Vulnerability discovery method and device
A vulnerability discovery and vulnerability technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problem of not being able to discover multiple input element vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined arbitrarily with each other.
[0054] First, Embodiment 1 of the present invention will be described with reference to the accompanying drawings.
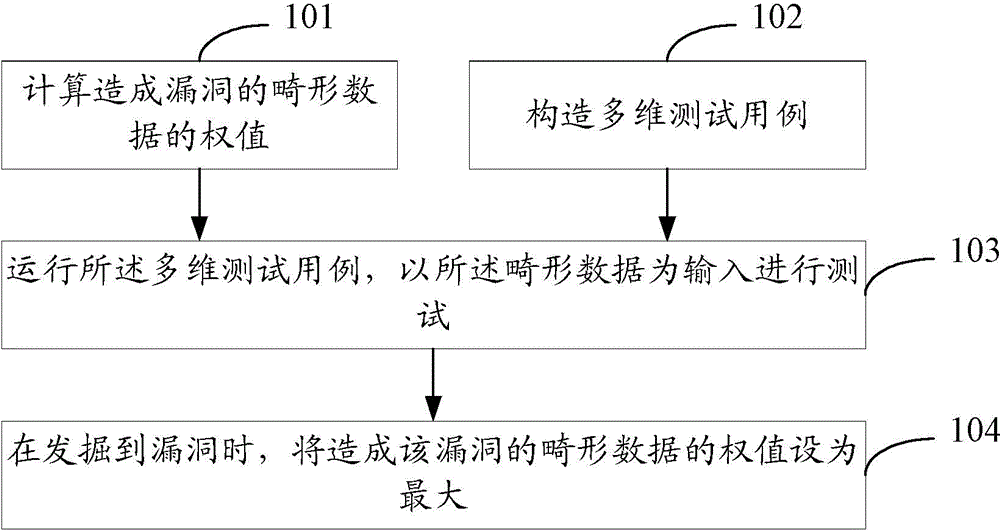
[0055] The embodiment of the present invention provides a vulnerability discovery method, using this method to complete the vulnerability discovery process as follows figure 1 shown, including:
[0056] Step 101, calculating the weight of the malformed data causing the loophole;
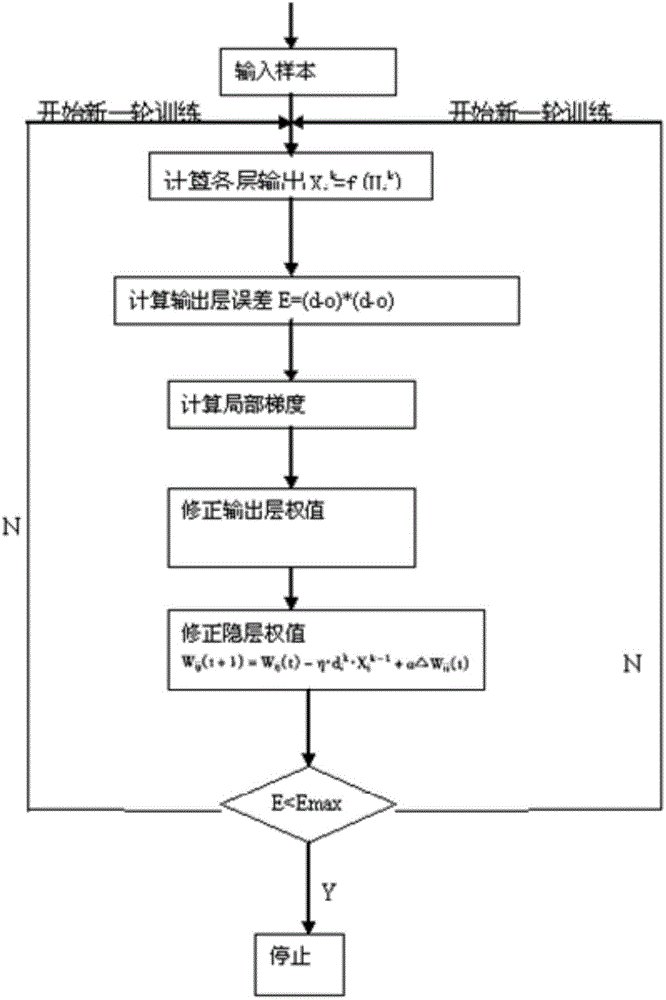
[0057] In this step, a learning neural network for malformed data is constructed to form a background analysis platform.
[0058] There are a lot of data that often cause loopholes, such as "0", ",", "%^#$", etc. When performing multi-dimensional fuzz testing, fuzz testing is performe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com