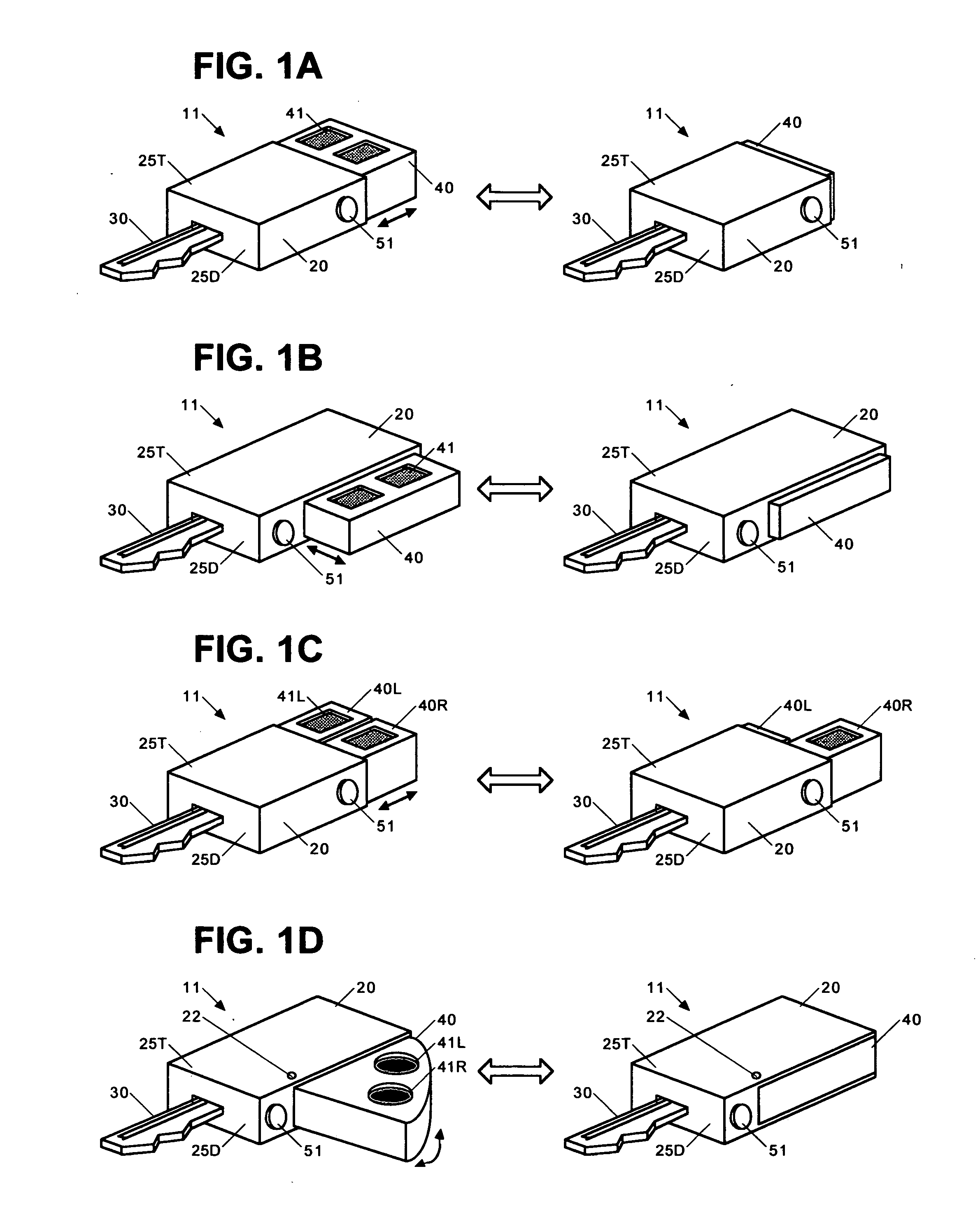
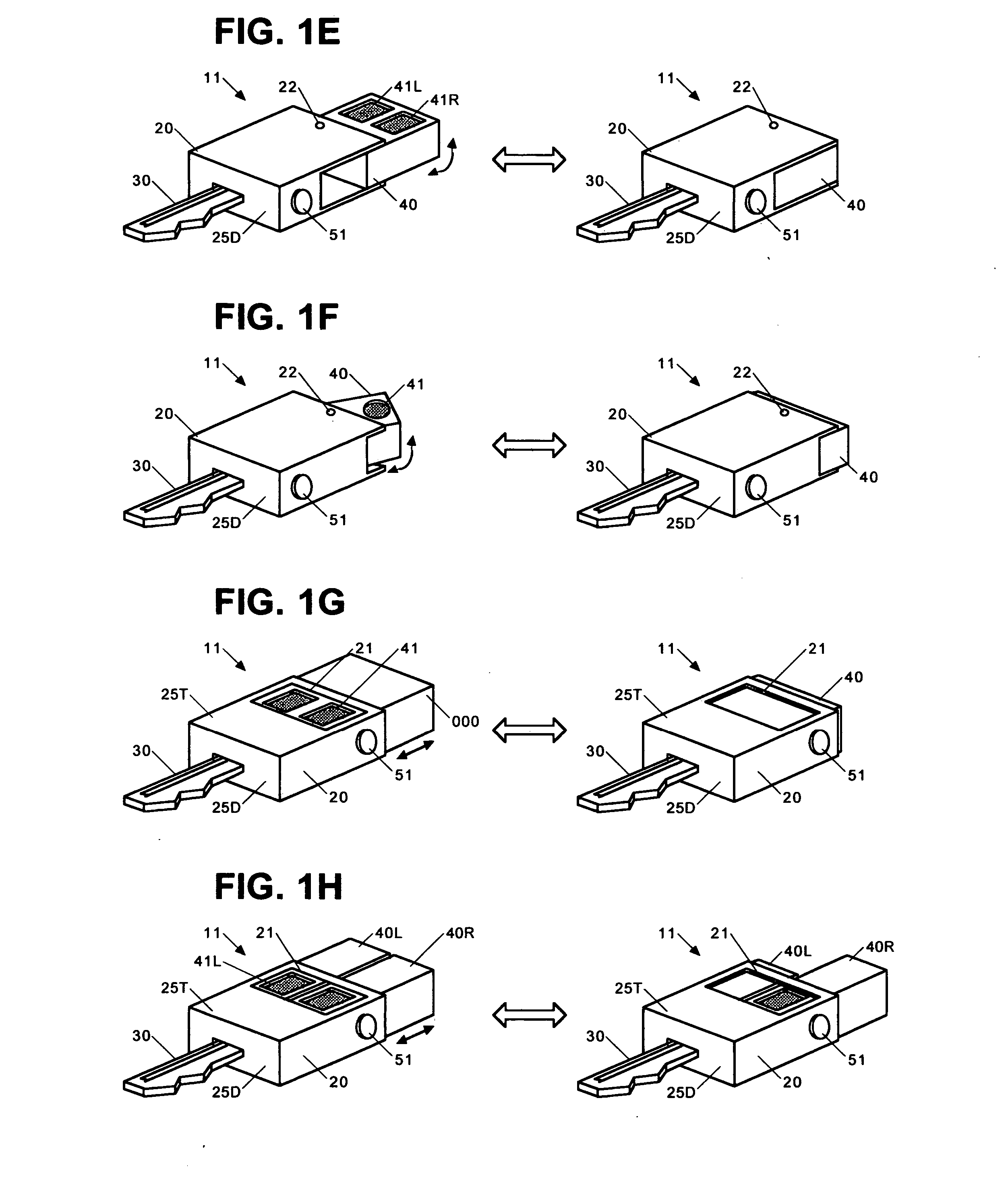
Patents
Literature
4088results about "Keys" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
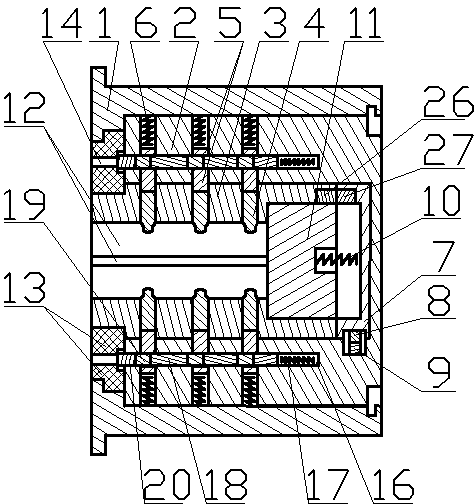
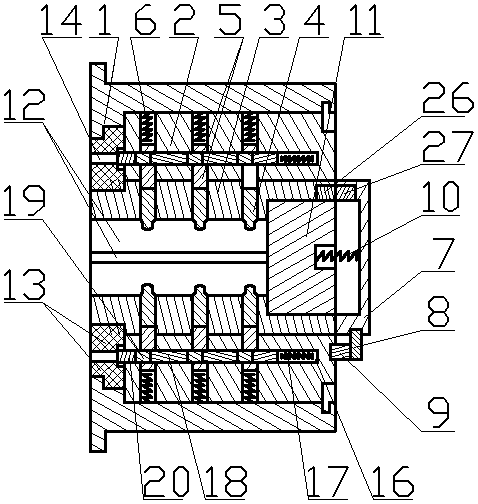
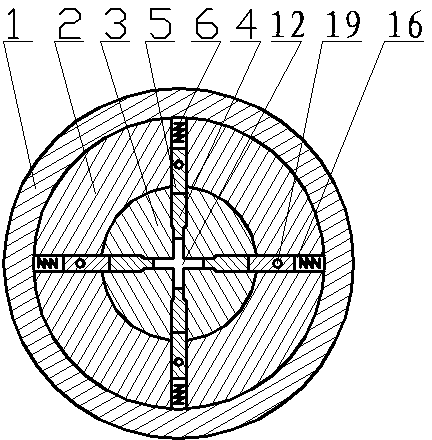
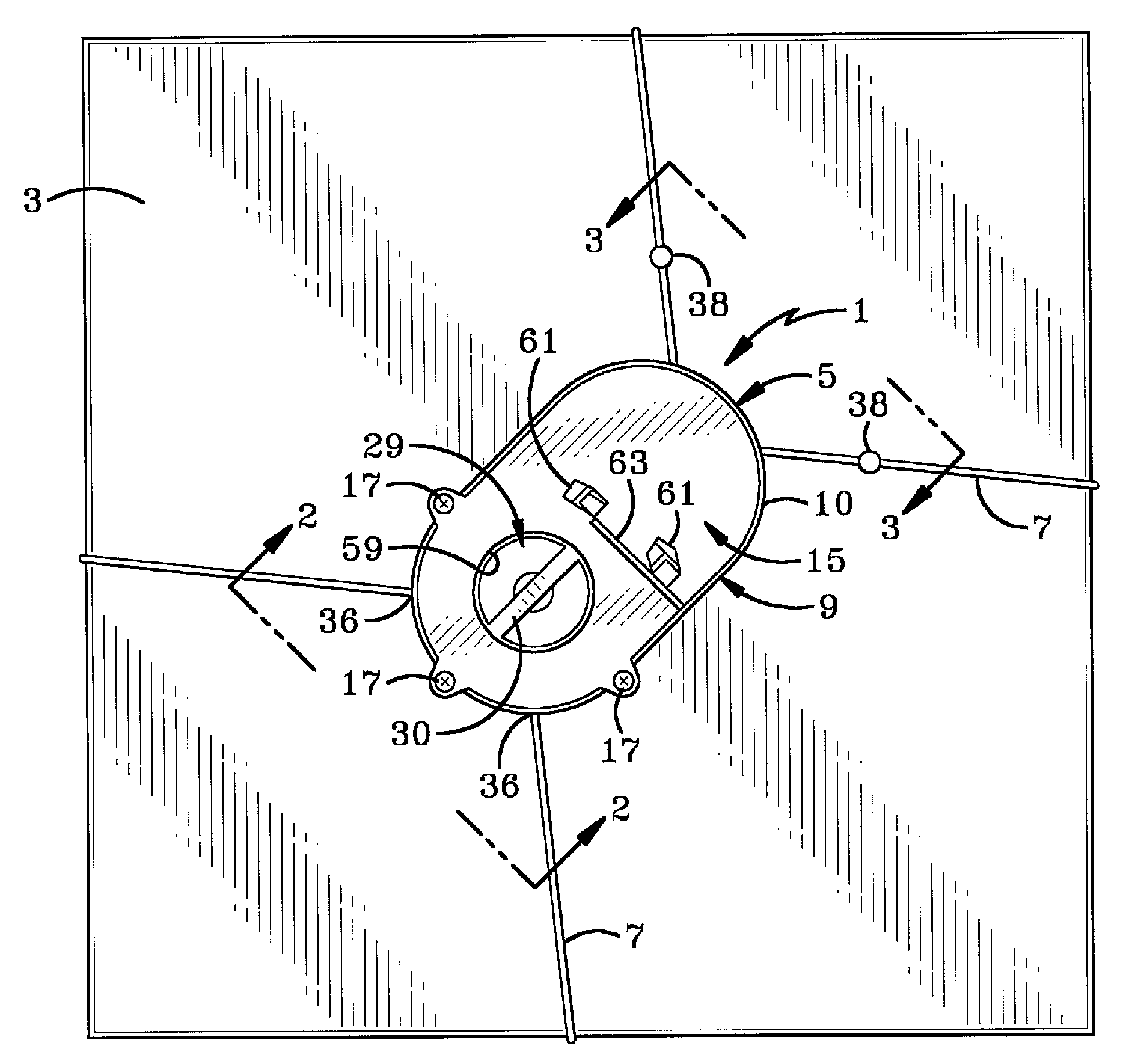
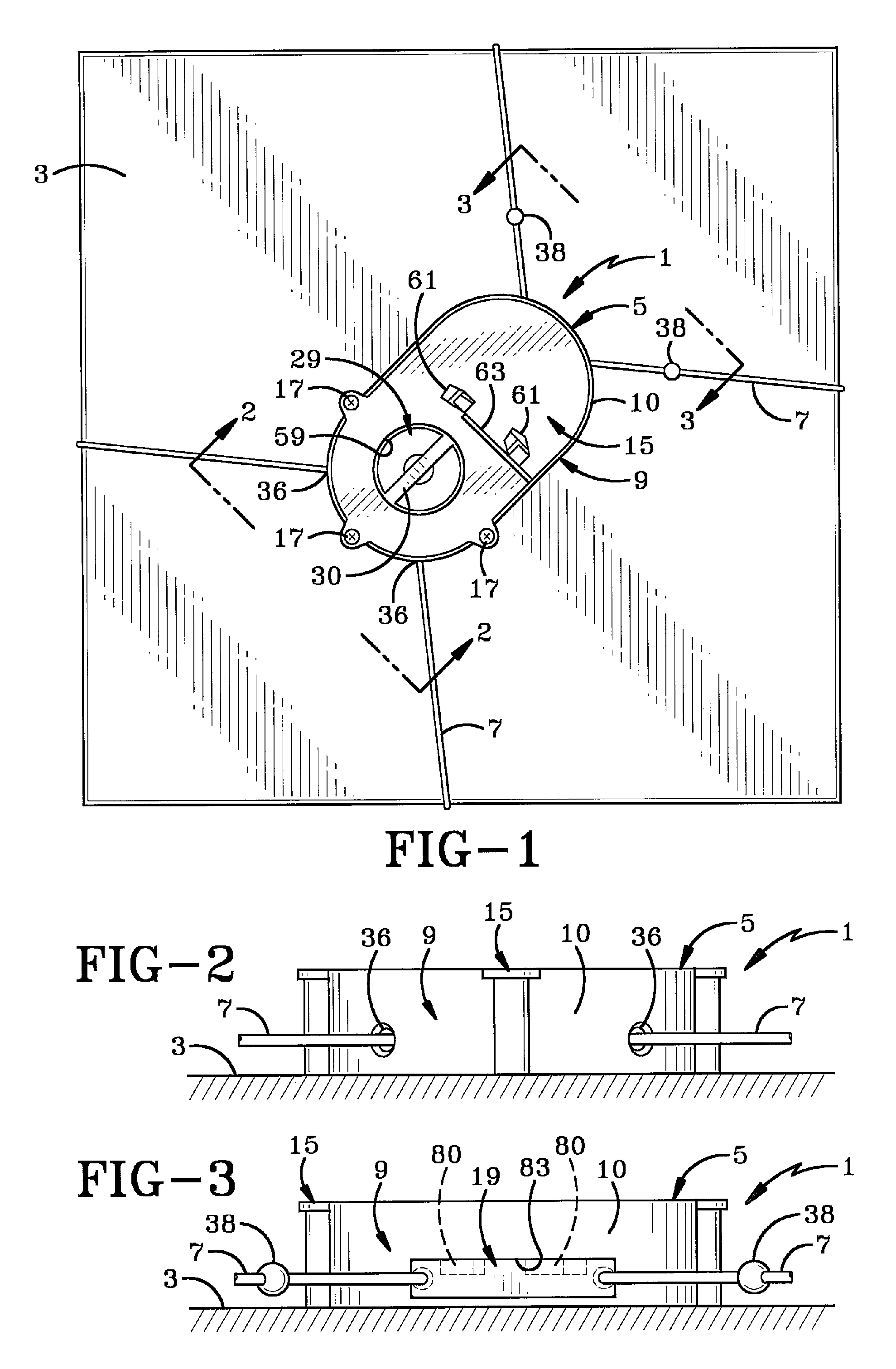
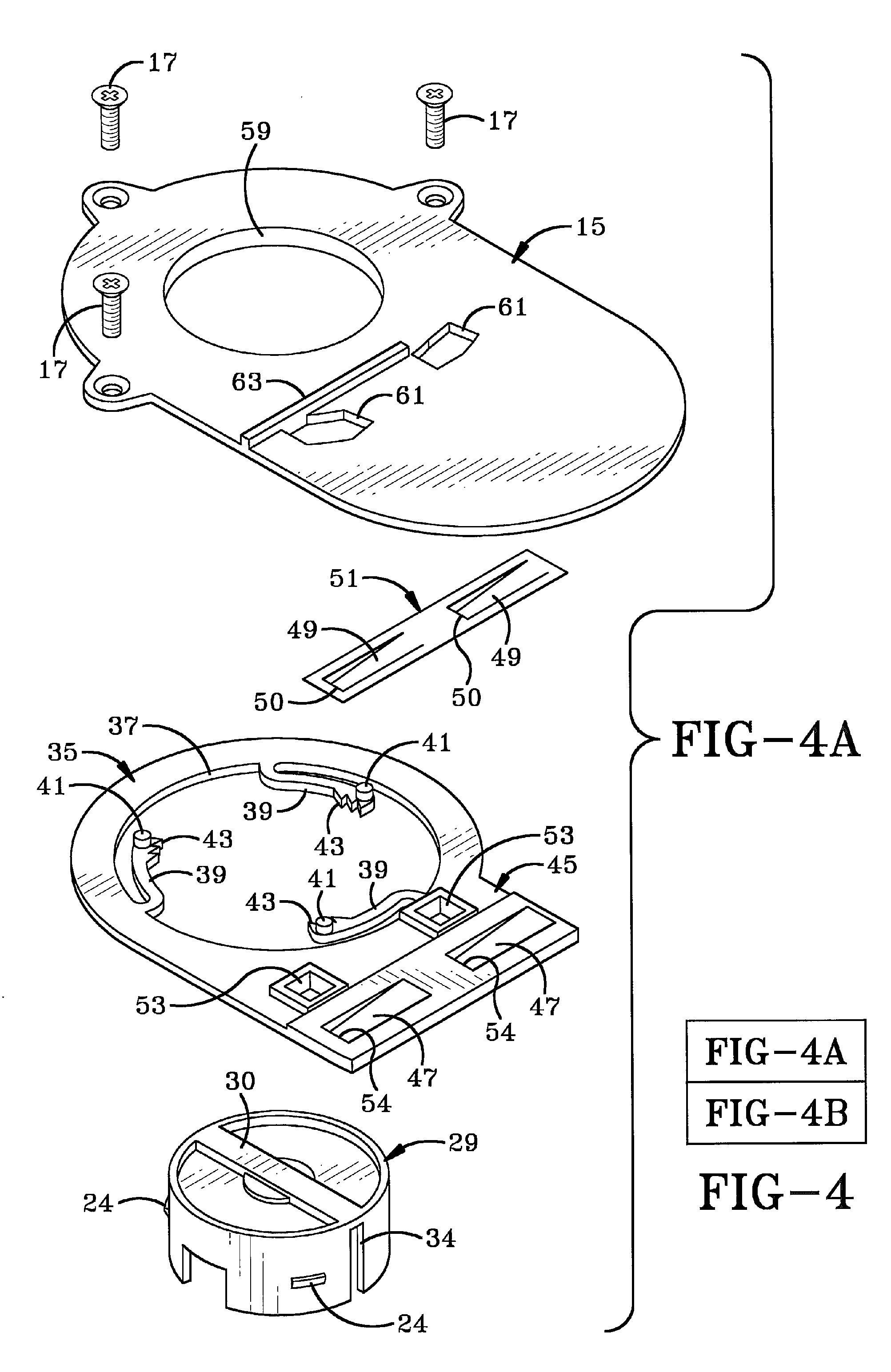
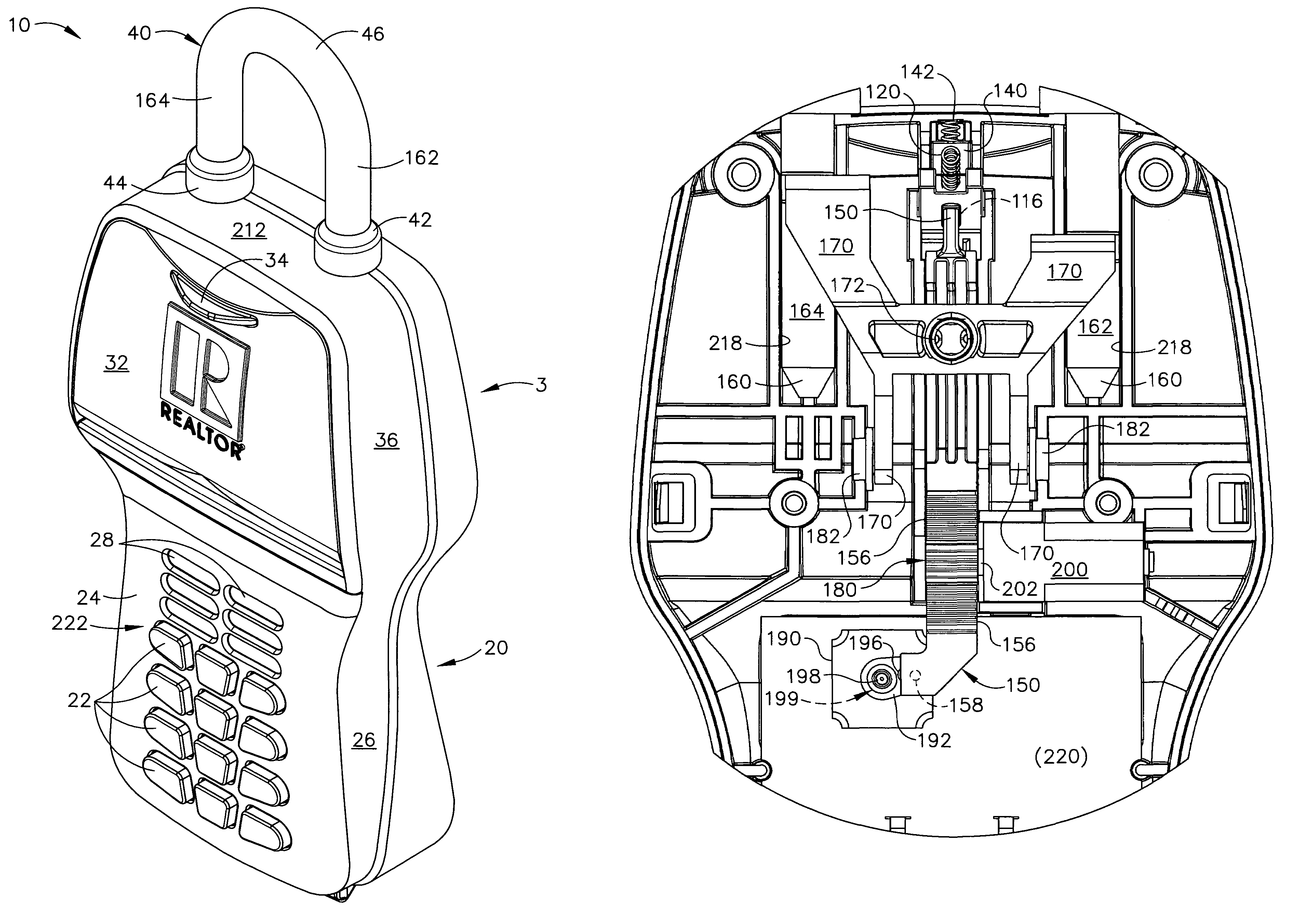
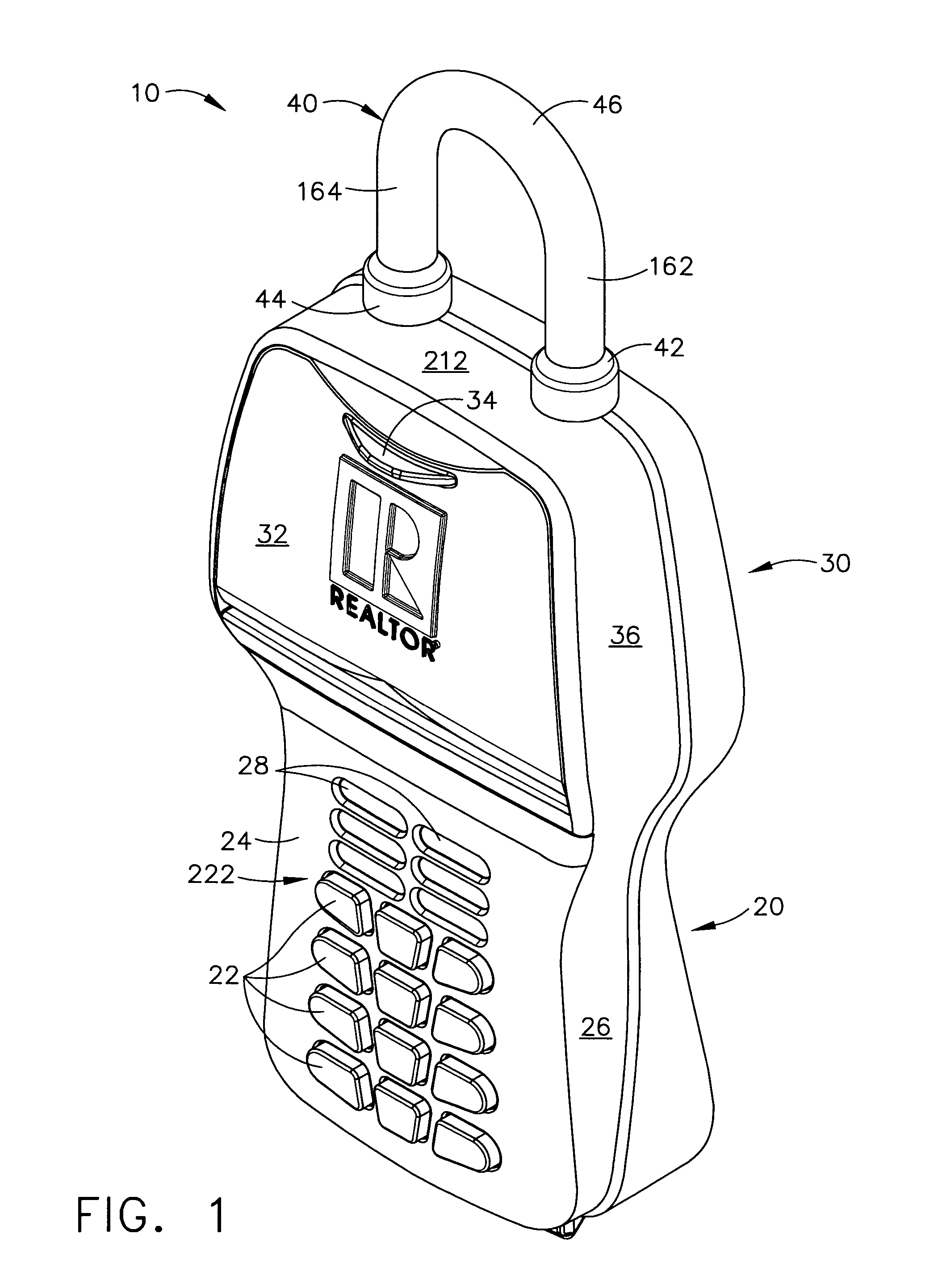
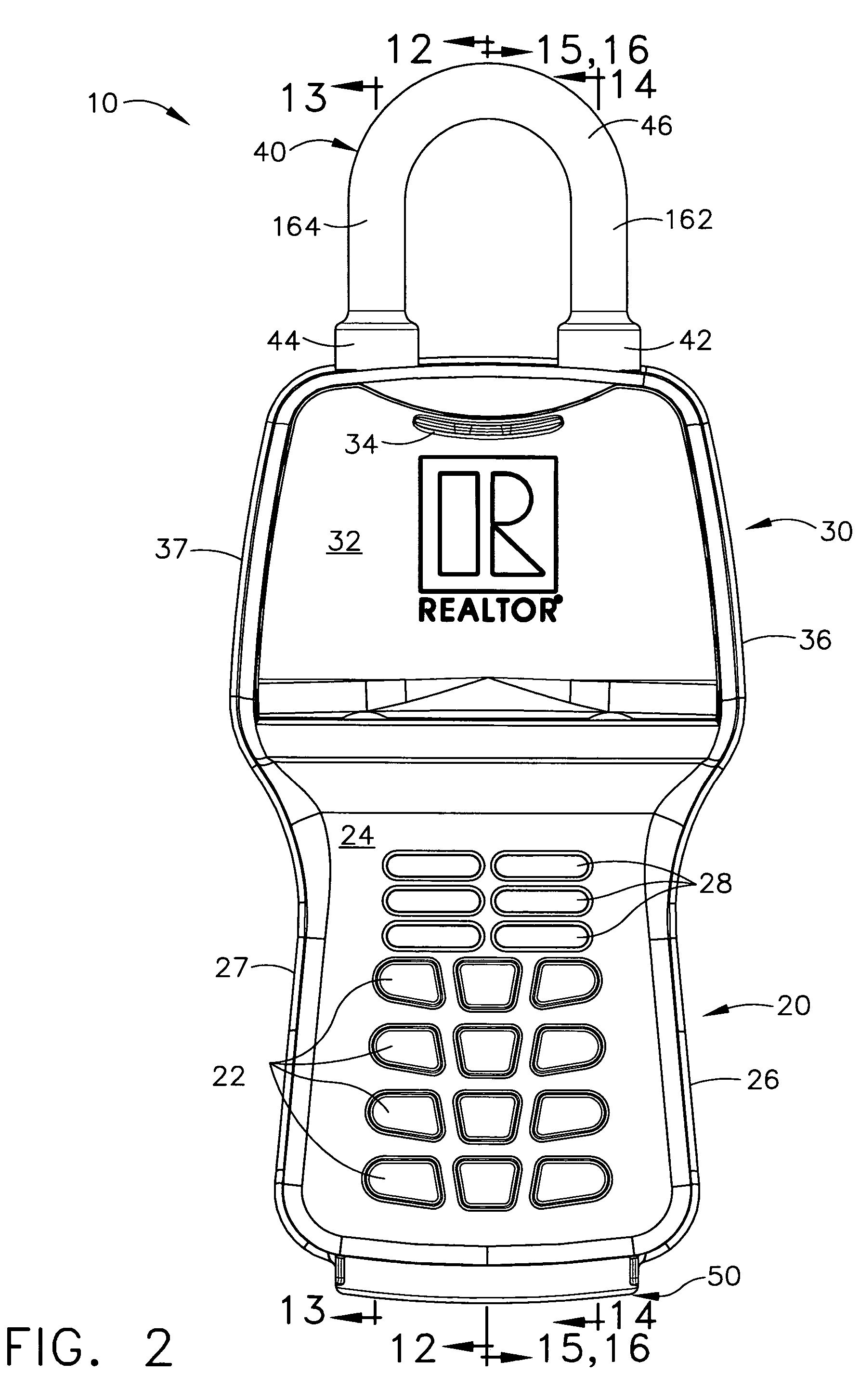
Automatic alarm invisible connection interlocking double-key anti-theft lock
InactiveCN104033024AInvisible Connection ImplementationReasonable structureNon-mechanical controlsKeysEngineeringKeyhole
The invention discloses an automatic alarm invisible connection interlocking double-key anti-theft lock. A fixed contact is arranged on a lock body or a fixed shell of the anti-theft lock, a specially-matched key hole and an invisible hole are formed in a lock cylinder, the front ends of the lock body and the lock cylinder are provided with interlocking covers, a locking needle hole is formed in a locking ejection column, an invisible connection device is arranged in the invisible hole, an invisible spring is installed in an invisible bearing hole in the back end of the invisible connection device, an interlocking hole in the lock body is provided with an interlocking spring, a centre, a locking needle and an abutting-against needle, a rotary contact is arranged on a rotary connection device, the rotary connection device is located behind the invisible connection device, an electronic telecontrol device, the rotary contact and the fixed contact are connected into a circuit of an electromagnet, and the electromagnet is connected with a locking transverse piece. The invisible connection device and a specially-matched key are disconnected, the invisible connection device and the rotary connection device are disconnected, the lock cylinder and the rotary connection device are disconnected, the electronic telecontrol device is invisibly installed in the circuit of the electromagnet, the ejection column can be transversely locked through the centre and the locking needle, an interlocking key and a specially-matched key are separated, and alarming, hiding, interlocking and multiple theft prevention of the anti-theft lock are achieved.
Owner:徐园植
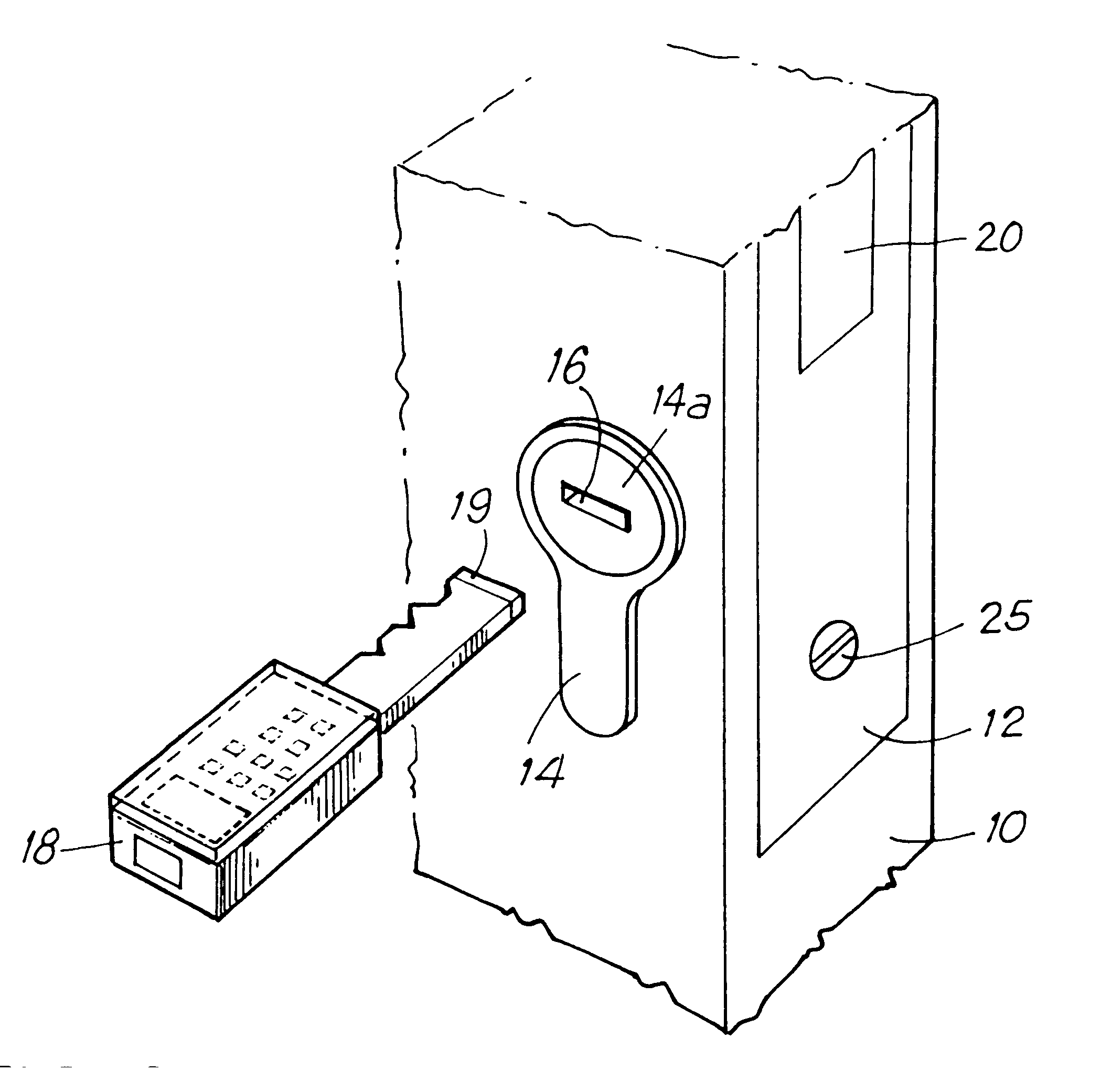
Programmable electronic locking device
InactiveUS6331812B1Simpler and cheapMitigate such drawbackElectric signal transmission systemsMultiple keys/algorithms usageEmbedded systemInput device
A programmable electronic closure system has a lock for operation by a key when an identification code of the key and a corresponding code of the lock match. The closure system can be programmed to modify the code data in both the key and the lock using an input device.
Owner:ELECTRONICS KEY SYST E K S R L
Electronic lock box using a biometric identification device
InactiveUS20070096870A1Reduce insecurityImprove securityElectric signal transmission systemsImage analysisEngineeringIdentification device
An improved electronic lock box system is provided for more secure control over the accessibility of a secure compartment in the electronic lock box, which is typically used to store a dwelling key. The new system uses biometric identification sensors to determine if the correct, authorized user is attempting to access the secure compartment of the electronic lock box. In one embodiment, the biometric identification sensor uses thermal scanning to detect a person's fingerprint pattern. This is compared to previously stored (enrollment) biometric identification information / data, and if the “live” (observed) biometric identification information / data sufficiently correlates to the stored enrollment biometric identification information / data, access will be granted.
Owner:SENTRILOCK
Novel magnetic mechanical anti-theft lock
The invention provides a novel magnetic mechanical anti-theft lock which comprises a wafer type key, a lock core rotor and a lock shell, and the wafer type key comprises a wafer; at least six magnetic blocks are arranged in the wafer, and the lock core rotor is a T-shaped cylinder on the appearance, and matches with the lock shell in a contacting way; a second magnetic spring blind hole and a magnetic spring are arranged in the position where the lock core rotor corresponds to the magnetic blocks, and the magnetic spring and the corresponding magnetic block are mutually repellent in terms of magnetism; an iron spring is respectively arranged in the position where the lock shell corresponds to the magnetic spring, and part of the iron spring convexly extends to the blind hole of the second magnetic spring; the bottom of the iron spring is also connected with a return spring, and the lock core fixing hole accommodates the narrow part of the lock core rotor. As the lock core of the lock has no key hole, destruction by tools such as a bolt driver, a screwdriver and the like can be prevented; besides, the key of the lock can not be easily duplicated, and the lock has multiple anti-theft functions, elegant appearance, strong invisibility and higher security.
Owner:泉州市科安盾智能锁业有限公司
Cable wrap security device
ActiveUS20080236209A1Avoid the needImprove sound transmissionClothing locksBelt retractorsEngineeringElectrical and Electronics engineering
A security device includes a locking member, a ratchet mechanism, and a plurality of cables. The cables are wrapped around all six sides of a box-like article. An attachment clip is releasably snap-fitted into the body of the security device and locked therein by a magnetically attractable member. The ratchet mechanism includes a spool and a locking pawl or lever. A top wall of the housing or locking clip has a key receiving recess for positioning the key for unlocking the clip from the housing and releasing the spool from the ratchet mechanism. The housing has a rotatable handle for manually rotating the internal spool to further tighten the cable about the article after the cable slack is taken up by an internal spring. An alarm system is contained in the housing and actuates an audible alarm upon certain unauthorized actions occurring. The spool is biased by the internal spring to automatically wind the cable onto the spool after the clip has been unlocked from the housing. Insertion of the clip into the housing automatically actuates the ratchet mechanism preventing movement of the cable in the unwind direction and activates the alarm system.
Owner:CHECKPOINT SYST INC
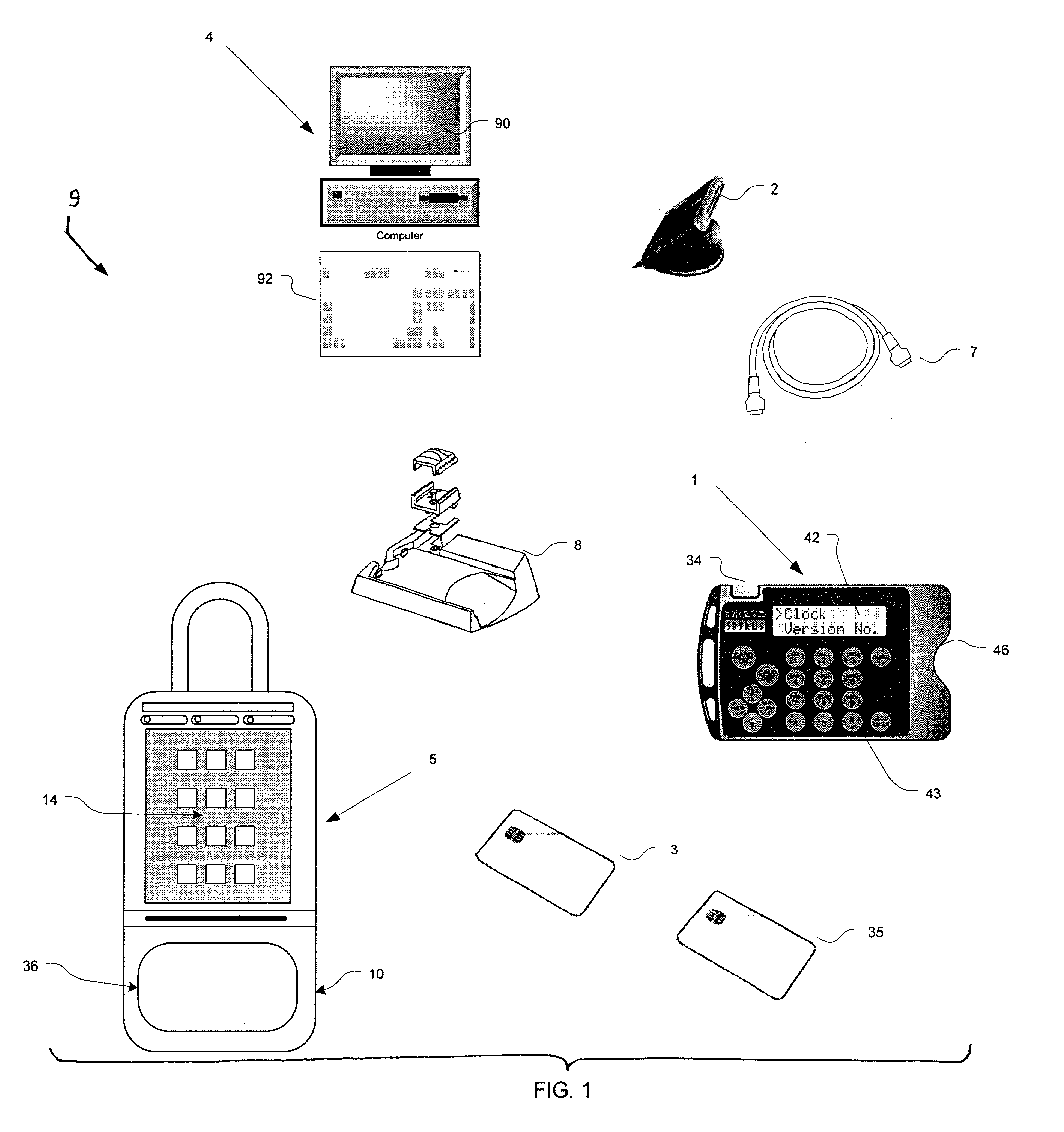
Electronic lock system and method for its use with card only mode
InactiveUS6989732B2Electric signal transmission systemsMultiple keys/algorithms usageMobile Telephone ServiceControl manner
An improved electronic lock system is provided for use with real estate lock boxes where there is the need for many people to access the secured compartment of the lock box in a controlled manner. Each user has an identification card with a non-volatile secure memory (known as a “smart card”), for exchanging data with the lock box, and with a portable computer capable of reading data from the smart card; or a cell phone can be used to gain access information from a central computer. The user first inserts the smart card into the connector attached to the lock box; the lock box reads the user's ID stored in the smart card memory and records this information in lock box memory. The lock box then transfers its access code information and other data to the smart card for further processing. The user then inserts the smart card in a portable card reader to learn the access code, or calls a central computer via a mobile phone system and interacts with the computer to elicit the necessary access code information. The access code is then manually keyed into the lock box keypad by the user to obtain access to the secure compartment. Other modes of operation include an “access token mode” and a “card only mode.”
Owner:SENTRILOCK
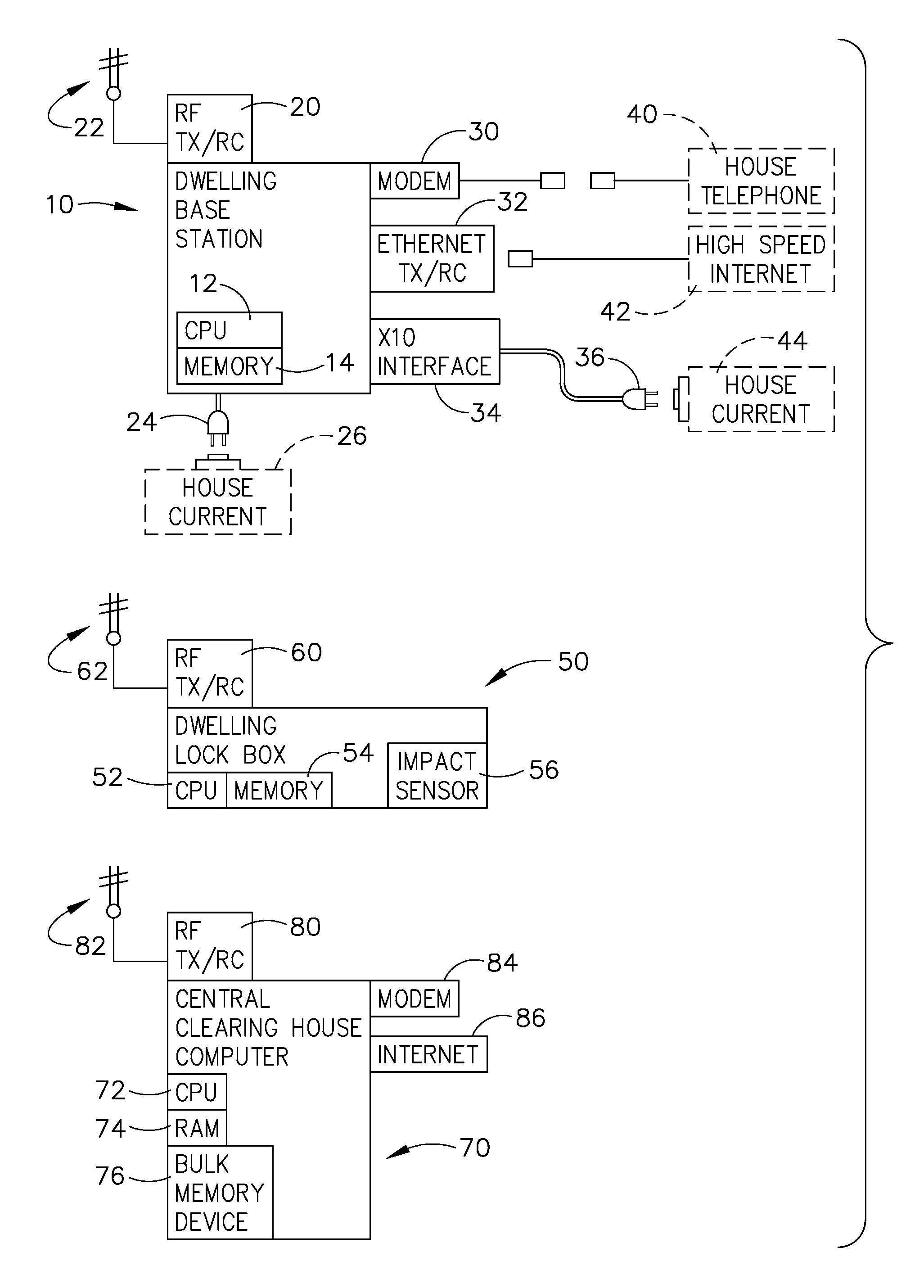
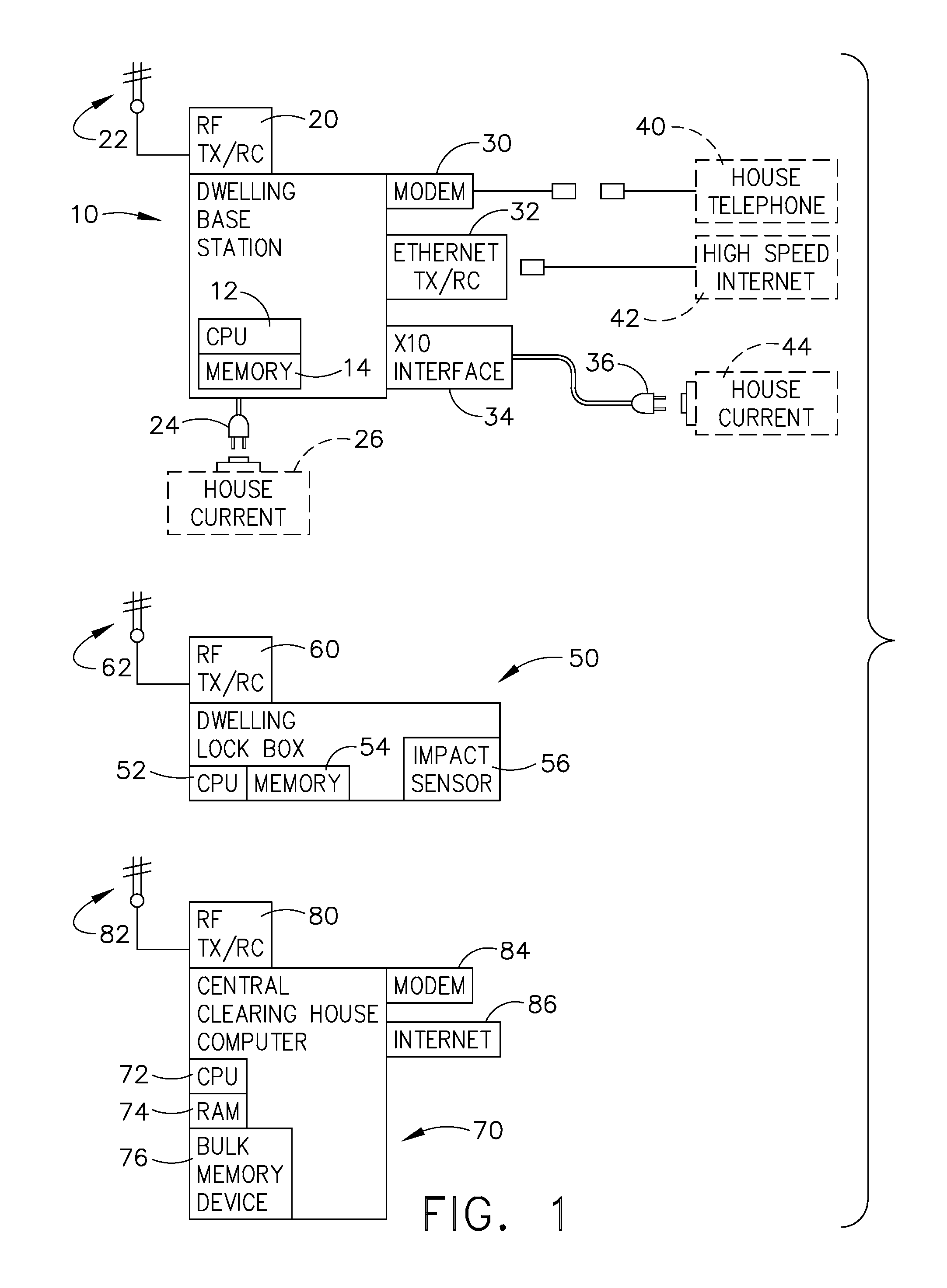
Electronic lock box with transponder based communications
InactiveUS20080246587A1Lack timelinessElectric signal transmission systemsDigital data processing detailsCommunications systemEngineering
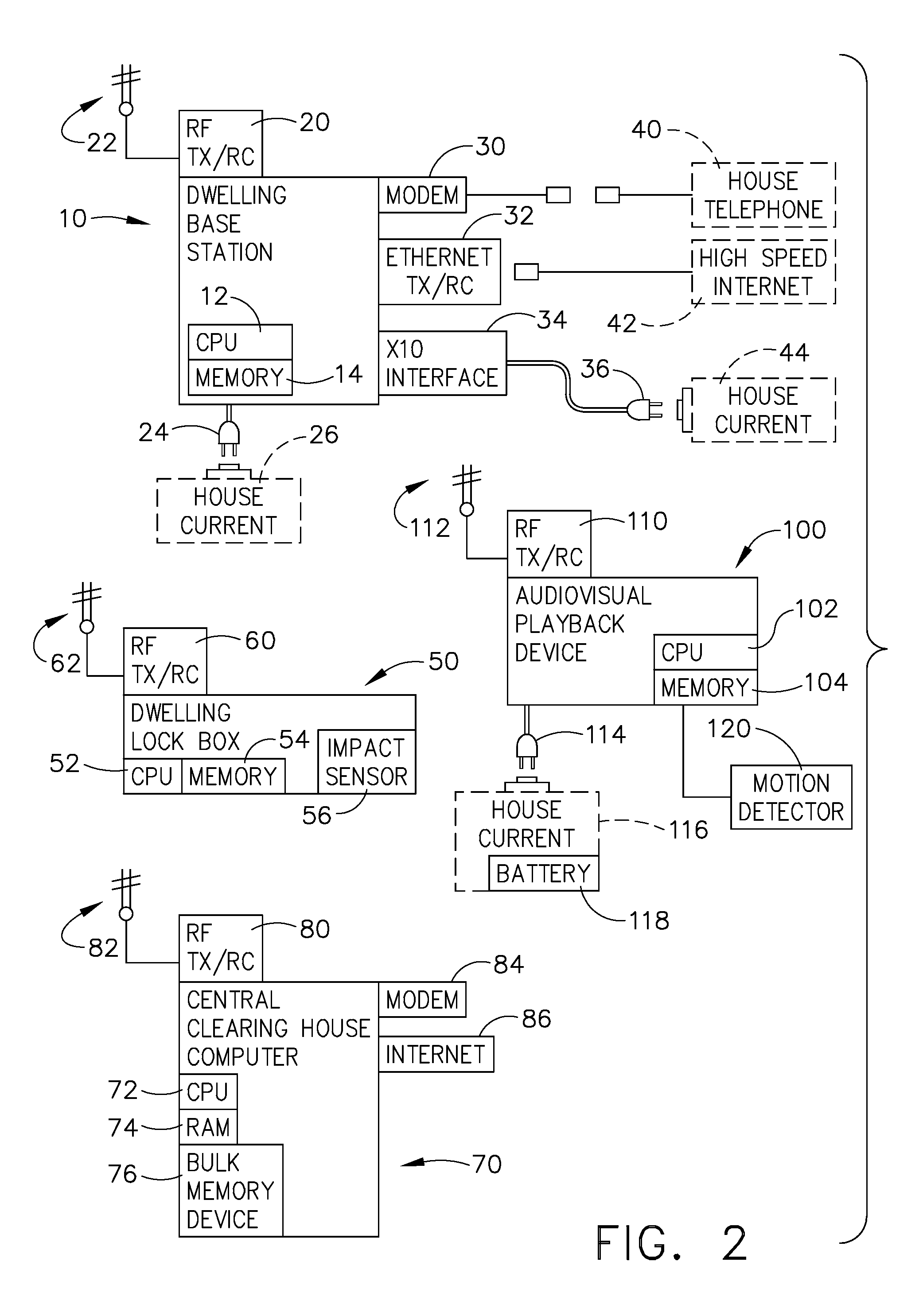
An electronic lock box contains a secure compartment for storing dwelling keys to a structure, and is typically mounted outside the dwelling structure. When properly instructed, usually with a coded message, the dwelling key can be accessed by opening the door to the secure compartment; such message can be manually entered on a keypad, or a programmed electronic key device can make the process more automatic. A lock box system uses a transponder at a dwelling base station (typically within the dwelling structure) to relay lock box status or access event information over a short range radio from the lock box to a remote central computer by using a more traditional communication system that is available within the dwelling. Additional sensors can be used to monitor the status of vandalism attempts. Furthermore, the lock box / transponder communications may be programmed so as to allow detection if the lock box is stolen.
Owner:SENTRILOCK
Electronic lock system and method for its use
ActiveUS7009489B2Accurate clearanceElectric signal transmission systemsMultiple keys/algorithms usageMobile Telephone ServiceControl manner
An improved electronic lock system is provided for use with real estate lock boxes where there is the need for many people to access the secured compartment of the lock box in a controlled manner. Each user has an identification card with a non-volatile secure memory (known as a “smart card”), for exchanging data with the lock box, and with a portable computer capable of reading data from the smart card; or a cell phone can be used to gain access information from a central computer. The user first inserts the smart card into the connector attached to the lock box; the lock box reads the user's ID stored in the smart card memory and records this information in lock box memory. The lock box then transfers its access code information and other data to the smart card for further processing. The user then inserts the smart card in a portable card reader to learn the access code, or calls a central computer via a mobile phone system and interacts with the computer to elicit the necessary access code information. The access code is then manually keyed into the lock box keypad by the user to obtain access to the secure compartment.
Owner:SENTRILOCK
Vehicle integration of ble nodes to enable passive entry and passive start features
ActiveUS20140240091A1Electric signal transmission systemsDigital data processing detailsTransmitted powerEngineering
A system and method for employing BLE nodes in a PEPS system to determine whether a FOB is within or outside of a vehicle. The method includes interrogating the FOB using a signal transmitted by a BLE device on the vehicle to determine whether the FOB is in a predetermined vicinity of the vehicle and receiving a Bluetooth signal at the BLE device that is transmitted by the FOB if the FOB is in the vicinity of the vehicle. The method also included determining a transmit power of the Bluetooth signal transmitted by the FOB and determining a receive power of the Bluetooth signal transmitted by the FOB and received by the BLE device. The method uses the transmit power and the receive power in a comparison process to determine whether the FOB is inside or outside of the vehicle.
Owner:GM GLOBAL TECH OPERATIONS LLC
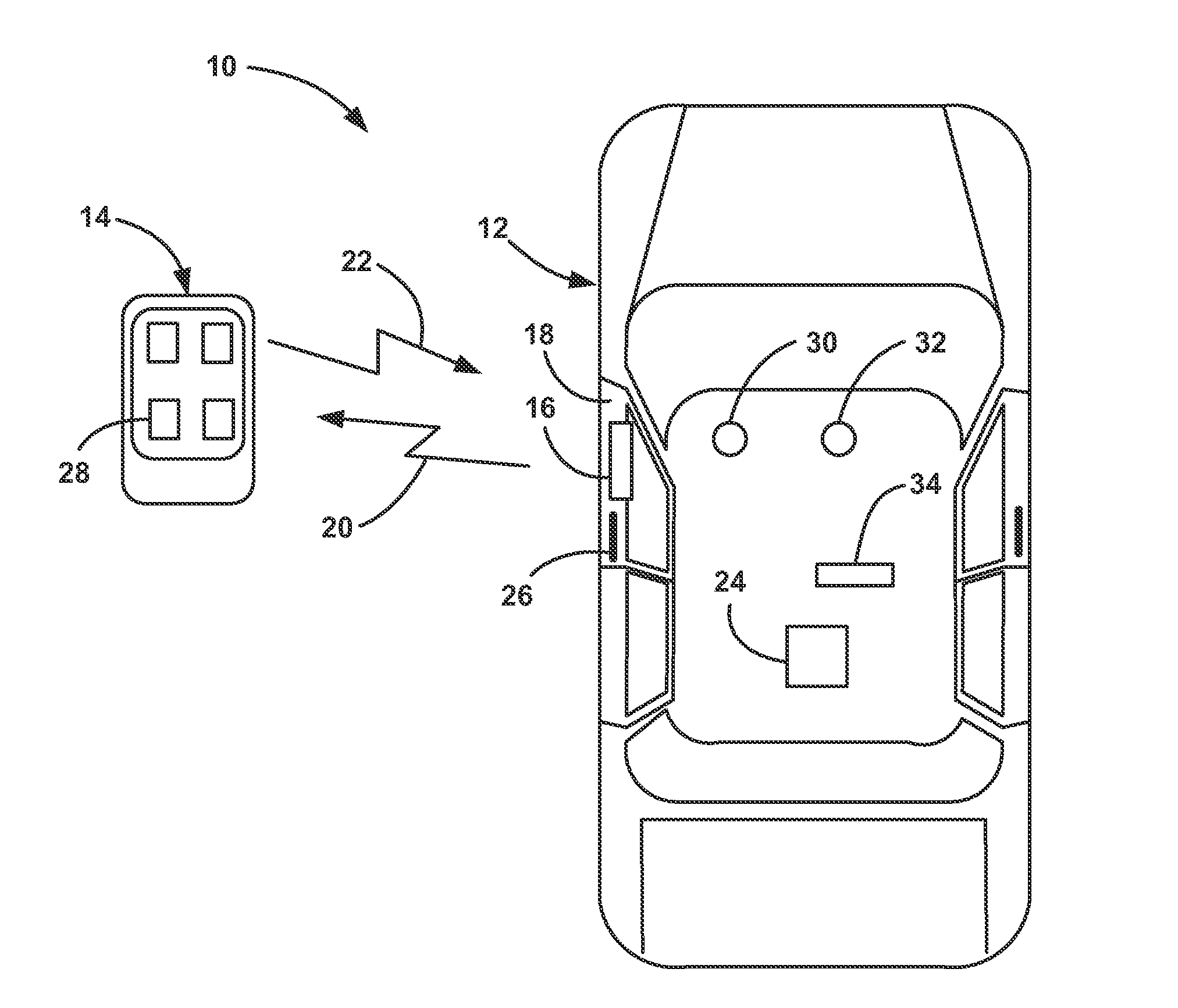
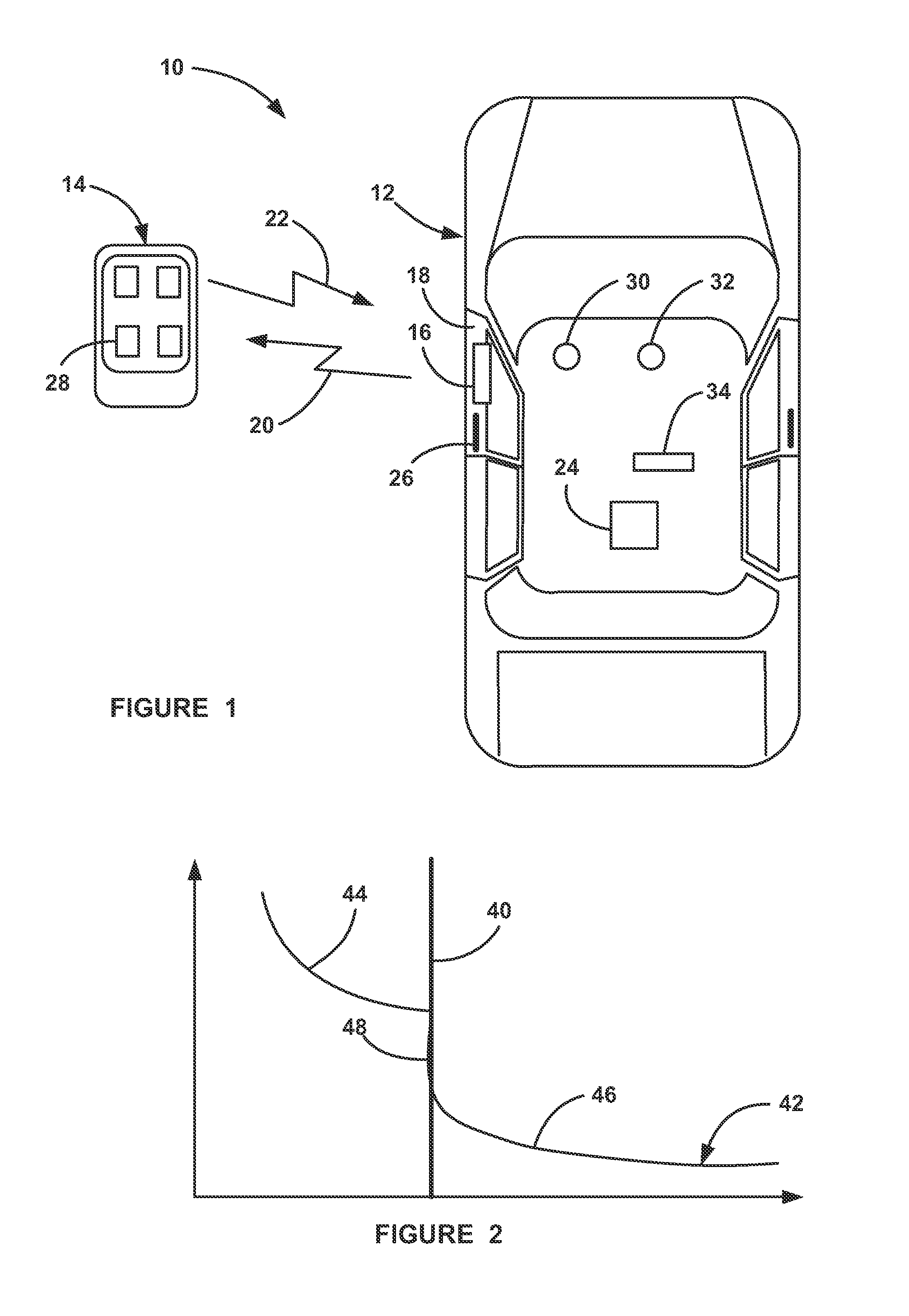
Key fob device and method
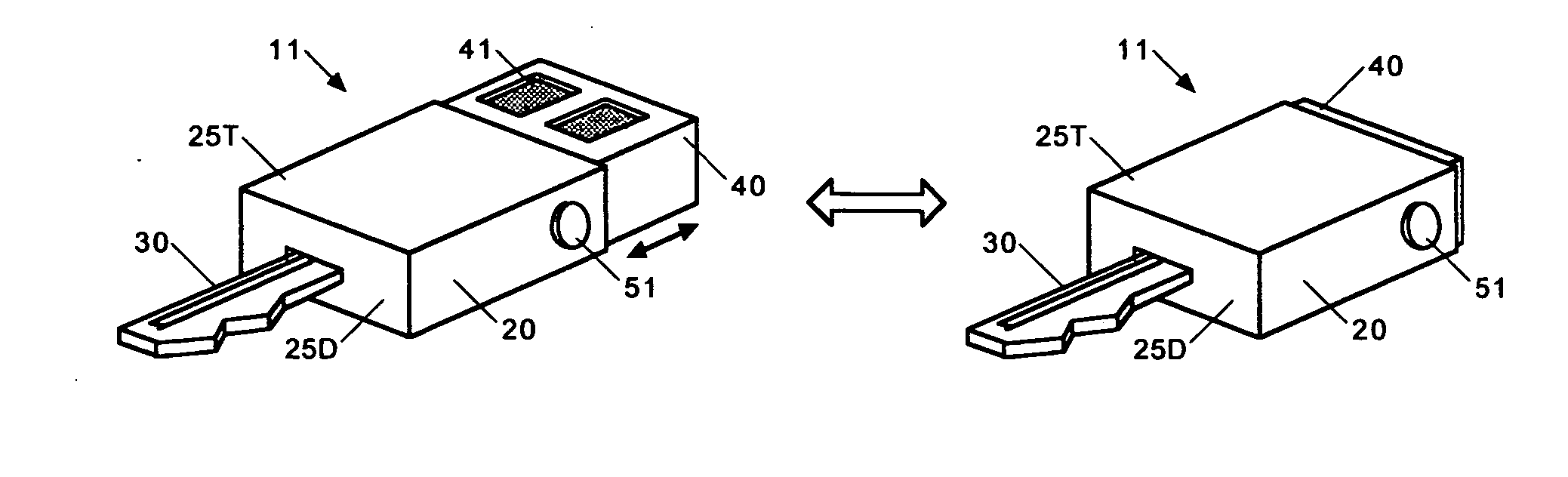
A device and method for a key fob. The key fob device can include a housing, a lid defining one or more apertures, a circuit board including one or more switches, and a flexible film coupled to the housing and / or the lid. The flexible film can include one or more contact surfaces and stylized graphics.
Owner:STRATTEC SECURITY +1
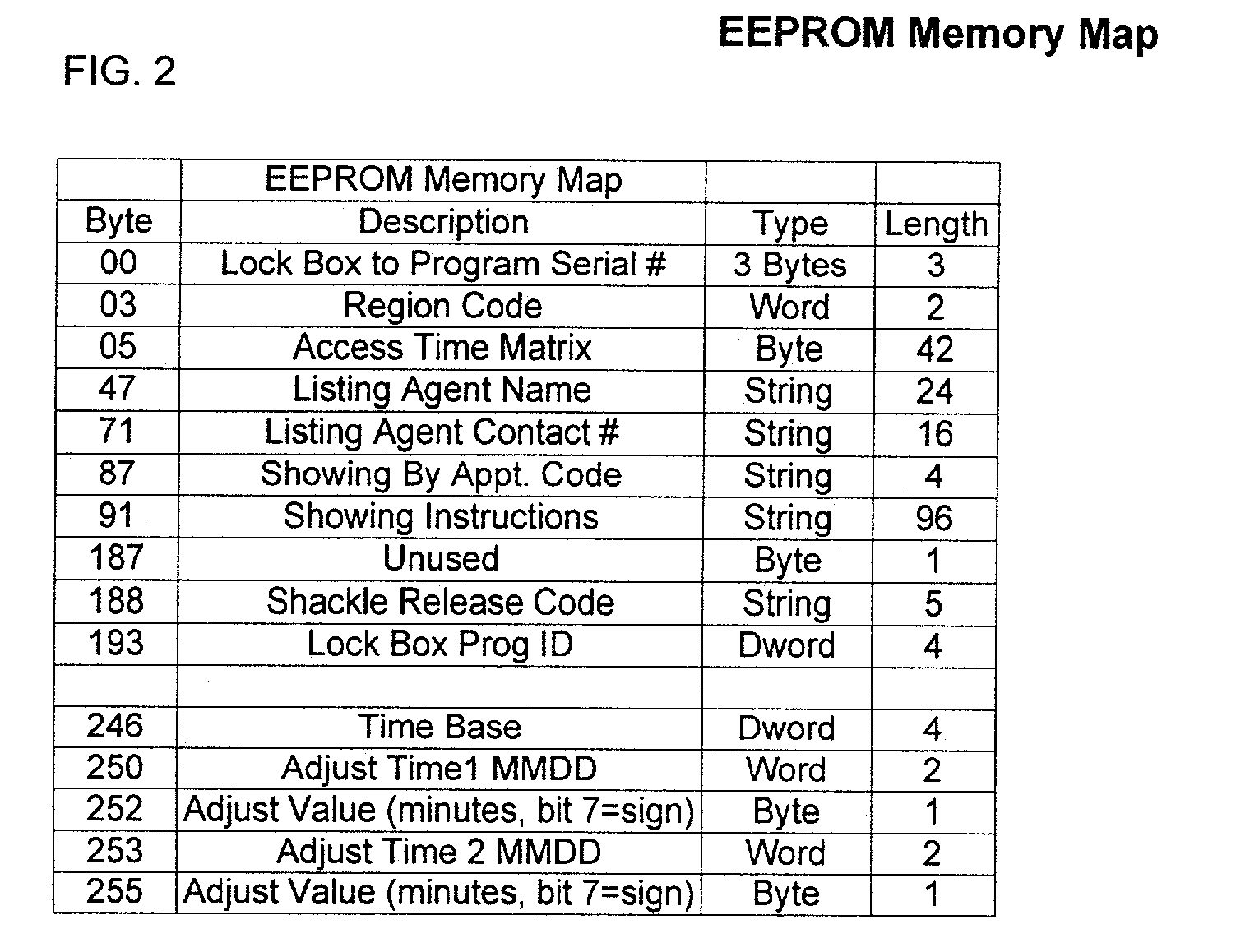
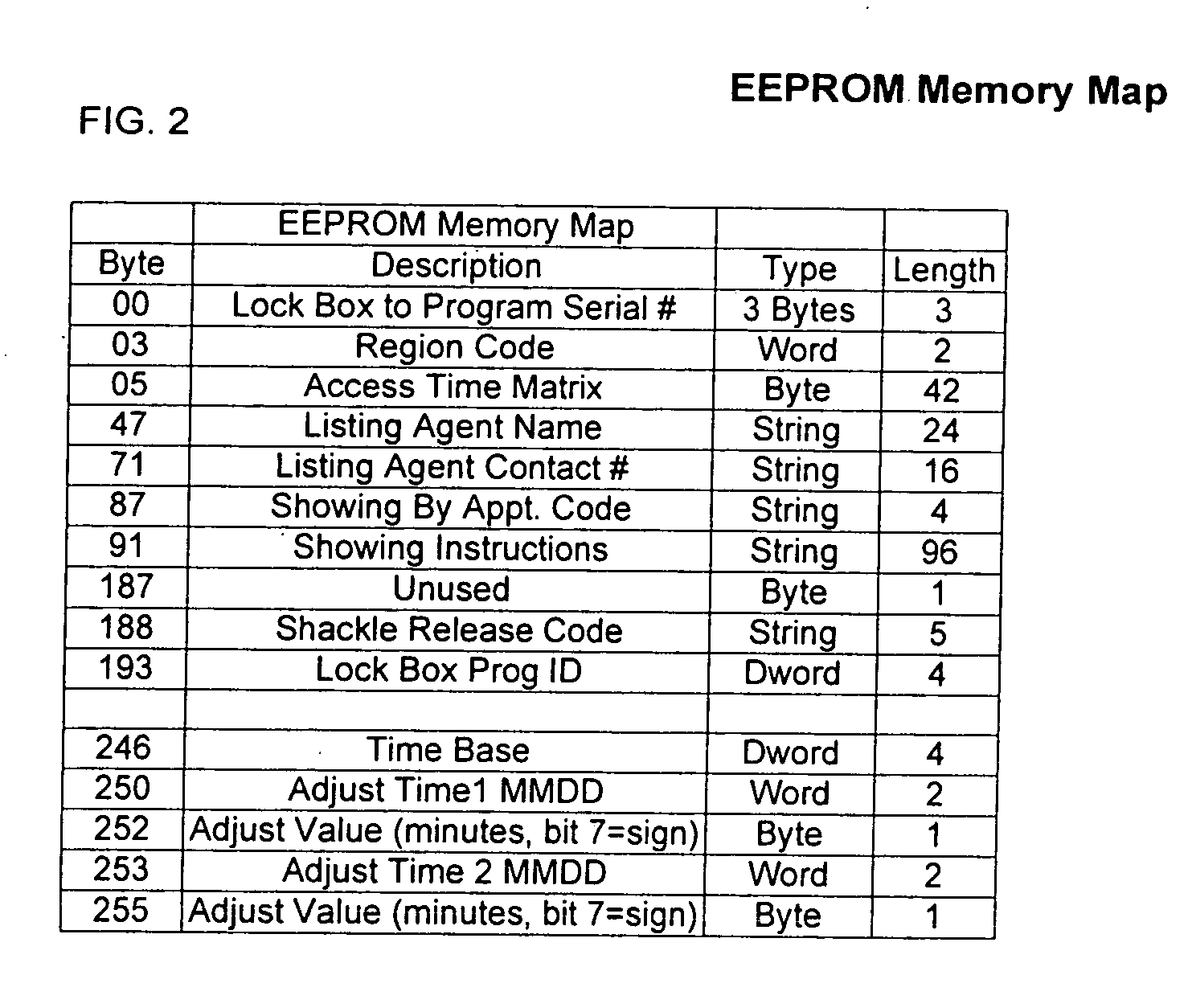
Electronic lock box with multiple modes and security states
InactiveUS20050206499A1Avoid damageProlong lifeElectric signal transmission systemsMultiple keys/algorithms usageSecure stateMultiple modes
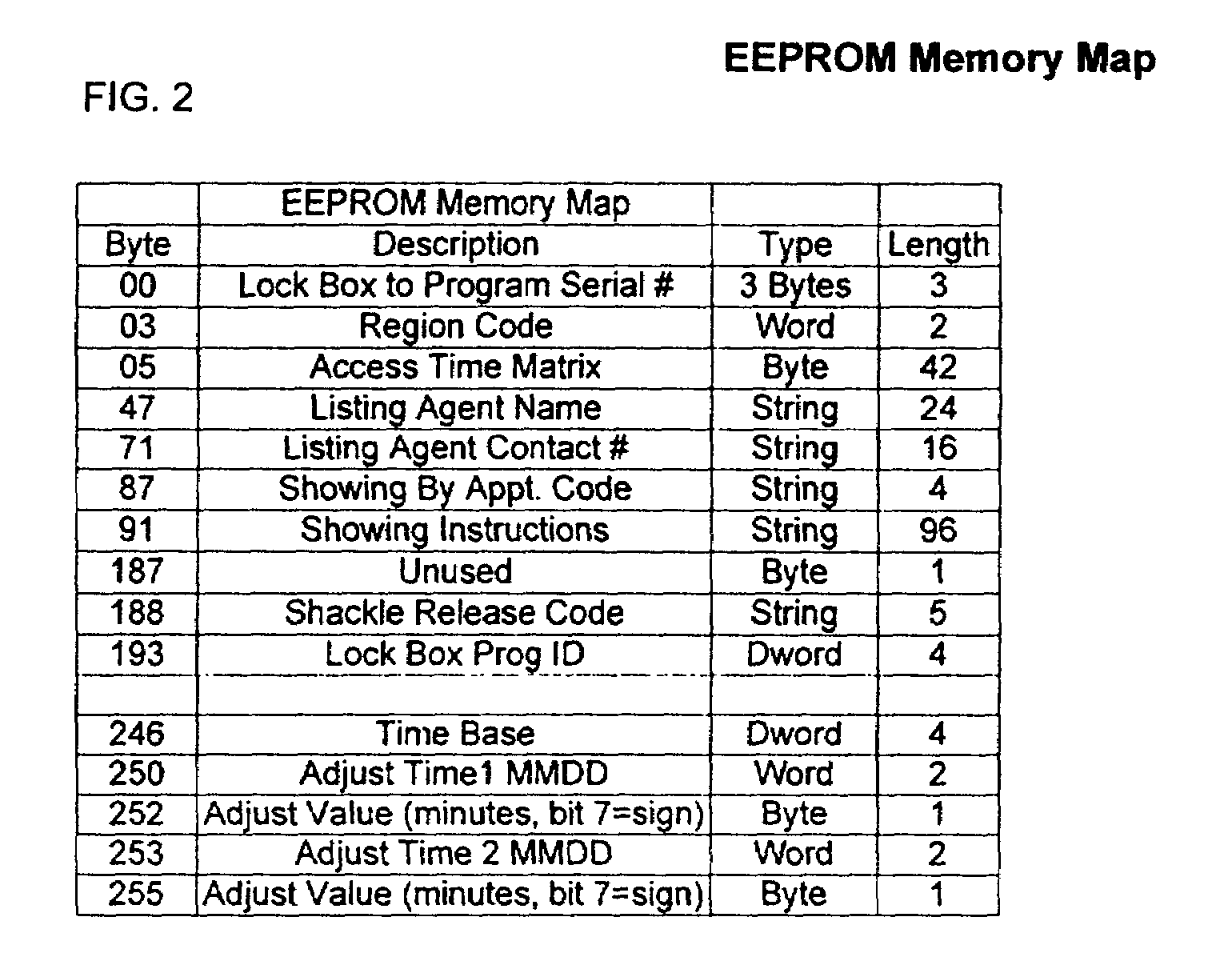
An electronic lock box contains a secure compartment for storing keys to a structure. A linear actuator moves in one direction opening the door to the secure compartment, and moves in the opposite direction releasing a shackle that holds the lock box to the structure. A lock box system uses an encryption algorithm to diversify user PIN data at a central computer, and stores that diversified information on a memory card for later use when the user attempts to access a lock box. The central computer and electronic lock box both keep track of system “epoch time,” and the memory card must be presented to the electronic lock box within a correct epoch time window for the diversified PIN data to be successfully decrypted and compared to the user's PIN data that is entered on a keypad of the electronic lock box.
Owner:SENTRILOCK
Rekeyable padlock with a lock cylinder having an enlarged viewing slot
InactiveUS6425274B1Improve visibilityGreat ease placingNon-mechanical controlsKeyhole guardsElectrical and Electronics engineering
This invention pertains to the lock cylinder of a rekeyable padlock. According to a preferred embodiment of the present invention, a rekeyable padlock is provided with a lock cylinder formed within. The lock cylinder includes a cylindrical core formed to receive a key and an outer casing formed around the core. A viewing opening is formed within the casing wall, the viewing opening allowing access to pin openings formed within the core to receive selected pins. The viewing opening is shaped such that it provides a viewing area larger than the pin openings, thereby allowing greater visibility when the pins are placed within the pin openings. The advantages of this viewing opening include greater ease in placing the pins into the pin openings and easier detection when a selected pin is the wrong length and does not sit flush within the lock cylinder core.
Owner:ABUS AUGUST BREMICKER SOEHNE AG
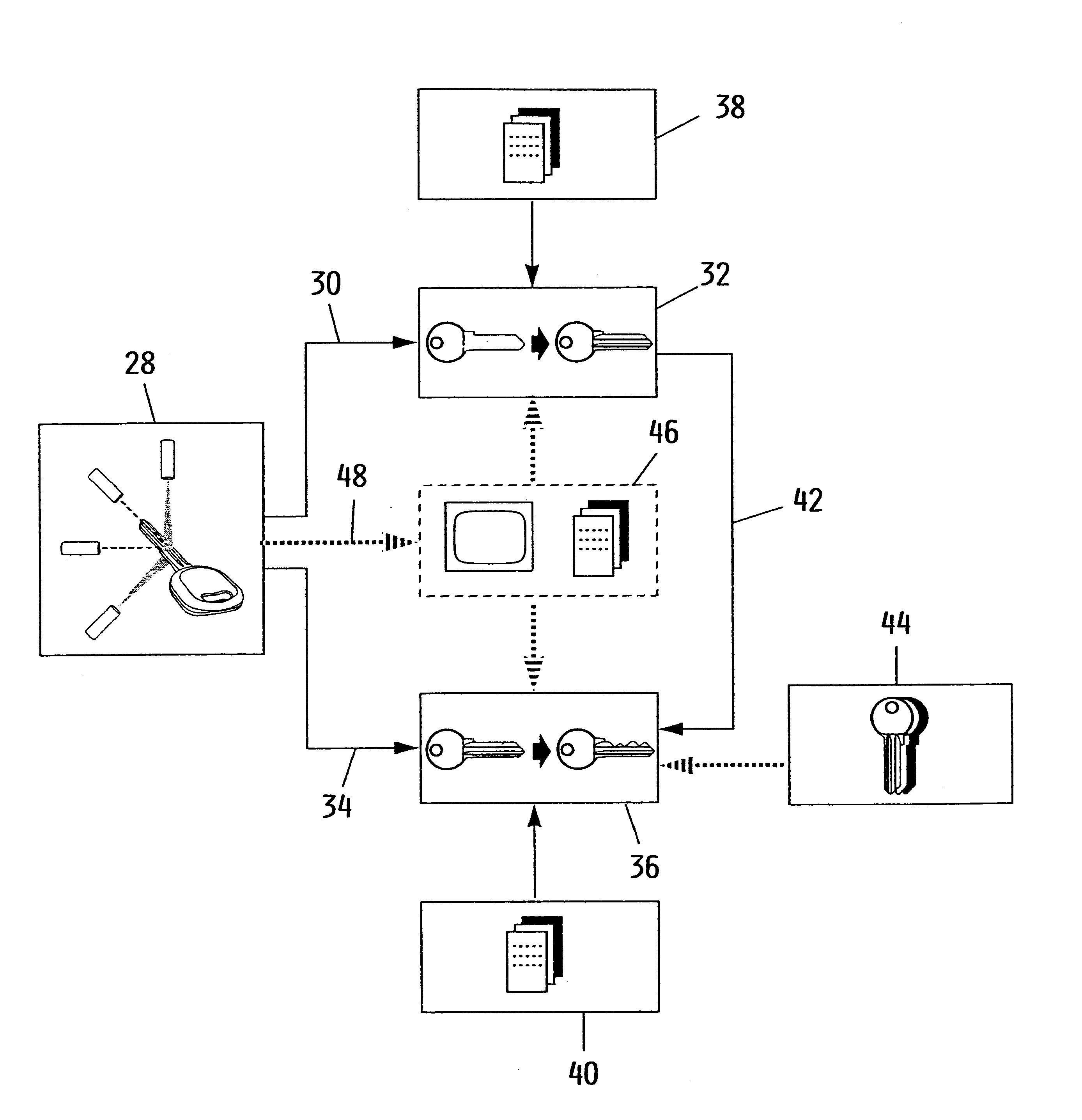
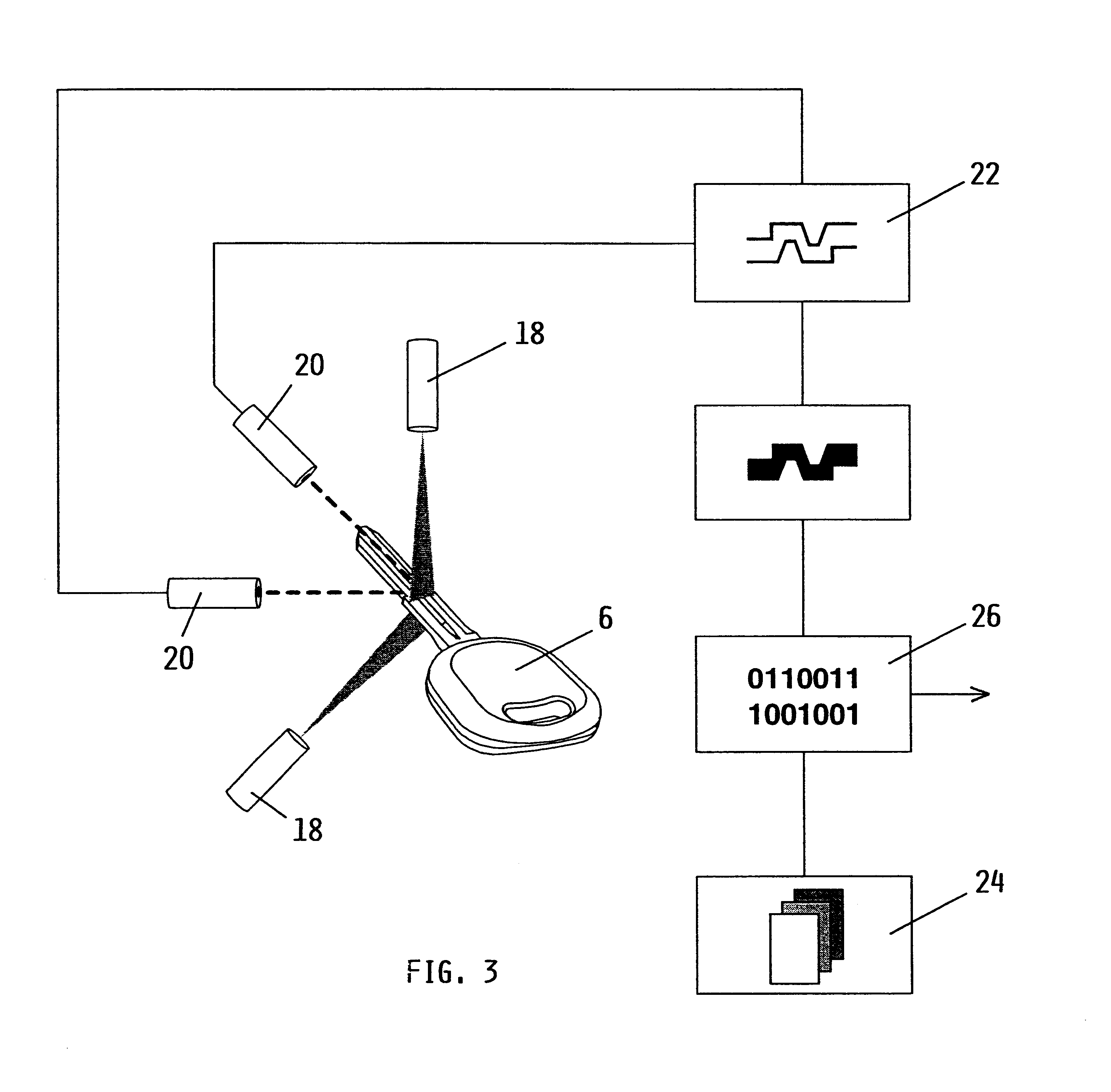
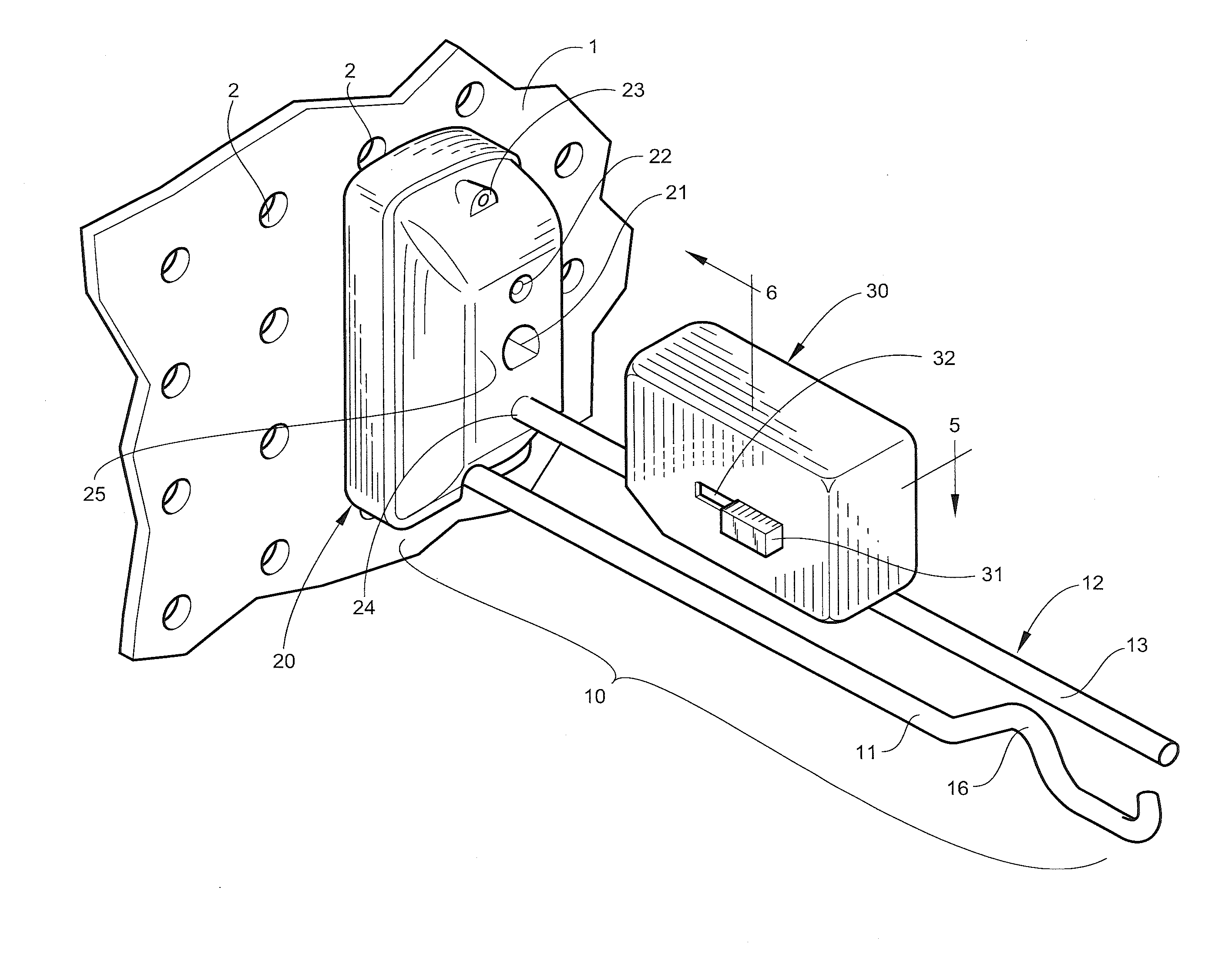
Method to identify a key profile, machine to implement the method and apparatus for the duplication of keys utilizing the machine
A method to identify a key profile, comprising:illuminating with two laminar beams emitted by two laser light sources said two sides of said shank of a key driven to move axially relative to said beams,reading with two video cameras, fixed relative to said sources and having their optical axis inclined to said planes in which said light beams lie, said two light profiles formed by said laminar beams striking said two surfaces of said shank of said keys,digitizing said optical images read in this manner, to obtain two sequences of signals representative of said profiles of said two lateral surface portions of said key, as instantaneously illuminated by said laminar beams and read by said video cameras,reconstructing from said signals, by means of a processor unit, a signal representative of the entire key profile, andcomparing said thus reconstructed signal with said signal representative of profiles stored in said processor unit to obtain data identifying said profile of said read key.
Owner:SILCA SPA
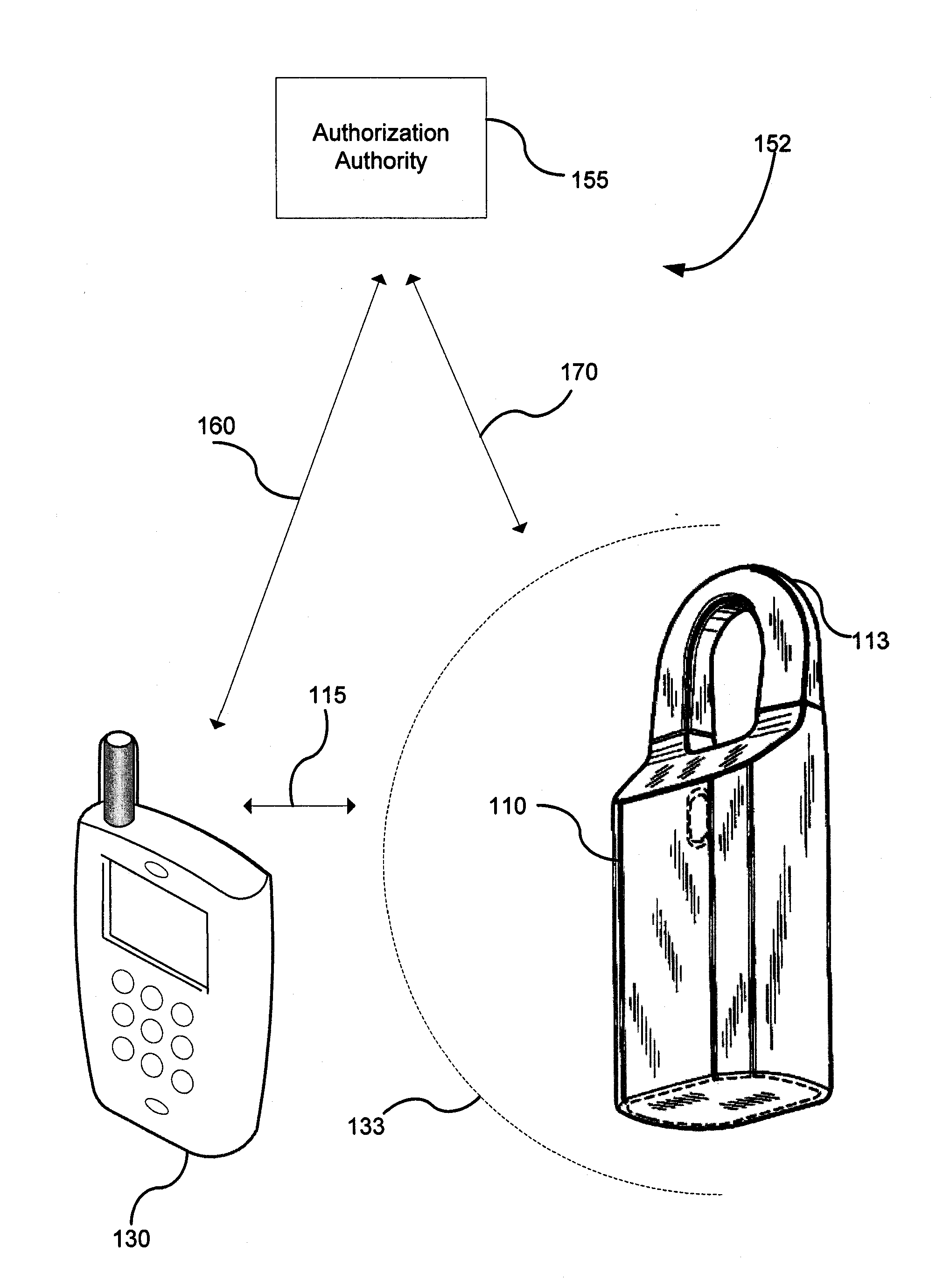
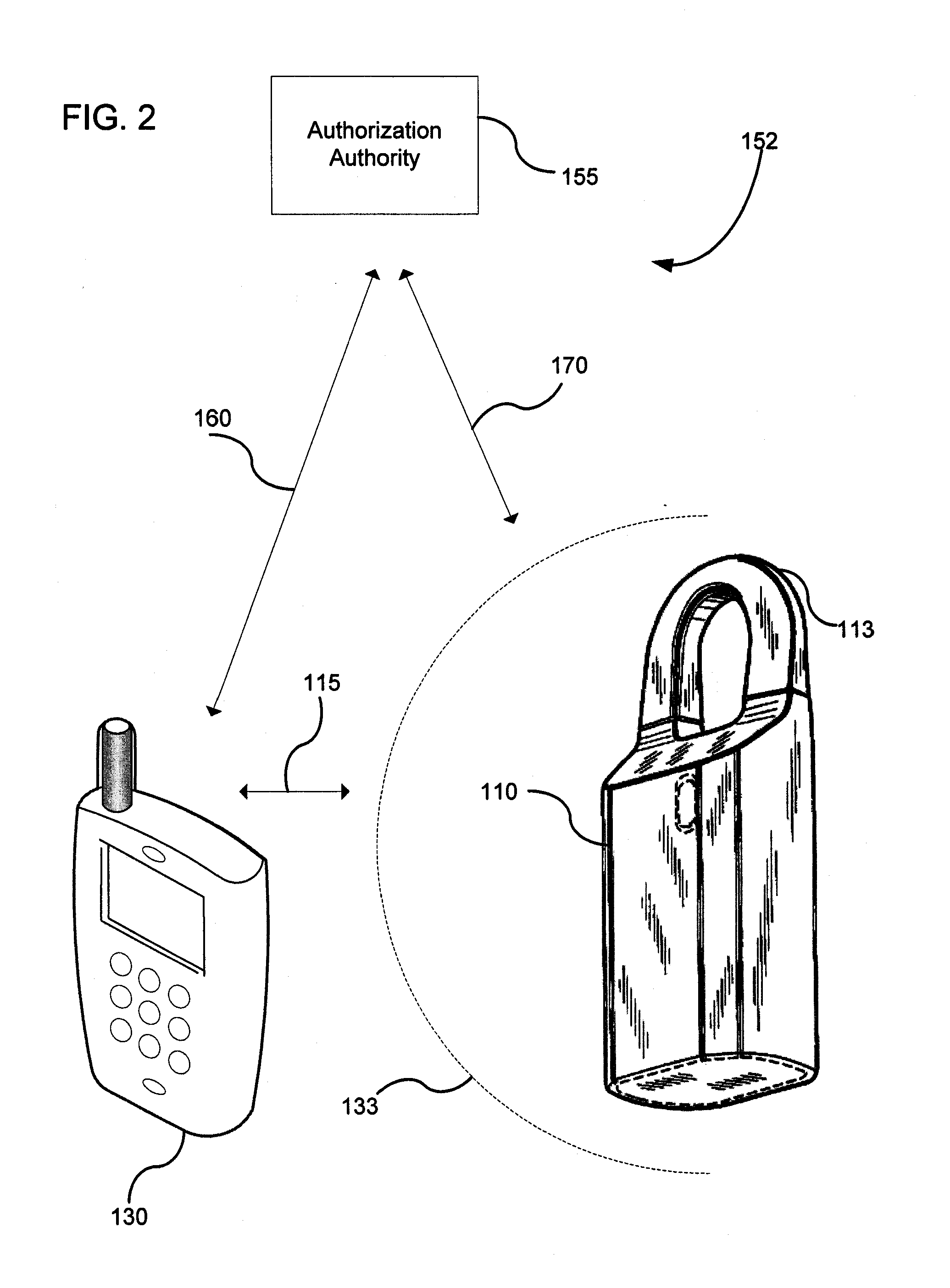
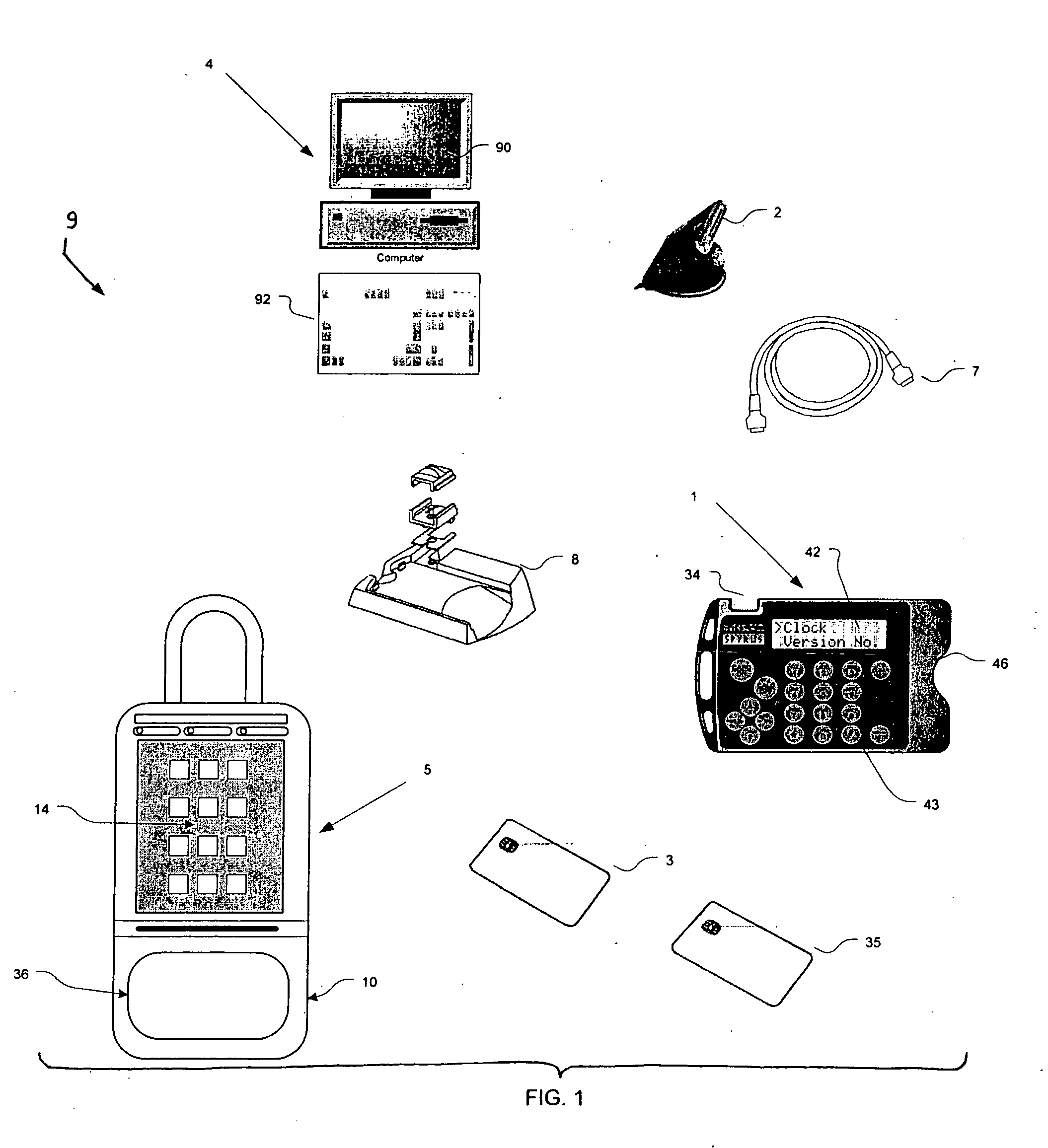
Method and apparatus for communicating access to a lockbox
InactiveUS20090153291A1Electric signal transmission systemsMultiple keys/algorithms usageComputer scienceSecurity system
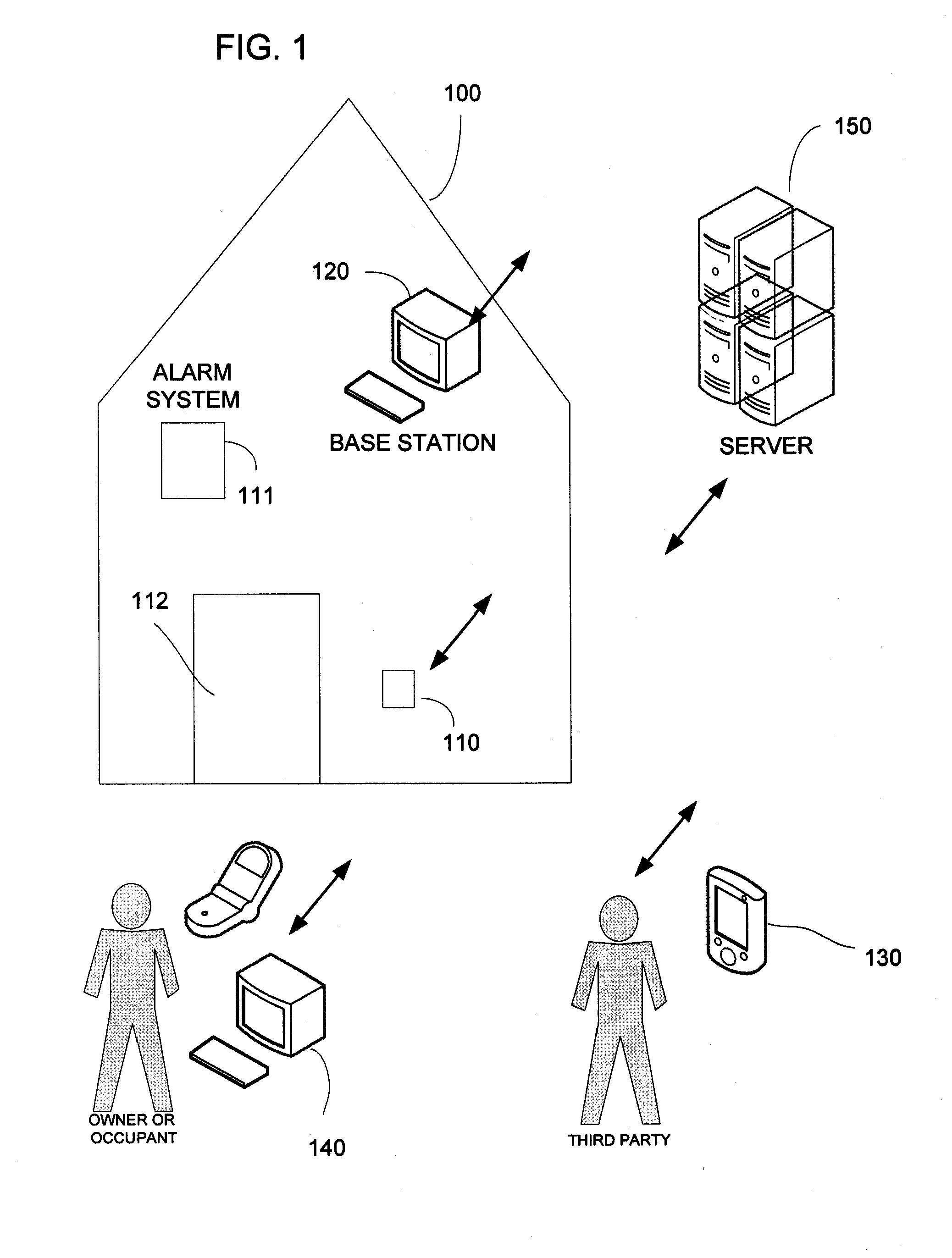
A real estate security system is described wherein access to a lockbox, that houses a key, causes automatic notification to an owner / occupant associated with the property. Such a communication can be used to alert the owner / occupant that a real estate showing is started or completed, that a friend or family member arrived home safely, that a property management accessed the house, or that emergency personnel accessed the house. The lockbox can include additional features that cause notification to the owner, such as automated sensing of tampering with the lockbox, or depressing a button on the lockbox to generate a signal to the owner / occupant of the property.
Owner:UTC FIRE & SECURITY AMERICAS CORPORATION INC
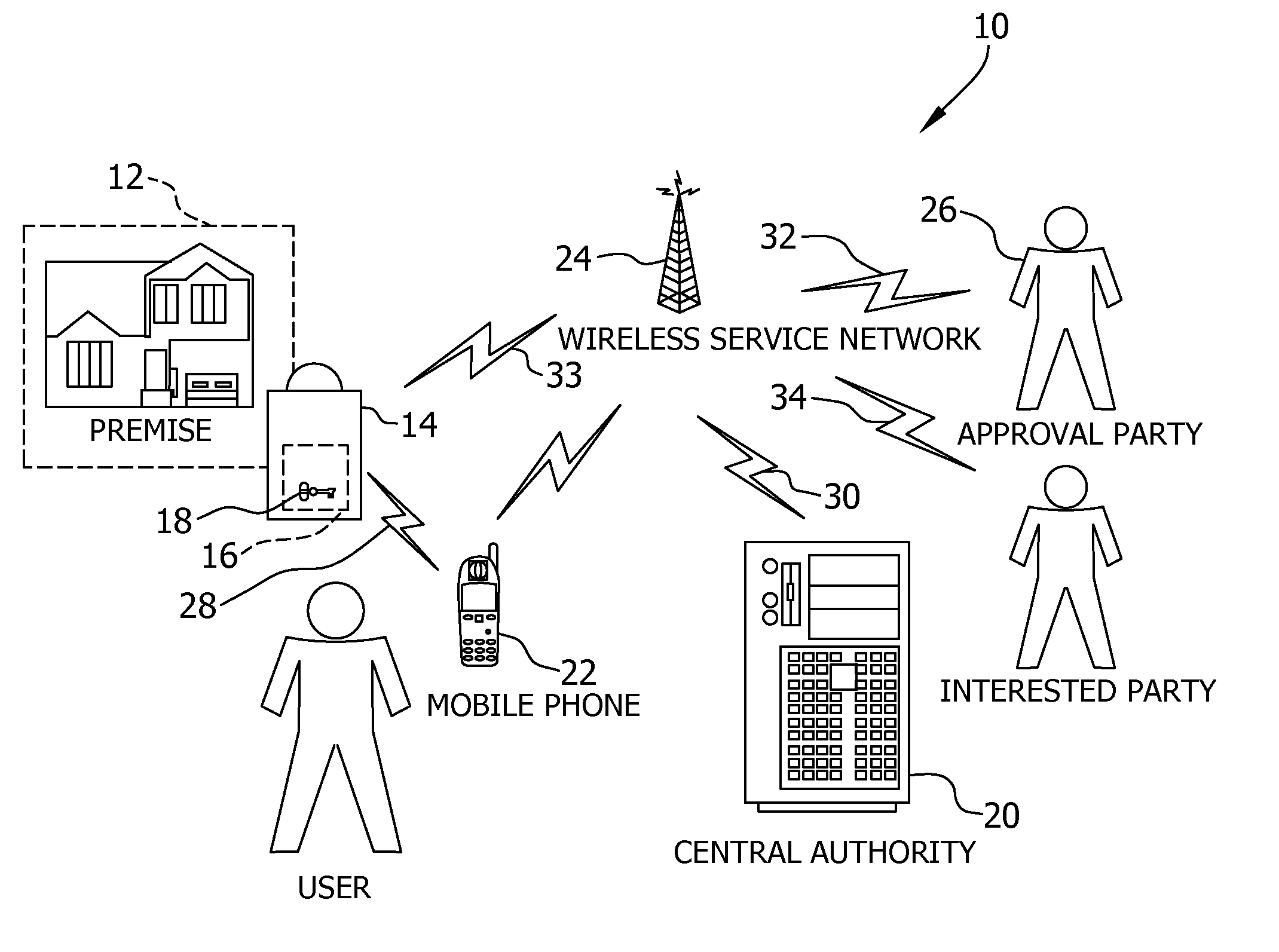
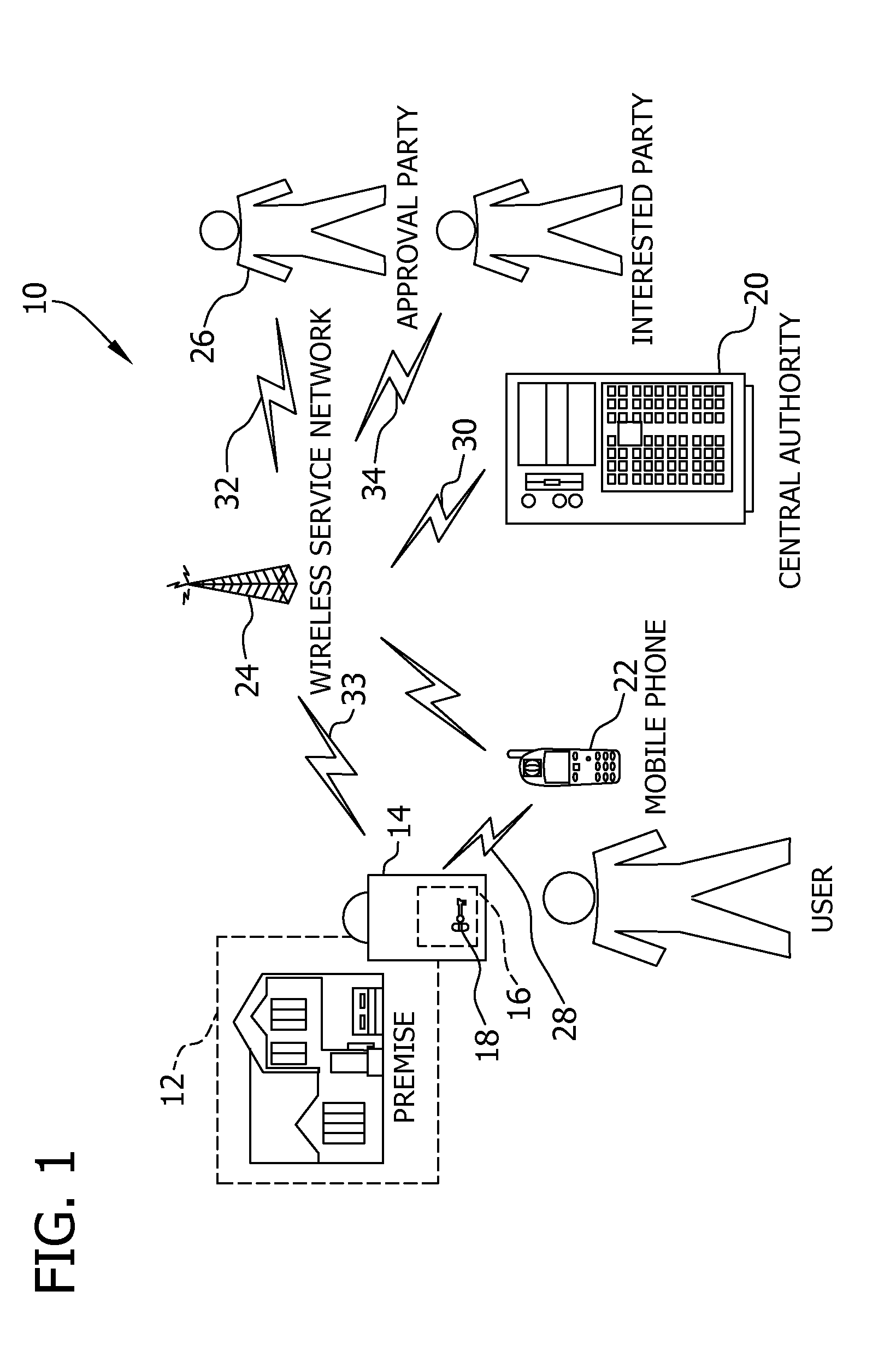
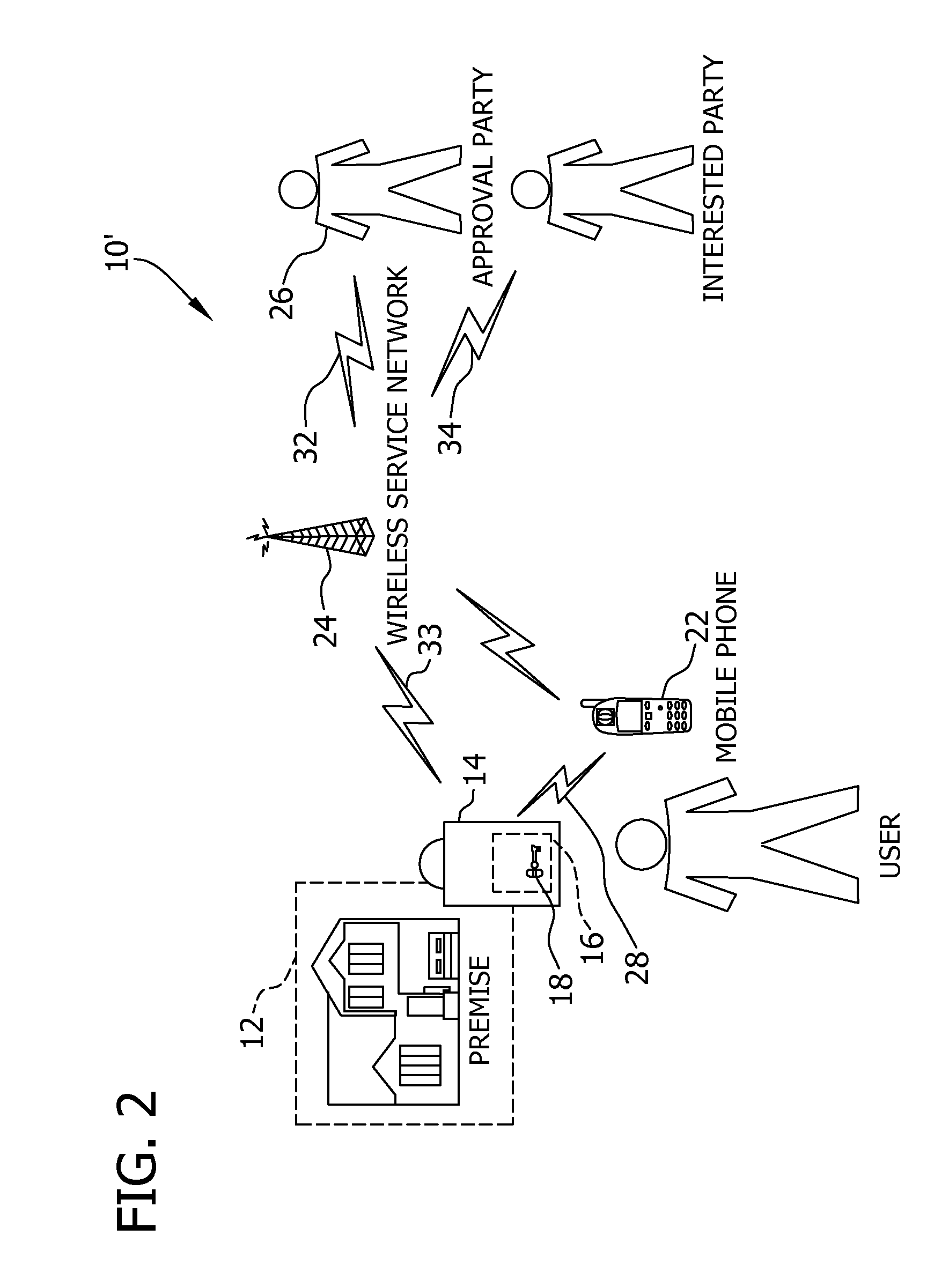
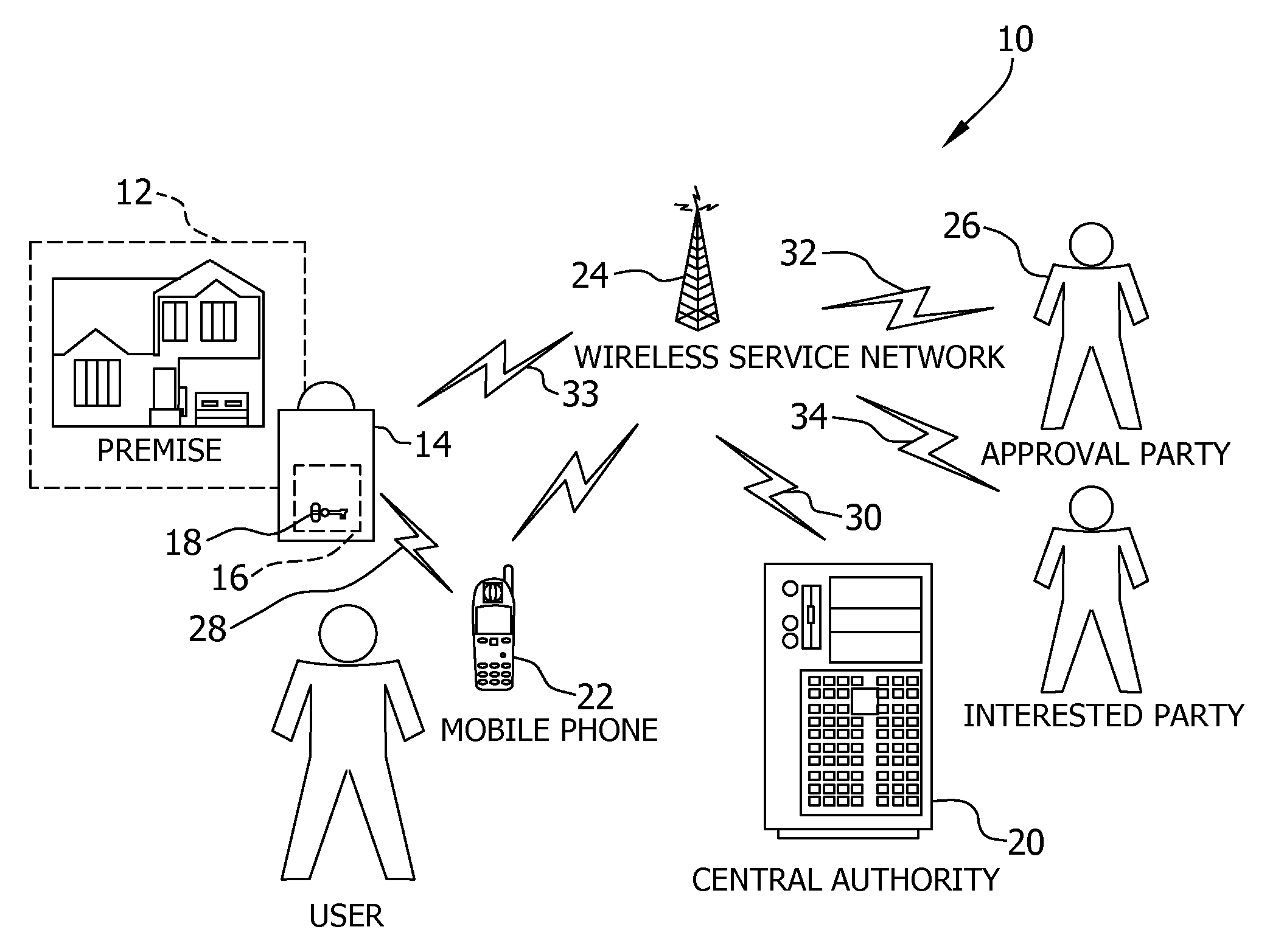
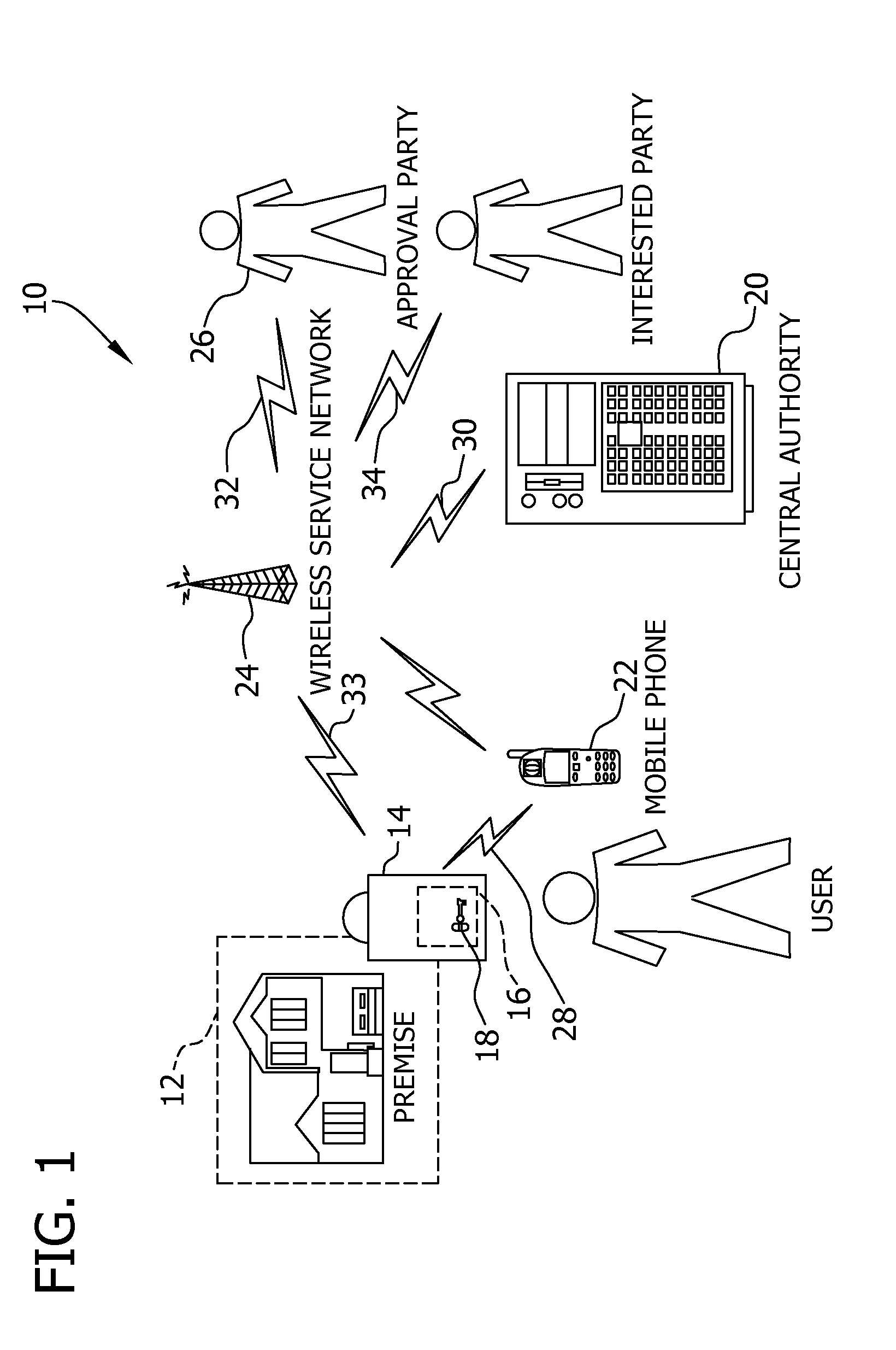
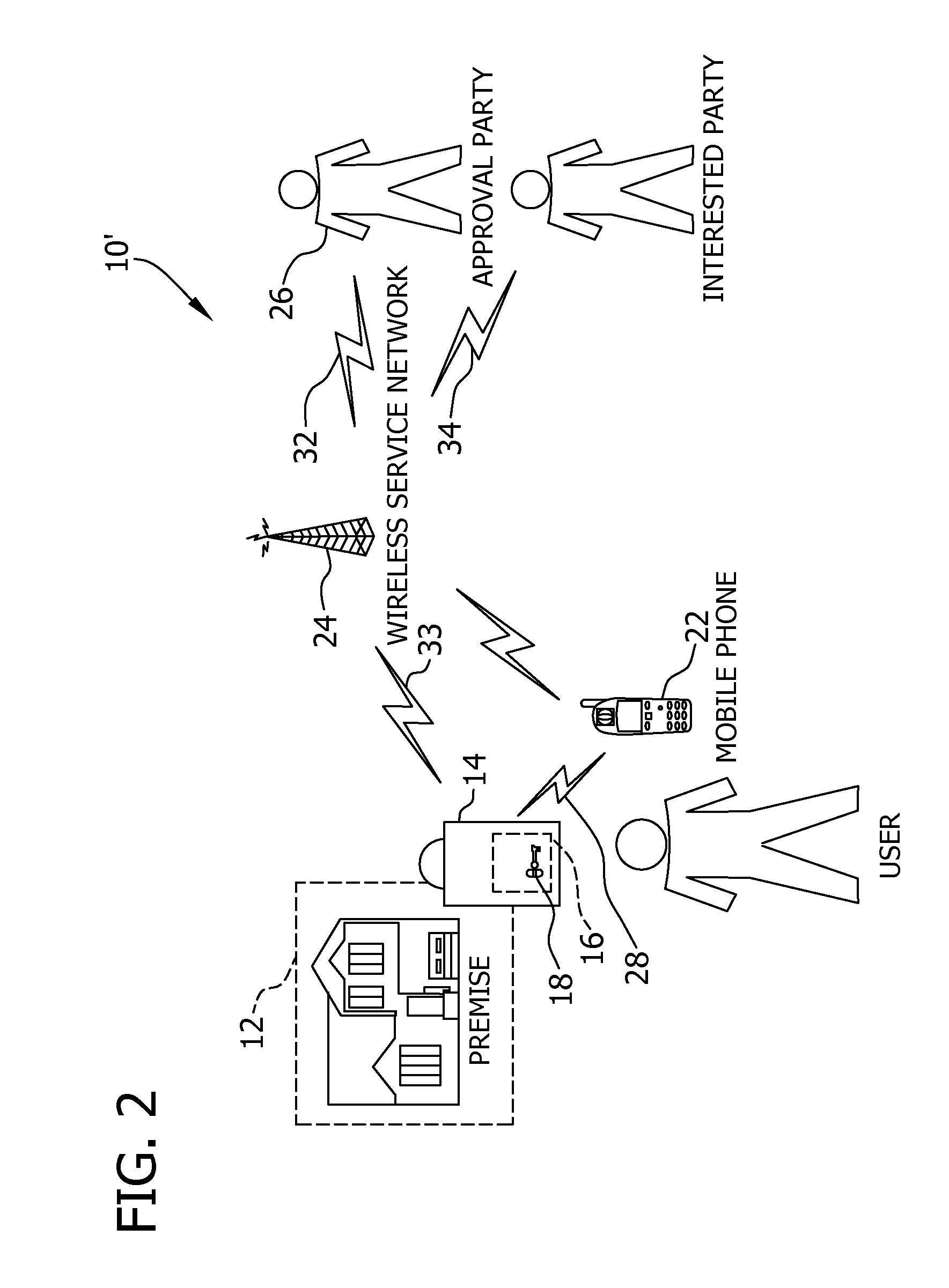
Key control with real time communications to remote locations
ActiveUS20110053557A1Electric signal transmission systemsUnauthorised/fraudulent call preventionControl systemMobile phone
A key control system includes at least one premise, a lockbox capable of securing a key to the premise and at least one mobile telephone associated with a user and having a stored access device program capable of communicating an access request to the lockbox. The premise is subject to authorized access by others, such as the user, based on preferences of an approval party established with the system. If specified by these preferences, the mobile telephone automatically initiates a communication to a selected destination to request approval of the access request.
Owner:UTC FIRE & SECURITY AMERICAS CORPORATION INC
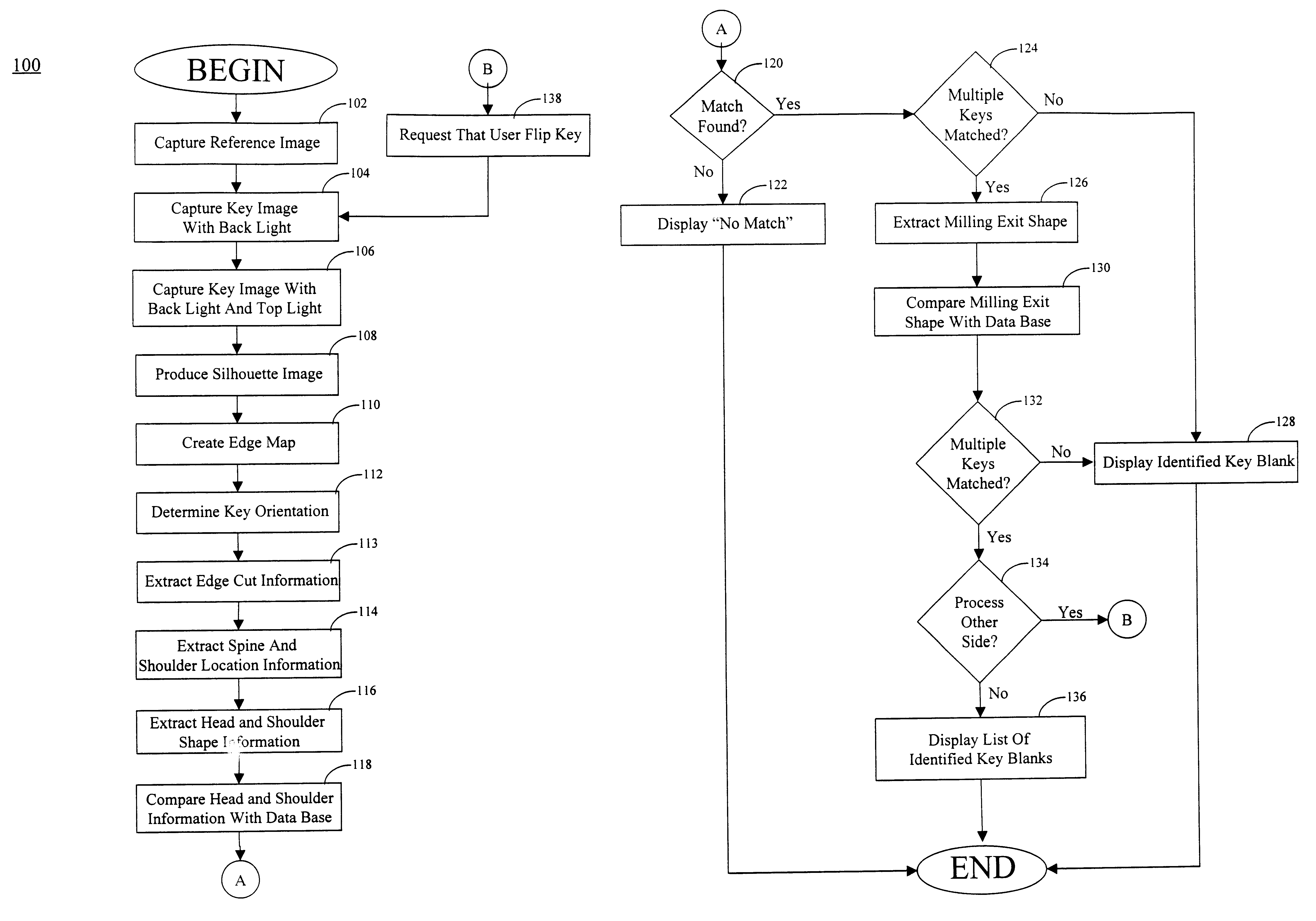
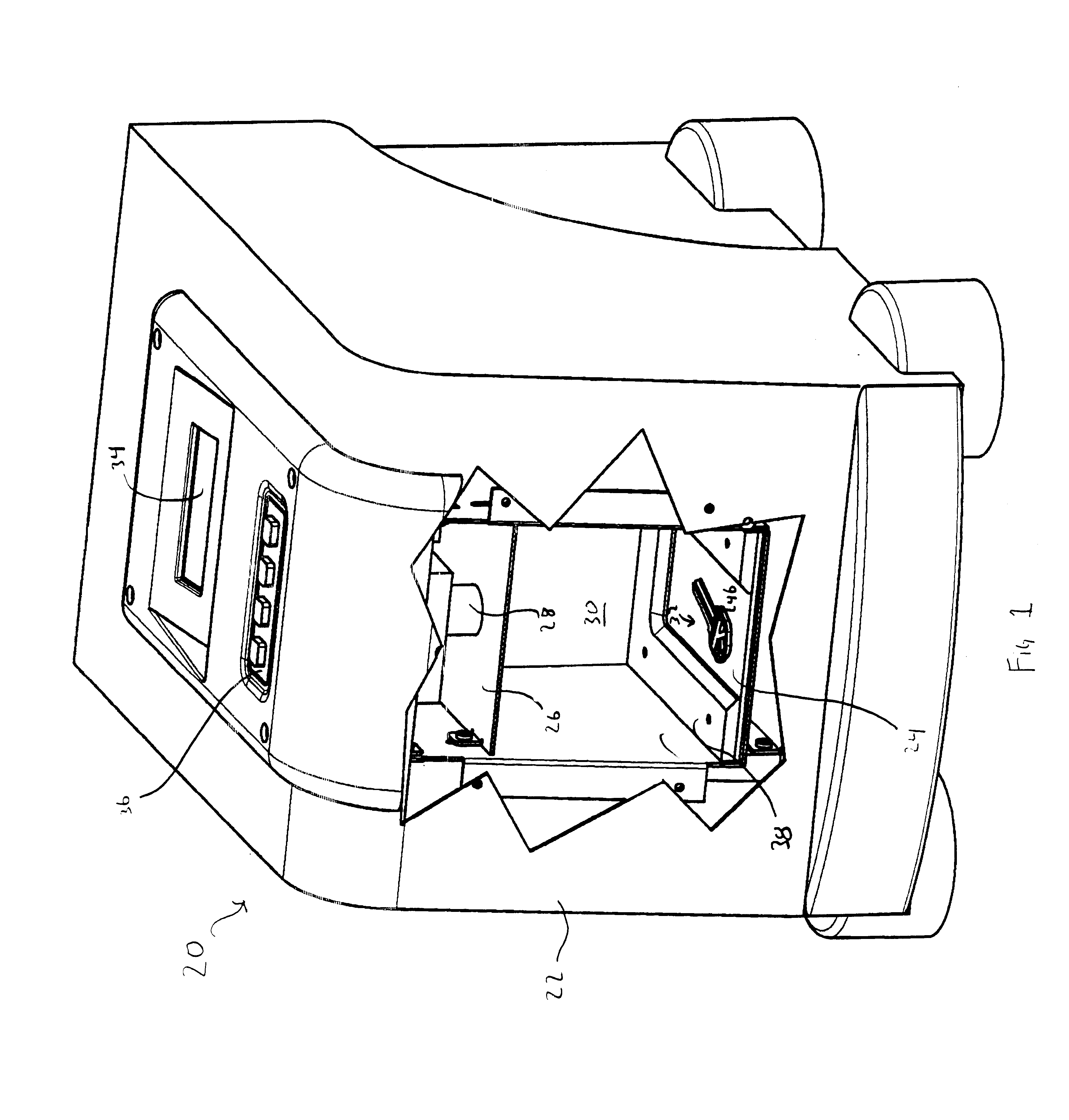
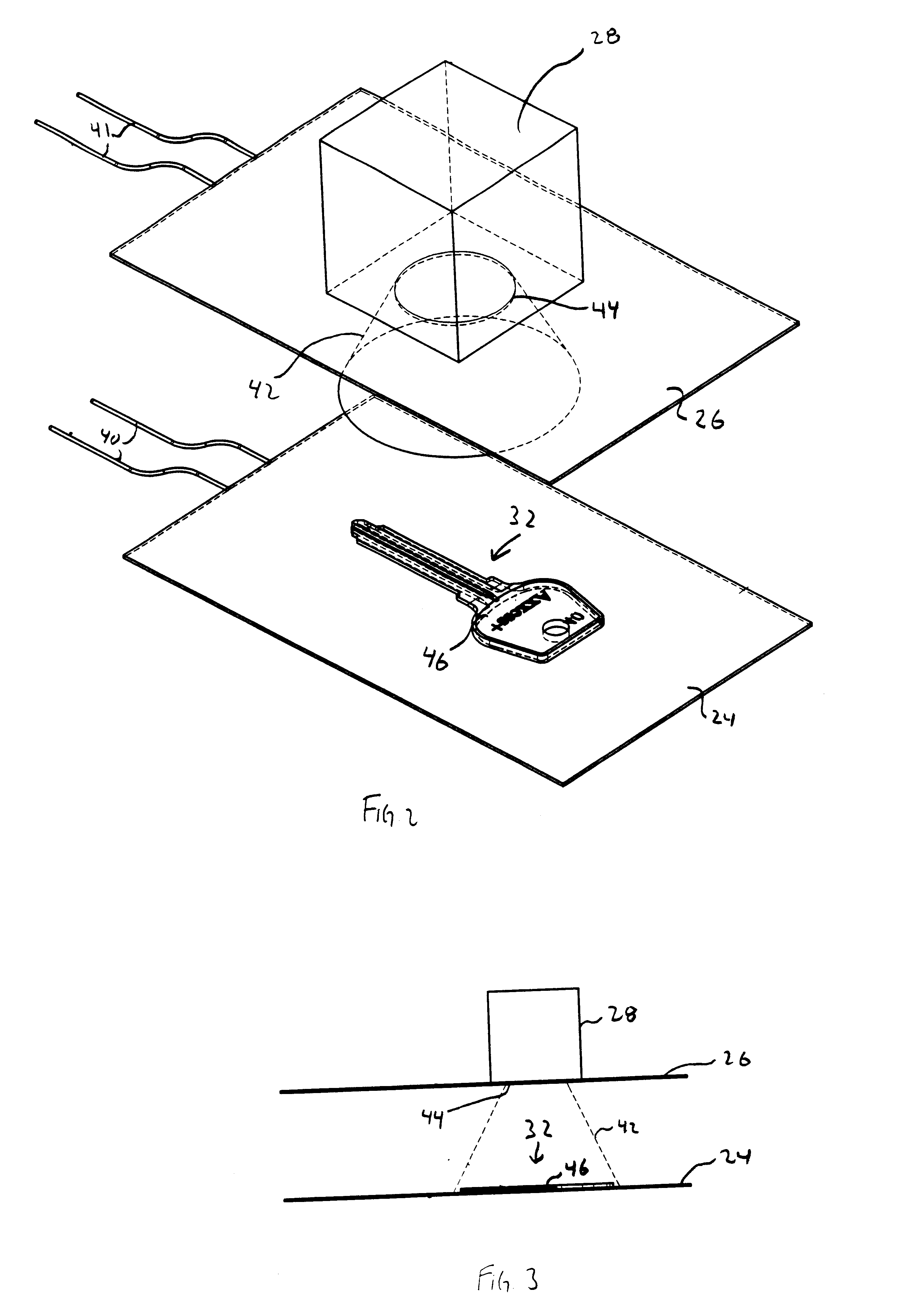
Key identification system
A system for identifying the key blank corresponding to a master key is provided. The system includes a first luminous surface and a second luminous surface. The second luminous surface is disposed opposite the first luminous surface such that the master key is disposable therebetween. The first and second luminous surfaces are operable to generate an image of the master key. A receiver is provided to capture the image of the master key. The system also includes a control having a memory that stores information on a plurality of key blanks. The control is operable to identify the key blank corresponding to the master key based on the image captured by the receiver.
Owner:THE HILLMAN GRP INC
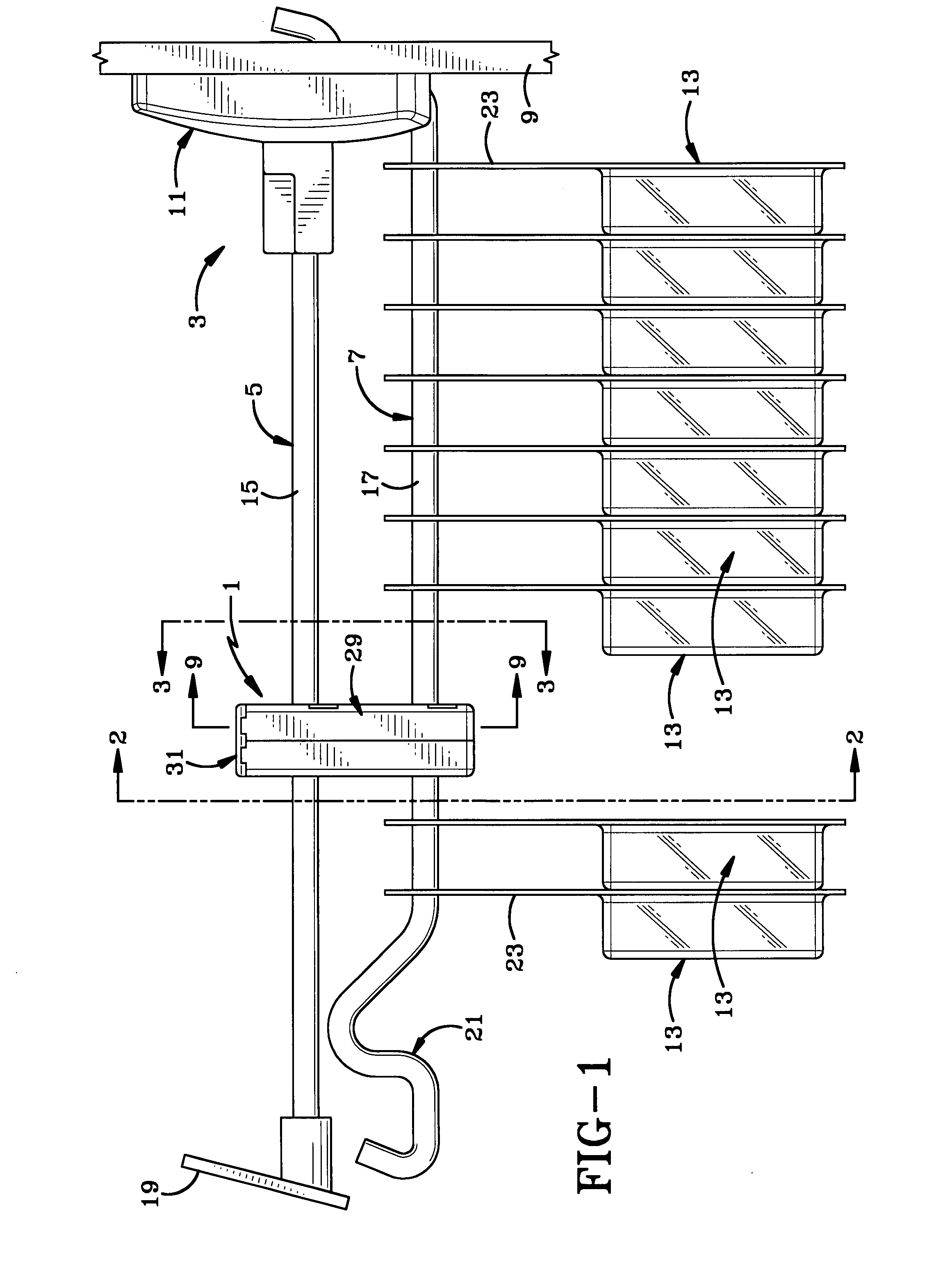
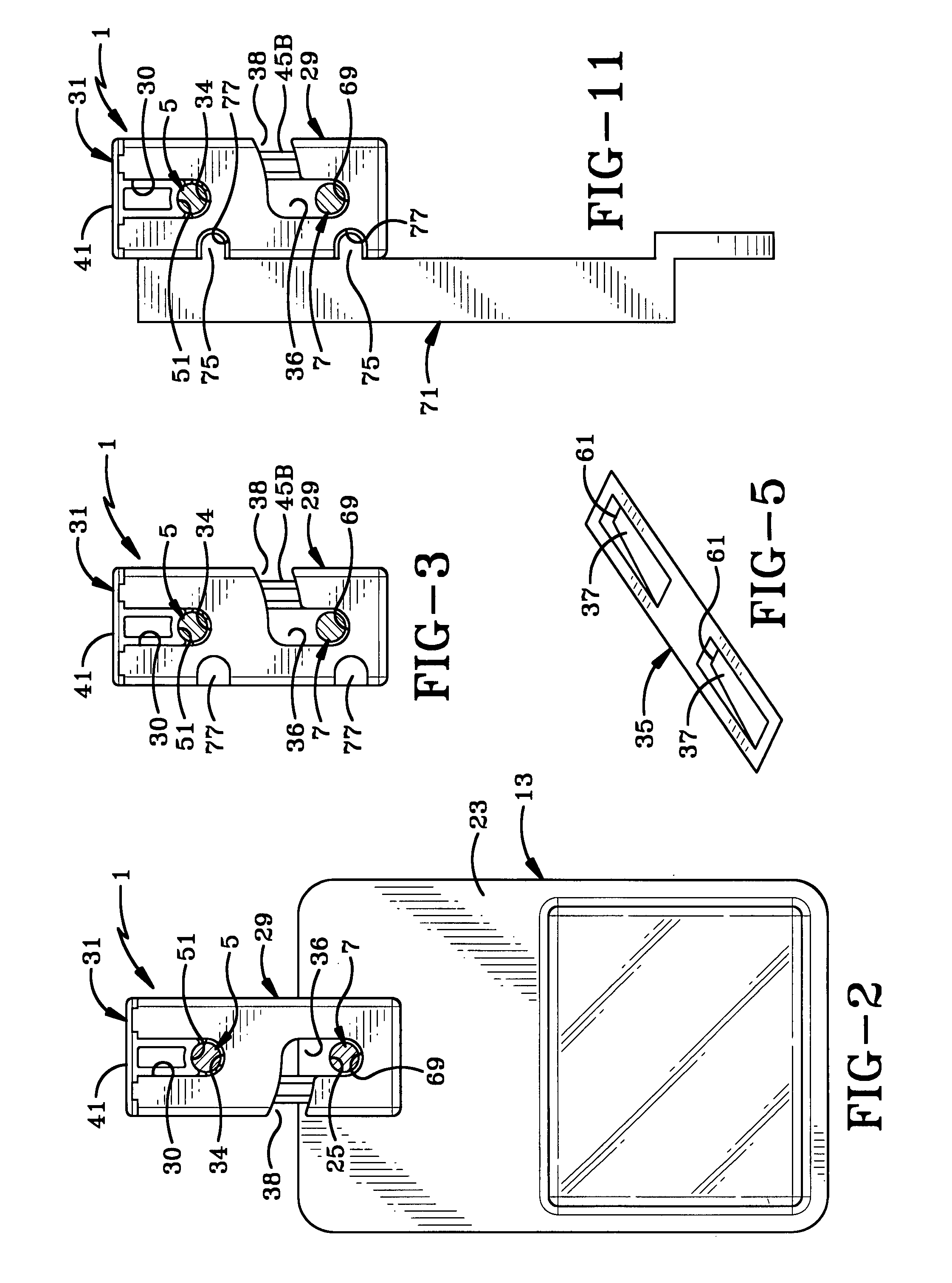
Electronic lock box with single linear actuator operating two different latching mechanisms
An electronic lock box contains a secure compartment for storing keys to a structure. A linear actuator moves in one direction opening the door to the secure compartment, and moves in the opposite direction releasing a shackle that holds the lock box to the structure. A lock box system uses an encryption algorithm to diversify user PIN data at a central computer, and stores that diversified information on a memory card for later use when the user attempts to access a lock box. The central computer and electronic lock box both keep track of system “epoch time,” and the memory card must be presented to the electronic lock box within a correct epoch time window for the diversified PIN data to be successfully decrypted and compared to the user's PIN data that is entered on a keypad of the electronic lock box.
Owner:SENTRILOCK
Combination non-programmable and programmable key for security device
A combination non-programmable and programmable key for a security device of the type used to display items of merchandise includes a non-programmable portion for cooperating with a mechanical lock of the security device and a programmable portion for cooperating with a sensor of the security device that is operatively coupled to an alarm for indicating a security threat to the security device or to an item of merchandise displayed on the security device. The non-programmable portion includes a side assembly having a magnet that cooperates with a magnetically attractable locking pin to unlock the mechanical lock of the security device. The programmable portion emits an energy signal that cooperates with the sensor of the security device to disarm the alarm and thereby permit the security device to be removed or an item of merchandise to be removed without the alarm indicating a security threat.
Owner:INVUE SECURITY PROD INC
Key storage and organization unit
InactiveUS20050199628A1Access is deniedProgramme controlComputer controlLocking mechanismEngineering
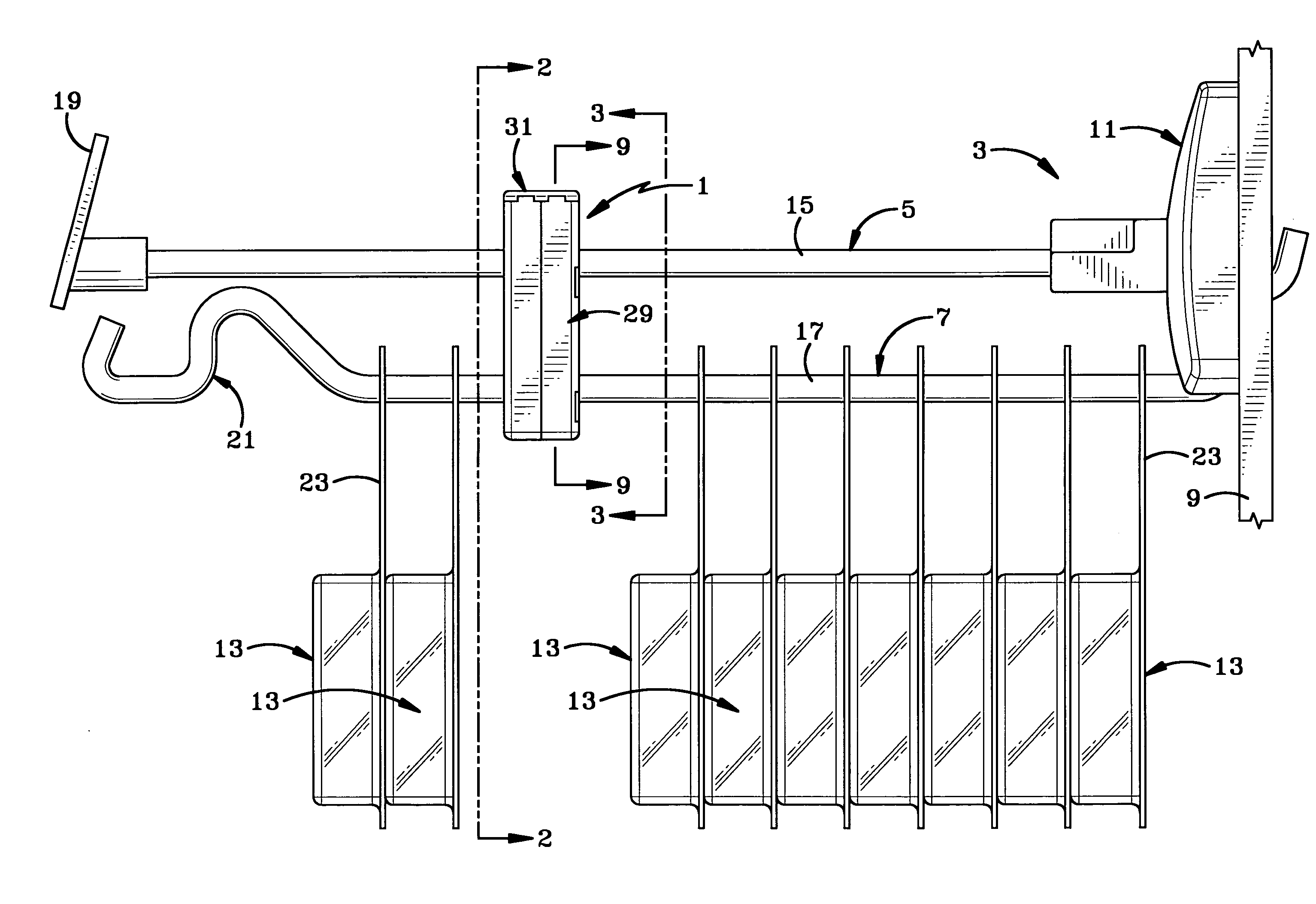
A key storage and organization unit includes a lockbox and a set of key file cards for retaining and storing keys in an organized manner. The lockbox includes a base and a cover that are secured by two closure latching members. When the two closure latching members are applied to the base and cover, a single locking mechanism can be applied to secure the lockbox. The lockbox is designed to receive multiple locking mechanisms, each capable of securing access to the lockbox.
Owner:MASTER LOCK COMANY LLC
Key imaging system and method
A key imaging system and method for identifying and matching a key blank with an original key when duplicating an original key by placing the key on a supporting flat surface and forming images of the grooves and indentations on the shank of the original key by illuminating the lateral surface containing the grooves and indentations and imaging those grooves and indentations by reflecting light off of the surrounding reflective surface and scattering light off of the grooves and indentations. The resultant images are scanned and recorded by means of a digital video camera / scanner. The scanned image is relayed to a computer where it is saved in computer memory. The saved image is compared to previously stored known original key blank images for the purpose of indicating a precise duplicate key blank matching the original key.
Owner:KABA ILCO CORP
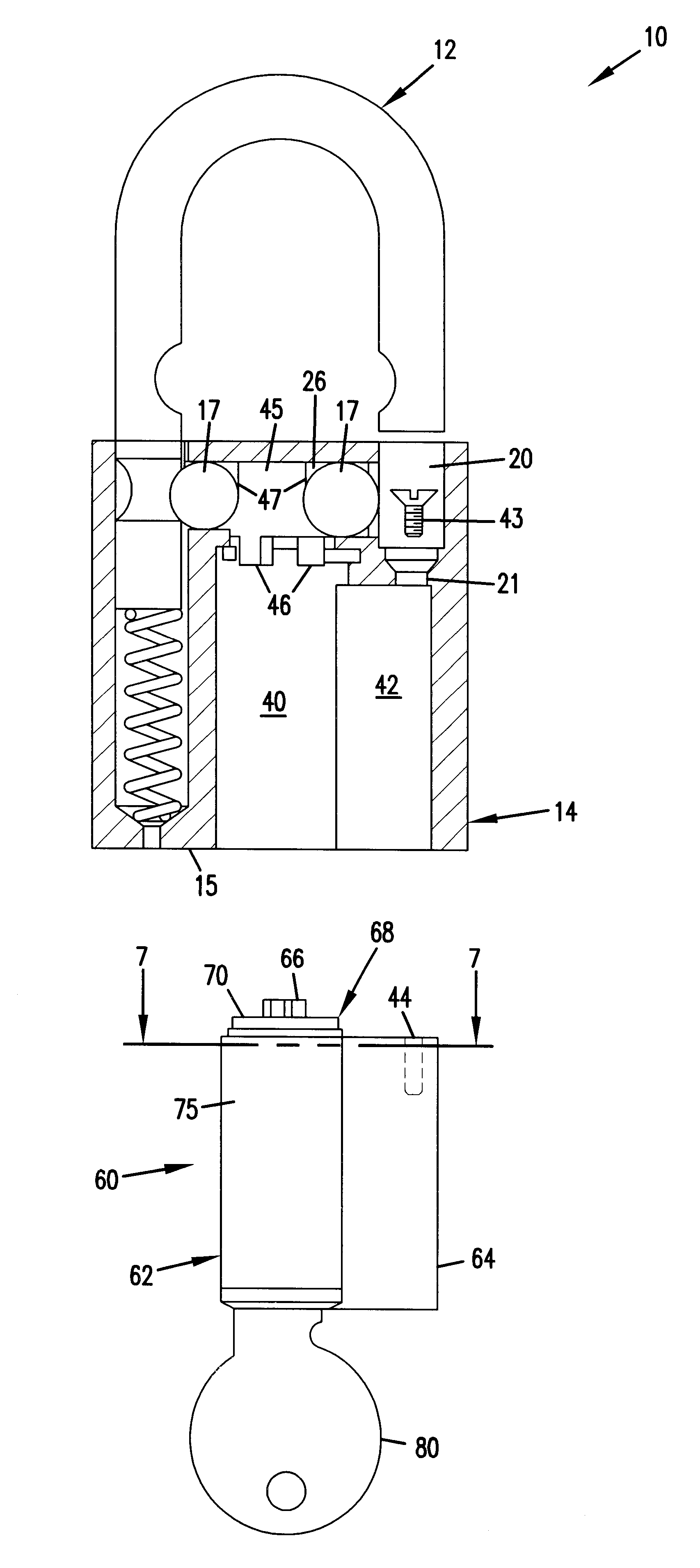
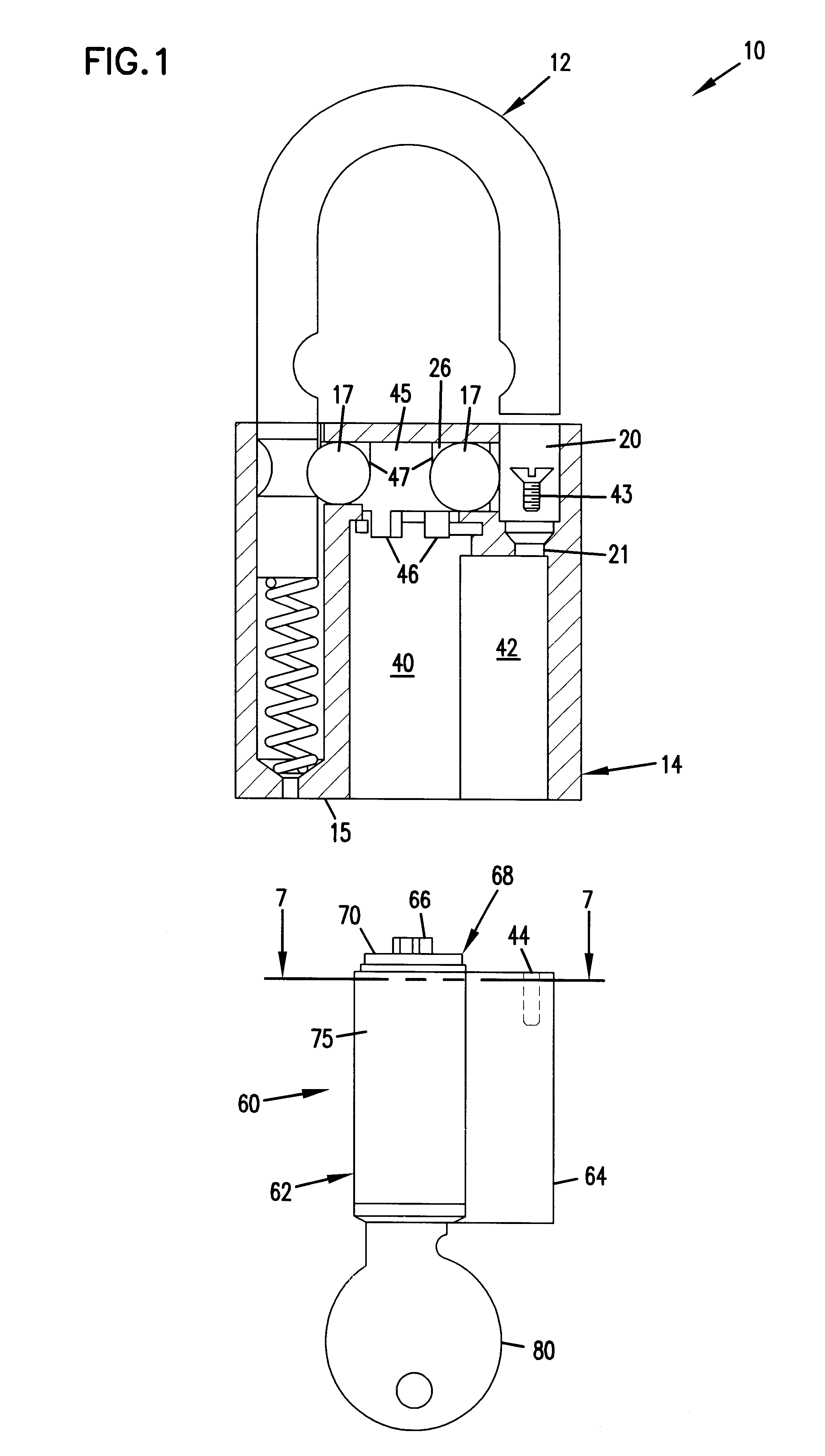
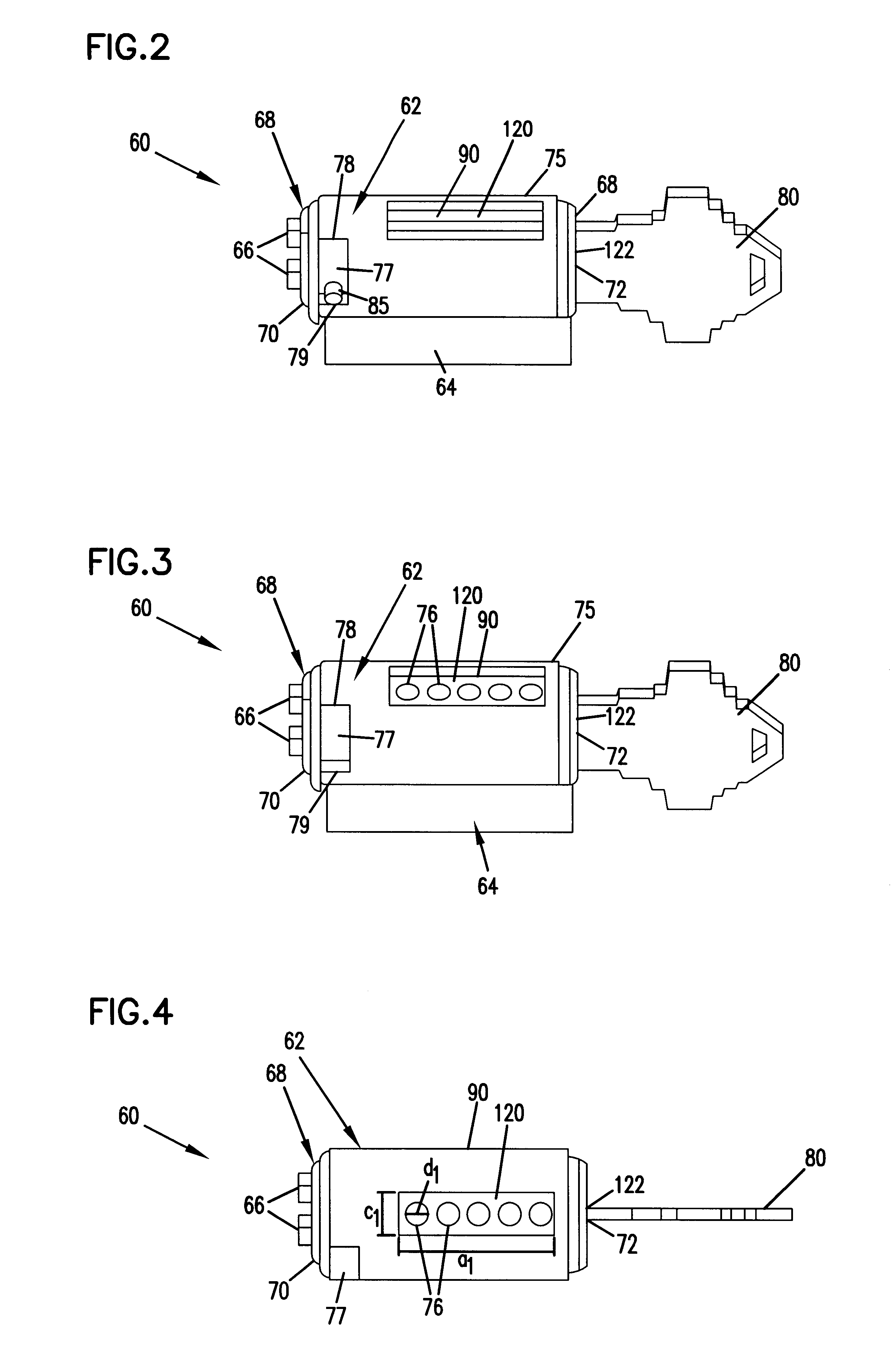
High security cylinder lock and key
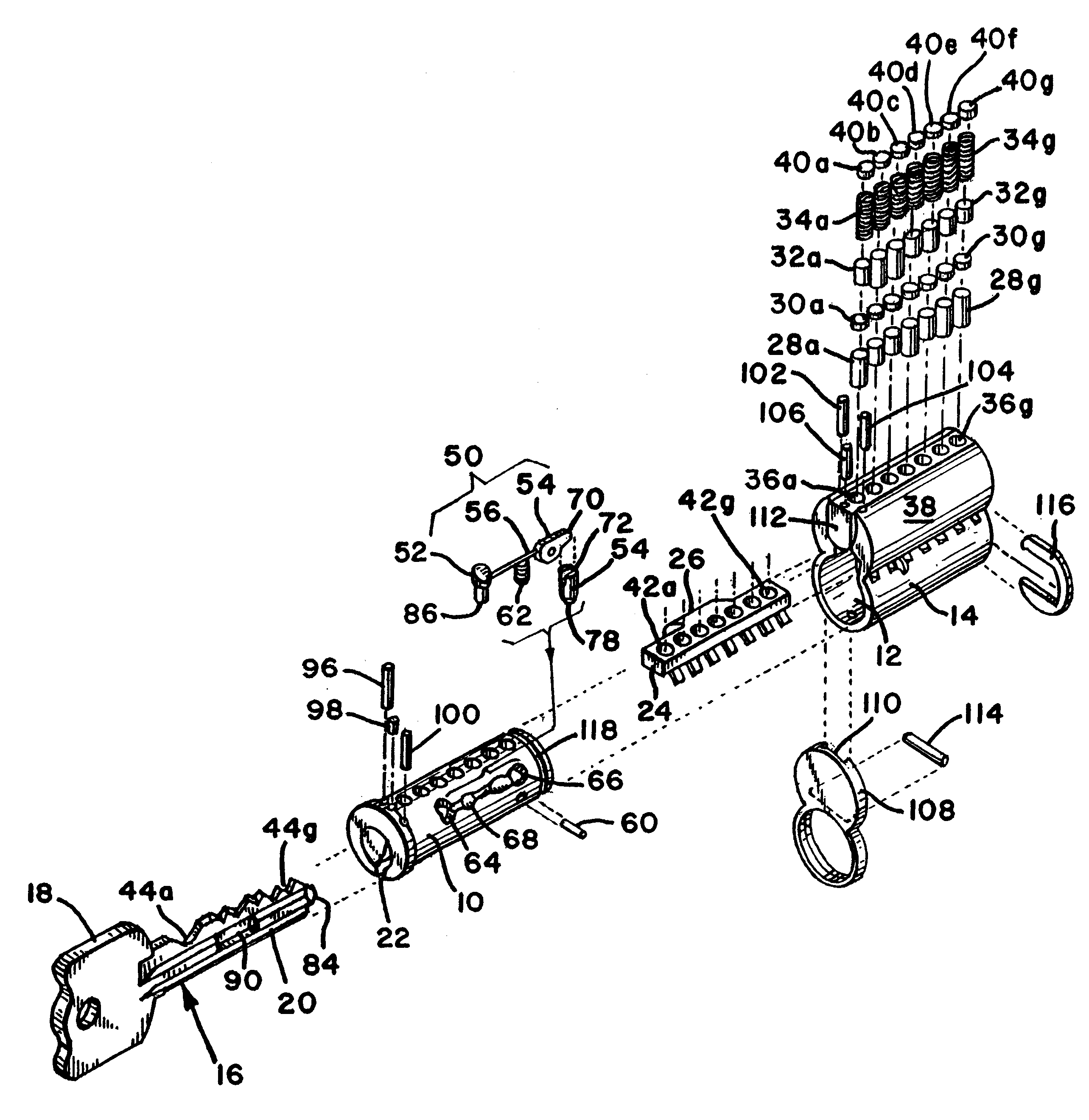
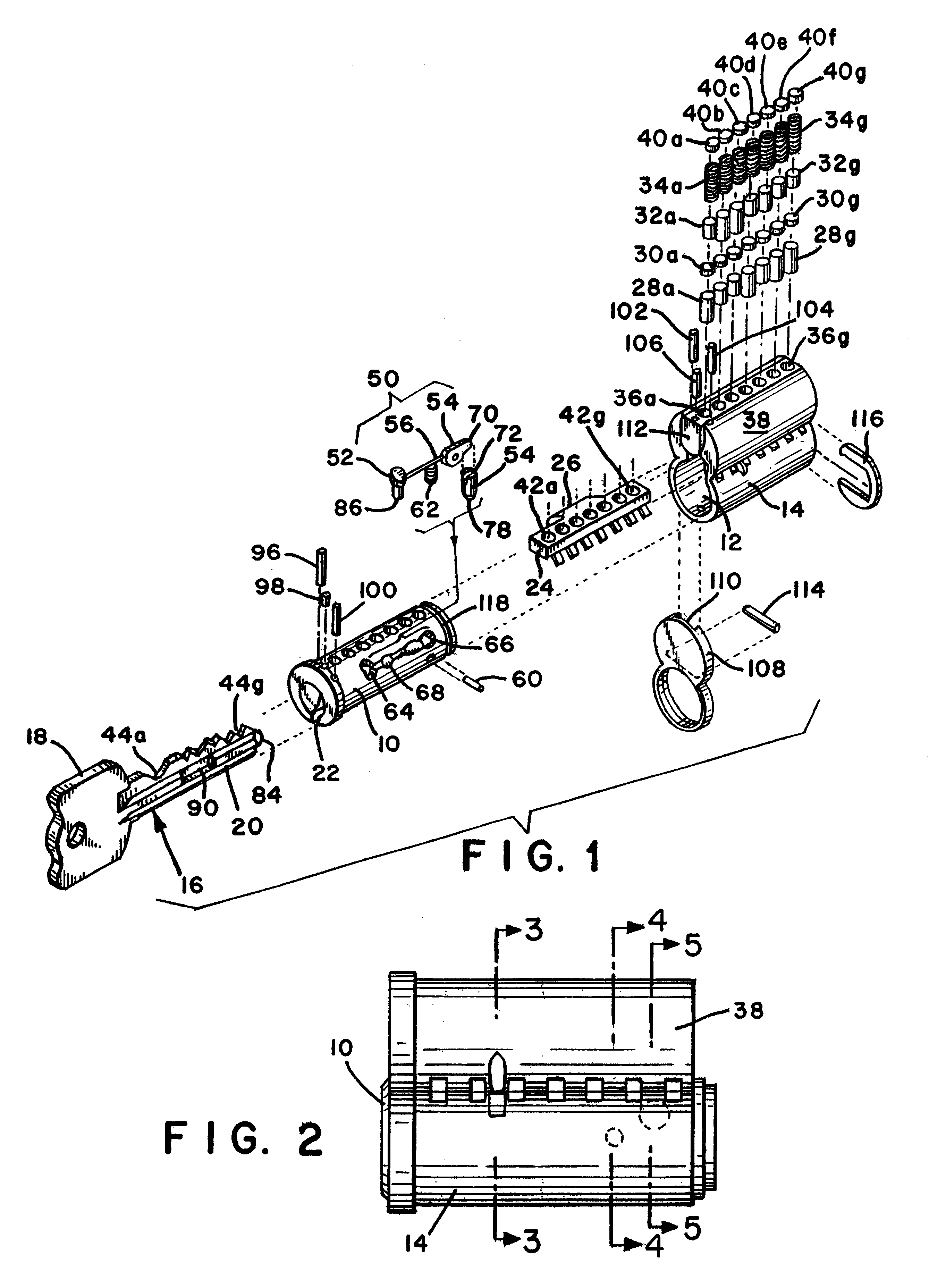
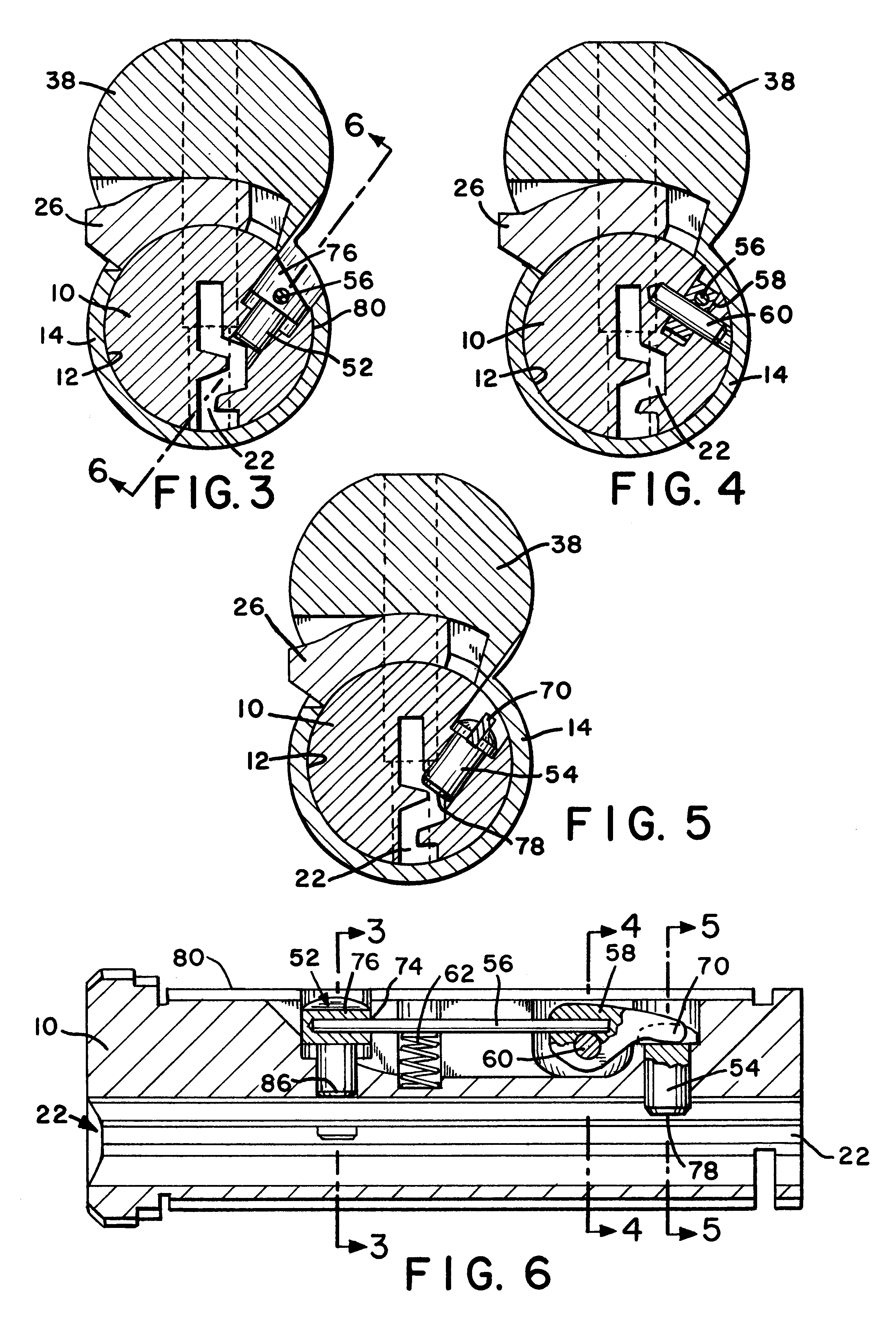
A cylinder lock includes a shell and a plug inside the shell. A locking pin, a sensor pin and a flexible coupling are mounted within the plug. The sensor pin moves the flexible coupling and the coupling moves the locking pin to an unlocked position when the correct key is inserted into a key slot in the plug. The key includes a locking pin receiving notch, to allow the locking pin to move to the unlocked position. The key also includes a contact surface that moves the sensor pin and thereby moves the locking pin to the unlocked position through the flexible coupling. When an incorrect key, without the locking pin receiving notch, is inserted, the flexibility of the flexible coupling allows the sensor pin to move without moving the locking pin. The cylinder lock may also include conventional pin tumblers. The receiving notch of the key may be provided with an alignment surface that cooperates with the locking pin to control the depth the key is inserted into the lock and allow keys of varying length to align relative to the pin tumblers of the cylinder lock.
Owner:MEDECO SECURITY LOCKS
Lock mechanism for display rod
InactiveUS7392673B2Quick removalSimple and compactClothing locksLocks for portable objectsLocking mechanismEngineering
Owner:INVUE SECURITY PROD INC
Key control with real time communications to remote locations
ActiveUS8437740B2Electric signal transmission systemsUnauthorised/fraudulent call preventionKey pressingControl system
Owner:UTC FIRE & SECURITY AMERICAS CORPORATION INC
Lock and key system with extra code combinations
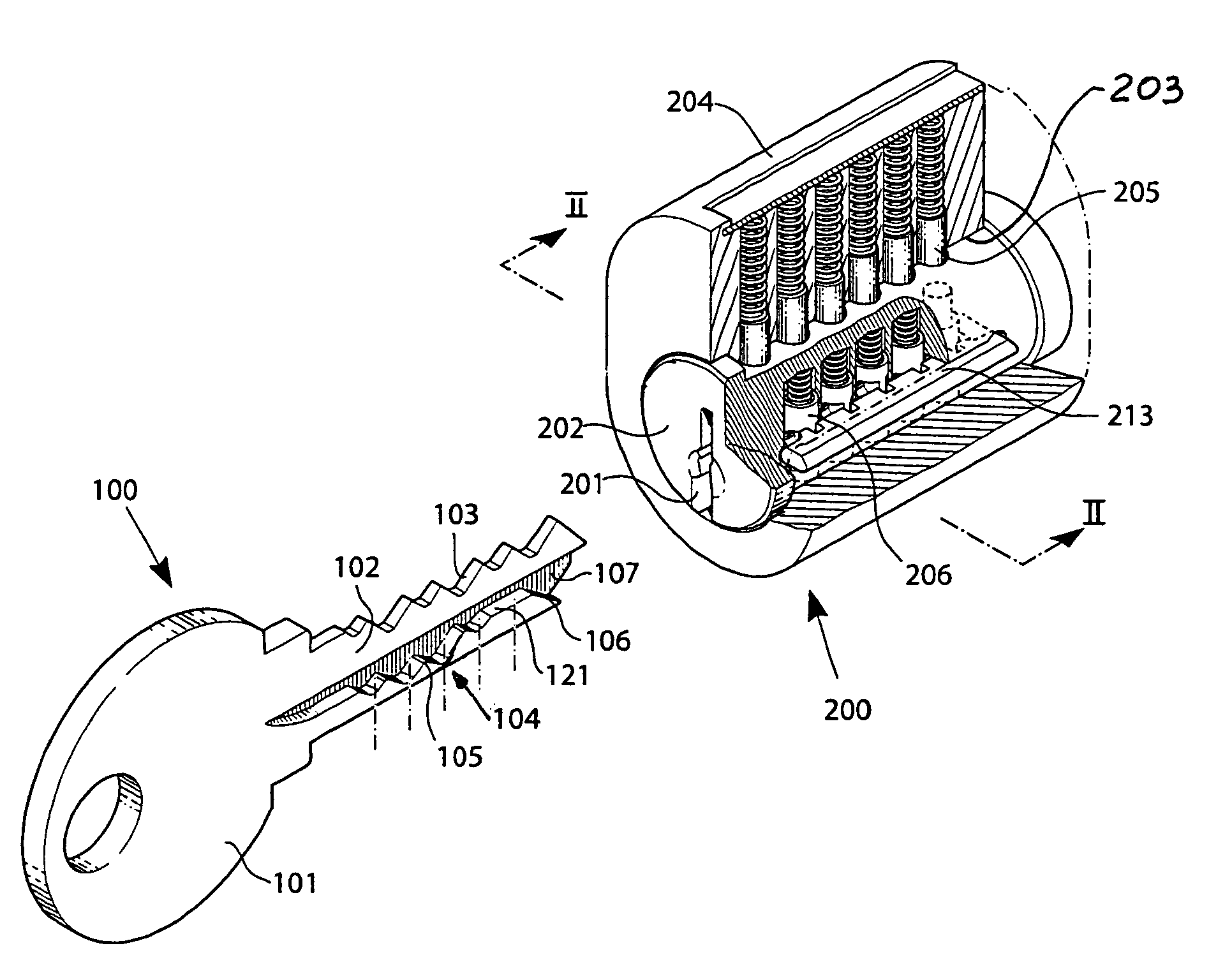
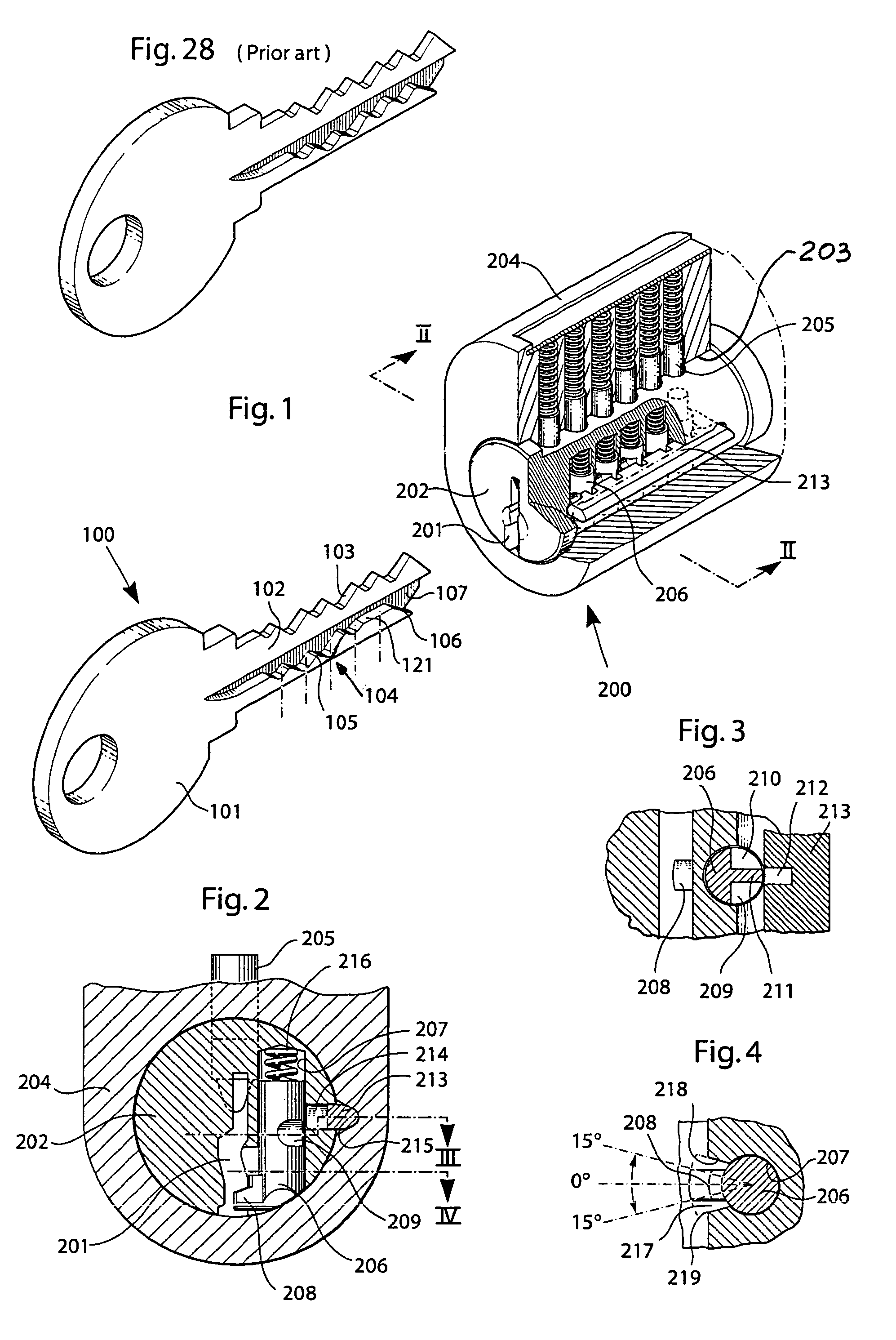
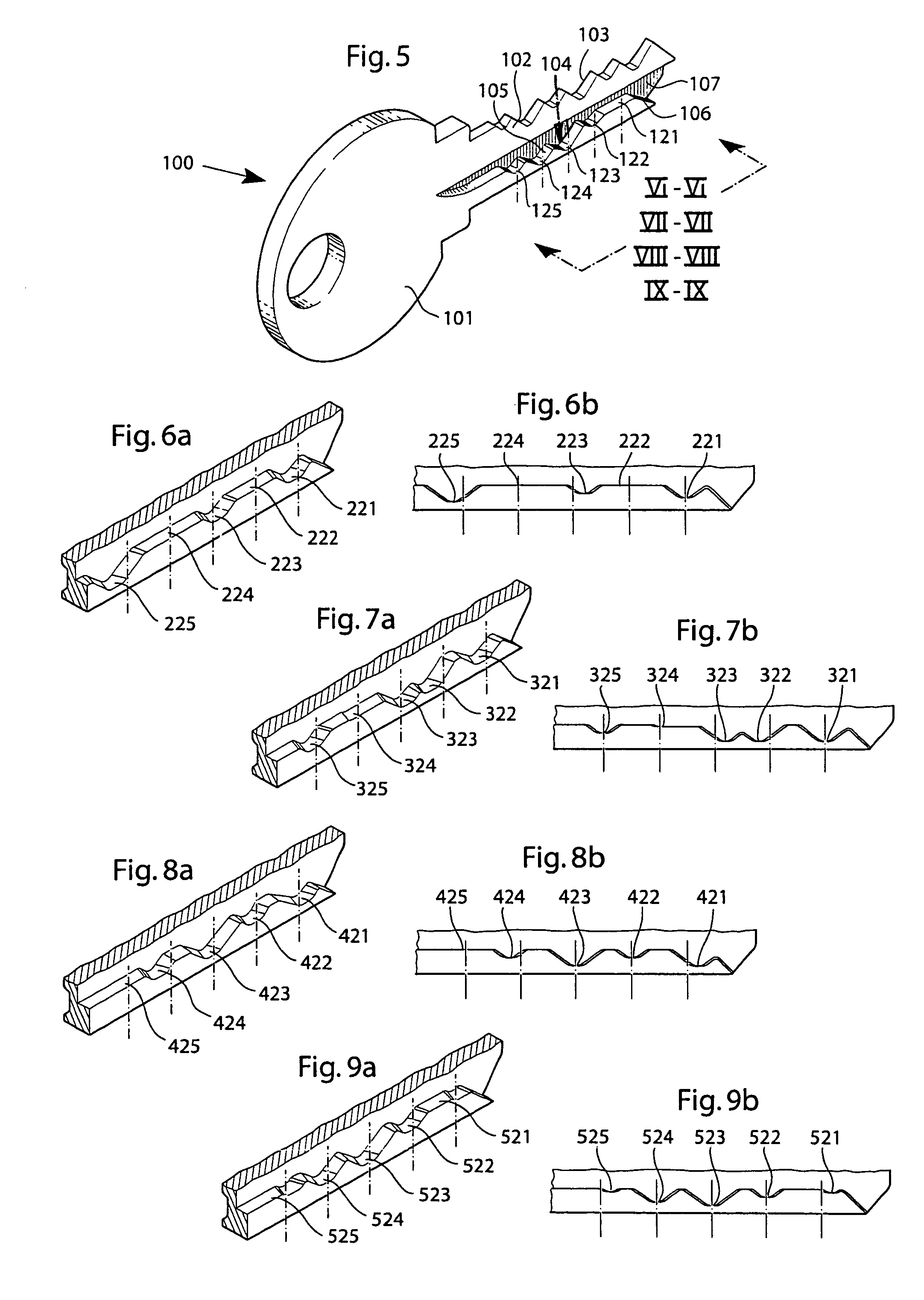
ActiveUS7159424B2Improve securityHighly controlled manufactureKeysCylinder locksLocking mechanismEngineering
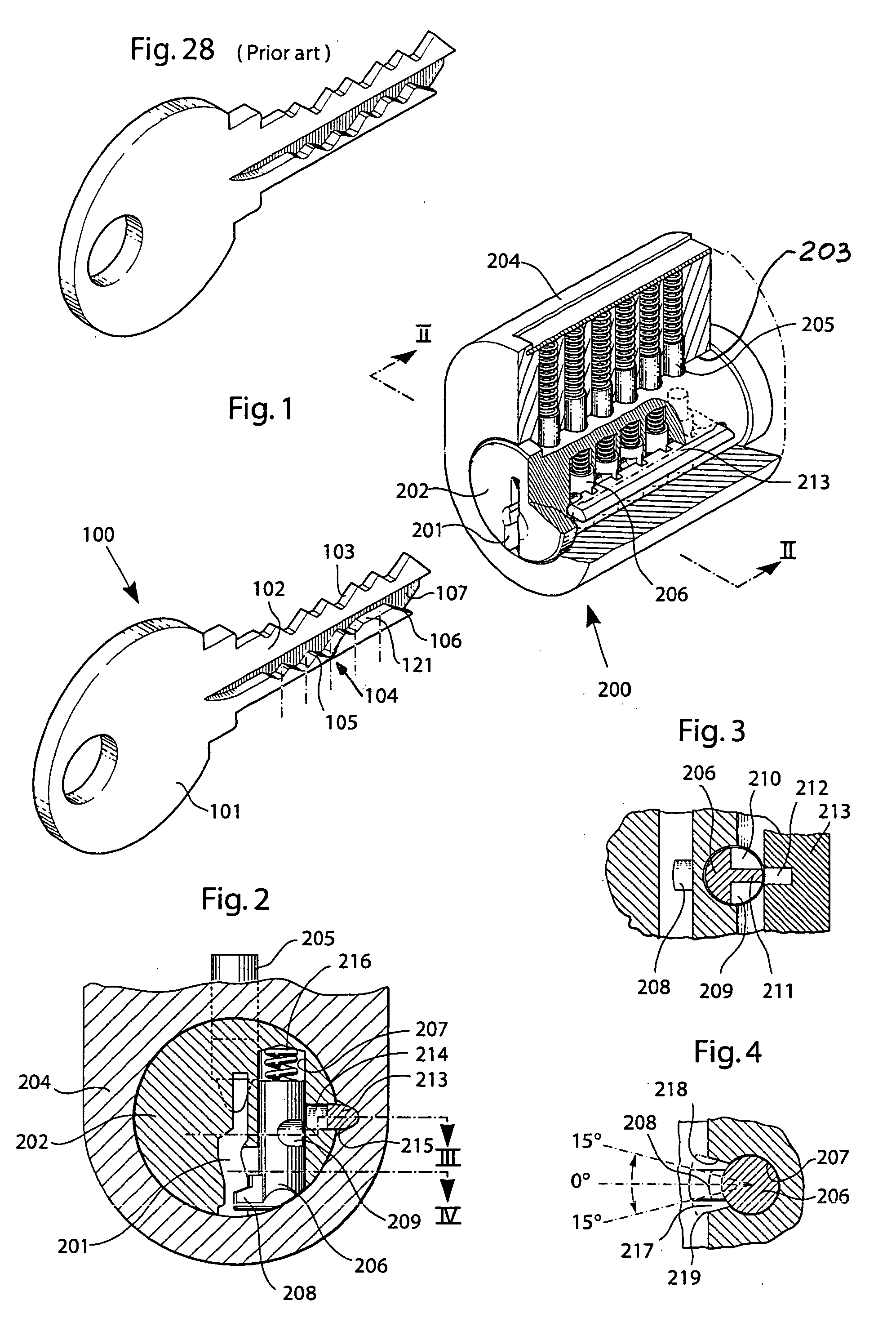
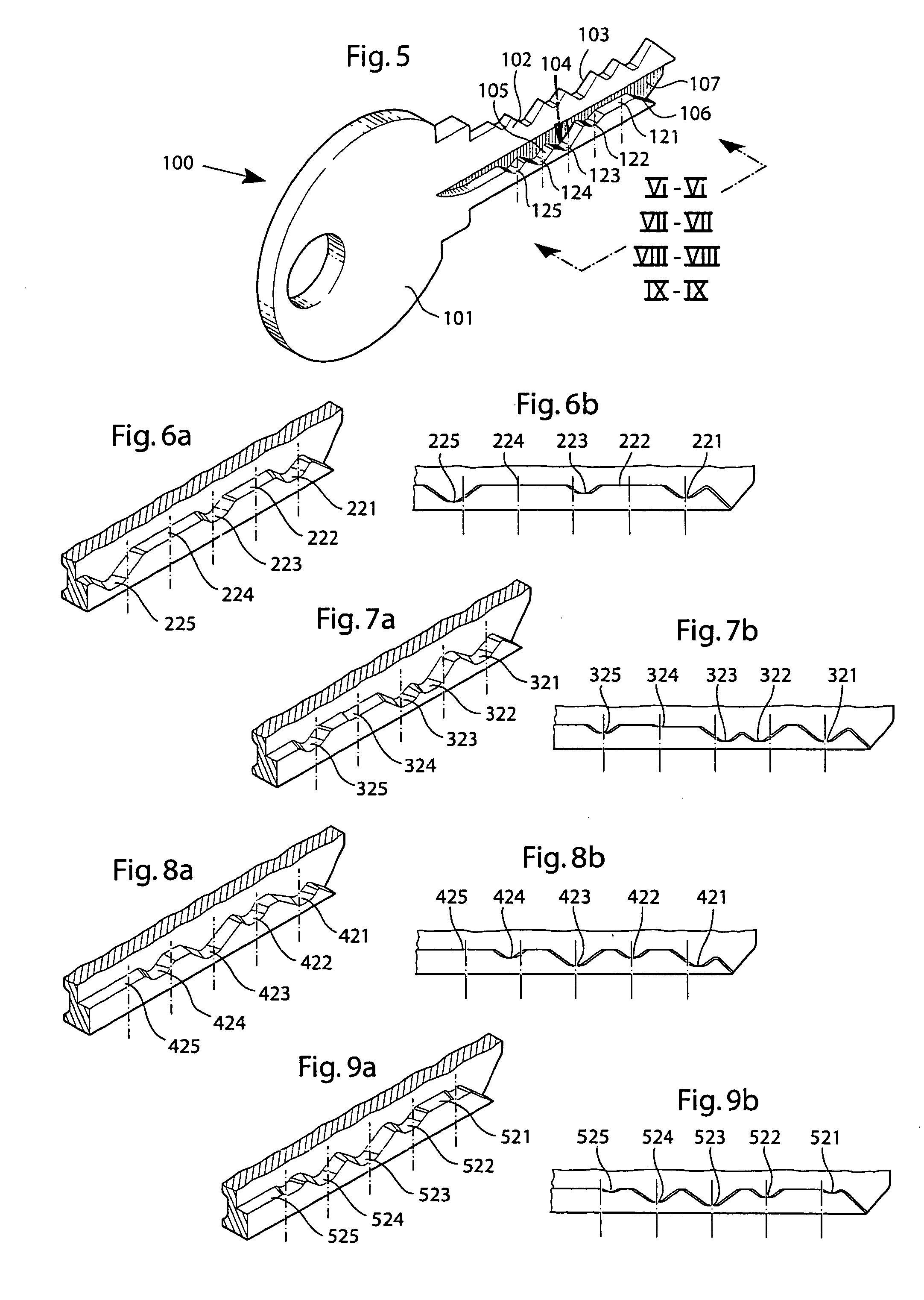
A high security lock and key system with an increased number of code combinations is disclosed. The system is of the kind where the blade of the key has a wave-like guiding surface (104) at the side of the key blade which, upon insertion into an associated lock having a rotatable key plug, engages with one or more side locking tumblers (206) in the lock cooperating with a side locking mechanism for locking the key plug against rotation. In order to provide an even higher number of possible code combinations, while preserving the overall dimensions of the locks and the keys of the system, the present invention provides for an extra code level (121) located at a longitudinally extending shelf surface, viz. at the upper boundary of the side material region where the wave-like guiding surface is cut at the side of the key blade. The invention also relates to a key (100) and a key blade as such, and to a lock (200) as such, for use in such a system.
Owner:WINLOC
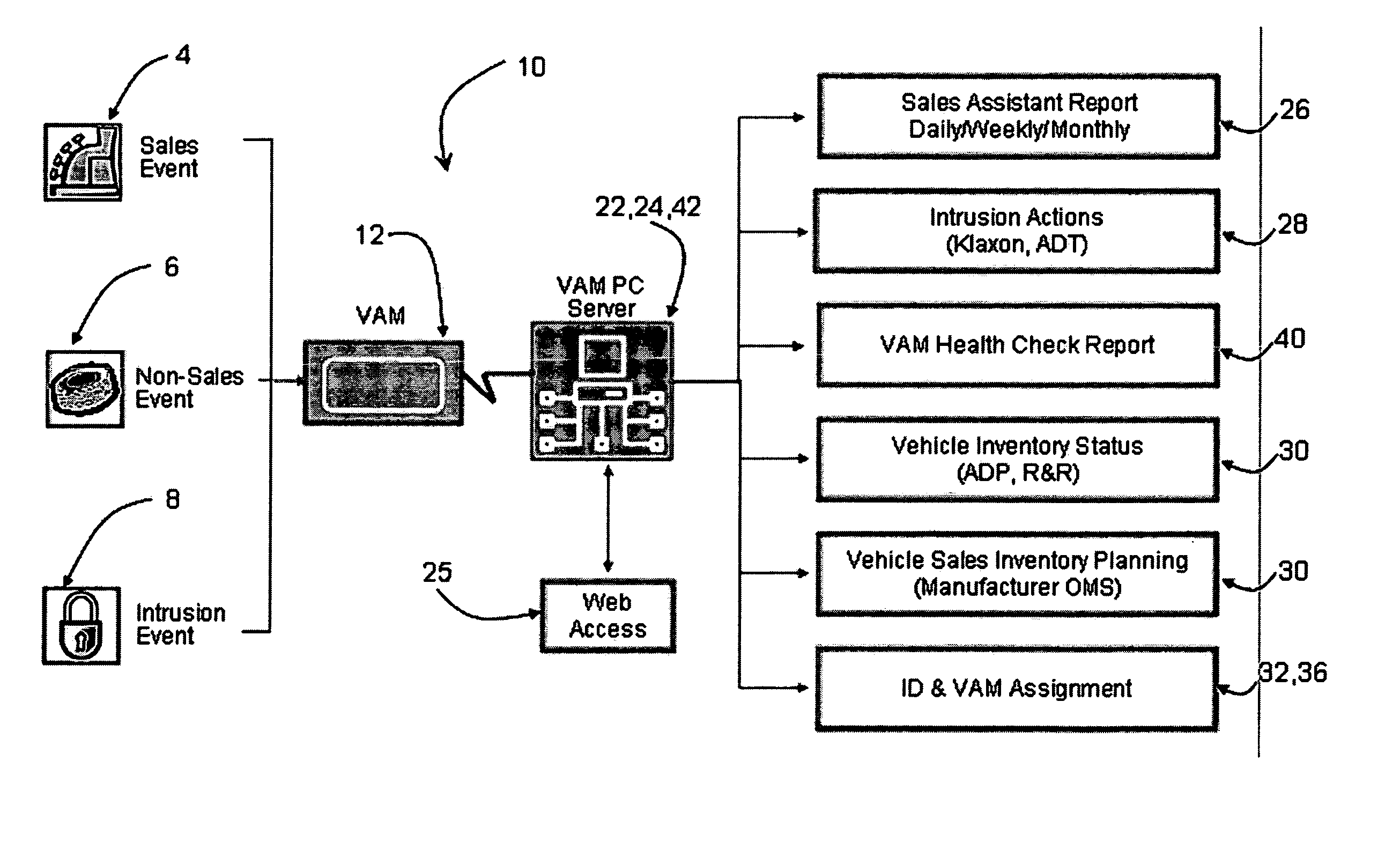
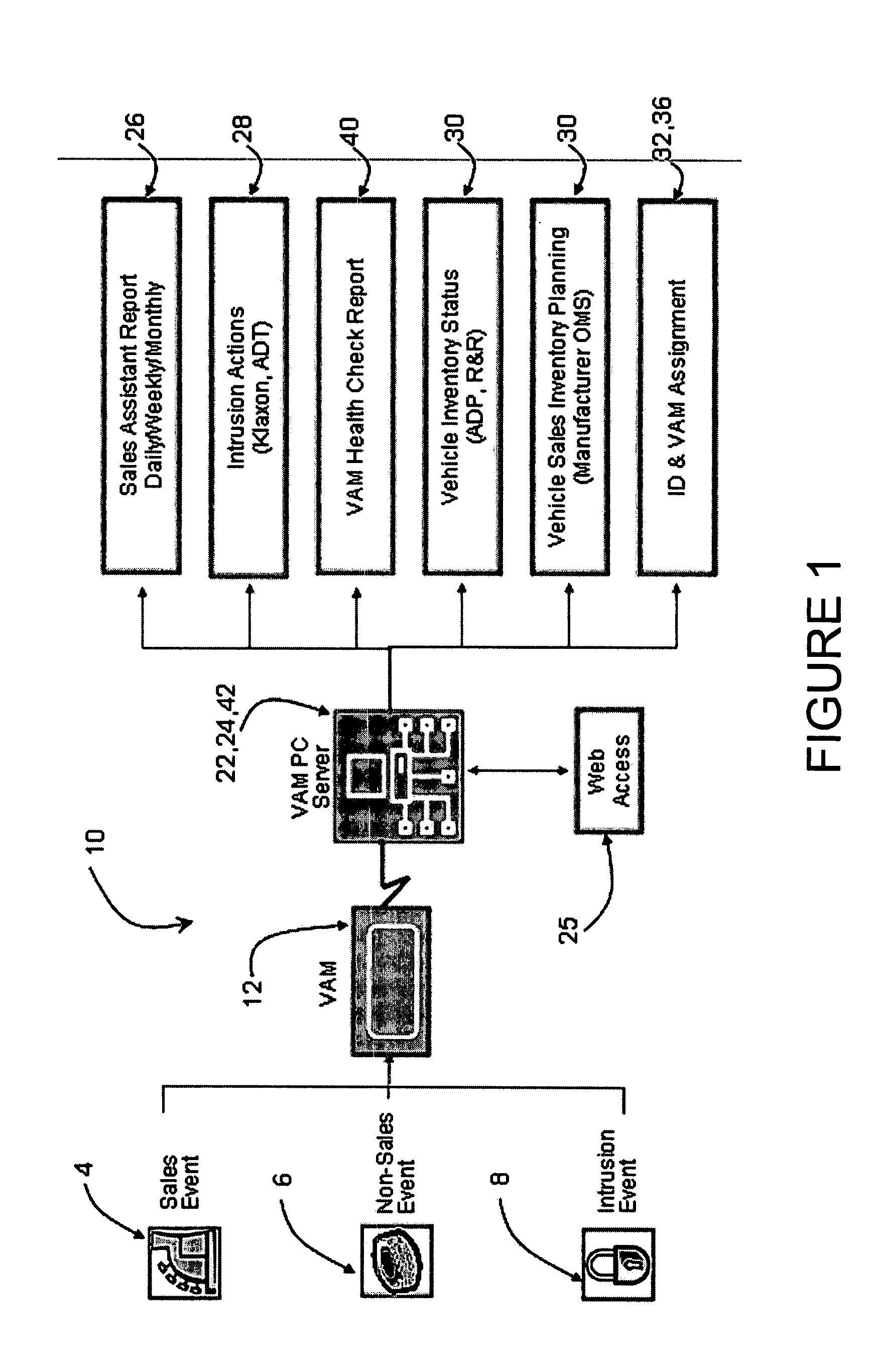
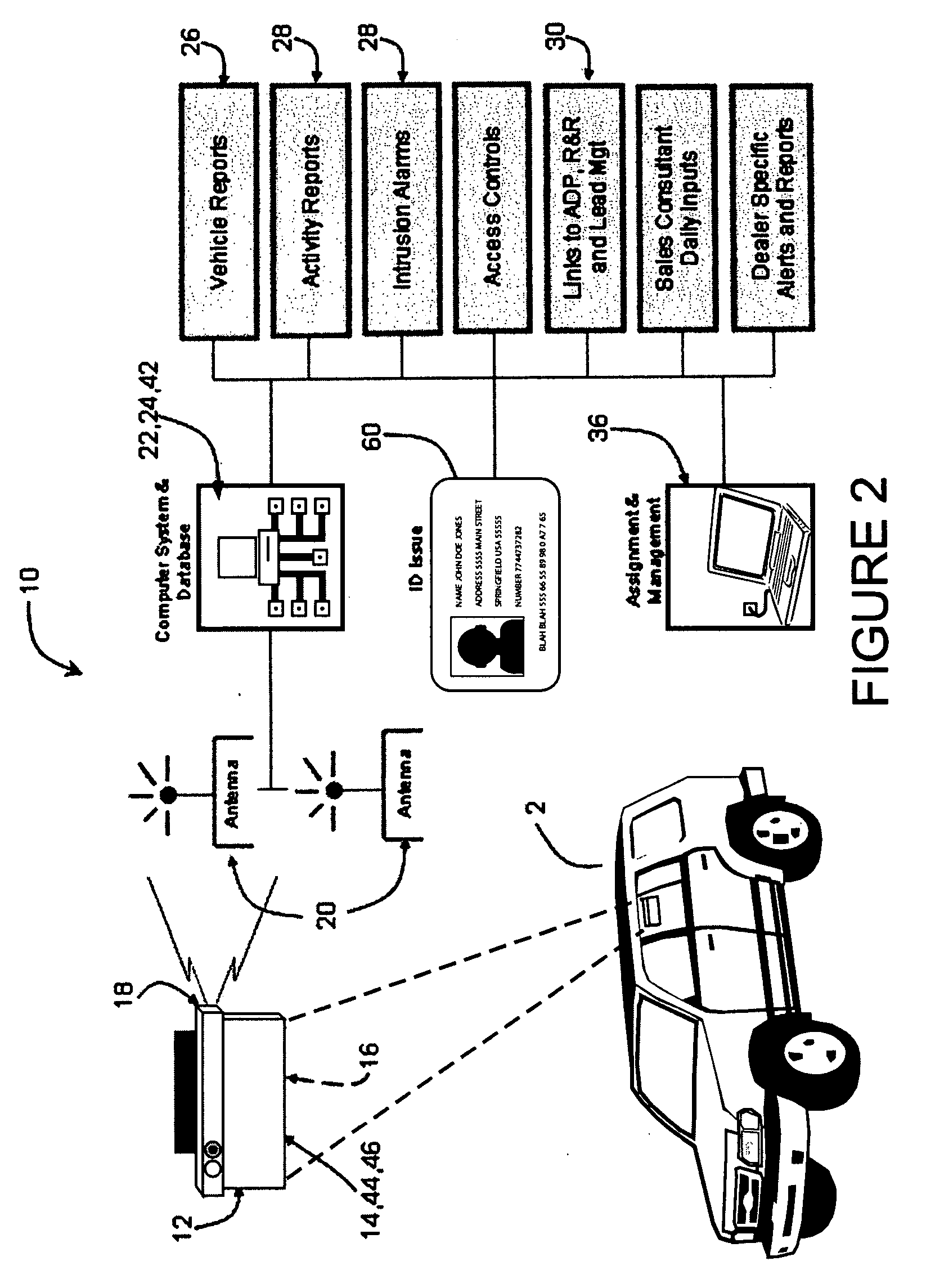
Vehicle activity module
ActiveUS20070273534A1Prevent copyingElectric signal transmission systemsDigital data processing detailsComputerized systemComputer module
Systems and methods are disclosed for maintaining security and data gathering for a number of vehicles. The systems include a vehicle activity module for each of the vehicles. The vehicle activity module has a wireless transmitter, a storage device, at least one sensor for receiving event information from identification devices, such as RFID cards, keypads, magnetic ID cards, and the like, a releasable key container, and a processor for accessing and analyzing information. The VAMs are wirelessly connected to a computer system. The VAMs control access to the keys, monitor information relating to access, and store and transmit information relating to sales events, non-sales events, and intrusion events. The VAMs are capable of autonomous operation, without the need to access the computer system to verify event information. The VAMs further include signal attenuating mechanisms to facilitate use of “smart keys.”
Owner:SENTRILOCK
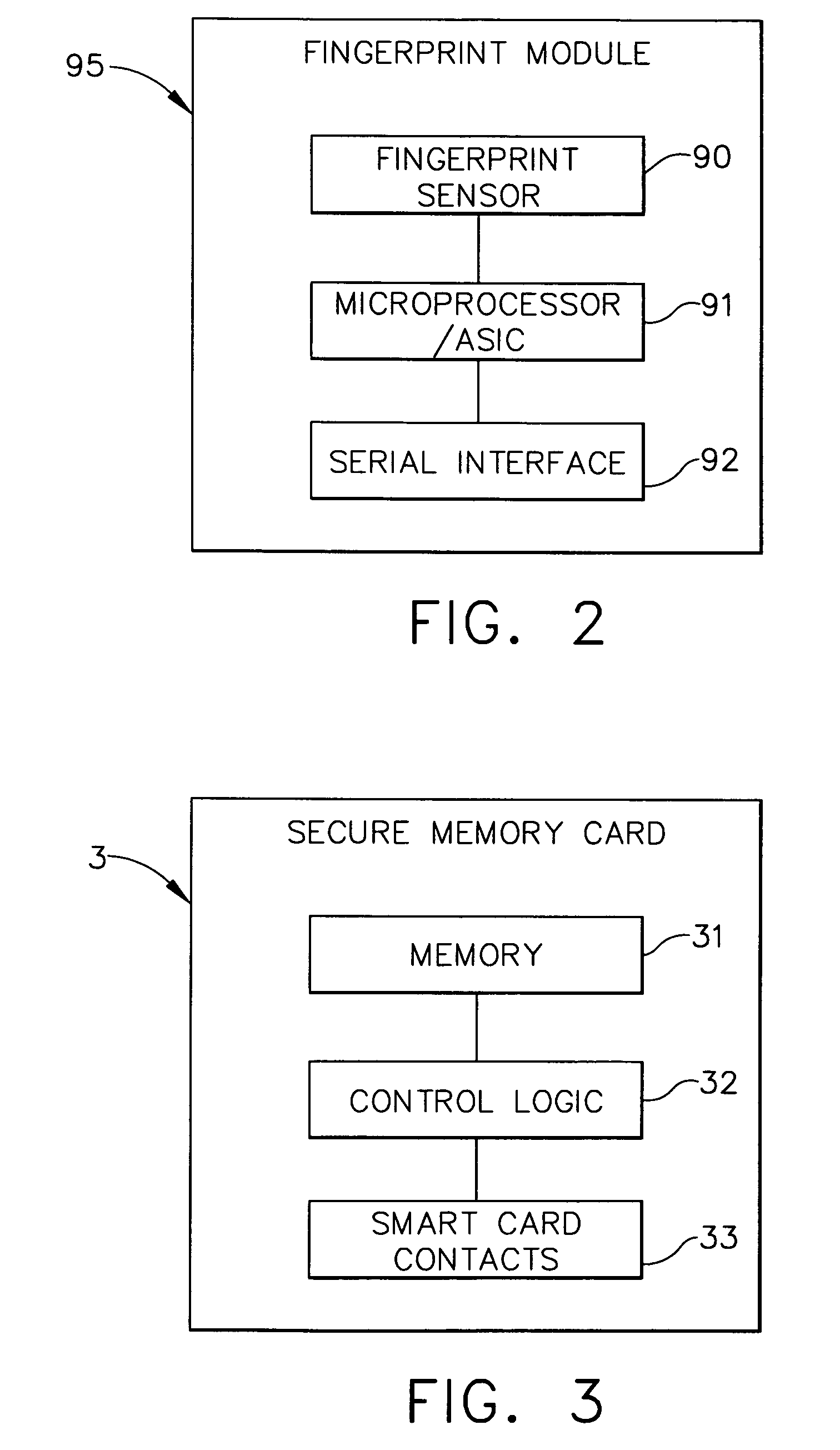
Electronic lock system and method for its use with a secure memory card
An improved electronic lock system is provided for use with real estate lock boxes. Each user has an identification card with a non-volatile secure memory for exchanging data with the lock box, and for exchanging data with a central computer. The user first inserts the card into a connector at the lock box, or at the central computer. The lock box or central computer must first enable (or unlock) the data in the card memory, and then can read the data stored in that card's memory and record this information in lock box memory. The card must then identify itself, and the user must identify himself / herself to the lock box or central computer. After the identification information is authenticated, the user can enter commands to the lock box; e.g., an access code is manually keyed into the lock box keypad by the user to obtain access to a secure compartment.
Owner:SENTRILOCK
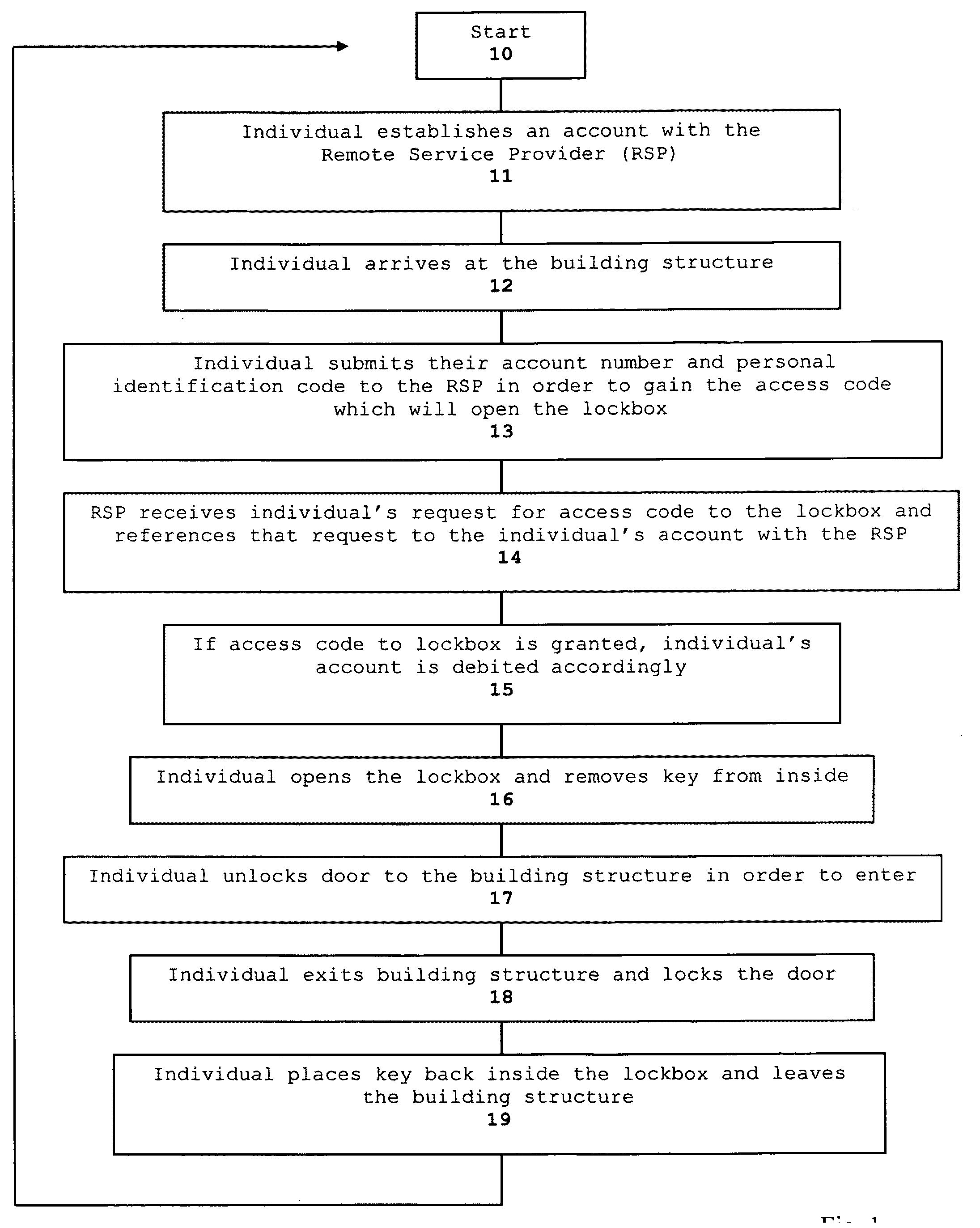
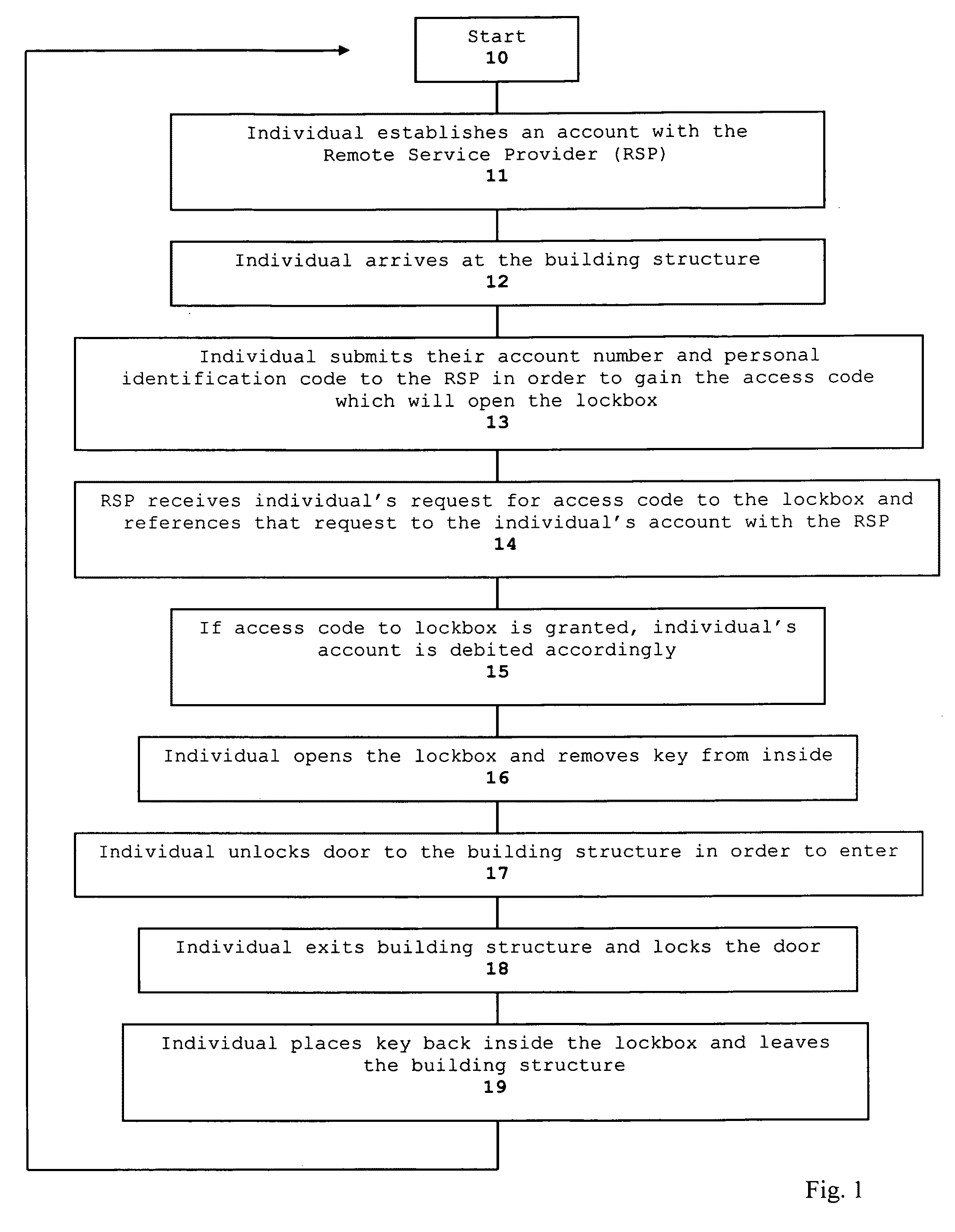
Method and system for real estate marketing
ActiveUS20100223170A1Shorter waiting periodIncrease volumeColor television detailsClosed circuit television systemsService provisionData science
A method and system for real estate marketing allows individuals from the general public to gain access to a real estate property that is placed for sale or lease for the purpose of inspection. Access to the real estate property may be granted to requesting individuals who hold valid user accounts with a Remote Service Provider which can authorize such access. Access to inspect real estate property may be granted based on a charged fee basis and can be monitored via video and / or audio surveillance equipment to safeguard against vandalism and / or inappropriate conduct at the property location.
Owner:BAHAR REUBEN
Lock and key system with extra code combinations
ActiveUS20050061043A1Improve securityHighly controlled manufactureKeysCylinder locksLocking mechanismEmbedded system
A high security lock and key system with an increased number of code combinations is disclosed. The system is of the kind where the blade of the key has a wave-like guiding surface (104) at the side of the key blade which, upon insertion into an associated lock having a rotatable key plug, engages with one or more side locking tumblers (206) in the lock cooperating with a side locking mechanism for locking the key plug against rotation. In order to provide an even higher number of possible code combinations, while preserving the overall dimensions of the locks and the keys of the system, the present invention provides for an extra code level (121) located at a longitudinally extending shelf surface, viz. at the upper boundary of the side material region where the wave-like guiding surface is cut at the side of the key blade. The invention also relates to a key (100) and a key blade as such, and to a lock (200) as such, for use in such a system.
Owner:WINLOC
Watch with function of vehicular intelligent key
ActiveCN103149830ADoes not increase thickness significantlyGood lookingKeysClockwork casesButton batteryIdentity recognition
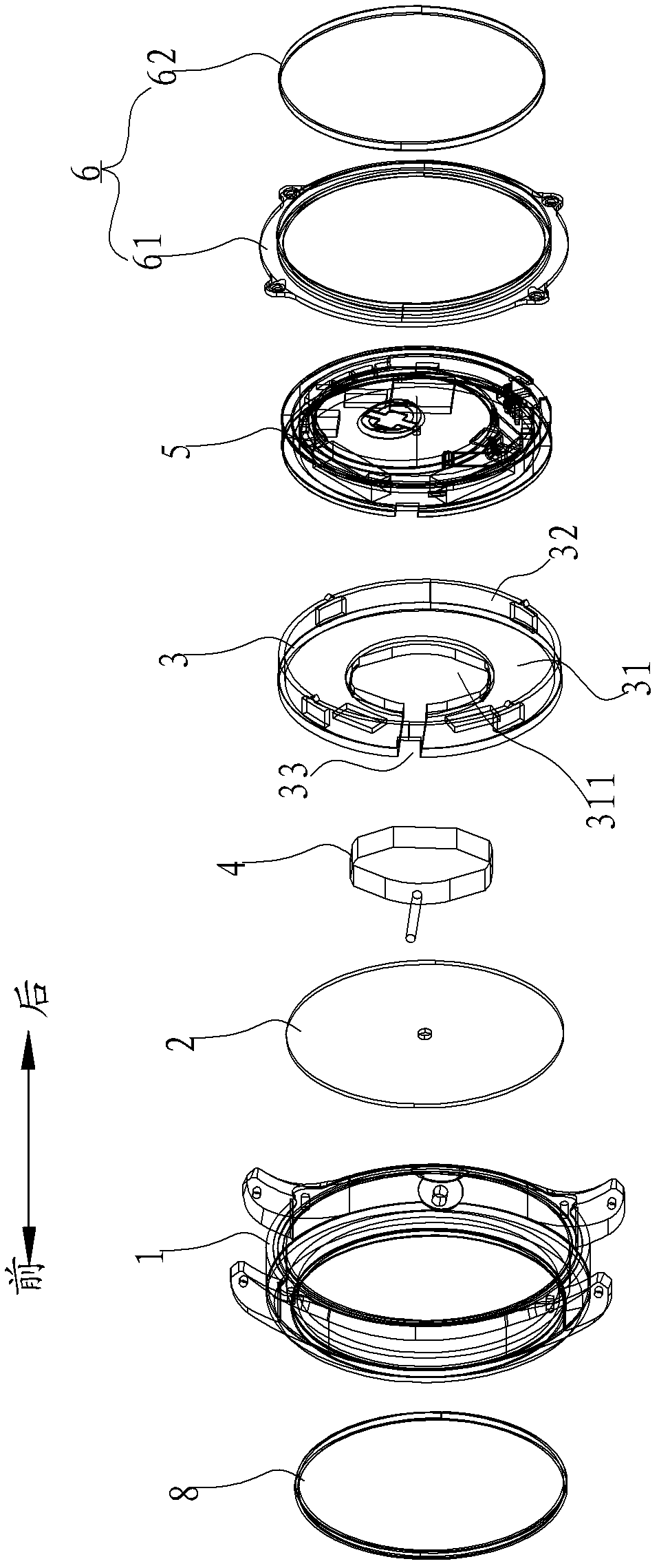
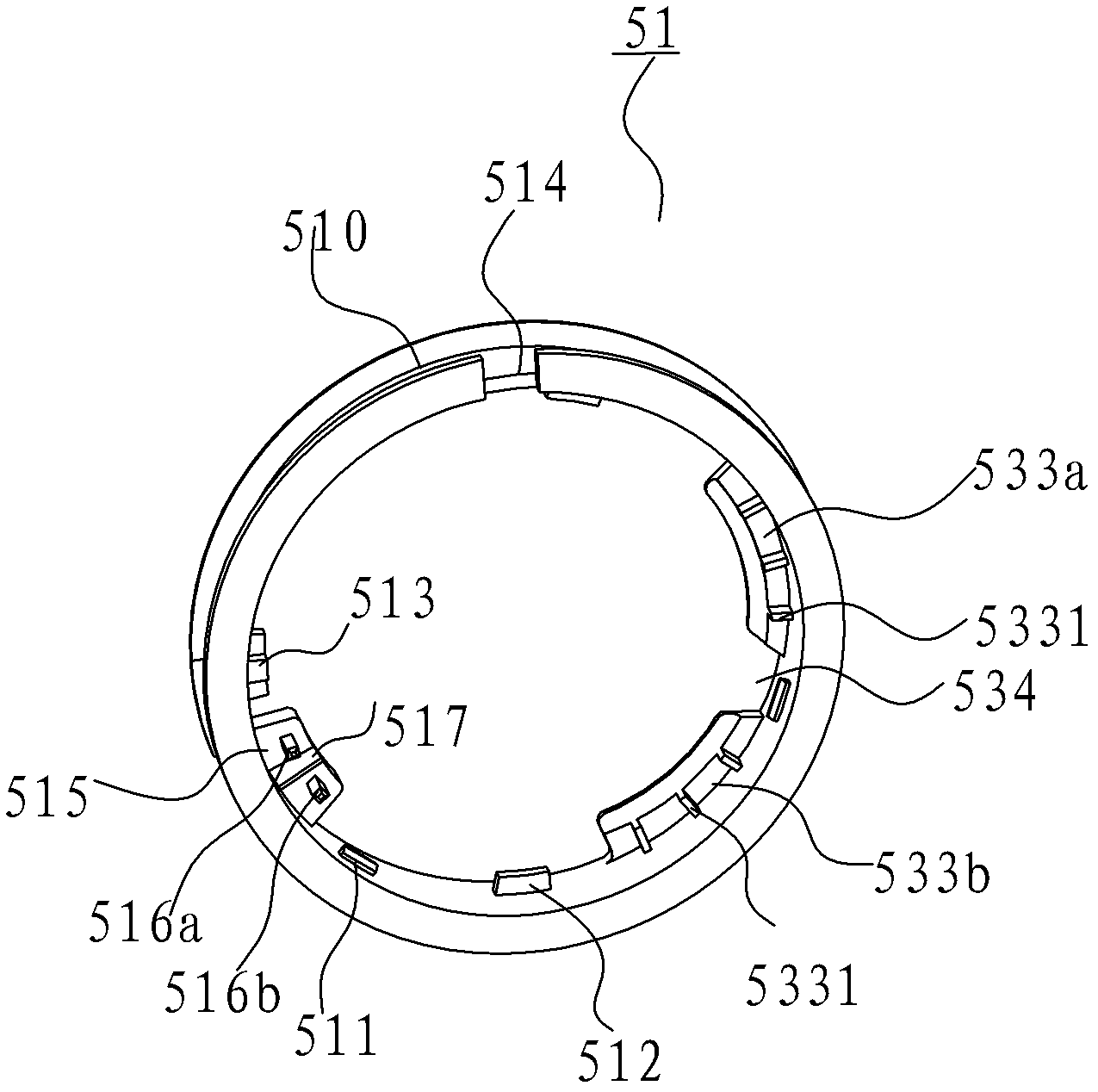
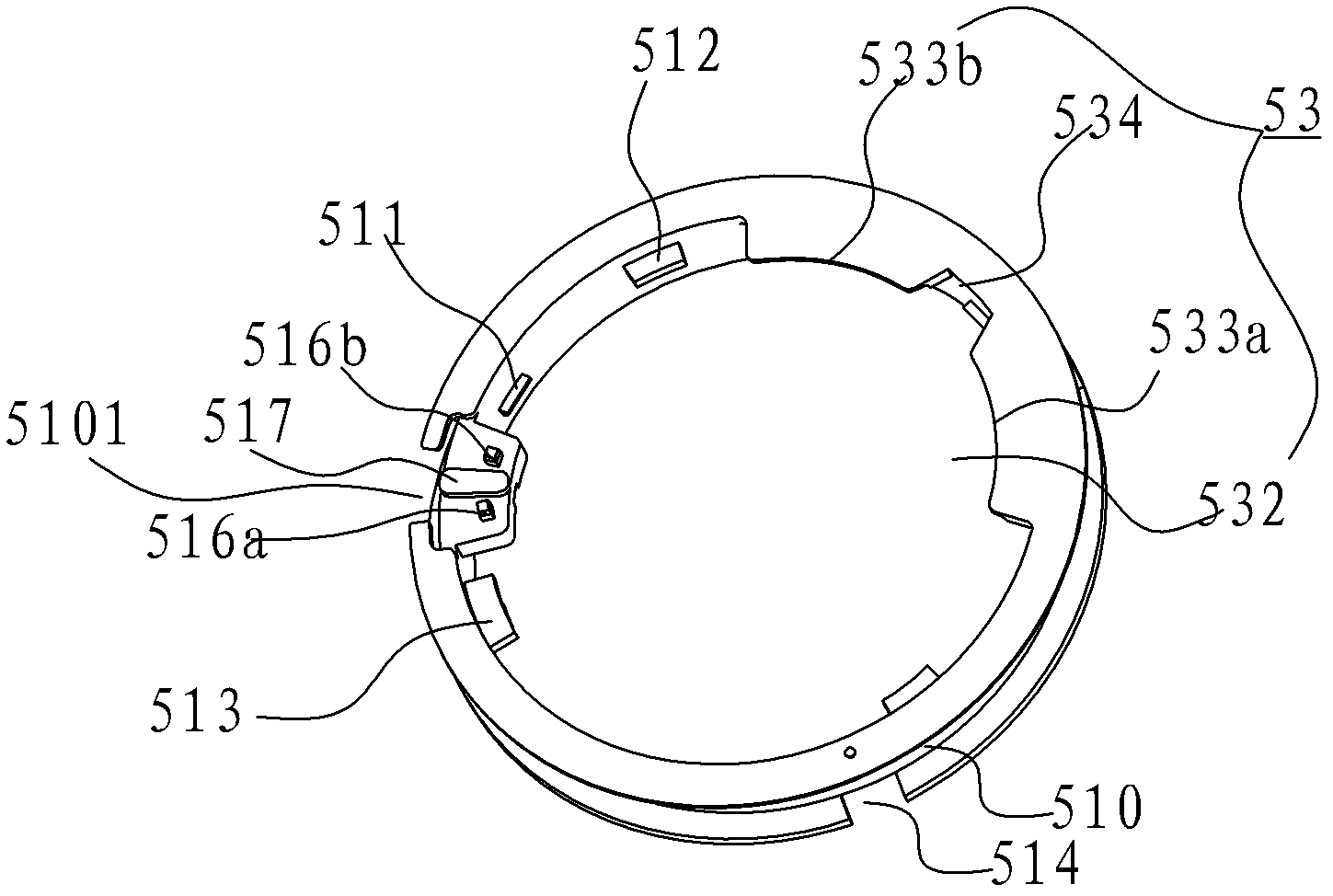
The invention discloses a watch with a function of a vehicular intelligent key. The watch comprises a watch shell body, an index dial, a movement and a vehicular controller. The vehicular controller is contained in the watch shell body and comprises a frame, a printed circuit board (PCB), a battery containing part, a button cell battery and a base cover, wherein the frame is roughly annular, and a coiling groove which is internally provided with antennae in a coiled mode is formed in the outer circumferential side of the frame; the PCB is arranged in one side, facing to the movement, of the frame in a clamped mode; the battery containing part is formed on the other side, away from the movement, of the frame, and is used for containing the button cell battery; and the base cover is connected with the watch shell body to seal the watch shell body. According to the watch with the function of the vehicular intelligent key, the vehicular controller is arranged in the watch, so that an identity recognition circuit of a car owner can be integrated into a quartz watch which is carried with the car owner. Therefore, the functions of identity recognition of the car owner and car burglary prevention can be achieved, in addition, the thickness of the watch cannot greatly increased, appearance is good, and carrying is convenient.
Owner:BYD CO LTD
Key assemblies and methods
InactiveUS20050012594A1Shorter length and widthMinimize actuationElectric signal transmission systemsDigital data processing detailsRemote controlMechanical engineering
The present invention generally relates to key assemblies and methods thereof for direct and remote control of operations of various devices including vehicles such as, e.g., automobiles or other land vehicles. More particularly, the present invention relates to a key assembly and related methods provided with a direct mechanism to directly lock and unlock a doors of a vehicle as well as a remote mechanism to lock and unlock the same door. Each of the direct and remote mechanisms is spatially disposed with respect to the other mechanism and / or operatively coupled to the other mechanism in order not to interfere the operation of the other mechanism and / or in order to reduce a characteristic dimension of such a key assembly. The key assemblies and related methods of this invention can be applied to any device of which the operations can be controlled by two or more different mechanisms, where one of such mechanisms may require a close disposition or a direct contact with the device for intended operations, while the other of such mechanisms does not require such a close disposition or direct contact for the same or similar intended operations.
Owner:SHIM YOUNGTACK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com