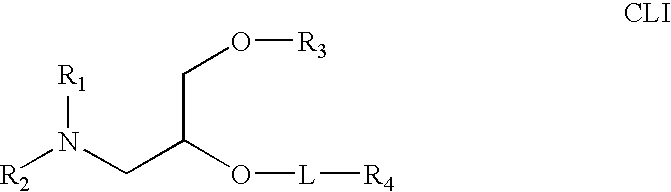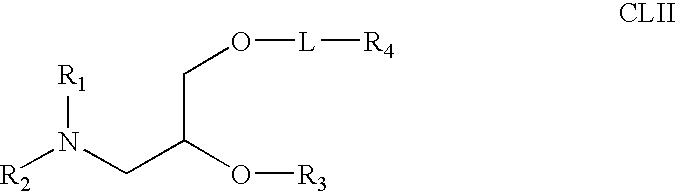Patents
Literature
2250 results about "Decoy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A decoy (derived from the duck-coy, "duck cage") is usually a person, device, or event meant as a distraction, to hide what an individual or a group might be looking for. Decoys have been used for centuries most notably in game hunting, but also in wartime and in the committing or resolving of crimes.
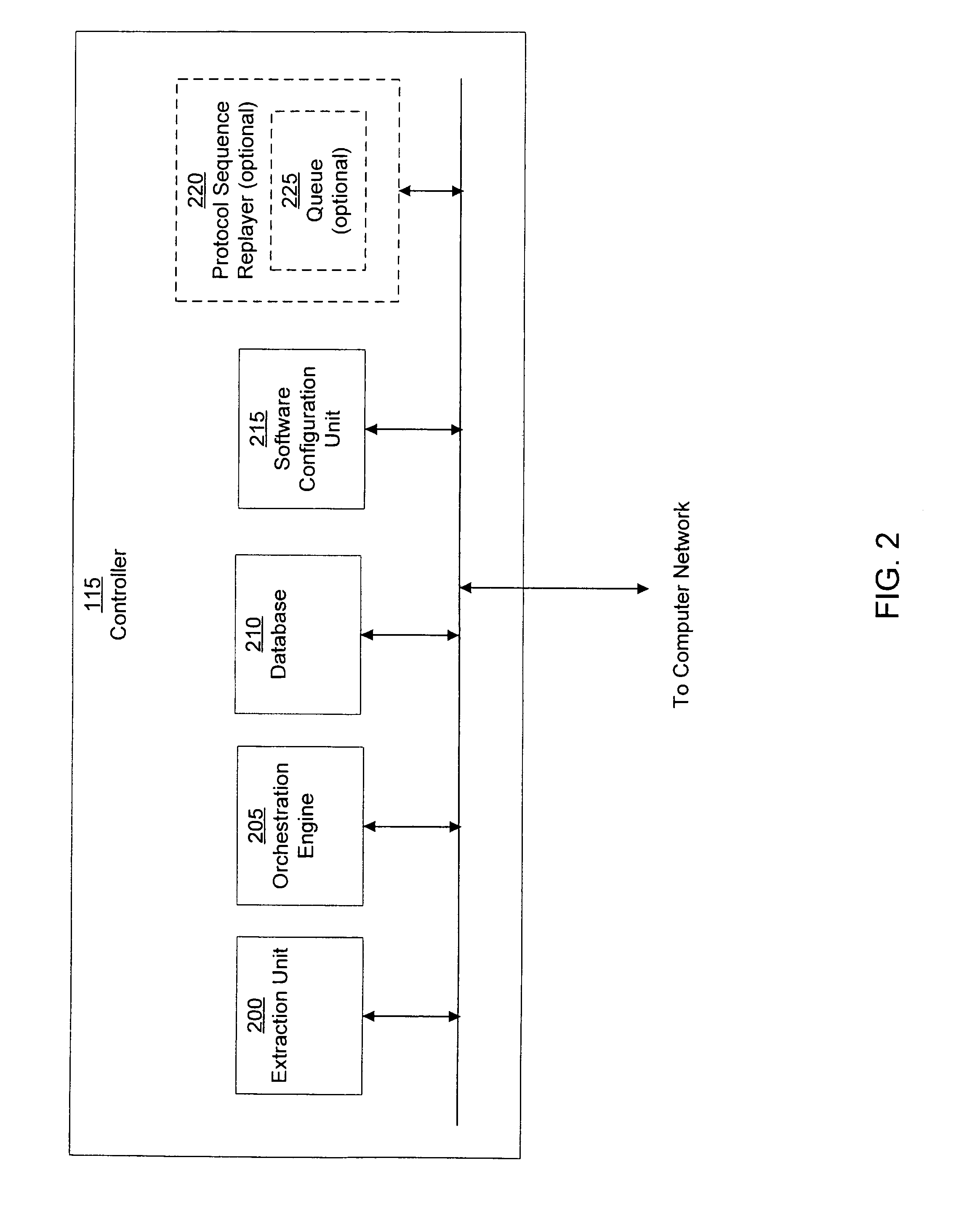
Methods, systems, and media for detecting covert malware
ActiveUS20110167494A1Reduce level of system knowledgeMemory loss protectionError detection/correctionDecoyApplication software
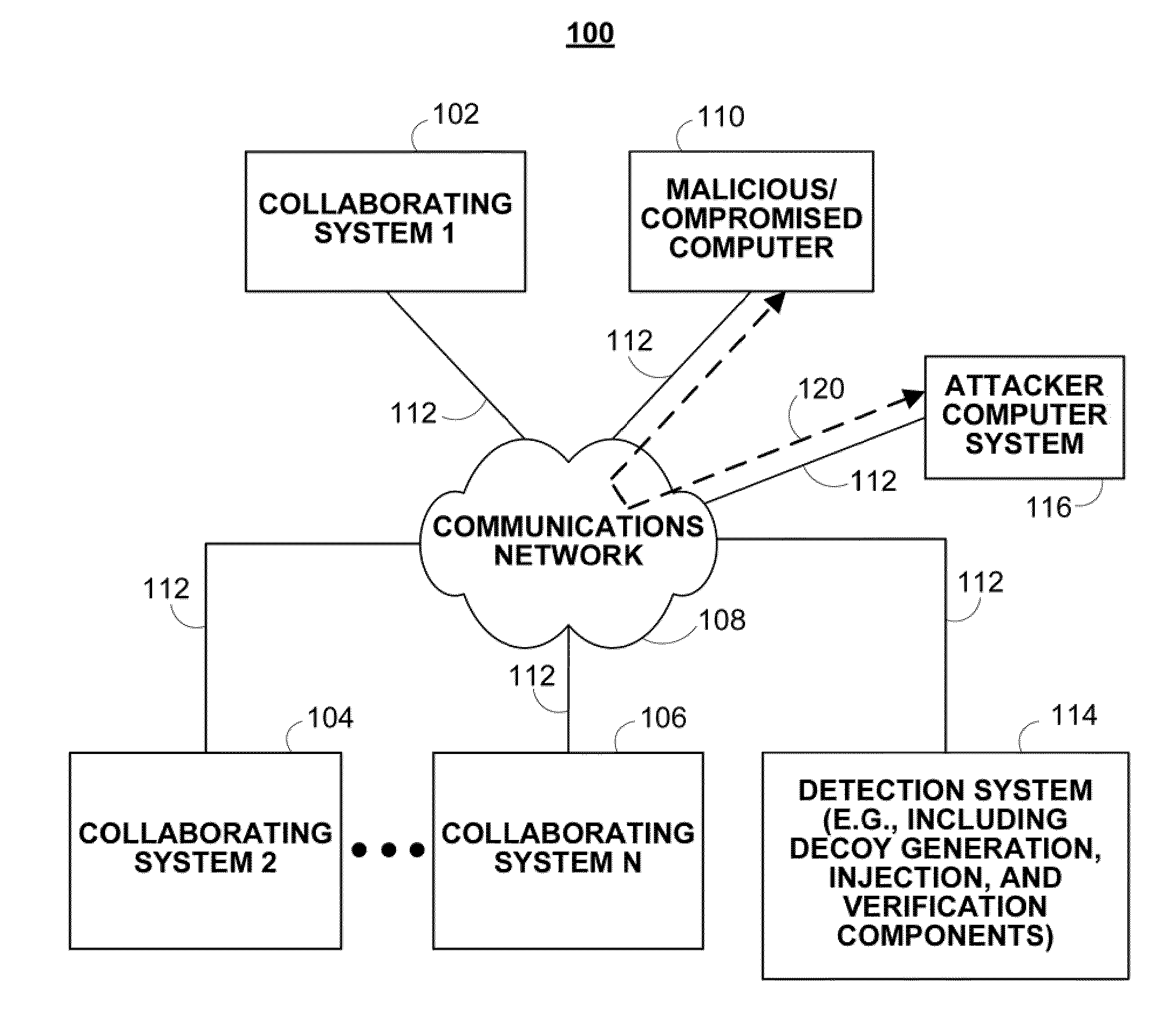
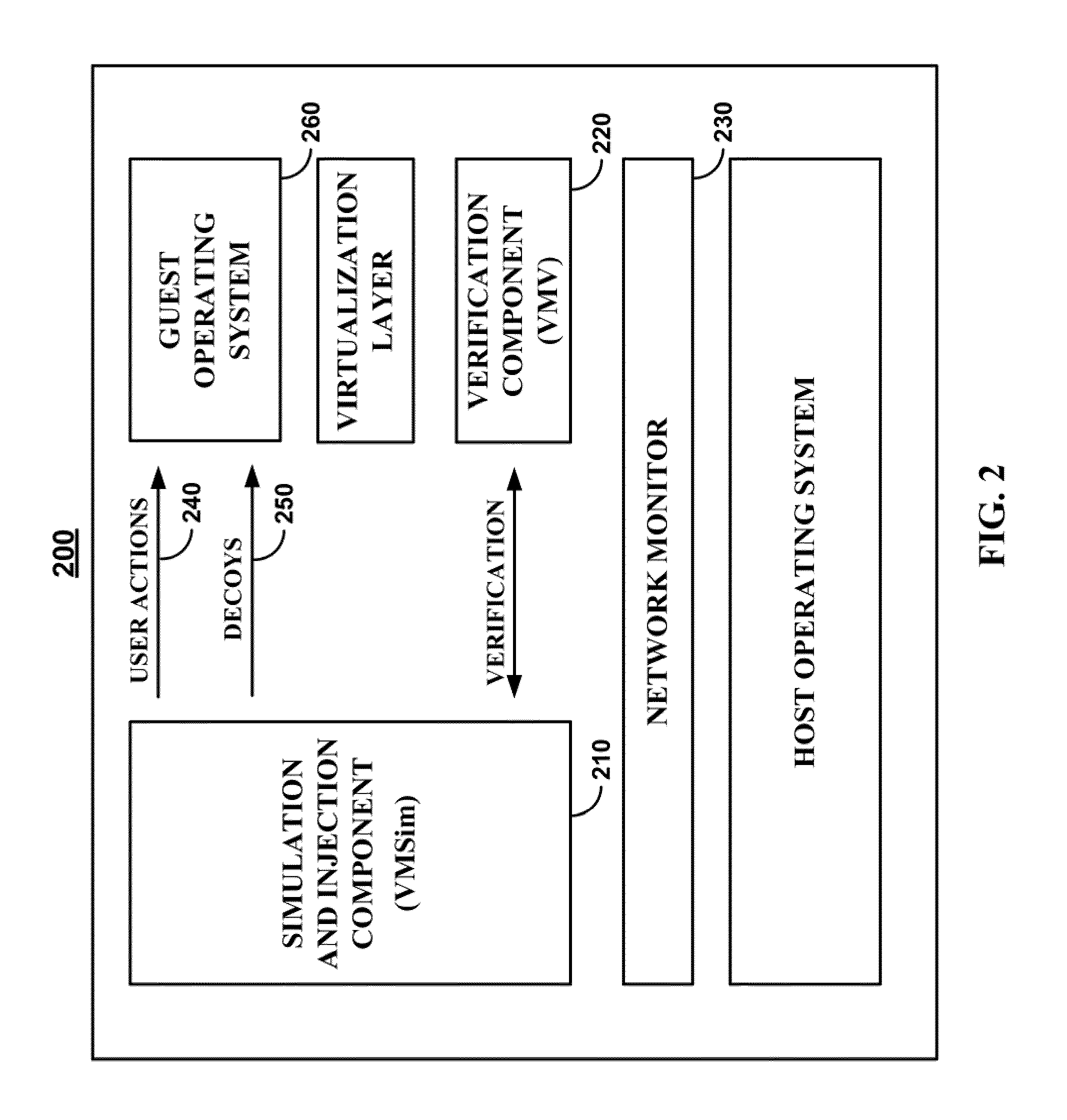
Methods, systems, and media for detecting covert malware are provided. In accordance with some embodiments, a method for detecting covert malware in a computing environment is provided, the method comprising: generating simulated user activity outside of the computing environment; conveying the simulated user activity to an application inside the computing environment; and determining whether a decoy corresponding to the simulated user activity has been accessed by an unauthorized entity.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
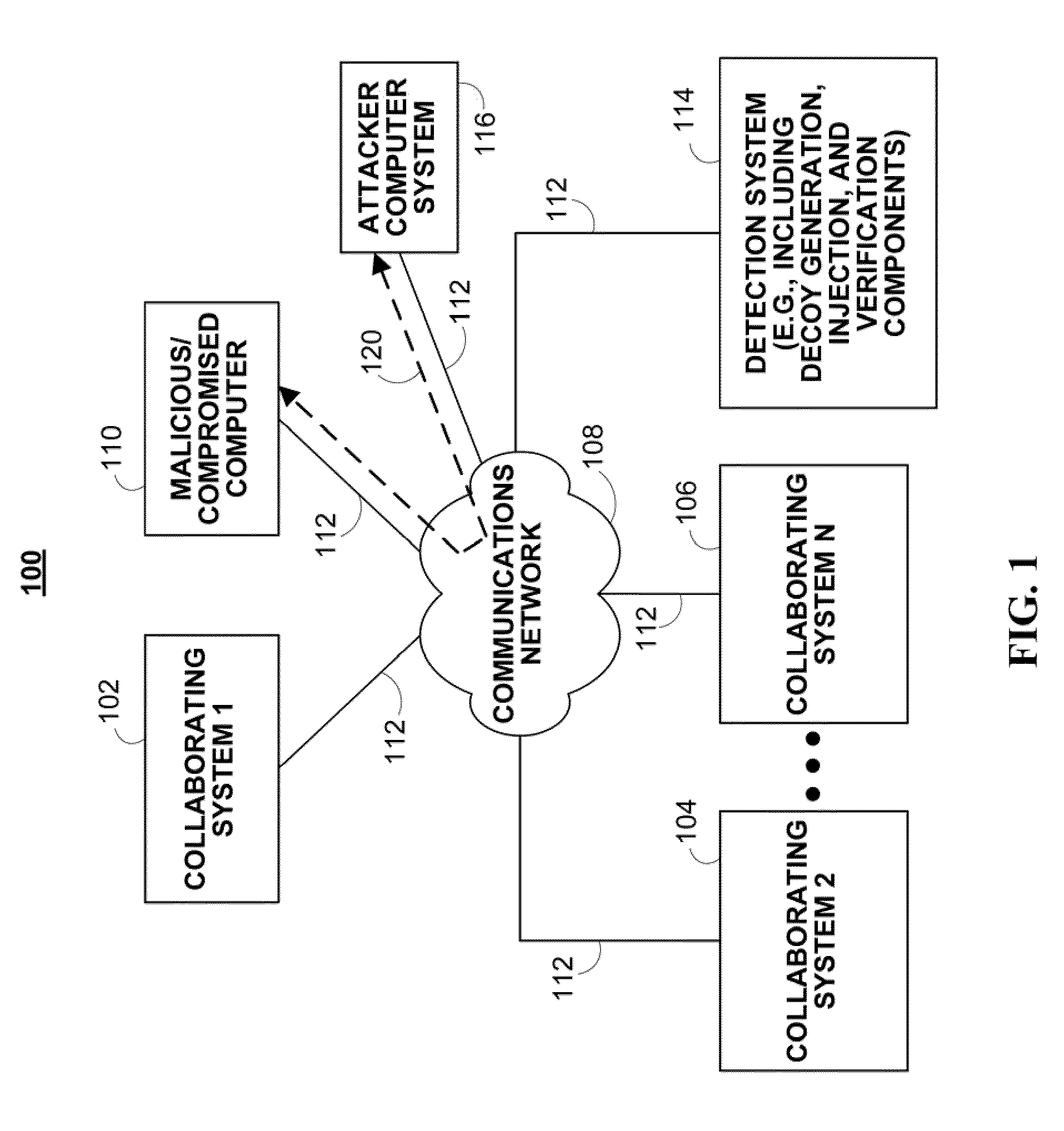
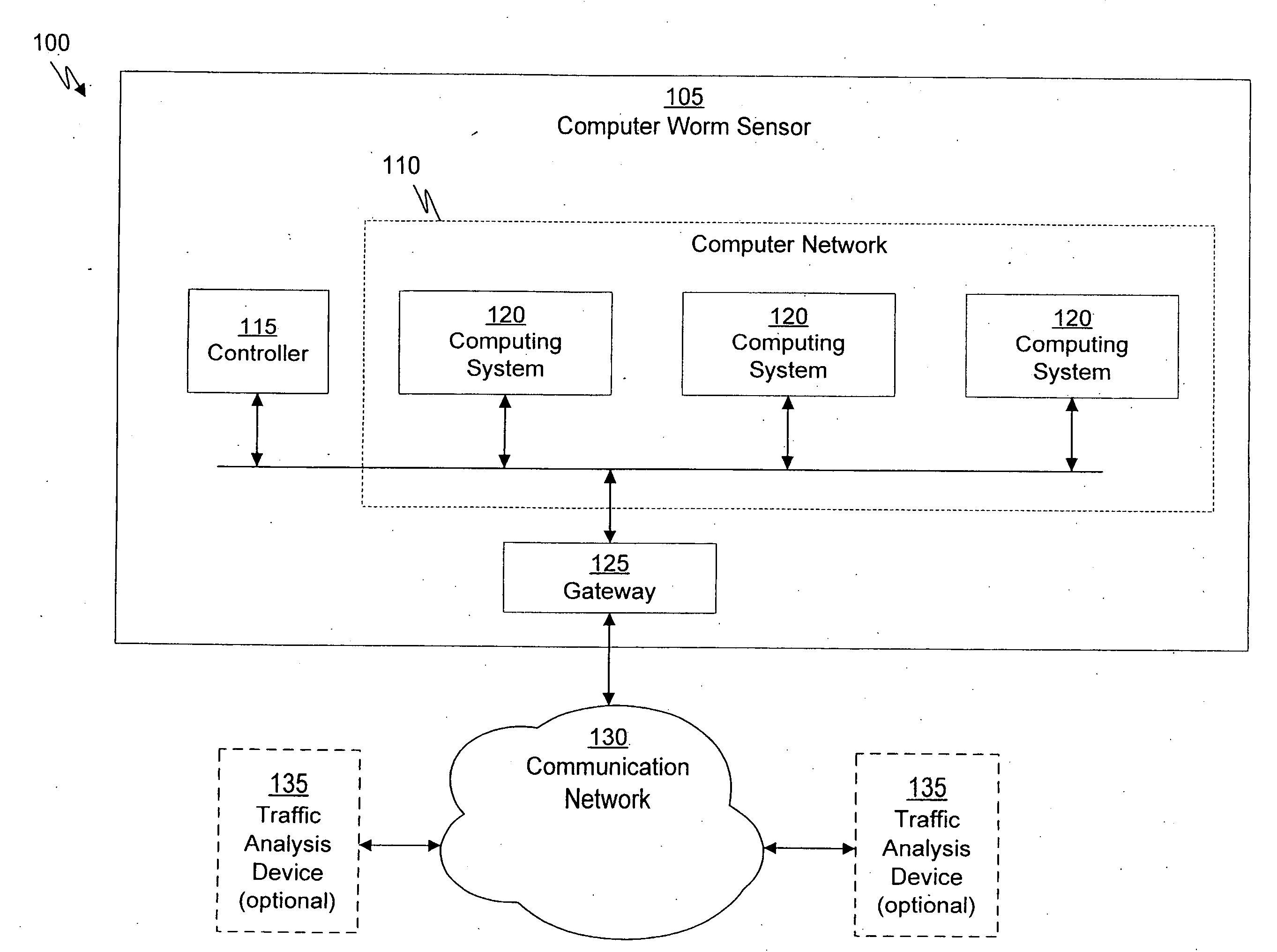
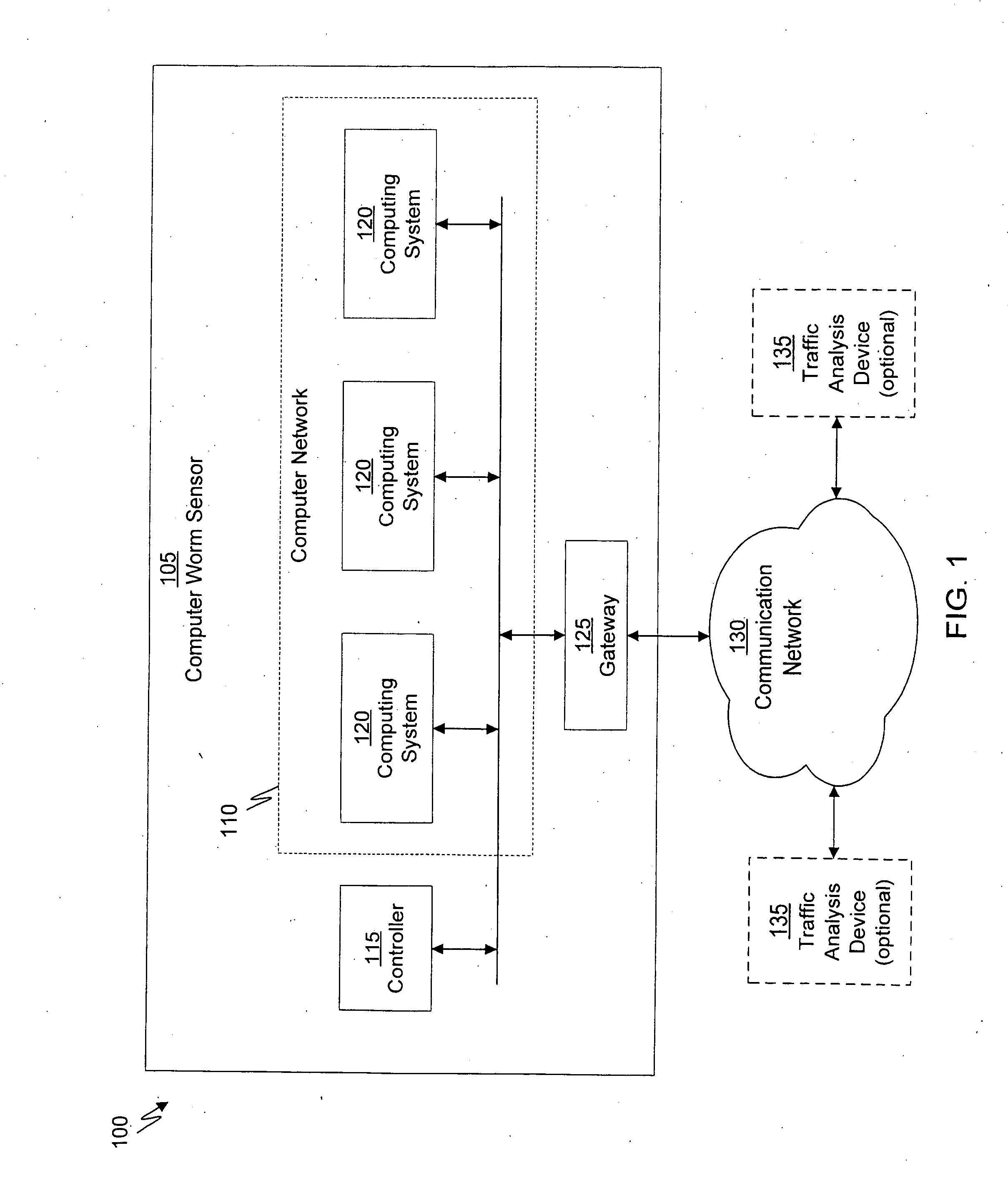
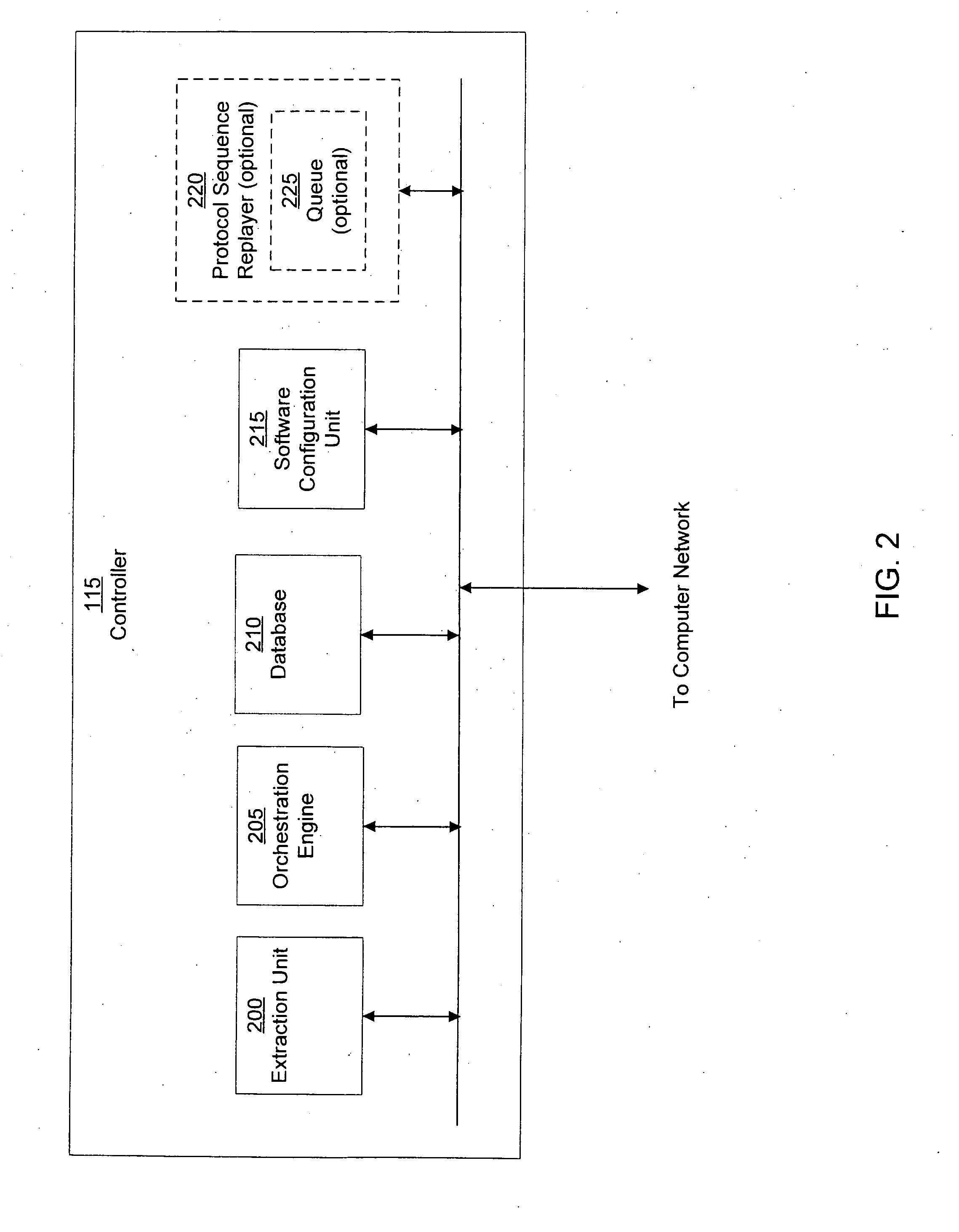
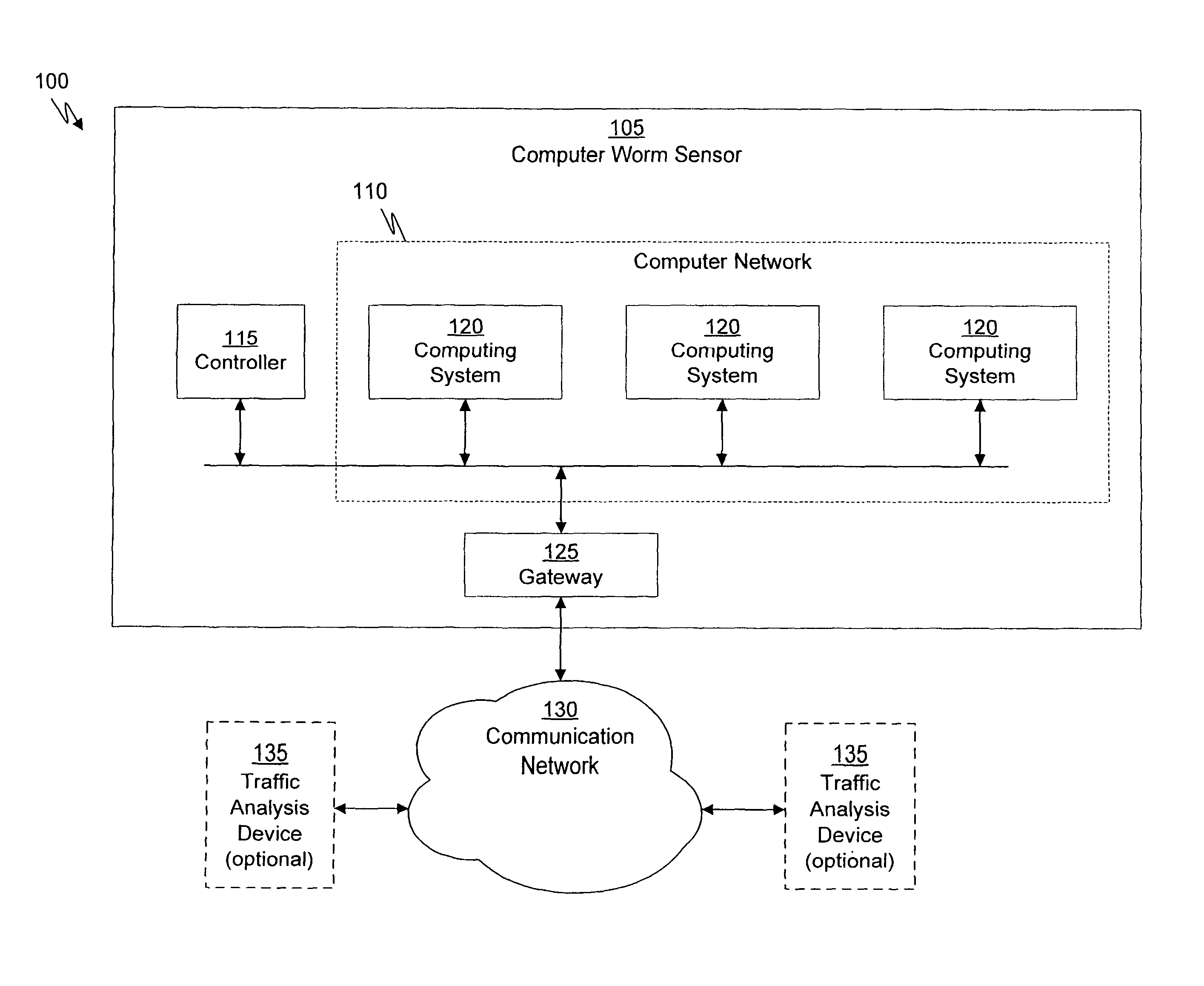
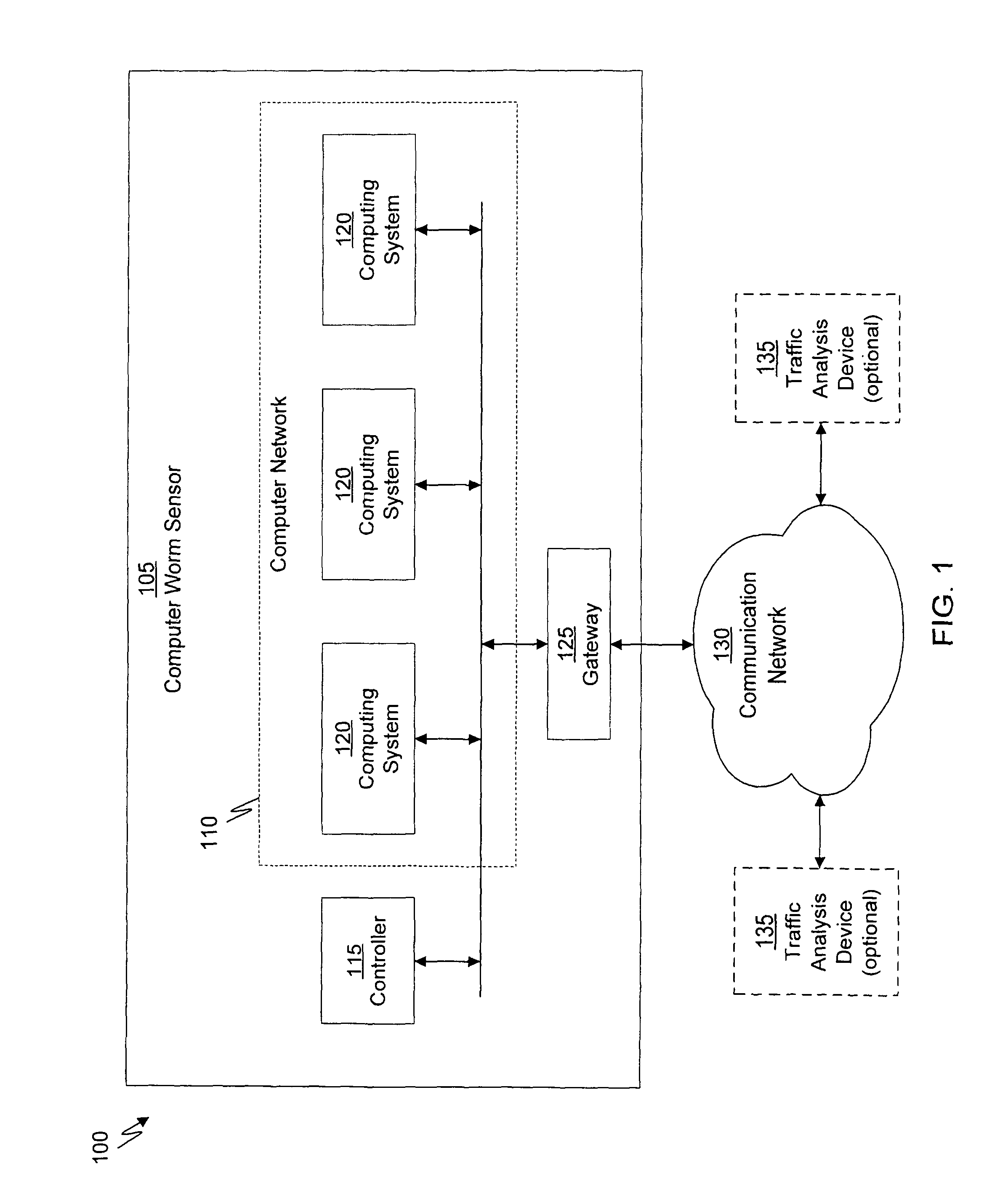
System and method of containing computer worms
ActiveUS20110099633A1Rapid responseMemory loss protectionError detection/correctionComputer wormNetwork activity
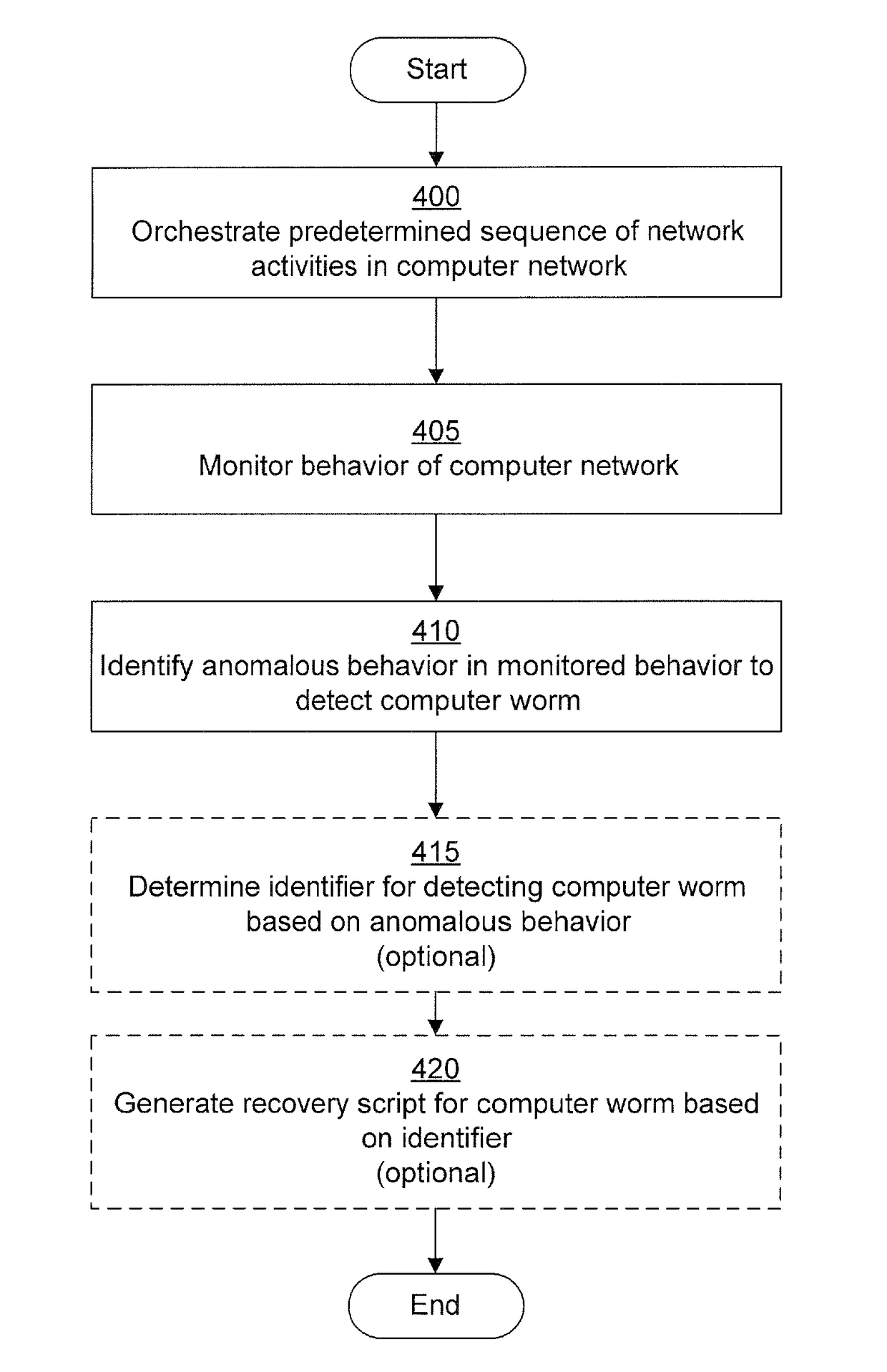
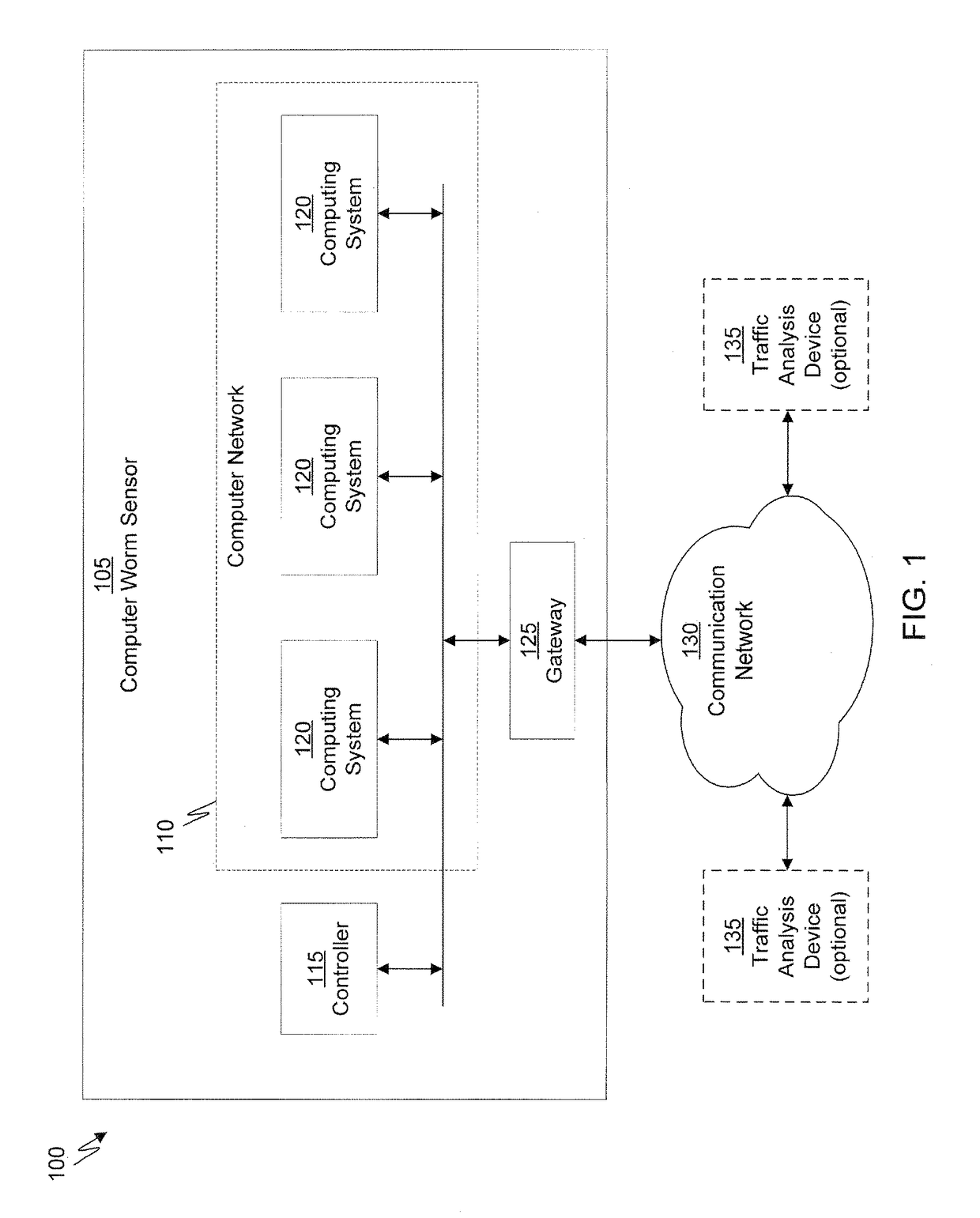
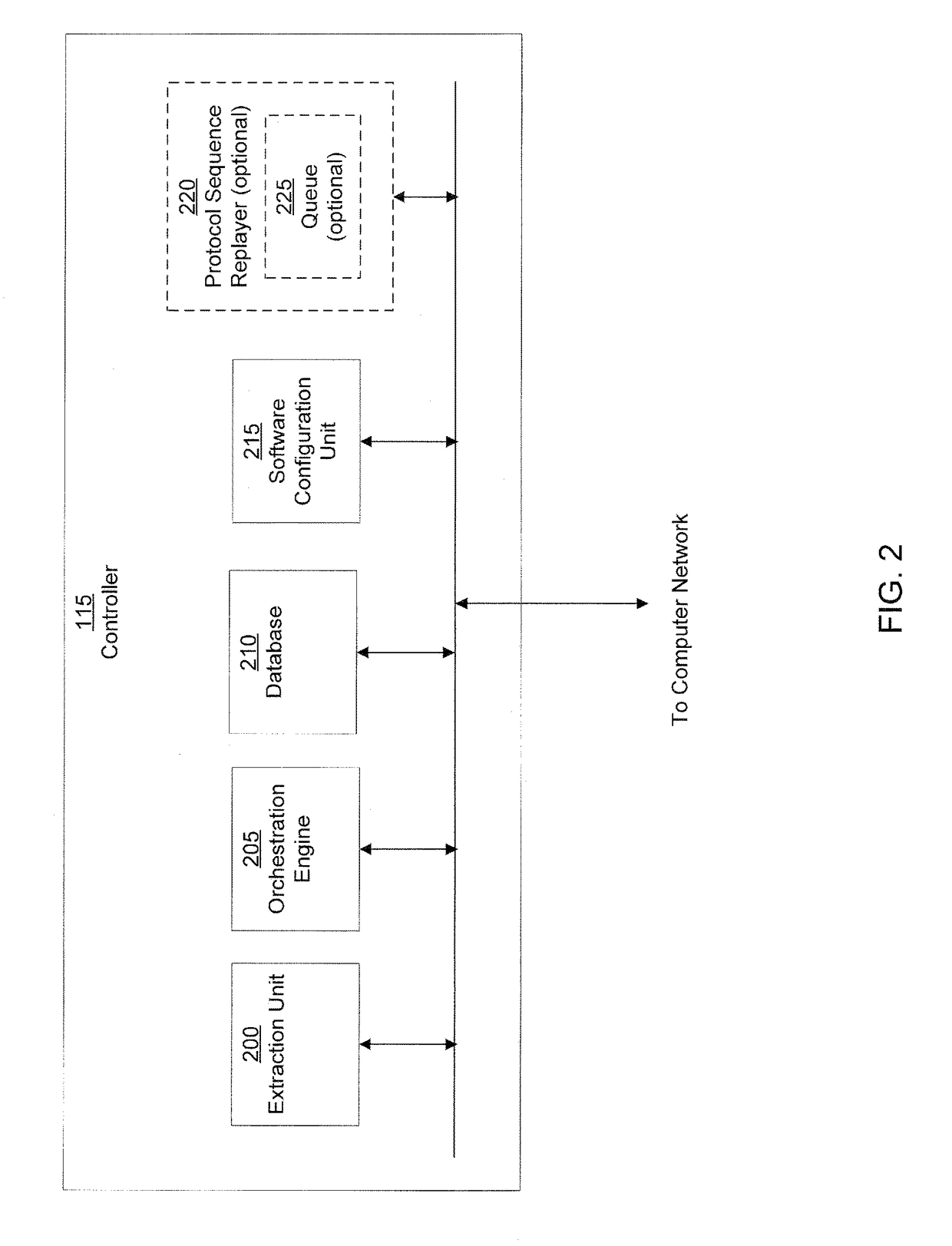
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
System and method of containing computer worms
ActiveUS8549638B2Rapid responseMemory loss protectionError detection/correctionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
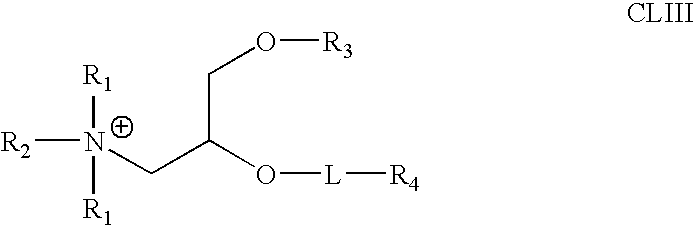
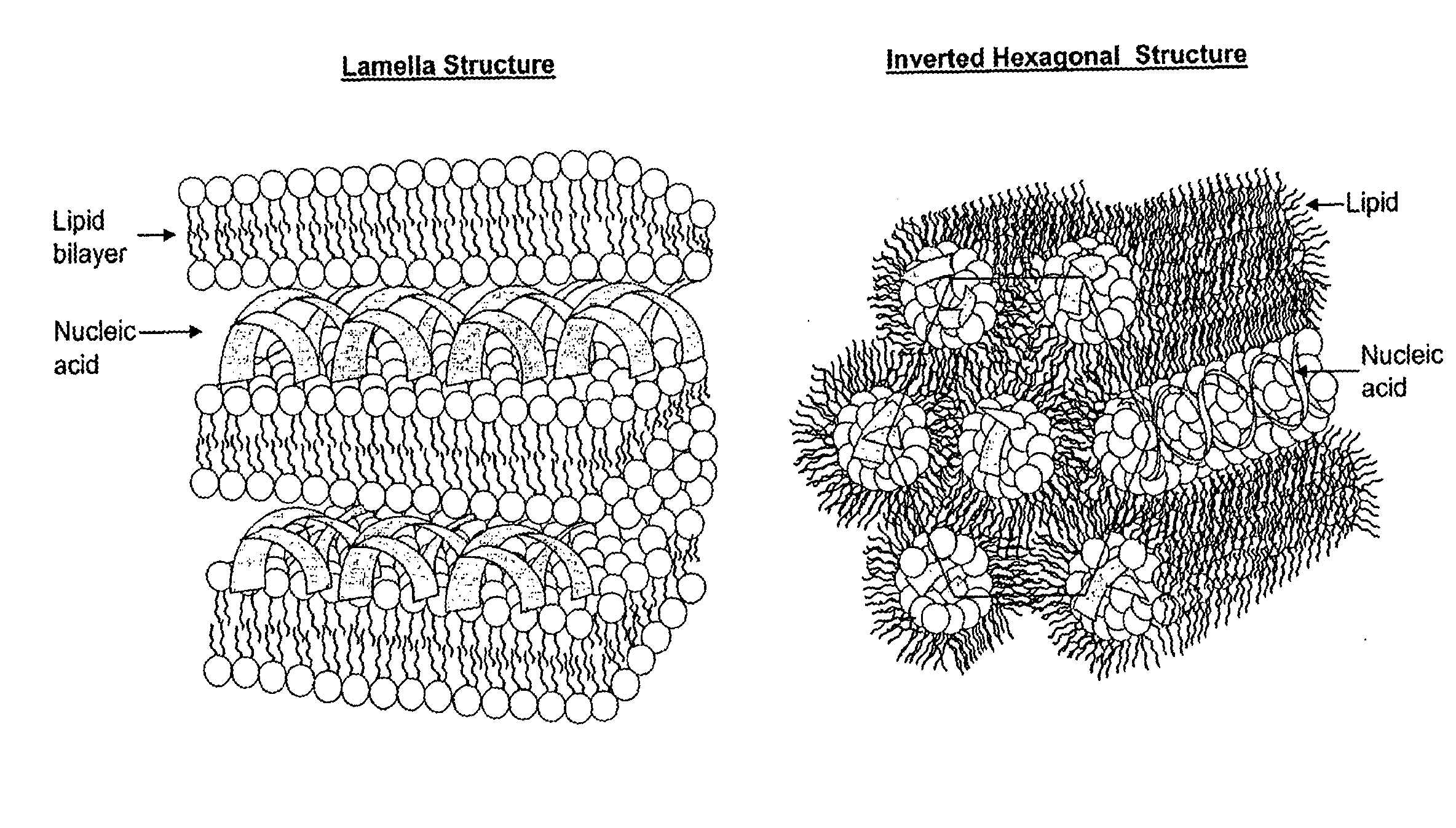
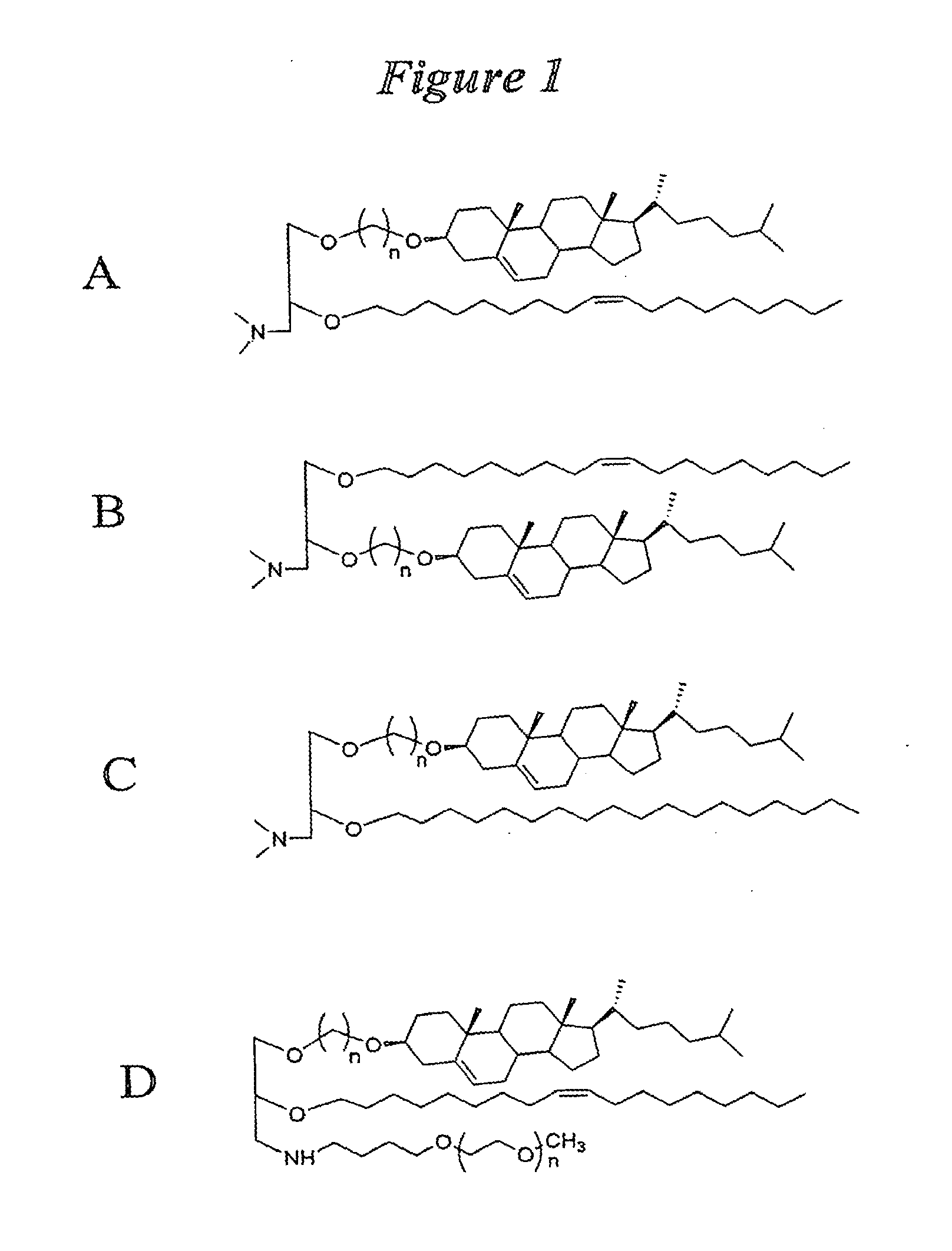
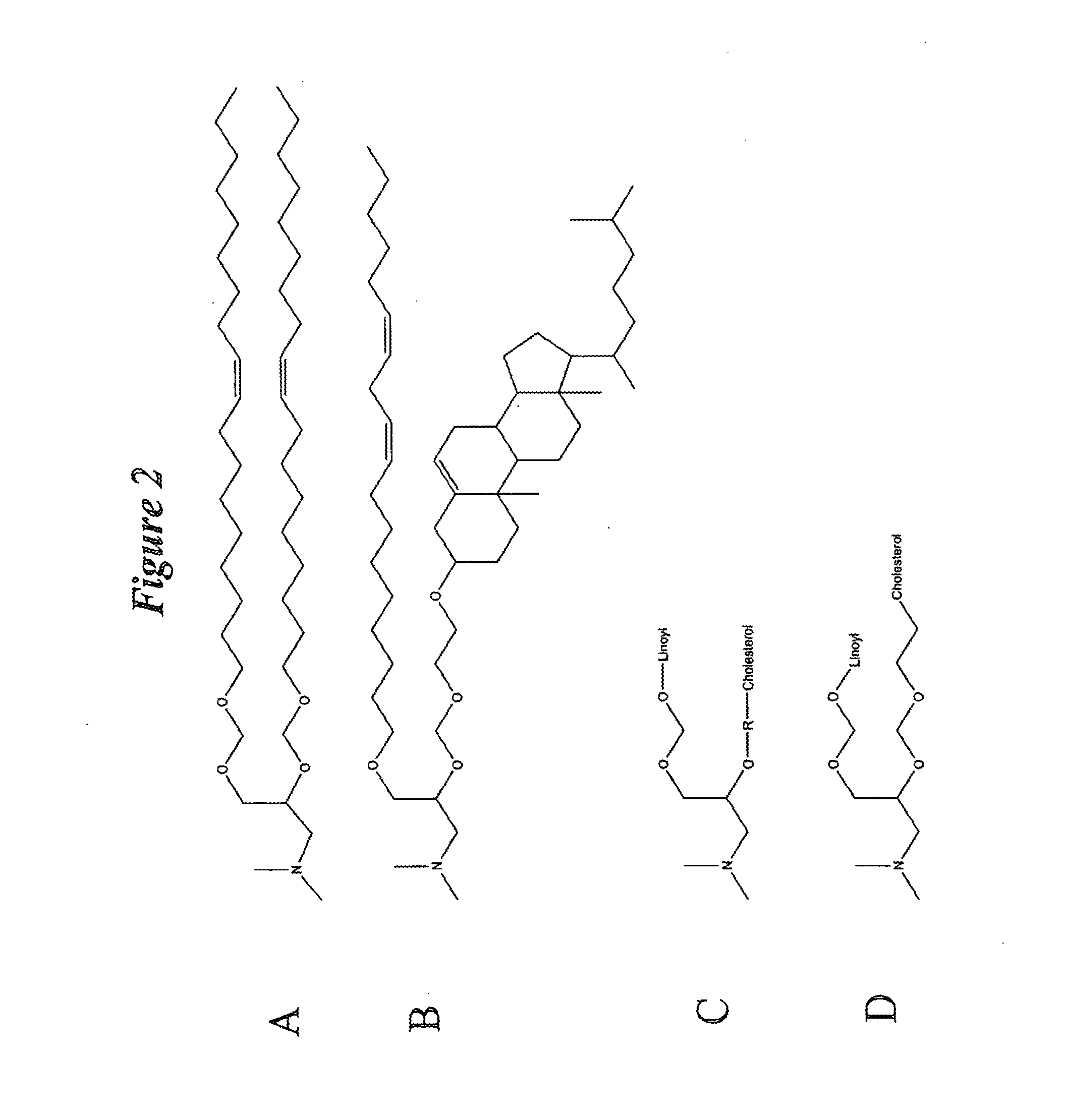
Lipid nanoparticle based compositions and methods for the delivery of biologically active molecules
The present invention relates to novel cationic lipids, transfection agents, microparticles, nanoparticles, and short interfering nucleic acid (siNA) molecules. The invention also features compositions, and methods of use for the study, diagnosis, and treatment of traits, diseases and conditions that respond to the modulation of gene expression and / or activity in a subject or organism. Specifically, the invention relates to novel cationic lipids, microparticles, nanoparticles and transfection agents that effectively transfect or deliver biologically active molecules, such as antibodies (e.g., monoclonal, chimeric, humanized etc.), cholesterol, hormones, antivirals, peptides, proteins, chemotherapeutics, small molecules, vitamins, co-factors, nucleosides, nucleotides, oligonucleotides, enzymatic nucleic acids, antisense nucleic acids, triplex forming oligonucleotides, 2,5-A chimeras, dsRNA, allozymes, aptamers, decoys and analogs thereof, and small nucleic acid molecules, such as short interfering nucleic acid (siNA), short interfering RNA (siRNA), double-stranded RNA (dsRNA), micro-RNA (miRNA), and short hairpin RNA (shRNA) molecules, to relevant cells and / or tissues, such as in a subject or organism. Such novel cationic lipids, microparticles, nanoparticles and transfection agents are useful, for example, in providing compositions to prevent, inhibit, or treat diseases, conditions, or traits in a cell, subject or organism. The compositions described herein are generally referred to as formulated molecular compositions (FMC) or lipid nanoparticles (LNP).
Owner:SIRNA THERAPEUTICS INC
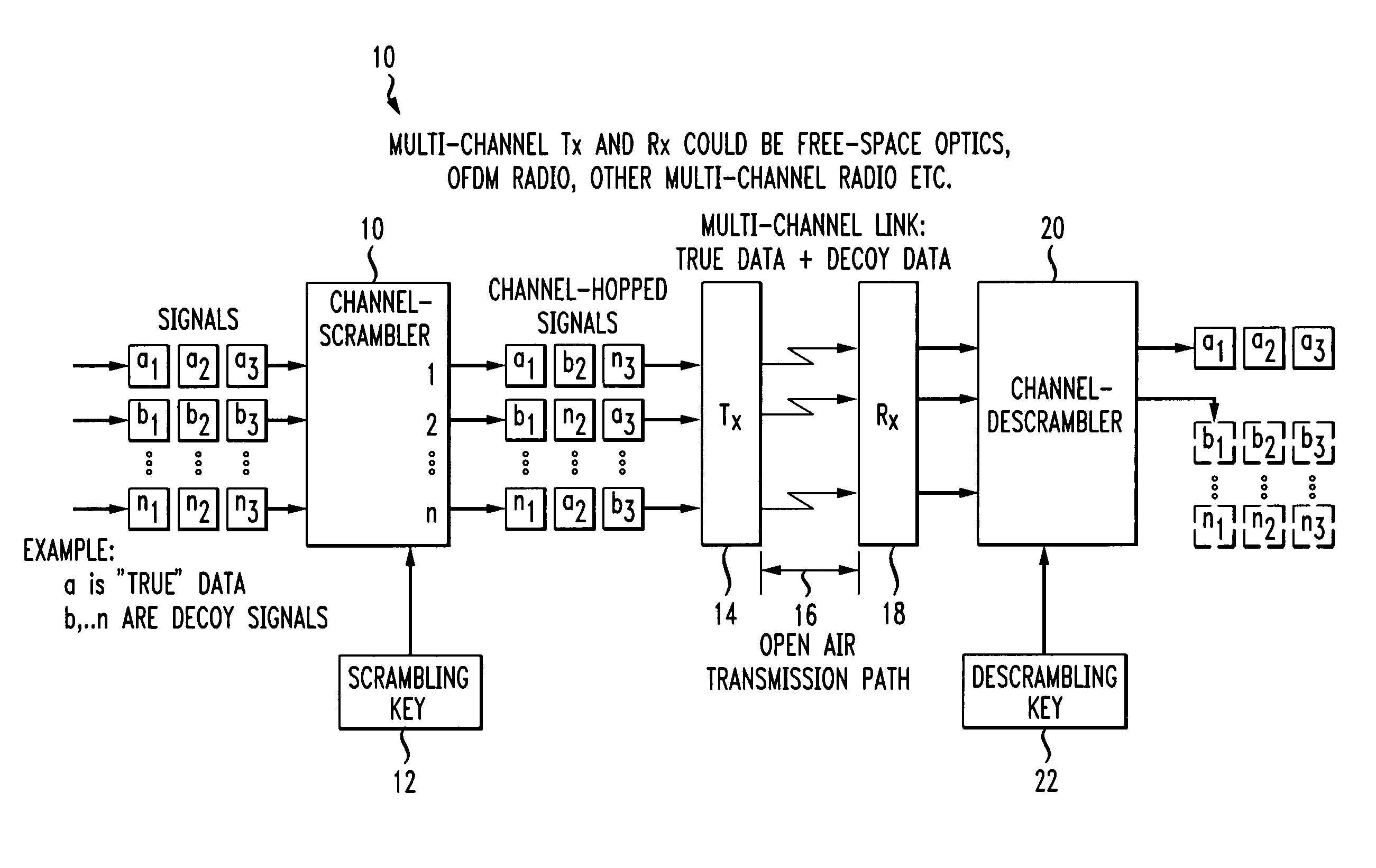
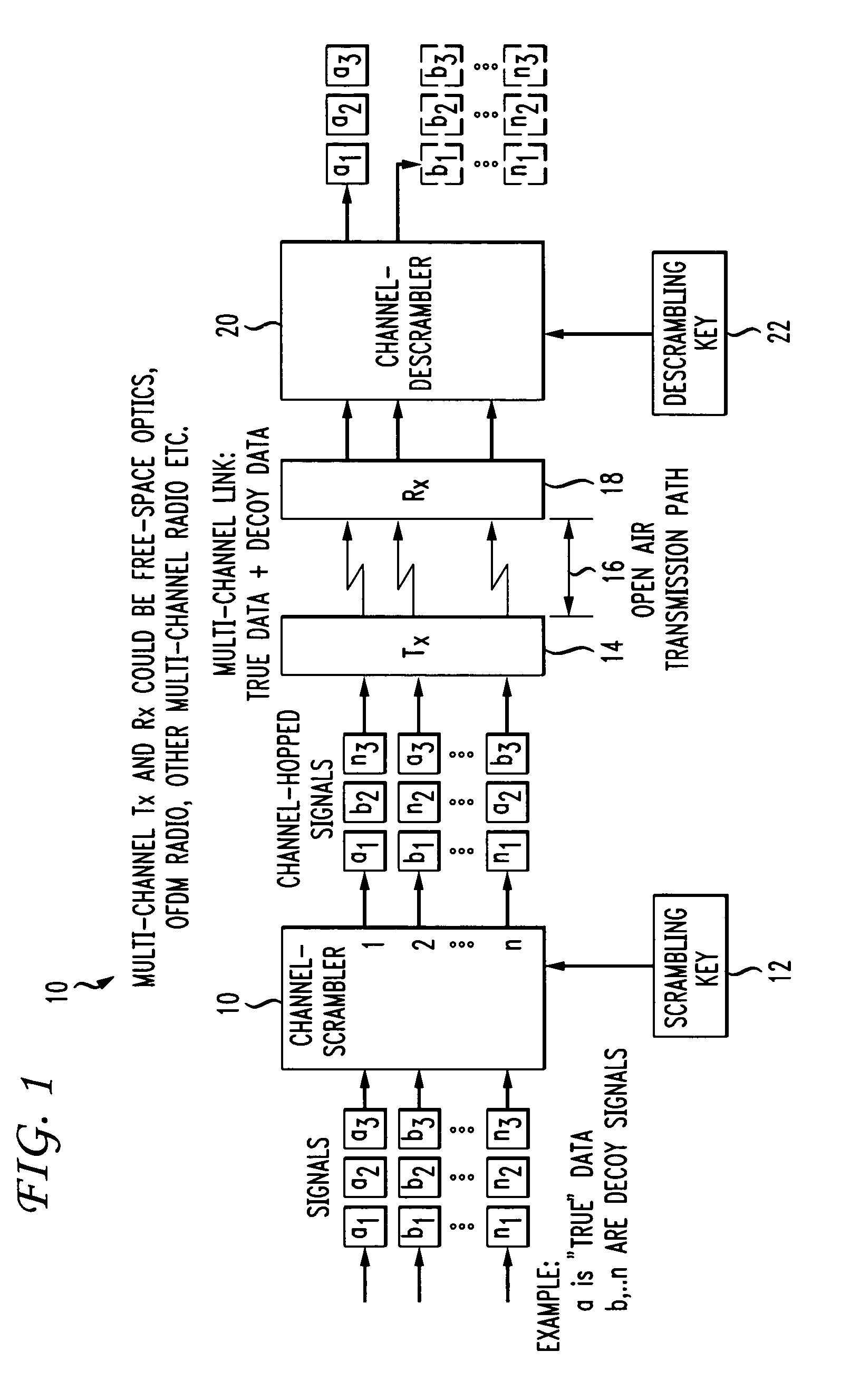
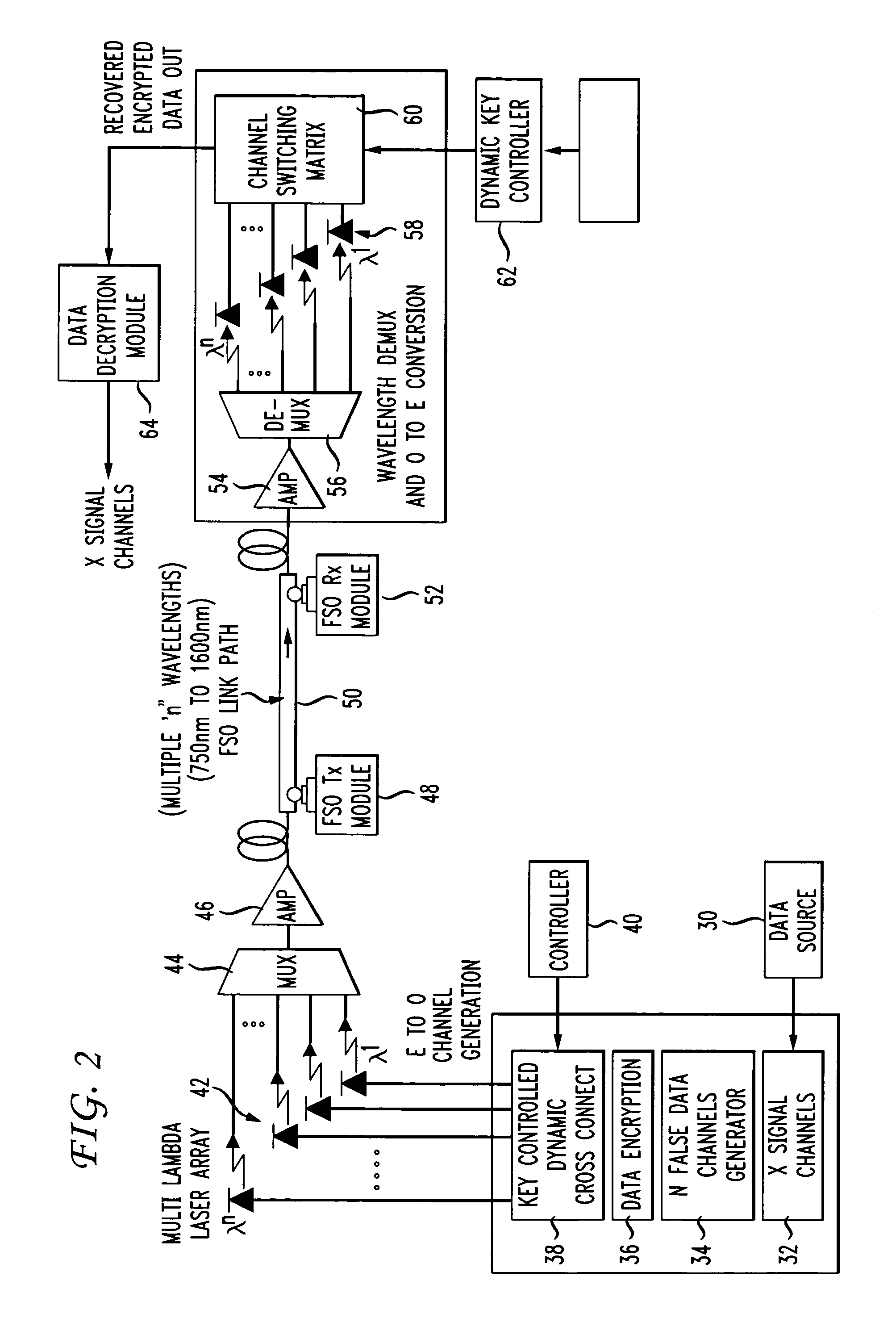
Secure open-air communication system utilizing multi-channel decoyed transmission
ActiveUS7848517B2Reduce the possibilitySufficient level of securityMultiplex system selection arrangementsSecret communicationCommunications systemDecoy
A secure, open-air communication system utilizes a plurality of “decoy” data signals to hide one or more true data signals. The true data signal(s) are channel hopped with the plurality of decoy data signals to form a multi-channel “scrambled” output signal that is thereafter transmitted in an open-air communication system. The greater the number of decoy signals, the greater the security provided to the open-air system. Further security may be provided by encrypting both the true and decoy signals prior to scrambling and / or by utilizing a spatially diverse set of transmitters and receivers. Without the knowledge of the channel assignment(s) for the true signal(s), an eavesdropper may be able to intercept (and, with time, perhaps descramble) the open-air transmitted signals, will not be able to distinguish the true data from the decoys without also knowing the channel assignment(s).
Owner:AT & T INTPROP II LP
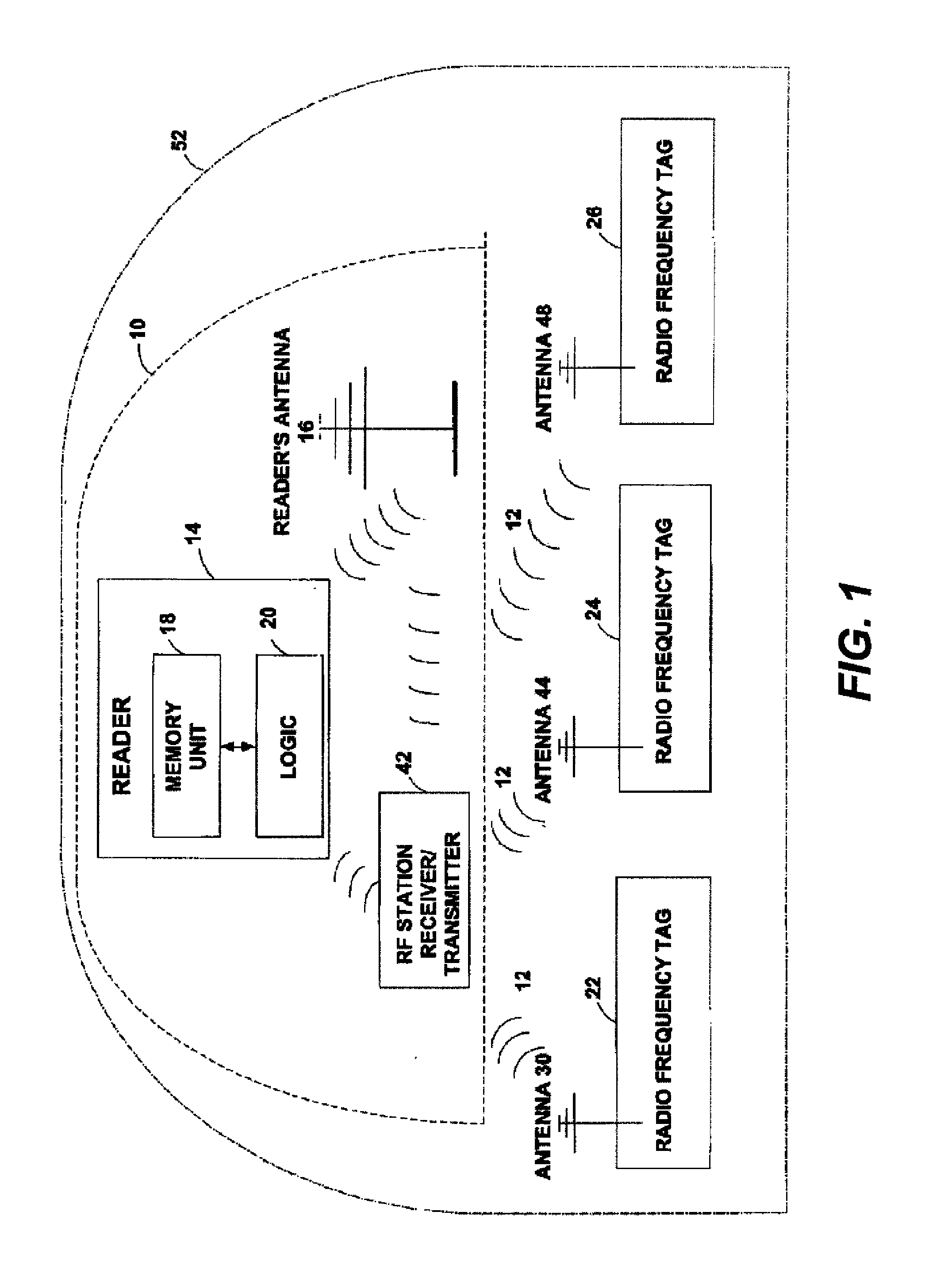
Detecting RFID tag and inhibiting skimming
InactiveUS20130106576A1Flush outsideIncrease the difficultySensing detailsCommunication jammingDecoyResponse Frequency
A method of detecting an RFID tag includes transmitting a bait RFID read signal at a bait power level and a simulated response signal at a simulated-response power level. A selected reader frequency is monitored for a selected detection time. A skimmer is determined to be present if a skimmer RFID read signal is detected during that time. If a skimmer is not determined to be present, multiple read signals are transmitted sequentially, each signal at a respective read power level. At least one of the read power levels is lower than the bait power level, at least one of the read power levels is lower than the simulated-response power level, and at least two of the read power levels are different from each other. A selected response frequency for a tag is monitored for a response from an RFID tag.
Owner:EASTMAN KODAK CO
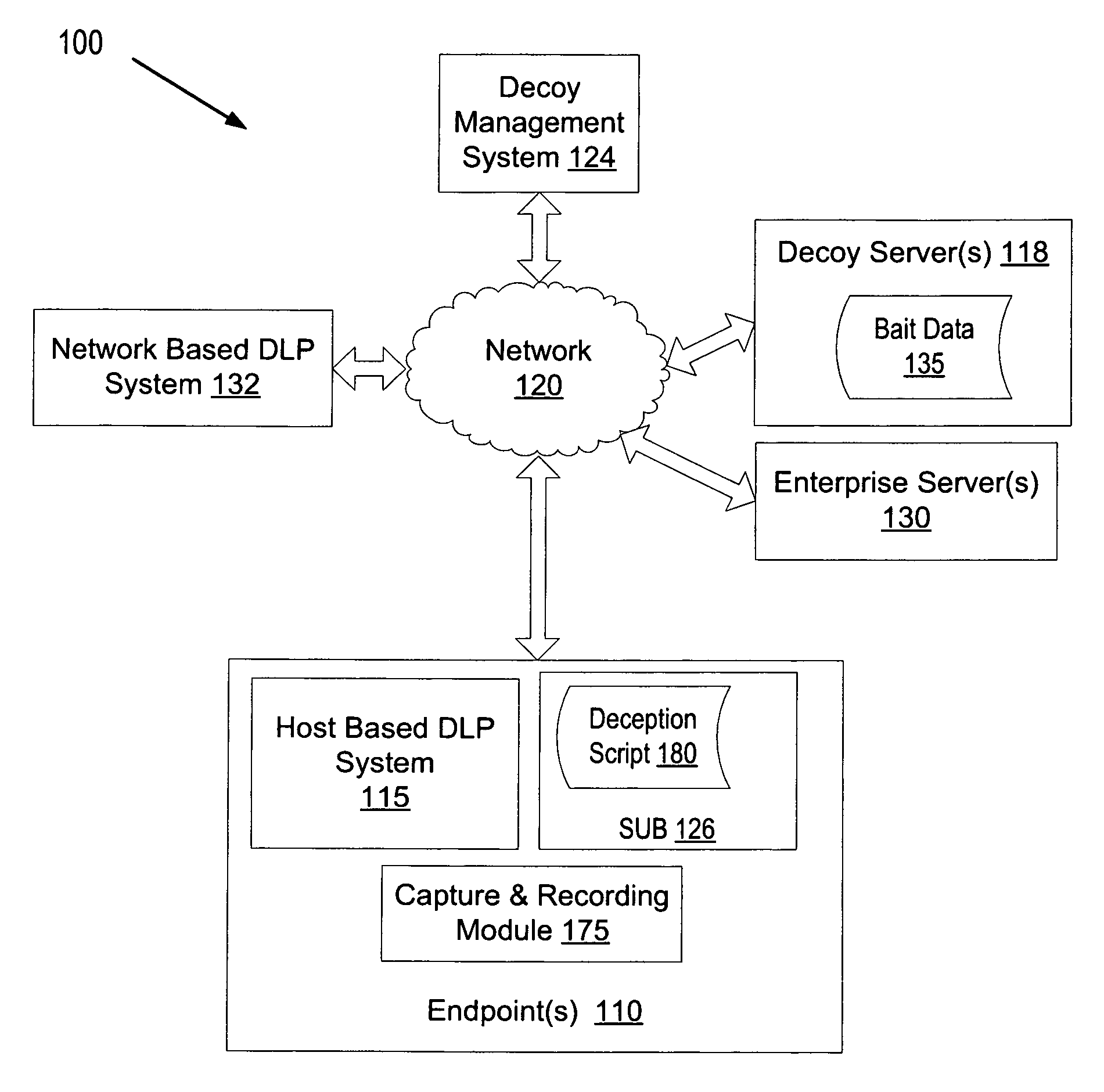
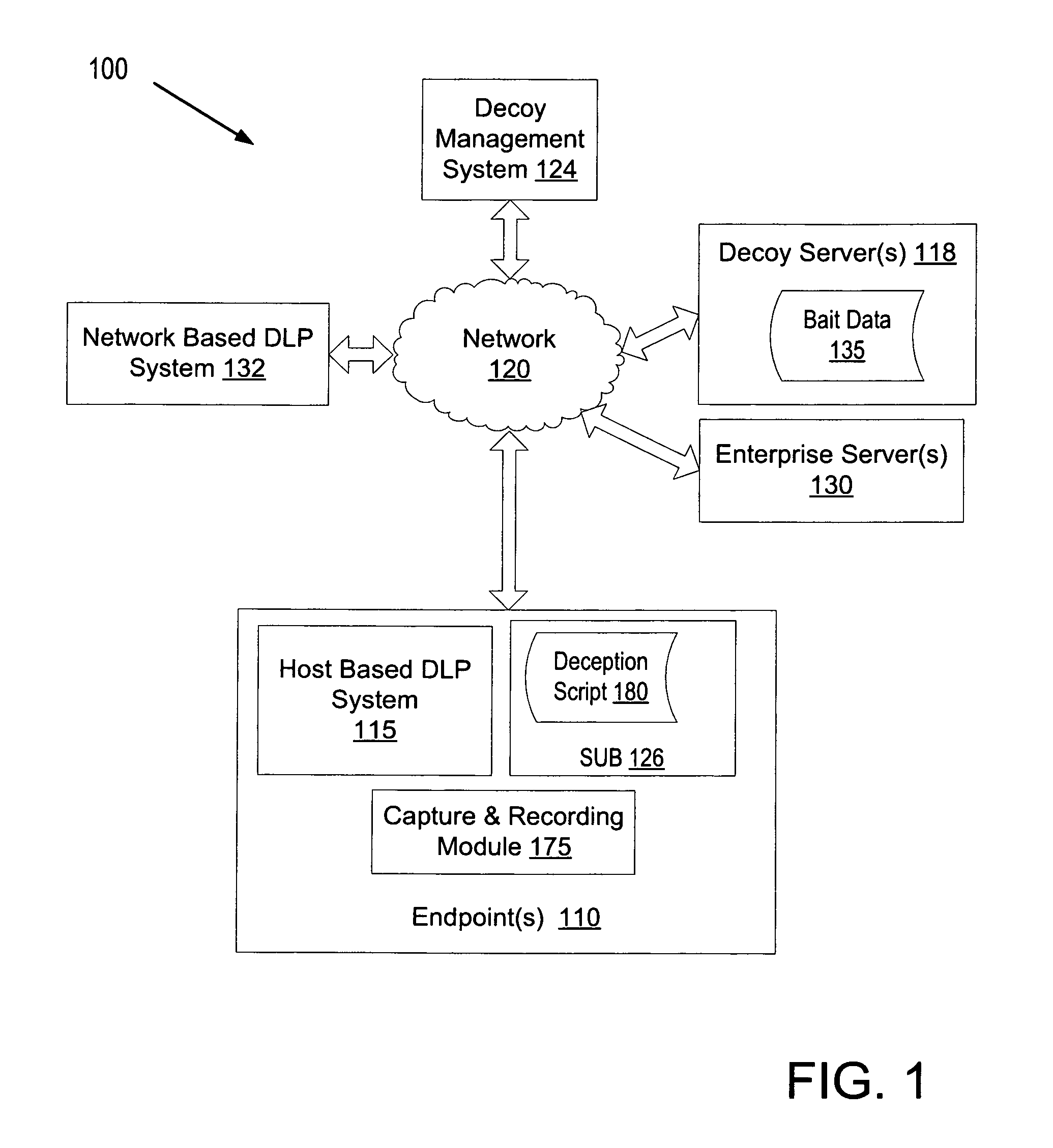
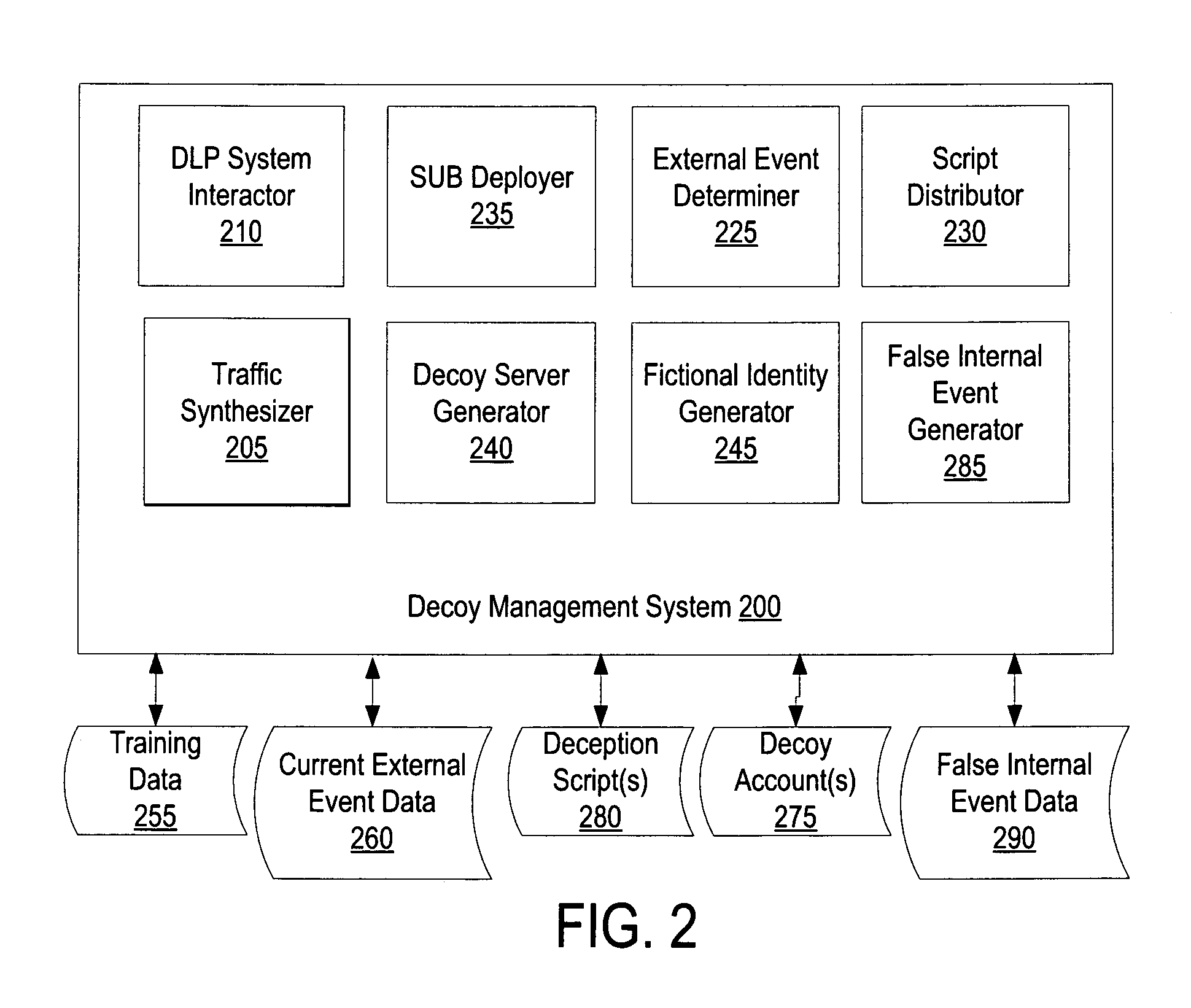
Using decoys by a data loss prevention system to protect against unscripted activity
A computing device executing a data loss prevention (DLP) system tracks bait data on at least one of the computing device or a network. The DLP system identifies a potential security threat in response to detecting unscripted activity associated with the bait data. The DLP system performs an action in response to identifying the potential security threat.
Owner:GEN DIGITAL INC +1
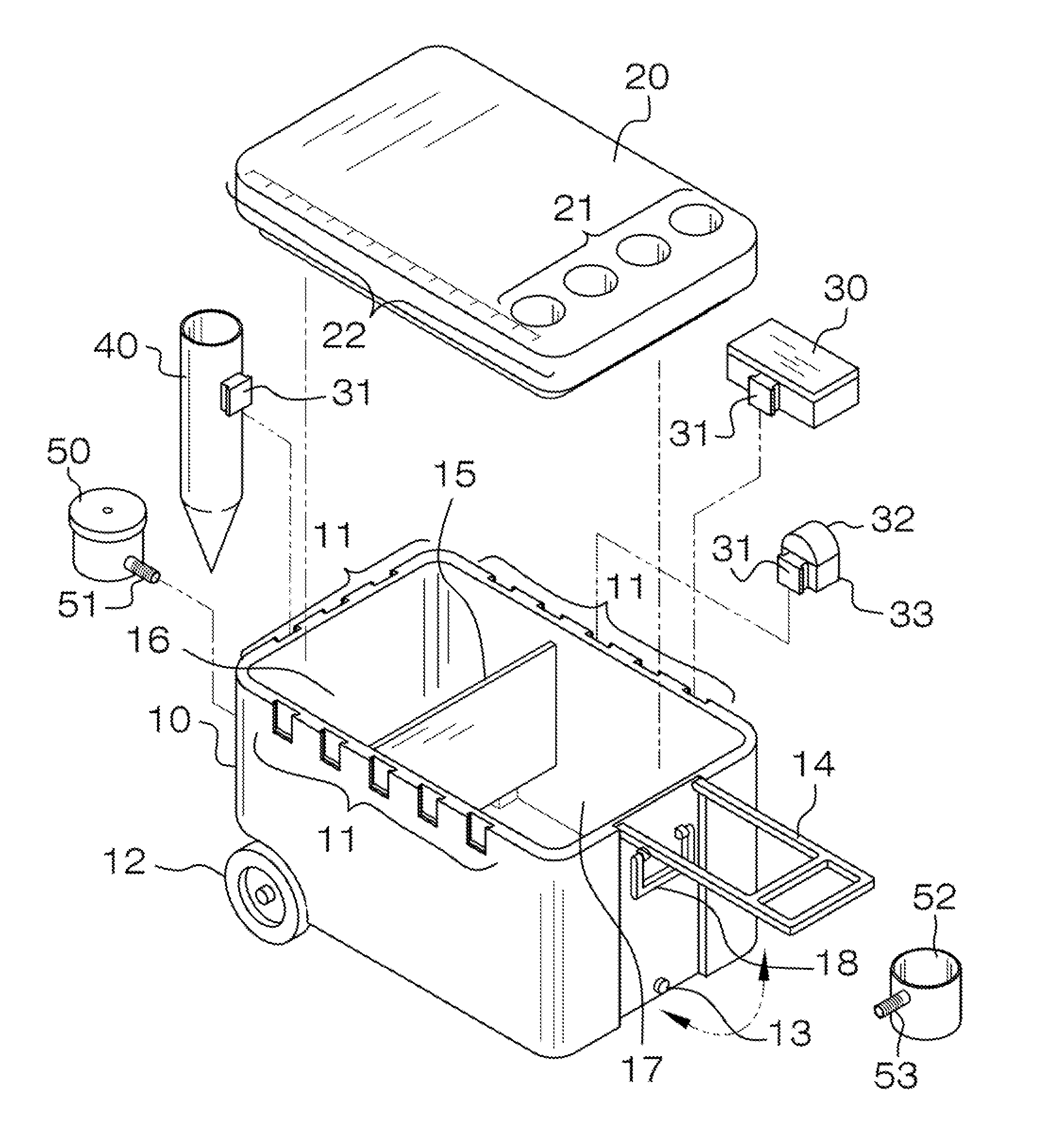
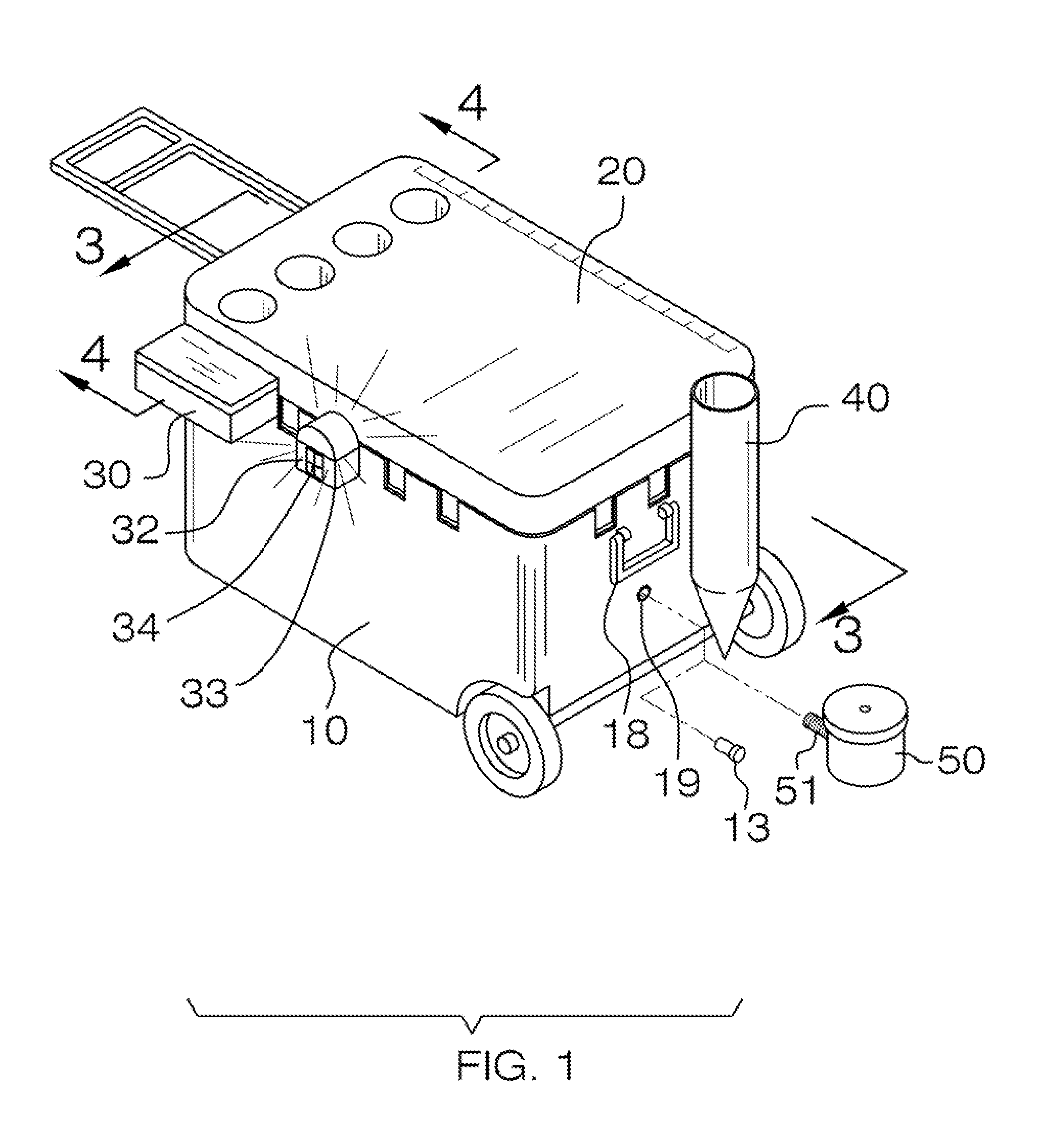
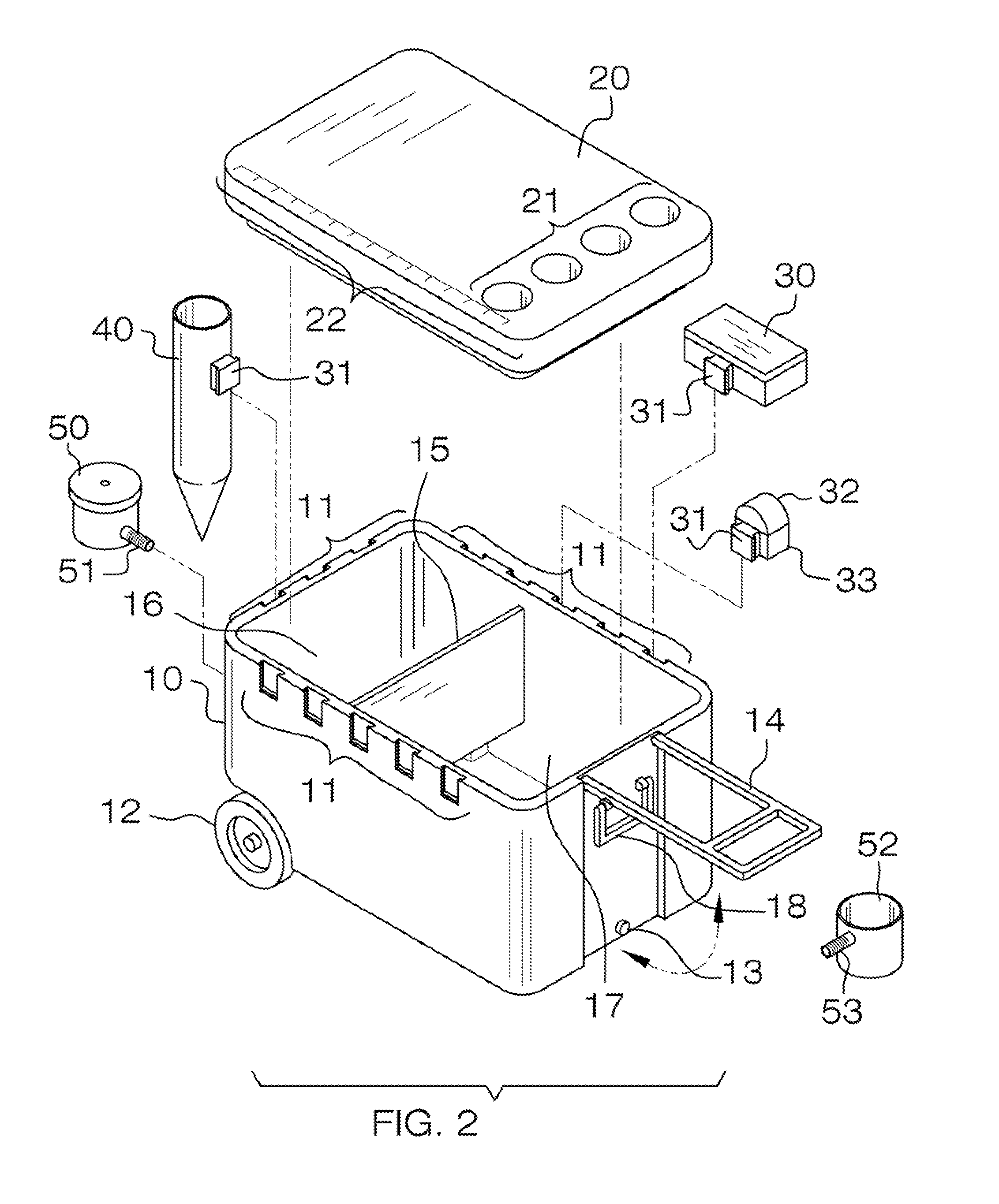
Fishing chest
The invention is a fishing cooler that has wheels and a handle. The fishing cooler also features a plurality of cup holders, an externally removable and attachable rod holder, and a tackle box that can be attached either internally or externally. The fishing cooler has two internal compartments. The first compartment is for storing bait, and is smaller than the second compartment, which is for storing caught fish. Water can pass between each compartment, and a drain plug enables evacuation of all water inside of the cooler. Integrated on top of the cooler is a measuring line for such uses as measuring caught fish. The handle is hingedly connected at one side of the cooler, and extends when in use to enable the end user to pull the cooler behind he or she. The cooler may also include a drain cup and aerator that can be attached to either of the two drain plug holes. A portable light may be attached to the cooler.
Owner:MACKAY MICHAEL VINCENT
System and method of detecting malicious content
ActiveUS9838416B1Rapid responsePlatform integrity maintainanceTransmissionComputer wormNetwork activity
A computer worm containment system comprises a detection system and a blocking system. The detection system orchestrates a sequence of network activities in a decoy computer network and monitors that network to identify anomalous behavior and determine whether the anomalous behavior is caused by a computer worm. The detection system can then determine an identifier of the computer worm based on the anomalous behavior. The detection system can also generate a recovery script for disabling the computer worm or repairing damage caused by the computer worm. The blocking system is configured to use the computer worm identifier to protect another computer network. The blocking system can also use the recovery script to disable a computer worm within the other network and to repair damage caused to the network by the worm.
Owner:FIREEYE SECURITY HLDG US LLC
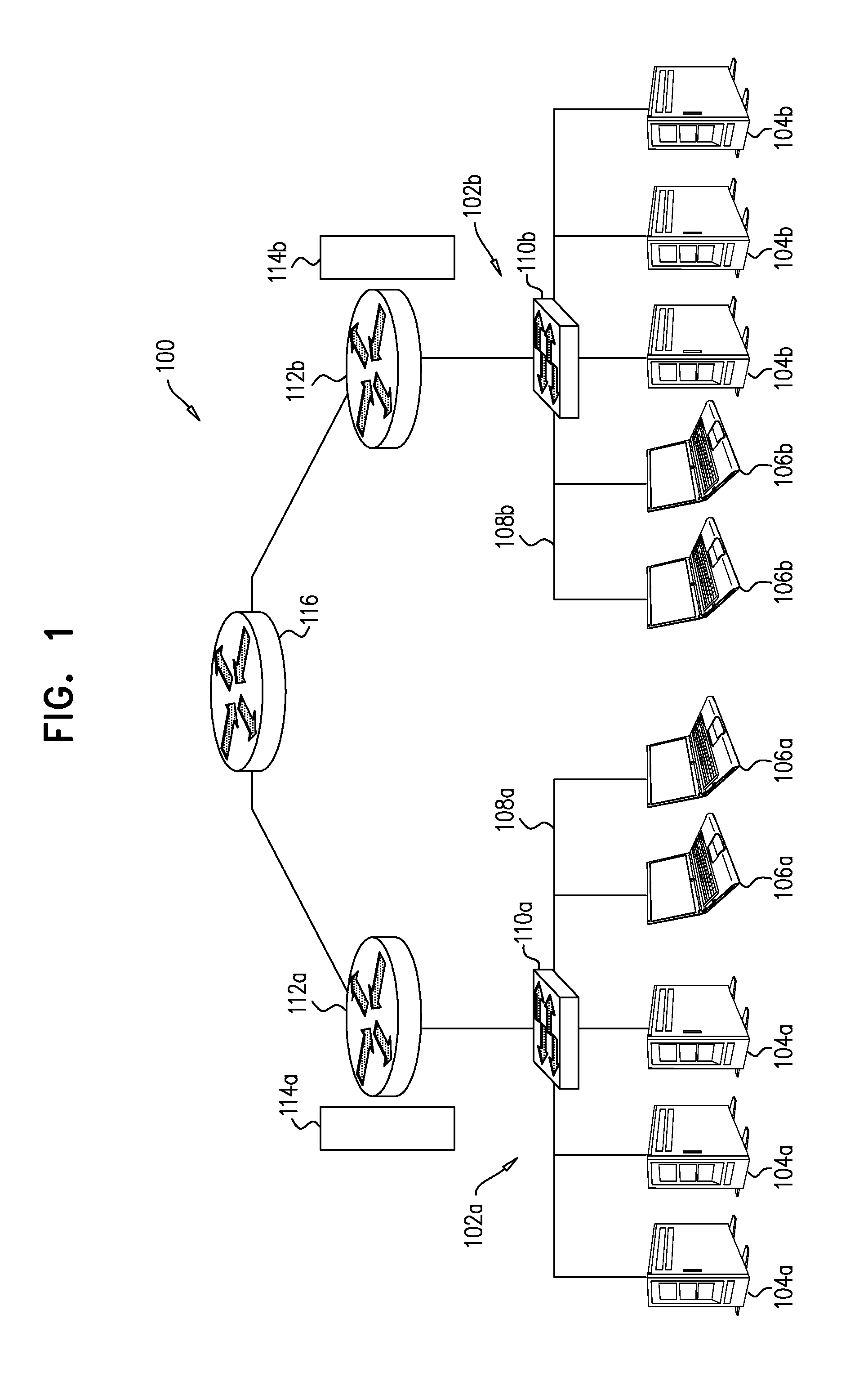
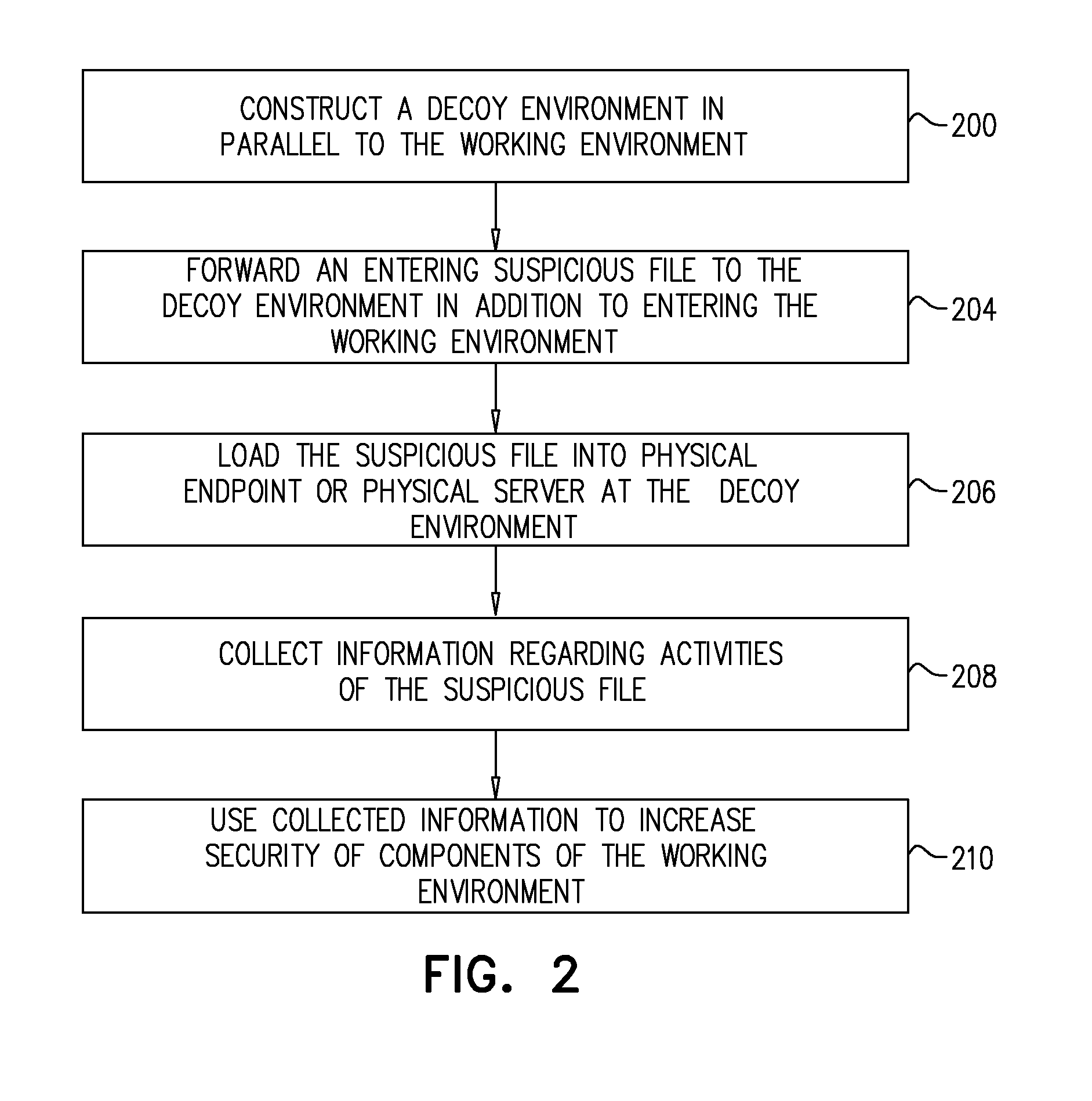
System and a Method for Identifying Malware Network Activity Using a Decoy Environment
A system for gathering information about malware and a method of use therefor, the system comprising a working environment including physical working environment servers, physical working environment endpoints, a working environment network, a switch, and a router directing traffic between said working environment network and an external network, a decoy environment including at least one physical machine, a decoy environment server, a decoy environment endpoint, a decoy environment network and a decoy environment router, a file directing mechanism directing at least some files to the decoy environment, and a threat tracking mechanism tracking and observing actions triggered by the files in the decoy environment.
Owner:FIDELIS SECURITY SYSTEMS
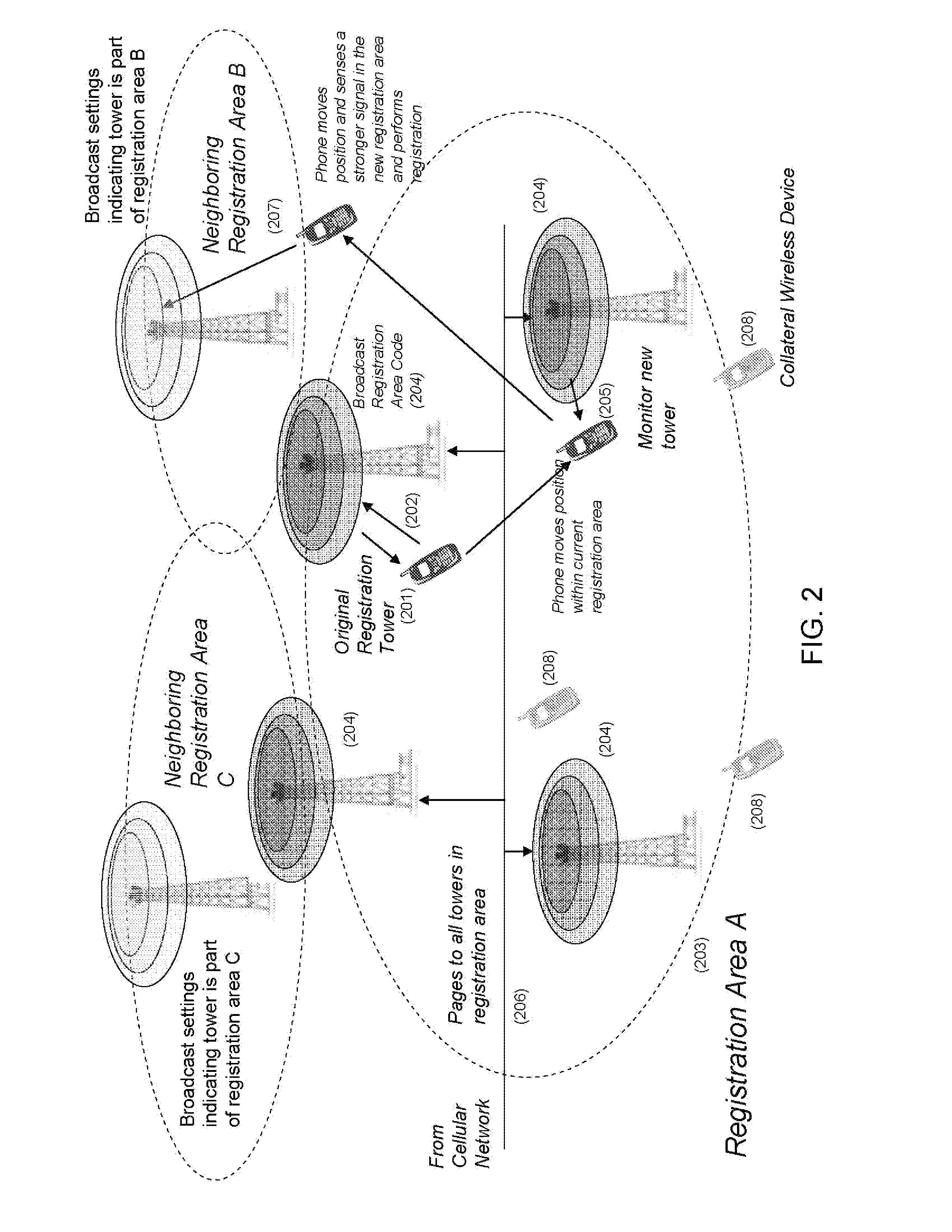
Methods of Remotely Identifying, Suppressing, Disabling and Access Filtering Wireless Devices of Interest Using Signal Timing and Intercept Receivers to Effect Power Reduction, Minimization of Detection, and Minimization of Collateral Interfernce.
InactiveUS20090311963A1Effectively disableEnergy efficient ICTCommunication jammingDecoySignal timing
Techniques for interfering with communications made according to a wireless standard between a beacon and a wireless device. The techniques determine a characteristic that is required by the standard for a signal produced during the communication. Then an interference signal is generated that is specifically adapted to the characteristic and interferes with the characteristic such that the wireless device and the beacon cannot interact as provided for the communication by the wireless standard. The techniques may be used to suppress legitimate wireless beacons in an operational area, to establish a baiting beacon in the operational area, or to interfere with communications between a wireless device and a baiting beacon or other beacon. The interference signal is specifically adapted to the characteristic in a way that greatly reduces the amount of power required for the interference signal and the conspicuousness of the interference signal.
Owner:L 3 COMM CORP
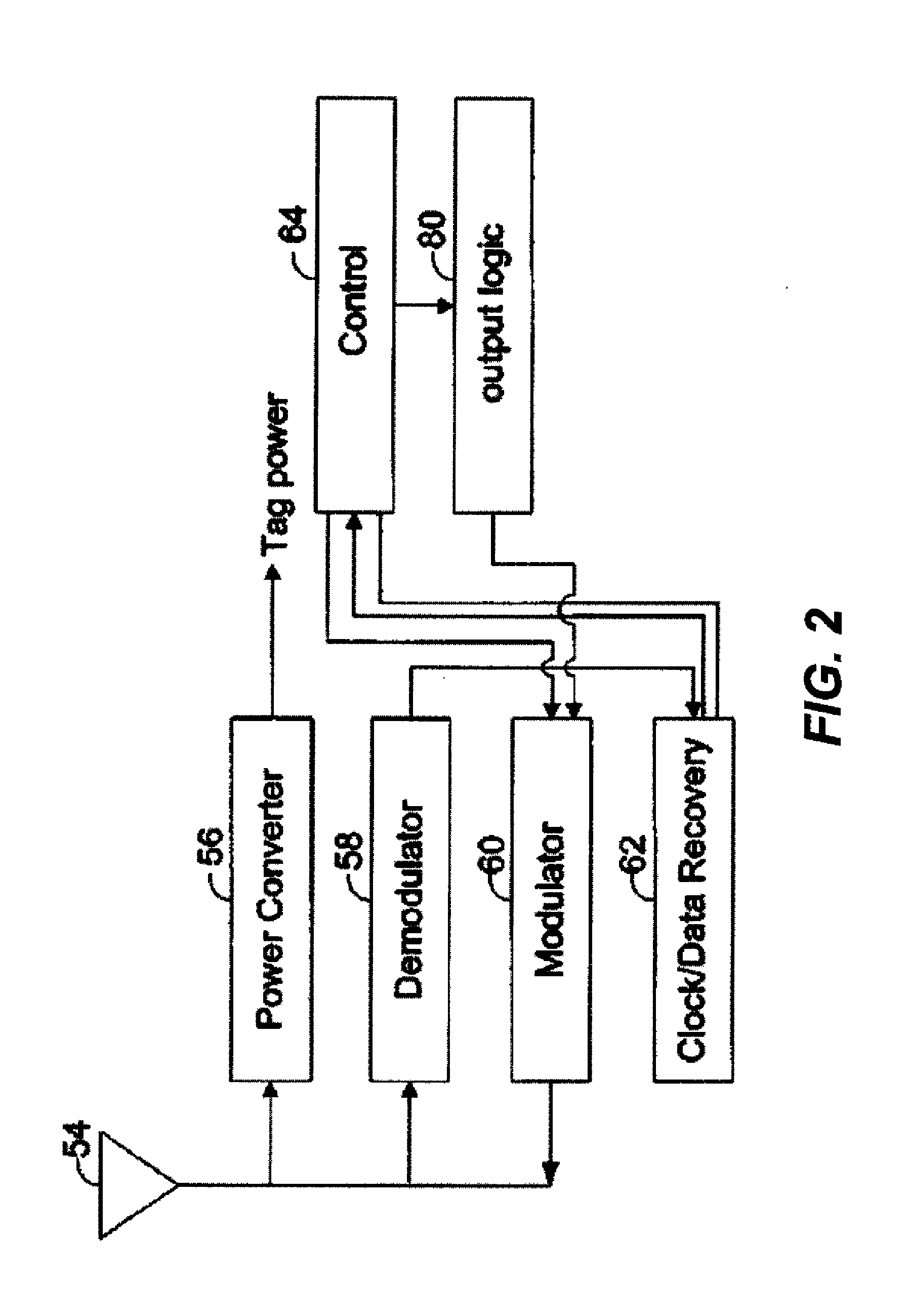
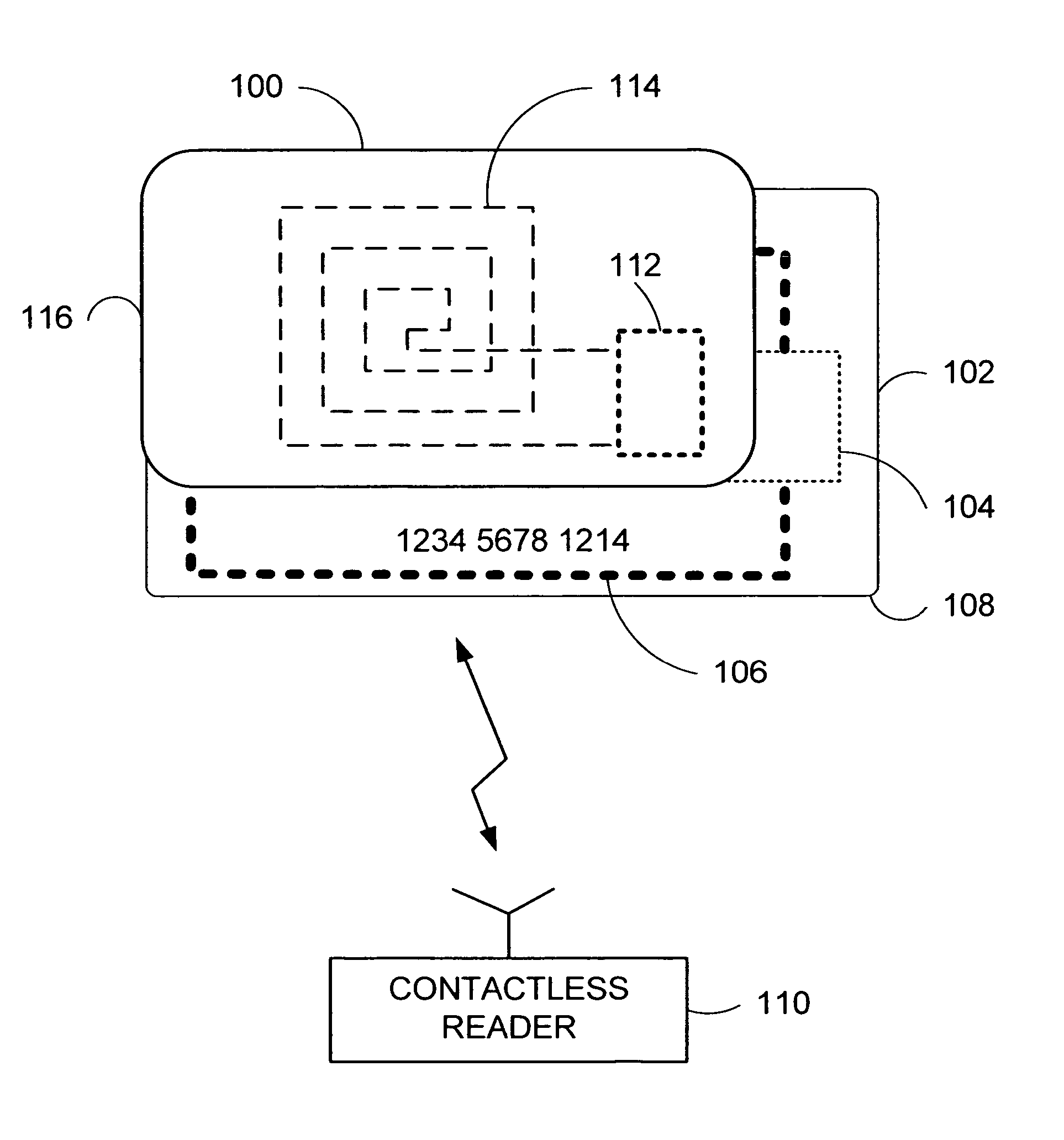
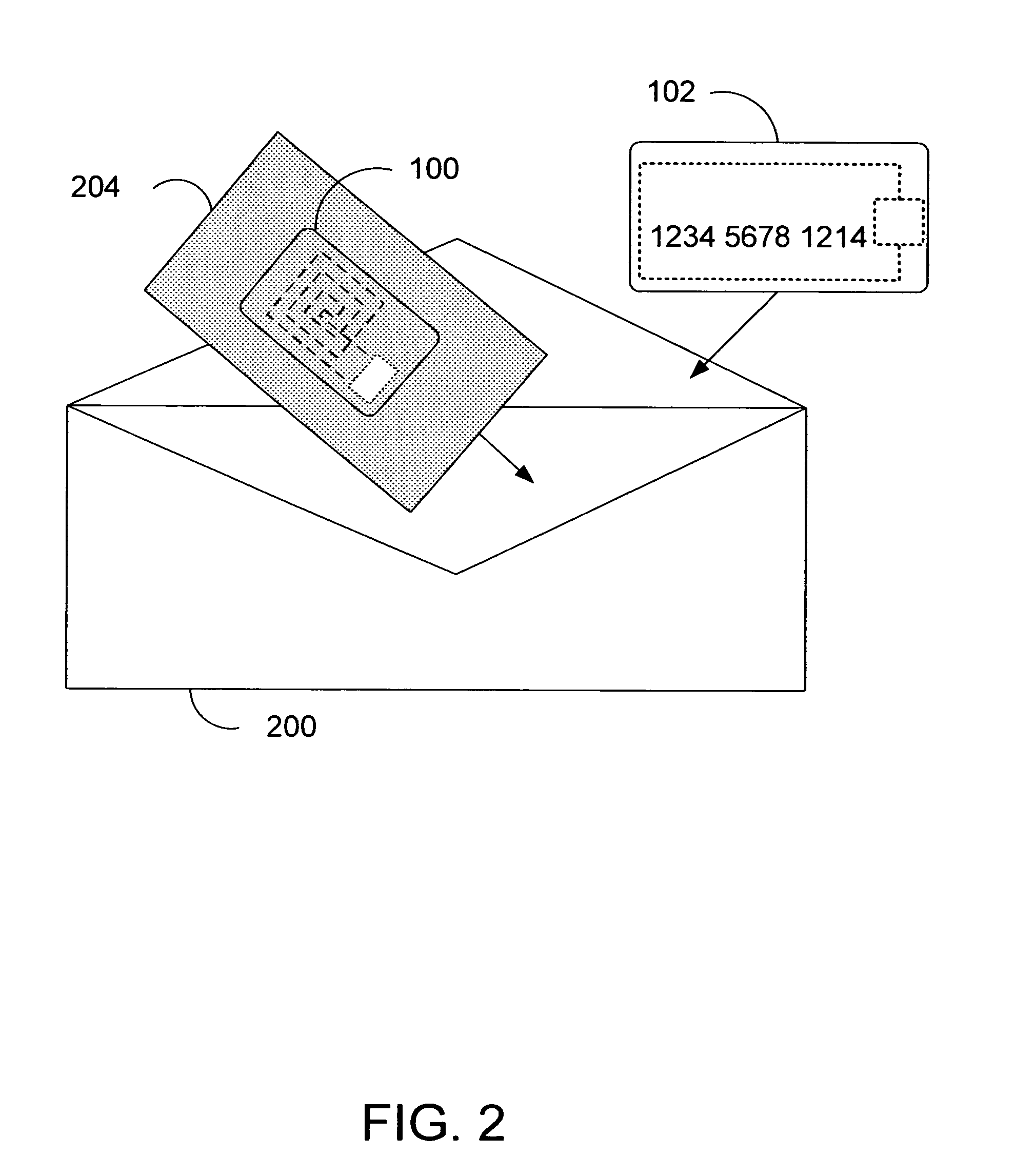
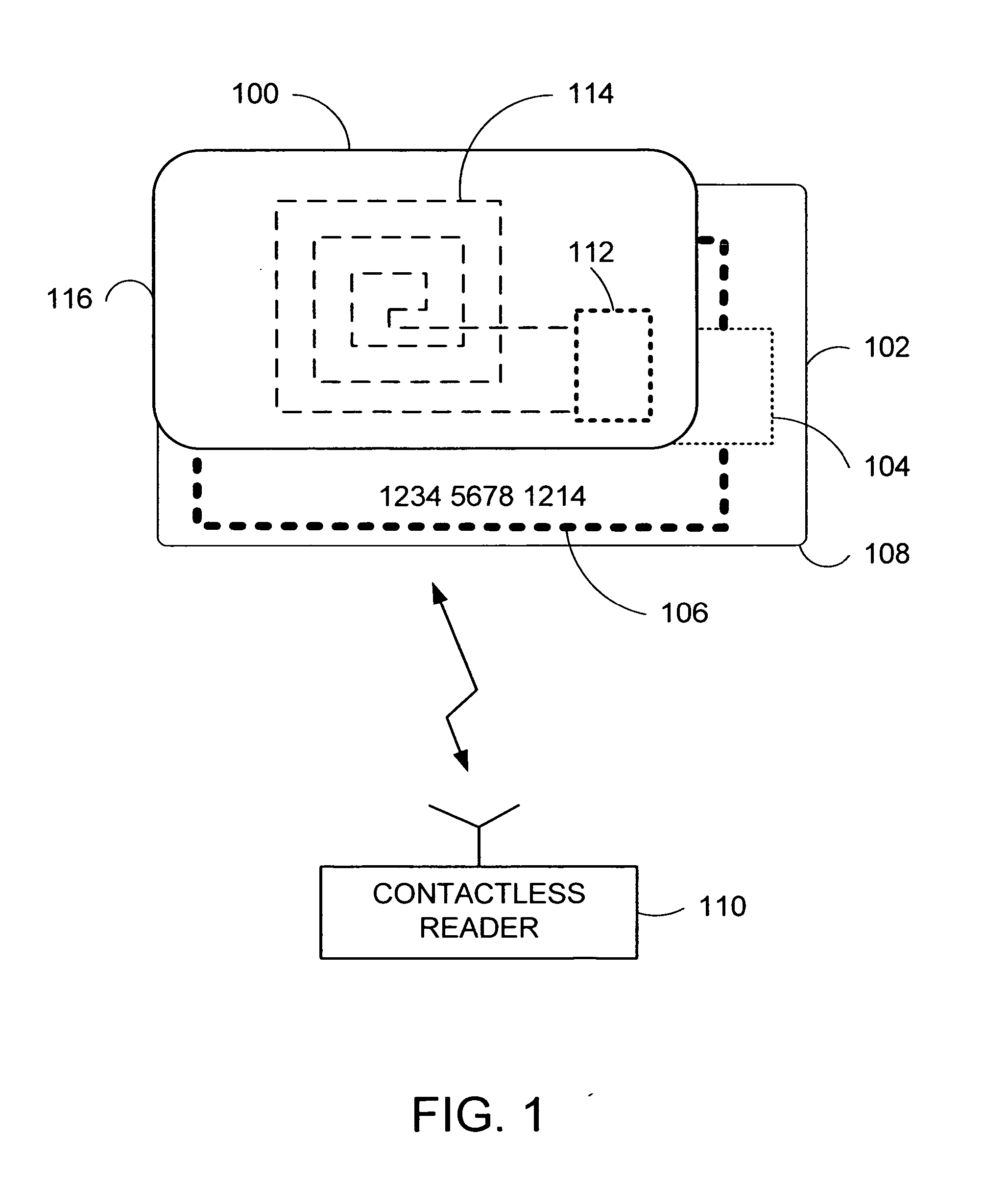
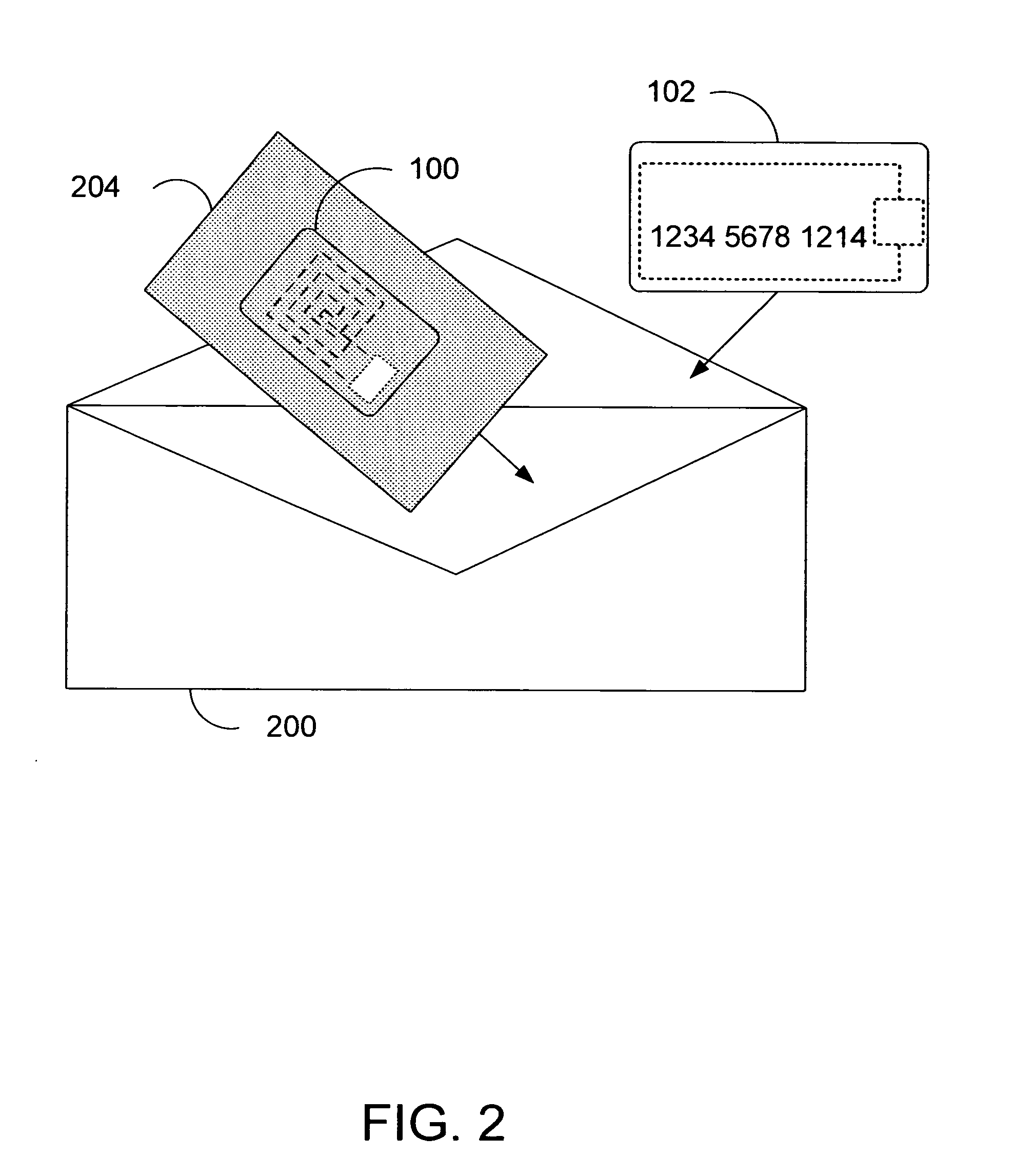
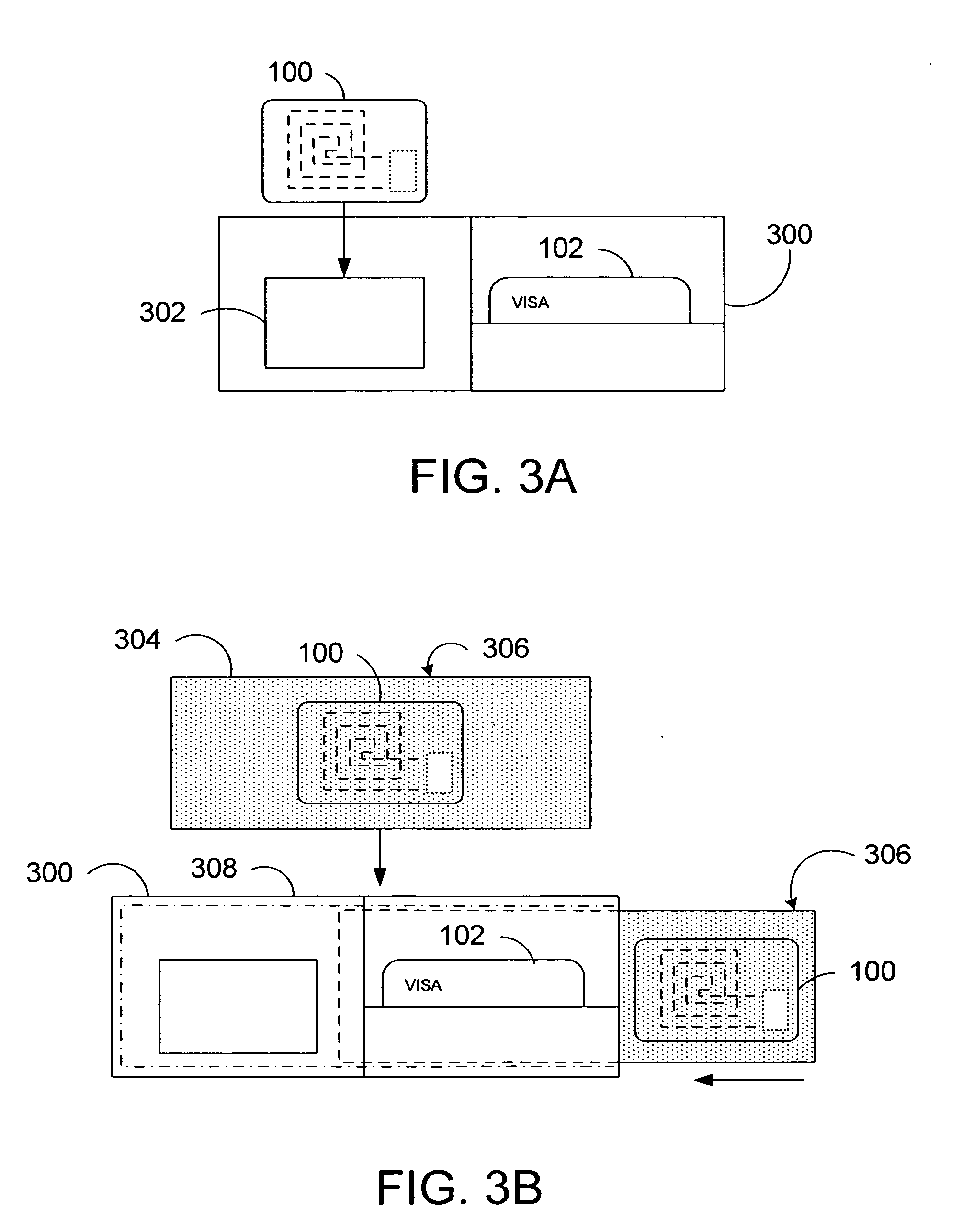
Apparatus and method for preventing wireless interrogation of portable consumer devices
ActiveUS7522905B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDecoySmart card
An apparatus and method is provided to prevent contactless portable electronic consumer devices such as an RF identification device (RFID), tokens, mini-cards, key fobs, cellular phones, smart card, etc. from being wirelessly interrogated. In one embodiment, a decoy circuit capable of detecting wireless interrogation signals transmitted to a contactless portable consumer device is used to prevent one or more interrogation devices from interrogating an authentic circuit in the contactless portable consumer device.
Owner:VISA USA INC (US)
Generating phish messages
Owner:OPSEC ONLINE LTD
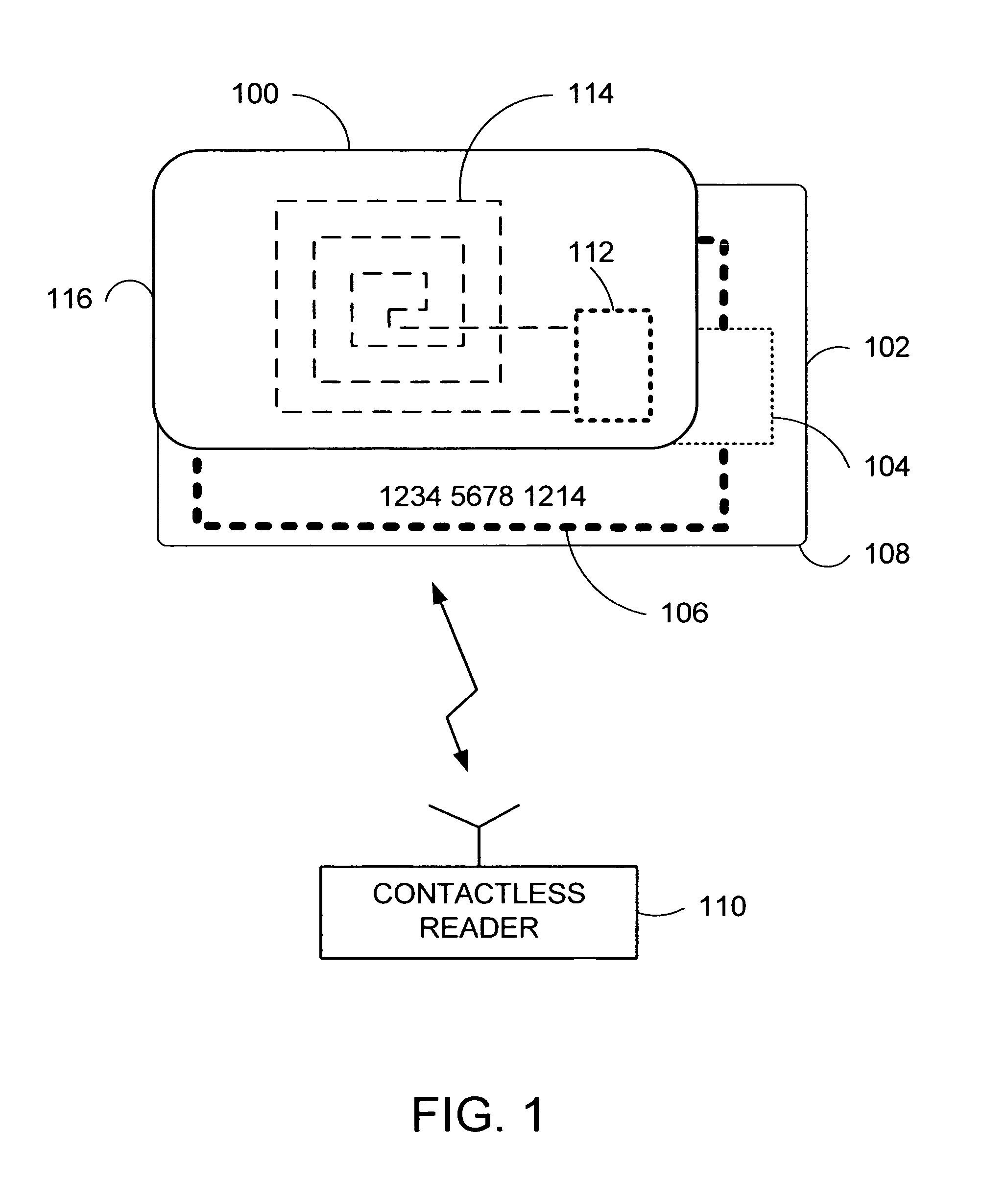
Apparatus and method for preventing wireless interrogation of portable consumer devices
ActiveUS20060293027A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsDecoySmart card
An apparatus and method is provided to prevent contactless portable electronic consumer devices such as an RF identification device (RFID), tokens, mini-cards, key fobs, cellular phones, smart card, etc. from being wirelessly interrogated. In one embodiment, a decoy circuit capable of detecting wireless interrogation signals transmitted to a contactless portable consumer device is used to prevent one or more interrogation devices from interrogating an authentic circuit in the contactless portable consumer device.
Owner:VISA USA INC (US)
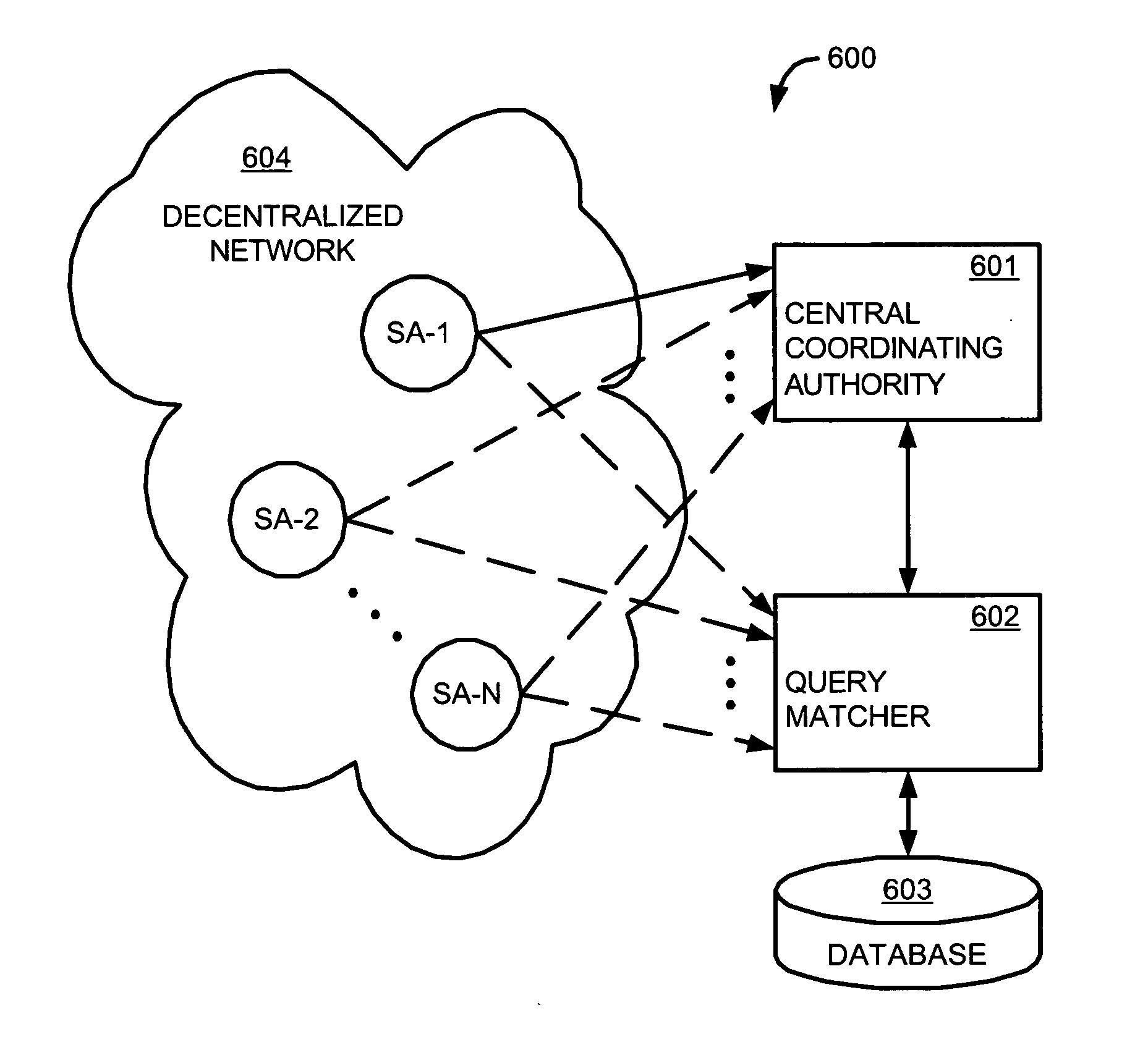
Demand based method for interdiction of unauthorized copying in a decentralized network
InactiveUS20050114709A1Digital data processing detailsUnauthorized memory use protectionDecoyNetwork communication
A multi-level and / or demand based method and apparatus for interdicting unauthorized copying in a decentralized network are described. In their preferred embodiments, the method and apparatus start out by performing search result manipulation to interdict unauthorized copying of protected files. If a trigger event is detected in network communications, however, such as a threshold number of requests being exceeded for a protected file by a network node, then the method floods that node with decoys of the protected file to enhance interdiction efforts.
Owner:MACROVISION CORP
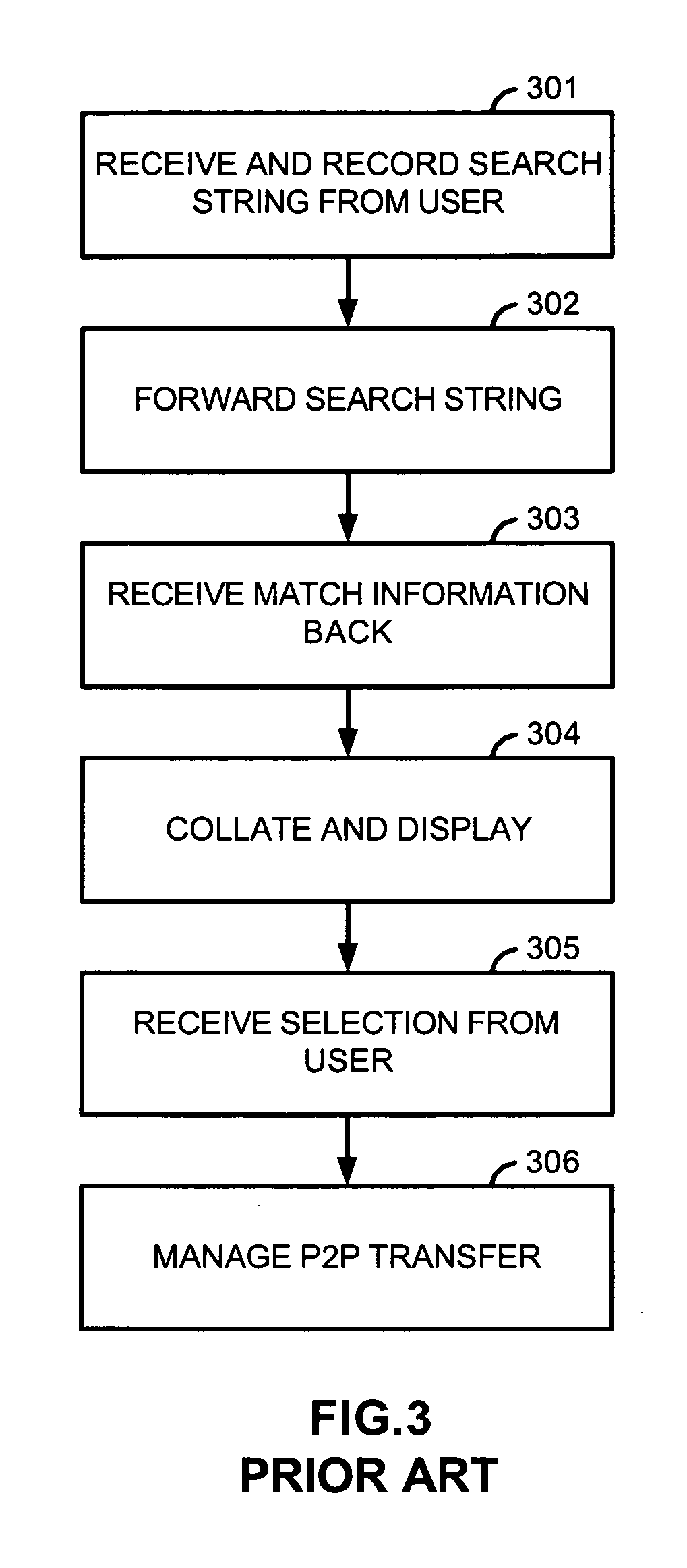
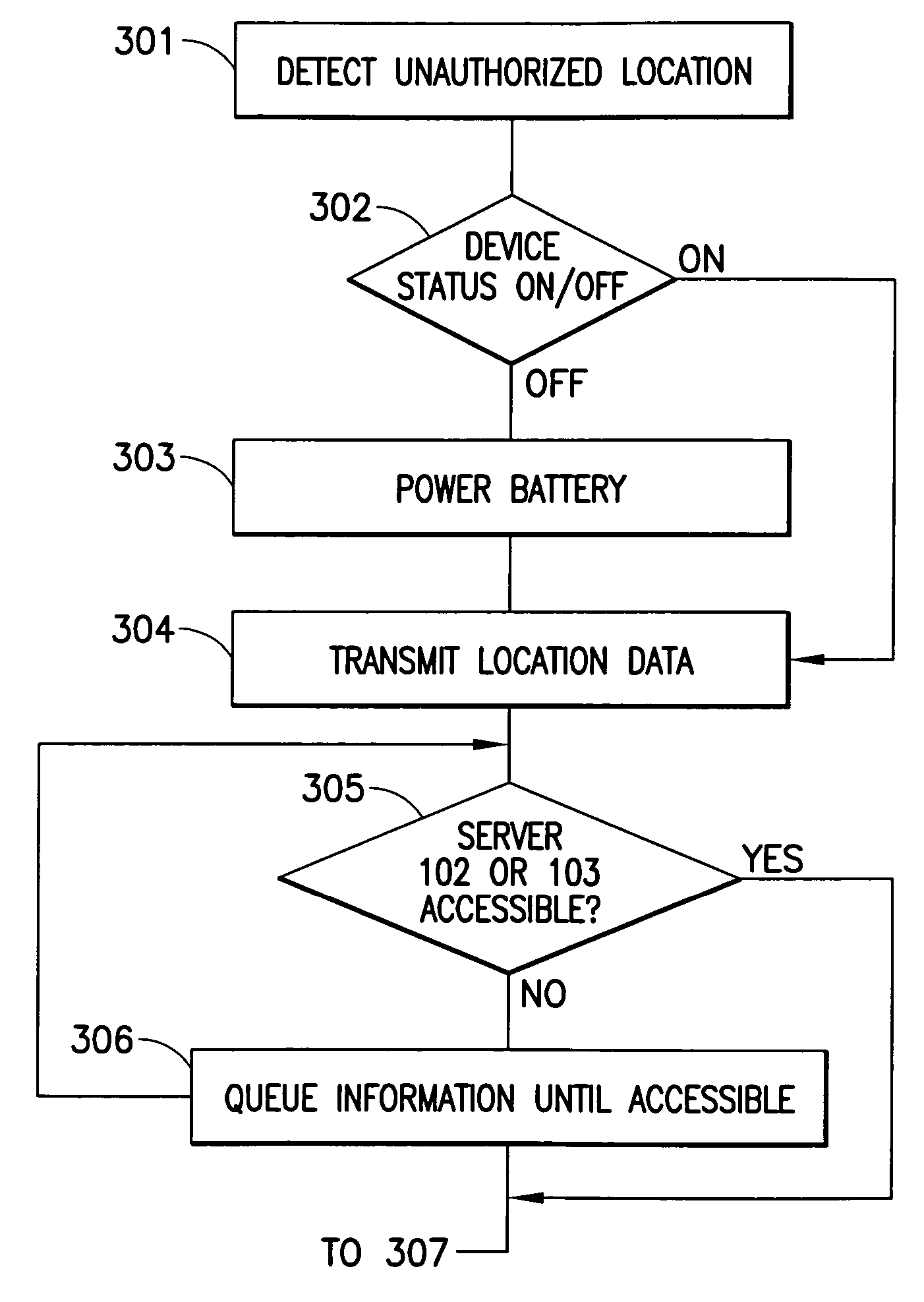
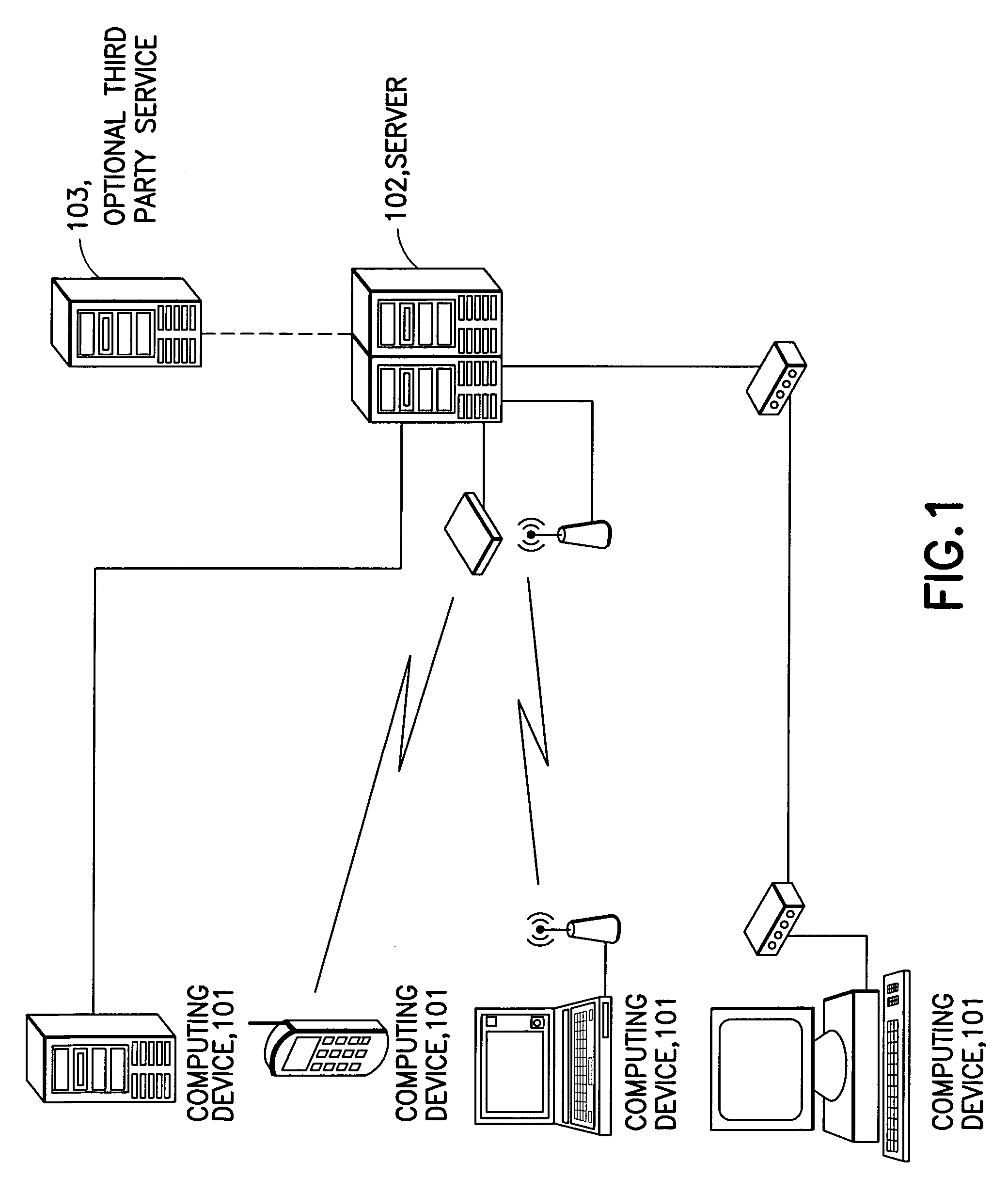
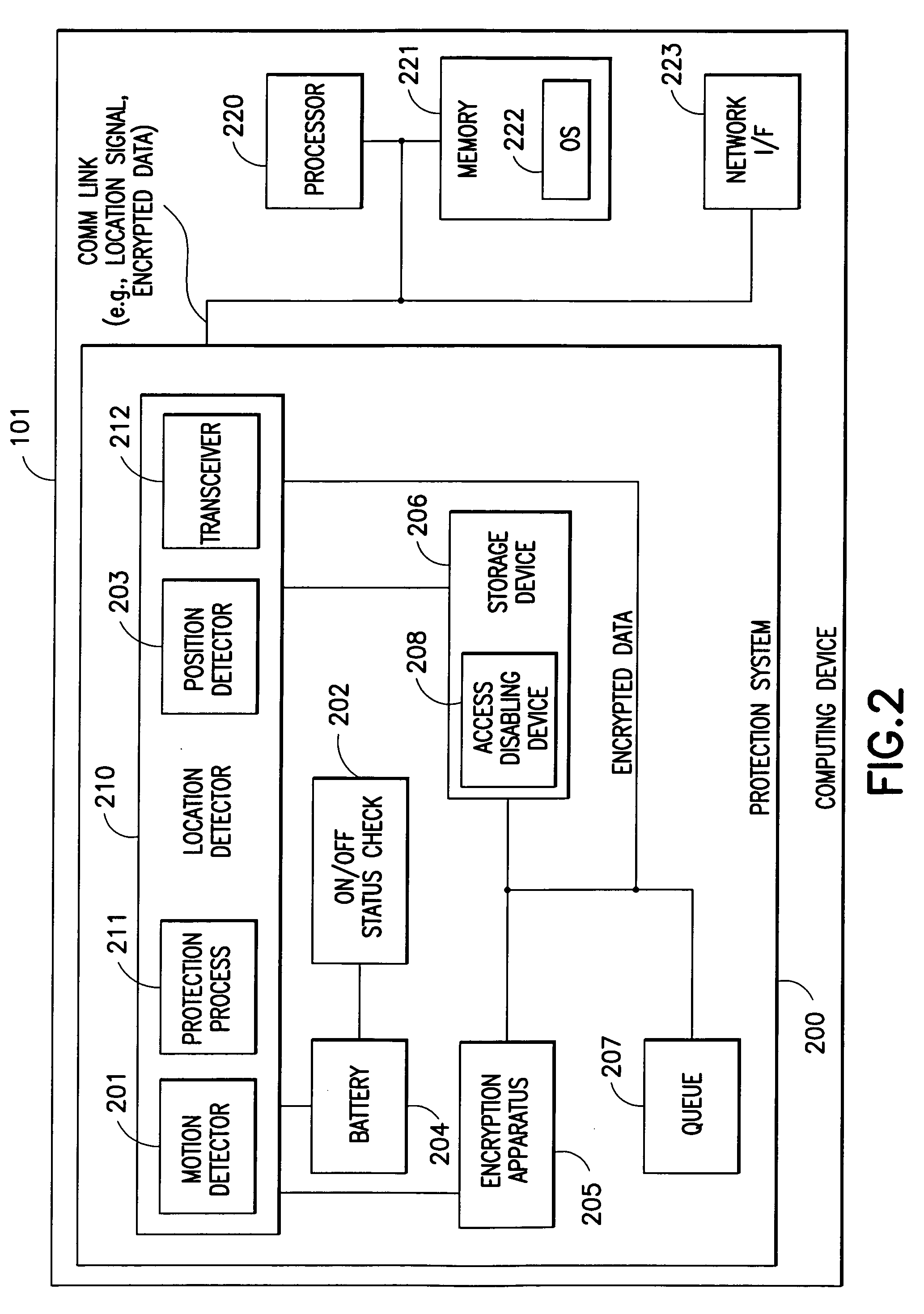
Protection of information in computing devices
ActiveUS20060112418A1Protect informationMemory loss protectionError detection/correctionDecoyComputer science
The present invention provides techniques for protecting information in a computing device. For instance, a location of the computing device is detected. It is determined whether the location is an unauthorized location. Access to the information is restricted in response to the location being an unauthorized location. As another example, information in a computing device may be protected by detecting location of the computing device. It is determined whether the location is an unauthorized location. One or more decoy files are created in the information in response to the location being an unauthorized location.
Owner:HCL TECH LTD
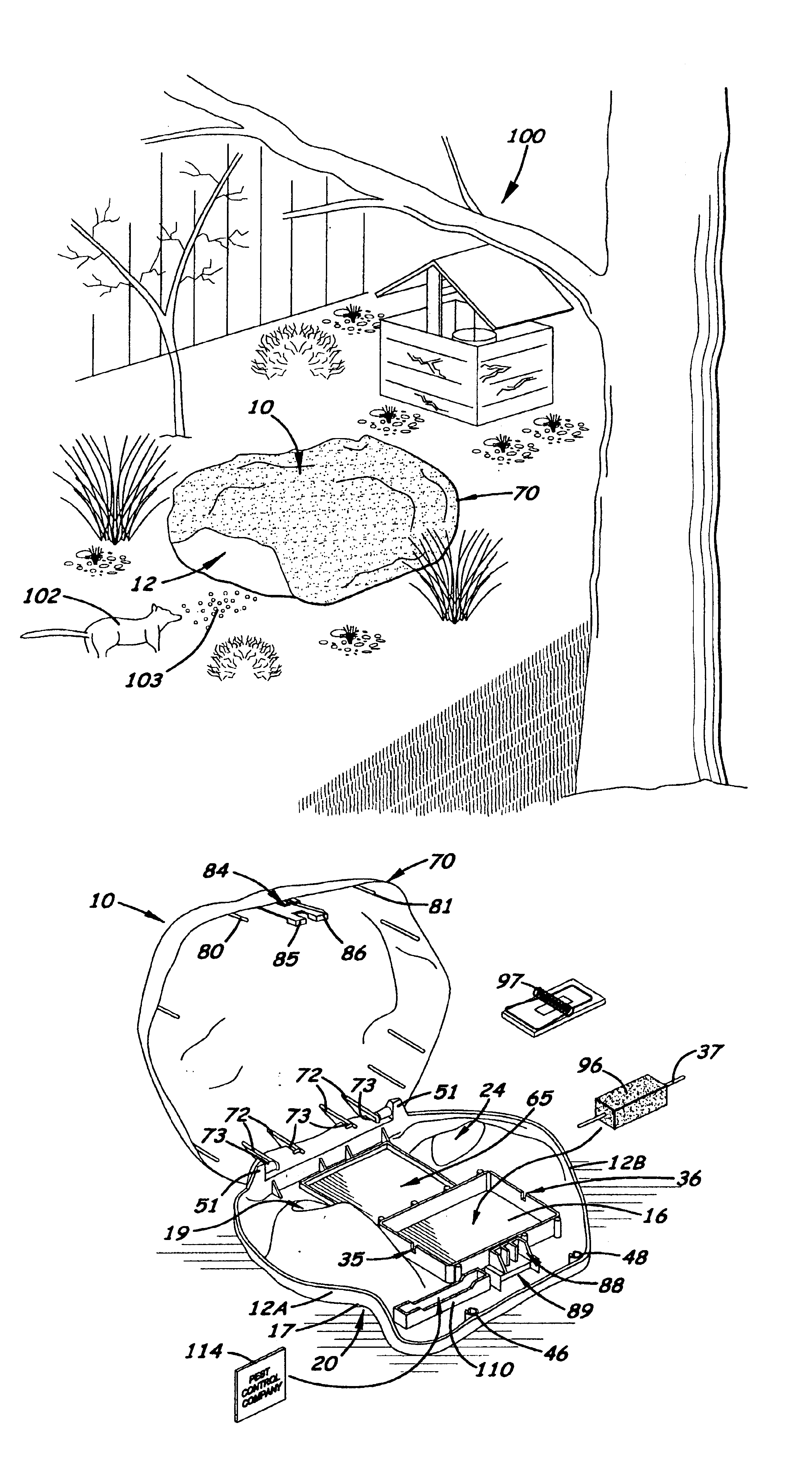
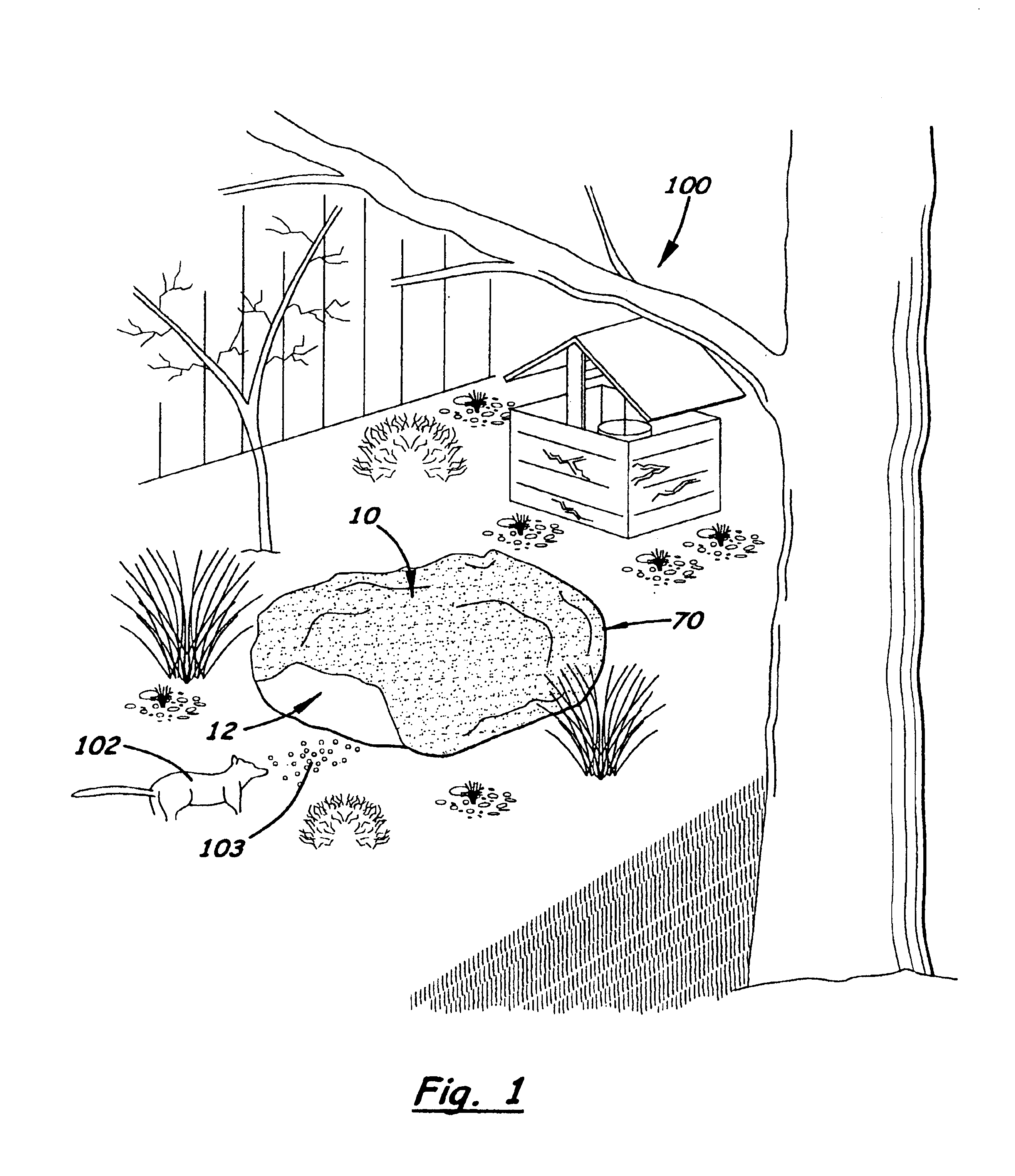
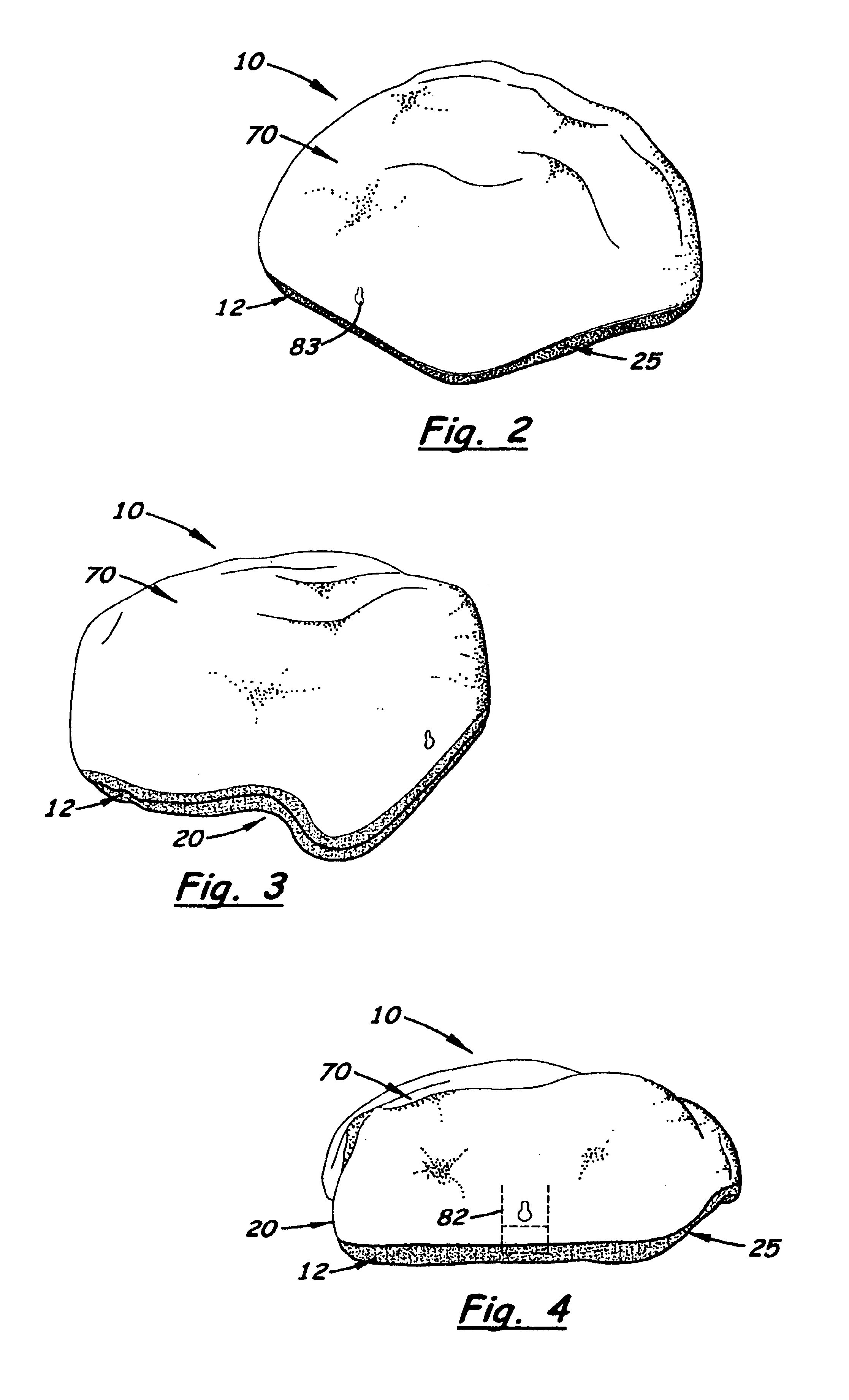
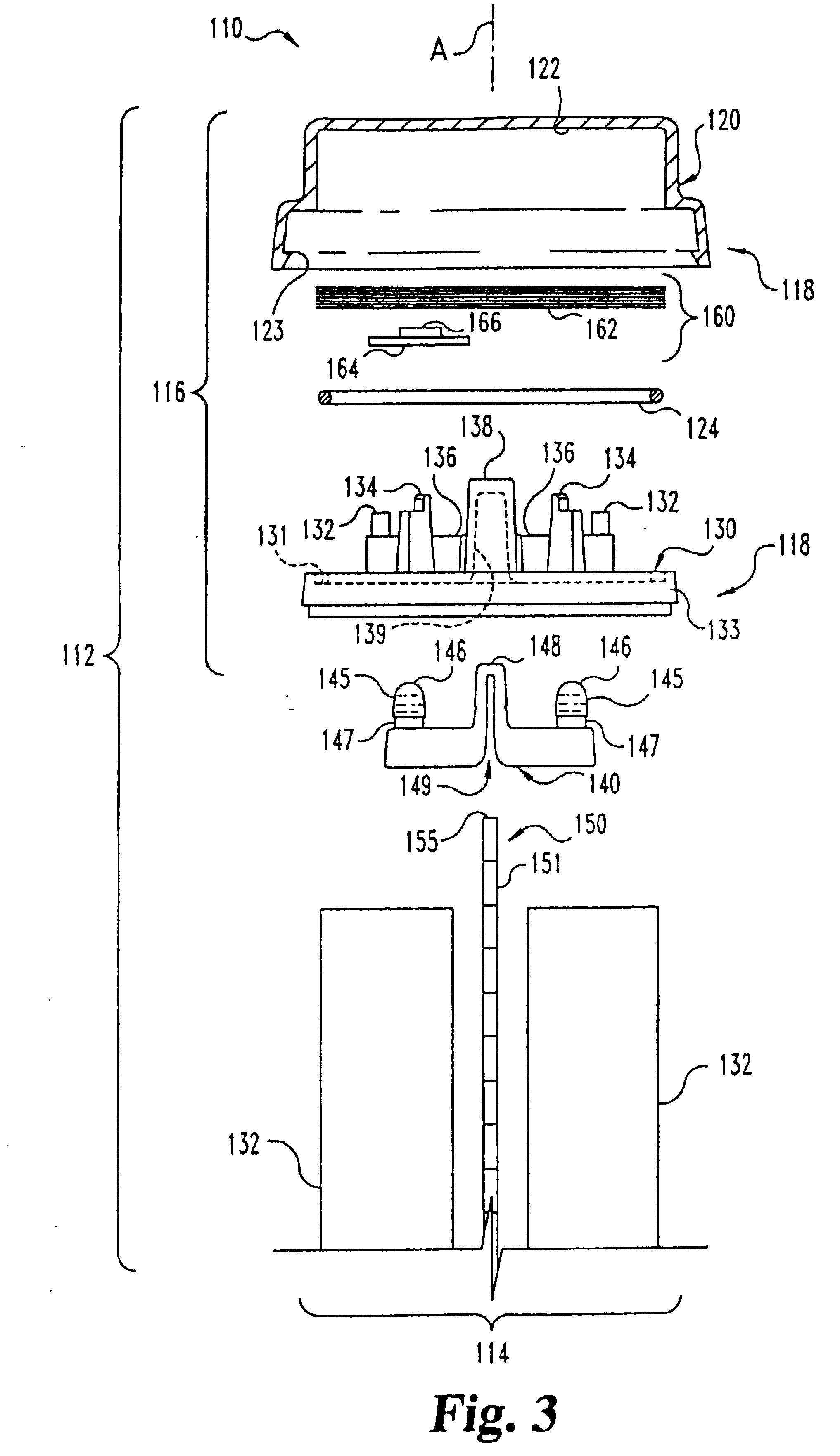
Rock simulating pest trap
A tamper-resistant pest trap that has an outer housing that simulates a rock typically found in a garden or landscape area around a residence or building. The outer housing includes a substantially flat bottom member and a pivotally attached upper dome-shaped lid member. When the lid member is closed over the bottom member, a large cavity is formed inside the trap. Formed on the bottom member are two, inward extending tunnel cavities that form two partially concealed tunnels that extend under the trap when the trap is placed on the ground. Formed on the perimeter edge of the outer housing is an outer pest opening. From on the bottom member directly over the tunnel cavity is an inner pest opening that allows a rodent to enter the large cavity after traveling through the tunnel. Formed inside the outer housing is a holding tray designed to hold a rodenocide or a mechanical trap capable of killing the rodent. An optional bait paper tray is also formed in the bottom member to hold bait paper. An optional lock is provided to prevent tampering and stake and hold-down chain are provided to attach the trays to the ground.
Owner:J L INNOVATIONS
Tamper resistant bait station for rats
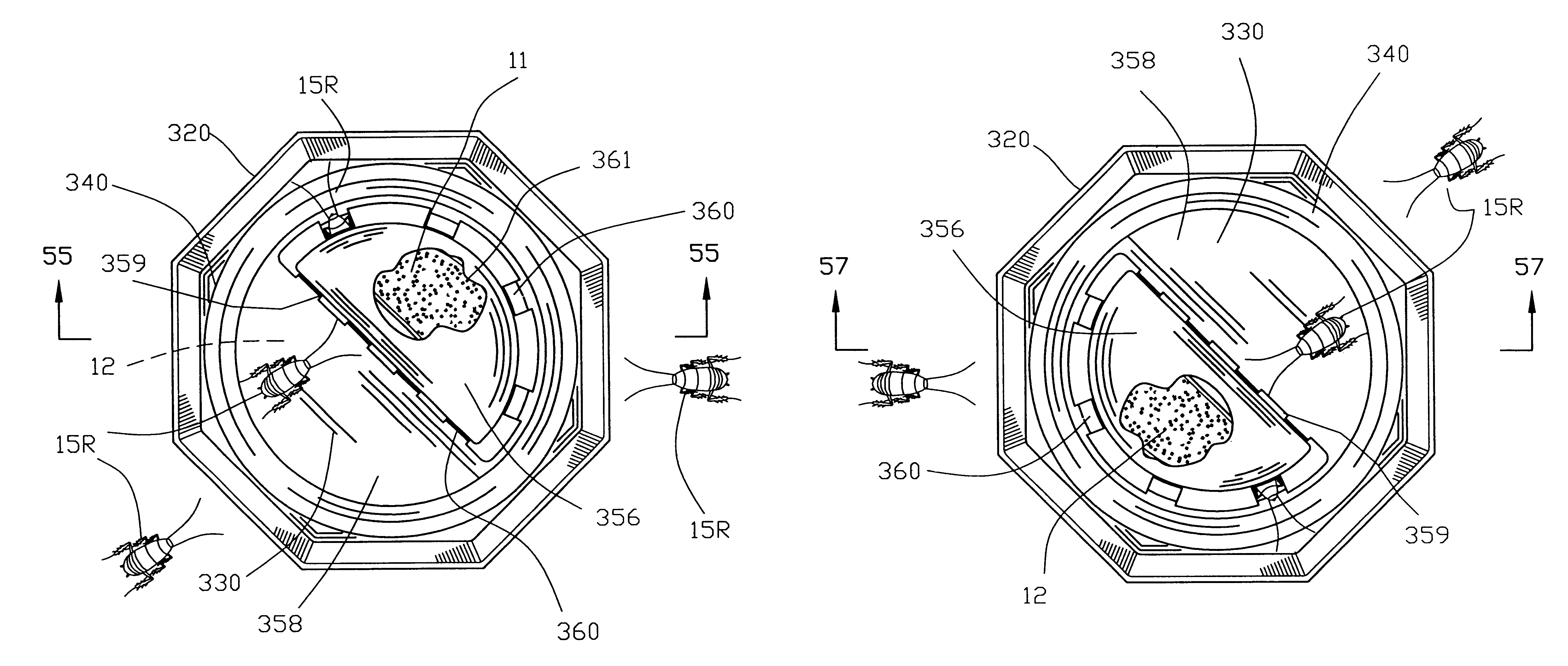
A bait station for containing rat poison contains a housing; at least one opening in the housing for a rat to enter; and a bait position in the housing for locating poisoned bait. A divider is provided between the bait position and each opening to prevent direct access to the bait from the opening, for example by a child. However, there are at least two different routes from the bait position leading to openings. Research has shown that rats, unlike mice, prefer not to eat in a confined space and it is believed that the choice of escape routes offered by the bait station of the invention encourages a rat to eat more of the bait. The bait station may include a hinged lid with locking means to prevent tampering with the bait.
Owner:DE SANGOSSE U S
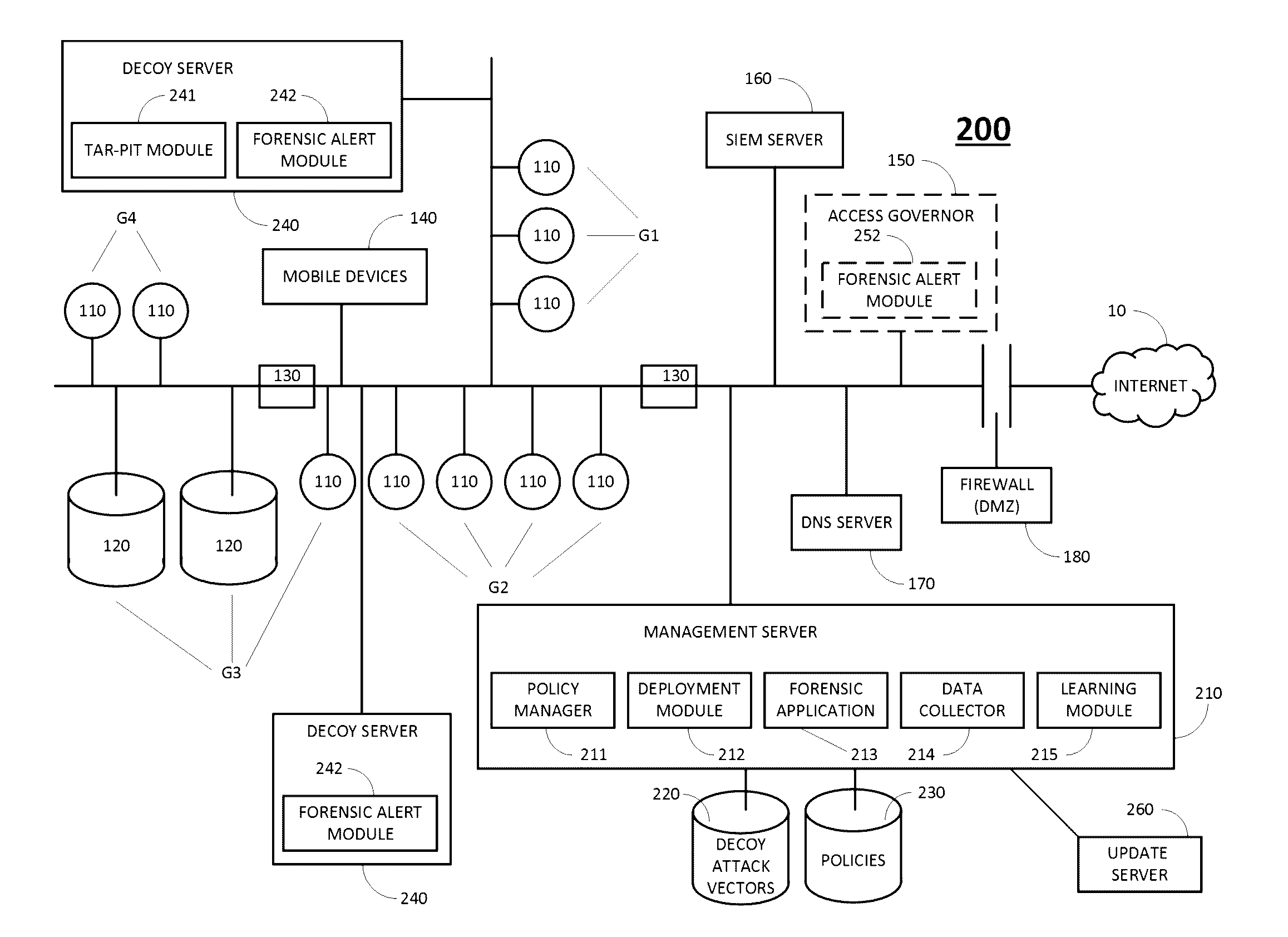
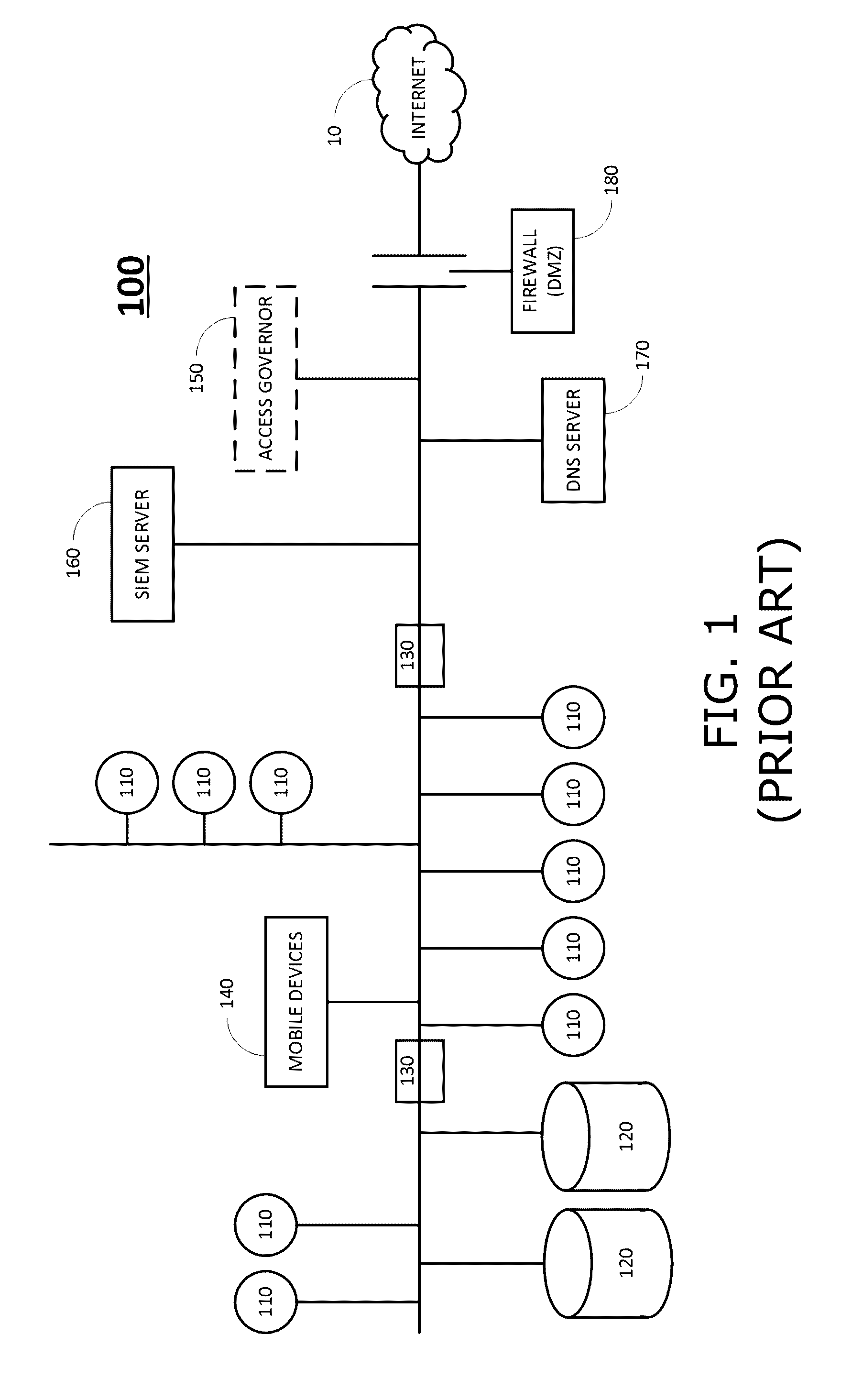
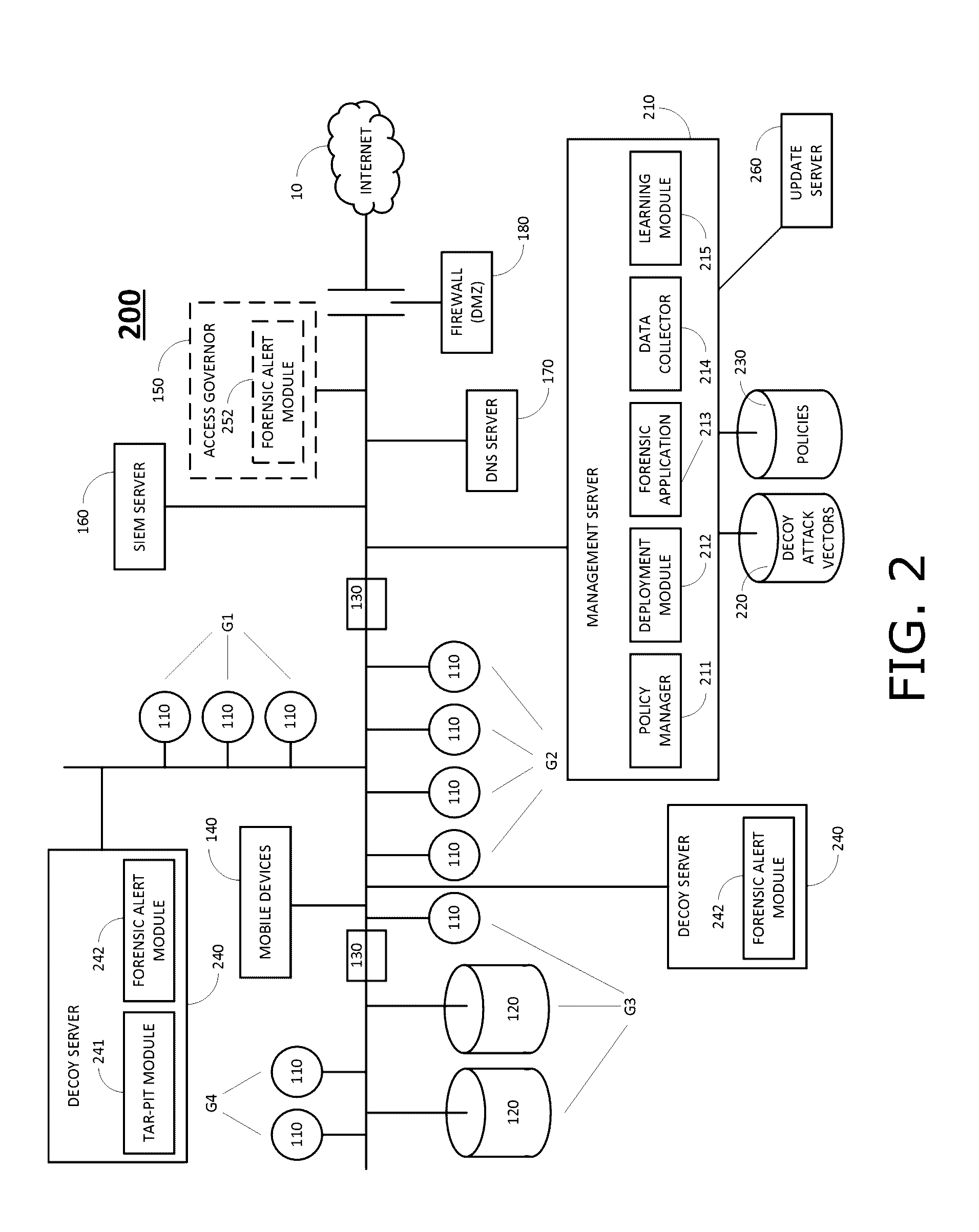
Automatically generating network resource groups and assigning customized decoy policies thereto
A cyber security system to detect attackers, including a data collector collecting data regarding a network, the data including network resources and users, a learning module analyzing data collected by the network data collector, determining therefrom groupings of the network resources into at least two groups, and assigning a customized decoy policy to each group of resources, wherein a decoy policy for a group of resources includes one or more decoy attack vectors, and one or more resources in the group in which the one or more decoy attack vectors are to be planted, and wherein an attack vector is an object of a first resource that may be used to access or discover a second resource, and a decoy deployer planting, for each group of resources, one or more decoy attack vectors in one or more resources in that group, in accordance with the decoy policy for that group.
Owner:ILLUSIVE NETWORKS LTD
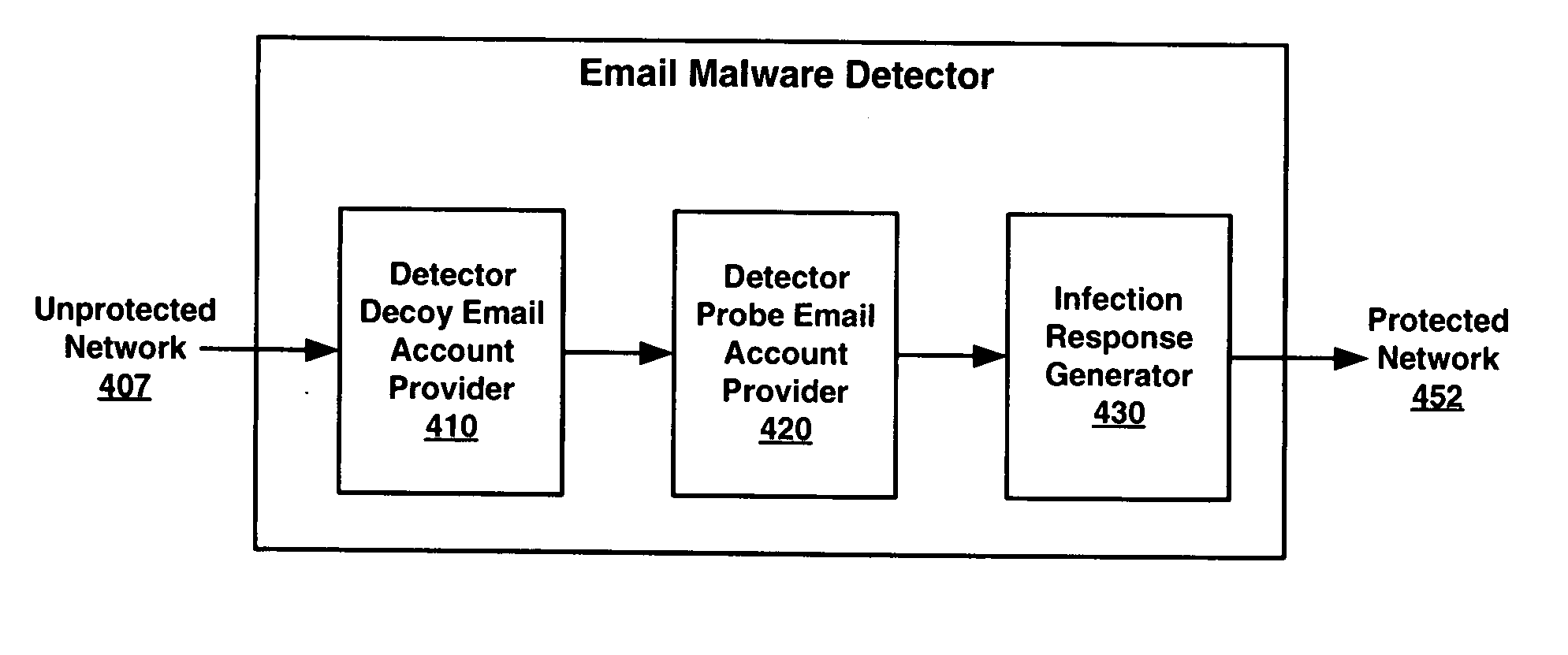
Method and apparatus for detecting and responding to email based propagation of malicious software in a trusted network
ActiveUS20070101430A1Memory loss protectionUser identity/authority verificationDecoyInternet privacy
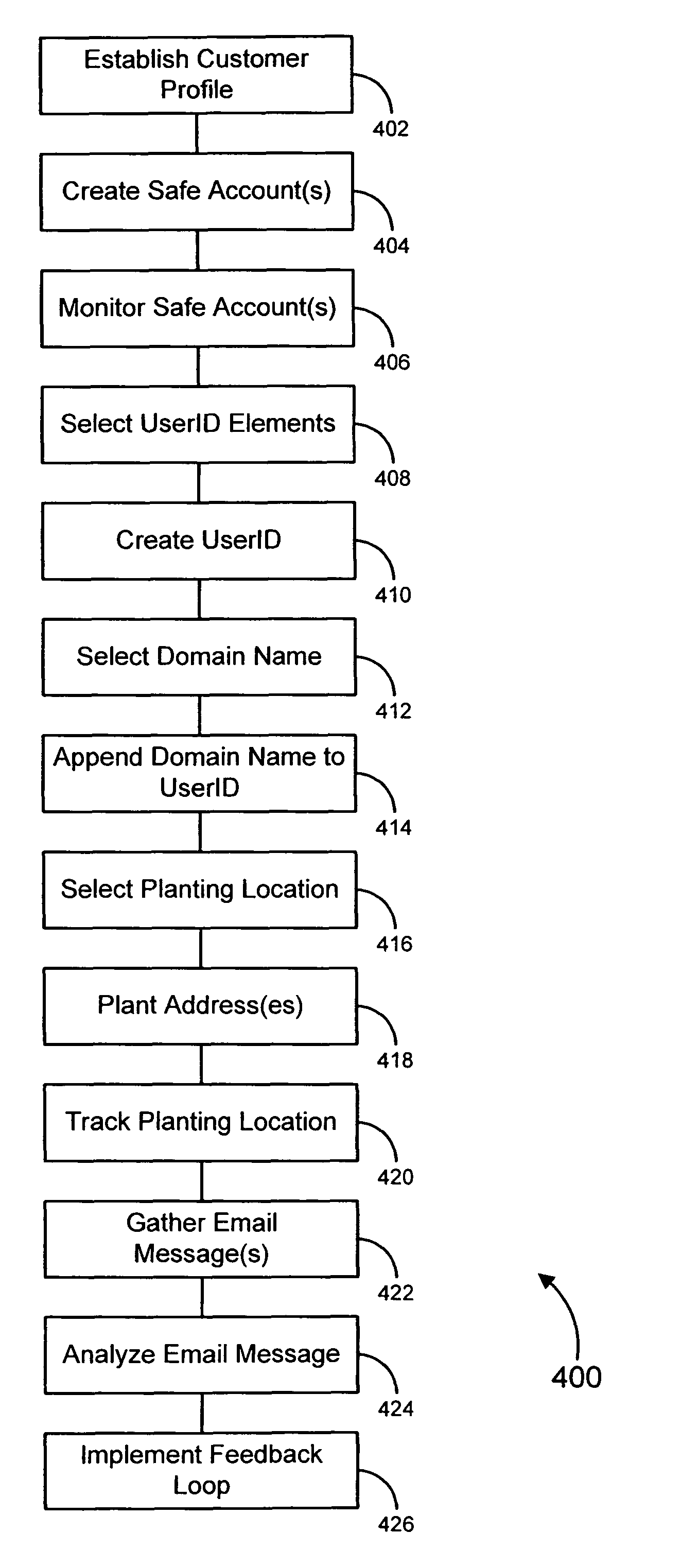
Embodiments of the invention provide a method and an apparatus for detecting and responding to email based propagation of malicious software (malware) in a trusted network. One embodiment provides a detector decoy email account to serve as generic bait for malicious software for a domain within the trusted network. In addition, at least one email account for the domain within the trusted network is provided as a detector probe account. In so doing, when the detector decoy email account receives an email from the detector probe account within the trusted network a policy based infection response rule is generated.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and apparatus for the detection, notification, and elimination of certain computer viruses on a network using a promiscuous system as bait
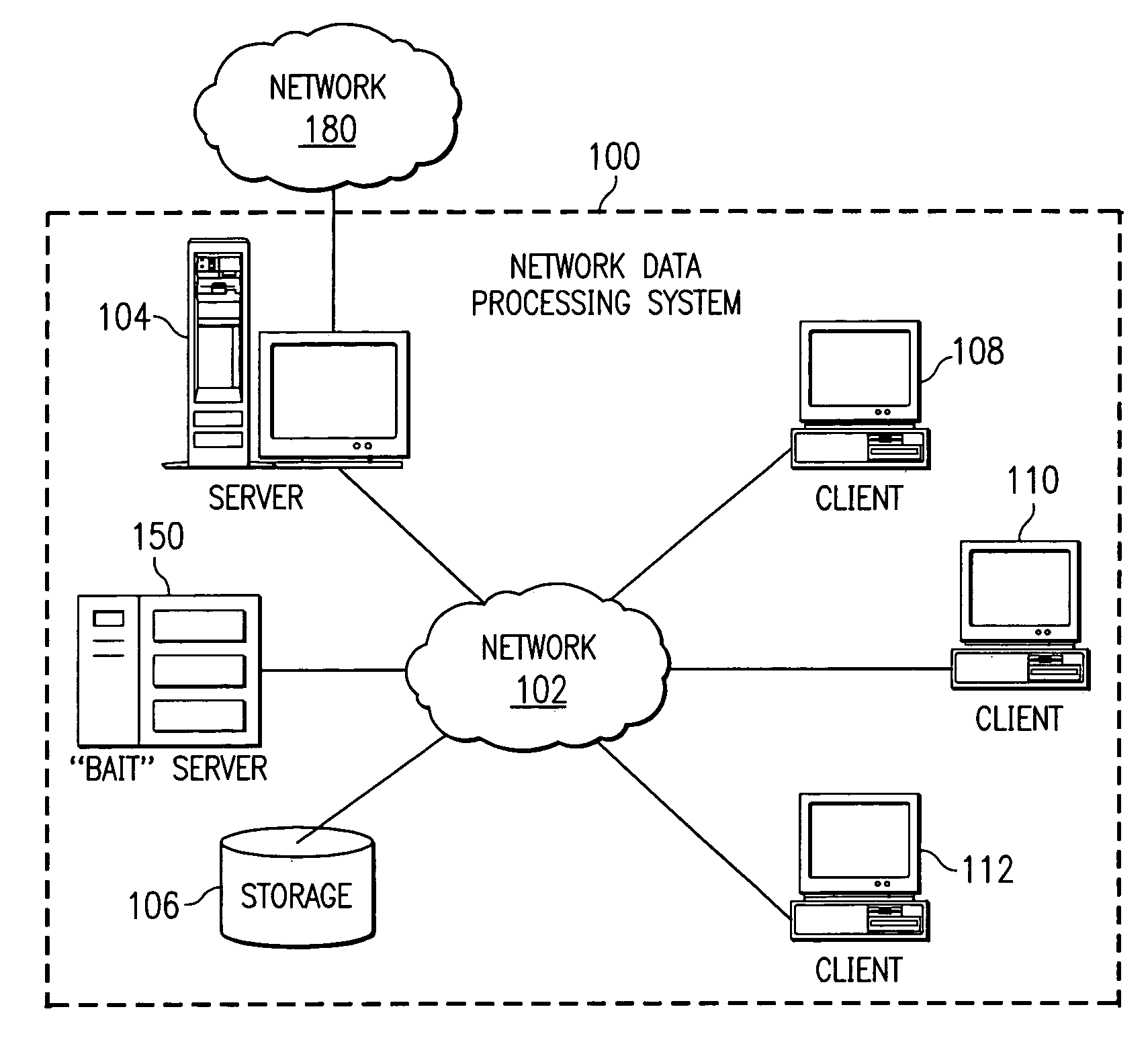
A method, computer program product, and network data processing system for identifying, locating, and deleting viruses is provided. In one embodiment, the network data processing system includes a local server, several client data processing systems, and a bait server. The address of the bait server is not published to the clients. Thus, any attempt to access the bait server would indicate the presence of a virus on the client attempting access. The bait server monitors itself and, responsive to an attempt from a client to access the bait server, broadcasts an indication that a virus attack is underway to all devices within the network. The bait server then ignores all further access requests by the offending client until it receives an indication that the offending client has been disinfected and directs the local server to disconnect the offending client(s) from the network. The bait server also notifies the local server and / or a network administrator of the problem and the identity of the offending client allowing appropriate action to be initiated to disinfect the offending client.
Owner:LENOVO PC INT
Multi-target-tracking optical sensor-array technology
ActiveUS7551121B1Highly accurate positional metricWide field-of-viewDirection controllersWeapon control systemsSensor arrayAviation
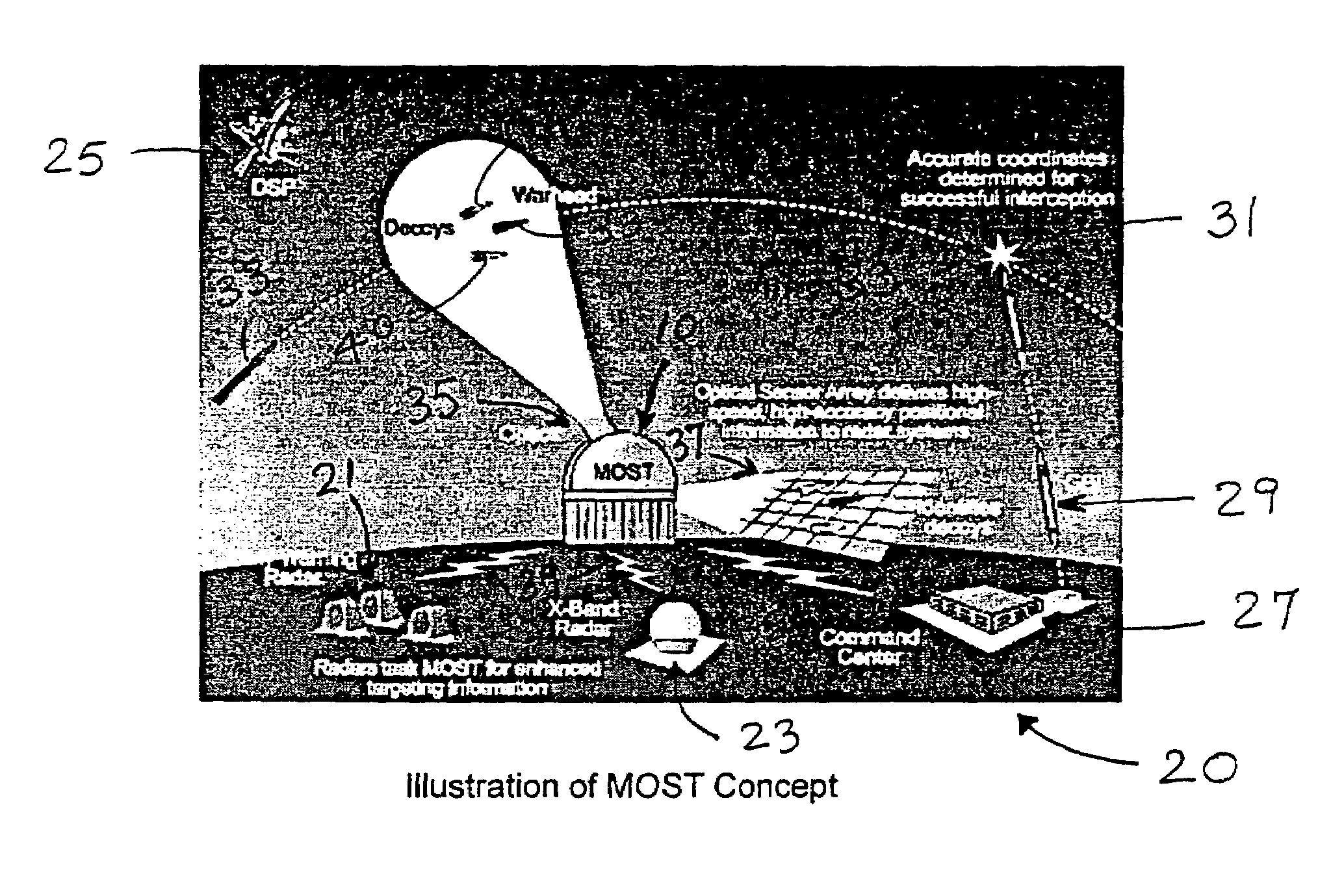
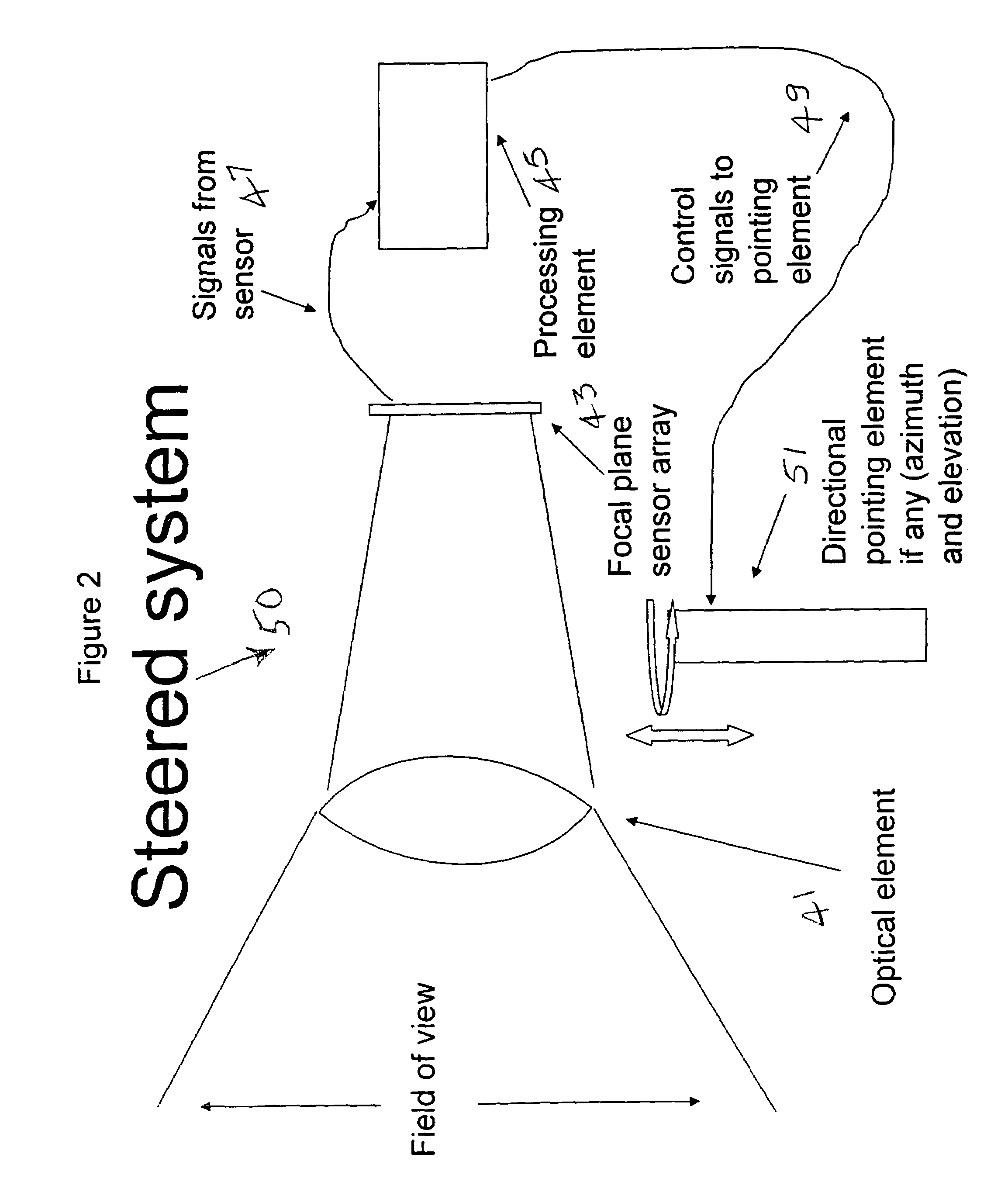
The multi-target tracking and discrimination system (MOST) fuses with and augments existing BMDS sensor systems. Integrated devices include early warning radars, X-band radars, Lidar, DSP, and MOST which coordinates all the data received from all sources through a command center and deploys the GBI for successful interception of an object detected anywhere in space, for example, warheads. The MOST system integrates the optics for rapid detection and with the optical sensor array delivers high-speed, high accuracy positional information to radar systems and also identifies decoys. MOST incorporates space situational awareness, aero-optics, adaptive optics, and Lidar technologies. The components include telescopes or other optical systems, focal plane arrays including high-speed wavefront sensors or other focal plane detector arrays, wavefront sensor technology developed to mitigate aero-optic effects, distributed network of optical sensors, high-accuracy positional metrics, data fusion, and tracking mounts. Field applications include space monitoring, battlefield artillery, battlefield management, ground defense, air defense, space protection, missile defense, gunfire detection, and the like.
Owner:OCEANIT LAB
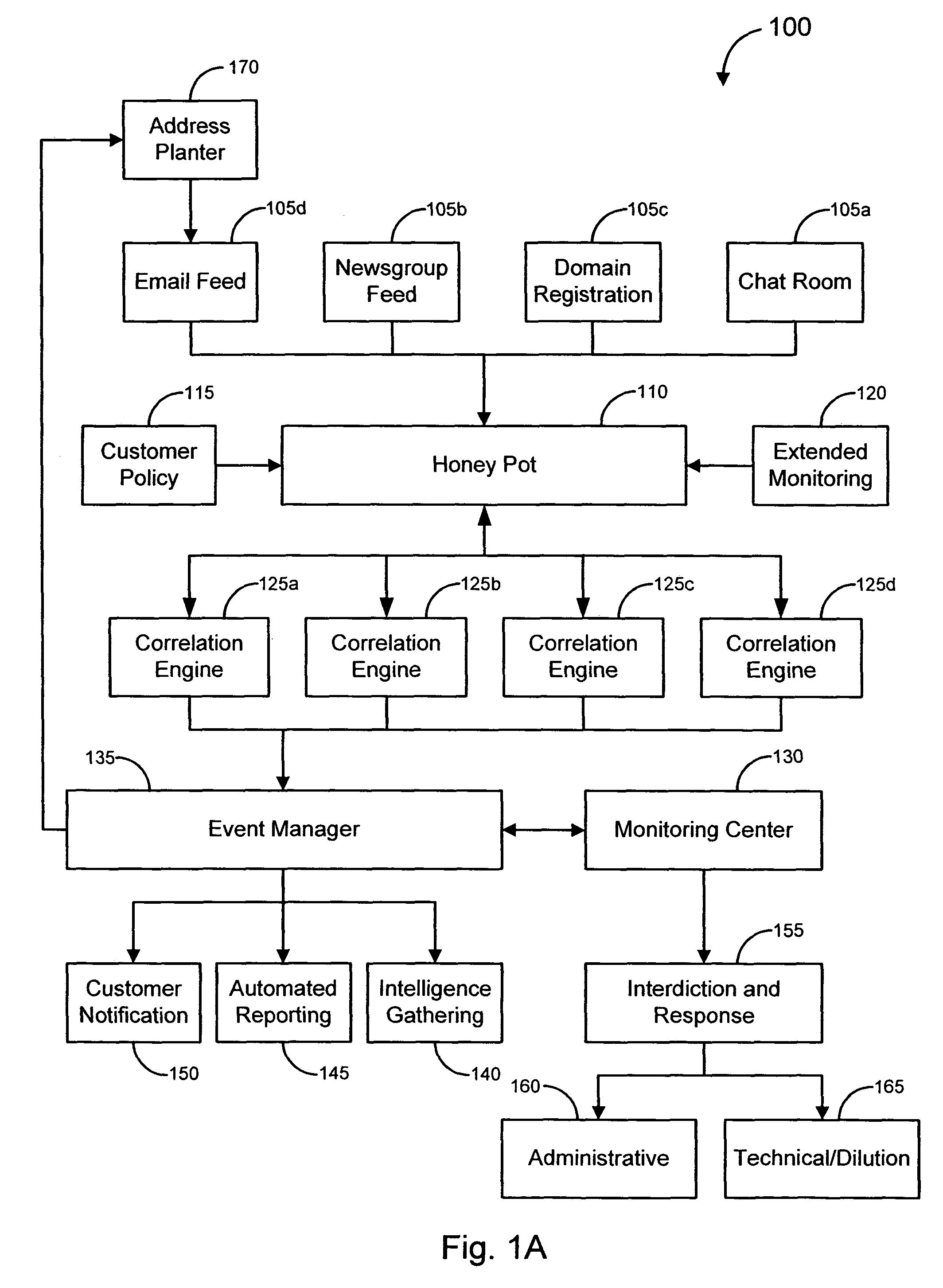
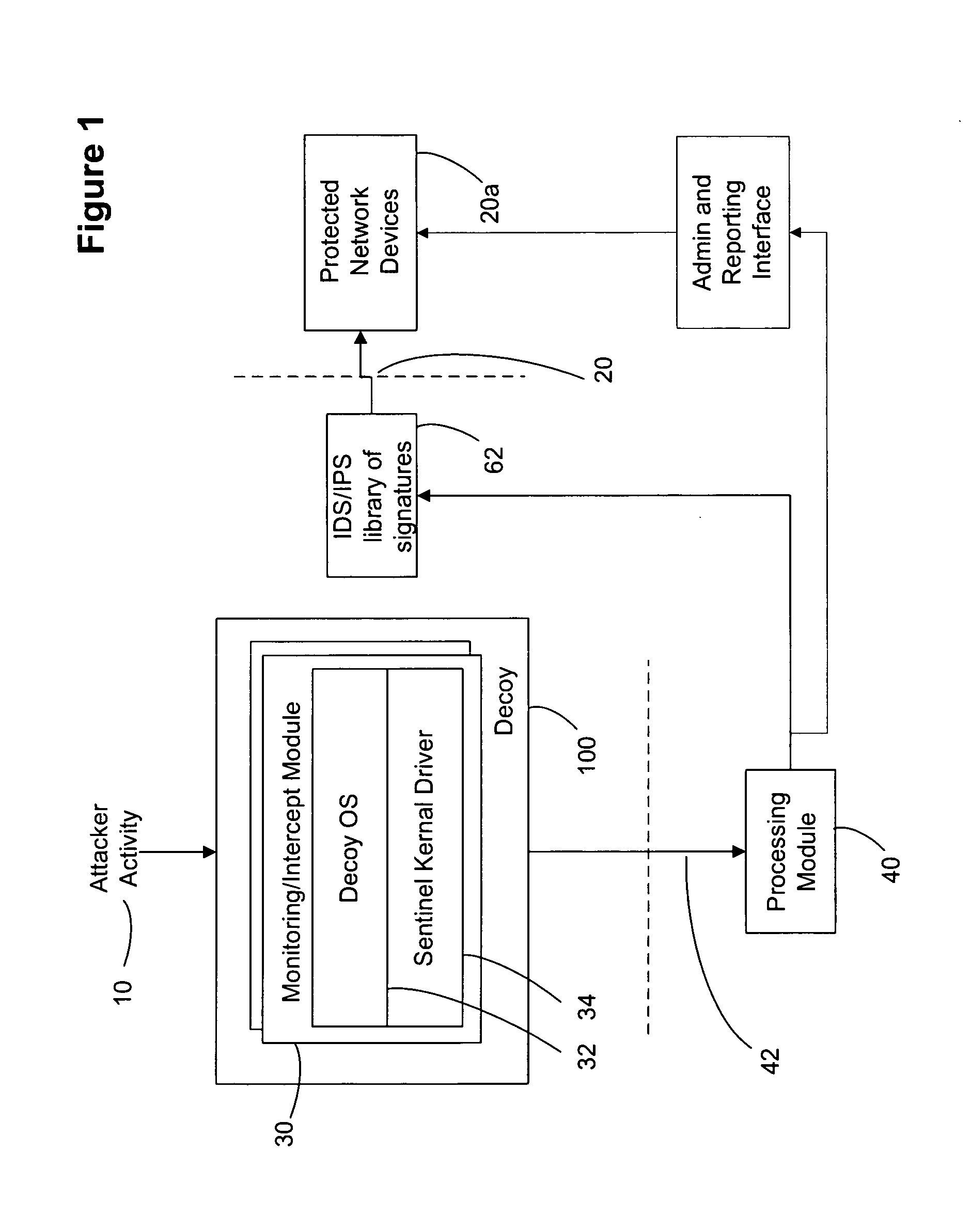
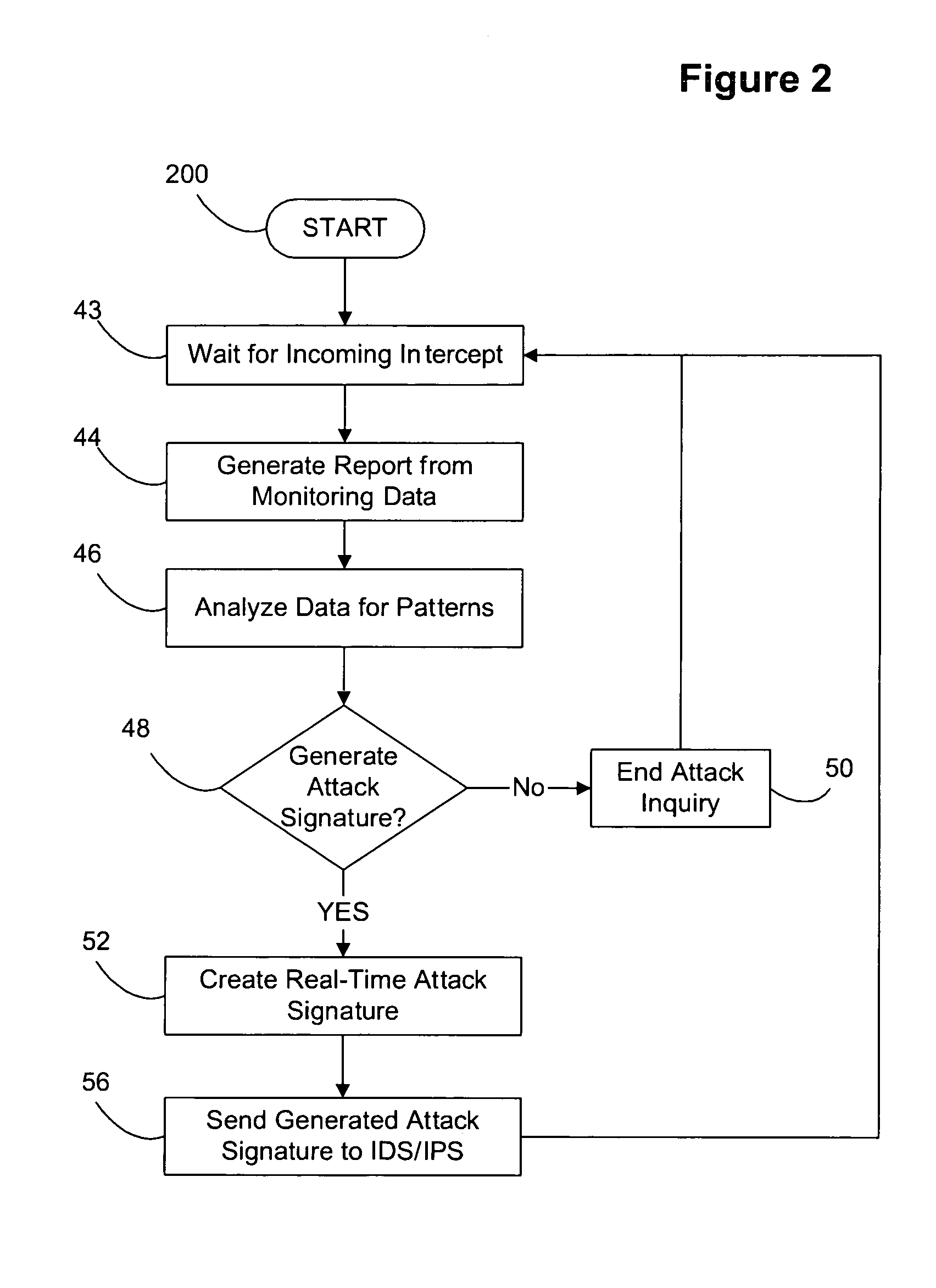
Decoy network technology with automatic signature generation for intrusion detection and intrusion prevention systems
ActiveUS20070271614A1Unauthorised/fraudulent call preventionDigital data processing detailsOperational systemDecoy
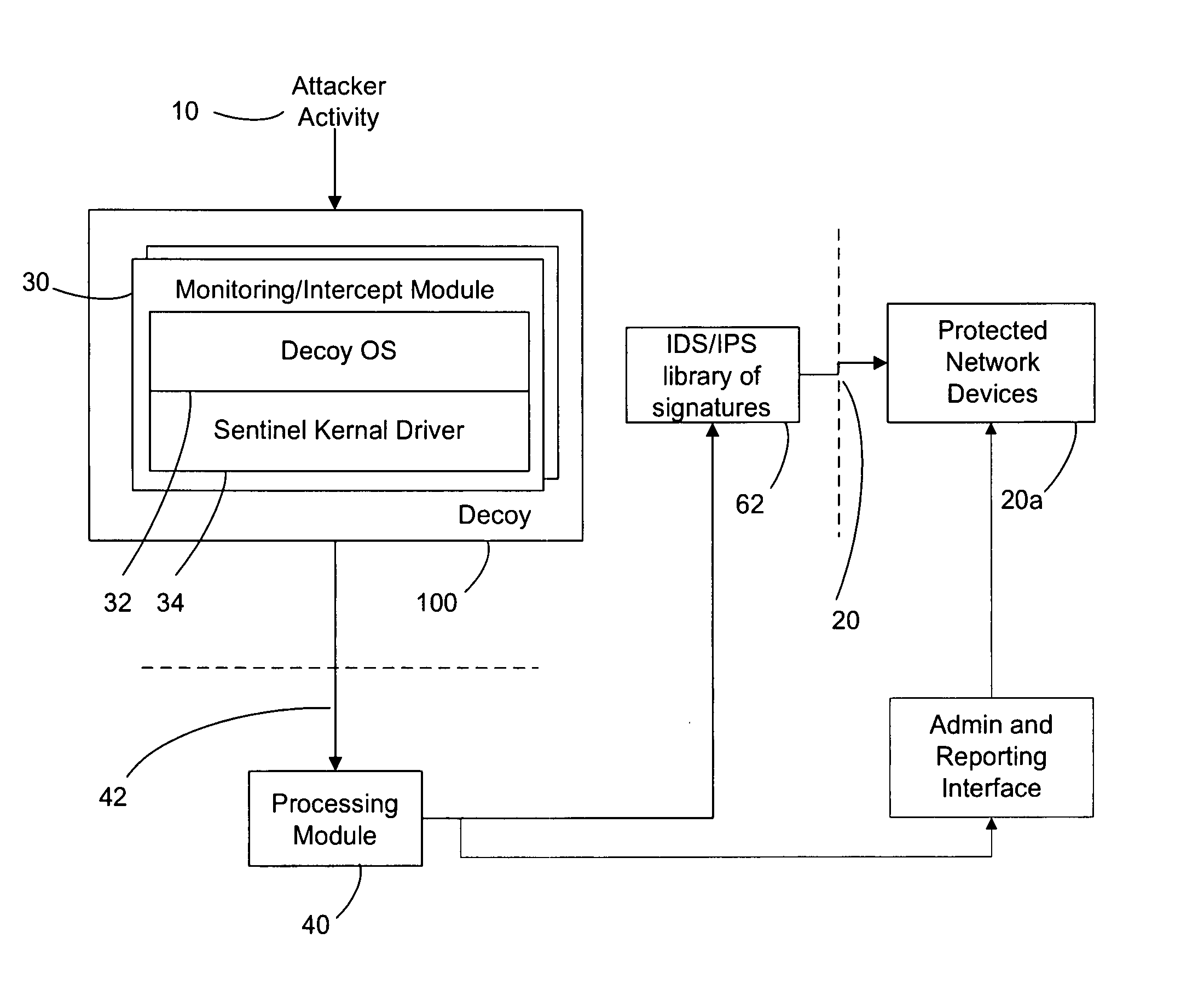
Improved methods and systems for decoy networks with automatic signature generation for intrusion detection and intrusion prevention systems. A modular decoy network with front-end monitor / intercept module(s) with a processing back-end that is separate from the protected network. The front-end presents a standard fully functional operating system that is a decoy so that the instigator of an attack is lead to believe a connection has been made to the protected network. The front-end includes a hidden sentinel kernal driver that monitors connections to the system and captures attack-identifying information. The captured information is sent to the processing module for report generation, data analysis and generation of an attack signature. The generated attack signature can then be applied to the library of signatures of the intrusion detection system or intrusion prevention system of the protected network to defend against network based attacks including zero-day attacks.
Owner:COUNTERTACK
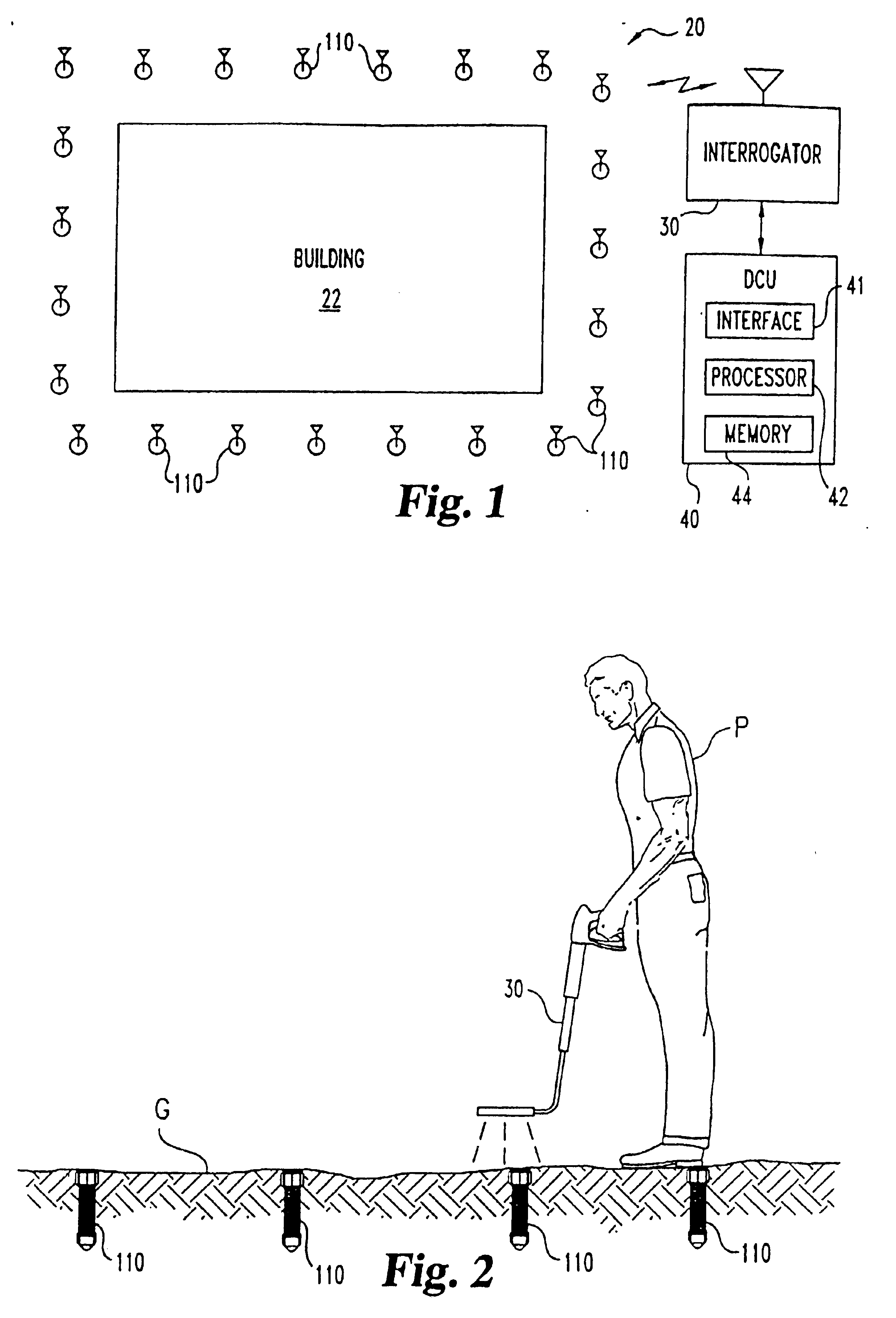
Sensing devices, systems, and methods particularly for pest control
A pest control system (20) includes pest control devices (110) installed about an area or building (22). These devices (110) each include a bait member and a communication circuit. The communication circuit may be in the form of a passive RF tag that transmits information indicative of bait status and an identifier unique to each pest control device (110). A hand held interrogator (30) is provided to locate and communicate with the pest control devices (110) via the communication circuit. A data collection unit (40) to accumulate data gathered from the pest control devices (110) may alternatively or additionally be utilized. The device (110) includes a sensor that has an electrically conductive pathway comprised of a nonmetallic material. Other pest control devices to detect varying nonzero levels of pest activity are also disclosed. Still another device includes one or more environmental sensors to further evaluate and predict pest behavior.
Owner:DOW AGROSCIENCES LLC
Device for delivering a poison to a pest
Owner:PLEASANTS DONALD A
Air-launchable aircraft and method of use
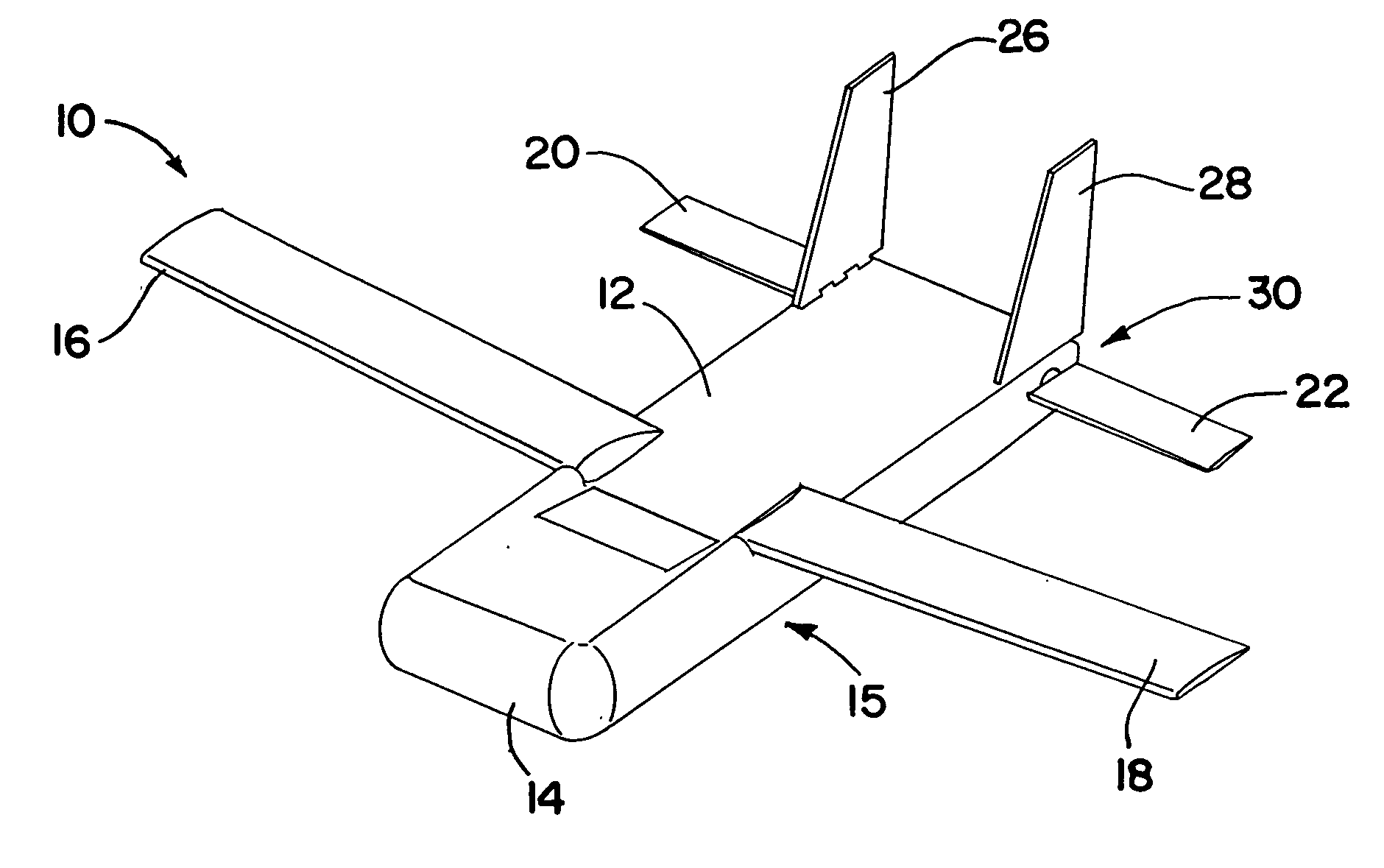
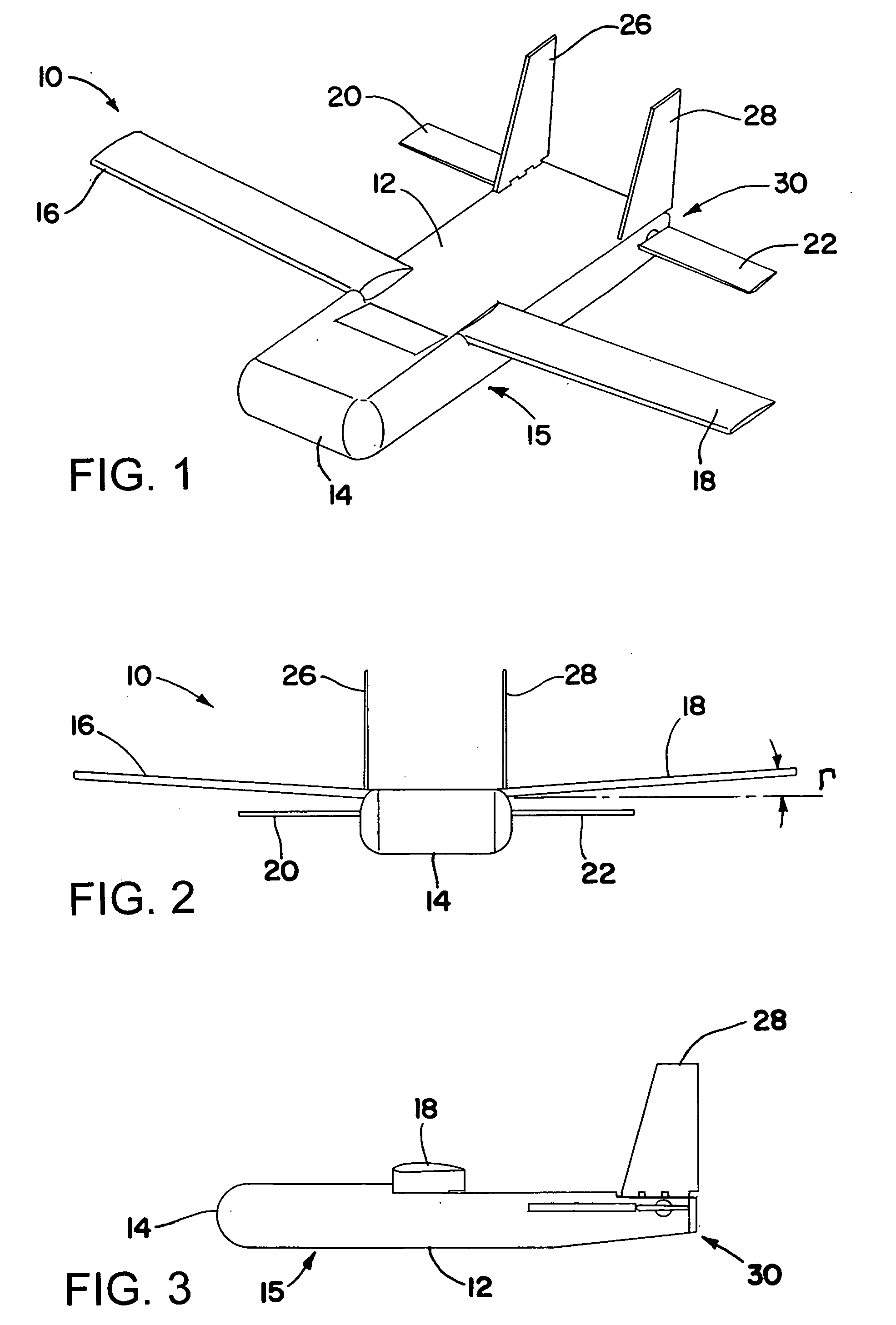
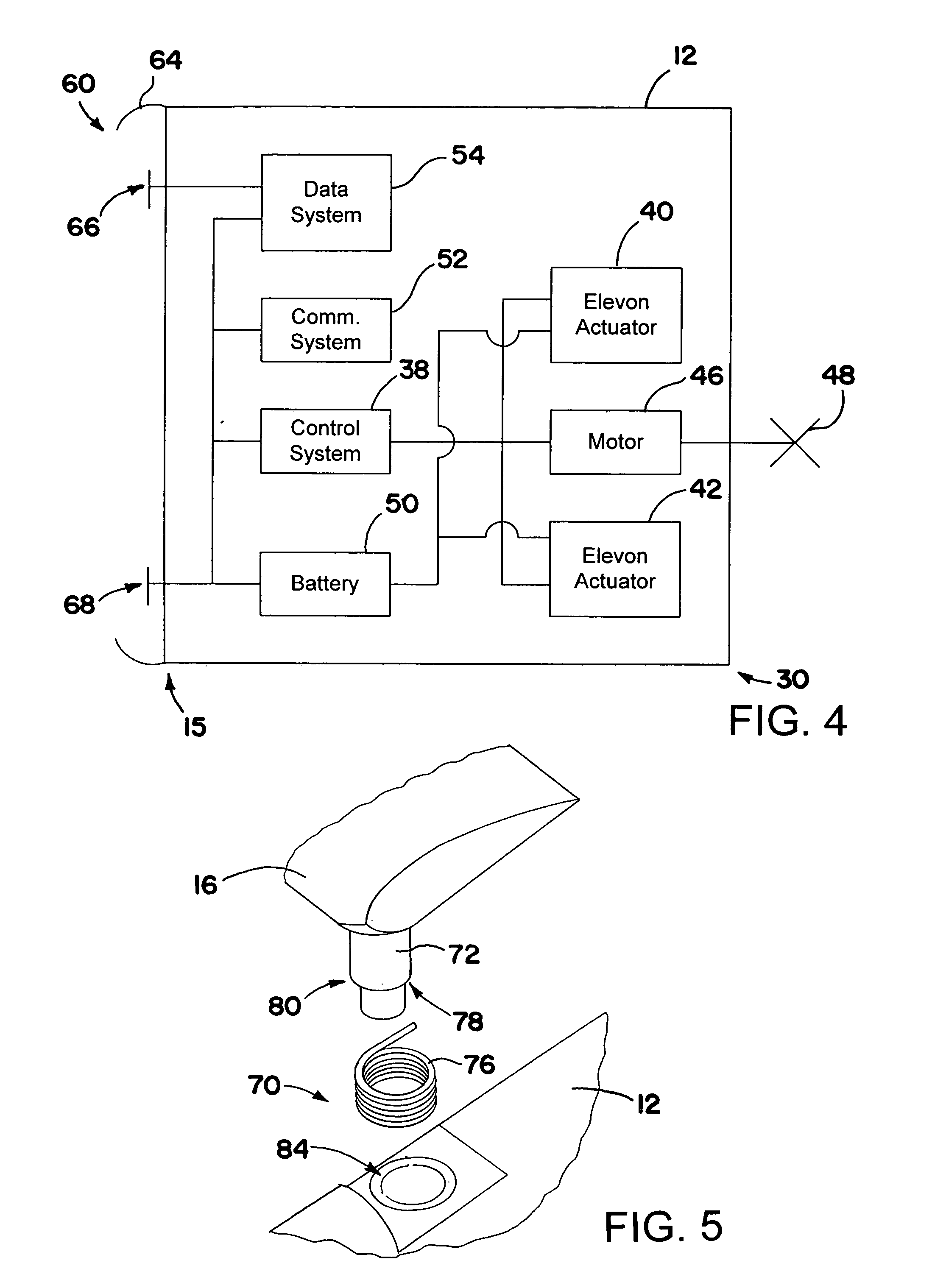
An air-launched aircraft includes deployable wings, elevons, and vertical fins that deploy from a fuselage during flight. The aircraft may include a control system for operating the elevons, a communication system, and batteries for powering the systems. In addition, the aircraft may include a payload module that mates with an interface in the fuselage. The payload module may include any of a variety of payloads, including cameras, sensors, and / or radar emitters. The aircraft may be powered or unpowered, and may be very small, for example, less than on the order of 10 kg (22 pounds). The aircraft may be employed at a low cost for any of a wide variety of functions, such as surveillance, or as a decoy. The deployable surfaces of the aircraft may be configured to deploy in a pre-determined order, allowing the aircraft automatically to enter controlled flight after being launched in a tumbling mode.
Owner:RAYTHEON CO
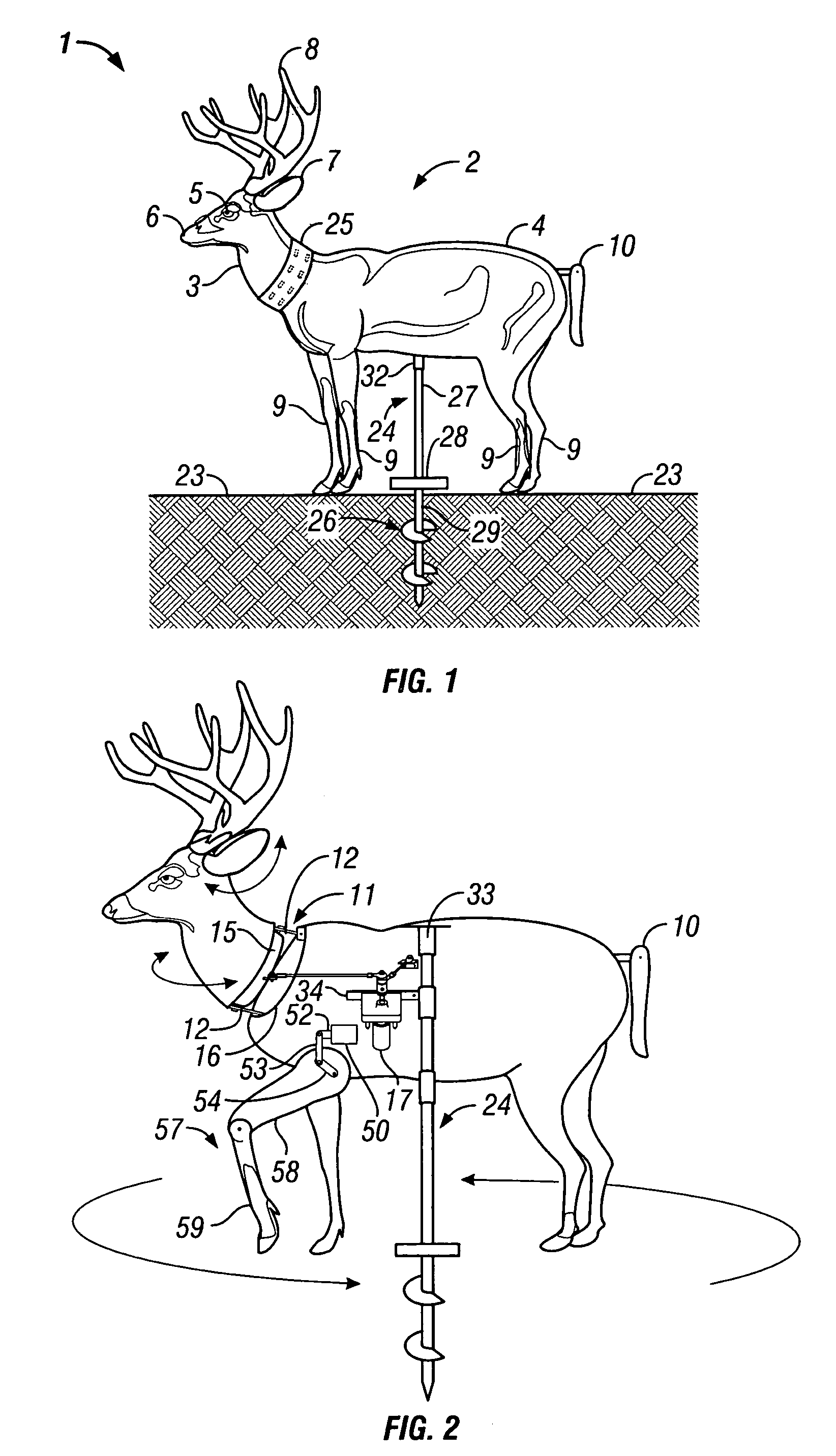
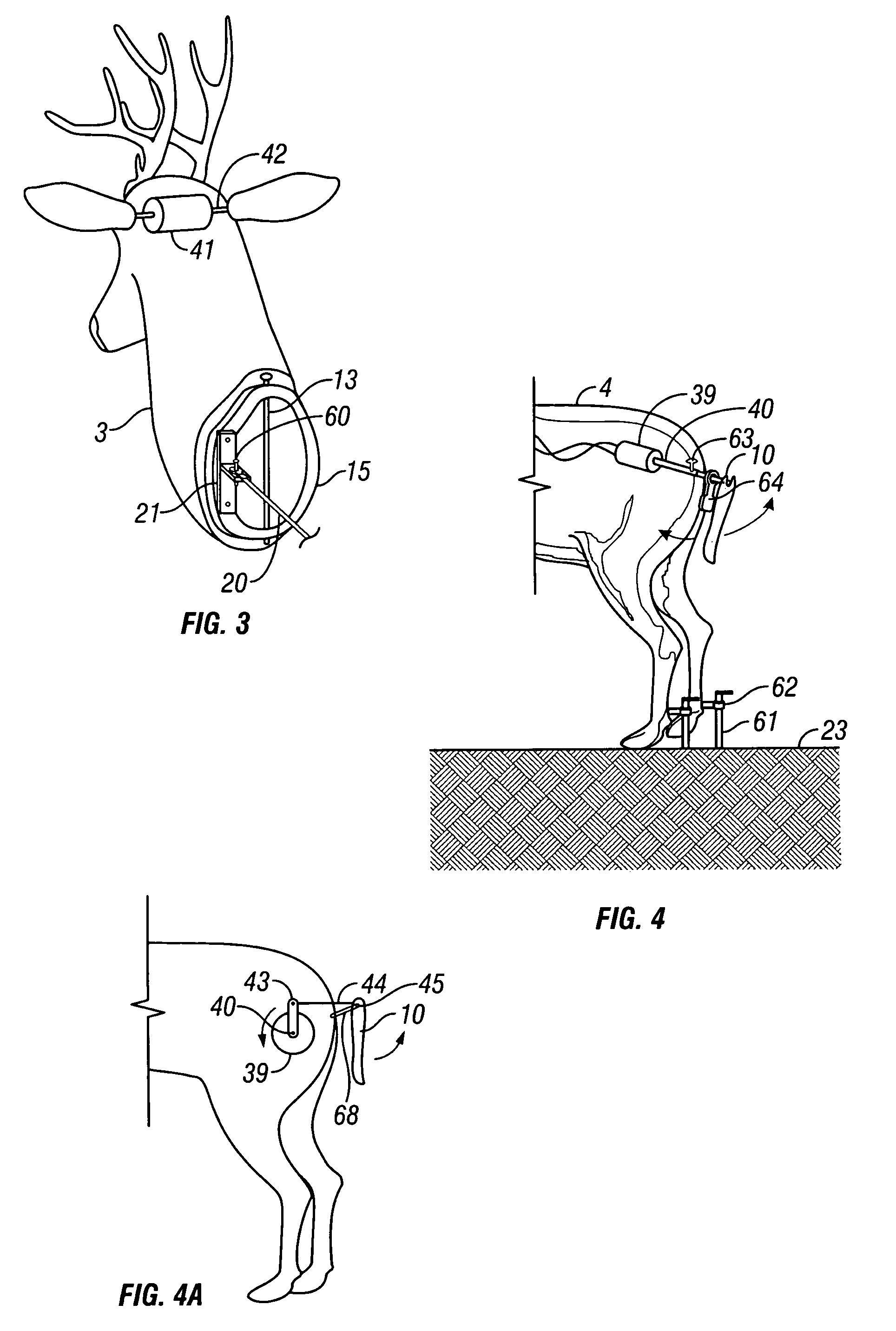
Motorized game decoy
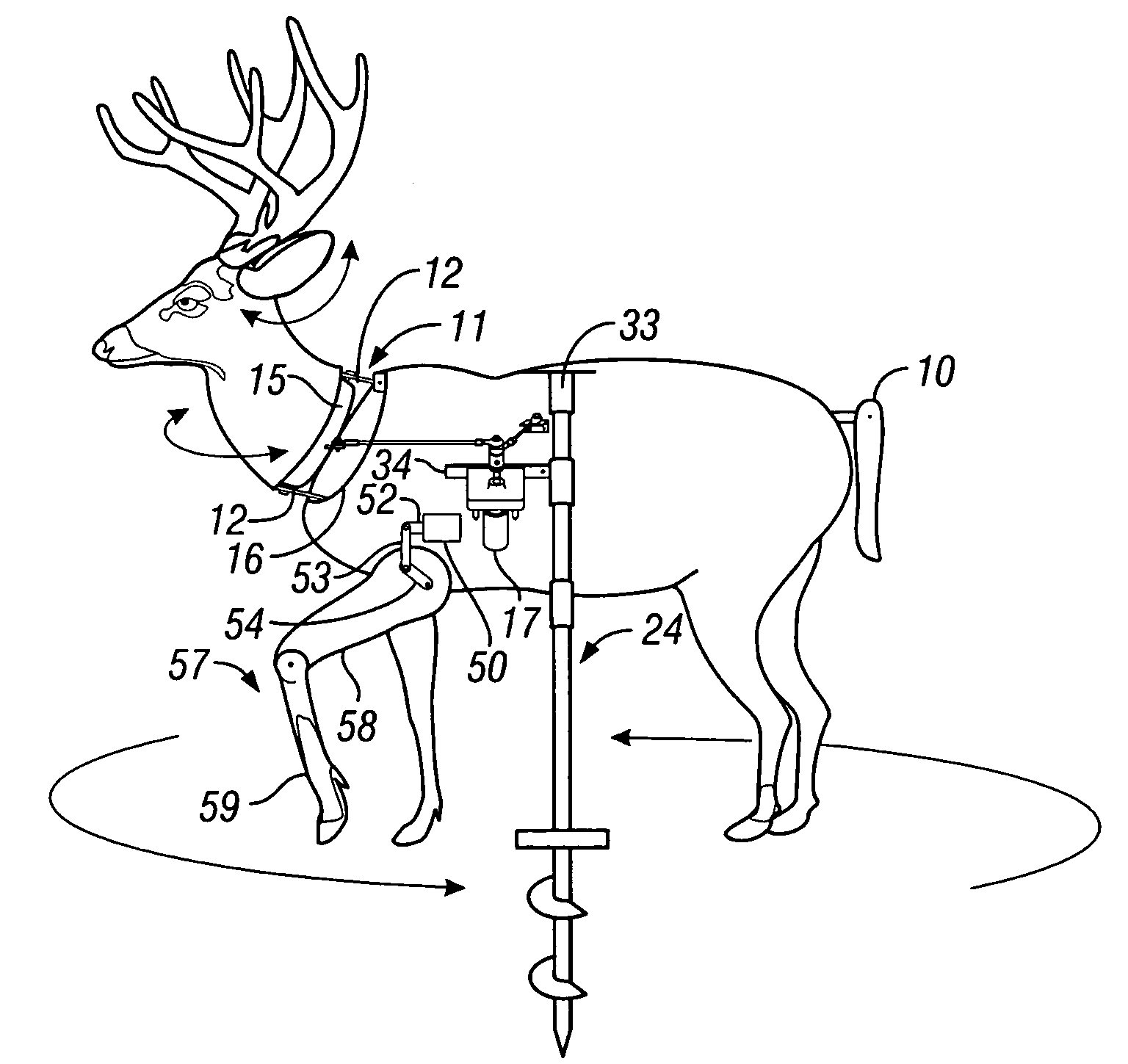
An improved motorized decoy is provided for attracting and holding the attention of a live game animal by simulating the appearance, movements, sounds, and smells of a live game animal or an animal that is native to the habitat of a selected game animal. The decoy includes a decoy body that may be bifurcated into a forward portion and a rear portion, one or more motors, and an optional support member. Together, the motors may produce, either individually or in combination, the following movements: (1) movement of the entire decoy body relative to a fixed ground position, (2) movement of the head and neck portion of the decoy body relative to the rear portion of the decoy body, (3) movement of the ears relative to the head and neck portion, (4) movement of the tail relative to the rear portion, and (5) movement of one or more legs relative to the rear portion. All of the above movements may be produced randomly and / or intermittently by virtue of a programmable modulator or a multi-cycle remote control. All of the above movements may also be produced in sequential order by virtue of a multi-cycle remote control. Additional features include detachable antlers, detachable genitalia, and a scent disperser for distributing a chemical attractant. The invention also includes a method for attracting a game animal to a target area.
Owner:HUNTWISE
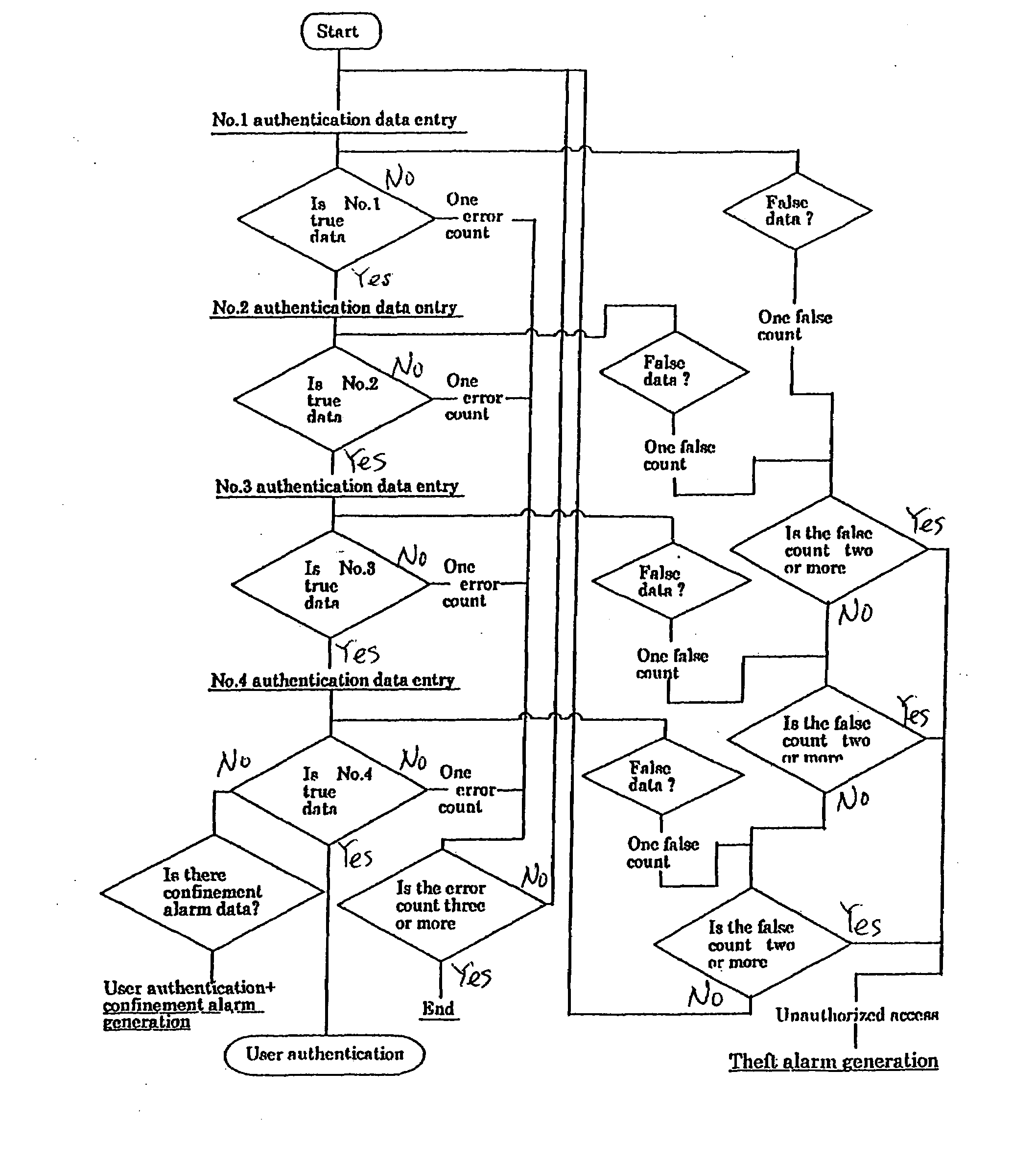
Mutual for reporting a theft in an authentication system
ActiveUS20090328162A1Inhibition of informationMemory loss protectionDigital data processing detailsThird partyPassword
Disclosed are protection of secret information including an encryption key and a system for reporting an emergency such as theft or confinement when secret information is accessed. Secret information includes a large quantity of decoy data and a piece / pieces of true and correct data mixed into the decoy data. The secret data including the decoy data and the true and correct data is two-dimensional code data the code of which is composed of groups of cells having different areas. The positions and order of storage of the true and correct data dispersedly mixed in the decoy data are determined and reported to the user. The user adds a predetermined alerting signal when inputting the password to tell that the user is under control of a third party. The system can detect the alerting signal and know that the user is in an abnormal state, performs normal identification procedures, and takes protection / preservation measures. Part of decoy data is specified as confinement report data and added to the true and correct data. Consequently at least a piece of confinement report data is included and therefore the user himself is judged to be under control of the third party. Then the user is identified and a confinement report alert is issued.
Owner:MNEMONIC SECURITY
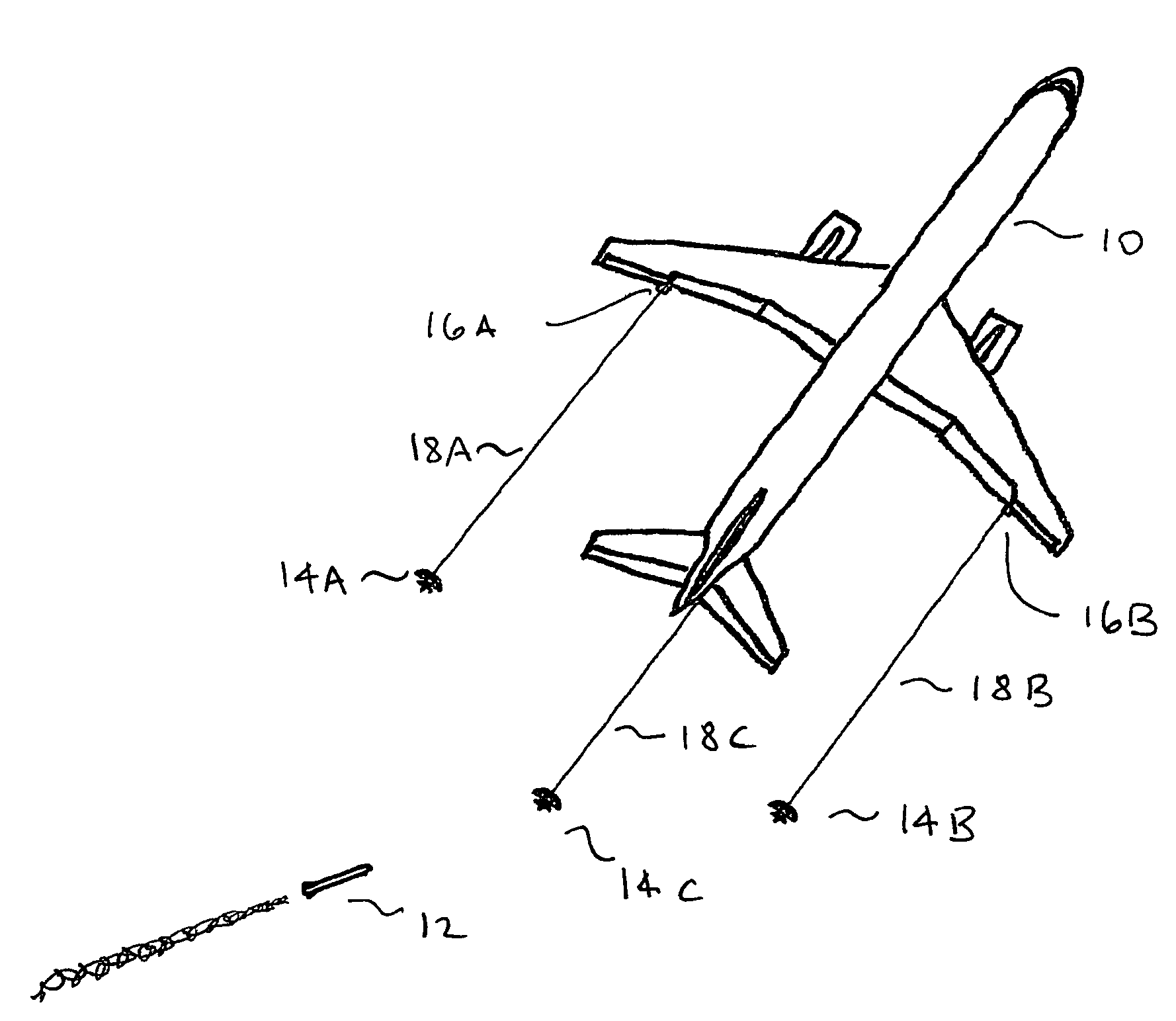
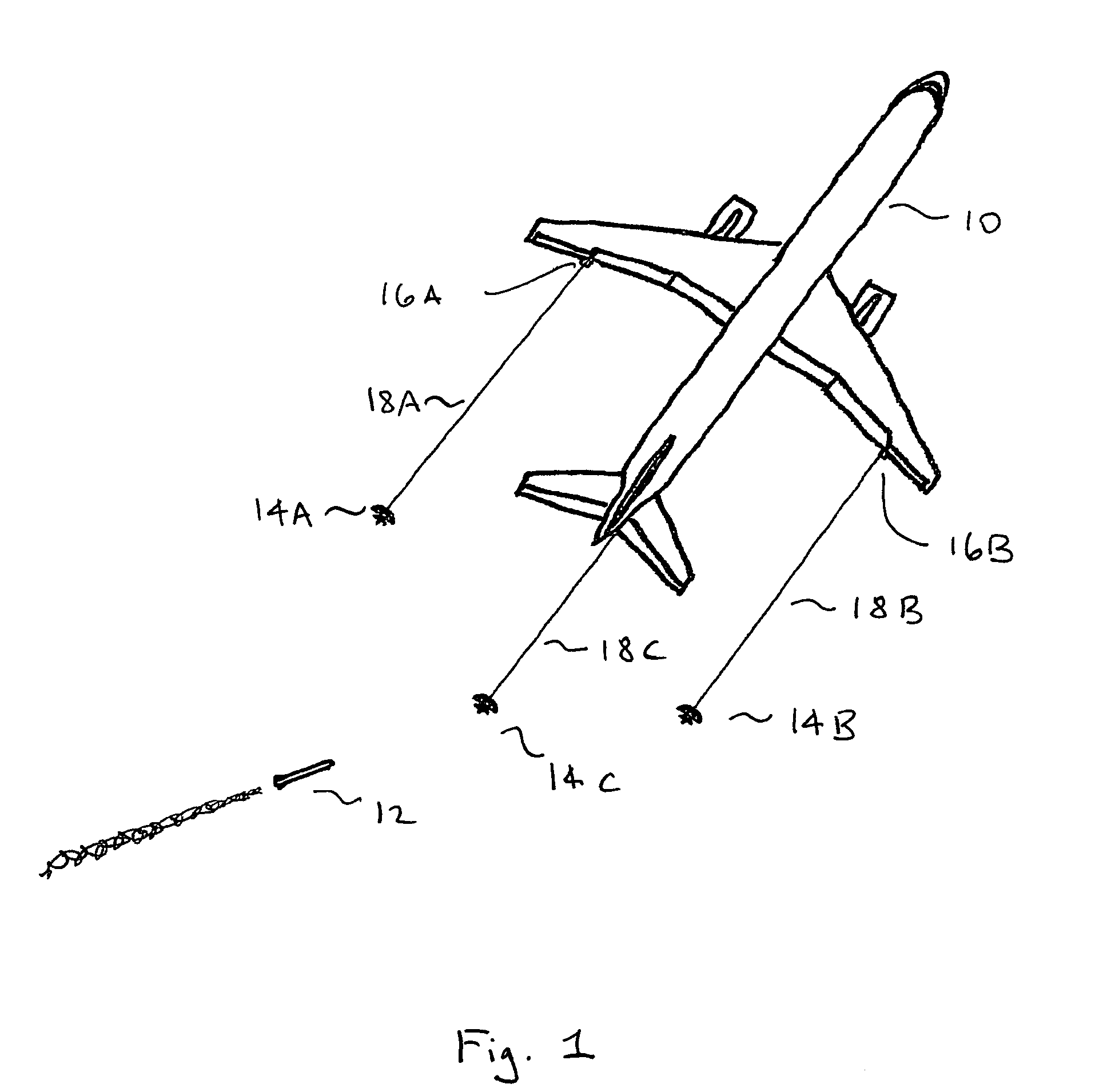
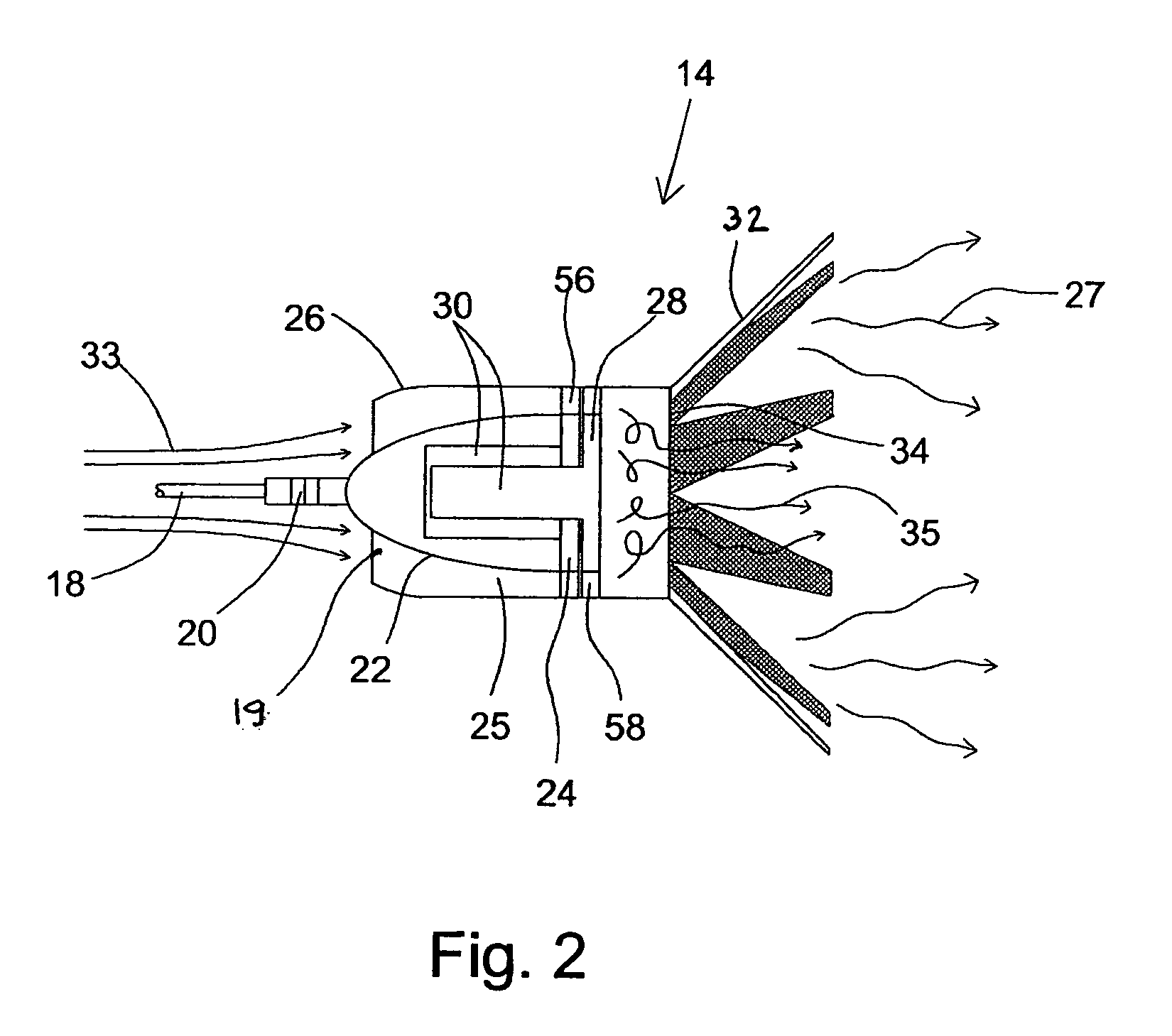
Self-powered tethered decoy for heat-seeking transport aircraft missile defense
A low-cost airliner defense system utilizing self powered, retrievable, towed decoys against man portable heat-seeking missile (MANPAD) systems provides both high power and a large IR radiating surface area. An efficient and lightweight integrated turbine-alternator extracts sufficient electric power from an air stream directed through a small decoy deployed and towed behind an aircraft during the vulnerable phases of a flight to power a large and intense IR emitter. Unfurled IR radiator “petals” present large area arrays of rear-facing IR emitters. During the high-altitude cruise phase the radiating petals furl down folding around the retrieved decoy body as it is stowed in a streamlined housing for minimizing fuel consumption and maneuverability penalties.
Owner:BURNS ALAN ALEXANDER
Lipid nanoparticle based compositions and methods for the delivery of biologically active molecules
The present invention relates to novel cationic lipids, transfection agents, microparticles, nanoparticles, and short interfering nucleic acid (siNA) molecules. The invention also features compositions, and methods of use for the study, diagnosis, and treatment of traits, diseases and conditions that respond to the modulation of gene expression and / or activity in a subject or organism. Specifically, the invention relates to novel cationic lipids, microparticles, nanoparticles and transfection agents that effectively transfect or deliver biologically active molecules, such as antibodies (e.g., monoclonal, chimeric, humanized etc.), cholesterol, hormones, antivirals, peptides, proteins, chemotherapeutics, small molecules, vitamins, co-factors, nucleosides, nucleotides, oligonucleotides, enzymatic nucleic acids, antisense nucleic acids, triplex forming oligonucleotides, 2,5-A chimeras, dsRNA, allozymes, aptamers, decoys and analogs thereof, and small nucleic acid molecules, such as short interfering nucleic acid (siNA), short interfering RNA (siRNA), double-stranded RNA (dsRNA), micro-RNA (miRNA), and short hairpin RNA (shRNA) molecules, to relevant cells and / or tissues, such as in a subject or organism. Such novel cationic lipids, microparticles, nanoparticles and transfection agents are useful, for example, in providing compositions to prevent, inhibit, or treat diseases, conditions, or traits in a cell, subject or organism. The compositions described herein are generally referred to as formulated molecular compositions (FMC) or lipid nanoparticles (LNP).
Owner:SIRNA THERAPEUTICS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com