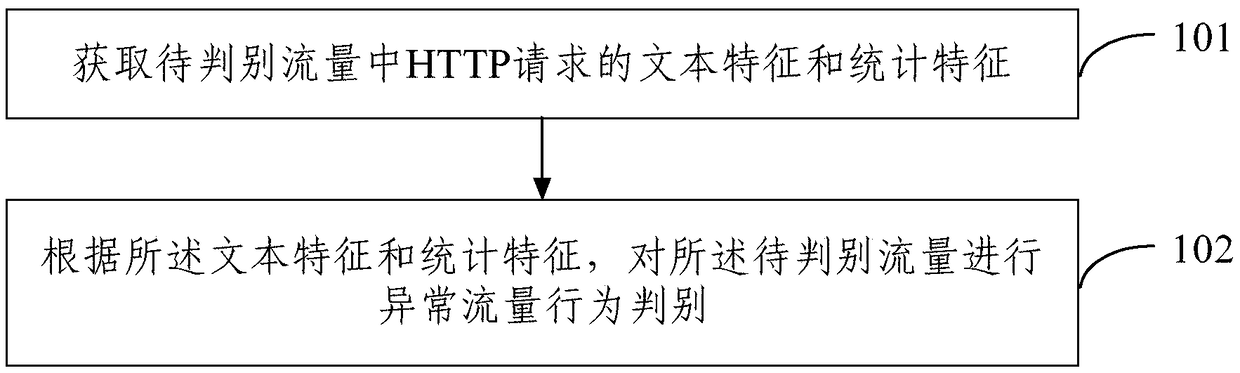
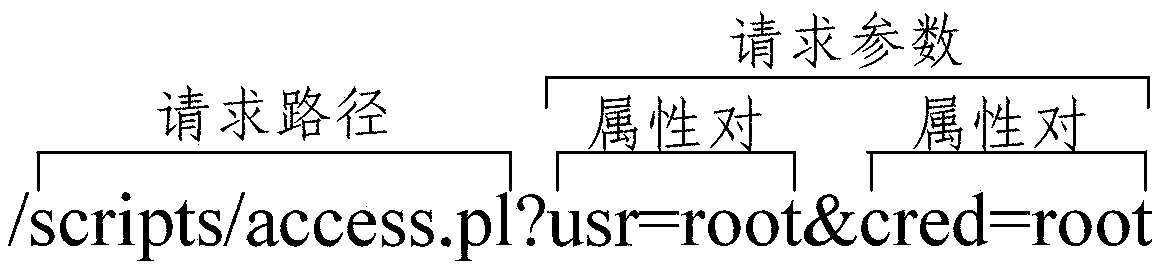
Abnormal flow behavior discrimination method and device
A technology of abnormal traffic and identification method, which is applied in the field of information security, can solve problems such as difficult identification of identification methods, and achieve the effect of efficient and accurate identification of abnormal traffic behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0057] When malicious code injection occurs, attackers are good at using specific combinations of non-alphanumeric as injections. Therefore, specific combinations of non-alphanumeric characters should be preserved when obtaining textual features of HTTP requests through the n-gram model. All letters, numbers and Chinese are regarded as the same symbols, and the conversion rules are shown in Table 3. Through the above conversion, while significantly reducing the dimensionality of text features, the relevant feature information for identifying abnormal traffic behaviors is effectively preserved.
[0058] Table 3. Character conversion rule table
[0059]
example 2
[0061] The method of obtaining character distribution features is as follows:
[0062] The HTTP request can output a total of 256 characters. The HTTP request "id=34232" is converted into a reverse order, and the distribution of related characters is 0.25, 0.25, 0.125, 0.125, 0.125, 0.125, followed by 248 0s.
[0063] For the character distribution feature, the above 256 characters can also be divided into 6 sets according to Table 4 in advance, so as to reduce the dimension of the character distribution feature.
[0064] Table 3. Character conversion rule table
[0065]
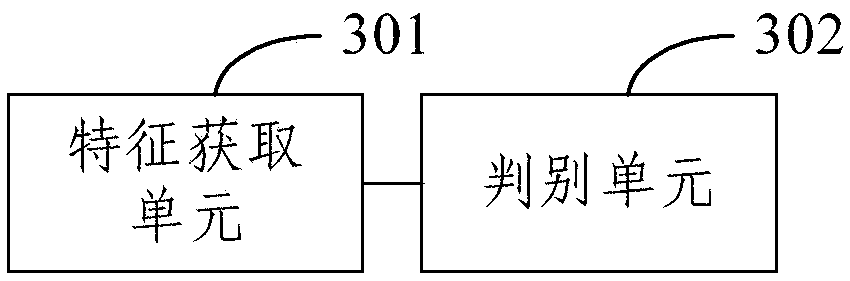
[0066] Based on any of the above method embodiments, image 3 It is a schematic structural diagram of an abnormal traffic behavior discrimination device according to an embodiment of the present invention, as shown in image 3 As shown, a device for discriminating abnormal traffic behavior includes:
[0067] A feature acquisition unit 301, configured to acquire textual features and statistical features...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com