Malicious behavior mining method and device
A behavioral and malicious technology, applied in the field of cloud computing, can solve problems such as inability to guarantee information security, difficulty in attack behavior, and easy access to network attacks, and achieve the effect of rapid judgment and accurate judgment results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
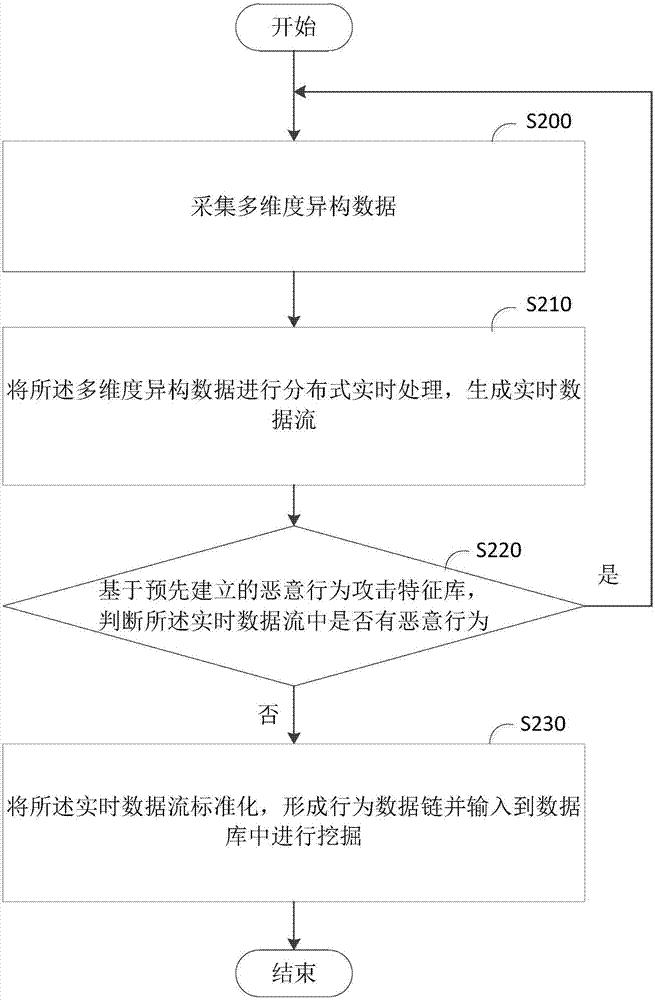
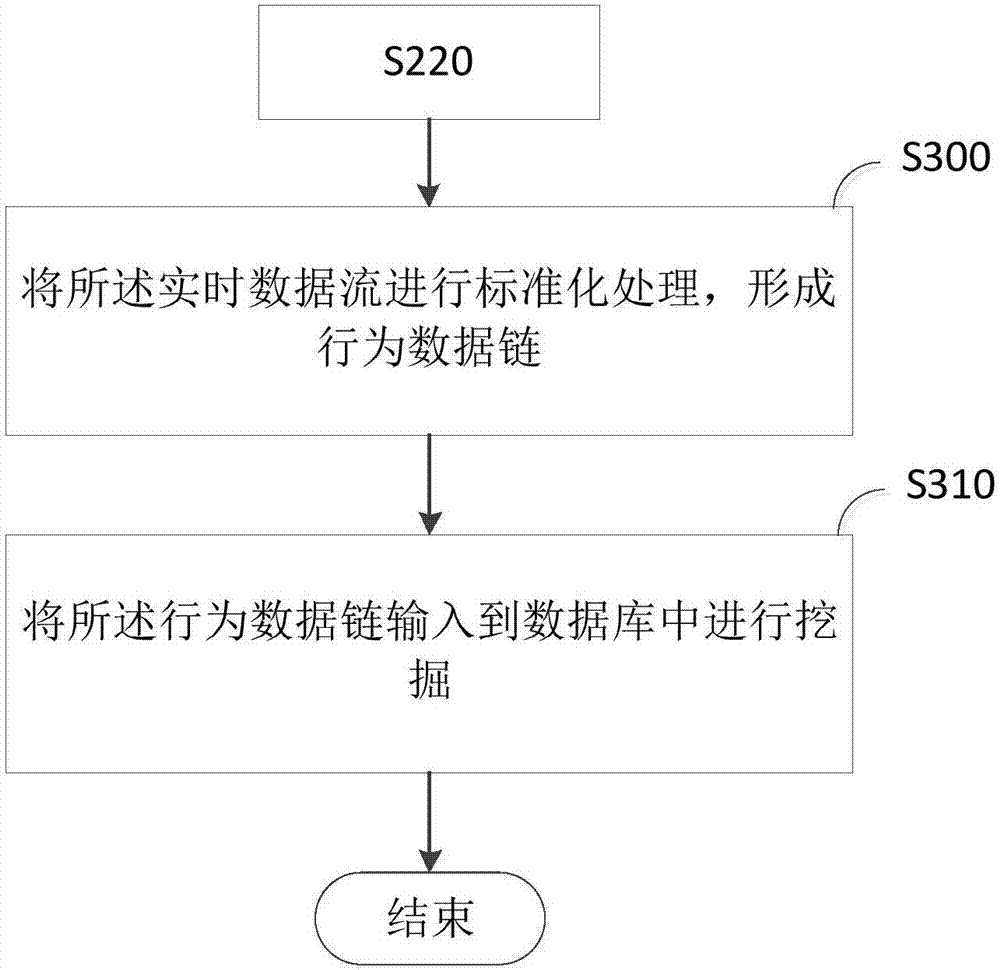
[0032] Please refer to figure 2 , This embodiment provides a malicious behavior mining method, the method includes:
[0033] Step S200: Collect multi-dimensional heterogeneous data;
[0034] In this embodiment, multi-dimensional heterogeneous data can be collected in real time from SDN, VMI, and entities. The multi-dimensional heterogeneous data can include: network data, access logs, data in virtual machines, and system logs. The multi-dimensional heterogeneous data can be common network intrusion monitoring information, which can specifically come from: system and network log files, network data, virtual machine data (through virtual machine introspection technology), directories and files Unexpected behavior; undesired behavior in program execution; physical form of intrusion information and data flow information in a certain period of time, etc.
[0035] Various behavior types are recorded in the log file, and each type contains different information, such as a network process ...
no. 2 example
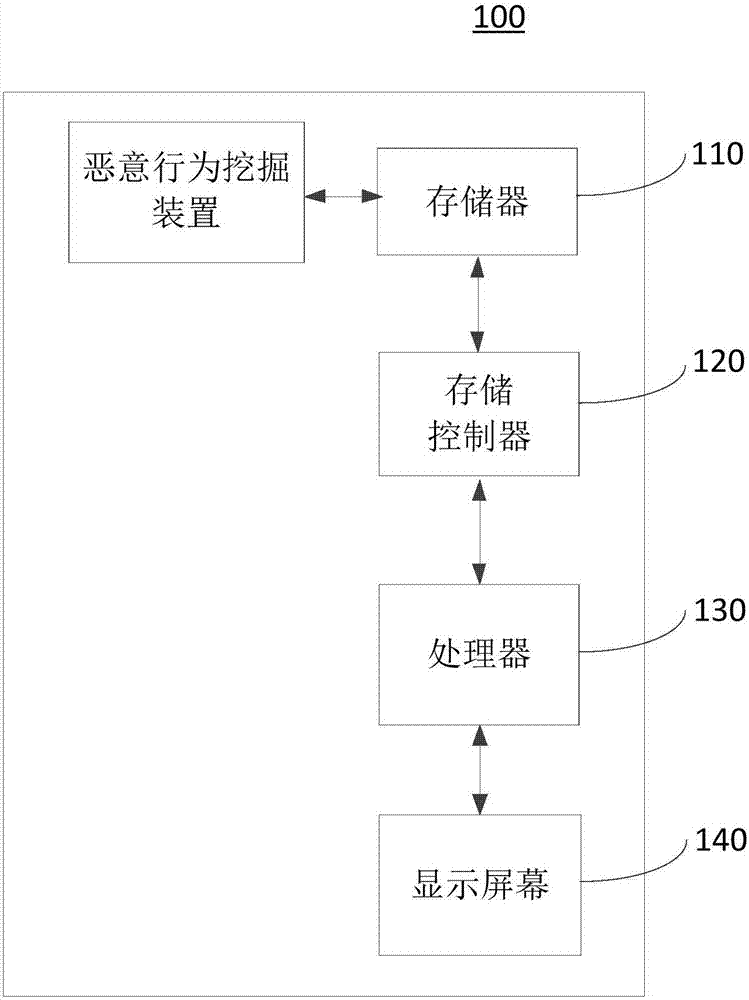
[0078] Please refer to Picture 9 , This embodiment provides a malicious behavior mining device 900, which includes:
[0079] The collection module 910 is configured to collect multi-dimensional heterogeneous data, where the multi-dimensional heterogeneous data includes: network data, access logs, data in virtual machines, and system logs;
[0080] The processing module 920 is configured to perform distributed real-time processing of the multi-dimensional heterogeneous data to generate a real-time data stream;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com