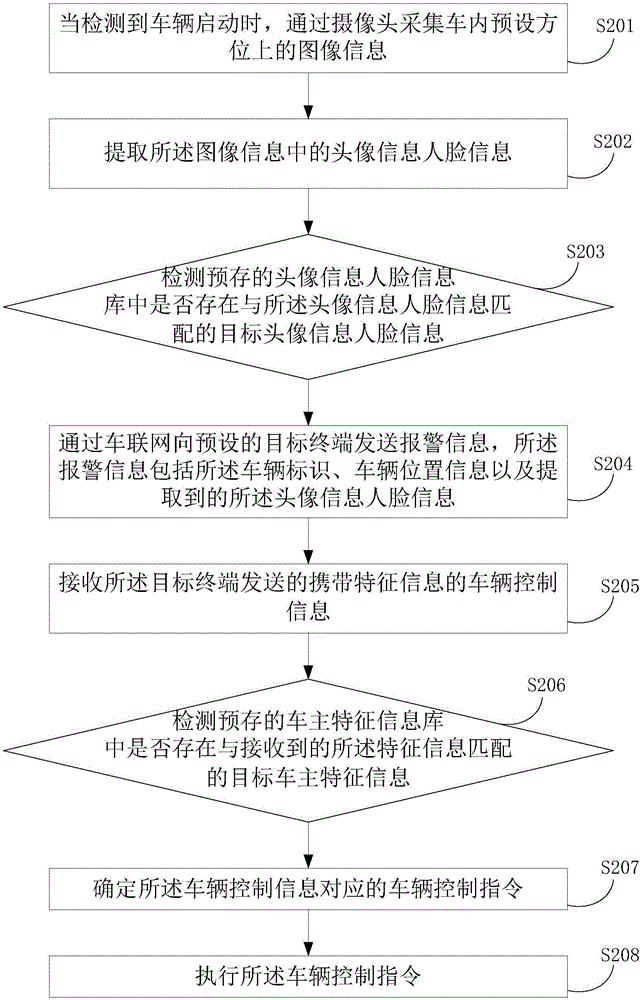
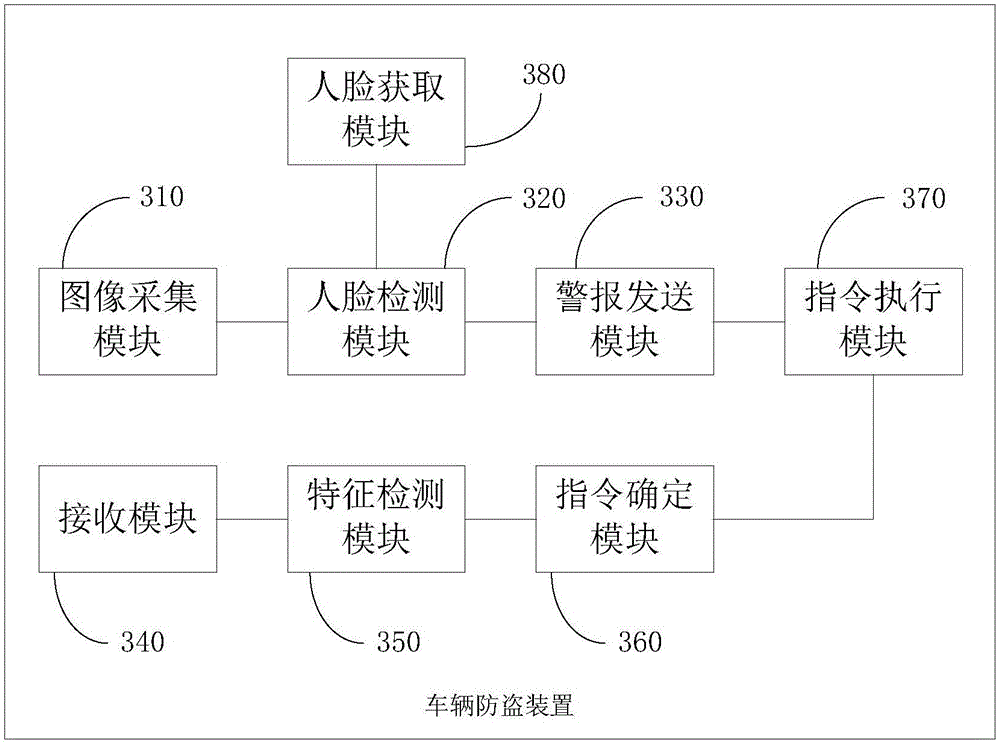
The invention provides a vehicle alarm method and device. The method includes the following steps that: when it is detected that a vehicle is started, image information in a preset direction in the vehicle is acquired through a camera; face information is extracted from the image information, whether target face information matched with the face information exists in a pre-stored face information library is detected; and if target face information matched with the face information does not exist in the pre-stored face information library, alarm information is sent to a preset target terminal through the Internet of Vehicles, wherein the alarm information contains a vehicle identifier, vehicle position information and the extracted face information. With the vehicle alarm method and device of the invention adopted, the vehicle can be tracked timely, and the risk of being stolen of the vehicle can be decreased.
Owner:LAUNCH TECH CO LTD
Vehicle anti-theft system and method of parking lot
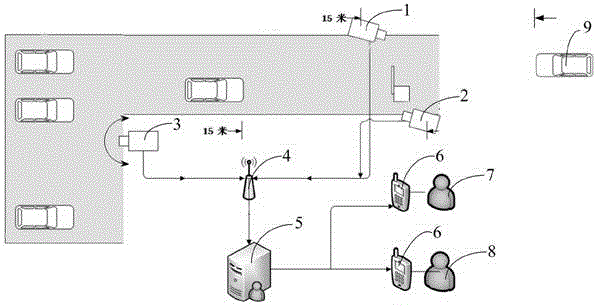
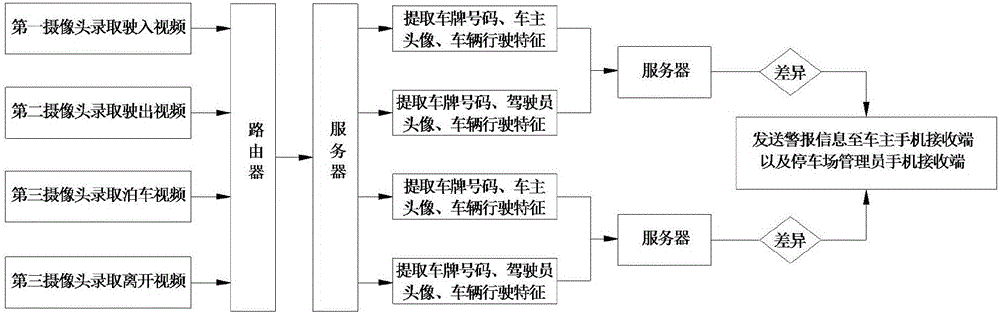
InactiveCN106710294AReduce the risk of theftImprove safety and reliabilityIndication of parksing free spacesCharacter and pattern recognitionDriver/operatorVehicle driving
The invention discloses a vehicle anti-theft system and method of a parking lot. A first camera collects entry data of vehicles, a second camera collects exit data of the vehicles, a third camera collects parking and departure data of the vehicles, the cameras transmit corresponding data to a server via a router in a WLAN communication protocol transmission manner, the server extracts and stores license plate numbers, vehicle owner / driver head portraits and vehicle driving features of the vehicles as basis information for monitoring examination, whether a vehicle has a risk of being stolen is detected in real time, and if YES, the server notifies the vehicle owner and a parking lot manager for confirmation timely, and the vehicle is not released unless both the vehicle owner and the parking lot manager confirm there is no risk. Compared with the prior art, the system and method can overcome management vulnerability of vehicle monitoring, reduces the risk of being stolen of the vehicles, and the vehicle anti-theft system is safer and more reliable.
Owner:中山大学南方学院
Electric motorcycle burglary prevention system
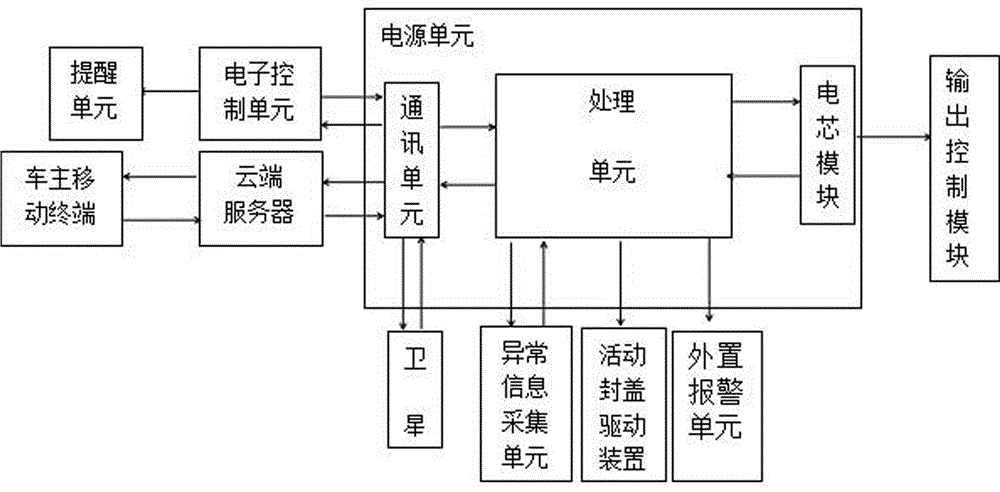
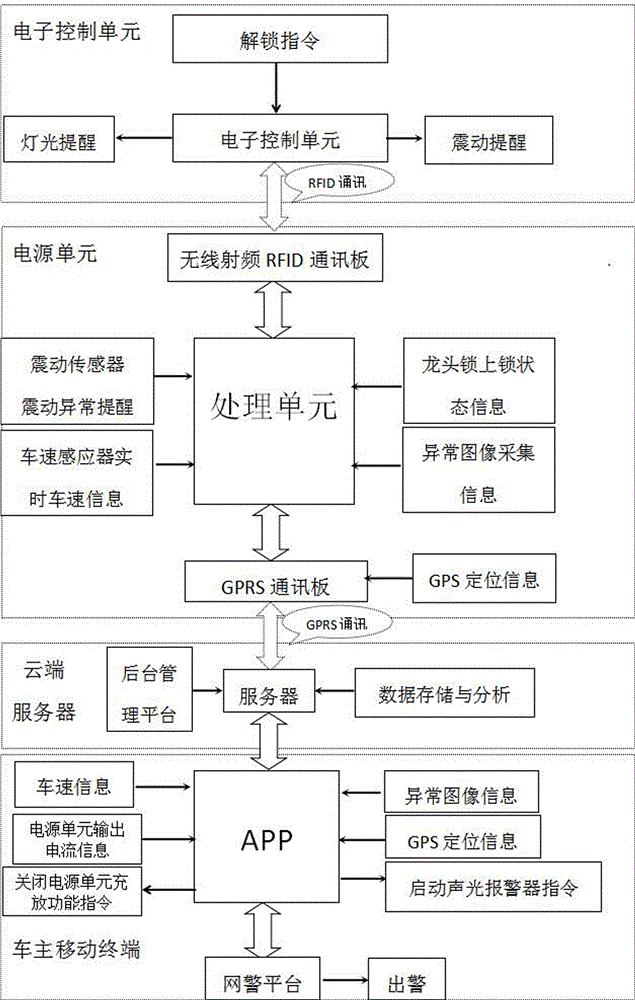
InactiveCN106741341AFacilitate the collection of alarms with confidenceReduce the risk of theftAnti-theft cycle devicesAnti-theft devicesAnti theftInformation transfer
The invention relates to the field of electric motorcycles, in particular to an electric motorcycle burglary protection system capable of acquiring abnormal condition, transmitting acquired information to a motorcycle owner mobile phone, making an output control unitclosea charging-discharging function of a power unit when a power supply is non-loaded and starting GPS positioning and an external alarm unit. The system comprises an electric motorcycle body and is characterized in that the power unit is carried in the motorcycle body, the power unit comprises a battery core module and an anti-theft module, the anti-theft module comprises a processing unit and a communication unit, the processing unit is connected with an abnormal information acquisition unit, an external alarm unit and a reminding unit electrically. The communication unit is connected with an electronic control unit and a motorcycle owner mobile terminal through a wireless link, an anti-theft movable seal cover and a corresponding driving device are arranged on the outer side of an electric motorcycle body locking cylinder and are electrically connected with a processing unit, and the system is used for blocking the lock cylinder while avoiding lock cylinder damage.
Owner:安徽登冠新能源电动车科技有限公司
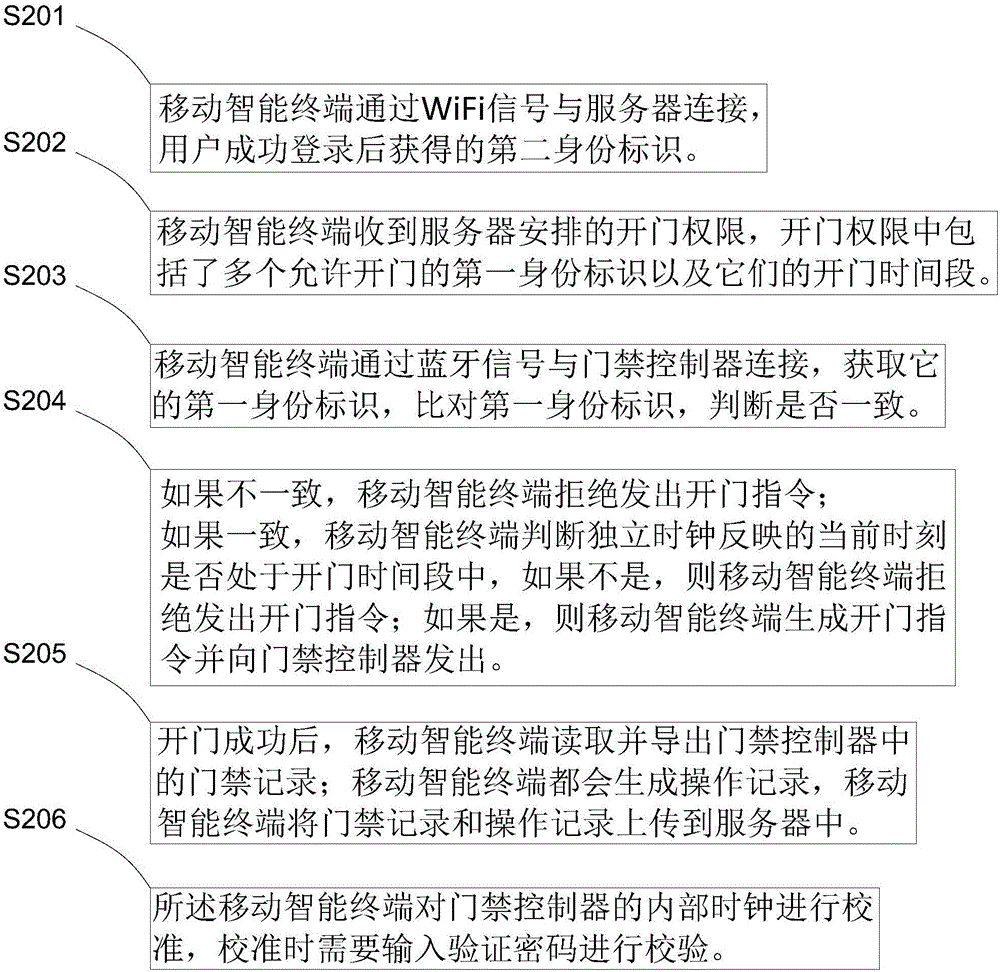
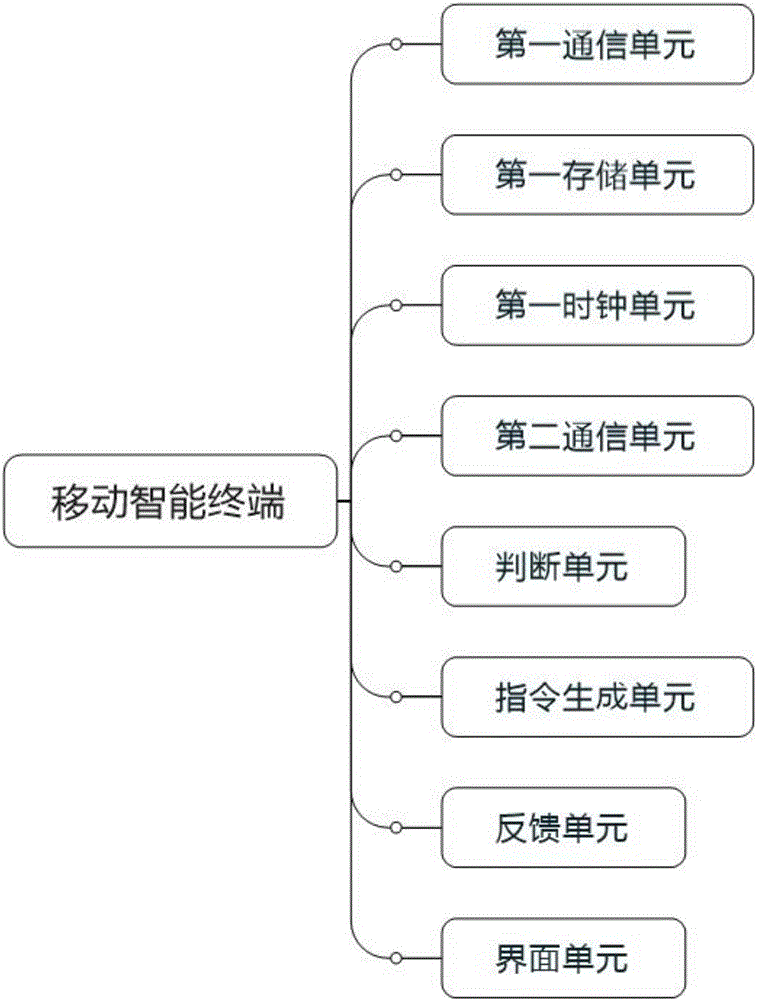
Access control system and method
The invention provides an access control method. An access controller is controlled by a mobile intelligent terminal to open a door. The method includes the steps that S1, the mobile intelligent terminal obtains a door opening authority; S2, the mobile intelligent terminal is connected with the access controller of a to-be-opened door and then judges whether the access controller conforms to the door opening authority or not, if yes, the mobile intelligent terminal sends a door opening instruction to the access controller and the access controller opens the door, and if not, the mobile intelligent terminal refuses to send the door opening instruction. The access control system is particularly suitable for the underground environment without an external network; the mobile intelligent terminal obtains the door opening authority on the ground and then moves to the underground, then the access controller can be controlled to open the door without the support of the external network; different from the door opening forms of keys and cards, copying is avoided, thievery risks are reduced, and safety and reliability are achieved.
Owner:常州市科能电器有限公司 +1
Lubricant dispenser
ActiveCN102341636AReduce the risk of theftSignal processingLubrication elementsElectronic controllerGas generator
A lubricant dispenser having a cartridge, a wall in the cartridge defining therein a lower chamber and an upper chamber, and a piston subdividing the lower chamber into a lower lubricant compartment and an upper gas compartment. The cartridge has an outlet opening into the lower lubricant compartment. A body of fluent lubricant fills the lower lubricant compartment. A housing in the upper chamber holds a gas generator connected through the wall to the gas compartment and electrically energizeable to generate gas and pressurize the gas compartment. A battery is secured to the housing. An electronic controller removably mounted in the upper chamber has electrical contacts connectable to the battery and to the gas generator. It is powerable by the battery for operating the gas generator and thereby pressurizing the gas compartment, moving the piston, and forcing the lubricant out of the outlet.
Owner:PERMA TEC
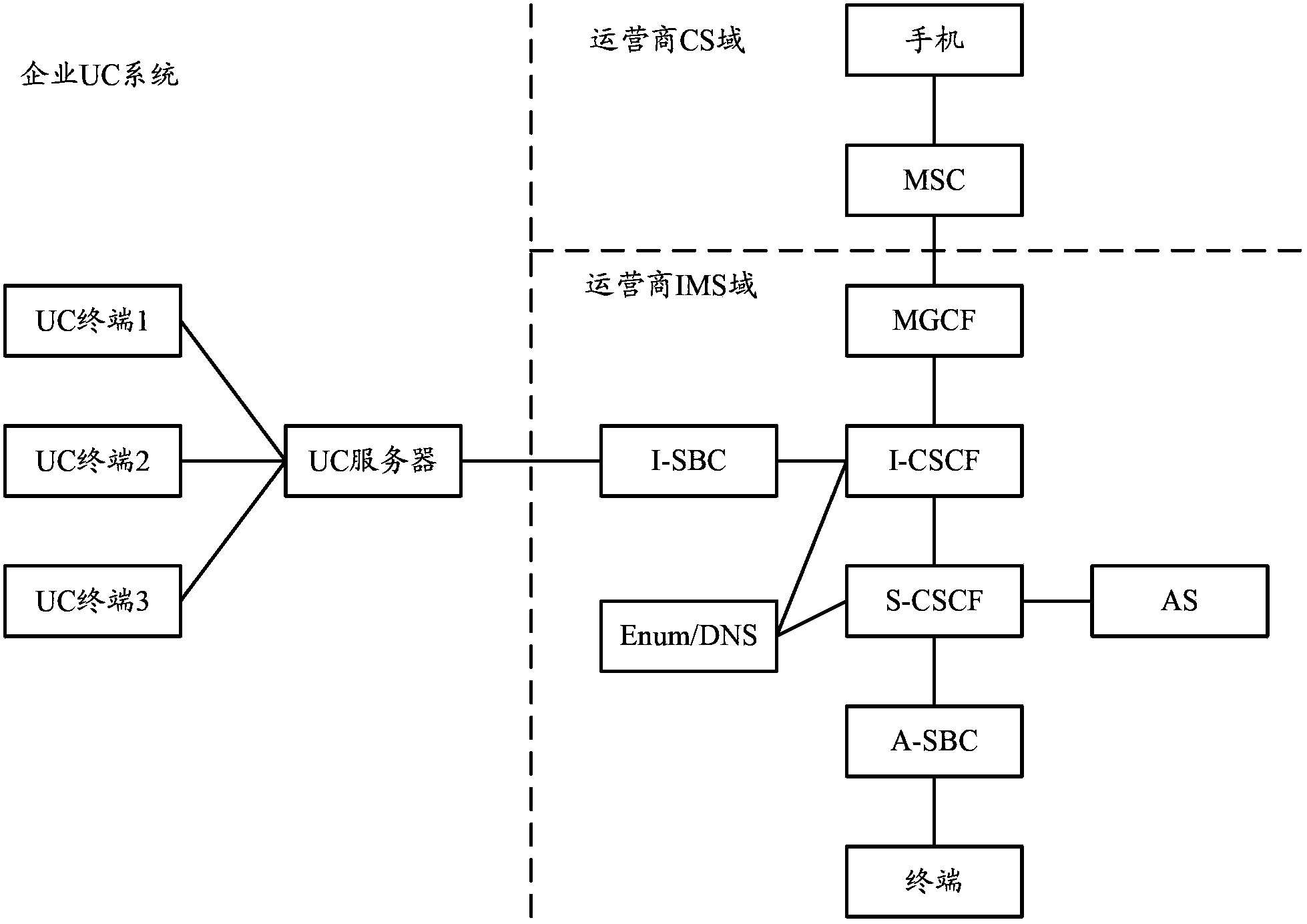
Method and equipment for realizing intercommunication of enterprise US system and IMS network
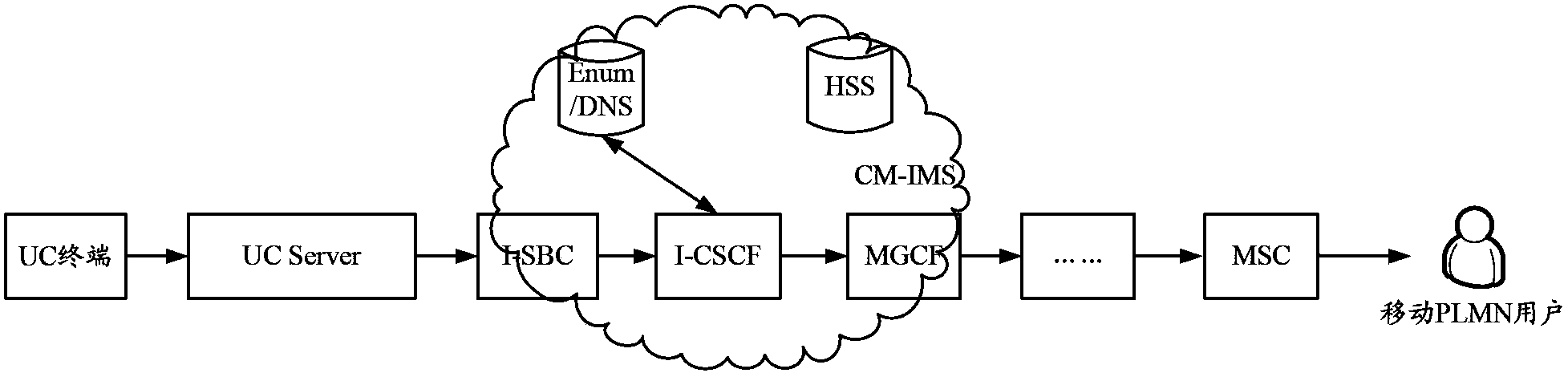
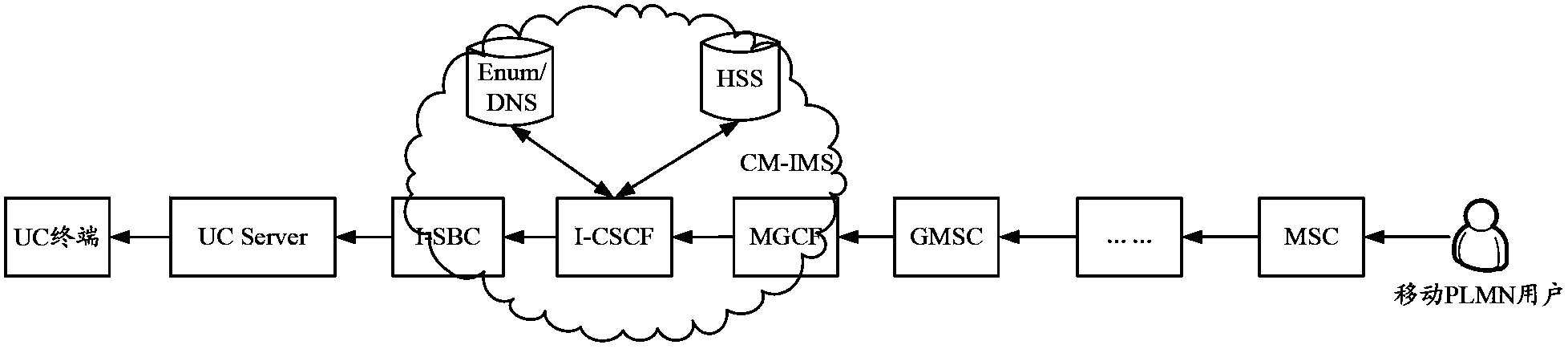
ActiveCN103905393AImprove interoperabilityReduce the risk of theftTransmissionNetwork data managementComputer scienceEnterprise it
An embodiment of the invention discloses a method and equipment for realizing intercommunication of an enterprise US system and an IMS network. The method includes: a gateway receives a message that a UC terminal is on line which is reported by a UC server, determines that the enterprise UC system carried in the message is a DID number corresponding to a number allocated to the UC terminal, and registers the DID number in the IMS network; and when the gateway receives a call request message of calling operator users which is initiated by the UC terminal, the gateway determines a DID number that a calling number carried in the call request message, the calling number is replaced with the DID number, and a call flow is initiated to the IMS network. In the method, business control of the UC terminal by an operator side is realized, and risks of theft-dialing are reduced.
Owner:CHINA MOBILE COMM GRP CO LTD
Anti-theft method and device of terminal and terminal equipment
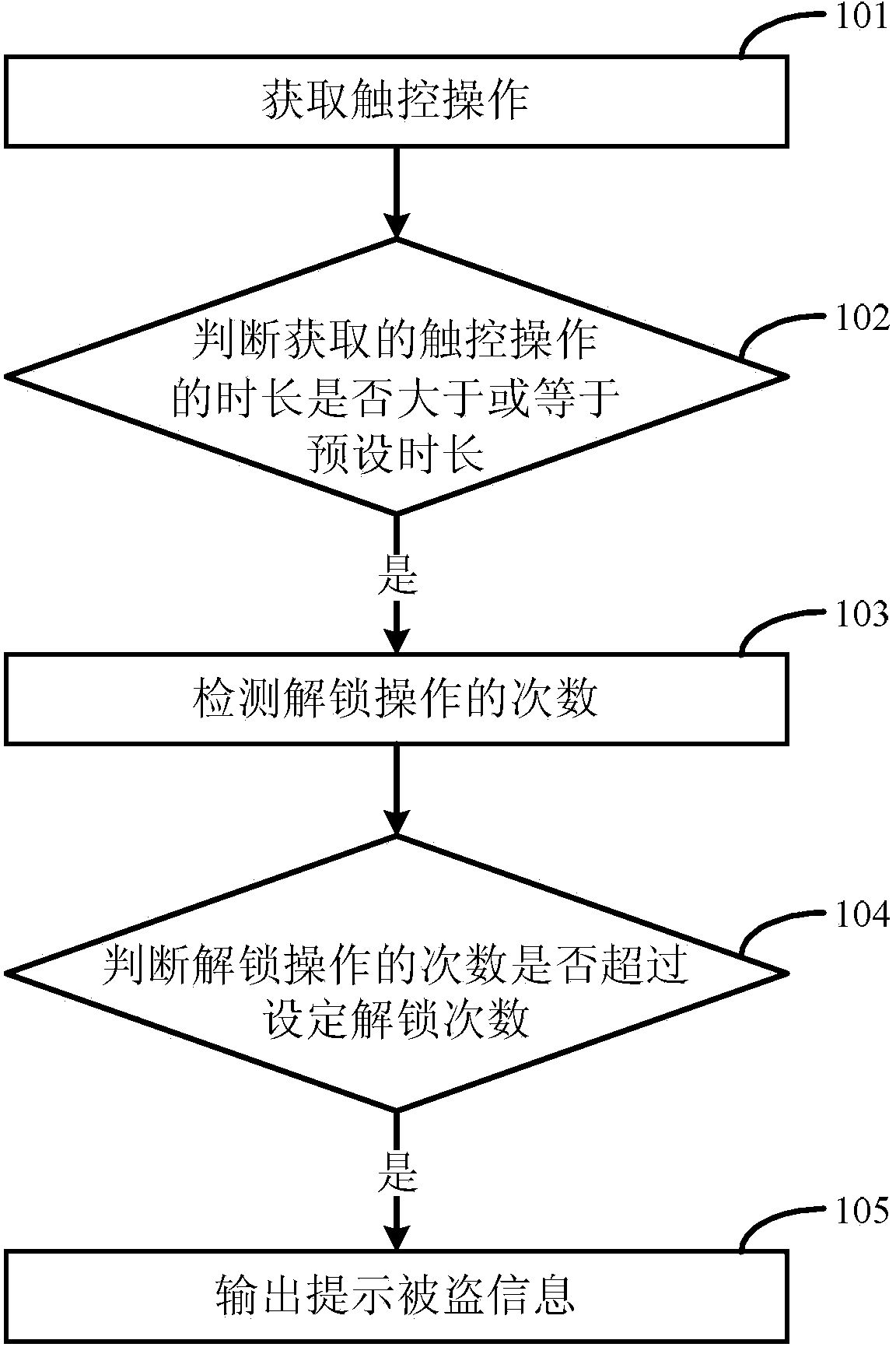
InactiveCN103679070AReduce the risk of theftIncrease standby timeInternal/peripheral component protectionInput/output processes for data processingTerminal equipmentComputer science
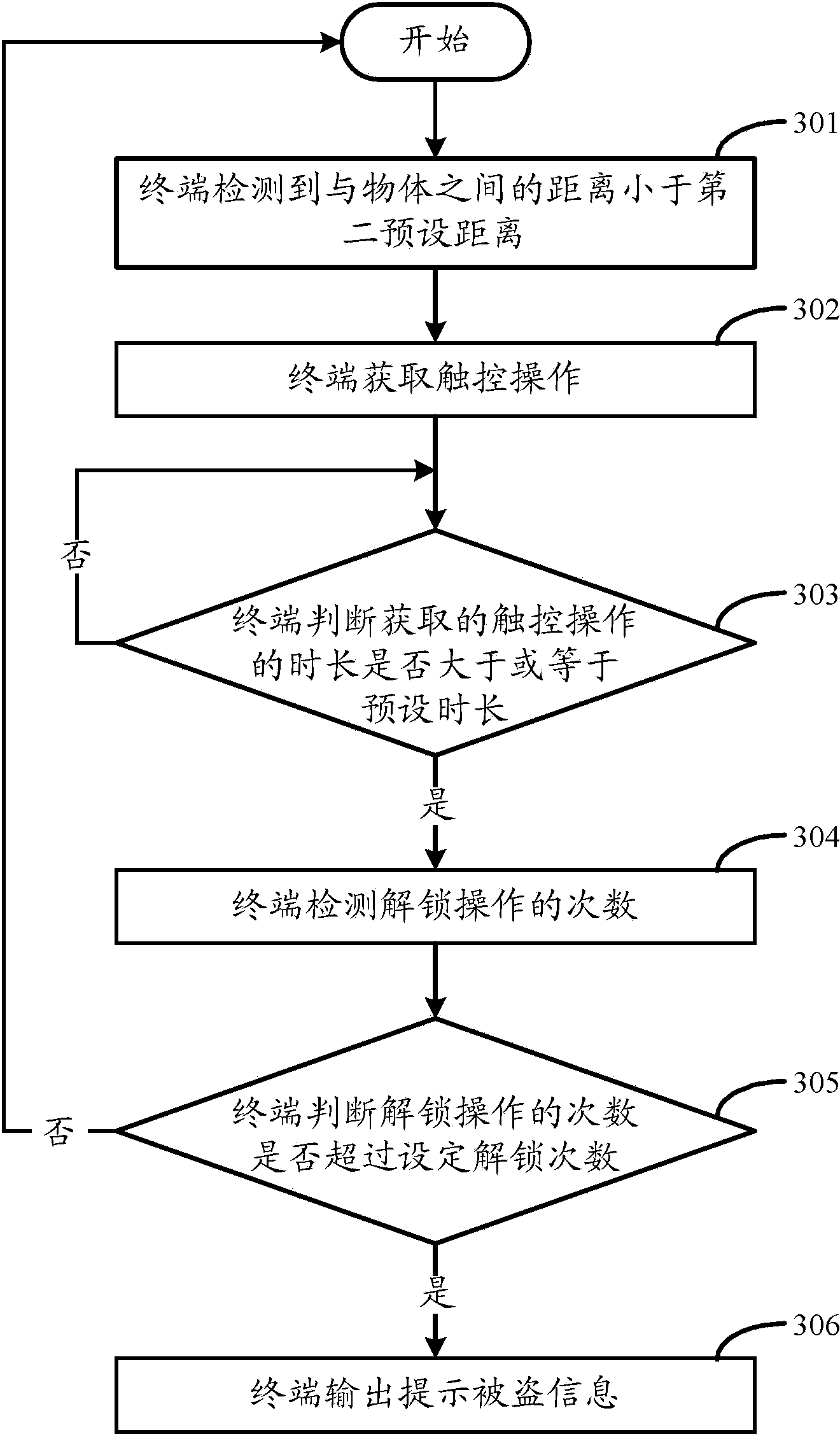
The invention discloses an anti-theft method and device of a terminal and terminal equipment. The anti-theft method and device of the terminal and the terminal equipment can prevent the terminal from being stolen right the first time, and effectively reduce the risk that the terminal is stolen. The anti-theft method comprises the steps of obtaining touch operation, judging whether the time length of the obtained touch operation is larger than a preset time length or not, detecting the number of unlocking operation times when the time length of the touch operation is judged to be not smaller than the preset time length, judging whether the number of the unlocking operation times is larger than the number of preset unlocking times or not, and outputting information prompting that the terminal is stolen when the number of the unlocking operation times exceeds the number of the preset unlocking times.
Owner:XIAOMI INC
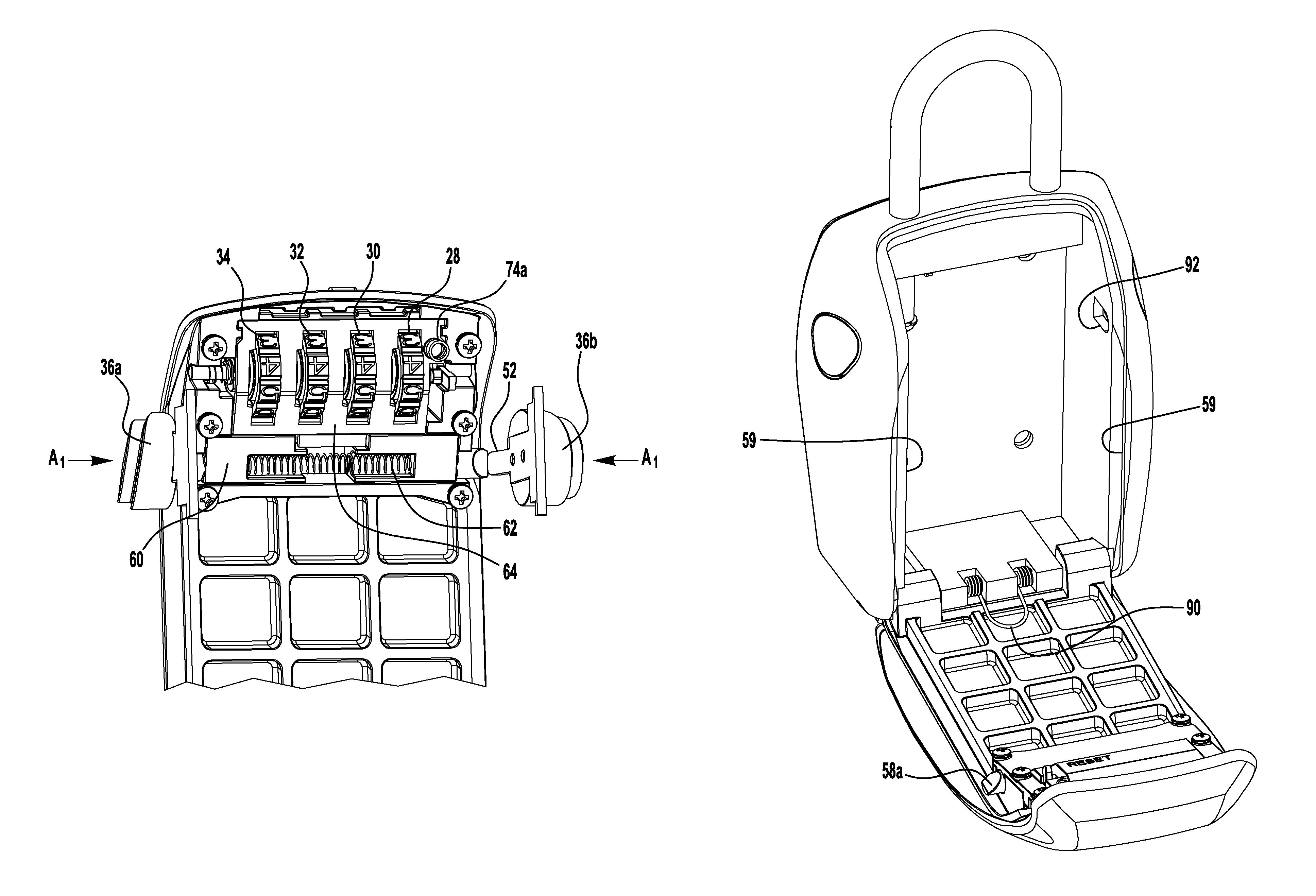
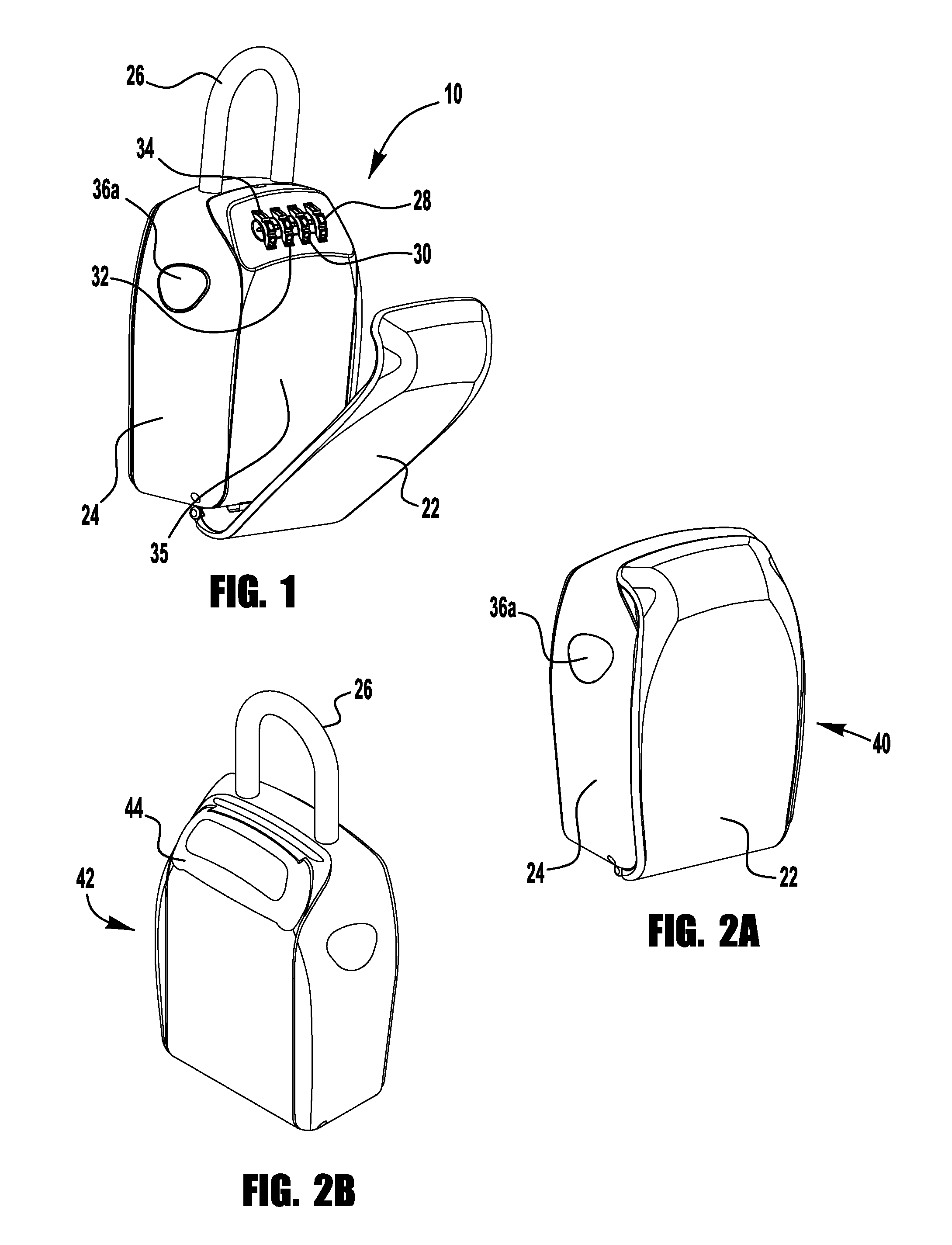
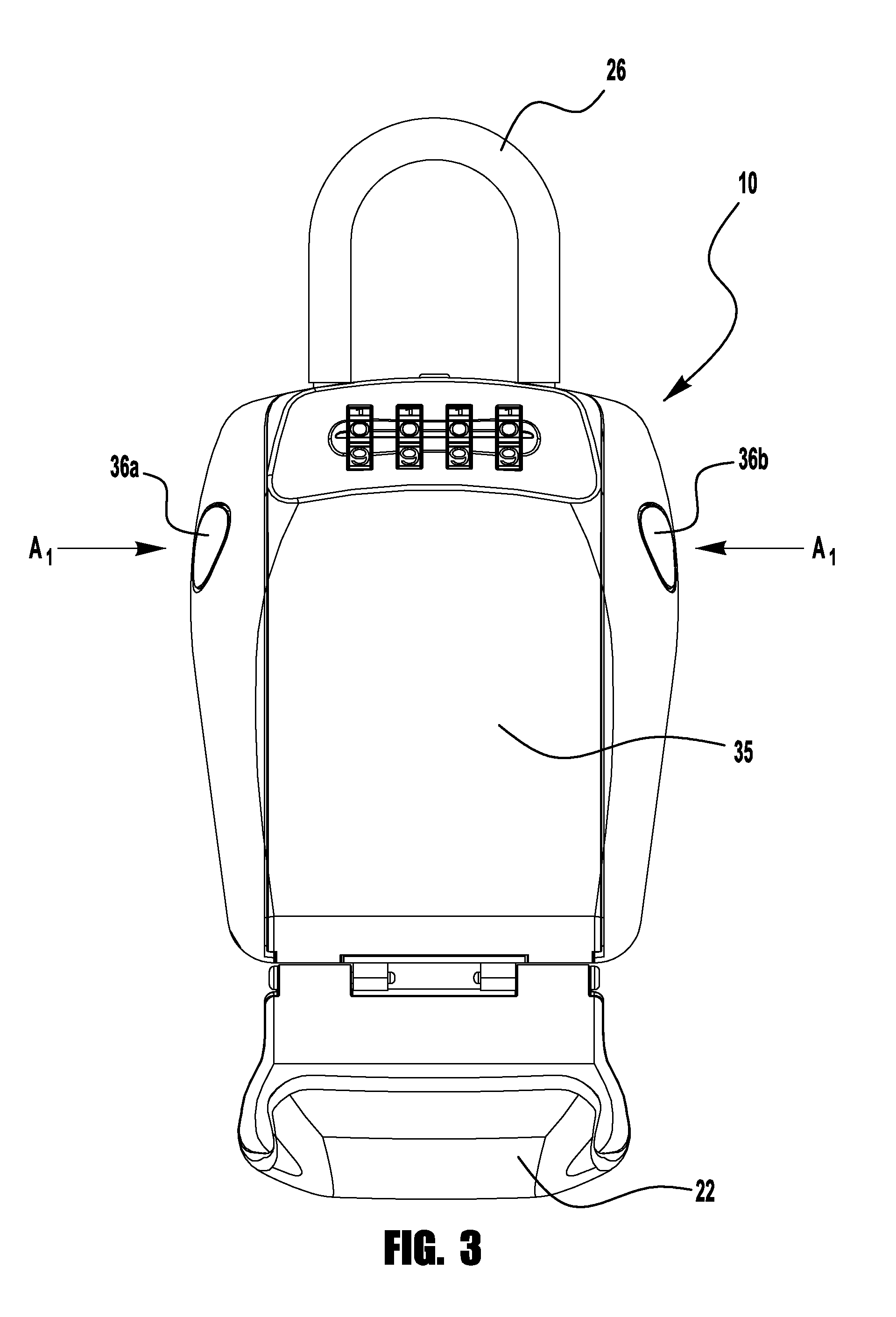
Safe with dual locking mechanism
A safe for providing security and storage of personal items. The safe includes a housing, a door, a user operable locking mechanism and a user operable release mechanism. The door can be opened only upon both proper manipulation of the user operable locking mechanism and proper manipulation of the user operable release mechanism. The user operable release mechanism is disposed to reduce the risk of theft of the contents of the safe by unauthorized attempts to manipulate the release mechanism. The safe may include a mounting arrangement for mounting the housing to a structure to reduce the risk of theft of the safe.
Owner:MASTER LOCK CO INC
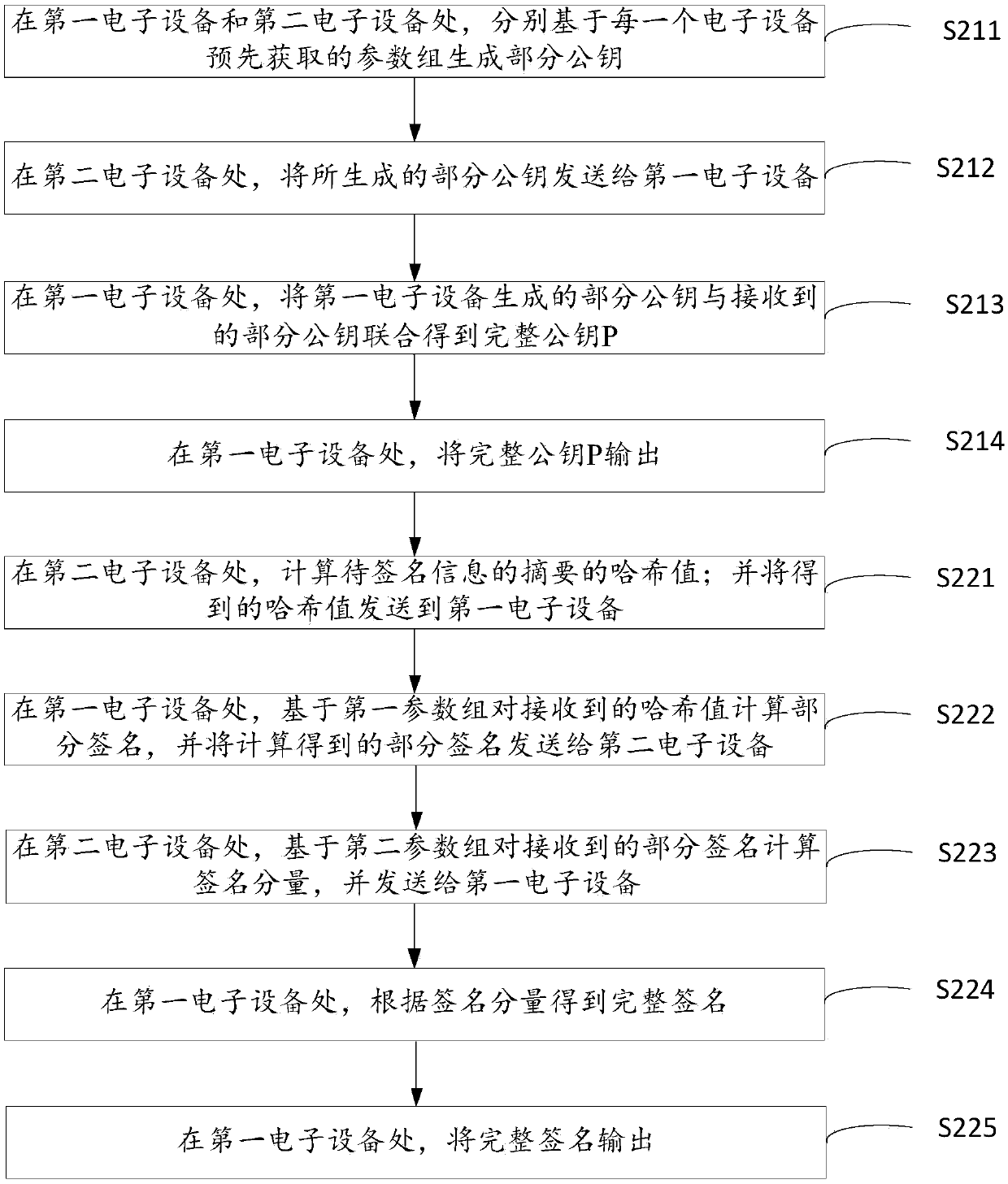
ECDSA algorithm-based signature generation method and apparatus, and data processing system
ActiveCN107911217AReduce the risk of theftIncrease the difficulty of being stolenKey distribution for secure communicationPublic key for secure communicationGeneration processData processing system
The embodiment of the disclosure relates to an ECDSA algorithm-based signature generation method and apparatus, and a data processing system. According to the embodiment of the disclosure, during thepublic key generation process, partial public keys are generated at two electronic devices based on different parameter groups; the partial public keys generated by the two electronic devices are combined to obtain an integrated public key, so that the private key is not generated completely at any electronic device. Therefore, no integrated private key can be obtained even when one electronic device is cracked, so that the difficulty of stealing the private key is improved and the risk of stealing the private key is reduced. Moreover, during the signature generation process, encryption is carried out at the two electronic device respectively based on different parameter groups, so that the signature operation process is completed.
Owner:陈彦丰 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com