Patents
Literature
4194 results about "Network Access Device" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
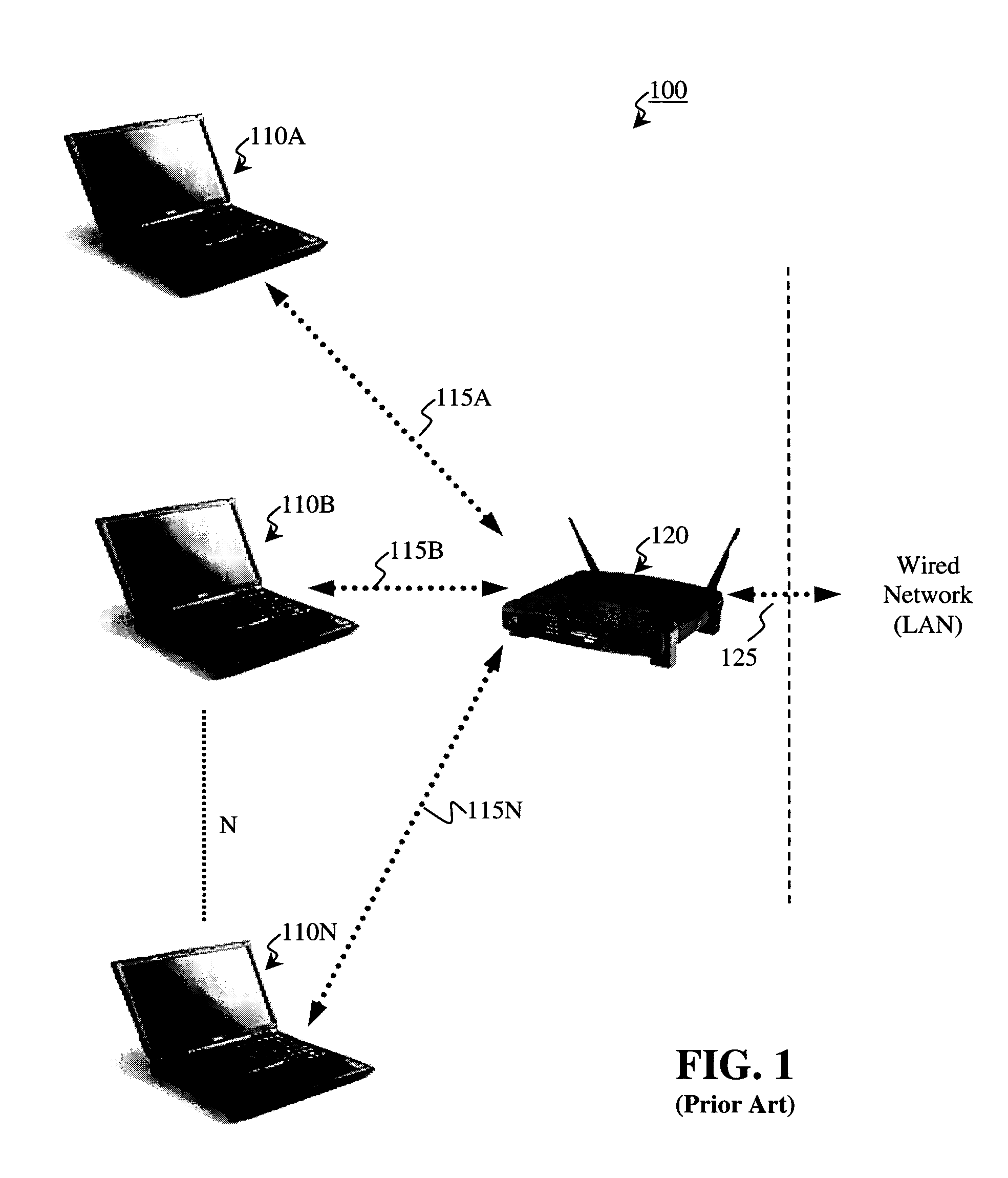
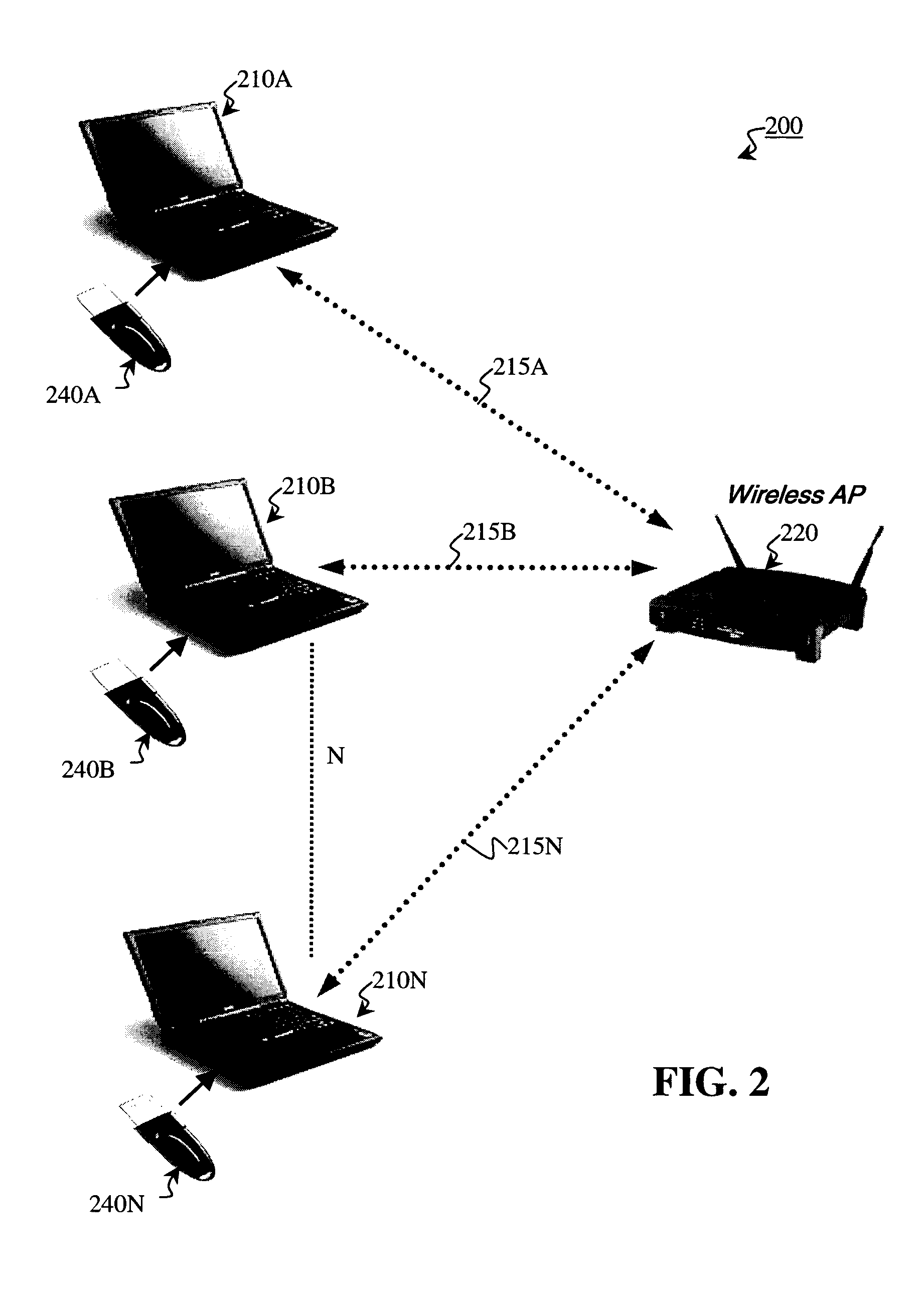
A Network Access Device (or NAD) is an electronic circuit that automatically connects a user to a preferred network. More generally, a NAD is any device that, when connected to, provides access to a larger communication network of some sort.
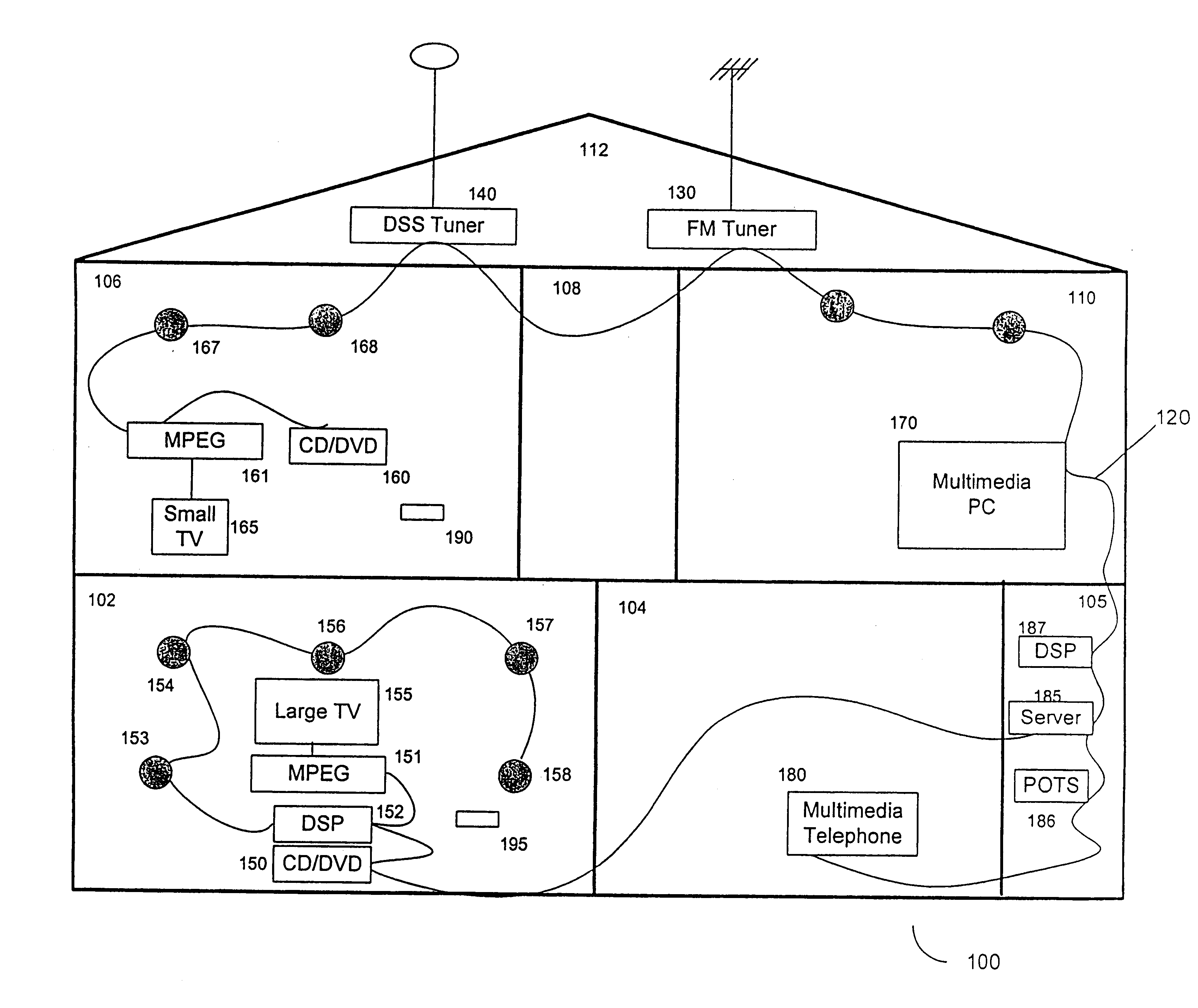
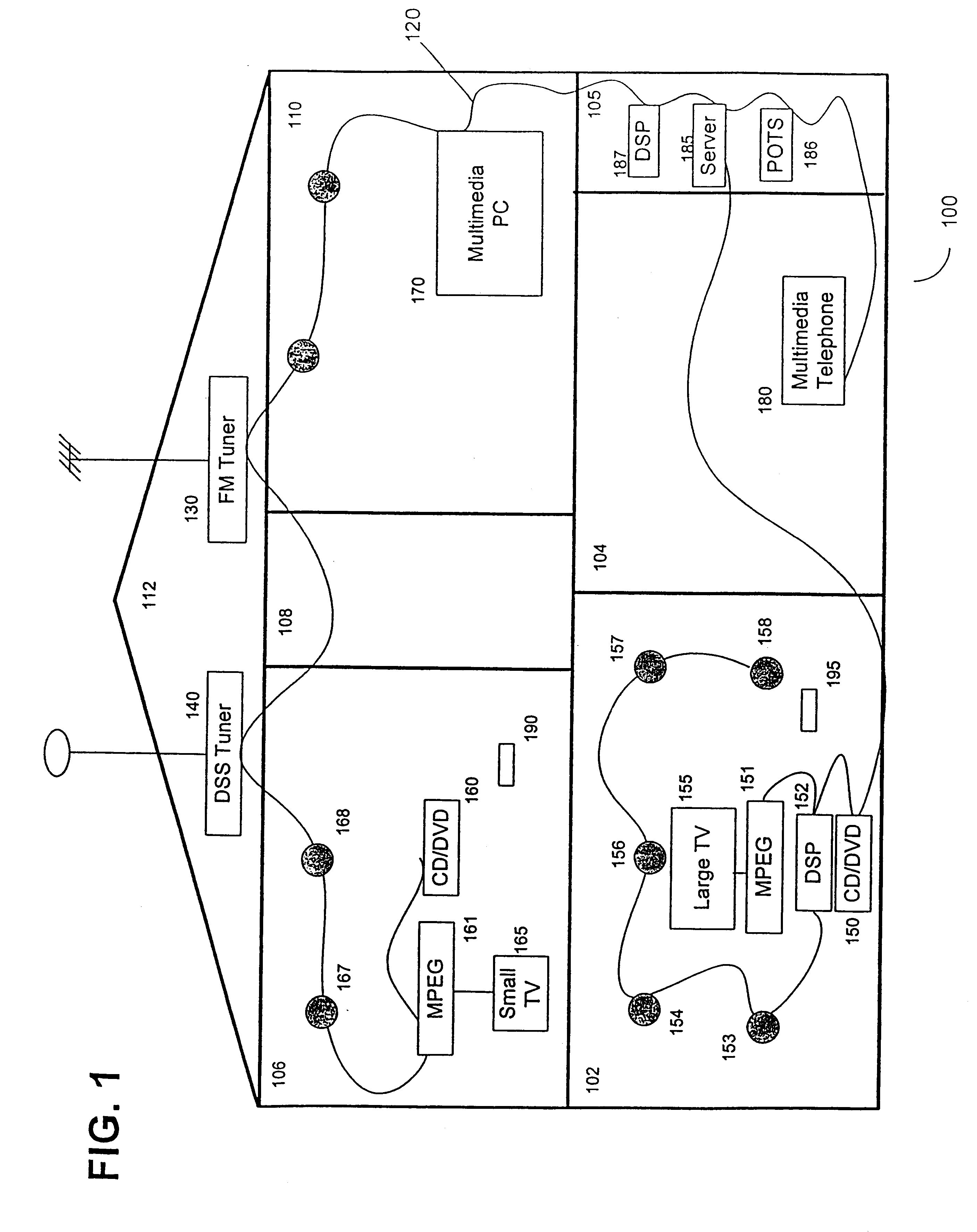
Synchronous network for digital media streams
InactiveUS6611537B1Avoid collisionPulse modulation television signal transmissionTime-division multiplexData streamNetwork clock
A network adapter for a synchronous logical ring network operates on existing physical twisted-pair telephone topologies. Information propagates around the logical ring, reaching every device on each revolution around the network. Network devices are full-duplex, transmitting and receiving information on every clock cycle. Network devices arbitrate to be elected the network clock device. By synchronizing all network devices to a single reference clock, and providing fixed frames of information propagating around the network at consistent time intervals, the logical ring network ensures that information propagates from one device to another at consistent time intervals. The fixed-length frames are divided into two independent streams: a data stream for the distribution of real-time continuous digital media streams; and a system command stream for the distribution of system commands.
Owner:CENTILLIUM COMM
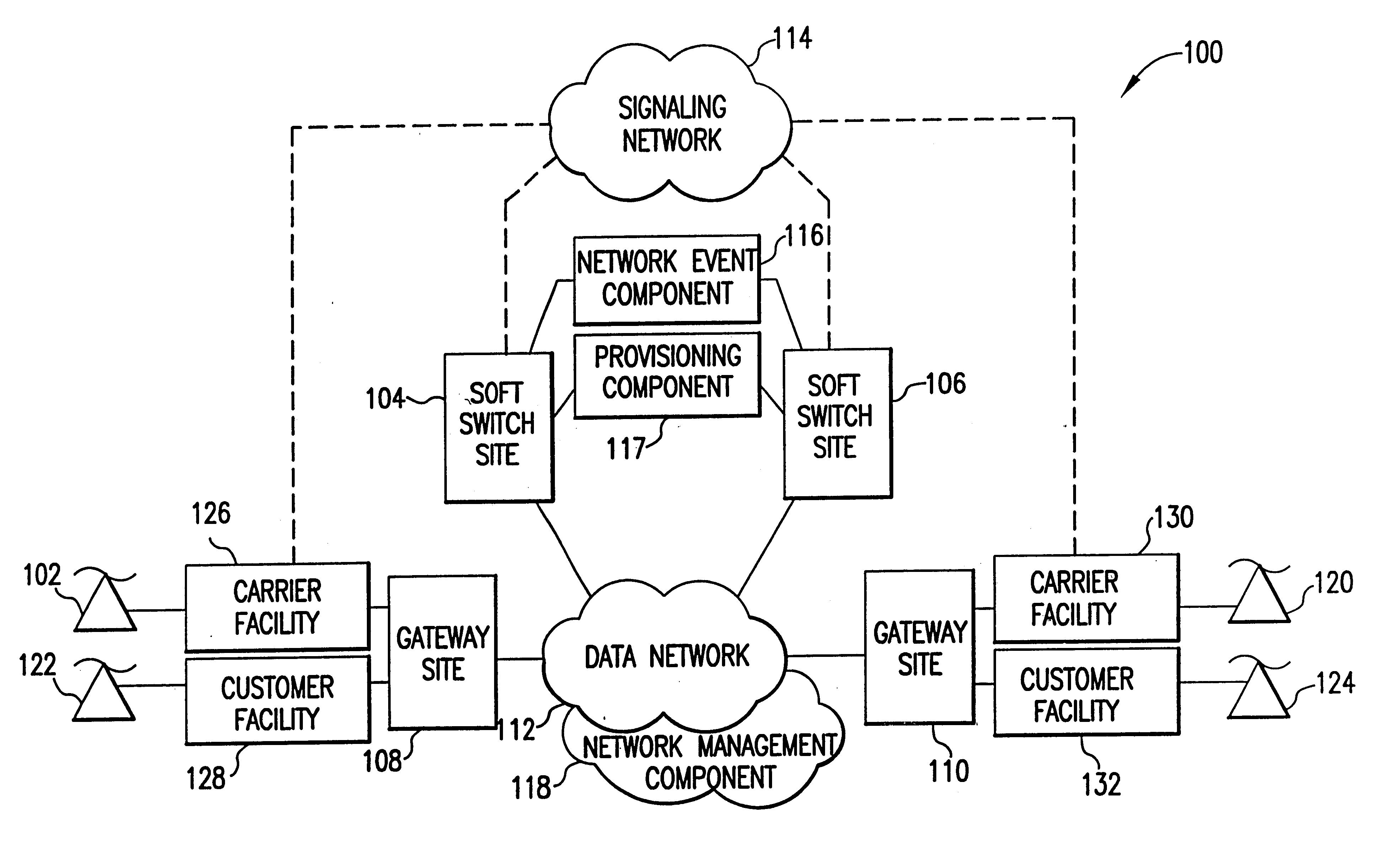
Voice over data telecommunications network architecture
InactiveUS6614781B1Interconnection arrangementsDc level restoring means or bias distort correctionNetwork operations centerNetwork architecture
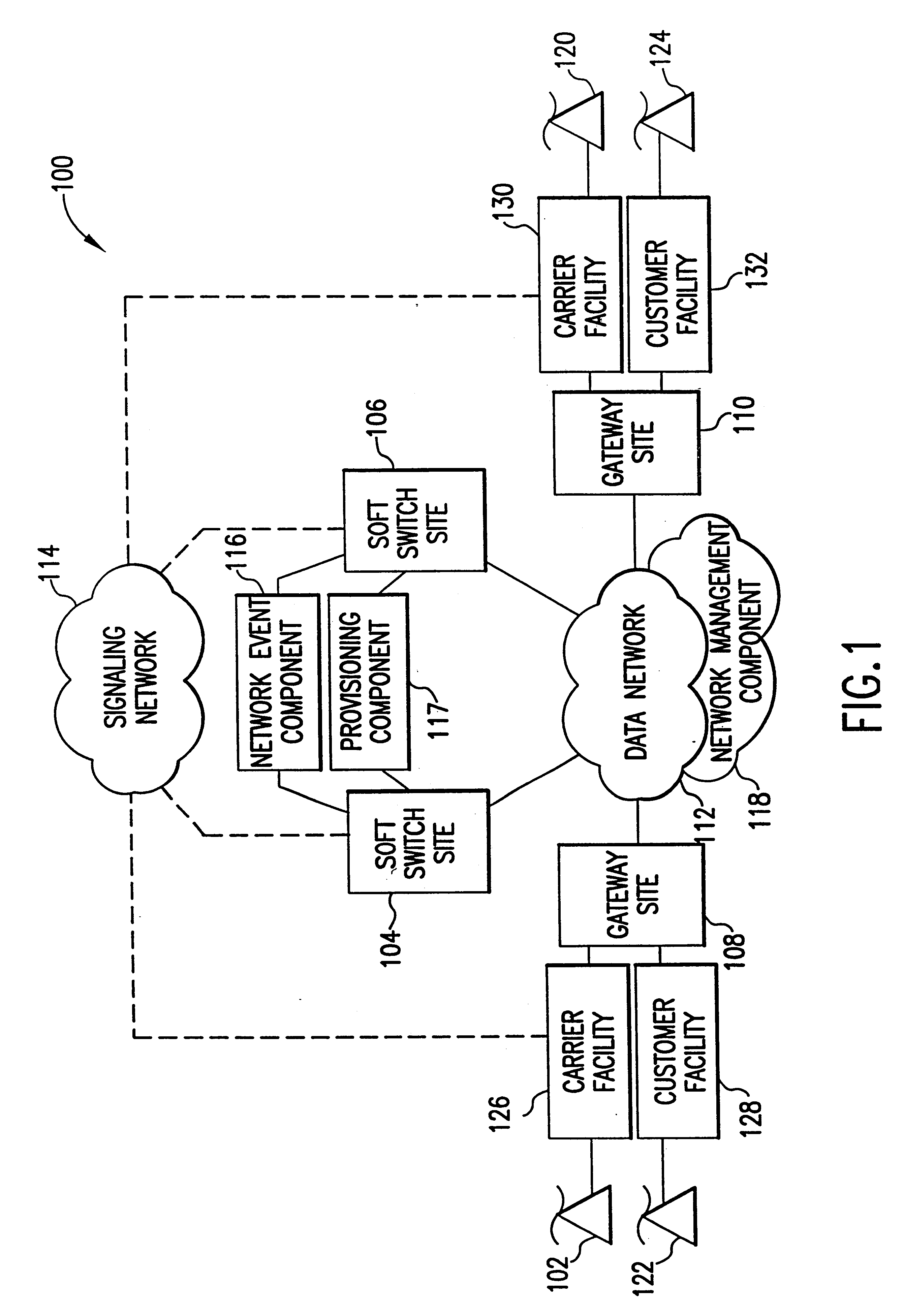
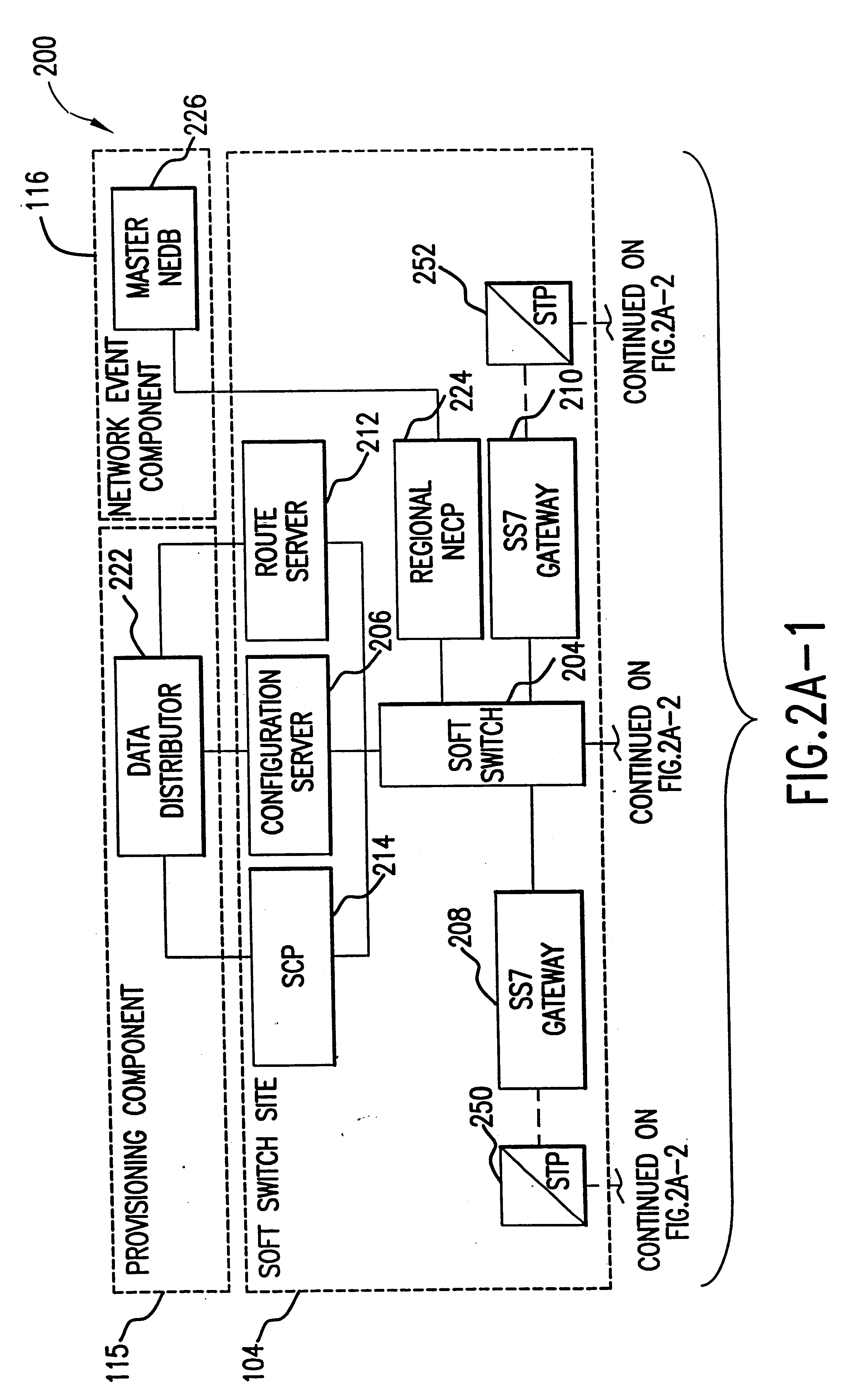
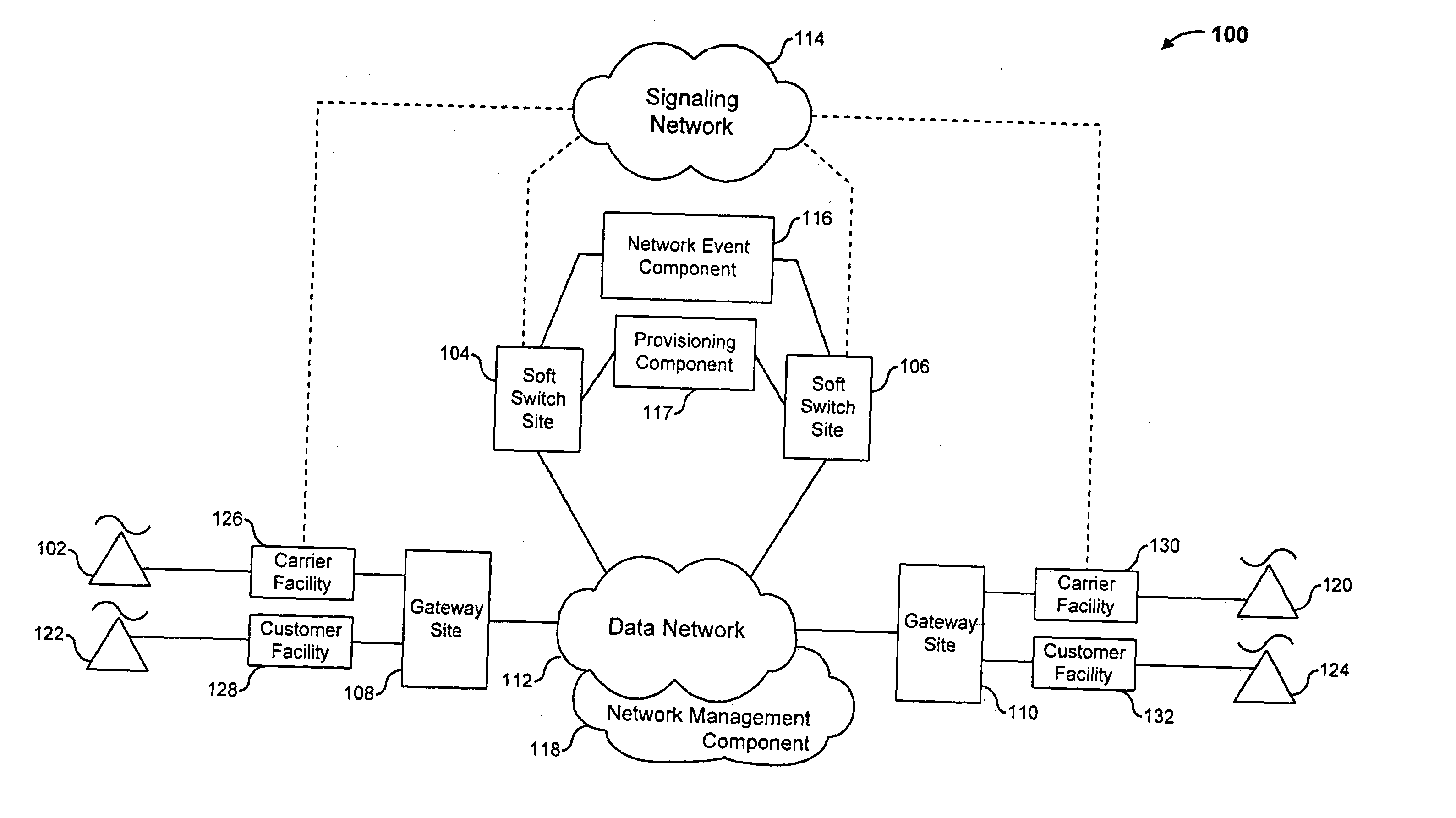
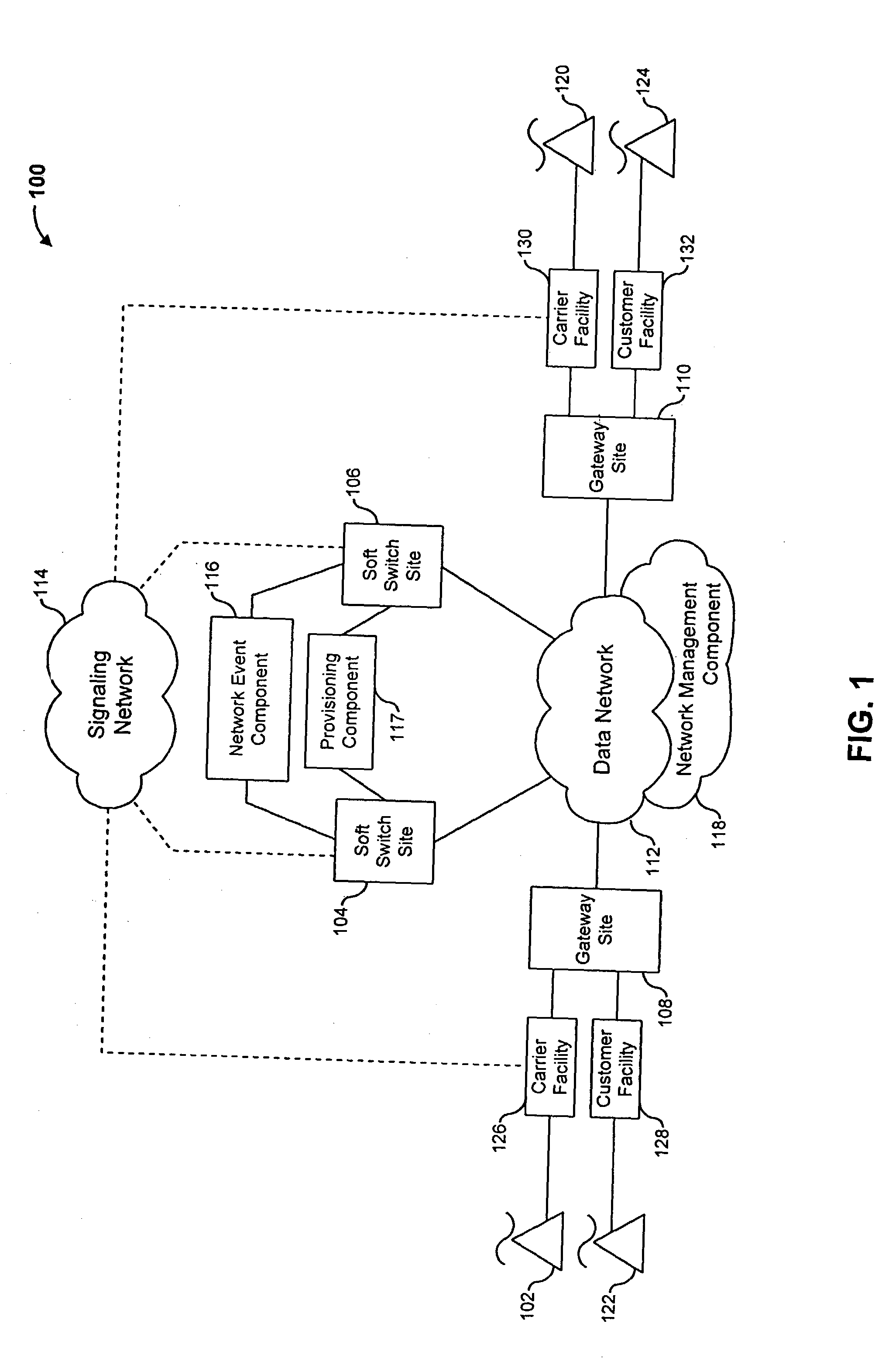
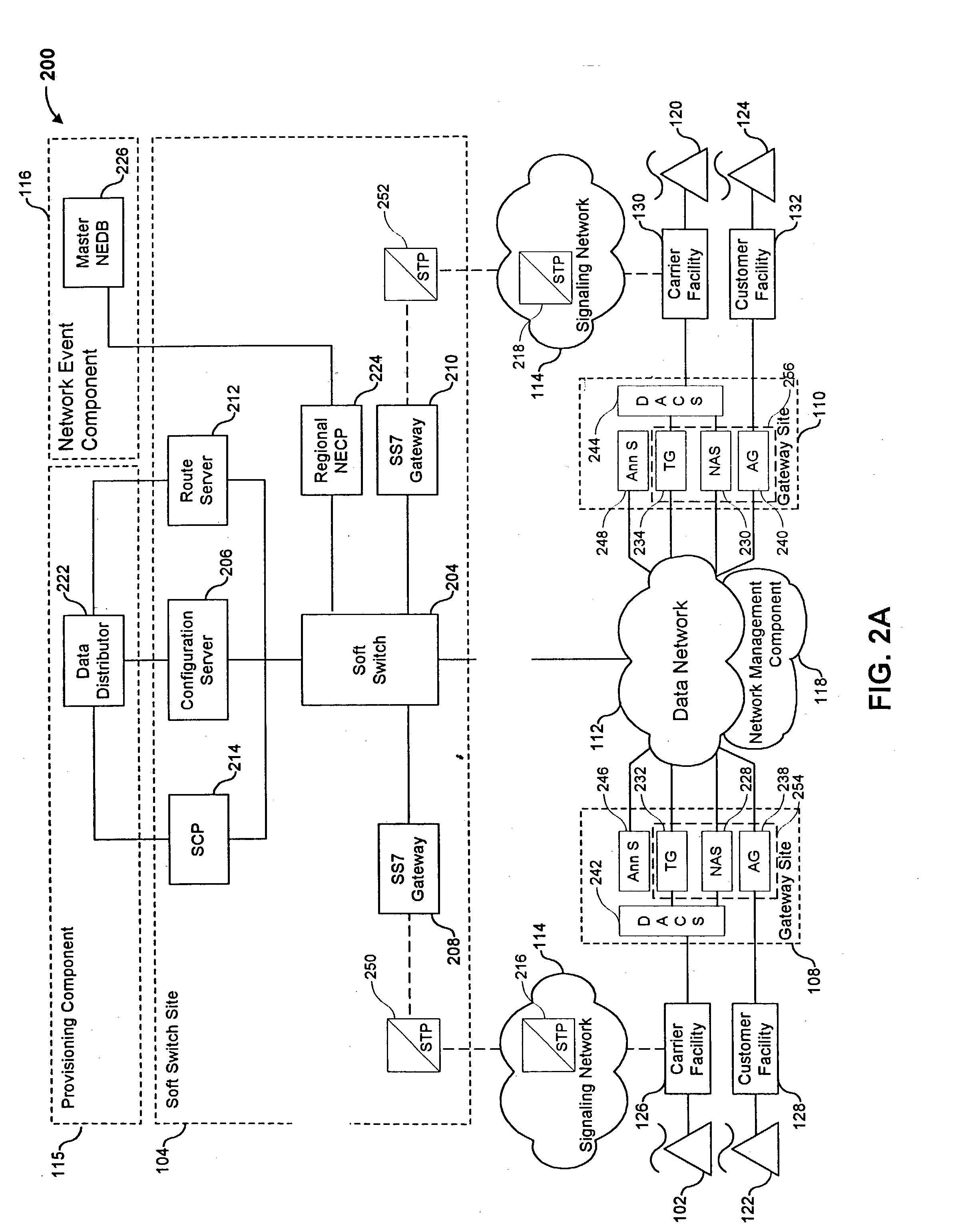
The present invention describes a system and method for communicating voice and data over a packet-switched network that is adapted to coexist and communicate with a legacy PSTN. The system permits packet switching of voice calls and data calls through a data network from and to any of a LEC, a customer facility or a direct IP connection on the data network. The system includes soft switch sites, gateway sites, a data network, a provisioning component, a network event component and a network management component. The system interfaces with customer facilities (e.g., a PBX), carrier facilities (e.g., a LEC) and legacy signaling networks (e.g., SS7) to handle calls between any combination of on-network and off-network callers.The soft switch sites provide the core call processing for the voice network architecture. The soft switch sites manage the gateway sites in a preferred embodiment, using a protocol such as the Internet Protocol Device Control (IPDC) protocol to request the set-up and tear-down of calls. The gateway sites originate and terminate calls between calling parties and called parties through the data network. The gateway sites include network access devices to provide access to network resources. The data network connects one or more of the soft switch sites to one or more of the gateway sites. The provisioning and network event component collects call events recorded at the soft switch sites. The network management component includes a network operations center (NOC) for centralized network management.
Owner:LEVEL 3 COMM LLC
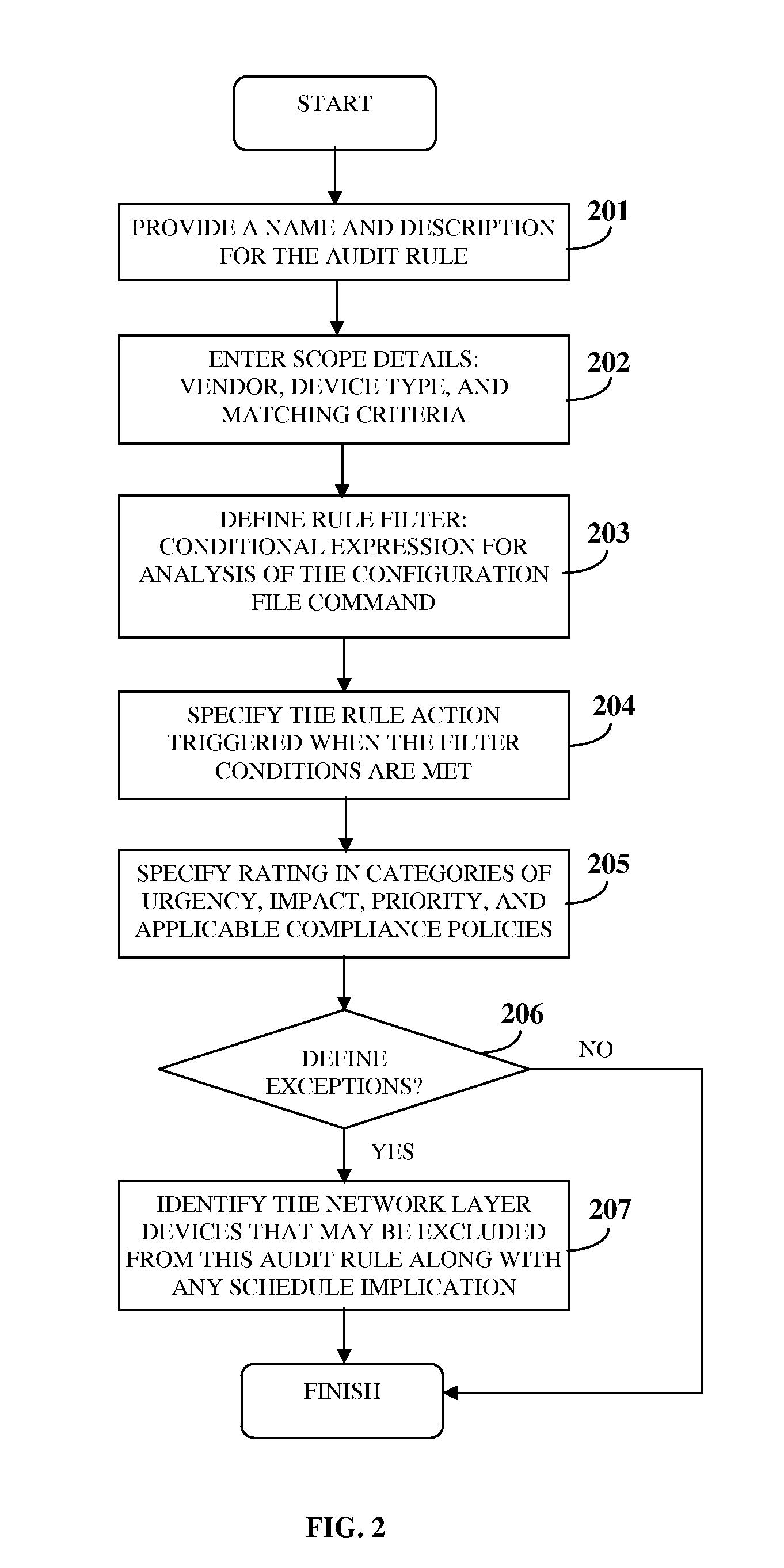
Audit Management System
InactiveUS20120102543A1Increase flexibilityIncrease speedComputer security arrangementsTransmissionGraphicsGraphical user interface
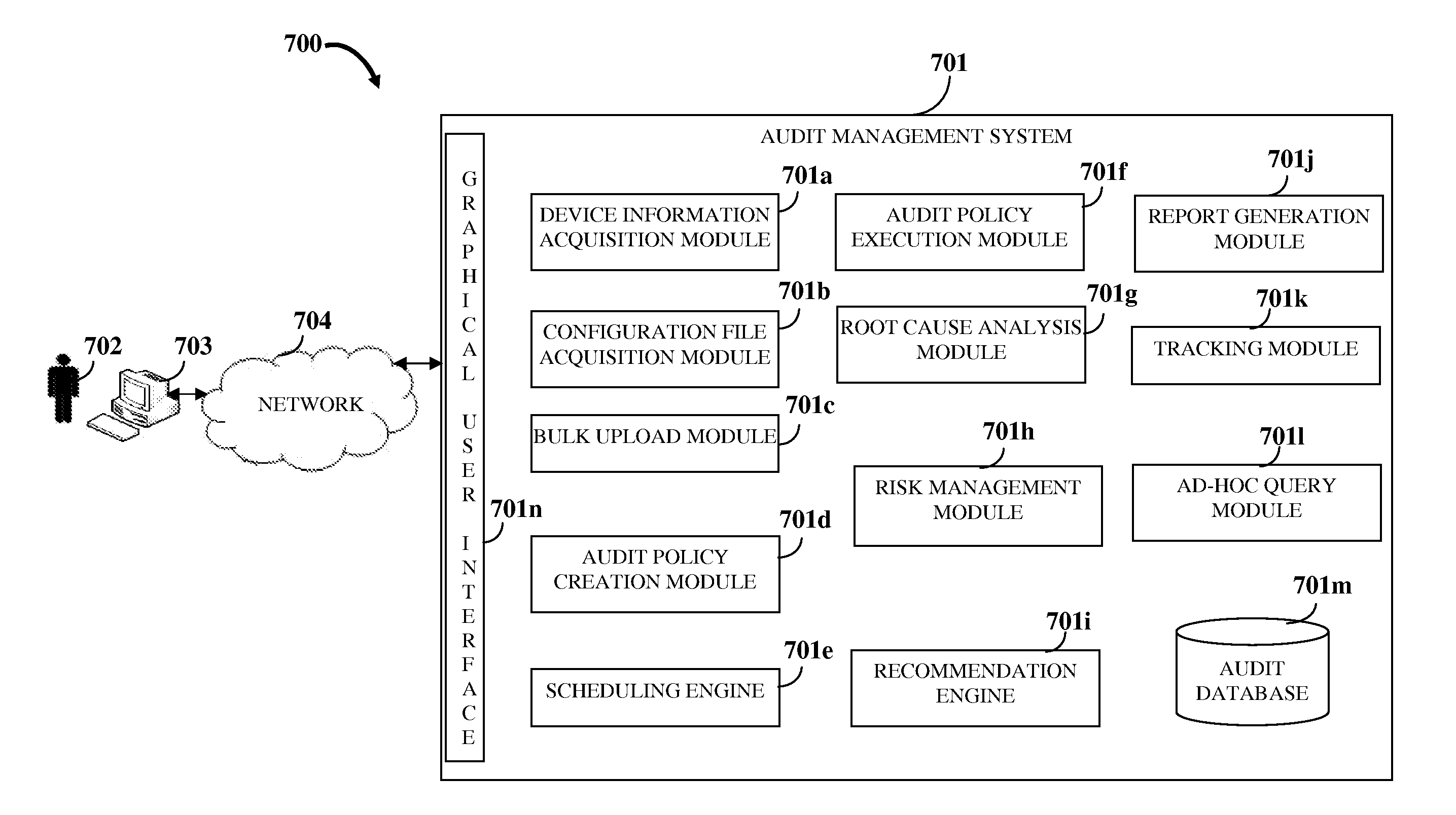
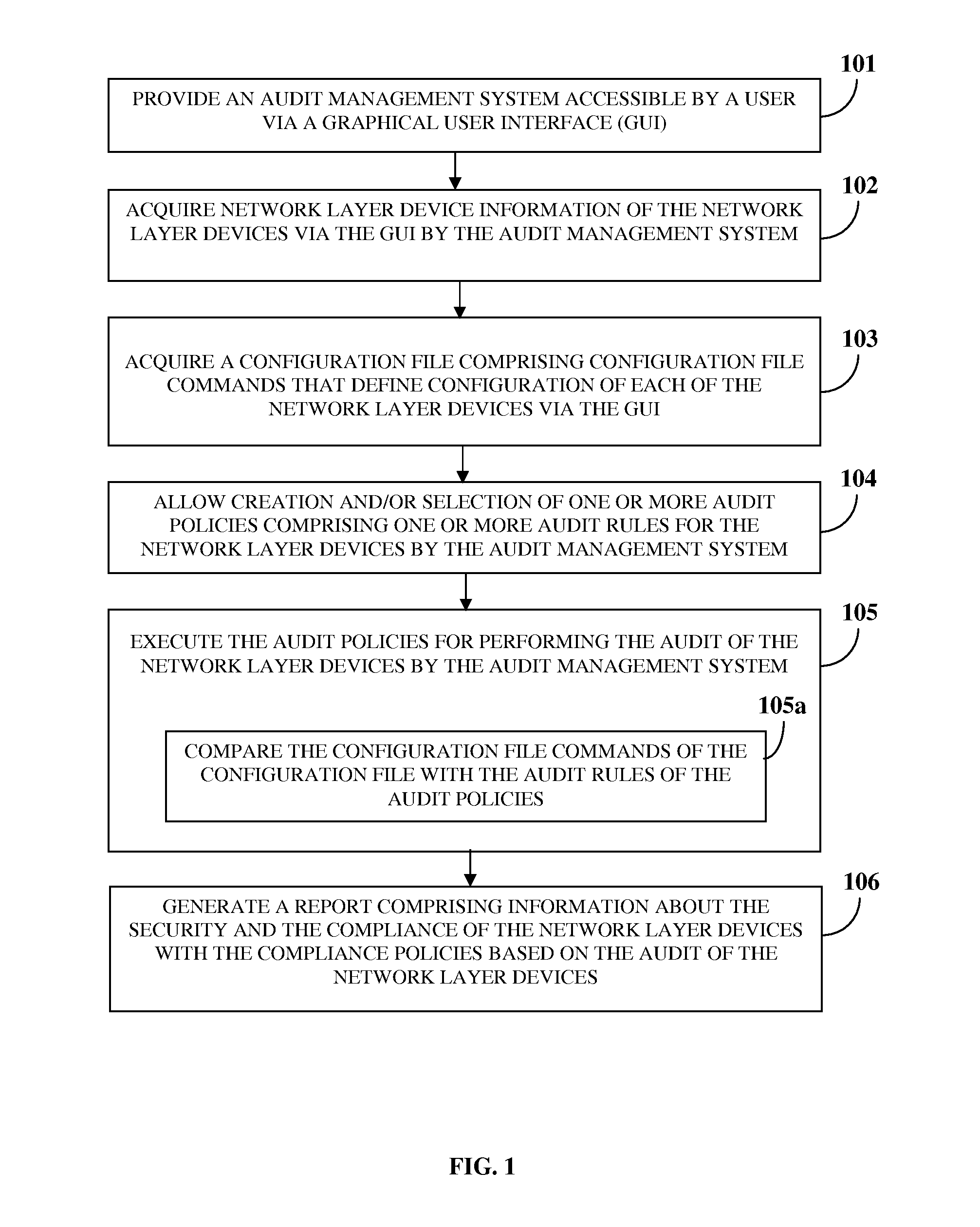
A computer implemented method and system for managing an audit of one or more network layer devices is provided. An audit management system accessible by a user via a graphical user interface acquires network layer device information of the network layer devices and a configuration file comprising configuration file commands. The audit management system allows creation and / or selection of one or more audit policies for the network layer devices. The audit policies comprise one or more audit rules that define functioning of the network layer devices for one or more compliance policies. The audit management system executes the audit policies for performing the audit of the network layer devices by comparing the configuration file commands of the configuration file with the audit rules of the audit policies, and generates a report comprising information about security and compliance of the network layer devices with the compliance policies based on the audit.
Owner:360 GRC
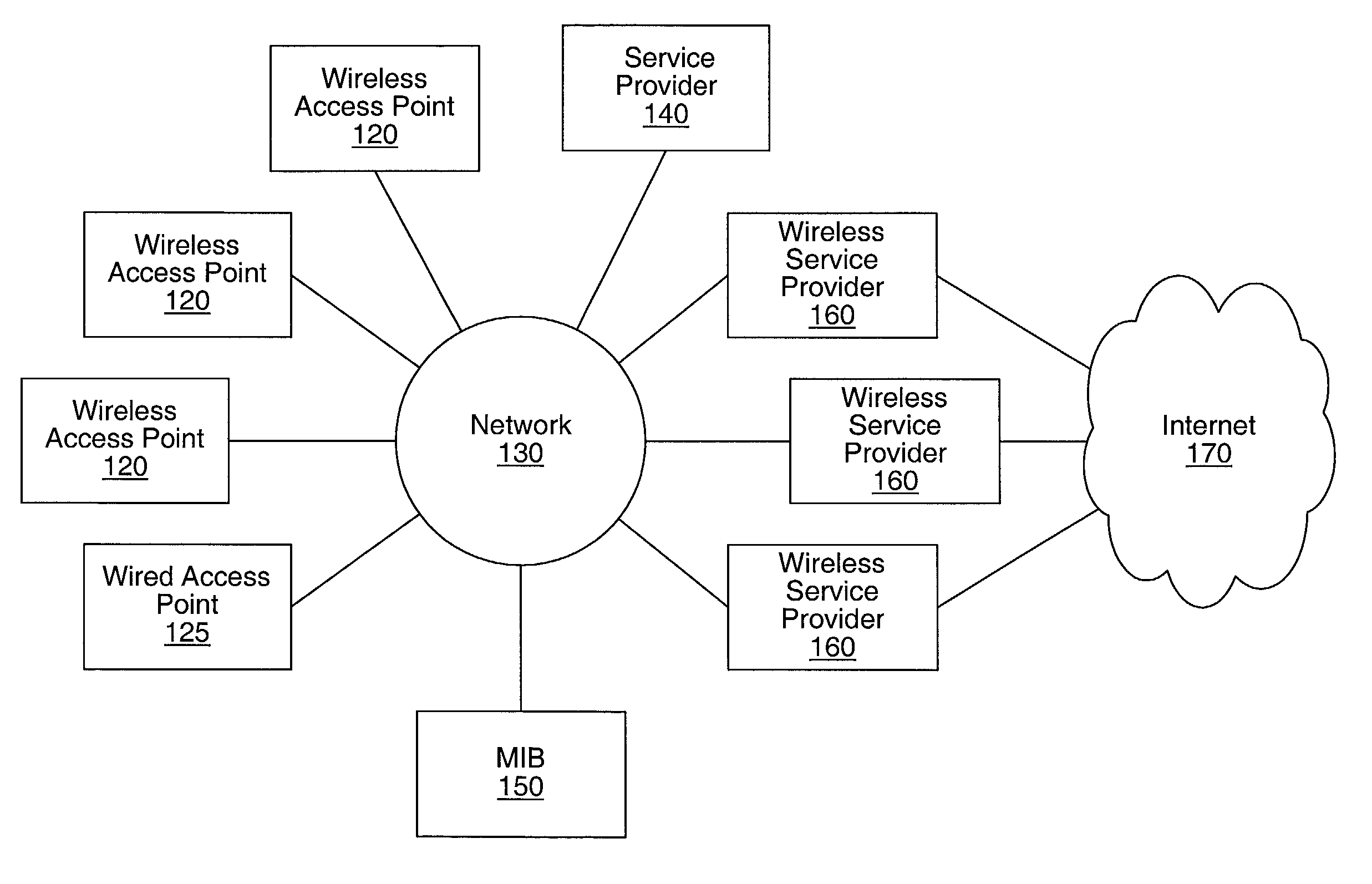
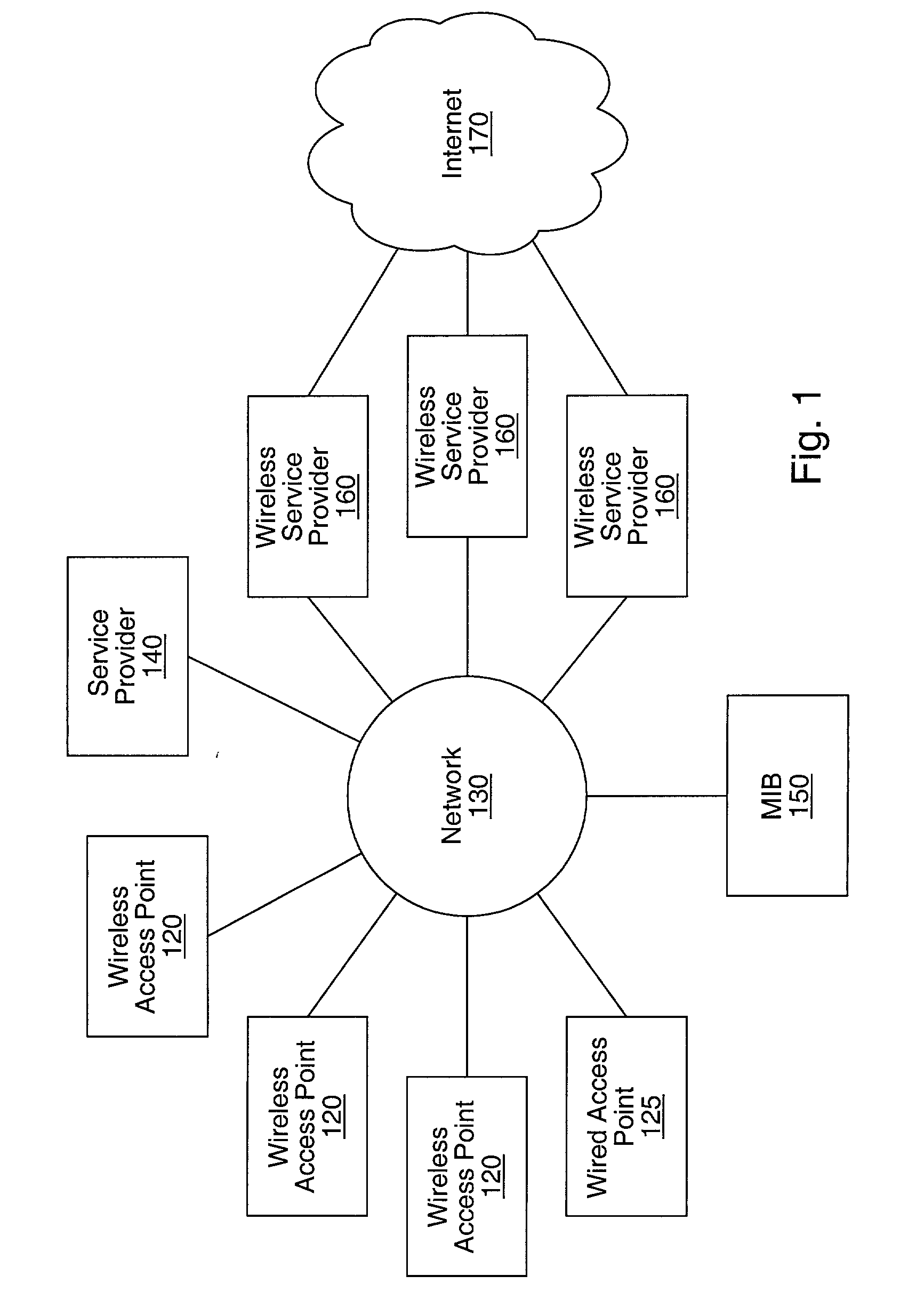
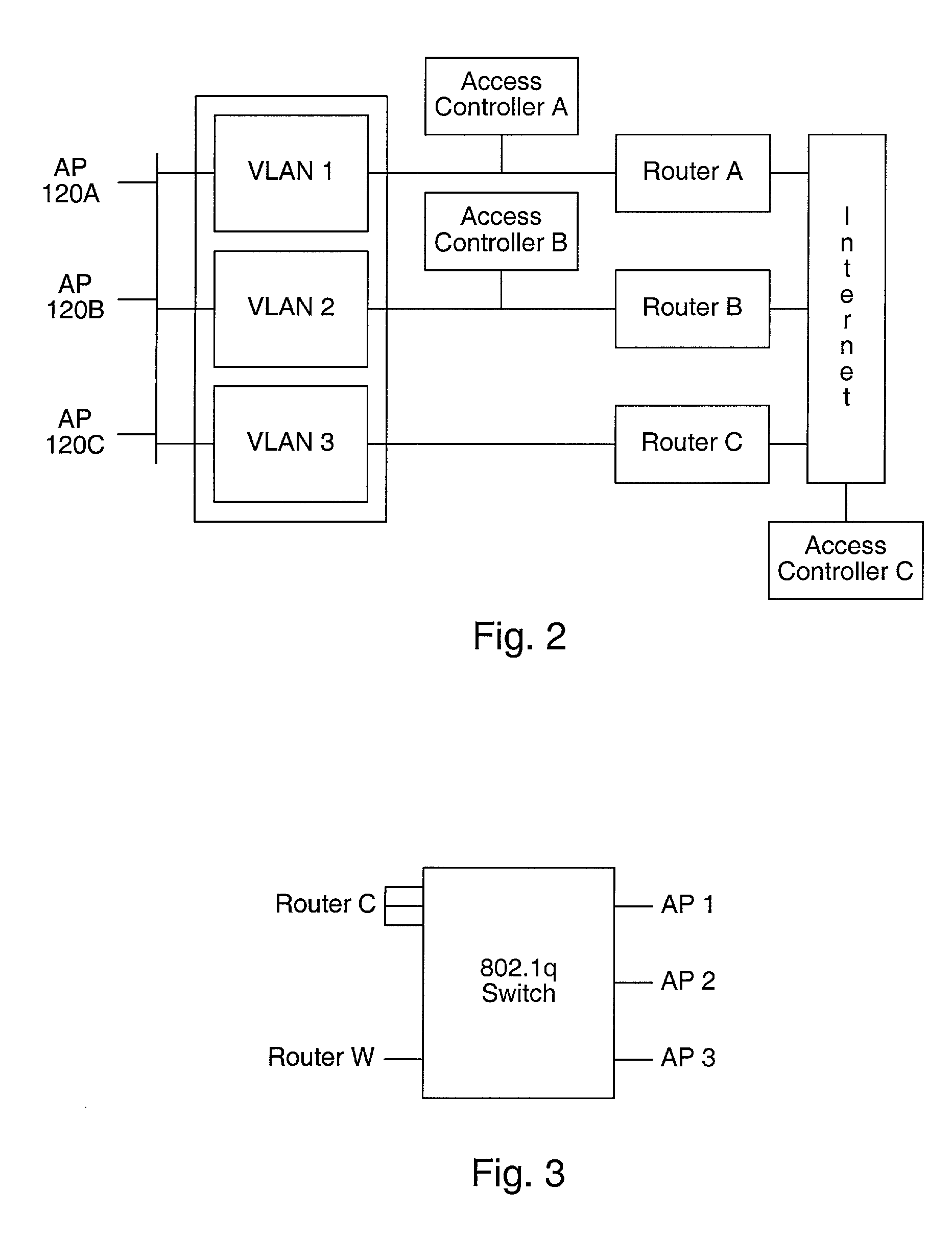
Distributed network communication system which allows multiple wireless service providers to share a common network infrastructure
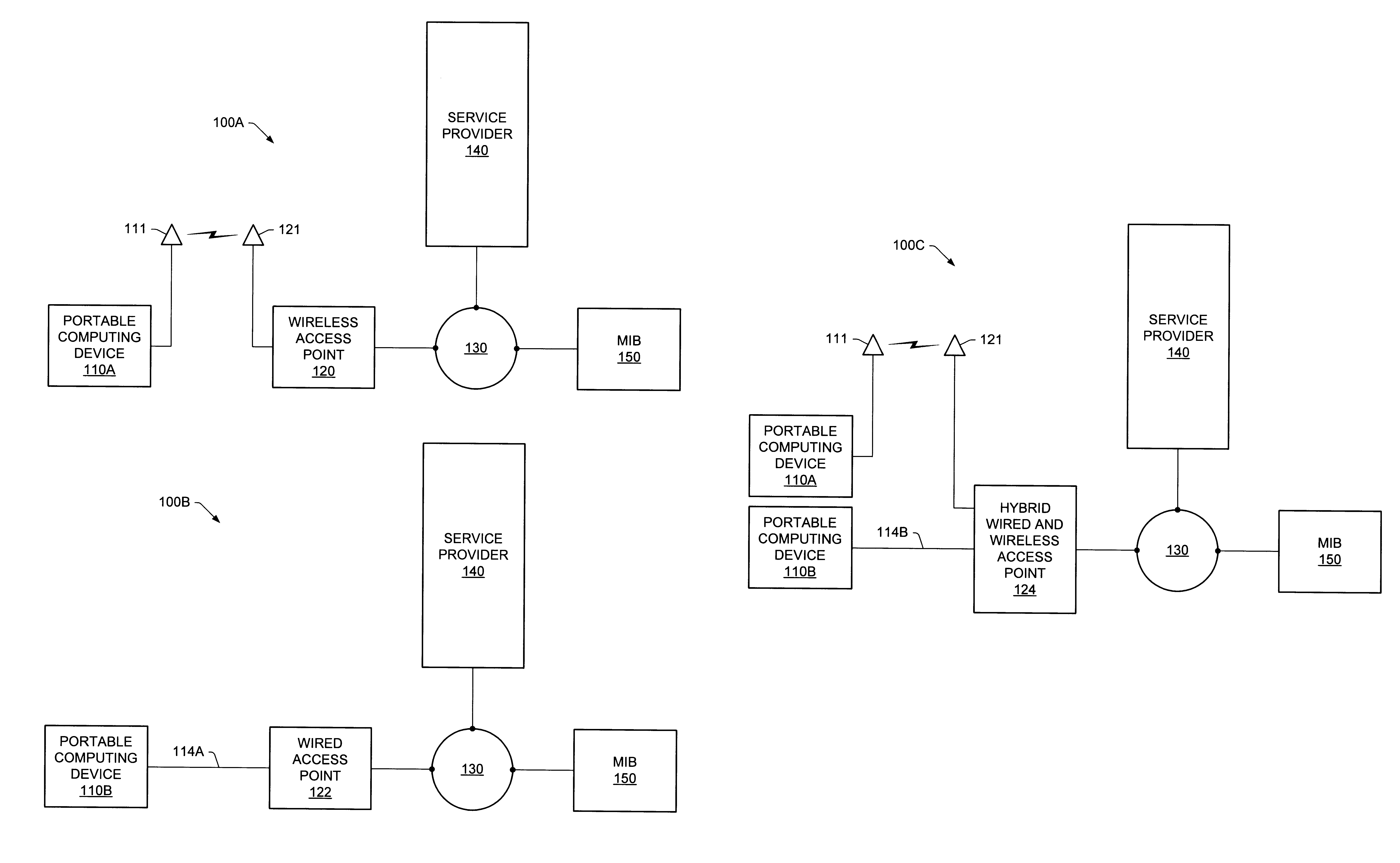
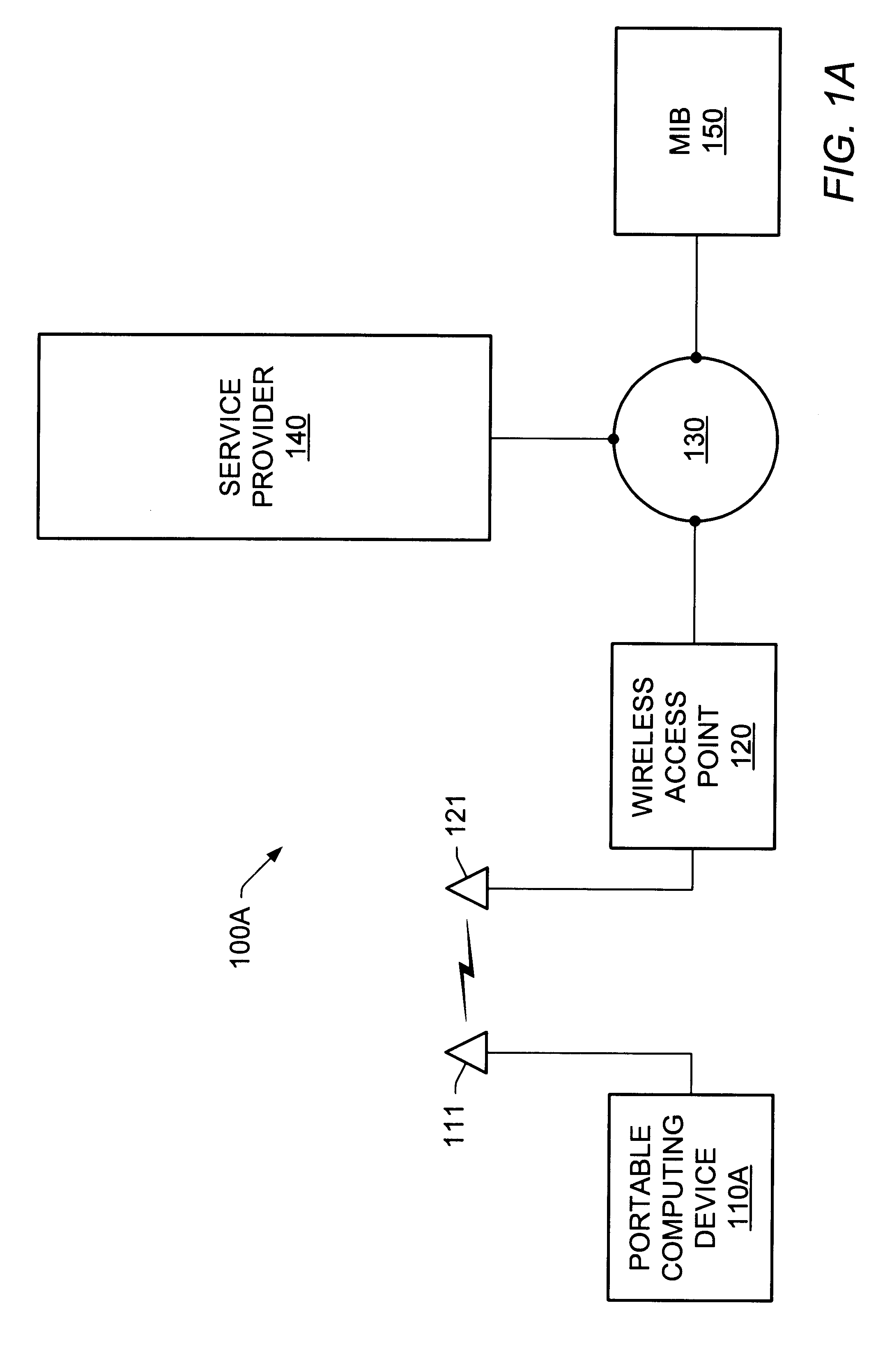
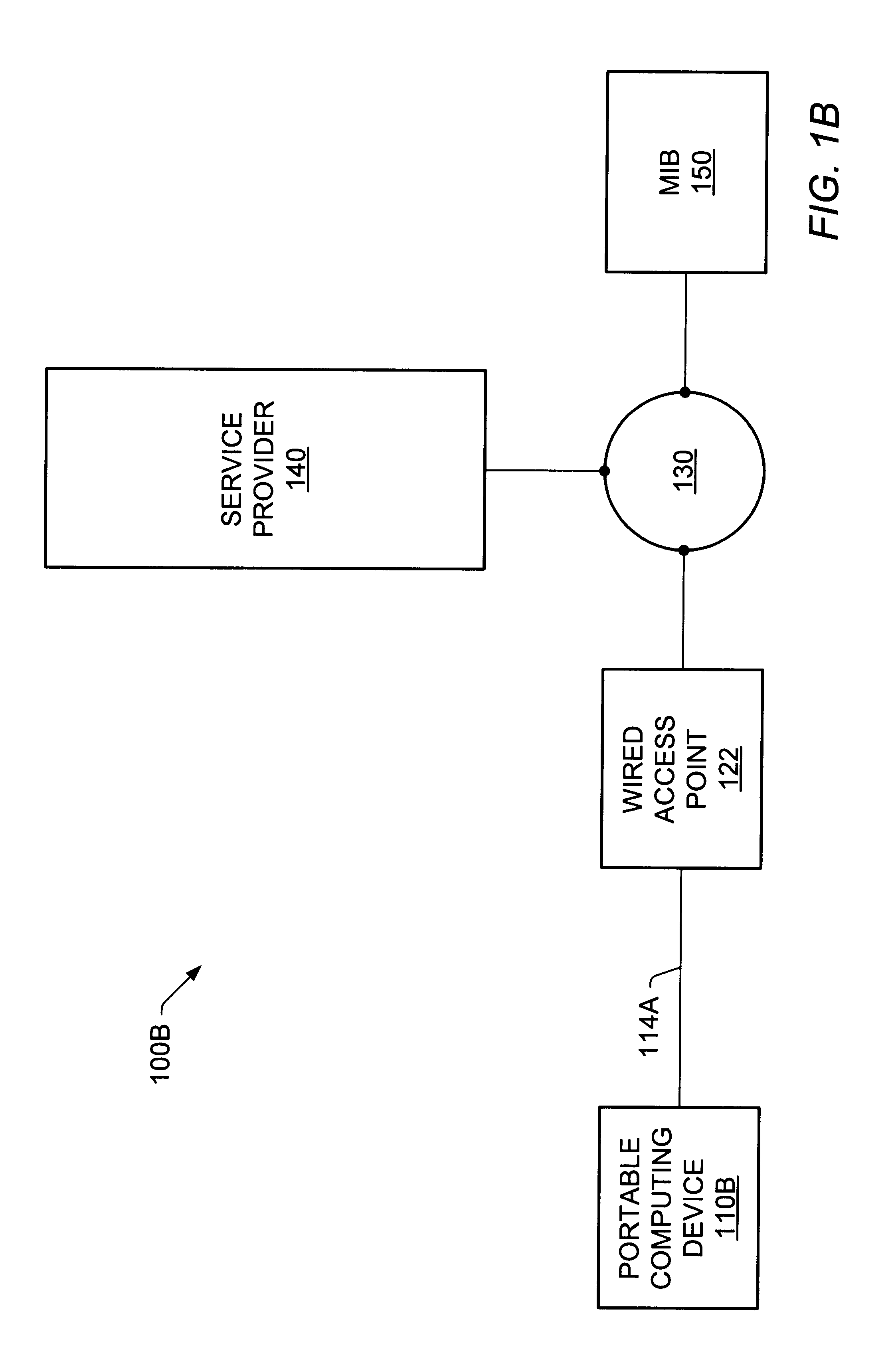
System and method for providing access to multiple wireless service providers (WSPs) on a shared network infrastructure. The system includes a plurality of access points (APs) coupled to a network which may be distributed in airports, mass-transit stations, businesses, etc. The network may couple to a wide area network, such as the Internet. Each AP may include a plurality of virtual APs (VAPs), each corresponding to a WSP. A portable computing device (PCD) of a user stores identification information indicating a WSP of a plurality of possible WSPs, and which may include an access level of the user. Each AP "listens for" or detects identification information associated with numerous WSPs. When the AP receives the identification information from the PCD, it determines the VAP / WSP for the PCD using the identification information. Network access is then provided to the PCD through the determined WSP at the determined access level.
Owner:CISCO TECH INC
Voice over data telecommunications network architecture
InactiveUS20040022237A1Interconnection arrangementsDc level restoring means or bias distort correctionNetwork operations centerNetwork architecture
Owner:LEVEL 3 COMM LLC
Method and apparatus for displaying health status of network devices
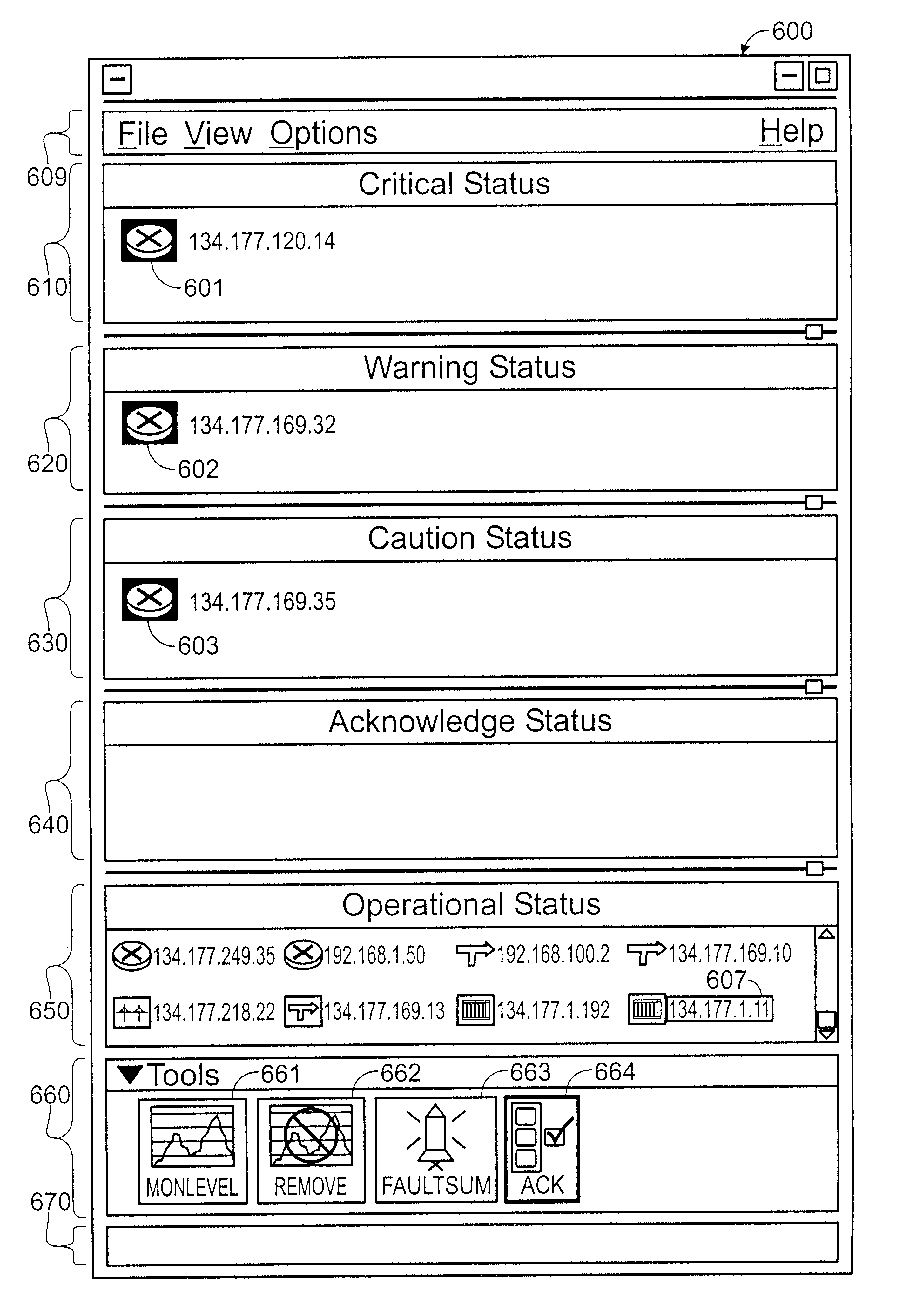
A method and apparatus for concurrently displaying from a single window on a network management station the health status of all network devices and objects of a computer network. The network devices may be categorized according to state or device type, as determined by the network manager. The method and apparatus provides a network manager with the ability to determine the current state of network devices and objects within an enterprise network and invoke further actions such as configuration, performance, fault, and security management tasks. The network manager can drag and drop icons from one network management system application window to another network management system application window to obtain fault information about network devices and objects, thus allowing multiple network management system applications to run concurrently on the same network management station. The network manager is further able to add new network devices and objects by dragging site, folder or device icons from one network management system application window to a second network management system application window for displaying the health status of the new devices. The dragged-in devices are added to the appropriate status panes within the second window according to the method of the present invention.
Owner:NORTEL NETWORKS LTD
Systems and methods for automatically configuring and managing network devices and virtual private networks
ActiveUS20060236095A1Multiple digital computer combinationsSpecial data processing applicationsComputer hardwareGraphics
Systems and methods are disclosed for automatically configuring, managing, and maintaining a network device or VPN using a public network such as the Internet. Initial configuration of a network device or VPN occurs upon a user entering minimal information via a simple HTML page. After receipt of this minimal information, the present invention automatically configures the network device or VPN without user intervention. Thereafter, a user may modify the network device or VPN configuration via an easy-to-use and easy-to-understand graphical user interface. Parameters are presented such that a user simply checks and unchecks boxes, or clicks on radio buttons, to configure network device parameters. Upon completion of the selection, the user clicks on save, and the configuration is automatically modified. In addition, upon a significant change to any network device, the changed network device automatically initiates reconfiguration of the network device or VPN with zero input from a user.
Owner:ANXEBUSINESS
Secure network access devices with data encryption
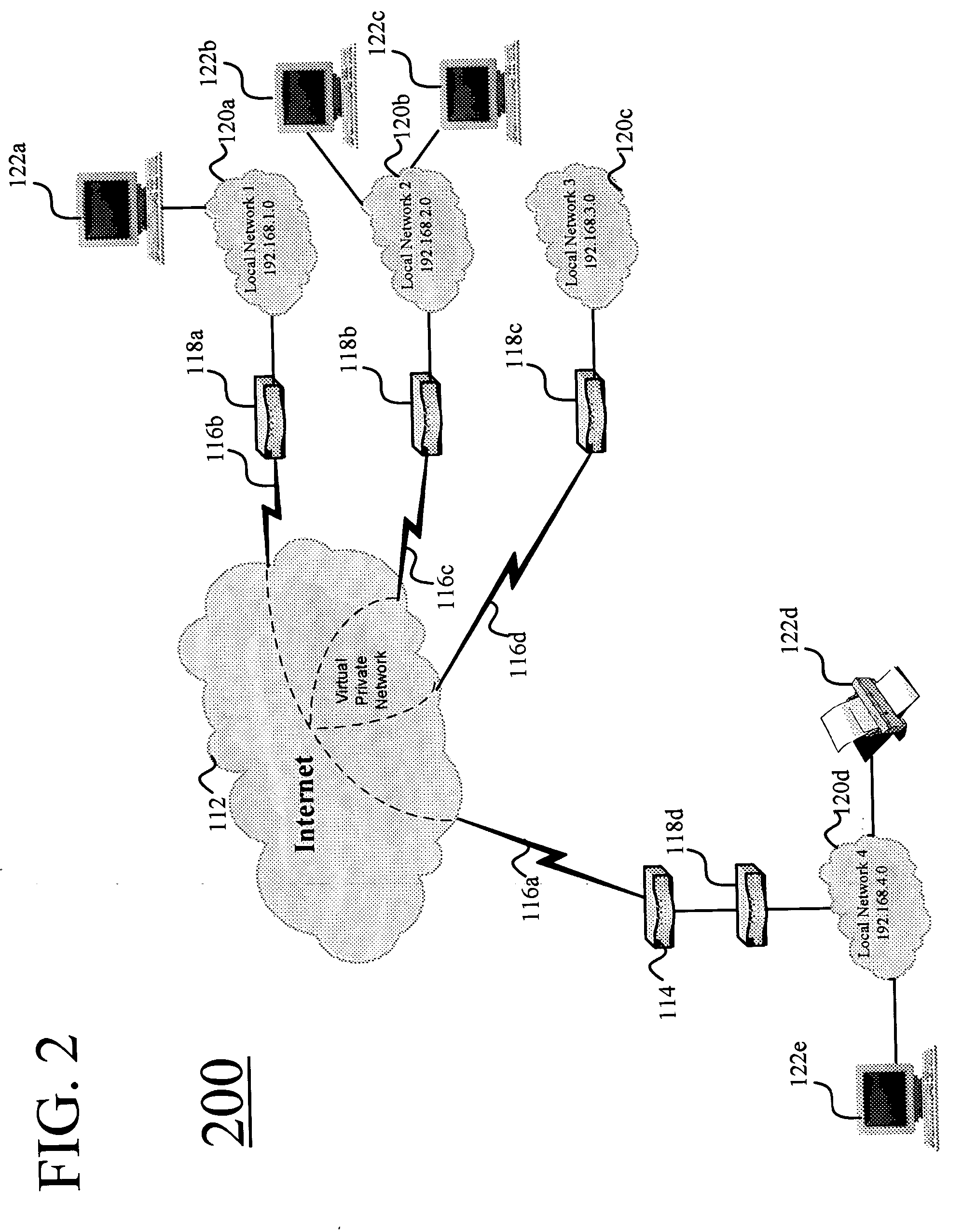
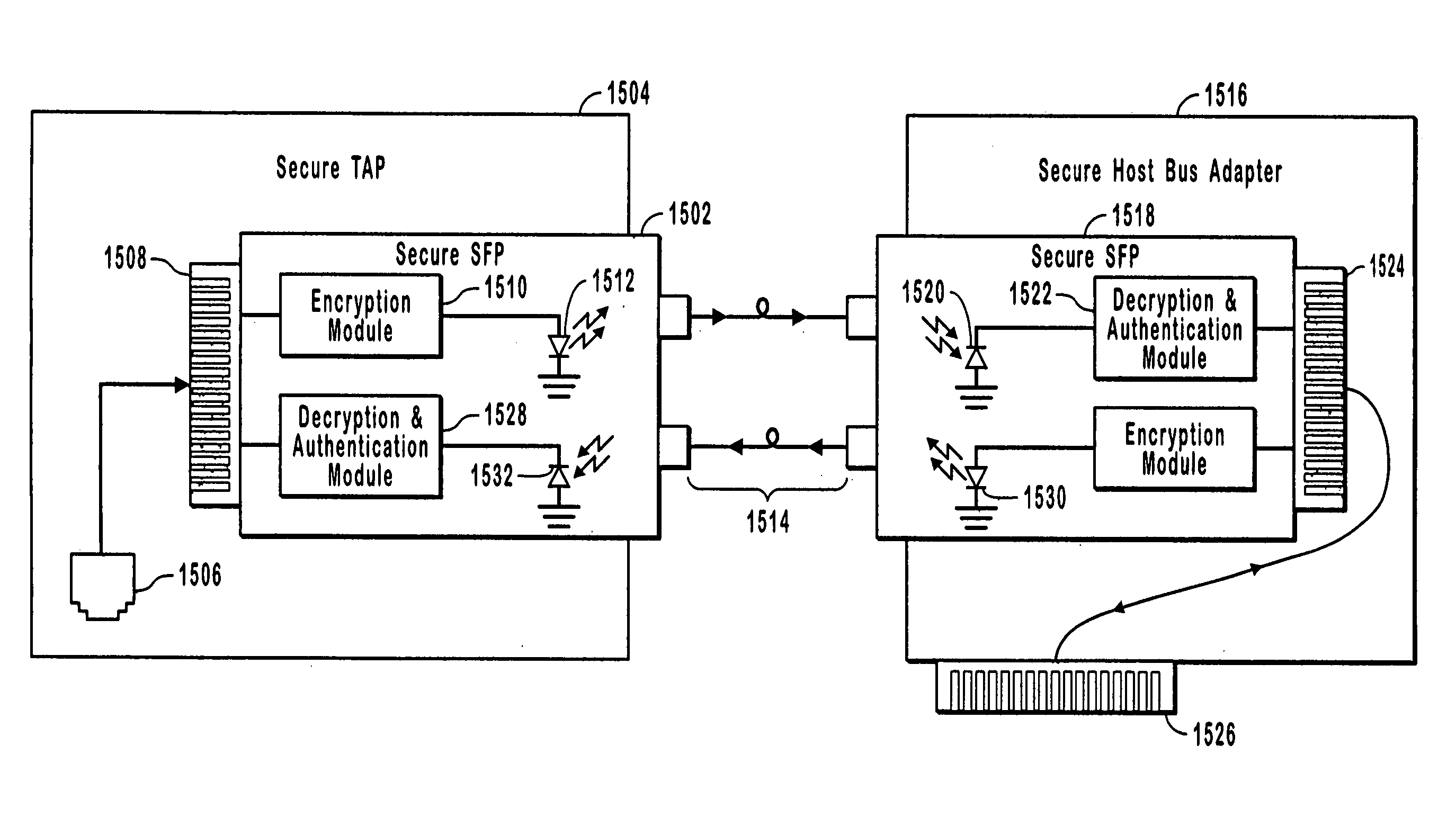
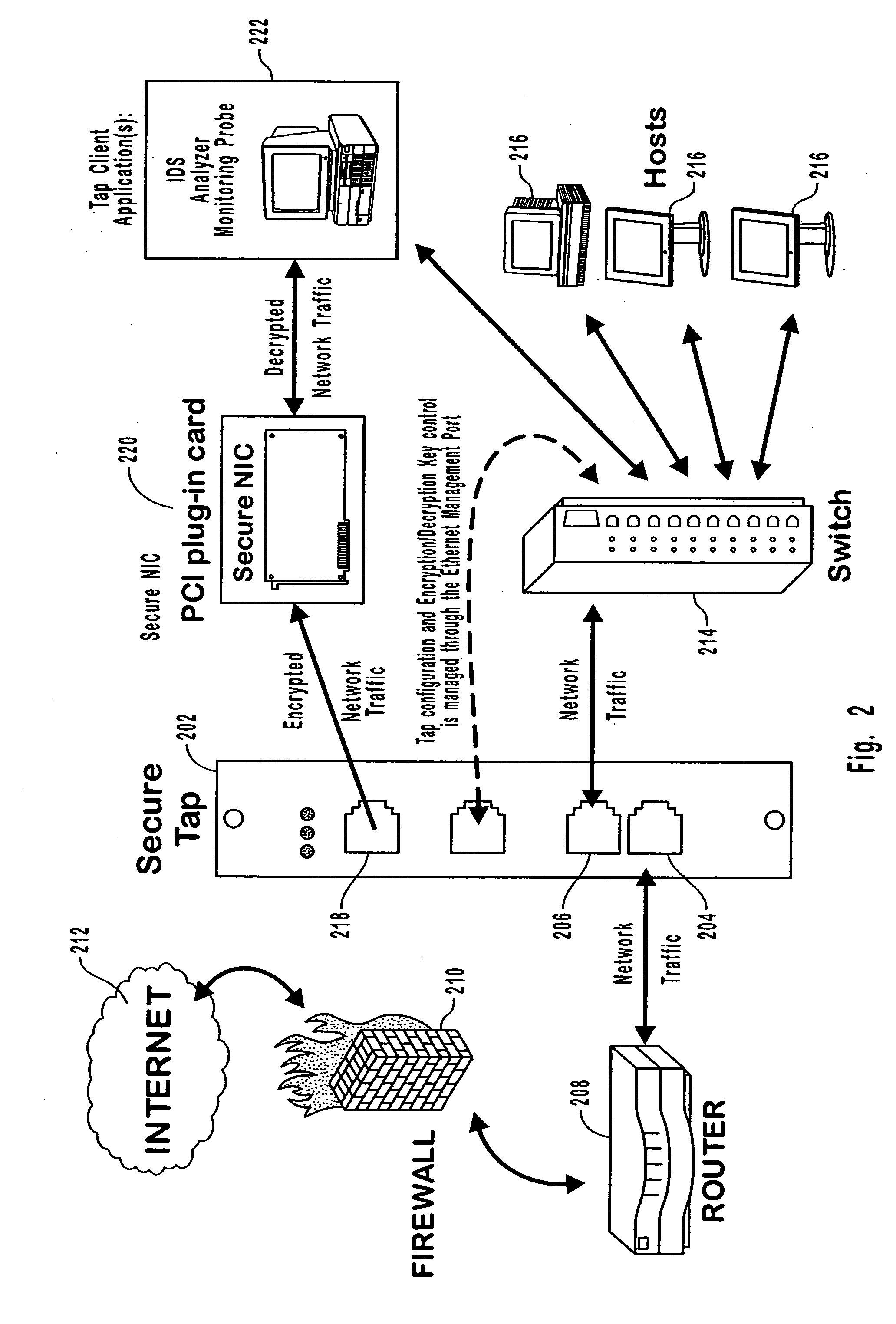
InactiveUS20050114663A1Avoid readingUser identity/authority verificationInternal/peripheral component protectionUsage dataEncryption
Secure point to point network communications. Secure point to point network communications are accomplished by sending data across a secure link. Trusted partners at the link are matched to each other. To ensure that no un-trusted partners are on the link, authentication is performed. One of the points may be a secure tap. The secure tap authenticates a trusted partner by receiving a hardware embedded encryption key or value derived from the hardware embedded encryption key from the trusted partner. Data sent on the trusted link is encrypted to prevent interception of the data. The secure tap polices the link to ensure that no un-trusted partners are attached to the link and that the trusted partner is not removed from the link. If un-trusted partners are added to the link or trusted partners removed from the link, the secure tap ceases sending data.
Owner:FINISAR
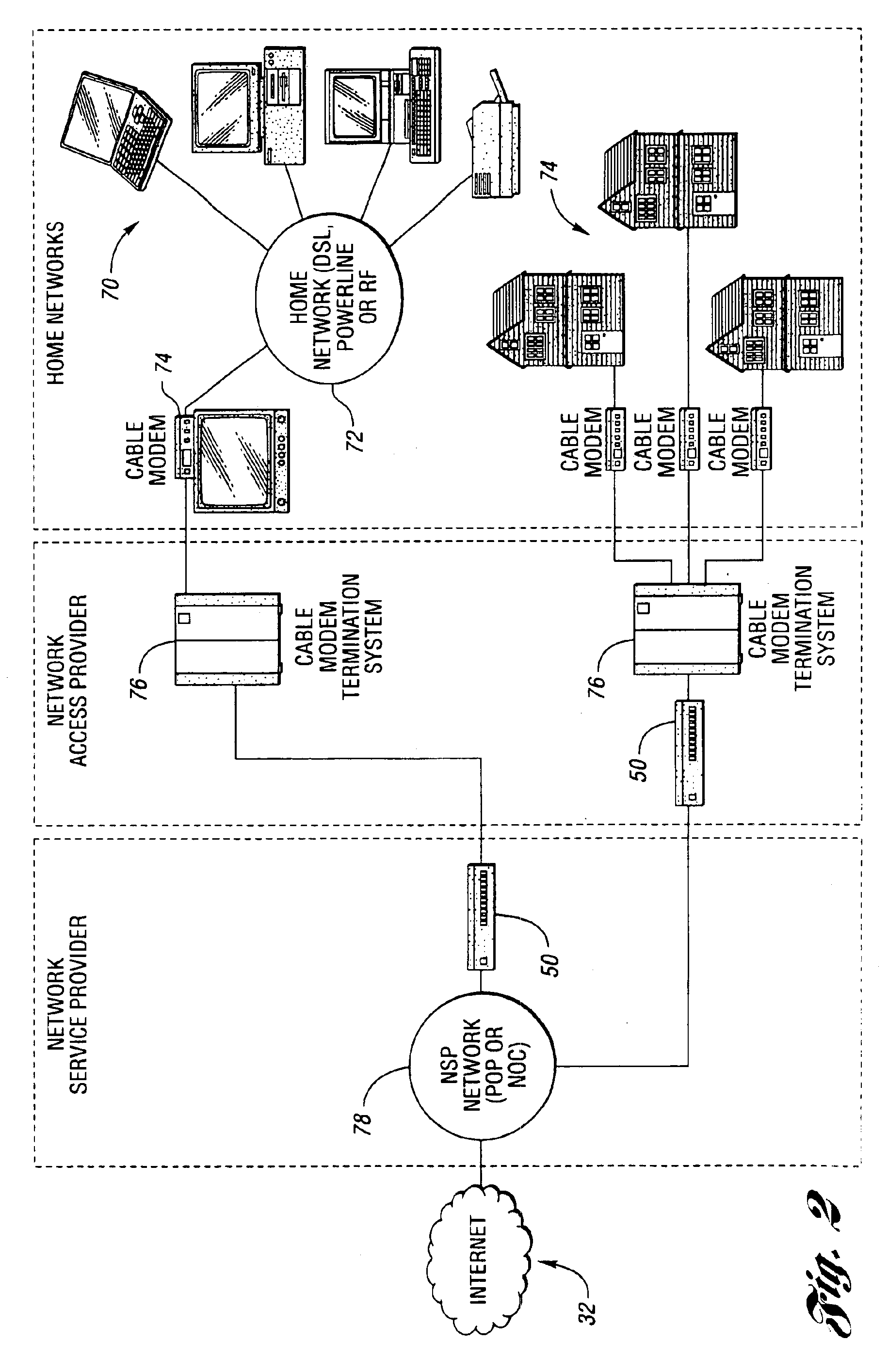
System and method for network access without reconfiguration
InactiveUS6857009B1Easy to addEasy to deleteTime-division multiplexData switching by path configurationDomain nameComputer compatibility
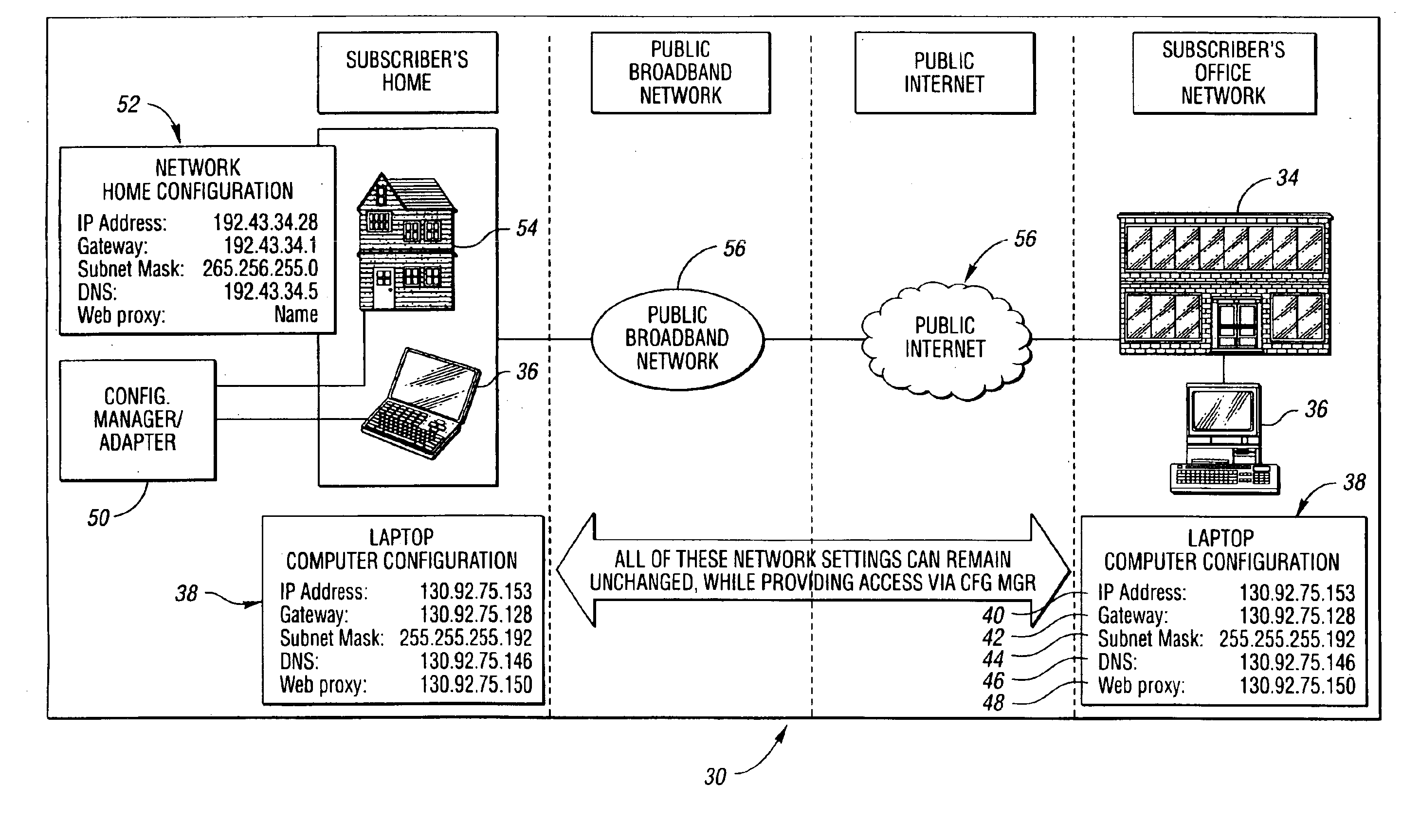
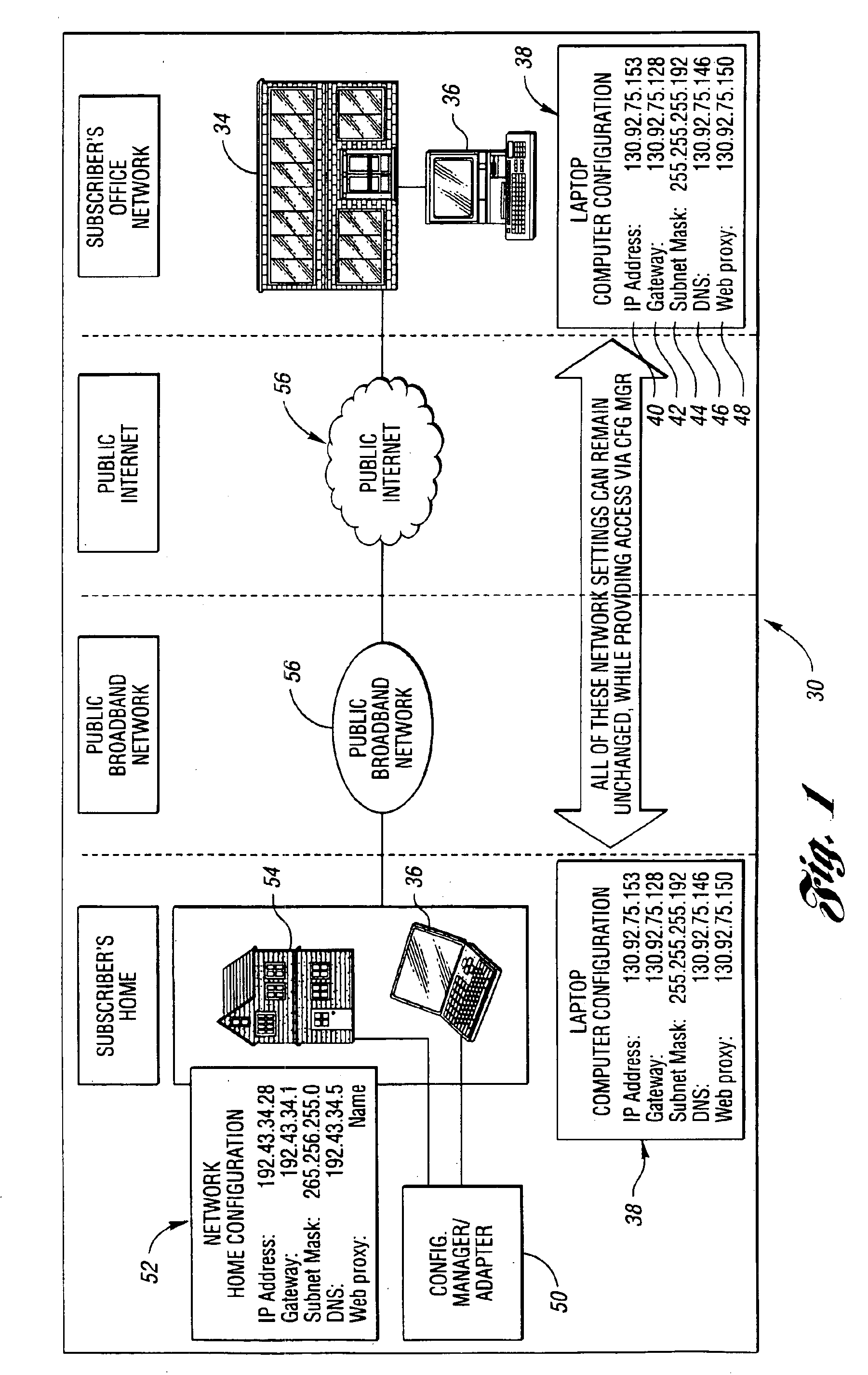
A system and method for providing connectivity to a foreign network for a device configured for communication over a home network without reconfiguring the device include intercepting packets transmitted by the device, selectively modifying intercepted packets which are incompatible with the foreign network to be compatible with network settings of the foreign network, and selectively providing network services for the device corresponding to network services available on the home network to reduce the delay associated with accessing the network services from the foreign network, or to provide network services otherwise inaccessible from the foreign network. Network services are provided by or through a configuration adapter connected to the device or to the foreign network. The configuration adapter accommodates incompatibilities resulting from proxy server requests, domain name server requests, and / or outgoing email service requests to provide transparent network access for mobile users without reconfiguration of the users computing device.
Owner:NOMADIX INC
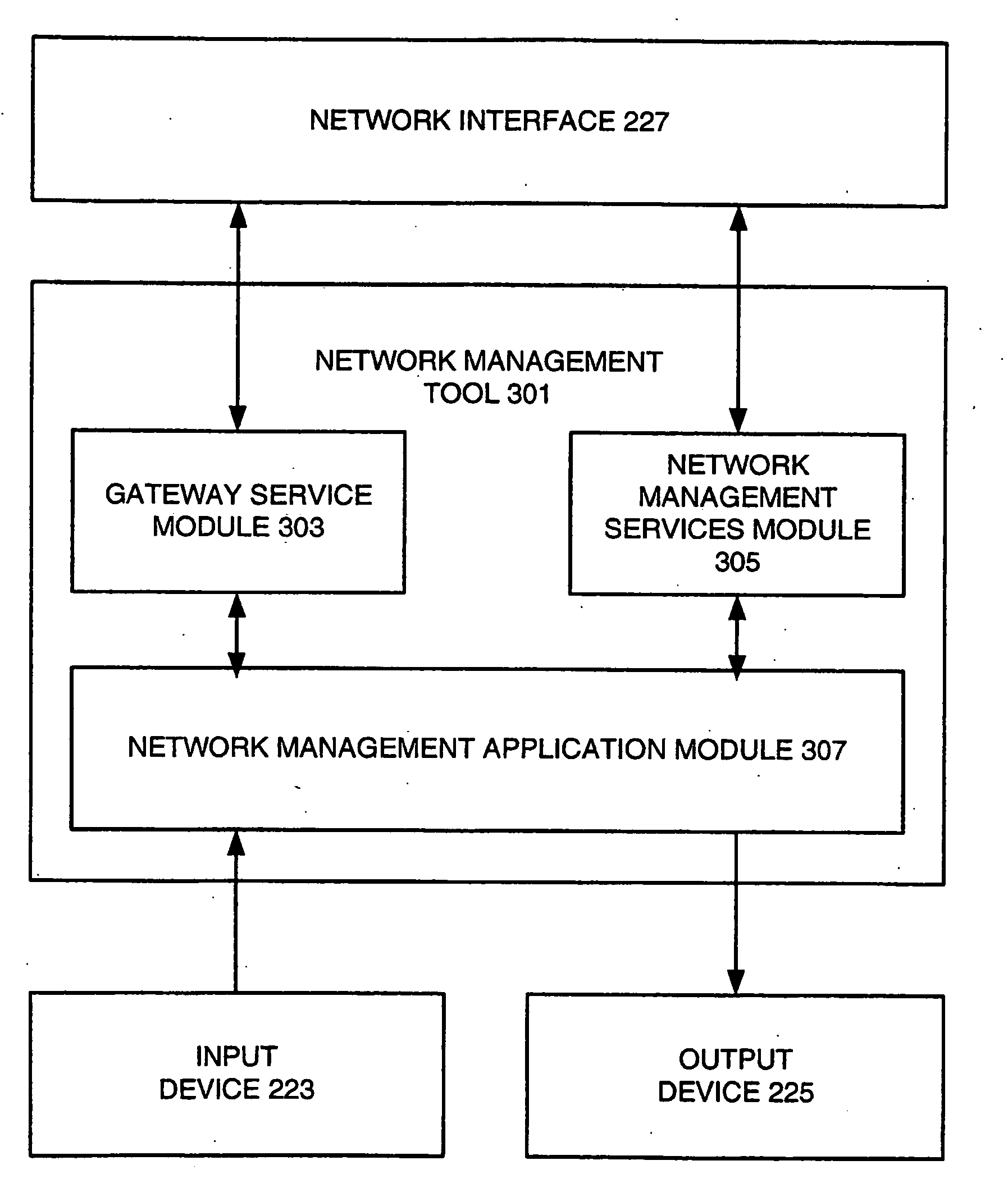
Network administration tool
InactiveUS20080052384A1Improve performanceImprove usabilityDigital computer detailsNetwork connectionsNetwork managementDistributed computing
Owner:CISCO TECH INC
Dynamic distribution of virtual machines in a communication network
In one embodiment, a method generally includes monitoring network traffic associated with a first network device comprising at least one of a plurality of virtual machines and determining if a parameter exceeds a predefined threshold at the first network device. If the parameter exceeds the predefined threshold, one of the virtual machines is selected to move to a second network device, the second network device selected based on network information, and the virtual machine is moved. An apparatus for resource allocation is also disclosed.
Owner:CISCO TECH INC
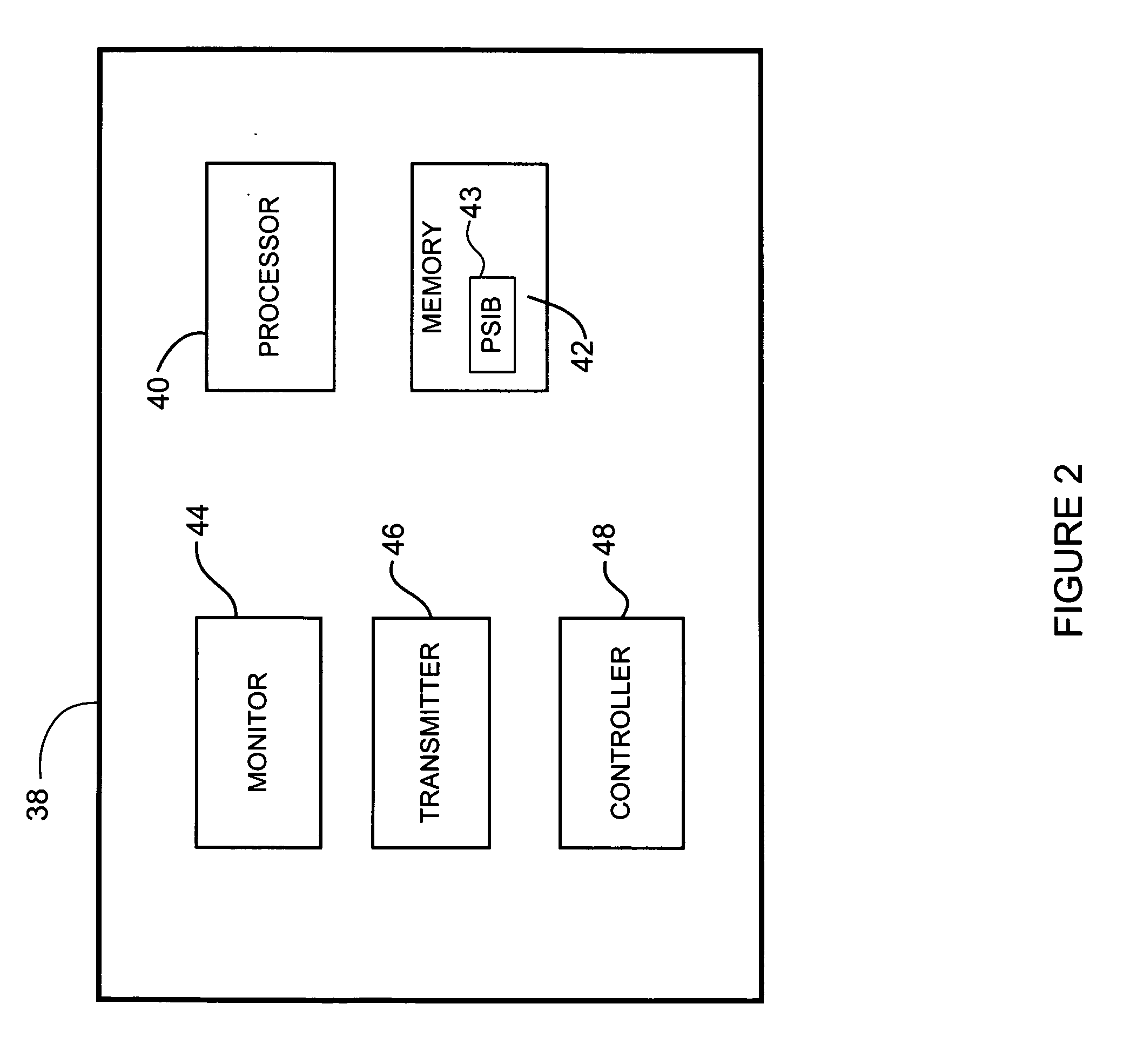
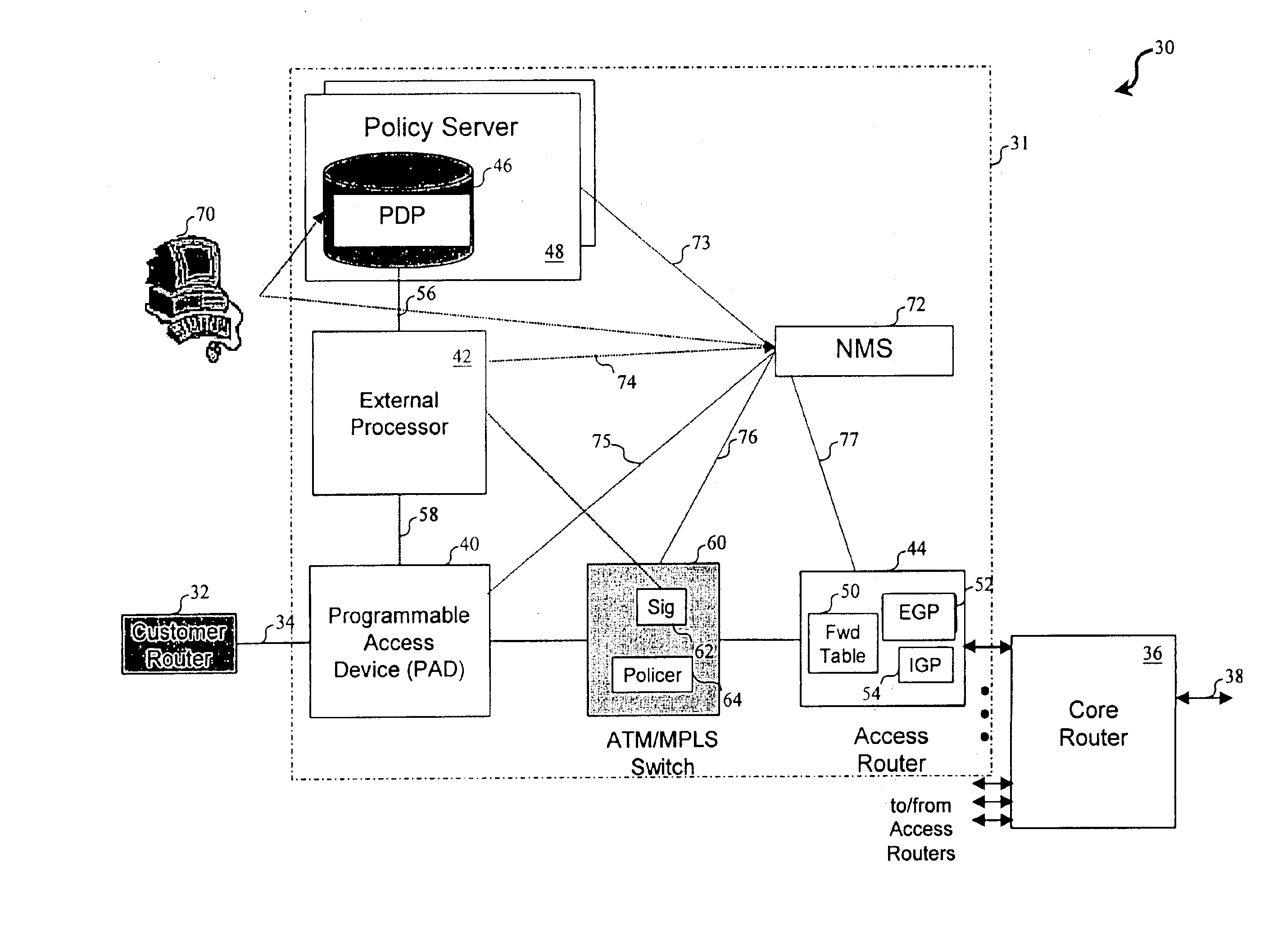
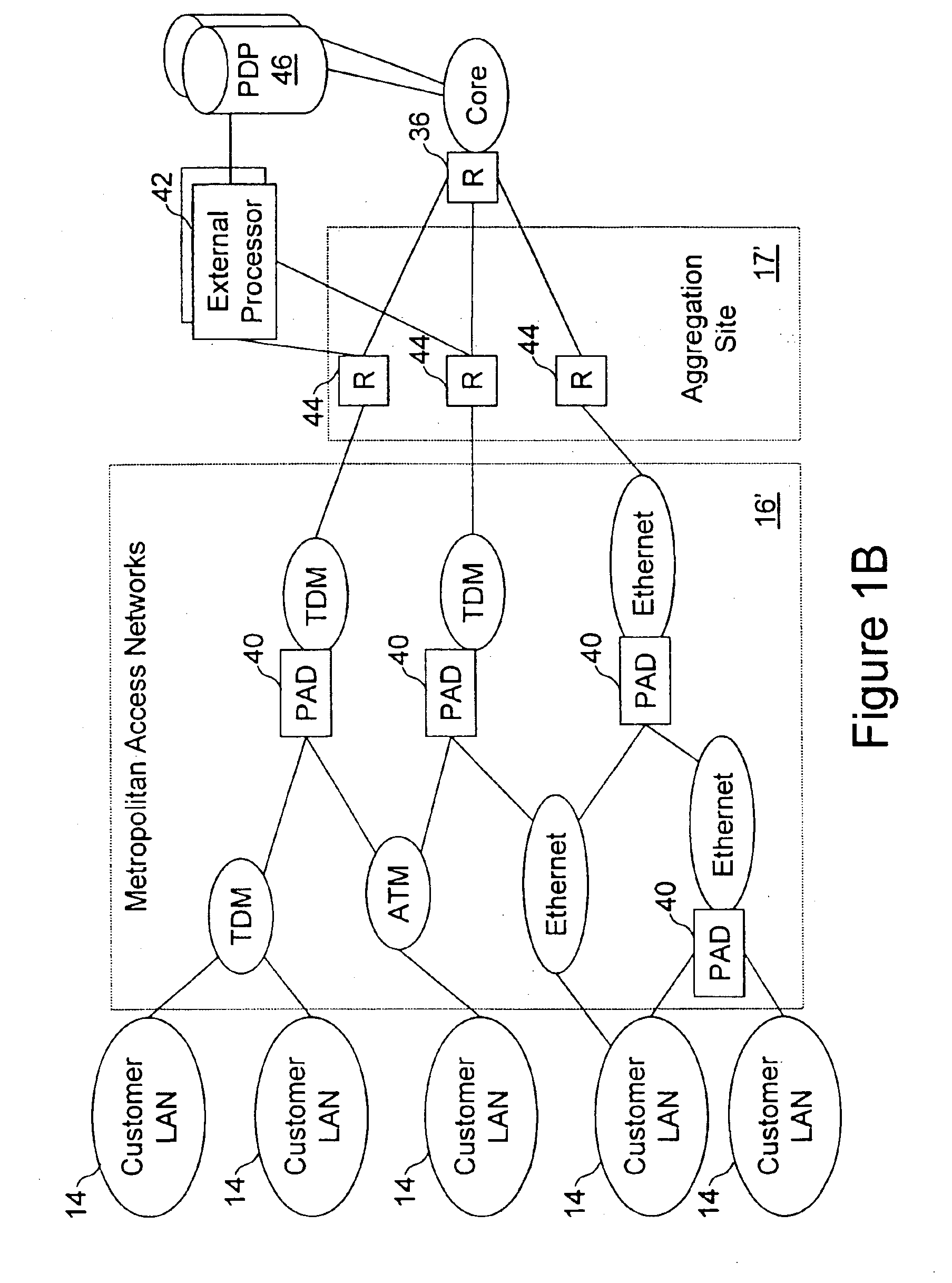
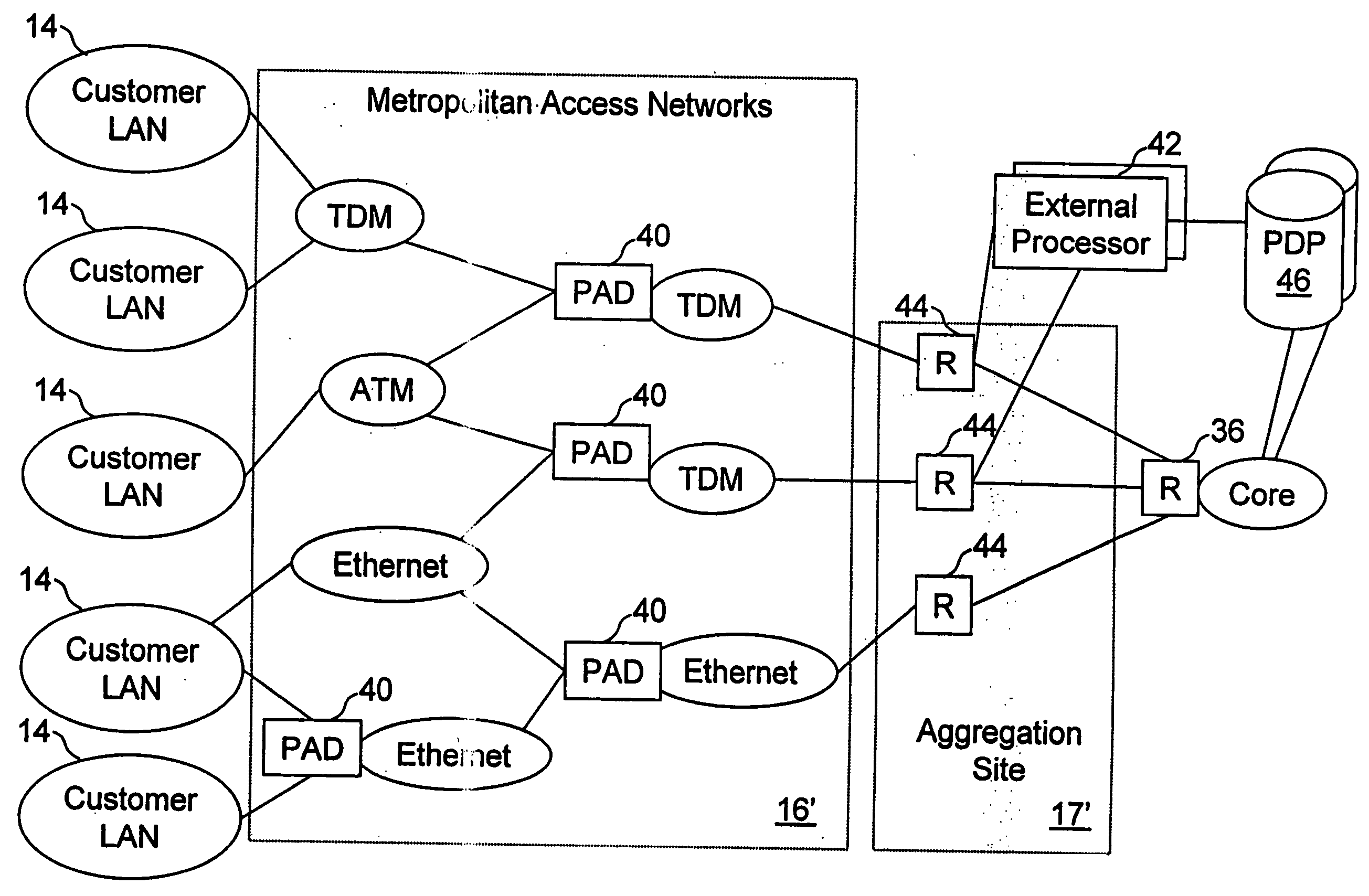
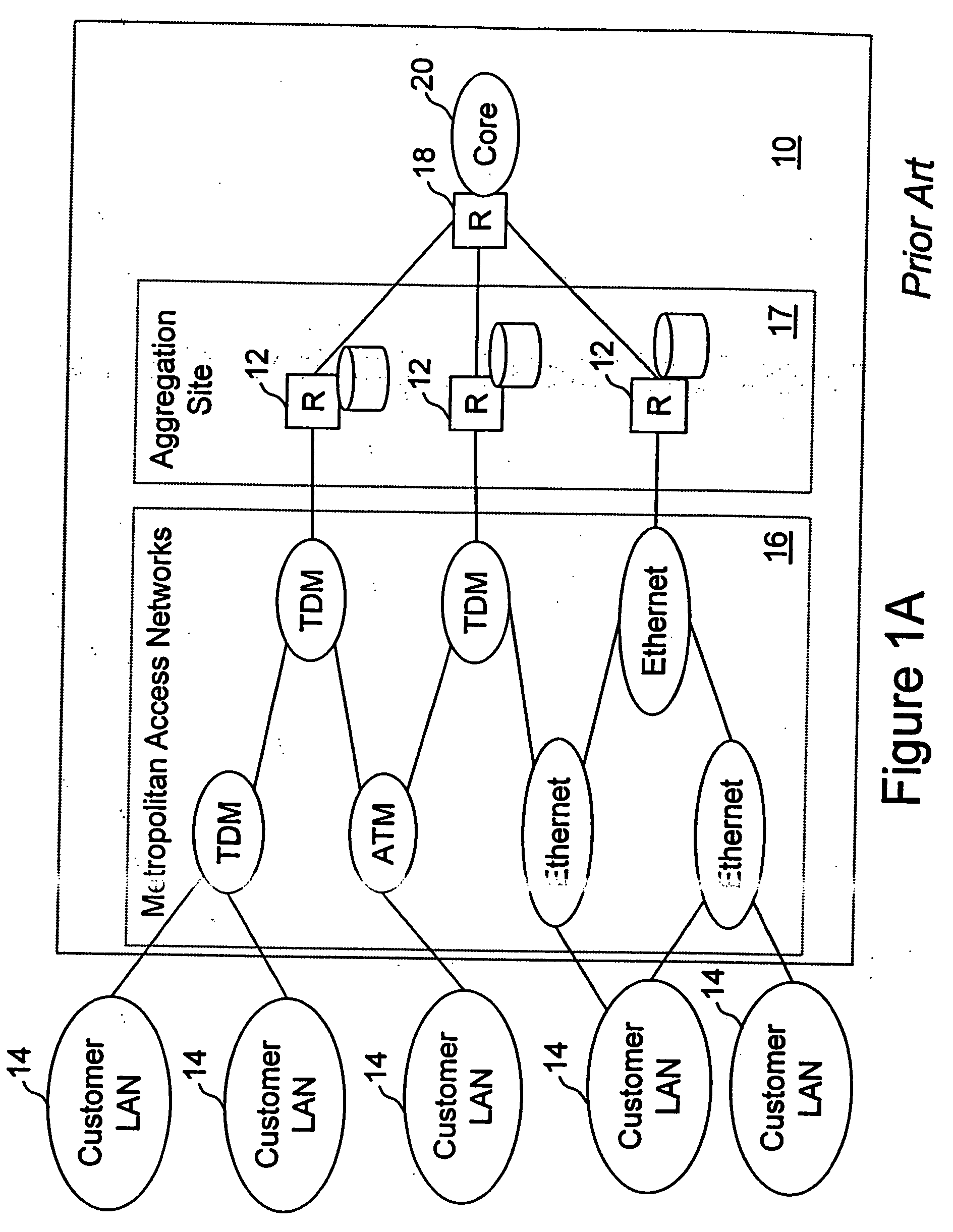
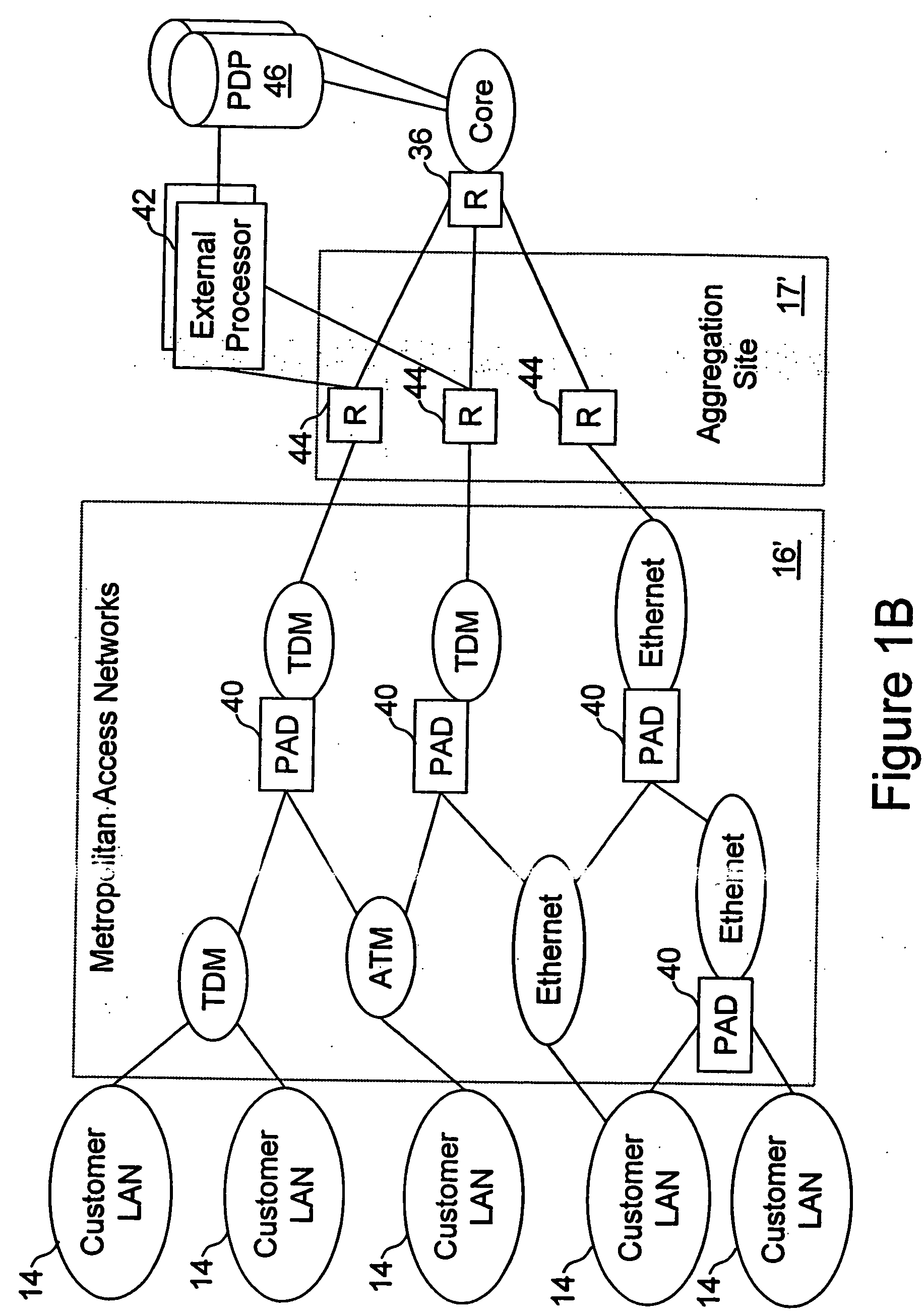
Network access system including a programmable access device having distributed service control
InactiveUS7046680B1Good extensibilityIncrease flexibilityData switching by path configurationMultiple digital computer combinationsProgrammable logic deviceMessage Passing Interface
A distributed network access system in accordance with the present invention includes at least an external processor and a programmable access device. The programmable access device has a message interface coupled to the external processor and first and second network interfaces through which packets are communicated with a network. The programmable access device includes a packet header filter and a forwarding table that is utilized to route packets communicated between the first and second network interfaces. In response to receipt of a series of packets, the packet header filter in the programmable access device identifies messages in the series of messages upon which policy-based services are to be implemented and passes identified messages via the message interface to the external processor for processing. In response to receipt of a message, the external processor invokes service control on the message and may also invoke policy control on the message.
Owner:VERIZON PATENT & LICENSING INC
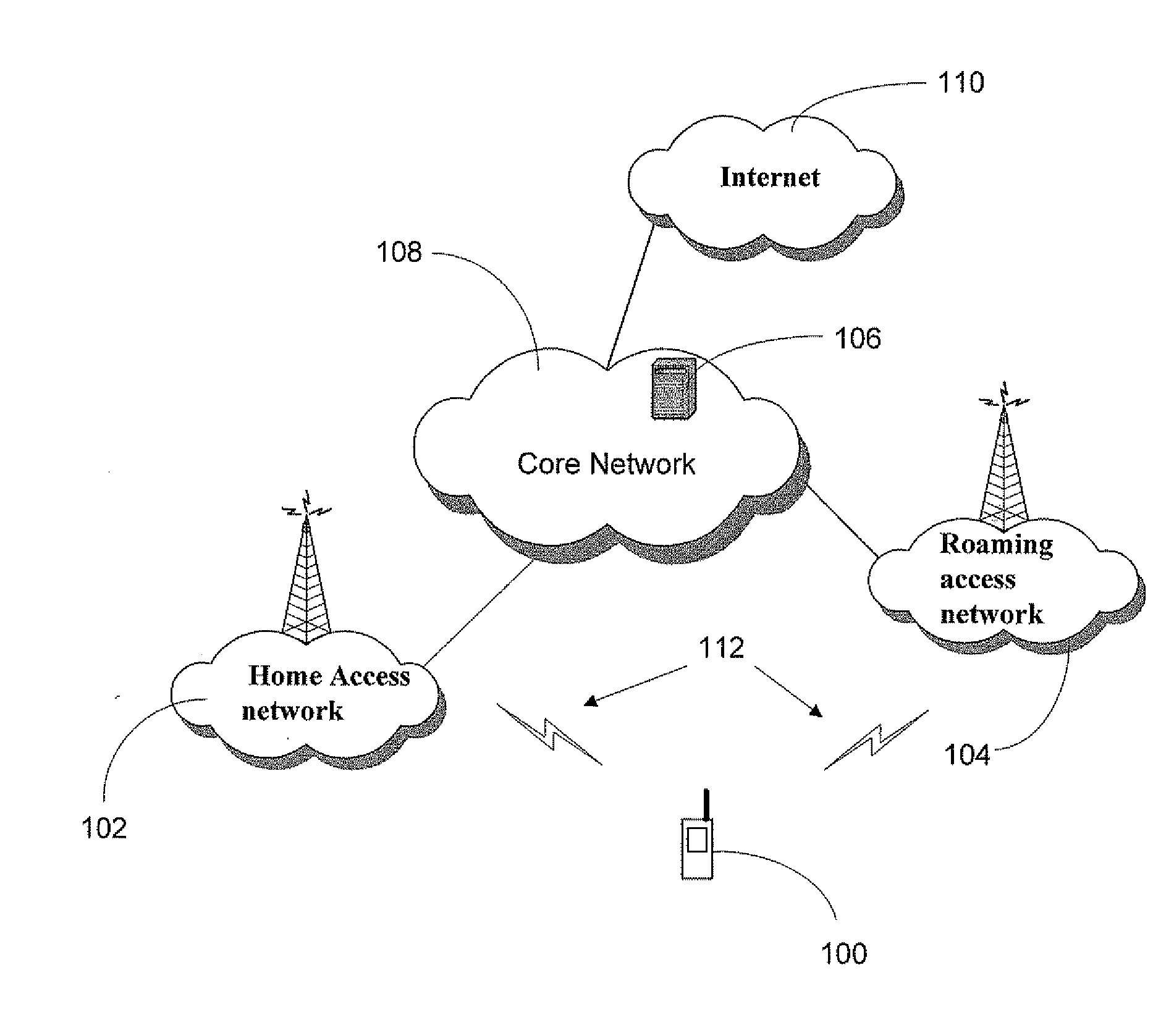
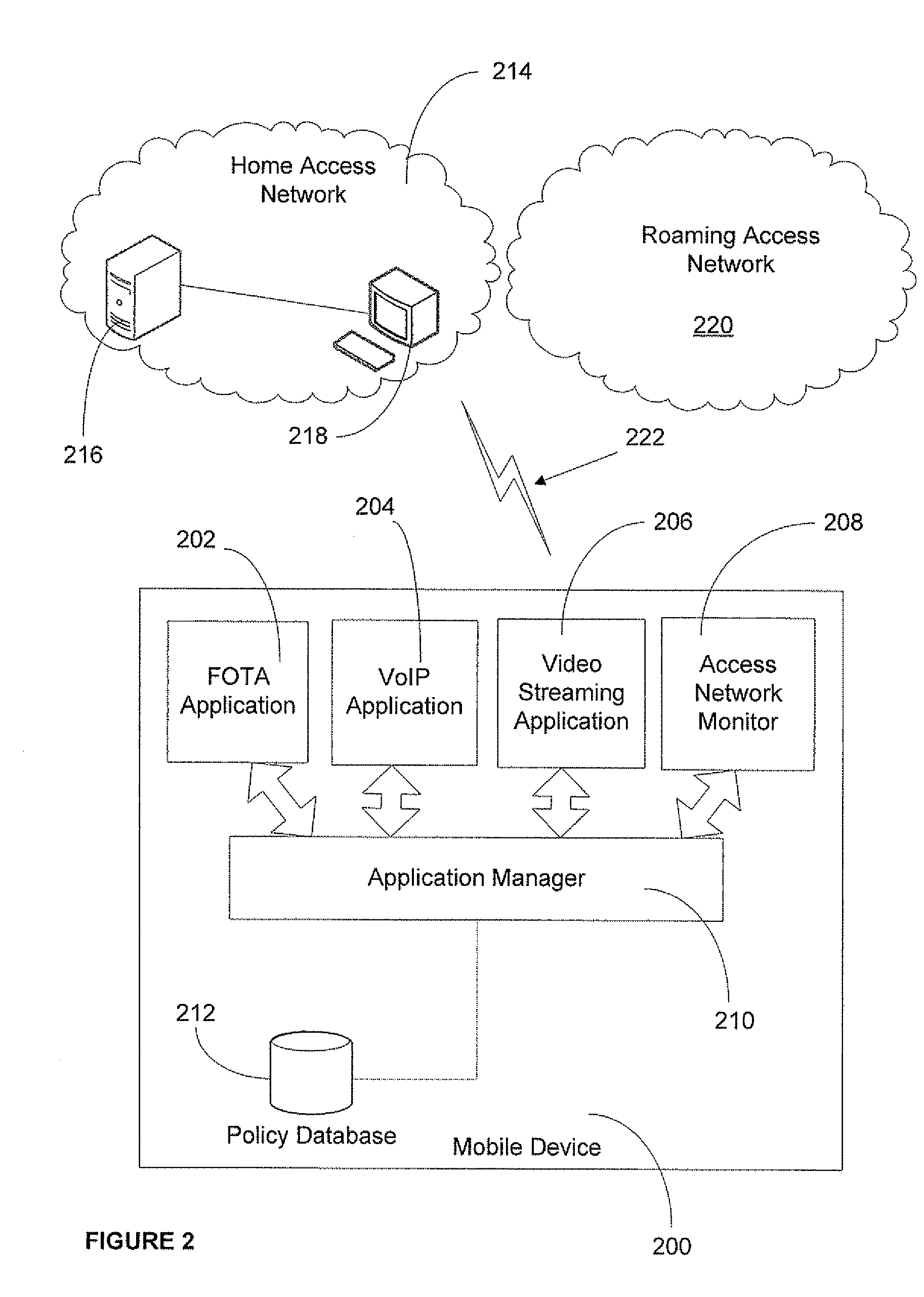
Application access control in a mobile environment
ActiveUS20080160958A1Avoid unwanted roaming chargeAvoid runningUnauthorised/fraudulent call preventionEavesdropping prevention circuitsData connectionAccess network
A system and method are described whereby a mobile device controls access to mobile applications based on access conditions associated with a current access network. To prevent mobile applications from running when the access conditions are not suitable, the mobile device includes a policy database used to store a list of access conditions that are inappropriate for launching the installed applications. The access conditions are based on the type of the current access network used by the mobile device for launching or maintaining the requested application session. The access conditions indicate whether the mobile device is currently accessing its home network or roaming on another provider's network. Similarly, the access conditions indicate the type of network access interface used by the current network to provide the data connection necessary to run the requested application. The policy database correlates predetermined actions with the access conditions associated with a given application session.
Owner:U S CELLULAR
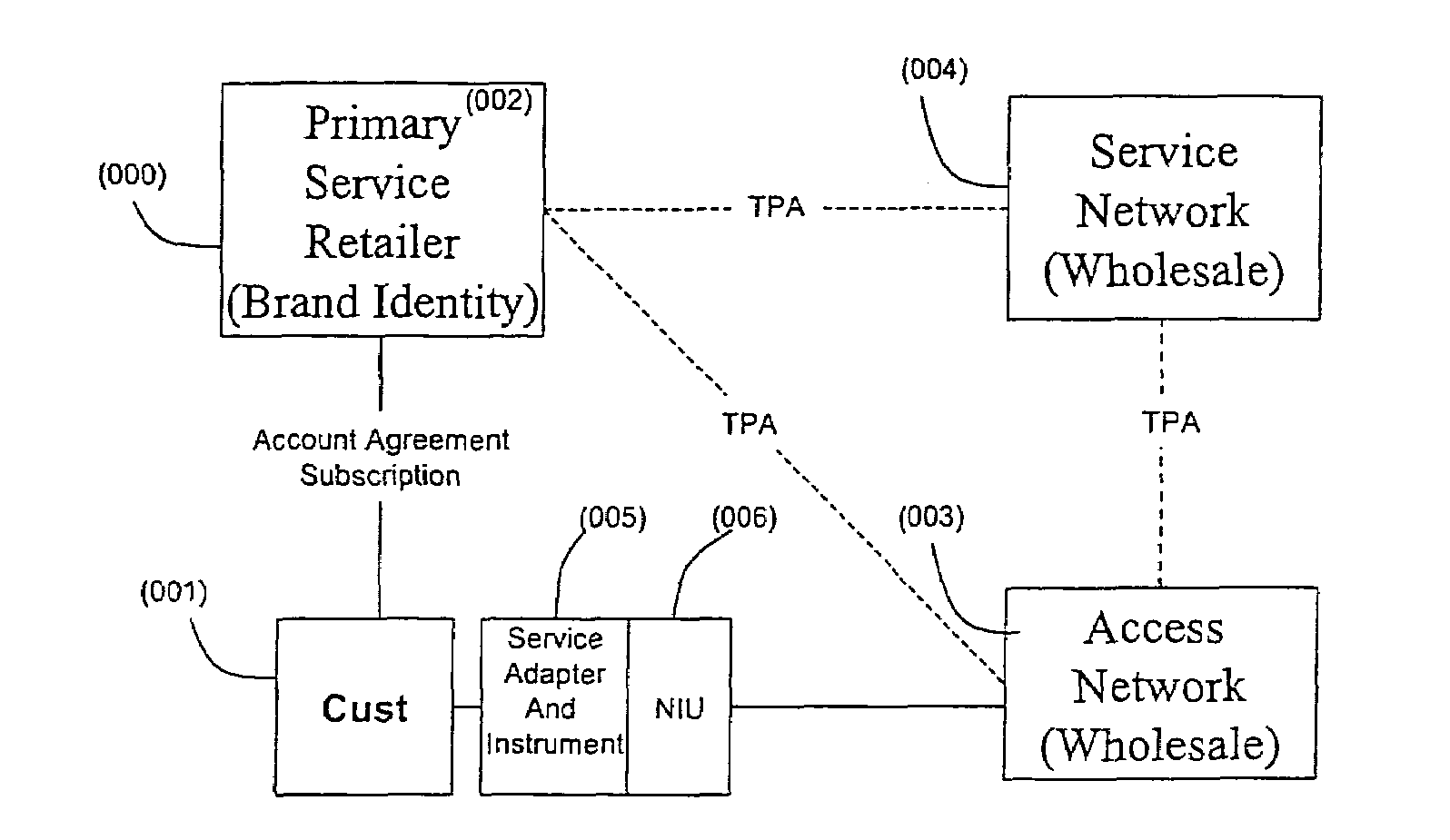
Intelligent network providing network access services (INP-NAS)
InactiveUS7496652B2Efficient use ofConsiderable timeBroadband local area networksMultiple digital computer combinationsIntelligent NetworkSmart network
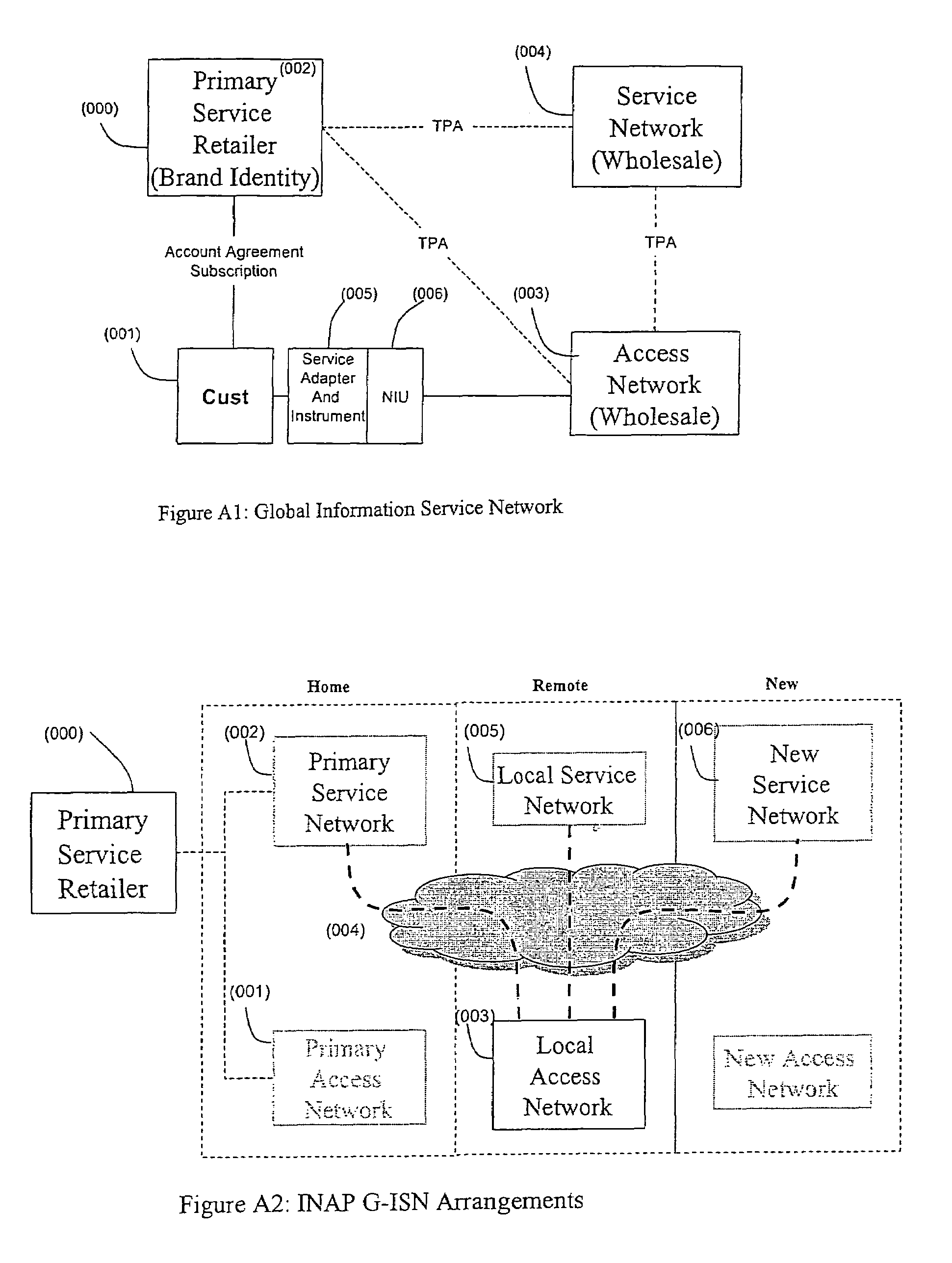
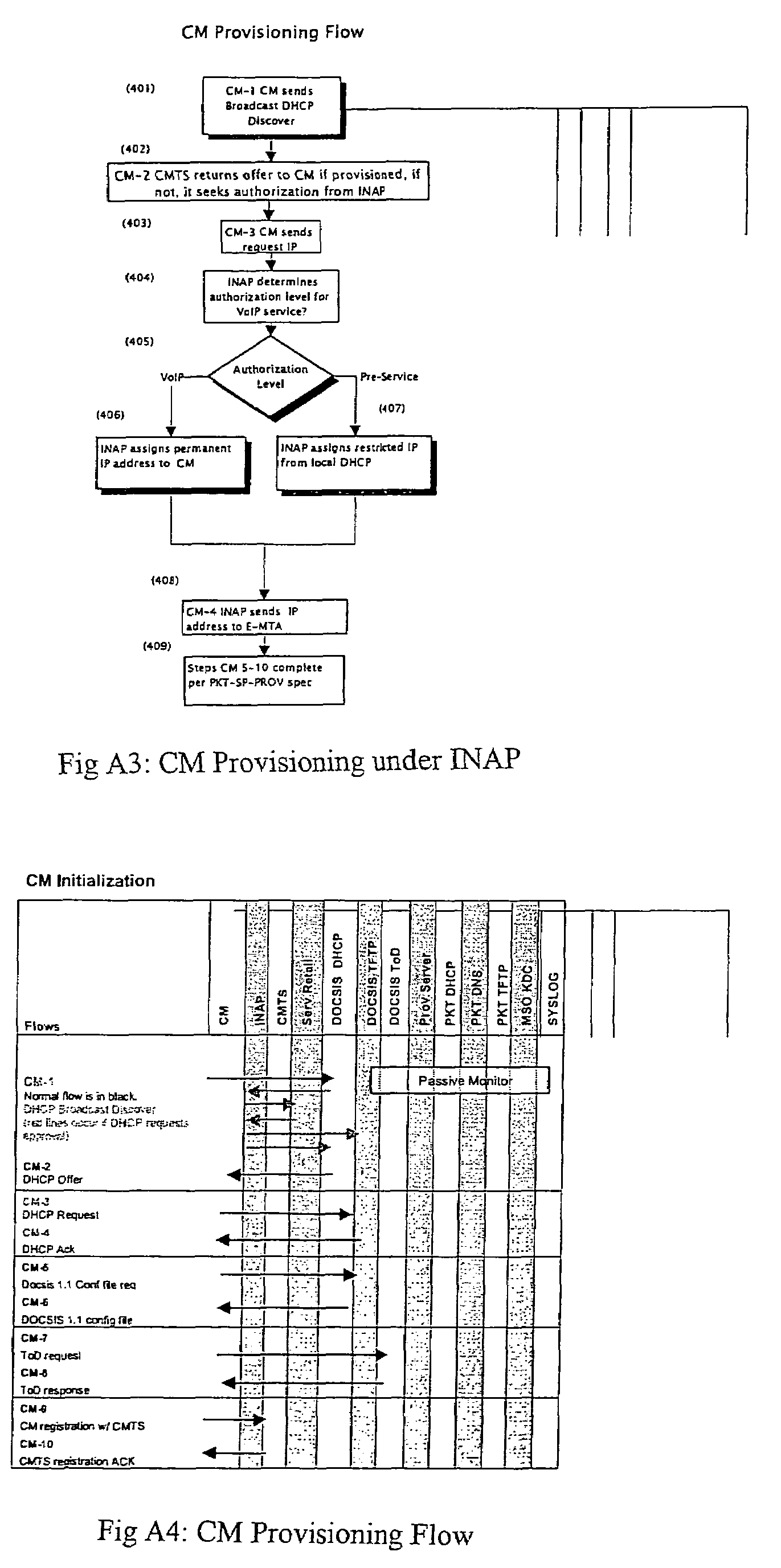
An open Information Services network architecture is disclosed which enables multiple business entities to assume specialized roles of access provider, service provider, and service retailer. The disclosed technology provides instant plug-and-play service, decouples access and service networks and provides seamless (single step) access enabling customers to maintain a service account regardless of location. The benefits of the disclosed technology, among others, include: Multi-level and multi-service registration; Broker Services providing customers with a choice of provider; Security Services relating to distribution; Revenue Assurance services, Gentle Reminder / Gentle Touch; Revenue Assurance services pertaining to usage integrity verification upon registration; mobile services derived from G-ISN; and claim benefits pertaining to LNP services derived from G-ISN.
Owner:AI-CORE TECH LLC +1
Network access system including a programmable access device having distributed service control
InactiveUS20050117576A1Good extensibilityIncrease flexibilityData switching by path configurationPacket communicationService control
A distributed network access system in accordance with the present invention includes at least an external processor and a programmable access device. The programmable access device has a message interface coupled to the external processor and first and second network interfaces through which packets are communicated with a network The programmable access device includes a packet header filter and a forwarding table that is utilized to route packets communication between the first and second network interfaces. In response to receipt of a series of packets, the packet header filter in the programmable access device identifies messages in the series of messages upon which policy-based services are to be implemented and passes identified messages via the message interface to the external processor for processing. In response to receipt of a message, the external processor invokes service control on the message and may also invoke policy control on the message.
Owner:VERIZON PATENT & LICENSING INC
Method and apparatus for generating a network topology representation based on inspection of application messages at a network device
ActiveUS7996556B2Multiple digital computer combinationsProgram controlRelevant informationContext based
A method is disclosed for generating a network topology representation based on inspection of application messages at a network device. According to one aspect, a network device receives a request packet, routes the packet to the destination, and extracts and stores correlation information from a copy of the request packet. When the network device receives a response packet, it examines the contents of a copy of the response packet using context-based correlation rules and matches the response packet with the appropriate stored request packet correlation information. It analyzes recorded correlation information to determine application-to-application mapping and calculate application response times. Another embodiment inserts custom headers that contain information used to match a response packet with a request packet into request packets.
Owner:CISCO TECH INC
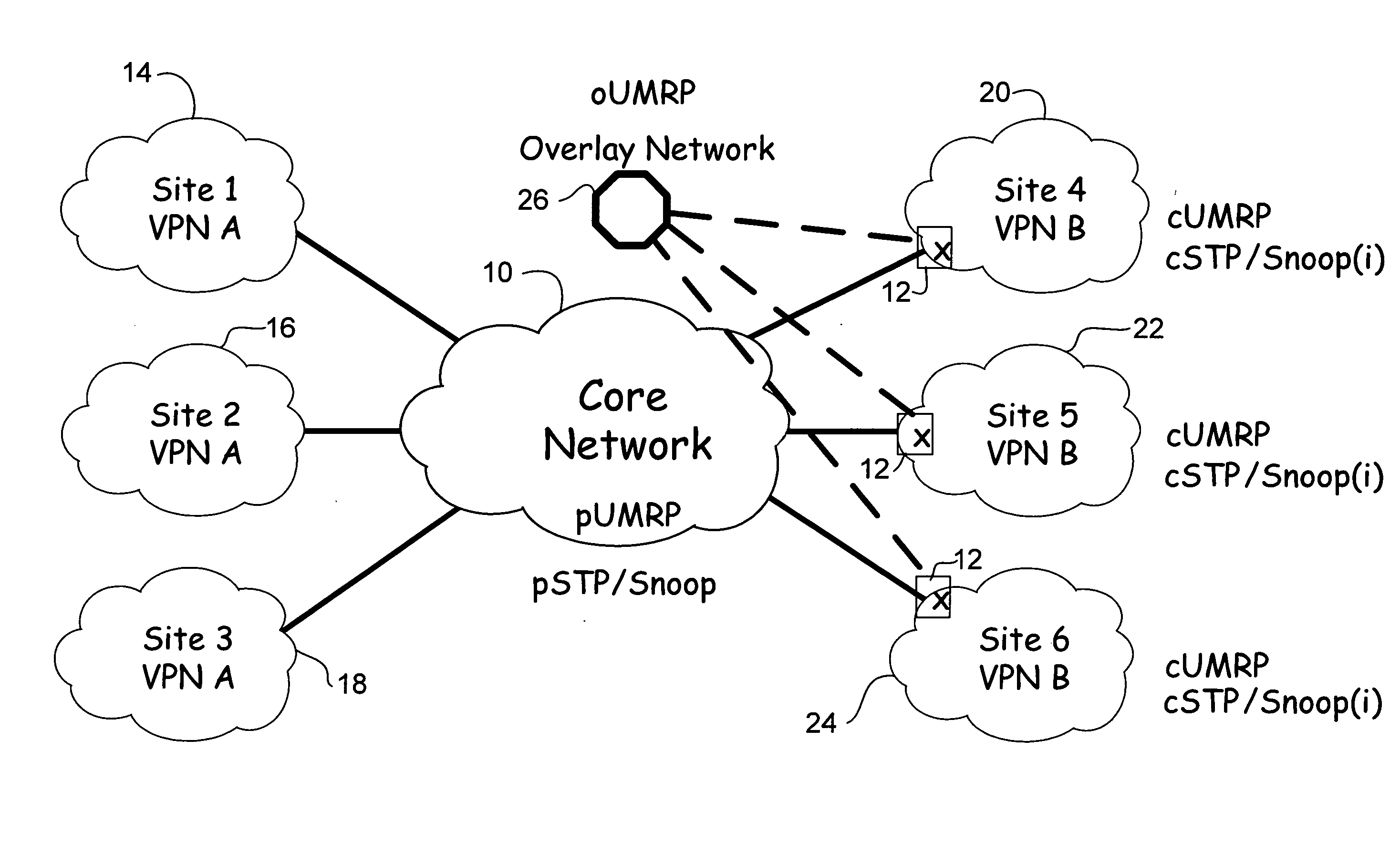
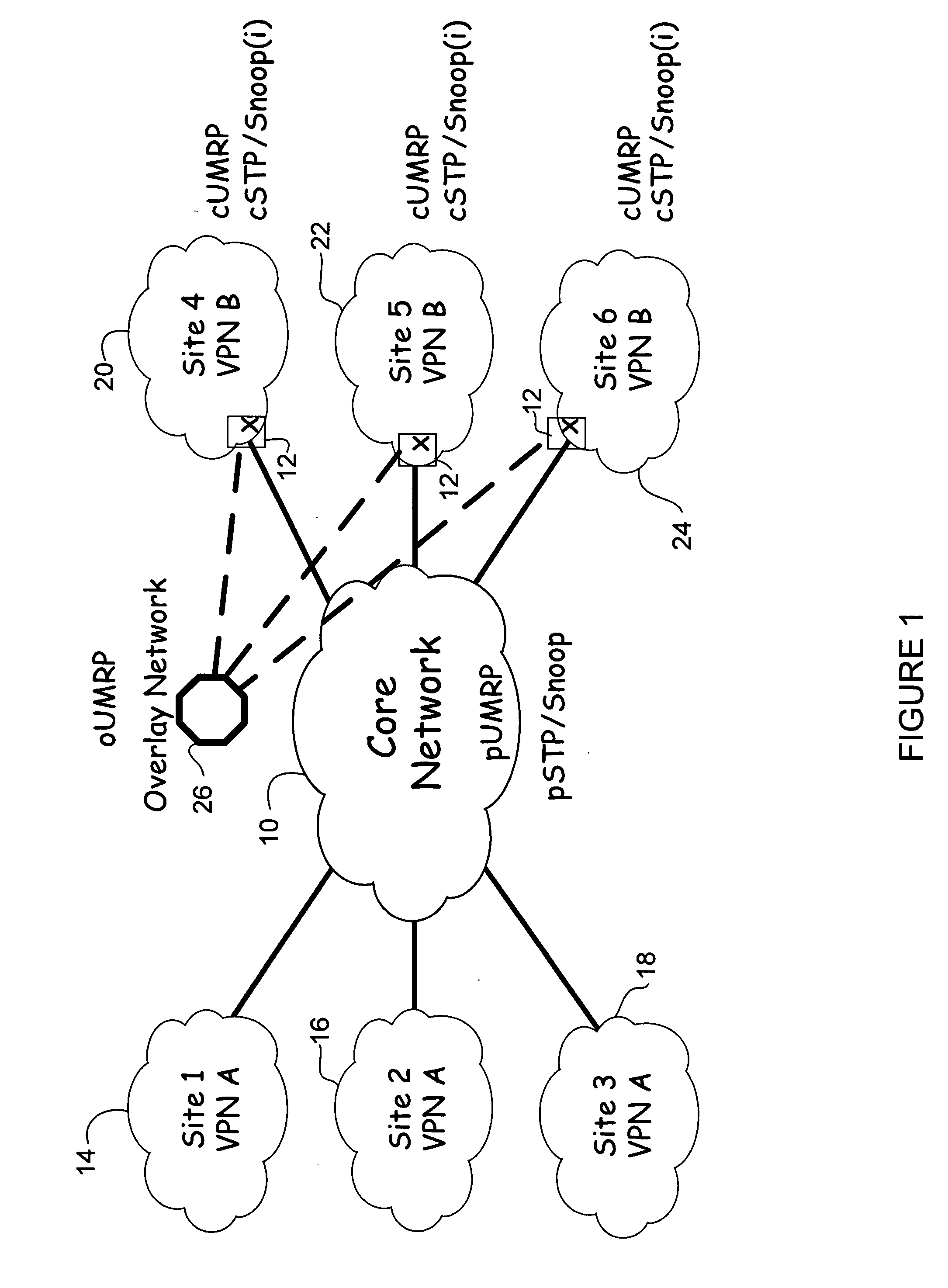
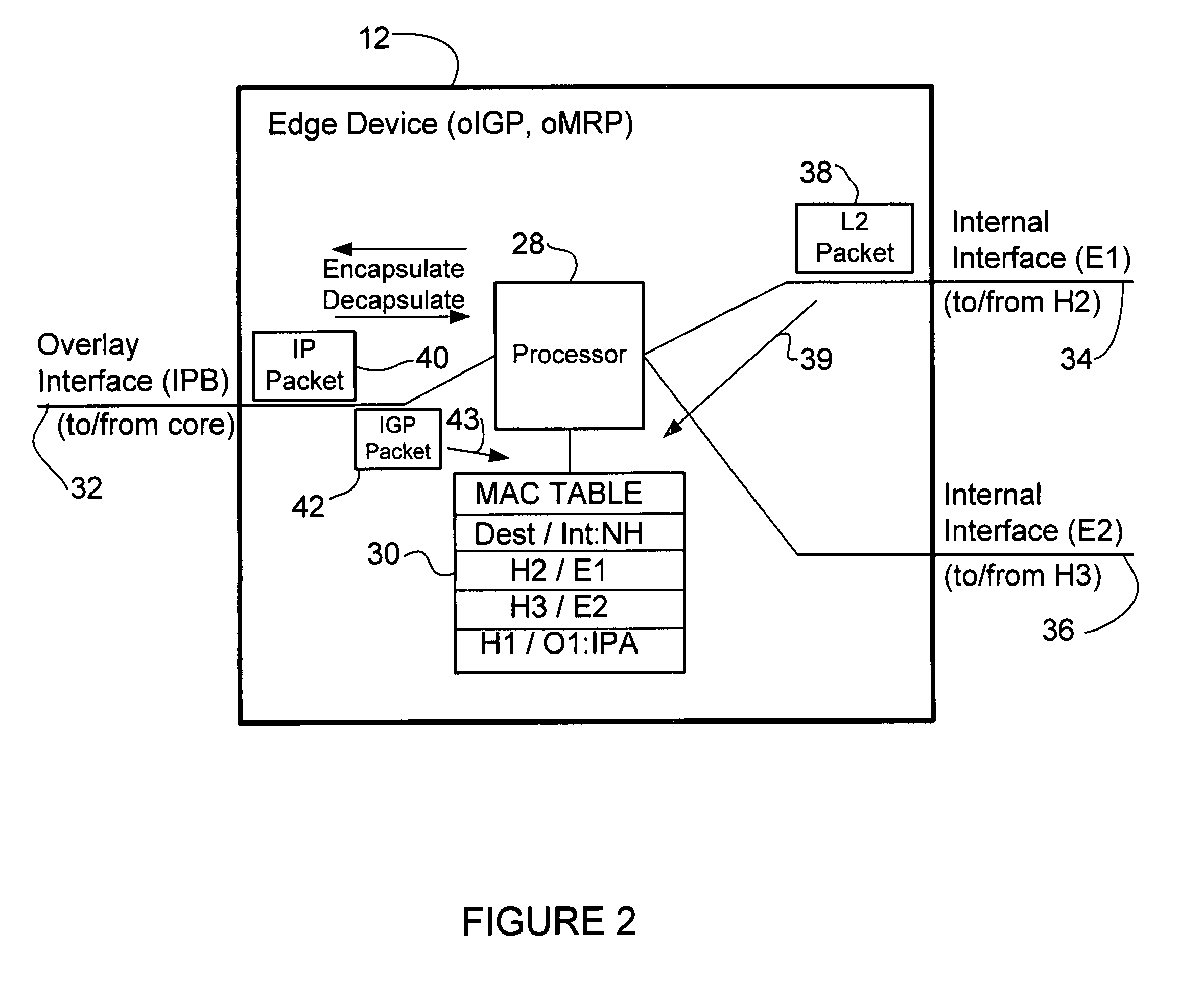
Overlay transport virtualization
ActiveUS20090037607A1Data switching by path configurationMultiple digital computer combinationsVirtualizationEdge device
In one embodiment, an apparatus includes one or more internal interfaces in communication with one or more network devices in a first network site through a Layer 2 link, an overlay interface in communication through a Layer 3 link with a core network connected to one or more other network sites, and a table mapping addresses for network devices in the other network sites to addresses of edge devices in the same network site as the network device. The apparatus further includes a processor operable to encapsulate a packet received at one of the internal interfaces and destined for one of the network devices in the other network sites, with an IP header including a destination address of the edge device mapped to the destination network device, and forward the encapsulated packet to the core network.
Owner:CISCO TECH INC
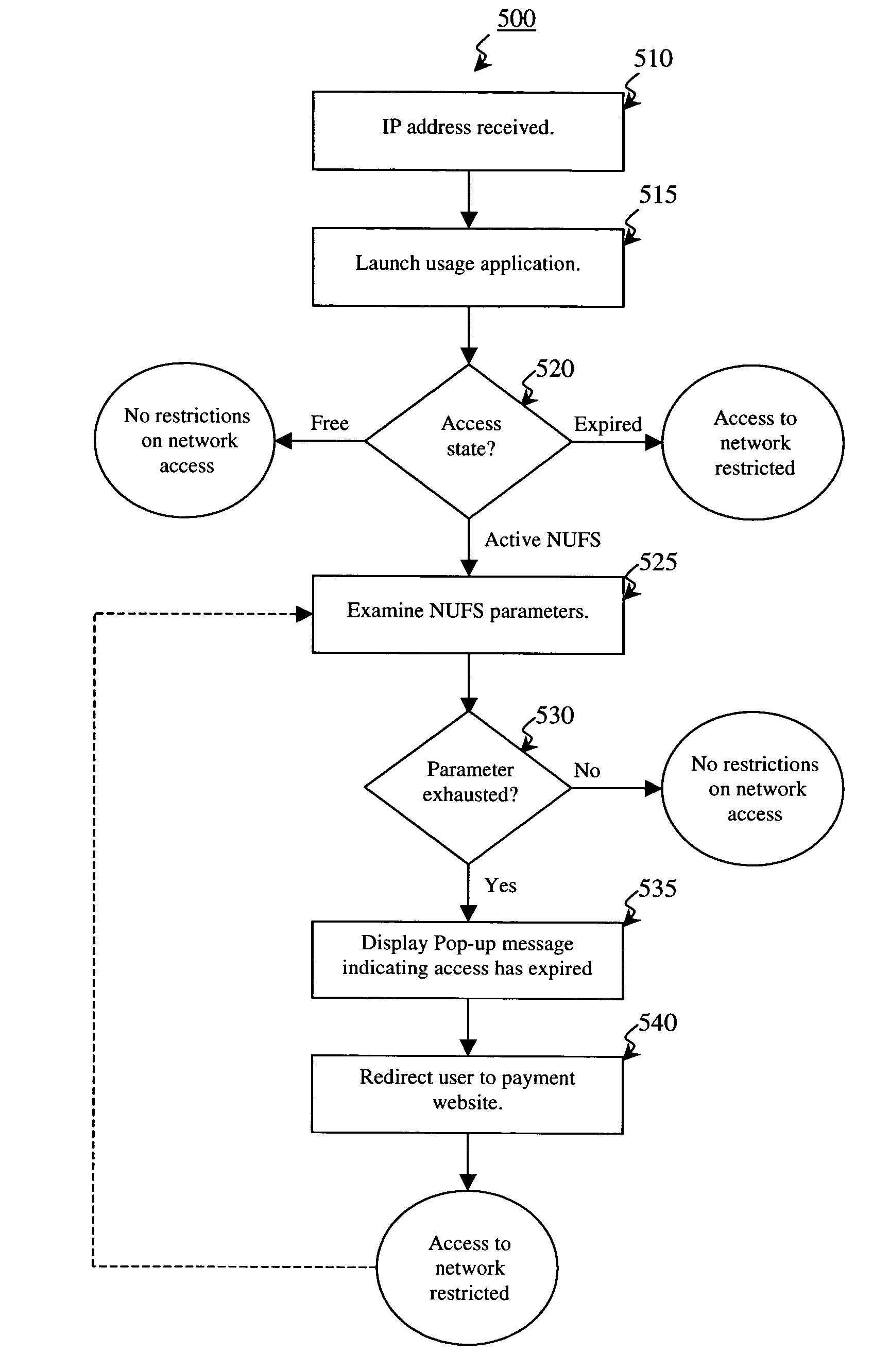
Self-managed network access using localized access management
ActiveUS7574731B2Provide usageAvoid modificationRandom number generatorsUser identity/authority verificationProgram planningBack end server
The invention provides a method and system for locally tracking network usage and enforcing usage plans at a client device. In an embodiment of the invention, a unique physical key, or token, is installed at a client device of one or more networks. The key comprises a usage application and one or more access parameters designated the conditions and / or limits of a particular network usage plan. Upon initial connection to the network, the usage application grants or denies access to the network based on an analysis of the current values of the access parameters. Therefore, network usage tracking and enforcement is made simple and automatic without requiring any back-end servers on the network while still providing ultimate flexibility in changing billing plans for any number of users at any time.
Owner:KOOLSPAN
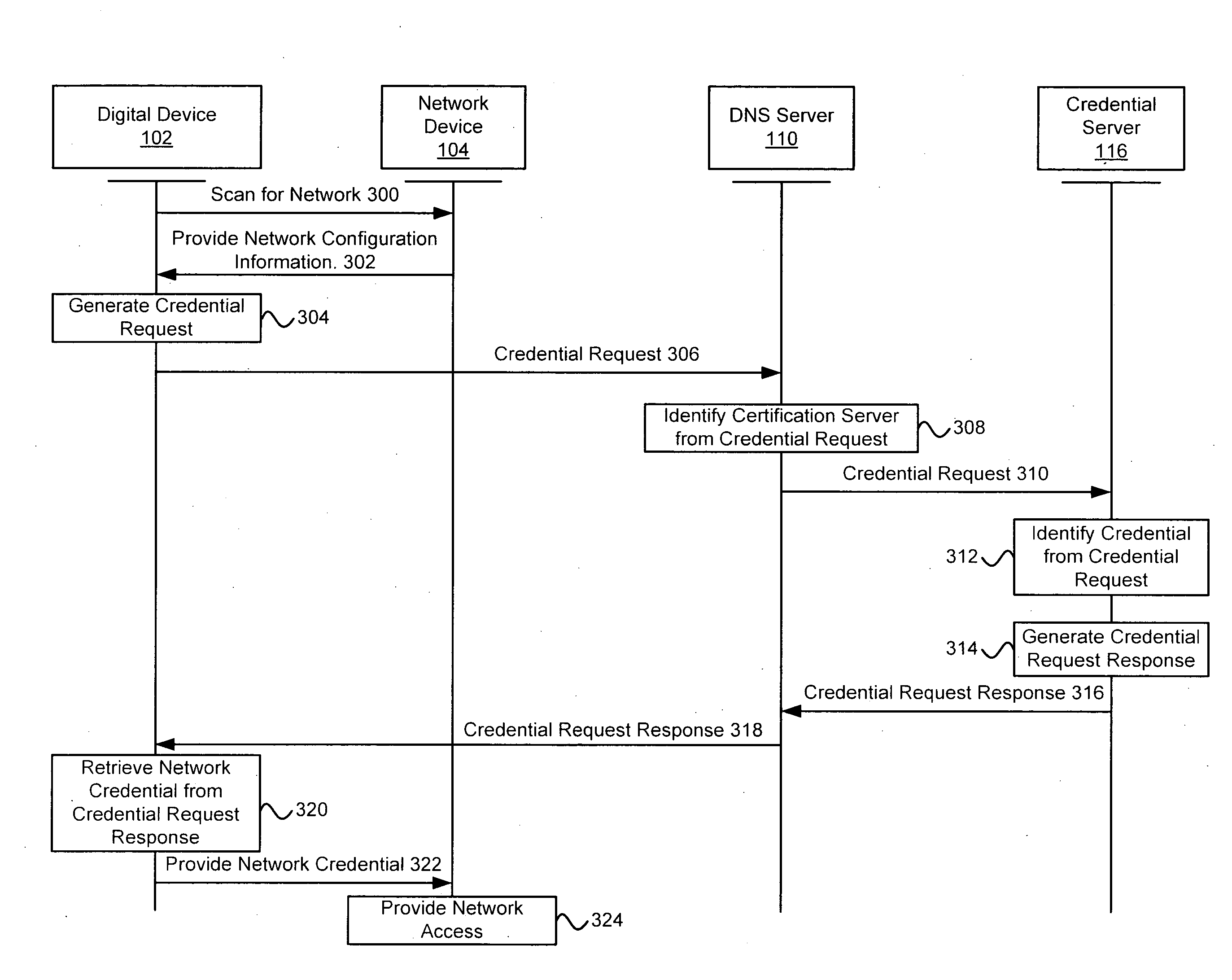
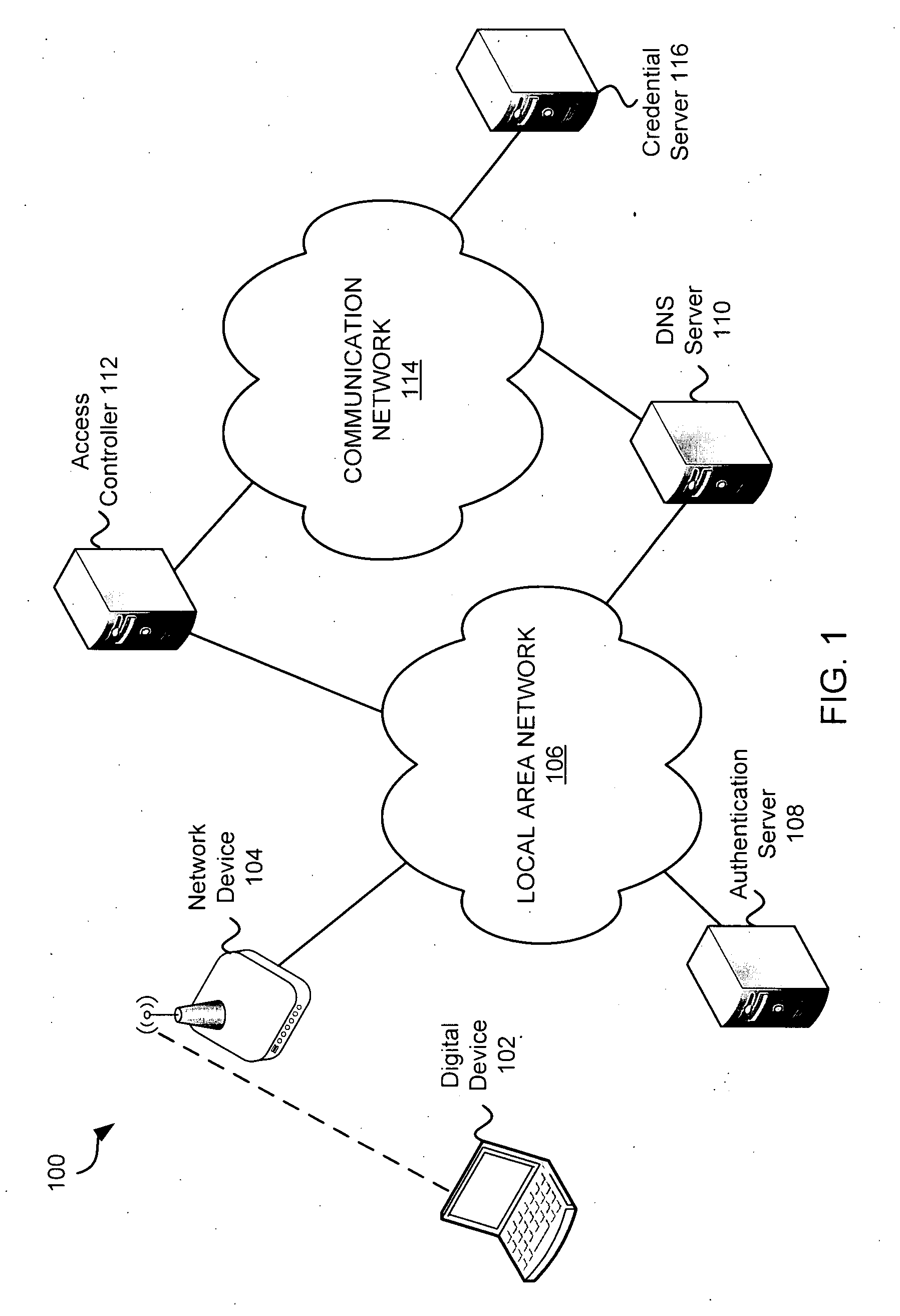
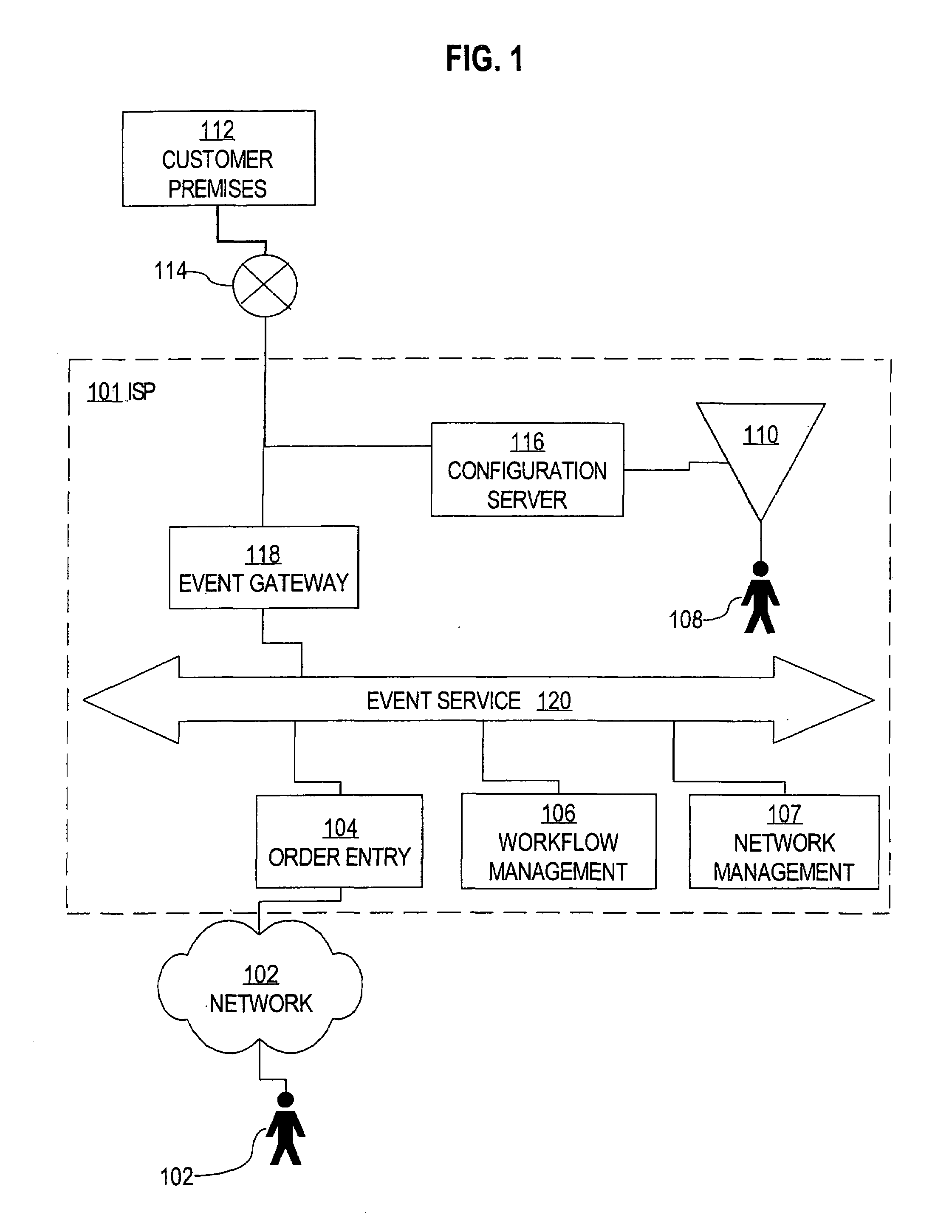
Systems and methods for acquiring network credentials
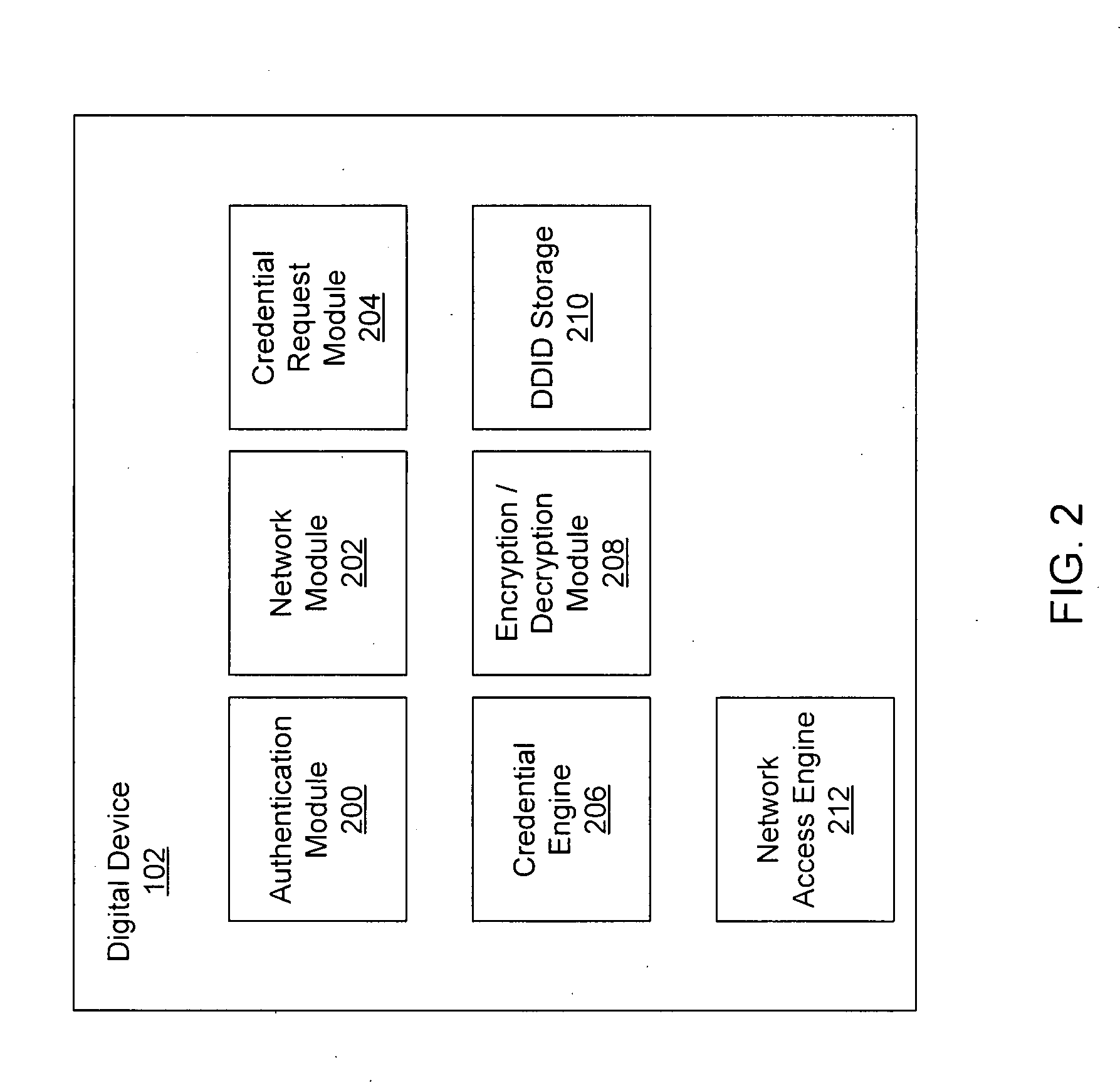
ActiveUS20080060066A1Digital data processing detailsAnalogue secracy/subscription systemsRequest–responseNetwork Access Device
Exemplary methods and systems for acquiring network credentials for network access are described. The exemplary method comprises receiving network configuration information from a network device on a communication network, generating a credential request, transmitting the credential request to a credential server over a standard protocol of the network device, receiving the credential request response, and providing a network credential from the credential request response to the network device to access the communication network.
Owner:CHANNEL IP BV
Fast flexible filter processor based architecture for a network device
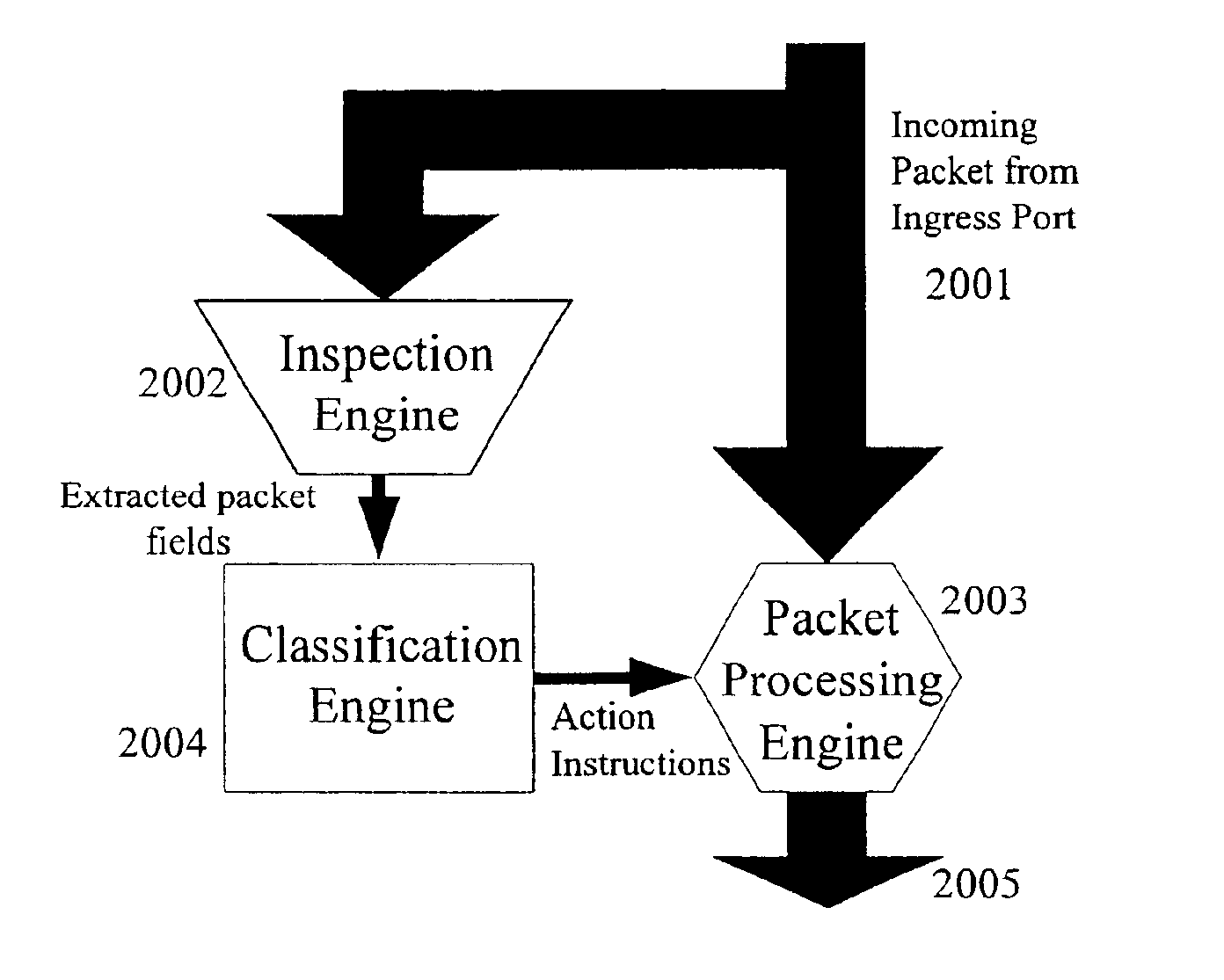
InactiveUS6876653B2Multiple digital computer combinationsStar/tree networksNetwork packetNetwork Access Device
A method of filtering data packets in a network device is disclosed. An incoming packet is received from a port and the incoming packet is inspected and packet fields are extracted. The incoming packet is classified based on the extracted packet fields and action instructions are generated. The incoming packet is then modified based on the action instructions. Further, the inspection and extraction includes applying inspection mask windows to any portion of the incoming packet to extract programmable packet fields.
Owner:AVAGO TECH INT SALES PTE LTD
Cable network repair control system
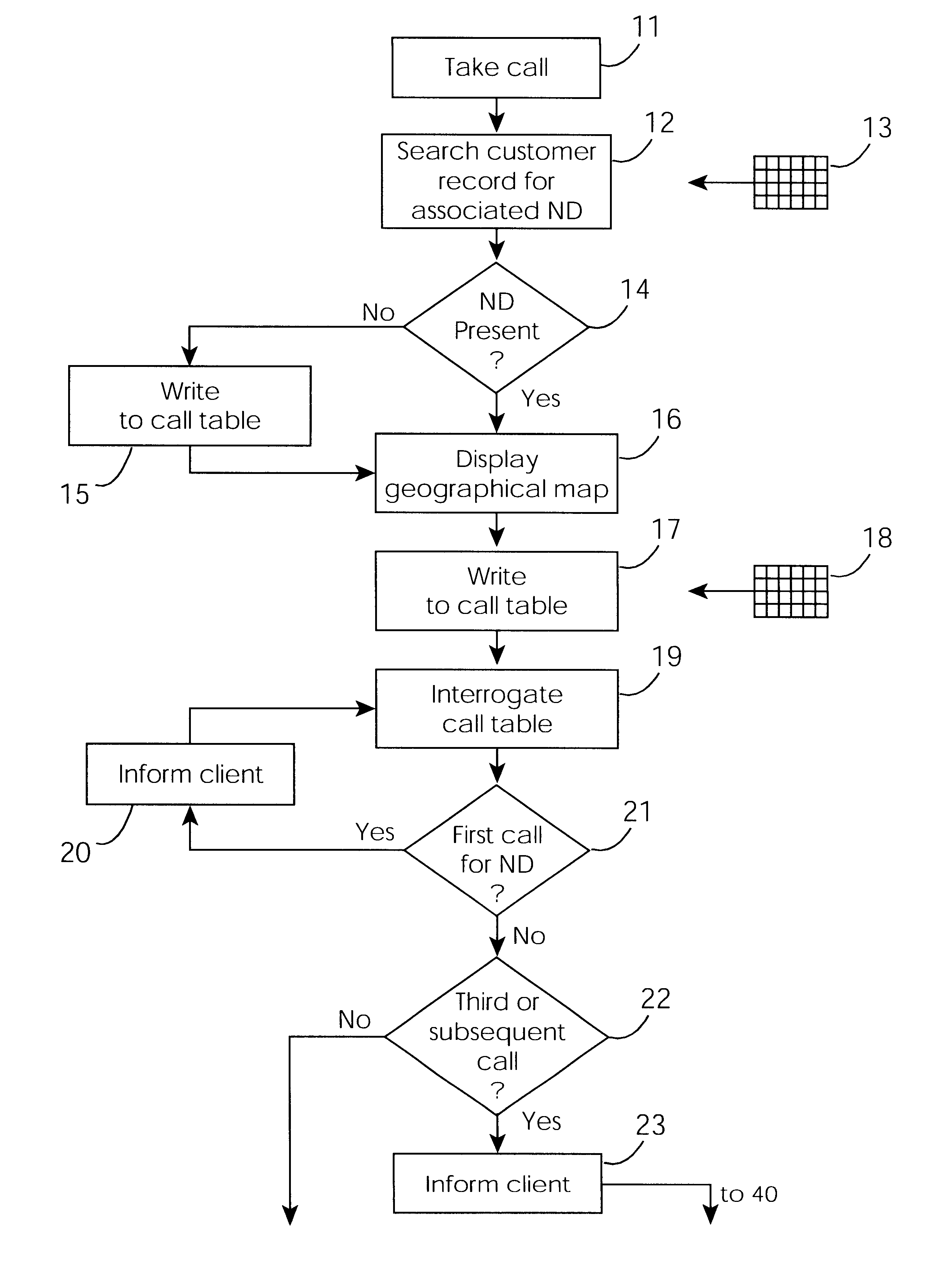
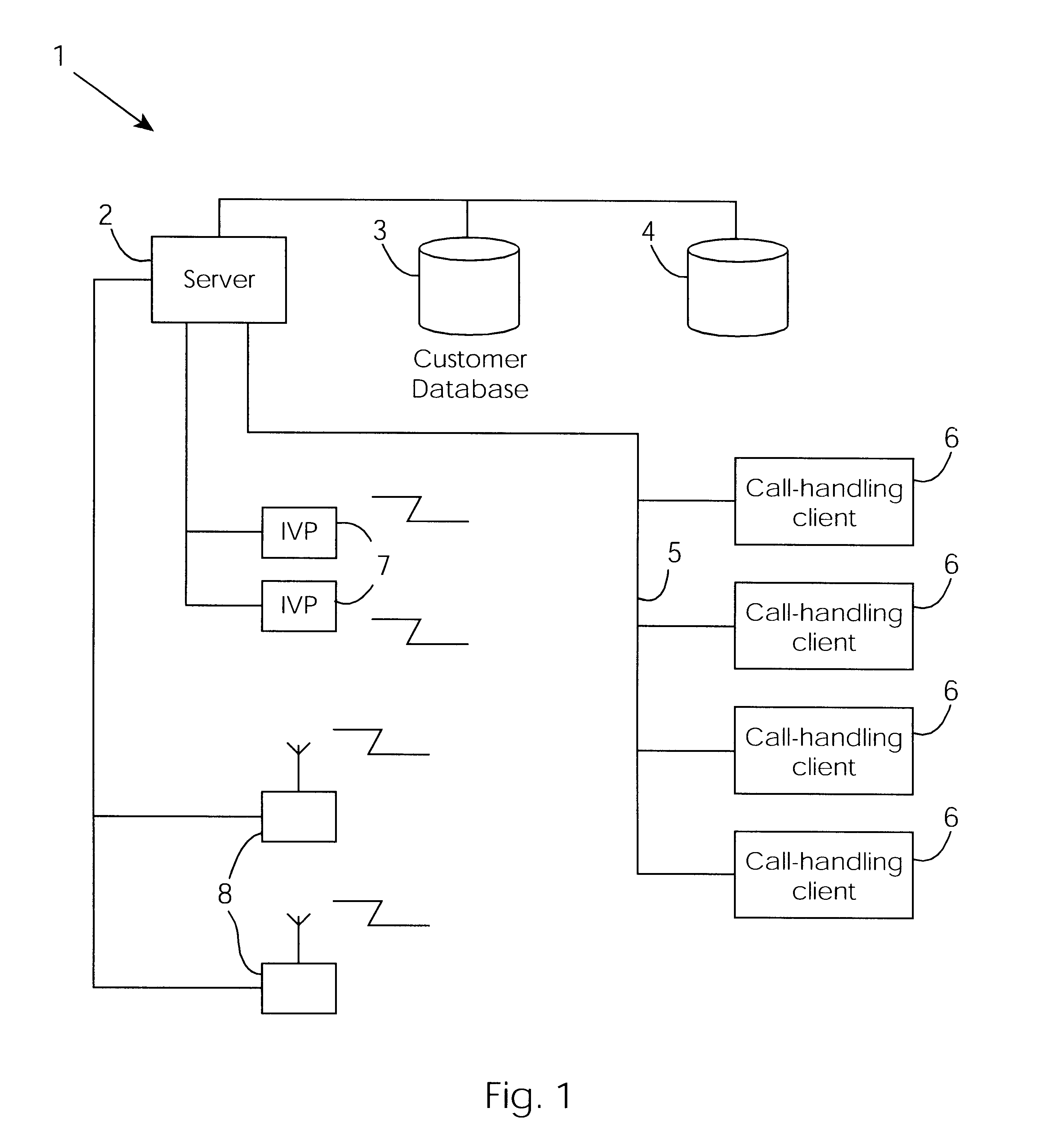
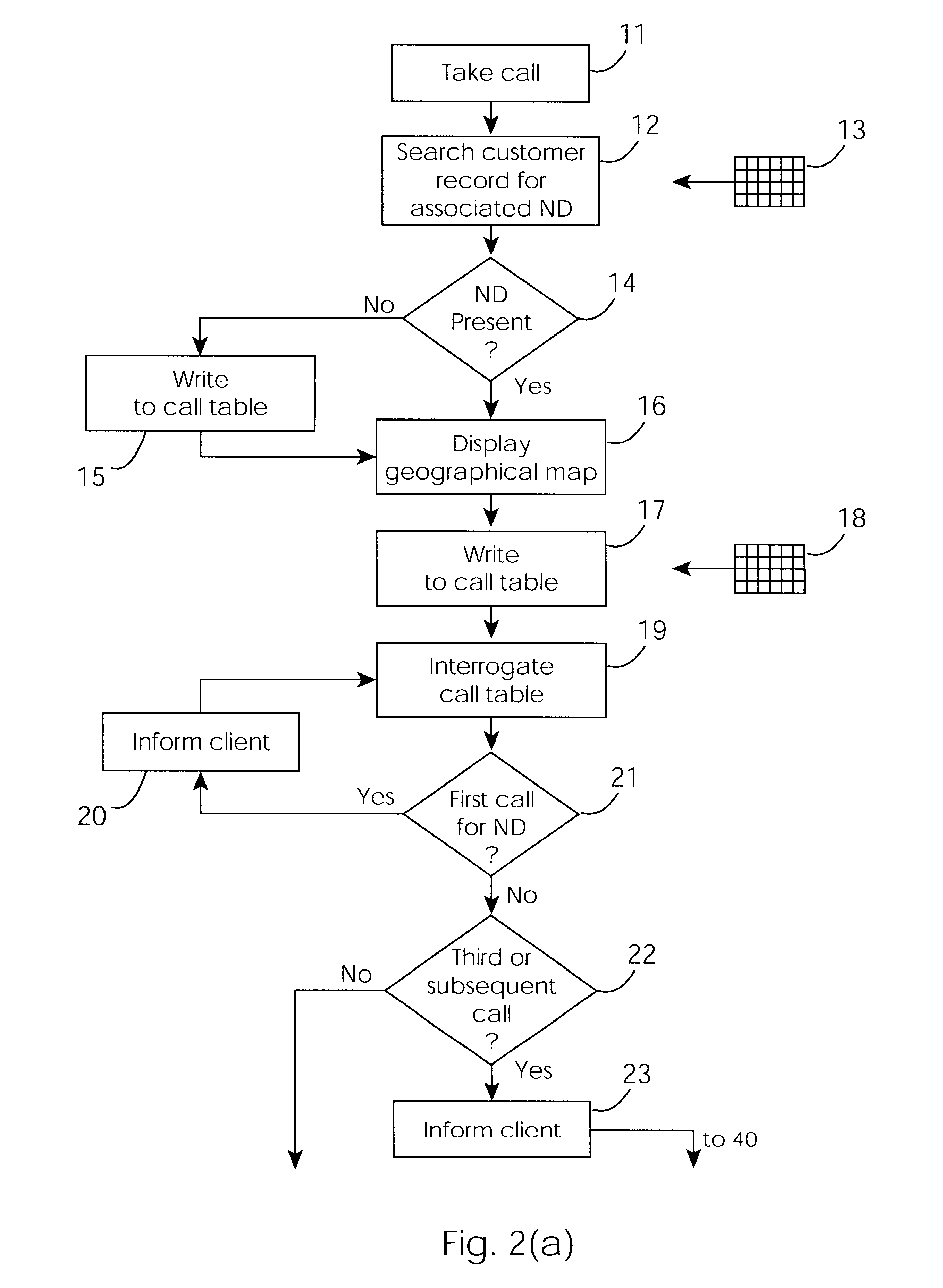
InactiveUS6671824B1Shorten the timeSupervisory/monitoring/testing arrangementsSubstation equipmentControl systemEngineering
A cable network repair control system including a server communicating with multiple call-handling clients in a trouble call center. The databases are used to automatically determine an associated network device for the customer who makes a trouble call. When a second call is received for a particular network device, an inferencing engine automatically operates to identify potential repairs crews and to control communication with them to ensure that optimum use of the repair crew time and quick repair. Various tables are generated dynamically and are used to update management status tables for reviewing of network repair status.
Owner:LAKEFIELD ETECH GROUP
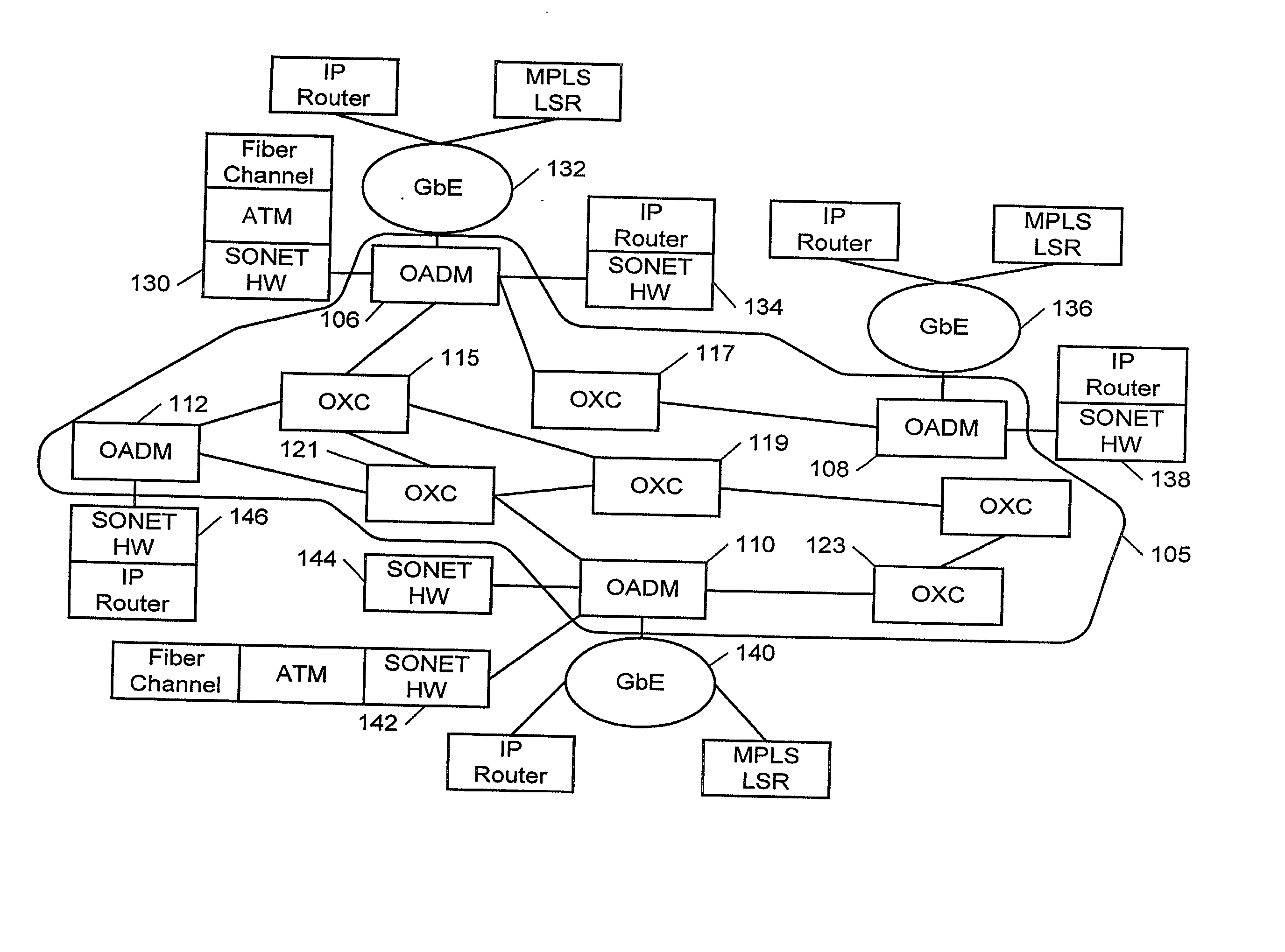
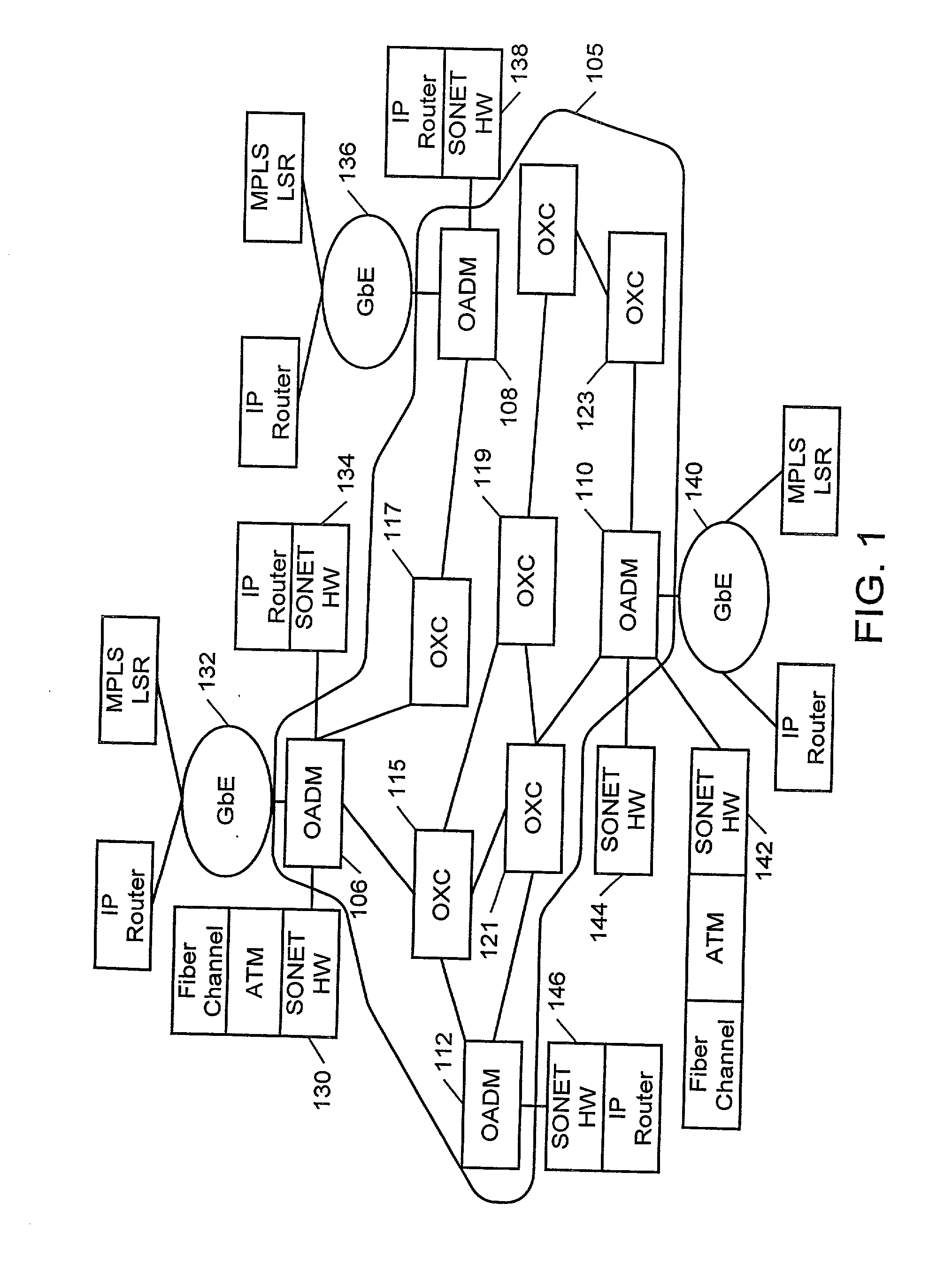
Protection switching for an optical network, and methods and apparatus therefor
InactiveUS20020176131A1Multiplex system selection arrangementsLaser detailsTraffic capacityLine card
An optical communications network having at least one optical switch connected to a network access device. The optical switch includes a first line card disposed along a first communications path over which a first optical signal is transmitted. The first line card is connected to the network access device. A second line card is disposed along a second communications path over which a second optical signal is transmitted. An inter-card communication channel is provided for bridging the second path to the first line card. The system enables the rapid switching of traffic from the first optical path to the second optical path.
Owner:FIRSTWAVE SECURE INTELLIGENT OPTICAL NETWORKS
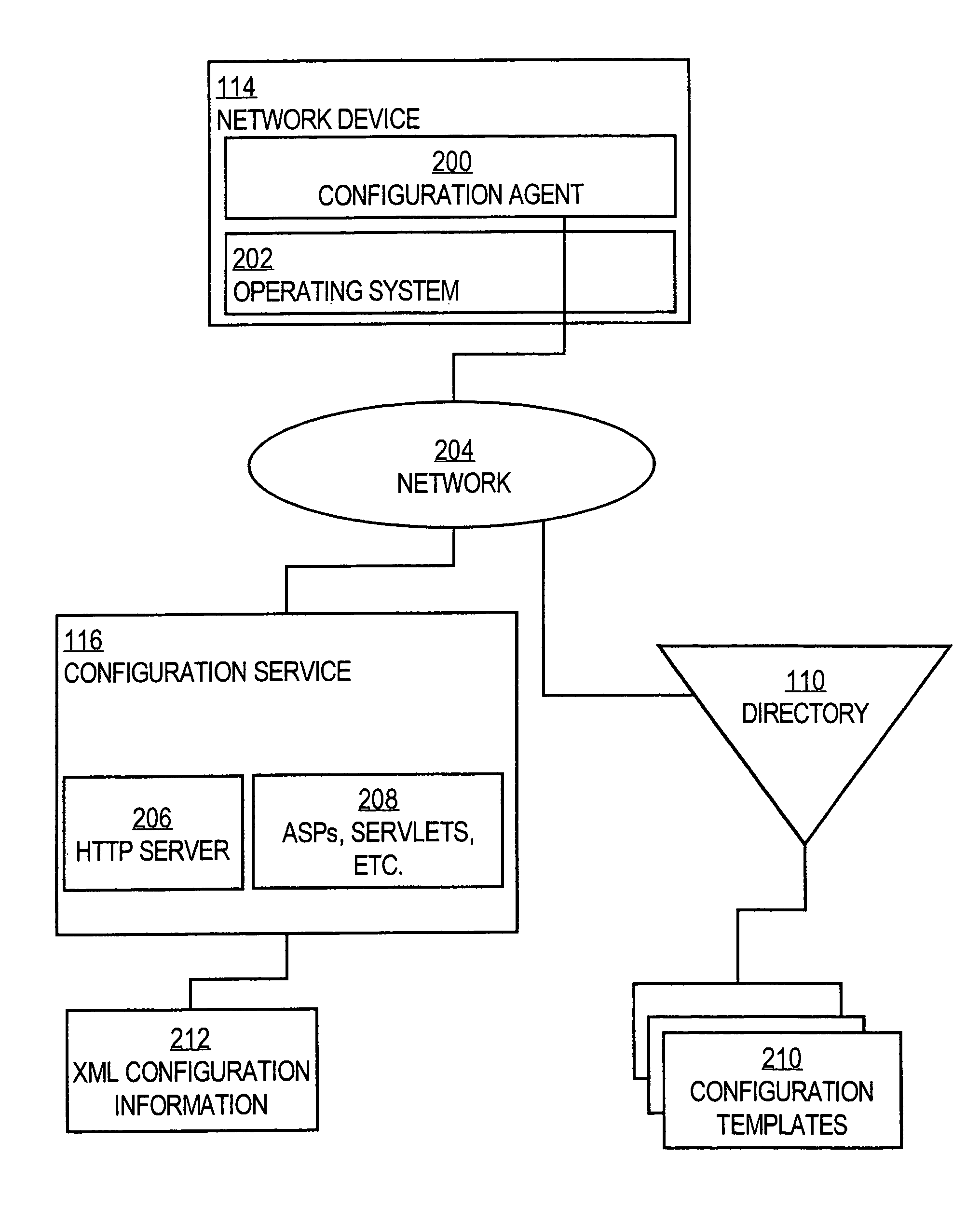
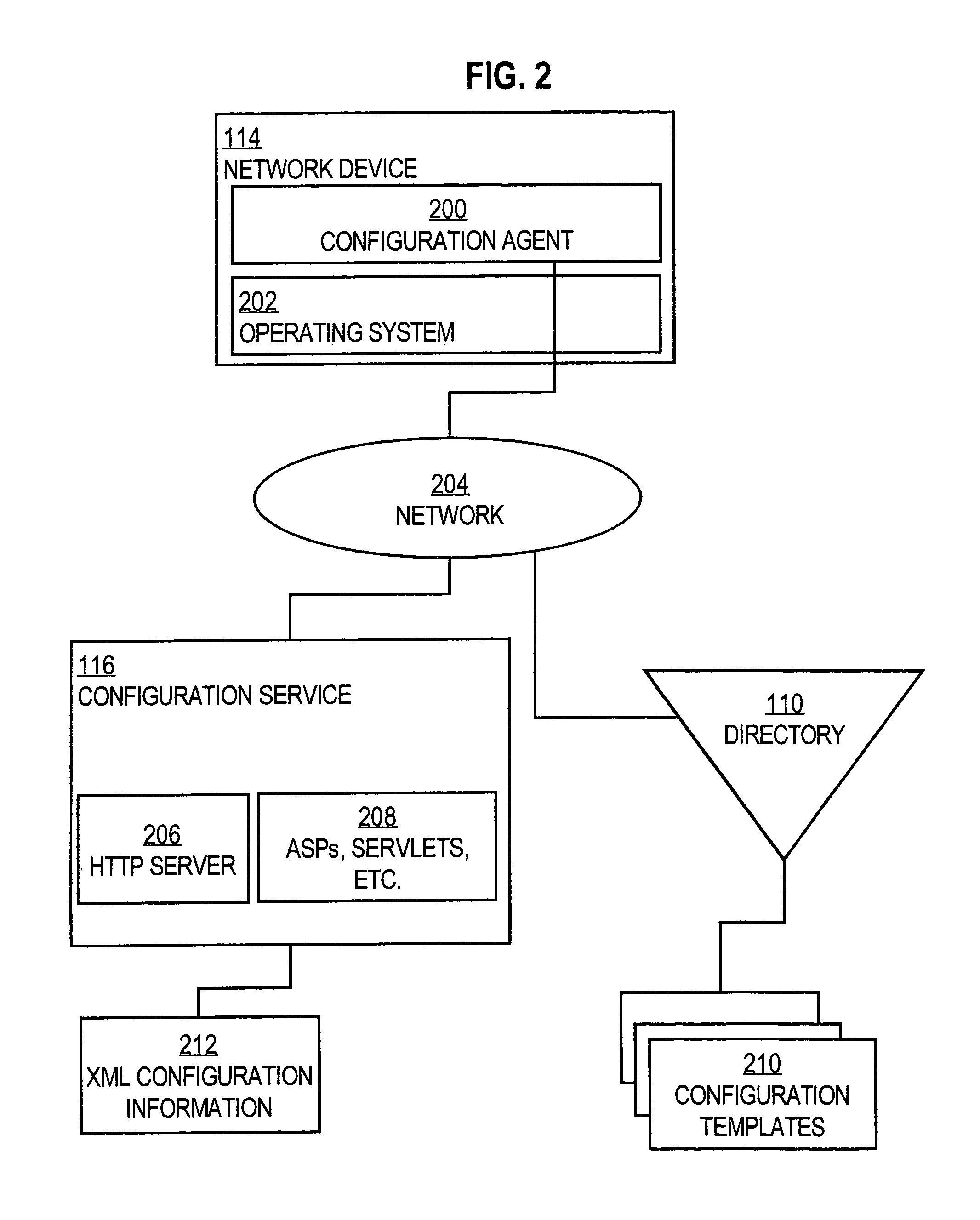
Method and apparatus for provisioning network devices using instructions in extensible markup language
InactiveUS7054924B1Reliable transportationMultiple digital computer combinationsTransmissionReliable transmissionExtensible markup
A method is disclosed for carrying out network device provisioning and configuration, and communication of other information to a network device, automatically and in an assured manner. A configuration service receives a request from a network device to provide configuration information. The configuration service retrieves a template representing the configuration from a storage location, e.g., a directory service. The configuration service also retrieves one or more parameter values specific to the device. Device-specific values are instantiated for the generic parameters in the template, based on the retrieved values. The resulting configuration is stored in XML format using XML tags to delimit configuration commands, tested for well-formed-ness, and syntax checked. A reliable transport protocol carries the configuration information to the device. At the device, a configuration agent syntax checks the embedded configuration information, and then applies the configuration information to the device. As a result, automatic network provisioning may be accomplished remotely, without requiring a skilled technician to visit customer premises to carry out configuration. The process may be integrated with an event service to enable multiple devices to concurrently receive re-configuration without special synchronization logic.
Owner:CISCO TECH INC
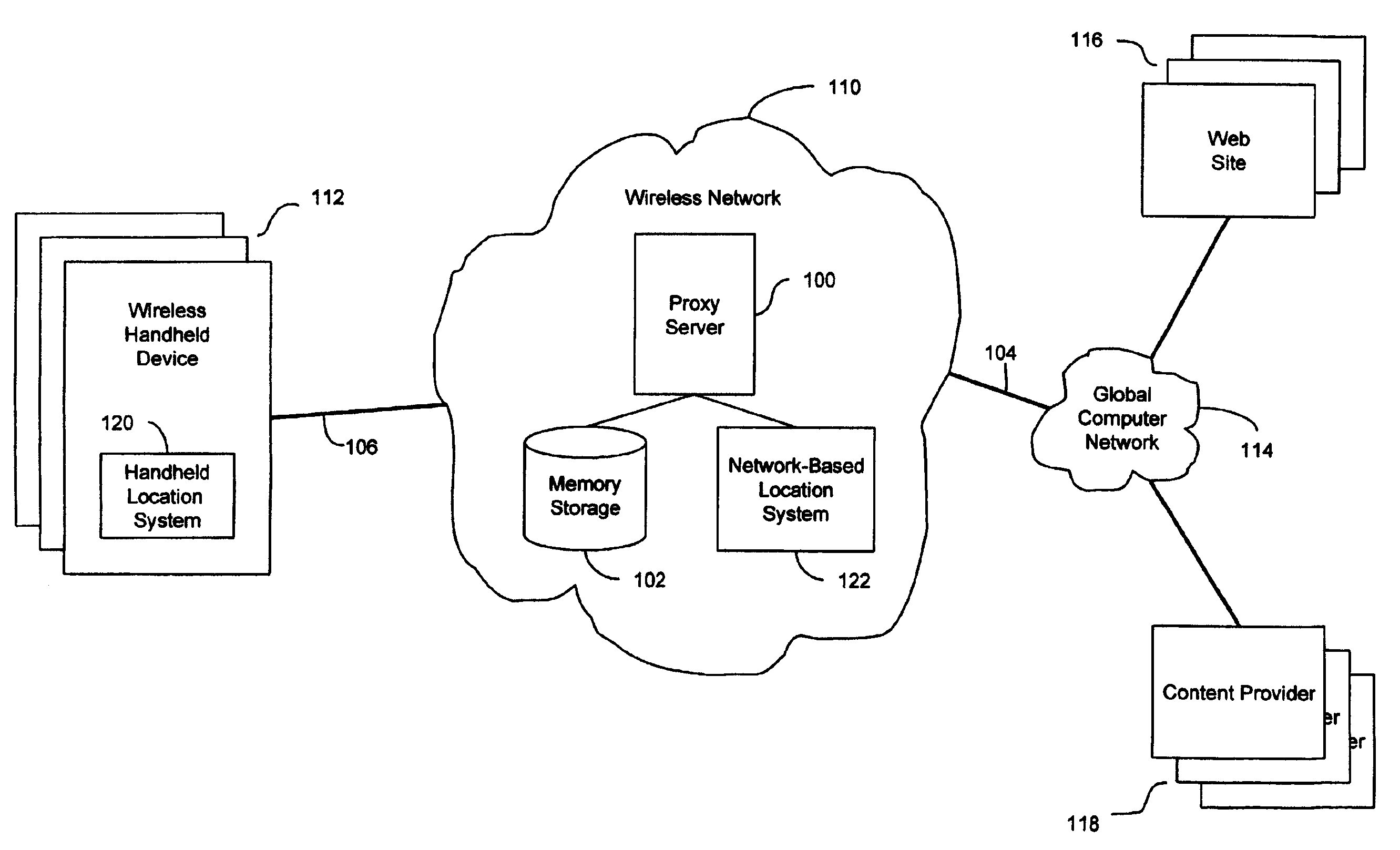
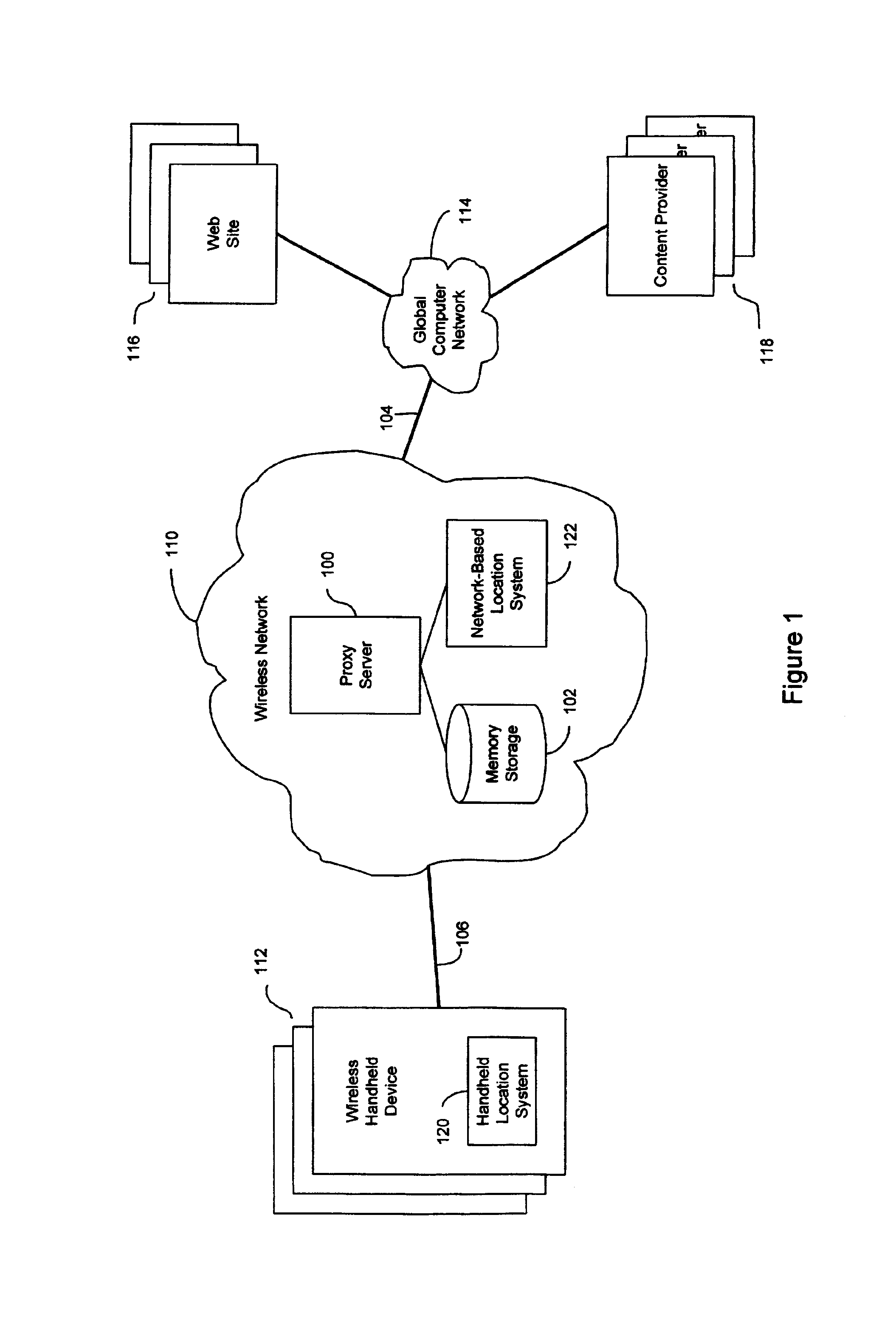
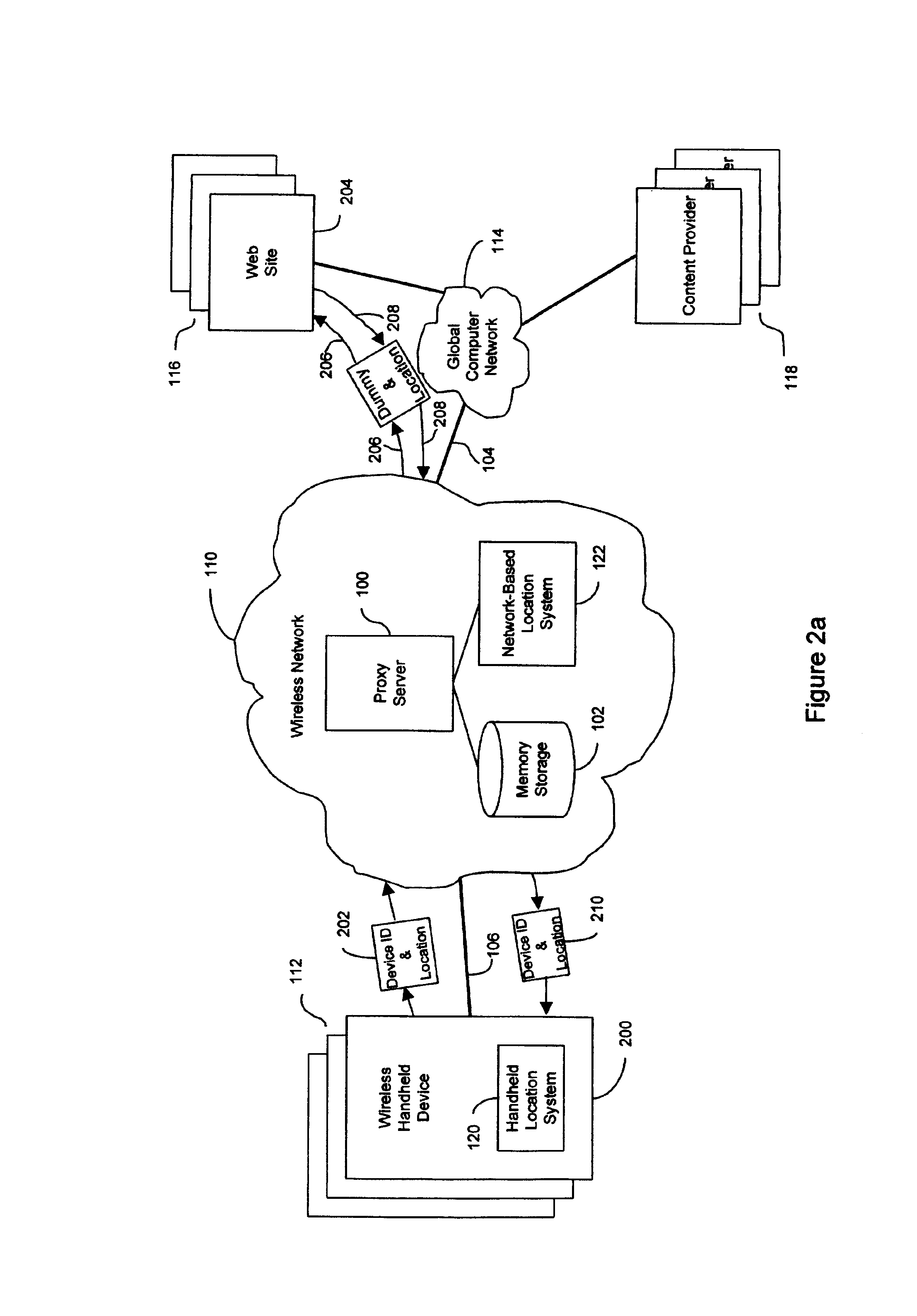
Anonymous location service for wireless networks
InactiveUS7069319B2Efficient content deliveryImprove identityDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving return messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identity information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
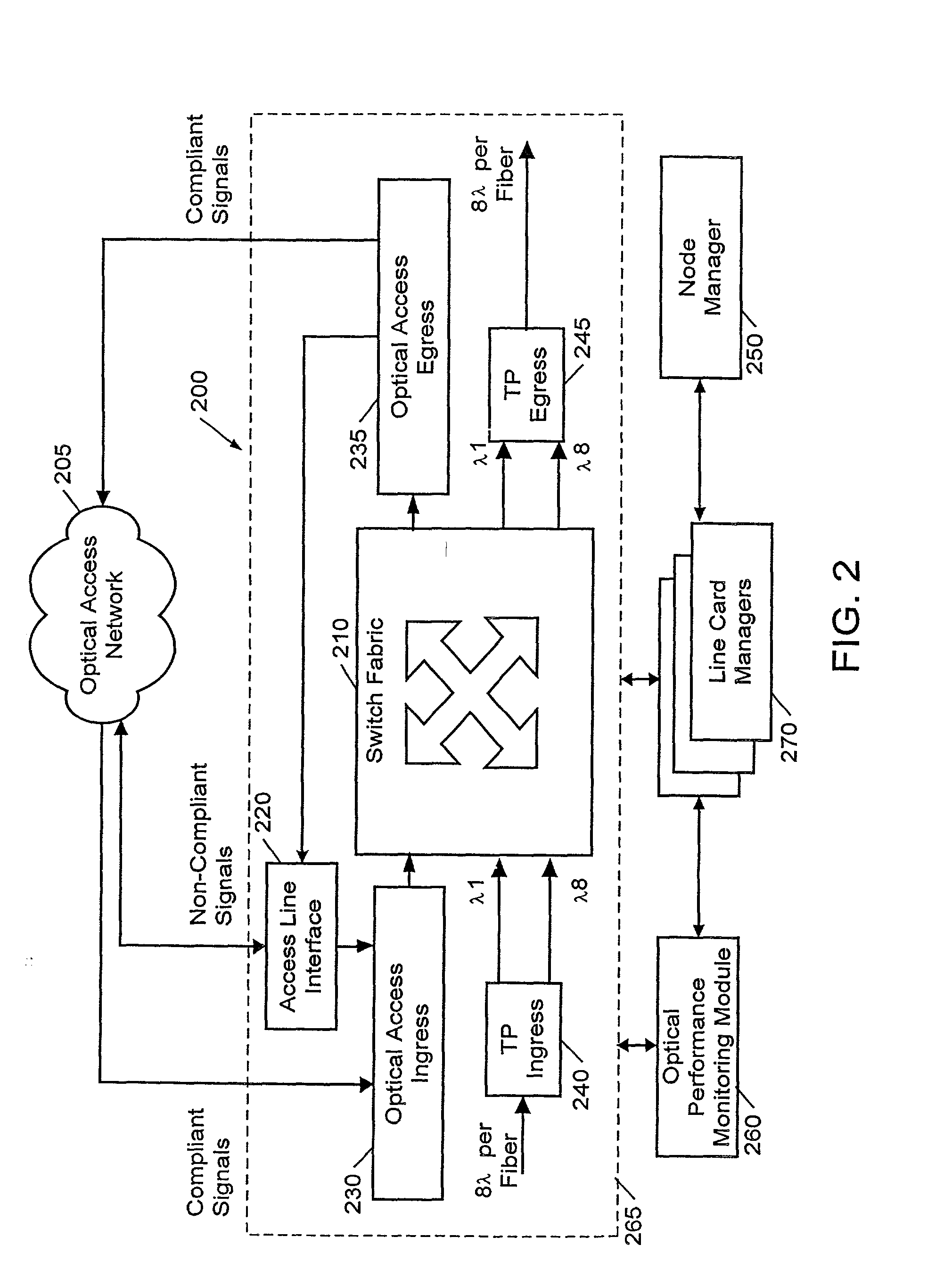
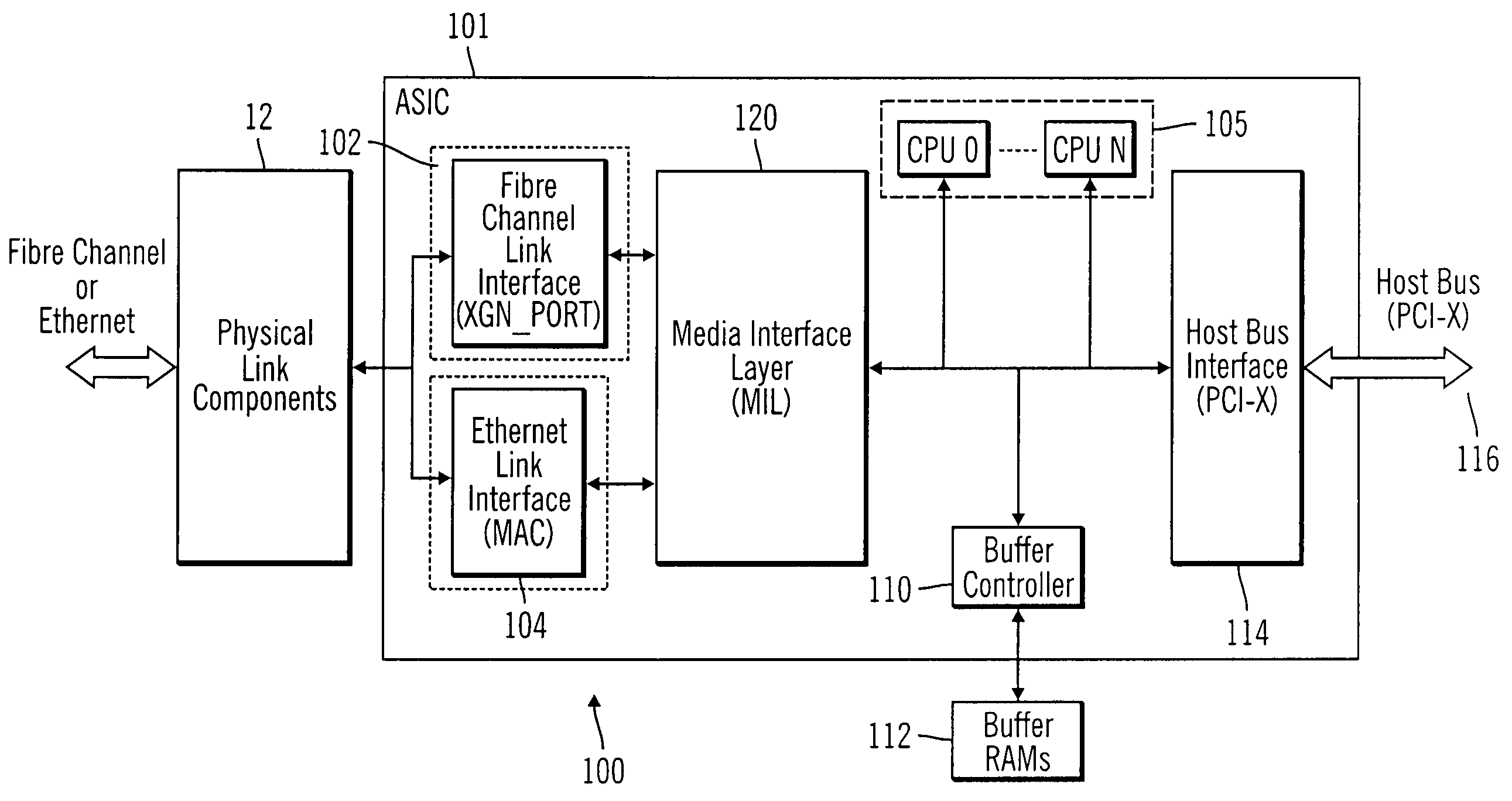
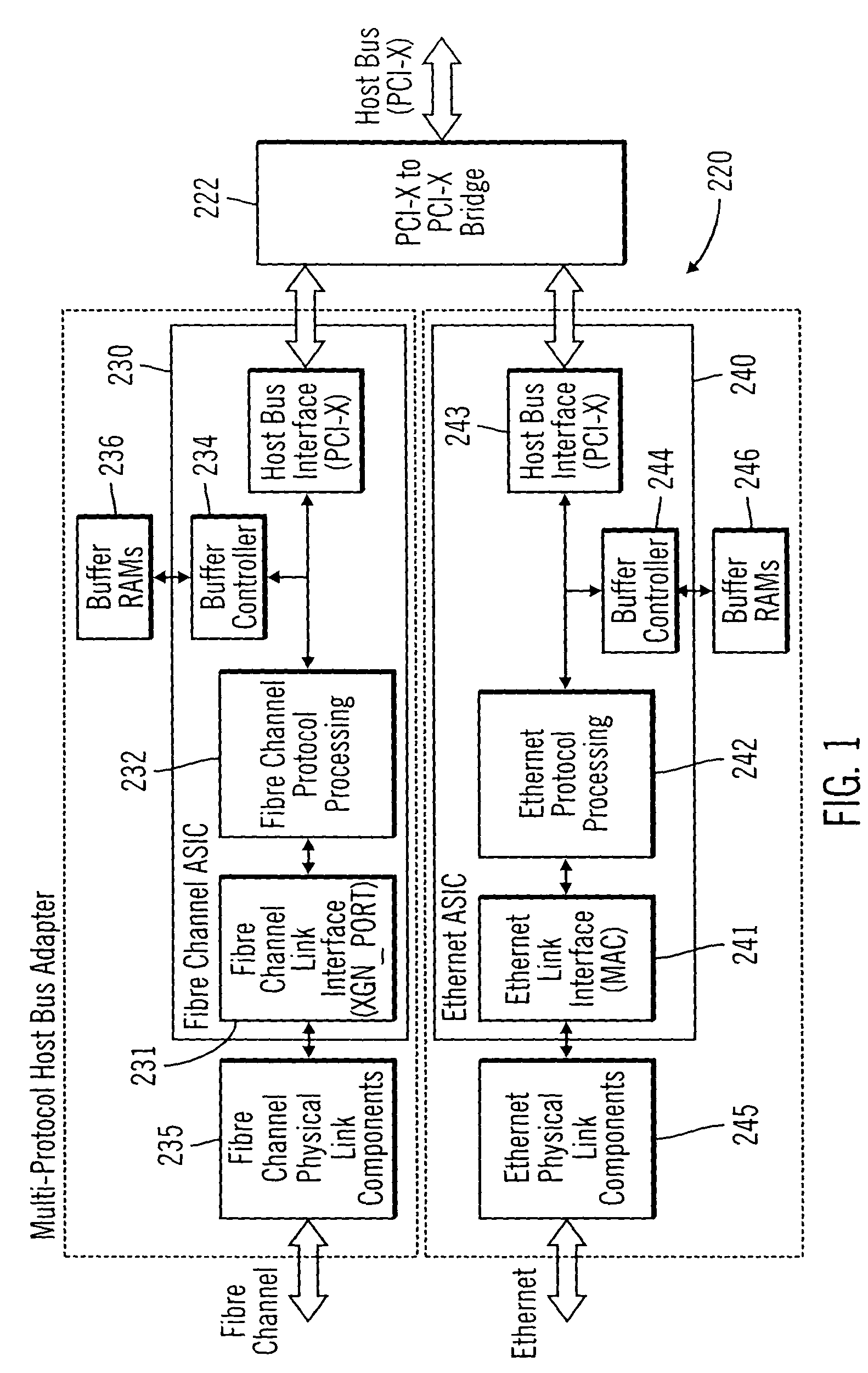
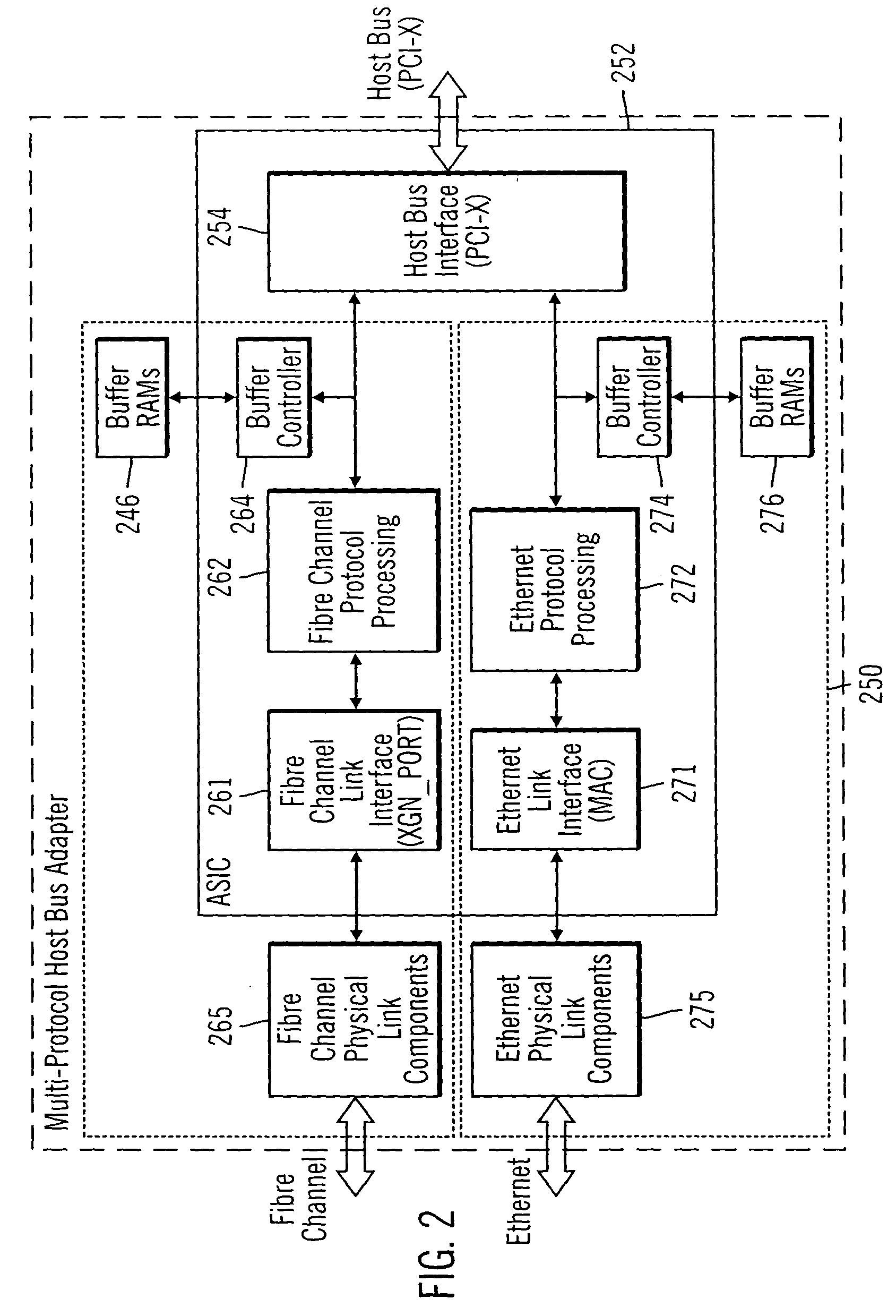
Integrated network interface supporting multiple data transfer protocols
InactiveUS20050066045A1Overcome limitationsTime-division multiplexMultiple digital computer combinationsData streamNetwork interface device
An integrated network interface device that supports data exchange in two or more high-speed network data transfer protocols that are based on different standards of network data transfer architectures, wherein an incoming data stream formatted in accordance with a particular network data transfer standard is processed into data not subject to the network data transfer standard to be output for further processing by a host. In one aspect, a network interface device is provided with a set of shared or common protocol independent physical link components that are used to identify the operating protocol of the incoming data, and a set of dynamically or statically re-configurable, shared or common protocol independent data transfer processing components that support data exchange via the physical link components for all the supported protocols, which may include a protocol specific link interface for each supported protocol.
Owner:WAVECREST LAB LLC +1
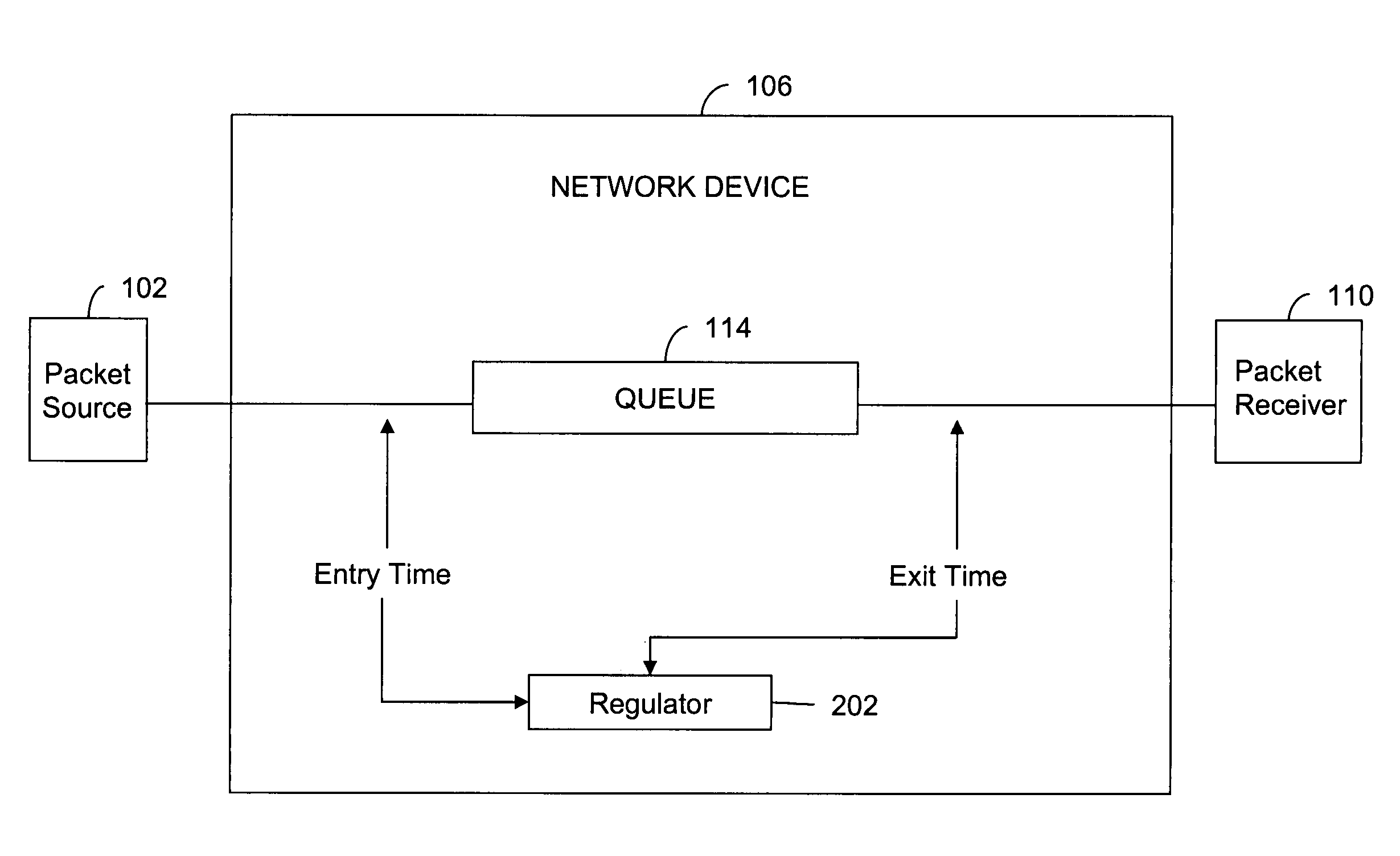
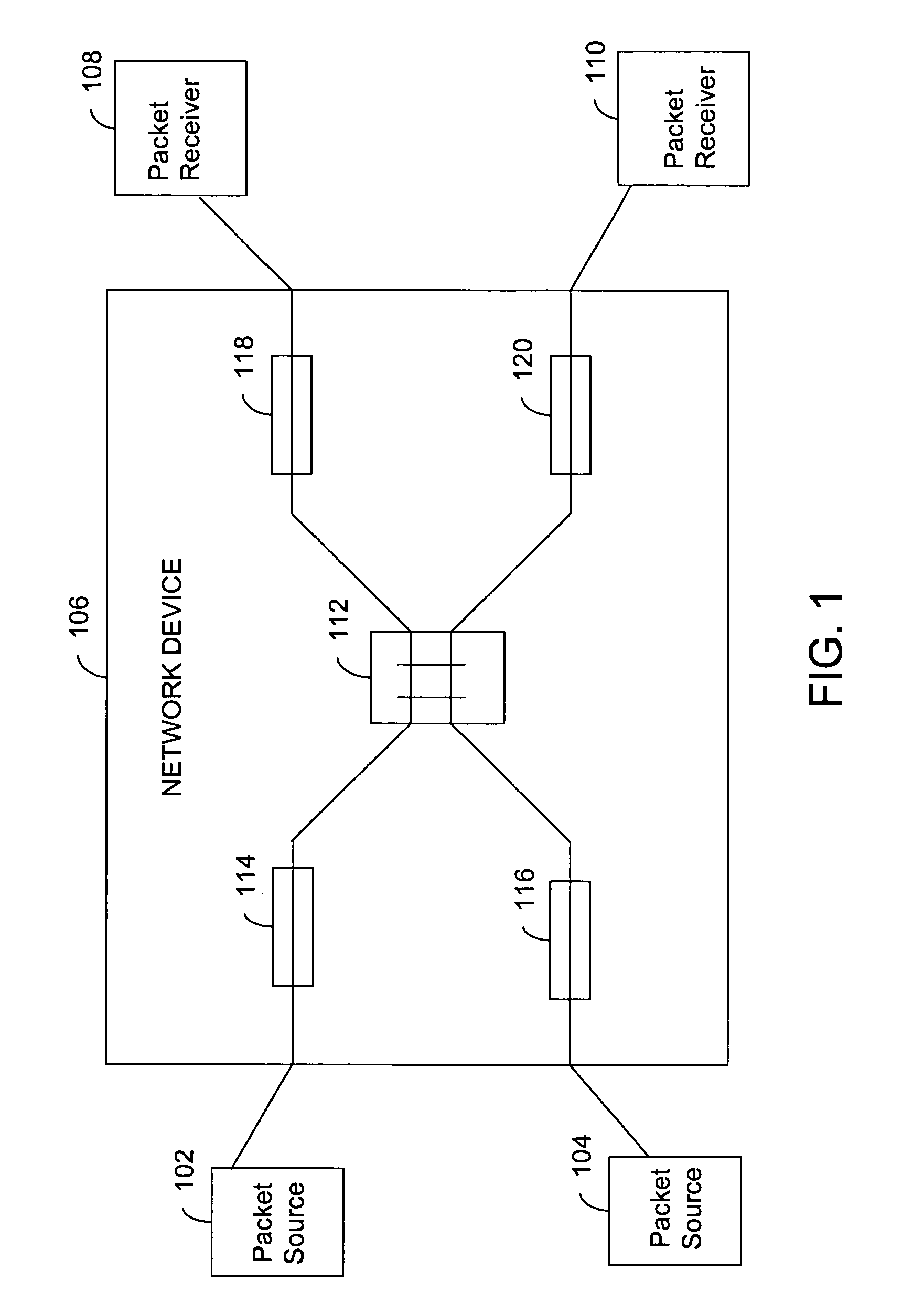
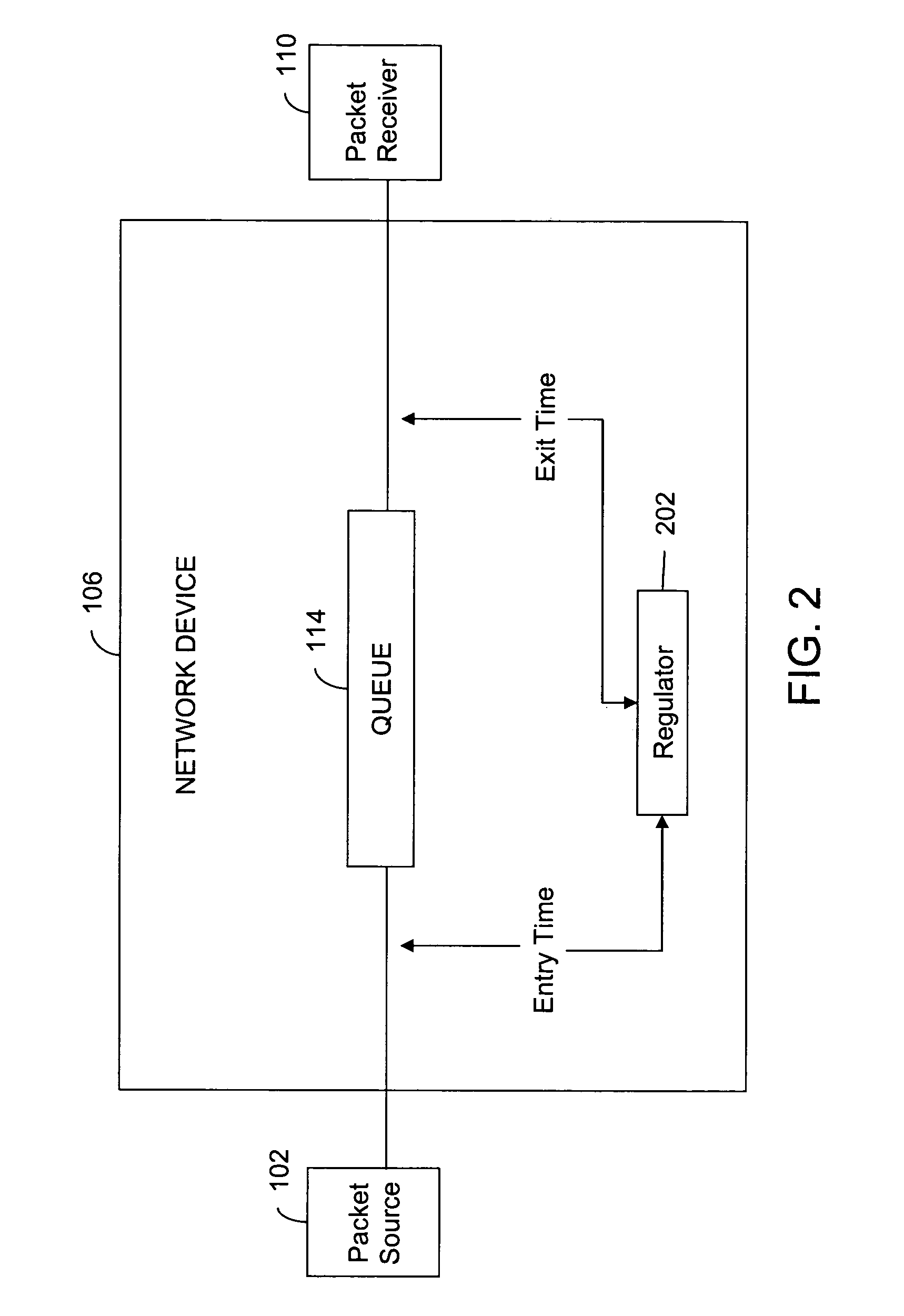
System and method for regulating data traffic in a network device
A method and a system for controlling a packet passing through a network device are provided. The method includes timestamping the packet with an arrival time when it arrives at the network device, and determining the time the packet spends in the network device. The time spent is calculated by comparing the arrival time stamp and the exit time stamp. Subsequently, the packet is labeled, based on a function of the determined time spent in the network device. The packet can be labeled, to be dropped, suppressed or temporarily stopped. The system for controlling the packet passing through the network device comprises the means for performing the above mentioned steps.
Owner:CISCO TECH INC
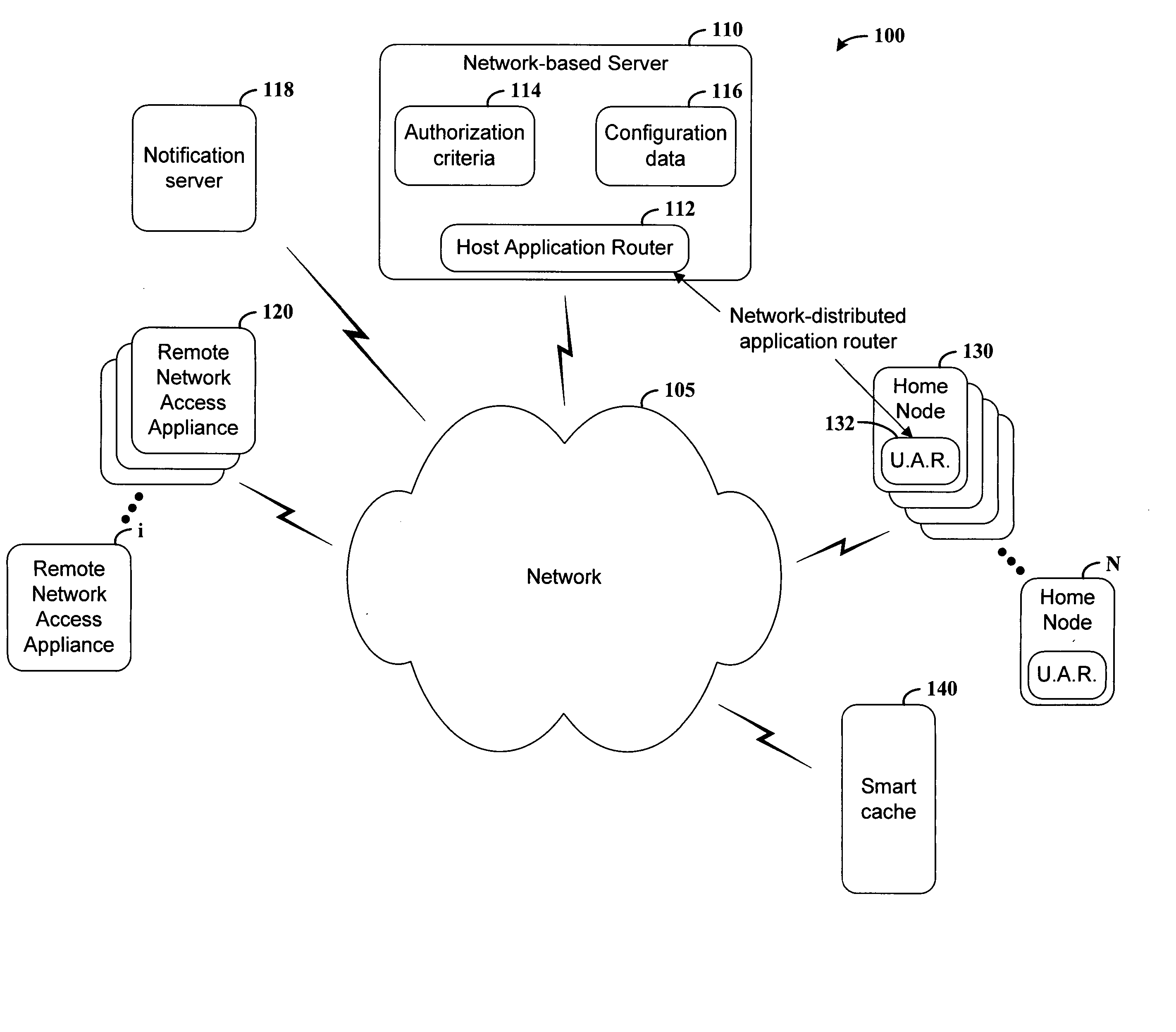
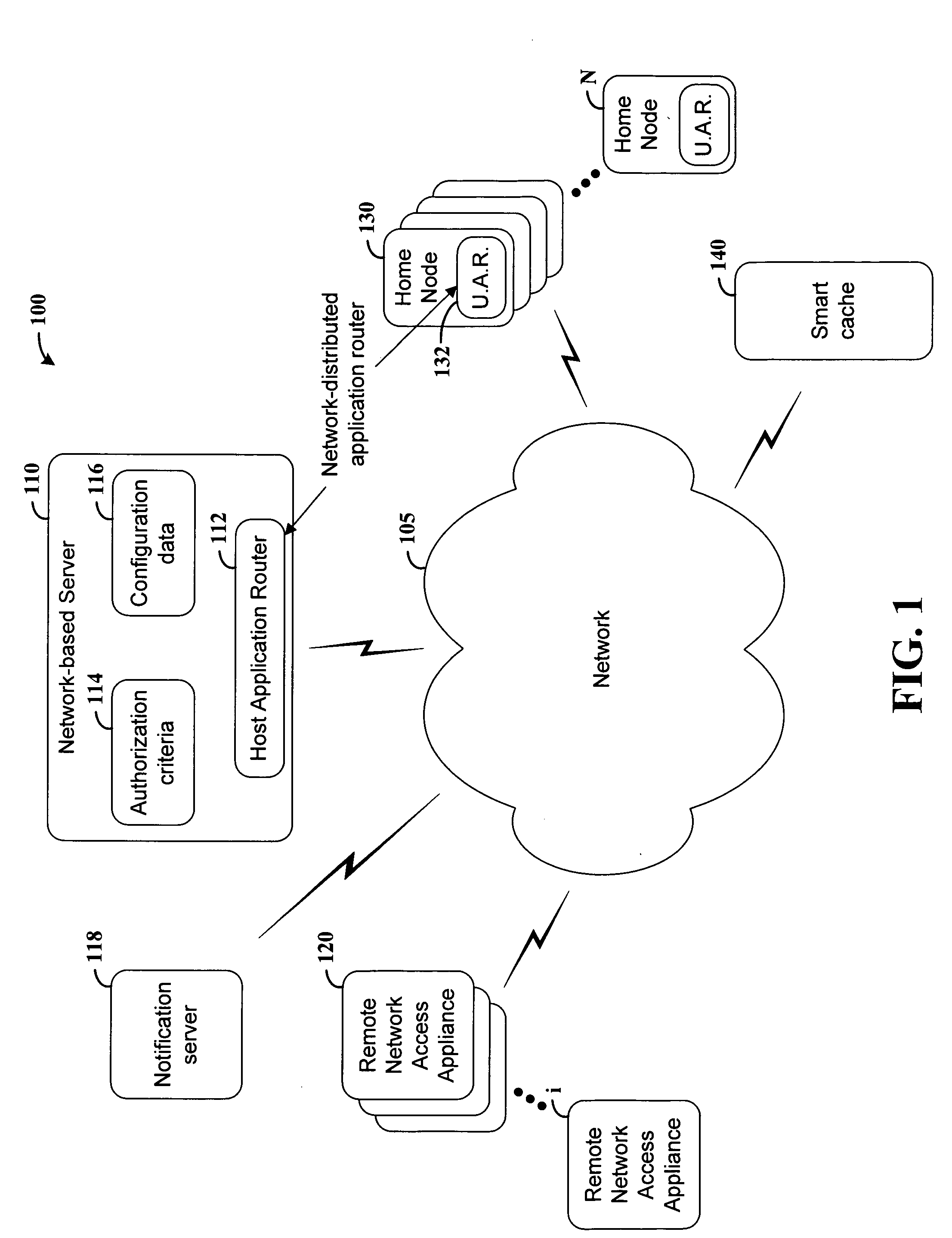
Network-distributed data routing
InactiveUS20060167985A1Facilitate delivery of contentEasy transferMultiple digital computer combinationsTransmissionTelecommunications linkData source
Data transfer over an network is effected in a manner that facilitates the use of available communications channels and makes possible enhanced data routing control and monitoring. According to an example embodiment of the present invention, data is transferred over a network having a plurality of communication links. A home (e.g., data source) node coupled to the network supplies data for transfer on the network. A network-distributed application routing controller is implemented at a host server and at the home node, and is configured for controlling the home node for passing data on the network. A data request from a remote network access appliance, such as a laptop or mobile telephone, is received at the host server. In response to the request, the host server implements the network-distributed application routing controller to transfer data from a home node to the remote network access appliance.
Owner:NOKIA CORP
Fast authentication and access control system for mobile networking
InactiveUS6856800B1Easy to switchReduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsExpiration TimeWeb authentication
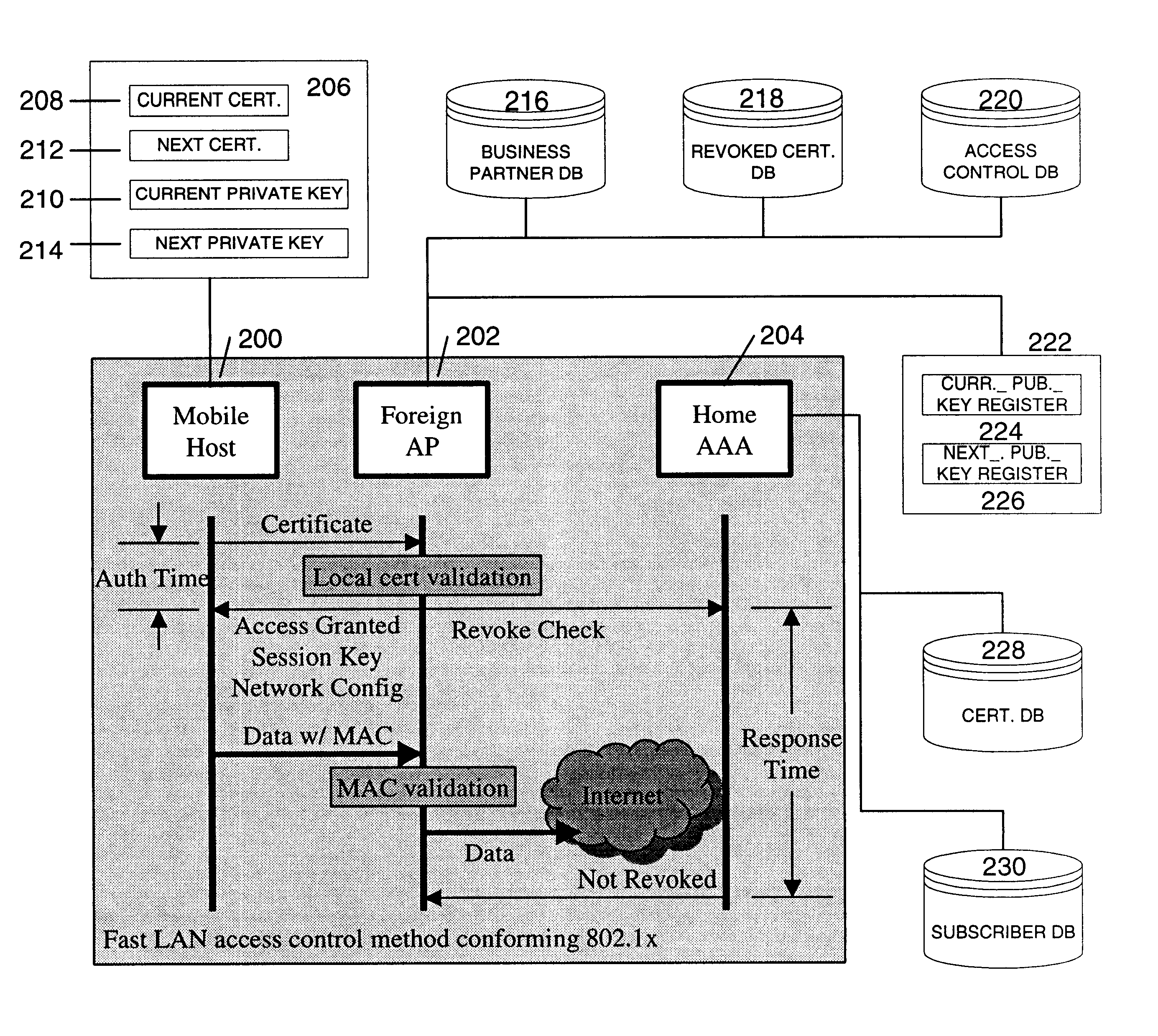
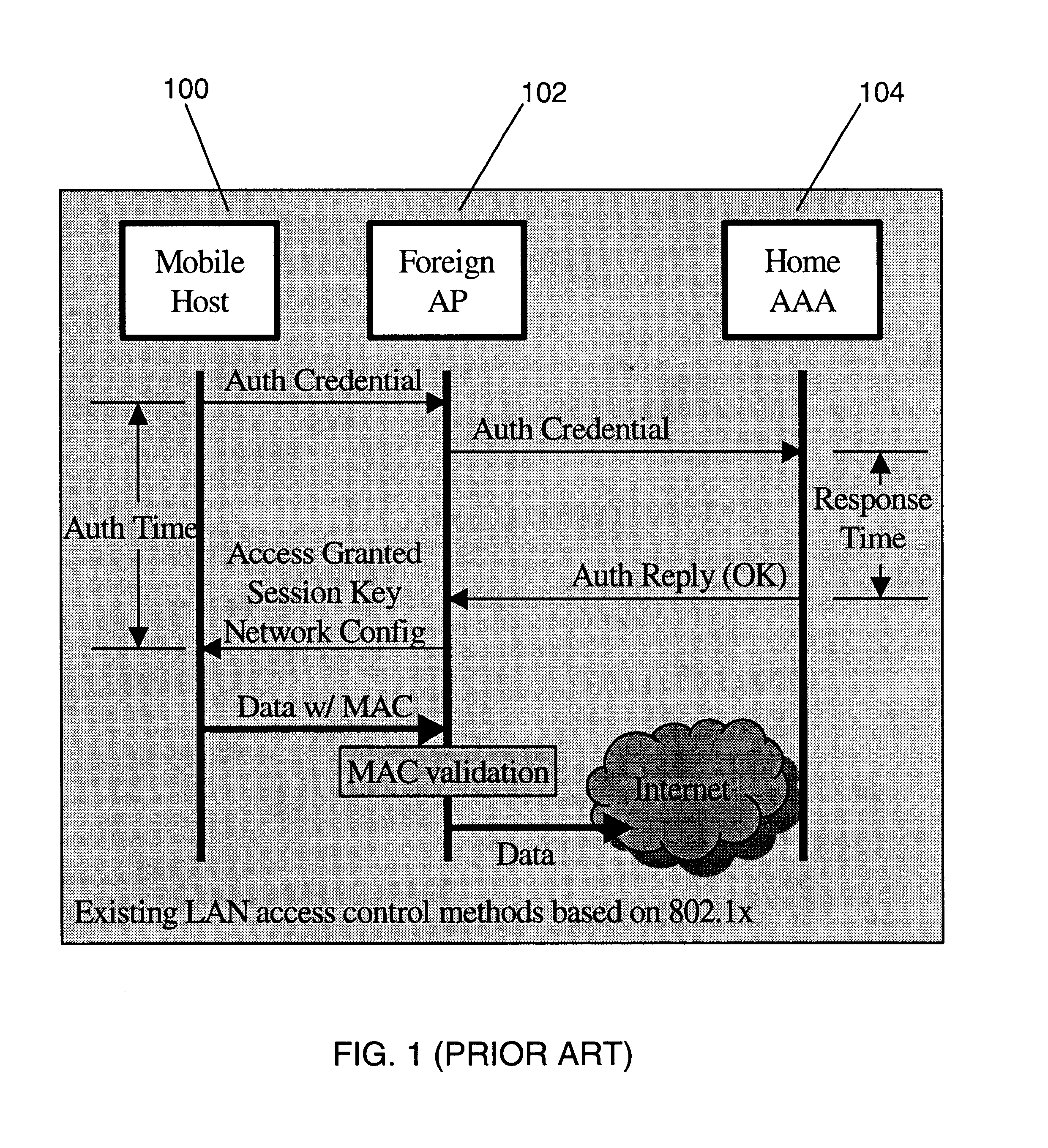
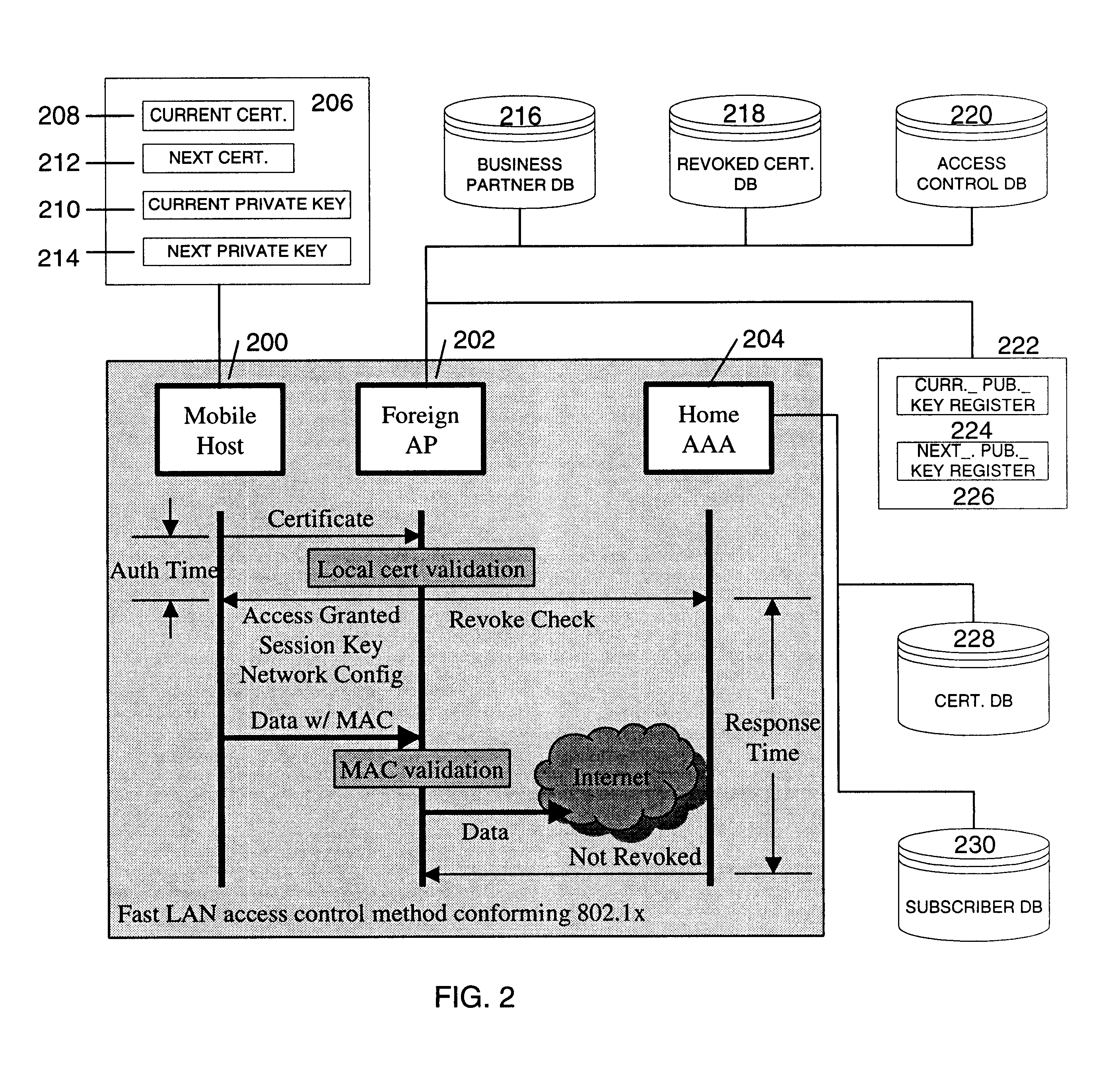
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Network communication service with an improved subscriber model using digital certificates
InactiveUS6571221B1Metering/charging/biilling arrangementsComputer security arrangementsGeolocationNetwork communication
A network communication service with an improved subscriber model. In one embodiment, a mobile user (MU), also referred to as a subscriber, may access the network service through a portable computing device (PCD) using a wireless (or wired) network interface card. Access points (APs) for the network may be widely distributed in various facilities. In one embodiment, the APs are arranged at known geographic locations and may provide geographic location information regarding the geographic location of the mobile user (MU). A digital certificate may be stored on the mobile user's PCD in order to allow access to the network. The digital certificate may store sponsorship information, including information regarding programs or entities in which the mobile user is a member or is affiliated. Each mobile user (subscriber) to the network service may have a "value bucket" which determines the amount of network access or service available to the user. Billing for access to the network communication service, i.e., the amount the "value bucket" is drained or filled, may be based on one or more of a number of factors, including information stored in the digital certificate, such as sponsorship information, the geographic location of the user, demographic information of the user, and charging information of the user.
Owner:WAYPORT
Unified network and physical premises access control server
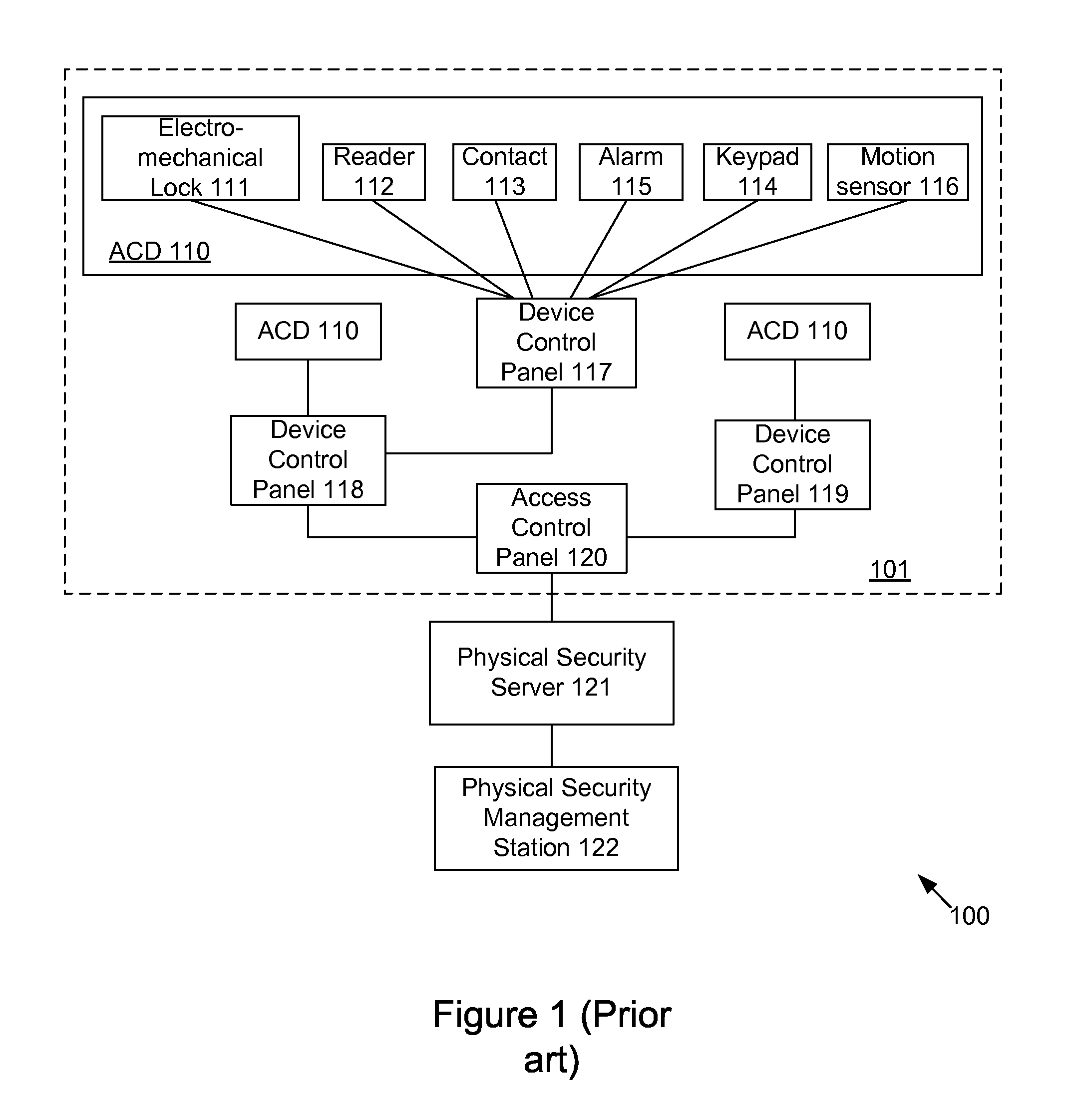
ActiveUS7437755B2Digital data processing detailsUser identity/authority verificationTime of dayNetwork Access Device
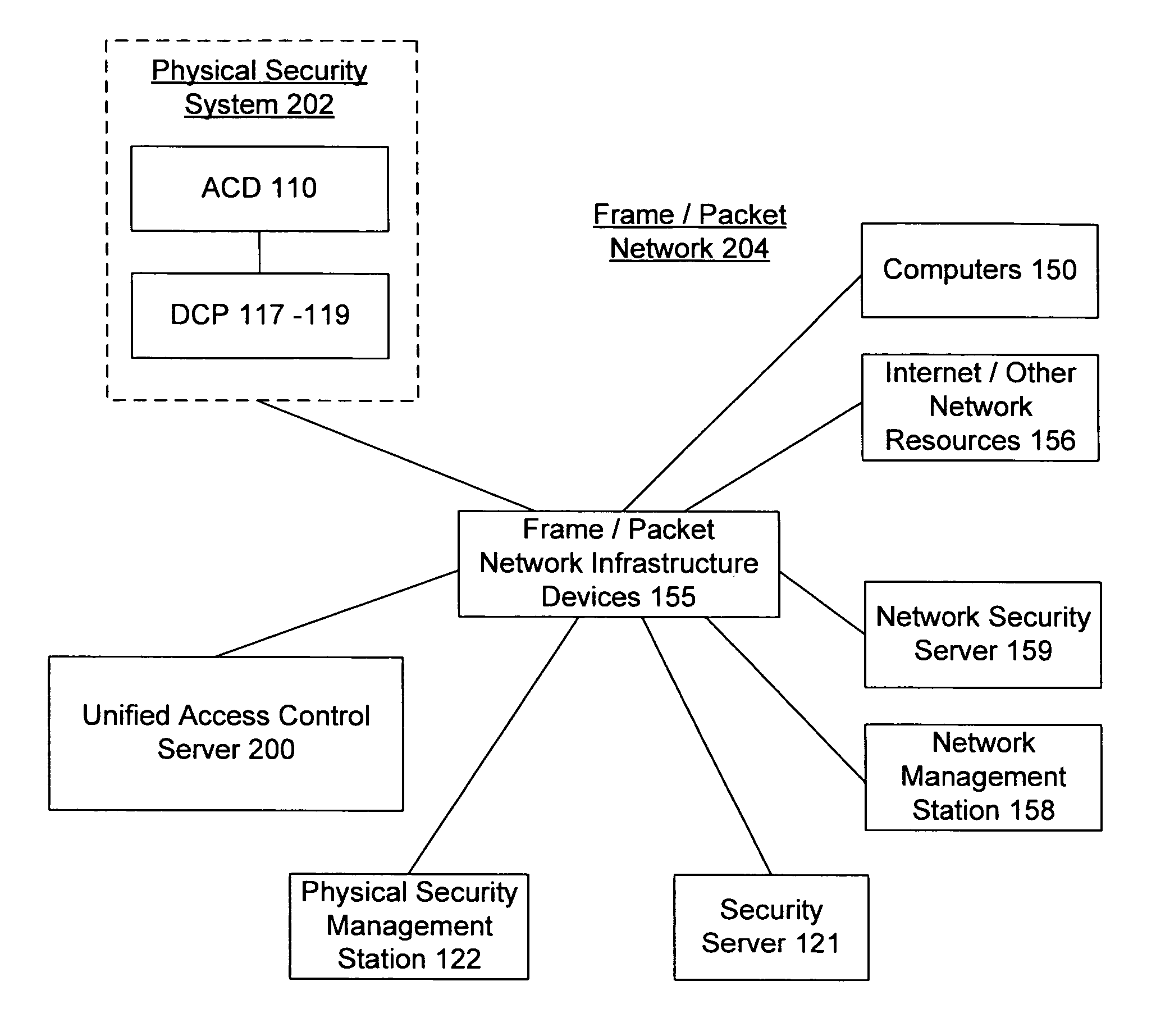
The present invention provides an access control server that holds information pertaining to both network access and facility access. The access control server enforces policies based on location, type of resource, time of day, duration, or other events, and logs all successful and unsuccessful attempts to access a given resource whether it be on the network or at the facility. The access control server operates off a common list or table of attributes and policies, or separate lists or tables of attributes and policies that are arbitrated by a credential verification and policy engine. This unified access control server implements protocols that work with network and / or physical premises-based devices. The unified access control server allows events in the facility to be associated with events on the network and vice versa and direct policies that may be executed in the physical or network realm.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com