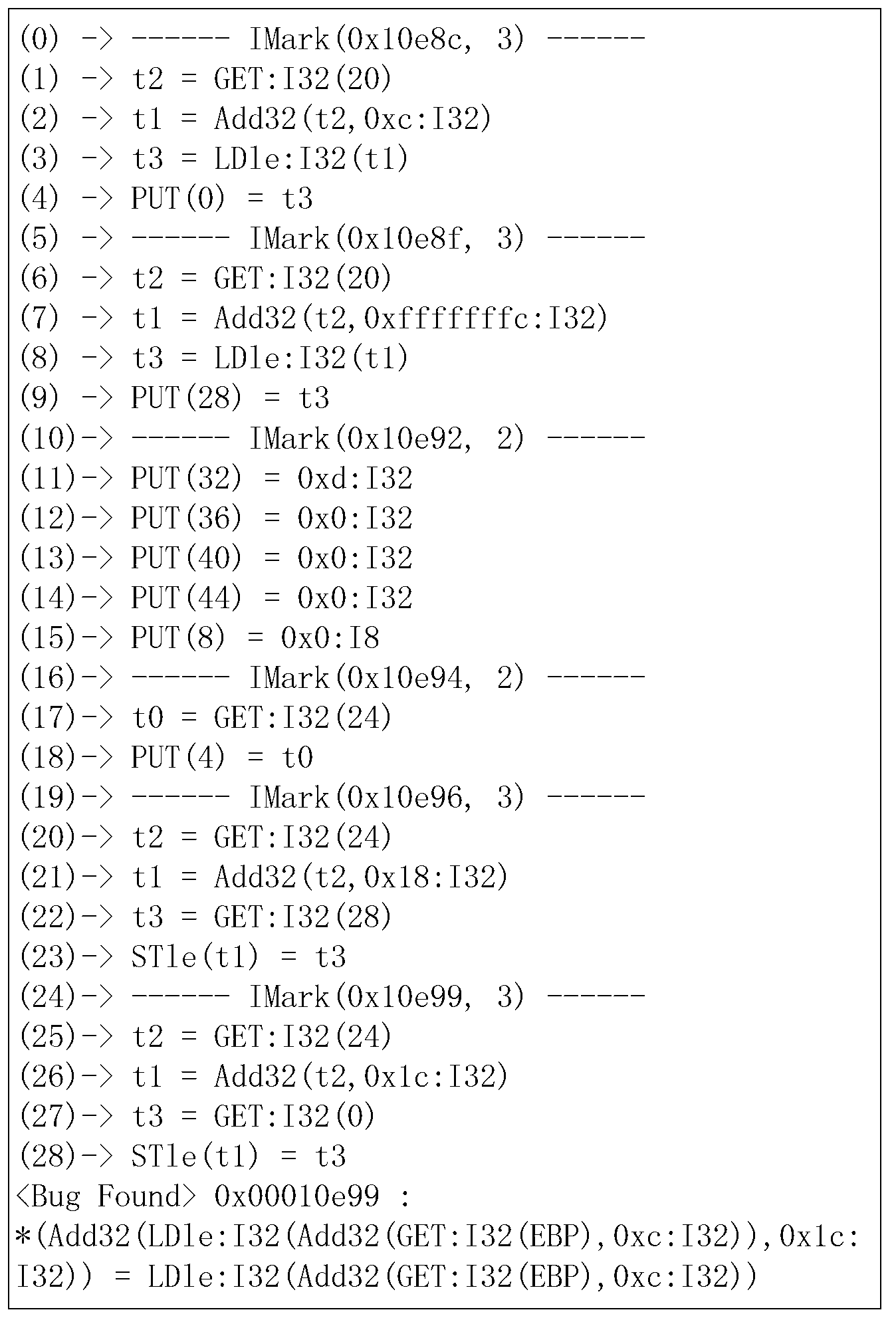
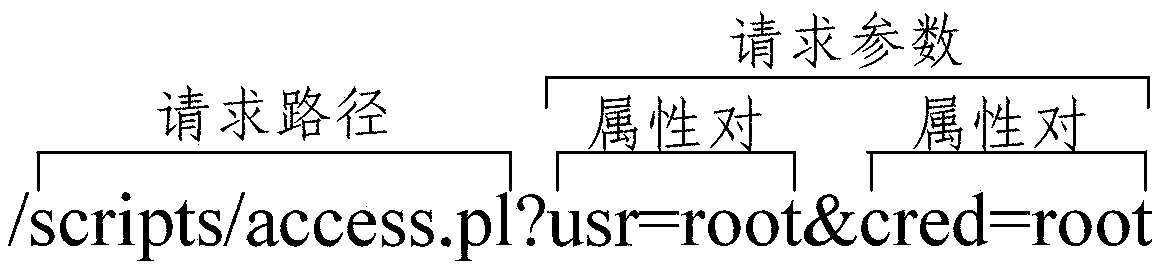
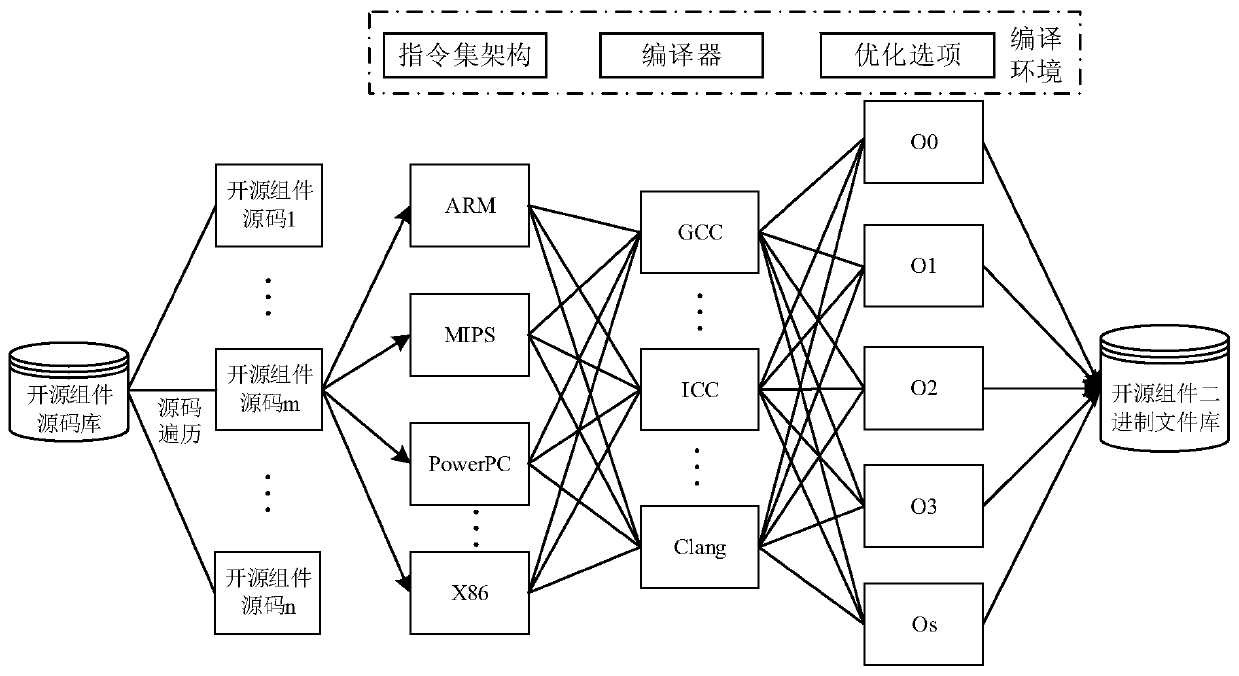
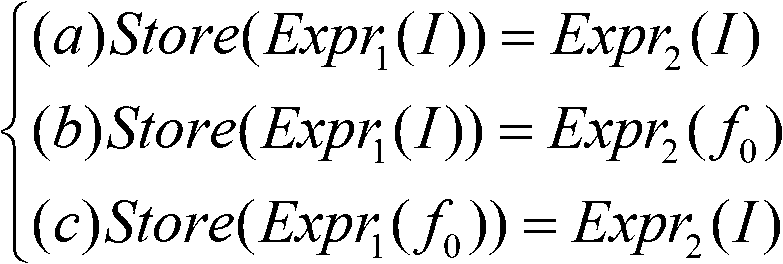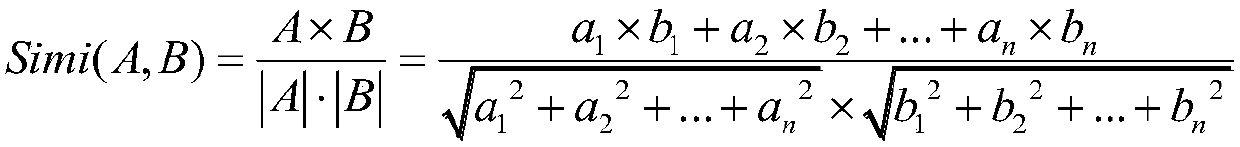Patents
Literature
107 results about "Vulnerability discovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
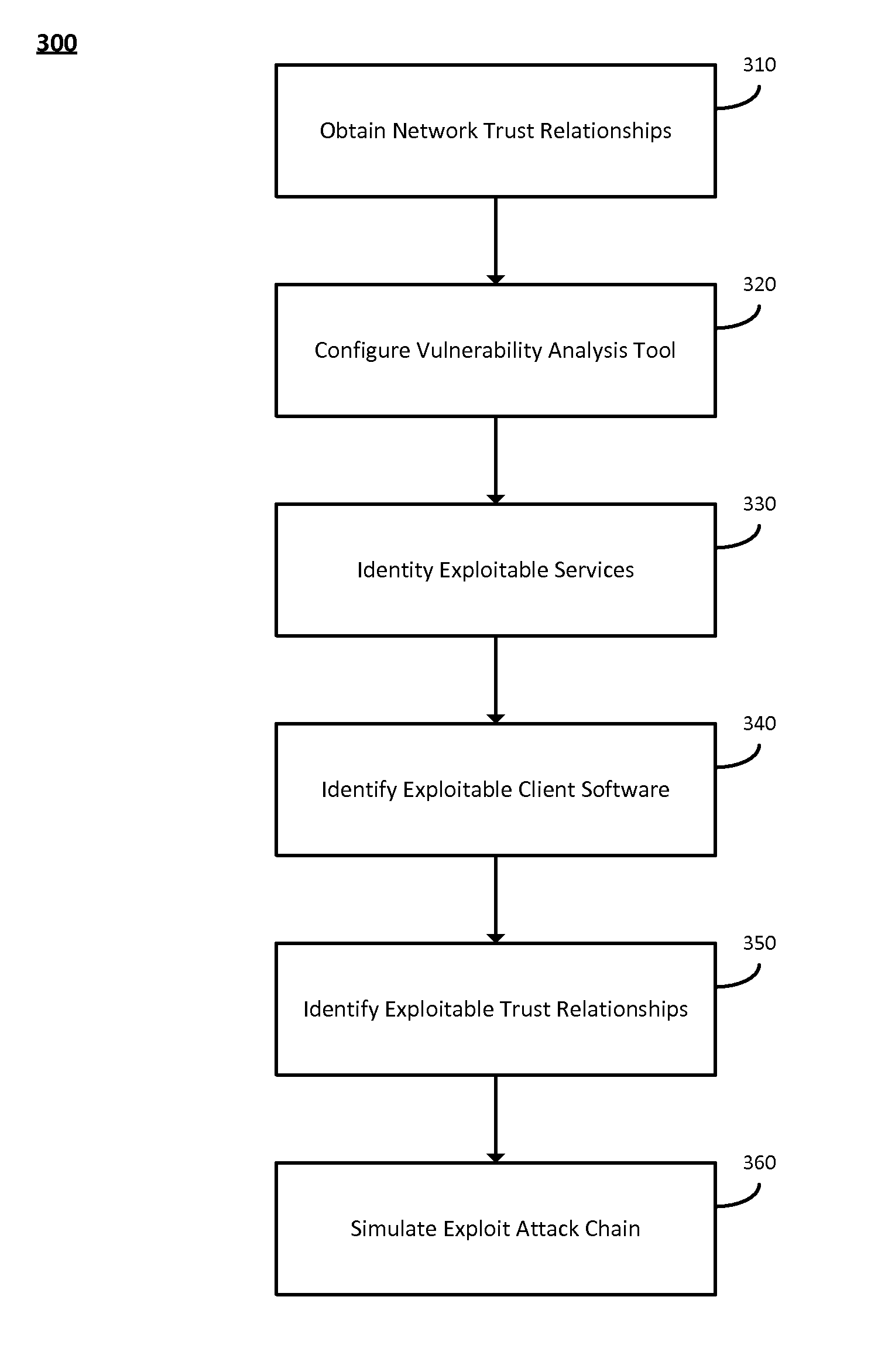
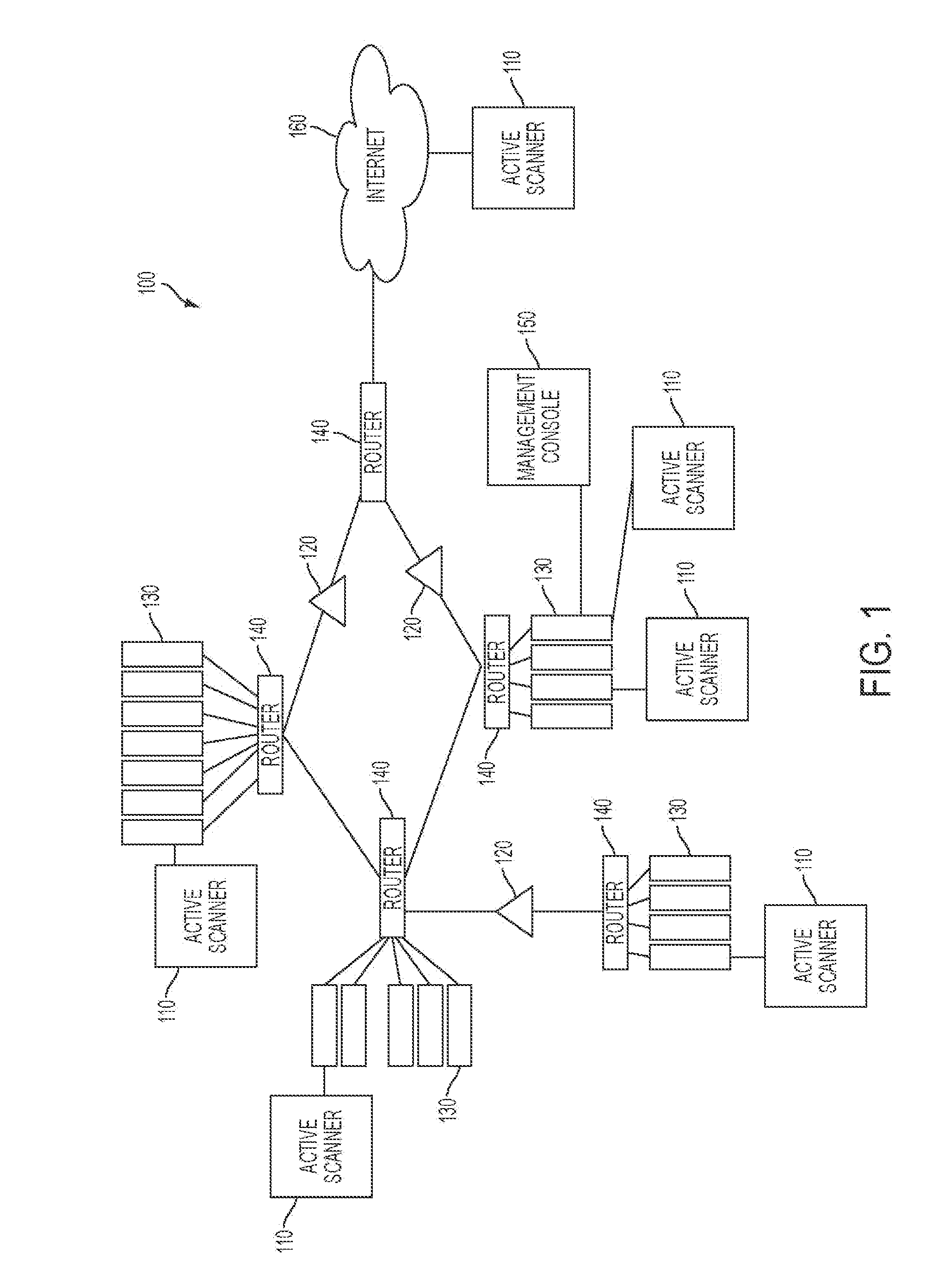
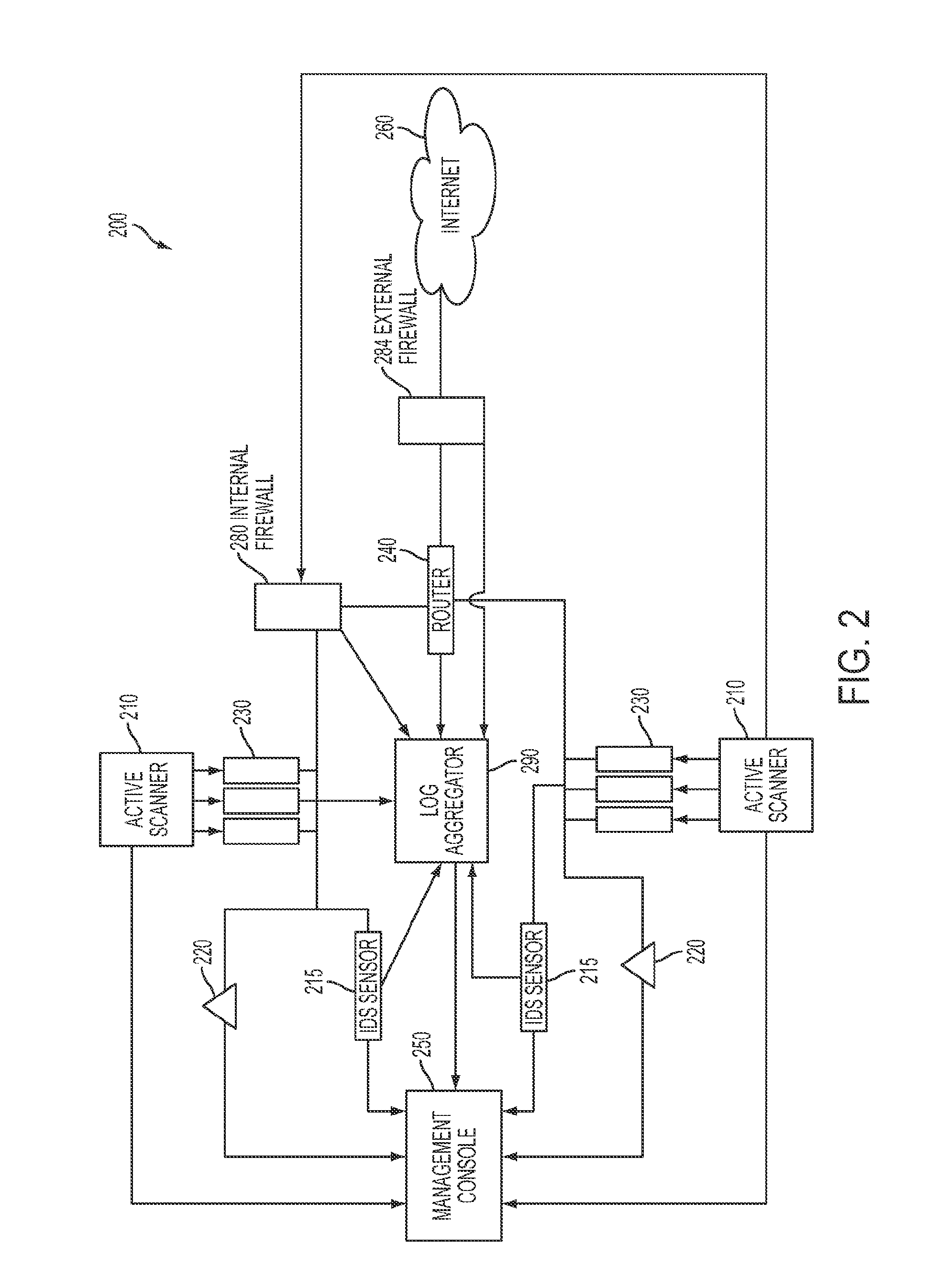
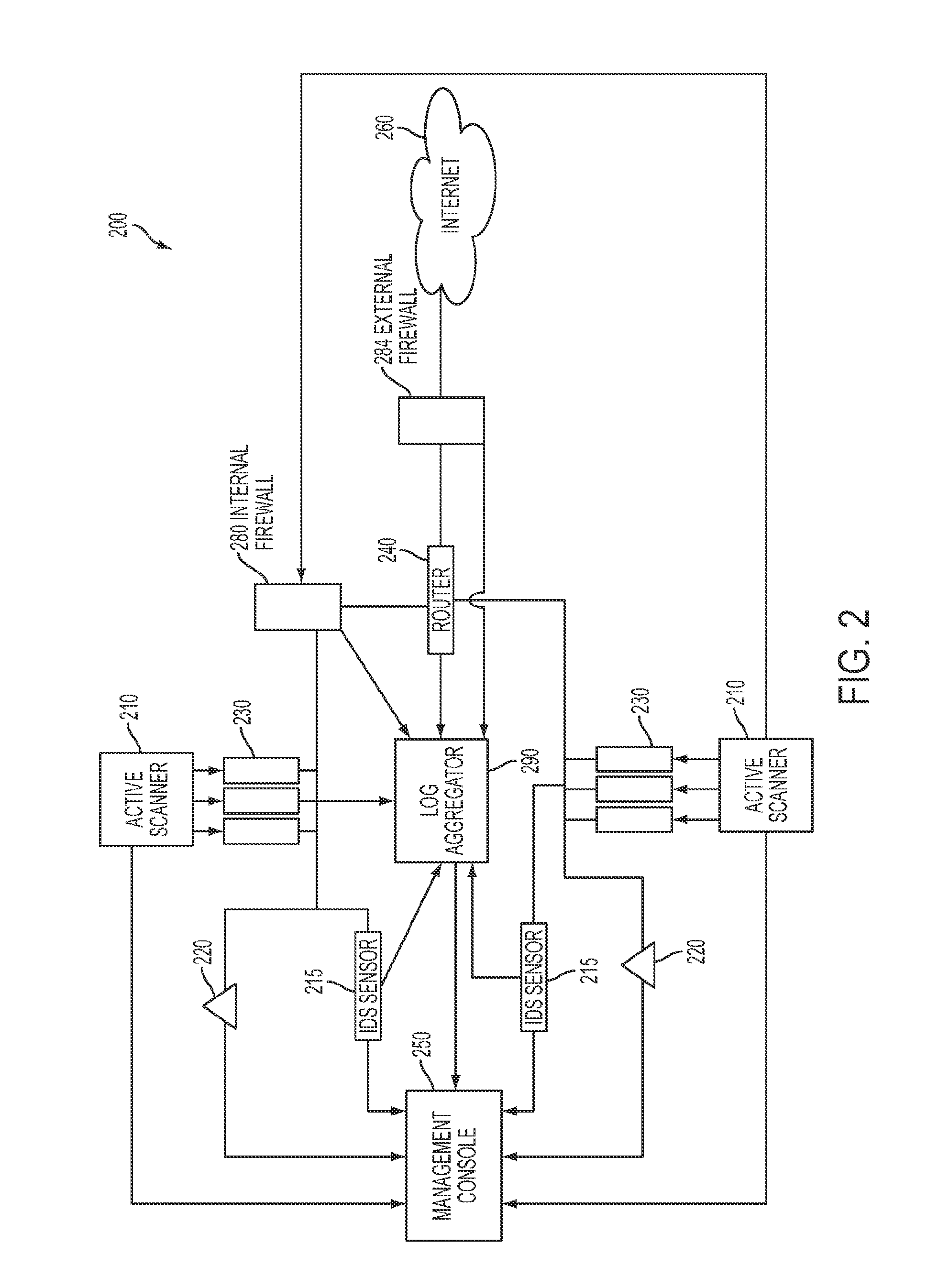
System and method for identifying exploitable weak points in a network
ActiveUS20140007241A1Low rateMemory loss protectionError detection/correctionOpen portTrust relationship
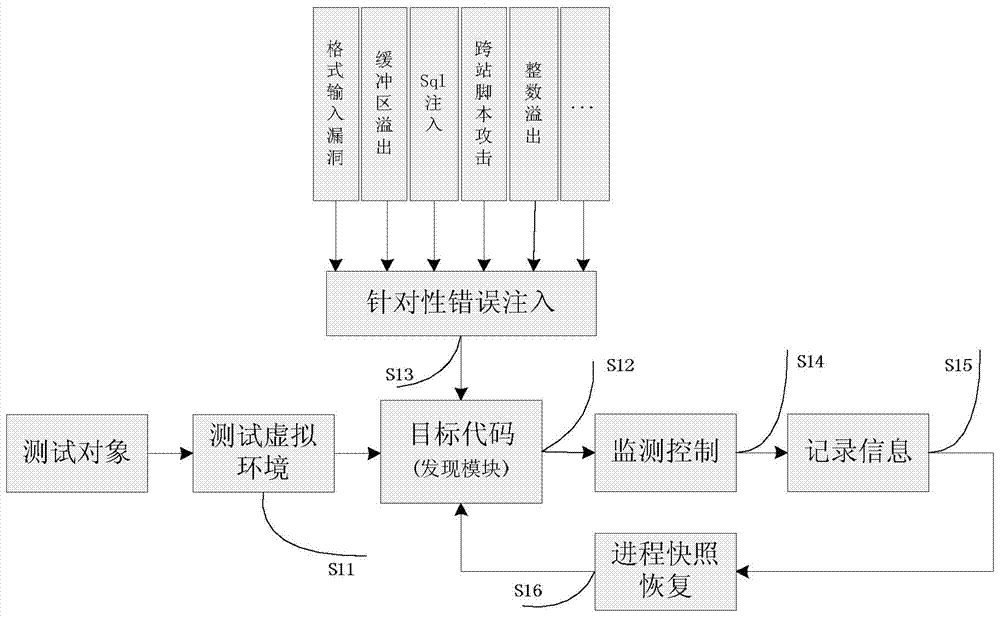
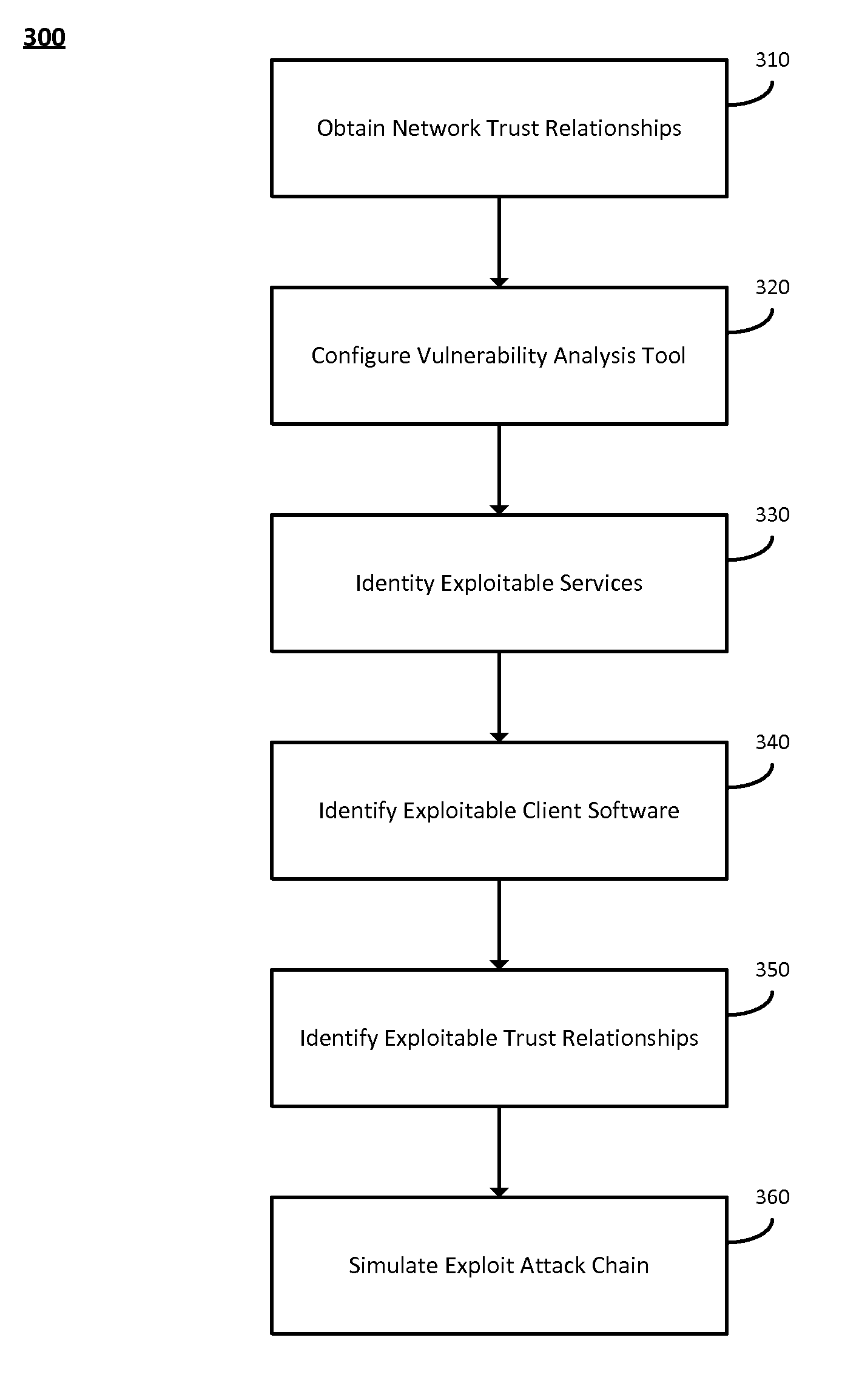
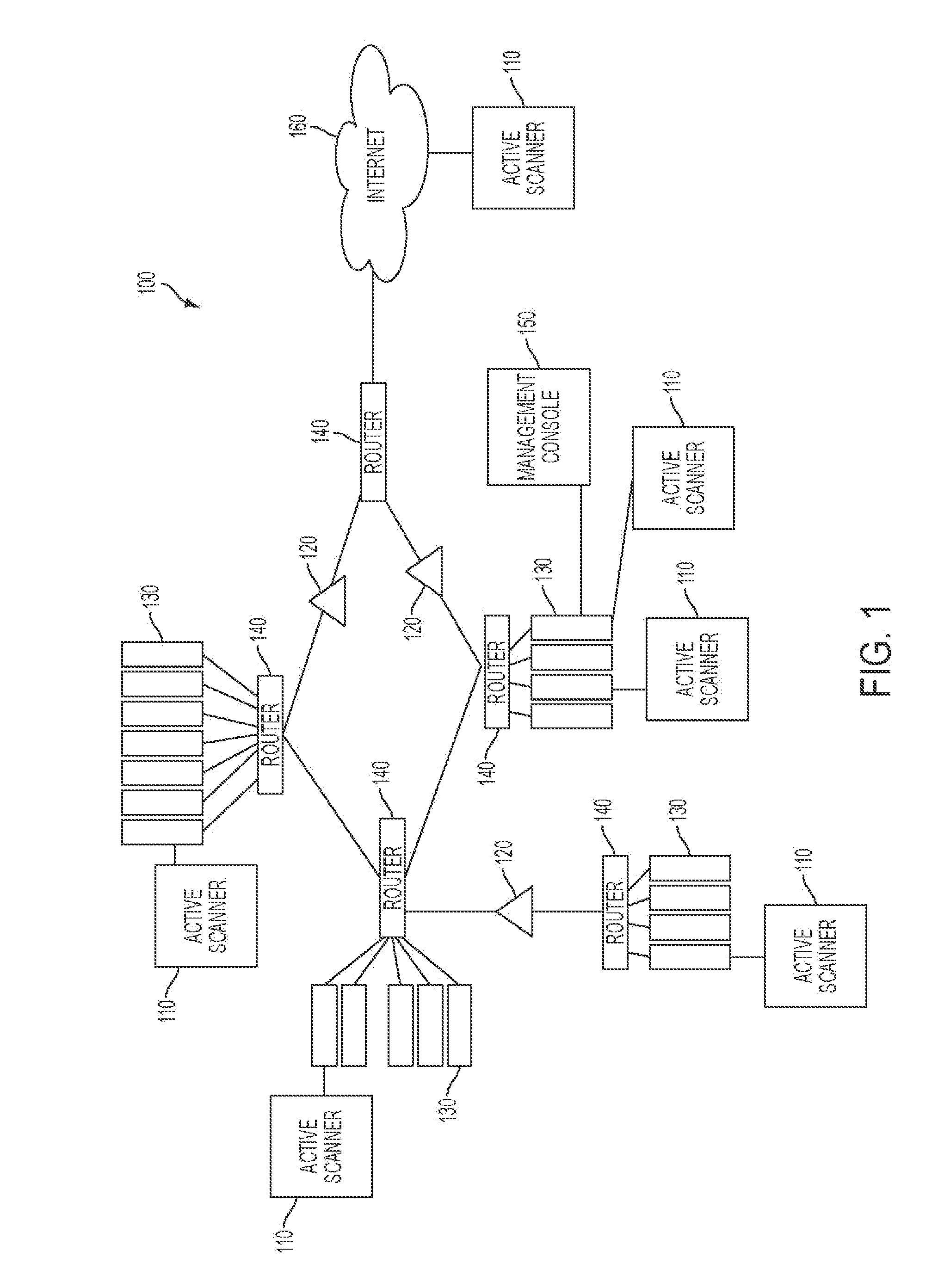
The system and method described herein may leverage passive and active vulnerability discovery to identify network addresses and open ports associated with connections that one or more passive scanners observed in a network and current connections that one or more active scanners enumerated in the network. The observed and enumerated current connections may be used to model trust relationships and identify exploitable weak points in the network, wherein the exploitable weak points may include hosts that have exploitable services, exploitable client software, and / or exploitable trust relationships. Furthermore, an attack that uses the modeled trust relationships to target the exploitable weak points on a selected host in the network may be simulated to enumerate remote network addresses that could compromise the network and determine an exploitation path that the enumerated remote network addresses could use to compromise the network.
Owner:TENABLE INC
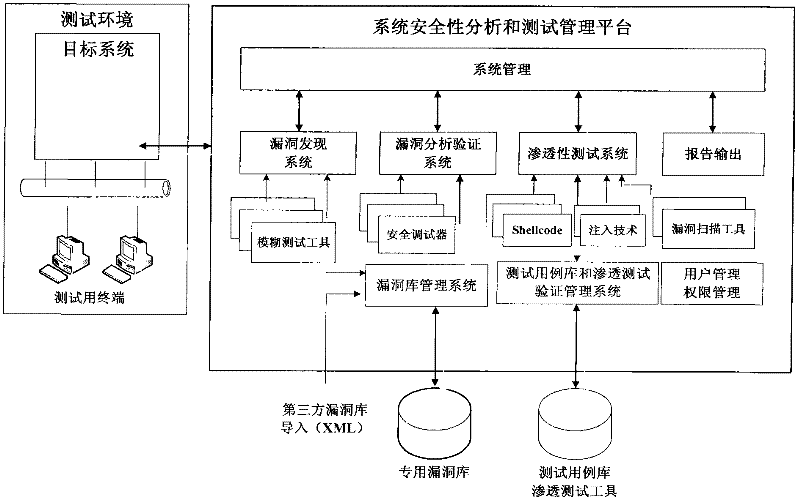
Detection device and method for security vulnerability of software
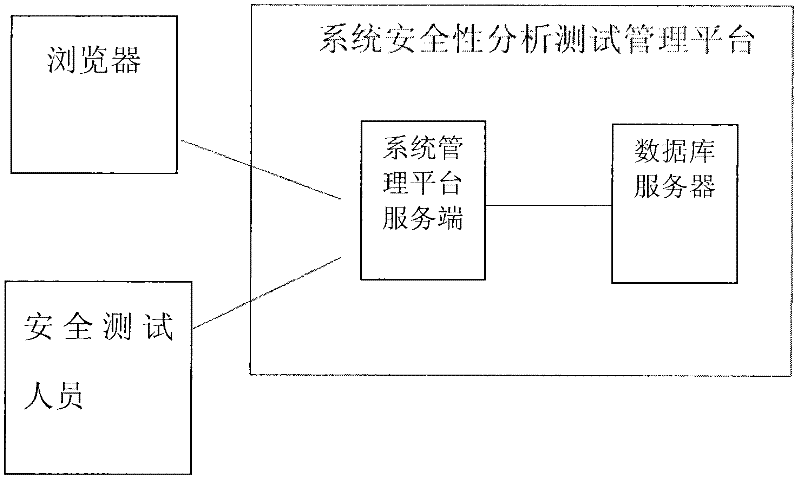
InactiveCN102541729ASatisfy attentionImprove use valueSoftware testing/debuggingSystems managementGoal system
The invention relates to the field of computers, in particular to a detection device and method for a security vulnerability of a dedicated information system. According to the detection device and method disclosed by the invention, a tester can not only access a target system to a testing network but also access the detection device to a production system by connecting a test terminal with the target system, wherein the target system is located in the production system. As the core of the detection device, a system security analysis and test management platform comprises a vulnerability discovering system, a vulnerability authenticating and analyzing system, a permeability testing system, a vulnerability library, a test case library, a report outputting system, a user and permission management system, a system management platform and the like. When the detection device and method for the security vulnerability of the software, provided by the invention, are adopted, the vulnerability can be found before the application of the software, and corresponding strategies can be provided, so that the detection device and method meet the requirement on the emphasis on information security in the current society in a better manner; and moreover, the detection device and method have a higher application value.
Owner:AVIATION IND INFORMATION CENT
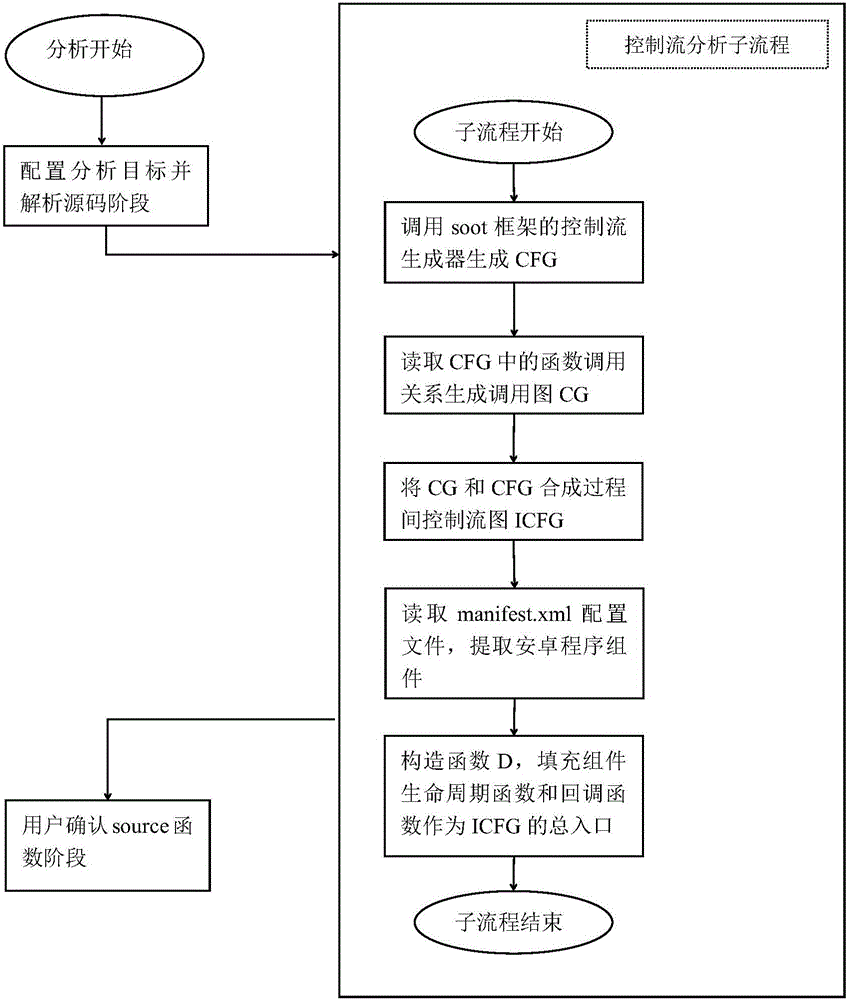
Static taint analysis and symbolic execution-based Android application vulnerability discovery method
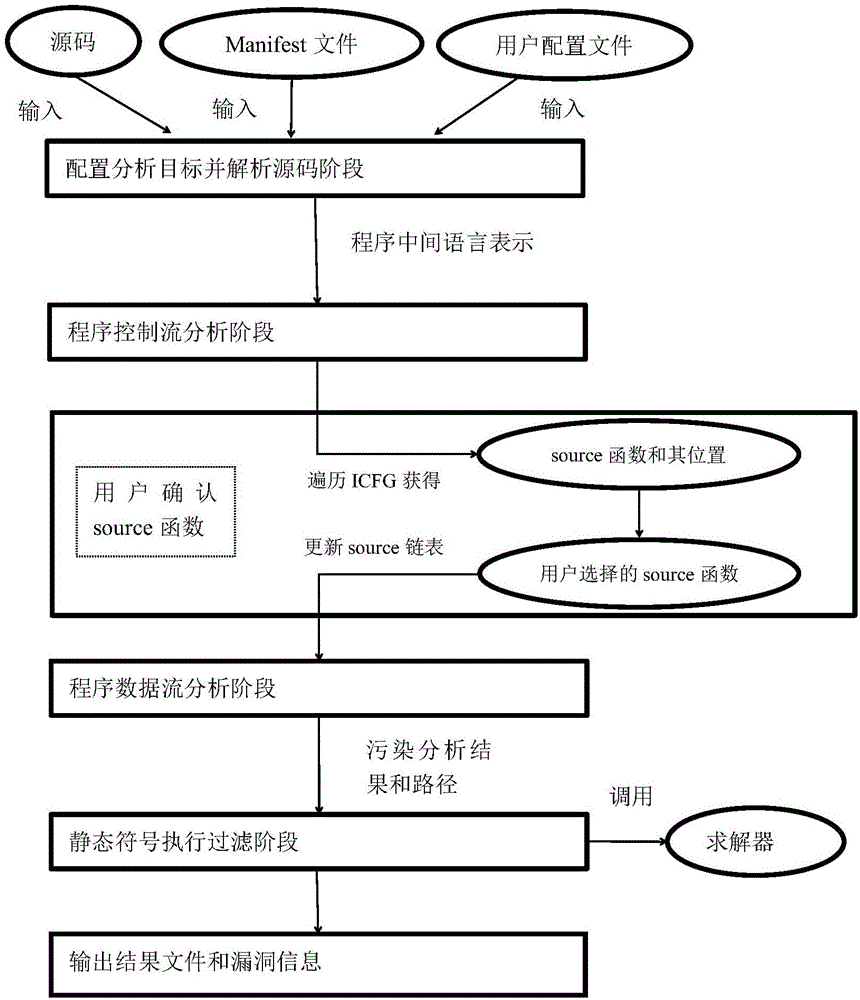
ActiveCN106709356ATargetedImprove efficiencyPlatform integrity maintainanceStatic timing analysisData stream
The invention discloses a static taint analysis and symbolic execution-based Android application vulnerability discovery method, and mainly aims at solving the problems that the analysis range is fixed, the memory consumption is huge and the analysis result is mistakenly reported in the process of discovering vulnerabilities by using the existing static taint analysis method. The method is realized through the following steps of: 1) configuring an analysis target and decompiling a program source code; 2) carrying out control flow analysis on the decompilation result; 3) selecting a source function by a user according to the control flow analysis result, so as to narrow an analysis target; 4) carrying out data flow analysis according to the control flow analysis result, so as to generate a vulnerability path; and 5) filtering the data flow analysis result by adoption of a static symbolic execution technology, taking the residual parts after the filtration as discovered vulnerabilities, warning the user and printing the vulnerability path. On the basis of the existing static taint analysis technology, the method disclosed by the invention has the advantages of extending the vulnerability discovery range, decreasing the memory consumption of vulnerability discovery and improving the accuracy of vulnerability discovery results, and can be applied to the discovery and research of Android application program vulnerabilities.
Owner:XIDIAN UNIV
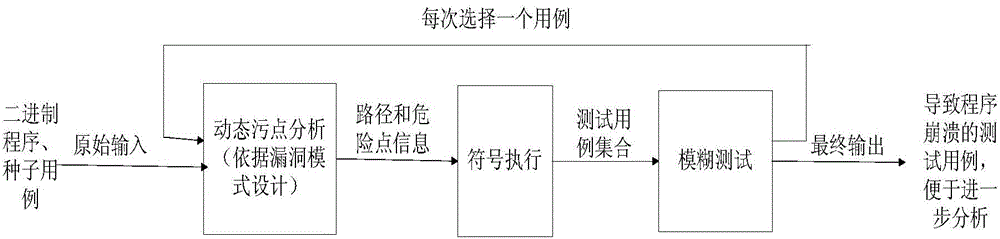
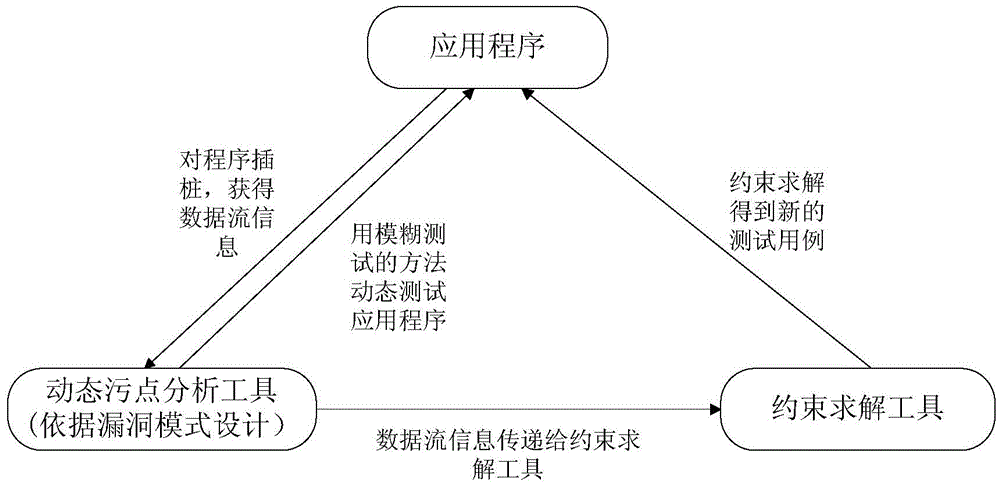
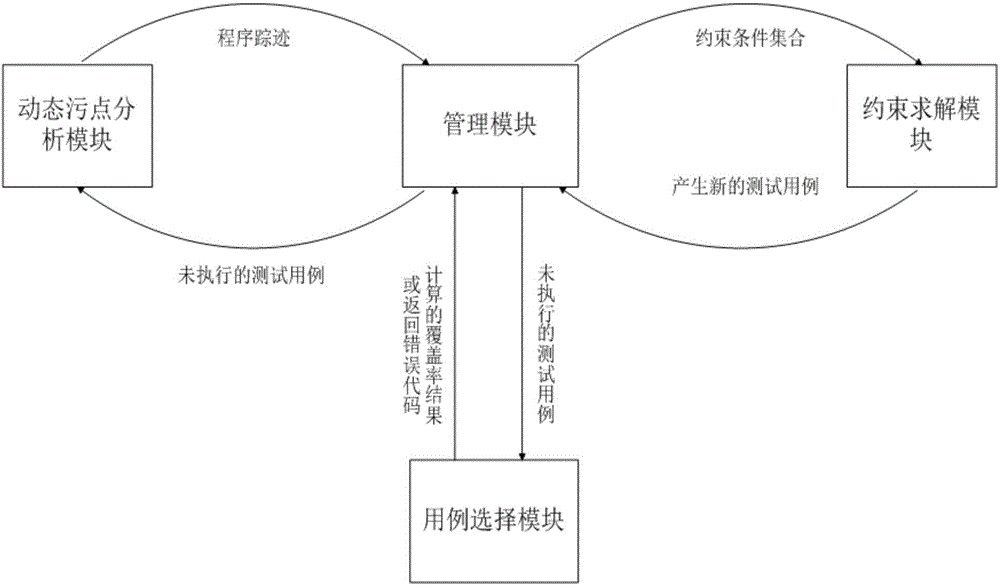
Mode-based dynamic vulnerability discovery integrated system and mode-based dynamic vulnerability discovery integrated method
InactiveCN104598383ABig blindnessImplement automated testingSoftware testing/debuggingComputer moduleComputer science
The invention relates to a mode-based dynamic vulnerability discovery integrated system and a mode-based dynamic vulnerability discovery integrated method. The mode-based dynamic vulnerability discovery integrated system comprises a dynamic taint analysis module, a test case selection module, a restraint solving module and a management module. The mode-based dynamic vulnerability discovery integrated method comprises the following steps: firstly, transmitting a seed case to an application program, tracking the transmission of taint data in the program by use of the dynamic taint analysis module, then expressing a transmission track by use of symbols, thereby obtaining a symbolized taint transmission path by virtue of combination of a dynamic taint analysis technology and a symbol execution technology; then by taking the symbolized taint transmission path as input of the restraint solving module, performing restraint solving to obtain a new test case, re-transmitting the test case to the application program, and further performing subsequent operations, wherein the whole process is performed under unified dispatching management of the management module. According to the mode-based dynamic vulnerability discovery integrated system and the mode-based dynamic vulnerability discovery integrated method, the automation degree and efficiency of dynamic vulnerability discovery for a binary program are improved, the generated test data accuracy and the efficiency are high, and thus a fuzzy test process is high in pertinency.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
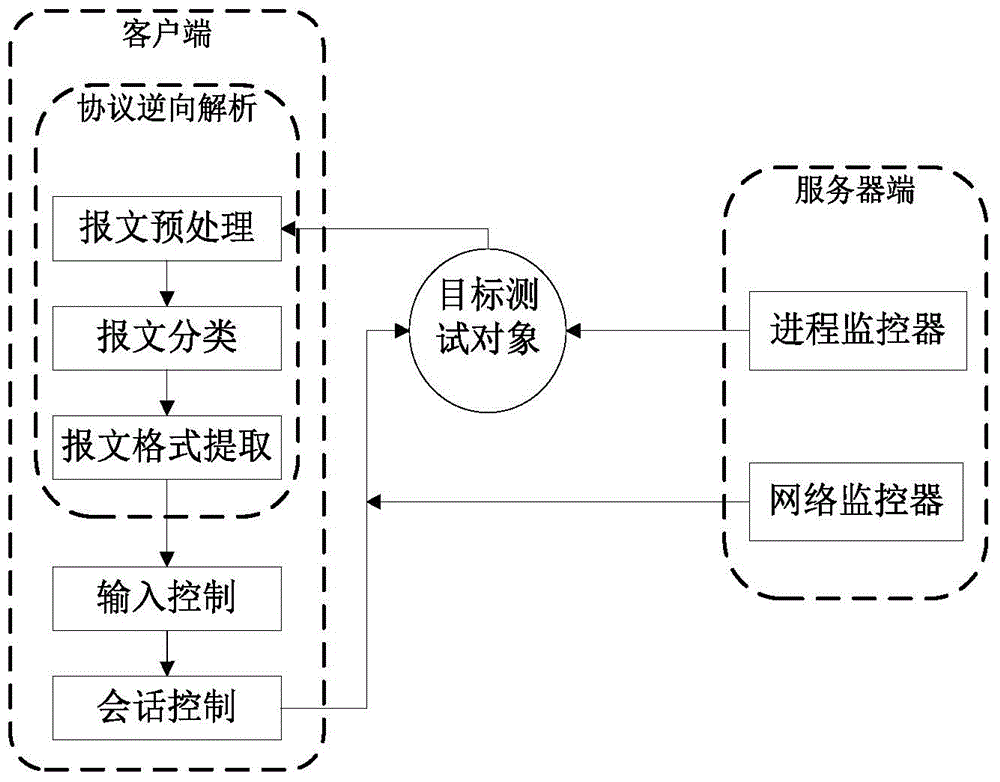
Automatic vulnerability discovery system and method based on protocol reverse parsing
InactiveCN104168288AImprove efficiencyHigh degree of automationTransmissionSession controlInput control
The invention relates to an automatic vulnerability discovery system and method based on protocol reverse parsing. The automatic vulnerability discovery system comprises a protocol reverse parsing module and a fuzz testing module, wherein the protocol reverse parsing module comprises a message preprocessing module, a message classifying module, a message format extracting module and the like, and the fuzz testing module comprises a process monitoring module, a network monitoring module, an input control module, a session control module and the like. The automatic vulnerability discovery system further comprises a server side and a client side, wherein the server side comprises a process monitoring module and a network monitoring module, and the client side comprises a message preprocessing module, a message classifying module, a message format extracting module, an input control module and a session control module. By means of the automatic vulnerability discovery system and method based on the protocol reverse parsing, the automation degree and efficiency of network service software vulnerability discovery are improved, the dependence on manual operation of the protocol analysis process is reduced, meanwhile the demand for the authority limit of a target object is reduced, and an application range is widened.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
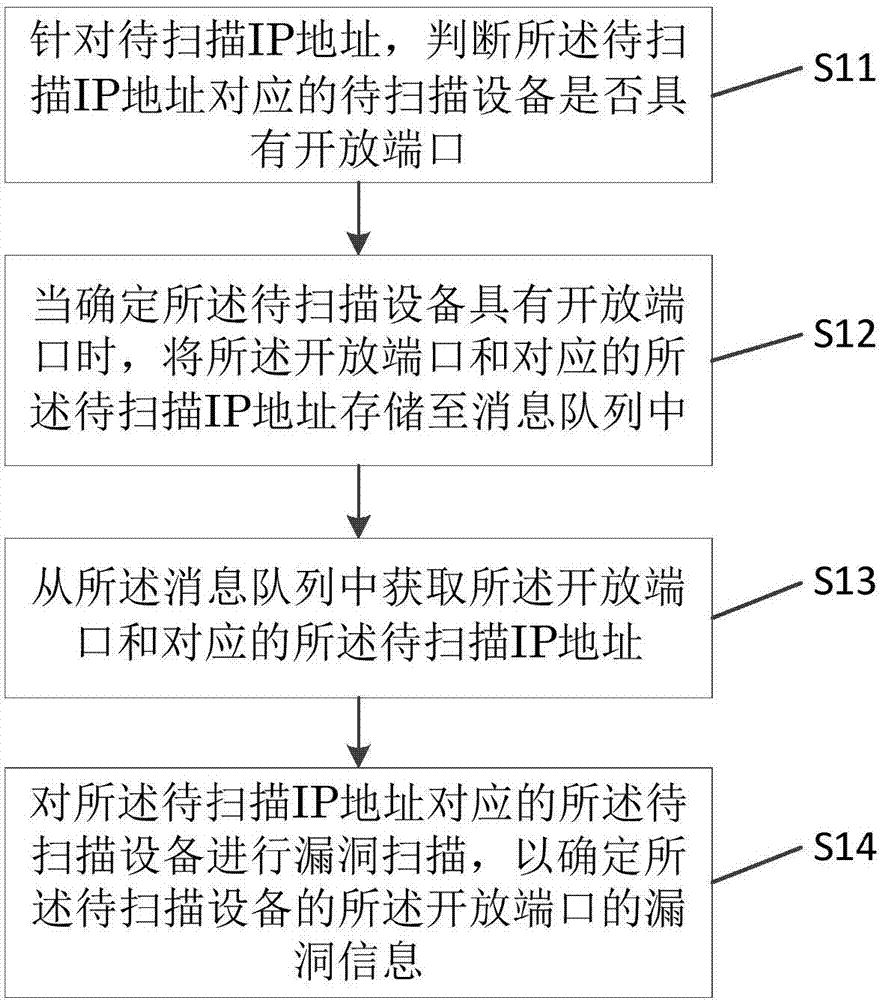
Vulnerability scanning method and device
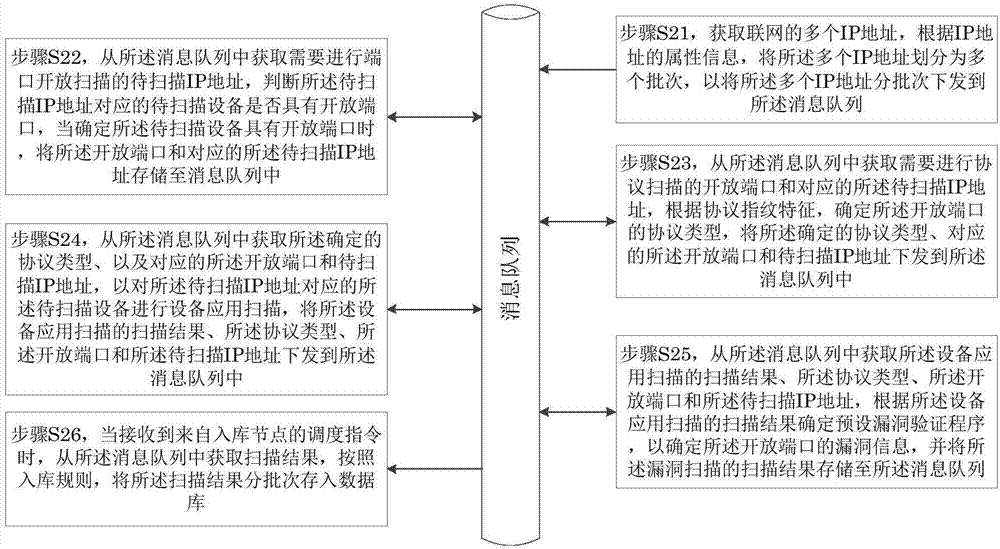
The invention provides a vulnerability scanning method and device. The method comprises a step of judging whether equipment to be scanned corresponding to an IP address to be scanned has an open port for the IP address to be scanned, a step of storing the open port and the corresponding IP address to be scanned into a message queue when a condition that the equipment to be scanned has the open port is determined, a step of obtaining the open port and the corresponding IP address to be scanned from the message queue, and a step of carrying out vulnerability scanning on the equipment to be scanned corresponding to an IP address to be scanned so as to determine the vulnerability information of the open port of the equipment to be scanned. Through the vulnerability scanning method and device, by using a message queue mechanism, the vulnerability discovery efficiency of online equipment corresponding to massive IP addresses is improved.
Owner:BEIJING KUANGEN NETWORK TECH
Binary program vulnerability discovery method and system
ActiveCN105678169AExcavate accuratelyAccurate locationPlatform integrity maintainanceCode conversionAssembly language
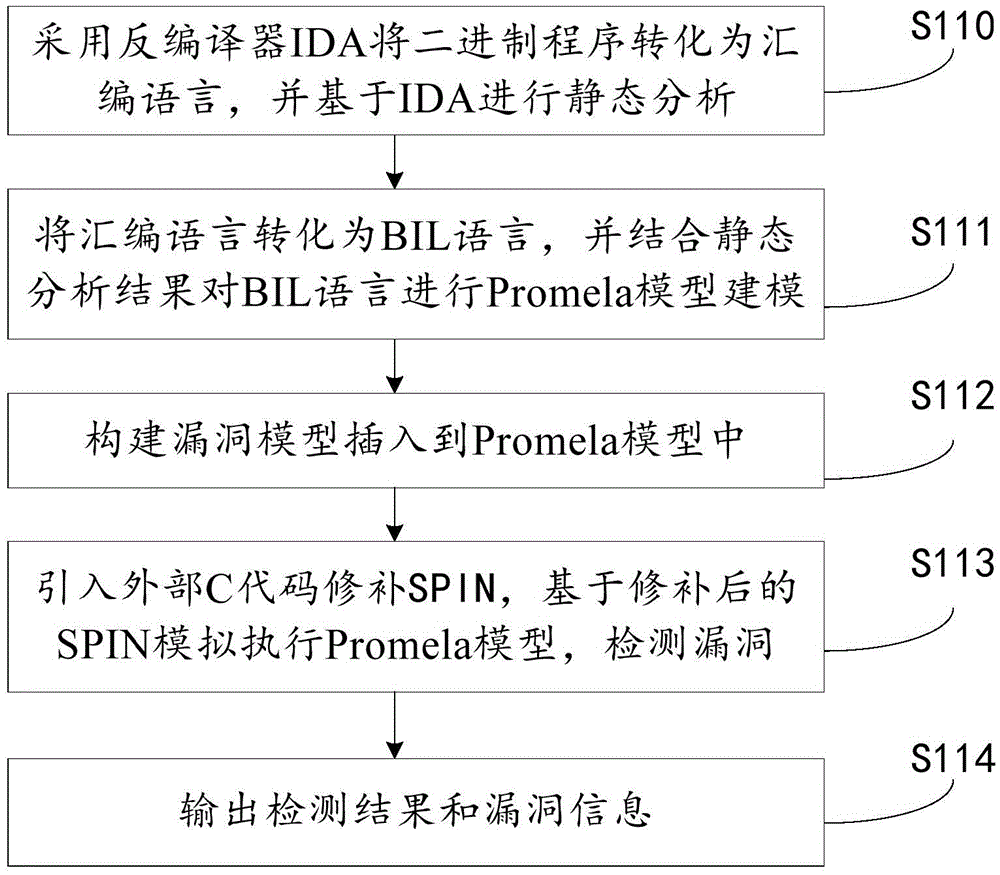
The invention provides a binary program vulnerability discovery method. The binary program vulnerability discovery method comprises steps of converting a target binary program into an assembly language, and carrying out static analysis to the assembly language; carrying out Promela model modeling to an intermediate language by combining the analysis result of the static analysis; establishing a vulnerability model and inserting the vulnerability model into the Promela model; introducing an external C code, simulating and executing the Promela model based on an SPIN, and detecting the vulnerability. The invention also provides a binary program vulnerability discovery system comprising a preprocessor module, a code conversion module and a model detection module. With respect to the binary program vulnerability discovery method and system, the intermediate language BIL is introduced to serve as a conversion bridge through which the binary program is converted into the Promela model, automatic modeling of the binary program is achieved, the embedded C function of the SPIN is employed to achieve simulation and execution, and the external C code is introduced to correct the defect of model detection. Experimental results show that the binary program vulnerability discovery method can effectively detect memory destructive vulnerabilities of binary programs.
Owner:XIAN HUMEN NETWORK TECH CO LTD
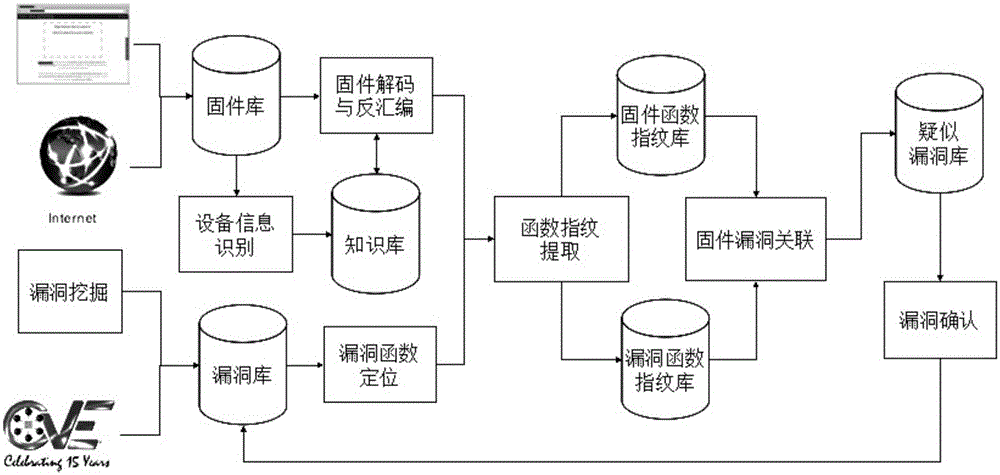
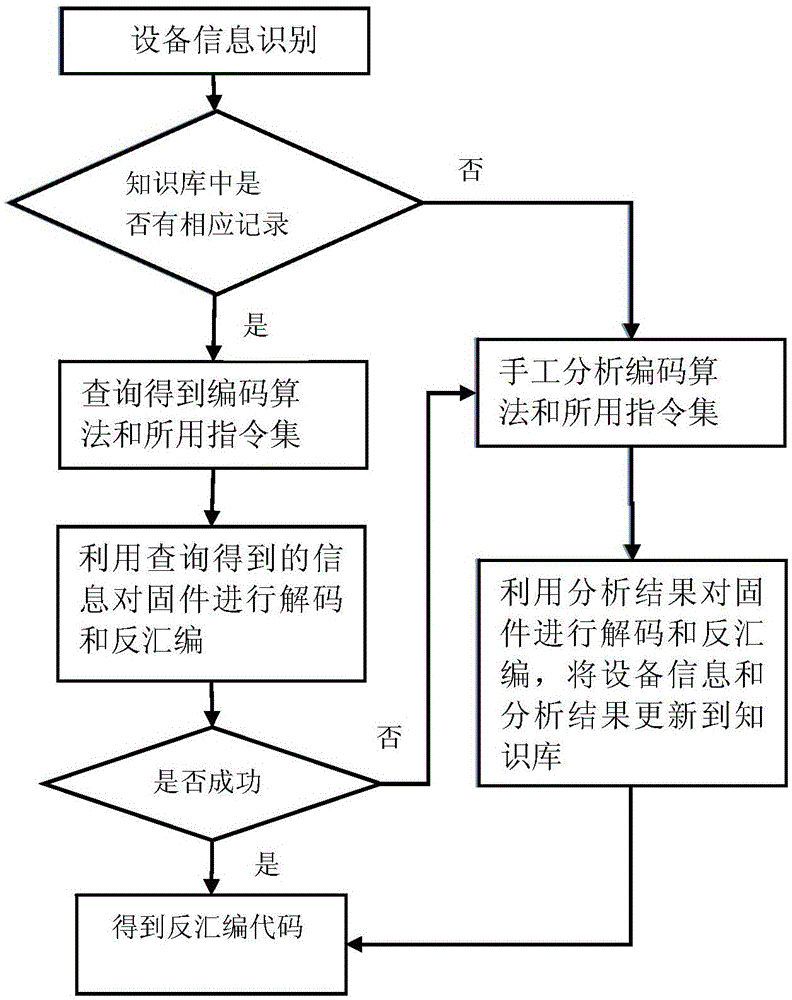
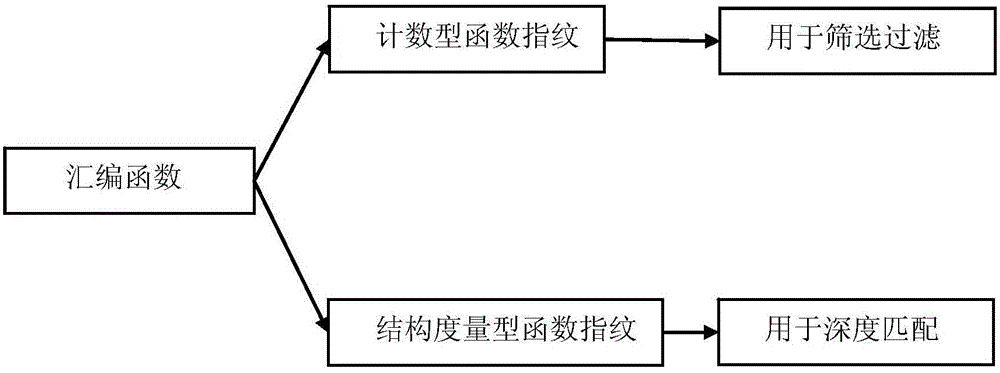
Embedded-device-oriented firmware vulnerability detection method and embedded-device-oriented firmware vulnerability detection system
ActiveCN106295335AGuaranteed strong robustnessHigh speedPlatform integrity maintainanceVulnerability discoveryFingerprint
The invention provides an embedded-device-oriented firmware vulnerability detection method and an embedded-device-oriented firmware vulnerability detection system, and relates to vulnerability discovery and analysis of firmware of embedded devices. By the method and the system, relevance among functions in the firmware can be utilized, and discovered firmware vulnerabilities are spread to other firmware automatically. The method mainly includes the steps of firmware crawling and vulnerability collection, equipment information extraction, firmware decoding and disassembling, fingerprint extracting and matching of functions, vulnerability verification and the like. The method and the device have the advantages that both matching speed and matching accuracy are taken into consideration through coordination between attribute counting type fingerprints and structure measurement type fingerprints, used fingerprint characteristics have features of trans-complier and trans-processor platforms, and accordingly, high robustness during matching is guaranteed.
Owner:INST OF INFORMATION ENG CAS
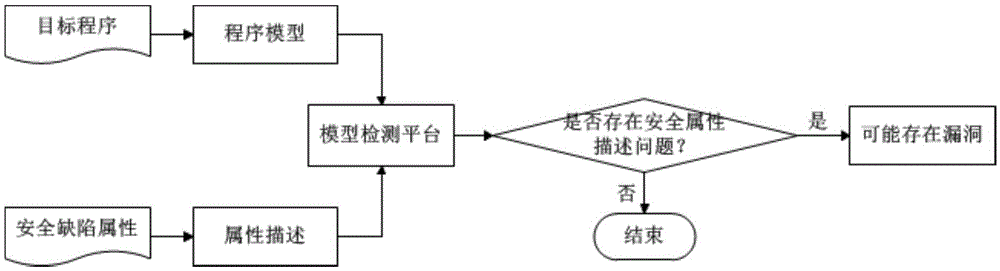
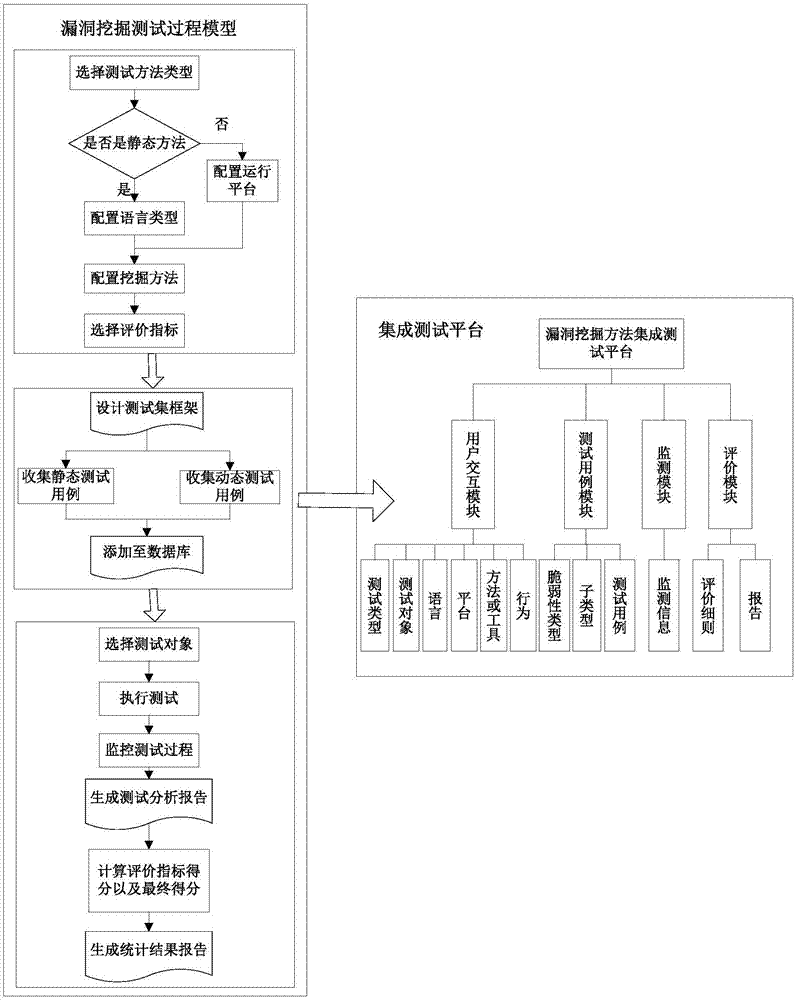
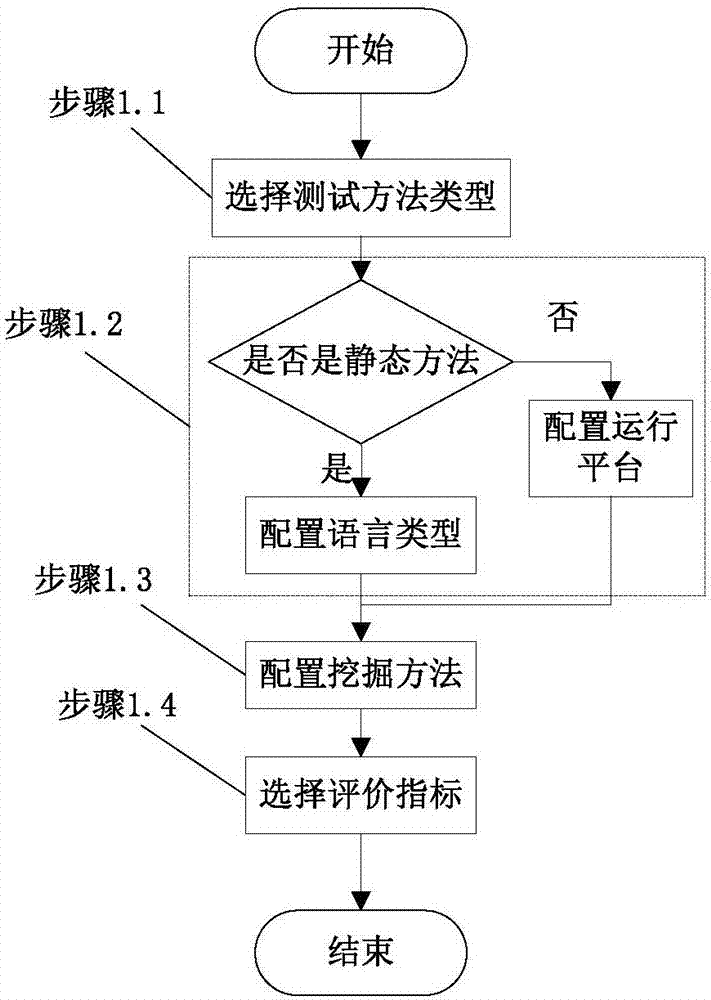
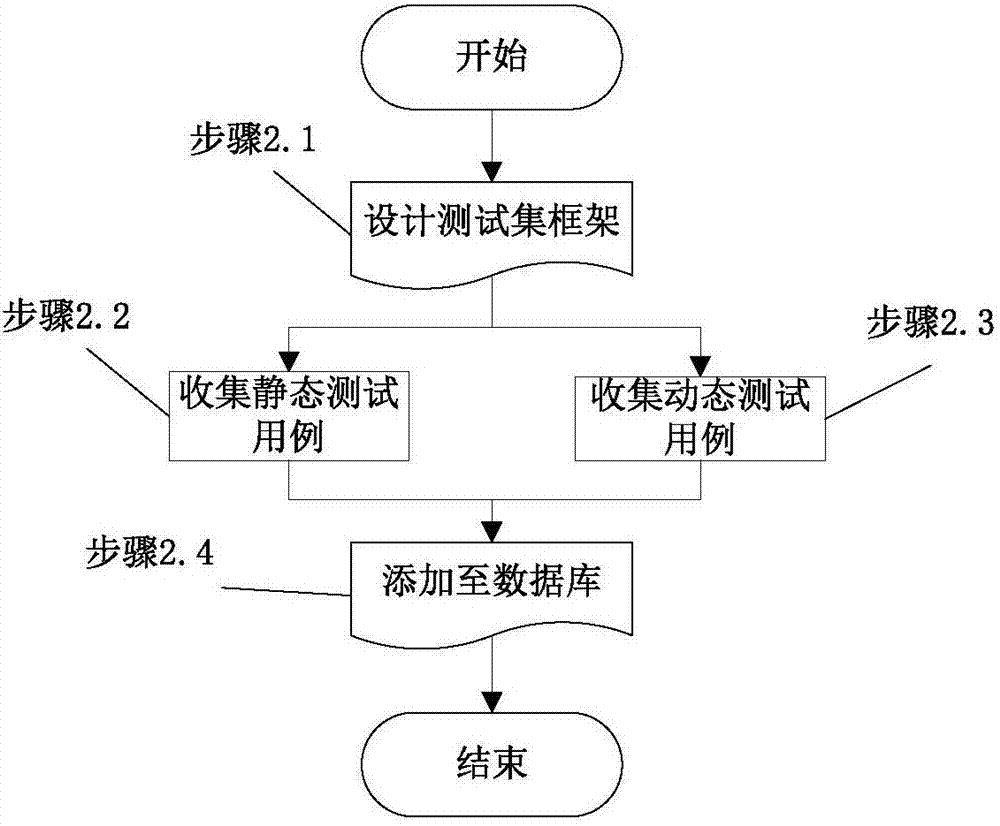
Test model and test method of vulnerability discovery technology
ActiveCN107368417AIncrease the level of automationEasy to useSoftware testing/debuggingPlatform integrity maintainanceIntegration testingTest analysis
The invention discloses a test model and test method of a vulnerability discovery technology, and belongs to the field of software engineering. The method includes the steps that 1, based on existing static and dynamic vulnerability discovery methods, a self-adaptive vulnerability discovery operation environment is constructed; 2, according to different vulnerability types, vulnerability languages and vulnerability trigger methods, a test case set is constructed and configured; 3, the vulnerability discovery test method is executed, the discovery test state is monitored, and meanwhile a test analysis report and statistical test results are output; 4, based on the vulnerability discovery test process model, an integrated test platform is designed and achieved, and the feasibility and validity of the vulnerability discovery test model are further verified. According to the test model and test method of the vulnerability discovery technology, existing typical vulnerability discovery methods and tools are accurately evaluated by means of a series of specific evaluation standards, moreover, comparative analysis is conducted on these methods and tools, and the test model and the test method have certain guiding significance for selection of the most suitable and the most efficient method or tool in the actual vulnerability discovery process.
Owner:中国人民解放军63928部队 +1
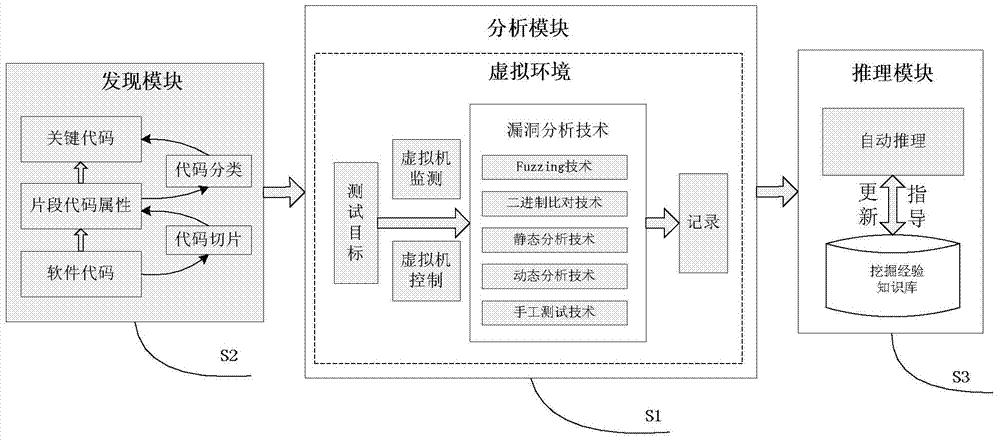
Software vulnerability discovery system and method based on attribute extraction
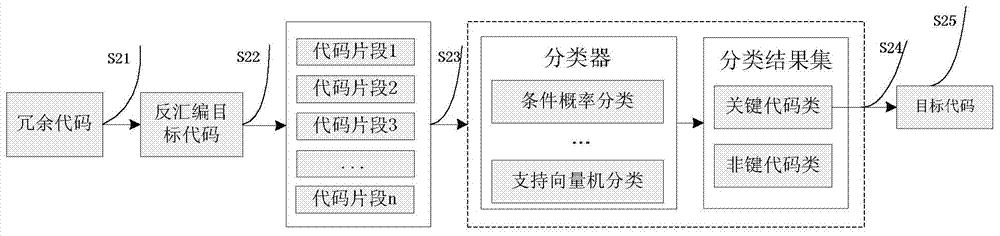
ActiveCN104268085ASimplify complexityImprove digging efficiencySoftware testing/debuggingComputer compatibilityData mining
The invention provides a software vulnerability discovery system and method based on attribute extraction and belongs to the field of computer safety. The system comprises a key code discovery module, a vulnerability analyzing module and a vulnerability deduction module. The method includes the following steps: extracting key codes of software to be tested; executing the software to be tested in the virtual machine environment and adopting a virtual machine fault injection engine and the key codes to conduct testing interaction and record a testing result; conducting deduction by combining the testing result and the discovery experience knowledge base. The system and the method effectively achieve complex causal relationship between uncertain software flaw and loopholes. The software vulnerability discovery system method based on the attribute extraction has certain advantages in the aspects of safety, flexibility and compatibility.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
System and method for identifying exploitable weak points in a network
The system and method described herein may leverage passive and active vulnerability discovery to identify network addresses and open ports associated with connections that one or more passive scanners observed in a network and current connections that one or more active scanners enumerated in the network. The observed and enumerated current connections may be used to model trust relationships and identify exploitable weak points in the network, wherein the exploitable weak points may include hosts that have exploitable services, exploitable client software, and / or exploitable trust relationships. Furthermore, an attack that uses the modeled trust relationships to target the exploitable weak points on a selected host in the network may be simulated to enumerate remote network addresses that could compromise the network and determine an exploitation path that the enumerated remote network addresses could use to compromise the network.
Owner:TENABLE INC
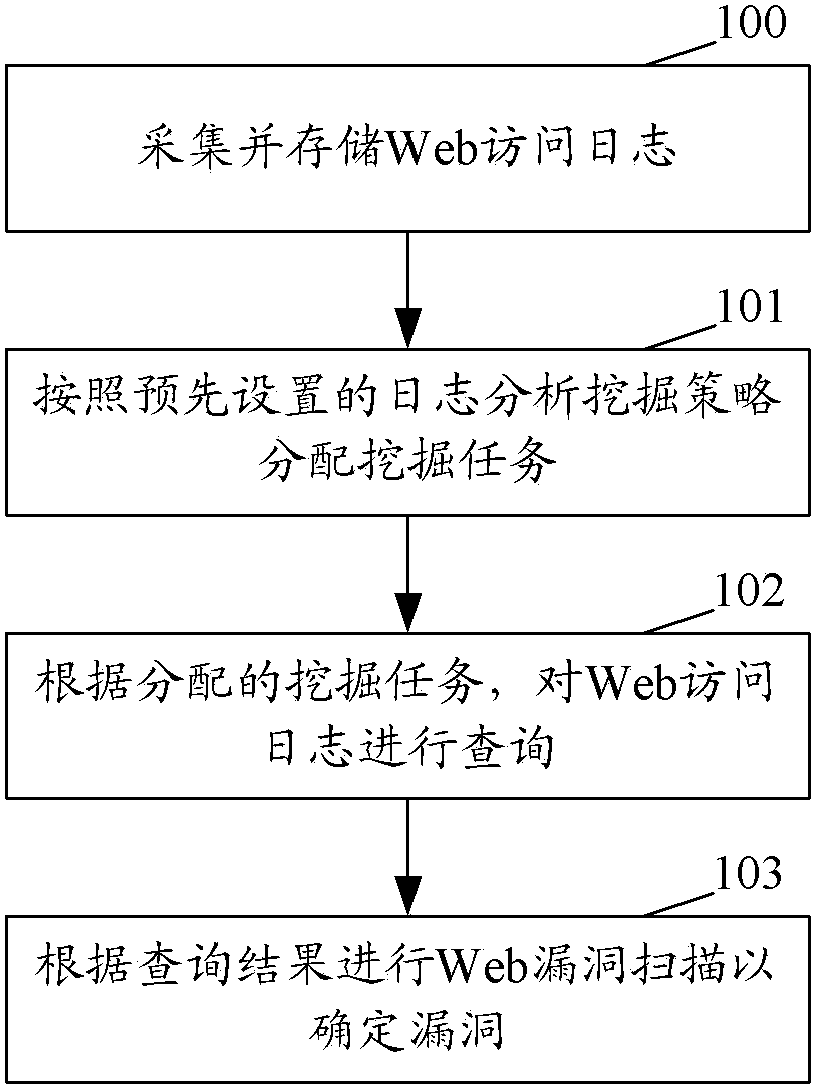
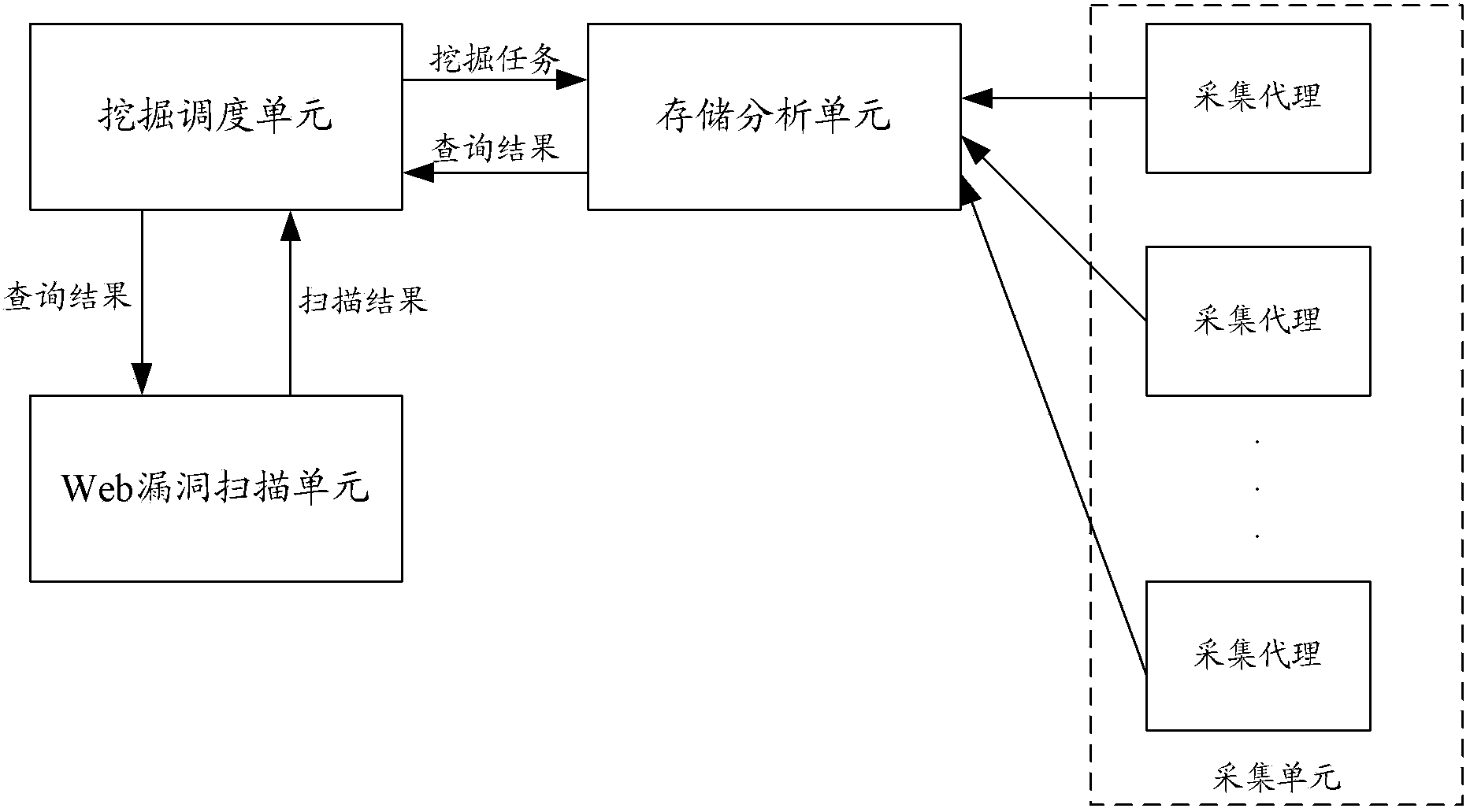
Web vulnerability discovery method and system
ActiveCN104144142AImprove accuracyGuaranteed accuracyTransmissionSpecial data processing applicationsVulnerability discoveryVulnerability scanning
The invention discloses a Web vulnerability discovery method and system. The web vulnerability discovery method includes the steps that Web access logs are collected and stored, discovery tasks are allocated according to a preset log analyzing and discovery strategy, the Web access logs are inquired according to the allocated discovery tasks, and Web vulnerability scanning is performed according to an inquiry result to determine vulnerability. According to the scheme, the capacity for storing, analyzing and inquiring mass data of the Hadoop framework and other big data analysis framework and the accuracy of Web vulnerability scanning are used for forming the close-loop vulnerability discovery method, and needle-in-the-haystack inquiries are avoided due to the targeted and objective inquiry, so that the inquiry efficiency is greatly improved, and accuracy of Web vulnerability discovery is ensured due to the accuracy of the Web vulnerability scanning technology. According to the Web vulnerability discovery method and system, the Web vulnerability are accurately analyzed and inquired under the mass data, so that accuracy and timeliness of Web vulnerability discovery are improved.
Owner:ALIBABA GRP HLDG LTD
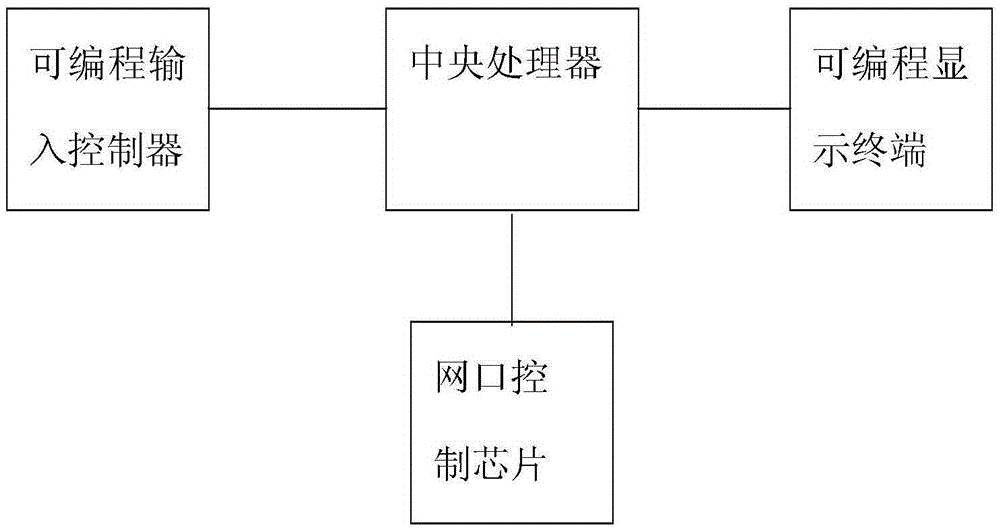
Industrial environment vulnerability discovering device and method
ActiveCN105404207APowerful and flexible graphical custom frameworkArbitrary manipulationProgramme controlComputer controlContent formatInternet access
The invention discloses an industrial environment vulnerability discovering device and method. The industrial environment vulnerability discovering device comprises a mainboard composed of a central processor and an internet access control chip, a programmable input controller and a programmable display terminal. The industrial environment vulnerability discovering is a method of discovering faults of a detected device through providing unexpected input for an application and monitoring abnormities in output of an external device, and the method realizes vulnerability discovery and security early-warning by discovering security vulnerabilities of an industrial control system through a fuzzy test. The device and method have the following advantages: 1, a professional protocol resource database is arranged; 2, a powerful flexible graphical customized framework is arranged; 3, a rich library of functions is arranged; 4, a customization function module is arranged; 5, a communication process design function is exhibited; 6, multiple test modes are exhibited; 7, an analysis report and a report template can be customized; and 8, a report content format can be customized.
Owner:CHINA ELECTRONICS CORP 6TH RES INST
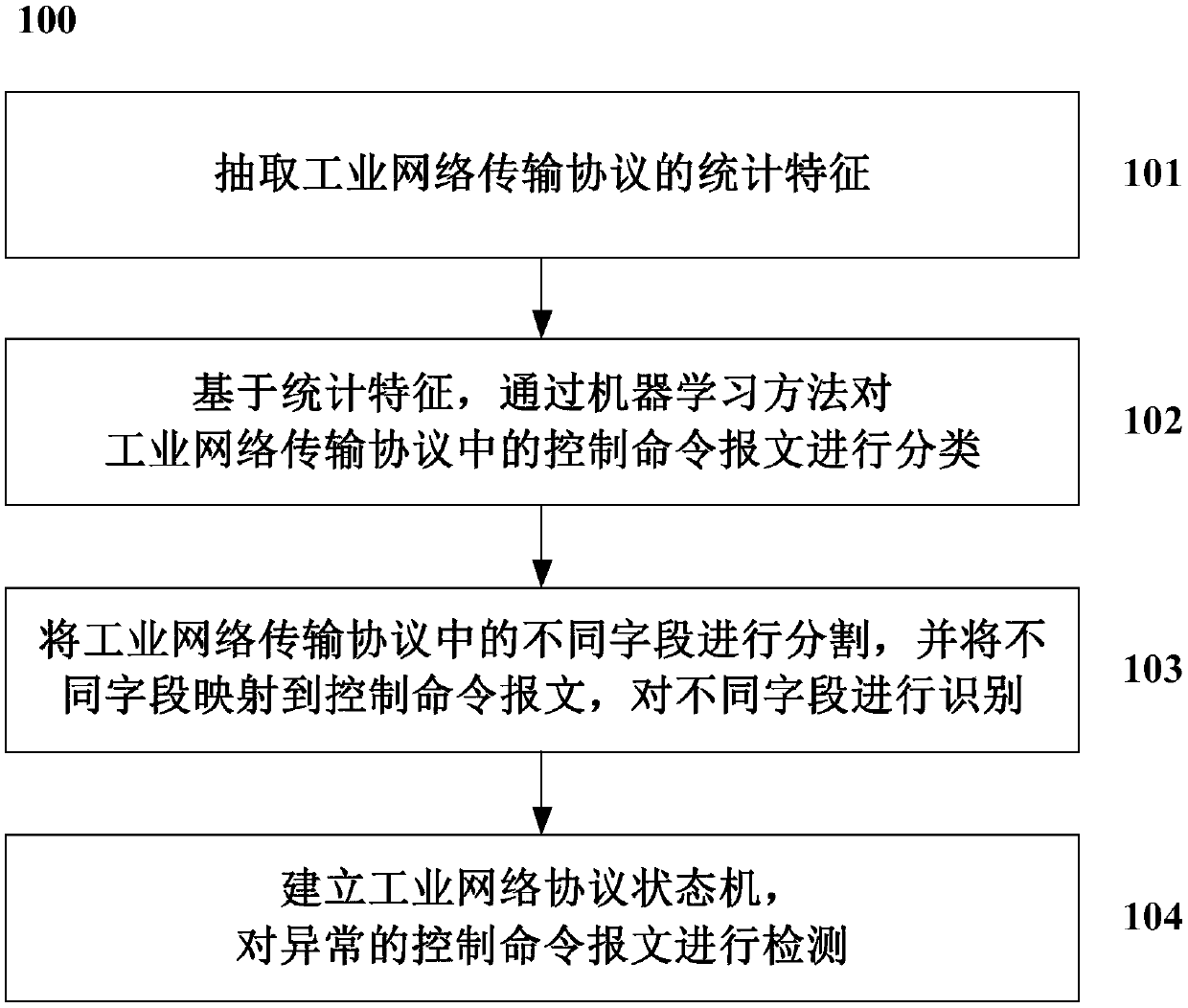
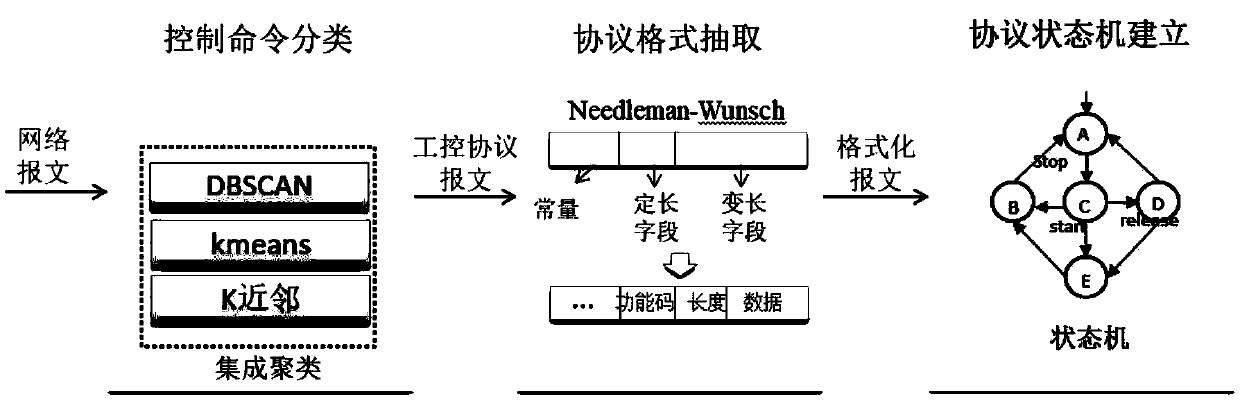
Method and system for analyzing industrial network transmission protocol
ActiveCN109547409AEnsure safetyPrevent malicious command attacksTransmissionTransmission protocolField mapping
The invention discloses a method and a system for analyzing an industrial network transmission protocol. The method comprises the steps of extracting statistical features of the industrial network transmission protocol; based on the statistical features, classifying control command messages in the industrial network transmission protocol via a machine learning method; segmenting different fields in the industrial network transmission protocol, and mapping the different fields to the control command messages, to recognize the different fields; and building an industrial network protocol state machine, and detecting the abnormal control command messages. According to the method and system provided by the invention, the important significance is provided for conducting researches in industrial control invasion detection, protocol security assessment and industrial protocol vulnerability discovery, and meanwhile the powerful support is provided foe ensuring the security of national infrastructures and core industrial control systems.
Owner:CHINA ELECTRIC POWER RES INST +3
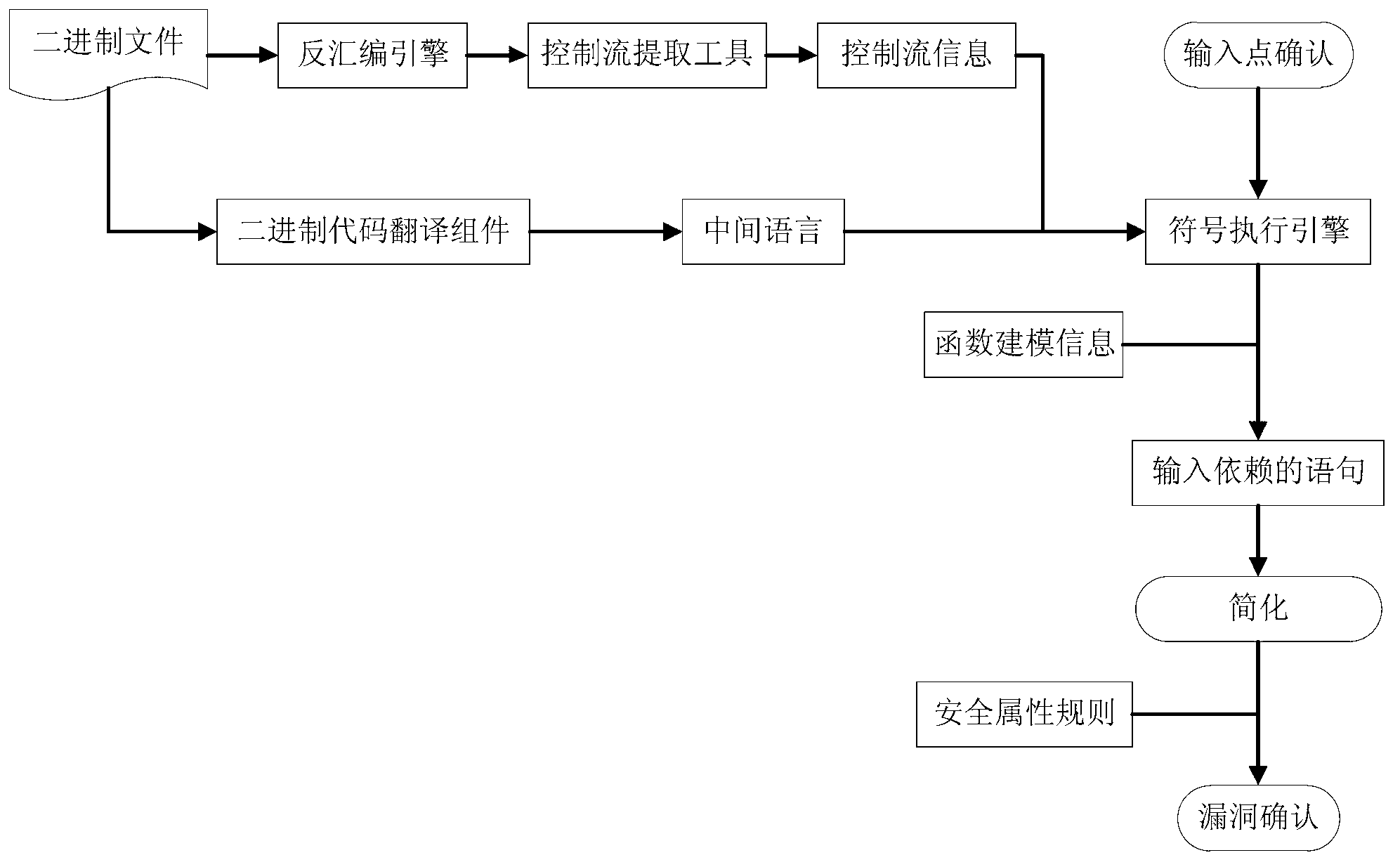
Method for binary code vulnerability discovery on basis of simple symbolic execution
The invention discloses a method for binary code vulnerability discovery on the basis of simple symbolic execution. The method comprises five steps that: firstly, binary codes are translated into an intermediate language with a static single assignment through a binary code translation component; and then, a disassembling engine is used to disassemble the binary codes, the control flow information of the binary codes is extracted, static symbolic execution is carried out in the intermediate language on the basis of the control flow information, an entrance point needs to be determined during the symbolic execution process, an input vector is converted into a symbol, and a called function is modeled. After the symbolic execution process is completed, the statement assembly of the intermediate language which depends on the input vector can be obtained, the statements of an assembly are simplified, and a vulnerability discovery confirmation report is generated after security attribute rules are used to confirm.
Owner:BEIHANG UNIV
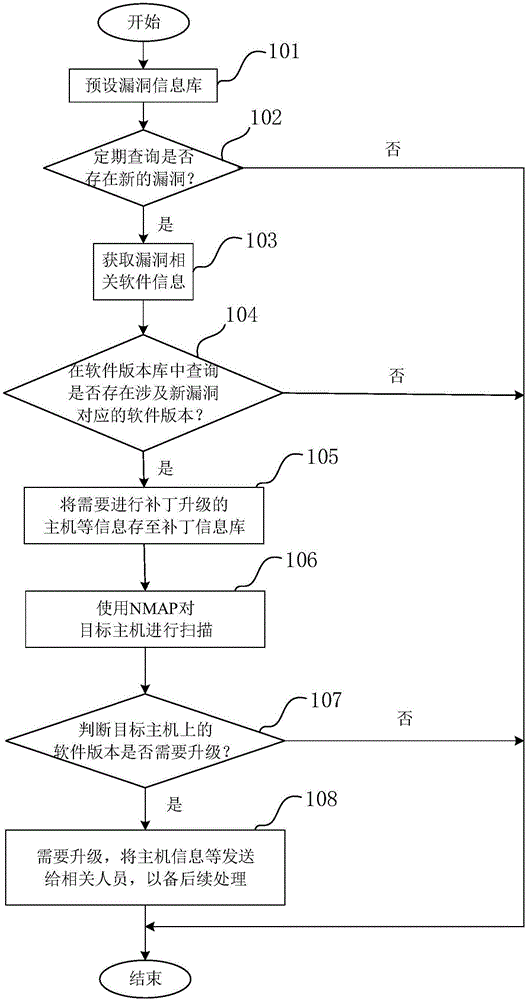
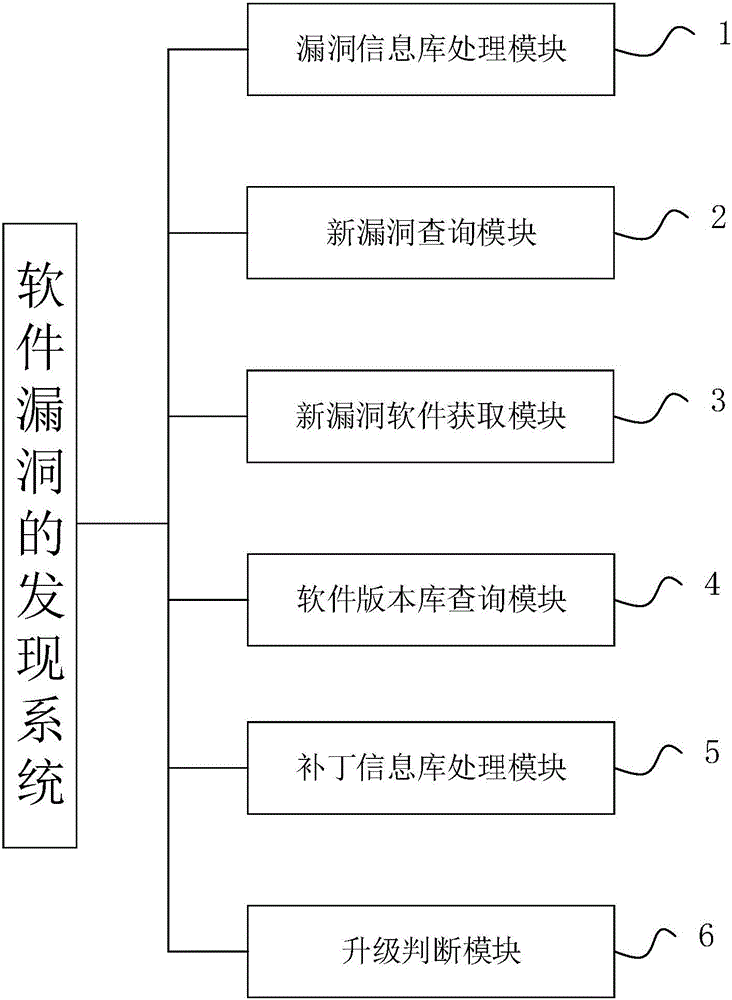
Software vulnerability discovery method and system
ActiveCN106503564AProcessing speedGet it in timePlatform integrity maintainanceVulnerability discoverySoftware engineering
The invention discloses a software vulnerability discovery method and system. The discovery method comprises the steps that 1, whether a new vulnerability exists or not is inquired regularly, and if yes, the step 2 is conducted; 2, vulnerability-related software information is acquired according to the new vulnerability, wherein the vulnerability-related software information comprises a name and a version of software affected by the new vulnerability; 3, whether software affected by the new vulnerability exists or not is inquired in a preset software version library according to the vulnerability-related software information, and if yes, to-be-analyzed host software information is output. According to the software vulnerability discovery method and system, vulnerability discovery can be automatically conducted, which software on a host in a to-be-analyzed network has the vulnerability and needs patch updating can be quickly, accurately and automatically identified, operation and maintenance engineers are free from heavy and complex work, and meanwhile harm caused by manual careless omissions to network security is avoided.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
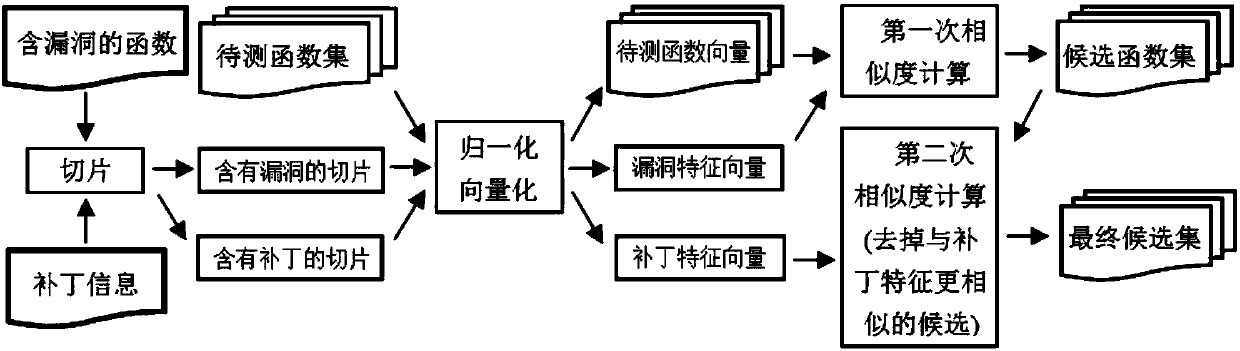
Similarity detection method for unknown vulnerability discovery based on patch information
ActiveCN108268777AReduce distractionsFix false positivesPlatform integrity maintainanceFeature vectorAlgorithm
The invention relates to a similarity detection method for unknown vulnerability discovery based on patch information. The method comprises steps as follows: a known vulnerability function and a patchfunction after patching are sliced, and slices containing vulnerability related statements and slices containing patch statements are generated; variable names, variable types and function call namesof a to-be-detected function, the vulnerability slices and the patch slices are subjected to symbol normalization; the to-be-detected function, the vulnerability slices and the patch slices are mapped to vector space to generate to-be-detected function characteristic vectors, vulnerability characteristic vectors and patch characteristic vectors, one vector is formed by each of the to-be-detectedfunction characteristic vectors, the vulnerability characteristic vectors and the patch characteristic vectors, and a value of each dimension of the one vector represents a product of the number of appearing times of the characteristic statement in the function and TF-IDF weight; after generation of the characteristic vectors, similarity of the characteristic vectors is calculated and sequencing is performed, and whether unknown vulnerability with the characteristics similar to those of known vulnerability in a to-be-detected function set is judged. According to the method, disturbance of vulnerability unrelated statements can be effectively reduced, and detection accuracy is improved.
Owner:RENMIN UNIVERSITY OF CHINA
Automatic vulnerability detection system and method based on port identification
InactiveCN109033844AQuick scanHigh speed scanPlatform integrity maintainanceRapid scanComputer science
The invention discloses an automatic vulnerability detection system based on port identification, includes a port quick scan module, a port protocol identification module, an asset classification storage module, a vulnerability verification module, an asset visualization display module, fast-scans that asset IP segment through the port fast-scan module, and outputs the result to the port protocolidentification module for fine service version fingerprint identification, classifies and stories the result after identification according to IP, port, service version in an asset classification storage module, and adds the filtered specific digital assets to the vulnerability validation module to begin vulnerability validation, at last, the t results are output and deliver to the operation and maintenance personnel for repair. The automatic vulnerability detection system and the automatic vulnerability detection method based on the port identification of the invention can complete the safetydetection of the enterprise assets within one hour of the vulnerability outbreak, greatly reduce the emergency response time and the human cost, and ensure that the enterprise completes the vulnerability discovery and repair before being attacked to the maximum extent.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
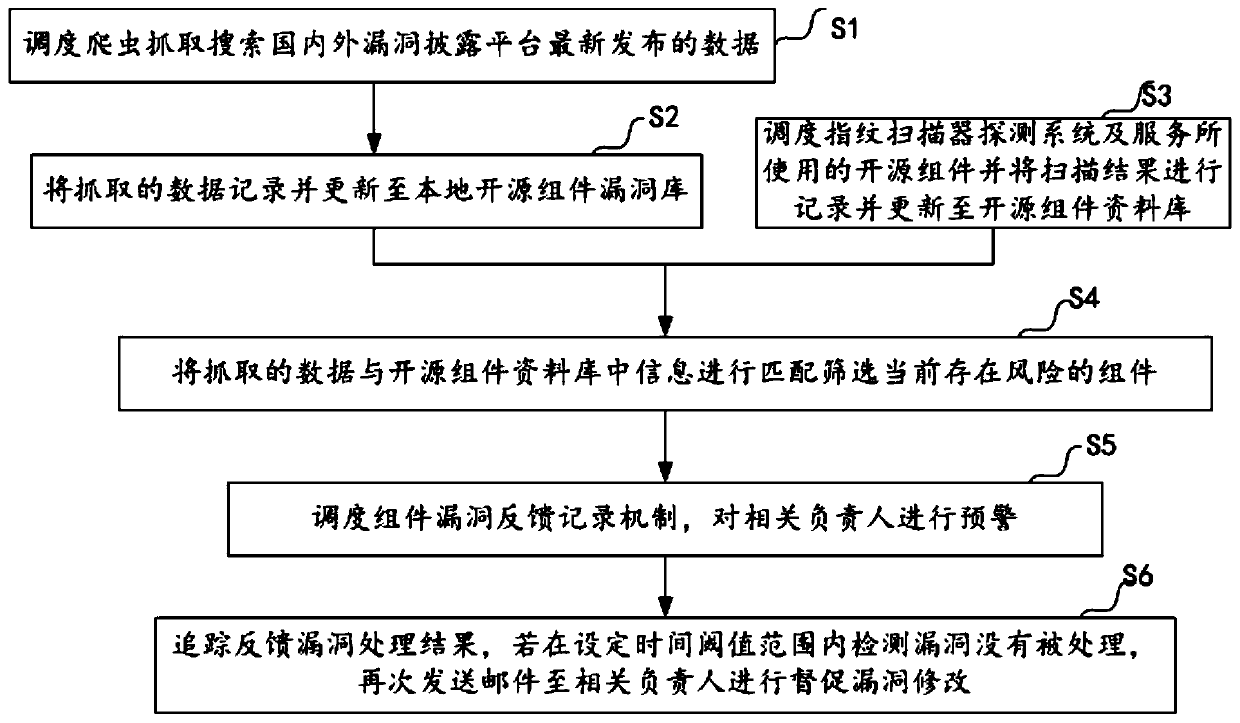
Automatic monitoring method and system for open source component vulnerabilities
InactiveCN110543767AImprove discoveryImprove efficiencyPlatform integrity maintainanceOpen sourceWorkload
The invention provides an automatic monitoring method and system for open source component vulnerabilities. The automatic monitoring method comprises the following steps: scheduling crawlers to searchand capture data newly published by bug disclosure platforms at home and abroad; recording the grabbed data and updating the grabbed data to a local open source component vulnerability library; scheduling an open source component used by the fingerprint scanner detection system and service, recording a scanning result and updating the scanning result to an open source component database; matchingthe grabbed data with information in an open source component database to screen components with risks at present; and performing early warning on related responsible persons by a scheduling component vulnerability feedback recording mechanism. The automatic monitoring method can realize Automatic vulnerability early warning tracking and security construction, so that security personnel only needto pay attention to screened vulnerabilities related to products and companies. Therefore, the extra-large workload is saved, and the security vulnerability discovery and tracking efficiency is improved; the vulnerability tracking range is expanded; and the latest burst vulnerability can be responded within 24 hours, so that the company network security response timeliness is improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
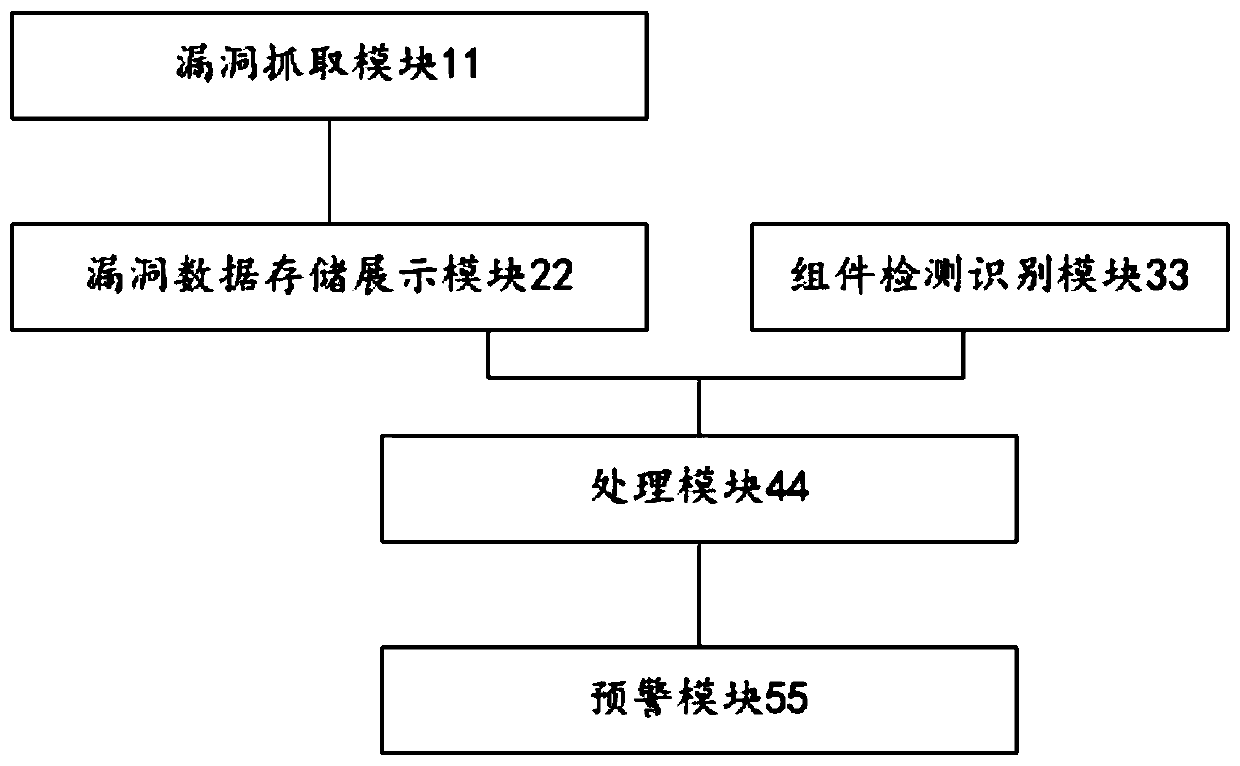
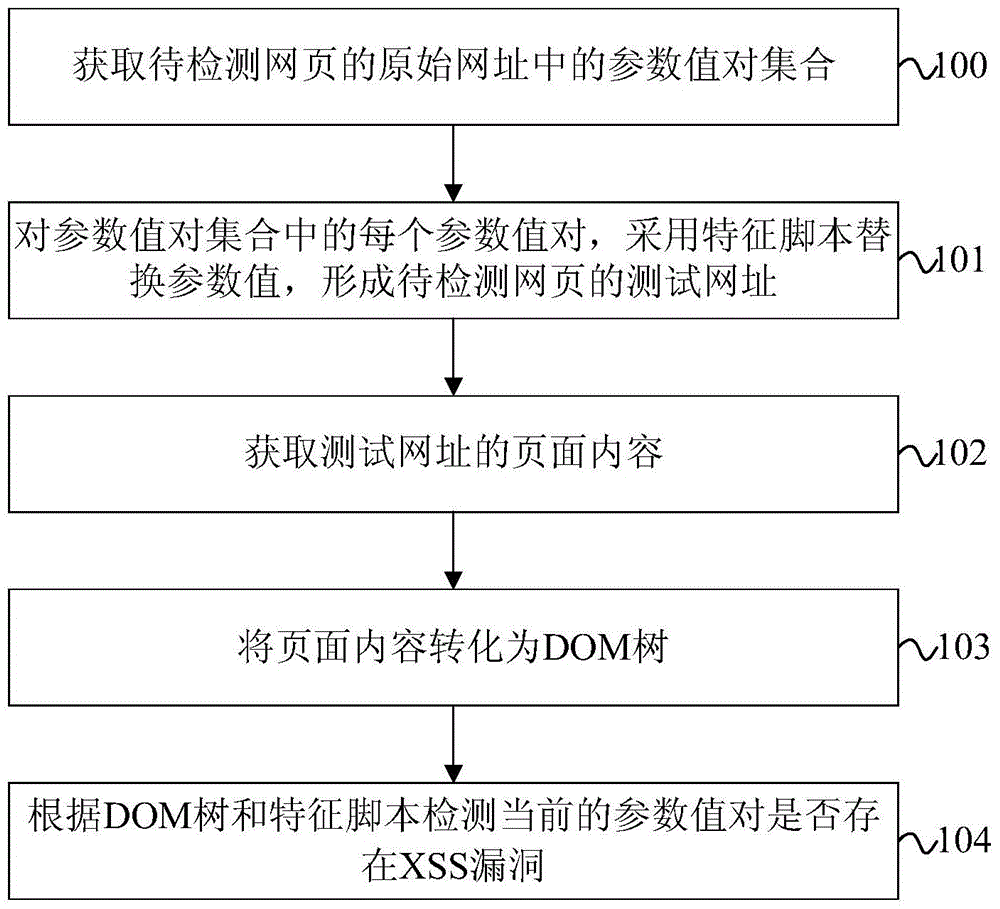
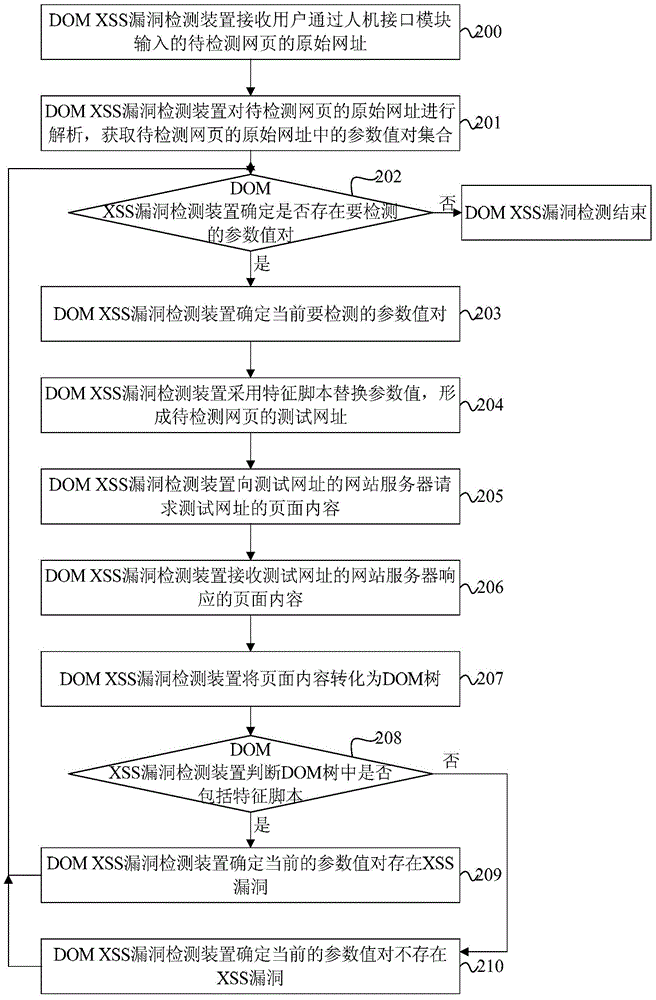
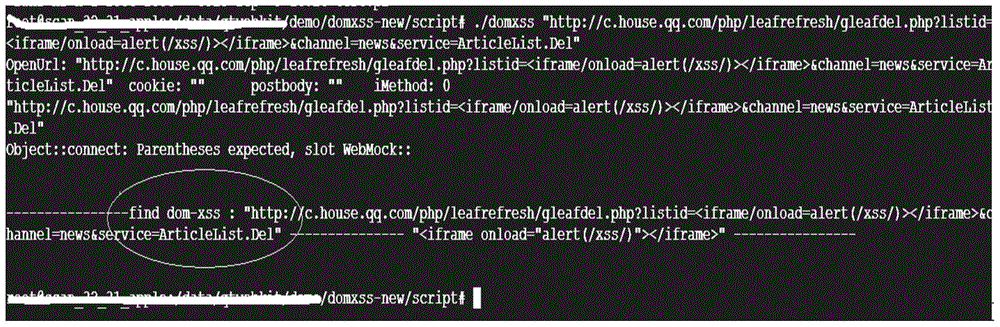
Cross-site scripting vulnerability detection method and device based on file object model
ActiveCN104636664AEfficient discoveryImprove vulnerability discovery capabilitiesPlatform integrity maintainancePattern recognitionDocumentation
Disclosed are a method, apparatus, and terminal for detecting a document object model-based cross-site scripting attack vulnerability. The method comprises: obtaining a set of parameter value pairs in the original URL of a webpage, the set of parameter value pairs including at least one parameter value pair; replacing parameter values of the parameter pairs with a feature script to form a test URL of the webpage, the feature script being malicious codes that contain malicious characters and can be uniquely identified in a document object model tree of the webpage; obtaining the page content corresponding to the test URL; converting the page content into the document object model tree; and detecting whether the cross-site scripting attack vulnerabilities are in the parameter value pairs according to the document object model tree and the feature script. By using the above solution, DOM XSS vulnerabilities can be effectively found only through searching the inserted feature script in the converted DOM tree and without triggering the execution of the feature script, thus greatly improving the ability of vulnerability discovery and the detection efficiency.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A program path sensitive grey box testing method and device
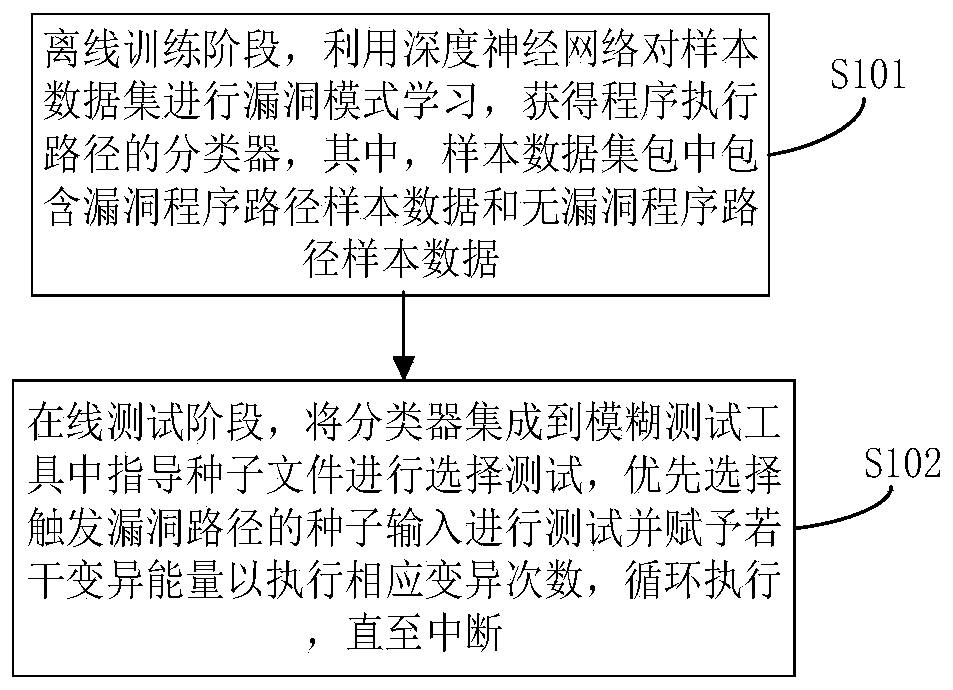
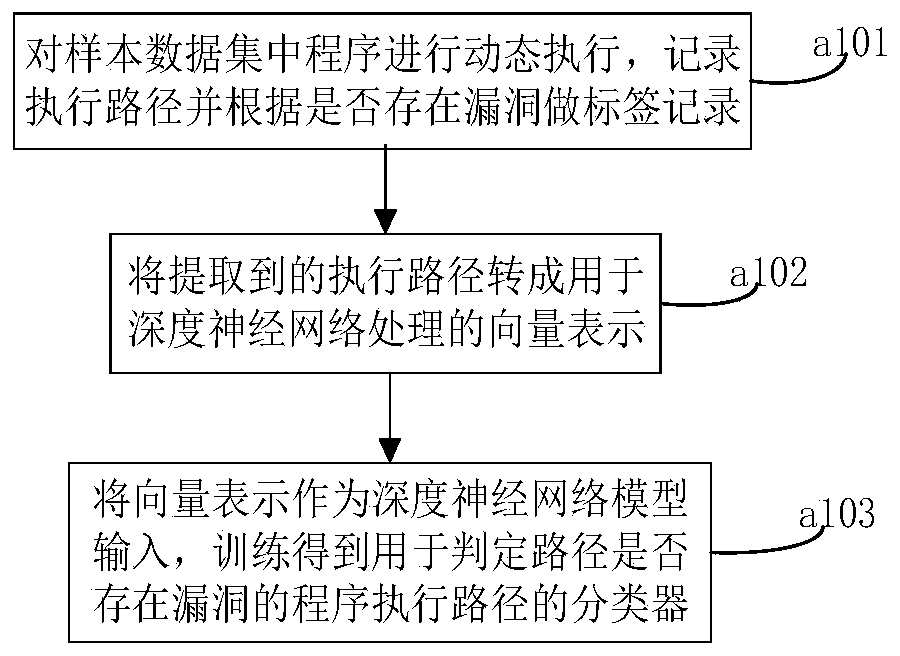
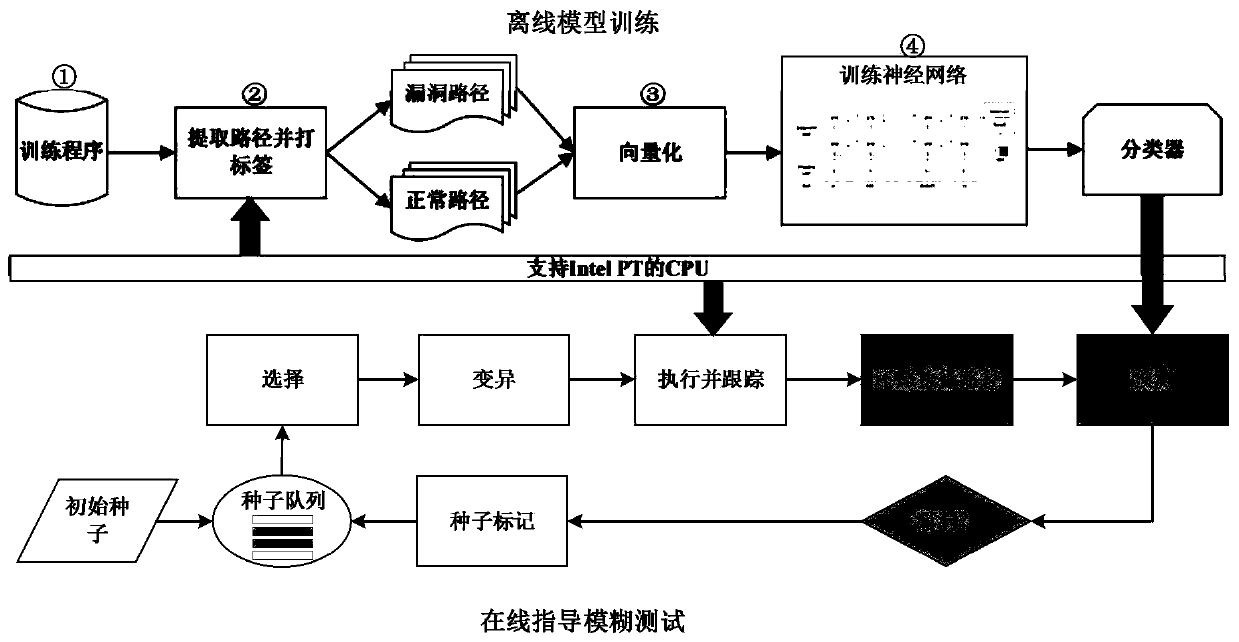
ActiveCN109902024AIncrease trigger rateImprove discovery efficiencySoftware testing/debuggingGray box testingData set
The invention belongs to the technical field of software testing. The invention particularly relates to a program path sensitive grey box testing method and device. The method comprises the steps thatin the offline training stage, vulnerability mode learning is conducted on a sample data set through a deep neural network, a classifier of a program execution path is obtained, and a sample data setpackage comprises vulnerability program path sample data and vulnerability-free program path sample data; and in an online test stage, the classifier is integrated into a fuzzy test tool to guide a seed file to perform a selection test, seed input triggering a vulnerability path is preferentially selected to perform the test, endowing the test with a plurality of variation energies to execute corresponding variation times, and performing cyclic execution until interruption. The method fills up the blank of vulnerability path sample influence analysis, does not depend on a complex dynamic analysis technology, does not bring about a large overhead problem, can be effectively combined with other grey box test technologies, improves vulnerability discovery efficiency, can be directly suitablefor a binary program, does not depend on a source code, and is high in applicability.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Method for SQL injection vulnerability discovery based on simulated attack extension
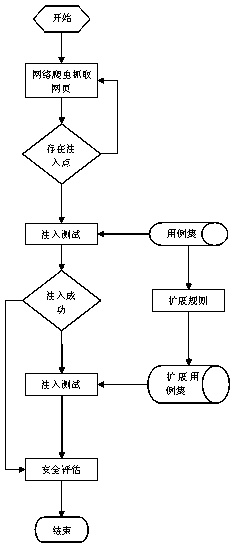
ActiveCN103780614AAchieve coverageImprove the detection rateTransmissionSQL injectionVulnerability discovery
The invention discloses a method for SQL injection vulnerability discovery based on simulated attack extension. The method comprises the step that simulated attack cases injected through an SQL are extended so as to be used for discovering coding vulnerability of a server side and preventing vulnerability existing in a safety verification mechanism injected through the SQL. According to the method, the requirement for devices is simple, the discovery rate of server vulnerability is high, and meanwhile the stability is good when the method is applied to servers of different types and conducts scanning operation in safety mechanisms of different levels.
Owner:JINHUA BIQI NETWORK TECH
Vulnerability detection method and device
InactiveCN105204985AResolve accuracySolve the problem of lagging in vulnerability miningSoftware testing/debuggingPlatform integrity maintainanceData sourceVulnerability discovery
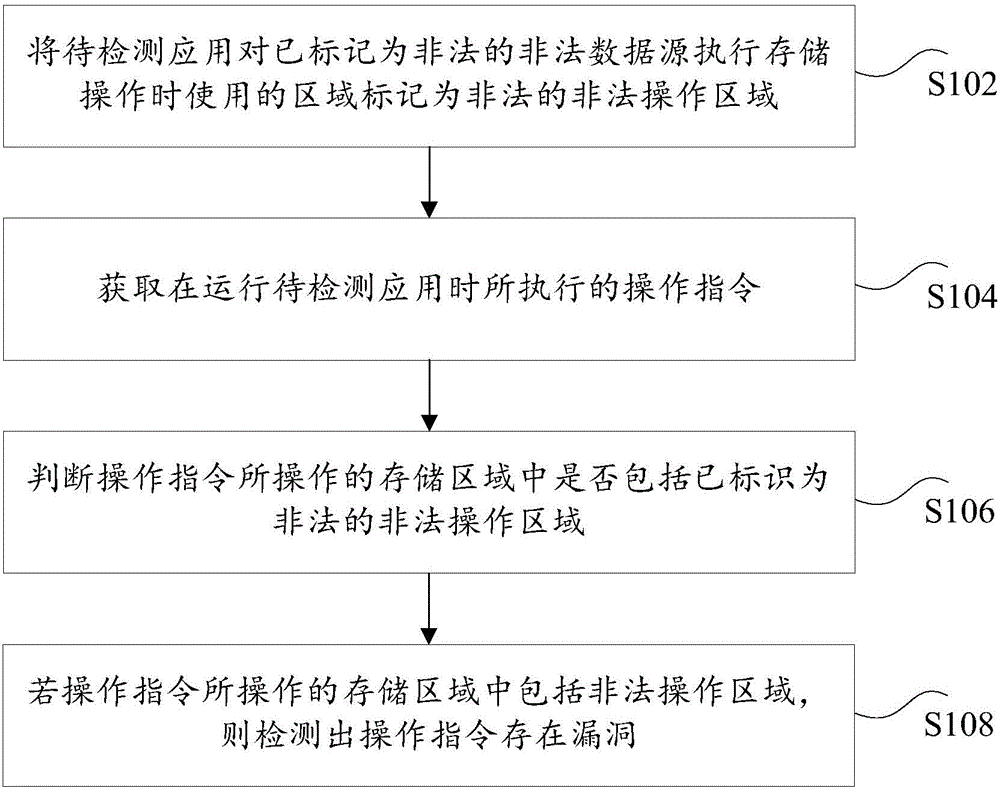
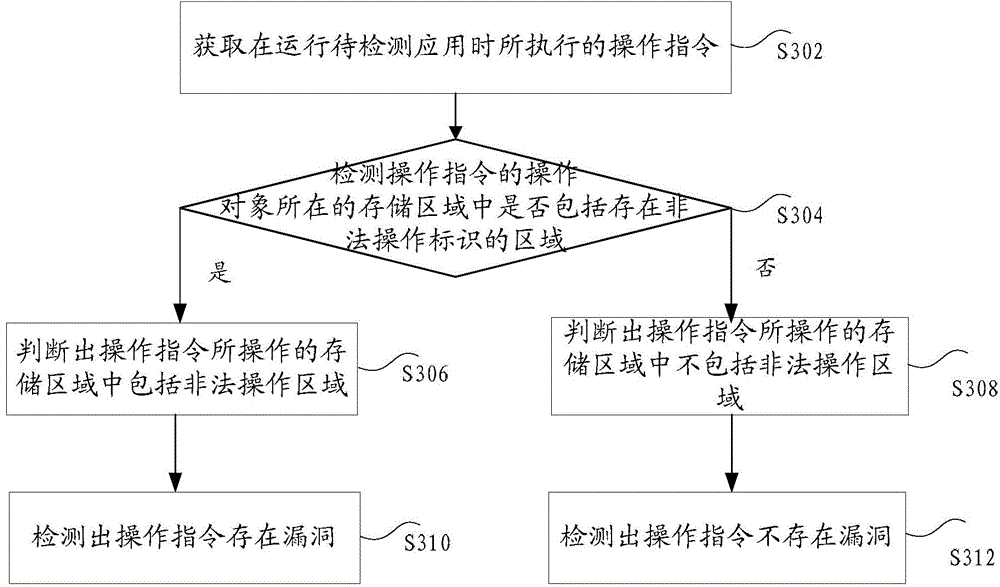
The invention discloses a vulnerability detection method and device. The method comprises the steps that the area used when an application to be detected executes storage operation on an illegal data source marked to be illegal is marked as an illegal operation area; an operation instruction executed when the application to be detected runs is obtained; whether a storage area operated by the operation instruction contains the illegal operation area marked to be illegal or not is judged; if yes, it is detected that the operation instruction has vulnerability. By the adoption of the vulnerability detection method and device, the problem that an existing black box vulnerability discovery method cannot detect the vulnerability accurately is solved, and the effect of detecting the vulnerability of the application to be detected accurately in real time is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Abnormal flow behavior discrimination method and device
ActiveCN108718306AEfficient and accurate identification of abnormal traffic behaviorTransmissionData miningArtificial intelligence
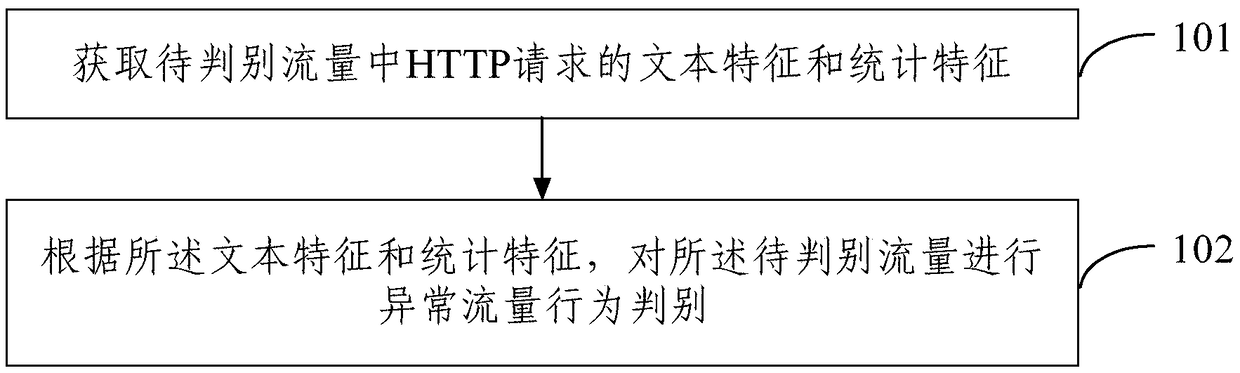
The embodiment of the invention provides an abnormal flow behavior discrimination method and device. The method comprises the steps that text features and statistical features of HTTP requests in to-be-discriminated flow are obtained; according to the text features and the statistical features, abnormal flow behavior discrimination is conducted on the to-be-discriminated flow, wherein the text features are output results obtained by inputting the HTTP requests in an n-gram model, and the statistical features comprise at least one of request path statistical features, request parameter statistical features, character distribution features, character frequency features, character entropy and keyword features of the HTTP requests. According to the abnormal flow behavior discrimination methodand device, by means of the text features and the statistical features which are obtained in the HTTP requests, the to-be-discriminated flow is subjected to abnormal flow behavior discrimination, efficient and accurate abnormal flow behavior discrimination is achieved, and important significance on information security protection and vulnerability discovery is achieved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
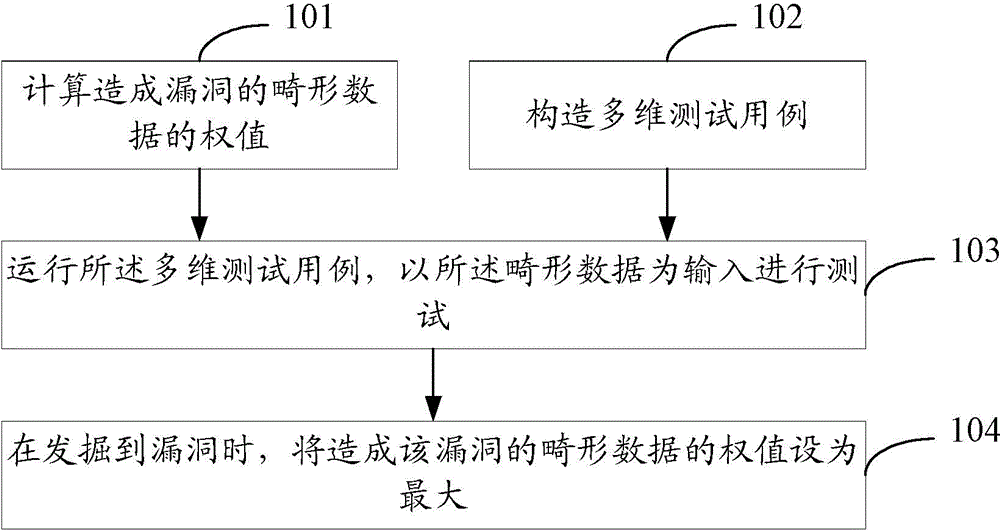
Vulnerability discovery method and device
The invention provides a method and device for discovering loopholes. It involves the field of work control network security; it solves the problem that the current test scheme cannot discover the loopholes jointly introduced by multiple input elements. The method includes: calculating the weight of the malformed data that causes the loophole; constructing a multi-dimensional test case; running the multi-dimensional test case, and testing with the malformed data as input; The weight is set to the maximum. The technical solution provided by the invention is applicable to the FUZZ technology, and realizes the discovery of multi-dimensional loopholes.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT +1
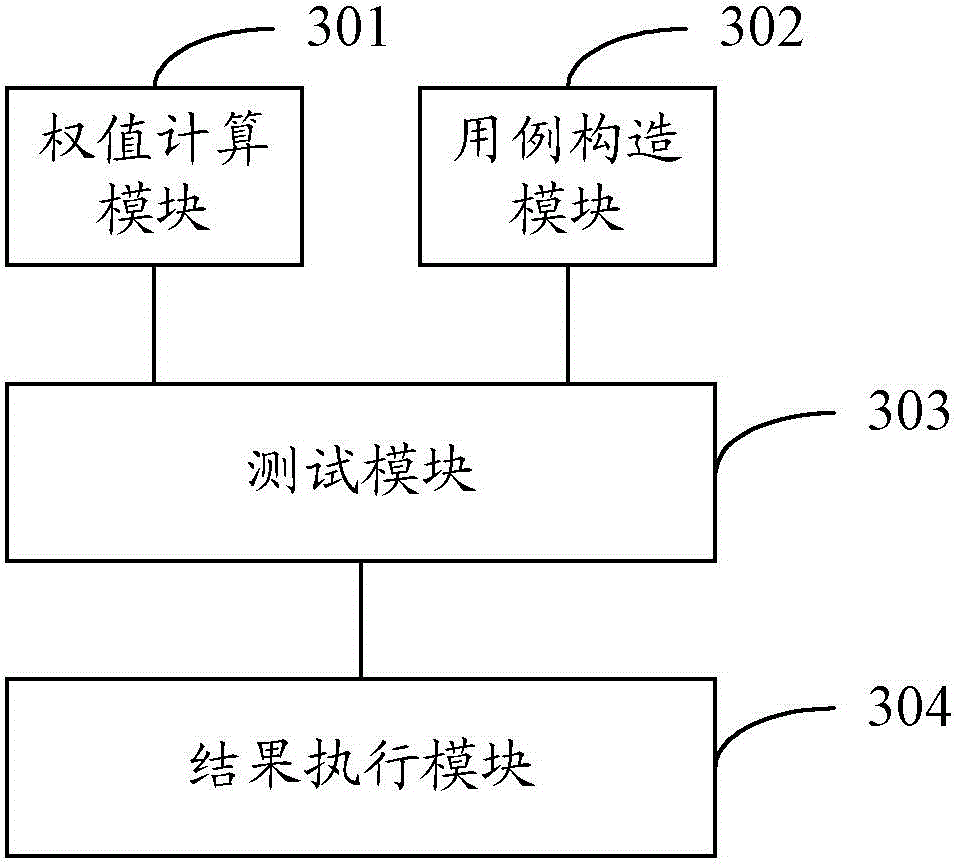
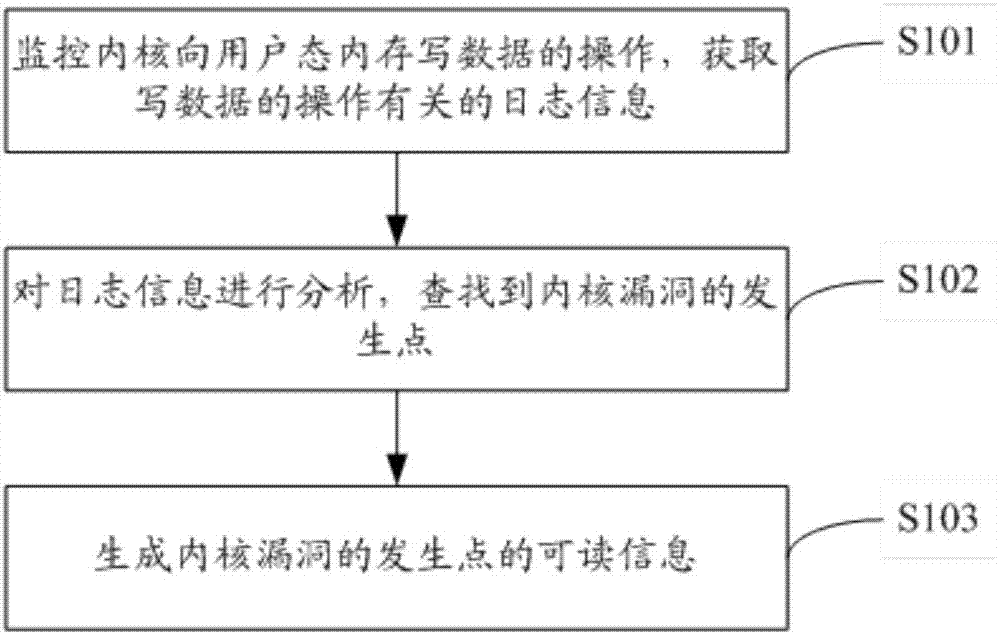
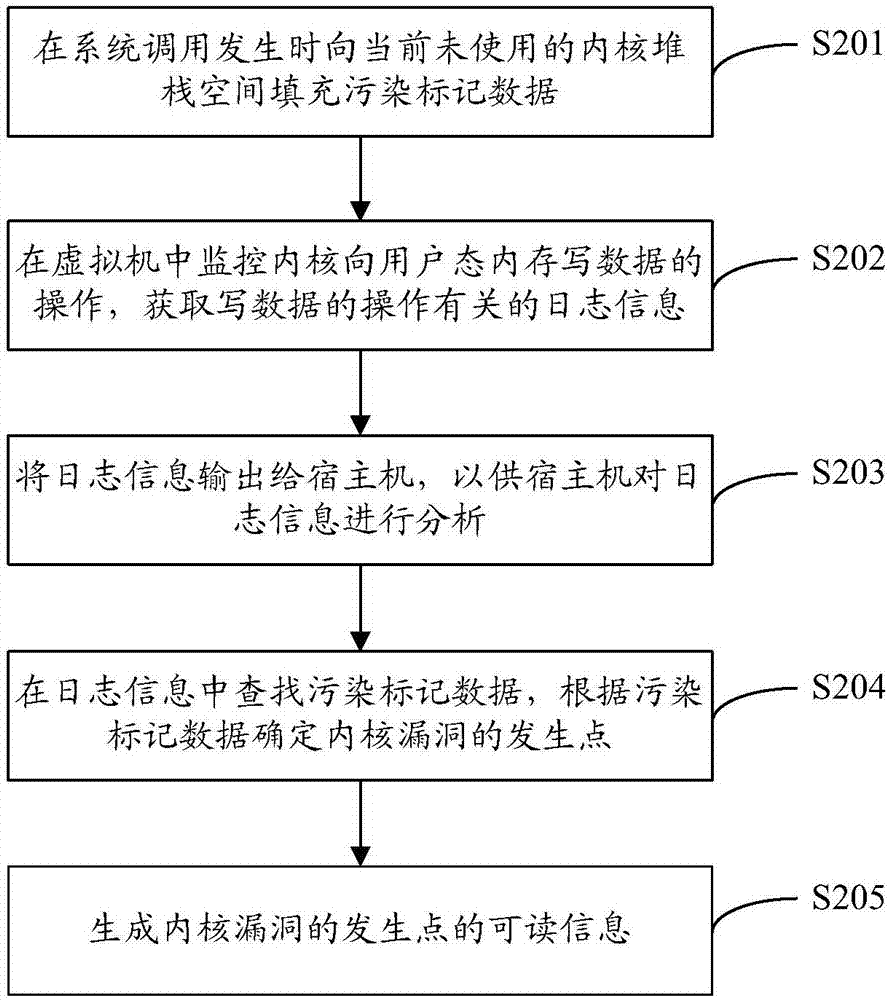
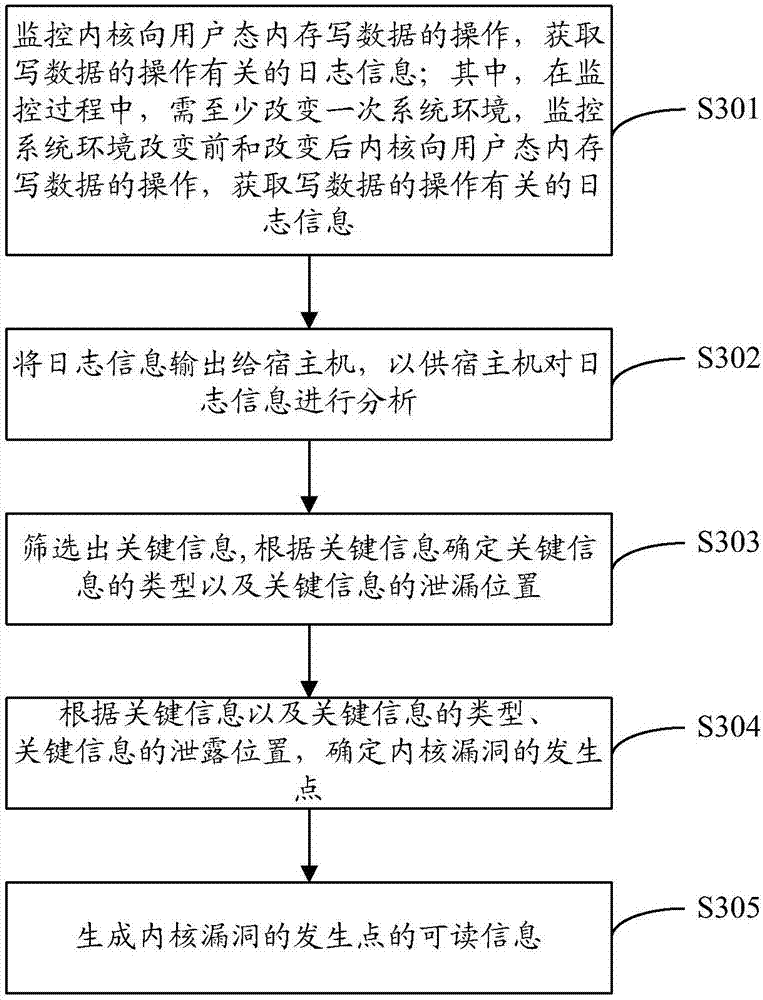
Kernel vulnerability discovery method and device, computing equipment and computer storage medium
ActiveCN107229867AAvoid operations such as attacksPlatform integrity maintainanceOperating systemVulnerability discovery
The invention discloses a kernel vulnerability discovery method and device, computing equipment and a computer storage medium. The kernel vulnerability discovery method includes the steps that operation of writing data in a user state memory by a kernel is monitored, and log information related with the operation of writing the data is acquired; the log information is analyzed, and an occurrence point of a kernel vulnerability is found out; readable information of the occurrence point of the kernel vulnerability is generated. According to the scheme, the leakage position, namely the occurrence point of the kernel vulnerability, of kernel information can be found out by analyzing the log information related with the operation of writing the data in the user state memory by the kernel, the vulnerability where the kernel information leaks can be easily, conveniently and efficiently found out in the mode, and following restoration is convenient.
Owner:BEIJING QIHOO TECH CO LTD
Vulnerability management system integrating vulnerability scanning engine and vulnerability work order management
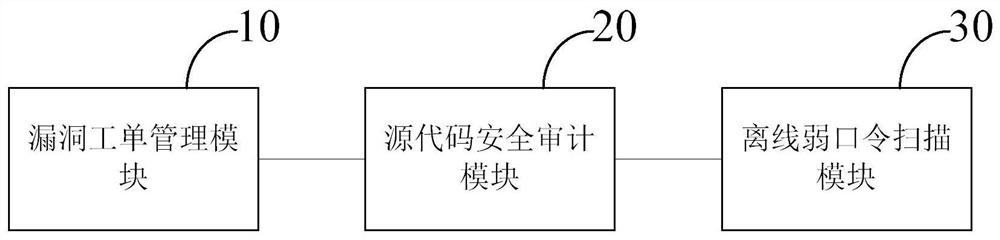
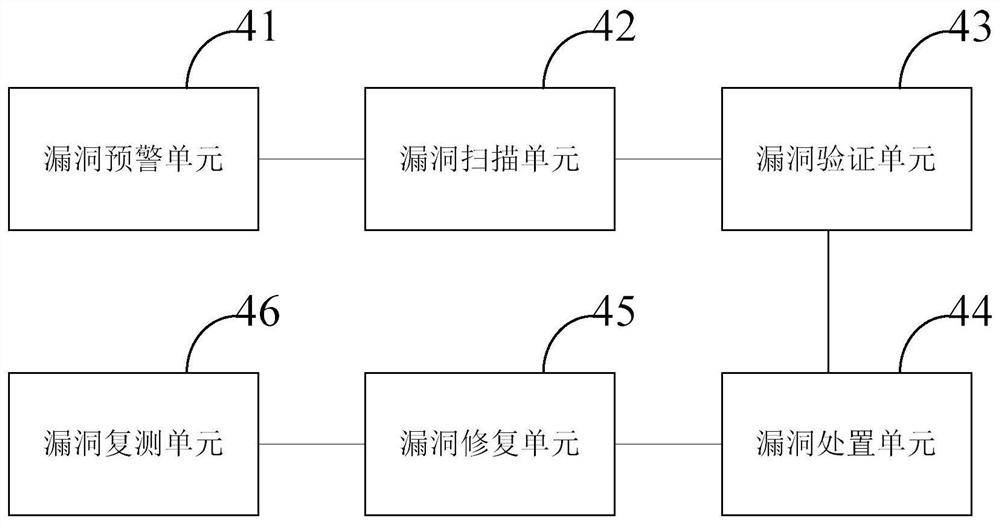
PendingCN113704767APlatform integrity maintainanceTransmissionAbstract syntax treeVulnerability scanning
The embodiment of the invention provides a vulnerability management system integrating a vulnerability scanning engine and vulnerability work order management, and the system comprises a vulnerability work order management module which is used for carrying out the work order issuing and management of five different vulnerability management stages: vulnerability discovery, vulnerability verification, vulnerability disposal, vulnerability reinforcement, and vulnerability retest; a source code security audit module which is used for performing comprehensive static analysis on the software source code, performing semantic analysis in combination with an AST abstract syntax tree, performing multi-level semantic analysis and function backtracking, and detecting to obtain security vulnerabilities existing in the software source code; an offline weak password scanning module which is used for acquiring a password file through an SSH protocol and uploading the password file in a manual mode, and discovering a weak password through Hash matching. According to the system, various vulnerability problems, including various security holes, security configuration problems and non-compliance behaviors, existing in the information system can be comprehensively and accurately detected.
Owner:北京凌云信安科技有限公司
Firmware vulnerability discrimination method and system based on open source component version identification
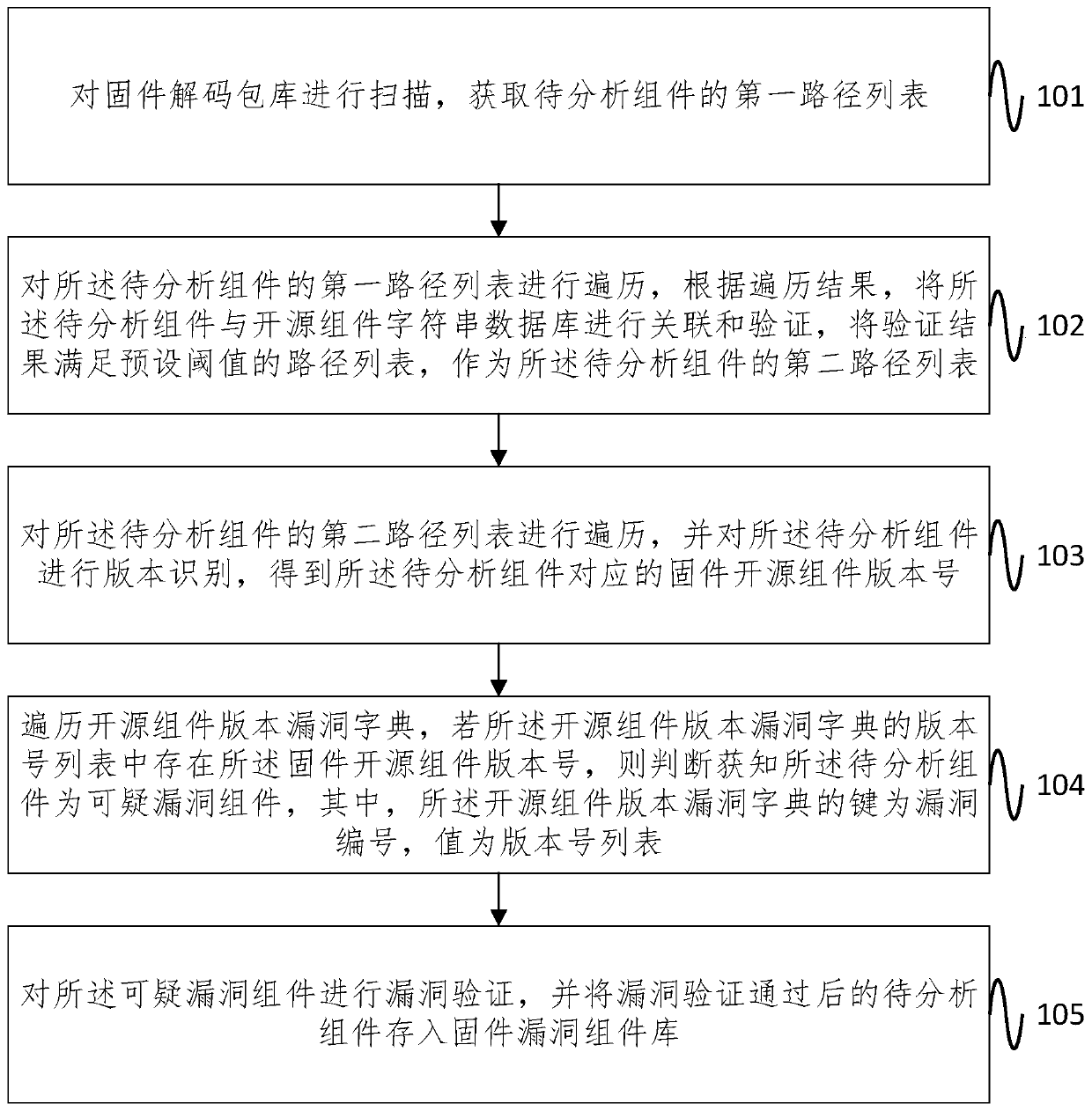
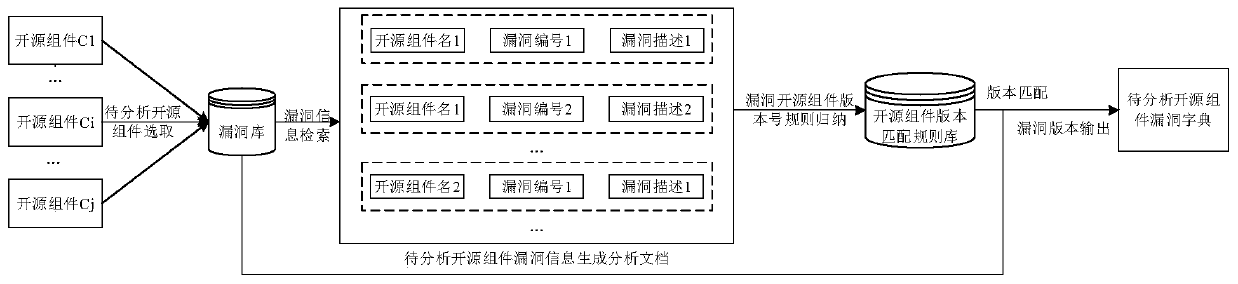
ActiveCN111400719AImprove reliabilityImprove efficiencyPlatform integrity maintainanceOther databases queryingPathPingString database
The embodiment of the invention provides a firmware vulnerability discrimination method and system based on open source component version identification, and the method comprises the steps: scanning afirmware decoding package library, and obtaining a first path list of a to-be-analyzed component; traversing the first path list of the to-be-analyzed component, and associating and verifying the to-be-analyzed component and the open source component string database to obtain a second path list of the to-be-analyzed component; carrying out the version identification on the to-be-analyzed component to obtain a firmware open source component version number corresponding to the to-be-analyzed component; traversing the open source component version vulnerability dictionary, and if a firmware opensource component version number exists in the open source component version vulnerability dictionary, judging and knowing that the to-be-analyzed component is a suspicious vulnerability component; performing vulnerability verification on the suspicious vulnerability component, and storing the to-be-analyzed component passing the vulnerability verification into a firmware vulnerability component library. According to the embodiment of the invention, suspicious vulnerabilities can be efficiently searched, the reliability of firmware security evaluation is high, and the vulnerability discovery efficiency and accuracy are improved.
Owner:INST OF INFORMATION ENG CAS
Vulnerability discovery method and device and electronic equipment
ActiveCN105512562AImprove accuracyShorten the timePlatform integrity maintainanceVulnerability discoveryDatabase
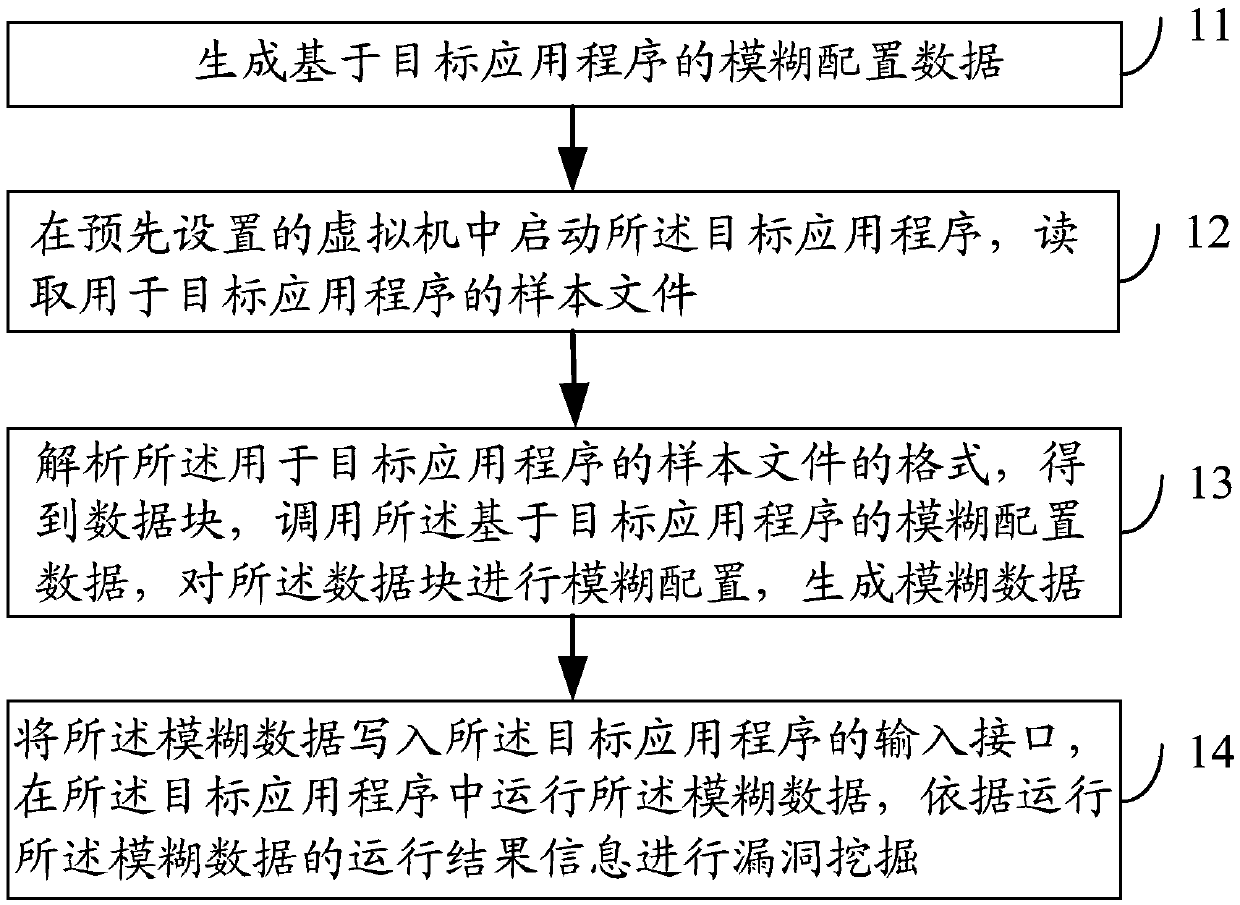
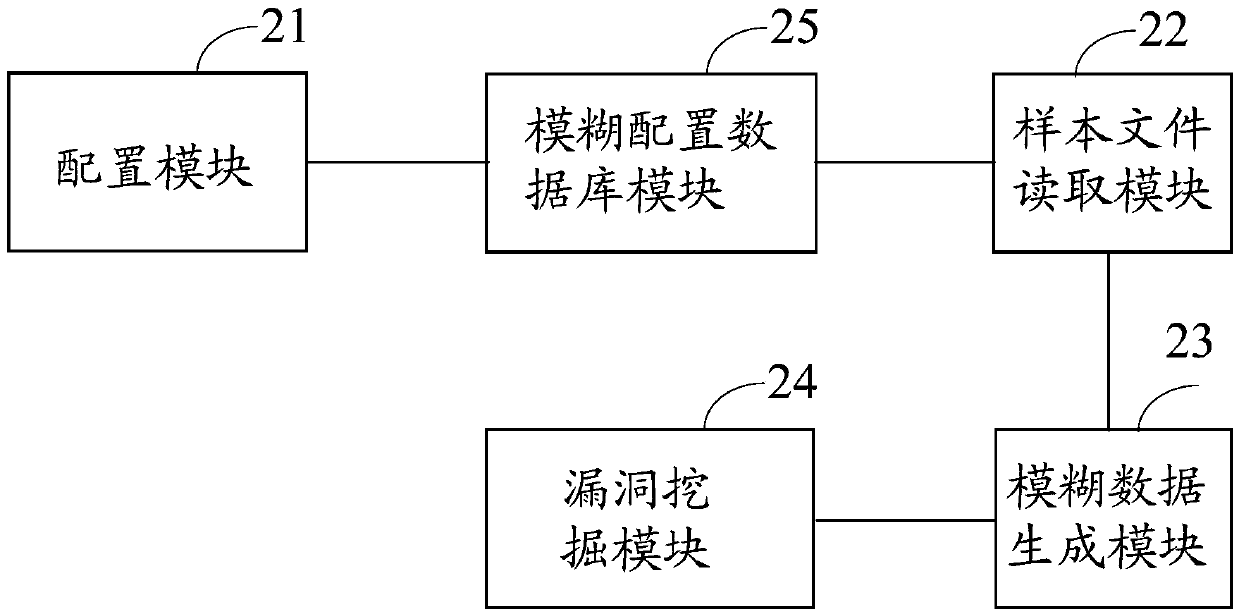
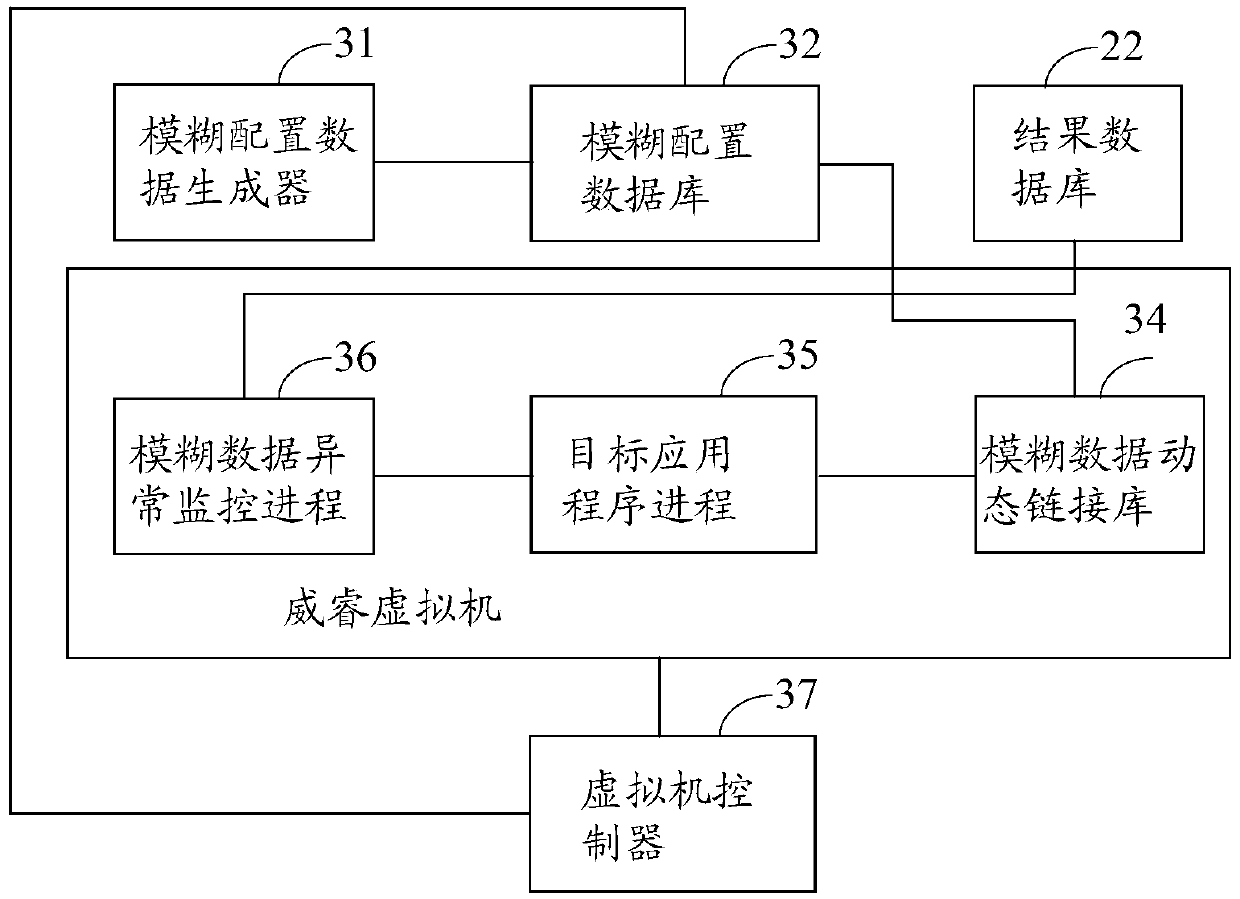
The embodiment of the invention discloses a vulnerability discovery method and device and electronic equipment. The method comprises the steps that fuzzy configuration data based on a target application program is generated; the target application program is started in a virtual machine arranged in advance, and a sample file for the target application program is read; the format of the sample file for the target application program is analyzed to obtain a data block, the fuzzy configuration data based on the target application program is called, and fuzzy configuration is carried out on the data block to generate fuzzy data; the fuzzy data is written into an input interface of the target application program, the fuzzy data runs in the target application program, and vulnerability discovery is carried out based on the information of a running result of the fuzzy data. By applying the vulnerability discovery method and device and the electronic equipment, the vulnerability discovery efficiency can be improved.
Owner:ZHUHAI BAOQU TECH CO LTD
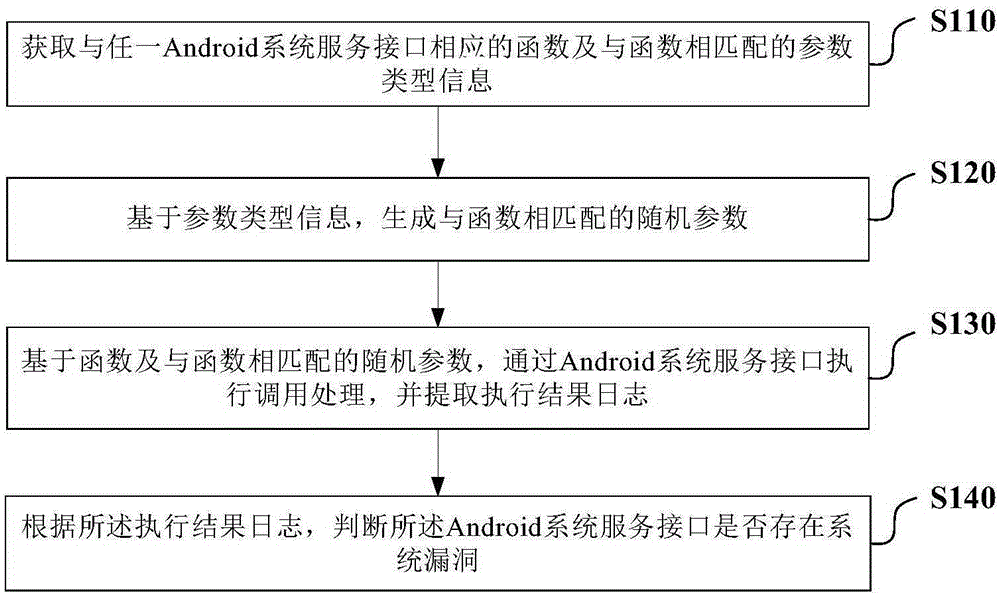
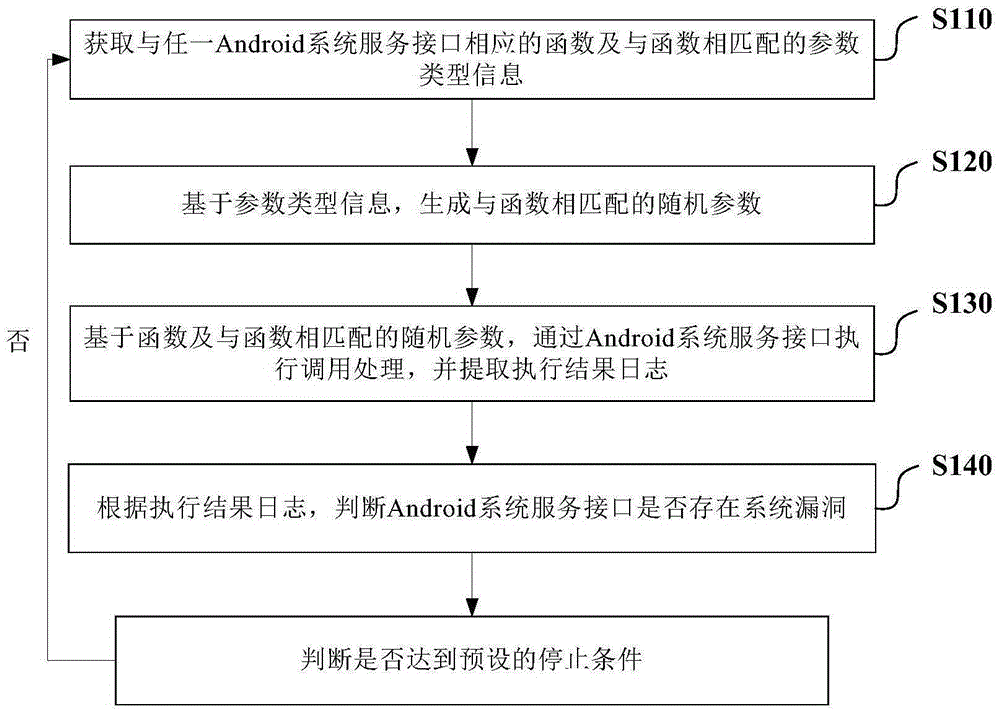
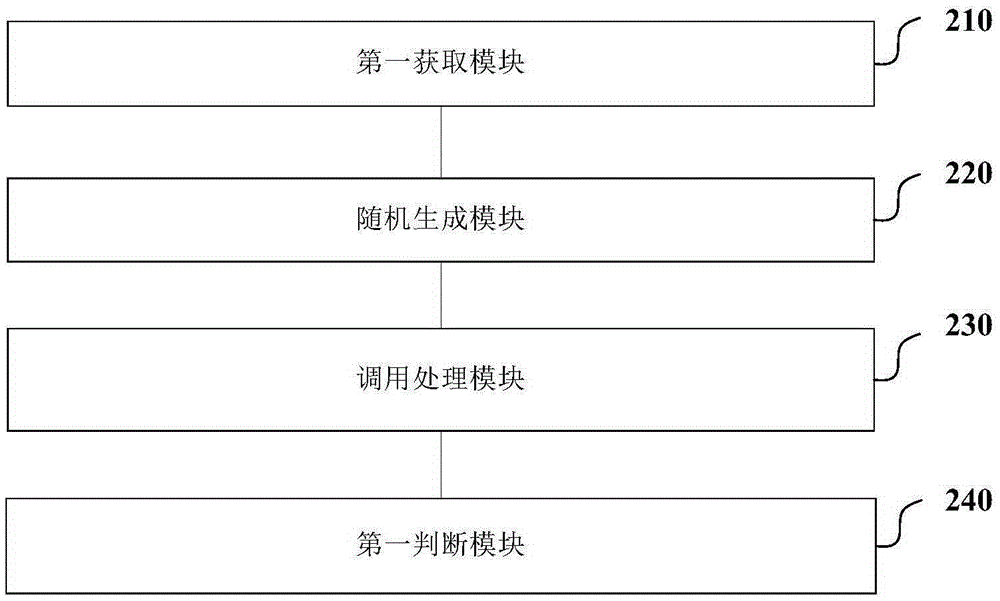
Method and system for vulnerability discovery of Android system
ActiveCN105243329AGuaranteed uptimeImprove user experiencePlatform integrity maintainanceRandom parametersComputer science
The invention provides a method and a system for vulnerability discovery of an Android system. The method comprises the following steps: obtaining a function corresponding to any Android system service interface and parameter type information matched with the function; generating a random parameter matched with the function on the basis of the parameter type information; executing call processing through the Android system service interface on the basis of the function and the random parameter matched with the function, and extracting an execution result log; and judging whether a system vulnerability exists in the Android system service interface according to the execution result log. According to the method and the system, the condition that call processing is executed through the Android system service interface is actively simulated; and the system crash condition is examined after call processing is ended, so that the call processing, which causes the crash, when executed by the Android system service interface in a practical application scene can be accurately predicted; and a repairing plan and a reliable basis can be provided for the discovered system vulnerabilities.
Owner:北京鸿享技术服务有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com