Identity authentication method, terminal device, authentication server, and electronic device
An authentication server and terminal equipment technology, applied in digital data authentication, electrical components, digital transmission systems, etc., can solve the problem that the authenticator cannot be authenticated or authorized, so as to reduce the risk of theft, facilitate operation, and ensure security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
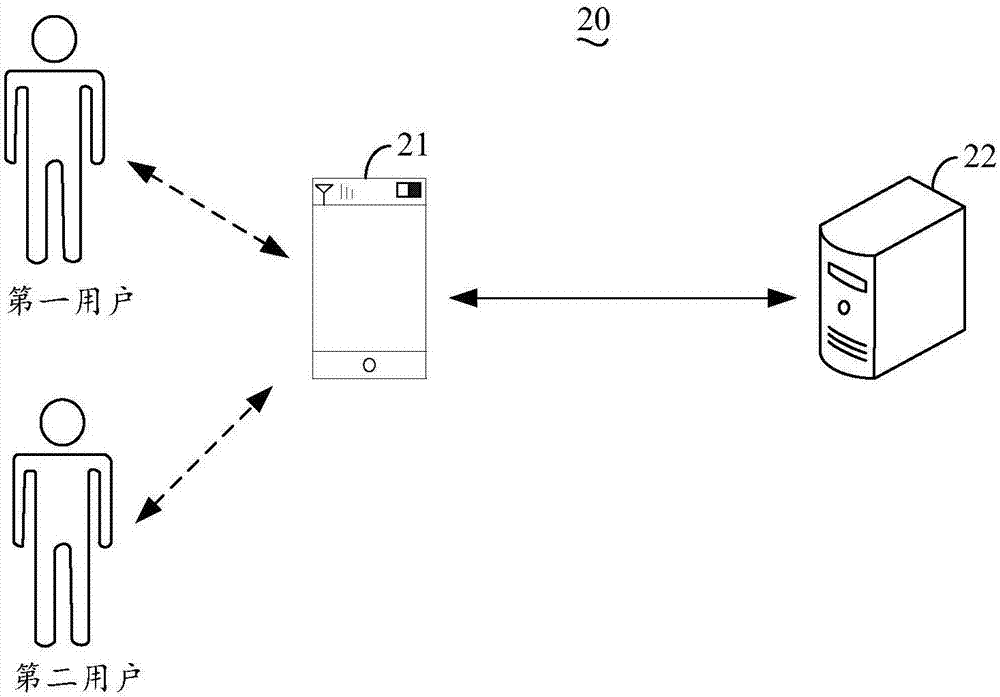
[0031] see figure 1 , figure 1 It is an application scenario diagram of identity authentication provided by the embodiment of the present invention. The identity authentication system 20 includes a terminal device 21 and an authentication server 22, wherein the terminal device 21 is configured with a biometric identification module, and the biometric identification module is used to identify a biometric feature, wherein a biometric feature refers to a unique identification of a user. Features. In this embodiment, the biological features may include features such as fingerprints, faces, irises, or palm prints. The terminal device 21 may be a smart phone, a tablet computer, a PDA (Personal Digital Assistant, handheld computer) and the like.
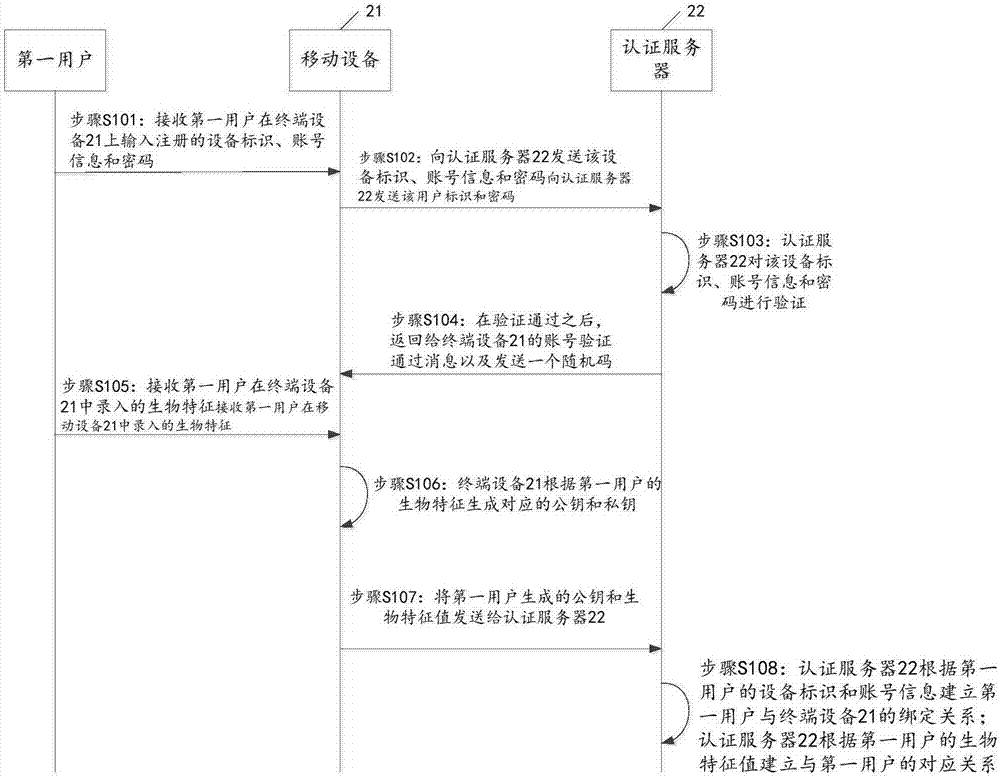
[0032]The terminal device 21 accepts the input of the first biometric feature of the first user, and acquires the account information of the first user and the device identification of the terminal device 21 . For example, in this embodi...
Embodiment 2
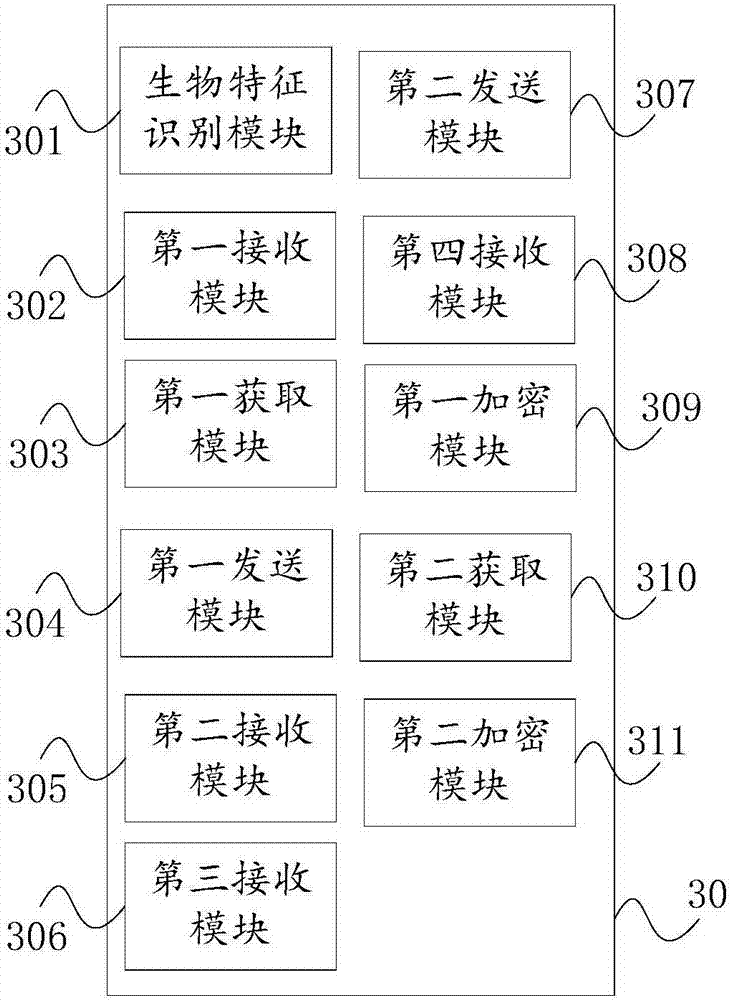
[0060] see image 3 , image 3 It is a schematic structural diagram of a terminal device provided in Embodiment 2 of the present invention. The terminal device 30 includes a biometric identification module 301, a first receiving module 302, a first acquiring module 303, a first sending module 304, a second receiving module 305, a third receiving module 306, a second sending module 307 and a fourth receiving module 308.
[0061]The biometric identification module 301 is configured to perform biometric identification. Wherein, the biometric feature refers to a feature that uniquely identifies the user. In this embodiment, the biometric feature may include features such as fingerprints, facial images, iris, or palm prints. The terminal device 21 may be a smart phone, a tablet computer, a PDA (Personal Digital Assistant, handheld computer) and the like.
[0062] The first receiving module 302 is configured to receive the inputted biometrics of the first user through the biomet...
Embodiment 3
[0075] see Figure 4 , Figure 4 It is a schematic diagram of an authentication server provided by Embodiment 3 of the present invention. The authentication server 40 includes a first receiving module 401 , a first returning module 402 , a second receiving module 403 , a generating module 404 and a second returning module 405 .
[0076] The first receiving module 401 is configured to receive identity authentication information sent by the terminal device, the identity authentication information carrying the account information of the first user, the first biometric feature of the first user and the device identification of the terminal device.
[0077] The first return module 402 is configured to return identity confirmation information to the terminal device after confirming the legal identity of the first user according to the identity authentication information.
[0078] The second receiving module 403 is configured to receive a verification request sent by the terminal d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com