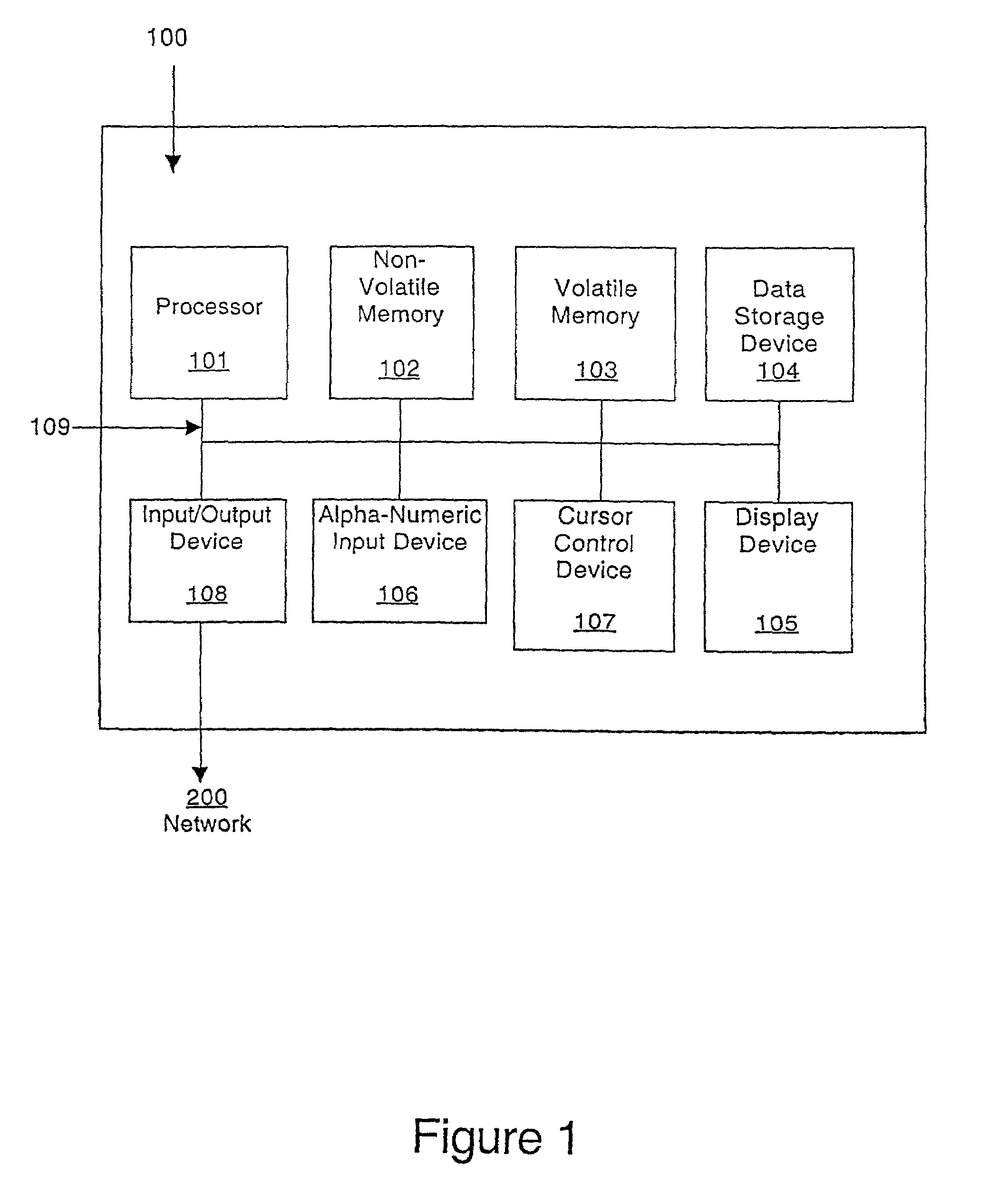
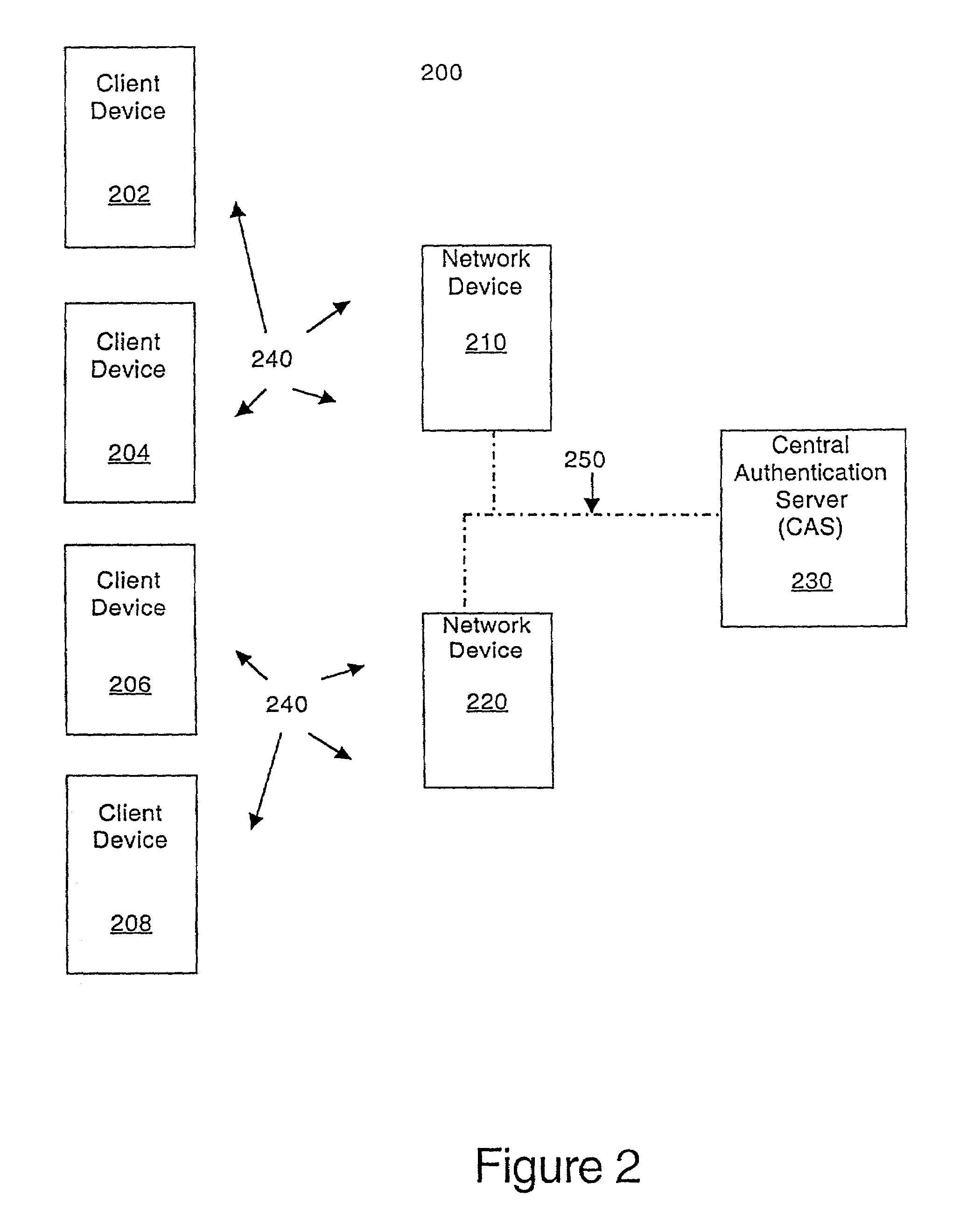
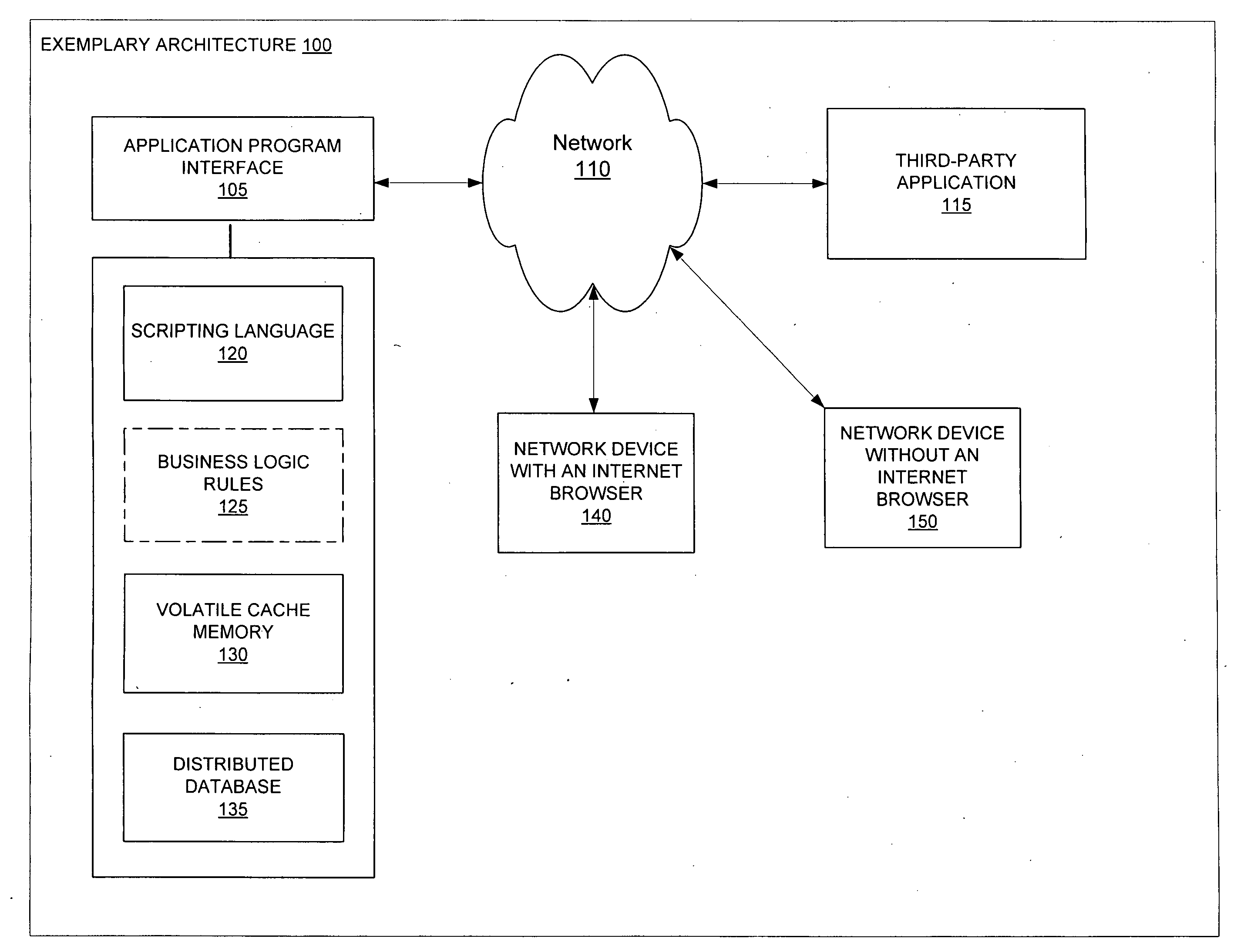
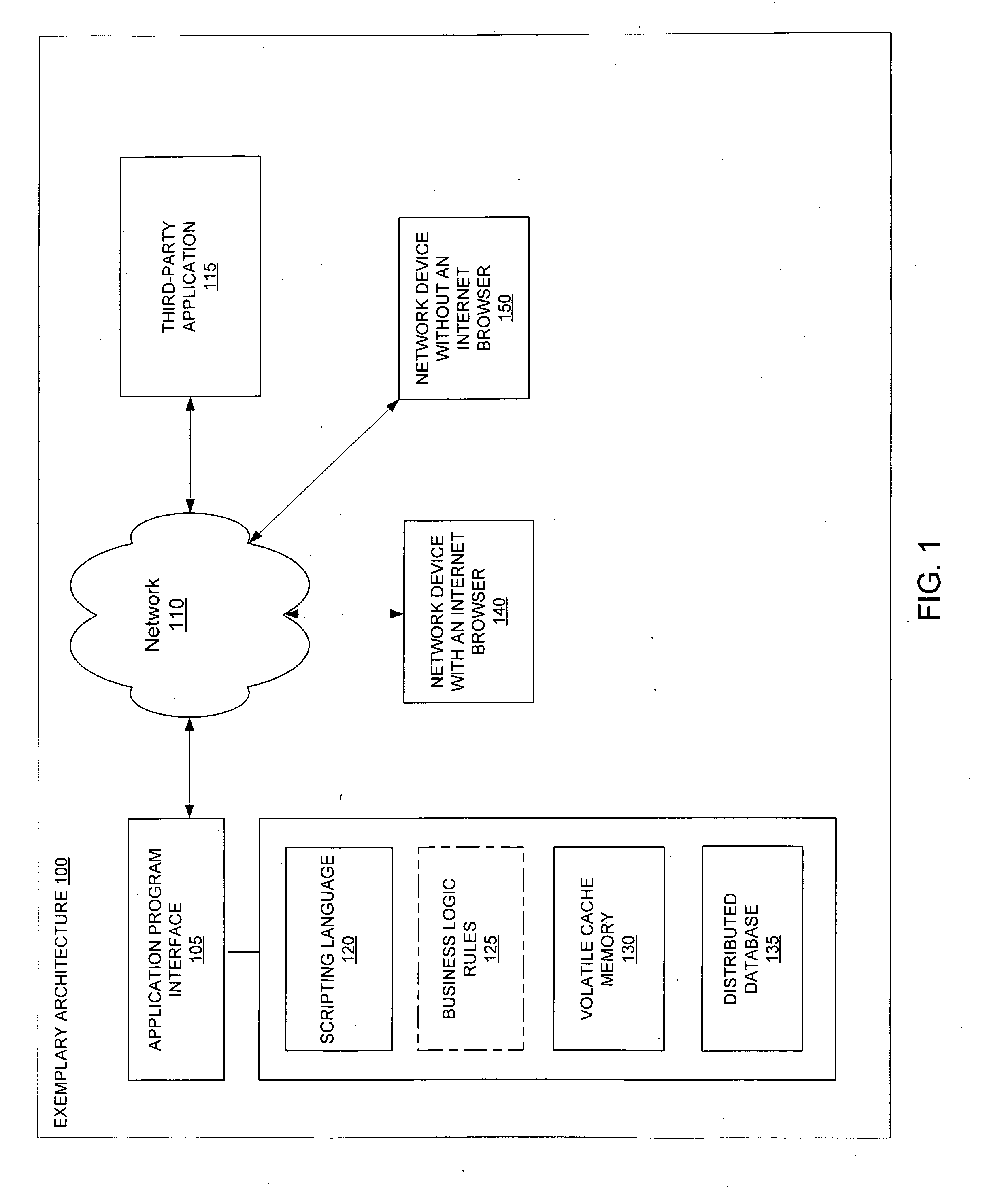
Patents
Literature
487 results about "Web authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
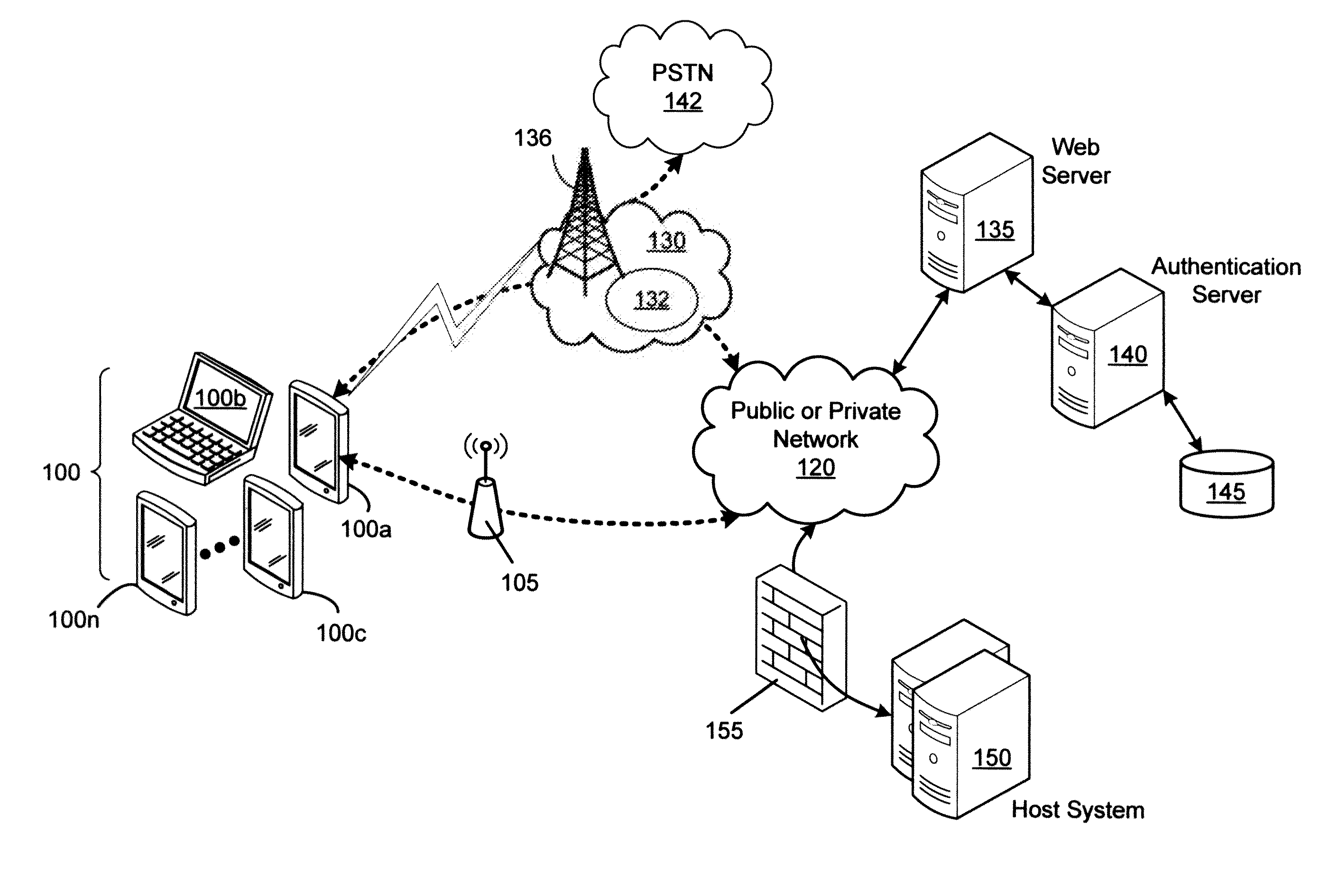
Web service authentication is the verification of a user’s identity before allowing access to a network or website. Certificates verify the identity of a Web server to users.
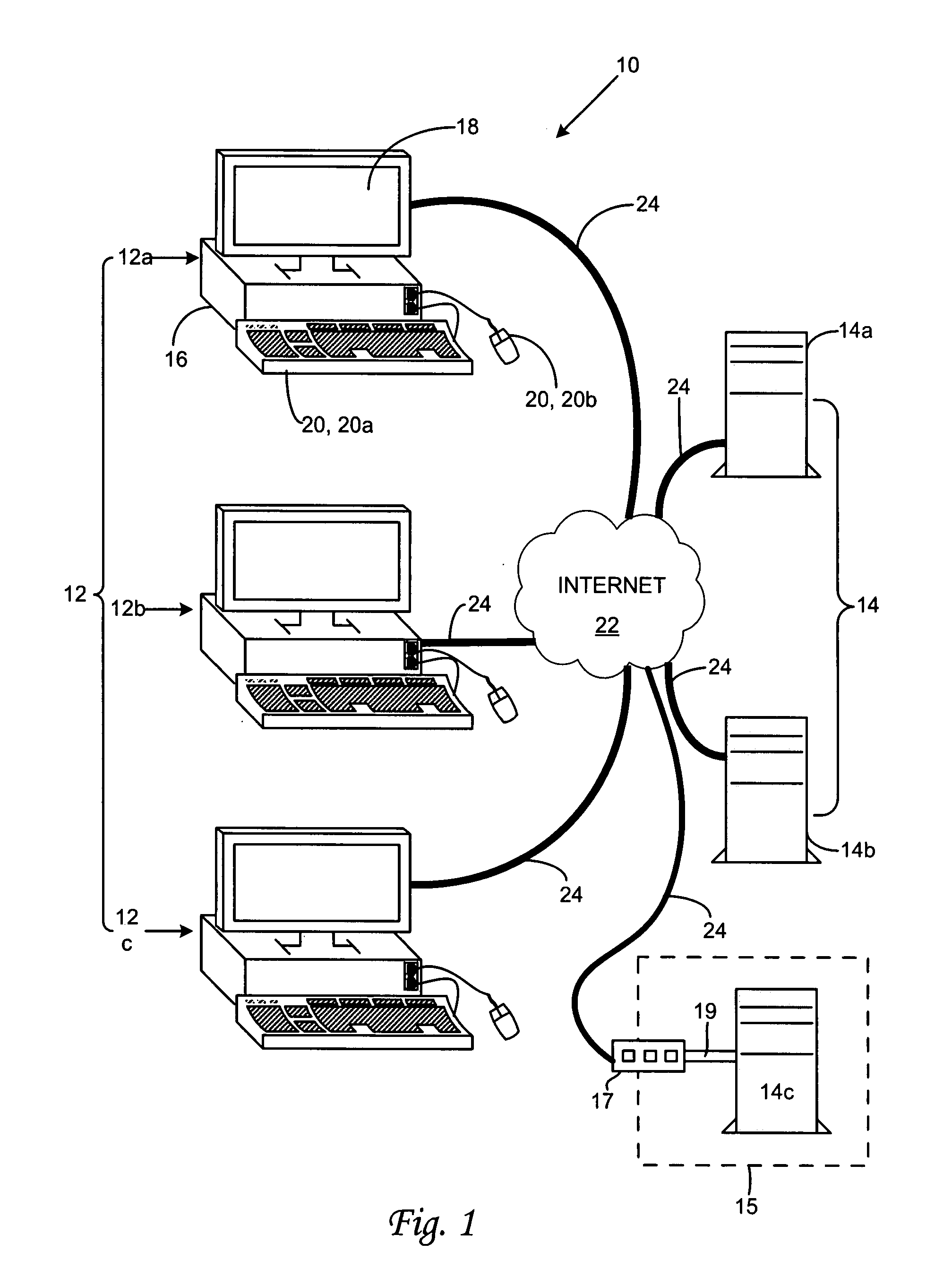
Authenticated access to internet based research and data services
InactiveUS6185567B1Data processing applicationsComputer security arrangementsData queryWeb authentication
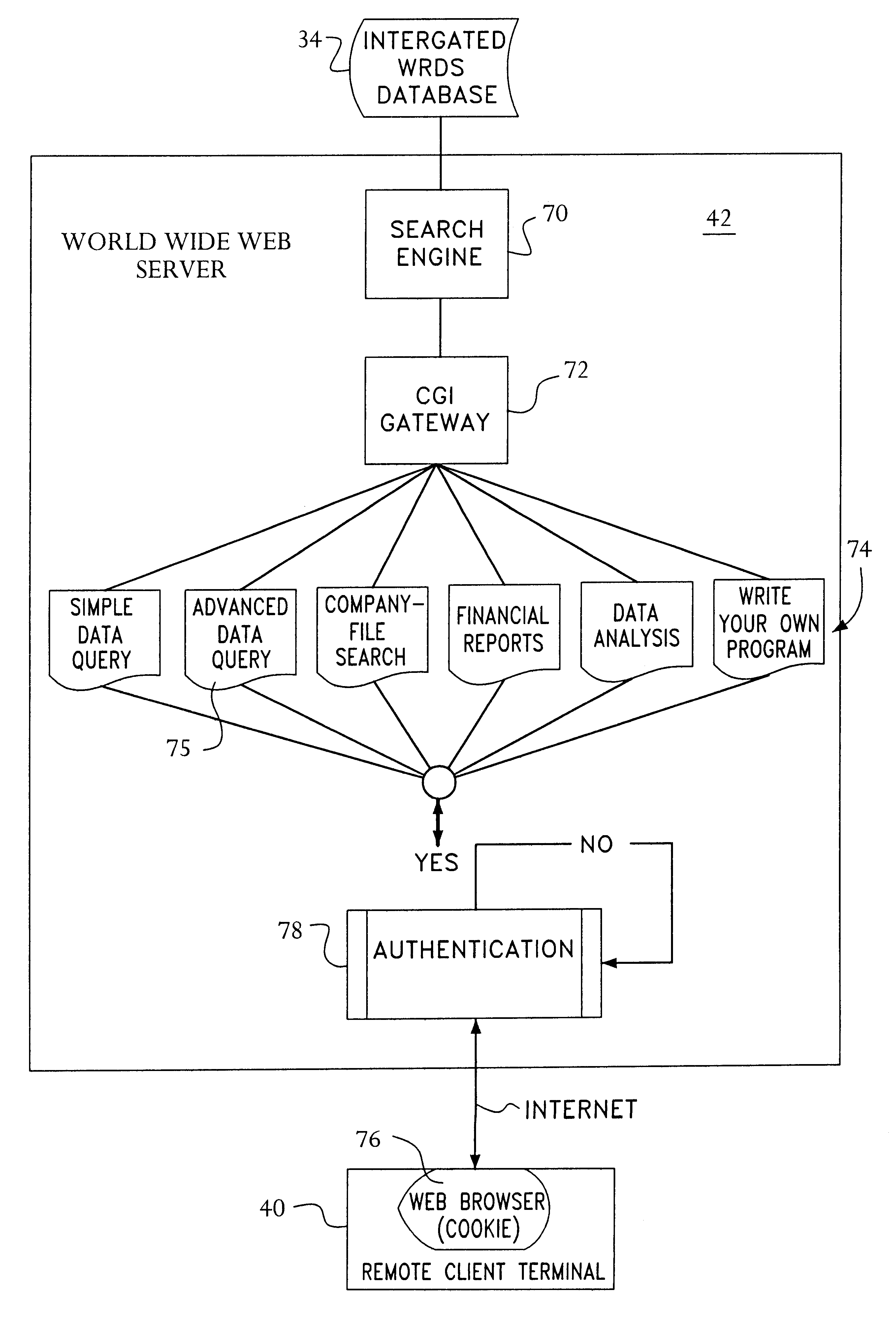
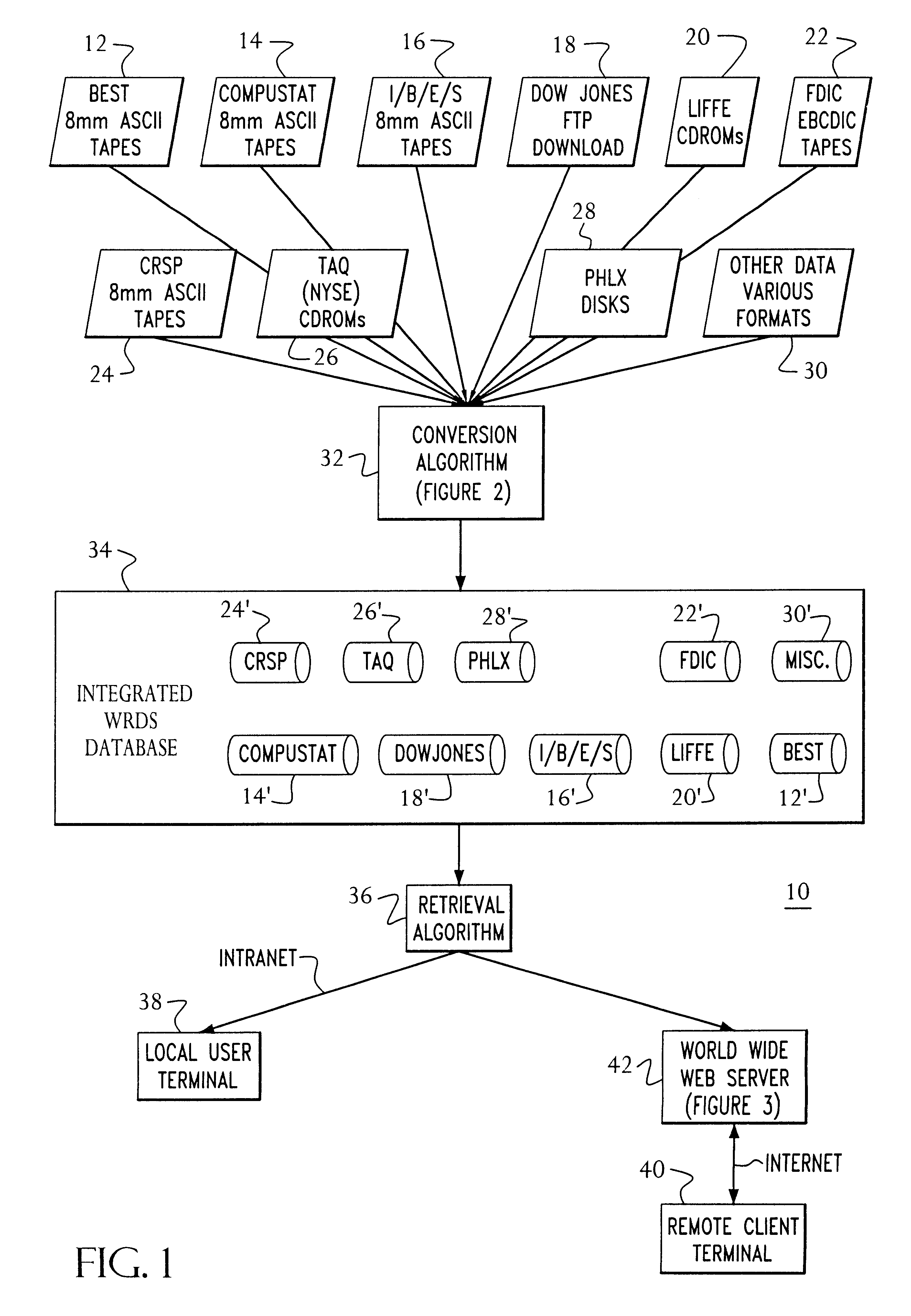
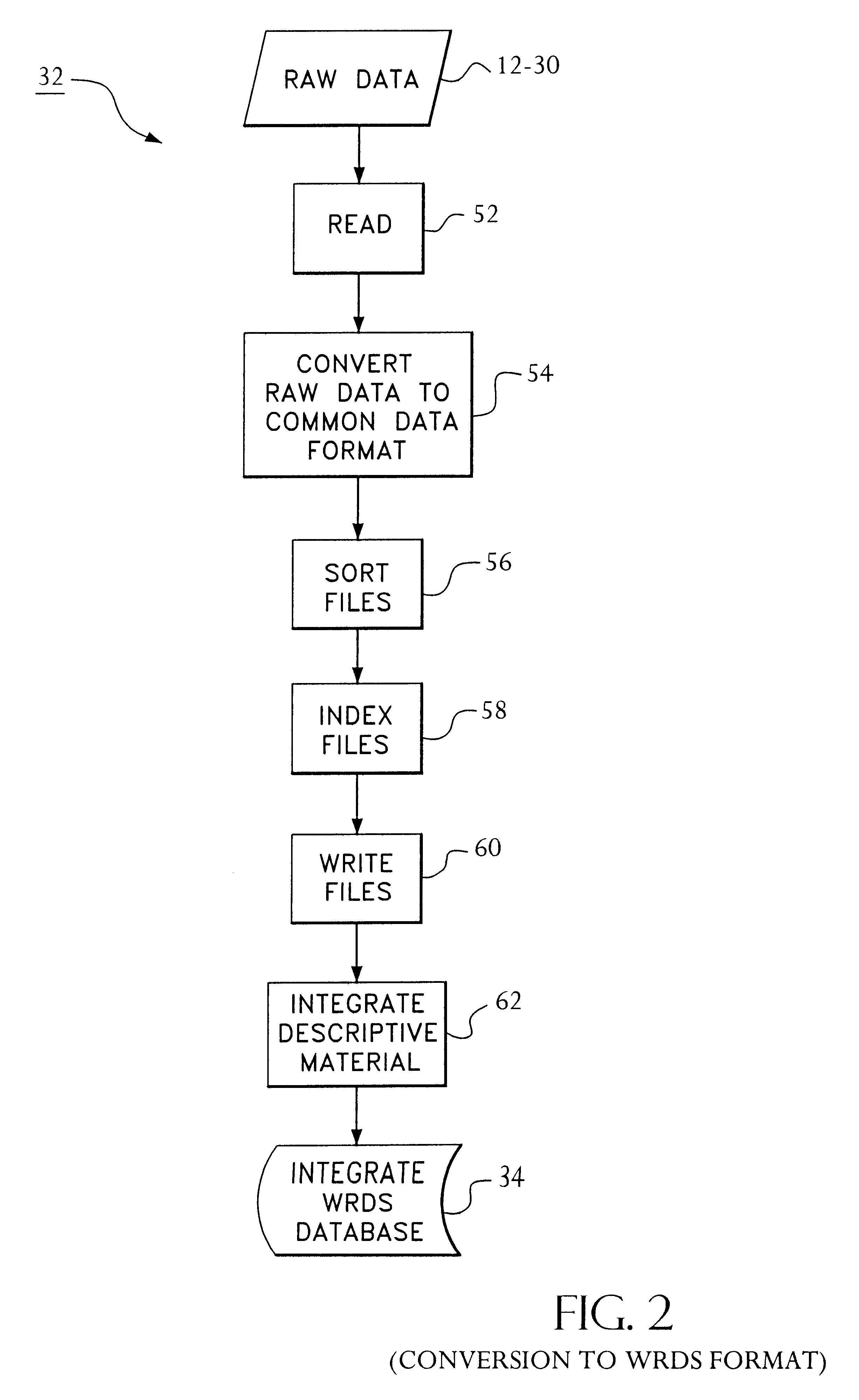
Access to a database is provided via the Internet using a World Wide Web server including a search engine, a CGI gateway and user selectable data queries for extracting data, generating reports, and the like. Access by the user is authenticated by querying the user's central machine for authentication. The authentication process operates by sending a page request from the web browser through three checkpoints before the requested page can be served to the web browser. The first checkpoint determines if the requested page is protected. If not, the requested page is served to the web browser. However, if the requested page is protected, the authentication process on the web server checks the host name of the system where the page request is coming from. If the domain of the requesting host is the same domain specified in the web authentication configuration, then the requested page is served to the web browser. However, if the page request is determined to come from outside of the domain of the web server, then the authentication process checks a "cookie" from the web browser to determine if the requesting user has been authenticated as an authorized user earlier in the same session. If the cookie has been "set" during the login procedure, then the requested page is served to the web browser. Otherwise, the user is prompted with a login page. After the user ends the web browser session, the cookie is cleared. Data Query software at the web server permits queries initiated via a web browser to be completed off-line and the results e-mailed to the initiator of the request.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
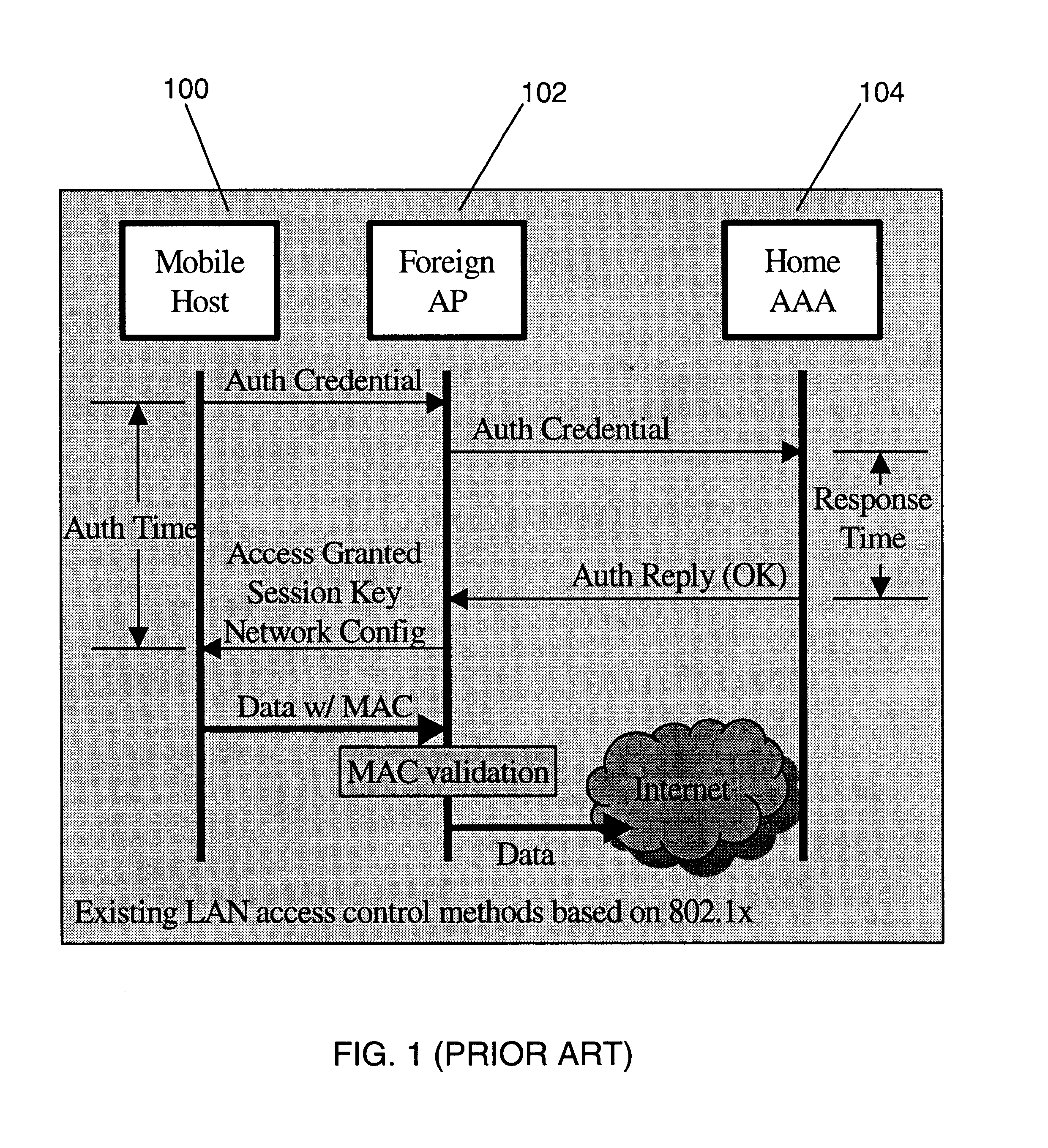
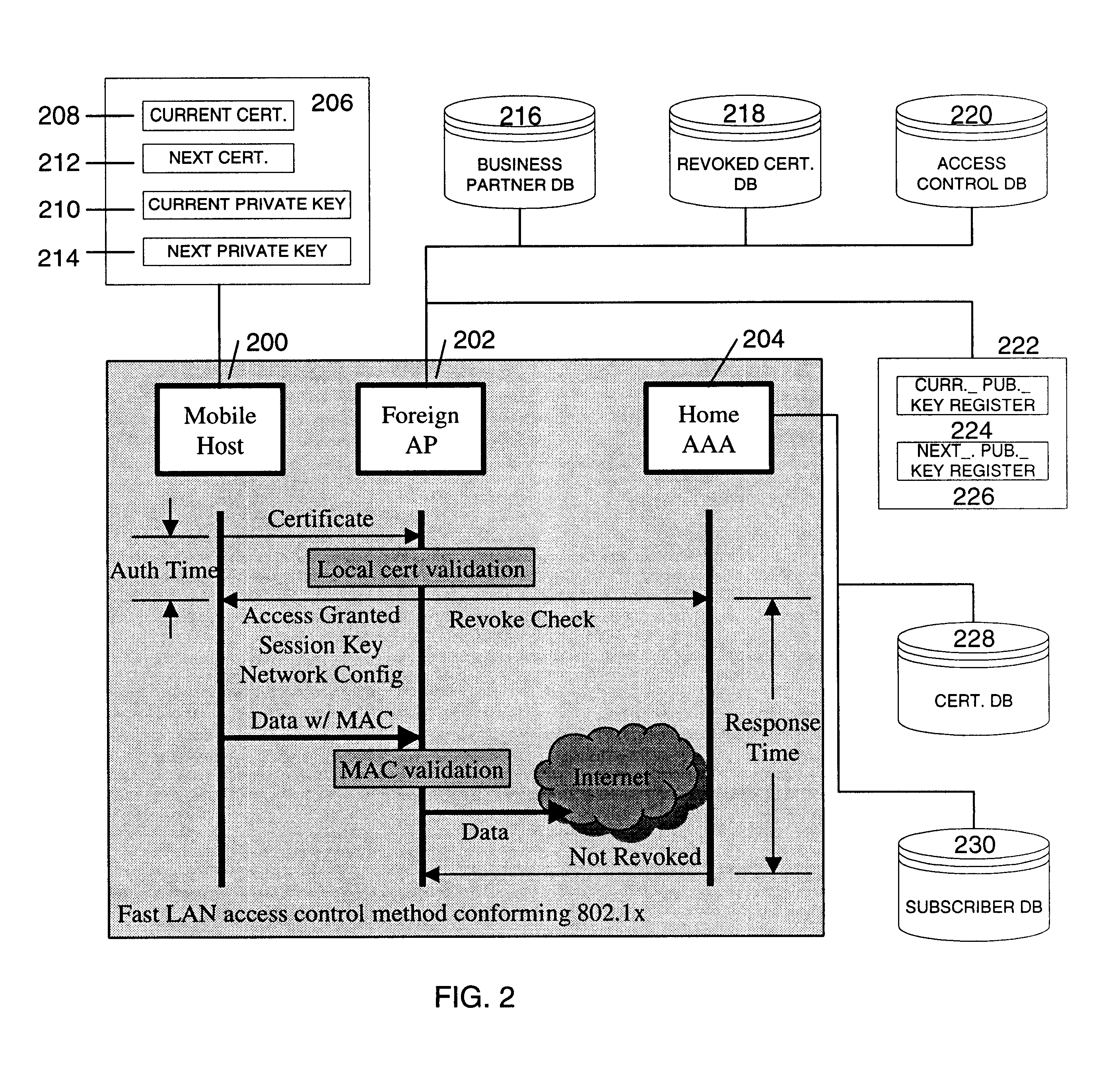
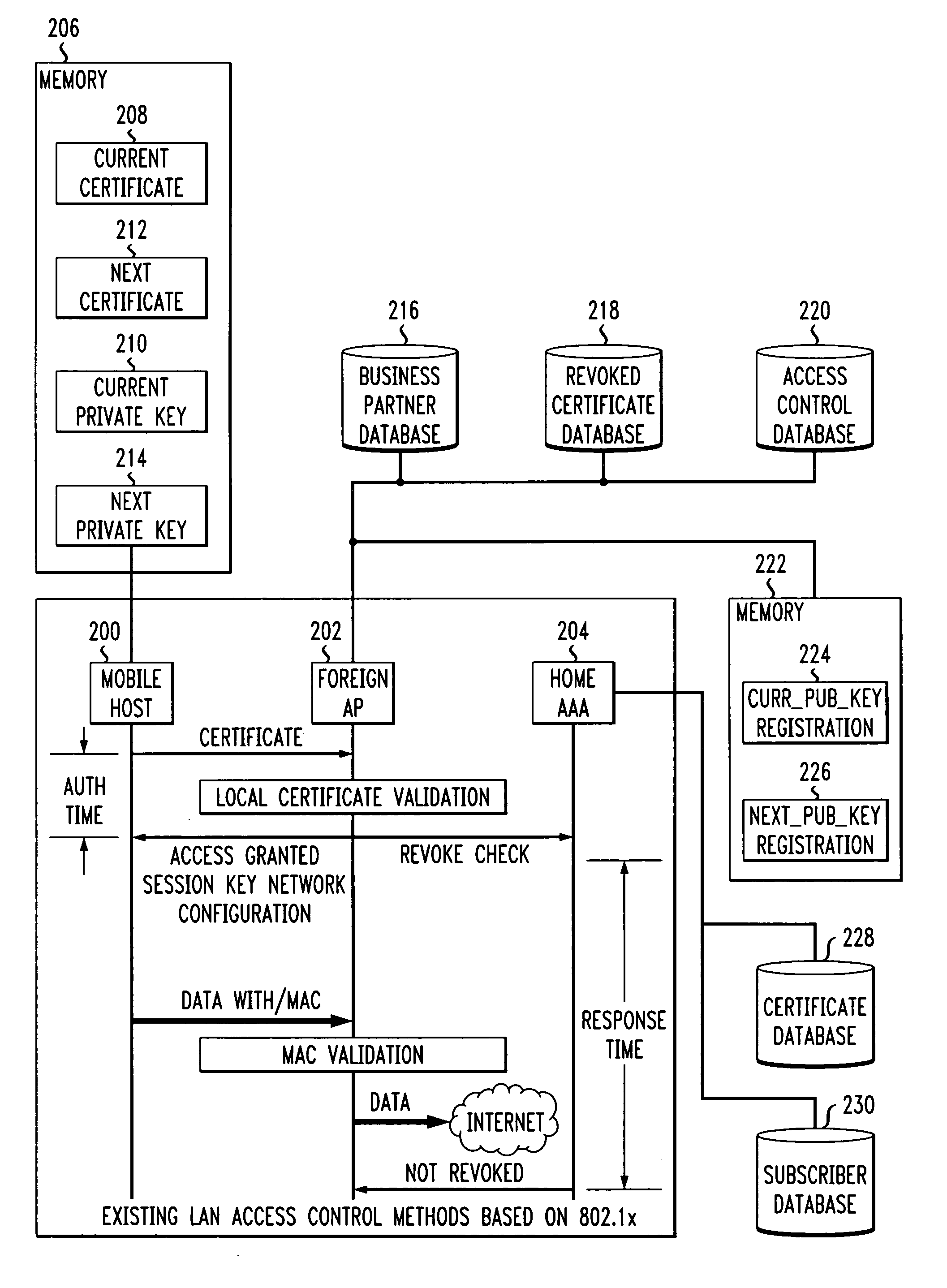
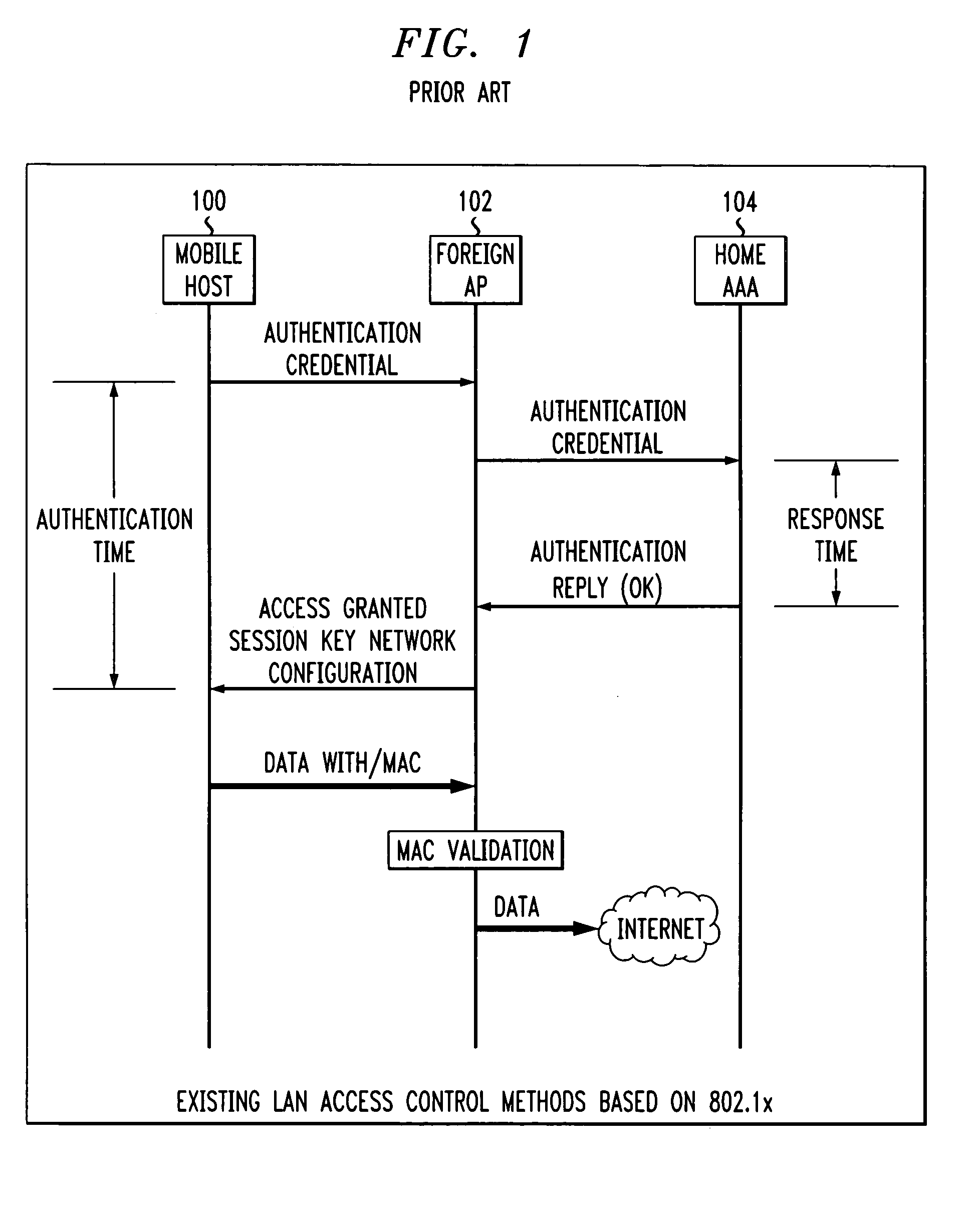
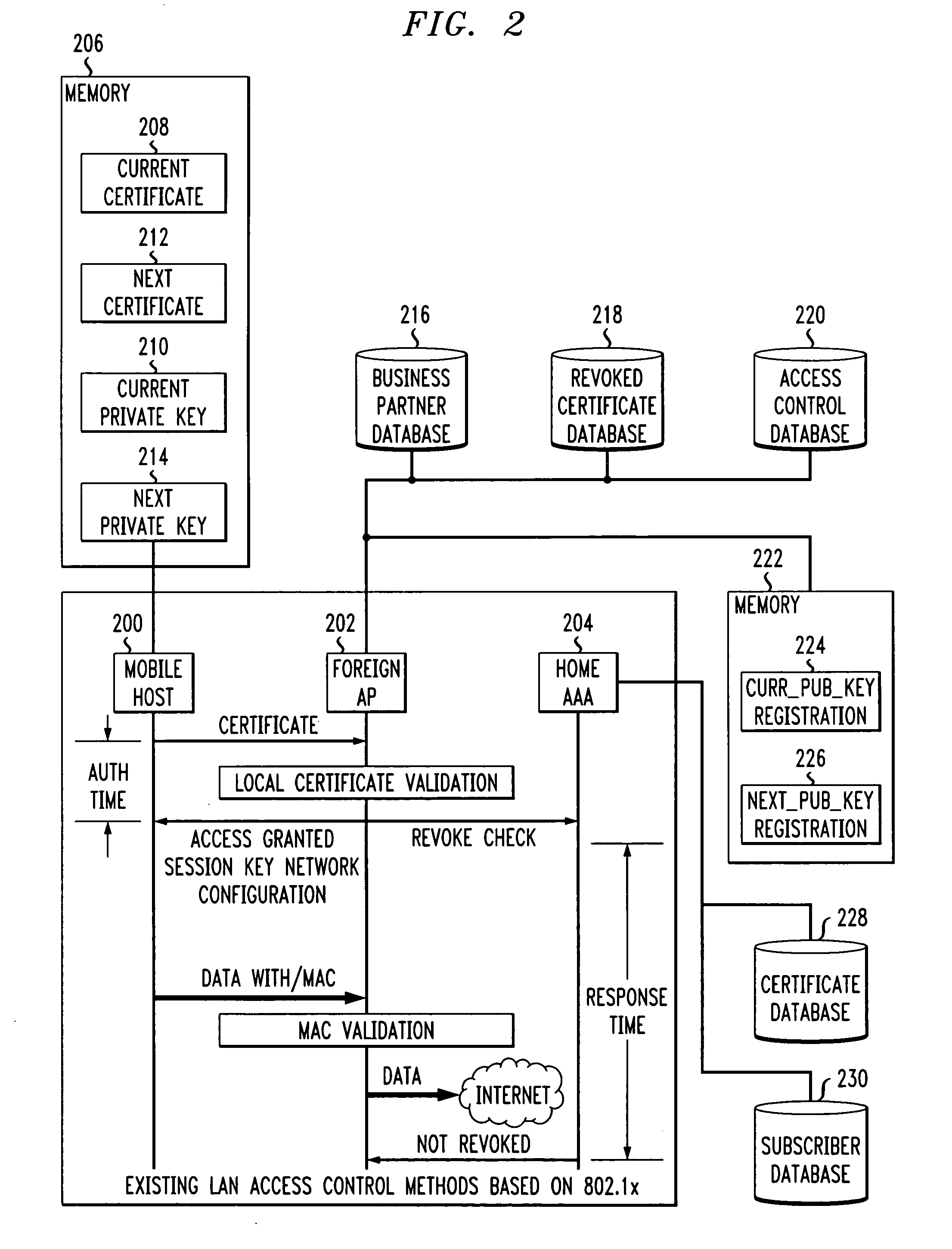
Fast authentication and access control system for mobile networking
InactiveUS6856800B1Easy to switchReduce certification timeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsExpiration TimeWeb authentication
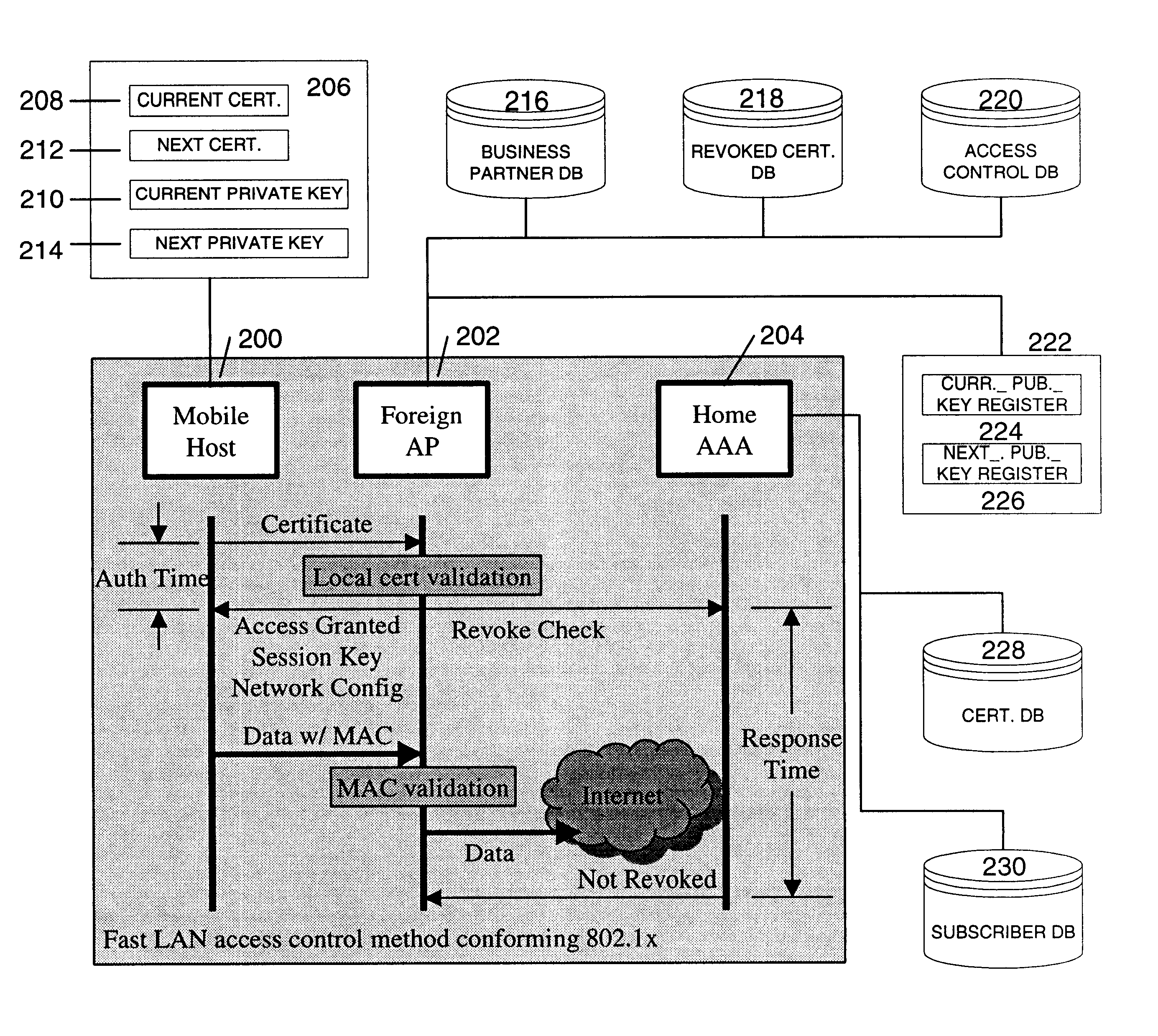
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
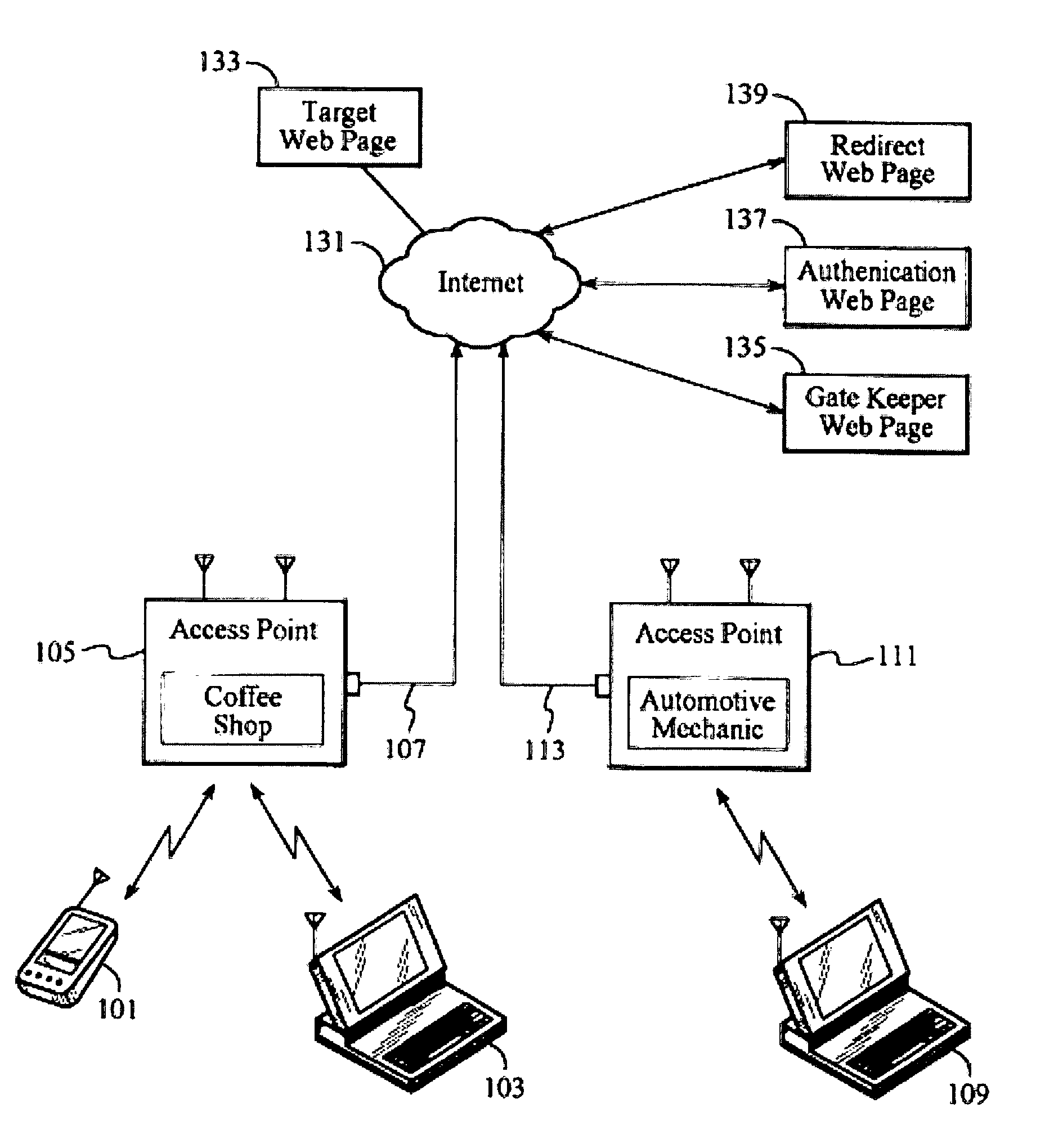
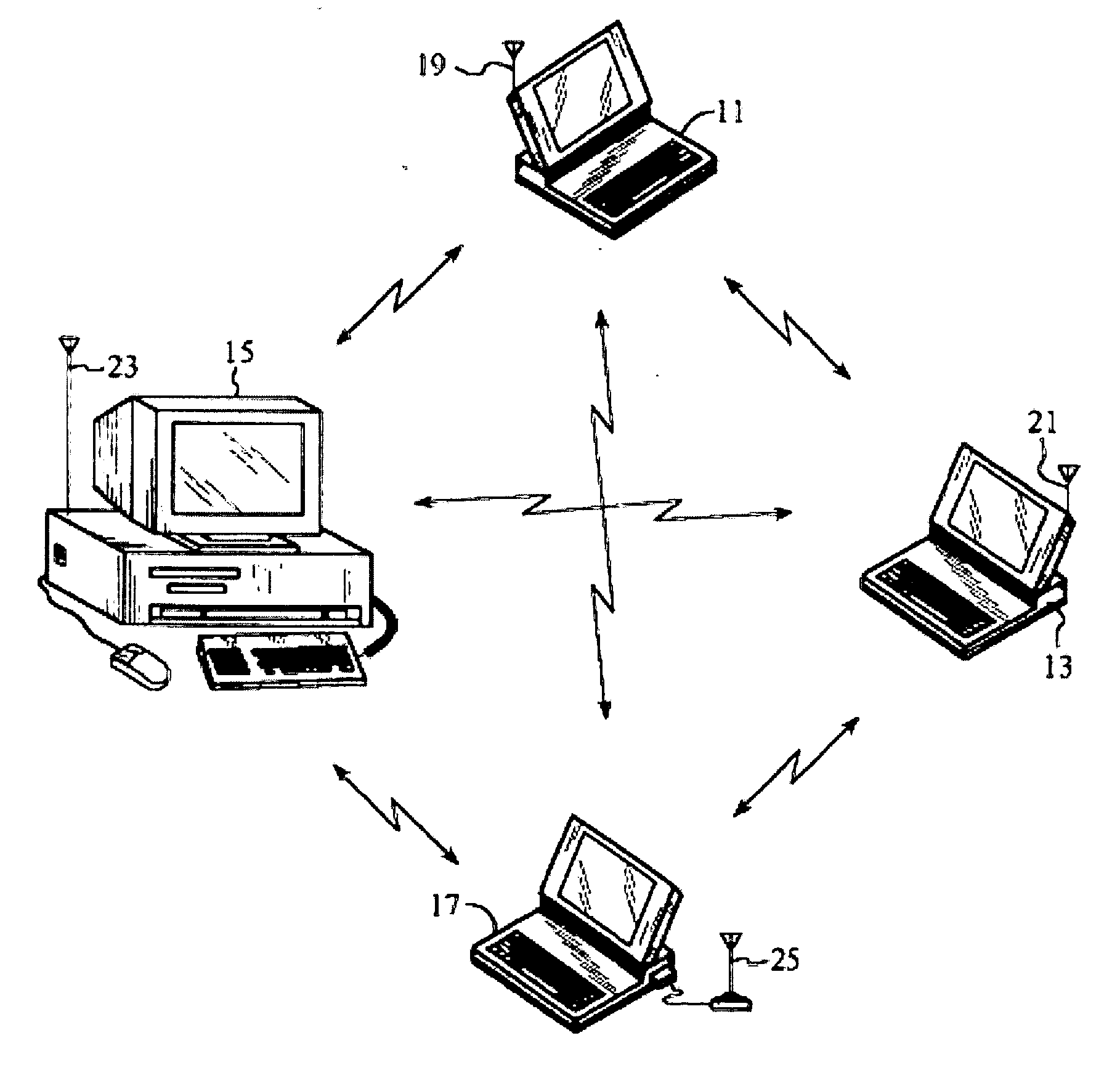
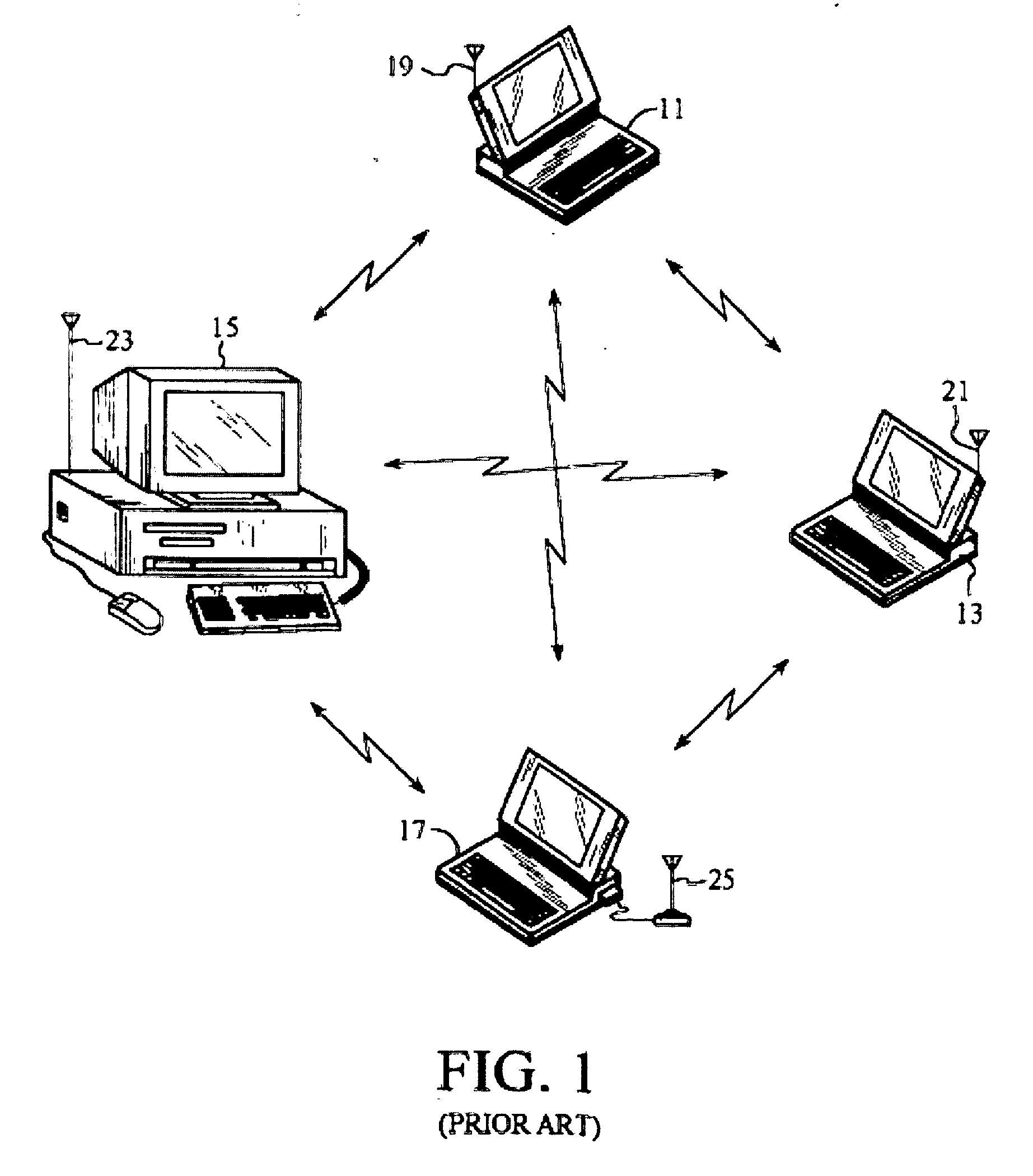
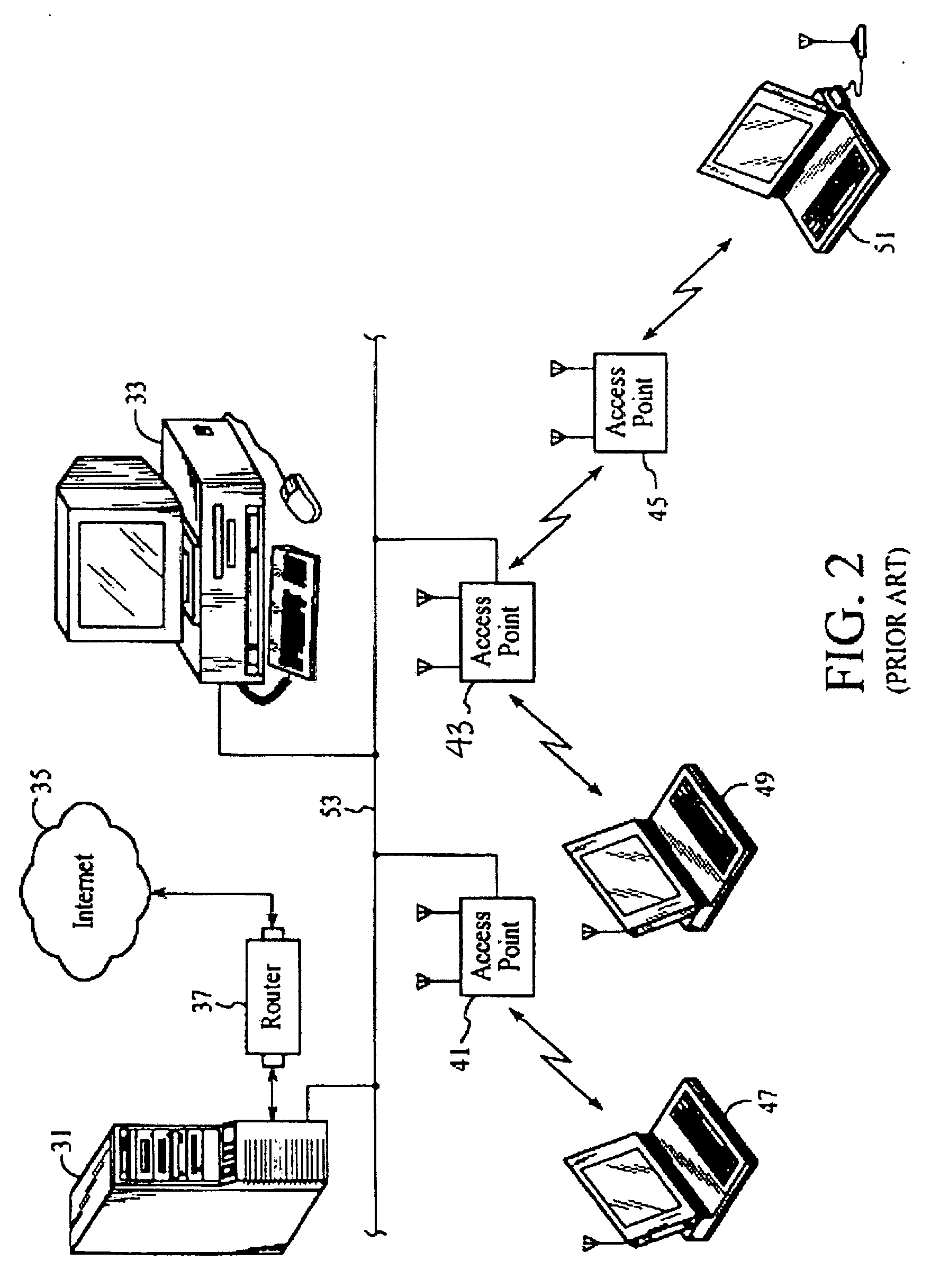
System for distributed network authentication and access control
InactiveUS7185360B1Facilitate wireless accessEasy accessError preventionFrequency-division multiplex detailsWeb authenticationGate-keeper
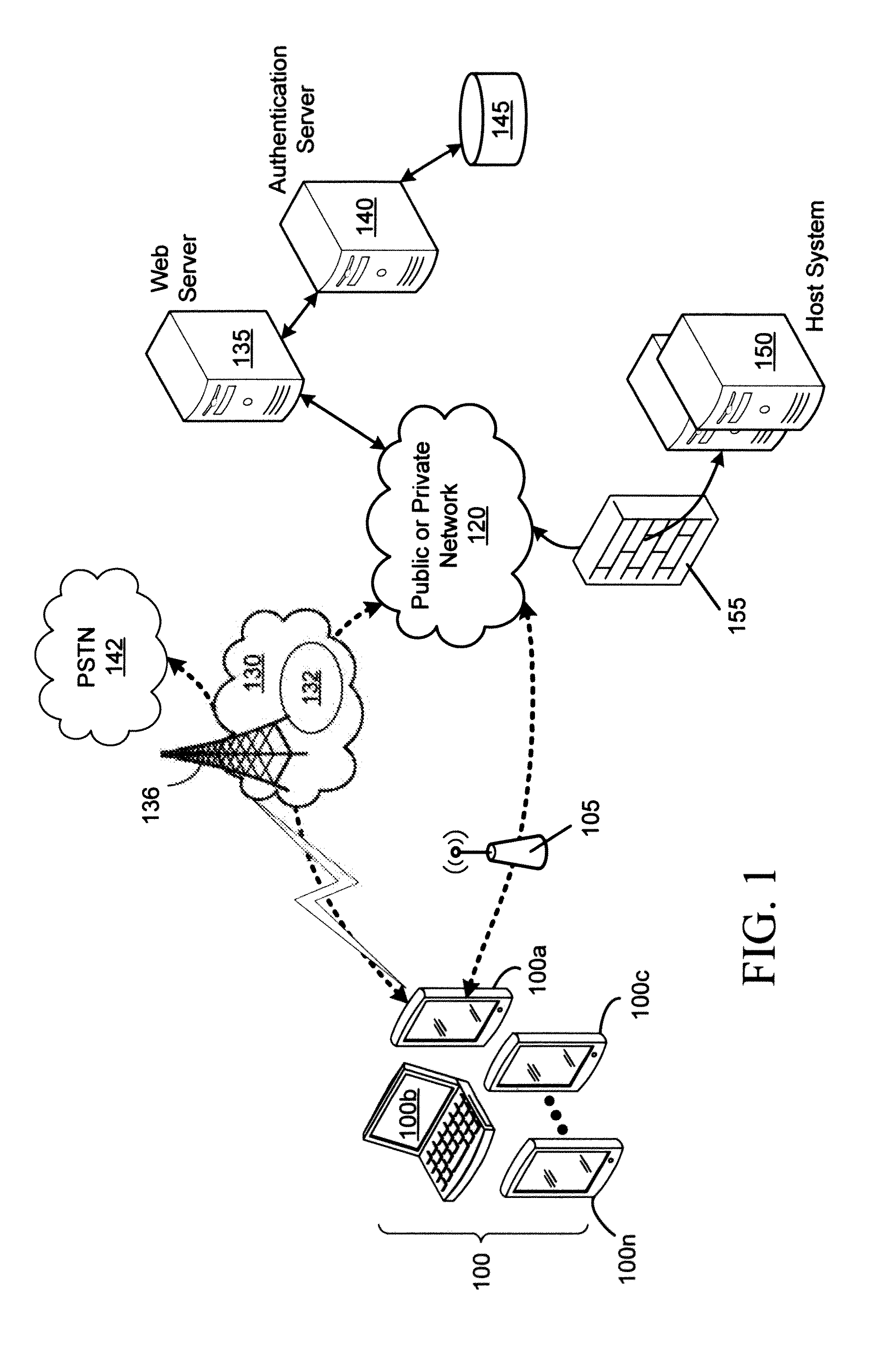
A user gains access to a private network by connecting to a network, either through a hardwired or wireless connection, and then initiates an Internet access request targeting any website. If the user is not already authorized for Internet access, then the user is sent to a first predetermined website that points the user to an authentication server accessible via the Internet. The authentication server sends the user an HTTP form pages requesting authentication information. When the user responds, a network monitoring device within the private network alters the form page to include the user's hardware address and an encoded ID based on the network's location. The authentication server forwards this data to a gate keeper server, which authenticates the new user and transmits an unblock message along with another encoded ID based on the network's location and the user's hardware address.
Owner:HEREUARE COMMUNICATIOINS
Secure authentication system and method
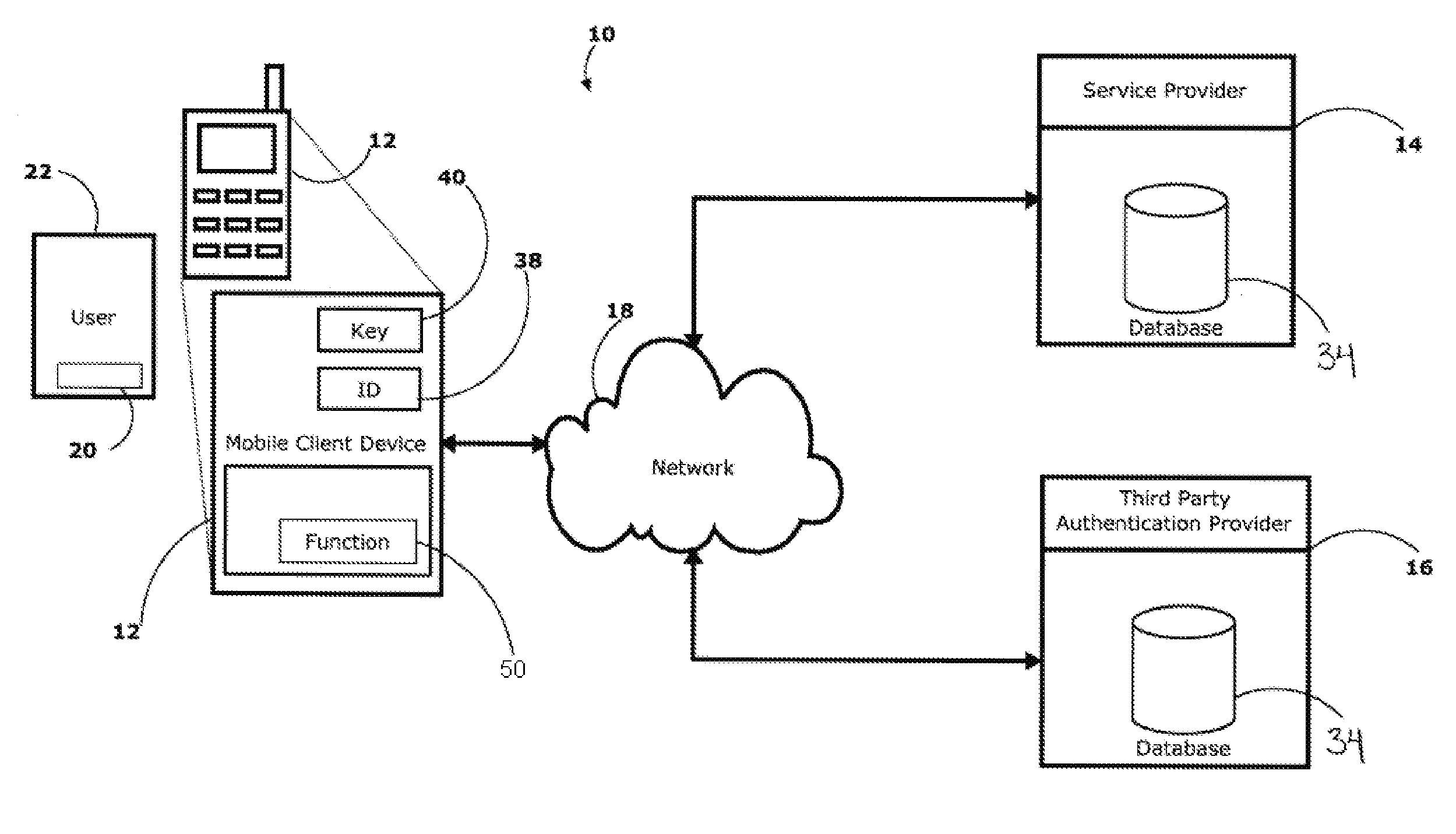
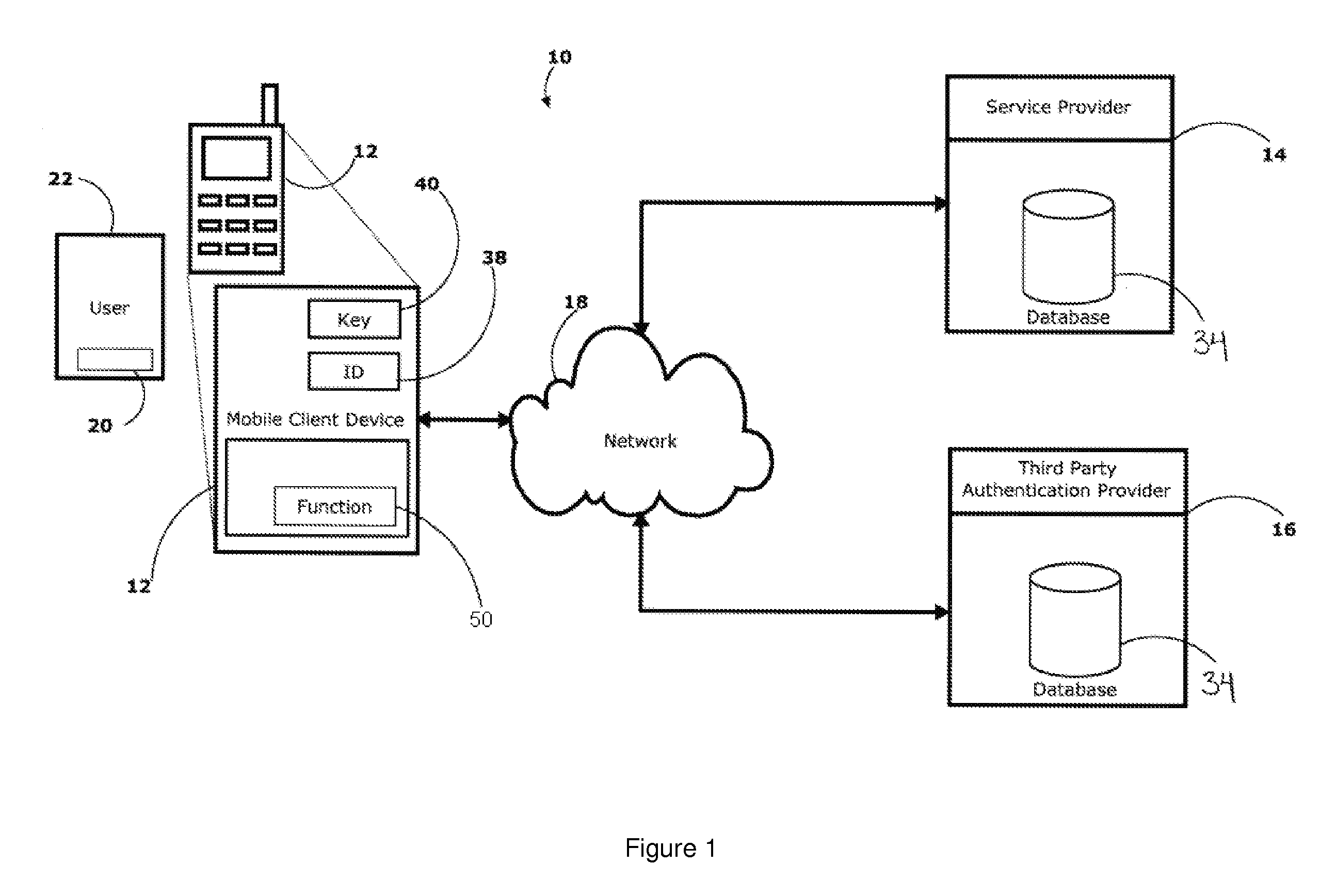
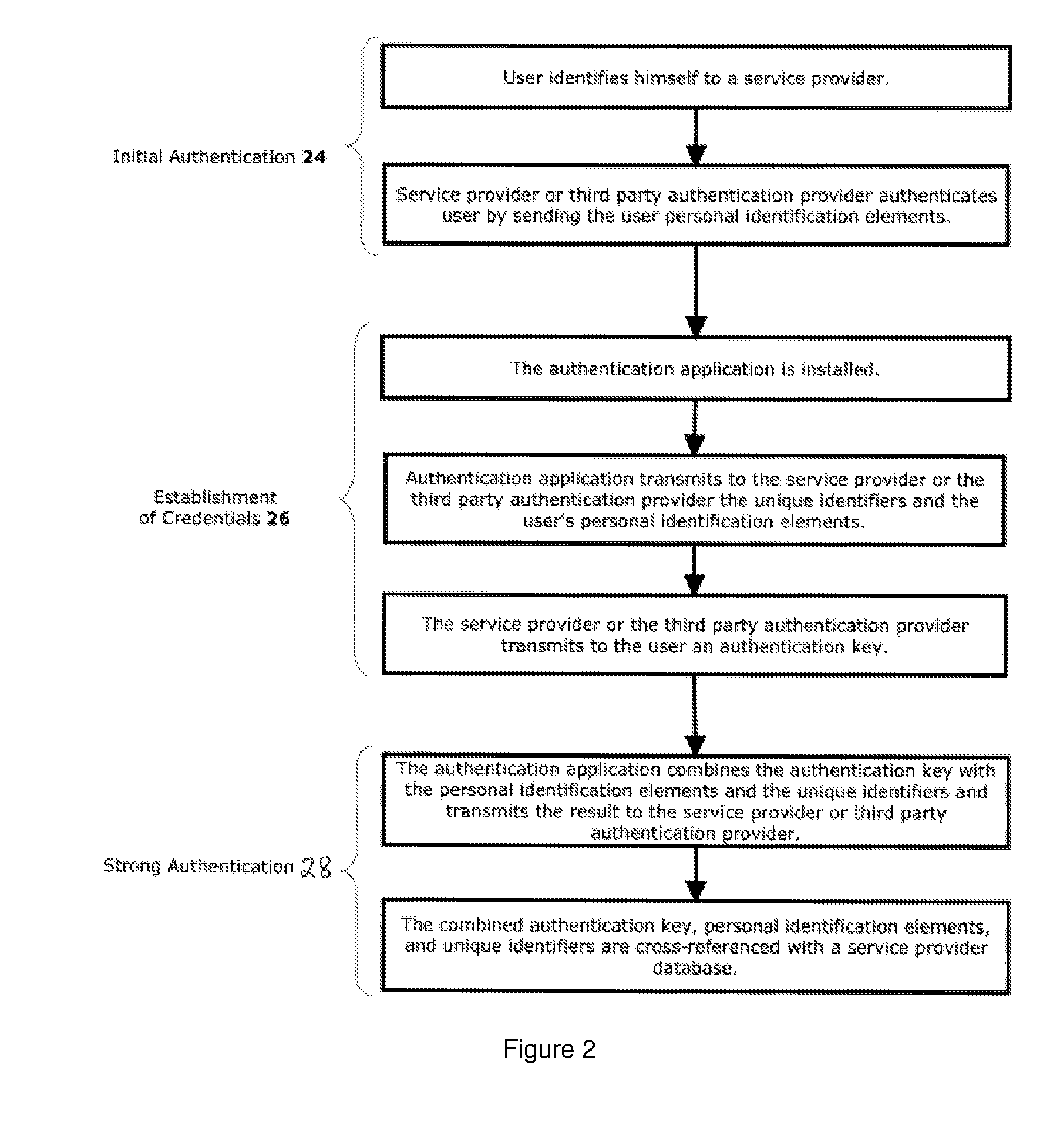
InactiveUS20110197267A1Digital data processing detailsUser identity/authority verificationWeb authenticationInternet privacy
There is disclosed a system and method for authenticating the identity of a user of a client device as part of a transaction between the client device and a server of a service provider over a communications network, the client device comprising a unique identifier. The system and method comprise one or more personal identification elements issued to the user based upon an initial authentication of the identity of the user, a credential issued to the client device by the service provider based upon the personal identification elements and the unique identifiers, and a trigger event for launching an authentication application installed on the client device. When the authentication application is launched by the trigger event, the authentication application transmits the one or more personal identification elements and the unique identifier in a combination with the credential to the server for authentication by the service provider.
Owner:LIPSO SYST INC
System and Method for Distributed Network Authentication and Access Control
InactiveUS20070124802A1Easy accessReduce difficultyRandom number generatorsUser identity/authority verificationWeb siteWeb authentication
A user gains access to a private network by connecting to a network, either through a hardwired or wireless connection, and then initiates an Internet access request targeting any website. If the user is not already authorized for Internet access, then the user is sent to a first predetermined website that points the user to an authentication server accessible via the Internet. The authentication server sends the user an HTTP form pages requesting authentication information. When the user responds, a network monitoring device within the private network alters the form page to include the user's hardware address and an encoded ID based on the network's location. The authentication server forwards this data to a gate keeper server, which authenticates the new user and transmits an unblock message along with another encoded ID based on the network's location and the user's hardware address.
Owner:HEREUARE COMMUNICATIOINS
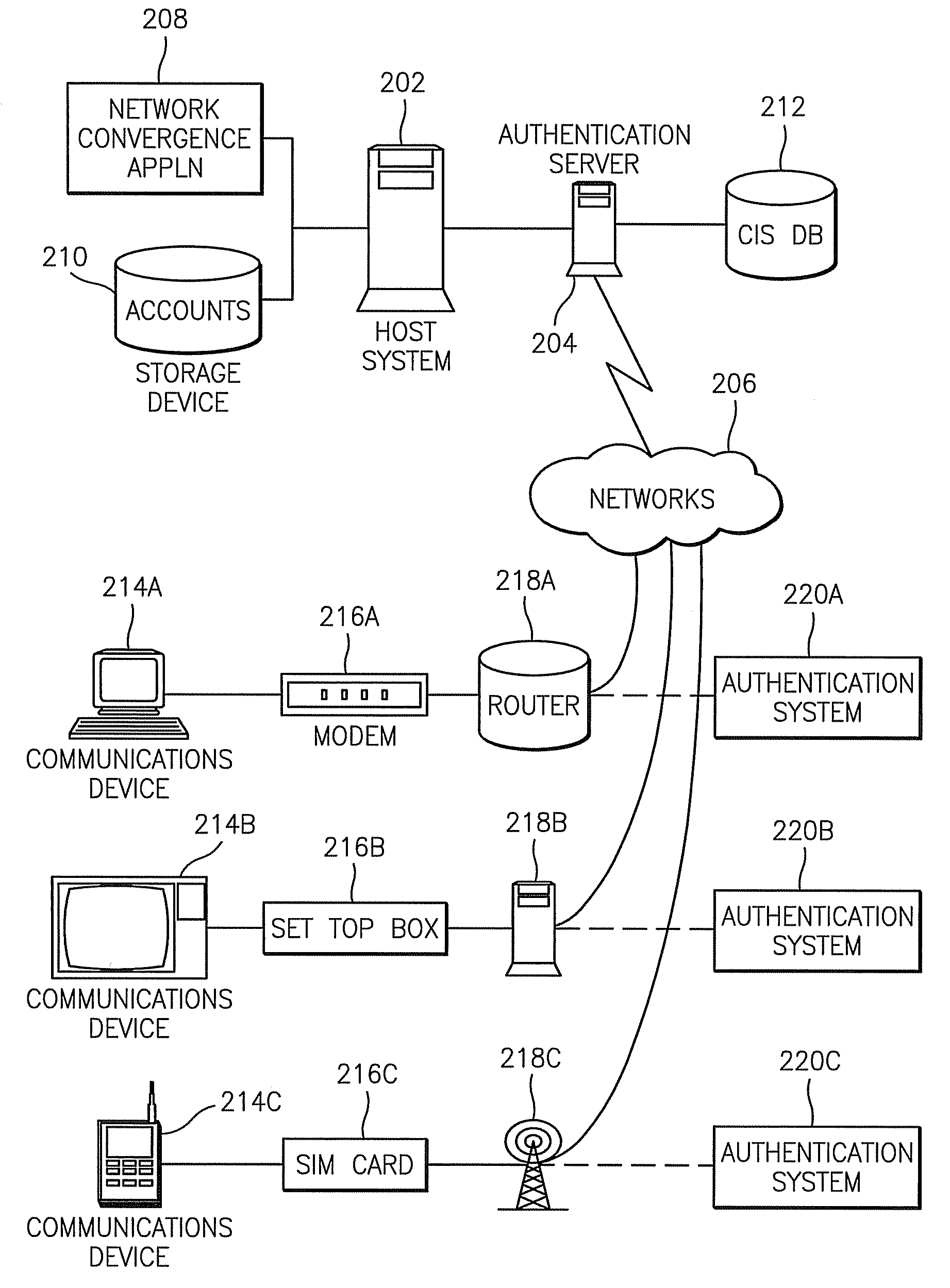
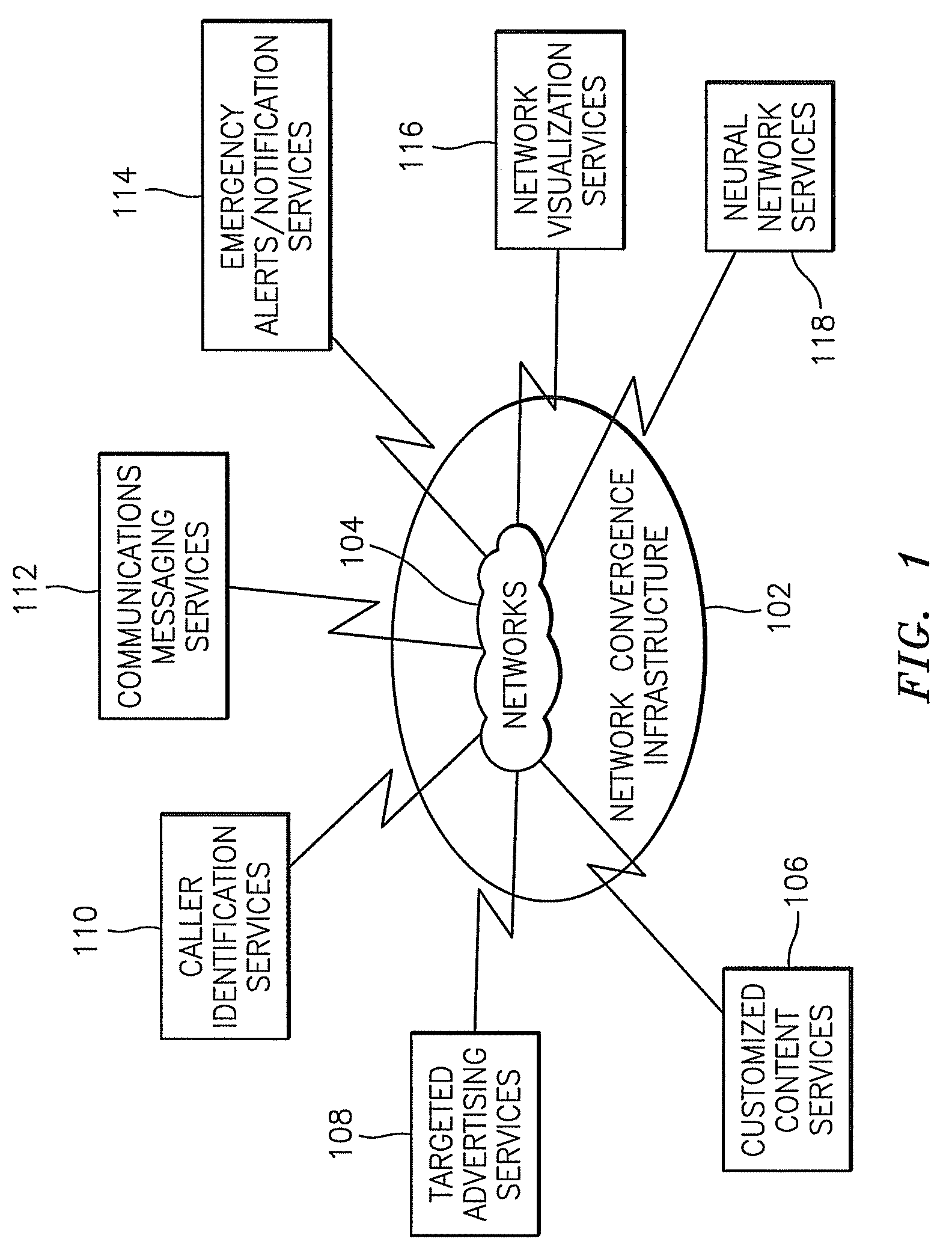
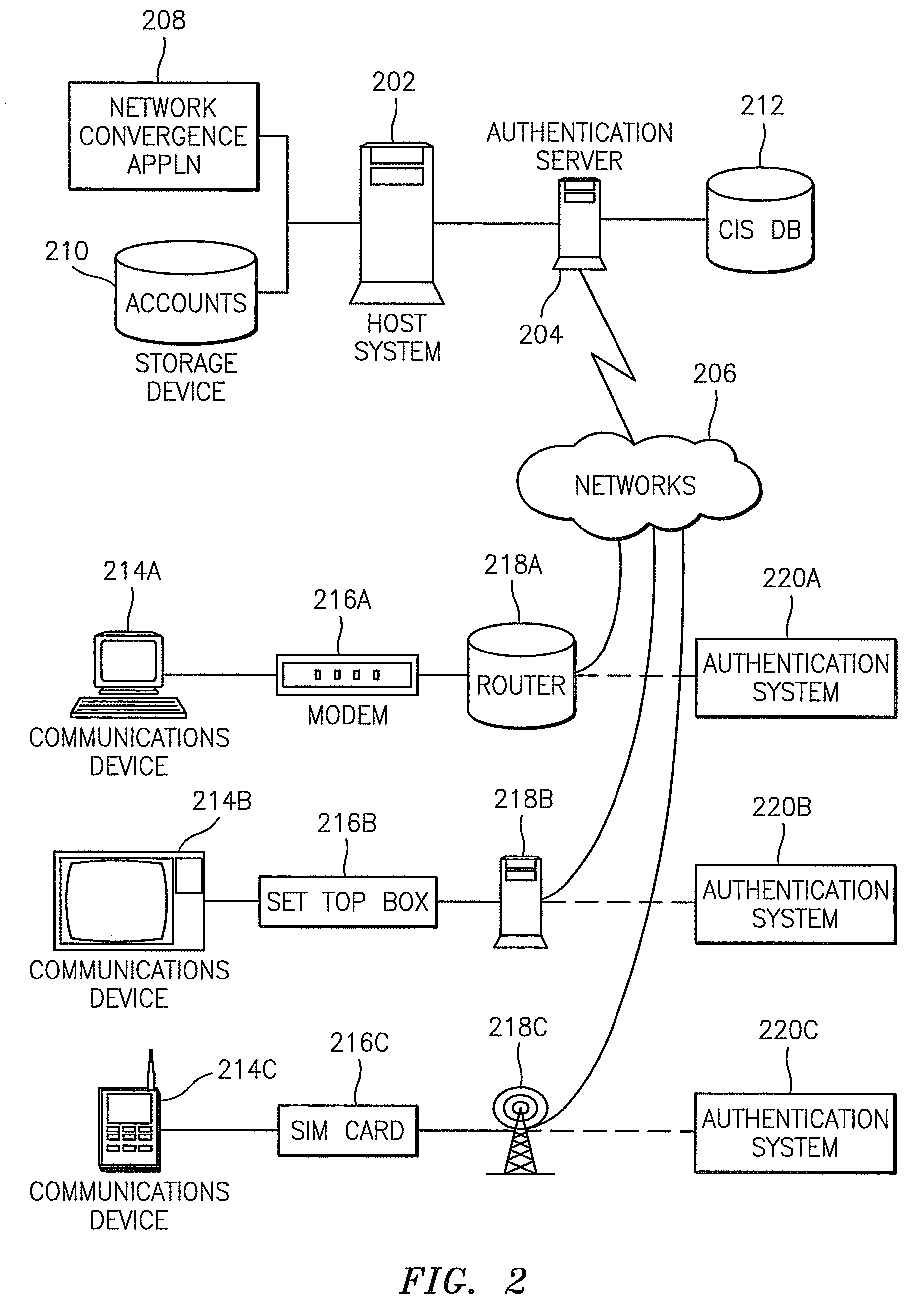
Methods, systems, and computer program products for providing network convergence of applications and devices
InactiveUS20070209065A1Digital data processing detailsUser identity/authority verificationNetwork ConvergenceWeb authentication
A method, system, and computer program product for providing network convergence of applications and devices across multiple types of networks are provided. The method includes receiving an identifier for a device and user credentials for an account. The account specifies network access privileges for a user. The method also includes authenticating the user credentials and storing the device identifier with the user credentials within the account upon successful authentication of the user credentials. The method further includes using the user credentials and an identifier of a respective selected device specified in the account to route a sign on request from the respective selected device to a network authentication element for providing a single sign on credential for a user of the respective selected device.
Owner:BELLSOUTH INTPROP COR
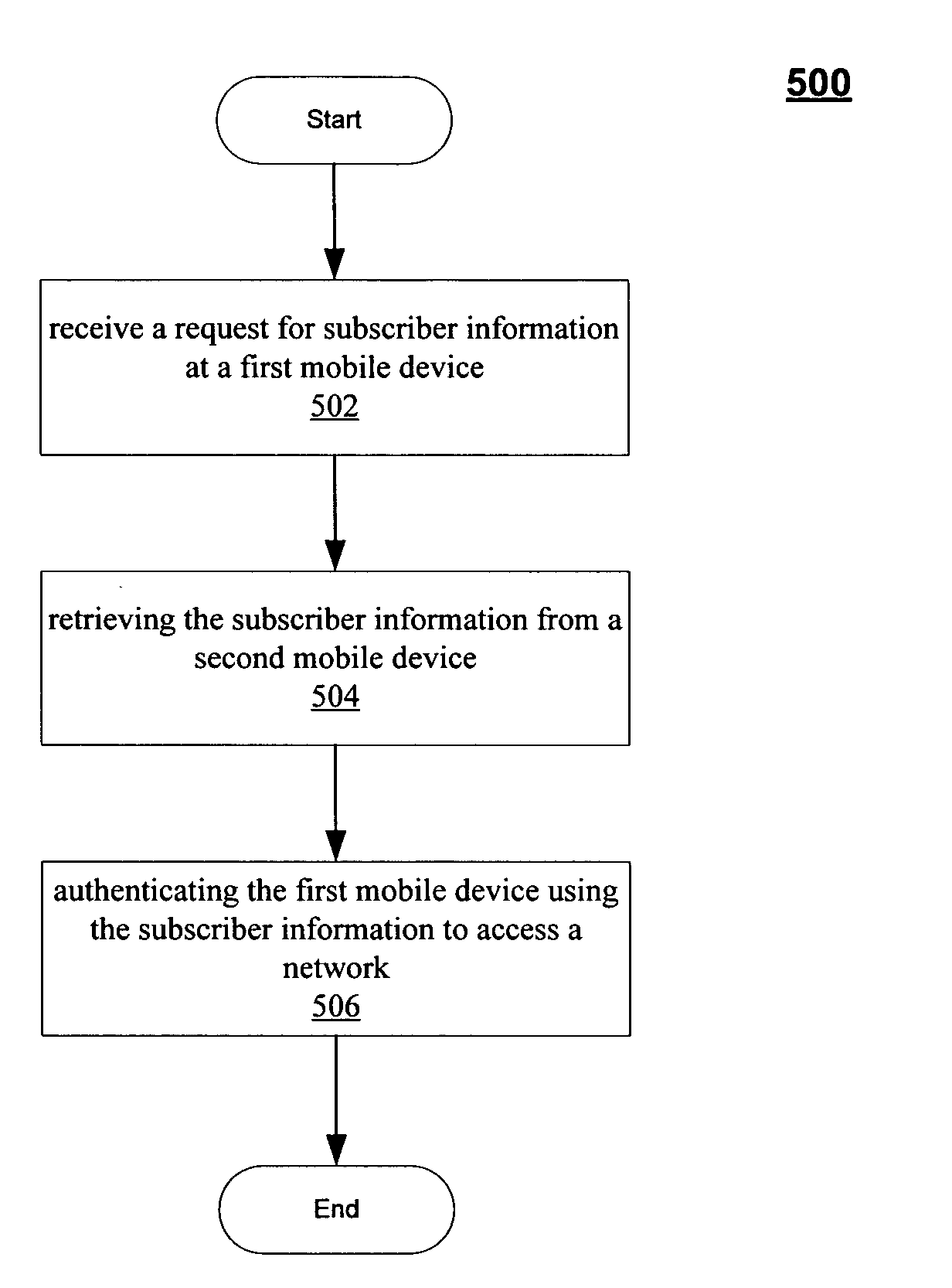
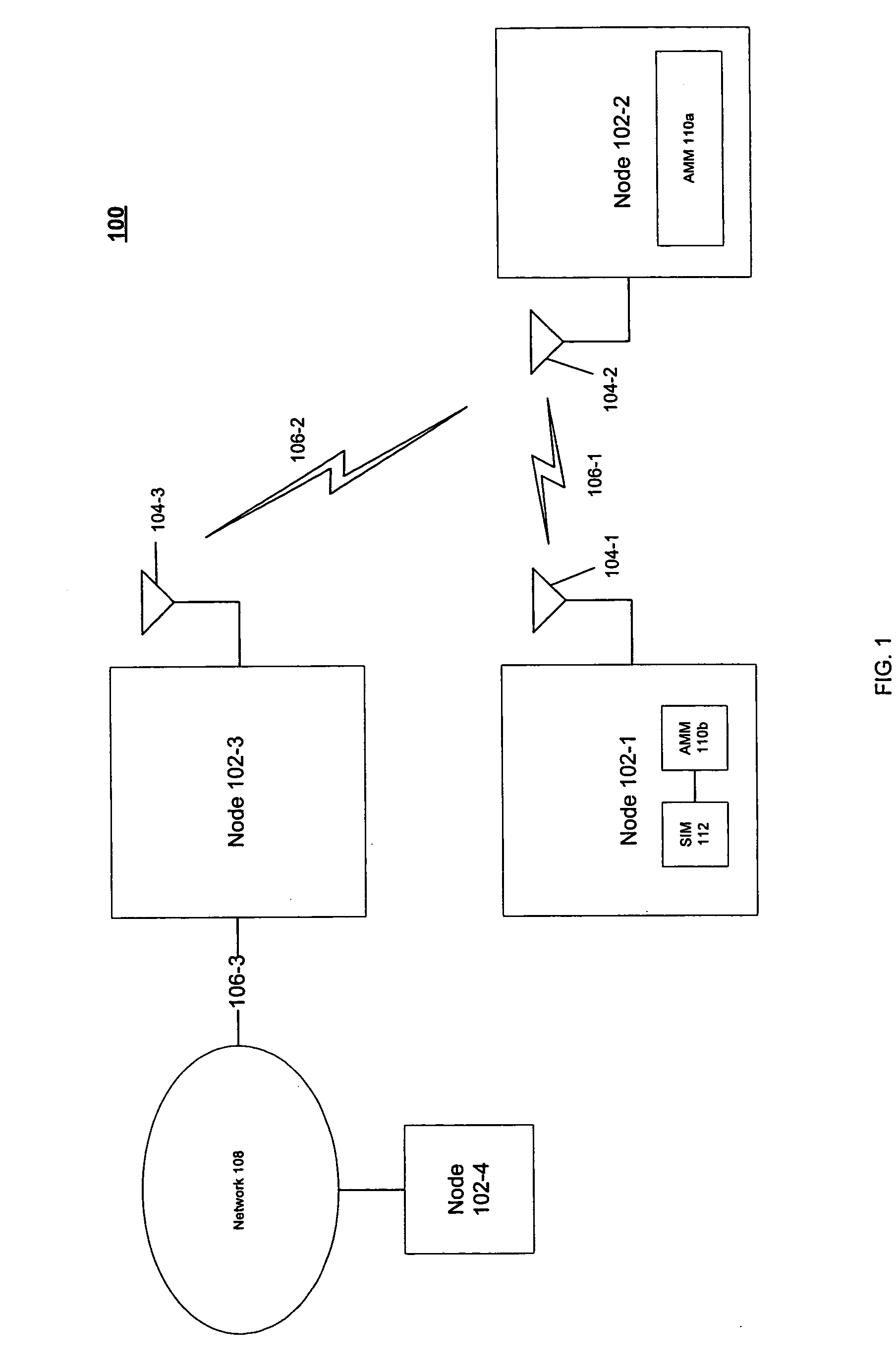
Techniques to manage network authentication
InactiveUS20060293028A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsWireless lanMobile device
A system, apparatus, method and article to manage network authentication are described. The apparatus may include an authentication management module to manage authentication of a first mobile device to access a wireless local area network using subscriber information stored on a second mobile device. Other embodiments are described and claimed.
Owner:INTEL CORP
Apparatus and method for automatically authenticating a network client
InactiveUS7231517B1Key distribution for secure communicationMultiple digital computer combinationsAccess networkWeb authentication
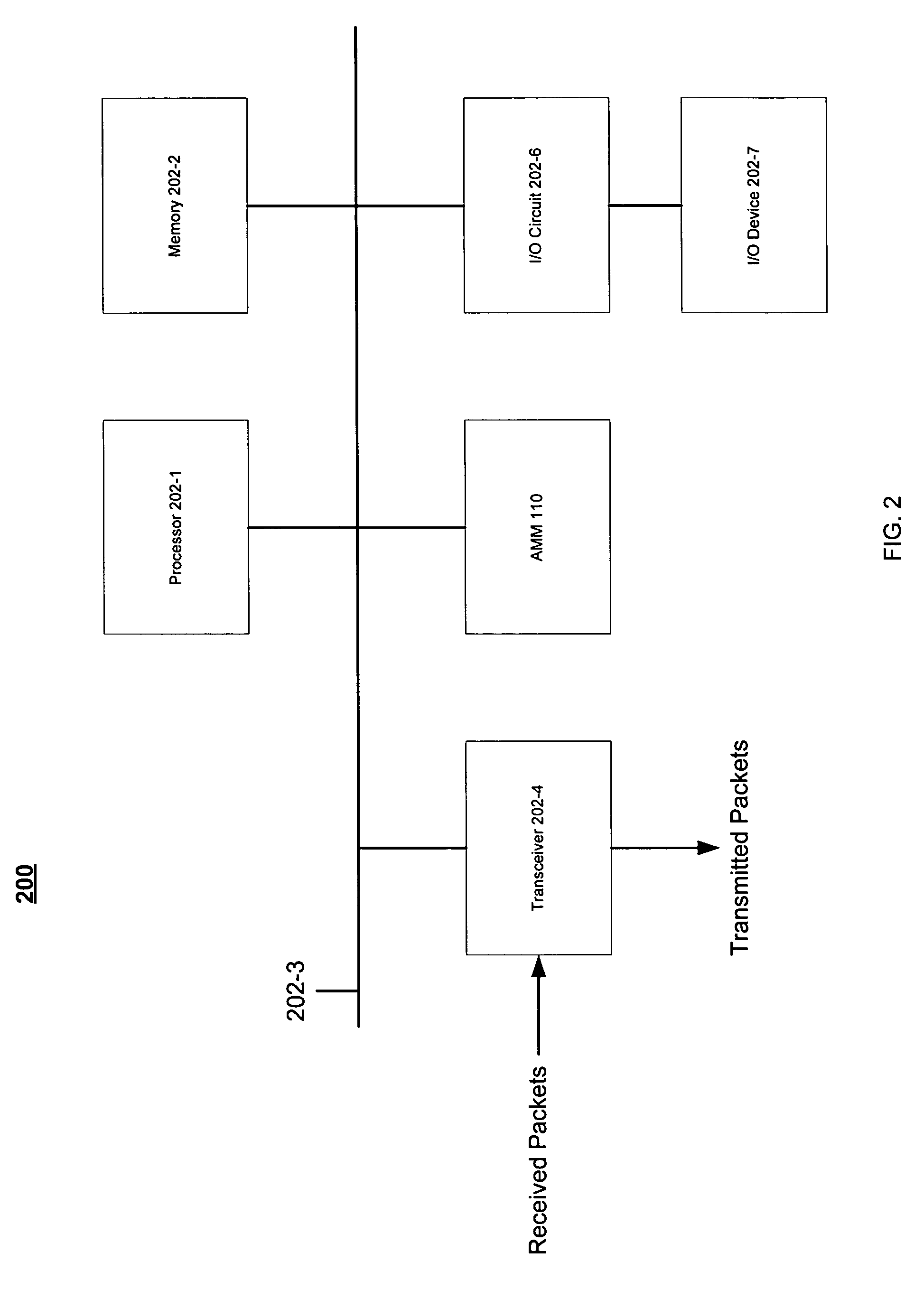
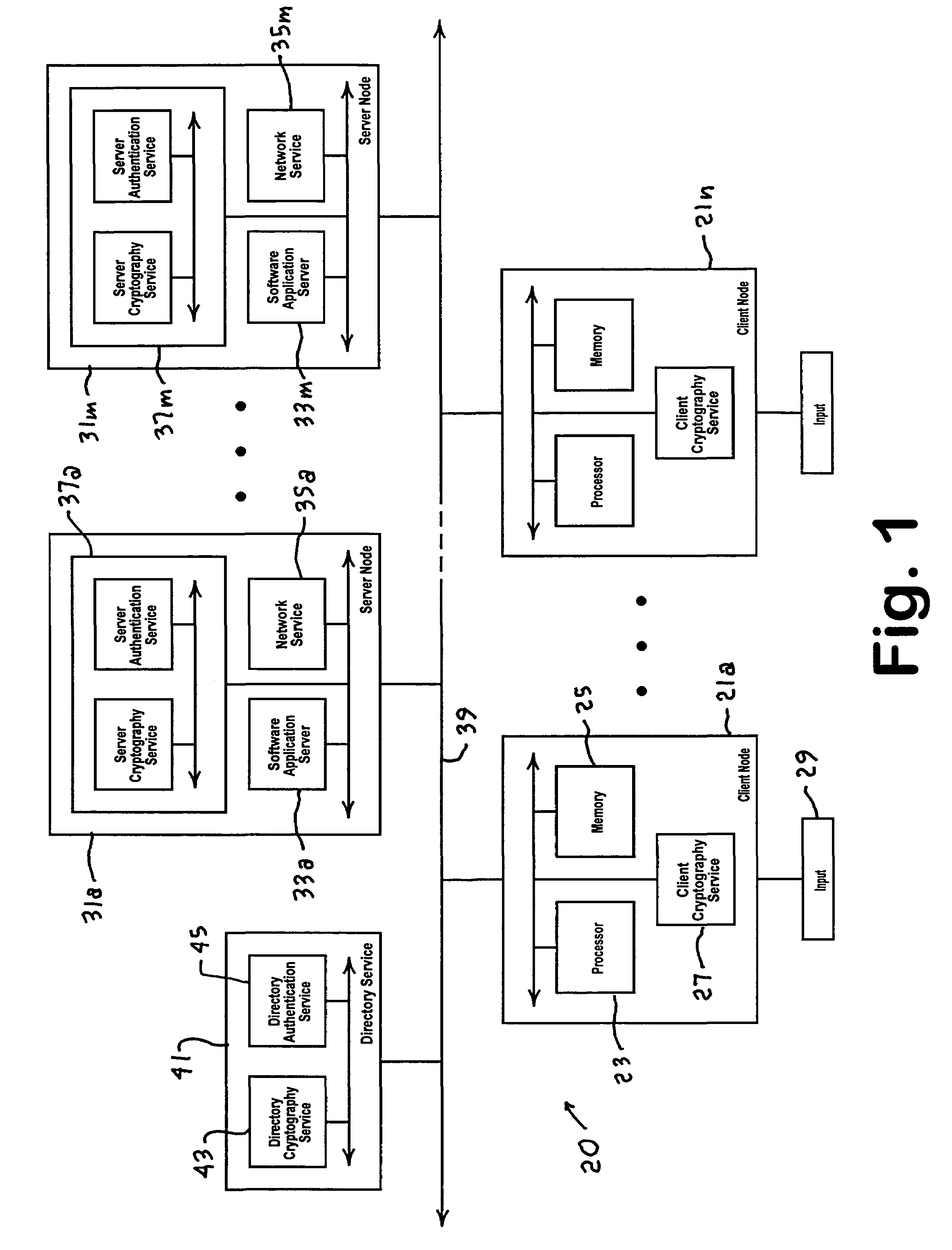
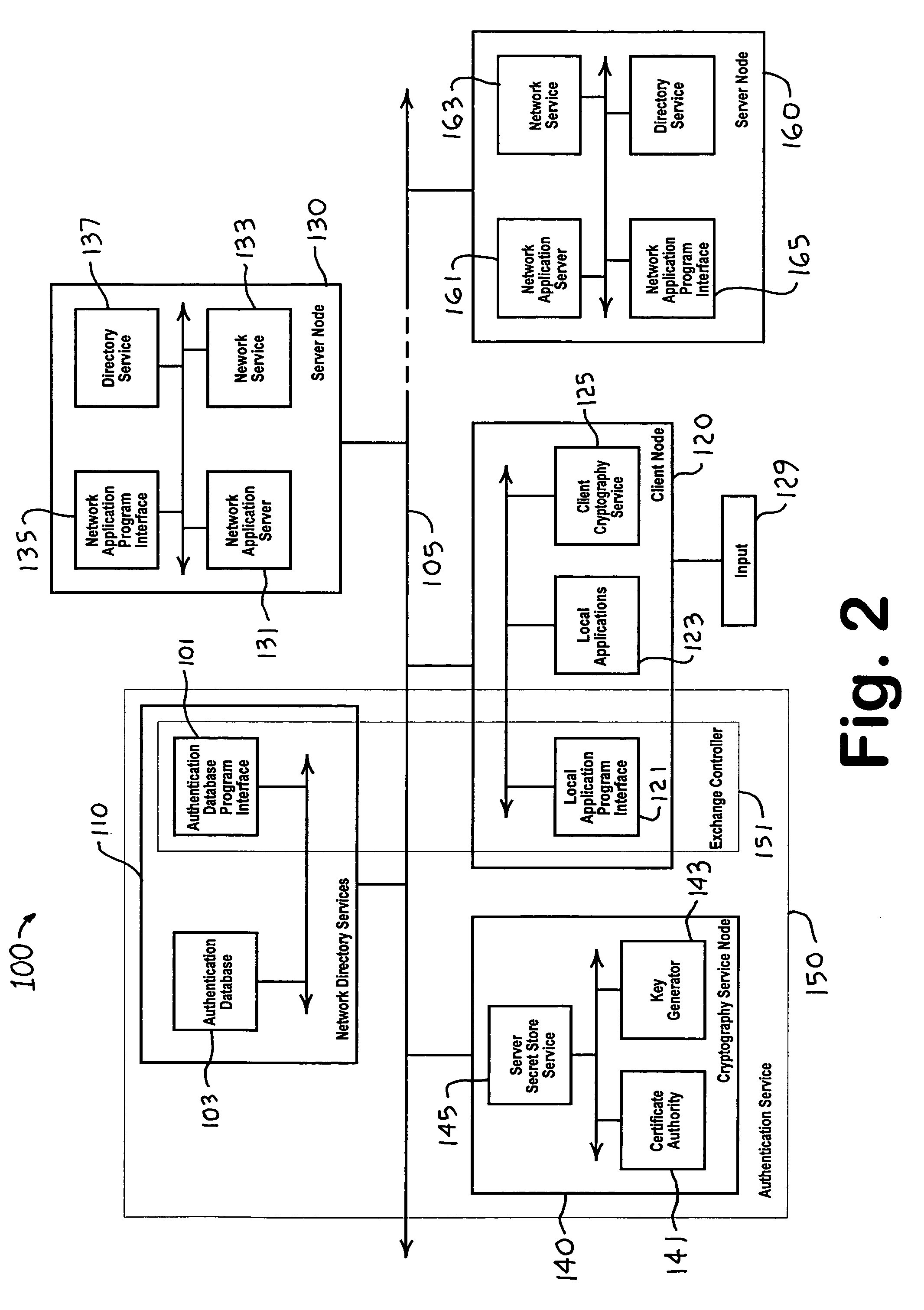
A distributed authentication system includes a cryptography service node, and a client node interface coupled to a network authentication database, for providing automatic authentication to enable the client node to access network resources, such as applications or services, resident in one or more network server nodes. Authentication secrets corresponding to the network resources are each encrypted with a respective strong key and stored in the authentication database. Authentication of the client node is accomplished with the retrieval of an authentication secret corresponding to a requested network resource. The retrieval process includes: i) decrypting the authentication secret using the strong key and encrypting the secret using a second key, and ii) sending a copy of the second key encrypted with a third key along with the encrypted secret to the requesting client node via a communication medium.
Owner:APPLE INC
Centralized identity authentication for electronic communication networks
InactiveUS7140036B2Easy to carryReduce demandDigital data processing detailsUser identity/authority verificationWeb authenticationElectronic communication
A method of centralized identity authentication for use in connection with a communications network includes registering users of the communications network such that each registered user's identity is uniquely defined and determinable, and registering a plurality of vendors having a presence on the communications network. The registered vendors selectively transact with registered users, wherein the transactions include: (i) the registered vendor selling goods and / or services to the registered user; (ii) the registered vendor granting the registered user access to personal records maintained by the registered vendor; and / or (iii) the registered vendor communicating to the registered user personal information maintained by the registered vendor. The method also includes each user's identity being authenticated over the communications network prior to completion of transactions between registered vendors and registered users.
Owner:CARDINALCOMMERCE CORP +2
Scheme for device and user authentication with key distribution in a wireless network
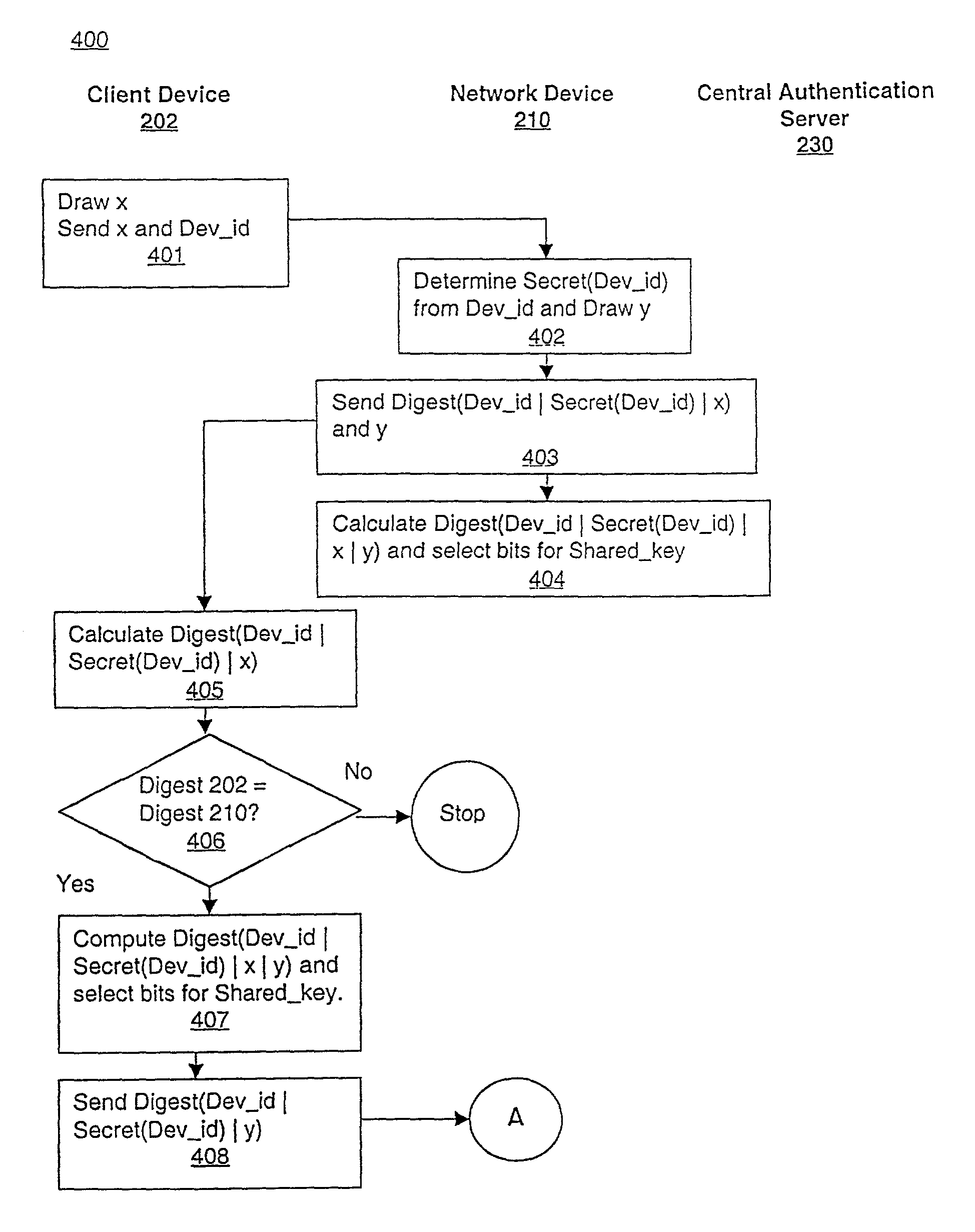
ActiveUS7350076B1Reduction in marketLarge processing capabilityRandom number generatorsUser identity/authority verificationWeb authenticationSecret share
In a computer network, a method of mutually authenticating a client device and a network interface, authenticating a user to the network and exchanging encryption keys. In one embodiment, the method comprises authenticating the client device at the local network device point, with which the client device exchanges an encryption key and then the user is authenticated by a central authentication server. In another embodiment, the method comprises authenticating the client device at the central authentication server, with which the client device exchanges a key which is passed to the network device with a secret shared between the central authentication server and the network device. In this embodiment, the user is also authenticated at the central authentication server.
Owner:VALTRUS INNOVATIONS LTD +1
Systems and methods for network authentication
ActiveUS20080313714A1Digital data processing detailsAnalogue secracy/subscription systemsDigital dataWeb based social networks
Exemplary systems and methods for network authentication are provided. Exemplary systems include an application program interface configured for receiving a request for an authentication code, a code generator in communication with the application program interface, the code generator configured to generate the authentication code, and the application program interface further configured to receive the generated authentication code and allow an application to communicate digital data with a web-based social network. Further systems include the generated authentication code being received from a network device without an Internet browser and the received generated authentication code allowing an application to communicate digital data with a web-based social network for an extended period of time. Exemplary methods include receiving a request for an authentication code, generating the authentication code, receiving the generated authentication code, and allowing an application to communicate digital data with a web-based social network.
Owner:META PLATFORMS INC
Computer network security system
ActiveUS7100054B2Improve security levelEasy to provideDigital data processing detailsUser identity/authority verificationThird partyInternet communication
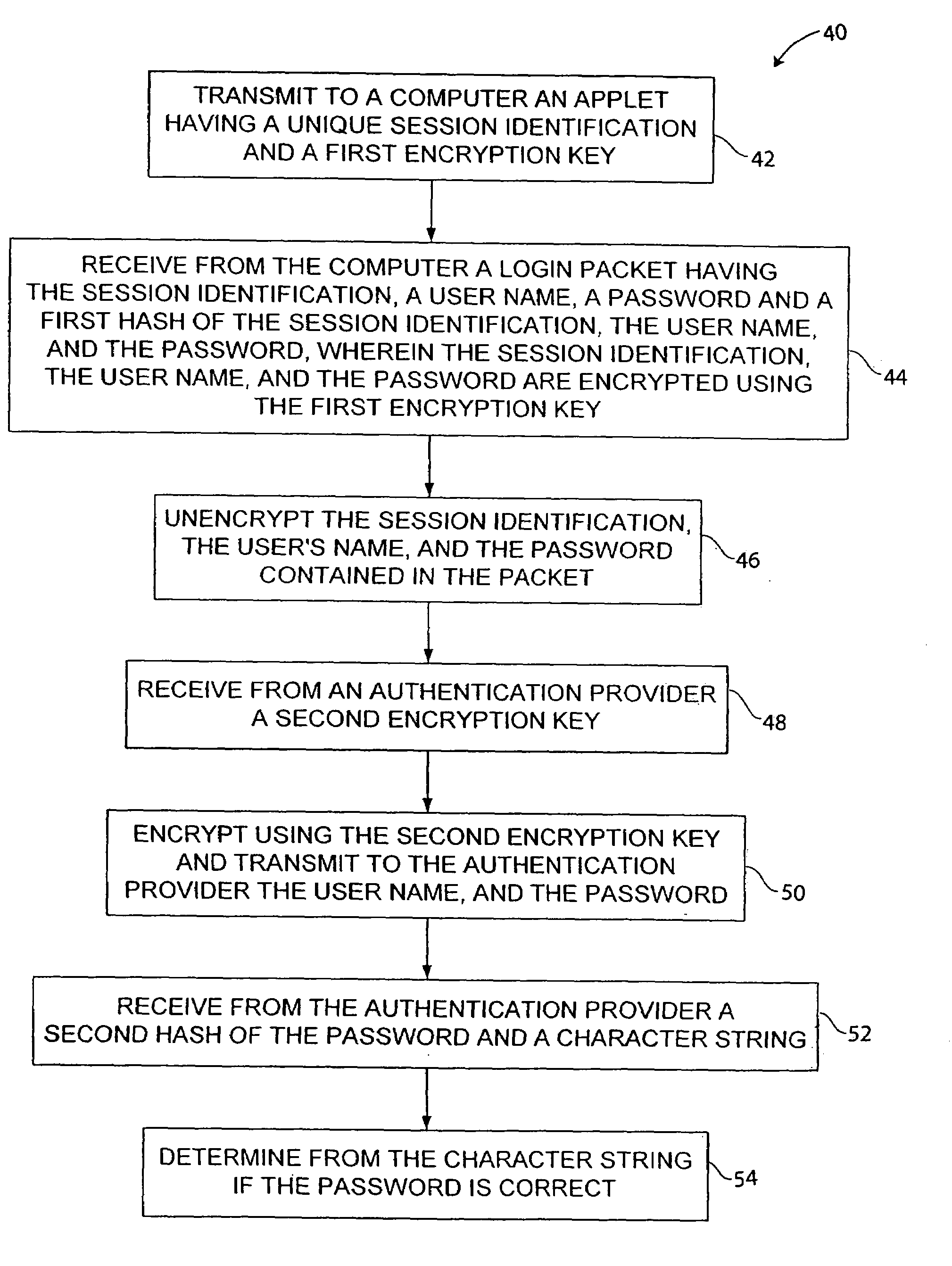
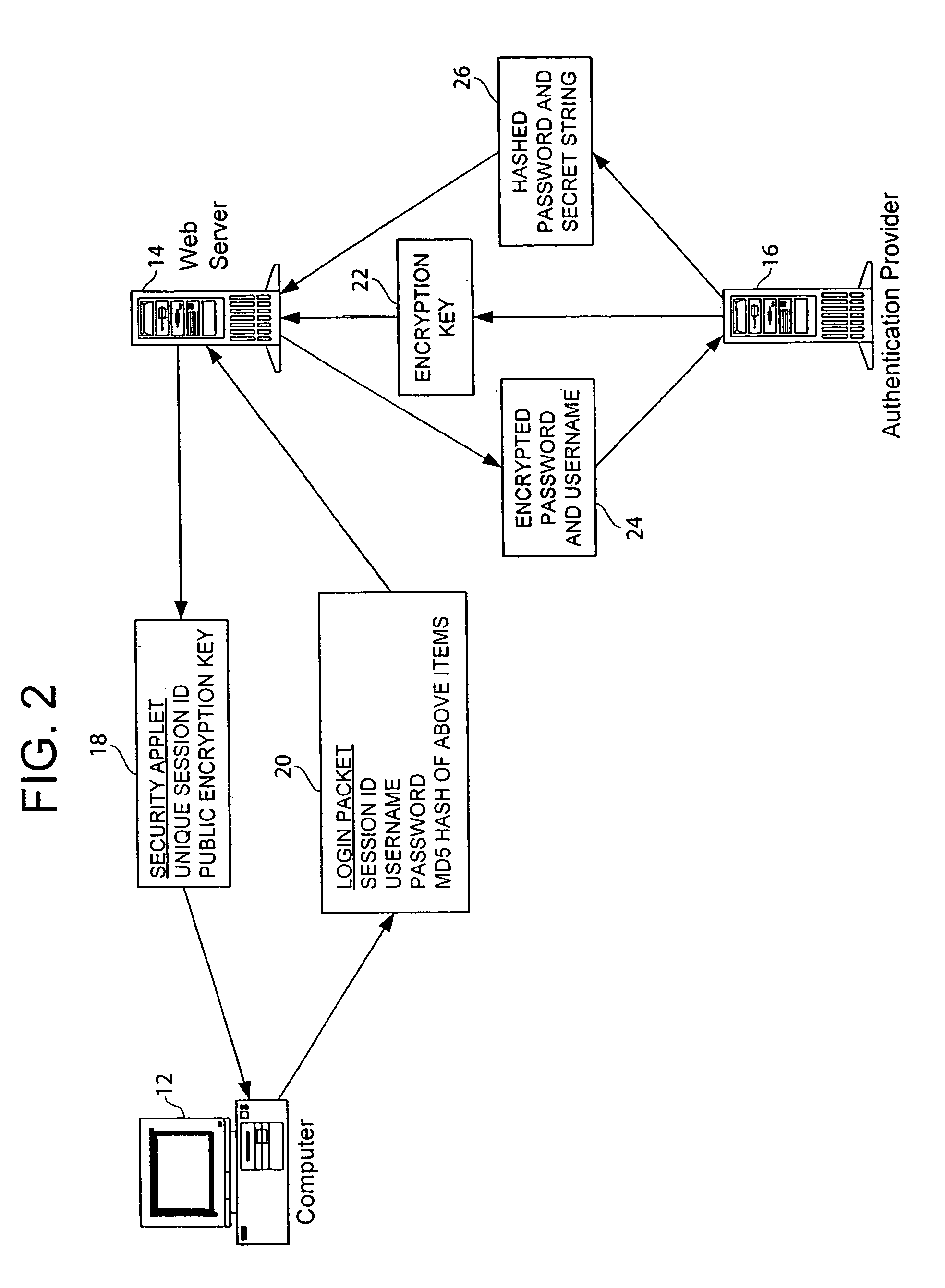
A method and system are provided for authenticating a user of a computer over a computer network. In one embodiment of the invention, the method includes transmitting an applet having a challenge string and a first encryption key, receiving a login packet having the challenge string and a password that is encrypted using the first encryption key, decrypting the password, receiving information from an authentication provider, and authenticating the password by using the information provided by the authentication provider. The challenge string can be either a sequence number or a session identifier. The authentication provider can be a software program or an authentication server. An advantage of embodiments of the present invention is that a computer can provide secure Internet communications using a web browser that does not support SSL and can provide secure integration with third party security systems.
Owner:AMERICA POWER CONVERSION CORP
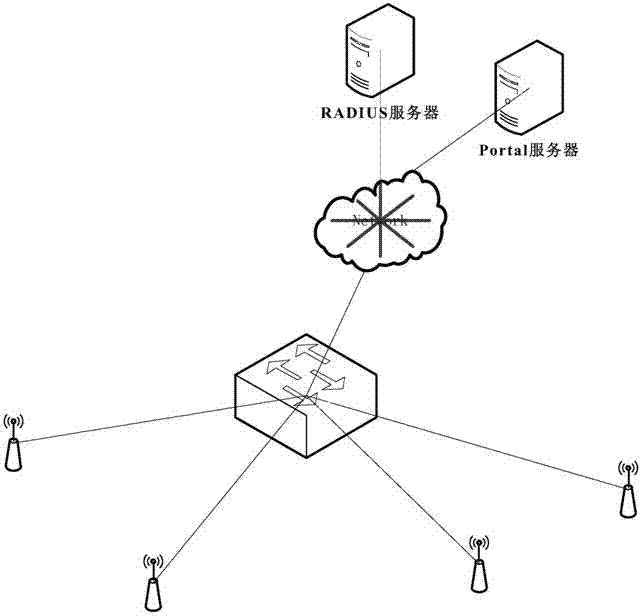
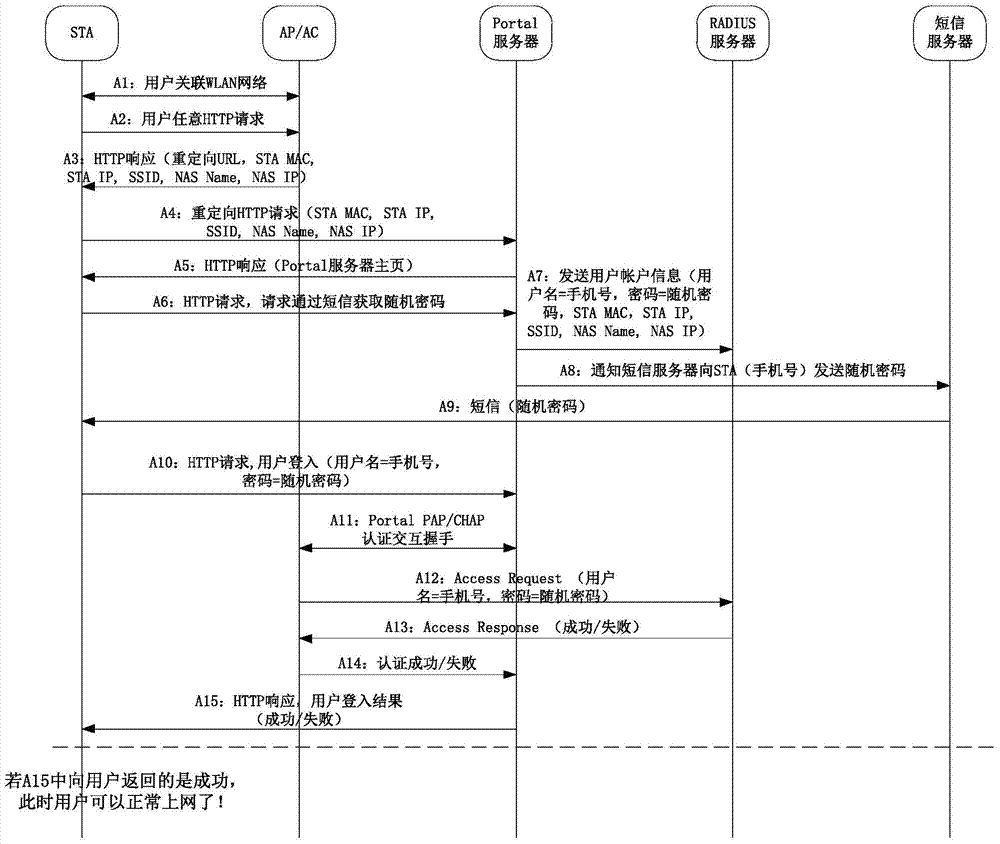
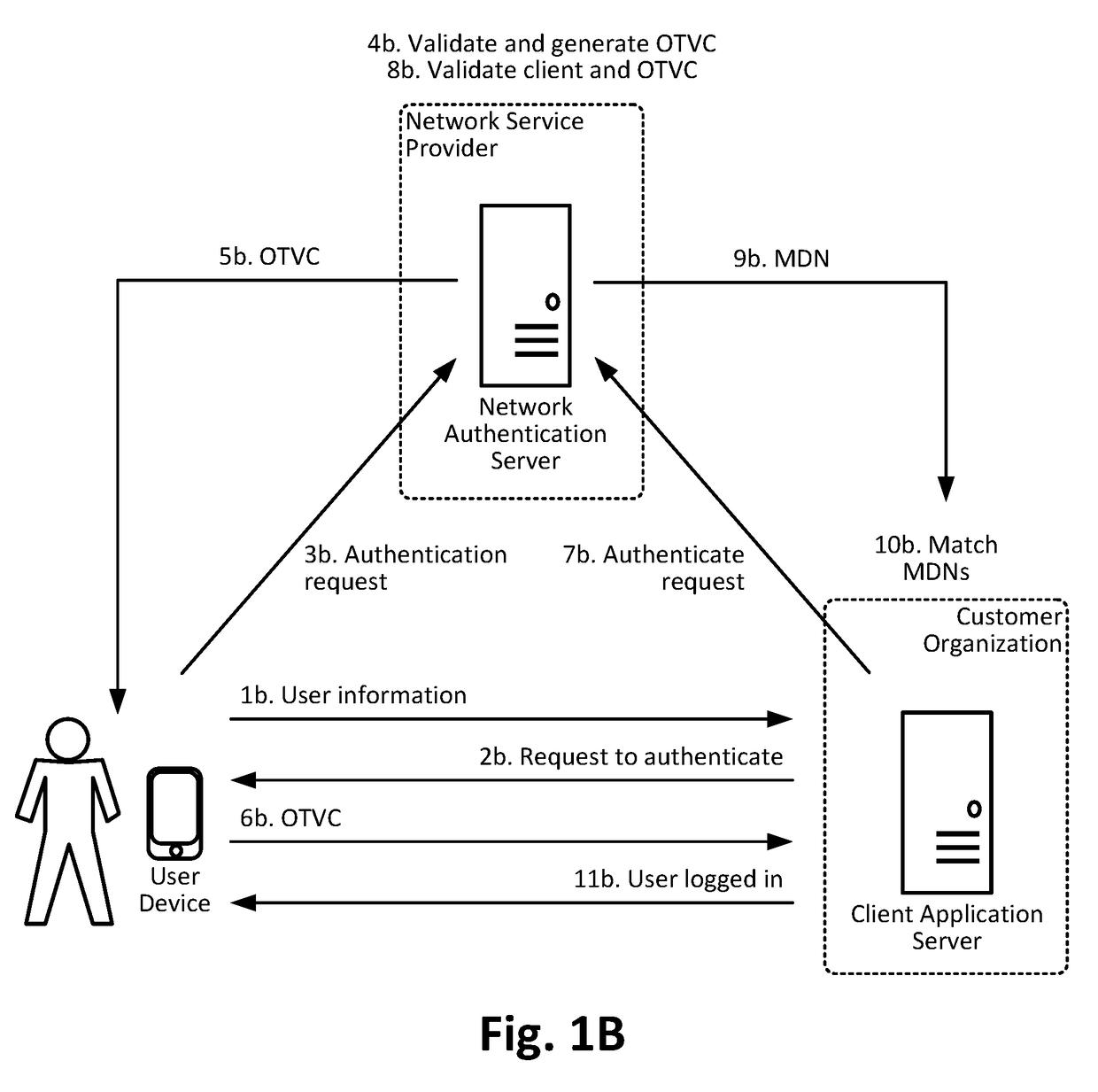
Perception-free WLAN (Wireless Local Area Network) authentication method fusing Portal/Web authentication and MAC (Media Access Control) authentication
The invention discloses a perception-free WLAN (Wireless Local Area Network) authentication method fusing Portal / Web authentication and MAC (Media Access Control) authentication. In the method, the characteristics and advantages of Portal / Web authentication and MAC authentication are fused. The method comprises the following steps: when a user terminal accesses a WLAN network for the first time, a user authenticates via a mobile phone number, and an AP (Access Point) or AC (Access Controller) serving as network access equipment transmits the MAC address information of the user terminal to an authentication server by controlling an HTTP (Hyper Text Transport Protocol) redirecting request of the user, so that the authentication server can correlatively bind user information with the unique identification MAC of the user terminal; when the user accesses the network once again or roams, the AP or AC of a WLAN infrastructure extracts the MAC address of the user terminal while the user terminal is correlating with the network, and network access authentication is completed for the user by using the MAC without perception of the user. The perception-free authentication method does not have any additional software installation requirement on a wireless terminal of the user, so that the user can obtain excellent authentication experience while accessing the WLAN network, and the identity-traceable network security requirement can be met.
Owner:SUZHOU HANMING TECH
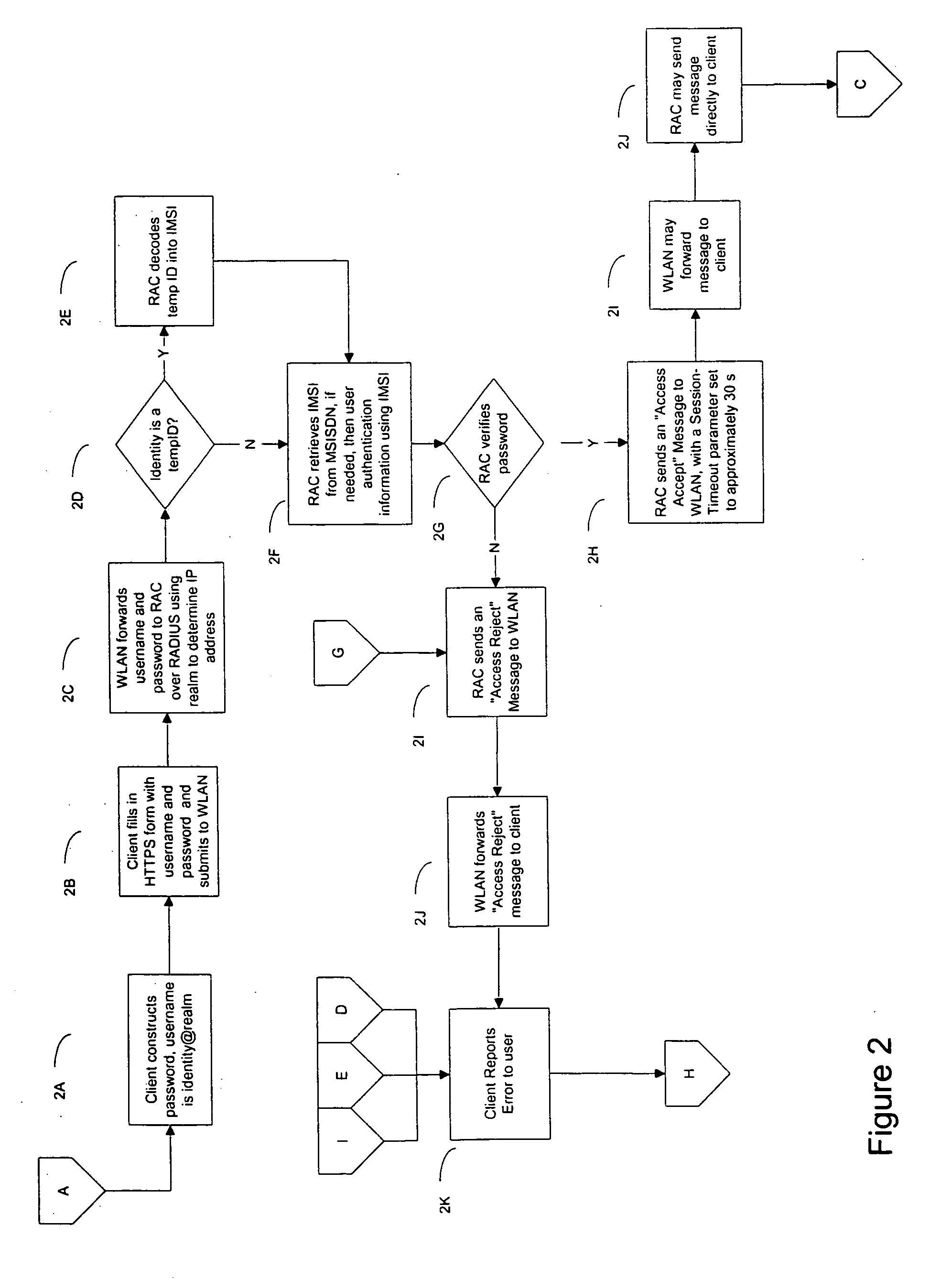
Method and system for providing SIM-based roaming over existing WLAN public access infrastructure
InactiveUS20050114680A1Prevent replay attacksUser identity/authority verificationNetwork topologiesWeb authenticationAccess method
A method and apparatus for performing SIM-based authentication and authorization in a WLAN Internet Service Provider (WISP) network supporting the universal access method (UAM) of authentication and authorization enabling roaming for customers of mobile service providers onto said networks. In addition, the invention provides a secure way of authenticating the customer's client device to the mobile service provider's network by employing temporary credentials for authentication that provide privacy of the user's identity and prevent replay attacks. Finally, if the WISP network supports the ‘pass-through’ facility, the authentication can be done more securely and quickly.
Owner:AZAIRE NETWORKS
Fast authentication and access control method for mobile networking
InactiveUS7174456B1Easy to switchReduce certification timeDigital data processing detailsUser identity/authority verificationExpiration TimeWeb authentication
A fast authentication and access control method of authenticating a network access device to a communications network having an access point communicating with a remote authentication (home AAA) server for the network access device. The method includes the step of receiving an access request having an authentication credential from the network access device at the access point. The authentication credential includes a security certificate having a public key for the network access device and an expiration time. The security certificate is signed with a private key for the remote authentication server. The access point locally validates the authentication credential by accessing the public key of the remote authentication server from a local database, and checking the signature and expiration time of the security certificate. If the authentication credential is validated at the access point, the access point grants the network access device conditional access to the network by sending an access granted message to the network access device. The access granted message includes a session key encrypted with a public key for the network access device. The session key is stored in a database associated with the access point. The access point contacts the remote authentication server to check a revocation status of the security certificate for the network access device. If the access point receives a message from the remote authentication server that the authentication credential for the network access device has been revoked, it suspends network access for the network access device.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
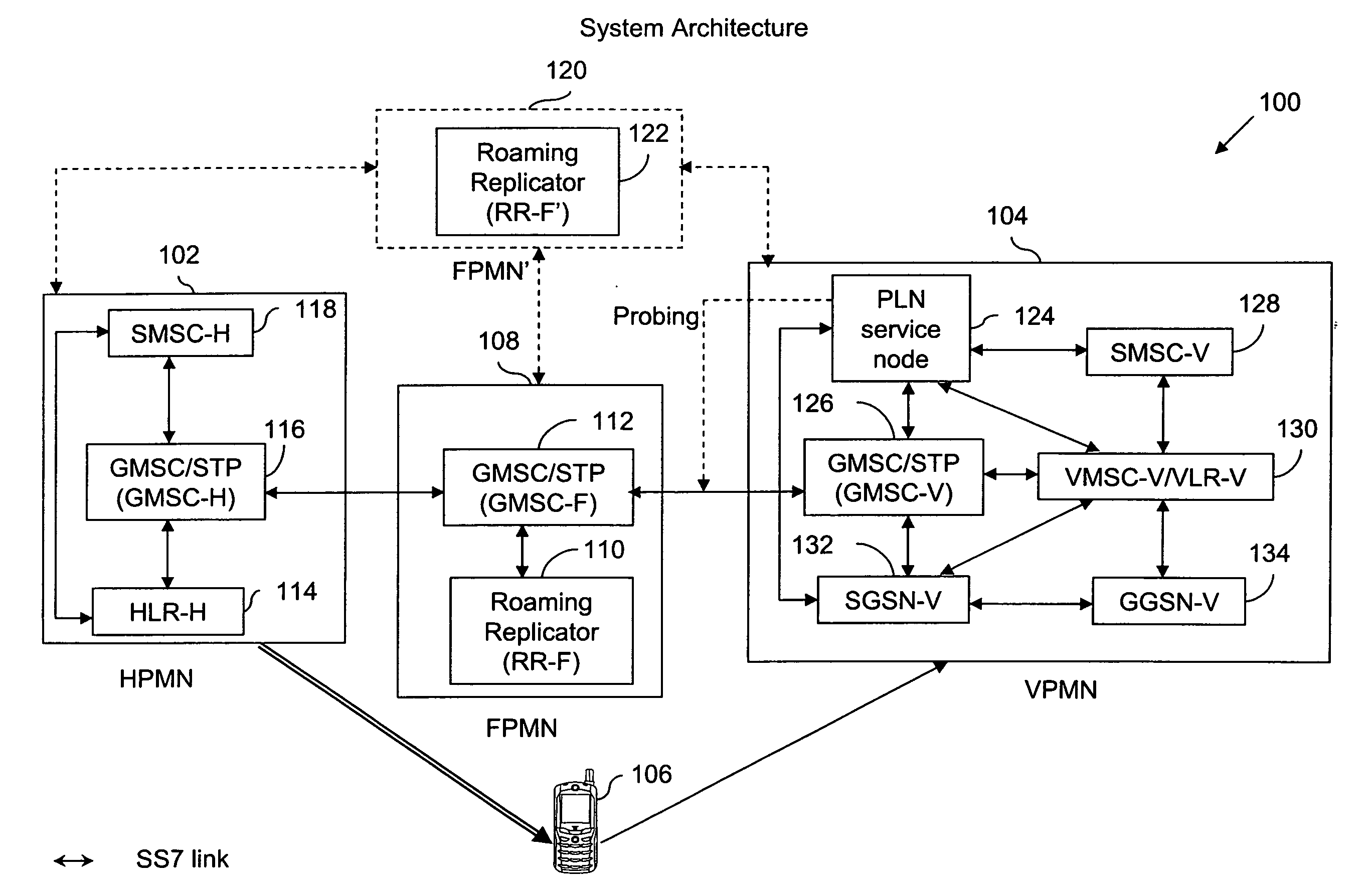
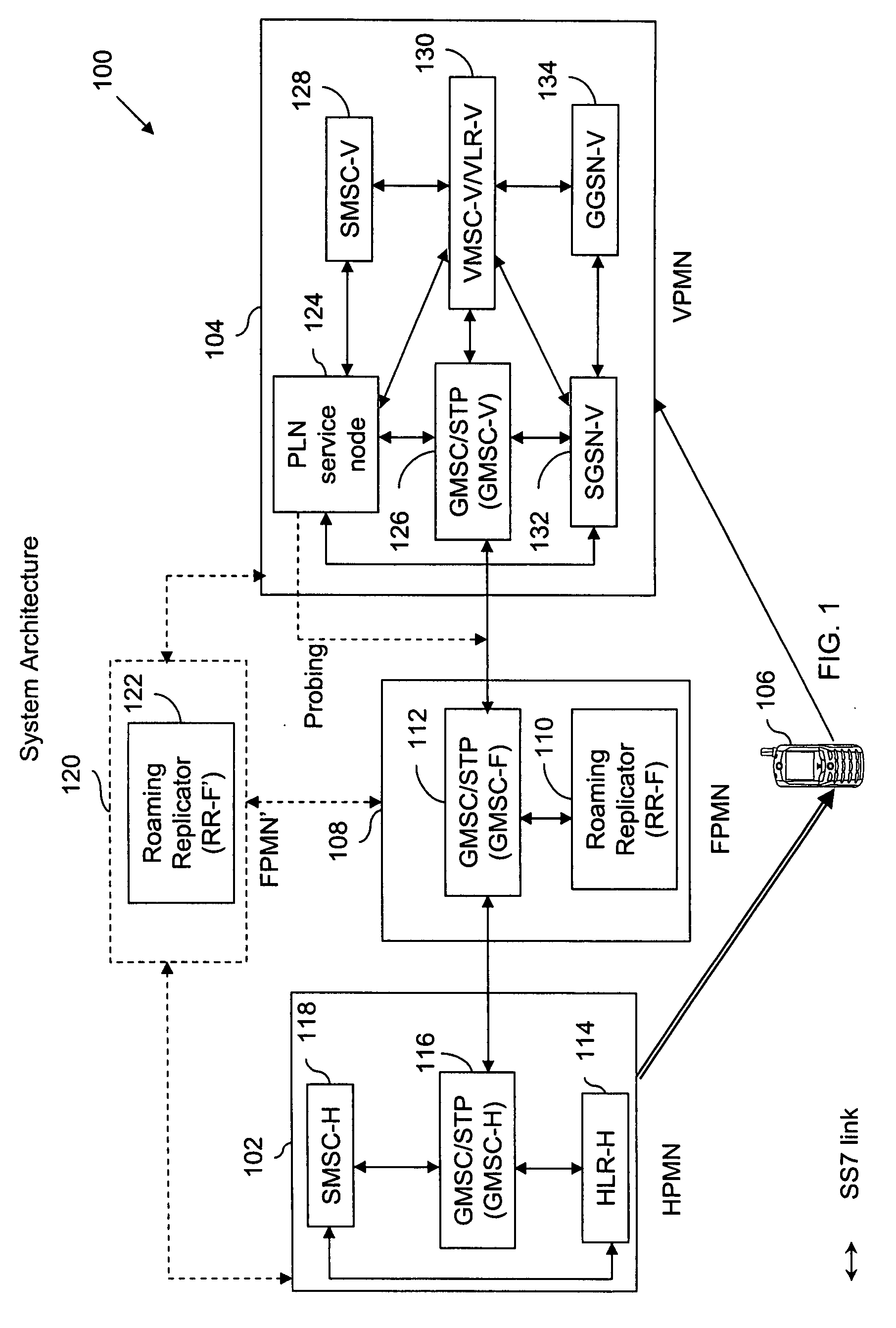
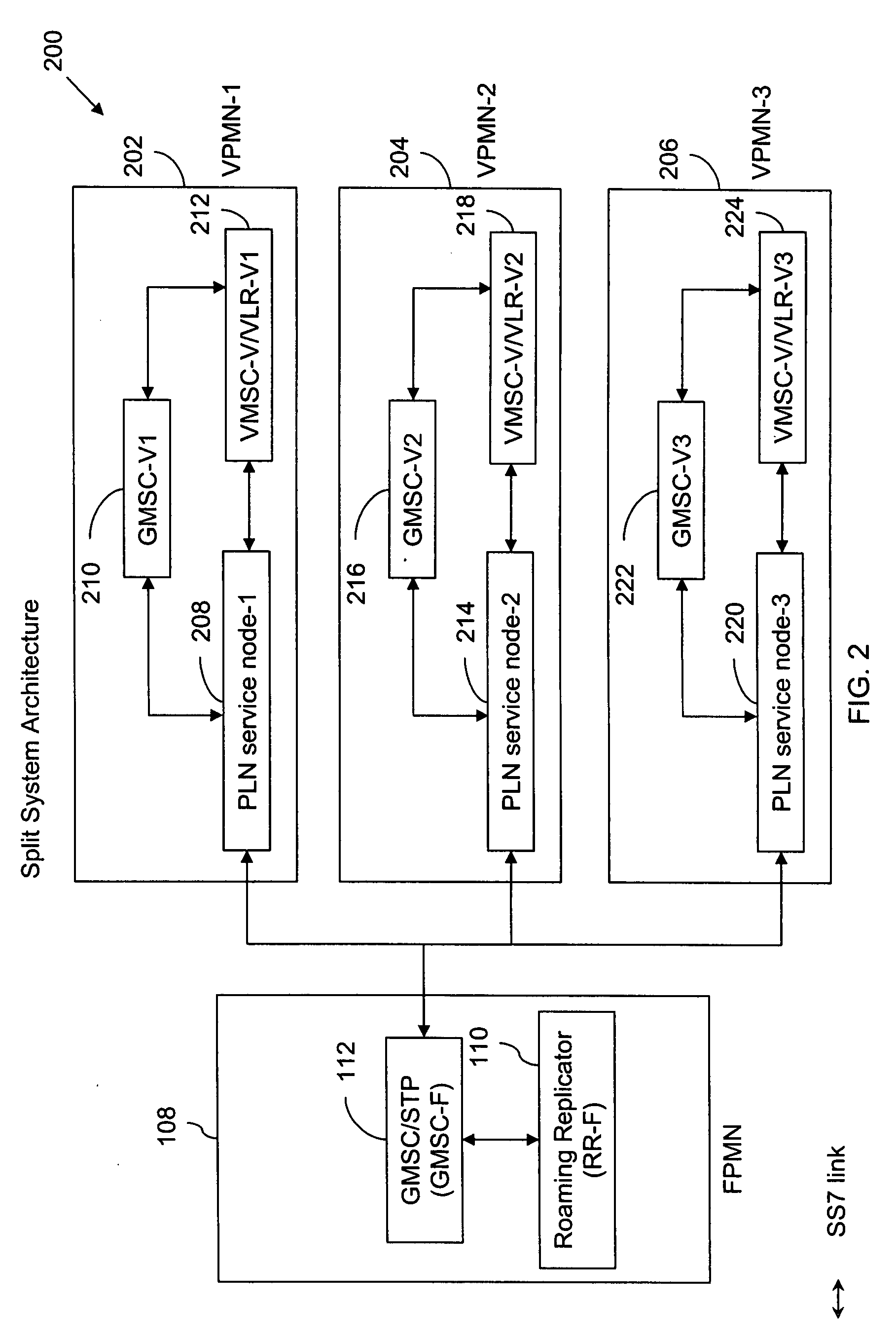
Method and system for providing PLN service to inbound roamers in a VPMN using a sponsor network when no roaming relationship exists between HPMN and VPMN
InactiveUS20070281687A1Facilitating mobile communicationRadio/inductive link selection arrangementsWireless commuication servicesWeb authenticationCall control
The present invention provides a method for facilitating mobile communication of a subscriber associated with a home network roaming in a visited network, even when the visited network has a No-Roaming Agreement (NRA) with the home network. The method includes detecting at a switching unit associated with the visited network, a registration attempt by the subscriber to register with the visited network. The method further includes authenticating by the switching unit, the subscriber with the home network via a sponsoring network that has a roaming agreement with the home network. Finally, the method includes sending by a service node, a trigger profile information to the switching unit in response to the registration attempt so as to enable redirection of call control associated with the subscriber to the service node. The service node thereafter allows the subscriber to perform call and non-call related mobile activities in the visited network.
Owner:ROAMWARE
System and method for secured network access
A method and system for secured network access is provided in accordance with the present invention. The method begins with receiving a login request from a client on a router. Thereafter, a certificate transfer instruction for the router to an authentication appliance is generated where the client lacks a copy of a client certificate. The client is authenticated with a challenge-response sequence, the response to which is deliverable through an out-of-band communications channel. Upon authentication, the client certificate and the client private key are transmitted to the client, which are used to authenticate the client to the network.
Owner:MULTIFACTOR CORP
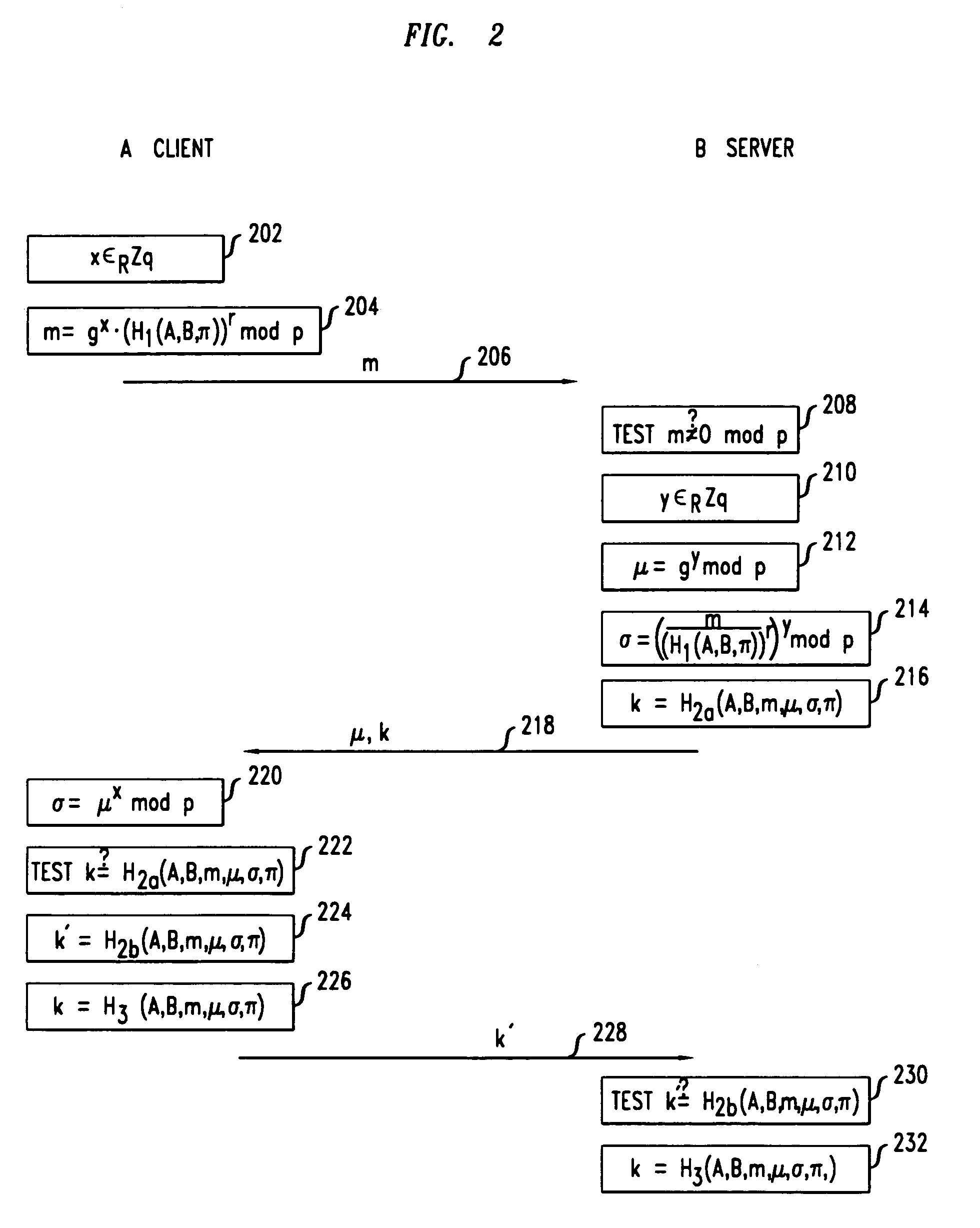
Secure mutual network authentication and key exchange protocol
InactiveUS7047408B1Key distribution for secure communicationUser identity/authority verificationKey exchangeSecure communication
Secure communication protocols are disclosed in which two parties generate a shared secret which may be used as a secure session key for communication between the parties. The protocols are based on Diffie-Hellman type key exchange in which a Diffie-Hellman value is combined with a function of at least a password using the group operation such that the Diffie-Hellman value may be extracted by the other party using the inverse group operation and knowledge of the password. In one embodiment, each of the parties explicitly authenticates the other party, while in another embodiment, the parties utilize implicit authentication relying on the generation of an appropriate secret session key to provide the implicit authentication. Typically, the parties will be a client computer and a server computer. In accordance with other embodiments of the invention, in order to protect against a security compromise at the server, the server is not in possession of the password, but instead is provided with, and stores, a so-called password verifier which is a function of the password and where the password itself cannot be determined from the value of the password verifier.
Owner:ALCATEL-LUCENT USA INC
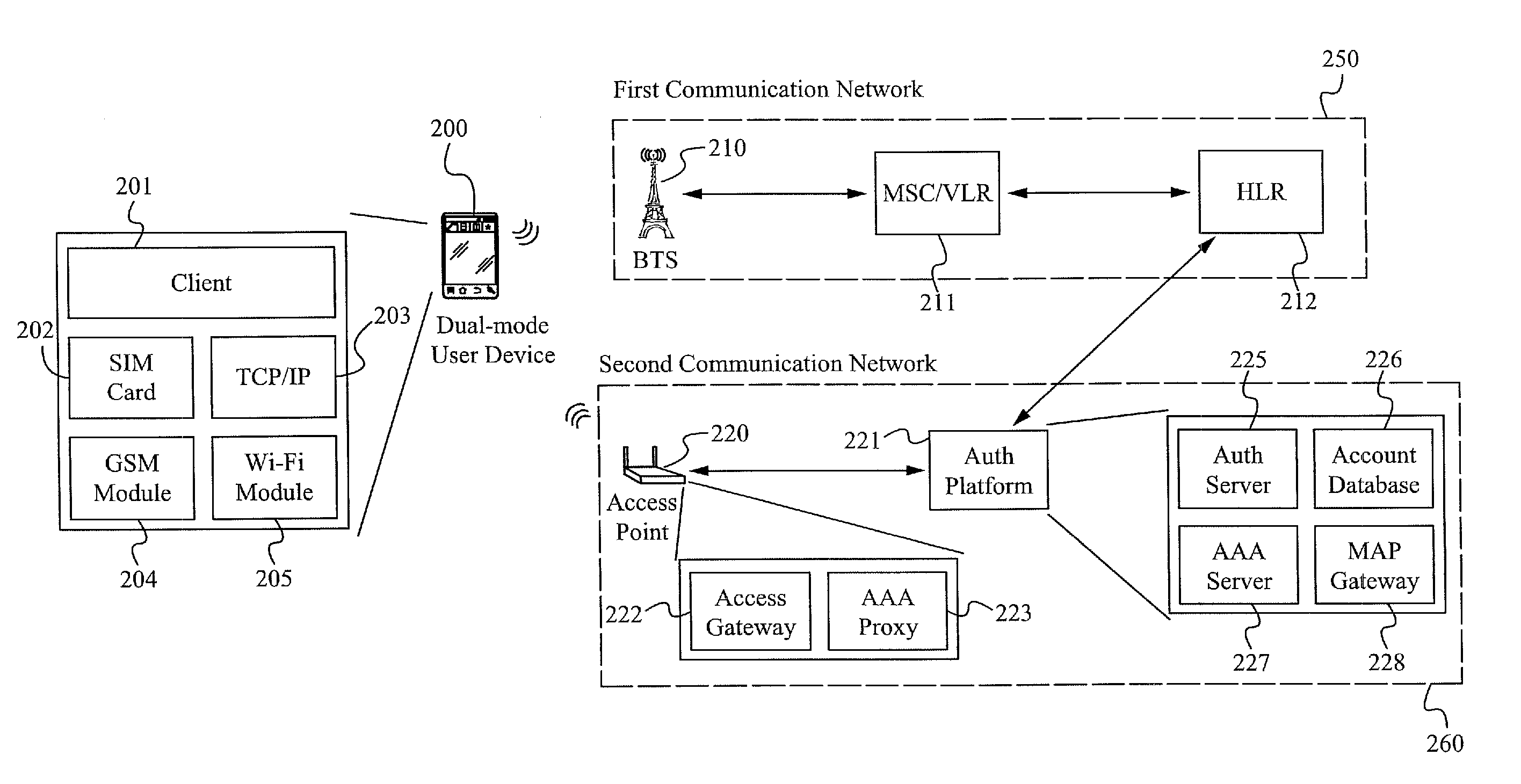
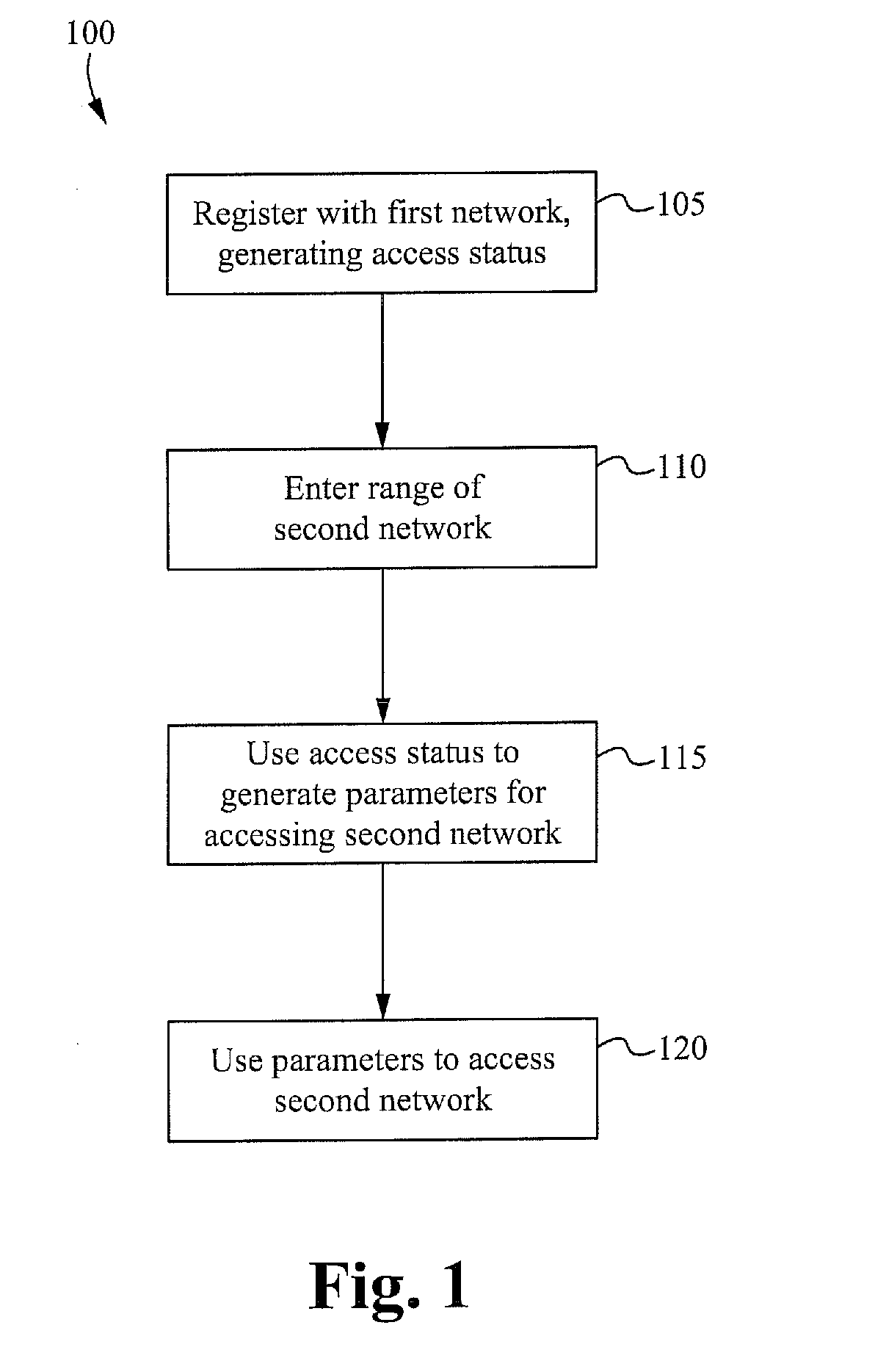
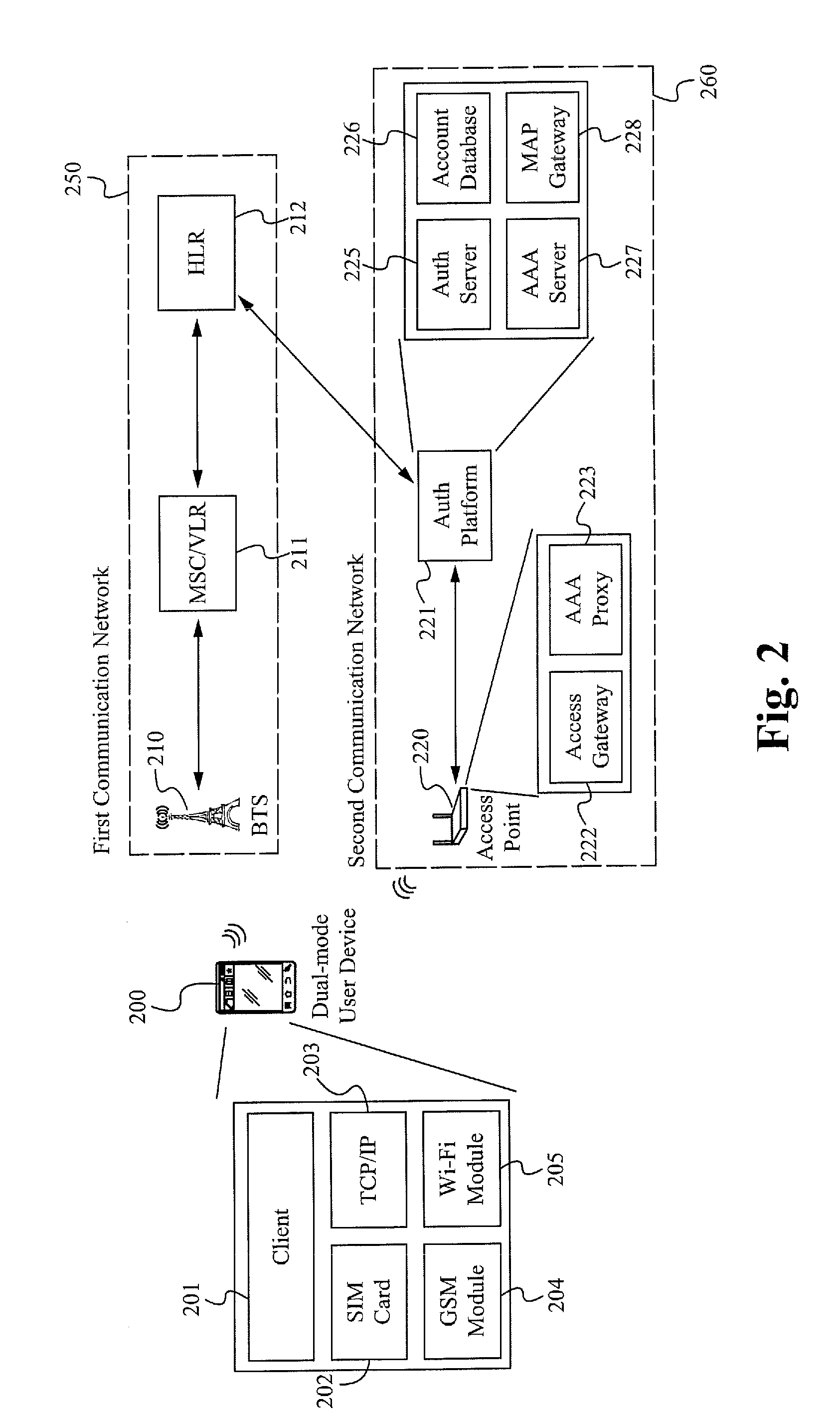
Method of and system for utilizing a first network authentication result for a second network
ActiveUS20120264402A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsWi-FiWeb authentication
A method and system for completing the authentication process in a second communication network (such as Wi-Fi or WiMAX) utilizes a user credential of a first communication network, such as GSM, UMTS, CDMA, or LTE. Preferably, the user credential is a SIM card, a USIM card, a R-UIM card, or a functionally similar component. The system includes a client and an authentication platform that retrieves Service State information of the user credential in the first communication network and passes the information to the authentication platform of the second communication network. The client is wanted access to the second communication network after the authentication platform validates the client's service and subscription status with the first communication network.
Owner:SYNIVERSE COMM LLC
Mitigation of application-level distributed denial-of-service attacks
ActiveUS20120260329A1Digital data processing detailsUser identity/authority verificationWeb authenticationMobile device
A system and method, implementable using an authenticating device, are provided for authenticating requesting devices such as mobile devices and other communication devices over a network. At least one group shared secret is provisioned on a plurality of requesting devices, which are further provided with other authentication credentials such as a shared secret for full authentication by the authenticating device. When authentication is sought, the requesting device transmits a pre-authentication request comprising one of the group shared secrets to the authenticating device, which verifies that group shared secret. The group shared secrets may be stored in volatile memory at the authenticating device. If the group shared secret is verified, the authenticating device will authenticate that same device in response to a subsequent authentication request.
Owner:MALIKIE INNOVATIONS LTD
Method and system for authentication using infrastructureless certificates
ActiveUS20050149723A1User identity/authority verificationSpecial data processing applicationsThird partyWeb authentication
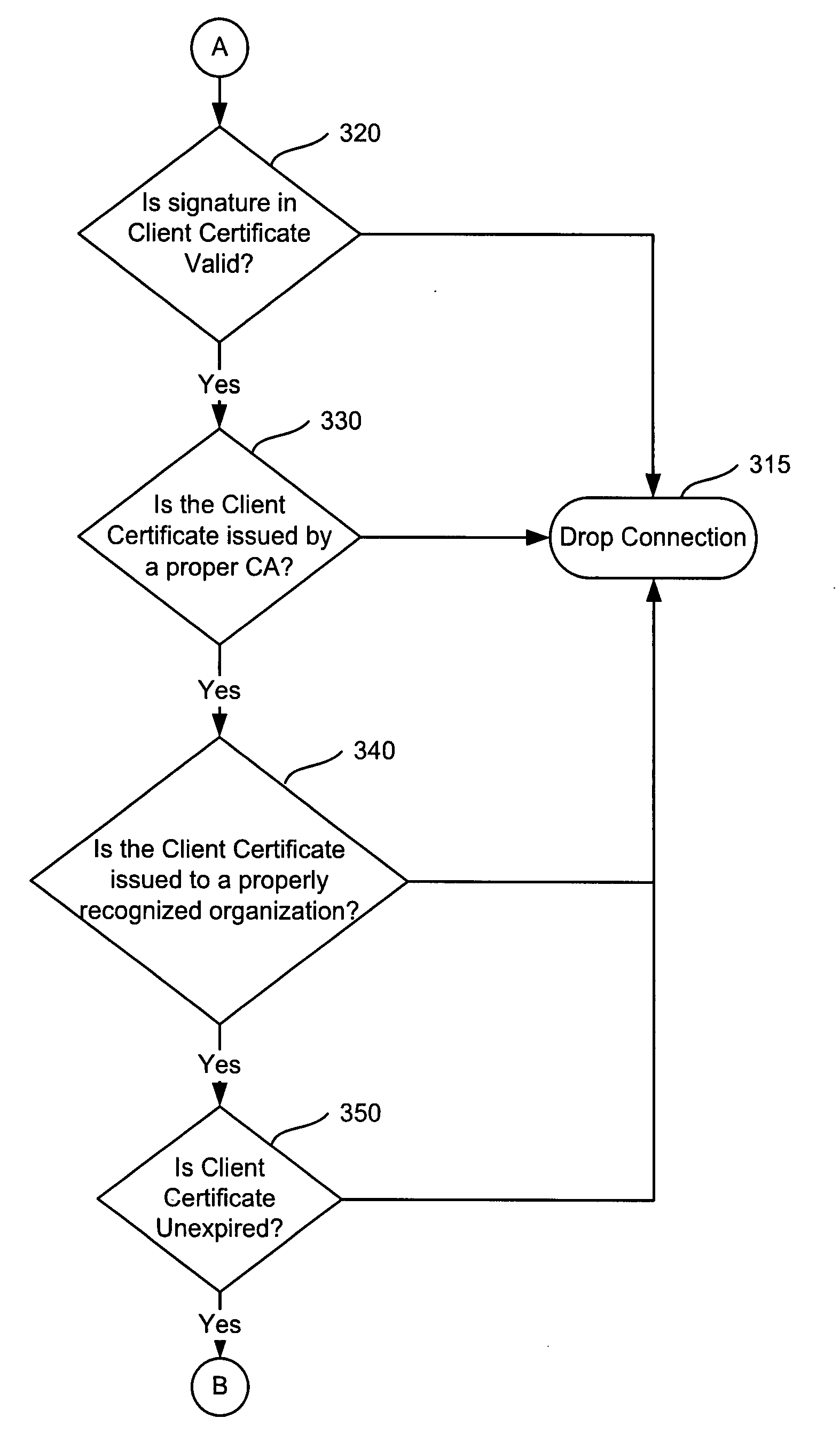
Methods and systems are directed to authenticating a client over a network. The client generates a certificate and sends it to a server through a trusted mechanism. The server is configured to store the received certificate. When the client requests authentication over the network, it provides the certificate again, along with a parameter associated with a secure session. The server verifies the parameter associated with the secure session and determines if the certificate is substantially the same as the stored certificate. The server authenticates the client over the network, if the certificate is determined to be stored. In another embodiment, the client transmits the certificate that is generated by a third party Certificate Authority (CA) based, in part, on the client's public key.
Owner:WSOU INVESTMENTS LLC
Authority setting method of user access network and equipment
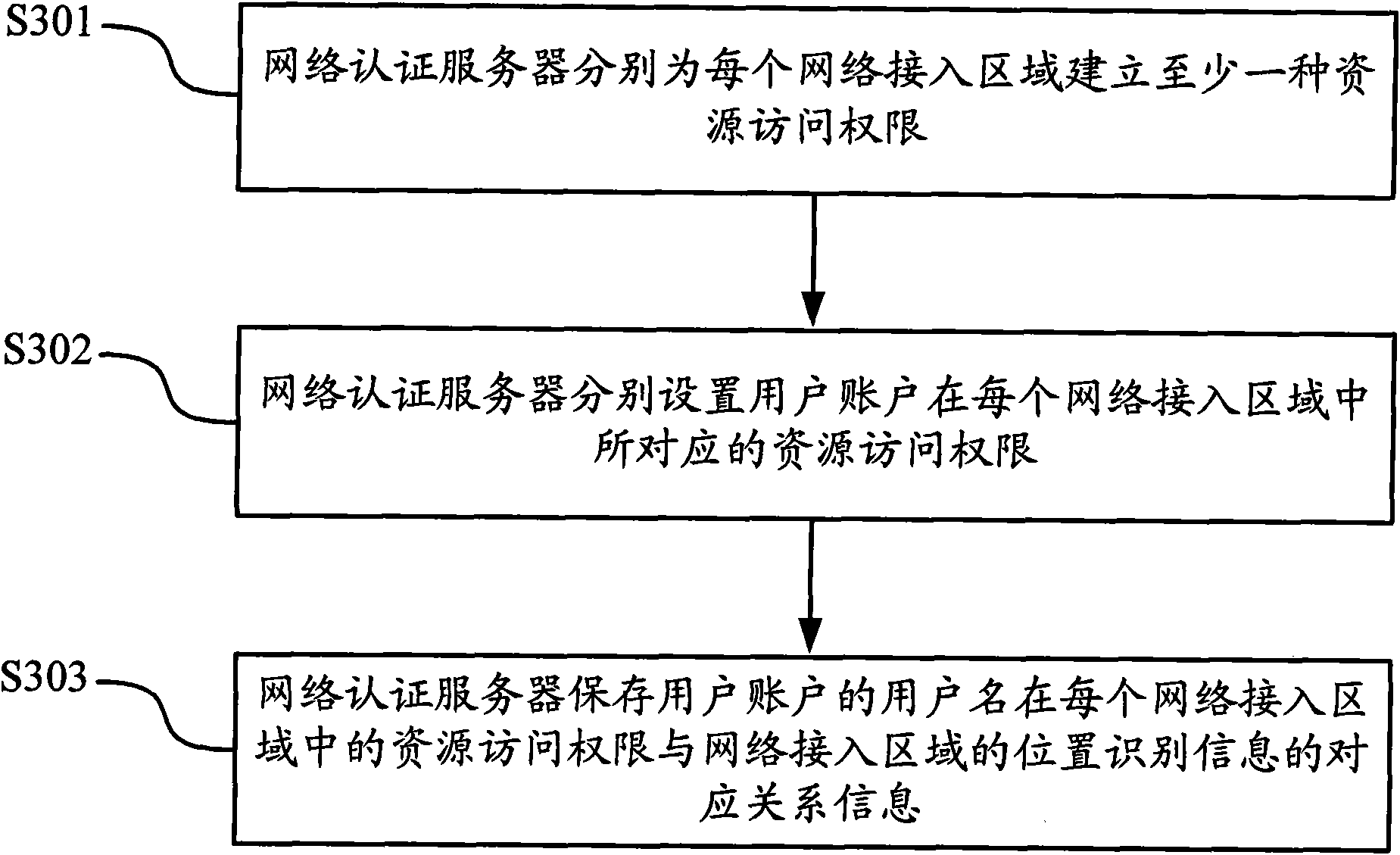
ActiveCN101582769AEasy to useImprove experienceUser identity/authority verificationLocation information based serviceAccess networkWeb authentication
The invention discloses an authority setting method of a user access network and equipment, which are applied to a network system comprising a network authentication server and a plurality of network access areas. The network authentication server stores access authority information of at least one user name in the plurality of network access areas respectively; when a user request is accessed, the user name and the position recognition information of the current network access area are provided, the corresponding resource access authority is obtained and network access is carried out. The invention realizes access authority allocation based on the actual access position of the user, can avoid that the access authority can not be controlled due to change of the access area, can adopt uniform access authority control for unfixed staff in all access areas, and adopts a single account number mode to access, thus providing convenience for use of users, improving network security of the network and simultaneously user experience.
Owner:NEW H3C TECH CO LTD
Authenticating clients to wireless access networks
InactiveUS20070180499A1Digital data processing detailsUser identity/authority verificationWi-FiAccess network
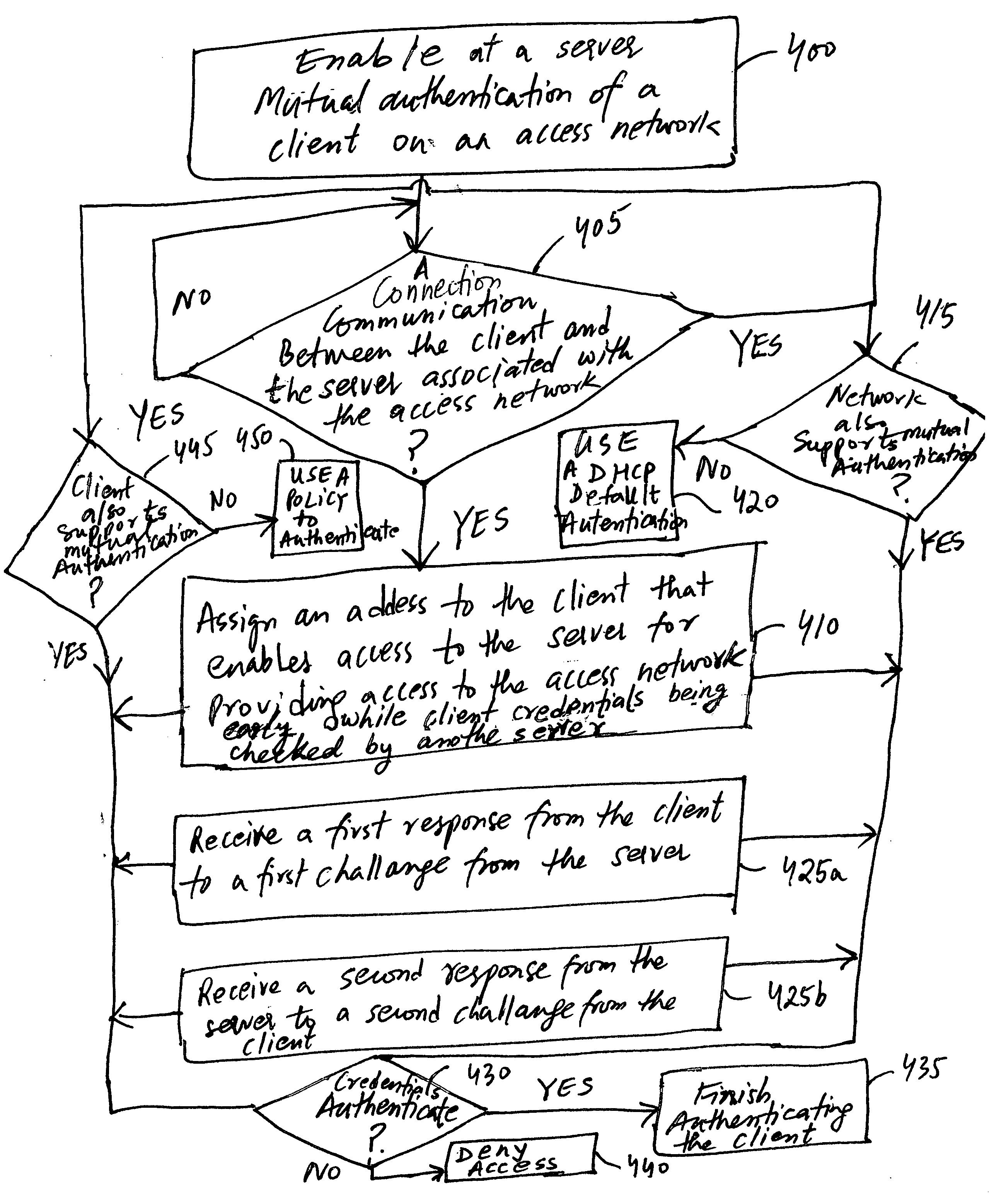
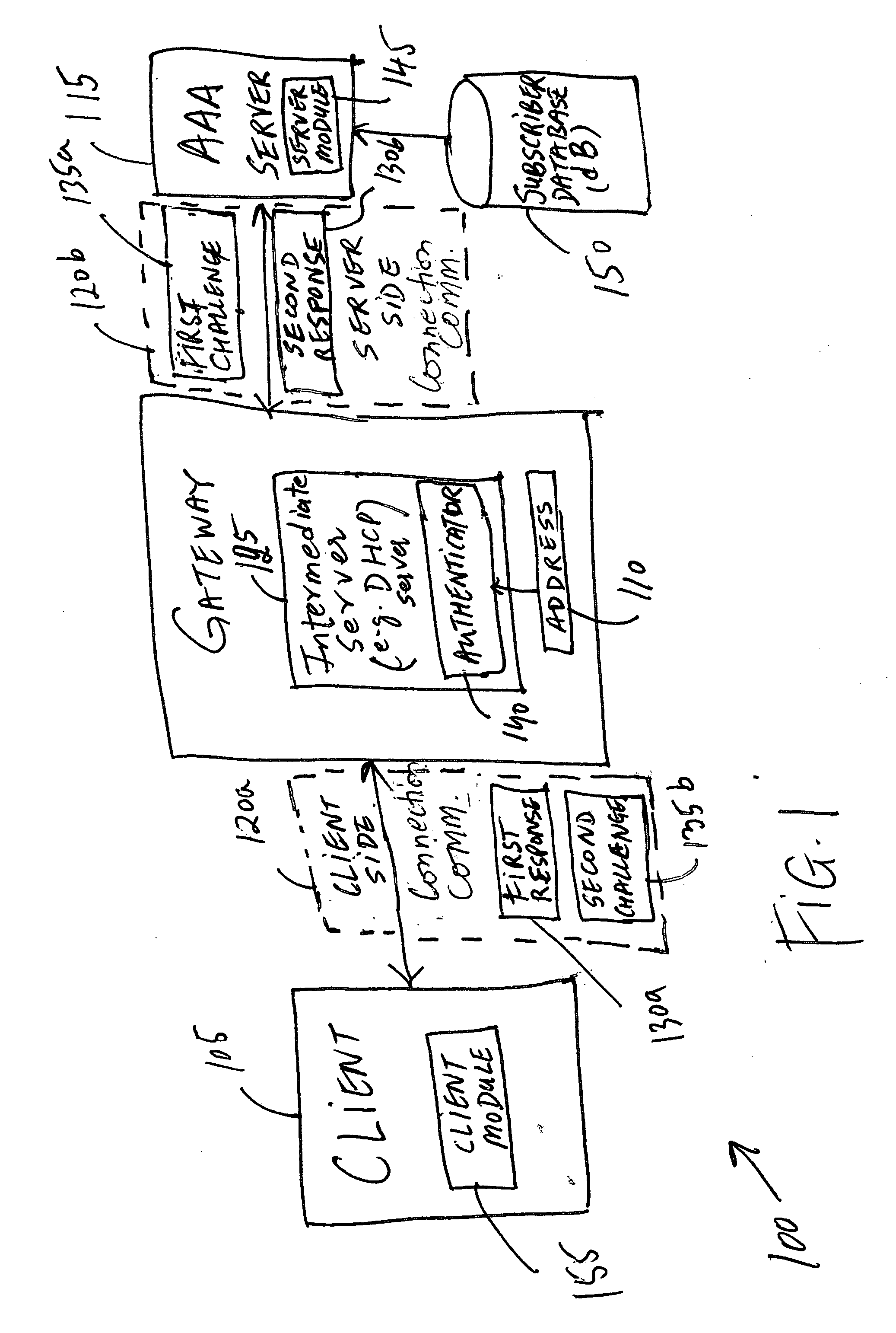
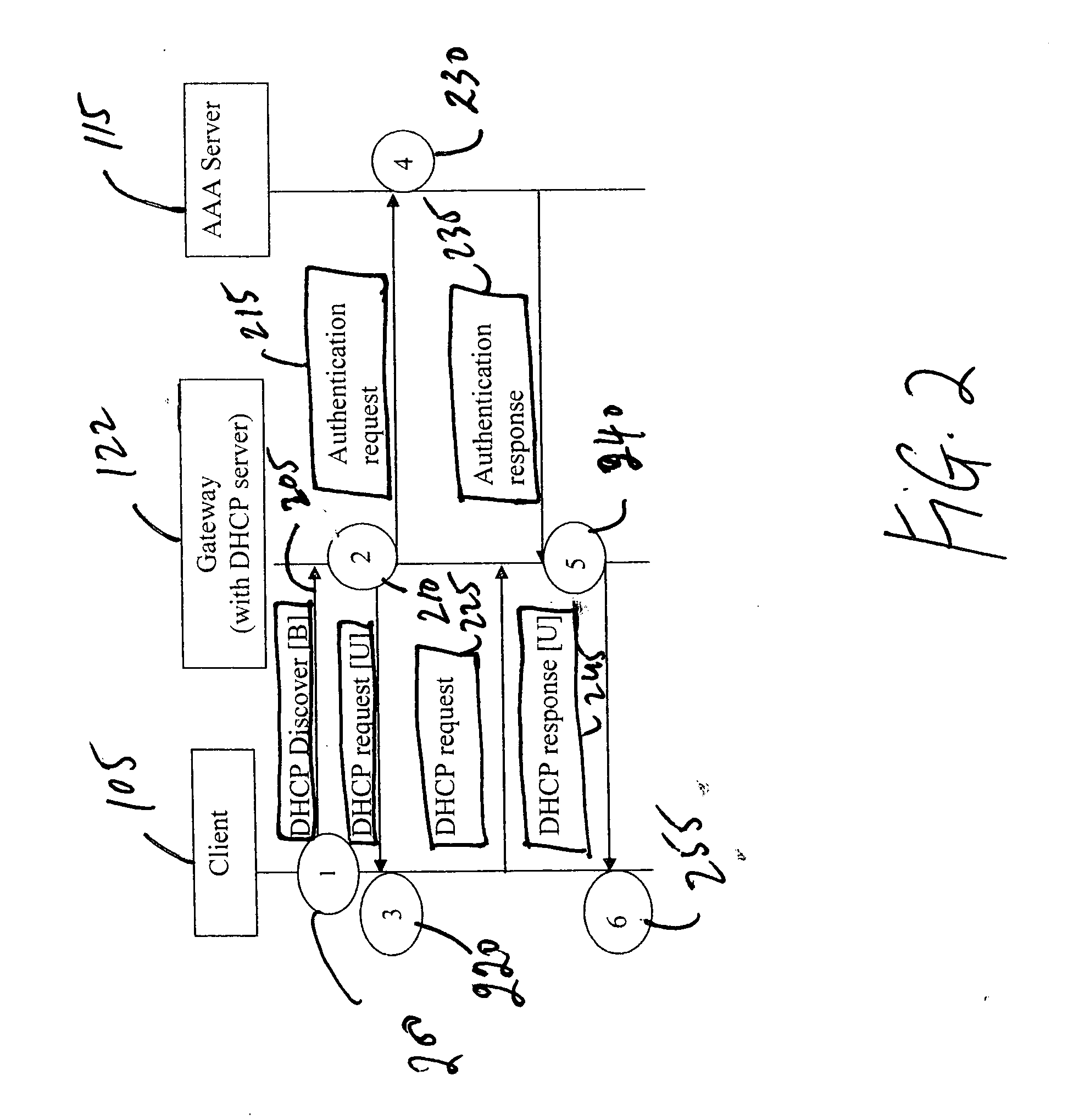
The present invention provides a method and an apparatus for authenticating a client on a wireless network having an address that enables access to a server associated with the wireless network. In one embodiment, a method calls for assigning the address to the client for providing access to the wireless network before finishing authenticating the client based on a first response from the client to a first challenge from the server and a second response from the server to a second challenge from the client in response to a communication between the client and the server over the wireless network. A wireless communication system includes a client module for authenticating a mobile device to a Wi-Fi network through an access point associated therewith. For the purposes of authentication, an intermediate server may enable a server module to mutually authenticate the mobile device and the Wi-Fi network based on exchange of signaling messages between the client module and a server module associated with the Wi-Fi network via the intermediate server.
Owner:LUCENT TECH INC
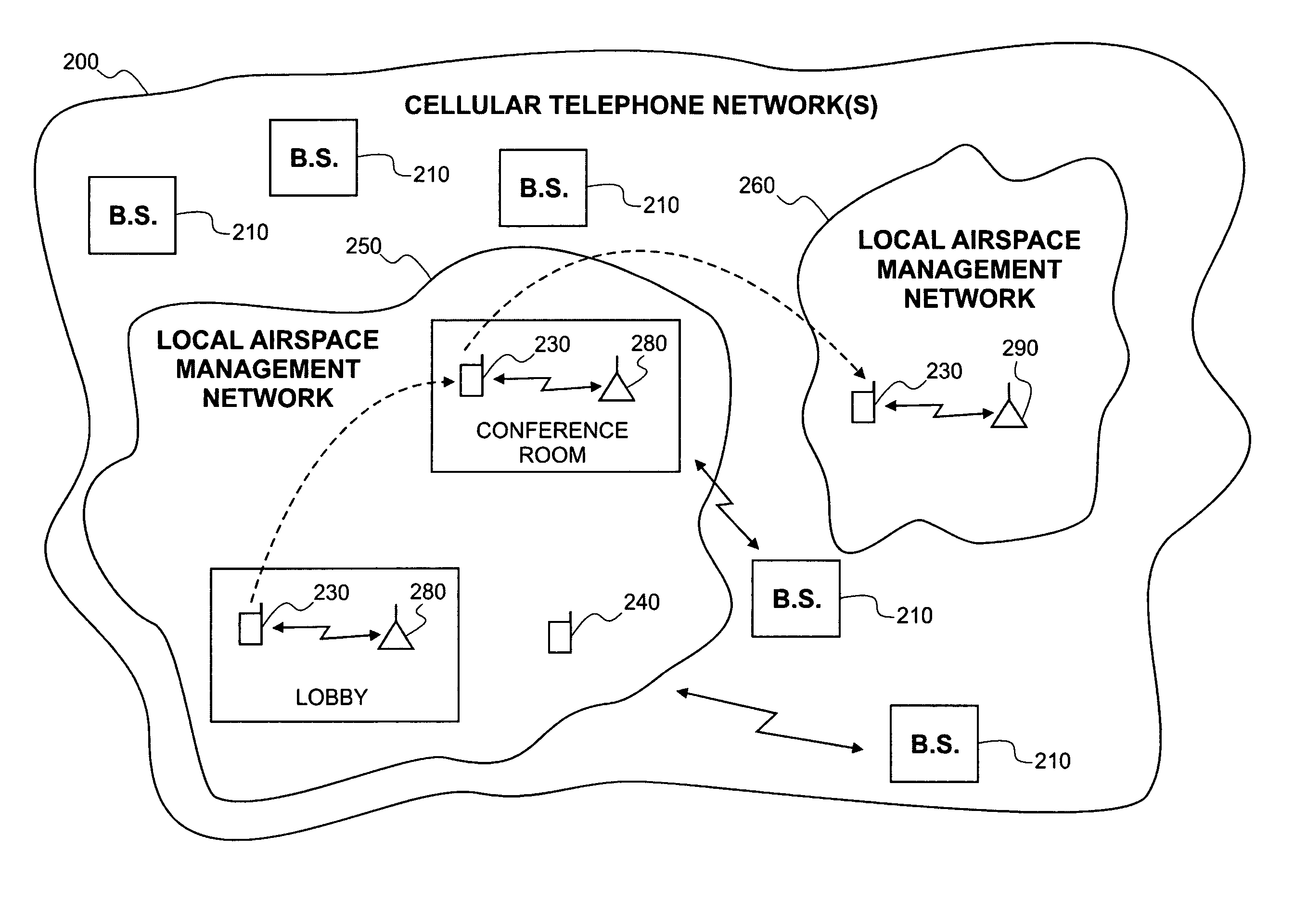
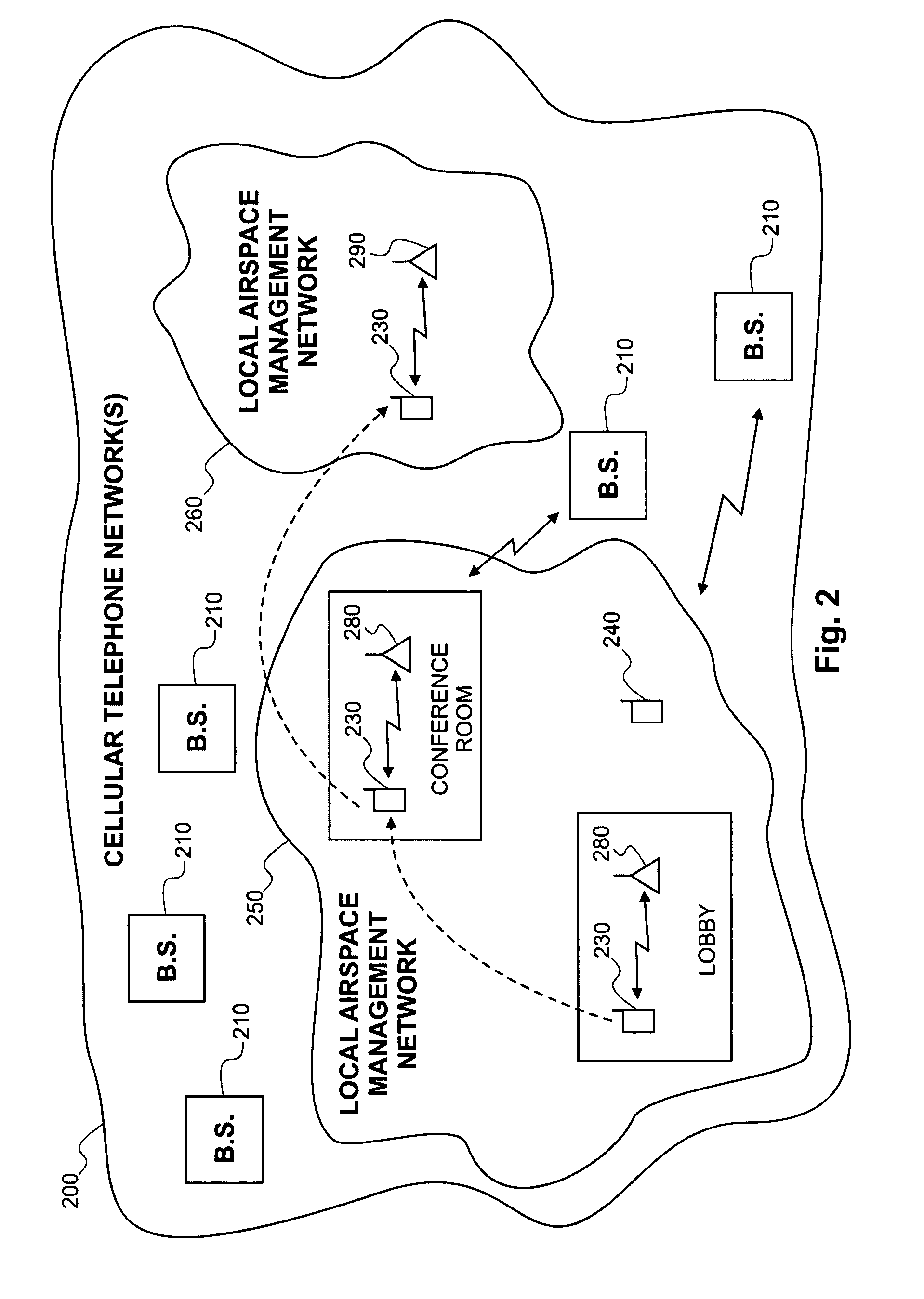
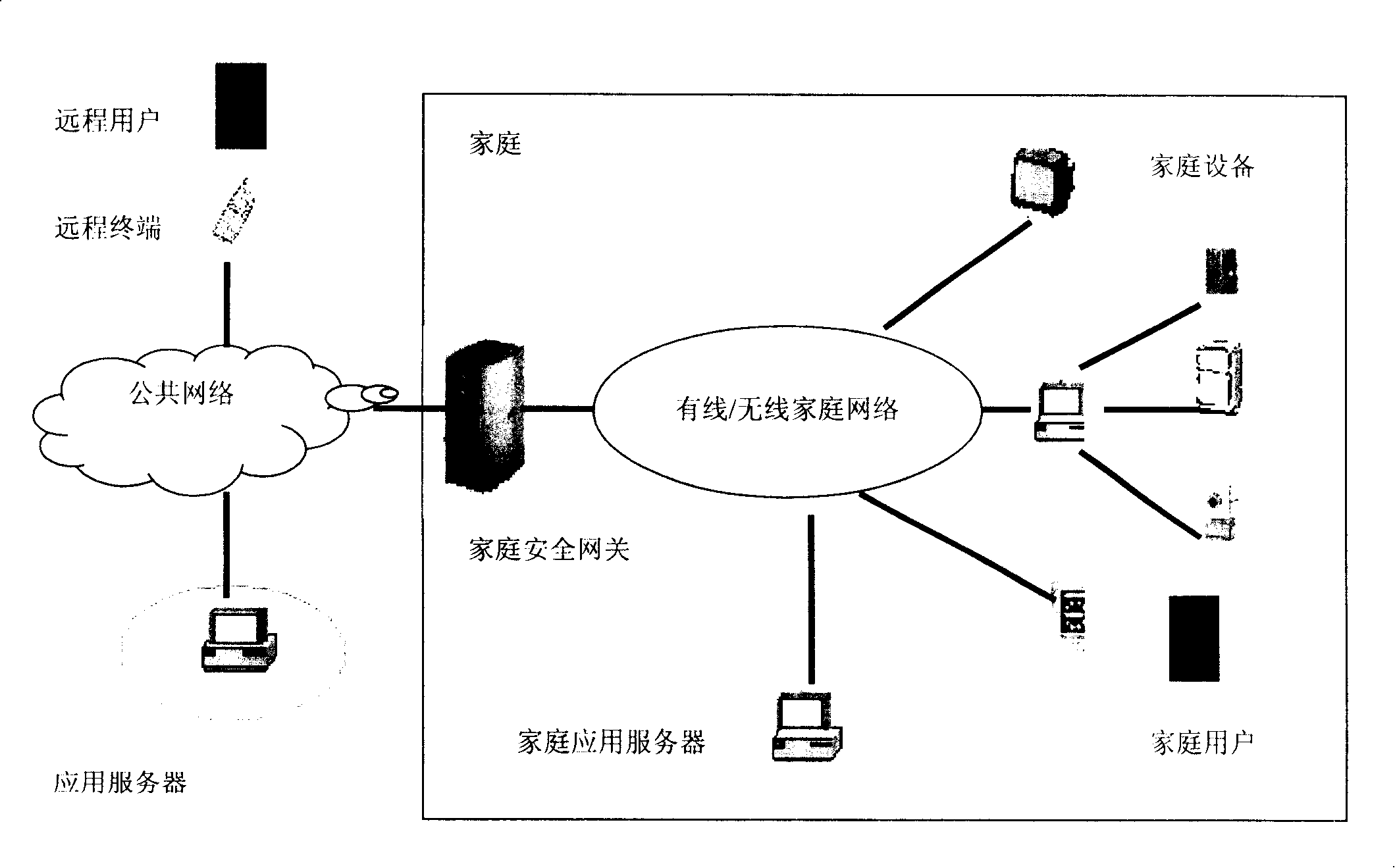
Local area wireless airspace management
A mobile wireless device that is implemented to provide personal communications services in a wireless communications network can be integrated with hardware and / or software to manage the device at the device level (e.g., control device usage or operation at the device) at the local level. Management can be implemented to be invisible to wireless device user such as to be implemented without requiring user initiation to acknowledge or allow management to proceed. Local management can be implemented on a real time basis to manage the usage or operation of a device, device components (hardware or software, peripherals (e.g., speaker, display, keyboard, microphone, etc.), or hardware (e.g., camera, voice recorder, etc.) or software integrated into the device. Different policies can be applied within a local airspace management network. A local airspace management network can be configured to interact with wireless devices to authenticate the user of a device. Security measures can also be implemented to assure that local airspace management is applied by a trusted network. Information associated with a local airspace management network such as user biometrics, trusted network certification, authentication information can be stored in a wireless device. A local airspace management network can include a transmitter and associated hardware and / or software that implement the local airspace management policy of an entity.
Owner:BALWANI RAMESH
System, method, apparatus and computer program product for facilitating digital communications
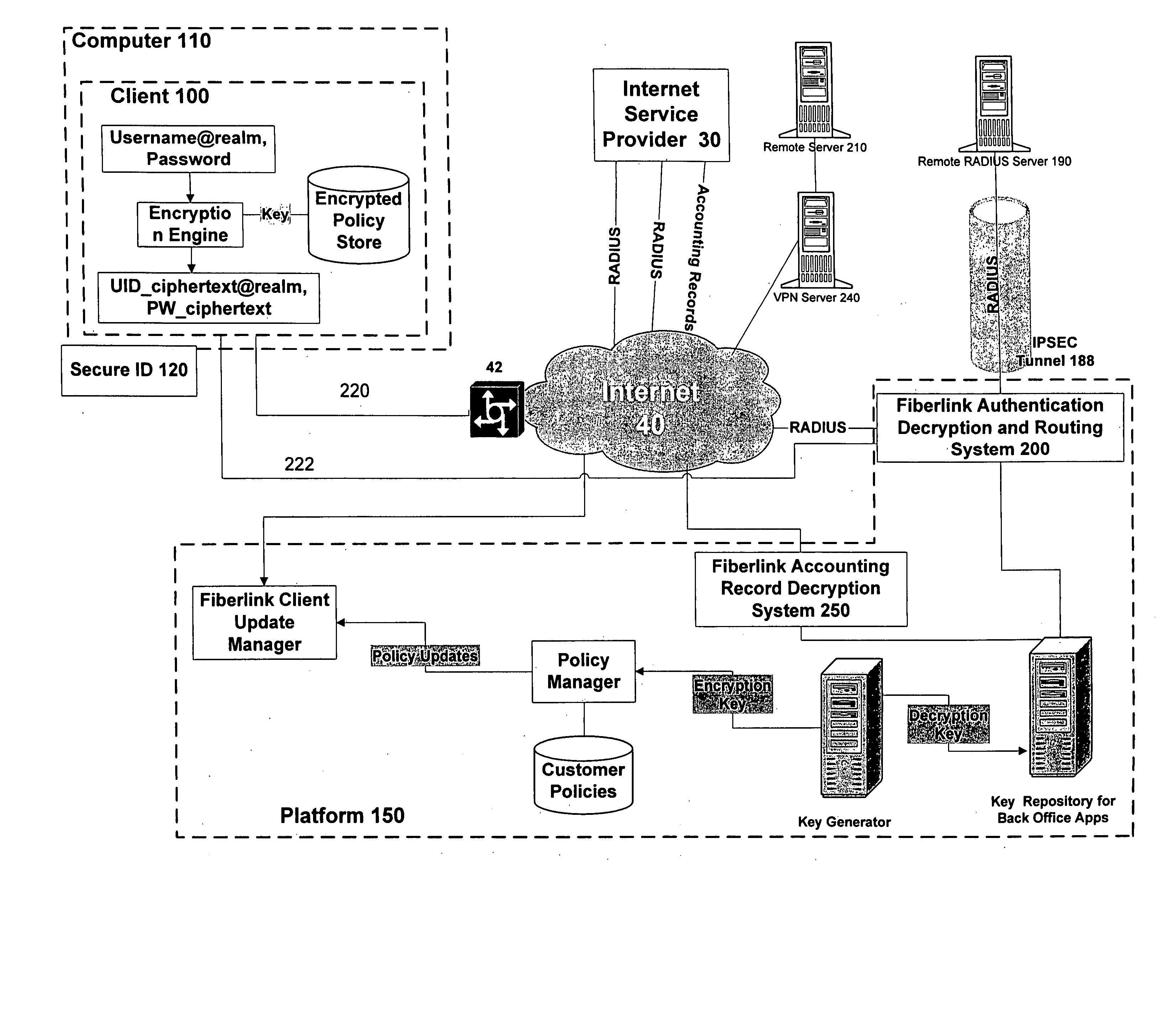
InactiveUS20050081045A1Hardware monitoringDigital data authenticationInternet communicationWeb authentication
A computer-implemented method and apparatus authenticates a user of a remote computer over a network. In one aspect of the present invention, an authentication challenge is received at said remote computer an authentication challenge message from an authentication server over a network, at least a portion of the network including an Internet communication link. A passcode is received at the remote computer. A response message to the authentication challenge is created, the response message including the passcode. The response message is transmitted from the remote computer to the authentication server over the network. The remote computer receives a verification message from the authentication server that the response message is verified.
Owner:IBM CORP
Network-based authentication and security services
ActiveUS20170171200A1User identity/authority verificationSecurity arrangementAuthentication systemWeb authentication
A user device may request access to a service provided by an application server. The application server may request that an identity server authenticate the user device. The identity server may have a network authentication system assist with the authentication of the user device. Once authenticated by the network authentication system, the application server may be informed and may grant the user device access to the requested service. Additionally, the identity server may help determine whether the user device is a security threat by comparing user information from the network authentication system with user information from the application server. Additionally, the network authentication system may provide the application server with user information to enable the application server to automatically register the user device for a particular service.
Owner:VERIZON PATENT & LICENSING INC
Method and network authentication server for controlling client terminal access to network appliance
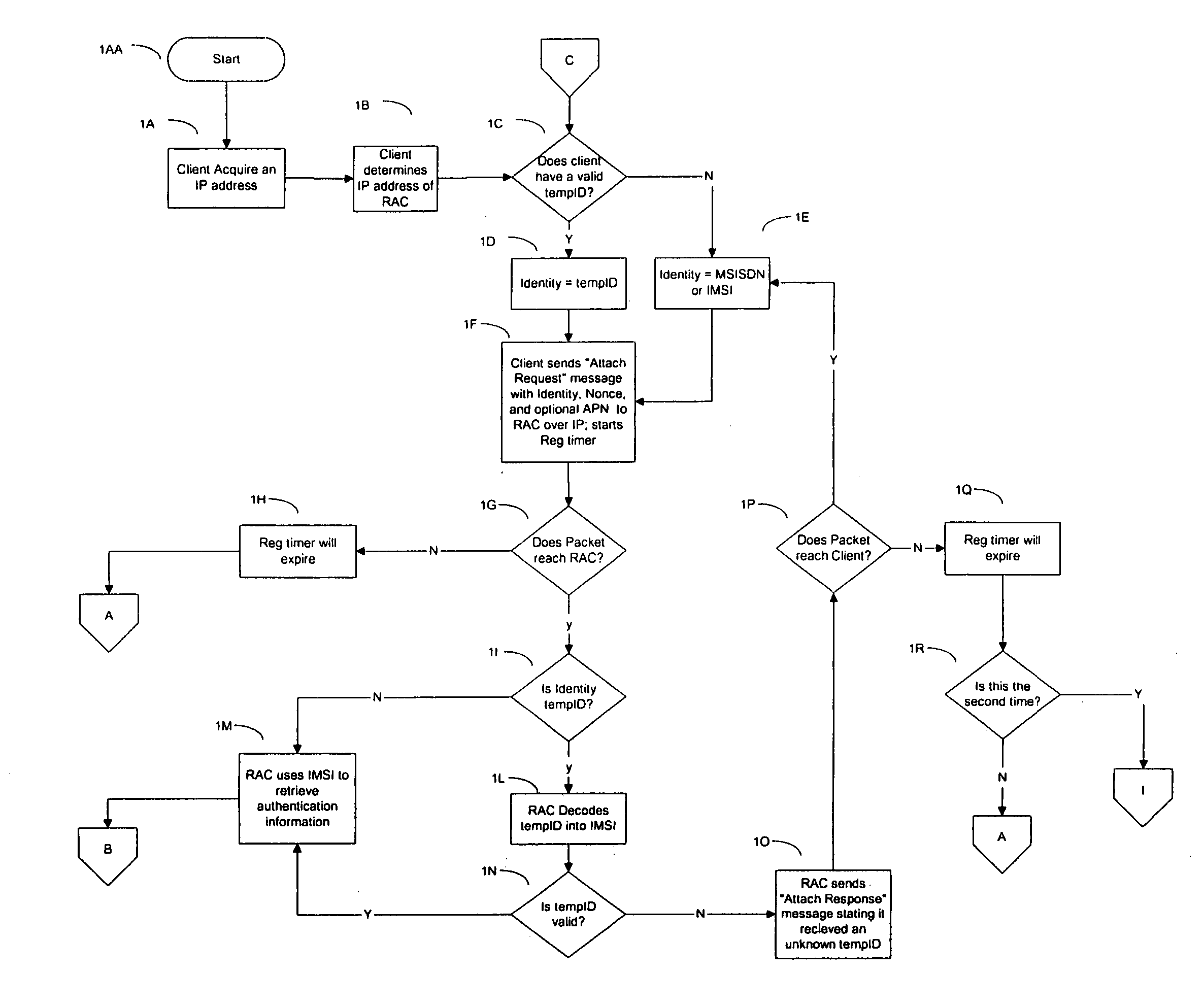
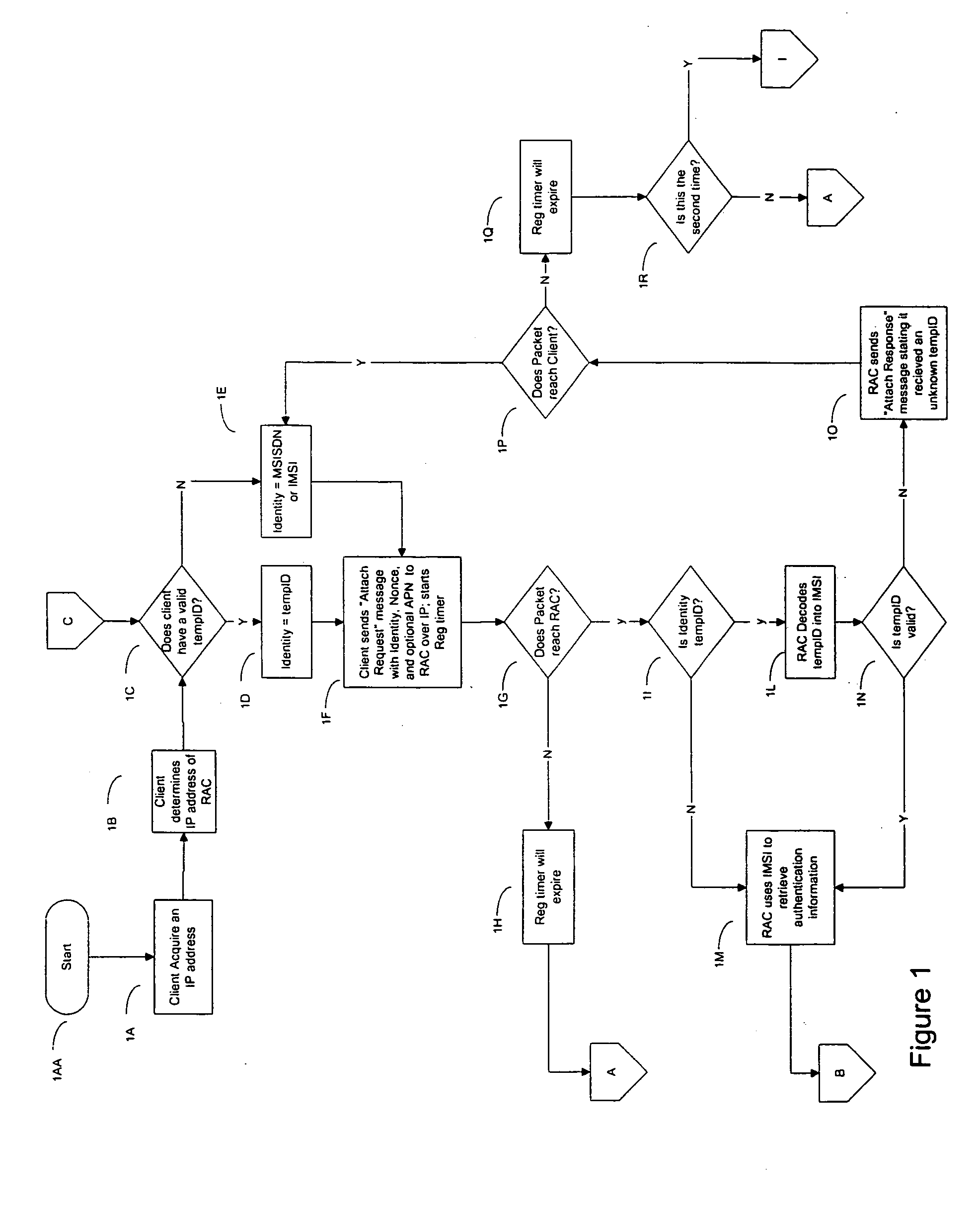
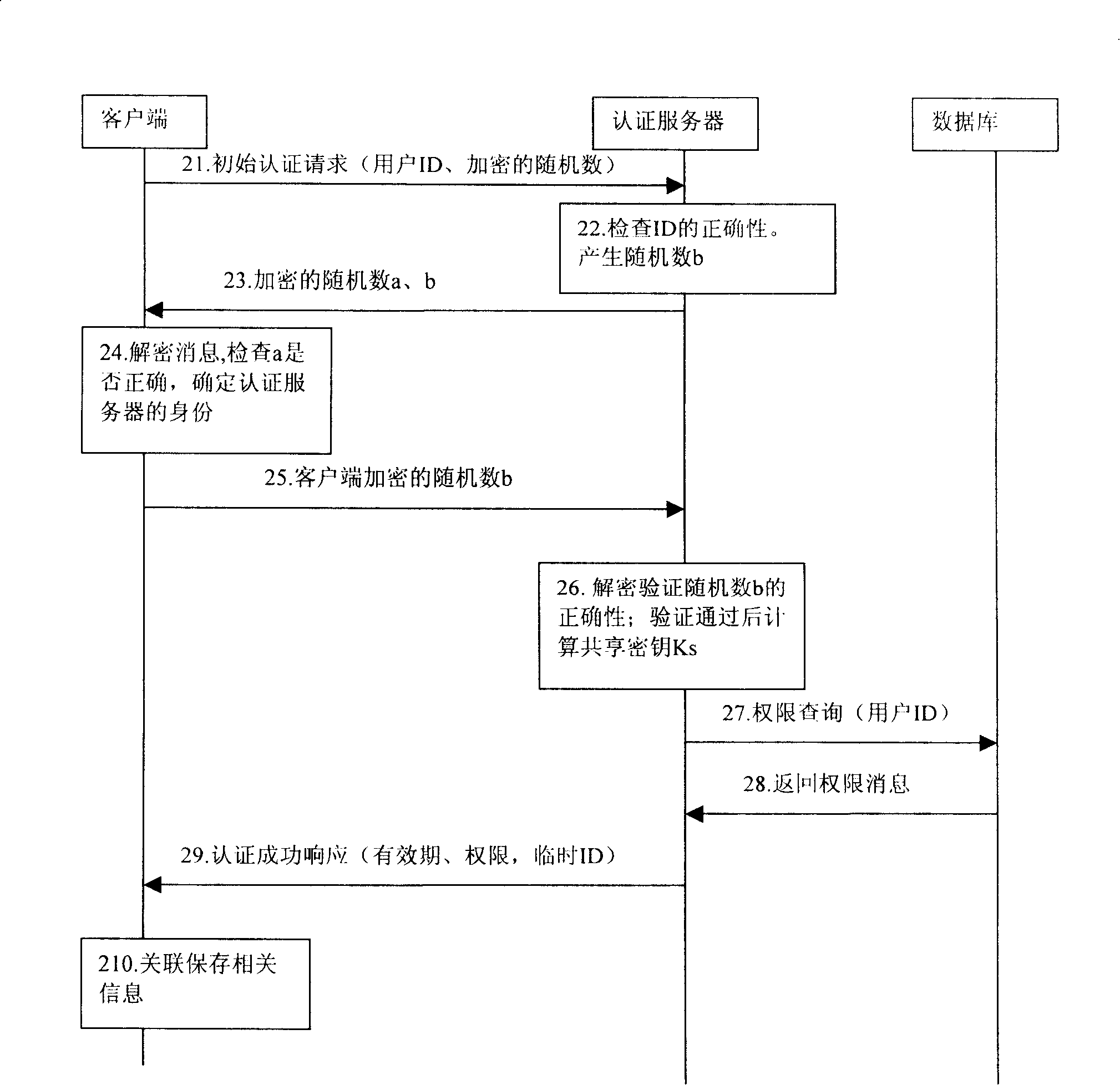
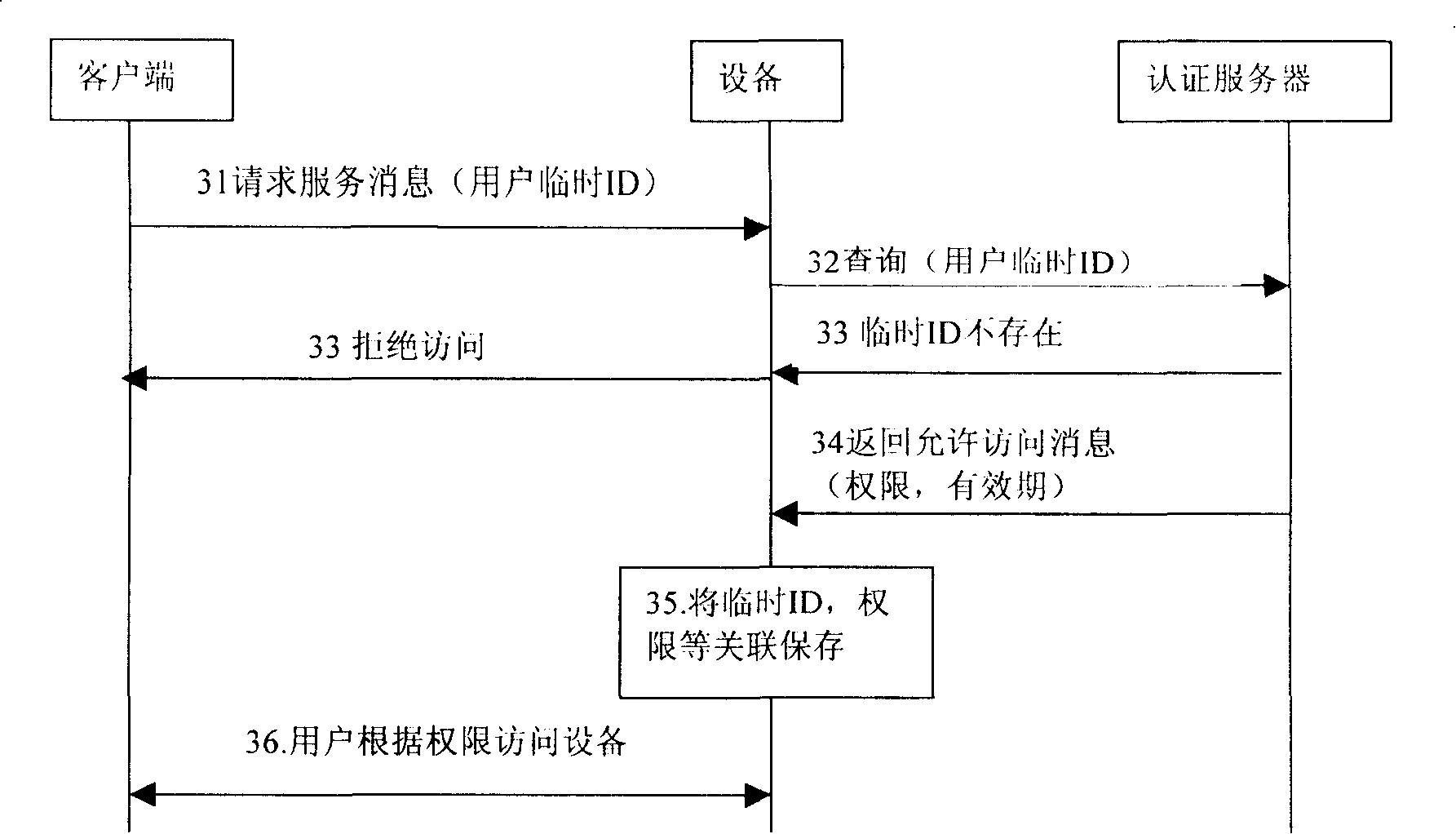
InactiveCN101222488AAccess controlUser identity/authority verificationAccess networkWeb authentication
The present invention provides a method for controlling client to access network equipment and a network authentication server. The method mainly comprises the following steps that: an authentication server in a network carries out identity authentication to a user through a user client ; after the user passes the identity authentication, the authentication server allocates authentication information to the user client ; the authentication information comprises a temporary ID and corresponding validity; the authentication server controls the user client to access equipment in the network according to the authentication information allocated to the user client. The method and the network authentication server of the present invention can realize authentication server safety in the network and control the access of user terminals to the equipment in the network effectively and conveniently.
Owner:HUAWEI TECH CO LTD +1
Control method, device and system for identifying login on basis of voiceprint
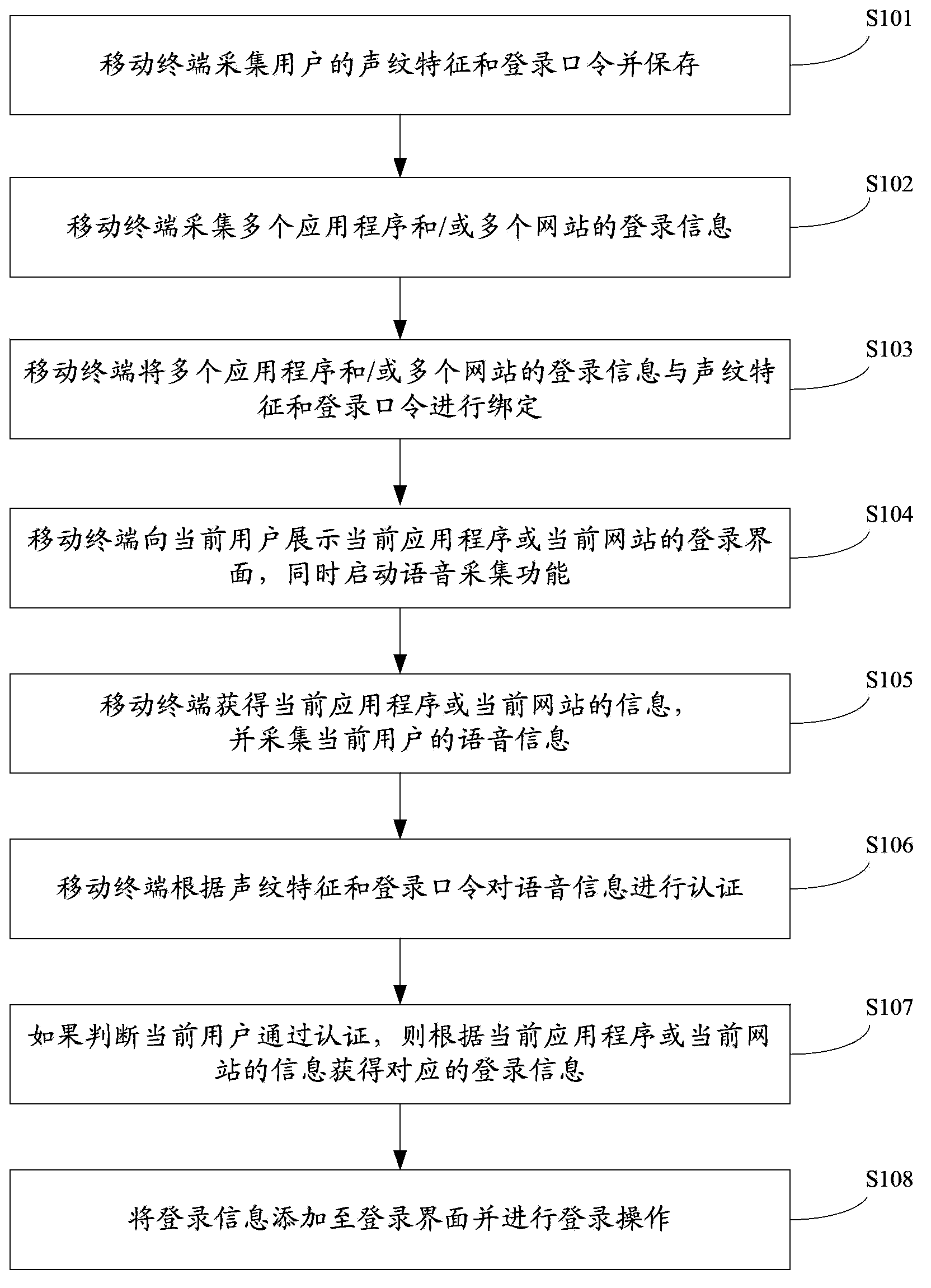
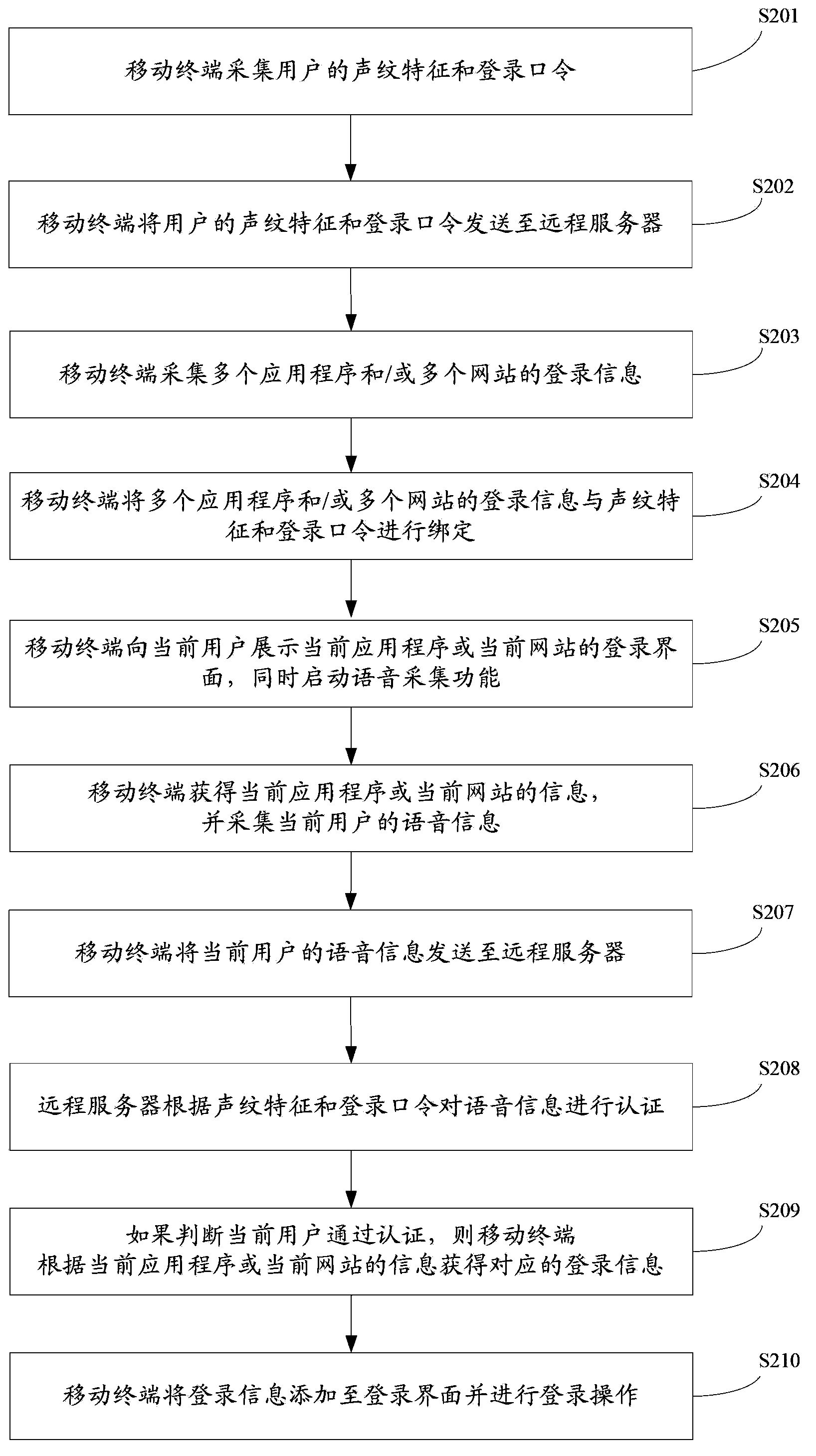
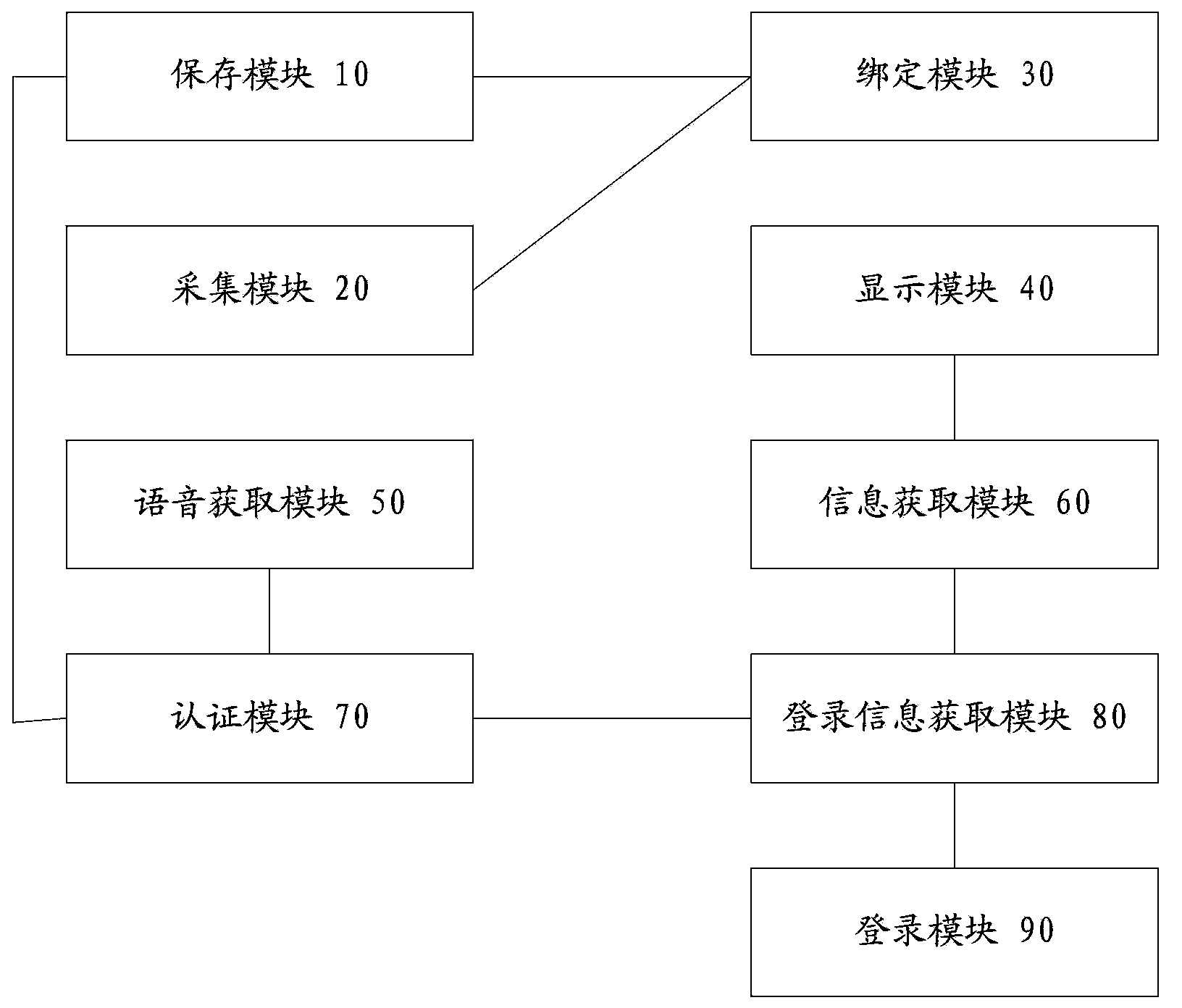
InactiveCN103546622AEasy accessAvoid manual entrySpeech analysisSubstation equipmentWeb authenticationComputer terminal
The invention provides a control method, a device and a system for identifying login on the basis of voiceprint. The control method includes steps of enabling a mobile terminal to acquire voiceprint features and login passwords of users and store the voiceprint features and the login passwords, acquiring login information of a plurality of application programs and / or a plurality of websites and binding the login information of the multiple application programs and / or the multiple websites to the voiceprint features and the login passwords; enabling the mobile terminal to display login interfaces of current application programs or current websites to current users, and starting a voice acquisition function; enabling the mobile terminal to acquire information of the current application programs or the current websites, and acquiring voice information inputted by the current users; enabling the mobile terminal to authenticate the voice information according to the voiceprint features and the login passwords; acquiring the corresponding login information according to the information of the current application programs or the current websites if the current users are authenticated; adding the login information to the login interfaces to perform login operation. The control method, the device and the system have the advantage that the network authentication safety and the network authentication convenience can be improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
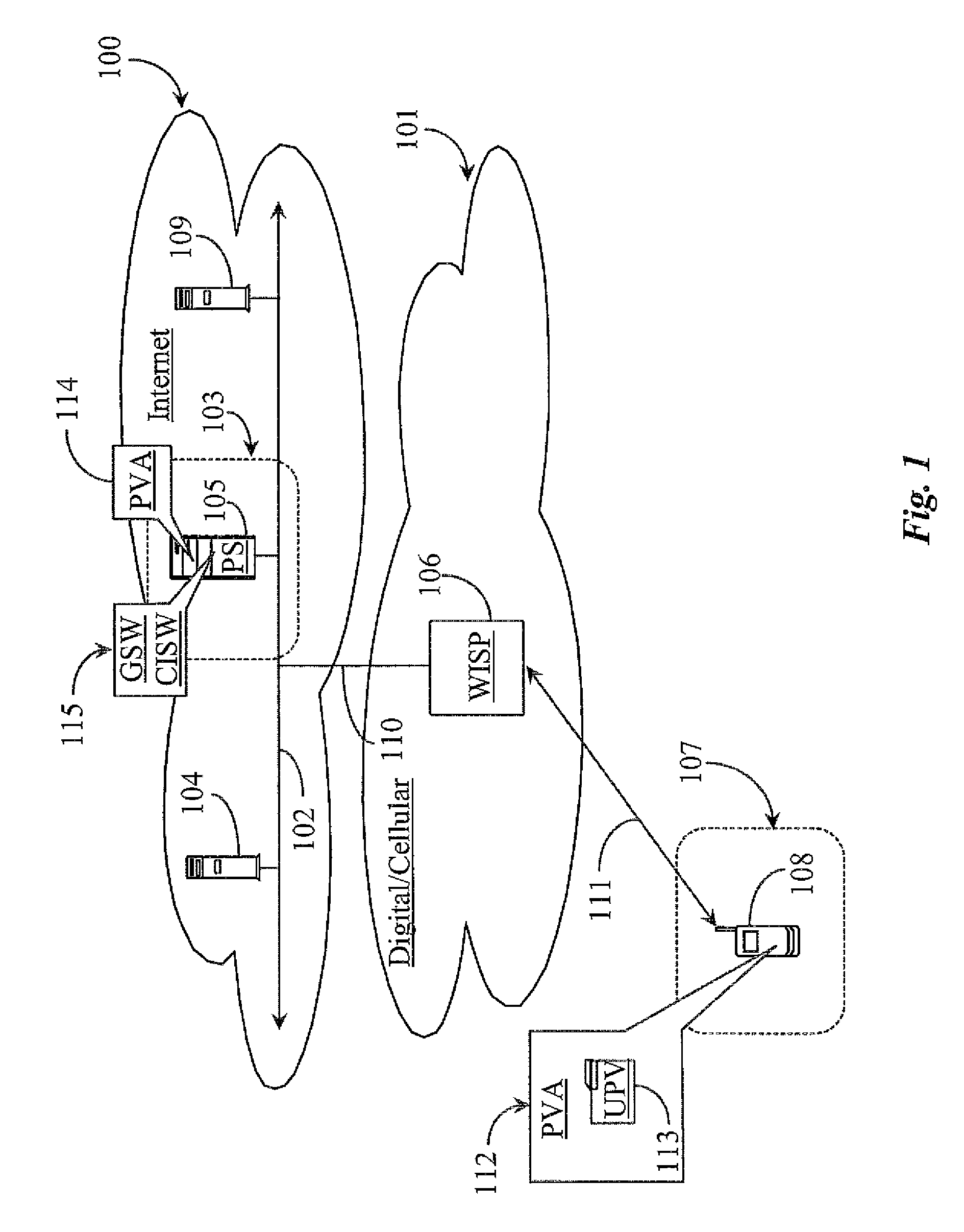
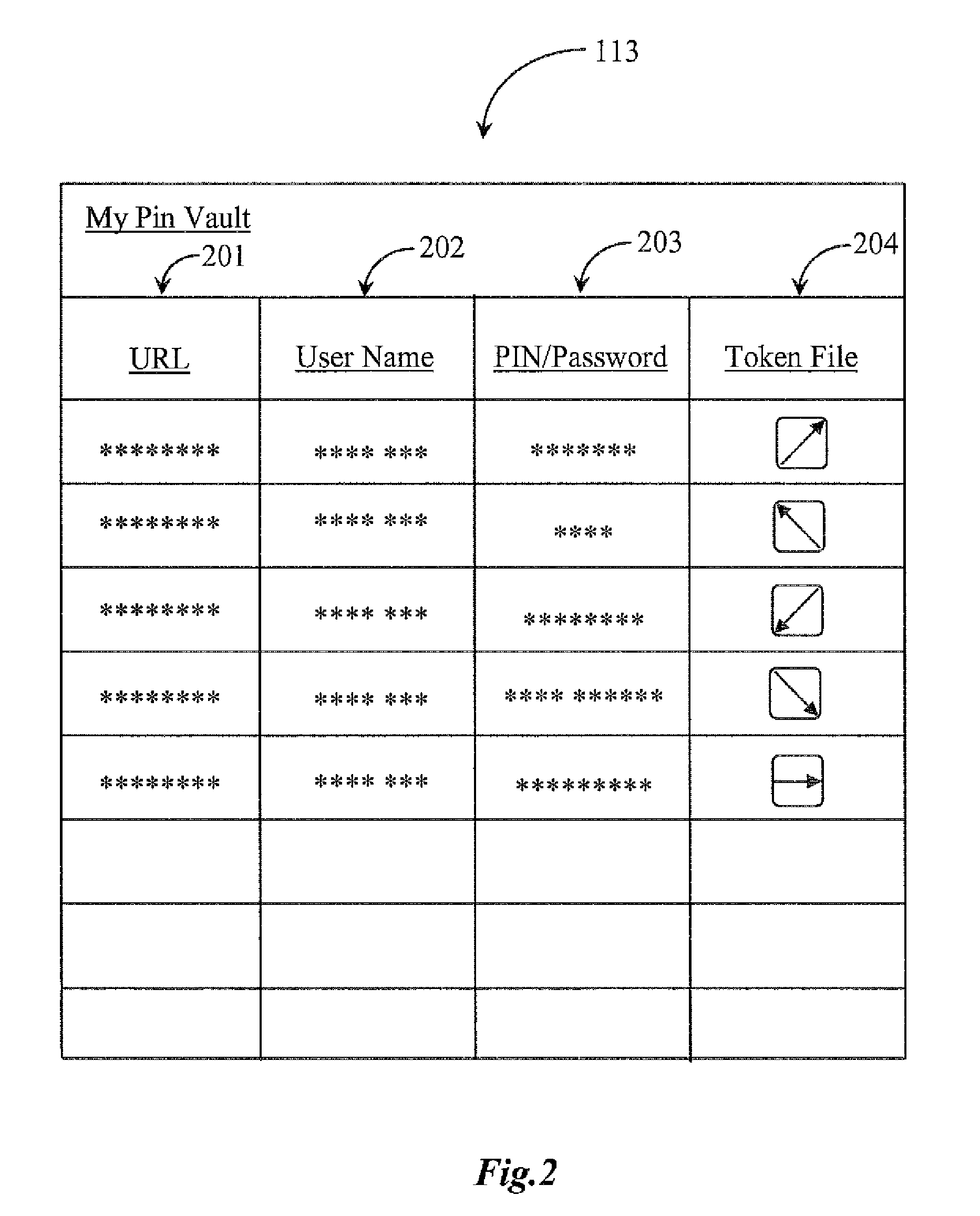
System for performing web authentication of a user by proxy
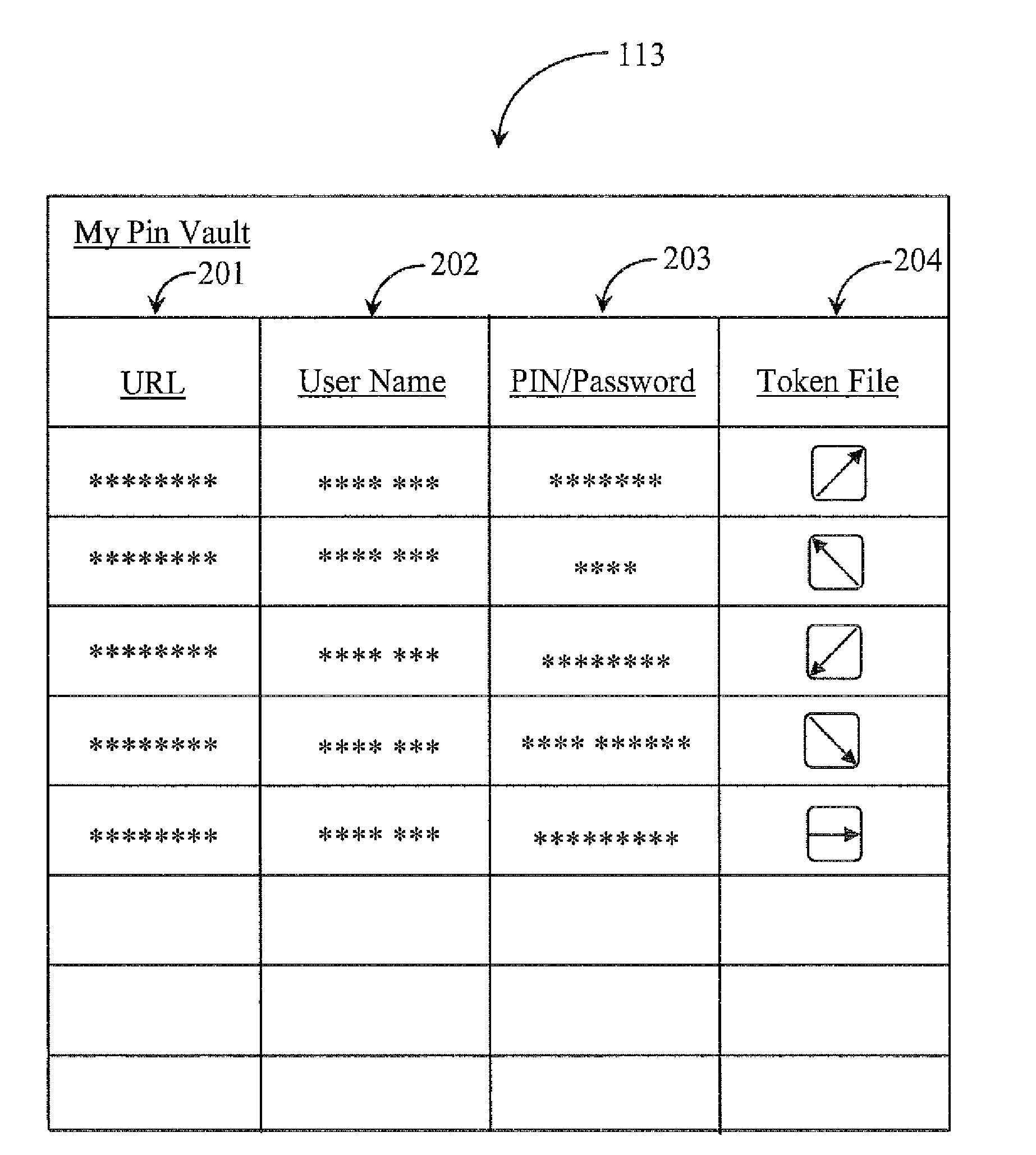
ActiveUS8261334B2Digital data processing detailsUser identity/authority verificationWeb siteWeb authentication
A data gathering system is guided by an Internet-capable appliance associated with a user, which has a Pin Vault software instance executing from a digital memory media coupled to the appliance and a Pin Vault file stored in a data repository coupled to the appliance. The Pin Vault file comprises data for authenticating the user to one or more web sites storing information of interest to the user, and the Pin Vault software cooperates with an Internet service to provide, from the Pin Vault, data as needed by the Internet service to log onto and authenticate as the user at the one or more web sites storing information of interest to the user, to gather information on behalf of the user. The data for authentication is never kept at the Internet service.
Owner:YODLEE COM INC
Wireless local area network (WLAN) authentication method and mobile terminal
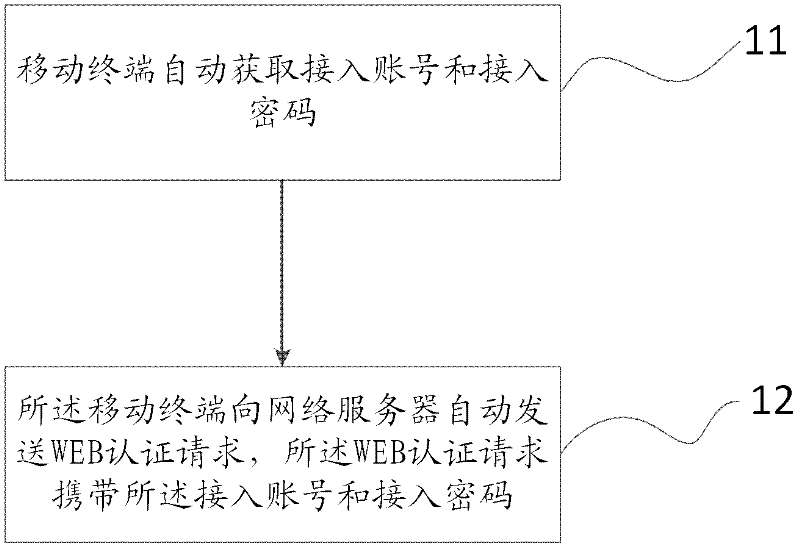
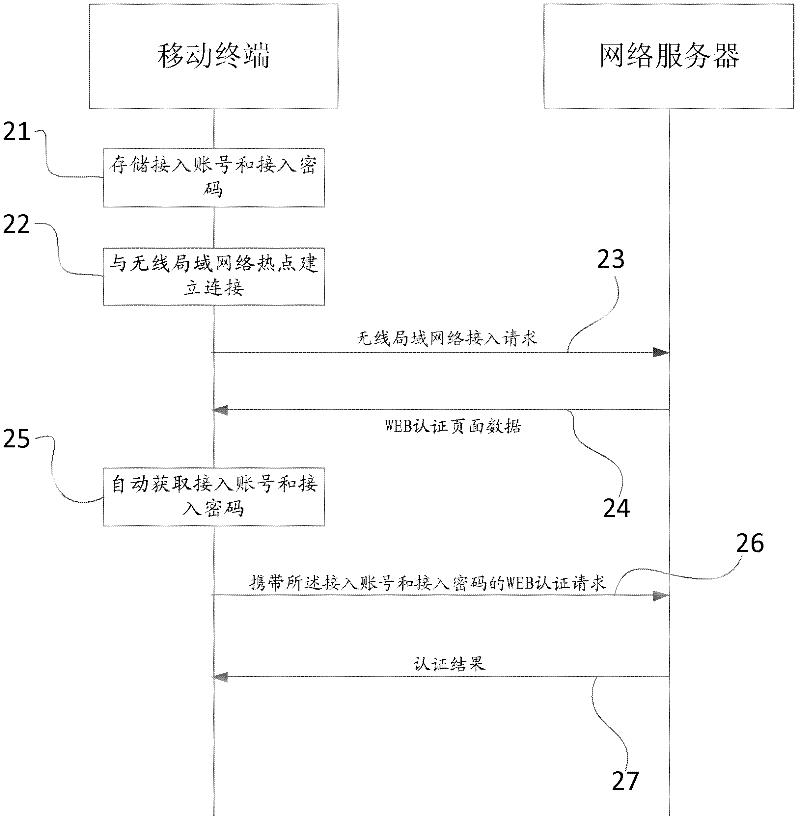
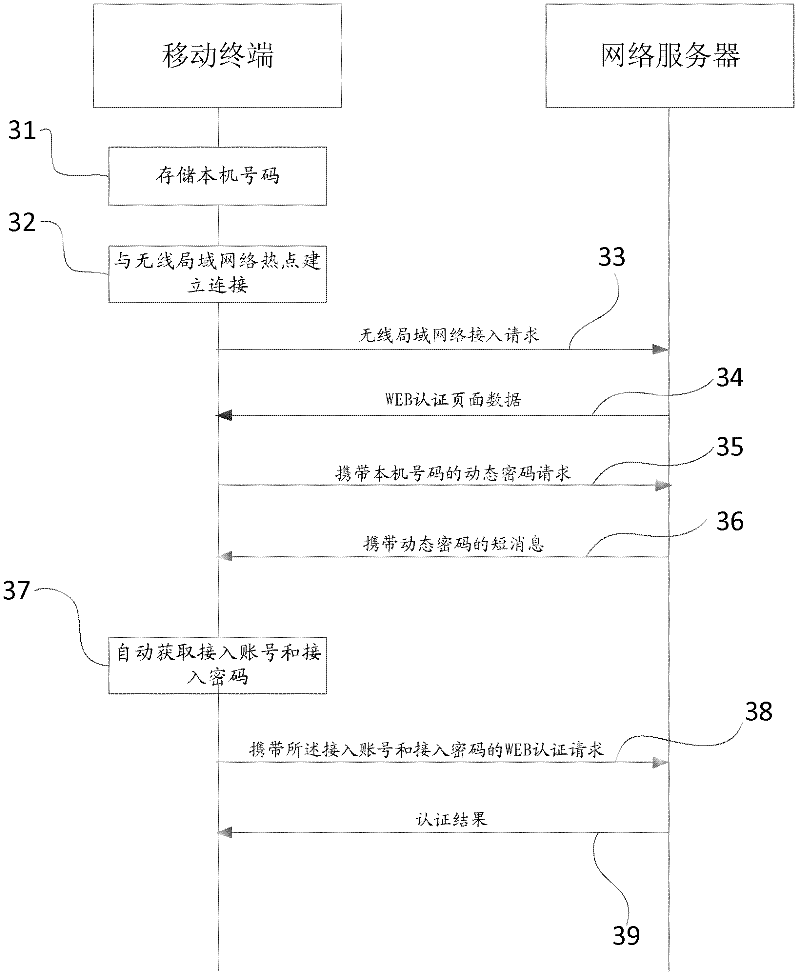
InactiveCN102378175AImprove experienceAvoid authentication operationsNetwork topologiesMessaging/mailboxes/announcementsWeb authenticationUser input
The embodiment of the invention discloses a wireless local area network (WLAN) authentication method. The method comprises the following steps of: a mobile terminal automatically obtains an access account number and an access password; and the mobile terminal automatically sends a WEB authentication request to a network server, wherein, the WEB authentication request carries the access account number and the access password. The embodiment of the invention further discloses the corresponding mobile terminal. By adopting the WLAN authentication method and the mobile terminal disclosed by the invention, the mobile terminal can automatically complete WEB authentication of a WLAN without inputting the account number and the password by a user and displaying a WEB authentication interface to the user, thus avoiding complicated authentication operation and improving the user experience.
Owner:HUAWEI DEVICE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com