Patents
Literature
3311results about "Communication jamming" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
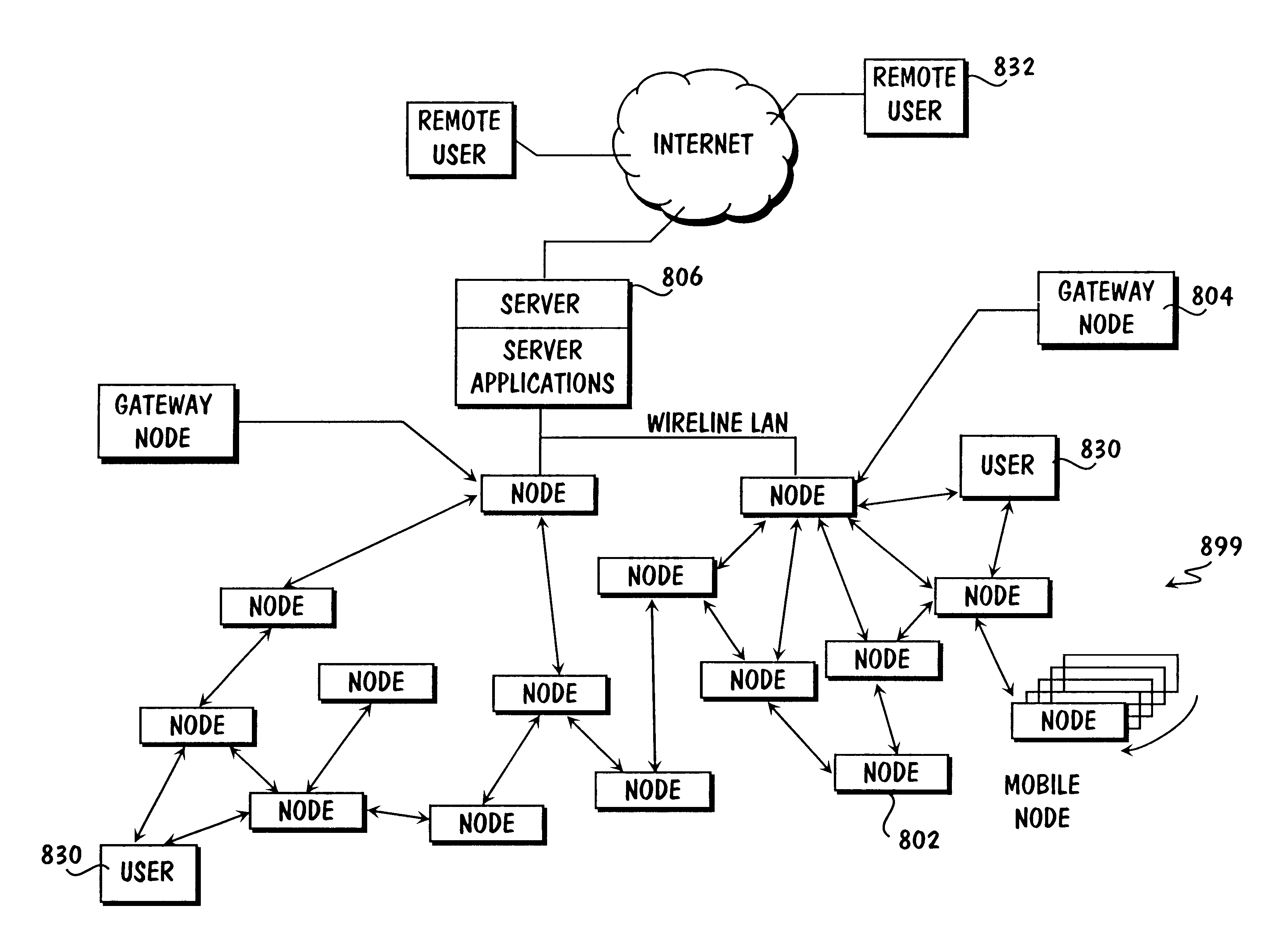
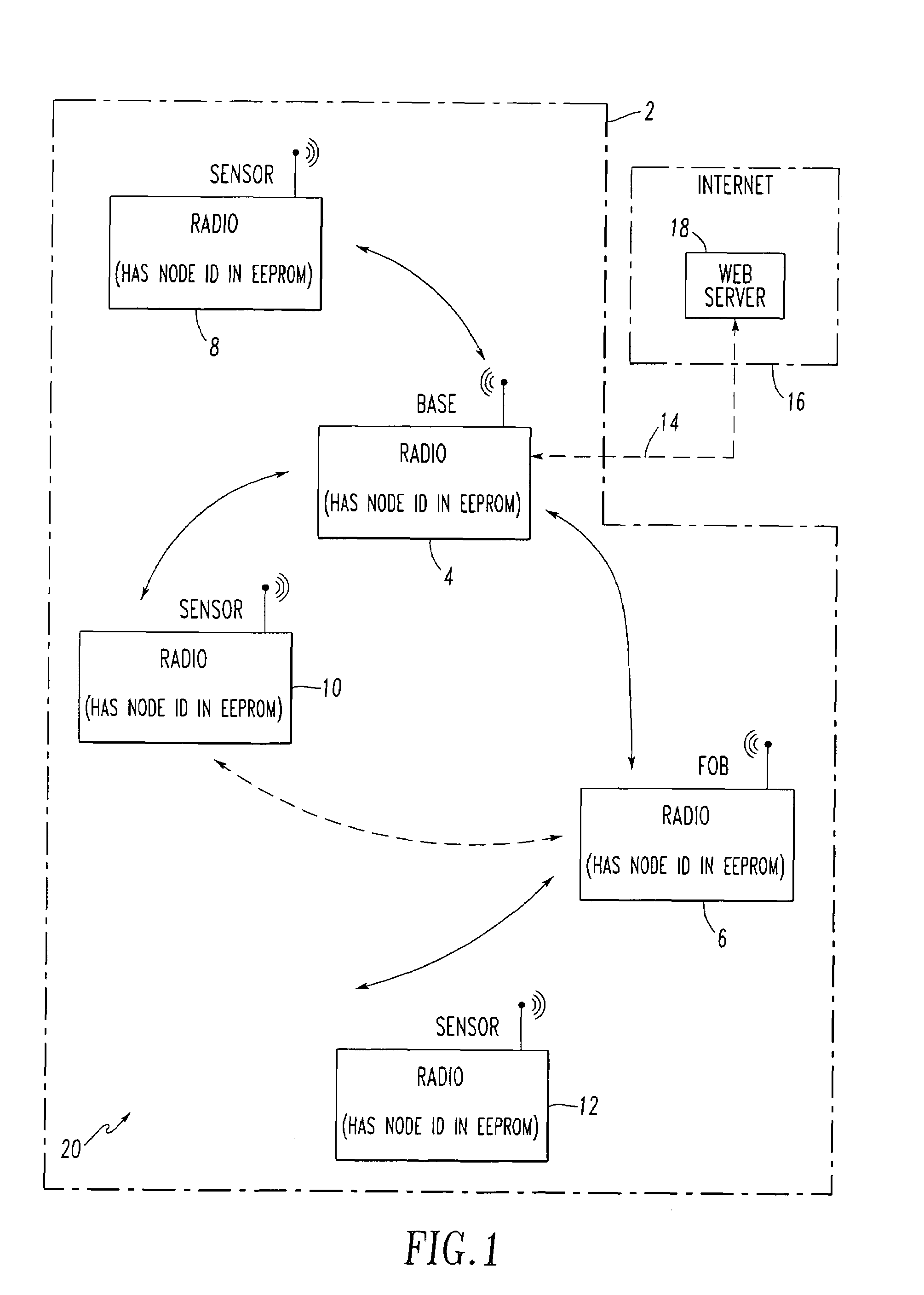
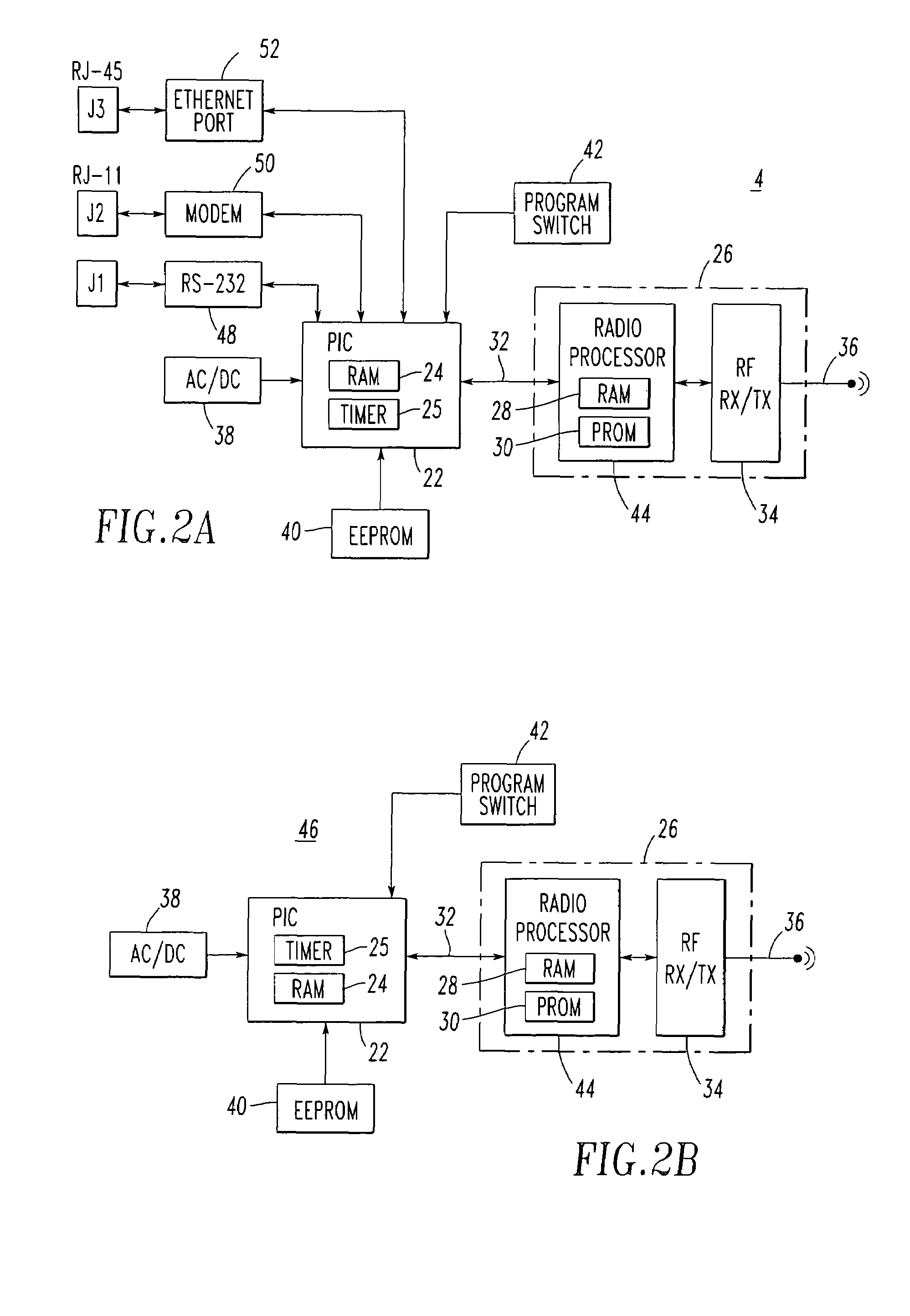
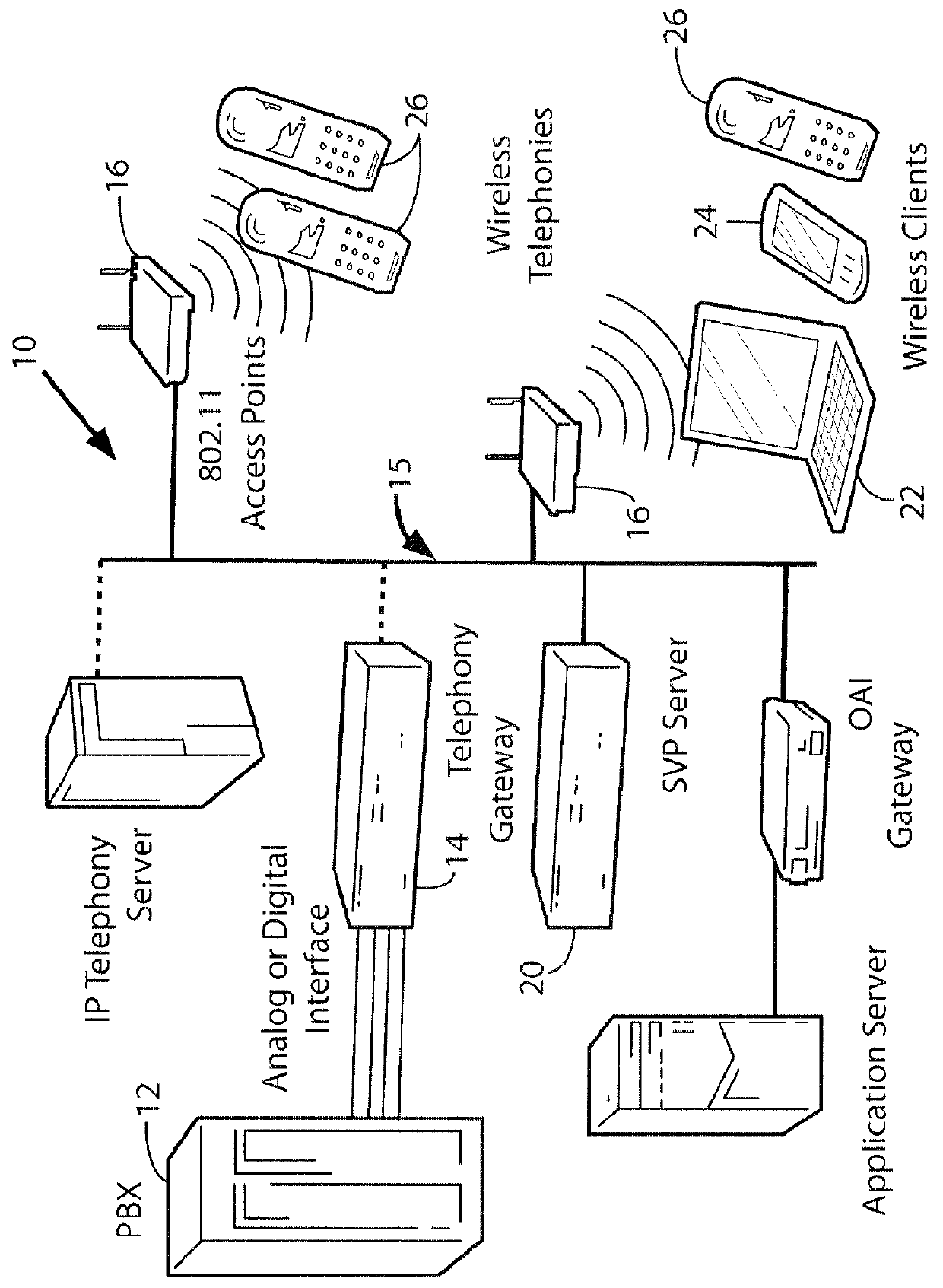
Method and apparatus for internetworked wireless integrated network sensor (WINS) nodes
InactiveUS6859831B1Ease real-time operating system issueImprove adaptabilitySpecific access rightsAnti-theft devicesReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
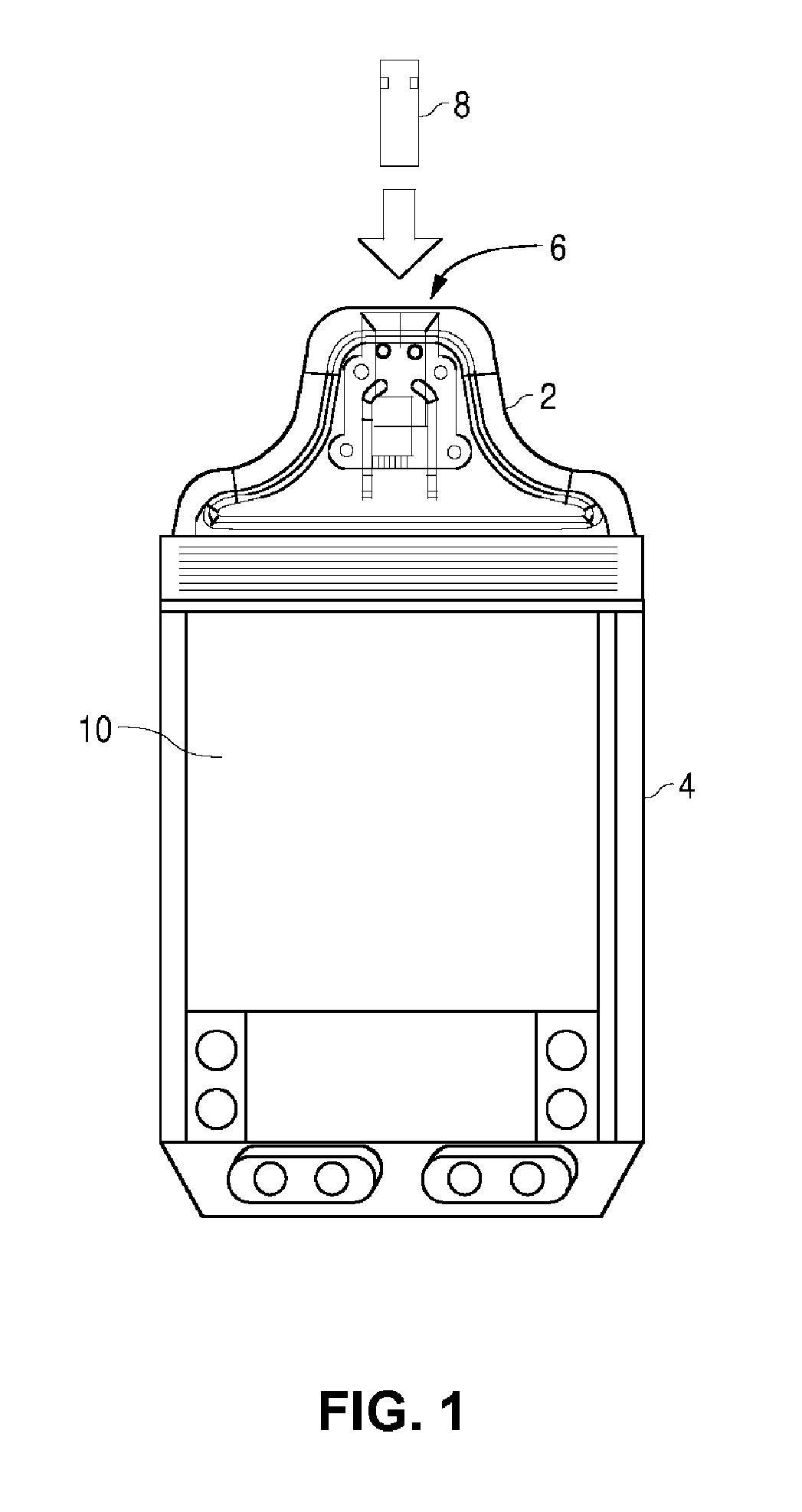
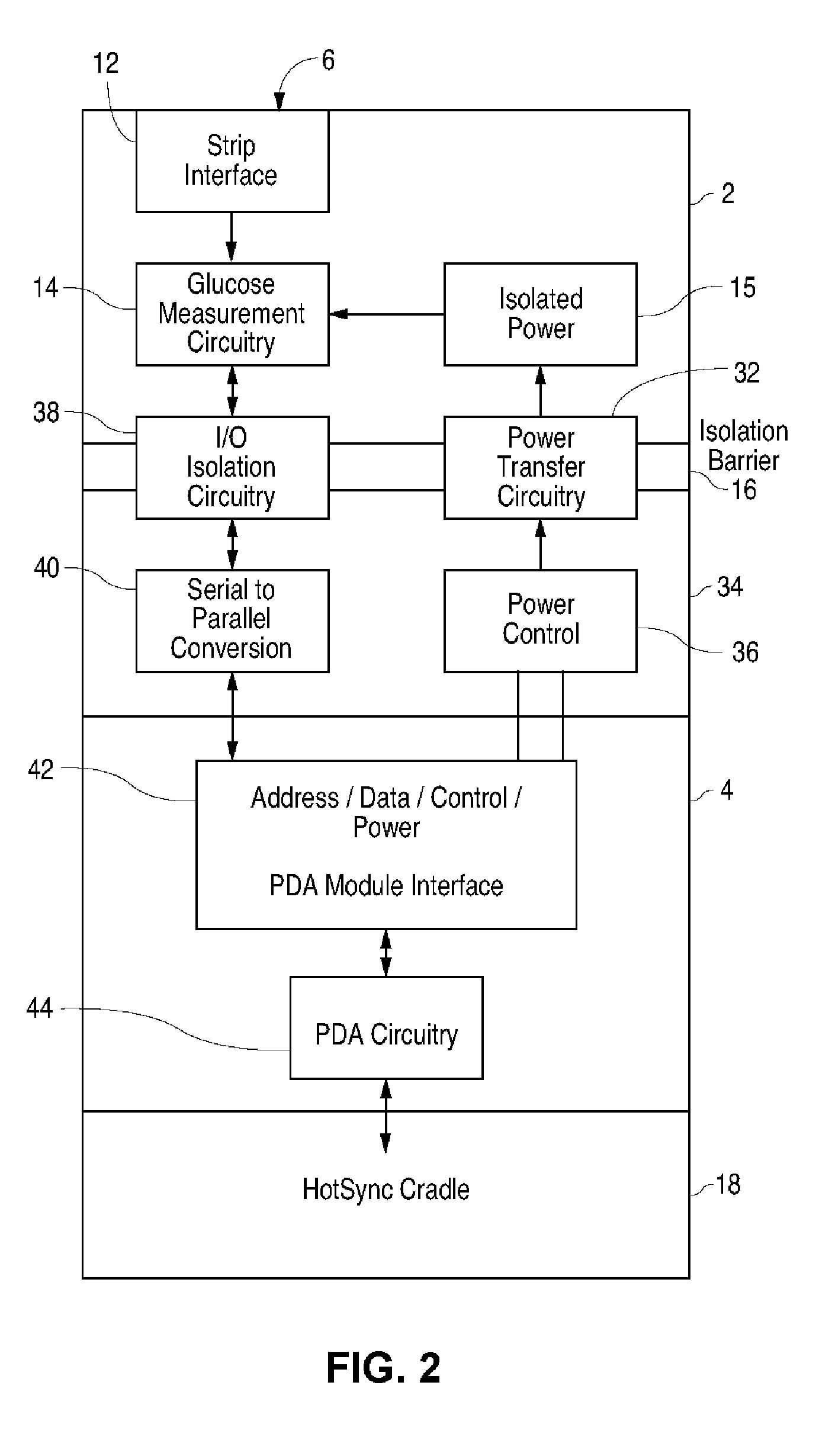
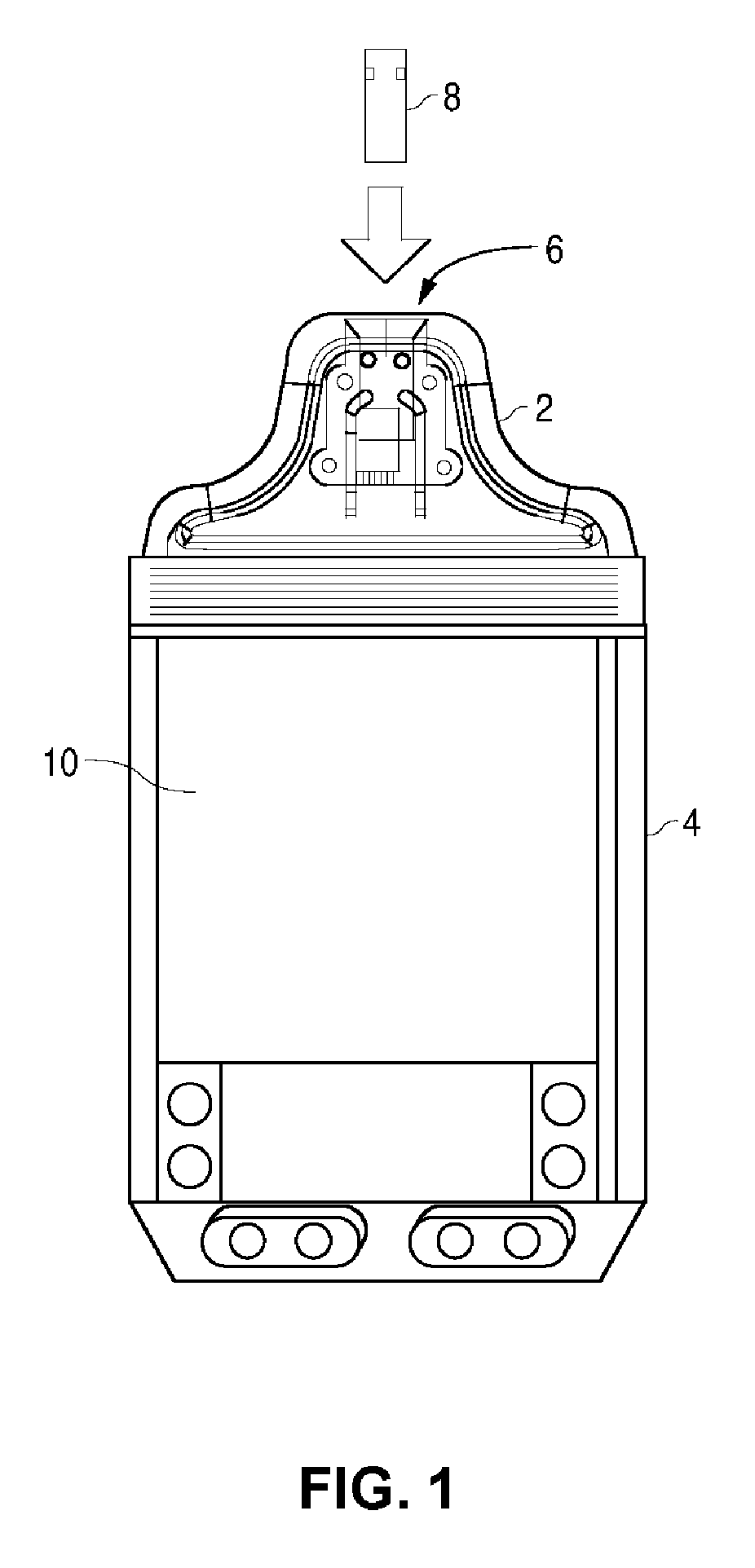
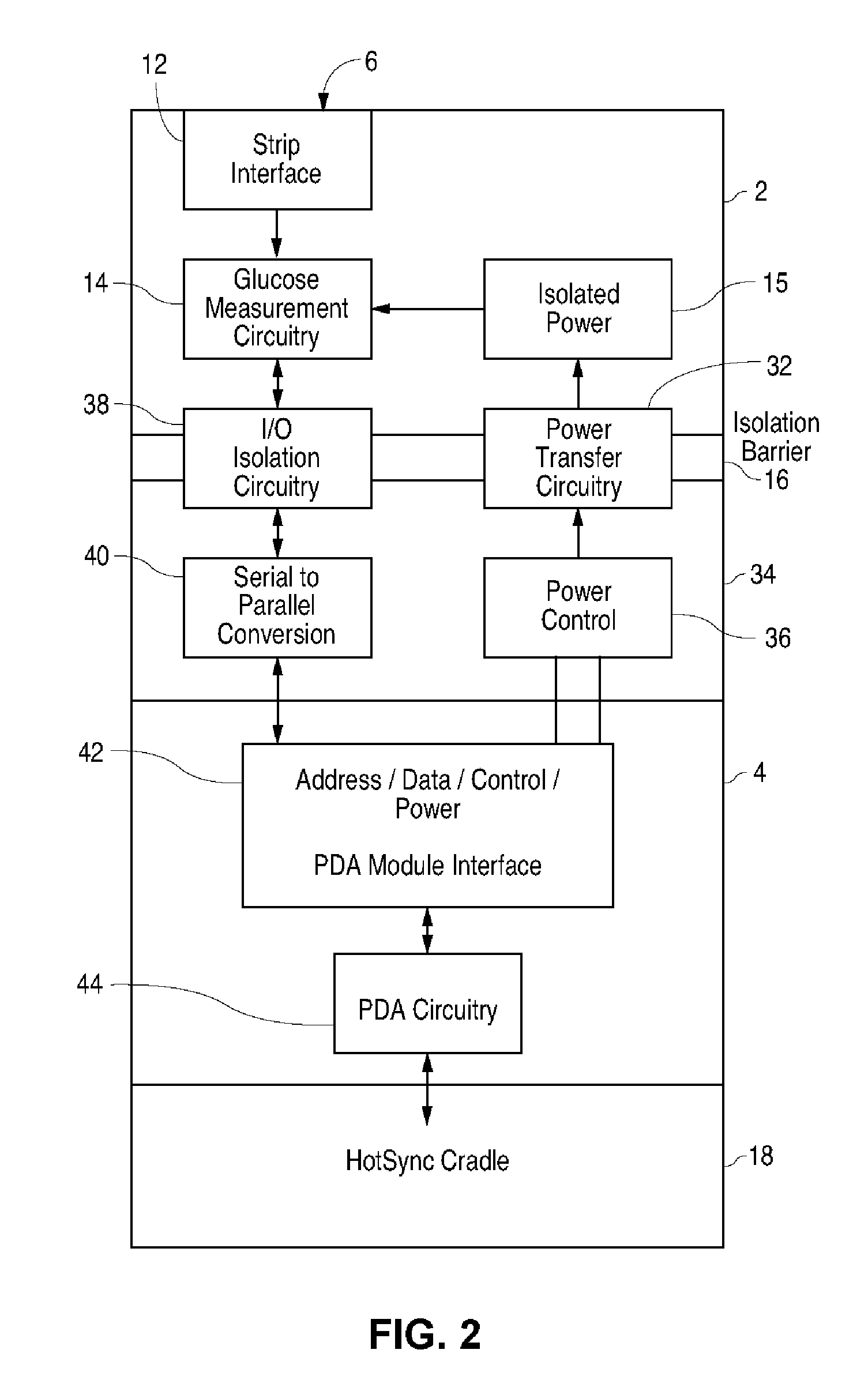
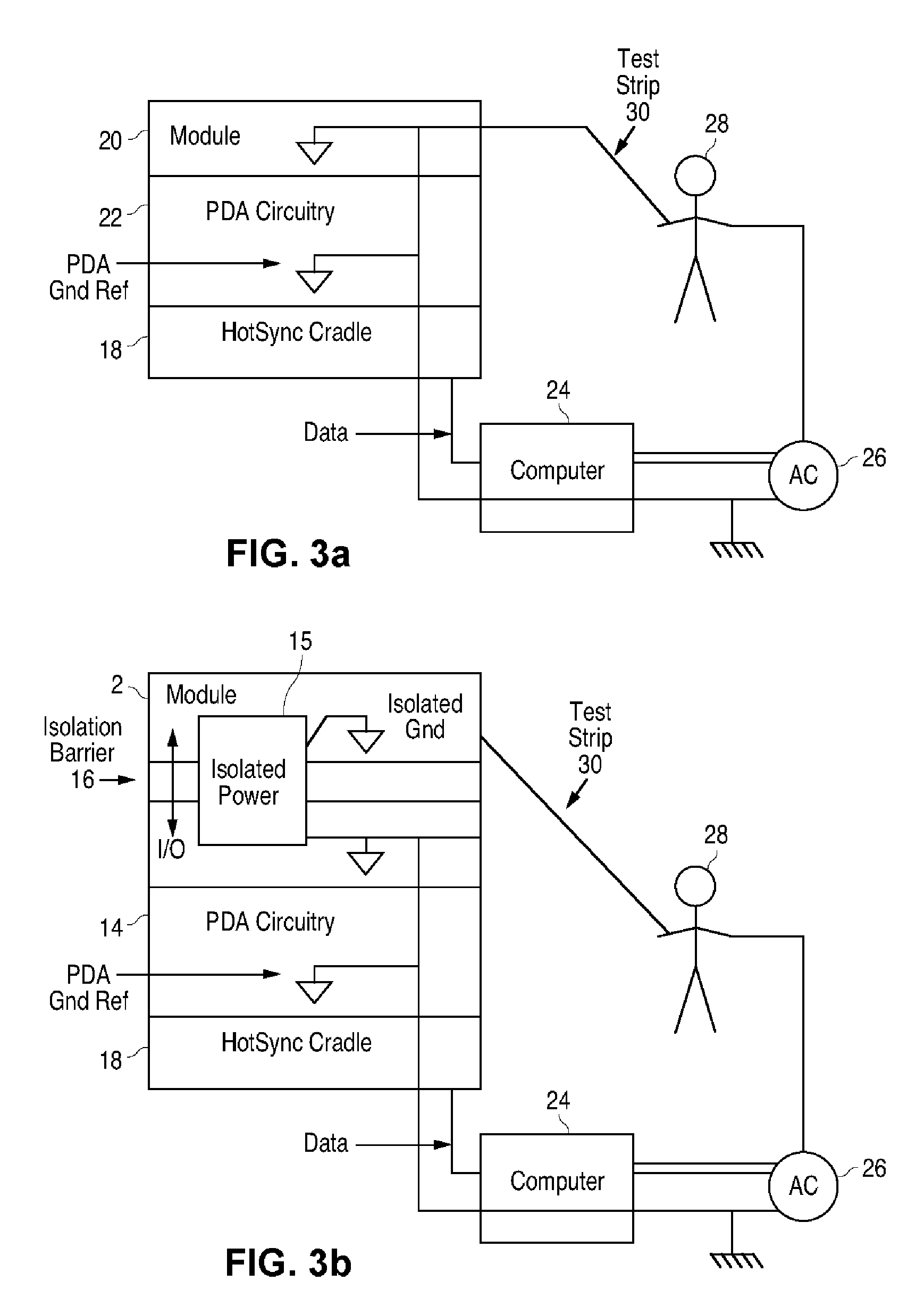
Blood glucose tracking apparatus and methods
ActiveUS20050239156A1Easy and precise applicationEfficient use ofBioreactor/fermenter combinationsBiological substance pretreatmentsHand heldComputer module
A measurement module for glucose testing includes a glucose testing measurement module housing, a test strip receptacle formed in the housing, and a connector portion formed in the housing and shaped to permit mechanical removable attachment of the housing to a hand-held computer. Electronics determine the amount of glucose present in a sample of body fluid, when the test strip is positioned in the receptacle and the body fluid is placed on a test strip, and communicate the glucose amount to the hand-held computer via the connector portion.
Owner:ABBOTT DIABETES CARE INC
Blood glucose tracking apparatus and methods
ActiveUS20050277164A1Easy and precise applicationEfficient use ofBioreactor/fermenter combinationsBiological substance pretreatmentsHand heldComputer module
Owner:ABBOTT DIABETES CARE INC
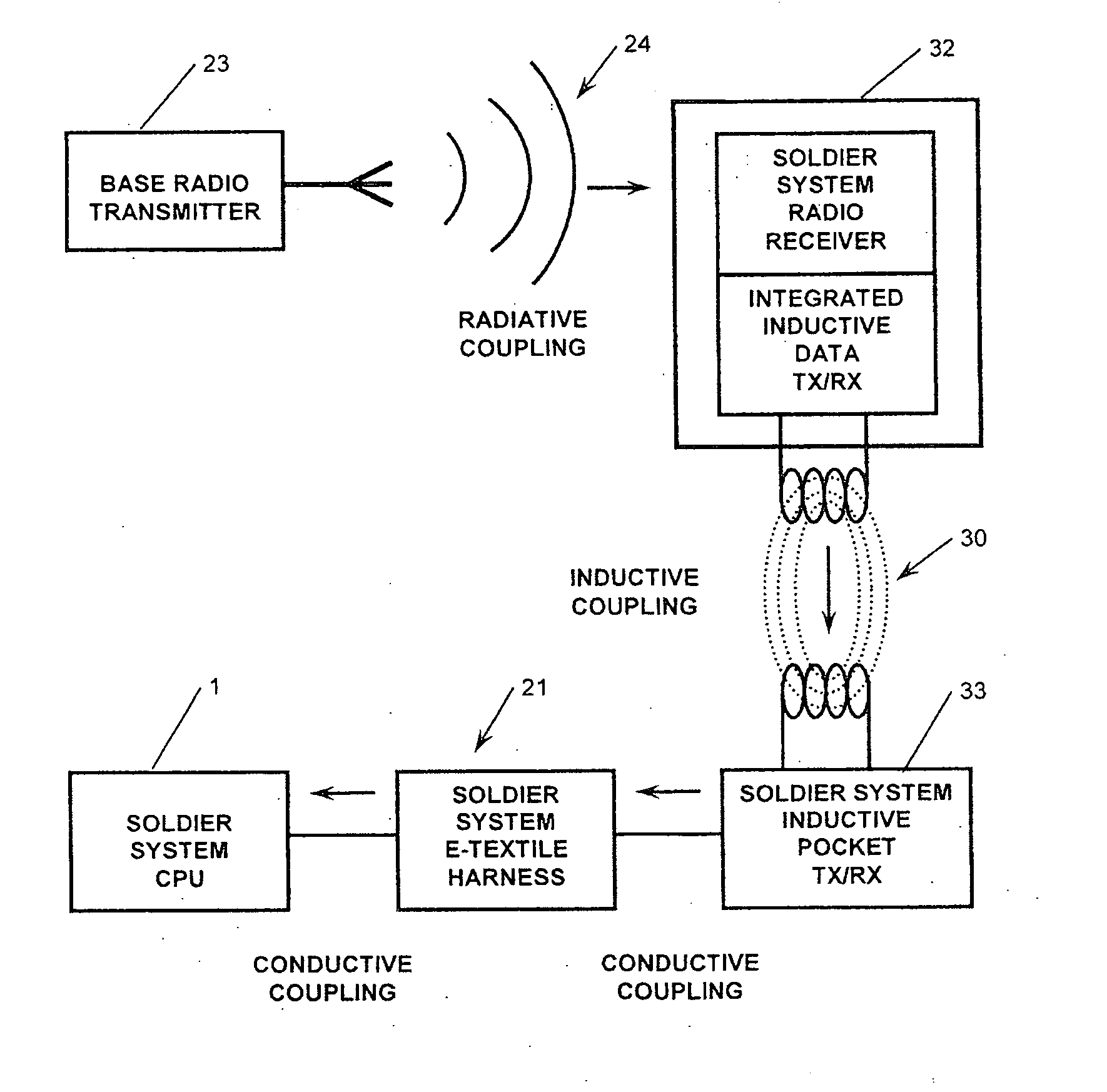
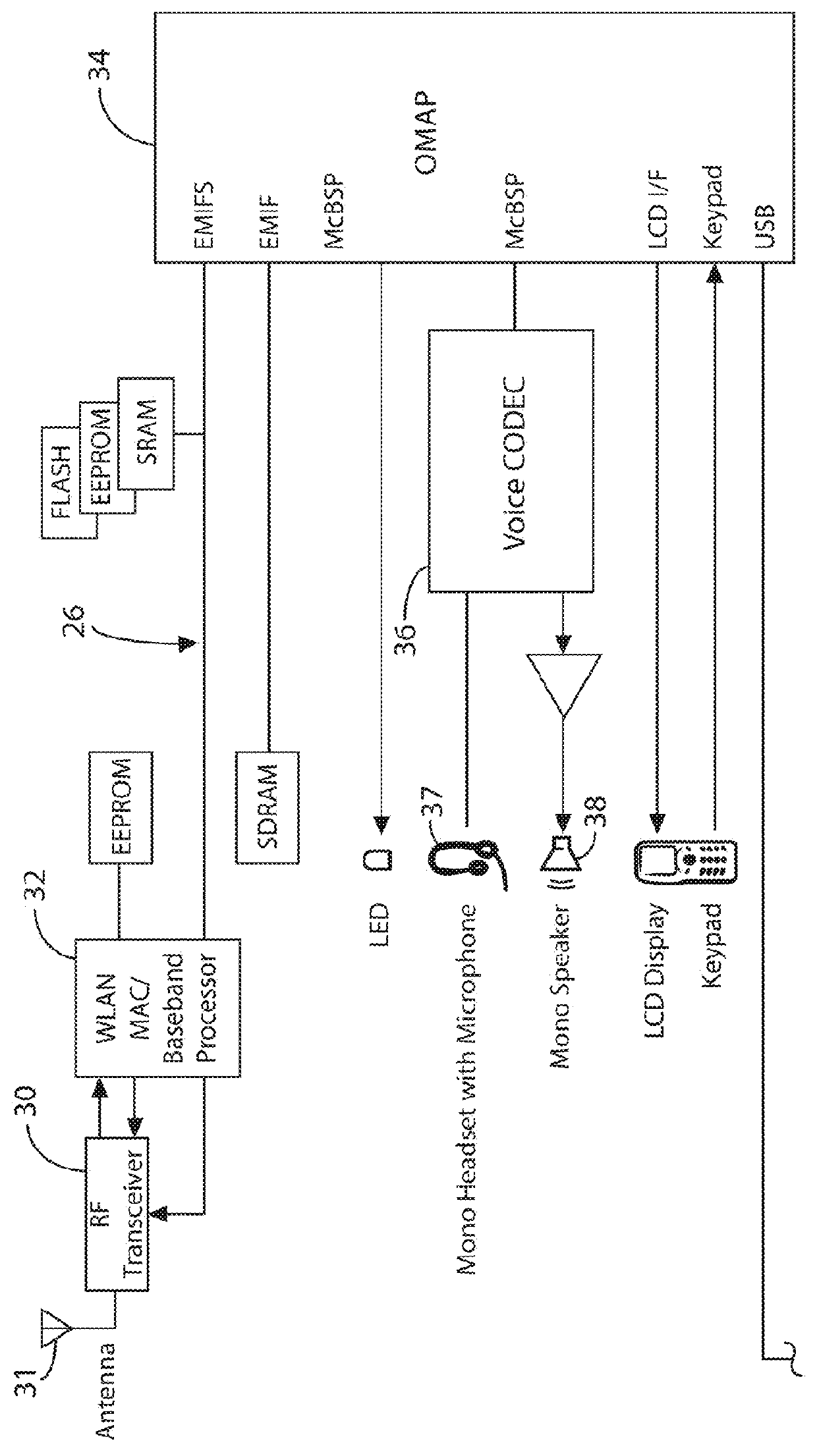
Soldier system wireless power and data transmission
An inductively coupled power and data transmission system include a main power source, apparel having an electrical conductor in electrical communication with the main power source, the apparel having a first inductively couplable power and data transmission sub-system to regulate power to the primary coil or coils and transmission of power and data by the primary coil or coils and reception of data by the primary coil or coils, and an independent device having a second inductively couplable power and data transmission sub-system so as to regulate reception of power and data by the secondary coil or coils and transmission of data from a secondary processor by the secondary coil or coils. The first and second primary coils transfer said power and data during inductive coupling, at electromagnetic radiation frequencies, between the first primary coil or coils and the secondary coil or coils.
Owner:CYNETIC DESIGNS
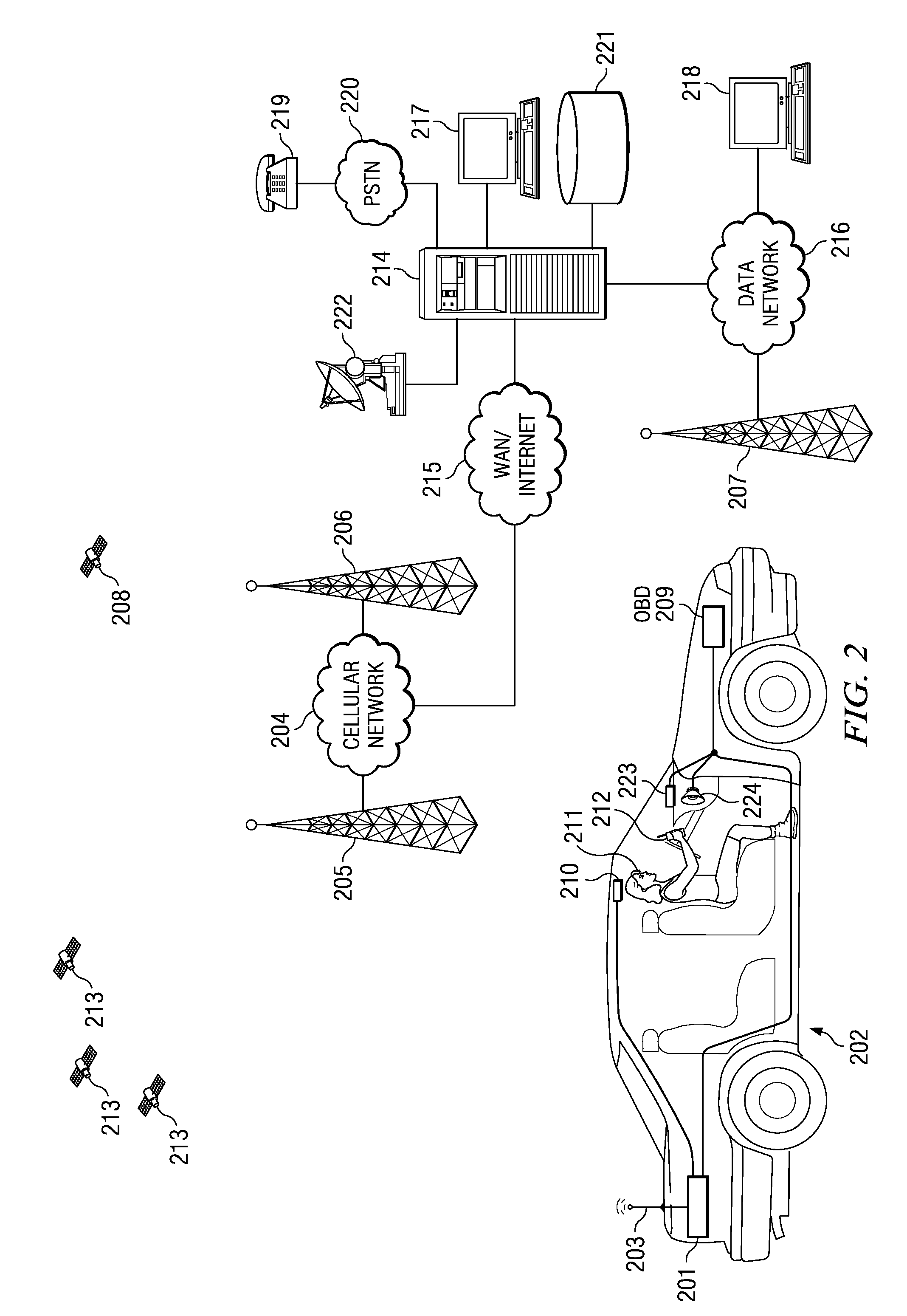
Vehicle data recorder and telematic device
InactiveUS20060212195A1Reduce drunk drivingReduce automobile theftVehicle testingRegistering/indicating working of vehiclesPersonalizationInformation processing
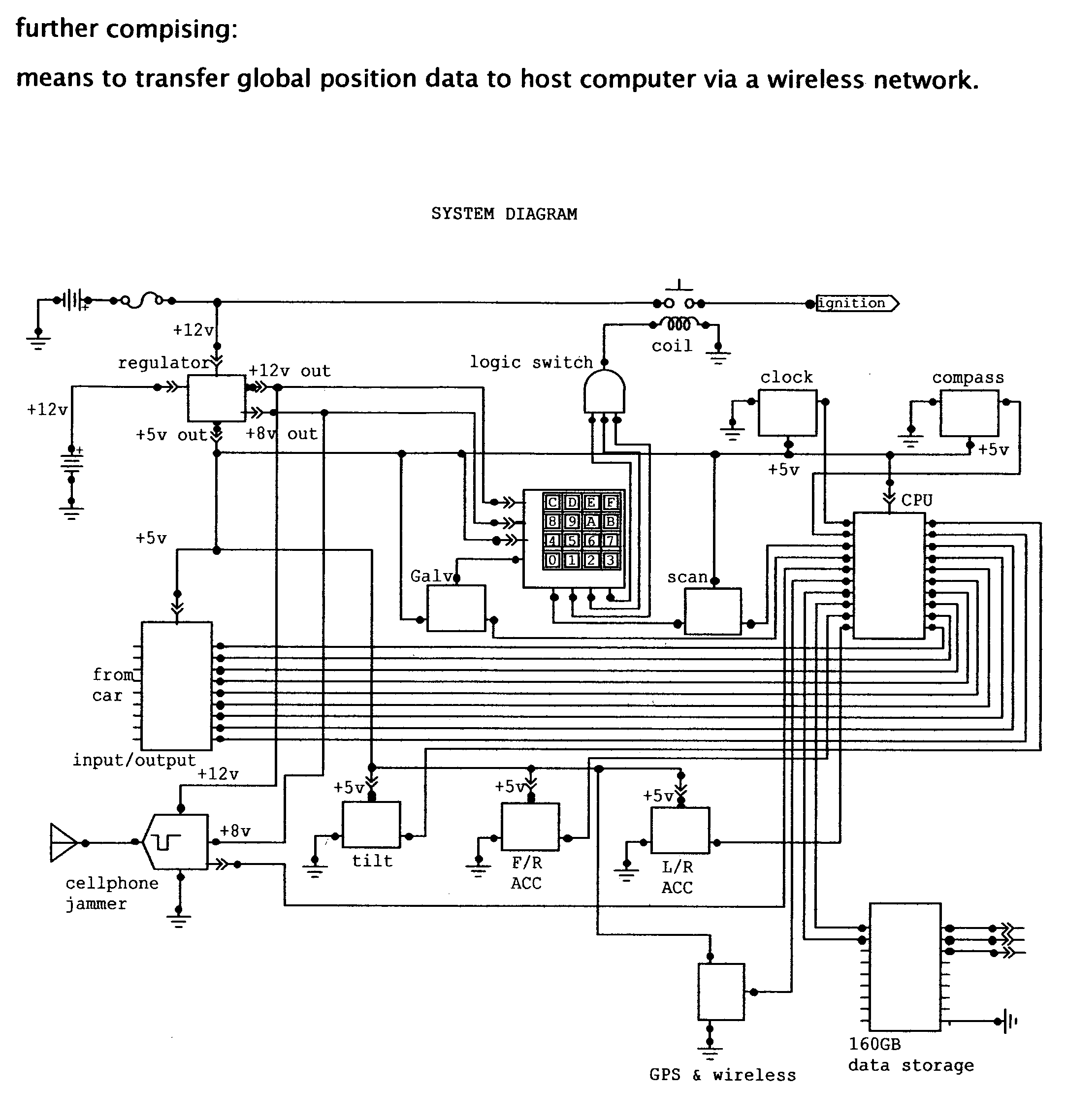
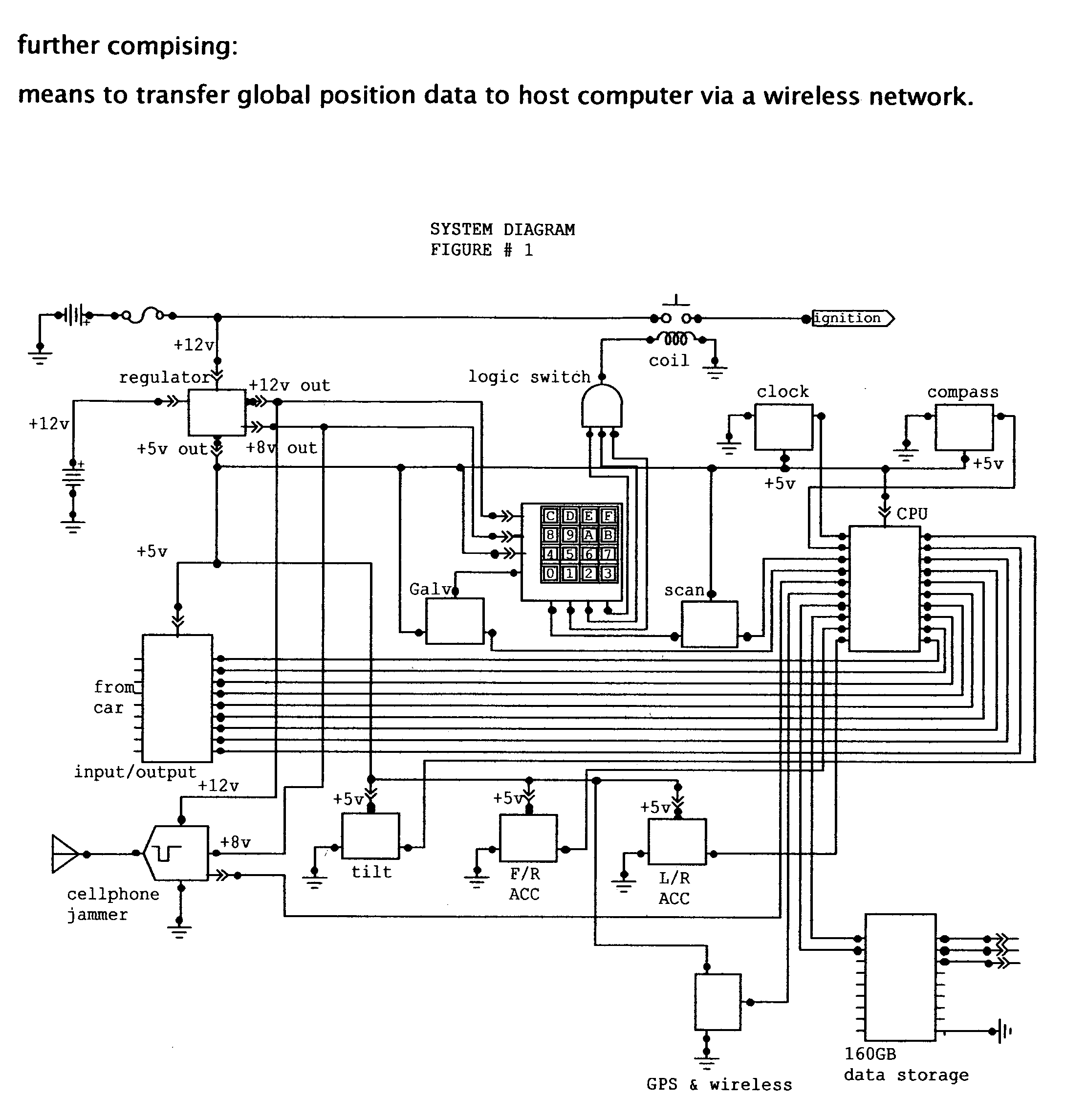
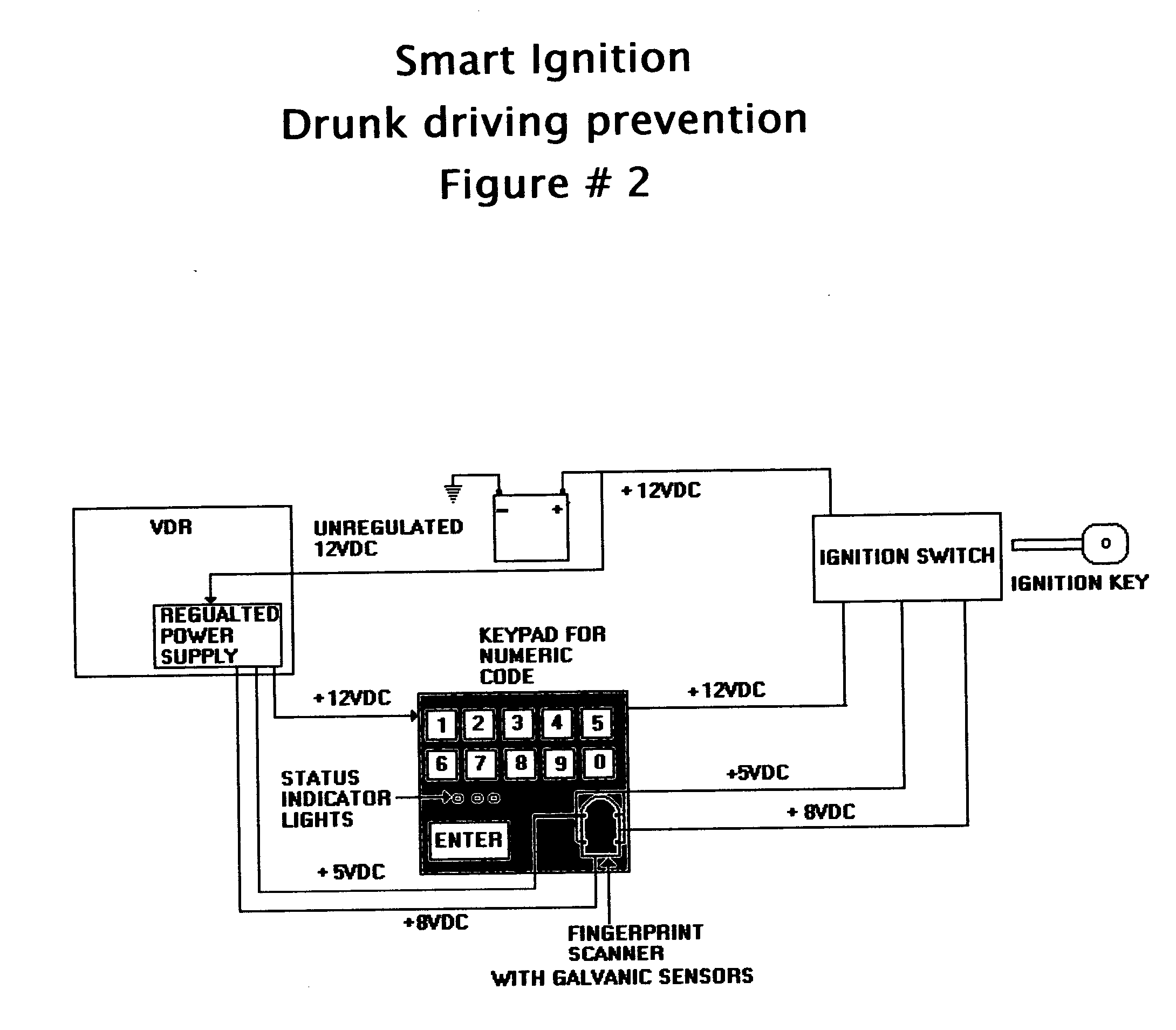
This invention is a vehicle data recorder with the capability to continuously record and store selected data on both driver and vehicle performance that will include but not be limited to, miles driven, speed, acceleration / deceleration, brake activation, seatbelt usage, vehicle direction, steering anomalies, global position, impact forces and direction, transmission status, and alcohol usage. Specifically, this recorder will have extended data storage capacity, a drunk driver prevention smart ignition, real-time GPS data, low-power cell phone jamming, and internal wireless communication capabilities. It uses microprocessor controlled electronics to record, store, and transmit both driver and vehicle performance data in a date and time stamped file which can be utilized to establish personalized insurance rates, assess road tax and use fees, locate “Amber alert” victims or stolen vehicles, and with it's on scene access, provide critical mechanism of injury information to emergency responders.
Owner:VEITH GREGORY W +1
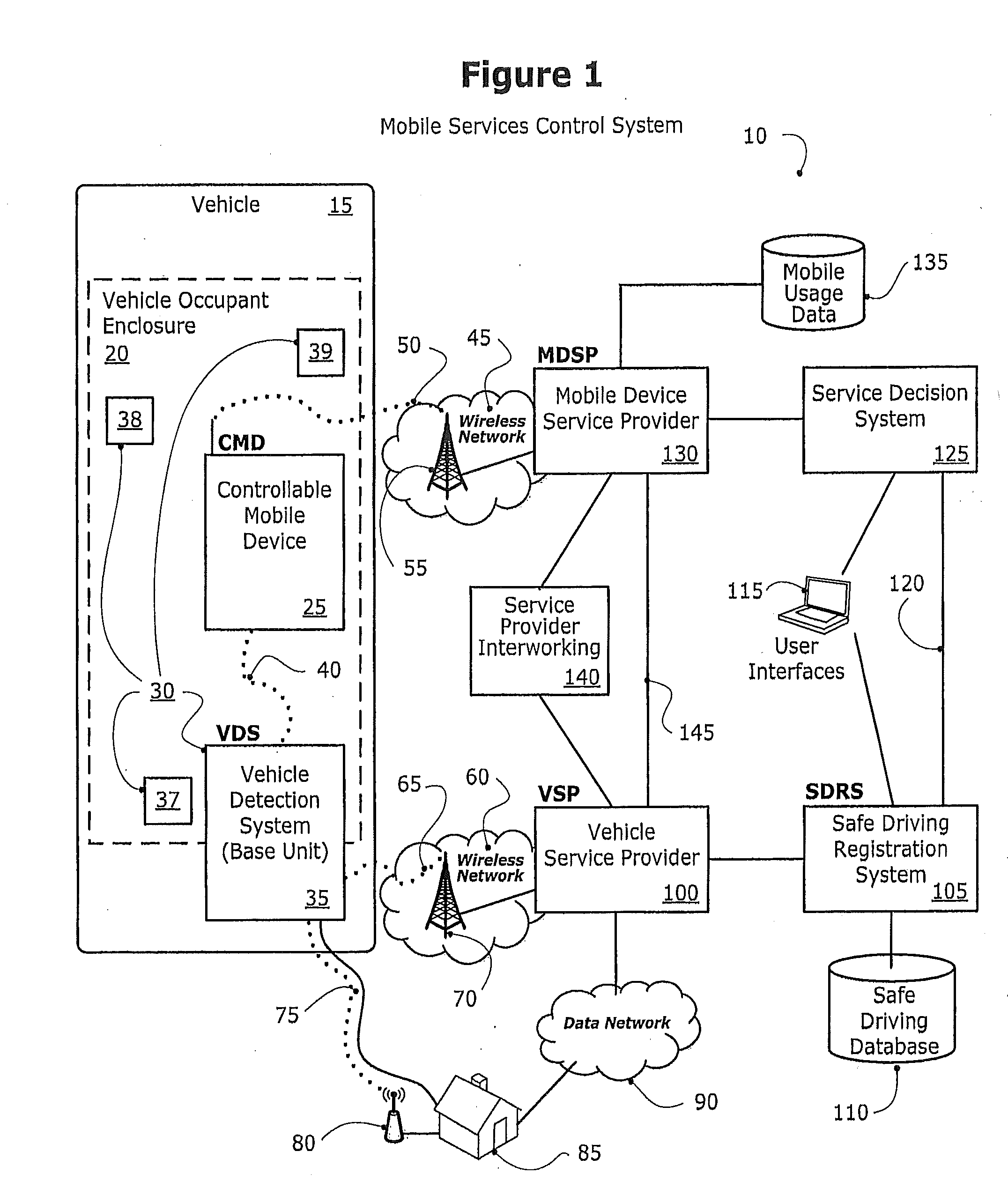
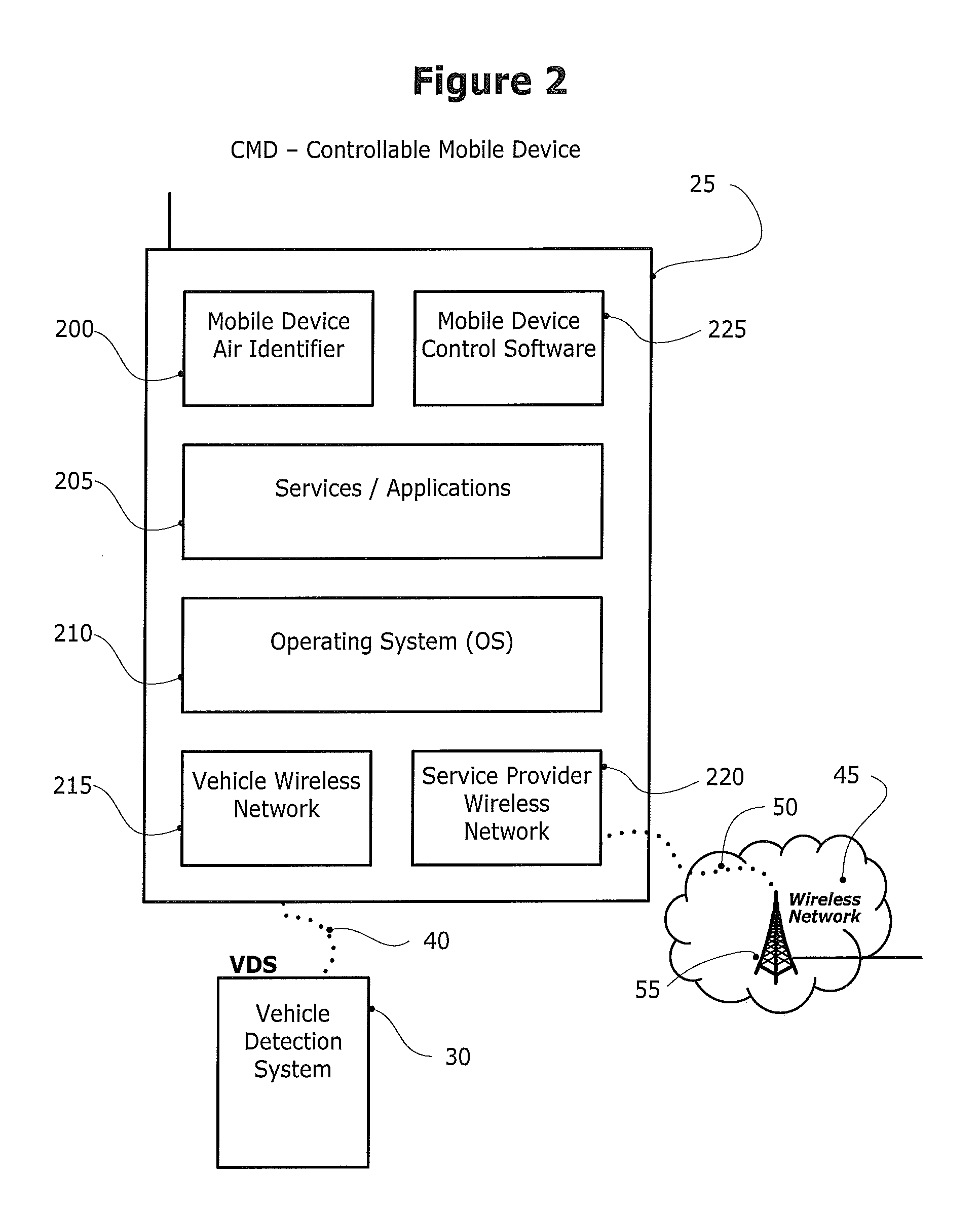
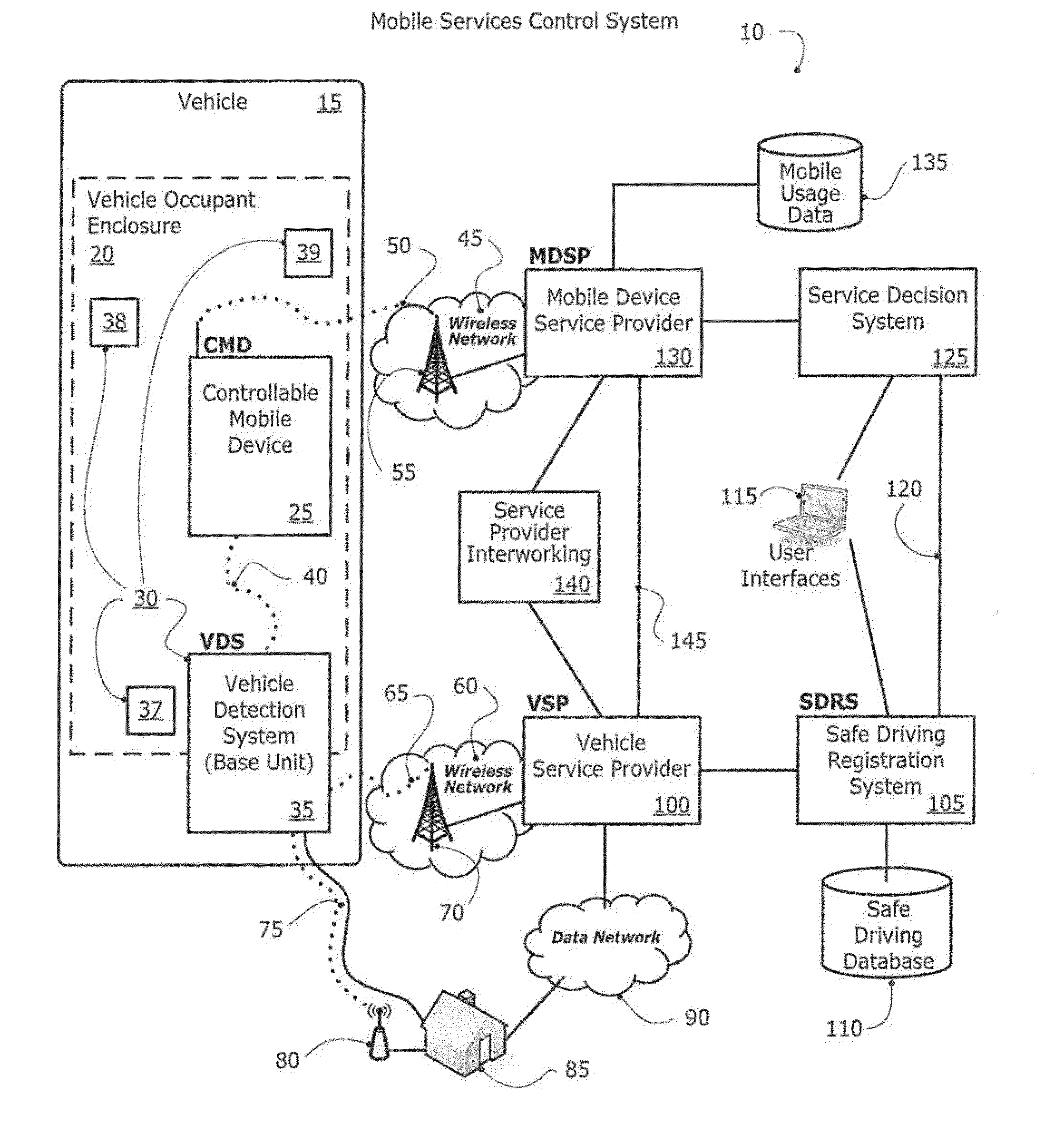
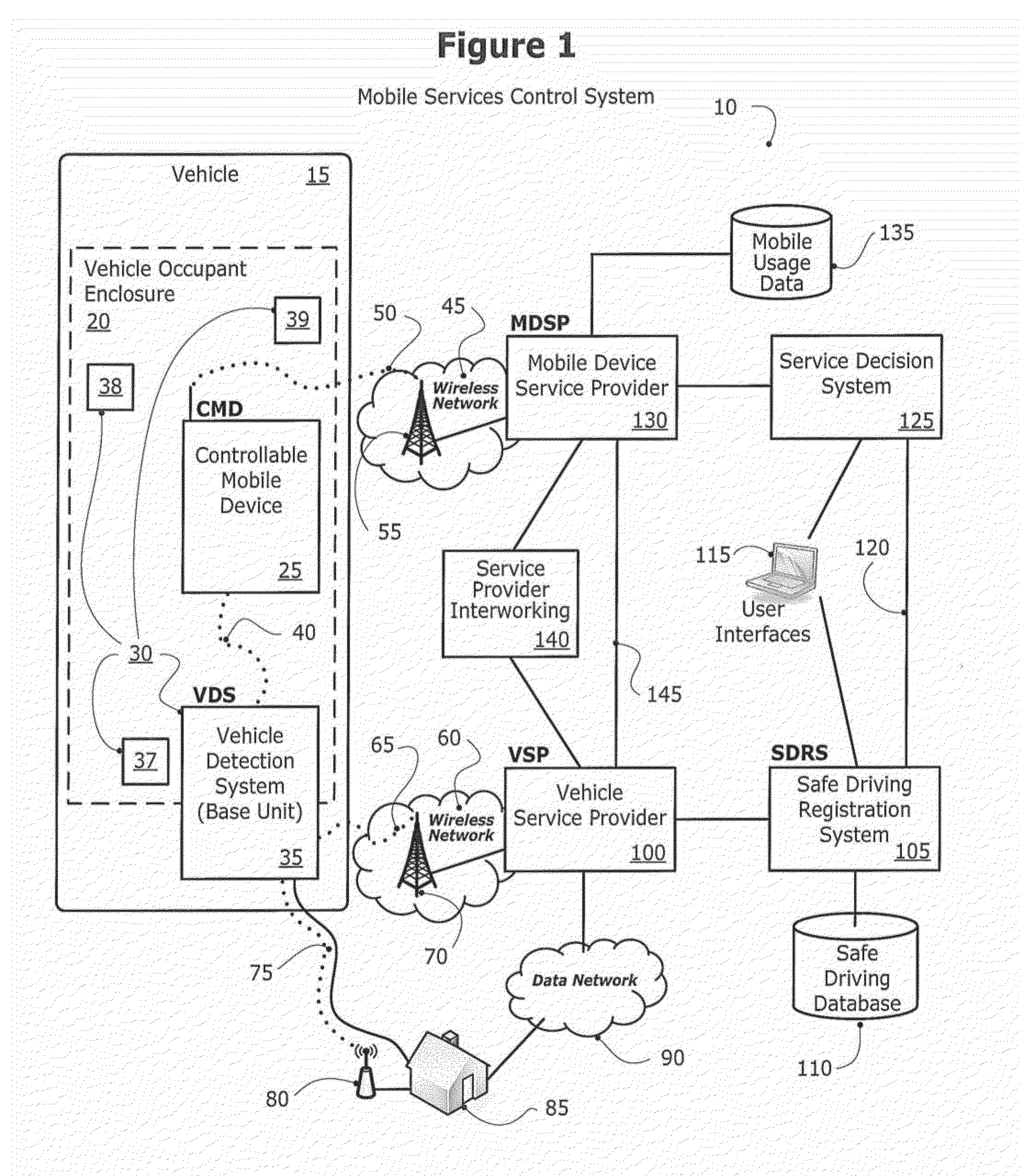
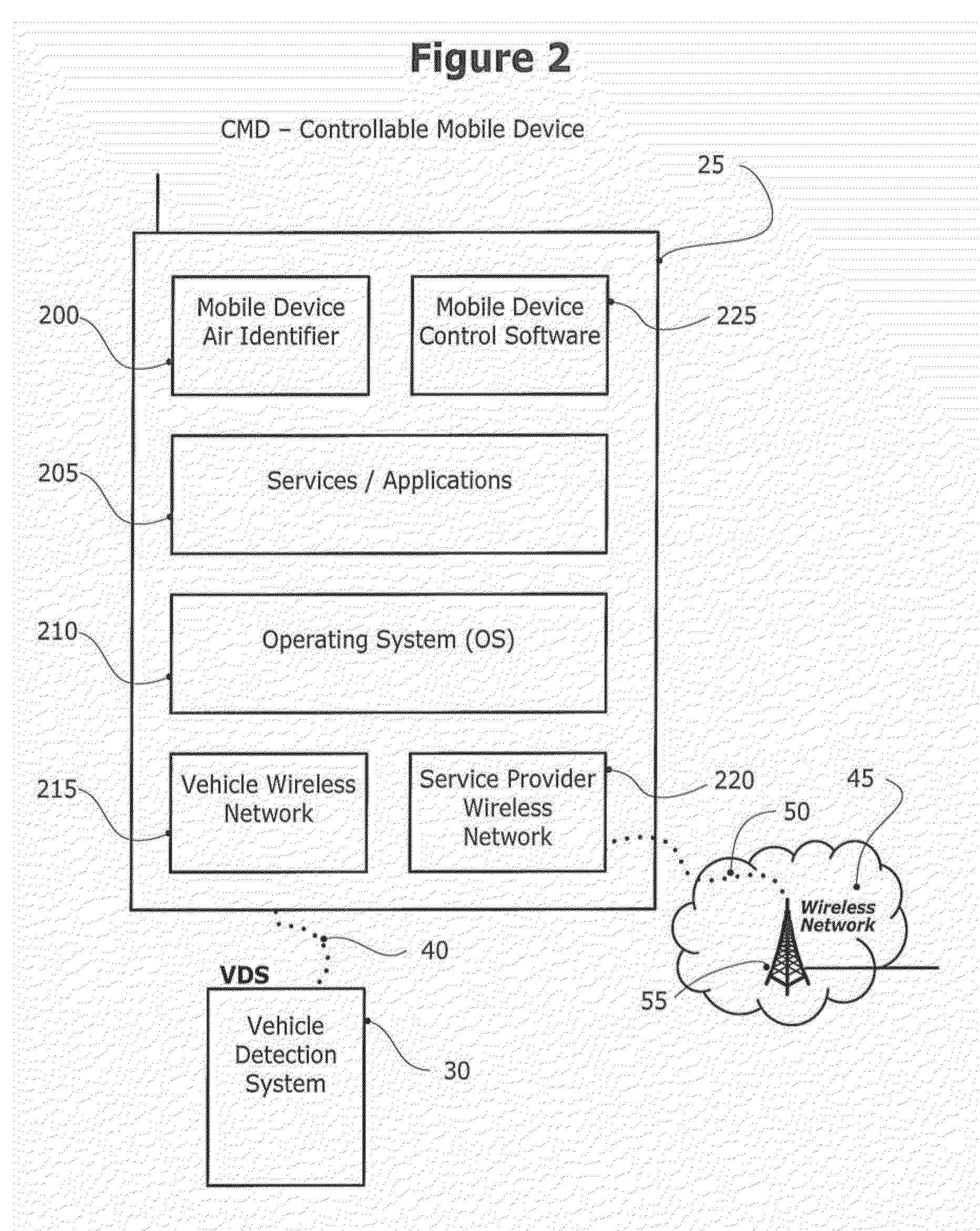
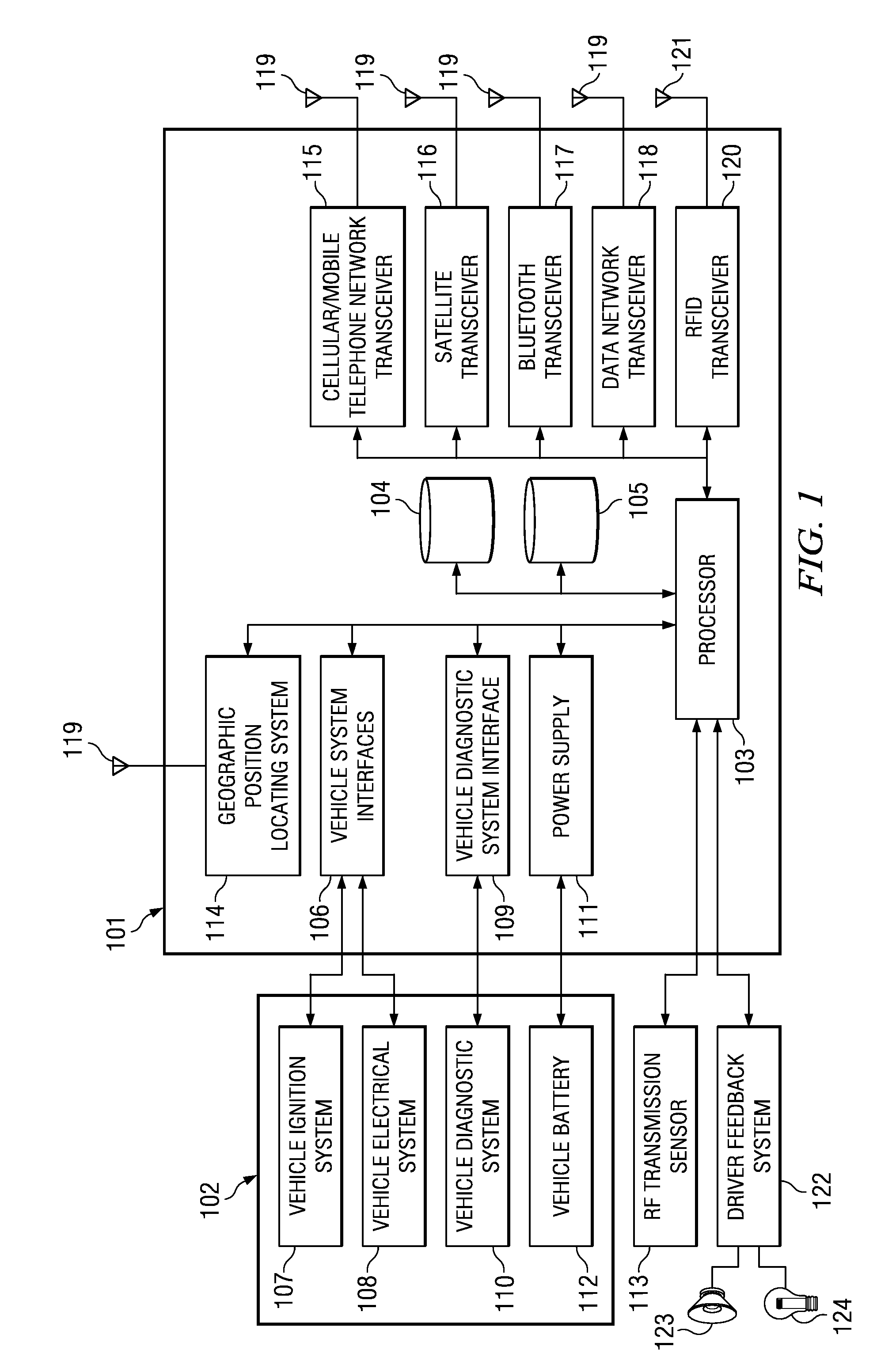
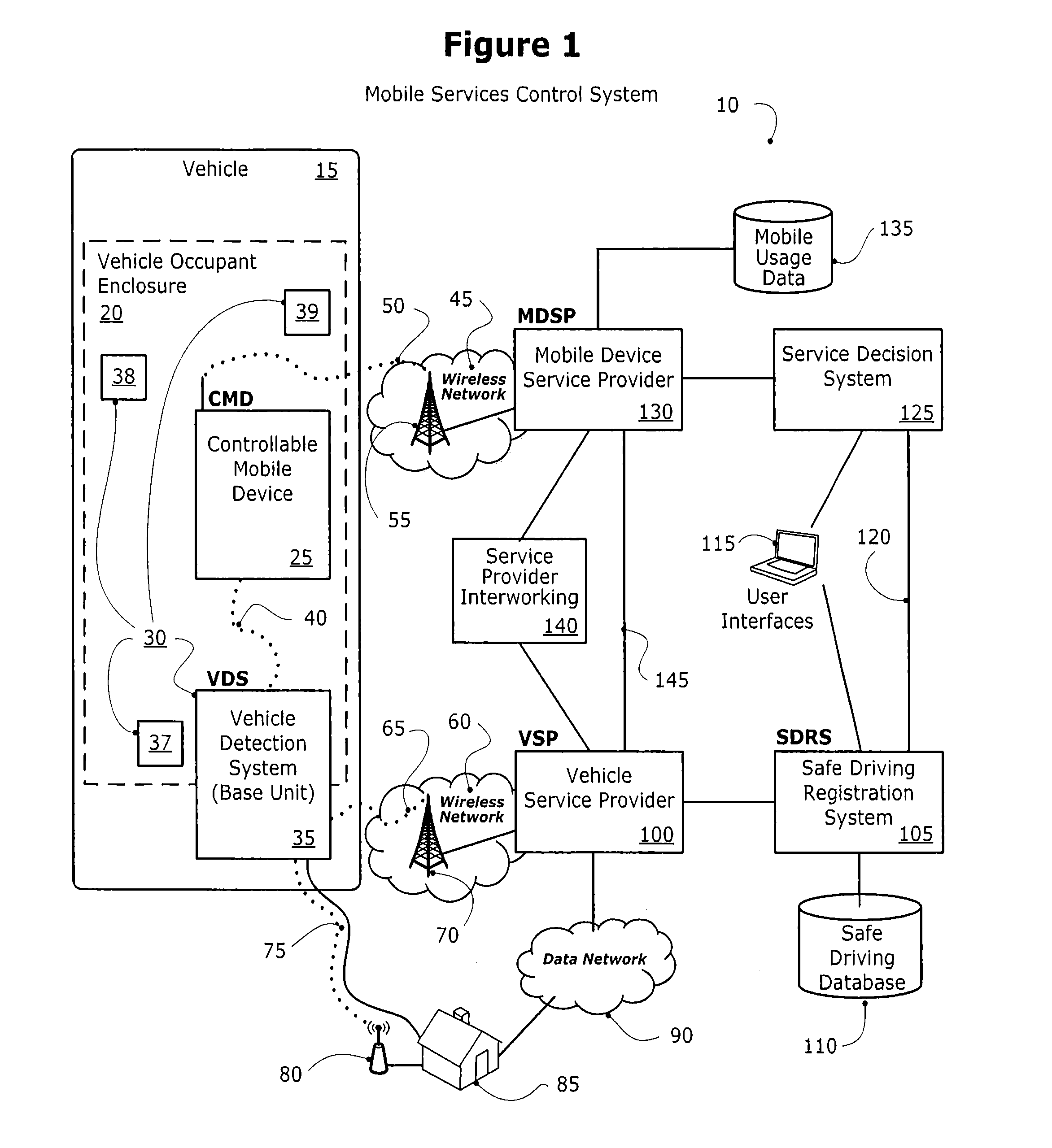
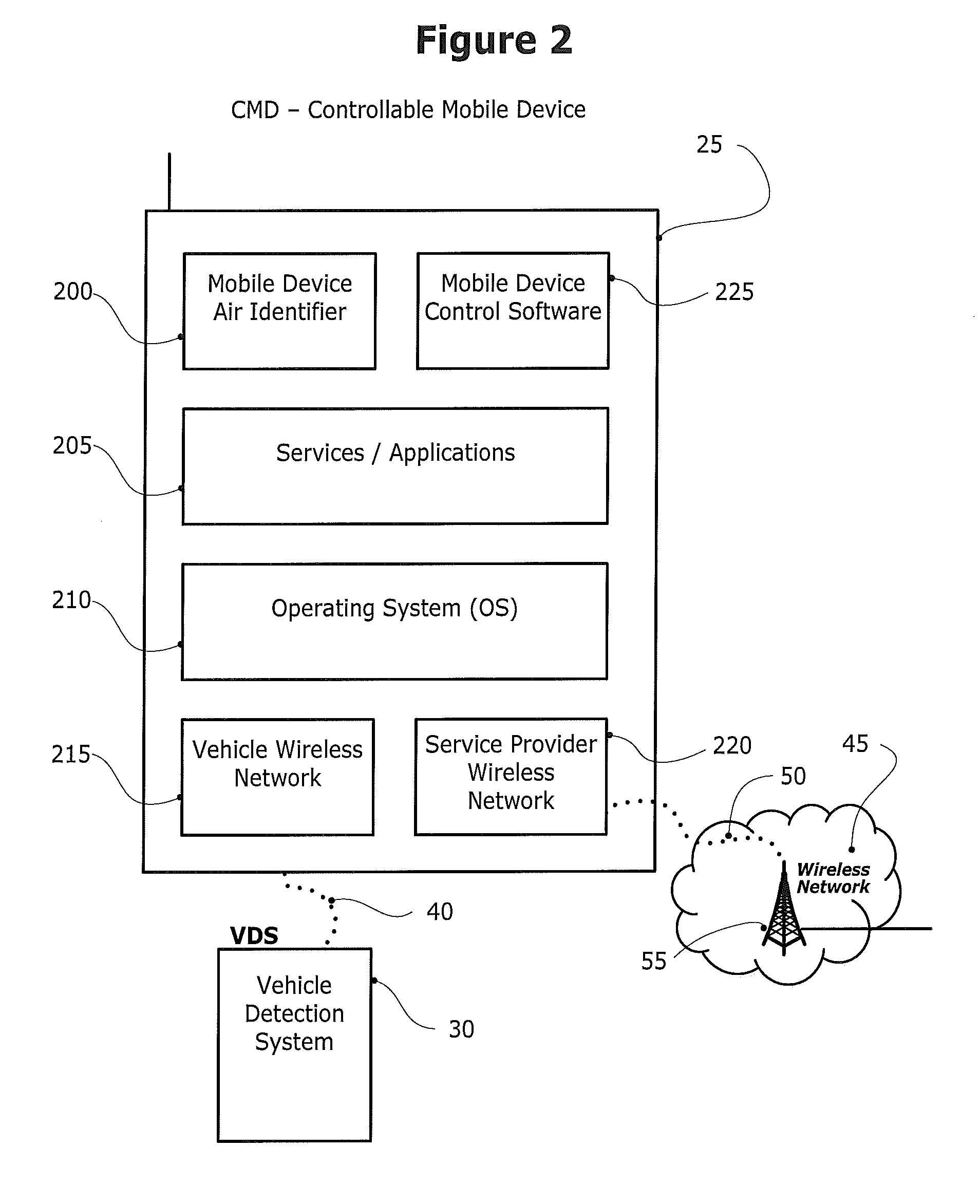
Method and system for controlling a mobile communication device in a moving vehicle
ActiveUS20110021234A1Assess restrictionParticular environment based servicesMobile vehicleControl system
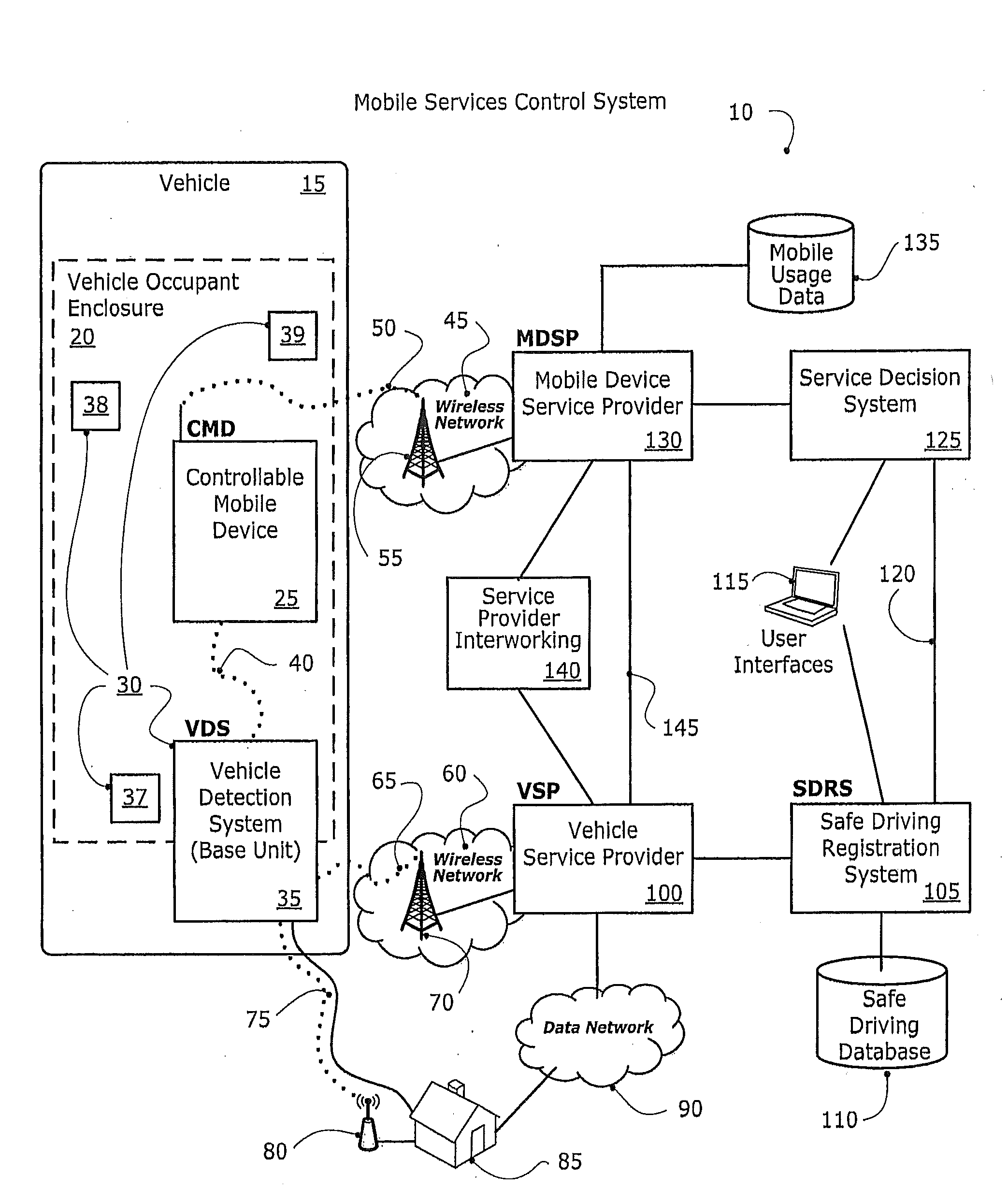
Disclosed herein is a method and system for detecting, monitoring and / or controlling one or more of mobile services for a mobile communication device (also referred to herein as a Controllable Mobile Device or CMD), and in particular, when the device is being used and the vehicle, operated by the user of the device, is moving. The present method and system determines whether the vehicle is being operated by a user that may also have access to a mobile communication device which, if used concurrently while the vehicle is in operation, may lead to unsafe operation of the vehicle. If the mobile services control system determines that a vehicle operator has potentially unsafe access to a mobile communication device, the mobile services control system may restrict operator access to one or more services that would otherwise be available to the operator via the mobile communication device.
Owner:KATASI
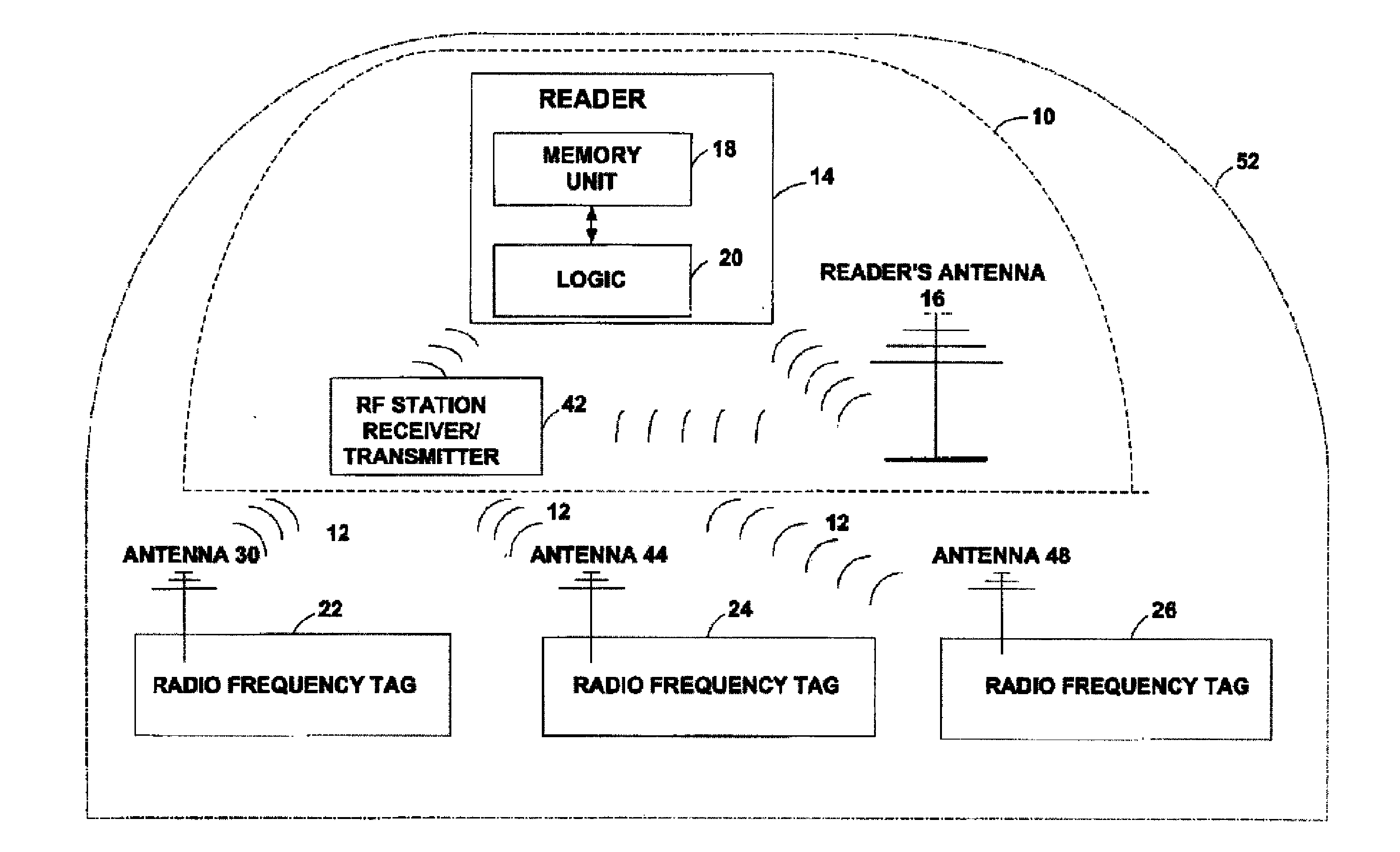
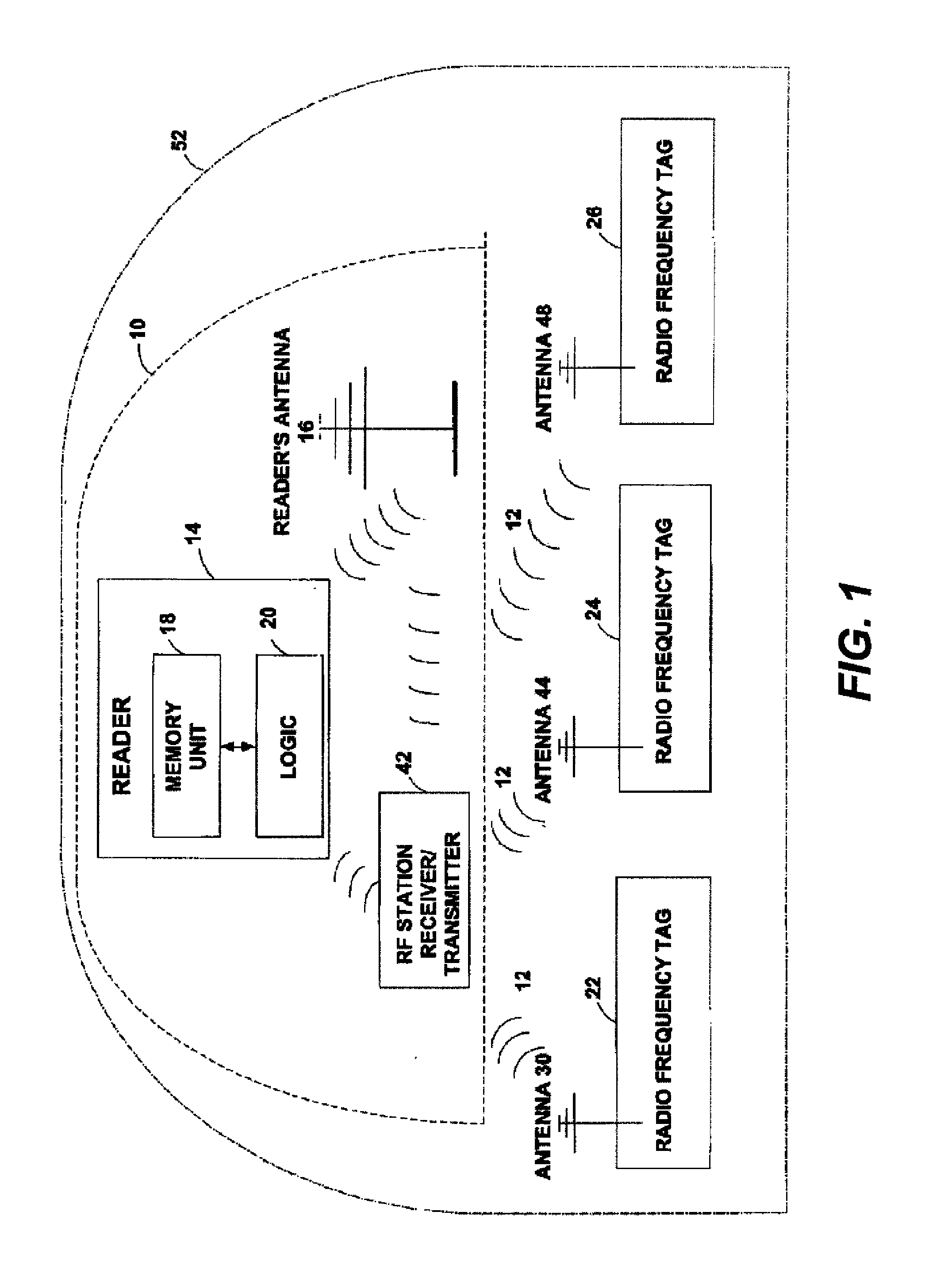
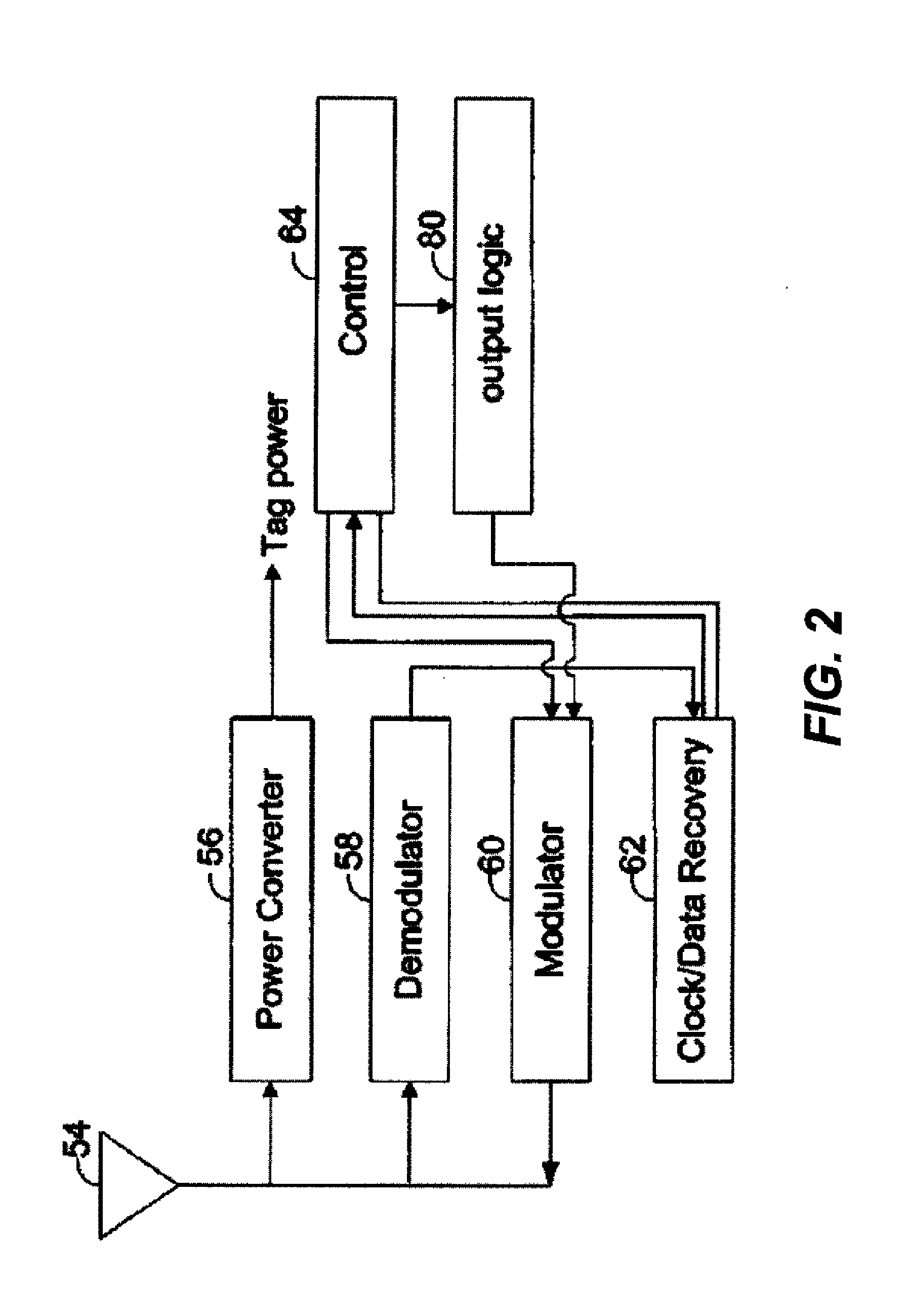
Method and apparatus for selective blocking of radio frequency identification devices
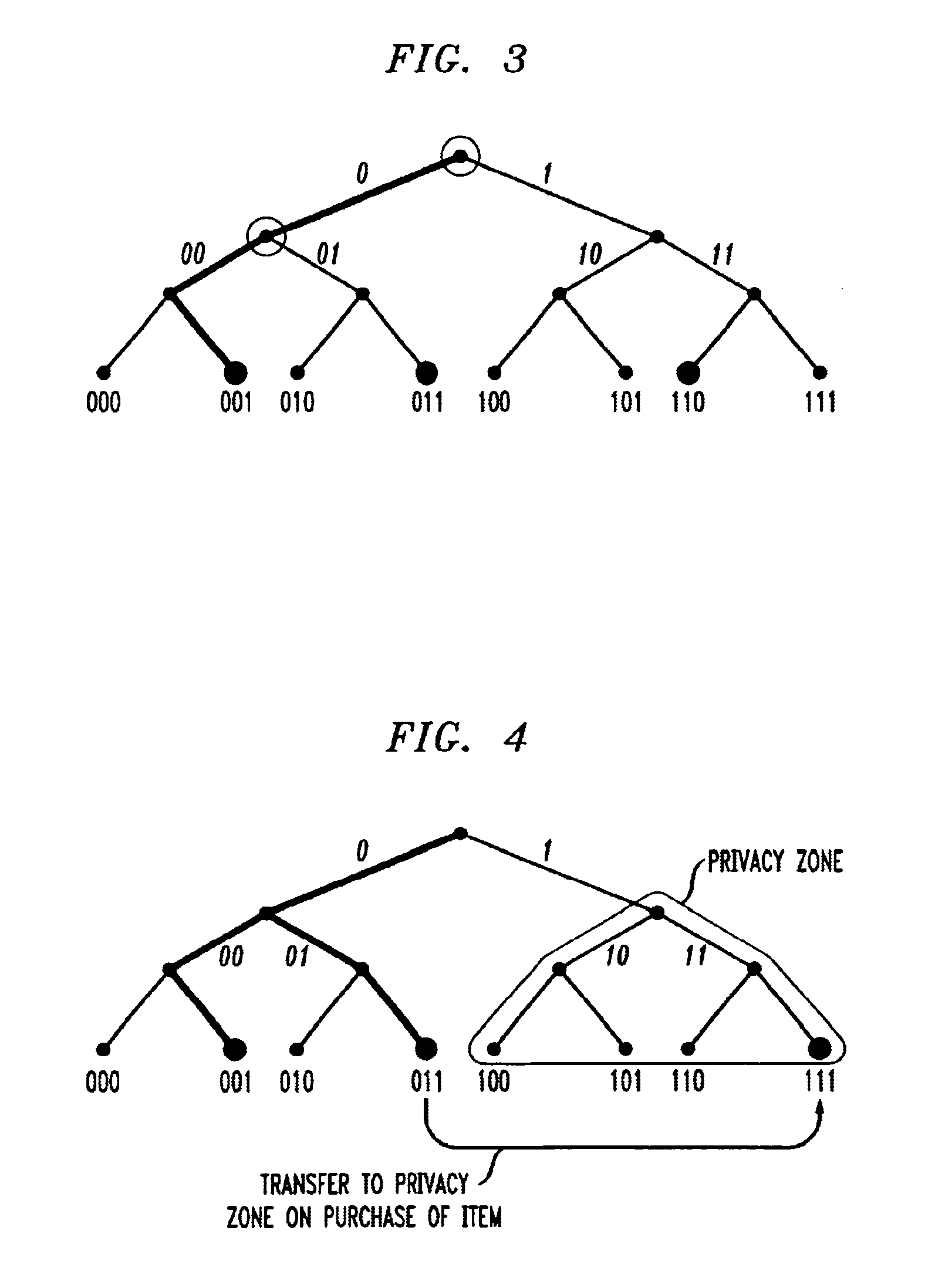
ActiveUS6970070B2Enhanced consumer privacyIncreased complexityMemory record carrier reading problemsTime-division multiplexComputer hardwareRadio-frequency identification
Techniques are disclosed for providing enhanced privacy in an RFID system comprising a plurality of RFID devices, each having an associated identifier, and at least one reader which communicates with one or more of the devices. A blocker device is operative to receive a communication directed from the reader to one or more of the RFID devices, and to generate, possibly based on information in the received communication, an output transmittable to the reader. The output simulates one or more responses from at least one of the RFID devices in a manner which prevents the reader from determining at least a portion of the identifier of at least one of the RFID devices. The blocker device may itself comprise one of the RFID devices. In an illustrative embodiment, the output generated by the blocker device interferes with the normal operation of a singulation algorithm implemented by the reader.
Owner:EMC IP HLDG CO LLC
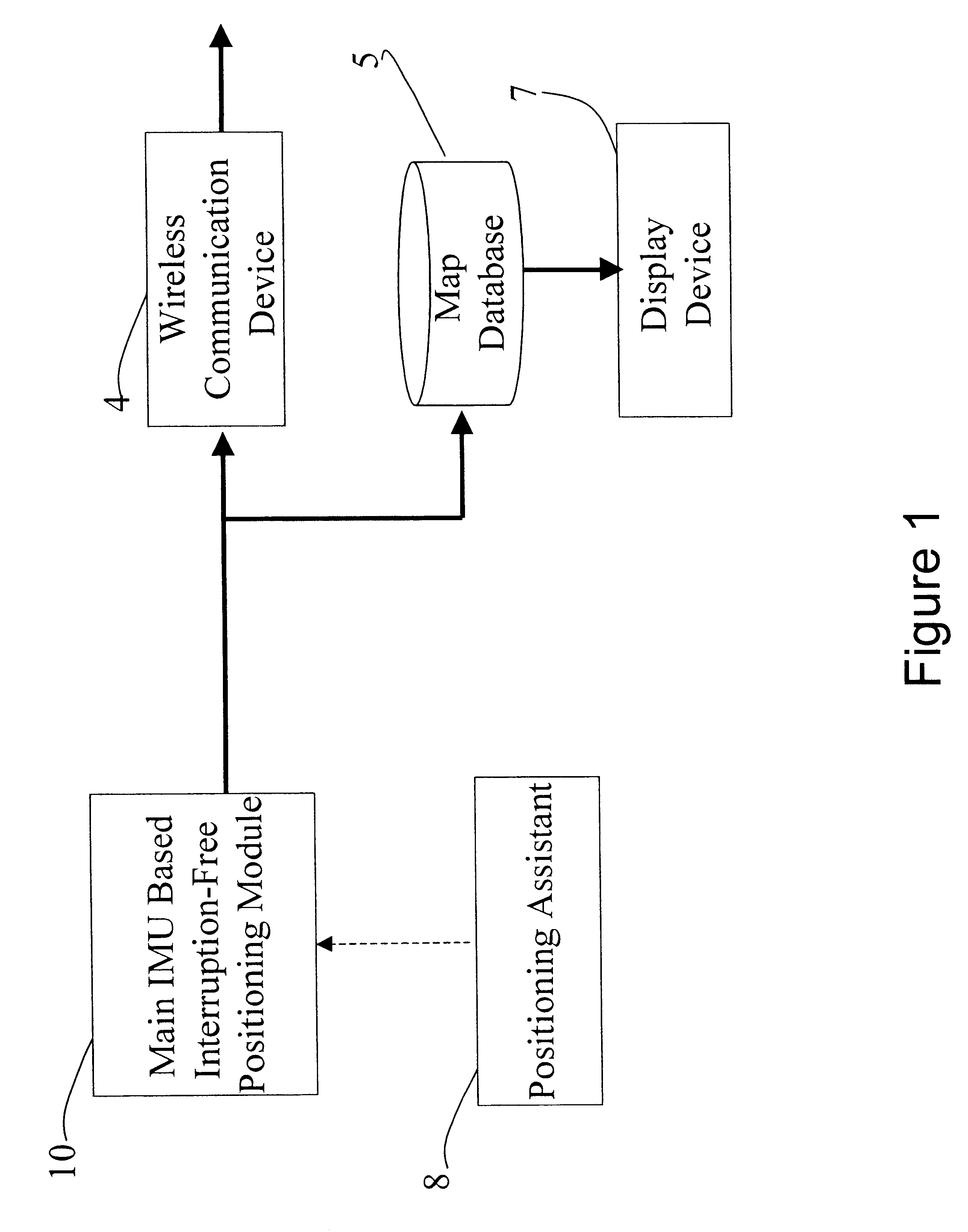
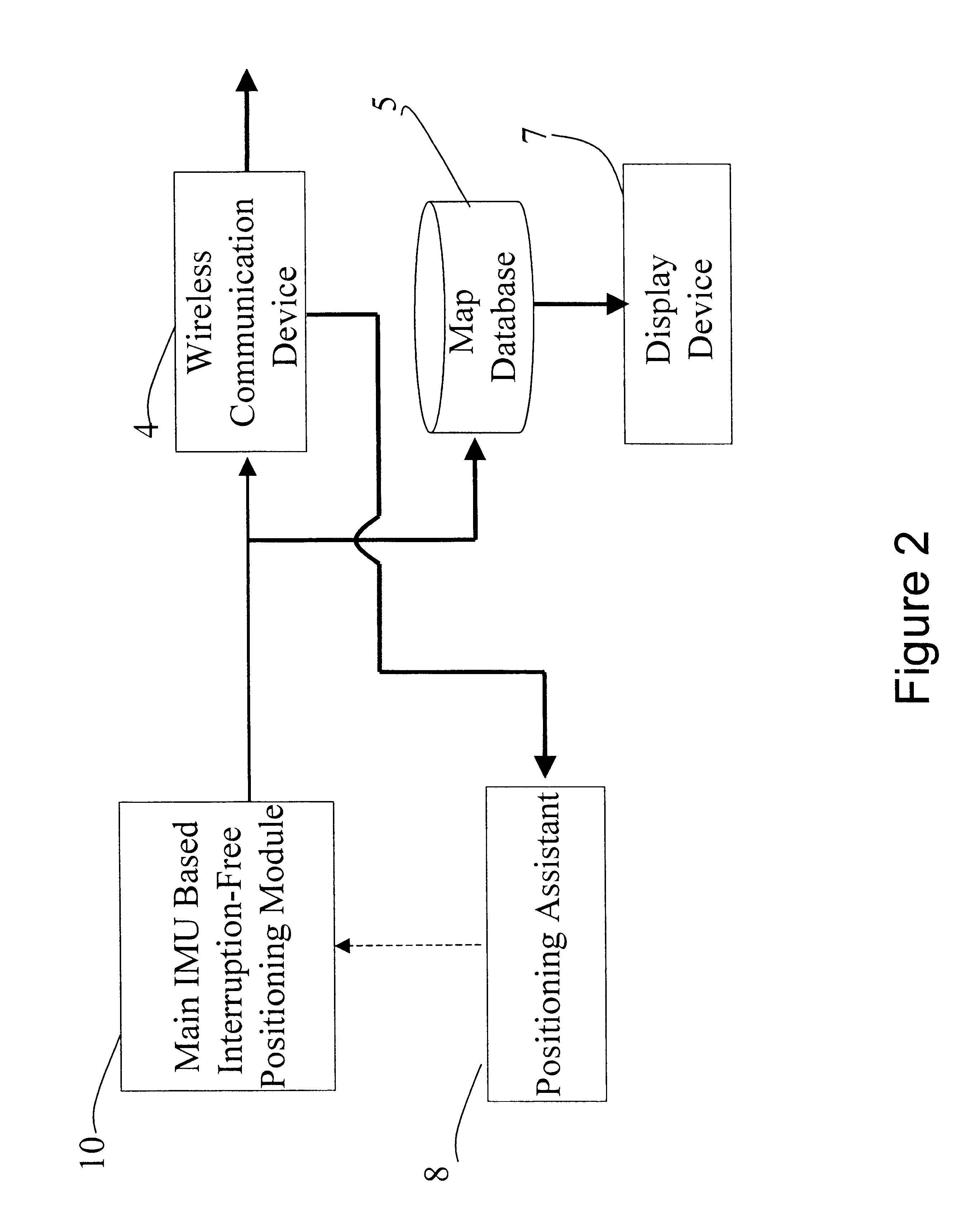
Interruption-free hand-held positioning method and system thereof
InactiveUS6415223B1Low costReduce power consumptionInstruments for road network navigationDirection finders using radio wavesDisplay deviceHand held
An interruption-free hand-held positioning method and system, carried by a person, includes an inertial measurement unit, a north finder, a velocity producer, a positioning assistant, a navigation processor, a wireless communication device, and a display device and map database. Output signals of the inertial measurement unit, the velocity producer, the positioning assistant, and the north finder are processed to obtain highly accurate position measurements of the person. The user's position information can be exchanged with other users through the wireless communication device, and the location and surrounding information can be displayed on the display device by accessing a map database with the person position information.
Owner:AMERICAN GNC
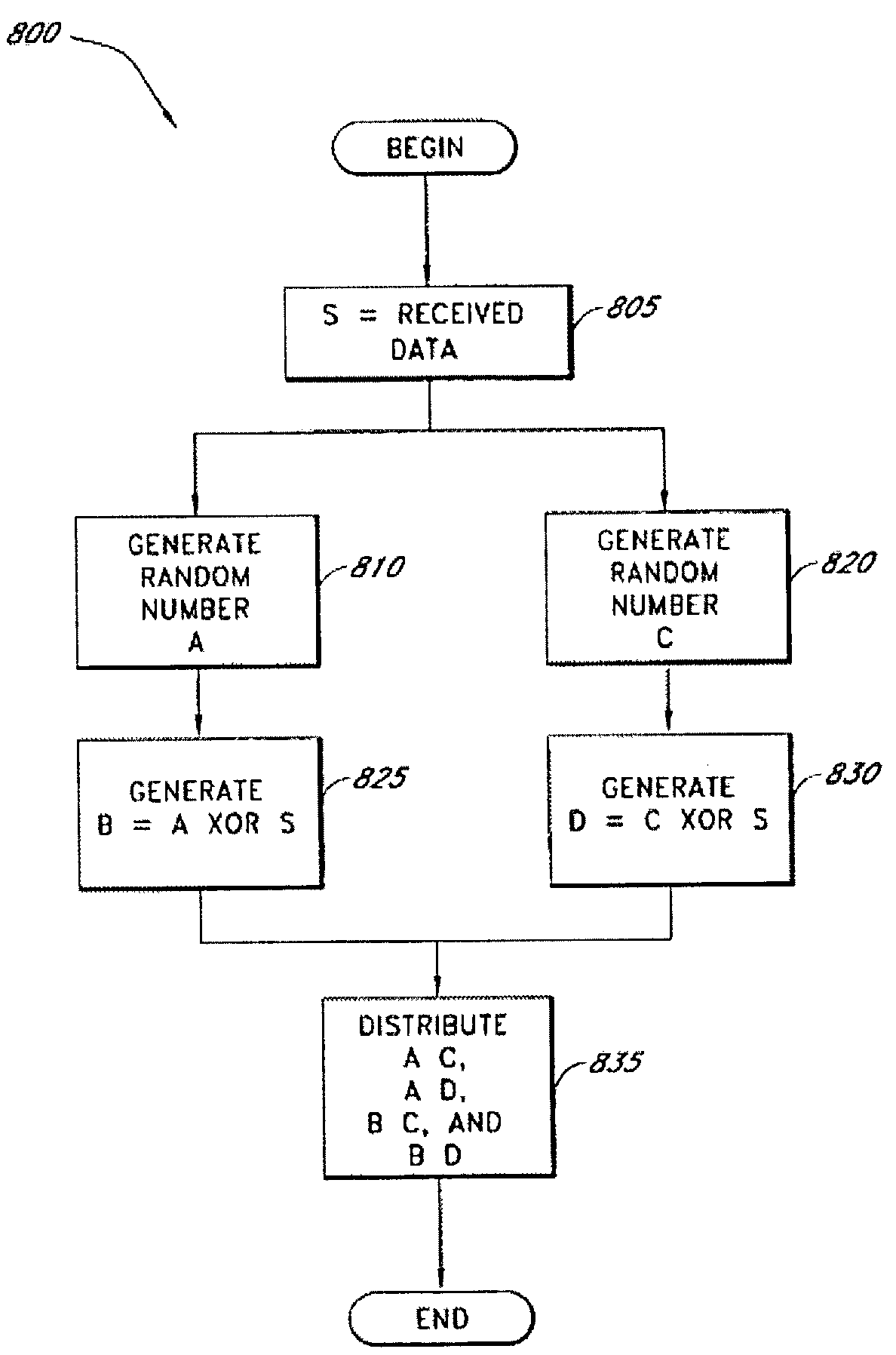
Secure data parser method and system
InactiveUS7391865B2Minimal compute resourceAvoid the needDigital data processing detailsUser identity/authority verificationGovernmental agencyVariospora
The present invention provides a method and system for securing sensitive data from unauthorized access or use. The method and system of the present invention is useful in a wide variety of settings, including commercial settings generally available to the public which may be extremely large or small with respect to the number of users. The method and system of the present invention is also useful in a more private setting, such as with a corporation or governmental agency, as well as between corporation, governmental agencies or any other entity.
Owner:SECURITY FIRST INNOVATIONS LLC
Disruption of speech understanding by adding a privacy sound thereto
InactiveUS7363227B2Lose abilityDisrupt abilitySecret communicationCommunication jammingAuditory systemSpeech sound
Owner:HERMAN MILLER INC
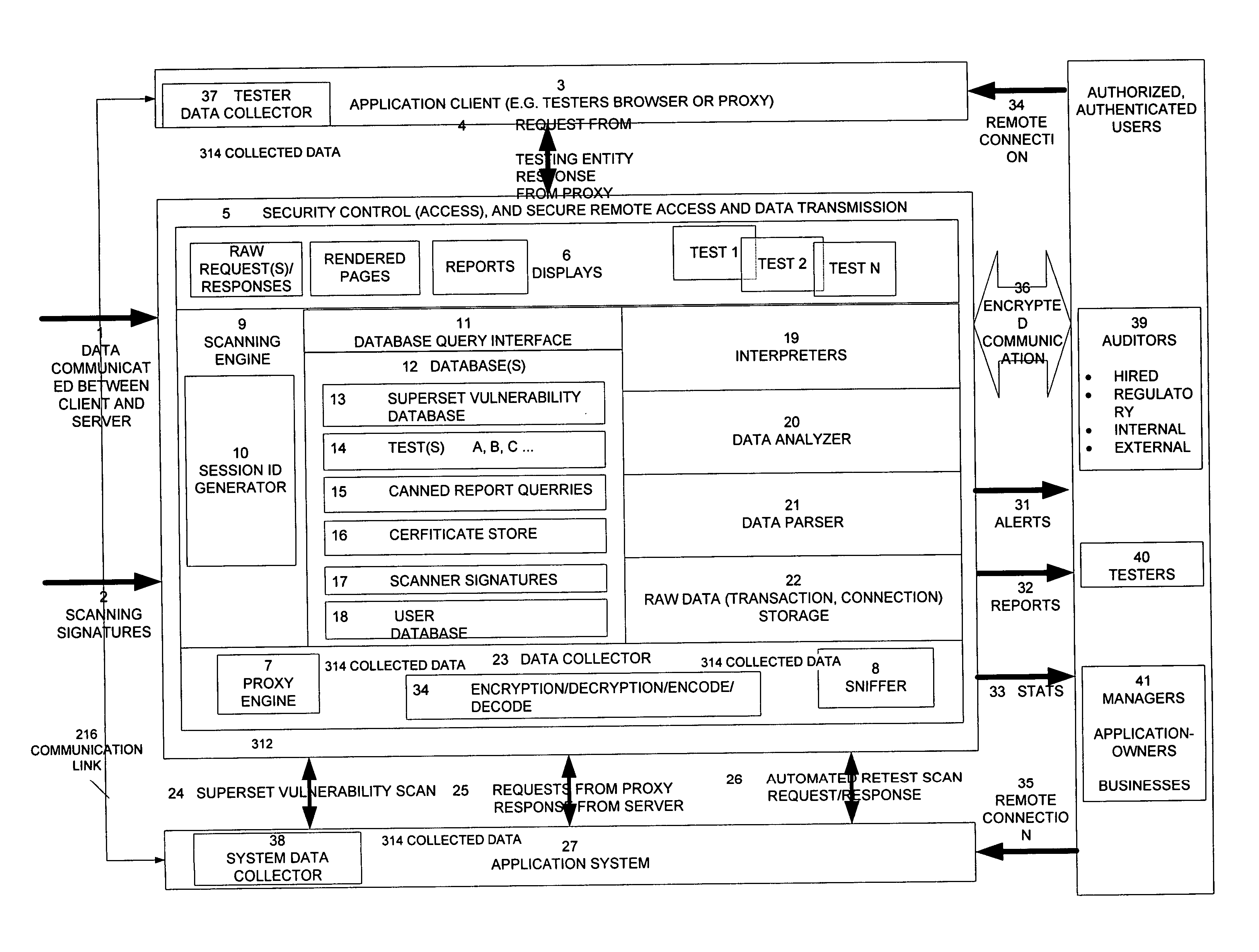
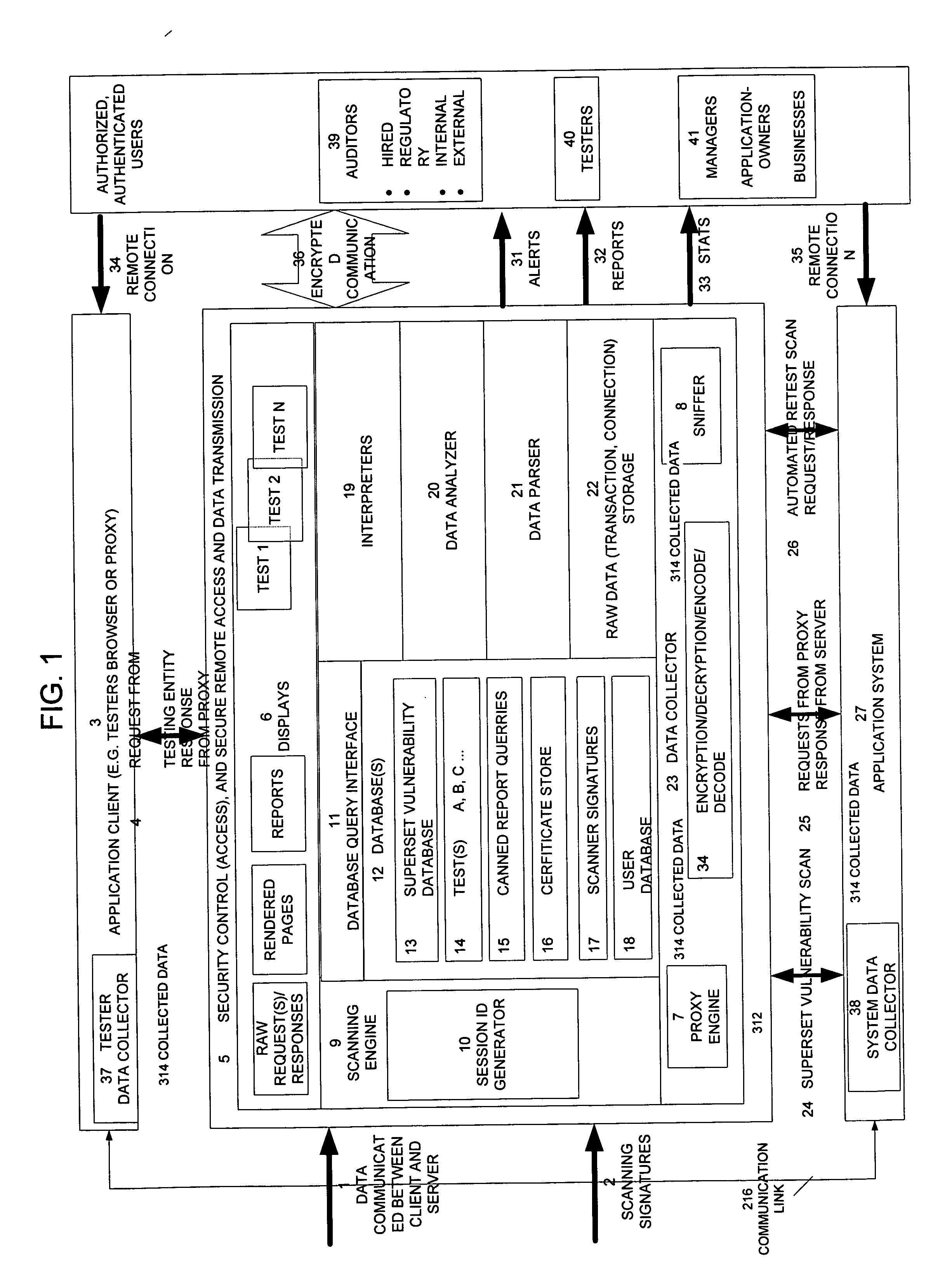
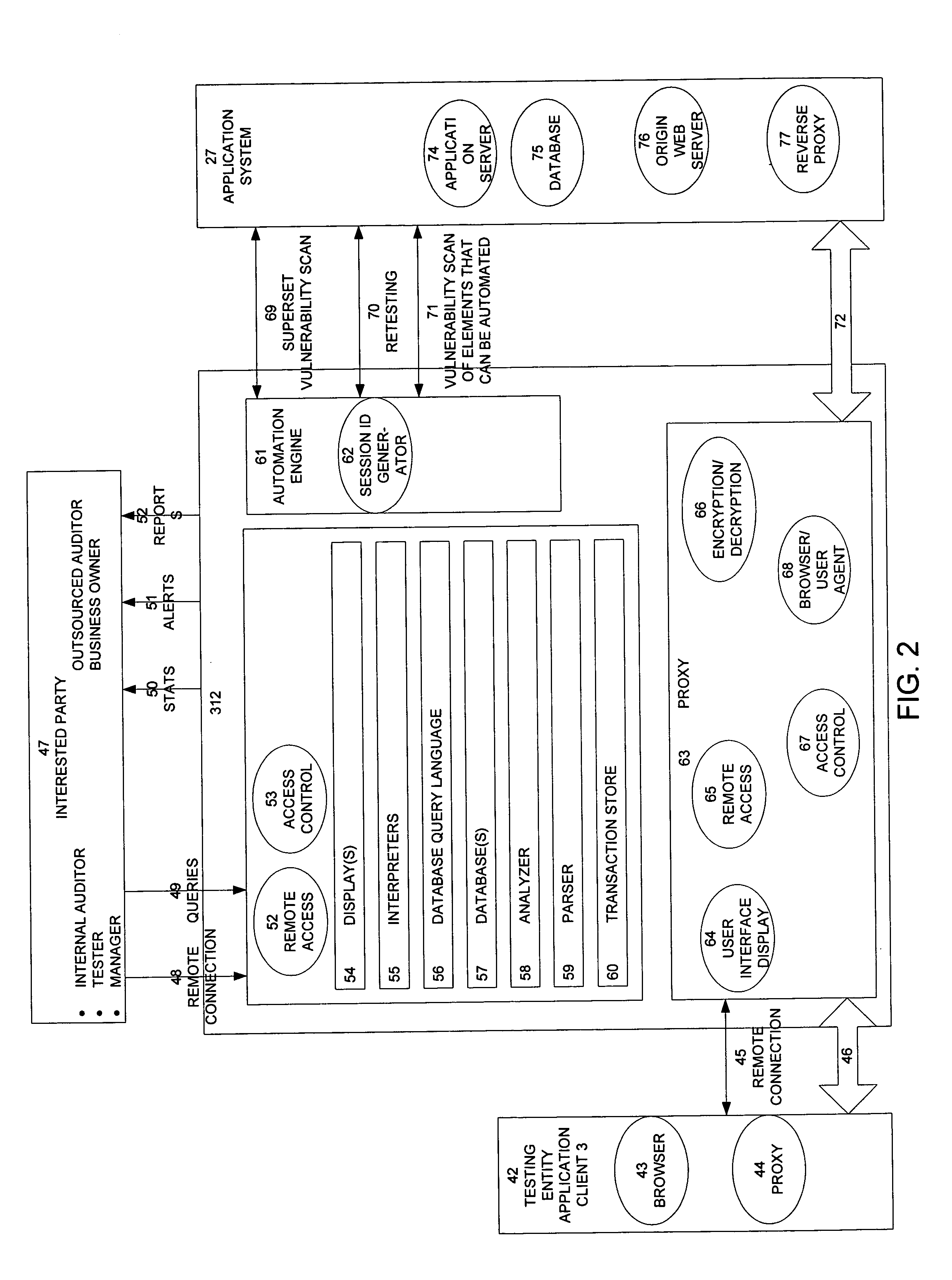
Method, system, and apparatus for managing, monitoring, auditing, cataloging, scoring, and improving vulnerability assessment tests, as well as automating retesting efforts and elements of tests
InactiveUS20050138426A1Streamline and improve test effortImprove consistencyDigital data processing detailsHardware monitoringAnalysis dataWeb application
A scalable method, system, and apparatus for non-intrusively auditing and improving security assessments includes capturing, storing, presenting, displaying, inspecting, monitoring, and analyzing data flow in client-server security assessments and / or network / infrastructure security assessments. The invention provides interested parties with a mechanism to non-intrusively audit in real-time the vulnerability test effort, as well as review, replay, and analyze all aspects of the security assessment during and after the test. For web application assessments, the data capture includes one of the following or some combination: an intermediary with all data passing through the intermediary; a sniffer that can passively extract all data being communicated between the application and tester; and a plurality of computing modules (e.g., software, appliances, etc.) installed in the tester environment or within the application system environment (e.g., software installed on the tester's computer, or on the computer where the intermediary is running, or software installed on the application systems proxy or web server, or an appliance in either environment) for storing, processing, analyzing, reporting, and displaying the data.
Owner:STYSLINGER BRIAN
Access system for a cellular network
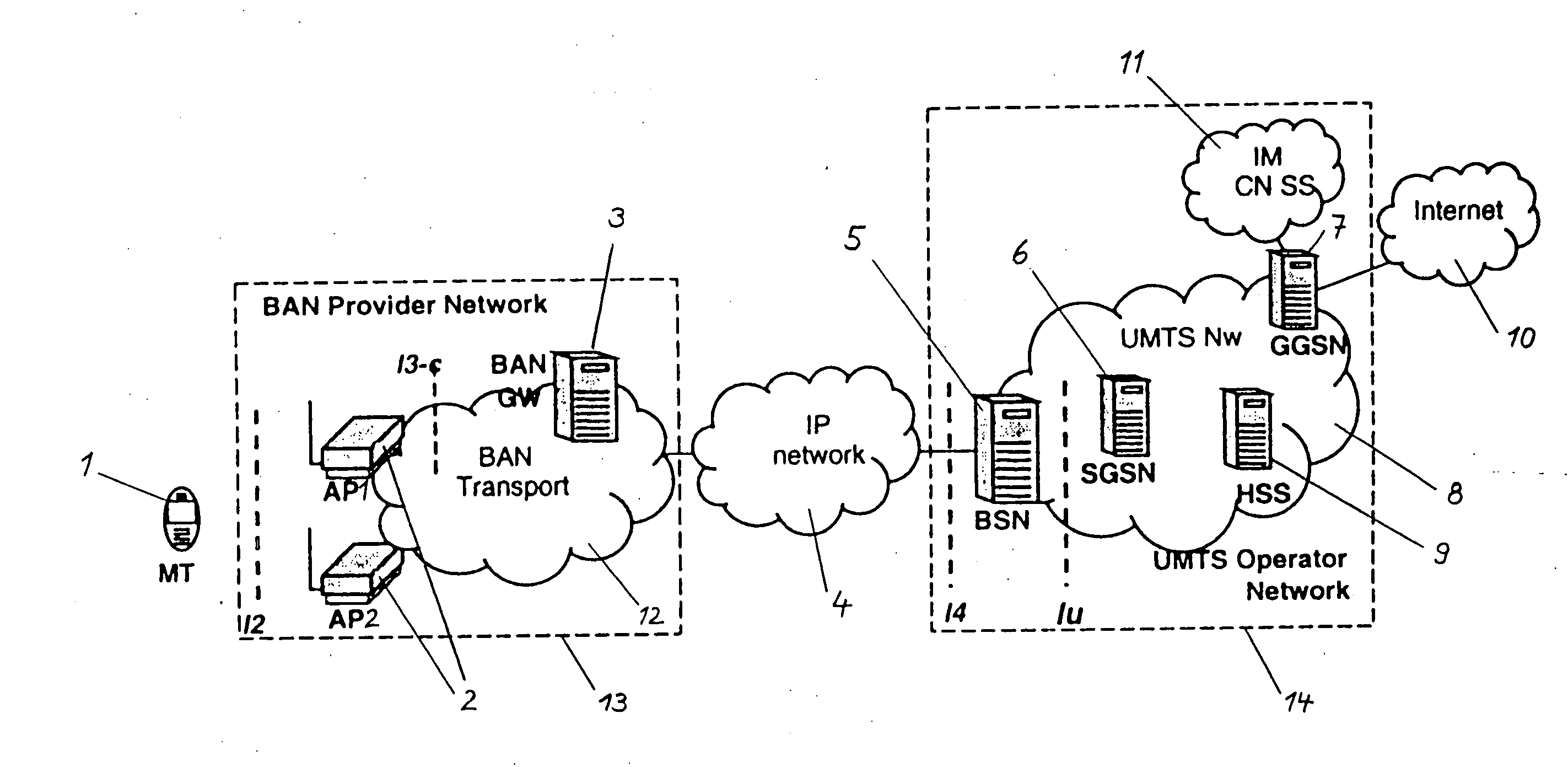
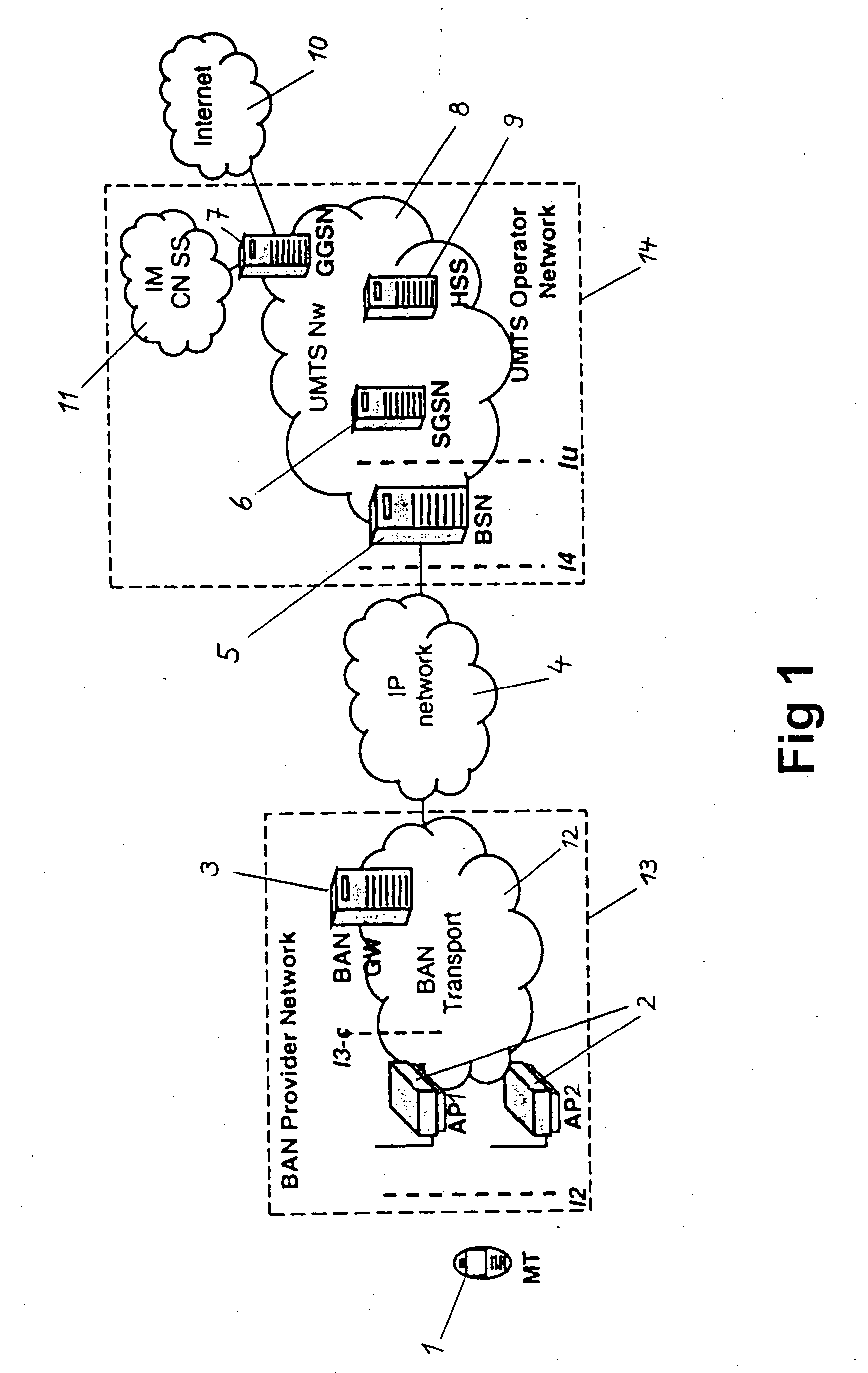
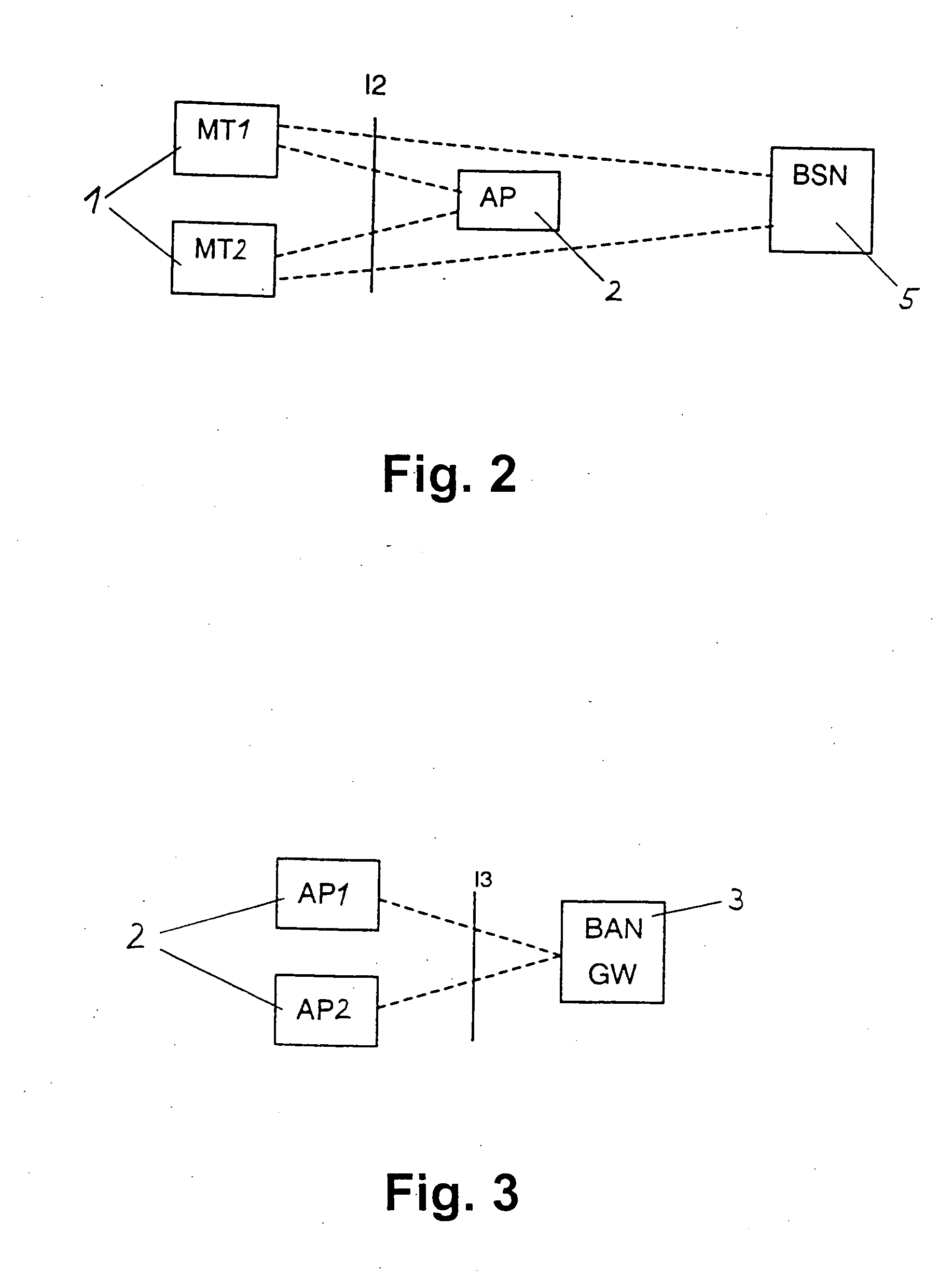
ActiveUS20050101245A1Improve facilitiesReasonable priceAssess restrictionTelephonic communicationAccess networkTerminal equipment
The present invention relates to a method and system for providing access to a cellular network (8), wherein a terminal device (1) is connected to an access device (2) according to access specifications of a broadband access network (12) which is not specifically designed to be used as a part of cellular network (8). The terminal device (1) indicates to the access device (2) that it wishes to be connected to the cellular network (8), and a session or call and a radio bearer is setup between the terminal device (1) and the cellular network (8). To achieve this, a service node (5) provided in the cellular network (8) requests a suitable access bearer from the access network (12) and the access device (2) sets up a corresponding access channel towards the terminal device (1). The terminal device (1) then associates the access channel to the correct radio bearer by using a corresponding identification. Thereby, service functions of the cellular network, e.g. UMTS services, can be distributed via any access network and existing broadband or high-speed access networks can be implemented in new cellular network structures. A huge capacity enhancement can thus be offered to the network operators of the cellular network without any standardization effort or license fee and at very small investment and maintenance costs.
Owner:NOKIA TECHNOLOGLES OY
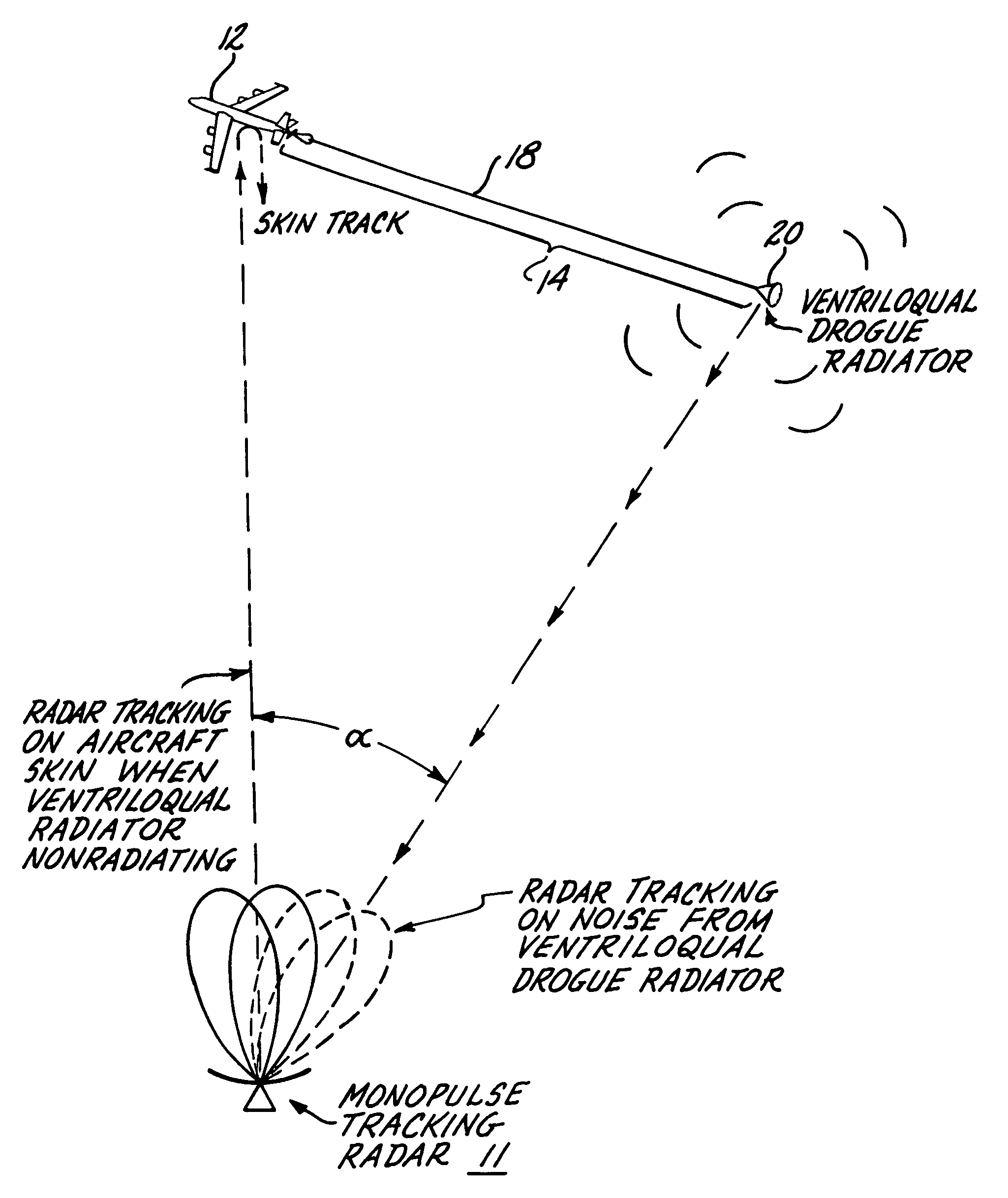
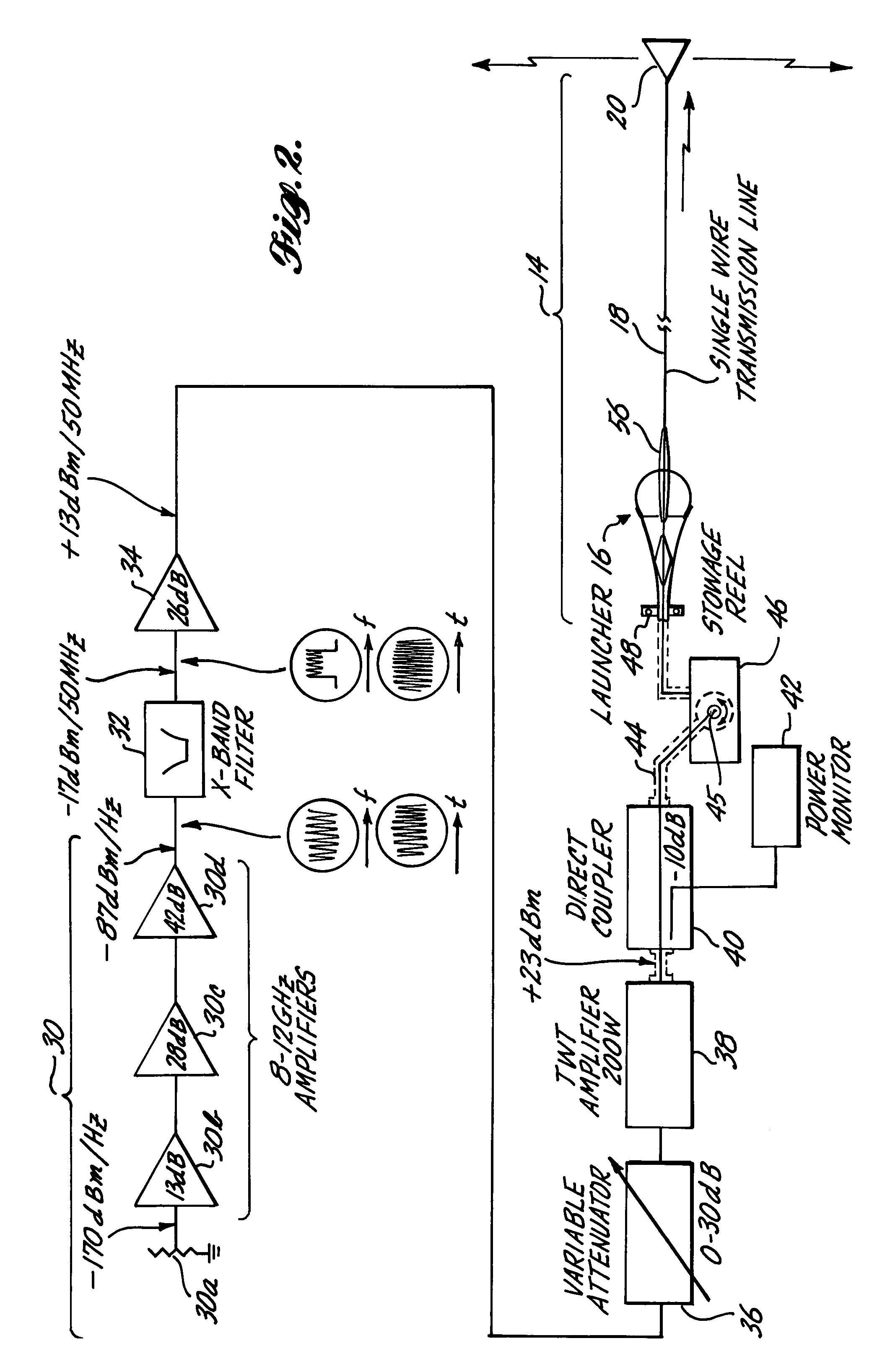
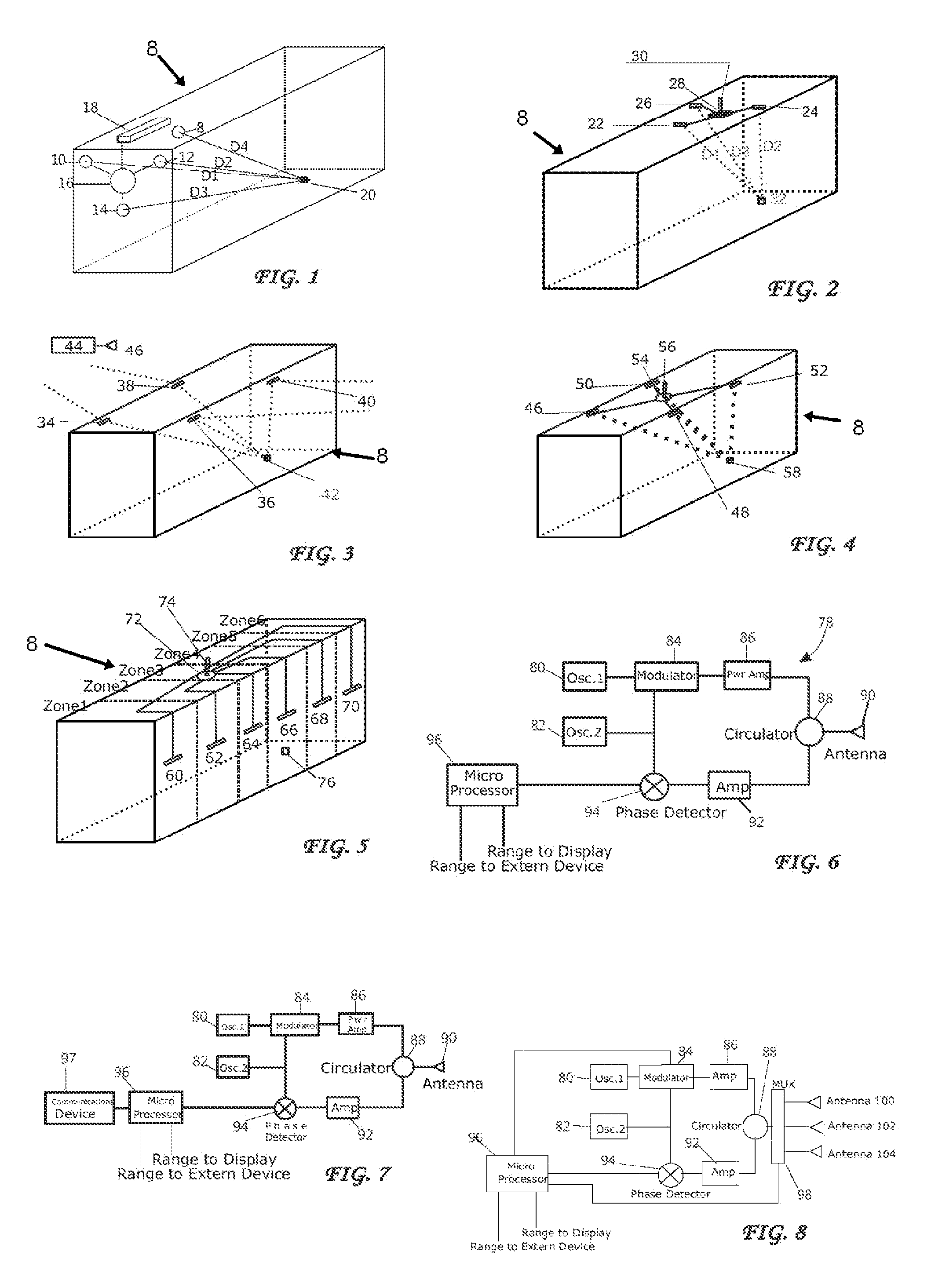
Airborne radar jamming system
A radar jamming signal generated by equipment carried by a target aircraft, is launched onto the leading end of a towed single wire transmission line so as to travel the length of the line as a nonradiating surface wave. A drogue radiator is attached to the trailing end of the line for radiating the jamming signal transversely of the towed line so as to be received by and cause jamming of tracking and / or fire control radar. The length of the single wire transmission line is selected so that the trailing radiator causes the jamming signal to emanate from a position sufficiently behind the aircraft so as to be outside the destructive radius of weapon fire directed at the apparent source of the jamming signal by fire control radar. A ventriloqual-like deception of the radar is thus achieved. A wave launcher couples the jamming signal to the leading end of the transmission line and for this purpose includes an electrically conducted horn-shaped structure, a tunable coaxial feed end at the constricted end of the horn structure, an inner transition conductor connecting the inner conductor of the coaxial feed to a leading end of the single wire transmission line, and a plurality of annular dielectric lenses and dielectric guides cooperatively shaped and fitted to the horn structure in a manner that effectively matches the bounded electromagnetic transmission wave characteristics of the coaxial feed cable with the surface wave transmission characteristics of the single wire transmission line. Coacting with the ventriloqual-like radiation of the jamming signal from the trailing end of the transmission line is an anti-integration network that hides the return radar signal reflected off the target aircraft in a signal energy “hole” created for such purpose in a secondary low level noise signal transmitted directly from the aircraft.
Owner:THE BOEING CO
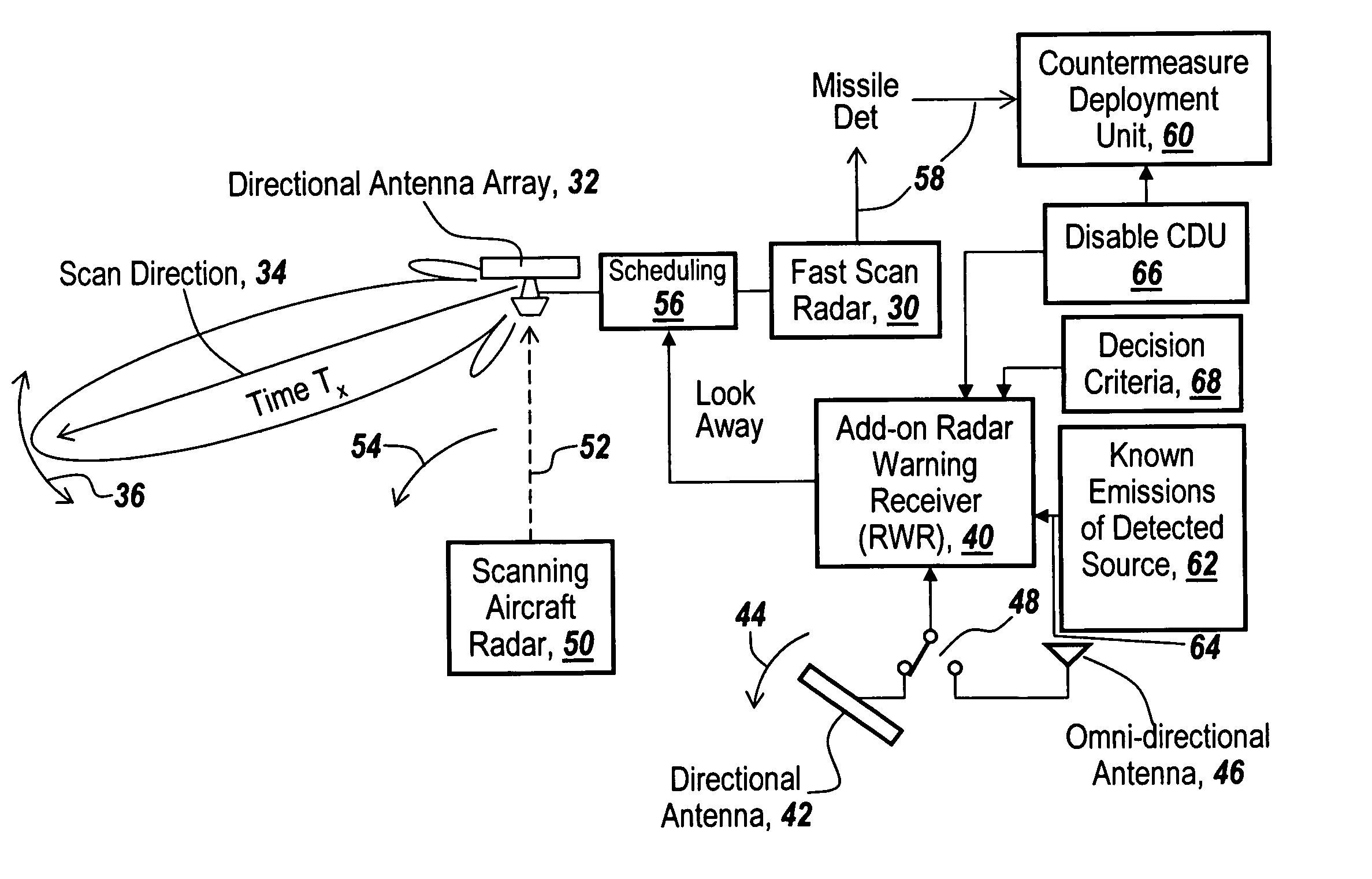
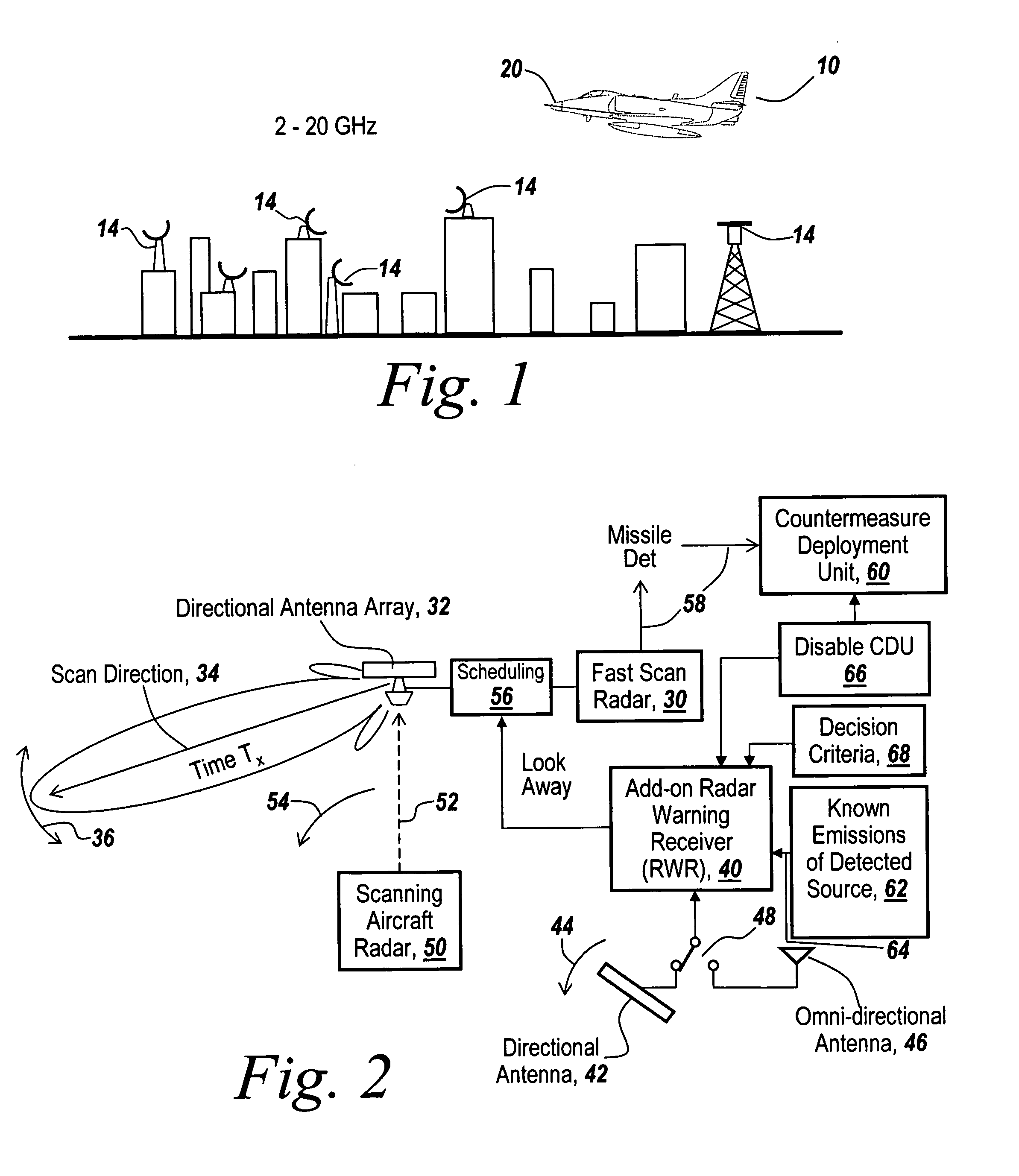
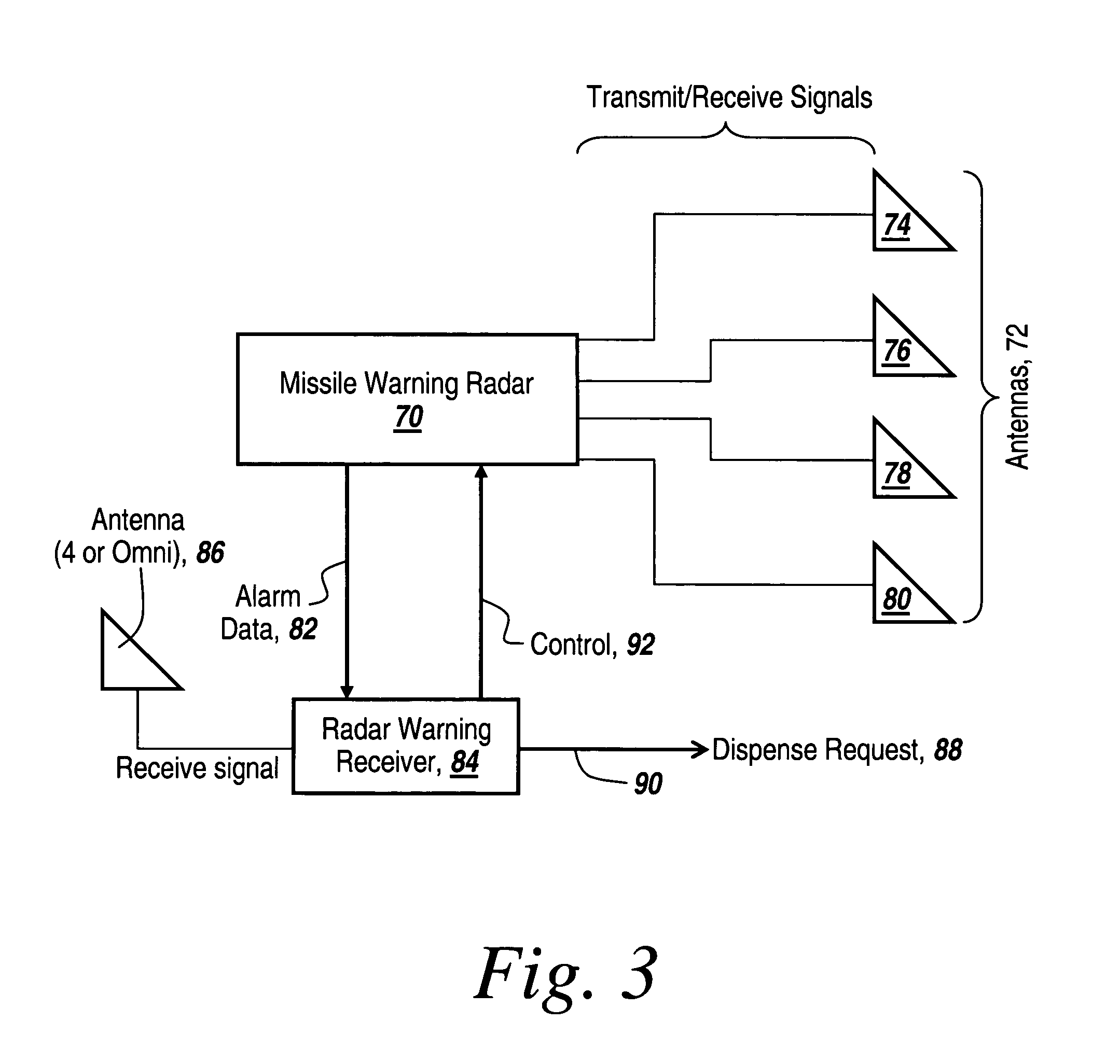
Method and apparatus for monitoring the RF environment to prevent airborne radar false alarms that initiate evasive maneuvers, reactionary displays or actions
InactiveUS7843375B1Accurate predictionLower false alarms without degrading system performanceCommunication jammingRadio wave reradiation/reflectionRadarFalse alarm
Rather than costly modifications to existing radars, a small, low cost radar warning receiver is used to monitor the RF environment. This add-on receiver can provide situational awareness including RF signal levels and angle of arrival, and recommend or provide antenna scanning synchronization, blanking inputs or gated reactionary outputs to or for the airborne radar. Utilization of this information can be used to reduce false alarms and improve system performance.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
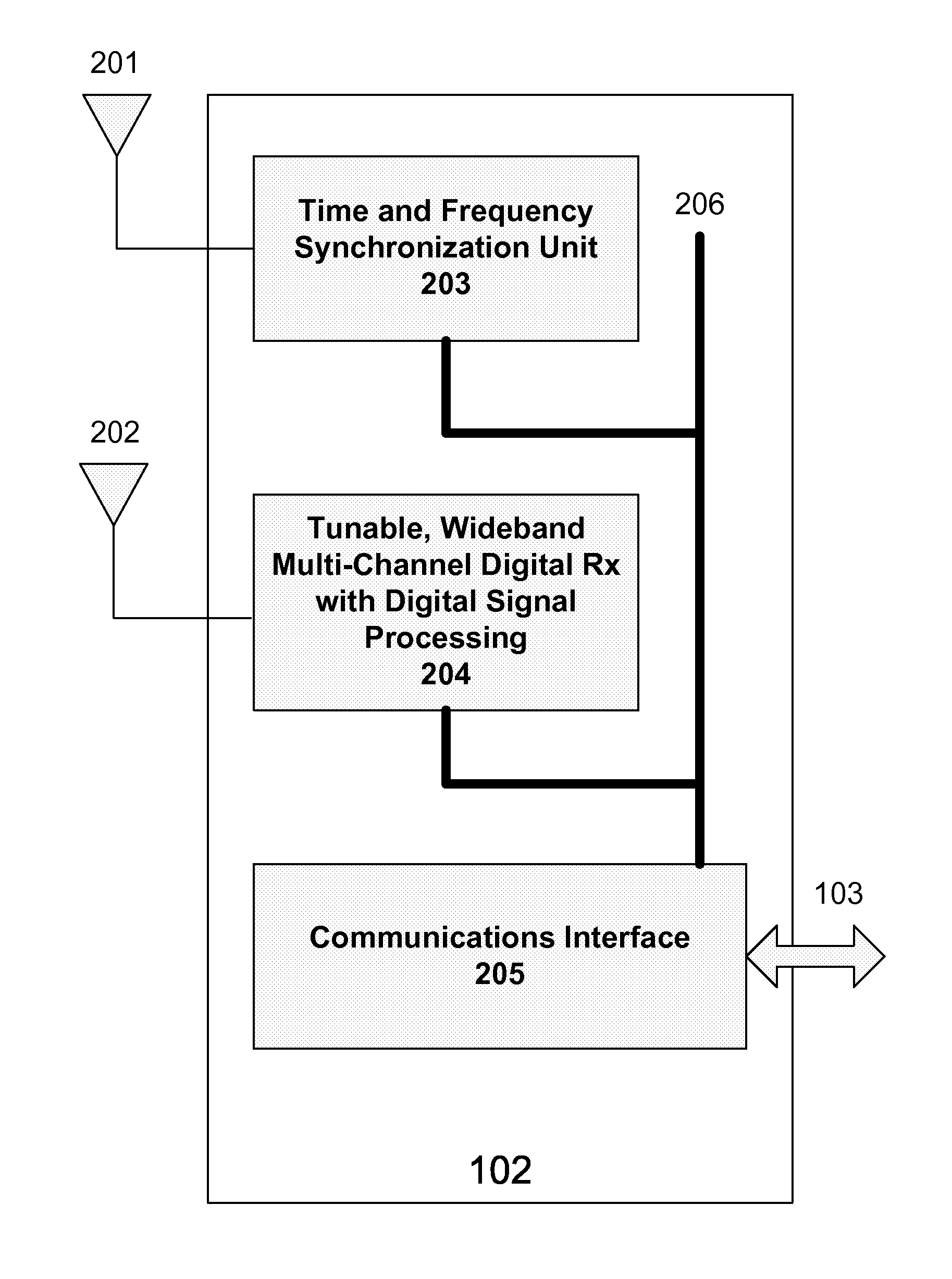
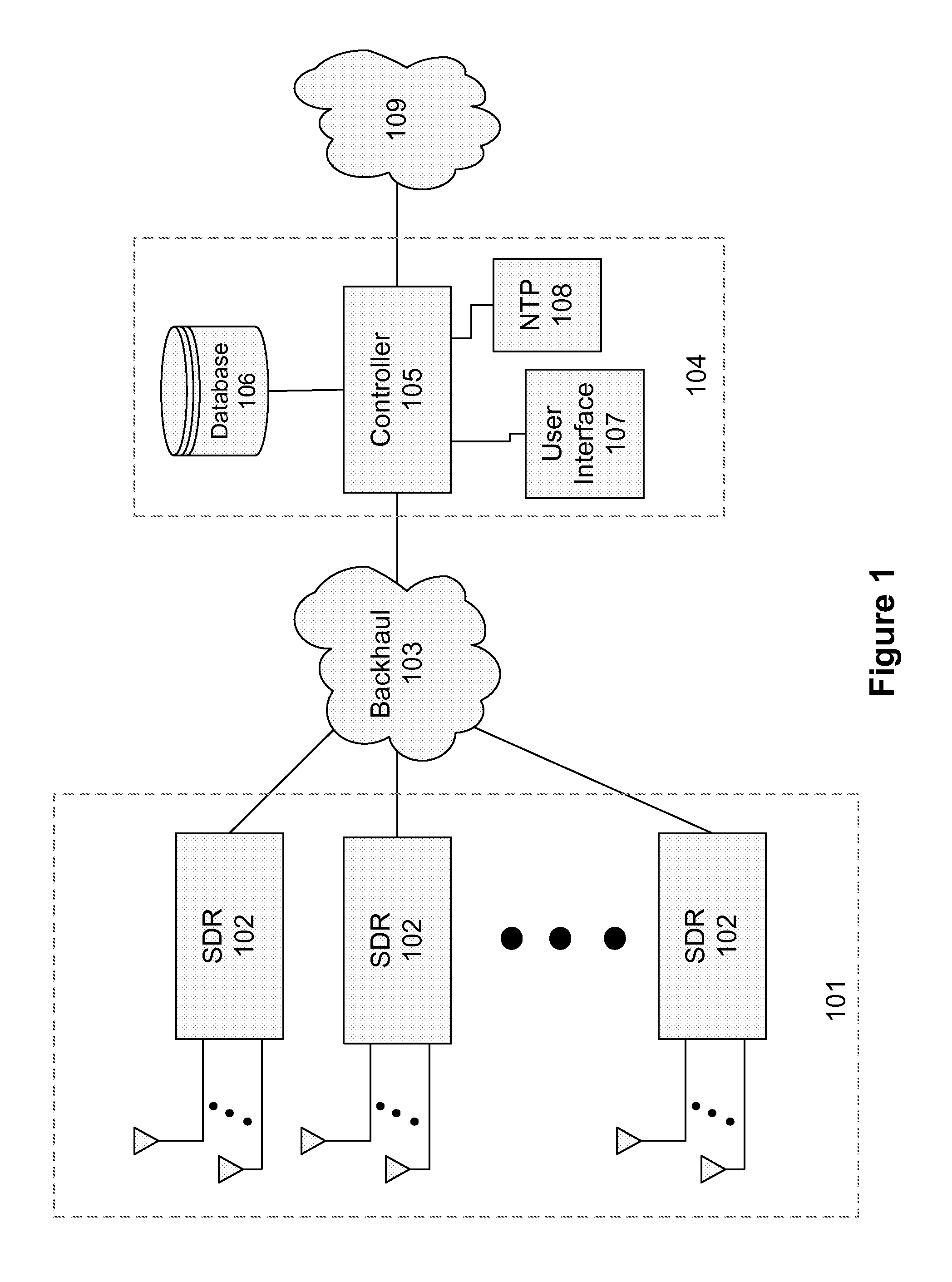
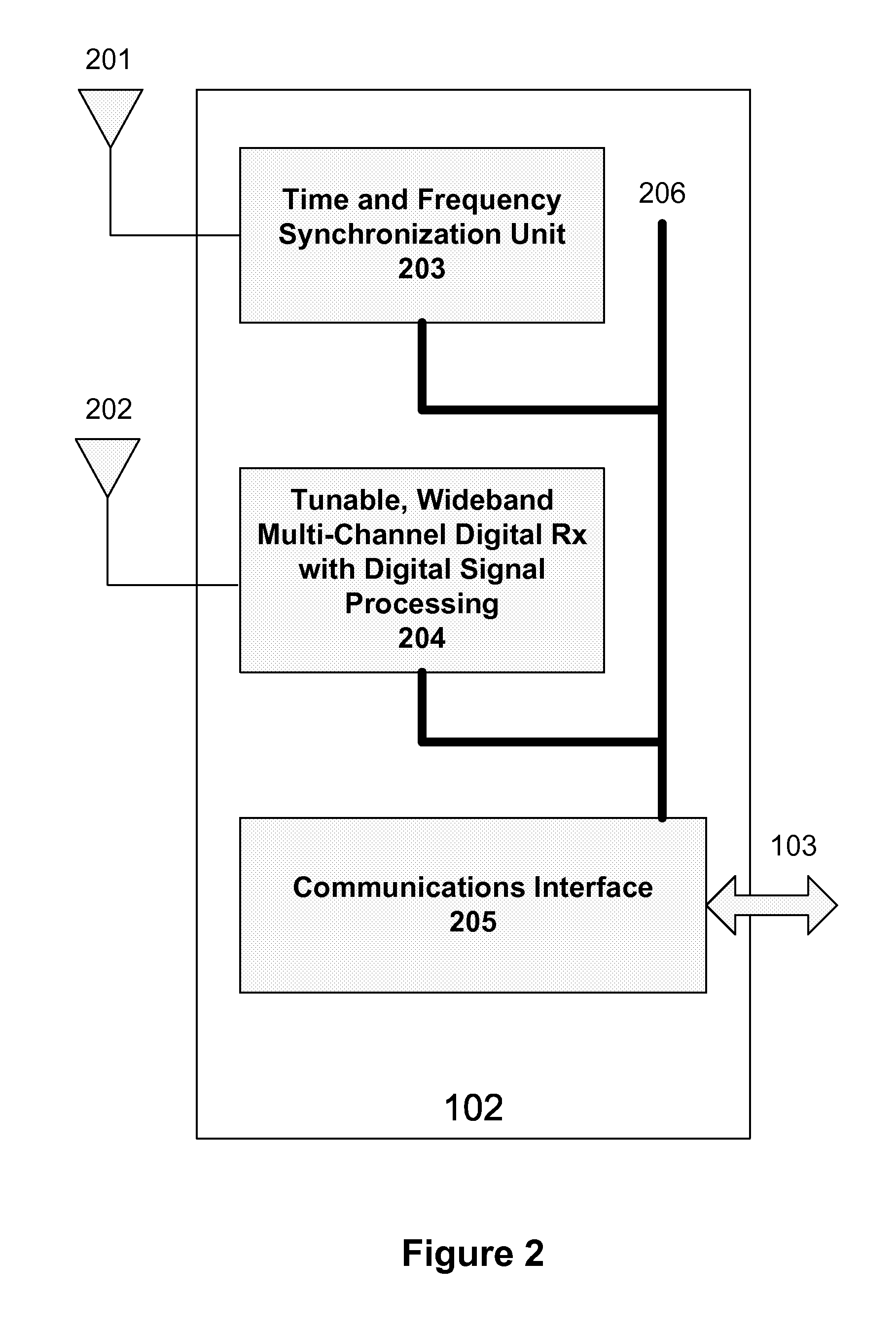
Interference detection, characterization and location in a wireless communications or broadcast system
ActiveUS20120032854A1Direction finders using radio wavesNetwork traffic/resource managementSoftware define radioTransmitted power
A Wide Area Sensor Network (WASN) is disclosed that utilizes wideband software defined radios (SDRs) to monitor RF energy over a wide frequency range, detect when critical frequencies are being jammed or otherwise interfered with, and locate the source of the interference so that the interference can be eliminated. The WASN may use one or more geolocation techniques In addition, the WASN may detect and locate unauthorized transmitters as well as estimate the transmitted power of authorized transmitters to assure they are not transmitting more power than authorized.
Owner:TRUE POSITION INC
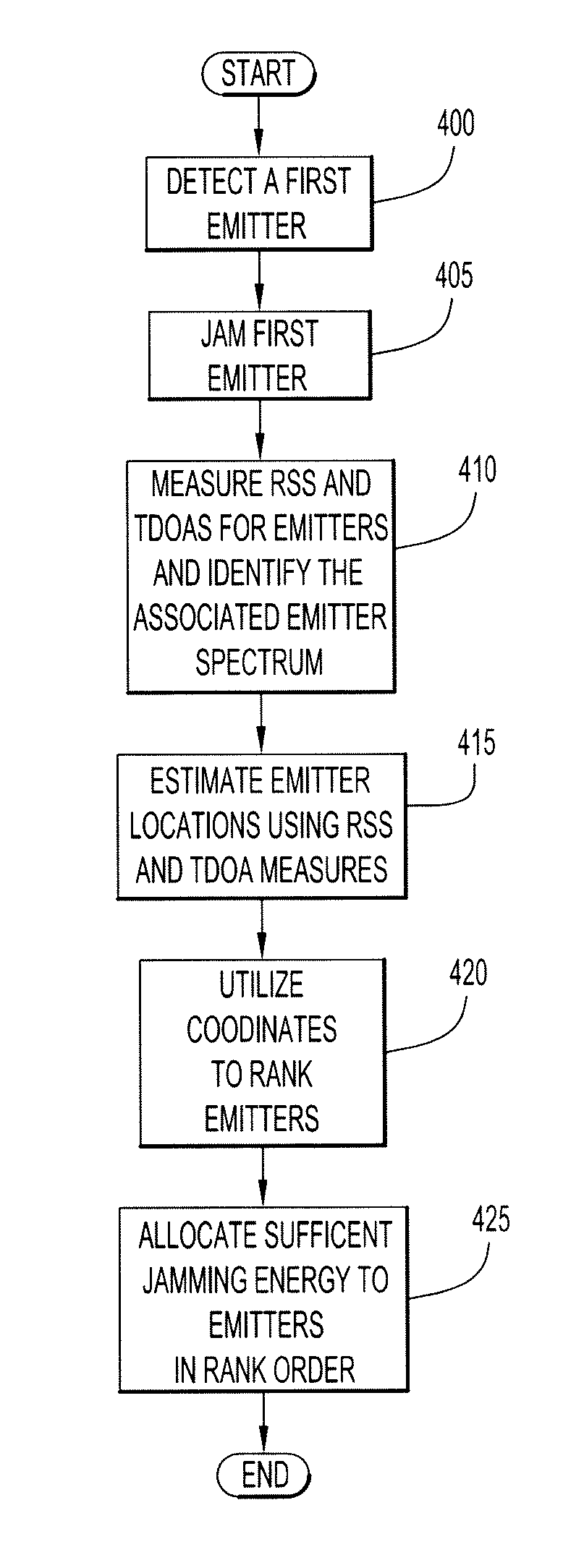
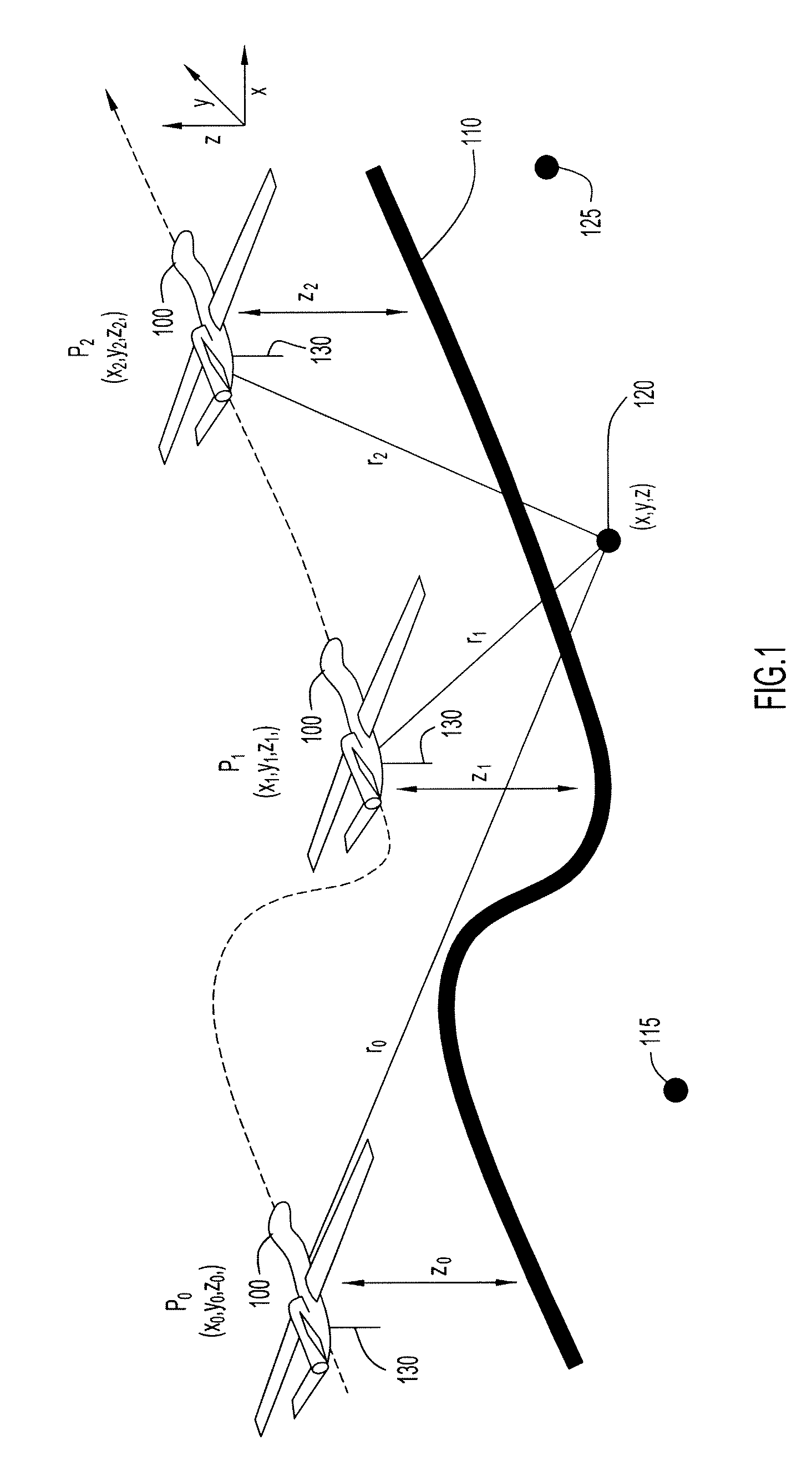
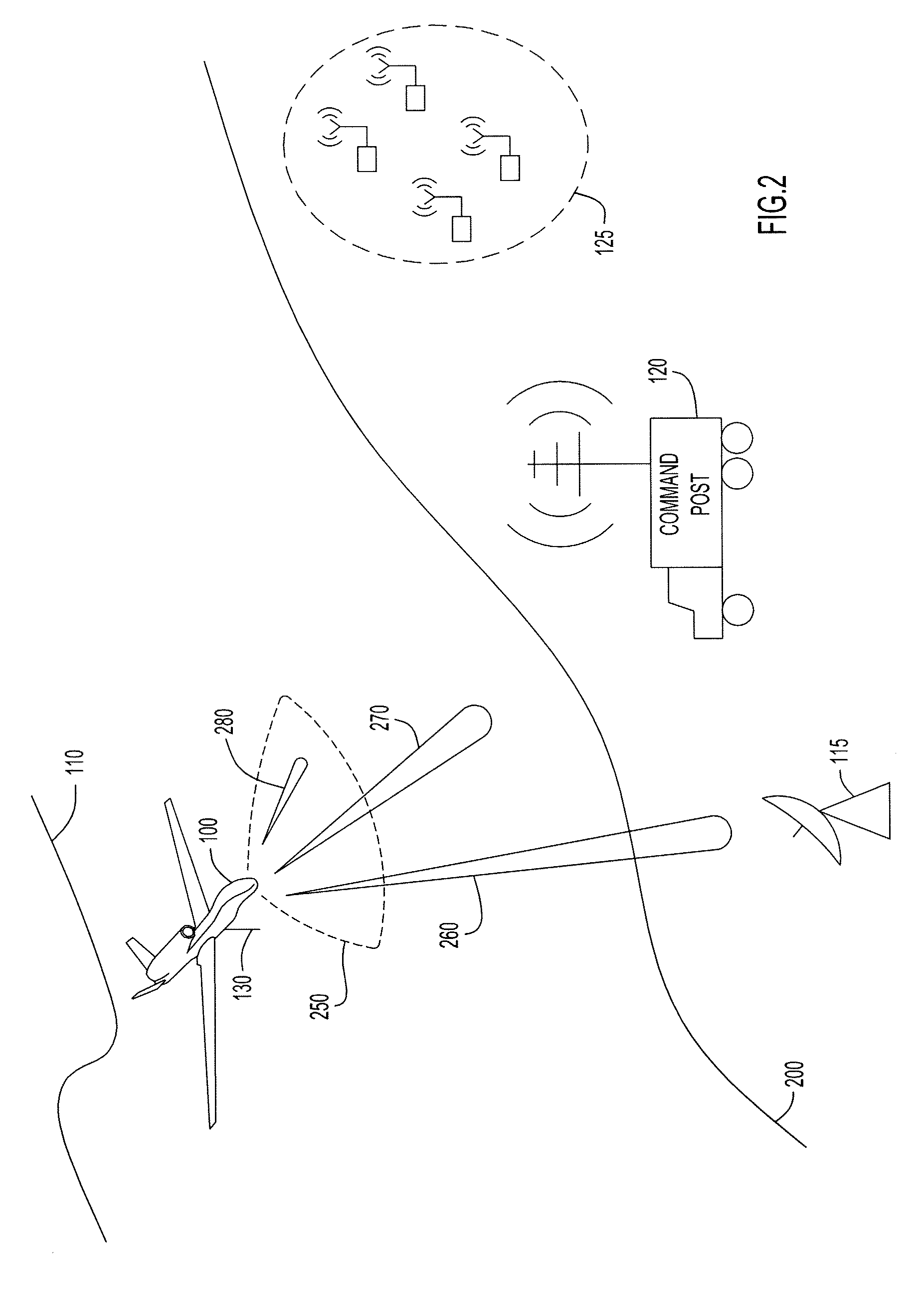
System and method for allocating jamming energy based on three-dimensional geolocation of emitters
ActiveUS8615190B2Cost-effectiveSmallWave based measurement systemsTelephonic communicationGeolocationEnergy based
According to an embodiment of the present invention jamming energy is allocated to a plurality of emitters based on a three-dimensional (3-D) emitter geolocation technique that determines the geolocation of radio frequency (RF) emitters based on energy or received signal strength (RSS) and / or time differences of arrival (TDOAs) of transmitted signals. The three-dimensional (3-D) emitter geolocations are used to rank emitters of interest according to distance and available radio frequency (RF) jamming energy is allocated to the emitters in rank order. The techniques may be employed with small unmanned air vehicles (UAV), and obtains efficient use of jamming energy when applied to radio frequency (RF) emitters of interest.
Owner:HARRIS CORP
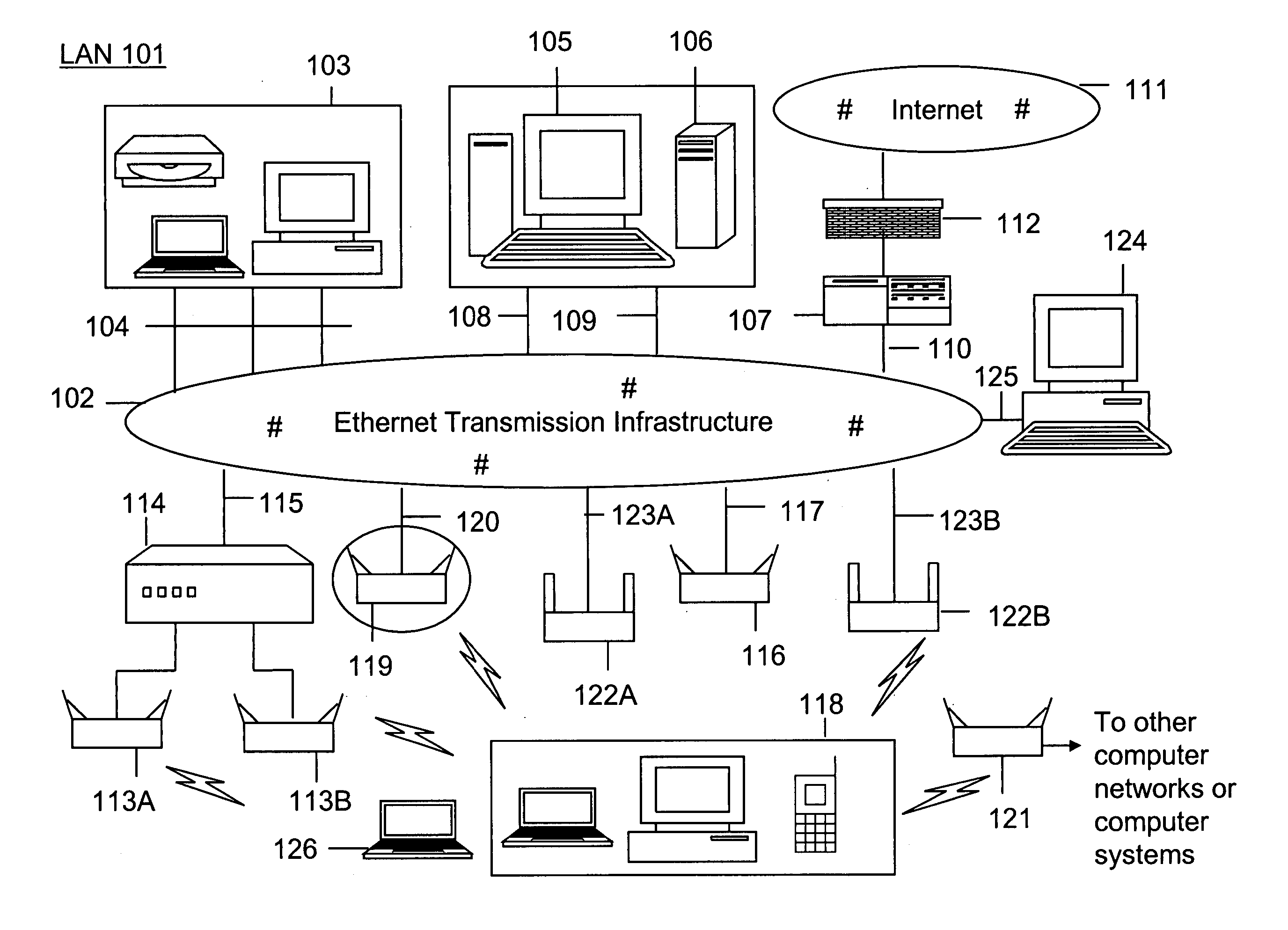
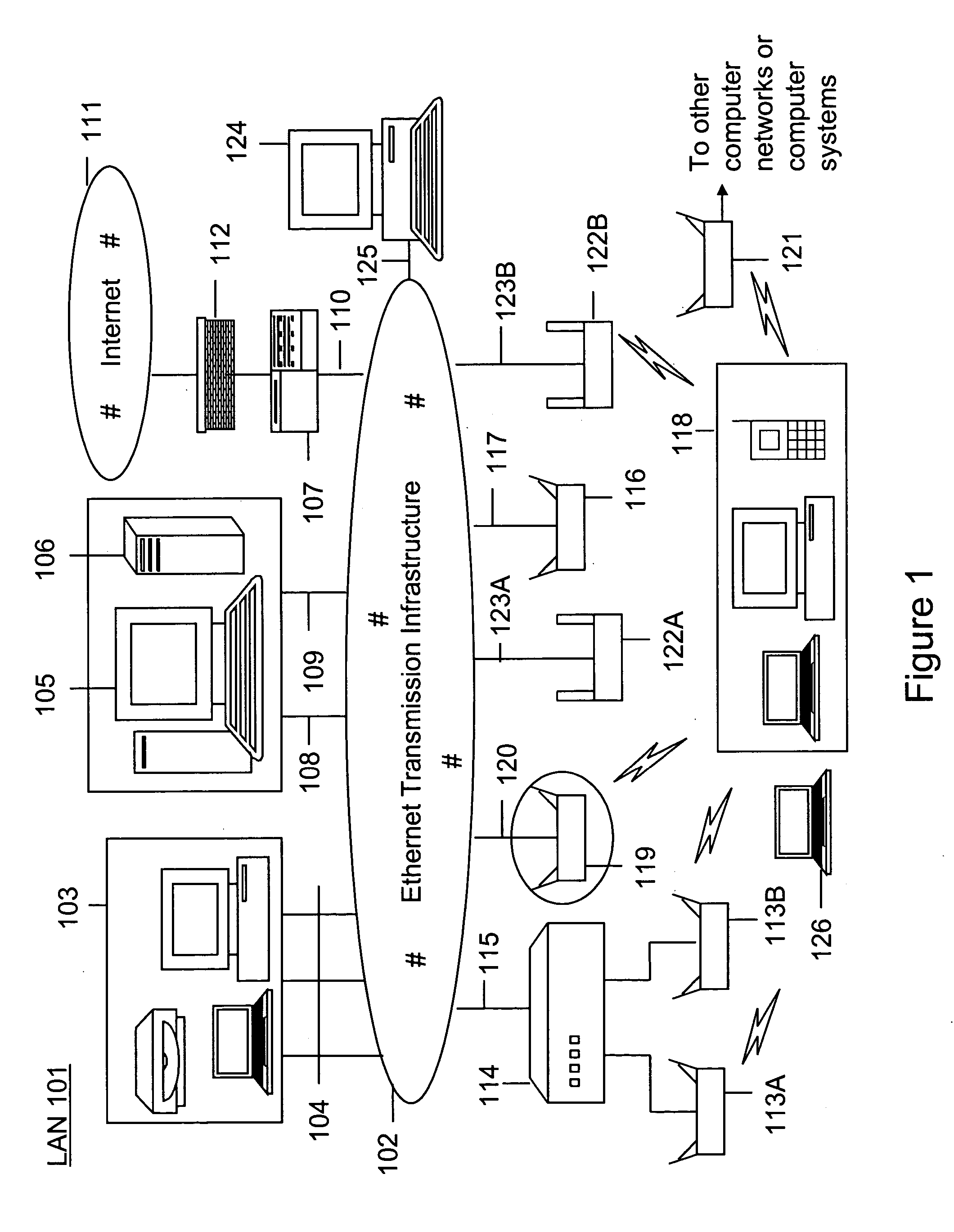
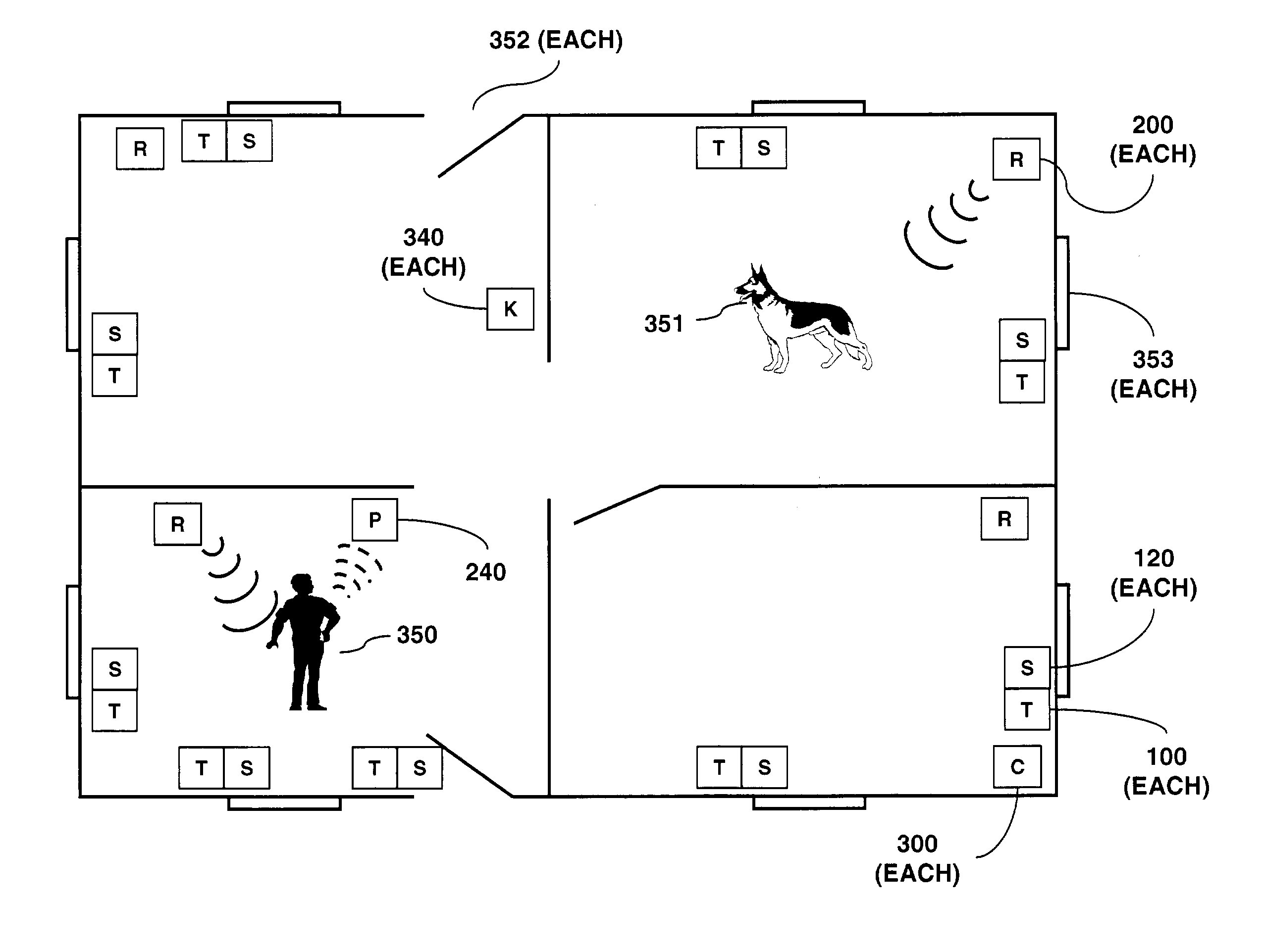
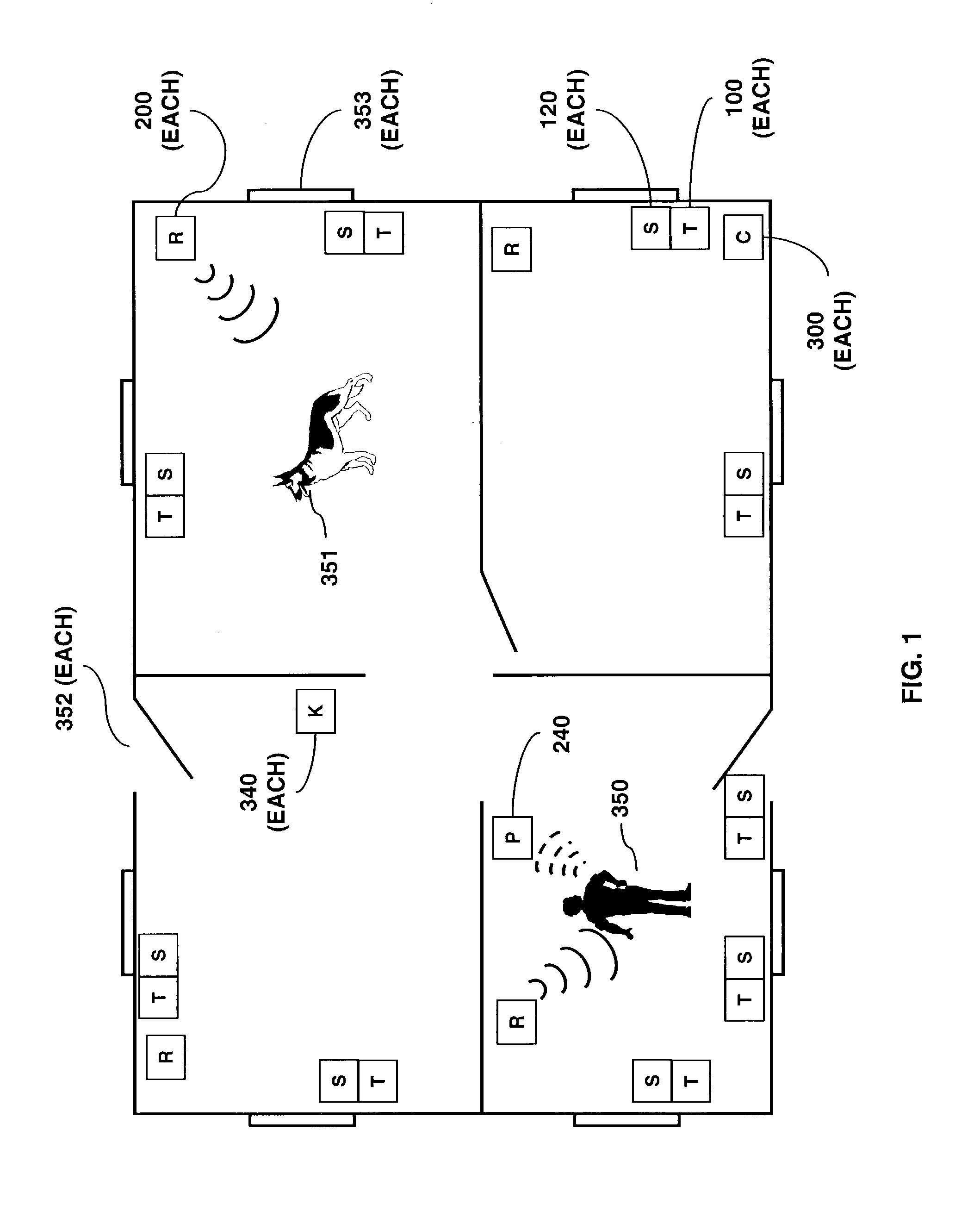
Method and system for monitoring a selected region of an airspace associated with local area networks of computing devices
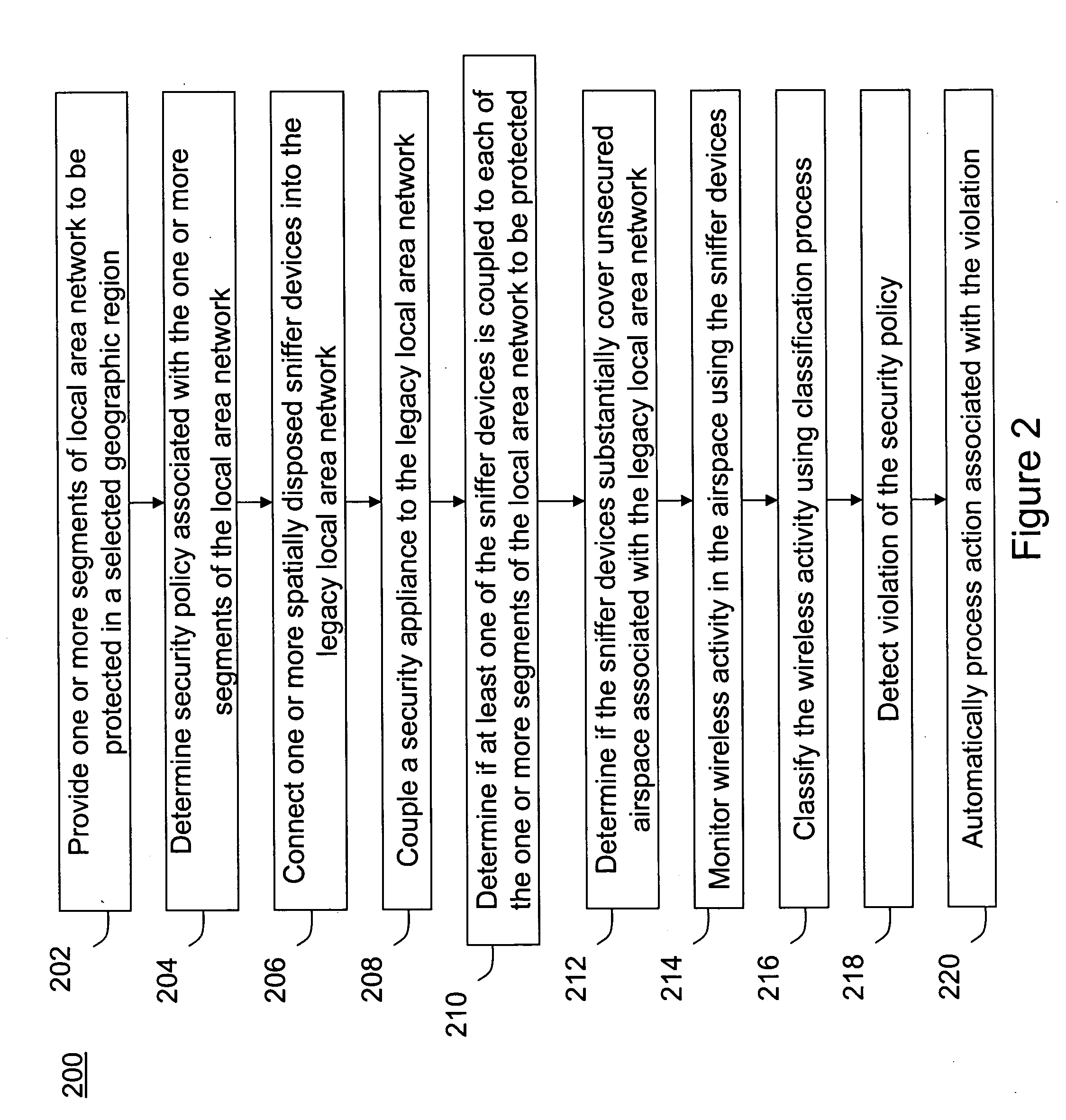
ActiveUS20050128989A1Easy to usePrevent unauthorized wireless accessWave based measurement systemsData switching by path configurationBody area networkGeographic regions
A method for monitoring a selected region of an airspace associated with local area networks of computing devices is provided. The method includes providing one or more segments of a legacy local area network to be protected in a selected geographic region. The legacy local area network is characterized by an unsecured airspace within the selected geographic region. The method includes determining a security policy associated with the one or more segments of the legacy local area network. The security policy at least characterizes a type of wireless activity in the unsecured airspace to be permitted, denied, or ignored. Additionally, the method includes connecting one or more sniffer devices into the legacy local area network. The one or more sniffer devices are spatially disposed within the selected geographic region to cause at least a portion of the unsecured airspace to be secured according to the security policy. Moreover, the method includes coupling a security appliance to the legacy local area network. The method also includes determining if at least one of the sniffer devices is coupled to each of the one or more segments of the legacy local area network to be protected and determining if the one or more sniffer devices substantially covers the portion of the unsecured airspace to be secured. The method additionally includes monitoring wireless activity in the airspace using the one or more sniffer devices, and automatically classifying, using a classification process, a portion of information associated with the monitoring of the wireless activity to at least determine if the wireless activity communicates to at least one of the one or more segments to be protected. Further, the method includes detecting a violation of the security policy based upon at least the classifying of the portion of the information from the monitoring of the wireless activity, and automatically processing an action associated with the violation in accordance to the security policy for the one or more segments in the legacy local area network to be protected.
Owner:ARISTA NETWORKS
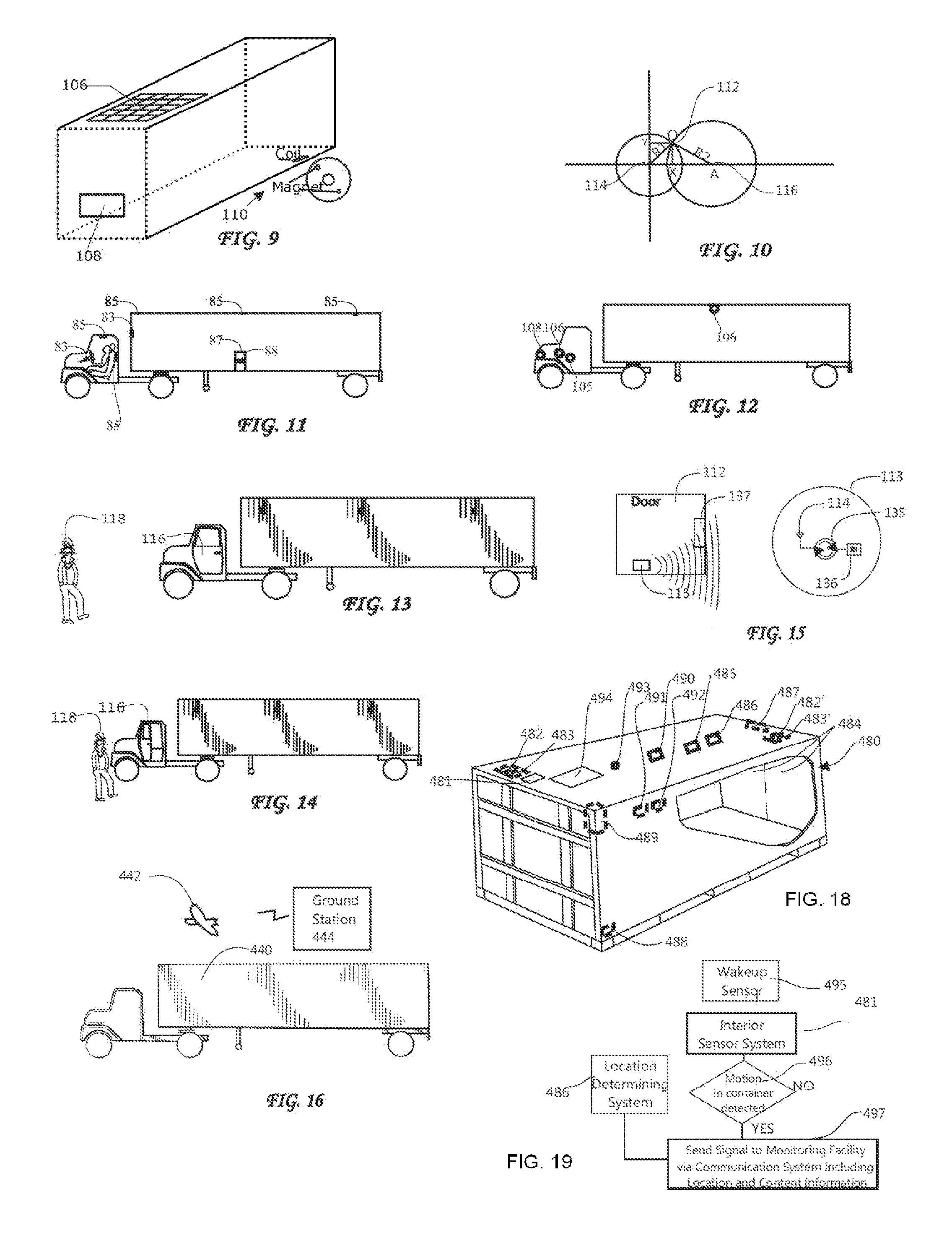
Cargo theft prevention using text messaging
InactiveUS20130033381A1Reducing and eliminating theftEfficient powerBraking element arrangementsBuilding locksDriver/operatorCargo container
Method for monitoring a cargo container in which a transmitter is arranged on the container and periodically transmits messages to a remote site or location according to a schedule of messages. When a message is not received according to the schedule, which may be the result of tampering with the transmitter or another nefarious action involving the container, it may be considered that the container has been stolen. A rate of transmission of the messages may be modified based on a condition of the vehicle, such as the presence of a driver inside the vehicle, a distance between a driver inside the vehicle and the vehicle, the vehicle being at rest after motion of the vehicle stops, a location of the vehicle, biometric identification of a driver of the vehicle and deviation of the vehicle from an expected route, and / or based on current time and weather around the vehicle.
Owner:INTELLIGENT TECH INT
Method and system for controlling and modifying driving behaviors
ActiveUS20140113619A1Improving insurance company performanceProvide controlRegistering/indicating working of vehiclesAssess restrictionDividing attentionEngineering
Disclosed herein is a method and system for detecting, monitoring and / or controlling one or more of mobile services for a mobile communication device (also referred to herein as a Controllable Mobile Device or CMD), and in particular, when the device is being used and the vehicle, operated by the user of the device, is moving. In addition, one aspect of the invention generally relates to a method and system for modifying a user's driving behaviors, in particular to a system and method for modifying a user's unsafe driving behaviors, e.g., using one or more services of a controllable mobile device while driving, by providing a score to the user rating indicating that they are using a mobile device in a distracting way, or driving in a manner that indicates that they are distracted.
Owner:KATASI
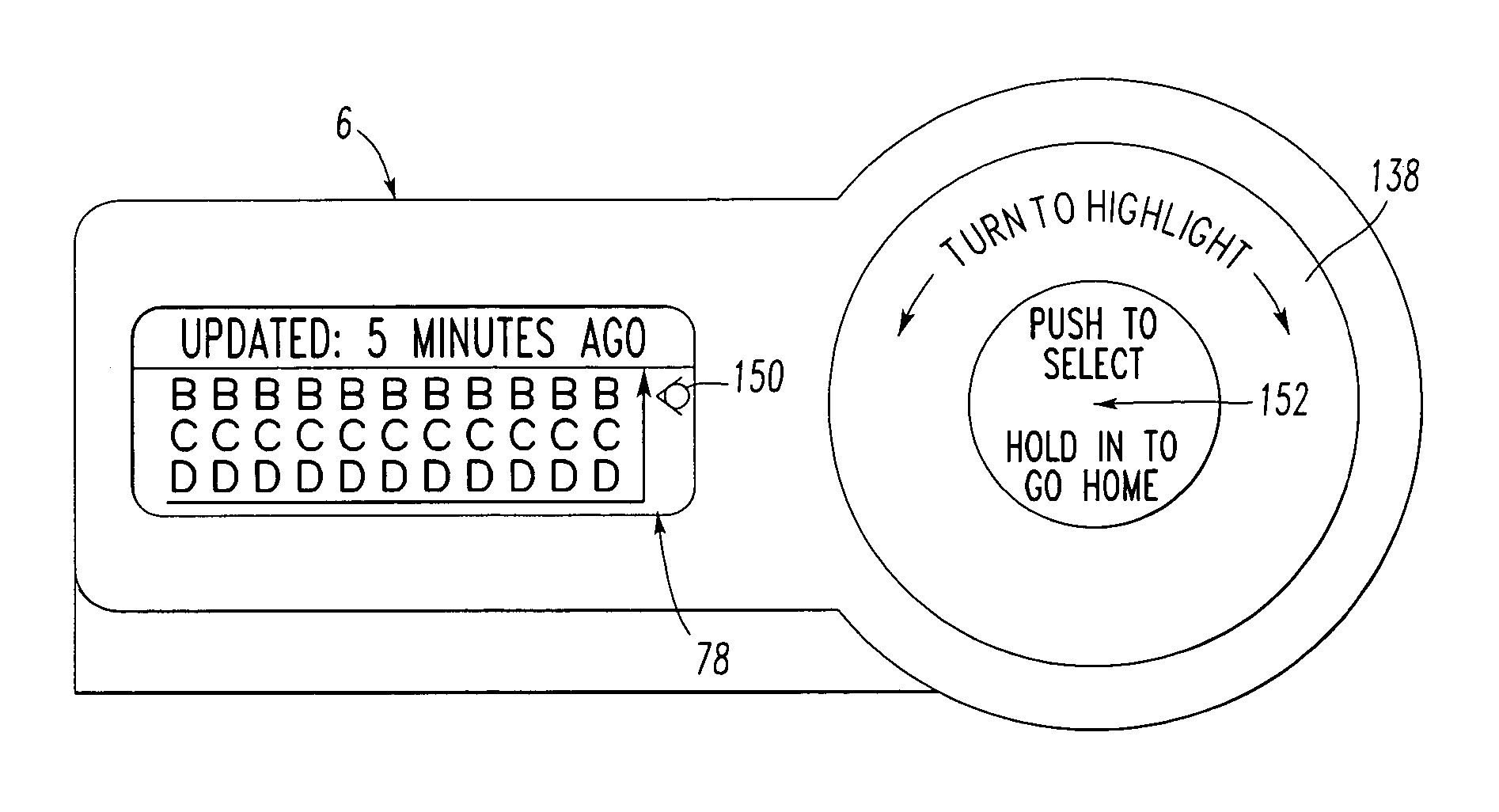
Home system including a portable fob having a rotary menu and a display
A home wellness system includes a server having a wireless transceiver, a plurality of sensors each of which has a wireless transceiver adapted to communicate sensor information to the server wireless transceiver, and a portable display and configuration fob, the portable fob includes a rotary thumbwheel encoder, a display and a wireless transceiver communicating with the server wireless transceiver, the thumbwheel encoder and the display cooperate to provide a first rotary menu for displaying the sensor information of the sensors and a second rotary menu for configuring the sensors.
Owner:EATON CORP
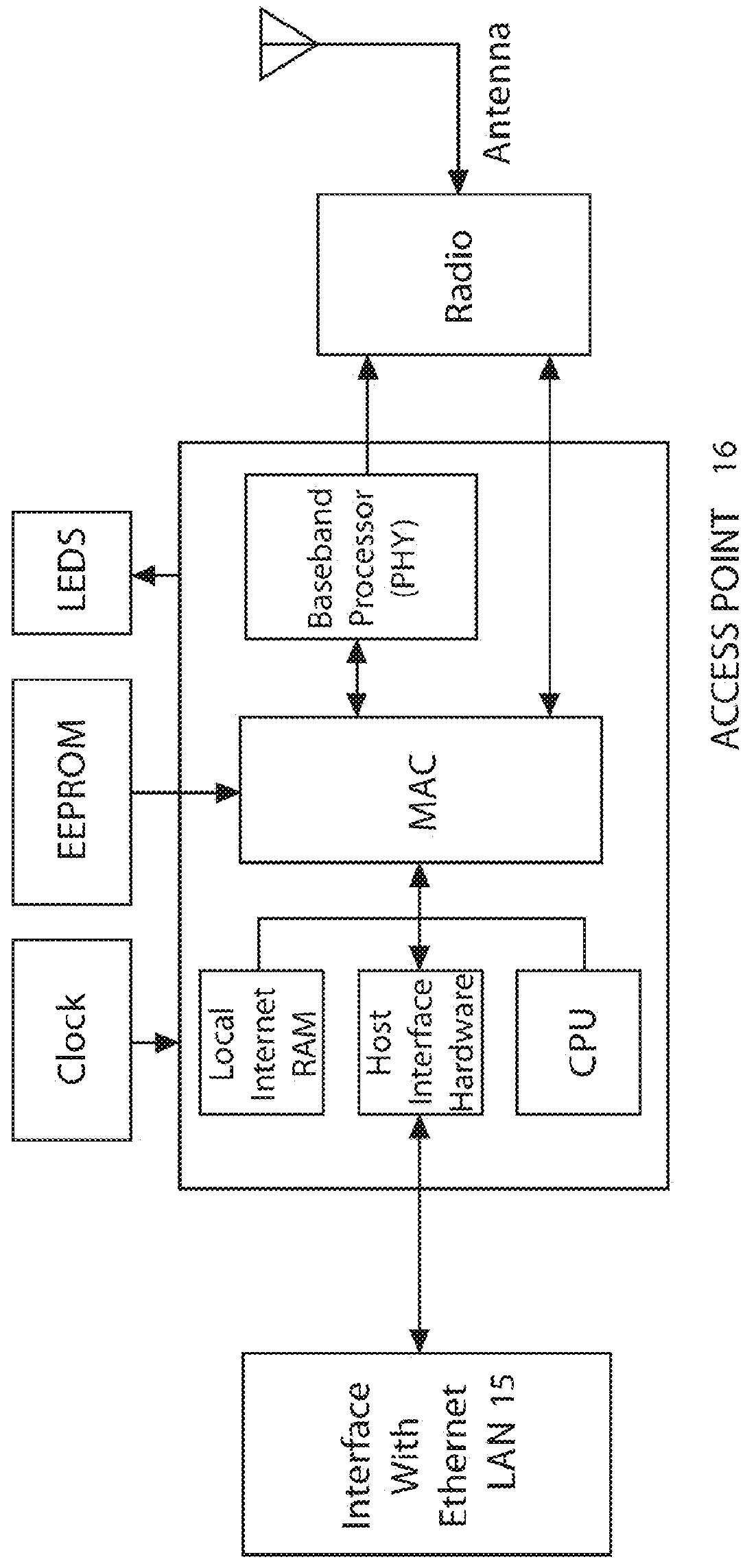
Communication network with secure access for portable users
InactiveUS8406427B2Multiple digital computer combinationsSecret communicationCommunications securityMedia access control
A communication network includes a local area network (LAN) and a wireless access point coupled to the LAN. In one embodiment, each access point includes a medium access control (MAC) stage, and a radio frequency (RF) transmitter / receiver for communicating unsecure message data via RF links with users of associated wireless devices. An optical transmitter / receiver in the access point enables the users to communicate secure message data over the LAN via free space optical (FSO) links with the users. The MAC stage operates (i) to direct unsecure data from the LAN to the wireless device users and to direct unsecure data from the users to the LAN, via the RF transmitter / receiver; and (ii) to direct secure data from the LAN to the wireless device users and to direct secure data from the users to the LAN, via the optical transmitter / receiver. An integrated VoIP / FSO portable handset is also disclosed.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Detecting RFID tag and inhibiting skimming
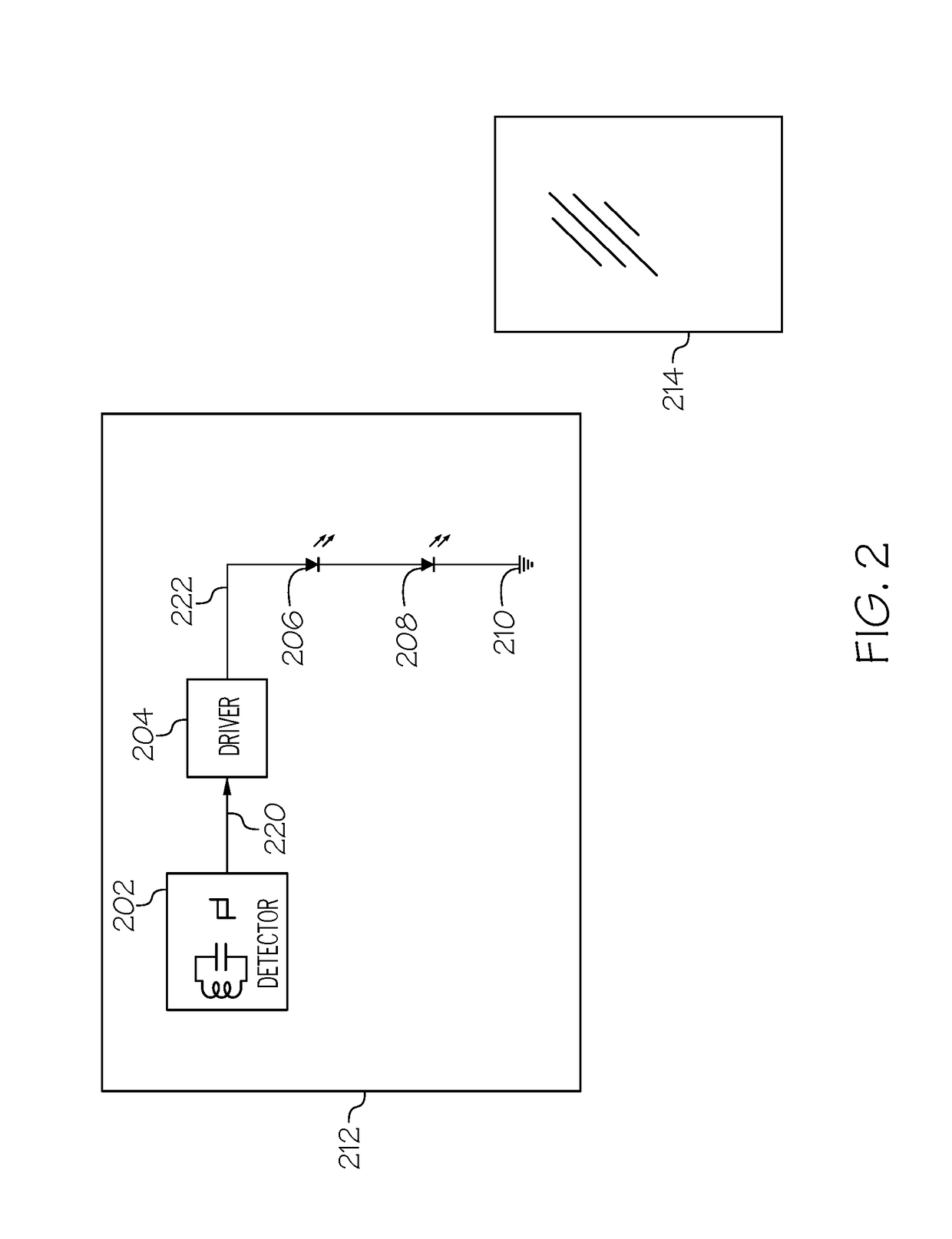
InactiveUS20130106576A1Flush outsideIncrease the difficultySensing detailsCommunication jammingDecoyResponse Frequency
A method of detecting an RFID tag includes transmitting a bait RFID read signal at a bait power level and a simulated response signal at a simulated-response power level. A selected reader frequency is monitored for a selected detection time. A skimmer is determined to be present if a skimmer RFID read signal is detected during that time. If a skimmer is not determined to be present, multiple read signals are transmitted sequentially, each signal at a respective read power level. At least one of the read power levels is lower than the bait power level, at least one of the read power levels is lower than the simulated-response power level, and at least two of the read power levels are different from each other. A selected response frequency for a tag is monitored for a response from an RFID tag.
Owner:EASTMAN KODAK CO
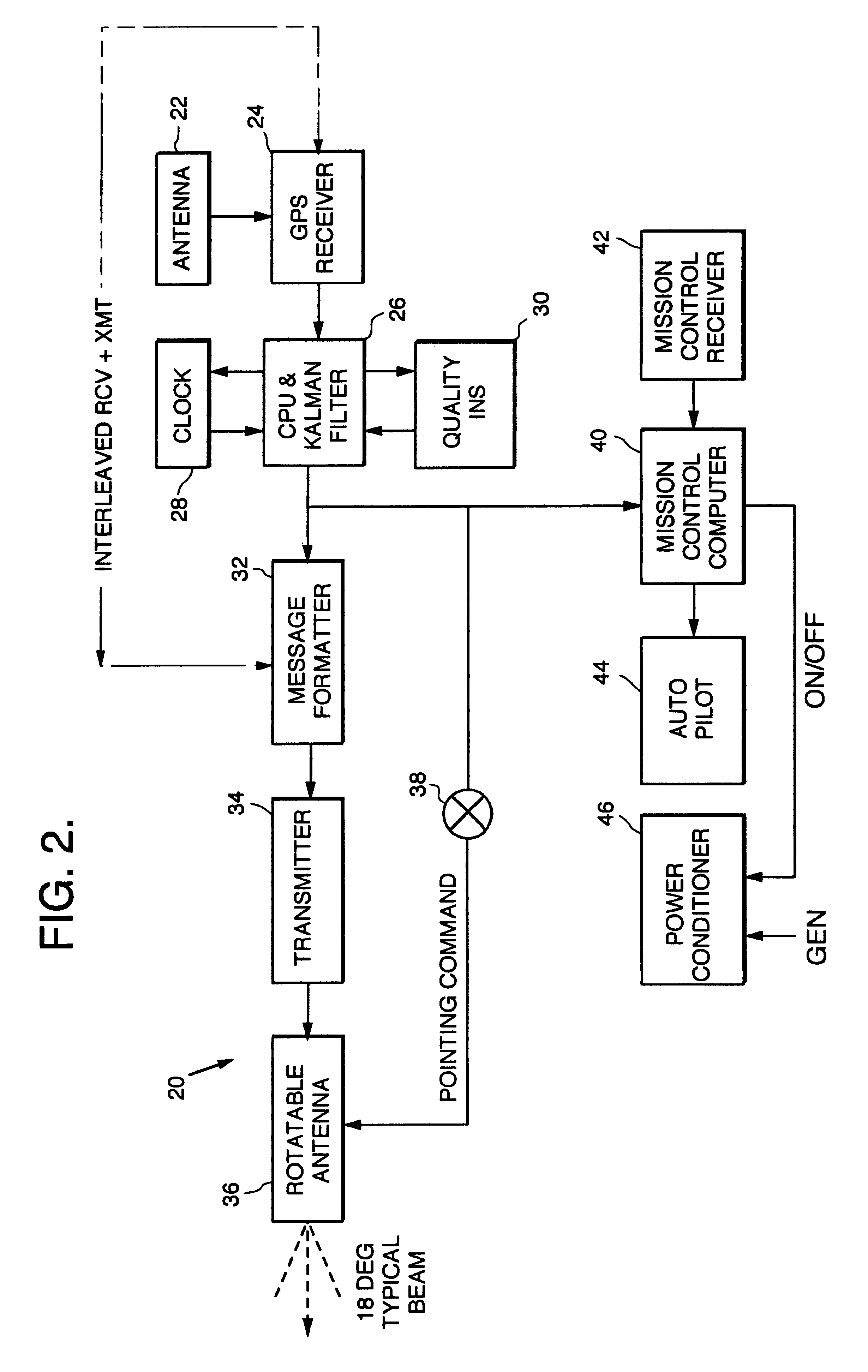
Airborne GPS guidance system for defeating multiple jammers
InactiveUS6300898B1Eliminate the effects ofDirection controllersBeacon systemsGuidance systemAnti jamming
A missile guidance system designed to operate on GPS signals in an anti-jamming environment. The inventive system includes first, second and third airborne vehicles (20). A GPS receiver (24) is mounted on each of the three vehicles (20) to receive signals transmitted from spaceborne satellites (14). Each vehicle (20) acts as a pseudo-satellite or "pseudolite'. The received GPS signals are processed by a processor (26) to provide a first intermediate signal indicating the position of the vehicle (20). This signal is retransmitted from each vehicle and received by a GPS receiver mounted on a missile. The received intermediate signal is processed on the missile to provide an output signal indicating the position thereof. The pseudolites would be airborne in the vicinity of a target area. Because the pseudolites are relatively close to the targets compared to a satellite in high altitude orbit and because the pseudolites would be able to transmit a kilowatt or more power, the signal strength may be improved significantly. To succeed as a jammer, a jammer, successful against GPS satellites, would need considerably more power to succeed against aircraft carried pseudolites. The pseudolite system delivers GPS signals into the target area 40-70 dB stronger than signals coming directly from GPS satellites. By timing the signals for 100% time coverage, enemy C / A code receivers will be jammed because they are limited to a J / S capability of 30 dB.
Owner:SCHNEIDER ARTHUR J +1
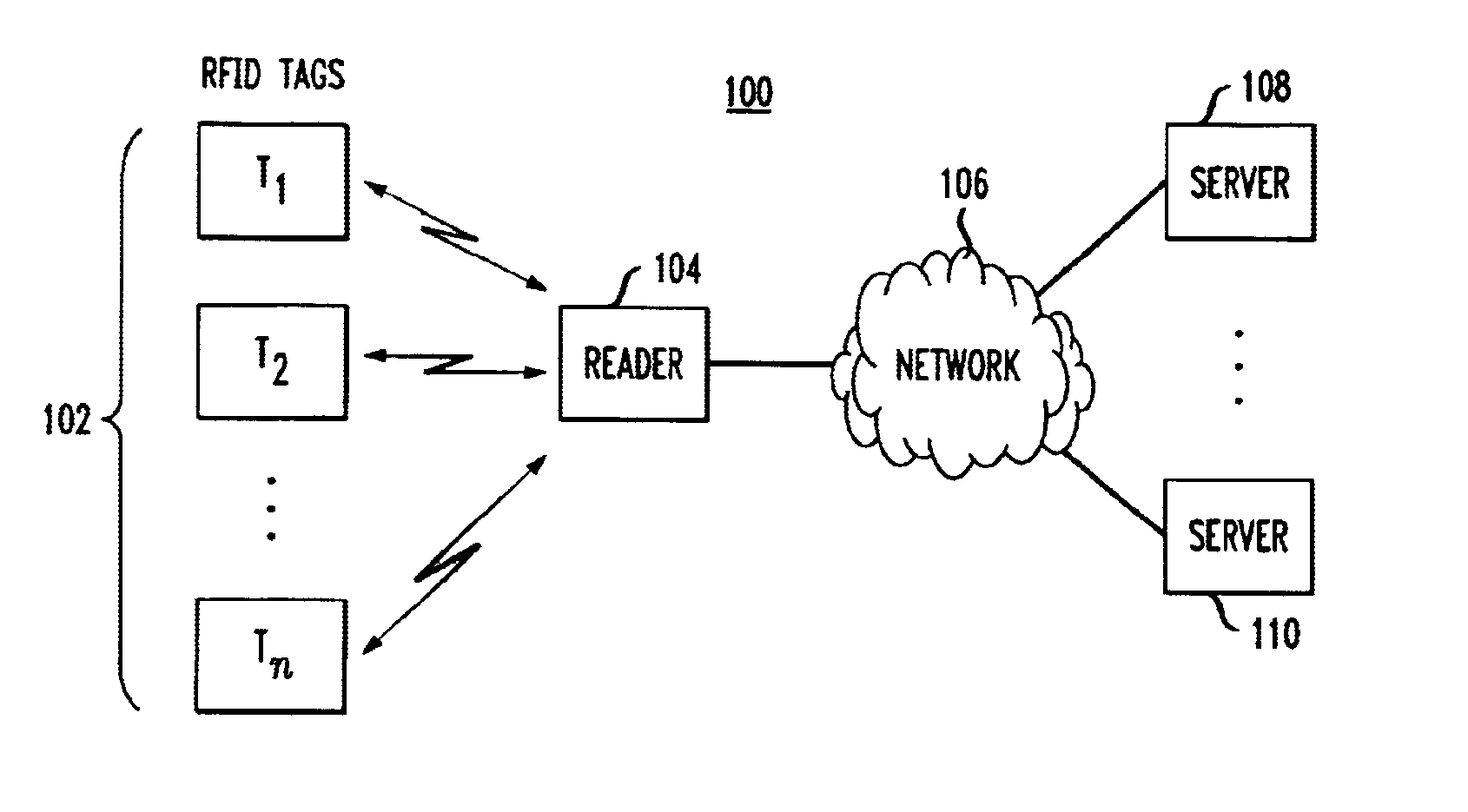
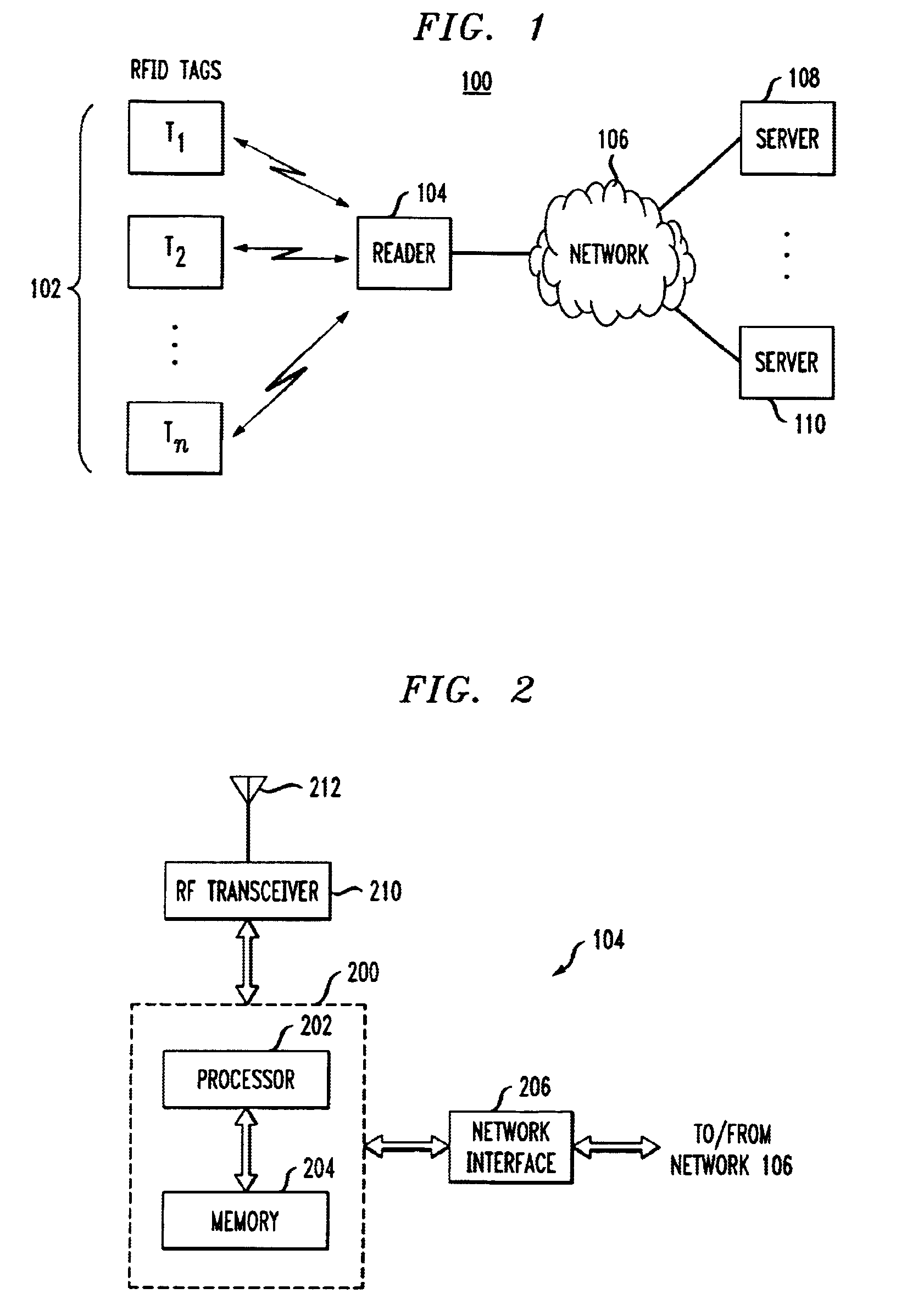
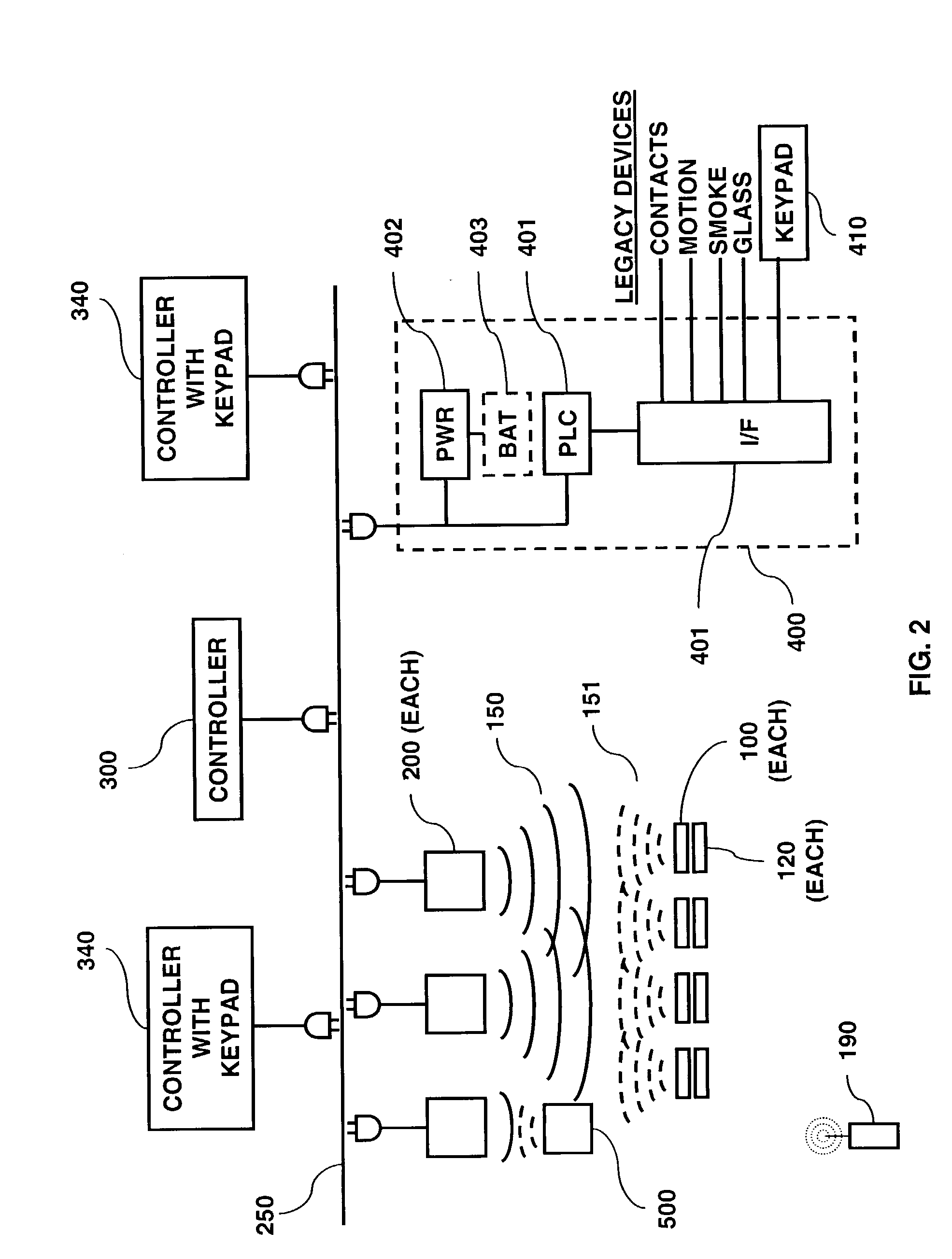
RFID reader for a security system
InactiveUS7057512B2Improve reliabilityBurglar alarm by openingFrequency-division multiplex detailsSecurity systemEmbedded system
An RFID reader for use in a security system based upon RFID techniques. The RFID reader can use power line carrier communications to communicate with the controllers in the security system. The RFID reader of the security system can be provided with multiple modulation techniques, multiple antennas, and the capability to vary its power level and carrier frequency. The controller of the security system determines which RFID readers may transmit, at what times, and the parameters with which to transmit. The RFID reader can detect interference or jamming, and respond. The RFID reader can transmit RF energy useful for detecting motion or for charging the batteries in RFID transponders. The RFID reader can receive wireless communications from active transmitters or from other RFID readers.
Owner:LIFESHIELD LLC
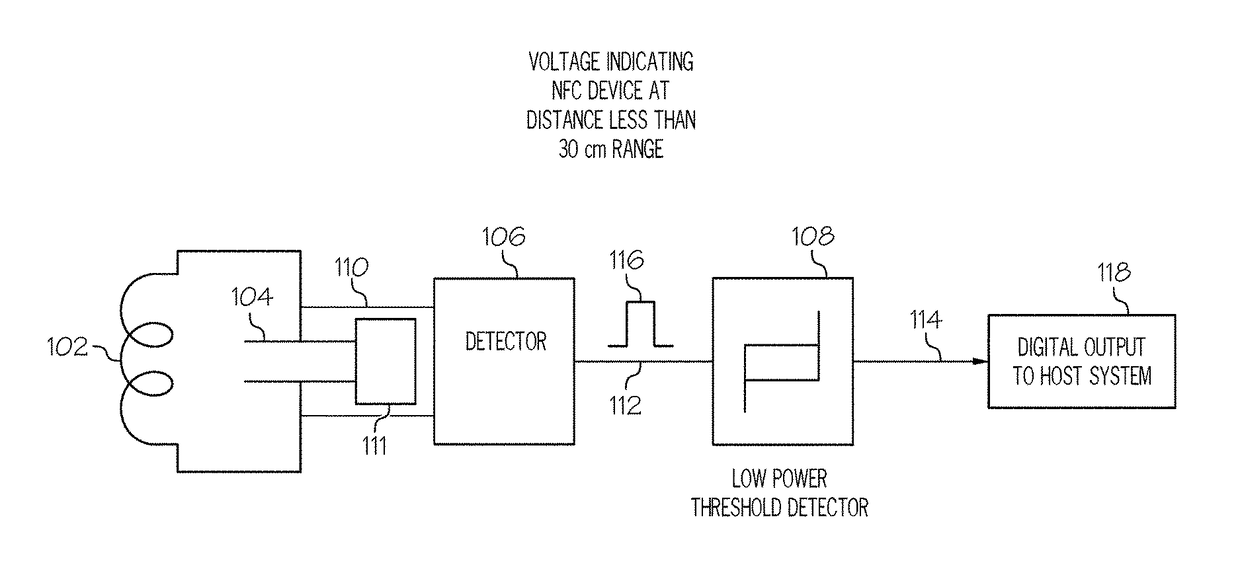
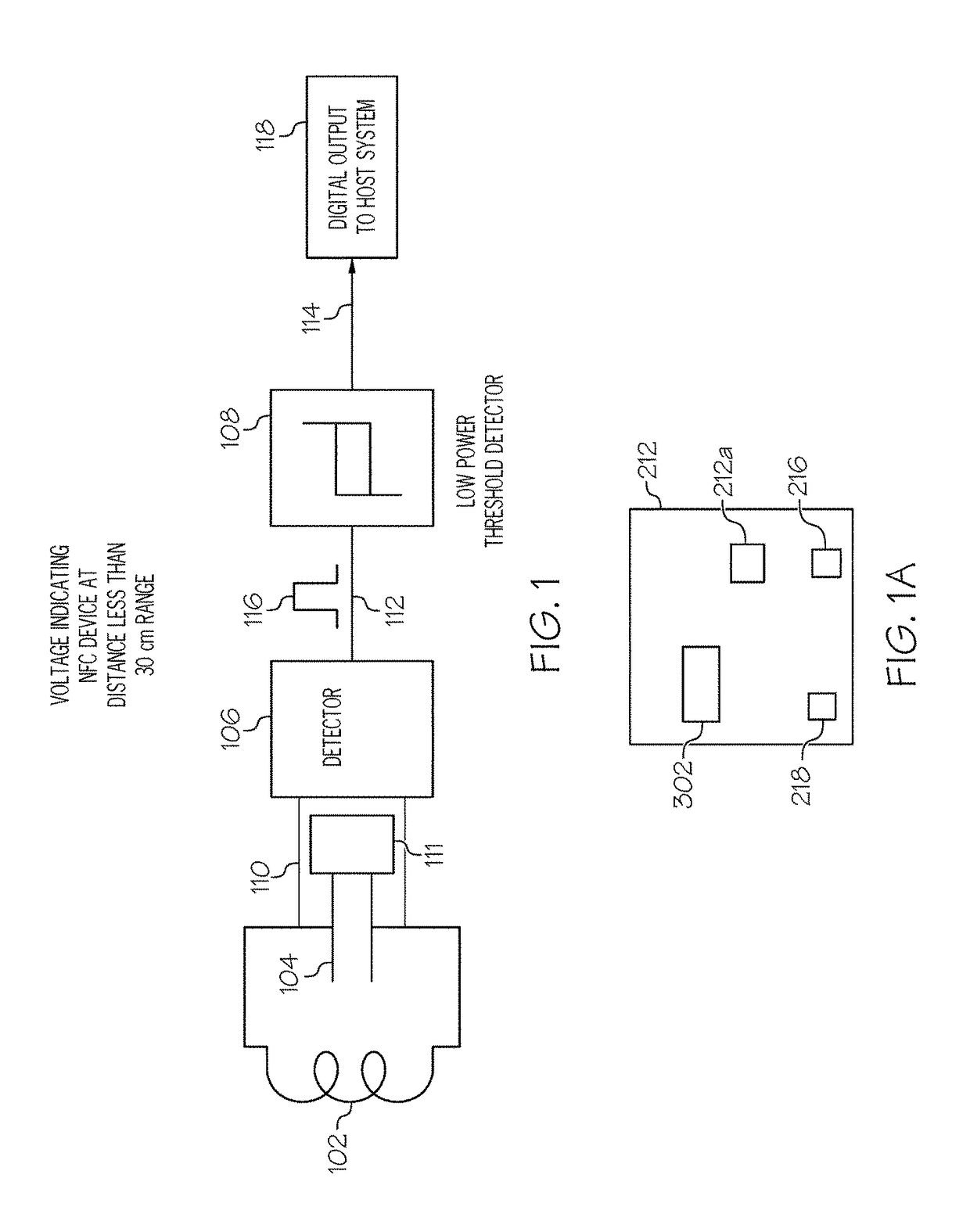
NFC tags with proximity detection
Owner:AVERY DENNISON CORP
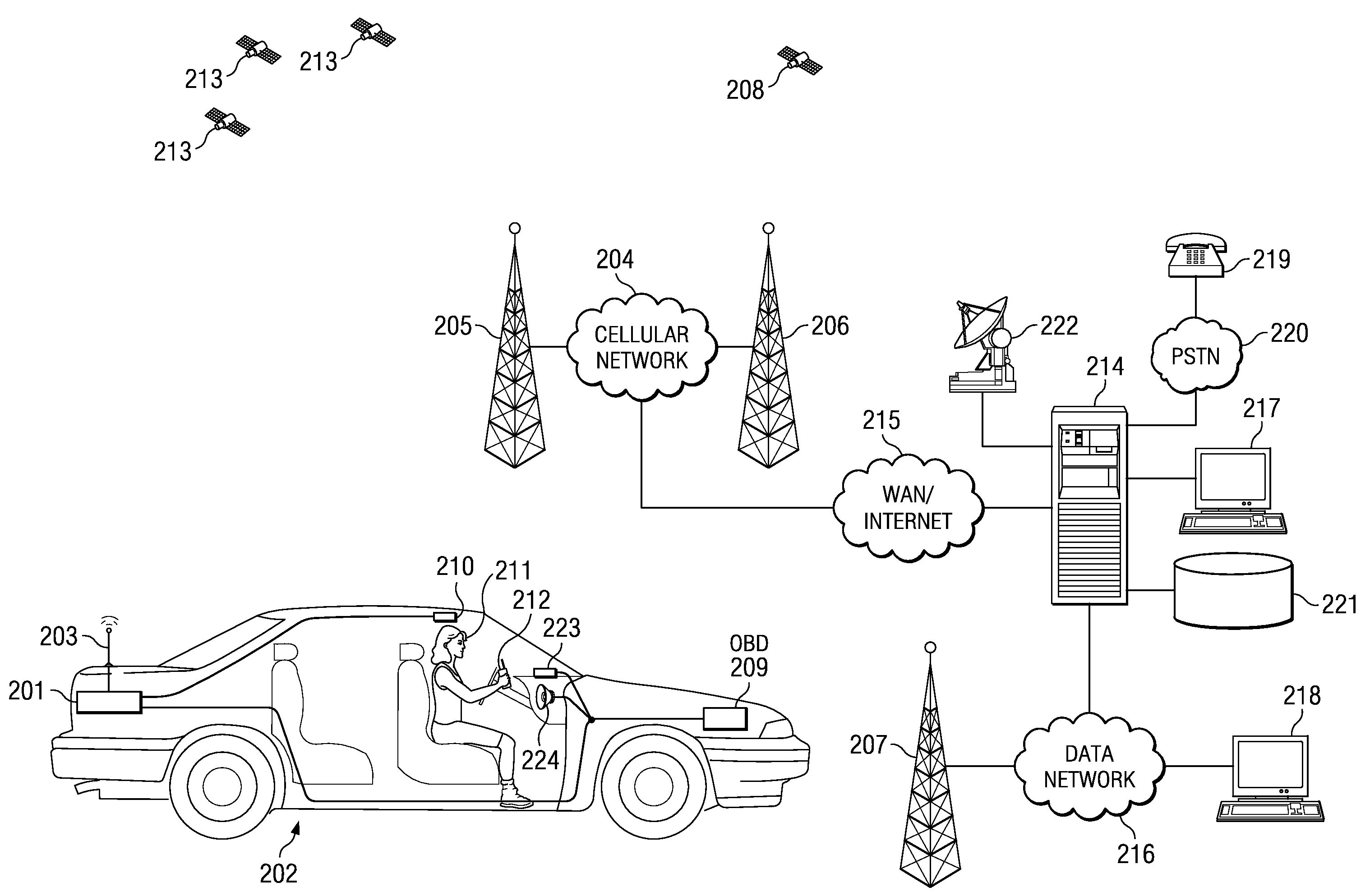
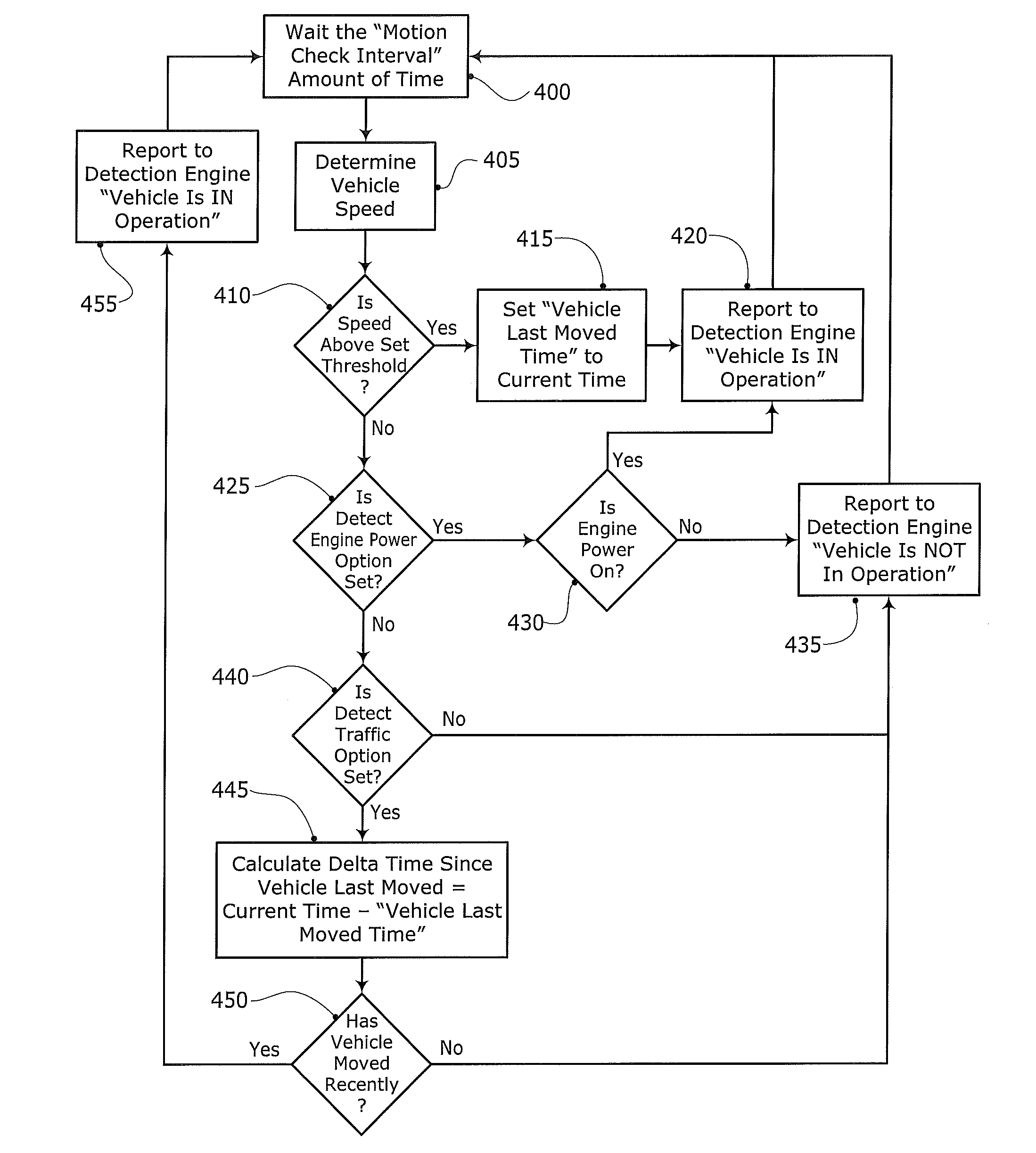
System and Method for Detecting Use of a Wireless Device in a Moving Vehicle
ActiveUS20090085728A1Registering/indicating working of vehiclesAssess restrictionMobile vehicleMonitoring system
A system and method for detecting use of a wireless device is disclosed. In one embodiment, wireless device activity data is received from a wireless network. User account data is searched using selected parameters from the wireless device activity data to identify one or more subscribers that are or were using a wireless device. One or more subscriber vehicles or vehicle monitoring systems associated with each of the one or more subscribers are identified. Vehicle operation data from one or more vehicle monitoring systems is received. The vehicle operation data is used to determine whether any of the one or more subscriber vehicles were moving during use of an associated wireless device.
Owner:IWI
Method and system for controlling a mobile communication device in a moving vehicle
ActiveUS20120244883A1Assess restrictionParticular environment based servicesMobile vehicleMobile device
A method and system is disclosed for performing a wireless location of a mobile communication device for detecting, monitoring and / or controlling one or more interactive mobile services capable of being activated by a user of the mobile device. When the mobile device is operated by the user, a wireless location is performed for determining whether such an interactive service, requested by the user, can be provided to the user. In one embodiment, a determination is made as to whether the mobile device resides in a container, e.g., a vehicle, for determining whether the interactive mobile service can be accessed by the user.
Owner:KATASI
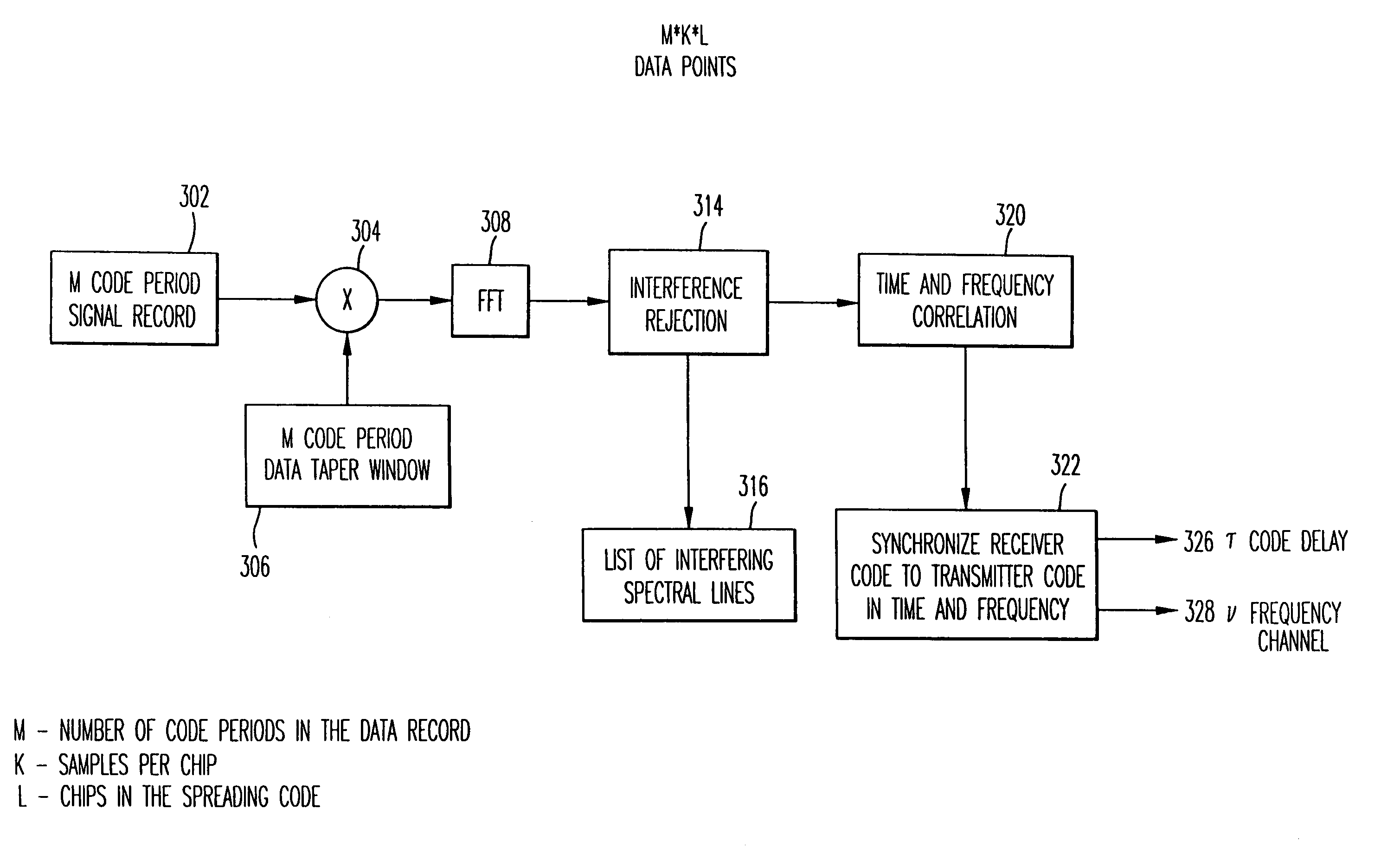
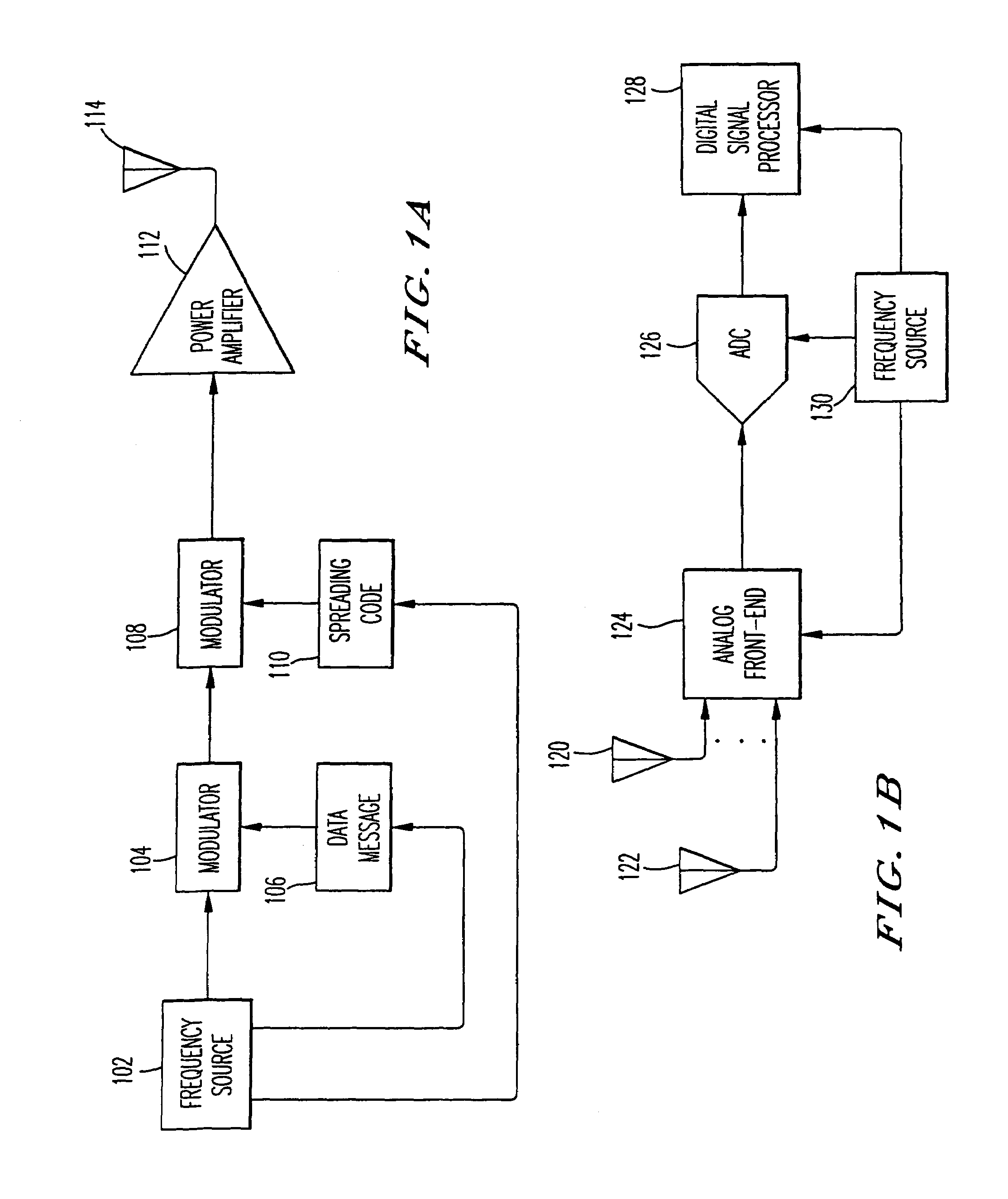
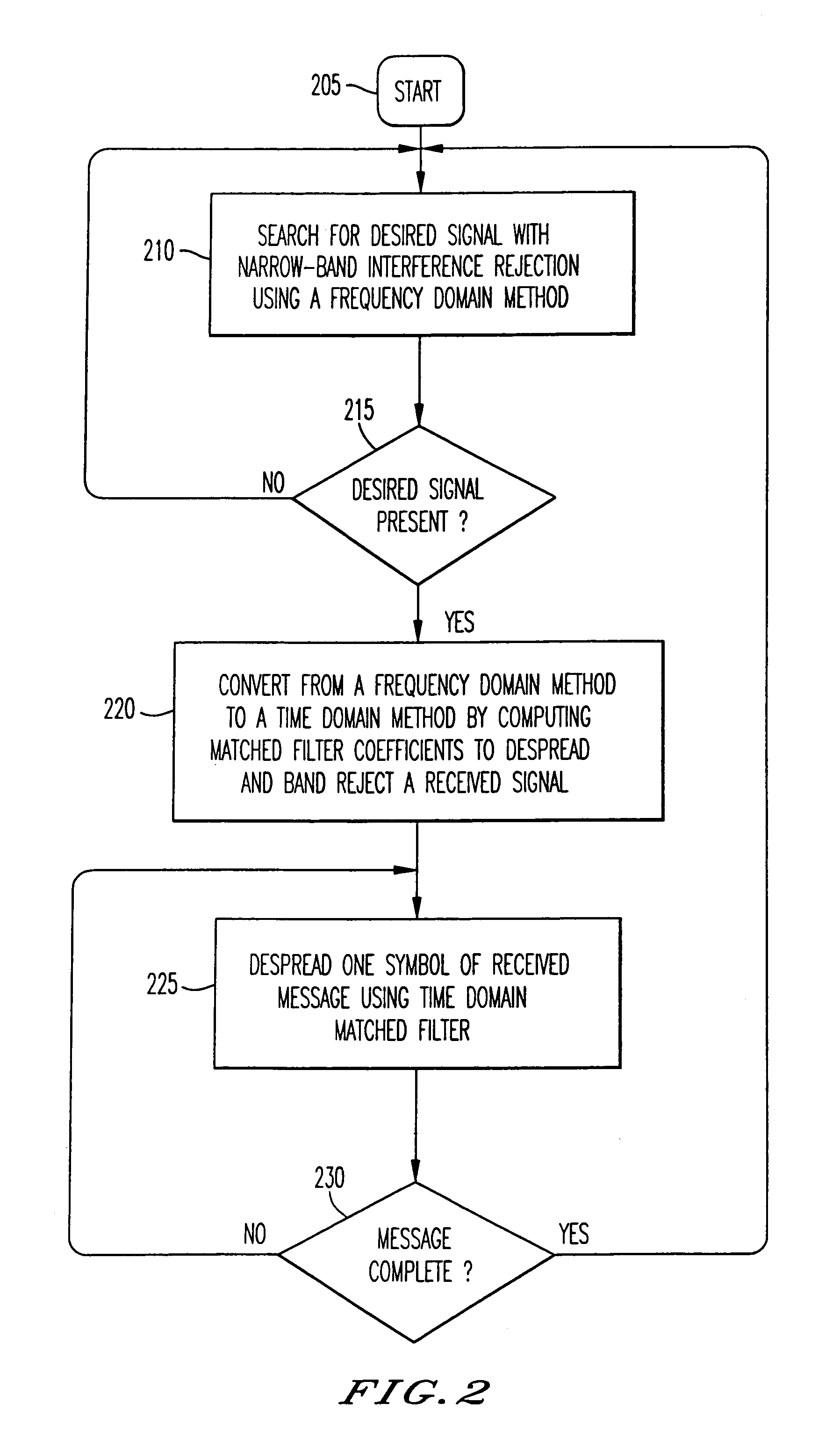
Narrow-band interference rejecting spread spectrum radio system and method
InactiveUS6975673B1Decrease requiredReduced computing resourceFrequency-modulated carrier systemsCommunication jammingTime domainDigital signal processing
A spread spectrum receiver and method having narrow-band interference rejection of narrow-band jamming signals using digital signal processing frequency domain techniques. The method performed in the receiver includes transforming the received signal to a frequency domain signal and identifying narrow-band interference components in the frequency domain signal; suppressing the identified narrow-band interference components by excising the identified narrow-band interference components from the frequency domain signal to produce an interference excised signal in the frequency domain, and storing in a memory frequencies corresponding to the identified narrow-band interference components; synchronizing a receiver code to a transmitter code in the frequency domain using the interference excised signal; generating coefficients for a time domain filter that includes notches at the frequencies corresponding to the excised narrow-band interference components and that jointly despreads and rejects narrow-band interference from the excised frequencies; applying the coefficients generated in the preceding step to the time domain filter, and despreading and filtering in real time in the time domain the received signal using the applied coefficients.
Owner:SENSUS SPECTRUM LLC
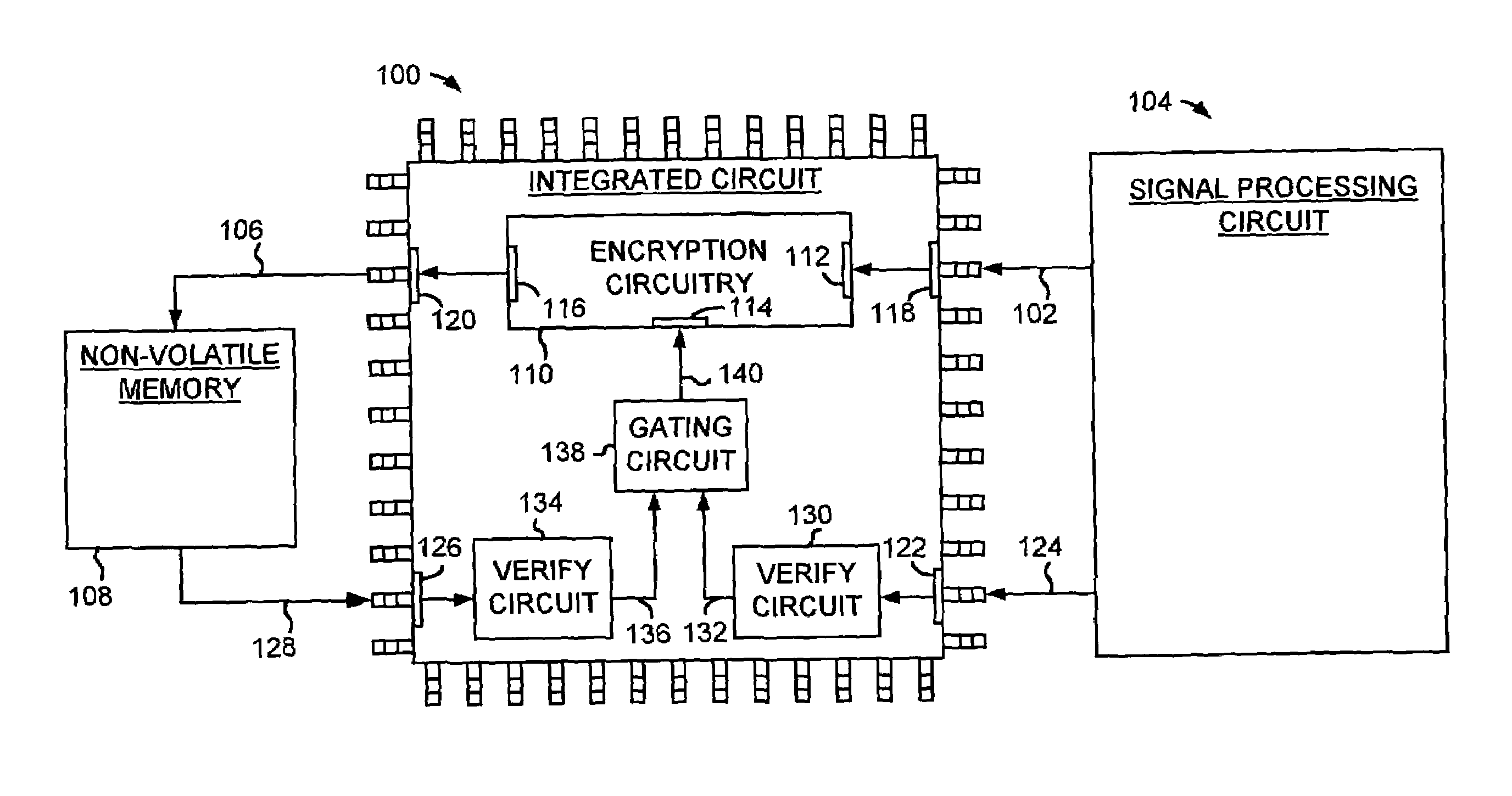
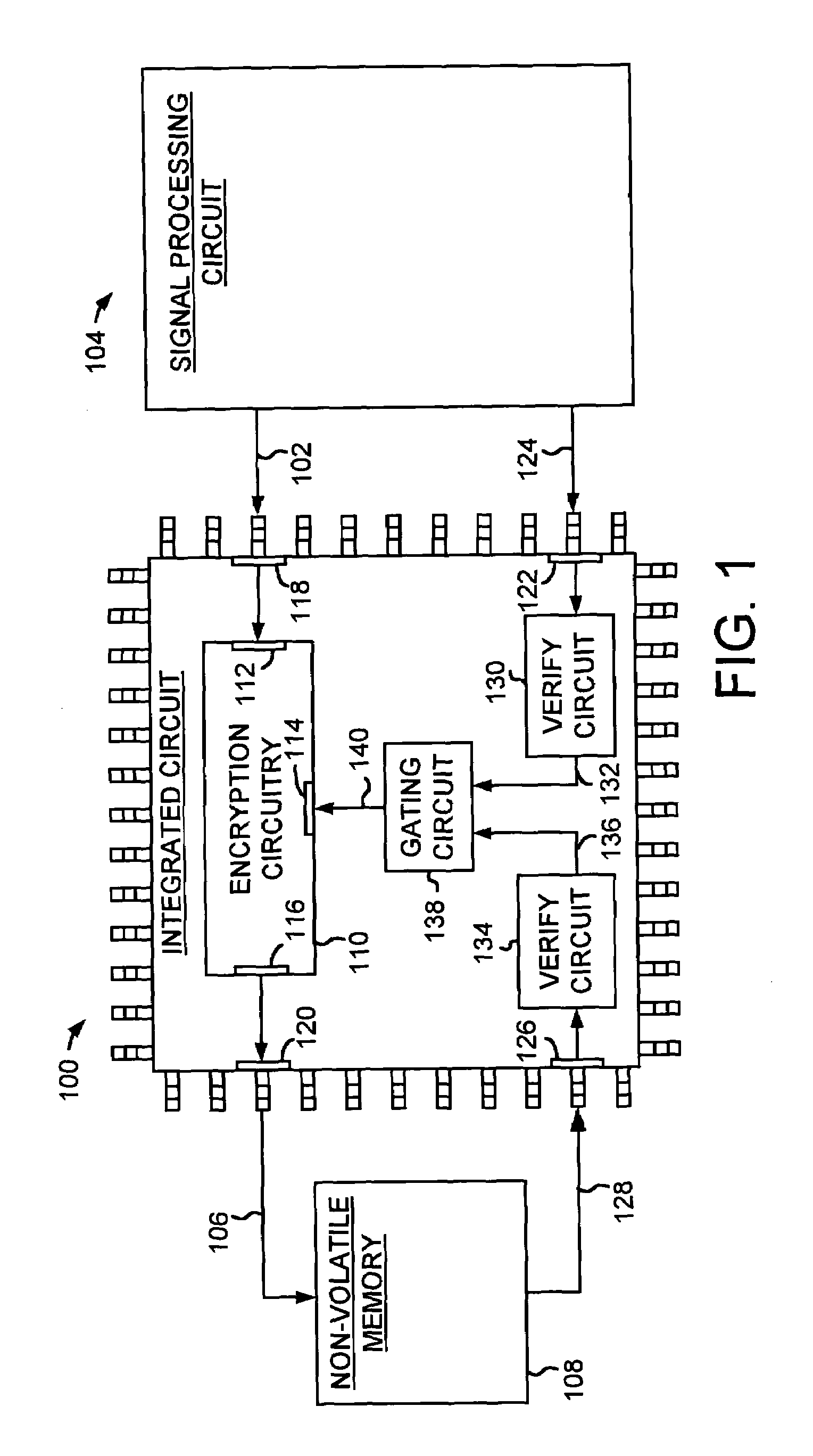
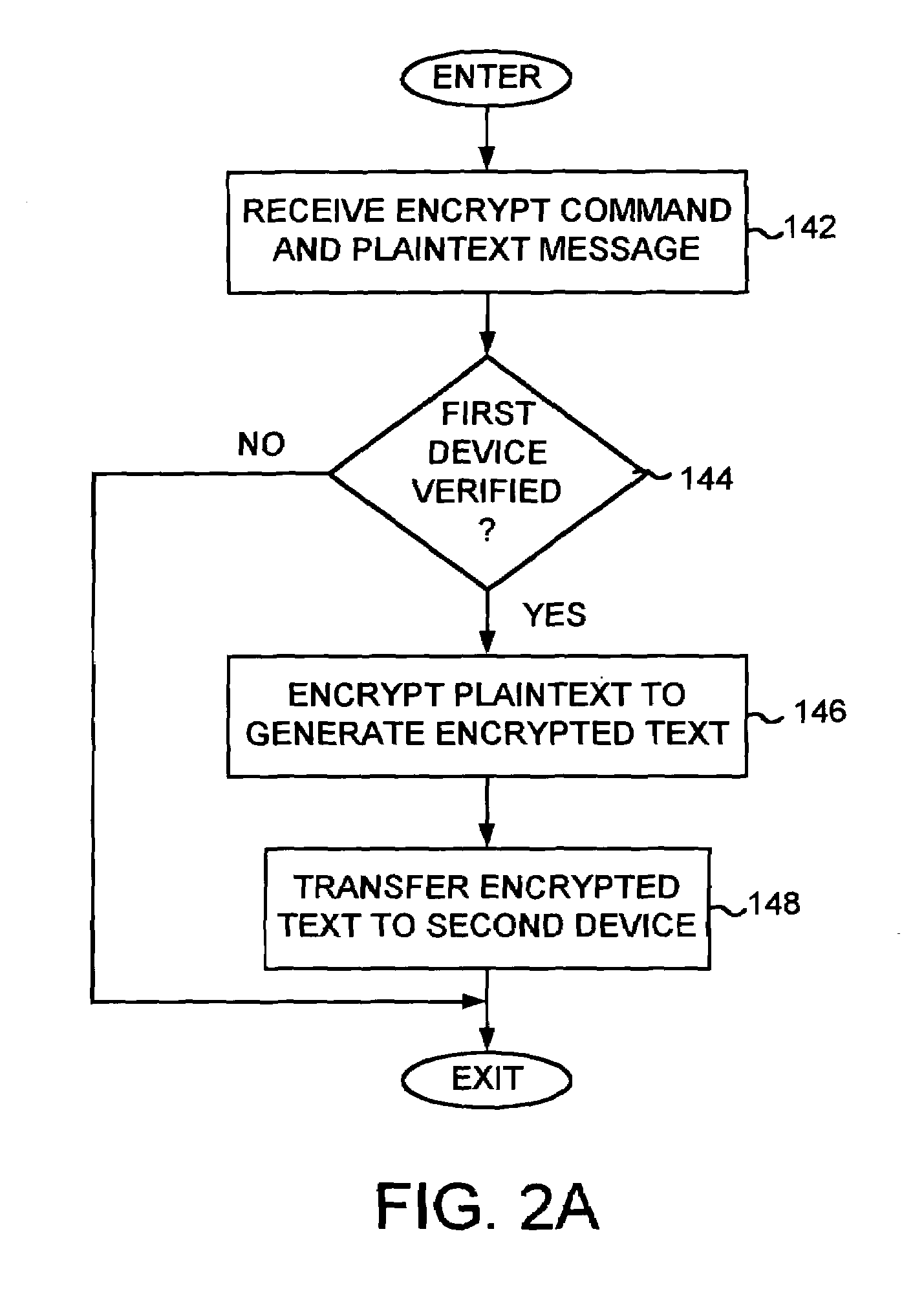
Integrated circuit comprising encryption circuitry selectively enabled by verifying a device
InactiveUS6973570B1Digital data processing detailsUser identity/authority verificationPlaintextIntegrated circuit
An integrated circuit is disclosed for selectively encrypting plaintext data received from a first device to produce encrypted data to send to a second device. The integrated circuit comprises controllable encryption circuitry comprising a data input, an enable input, and a data output. The integrated circuit further comprises a plaintext input for providing the plaintext data to the data input, an encrypted text output for providing the encrypted data from the data output, and a first control input for receiving a first device authentication signal for authenticating the first device. The integrated circuit further comprises a verification circuit responsive to the first device authentication signal for producing a first verification signal for use in controlling the enable input of the encryption circuitry to enable the encryption circuitry to provide the encrypted data via the encrypted text output.
Owner:WESTERN DIGITAL VENTURES
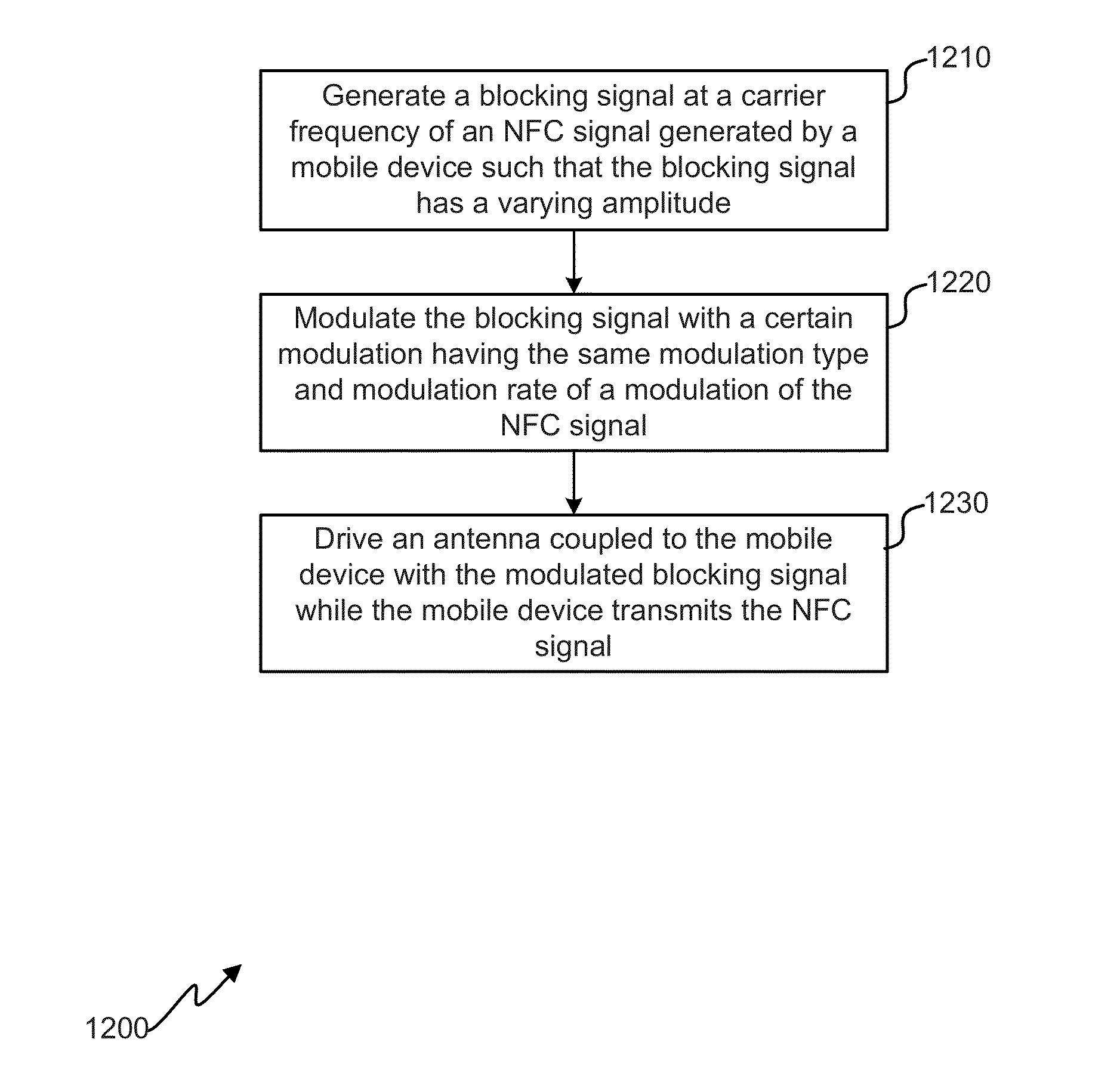
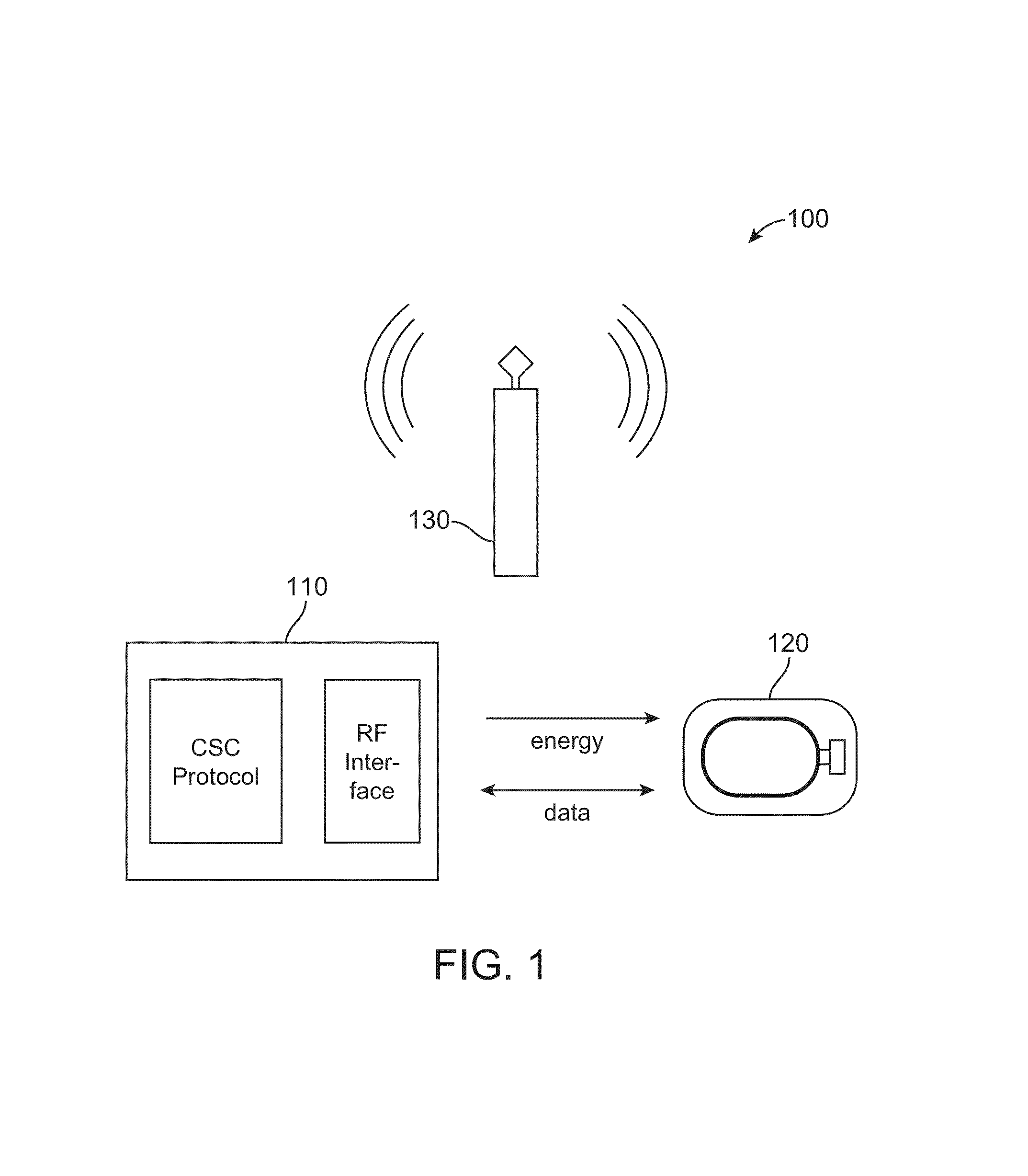
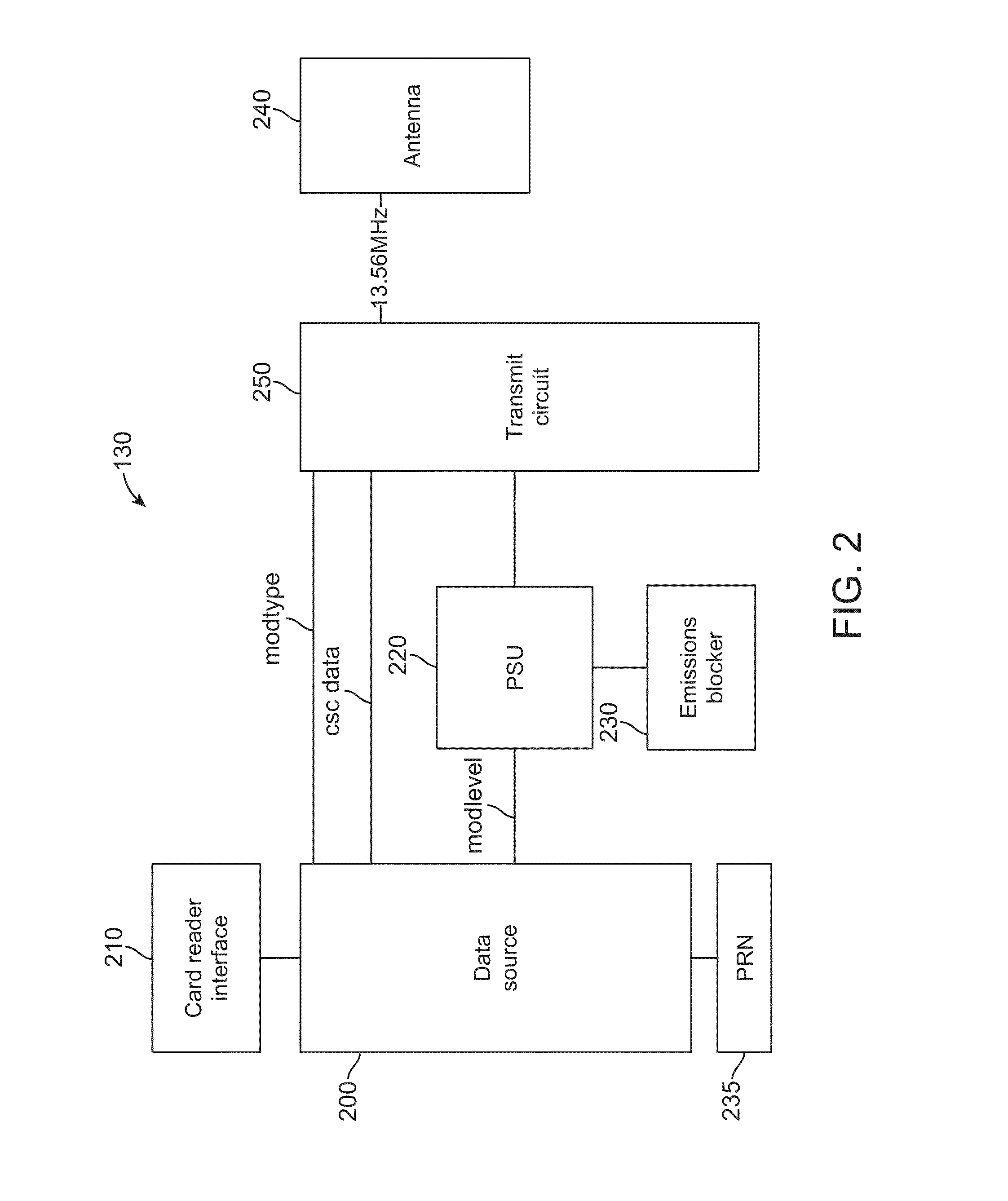
Protection of near-field communication exchanges
ActiveUS20130130614A1Efficiently maskedNear-field transmissionSensing record carriersEngineeringData exchange
Techniques are disclosed for protecting communication of an NFC-enabled device by generating one or more blocking signals during an NFC data exchange. The blocking signal(s) can include a similar carrier frequency, modulation type, and / or modulation rate an NFC signal, thereby effectively masking the NFC signal. Furthermore, the blocking signal(s) can have a varying amplitude and / or length, which can further mask when an NFC signal is transmitted.
Owner:CUBIC CORPORATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com