Patents
Literature
433 results about "Symbolic execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
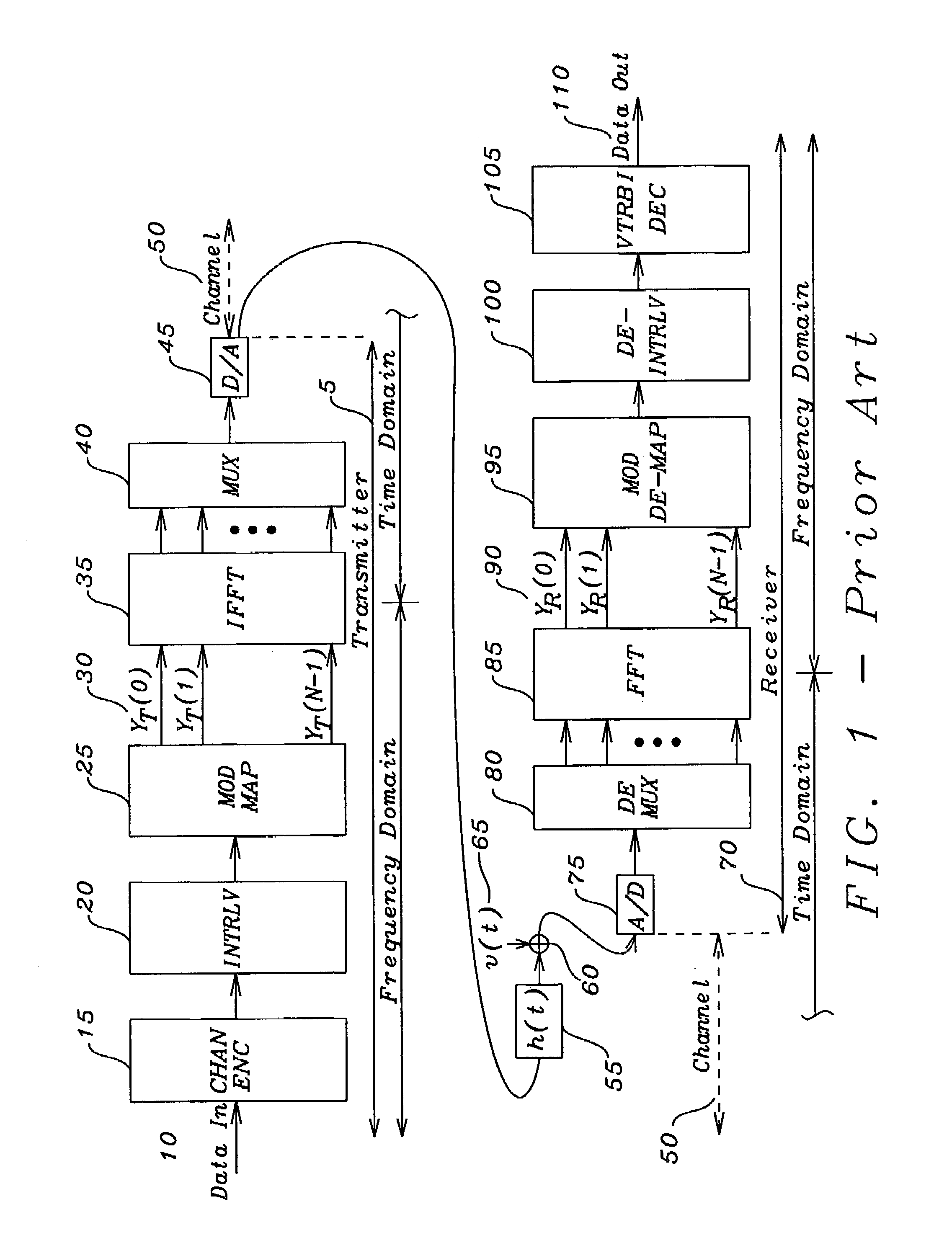
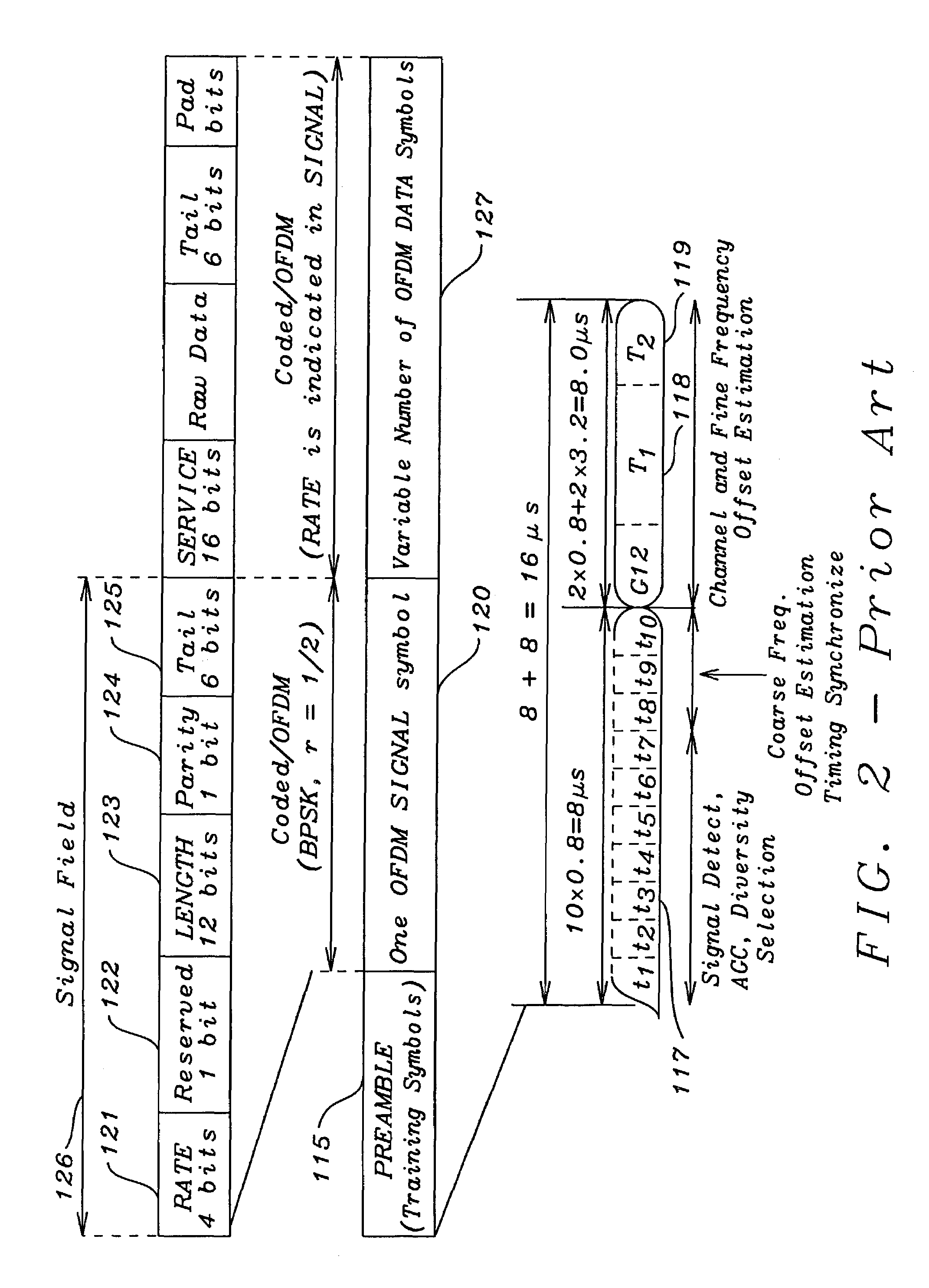
In computer science, symbolic execution (also symbolic evaluation) is a means of analyzing a program to determine what inputs cause each part of a program to execute. An interpreter follows the program, assuming symbolic values for inputs rather than obtaining actual inputs as normal execution of the program would, a case of abstract interpretation. It thus arrives at expressions in terms of those symbols for expressions and variables in the program, and constraints in terms of those symbols for the possible outcomes of each conditional branch.
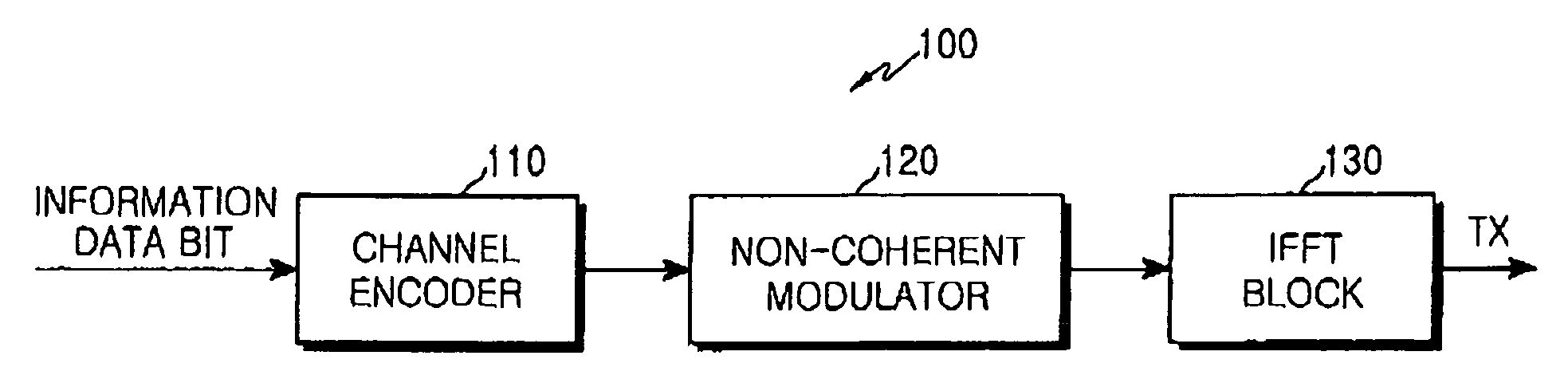
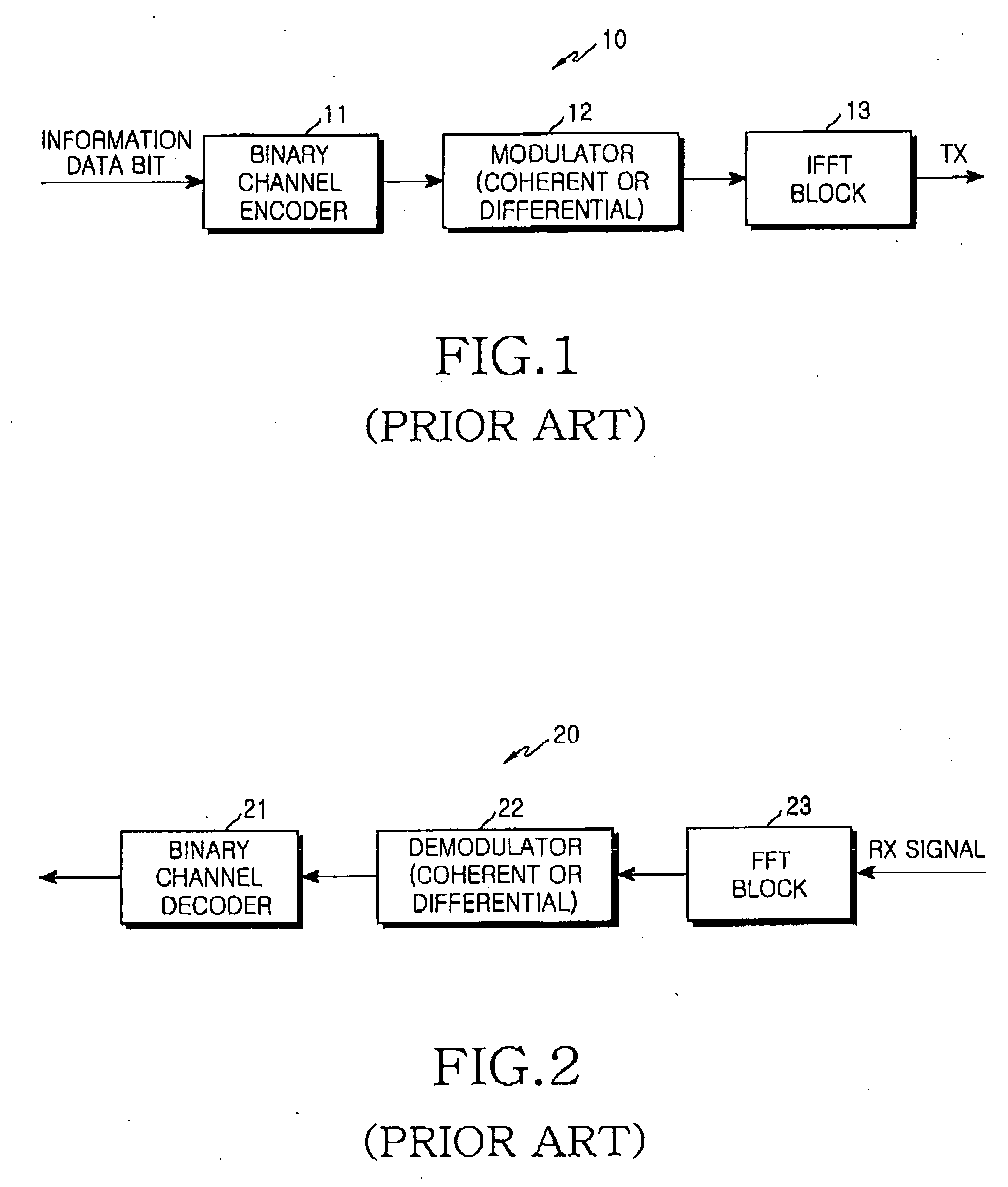
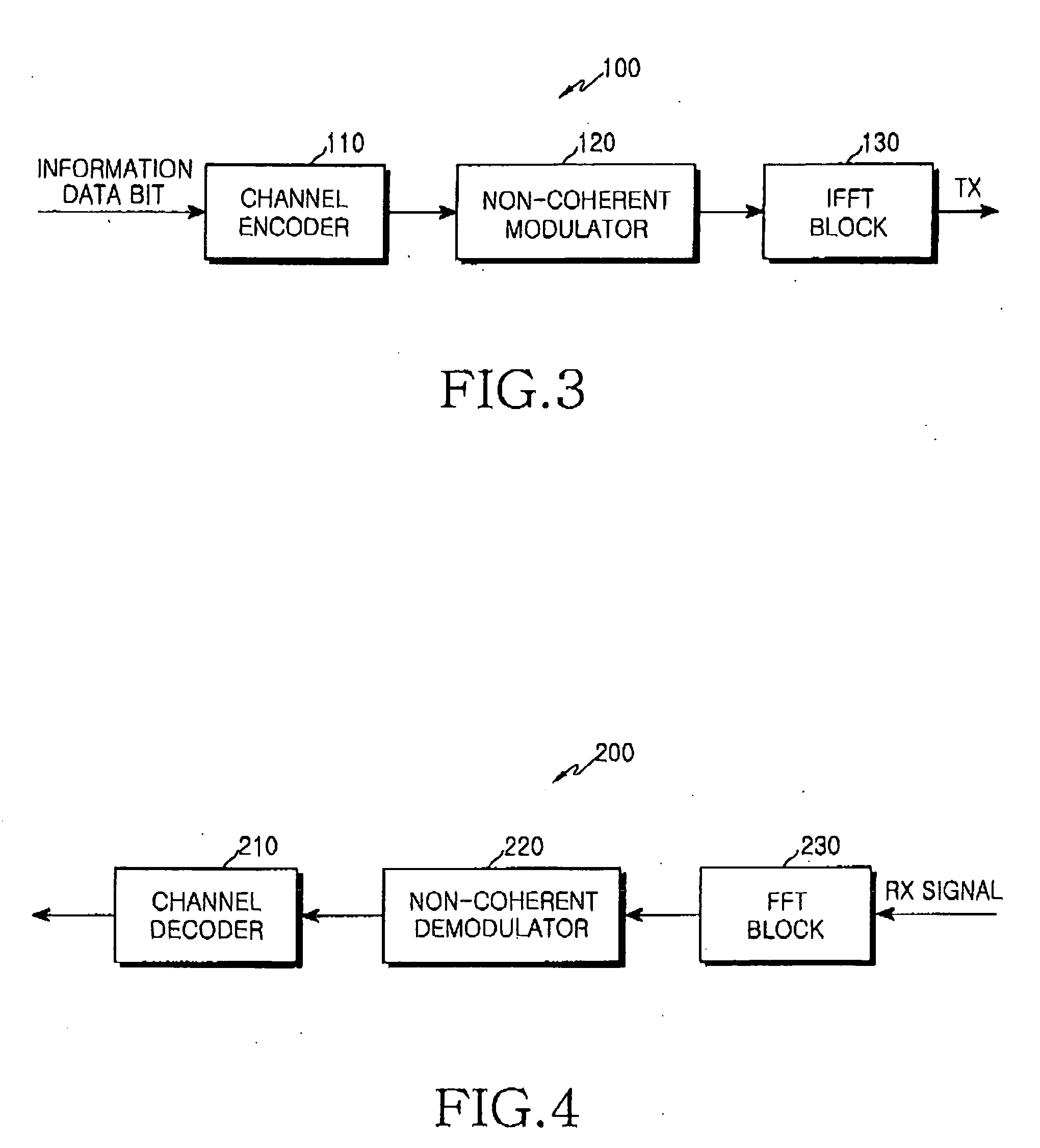
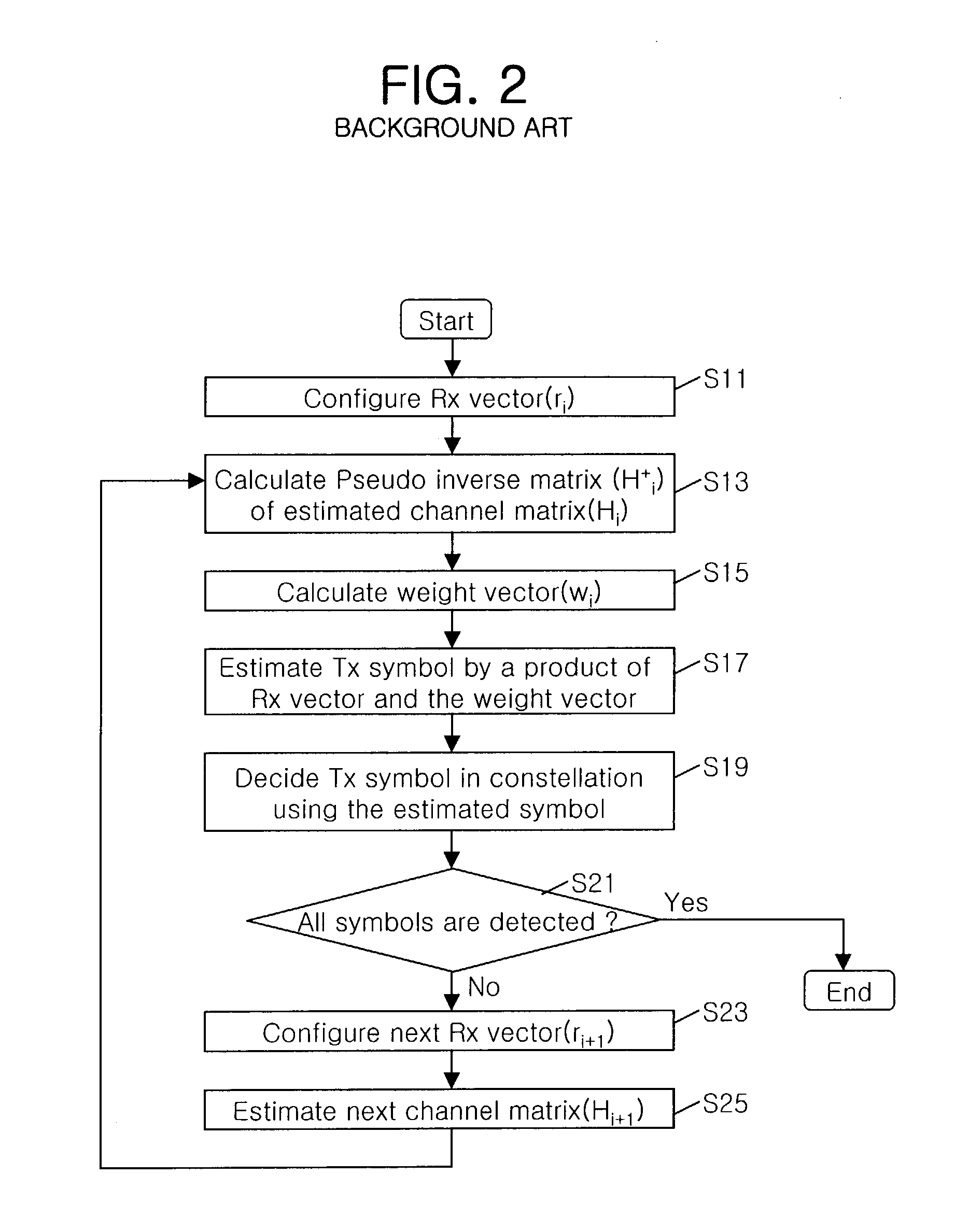
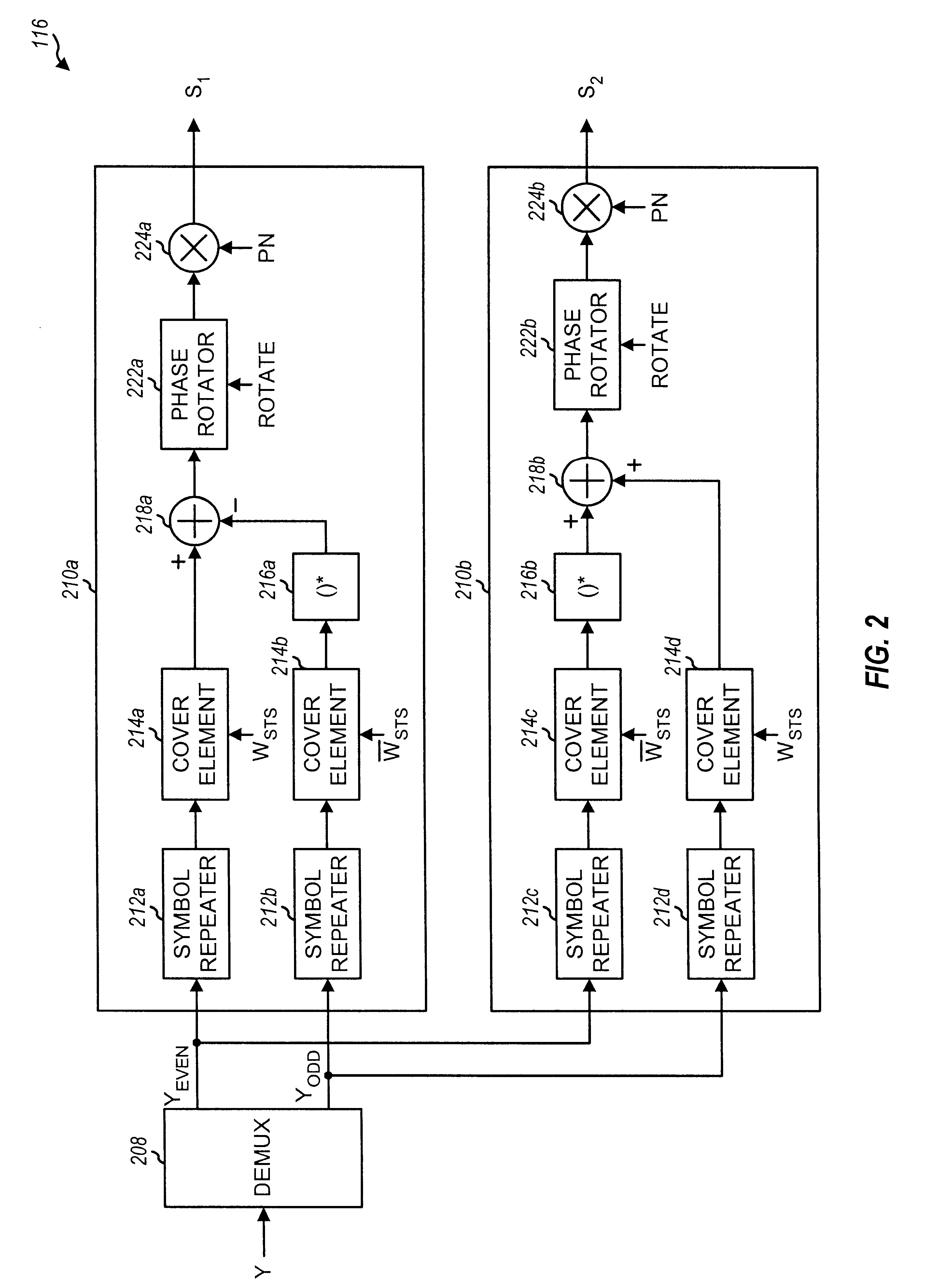
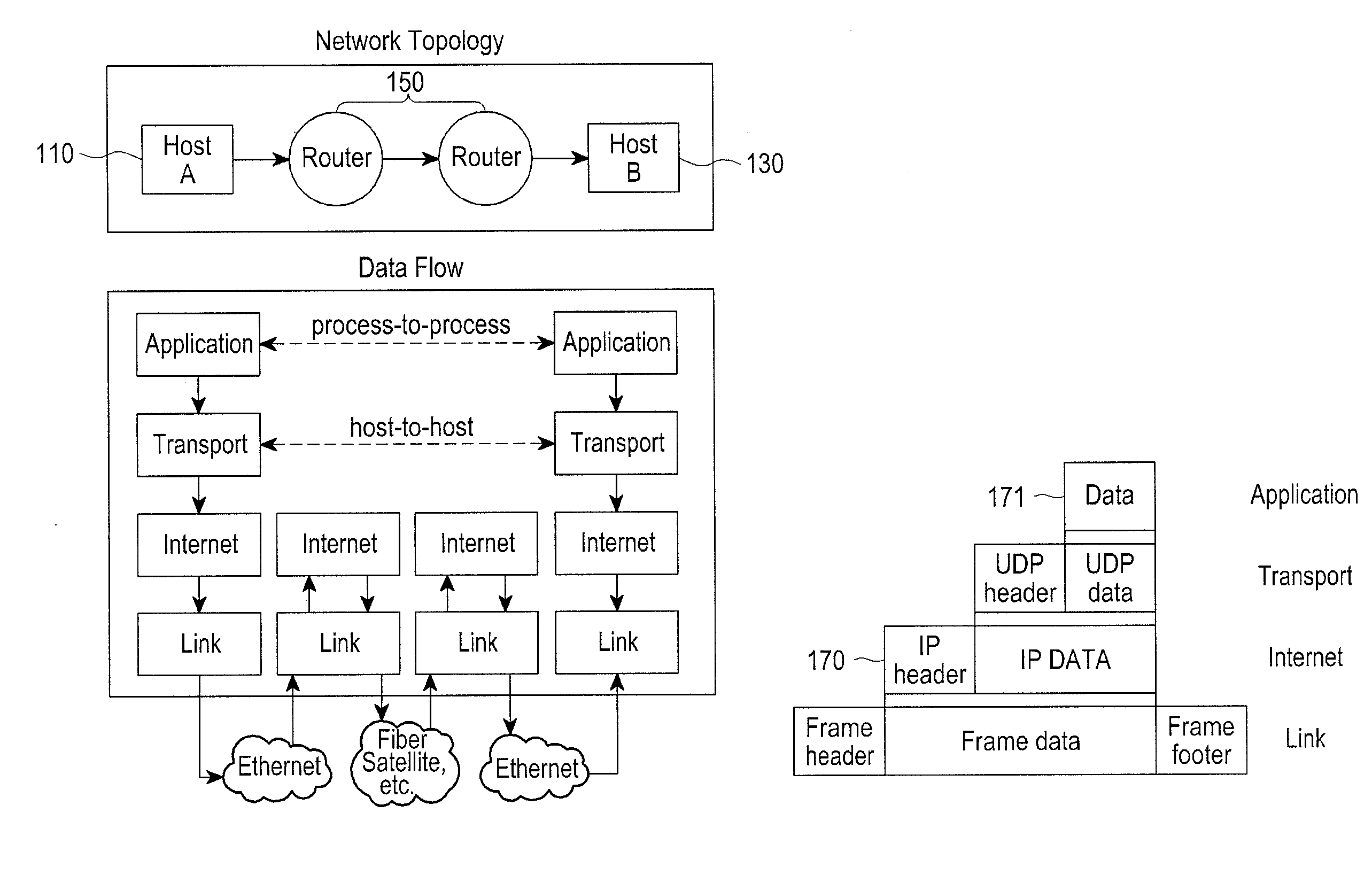
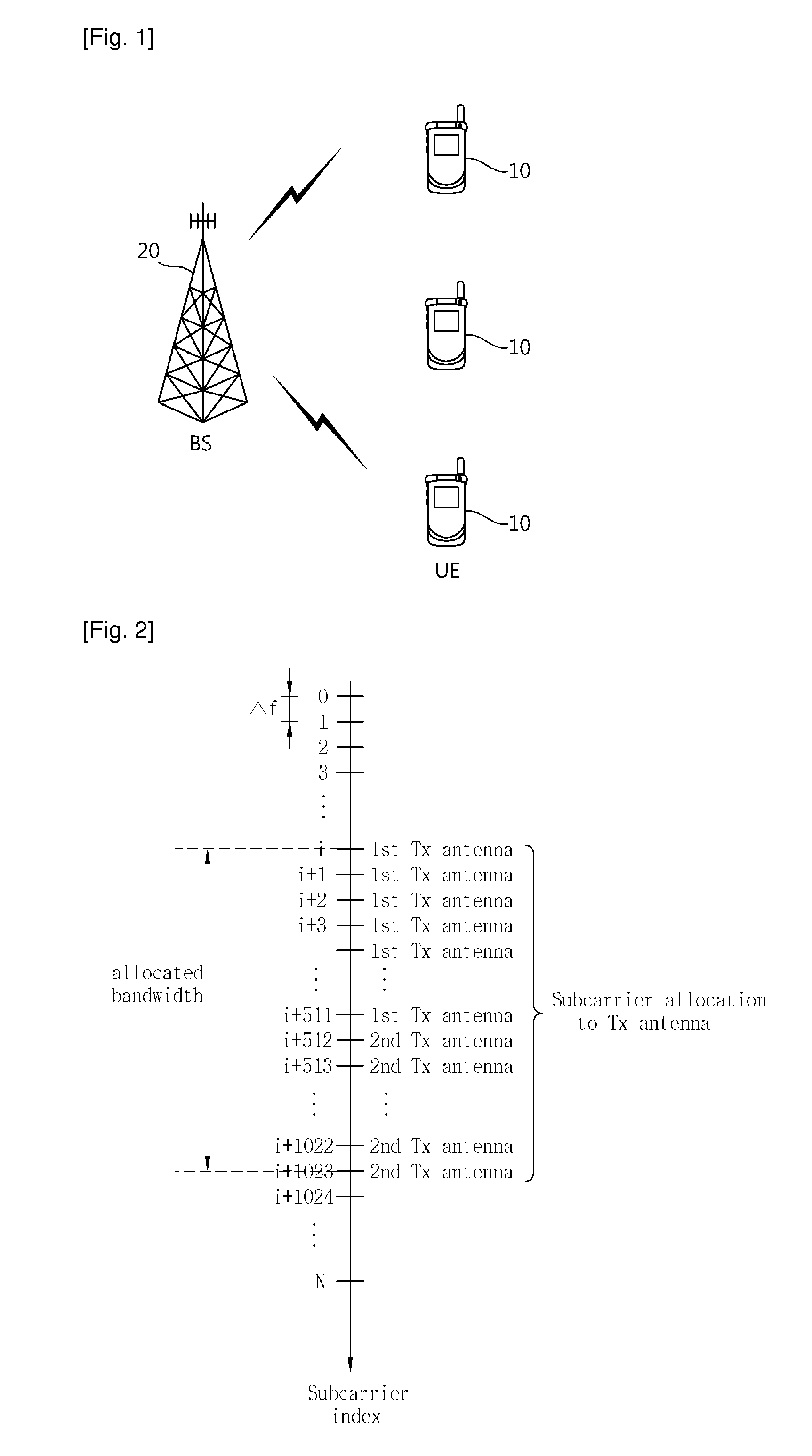
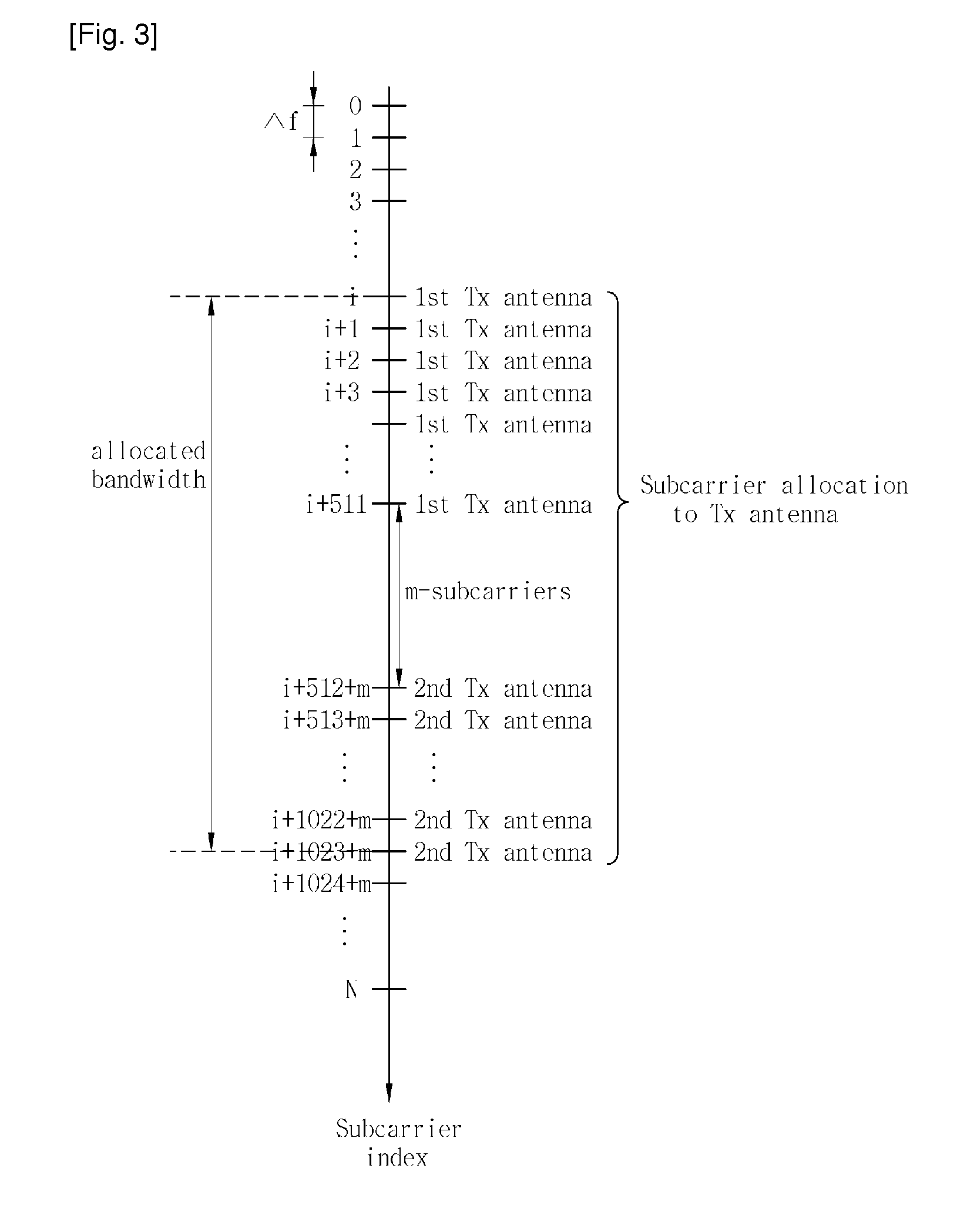
Method and apparatus for transmitting uplink acknowledgement information in an OFDMA communication system
ActiveUS20050286402A1Guaranteed normal transmissionImprove reliabilityError prevention/detection by using return channelTransmission path divisionFast Fourier transformCommunications system
A method and apparatus for transmitting uplink acknowledge information (ACK) in a communication system using an orthogonal frequency division multiple access (OFDMA) scheme. The method includes receiving a data bit for the uplink ACK; outputting codewords corresponding to the data bit; performing quadrature phase shift keying (QPSK) modulation on symbols for ACK vector indexes corresponding to the codewords for the received data bit; performing inverse fast Fourier transform (IFFT) on a transmission signal having subcarrier clusters to which the modulated transmission symbols are allocated; and transmitting the IFFT-processed transmission signal.
Owner:SAMSUNG ELECTRONICS CO LTD
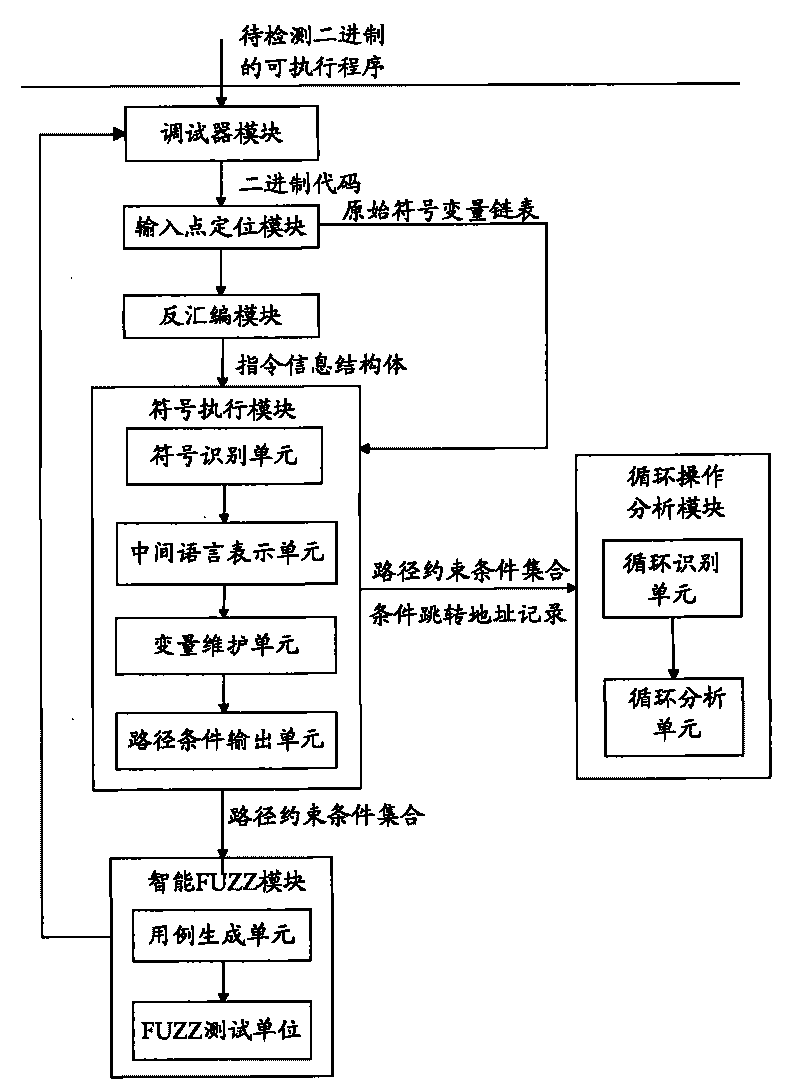
Detector for binary-code buffer-zone overflow bugs, and detection method thereof
InactiveCN101714118AGuaranteed feasibilityGuaranteed accuracyMultiprogramming arrangementsSoftware testing/debuggingBuffer overflowSource code
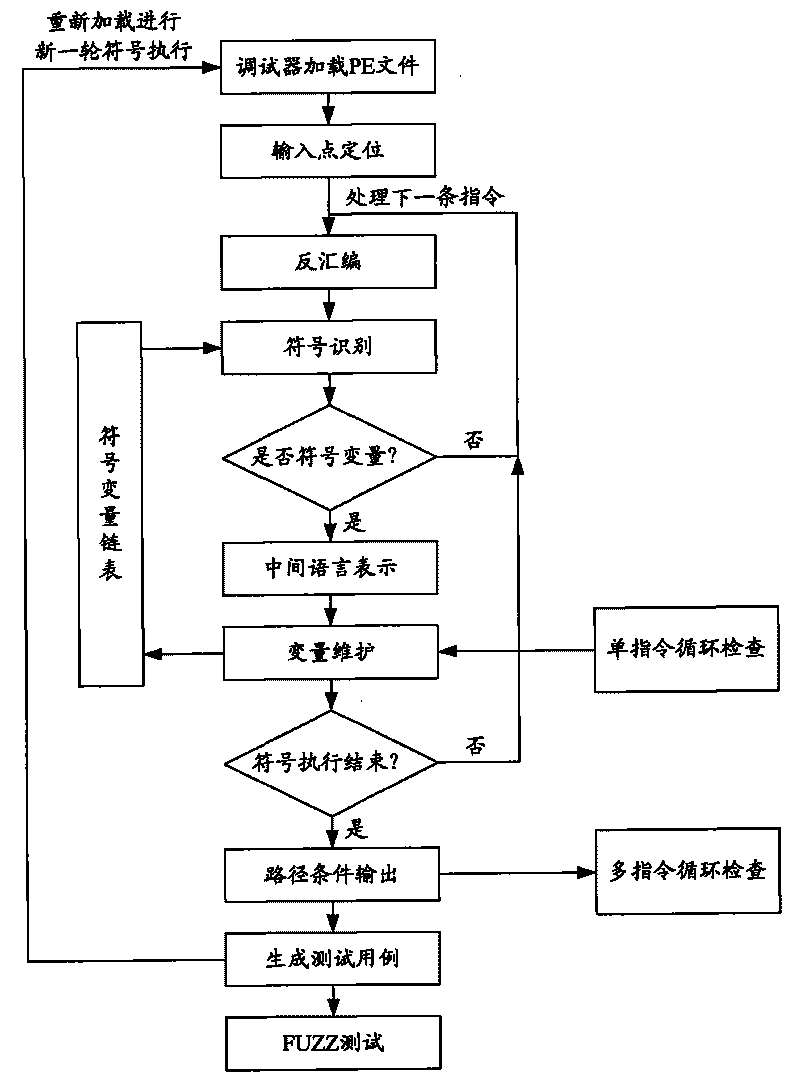
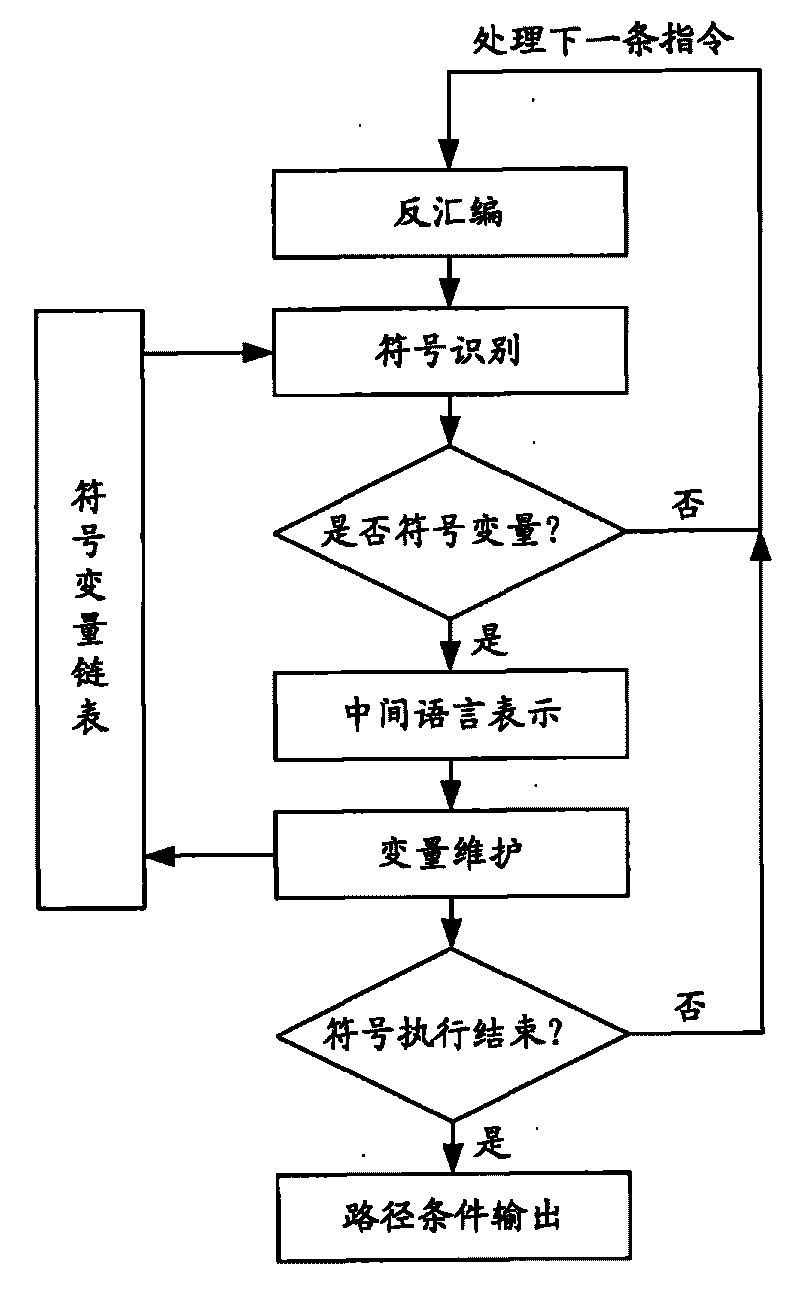
The invention provides a detector for binary-code buffer-zone overflow bugs, and a detection method thereof. The detector comprises six functional modules, namely a debugger module, an input point positioning module, a disassembling module, a symbolic execution module, a loop operation analysis module and an intelligent FUZZ test module. Differing from static symbolic execution, the detection method dynamically loads programs through the self-developed debugger module to synchronously performing symbolic execution and single-step practical execution, and then applies a model to solve each difficulty in binary code analysis so as to test path coverage and detect overflow bugs in accordance with all executable programs of PE format under a Windows platform. The detection can also provide propagation paths of input data and other important information related to bug formation cause while positioning the bugs, only analyzes the selves of the executable programs, needs no source codes, is unrelated to the species of source codes and development tools, and is extensive in applicable occasions, so the detection method has good prospects for popularization and application.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Apparatus and method for transmitting signal in mobile communication system
InactiveUS7068981B2Easy to detectSpatial transmit diversityMultiplex communicationMobile communication systemsBeamforming
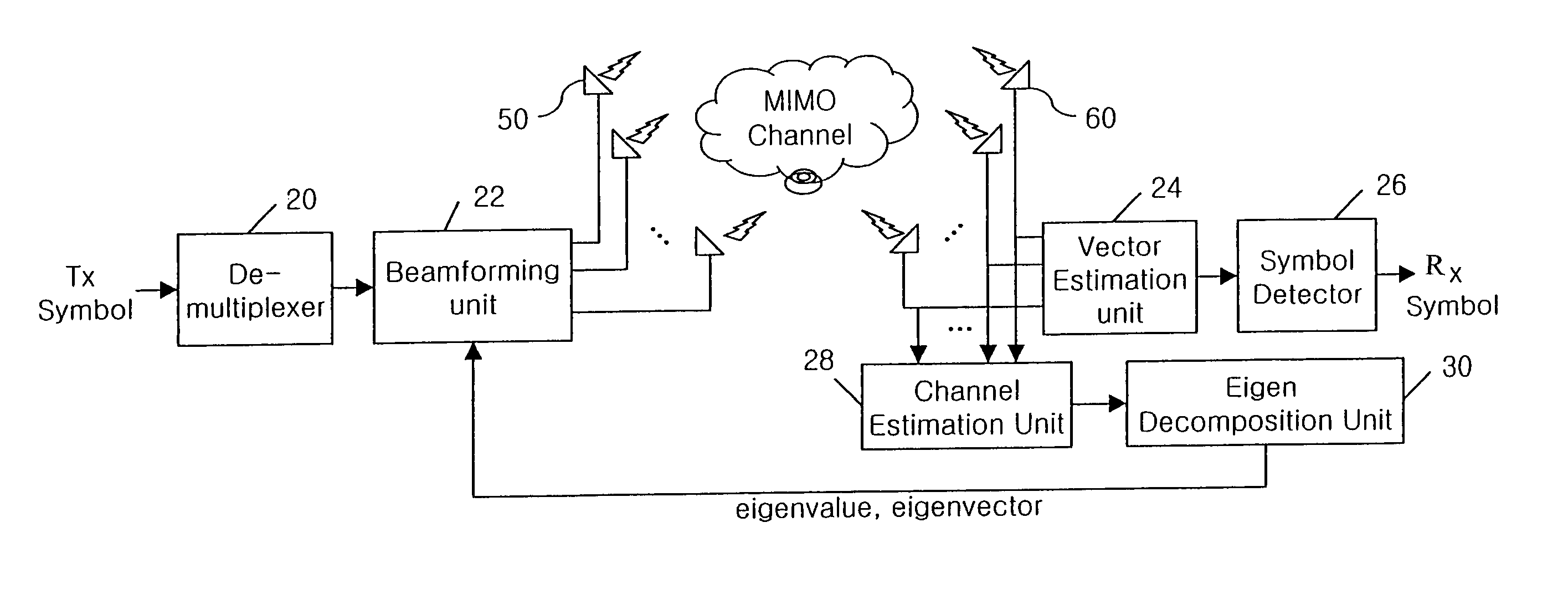
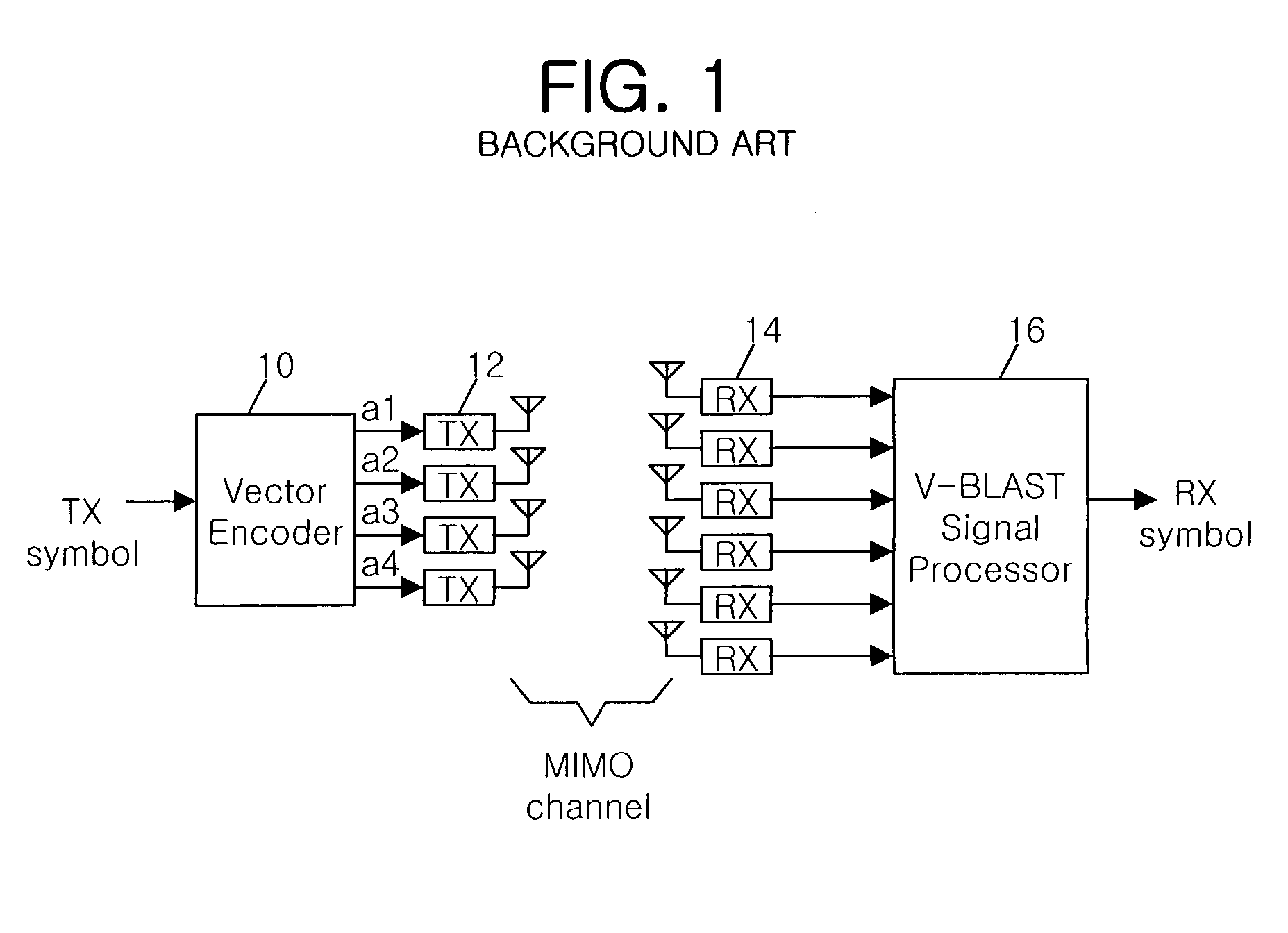
A signal transmission apparatus and method for a mobile communication system are disclosed. Beamforming is performed on each symbol using the correlation as well as the independence between antennas, and then the beamformed symbols are transmitted. Thus, both the correlation between antennas and the independence between antennas are all considered, so that the gain according to the correlation between antennas can be also obtained. In addition, the additional gain would lead to enhancement of the symbol detection capability of the sending end, so that performance of the MIMO system can be remarkably heightened.
Owner:LG ELECTRONICS INC
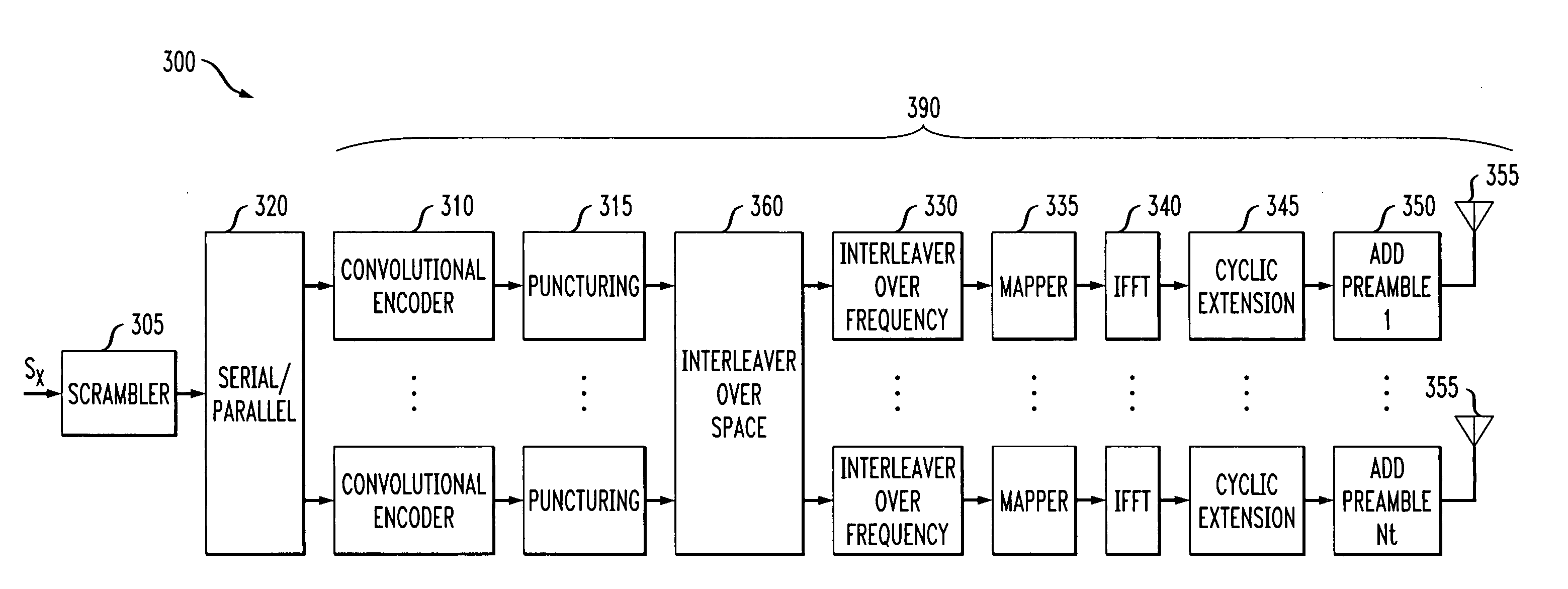
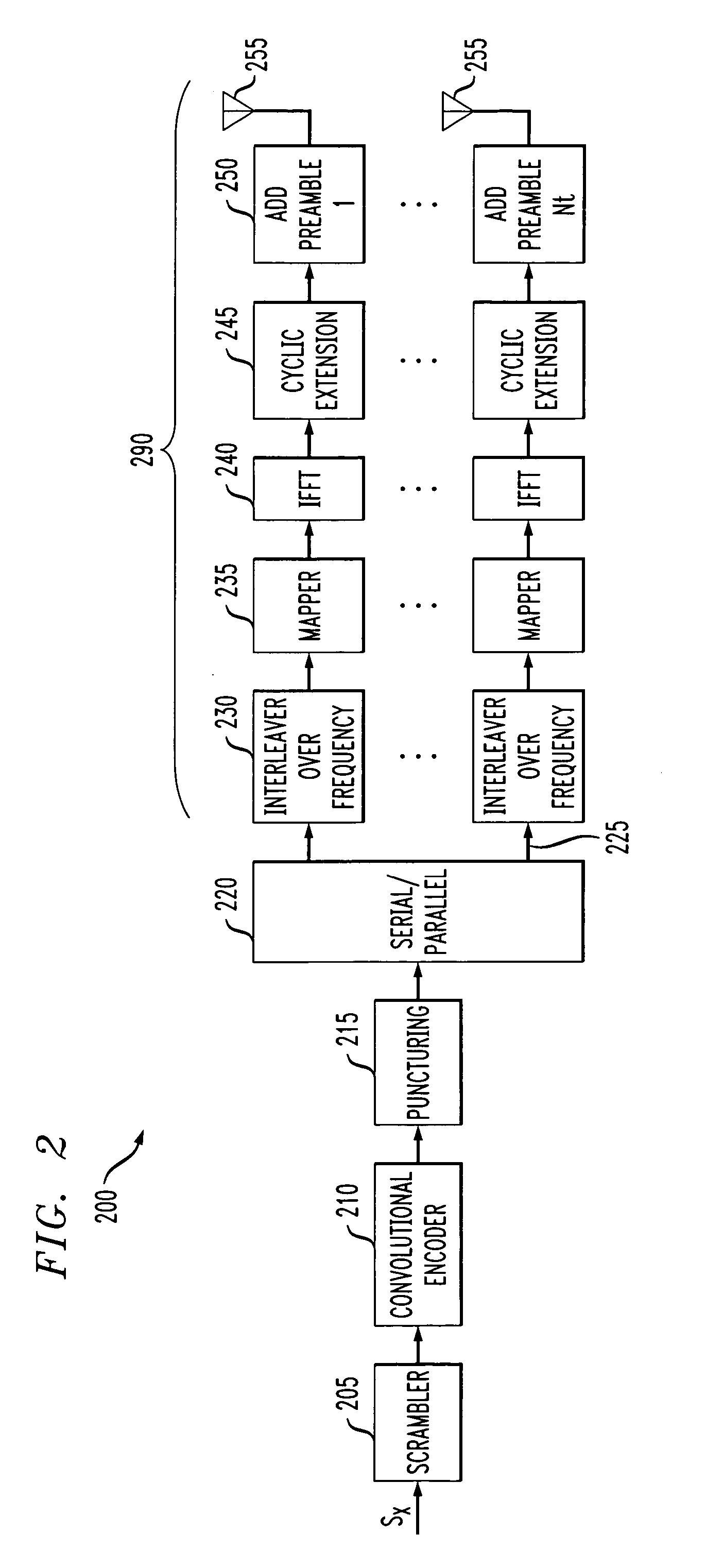
Method and apparatus for space interleaved communication in a multiple antenna communication system
InactiveUS20060018247A1Improve performanceMulti-frequency code systemsOrthogonal multiplexCommunications systemDiversity scheme
Methods and systems are disclosed for space interleaved communication of data in a multiple antenna communication system. Data is interleaved over space by interleaving the data over a plurality of transmit branches in the multiple antenna system. The disclosed spatial interleaving increases the performance gains resulting from the spatial transmit diversity of the multiple antenna communication system. Spatial interleaving can be performed, for example, over the bits before the bits are interleaved over frequency. In another variation, spatial interleaving is performed over the symbols after the bits are mapped to symbols.
Owner:AGERE SYST INC
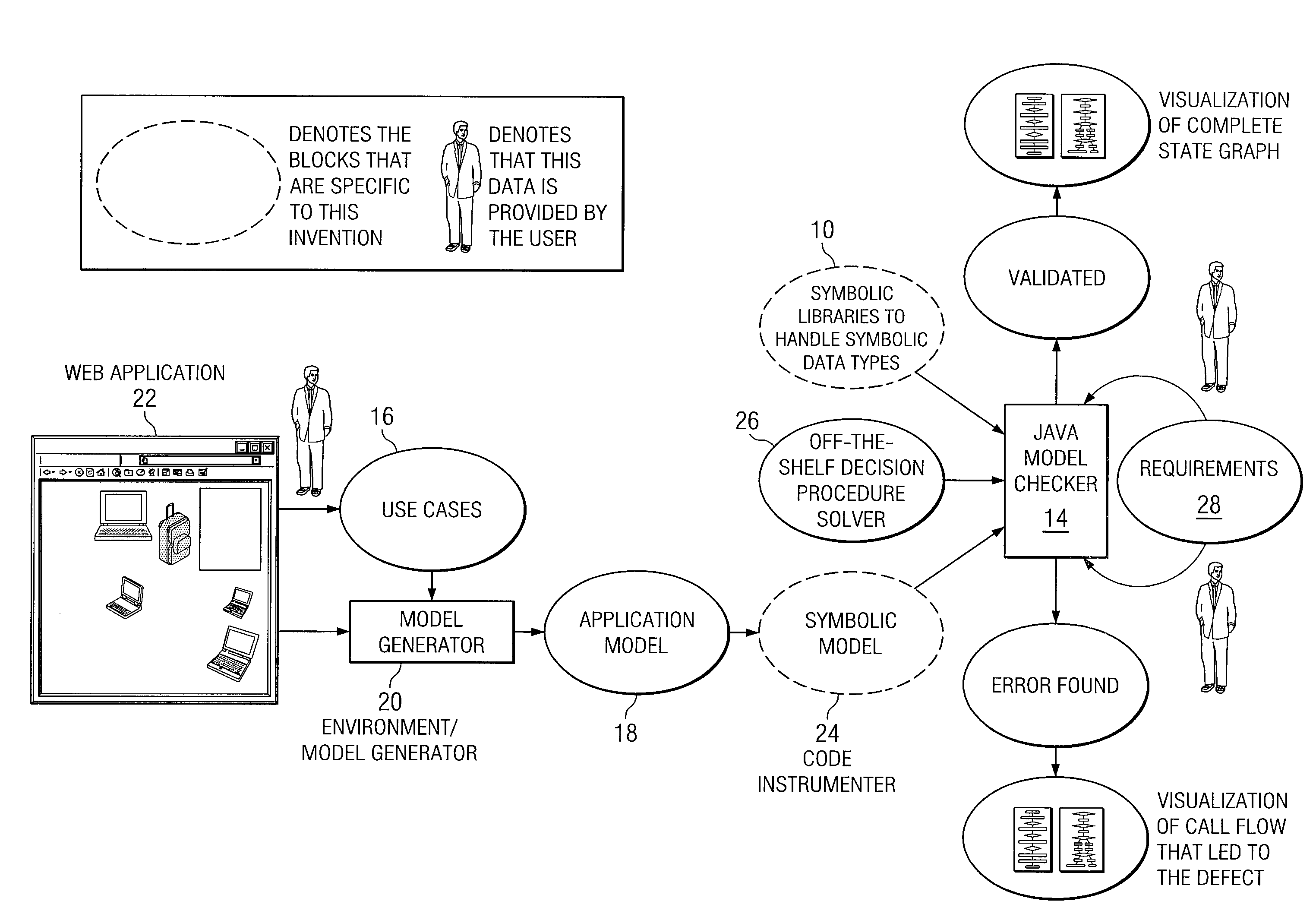
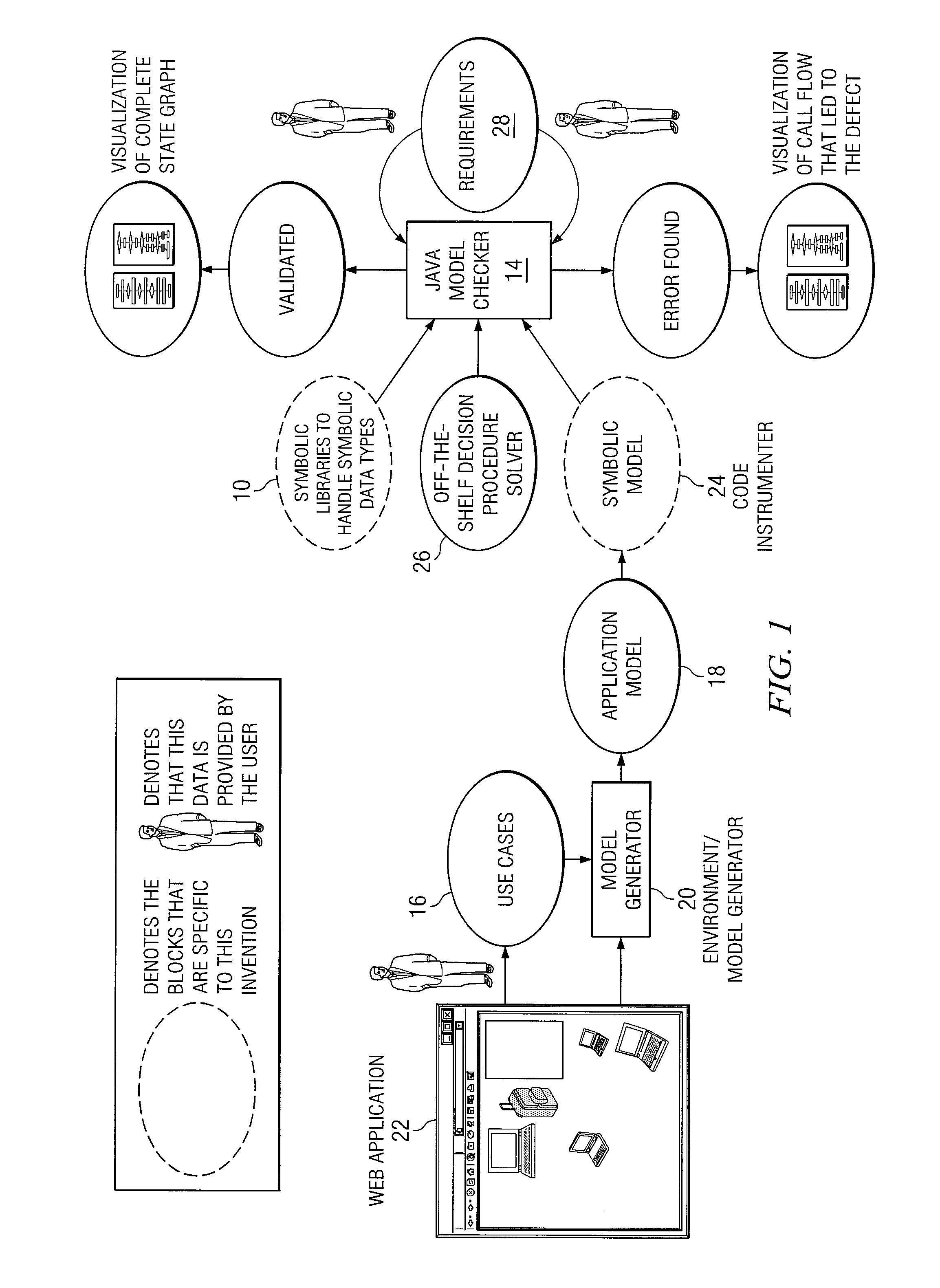
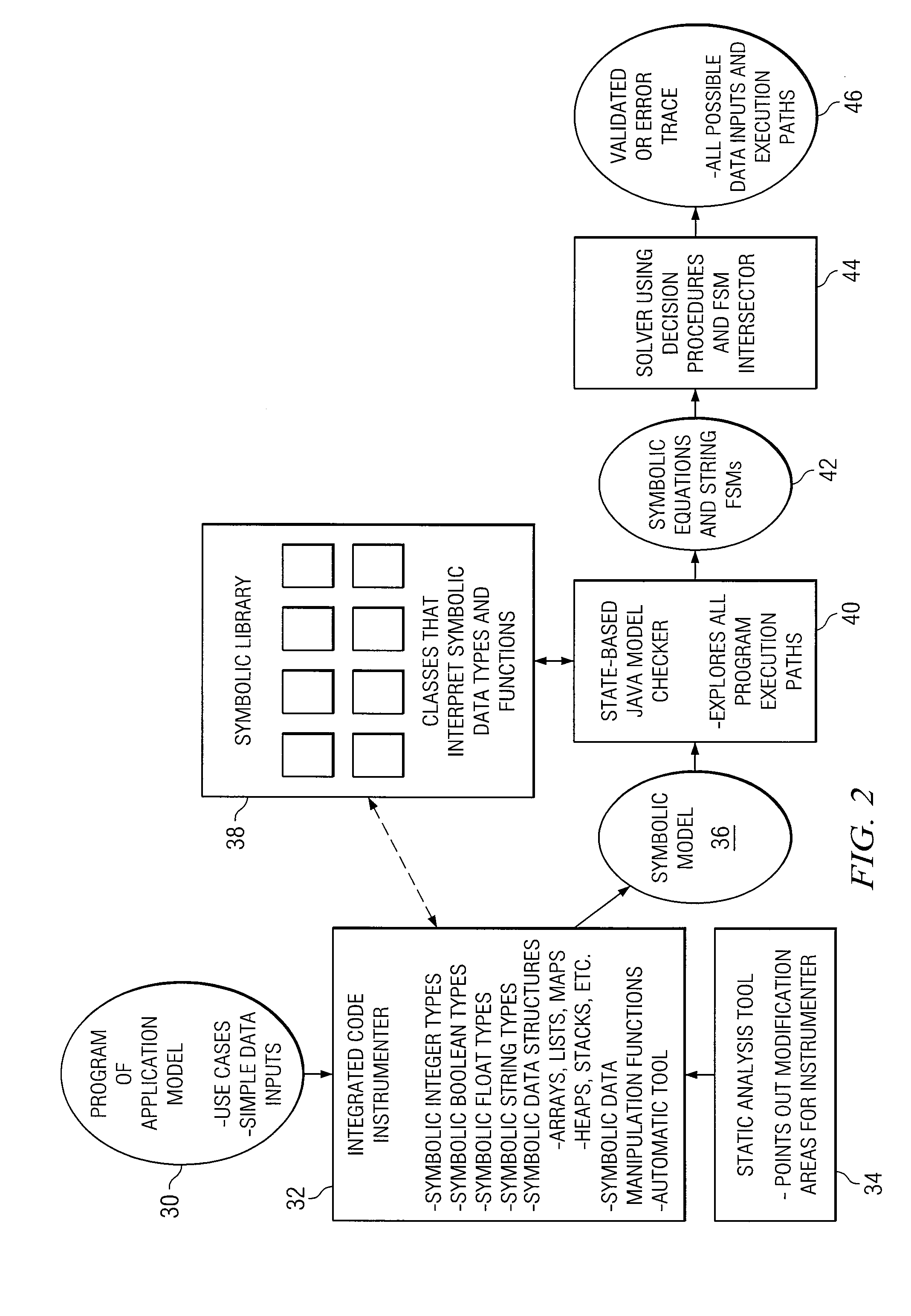
System and Method for Providing Symbolic Execution Engine for Validating Web Applications
InactiveUS20090089759A1Eliminates and reduces of disadvantageEliminates and reduces of and problemError detection/correctionSpecific program execution arrangementsWeb applicationApplication software
In accordance with a particular embodiment of the present invention, a method is offered that includes generating a symbolic string manipulation class library for one or more web applications. The manipulations are generalized into a string manipulation symbolic algebra. The method also includes performing symbolic execution for one or more web applications. Typically, a Java model checker is augmented to check for certain types of requirements or properties in performing the symbolic execution. If an error scenario exists, a solution to a set of symbolic constraints is obtained, and the solution is mapped back to a source code to obtain an error trace and a test case. In still other specific embodiments, requirements or properties are encoded through templates and checked using public domain decision procedures. The properties or requirements can relate to security validation. The symbolic execution can be customized and tuned for Java-based web applications.
Owner:FUJITSU LTD
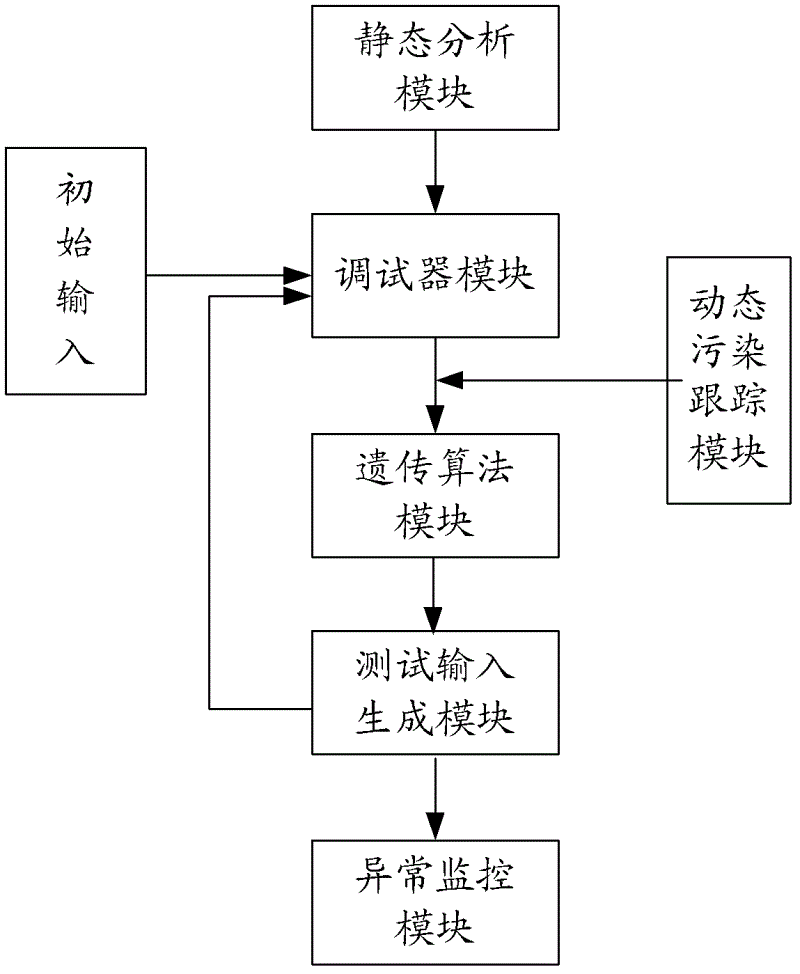
Excavating device and excavating method of binary system program loopholes
InactiveCN102622558AAvoid blindnessPath maximizationPlatform integrity maintainanceTest inputTheoretical computer science
Provided are an excavating device and an excavating method of binary system program loopholes. The excavating device is provided with a static analysis module, a debugger module, a genetic algorithm module, a test input generation module and an abnormal monitoring module which are sequentially connected and a dynamic pollution tracking module located between the debugger module and the genetic algorithm module. The excavating device is guided to generate a test case by aid of a fitness function of the genetic algorithm, the multi-objective fitness function is designed, and the test case is evaluated in view of quantification. Dynamic pollution tracking is used for identifying key bytes in input files to narrow search space of the genetic algorithm. The excavating device combines advantages of the genetic algorithm and the dynamic pollution tracking and is guided to generate the test case, so that the generated test case is strong in pertinence, generated test data are high in accuracy and efficiency, further qualitative analysis and quantitative calculation are combined, and therefore path explosion in binary system program testing based on the symbolic execution and constraint solving technology is avoided.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and apparatus for demodulating signals processed in a transmit diversity mode
InactiveUS6628702B1Reduce complexityLow costSpatial transmit diversityCode division multiplexCommunications systemTransmit diversity
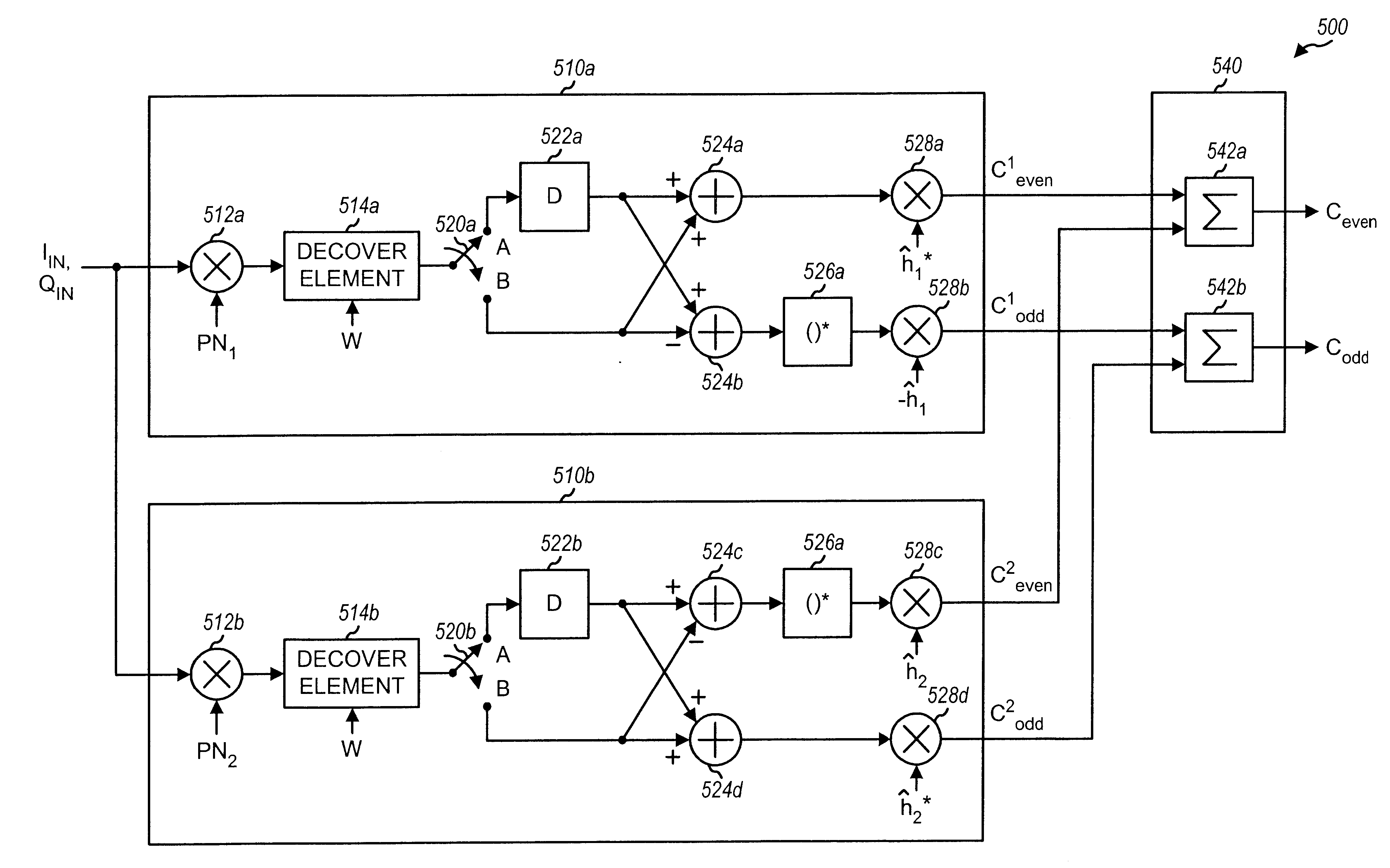
Demodulator architectures for processing a received signal in a wireless communications system. The demodulator includes a number of correlators coupled to a combiner. Each correlator typically receives and despreads input samples (which are generated from the received signal) with a respective despreading sequence to provide despread samples. Each correlator then decovers the despread samples to provide decovered "half-symbols" and further demodulates the decovered half-symbols with pilot estimates to generate correlated symbols. The decovering is performed with a Walsh symbol having a length (T) that is half the length (2T) of a Walsh symbol used to cover the data symbols in the transmitted signal. The combiner selectively combines correlated symbols from the assigned correlators to provide demodulated symbols. One or more correlators can be assigned to process one or more instances of each transmitted signal. The pilot estimates used within each assigned correlator to demodulate the decovered half-symbols are generated based on the signal instance being processed by that correlator.
Owner:QUALCOMM INC
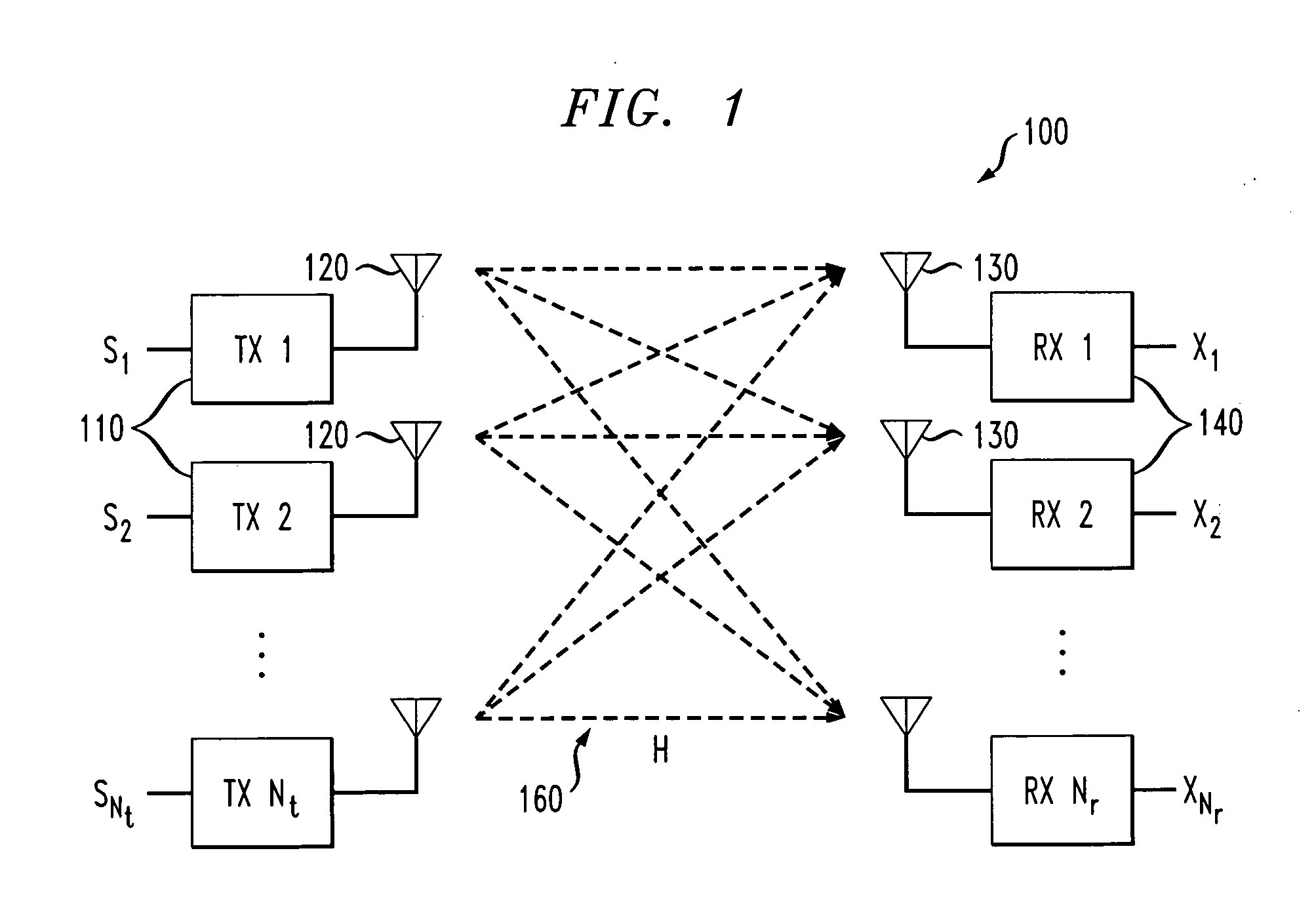
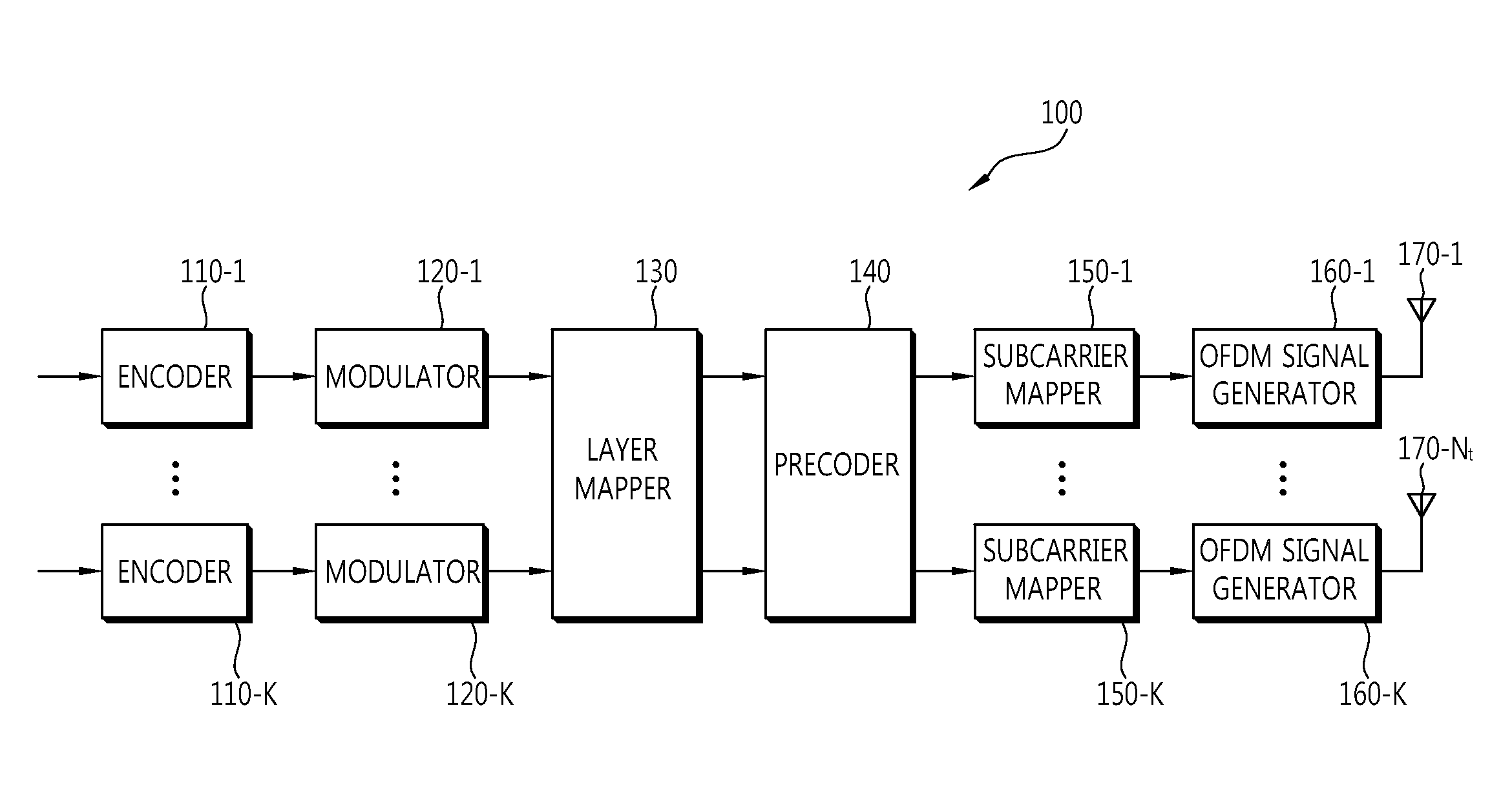
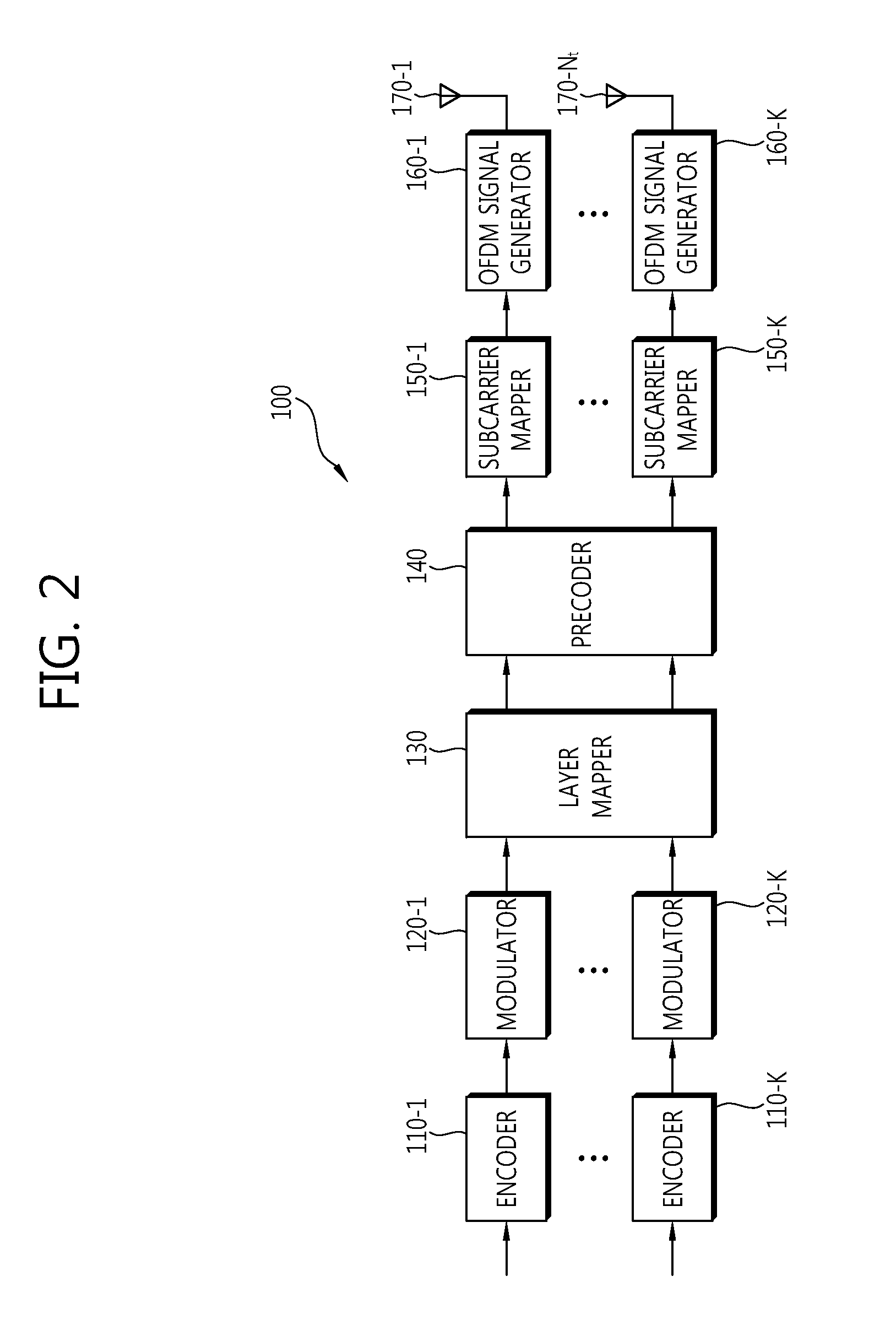
Method for transmitting data in multiple antenna system
ActiveUS20110158219A1Effective applicationFrequency-division multiplexInter user/terminal allocationTelecommunicationsPrecoding matrix
A method of sending data in a multiple antenna system according to an aspect of the present invention includes performing precoding on received symbols based on a second codebook generated from a first codebook for a plurality of transmission antennas and sending the precoded symbols. The second codebook is a codebook for transmission antennas which are a multiple of an integer of the plurality of transmission antennas, and a precoding matrix included in the second codebook is generated by a combination of precoding matrices included in the first codebook.
Owner:LG ELECTRONICS INC
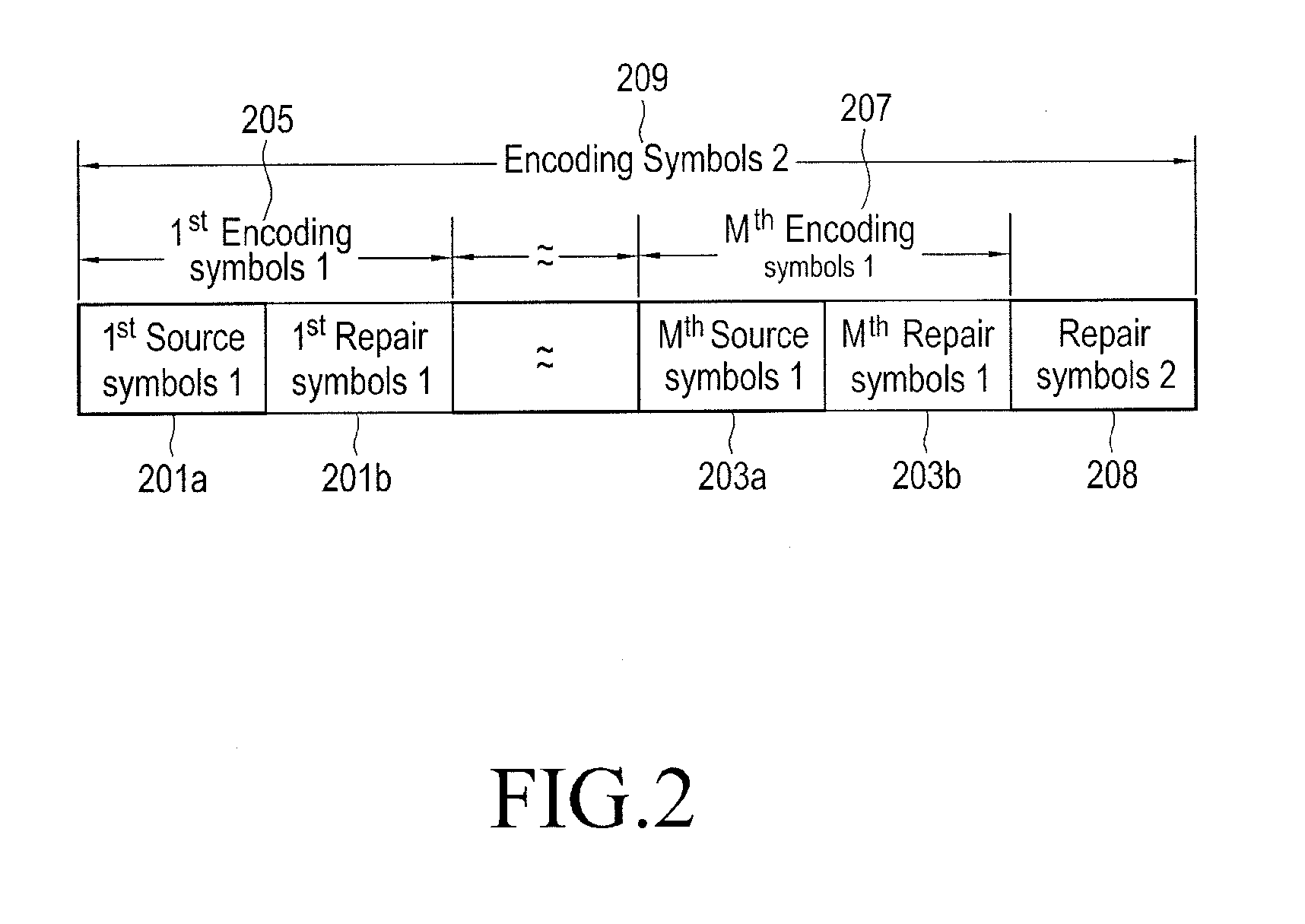
Method for generating forward error correction packet in multimedia system and method and apparatus for transmitting and receiving forward error correction packet
ActiveUS20130013982A1Avoid packet lossCode conversionError correction/detection using block codesForward error correctionMultimedia system
A method and apparatus for transmitting a Forward Error Correction (FEC) packet block including a plurality of FEC packets in a multimedia system are provided. The method includes generating a plurality of first FEC packet blocks by performing a first FEC encoding on a plurality of source symbols, each of the plurality of first FEC packet blocks including at least one source packet and at least one repair packet for repair of each of the at least one source packet, generating a second FEC packet block by performing a second FEC encoding on the plurality of first FEC packet blocks, the second FEC packet block including at least one repair packet for the plurality of first FEC packet blocks, and transmitting the second FEC packet block that includes, in header information of each of the at least one source packet and the at least one repair packet.
Owner:SAMSUNG ELECTRONICS CO LTD
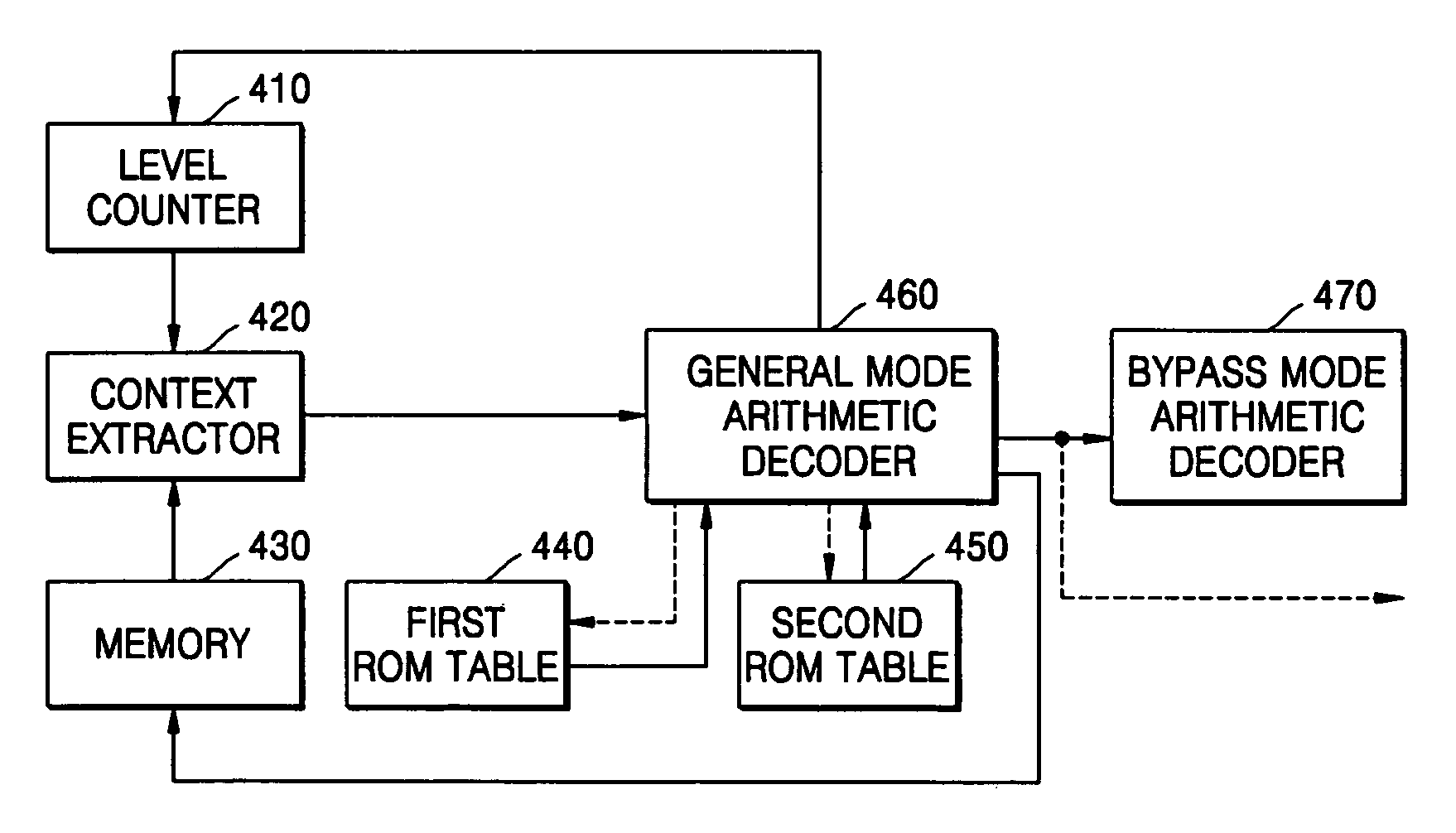
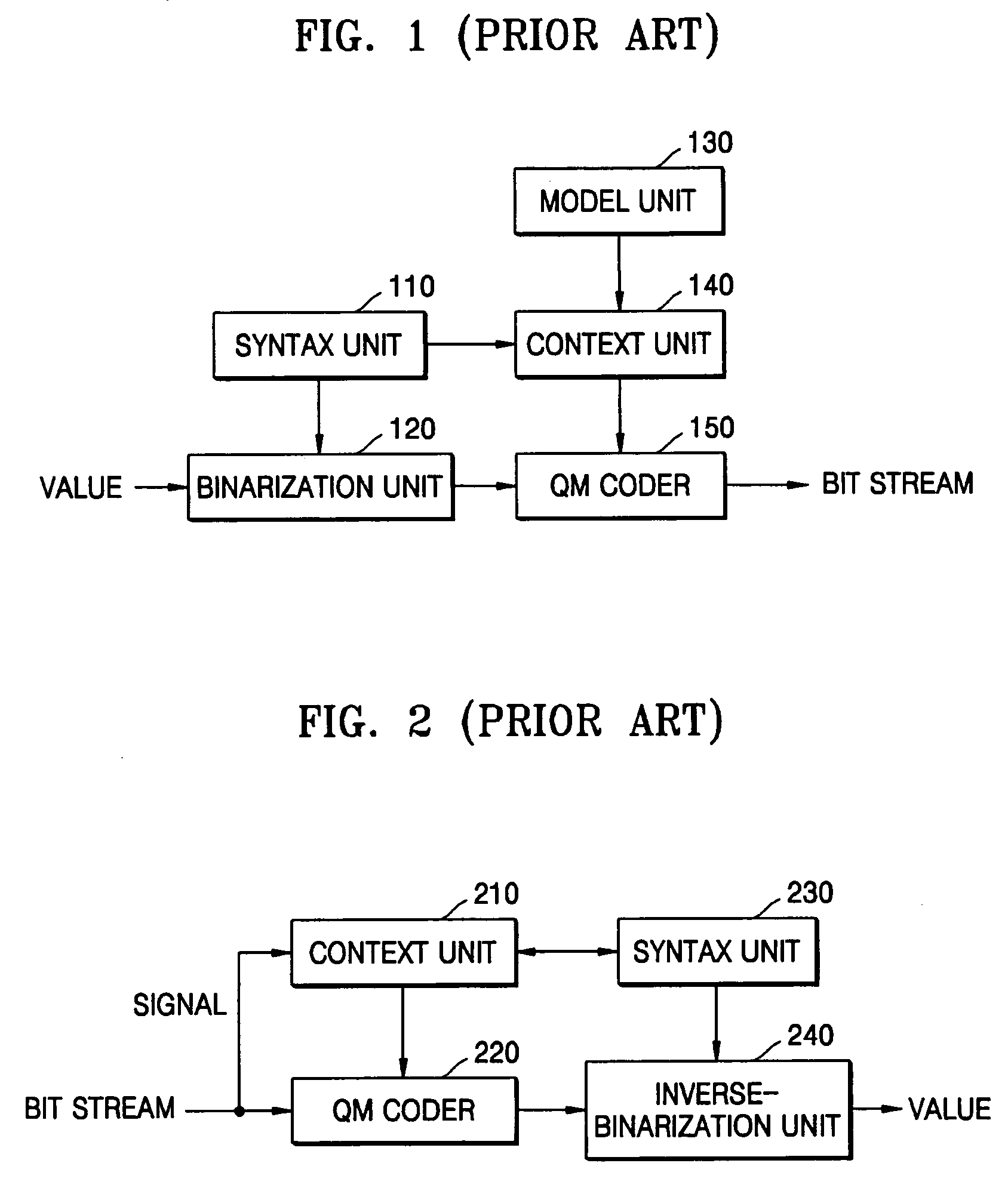
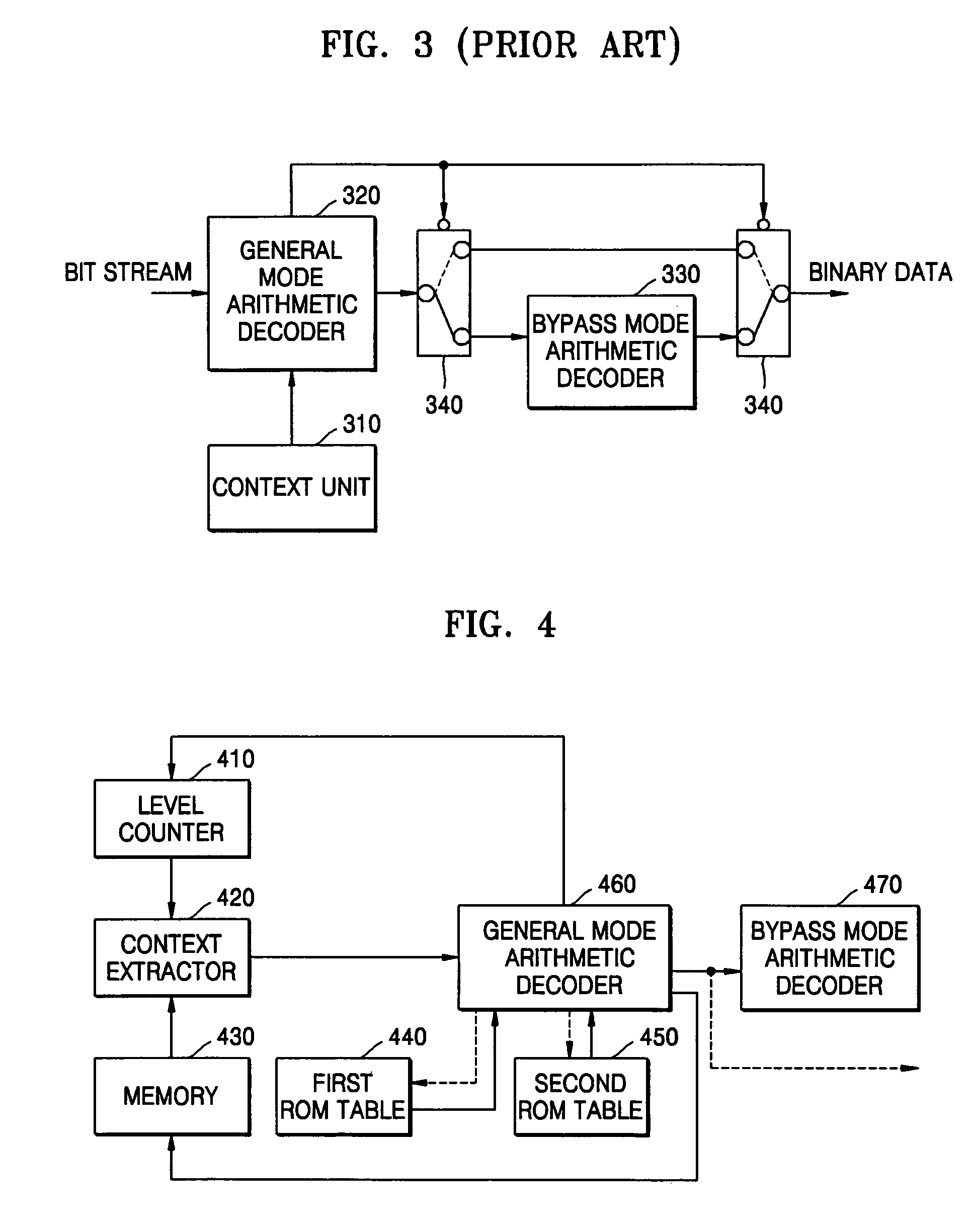
Context-based adaptive binary arithmetic coding method and apparatus
There are provided a context-based adaptive binary arithmetic decoding method and apparatus. The context-based adaptive binary arithmetic decoding apparatus includes: a context extractor extracting a plurality of contexts from a storage unit storing contexts each including a state value for probability characteristic; a first ROM table storing current probability information so that a current binary symbol of the bit stream is decoded according to a state value of each context; a second ROM table storing predicted probability information so that a next binary symbol of the bit stream is decoded according to a state value of each context; a general mode arithmetic decoder, which performs pipeline processing, loading current probability information from the first ROM table on the basis of a current state value of a context extracted from the context extractor to decode a first binary symbol, and loading predicted probability information from the second ROM table to decode a next remaining binary symbol while decoding the remaining binary symbols; and a bypass mode arithmetic decoder, including a plurality of calculators for parallel processing, simultaneously decoding a plurality of corresponding binary symbols of the bit stream, to perform arithmetic decoding on the remaining symbols if a predetermined condition is satisfied while the general mode arithmetic decoder performs arithmetic decoding on the corresponding symbols of the bit stream. Therefore, by implementing a hardware suitable for context-based adaptive binary arithmetic decoding, it is possible to enhance a decoding speed.
Owner:SAMSUNG ELECTRONICS CO LTD
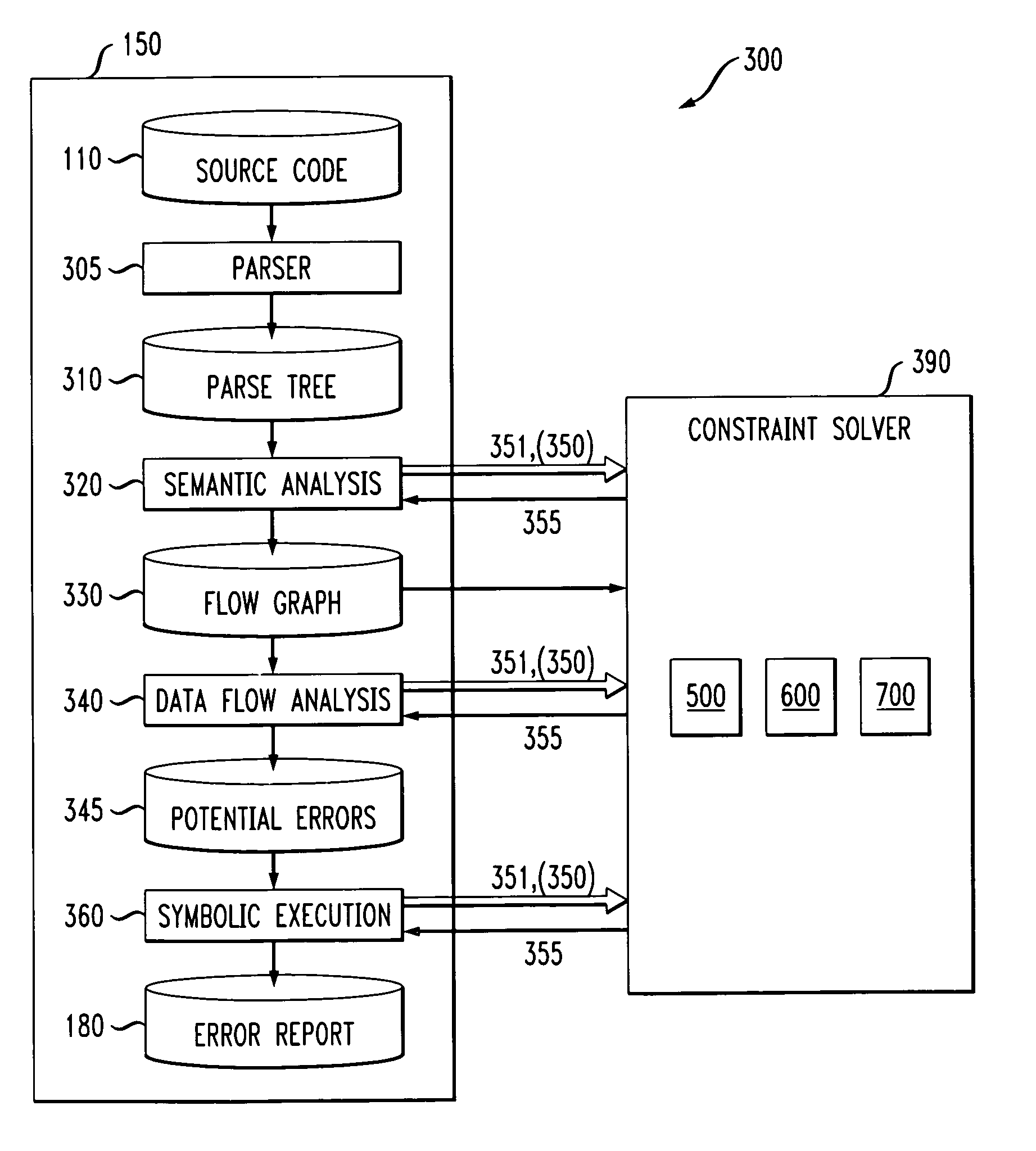
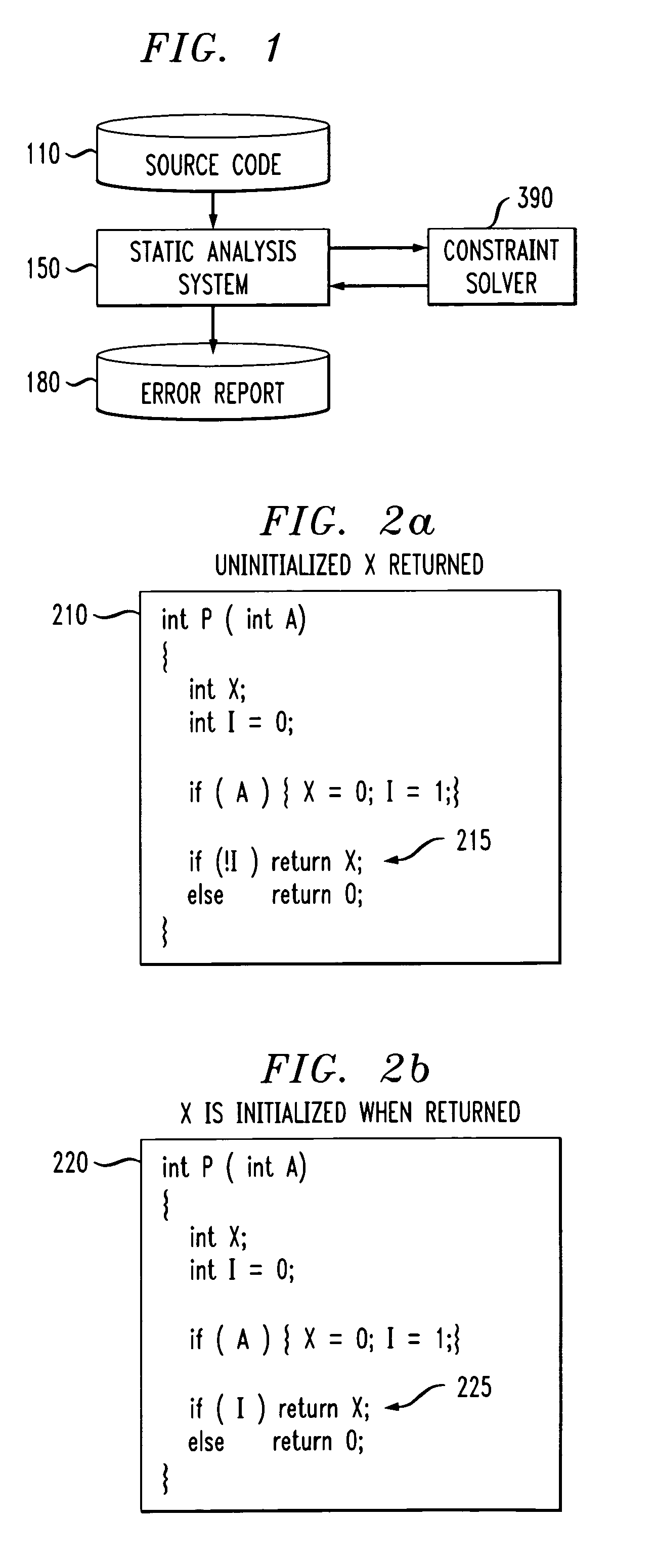
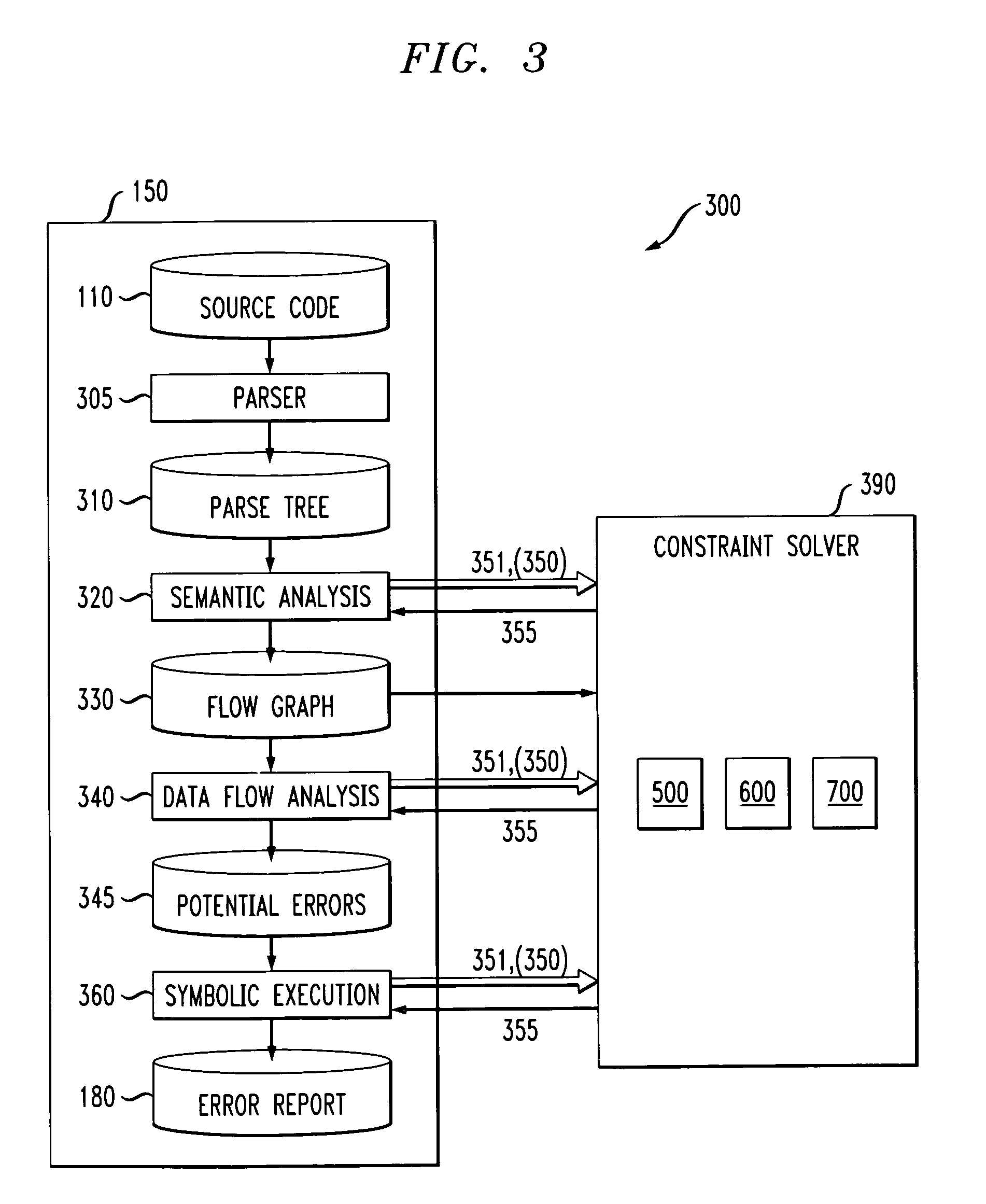
Method and apparatus for finding errors in software programs using satisfiability of constraints
InactiveUS7089542B2Efficient and accurateHandled satisfactorilyError preventionError detection/correctionRewrite ruleSemantics
A method and apparatus are provided for analyzing software programs. The invention combines data flow analysis and symbolic execution with a new constraint solver to create a more efficient and accurate static software analysis tool. The disclosed constraint solver combines rewrite rules with arithmetic constraint solving to provide a constraint solver that is efficient, flexible and capable of satisfactorily expressing semantics and handling arithmetic constraints. The disclosed constraint solver comprises a number of data structures to remember existing range, equivalence and inequality constraints and incrementally add new constraints. The constraint solver returns an inconsistent indication only if the range constraints, equivalence constraints, and inequality constraints are mutually inconsistent.
Owner:IBM CORP
Method and apparatus for data transmission
ActiveUS20100246712A1Increase flexibilityPolarisation/directional diversityFrequency diversityResource elementData transmission
A method for data transmission is disclosed. The method includes: performing, by a system, resource element mapping on modulation symbols which include data to be transmitted and reference signals and which are allocated to antenna ports of a designated type; performing antenna port mapping on the modulation symbols which are through the resource element mapping; and generating Orthogonal Frequency Division Multiplexing (OFDM) signals based on the modulation symbols which are through the antenna port mapping and transmitting the OFDM signals via physical antennas. The present invention also discloses an apparatus for data transmission. In the method and apparatus provided by the present invention, through establishing a mapping relationship between physical antenna elements and antenna ports, beamforming weights are added to modulation symbols of users at the same time. Thus, beamforming operation of the users is implemented. Accordingly, the system may support flexible beamforming transmission on frequency-domain, which greatly improves the flexibility of data transmission of the system.
Owner:DATANG MOBILE COMM EQUIP CO LTD
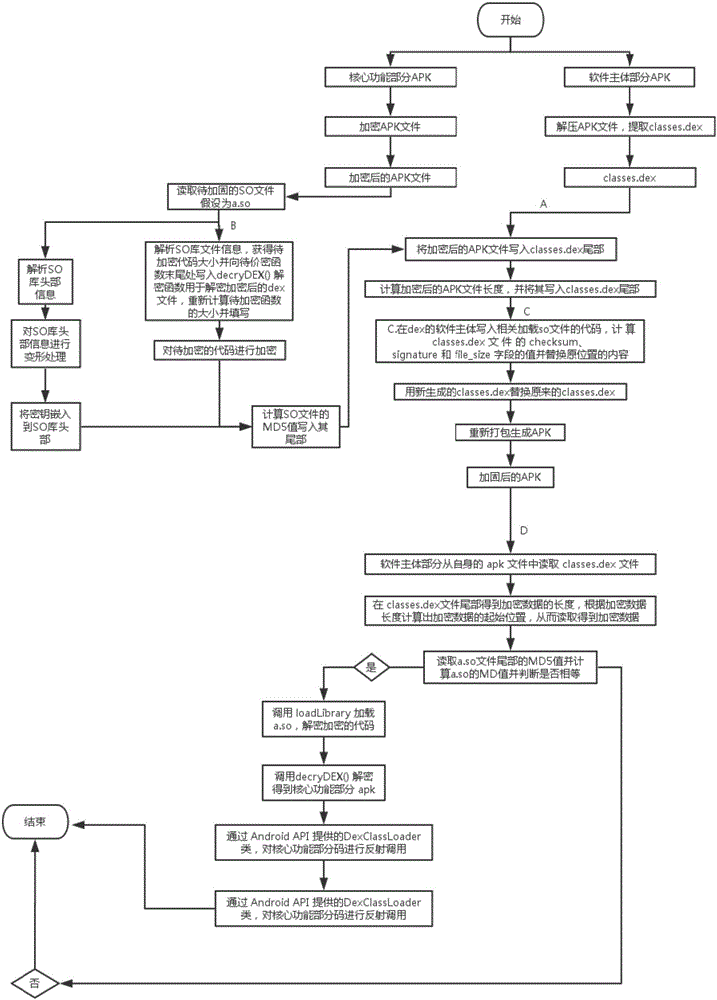
Android application strengthening method based on dynamic execution of dex and so files
PendingCN106203006AAvoid exposureAvoid gettingDigital data protectionProgram/content distribution protectionComputer hardwarePlaintext
The invention discloses an Android application strengthening method based on dynamic execution of dex and so files. Through an encryption method, key codes of an Android application are strengthened such that codes of the Android application are protected. The strengthening method comprises an encryption process and a decryption process and comprises following steps: strengthening key codes of the Android application during the encryption process; and decrypting when dynamic execution of the Android application. The Android application strengthening method based on dynamic execution of dex and so files has following beneficial effects: the C++ language is utilized for writing core dex decryption functions so that difficulty in decompilation is increased and the dex decryption functions are present in the form of a dynamic link library and encrypted; compared with the method of core dex dual encryption, key codes of the dynamic link library are encrypted and a JNI calling mechanism is removed during encryption; therefore, plaintext so files encrypted during encryption do not exist in a hard disk and stored in a memory; and the Android application strengthening method is higher in safety.
Owner:北京鼎源科技有限公司
Method and apparatus for uplink carrier frequency synchronization and antenna weight vector estimation in OFDMA system having smart antenna
InactiveUS20060233270A1Improve transmission performanceLine-faulsts/interference reductionSecret communicationTime domainSmart antenna
Provided are a method and apparatus for uplink carrier frequency synchronization and antenna weight vector estimation in an Orthogonal Frequency Division Multiple Access System (OFDMA) having a smart antenna. The inventive method comprises the steps of receiving and storing training symbols in the time domain transmitted to estimate an antenna weight vector during a training symbol transmission interval; estimating carrier frequency offsets using training symbols in the frequency domain that are obtained by performing a Fast Fourier Transformation (FFT) algorithm with respect to the training symbols received during the training symbol transmission interval; compensating the stored training symbols in the time domain based on the estimated carrier frequency offsets; and estimating an antenna weight vector using training symbols in the frequency domain that are obtained by applying an FFT algorithm with respect to the training symbols in the time domain derived by compensating the carrier frequency offsets during the training symbol transmission interval.
Owner:ELECTRONICS & TELECOMM RES INST +1
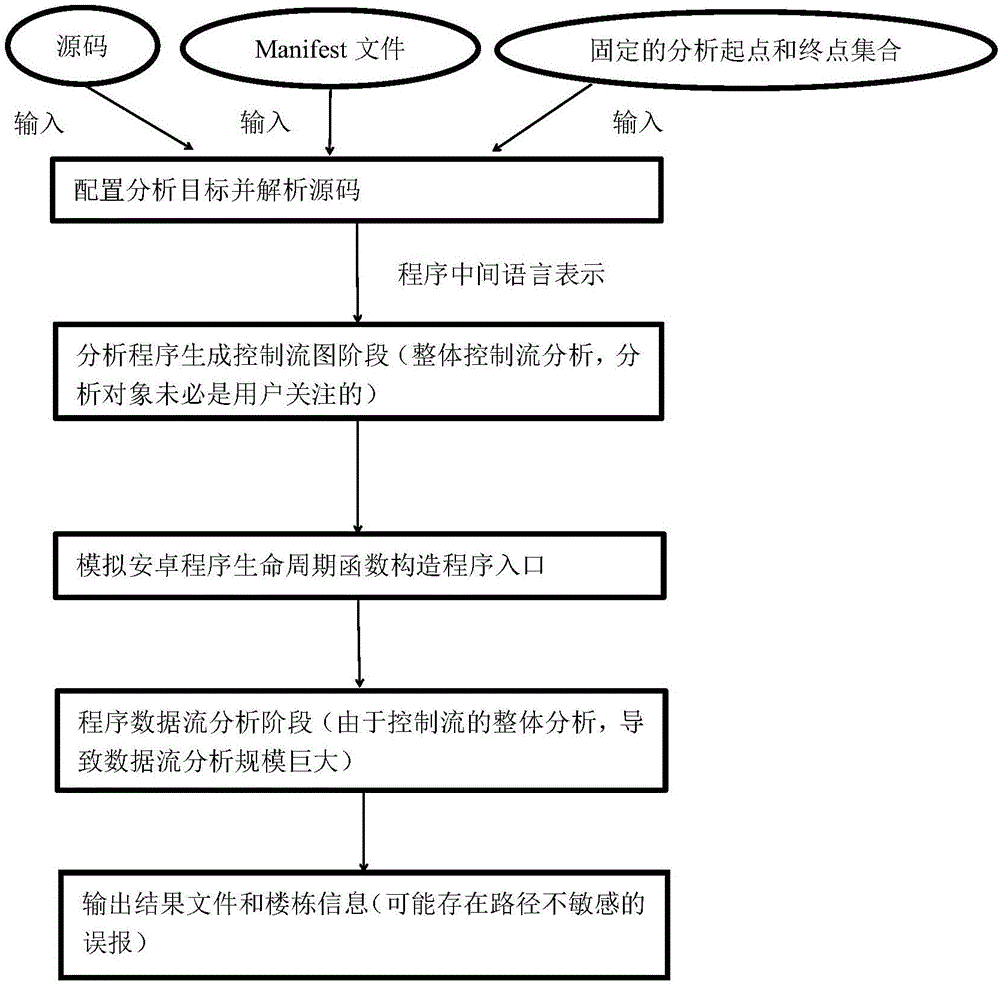
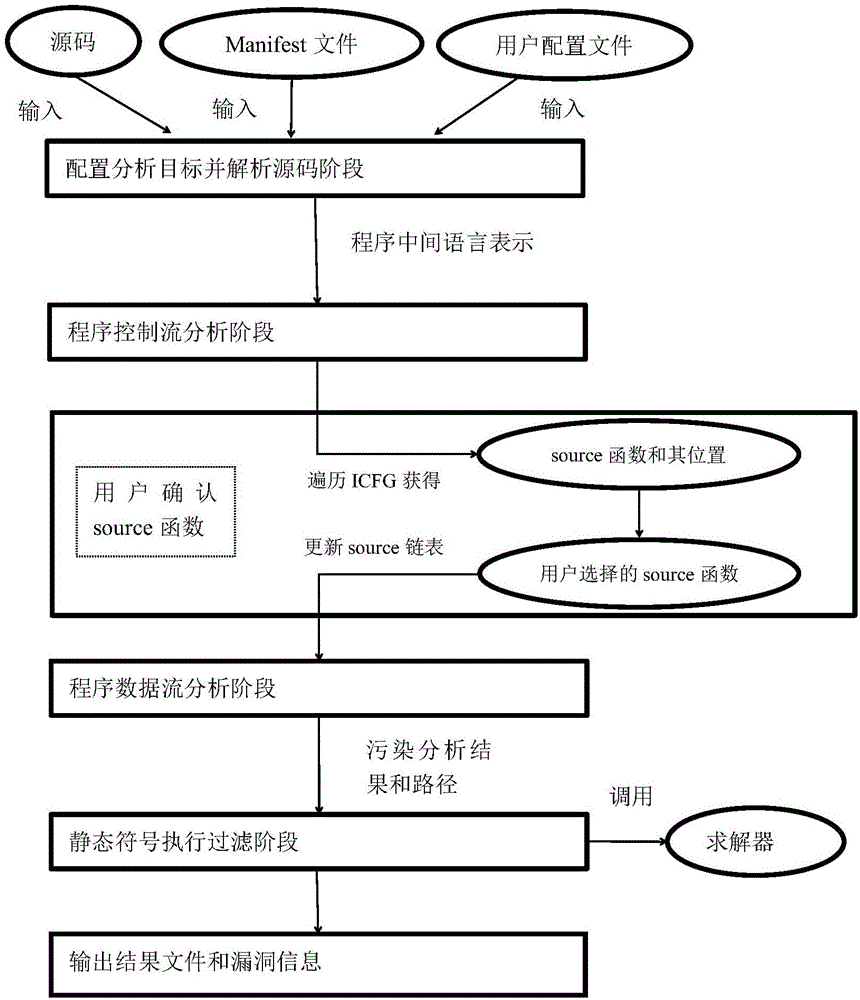
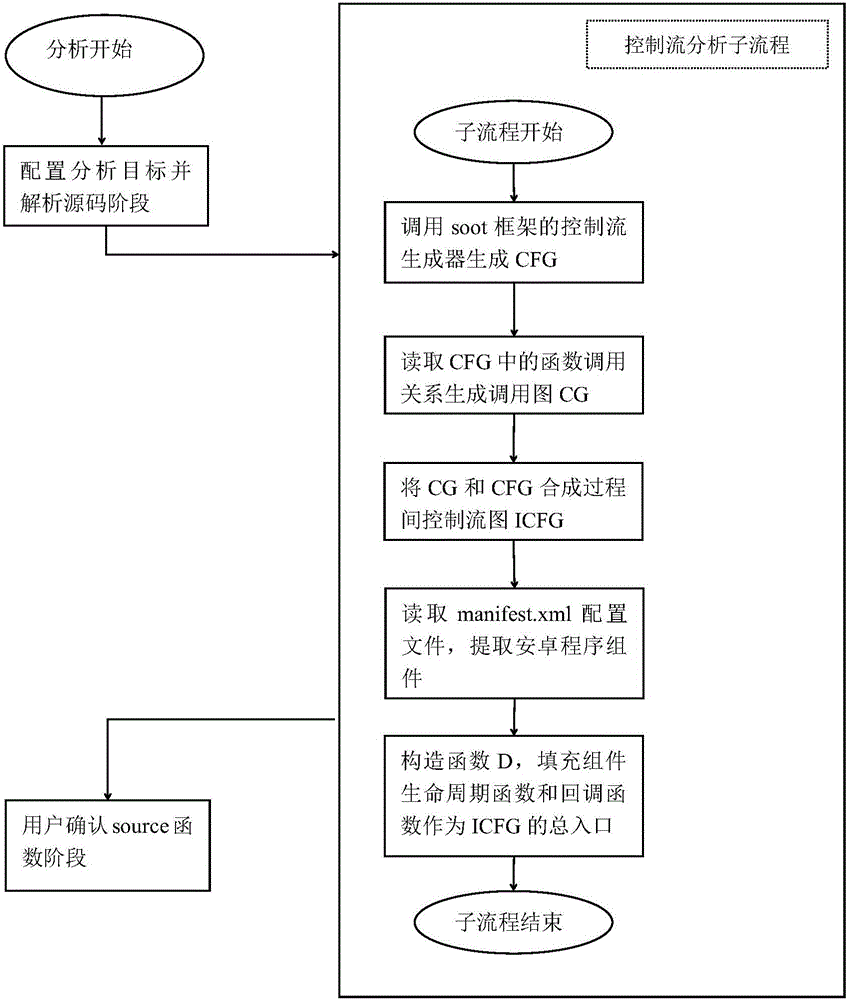
Static taint analysis and symbolic execution-based Android application vulnerability discovery method
ActiveCN106709356ATargetedImprove efficiencyPlatform integrity maintainanceStatic timing analysisData stream
The invention discloses a static taint analysis and symbolic execution-based Android application vulnerability discovery method, and mainly aims at solving the problems that the analysis range is fixed, the memory consumption is huge and the analysis result is mistakenly reported in the process of discovering vulnerabilities by using the existing static taint analysis method. The method is realized through the following steps of: 1) configuring an analysis target and decompiling a program source code; 2) carrying out control flow analysis on the decompilation result; 3) selecting a source function by a user according to the control flow analysis result, so as to narrow an analysis target; 4) carrying out data flow analysis according to the control flow analysis result, so as to generate a vulnerability path; and 5) filtering the data flow analysis result by adoption of a static symbolic execution technology, taking the residual parts after the filtration as discovered vulnerabilities, warning the user and printing the vulnerability path. On the basis of the existing static taint analysis technology, the method disclosed by the invention has the advantages of extending the vulnerability discovery range, decreasing the memory consumption of vulnerability discovery and improving the accuracy of vulnerability discovery results, and can be applied to the discovery and research of Android application program vulnerabilities.
Owner:XIDIAN UNIV
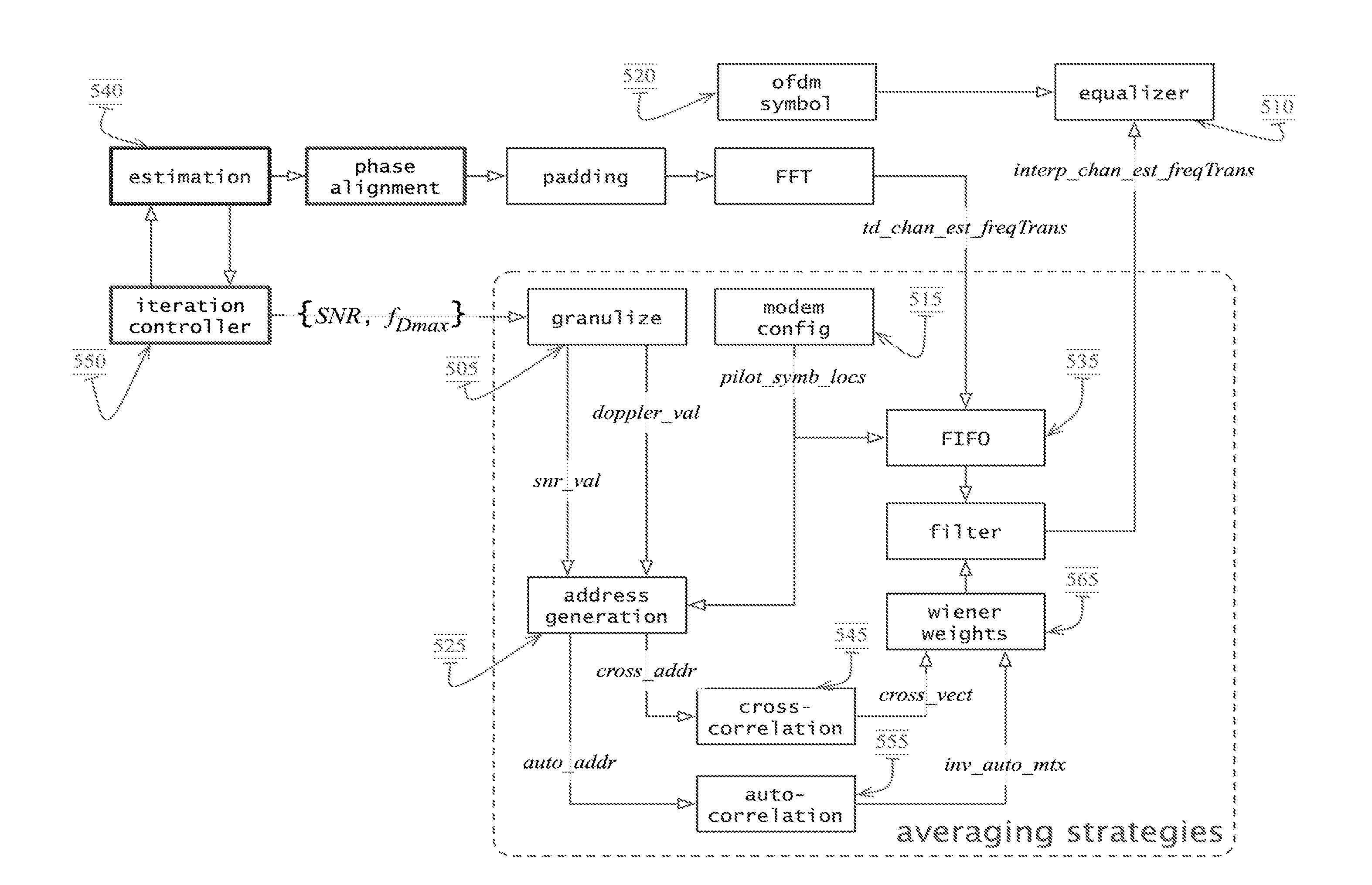
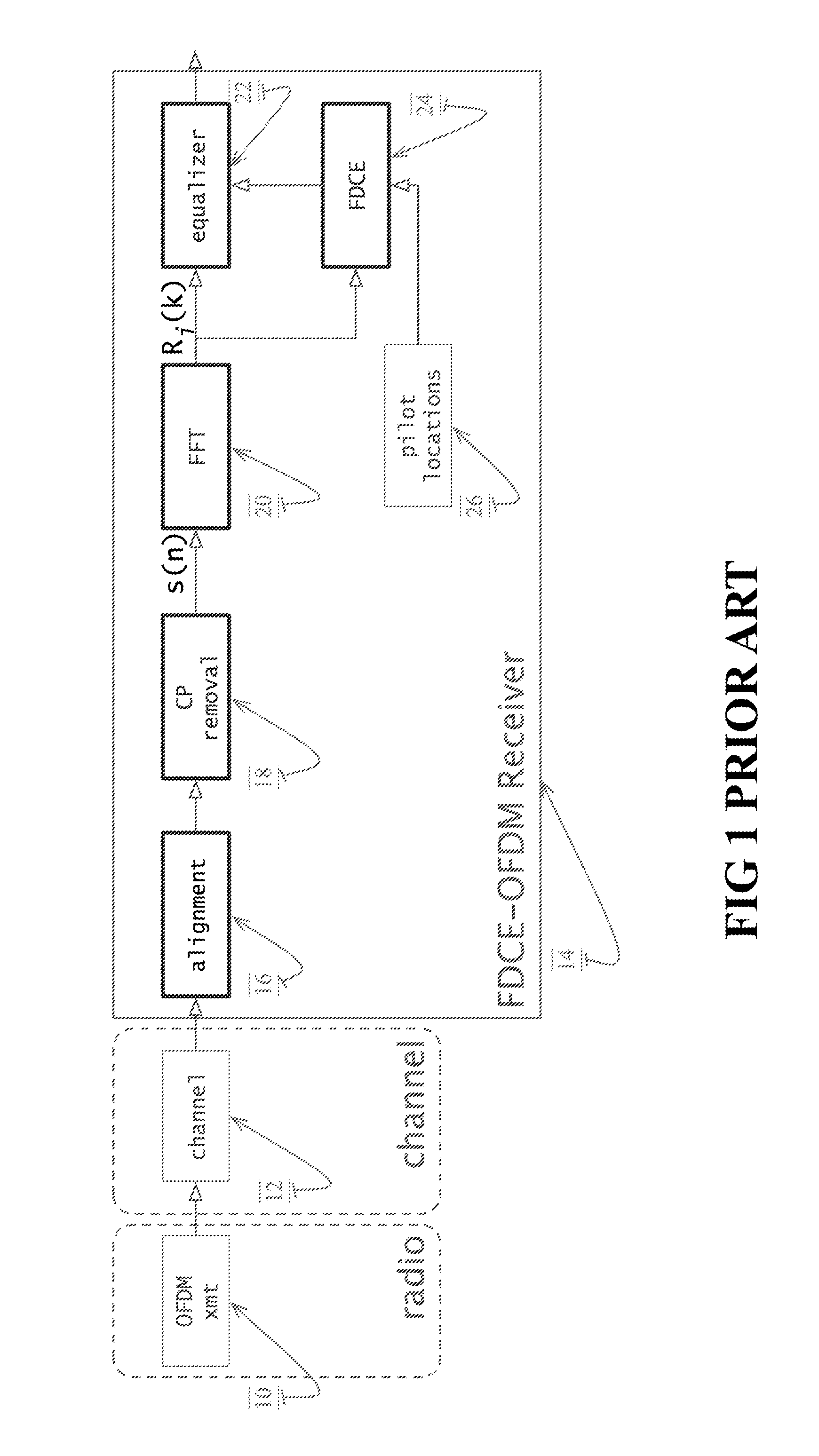
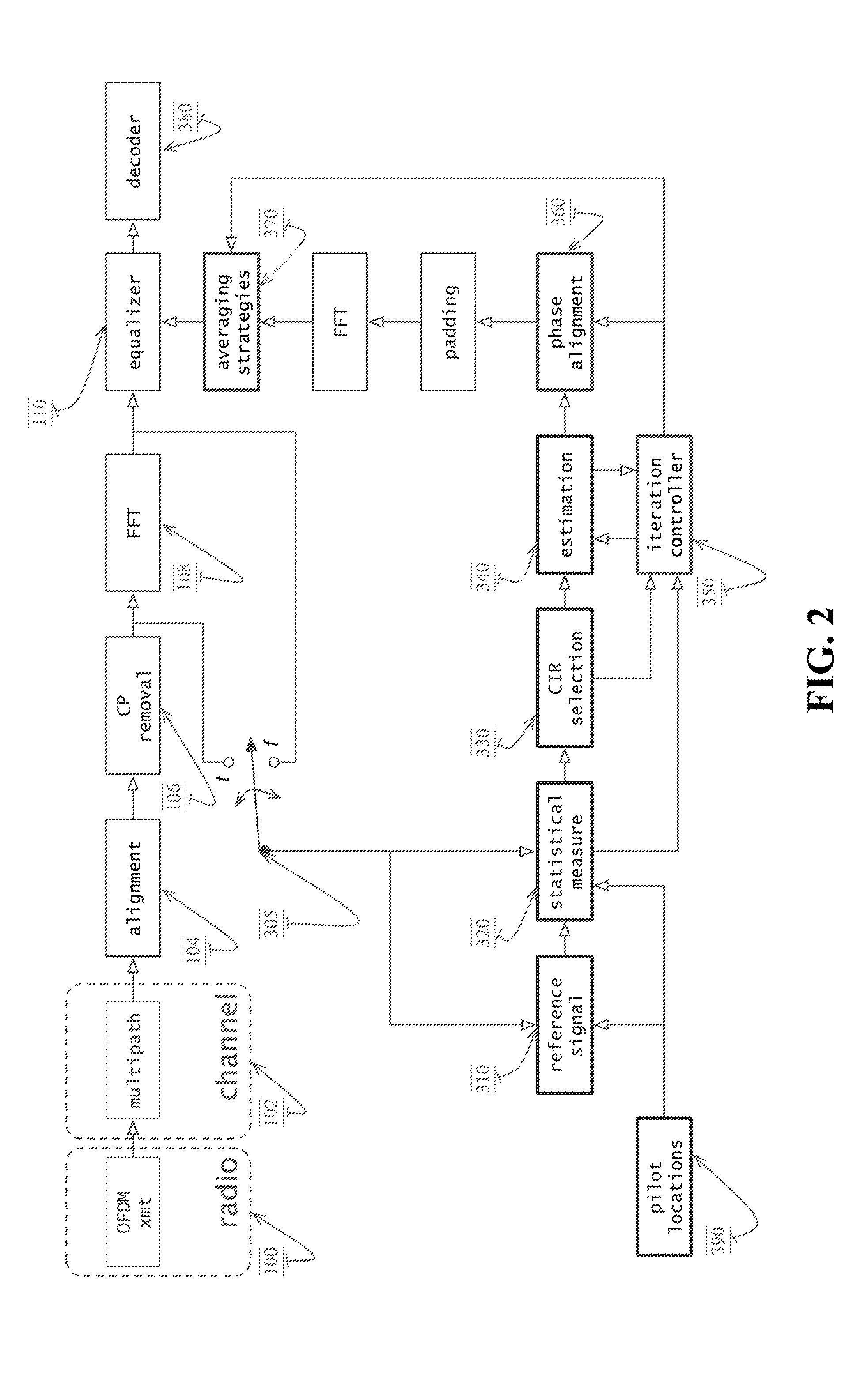
OFDM Receiver With Time Domain Channel Estimation
ActiveUS20130121392A1Multiple-port networksDelay line applicationsFinite impulse responseTime domain
An OFDM communication system performs time domain channel estimation responsive to received symbols before the symbols are processed by a fast Fourier transform. The communication system generates virtual pilots from actual pilots to improve the stability and quality of channel estimation. The system generates a reference signal from the actual and virtual pilots and correlates the resulting reference signal with a signal responsive to the received symbol to generate an initial channel impulse response (CIR) and to determine statistics about the channel. In some circumstances, the resulting reference signal is correlated with a modified symbol in which the actual and virtual pilot locations are emphasized and the data locations are deemphasized. Time domain channel estimation iteratively improves on the initial CIR. The system determines channel estimates for data only symbols through averaging such as interpolation.
Owner:ACORN TECH INC
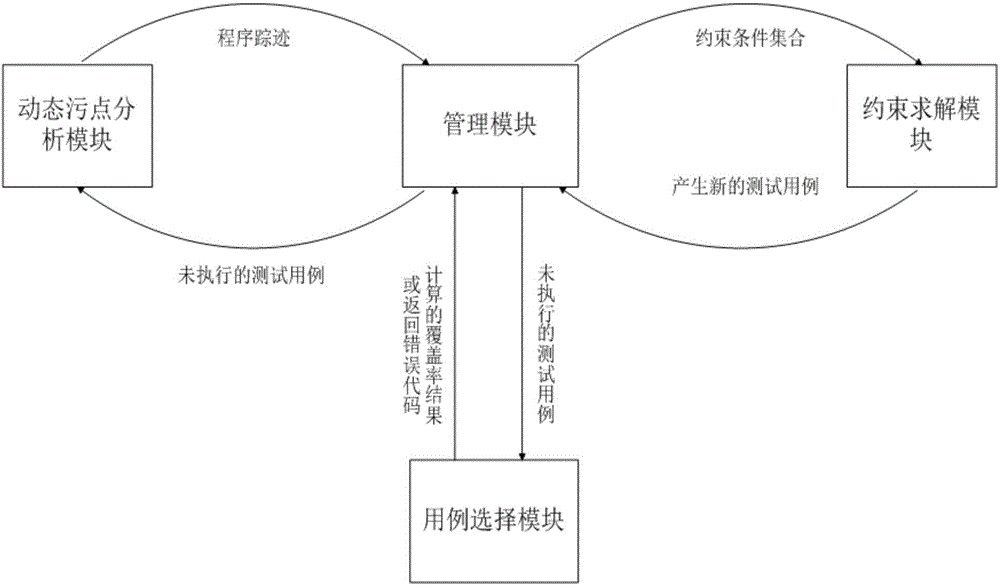
Mode-based dynamic vulnerability discovery integrated system and mode-based dynamic vulnerability discovery integrated method
InactiveCN104598383ABig blindnessImplement automated testingSoftware testing/debuggingComputer moduleComputer science
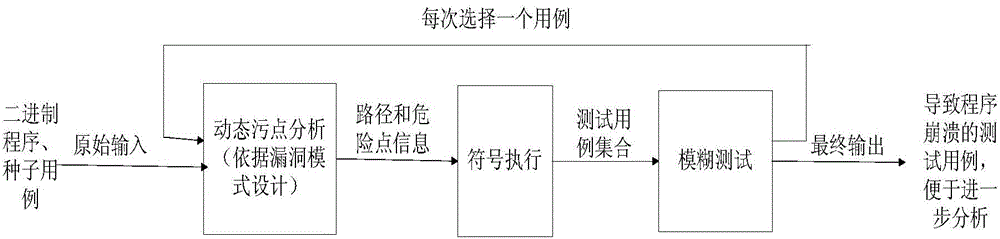
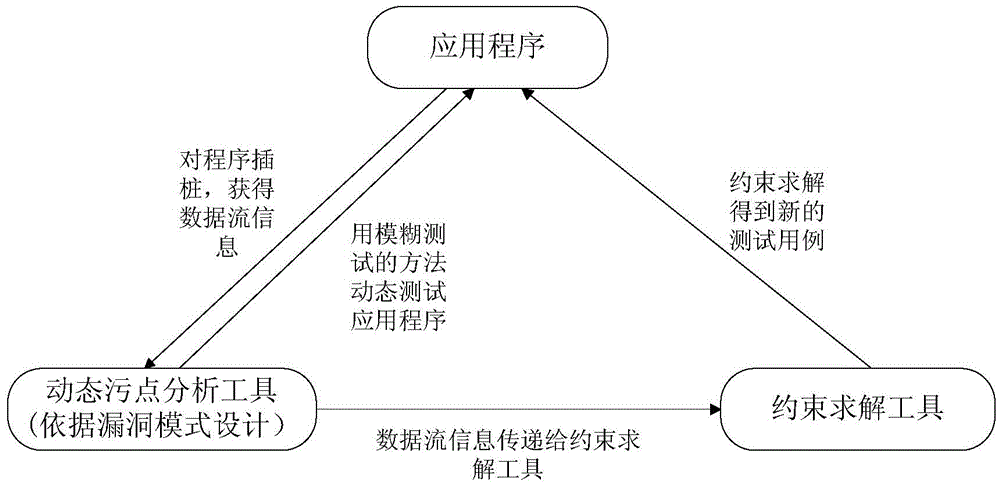
The invention relates to a mode-based dynamic vulnerability discovery integrated system and a mode-based dynamic vulnerability discovery integrated method. The mode-based dynamic vulnerability discovery integrated system comprises a dynamic taint analysis module, a test case selection module, a restraint solving module and a management module. The mode-based dynamic vulnerability discovery integrated method comprises the following steps: firstly, transmitting a seed case to an application program, tracking the transmission of taint data in the program by use of the dynamic taint analysis module, then expressing a transmission track by use of symbols, thereby obtaining a symbolized taint transmission path by virtue of combination of a dynamic taint analysis technology and a symbol execution technology; then by taking the symbolized taint transmission path as input of the restraint solving module, performing restraint solving to obtain a new test case, re-transmitting the test case to the application program, and further performing subsequent operations, wherein the whole process is performed under unified dispatching management of the management module. According to the mode-based dynamic vulnerability discovery integrated system and the mode-based dynamic vulnerability discovery integrated method, the automation degree and efficiency of dynamic vulnerability discovery for a binary program are improved, the generated test data accuracy and the efficiency are high, and thus a fuzzy test process is high in pertinency.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
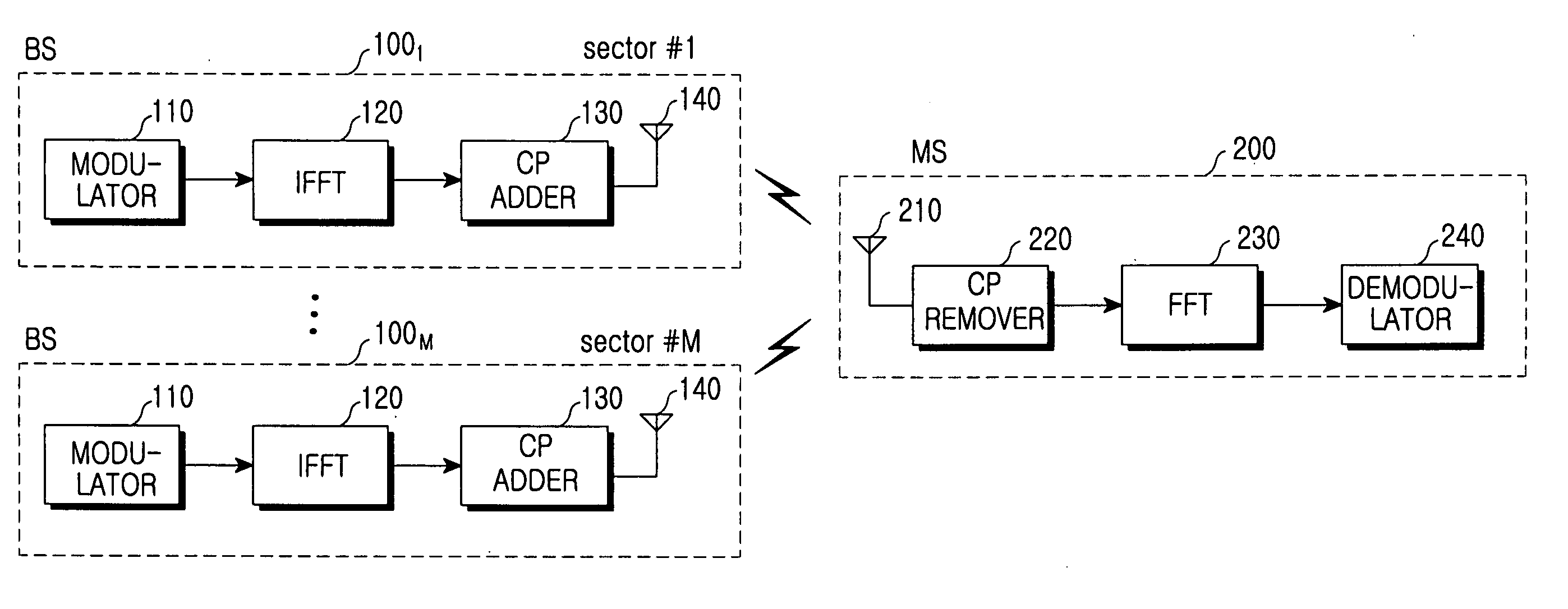
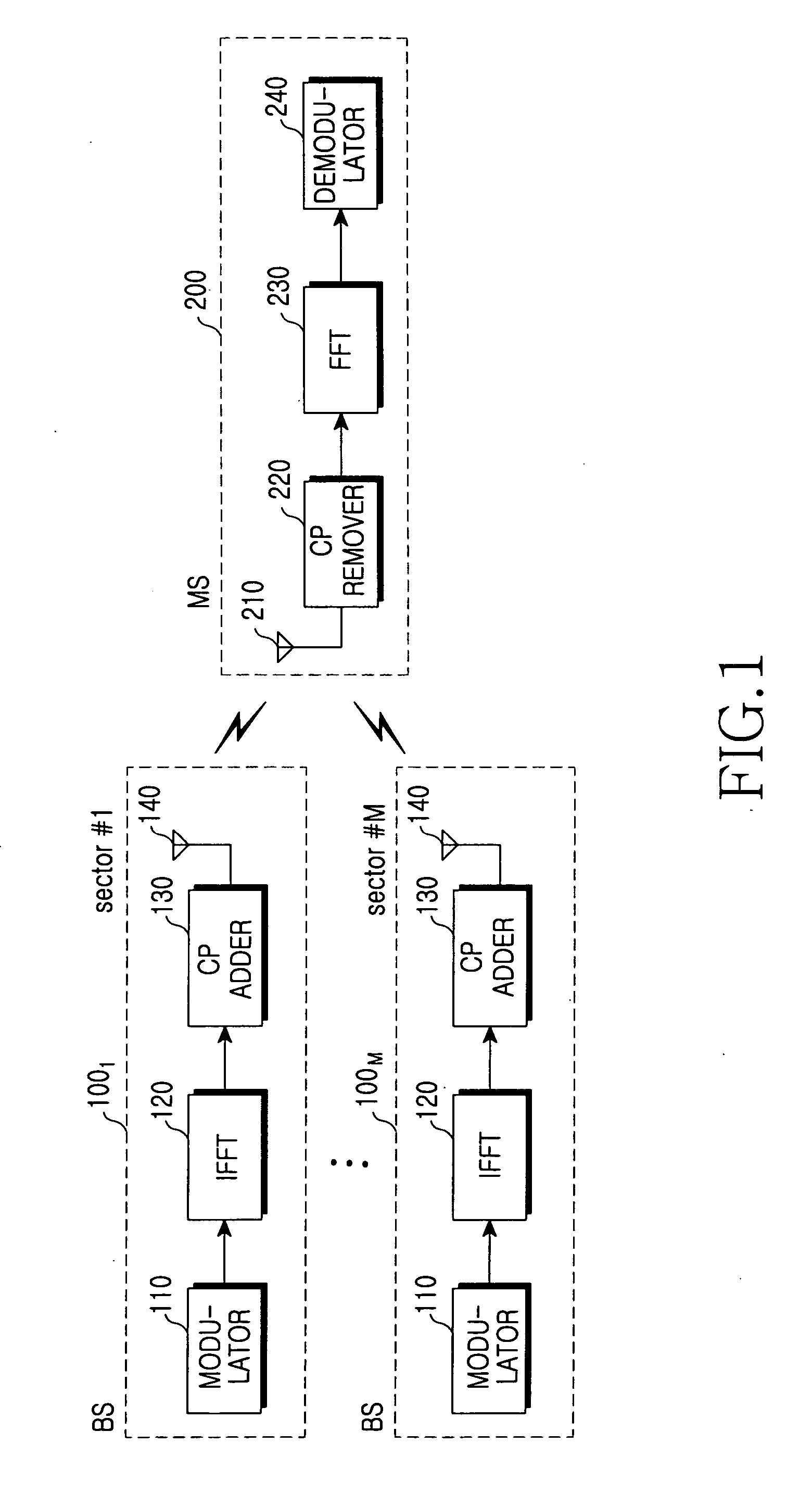
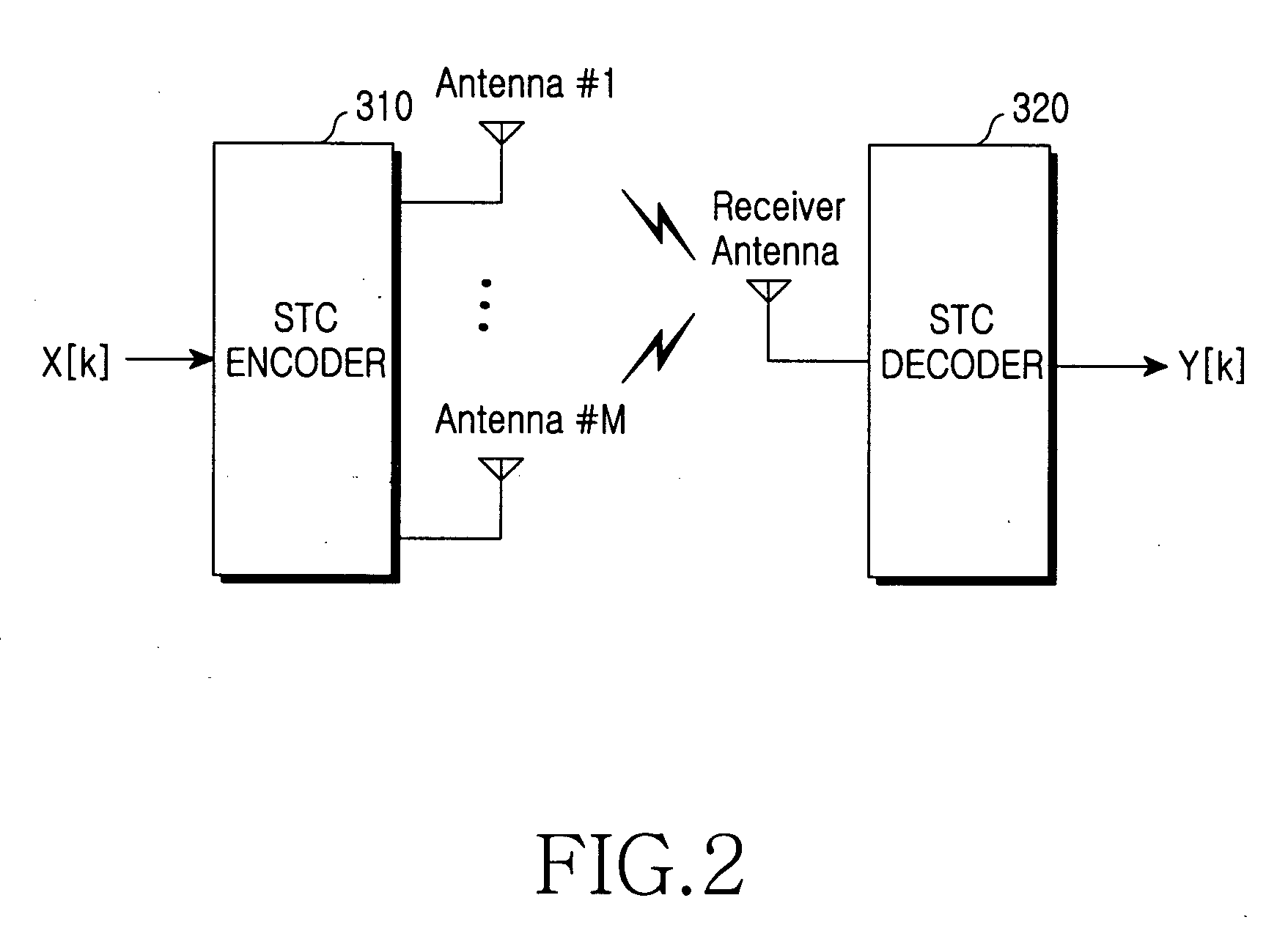
OFDM symbol transmission method and apparatus for providing sector diversity in a mobile communication system, and system using the same
InactiveUS20050286462A1Improved sector diversitySite diversityRadio/inductive link selection arrangementsOriginal dataMobile station
An orthogonal frequency division multiplexing (OFDM) system with a multicell or multisector structure includes a plurality of base stations and mobile stations. Each of the base stations interleaves data for transmission to the mobile station, performs space-time coding (STC) on the interleaved data into a plurality of space-time code streams, selects one of the space-time code streams every predetermined code stream selection period such that different space-time code streams are transmitted to at least one cell or sector from among cells or sectors formed by the base station and other base stations, and outputs the selected space-time code stream as an OFDM symbol. Each of the mobile stations STC-decodes a space-time code stream obtained by performing Fourier transform on the OFDM symbol, deinterleaves the STC-decoded data, and channel-decodes the deinterleaved data into its original data.
Owner:SAMSUNG ELECTRONICS CO LTD
Methods and systems for transceiving chaotic signals
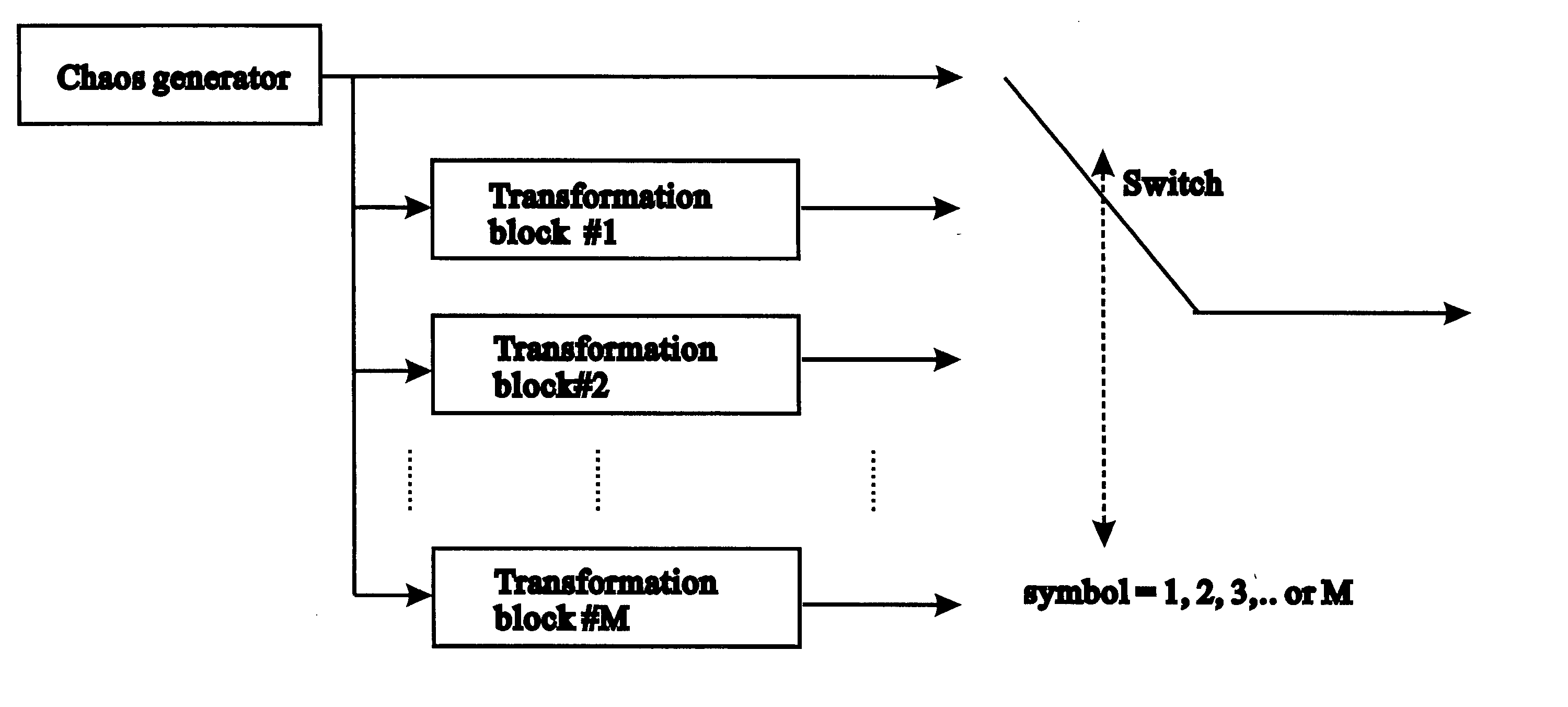
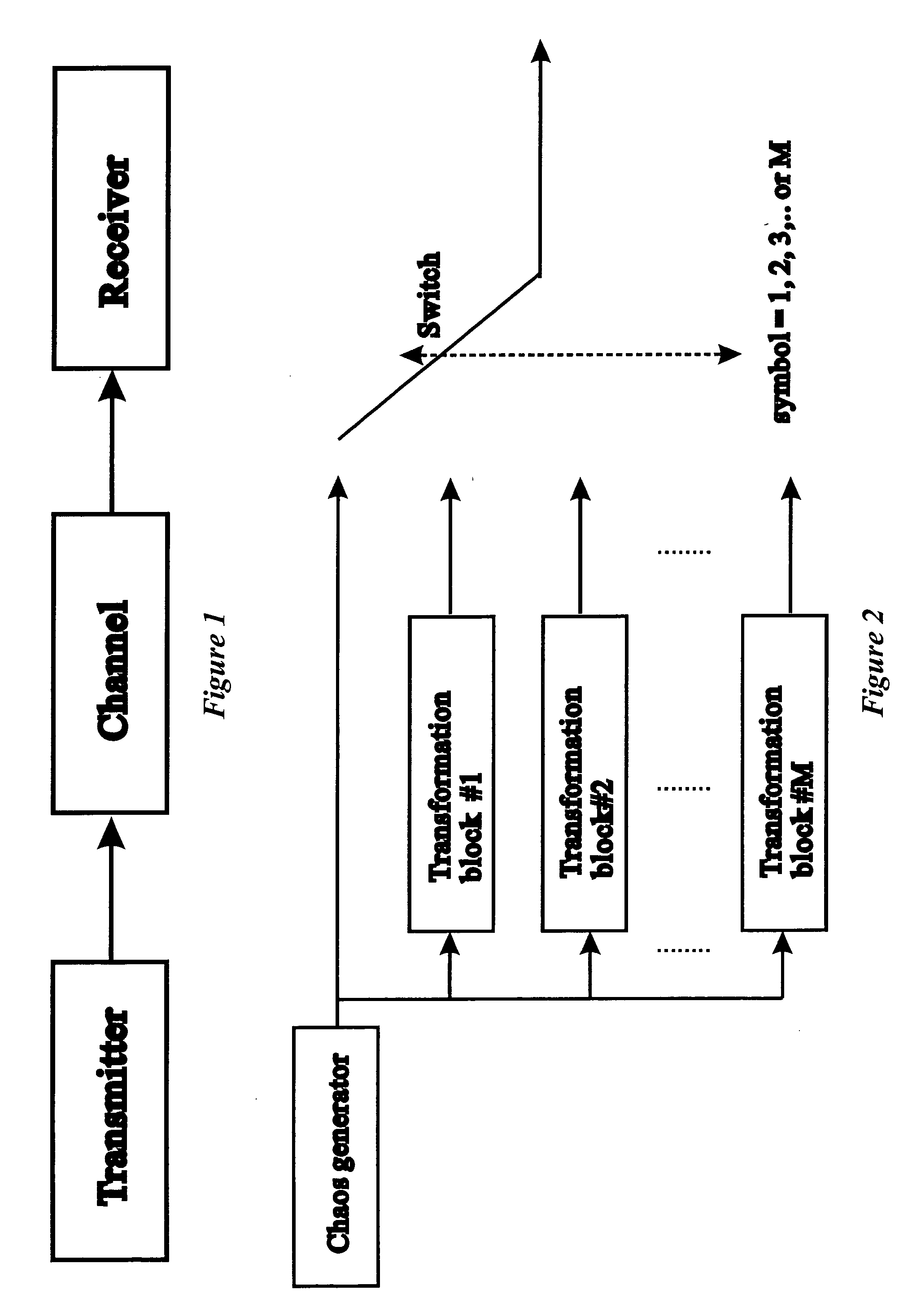
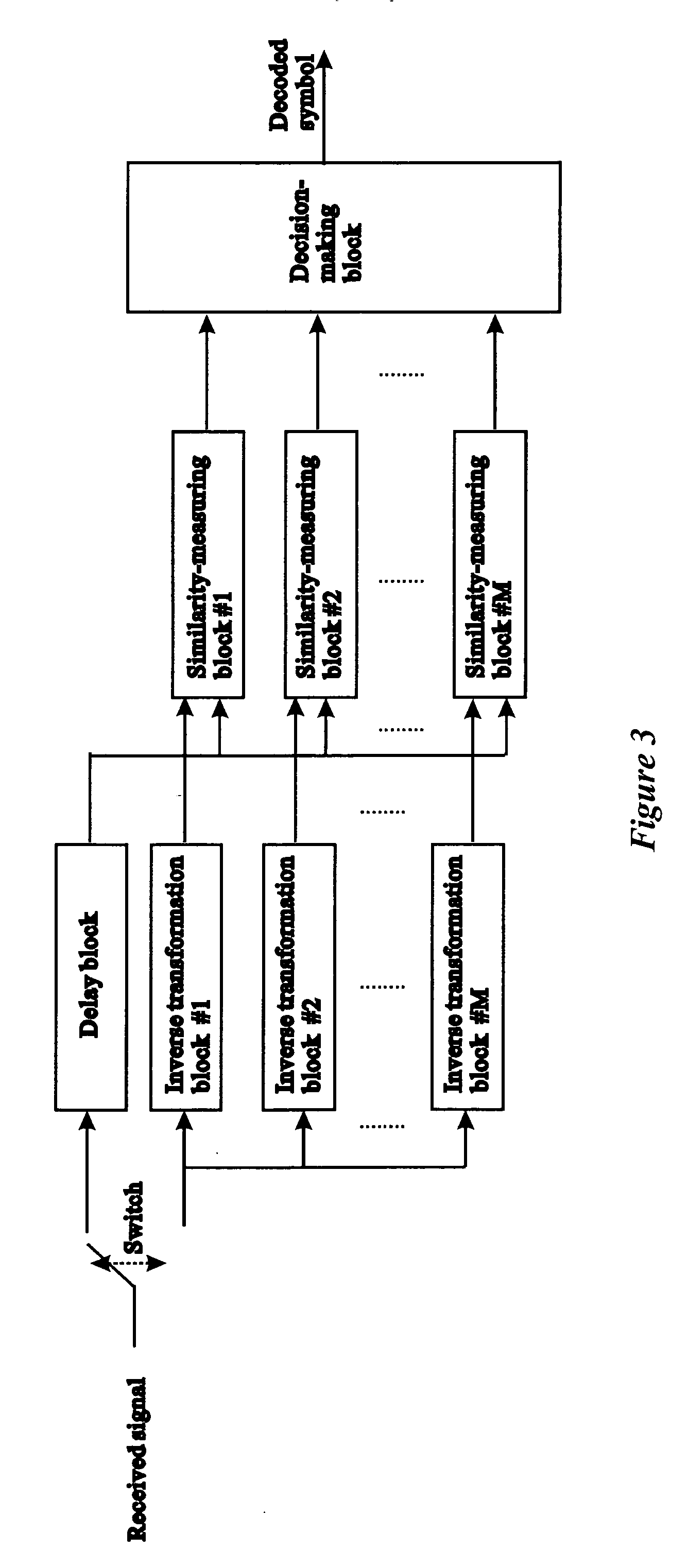
ActiveUS20050249271A1Modulated-carrier systemsSecuring communicationFrequency spectrumCommunications system
A digital communication system based on the use of chaotic carriers is disclosed. For each symbol to be sent, the transmitter sends a reference chaotic signal followed by a transformed version of the reference chaotic signal. For different symbols, different transformations are performed. Also, the transformations are designed such that the transformed versions of the reference chaotic signal do not resemble the original reference chaotic signal. As a consequence, little information can be deduced by inspecting the frequency spectrum of the transmitted signal. Moreover, even if the communication could be detected, it is difficult to decode the messages because there are numerous transformations possible.
Owner:THE HONG KONG POLYTECHNIC UNIV
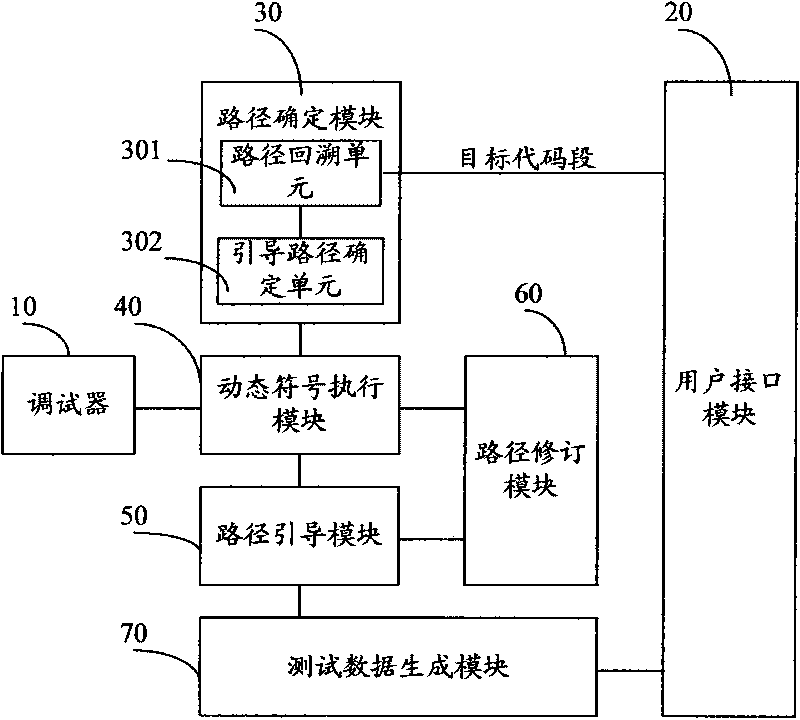
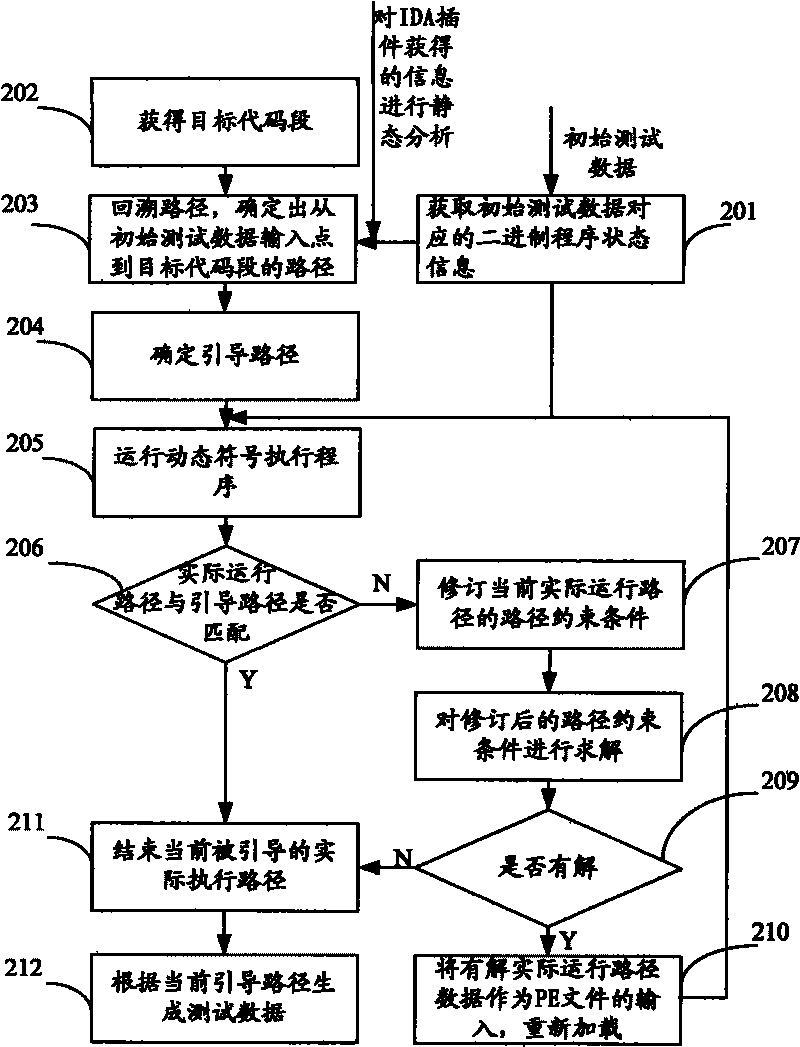
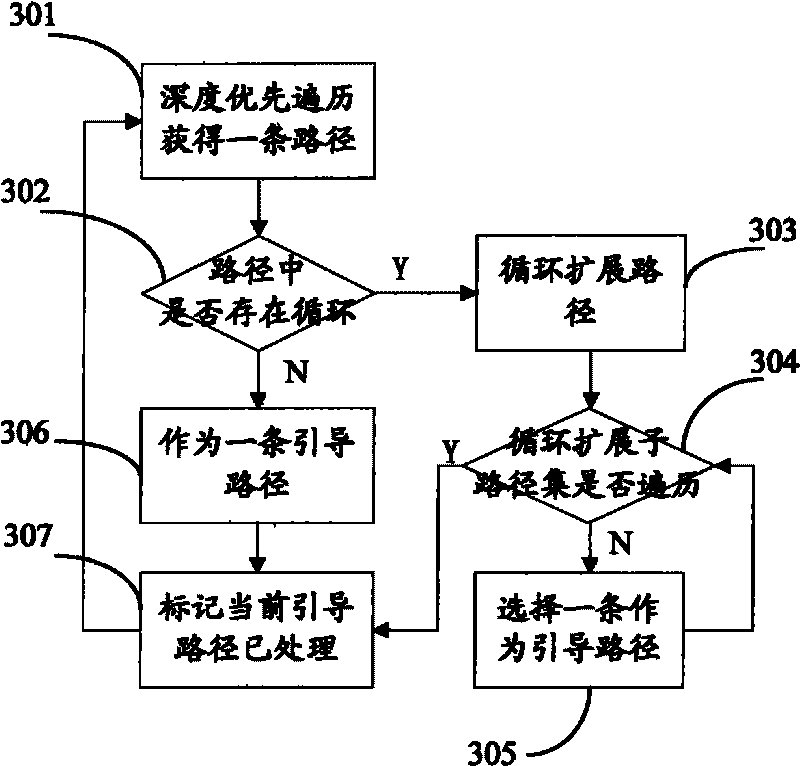
Test data generating device and method based on binary program
InactiveCN101714119AImprove effectivenessImprove accuracySoftware testing/debuggingCorresponding conditionalSensitivity analyses
The invention relates to test data generating device and method based on a binary program. The test data generating method mainly comprises the following steps of: operating a dynamic symbol executing program for the state information of the binary program which corresponds to a guide path and initial test data; obtaining corresponding conditional jump address information according to an operating result; matching an actual operation path which corresponds to the initial test data with the guide path on the basis of the obtained conditional jump address information; and generating the test data which corresponds to the actual operation path and is matched with the guide path. The invention combines the advantages of static analysis and dynamic analysis and can enhance the availability and the accuracy of symbolic execution and the accuracy degree of the generated test data and generate the test data used for carrying out path sensitivity analysis on a key code segment, thereby effectively mitigating the problem of path explosion in the symbolic execution.
Owner:BEIJING UNIV OF POSTS & TELECOMM
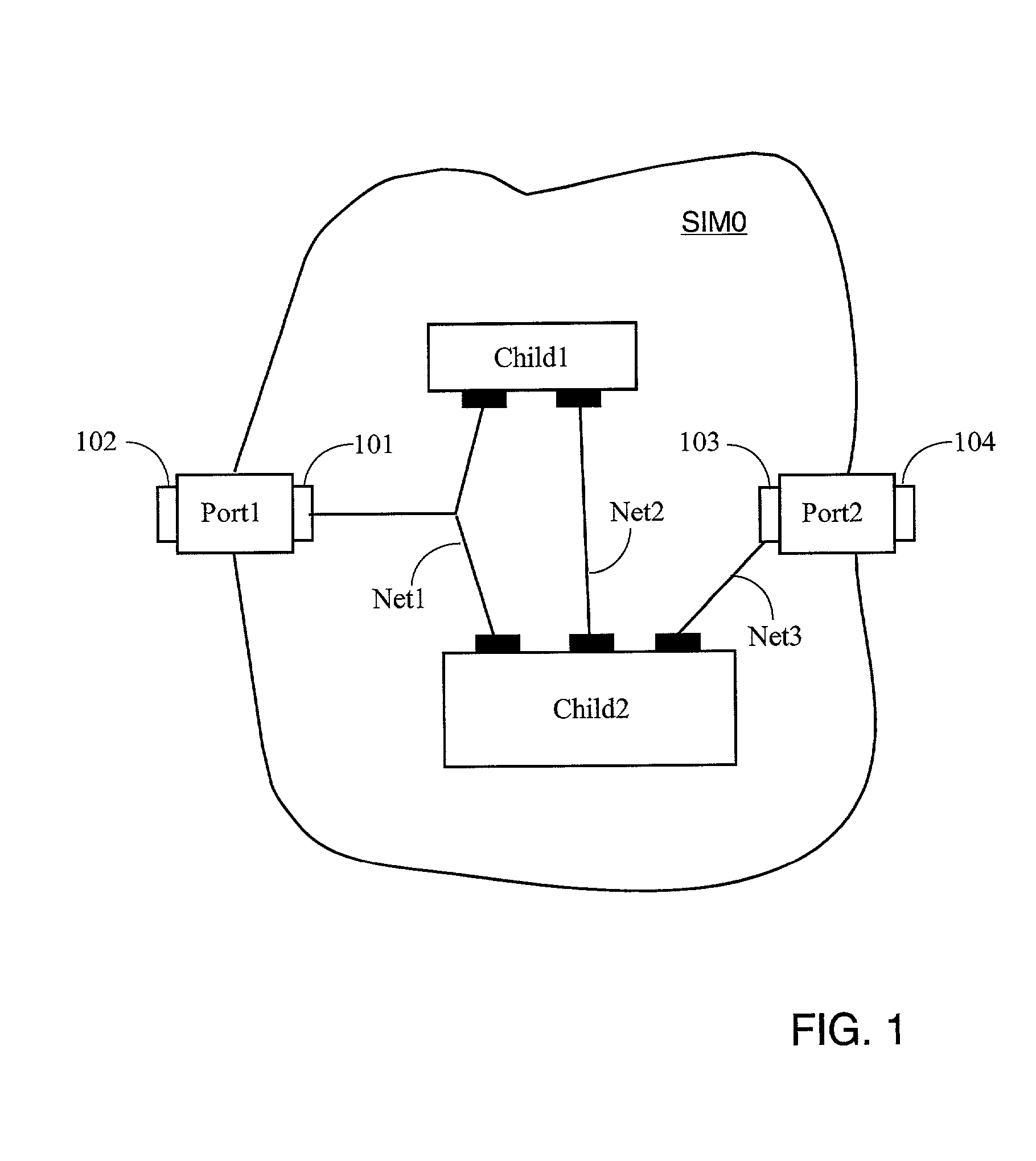
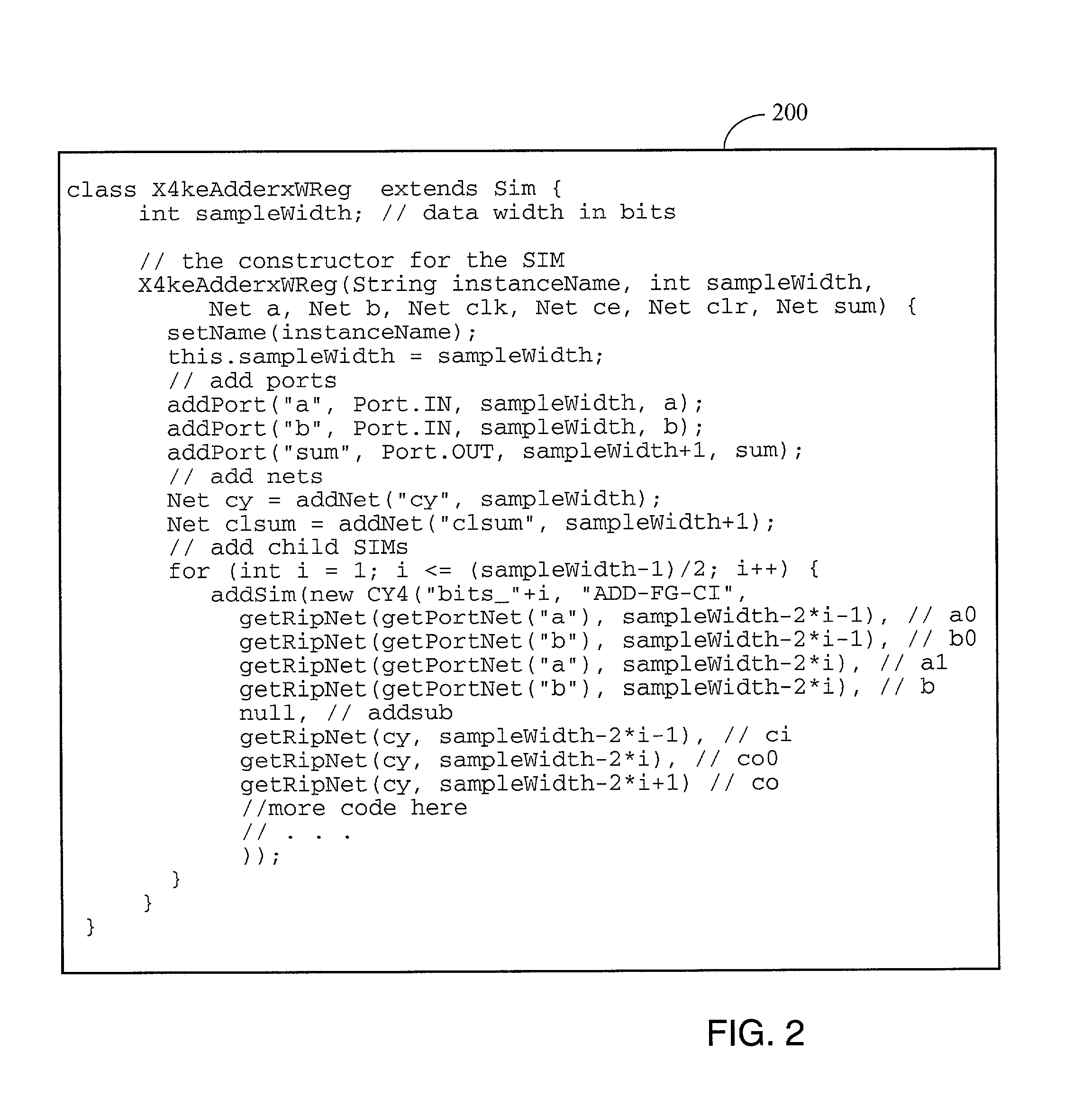
Methods and media for utilizing symbolic expressions in circuit modules
InactiveUS20010001881A1Simple designEasy to useCAD circuit designSpecial data processing applicationsProgrammable logic deviceTheoretical computer science
The invention provides parametric modules called Self Implementing Modules (SIMs) for use in programmable logic devices such as FPGAs. The invention further provides tools and methods for generating and using SIMs. SIMs implement themselves at the time the design is elaborated, targeting a specified FPGA according to specified parameters that may, for example, include the required timing, data width, number of taps for a FIR filter, and so forth. In one embodiment, the SIM parameters may be symbolic expressions, which may comprise strings or string expressions, logical (Boolean) expressions, or a combination of these data types. The variables in these expressions are either parameters of the SIM or parameters of the "parent" of the SIM. Parametric expressions are parsed and evaluated at the time the SIM is elaborated; i.e., at run-time, usually when the design is mapped, placed, and routed in a specific FPGA. The use of parametric expressions interpreted at elaboration time allows dynamic inheritance and synthesis of actual parameter values, rather than the static value inheritance commonly found in programming languages such as C++ and Java.
Owner:XILINX INC
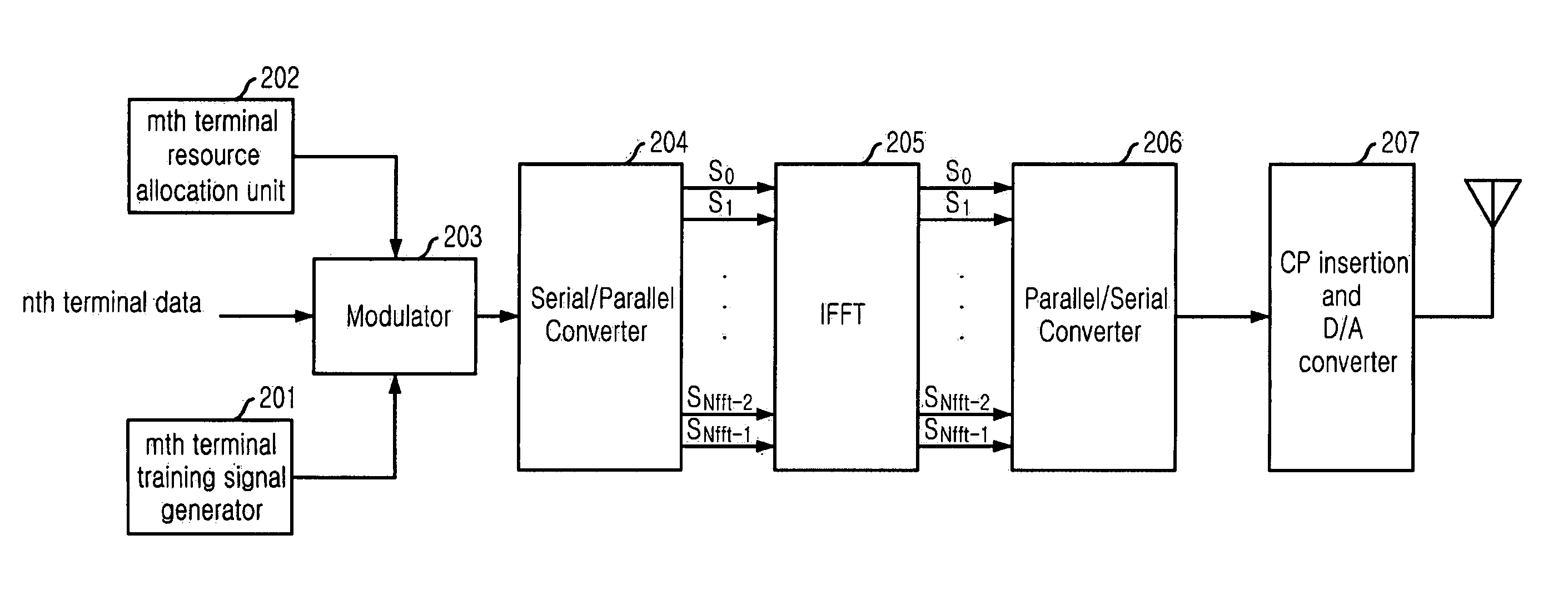
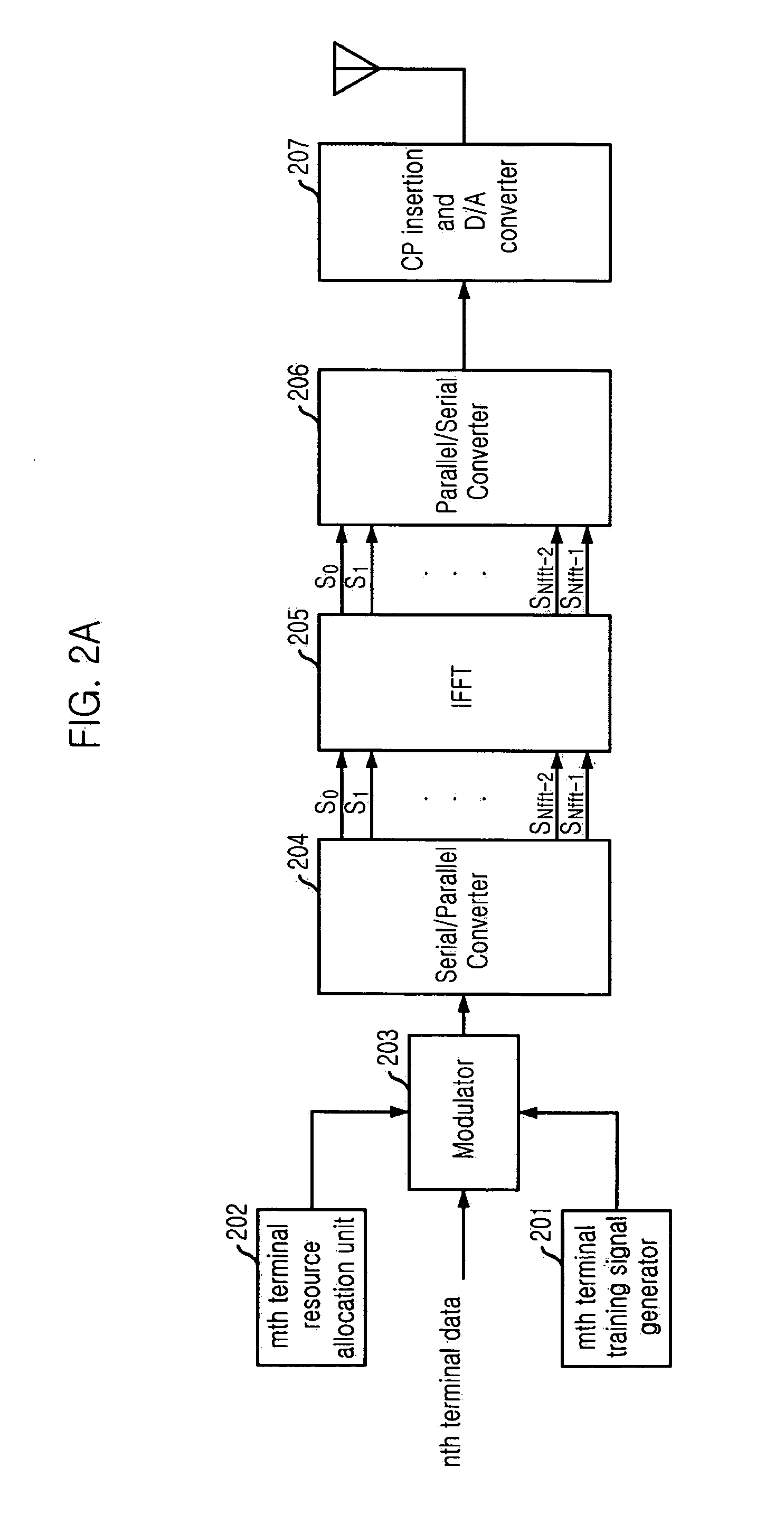
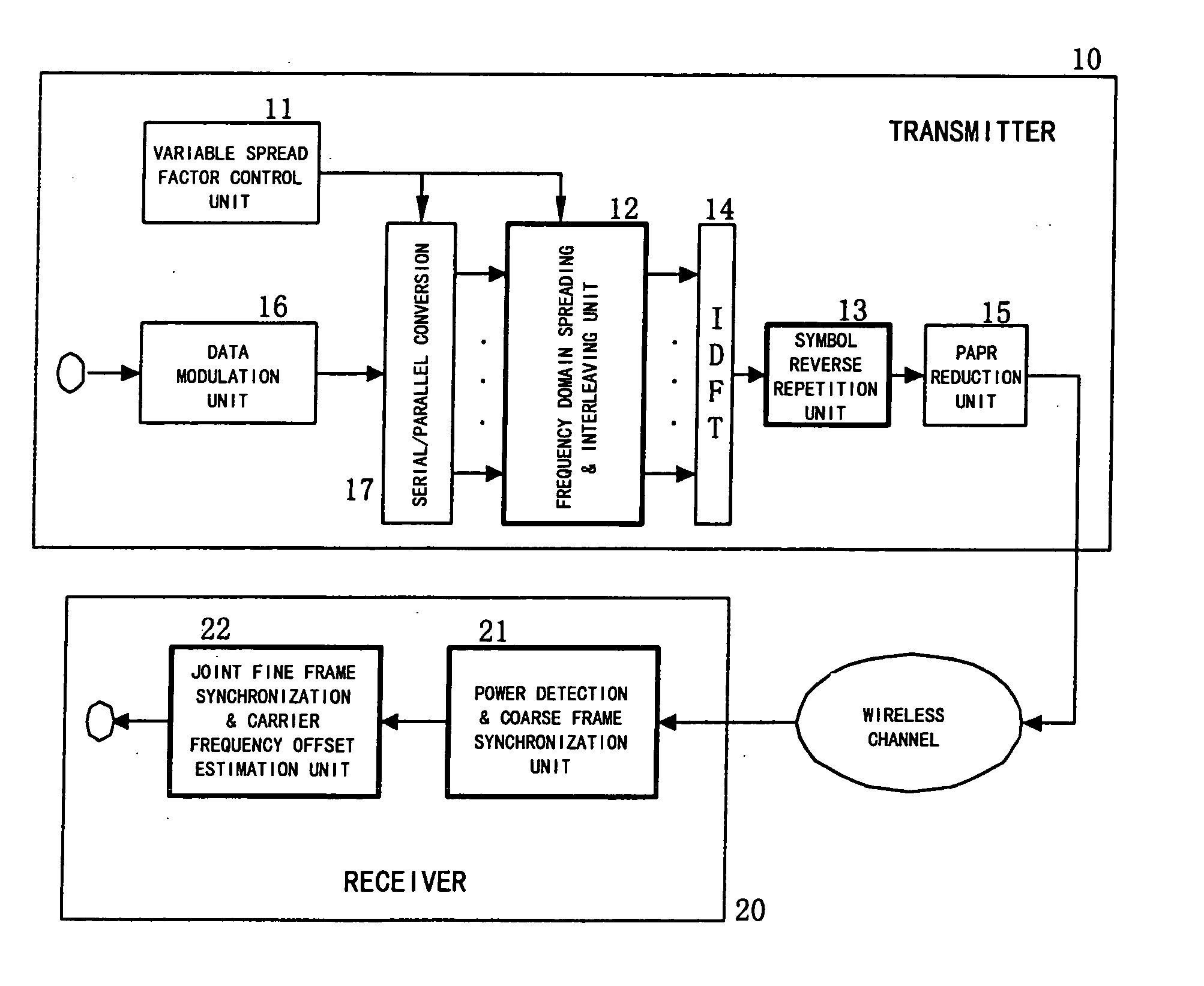
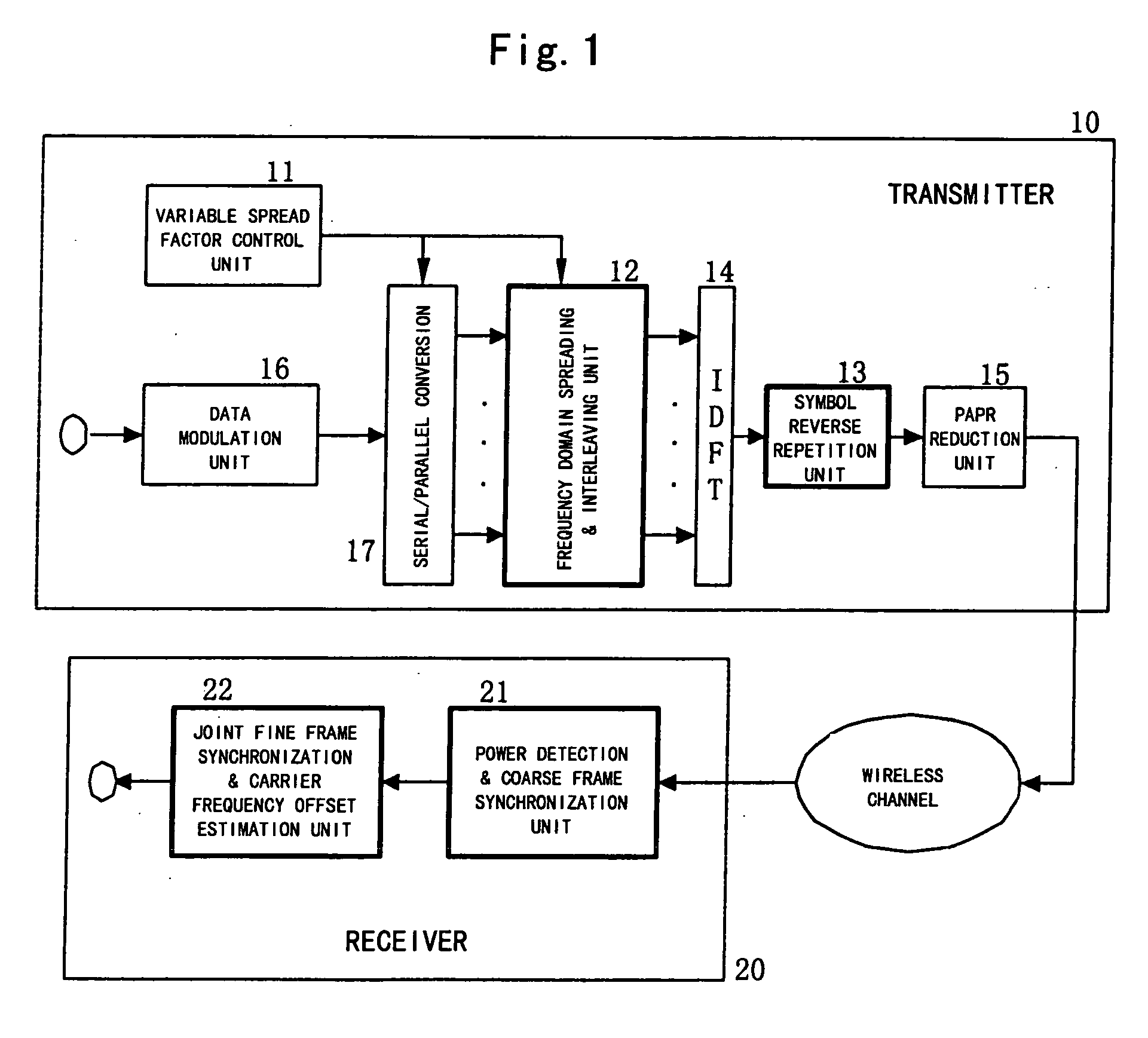
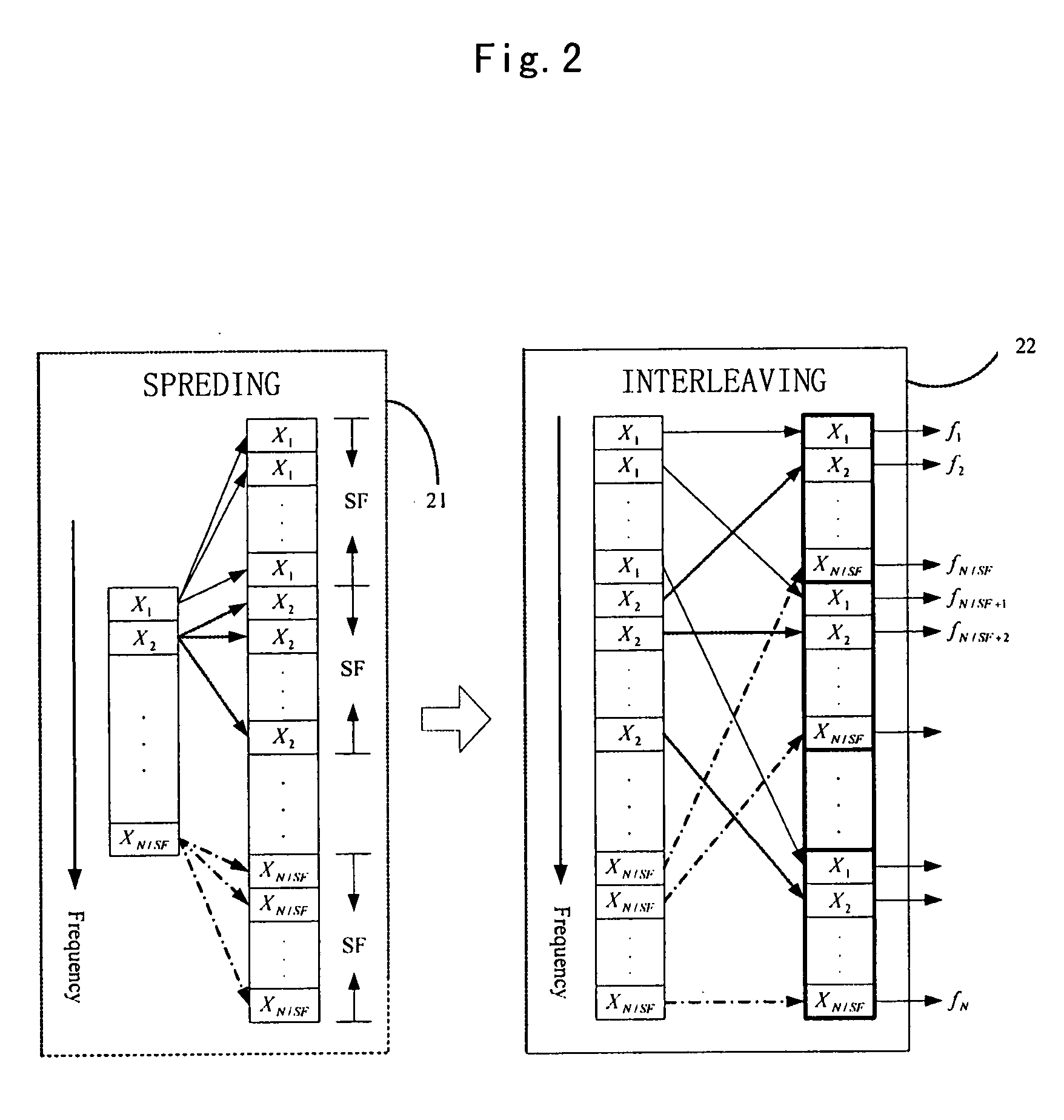
Method for joint time synchronization and frequency offset estimation in OFDM system and apparatus of the same
InactiveUS20060133526A1Improve accuracyReduce loss rateAmplitude-modulated pulse demodulationSecret communicationCarrier frequency offsetSpreading factor
Embodiments of the present invention include a method for performing joint time synchronization and carrier frequency offset estimation in a wireless communication system, comprising steps of: on a transmitter: performing frequency domain spreading and interleaving on input data by using a predetermined spreading factor (SF) to generate a frequency domain training symbol; performing Inverse Discrete Fourier Transformation (IDFT) on the generated frequency domain training symbol to generate a first time domain training symbol; reversely copying the generated first time domain training symbol to a second time domain training symbol such that a complete training sequence is formed; and on a receiver: detecting an average power of received signals to judge the coming of a training sequence, and performing coarse frame synchronization; performing joint fine frame synchronization and carrier frequency offset estimation based on a received training sequence; and compensating for the carrier frequency offset based on the carrier frequency offset estimation result so as to eliminate the carrier frequency offset. In addition, embodiments of the present invention also include an apparatus for performing joint time synchronization and carrier frequency offset estimation and a method for generating a training sequence.
Owner:THE PROCTER & GAMBLE COMPANY +1
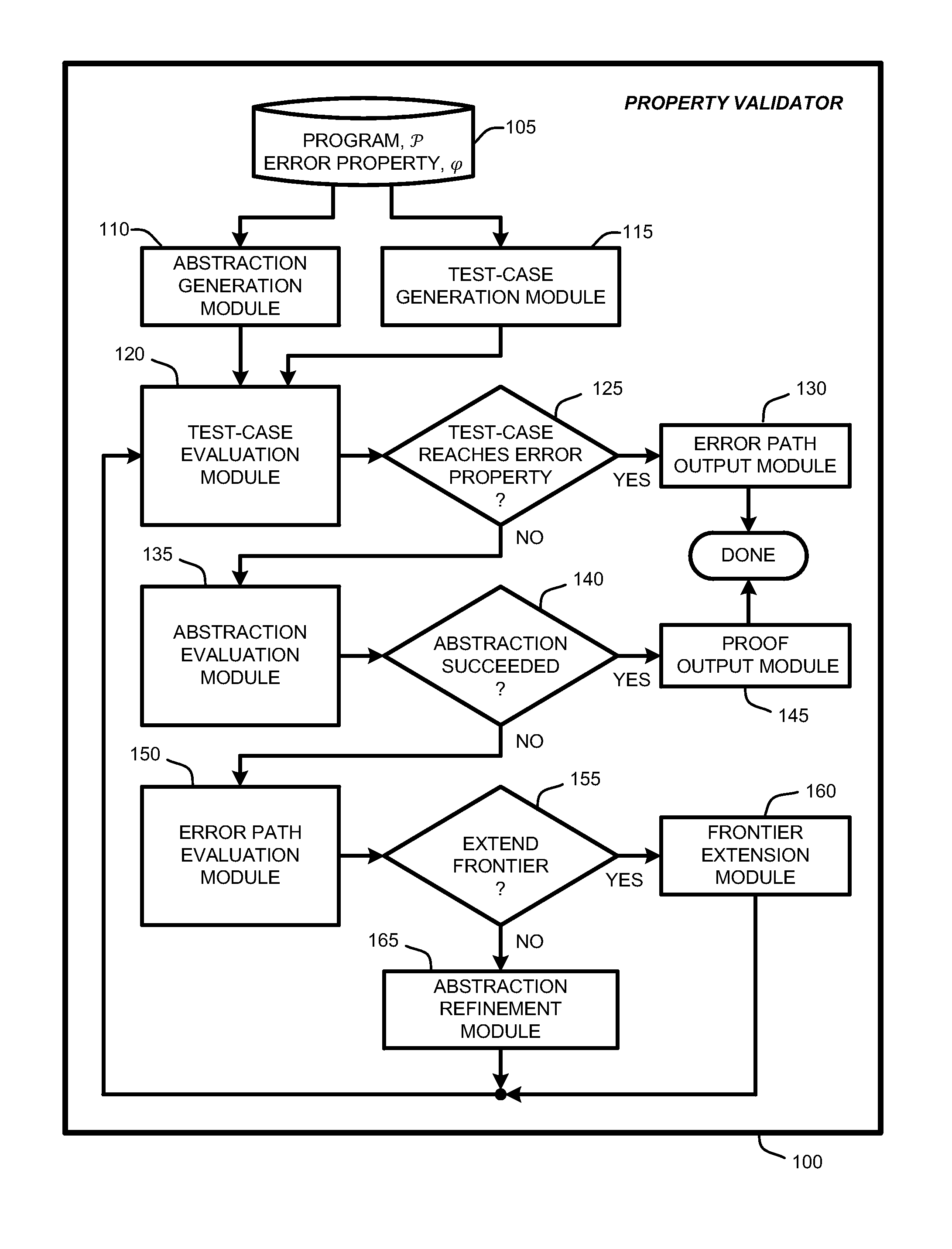
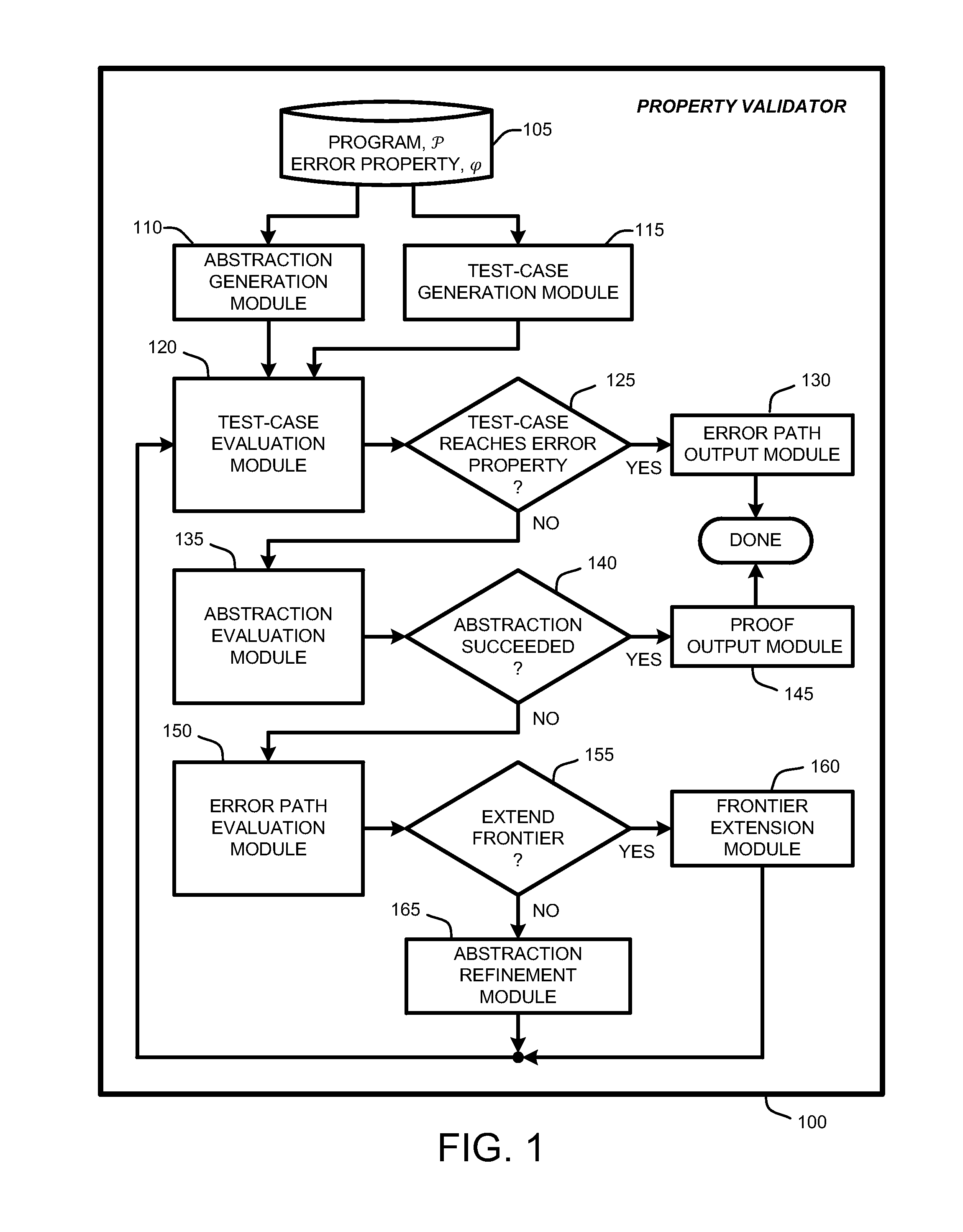
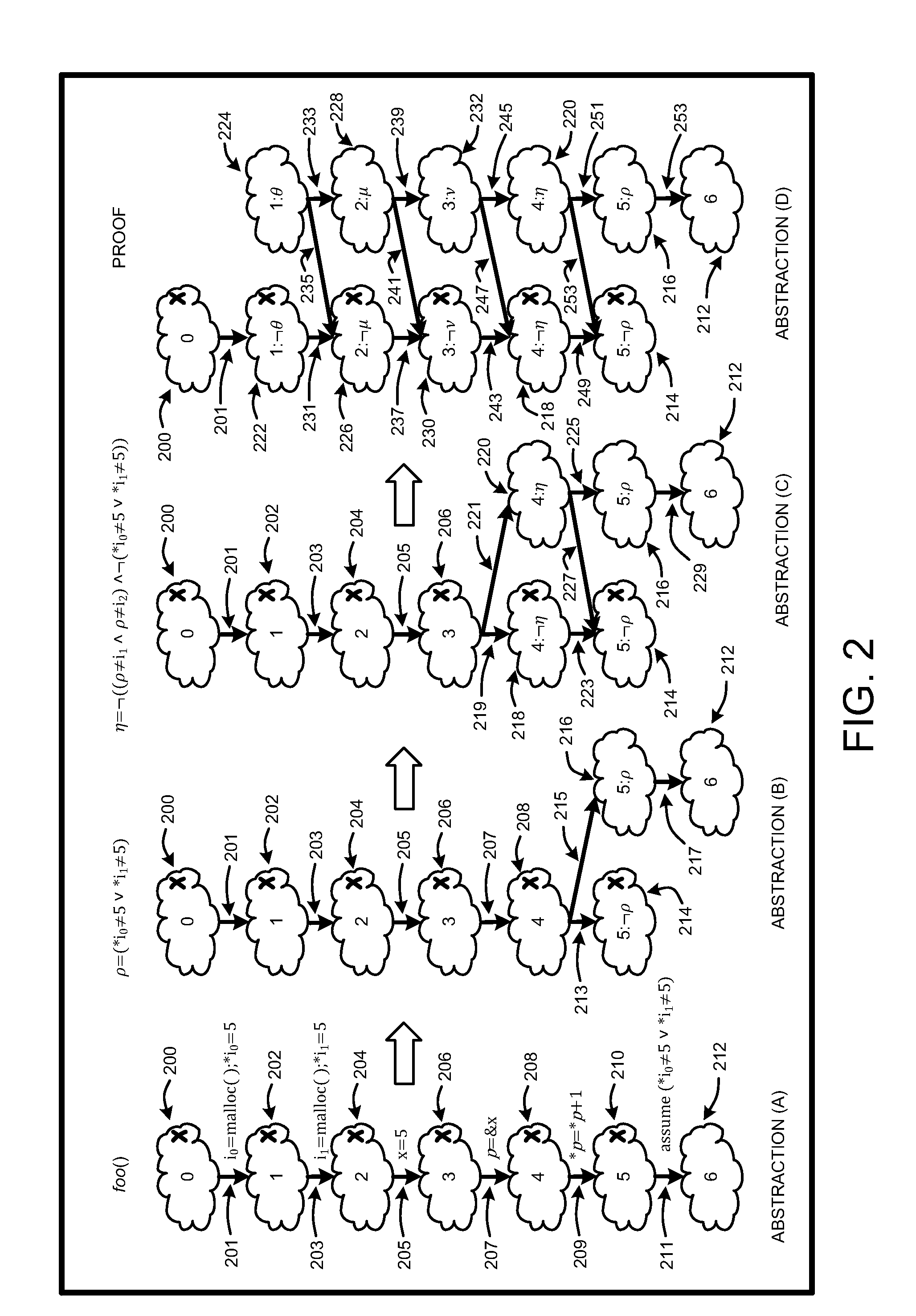
Generation and evaluation of test cases for software validation and proofs
InactiveUS20090282289A1Computationally efficientSoftware testing/debuggingState spaceProgram testing
A “property checker” uses light-weight symbolic execution to prove that software programs satisfy safety properties by simultaneously performing program testing and program abstraction. A simple example of safety properties includes conditions that must be satisfied for proper program execution, such as whether an application properly interfaces with API methods or functions. Program tests are an “under-approximation” of program behavior, and abstractions are an “over-approximation” of the program. This simultaneous testing either finds a test-case that reaches an error state, or finds an abstraction showing that no path in the state space of the program can reach any error state. If a test-case reaches an error state, the property checker has discovered a violation of the safety property. Conversely, if no path in the state space can reach any error state, the property checker has proved that the program satisfies the desired safety property.
Owner:MICROSOFT TECH LICENSING LLC
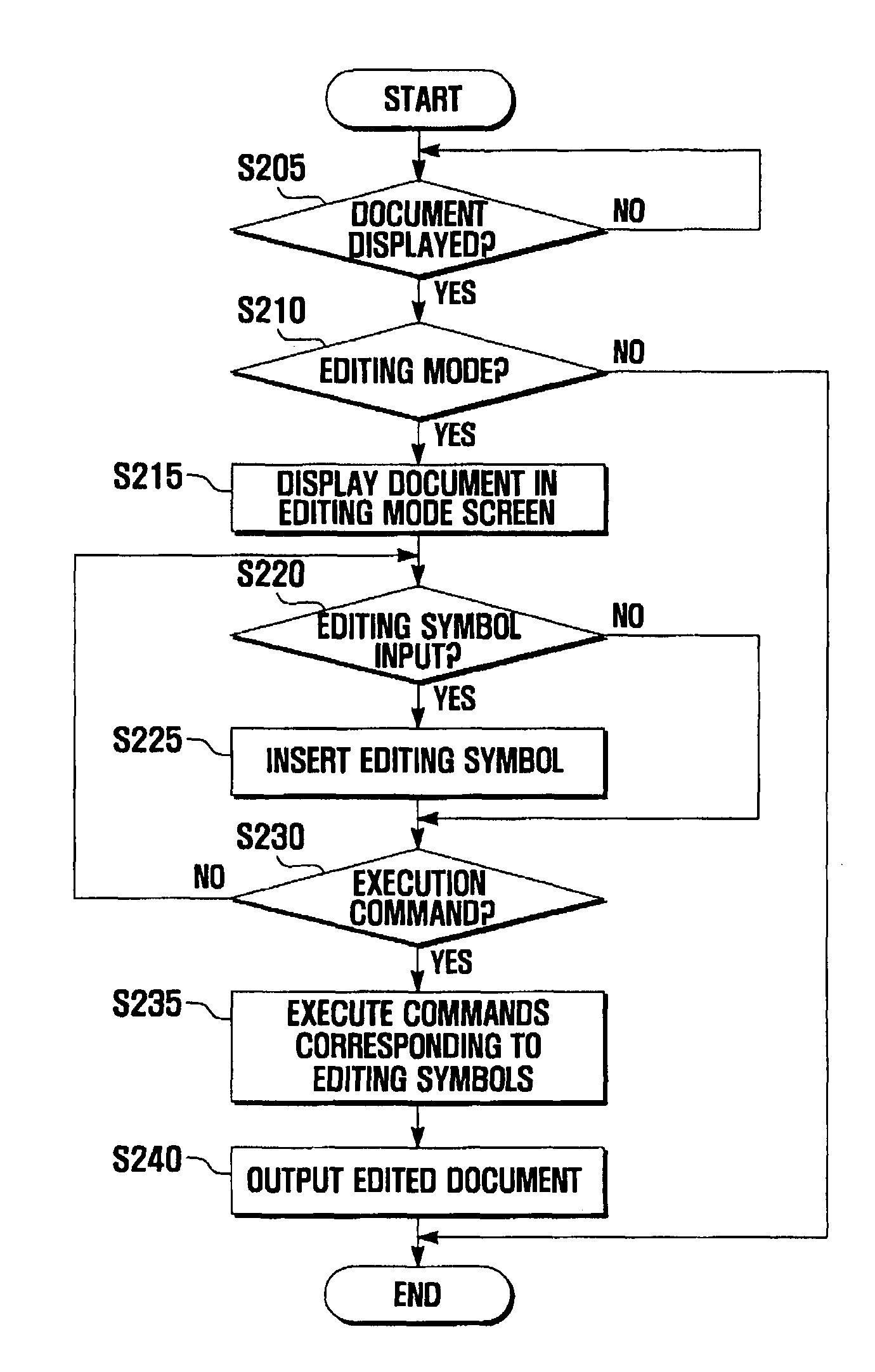
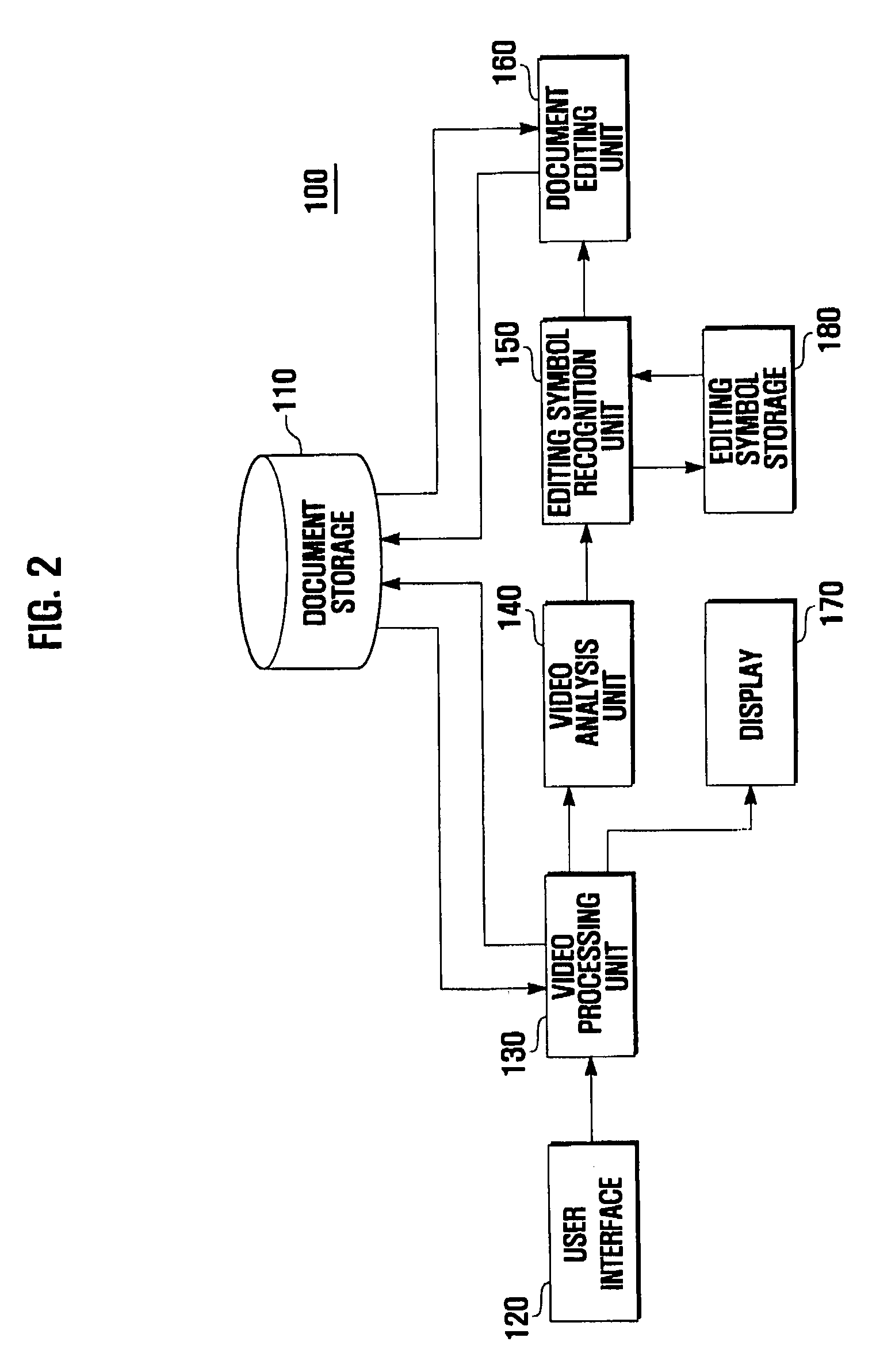
Touch screen-based document editing device and method
InactiveUS8042042B2Facilitates editing of a documentIncrease distanceNatural language data processingSpecial data processing applicationsComputer graphics (images)Paper document
Owner:SAMSUNG ELECTRONICS CO LTD
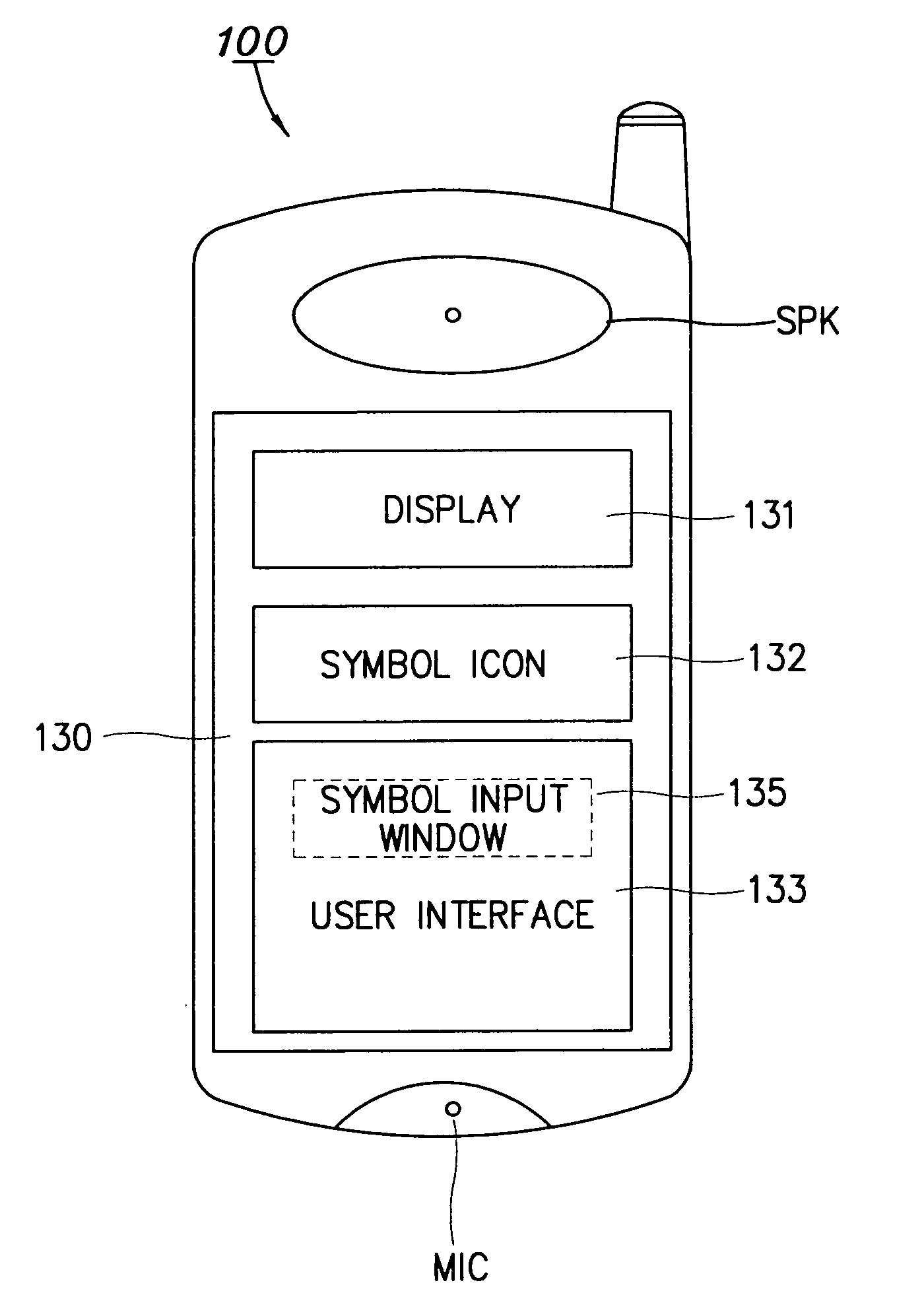
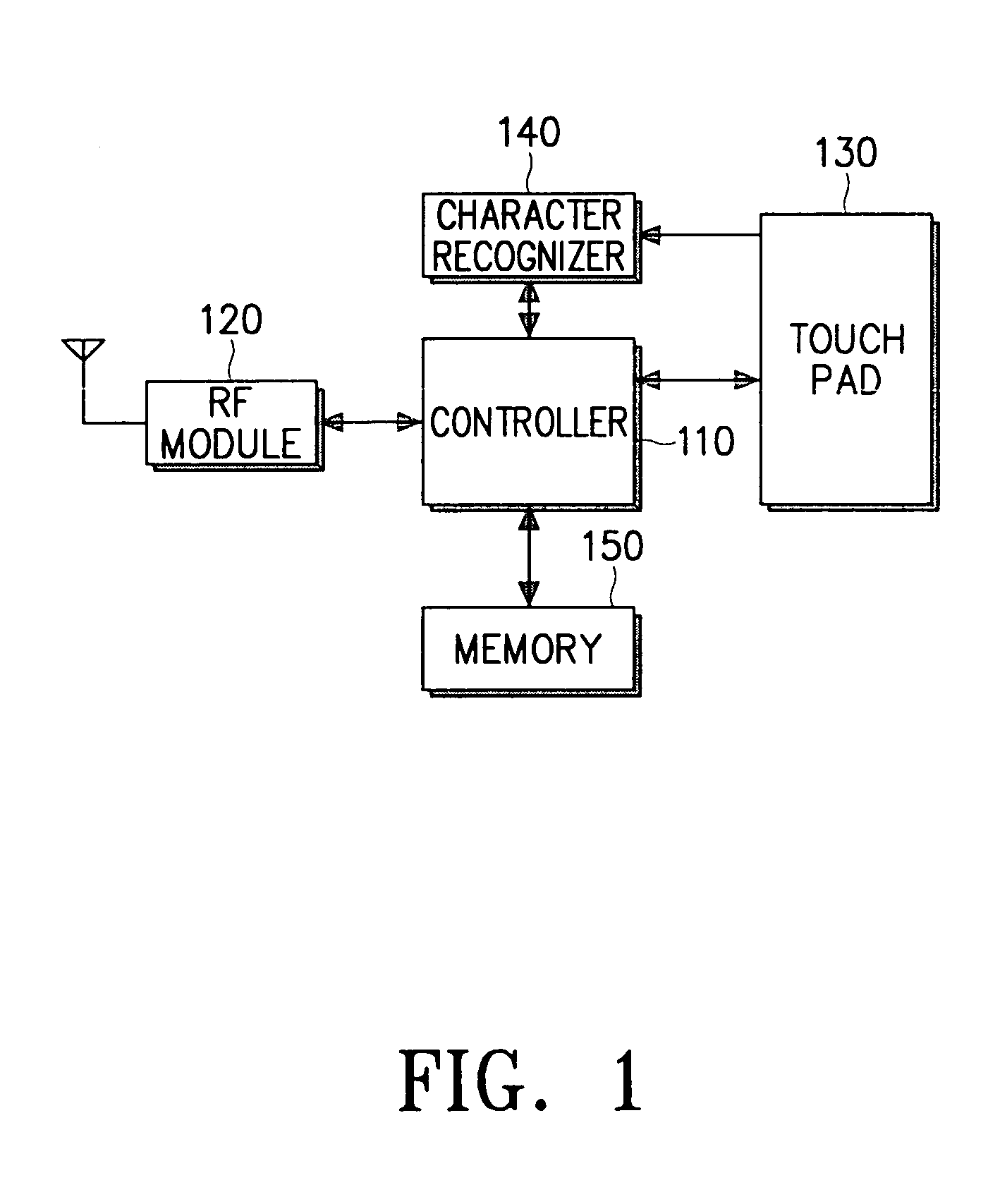
Speed dialing method using symbols in communication terminal having touch pad
InactiveUS7020269B1Subscriber signalling identity devicesAutomatic exchangesTouchpadArtificial intelligence
A method for performing speed dialing using symbols in a communication terminal having a touch pad is disclosed. The method comprises registering a symbol in association with a phone number; comparing a symbol input by a user from the touch pad with the registered symbol; and reading, when the input symbol is identical to the registered symbol, said phone number registered in associated with the registered symbol and automatically dialing the read phone number. An error message, or a re-input request message, is displayed when the input symbol is not identical to a registered symbol.
Owner:SAMSUNG ELECTRONICS CO LTD
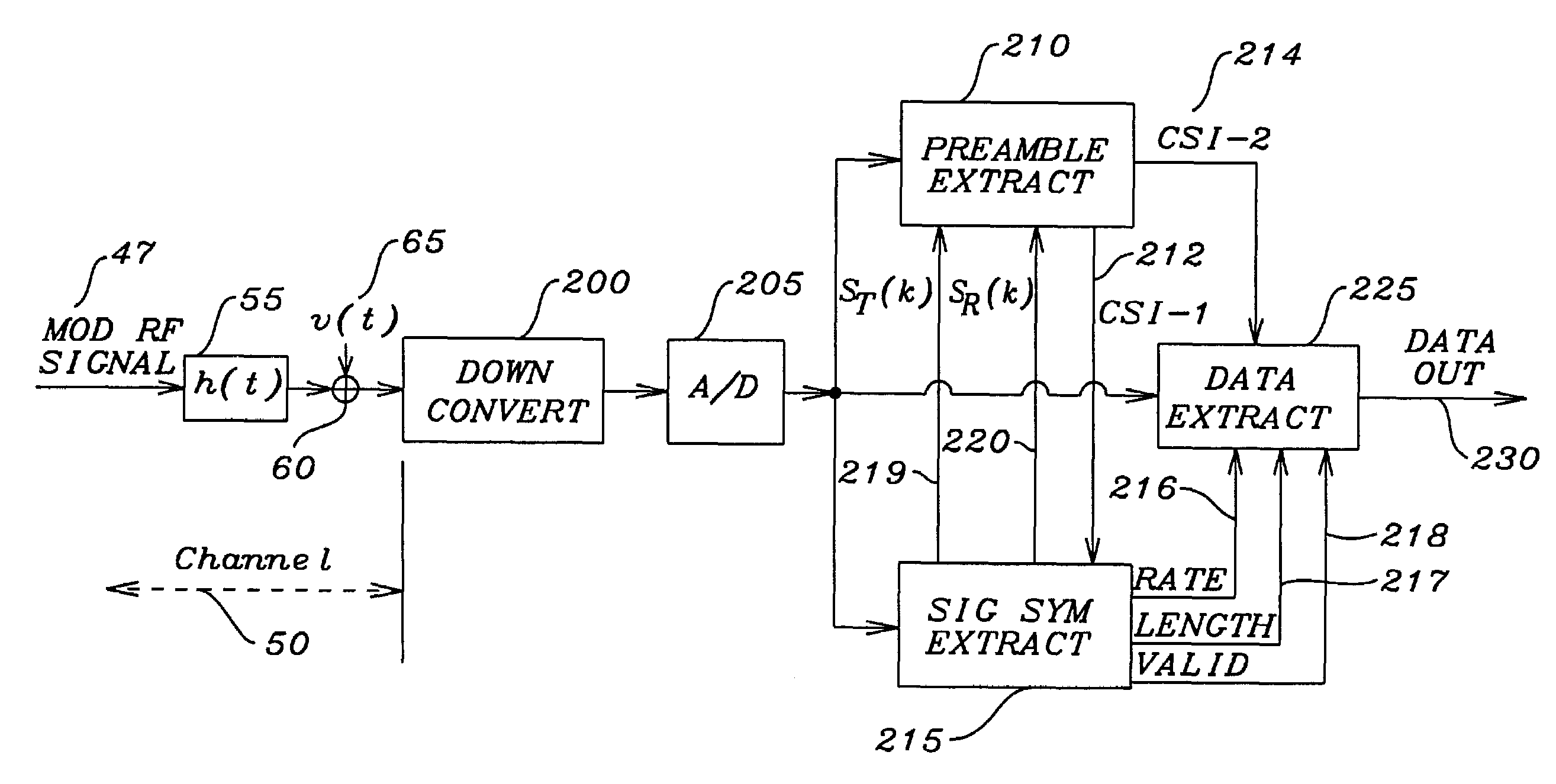
Method for reducing channel estimation error in an OFDM system
InactiveUS7260055B2Error preventionFrequency-division multiplex detailsChannel state informationVirtual training
A method for channel response estimation for an OFDM communication system based on a certain normal training symbols plus one virtual training symbol begins with receiving at least one preamble symbol of a transmitted data frame. A first channel state information is estimated from the at least one preamble symbol. At least one signalling symbol is then received and equalized and a rate factor and a length factor are extracted from the at least one signalling symbol. A virtual training symbol is formed from the rate factor and the length factor. A second channel state information is estimated from the at least one preamble symbol and the virtual training symbol. The data symbols are equalized by performing channel correction on data symbols with the second channel estimation and pilot sub-carriers in each of the plurality of data symbols.
Owner:AGENCY FOR SCI TECH & RES
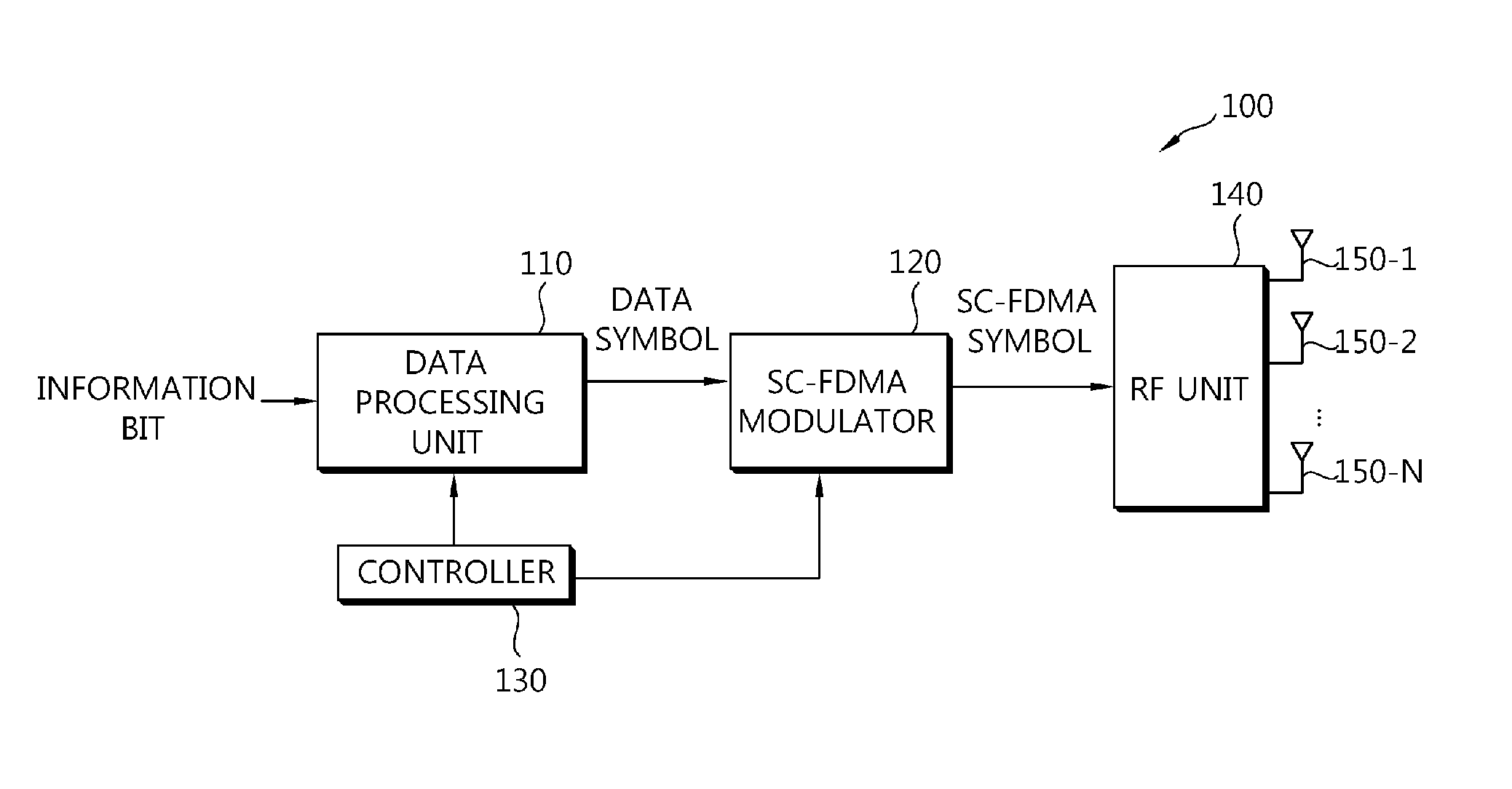
Apparatus and method for data transmission in sc-fdma system with multiple antennas
ActiveUS20110149944A1Reduce the ratioRadio transmissionMulti-frequency code systemsCarrier signalPeak value
According to an aspect of the present invention, an apparatus for data transmission is provided. The apparatus includes a data processing unit generating a data symbol by performing channel coding and constellation mapping on an information bit, a single carrier-frequency division multiple access (SC-FDMA) modulator generating an SC-FDMA symbol by performing discrete Fourier transform (DFT) on the data symbol, by mapping the DFT performed-data symbol to subcarriers, and by performing inverse fast Fourier transform (IFFT) on the subcarrier mapped-DFT performed-data symbol, and a plurality of transmit antennas transmitting the SC-FDMA symbol. A single carrier-frequency division multiple access (SC-FDMA) system can effectively use frequency switched transmit diversity (FSTD) to reduce a peak-to-average power ratio (PAPR) and to maintain a single-carrier property.
Owner:LG ELECTRONICS INC
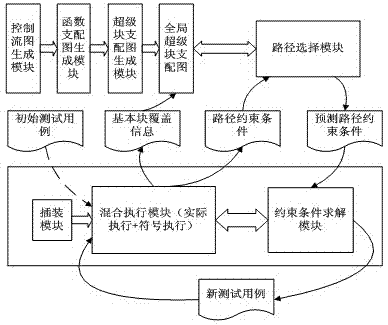
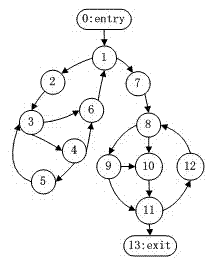
Dynamic symbolic execution method and device thereof based on overall situation super block dominator graph
ActiveCN103116540AImprove execution efficiencyAlleviate the path explosion problemSoftware testing/debuggingAlgorithmTheoretical computer science
The invention provides a dynamic symbolic execution method and a device of the dynamic symbolic execution method based on an overall situation super block dominator graph and belongs to the field of computer software testing and software security. The method is as follows: a control flow diagram of a tested executable program is obtained, and the control flow diagram is transformed to a super block dominator graph according to relevant theories of a dominance relation. Each nodal point in the super block dominator graph is marked with 'weight' which is updated before symbolic execution at each time, and the 'weight' indicates the least number of basic blocks which can be covered when the nodal point is executed. When one dynamic symbolic execution is over, the nodal point with the largest 'weight' value is selected from the super block dominator graph, and corresponding forecasting path constraint conditions are generated, and then a new testing use case is generated by solving of a solver, so that the next execution is driven. Compared with the prior art, the dynamic symbolic execution method and the device of the dynamic symbolic execution method based on the overall situation super block dominator graph are capable of covering code blocks as many as possible with least testing use cases, so that the growth rate of the code coverage rate is effectively accelerated, and the problem of path explosion is relieved. The dynamic symbolic execution method and the device of the dynamic symbolic execution method based on the overall situation super block dominator graph is of great importance for the performance of testing large-scale utility software of the dynamic symbolic execution.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Vulnerability detection system aiming at binary executable files and combining fuzz testing with symbolic execution
ActiveCN108052825ASpeed up explorationRun fastSoftware testing/debuggingPlatform integrity maintainanceData setParallel computing
The invention discloses a vulnerability detection system aiming at binary executable files and combining fuzz testing with symbolic execution, belongs to computer vulnerability detection software development technology and aims to increase detection depth and improve detection efficiency in binary file vulnerability detection scenes. The vulnerability detection system comprises a fuzzifier modulethrough optimization design, a symbolic execution module through optimization design and a fuzzifier skip symbol scheduling execution module, and a cache explorer and a task cooperation module are introduced. Advantages of fuzz testing and symbolic execution are combined for vulnerability detection of binary execution files. Evaluation experiments are conducted on the system, an application program provided by a qualification test of DARPA network challenge is adopted as a dataset, and contrast experiments are set on three objects including single fuzz testing, single symbolic execution and avulnerability mining system realized by the system. The system has remarkable effect, exploration of binary program compartment is accelerated, and running speed of the vulnerability mining system isincreased greatly.
Owner:HARBIN INST OF TECH
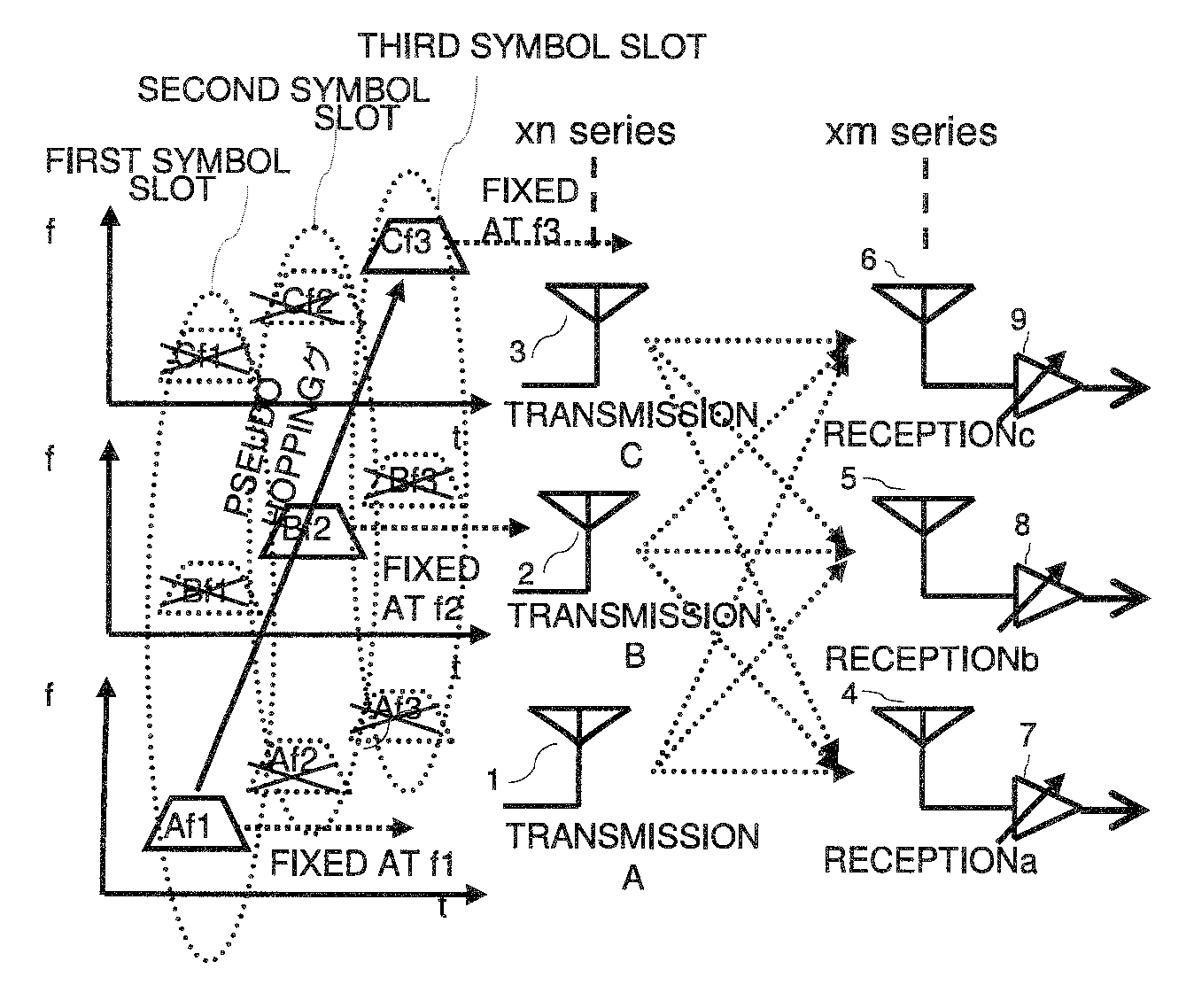
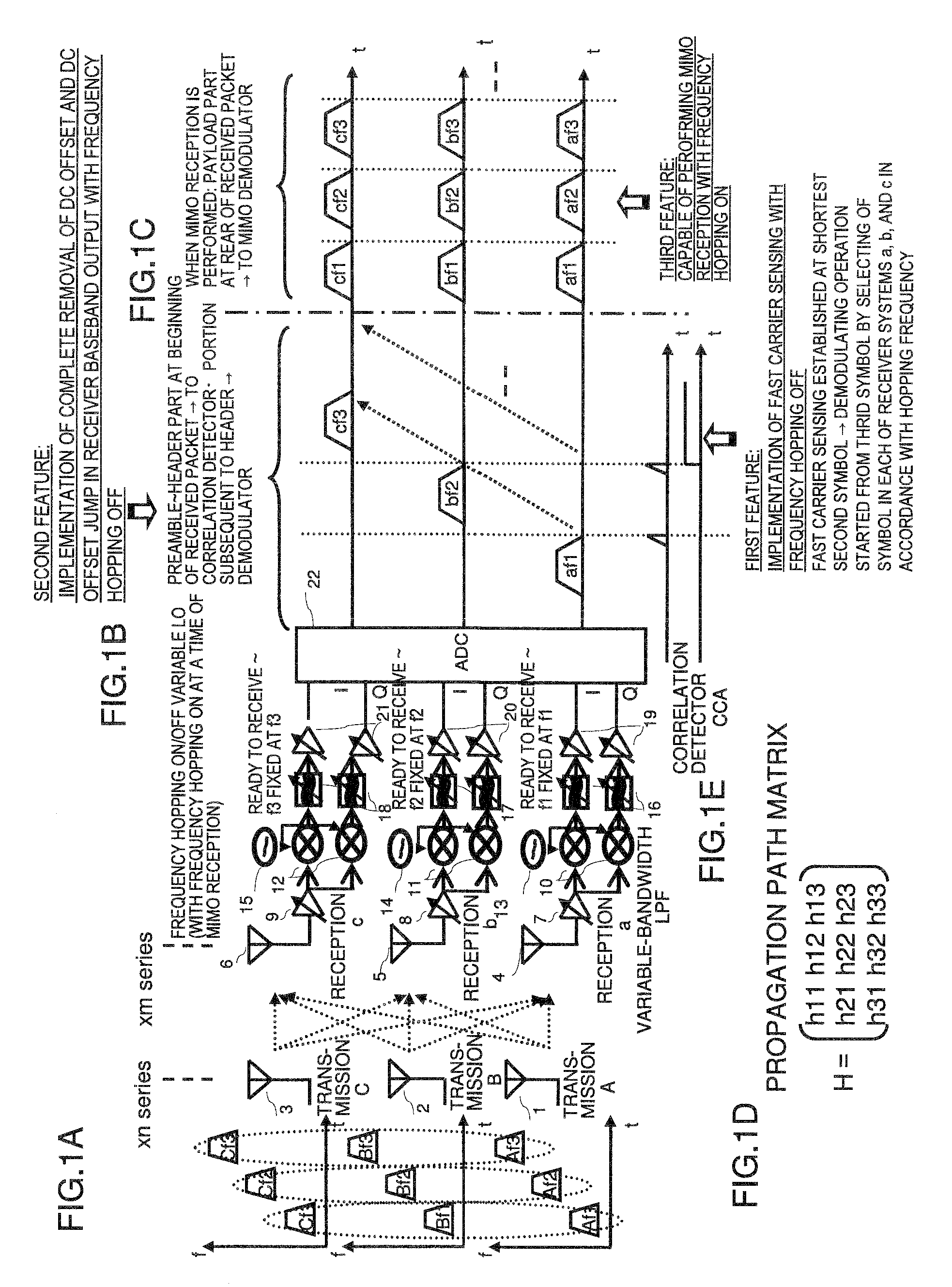
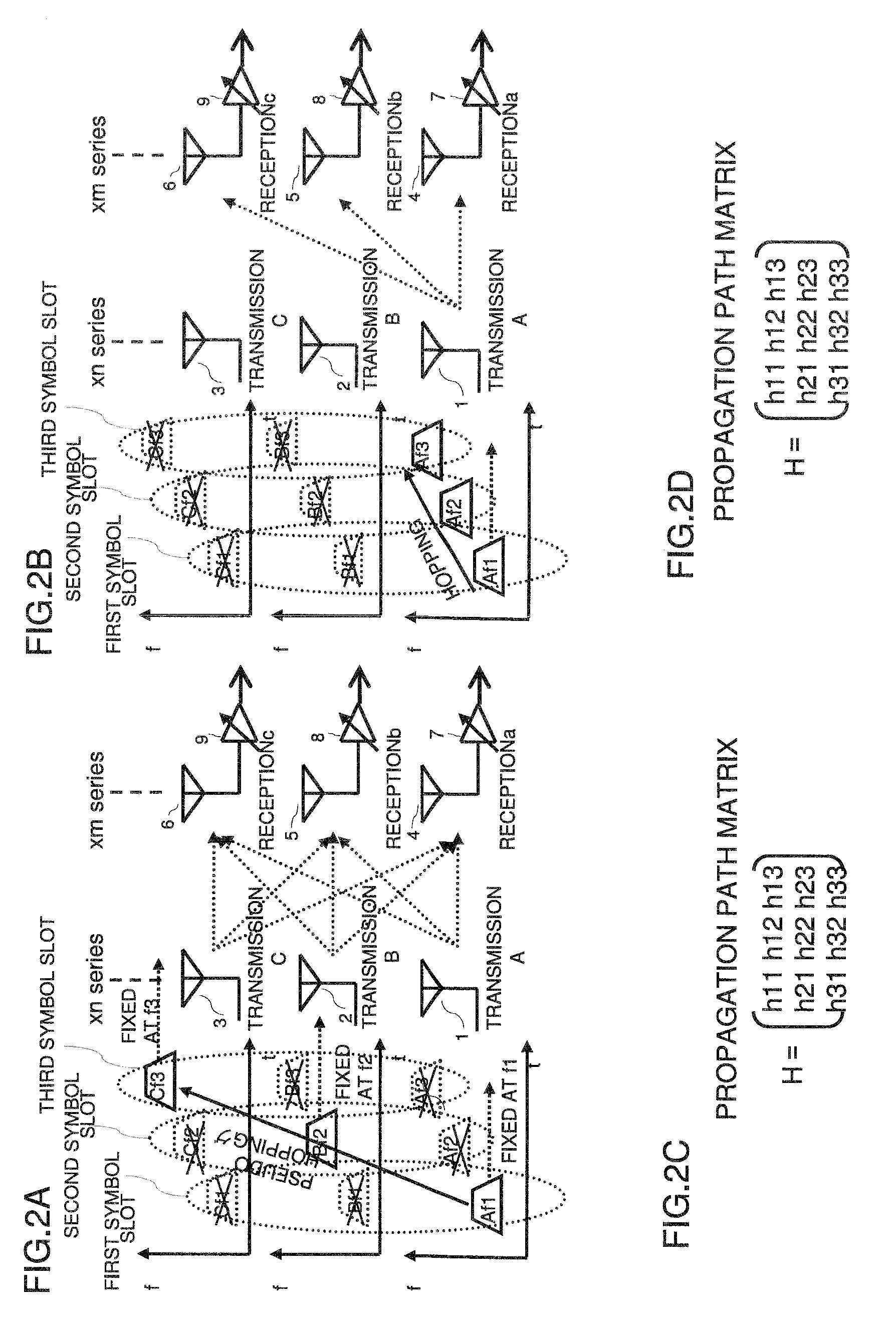
Wireless communication apparatus and a reception method involving frequency hopping
InactiveUS20090279588A1Solve the real problemIncrease speedSpatial transmit diversityModulated-carrier systemsBandpass filteringEngineering
Disclosed is a receiver of a direct conversion receiving scheme in which a packet is transmitted or received while performing frequency hopping for each symbol and demodulation is started by carrier sensing at the beginning of the packet, which performs demodulation without hopping frequencies of LOs of receiving systems to reliably execute fast carrier sensing and hopping synchronization at the beginning of the packet and remove the DC offset jump. At a time of demodulation of a payload part, the frequencies of LOs of the receiving system are hopped to allow a transition of MIMO. Further, by concurrently using complex bandpass filters while fixing all the LOs at a center LO frequency, complete removal of the DC offset jump over the entire length of the packet and MIMO can be simultaneously implemented.
Owner:RENESAS ELECTRONICS CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com