Patents
Literature
34results about How to "Solve security protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
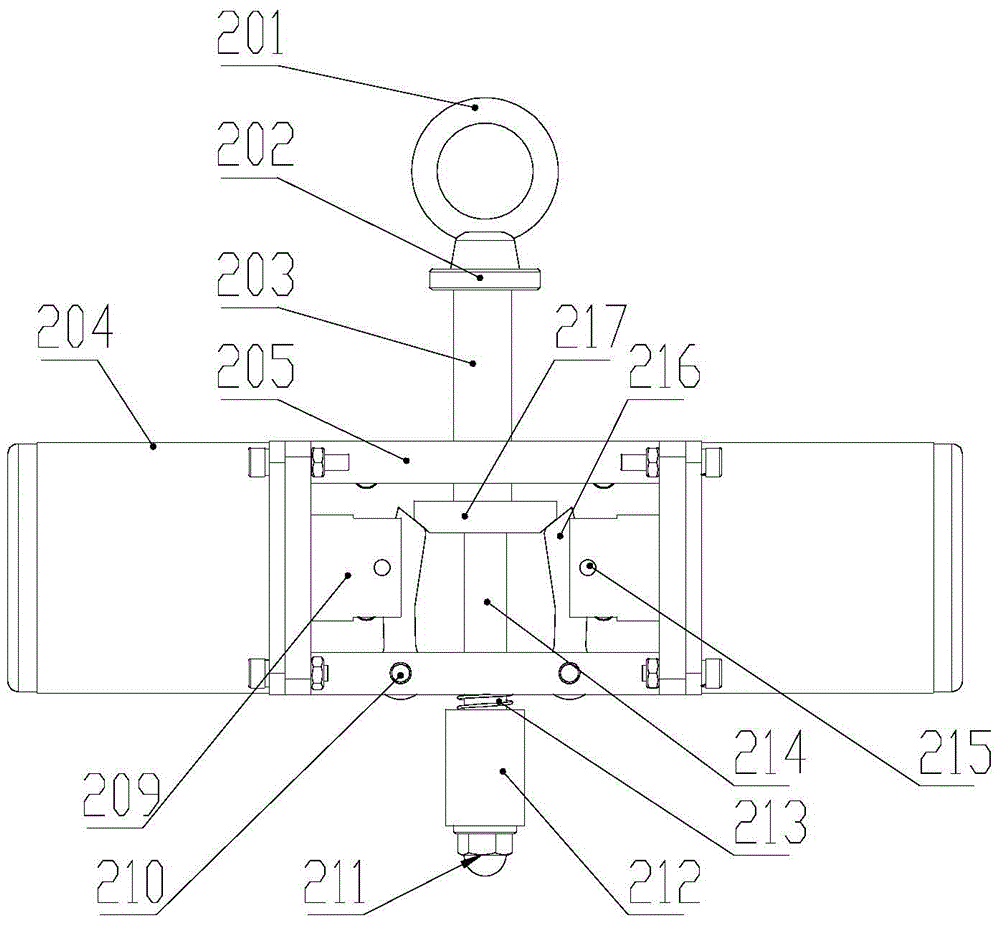
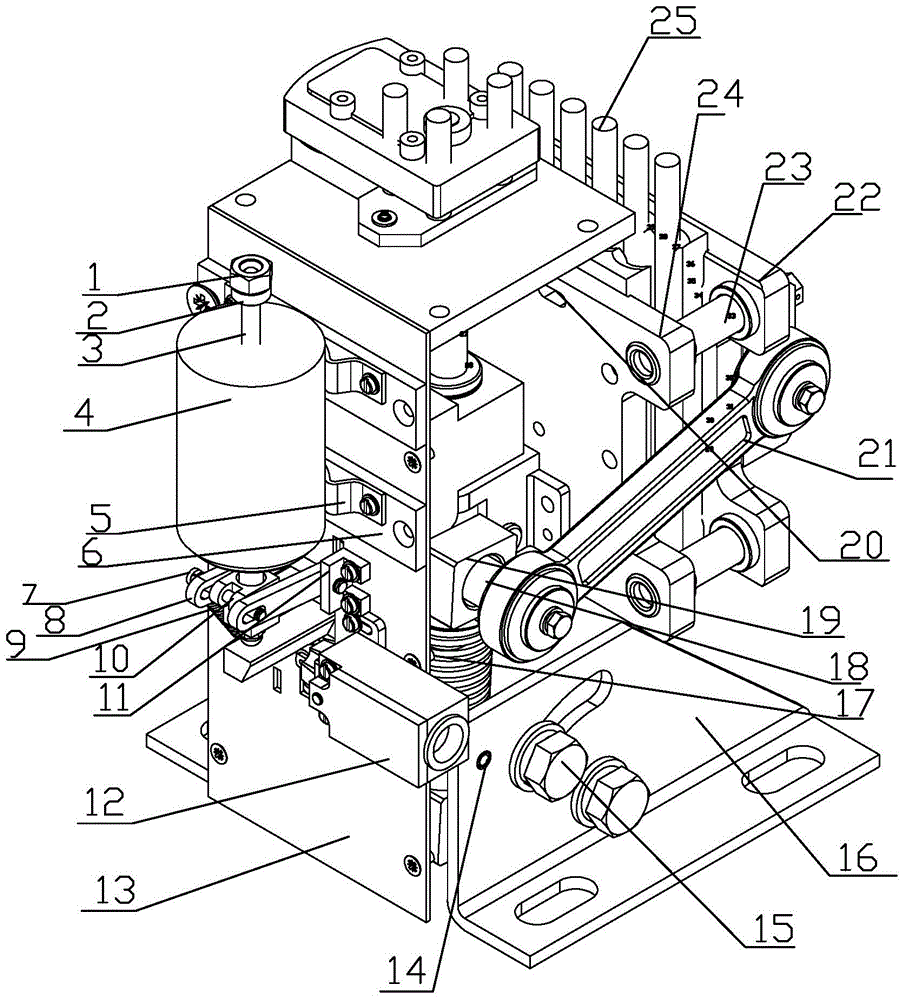
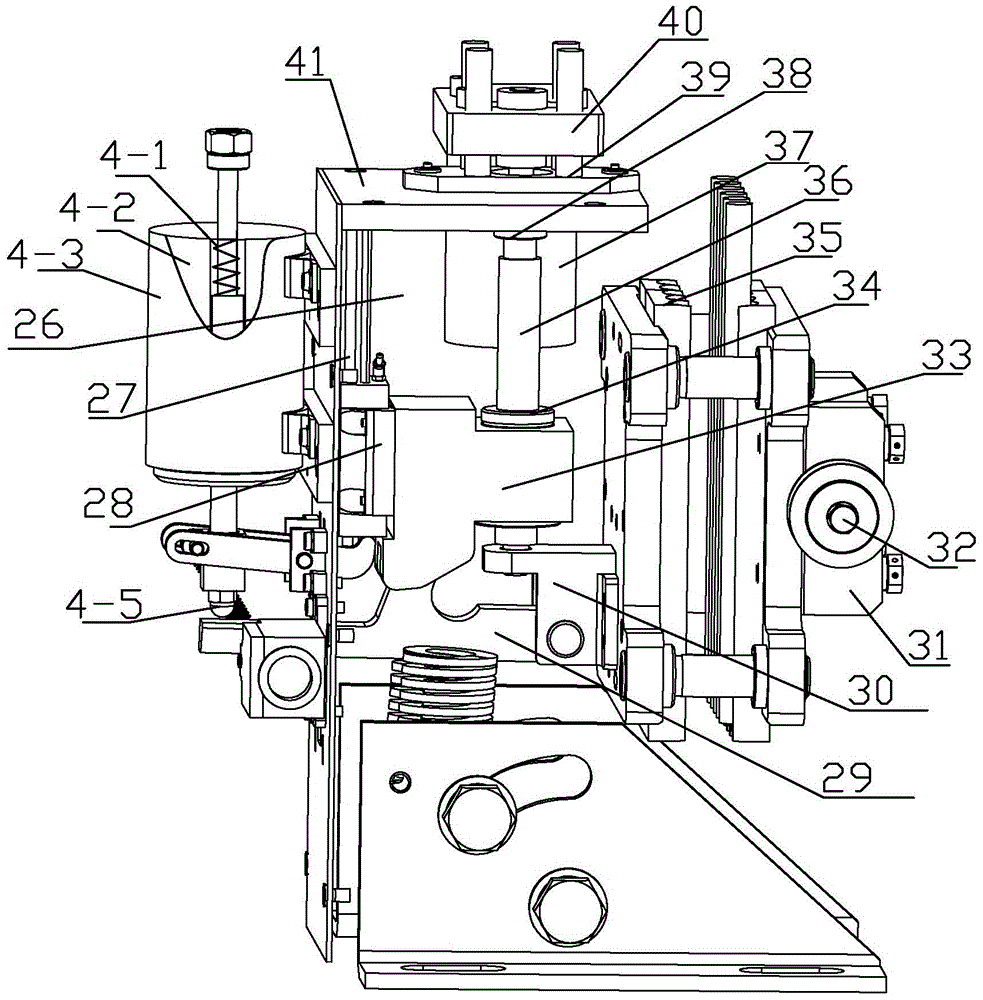
Method, device and system for safety protection used in failure of putting away oar of blade of wind turbine generator
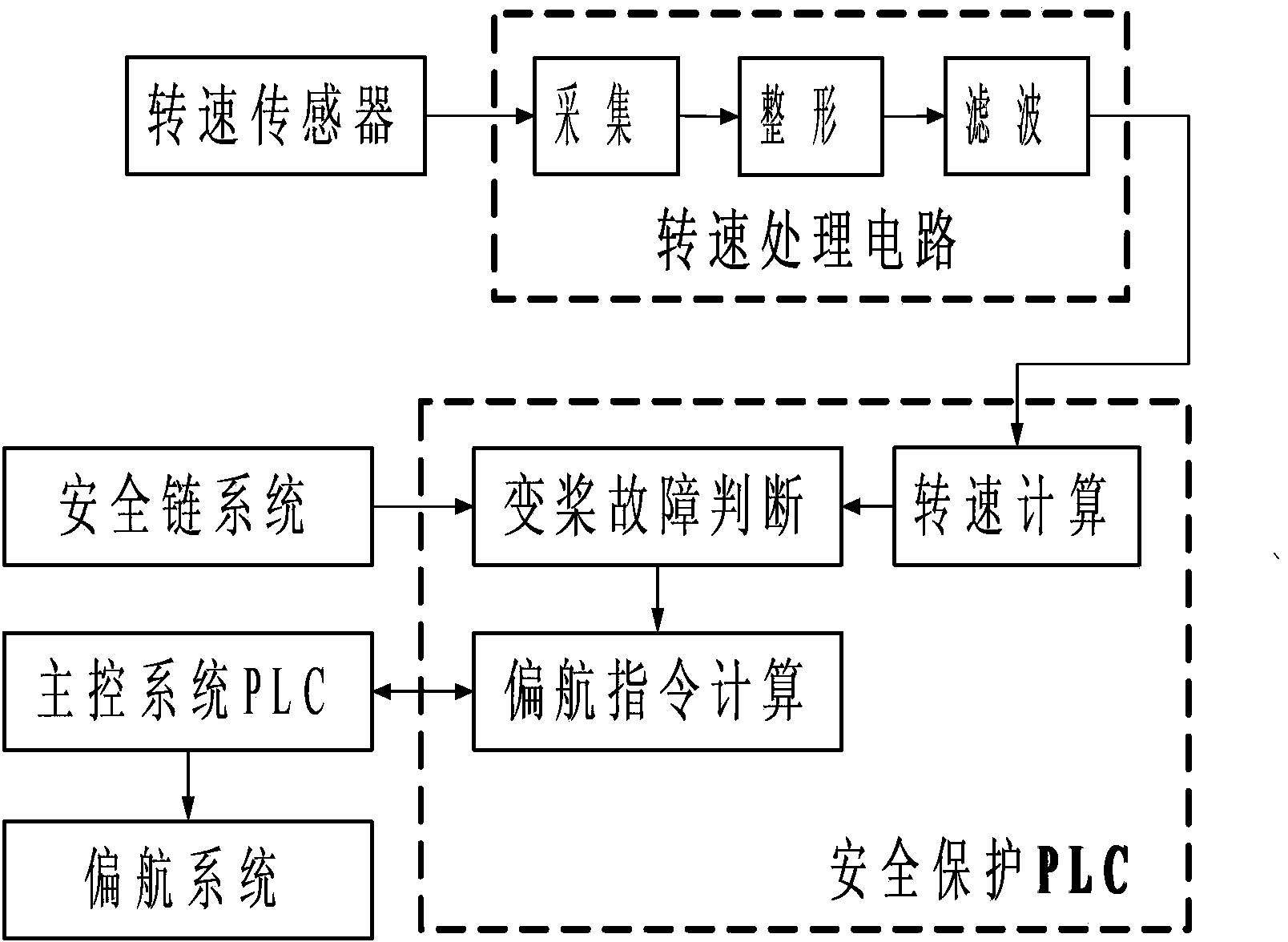
ActiveCN102828909ASolve security protectionReduce the risk of speedingWind motor controlMachines/enginesElectricityProgrammable logic controller
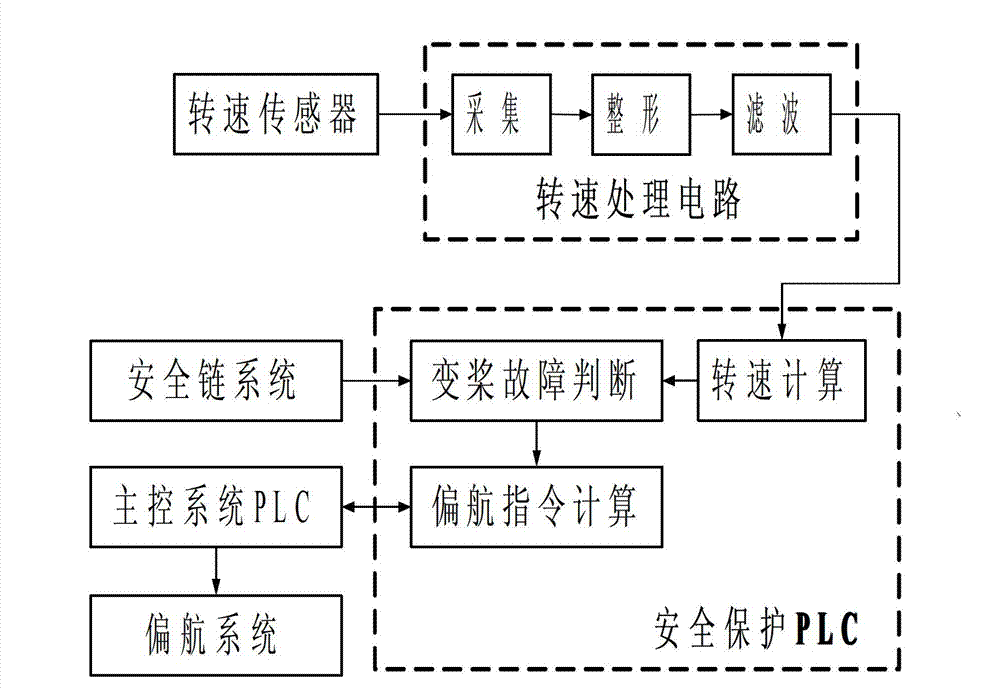
The invention discloses a method, a device and a system for safety protection used in failure of putting away an oar of a blade of a wind turbine generator. The method comprises the following steps: collecting and computing a real-time rotating speed of a blade hub; after a safety chain system sends a stopping command, if the rotating speed of the blade hub is continuously increased, judging a pitch control system to have a fault of putting away the oar; computing a yaw angle command; sending the computed yaw angle command to a master control PLC (Programmable Logic Controller), and controlling a yaw system to carry out a yaw action through the master control PLC. The system comprises a rotating speed computing module, a pitch control fault judging module and a yaw command computing module. The device comprises a safety protection controller internally provided with the system and connected with the safety chain system and the master control PLC; a rotating sensor used for collecting the real-time rotating speed of the blade hub; and a rotating speed processing circuit connected with the rotating speed sensor and the safety protection controller. According to the invention, the overspeed risk of the wind turbine in a stopping process is reduced, and the safety of the wind turbine and the reliability of judgment of the pitch control fault are improved.
Owner:GUODIAN UNITED POWER TECH
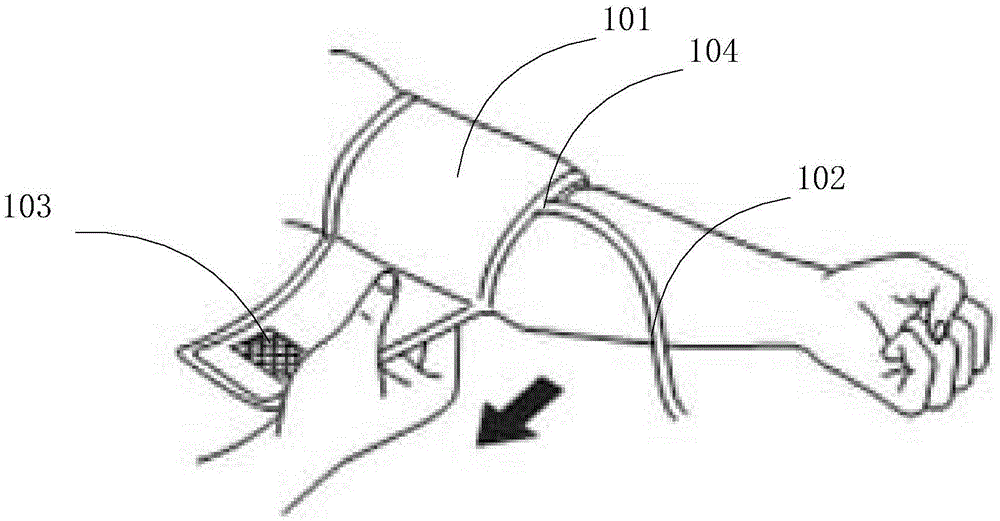
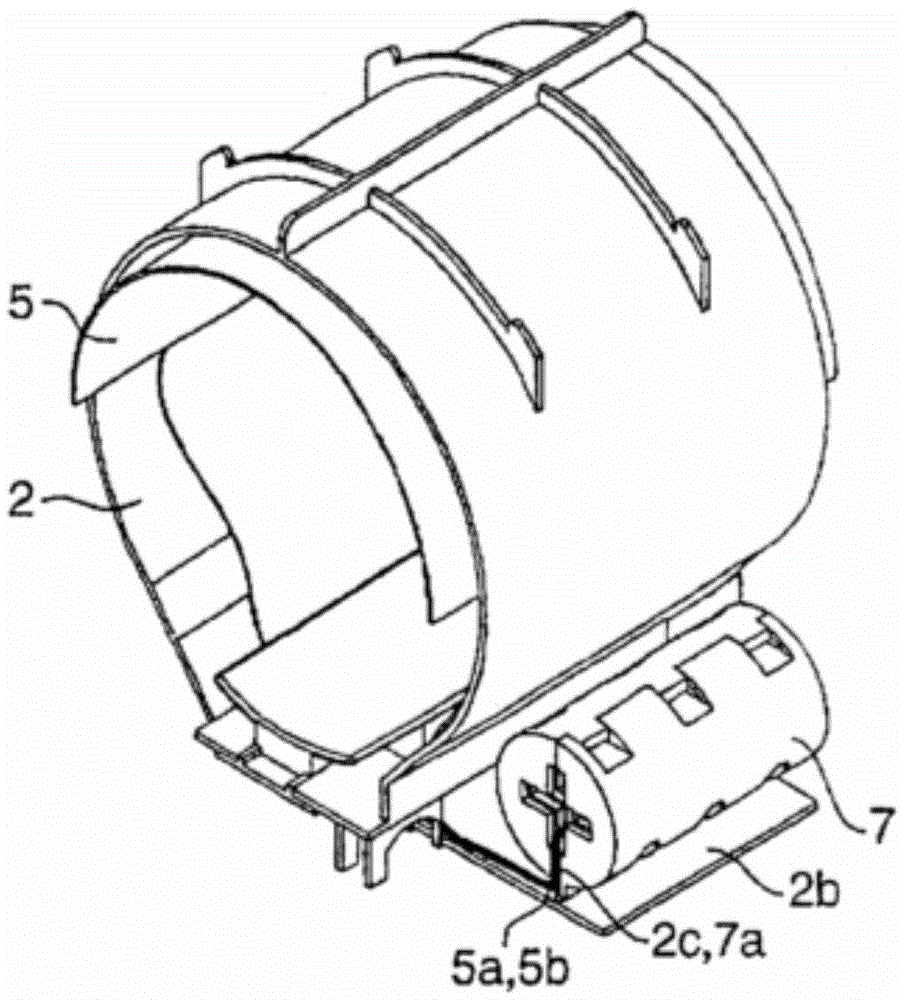
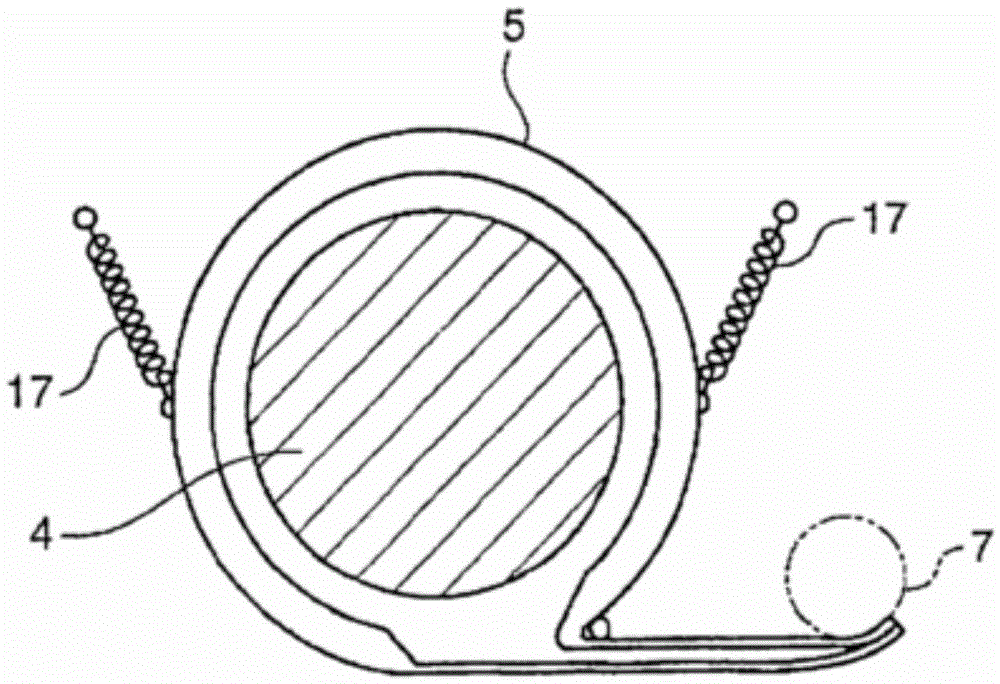
Device and method for winding or unwinding cuff
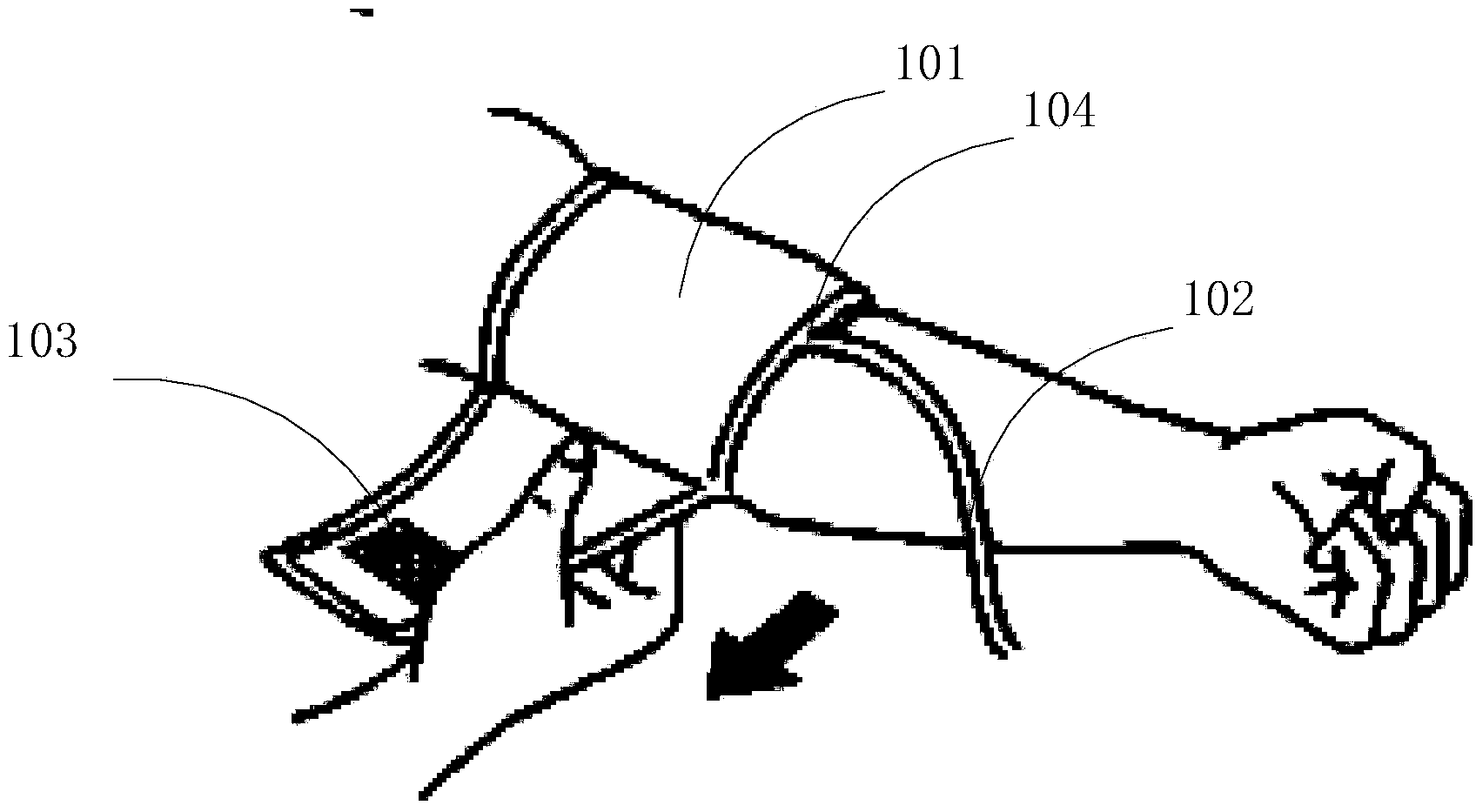
ActiveCN103932690ASolve the problem that the measurement posture cannot be adjusted according to the height and arm length of the measured objectAvoid measurement errorsEvaluation of blood vesselsAngiographyBarrel Shaped
The invention provides a device and method for winding or unwinding a cuff. The device for winding or unwinding the cuff comprises a winding mechanism, the cuff attached to the inner portion of the winding mechanism and a control part used for controlling the winding mechanism to carry out winding or unwinding. The device is characterized in that the winding mechanism is made to carry out winding or unwinding in a barrel shape through the control part to wind or unwind the cuff in the winding mechanism, so that the cross section area of the winding mechanism is changed.
Owner:BEIJING CHIOY MEDICAL TECH CO LTD
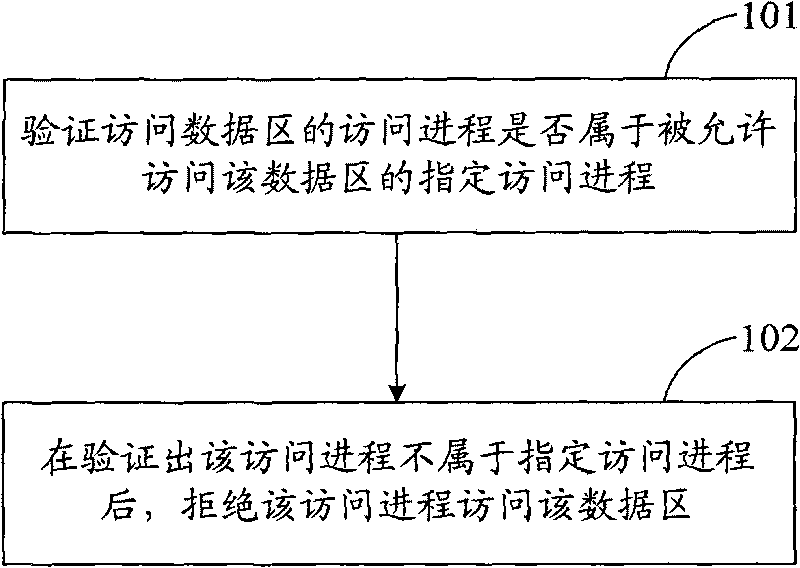
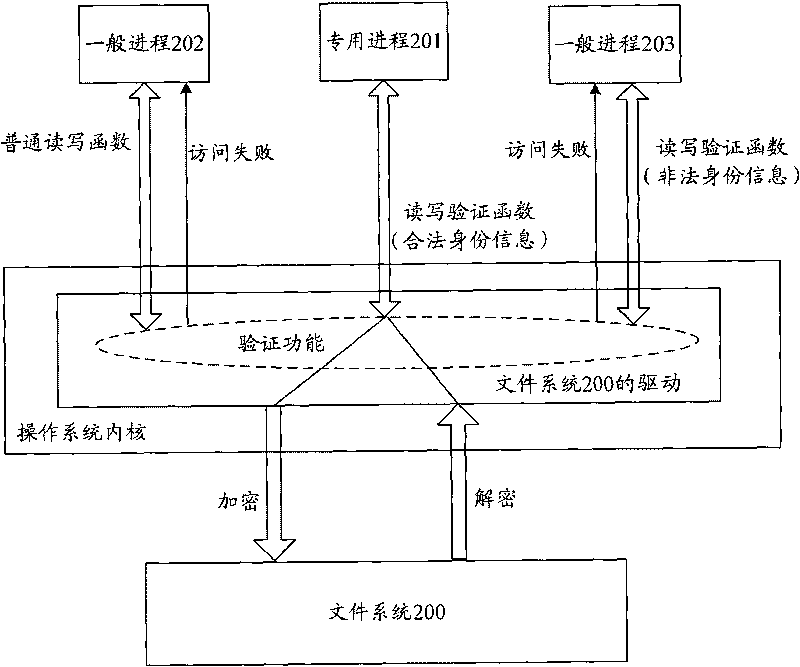
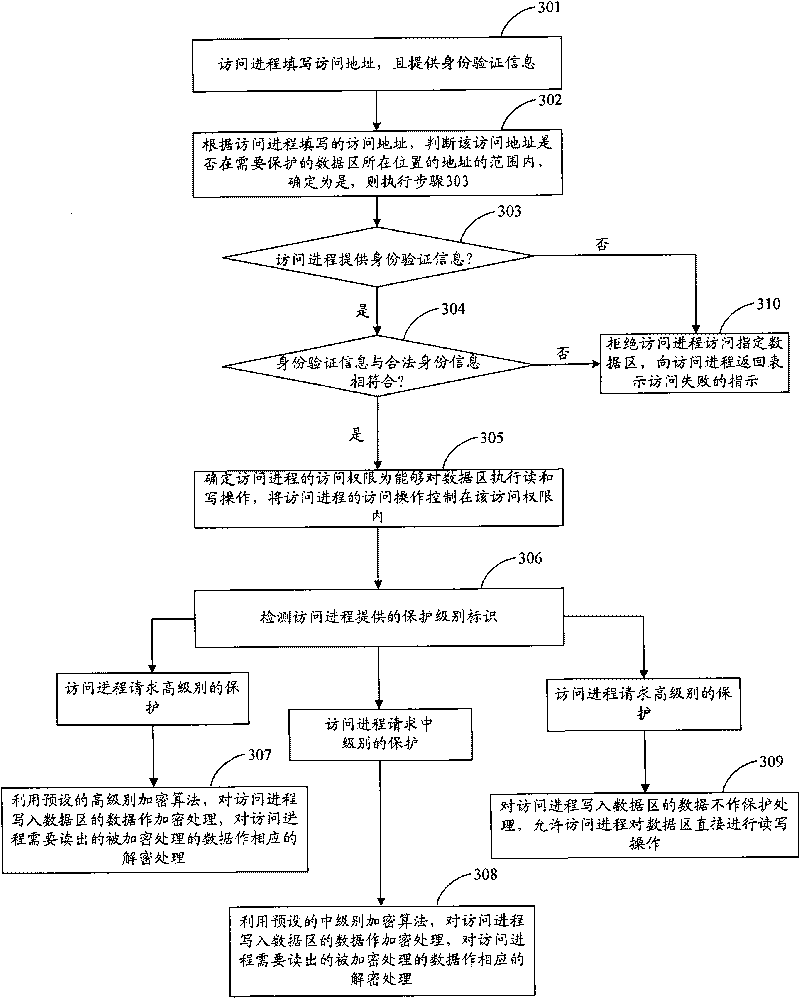
Access control method, access control device and terminal device
InactiveCN101739361AEffective access controlAccess controlUnauthorized memory use protectionTerminal equipmentAccess control
The implementation of the invention provides an access control method, an access control device and an accessing device. The method includes: whether the access process accessing data area is assigned to the designated access process of the data area allowed to be accessed is verified; the data area is used for storing data; and after the access process is verified not to be assigned to the designated access process, the access process is rejected to access the data area. The technical scheme provided by the implementation of the invention can effectively control the access of access process on data area, reject illegal access process to access the data area and effectively ensure the data of the data area to be safe.
Owner:LENOVO (BEIJING) CO LTD
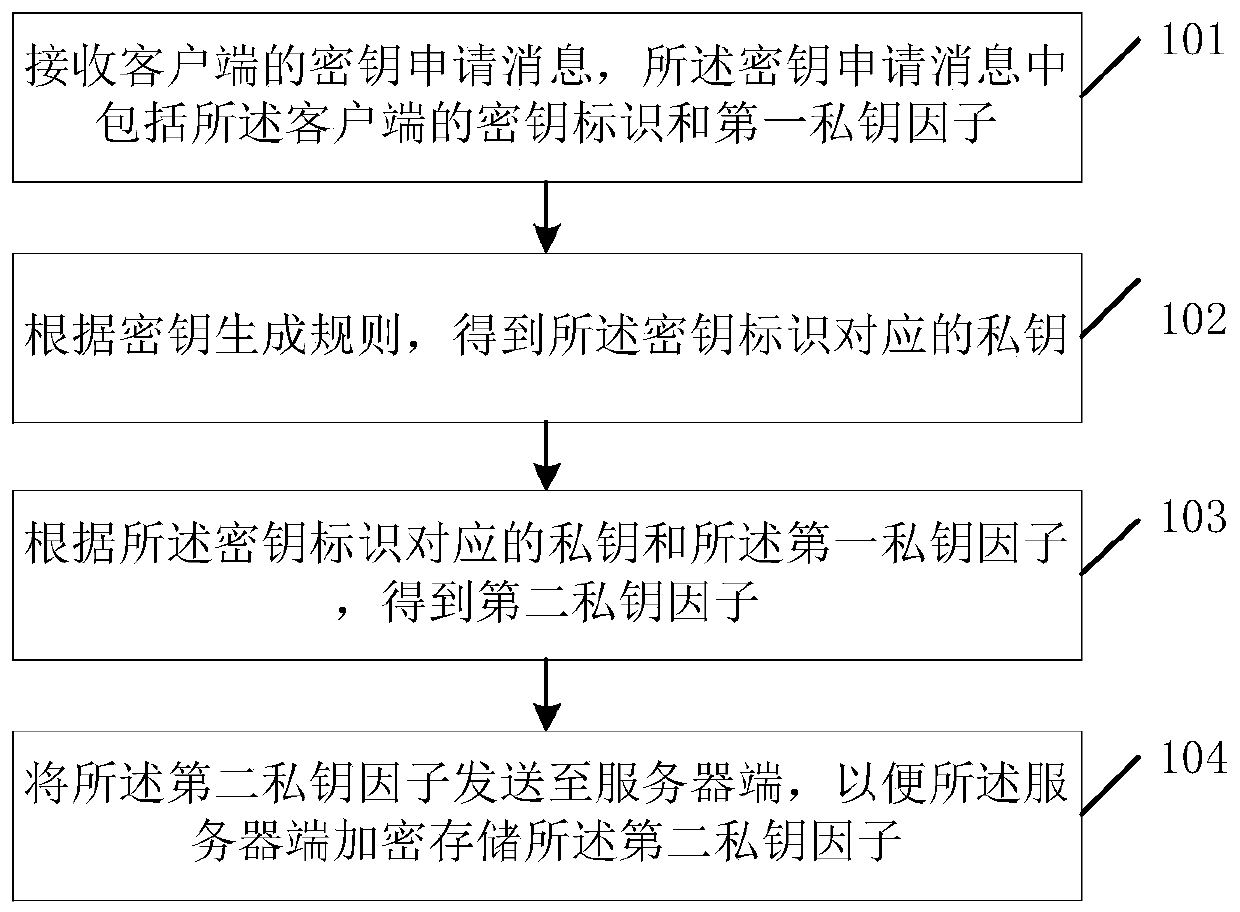
Private key processing method based on SM2 algorithm, terminal and key center
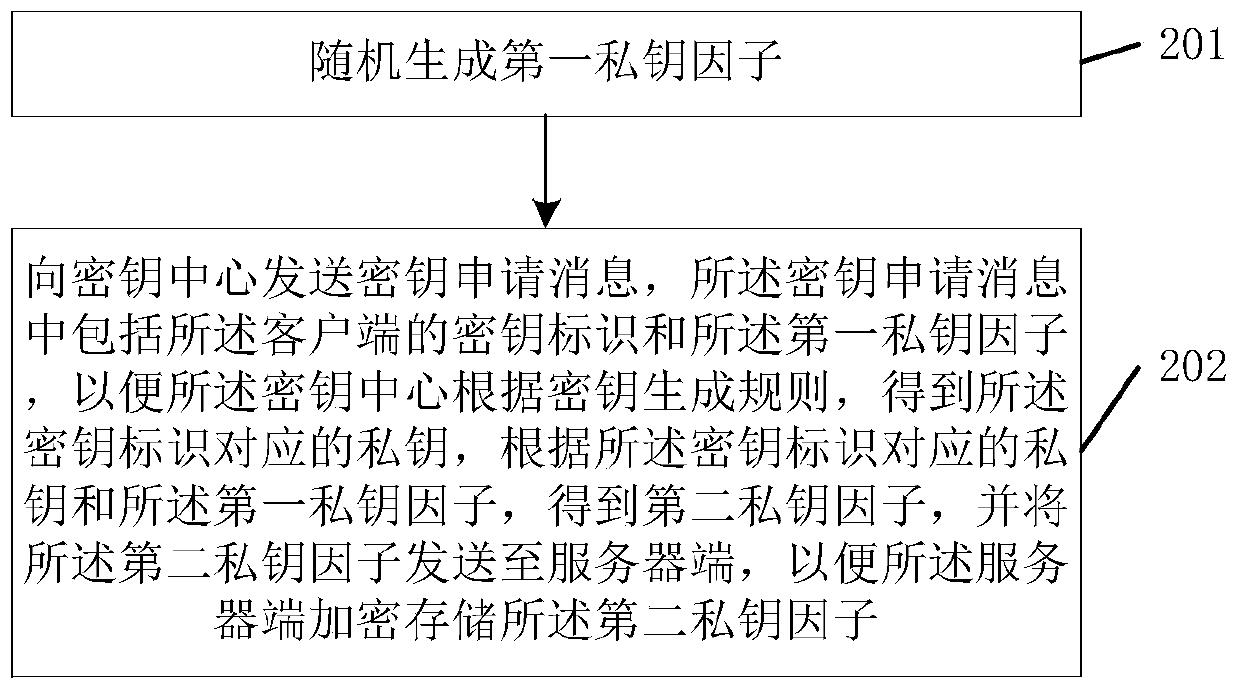
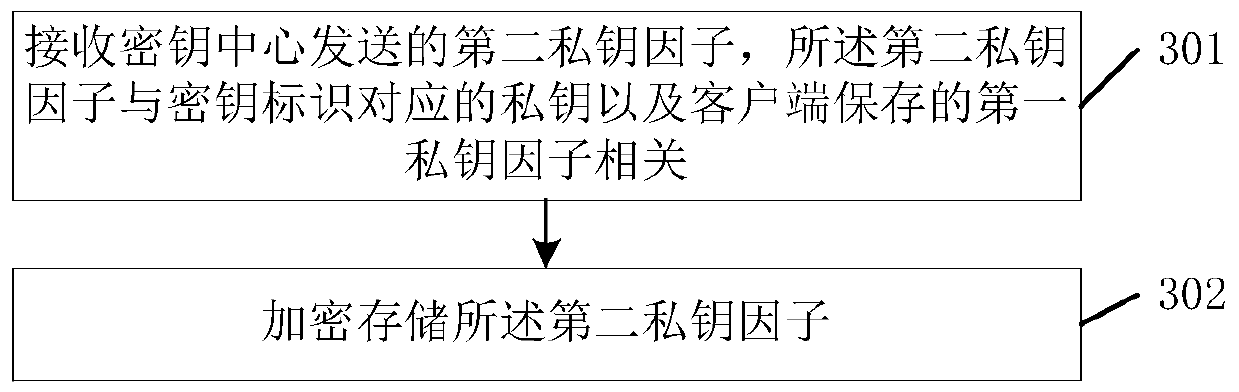
ActiveCN110391900ASolve security protectionTroubleshoot recovery issuesKey distribution for secure communicationUser identity/authority verificationClient-sideInformation security
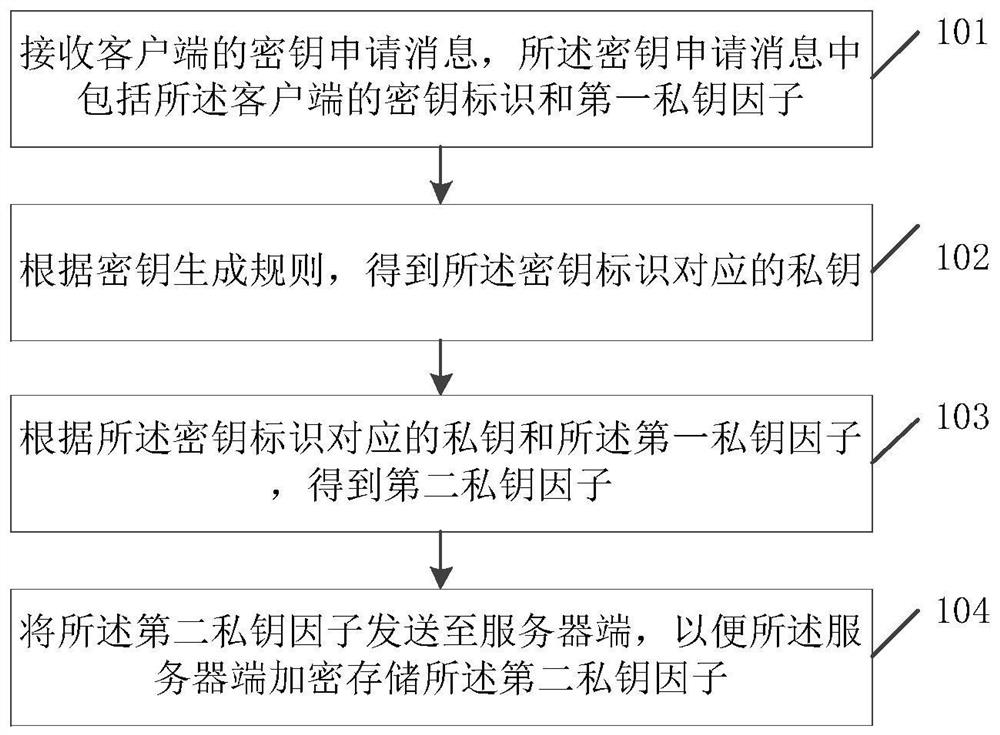
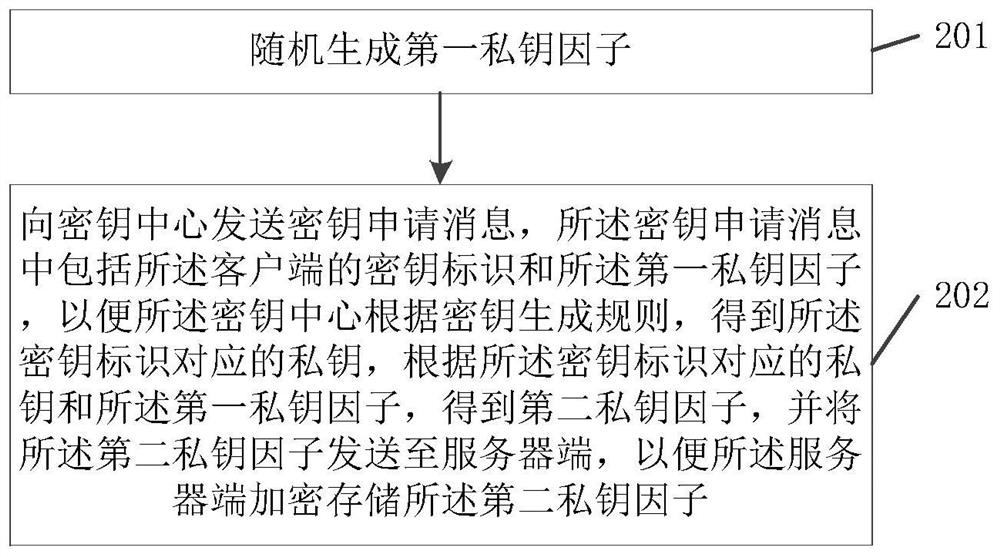
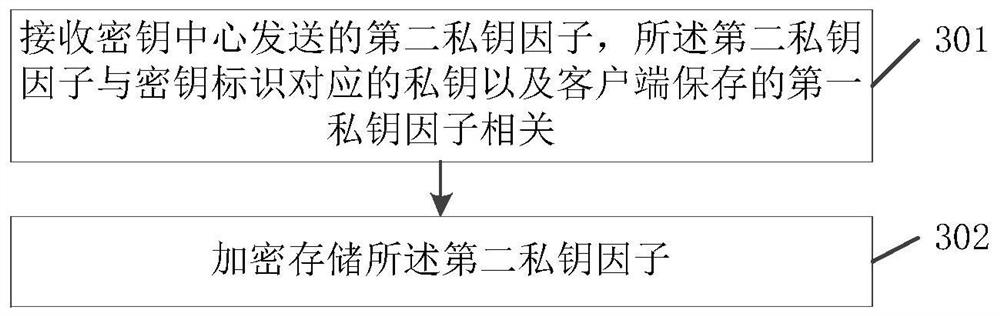
The invention relates to the technical field of information security, discloses a private key processing method based on an SM2 algorithm, a terminal and a key center, and solves the security protection problem of a private key in an open environment in the prior art. The method is applied to a key center, and comprises the following steps: receiving a key application message of a client, the keyapplication message comprising a key identifier and a first private key factor of the client; obtaining a private key corresponding to the key identifier according to a key generation rule; obtaininga second private key factor according to a private key corresponding to the key identifier and the first private key factor; and sending the second private key factor to a server, so that the server encrypts and stores the second private key factor. The embodiment of the invention is suitable for the decentralized storage and use process of the private key in the open environment.
Owner:JIN SHANG BO CHUANG BEIJING SCI & TECH CO LTD
Gas-fired heating wall-mounted stove and operation control method thereof
The invention provides a gas-fired heating wall-mounted stove which is used for a fan forcedly discharging smoke and an operation control method of the wall-mounted stove. The fan is a Hall fan provided with a Hall sensor, and a carbon monoxide concentration sensor is arranged in a smoke pipe or an exhaust pipe of the fan. The operation control method of the wall-mounted stove comprises the steps that 1, a power supply is turned on, and the gas-fired heating wall-mounted stove and a water pump are started after a heating system is full of water; 2, the fan is started, and after the Hall sensor detects that a fan motor normally operates, an ignition needle is started and meanwhile a gas valve is turned on to complete ignition; 3, after ignition is completed, a sensing needle detects a flame signal, the Hall sensor detects that the fan motor normally operates, and the carbon monoxide concentration sensor detects smoke; 4, the wall-mounted stove is automatically shut down once an abnormal situation occurs, the specific situation is that the sensing needle cannot detect the flame signal, or water pressure in the stove is insufficient, or the water temperature in the stove is too high, or the rotation speed of the fan motor is too low, or the carbon monoxide concentration in the smoke exceeds standard. The gas-fired heating wall-mounted stove can monitor whether smoke discharge during working of the wall-mounted stove is normal or not at the right moment, and it is effectively ensured that the wall-mounted stove safely operates.
Owner:GUANGZHOU DEVOTION HOME ENVIRONMENT TECH CO LTD
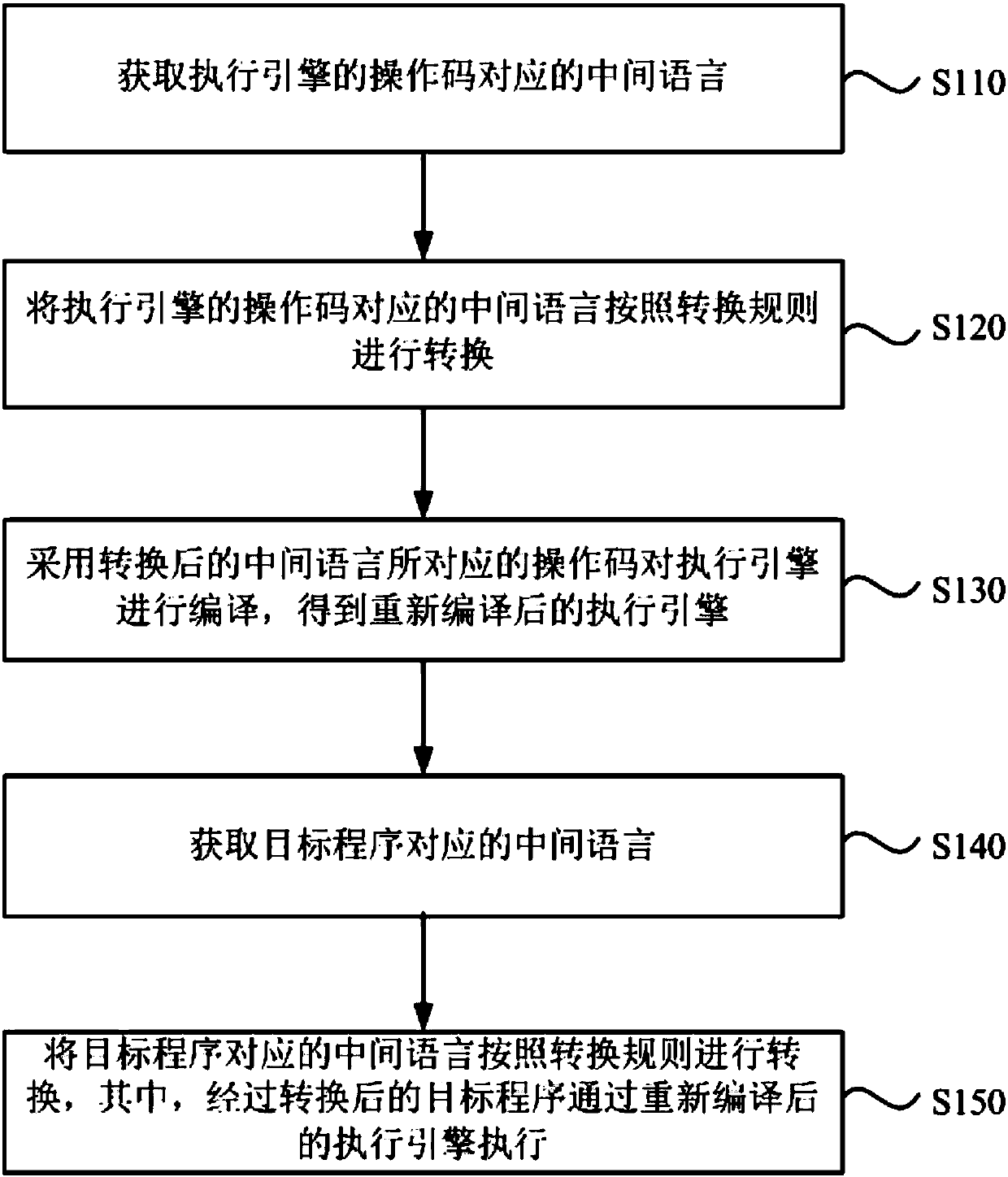
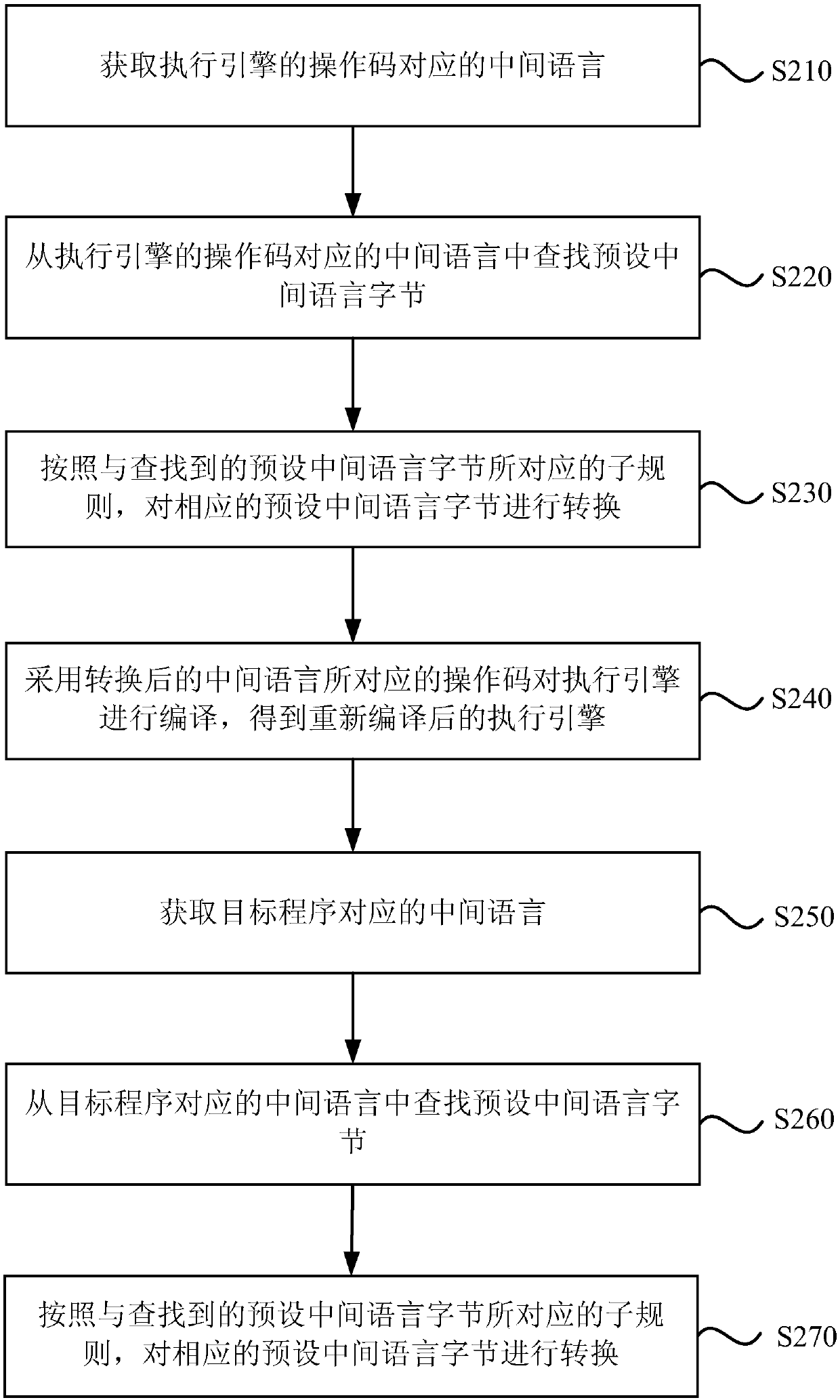
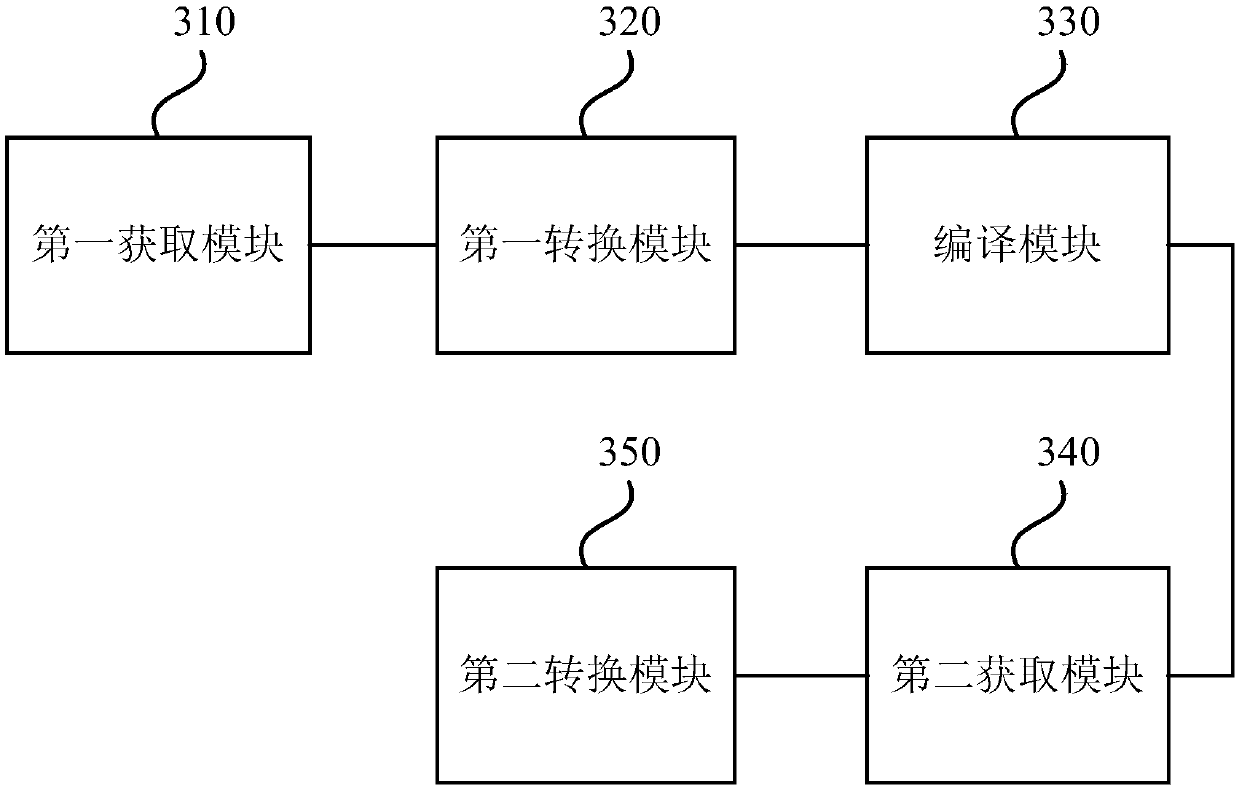
Protection method and device for target program, equipment and storage medium
ActiveCN107657154ASolve security protectionProgram/content distribution protectionCode compilationSoftware engineeringIntermediate language
The embodiment of the invention discloses a protection method and device for a target program, equipment and a storage medium. The method comprises the following steps that: obtaining an intermediatelanguage corresponding to the operation code of an execution engine; converting the intermediate language corresponding to the operation code of the execution engine according to a conversion rule; adopting the operation code corresponding to the converted intermediate language to compile the execution engine to obtain the recompiled execution engine; obtaining the intermediate language corresponding to a target program; and converting the intermediate language corresponding to the target program according to the conversion rule, wherein the converted target program is executed through the recompiled execution engine. Through the technical scheme of the method, the safety protection problem of a unity 3d program can be solved.
Owner:BEIJING SENSESHIELD TECH
Information monitoring method, equipment and information monitoring system
InactiveCN105163330ASolve the problem of effective security protectionSolve security protectionWireless communicationCrowdsInformation monitoring
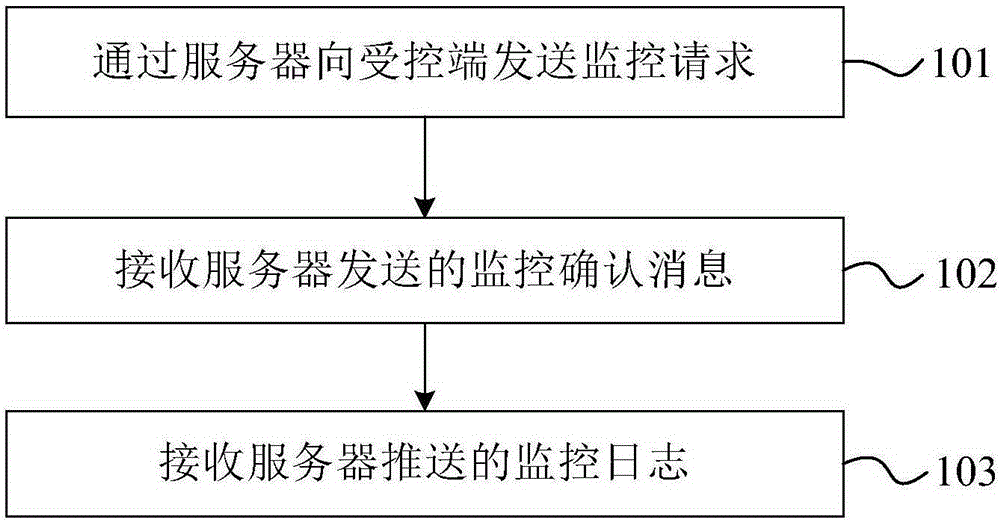
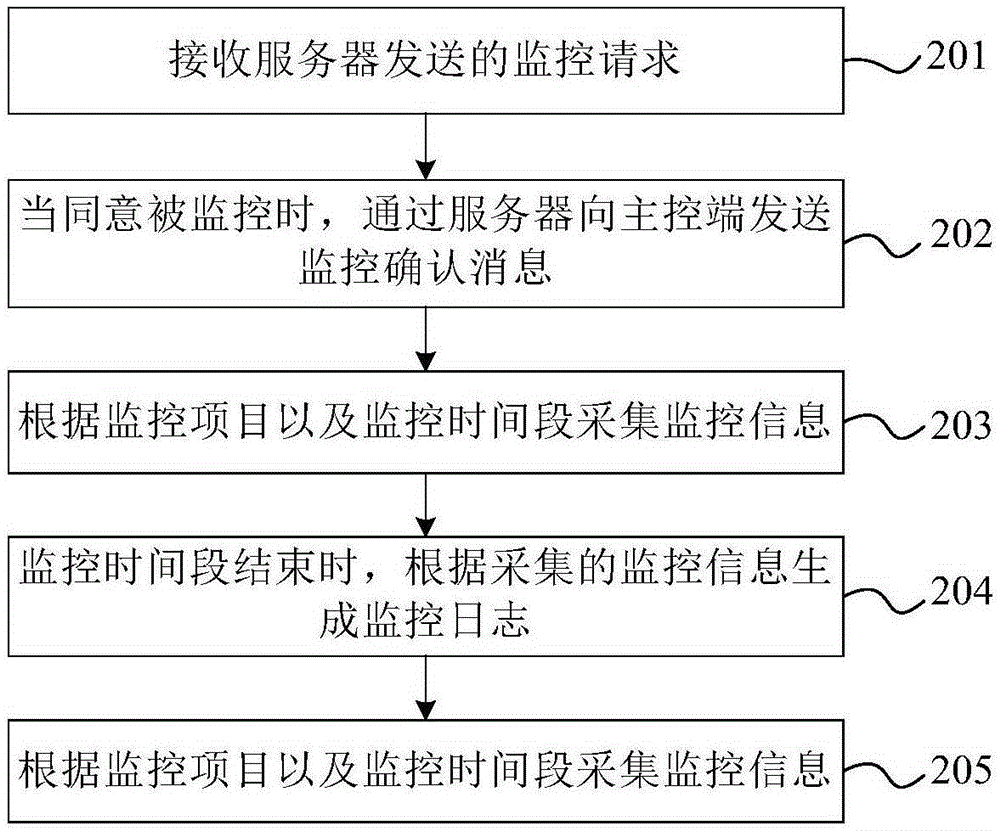
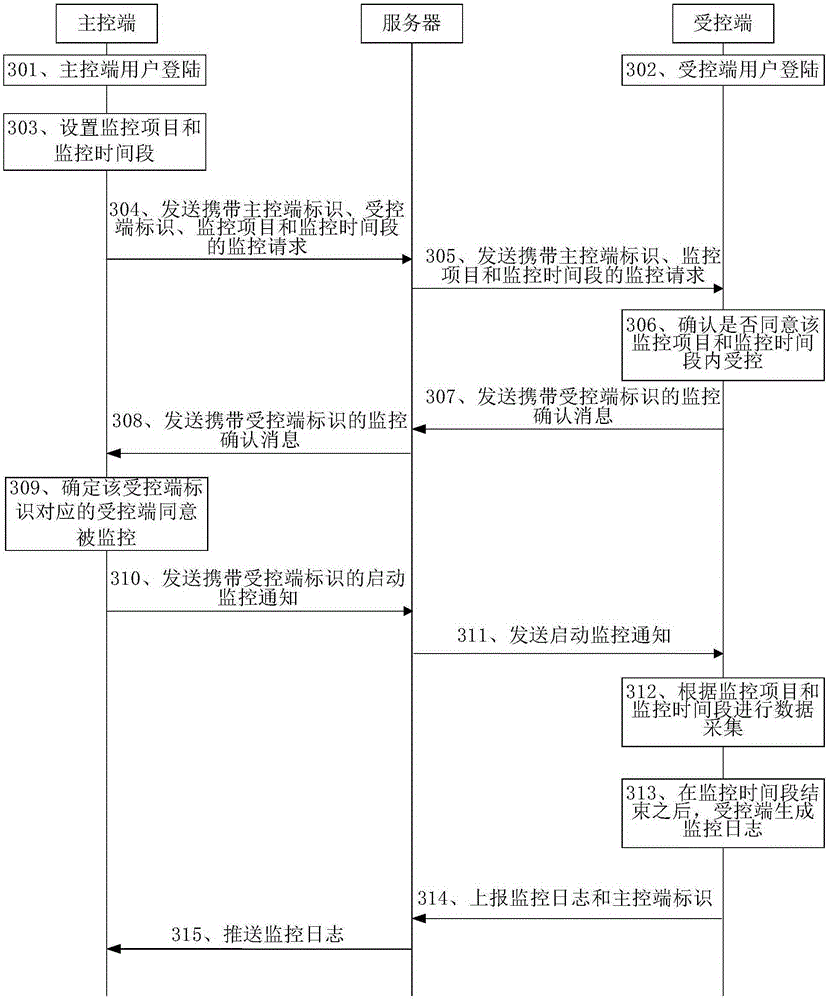
The invention provides an information monitoring method, equipment and an information monitoring system. The information monitoring method comprises the steps of sending a monitoring request to a controlled terminal through a server, wherein the monitoring request carries a main control terminal identifier, a monitoring item and a monitoring time period; receiving a monitoring confirmation message sent by the server, wherein the monitoring confirmation message is received by the server and sent by the controlled terminal; and receiving a monitoring log pushed by the server, wherein the monitoring log is acquired by the controlled terminal according to the monitoring item and the monitoring time period and reported to the server at the end of the monitoring time period. Through adopting the scheme provided by the invention, monitoring is carried out on the crowds to be monitored through communication equipment such as a mobile terminal, thereby solving a problem of carrying out effective security protection on the crowds to be monitored such as the old, the juveniles and the like.
Owner:SHENZHEN TINNO WIRELESS TECH
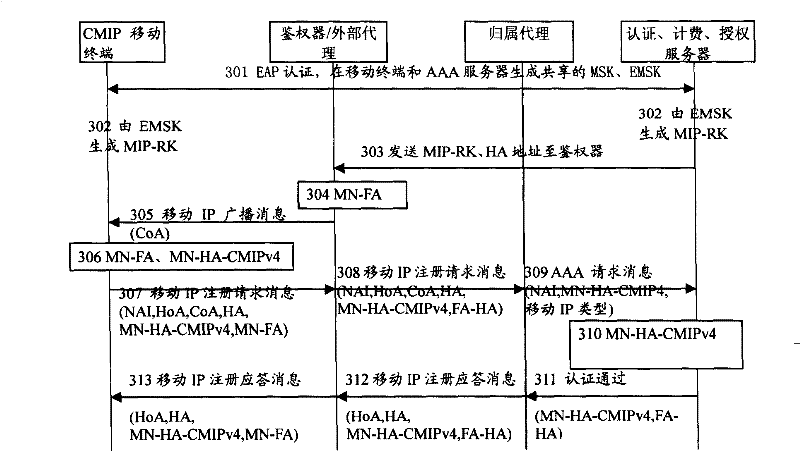
Method, system and mobile terminal for wireless network to capture mobile IP style of mobile terminal
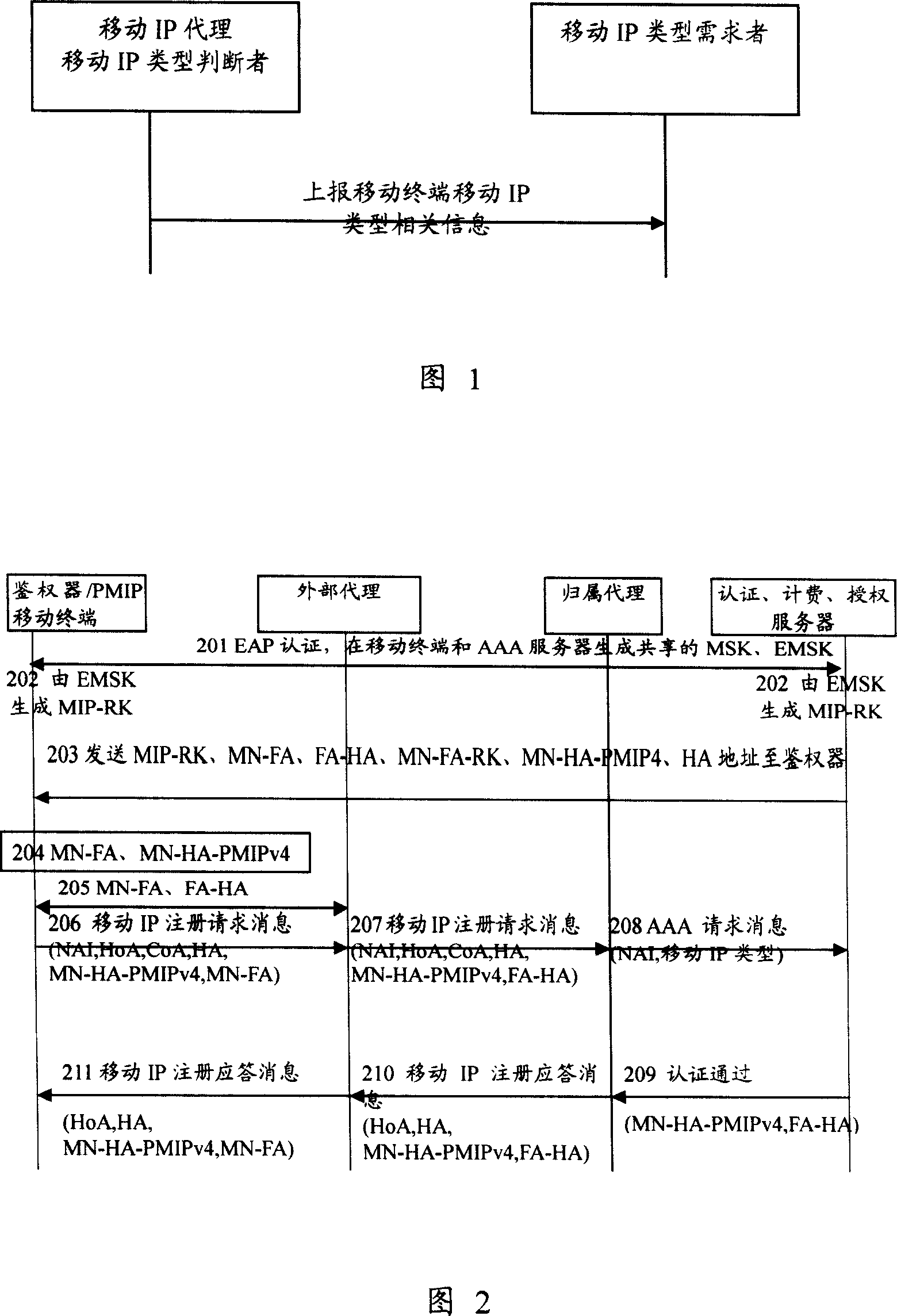
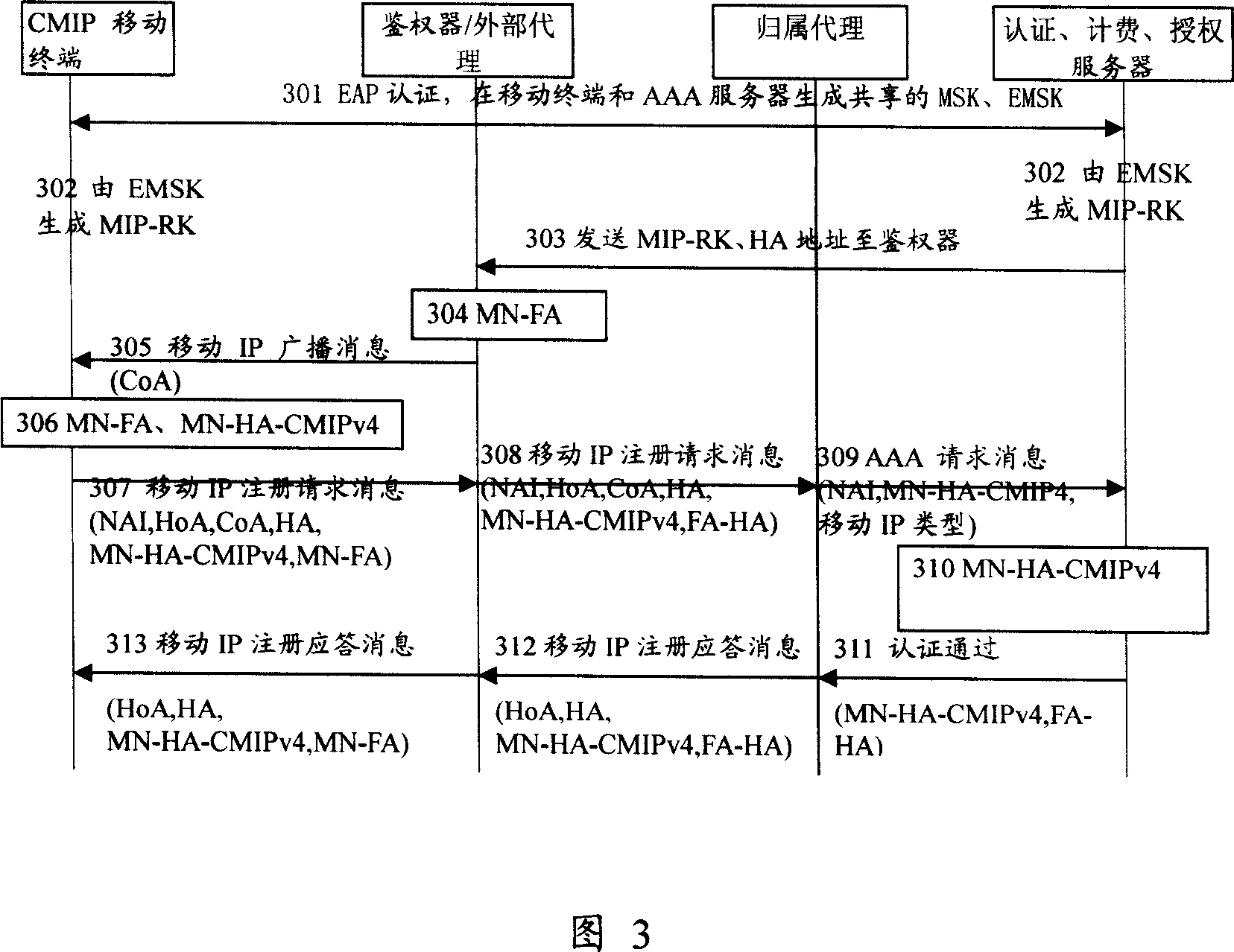
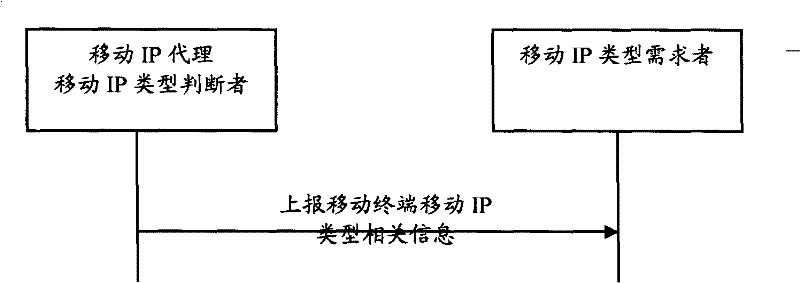
ActiveCN101106806ASolve security protectionKey distribution for secure communicationMultiple keys/algorithms usageRelevant informationTelecommunications
The invention provides a method for obtaining mobile IP type of a mobile terminal in a wireless network: a mobile IP proxy server reports related information of a mobile IP type to a user, who requires a mobile IP type, according to the mobile IP type identifying field in a mobile IP logging request message of a mobile terminal. A system for imparting a mobile IP type to a mobile terminal in a wireless network at least includes: a mobile terminal, a mobile IP proxy server, and a user who requires a mobile IP type. The mobile terminal transmit a mobile IP logging request message to a mobile IP proxy server for performing mobile IP logging in; and the mobile IP proxy server reports mobile IP type related information of the mobile terminal to the user who requires a mobile IP type according to the mobile IP type identifying field in a mobile IP logging request message. The invention also provides a mobile terminal for wireless network, when the mobile terminal is logged in a network for the first time or keywords for the mobile terminal is needed to be updated, the mobile terminal transmits mobile IP logging request message to a mobile IP proxy serve for performing mobile IP logging in, and a mobile IP type identifying field for identifying mobile IP type of the mobile terminal is included in the mobile IP logging request message.
Owner:HUAWEI TECH CO LTD
Data encryption processing method for performing signature verification on application program interface
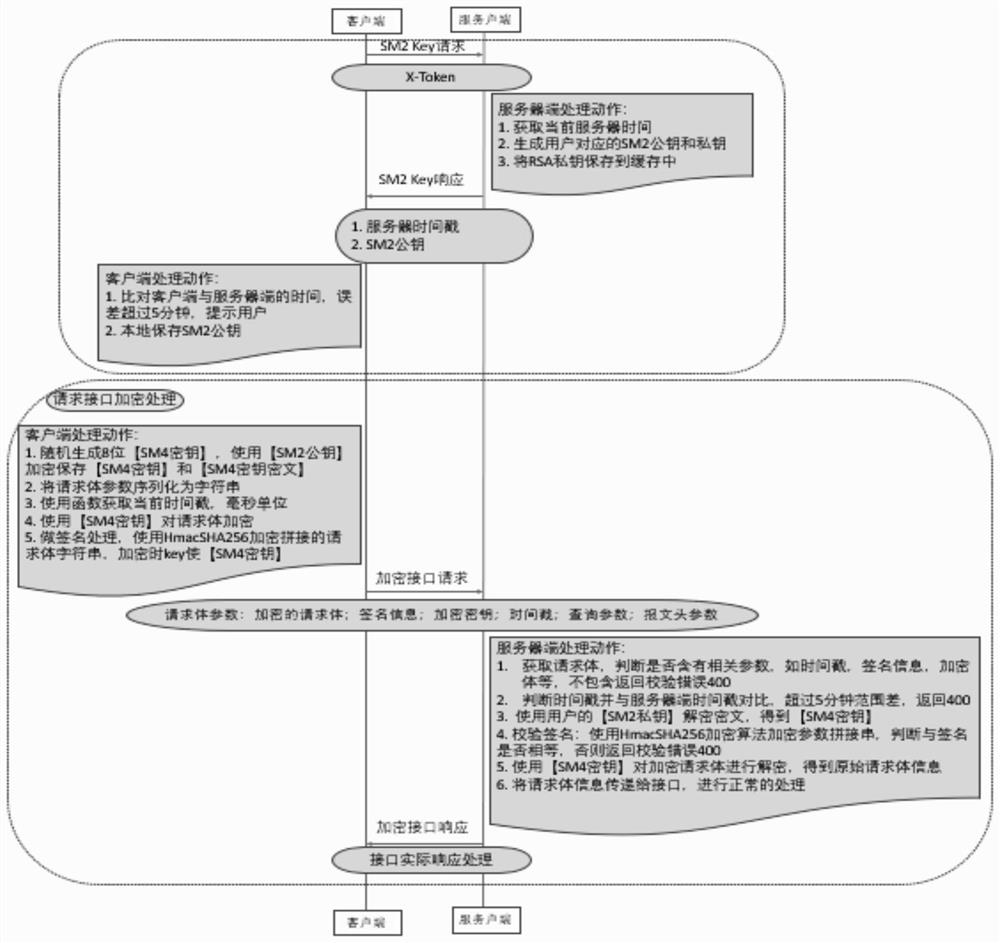
PendingCN114553416AStrengthen safe and orderly useAchieve non-repudiationKey distribution for secure communicationUser identity/authority verificationProgramming languageApplication procedure
A data encryption processing method for performing signature verification on an application program interface comprises the following steps: before a client of an application program sends a request to a corresponding server interface, firstly obtaining an exclusive asymmetric key through a server, thereby ensuring the security of the server accessing the client; when a client initiates an interface request to a corresponding server interface, a generated symmetric key is matched with a hash algorithm to encrypt data of a request body and generate a signature body of the request body, the server forms a signature verification body by using received request body parameters through the same encryption algorithm, and the signature body is verified through the signature and signature verification process. The anti-repudiation of the data original issuing behavior and the anti-repudiation of the data receiving behavior are realized; according to the invention, the non-repudiation of data request and transmission is realized by carrying out the encryption processing of signature verification on the data receiving and transmitting voucher; the safe and orderly use of the application program interface is enhanced, and the credibility, the safety and the traceability of the original request interface of the application program are ensured.
Owner:北京友普信息技术有限公司
Method, device and system for safety protection used in failure of putting away oar of blade of wind turbine generator
ActiveCN102828909BSolve security protectionReduce the risk of speedingWind motor controlMachines/enginesElectricityProgrammable logic controller
The invention discloses a method, a device and a system for safety protection used in failure of putting away an oar of a blade of a wind turbine generator. The method comprises the following steps: collecting and computing a real-time rotating speed of a blade hub; after a safety chain system sends a stopping command, if the rotating speed of the blade hub is continuously increased, judging a pitch control system to have a fault of putting away the oar; computing a yaw angle command; sending the computed yaw angle command to a master control PLC (Programmable Logic Controller), and controlling a yaw system to carry out a yaw action through the master control PLC. The system comprises a rotating speed computing module, a pitch control fault judging module and a yaw command computing module. The device comprises a safety protection controller internally provided with the system and connected with the safety chain system and the master control PLC; a rotating sensor used for collecting the real-time rotating speed of the blade hub; and a rotating speed processing circuit connected with the rotating speed sensor and the safety protection controller. According to the invention, the overspeed risk of the wind turbine in a stopping process is reduced, and the safety of the wind turbine and the reliability of judgment of the pitch control fault are improved.
Owner:GUODIAN UNITED POWER TECH
JavaScript engine memory information leakage defense method and system based on runtime randomization
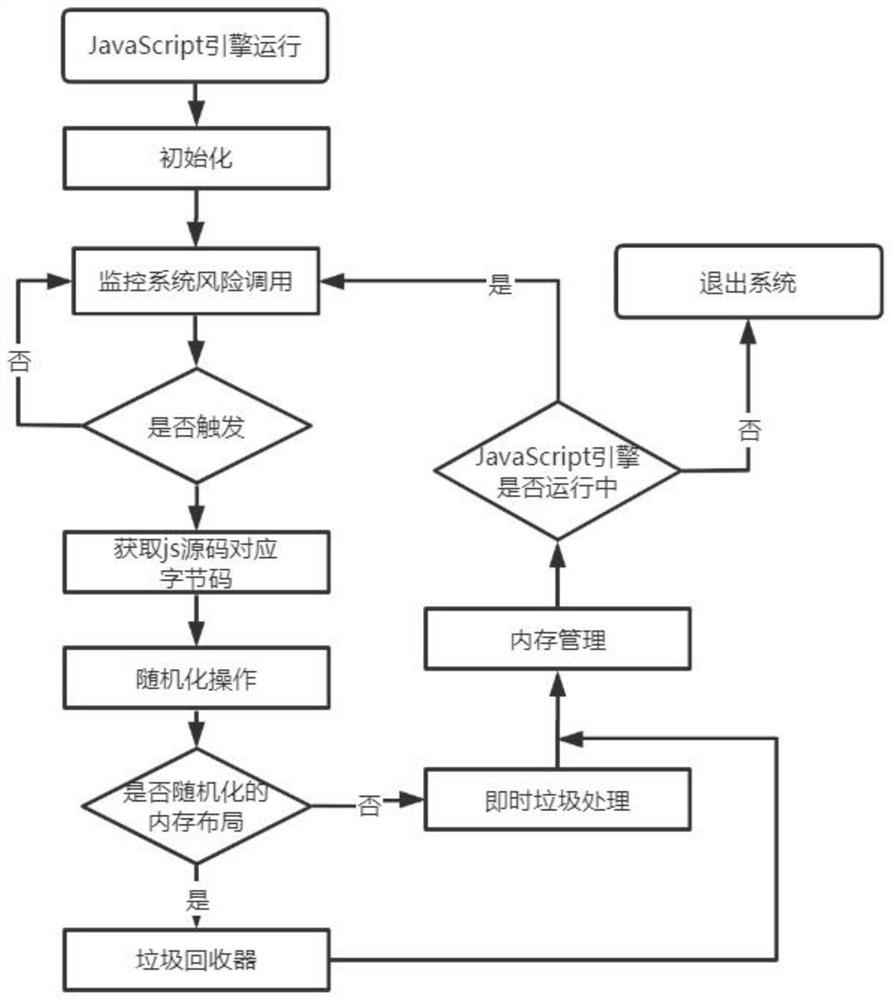
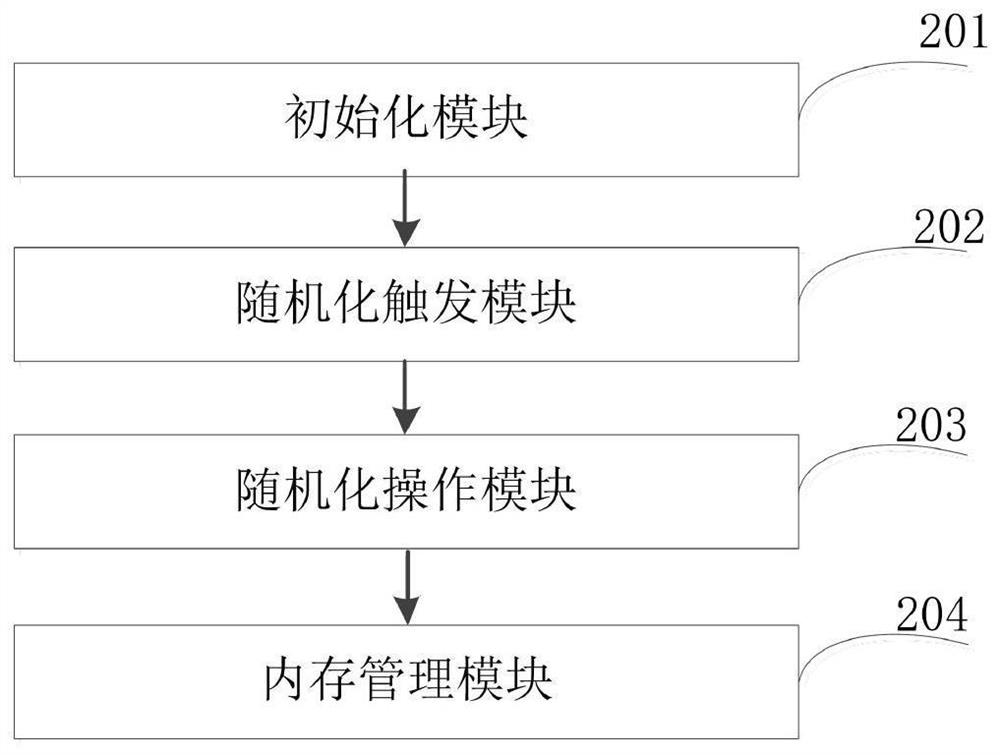
PendingCN111797388AIncrease unpredictabilityAchieve defensePlatform integrity maintainanceSoftware simulation/interpretation/emulationAttackInit
The invention discloses a JavaScript engine memory information leakage prevention method and system based on runtime randomization. The method comprises the following steps of step 1), initializing the system, carrying out initialization setting on a JavaScript engine-based runtime randomization system; 2) monitoring a risk behavior causing memory information leakage in a JavaScript engine runningprocess, and triggering a randomized system to execute during running; 3) realizing randomized operation of the JS engine; and 4) managing the memory in the operation process of the randomized systemduring operation, thereby realizing recovery management of memory garbage generated during operation of the randomized system during operation. The method is advantaged in that a security protectionproblem of dynamically generating the code by the JavaScript engine can be solved, and the capacity of the JS engine for coping with attacks based on memory information leakage is effectively improved.
Owner:WUHAN UNIV
A wire rope brake
ActiveCN104555789BRealize automatic resetSolve security protectionElevatorsHoisting equipmentsCamEnergy storage
Owner:HANGZHOU HUNING ELEVATOR PARTS CO LTD
High-voltage electrical apparatus insulation paint and preparation method thereof
InactiveCN107201148AGood flame retardantGood insulation effectFireproof paintsAnti-corrosive paintsChemistryPolyamide
The invention discloses high-voltage electrical apparatus insulation paint which comprises the following components in parts by weight: 60-80 parts of epoxy resin, 30-40 parts of organic silicon rubber, 20-30 parts of thermosetting resin, 15-35 parts of carbonate resin, 10-30 parts of nano-montmorillonite, 10-20 parts of talcum powder, 5-15 parts of light calcium carbonate, 3-8 parts of titanium dioxide, 5-10 parts of an organic solvent, 2-8 parts of amino polyamide, 5-10 parts of nanometer titania, 5-15 parts of calcium chloride, 8-15 parts of a composite flame retardant and 3-8 parts of a cross-linking agent. The high-voltage electrical apparatus insulation paint disclosed by the invention has excellent flame-retardant and insulating properties, so that the safety protection of high-voltage electrical apparatus equipment is achieved.
Owner:HEFEI OUSHIJIA ELECTRICAL & MECHANICAL EQUIP CO LTD
Flame retardant dipping device for foam plastic board
The invention discloses a flame retardant impregnating device for a foam plastic board, and relates to the technical field of mechanical equipment.The flame retardant impregnating device comprises a machine shell, an impregnating bin is fixedly connected to the inner side wall of the machine shell, an air suction pipe is fixedly connected to the right side wall of the impregnating bin, and an air suction pump is fixedly connected to the side wall of the right end of the machine shell; the right end of the air suction pipe penetrates through the machine shell and is fixedly connected with the output end of an air suction pump, a first valve is fixedly connected to the upper end of the left side wall of the dipping bin, a first water pipe is fixedly connected to the middle of the left side wall of the dipping bin, the left end of the first water pipe penetrates through the machine shell, and a second valve is fixedly connected to the middle of the first water pipe. The end, away from the machine shell, of the first water pipe is fixedly connected with a material storage tank, and the top end of the material storage tank is fixedly connected with a feeding port. By changing the pressure intensity in the impregnation bin, a flame retardant can be fully impregnated on a plastic plate, the possibility of incomplete impregnation is reduced, and the flame retardant strength of the plastic plate is improved.
Owner:湖南省源塑管道有限公司
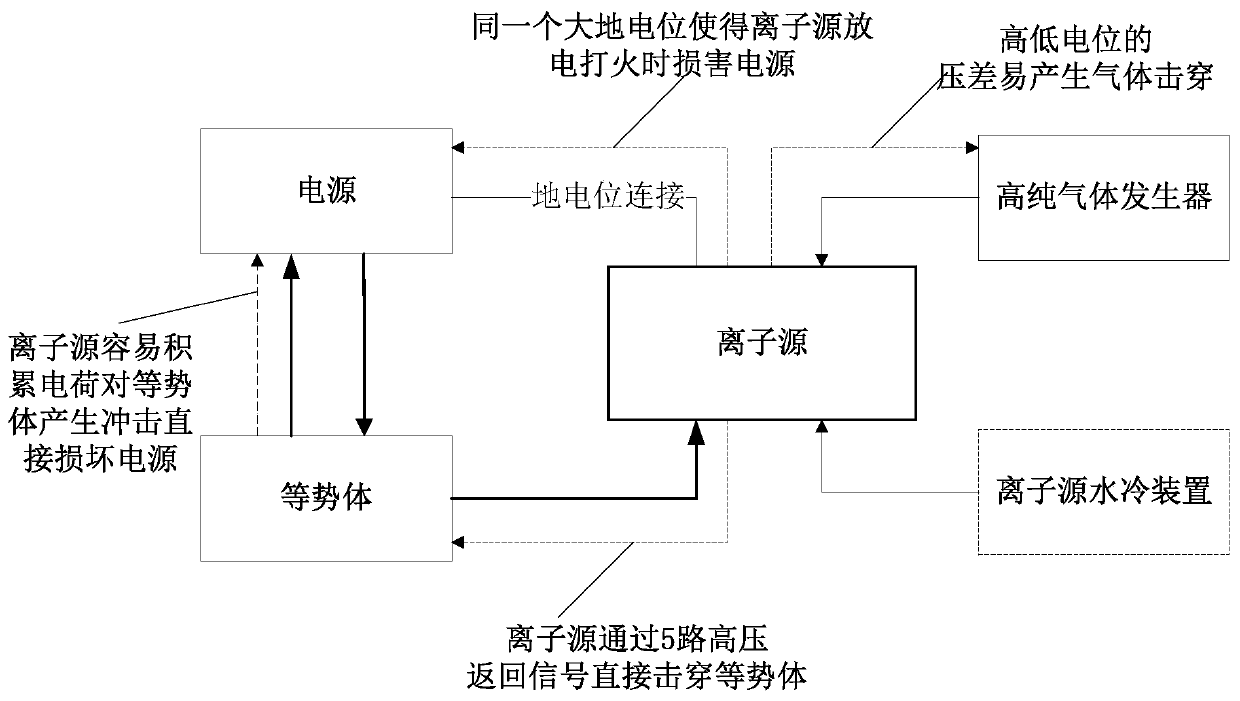
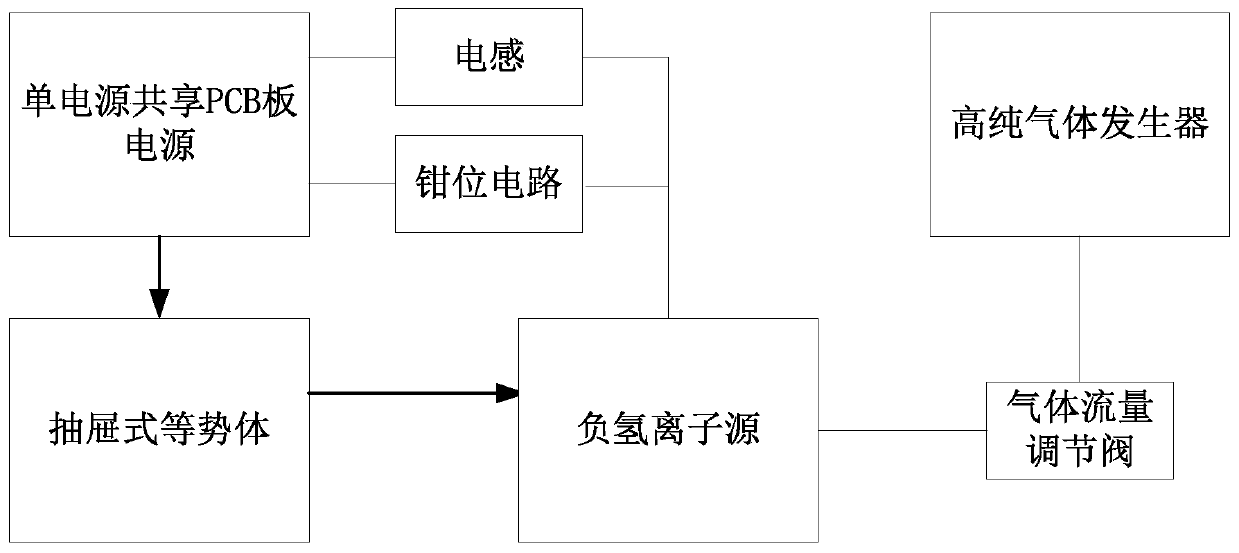
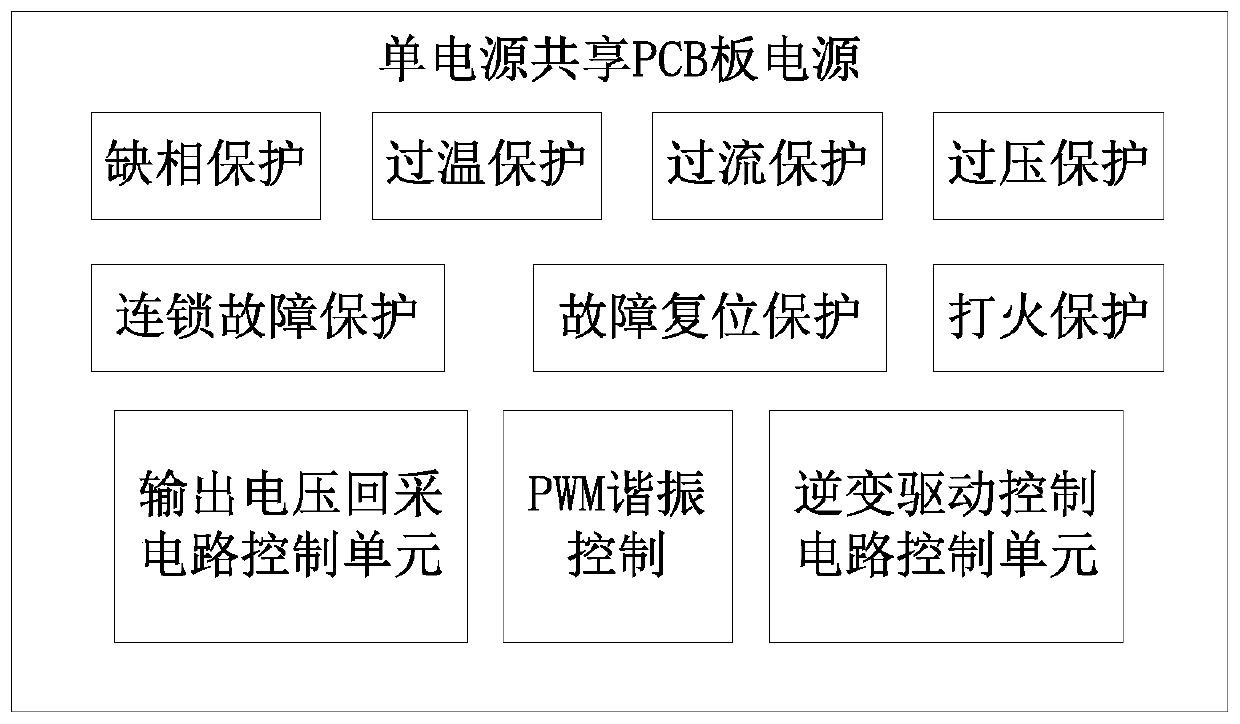
Safety protection device for high-current negative hydrogen ion source
PendingCN111341633ASolve security protectionGuaranteed power supplyElectric discharge tubesEngineeringGas supply
The invention discloses a safety protection device for a high-current negative hydrogen ion source. The device comprises an ion source which is used for generating negative hydrogen ions, a high-purity gas generator which is used for supplying gas to the negative hydrogen ion source, and a power supply which is used for supplying power to the negative hydrogen ion source; a high-voltage equipotential body is further arranged between the power supply and the negative hydrogen ion source, and the power supply supplies power to the negative hydrogen ion source through the high-voltage equipotential body; a load discharge prevention device is also arranged between the power supply and the negative hydrogen ion source; a high-potential gas flow regulating valve is also arranged between the high-purity gas generator and the negative hydrogen ion source; the power supply is a single-power-supply shared PCB power supply; the high-voltage equipotential body is a drawer type equipotential body;the ground potential of the power supply end and the ground potential of the negative hydrogen ion source end are the same ground potential, and the high potential of the high-voltage equipotential body end and the high potential of the negative hydrogen ion source end are the same high potential of -30 KV or above. All the parts are organically combined, all the parts support and depend on one another after combination, and the overall safety protection problem of the high-current negative hydrogen ion source is solved.
Owner:CHINA INSTITUTE OF ATOMIC ENERGY
An automatic reset wire rope brake
The invention discloses an automatic resetting steel wire rope brake, which comprises two side plates, a fixed brake plate, a moving brake plate, a motor lead screw and push block resetting mechanism, an electromagnet resetting mechanism and an electromagnetic triggering mechanism, wherein the fixed brake plate and the moving brake plate are arranged in parallel, and an interval is kept between the opposite clamping surfaces of the fixed brake plate and the moving brake plate; two sides of the moving brake plate are respectively and rotatably matched with one end of a link arm, and the moving brake plate can do translational motion towards or away from the fixed brake plate under the drive of the two link arms; the other end of each of the two link arms is rotatably matched with one end of a sliding axle; two ends of the sliding axle are respectively in sliding fit with arc-shaped grooves of the two side plates; a hooking part is formed on a swing-type latch hook, and is used for hooking and locking the sliding axle; the swing end of the swing-type latch hook is triggered by the electromagnetic or mechanical triggering mechanism to enable the swing end to release the sliding axle; the electromagnetic triggering mechanism, the latch hook, the sliding axle and the moving brake plate are promoted to reset by the motor lead screw and push block resetting mechanism through the electromagnet resetting mechanism. According to the automatic resetting steel wire rope brake disclosed by the invention, elevator ascending and descending over-speed protection and car accidental movement protection can be realized simultaneously.
Owner:HANGZHOU HUNING ELEVATOR PARTS CO LTD
A mobile proxy safeguarding method similar to biological self-protection
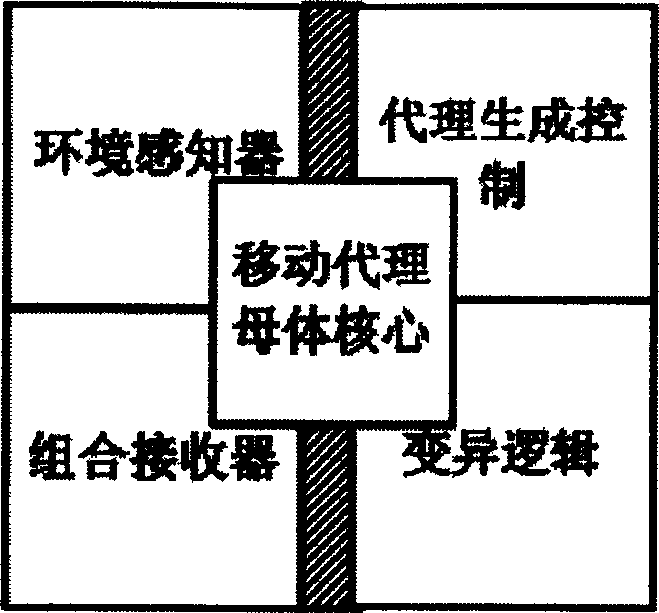
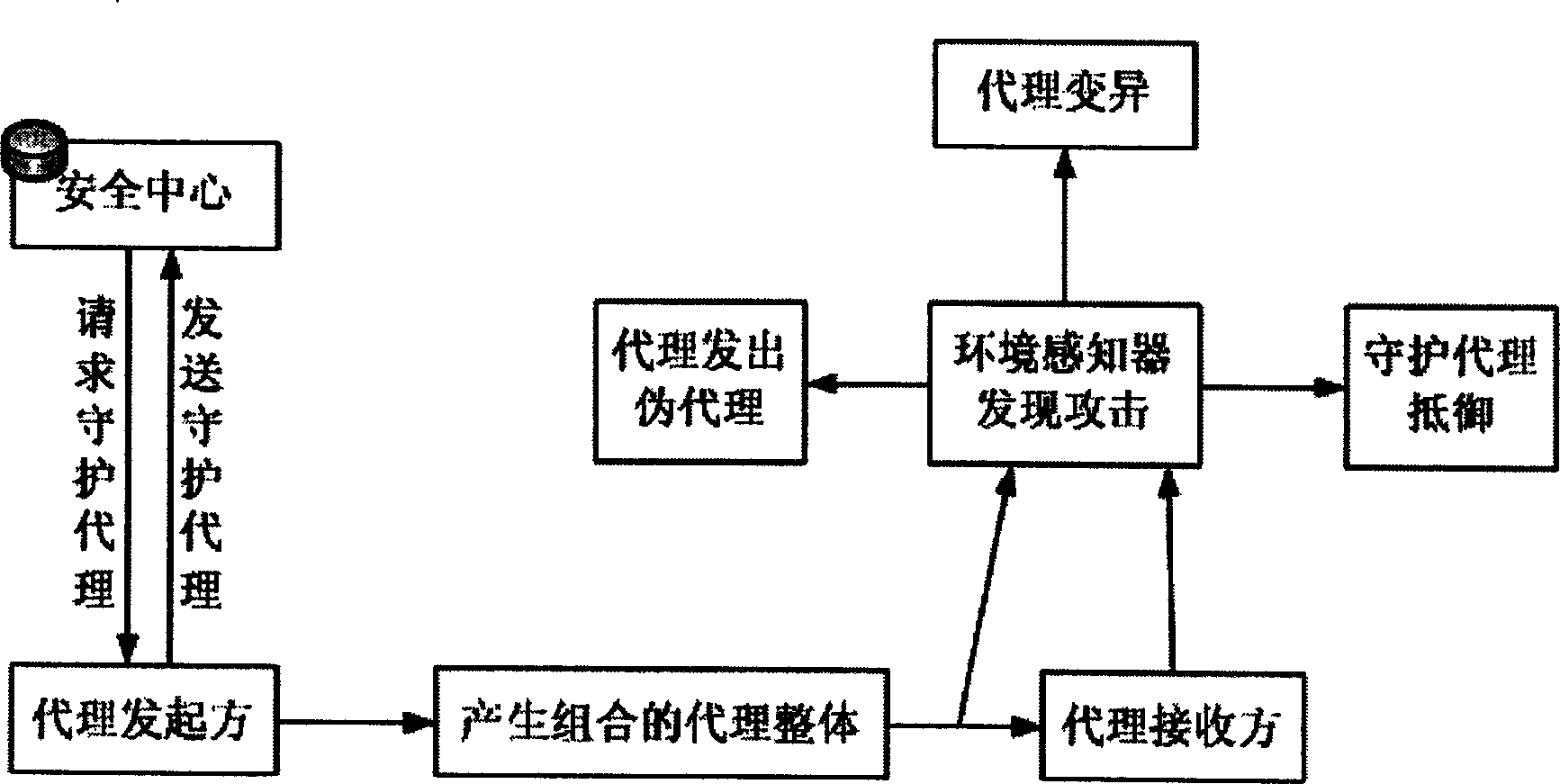
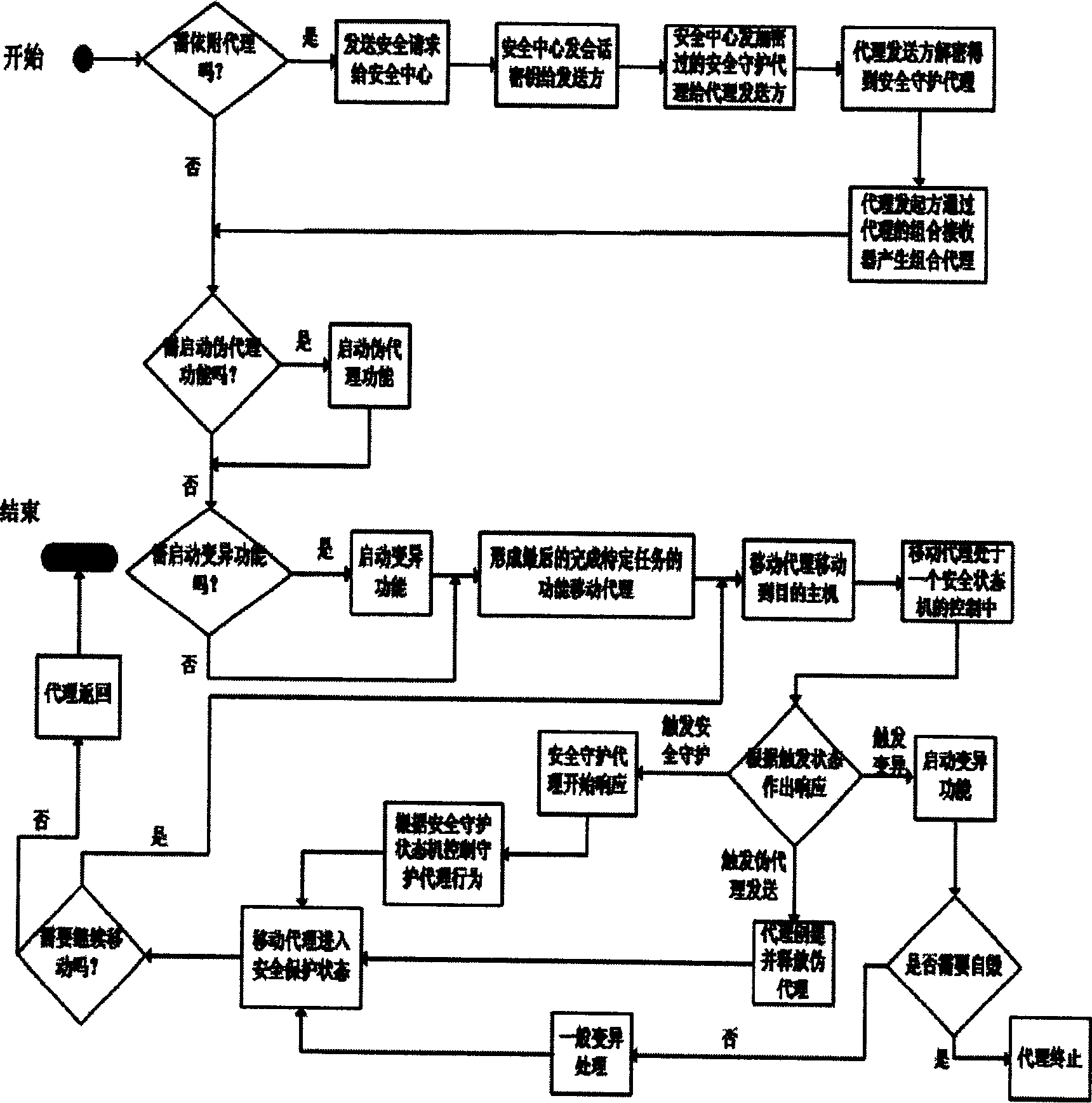
InactiveCN1655524AProtection reachedSolve security protectionData switching networksSecuring communicationSecurity solutionByte
This invention relates to moving agent safety protective method similar to the biological creature, which is mainly used to solve the moving agent safety problem and introduces multiple functions agent and refers to the biological creature self-protection method. Comparing with the traditional structure, this invention adds four parts: environment appreciation device, agent generation control logics and combination receiver and aberrance logic control.
Owner:NANJING UNIV OF POSTS & TELECOMM
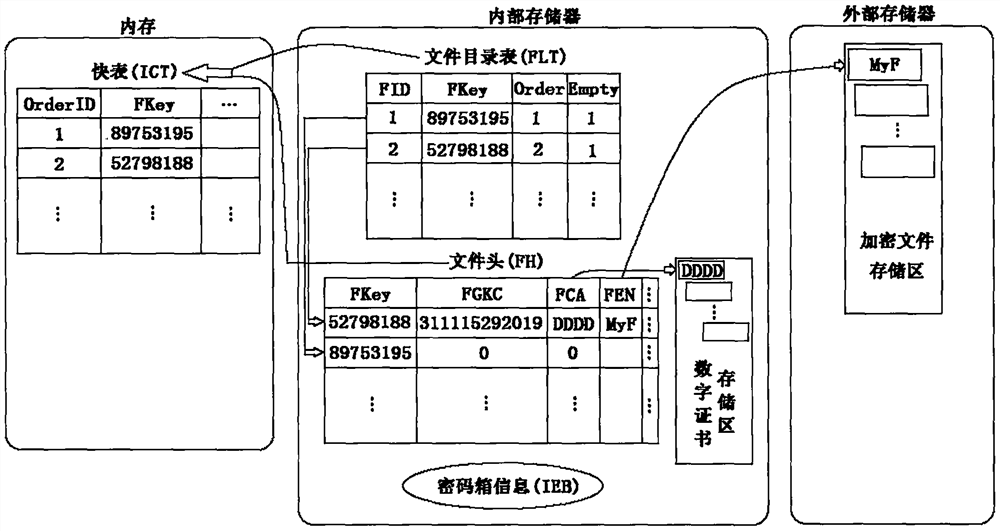
Android file code box system based on double chaotic hash file control
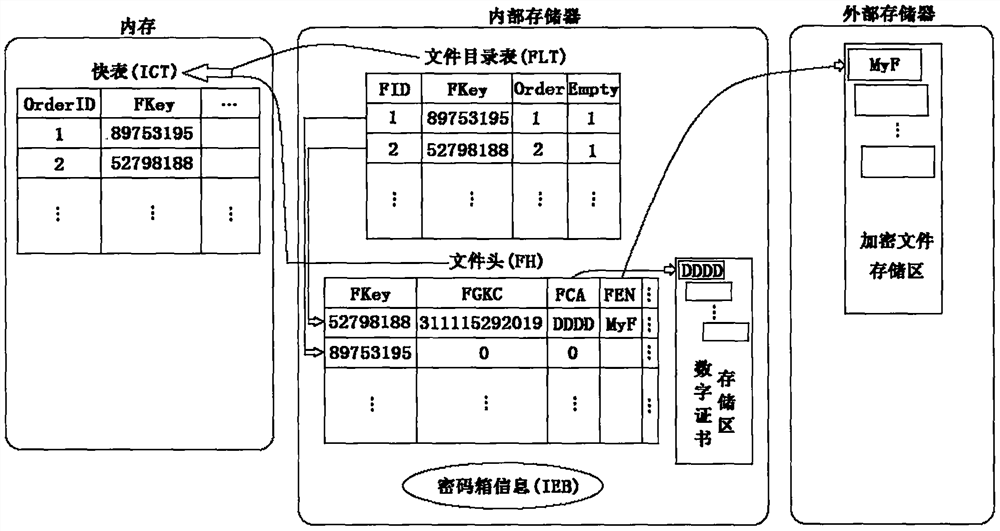
ActiveCN112380559AWill not crowdSolve conflictsDigital data protectionDigital data authenticationInternal memoryExternal storage
The invention provides an android file code box system based on double chaotic hash file control, which has the functions of reading a system data structure file in an internal memory after successfullogin in an android system, establishing a fast table in the memory, and storing the fast table in the internal memory. Rapid browsing, adding, modifying, deleting, backing up and reconstructing operations on the encrypted file stored in the external memory are realized; When the user exits, the content of the fast table is written back into the data structure file. Mobile phone configuration andpersonal safety requirements of the user are fully considered, the storage space of the user is prevented from being forcibly occupied, and the user can flexibly set different file safety protectionlevels. According to the system, a new data structure file is designed according to the characteristics of the Android system to realize file control, so that the trouble that a user sets different passwords for encrypting a plurality of files is avoided, and a function of protecting copyright files is provided; and through the system reconstruction function, the attack of illegal users is avoided, the security is greatly improved, and the operation speed is higher.
Owner:JILIN UNIV
Method, system and mobile terminal for wireless network to capture mobile IP style of mobile terminal
ActiveCN101106806BSolve security protectionKey distribution for secure communicationWireless network protocolsEngineeringProxy server
The invention provides a method for obtaining mobile IP type of a mobile terminal in a wireless network: a mobile IP proxy server reports related information of a mobile IP type to a user, who requires a mobile IP type, according to the mobile IP type identifying field in a mobile IP logging request message of a mobile terminal. A system for imparting a mobile IP type to a mobile terminal in a wireless network at least includes: a mobile terminal, a mobile IP proxy server, and a user who requires a mobile IP type. The mobile terminal transmit a mobile IP logging request message to a mobile IPproxy server for performing mobile IP logging in; and the mobile IP proxy server reports mobile IP type related information of the mobile terminal to the user who requires a mobile IP type according to the mobile IP type identifying field in a mobile IP logging request message. The invention also provides a mobile terminal for wireless network, when the mobile terminal is logged in a network for the first time or keywords for the mobile terminal is needed to be updated, the mobile terminal transmits mobile IP logging request message to a mobile IP proxy serve for performing mobile IP logging in, and a mobile IP type identifying field for identifying mobile IP type of the mobile terminal is included in the mobile IP logging request message.
Owner:HUAWEI TECH CO LTD
A flexible guiding special elevator car stabilization device and method
ActiveCN104150336BSolve the stop swingSolve security protectionElevatorsMine liftsLocking mechanismEngineering
The invention relates to a flexible guiding special lift car stabilizing device and method. The device is composed of a stabilizing support, a connecting mechanism and a self-locking mechanism. The connecting mechanism comprises connecting plates, final limit cams and stabilizing bars, and the self-locking mechanism comprises rockers, return springs, driving bolts, bearings, driven bolts and pins. When a lift stops on a floor, a car door is opened to drive the connecting mechanism to release self locking, the stabilizing bars are pushed into a shaft support so as to stabilize the lift car, and the self-locking mechanism returns to the self-locking state. After unloading and loading, the car door is closed, the connecting mechanism is driven to release self locking, the stabilizing bars are withdrawn, the self-locking mechanism performs self locking again, and the lift runs normally. The problem that the lift car sways when people or cargos enter or exit from the flexible guiding mining lift is solved, various safety problems caused by partial swaying during rerunning of the lift car are avoided, the lift car can be started stably after stopping on one floor, reliability and stability of the lift are improved, driving does not need to be set independently, and the flexible guiding special lift car stabilizing device is simple in structure, good in lift car stabilizing effect, low in cost and safe and reliable.
Owner:DONGNAN ELEVATOR +1
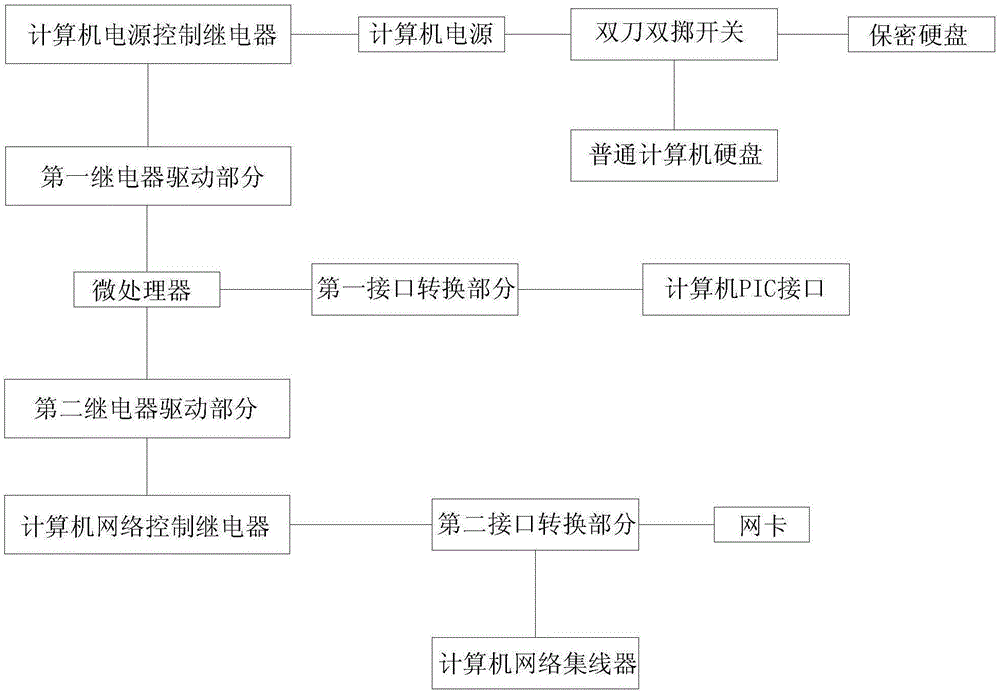
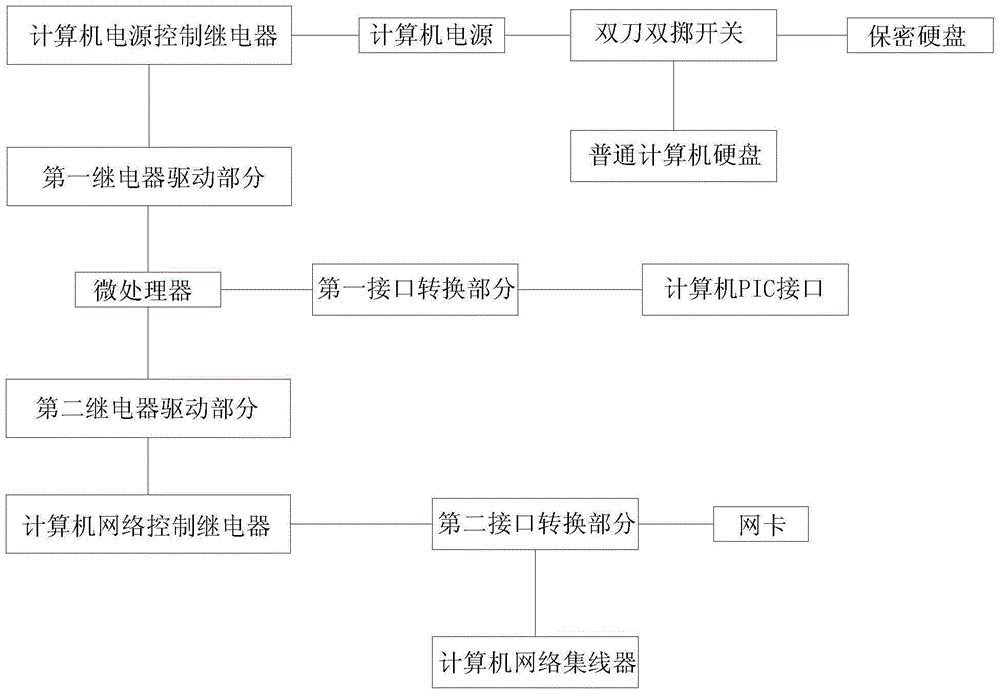
Computer data security control device and control method thereof
InactiveCN105138909ASolve the problem of information security protectionSolve security protectionDigital data authenticationPlatform integrity maintainanceStructure of Management InformationOptimal control
The invention discloses a computer data security control device. The computer data security control device comprises a microprocessor, relay drive parts, a computer power source control relay, a computer network control relay, a computer power source, a double-pole-double-throw switch, computer hard disks, interface conversion parts, a network card and a computer network hub. The relay drive parts comprise a first relay drive part and a second relay drive part. The computer hard disks comprise a secrecy hard disk and a common computer hard disk. The interface conversion parts comprise a first interface conversion part and a second interface conversion part. As the microprocessor is adopted for controlling a relay driver, information safety protection of the hard disks of a computer and safety protection after the computer is networked are effectively achieved, the optimal control combination is achieved, the computer data security control device is simple in structure, low in cost and easy to popularize, the control method is high in sensitivity, and once an alien invader enters, the computer data security control device immediately stops the alien invader from entering.
Owner:NANYANG INST OF TECH
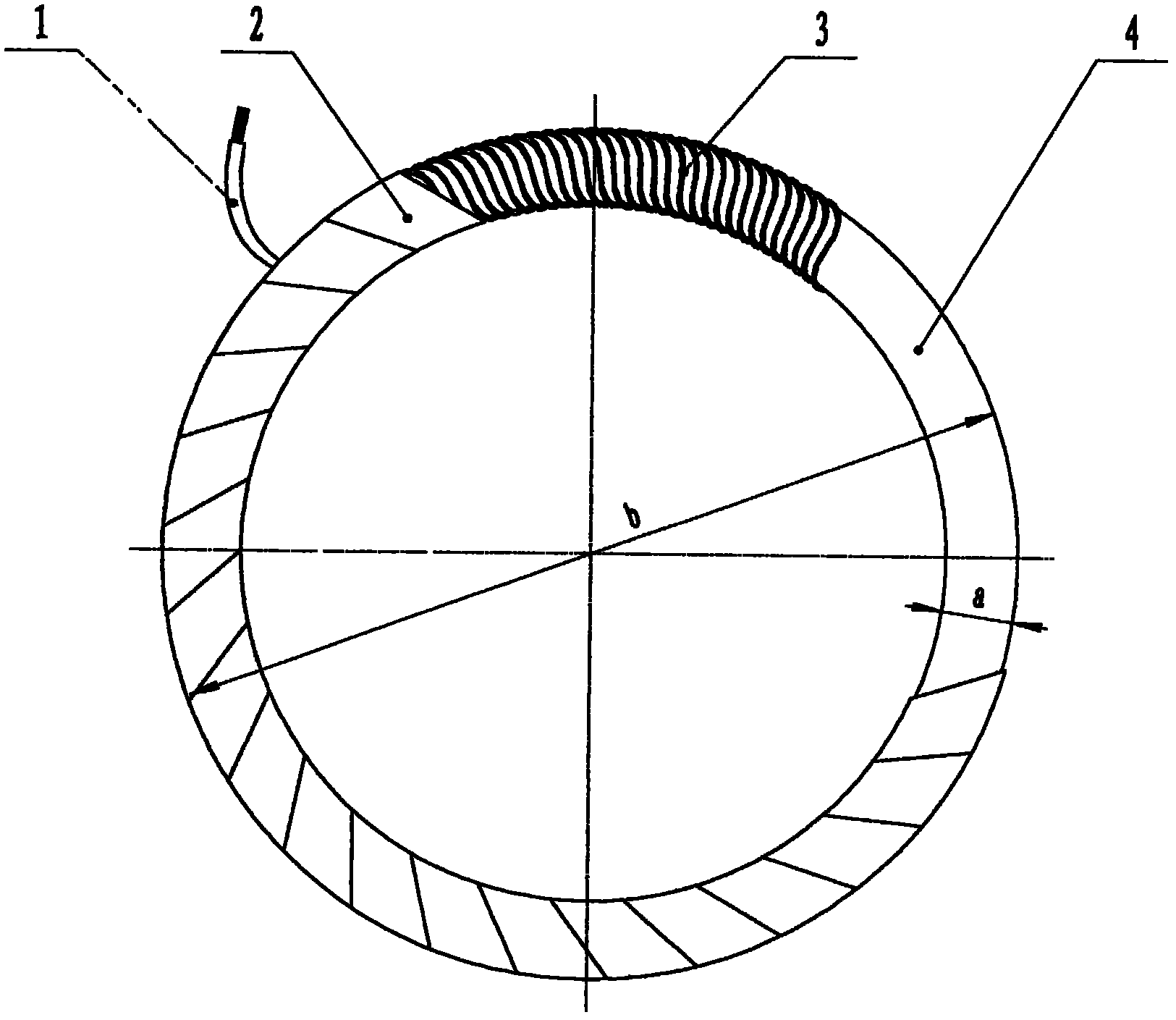
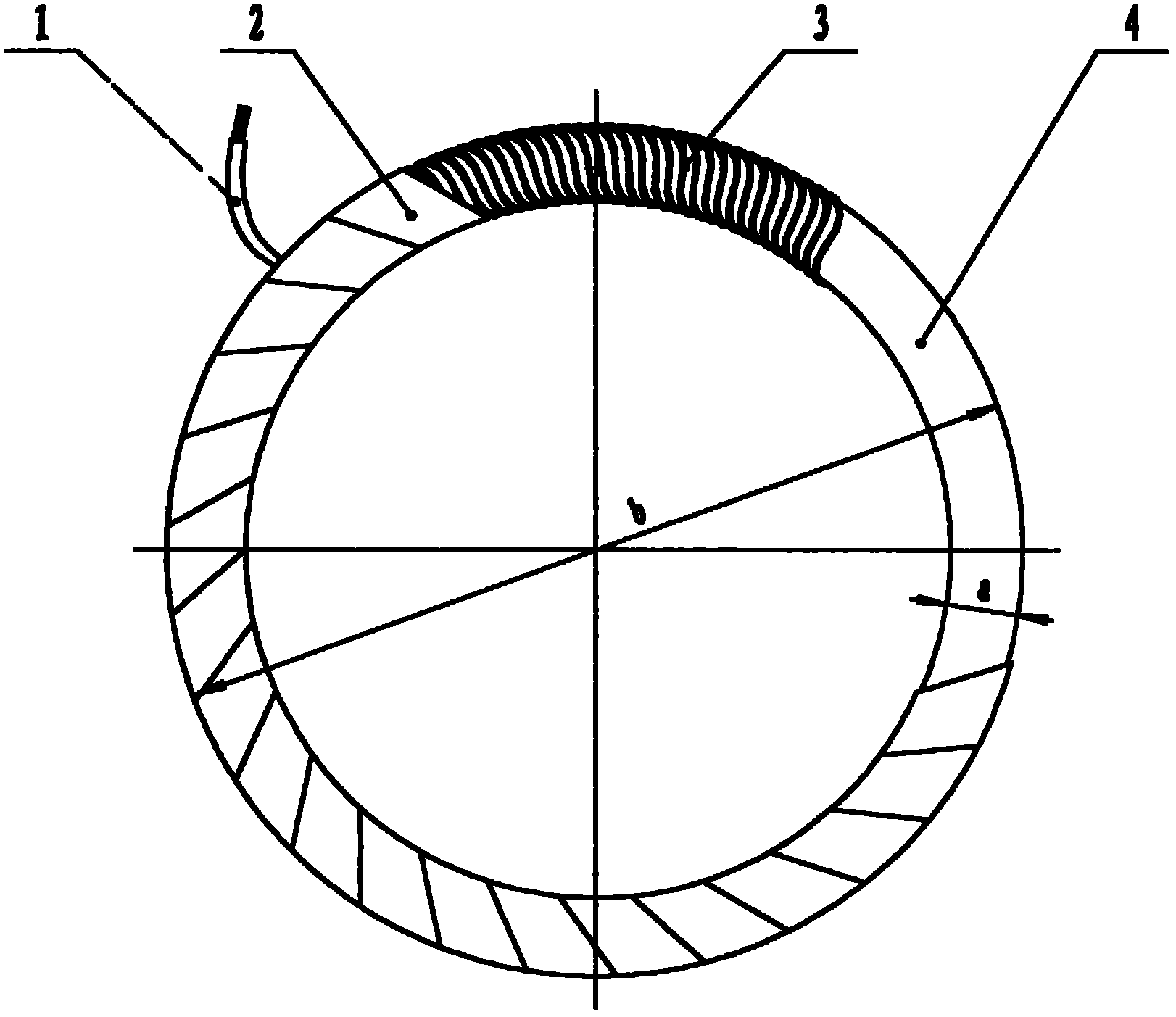
Lead-out end phase-failure protection method for leakage circuit breaker
InactiveCN102222888ASolve the security protection problem of lack of phaseSolve security protectionSwitch operated by current/voltage unbalanceSwitch operated by falling voltageProtection procedureEngineering
A lead-out end phase-failure protection method for a leakage circuit breaker adopts the following four measures: the first measure is the selection of an acquisition signal, namely, a lead-out end phase-failure current change is acquired as a signal; the second measure is the fabrication of current inductive elements, namely, a plastic loop (4) is used as a core, an enameled wire layer (3) and an insulating tape layer (2) are wound around the exterior of the core, and the two ends of the enameled wire are led out by two insulating leads 1; the third measure is the installation of a leakage circuit breaker with a lead-out end phase-failure protection function, namely, three current inductive elements are respectively arranged on three live wires between a zero sequence mutual inductor (6) and a lead-out column (8) in a common leakage circuit breaker (5); and the fourth measure is the setting of a lead-out end phase-failure protection procedure for the leakage circuit breaker, namely, the current inductive elements collect the current change information caused by the phase failure, transfer to an AD conversion processor and then send to a microprocessor, the microprocessor instructs to alarm and implements break-brake protection after comprehensive analysis. The method solves the lead-out end phase-failure problem that is long for being solved and cannot be solved and fills in the gap in the field of phase failure protection.
Owner:浙江豪顿电气有限公司
A method of protecting computer data security
InactiveCN105138909BSolve the problem of information security protectionSolve security protectionDigital data authenticationPlatform integrity maintainanceControl systemComputer module
The invention discloses a computer data security control device. The computer data security control device comprises a microprocessor, relay drive parts, a computer power source control relay, a computer network control relay, a computer power source, a double-pole-double-throw switch, computer hard disks, interface conversion parts, a network card and a computer network hub. The relay drive parts comprise a first relay drive part and a second relay drive part. The computer hard disks comprise a secrecy hard disk and a common computer hard disk. The interface conversion parts comprise a first interface conversion part and a second interface conversion part. As the microprocessor is adopted for controlling a relay driver, information safety protection of the hard disks of a computer and safety protection after the computer is networked are effectively achieved, the optimal control combination is achieved, the computer data security control device is simple in structure, low in cost and easy to popularize, the control method is high in sensitivity, and once an alien invader enters, the computer data security control device immediately stops the alien invader from entering.
Owner:NANYANG INST OF TECH
Flexible guiding special lift car stabilizing device and method
ActiveCN104150336ASolve the stop swingSolve security protectionElevatorsMine liftsLocking mechanismSelf locking
The invention relates to a flexible guiding special lift car stabilizing device and method. The device is composed of a stabilizing support, a connecting mechanism and a self-locking mechanism. The connecting mechanism comprises connecting plates, final limit cams and stabilizing bars, and the self-locking mechanism comprises rockers, return springs, driving bolts, bearings, driven bolts and pins. When a lift stops on a floor, a car door is opened to drive the connecting mechanism to release self locking, the stabilizing bars are pushed into a shaft support so as to stabilize the lift car, and the self-locking mechanism returns to the self-locking state. After unloading and loading, the car door is closed, the connecting mechanism is driven to release self locking, the stabilizing bars are withdrawn, the self-locking mechanism performs self locking again, and the lift runs normally. The problem that the lift car sways when people or cargos enter or exit from the flexible guiding mining lift is solved, various safety problems caused by partial swaying during rerunning of the lift car are avoided, the lift car can be started stably after stopping on one floor, reliability and stability of the lift are improved, driving does not need to be set independently, and the flexible guiding special lift car stabilizing device is simple in structure, good in lift car stabilizing effect, low in cost and safe and reliable.
Owner:DONGNAN ELEVATOR +1
Device and method for tightening or loosening a cuff
ActiveCN103932690BSolve for uniformitySolve the comfortEvaluation of blood vesselsAngiographyBarrel ShapedEngineering
The invention provides a device and method for winding or unwinding a cuff. The device for winding or unwinding the cuff comprises a winding mechanism, the cuff attached to the inner portion of the winding mechanism and a control part used for controlling the winding mechanism to carry out winding or unwinding. The device is characterized in that the winding mechanism is made to carry out winding or unwinding in a barrel shape through the control part to wind or unwind the cuff in the winding mechanism, so that the cross section area of the winding mechanism is changed.
Owner:BEIJING CHIOY MEDICAL TECH CO LTD
Preparation method of microsphere for detonation of blasting in oil field layer
The invention discloses a preparation method of a microsphere for detonation of blasting in an oil field layer. The method comprises the following steps of: evenly mixing raw materials to obtain powder; then adding a collodion acetone solution in partial powder, stirring and agglomerating, and then carrying out forced screening to obtain a qualified product; subsequently, placing the qualified product in a sugar-coating machine, spraying a lac ethanol solution, scattering the powder so that the qualified product rounds as a ball and is enlarged, and screening to obtain a semi-finished product; placing the semi-finished product in the sugar-coating machine, spraying the collodion acetone solution, scattering the powder so that the semi-finished product rounds as a ball and is enlarged, andscreening to obtain a qualified semi-finished product; and placing the qualified semi-finished product in the sugar-coating machine for primary cladding and cladding, and drying to obtain the microsphere with the particle size of 1mm-3mm. The microsphere prepared by the method of the invention is easily transported in the rock seam at the bottom of an oil well; the detonation blasting effect of the microsphere is good, and the success rate of the ignition reaches 100%, thereby effectively improving the oil-production efficiency of the oil field; and the microsphere is safe and reliable and has low cost.
Owner:西安石油大油气科技有限公司 +1
Android file lockbox system based on double chaotic hash file control
ActiveCN112380559BWill not crowdSolve conflictsDigital data protectionDigital data authenticationInternal memoryExternal storage
The present invention provides an Android file password box system based on double chaotic hash file control. Quick browse, add, modify, delete, backup and rebuild operations of encrypted files in the external storage; when the user exits, the content of the fast table is written back to the data structure file. The invention fully considers the user's mobile phone configuration and personal security requirements, avoids mandatory occupation of the user's storage space, and the user can flexibly set different file security protection levels. According to the characteristics of the Android system, this system designs a new data structure file to realize the control of the file, avoids the trouble of users setting different passwords for encrypting multiple files, and provides the function of protecting copyright files; and the system reconstruction function avoids illegal users. The attack greatly improves security and runs faster.
Owner:JILIN UNIV
Display for protecting data
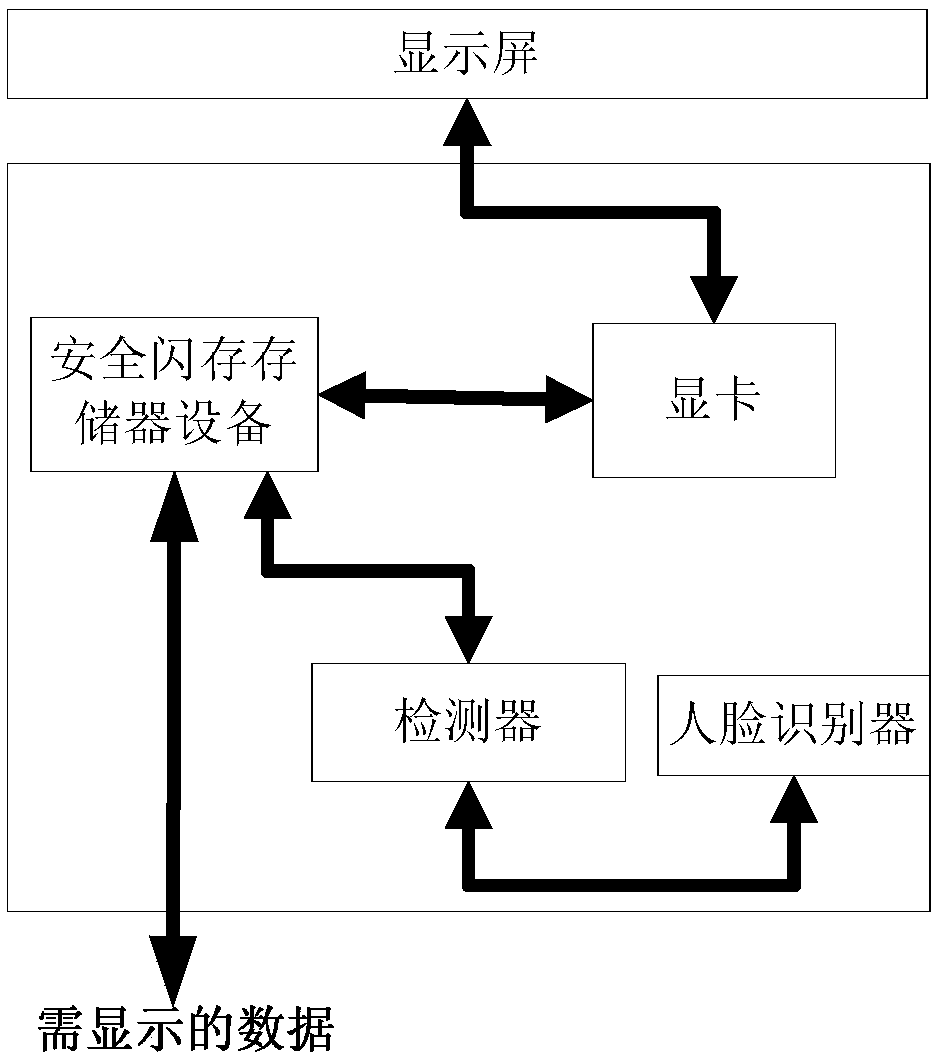
PendingCN110443082ASolve security protectionDigital data protectionInternal/peripheral component protectionGraphic cardDisplay device
The invention discloses a display for protecting data. The display comprises a display screen, a display card, a secure flash memory device and a detector. The detector detects whether the display isin a safe environment or not, if the display is in the safe environment, the safe flash memory device is controlled to process the data needing to be sent to the display card to be displayed, and theprocessed result is sent to the display card to be displayed. If the terminal is in the unsafe environment, the data needing to be sent to the display card to be displayed is not processed, but the data is directly sent to the display card, so that the displayed data is effectively protected.
Owner:拉萨经济技术开发区凯航科技开发有限公司
Deep foundation pit safety protection device for building construction
InactiveCN112081113AImprove protectionEnsure safetyFencingExcavationsArchitectural engineeringBuilding construction
The invention discloses a deep foundation pit safety protection device for building construction. The deep foundation pit safety protection device comprises first protection plates which are symmetrically installed, wherein second protection plates are symmetrically installed between the first protection plates; connecting clamping strips are installed on the two side edges of each second protection plate; connecting clamping grooves matched with the connecting clamping strips are formed in the positions, close to one side edges of the second protection plates and corresponding to the connecting clamping strips, of the first protection plates; connecting frames are installed at the two ends of the side edges, close to each other, of the second protection plates; supporting strip plates arefixedly installed inside the connecting frames; locking bolts are installed on the sides, close to each other, of the supporting strip plates and located at the ends, close to the first protection plates, of the connecting frames in a penetrating mode; threaded locking grooves matched with the locking bolts are formed in the positions, corresponding to the locking bolts, of the first protection plates; and connecting blocks are fixedly installed between the second protection plates and located on the side edges, close to each other, of the supporting strip plates.
Owner:青岛环城建工集团有限公司
Private key processing method, terminal and key center based on sm2 algorithm
ActiveCN110391900BSolve security protectionTroubleshoot recovery issuesKey distribution for secure communicationUser identity/authority verificationAlgorithmEngineering
The invention relates to the technical field of information security, discloses a private key processing method based on an SM2 algorithm, a terminal and a key center, and solves the security protection problem of a private key in an open environment in the prior art. The method is applied to a key center, and the method includes: receiving a key request message from a client, where the key request message includes a key identifier and a first private key factor of the client; according to a key generation rule, obtaining the private key corresponding to the key identifier; obtaining a second private key factor according to the private key corresponding to the key identifier and the first private key factor; sending the second private key factor to the server, so that the server side encrypts and stores the second private key factor. The embodiment of the present invention is applicable to the process of decentralized storage and use of private keys in an open environment.
Owner:JIN SHANG BO CHUANG BEIJING SCI & TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com