A SQL injection attack detection method and system
A technology for injecting attack and detection methods, applied in transmission systems, digital transmission systems, instruments, etc., can solve the problems of easy spoofing of attack signatures and inaccurate extraction of attack signatures, and overcome difficulties in extraction and deception, No need for frequent updates, reducing the effect of false positive rate and false negative rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
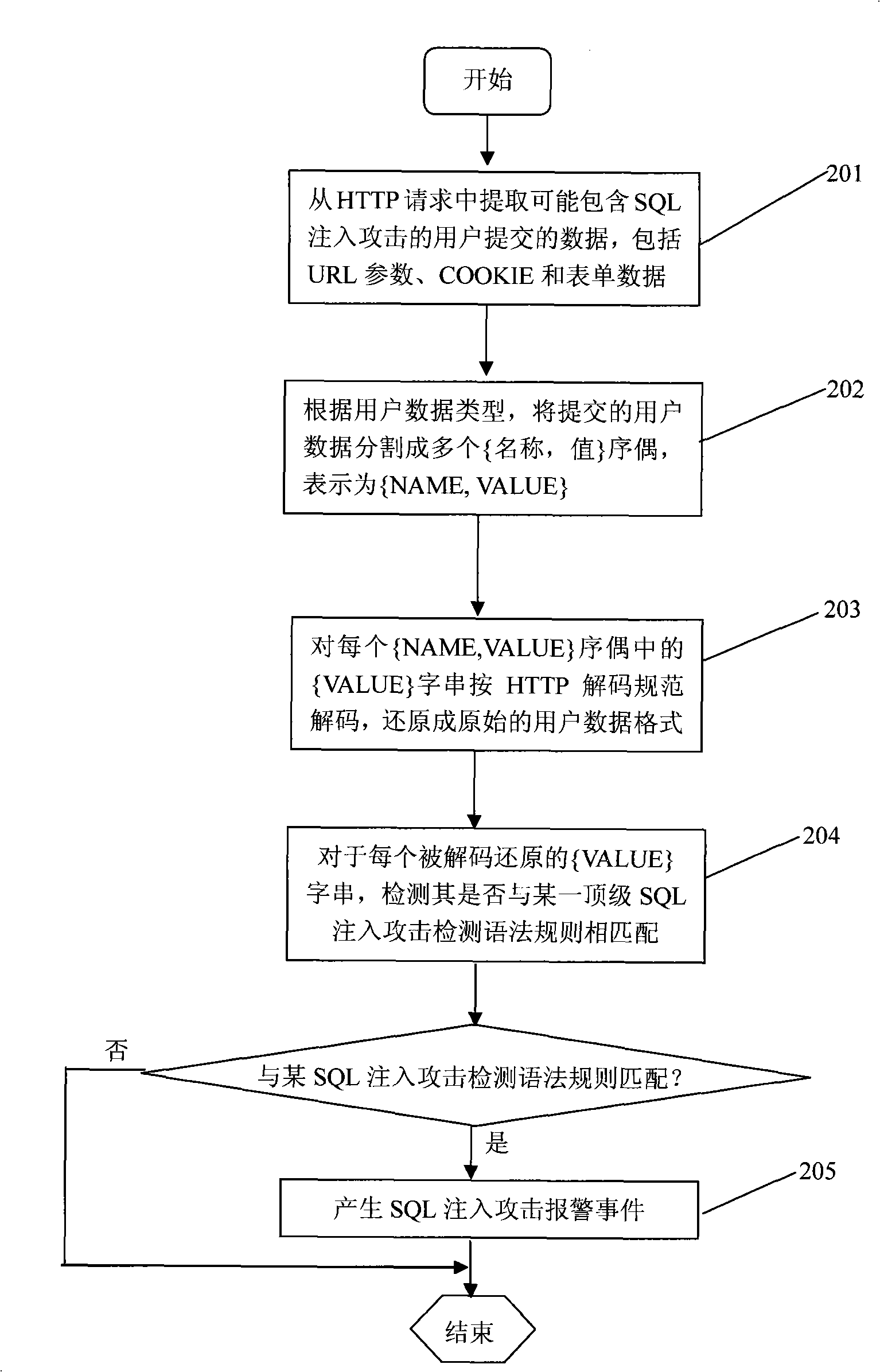
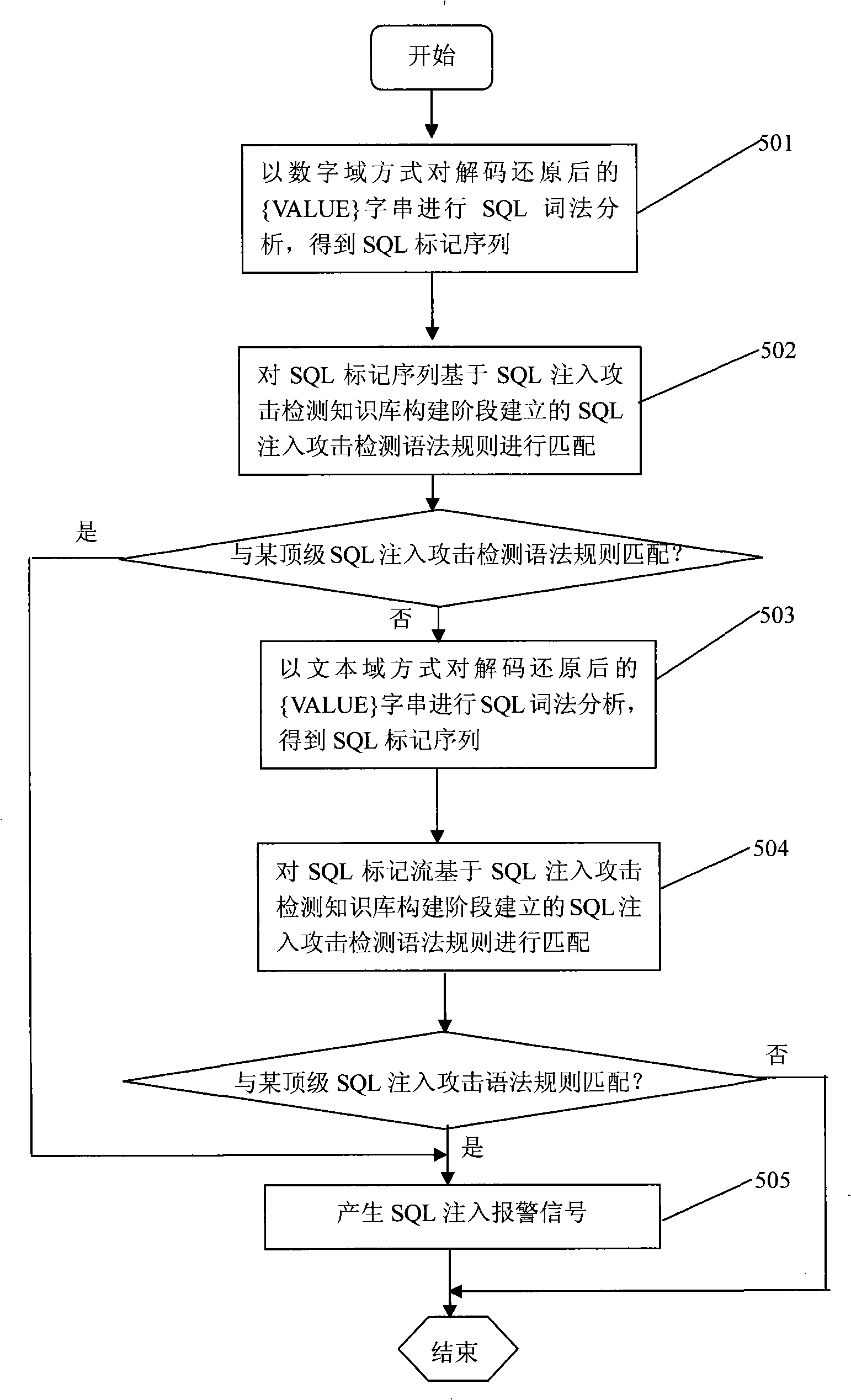
[0039] The SQL injection attack detection method of the present invention includes two working stages: a SQL injection attack detection knowledge base construction stage and a real-time SQL injection attack detection stage.
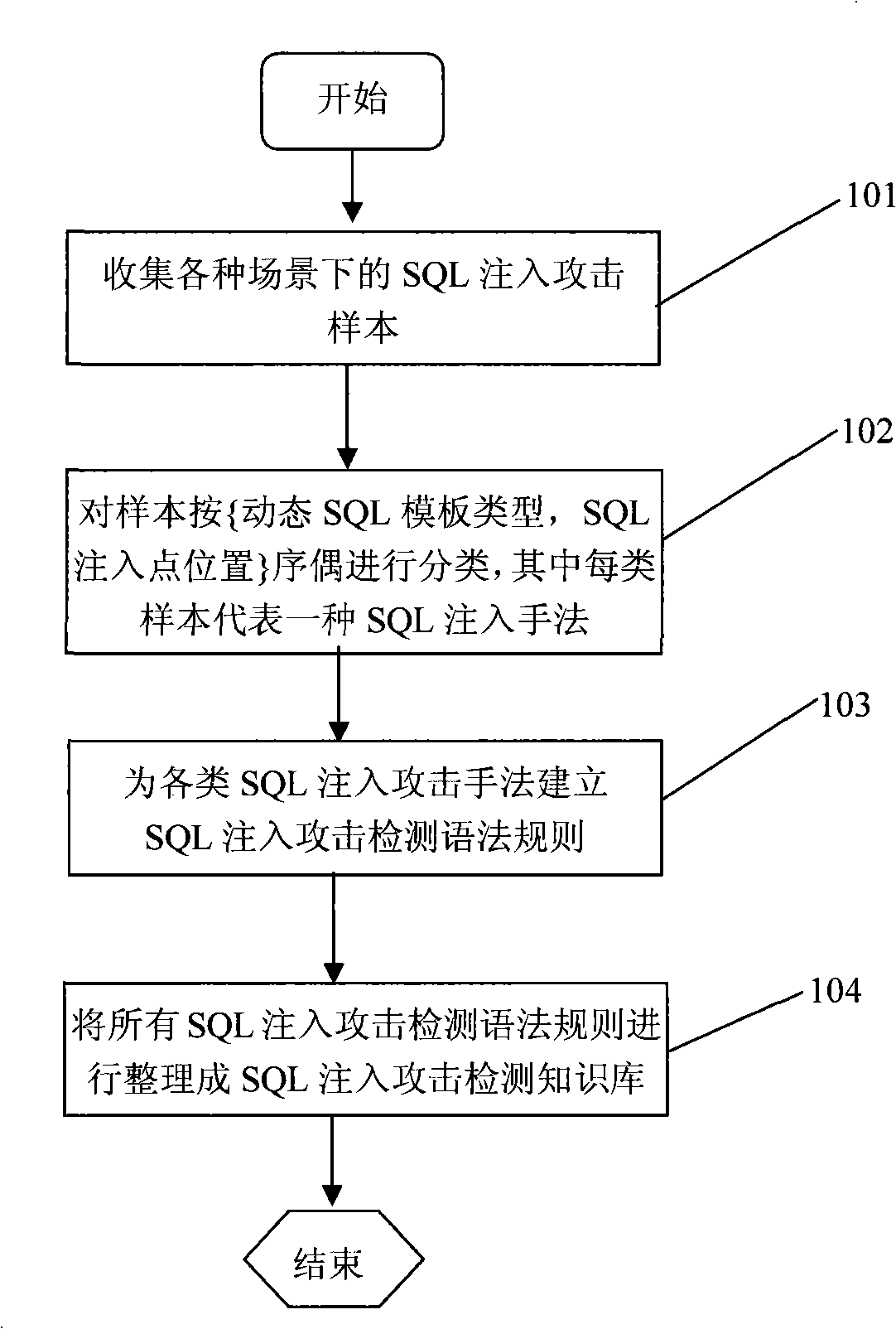
[0040] as attached figure 1 As shown, the SQL injection attack detection knowledge base construction phase includes the following steps:
[0041] 101) Collect SQL injection attack samples in various scenarios;
[0042] The root of the SQL injection vulnerability lies in the use of dynamic SQL functions supported by various relational databases in the development of Web database programs. Various popular relational databases including MS SQL Server, ORACLE, DB2, Informix, MySQL, PostgreSQL, etc. all support the use of dynamic SQL functions in the development of Web database programs. In general Web database program development, d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com