Anti-theft method and device of terminal and terminal equipment
An anti-theft method and anti-theft device technology, applied in the input/output process of data processing, instruments, electronic digital data processing, etc., can solve the problems of endangering personal property safety, lack of quality, and life impact, and increase the standby time , save resource consumption, and reduce the risk of terminal theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
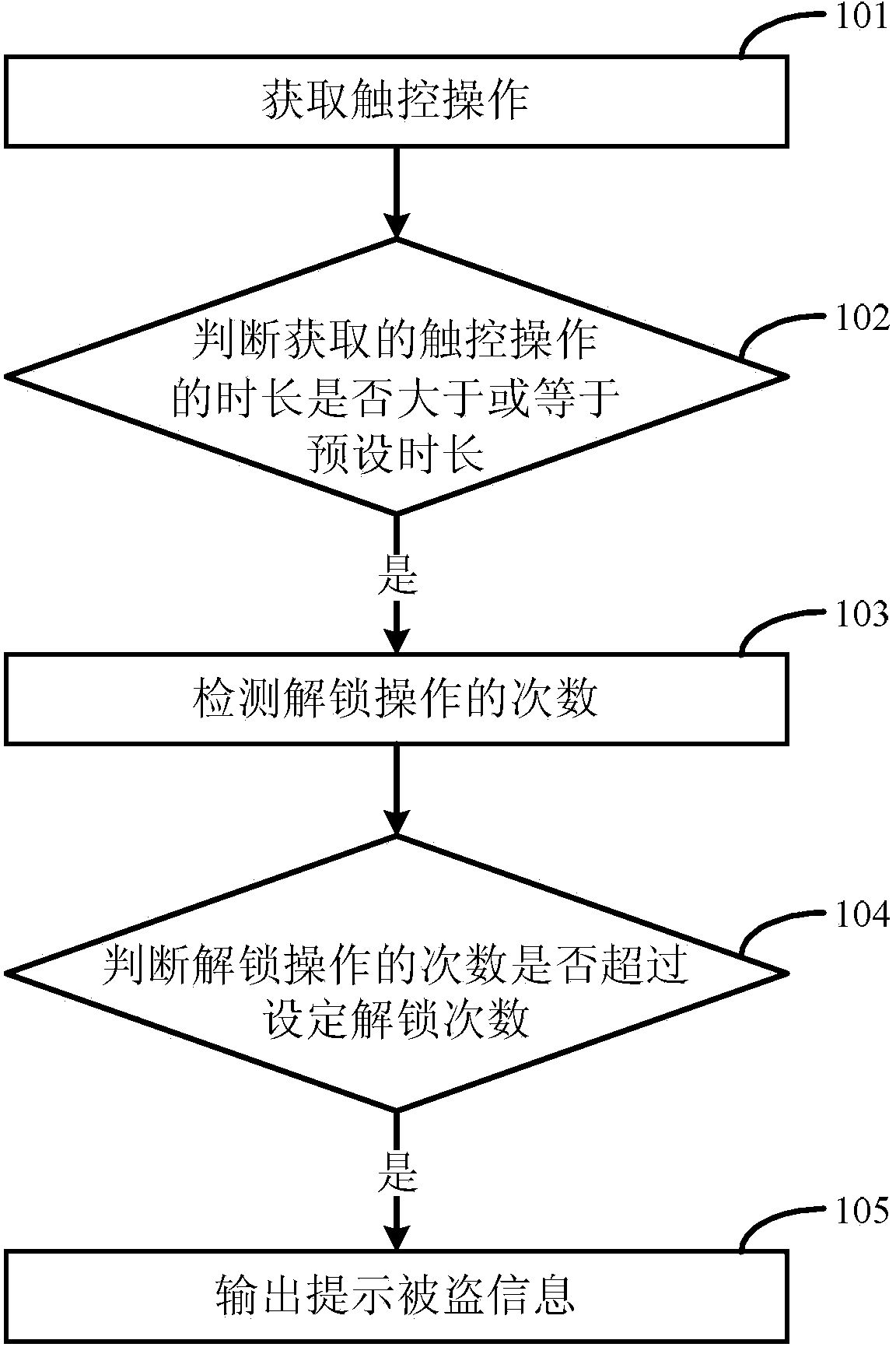
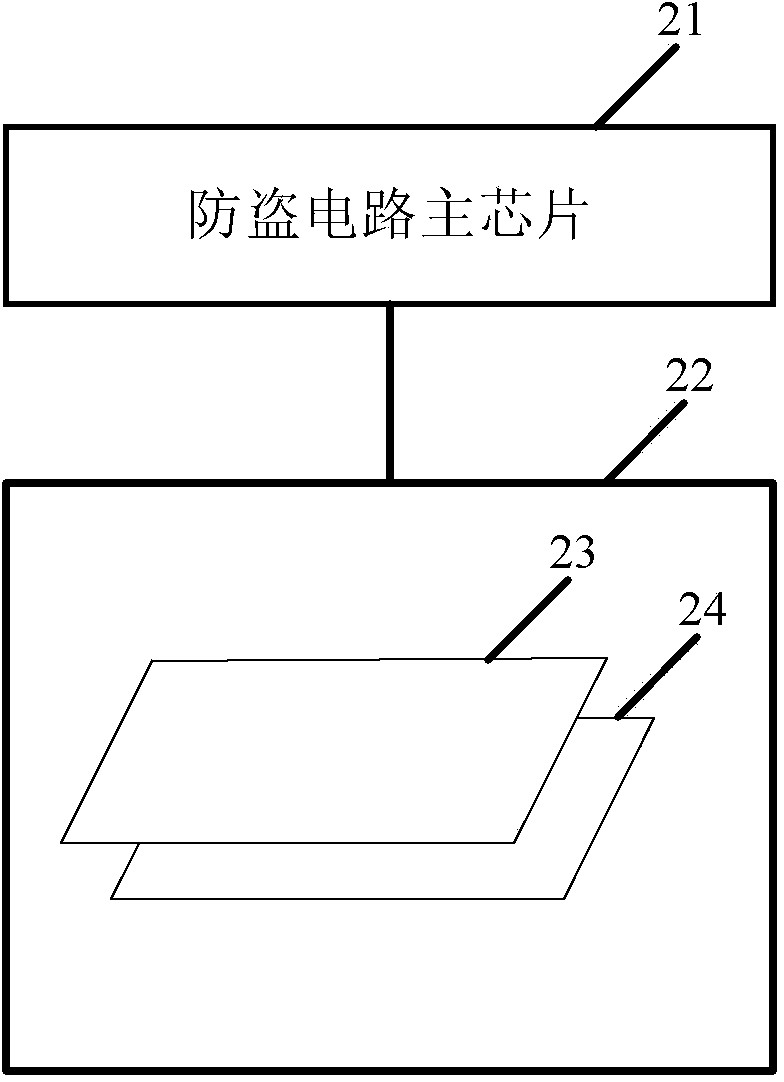
[0085] In Embodiment 1, the distance sensor on the terminal is used to detect the distance between the terminal and the object, and when the distance between the terminal and the object is detected to be less than the second preset distance, the anti-theft circuit designed on the terminal (such as figure 2 shown) to detect whether an object touches the terminal. like image 3 As shown, a terminal anti-theft method includes the following steps:
[0086] In step 301, the terminal detects that the distance to the object is less than a second preset distance, and the method of this embodiment can be applied to terminal devices such as smartphones and tablet computers.
[0087] The distance sensor on the terminal can be used to detect the distance between the terminal and the object. When it is detected that the distance between the terminal and the object is less than the second preset distance, the distance sensor will set the distance between the terminal and the object to be ...
Embodiment 2
[0097] In the second embodiment, the terminal is associated with the setting terminal, and when the distance between the terminal and the setting terminal exceeds the first preset distance, the stolen information is sent to the setting terminal, and the user can start from the setting terminal at the first time. You can get prompt information at the designated terminal, effectively reducing the risk of the terminal being stolen. like Figure 4A As shown, a terminal anti-theft method includes the following steps:
[0098] In step 401, the terminal detects and sets the distance between the terminals. The method of this embodiment can be applied to terminal devices such as smartphones and tablet computers.
[0099] In step 402, when it is detected that the distance from the set terminal exceeds the first preset distance, the terminal sends a stolen message to the set terminal.
[0100] In step 403, the terminal obtains a touch operation.
[0101] Wherein, the touch operation m...
Embodiment 3
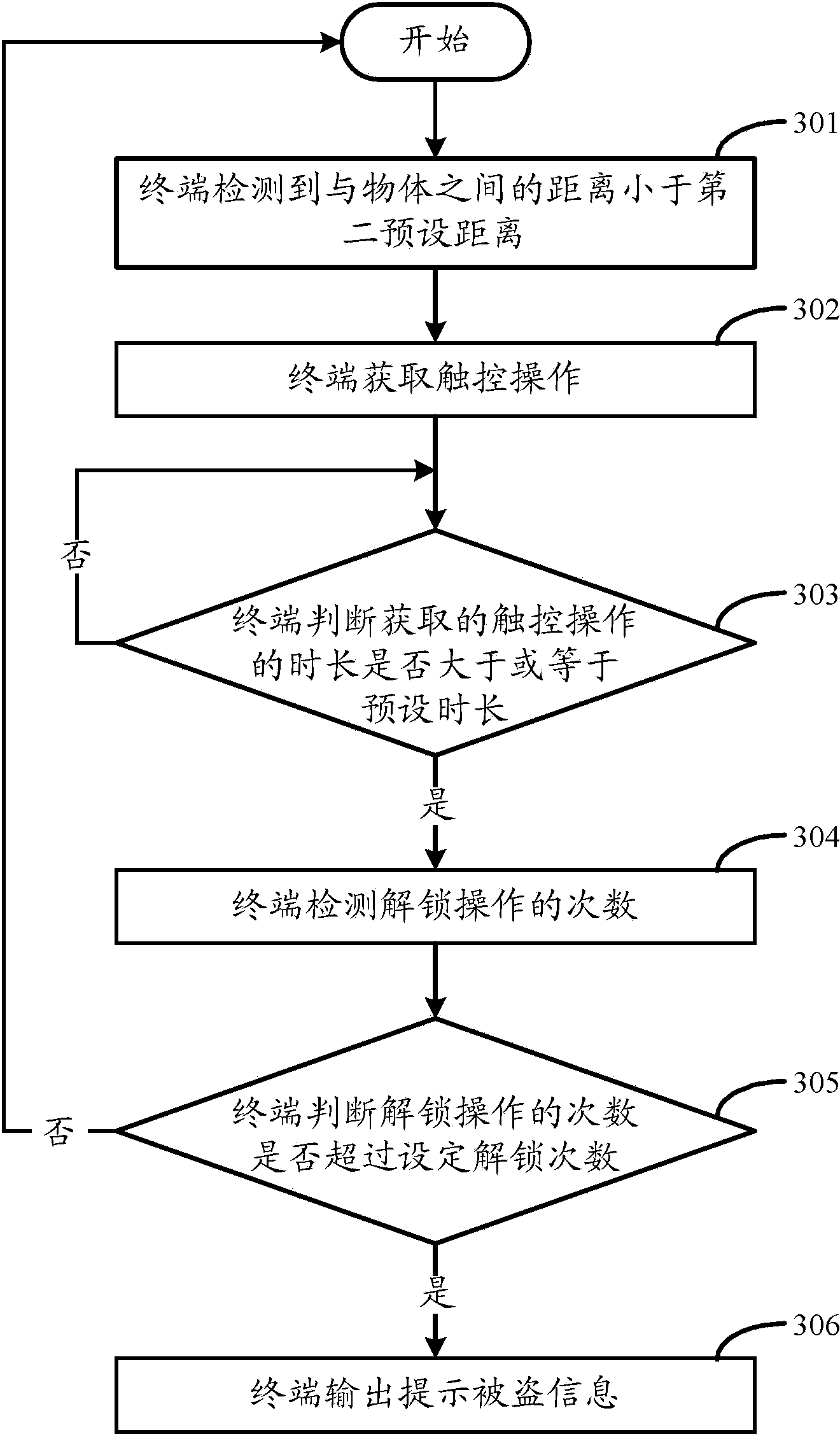
[0109] In the third embodiment, the stolen information is output to the setting terminal or the server, and the setting terminal or server outputs the prompting information, so that the user can receive the prompting information in time to prevent the terminal from being stolen. like Figure 4B As shown, a terminal anti-theft method includes the following steps:
[0110] In step 411, the terminal detects that the distance to the object is less than the second preset distance, and the method of this embodiment can be applied to terminal devices such as smartphones and tablet computers.
[0111] In step 412, the terminal obtains a touch operation.
[0112]In step 413 , the terminal judges whether the acquired duration of the touch operation is greater than or equal to the preset duration, if yes, proceeds to step 414 ; otherwise, returns to continue execution of step 413 .
[0113] In step 414, the terminal detects the number of unlocking operations.
[0114] In step 415, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com