Duplicate coding internet of things traceability security label and 2-dimensional bar code security traceability method
A technology of anti-counterfeiting labels and two-dimensional codes, which is applied to collaborative devices, record carriers used by machines, instruments, etc., can solve the problems of being easy to be copied, and achieve the effect of not easy to copy and good security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
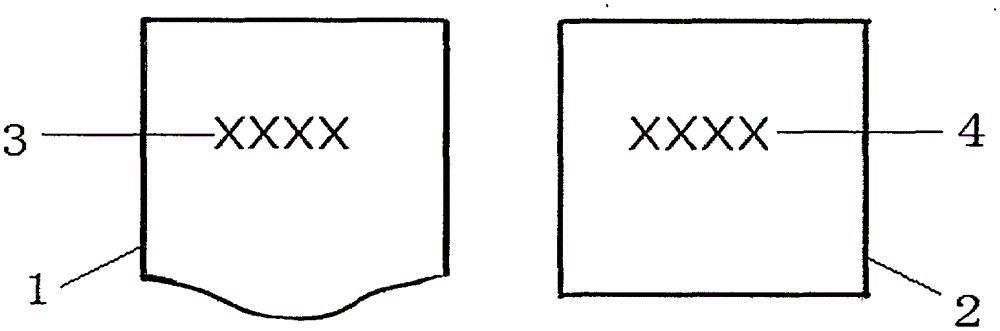
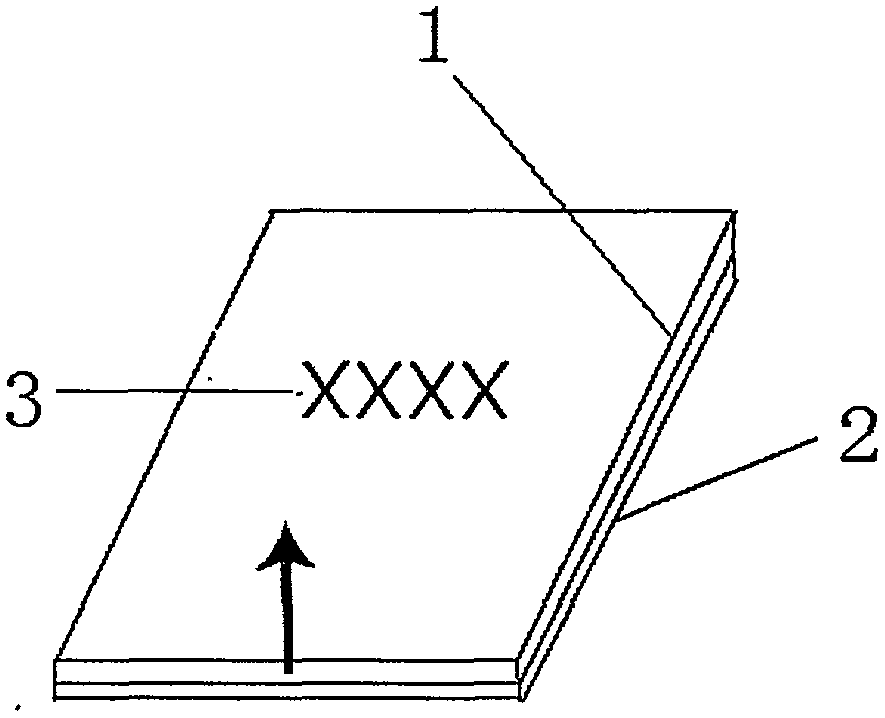
[0038] see figure 1 and figure 2 , the Internet of Things traceability anti-counterfeiting label of this double code includes a QR code, an upper label 1 and a lower label 2; the QR code includes a QR code outer code 3 and a QR code inner code 4; the QR code outer code 3 setting On the upper label 1, it is used for commodity traceability query; the two-dimensional code internal code 4 is set on the lower label 2, used for anti-counterfeiting verification; only the edge is bonded between the upper label 1 and the lower label 2, and the upper label 2 is set. tear mouth. Both the outer code 3 of the QR code and the inner code 4 of the QR code are composed of URL, version number, product ID, service group, carrier category and manufacturer-defined data, and the outer code 3 of the QR code and the inner code of the QR code 4 are all one type of two-part, that is, two-part code; the carrier type of the outer code 3 of the two-dimensional code adopts W to represent the outer code;...
Embodiment 2
[0129] see figure 1 , figure 2 and image 3 , the two-dimensional code anti-counterfeit traceability method includes the following steps:
[0130] Make a double-coded Internet of Things traceability anti-counterfeiting label: the two-dimensional code includes the outer code 3 of the two-dimensional code and the inner code 4 of the two-dimensional code; set the outer code 3 of the two-dimensional code on the upper label 1 for commodity traceability query; The inner code 4 of the two-dimensional code is set on the lower label 2 for anti-counterfeiting verification; only the edge is bonded between the upper label 1 and the lower label 2 and there is a tear on the upper label 1; the outer code 3 of the two-dimensional code and the second The internal code 4 of the two-dimensional code is composed of URL, version number, product ID, service group, carrier category, and manufacturer-defined data, and the external code 3 of the two-dimensional code and the internal code 4 of the t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com