Patents
Literature
236results about How to "Not easy to copy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
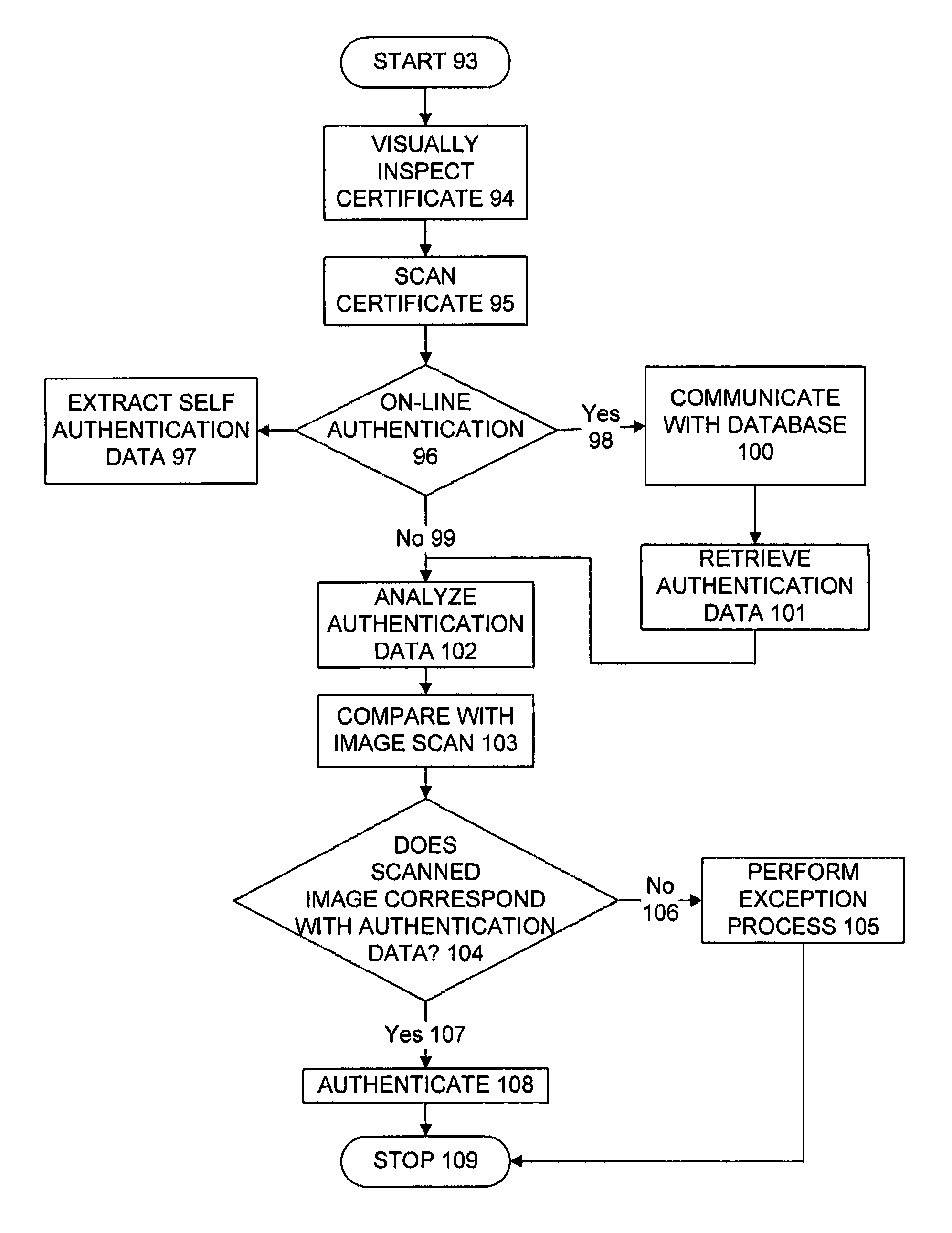
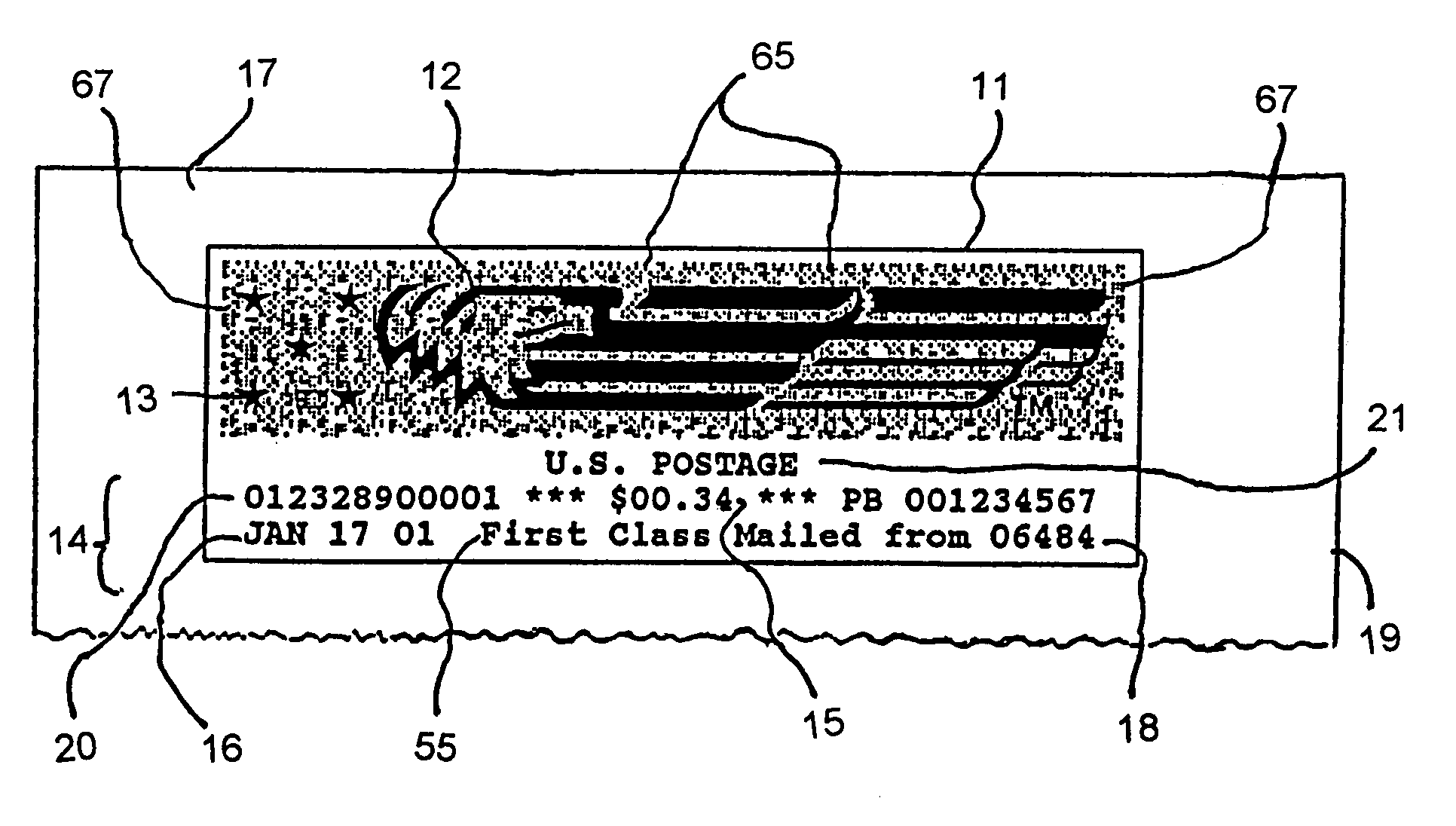
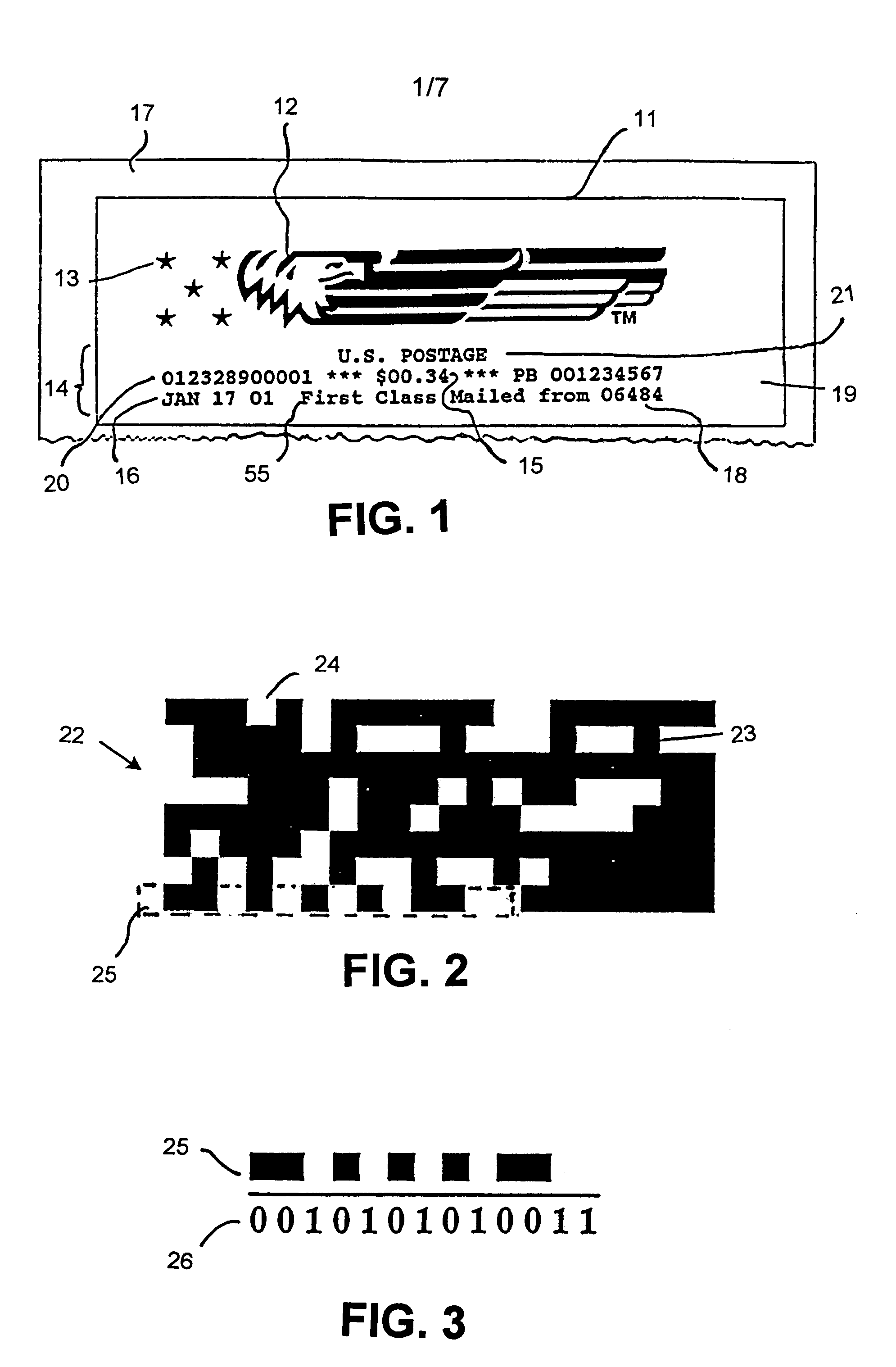
Authentication method and system
InactiveUS8171567B1Low densityStable positionDigital data processing detailsUser identity/authority verificationEngineeringReproduction
The present invention provides a method and apparatus for the production and labeling of objects in a manner suitable for the prevention and detection of counterfeiting. Thus, the system incorporates a variety of features that make unauthorized reproduction difficult. In addition, the present invention provides a system and method for providing a dynamically reconfigurable watermark, and the use of the watermark to encode a stochastically variable property of the carrier medium for self-authentication purposes.
Owner:COPILOT VENTURES FUND III
RFID tracking of anesthesiologist and patient time
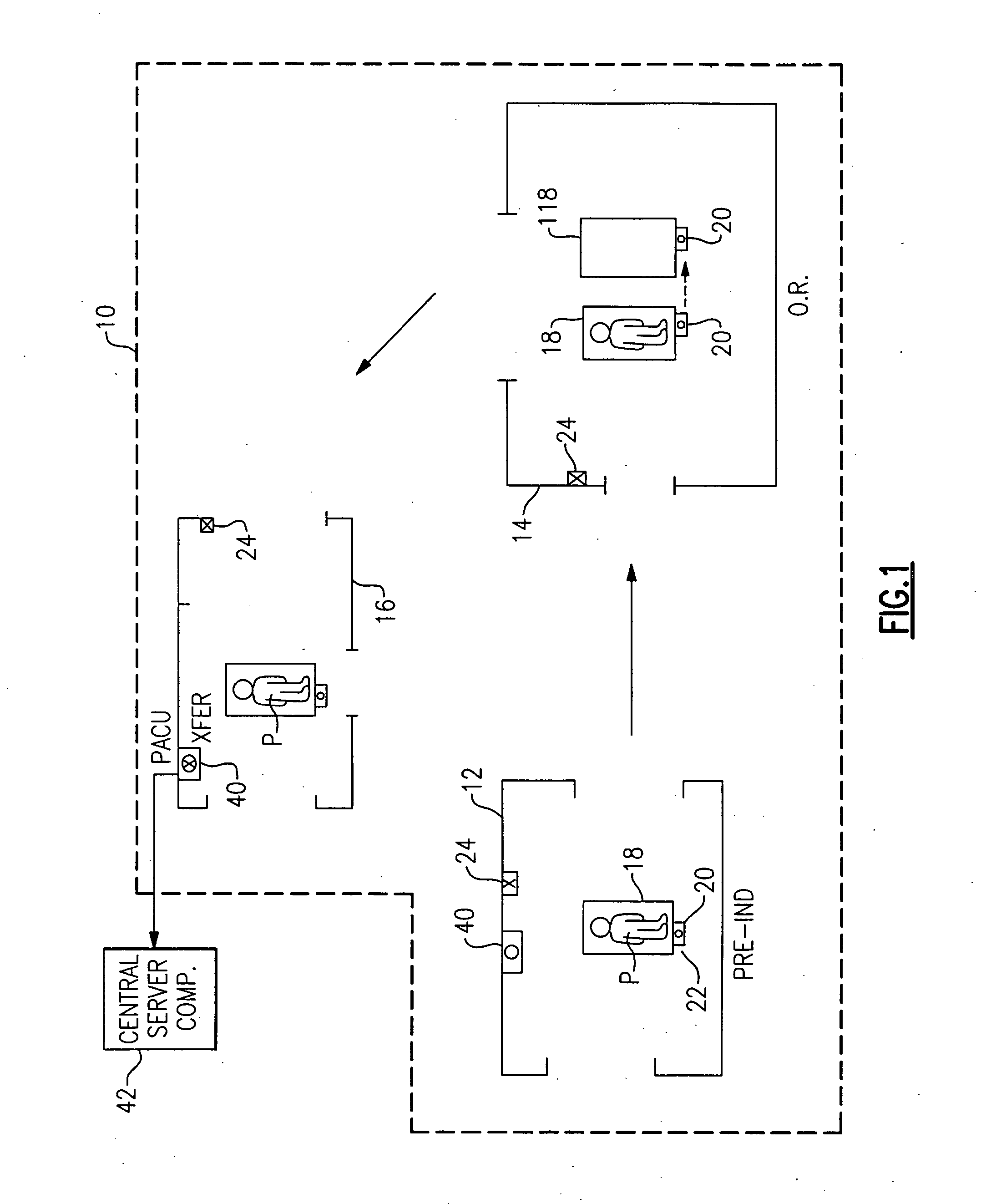
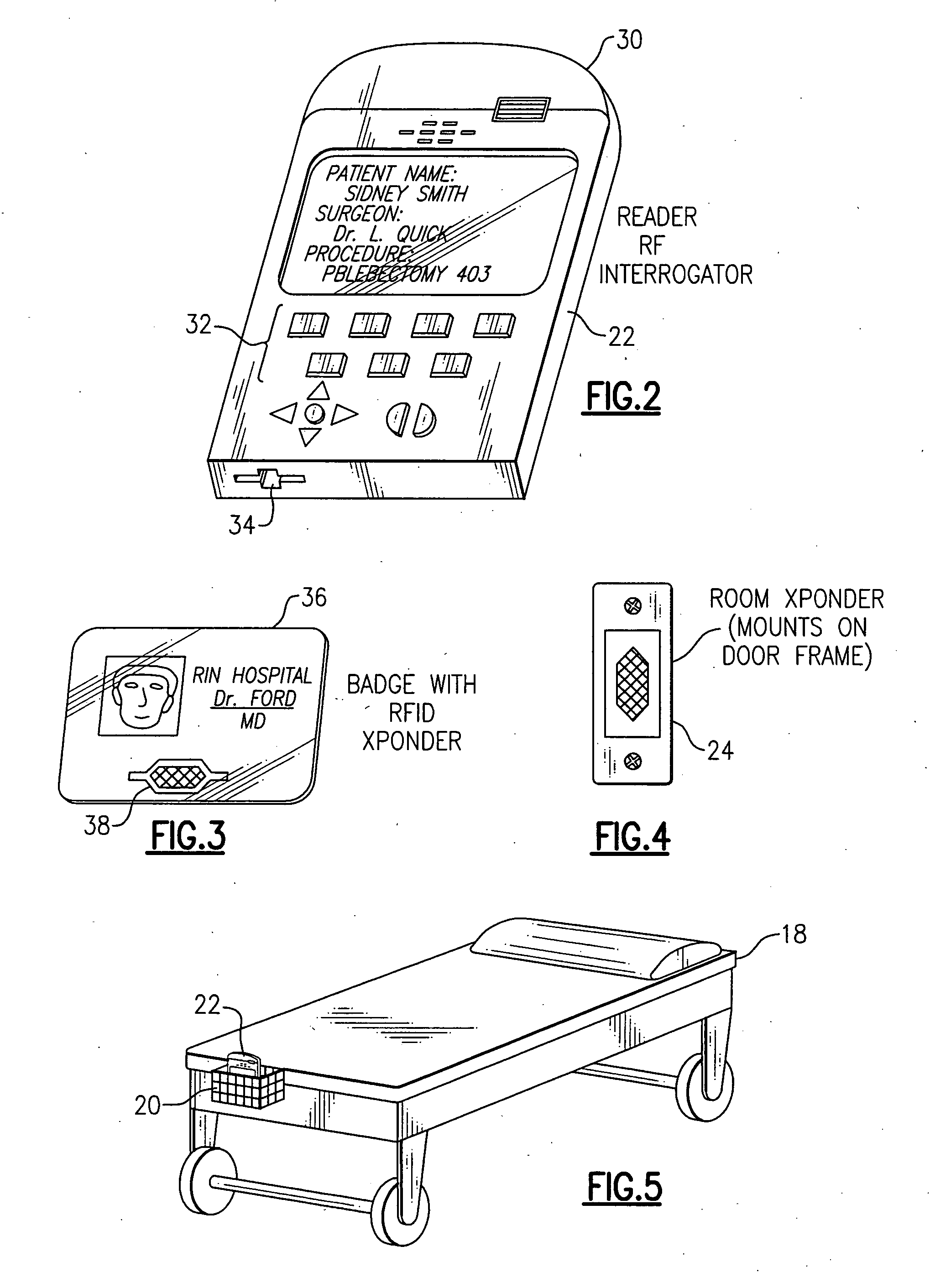
InactiveUS20050149358A1Simple methodNot easy to copyElectric signal transmission systemsMechanical/radiation/invasive therapiesHand heldOperating theatres
RFID-based system for tracking billable anesthesiology time in a surgical environment employs hand-held RFID reader devices that record and store timed anesthesia events for each surgical patient. Each patient is assigned a reader device, uploaded with patient data. Each anesthesiology professional has an identifying RFID transponder, and room transponders are located on wall or doorway of each room in the surgical suite. A download cradle is used for downloading the patient data collected during surgery to a central computer. The reader devices are synchronized to a high-accuracy clock, eliminating time accounting problems associated with concurrency and discontinuous time.
Owner:SACCO LISA M +1
Method of implementing digital payments
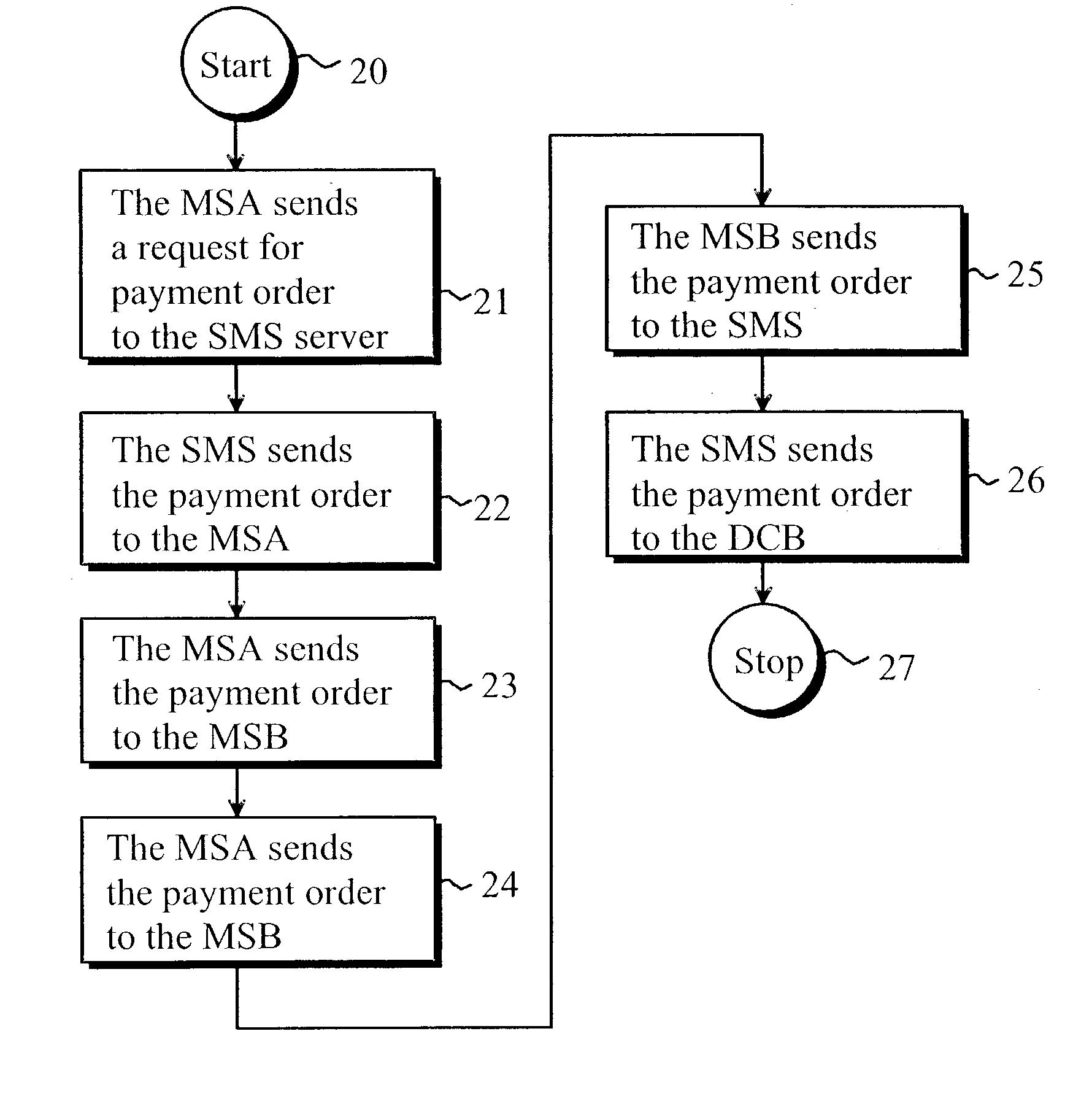
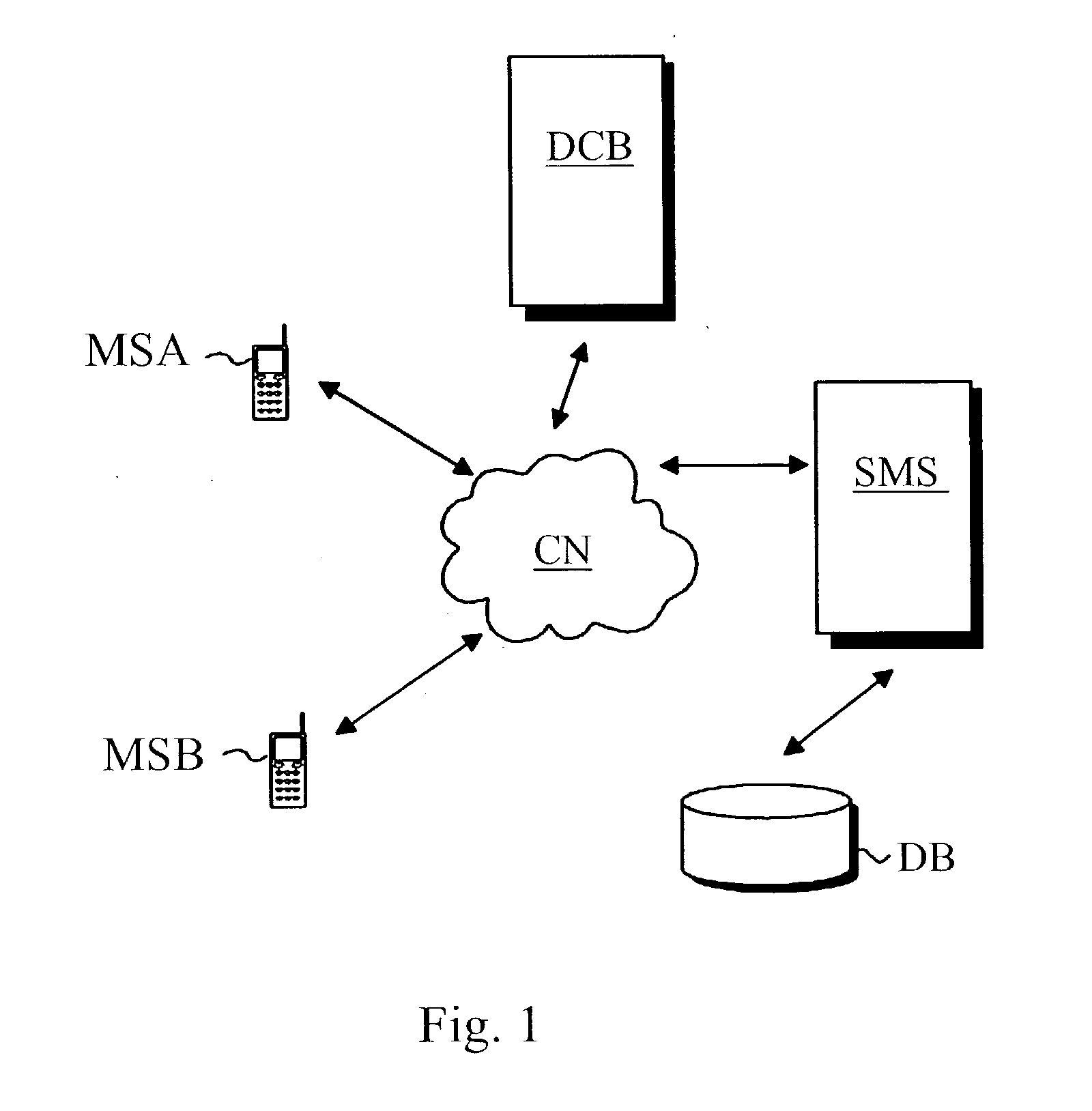
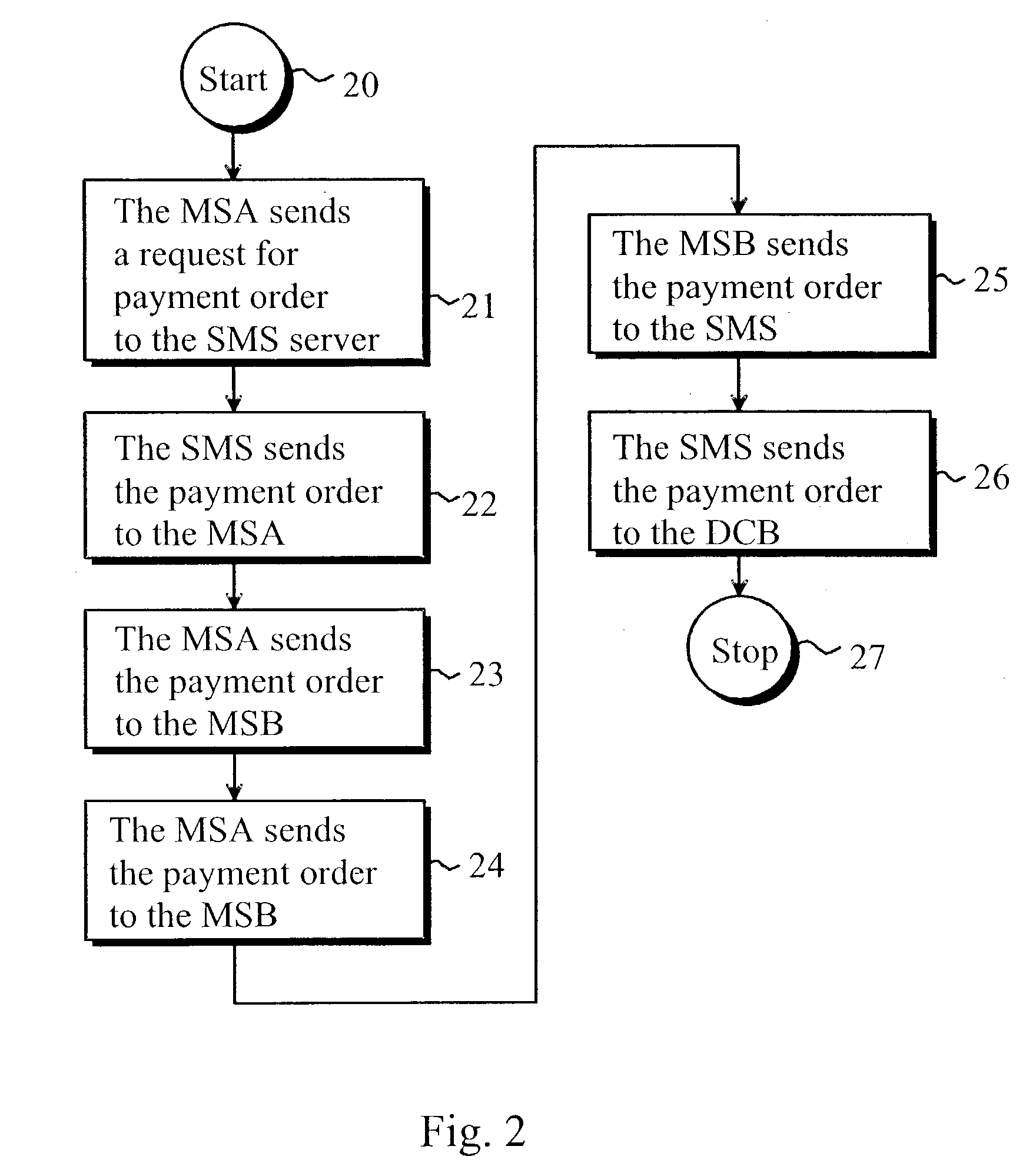
ActiveUS20030126078A1Eliminate, orAlleviate, the drawbacks and deficienciesFinanceComputer security arrangementsPaymentTerminal equipment
A method for transferring a digital payment order from a first terminal device to a second terminal device, and for saving the payment order on a payment order server. A payment order request is sent from the first terminal device to the payment order server and, in response, the requested payment order is sent from the payment order server to the first terminal device. The payment order is thereafter transmitted from the first terminal device to the second terminal device, and the payment order is then transferred from the second terminal device to the payment order server to be honored. A message confirming the honoring of the payment order is sent to the second terminal device.
Owner:MIND FUSION LLC
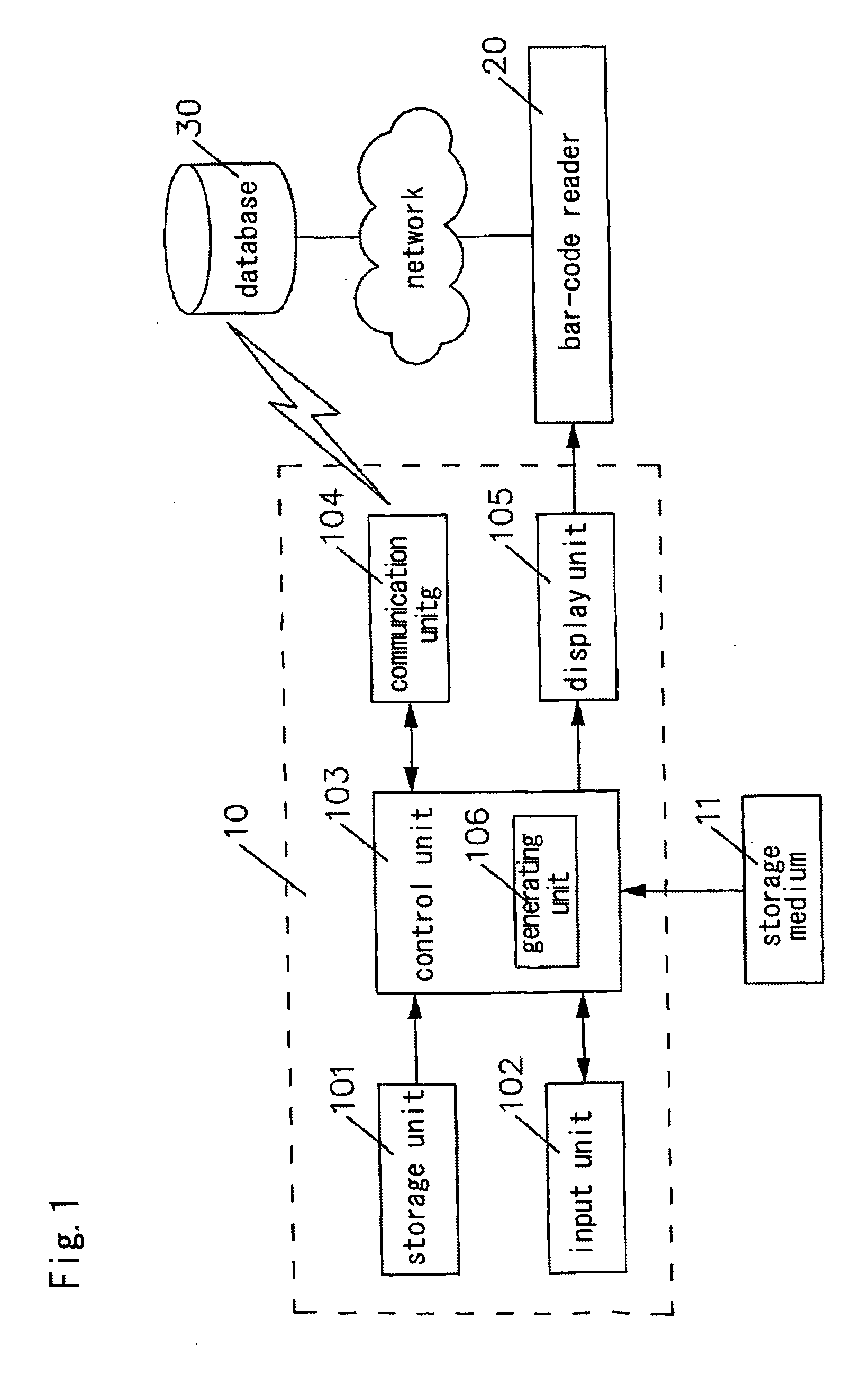
Dynamic bar code display apparatus, dynamic bar code generation method, and storage medium generation dynamic bar code
InactiveUS20060054695A1Increase volumeNot easy to copyCo-operative working arrangementsBuying/selling/leasing transactionsBarcodeComputer science
By changing methods from the conventional method in which a plurality of bar codes are arranged in the space for use to the method of the invention in which a plurality of bar codes are used according to time, so that the conventional bar codes which are displayed in a fixed fashion are changed over to dynamic bar codes which are displayed dynamically, a dynamic bar code display apparatus for displaying bar codes which are difficult to be copied and which increases the volume of data of the bar codes, a dynamic bar code generation method and a storage medium which generates dynamic bar codes can be provided. The bar code display apparatus comprises a storage means in which bar code images are stored, a display means for displaying at least two or more bar codes continuously and a control means for controlling the display means.
Owner:GLOBAL VALUE
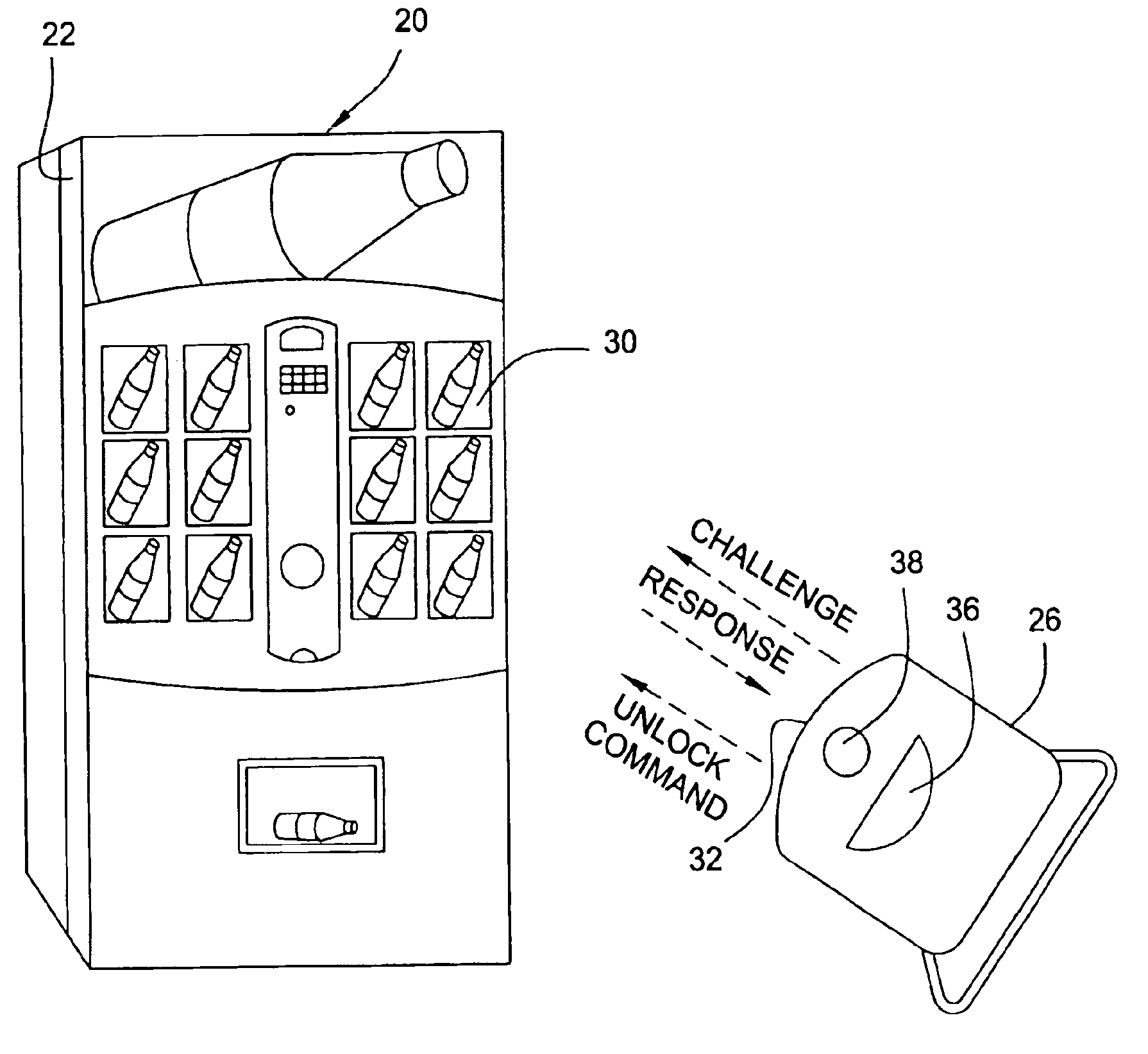
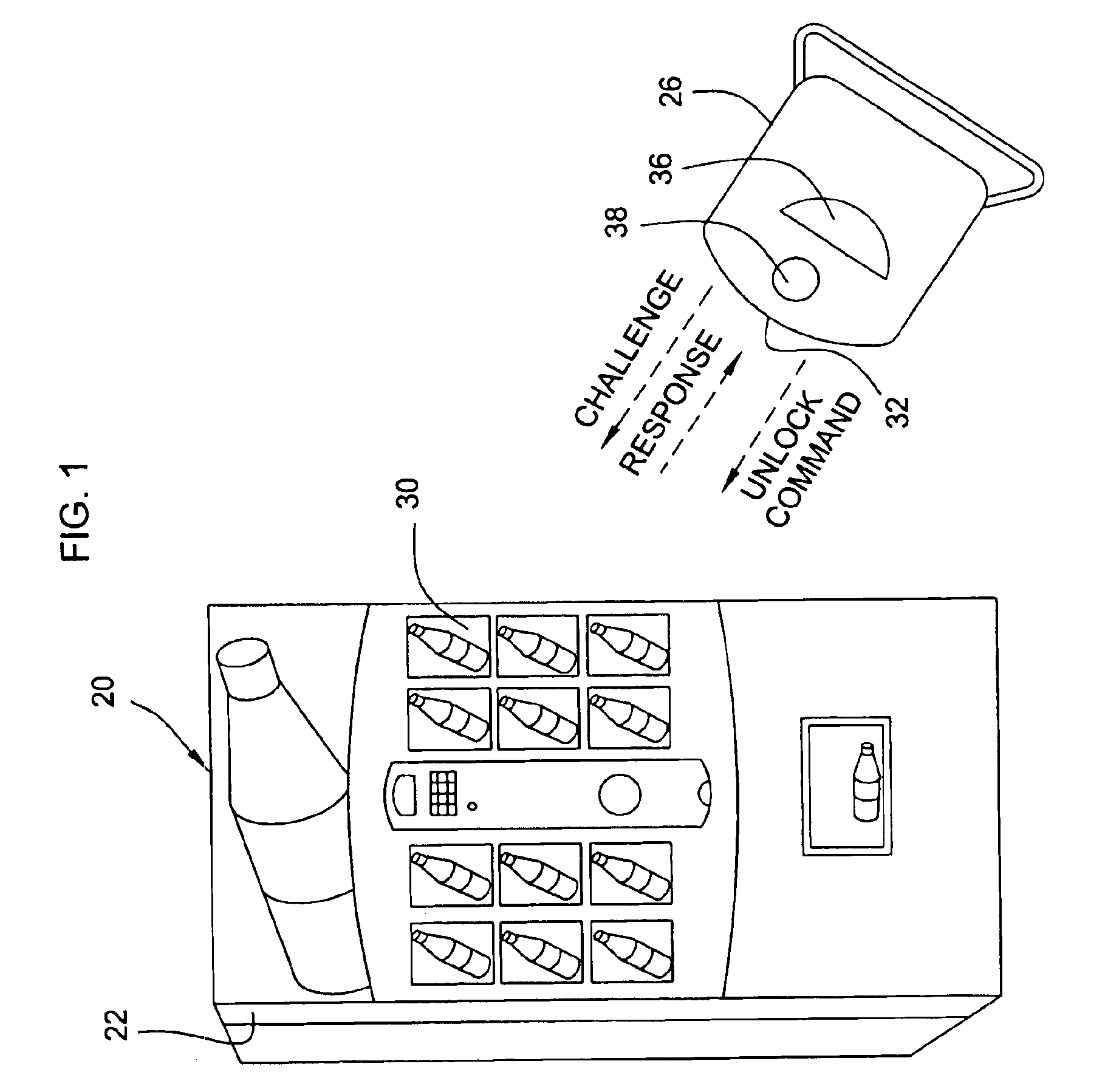
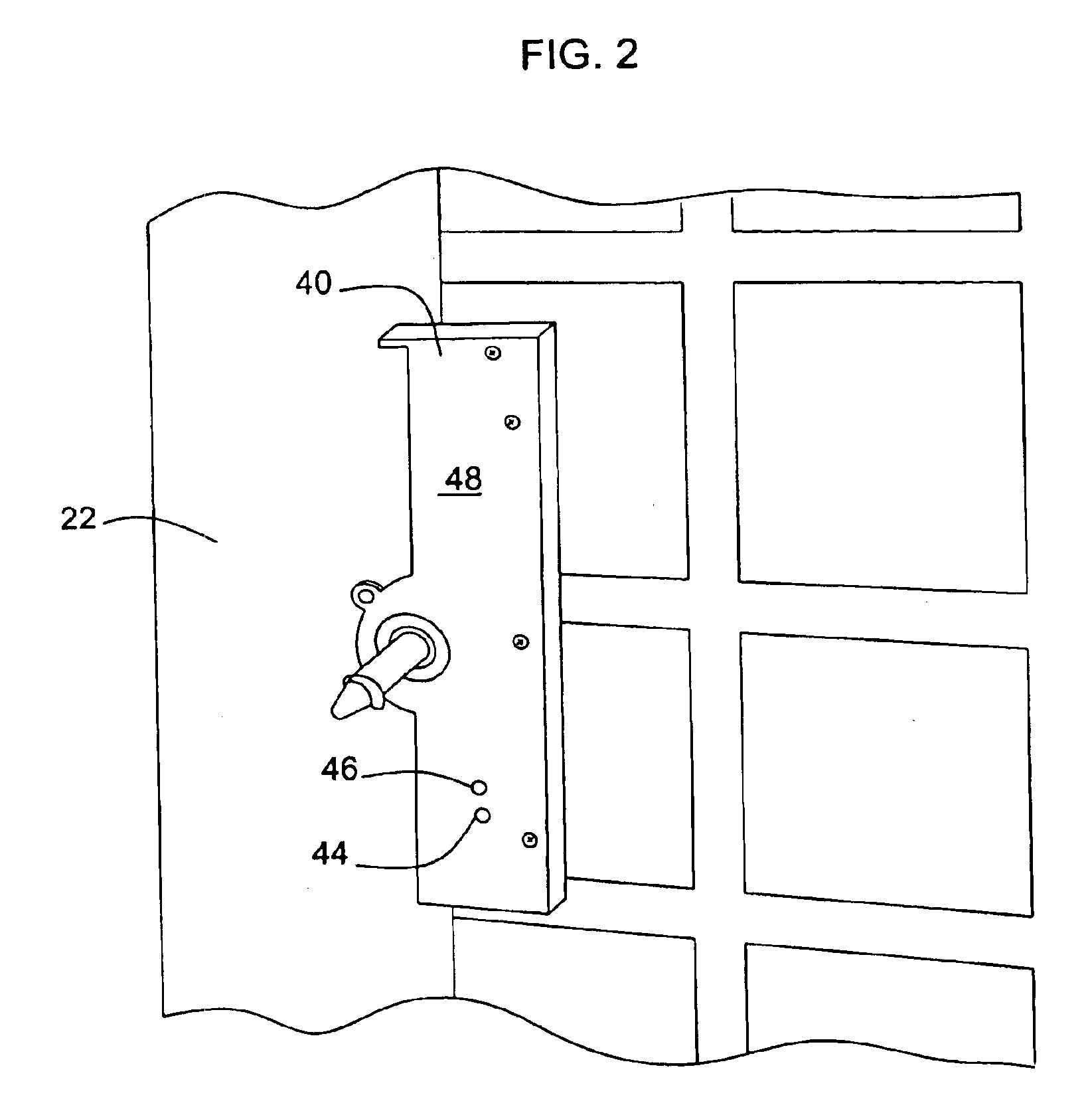
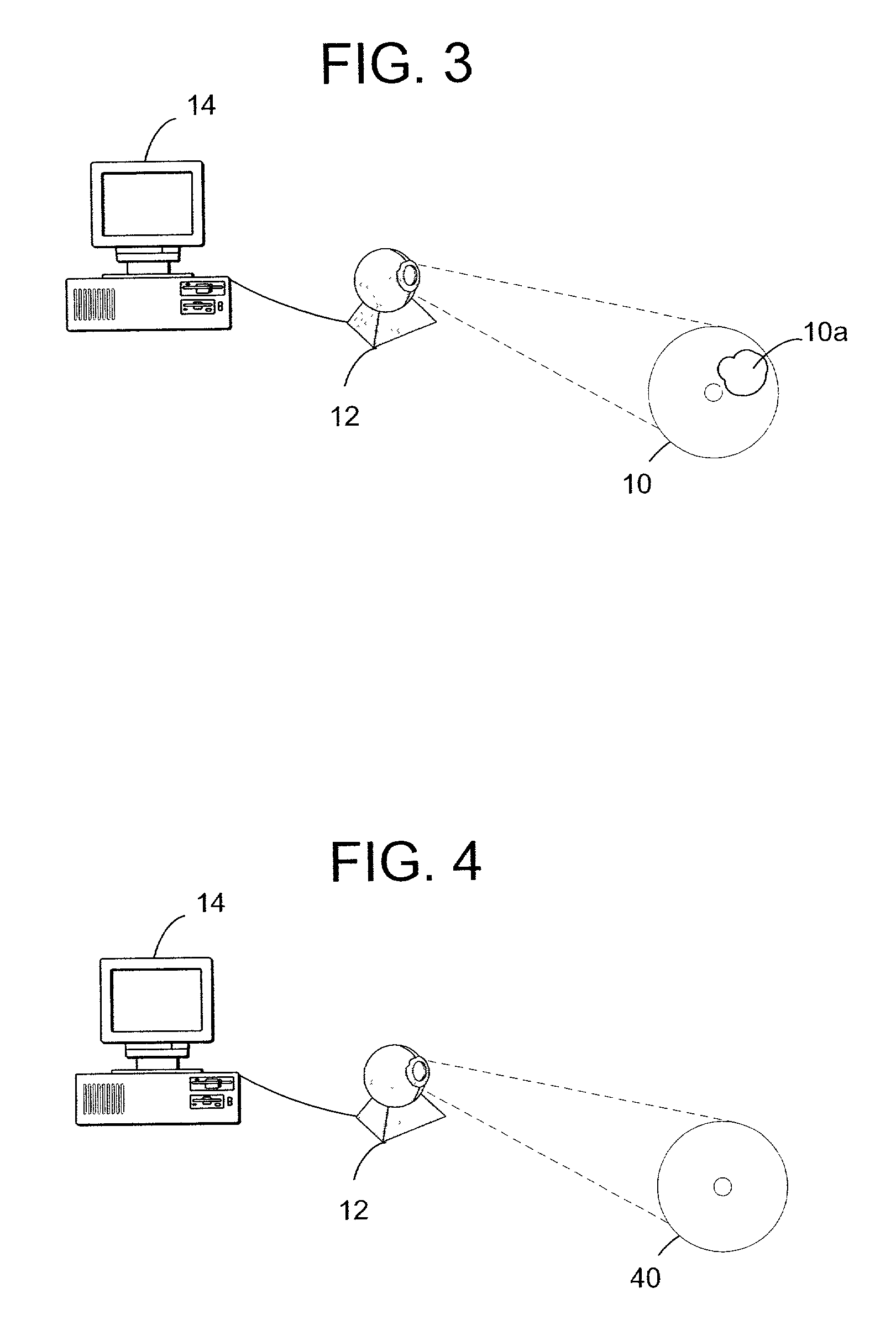
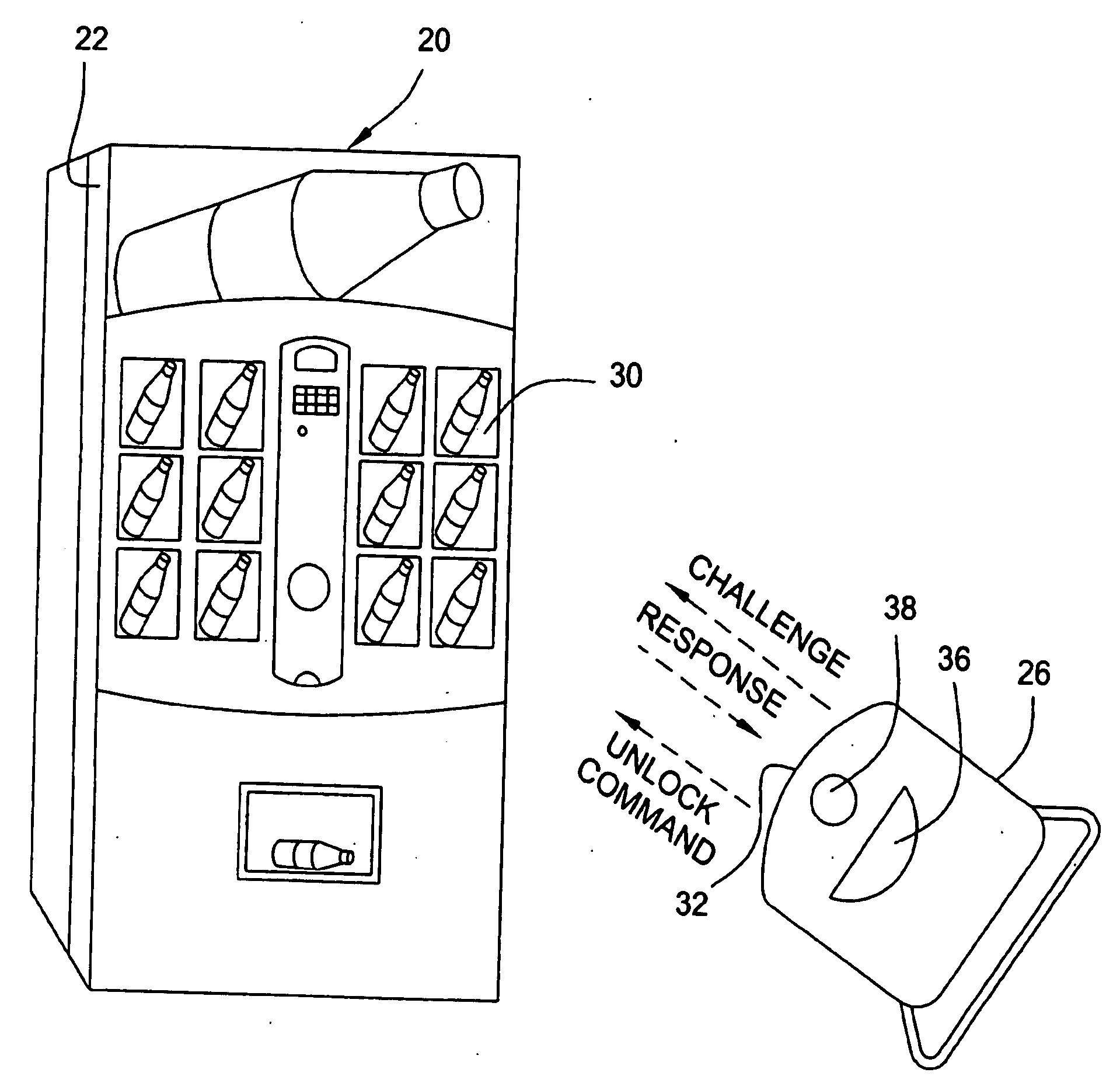
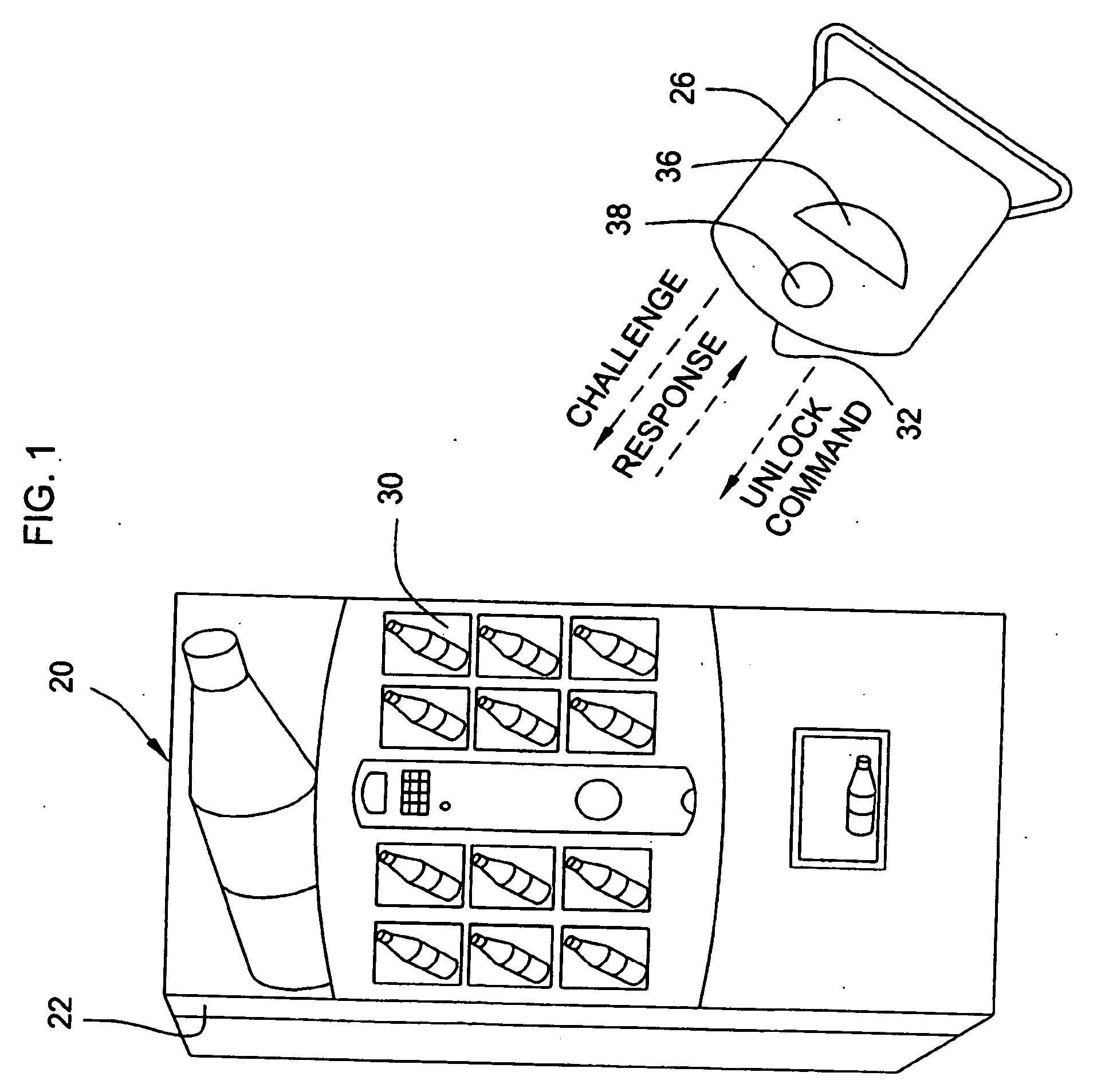
Vending machines with field-programmable locks
InactiveUS6900720B2Easily and inexpensively programmedImprove the level ofFrequency-division multiplex detailsDigital data processing detailsBiological activationHome based
Owner:MICRO ENHANCED TECH
Device for treating flat material
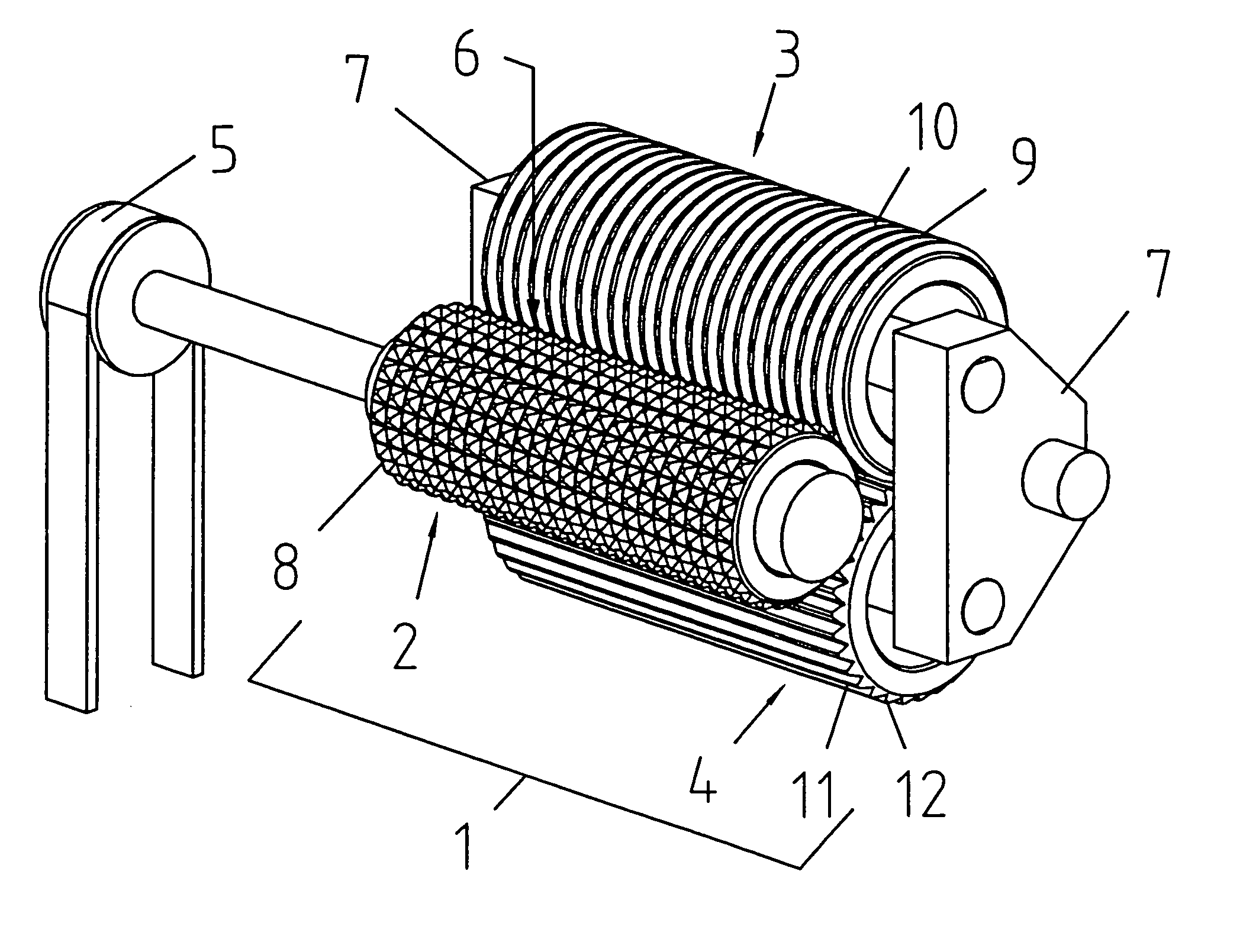
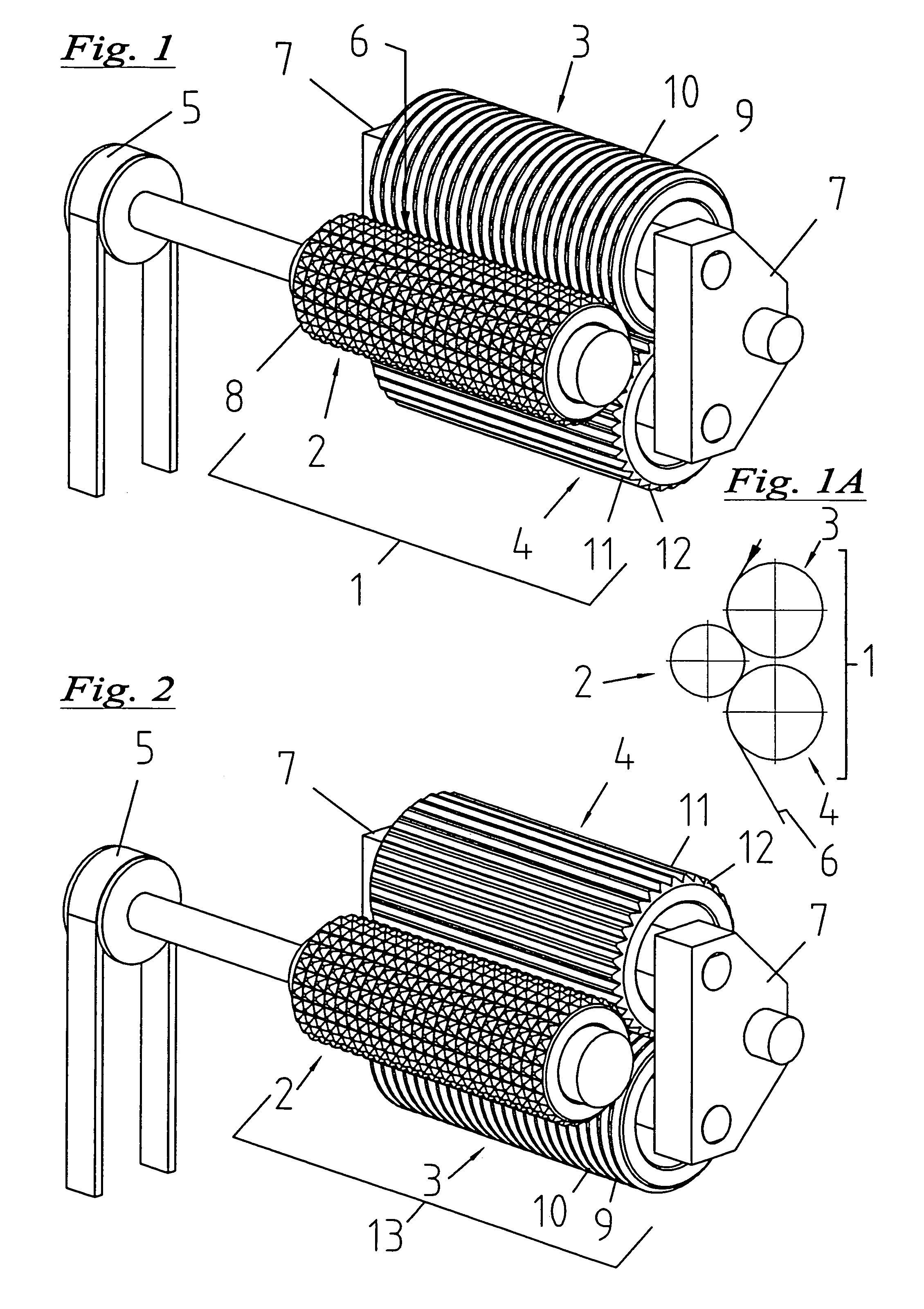
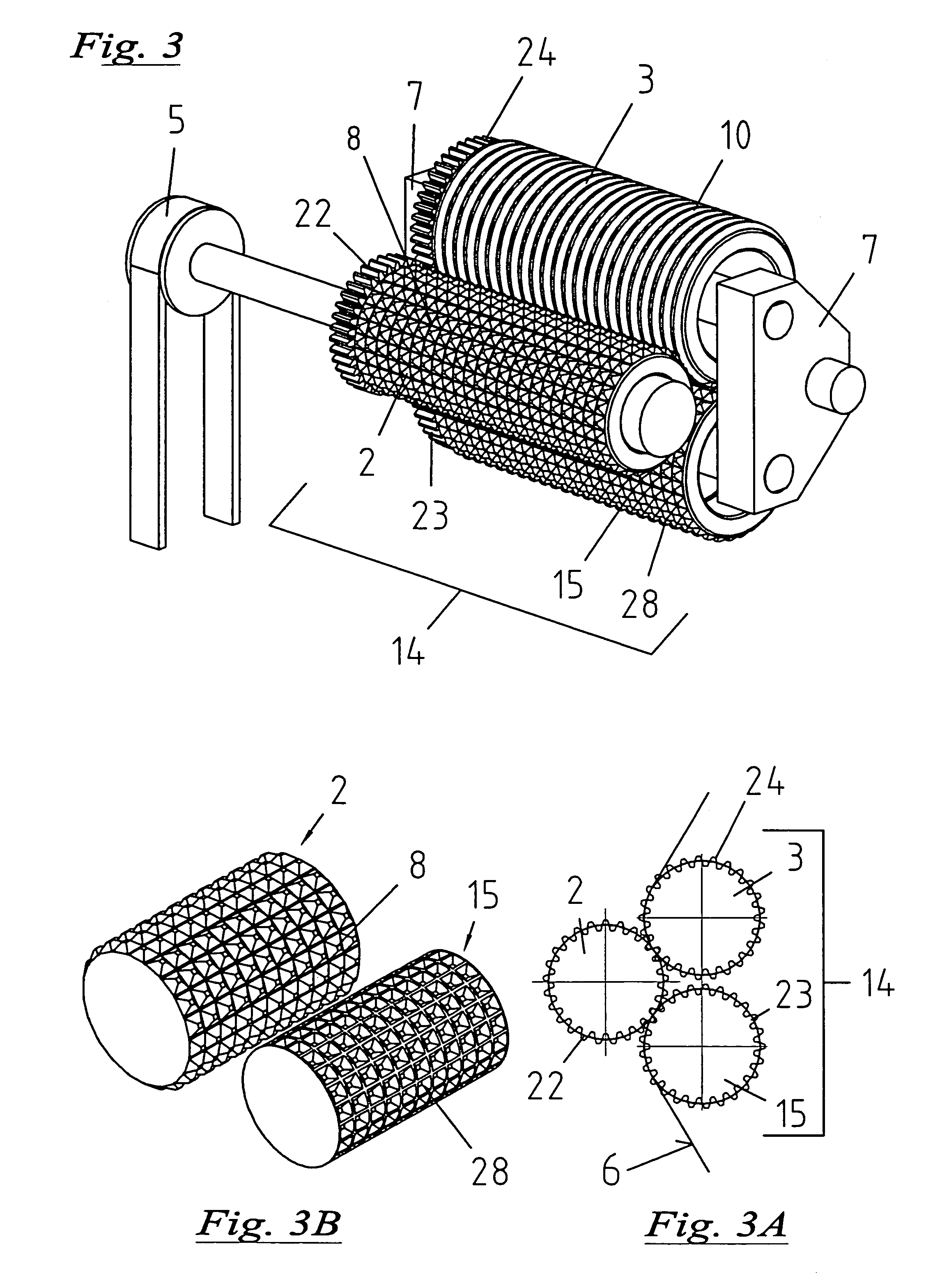
InactiveUS7147453B2Not easy to copyImprove accuracyMechanical working/deformationDough-sheeters/rolling-machines/rolling-pinsEngineeringMechanical engineering
The invention relates to a device for embossing and / or glazing films. The device for embossing includes a first and second embossing roll, through which flat material can be fed under pressure, in order to create a pattern. An additional embossing roll is connected downstream of the second embossing roll, this additional embossing roll interacting with the first or preceding embossing roll. The patterned flat material may be fed between these embossing rolls, in order to be embossed again with essentially the same pattern. In a simplified embodiment, only a total of two rolls are used. In order to achieve as precise an embossing as possible, with special effects, the first driven embossing roll is provided with teeth, while at least one other embossing roll comprises rings or longitudinal ribs, or is smooth.
Owner:BOEGLL GRAVURES SA
Identification document with three dimensional image of bearer
InactiveUS20050109850A1Increase in costImprove printing qualityRecord carriers used with machinesVerifying markings correctnessCamera lensComputer science
An identification document includes a lens system and a specially prepared photo of a document bearer. The lens system and the specially prepared photo cooperate to create a three dimensional photo effect. The document includes two or more document layers. There is a lens structure in one of the document layers, and it includes lens elements. A photo is printed on one or more of the document layers. The photo depicts the document bearer, and includes two or more separate images of the bearer from different perspectives. Parts of the separate images are interleaved together into sets, and the sets are positioned relative to corresponding lens elements of the lens structure. These sets include parts of the separate images such that when viewed through the lens structure, the parts are viewed simultaneously making the subject appear three-dimensional to a viewer.
Owner:L 1 SECURE CREDENTIALING
Two dimensional barcode and method of authentication of such barcode
ActiveUS20160267369A1Easy to detectConvenient verificationPaper-money testing devicesRecord carriers used with machinesGraphicsBarcode reader
A method is disclosed for creating a 2D barcode. In an embodiment, the method includes: embedding primary information that can be read by a 2D-barcode-reader in a primary information pattern, and embedding secondary information that is made difficult to reproduce without alteration in a visible pattern. In an embodiment, the visible pattern is embedded within the barcode in at least one area that does not contain any primary information
Owner:SCANTRUST
Head-mounted display device, control method for the head-mounted display device, and authentication system
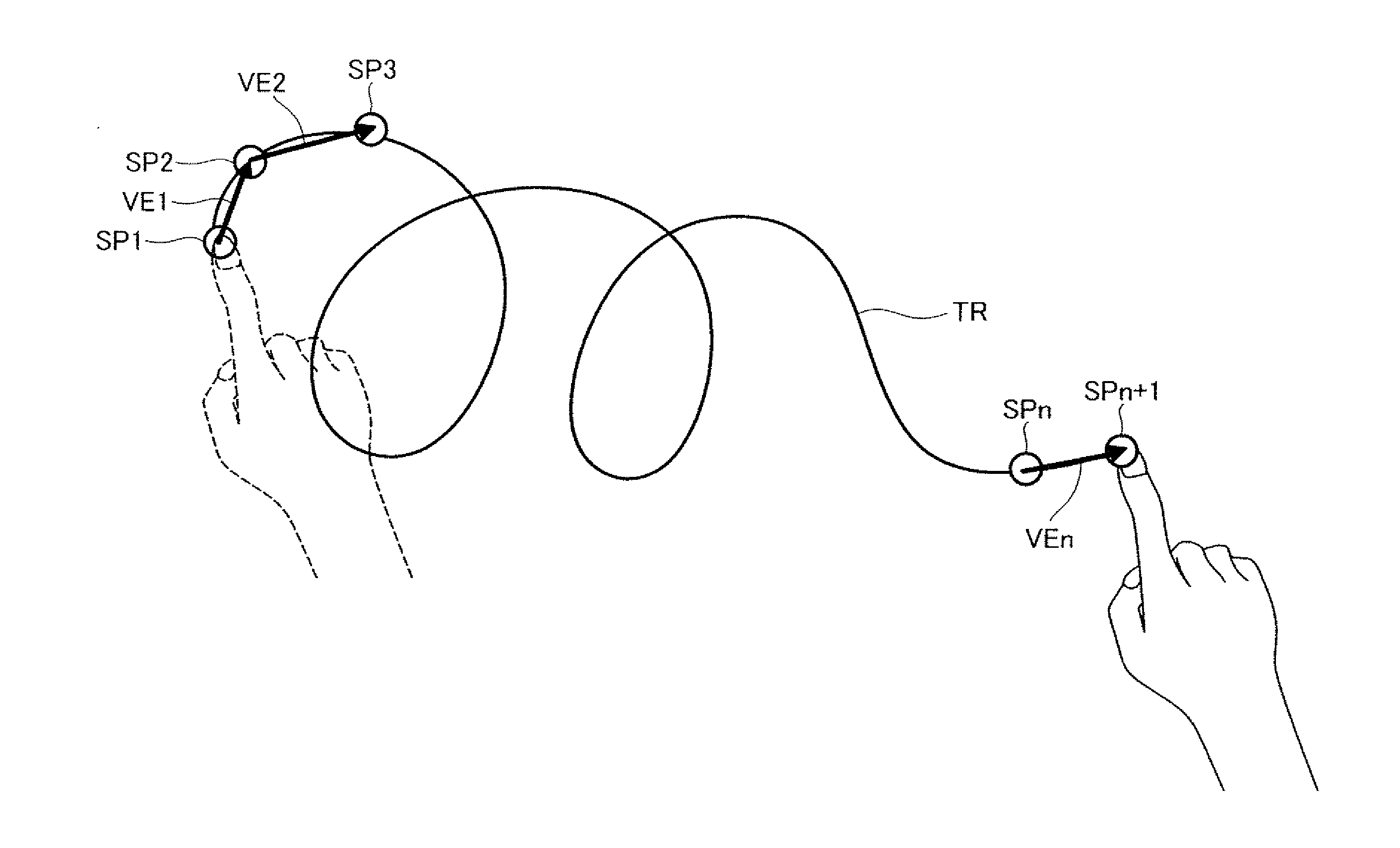
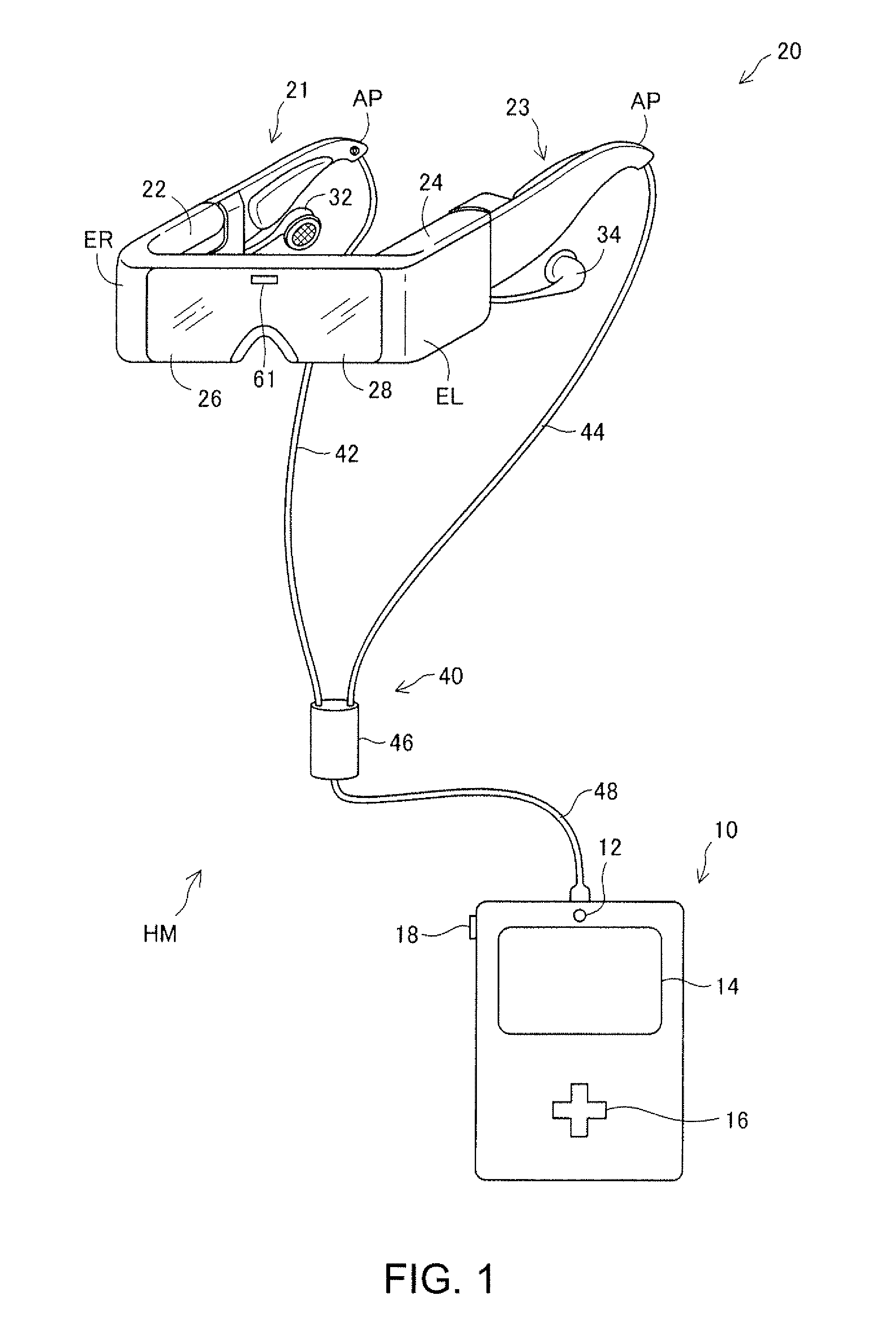
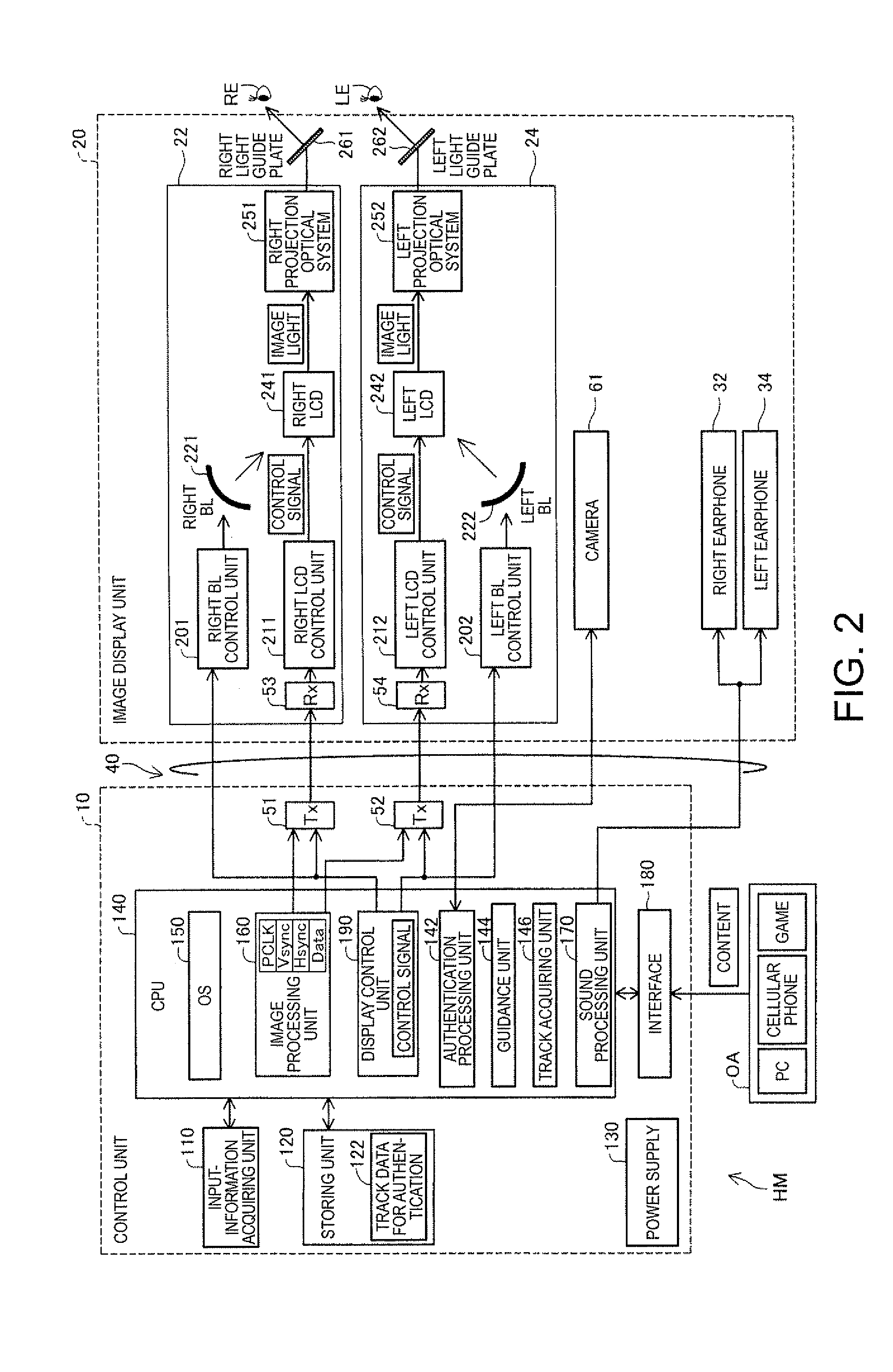
ActiveUS20140071041A1Reduce riskImprove securityInput/output for user-computer interactionCathode-ray tube indicatorsVisual field lossDisplay device
A head-mounted display device that enables a user to simultaneously visually recognize a virtual image and an outside scene includes a photographing unit configured to photograph at least a part of a visual field direction of the user in a state in which the user wears the head-mounted display device and acquire a motion of the user; a track acquiring unit configured to acquire a track of the motion of the user from the motion photographed by the photographing unit; and an authentication processing unit configured to authenticate, using the track acquired by the track acquiring unit, whether the user is a proper user.
Owner:SEIKO EPSON CORP
Tamper-resistant non-volatile memory device
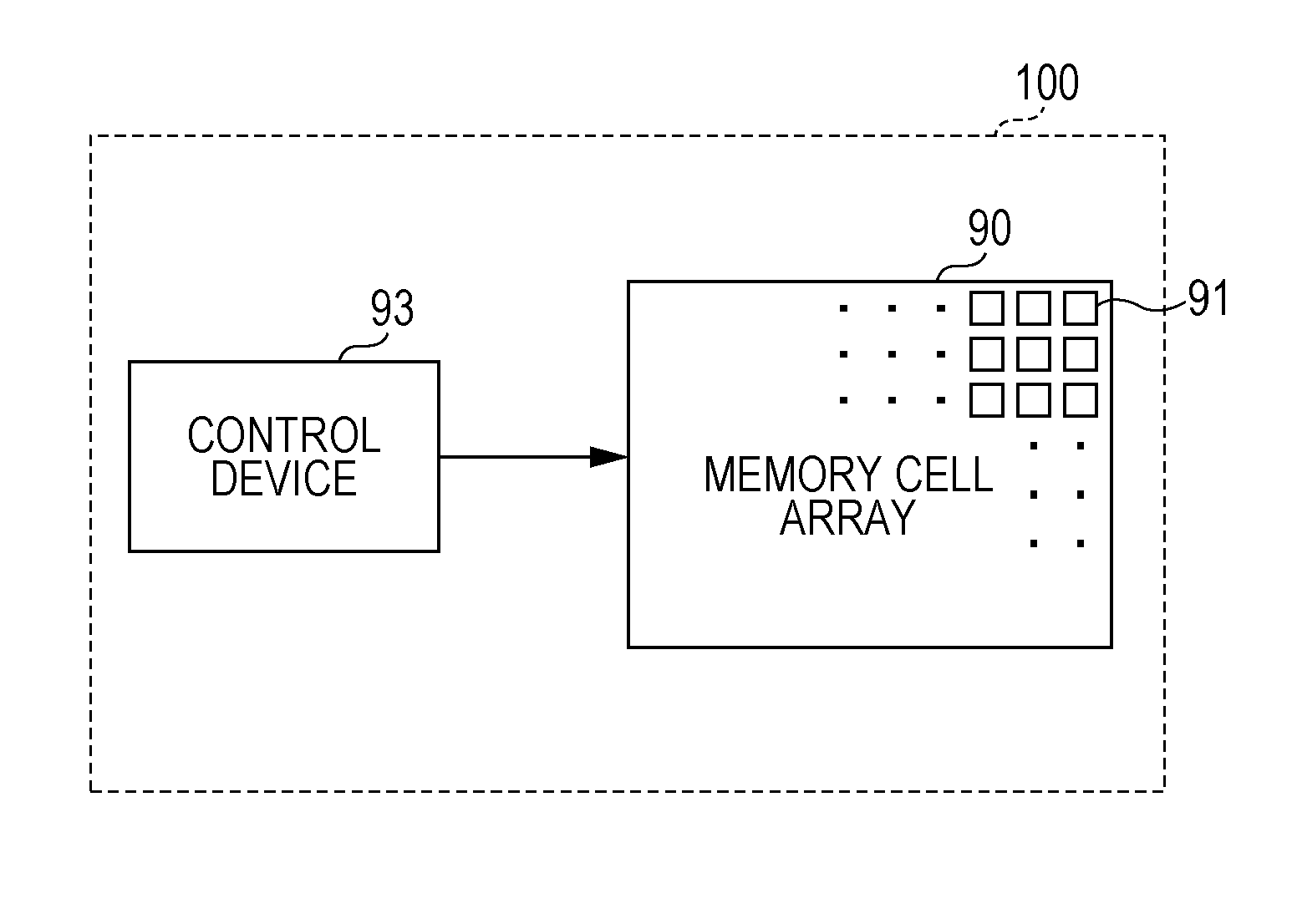
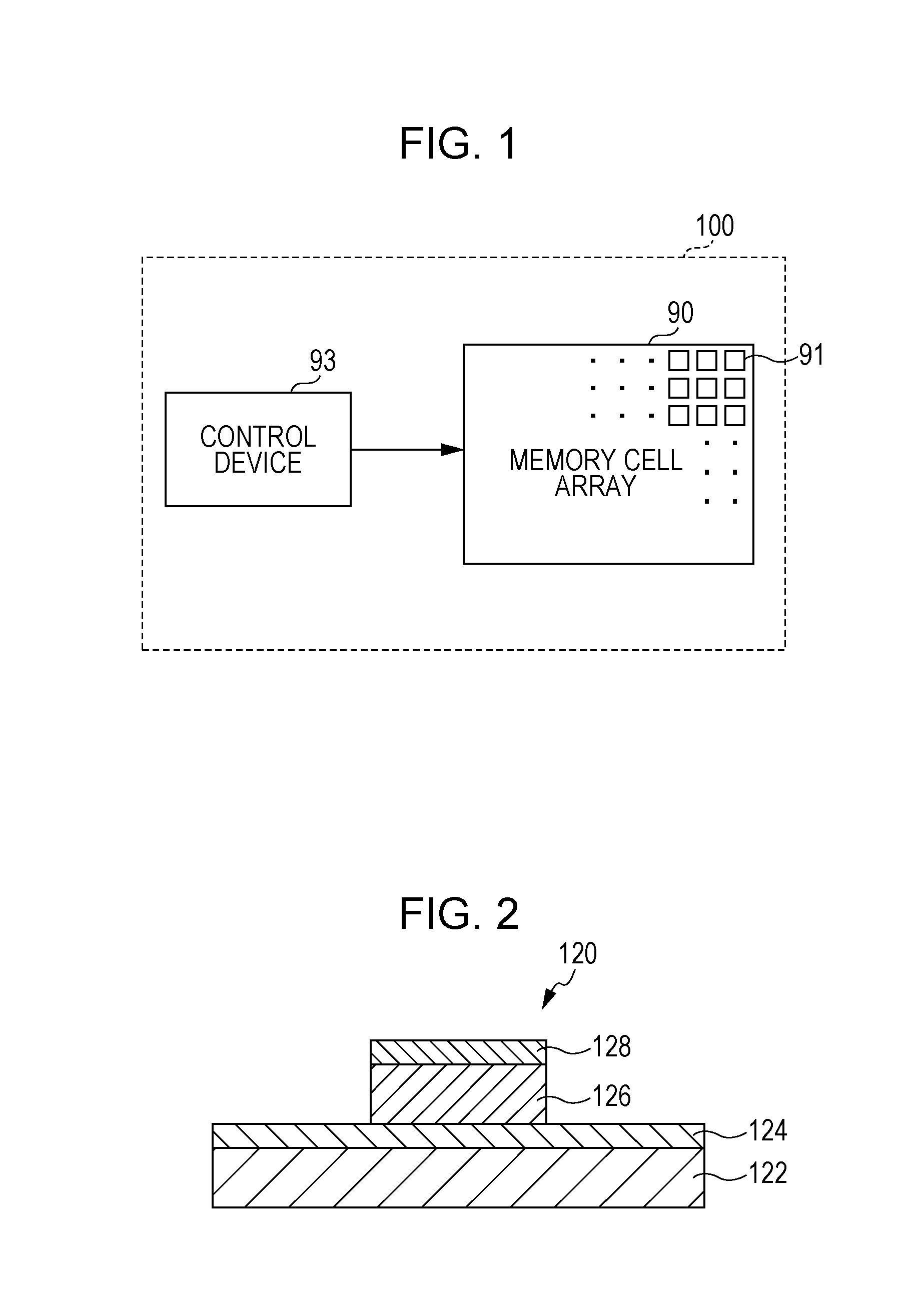
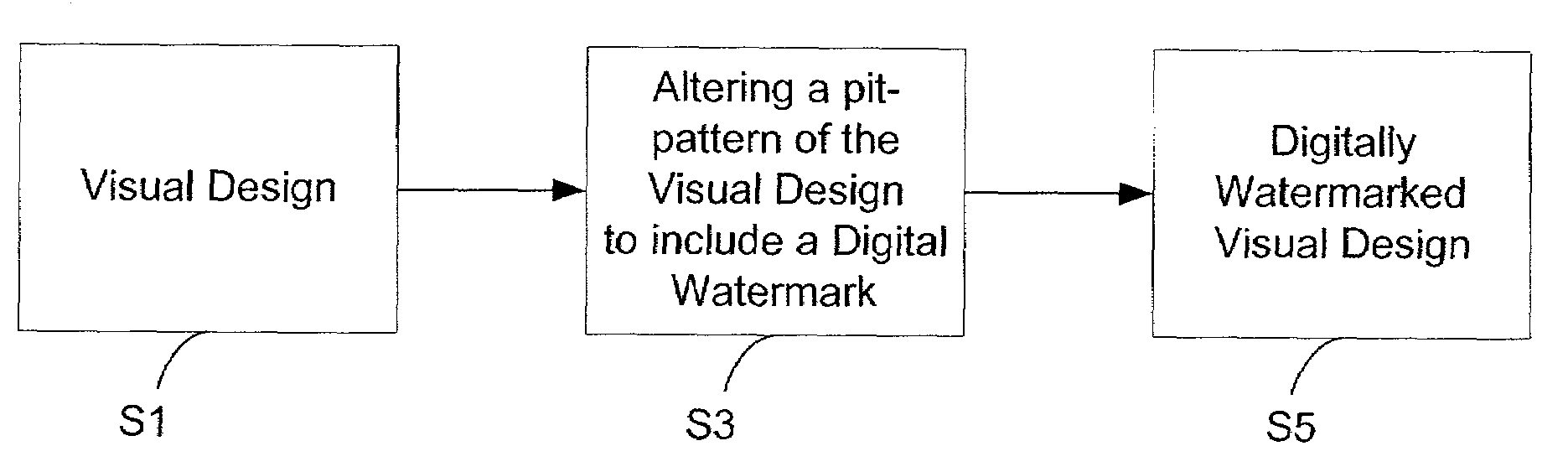
ActiveUS20160148679A1Difficult to duplicateHigh resistanceRead-only memoriesDigital storageData AdjustmentsDigital data
A non-volatile memory device includes a memory cell array including memory cells, a read circuit that, in operation, obtains pieces of resistance value information each relating to the resistance value of one of the memory cells, an arithmetic circuit that, in operation, calculates a binary reference value based on at least a part of the pieces of resistance value information, and a data adjustment circuit. In operation, the read circuit assigns, based on the binary reference value, 0 or 1 to each of the pieces of resistance value information. In operation, the data adjustment circuit determines whether to adjust the binary reference value, in accordance with a difference between the numbers of pieces of digital data “0” and digital data “1” in the pieces of digital data.
Owner:PANASONIC SEMICON SOLUTIONS CO LTD
Digitally watermarking physical media
InactiveUS7248715B2Little and no production costMinimal costCharacter and pattern recognitionImage data processing detailsThe InternetVisual perception
A digital watermark is embedded through varying pit locations on a data side of a CD, SACD or DVD. In one embodiment, a pattern of pits or data indentations forms a visual design on the data side. A watermark is embedded by slightly varying various pit locations within the visual design. In another embodiment, the varied pit locations are imperceptible or nearly imperceptible to human observation. The digital watermark is used as a counterfeit deterrent and as an identifier. Once extracted, the identifier is used to link to related content via the internet.
Owner:DIGIMARC CORP
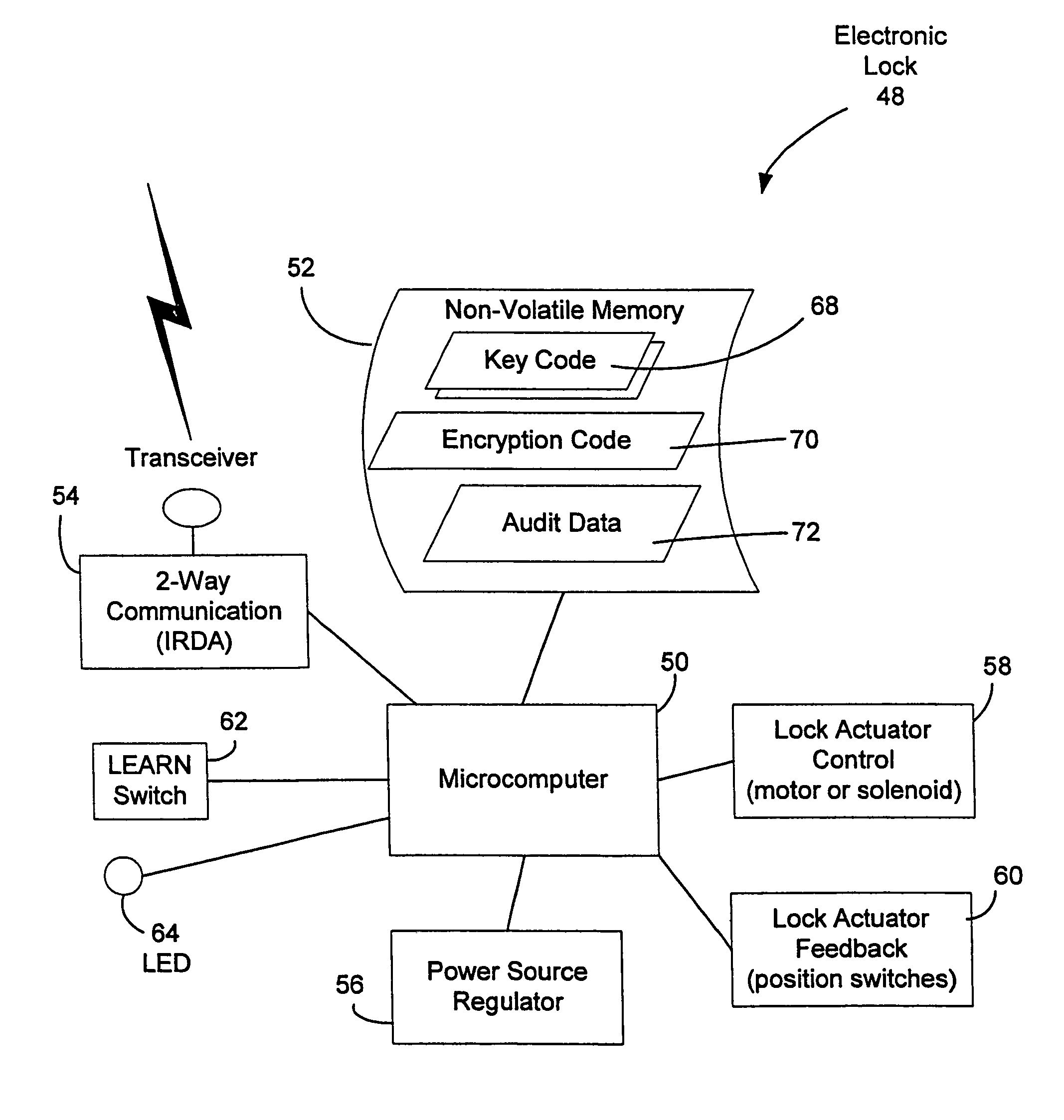
Vending machines with field-programmable locks
InactiveUS7821395B2Easy and inexpensiveReduce theft and fraudFrequency-division multiplex detailsDigital data processing detailsEngineeringHand held
A vending machine uses a field-programmable electronic lock that learns a key code from a corresponding electronic key, a hand-held program unit, or an external computing device via wireless communications. In one mode, the electronic lock has a learning process activation device that is accessible only when the door of the vending machine is in the open position. In another mode, the electronic lock is programmed in the field without first opening the vending machine. A program command and access control data including a new access code are transmitted wirelessly from a hand-held program unit or the like. Alternatively, an external computing device is used to program the electronic lock via long-range wireless communications, and an electronic key is then used to open the electronic lock to physically access the vending machine.
Owner:MICRO ENHANCED TECH
System and Method for Device Bound Public Key Infrastructure
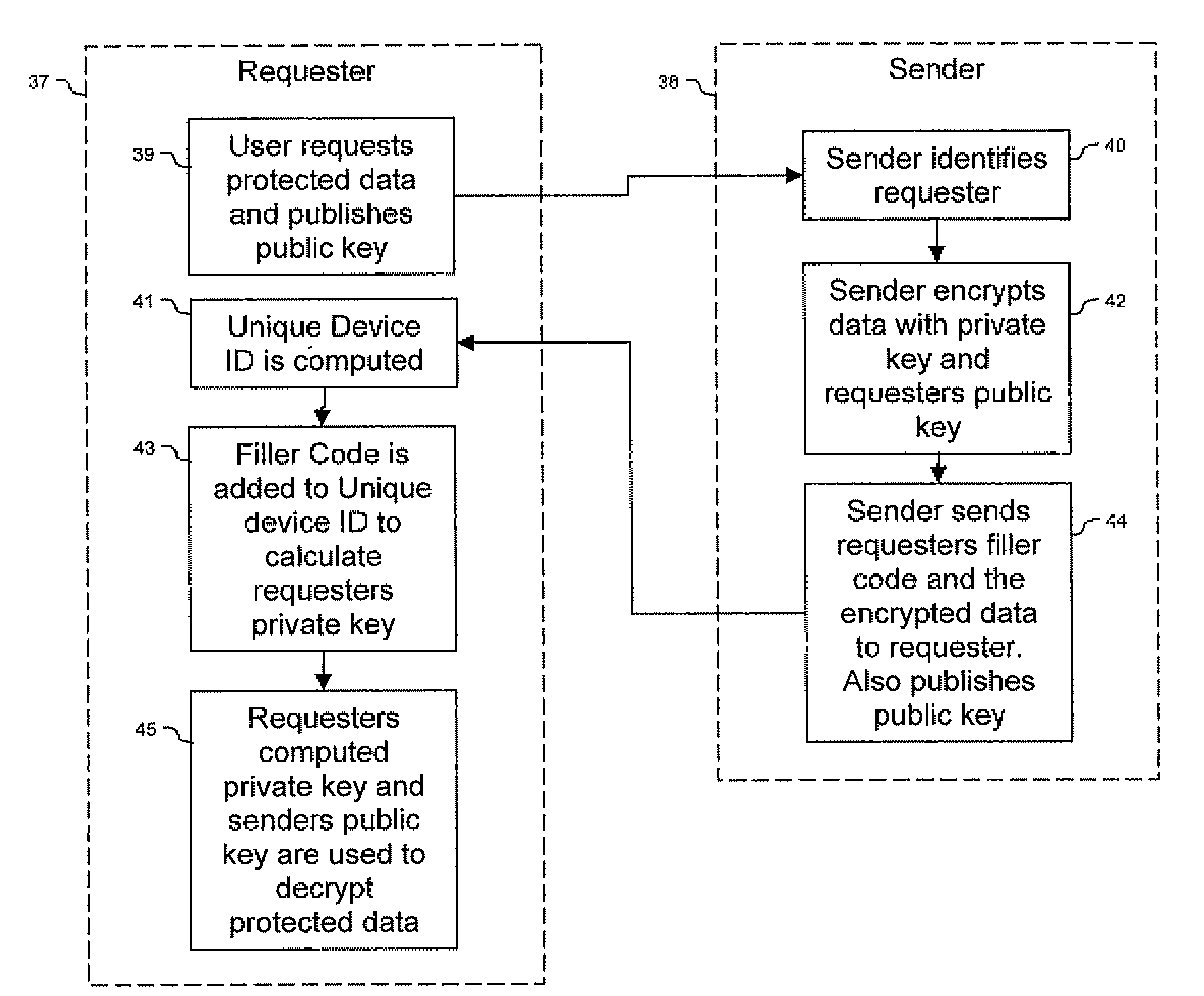
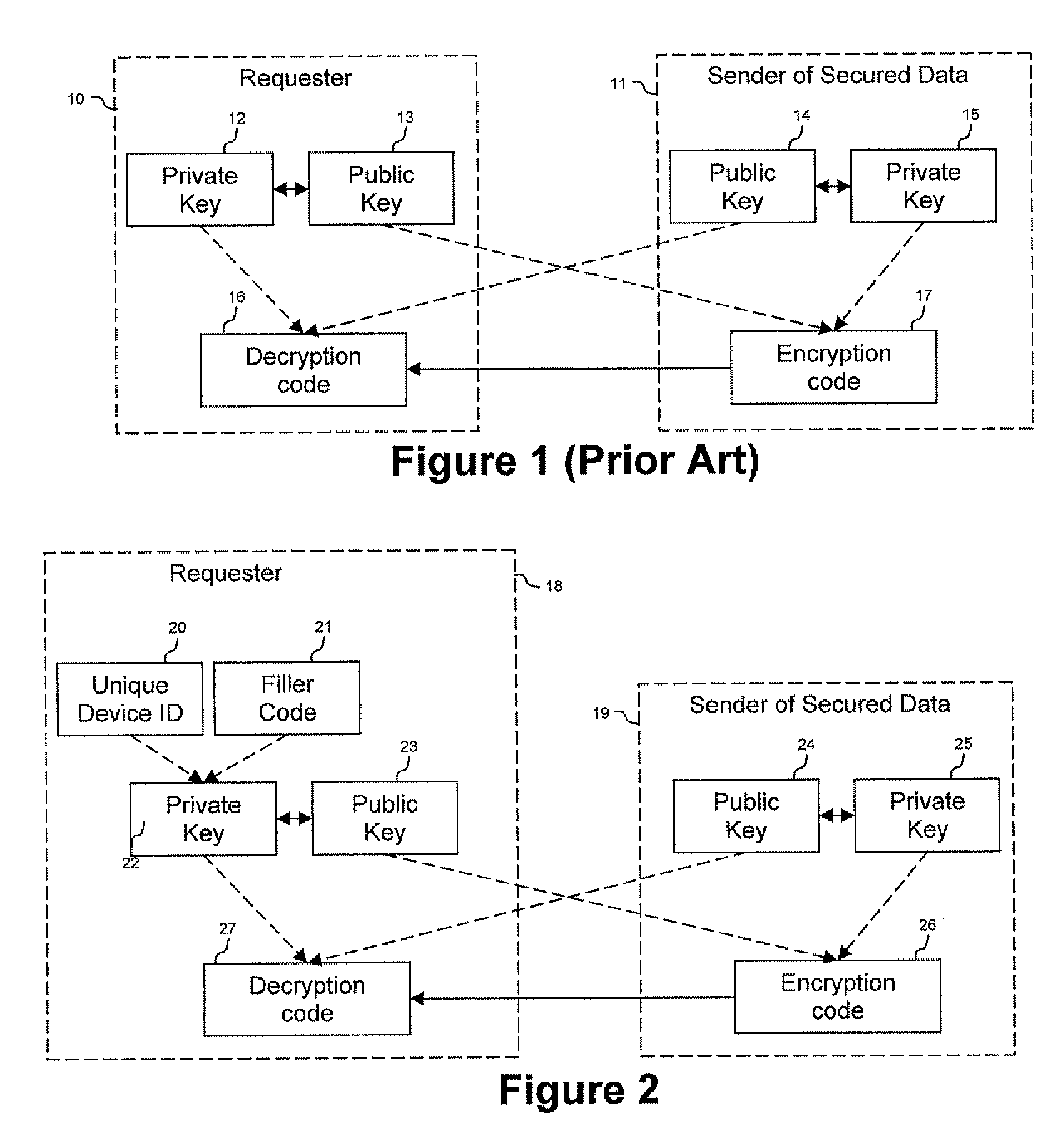
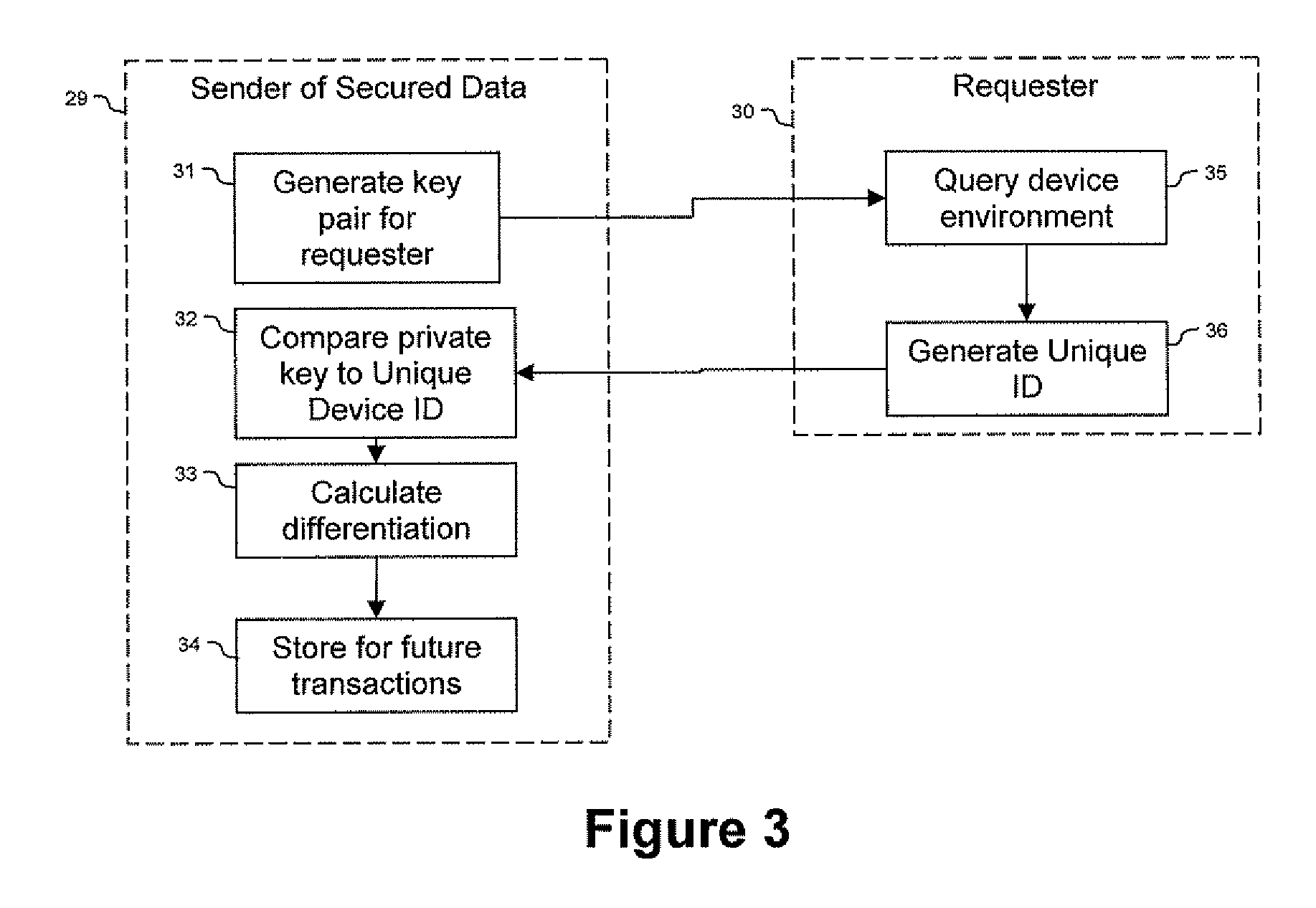
ActiveUS20090150674A1Not easy to copyNot easy to be stolenDigital data processing detailsUser identity/authority verificationSecure communicationUnique device identifier
Techniques are provided secured communication of data, such as in the context of a public key infrastructure (PKI). In one embodiment, the technique may involve using a private key that is bound to the device requesting the secure data, thereby making it harder for someone to copy, steal or fake. The private key may be generated by adding a filler code to a unique device identifier. The identifier may be based on at least one user-configurable parameter and at least one non-user-configurable parameter of the device.
Owner:DEVICE AUTHORITY LTD
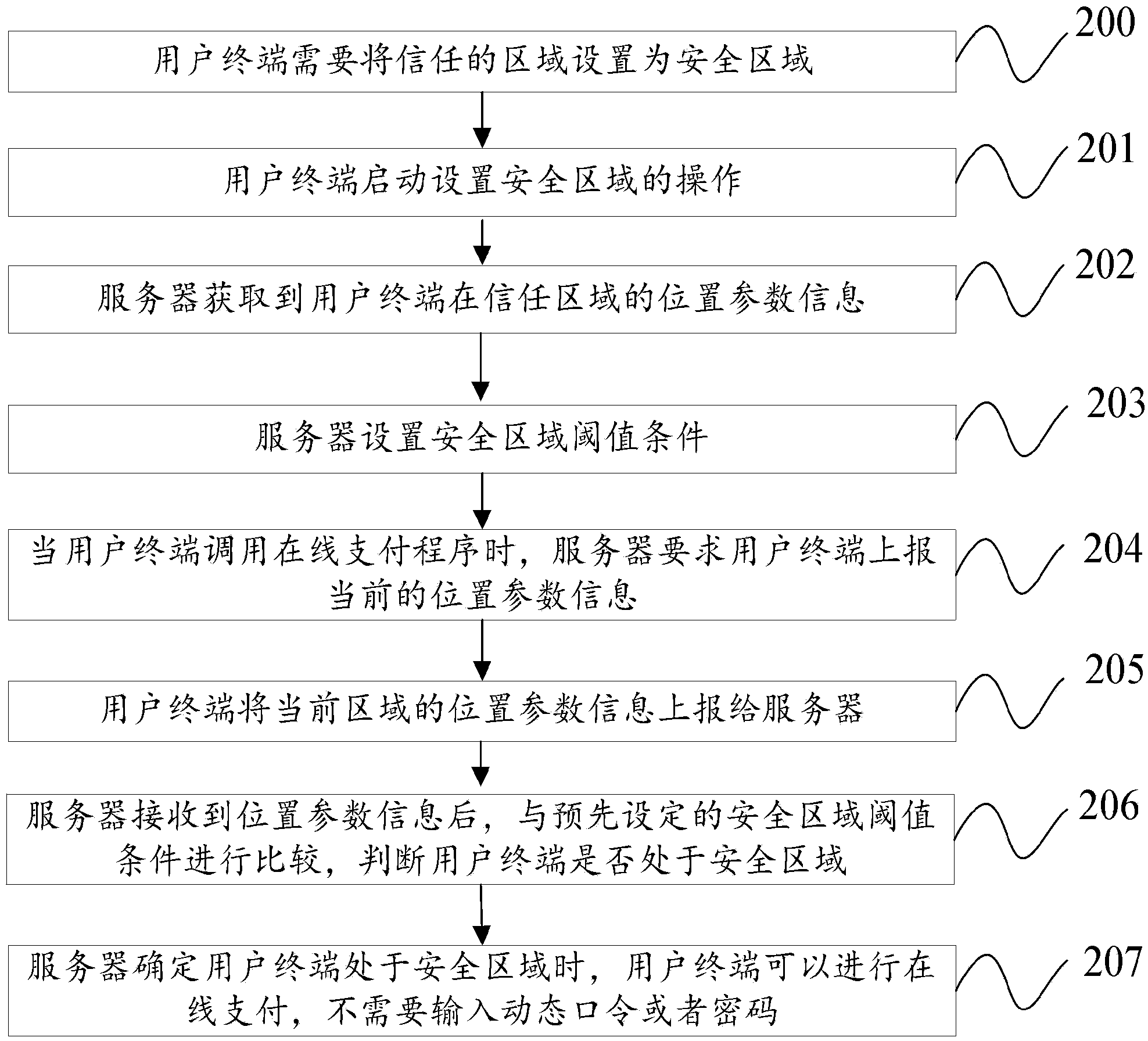
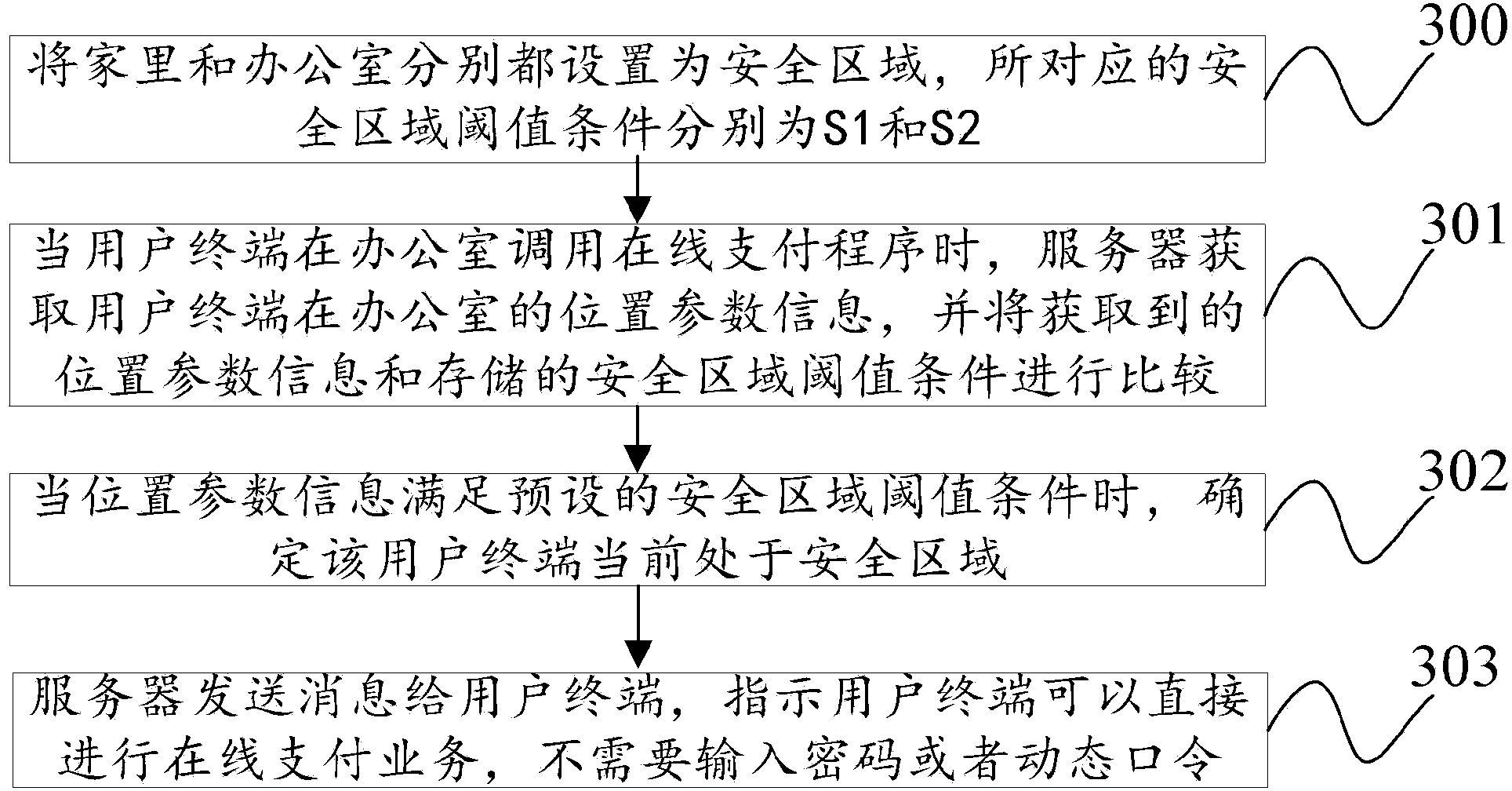
Safe region recognition method and device, and user terminal
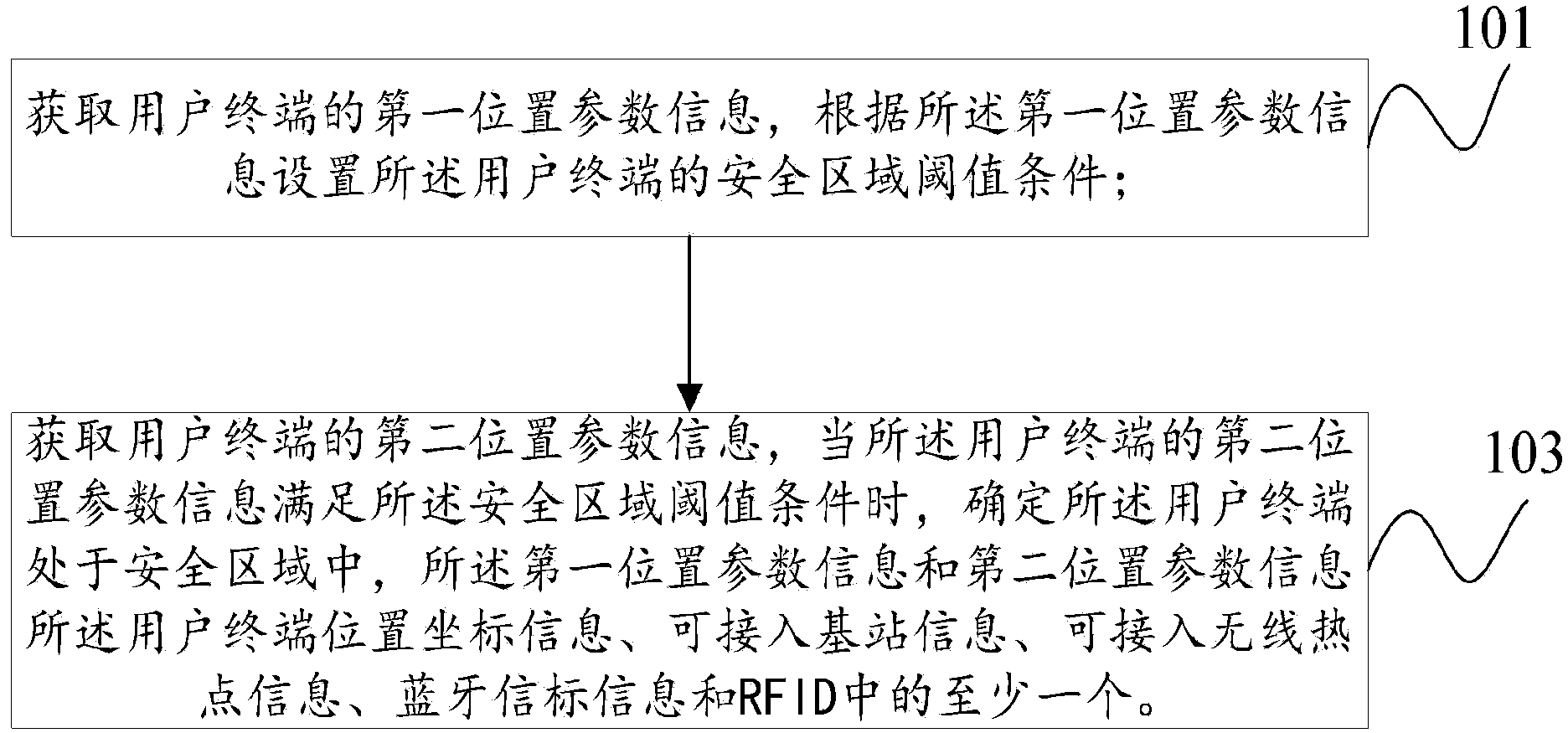
InactiveCN103874021AImprove experienceOperational intelligenceLocation information based serviceSecurity arrangementBluetoothComputer science
The embodiment of the invention provides a safe region recognition method and device, and a user terminal. The method includes the steps of firstly, obtaining first position parameter information of the user terminal, and setting the safe region threshold value condition of the user terminal according to the first position parameter information; secondly, obtaining second position parameter information of the user terminal, and when the second position parameter information of the user terminal meets the safe region threshold value condition, determining that the user terminal is located in a safe region, wherein the first position parameter information and the second position parameter information respectively include at least one of position coordinate information, access base station information, access wireless hot point information, Bluetooth beacon information and RFID information of the user terminal. According to the safe region recognition method and device, and the user terminal, the safe region can be set for the user terminal, and the user terminal can rapidly and conveniently execute mobile application services in the safe region.
Owner:YINLIAN FINANCIAL INFORMATION SERVICE BEIJING CO LTD
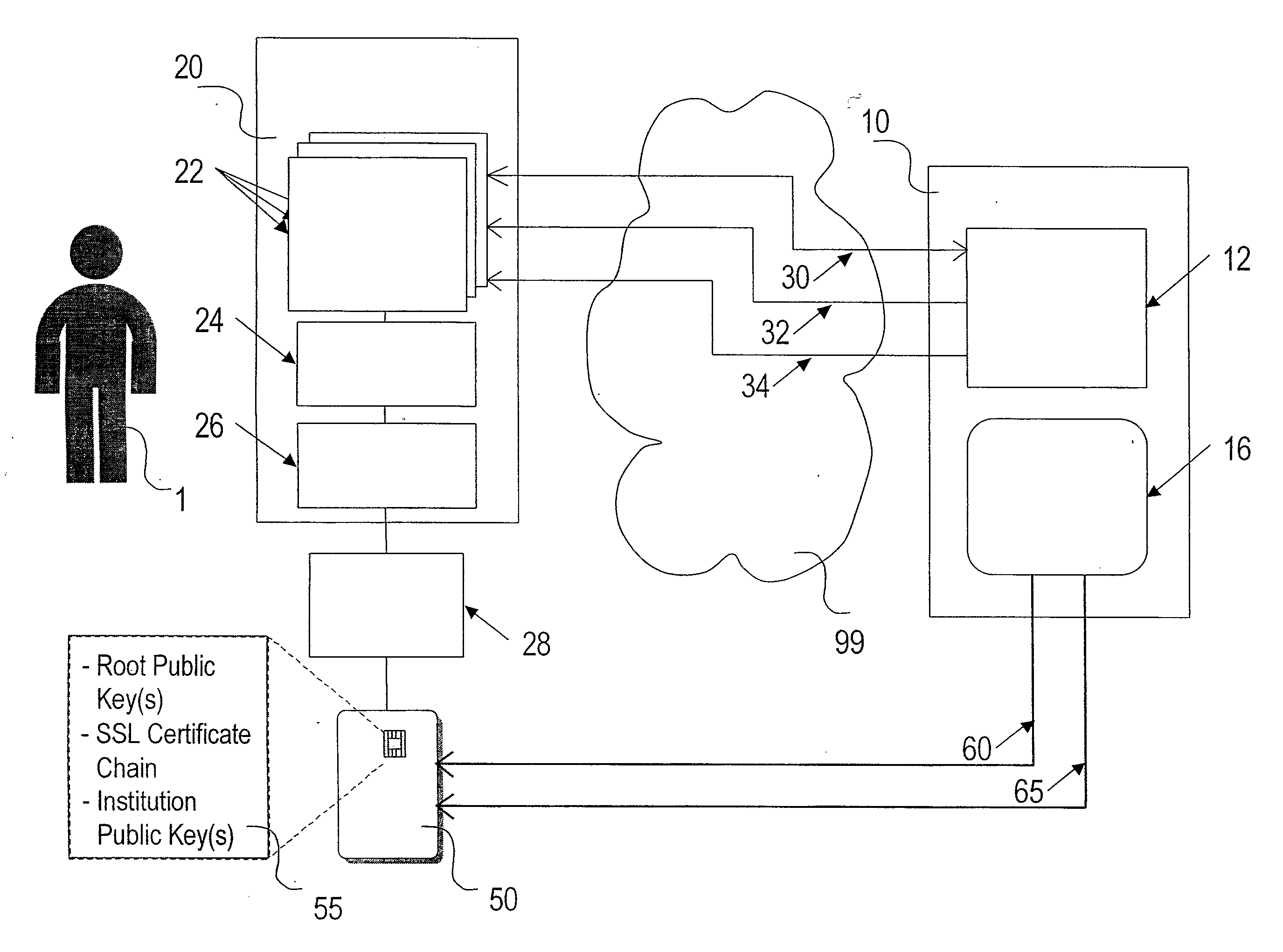
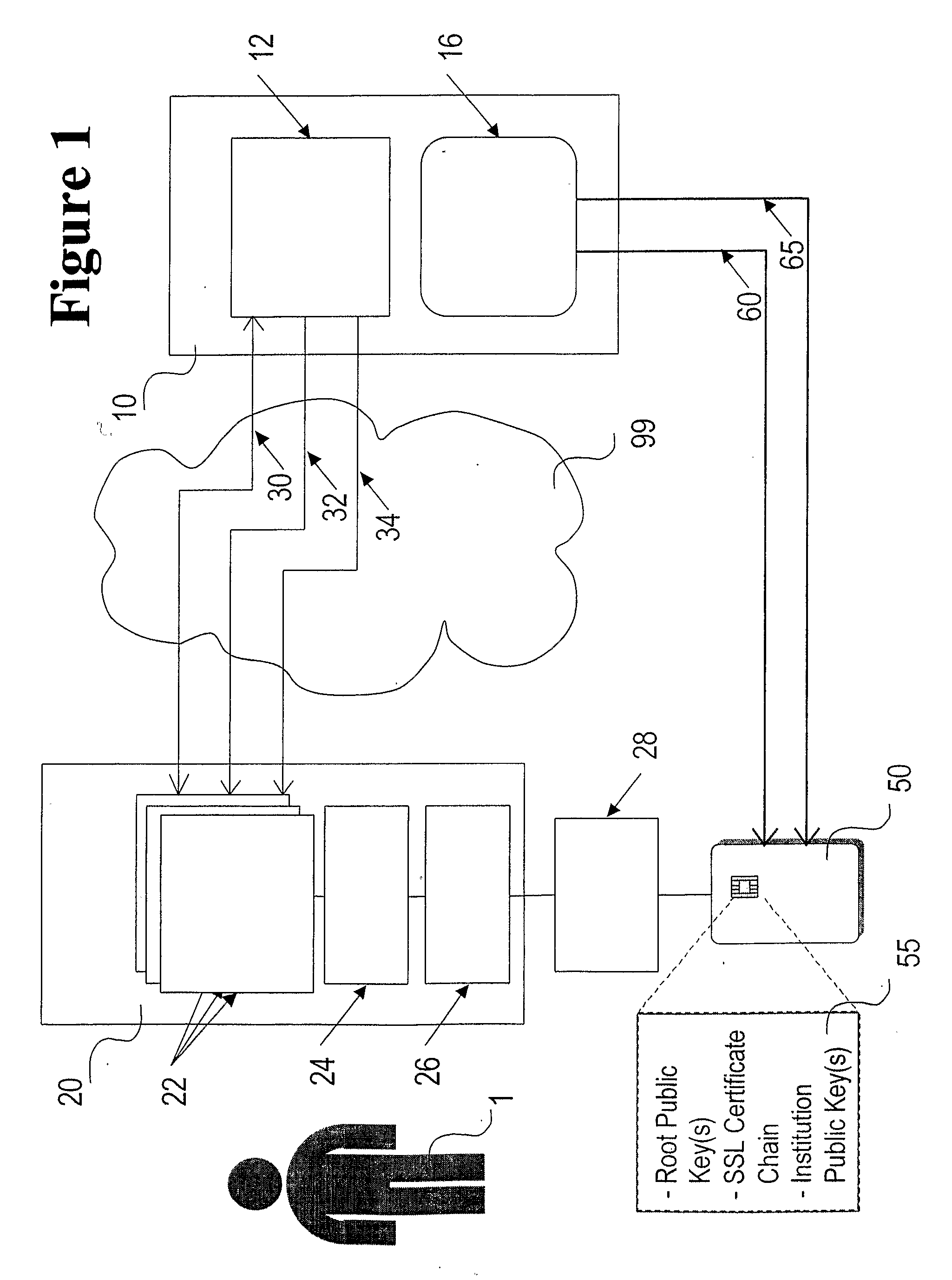
Means and Method of Using Cryptographic Device to Combat Online Institution Identity Theft
InactiveUS20080288790A1Improve securityProcess safetyUnauthorized memory use protectionHardware monitoringWeb siteIdentity theft
Whereas smartcards and similar cryptographic devices may customarily be used to protect against personal identity theft, this invention stores Public Keys of an institution in cryptographic devices issued by the institution to its customers, in order to protect the institution's identity from being stolen. The invention improves the security of electronic business applications using Secure Sockets Layer, Secure E-mail, Object Signing and similar low level electronic business security functions by storing various Public Keys of the institution within the cryptographic device. The invention thereby helps to reduce the likelihood of “ghosting” an institution's web site (where an illegitimate web site seeks to mimic a genuine web site in order to defraud customers), and provides a means to overcome the problem of “phishing” (where illegitimate e-mails purporting to be from the institution are sent to customers in order to elicit personal information).
Owner:LOCKSTEP CONSULTING
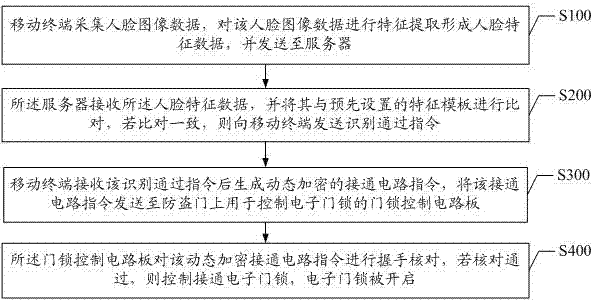
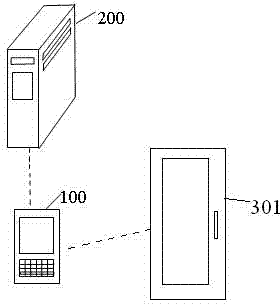
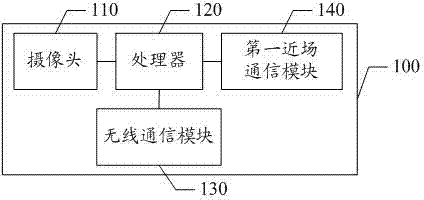
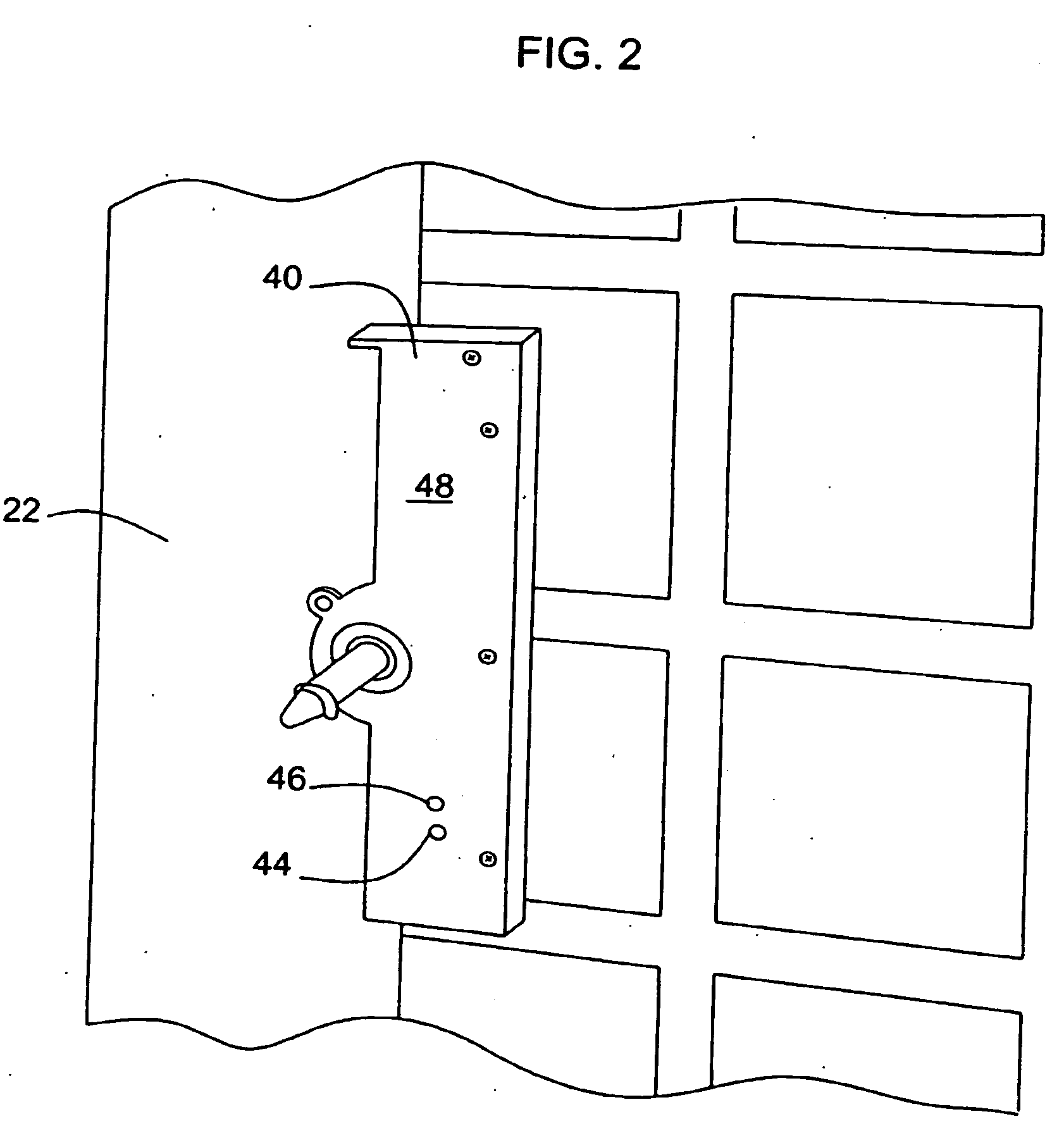
Door lock control method and system
ActiveCN103927802AReduce workloadEnsure safetyCharacter and pattern recognitionIndividual entry/exit registersFeature extractionControl system
The invention discloses a door lock control method and a door lock control system. The method comprises the following steps: A, a mobile terminal acquires the facial image data and carries out feature extraction to form facial feature data to be sent to a server; B, the server receives the facial feature data and compares the facial feature data with preset feature template, and if consistent, sending an identification passing instruction to the mobile terminal; C, the mobile terminal receives the identification passing instruction and then generates a dynamically encrypted circuit connecting instruction and sending to a door lock control circuit board; D, the door lock control circuit board carries out handshaking checking on the dynamically encrypted circuit connecting instruction, and if the checking passes, controlling to connect an electronic door lock. According to the invention, the mobile terminal and the server are utilized to realize the facial identification technology and are organically combined with control on the electronic door lock, so as to realize the intelligent unlocking function with low cost; the system avoids the problem that common door locks and locks with magnetic card swiping function are easy to be duplicated, and improves the domestic antitheft security level.
Owner:SHENZHEN WAVE KINGDOM CO LTD
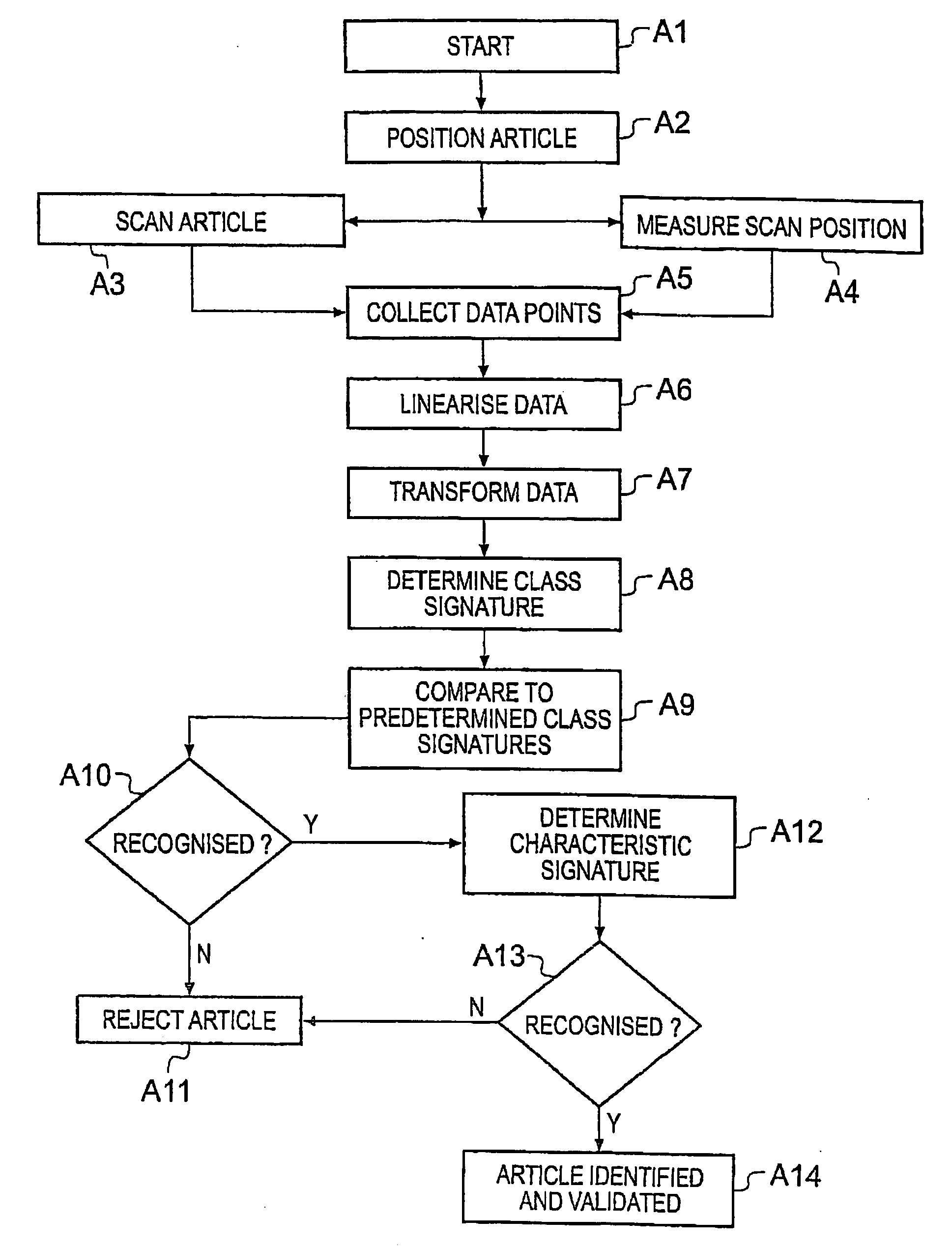
Authenticity Verification Methods, Products and Apparatuses
InactiveUS20080260199A1Increase the number ofNot easy to copyDigitally marking record carriersPaper-money testing devicesCardboardComputer science
A method and apparatus for determining a class signature from an article made of paper or cardboard in order to identify a generic type of class to which the article belongs. An optical beam illuminates the article and a detector arrangement collects data points from light scattered from many different parts of the article as the article is scanned by the beam. The class signature derives from intrinsic properties imparted to the paper / cardboard during manufacture by, it is believed, the screen used during dewatering of paper pulp. Detection of the class signature allows the manufacturer or the particular paper making machine that made the paper to be identified.
Owner:INGENIA HLDG LTD
Diffractive optical security device
InactiveUS20070081246A1High level of security against counterfeitingMitigate such drawbackDiffraction gratingsInformation cardsRefractive indexMirror image
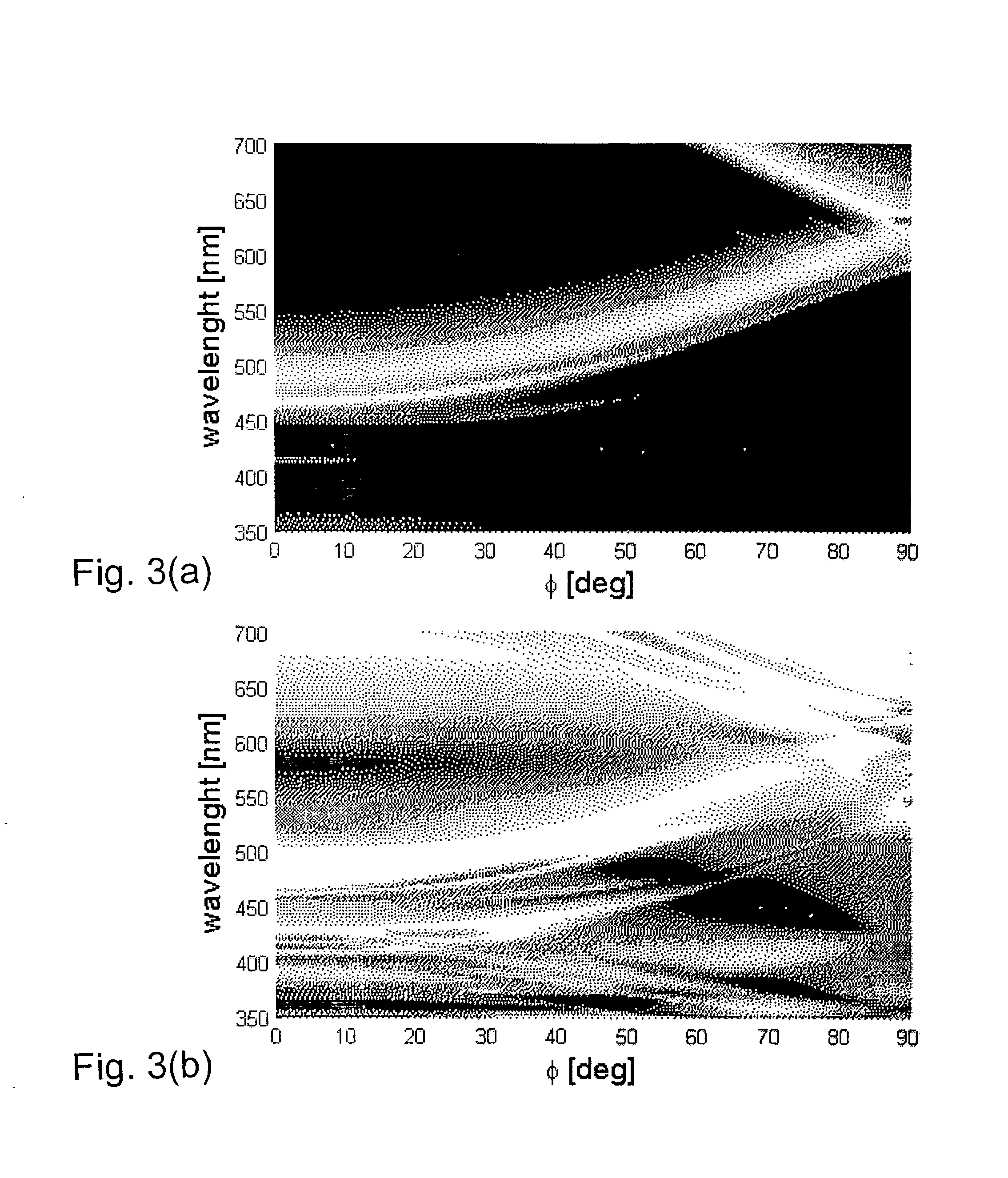
The diffractive optical device (1) can be used as a security device in the fields of authentication, identification and security. It comprises a zero-order diffractive color filter (3). The diffractive color filter may consist of a microstructured high-index layer (32) embedded between two low-index layers (31, 33). A mirror layer (4) for reflecting towards the diffractive color filter (3) at least part of light transmitted through the diffractive color filter (3) are provided beneath the diffractive color filter. Thanks to the mirror layer (4), the device (1) has a much higher reflected intensity and much more complex spectra than prior-art diffractive color filters.
Owner:CSEM CENT SUISSE DELECTRONIQUE & DE MICROTECHNIQUE SA RECH & DEV
Method for embedding information in an image
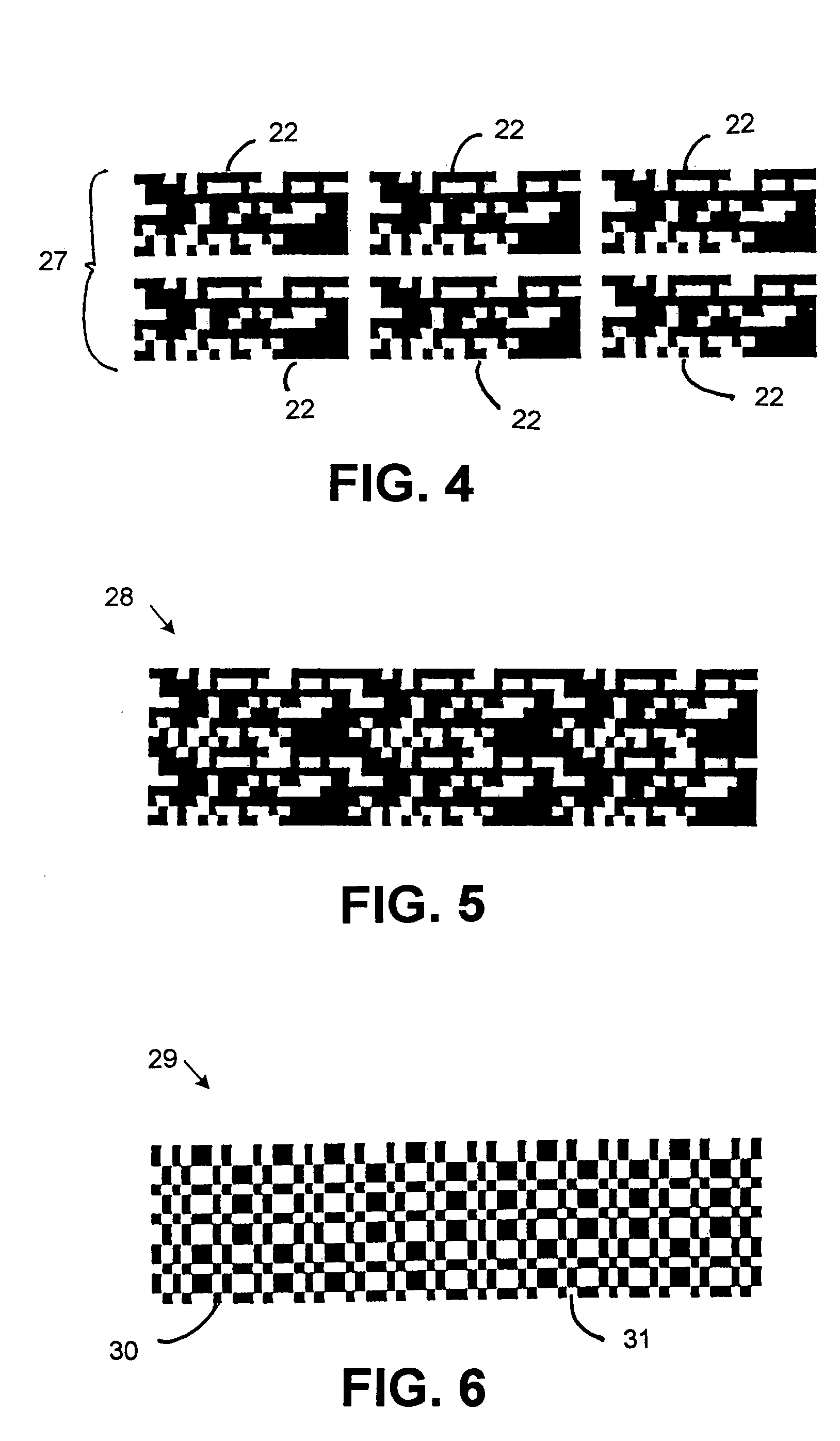
InactiveUS7191336B2Reduce productionDifficult to imageUser identity/authority verificationFranking apparatusArray data structureComputer graphics (images)
A method for producing a background image representing data. The background image is created by; producing a first encoding of data into a first binary array; producing a second encoding of the data into a second binary array; representing the first binary array as a first set of modules of a first size of n×n pixels wherein each pixel is either white or black and every pixel in the module is identical to every other picture in the module on nodes of a first lattice, representing the second binary array as a first set of modules of a second size, of m×m wherein each pixel is either white or black and every pixel in the module is identical to every other pixel in the module, which is smaller than the first size on nodes of a second lattice, combining the first and second sets of modules; and printing the first and second sets of modules.
Owner:PITNEY BOWES INC
Duplicate coding internet of things traceability security label and 2-dimensional bar code security traceability method
InactiveCN105469132ANot easy to copyImprove securityCo-operative working arrangementsCommerceSecurity functionHandset
The invention discloses a duplicate coding internet of things traceability security label, comprising a 2-dimensional bar code, an upper layer label and a lower layer label. The 2-dimensional bar code comprises a 2-dimensional bar code external code and a 2-dimensional bar code internal code, wherein the 2-dimensional bar code external code is arranged on the upper layer label and used for goods traceablility querying; the 2-dimensional bar code internal code is arranged on the lower layer label and used for security verification; the upper layer label and the lower layer label only have edges jointed, and the upper layer label is provided with a tearing port; the 2-dimensional bar code internal code is used for a consumer to perform network security verification through handset scanning, the security verification being performed only once. After security verification, the security function of the 2-dimensional bar code internal code is immediately disabled, and scanning the 2-dimensional bar code internal code is equal to scanning a torn 2-dimensional bar code external code. The invention also discloses a 2-dimensional bar code security traceability method which is hard to copy and has high security.
Owner:SHANGHAI ZHONGSHUO INFORMATION TECH
Vending machines with field-programmable electronic locks
InactiveUS20070096867A1Easily and inexpensively programmedImprove the level ofElectric signal transmission systemsMultiple keys/algorithms usageService personnelBiological activation
A vending machine uses a field-programmable electronic lock that learns a key code from a corresponding electronic key. The electronic lock has a learning process activation device that is accessible when the door of the vending machine is in the open position. Using the learning process activation device, a service person activates the electronic lock to perform a key code learning operation, in which the electronic lock receives a key code transmitted from an electronic key and stores the key code in a non-volatile memory for future access control of the vending machine. Data encryption is employed in the communications between the key and the lock to ensure the security of the communications. A communication device installed in the vending machine for communicating with a home base computer allows the operation of the electronic lock to be remotely controlled for access control and auditing purposes.
Owner:DENISON WILLIAM D +2
Two-dimensional code, encoding and identification method thereof and product with anti-counterfeiting function
ActiveCN108764420ARich Personalization FeaturesFlexible Personalization FeaturesRecord carriers used with machinesGraphicsDimensional modeling
Owner:CHINA BANKNOTE SECURITY PRINTING TECH RES INST CO LTD +1
Method and Apparatus for Accessing Proteceted Data
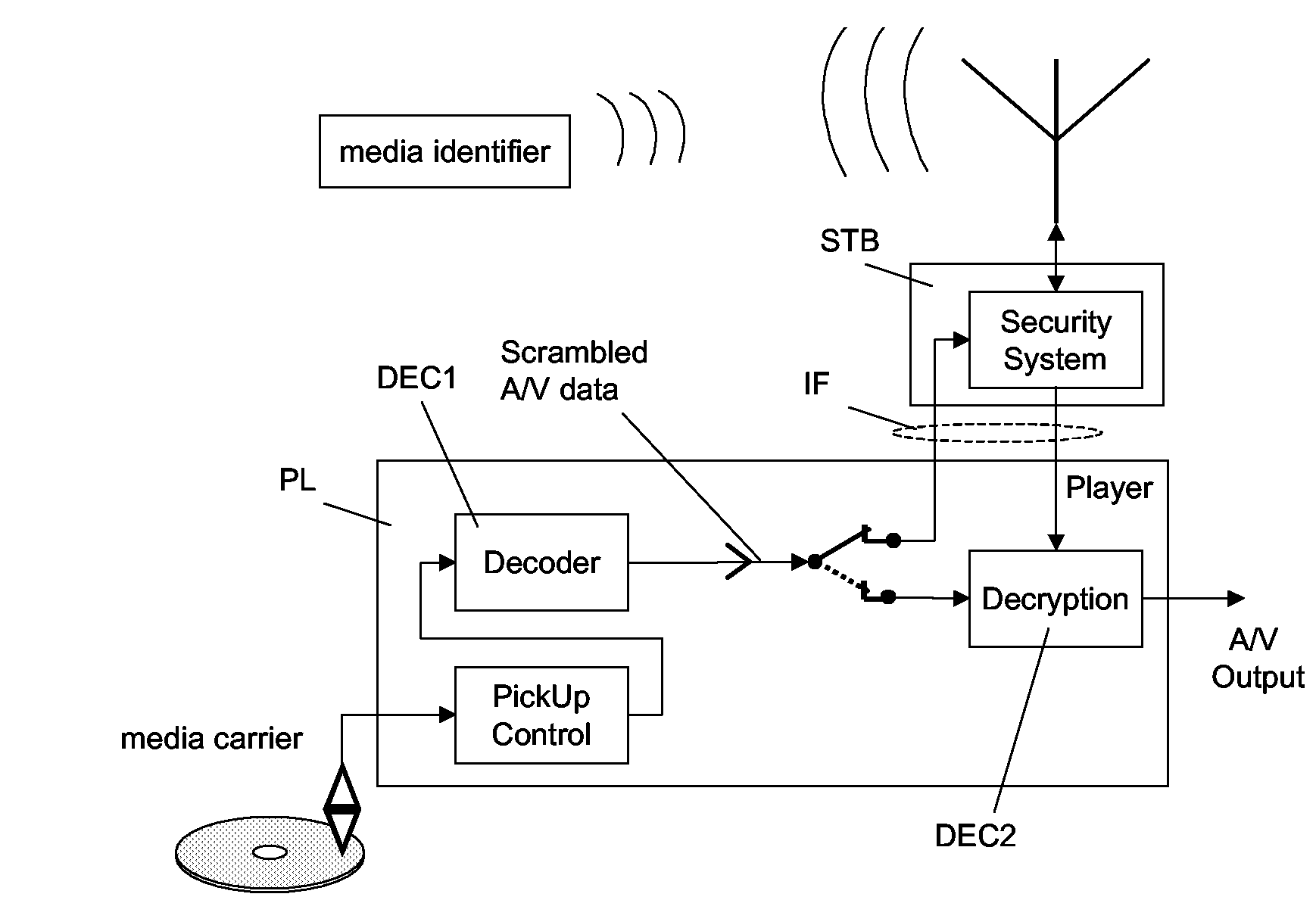
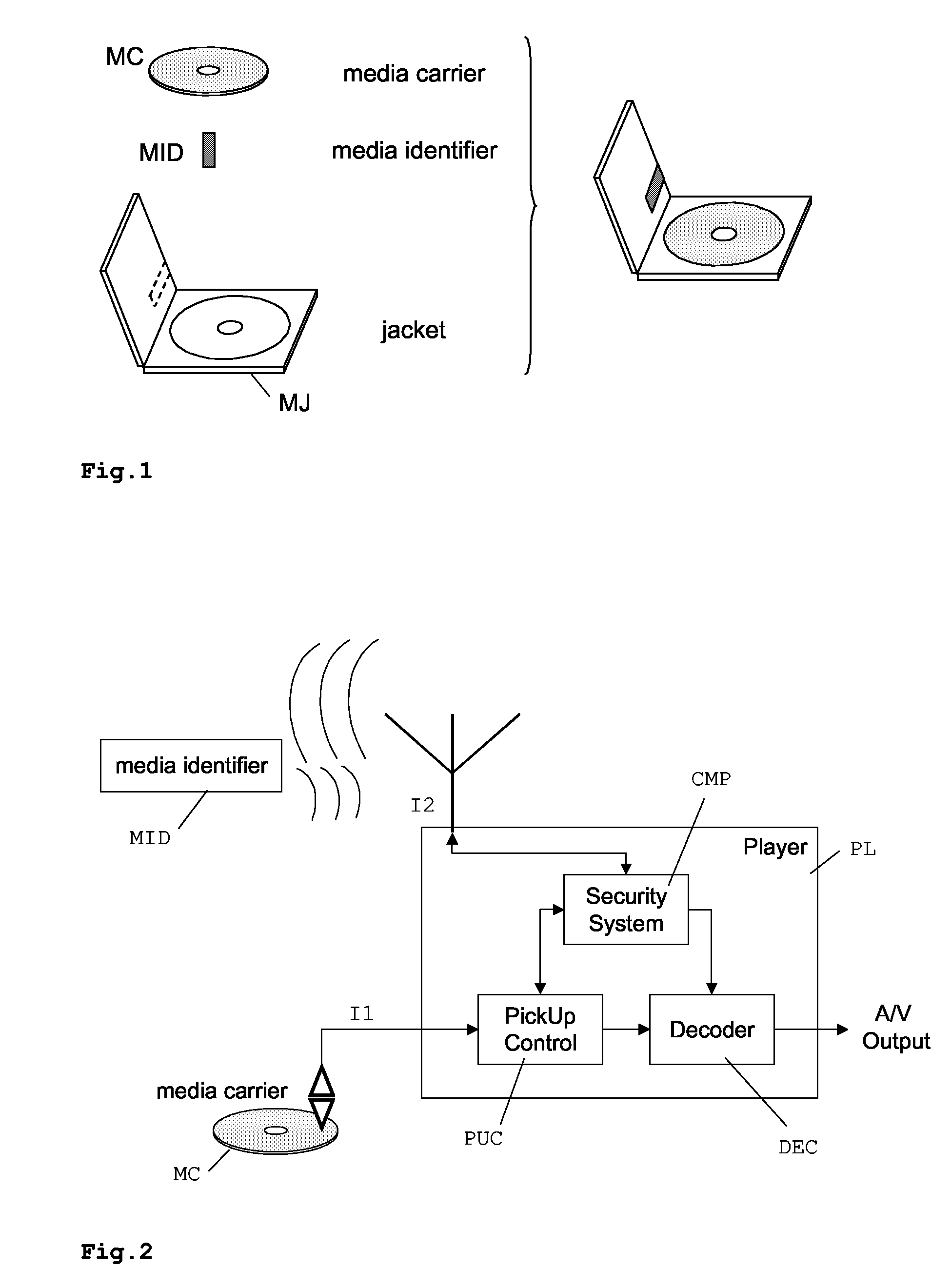
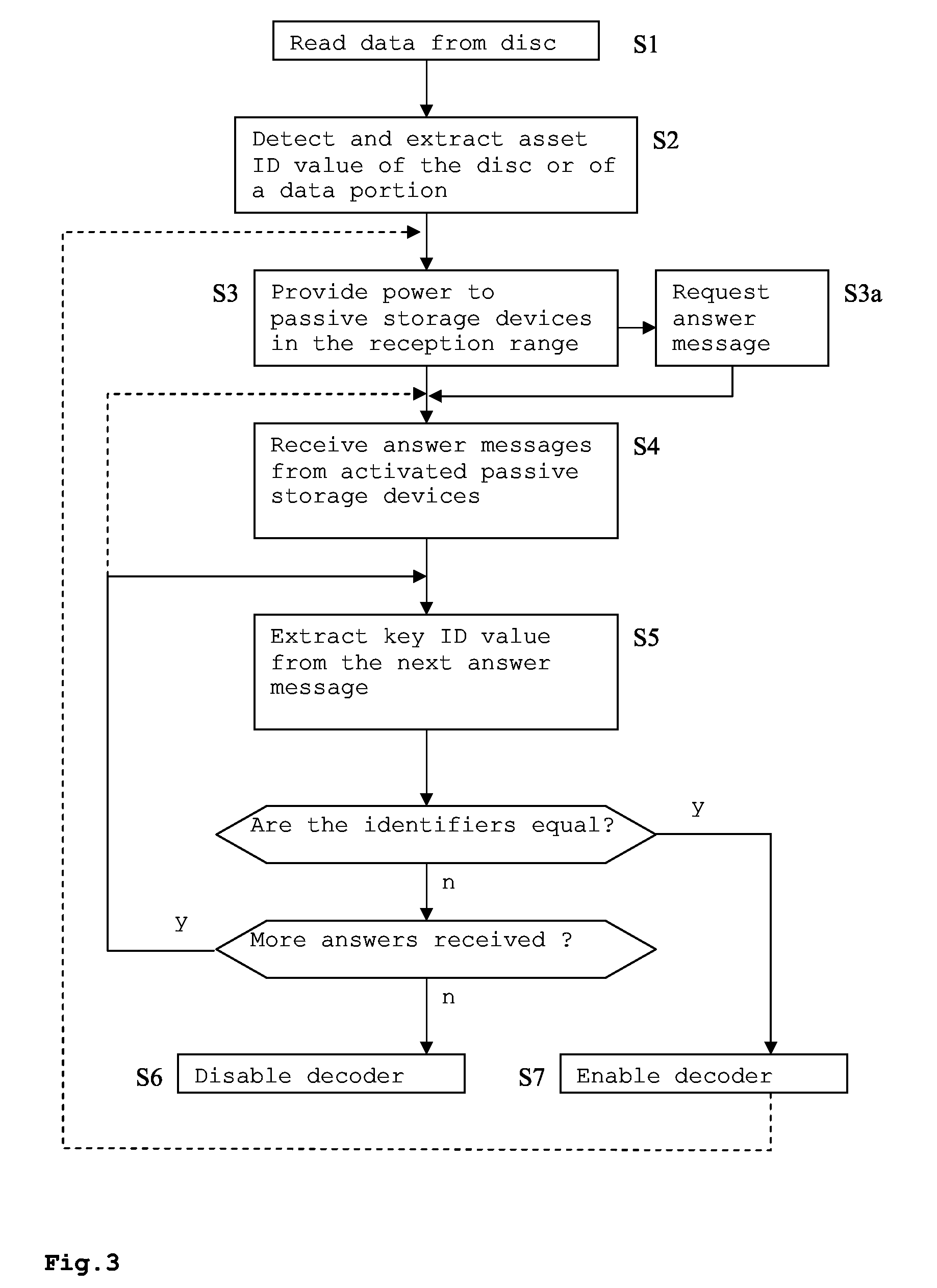
InactiveUS20080199006A1Preserving content rightPrevent illegal useAccessories for auxillary signalsRecord information storageContent IdentifierApplication software
Consumers of content protected multimedia data, such as e.g. commercially available video DVDS, want to take backup copies of these data, and want to be free to play the data on any suitable playback device, while content providers want to protect these data against pirate copying. The disclosed method for accessing application data from a first storage medium, e.g. CD, uses an electronic key for decoding or converting the application data. One or more content identifiers are attached to the application data or the first storage medium. The key is stored on a copy-protected separate second storage medium, e.g. RFID tag, and compared with the content identifier. Playback or format conversion of the application data is only possible when the second storage medium is available. This allows the application data to be copied, distributed or format converted, while simultaneously preserving the content rights of the data because only one copy can be used at a time.
Owner:THOMSON LICENSING SA
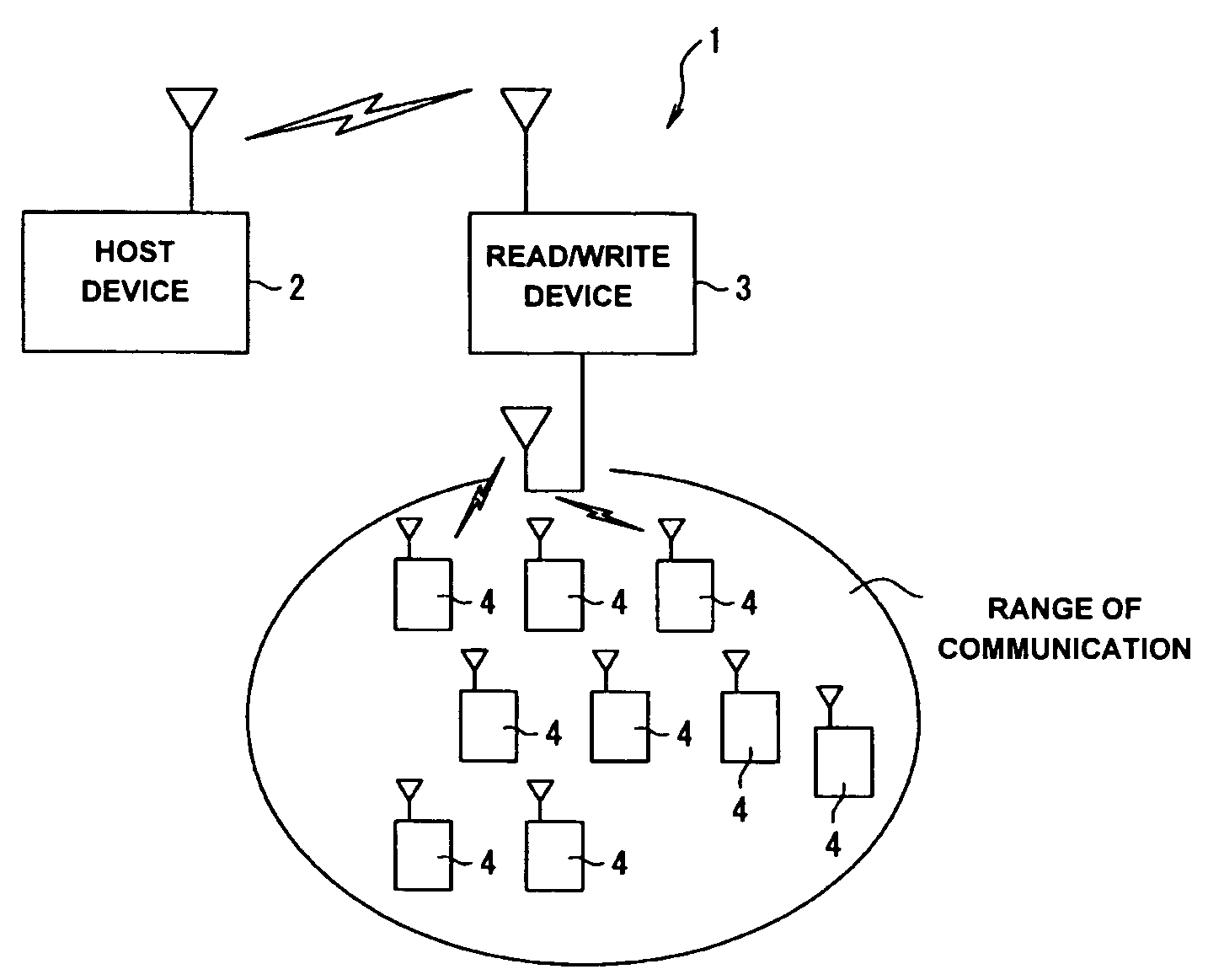
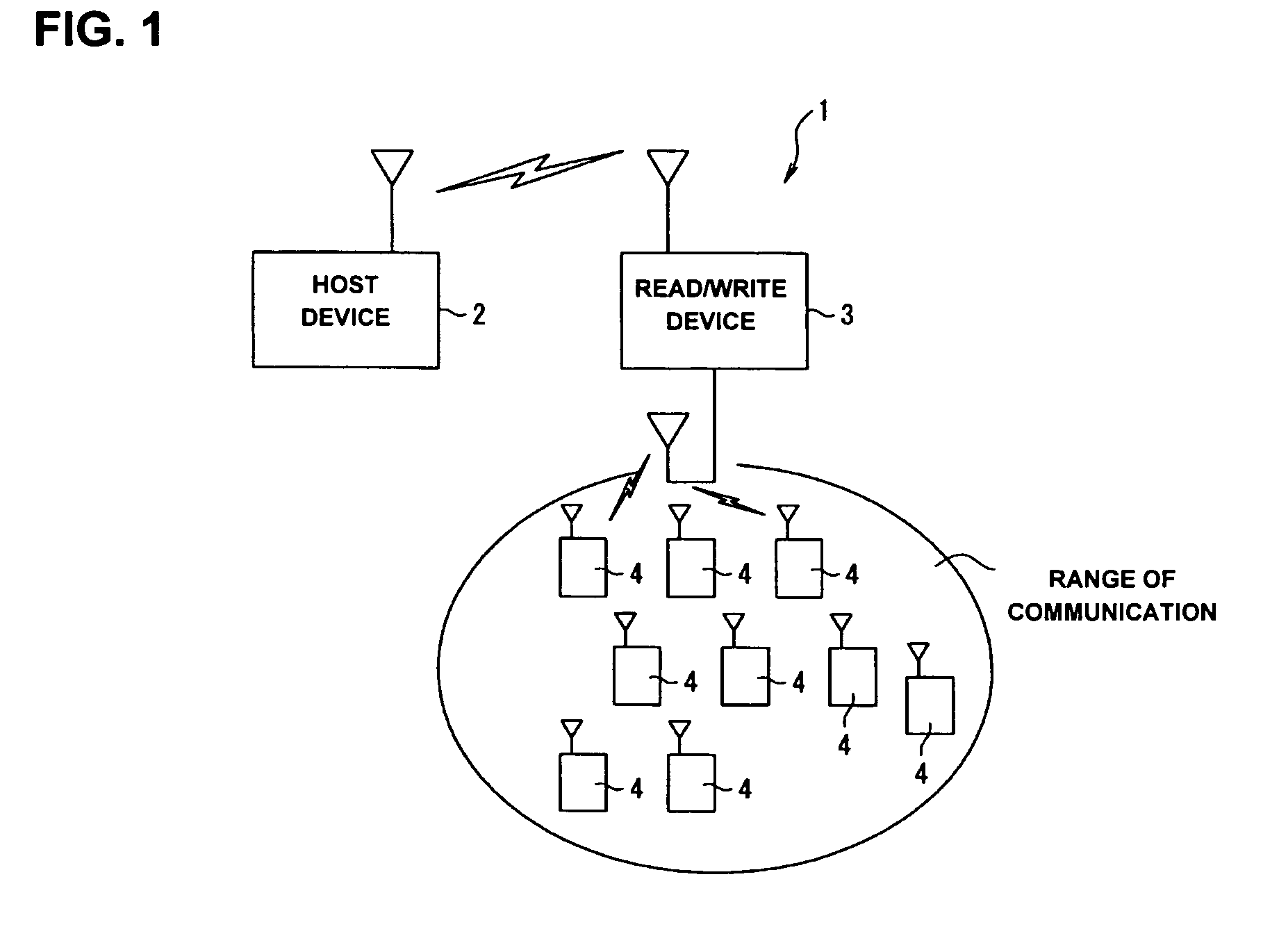
Contactless identification tag, data communication system and contactless identification tag control program
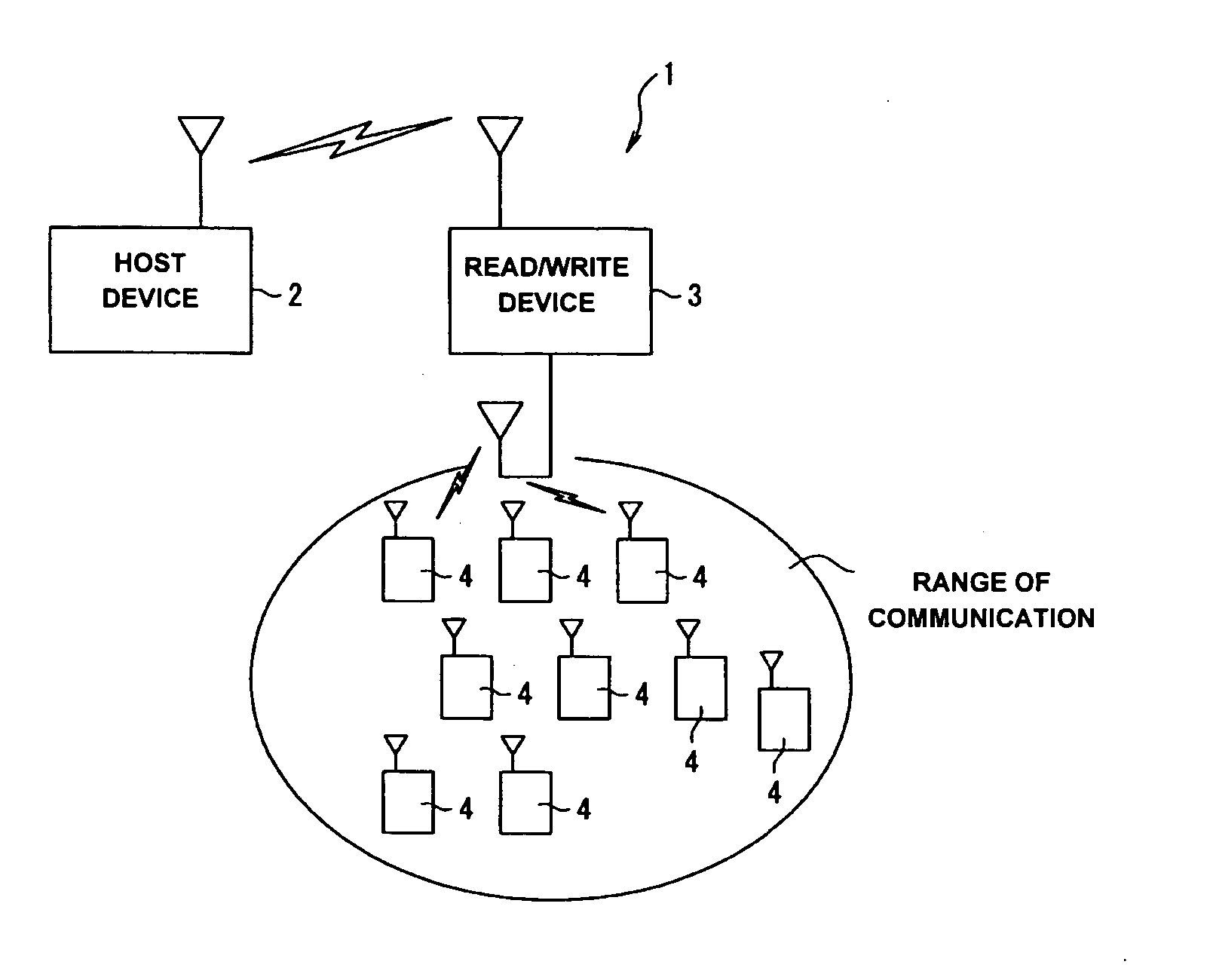
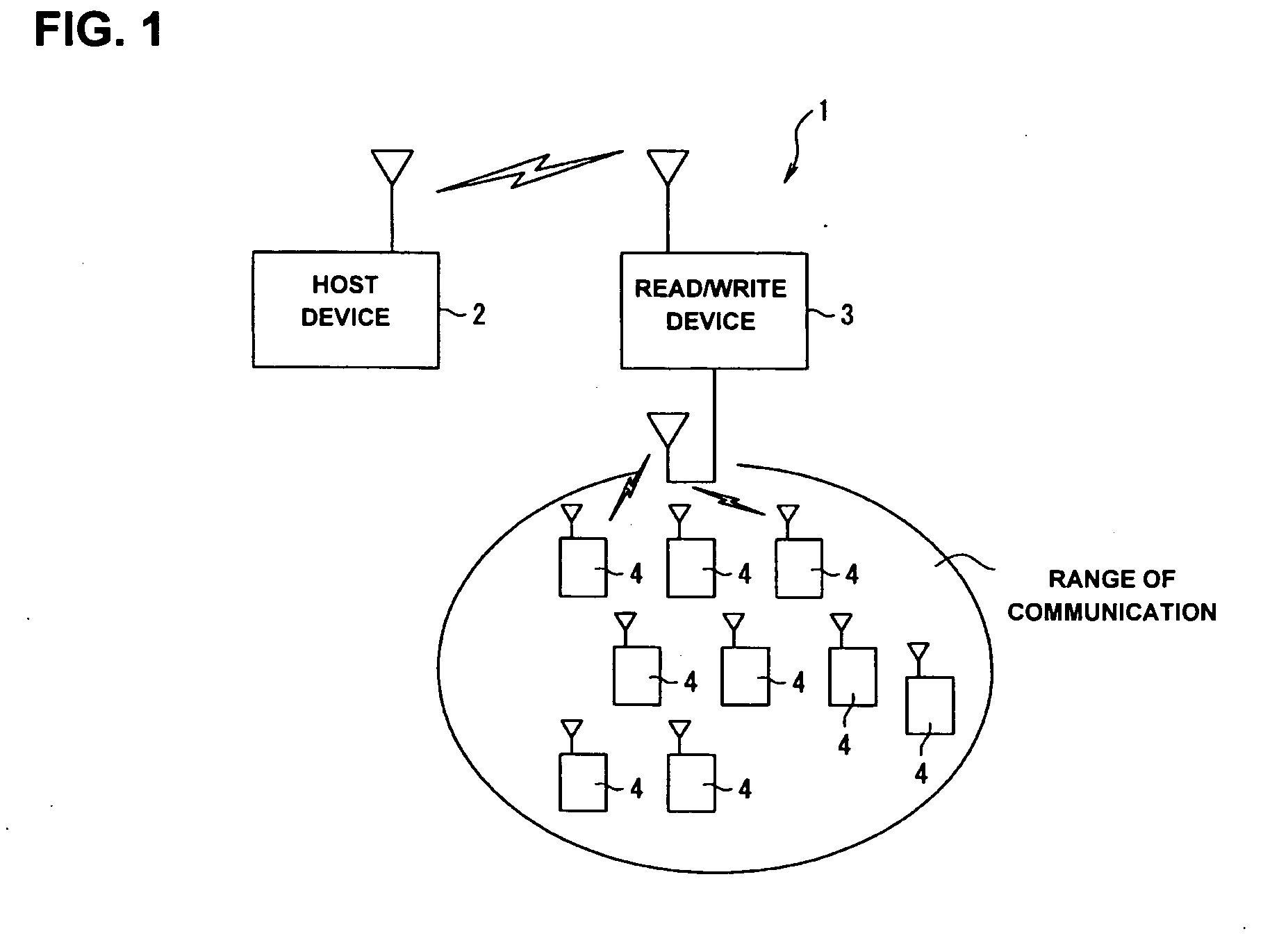
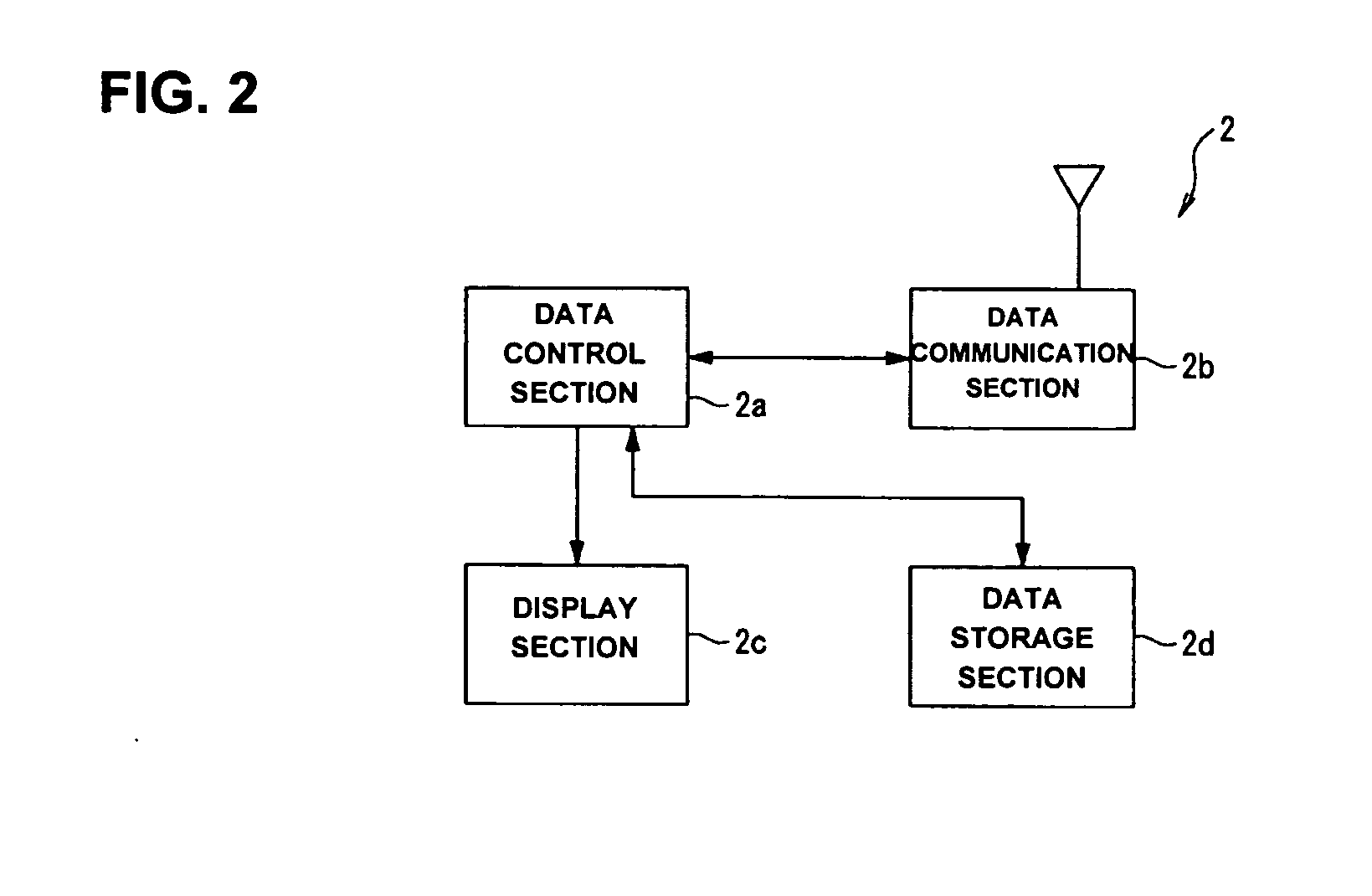
InactiveUS20050127180A1Prevent unnecessary communicationReduce probabilityMemory record carrier reading problemsCo-operative working arrangementsData transmissionInstruction data
A data communication system includes a host device, a reader / writer device and a plurality of contactless identification tags. The contactless identification tag includes a data reception section, a data transmission section, a data control section, a data storage section, a driving electric current generation section and a coil antenna. In response to a command from the reader / writer device, the data control section generates a random number, and sets a time slot number based on the random number and a unique identification number stored in advance in the data storage section.
Owner:SEIKO EPSON CORP
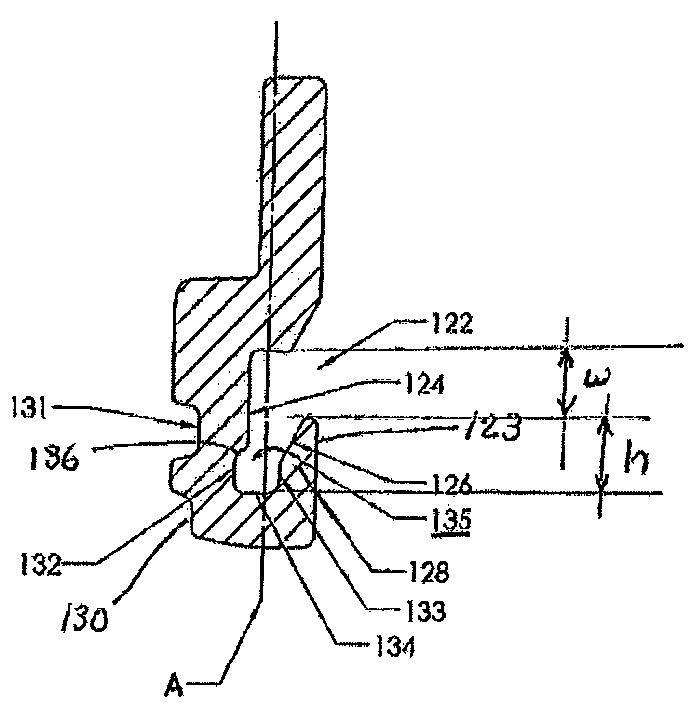
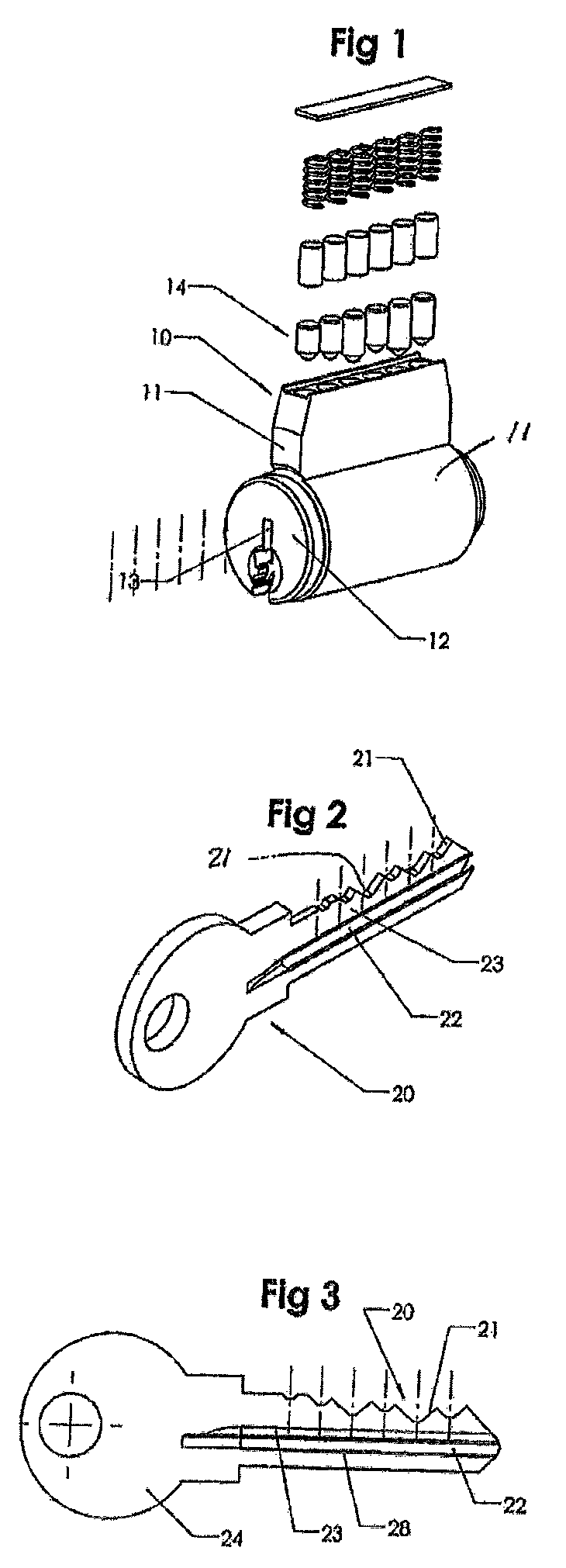
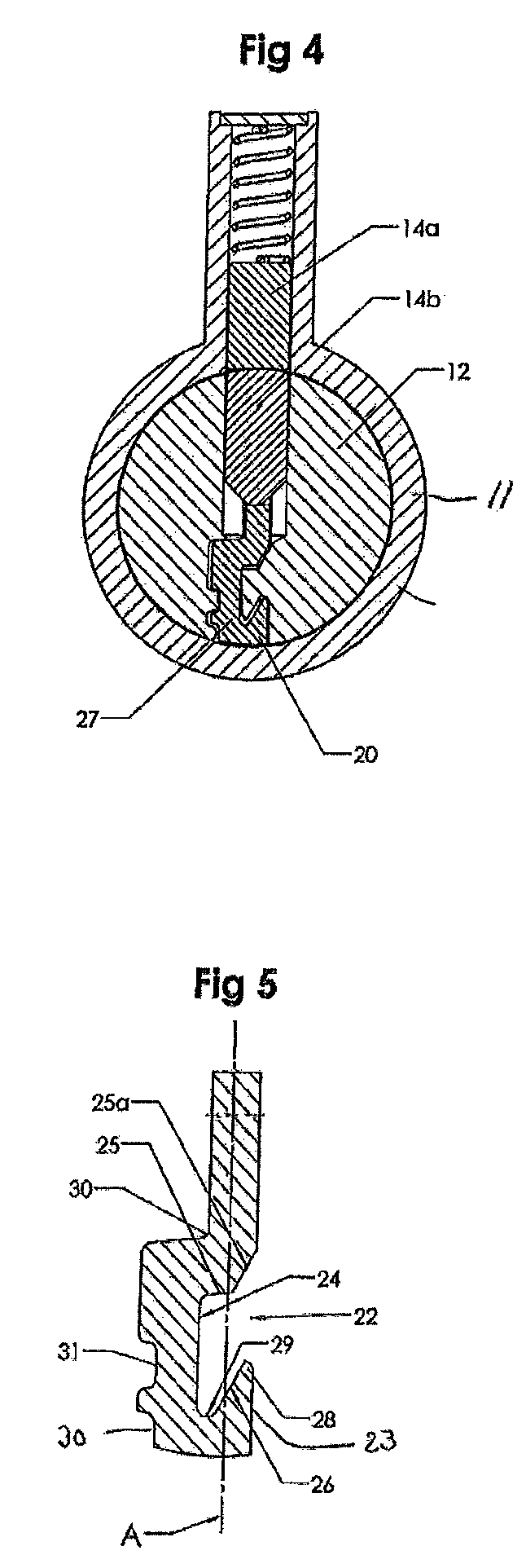
Profiled key for cylinder locks
A key for use in a cylinder lock with a rotatable key plug having a profiled keyway including a longitudinal profile rib at a side wall of the keyway. The key has an elongated, substantially flat key blade (120; 120′) having a longitudinal profile groove (122; 122′) extending along at least a portion of the length of the key blade. The groove has an undercut portion (129) adjacent to a ridge portion (128, 128′), the outside of which forms part of a side surface (123; 123′) of the key blade and the inside of which comprises a side wall portion (126; 126′) being inclined and facing the bottom wall (124; 124′) of the groove. The undercut portion (129; 129′) of the groove is expanded, at its innermost part adjacent to the inclined side wall portion (126; 126′), into a longitudinally extending pocket (135; 135′).
Owner:WINLOC
Contactless identification tag, data communication system and contactless identification tag control program
InactiveUS7243855B2Reduce probabilityIncrease the number ofMemory record carrier reading problemsCo-operative working arrangementsData controlCommunications system
A data communication system includes a host device, a reader / writer device and a plurality of contactless identification tags. The contactless identification tag includes a data reception section, a data transmission section, a data control section, a data storage section, a driving electric current generation section and a coil antenna. In response to a command from the reader / writer device, the data control section generates a random number, and sets a time slot number based on the random number and a unique identification number stored in advance in the data storage section.
Owner:SEIKO EPSON CORP
Cloud platform-based combined safety lock system and control method thereof
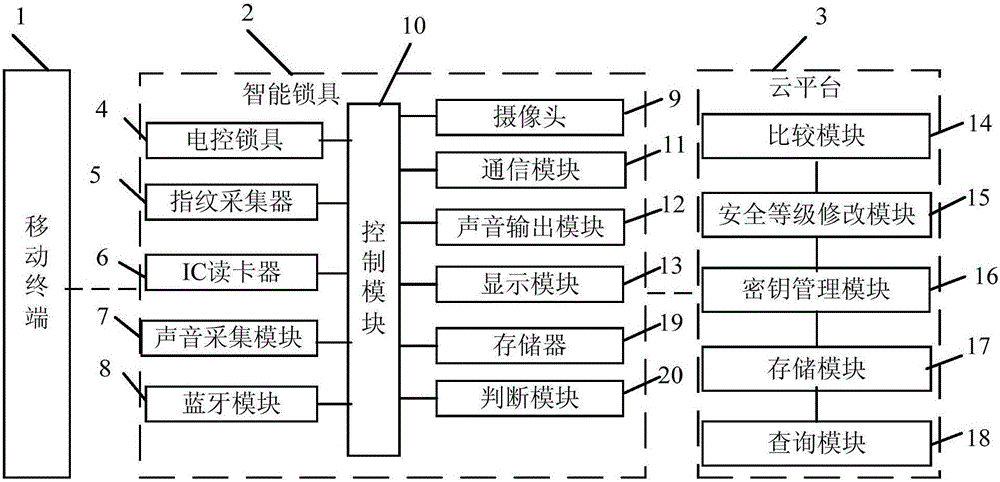
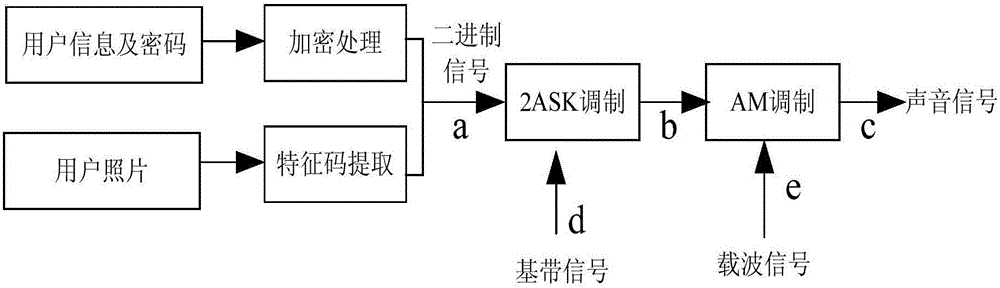
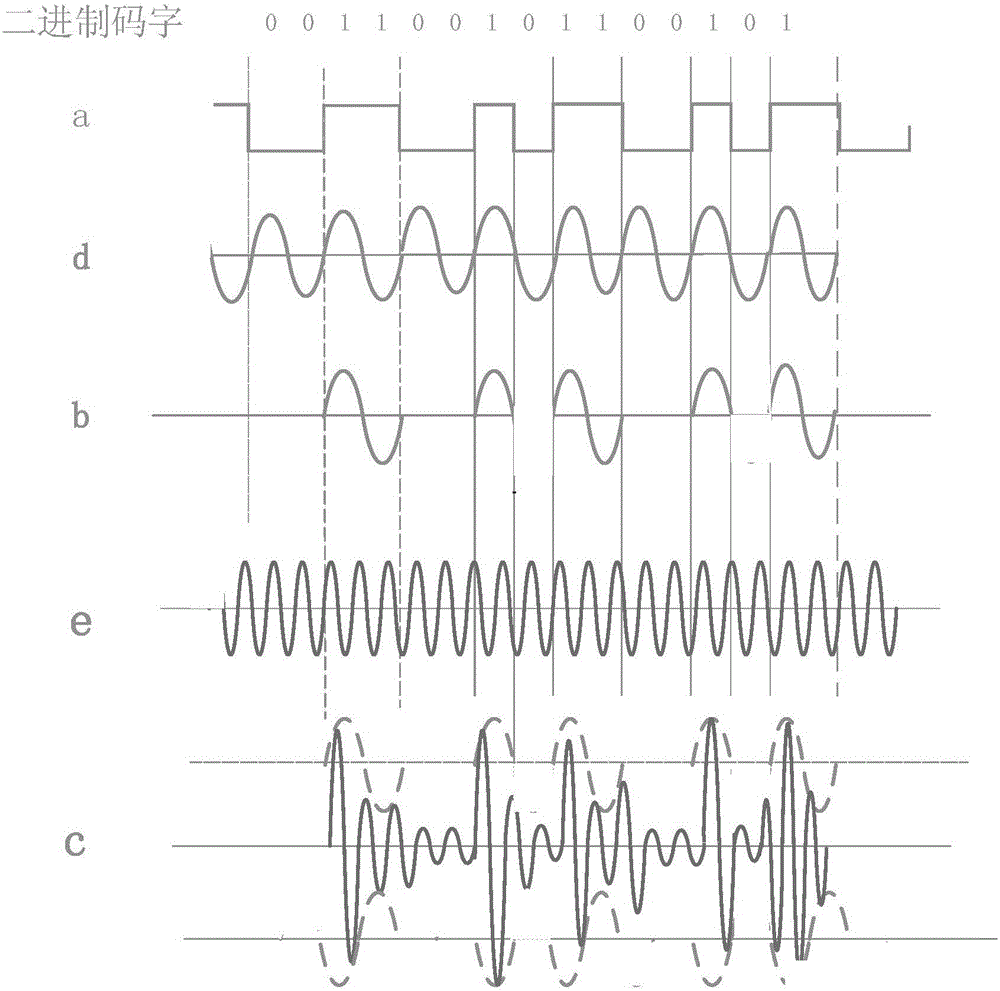
InactiveCN106023369AImprove securityModify security levelIndividual entry/exit registersElectronic control systemPassword
The invention discloses a cloud platform-based combined safety lock system and a control method thereof. The system comprises a cloud platform, a mobile terminal and an intelligent lock connected to cloud; an unlock APP is installed in the mobile terminal and used for receiving a locking password and transmitting it to the intelligent lock or for encrypting the unlocking password and modulating it into an acoustic signal transmitted to the intelligent lock, and the unlocking password is characteristic values of the face of an unlocking user or user information and password entered by the unlocking user; the intelligent lock comprises a control module and the following items connected with the control module: an electronic control module, a fingerprint acquirer, an IC (integrated circuit) card reader, a sound acquisition module, a Bluetooth module, a communication module, a storage and a judging module; the cloud platform comprises a comparison module, a safety level correcting module, a key management module and a storage module. The safety level herein may be adjusted in real time, the system is applicable to places with different safety level requirements or requiring frequent safety level adjustment, and the system enables real-time management for all intelligent locks connected to the cloud platform.
Owner:CHONGQING UNIV OF TECH
Personalized user authentication process
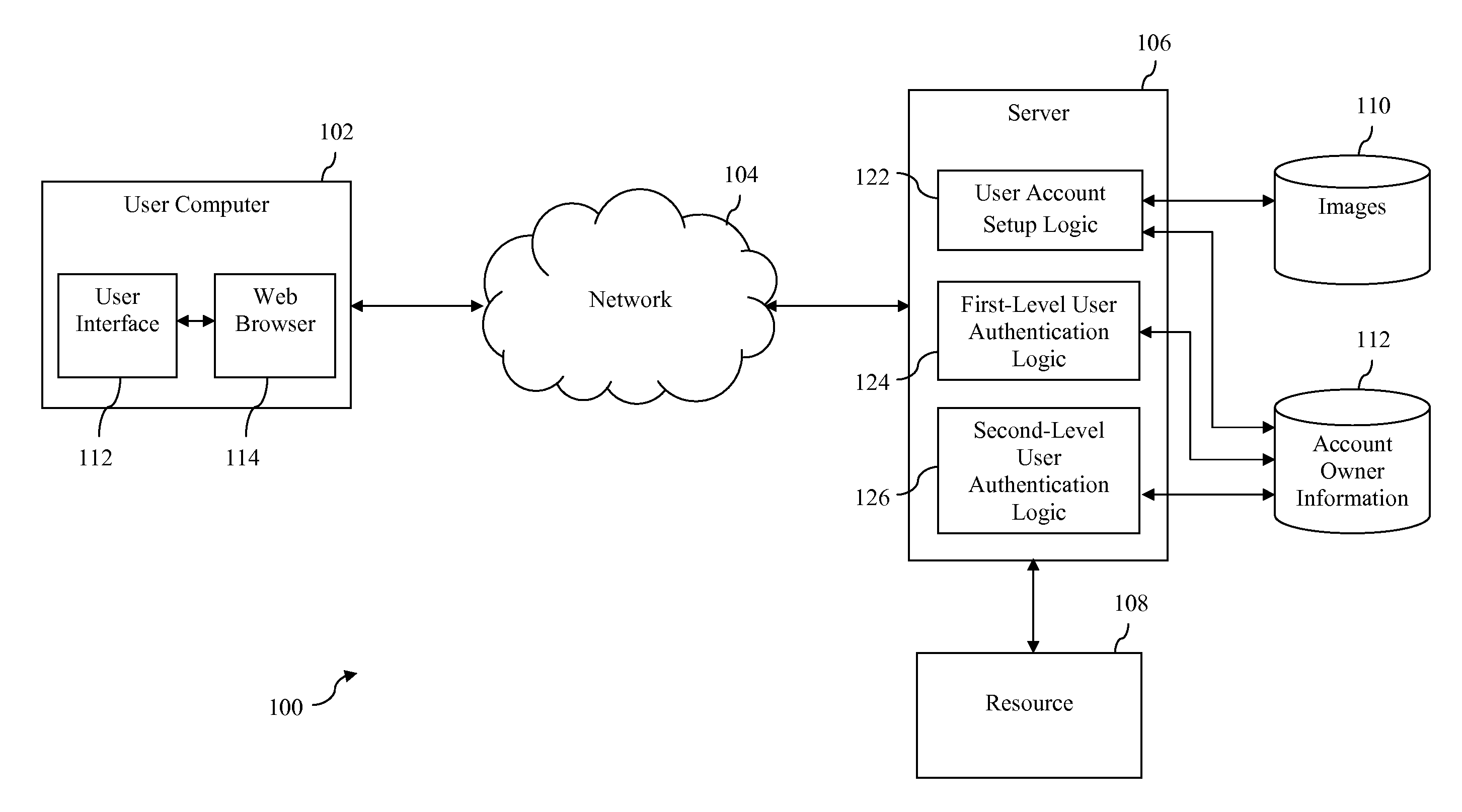
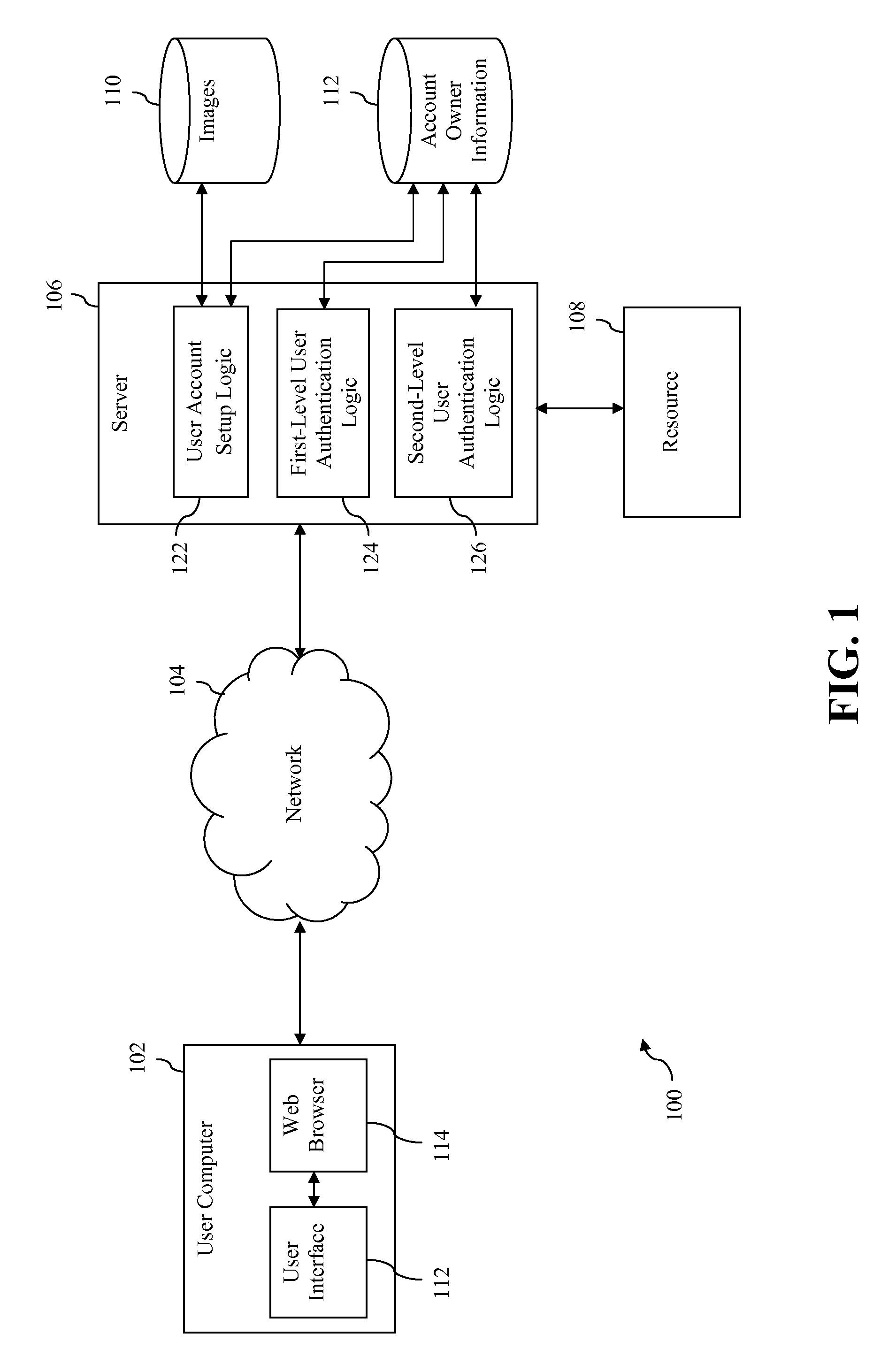
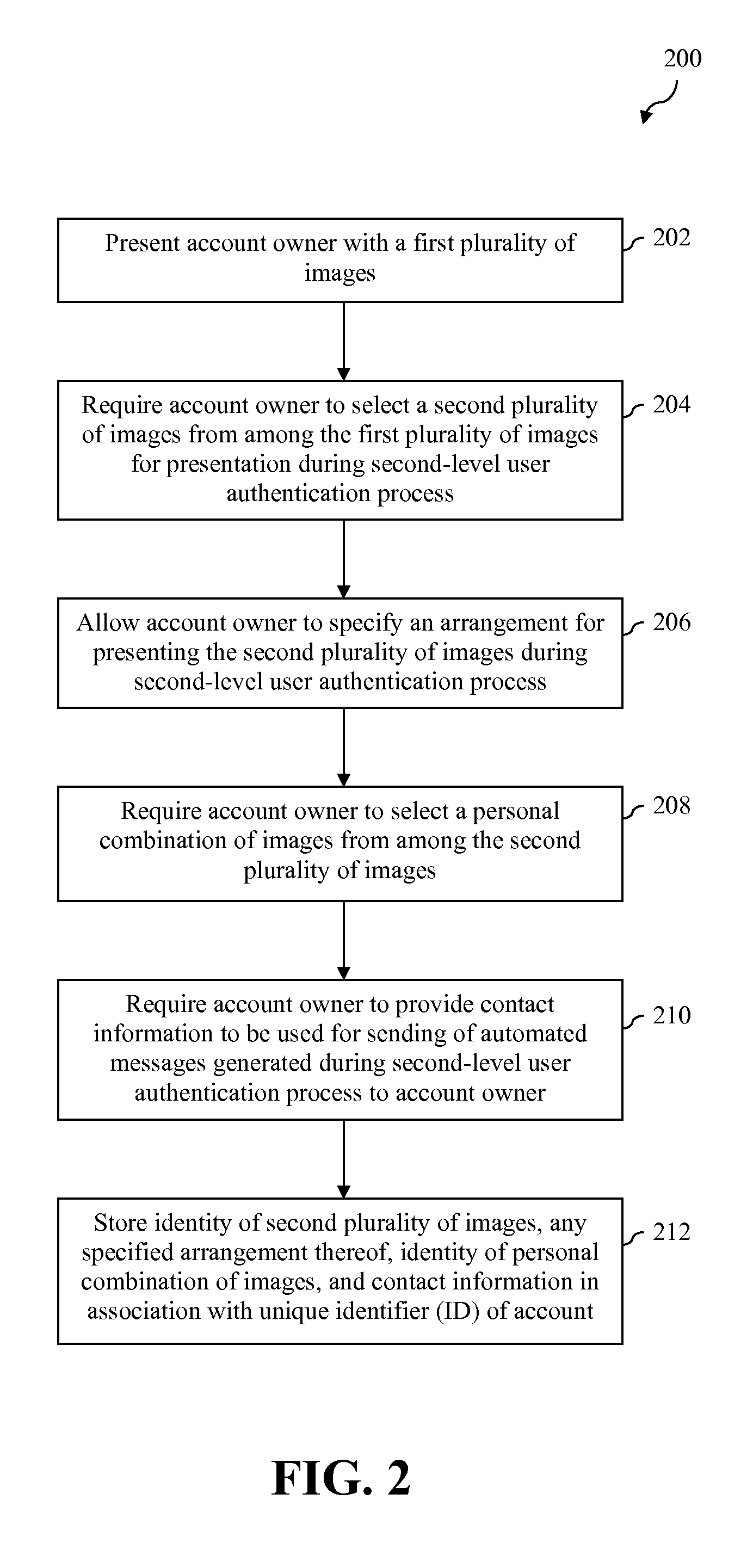
InactiveUS20100083353A1Maintaining ease-of-useImprove security levelDigital data processing detailsUser identity/authority verificationPersonalizationUser authentication
A system and method for authenticating a user seeking access to a resource via a computer is described herein. In accordance with one embodiment, a person authorized to control access to the resource selects a personalized combination of non-text elements, a collection of non-text elements from which the combination must be selected, and an arrangement in which the collection of non-text elements is presented to the user. When the user attempts to access the resource, the system presents the collection of non-text elements to the user and requires the user to select a combination of non-text elements from among the collection of non-text elements that matches the personalized combination previously selected by the person authorized to control access to the resource.
Owner:OATH INC
Metameric security devices using an active material
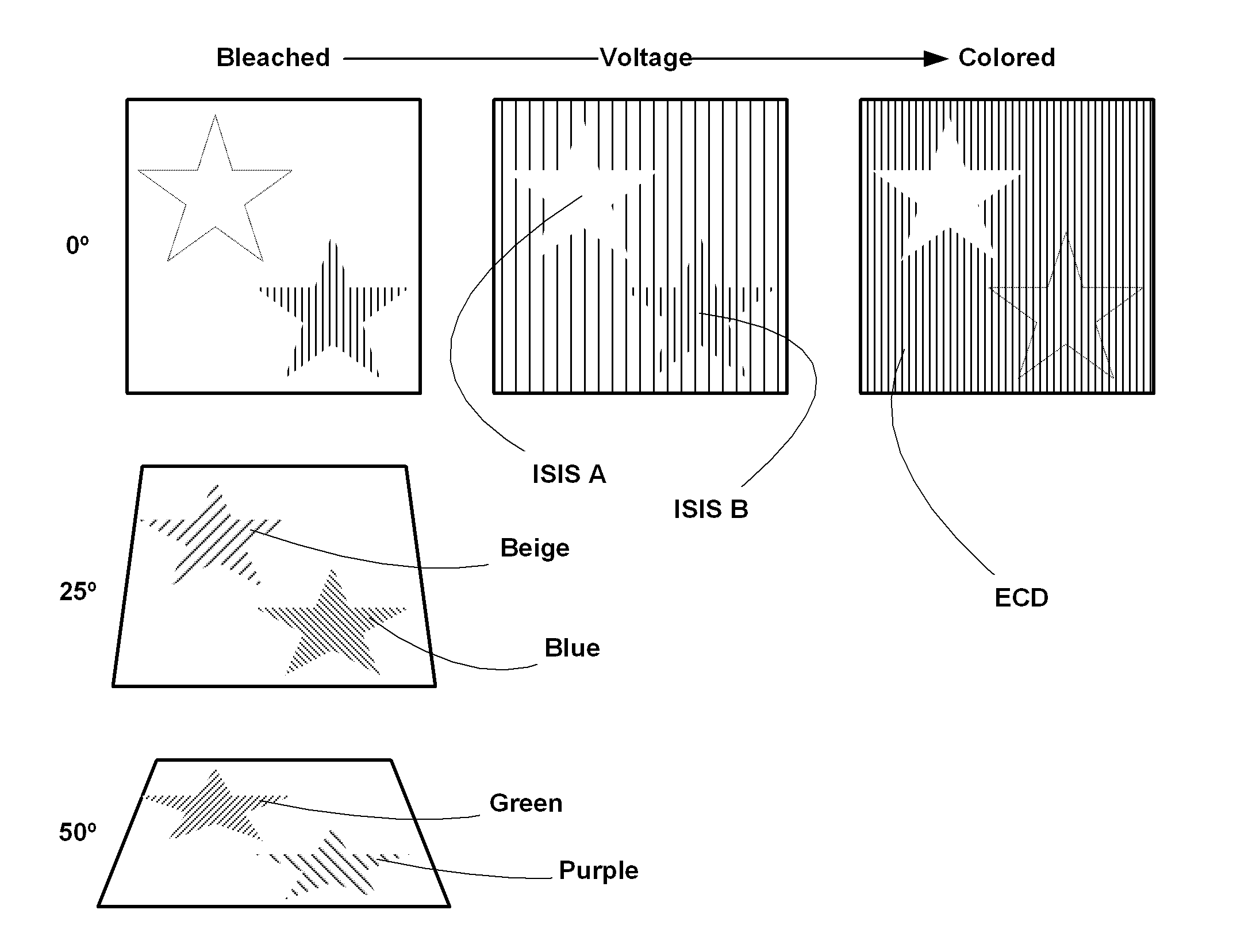
ActiveUS20130147179A1Not easy to copyImprove performanceOther printing matterCoding/ciphering apparatusElectricityChange color
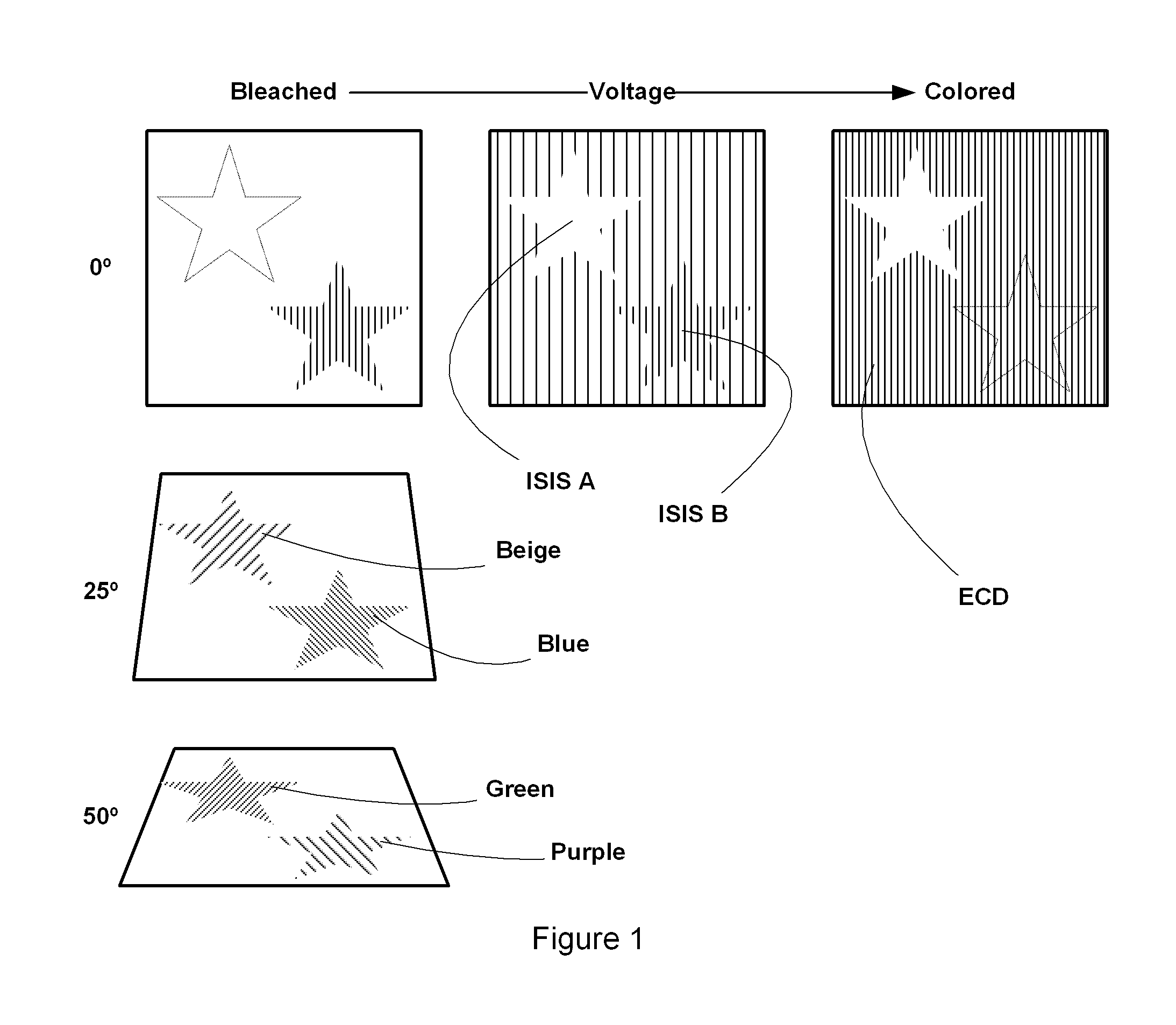
An integrated security structure is provided employing an external source of energy to change the appearance of the structure rendering the structure more challenging to duplicate due to its complexity. The security structure includes a substrate forming part of a bank note, identification document, or other security device; an active device within the substrate changing color between at least two colors wherein a color of the substrate surrounding the active device matches one of the at least two colors to form a metameric device. At least one Interference Security Image Structure (ISIS) is configured to be metameric with a bleached state of the active device and is therefore invisible at normal incidence. Another ISIS is metameric with the colored state of the electrochromic device and consequently becomes invisible during coloration. When the whole device is tilted, both ISIS's change color while the rest of the device essentially remains the same.
Owner:POLYVALOR LP
Data encryption method and system
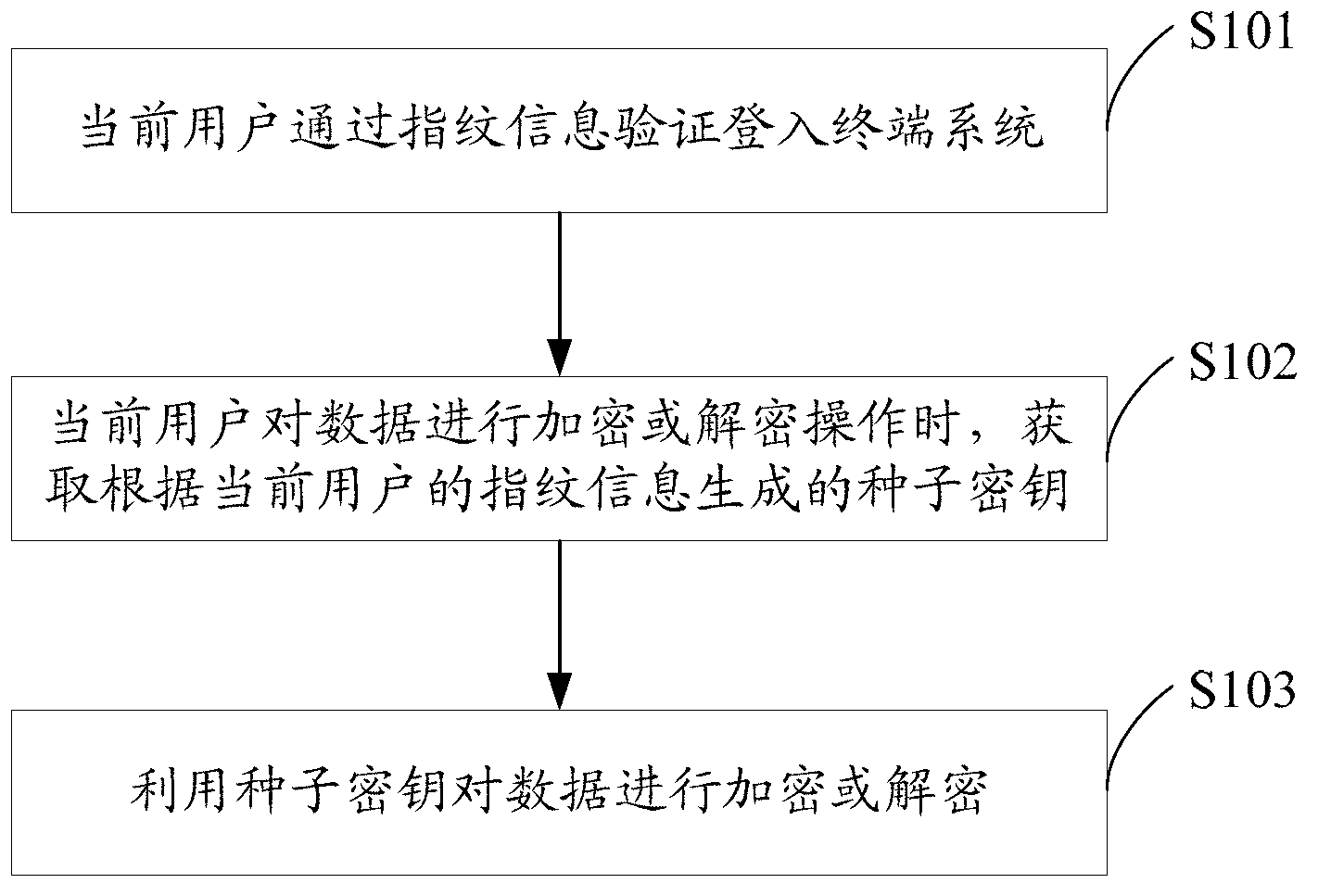
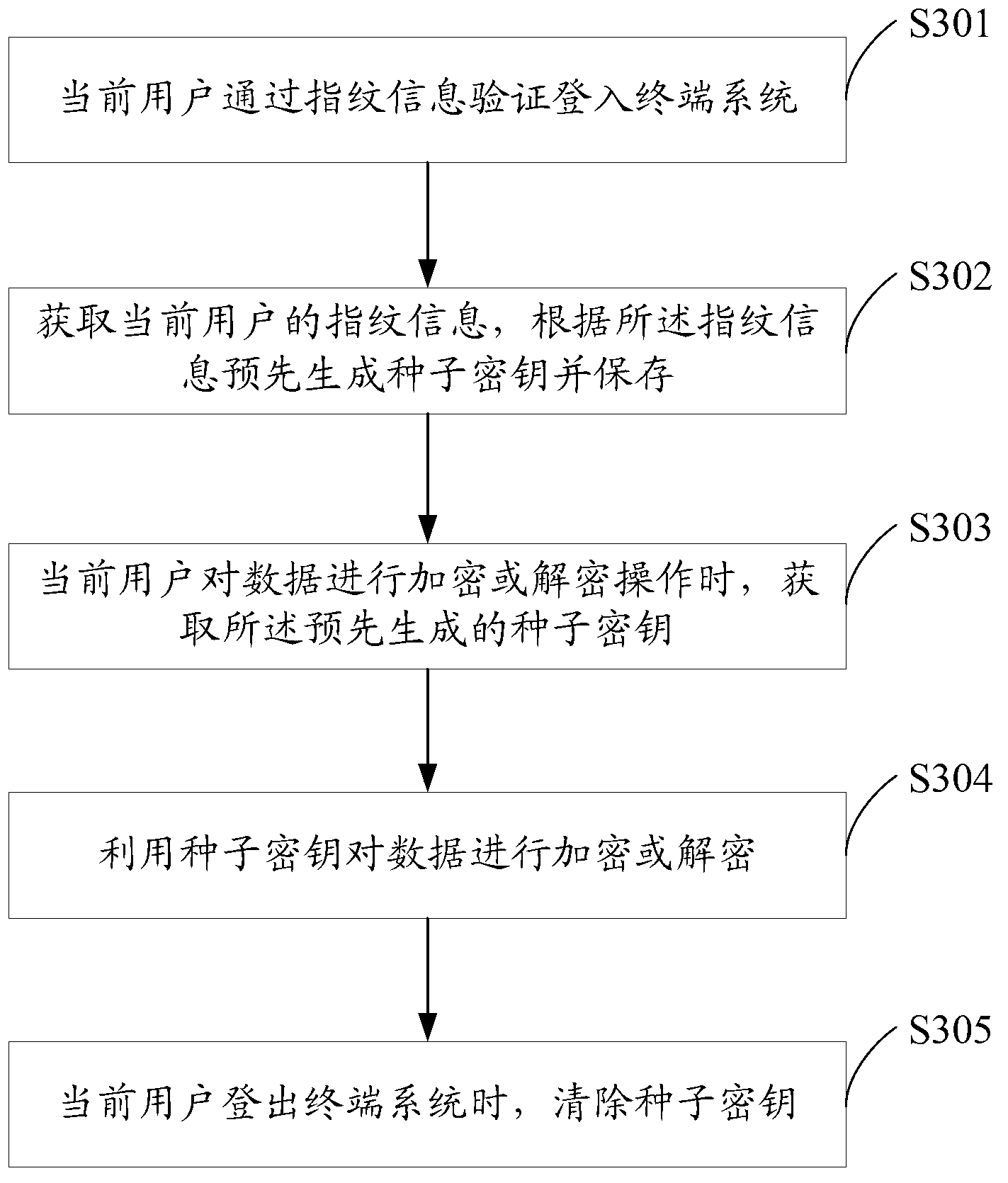
InactiveCN103236930AImprove securityNot easy to loseUser identity/authority verificationCharacter and pattern recognitionComputer scienceTerminal system
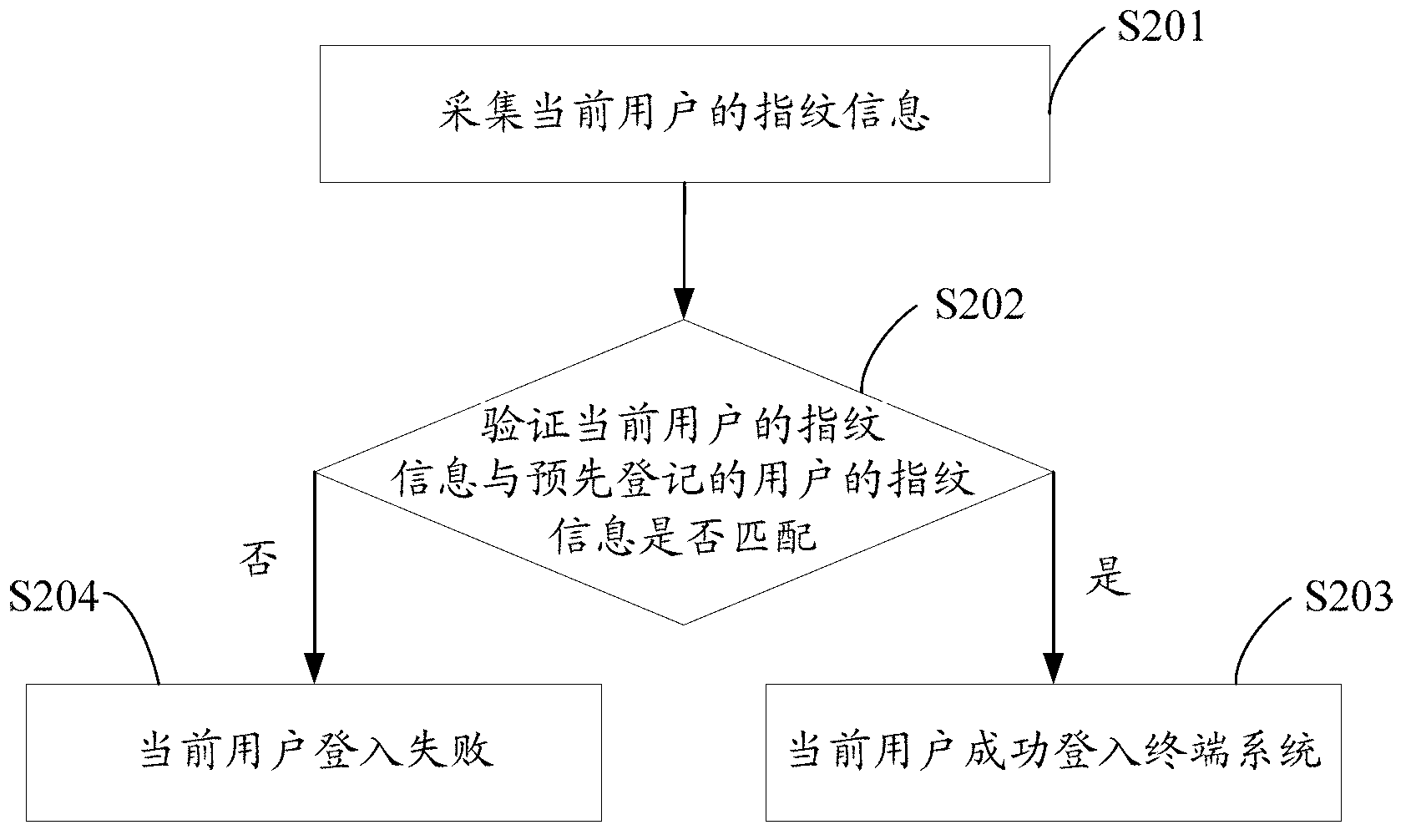
The invention discloses a data encryption method and system. The data encryption method comprises the steps of obtaining a cipher key which is generated according to fingerprint information of a current user when the current user conducts encryption or decryption operation to data; and encrypting or decrypting the data by using the cipher key. Since the fingerprint information of users is different, the cipher keys which are generated according to the fingerprint information are different, i.e. each user owns a unique cipher key and further owns a unique data encryption method. The cipher key is generated according to the fingerprint information through a preset rule in terminal systems. Even though the finger information of the users is illegally copied and stolen, encrypted files in the terminal systems cannot be decrypted in other systems, so that the security of user data is greatly improved.
Owner:NUBIA TECHNOLOGY CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com