Detecting method and detecting device for network attack
A network attack and detection method technology, applied in the field of cloud computing, can solve problems such as low mining accuracy, network traffic growth, and accuracy reduction, and achieve the effect of improving mining accuracy and solving detection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
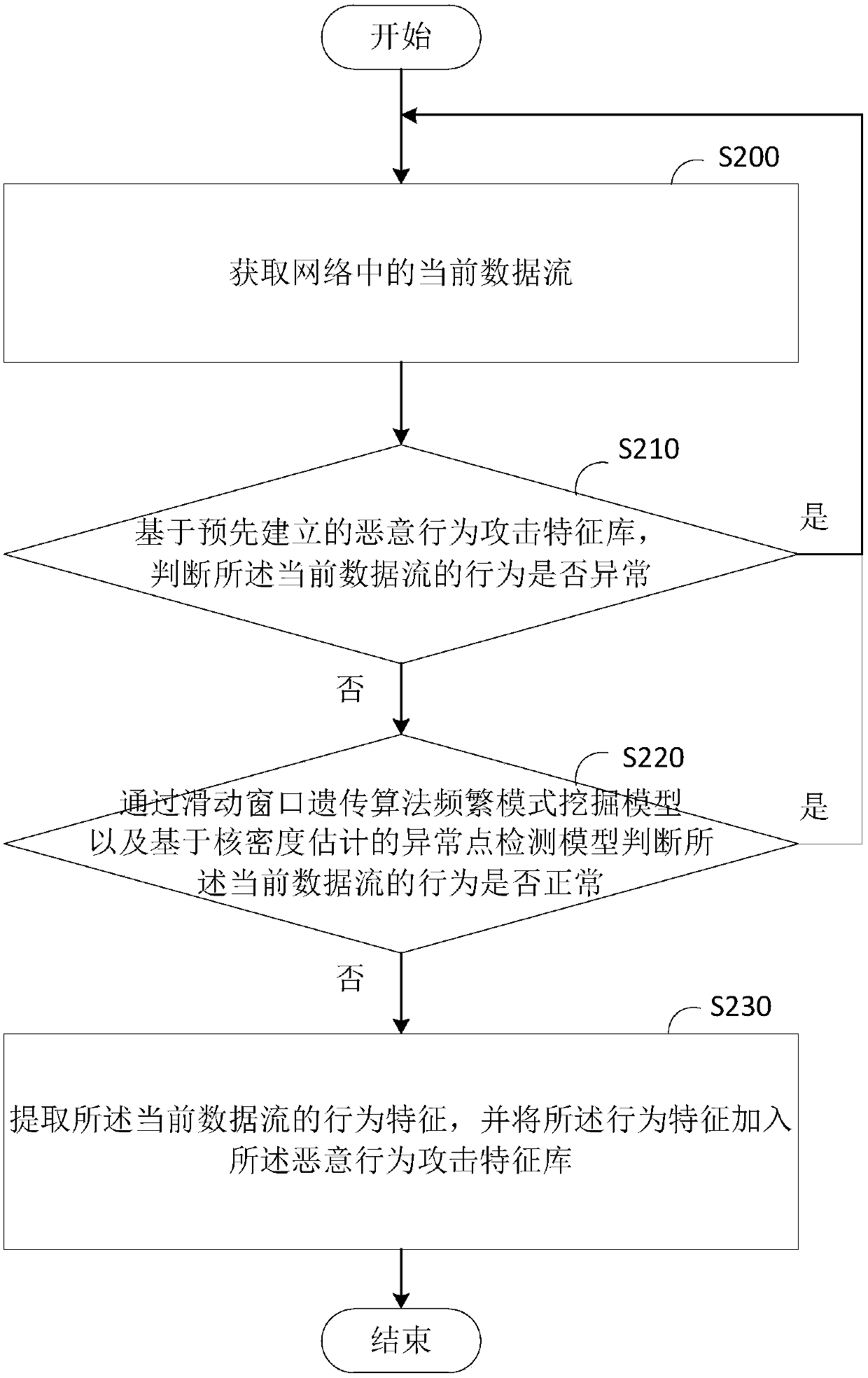
[0033] Please refer to figure 2 , the present embodiment provides a network attack detection method, the method comprising:
[0034] Step S200: Obtain the current data flow in the network;
[0035] In this embodiment, the current data flow that may include normal traffic, attack traffic, and malicious traffic can be obtained in real time through the OpenFlow switch under the SDN framework.
[0036] Step S210: Based on the pre-established malicious behavior attack signature database, determine whether the behavior of the current data flow is abnormal;
[0037] In this embodiment, the malicious behavior attack feature library may be obtained by training network traffic through machine learning or deep learning models. It can be understood that the malicious behavior supply feature library contains a large number of normal behavior traffic features The normal behavior pattern library composed of the abnormal behavior pattern library and the abnormal behavior pattern library co...
no. 2 example
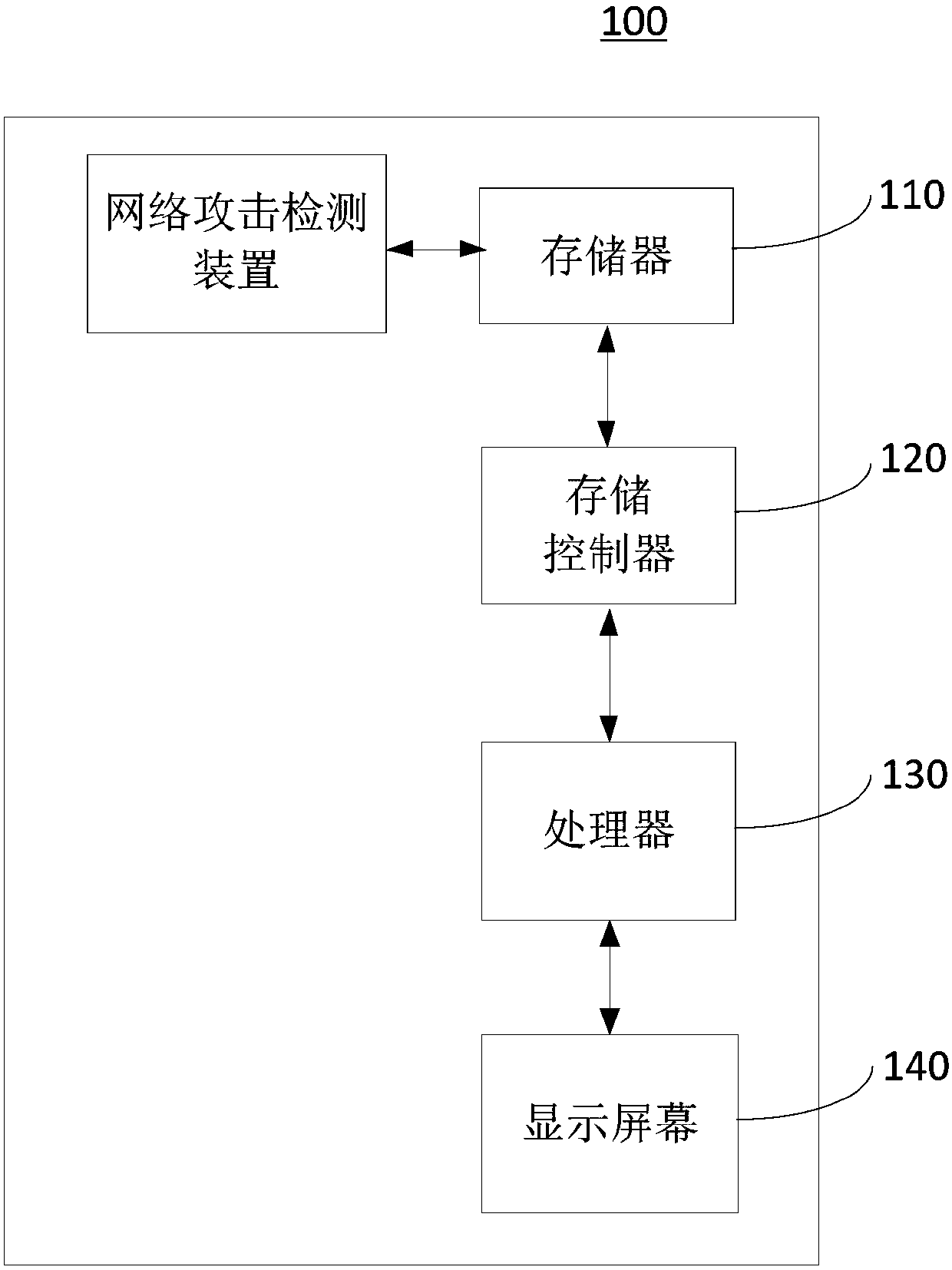
[0072] Please refer to Figure 7 , this embodiment provides a network attack detection device 700, which includes:
[0073] An acquisition module 710, configured to acquire the current data flow in the network;
[0074] A primary detection module 720, configured to determine whether the behavior of the current data flow is abnormal based on a pre-established malicious behavior attack signature database;
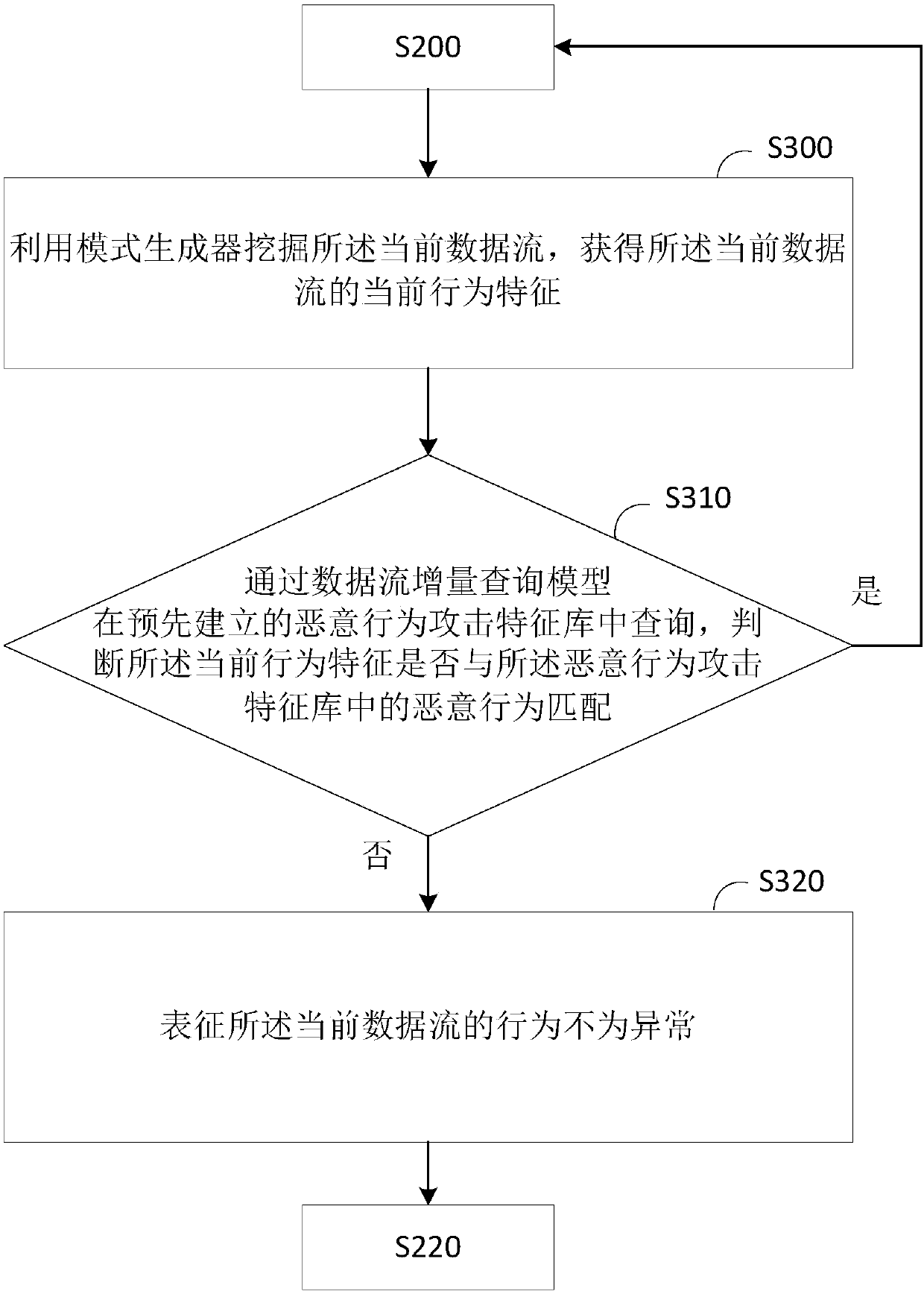
[0075] The secondary detection module 730 is used to determine whether the behavior of the current data stream is normal through the sliding window genetic algorithm frequent pattern mining model and the outlier detection model based on kernel density estimation when the behavior of the current data stream is not abnormal ;
[0076] The extracting module 740 is configured to extract behavior features of the current data stream when the behavior of the current data stream is abnormal, and add the behavior features to the malicious behavior attack feature library.
[0077] P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com