Patents
Literature
35 results about "String database" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Online procurement of biologically related products/services using interactive context searching of biological information
InactiveUS20050240352A1Reduce deliveryBiological testingSpecial data processing applicationsString databaseInformation system
Systems and methods for procuring biologically related products available on a vendor Website are described which involve user-server interfacing with a Web based browser to retrieve database files representing available target products via processing biological context searches on named annotated text string databases.
Owner:LIFE TECH CORP
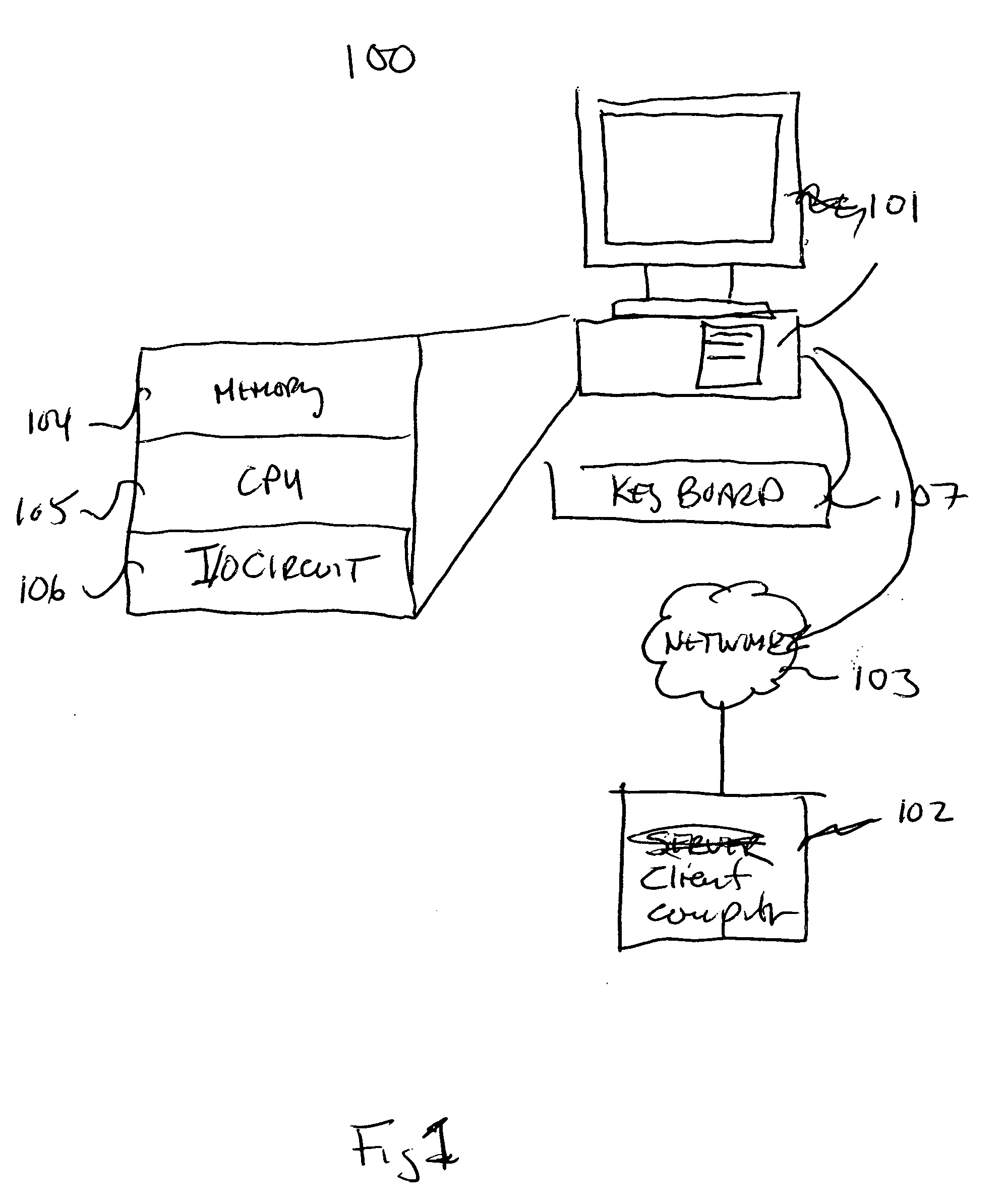
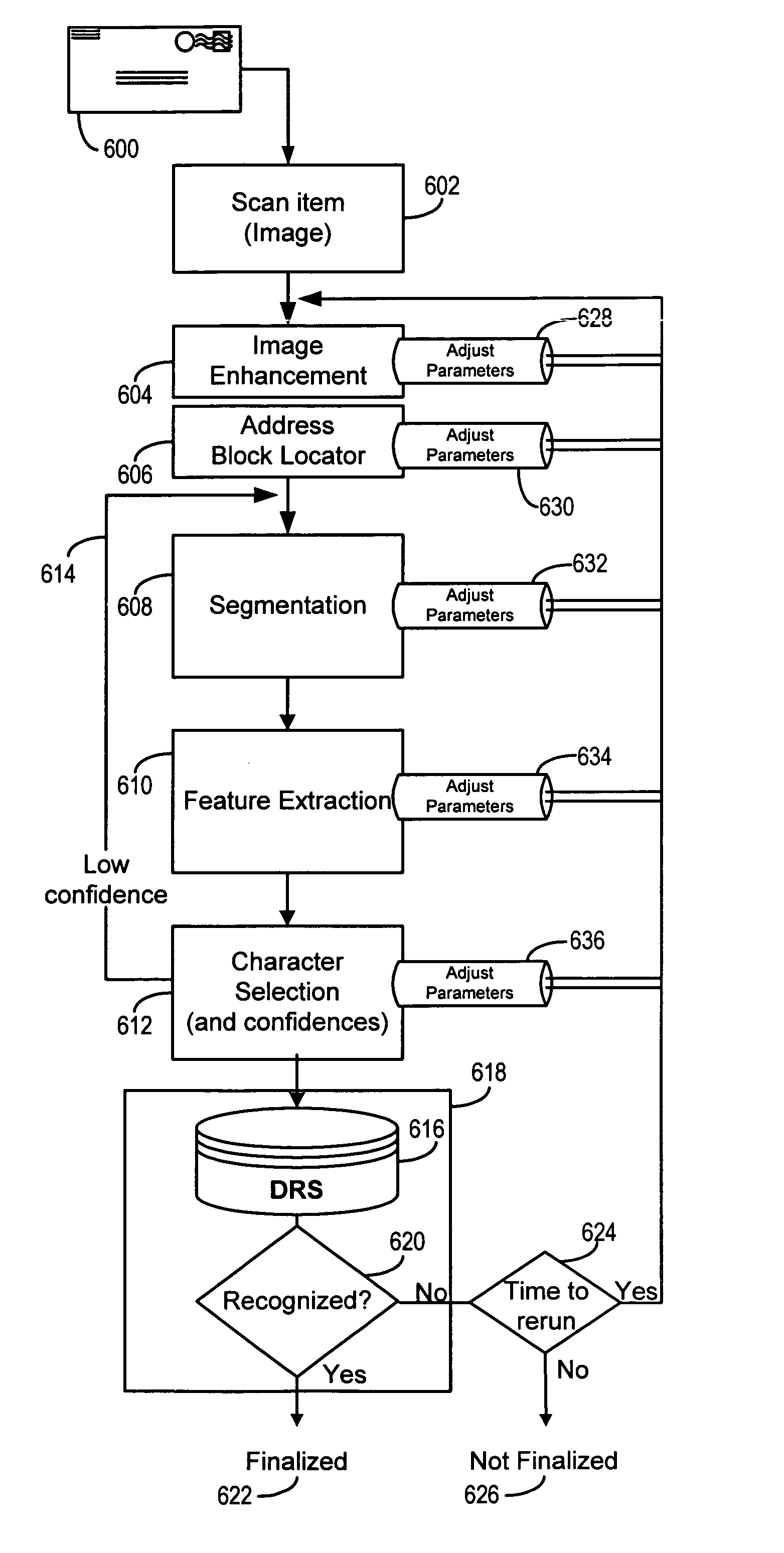
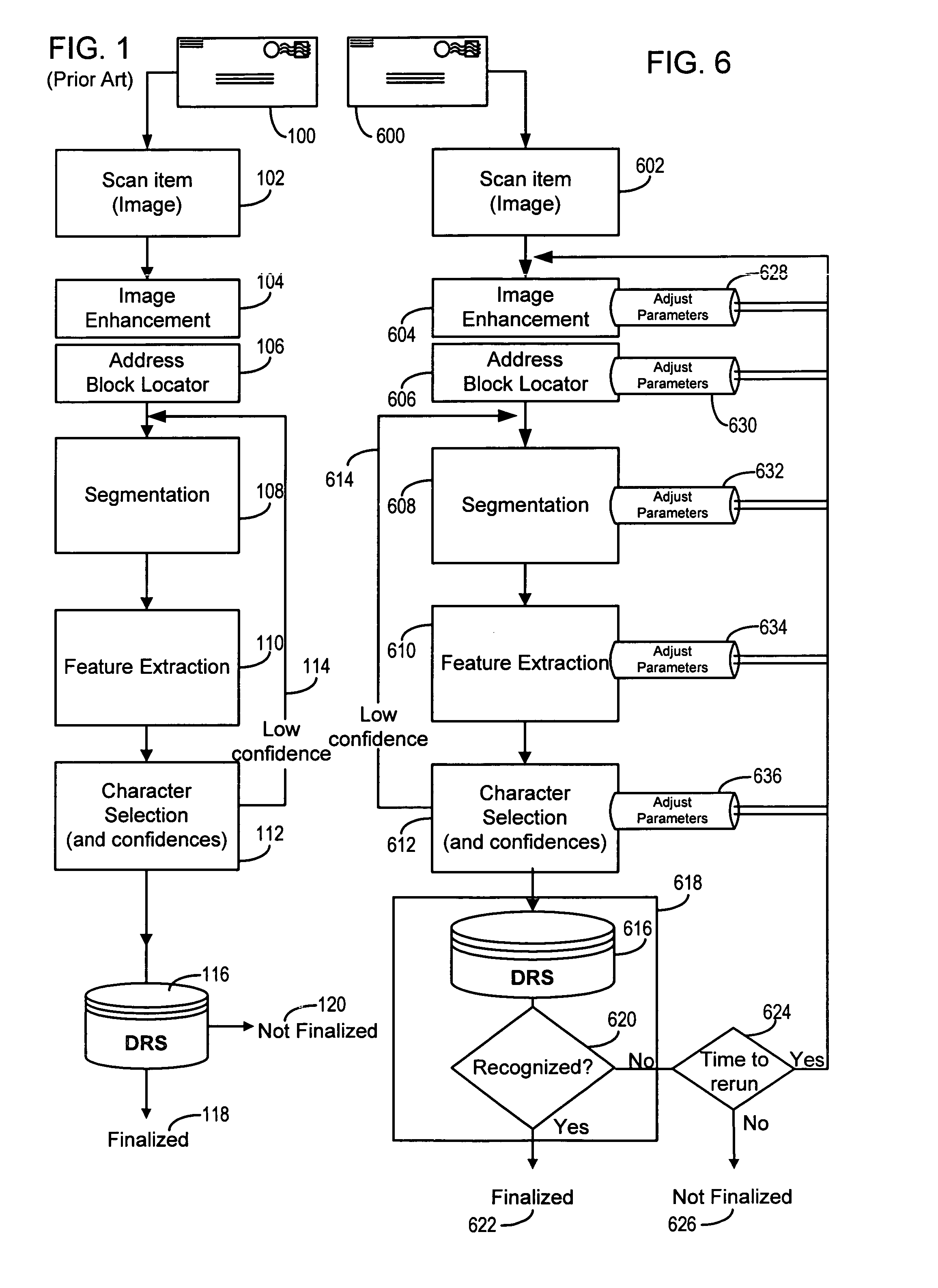
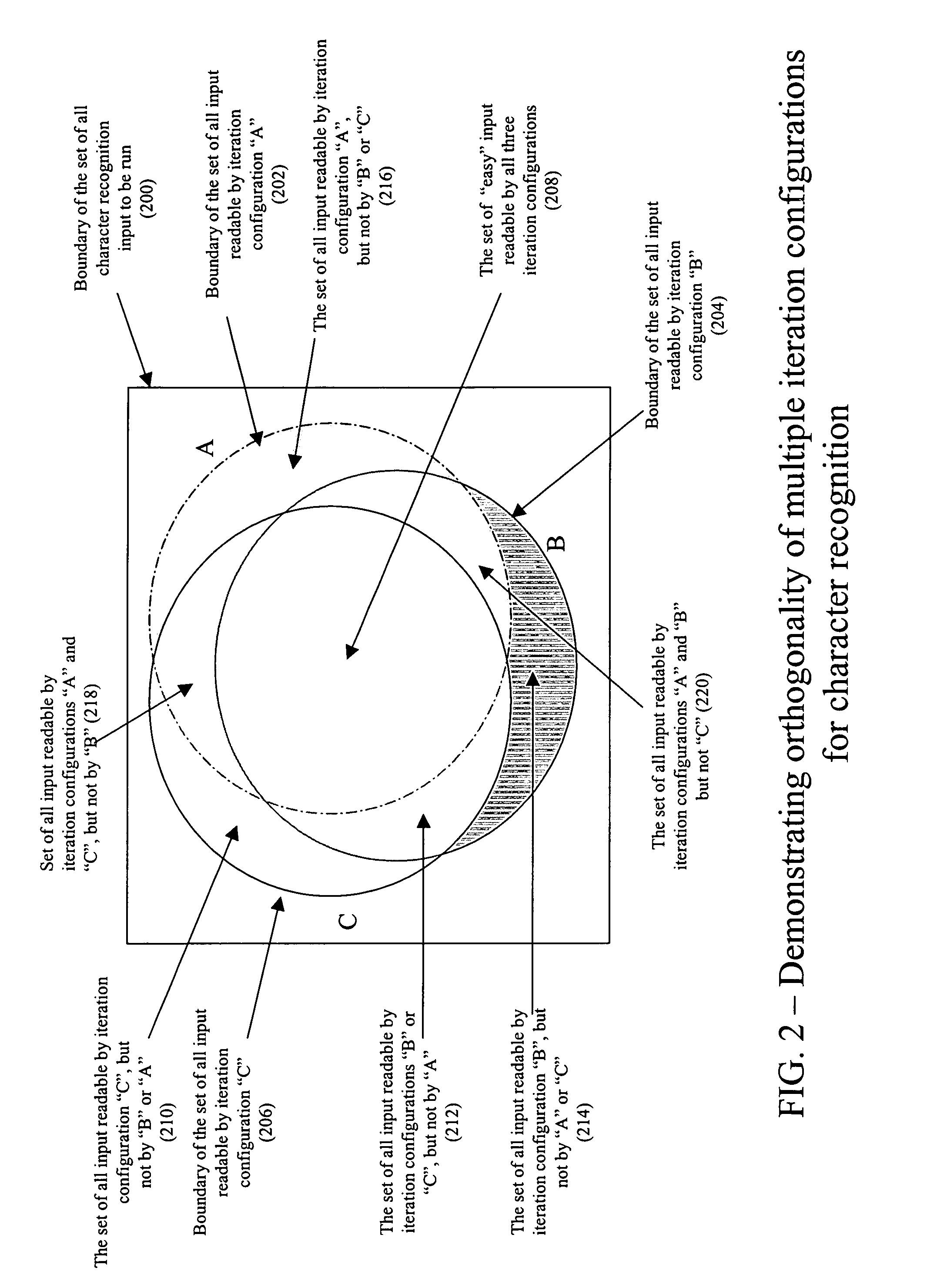
Orthogonal technology for character recognition
The present invention encompasses a self-orthogonal character recognition engine for executing an iterative method employing a database of predetermined character strings. The method receives a digital representation of a character string. It then generates a proposed result string by applying to the captured digital image a predetermined recognition routine including one or more recognition subroutines. Each recognition subroutine employs an initial parameter setting. Next, if the proposed result string does not match any of the predetermined character strings in the database, the initial parameter setting of a recognition subroutine is changed to a next setting. The recognition process is then repeated using the next parameter setting to generate and test a next result string. The process can be repeated iteratively until a result string is verified or the process times out.
Owner:MATTHEWS INT CORP
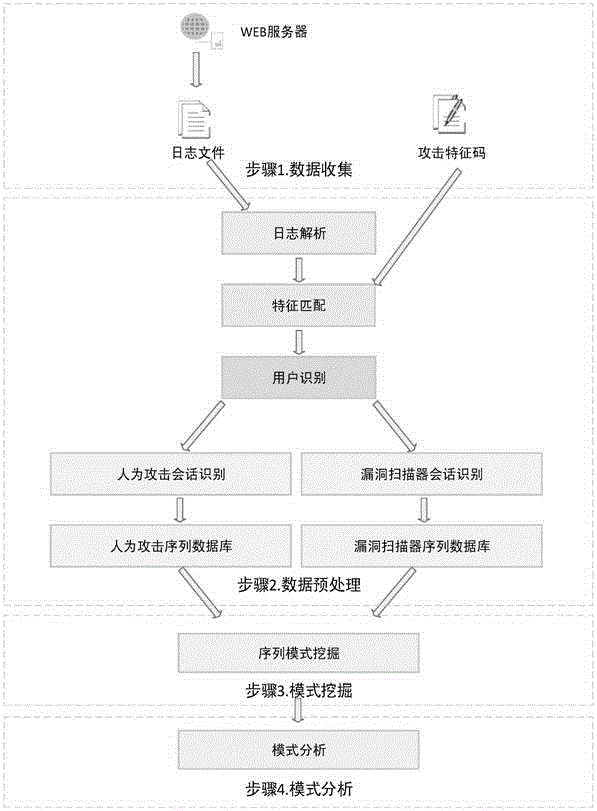
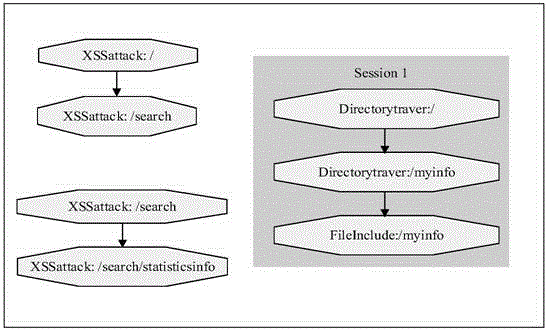
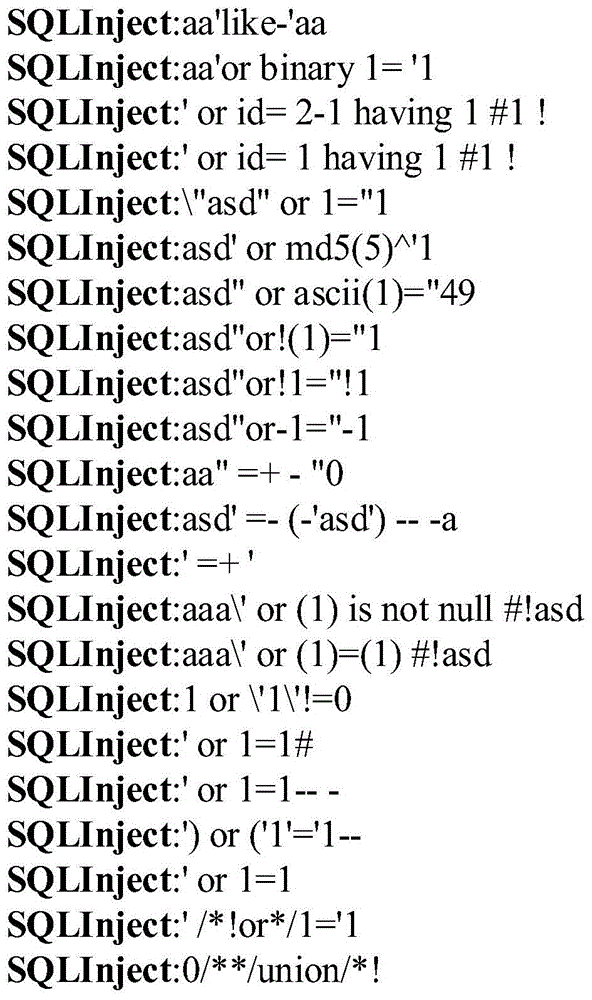
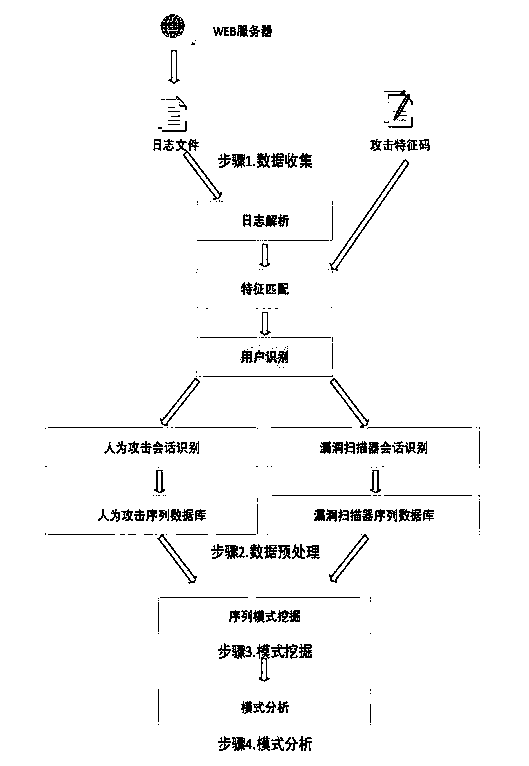
Method for mining attack frequent sequence mode from Web log
ActiveCN105721427ATransmissionSpecial data processing applicationsSequence databaseUniform resource locator
The invention relates to data mining in the field of network security and especially relates to a method for mining an attack frequent sequence mode from a Web log. The method comprises the following steps: collecting website access log files, website information and attack feature codes; analyzing a website log structure, matching analyzed URLs with the collected attack feature codes, obtaining attack records, and clearing up the URLs; performing user identification on attack log data and distinguishing manual attacks and attacks of a loophole scanner; respectively performing session identification to obtain a sequence database of the manual attacks and a sequence database of the loophole scanner; converting a character string database into a digital database, and respectively mining a frequent sequence of the sequence database by use of a sequence mode mining method; and maximizing the frequent sequence obtained through mining and converting a sequence mode into visual figure language. The process is indicated in the first graph. The method provided by the invention can realize visualization of an attack mode and explores a scanning sequence in the loophole scanner.
Owner:HUNAN UNIV
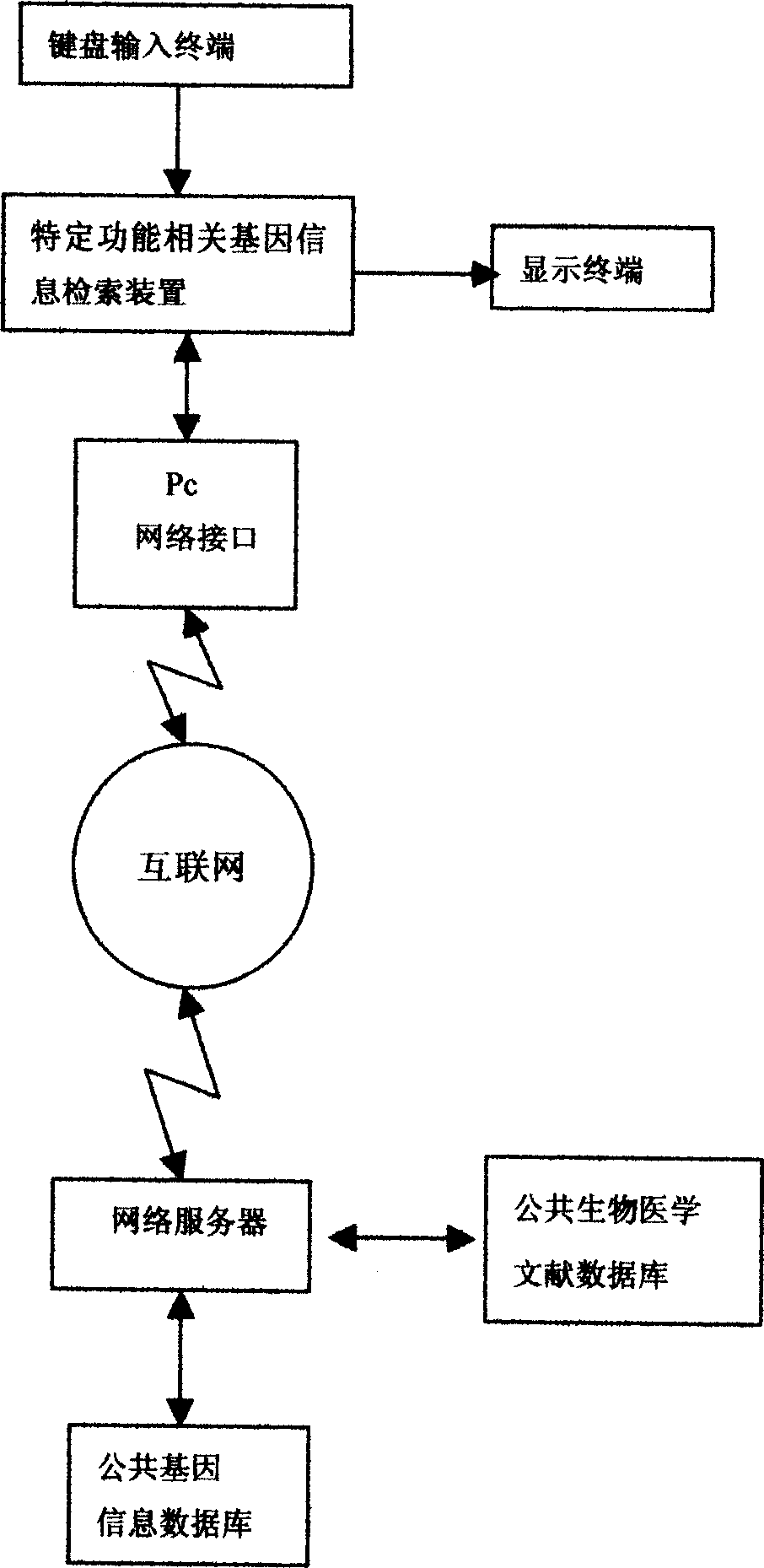
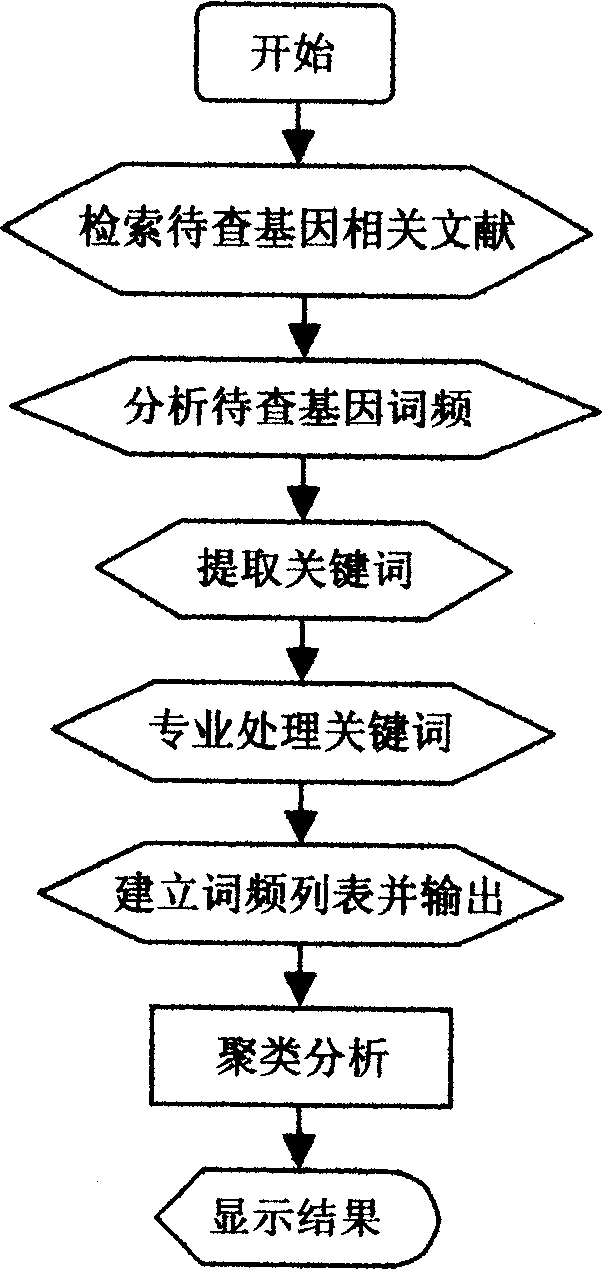
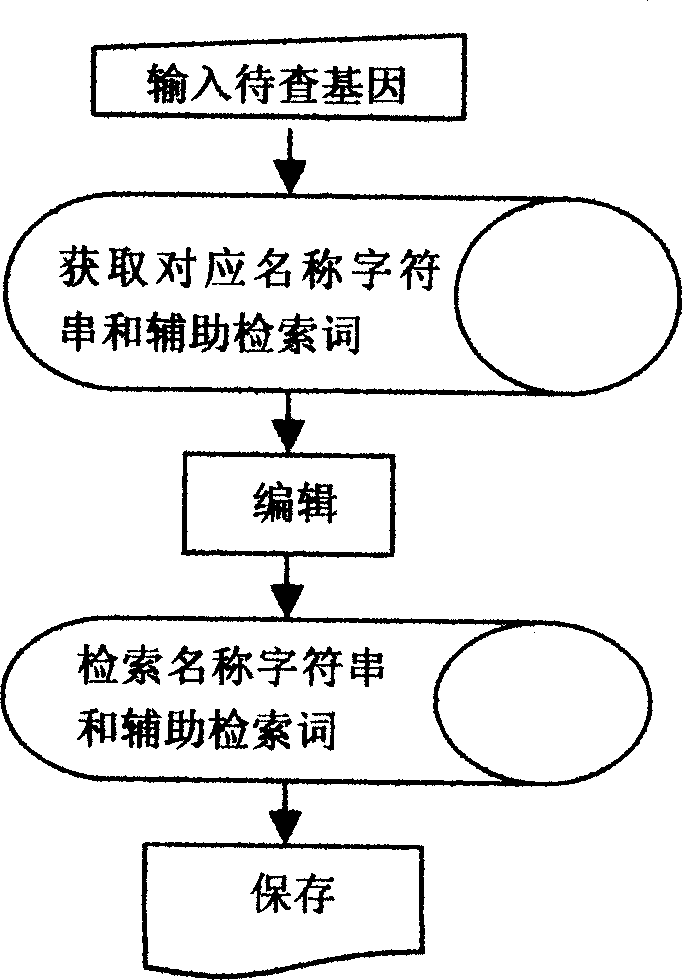
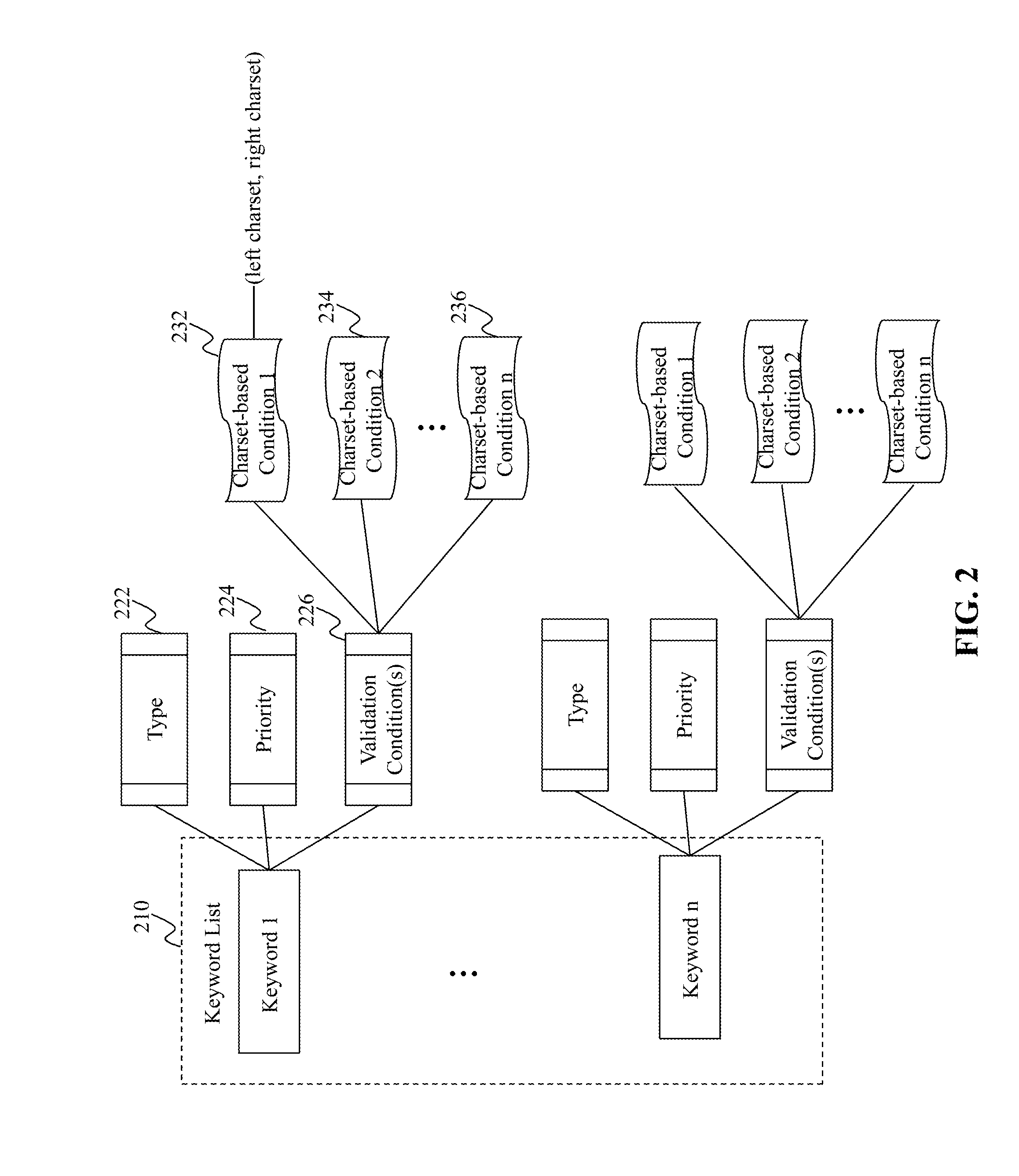
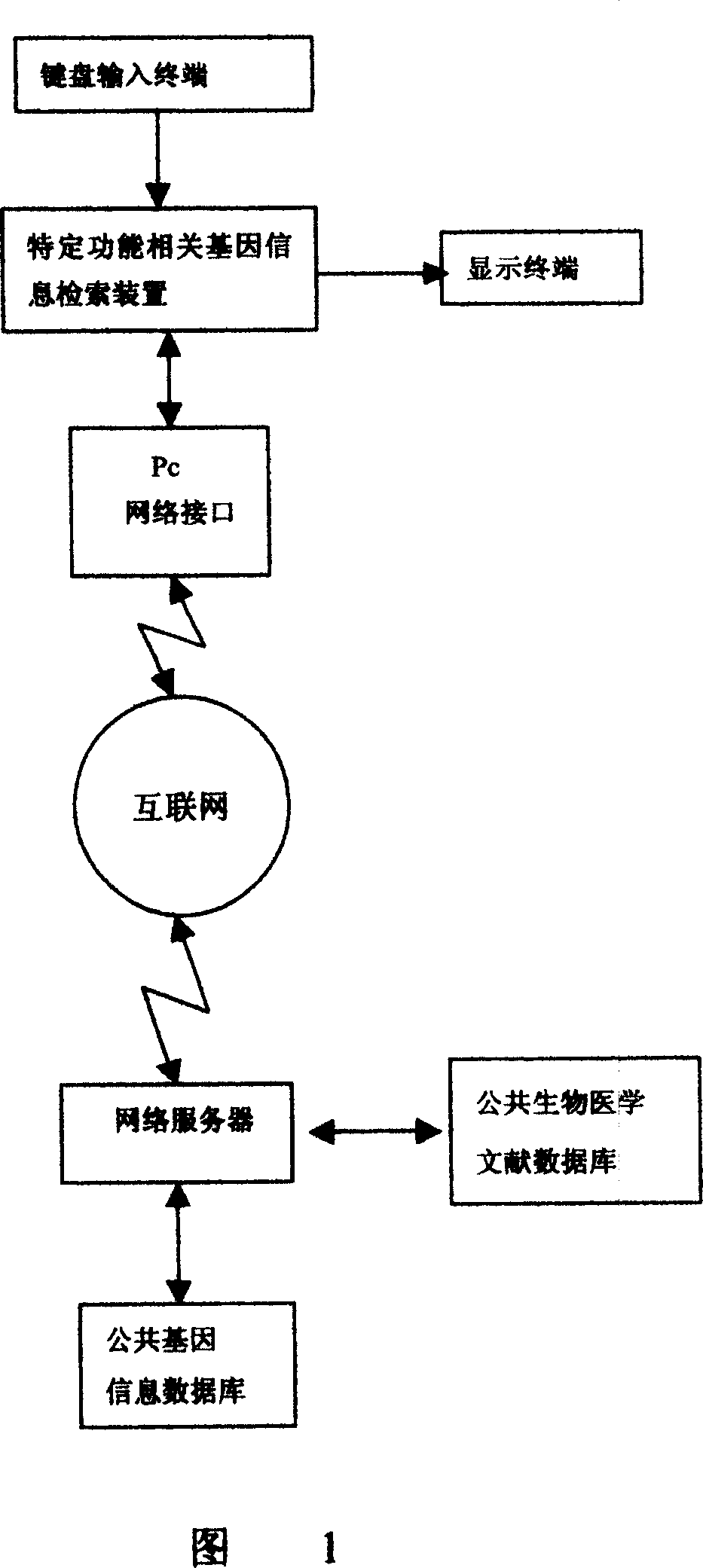
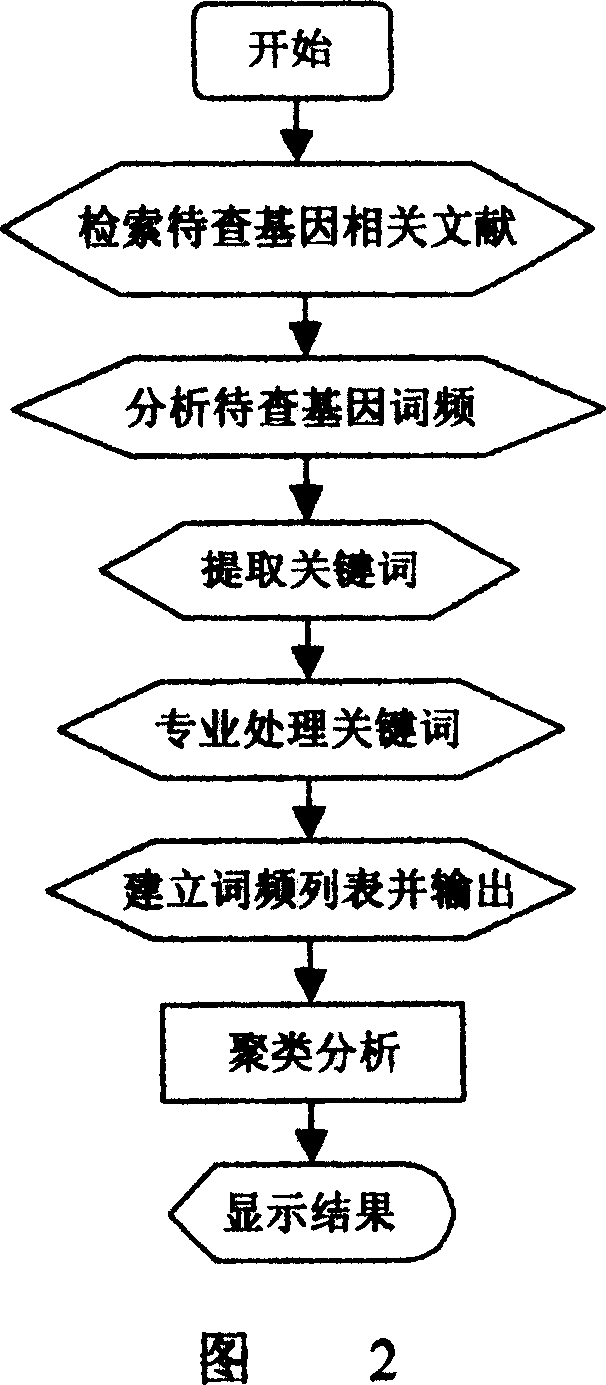
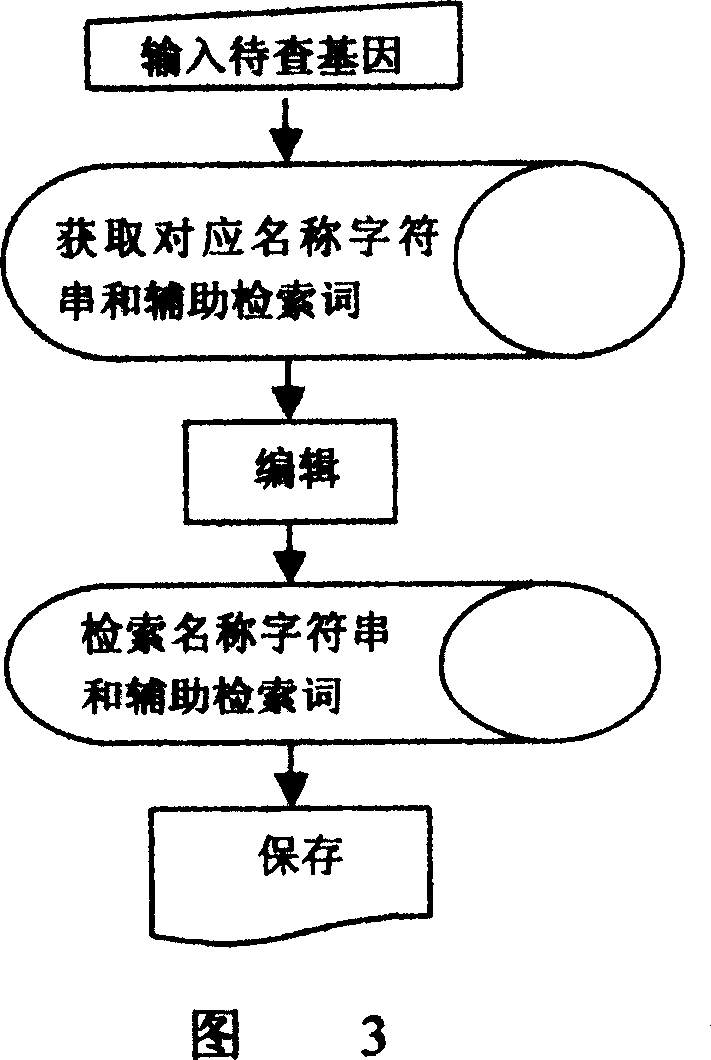
Specific function-related gene information searching system and method for building database of searching workds thereof
InactiveCN1744080AGood technical effectReduce duplication of effortSpecial data processing applicationsSpecific functionString database
The system searches out relevant documents of gene to be searched through following devices and steps: computer of having input function and display terminal, database of docuterm for document composed of database of gene name, database of word frequency base value, character-string database and database of assistant docuterm, as well as public database of biomedicine document entered through network server. The method includes following steps: carrying out analysis of word frequency, picking out keywords of gene; through professional process, building list of word frequency; finally, searching out information of gene relevant to specific function through cluster analysis. Features are: accurate positioning, searching in quick speed, avoiding rehandling so as to save human and material resources greatly, and suitable commercial development.
Owner:SOUTHERN MEDICAL UNIVERSITY
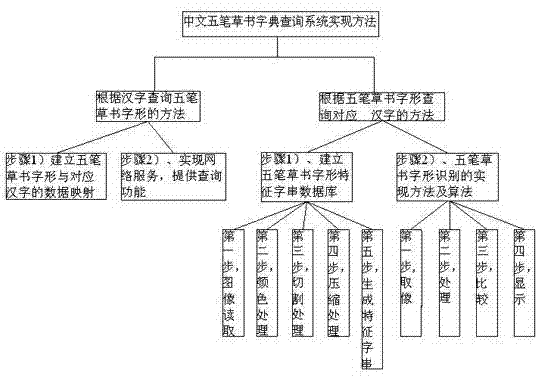
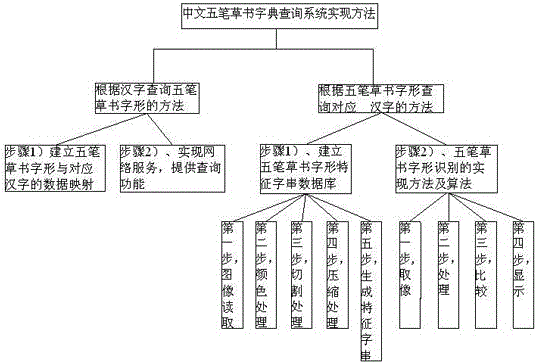
Implement method for Chinese wubi cursive script dictionary query system
ActiveCN103778250AEasy to knowEasy to learnStill image data retrievalSpecial data processing applicationsNatural language processingChinese characters
The invention relates to an implement method for a Chinese wubi cursive script dictionary query system. The method comprises a wubi cursive script character pattern query method as per Chinese character and a corresponding Chinese character query method as per wubi cursive script character pattern, wherein the wubi cursive script character pattern query method as per Chinese character comprises the following two steps: establishing a data mapping between a wubi cursive script character pattern and a corresponding Chinese character, and realizing web service and providing query function; the corresponding Chinese character query method as per wubi cursive script character pattern comprises the following two steps: establishing a characteristic word string database for a wubi cursive script character pattern, and establishing implement method and algorithm for recognizing the wubi cursive script character pattern. The implement method provided by the invention is original, and through applying the Chinese wubi cursive script query system established in the method, devotees of wubi cursive script can figure out the style of writing of corresponding wubi cursive script as per Chinese character, learners of wubi cursive script can query the corresponding Chinese character of a certain wubi cursive character pattern, and the method is beneficial for people to understand and learn Chinese wubi cursive script and is beneficial for worldwide popularization and application of Chinese cursive script.
Owner:张朝亮
High speed cache data pre-fetching method based on increment type closed sequence dredging
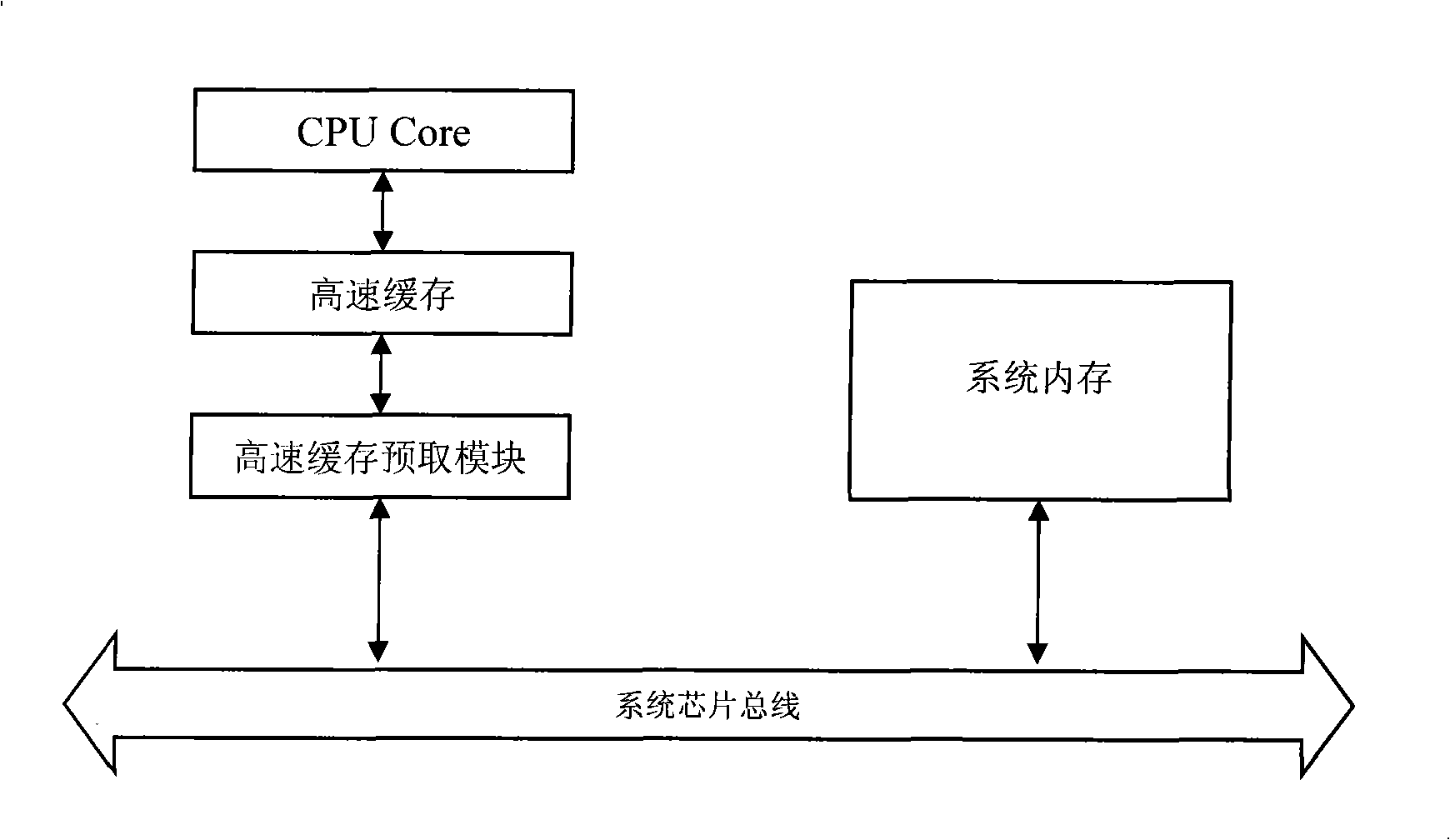
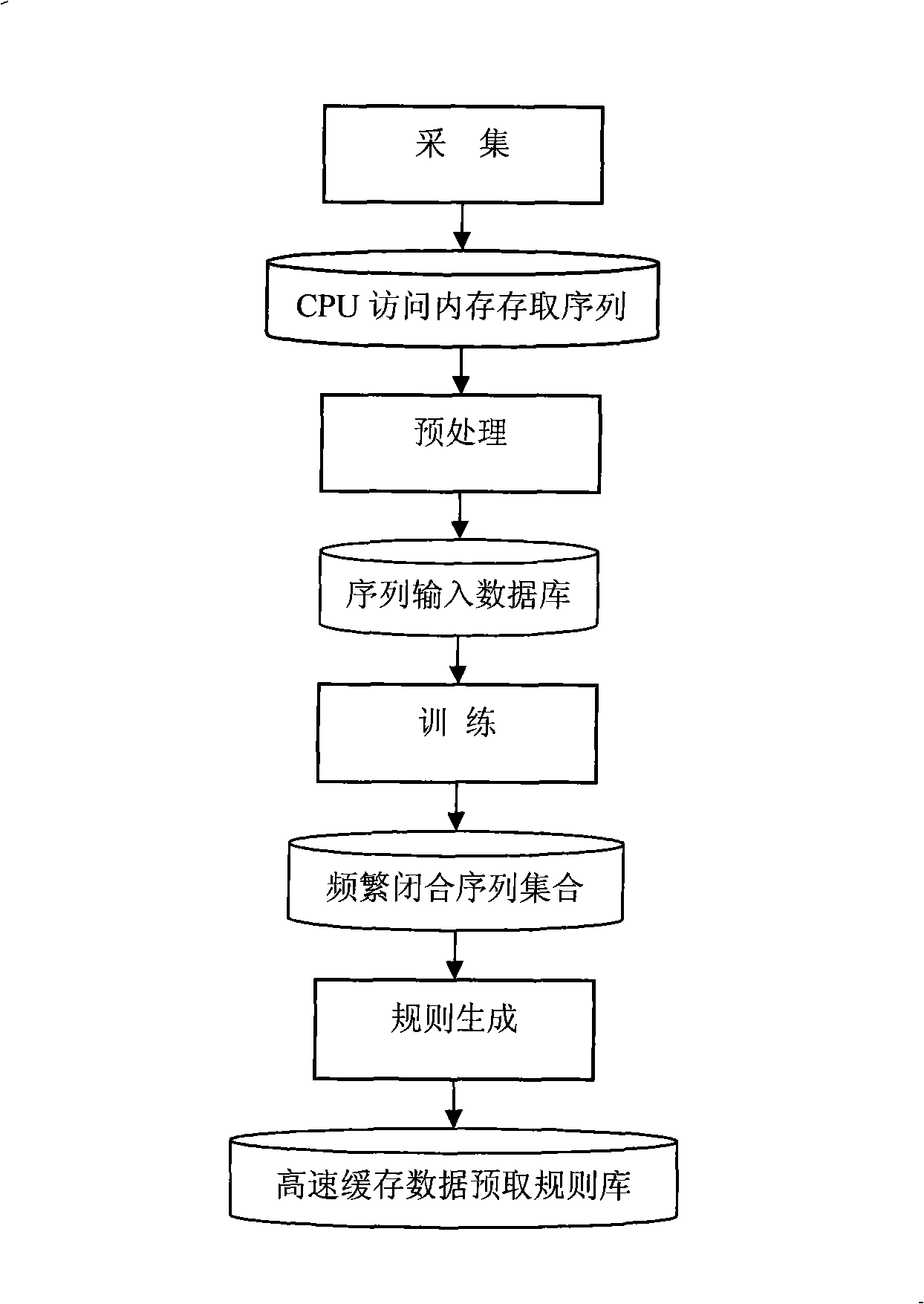
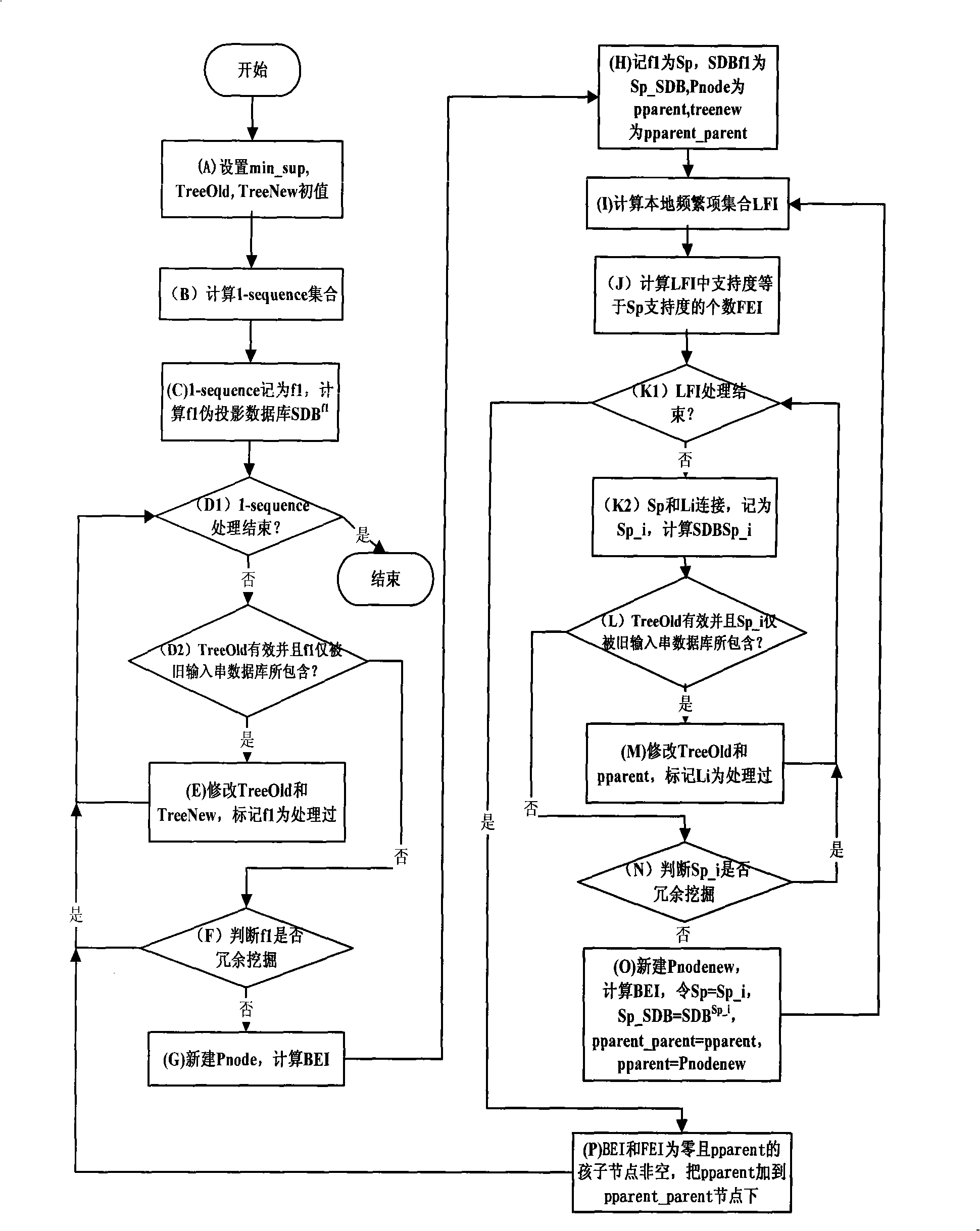
InactiveCN101266578AImprove hit rateSave running spaceMemory adressing/allocation/relocationSpecial data processing applicationsString databaseData access
The invention discloses a prefetching method of cache data based on an incremental closing sequence mining. Through collecting the data access sequence of visiting the memory by the CPU, the data access sequence is transferred into a sequence input database, mining a frequent closed sequence adopting the incremental closing sequence mining arithmetic, extracting a cache data prefetching rule to use to conduct the data prefetching of the cache, so that there are semantic link and data prefetching intelligent between the data blocks, which enhances the hit ratio of the cache. The invention can mine the inputted sequence in an incremental way according to the environmental change in real time. Maintaining mass candidate closed sequences is not needed, so that a lot of space is saved, enhanced the hit ratio of the cache by 12%-25%. The invention has universality, being easy to widely apply to the real time environment that the sequence input string database is dynamic update, the range of variation is small, and the frequency is high.
Owner:ZHEJIANG UNIV
Authentication method and system for CAPTCHA Turing test based on static characters
InactiveCN103093138AIncrease the difficultyStrong defenseDigital data authenticationString databaseSemantics
The invention discloses an authentication method and a system for CAPTCHA Turing test based on static characters. The authentication method and the system for the CAPTCHA Turing test based on the static characters include the following steps of establishing a communication connection between a server and a client, selecting randomly a static string in a static string database stored the server in advance, segmenting the static string into single characters, then calling a character image to generate a function which converts single characters into image representation, placing the single characters represented by the image into a region formed by a circular or elliptic boundary to show as a verification code on the client so as to carry out the Turing test CAPTCHA. Utilizing the region formed by the circular or elliptic boundary to place the verification code, the method can effectively prevent the character from being segmented by conventional pixel segmentation, and thus increases the difficulty of attack. The method carries out distortion, mirror image, and increasing interference lines for characters. The method carries out the characters arrangement according to the specific semantics of the characters and increases more human participation and can guarantee the safe man-machine interaction.
Owner:COMMUNICATION UNIVERSITY OF CHINA
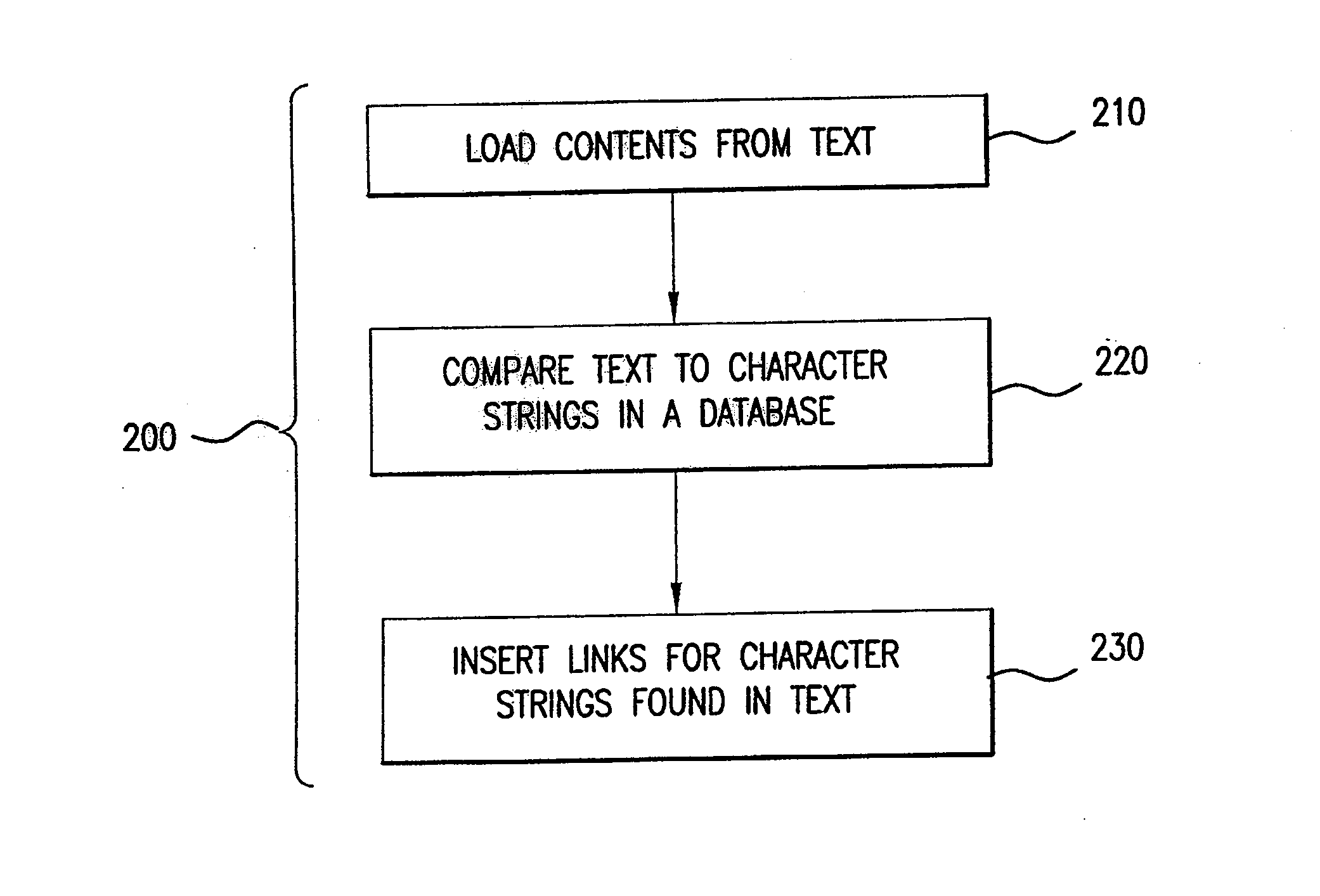
Automatically inserting relevant hyperlinks into a webpage
A methodology through which a host site may automatically insert relevant links into a set of text. In this methodology, the contents of the text are compared against a database containing character strings, and the character strings from the database contained in the text are identified. Each of the character strings in the database has an associated link that connects to other webpages on the same website or other websites. For each character string of the database found in the contents of the text, the associated link is inserted into the text. In this way, only relevant links are inserted into the text.
Owner:EBAY INC
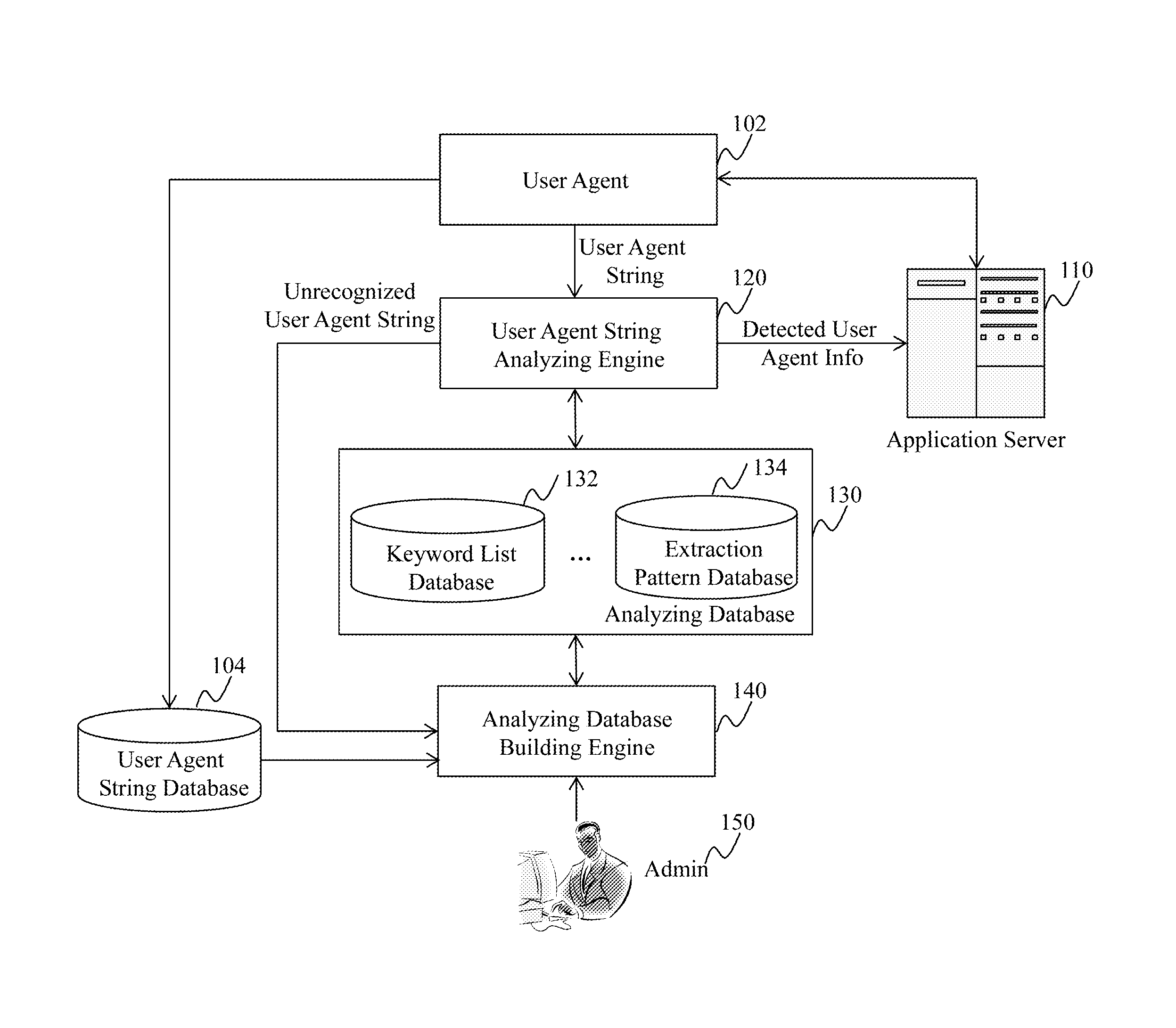
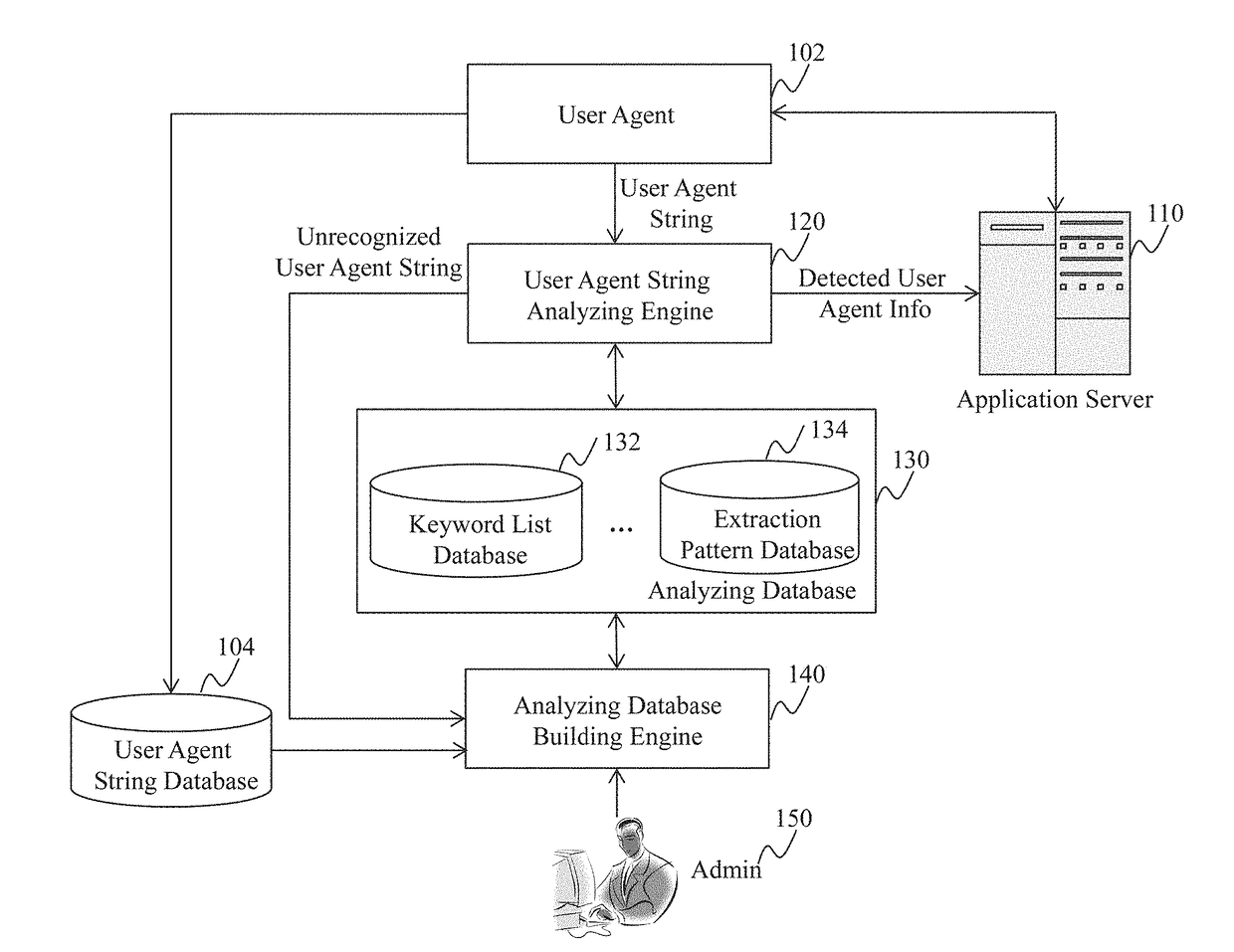
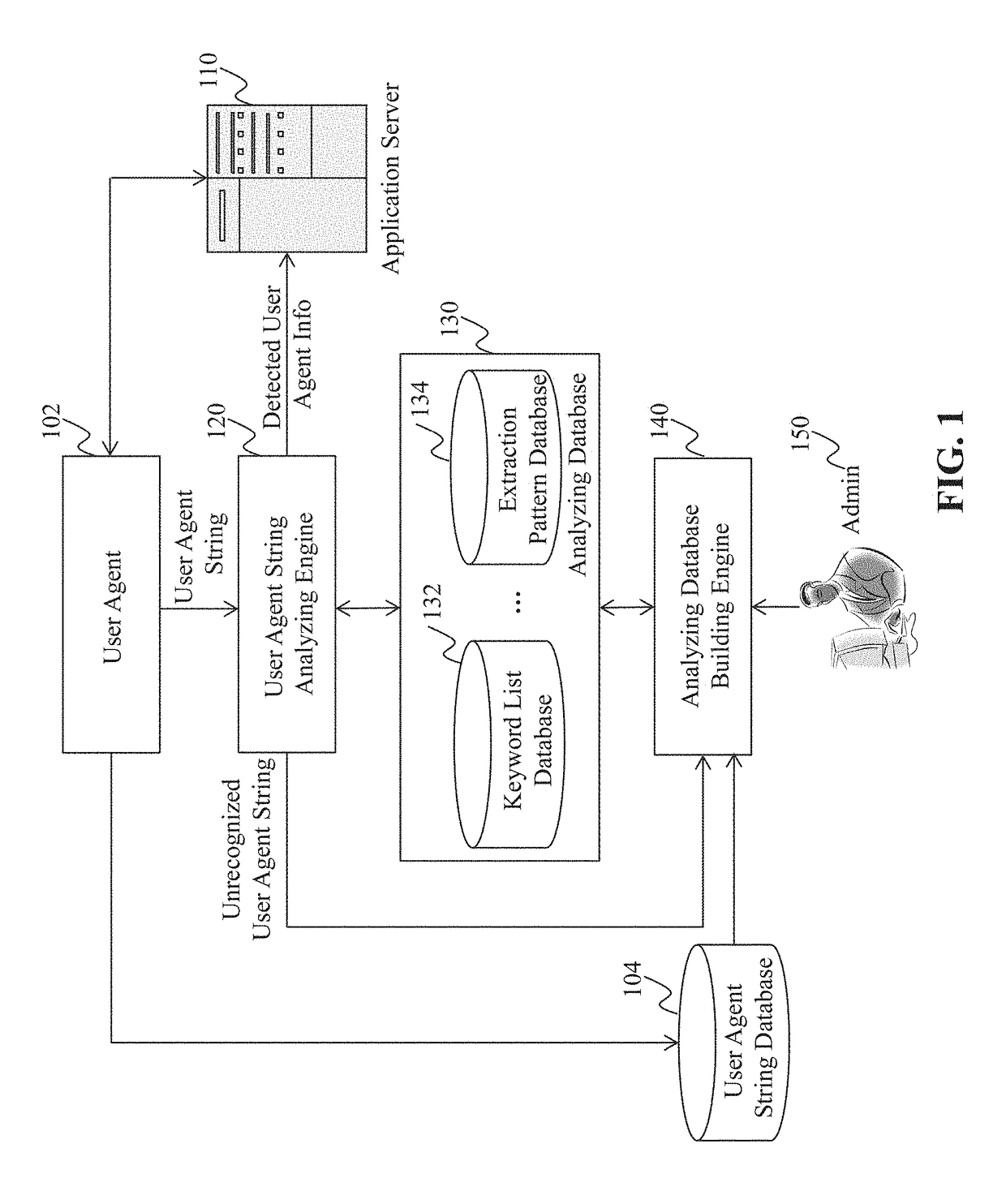
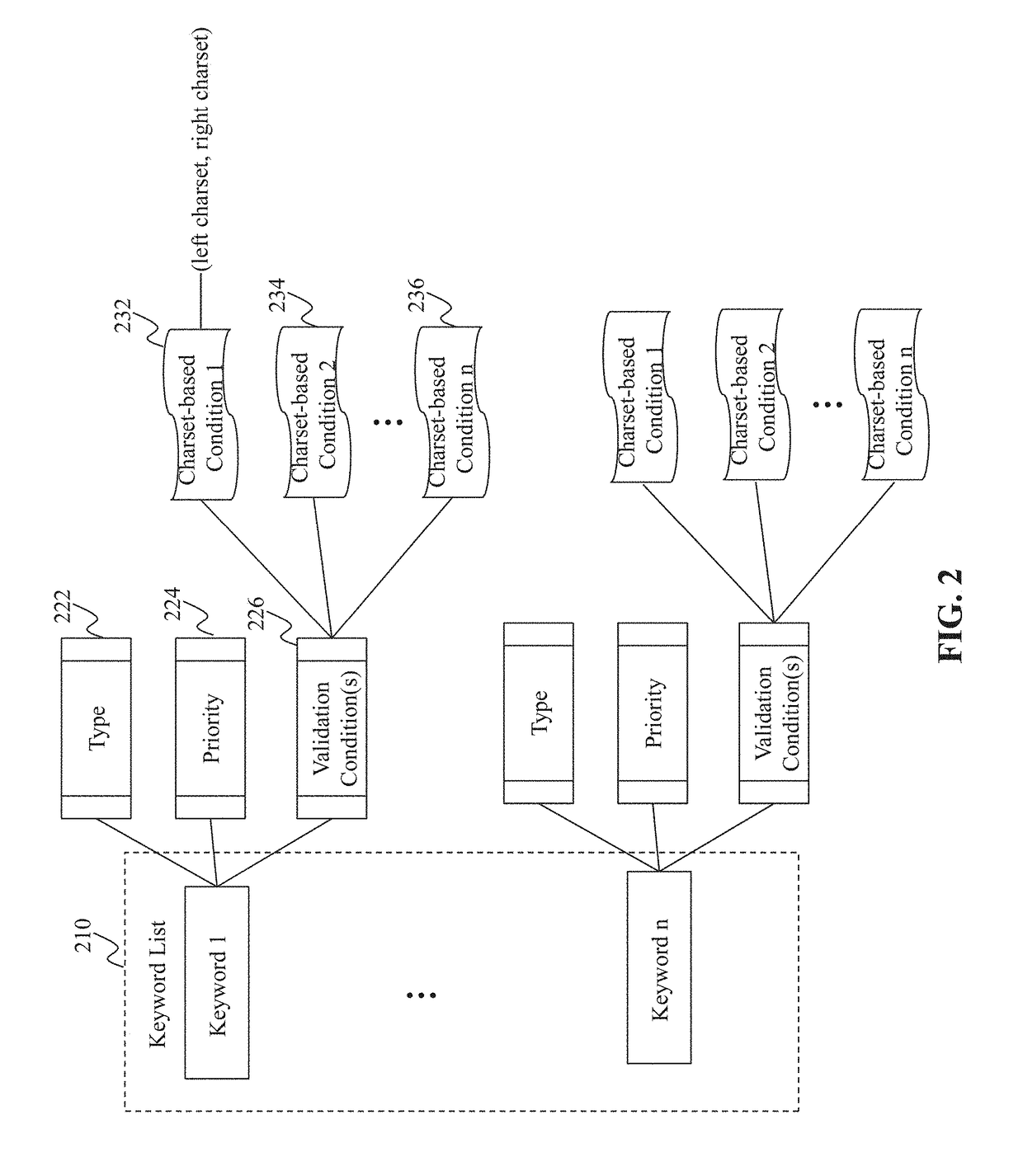
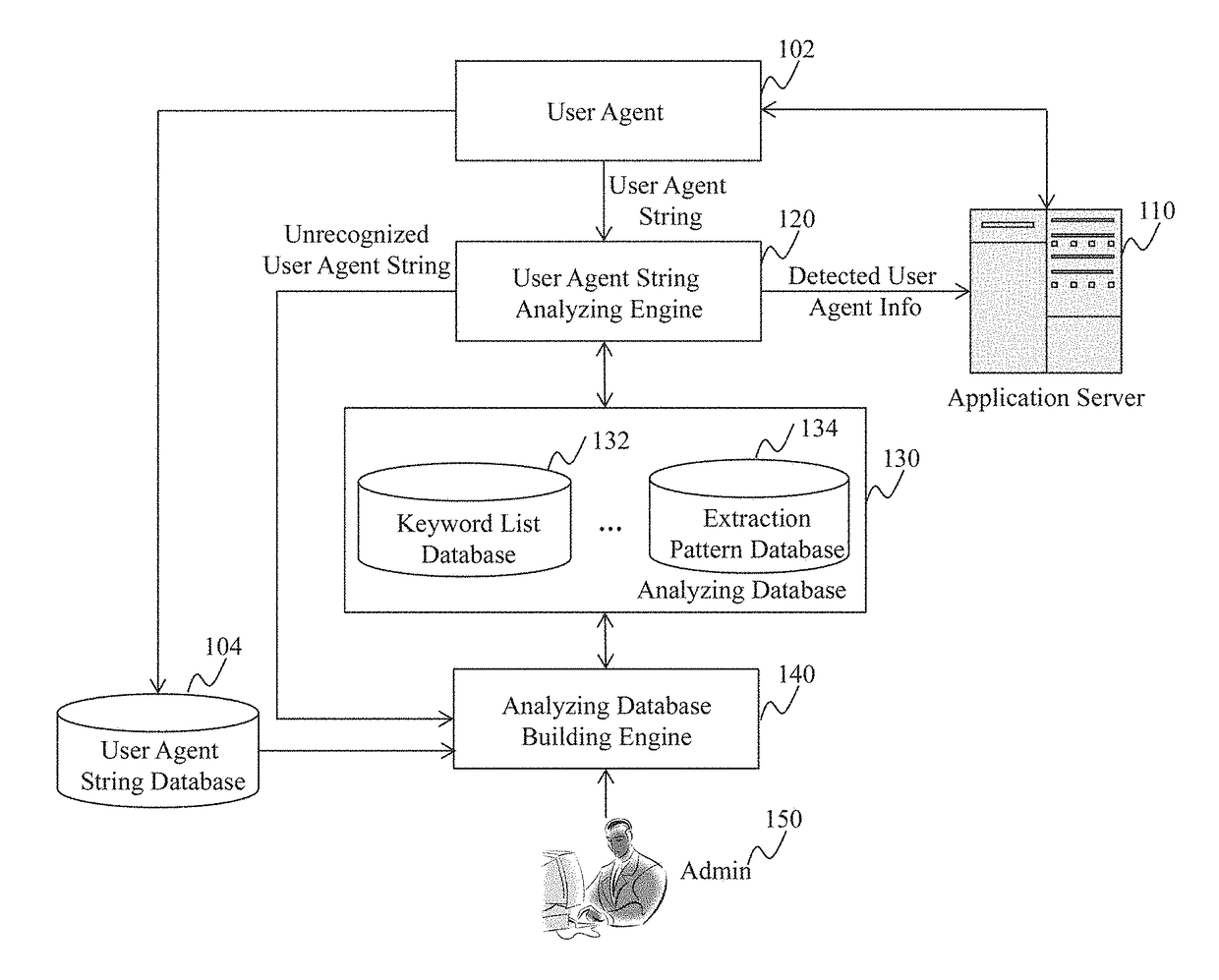
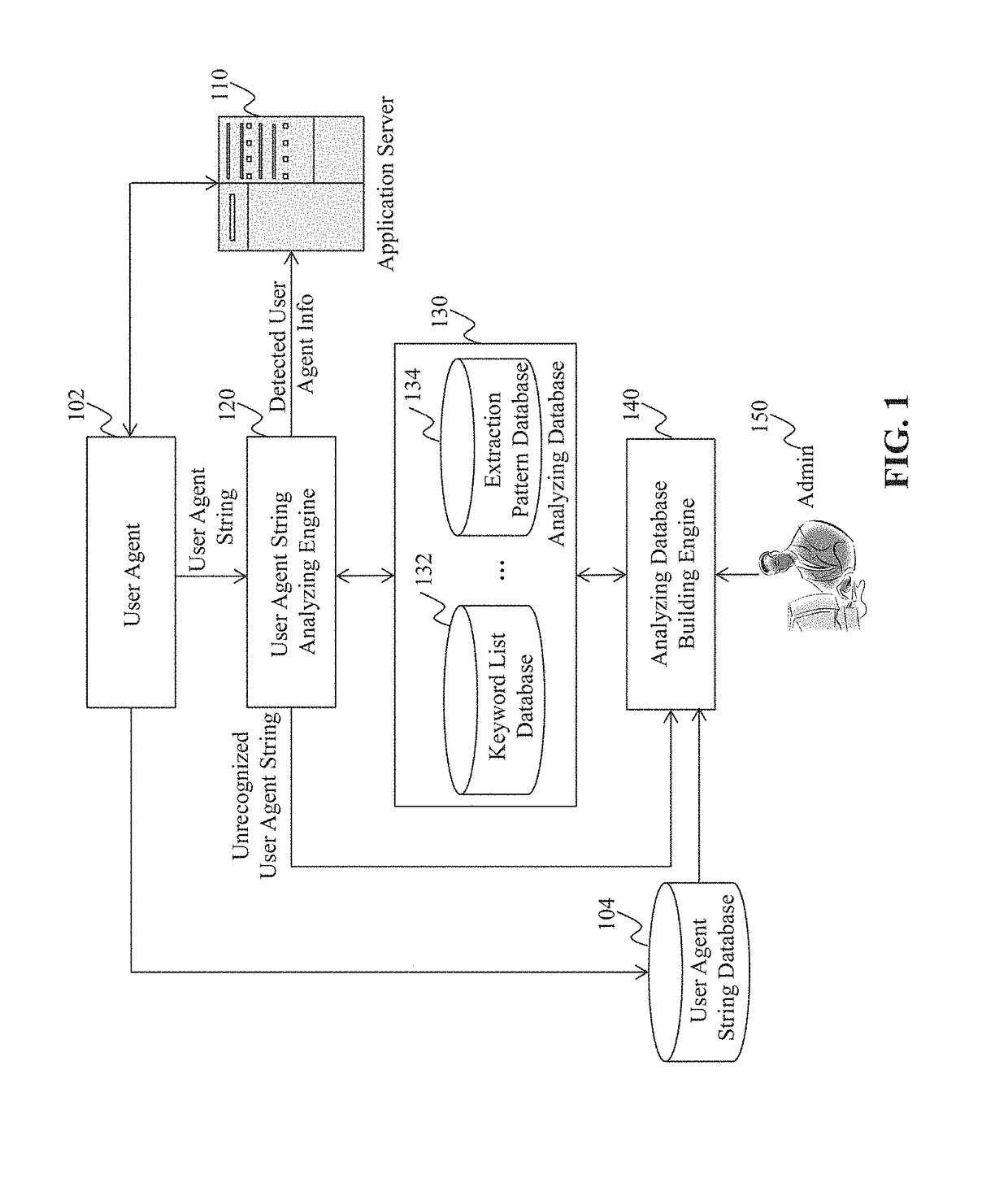
Method and System for Providing a User Agent String Database
Method, system, and programs for determining a keyword from user agent strings are disclosed. In one example, a plurality of user agent strings is received. The plurality of user agent strings is grouped into one or more clusters. The one or more clusters comprise a first cluster that includes two or more user agent strings. The two or more user agent strings in the first cluster are compared. Based on the comparing, a keyword is determined from the first cluster. The keyword represents a type of user agent information.
Owner:YAHOO ASSETS LLC
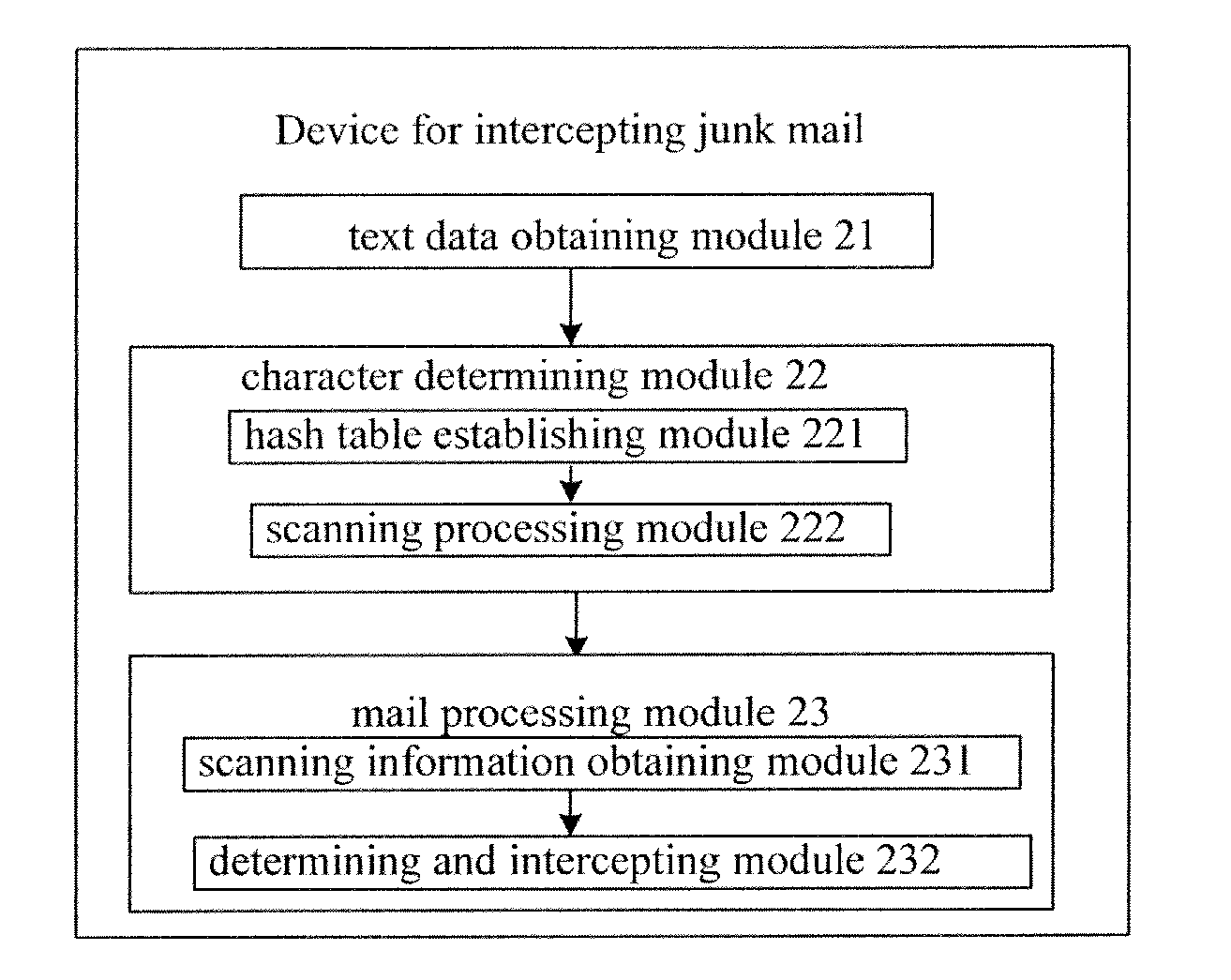
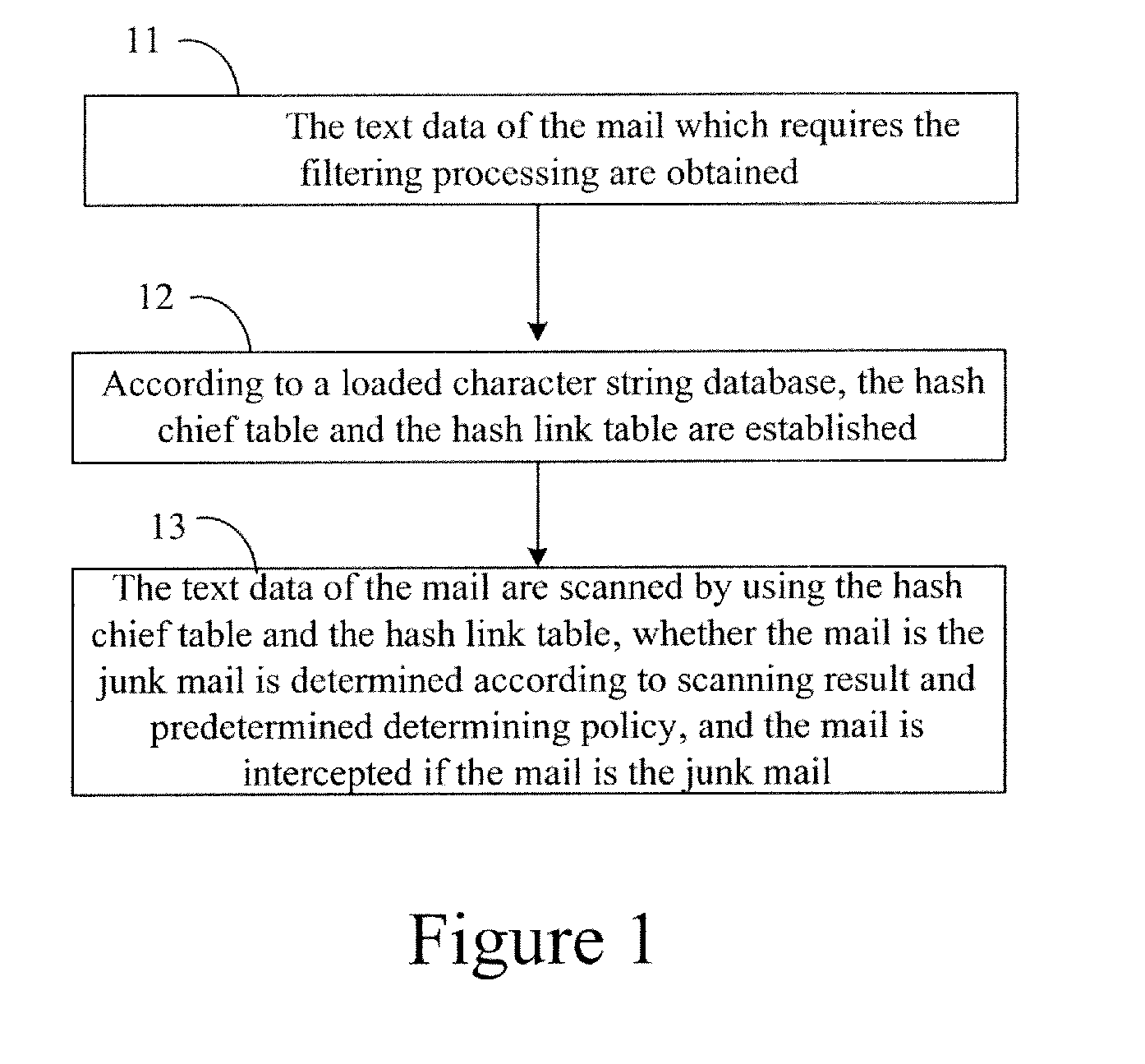
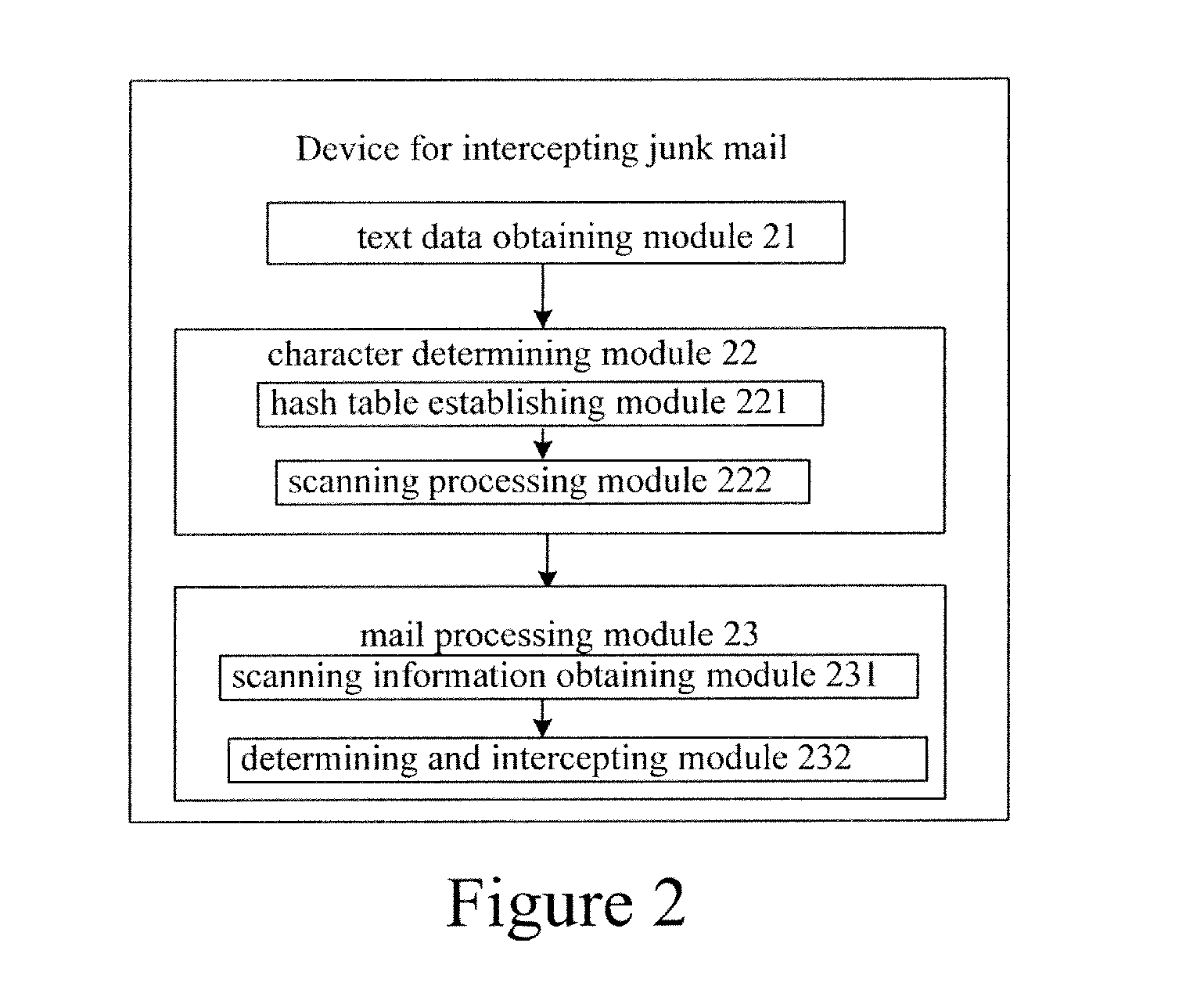
Method and device for intercepting junk mail
InactiveUS20110202620A1Improve efficiencySolve the slow scanning speedMultiple digital computer combinationsData switching networksString databaseData mining
A method and a device for intercepting a junk mail are provided. The method mainly includes: A: obtaining text data of a mail which requires filtering processing; B: determining whether the text data contain a keyword in a string contained in a string database for mail filtering, and if the text data contain the keyword in the string contained in the string database for mail filtering, further determining whether the text data comprise a string corresponding to the keyword contained in the string database; and C: determining whether the mail is a junk mail according to a result of the further determining and according to a predetermined determining policy, and intercepting the mail if the mail is the junk mail. By the method and device, the scanning efficiency and the scanning speed can be improved, and real-time filtering for the mail can be implemented even when the string database has a relatively large dimension.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and device for retrieving work order address of power distribution network
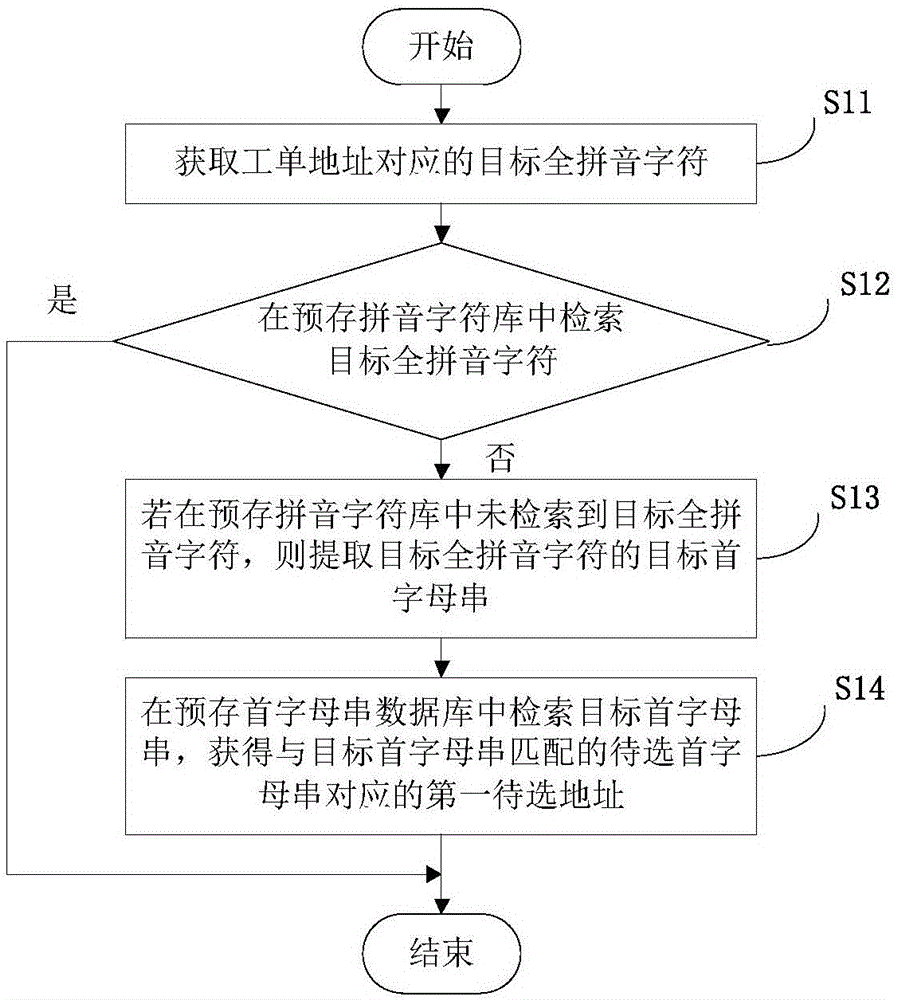
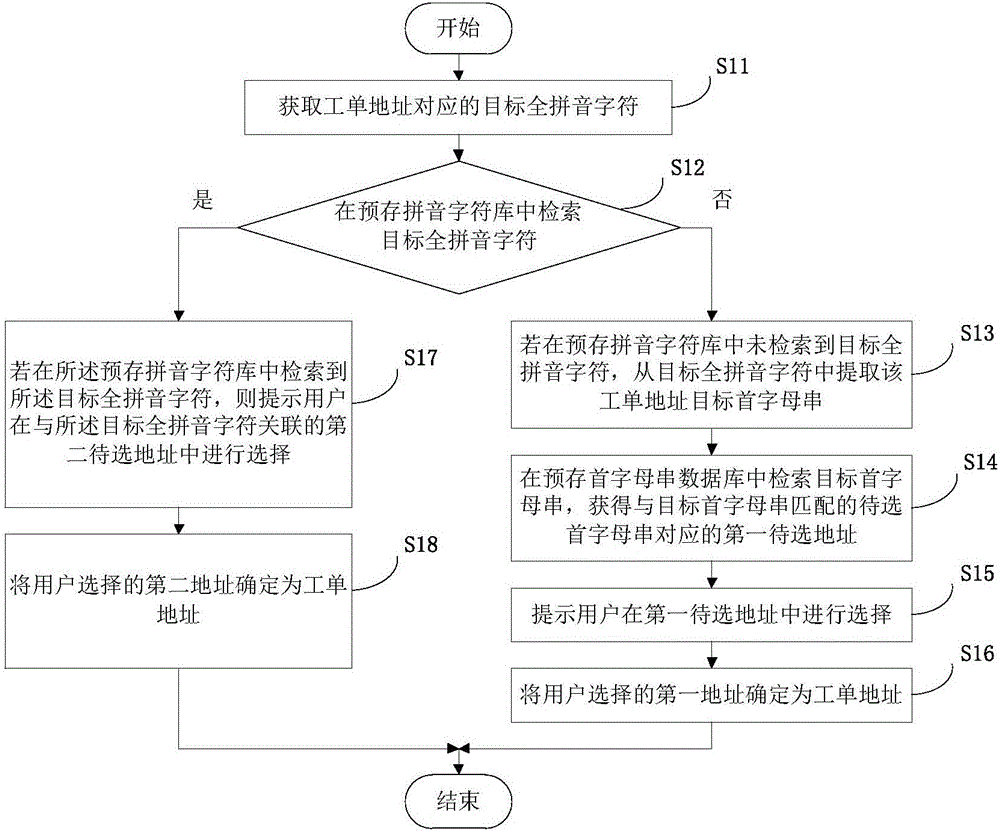
ActiveCN106503033AImprove processing efficiencyRealize automatic error correctionData processing applicationsSystems intergating technologiesString databaseProcess efficiency
The invention provides a retrieval method for a work order address of a power distribution network and a retrieval device of the work order address of the power distribution network. The method comprises the steps that a target full-spelling character corresponding to the work order address is acquired; the target full-spelling character is retrieved in a pre-stored spelling character library; if the target full-spelling character is not retrieved in the pre-stored spelling character library, a target initial letter string of the target full-spelling character can be extracted; and the target initial letter string is retrieved in a pre-stored initial letter string database, and a first candidate address corresponding to a candidate initial letter string matched with the target initial letter string can be obtained. According to the scheme, retrieval are conducted for twice in different scopes, so that wrongly writer characters, homophonic characters, character surplus, character lack and so forth appearing in client address information can be corrected automatically, and thus the correct work order address can be found rapidly and accurately. In this way, situations such as confirmation of the work order address based on repeated contact with a client, and wrong work assignment caused by the wrong work order address can be avoided, and processing efficiency of work orders of the power distribution network can be increased.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
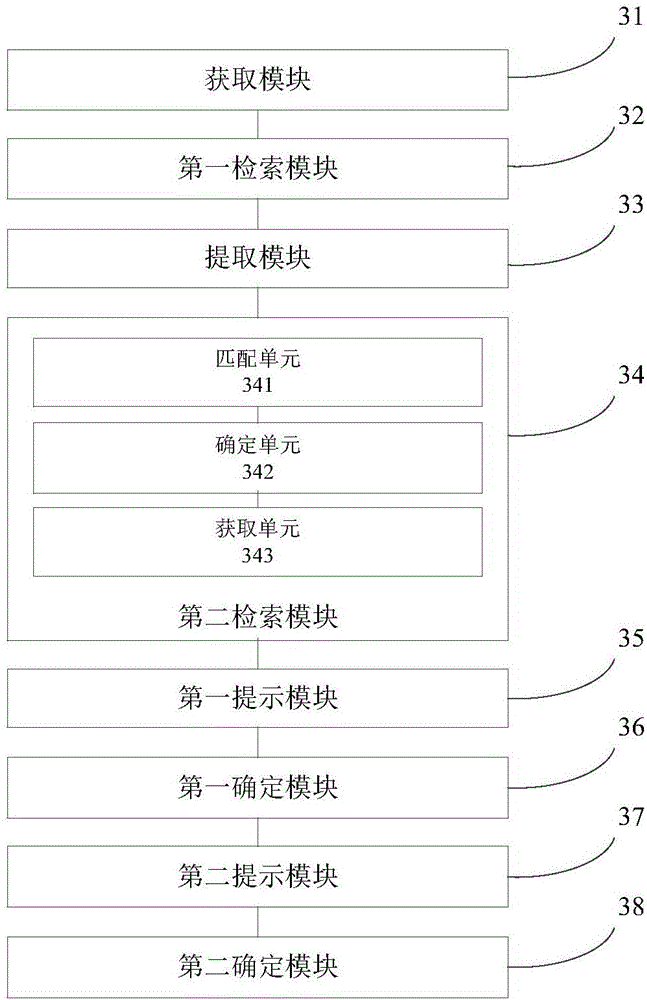
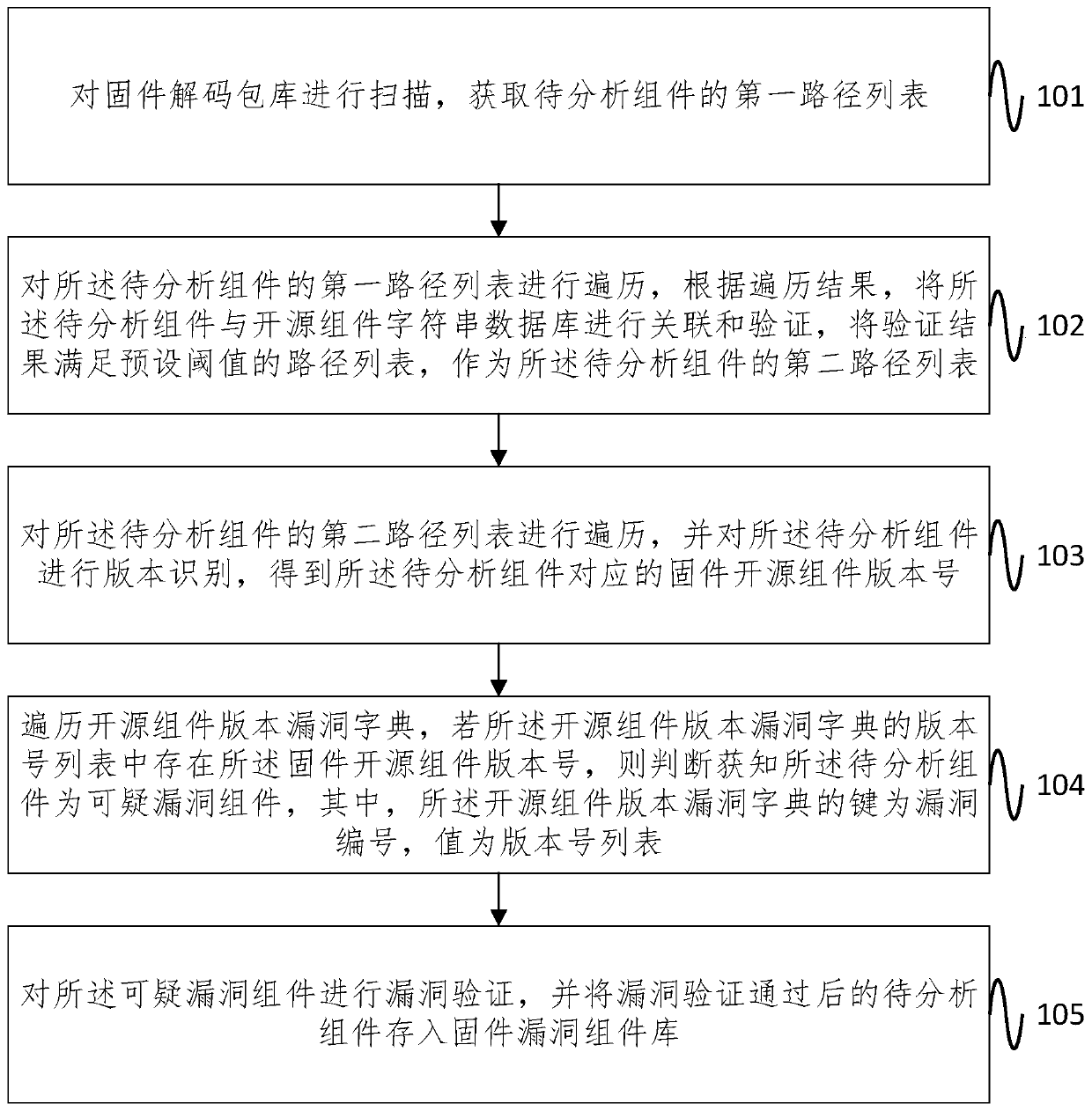
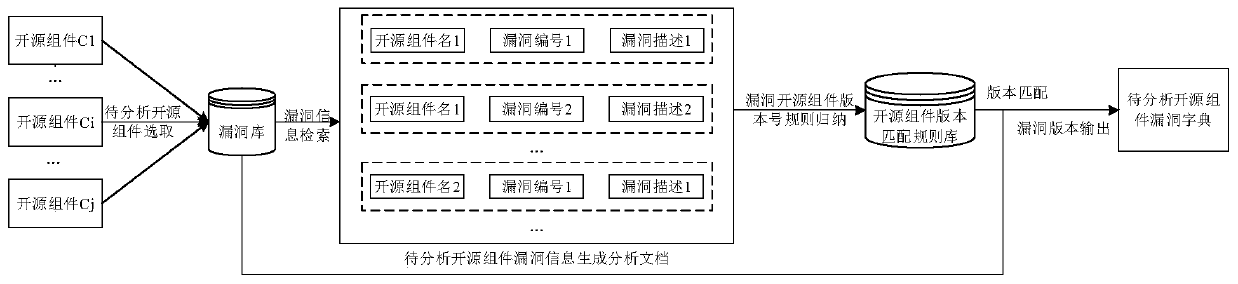
Firmware vulnerability discrimination method and system based on open source component version identification
ActiveCN111400719AImprove reliabilityImprove efficiencyPlatform integrity maintainanceOther databases queryingPathPingString database
The embodiment of the invention provides a firmware vulnerability discrimination method and system based on open source component version identification, and the method comprises the steps: scanning afirmware decoding package library, and obtaining a first path list of a to-be-analyzed component; traversing the first path list of the to-be-analyzed component, and associating and verifying the to-be-analyzed component and the open source component string database to obtain a second path list of the to-be-analyzed component; carrying out the version identification on the to-be-analyzed component to obtain a firmware open source component version number corresponding to the to-be-analyzed component; traversing the open source component version vulnerability dictionary, and if a firmware opensource component version number exists in the open source component version vulnerability dictionary, judging and knowing that the to-be-analyzed component is a suspicious vulnerability component; performing vulnerability verification on the suspicious vulnerability component, and storing the to-be-analyzed component passing the vulnerability verification into a firmware vulnerability component library. According to the embodiment of the invention, suspicious vulnerabilities can be efficiently searched, the reliability of firmware security evaluation is high, and the vulnerability discovery efficiency and accuracy are improved.
Owner:INST OF INFORMATION ENG CAS
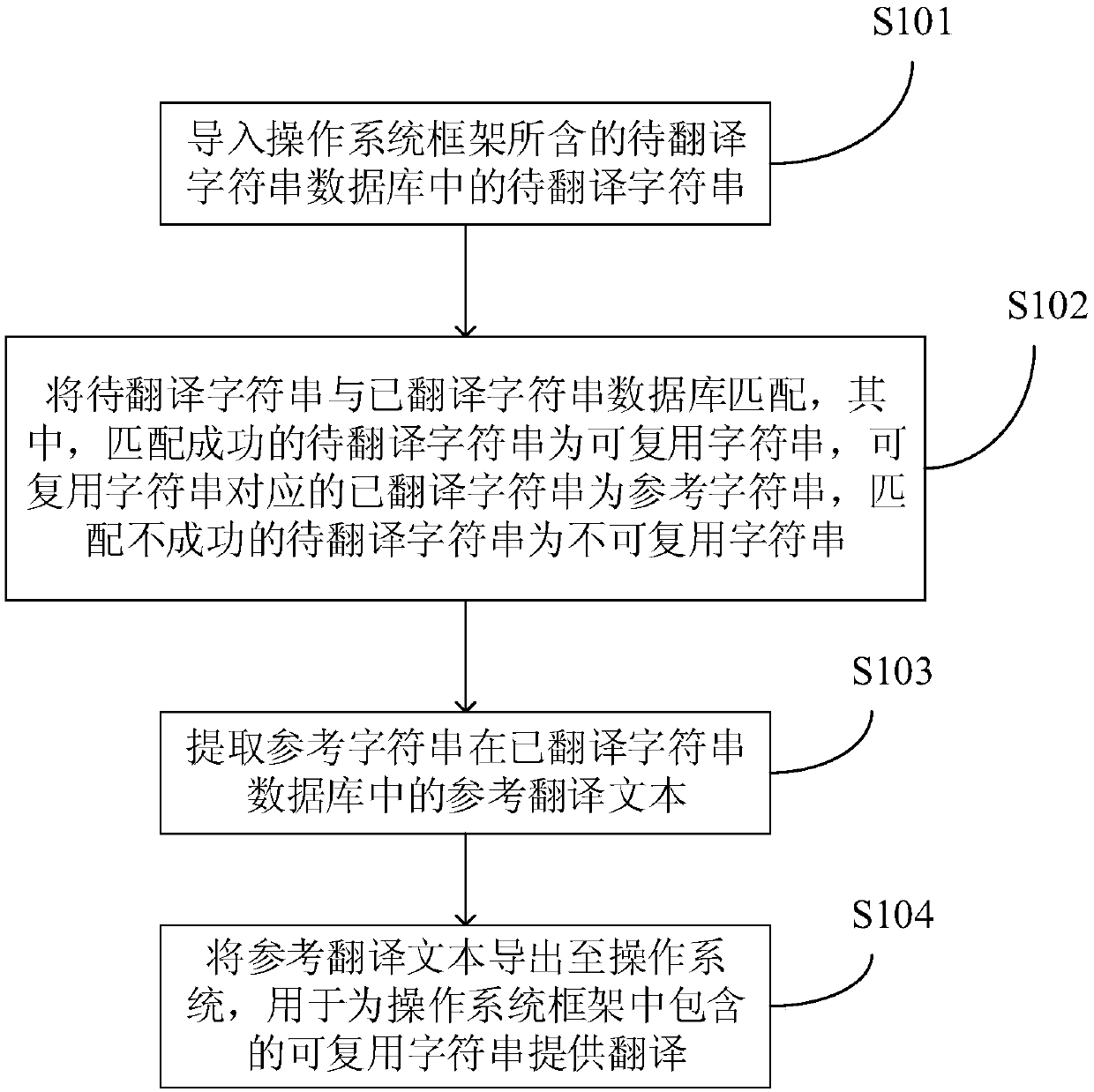
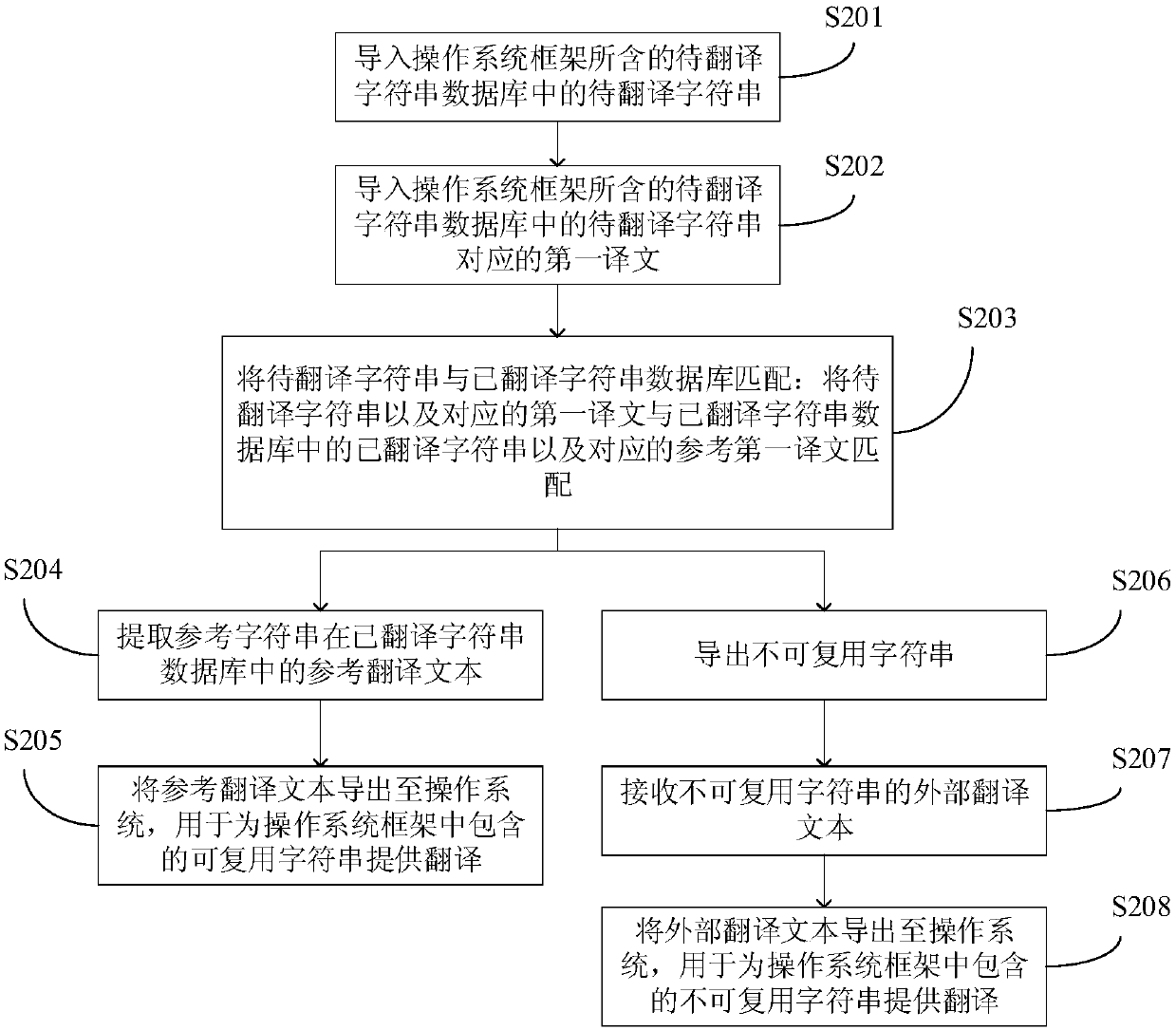
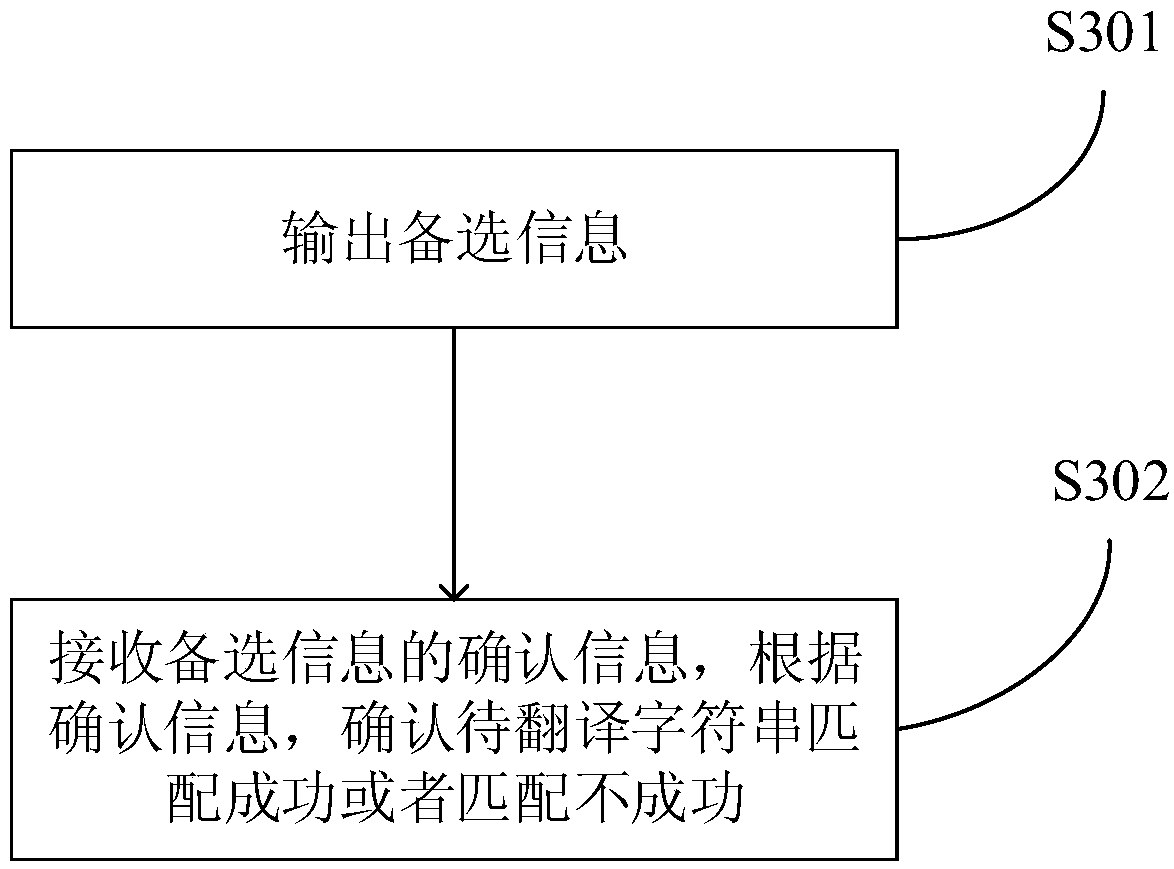
Translation method of operating system framework, mobile terminal and storage device
InactiveCN107741931AReduce duplicate translationsReduce translation costsNatural language translationSpecial data processing applicationsProgramming languageOperational system
The application discloses a translation method of an operating system framework, a mobile terminal and a storage device. The method includes: importing to-be-translated character strings in a to-be-translated character string database contained by the operating system framework; matching the to-be-translated character strings with a translated character string database, wherein to-be-translated character strings which are successfully matched are reusable character strings, translated character strings corresponding to the reusable character strings are reference character strings, and to-be-translated character strings which are not successfully matched are non-reusable character strings; extracting reference translation text of the reference character strings in the translated characterstring database; and exporting the reference translation text to an operating system to use the same to provide translation for the reusable character strings contained in the operating system framework. According to the method, repeated translation of the reusable character strings can be reduced, and thus translation costs are saved.
Owner:JRD COMM (SHENZHEN) LTD
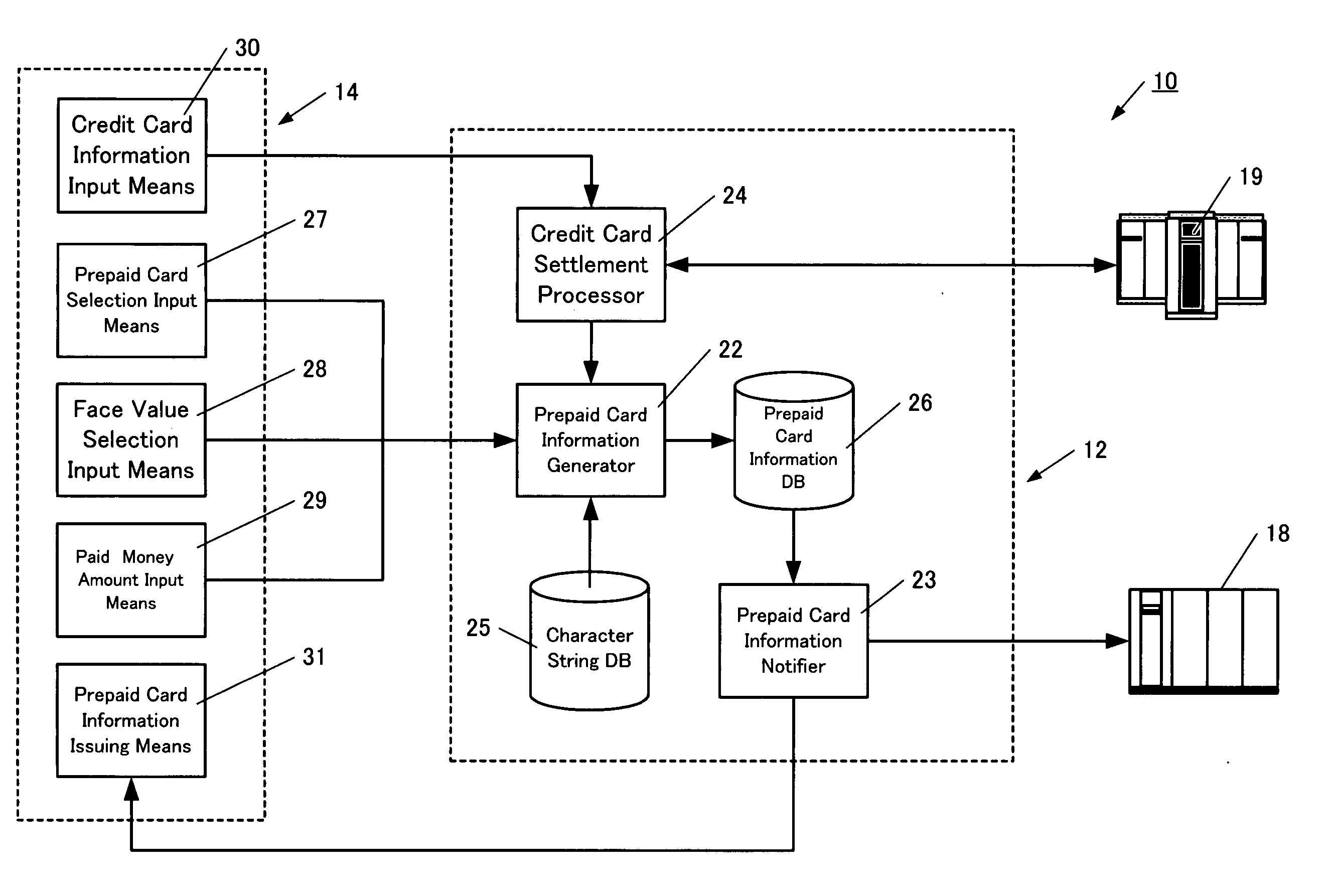
Prepaid card information issuing system, call rate settlement system, communication rate settlement system, and expense settlement system
InactiveUS20050015331A1Decreases communication rateEliminate riskFinanceCredit schemesComputer hardwareBarcode reader
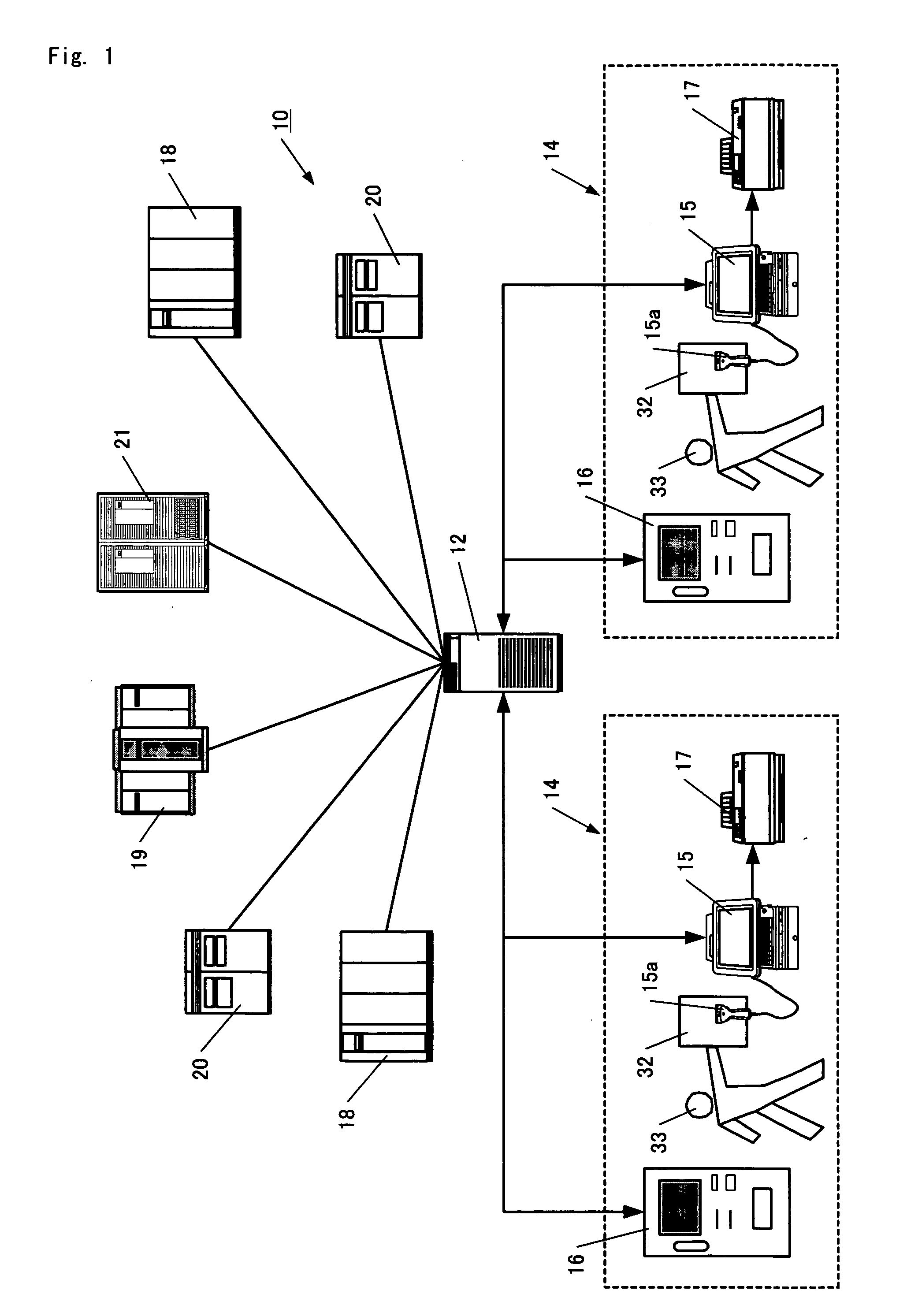
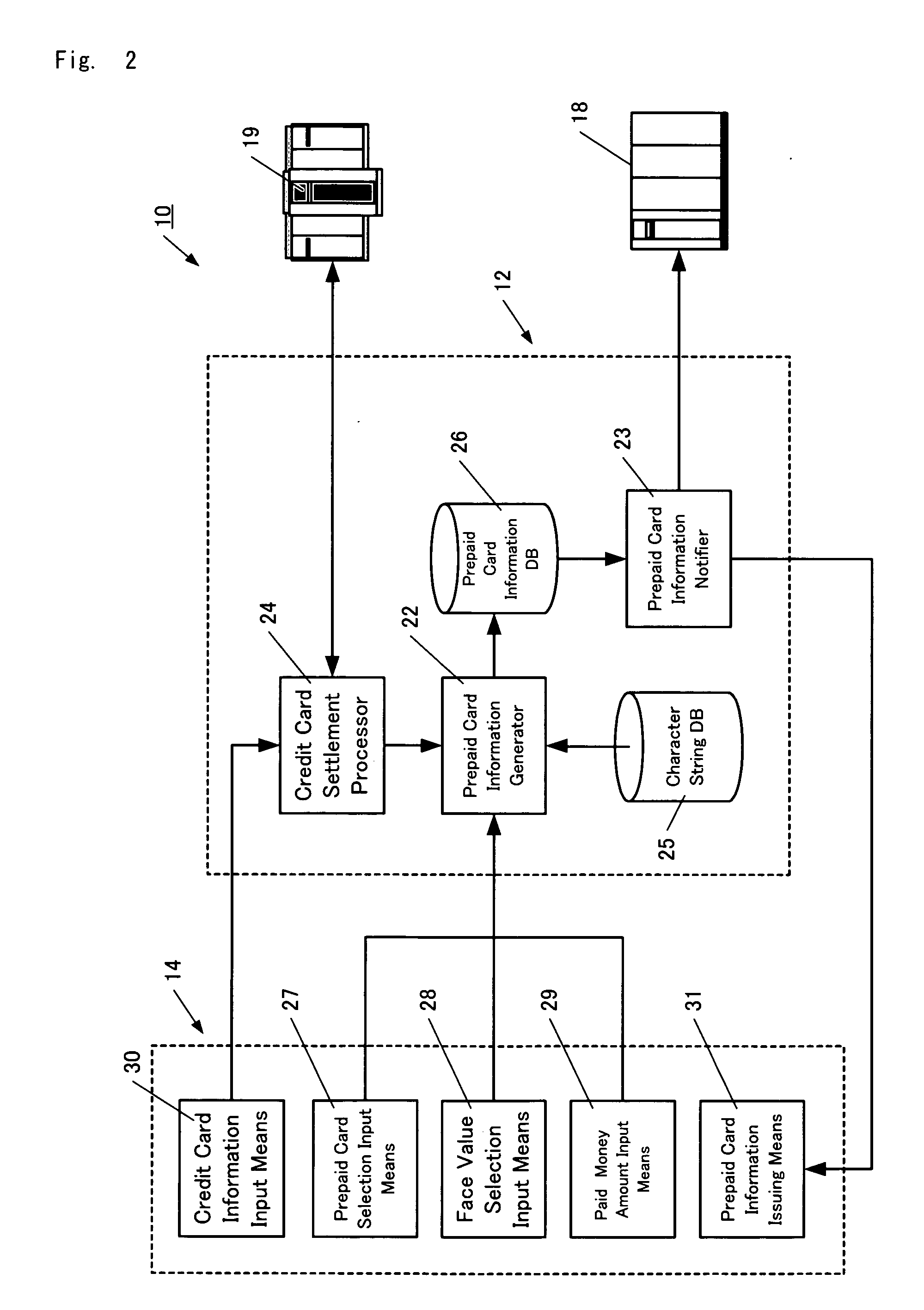
A prepaid card information issuing system 10 comprising a character string data base 25 for storing a plurality of character strings each consisting of a predetermined number of digits, a selection sheet 32 on which barcodes 35, 36 for identifying the type and face value of a prepaid card are displayed, a barcode reader 15a for reading out the barcodes 35, 36 to input the type and face value of the prepaid card, paid amount of money input means for inputting the amount of cash paid, prepaid card information generator 22 for generating prepaid card information by associating some character string in the character string data base 25 with the face value concerned when the face value of the prepaid card thus selected is coincident with the paid money amount, a prepaid card information data base 26 for storing prepaid card information, and prepaid card information issuing means 31.
Owner:GREAT INFORMATION
Character string matching method based on finite state automation and content filtering equipment
InactiveCN101876986BReduce latencyImprove processing speedSpecial data processing applicationsAlgorithmString database
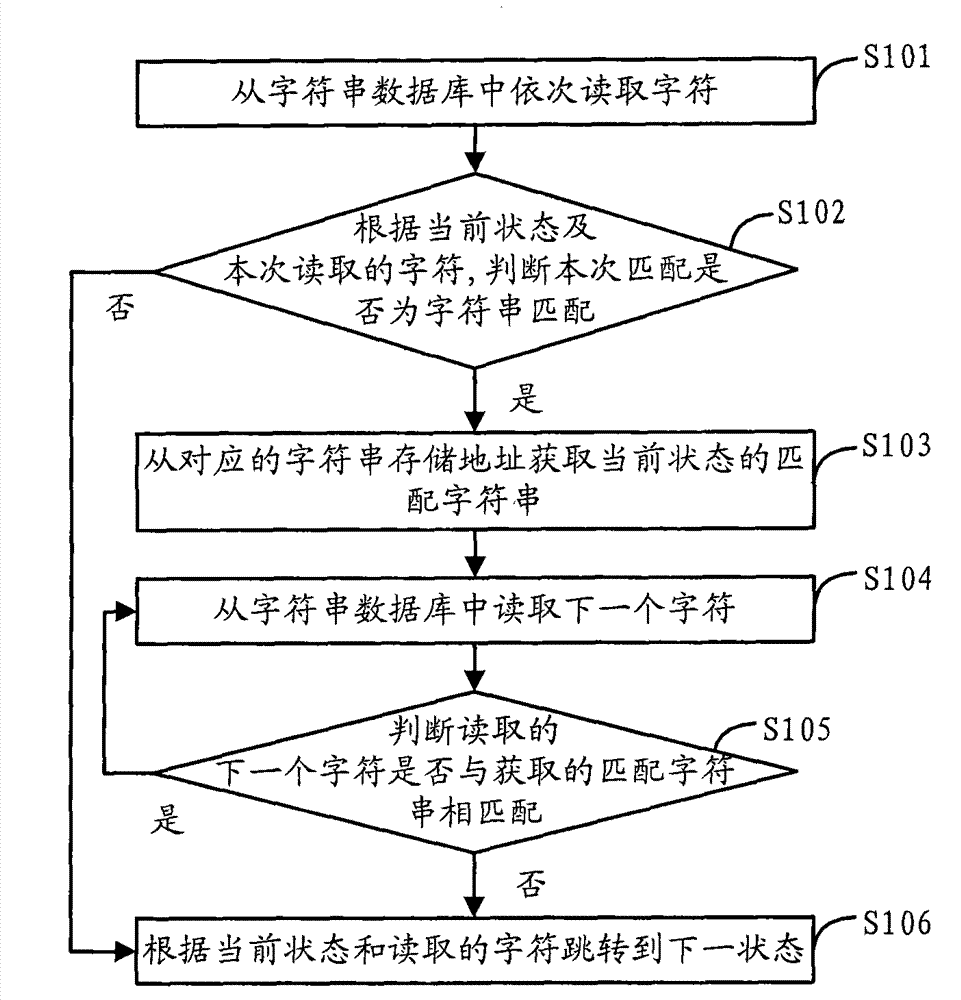
The invention discloses a character string matching method based on a finite state automation and content filtering equipment. The character string matching method comprises the step of combining two sequence-associated states meeting the set conditions in a DFA (Deterministic Finite Automaton) to obtain a combined DFA; the corresponding matching process of character strings comprises the following steps of: sequentially reading characters from a character string database and judging whether the matching is character string matching according to the current state and the read characters; if not, skipping to the next state according to the current state and the read characters; if so, acquiring a matched character string of the current state from the corresponding storage address of the character string, reading next character and judging whether to be matched with next character matched with the character string or not; during matching, continuously reading next character and skippingto the next state until the character strings are successfully matched; and if not, skipping to the next state according to the current state and the read characters. By using the method, the times for accessing a memory during the matching of the character strings can be reduced and the speed and the efficiency for the matching of the character strings can be improved.
Owner:RUIJIE NETWORKS CO LTD
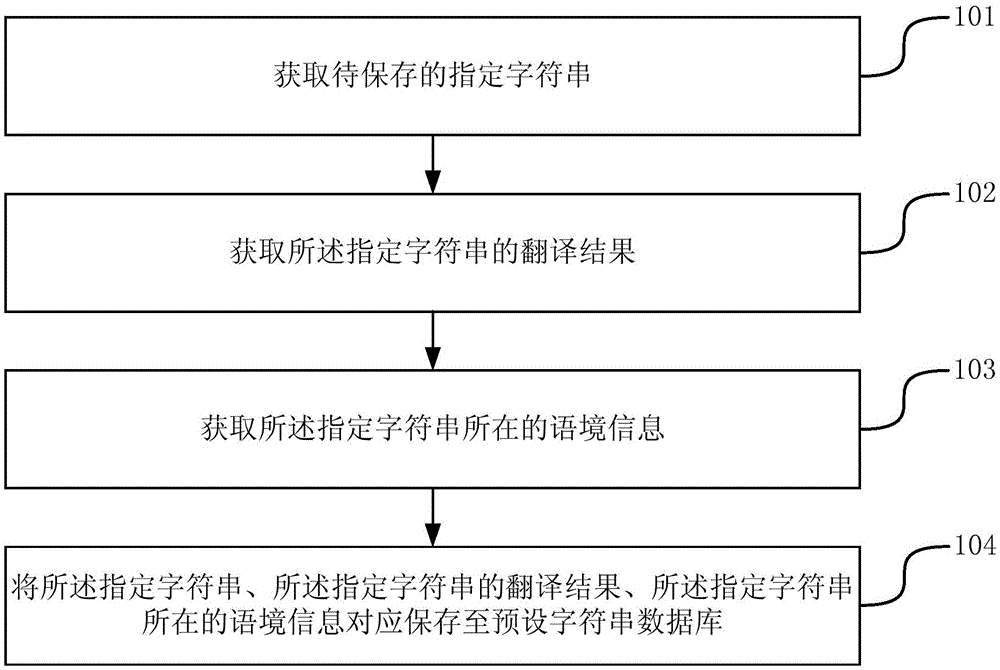
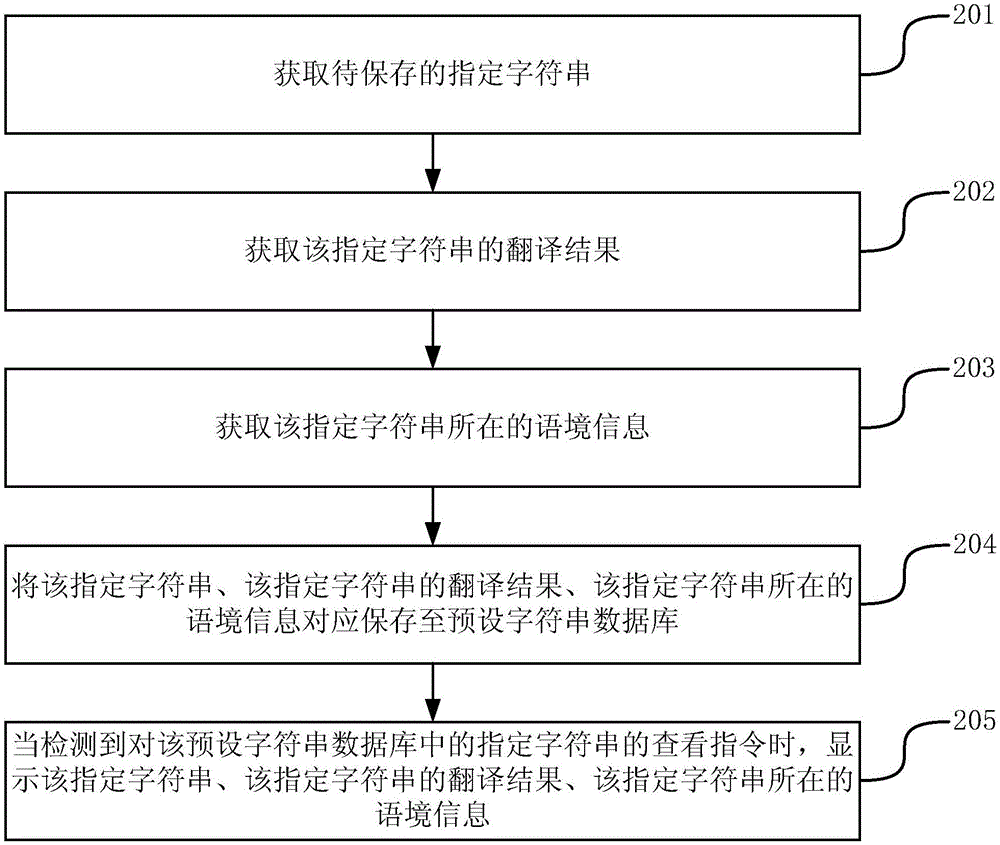
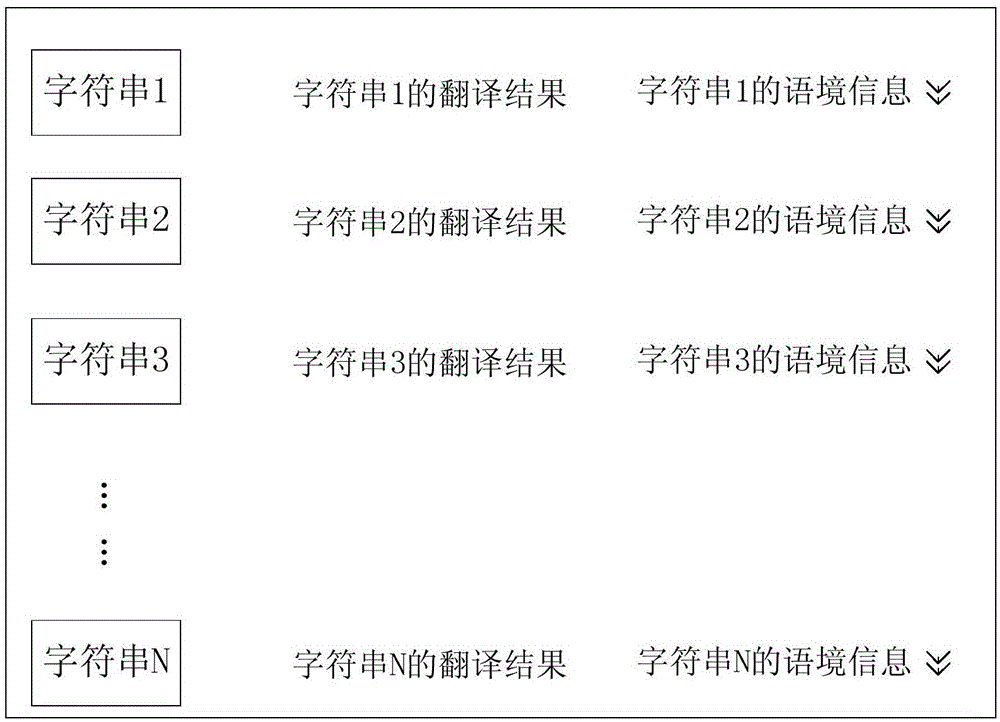
Character string saving method and device
InactiveCN105159893AGood reminderQuick recallNatural language translationSpecial data processing applicationsAlgorithmTheoretical computer science
The invention provides a character string saving method and device and belongs to the technical field of networks. The method comprises obtaining a specified character string to be saved, obtaining a translation result of the specified character string, obtaining the information of a context of the specified character string, and correspondingly saving the specified character string, the translation result of the specified character string and the information of the context of the specified character string in a preset character string database. According to the character string saving method, as the information of the context of the specified character string is saved while the specified character string is saved, the character string and the information of the context of the character string can be displayed simultaneously when a view instruction from a user to the character string in the preset character string database is detected, and therefore, the effect of reminding is improved, and the user can quickly recall the character string and the use scene thereof.
Owner:XIAOMI INC
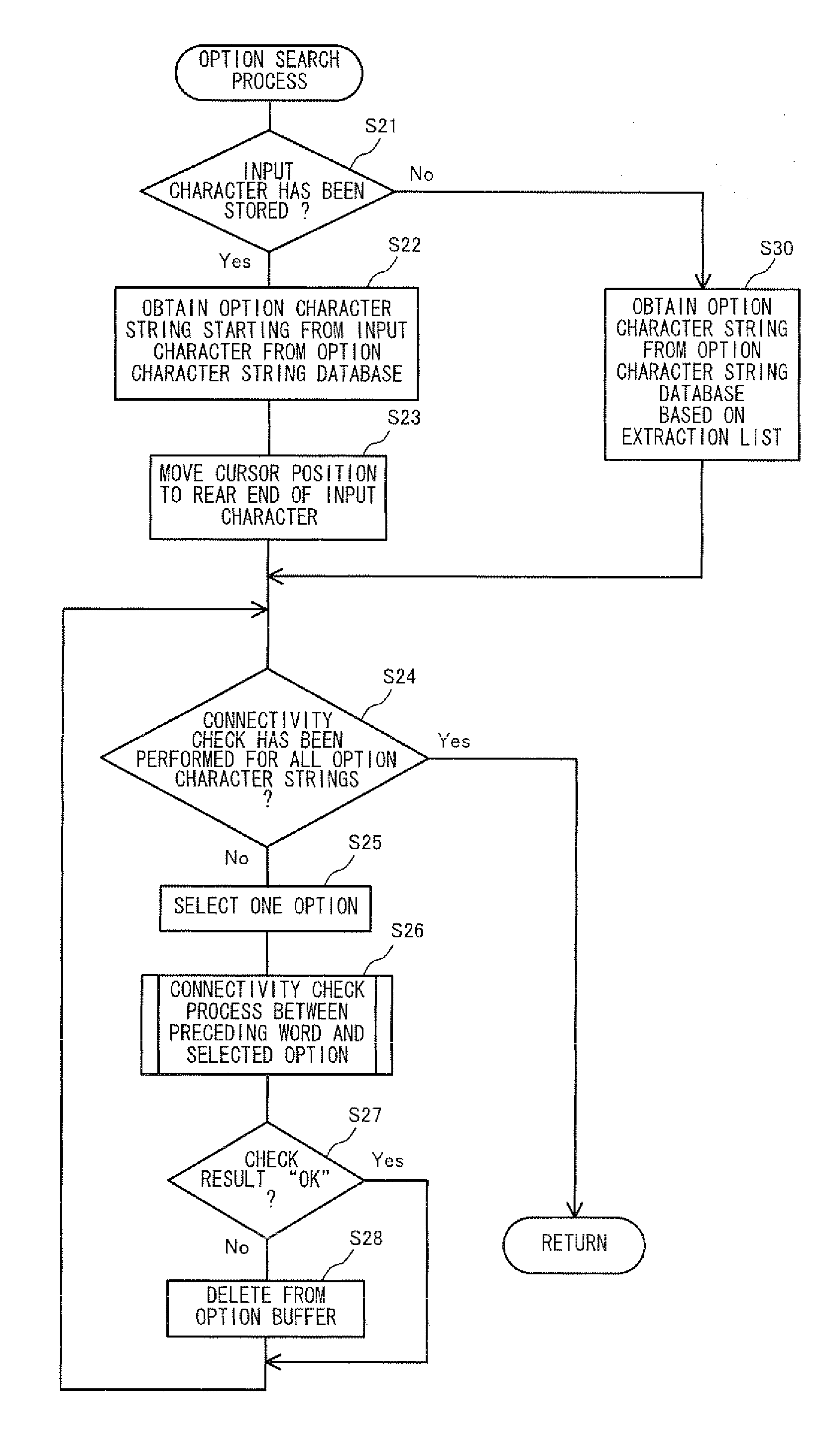
Computer readable storage medium having input program stored therein, system, and input method
ActiveUS20110231427A1Effective preventionEffectively preventing the sameDigital data processing detailsNatural language data processingProgramming languageTheoretical computer science
Upon receiving an input of an input character a1 by a user, a game apparatus stores the received input character a1 as an unfixed character, and displays the stored unfixed character a1. The game apparatus obtains option character strings a2 corresponding to the input character a1 from an option character string database, and receives an operation which the user performs for selecting an option character string a2 from the obtained option character strings a2. Upon receiving the operation for selecting an option character string a2, the game apparatus determines the selected option character string a2 to be a fixed character string, and stores the determined fixed character string, and then outputs the stored fixed character string. Here, only when receiving the operation for selecting an option character string, the game apparatus determines a fixed character string.
Owner:NINTENDO CO LTD
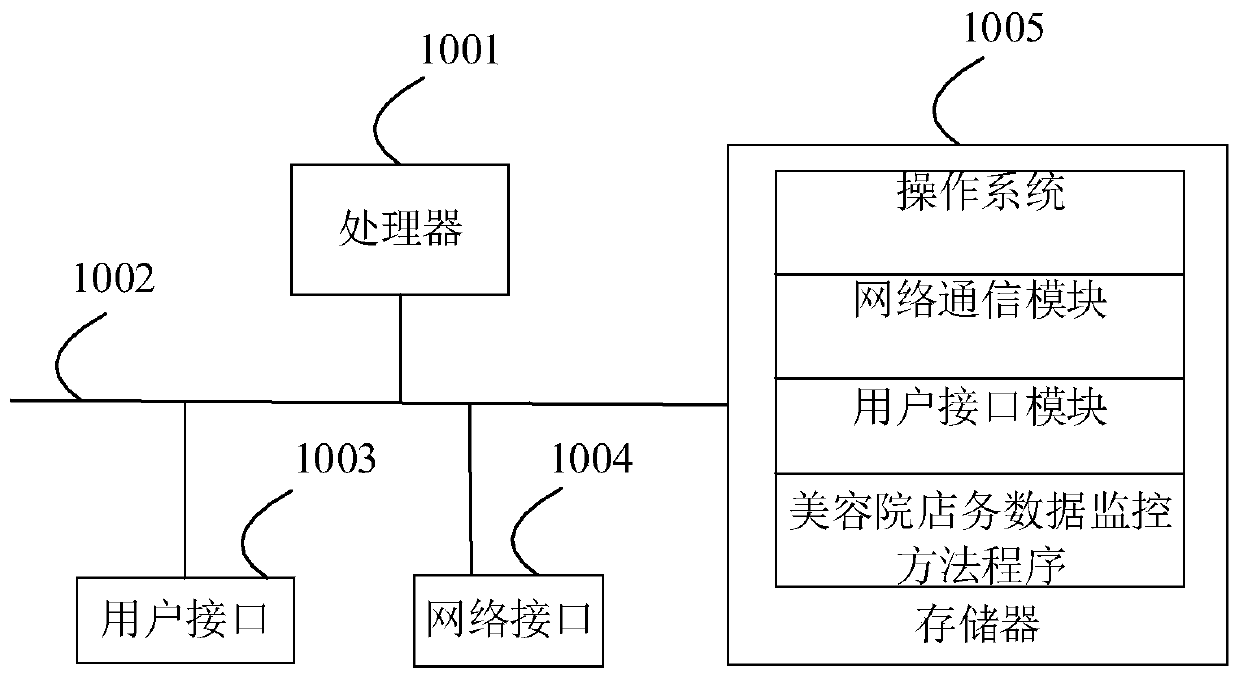
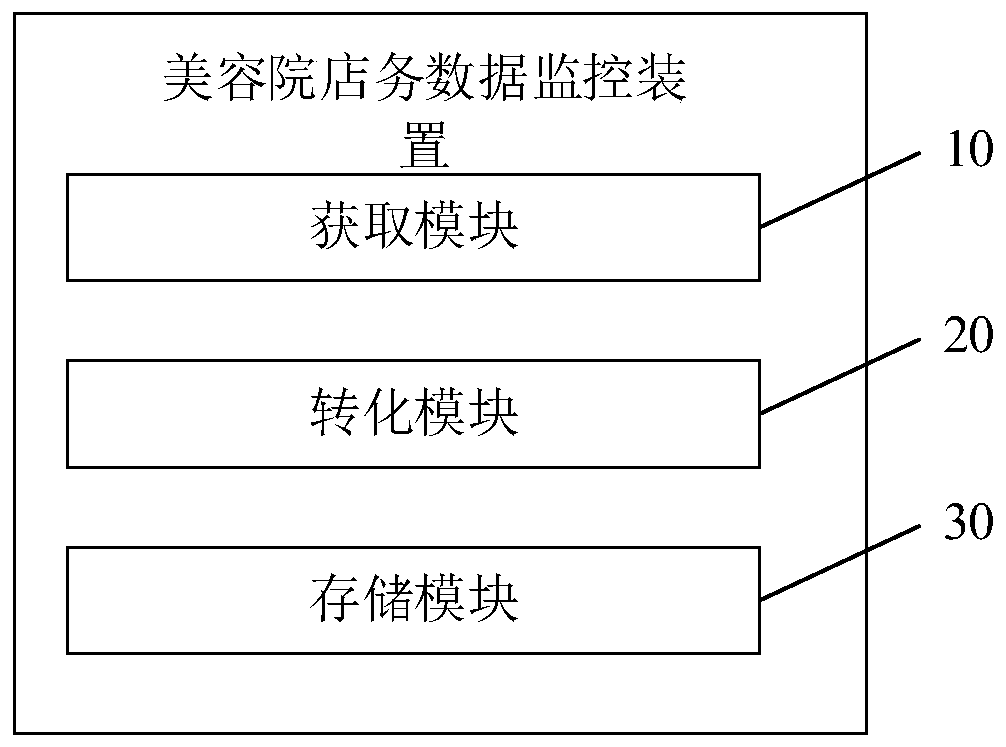
Beautifying home shop data monitoring method and device, equipment and medium
InactiveCN110717078AIncrease controlEasy to understandDigital data protectionOther databases queryingData authenticityString database
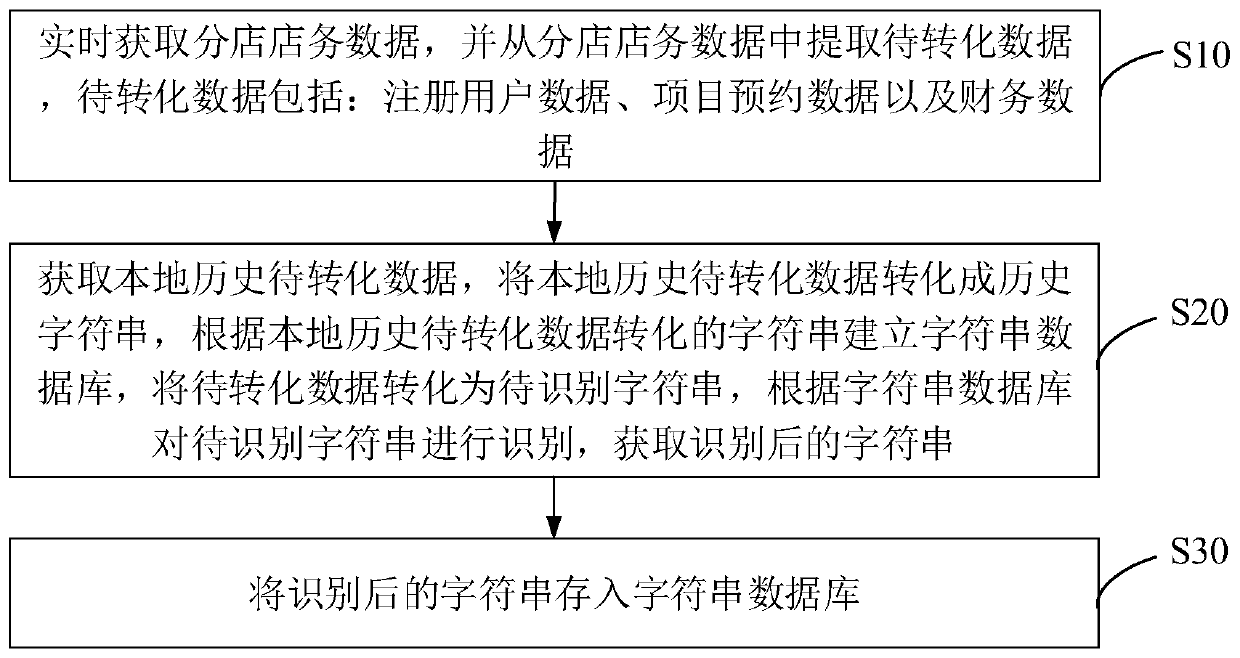
The invention provides a beauty salon shop data monitoring method and device, equipment and a medium. The method comprises the steps of acquiring branch store affair data in real time, extracting to-be-converted data from the branch store affair data, wherien the to-be-converted data comprise registered user data, project reservation data and financial data; acquiring local historical to-be-converted data, converting the local historical to-be-converted data into a historical character string, establishing a character string database according to the character string converted from the local historical to-be-converted data, converting the to-be-converted data into a to-be-identified character string, identifying the to-be-identified character string according to the character string database, and acquiring an identified character string; storing the identified character string into a character string database. The store data is converted into the character string form, the monitoring strength of a head office on the branch store data can be enhanced. Meanwhile, the store data is encrypted, and the store data is decrypted before conversion, so that the data can be effectively prevented from being tampered, and the authenticity of the branch store data is improved.
Owner:武汉安诠加信息技术有限公司
Method and System for Providing a User Agent String Database
Method, system, and programs for determining a keyword from user agent strings are disclosed. In one example, a plurality of user agent strings is received. The plurality of user agent strings is grouped into one or more clusters. The one or more clusters comprise a first cluster that includes two or more user agent strings. The two or more user agent strings in the first cluster are compared. Based on the comparing, a keyword is determined from the first cluster. The keyword represents a type of user agent information.
Owner:YAHOO ASSETS LLC
Map data base system of multi-nation language
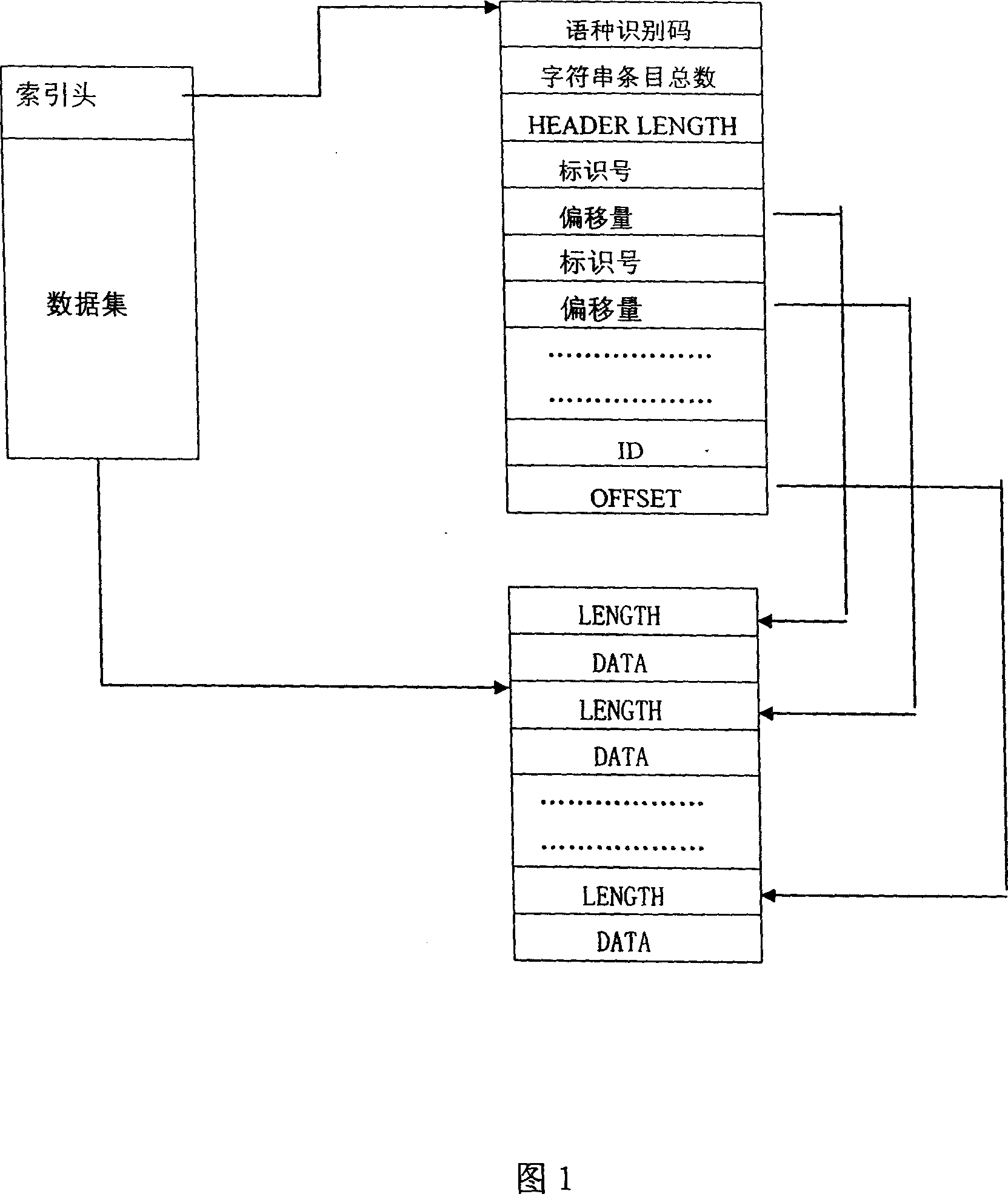
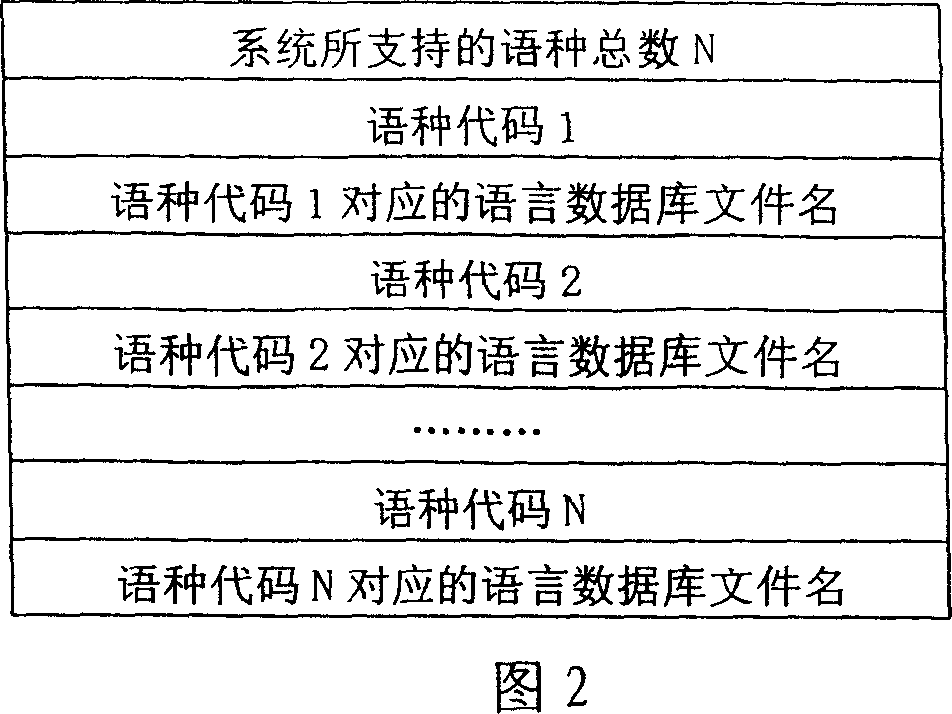
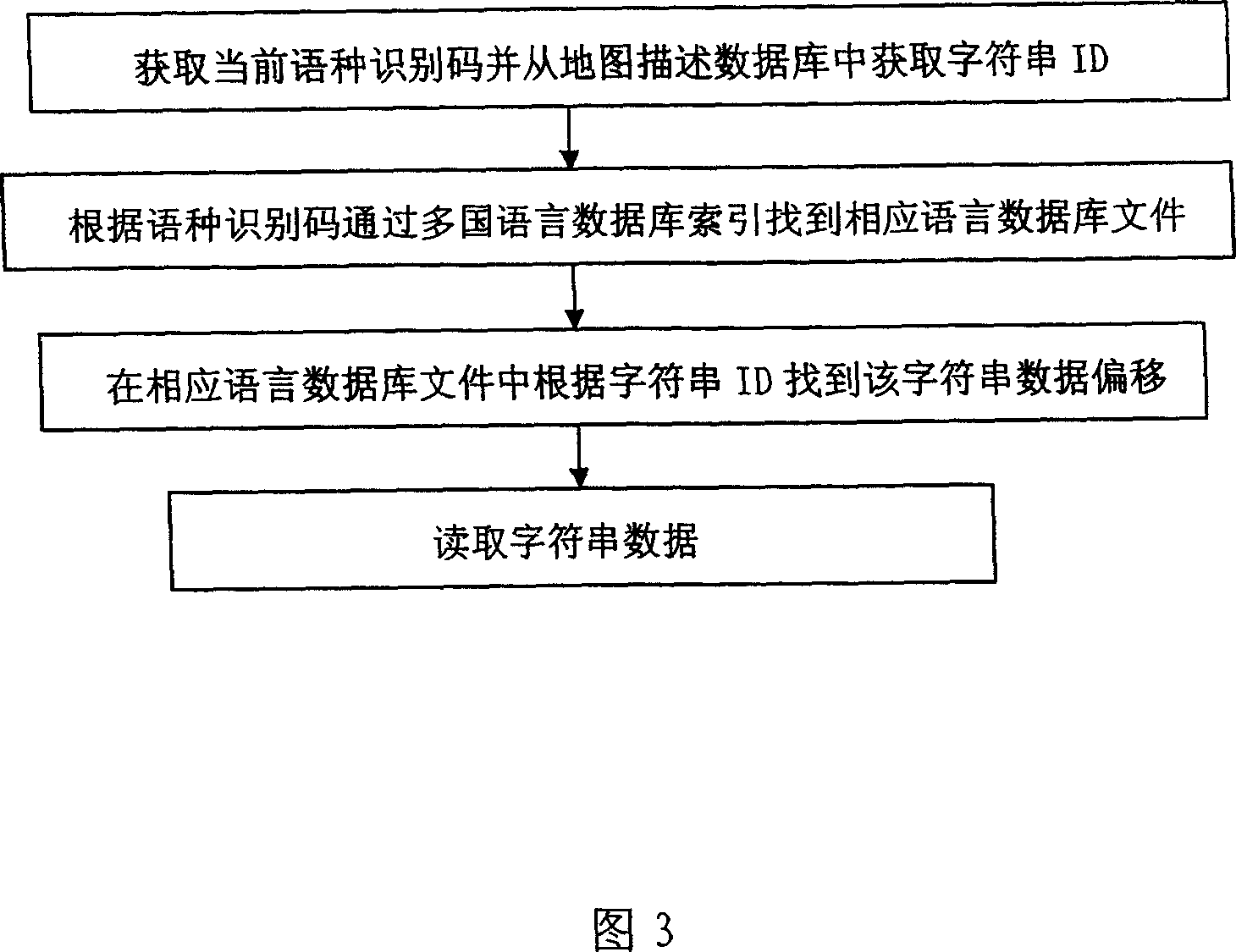
InactiveCN1955954AEasy maintenanceImprove compatibilitySpecial data processing applicationsData setDatabase index
A databank system of map with multinational languages comprises map description databank, multinational language character string databank, index of multinational language databank. It is featured as forming independent databank of each language by index head, data set, one independent identification number for each character string and identification code of language type; and arranging index information by index head according to identification number sequence.
Owner:YINGHUADA (SHANGHAI) ELECTRONIC CO LTD
Token-based web browsing with visual feedback of disclosure
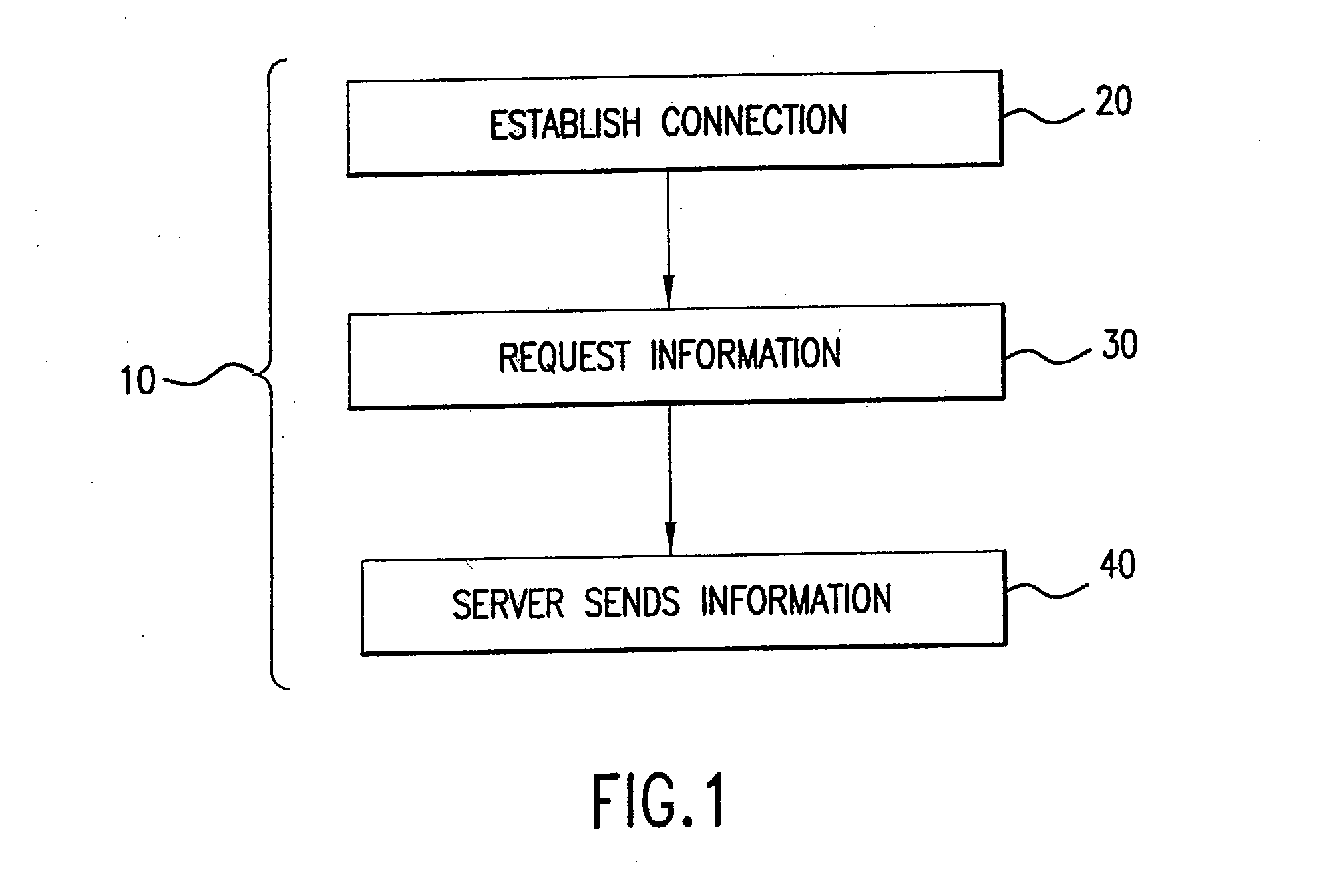
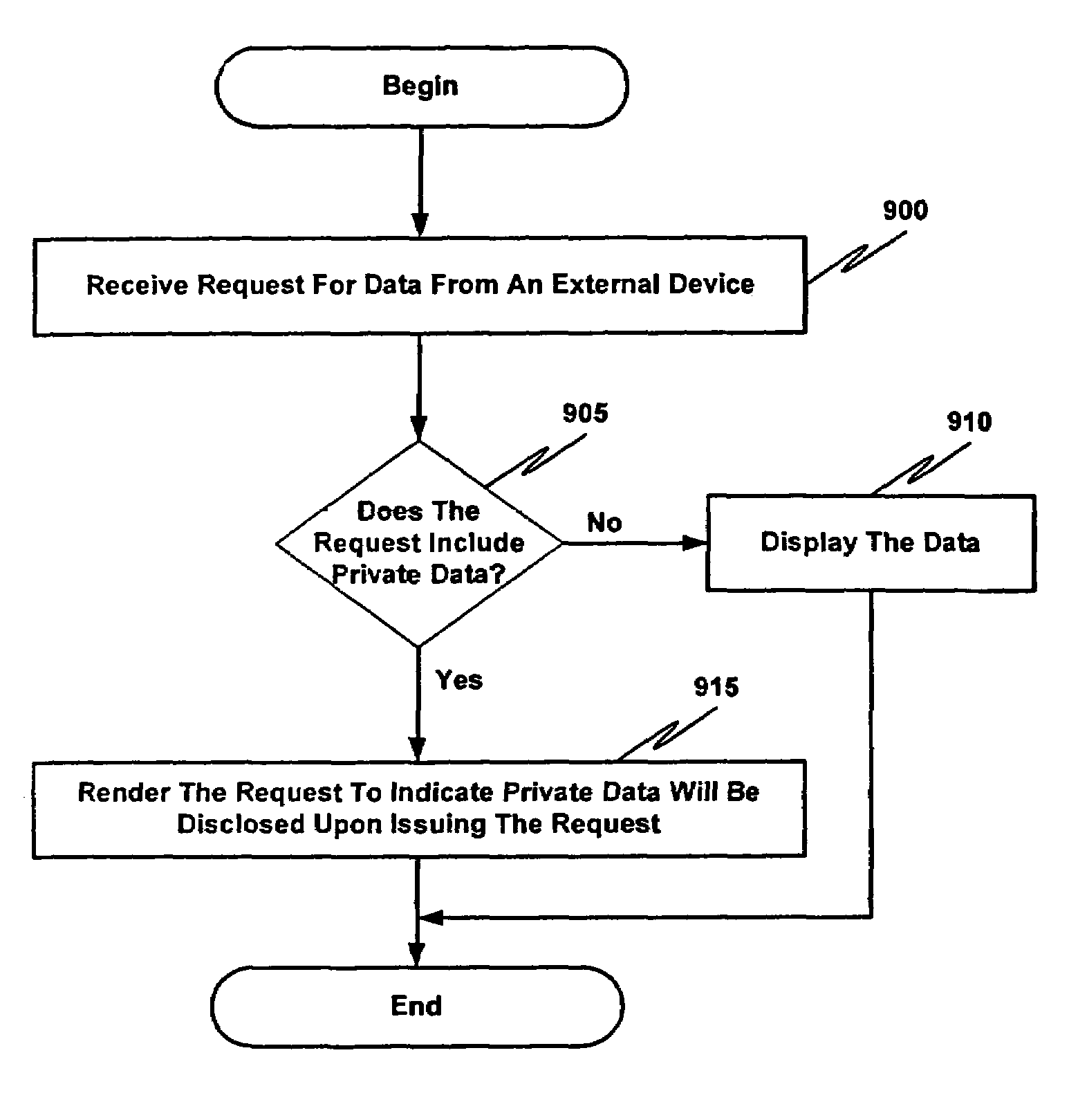
InactiveUS7310662B2Digital data processing detailsMultiple digital computer combinationsHyperlinkUser input
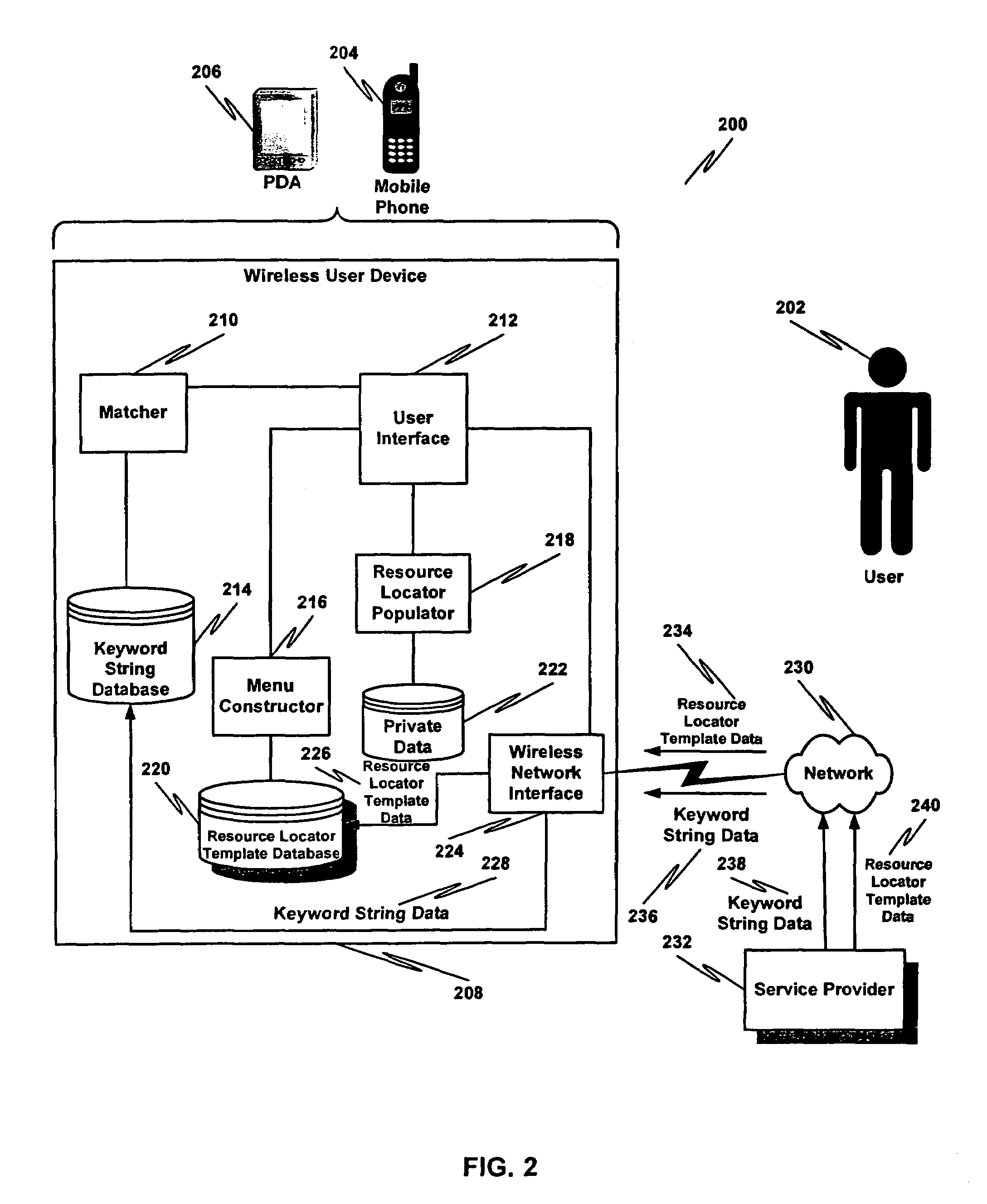
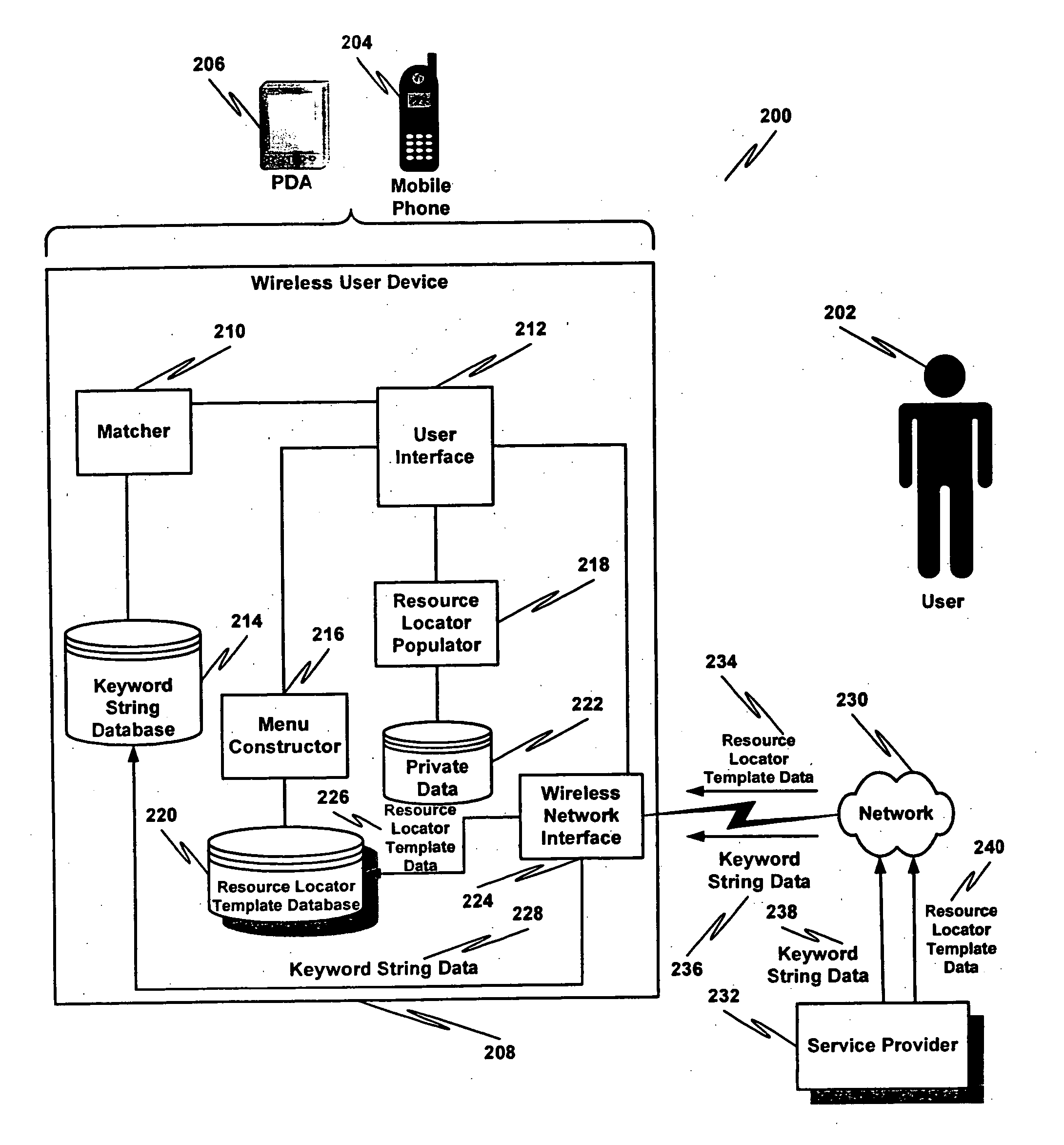
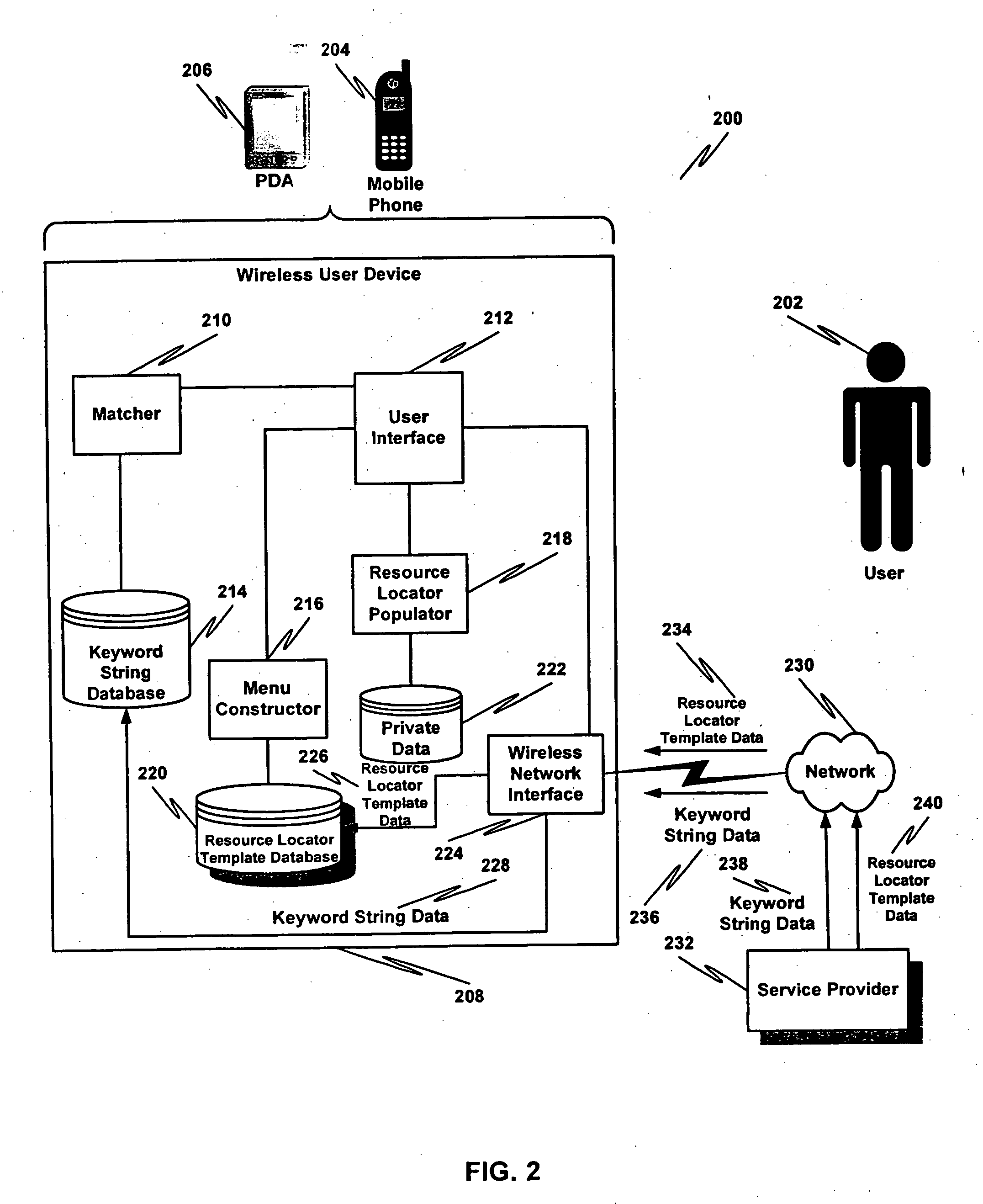
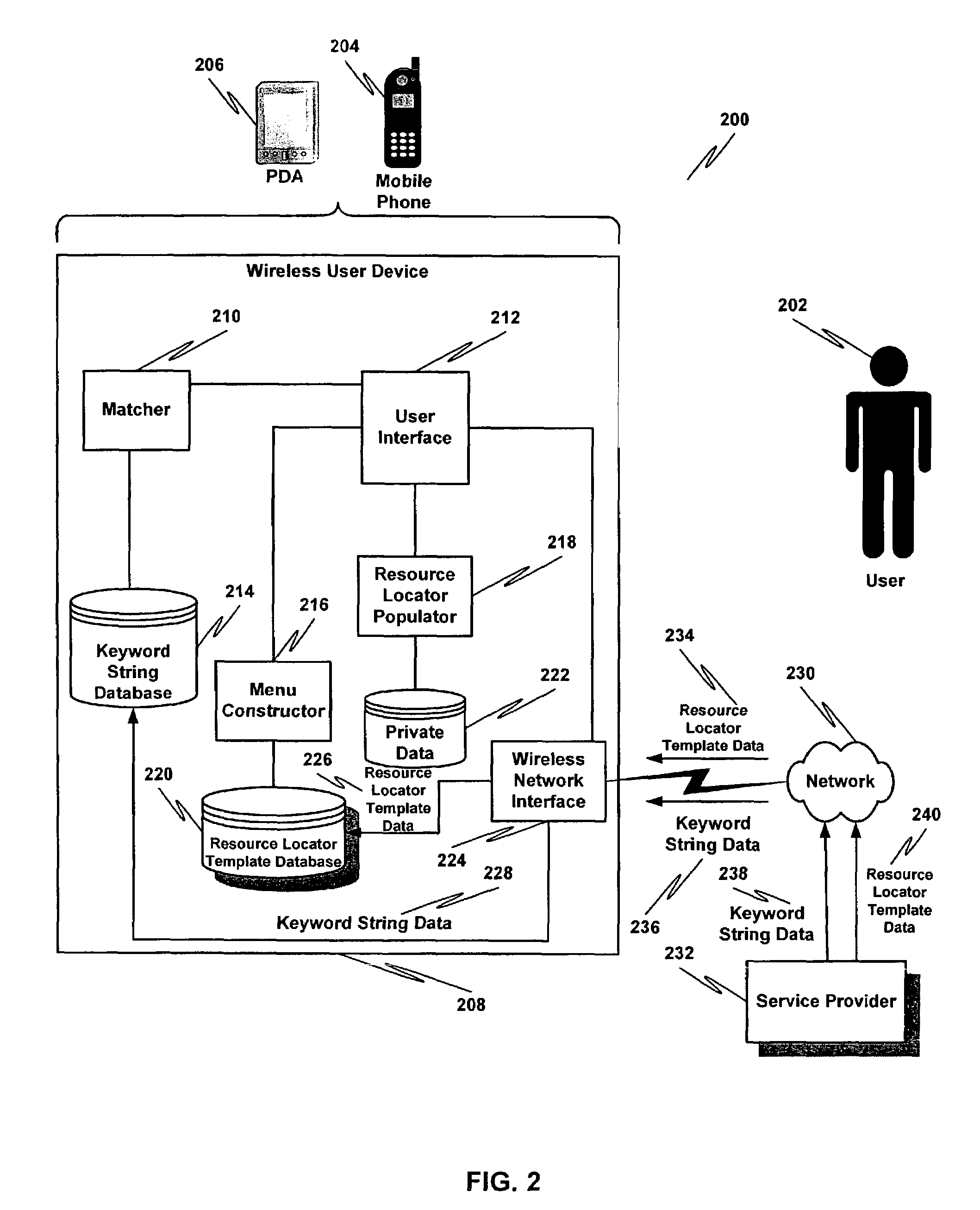
A data communications network may be browsed using one or more tokens by receiving an input keyword string from a user, determining whether there is a match between the input keyword string and a database of keyword strings, determining a category of the keyword string, rendering to the user at least one service identifier associated with the category, receiving a user-selected service identifier in response to the rendering, substituting at least one variable in a resource locator template associated with the service with a string based at least in part on the keyword string entered by the user and launching the resource locator. According to one aspect, a special rendering of a hyperlink corresponding to the resource locator is used to indicate private data will be disclosed upon launching the resource locator.
Owner:SIERRA WIRLESS INC
Token-based web browsing with visual feedback of disclosure
InactiveUS20060277274A1Digital data processing detailsMultiple digital computer combinationsHyperlinkUser input
A data communications network may be browsed using one or more tokens by receiving an input keyword string from a user, determining whether there is a match between the input keyword string and a database of keyword strings, determining a category of the keyword string, rendering to the user at least one service identifier associated with the category, receiving a user-selected service identifier in response to the rendering, substituting at least one variable in a resource locator template associated with the service with a string based at least in part on the keyword string entered by the user and launching the resource locator. According to one aspect, a special rendering of a hyperlink corresponding to the resource locator is used to indicate private data will be disclosed upon launching the resource locator.
Owner:SIERRA WIRELESS
Token-based Web browsing with visual feedback of disclosure
InactiveUS7167905B2Digital data processing detailsMultiple digital computer combinationsHyperlinkUser input
A data communications network may be browsed using one or more tokens by receiving an input keyword string from a user, determining whether there is a match between the input keyword string and a database of keyword strings, determining a category of the keyword string, rendering to the user at least one service identifier associated with the category, receiving a user-selected service identifier in response to the rendering, substituting at least one variable in a resource locator template associated with the service with a string based at least in part on the keyword string entered by the user and launching the resource locator. According to one aspect, a special rendering of a hyperlink corresponding to the resource locator is used to indicate private data will be disclosed upon launching the resource locator.
Owner:SIERRA WIRELESS
Specific function-related gene information searching system and method for building database of searching workds thereof
InactiveCN100343852CReduce duplication of effortHigh speedSpecial data processing applicationsSpecific functionString database
The system searches out relevant documents of gene to be searched through following devices and steps: computer of having input function and display terminal, database of docuterm for document composed of database of gene name, database of word frequency base value, character-string database and database of assistant docuterm, as well as public database of biomedicine document entered through network server. The method includes following steps: carrying out analysis of word frequency, picking out keywords of gene; through professional process, building list of word frequency; finally, searching out information of gene relevant to specific function through cluster analysis. Features are: accurate positioning, searching in quick speed, avoiding rehandling so as to save human and material resources greatly, and suitable commercial development.
Owner:SOUTHERN MEDICAL UNIVERSITY
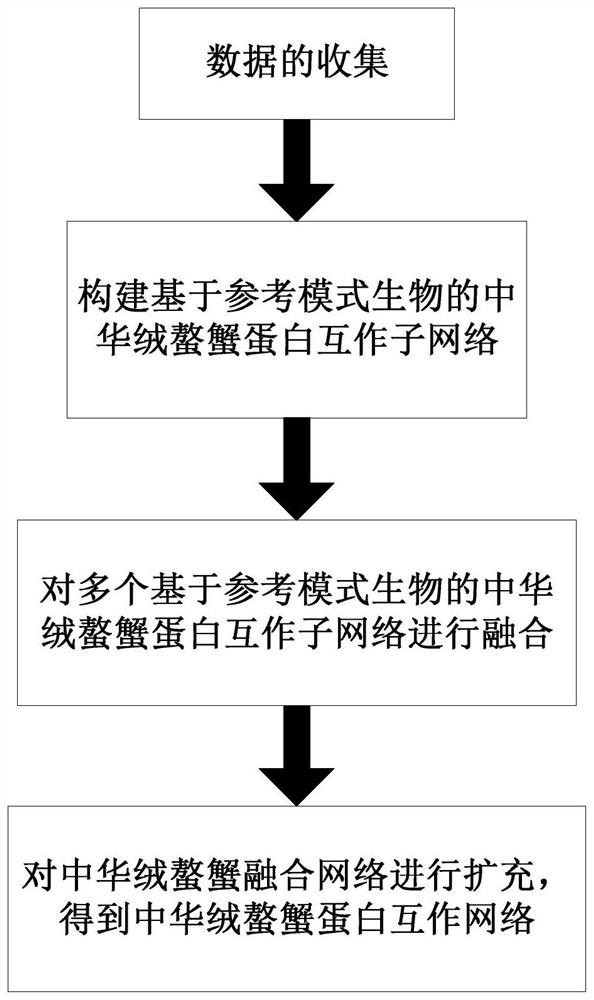
Method for constructing Eriocheir sinensis protein interaction network
PendingCN114822687AWide variety of sourcesQuality improvementProteomicsGenomicsString databaseEriocheir japonica sinensis
The invention discloses a method for constructing a protein interaction network of Eriocheir sinensis, which comprises the following steps of: collecting data: taking organisms in a PINA database as reference mode organisms, obtaining protein sequence information of the reference mode organisms, and respectively obtaining protein interaction information of each reference mode organism from the PINA database and an STRING database; constructing an Eriocheir sinensis protein interaction sub-network based on a reference mode organism; fusing the plurality of Eriocheir sinensis protein interaction sub-networks based on the reference pattern organisms; and expanding the Eriocheir sinensis fusion network to obtain the Eriocheir sinensis protein interaction network. The Eriocheir sinensis protein interaction network constructed by using the method disclosed by the invention is the Eriocheir sinensis protein interaction network with the largest scale and the largest number of protein and protein interaction relationships at present, so that richer information is provided for biological analysis performed by using the network.
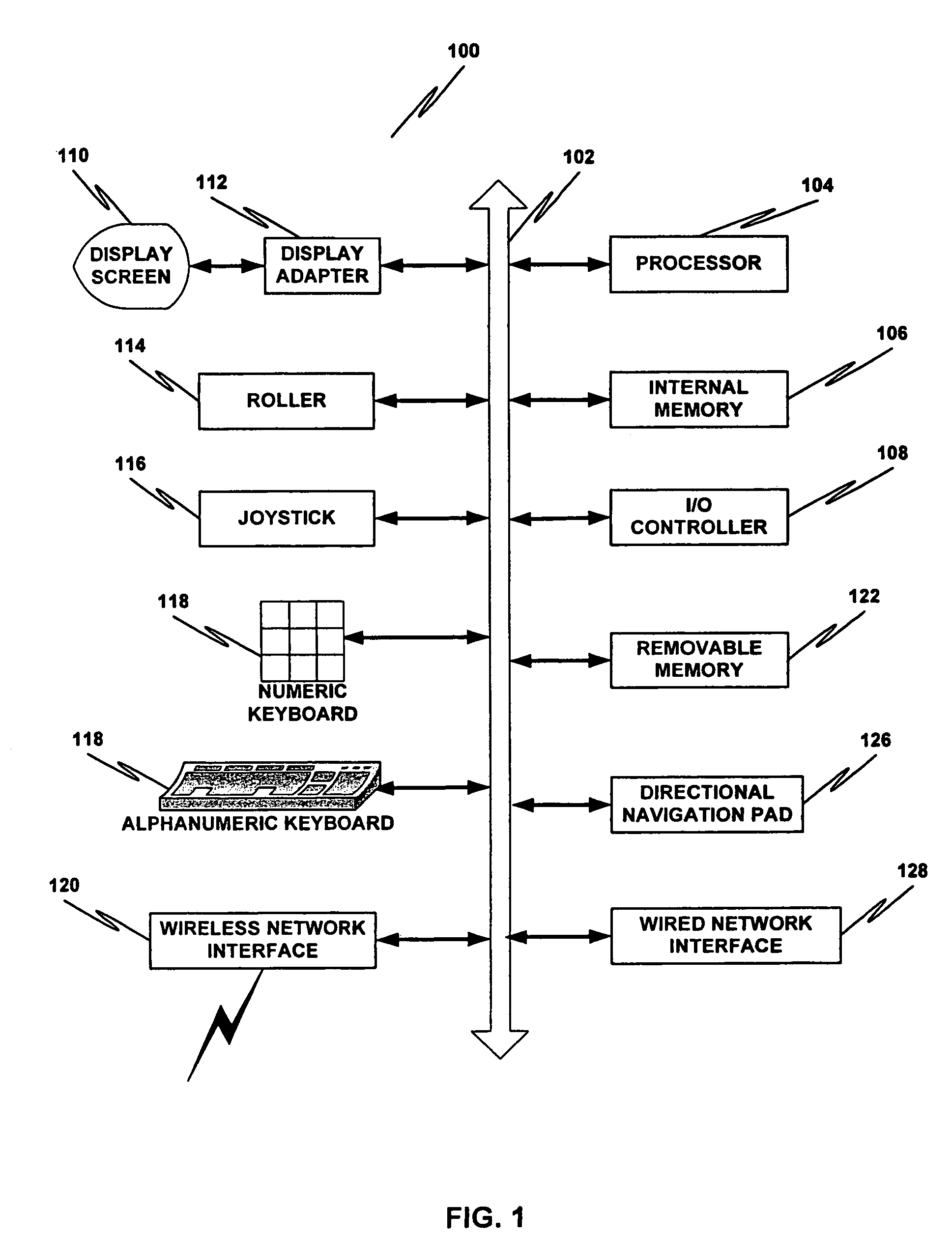
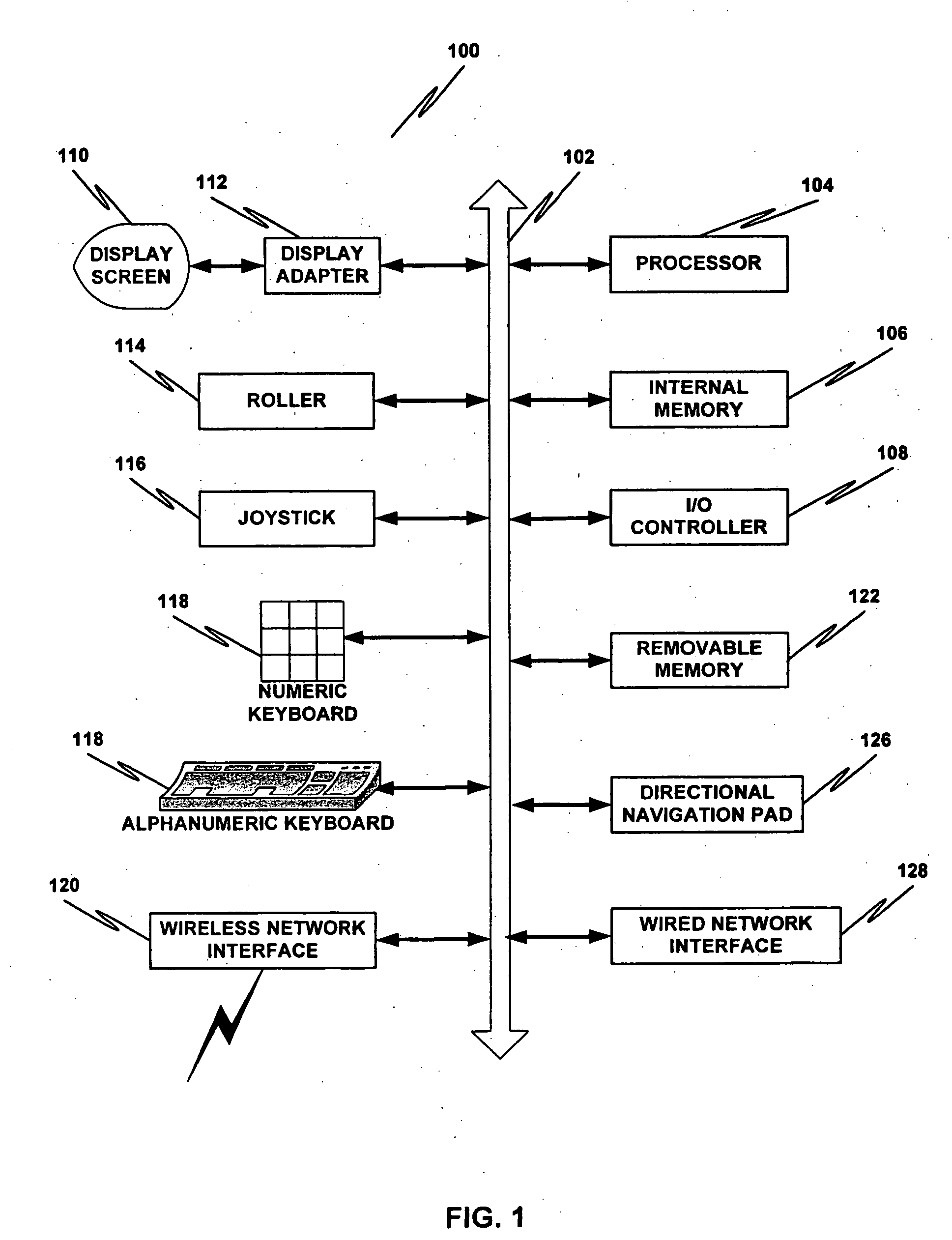
Owner:TIANJIN NORMAL UNIVERSITY
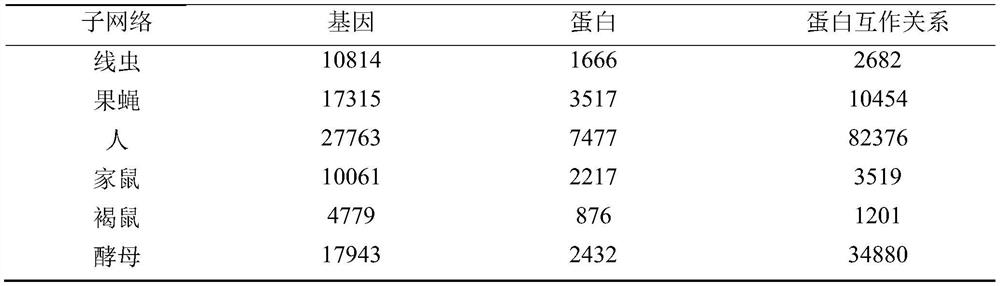
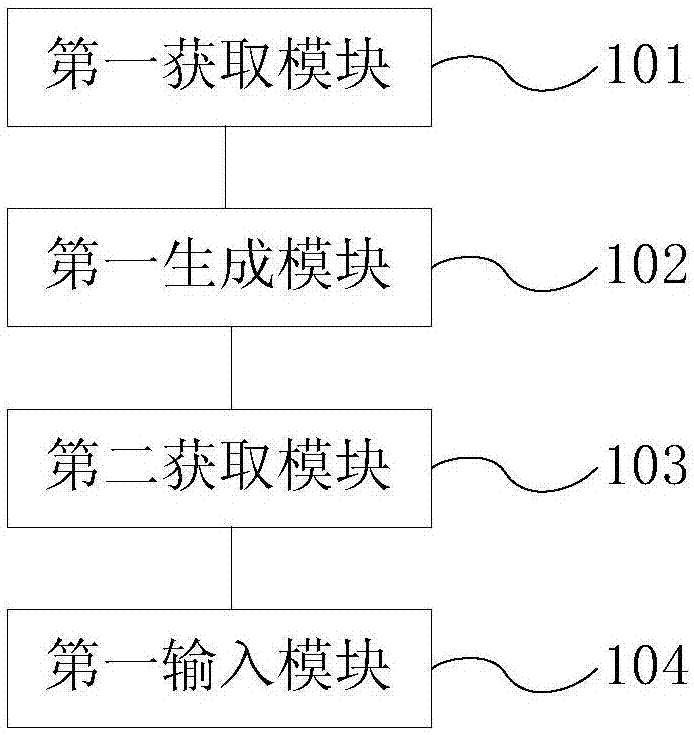
Character string translation processing method and device of electronic terminal
InactiveCN107402918ASave human effortThe process of reducing manpower for translationNatural language translationExecution for user interfacesAlgorithmTheoretical computer science
The invention provides a character string translation processing method and device of an electronic terminal. The method includes: acquiring a first character string translated from a second character string from a character string database; generating first data content according to the first character string, wherein the first data content records the first character string translated from the second character string; acquiring the second character string from a first code and a first location path of the second character string in the first code; inputting the first character string in the first data content to the corresponding position of the first code. Translation is performed with the first character string translated in the character string database, the human translation process is reduced, and working efficiency is increased.
Owner:SHANGHAI GREEN ORANGE IND
Computer-aided translation method and system for voice sequence and visual terminal
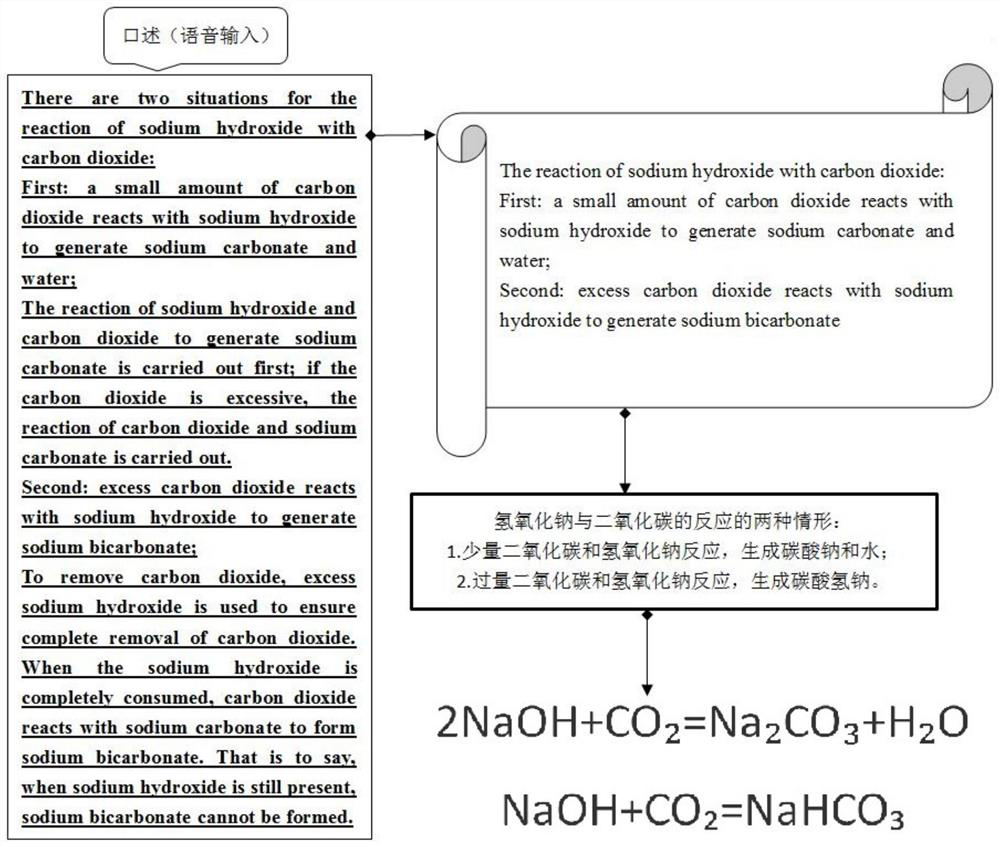
PendingCN114818747AMaintain integrityMaintain readabilityNatural language translationSpeech recognitionSpeech translationString database
The invention provides a computer-aided translation method and system for a voice sequence and a visual terminal, and belongs to the technical field of computer-aided translation. The method comprises the following steps: translating a voice sequence of a first source language into a text sequence of a second target language, displaying a target text string in a predetermined picture format, and meanwhile, performing voice broadcast on an output text sequence of the second target language. The system comprises a recording storage subsystem, a pause point detection subsystem, a sequence segmentation subsystem, a target voice string recognition subsystem, a voice-to-text subsystem, an abstract generation subsystem, a text translation subsystem, a display subsystem, a voice broadcast subsystem, a sequence merging subsystem, a target voice string database and a target text string picture database. The invention further provides a visual terminal for implementing the method. According to the method, quick recognition and translation output display of key target voice strings can be realized for voice input sequences, and readability and relative integrity of translation results are realized while real-time performance of voice translation is ensured.
Owner:IOL WUHAN INFORMATION TECH CO LTD
Implementation method of Yizitong Chinese Wubi cursive dictionary query system
ActiveCN103778250BEasy to knowEasy to learnStill image data retrievalSpecial data processing applicationsNatural language processingChinese characters
The invention relates to an implement method for a Chinese wubi cursive script dictionary query system. The method comprises a wubi cursive script character pattern query method as per Chinese character and a corresponding Chinese character query method as per wubi cursive script character pattern, wherein the wubi cursive script character pattern query method as per Chinese character comprises the following two steps: establishing a data mapping between a wubi cursive script character pattern and a corresponding Chinese character, and realizing web service and providing query function; the corresponding Chinese character query method as per wubi cursive script character pattern comprises the following two steps: establishing a characteristic word string database for a wubi cursive script character pattern, and establishing implement method and algorithm for recognizing the wubi cursive script character pattern. The implement method provided by the invention is original, and through applying the Chinese wubi cursive script query system established in the method, devotees of wubi cursive script can figure out the style of writing of corresponding wubi cursive script as per Chinese character, learners of wubi cursive script can query the corresponding Chinese character of a certain wubi cursive character pattern, and the method is beneficial for people to understand and learn Chinese wubi cursive script and is beneficial for worldwide popularization and application of Chinese cursive script.
Owner:张朝亮
Method and system for providing a user agent string database
Method, system, and programs for determining a keyword from user agent strings are disclosed. In one example, a plurality of user agent strings is received. The plurality of user agent strings is grouped into one or more clusters. The one or more clusters comprise a first cluster that includes two or more user agent strings. The two or more user agent strings in the first cluster are compared. Based on the comparing, a keyword is determined from the first cluster. The keyword represents a type of user agent information.
Owner:YAHOO ASSETS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com