Method and network authentication server for controlling client terminal access to network appliance
A technology for authentication server and client control, applied in the field of network security, it can solve the problems of complicated user operation server control, etc., and achieve the effect of effective and convenient access.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Embodiments of the present invention provide a method for controlling client access to network equipment and a network authentication server.
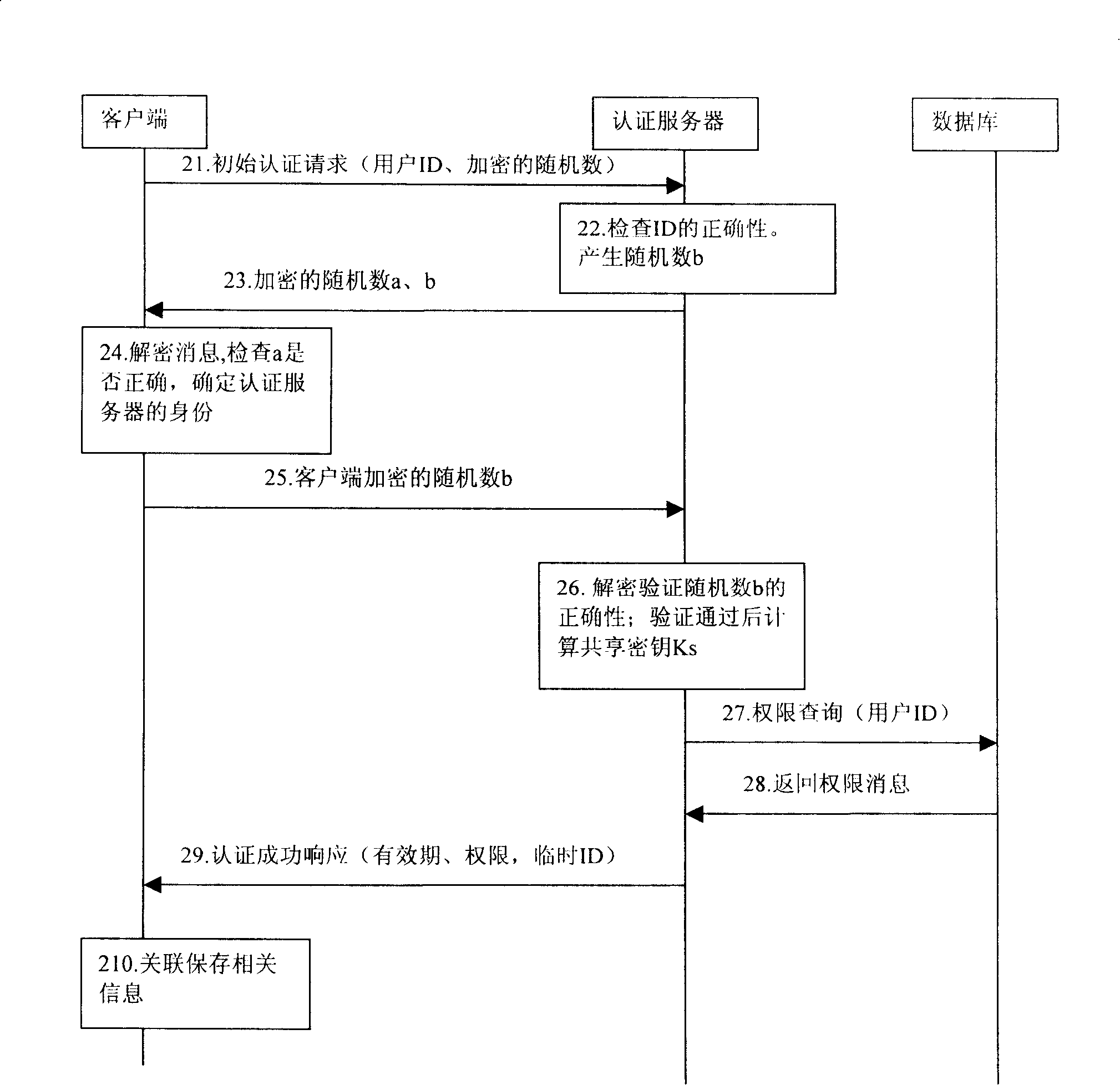
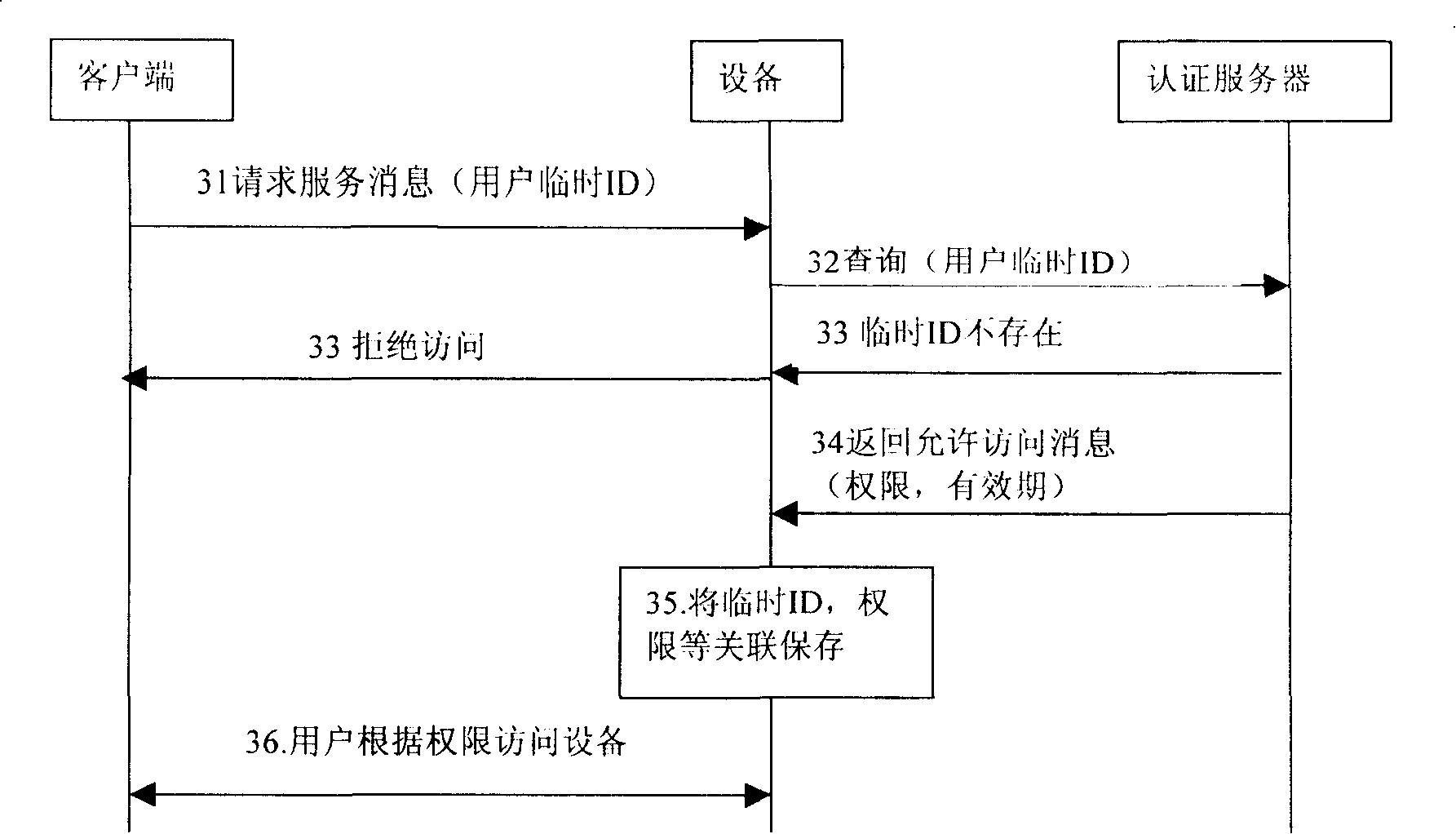
[0032] The main processing flow of the method described in the embodiment of the present invention is as follows: the authentication server in the network and the client of the user first use the public key cryptosystem to perform two-way identity authentication, and the authentication server assigns a temporary ID to the client of the user And the corresponding expiration date, as well as permission information. Then, the client controlling the user uses the temporary ID to access devices in the network within the validity period.
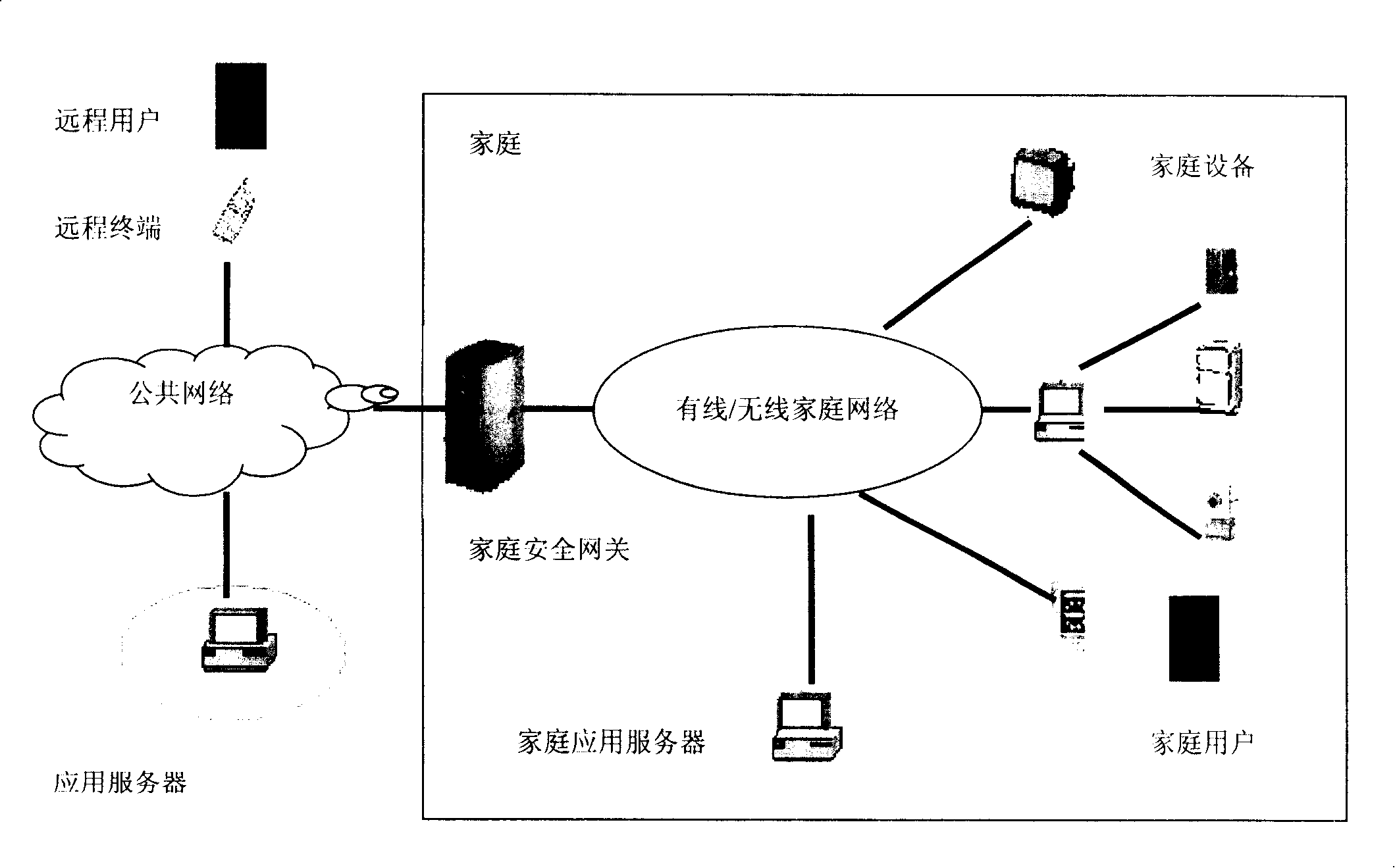
[0033] The method described in the embodiment of the present invention is applicable to various small local area networks, for example, a home network.
[0034] Taking a home network as an example, the processing flow of the embodiment of the method of the present invention mainly includes the foll...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com