Access control system and method
A management method and access control technology, which is applied in the access control management system and its management field, can solve problems such as inability to communicate, scattered distribution of substations, low difficulty in copying cards, etc., and achieve the effect of reducing the risk of theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
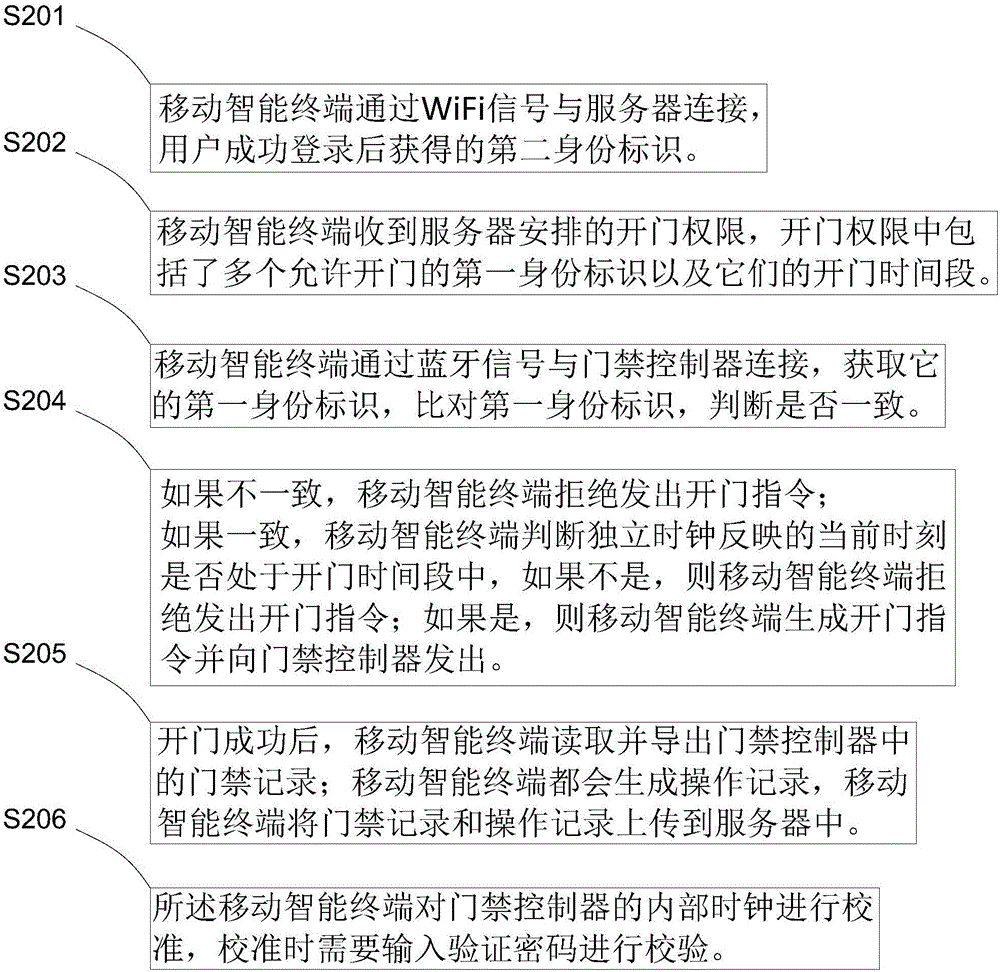
[0091] Such as image 3 As shown, the present invention provides a first embodiment of a mobile smart terminal, including:
[0092] The first communication unit is used to connect with the server and send user identity verification information to the server; after the verification is passed, obtain the second identity mark; it is also used to obtain the door opening authority from the server; each access controller corresponds to a first identity mark, The door-opening authority includes at least one first identification of an access controller that is allowed to open the door and their opening time periods;
[0093] The first storage unit is used to store the authority to open the door;
[0094] a first clock unit, configured to form an independent clock;
[0095] The second communication unit is used to connect with the access controller to obtain the first identity of the access controller to be opened;
[0096] Judging unit: used to verify whether the first identity of ...
Embodiment 2
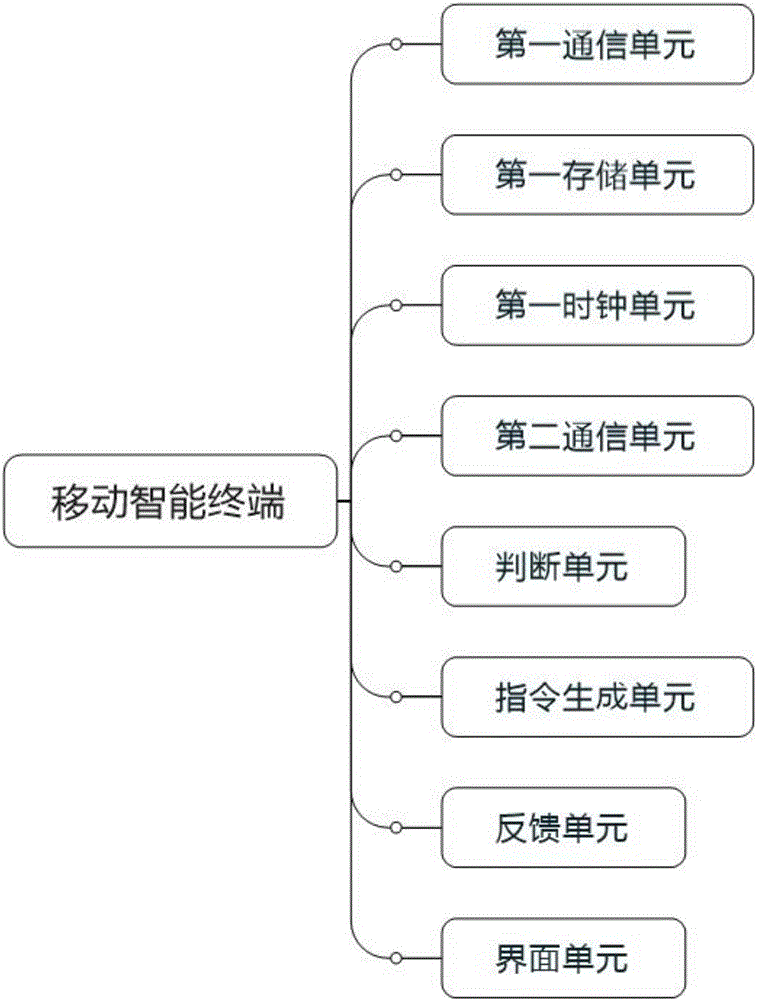
[0102] Such as Figure 4 As shown, the present invention provides a second embodiment of a mobile smart terminal. Compared with the first embodiment, the mobile smart terminal also includes:
[0103] An operation record unit, configured to generate an operation record corresponding to the second identity;
[0104] The second communication unit is also used to obtain the access control record corresponding to the first identity from the access control controller;
[0105] The first storage unit is also used for storing operation records and access control records;
[0106] The first communication unit is also used to transmit the operation record and access control record to the server.
Embodiment 3
[0107] Such as Figure 5 As shown, the present invention provides a third embodiment of a mobile smart terminal. Compared with the second embodiment, the mobile smart terminal also includes:
[0108]An encryption unit, configured to encrypt the setting operation of the first clock unit;
[0109] a decryption unit, configured to decrypt the encrypted first clock unit;
[0110] Calibration unit for synchronizing the stand-alone clock with the network clock on the server.
[0111] Such as Image 6 As shown, the invention provides a kind of access controller, comprising:
[0112] The third communication unit is used to connect with the mobile smart terminal to obtain the door opening instruction;
[0113] The lock control unit is used to control the opening or closing of the door lock.
[0114] An access control record unit, configured to generate an access control record corresponding to the first identity;
[0115] The second clock unit is used to reflect the current momen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com