Patents
Literature
68results about How to "Eliminates and reduces of disadvantage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
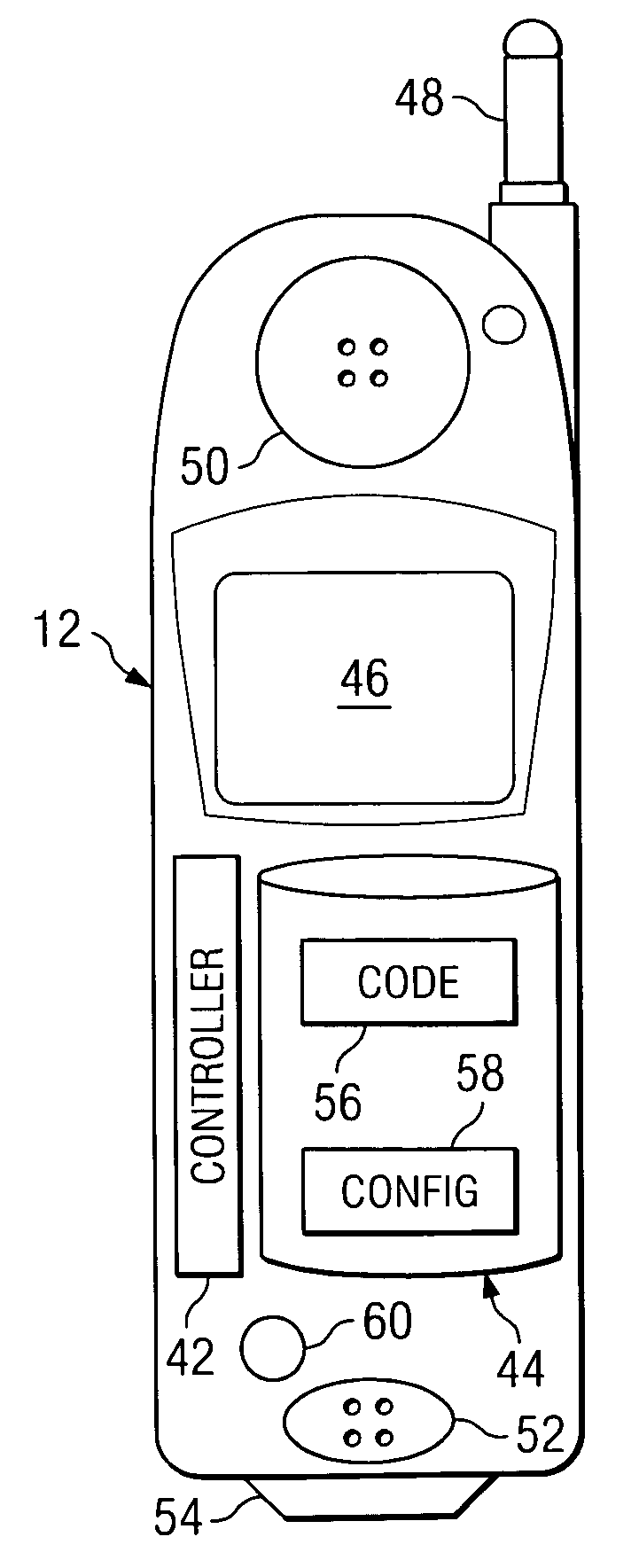
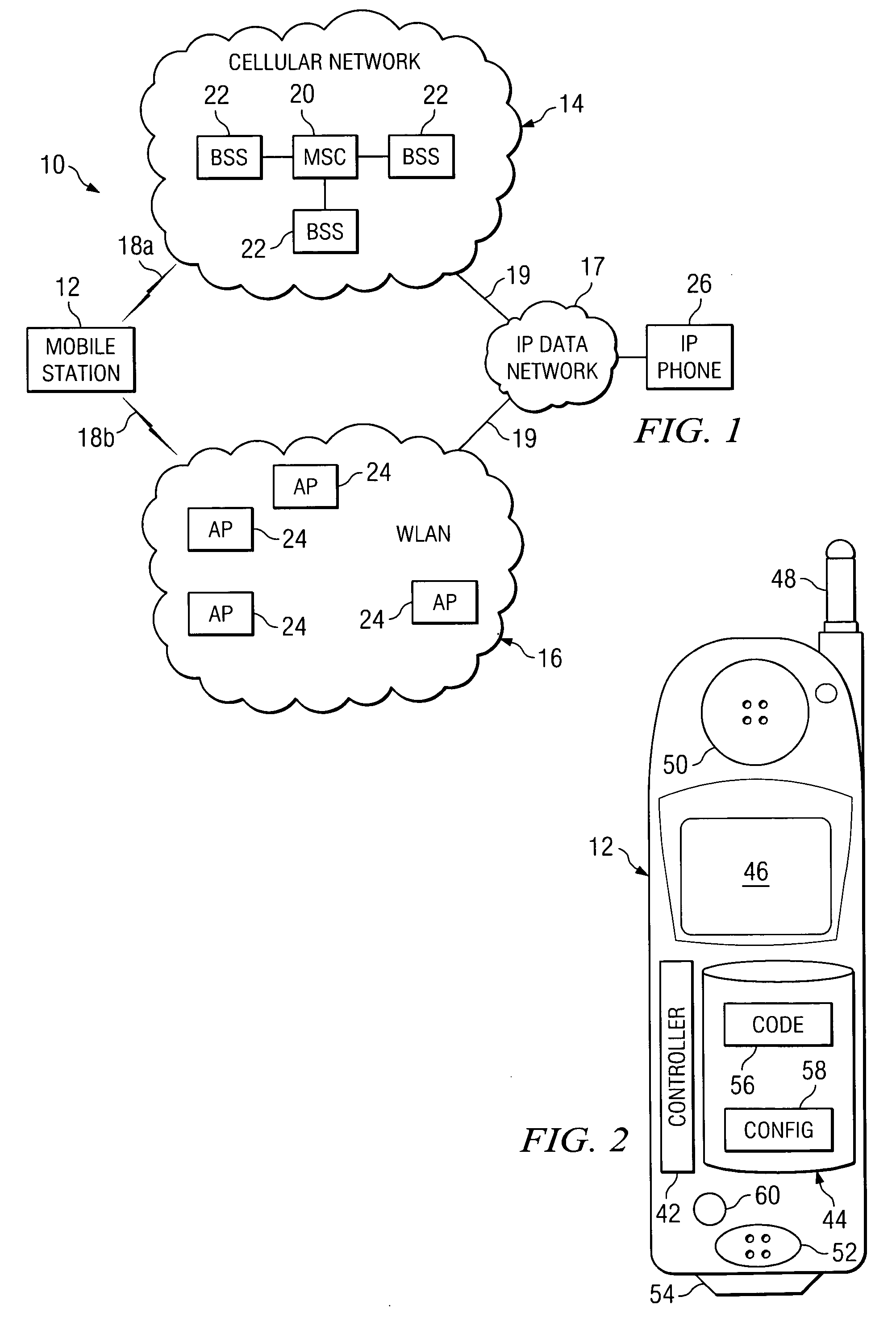
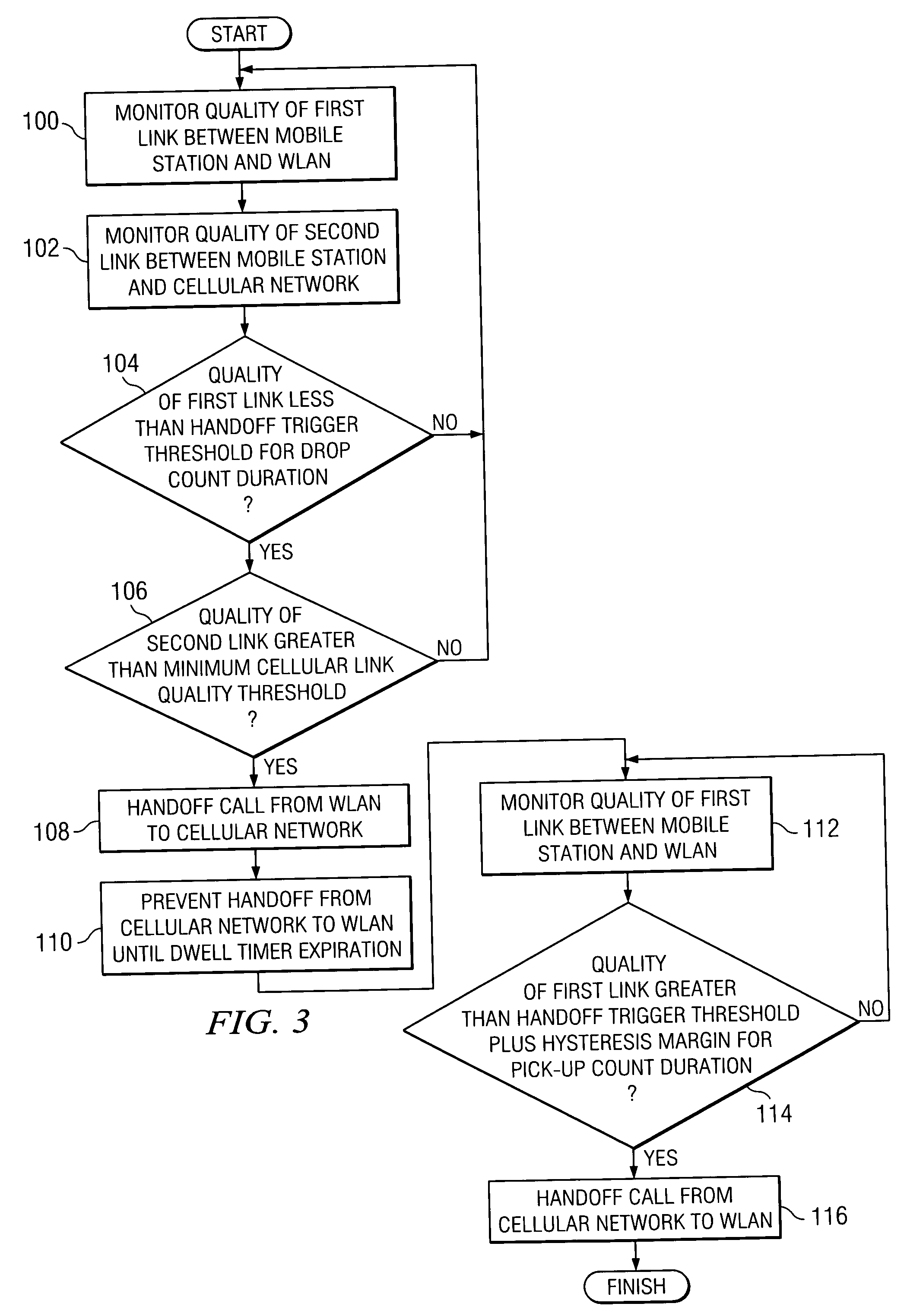
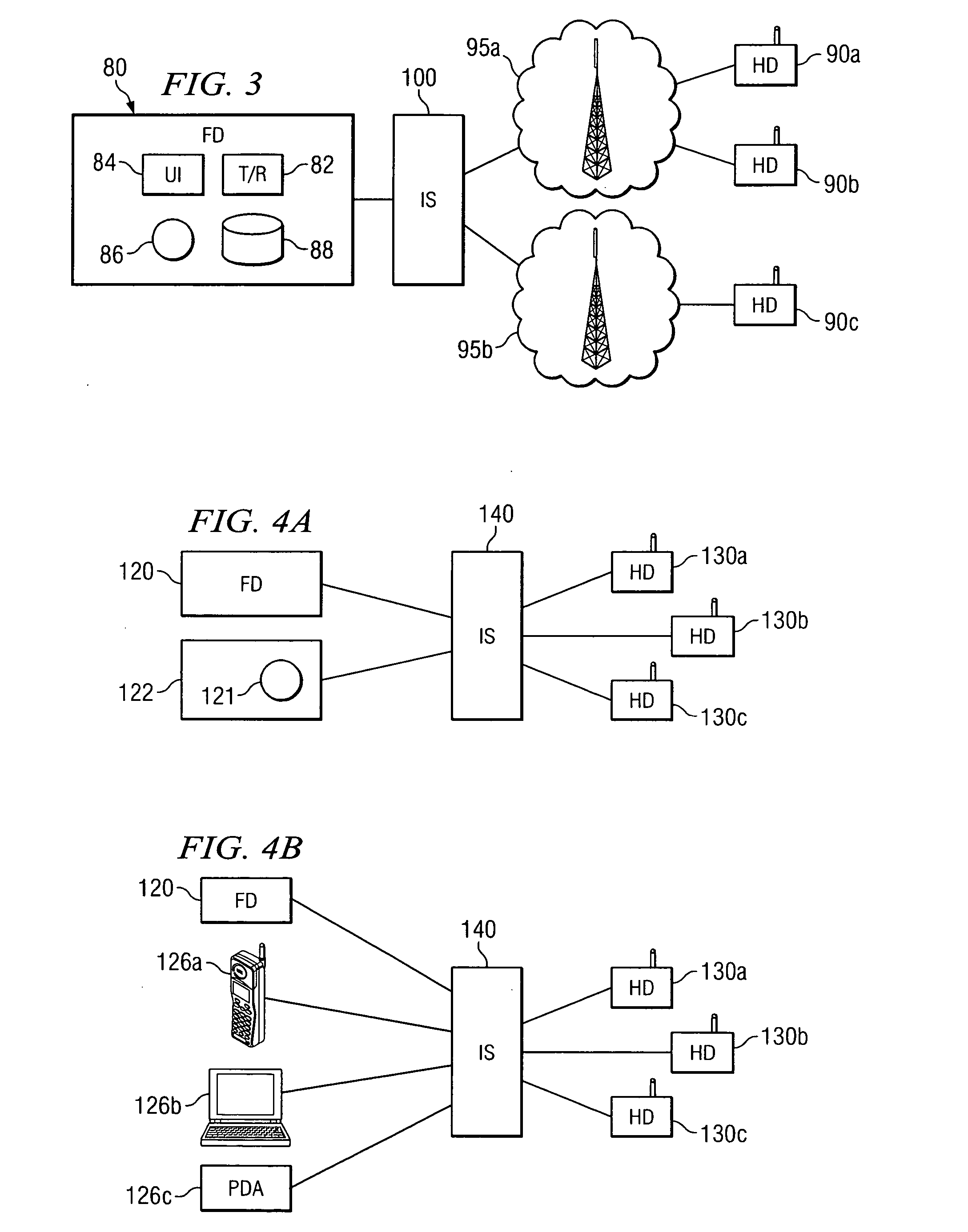
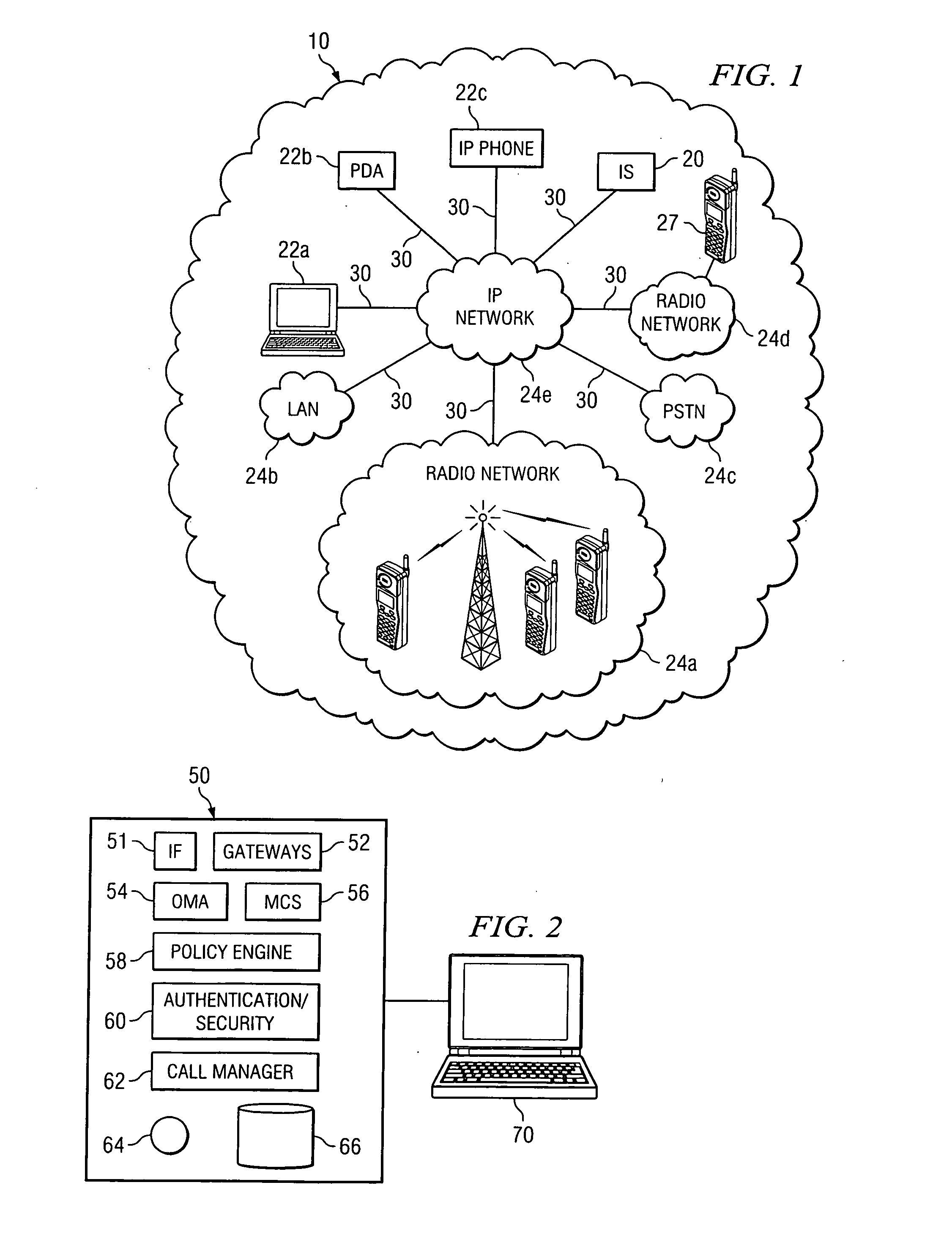
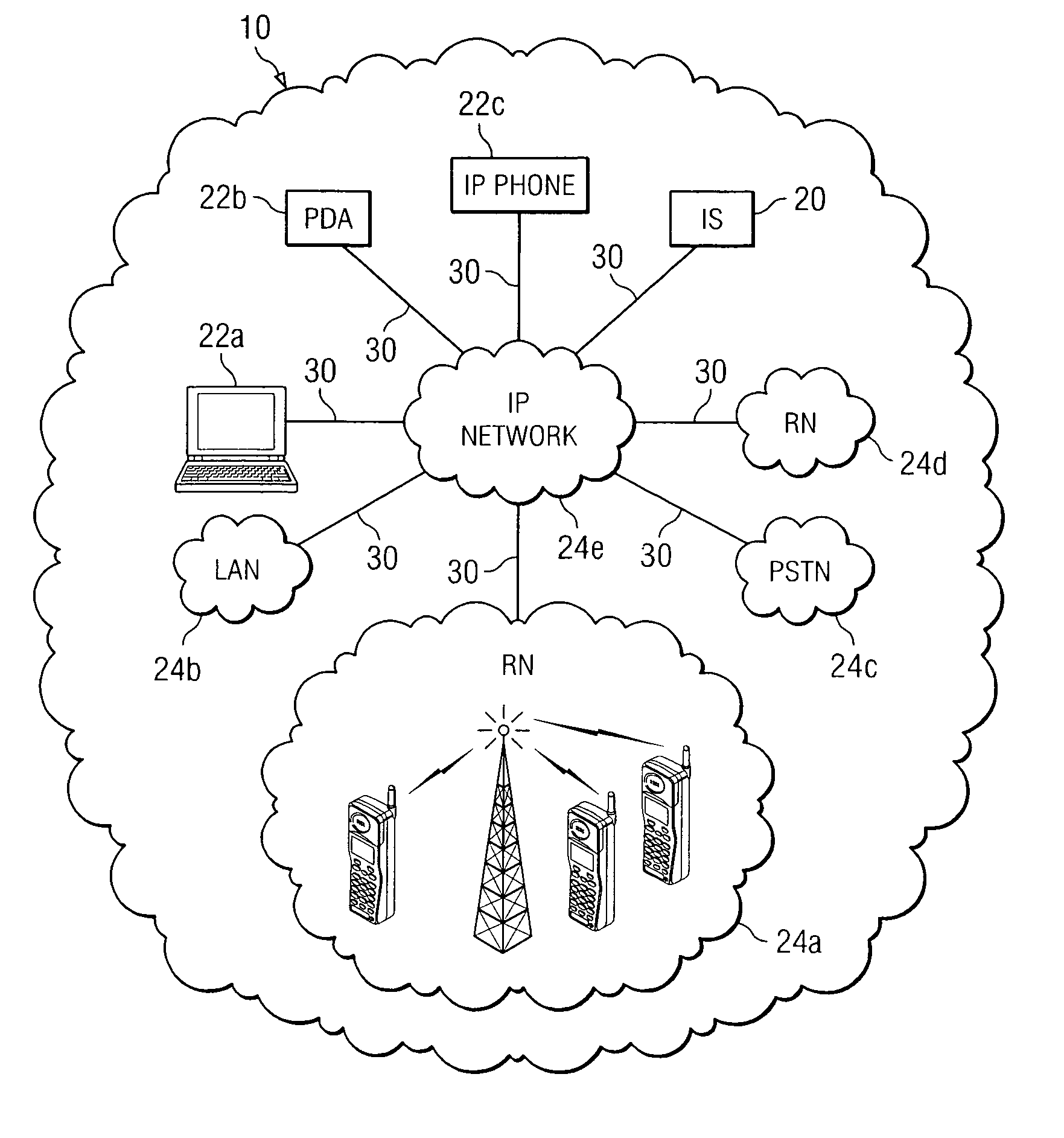
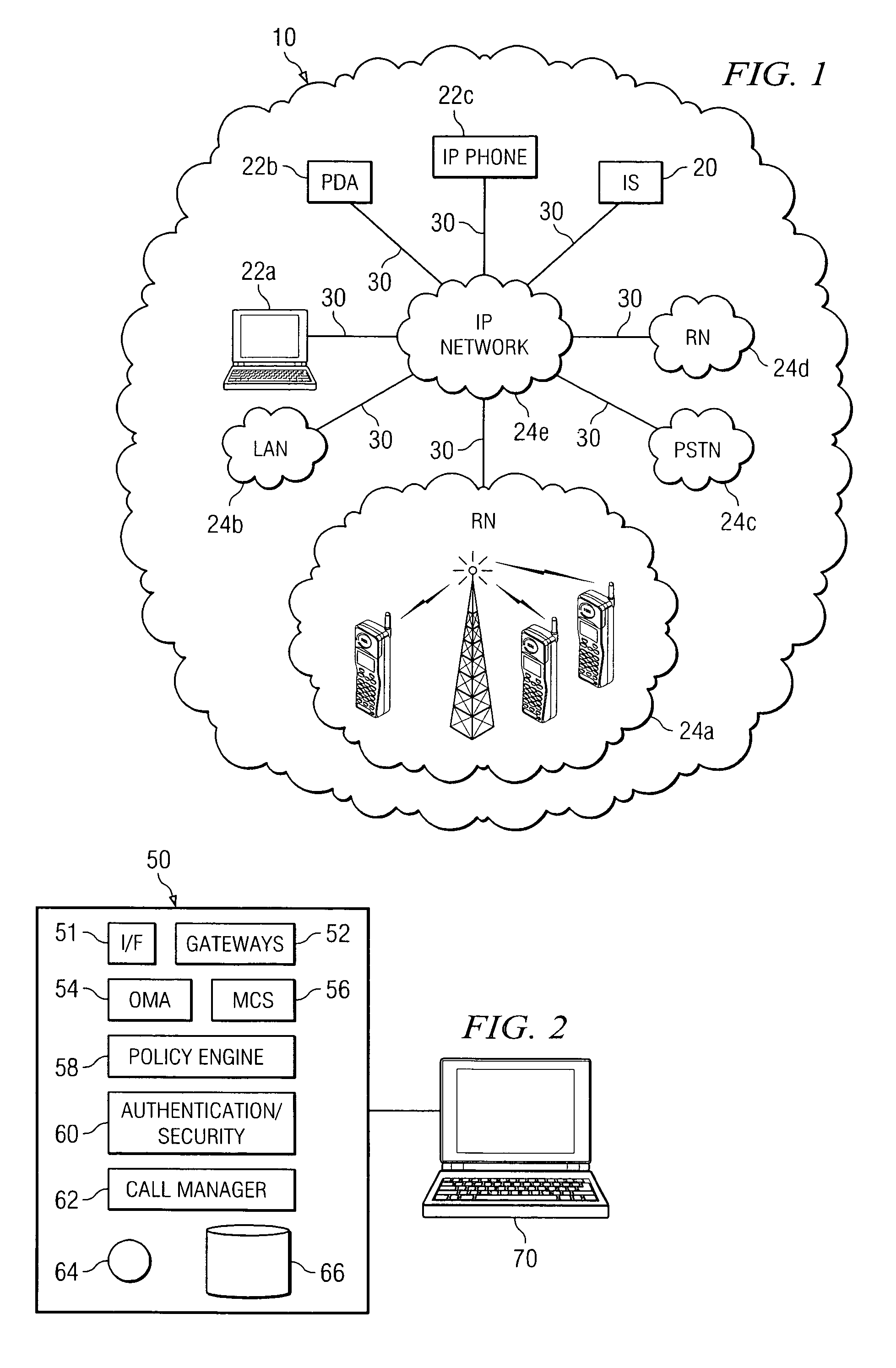
Method and system for triggering handoff of a call between networks
ActiveUS20050059400A1Eliminates and reduces of disadvantageEliminates and reduces of and problemNetwork topologiesMultiple digital computer combinationsMobile stationHand-off
A method for handing off a call between networks includes monitoring a quality of a first link between a mobile station and a wireless local area network (WLAN) when the mobile station is actively connected with the WLAN on a call and monitoring a quality of a second link between the mobile station and a cellular network when the mobile station is actively connected with the WLAN on the call. The method also includes handing off the call from the WLAN to the cellular network when the quality of the first link is less than a handoff trigger threshold for a drop count duration and when the quality of the second link is greater than a minimum cellular link quality threshold.
Owner:CISCO TECH INC
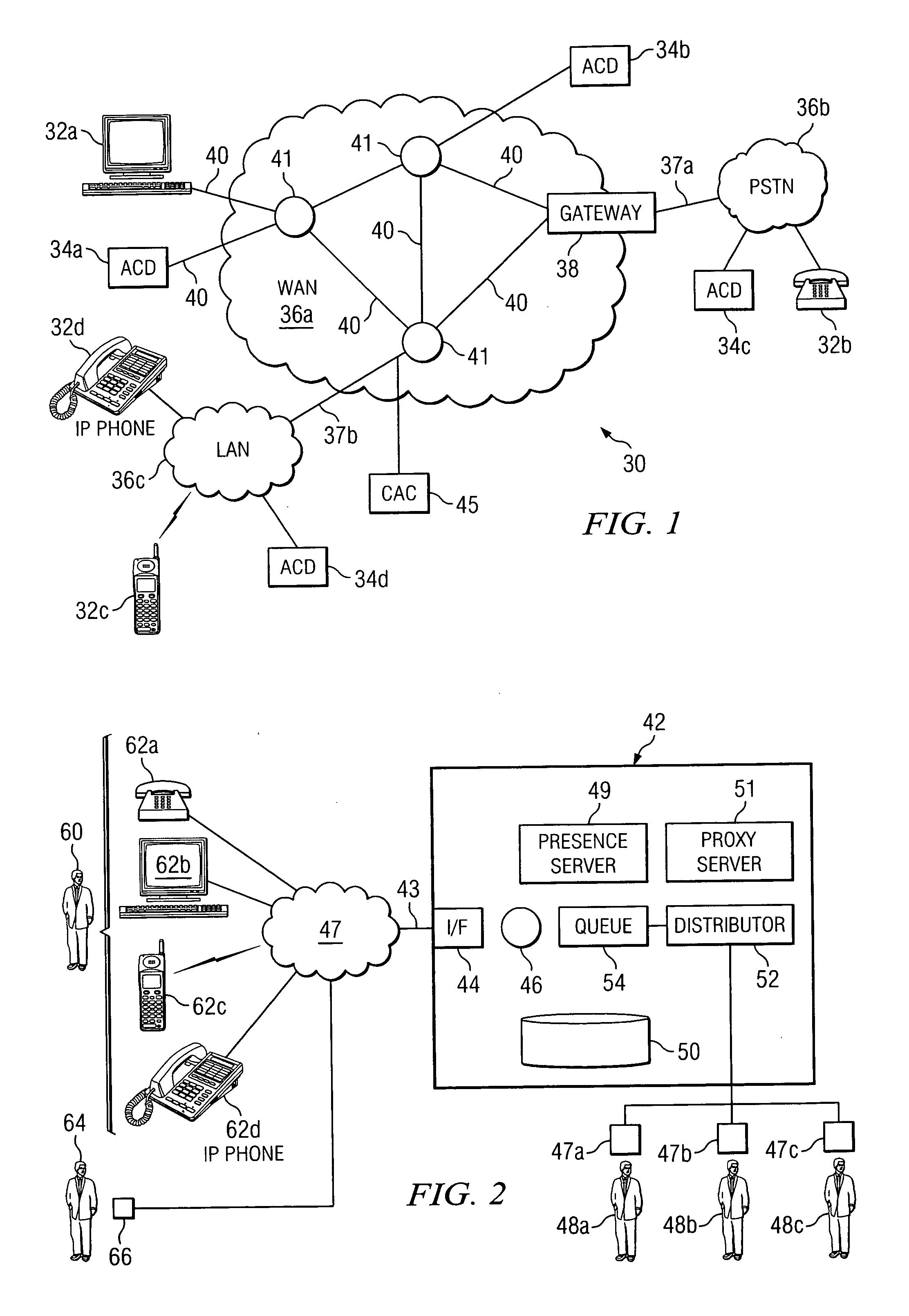
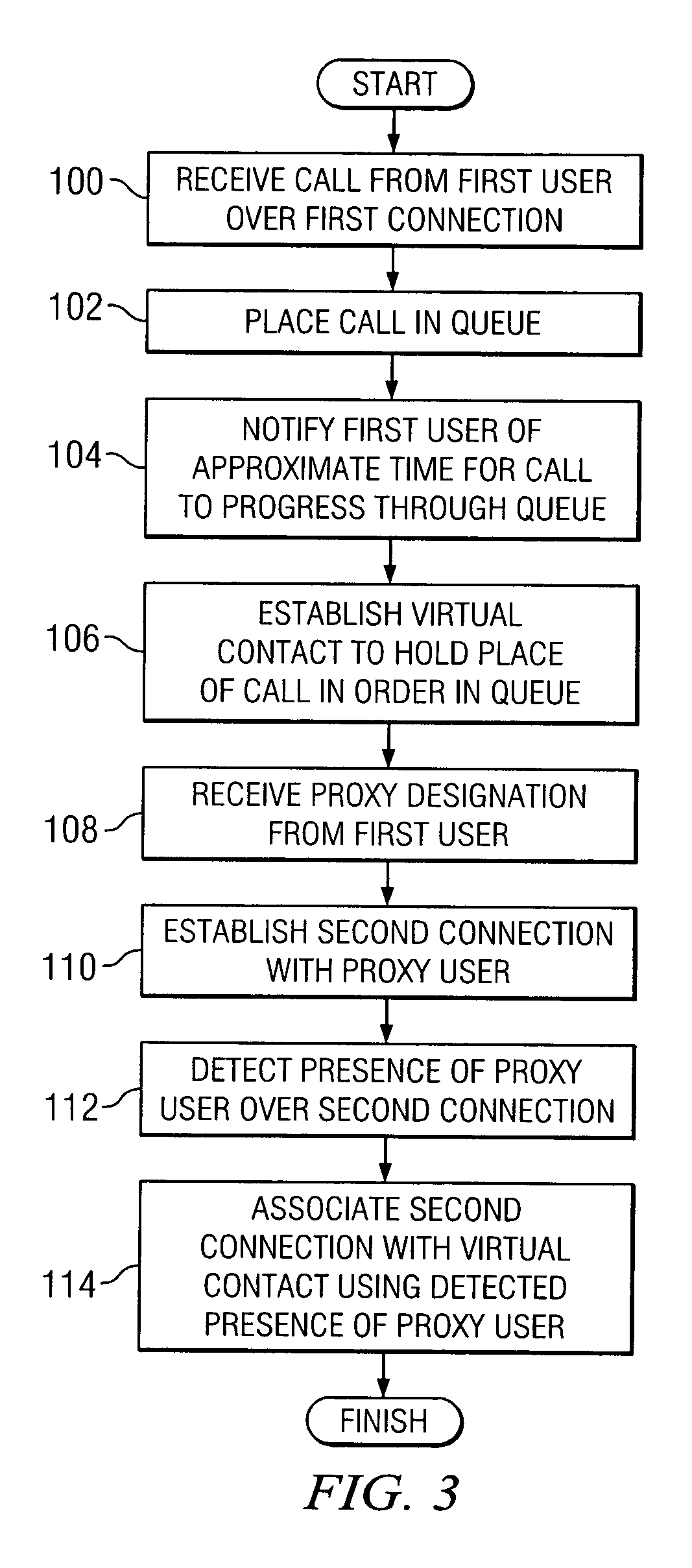
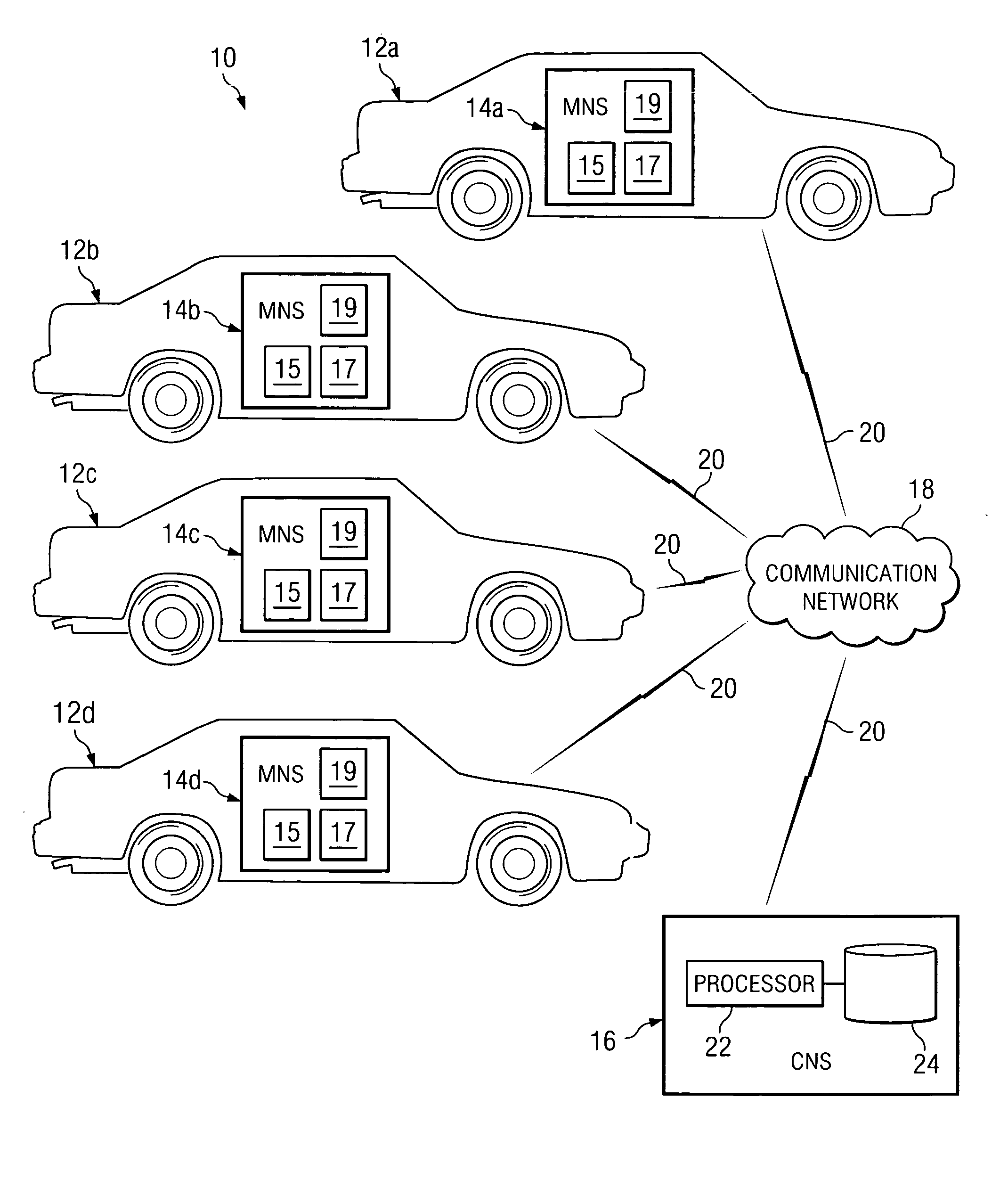
Method and system for managing calls of an automatic call distributor
ActiveUS20050047581A1Eliminates and reduces of disadvantageEliminates and reduces of and problemManual exchangesAutomatic exchangesTelecommunications
A method for utilizing proxy designation in a call system includes receiving a call from a first user over a first connection with a first endpoint of the first user. The method includes receiving a proxy designation from the first user. The proxy designation comprises a proxy user designated to handle the call for the first user. The method also includes establishing a second connection with the proxy user and detecting the presence of the proxy user over the second connection.
Owner:CISCO TECH INC
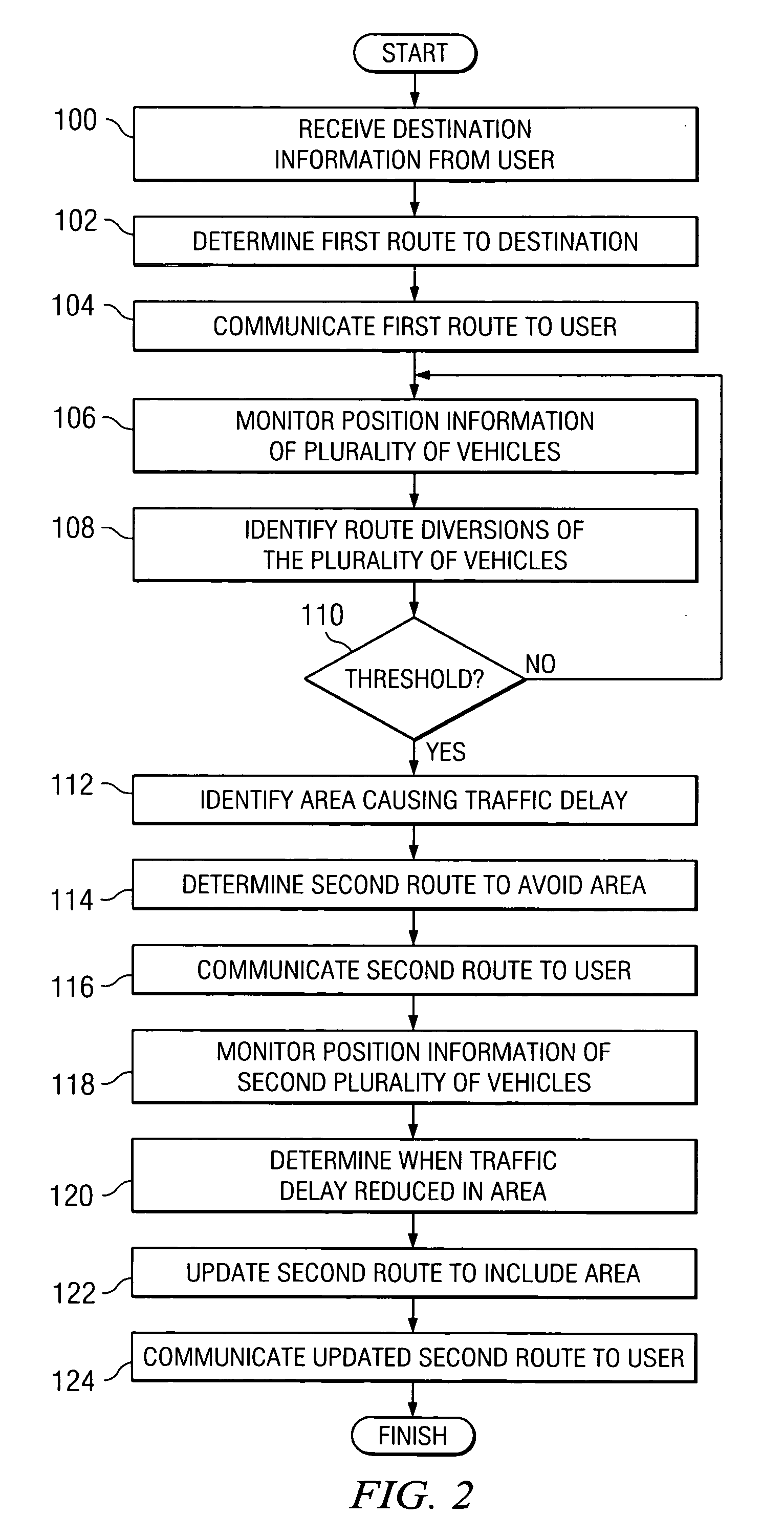
Method and system for communicating navigation information
ActiveUS20050131643A1Eliminates and reduces of disadvantageEliminates and reduces of and problemInstruments for road network navigationRoad vehicles traffic controlReal-time computingMarine navigation
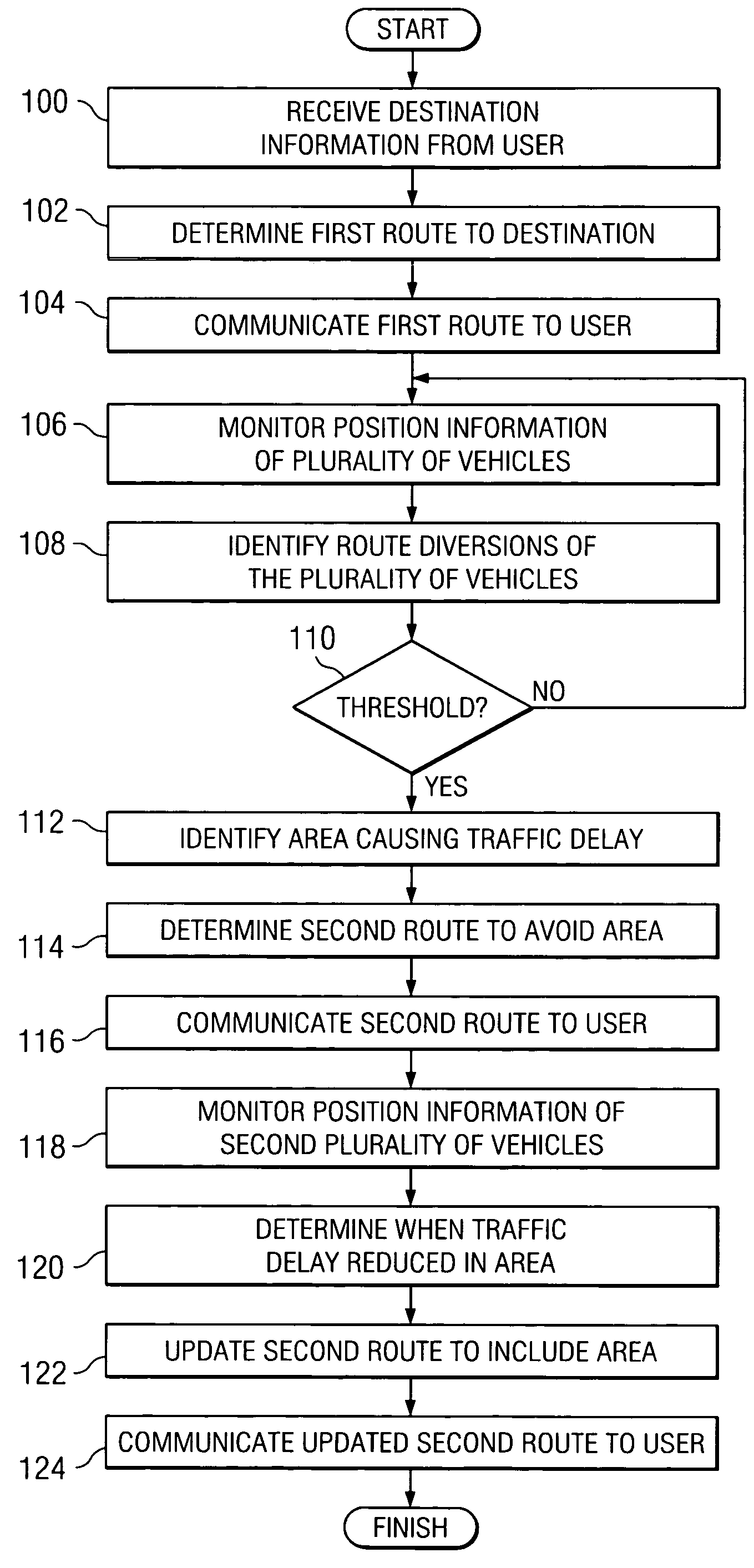
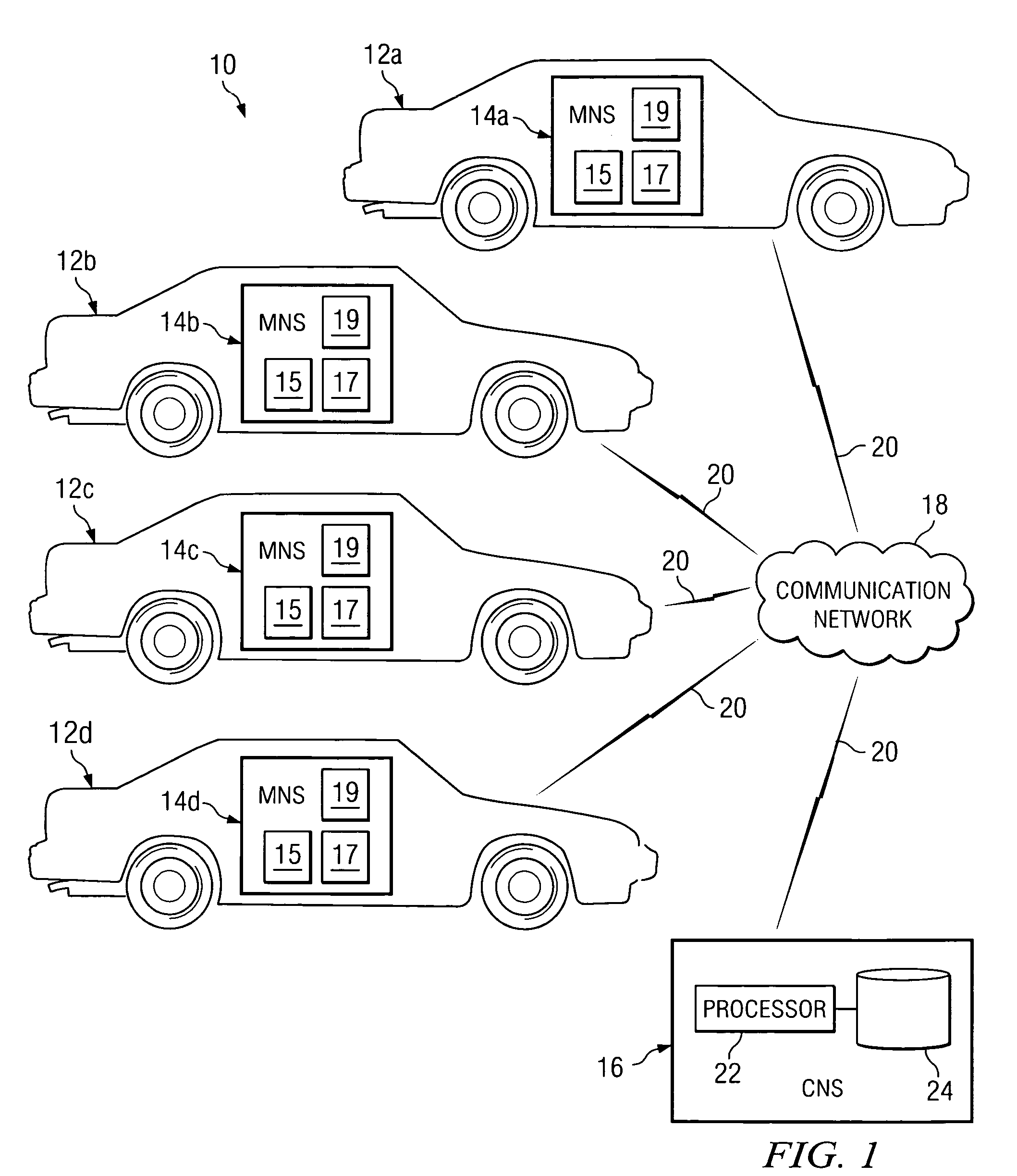
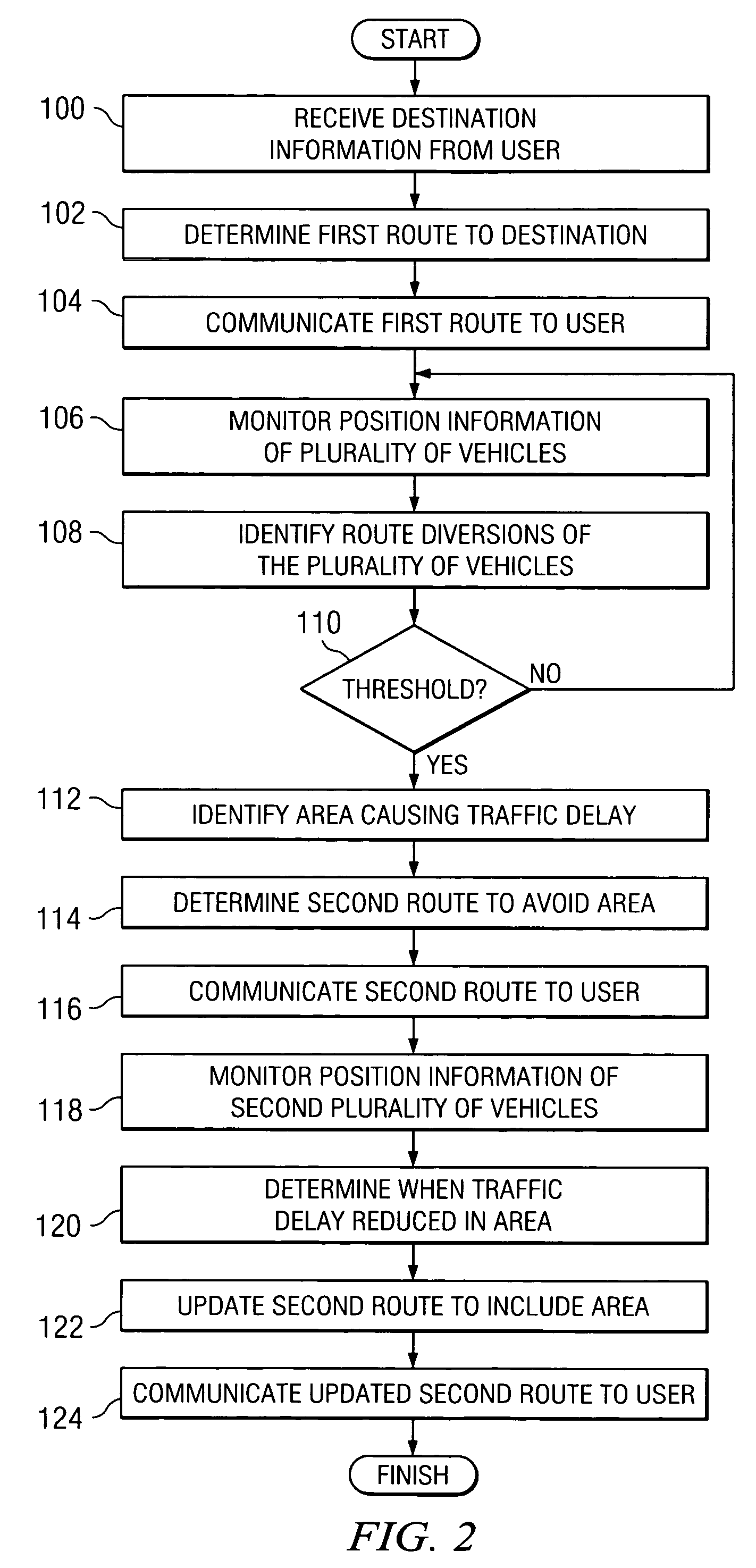
A method for communicating navigation information includes receiving destination information from a user. The destination information comprises a desired destination of the user. The method includes determining a first route to the destination and communicating the first route to the user. The method includes monitoring position information of a plurality of vehicles and identifying an area causing traffic delay using the position information of the plurality of vehicles. The method also includes determining a second route to the destination to avoid the area and communicating the second route to the user.
Owner:CISCO TECH INC
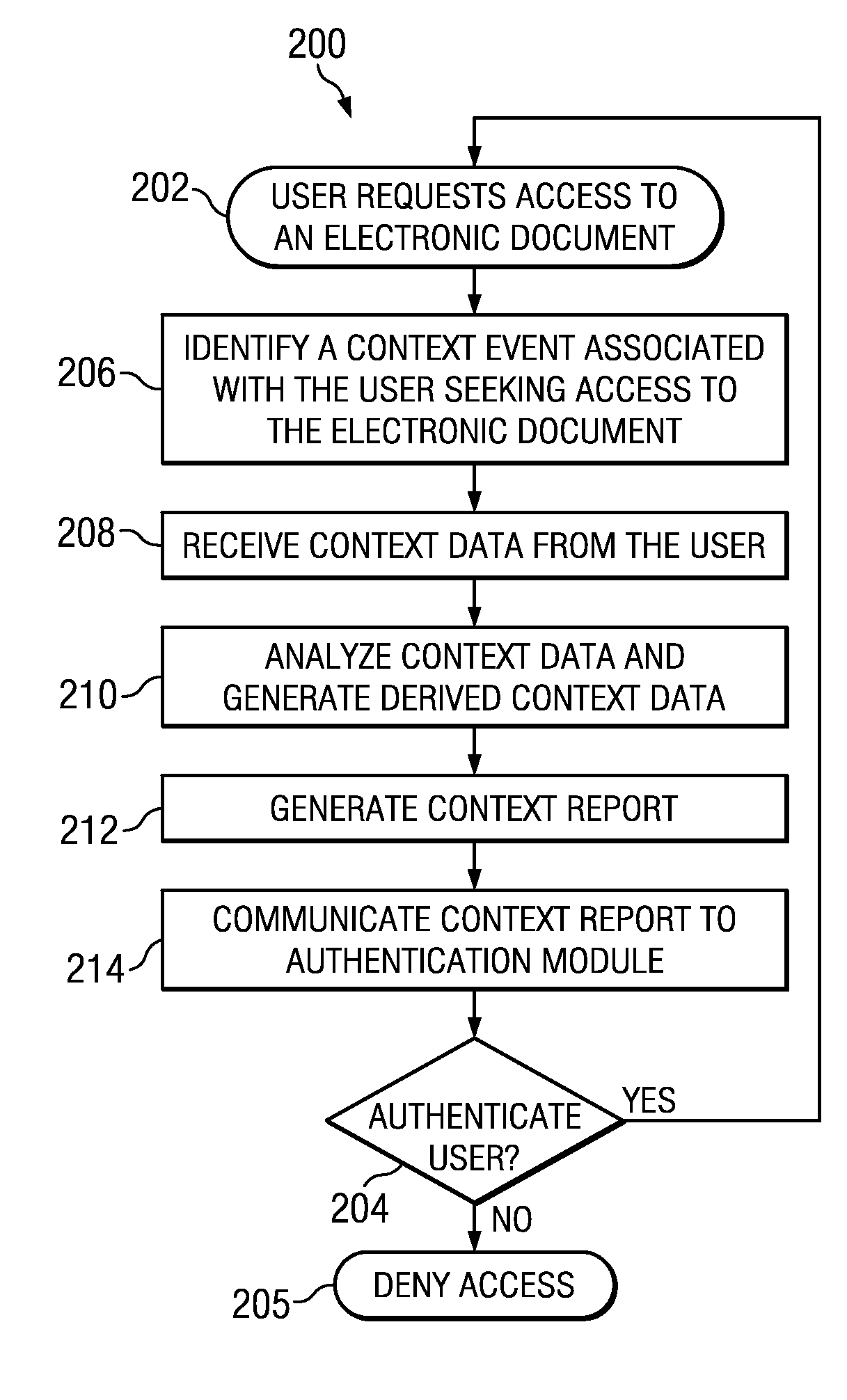
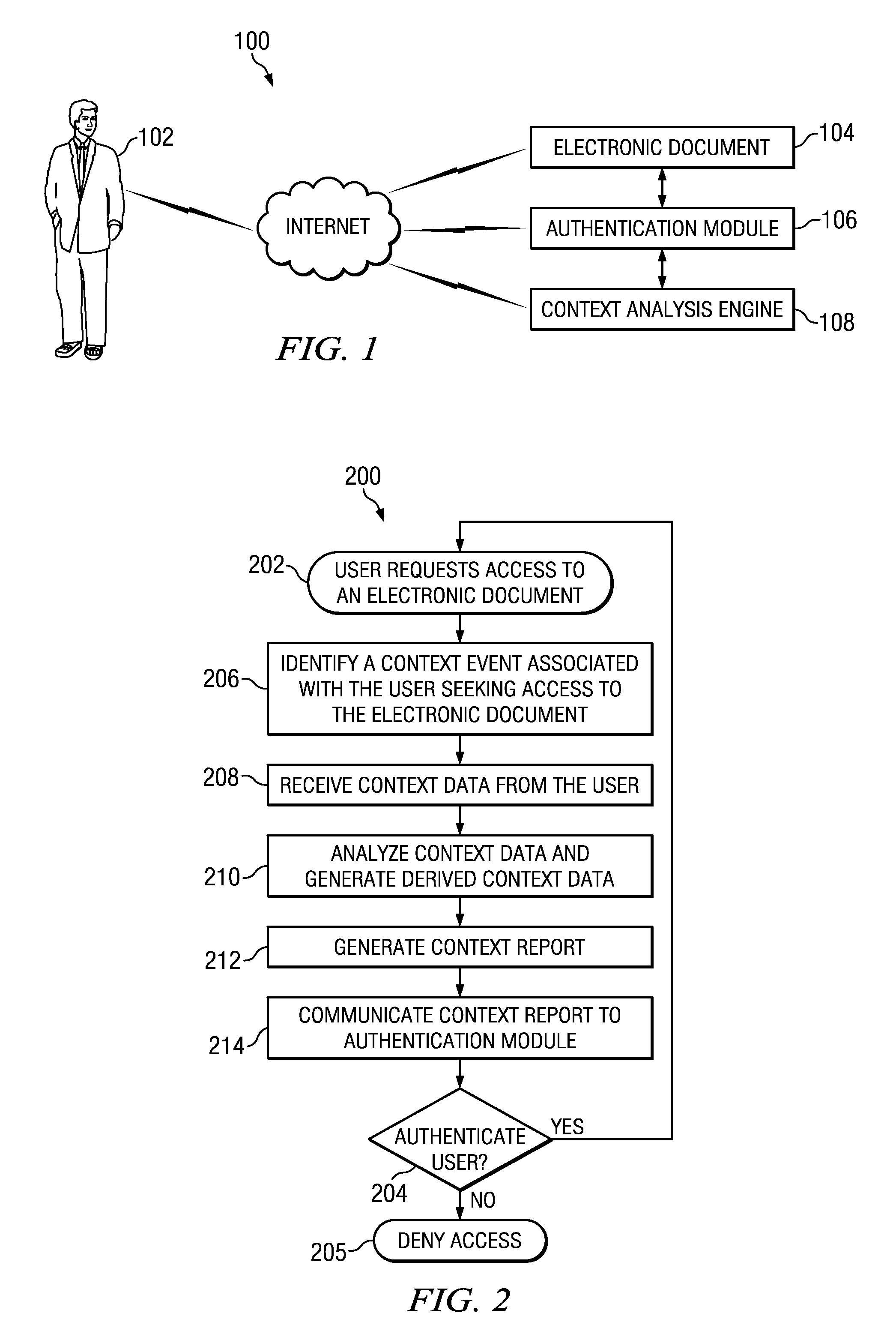
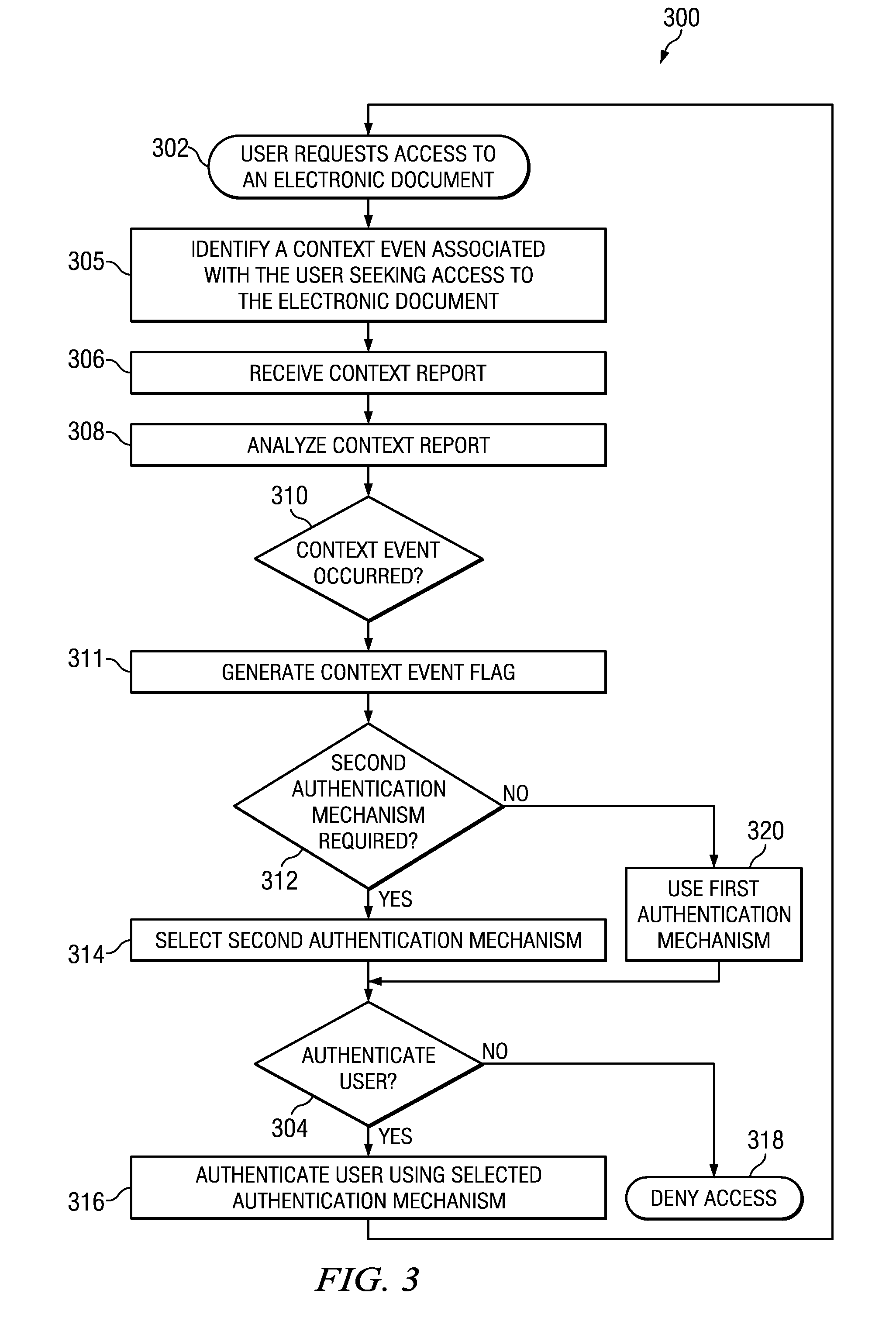
Method and apparatus for periodic context-aware authentication
InactiveUS20110314549A1Eliminates and reduces of disadvantageEliminates and reduces of and problemMemory loss protectionDigital data processing detailsMultiple contextElectronic document
A method for authenticating access to an electronic document. The method includes identifying a context event associated with a user seeking access to the electronic document, receiving from the user a plurality of context data, and analyzing the plurality of context data to generate a one or more derived context data. The method may also include receiving from an authentication module a context request, and in response to the context request, generating a context report, wherein the context report includes at least the one or more derived context data, and is configured to enable the authentication module to authenticate the user's access to the electronic document using a first authentication mechanism. The method may also include communicating the context report to the authentication module, monitoring the user to identify an occurrence of the context event, and upon identifying the occurrence of the context event, generating a context event flag, the context event flag configured to inform the authentication module to reauthenticate the user's access to the electronic document.
Owner:FUJITSU LTD
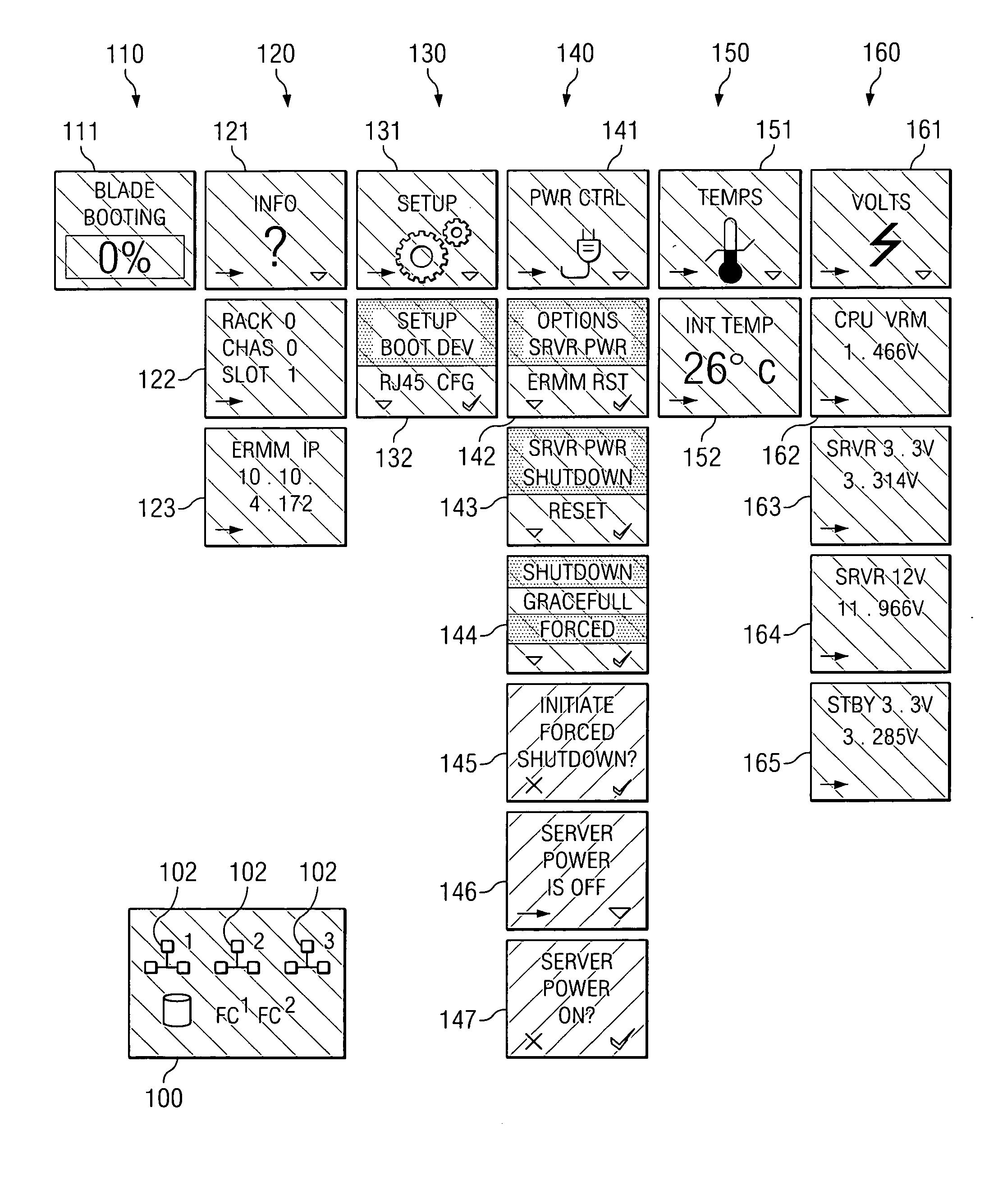
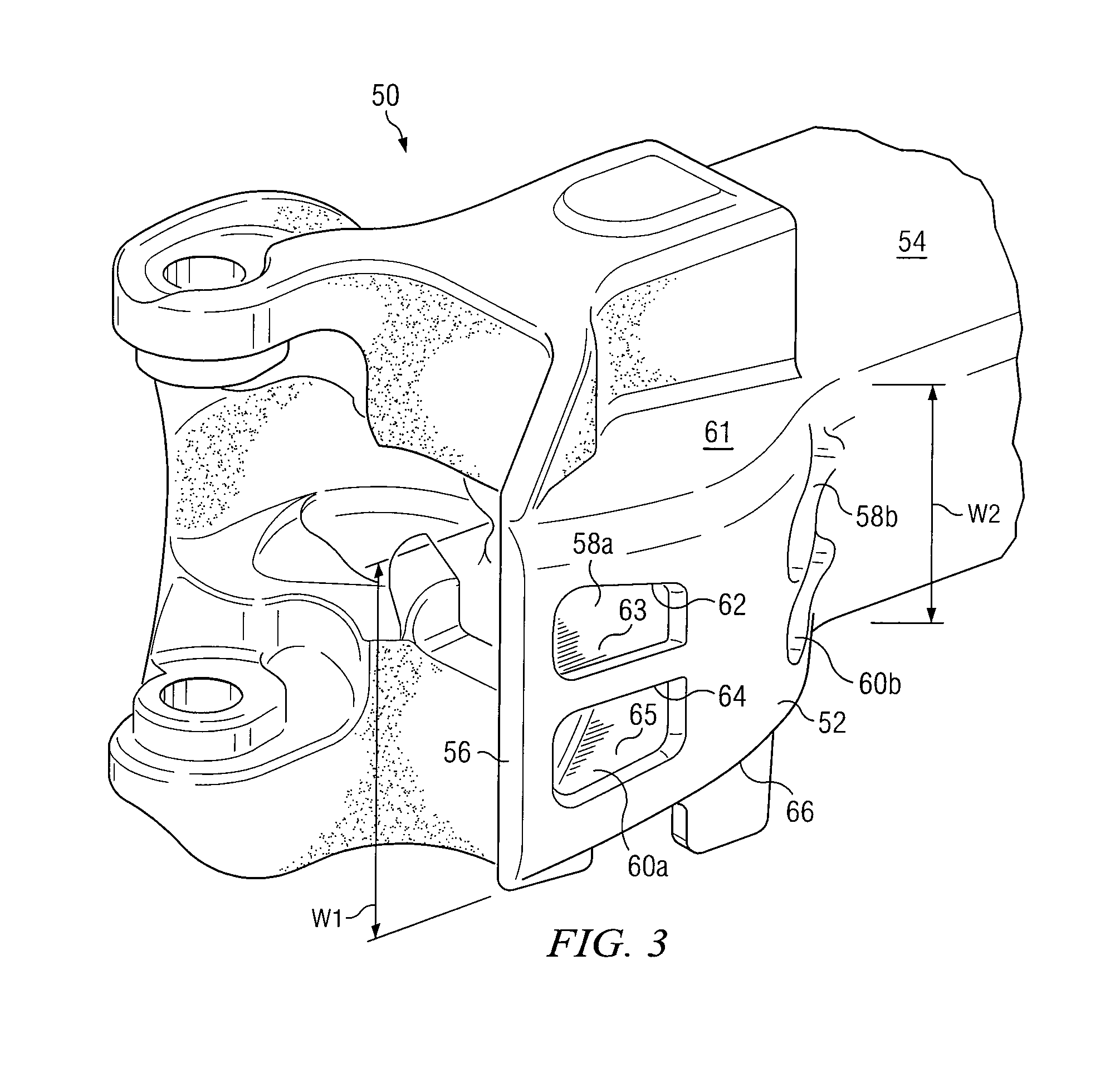
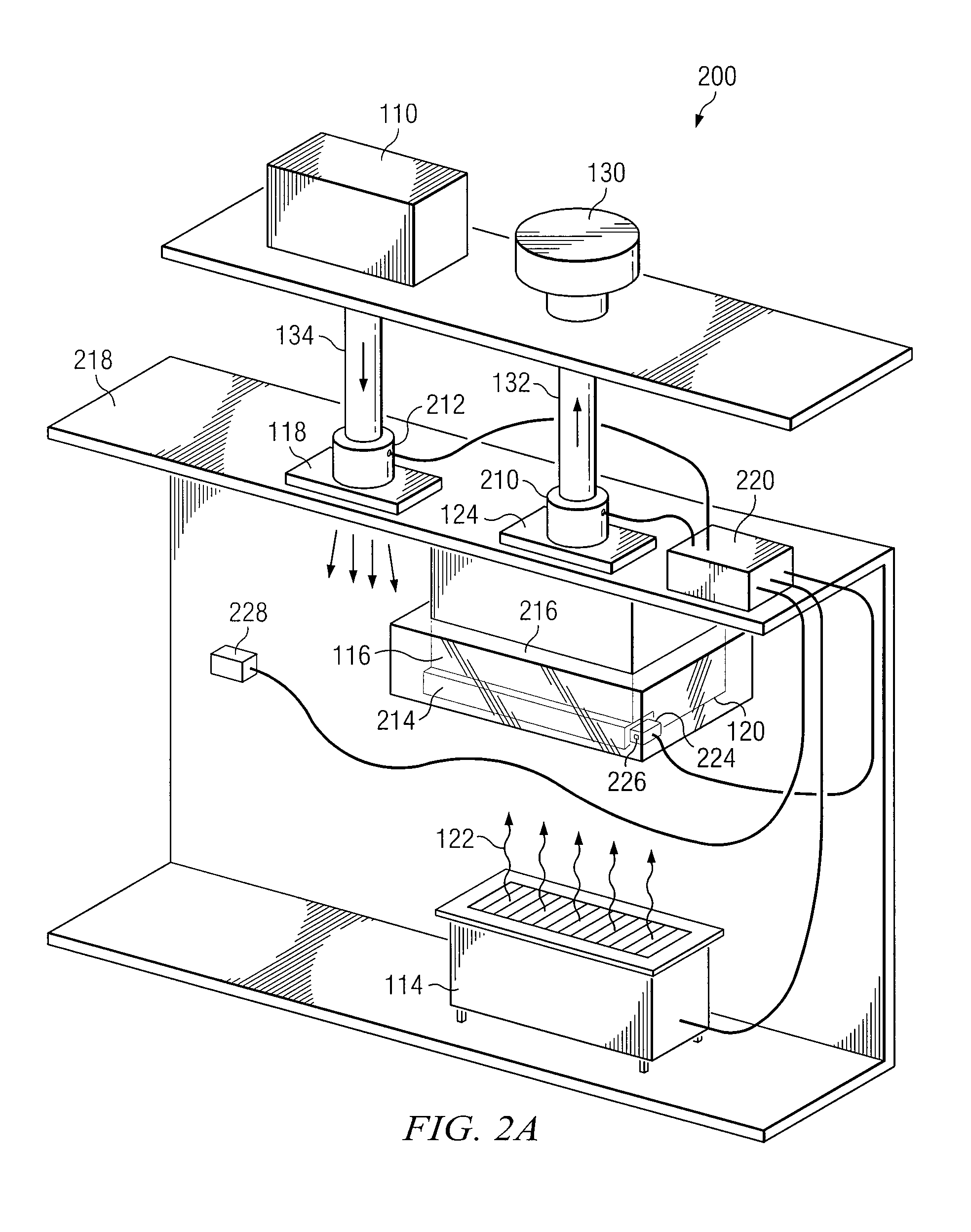
System and method for displaying chassis component information
ActiveUS20050195075A1Eliminates and reduces of disadvantageEliminates and reduces of and problemServersElectric lighting sourcesEmbedded systemBlade server
A system for displaying chassis component information includes a chassis and a plurality of server blades each coupled to the chassis. Each server blade comprises a respective liquid crystal display (LCD) positioned upon the server blade. The respective LCD is operable to display chassis component information.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
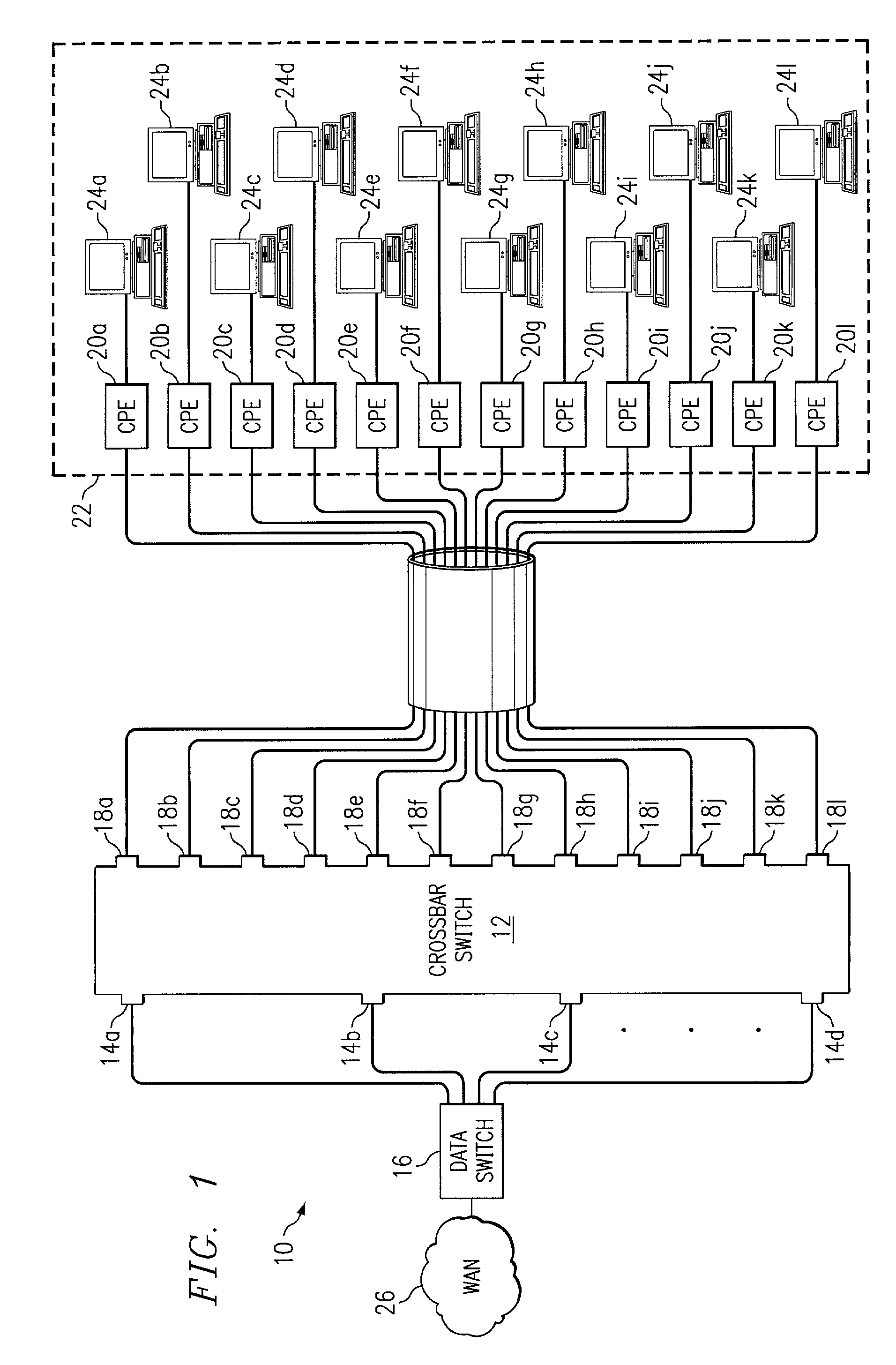
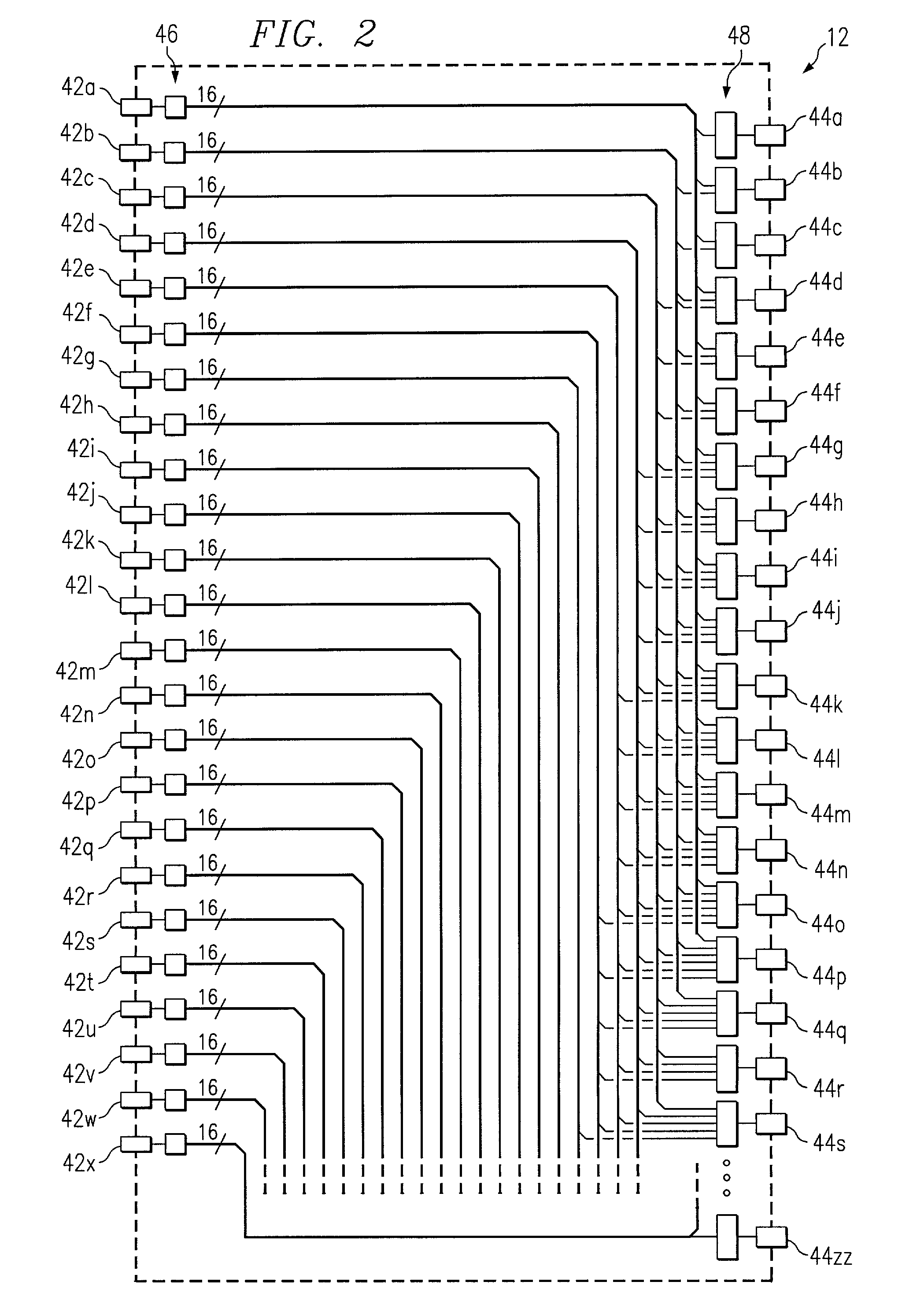
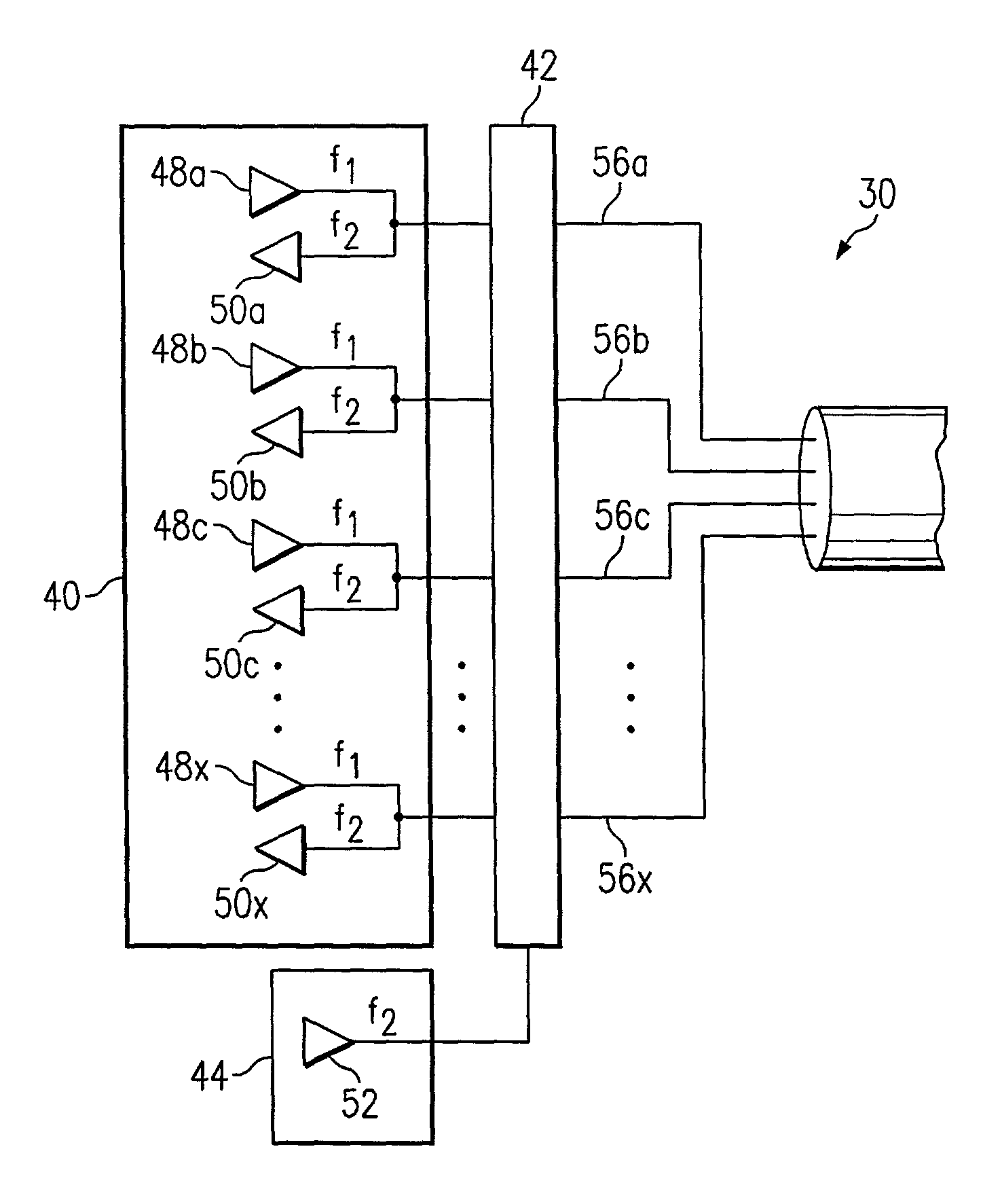
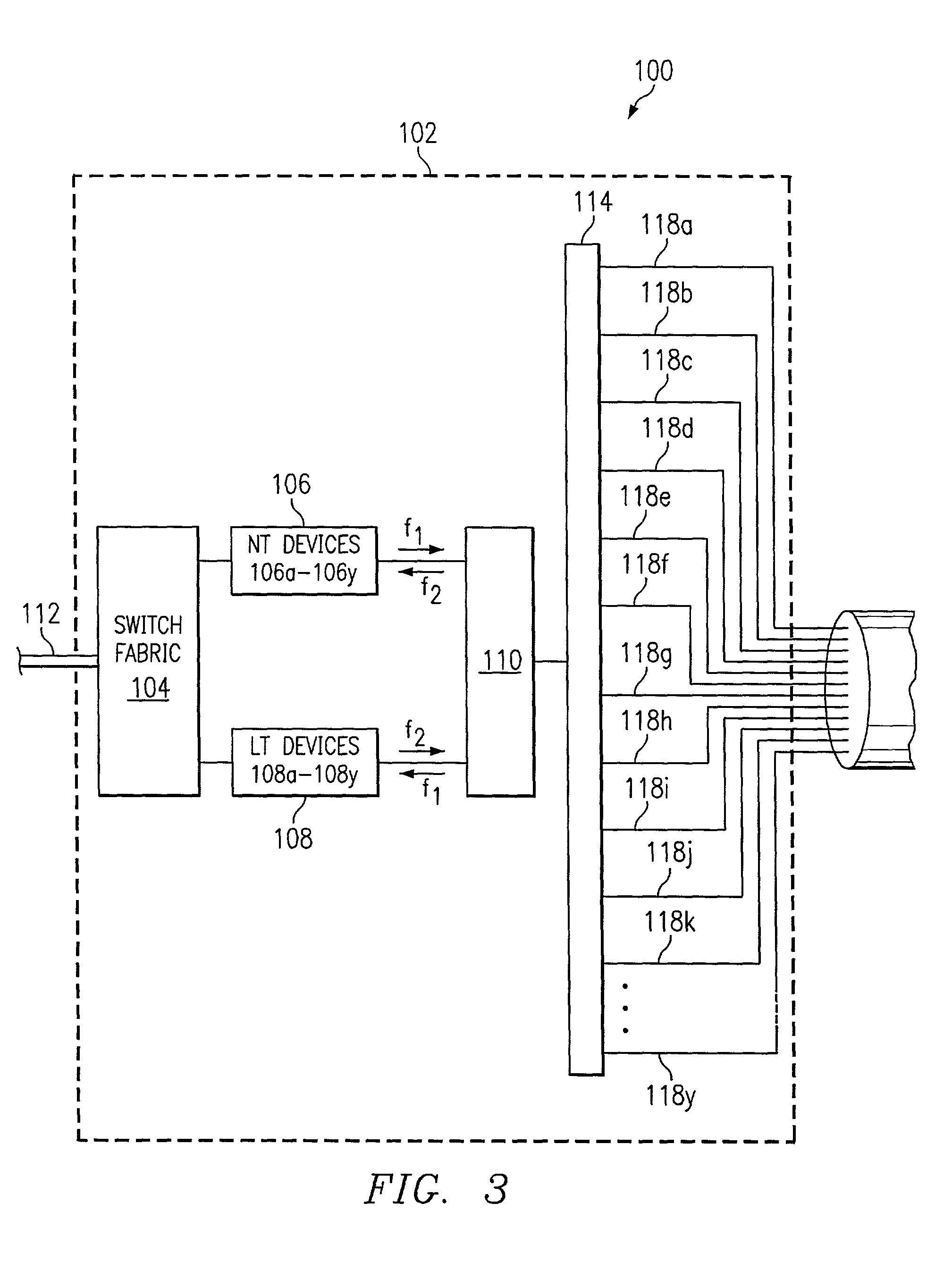
Method and system for distributing data communications utilizing a crossbar switch
InactiveUS7161936B1Eliminates and reduces of disadvantageEliminates and reduces of and problemCircuit switching systemsTime-division multiplexing selectionCrossbar switchEngineering
A solid-state crossbar switch for transmitting data traffic includes a first number of input ports. Each input port is operable to receive DSL data from a data switch. The crossbar switch also includes a second number of output ports. Each output port is capable of being coupled to a customer premise equipment (CPE) device. The crossbar switch includes a third number of 1×N solid-state analog switches. Each 1×N solid-state analog switch is operable to couple one of the input ports with N output ports. Each input port may be coupled to one of the analog switches. The second number of output ports may be greater than N. The crossbar switch may include a sweeper port coupled to each output port. The sweeper port is operable to monitor each output port to detect an active connection of a CPE device to one of the output ports.
Owner:CISCO TECH INC
Method and system for providing a proxy media service
ActiveUS20070105579A1Eliminates and reduces of disadvantageEliminates and reduces of and problemConnection managementBroadcast service distributionHigh bandwidthPush-to-talk
A method for providing a push-to-talk proxy media service includes receiving a plurality of monitored push-to-talk communication streams over a high bandwidth connection and mixing the plurality of monitored push-to-talk communication streams into a mixed communication stream. The method also includes transmitting the mixed communication stream to a user endpoint over a low bandwidth connection.
Owner:STA GRP LLC
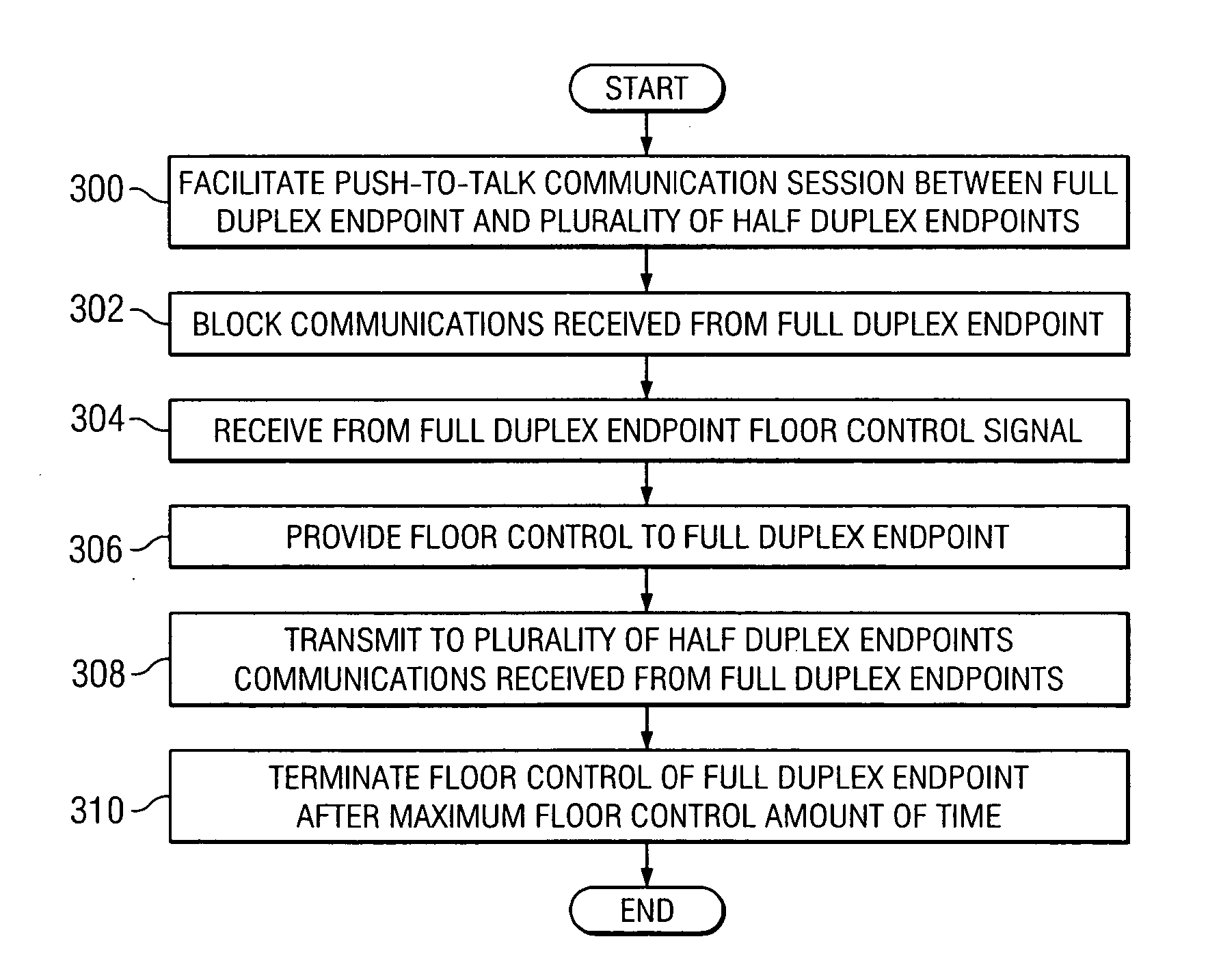
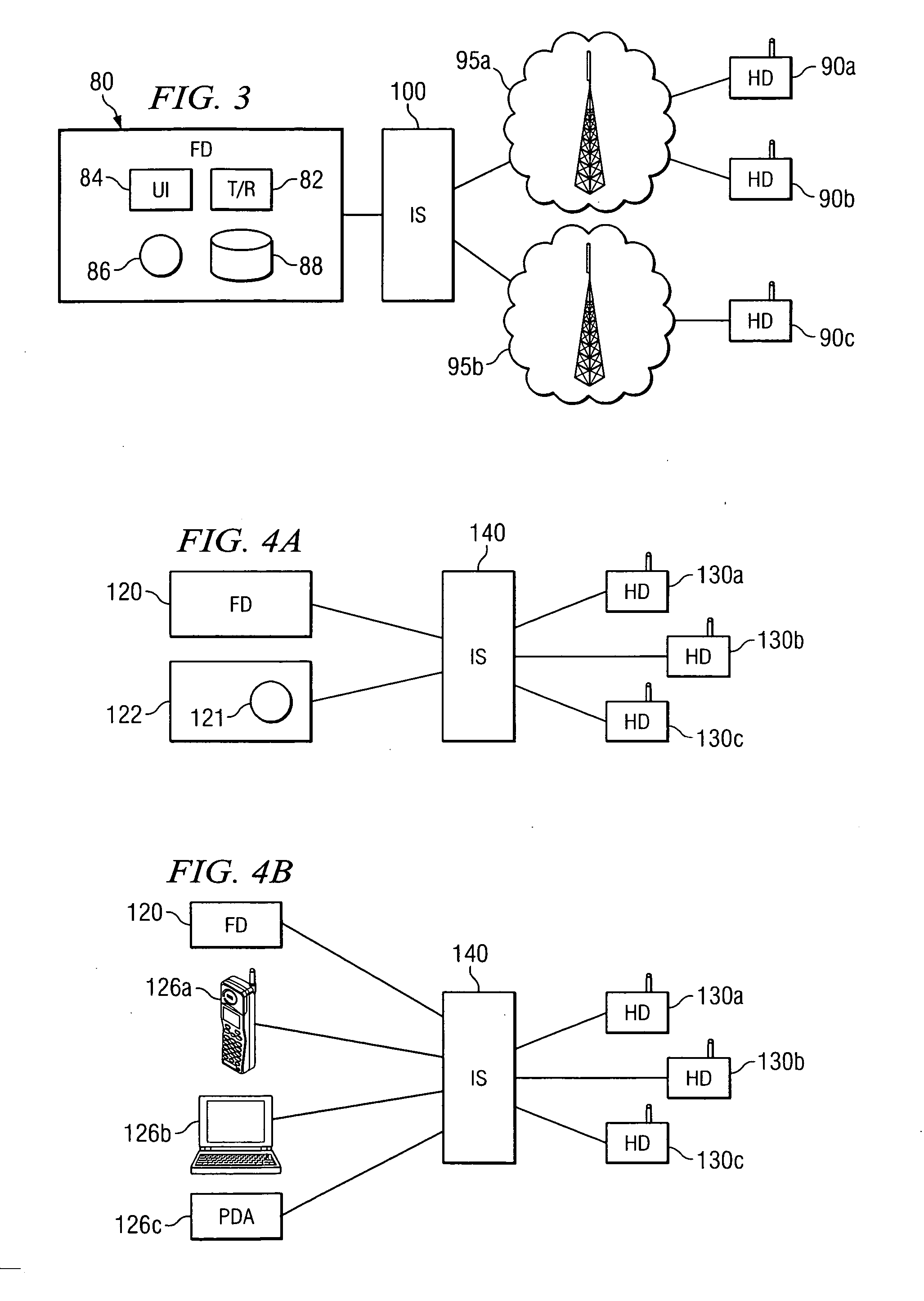
Method and system for providing a push-to-talk communication session using a control endpoint
InactiveUS20070105578A1Eliminates and reducesEliminates and reduces of disadvantageNetwork topologiesRadio/inductive link selection arrangementsControl signalPush-to-talk
A method for providing a push-to-talk communication session using a control endpoint includes facilitating a push-to-talk communication session among a full duplex endpoint supporting simultaneous two-way communication and a plurality of half duplex endpoints. Communications are received from and transmitted to the full duplex endpoint along a two-way communications path. The method includes blocking communications received from the full duplex endpoint while one of the plurality of half duplex endpoints has floor control in the communication session and receiving, from a control endpoint separate from the full duplex endpoint, a floor control signal comprising a request to transmit communications in the communication session. The method includes, in response to receiving the floor control signal, providing floor control to the full duplex endpoint and transmitting to the plurality of half duplex endpoints communications received from the full duplex endpoint.
Owner:STA GRP LLC
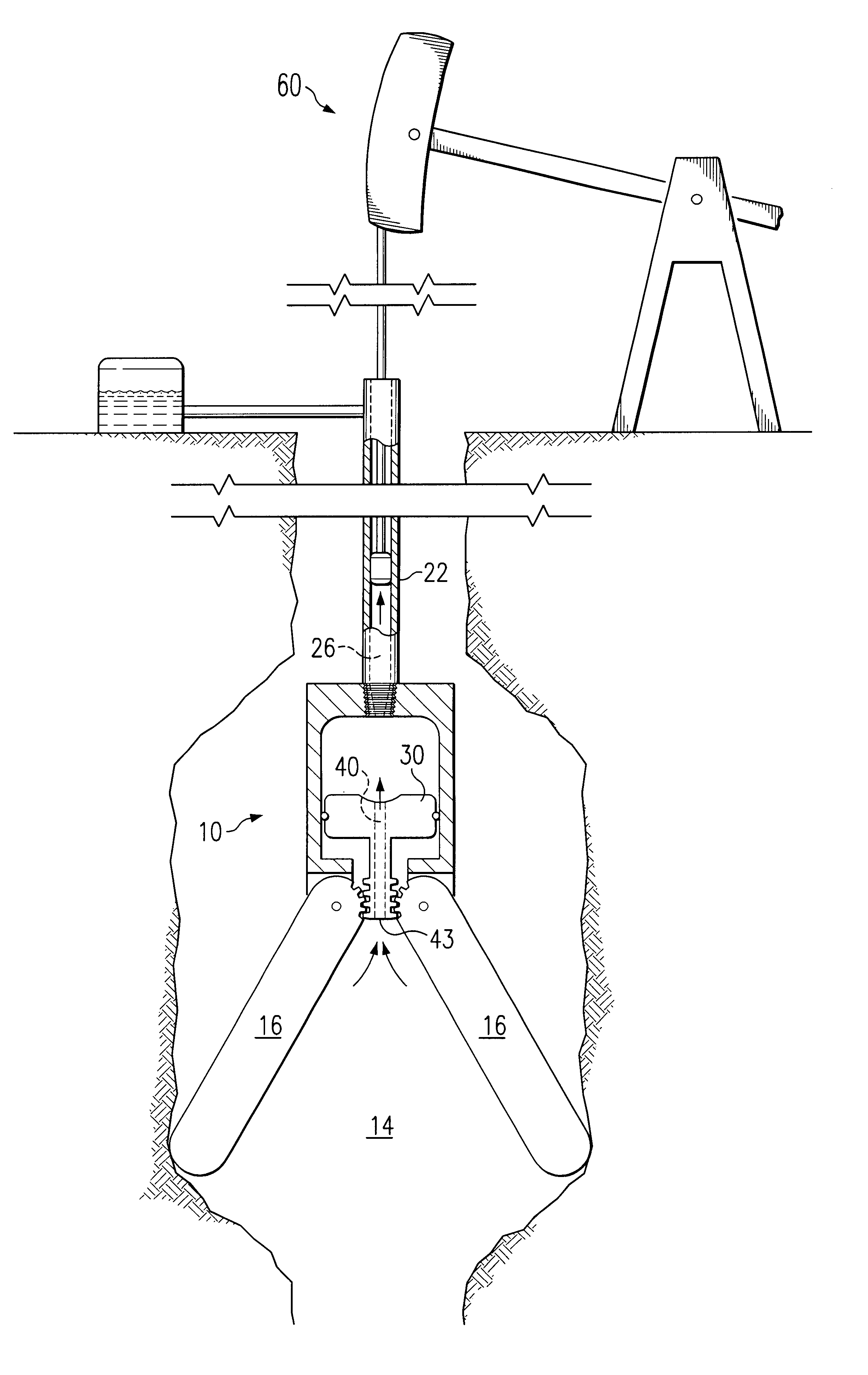
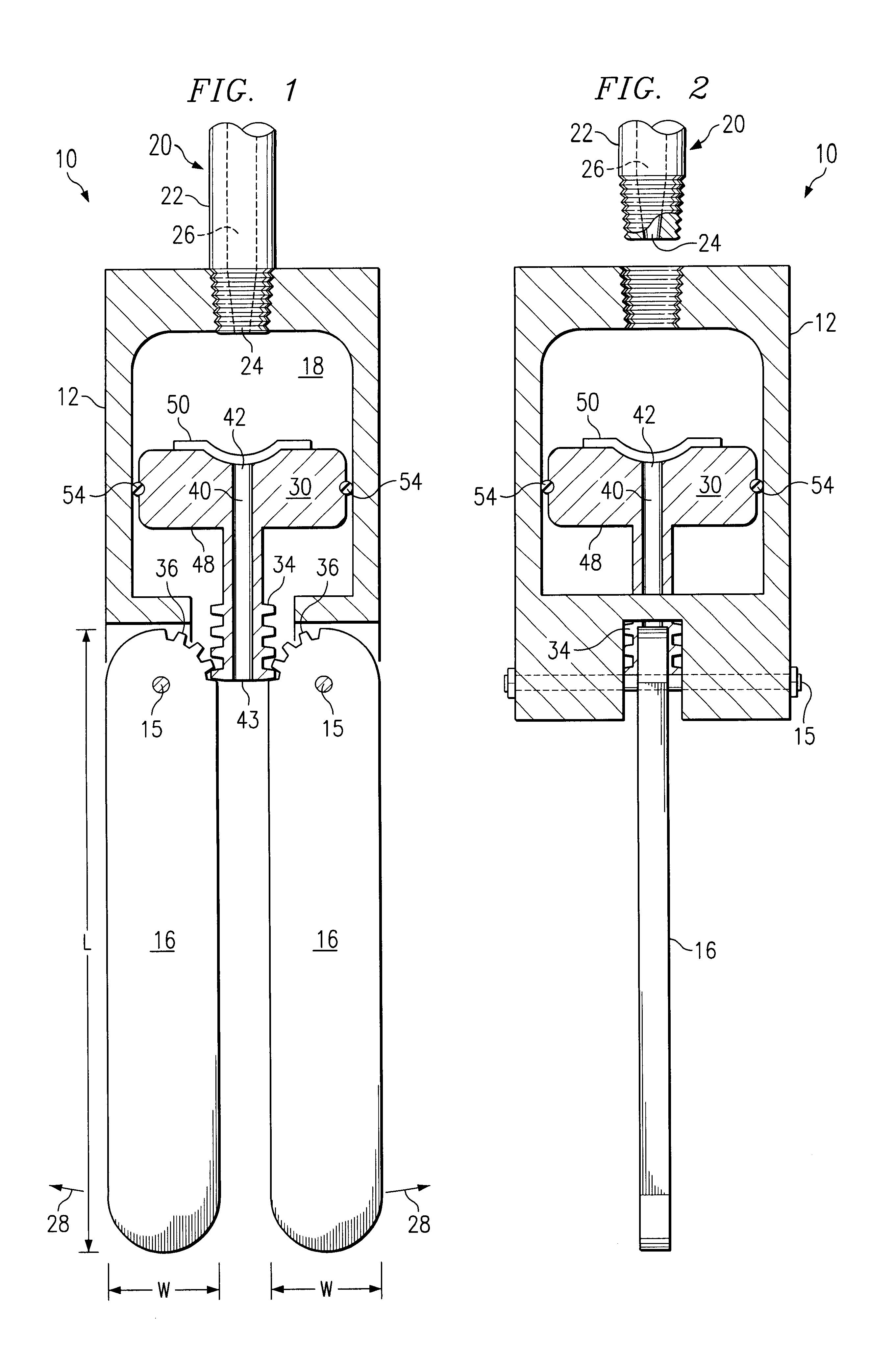
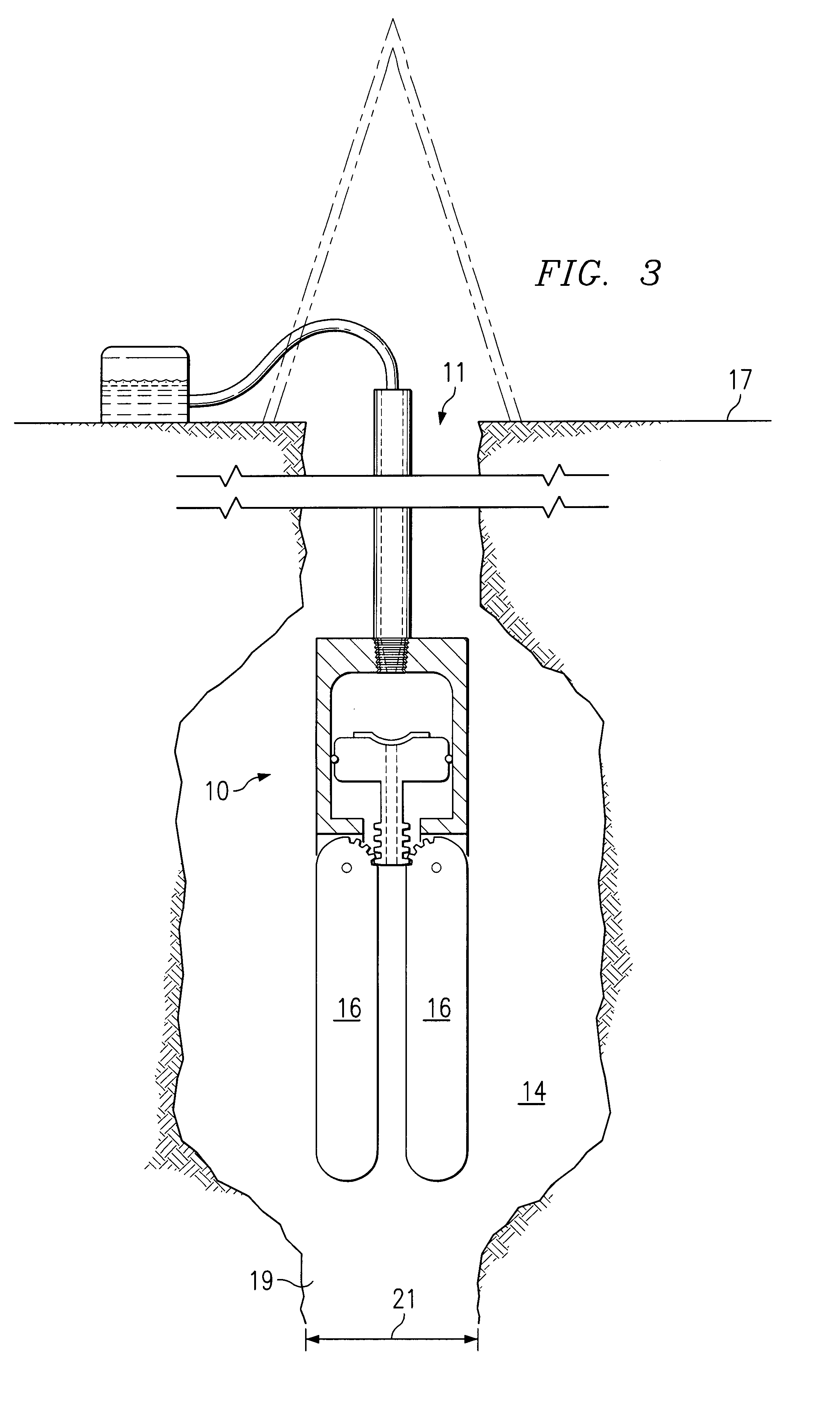
Cavity positioning tool and method
InactiveUS6851479B1Eliminates and reduces of disadvantageEliminates and reduces of and problemSurveyFluid removalAxial forceMechanical engineering
A cavity positioning tool includes a housing adapted to be coupled to a downhole string. The cavity positioning tool includes at least one blunt arm pivotally coupled to the housing. Each blunt arm is configured to contact a surface of the cavity to position the tool in the cavity. The cavity positioning tool also includes a piston slidably disposed within the housing. The piston is operable to engage each blunt arm. The piston is also operable to receive an axial force operable to slide the piston relative to the housing. The sliding of the piston extends each blunt arm radially outward relative to the housing from a retracted position.
Owner:EFFECTIVE EXPLORATION
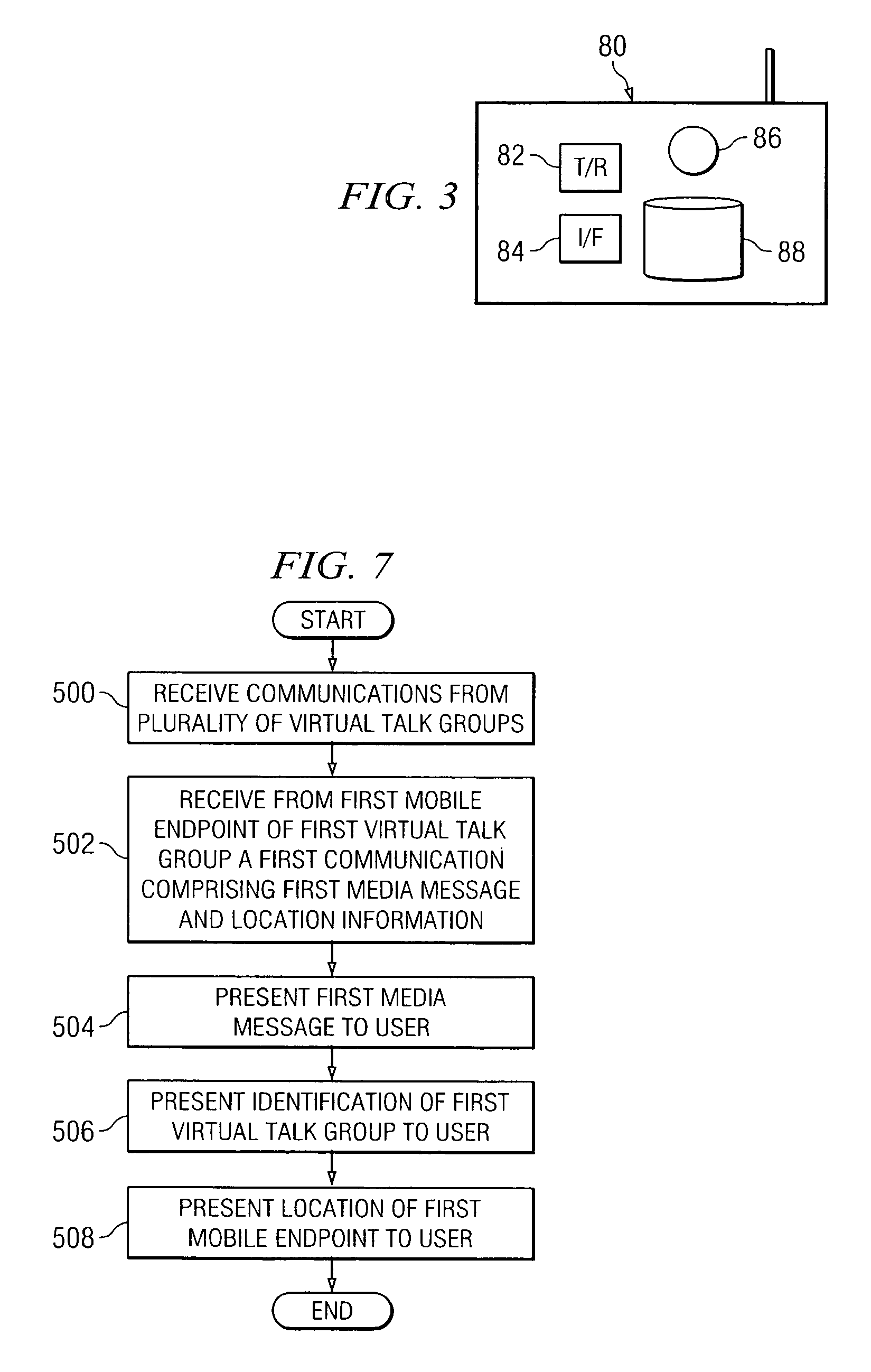
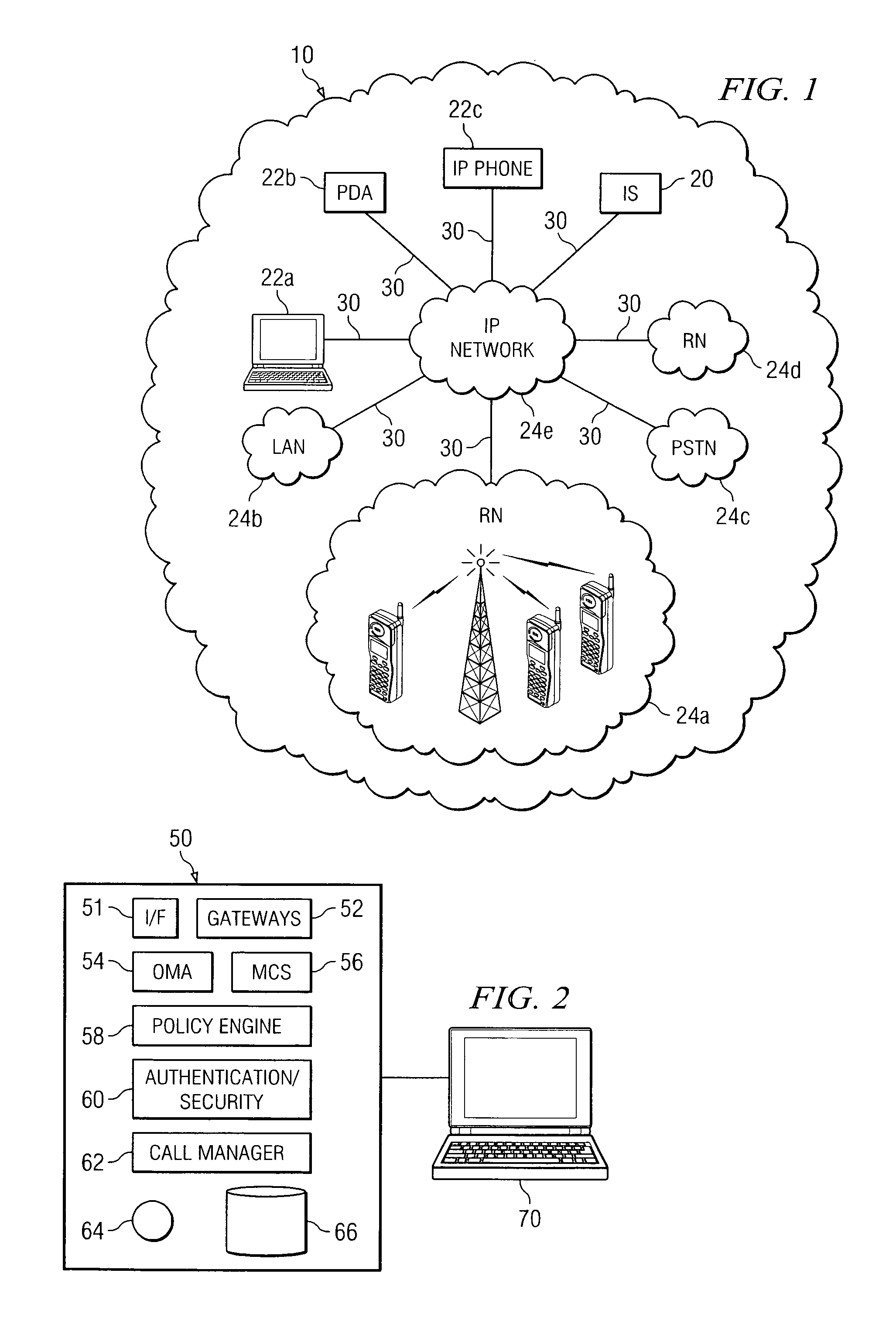
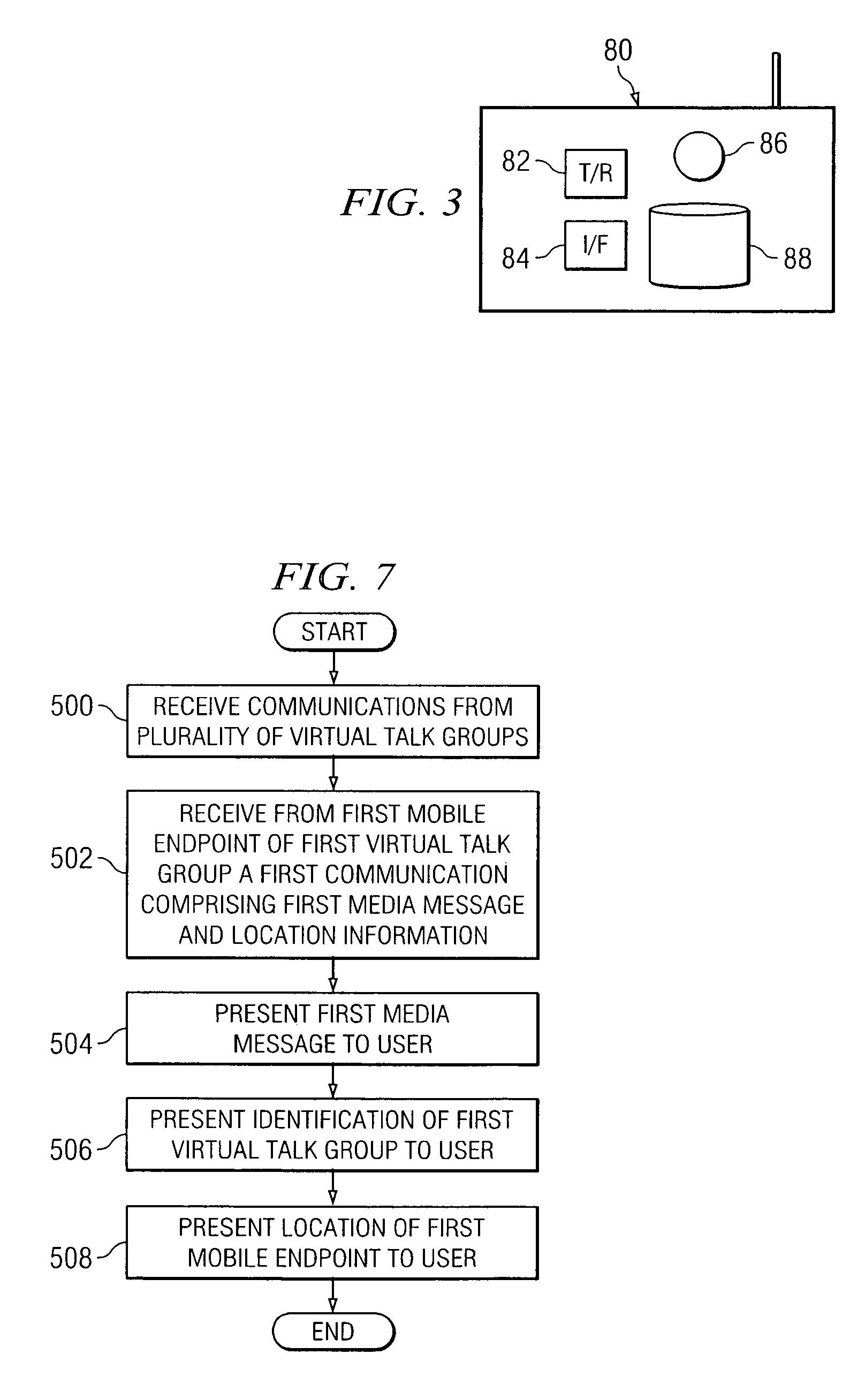
Method and system for managing virtual talk groups
ActiveUS20070239824A1Eliminates and reduces of disadvantageEliminates and reduces of and problemSpecial service for subscribersConnection managementDistributed computingInteroperability Problem
A method for managing virtual talk groups includes facilitating communications from a plurality of endpoints via an interoperability system. The plurality of endpoints comprises endpoints of different communication networks. The method includes configuring a virtual talk group comprising a first group of the plurality of endpoints and assigning to at least one endpoint of the first group of the plurality of endpoints of the virtual talk group functionality with respect to the interoperability system based on a relative priority of the at least one endpoint to other endpoints of the first group of the plurality of endpoints.
Owner:STA GRP LLC
Method and system for providing interoperable communications with location information
InactiveUS20070037596A1Eliminates and reduces of disadvantageEliminates and reduces of and problemNetwork topologiesConnection managementTelecommunicationsComputer science
Owner:CISCO TECH INC
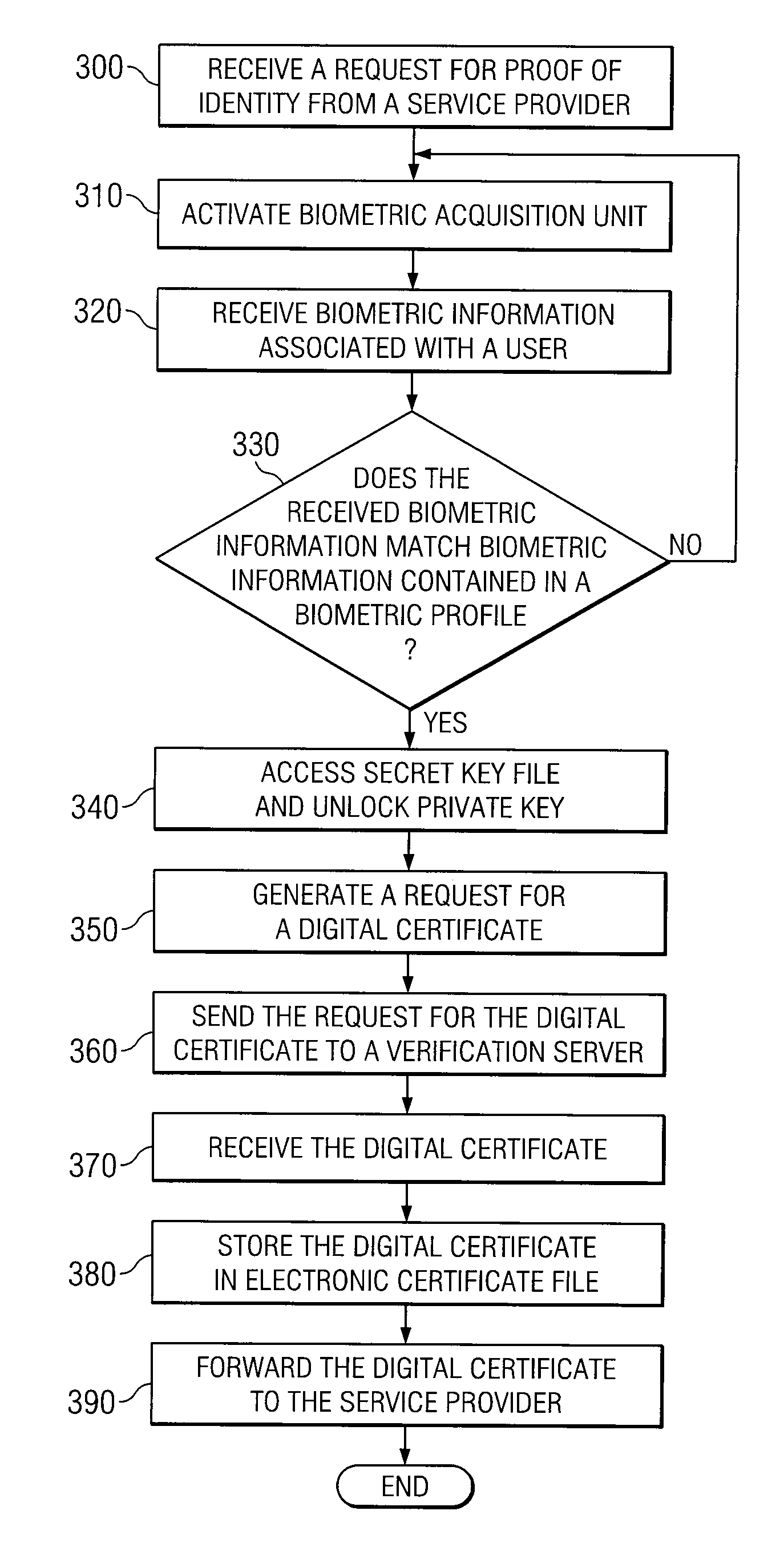
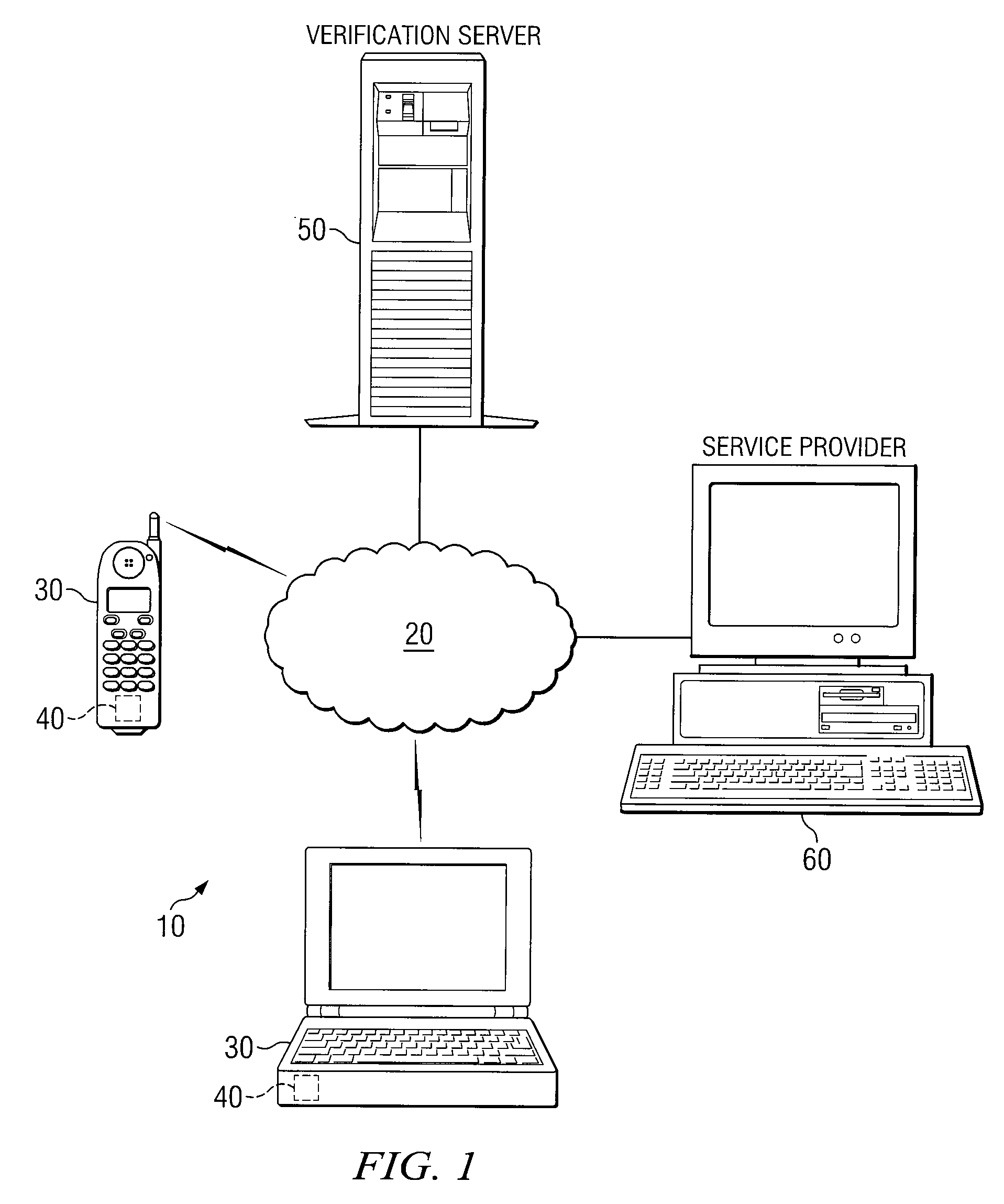
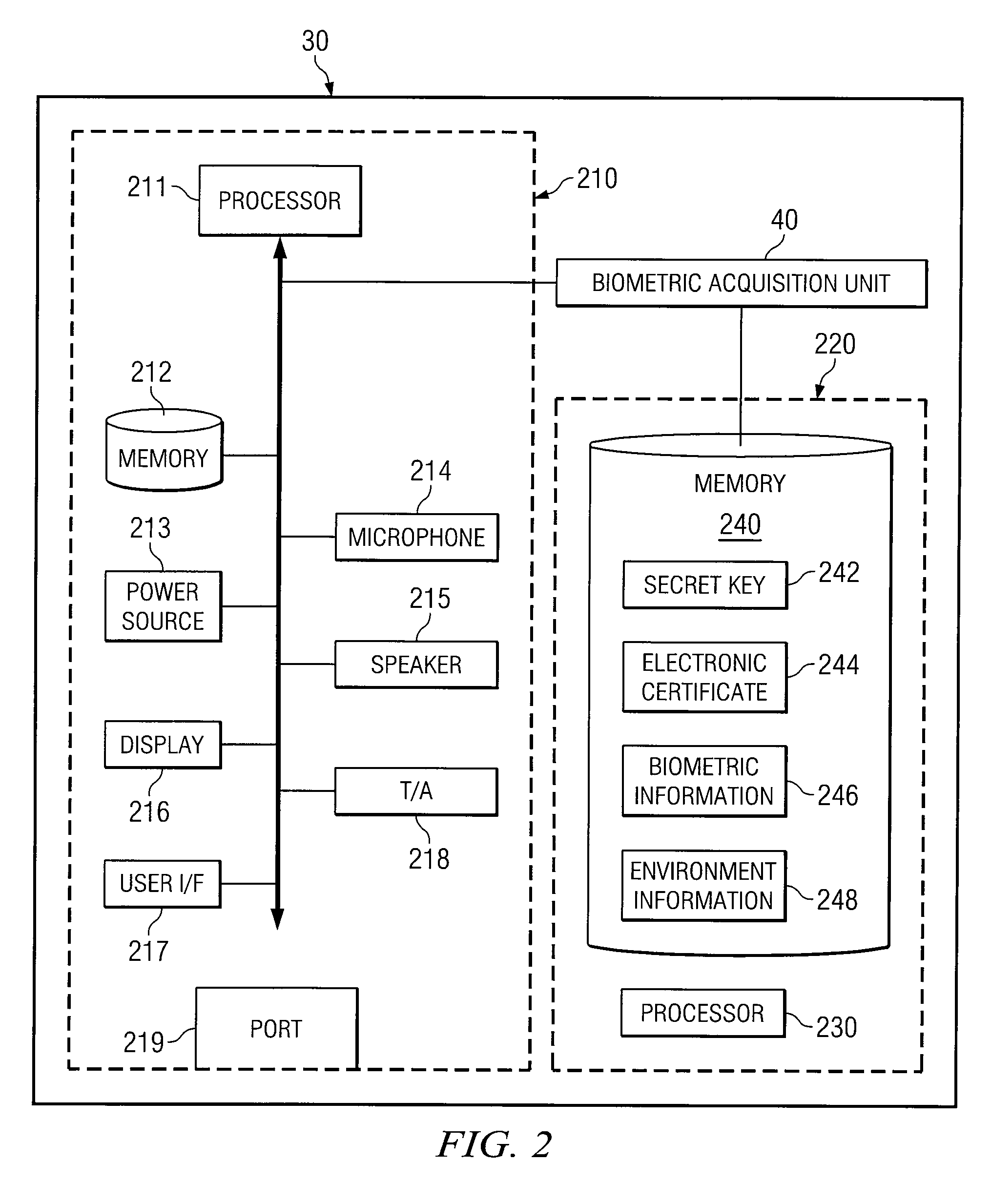
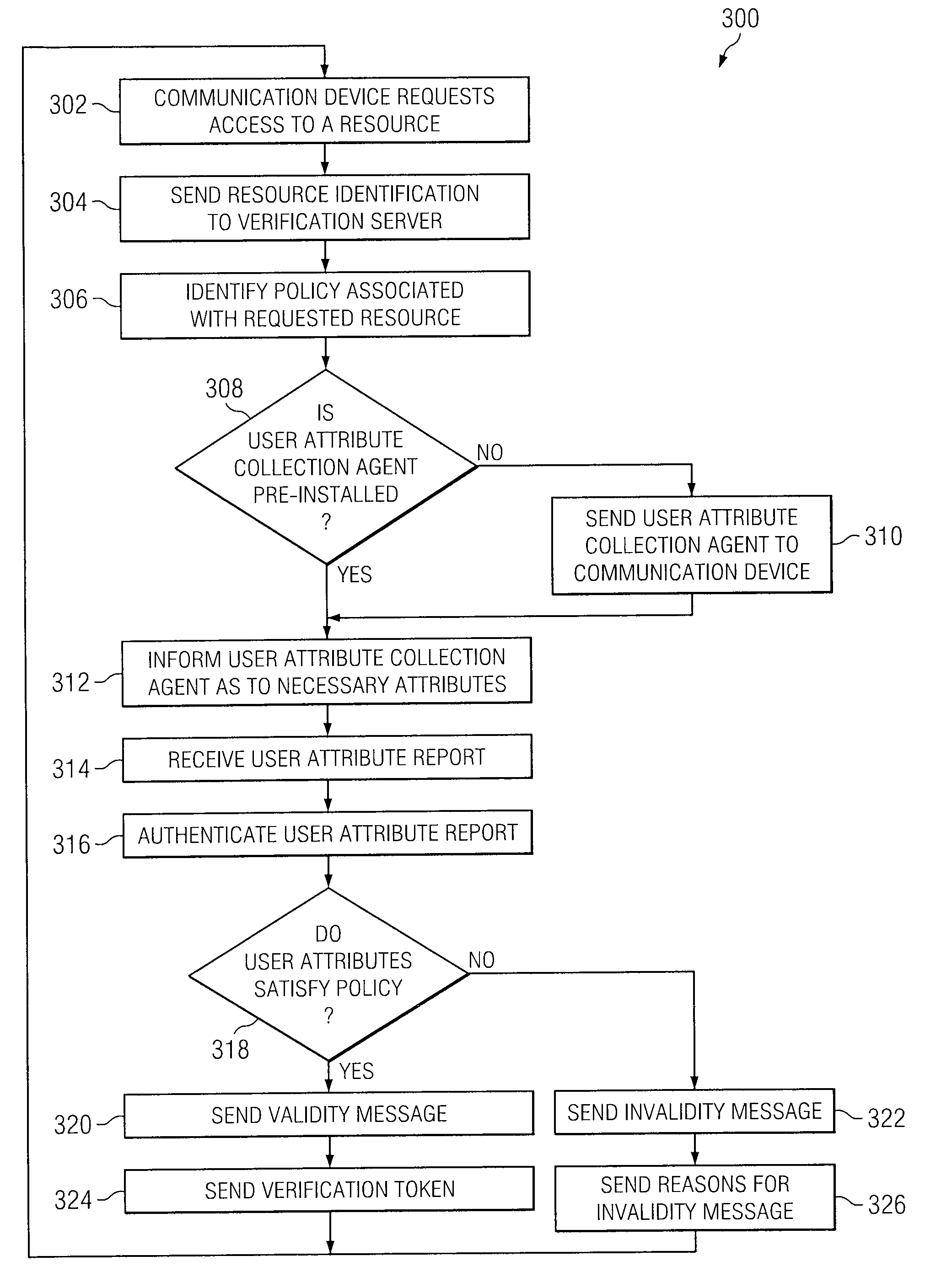
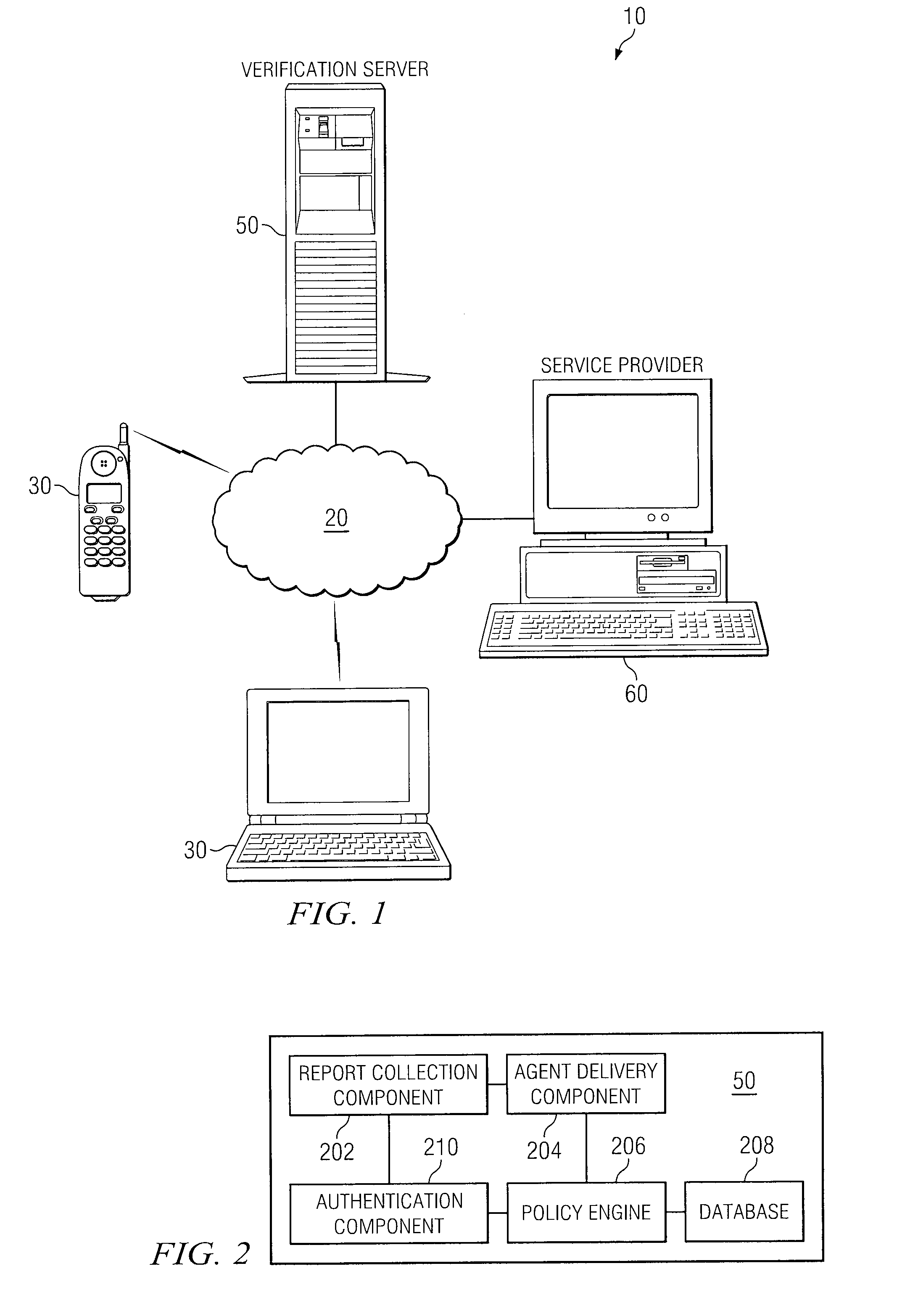
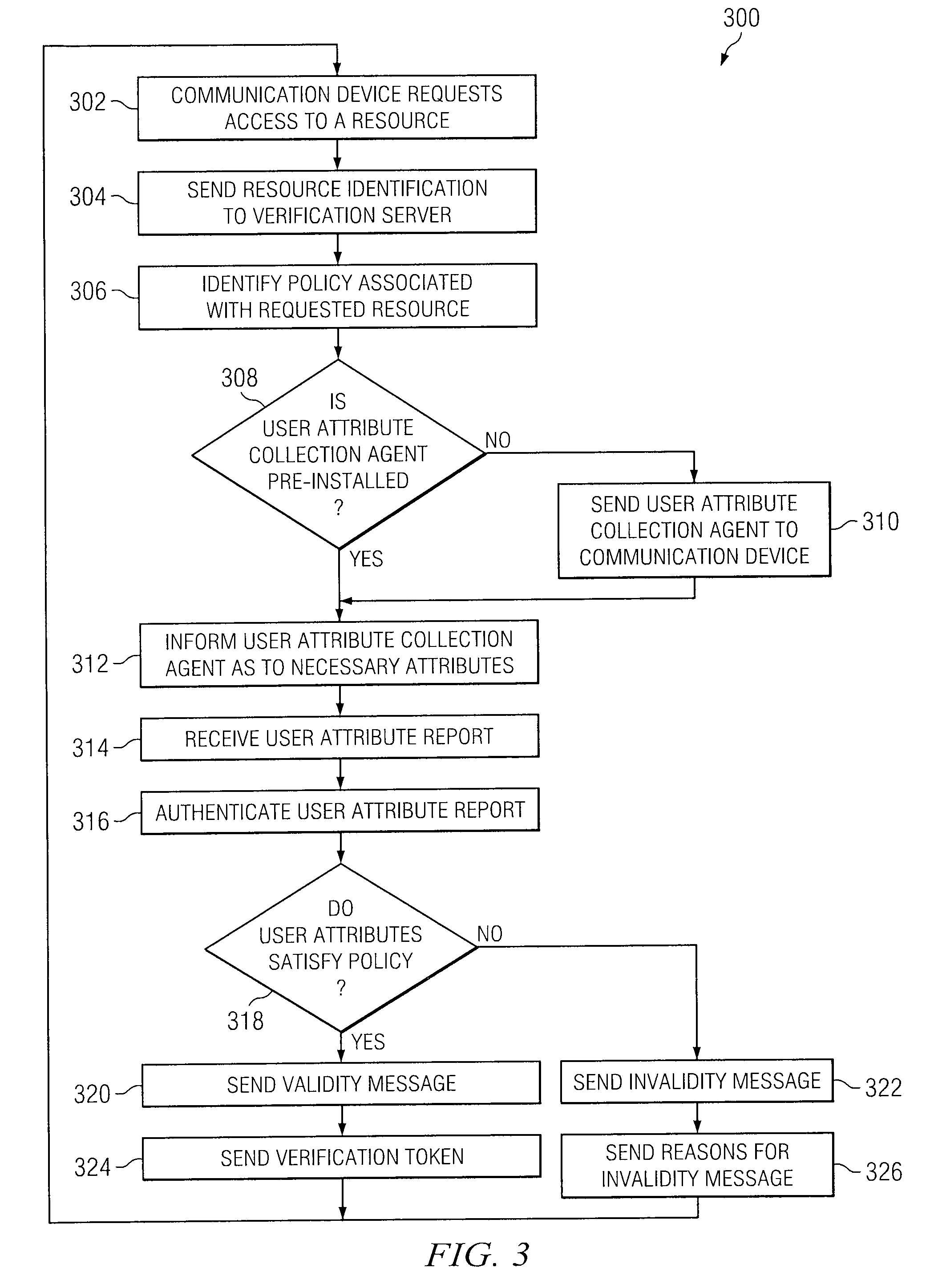
Method and Apparatus for Identity Verification
InactiveUS20090235068A1Eliminates and reduces of disadvantageEliminates and reduces of and problemDigital data processing detailsUser identity/authority verificationService provisionCommunication device
A method for identity verification includes receiving a request for proof of identity from a service provider and receiving biometric information associated with a user of a communication device. The method also includes determining that the received biometric information matches a biometric profile that contains biometric information associated with a registered user of the communication device. The method also includes unlocking a private key associated with the registered user in response to determining that the received biometric information matches a biometric profile and sending a request for a digital certificate that is signed with the private key associated with the registered user. The method further includes receiving the digital certificate that includes a public key associated with the registered user and satisfies the request for proof of identity. The method also includes with forwarding the digital certificate to the service provider.
Owner:FUJITSU LTD
Method and system for communicating navigation information
ActiveUS7035734B2Eliminates and reduces of disadvantageEliminates and reduces of and problemInstruments for road network navigationRoad vehicles traffic controlTraffic delayReal-time computing
A method for communicating navigation information includes receiving destination information from a user. The destination information comprises a desired destination of the user. The method includes determining a first route to the destination and communicating the first route to the user. The method includes monitoring position information of a plurality of vehicles and identifying an area causing traffic delay using the position information of the plurality of vehicles. The method also includes determining a second route to the destination to avoid the area and communicating the second route to the user.
Owner:CISCO TECH INC
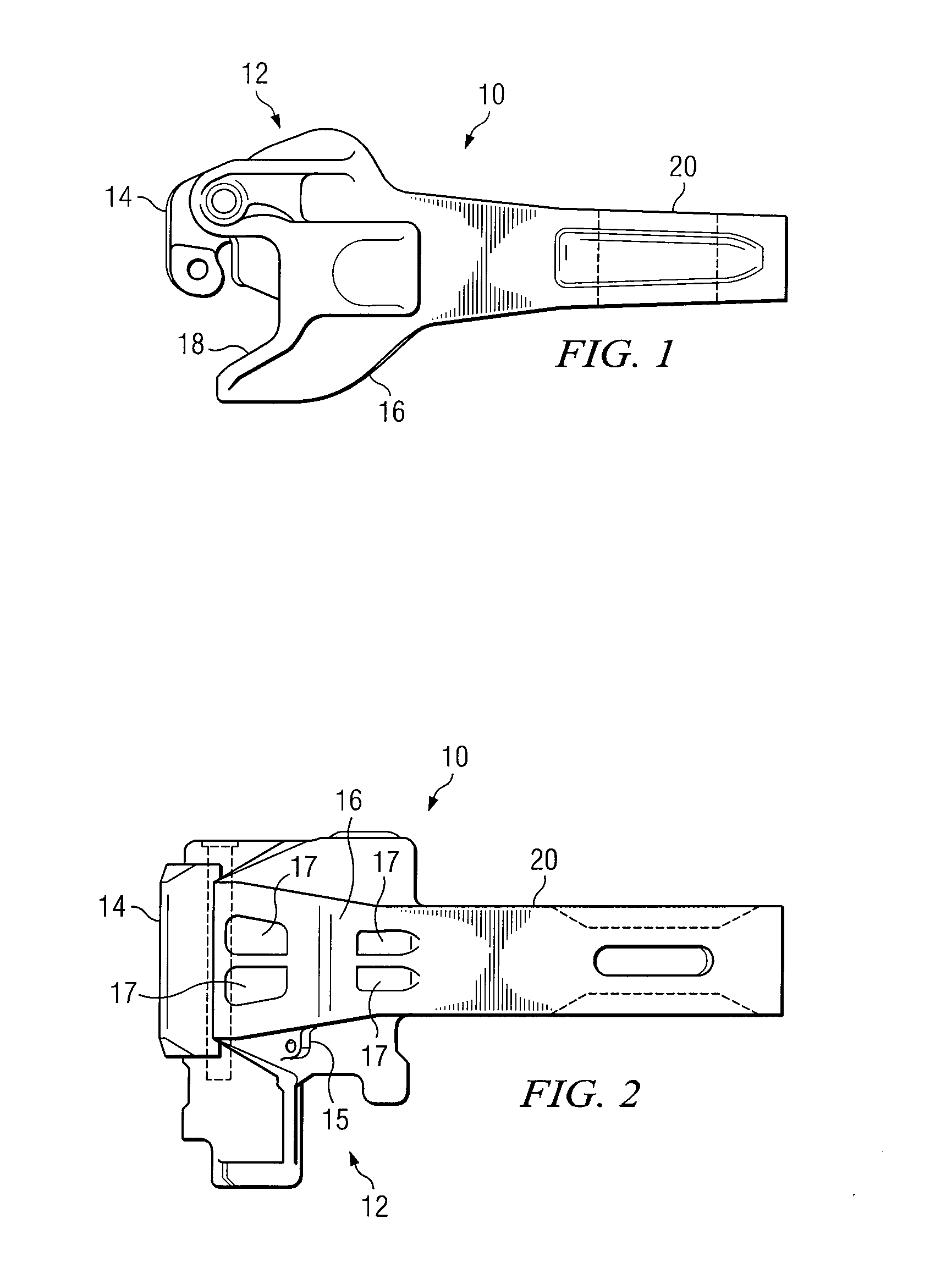
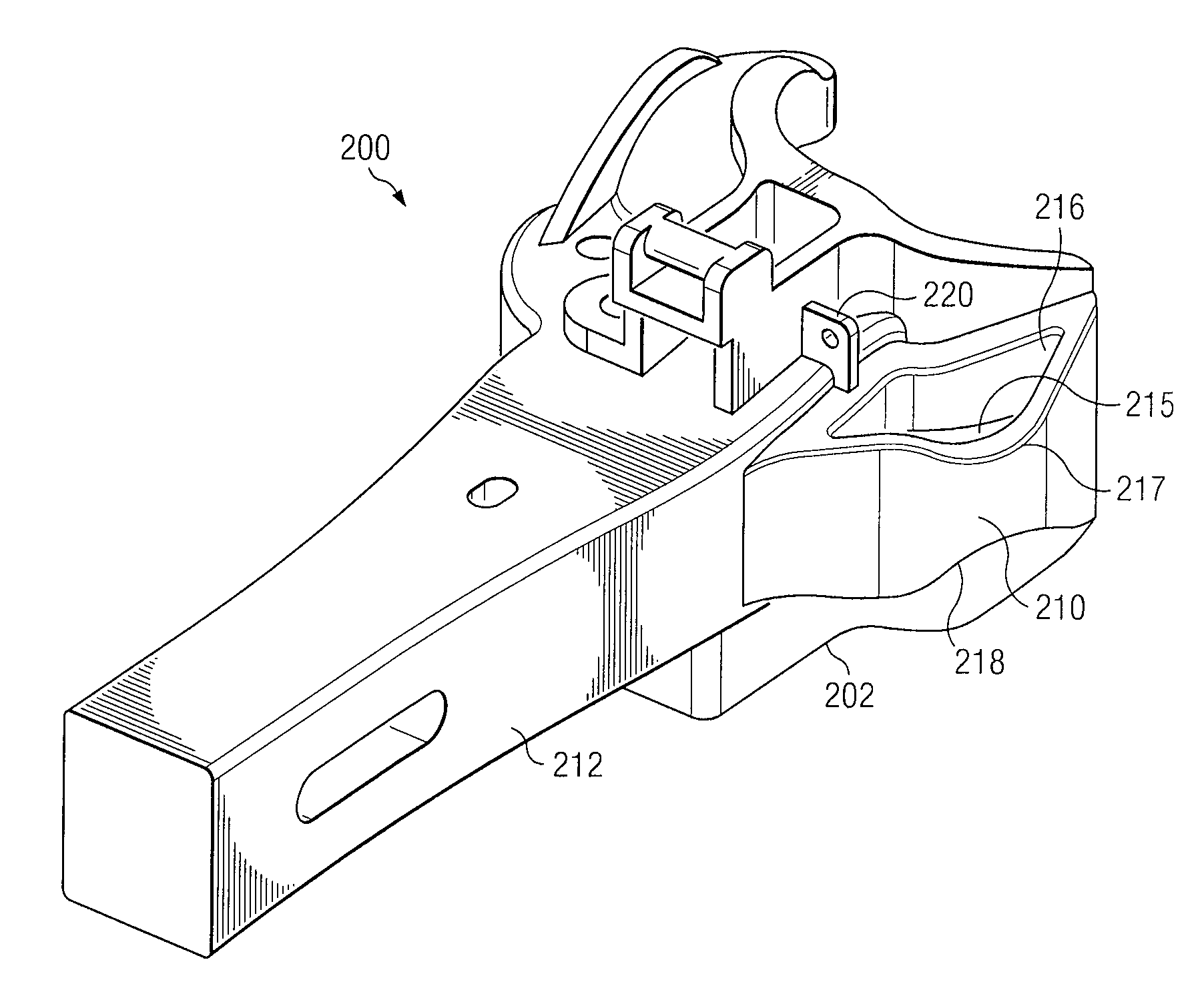
Railcar Coupler System and Method
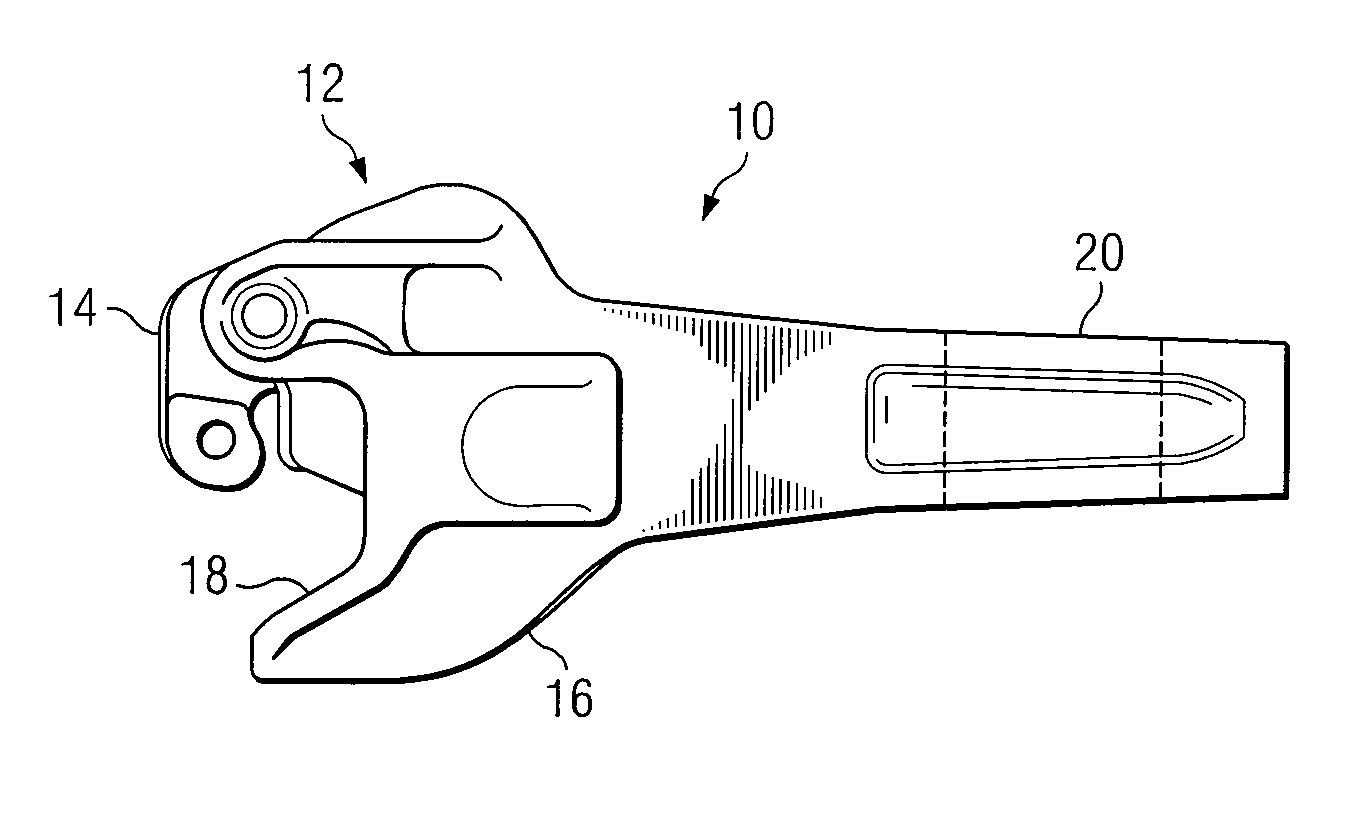
ActiveUS20080128377A1Eliminates and reduces of disadvantageEliminates and reduces of and problemRailway coupling accessoriesEngineeringMechanical engineering
A railcar coupler includes a coupler head portion extending from a shank portion. The coupler head portion is configured to couple to a first coupler knuckle for coupling the railcar coupler to a second railcar coupler of an adjacent railcar. The coupler head portion comprises a nose portion and a gathering face extending from the nose portion for engaging a second coupler knuckle coupled to the second railcar coupler. The coupler head portion comprises a guard arm portion extending from the nose portion towards the shank portion. The guard arm portion comprises a minimum width less than a width of the shank portion where the guard arm portion meets the shank portion.
Owner:MCCONWAY & TORLEY LLC
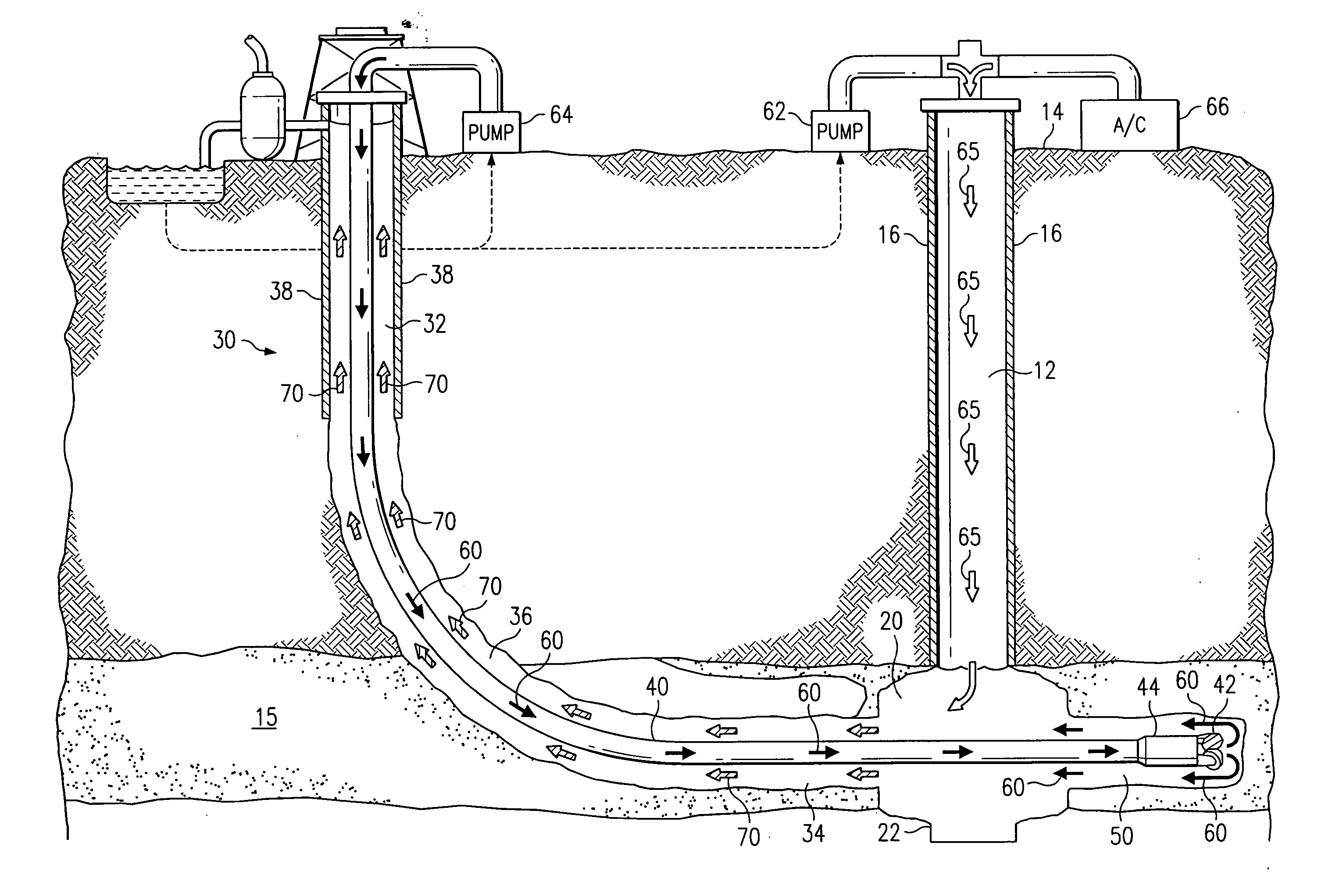
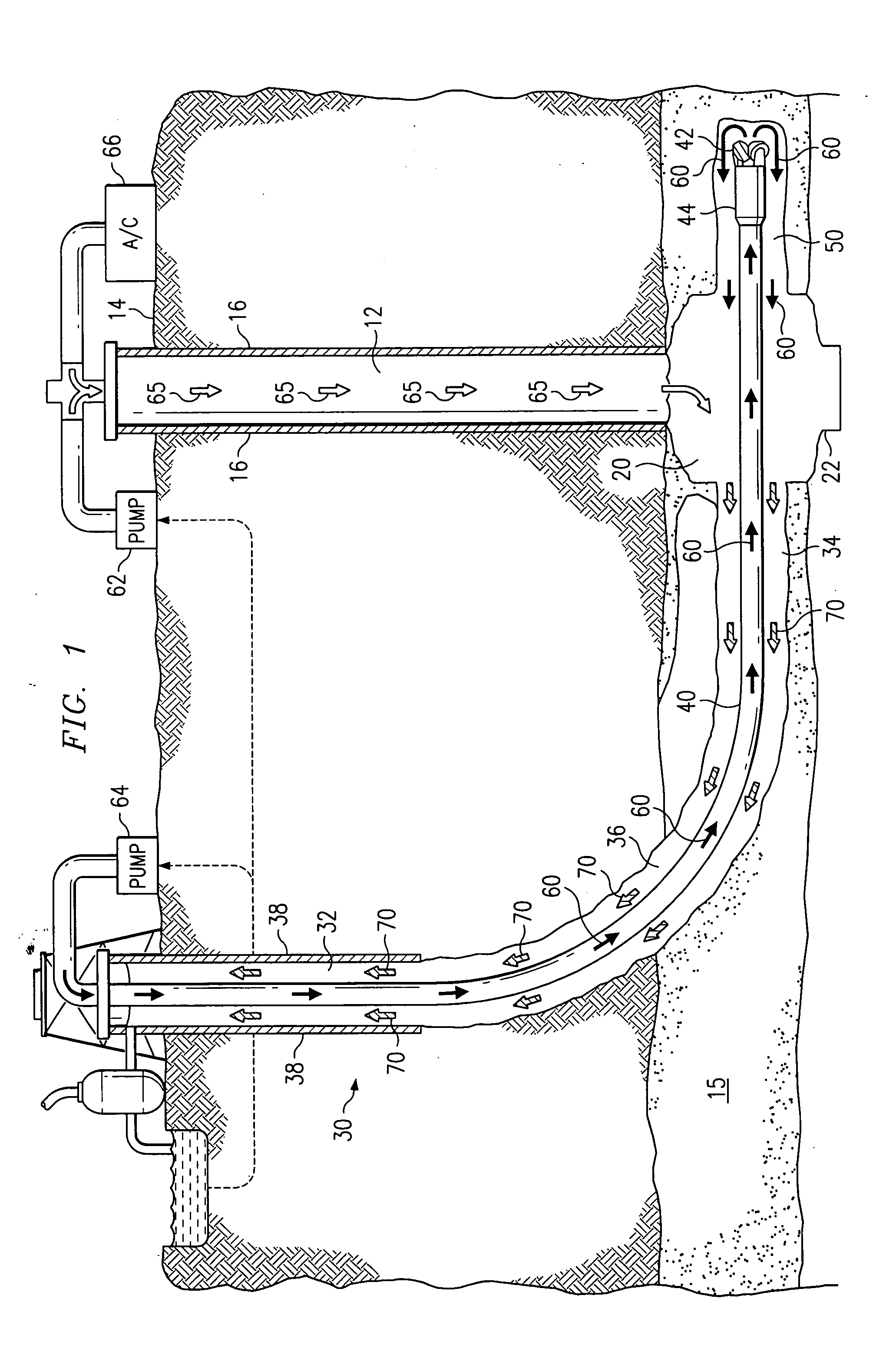
Method and system for controlling pressure in a dual well system
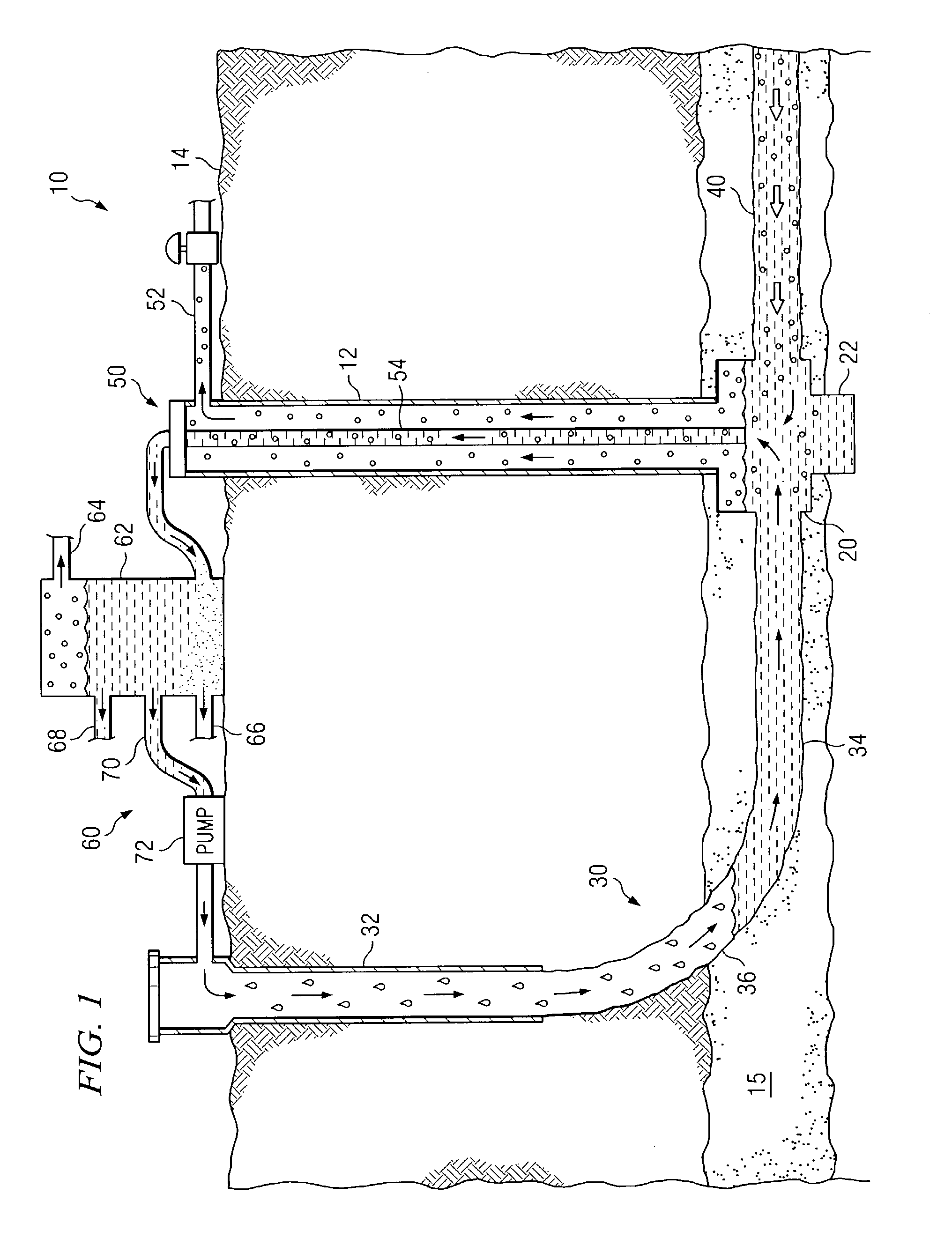
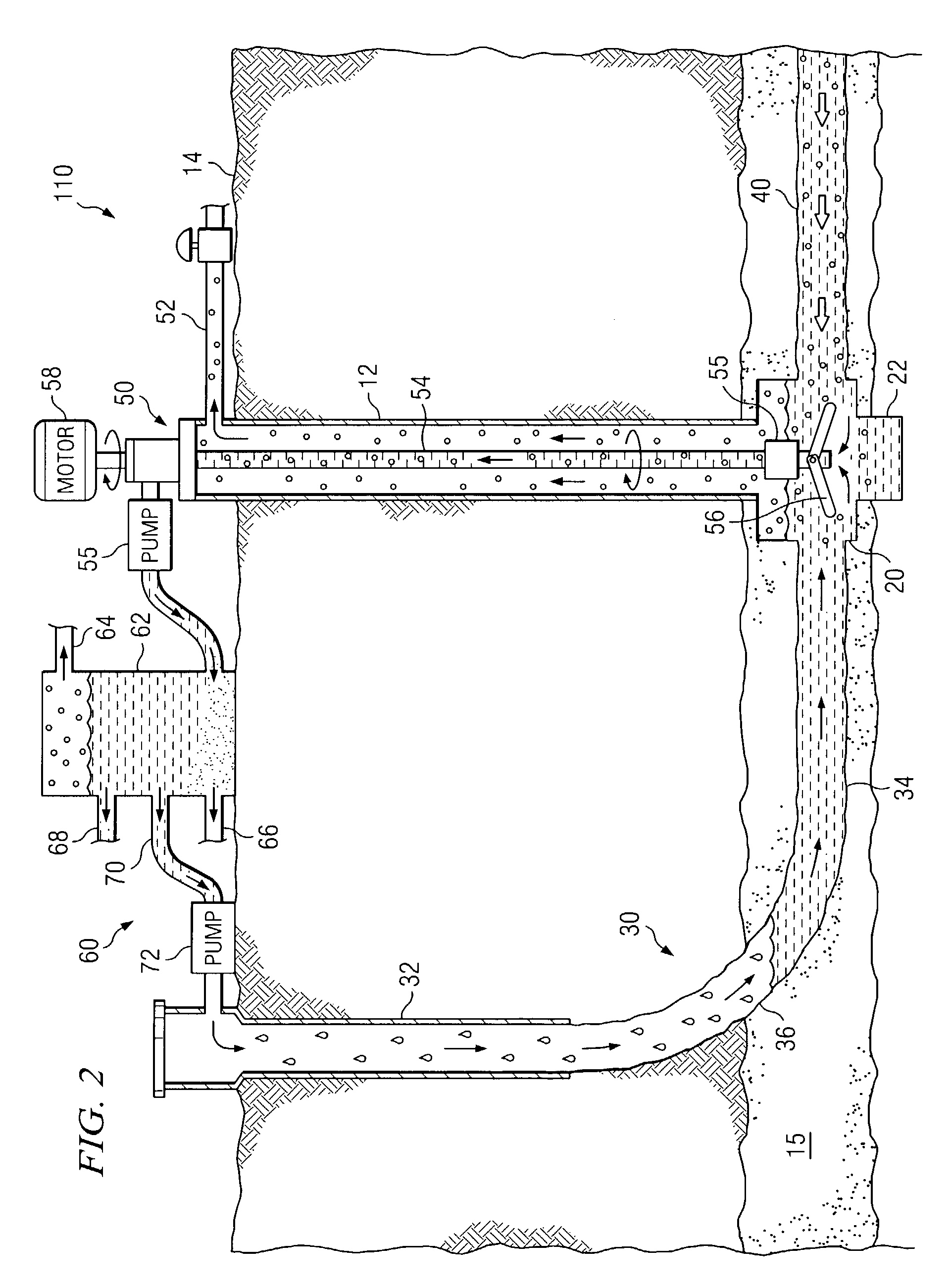
InactiveUS20050115709A1Eliminates and reduces of disadvantageEliminates and reduces of and problemFluid removalDirectional drillingWell drillingHydrology
A method for controlling pressure of a dual well system includes drilling a substantially vertical well bore from a surface to a subterranean zone and drilling an articulated well bore from the surface to the subterranean zone using a drill string. The articulated well bore is horizontally offset from the substantially vertical well bore at the surface and intersects the substantially vertical well bore. The method includes drilling a drainage bore into the subterranean zone. The method includes pumping a drilling fluid through the drill string when drilling the drainage bore. The method includes pumping a pressure fluid down the substantially vertical well bore when drilling the drainage bore. The pressure fluid mixes with the drilling fluid to form a fluid mixture returning up the articulated well bore which forms a frictional pressure that resists fluid flow from the subterranean zone.
Owner:EFFECTIVE EXPLORATION
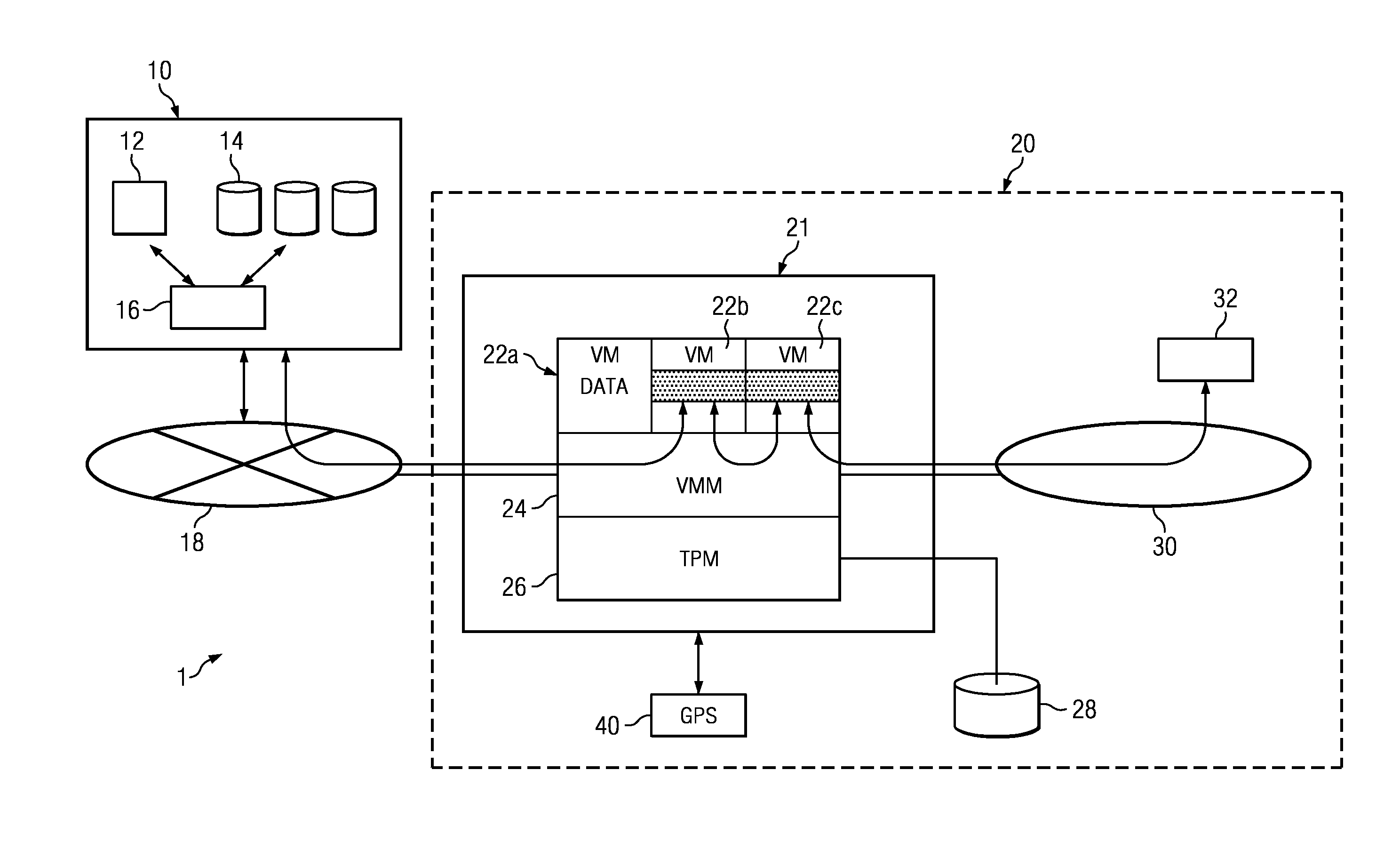
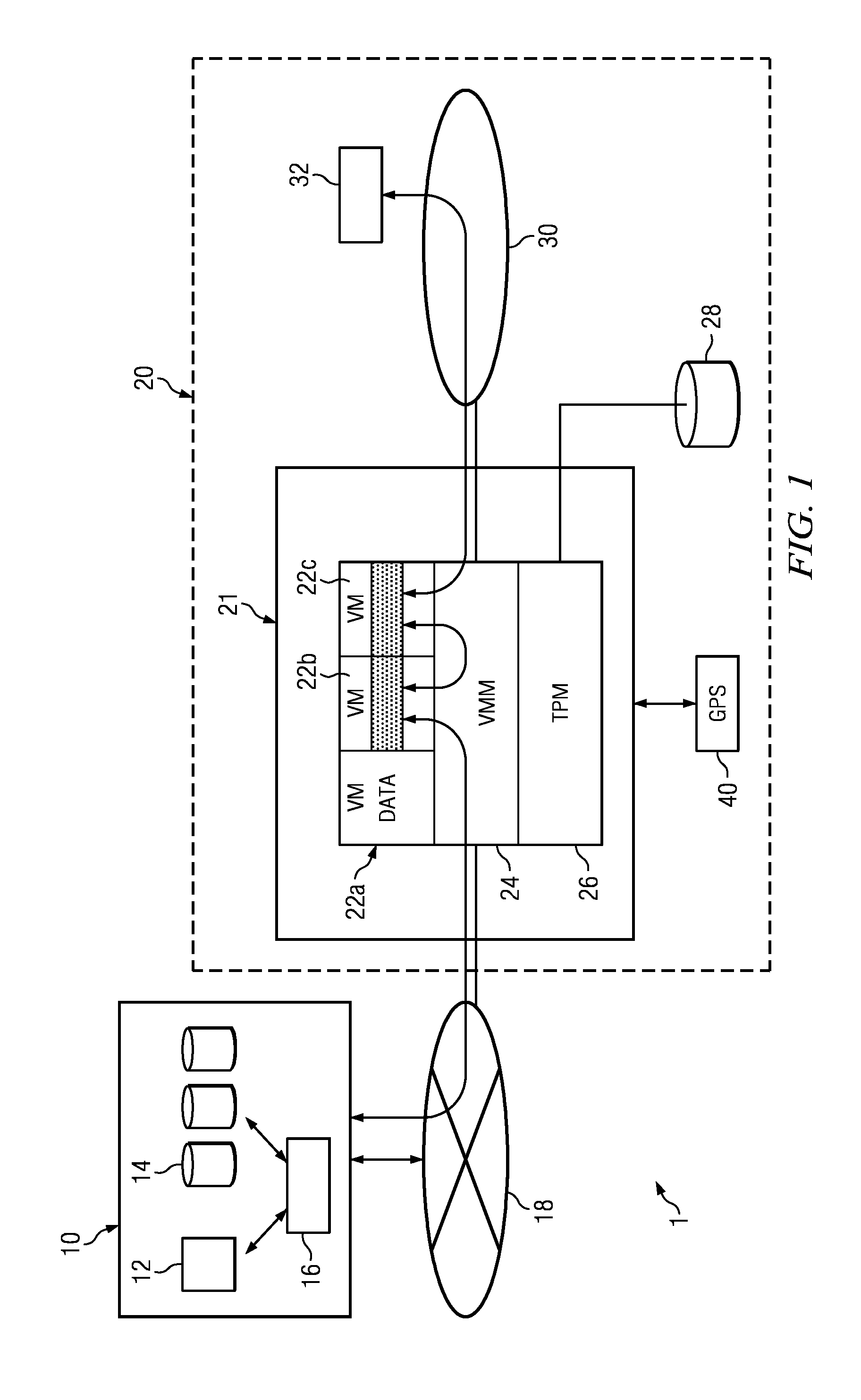
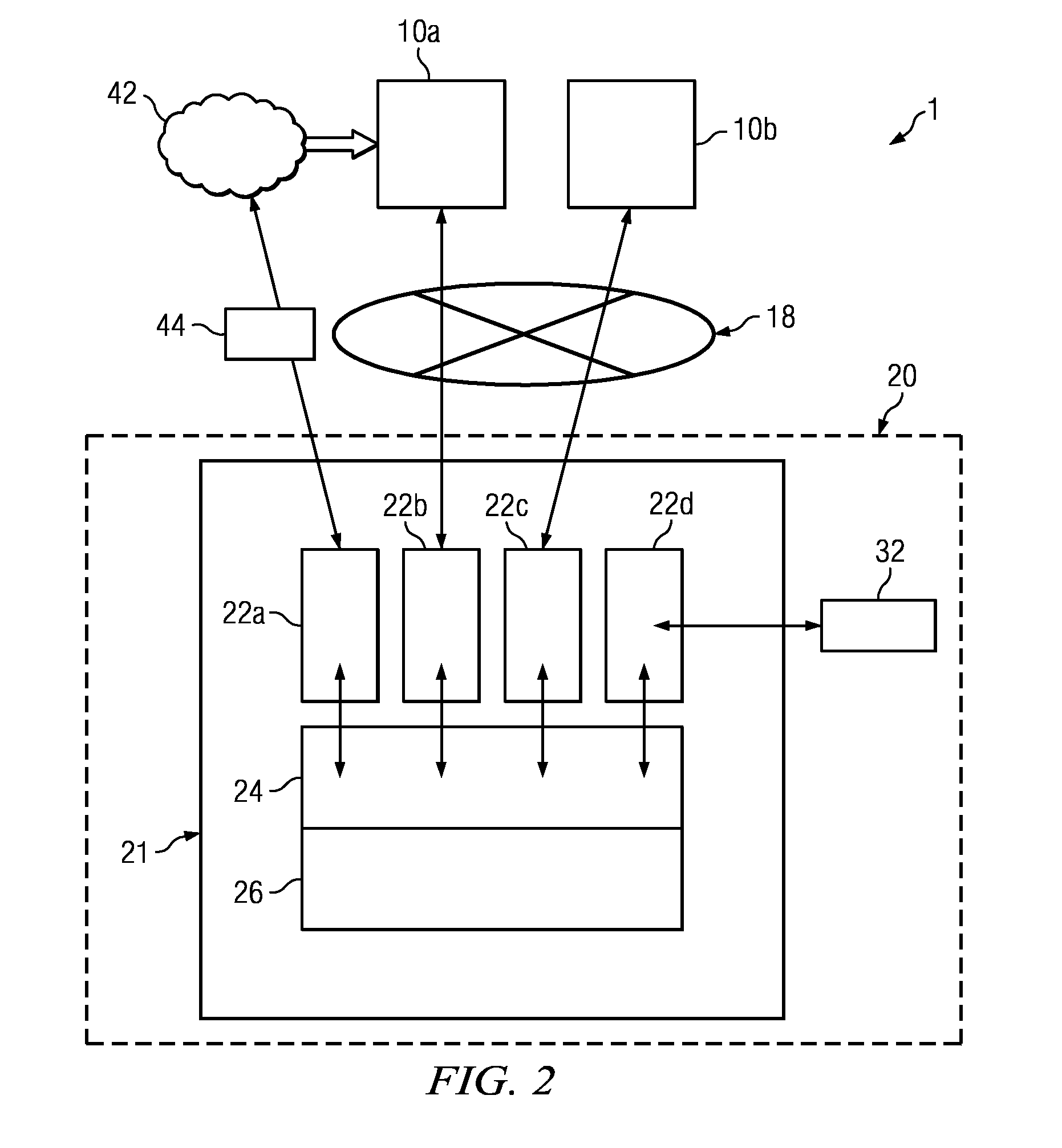
System and methods for remote maintenance in an electronic network with multiple clients
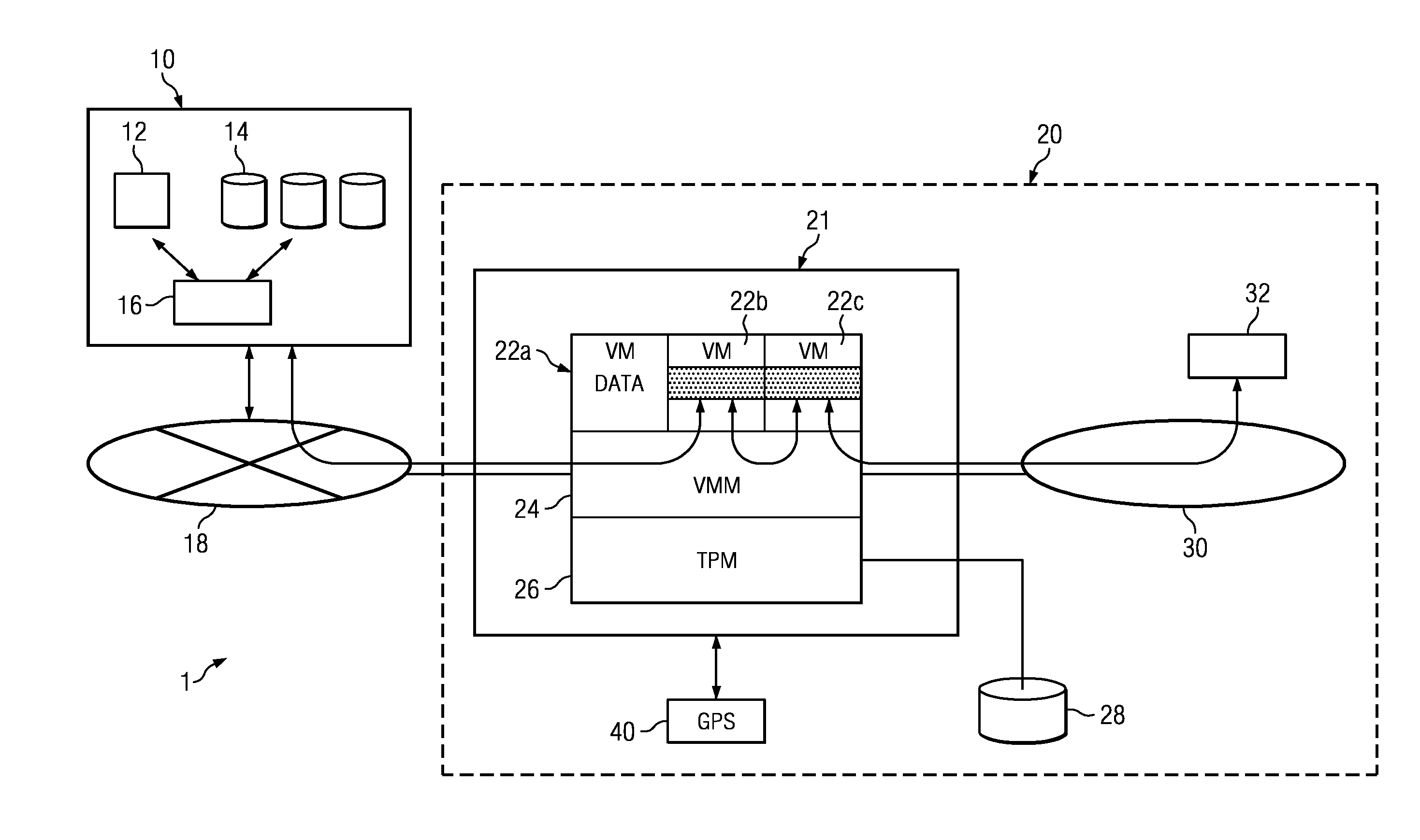
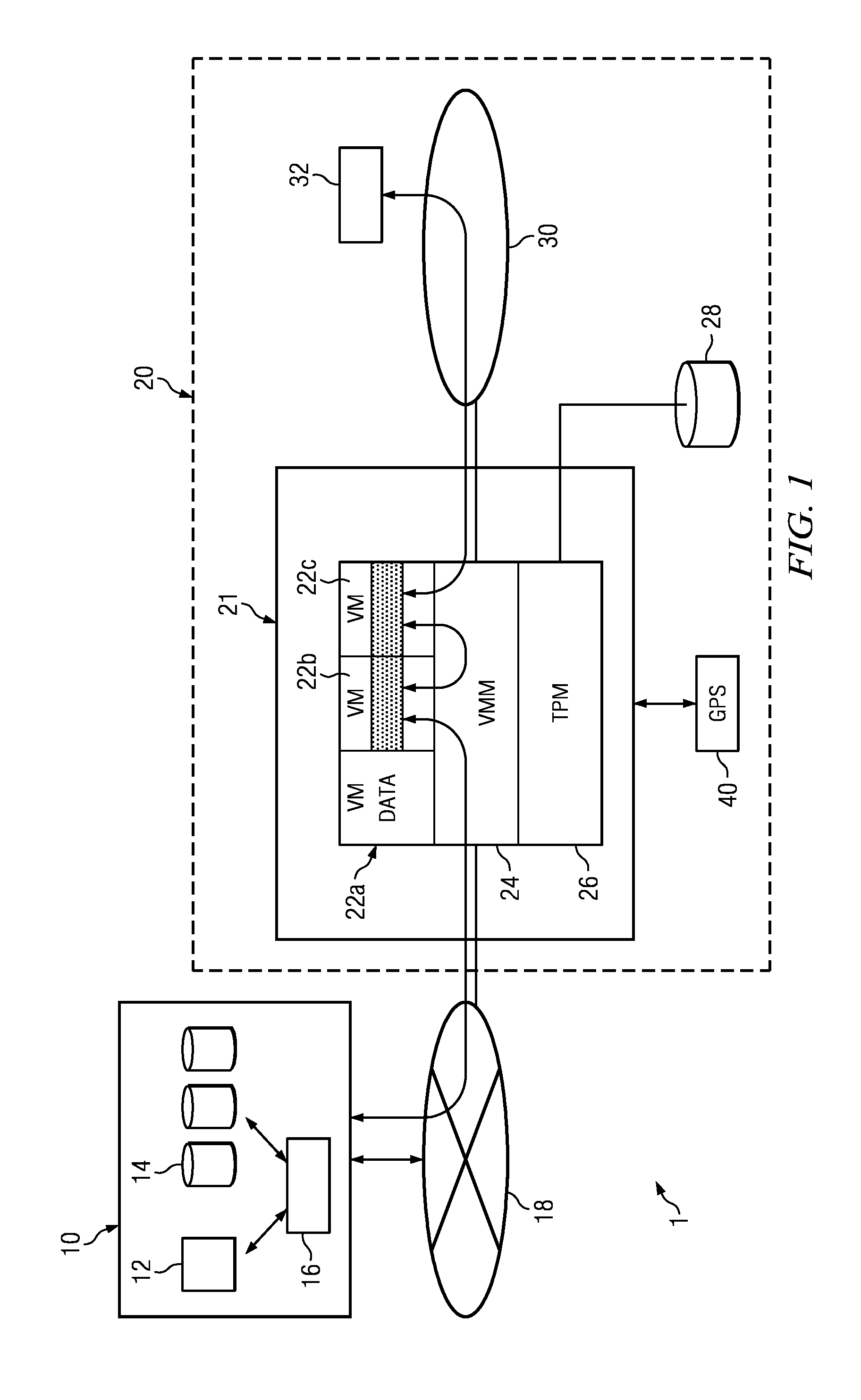
InactiveUS20110239210A1Eliminates and reduces of disadvantageEliminates and reduces of and problemWeb data indexingDigital data protectionData setData center
According to one embodiment, a client system supported by remote maintenance in an electronic network configured to serve a plurality of clients may include an electronic network, a plurality of storage resources, a first virtual machine, a second virtual machine, and a virtual machine manager. The electronic network may include a plurality of processing resources and a communication bus. The plurality of storage resources may be accessible by the plurality of processing resources. The plurality of storage resources may include a computer readable memory. The first virtual machine may handle a first data set associated with the client system. The first virtual machine may include an operating system and a reporting agent. The second virtual machine may handle a second data set associated with an external data center. The virtual machine manager may be configured to manage data transfer between the first virtual machine and the second virtual machine. The second virtual machine may be configured to assess a state of the first virtual machine and identify a software update for installation on the first virtual machine. The virtual machine manager may manage an attestation process for the first virtual machine prior to delivering or installing the software update on the client system using the first virtual machine.
Owner:FUJITSU LTD
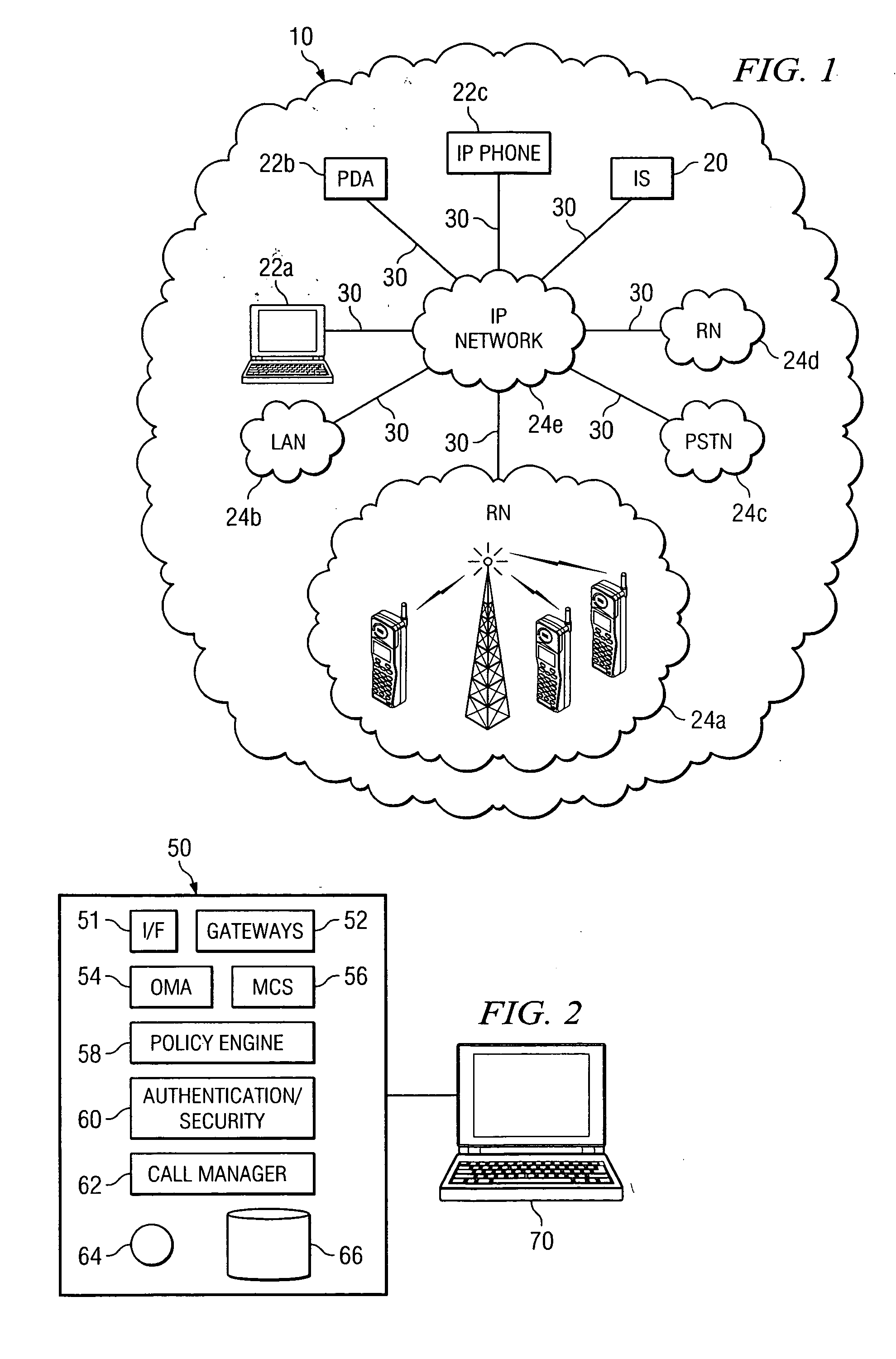
Method and system using presence information to manage network access
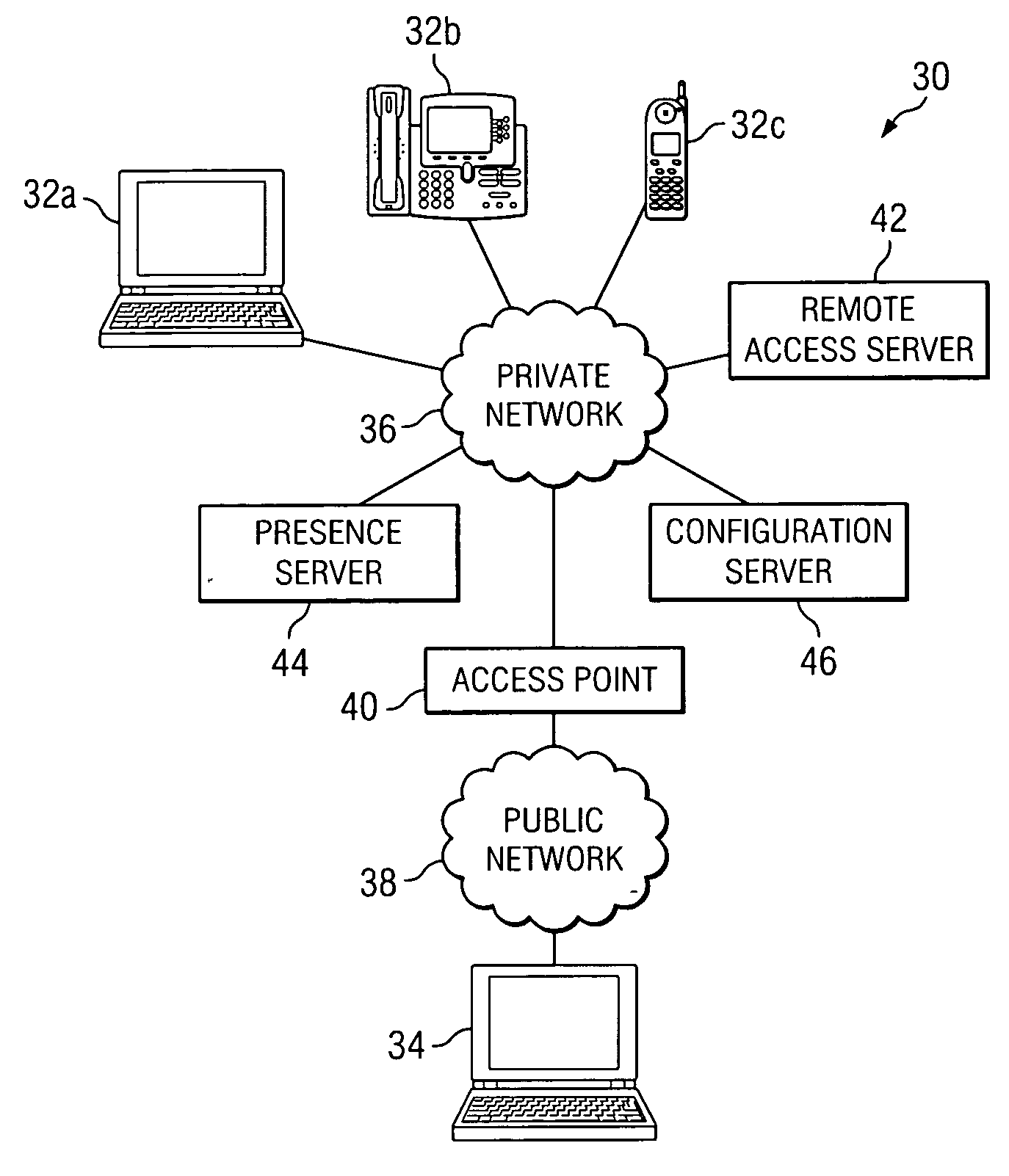
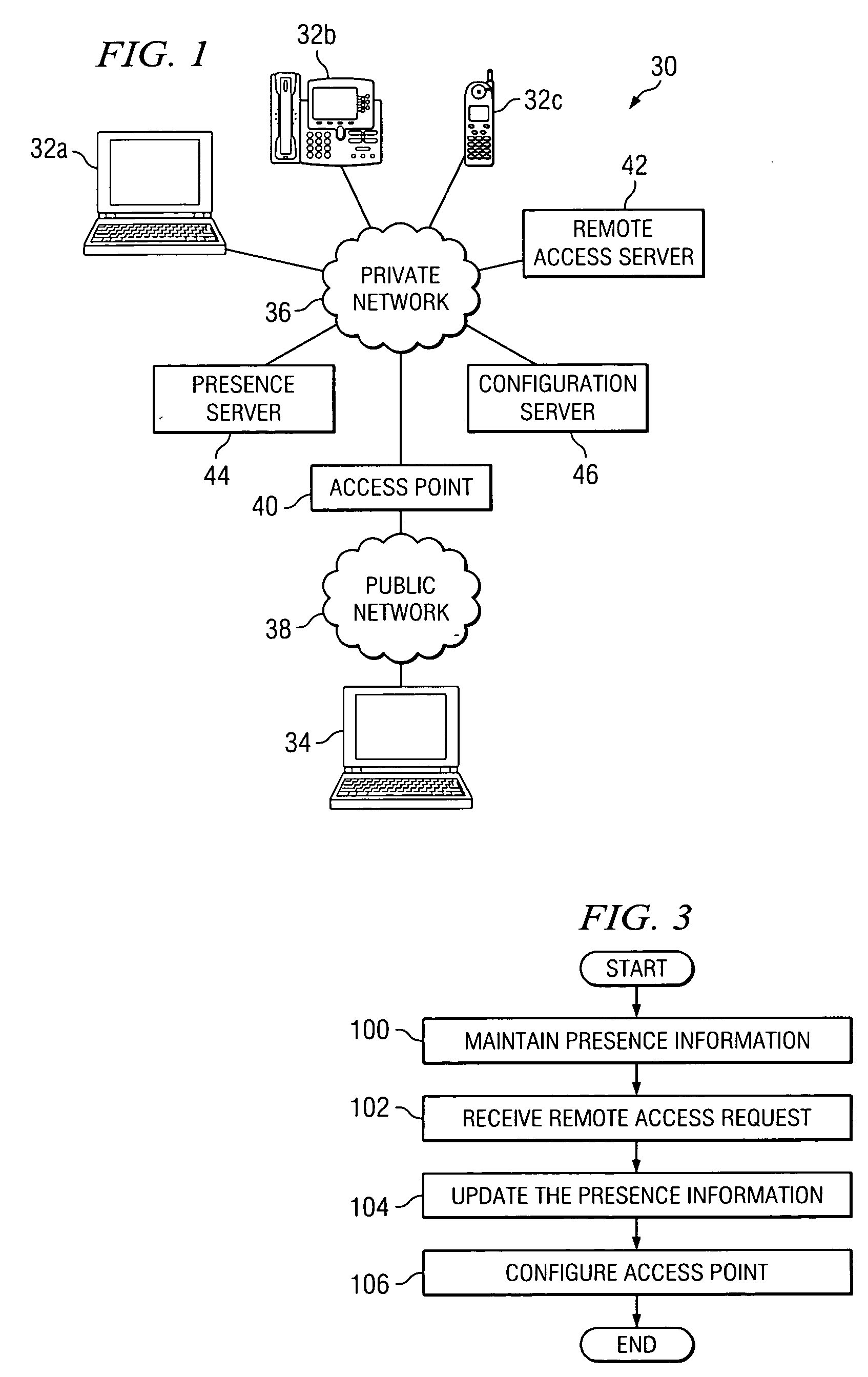
ActiveUS20060259958A1Eliminates and reduces of disadvantageEliminates and reduces of and problemDigital data processing detailsUser identity/authority verificationAuto-configurationIp address
In accordance with a particular embodiment of the present invention, a method using presence information to manage network access includes maintaining presence information for an end user. When a remote access request is received from the end user at a remote endpoint, the presence information for the end user is updated to identify the presence of the end user at one or more network endpoints associated with a private network. An access point to the private network is then automatically configured to allow any communications addressed to an IP address associated with the one or more network endpoints to pass through the access point.
Owner:CISCO TECH INC
Method and system for communicating media based on location of media source
ActiveUS20070036100A1Eliminates and reduces of disadvantageEliminates and reduces of and problemBroadcast service distributionRadio/inductive link selection arrangementsComputer scienceReal-time computing
Owner:CISCO TECH INC
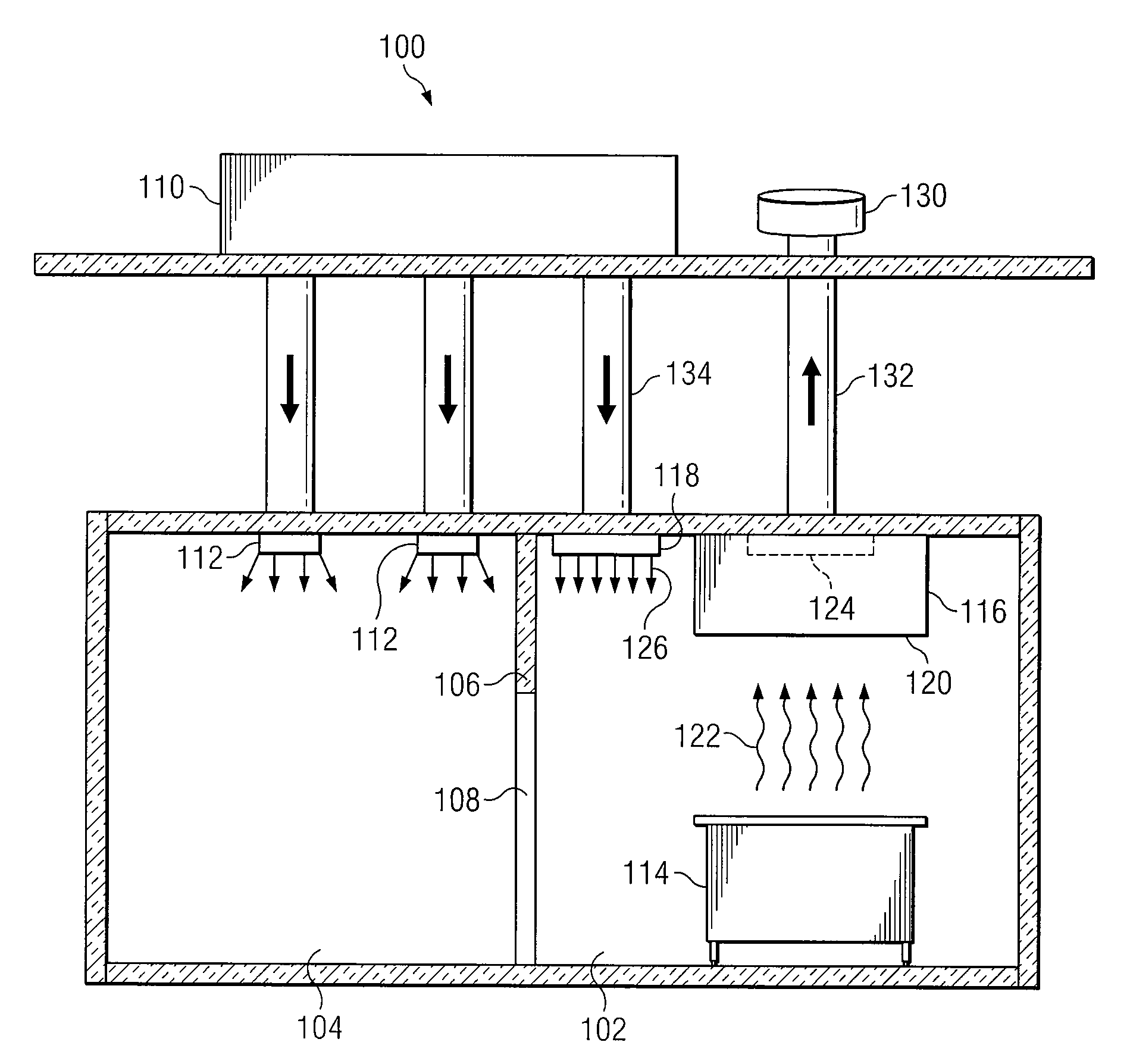
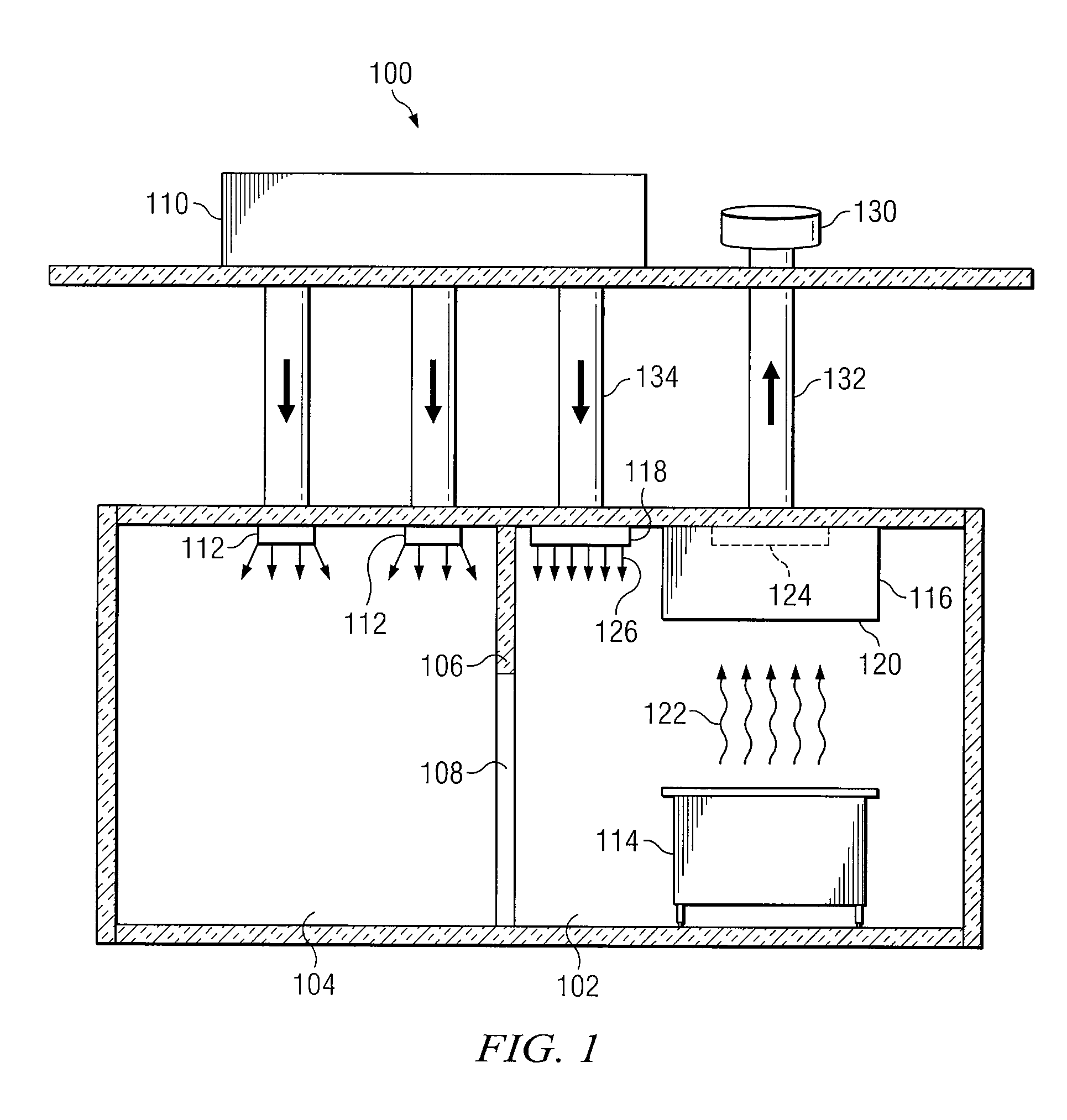
Autonomous Ventilation System
InactiveUS20080274683A1Eliminates and reduces of disadvantageEliminates and reduces of and problemMechanical apparatusDomestic stoves or rangesAir contaminantEngineering
An autonomous ventilation system includes a variable-speed exhaust fan, a controller, an exhaust hood, and a spillage sensor. The exhaust fan removes air contaminants from an area. The controller is coupled to the exhaust fan and adjusts the speed of the exhaust fan. The exhaust hood is coupled to the exhaust fan and directs air contaminants to the exhaust fan. The spillage sensor is coupled to the controller, detects changes in an environmental parameter in a spillage zone adjacent to the exhaust hood, and communicates information relating to detected changes in the environmental parameter to the controller. The controller adjusts the speed of the exhaust fan in response to information relating to detected changes in the environmental parameter.
Owner:HALTON GROUP LTD
Method and system for measuring crosstalk utilizing a crossbar switch
InactiveUS7154845B1Eliminates and reduces of disadvantageEliminates and reduces of and problemInterconnection arrangementsSubstations coupling interface circuitsService systemSolid-state
A method for measuring crosstalk in a data service system includes transmitting a signal using a first device. The first device is coupled to a solid state crossbar switch. The method includes coupling the first device using the crossbar switch to a first data line coupled to the crossbar switch such that the signal communicates over the first data line. The first data line is capable of being coupled to a customer premise equipment (CPE) device. The method includes coupling a first number of second devices coupled to the crossbar switch to a second number of data lines coupled to the crossbar switch using the crossbar switch. Each second number of data lines is capable of being coupled to a CPE device. The method also includes monitoring the second number of data lines for near end crosstalk (NEXT) generated by the signal communicating over the first data line using the first number of second devices. The method may also include monitoring at least one of a third number of data lines for far end crosstalk (FEXT) generated by a signal communicating over the third number of data lines. The third number of data lines comprises the first data line and the second number of data lines.
Owner:CISCO TECH INC
Railcar coupler system and method
ActiveUS7757871B2Eliminates and reduces of disadvantageEliminates and reduces of and problemRailway coupling accessoriesEngineeringMechanical engineering
A railcar coupler includes a coupler head portion extending from a shank portion. The coupler head portion is configured to couple to a first coupler knuckle for coupling the railcar coupler to a second railcar coupler of an adjacent railcar. The coupler head portion comprises a nose portion and a gathering face extending from the nose portion for engaging a second coupler knuckle coupled to the second railcar coupler. The coupler head portion comprises a guard arm portion extending from the nose portion towards the shank portion. The guard arm portion comprises a minimum height less than a height of the shank portion where the guard arm portion meets the shank portion.
Owner:MCCONWAY & TORLEY LLC
Method and Apparatus for Identity Verification
InactiveUS20110072502A1Improve protectionImprove reliabilityDigital data processing detailsUser identity/authority verificationCommunication deviceAuthentication
A method for identity verification includes receiving a request for proof of identity from a service provider and receiving biometric information associated with a user of a communication device. The method also includes determining that the received biometric information matches a biometric profile that contains biometric information associated with a registered user of the communication device. The method also includes unlocking a private key associated with the registered user in response to determining that the received biometric information matches a biometric profile and sending a request for a digital certificate that is signed with the private key associated with the registered user. The method further includes receiving the digital certificate that includes a public key associated with the registered user and satisfies the request for proof of identity. The method also includes with forwarding the digital certificate to the service provider.
Owner:FUJITSU LTD
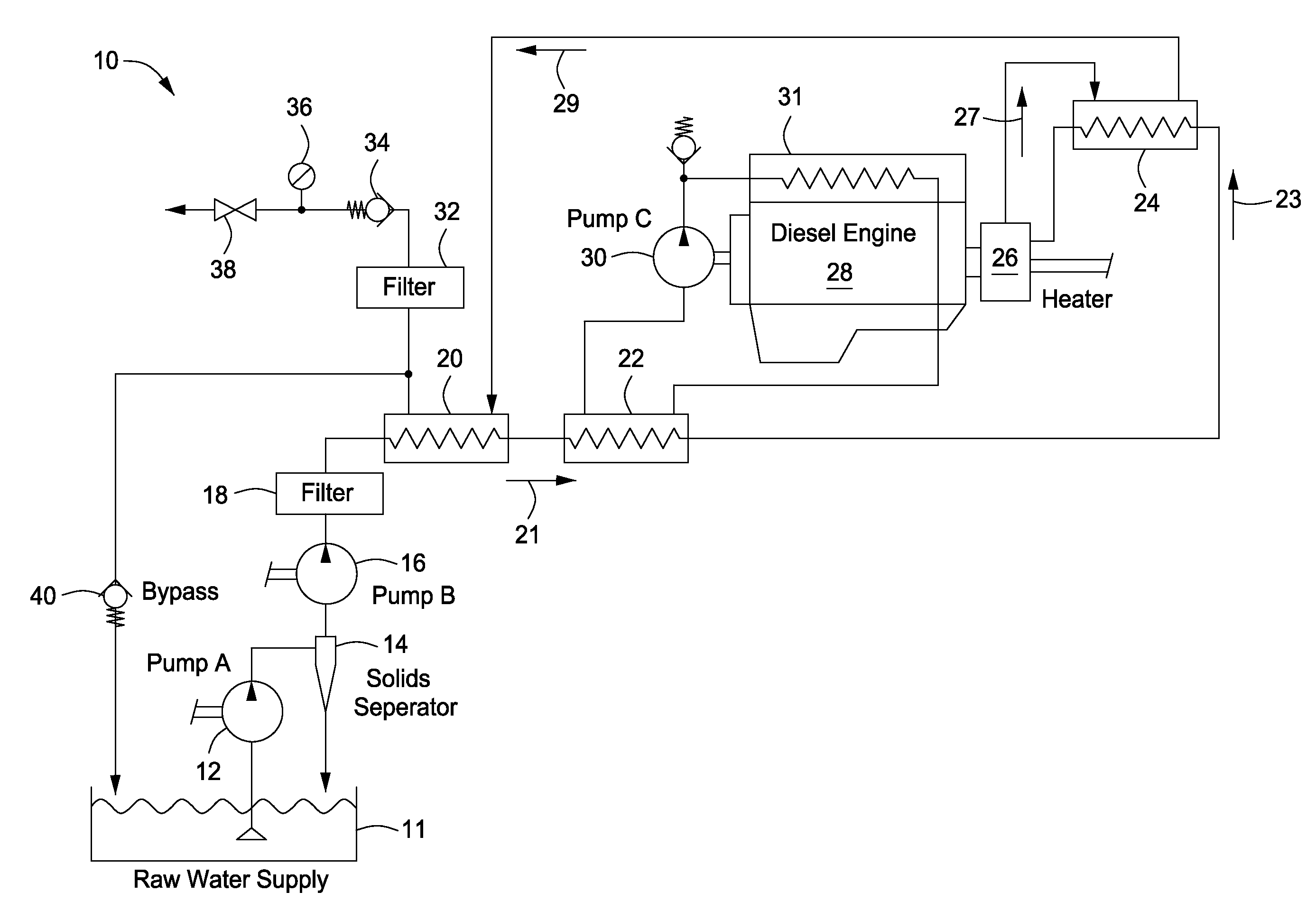
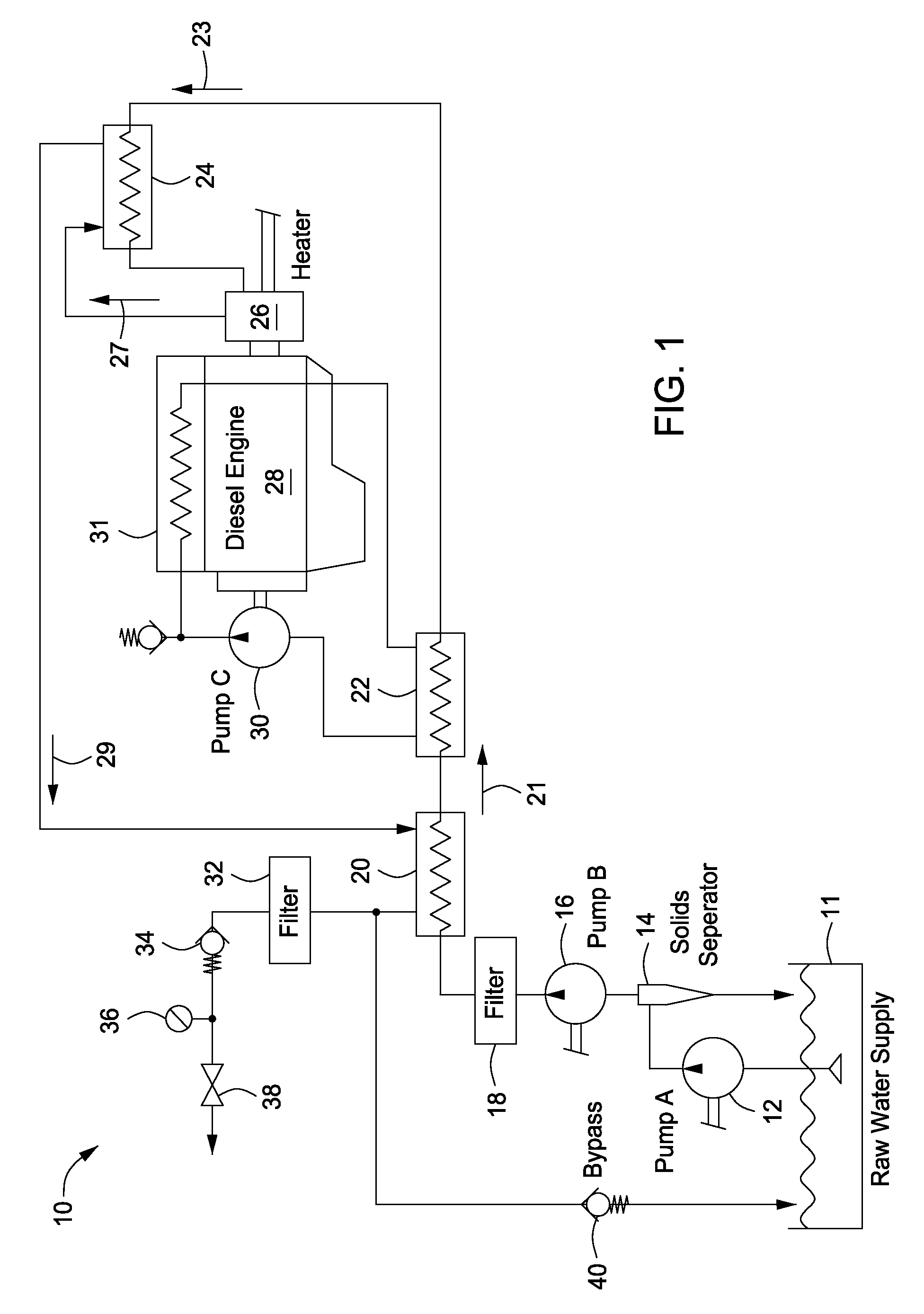
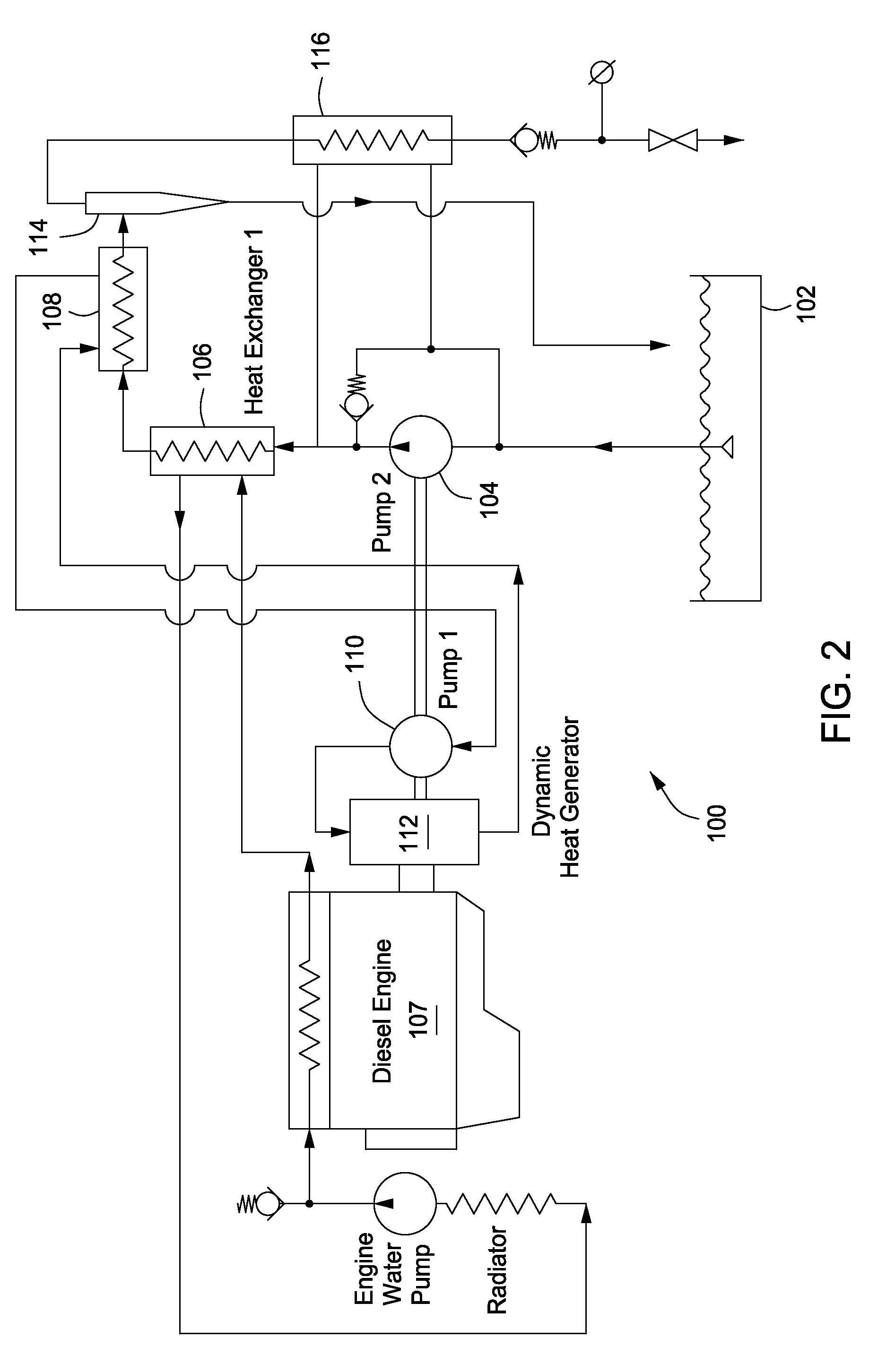
System and method for producing hot water without a flame
InactiveUS7866380B2Eliminates and reduces of disadvantageEliminates and reduces of and problemWater/sewage treatment with mechanical oscillationsWater/sewage treatment by magnetic/electric fieldsWater useWater source
The present invention provides a system and method for producing hot water without a flame. The system and method heats water to at least a specified temperature without a flame by providing a source of water and a prime mover, pumping water from the source of water into one or more heat exchangers, pre-heating the water using the one or more heat exchangers, heating the pre-heated water to at least the specified temperature without a flame using a dynamic heat generator driven by the prime mover, using the heated water in the one or more heat exchangers to pre-heat the water and providing the heated water to an output.
Owner:CLOUDBURST SOLUTIONS +1
Method and System for Managing a Plurality of Virtual Talk Groups
InactiveUS20070280203A1Eliminates and reduces of disadvantageEliminates and reduces of and problemData switching by path configurationNetwork connectionsComputer scienceDistributed computing
Owner:CISCO TECH INC
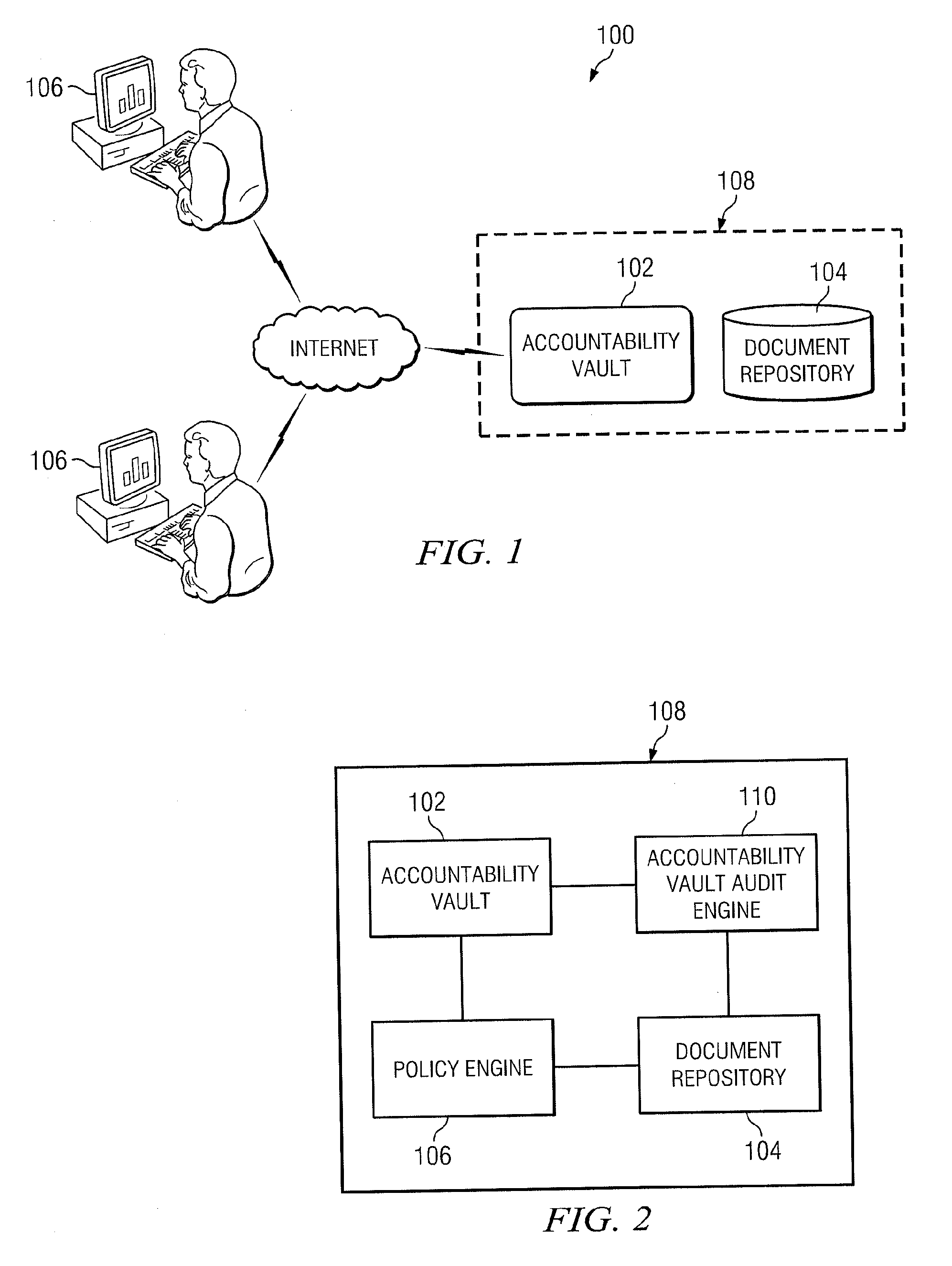
Method and Apparatus for Sharing Documents
ActiveUS20110126008A1Eliminates and reduces of disadvantageEliminates and reduces of and problemDigital data processing detailsAnalogue secracy/subscription systemsElectronic documentDocumentation
A method for securely sharing electronic documents on a document storage system. The method includes receiving an electronic document from a creating user, generating an encryption key unique to the electronic document, encrypting the electronic document using the encryption key to create an encrypted electronic document, and communicating the encrypted electronic document to a document repository for storage / The method also includes identifying a resource locator for uniquely identifying the storage location of the encrypted electronic document and communicating the encryption key and the resource locator to the creating user. The method also includes receiving the encryption key and the resource locator from a requesting user, retrieving the encrypted electronic document from the document repository using the resource locator, decrypting the encrypted electronic document using the encryption key, and communicating the decrypted electronic document to the requesting user.
Owner:FUJITSU LTD
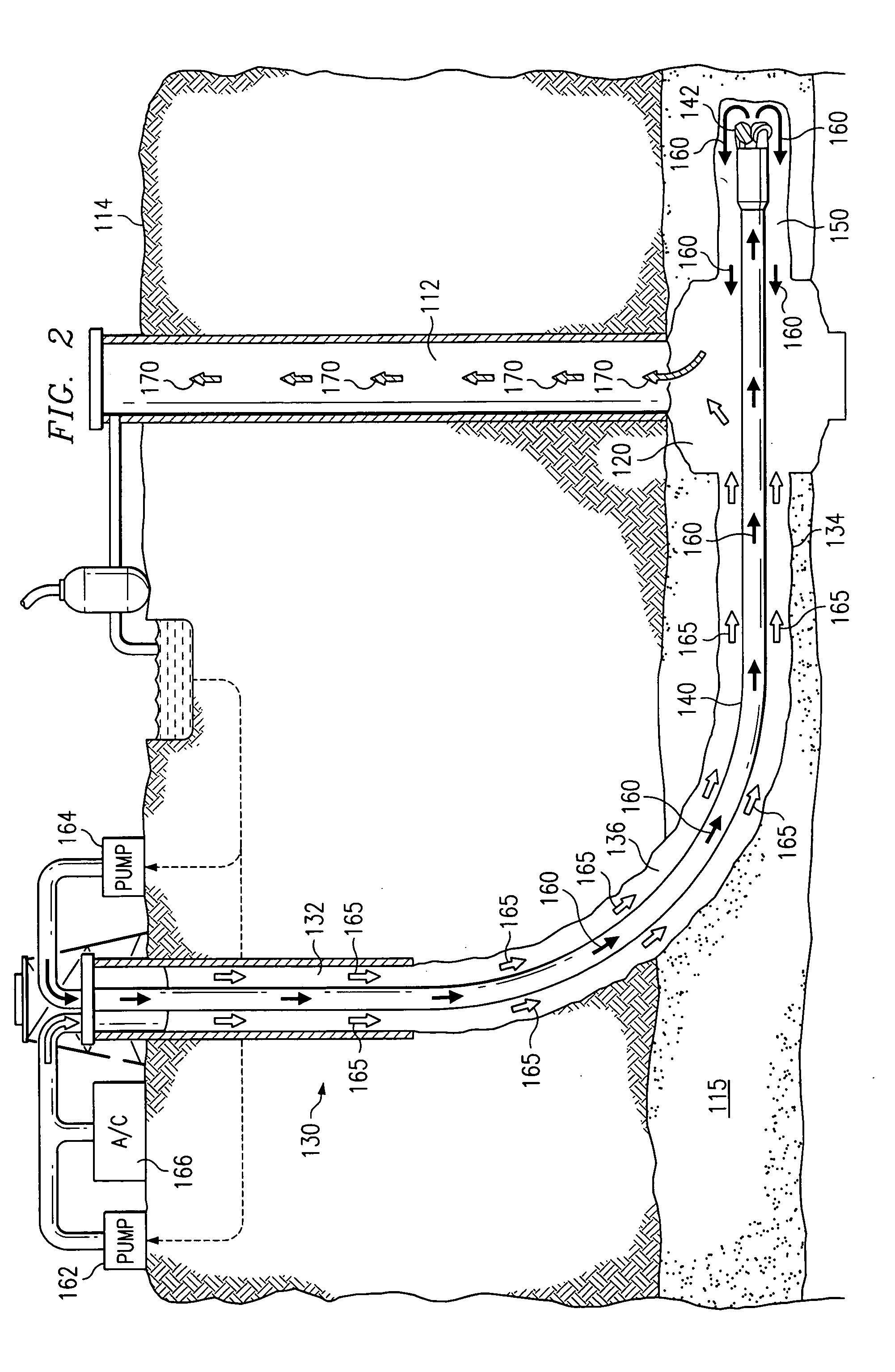
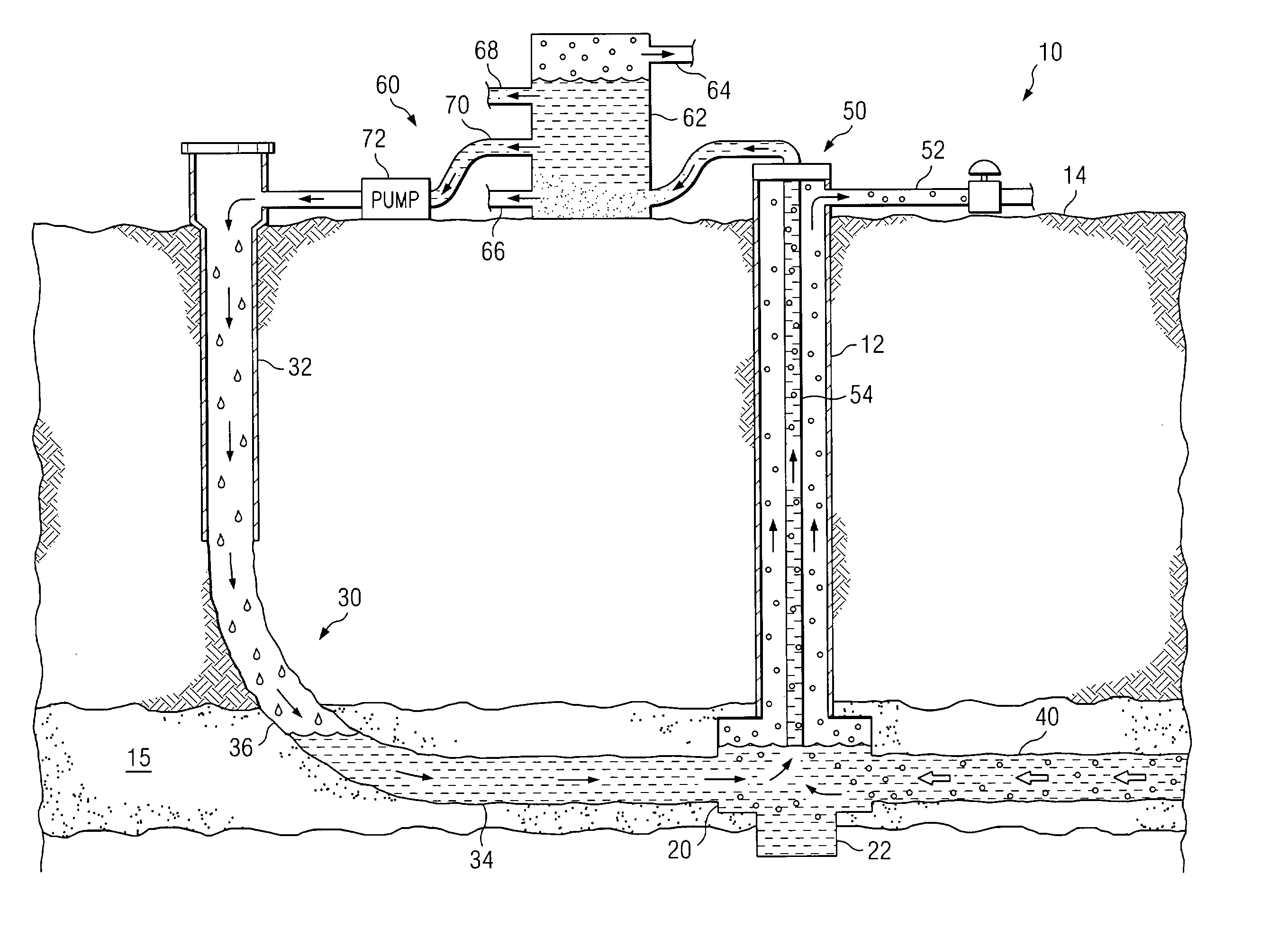
Method and system for recirculating fluid in a well system
InactiveUS7134494B2Eliminates and reduces of disadvantageEliminates and reduces of and problemCleaning apparatusFluid removalWellboreWater resource management
A method for recirculating fluid in a well system includes drilling a first well bore from a surface to a subterranean zone, and drilling an articulated well bore that is horizontally offset from the first well bore at the surface and that intersects the first well bore at a junction proximate the subterranean zone. The method also includes drilling a drainage bore from the junction into the subterranean zone, and receiving gas, water and particles produced from the subterranean zone at the junction via the drainage bore. The gas, water, and particles are received from the junction at the surface, and the water is separated from the gas and the particles. The method also includes determining an amount of water to circulate, and recirculating a portion of the separated water according to this determination.
Owner:EFFECTIVE EXPLORATION
System and methods for remote maintenance in an electronic network with multiple clients
InactiveUS9059978B2Eliminates and reduces of disadvantageEliminates and reduces of and problemKey distribution for secure communicationWeb data indexingData setData center
According to one embodiment, a client system supported by remote maintenance in an electronic network configured to serve a plurality of clients may include an electronic network, a plurality of storage resources, a first virtual machine, a second virtual machine, and a virtual machine manager. The electronic network may include a plurality of processing resources and a communication bus. The plurality of storage resources may be accessible by the plurality of processing resources. The plurality of storage resources may include a computer readable memory. The first virtual machine may handle a first data set associated with the client system. The first virtual machine may include an operating system and a reporting agent. The second virtual machine may handle a second data set associated with an external data center. The virtual machine manager may be configured to manage data transfer between the first virtual machine and the second virtual machine. The second virtual machine may be configured to assess a state of the first virtual machine and identify a software update for installation on the first virtual machine. The virtual machine manager may manage an attestation process for the first virtual machine prior to delivering or installing the software update on the client system using the first virtual machine.
Owner:FUJITSU LTD
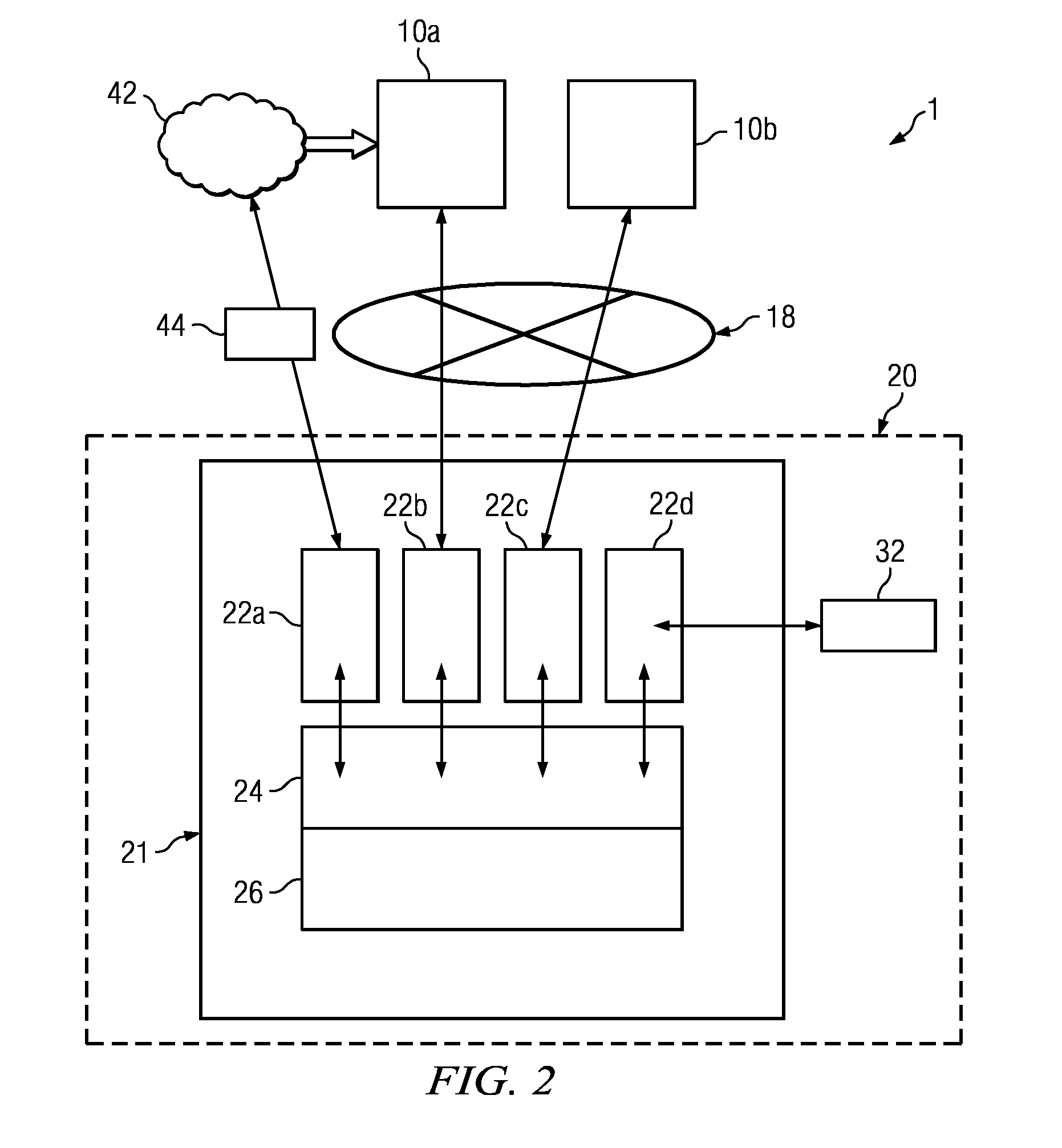
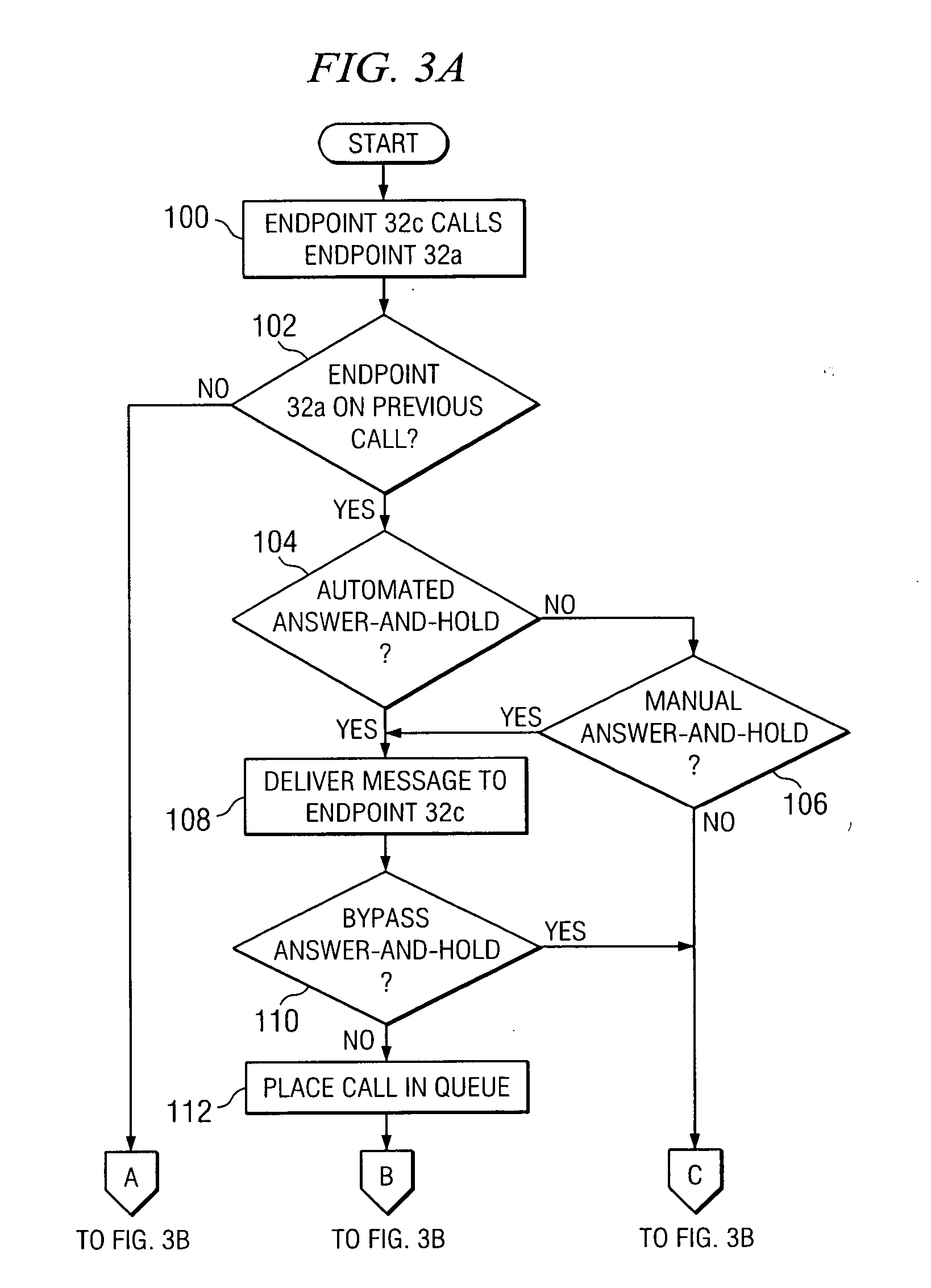
Method and system for the automated answering and holding of a call
InactiveUS20060154654A1Eliminates and reduces of disadvantageEliminates and reduces of and problemSpecial service for subscribersTelecommunications
In accordance with a particular embodiment of the present invention, a method for the automated answering and holding of a call includes receiving an incoming call directed to a first endpoint from a second endpoint. A detection is made that the first endpoint is communicating with a third endpoint on a previous call. An indication is received from a recipient of the incoming call that the recipient desires the incoming call to be automatically answered and held. The incoming call from the second endpoint is automatically answered without interrupting the previous call, and the incoming call from the second endpoint is placed in a queue.
Owner:CISCO TECH INC
Method and system to protect the privacy of presence information for network users
ActiveUS20060258332A1Eliminates and reduces of disadvantageEliminates and reduces of and problemMetering/charging/biilling arrangementsUnauthorised/fraudulent call preventionRegistration statusPrivacy protection
In accordance with a particular embodiment of the present invention, a method for providing privacy protection to network users includes receiving a subscription request from a first end user. The subscription request identifies a second end user for whom the first end user would like to become a registered presence watcher. A cost to be assessed to become the registered presence watcher of the second end user is determined, and the first user is registered as the registered presence watcher of the second end user.
Owner:CISCO TECH INC
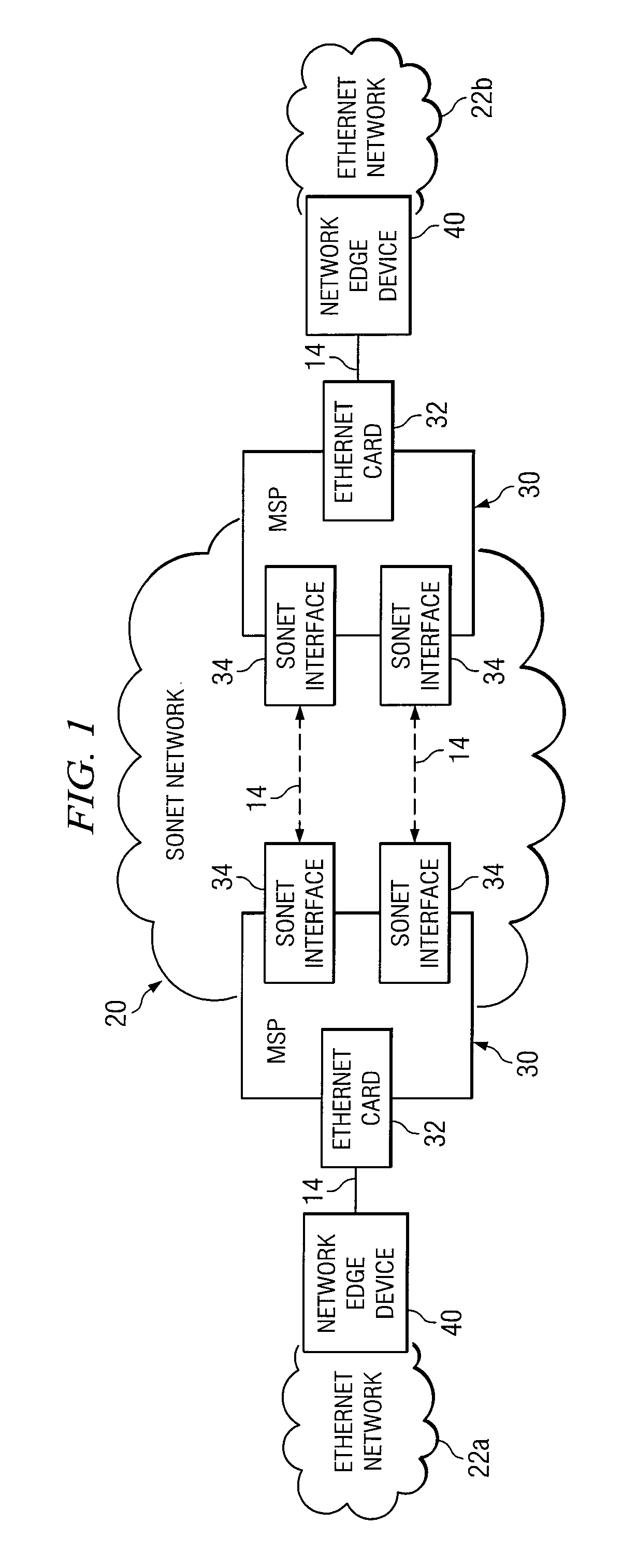
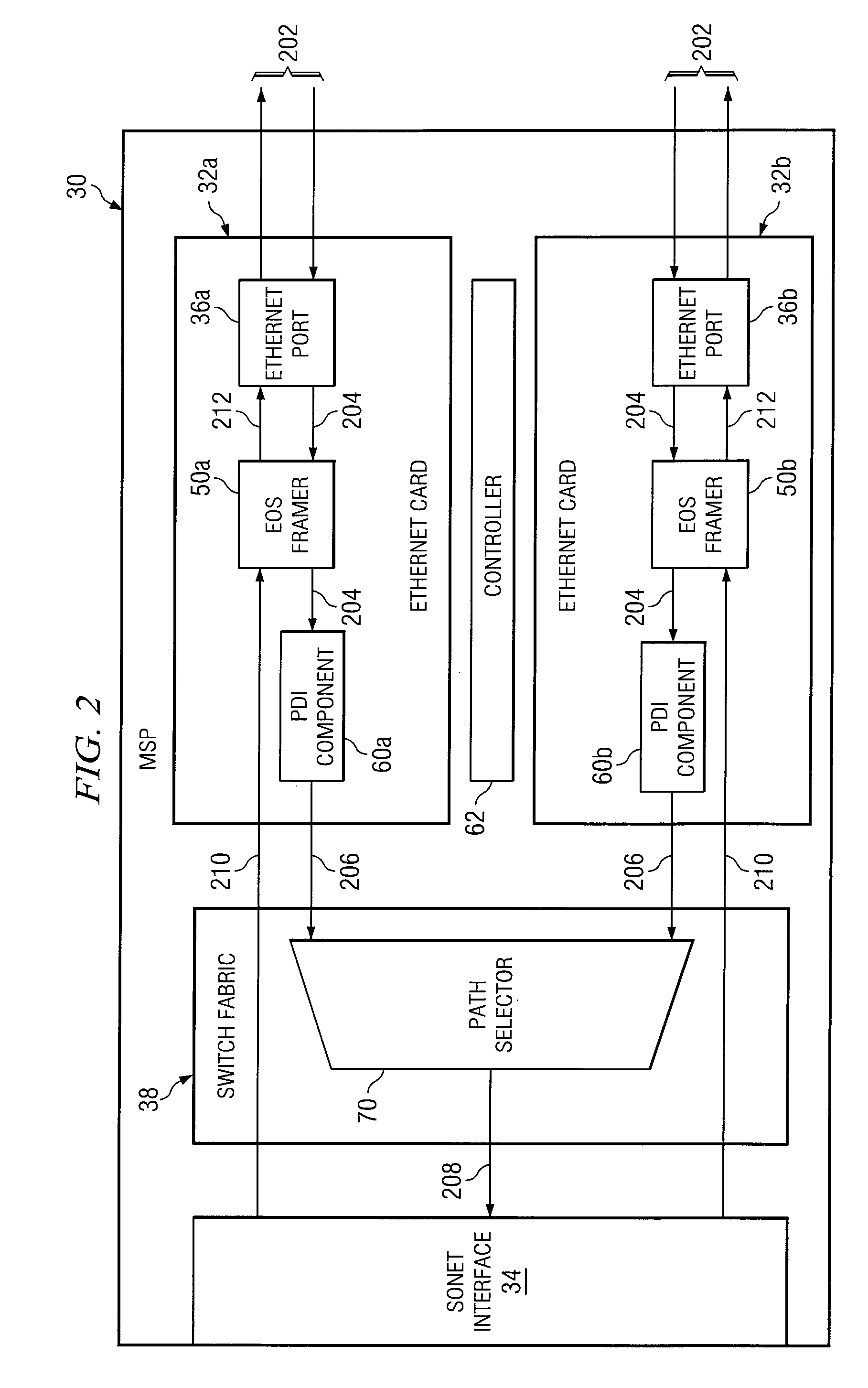
Method and System for Providing Ethernet Protection
InactiveUS20080124073A1Eliminates and reduces of disadvantageEliminates and reduces of and problemLaser detailsError preventionTraffic capacityComputer science
A method is provided for providing protection of a local area network (LAN) connection that includes providing first and second LAN cards in a multi-service platform. The first and second LAN cards each include at least one port. The first and second LAN cards are coupled to a network edge device through their respective ports to communicate LAN traffic. The method also includes designating the first LAN card as an active card and the second LAN card as an inactive card. The method further includes detecting a network failure associated with the first LAN card. The method further includes protecting LAN traffic communicated between the second LAN card and the LAN by designating the second LAN card as an active card and the first LAN card as an inactive card.
Owner:FUJITSU LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com