Method for tampering secret stealing information on power line and preventing interference
A power line and stealing technology, applied in the direction of reducing electrical interference, distribution line transmission system, electrical components, etc., can solve the problems of easy data theft and inability to tamper with signals
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
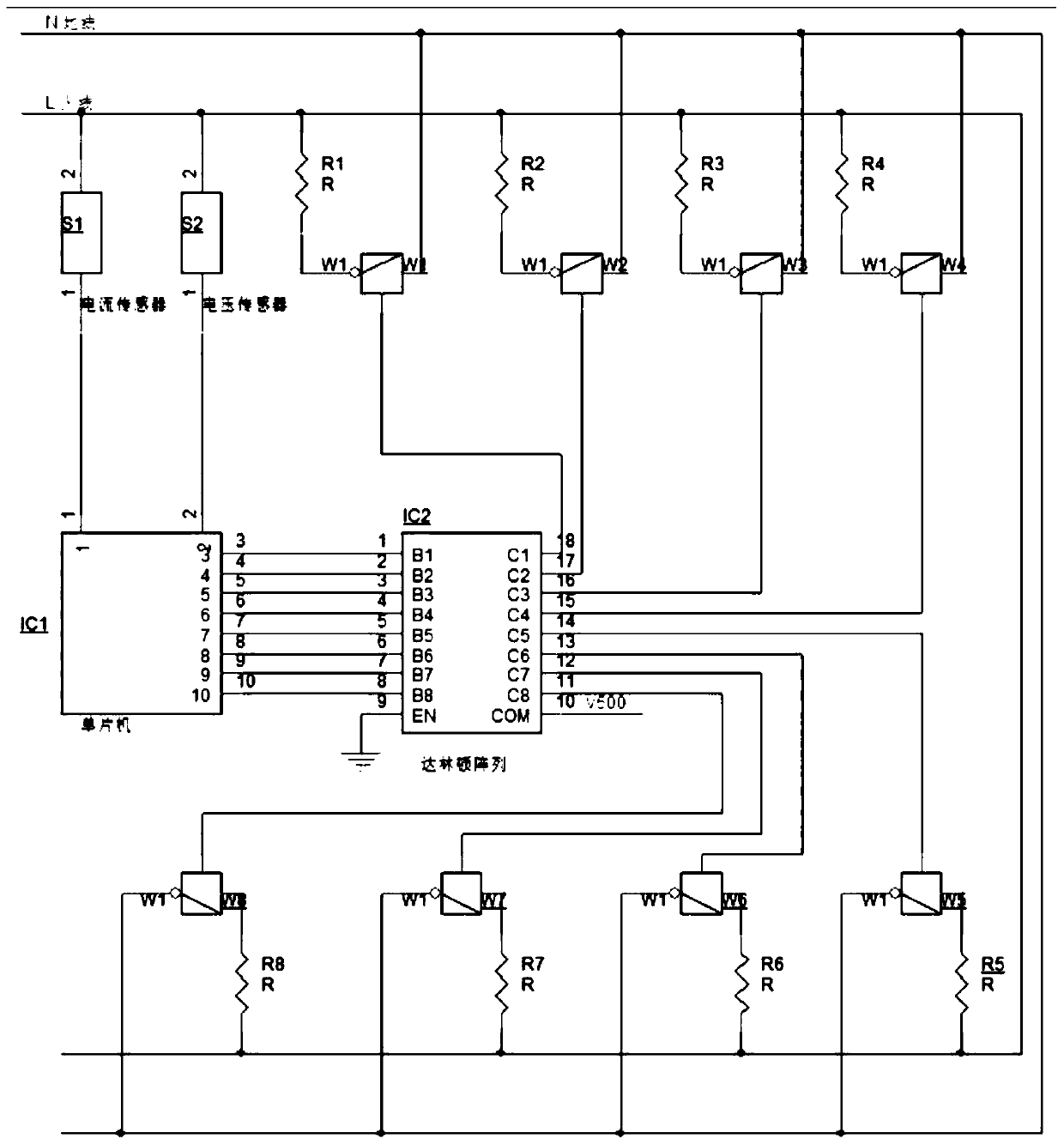
[0021] Such as figure 1 As shown, the embodiment of the present invention provides a method for tampering with stolen information on a power line and preventing interference, including the following steps:
[0022] 1) Install current and voltage sensors on both the live wire and the neutral wire, and then connect the current and voltage sensors to the ADC of the single-chip MCU;
[0023] 2) Use the single-chip microcomputer to perform high-speed sampling of the power information. The single-chip microcomputer performs AD conversion on the information on the current and voltage sensors. After calculation, it is judged whether there is any stolen information transmitted on the power line. If there is any stolen information transmitted, the wave of the stolen information is calculated. Baud rate, amplitude and waveform start time;
[0024] 3) The single-chip computer calculates the load value required to generate the information with the same amplitude according to the amplitude...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com