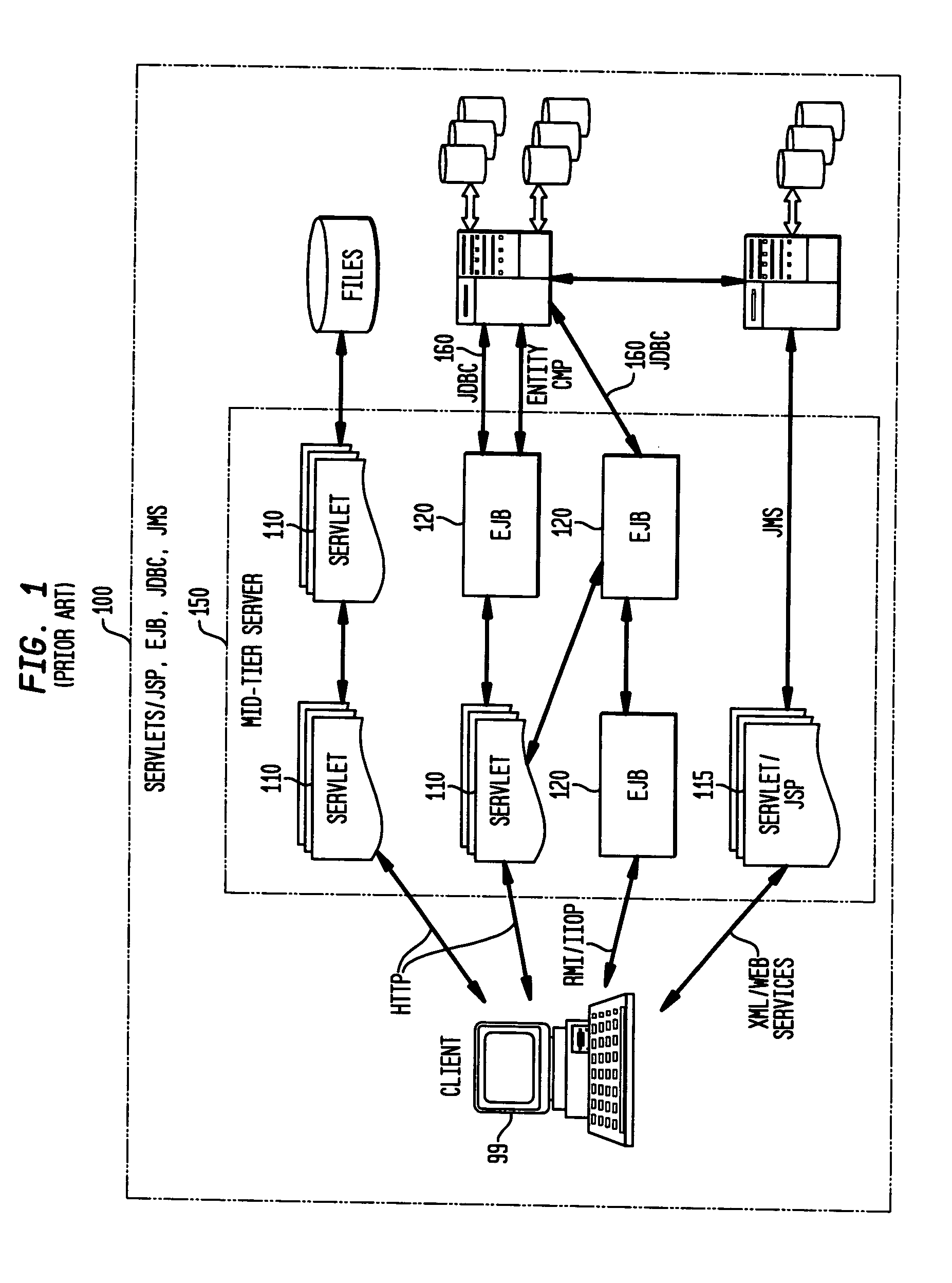
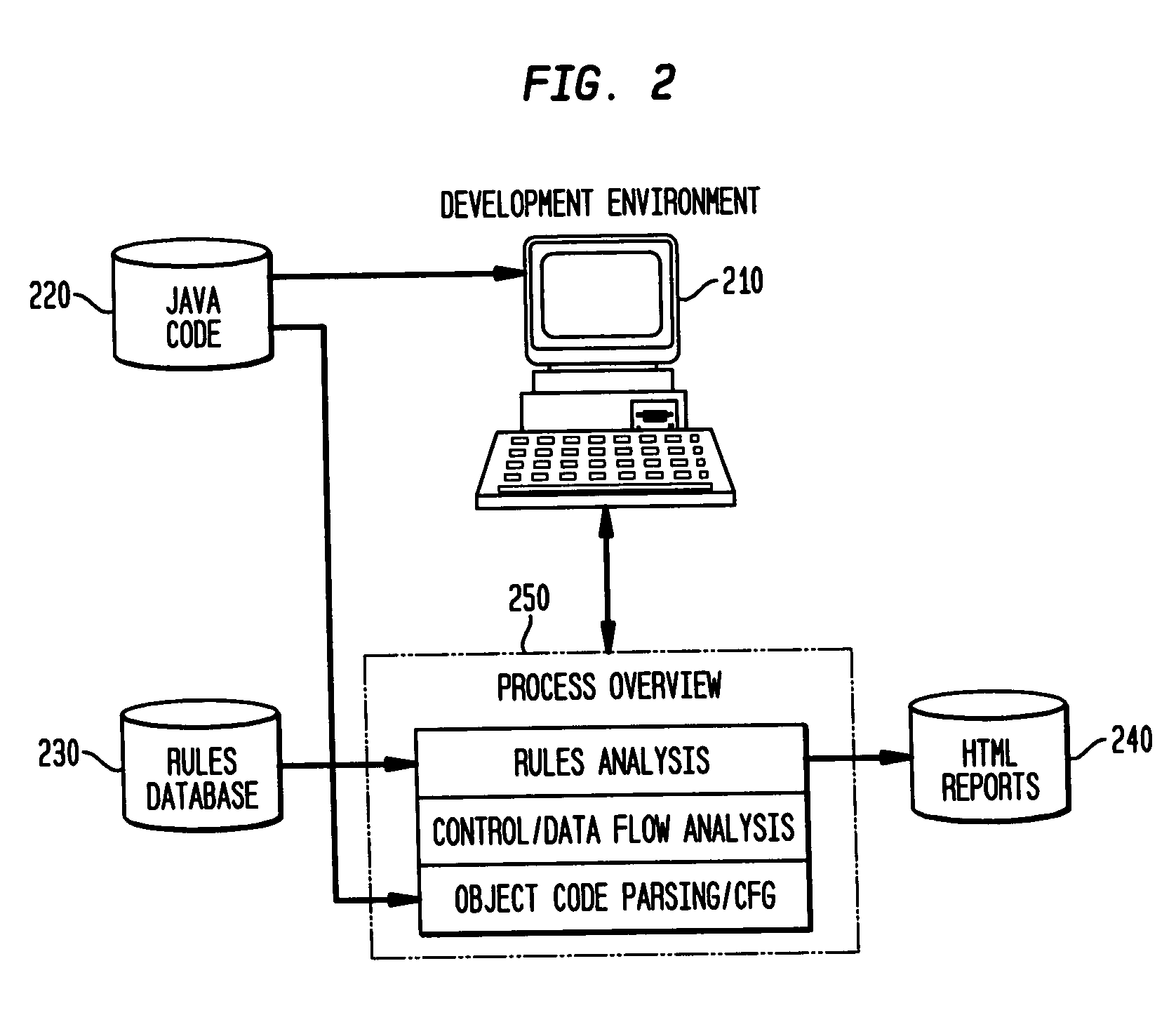
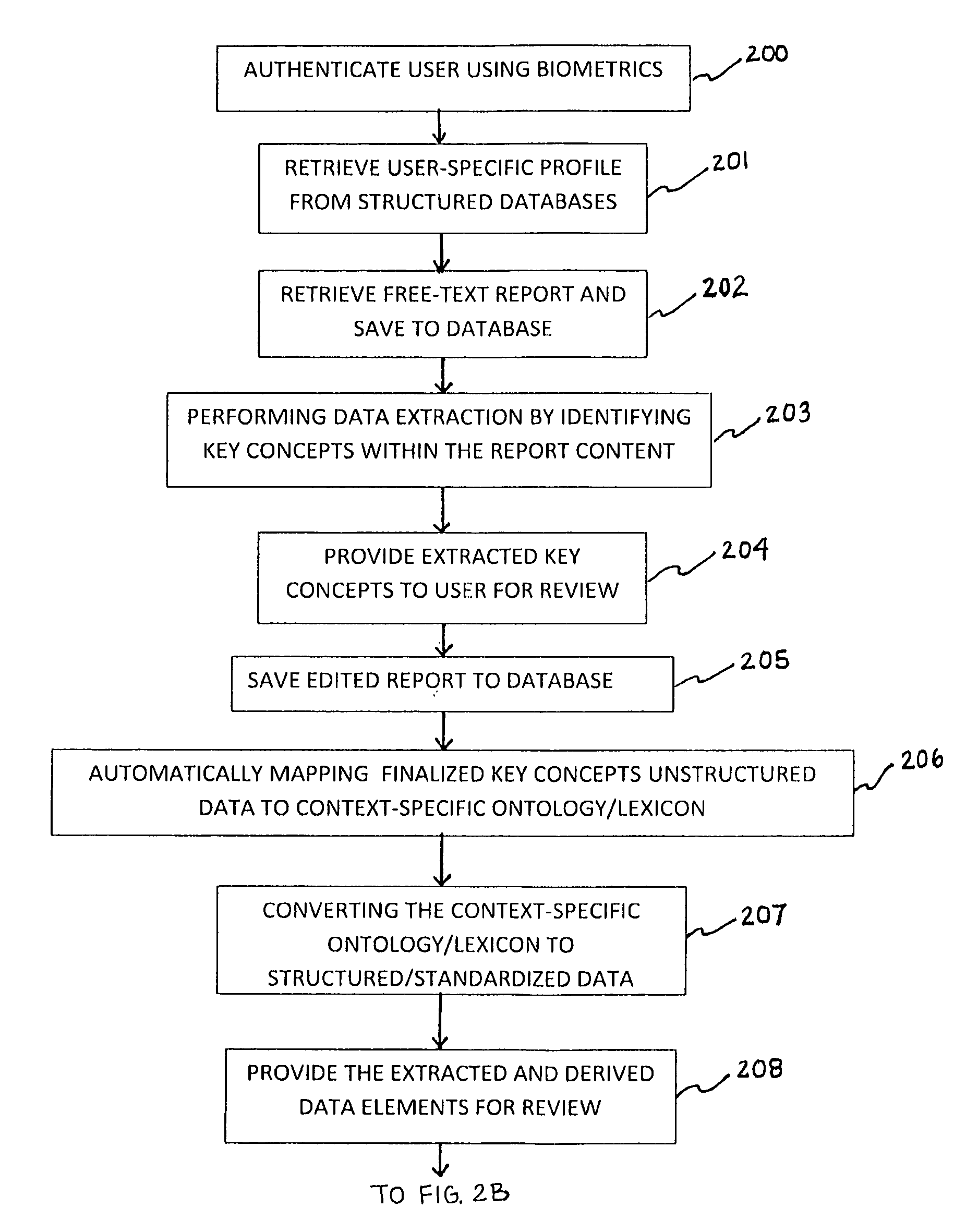
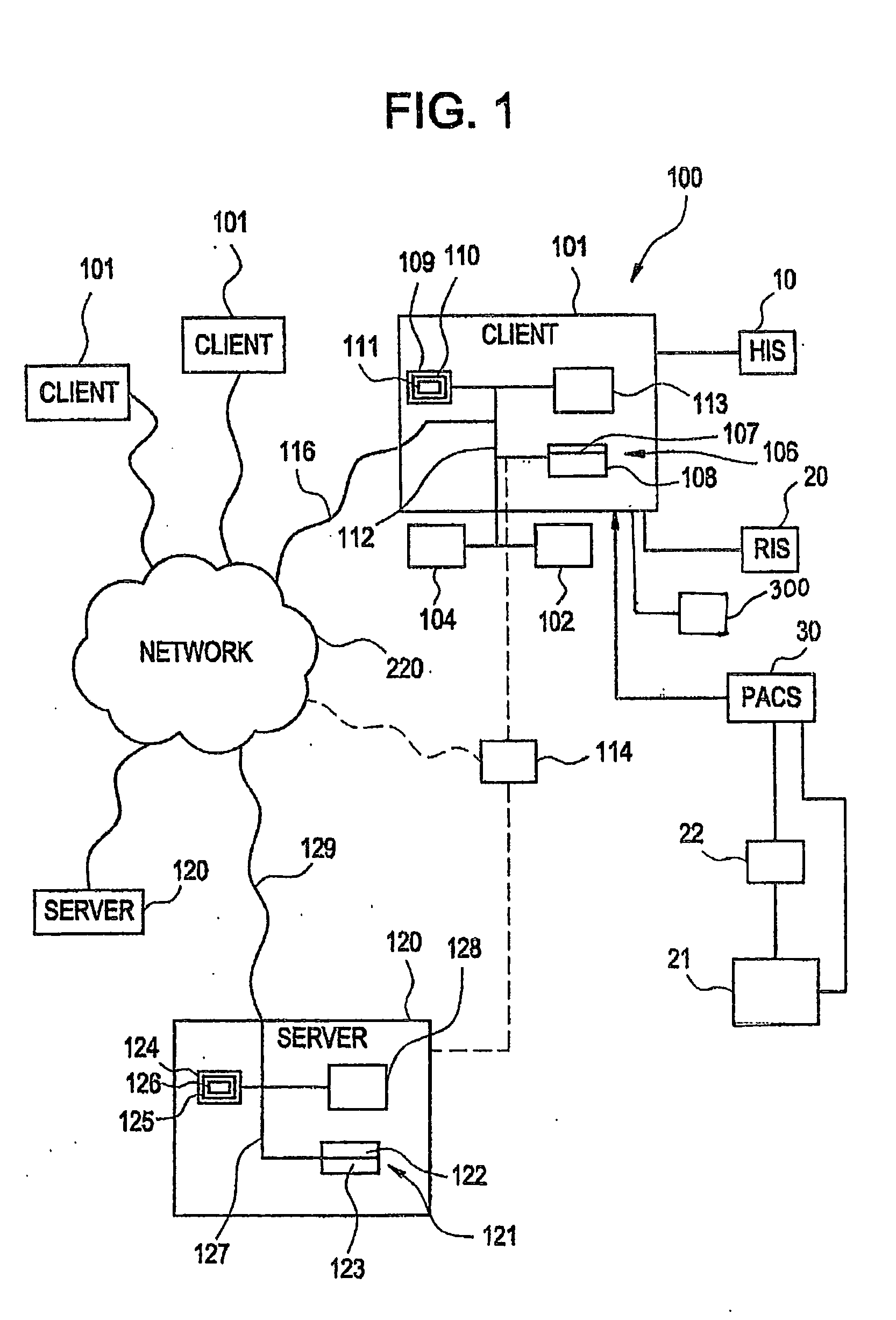
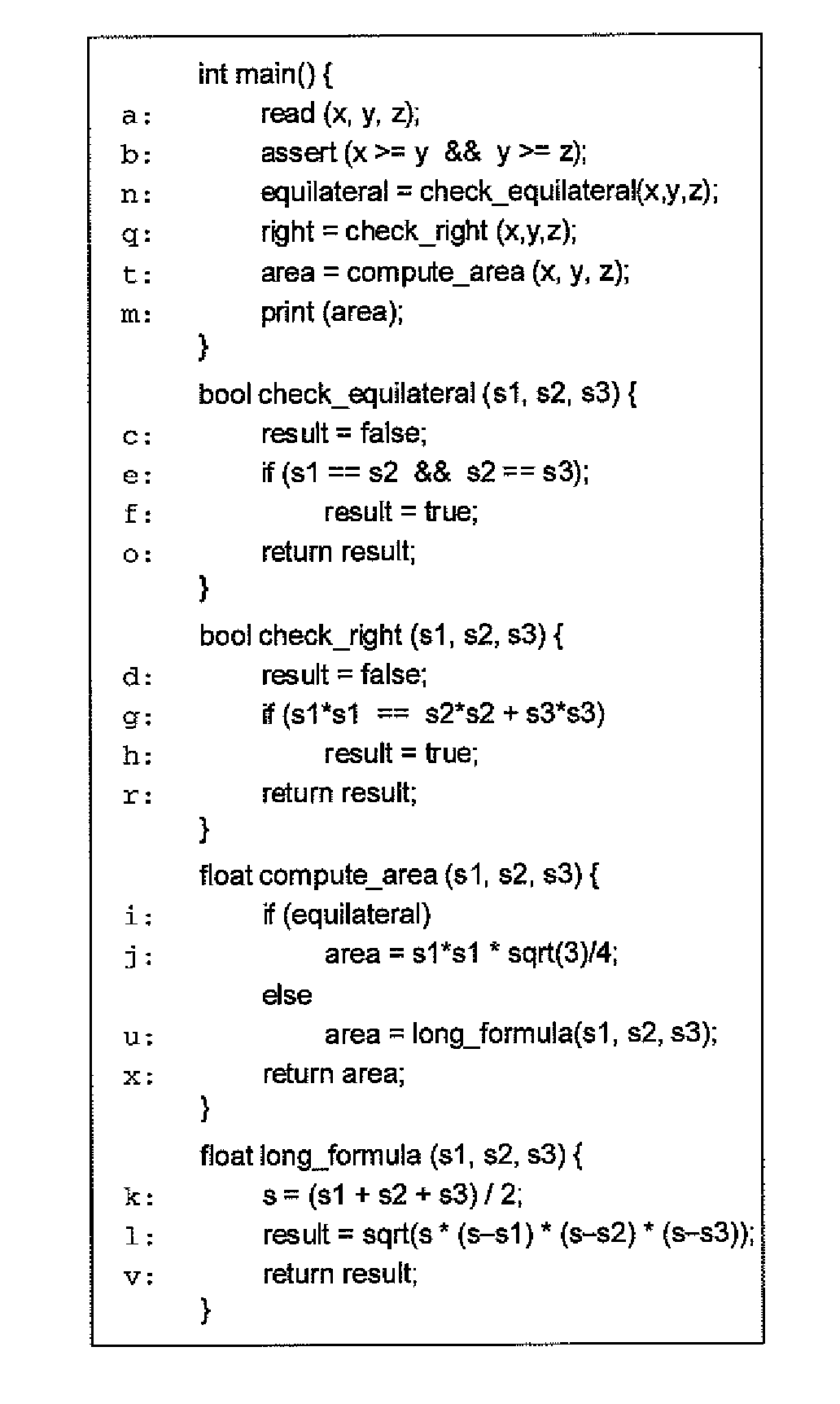
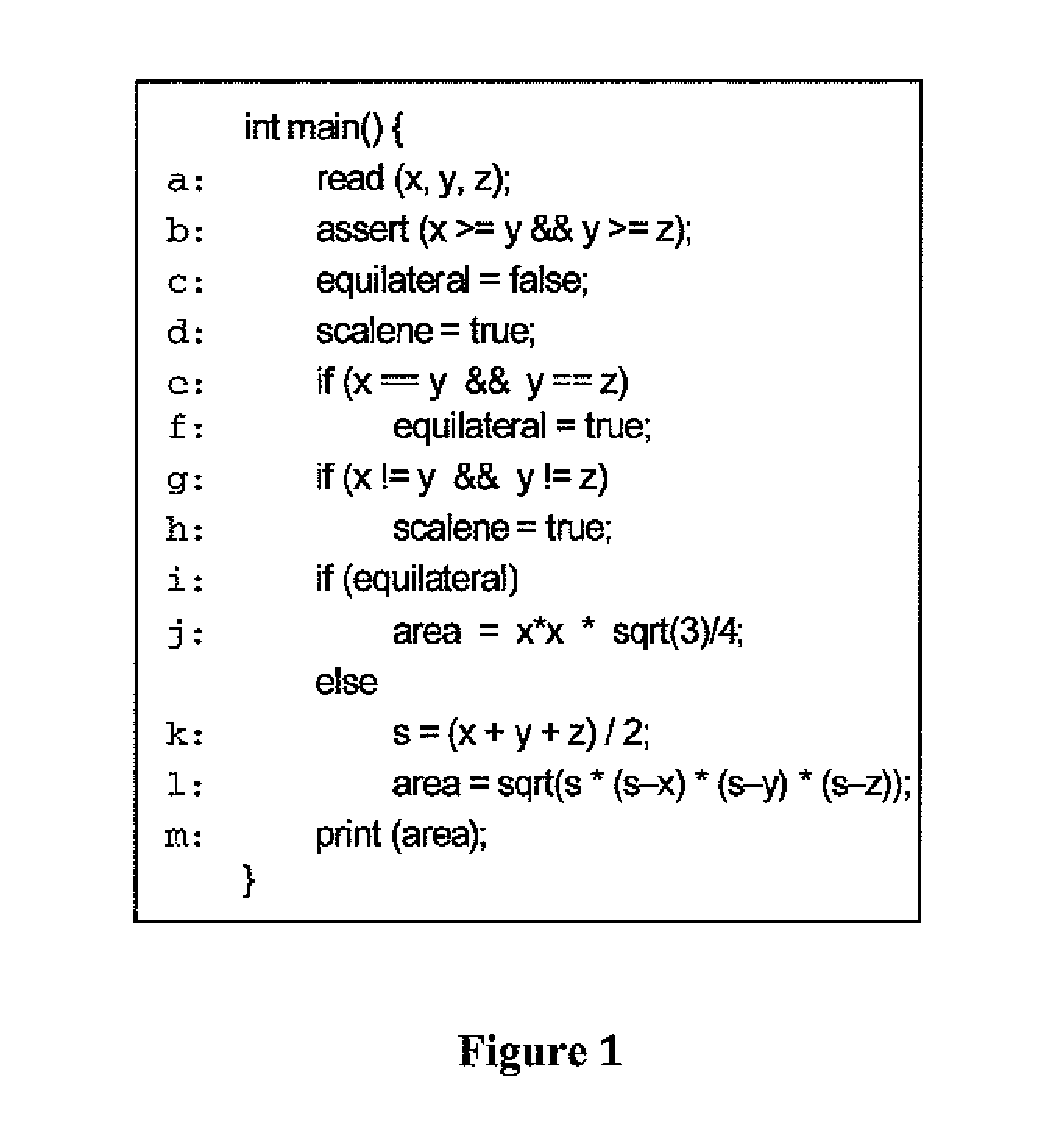
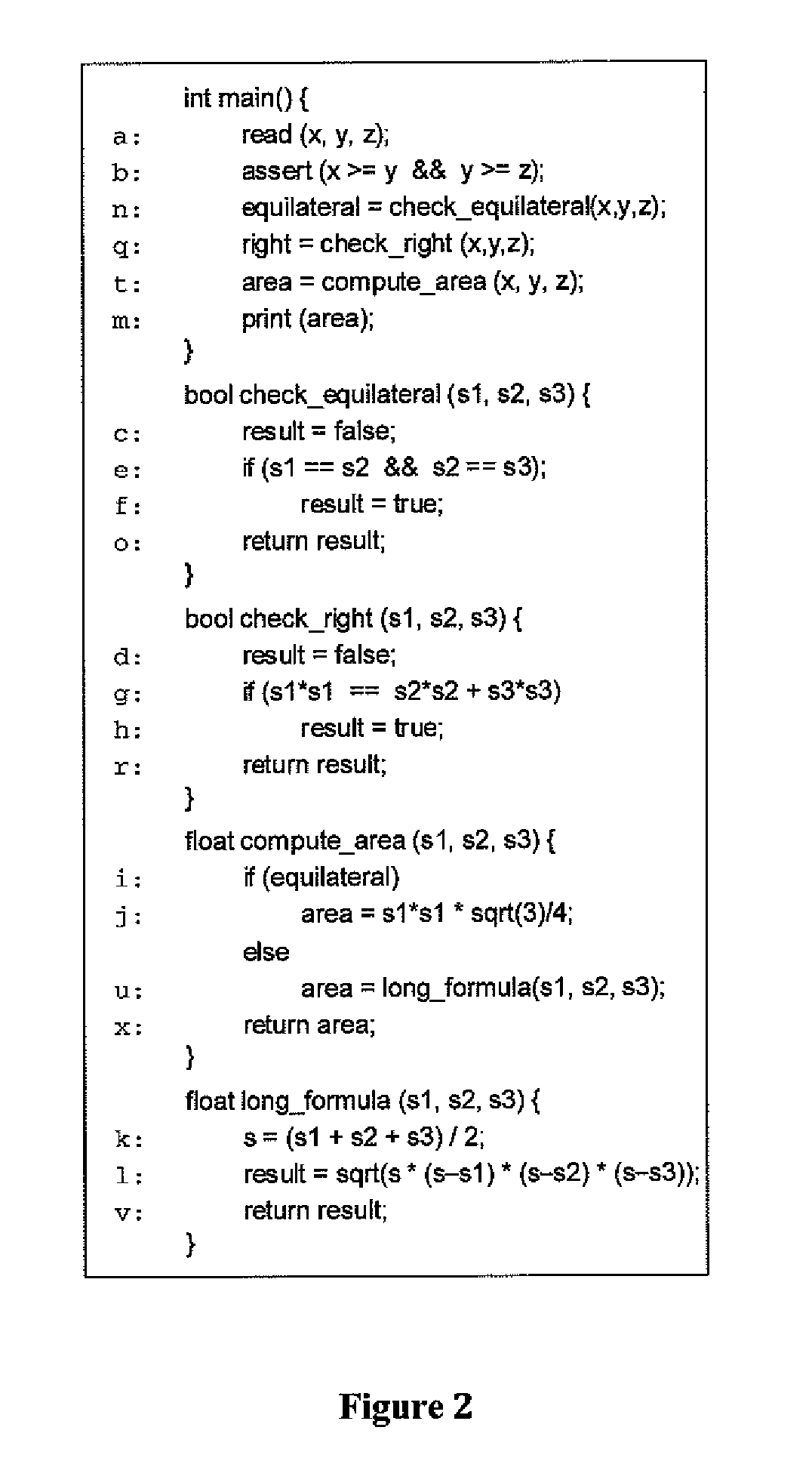
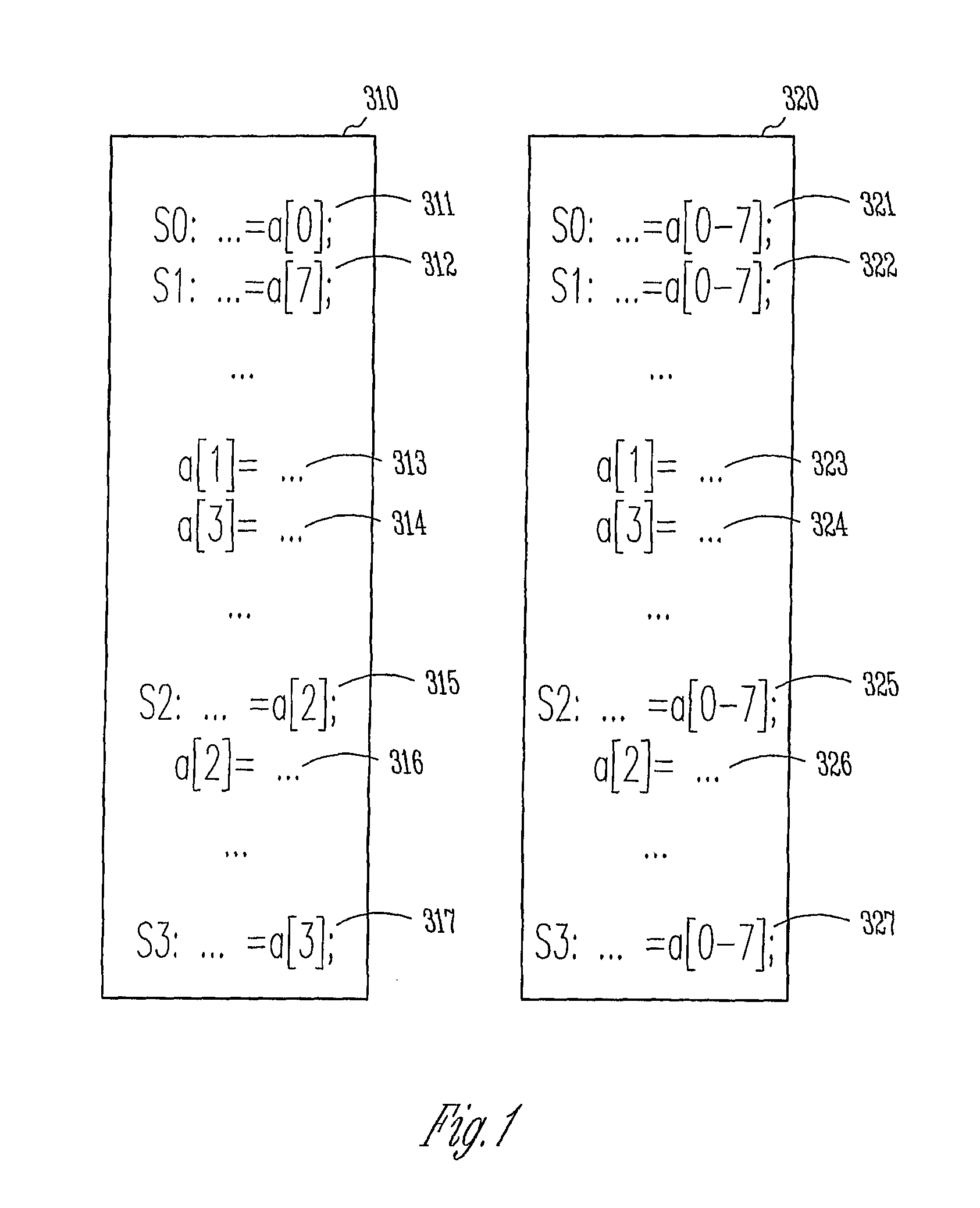Patents
Literature
337 results about "Data-flow analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
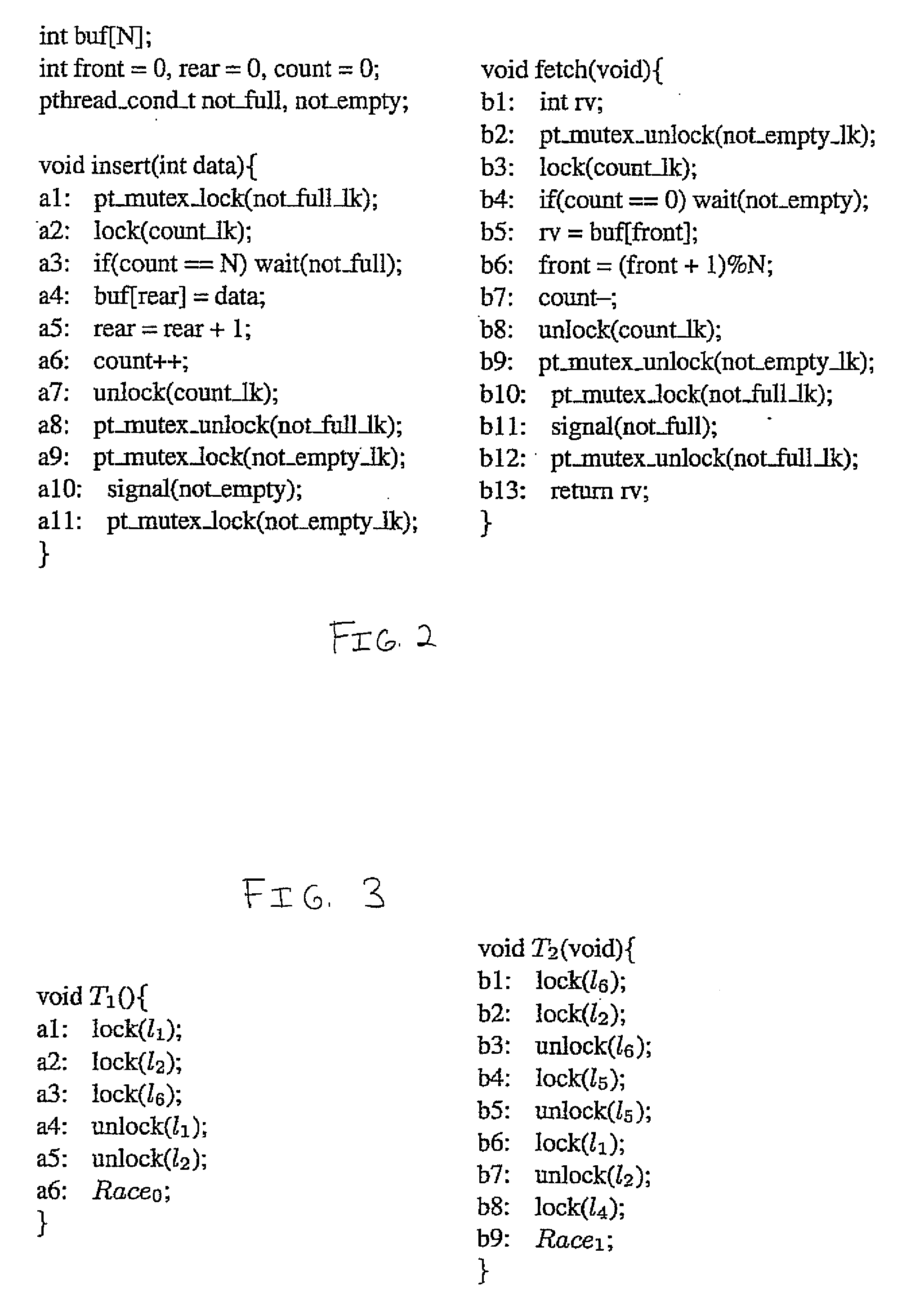
Data-flow analysis is a technique for gathering information about the possible set of values calculated at various points in a computer program. A program's control flow graph (CFG) is used to determine those parts of a program to which a particular value assigned to a variable might propagate. The information gathered is often used by compilers when optimizing a program. A canonical example of a data-flow analysis is reaching definitions.
Detecting exploit code in network flows
InactiveUS20090328185A1Memory loss protectionUnauthorized memory use protectionData streamNetwork packet
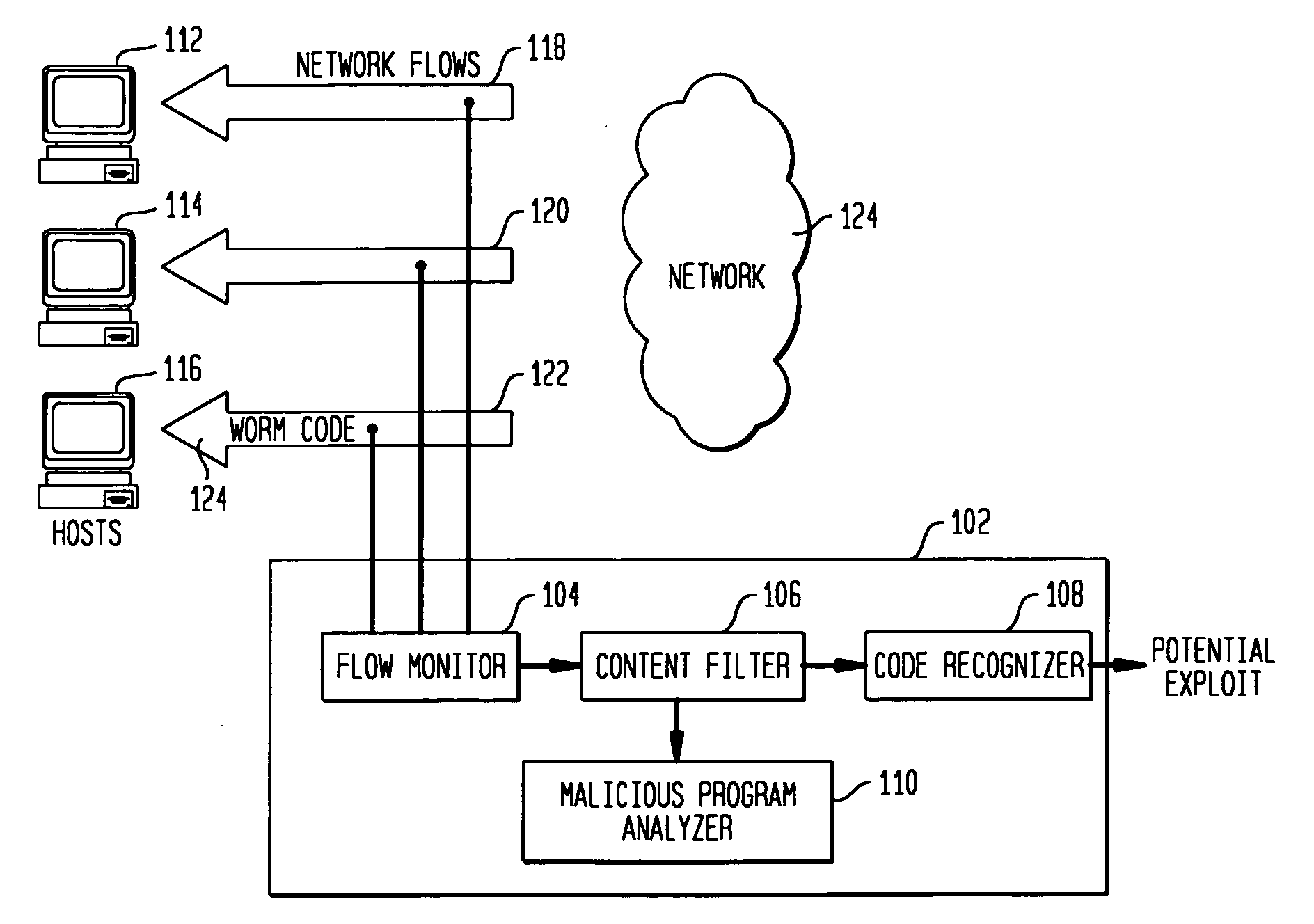
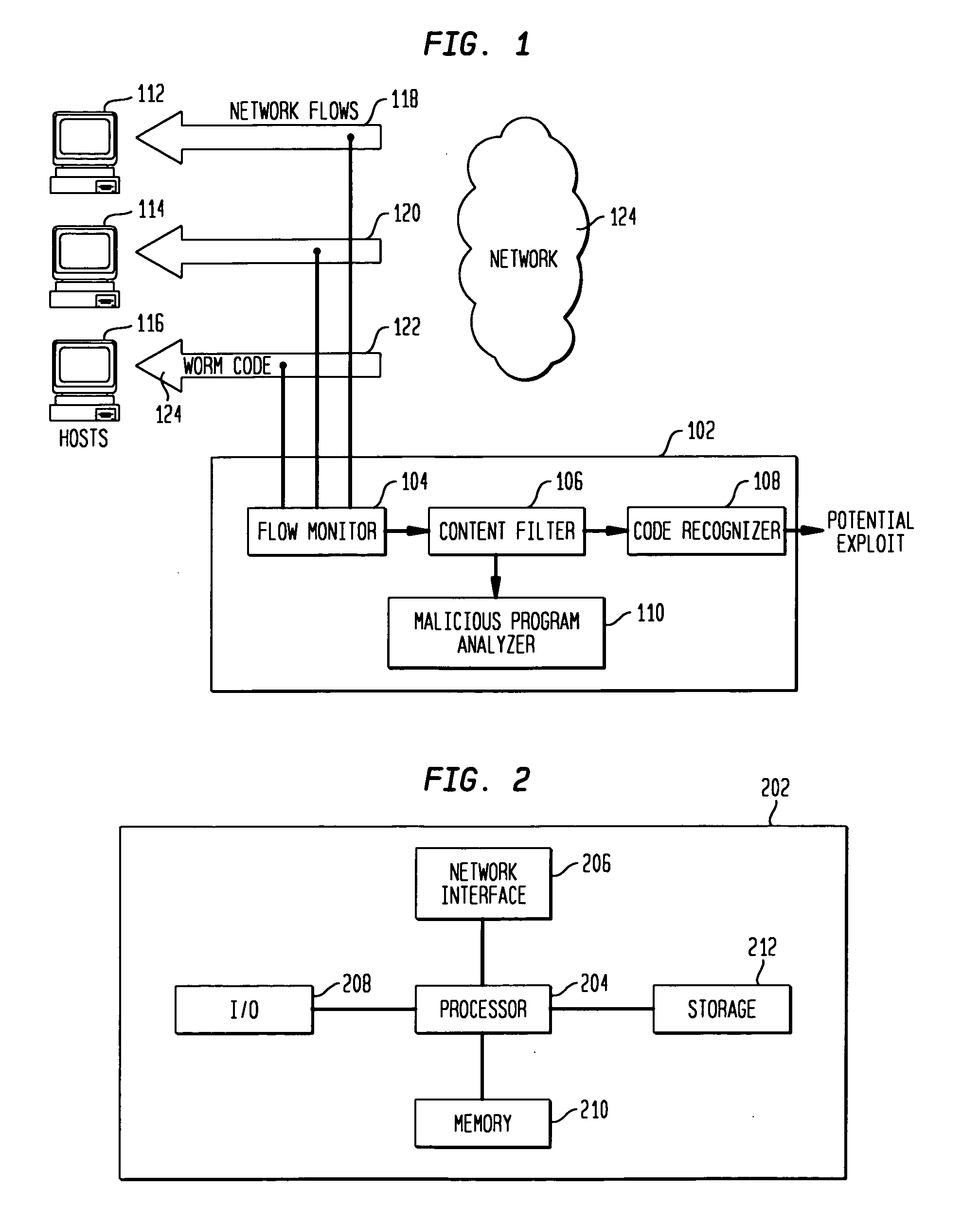
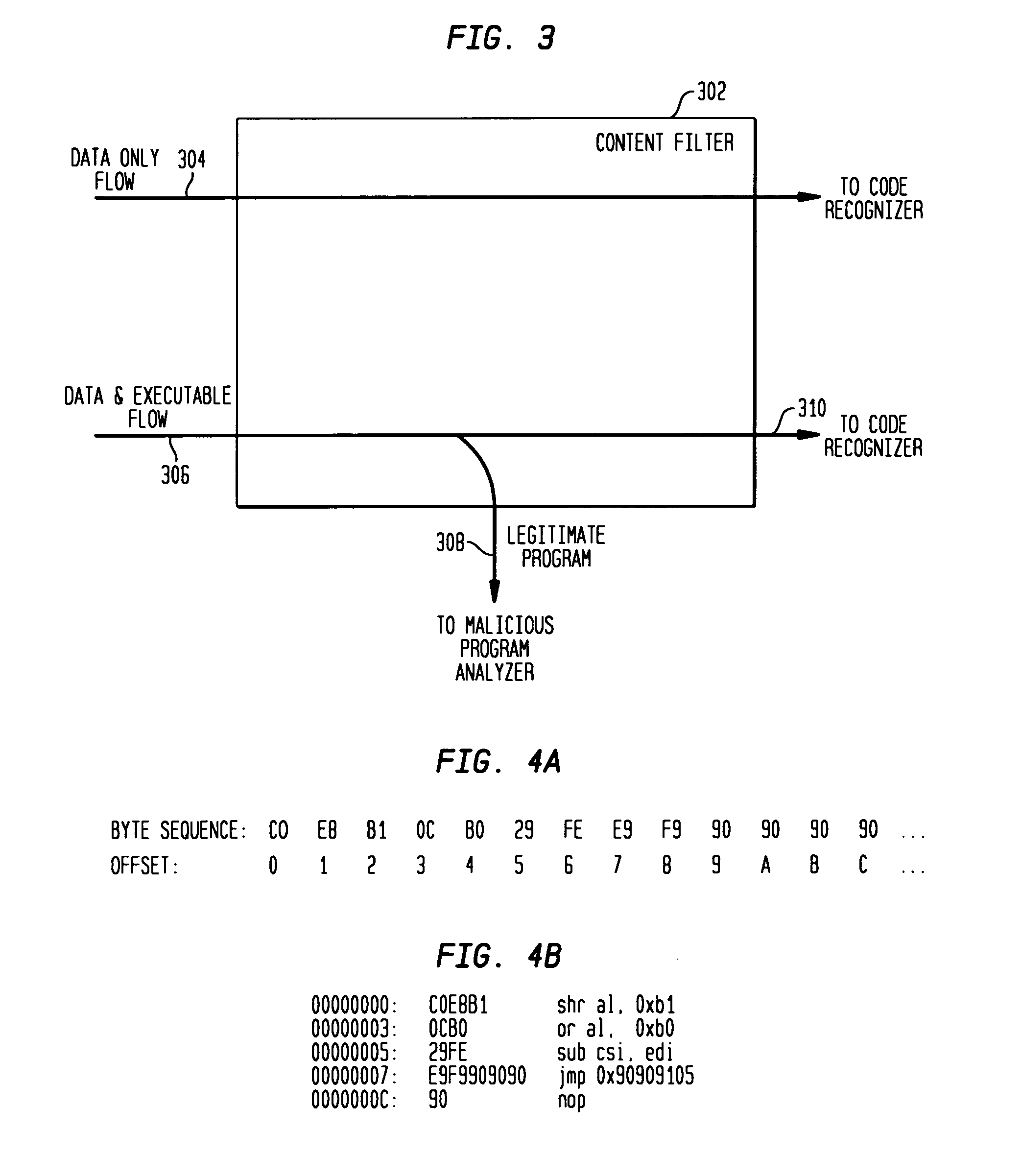
Disclosed is a method and apparatus for detecting exploit code in network flows. Network data packets are intercepted by a flow monitor which generates data flows from the intercepted data packets. A content filter filters out legitimate programs from the data flows, and the unfiltered portions are provided to a code recognizer which detects executable code. Any embedded executable code in the unfiltered data flow portions is identified as a suspected exploit in the network flow. The executable code recognizer recognizes executable code by performing convergent binary disassembly on the unfiltered portions of the data flows. The executable code recognizer then constructs a control flow graph and performs control flow analysis, data flow analysis, and constraint enforcement in order to detect executable code. In addition to identifying detected executable code as a potential exploit, the detected executable code may then be used in order to generate a signature of the potential exploit, for use by other systems in detecting the exploit.
Owner:TELCORDIA TECHNOLOGIES INC
Static analysis based error reduction for software applications
InactiveUS20050015752A1Easy to liftSimple technologyError detection/correctionSpecific program execution arrangementsError reductionMaintainability
A system and method for providing “static analysis” of programs to aid in improving runtime performance, stability, security and privacy characteristics of deployed application code. The method includes performing a set of analyses that sifts through the program code and identifies programming security and / or privacy model coding errors. In particular the invention focuses on identifying coding errors that cause loss of correctness, performance degradation, security, privacy and maintainability vulnerabilities. A deep analysis of the program is performed using detailed control and data flow analyses. These deeper analyses provide a much better perspective of the overall application behavior. This deep analysis is in contrast to shallow analyses in current industry tools, which inspect or model a single or a few classes at a time.
Owner:IBM CORP
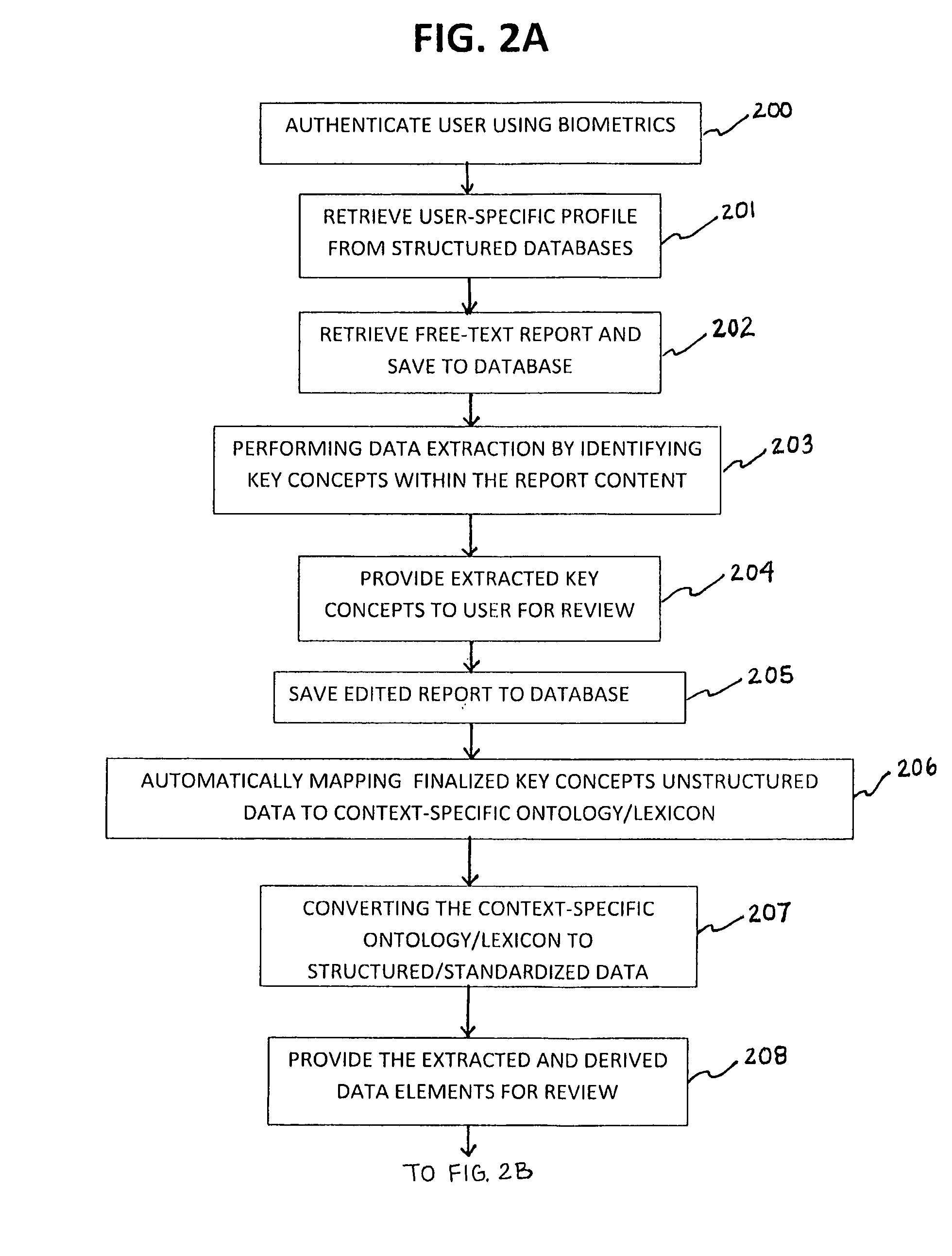
Method of extracting real-time structured data and performing data analysis and decision support in medical reporting
InactiveUS20100145720A1Medical data miningData processing applicationsTime structureTreatment options
The present invention relates to a methodology for the conversion of unstructured, free text data (contained within medical reports) into standardized, structured data, and also relates to a decision support feature for use in diagnosis and treatment options.
Owner:REINER BRUCE
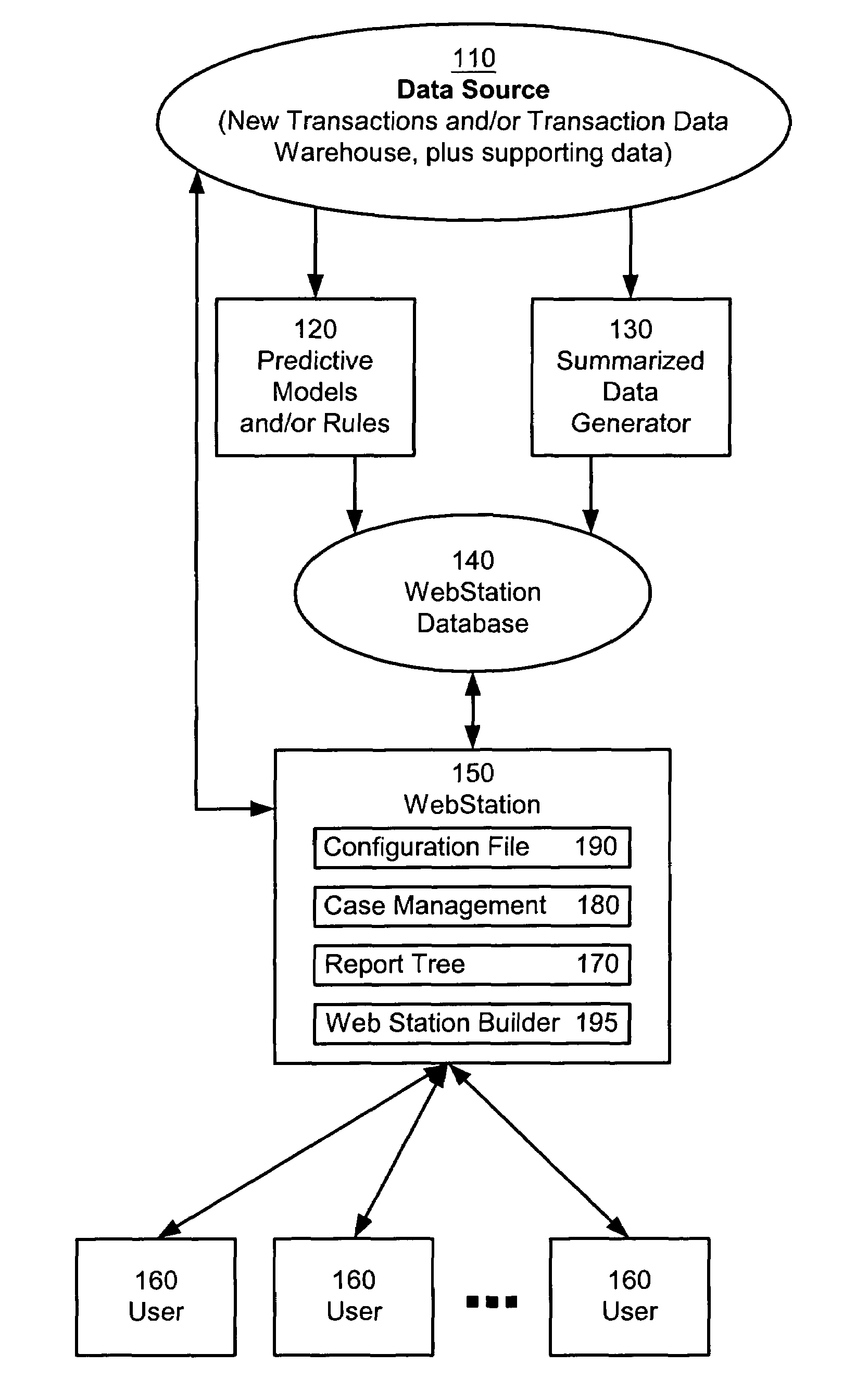
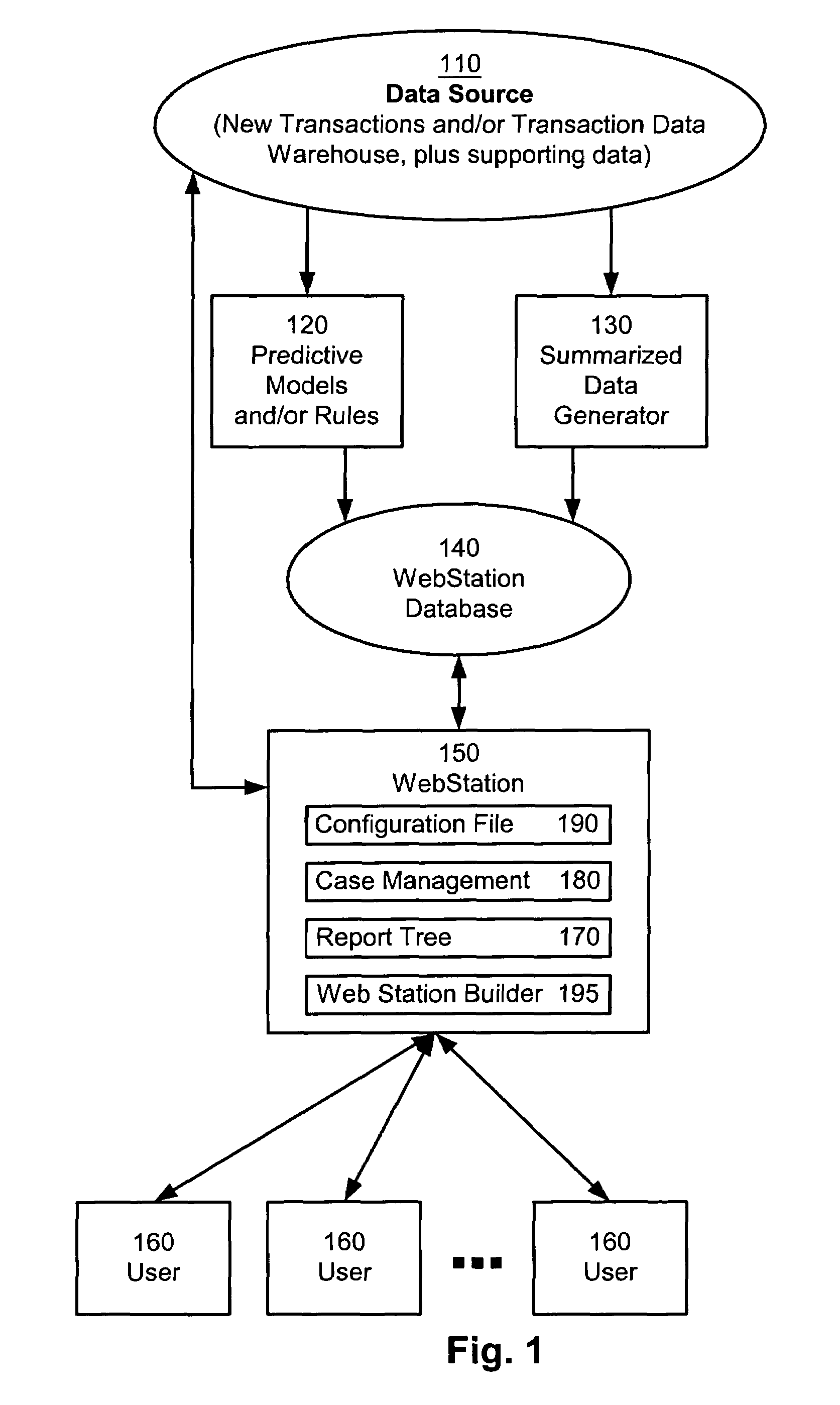
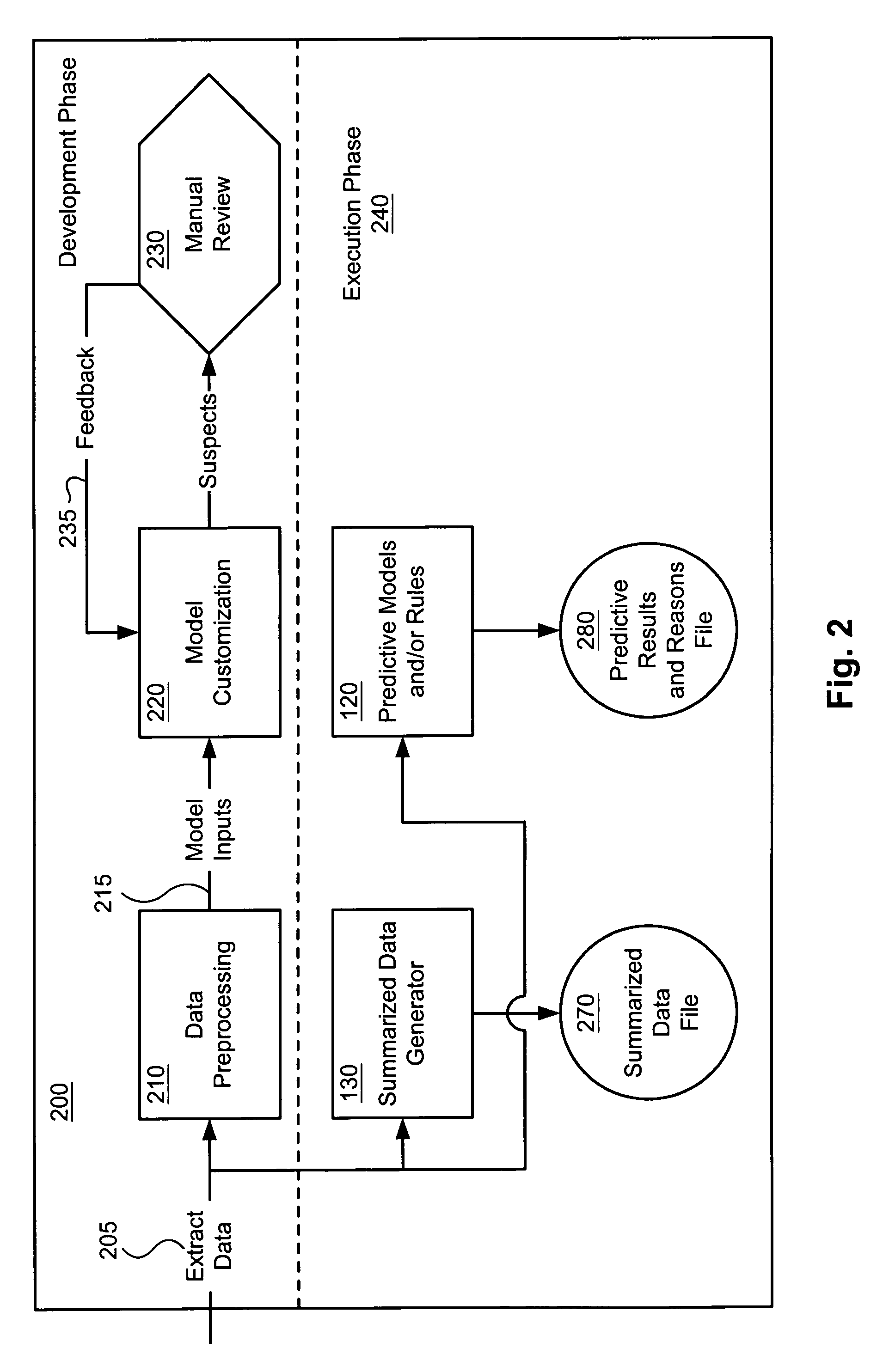
Webstation: configurable web-based workstation for reason driven data analysis
ActiveUS7418431B1Overcome limitationsQuick navigationDigital computer detailsDigital dataFrame basedWorkstation
Owner:FAIR ISAAC & CO INC
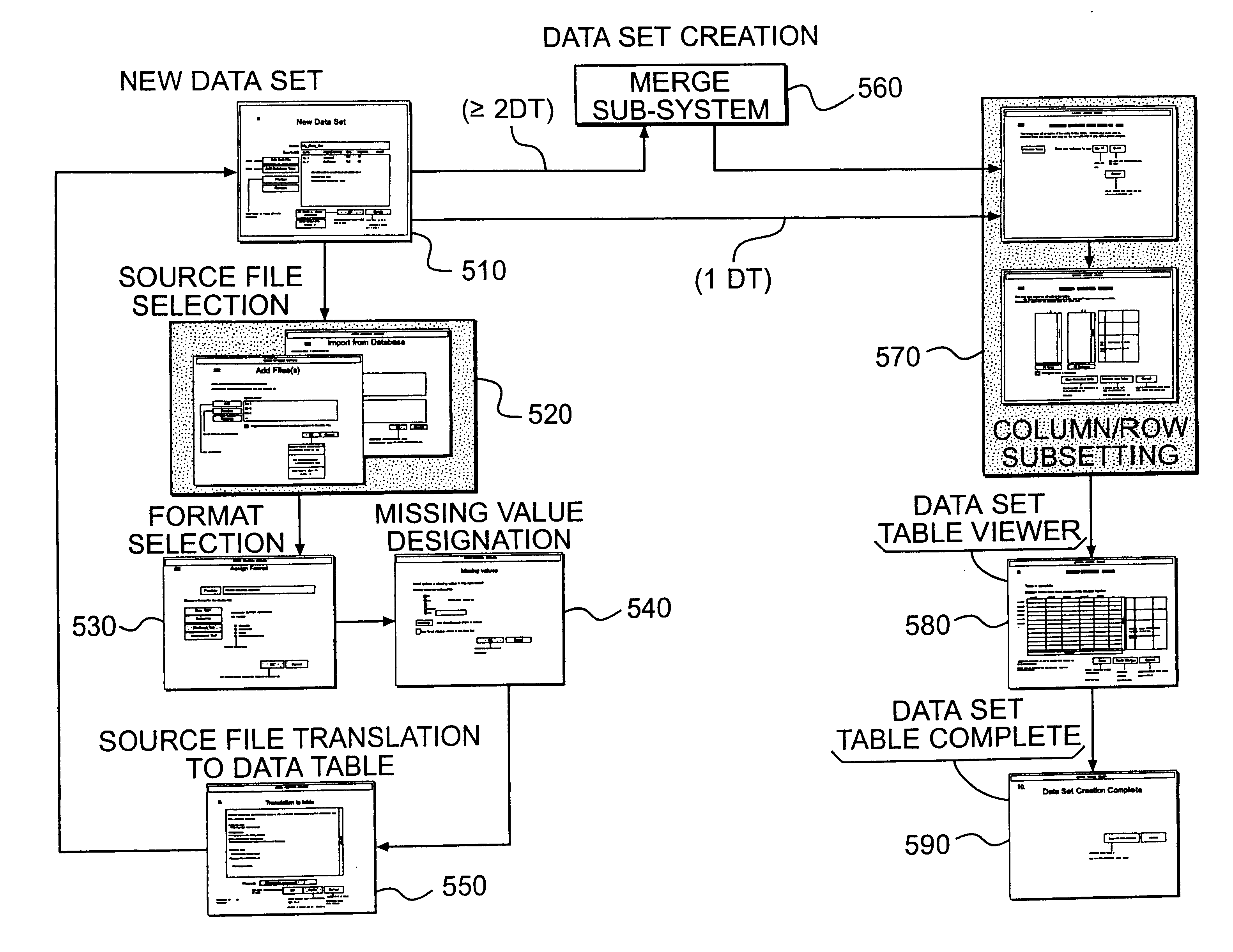
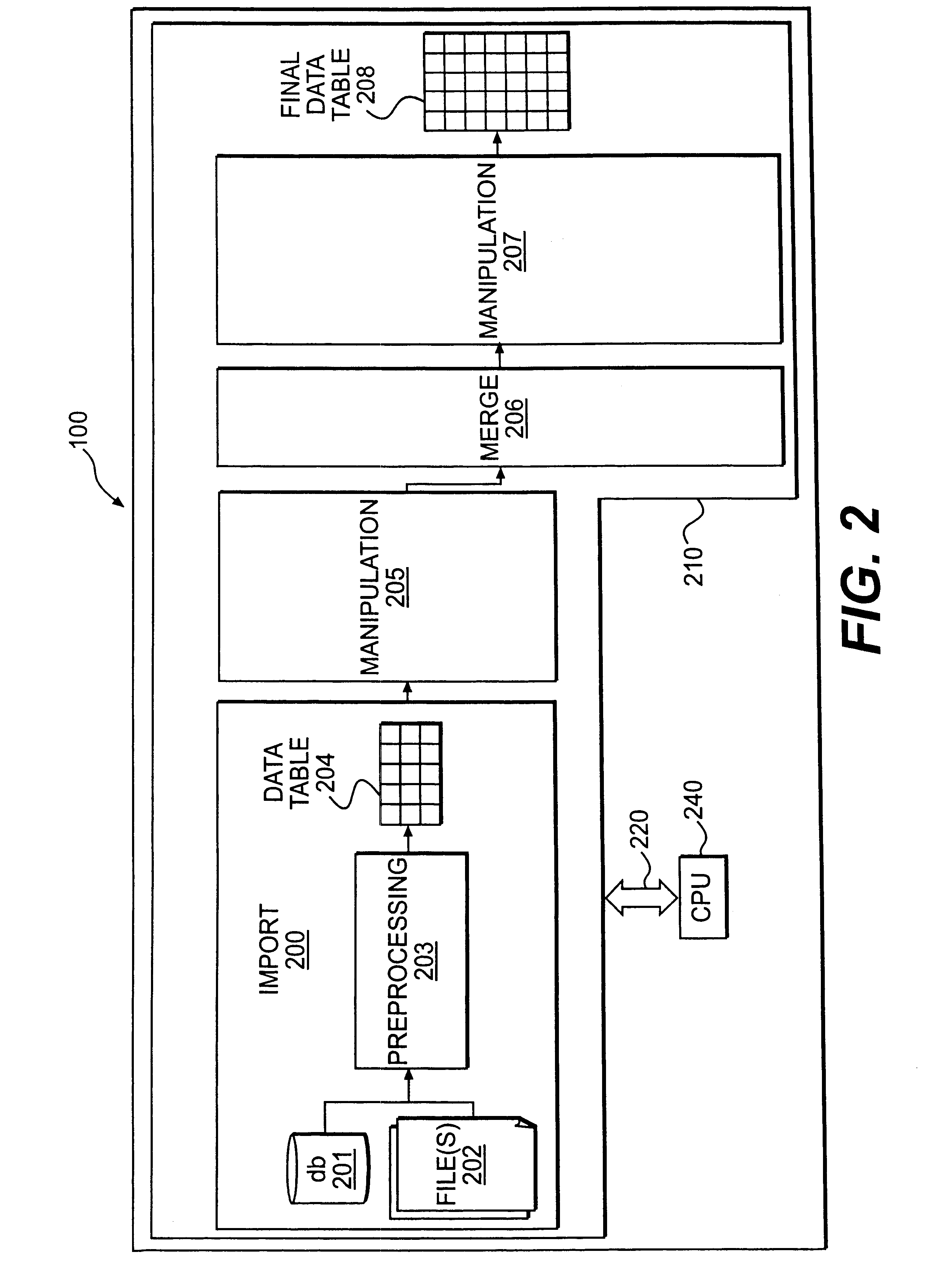
Data import system for data analysis system
A data import system enables access to data of multiple types from multiple data sources of different formats and provides an interface for importing data into a data analysis system. The interface enables a user to customize the formatting of the data as the data is being imported into a data analysis system. A user may select first user defined options for operating on a first data set received during a data importation process. An intermediate representation of the data set is generated based on the user first defined options. A user may specify second user defined options based on the intermediate representation during the data importation process. The second user defined options are processed to produce a final data representation of the data set to be used for analysis of the data. The intermediate representation may be a data table. The processing of a data set may include merging a first and second data set to produce the final data representation. The second user defined options may enable a user to select a basic operation for merging the data sets or to select a non-basic operation for merging the data sets. The basic operation may combine data sets in response to a user's selection of a first graphical interface control, and the non-basic operation may combine the data sets based on user selection of at least two graphical interface controls from a group of graphical interface controls.
Owner:BATTELLE MEMORIAL INST
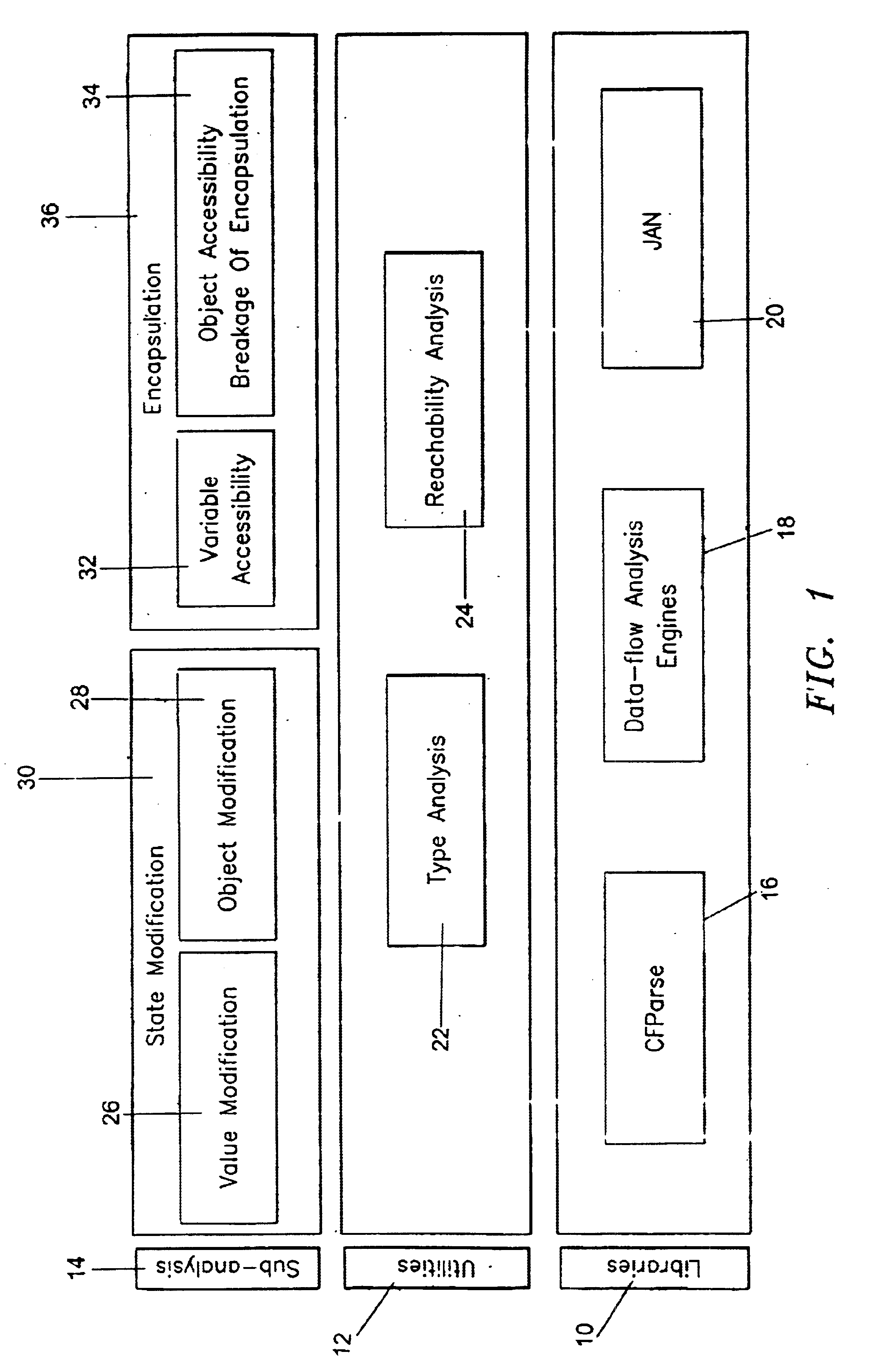
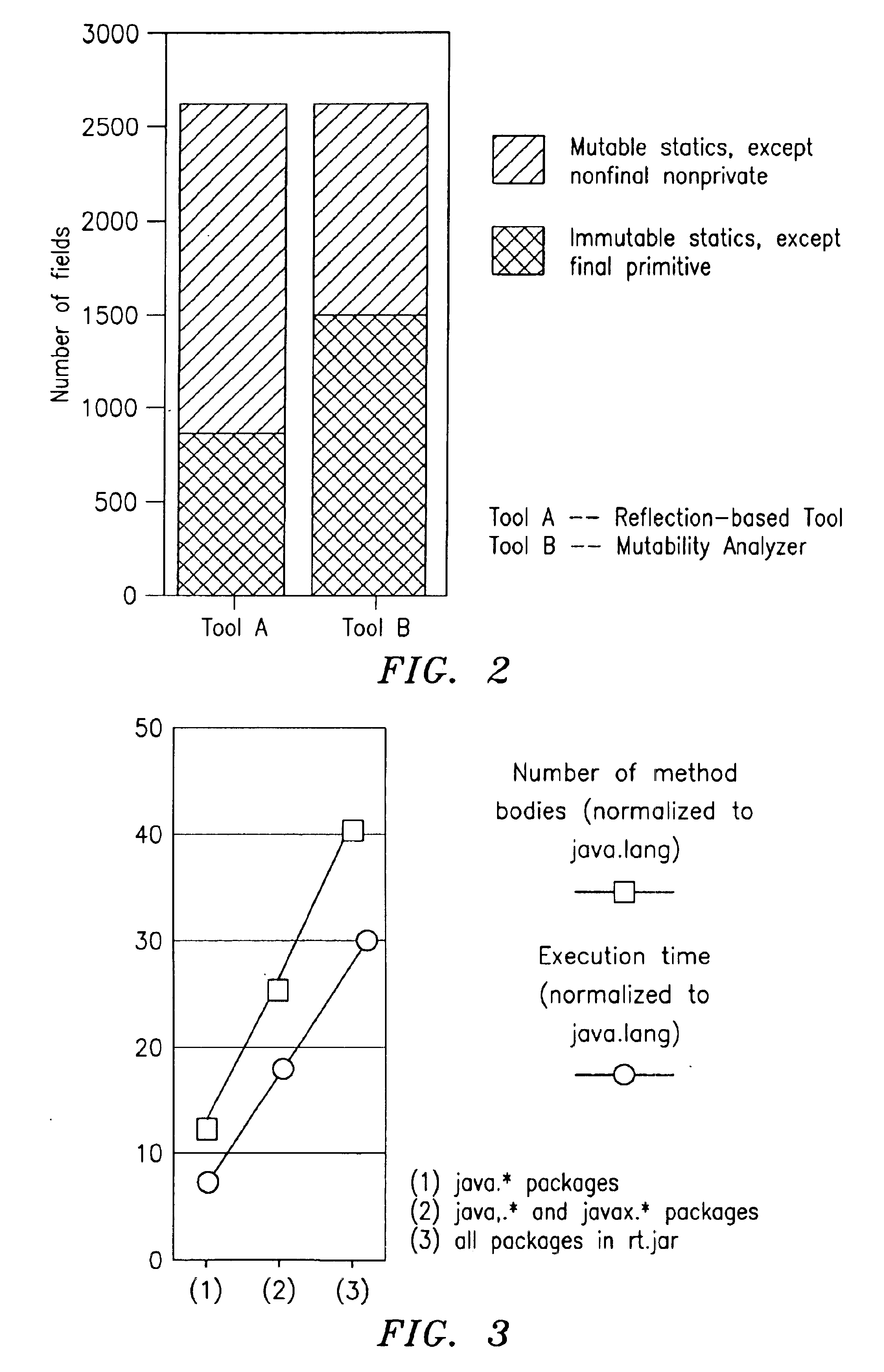
Mutability analysis in Java
InactiveUS6925638B1Reduce security risksEnsure maintenanceSoftware engineeringSpecific program execution arrangementsExtensibilityHuman language
A system and method for detecting the mutability of fields and classes in an arbitrary program component written in an object oriented programming language is disclosed. A variable is considered to be mutable if a new value is stored into it, as well as if any of its reachable variables are mutable. The system and method uses a static analysis algorithm which can be applied to any software component rather than whole programs. The analysis classifies fields and classes as either mutable or immutable. In order to facilitate open-world analysis, the algorithm identifies situations that expose variables to potential modification by code outside the component, as well as situations where variables are modified by the analyzed code. An implementation of the analysis is presented which focuses on detecting mutability of class variables, so as to avoid isolation problems. The implementation incorporates intra- and inter-procedural data-flow analyses and is shown to be highly scalable. Experimental results demonstrate the effectiveness of the algorithms.
Owner:IBM CORP
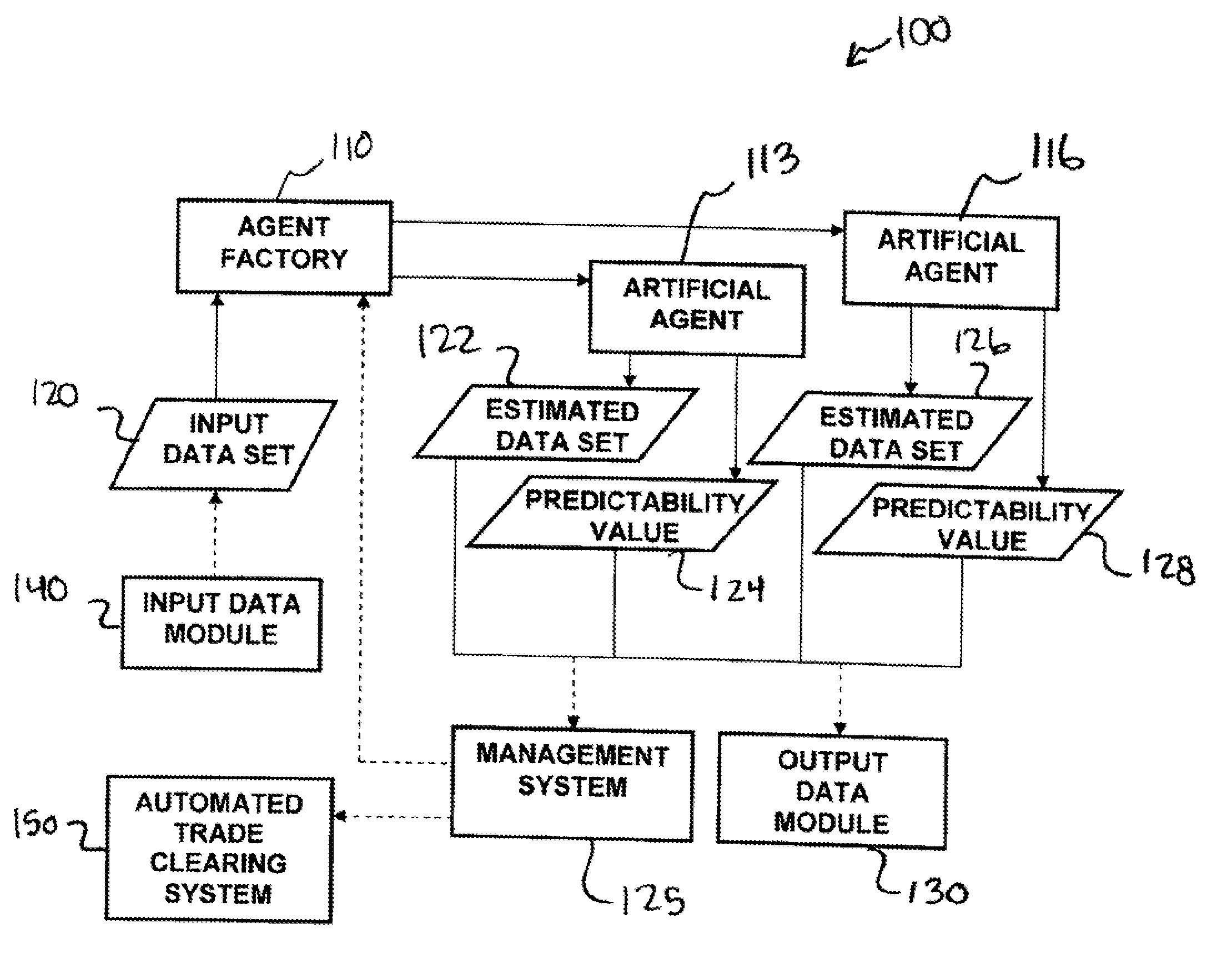
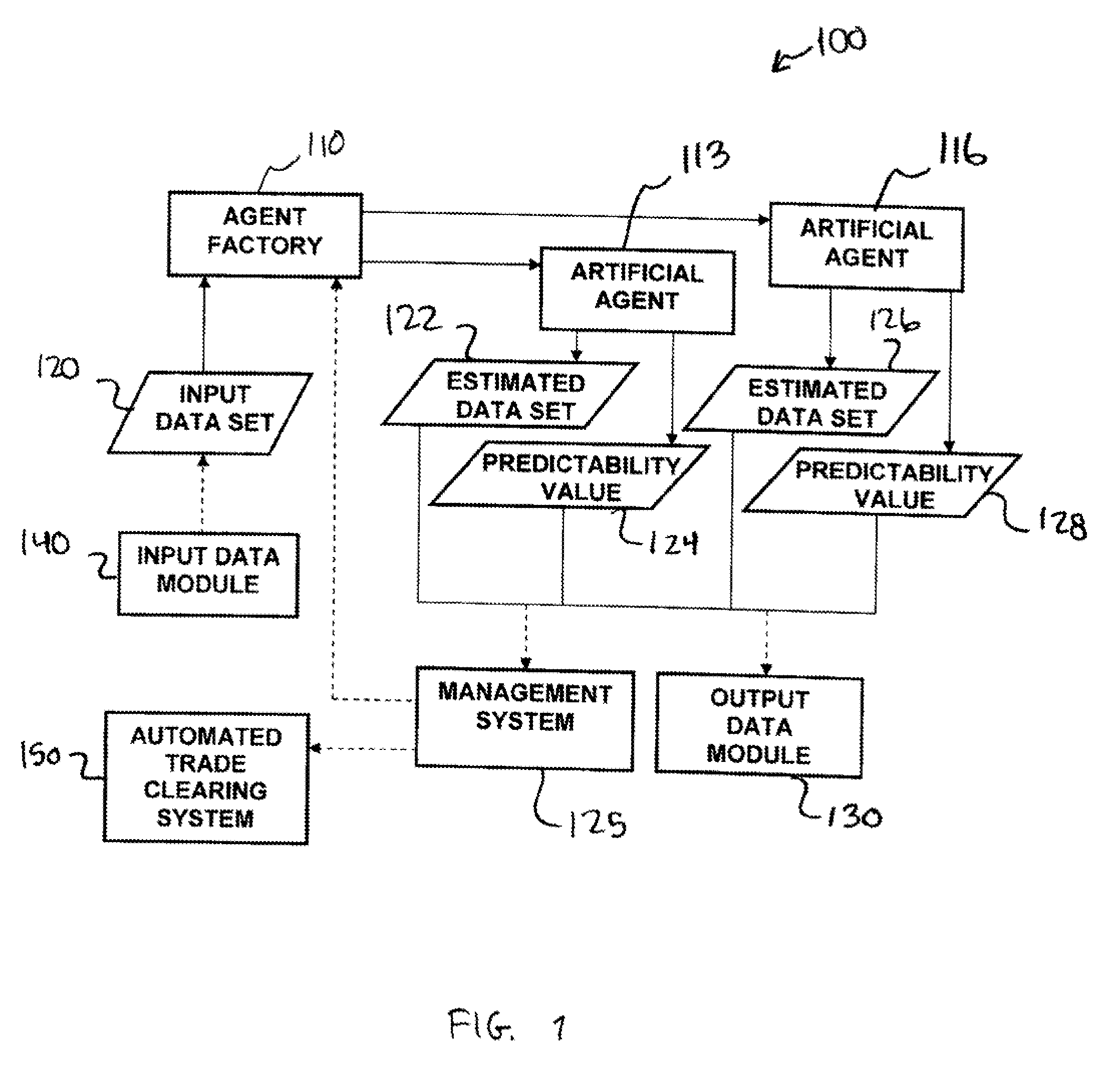
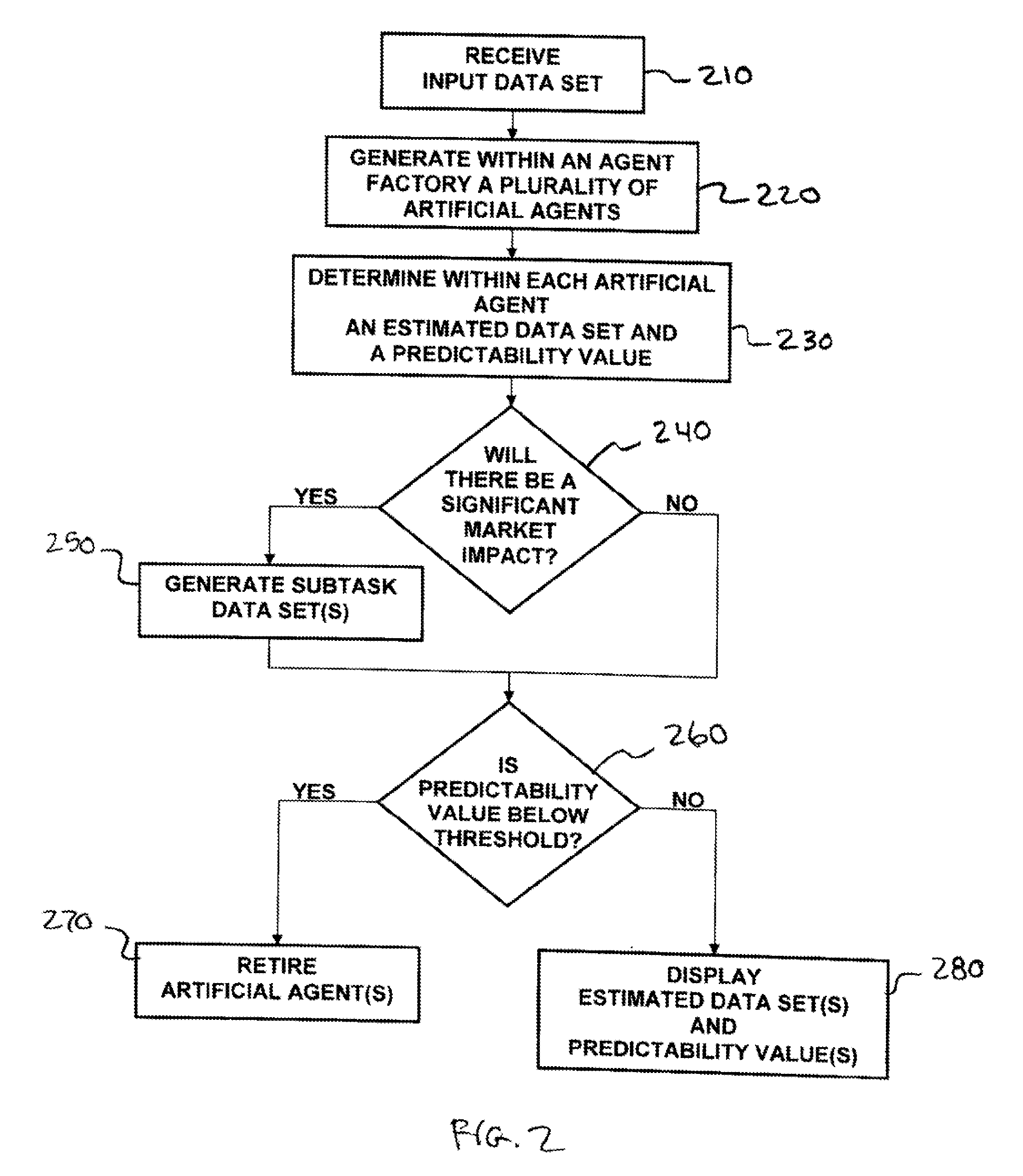
Methods and apparatus for self-adaptive, learning data analysis
Methods and apparatus for analyzing financial data generally includes a predictive modeling system. The predictive modeling system may include an artificial agent responsive to an input data set. The artificial agent may produce an estimated data set including a market conditions data set. The market conditions data may include an estimate of at least one of liquidity of a market, strategy of a counterparty, and an effect of information leakage. The artificial agent may determine a predictability value for the estimated data set. The predictive modeling system may also include an agent factory responsive to the input data set. The agent factory may generate an artificial agent in response to the input data set.
Owner:ADAPTIV TECH
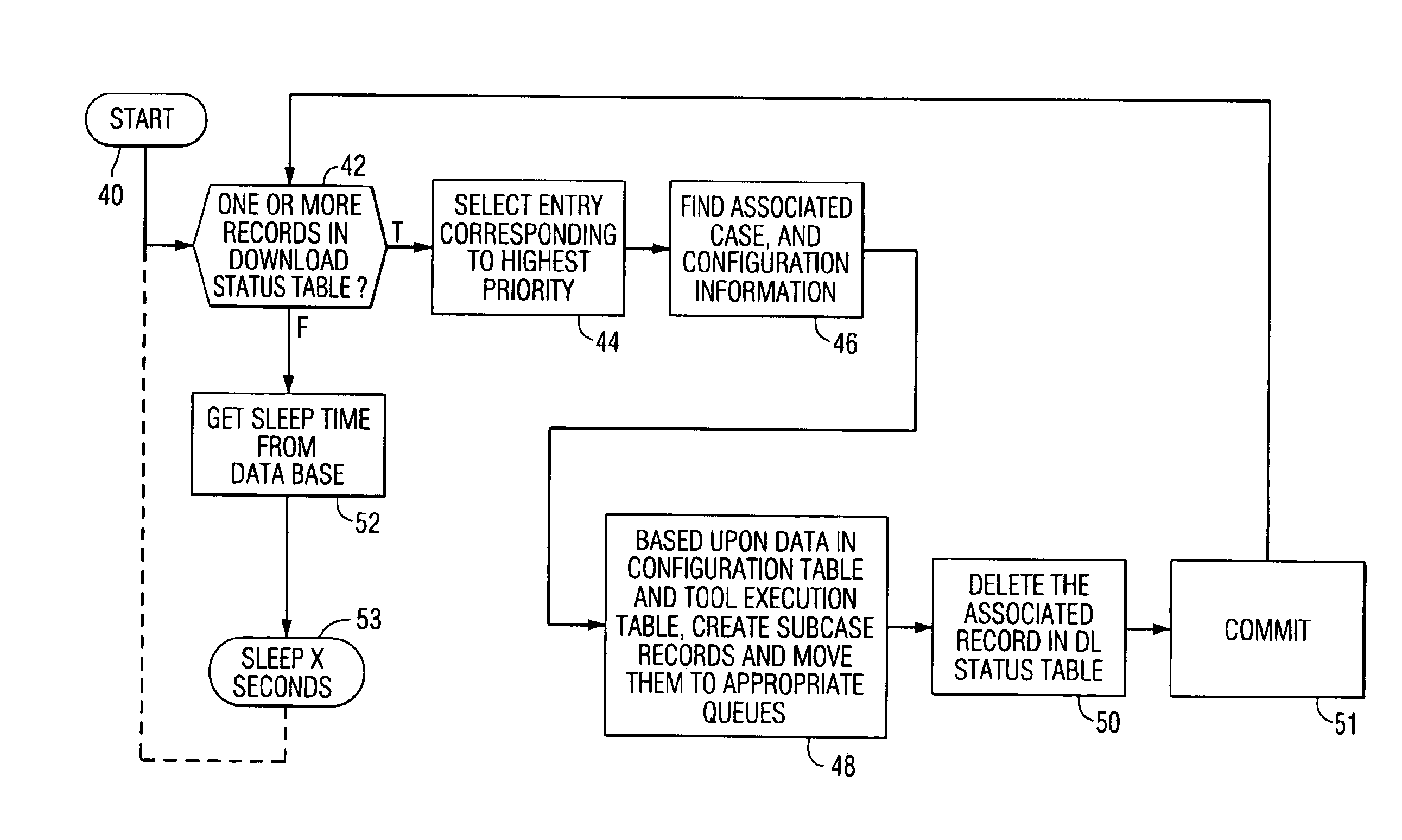
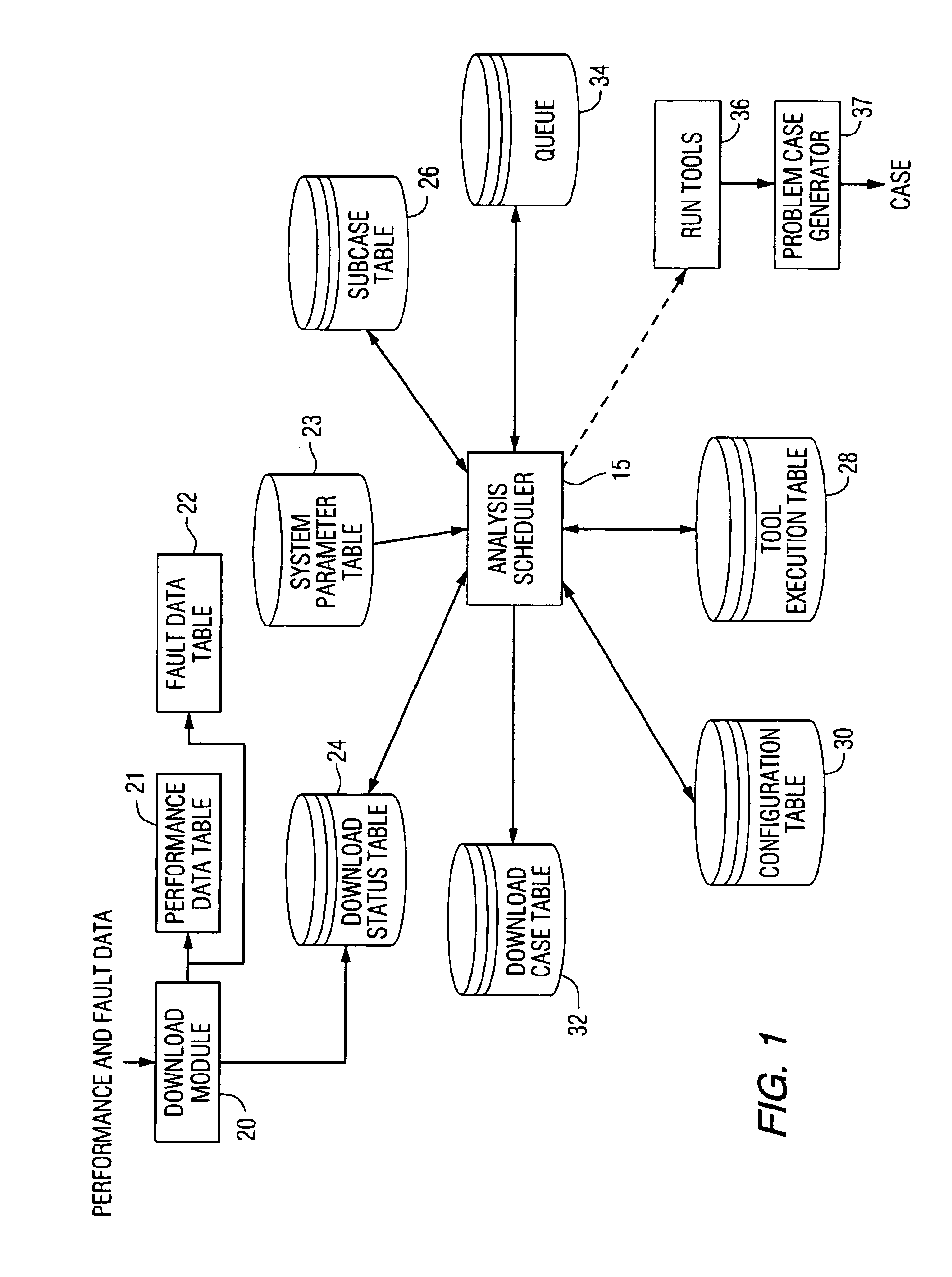
Apparatus and method for performance and fault data analysis
InactiveUS7013239B2Easily overload a human operatorEfficient and productiveVehicle testingRegistering/indicating working of vehiclesAnalysis toolsAutomatic processing
An analysis scheduler for scheduling the automatic processing of performance data through a plurality of analysis tools is disclosed. Performance data provided to some of the tools by the analysis scheduler may be specified to be within a predetermined (but variable) look-back period. The analysis tools identify faults and anomalous conditions and also create repair recommendations, and automatically create problem cases when conditions warrant, or update existing problem cases with additional data, all under control of the analysis scheduler. The problem cases are reviewed by a human user and then forwarded to the railroad for implementation.
Owner:GENERAL ELECTRIC CO
Mass customization configurator
InactiveUS7472043B1Accelerate time to marketReducing the engineering life cycleThermometer detailsDigital computer detailsAuto-configurationBill of materials
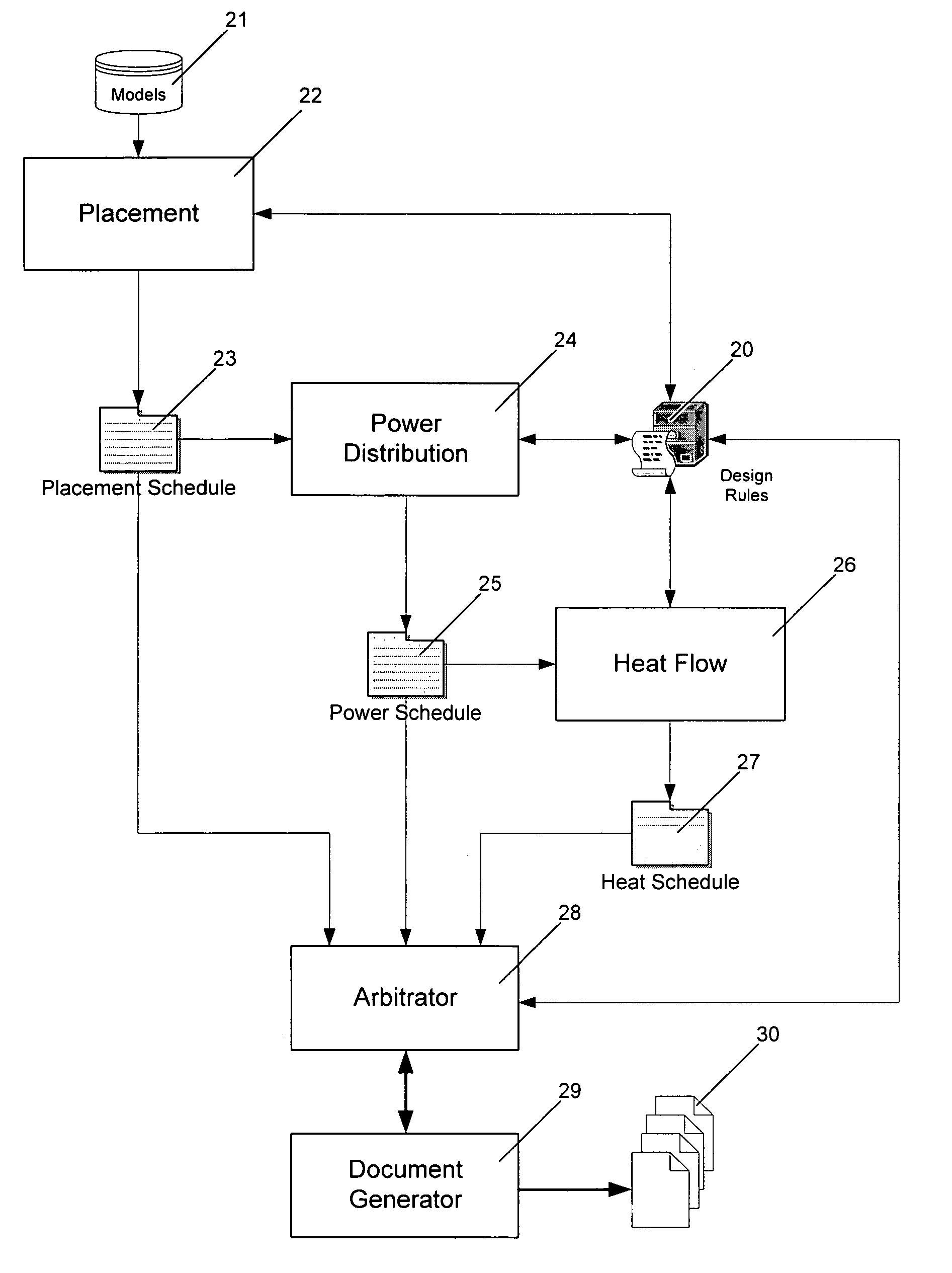
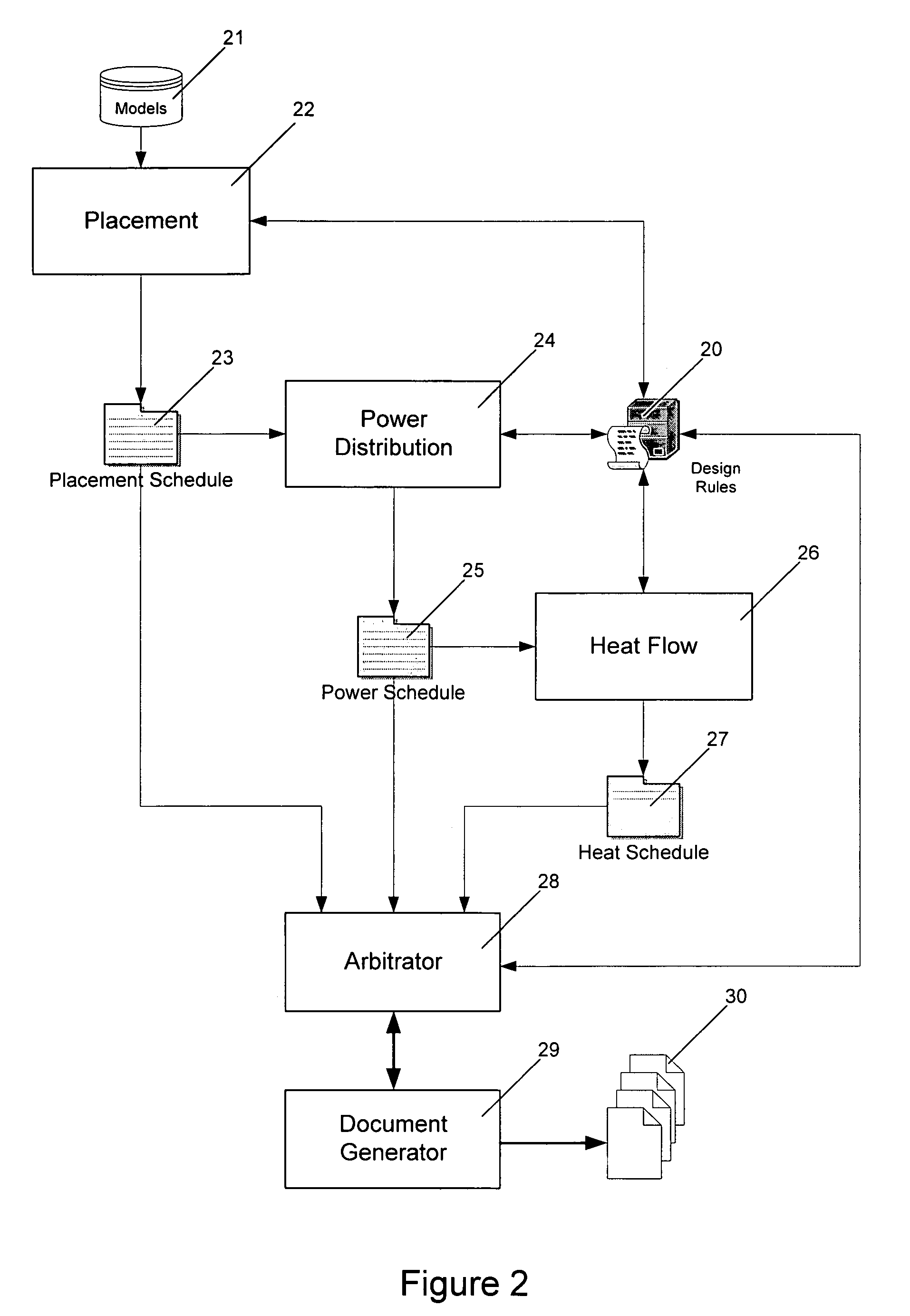
The present invention provides an automated configuration system and method for electronics enclosures. The system receives user requirements generates a configuration including placement schedule, power usage schedules and heat flow schedules. Included as output of the system is a bill of materials, an equipment layout drawing and pricing based on predetermined material and labor pricing. Methods for generating a configuration are described that include iteratively repeating combinations of the steps of generating design rules, deriving a placement schedule, mapping the distribution of power usage within the enclosure and producing a heat flow analysis. Processes used to generate the configuration can be controlled by design rules derived from user requirements.
Owner:TELLABS BEDFORD
Traffic flow surveying and handling method based on unmanned aerial vehicle high-definition video
ActiveCN103413444AHigh precisionOvercome inherent difficultiesImage analysisDetection of traffic movementHigh-definition videoSignal timing
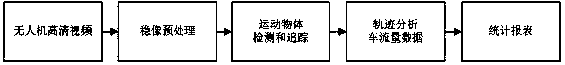
The invention provides a traffic flow surveying and handling method based on an unmanned aerial vehicle high-definition video. The method comprises the steps of video capture, wherein an unmanned aerial vehicle is made to hover over a selected urban road intersection for high-definition video shooting; image stabilization and pre-processing, wherein the high-definition video is copied, stabilization and pre-processing are carried out on images, and then an image sequence is output; detection and tracking, wherein detection and tracking are carried out on moving objects with the image sequence treated with image stabilization as source data; analysis and statistics, wherein traffic flow analysis and statistics are carried out on a target ID which is tracked down and the current coordinates of motion; output, wherein traffic flow statistical data are transmitted to a client-side graphical interface for display, and then data and statements are generated. The traffic flow surveying and handling method based on the unmanned aerial vehicle high-definition video is capable of obtaining various high-accuracy traffic data, reducing the workload of field survey remarkably, preventing the traffic from being affected, obtaining statistic data of all traffic flows in twelve directions of the intersection, and providing data support for congestion control such as intersection signal timing optimization and traffic channeling improvement.
Owner:SHENZHEN WISESOFT TECH DEV
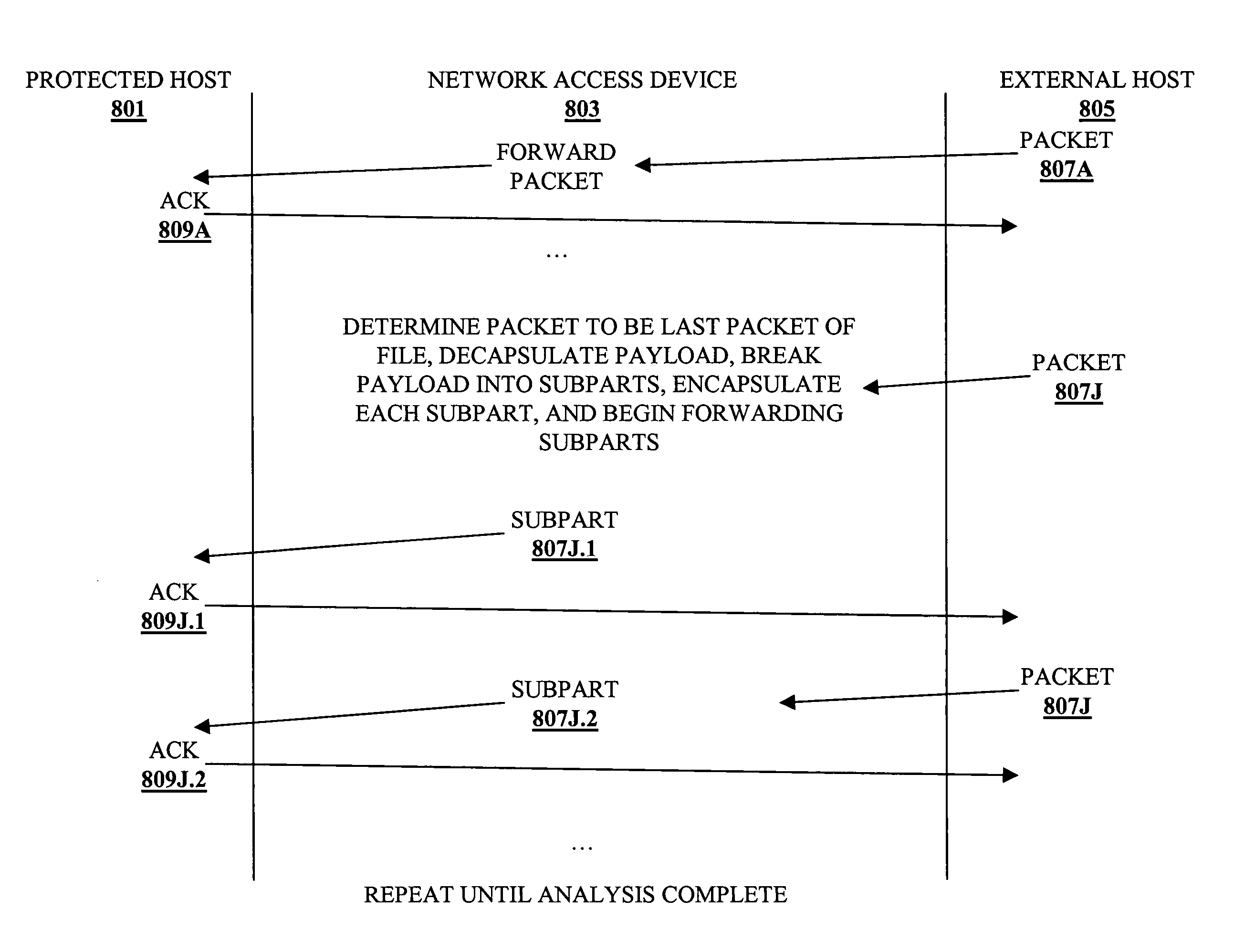
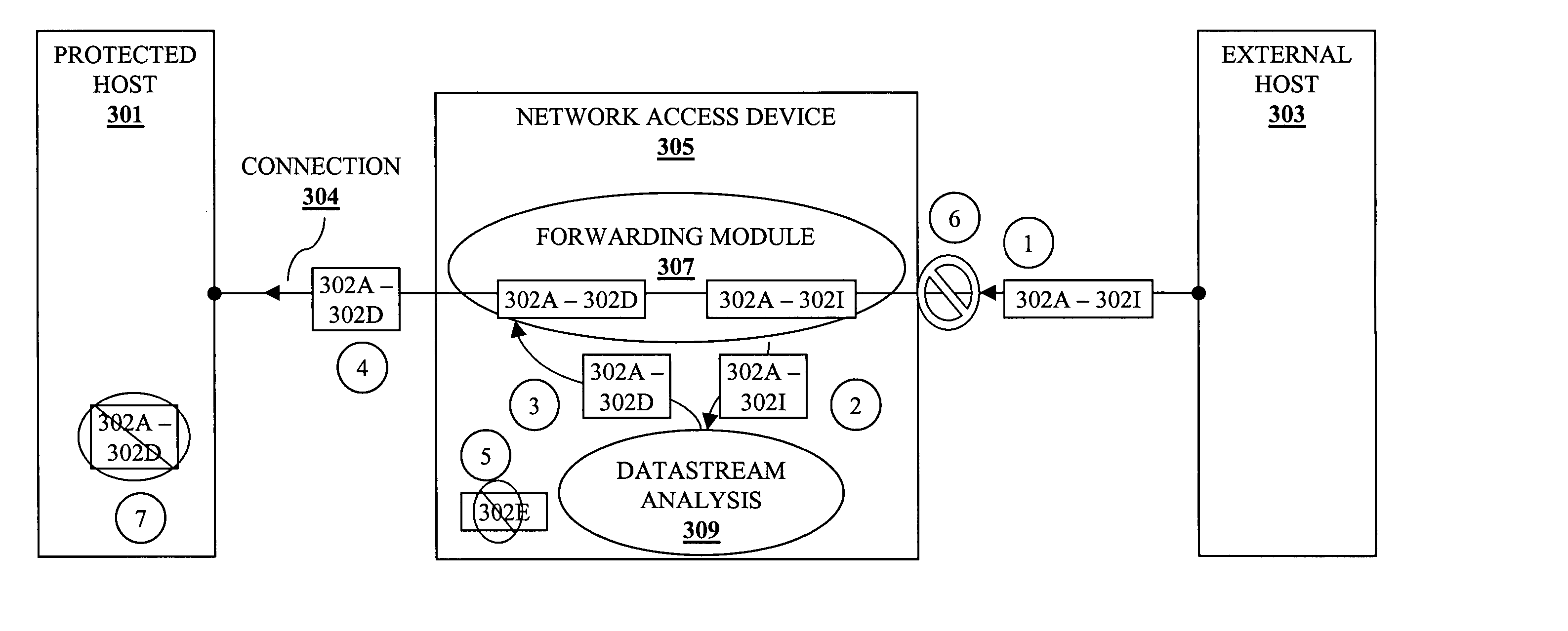
Method and apparatus for datastream analysis and blocking
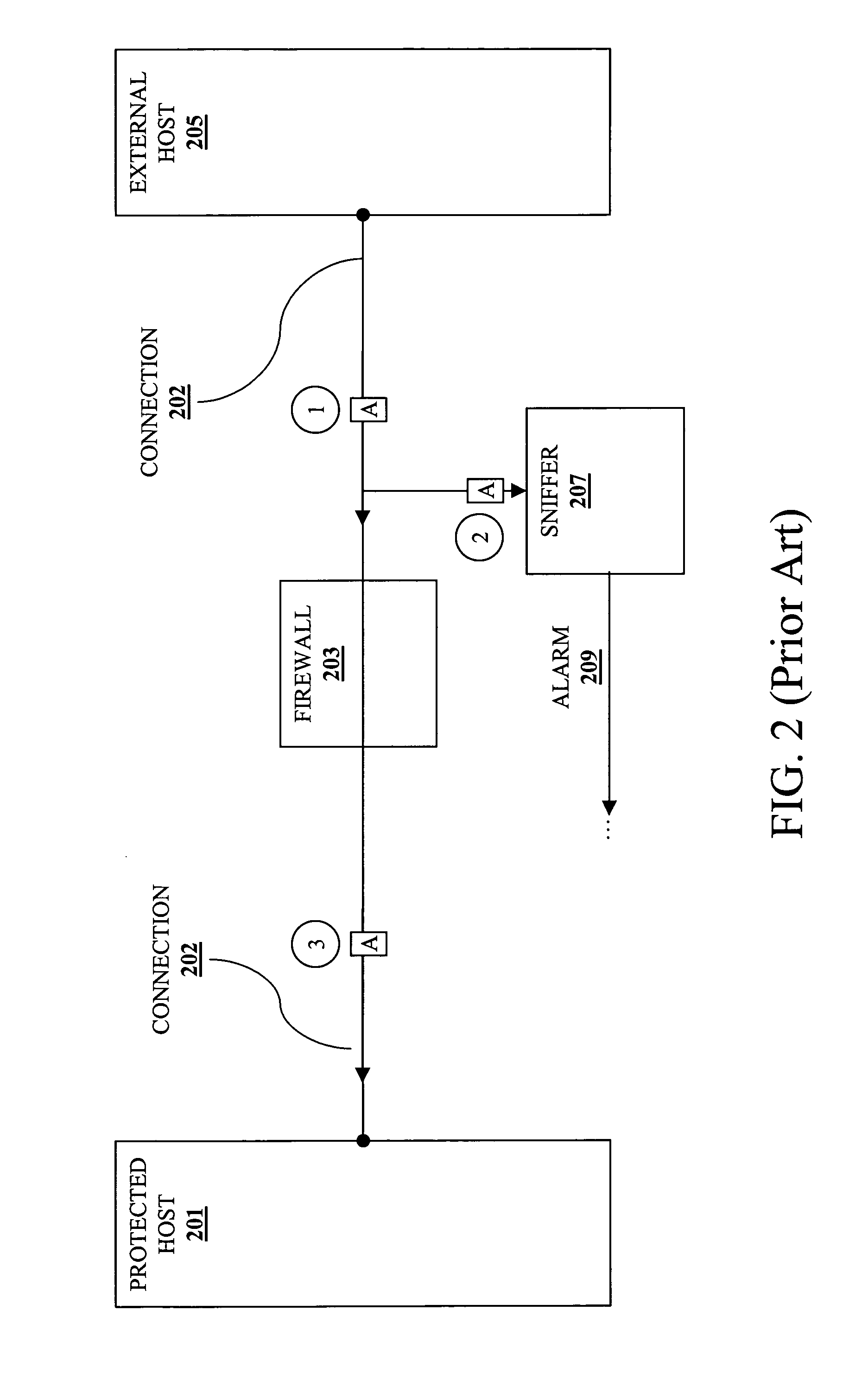
A method and apparatus for datastream analysis and blocking. According to one embodiment of the invention, a network access device, analyzes (without proxying) each of a stream of packets traversing a single connection through the network access device from an external host to a protected host. In addition, the network access device forwards each allowed packet of the stream of packets as long as the connection is active. However, if one of the stream of packets is determined to be disallowed as a result of the analyzing, then the network access device discards the disallowed packet and terminates the connection, causing the protected host to discard those packets received on the terminated connection.
Owner:MICRON TECH INC +1
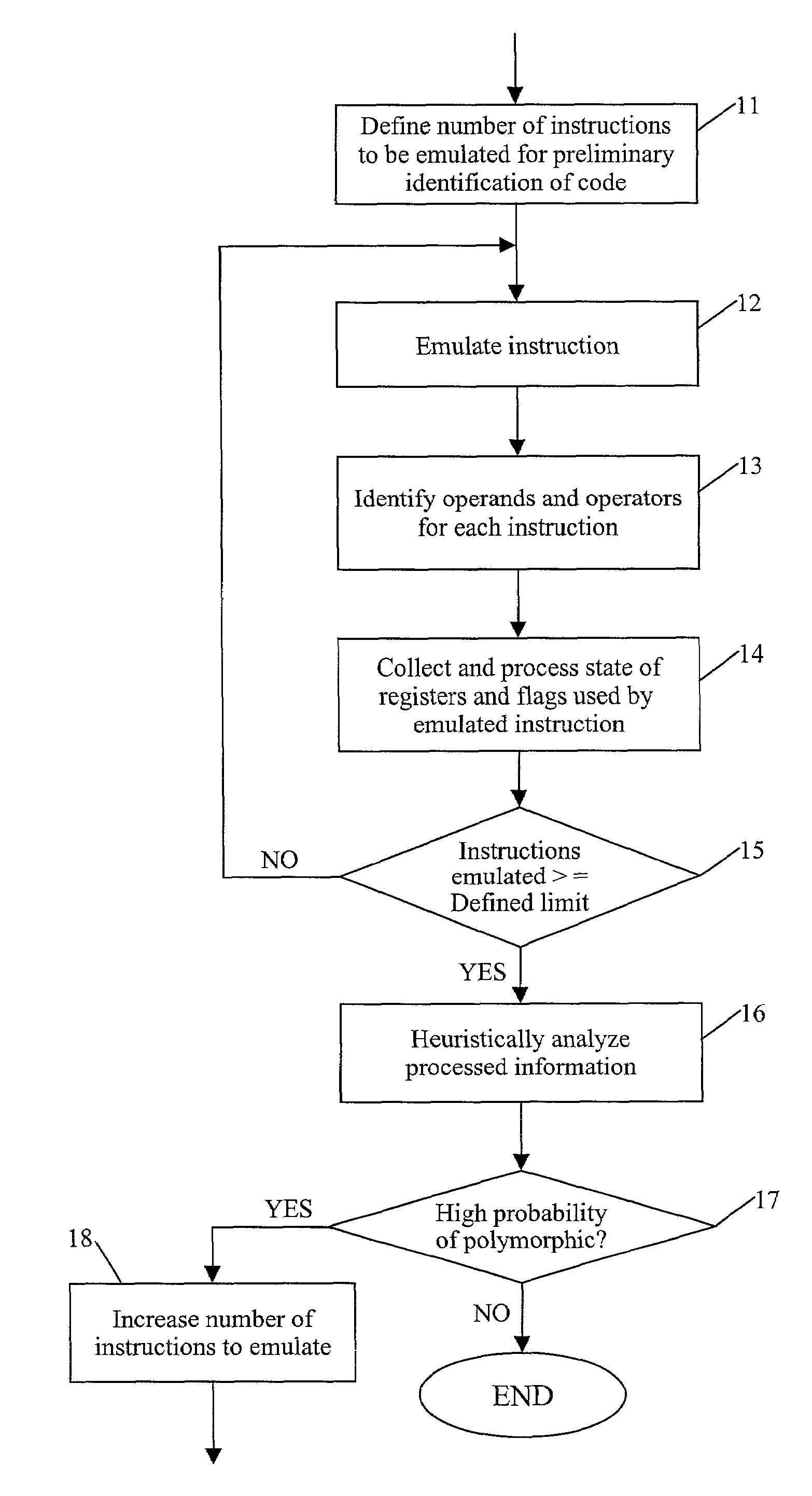
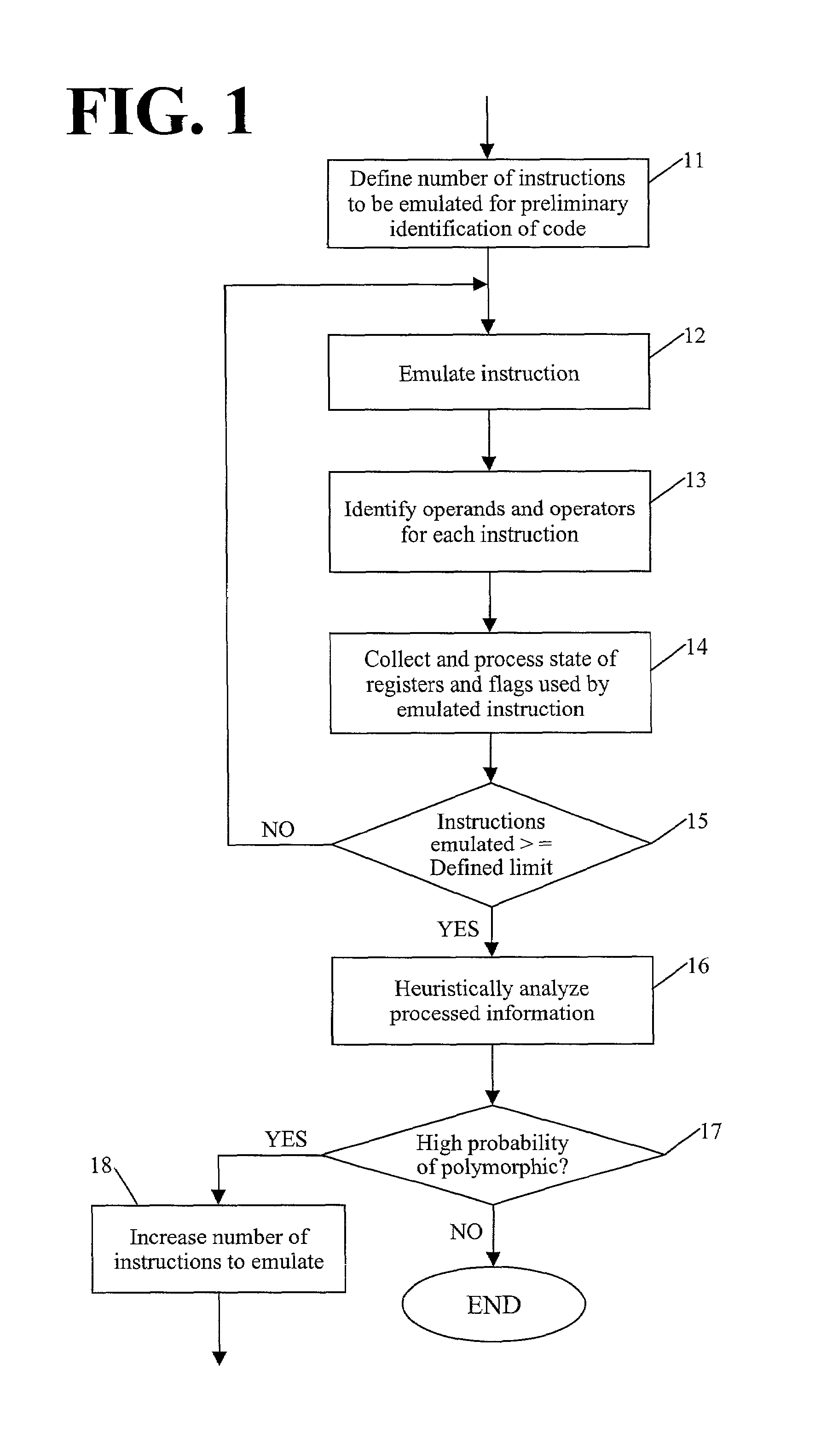
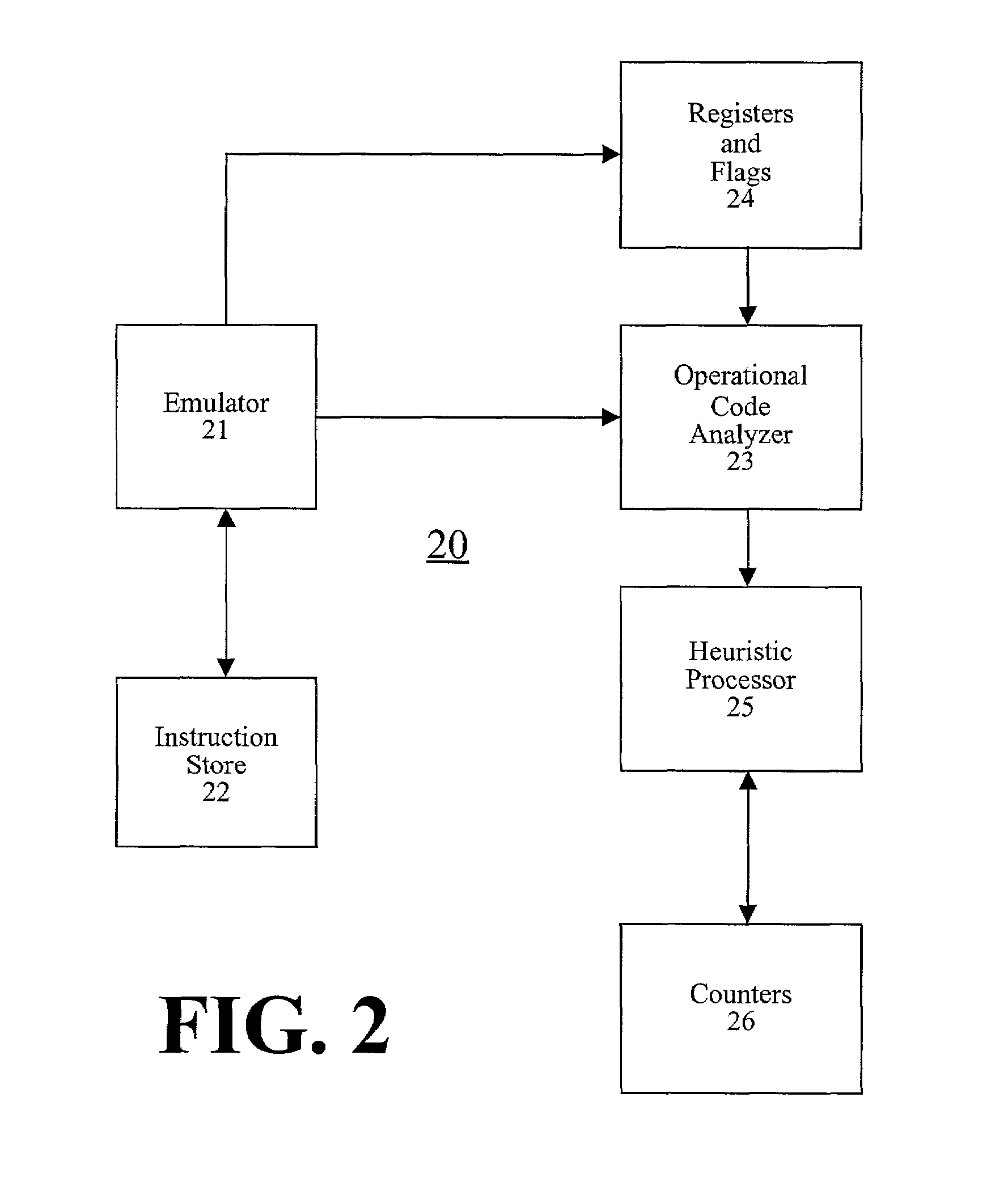
Detection of polymorphic virus code using dataflow analysis
A method and apparatus for detecting polymorphic viral code in a computer program is provided. The apparatus comprises an emulator, an operational code analyzer and an heuristic analyzer. The emulator emulates a selected number of instructions of the computer program. The operational code analyzer collects and stores information corresponding to operands and operators used in the instructions and the state of registers / flags after each emulated instruction execution. The heuristic analyzer determines a probability that the computer program contains viral code based on an heuristic analysis of register / flag state information supplied by the operational code analyzer.
Owner:COMP ASSOC THINK INC
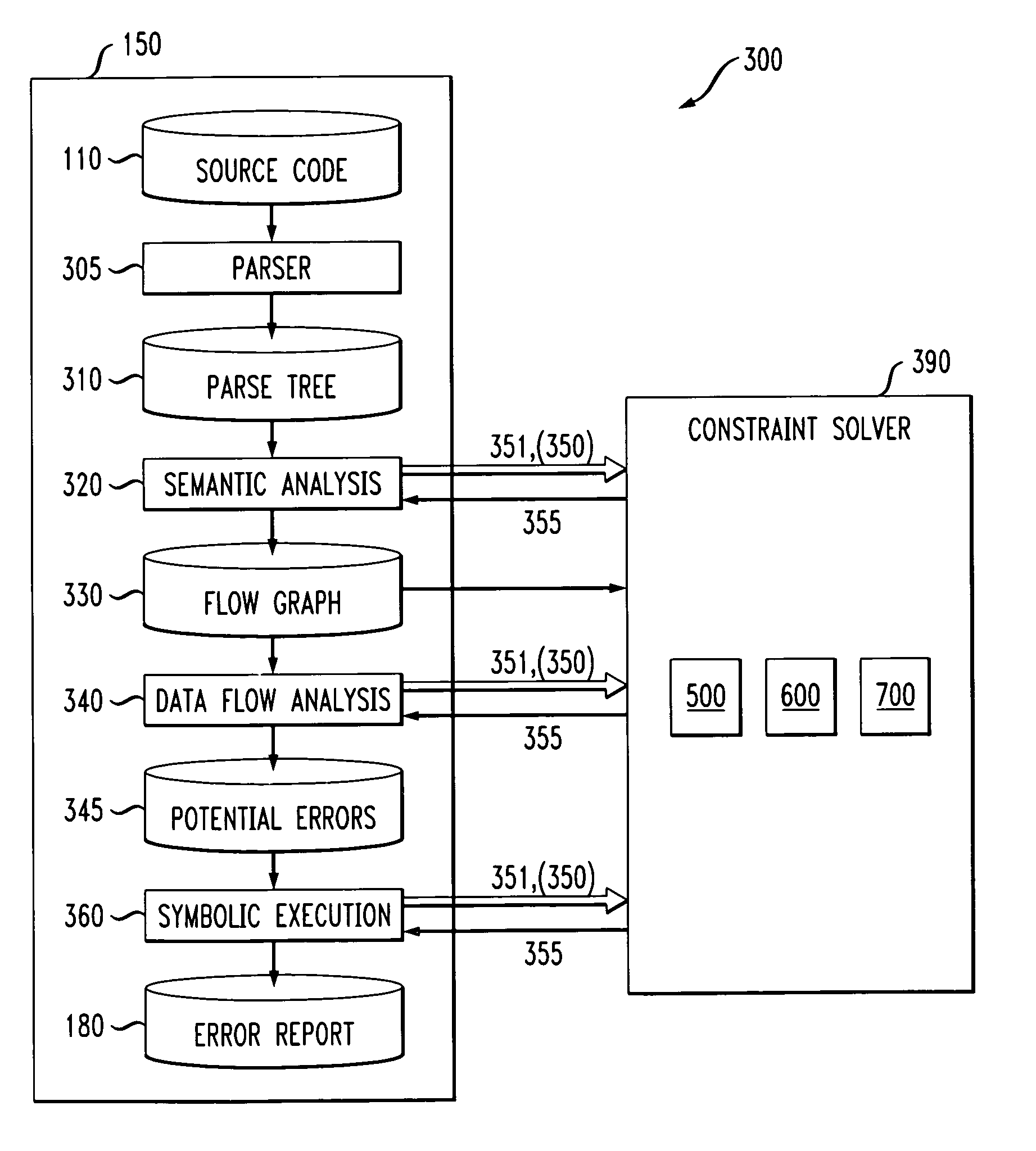
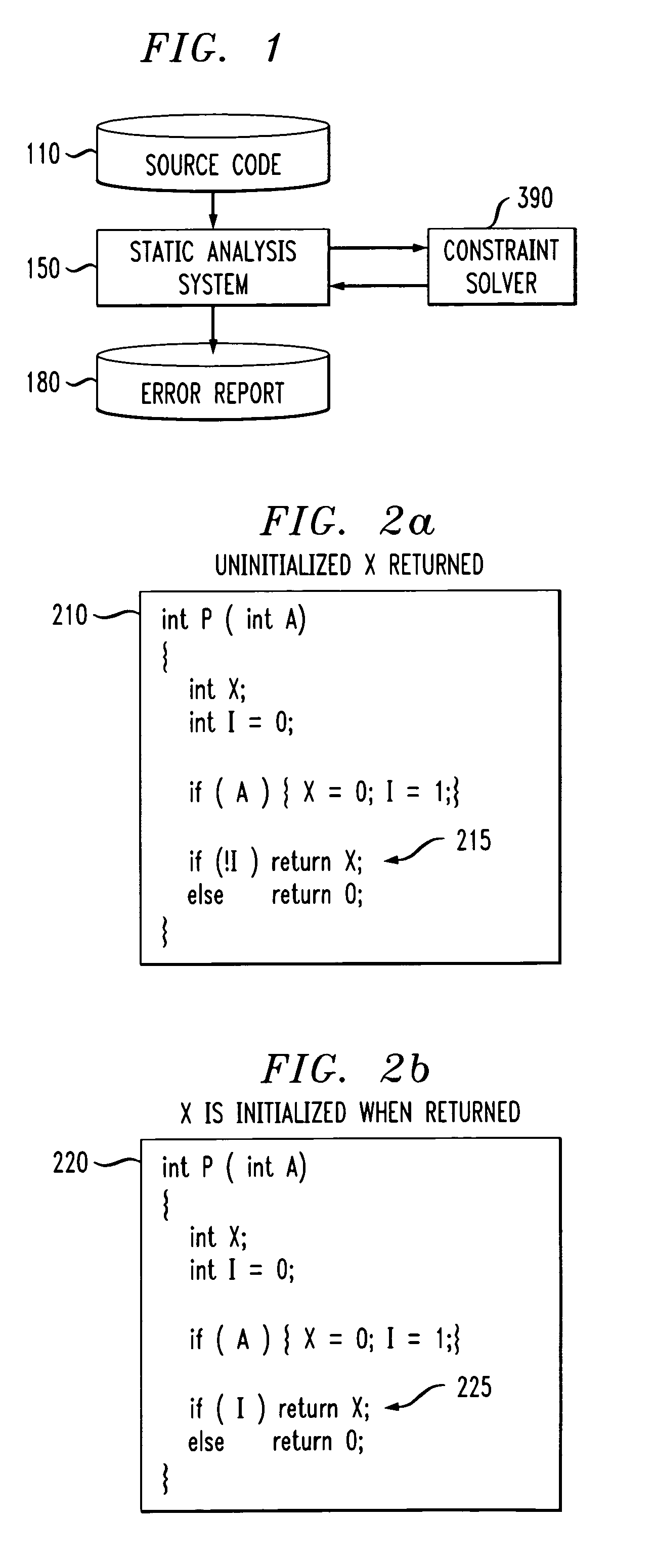
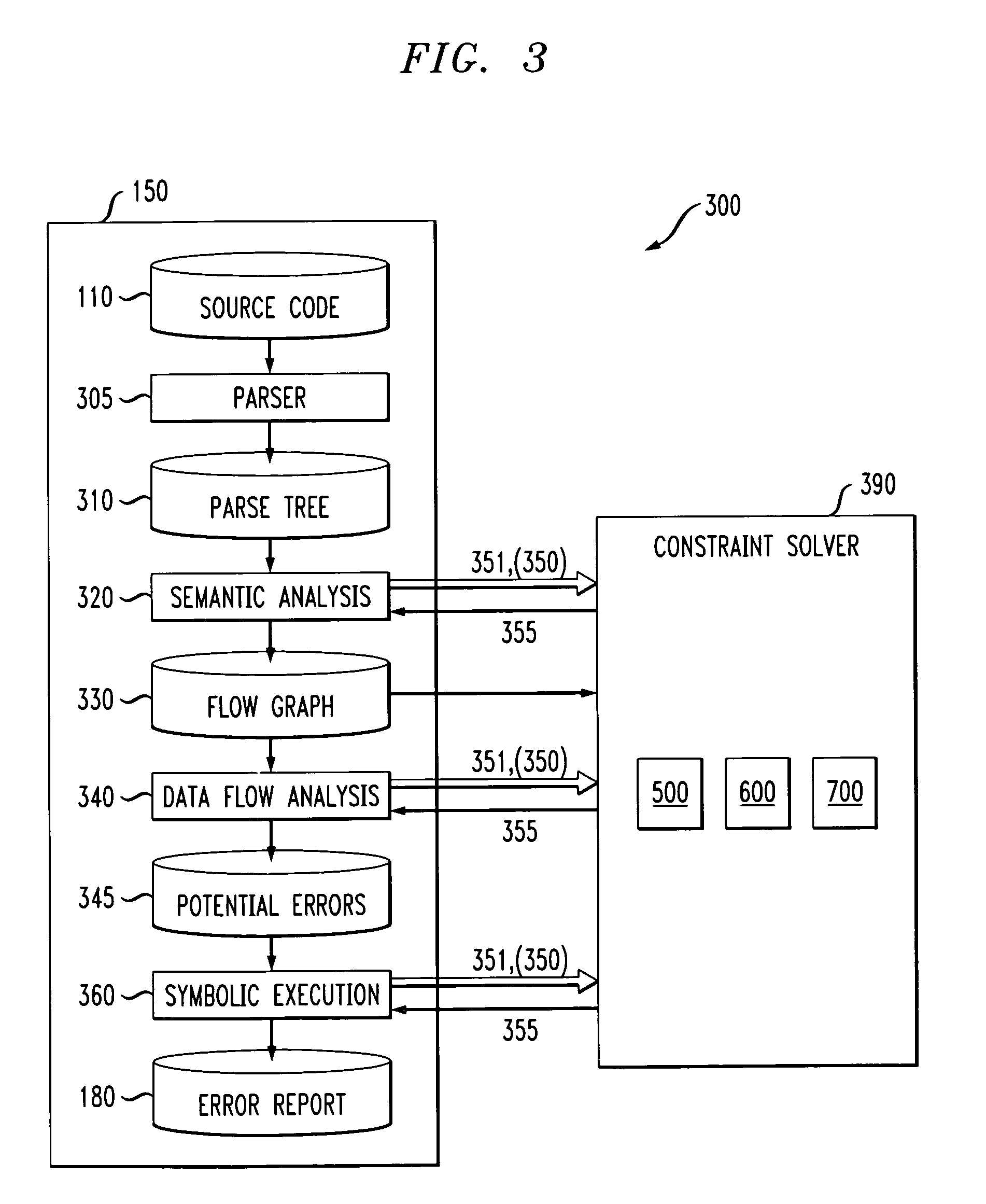
Method and apparatus for finding errors in software programs using satisfiability of constraints
InactiveUS7089542B2Efficient and accurateHandled satisfactorilyError preventionError detection/correctionRewrite ruleSemantics
A method and apparatus are provided for analyzing software programs. The invention combines data flow analysis and symbolic execution with a new constraint solver to create a more efficient and accurate static software analysis tool. The disclosed constraint solver combines rewrite rules with arithmetic constraint solving to provide a constraint solver that is efficient, flexible and capable of satisfactorily expressing semantics and handling arithmetic constraints. The disclosed constraint solver comprises a number of data structures to remember existing range, equivalence and inequality constraints and incrementally add new constraints. The constraint solver returns an inconsistent indication only if the range constraints, equivalence constraints, and inequality constraints are mutually inconsistent.
Owner:IBM CORP
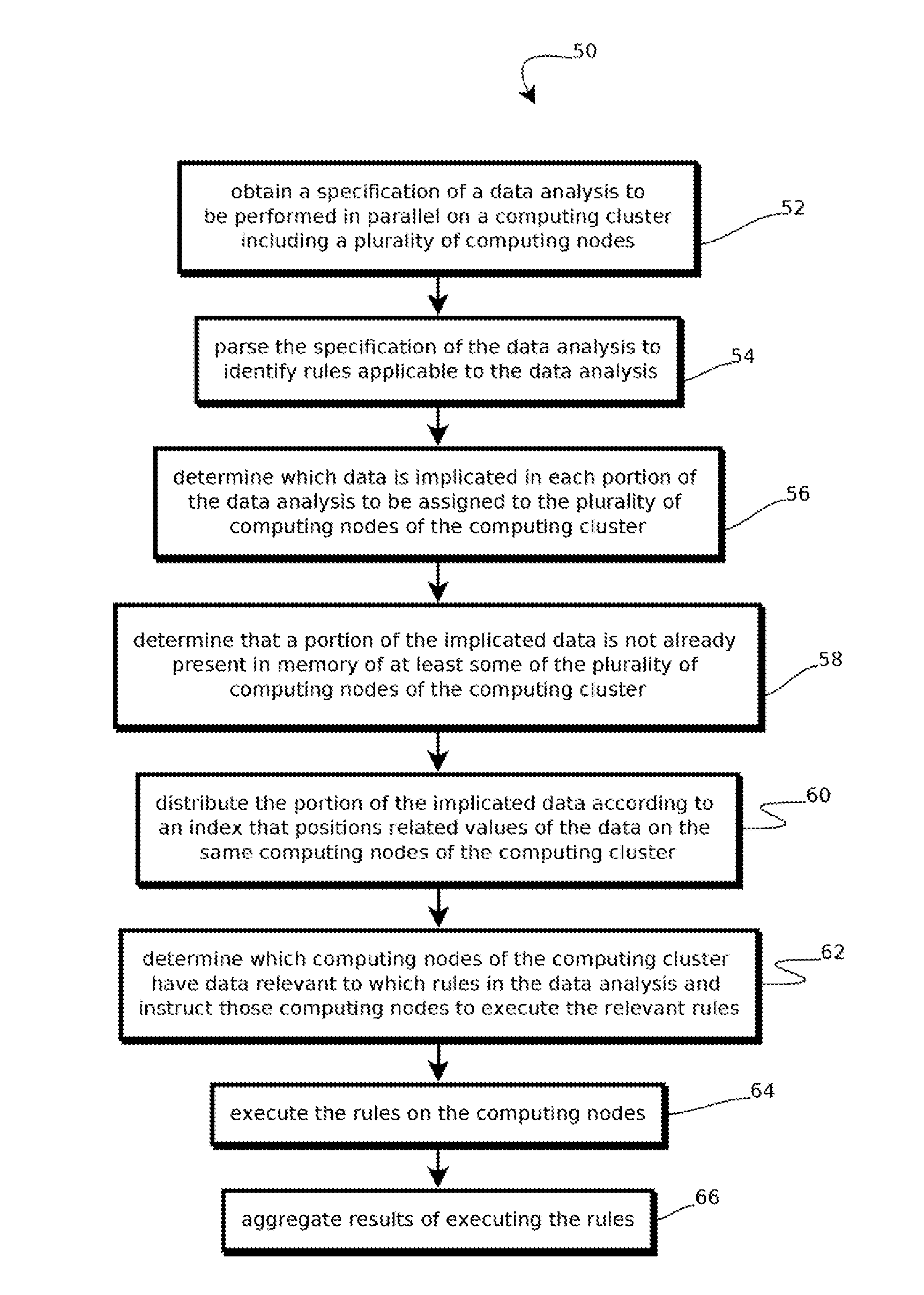
Scripting distributed, parallel programs
ActiveUS20160112531A1Program controlGeographical information databasesData-flow analysisData analysis
Provided is a process having steps including obtaining a specification of a data analysis to be performed in parallel on a computing cluster; parsing the specification of the data analysis; determining which data is implicated in each portion of the data analysis to be assigned to a plurality of computing nodes of the computing cluster; determining that a portion of the implicated data is not already present in memory of at least some of the plurality of computing nodes of the computing cluster; distributing the portion of the implicated data according to an index that positions related values of the data on the same computing nodes of the computing cluster; determining which computing nodes of the computing cluster have data relevant to which rules in the data analysis and send relevant rules to the corresponding computing nodes; executing the rules on the computing nodes; and aggregating results of executing the rules.
Owner:PLACEIQ
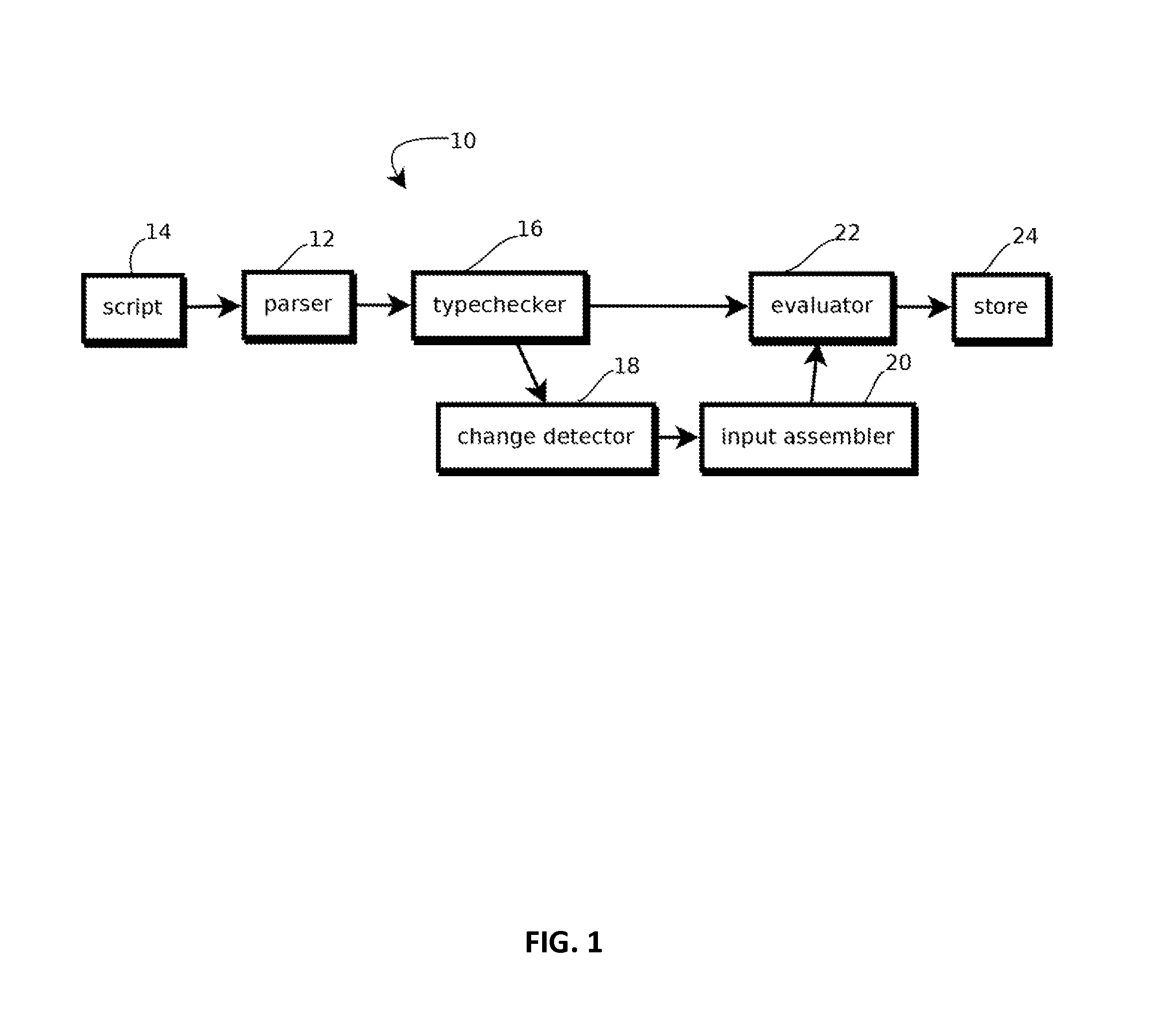
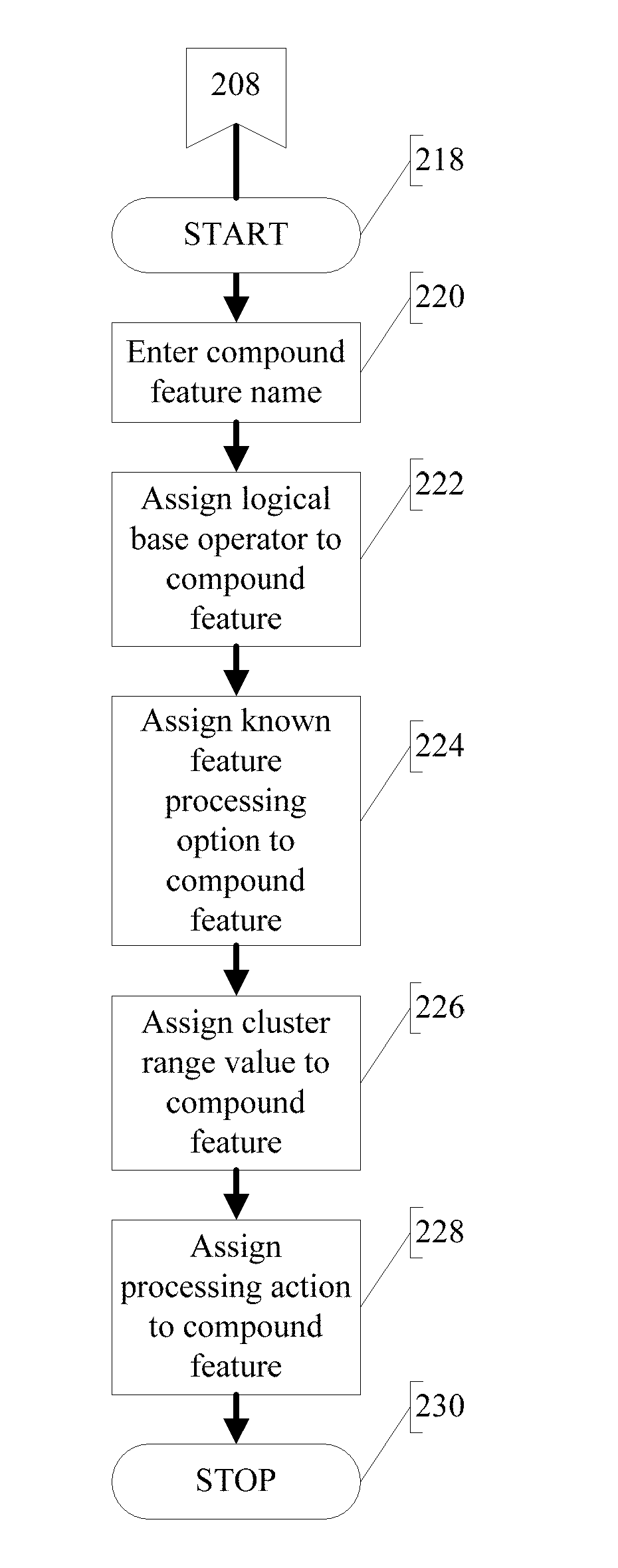
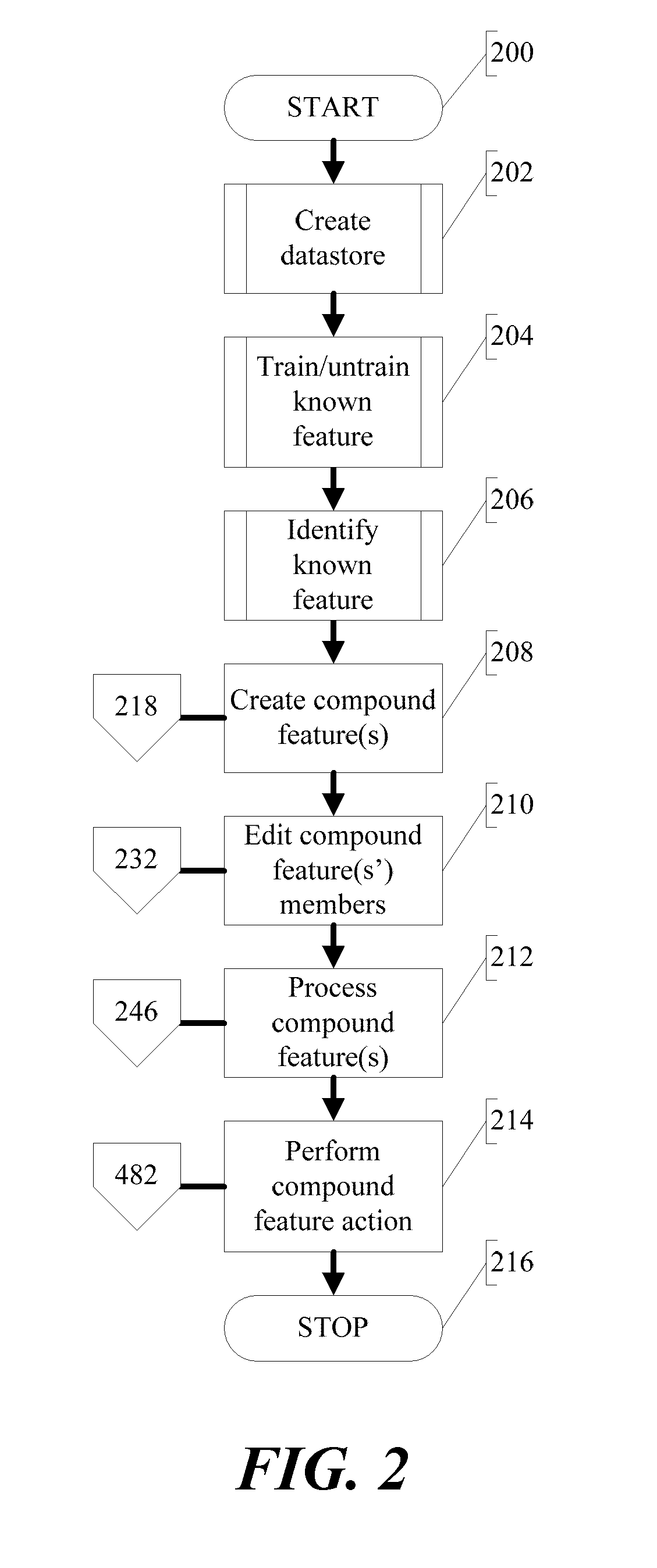
Methods and systems for compound feature creation, processing, and identification in conjunction with a data analysis and feature recognition system
ActiveUS20090231359A1Conducive to interpretationImprove perceptionCathode-ray tube indicatorsChaos modelsAnalysis dataData discrimination
Methods and systems for creation, processing, and use of compound features during data analysis and feature recognition are disclosed herein. In a preferred embodiment, the present invention functions to apply a new level of data discrimination during data analysis and feature recognition events such that features are more easily discerned from the remainder of the data pool using processing techniques that are more conducive to human visualizations, perceptions, and / or interpretations of data. This is accomplished using an example tool that allows previously processed and identified features (hereafter “known features”) to be aggregated so as to aid the system in recognizing abstract data features, preferably using Boolean operators and user-assigned hit weight values across desired cluster ranges surrounding analyzed data elements.
Owner:INTELLISCI CORP
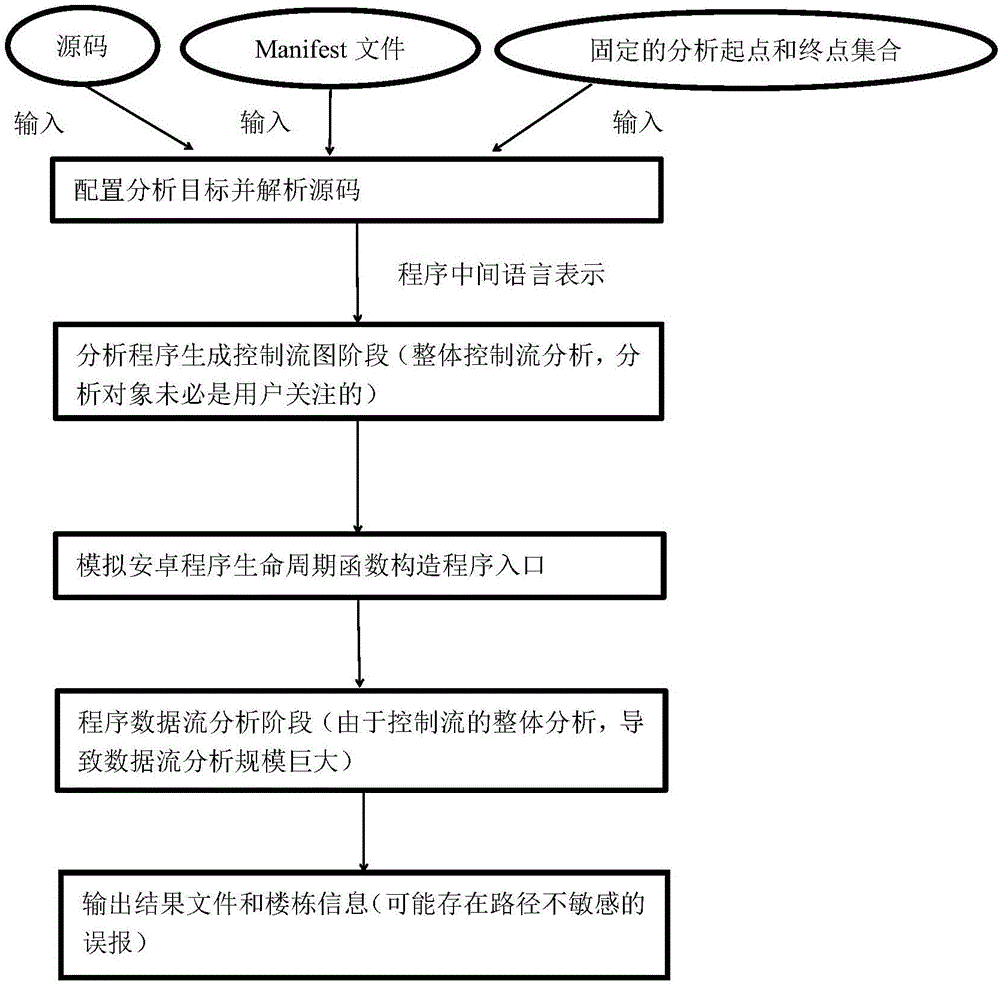
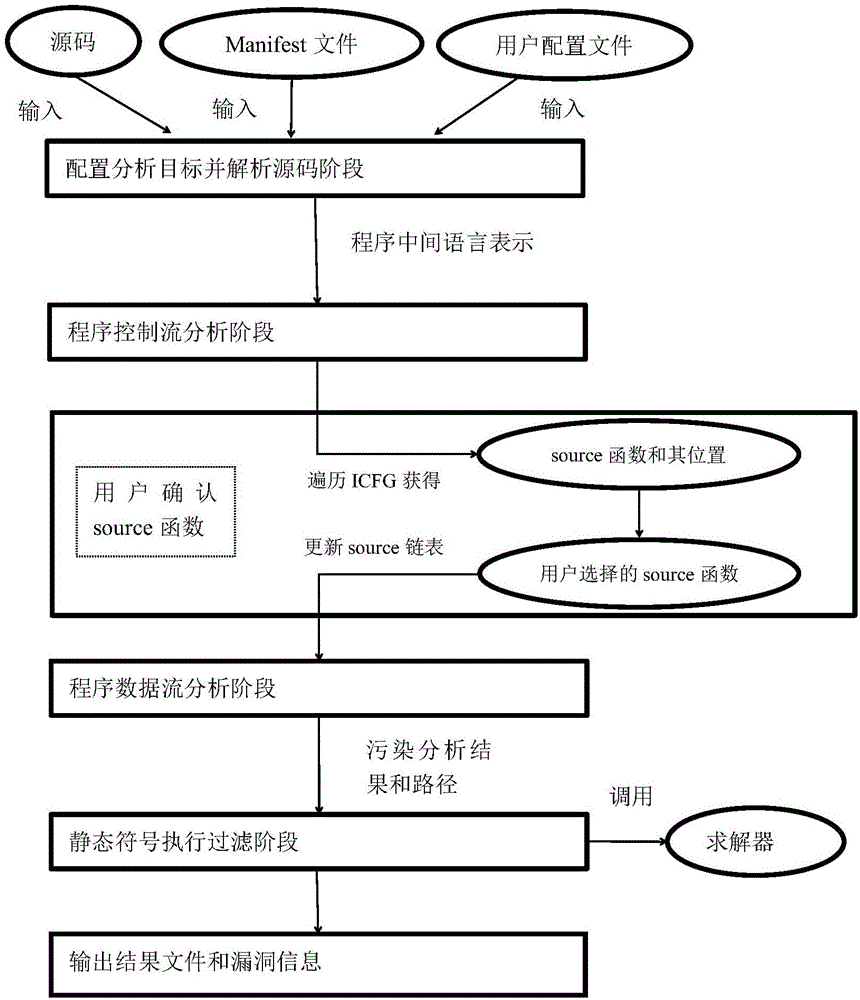
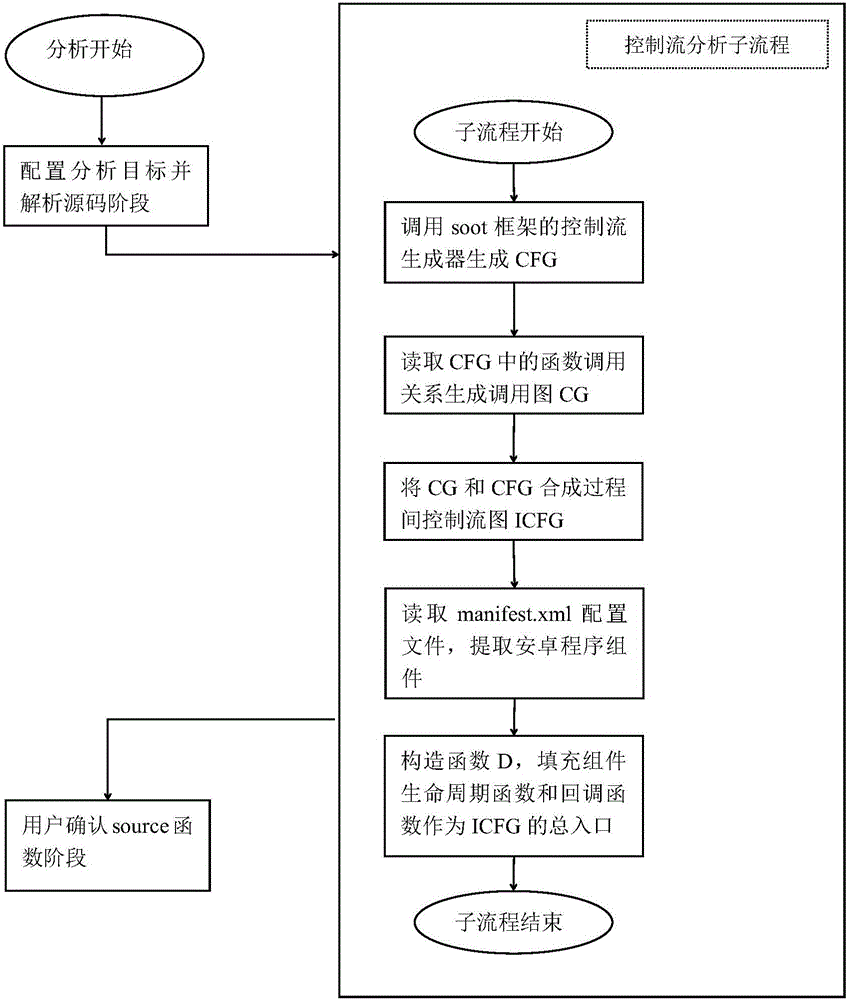
Static taint analysis and symbolic execution-based Android application vulnerability discovery method
ActiveCN106709356ATargetedImprove efficiencyPlatform integrity maintainanceStatic timing analysisData stream
The invention discloses a static taint analysis and symbolic execution-based Android application vulnerability discovery method, and mainly aims at solving the problems that the analysis range is fixed, the memory consumption is huge and the analysis result is mistakenly reported in the process of discovering vulnerabilities by using the existing static taint analysis method. The method is realized through the following steps of: 1) configuring an analysis target and decompiling a program source code; 2) carrying out control flow analysis on the decompilation result; 3) selecting a source function by a user according to the control flow analysis result, so as to narrow an analysis target; 4) carrying out data flow analysis according to the control flow analysis result, so as to generate a vulnerability path; and 5) filtering the data flow analysis result by adoption of a static symbolic execution technology, taking the residual parts after the filtration as discovered vulnerabilities, warning the user and printing the vulnerability path. On the basis of the existing static taint analysis technology, the method disclosed by the invention has the advantages of extending the vulnerability discovery range, decreasing the memory consumption of vulnerability discovery and improving the accuracy of vulnerability discovery results, and can be applied to the discovery and research of Android application program vulnerabilities.
Owner:XIDIAN UNIV
Method and apparatus for datastream
ActiveUS20050097358A1Memory loss protectionDigital data processing detailsComputer networkData stream
A method and apparatus for datastream analysis and blocking. According to one embodiment of the invention, a network access device, analyzes (without proxying) each of a stream of packets traversing a single connection through the network access device from an external host to a protected host. In addition, the network access device forwards each allowed packet of the stream of packets as long as the connection is active. However, if one of the stream of packets is determined to be disallowed as a result of the analyzing, then the network access device discards the disallowed packet and terminates the connection, causing the protected host to discard those packets received on the terminated connection.
Owner:MICRON TECH INC +1
Realization method for parallelization of single-threading program based on analysis of data flow
InactiveCN101515231AImprove execution efficiencyImprove utilization efficiencyConcurrent instruction executionProgram instructionData dependence
The invention discloses a realization method for the parallelization of the single-threading program based on the analysis of data flow. In the invention, by analyzing the data dependence among the instructions in the single-thread program, the single-threading program is transformed to a multi-threading program, the dependence among the instructions in the single-thread program includes a data dependence and a control dependence, wherein the control dependence is a dependence for the control condition value and a special data dependence. In the process of thread analyzing, the invention can take regard of the balance of the thread communication expense and the thread after analyzing. The invention has the advantage that the different parts of the single-threading program are executed in parallel, thus reducing the program executing time and improving the program executing efficiency. The method for the parallelization of the single-threading program is in particular suitable for the current multi-core structure.
Owner:ZHEJIANG UNIV
Tractable dataflow analysis for concurrent programs via bounded languages
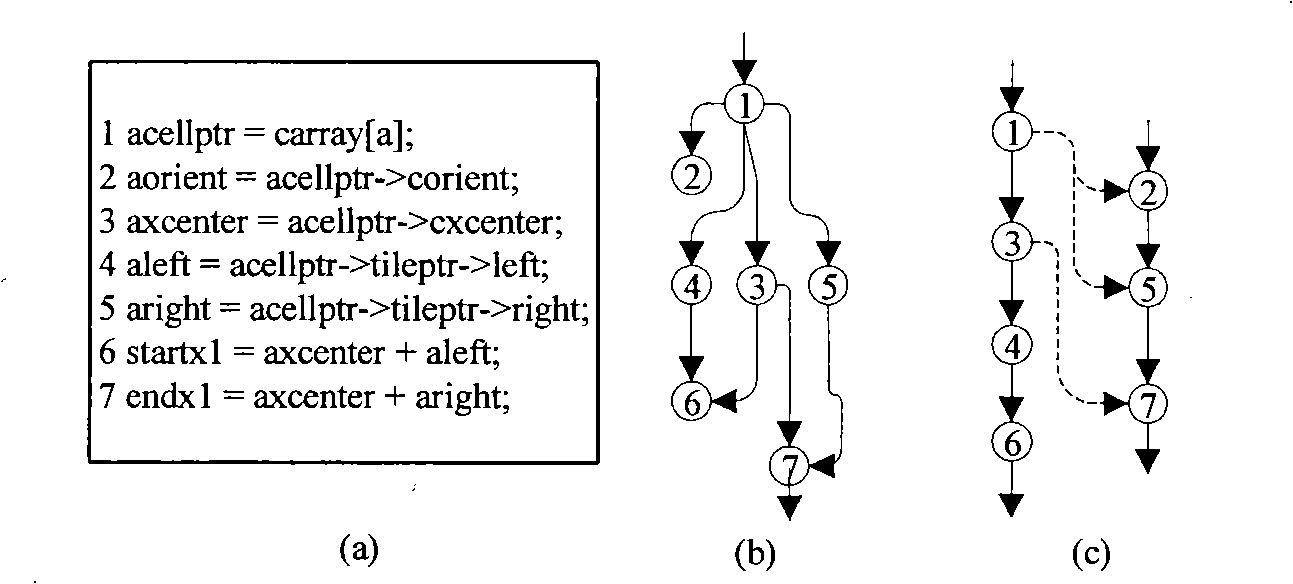
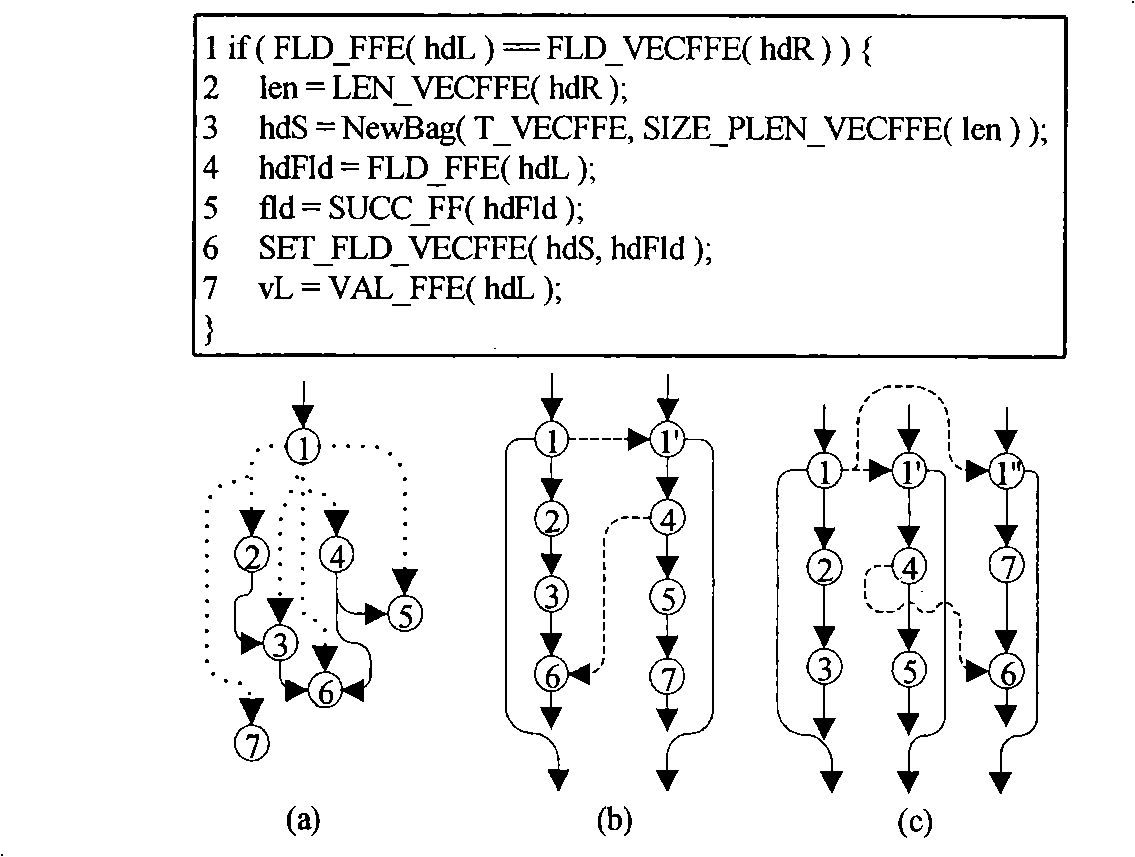
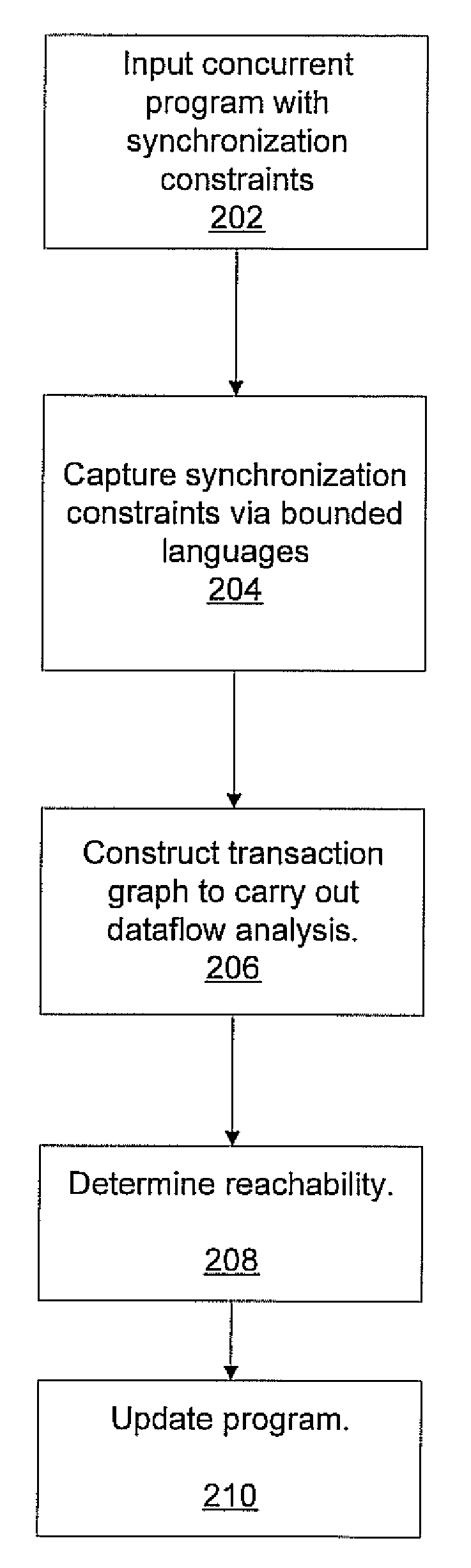
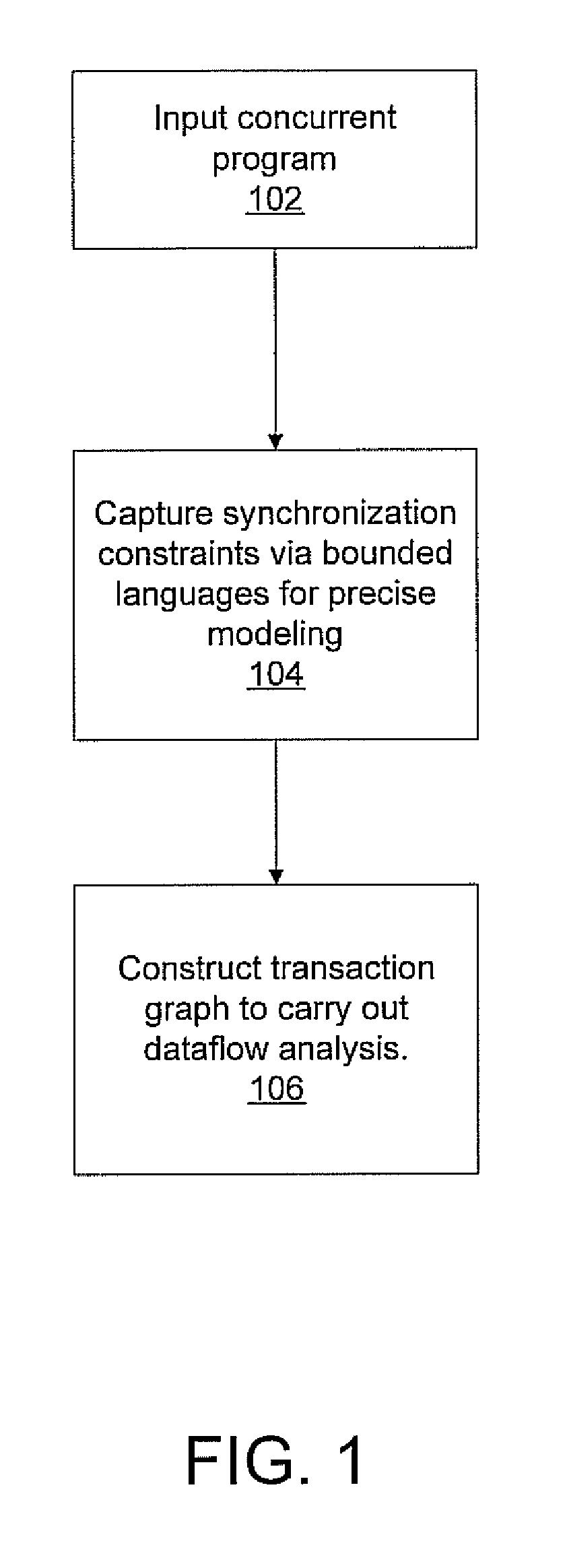
InactiveUS20090193417A1Enhanced couplingError detection/correctionMultiprogramming arrangementsHuman languageDataflow
A system and method for dataflow analysis includes inputting a concurrent program comprised of threads communicating via synchronization primitives and shared variables. Synchronization constraints imposed by the primitives are captured as an intersection problem for bounded languages. A transaction graph is constructed to perform dataflow analysis. The concurrent program is updated in accordance with the dataflow analysis.
Owner:NEC LAB AMERICA
System and method for optimizing operations via dataflow analysis
InactiveUS7185327B2Increase speedGood flexibilitySoftware engineeringSpecific program execution arrangementsGraphicsIntermediate language
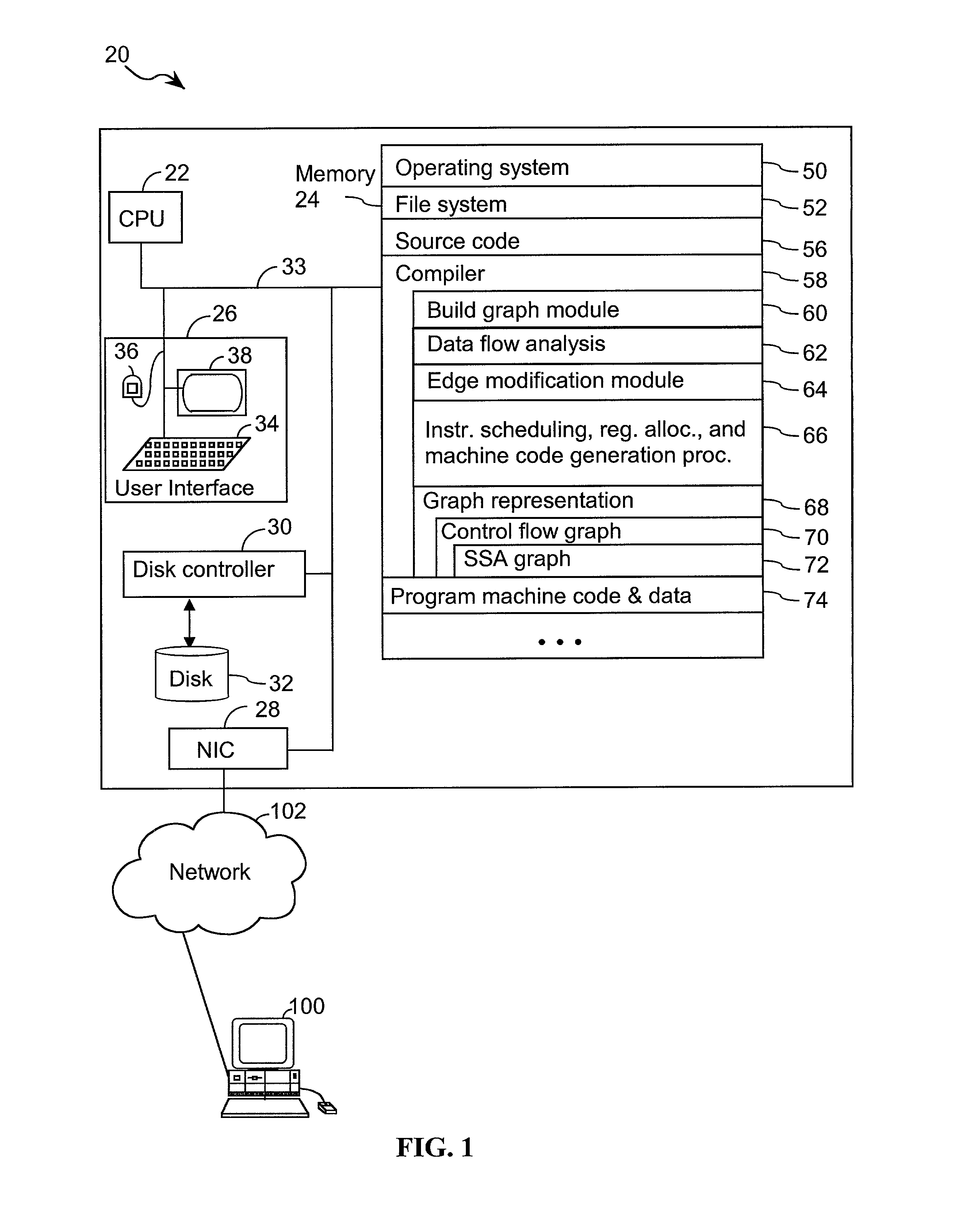
A method for modifying serial dependencies in a procedure includes a step of building a graph representation of the procedure. The graph representation has an origin as well as a unique position, relative to the origin, for each memory operation in the procedure. Each memory operation in the representation is designated with a location type. Each of these location types are based on one or more characteristics of the corresponding memory operation that are sufficient to notify the compiler that the memory operation accesses a distinct or disjoint memory location. Memory operations having the same location type as subsequent memory operations are identified. When the graph representation does not include additional memory operations of the same location type between pairs of such memory operations, the subsequent memory operation is moved to a position in the intermediate representation that is closer to the origin.
Owner:HEWLETT PACKARD DEV CO LP
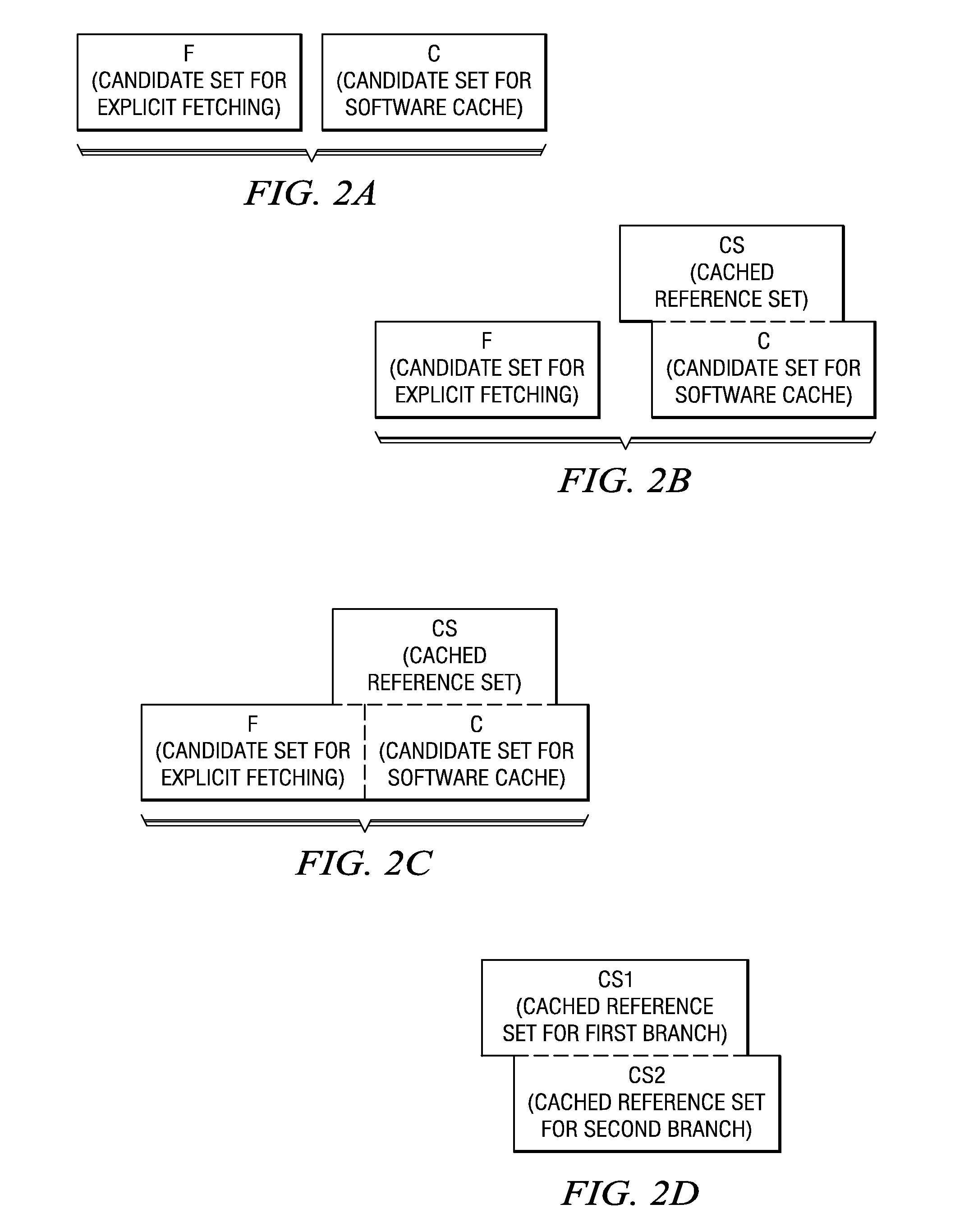
Compiler implemented software cache apparatus and method in which non-aliased explicitly fetched data are excluded
InactiveUS20070261042A1Keep properlyReduce in quantitySoftware engineeringProgram controlParallel computingSoftware cache
A compiler implemented software cache apparatus and method in which non-aliased explicitly fetched data are excluded are provided. With the mechanisms of the illustrative embodiments, a compiler uses a forward data flow analysis to prove that there is no alias between the cached data and explicitly fetched data. Explicitly fetched data that has no alias in the cached data are excluded from the software cache. Explicitly fetched data that has aliases in the cached data are allowed to be stored in the software cache. In this way, there is no runtime overhead to maintain the correctness of the two copies of data. Moreover, the number of lines of the software cache that must be protected from eviction is decreased. This leads to a decrease in the amount of computation cycles required by the cache miss handler when evicting cache lines during cache miss handling.
Owner:IBM CORP
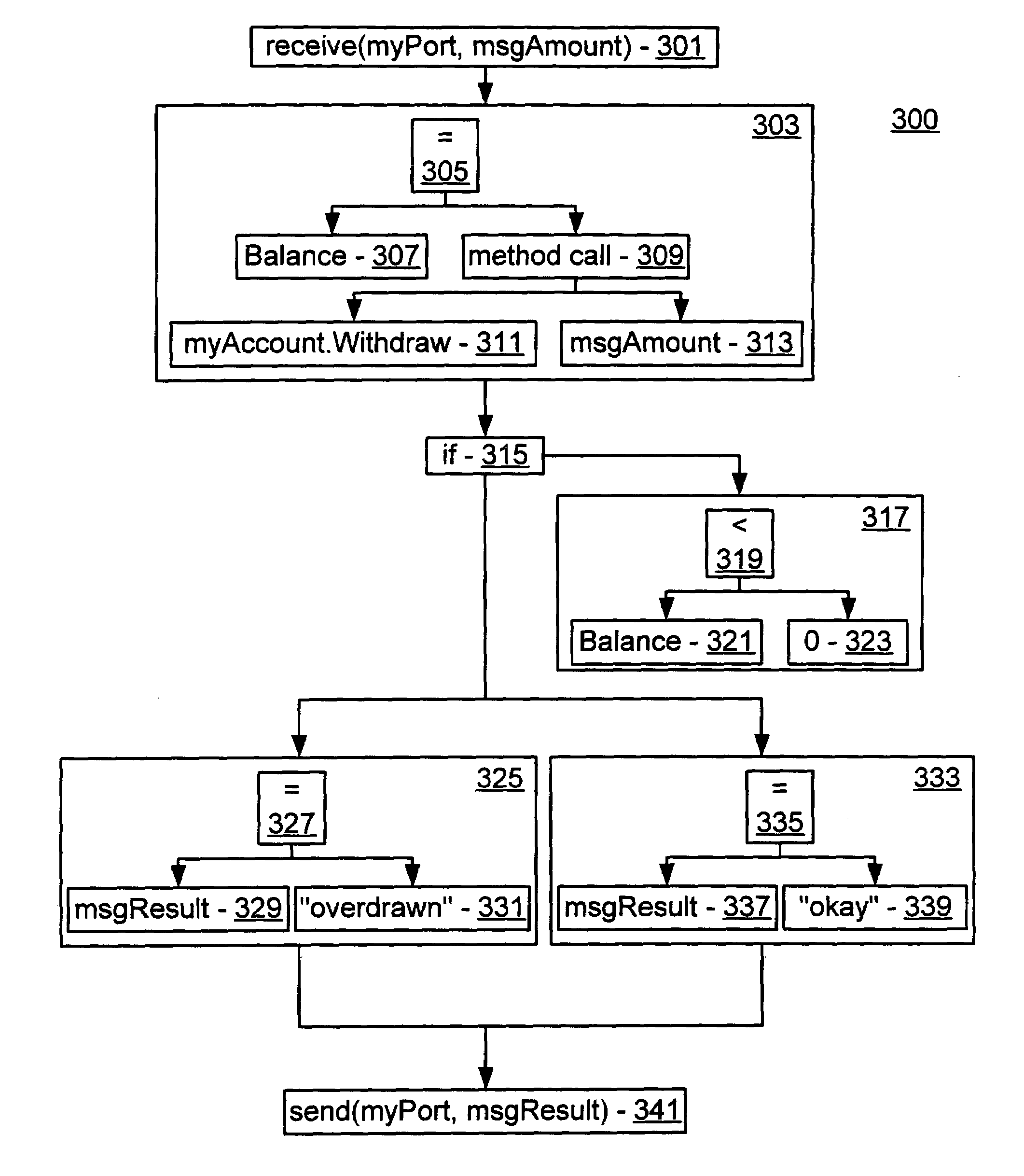
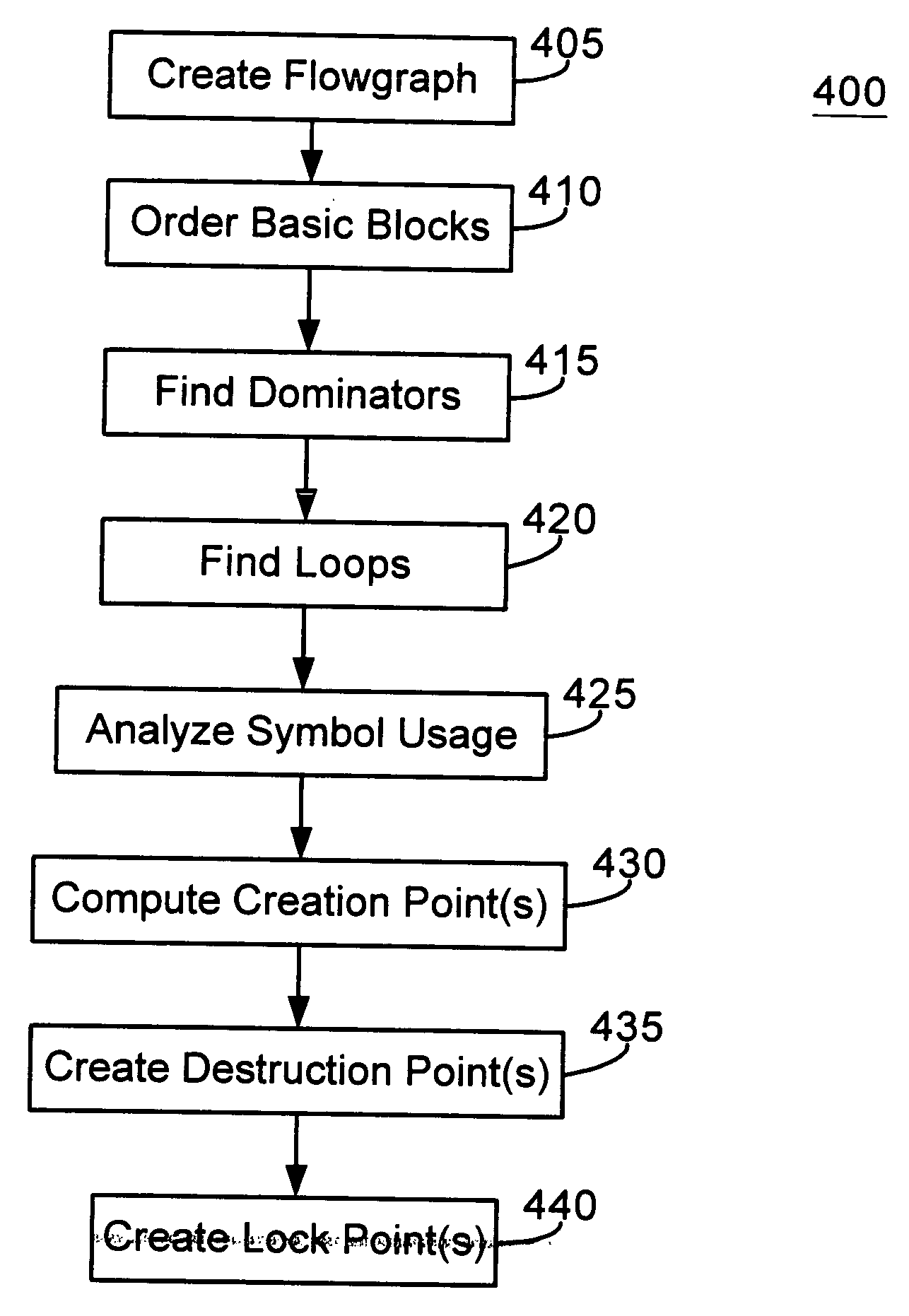
Data flow analysis of transactional processes
A XLANG / s compilation method is provided that uses data flow analysis of a program's flow graph to determine lifetimes of a data object. A flowgraph is created according to abstract computer instructions. A depth-first order is assigned to basic blocks and a dominance relationship between the basic blocks is determined. A determination is made as to whether any loops are present within the flowgraph and, if so, the loops are identified. A creation point, destruction point and lock point for the data object is determined. Instructions are inserted into the computer code to create the at least one data object at the creation point, to destroy the data object at the destruction point and to lock the data object at the lock point.
Owner:MICROSOFT TECH LICENSING LLC
Super-region instruction scheduling and code generation for merging identical instruction into the ready-to-schedule instruction
InactiveUS7069555B1Increasing instruction level parallelismImprove the level ofSoftware engineeringDigital computer detailsControl flowScheduling instructions
Systems and methods perform super-region instruction scheduling that increases the instruction level parallelism for computer programs. A compiler performs data flow analysis and memory interference analysis on the code to determine data dependencies between entities such as registers and memory locations. A region tree is constructed, where the region tree contains a single entry block and a single exit block, with potential intervening blocks representing different control flows through the region. Instructions within blocks are moved to predecessor blocks when there are no dependencies on the instruction to be moved, and when the move results in greater opportunity for instruction level parallelism. Redundant instructions from multiple paths can be merged into a single instruction during the process of scheduling. In addition, if a dependency can be removed the method transforms the instruction into an instruction that can be moved to a block having available resources.
Owner:MICROSOFT TECH LICENSING LLC
Machine learning data analysis system and method
Owner:GAMALON INC
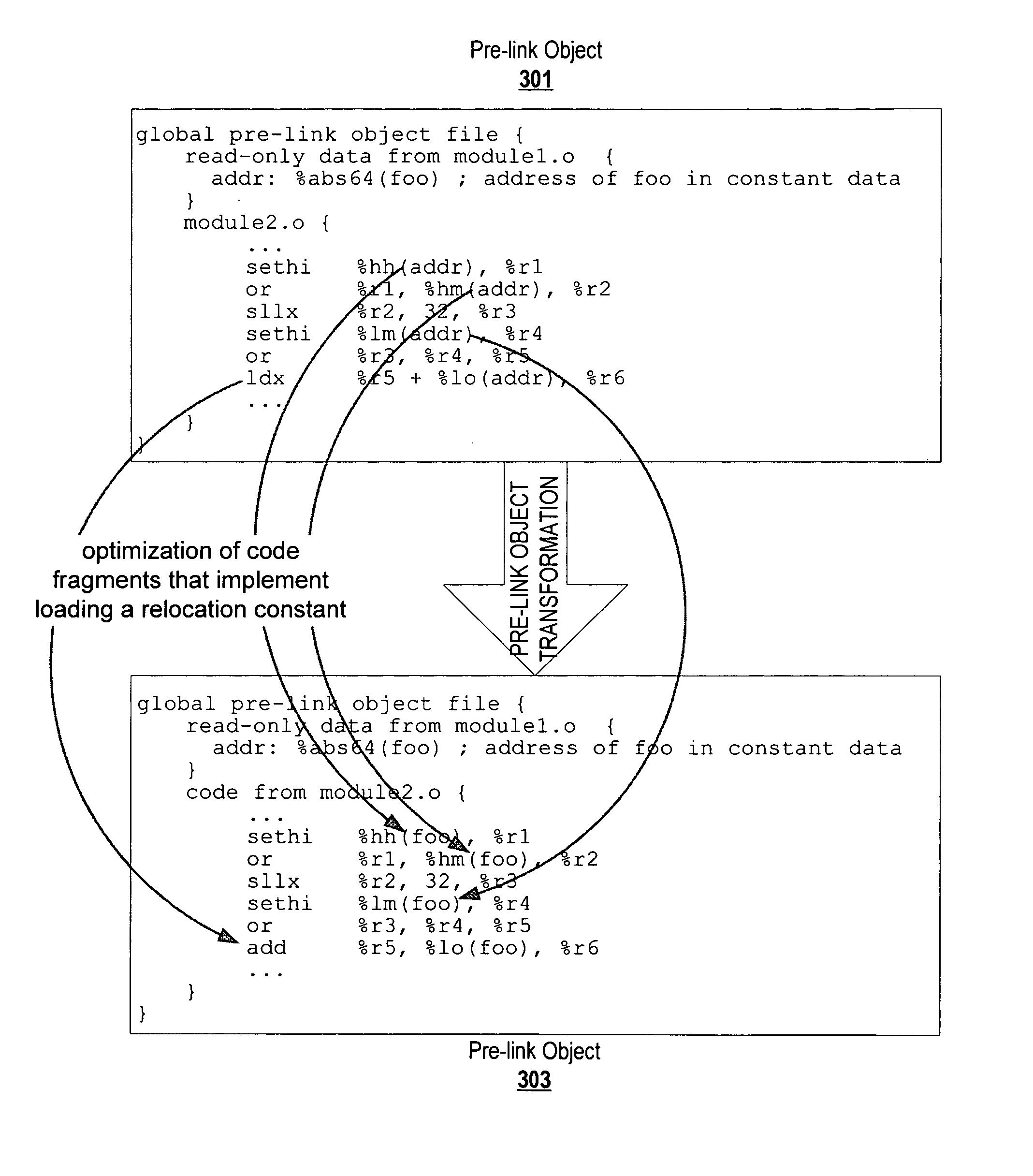
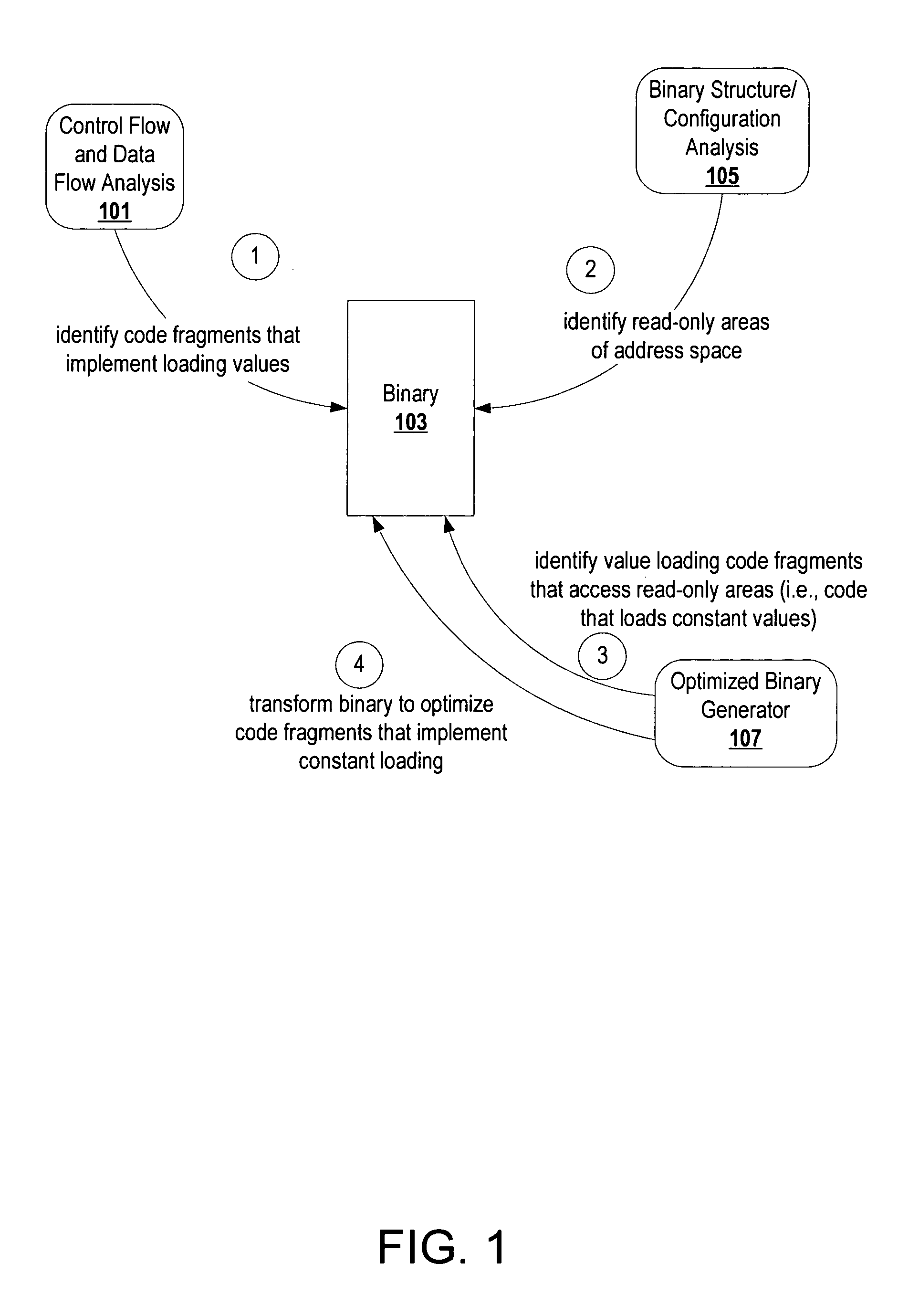
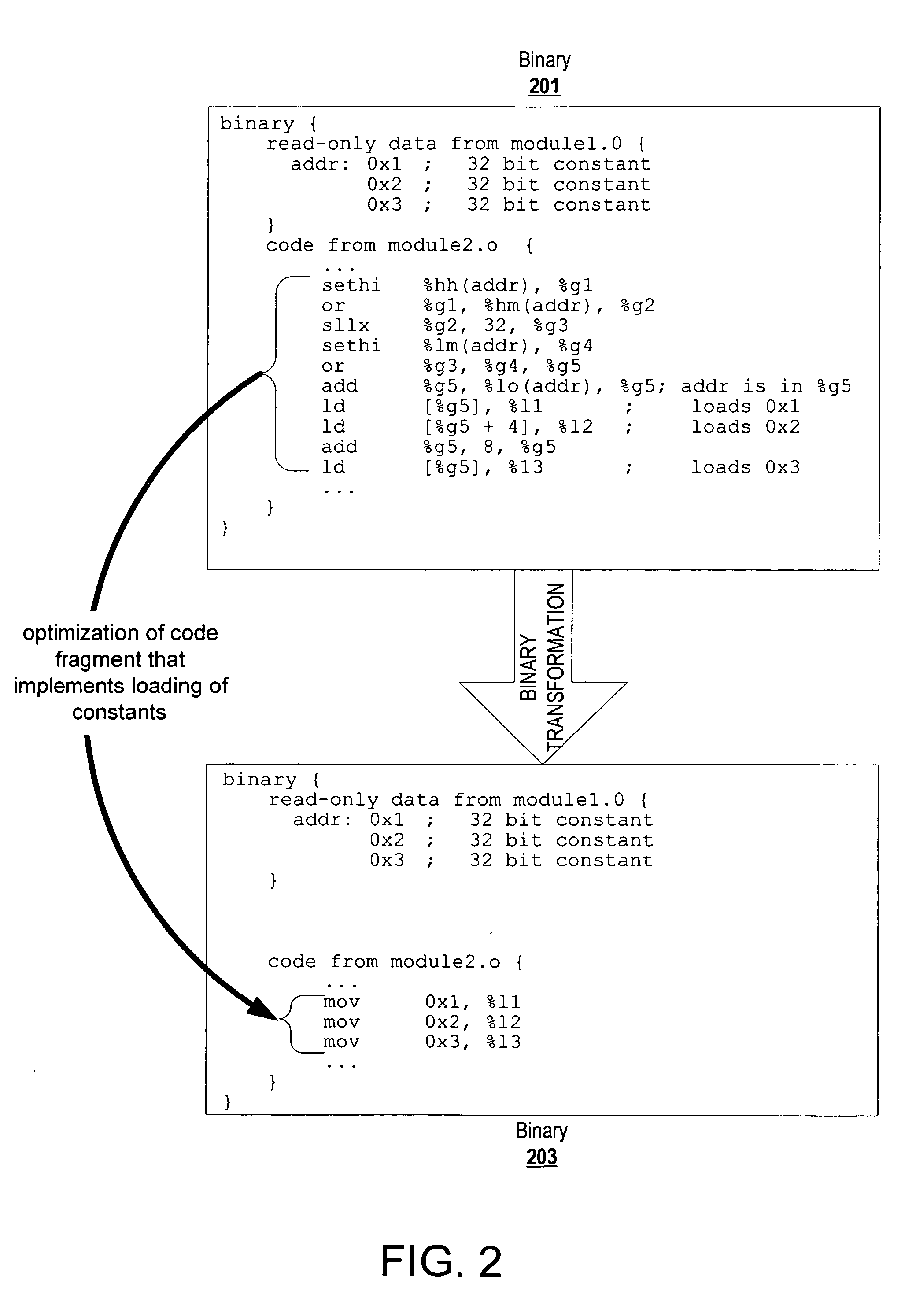
Code transformation to optimize fragments that implement constant loading
ActiveUS20070226717A1Relieve pressureEliminate operationSoftware engineeringSpecific program execution arrangementsConfiguration analysisInline function
Owner:ORACLE INT CORP
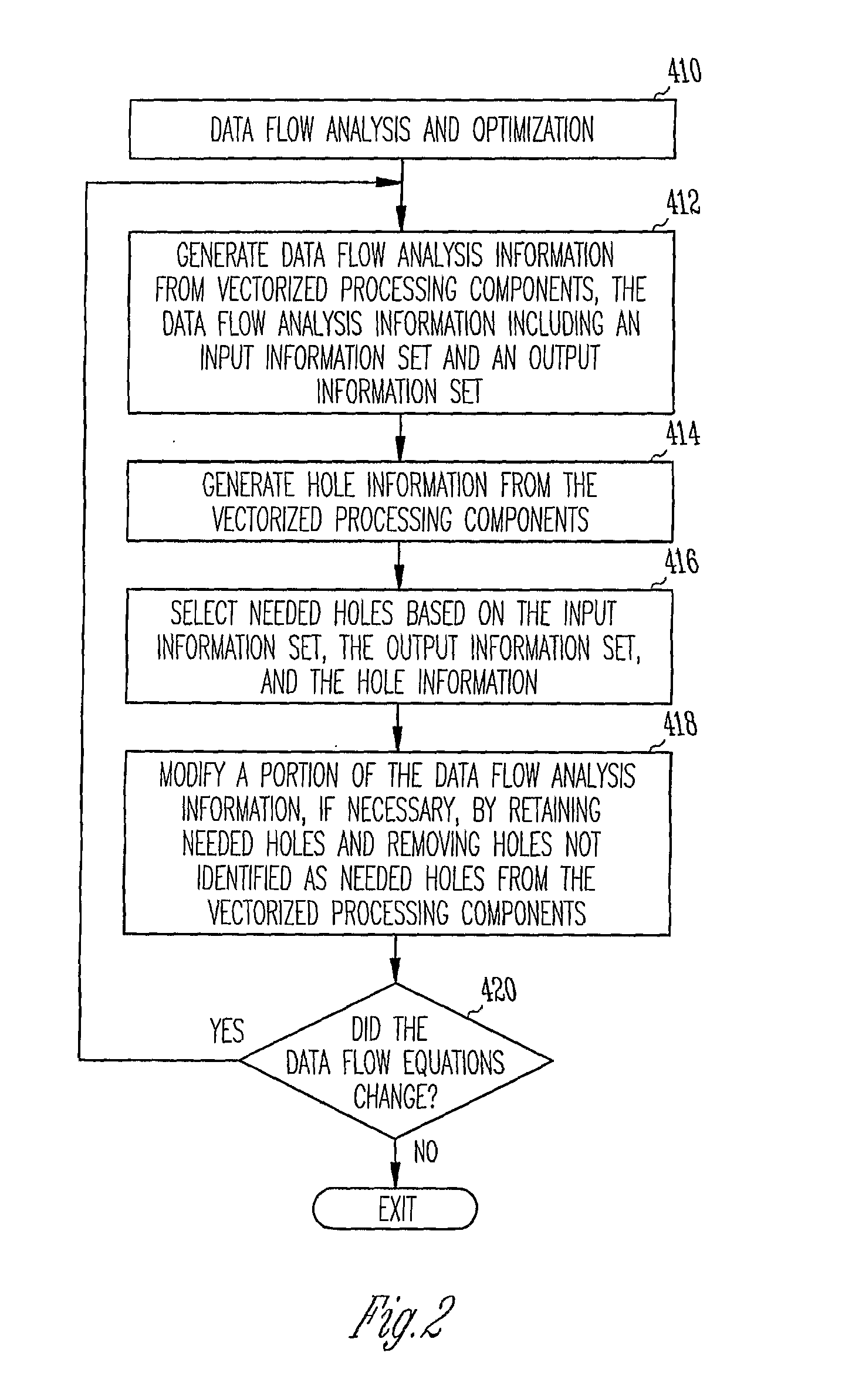
Computer-Implemented Method and System for Improved Data Flow Analysis and Optimization
A computer-implemented method and system for improved data flow analysis and optimization are disclosed. The method and system generates data flow analysis information from vectorized processing components, the data flow analysis information including an input information set and an output information set, generates hole information from the vectorized processing components, selects needed holes based on the input information set, the output information set, and the hole information, and modifies a portion of the data flow analysis 10 information by retaining needed holes and removing holes not identified as needed holes from the vectorized processing components.
Owner:INTEL CORP
Data flow analysis of transactional processes
A XLANG / s compilation method is provided that uses data flow analysis of a program's flow graph to determine lifetimes of a data object. A flowgraph is created according to abstract computer instructions. A depth-first order is assigned to basic blocks and a dominance relationship between the basic blocks is determined. A determination is made as to whether any loops are present within the flowgraph and, if so, the loops are identified. A creation point, destruction point and lock point for the data object is determined. Instructions are inserted into the computer code to create the at least one data object at the creation point, to destroy the data object at the destruction point and to lock the data object at the lock point.
Owner:MICROSOFT TECH LICENSING LLC
Data mining system for AIS information source based on big data platform
InactiveCN110188093AAccurate extractionReduce computational overheadSpecial data processing applicationsDatabase indexingDensity distributionData platform
The invention discloses a data mining system for an AIS information source based on a big data platform. The data mining system comprises a data acquisition system, a data storage system, a data mining system and a data analysis system, wherein the data storage system is a distributed storage system, and the data mining system comprises the classified statistics of the data, the target motion characteristic analysis, the target density distribution analysis, the target track distribution analysis, the activity rule analysis and the abnormal behavior detection analysis. According to the data mining system, the tasks are mined through AIS data, such as the track mode mining, the track uncertainty, the abnormal value detection, the stay points and the classification. For example, the abnormalvalue detection can find an abnormal behavior ship, the classficiation helps to analye the joint features, such as navigation conditions, etc., of different types of ships, and the stay point detection can help to determine a hot spot port and laterally understand the import and export trade indexes of the port.
Owner:江苏锐天智能科技股份有限公司
Detection of global metamorphic malware variants using control and data flow analysis
InactiveUS20120072988A1Easily defeatedSimple structureMemory loss protectionError detection/correctionData streamFeature extraction
Malware feature extraction derives semantic summaries of executable malware using global, inter-procedural program analysis techniques. A combination of global, inter-procedural program analysis techniques constructs semantic summaries of malware which automatically detect and discard any noise introduced by transformations and capture the essence of the underlying computations in a succinct form. This is achieved in two ways. First, global control flow analysis techniques are used to derive a high level representation of malware code that, for instance, removes the effects of subroutine calls. Second, global data flow analysis techniques are employed to detect and remove all spurious elements of malware that do not contribute towards its underlying computation, thereby preventing the resulting summaries from being “corrupted” with unnecessary, extraneous elements.
Owner:TT GOVERNMENT SOLUTIONS
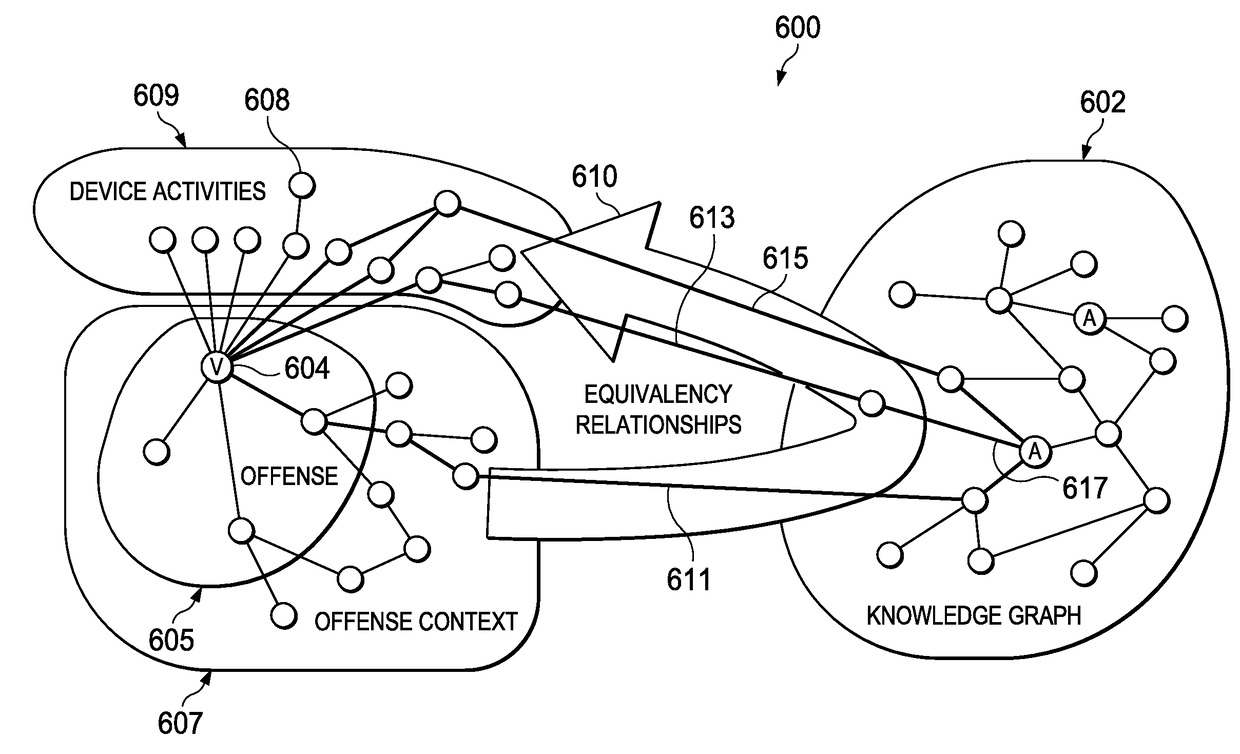
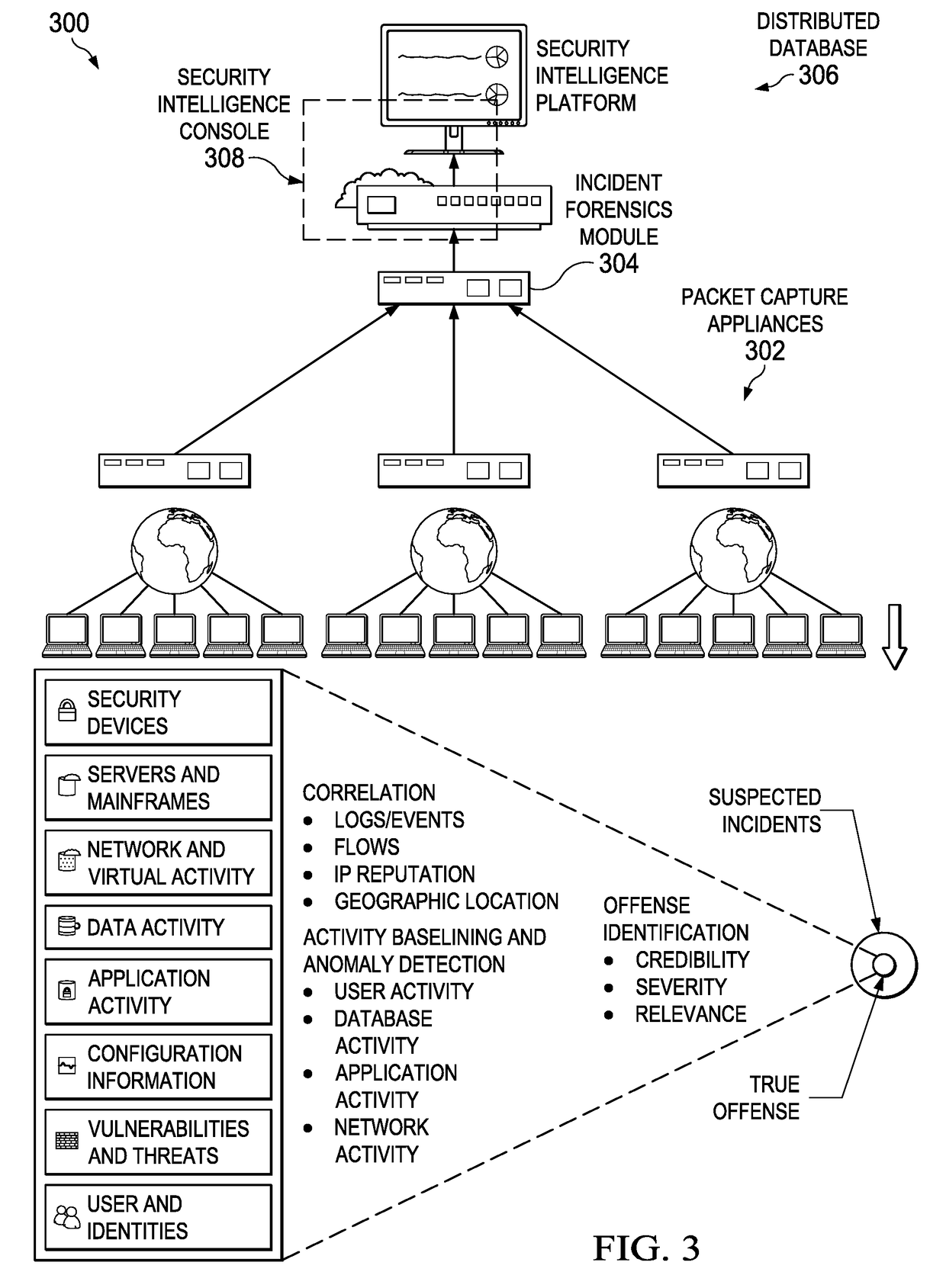
Cognitive analysis of security data with signal flow-based graph exploration
This disclosure provides for a signal flow analysis-based exploration of security knowledge represented in a graph structure comprising nodes and edges. “Conductance” values are associated to each of a set of edges. Each node has an associated “toxicity” value representing a degree of maliciousness associated with the node. The conductance value associated with an edge is a function of at least the toxicity values of the nodes to which the edge is incident. A signal flow analysis is conducted with respect to an input node representing an observable associated with an offense. The flow analysis seeks to identify a subset of the nodes that, based on their conductance values, are reached by flow of a signal representing a threat, wherein signal flow over a path in the graph continues until a signal threshold is met. Based on the analysis, nodes within the subset are designated as hypothesis nodes for further examination.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com