Vulnerability detection system aiming at binary executable files and combining fuzz testing with symbolic execution
A technology for symbolic execution and vulnerability detection, applied in the field of vulnerability detection systems, can solve problems such as low detection efficiency and insufficient detection depth, and achieve the effects of accelerating running speed, improving detection efficiency, and improving crashes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
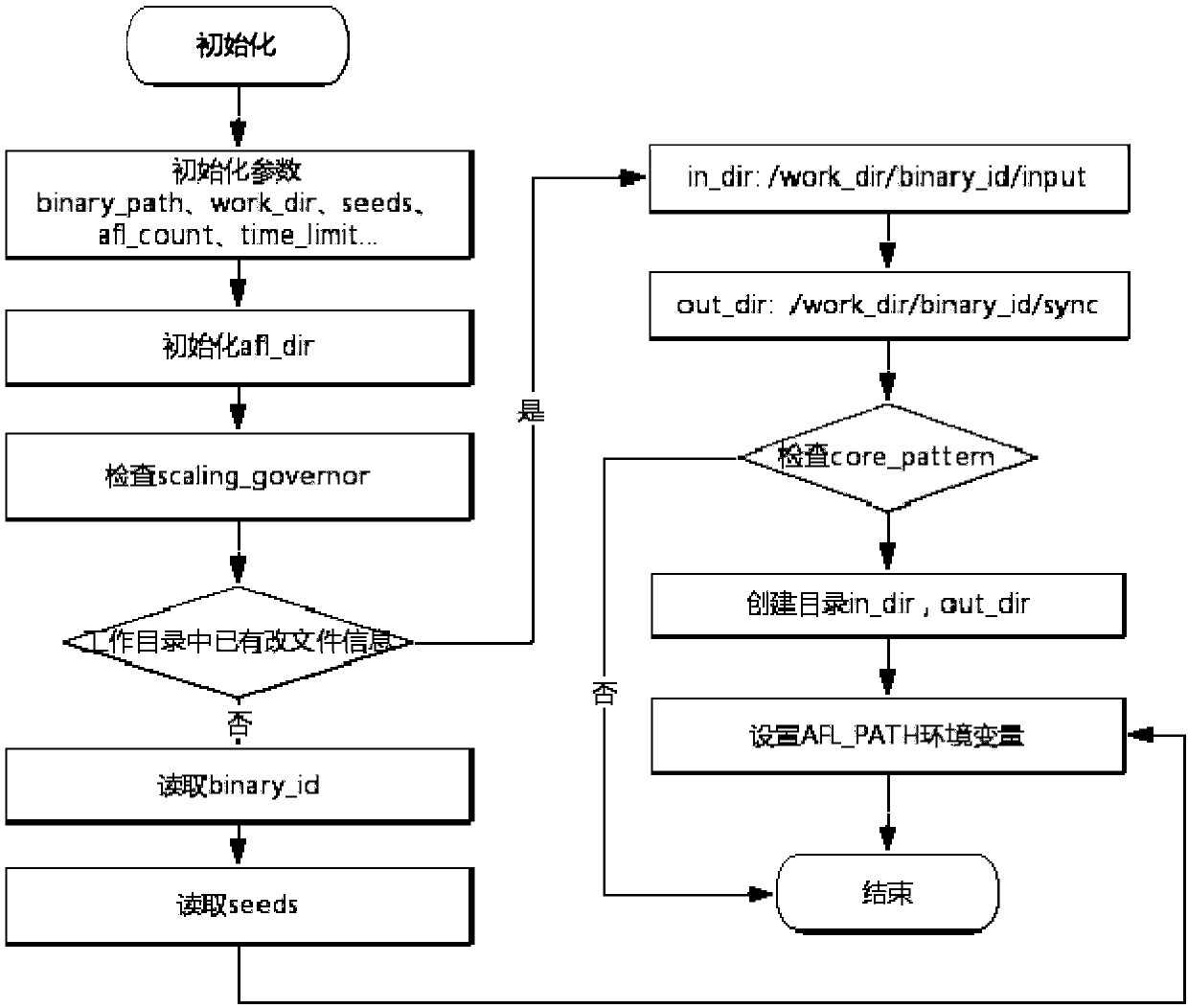
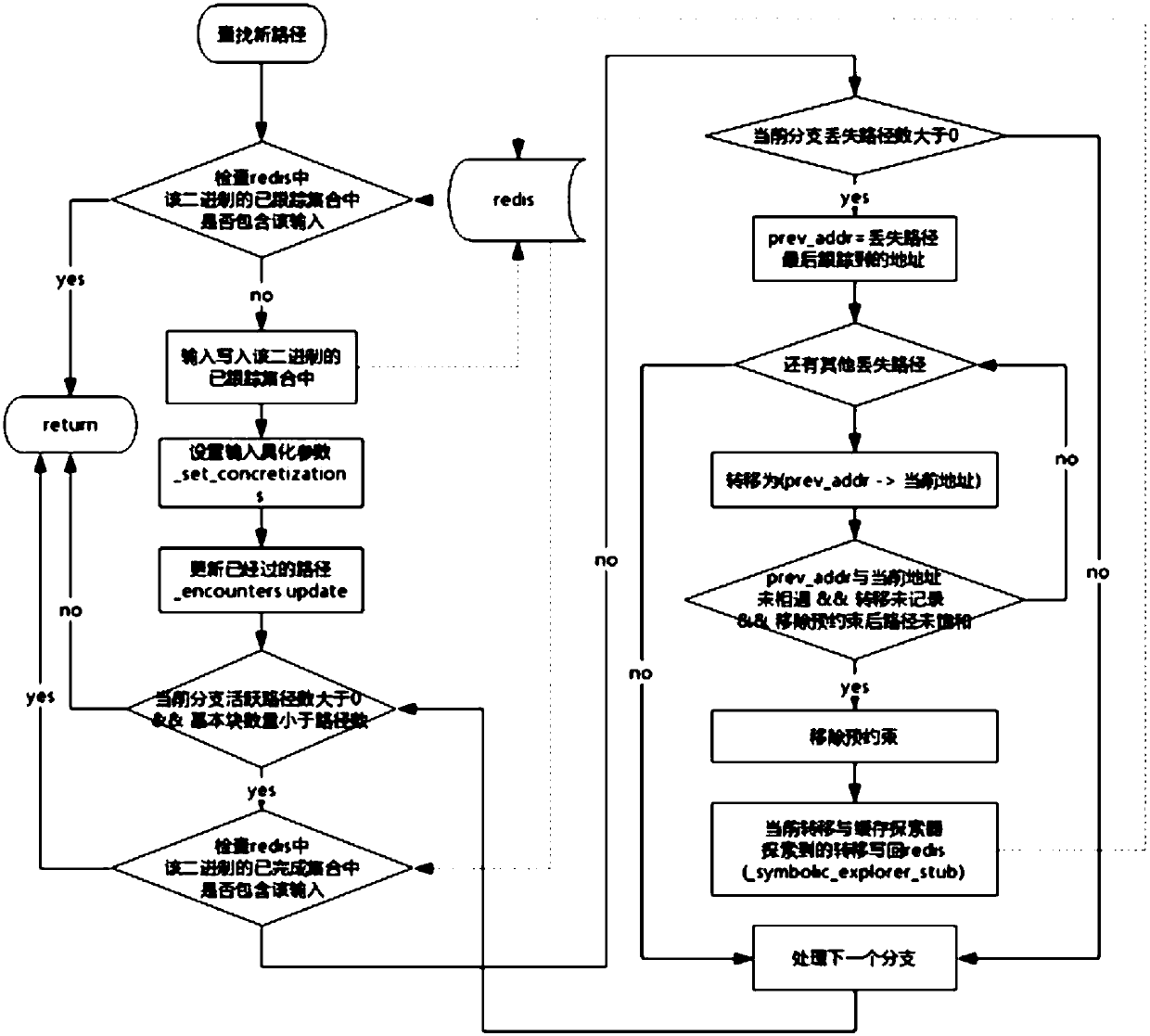
[0080] combine Figure 1 to Figure 6 , this embodiment describes the implementation of the vulnerability detection system that combines fuzzing and symbolic execution of binary executable files as follows:
[0081] 1. Optimal design of the fuzzer module
[0082] The optimized fuzzer module has the following characteristics:
[0083] 1) It can automatically generate custom input data and monitor the abnormality of the program;
[0084] 2) Regardless of whether there is source code or no source code, the system can monitor the abnormal situation of the software, and find as many defects as possible that cause the system to crash;
[0085] 3) The crash of the program can be located and recorded in time.
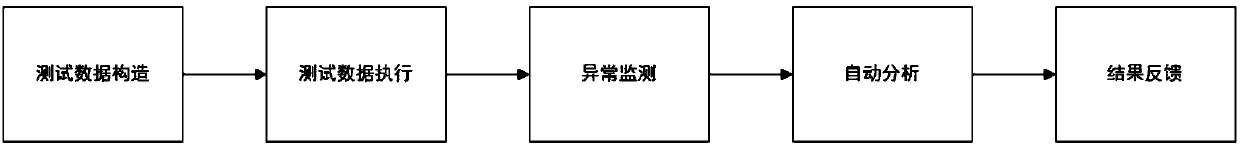
[0086] According to the optimization goal of the fuzzer, that is, the independence and scalability between modules, the optimized fuzzer mainly includes five modules: data generation, data input execution, vulnerability generation monitoring, false positive automatic analysis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com