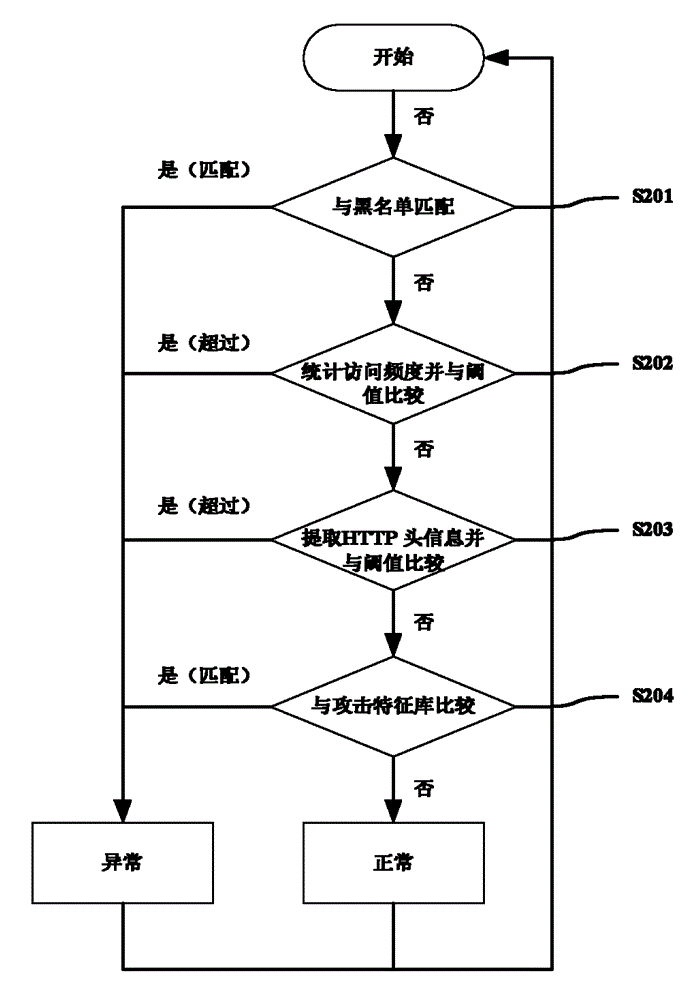
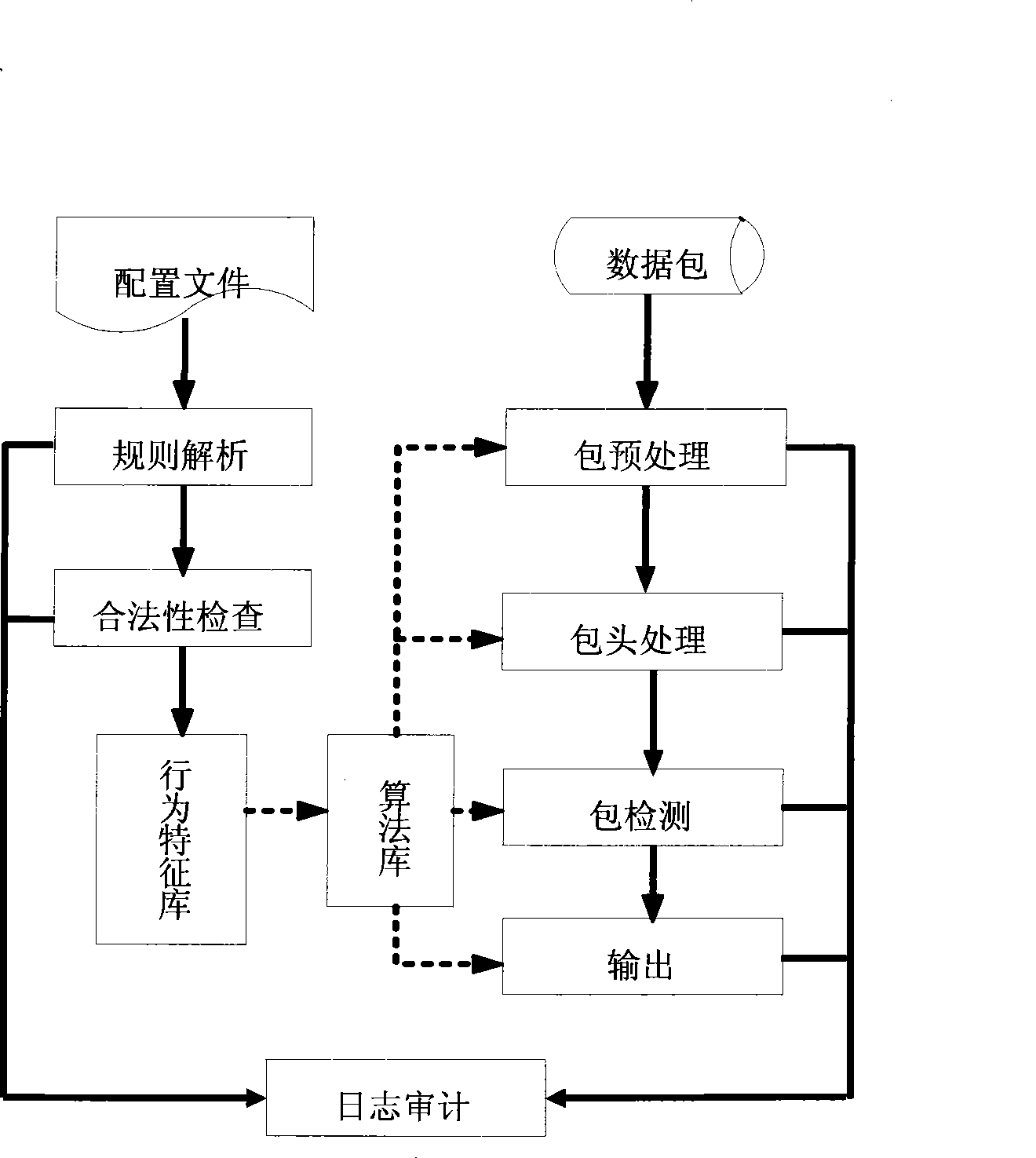
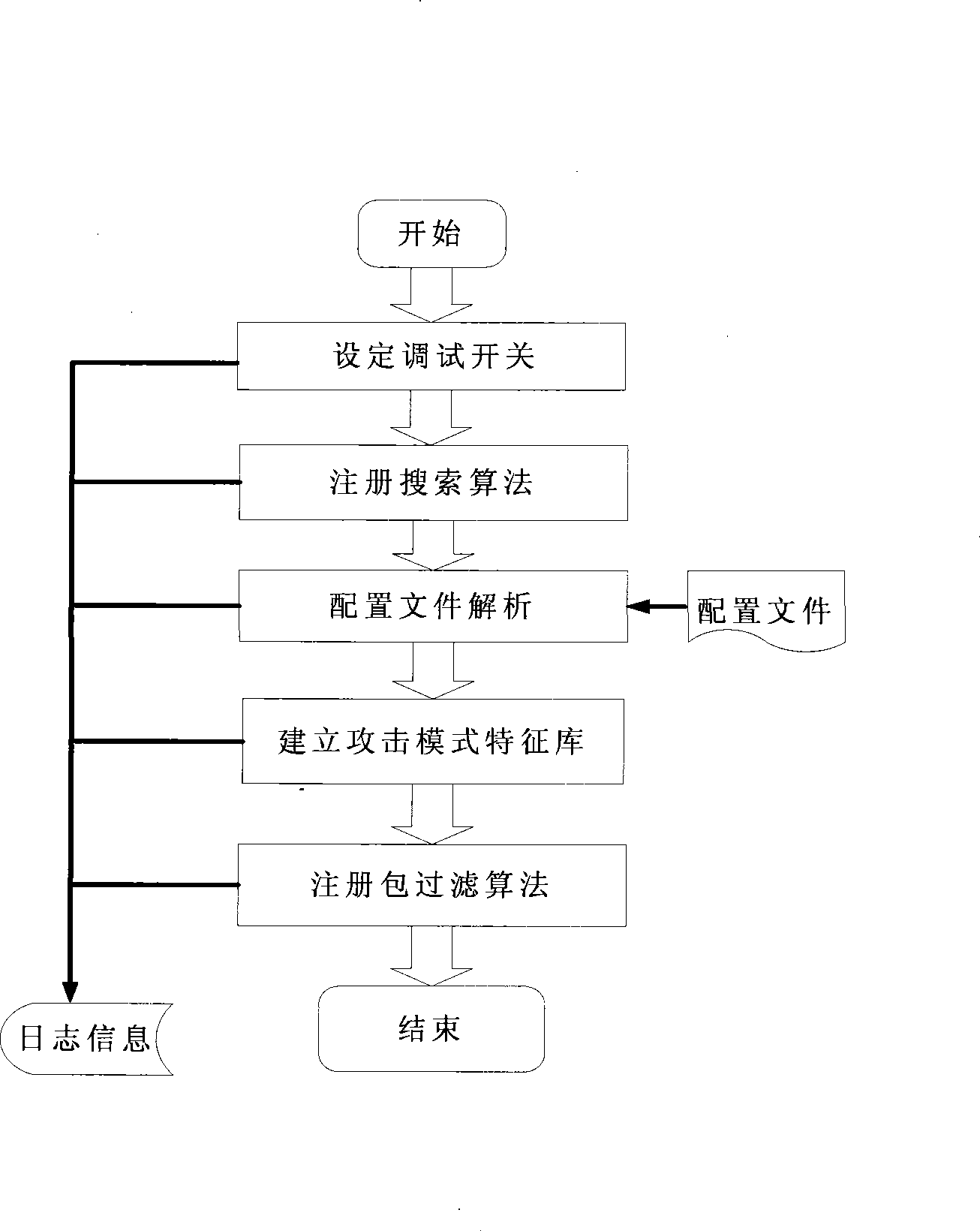
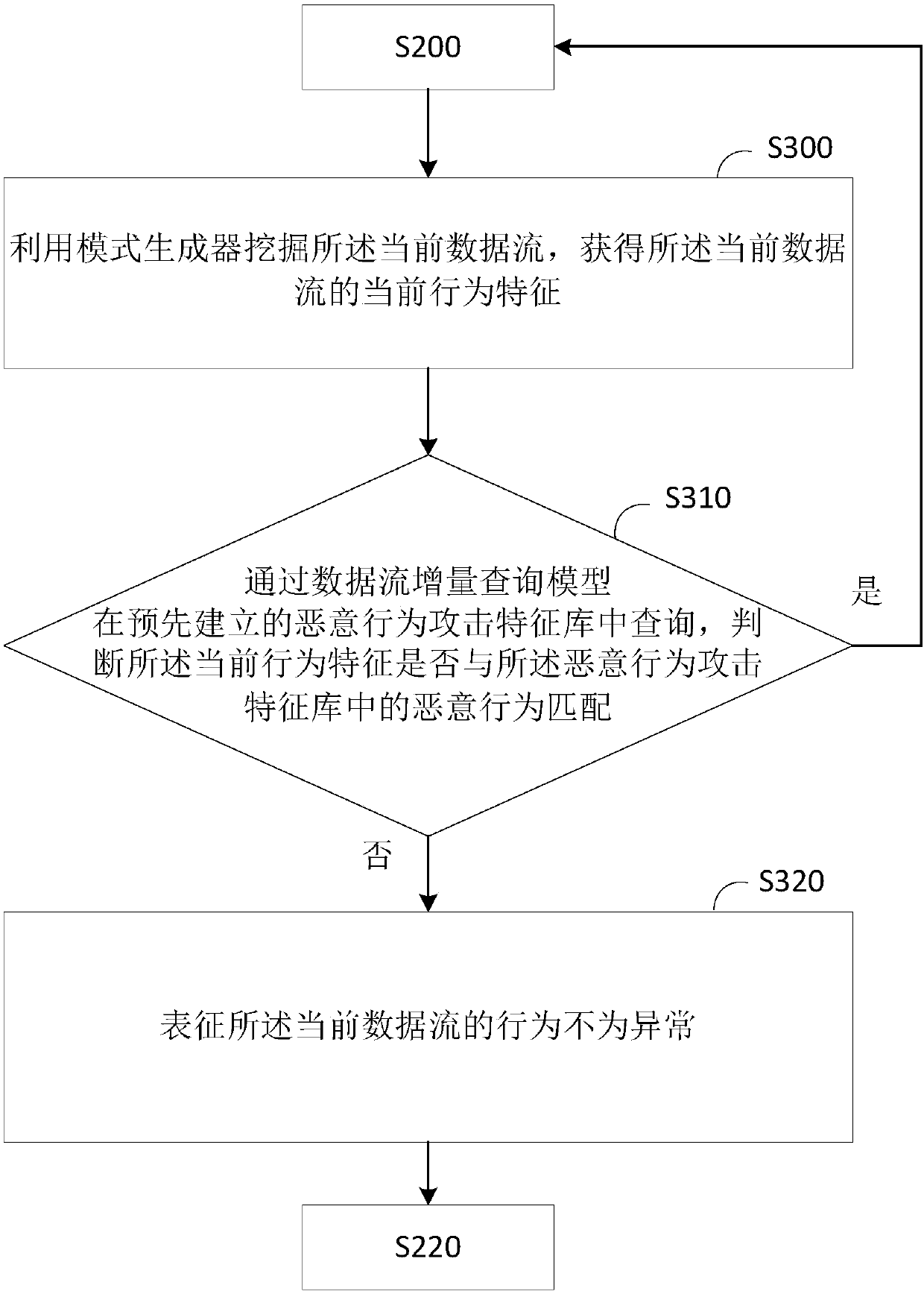
Patents
Literature
278 results about "Attack signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
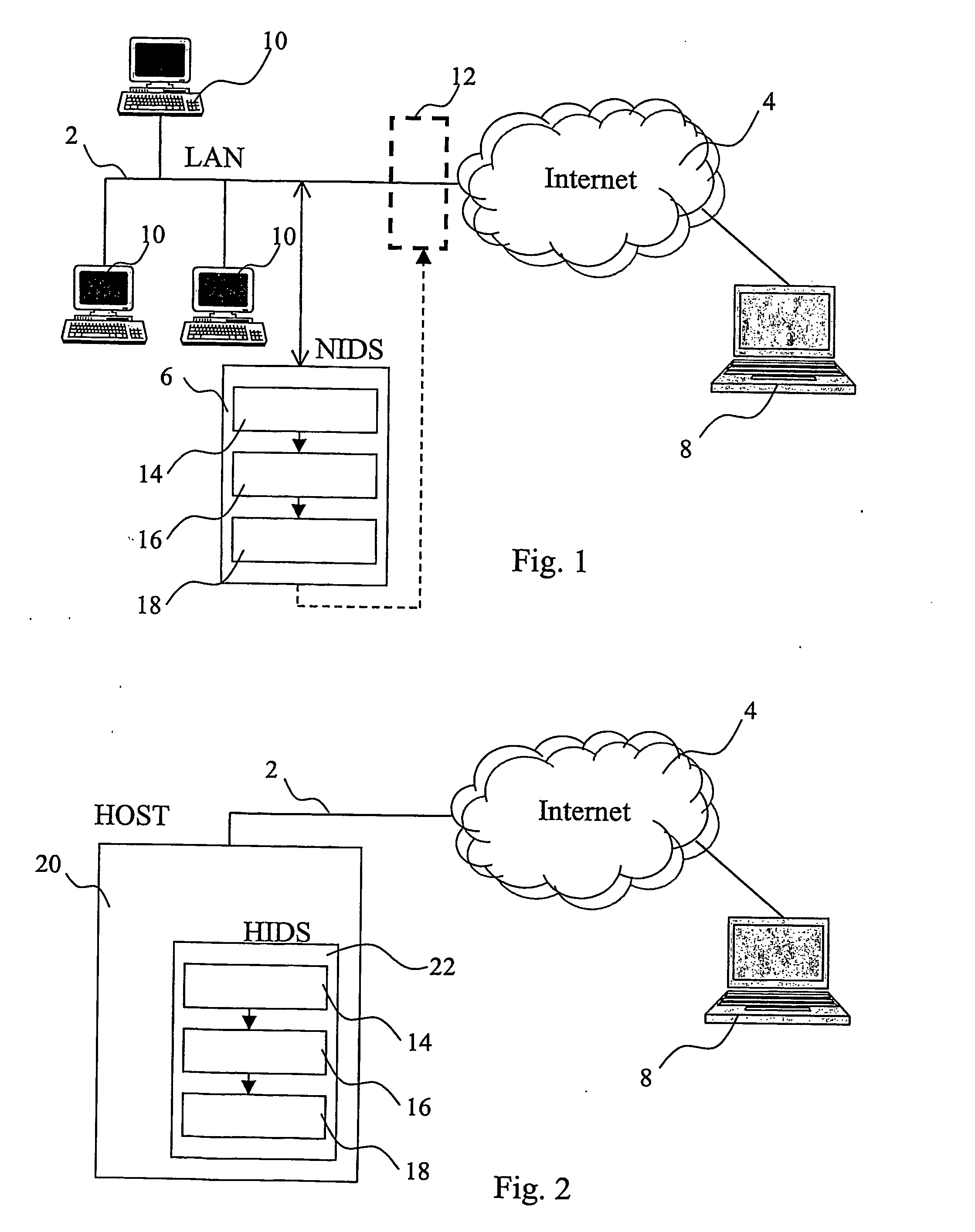
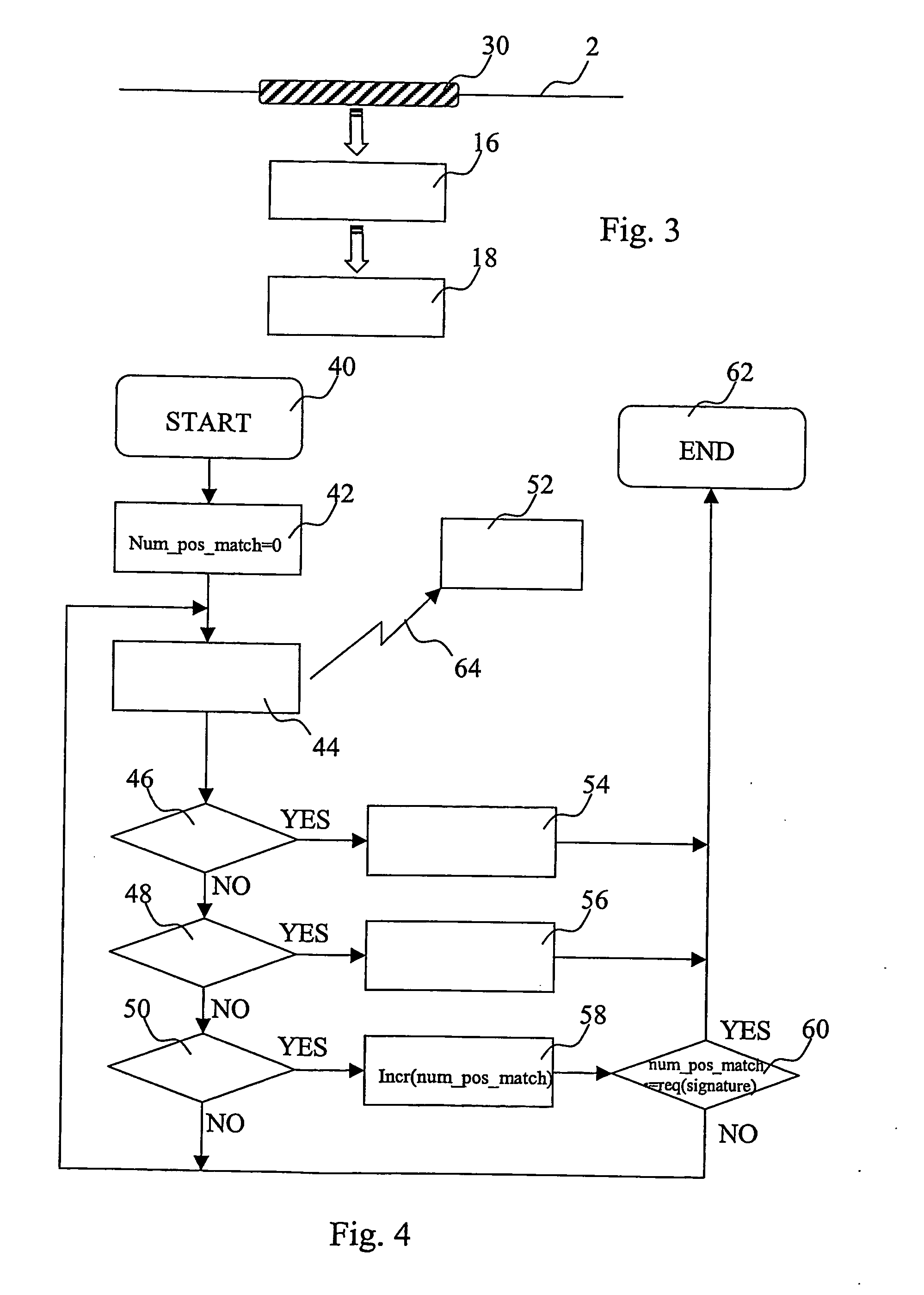
Attack signature. A file containing a data sequence used to identify an attack on the network, typically using an operating system or application vulnerability. Such signatures are used by an Intrusion Detection System (IDS) or firewall to flag malicious activity directed at the system.
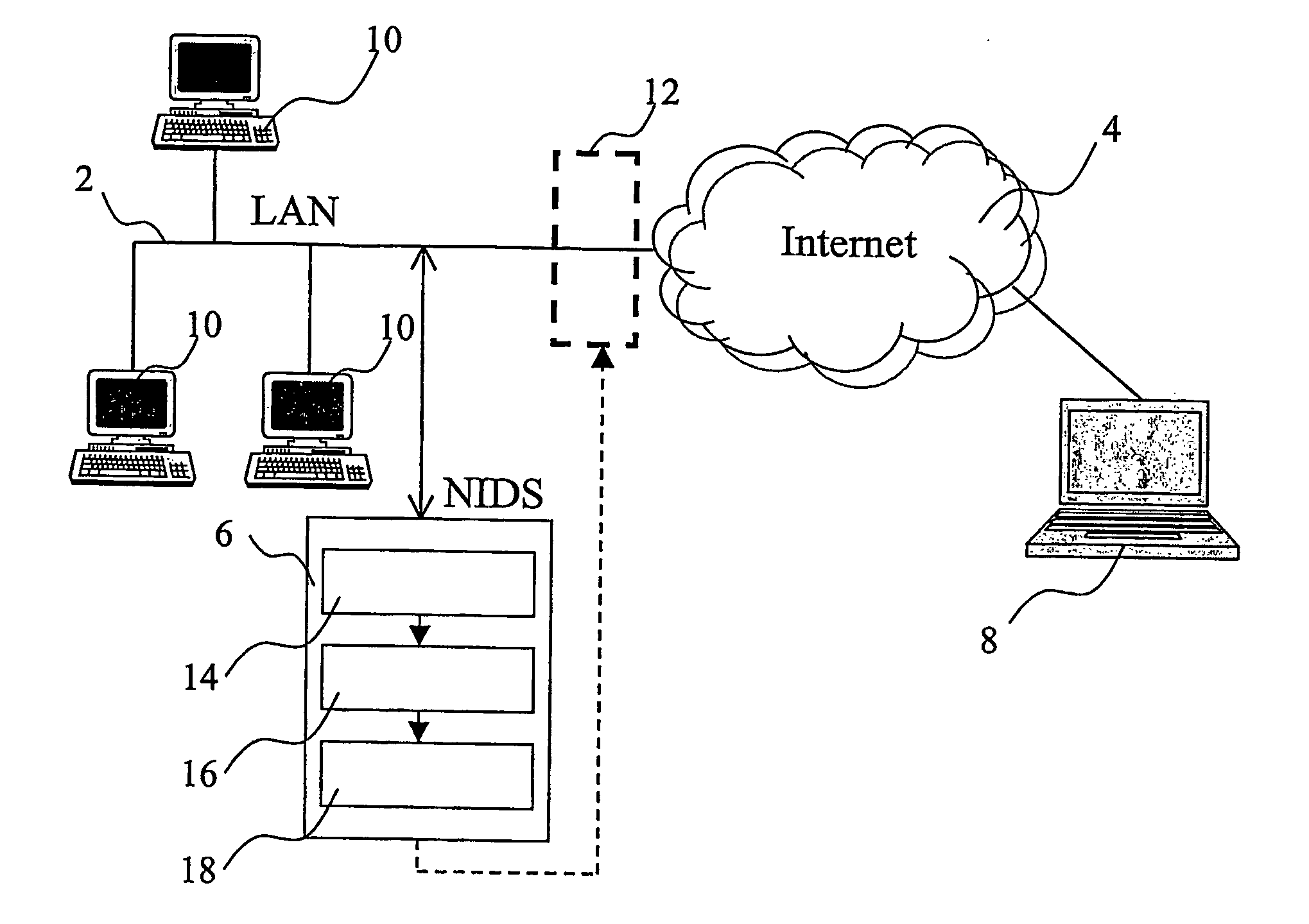
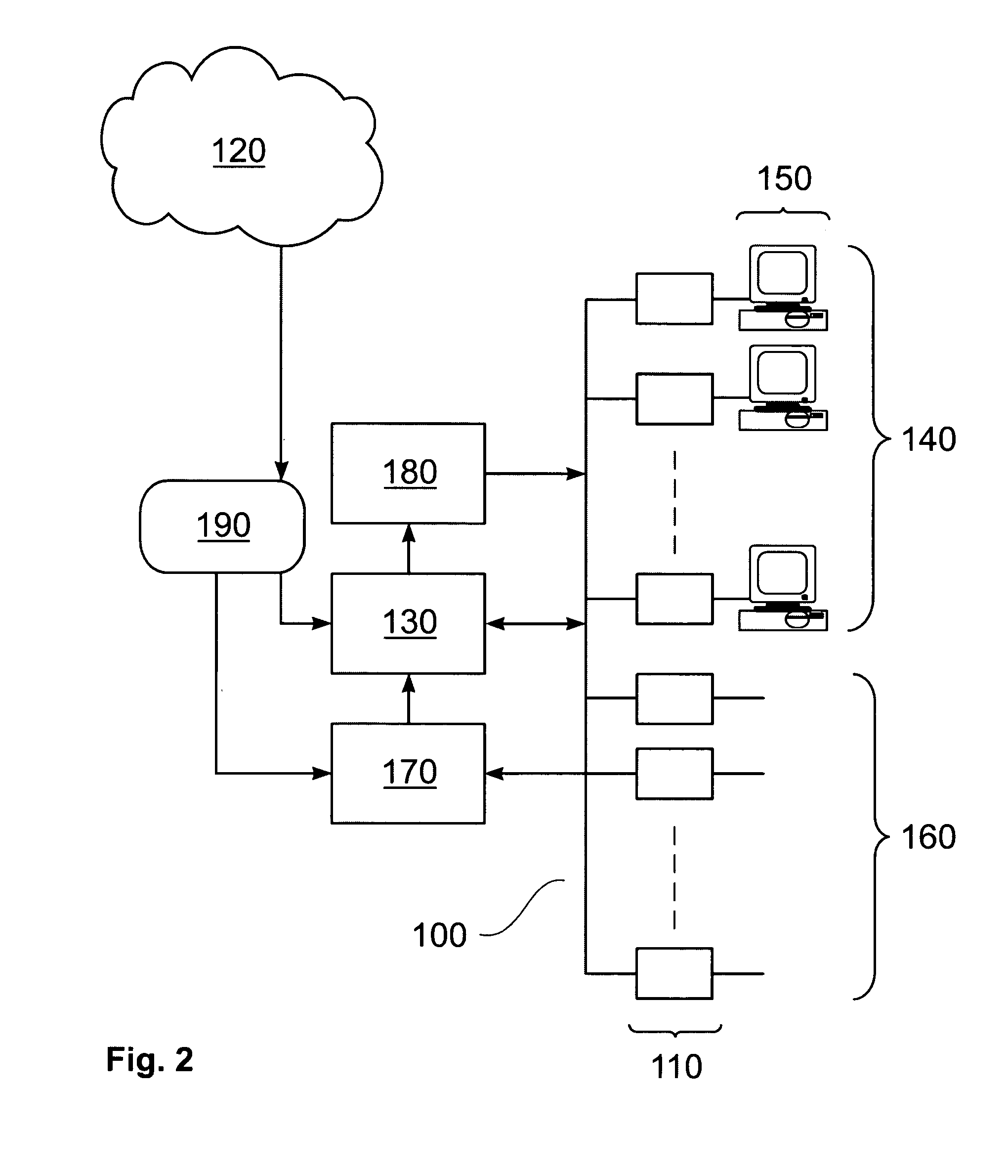
Inline intrusion detection
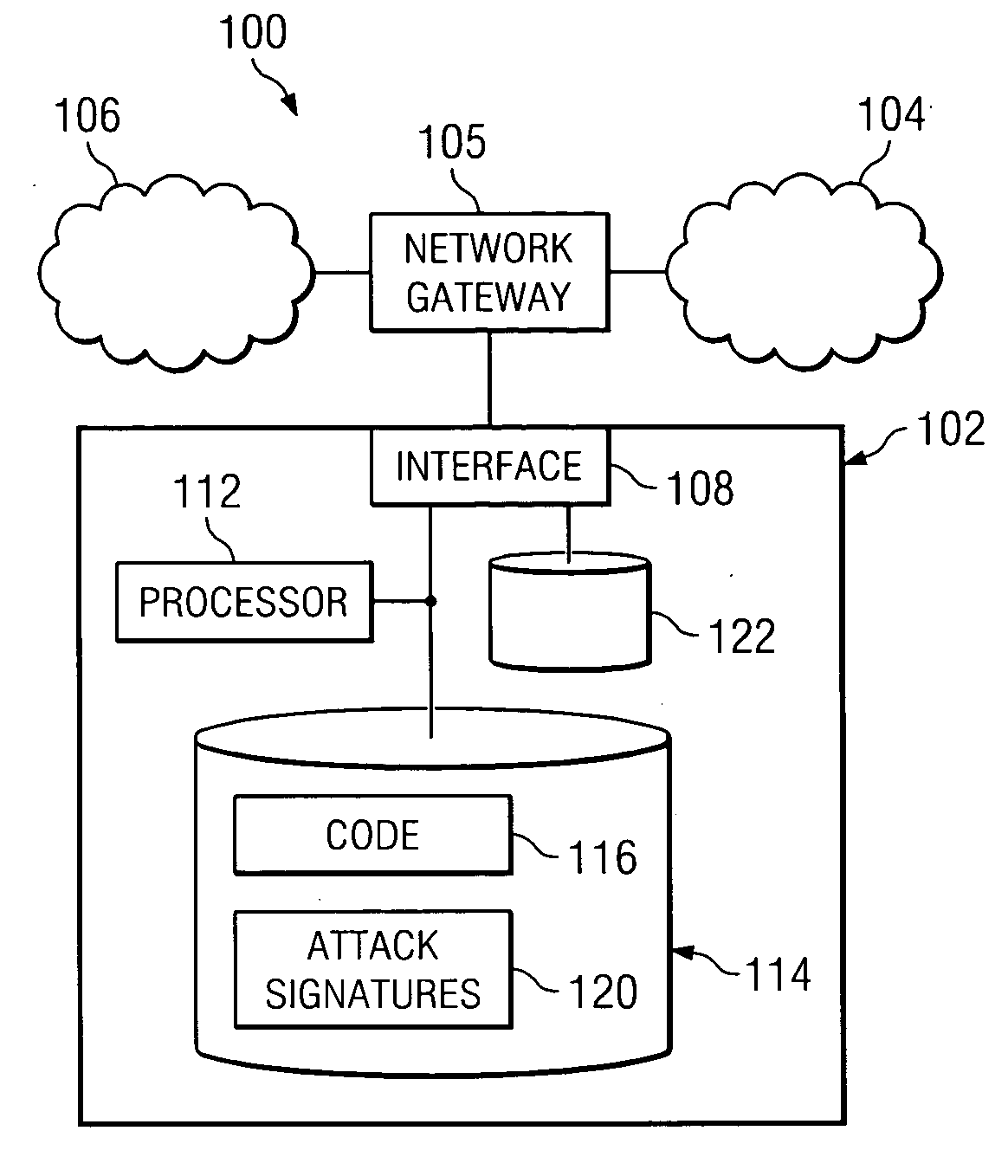
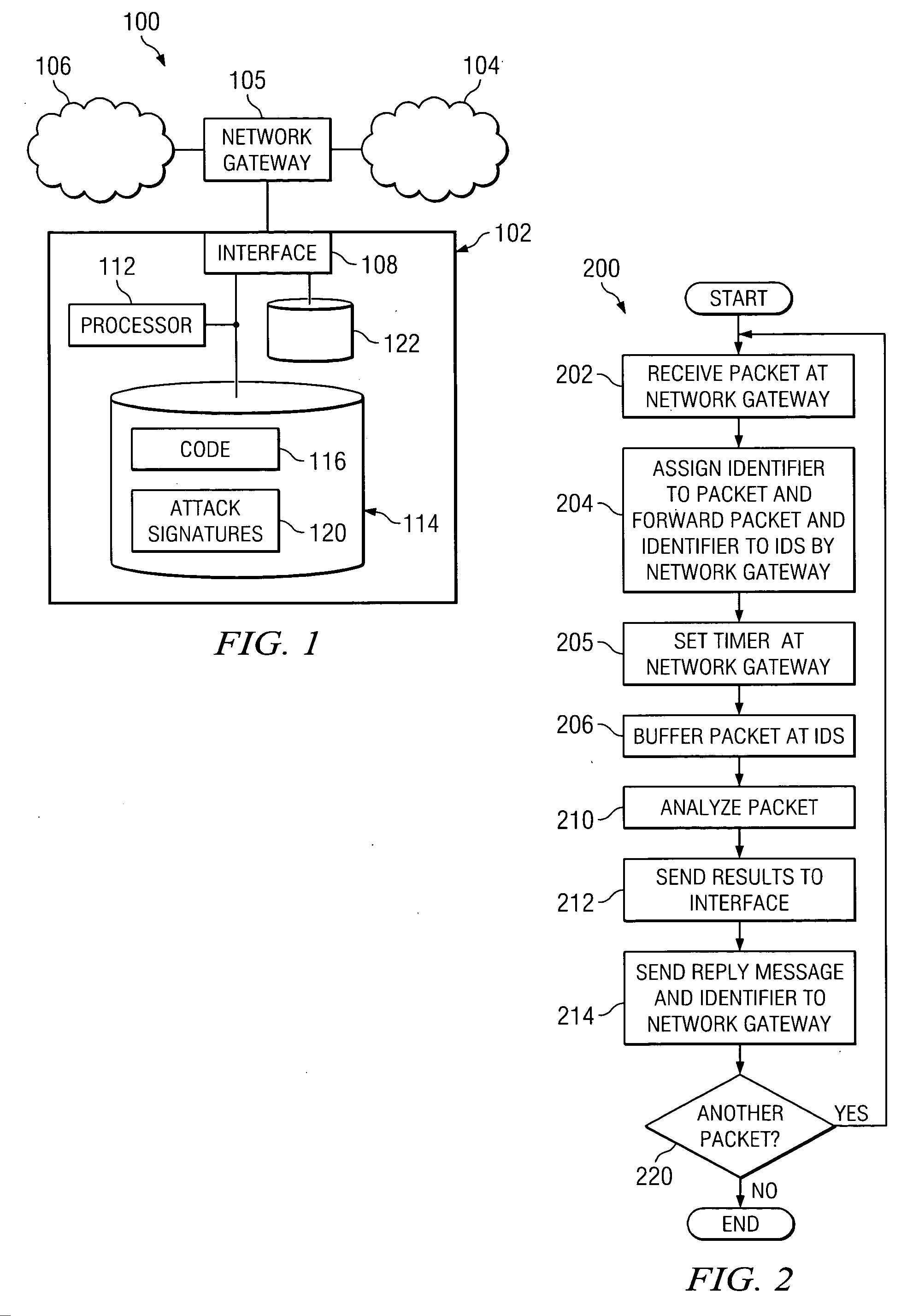
ActiveUS20060161983A1Save memorySave bus resourcesMemory loss protectionError detection/correctionAttack signature
A method for inline intrusion detection includes receiving a packet at a network gateway, storing the packet, and assigning an identifier to the packet. The method also includes transmitting a copy of the packet and the identifier from the network gateway to an intrusion detection system and analyzing the copy of the packet by the intrusion detection system to determine whether the packet includes an attack signature and communicating a reply message from the intrusion detection system to the network gateway. The reply message includes the identifier and is indicative of the results of the analysis. The size of the reply message is less than the size of the packet.
Owner:CISCO TECH INC
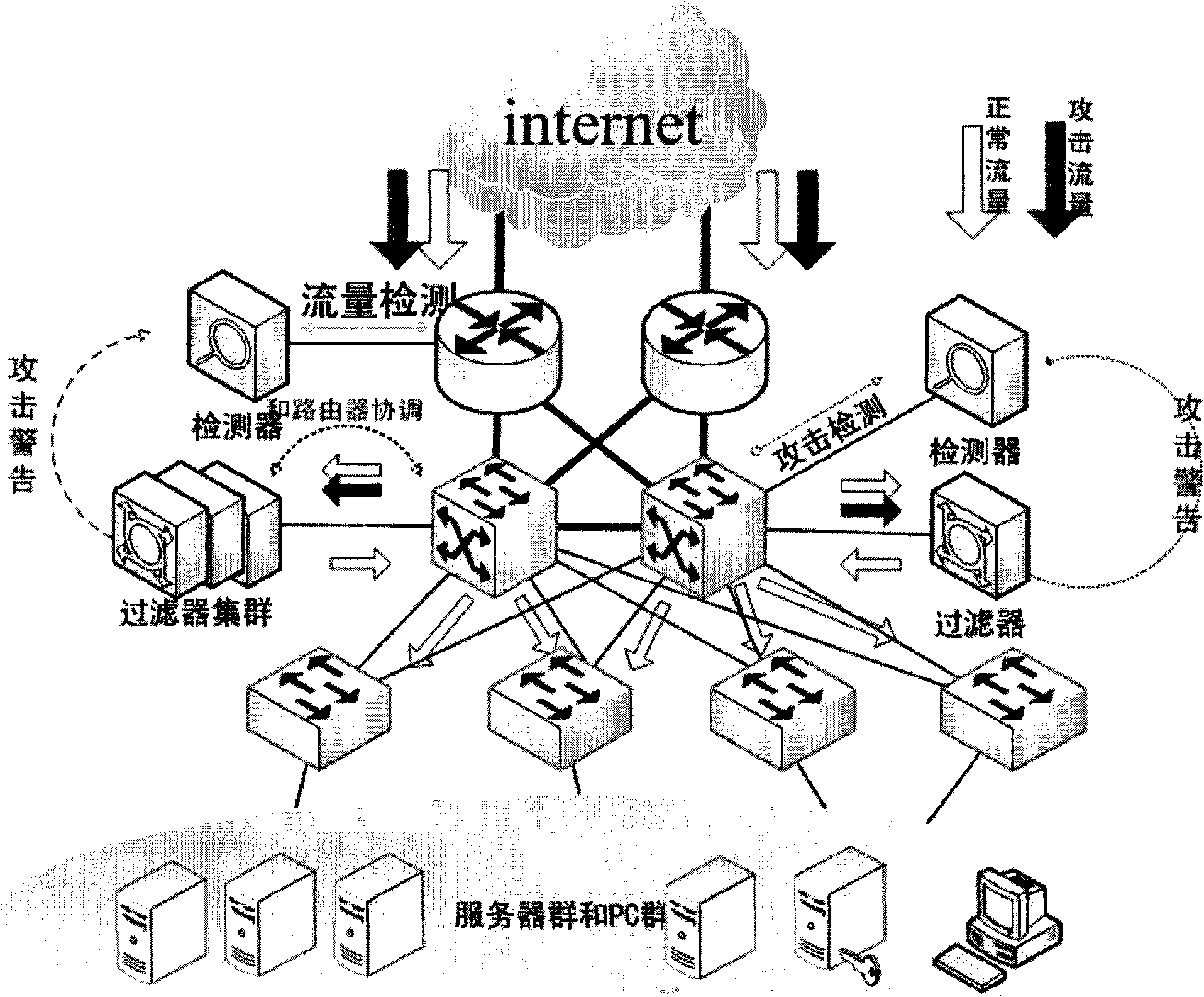
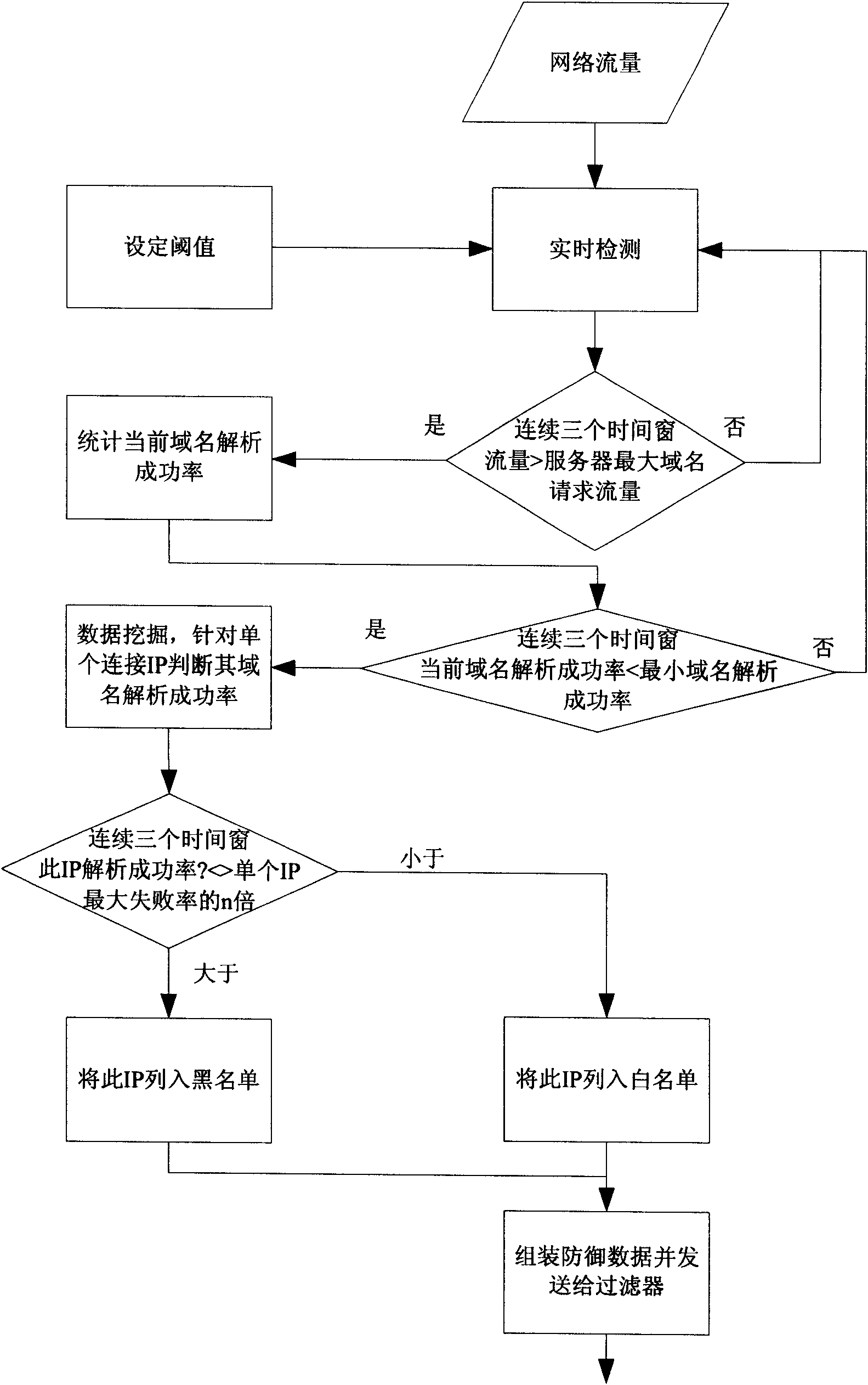
Security gateway system for resisting DDoS attack for DNS service
The invention discloses a high-efficiency anti-DDoS security gateway system, which can effectively detect and defend a DNS denial-of-service attack. The system comprises two core components, namely a detector and a filter. The system supports two deploying ways, namely serial connection and bypass. A detecting method is based on the self-learning network flow state statistic and characteristic disinterment, achieves the detection and positioning of the network abnormal flow by setting network performance parameter thresholds, and can effectively identify the suspected attack flow. A defending method carries out a thought of deep defense, and the system is deployed with two defense steps of attack characteristic defense and baseline defense so as to ensure the attack defending effect of thesystem under normal network condition and the basic defense capacity of the system in the individual and severe attack environment. The methods can effectively improve the security and attack resista nce of a DNS server and can ensure the normal operation of the DNS service.
Owner:ZHONGKE INFORMATION SECURITY COMMON TECH NAT ENG RES CENT CO LTD
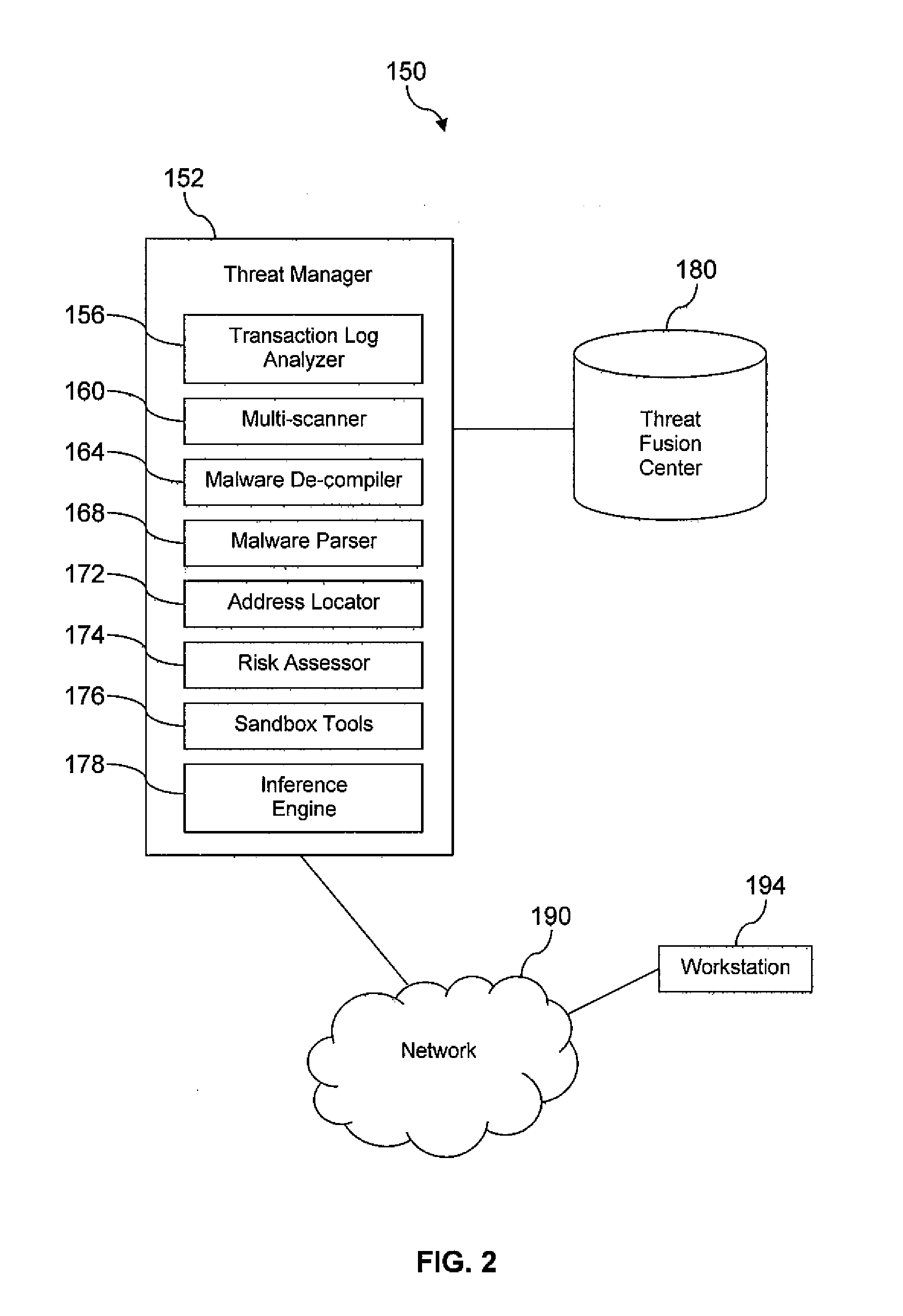
Electronic Crime Detection and Tracking
A system for electronic crime reduction is provided, comprising a computer system, a database, a malware de-compiler, a malware parser, and an inference engine. The database contains information that associates electronic crime attack signature data with at least one of an individual, a group, and a location. The malware de-compiler, when executed on the computer system, translates a first malware executable to an assembly language version. The first malware is associated with an electronic crime that has been committed. The malware parser, when executed on the computer system, analyzes the assembly language version to identify distinctive coding preferences used to develop the first malware. The inference engine, when executed on the computer system, analyzes the distinctive coding preferences identified by the malware parser application in combination with searching the database to identify one of an individual, a group, and a location associated with the electronic crime.
Owner:GOOGLE LLC
Decoy network technology with automatic signature generation for intrusion detection and intrusion prevention systems
ActiveUS20070271614A1Unauthorised/fraudulent call preventionDigital data processing detailsOperational systemDecoy
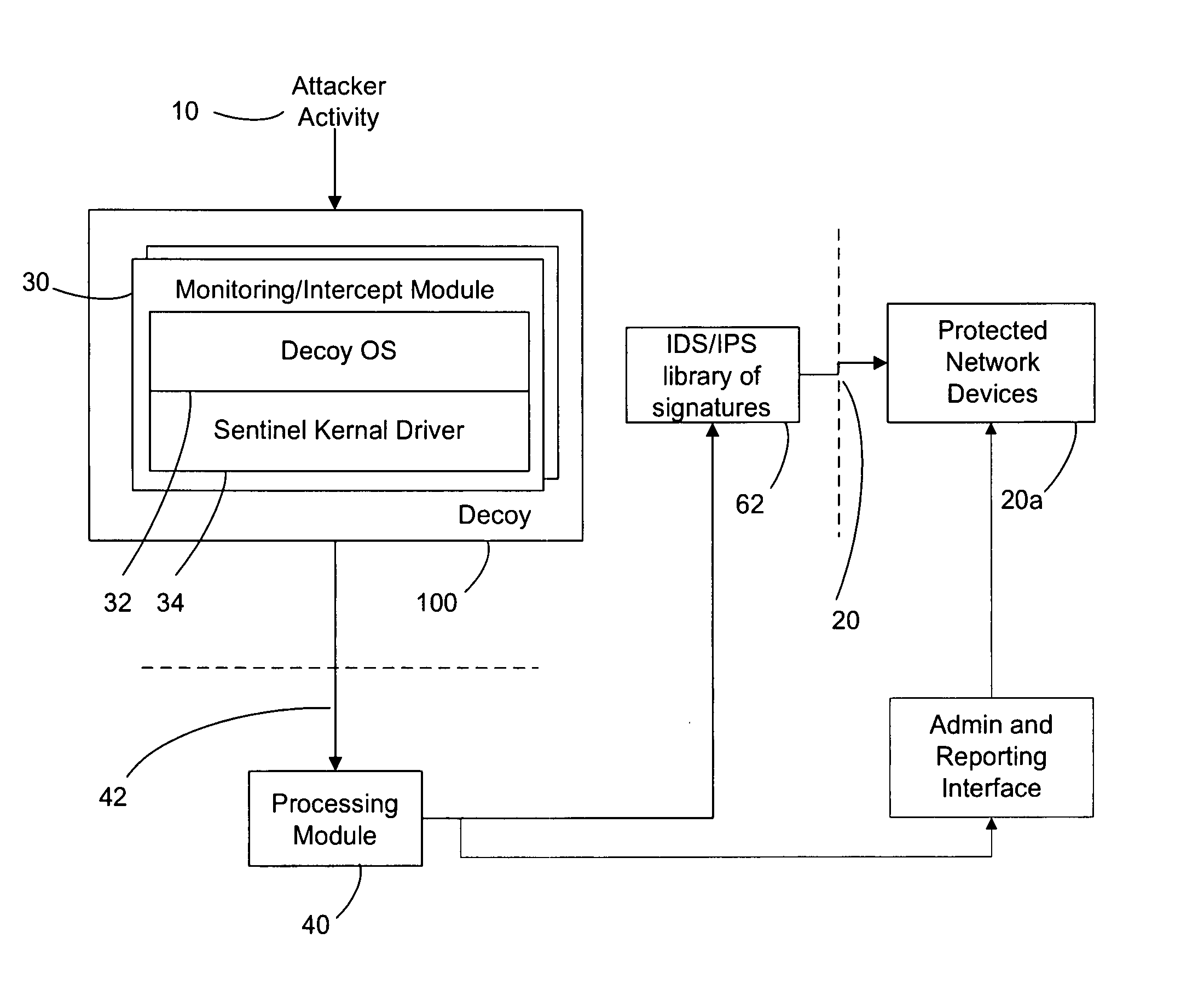
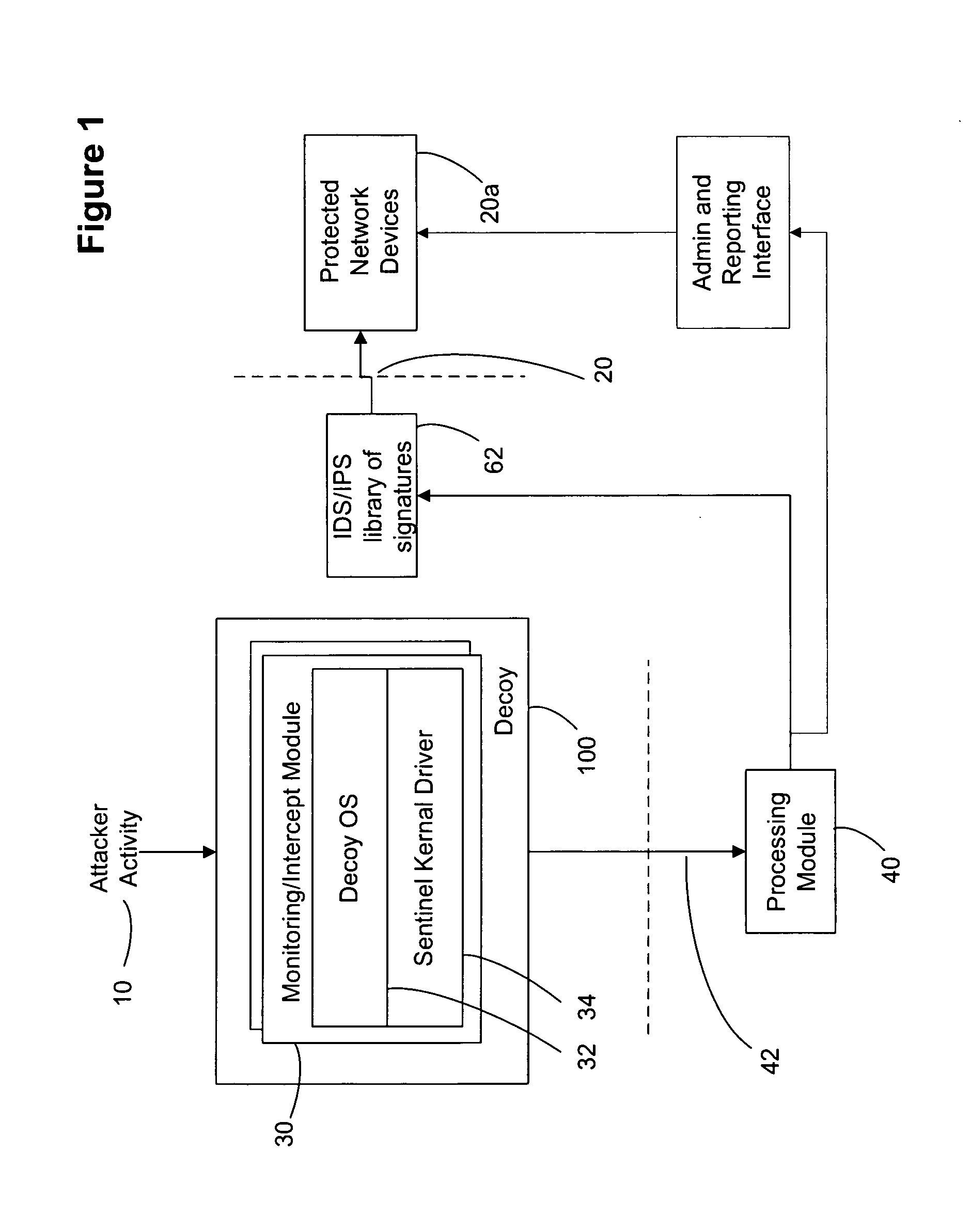
Improved methods and systems for decoy networks with automatic signature generation for intrusion detection and intrusion prevention systems. A modular decoy network with front-end monitor / intercept module(s) with a processing back-end that is separate from the protected network. The front-end presents a standard fully functional operating system that is a decoy so that the instigator of an attack is lead to believe a connection has been made to the protected network. The front-end includes a hidden sentinel kernal driver that monitors connections to the system and captures attack-identifying information. The captured information is sent to the processing module for report generation, data analysis and generation of an attack signature. The generated attack signature can then be applied to the library of signatures of the intrusion detection system or intrusion prevention system of the protected network to defend against network based attacks including zero-day attacks.
Owner:COUNTERTACK
Method and system for detecting unauthorized use of a communication network
ActiveUS20060242703A1Less proneMemory loss protectionError detection/correctionPattern matchingAlert state
A system for detecting unauthorised use of a network is provided with a pattern matching engine for searching attack signatures into data packets, and with a response analysis engine for detecting response signatures into data packets sent back from an attacked network / computer. When a suspect signature has been detected into a packet, the system enters an alarm status starting a monitoring process on the packets sent back from the potentially attacked network / computer. An alarm is generated only in case the analysis of the response packets produces as well a positive result. Such intrusion detection system is much less prone to false positives and misdiagnosis than a conventional pattern matching intrusion detection system.
Owner:III HLDG 1
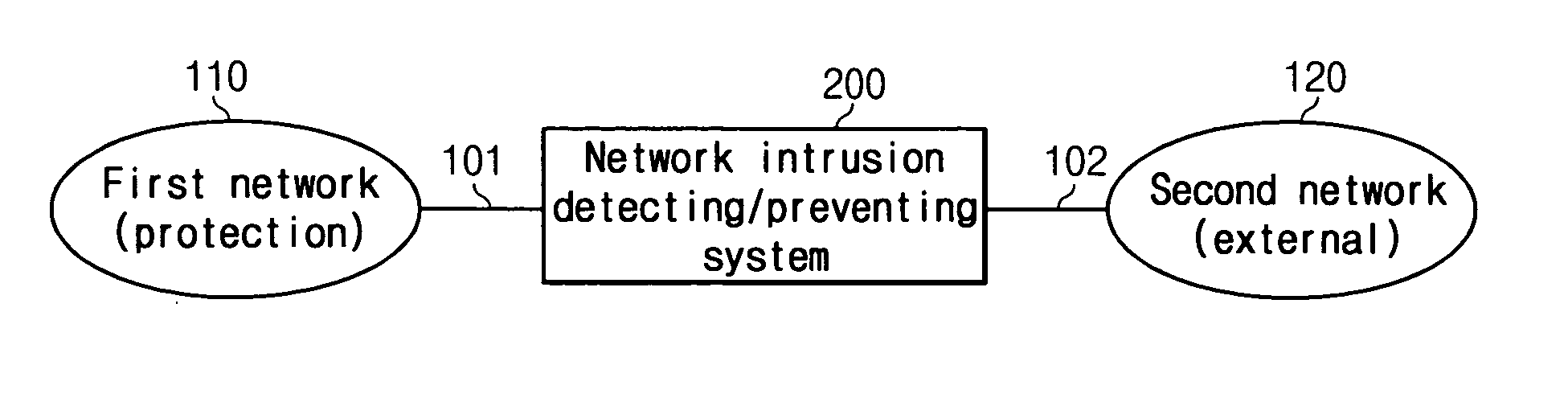
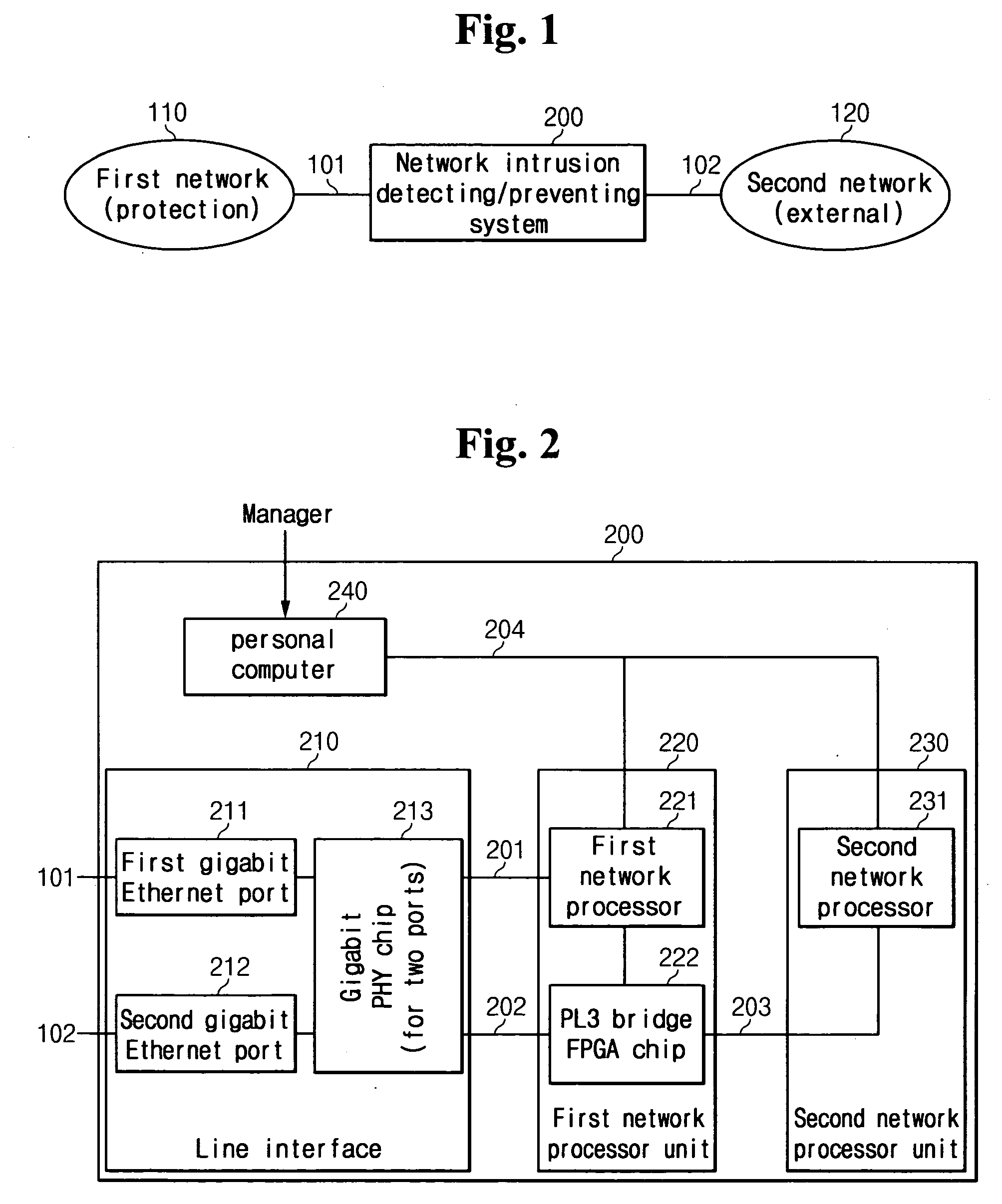
In-line mode network intrusion detect and prevent system and method thereof
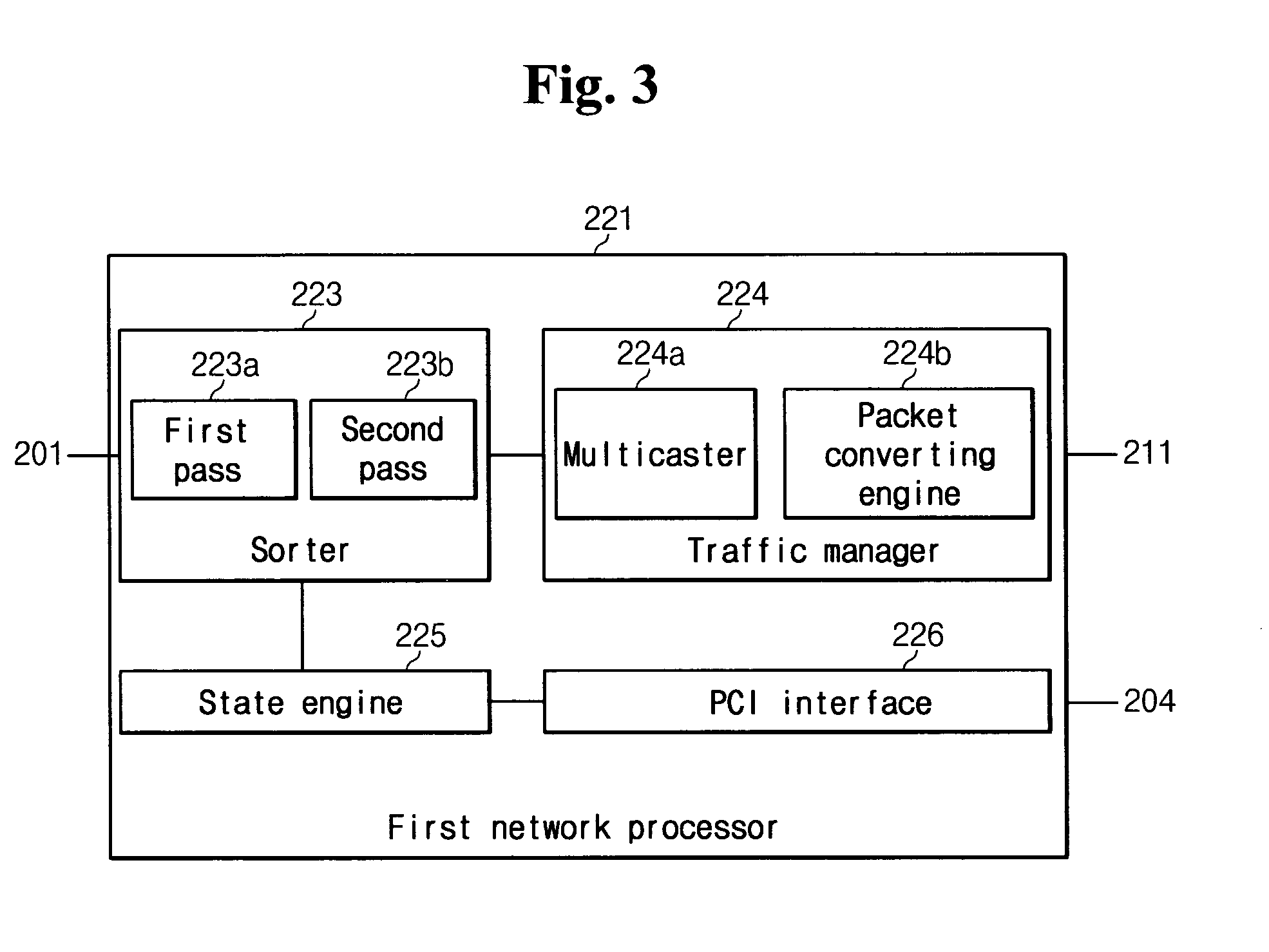
InactiveUS20050076227A1Respond quicklyProcess stabilityUser identity/authority verificationUnauthorized memory use protectionComputer networkNetwork processor
Disclosed is an in-line mode network intrusion detecting and preventing system coupled between a protection network and an external network, for detecting intrusion states between the networks and preventing the intrusion. The system comprises a first network processor unit for monitoring the packets communicated between the networks to collect various statistical data, and performing a packet filtering process according to a packet preventing rule and a packet sensing process according to a sensing rule; and a second network processor unit for checking payloads of the packets with reference to attack signatures to detect the attack states to one of the networks.
Owner:ELECTRONICS & TELECOMM RES INST
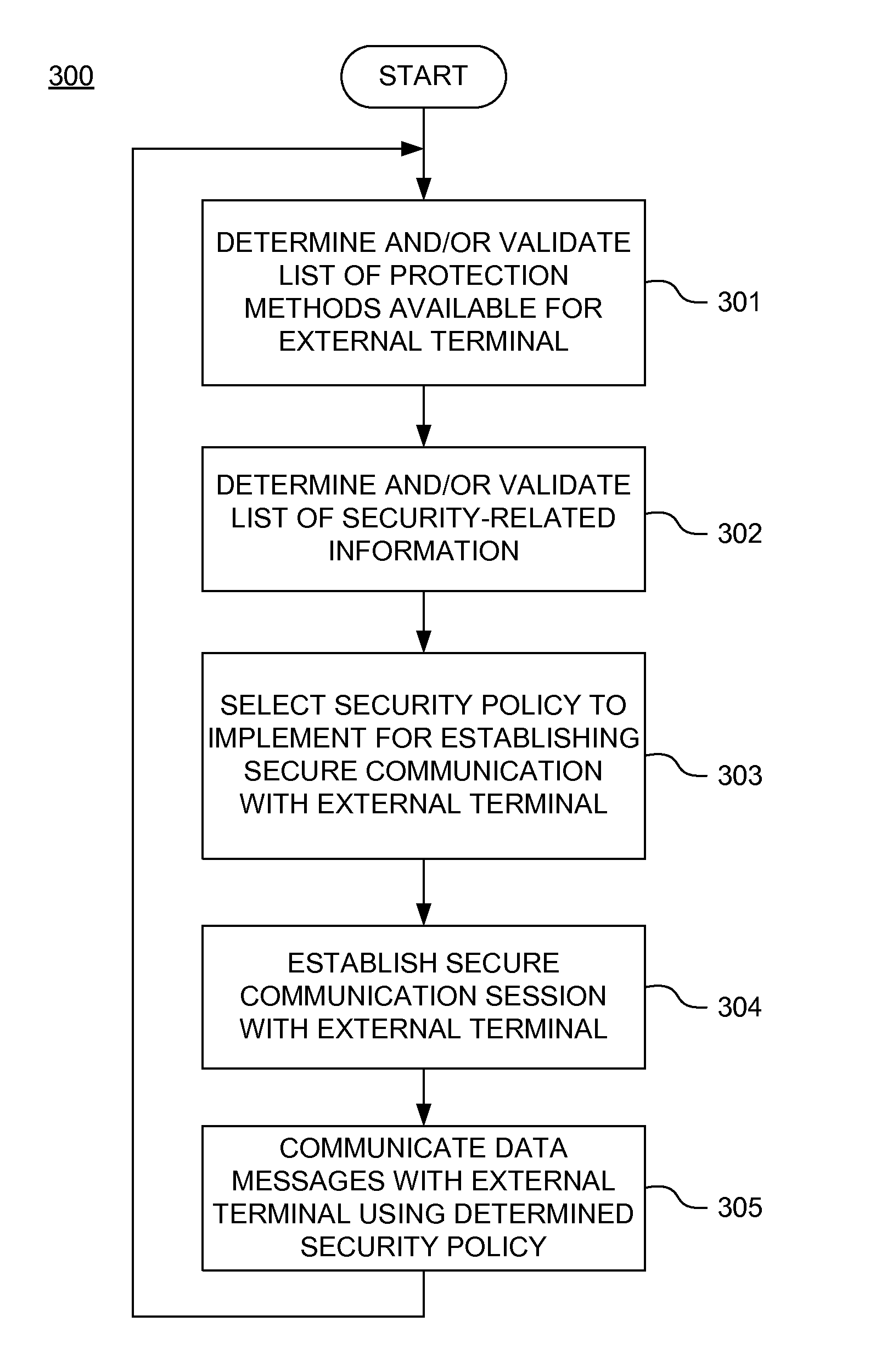
Dynamically reacting policies and protections for securing mobile financial transaction data in transit
ActiveUS20110178933A1Shorten the time to marketAcceptable levelFinanceMemory loss protectionEngineeringFinancial transaction
A secure mobile financial transaction is provided by receiving, over a communication network, a list of protection mechanisms available for implementation by an external terminal. Security-related data is received from one or more sensors and an attack signature is computed based on the security-related data. An appropriate security policy is selected from multiple security policies stored in a database based on the list of protection mechanisms and the attack signature. A secure communication session is established between the external terminal and an internal network component according to the selected security policy. A data message associated with a mobile financial transaction is communicated over the communication network during the communication session.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Network security accident classification and predicting method and system
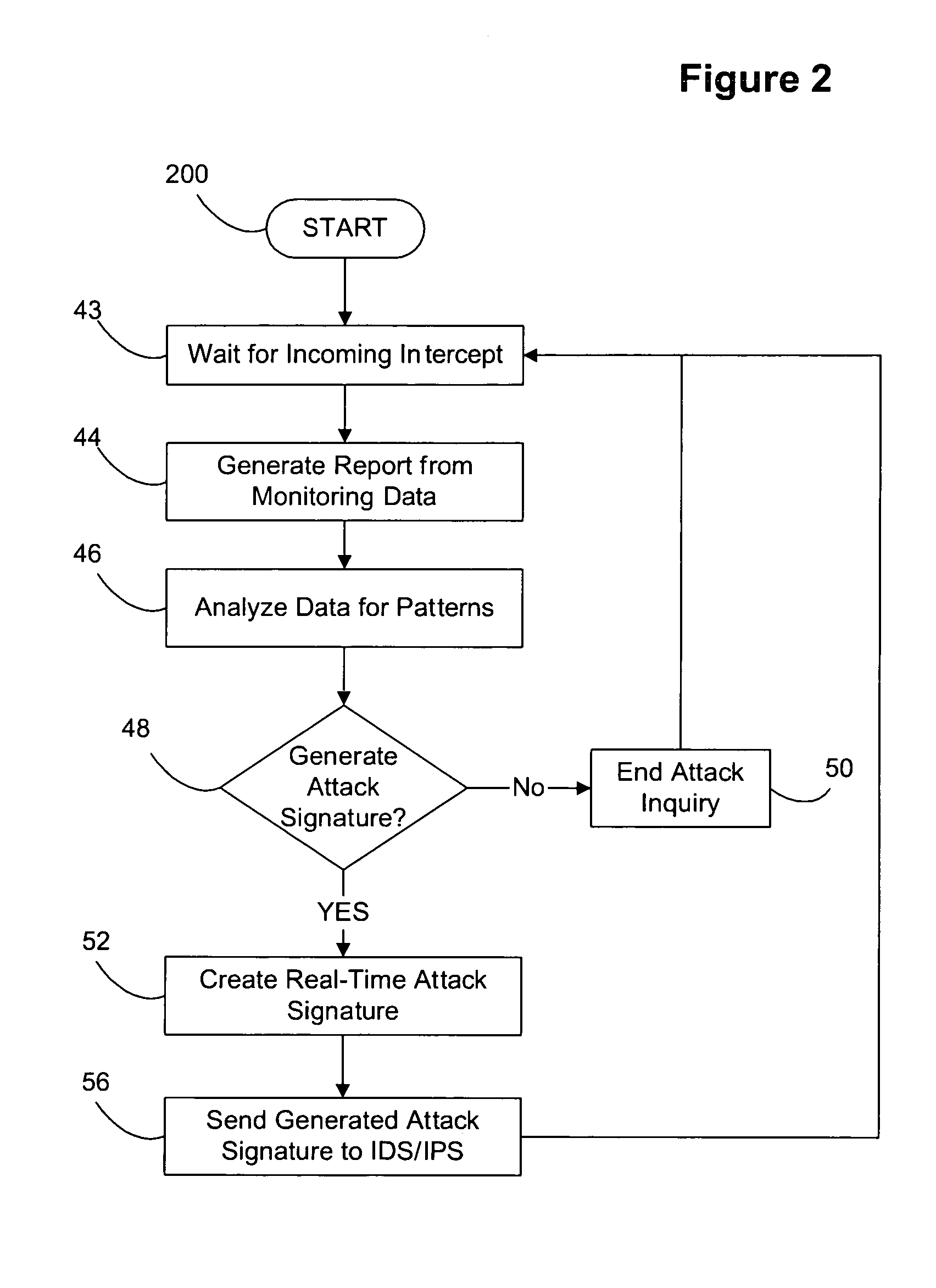
ActiveCN107241352AImprove classification efficiencySave time and costTransmissionNetwork attackTime cost
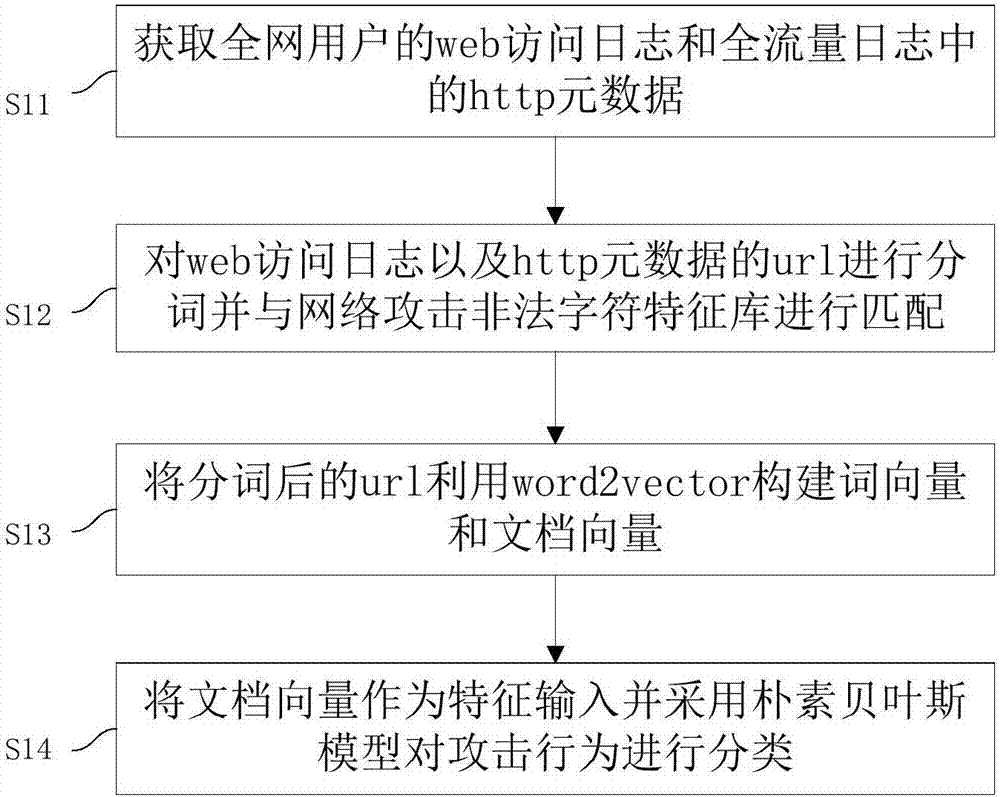
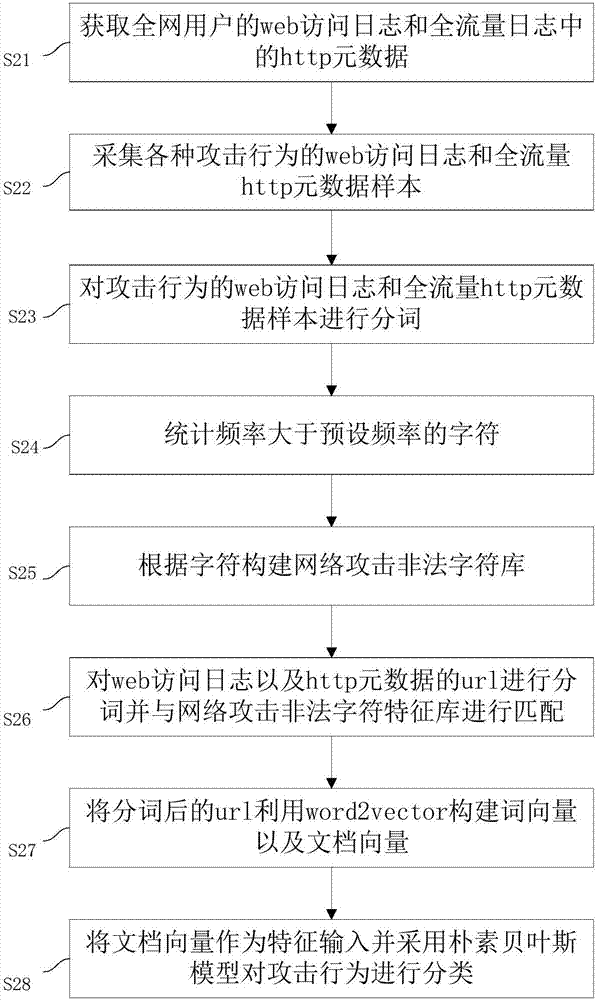
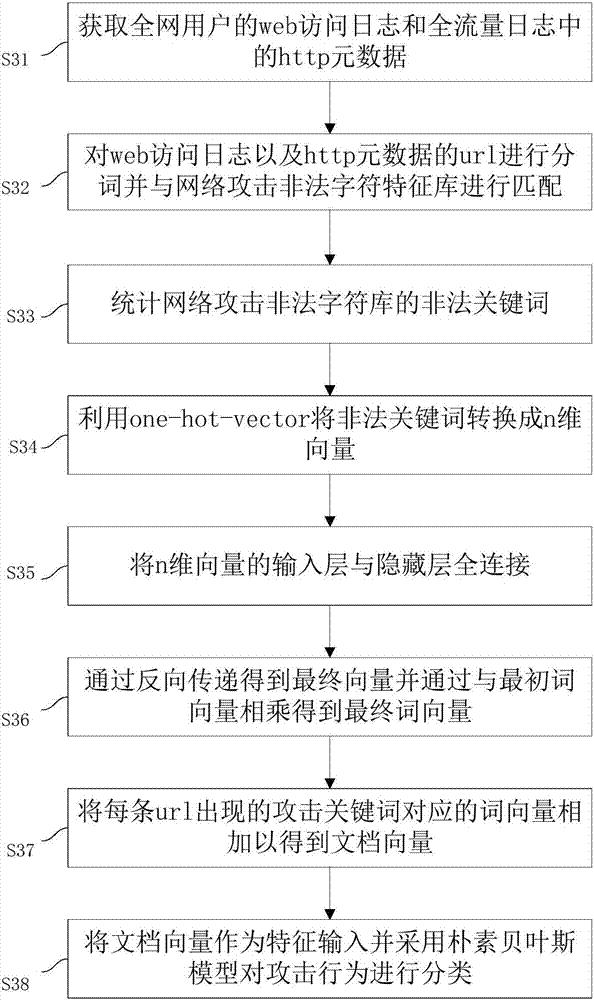
The invention discloses a network security accident classification and predicting method and a system, which are used for solving the problems of the prior art on lacking the capability of timely finding the characteristics of attack behaviors and accurately classifying the attack behaviors. The method comprises the following steps: S1. acquiring web access log of users in a whole network and http metadata in full-flow log; S2. segmenting the web access log and the url of the http metadata, and matching with a network attach illegal character feature library; S3. constructing a word vector and a document vector of the segmented url by utilizing word2vector; and S4. inputting the document vector as a feature and classifying the attack behavior by adopting a naive bayes model. The real-time monitoring of key points can be realized, the abnormal behavior carrying mainstream attack feature can be found by means of machine learning, the classification efficiency of network attack behaviors can be improved, and the time cost of manual check can be lowered, continuously changed attack behaviors can be adapted, and the classification detection accuracy can be enhanced, thus providing guarantee for network security.
Owner:ZHEJIANG PONSHINE INFORMATION TECH CO LTD
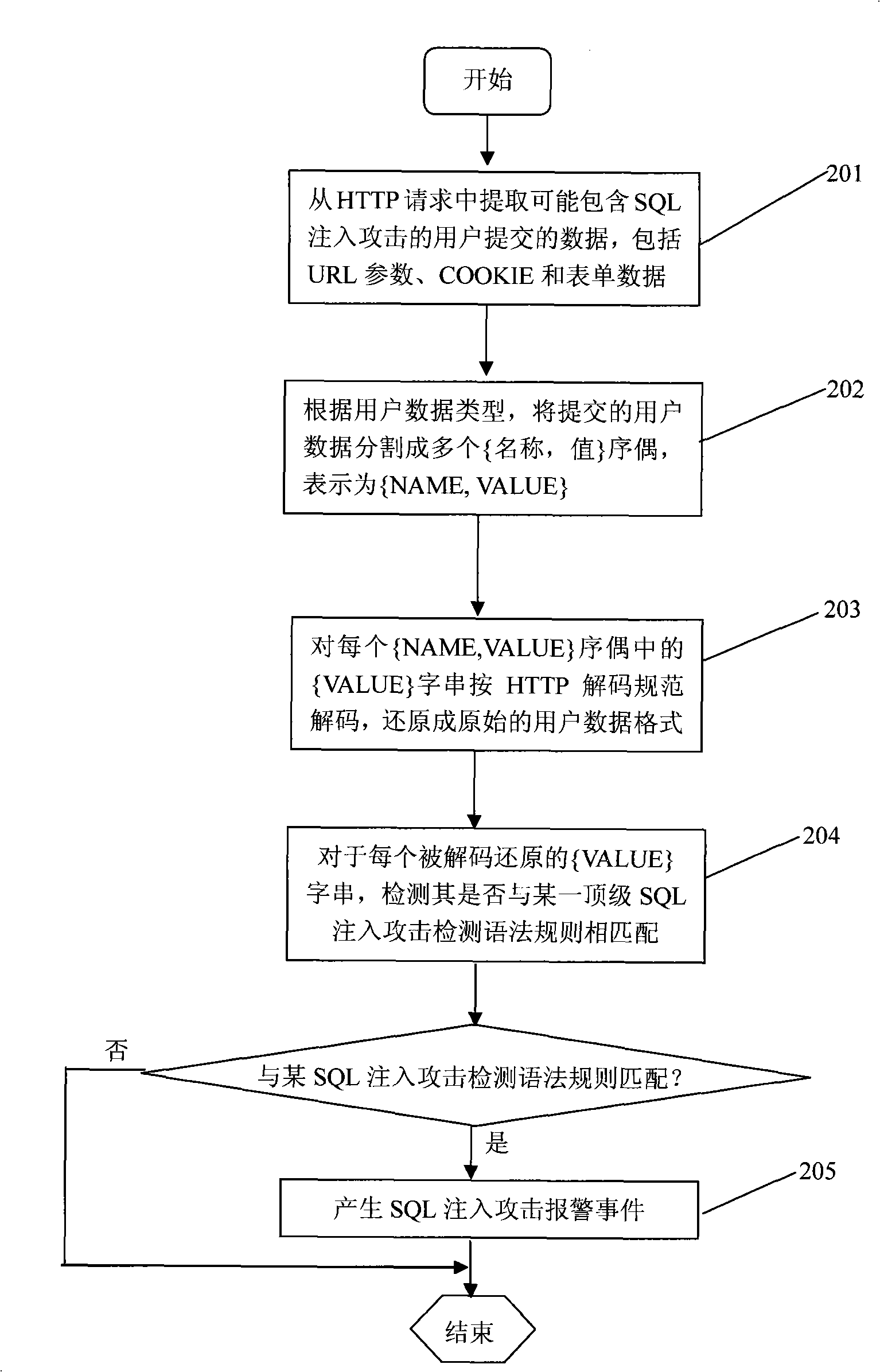
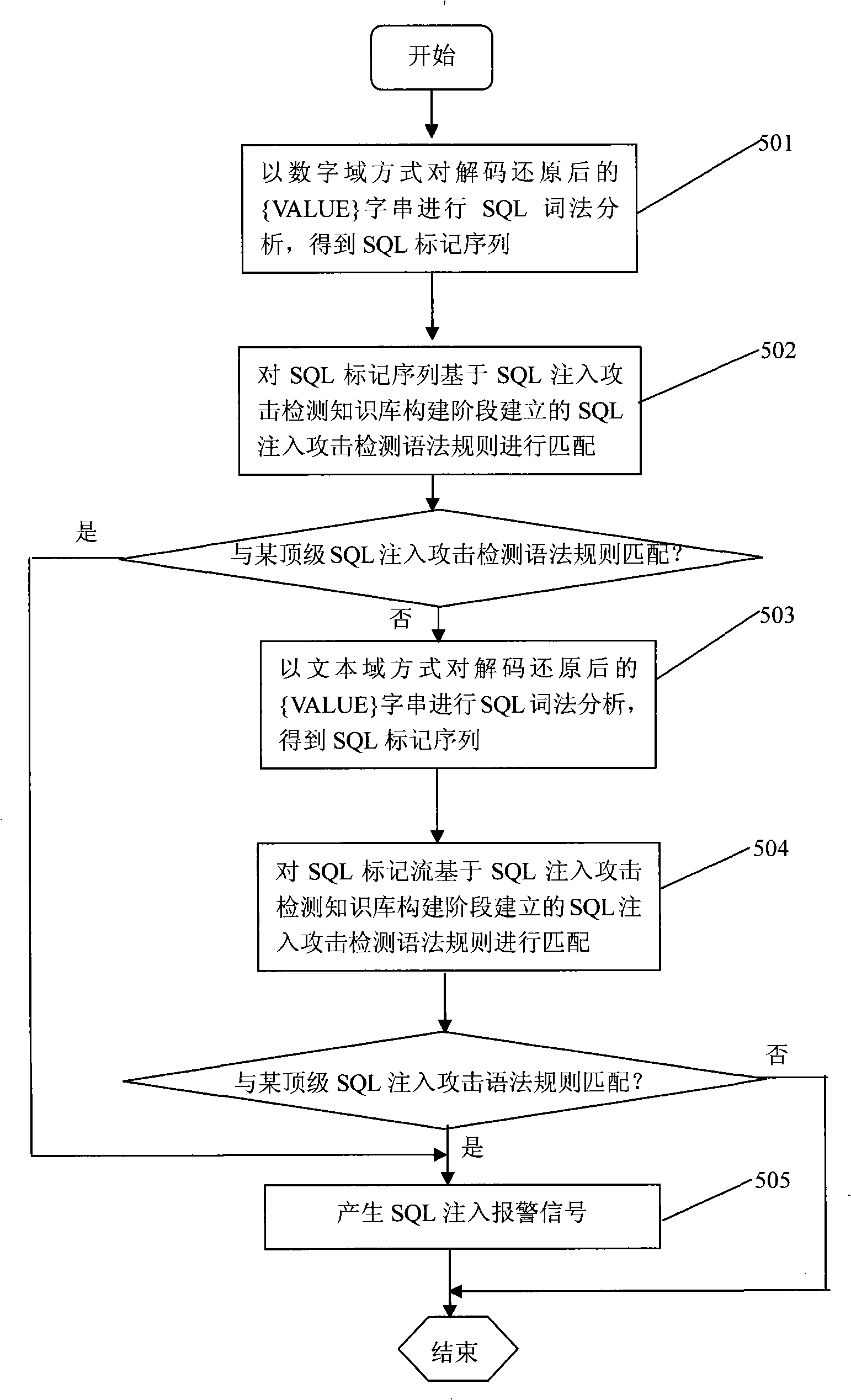
A SQL injection attack detection method and system
InactiveCN101267357AOvercoming difficult extractionOvercome shortcomings such as being easily deceivedUser identity/authority verificationData switching networksSQL injectionUser input
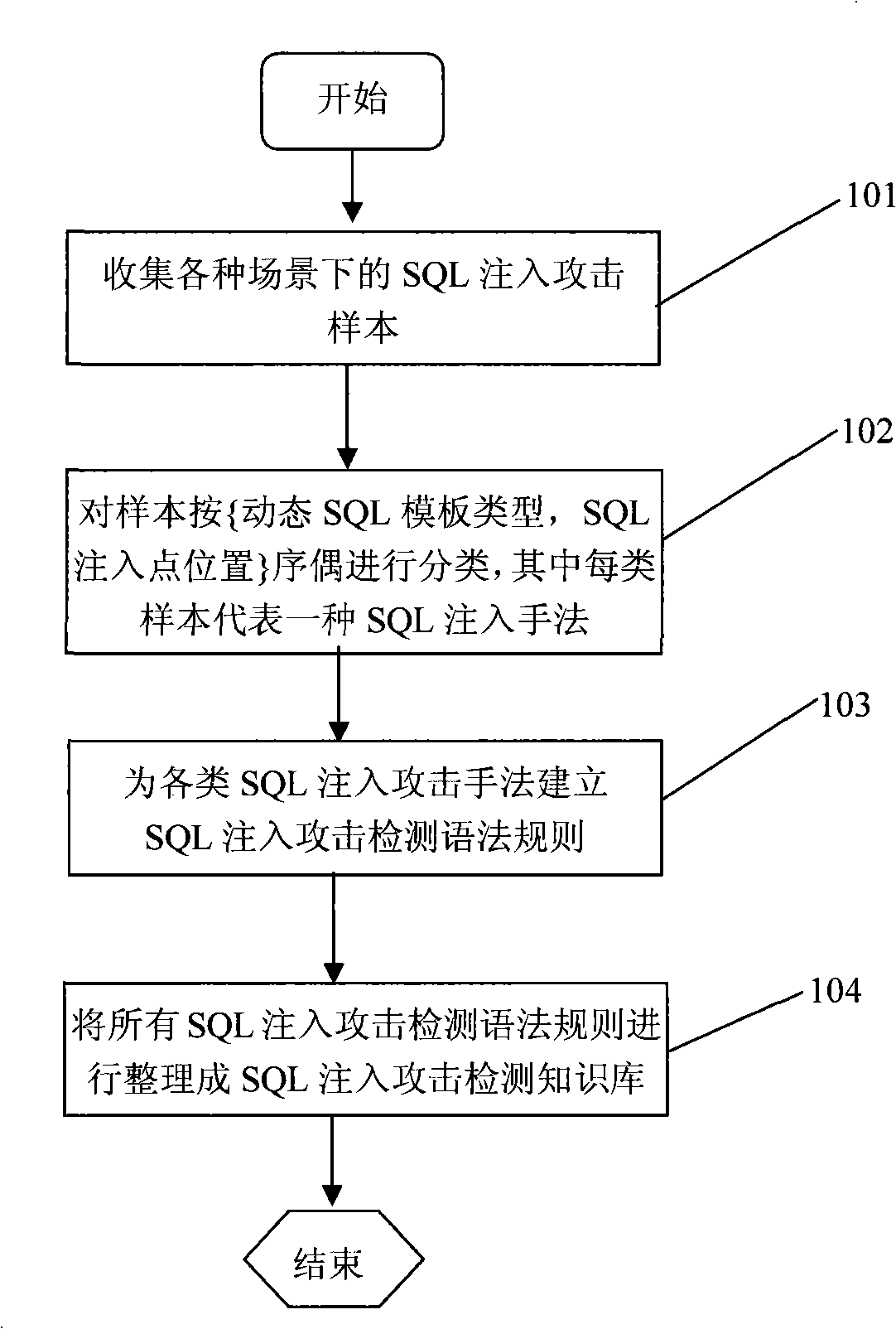
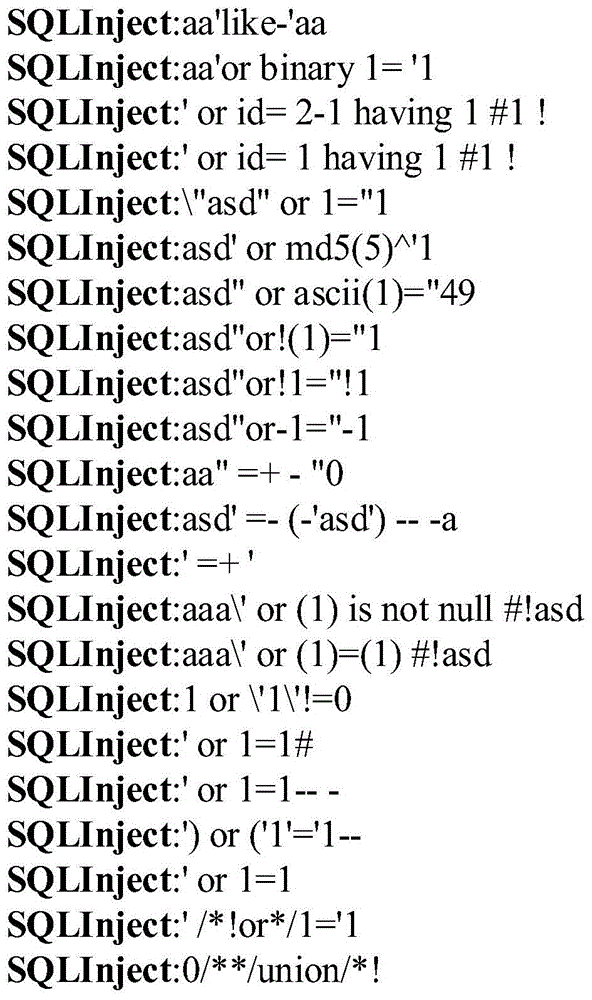
An SQL injection attack detecting method and system are provided, comprising building phase of SQL injection attack detecting knowledge base and detecting phase for real-time SQL injection attack. The build of SQL injection attack detecting knowledge base comprises collection of SQL injection attack sample for sorts of scenes, classification of SQL injection ways, and build of SQL injection attack detecting grammar rules aiming at sorts of SQL injection ways; the detecting phase for real-time SQL injection attack comprises extraction and decoding of user inputting data in HTTP request message and matching of the SQL injection attack detecting grammar rules and so on. This invention defines the SQL injection attack detecting grammar rules by using SQL grammar instead of defining the SQL injection attack detecting grammar rules based on the traditional attack characteristic. The invention overcomes shortcomings of uneasy extraction and inclined fraud of the attach characteristic sign of the SQL injection attack incident, which significantly reduces rate of wrong report and rate of missing report while invading the detecting system for detecting SQL injection attack.
Owner:BEIJING VENUS INFORMATION TECH
Attack signature generation
InactiveUS20070094728A1Raise the possibilityAccurate detectionMetering/charging/biilling arrangementsMemory loss protectionData processing systemNetwork addressing
The present invention provides a method for generating from requests from a first data network attack signatures for use in a second data network having a plurality of addresses assigned to data processing systems, the method comprising receiving data traffic from the first data network addressed to a number of unassigned addresses in a third data network; inspecting several incidents of the received data traffic for a common data pattern, upon finding a said data pattern, determining from the corresponding data traffic the attack signature for use in detecting attacks for the second data network. The invention also provides an apparatus for generating from requests on a first data network attack signatures for use in a second data network having a plurality of addresses assigned to data processing systems. The present invention further extends to a computer program element comprising computer program code means which, when loaded in a processor of a data processing system, configures the processor to perform a method for detecting attacks on a data network as hereinbefore described. The present invention further extends to a method of supporting an entity in the handling of a detected attack.
Owner:IBM CORP
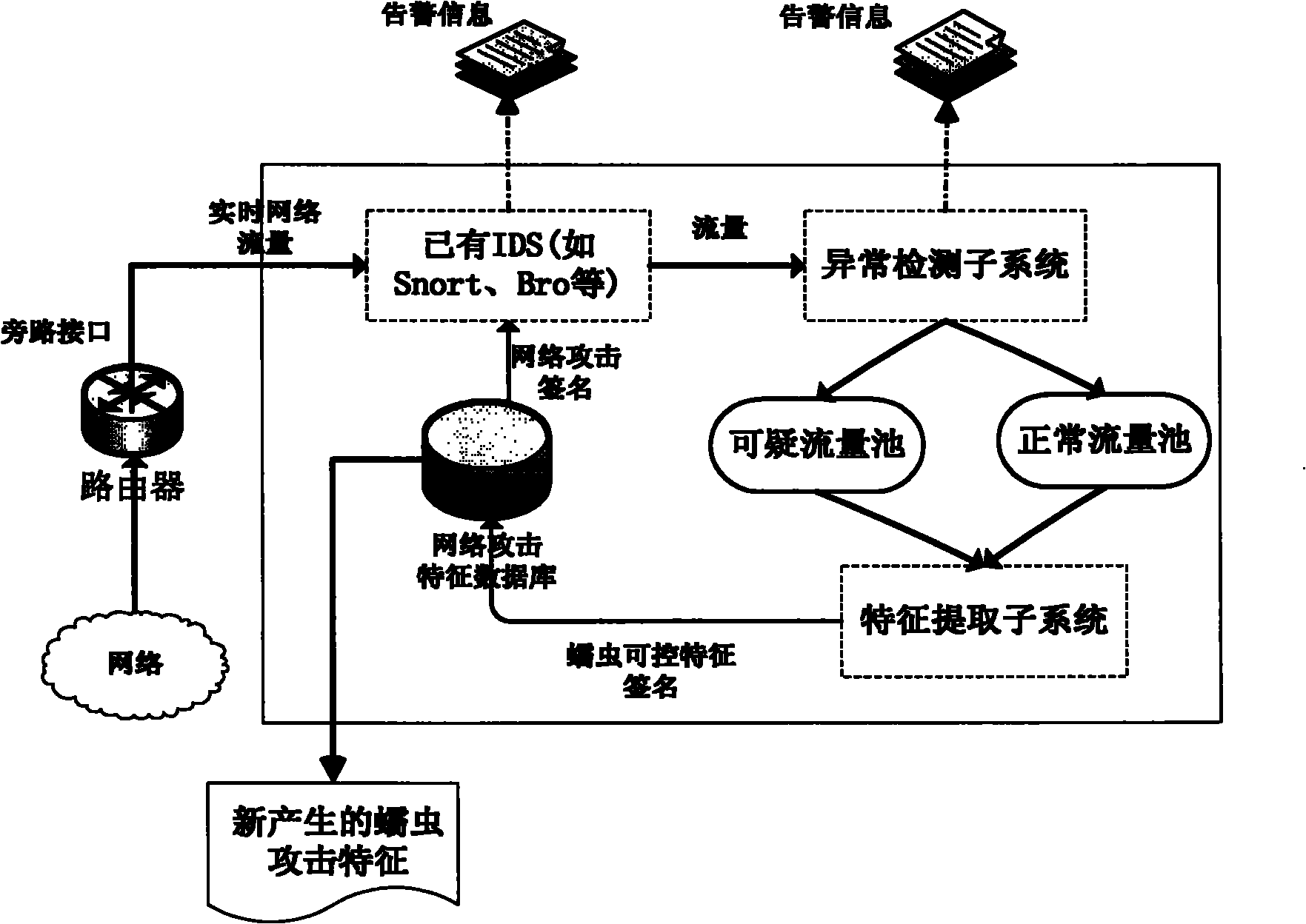
Network worm detection and characteristic automatic extraction method and system
InactiveCN101895521AStop the spreadAccurate discoveryData switching networksFeature extractionAnomaly detection
The invention discloses a network worm detection and characteristic automatic extraction method and a network worm detection and characteristic automatic extraction system and belongs to the technical field of network safety. The method comprises the following steps of: 1) performing abnormal detection on captured network data packets, and dividing the data packets into suspicious network flow and normal network flow according to detection results; 2) storing the suspicious network flow in a suspicious flow pool, and storing the normal network flow in a normal flow pool; 3) clustering the network flow in the suspicious flow pool and the normal flow pool, and extracting a characteristic signature; and 4) updating the extracted characteristic signature in a network attack database, and detecting the network worm. The system comprises an abnormal detection subsystem, a characteristic extraction subsystem, a network attack characteristic database, and a misuse detection system. The methodand the system can more accurately and timely discover the network worm, can automatically extract the worm characteristics and update the attack characteristic database of the existing misuse detection system. Therefore, the aim of suppressing worm propagation is really fulfilled.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
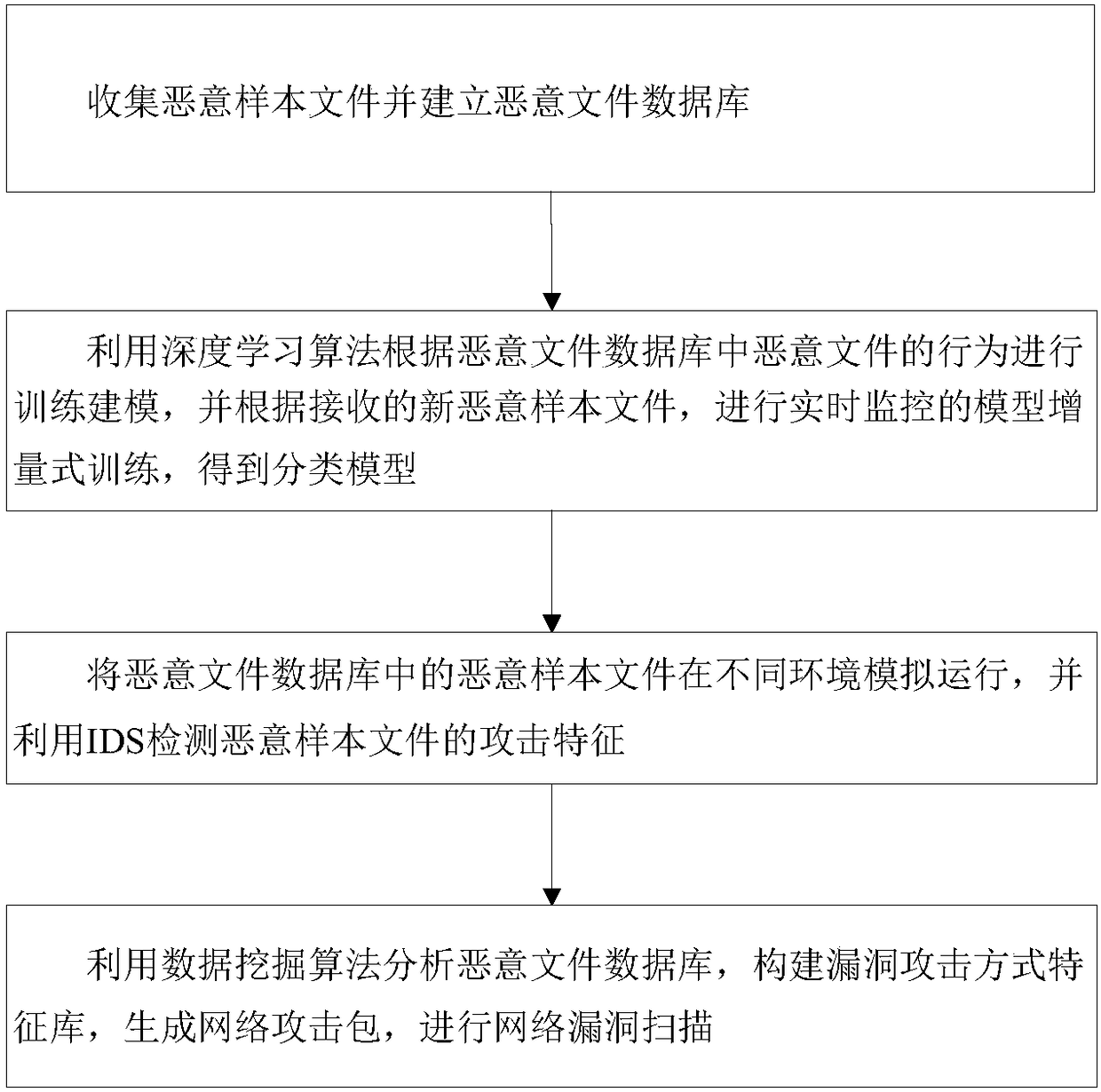
Deep learning-based network intrusion detection and vulnerability scanning method and devices
The invention discloses a deep leaning-based network intrusion detection and vulnerability scanning method and devices. The method comprises the steps of collecting malicious sample files and buildinga malicious file database; performing training modeling according to behaviors of malicious files in the malicious file database by using a deep learning algorithm, performing real-time monitored model incremental training according to received new malicious sample files, so as to obtain classified models; simulating and running the malicious sample files in the malicious file database in different environments, and detecting an attack characteristic of the malicious sample files by using IDS; and analyzing the malicious file database by using a data mining algorithm, building a vulnerabilityattack manner characteristic library, generating a network attack package, and scanning network vulnerabilities.
Owner:JINING POWER SUPPLY CO OF STATE GRID SHANDONG ELECTRIC POWER CO +1
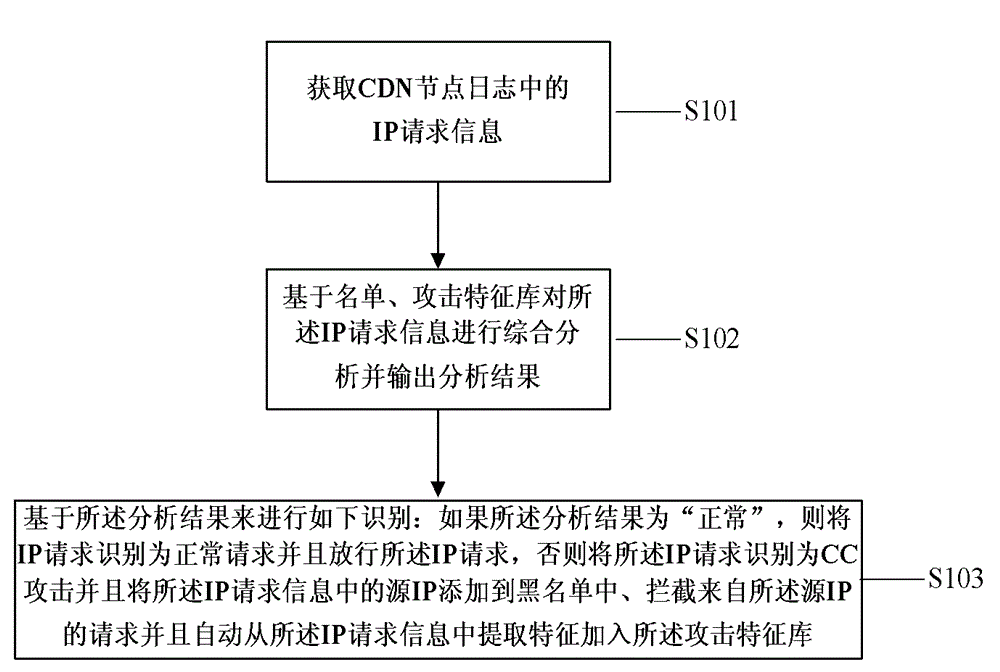
Method and apparatus for recognizing CC attacks based on log analysis
ActiveCN104065644AAchieve the purpose of automatic learningTransmissionSpecial data processing applicationsInternet ProtocolAttack signature
The invention relates to a method and an apparatus for recognizing CC (Challenge Collapsar) attacks based on log analysis. The method for recognizing CC attacks based on log analysis comprises the steps of obtaining IP (Internet Protocol) request information in logs, comprehensively analyzing the IP request information based on a list and an attack characteristic library and outputting an analysis result, and carrying out recognition based on the analysis result, namely recognizing IP requests as normal requests and releasing the IP requests if the analysis result is normal, and otherwise, recognizing the IP requests as the CC attacks, and adding source IPs in the IP request information to a blacklist, intercepting requests from the source IPs and automatically extracting characteristics from the IP request information and adding the characteristics to the attack characteristic library.
Owner:BEIJING KNOWNSEC INFORMATION TECH
Attack prevention system based on structured query language (SQL)
ActiveCN101448007AImprove accuracyNo false positivesData switching networksSpecial data processing applicationsFeature extractionApplication server
The invention provides a modified misuse-type structured query language (hereinafter referred as to SQL) attack defense system which is based on application system services and an SQL-injected characteristic extraction malicious attack behavior characteristic library and combined with the SQL request of the characteristic library to a user to carry out strict test and block the SQL request with the attack characteristics according to test results, so as to provide the security protection for the database and the corresponding audit record. The invention can be flexibly allocated to boundary defense devices, application servers, database servers and various security audit software, and the SQL attack behavior characteristic library can be updated at any time when the application environment is changed and a new attack type or normal behavior pattern appears.
Owner:CHINA ELECTRIC POWER RES INST +2
Method for mining attack frequent sequence mode from Web log
ActiveCN105721427ATransmissionSpecial data processing applicationsSequence databaseUniform resource locator
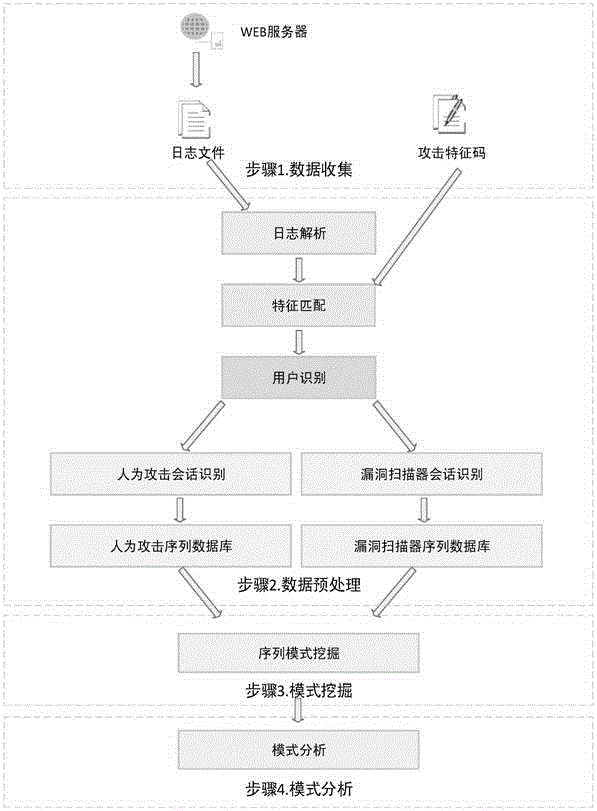
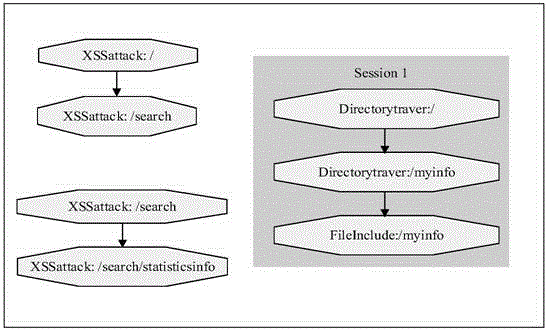
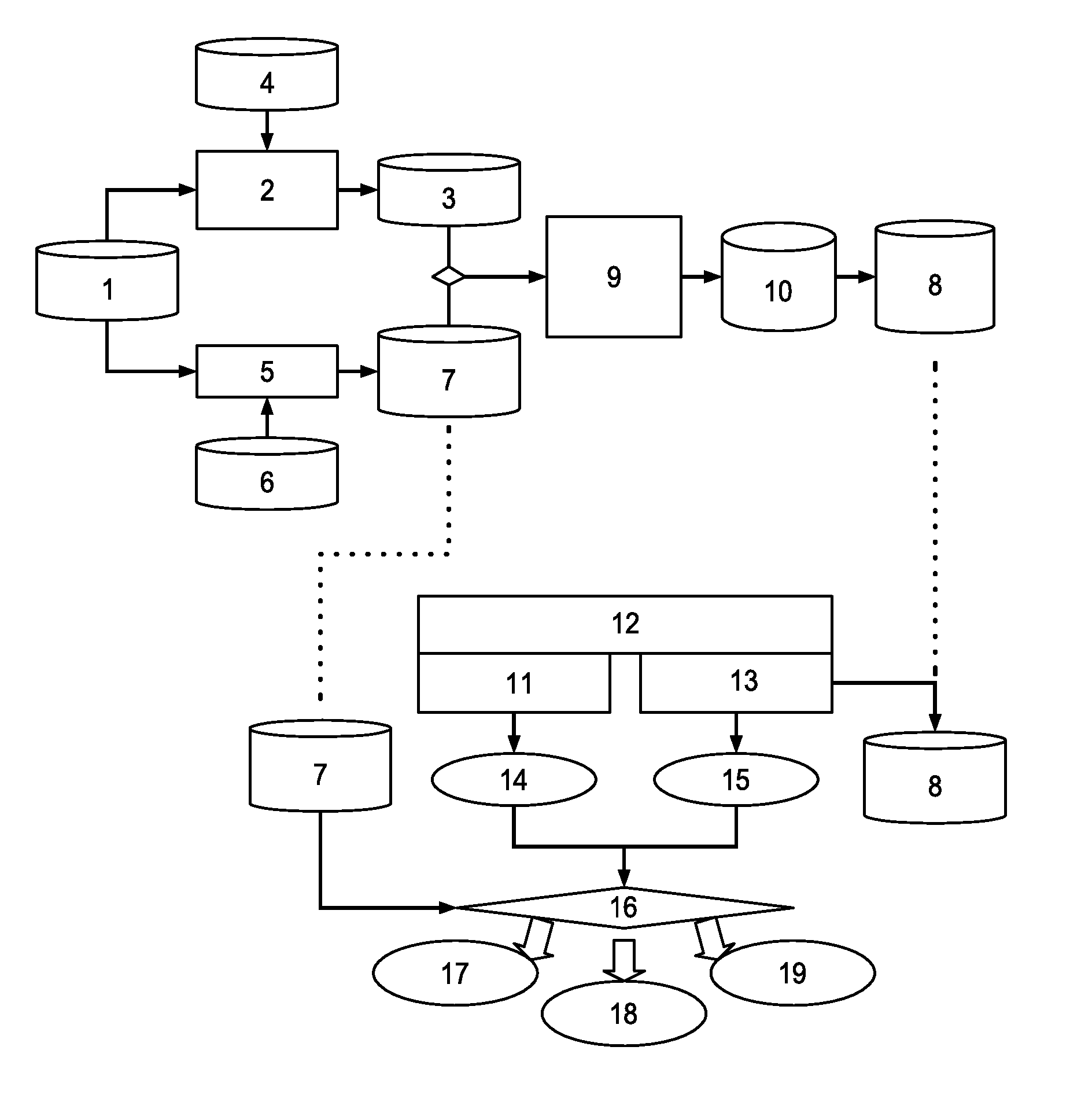
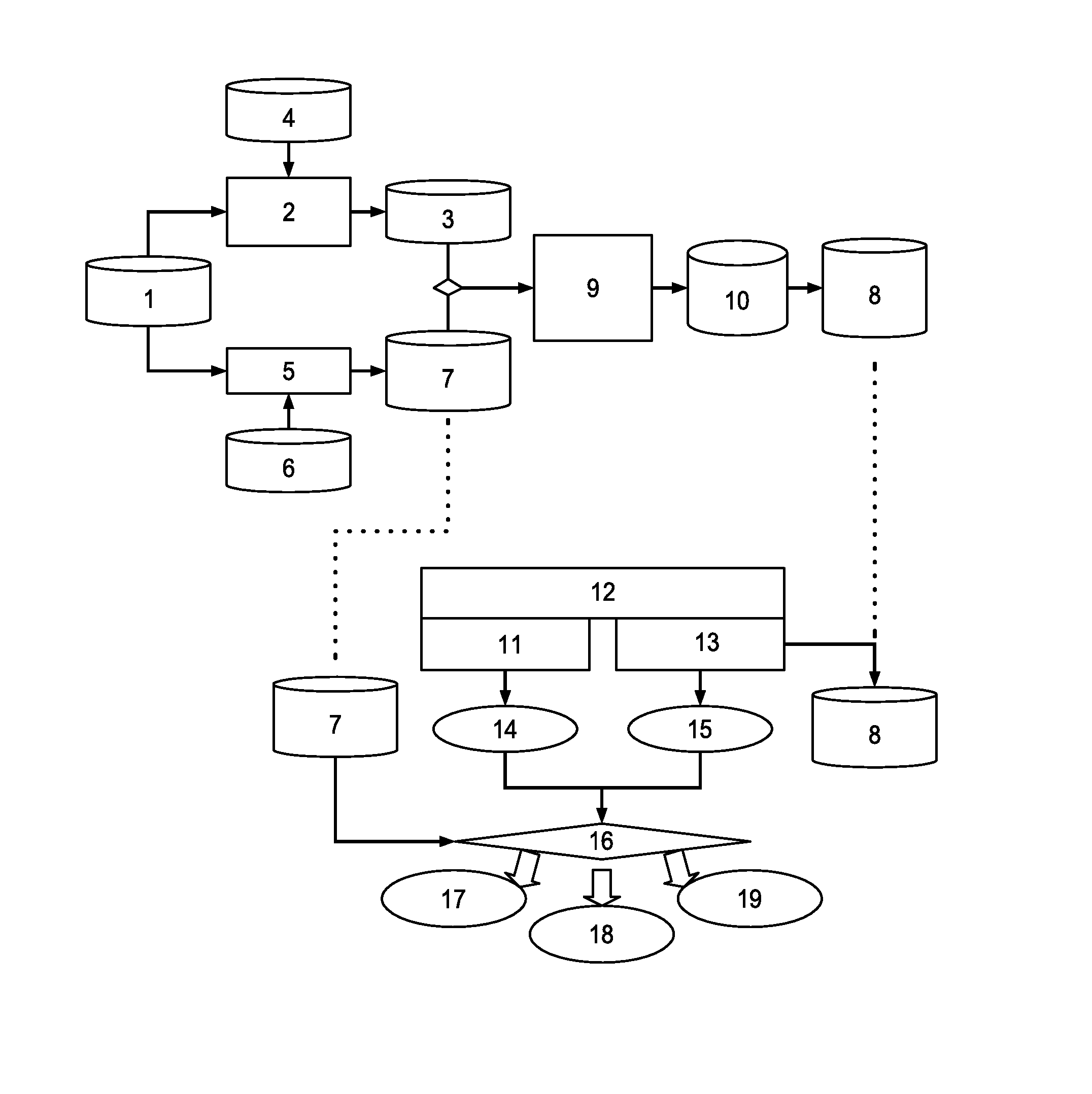
The invention relates to data mining in the field of network security and especially relates to a method for mining an attack frequent sequence mode from a Web log. The method comprises the following steps: collecting website access log files, website information and attack feature codes; analyzing a website log structure, matching analyzed URLs with the collected attack feature codes, obtaining attack records, and clearing up the URLs; performing user identification on attack log data and distinguishing manual attacks and attacks of a loophole scanner; respectively performing session identification to obtain a sequence database of the manual attacks and a sequence database of the loophole scanner; converting a character string database into a digital database, and respectively mining a frequent sequence of the sequence database by use of a sequence mode mining method; and maximizing the frequent sequence obtained through mining and converting a sequence mode into visual figure language. The process is indicated in the first graph. The method provided by the invention can realize visualization of an attack mode and explores a scanning sequence in the loophole scanner.
Owner:HUNAN UNIV
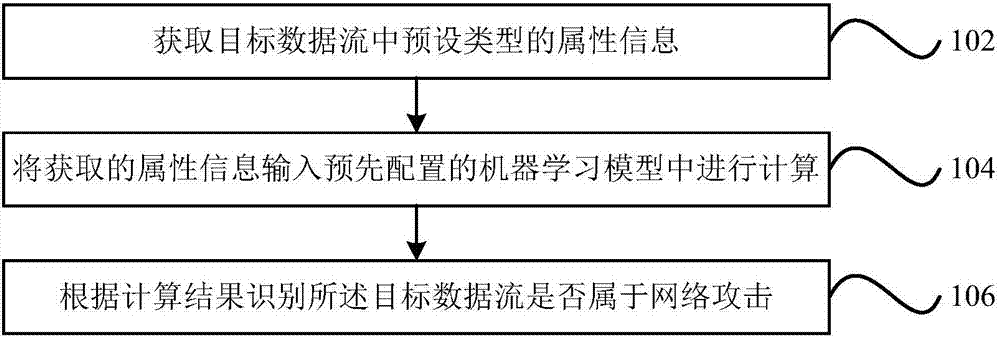
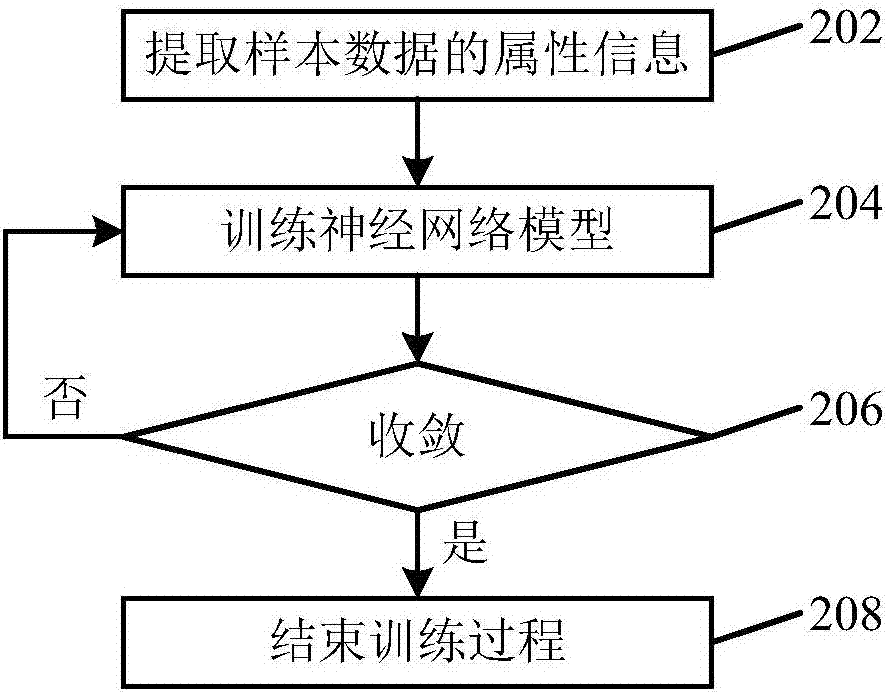
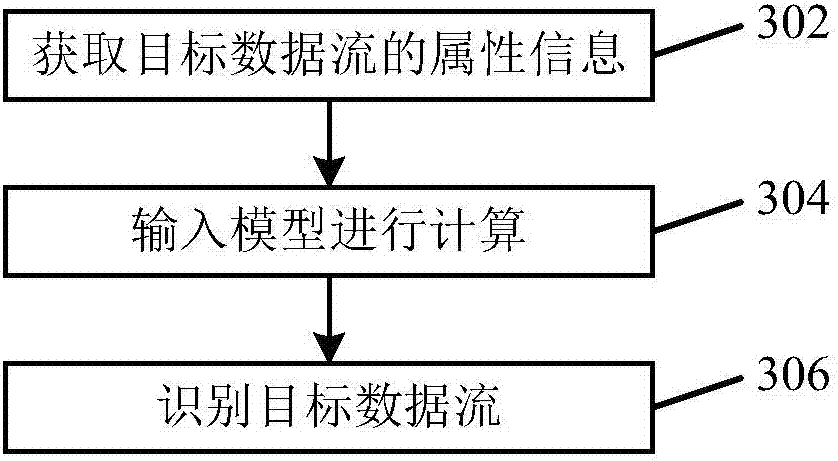
Network attack identification method and device as well as computer readable storage medium
The application provides a network attack identification method and device as well as a computer readable storage medium. The method may include the following steps: acquiring a preset type of attribute information in a target data stream; inputting the acquired attribute information into a preconfigured machine learning model for calculation, wherein the machine learning model is obtained by training sample data through a supervised learning algorithm; and identifying whether the target data stream belongs to network attacks according to a calculation result. According to the technical scheme provided by the application, the data stream that belongs to the network attacks can be effectively identified; and meanwhile, the network attacks can be identified without extracting attack features, and messages that are transmitted through covert channels, encrypted channels and other modes and belong to the network attacks can be identified.
Owner:HANGZHOU DPTECH TECH
Intrusion detection method and system
ActiveUS20100287615A1Efficient methodMemory loss protectionError detection/correctionGoal systemSecurity alarm
Intrusion detection method for detecting unauthorized use or abnormal activities of a targeted system of a network, comprising the steps: creating defined preconditions for each vulnerability related to the targeted system and / or for each attack that exploit one or several vulnerabilities; creating assurance references corresponding to said defined preconditions and considering the targeted perimeter capturing data related to the targeted system; comparing captured data with attack signatures for generating at least one security alert when captured data and at least one attack signature match; capturing assurance data from monitoring of the targeted perimeter comparing assurance data, issued from assurance monitoring of the targeted perimeter, with assurance references for generating assurance information when said data issued from assurance monitoring and at least one assurance reference match retrieving the preconditions of the generated security alert checking if assurance information corresponding to said preconditions has been retrieved generating a verified security alarm when generated security alert and its retrieved precondition match with at least one corresponding assurance information filtering said security alert when no match has been found between its retrieved preconditions and at least one corresponding assurance information; emitting a non verified security alert when no preconditions have been retrieved for this alert and / or no assurance reference corresponding to said preconditions has been defined.
Owner:ALCATEL LUCENT SAS
Agent-based intrusion detection system
ActiveUS7370358B2Messaging overhead can be very lowFirmly connectedMemory loss protectionDigital data processing detailsSystems designMessage passing
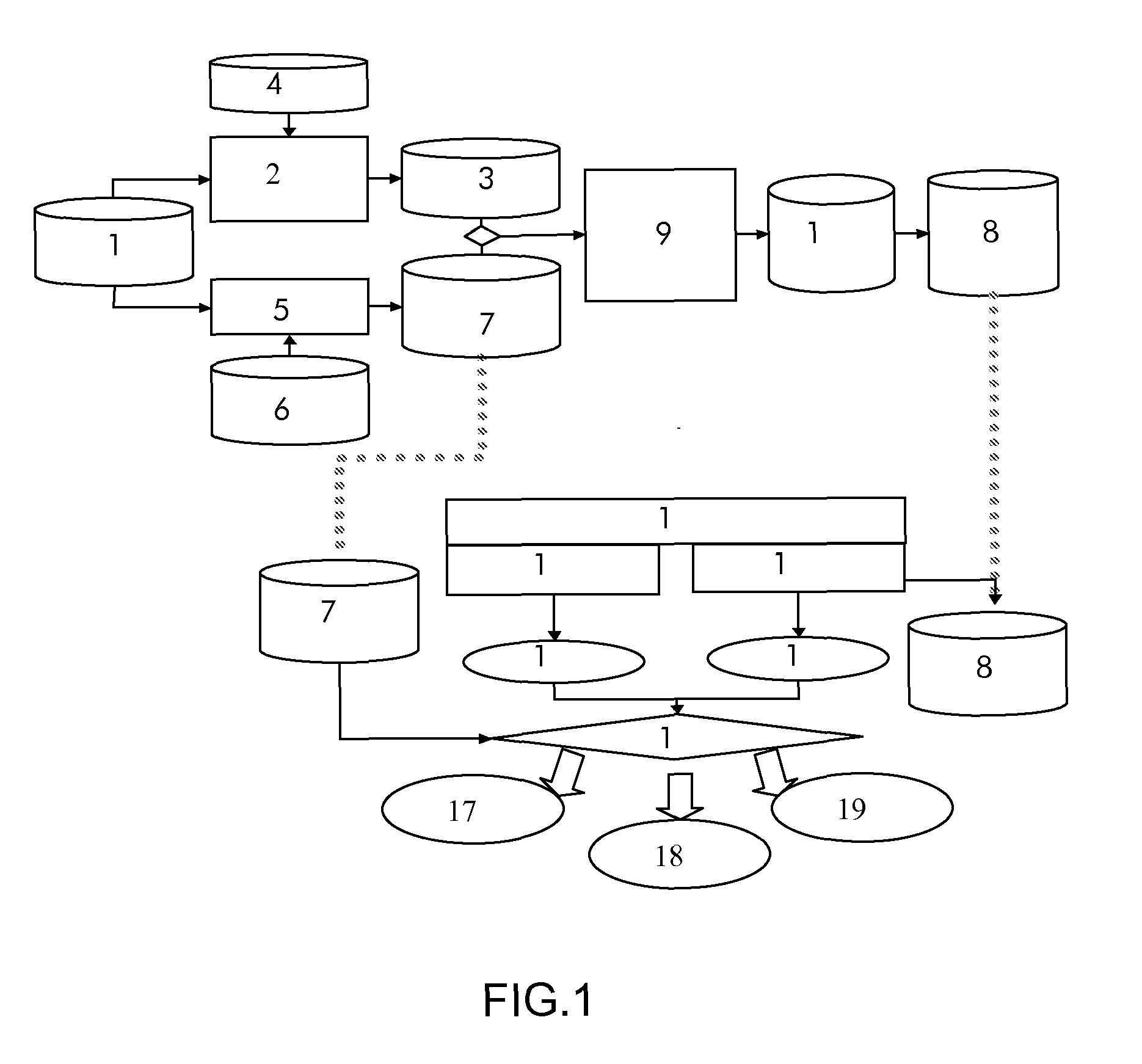
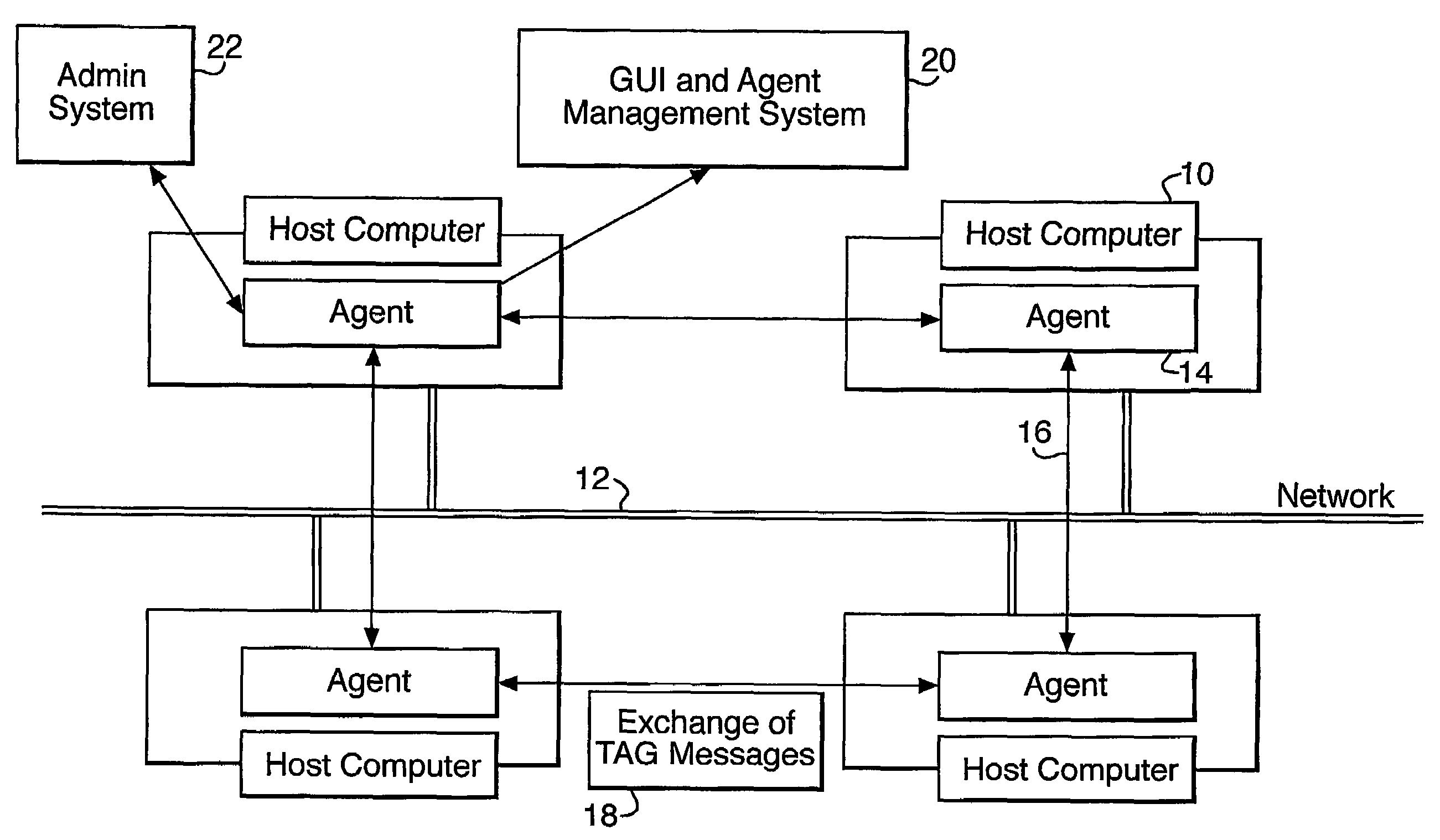
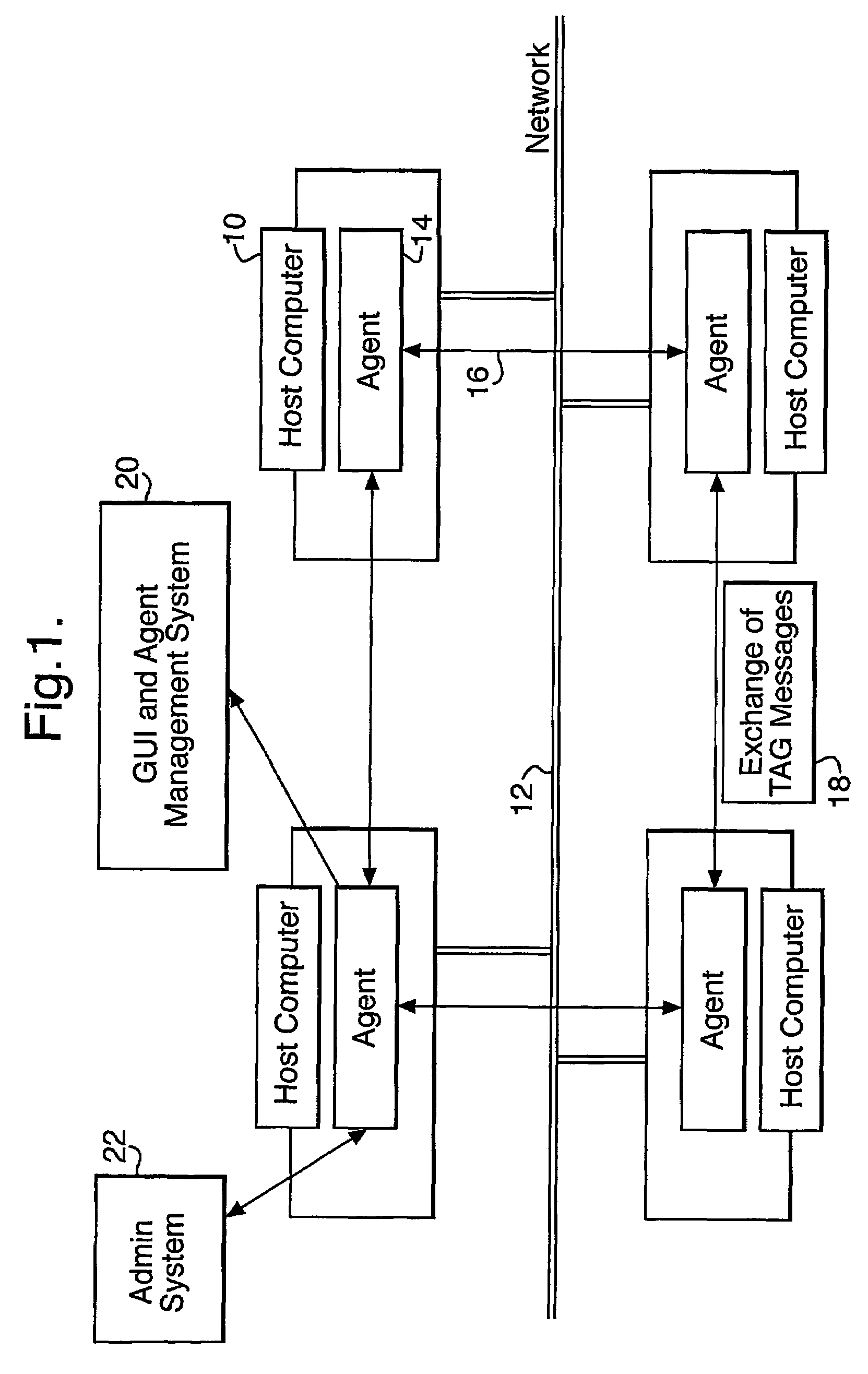
A computer security system uses a plurality of co-operating software agents to protect a network against attack. Individual agents at each node the network co-operatively act to detect attacks and to share attack signatures and solutions via a message exchange mechanism. A global internal measurement of the overall health of the group of agents may be used as an indicator of a possible attack. In larger networks, the agents may be formed a plurality of separate autonomous groups, with a common group identity being automatically maintained by the message passing mechanism. Individual groups may be located by a system designer in separate cells or domains within the network, so that if one cell becomes compromised the rest of the network is not affected.
Owner:BRITISH TELECOMM PLC
Attack detection method and system for WEB
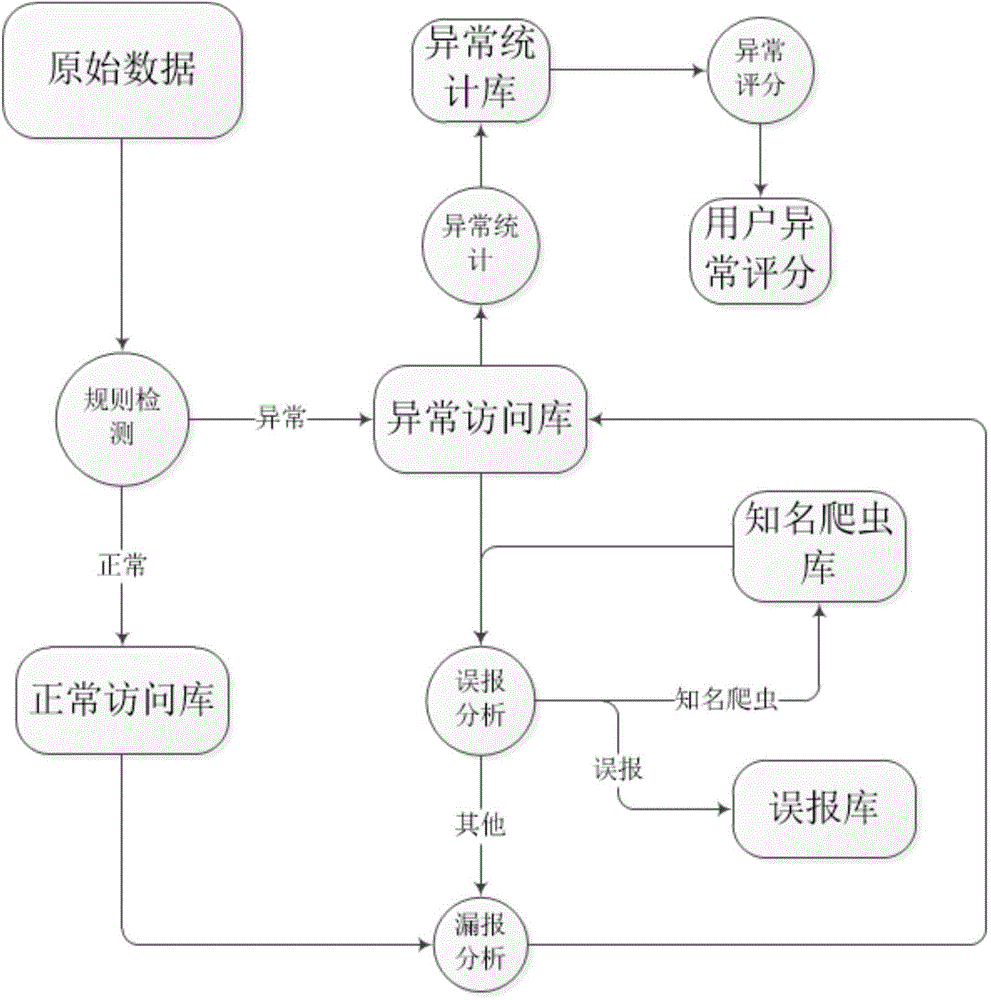
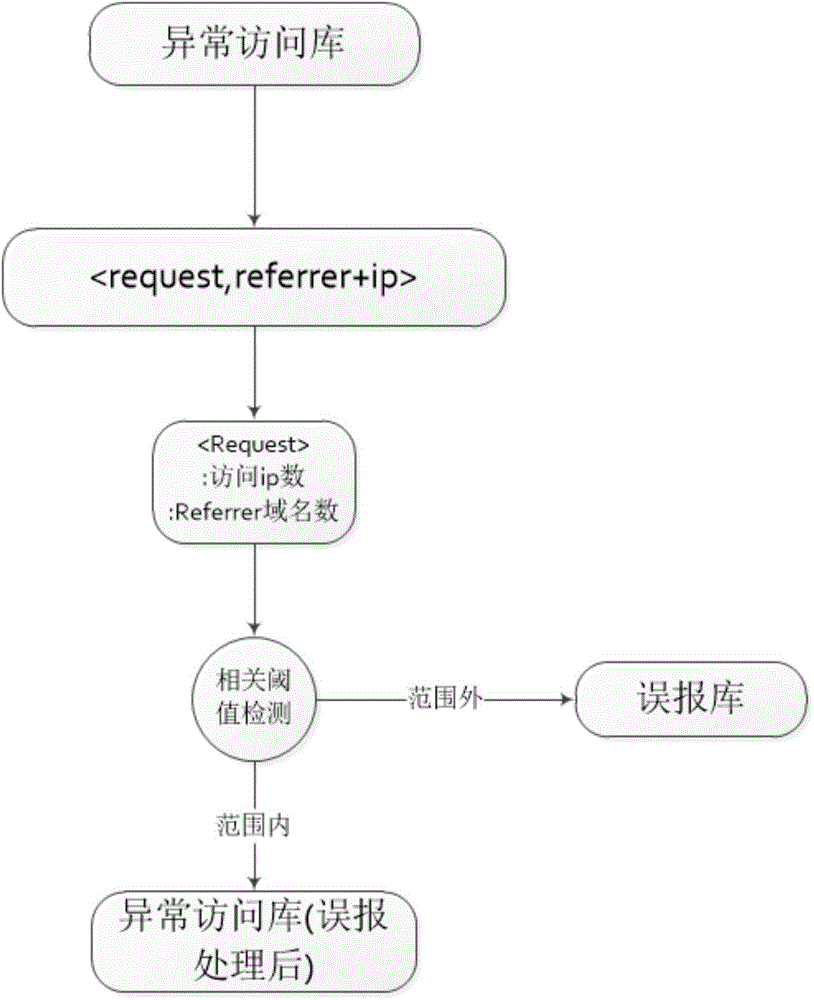
The invention discloses an attack detection method and system for WEB; the method comprises the following steps: firstly implementing attack characteristic detection to the url accessed by a user; then implementing misinformation analysis and fail-to-declare analysis treatment to the detection result, wherein the misinformation analysis mainly solves the misinformation caused by normal embedded resources of the website and the web crawlers, the fail-to-declare analysis is to treat the undetected abnormal behaviors conducted by the detected abnormal users. Based on the results of the treatment above, calculating the total normal access time of each abnormal user under each domain name; when the access time is less than the average value of all users, taking the ratio between the access time and the average value as an abnormality scoring index of the abnormal user; otherwise, the abnormality score is a weighted value w of the ratio between the access time and the maximum access time of all users. By the misinformation analysis and fail-to-declare analysis treatment, the efficiency of the attack detection method and system for WEB is significantly increased.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Automated network attack characteristic generation method
ActiveCN101616151AEasy to findEasy extractionData switching networksSpecific program execution arrangementsGeneration processSequence processing
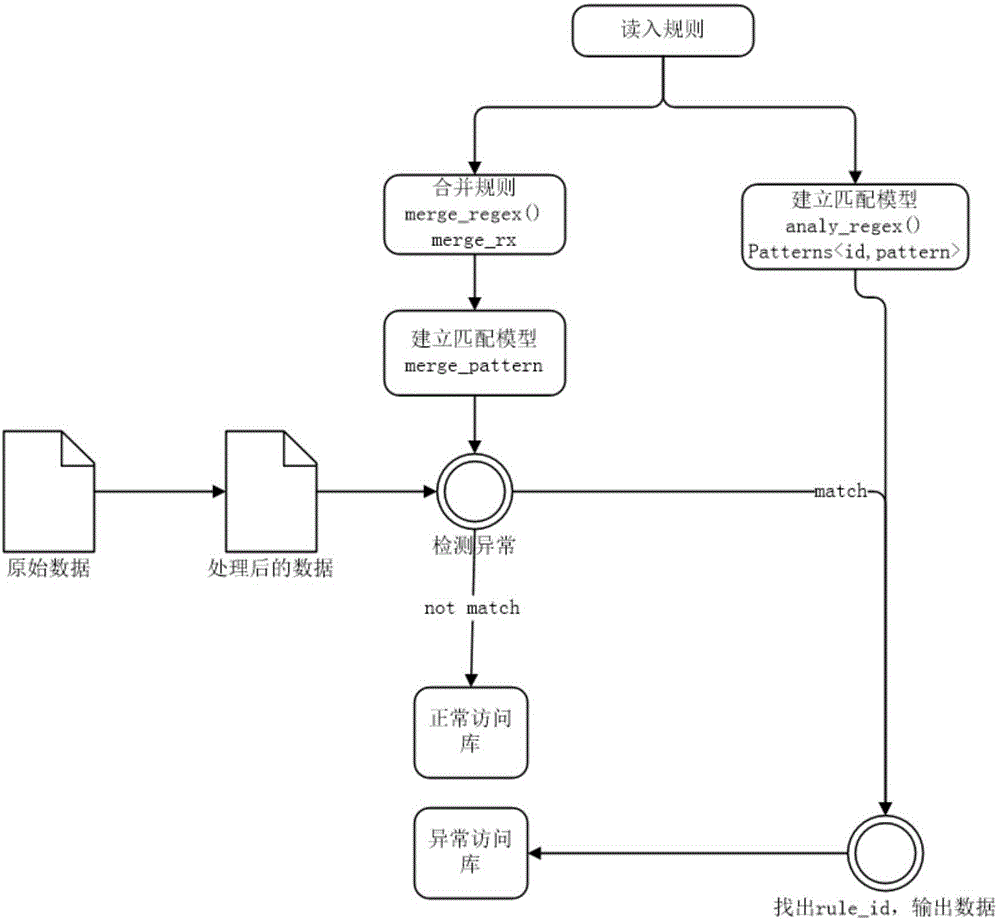
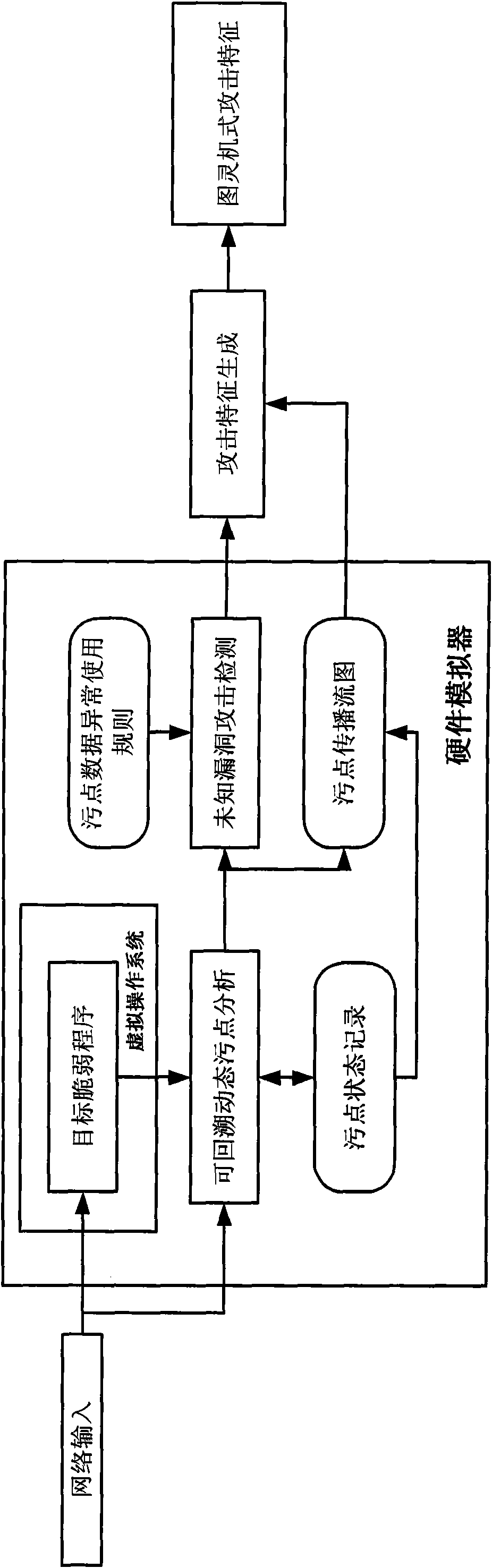
The invention discloses an automated network attack characteristic generation method, comprising the following steps: 1) a virtual operating system is installed in a virtual host, an operation environment coincident with the real application of a brittle program is configured, and a taint data operation rule is configured; 2) the brittle program is started, all network input thereof is marked as the taint data to be monitored, the state of the taint data is recorded, and relative operation command of the taint data is recorded to form a taint transmission flow graph; 3) when the abnormal operation of the taint data is detected, a command sequence operated and handled by the brittle the taint data starting from the input data pack is obtained from the taint transmission flow graph; 4) the command sequence is processed to be a compiling performing command, and a judging output sentence is added to generate Turing-type attack characteristics. The method of the invention is favourable for finding unknown bug attack behaviour and extracting the attack flow and has no need of obtaining brittle program source code, the generated attack characteristics are more accurate, and the attack characteristic generation process is automatic and quick.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
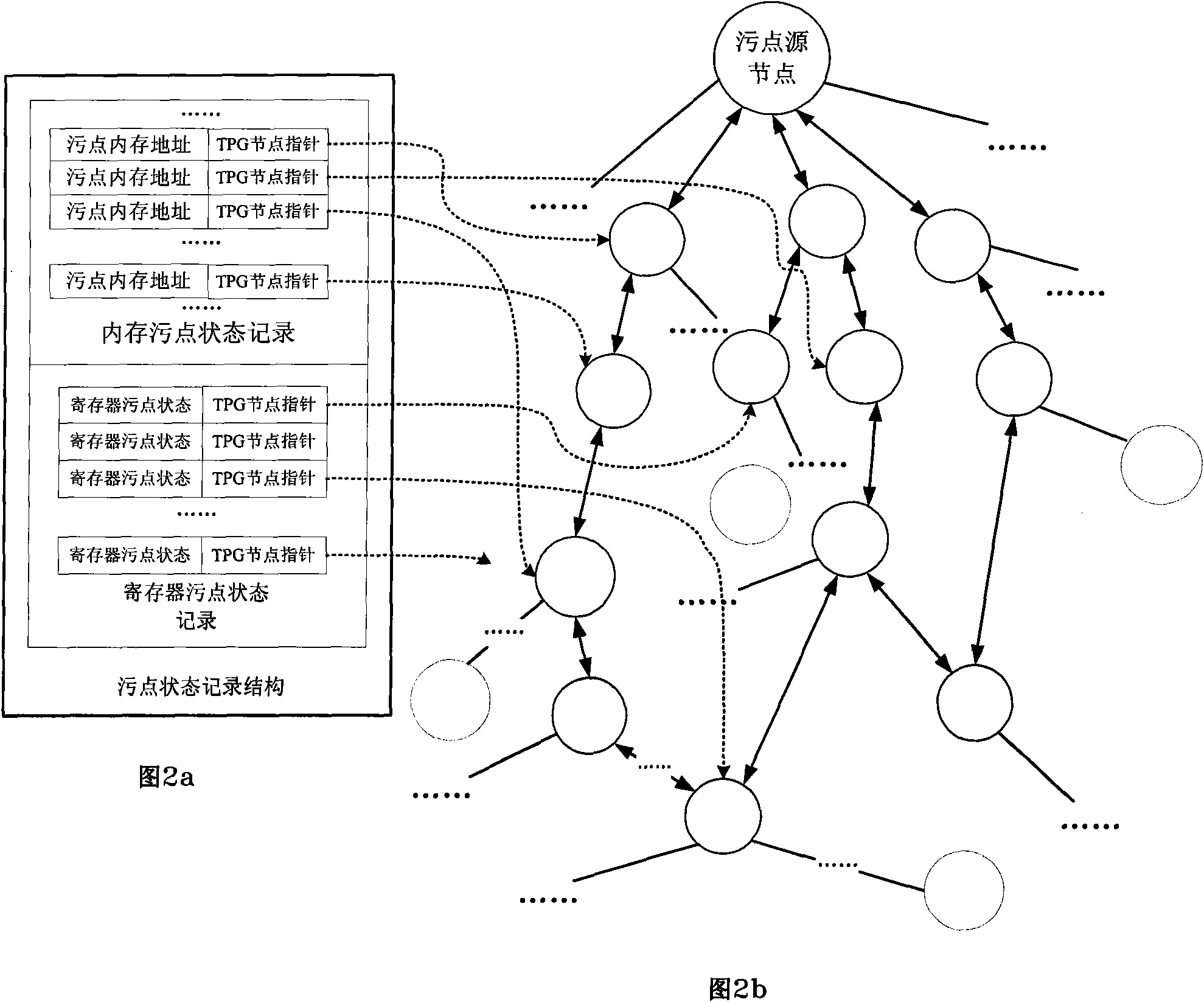
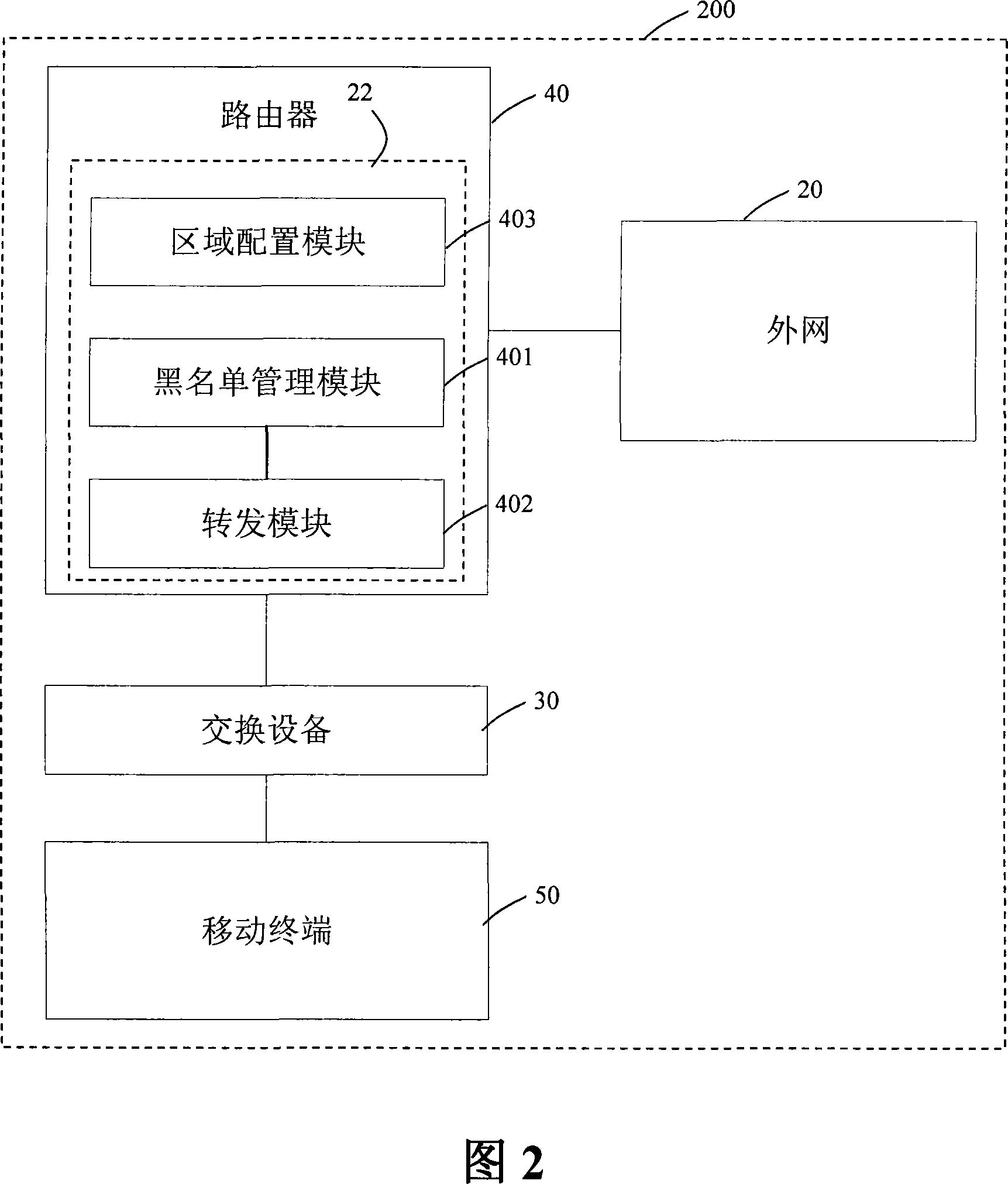
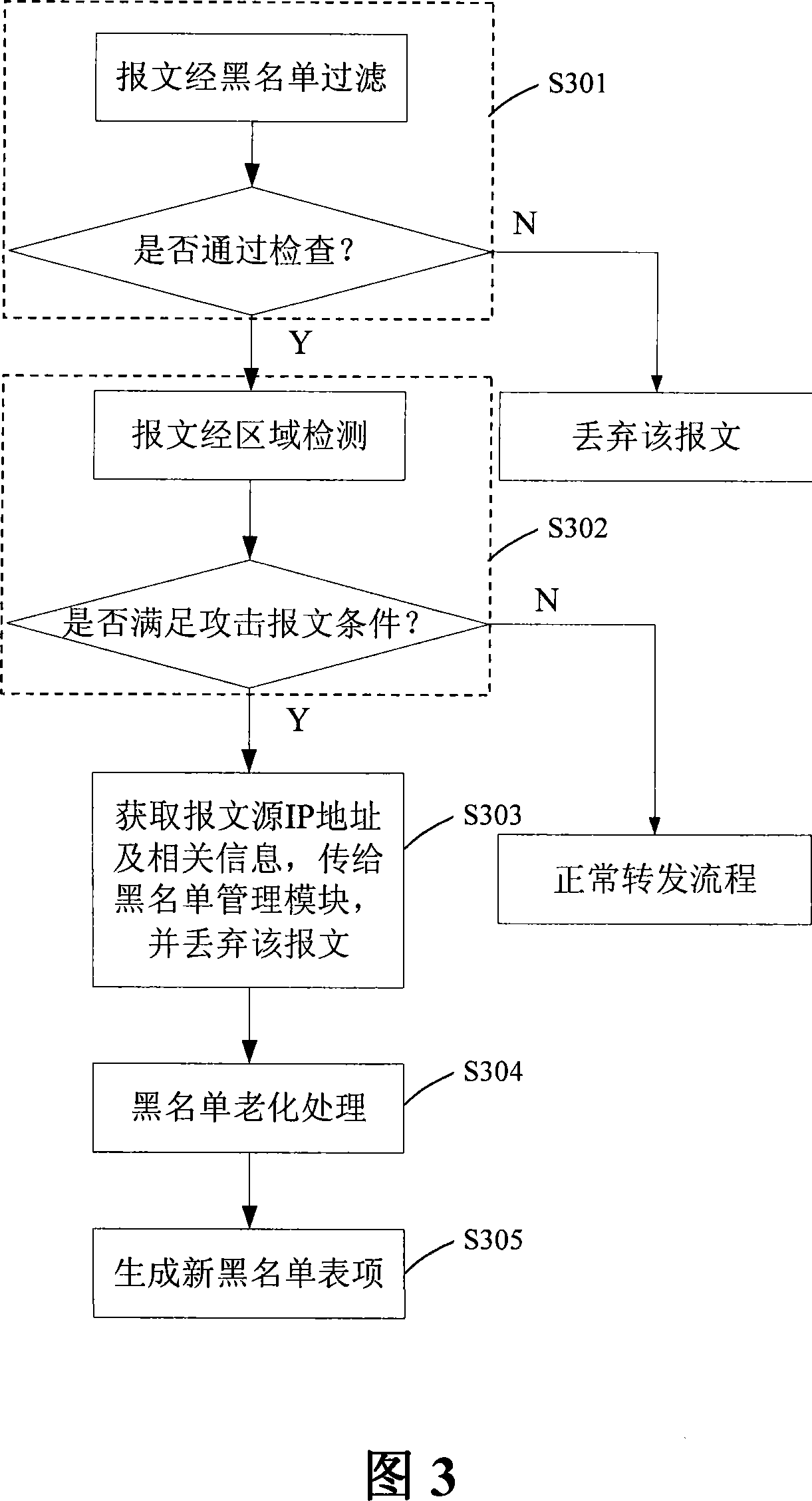
A blacklist real time management method and device
InactiveCN101188612AImprove securityImprove real-time performanceData switching networksSpecial data processing applicationsCommunications systemReal time management
The invention discloses a method for real-time blacklist management and the device thereof, wherein, the method comprise the following steps: step one, a transmission module sends detected message information with attack signature to a blacklist management module, and discards the message; step two, the blacklist management module searches all the blacklist list items in the blacklist, deletes aged blacklist list items, and adds the information into the blacklist list items. The invention adopts a module optimization treatment mode, obtains technical and security progresses, and truly achieves the effect of the real-time blacklist management. No information interaction exists between the modules, therefore the designs in the modules are required to be compactor and more logical, thereby the real time and the stability of the blacklist management are better, and the security of a communication system is higher.
Owner:ZTE CORP
Device and method for specifically and dynamically deploying and capturing malicious samples by using honeypot
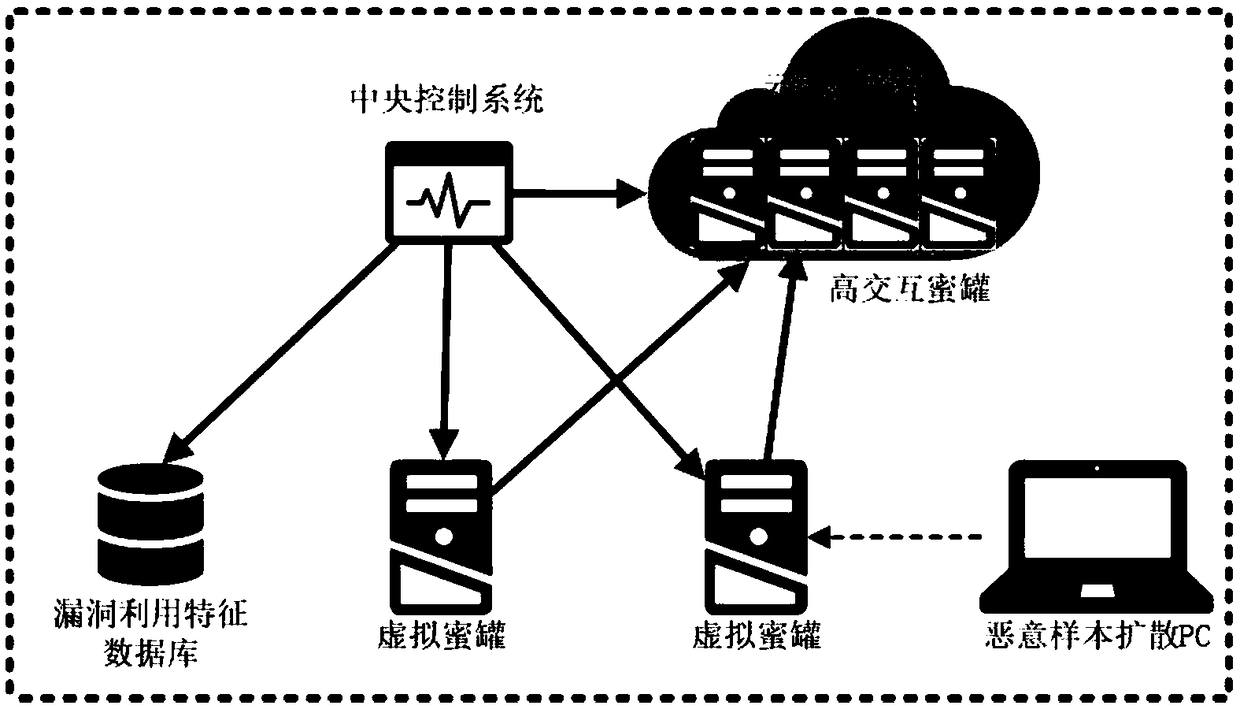
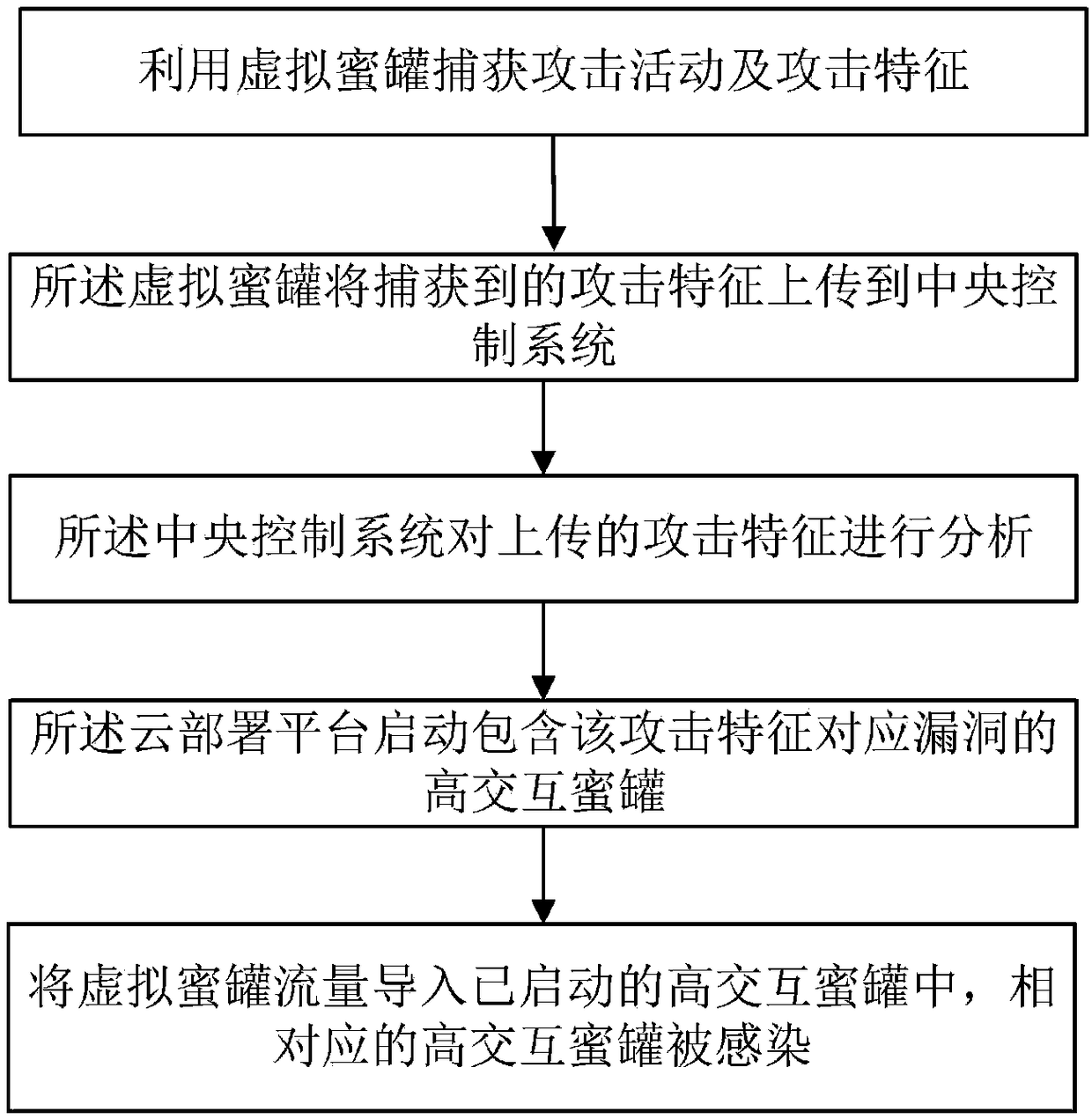
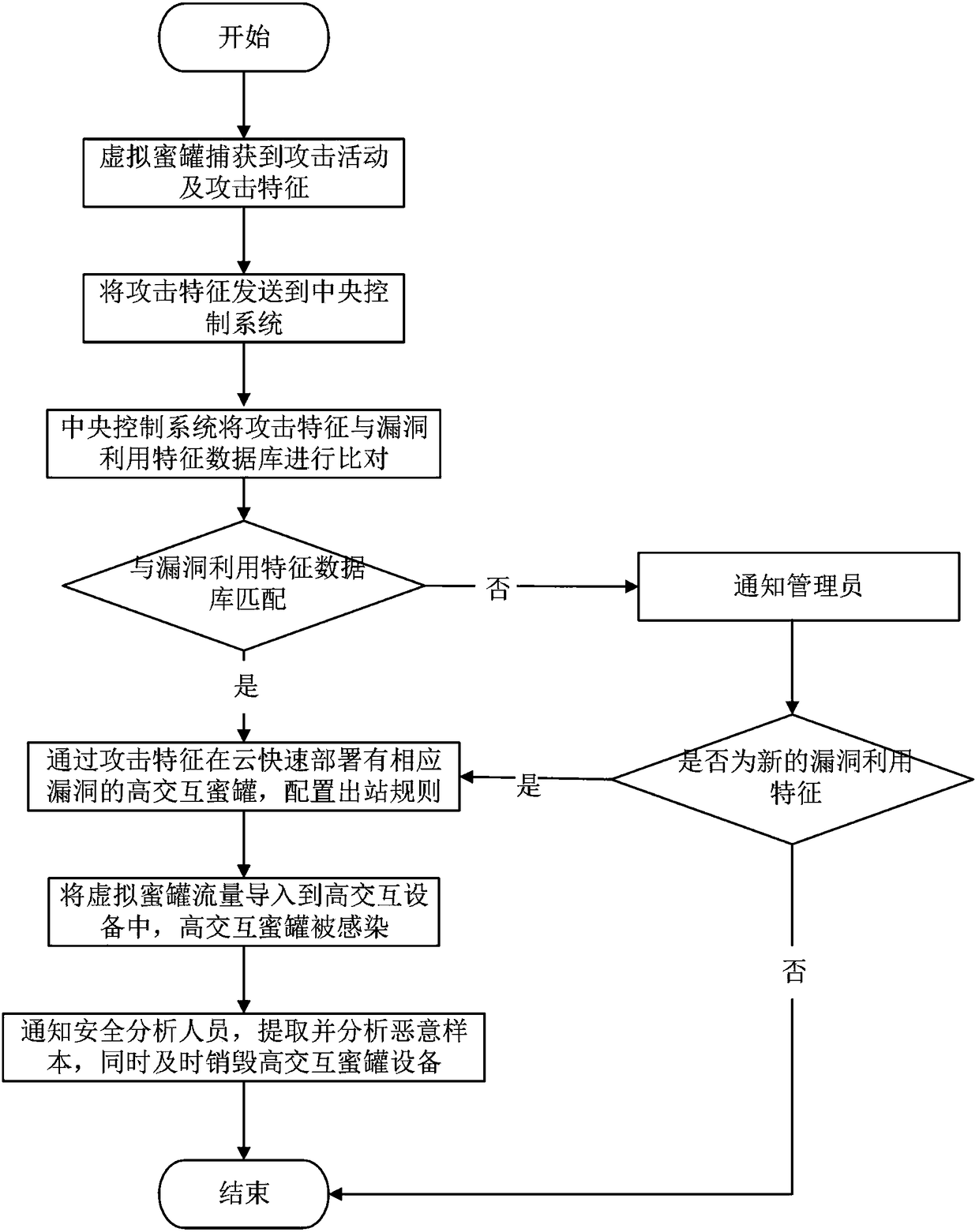
The application relates to a device and a method for specifically and dynamically deploying and capturing malicious samples by using a honeypot. The device comprises a virtual honeypot, a central control system and a cloud deployment platform. The method comprises the following steps: capturing attack activities and attack features by using the virtual honeypot; uploading the captured attack features to the central control system by the honeypot; analyzing the uploaded attack features by the central control system; starting a high interaction honeypot of vulnerabilities corresponding to the attack features by the cloud deployment platform; and importing virtual honeypot traffic into the started high interaction honeypot, wherein the corresponding high interaction honeypot is infected. According to the device and the method, a low interaction honeypot cooperates with the high interaction honeypot based on a vulnerability service or system; the malicious samples are detected rapidly by using the low interaction honeypot; the high interaction honeypot based on the vulnerability service or system is deployed rapidly by the cloud deployment platform; and the high interaction honeypot based on the vulnerability service or system cooperates with the low interaction honeypot to realize capturing of the malicious samples.
Owner:北京经纬信安科技有限公司
Method for detecting WEB service abnormality
The invention relates to a method for detecting WEB service abnormality, which comprises the following steps: analyzing and establishing a corresponding relation between a state of a Web server (4) and a behavior of communication message; detecting and analyzing network communication message in real time, and acquiring the state of the Web server (4) and transition thereof according to the behavior of the communication message; and judging and reporting whether the Web server is subjected to unknown denial service attack according to the state transition condition of the Web server (4). By analyzing and establishing the corresponding relation between the state of the Web server and the behavior of the communication message, detecting the message in real time and analyzing the corresponding state and transition of the Web server, the method can discover the abnormal state of the Web server, and can warn and stop the unknown denial service attack, and prevent, extract and record the network message with attack characteristics compared with the prior method.
Owner:BEIJING VENUS INFORMATION TECH +1
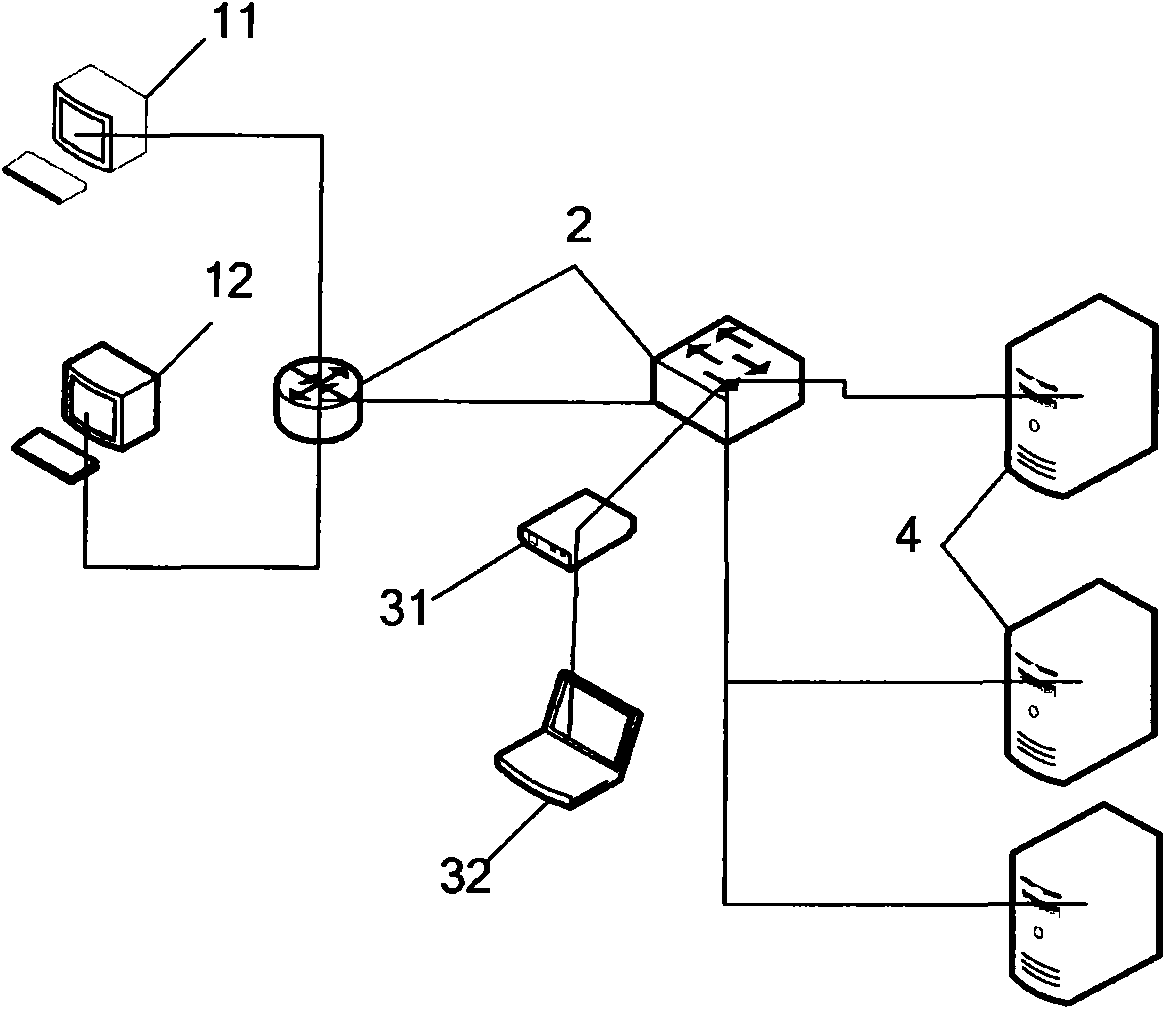
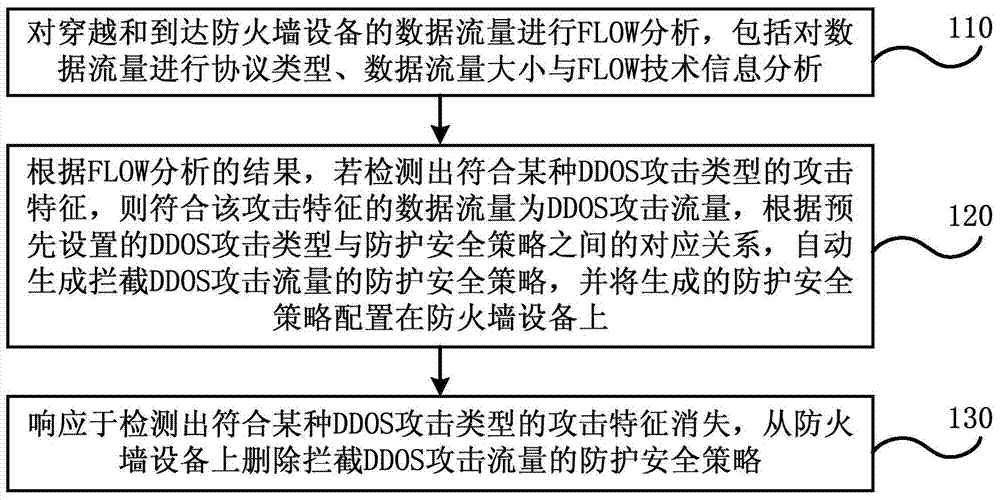
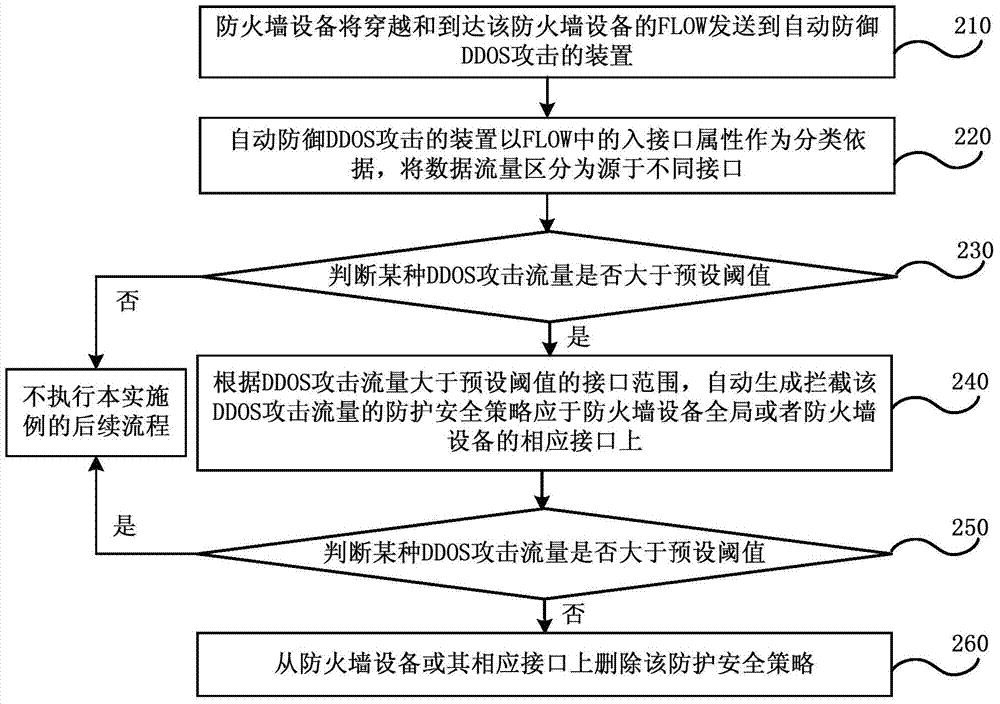
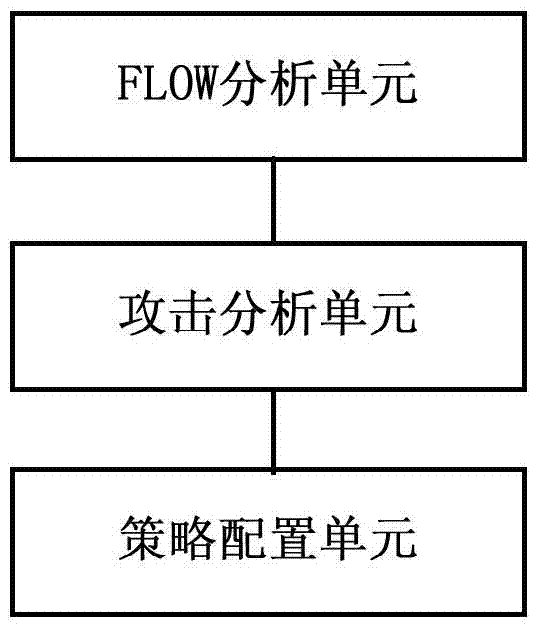
Method and device for automatic defense distributed denial of service attack of firewall
ActiveCN104519016AAutomatic defense implementationImprove work efficiencyTransmissionSecurity ruleSecurity policy
Embodiments of the invention disclose a method and a device for automatic defense distributed denial of service attack of a firewall. The method comprises: performing FLOW analysis on data traffic passing through and reaching a firewall device; according to the result of the FLOW analysis, if the result is detected to conform to attack characteristics of a certain distributed denial of service (DDOS) attack type, and the data traffic conforming the attack characteristics is DDOS attack flow, according to correspondence between DDOS attack types and protection security strategy arranged in advance, automatically generating protection security strategy holding up DDOS attack flow, and configuring the generated protection security strategy on the firewall device; and responding to disappearing of the attack characteristics which conform to a certain DDOS attack type, deleting the protection security strategy from the firewall device, the strategy holds up the DDOS attack flow. The method does not need to configure the protection security strategy in a safety regulation base of the firewall device in advance, and automatic defense of DDOS attack can be realized on a universal firewall device.
Owner:CHINA TELECOM CORP LTD
Intrusion detection method and system
ActiveUS8418247B2Efficient methodMemory loss protectionError detection/correctionGoal systemSecurity alarm
A technique is provided for detecting unauthorized use or abnormal activities of a targeted system of a network. The technique includes a comparison of captured data that relates to a targeted system with attack signatures to generate a security alert when the captured data and an attack signature match, a comparison of assurance metrics data from a monitored targeted perimeter with assurance references to generate assurance information when the assurance metrics data and an assurance reference match, a generation of a verified security alarm when the security alert and associated preconditions match a corresponding assurance information, a filtering of the security alert when no match has been found between the associated retrieved preconditions and the corresponding assurance information, and an emitting of a non verified security alert when no preconditions have been retrieved for the security alert and / or no assurance reference corresponding to the preconditions has been defined.
Owner:ALCATEL LUCENT SAS
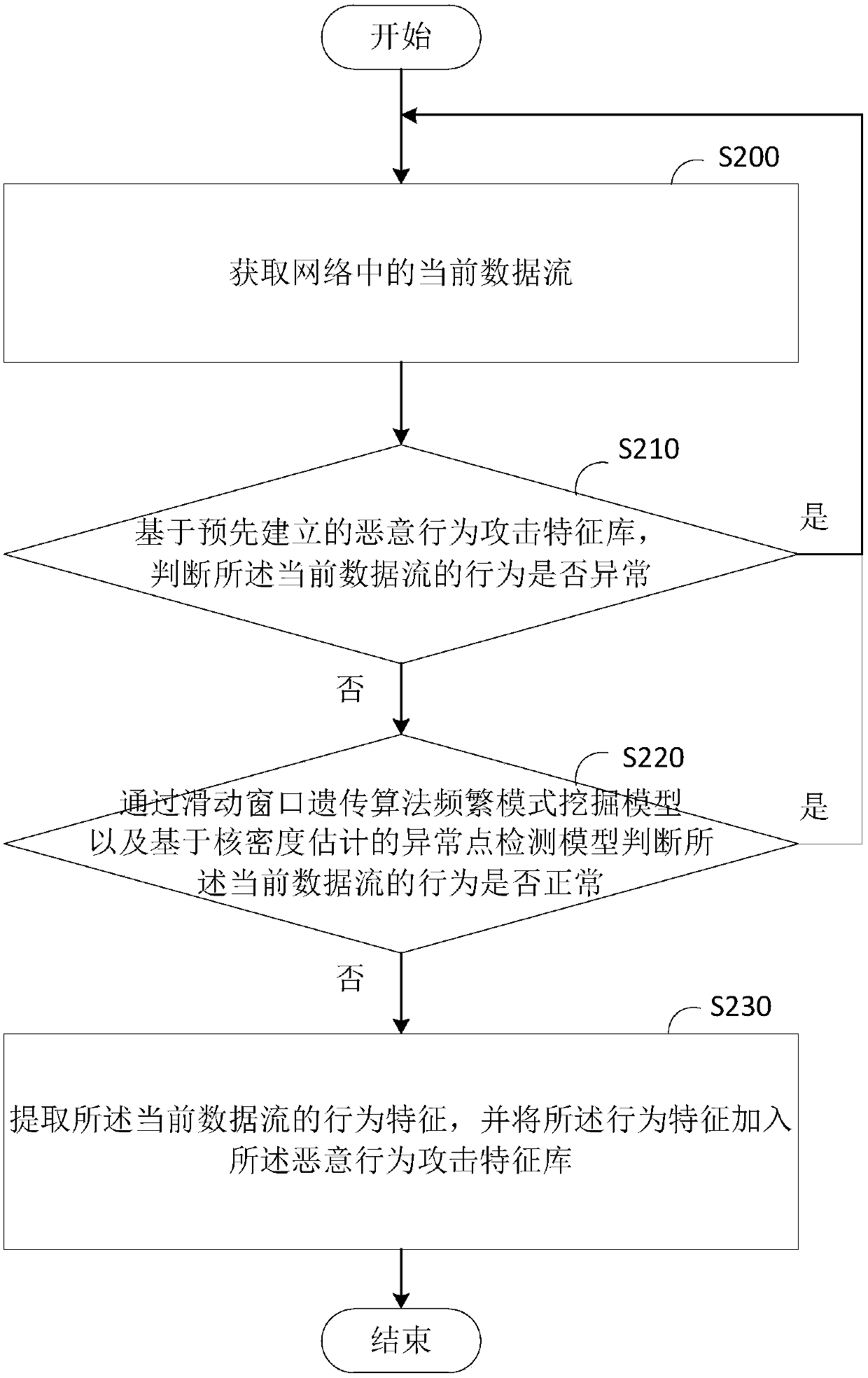
Detecting method and detecting device for network attack
The invention provides a detecting method and a detecting device for network attack and relates to the technical field of cloud computing. The detecting method for the network attack comprises the following steps: acquiring a current data flow in the network; based on a pre-established malicious act attack signature database, judging whether the behavior of the current data flow is abnormal or not; when the behavior of the current data flow is no, judging whether the behavior of the current data flow is normal or not by using a sliding window genetic algorithm frequent pattern mining model andan abnormal point detection model estimated based on nuclear density; when the behavior of the current data flow is no, extracting behavior characteristics of the current data flow, and adding the behavior characteristics into the malicious act attack signature database. According to the detecting method and the detecting device provided by the invention, by adopting a nested sliding window genetic algorithm frequent pattern mining model, the problems that a frequent mode, based on single-time scanning, of the current data flow is not high in mining accuracy, untimely processing of data is caused by high-speed growth of network data and the accuracy of a conventional intrusion detection technique is reduced due to complexity of a cloud computing environment network can be effectively solved.
Owner:HUAZHONG NORMAL UNIV
Malware Detection for SMS/MMS Based Attacks
Devices, systems, and methods are disclosed which utilize lightweight agents on a mobile device to detect message-based attacks. In exemplary configurations, the lightweight agents are included as contacts on the mobile device addressed to an agent server on a network. A malware onboard the mobile device, intending to propagate, unknowingly addresses the lightweight agents, sending messages to the agent server. The agent server analyzes the messages received from the mobile device of the deployed lightweight agents. The agent server then generates attack signatures for the malware. Using malware propagation models, the system estimates how many active mobile devices are infected as well as the total number of infected mobile devices in the network. By understanding the malware propagation, the service provider can decide how to deploy a mitigation plan on crucial locations. In further configurations, the mechanism may be used to detect message and email attacks on other devices.
Owner:AT&T INTPROP I L P
Malicious behavior mining method and device
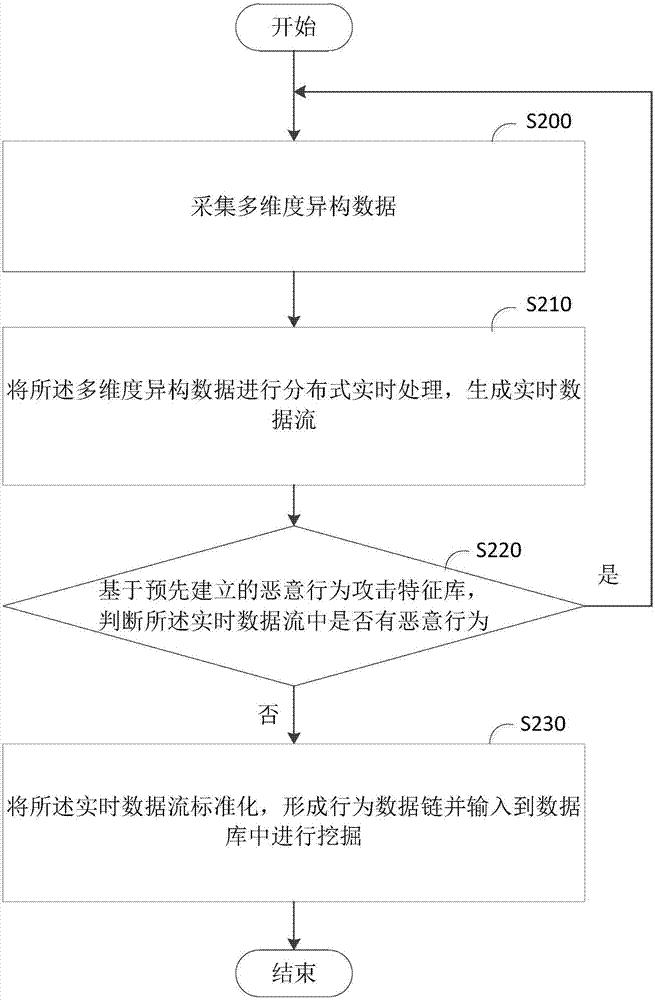
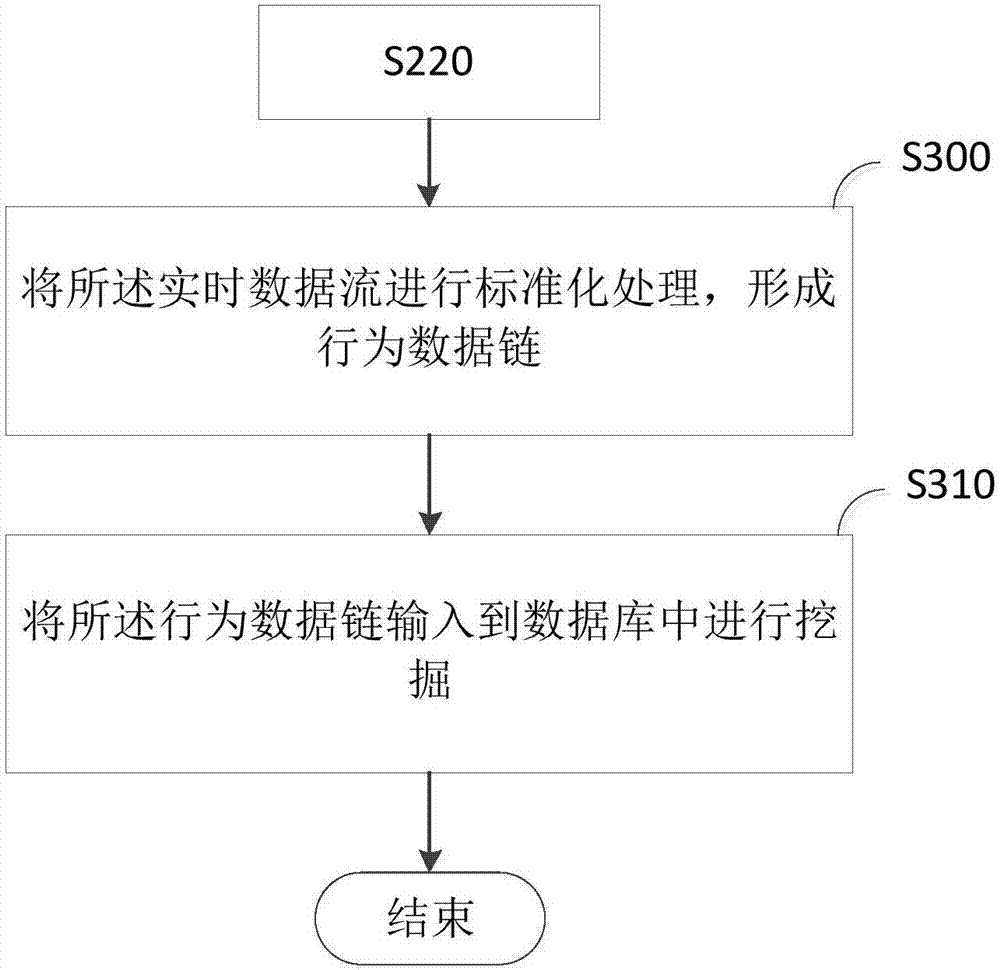
ActiveCN107992746AThe judgment result is accurateComplete judgmentPlatform integrity maintainanceMulti-dimensional databasesReal-time dataData stream
The invention provides a malicious behavior mining method and a malicious behavior mining device and relates to the technical field of cloud computing. The malicious behavior mining method includes the steps of collecting multi-dimensional heterogeneous data, conducting the distributed real-time processing of the multi-dimensional heterogeneous data and generating real-time data flows, determiningwhether malicious behavior exists in the real-time data flows based on a pre-established malicious behavior attack feature library, standardizing the real-time data flows and forming a behavioral data link to be input into a database to conduct mining if no malicious behavior exists in the real-time data flows. The malicious behavior mining method has the advantages that the attack feature library can be obtained through the training of extracted data features in each dimension, and whether malicious behavioral data exists can be quickly determined when real time data is dealt with; furthermore, the feature library can be constantly updated through the data, the method model is accurate in result determination, and a large amount of complex data can be completely, quickly and continuouslyjudged.
Owner:HUAZHONG NORMAL UNIV
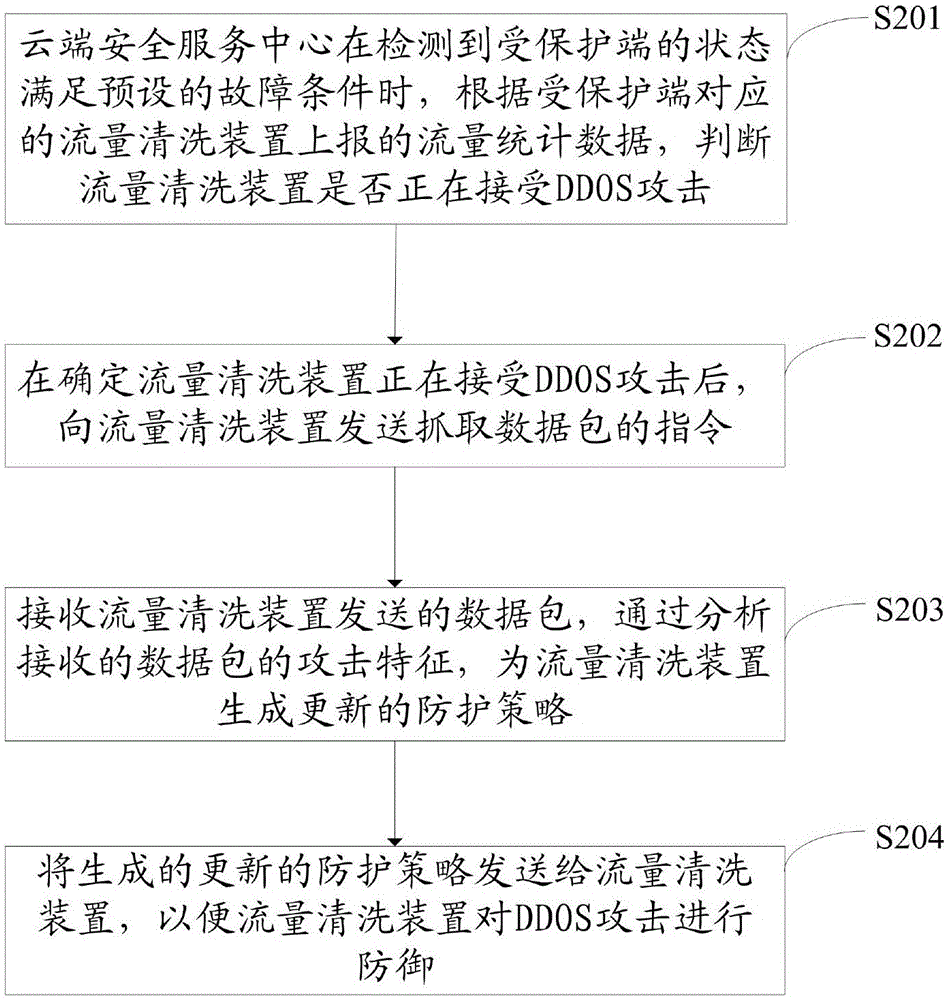
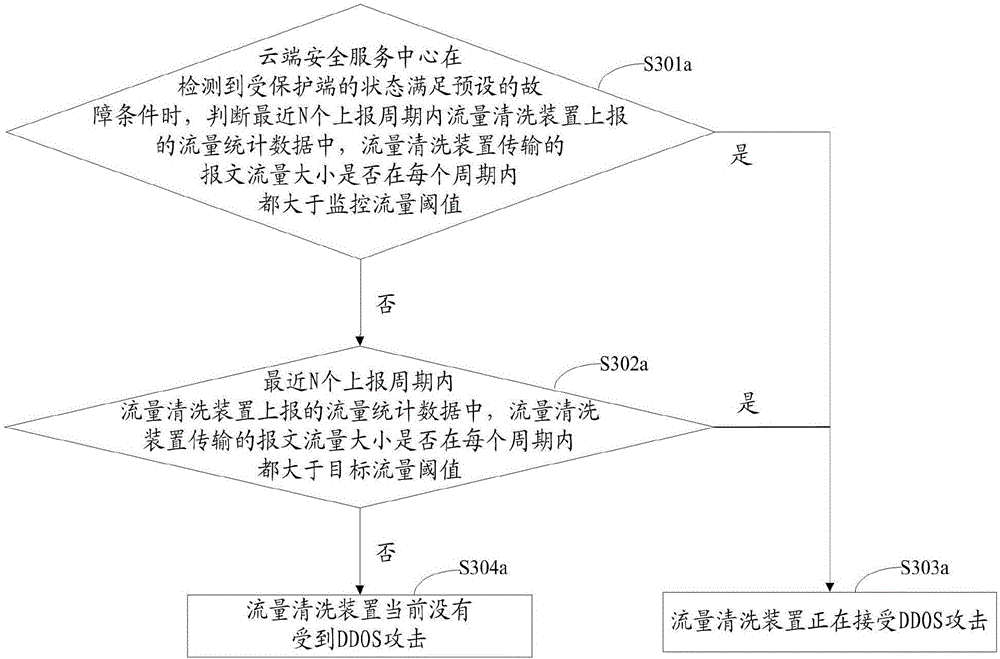
Method and device for defending distributed denial of service attack
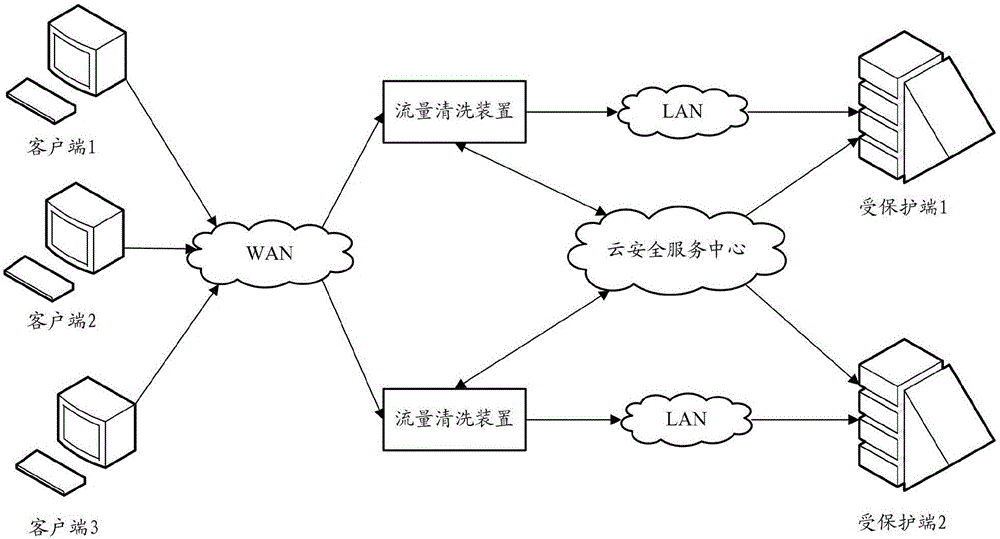
InactiveCN106357685AEffective protectionImprove the ability to defend against DDOS attacks in real timeTransmissionAttack signatureTraffic volume
The invention relates to the technical field of network safety and especially relates to a method and a device for defending distributed denial of service (DDOS) attack. The method and device are used for solving the problem in the prior art that a protected terminal can not be effectively protected in real time when a flow cleaning device encounters with DDOS attack. The method provided by the embodiment of the invention comprises the following steps: judging if the flow cleaning device encounters with DDOS attack according to a flow statistic data reported by the flow cleaning device corresponding to the protected terminal when a cloud security service center detects that the state of the protected terminal meets a preset fault condition; sending an instruction for capturing the message to the flow cleaning device after confirming that the flow cleaning device encounters with DDOS attack; receiving the message sent by the flow cleaning device and generating an updating defense strategy for the flow cleaning device by analyzing the attack features of the received message; and sending the generated updating defense strategy to the flow cleaning device, so that the flow cleaning device defends the DDOS attack.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
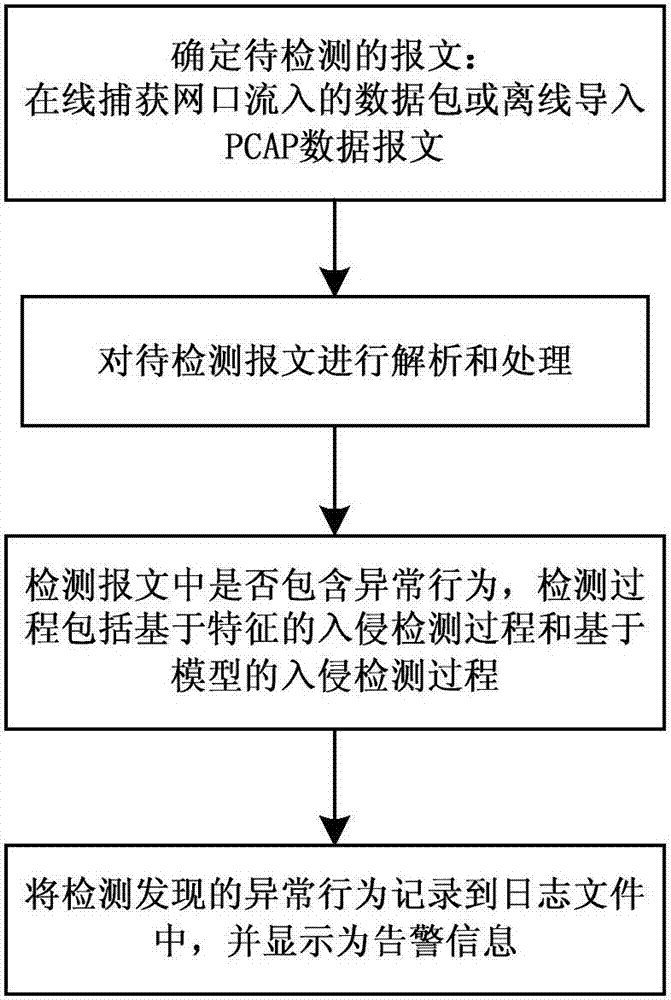
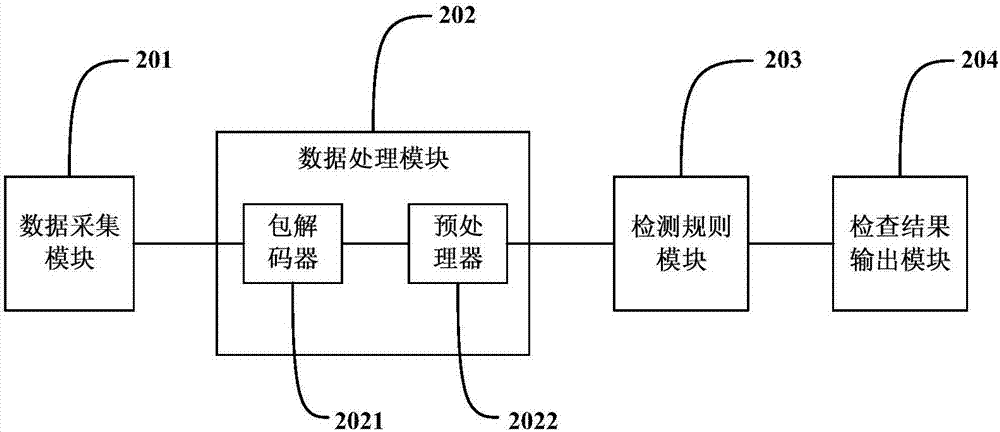
IEC60870-5-104 Protocol-based SCADA (supervisory control and data acquisition) network intrusion detection method and system
InactiveCN106911514AImprove network securityPrevent intrusionData switching networksSCADAData acquisition
The invention discloses an IEC60870-5-104 Protocol-based SCADA (supervisory control and data acquisition) network intrusion detection method and system. According to the method, the detection processes of the method include a feature-based intrusion detection process and a model-based intrusion detection process. According to the feature-based intrusion detection process, matching is performed on a message to be detected and a rule database of attack features, if the message to be detected is matched with the rule database of attack features, a corresponding alarm is generated and stored in a log file. According to the model-based intrusion detection process, models that characterize specific protocol expected behaviors are established, if it is detected that the message violates the models, a corresponding alarm is generated and is stored in the log file. With the IEC60870-5-104 Protocol-based SCADA (supervisory control and data acquisition) network intrusion detection method and system of the invention adopted, the network security of an IEC / 104 protocol-based SCADA system can be improved.
Owner:JIANGSU ELECTRIC POWER RES INST +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com