Access control method, access control device and terminal device
An access control and access-allowing technology, applied in the information field, can solve the problems of difficult to ensure data security and difficult access to data areas, and achieve the effect of avoiding illegal access, ensuring data security, and improving data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
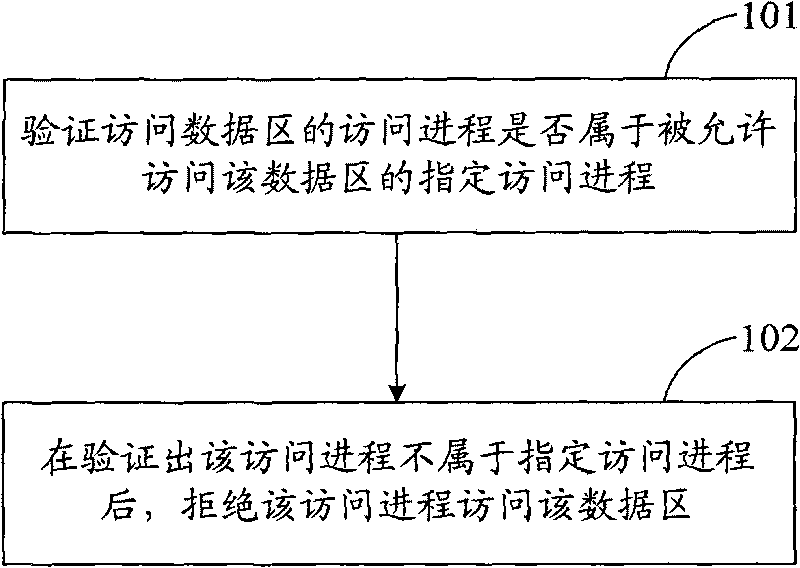
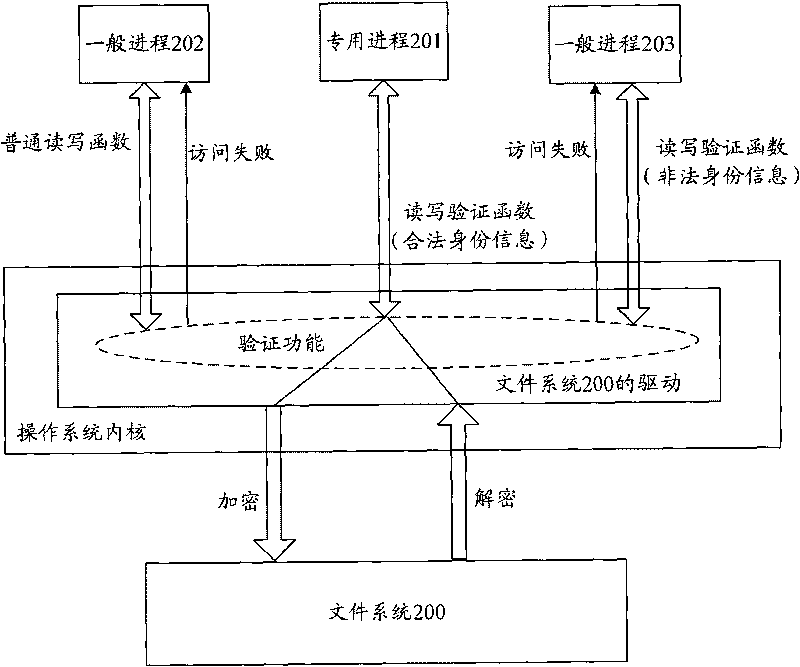
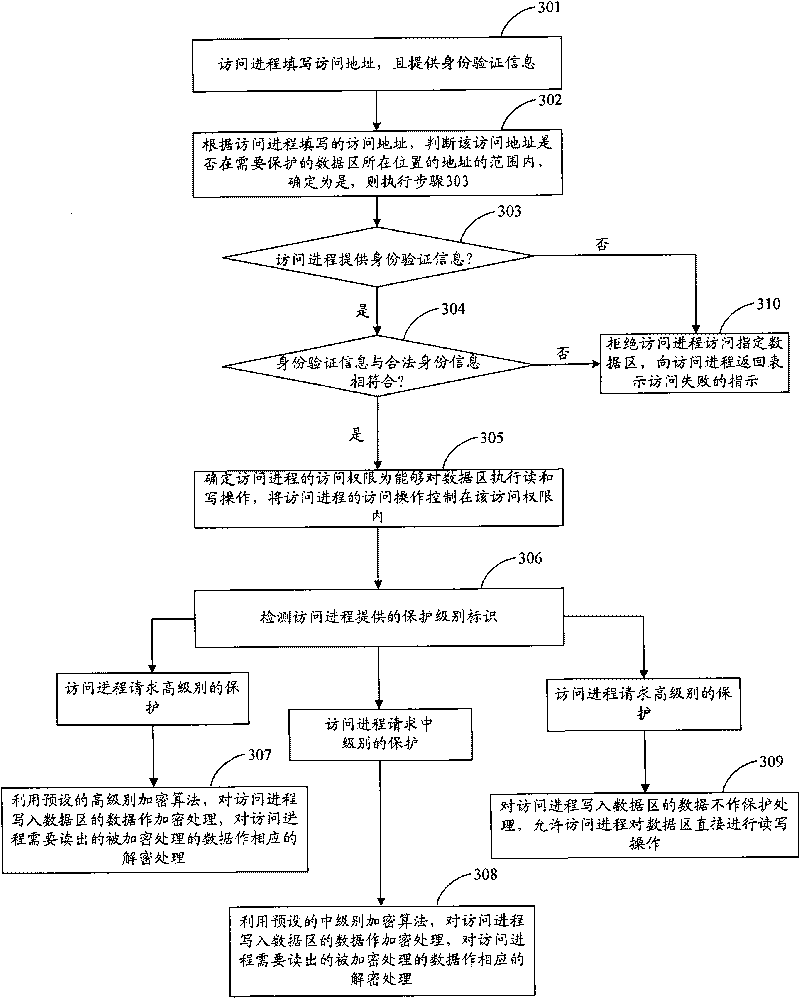
[0069] The reason why it is difficult for the prior art to effectively control the access of the access process to the data area is that the prior art only verifies the validity of the identity of the user using the access process before the access process accesses the data area, and does not verify the validity of the access process. It does legality verification itself, which leads to security risks that illegal processes can also access the data area once the data area is mounted.
[0070] In the specific implementation of the present invention, consider starting from the essence of the access operation, do legal identity verification to the access process that performs the access operation, and be verified as a legal access process to allow access to the data area, otherwise it is not allowed to access, so as to realize data access. Zone access control. Wherein, the accessing process may include all processes expecting to access the data area to be protected. For example,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com