ECDSA algorithm-based signature generation method and apparatus, and data processing system
A technology for generating signatures and algorithms, applied in digital transmission systems, transmission systems, secure communication devices, etc., can solve the problems that the holder of the private key is easy to be attacked, the private key is easy to be stolen, and the encryption system fails, etc. The risk of private key being stolen, the effect of increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] It should be understood that the specific embodiments described here are only used to explain the present disclosure, not to limit the present disclosure.
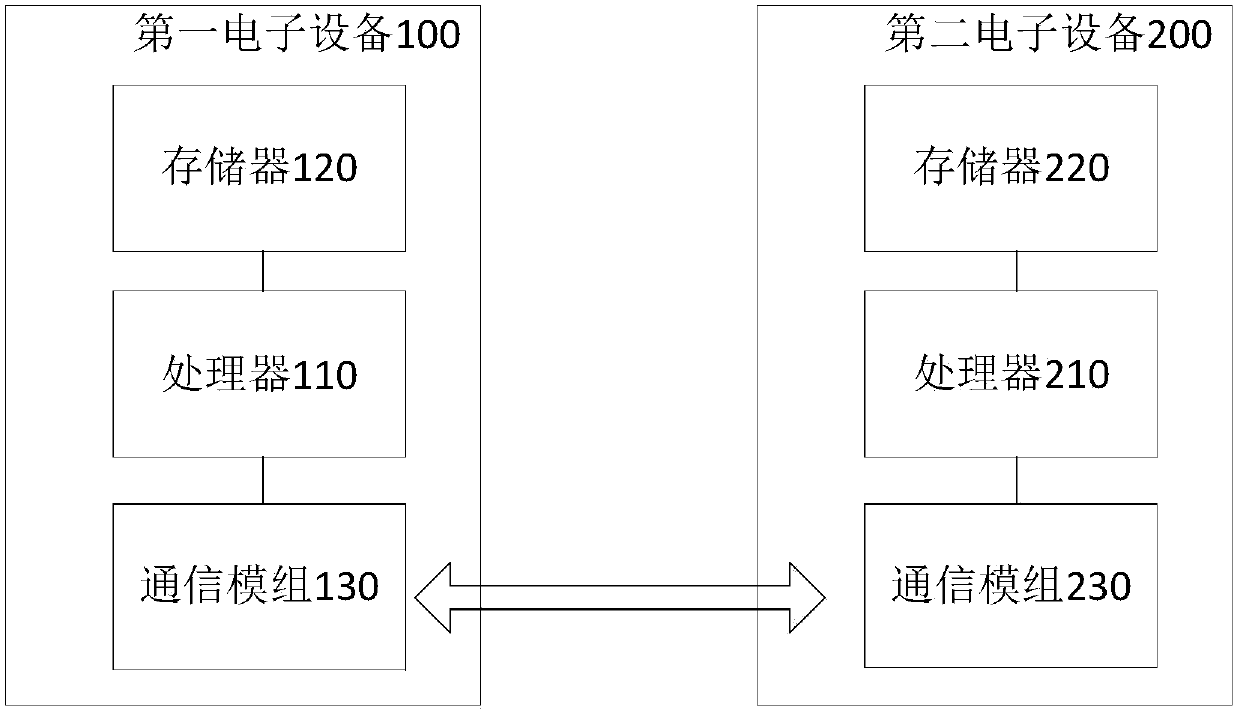
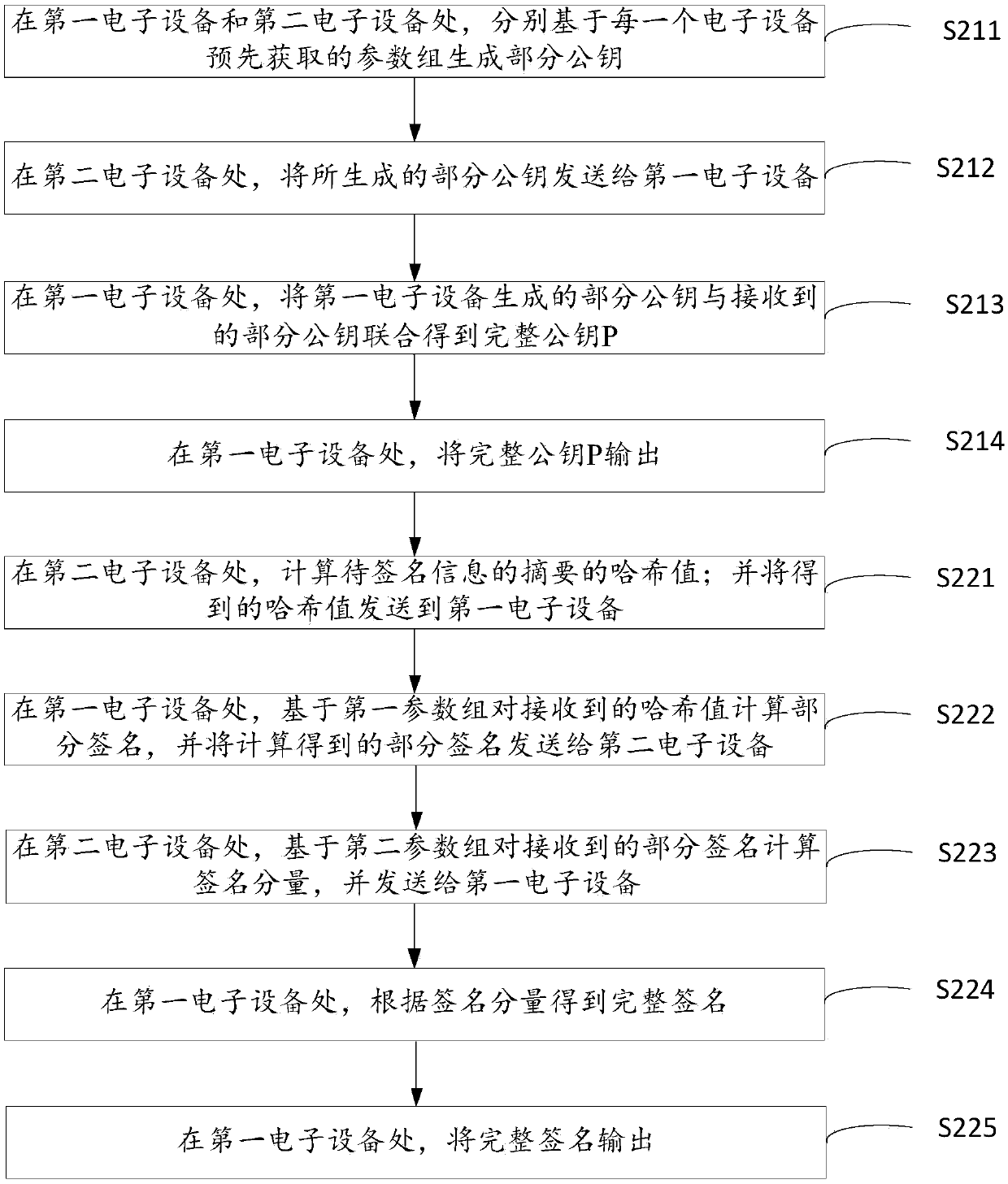
[0057] figure 1 A schematic diagram showing the structure of the signature system provided by an embodiment of the present disclosure, figure 1 The scenario shown in is a typical application scenario of the signature generation method based on the ECDSA algorithm provided by an embodiment of the present disclosure. Please refer to figure 1 , the system includes at least two electronic devices, which are referred to as a first electronic device 100 and a second electronic device 200 for convenience of description. continue to refer figure 1 , the first electronic device 100 includes a processor 110 , a memory 120 and a communication module 130 ; and the corresponding first electronic device 200 includes a processor 210 , a memory 220 and a communication module 230 . In each electronic device, the communication mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com