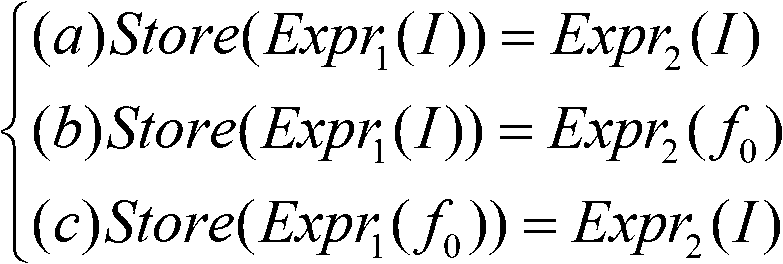Method for binary code vulnerability discovery on basis of simple symbolic execution
A binary code and symbolic execution technology, applied in the field of binary code vulnerability mining, can solve problems such as inaccessible source code, danger, and inability to know that the program path has been executed, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The method of the present invention will be further described in detail below in conjunction with the accompanying drawings and the implementation of the present invention.
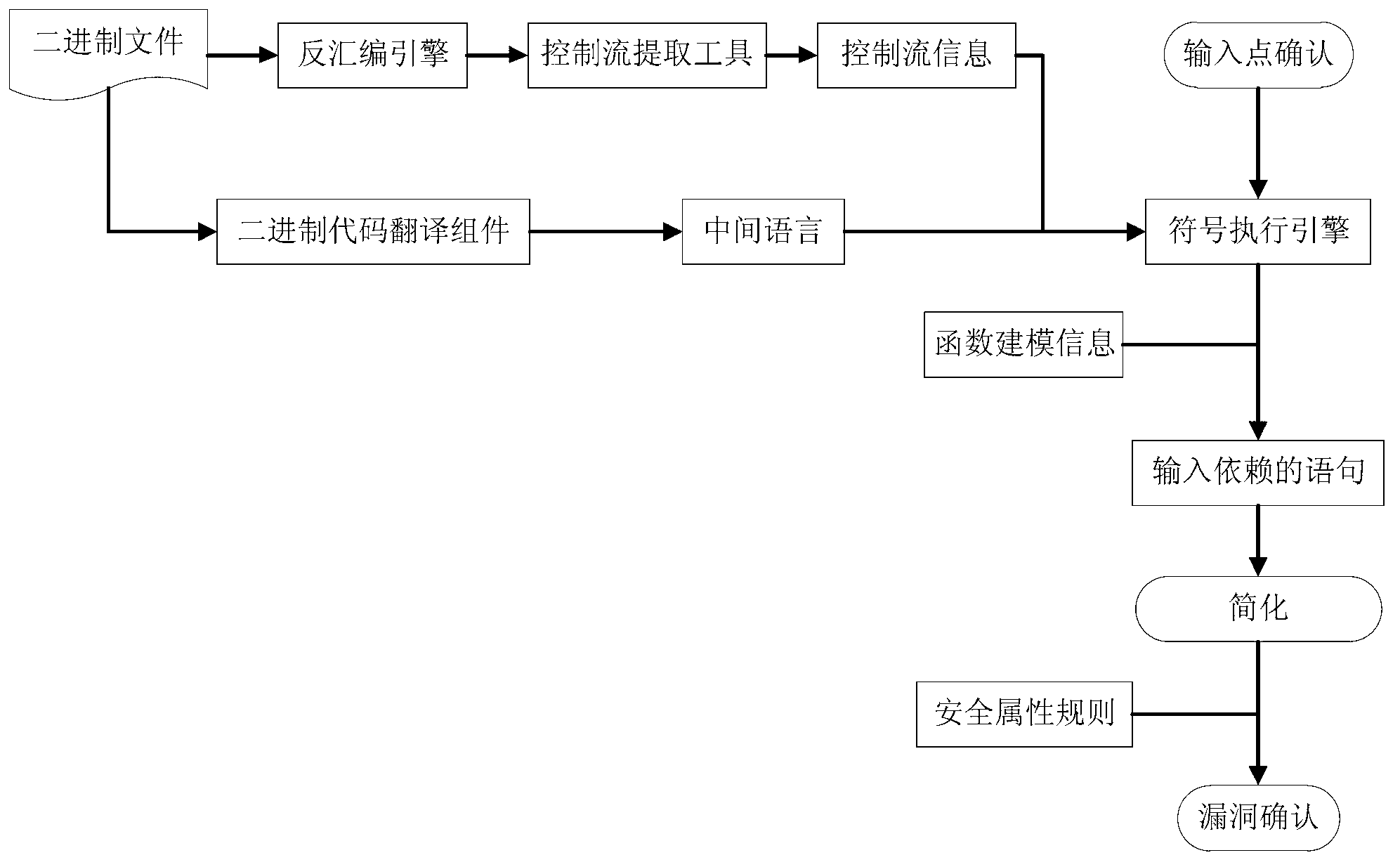
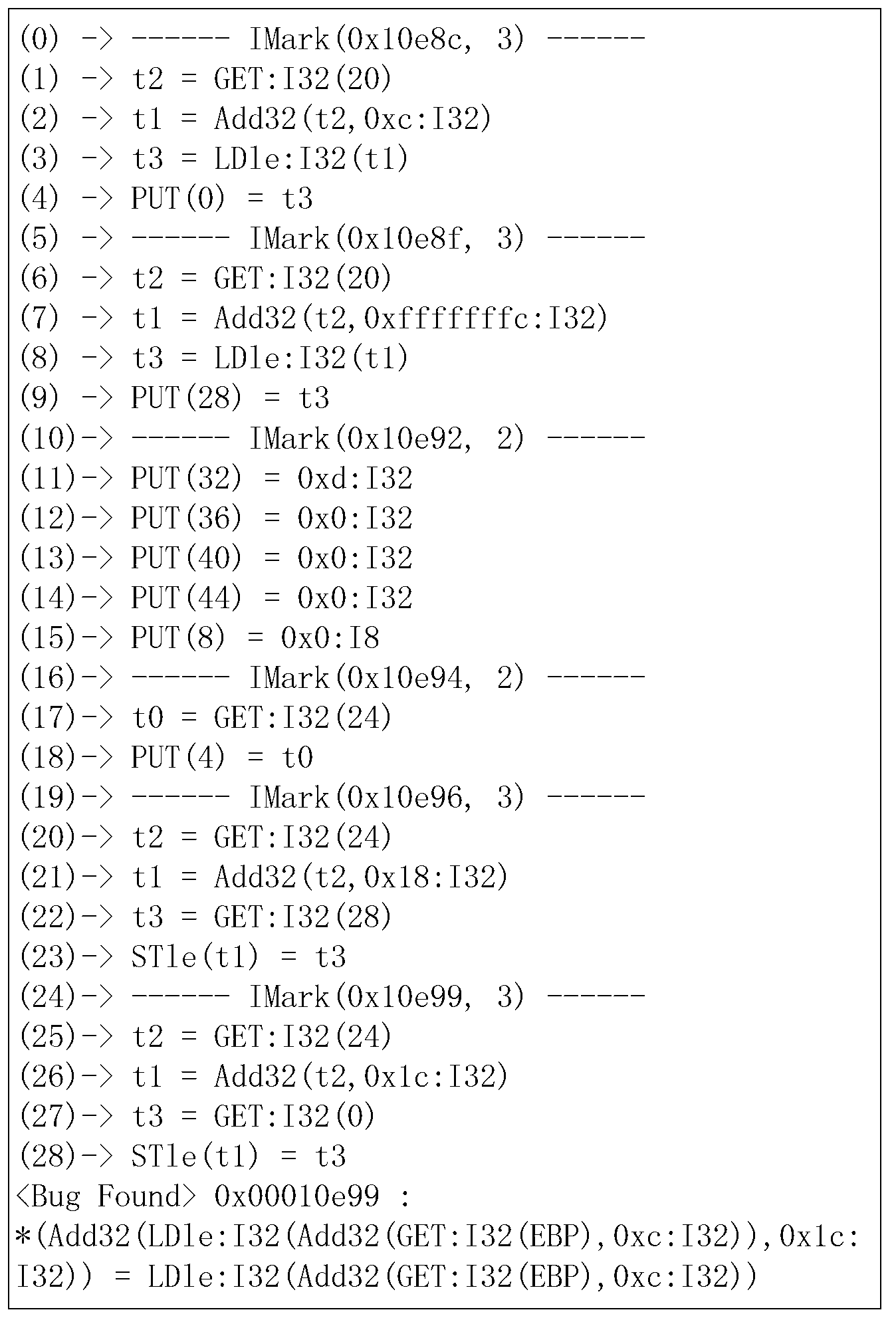
[0062] The basic idea of the present invention is: convert the binary code into an intermediate language, and then combine the control flow information, input point information, and function modeling information to perform symbolic execution on the intermediate language. After the symbolic execution process is completed, the obtained and input A collection of intermediate language statements of related instructions, according to certain security attribute rules, judge whether there are loopholes in these statements.
[0063] figure 1 It is a schematic flow diagram of the binary code vulnerability mining method based on simple symbol execution, as shown in figure 1 As shown, the method includes the following steps:
[0064] Step A: Hand the binary code to the disassembly engine, decode it into a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com